Patents
Literature
319 results about "Access structure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Access structures are used in the study of security system where multiple parties need to work together to obtain a resource. Groups of parties that are granted access are called qualified. In set theoretic terms they are referred to as qualified sets. In turn, the set of all such qualified sets is called the access structure of the system. Less formally it is a description of who needs to cooperate with whom in order to access the resource. In its original use in cryptography, the resource was a secret shared among the participants. Only subgroups of participants contained in the access structure, are able to join their shares to recompute the secret. More generally, the resource can also be a task that a group of people can complete together, such as creating a digital signature, or decrypting an encrypted message.
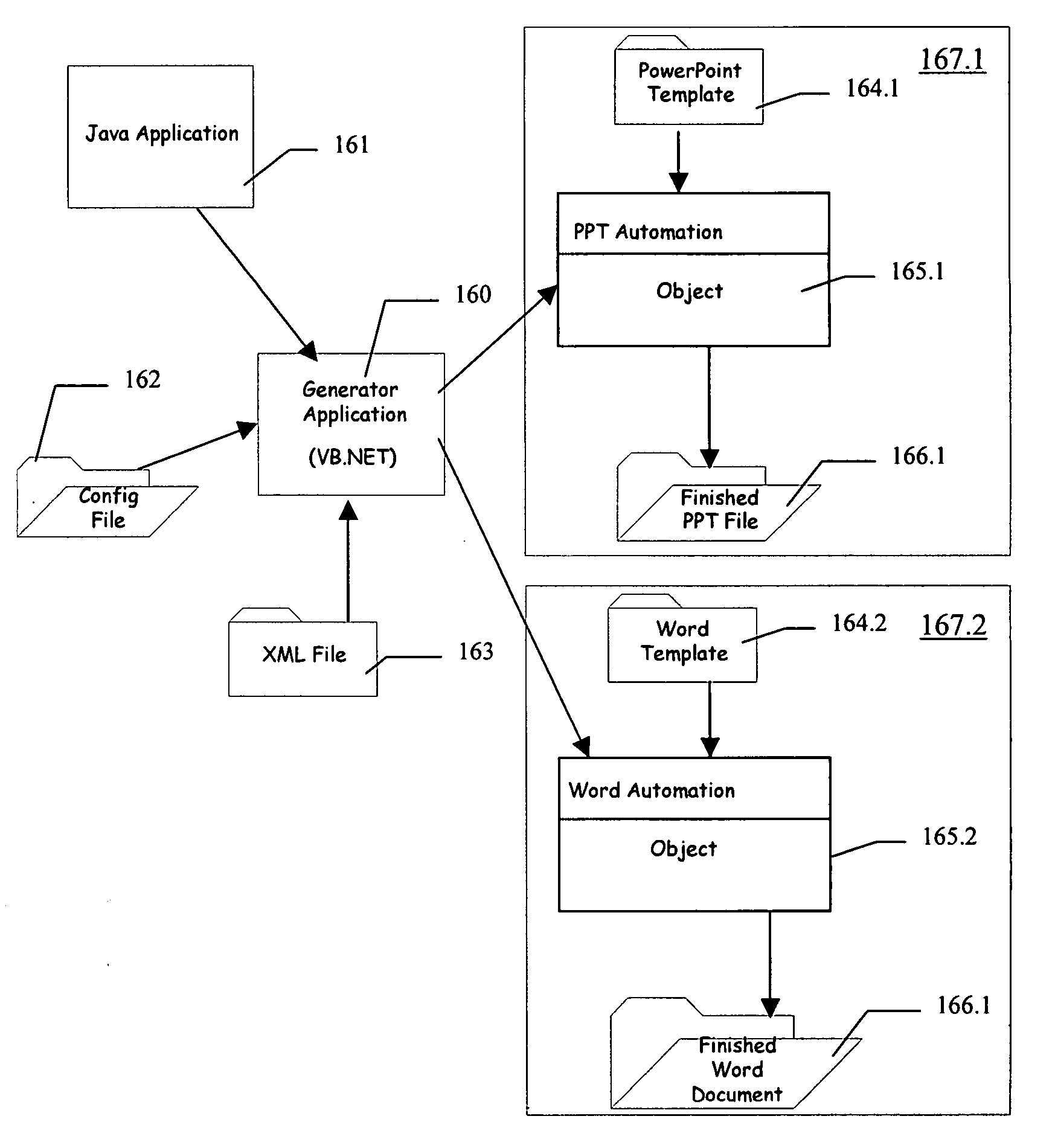
Presentation generator
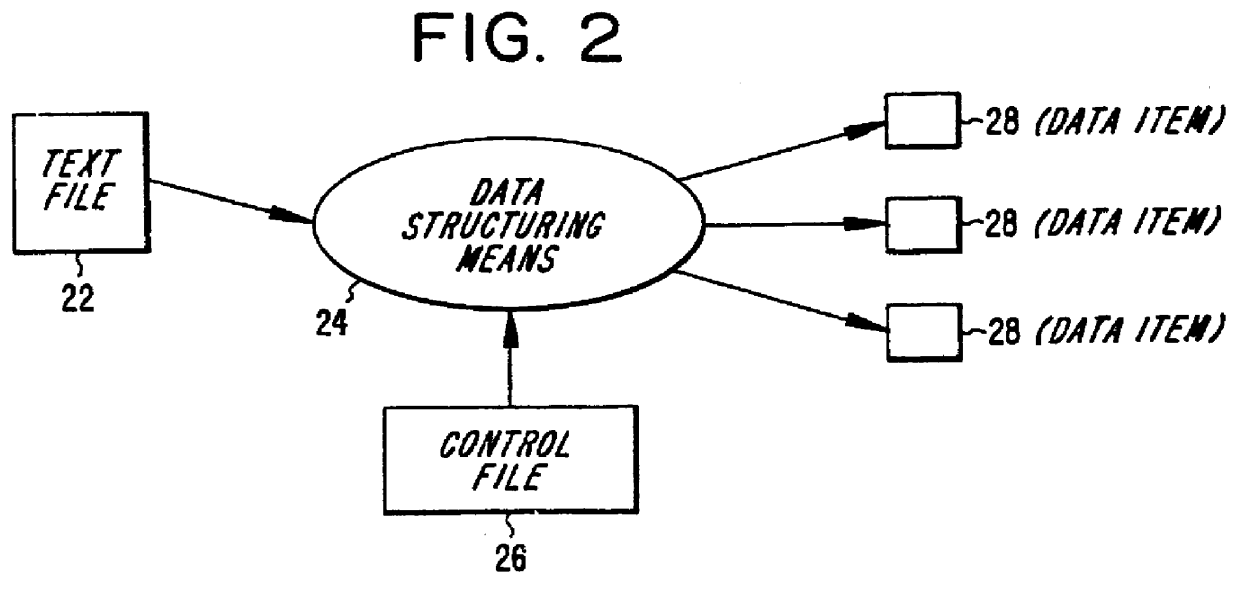
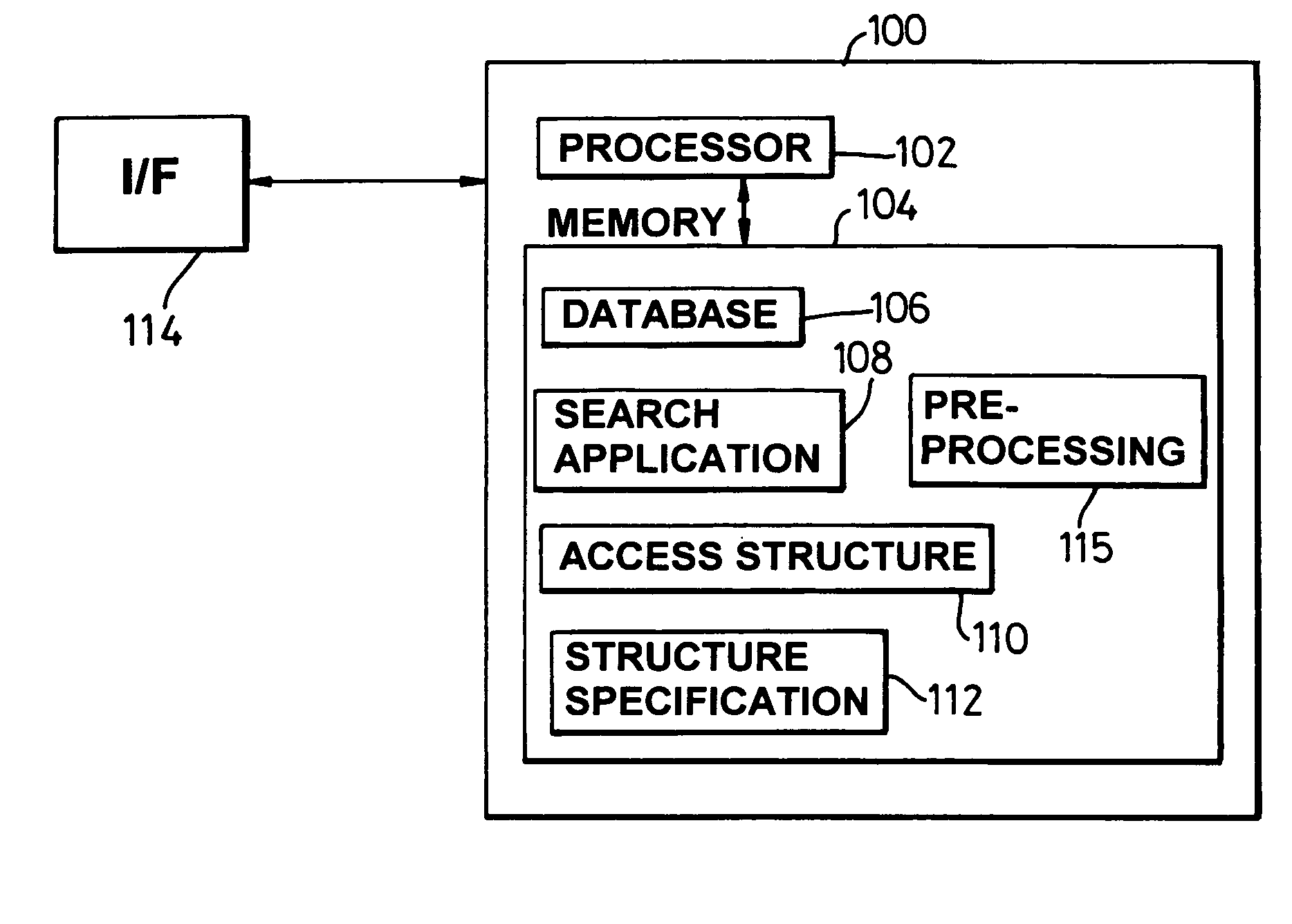
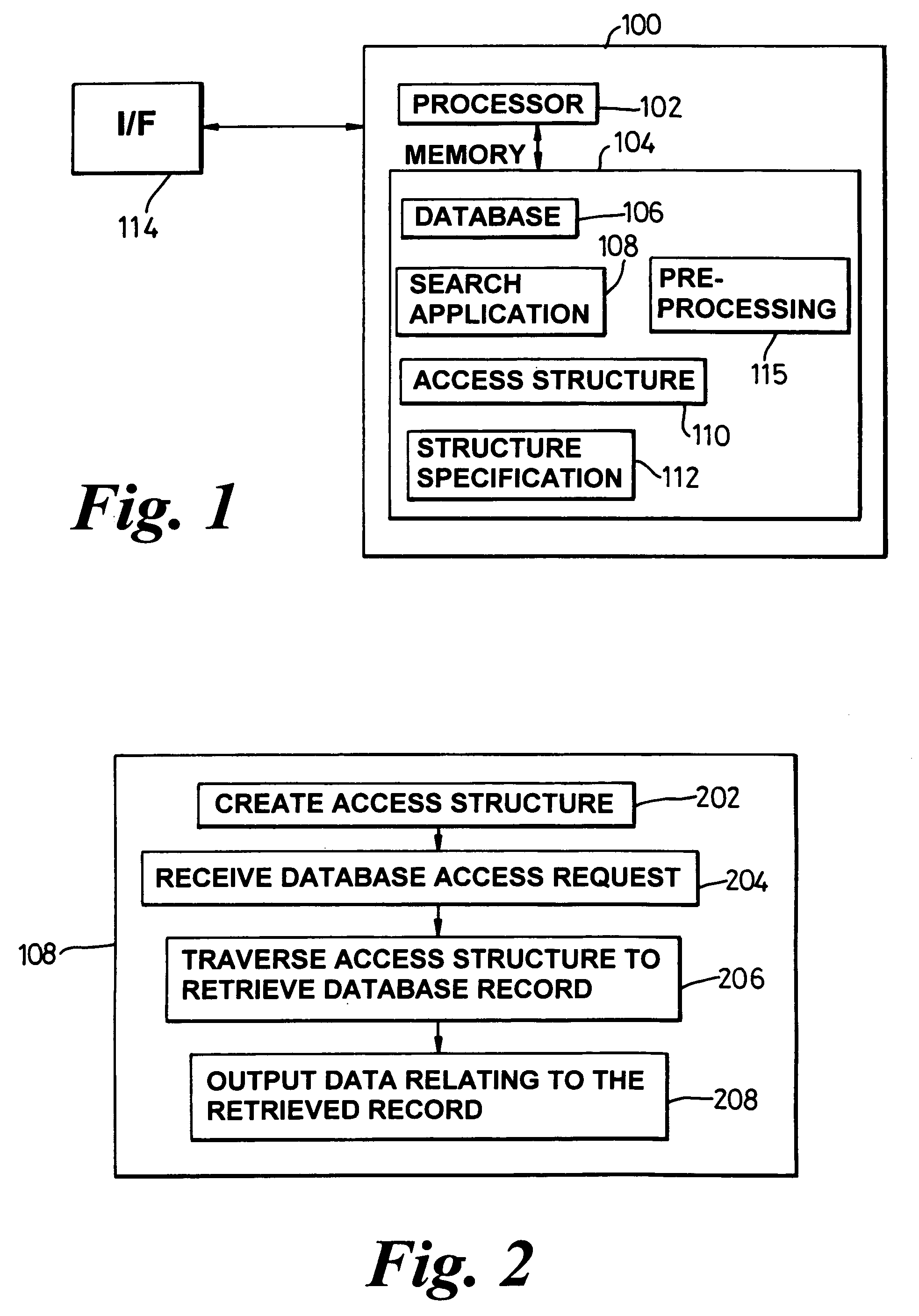
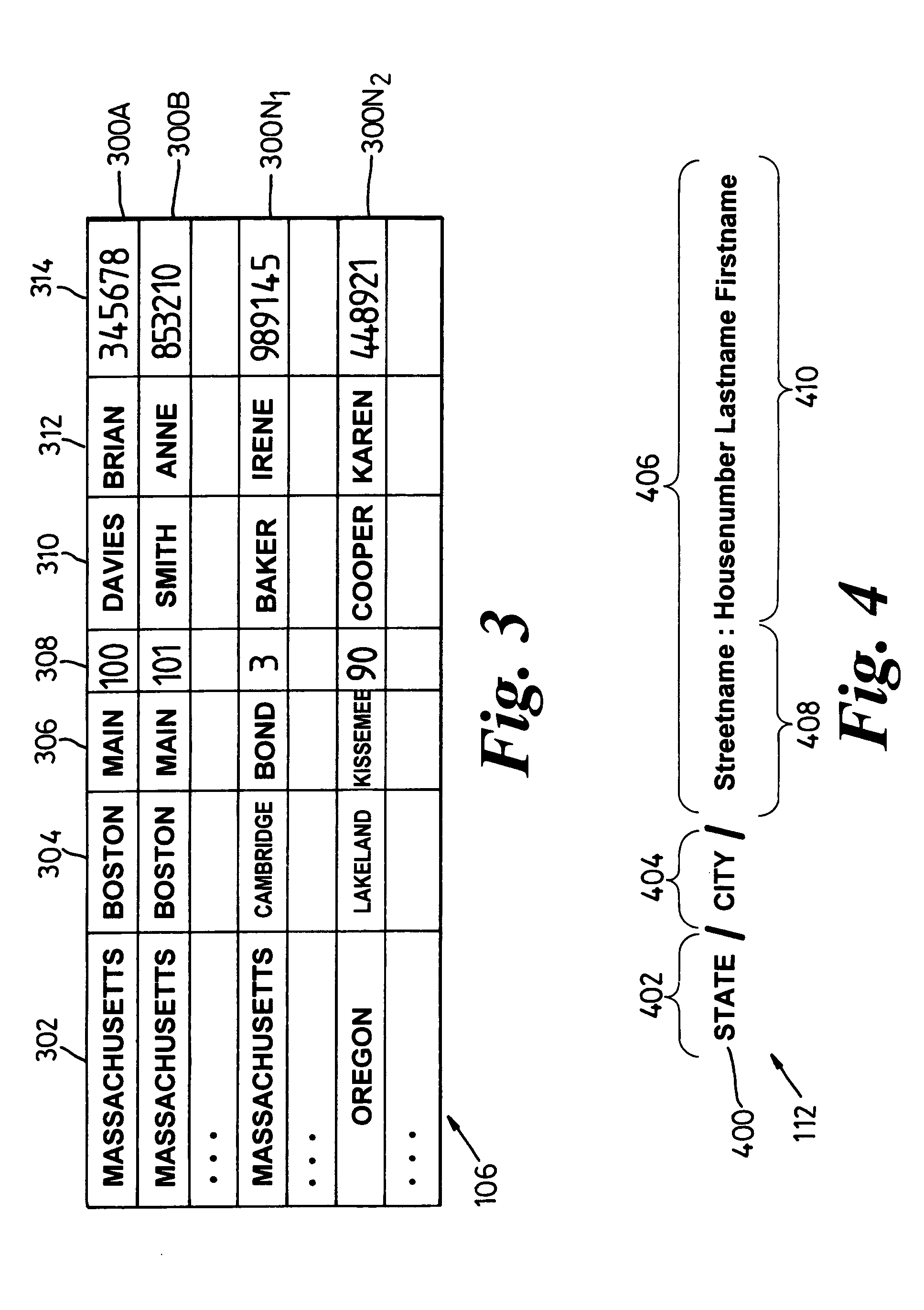
A presentation generator may access one or more data sources structured into data fields. The user may create or modify a template by inserting one or more tags corresponding to data fields in the template. The template may also have one or more processing instructions for indicating the data sources and how the data sources should be queried. The processing instructions may also indicate how the data is to be grouped across various slides, pages, sections, etc. The generator may build the presentation based on the template, its tags, and its processing instructions. The resulting presentation may be accessed by a user-friendly application, such