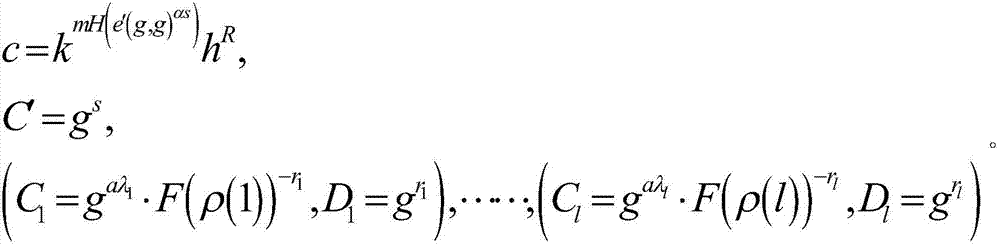BGN type cryptograph decryption outsourcing scheme based on attributes
A technology of ciphertext and attributes, applied in the field of information security, can solve problems such as illegal reading of ciphertext
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0107] 实施例1:基于属性的BGN型密文解密外包方案
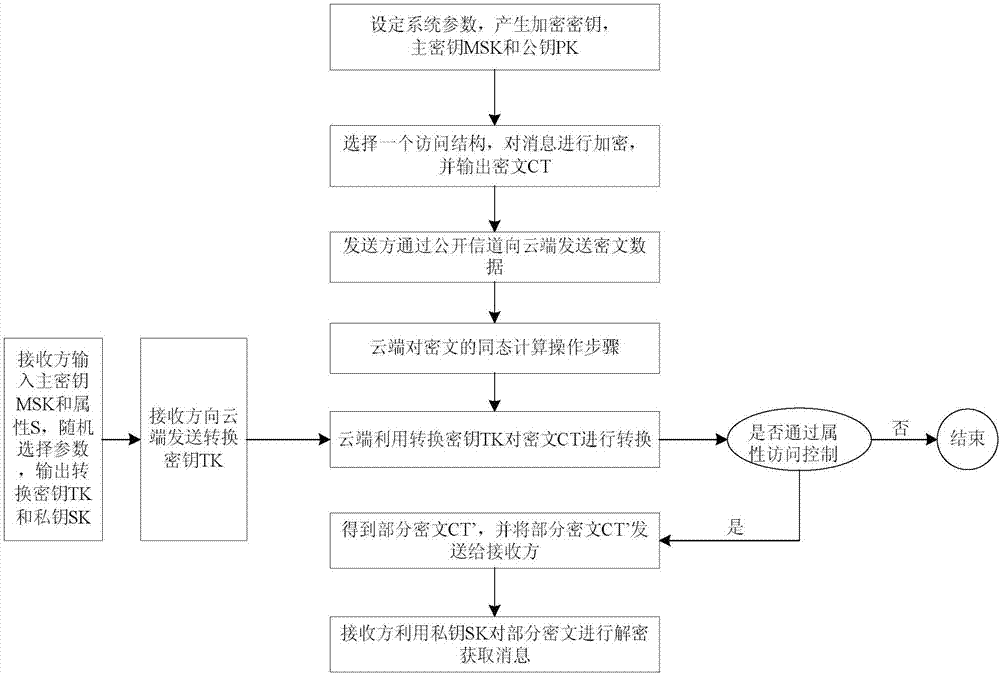
[0108] Such as figure 1 所示的基于属性的BGN型密文解密外包方案,其具体步骤如下:
[0109] 步骤(1):设定系统参数,产生加密密钥,主密钥MSK和公钥PK,步骤(1)具体过程如下:
[0110] 步骤(1-1):设定系统参数,输入安全参数λ和属性空间U,其中U={0,1} * ;所输入的安全参数λ的取值比较大,本实施例中,λ选择1024bit大小,足以保证方案的安全性。
[0111] 步骤(1-2):运行算法ξ(λ),得到元组(q 1 ,q 2 ,G,G 1 ,e)和双线性映射e:G×G→G 1 , where q 1 ,q 2 为素数,G,G 1 都是阶为n=q 1 q 2 的群;ξ(λ)是公开的参数产生算法,q 1 ,q 2 为大素数,本实施例中选择q 1 ,q 2 为512bit大小的素数。
[0112] 步骤(1-3):在群G中随机选择生成元k,u,并令 则h是群G的q 1 阶子群生成元,再随机选择阶为p的素数阶群G′和G′ T ,令g为群G′的一个生成元,得到双线性映射e′:G′×G′→G′ T .
[0113] 步骤(1-4):随机选择由{0,1} * 映射到G′的哈希函数F和由G′ T 映射到(0,1)的哈希函数H,随机选择系数α,a∈Z p ,即α、a均在模p的整数域上随机选择,Z p 即为模p的整数域,则算法的主密钥表示为:MSK=(g α ,PK);
[0114] 公钥表示为:PK=(n,g,k,h,e,e′(g,g) α , g a ,F,H,G,G 1 ).
[0115] 步骤(1)中所使用的哈希函数F和哈希函数H均为公开的国产哈希函数SM3算法。
[0116] 步骤(2):发送方选择一个访问结构,对消息进行加密,并生成密文CT,步骤(2)具体过程如下:
[0117] 步骤(2-1):发送方选择LSSS访问结构(M,ρ),其中,M是一个与属性有关的l×n的矩阵,ρ是与M的行元素M i 相关的函数,表示可以将矩阵M的每一行对应到访问结构中某一元素的映射,i=1,2,…,l。
[0118] 步骤(2-2):随机选择n个Z p...
Embodiment 2
[0141] Example 2: Attribute-based BGN-type ciphertext decryption outsourcing scheme
[0142] The specific plan is as follows:
[0143] Step (1): Set system parameters, generate encryption key, master key MSK and public key PK, the specific process of step (1) is as follows:
[0144] Step (1-1): Set system parameters, input security parameter λ and attribute space U, where U={0,1} * ; The value of the input security parameter λ is relatively large. In this embodiment, λ is selected as 1024bit, which is sufficient to ensure the security of the scheme.
[0145] Step (1-2): Run the algorithm ξ(λ) to get the tuple (q 1 ,q 2 ,G,G 1 , e) and bilinear map e:G×G→G 1 , where q 1 ,q 2 is a prime number, G, G 1 Both are of order n=q 1 q 2 group of ; ξ(λ) is a public parameter generation algorithm, q 1 ,q 2 is a large prime number, select q in this embodiment 1 ,q 2 It is a prime number of 512bit size.
[0146] Step (1-3): Randomly select generators k, u in the group G, and ...
Embodiment 3
[0185] Example 3: Attribute-based BGN-type ciphertext decryption outsourcing scheme
[0186] The specific plan is as follows:
[0187] Step (1): Set system parameters, generate encryption key, master key MSK and public key PK, the specific process of step (1) is as follows:
[0188] Step (1-1): Set system parameters, input security parameter λ and attribute space U, where U={0,1} * ; The value of the input security parameter λ is relatively large. In this embodiment, λ is selected as 1024bit, which is sufficient to ensure the security of the scheme.
[0189] Step (1-2): Run the algorithm ξ(λ) to get the tuple (q 1 ,q 2 ,G,G 1 , e) and bilinear map e:G×G→G 1 , where q 1 ,q 2 is a prime number, G, G 1 Both are of order n=q 1 q 2 group of ; ξ(λ) is a public parameter generation algorithm, q 1 ,q 2 is a large prime number, select q in this embodiment 1 ,q 2 It is a prime number of 512bit size.
[0190] Step (1-3): Randomly select generators k, u in the group G, and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com