as a word processor, slide program, spreadsheet, report viewer, or other application. The user may update part or all of the presentation using information on the queries and data sources embedded in the presentation itself.
Owner:ACCENTURE GLOBAL SERVICES LTD
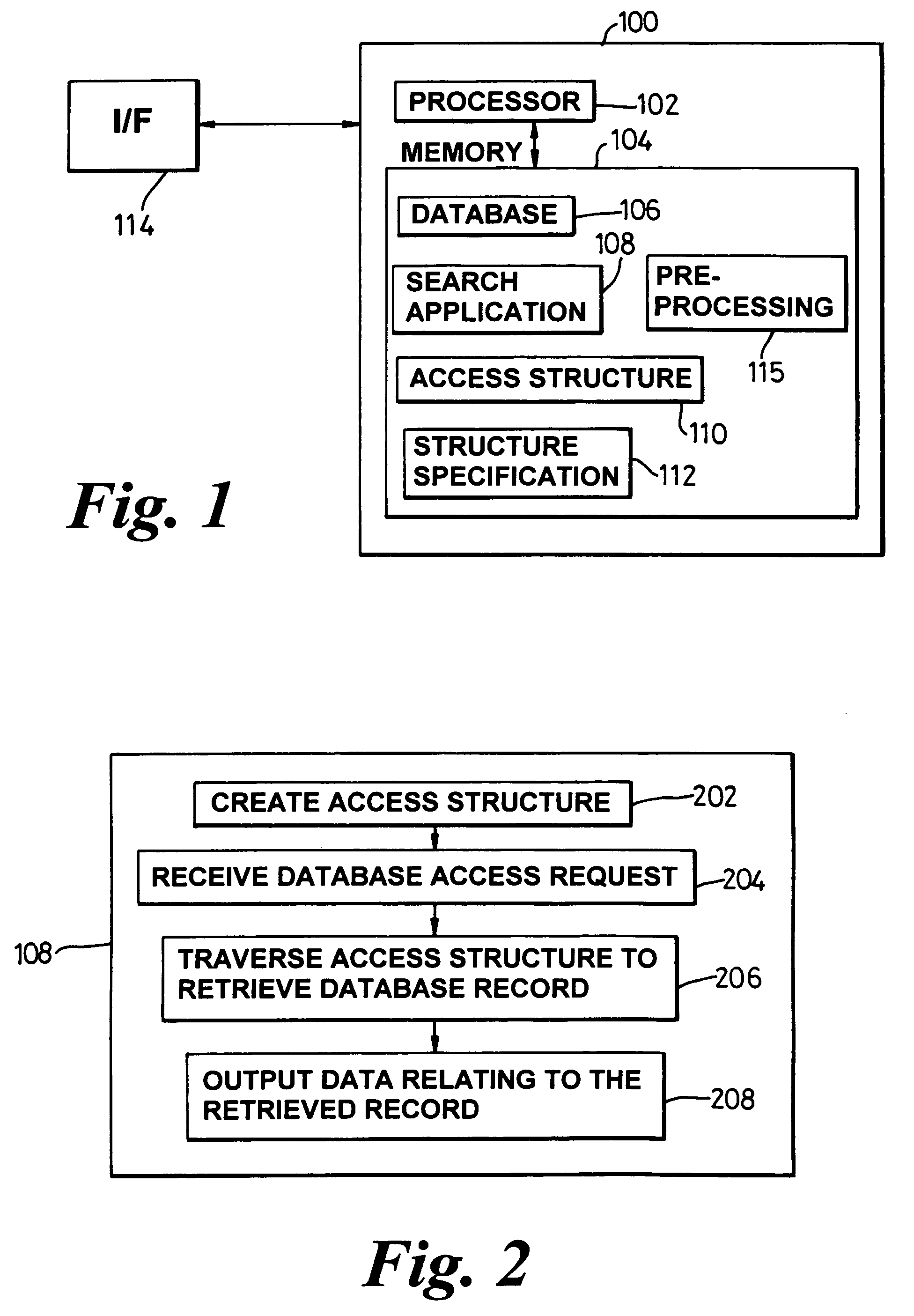
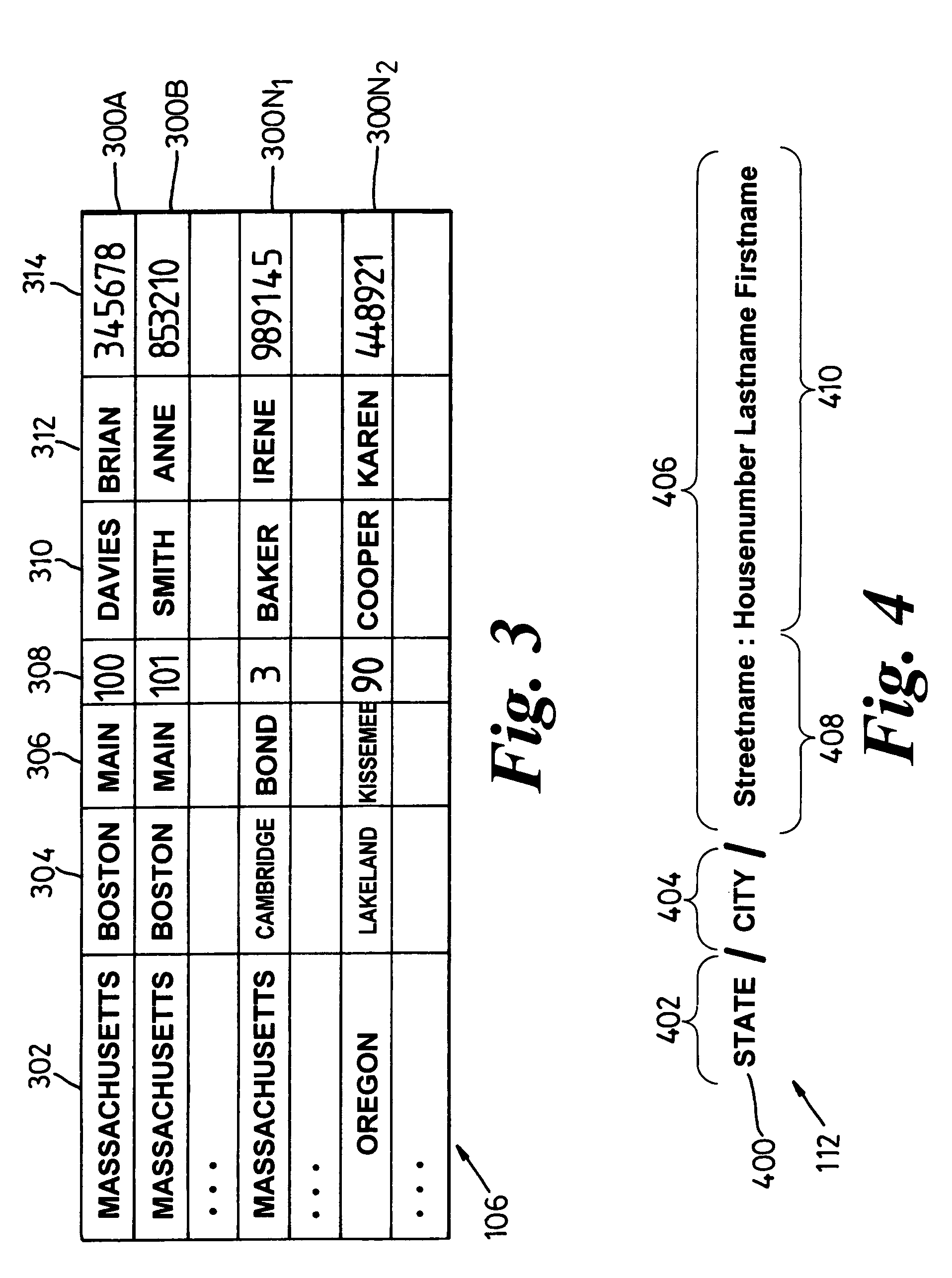
System, method and technique for searching structured databases
ActiveUS7403941B2Reliable resultsData processing applicationsDigital data information retrievalAccess structureTree (data structure)
Owner:APPLE INC
Lancet depth adjustment assembly
A lancet depth adjustment assembly structured to be used use with a lancet device of the type including a lancet disposed movably within a housing so as to pass into a piercing orientation wherein a piercing tip of the lancet protrudes from a piercing aperture defined in the housing. The lancet depth adjustment assembly includes a depth adjustment element movably secured in overlying relation to the piercing aperture of the housing and having a piercing access structured to permit passage of the piercing tip of the lancet therethrough. The depth adjustment element is structured to be interposed between a finger of a patient and the piercing aperture so as to define a spacing therebetween, and accordingly define a depth to which the piercing tip, which protrudes a defined amount from the housing, penetrates the body part. Furthermore, the depth adjustment element is constructed of a varying thickness so as to vary the spacing between the body part and the piercing aperture in accordance with a thickness of a portion of the depth adjustment element disposed in overlying relation to the piercing aperture at a time of operation of the lancet device.
Owner:SCHRAGA STEVE
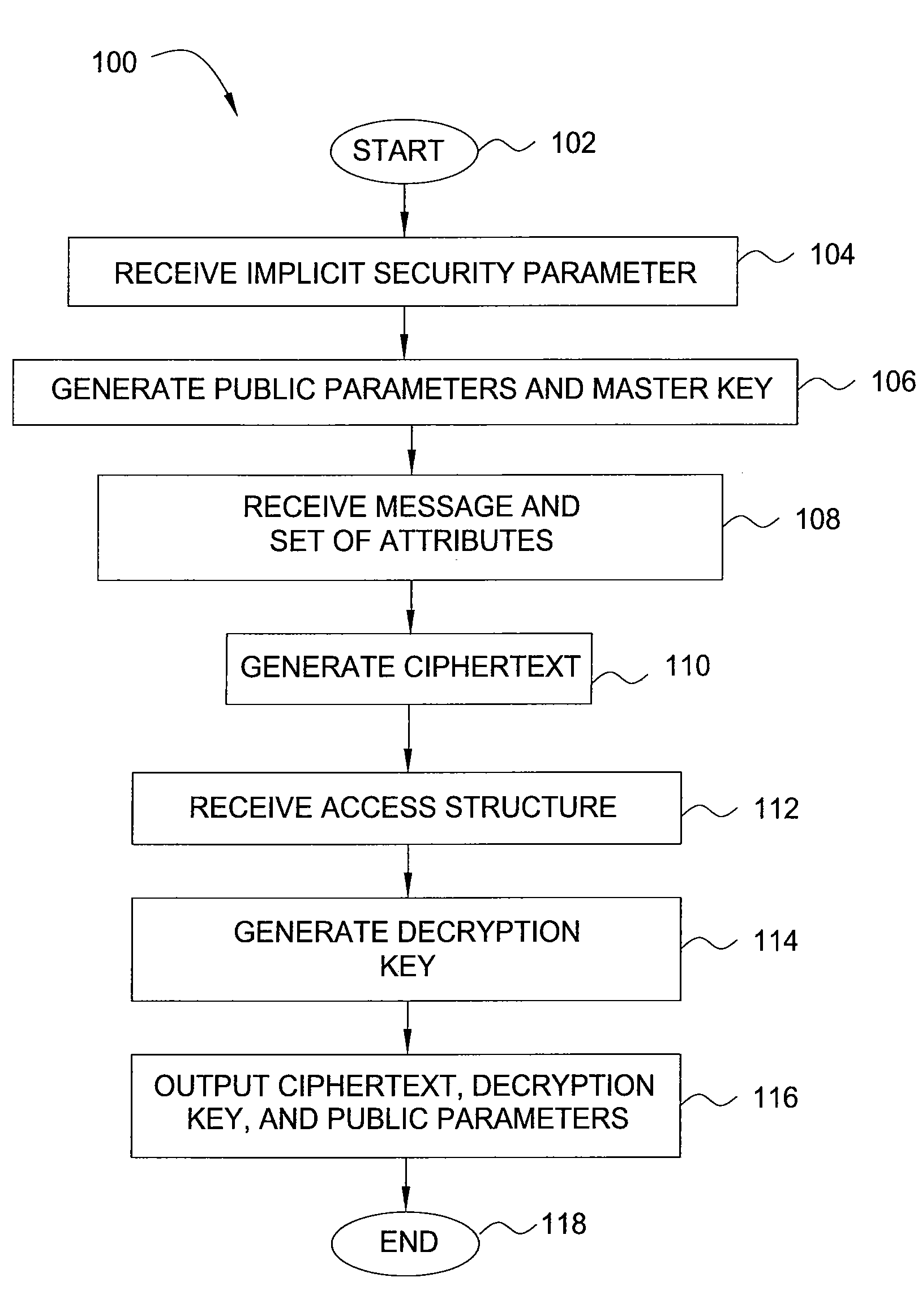
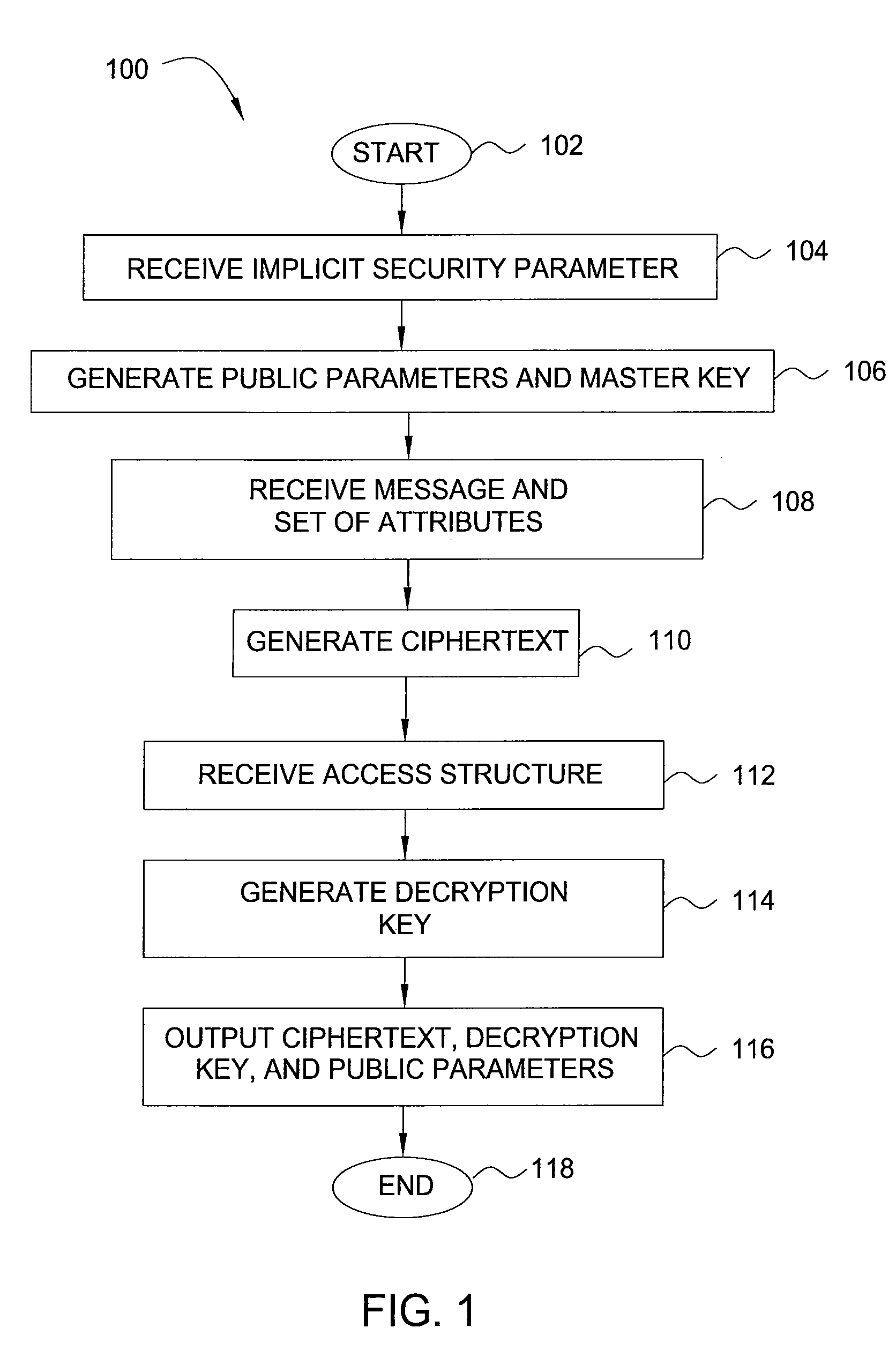
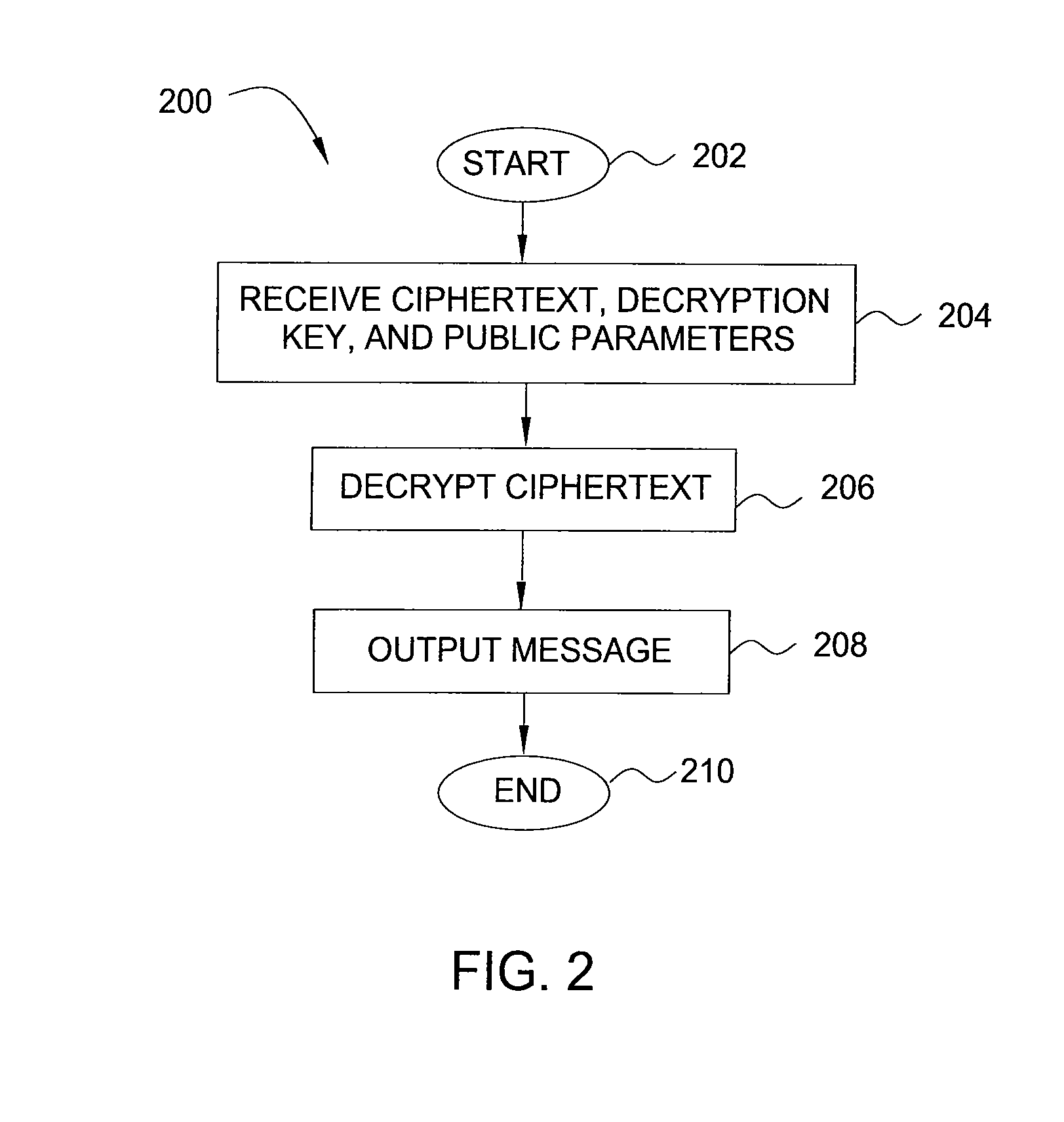
Method and apparatus for encrypting data for fine-grained access control
InactiveUS20090080658A1Encryption apparatus with shift registers/memoriesDigital data processing detailsAccess structureCiphertext
In one embodiment, the present invention is a method and apparatus for encrypting data for fine-grained access control. One embodiment of a method for encrypting data includes encrypting the data as a ciphertext, labeling the ciphertext with a set of one or more descriptive attributes, generating a decryption key for decrypting the ciphertext, associating an access structure with the decryption key, such that the data is recoverable from the ciphertext using the decryption key only if the set of one or more descriptive attributes satisfies the access structure, and outputting the ciphertext and the decryption key.
Owner:RGT UNIV OF CALIFORNIA +1
Computer-implemented control of access to atomic data items
InactiveUS6052688AEasy accessData processing applicationsDigital data information retrievalData processing systemAccess structure
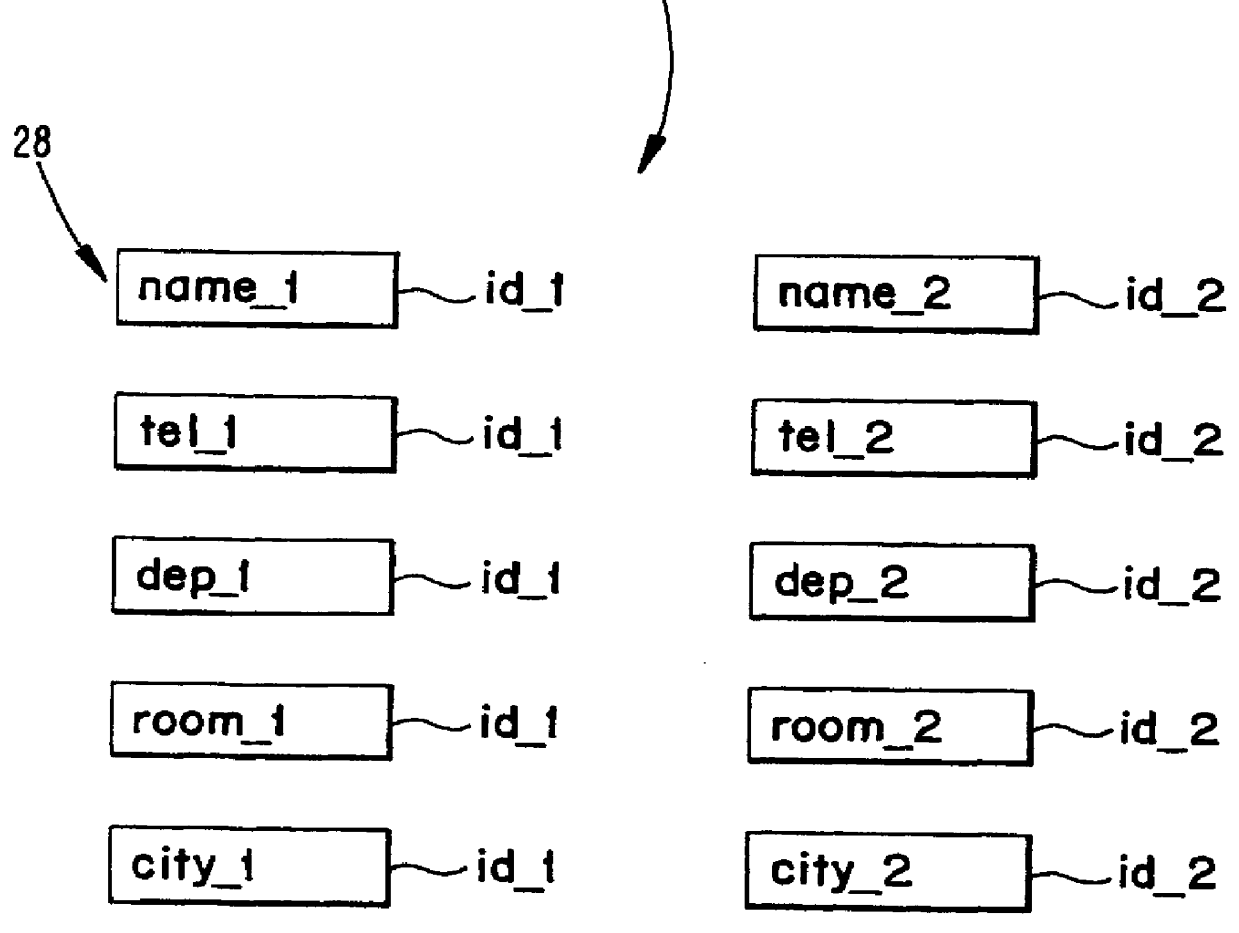
A method and a system for accessing data in a computer-based data processing system is described. The method comprises the steps of initiating and maintaining data access nodes in a variable access structure. Each access node is provided with references to other access nodes and / or to data items representing an object, each data item carrying only the amount of information which is relevant for its purpose. The data items or the references are provided with a time parameter thus enabling version control and the possibility to handle static or slowly changing data and frequently changed and updated data in a corresponding manner. The access nodes comprise access control parameters for access control from a safety point of view as well as for enabling different views of the access structure and underlying data and objects.
Owner:RPX CORP
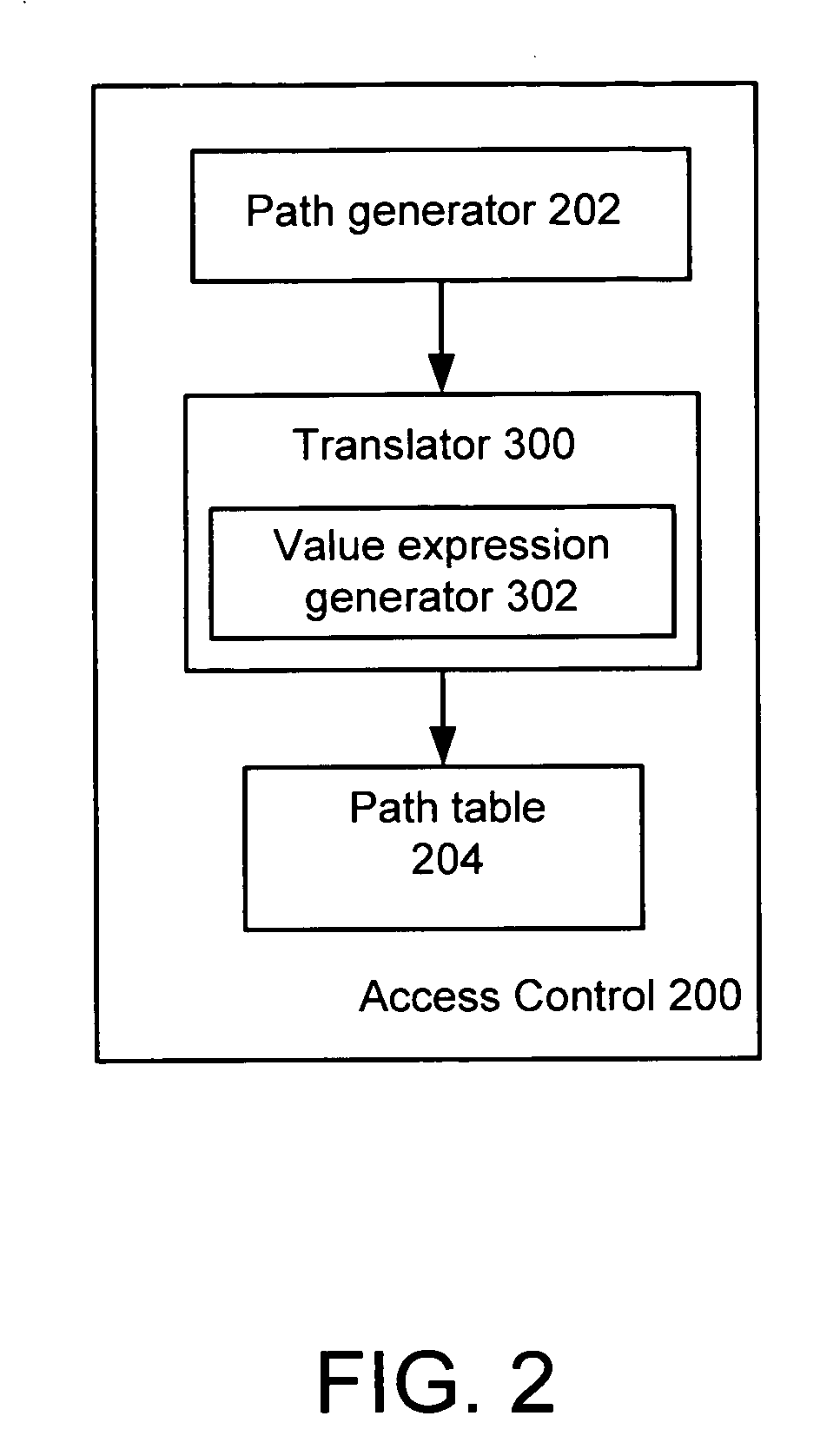
Method and system for providing path-level access control for structured documents stored in a database
ActiveUS20050076030A1Easy to processRestricted evaluationDigital data processing detailsRelational databasesAccess structurePaper document
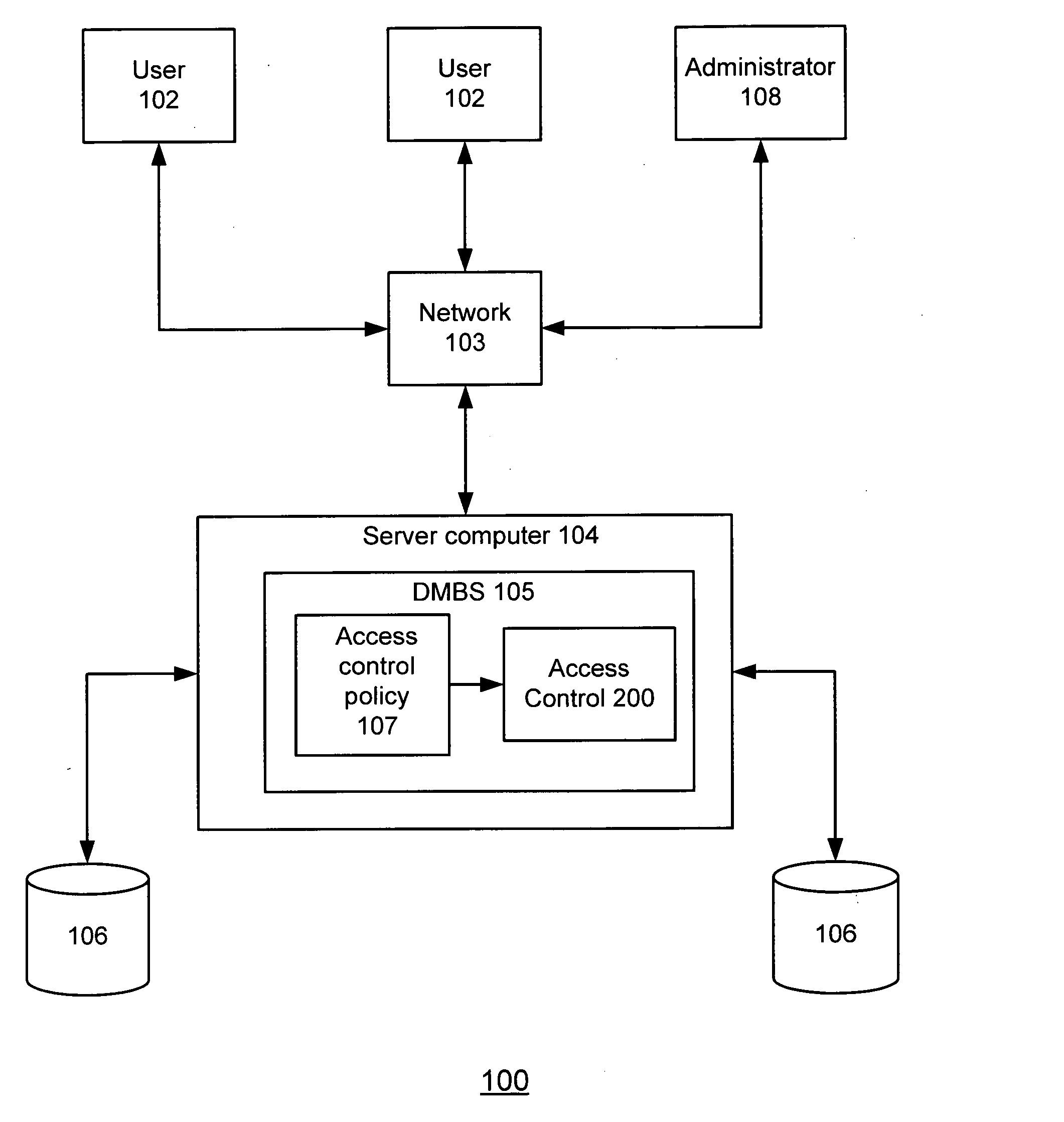
An improved method and system for providing path-level access control to a structured document in a collection stored in a database, where the structured document includes a plurality of nodes is disclosed. The method includes the steps of providing an access control policy for the collection, where the access control policy comprises a plurality of access control rules, generating a path for each node of the plurality of nodes in the document, and generating for each path associated with a node a corresponding value expression based on at least one access control rule of the plurality of access control rules. According to the method and system of the present invention, the corresponding value expression is utilized during access control evaluation to determine whether a user is allowed to access a node in the structured document.
Owner:IBM CORP
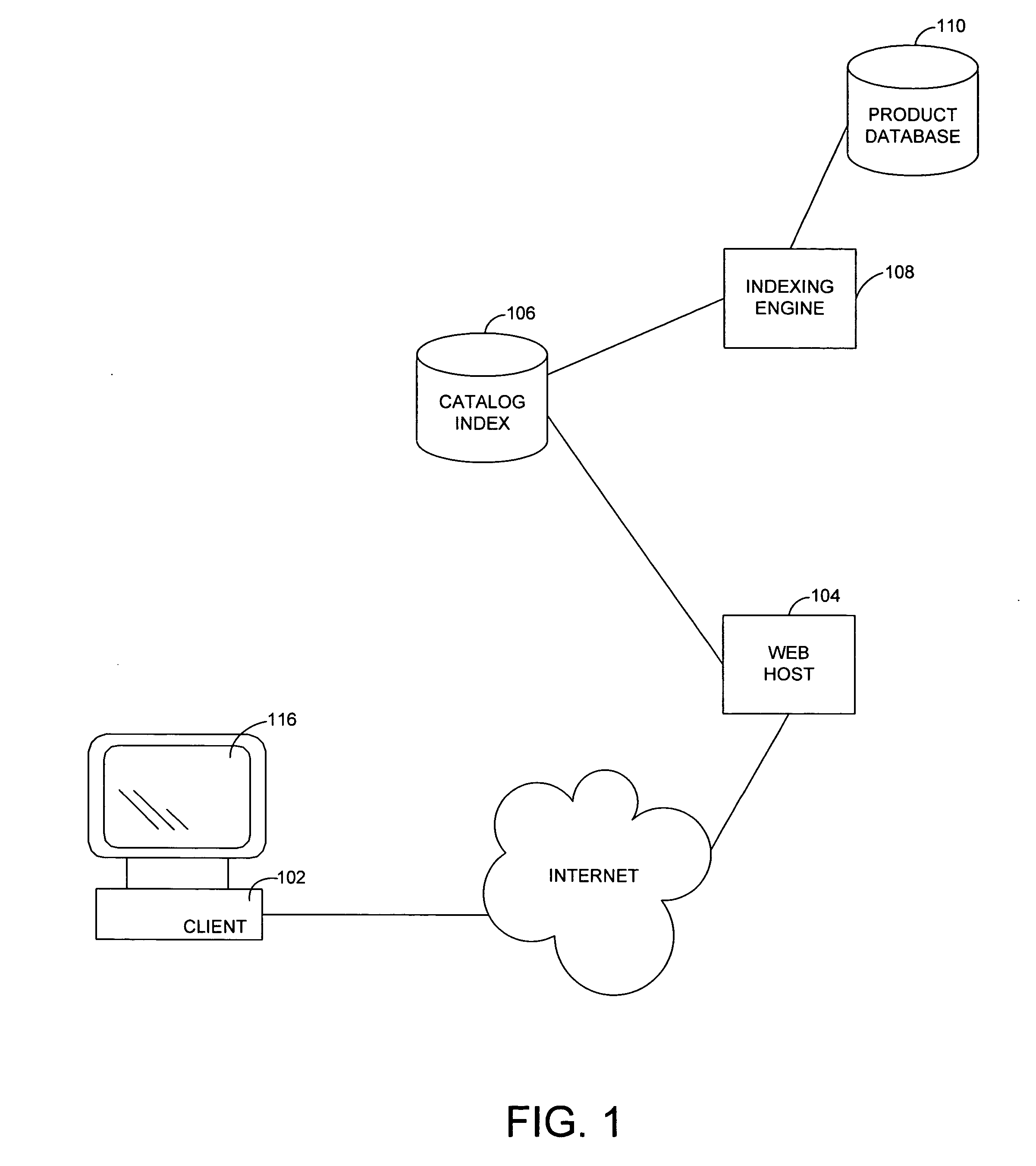
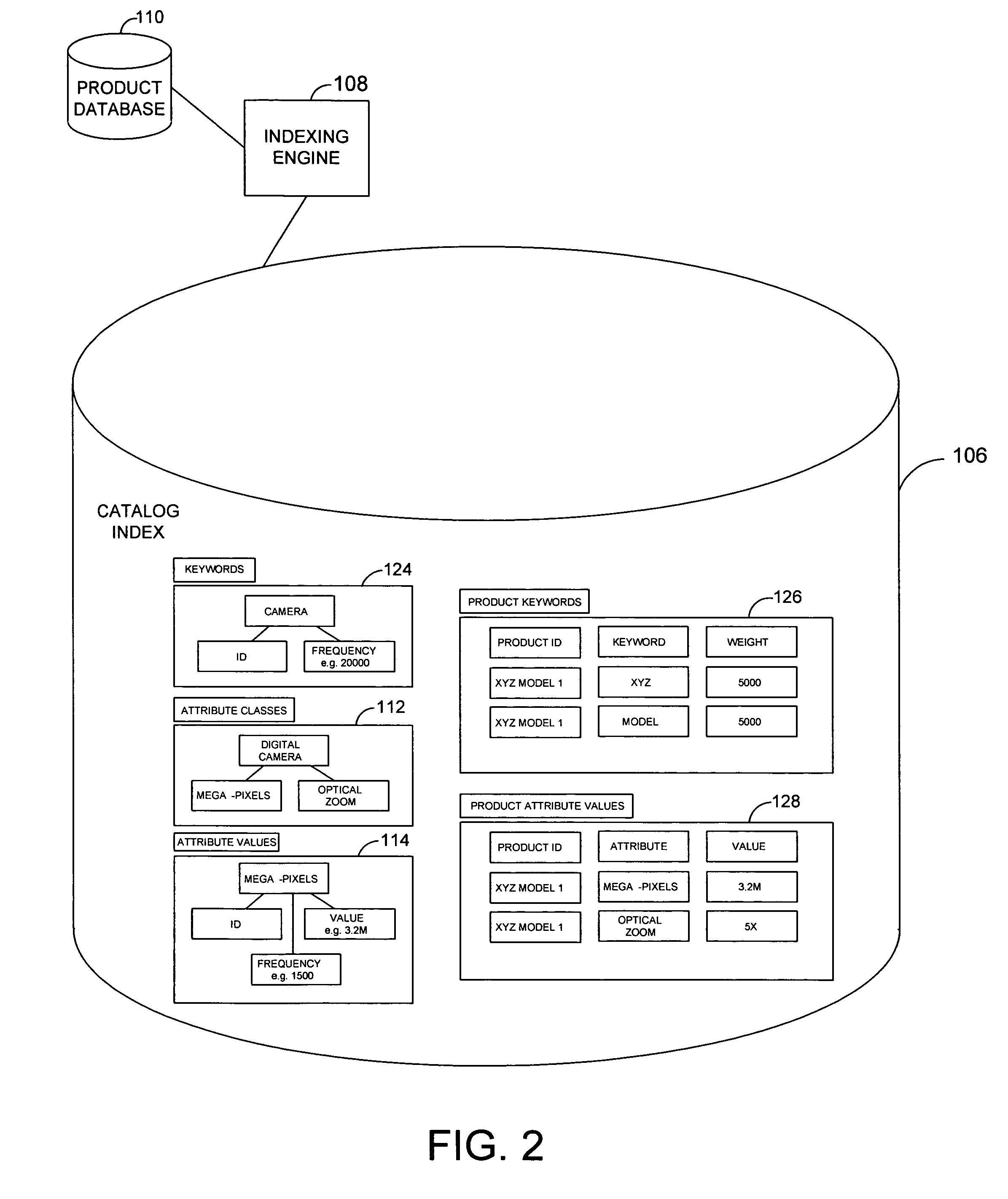
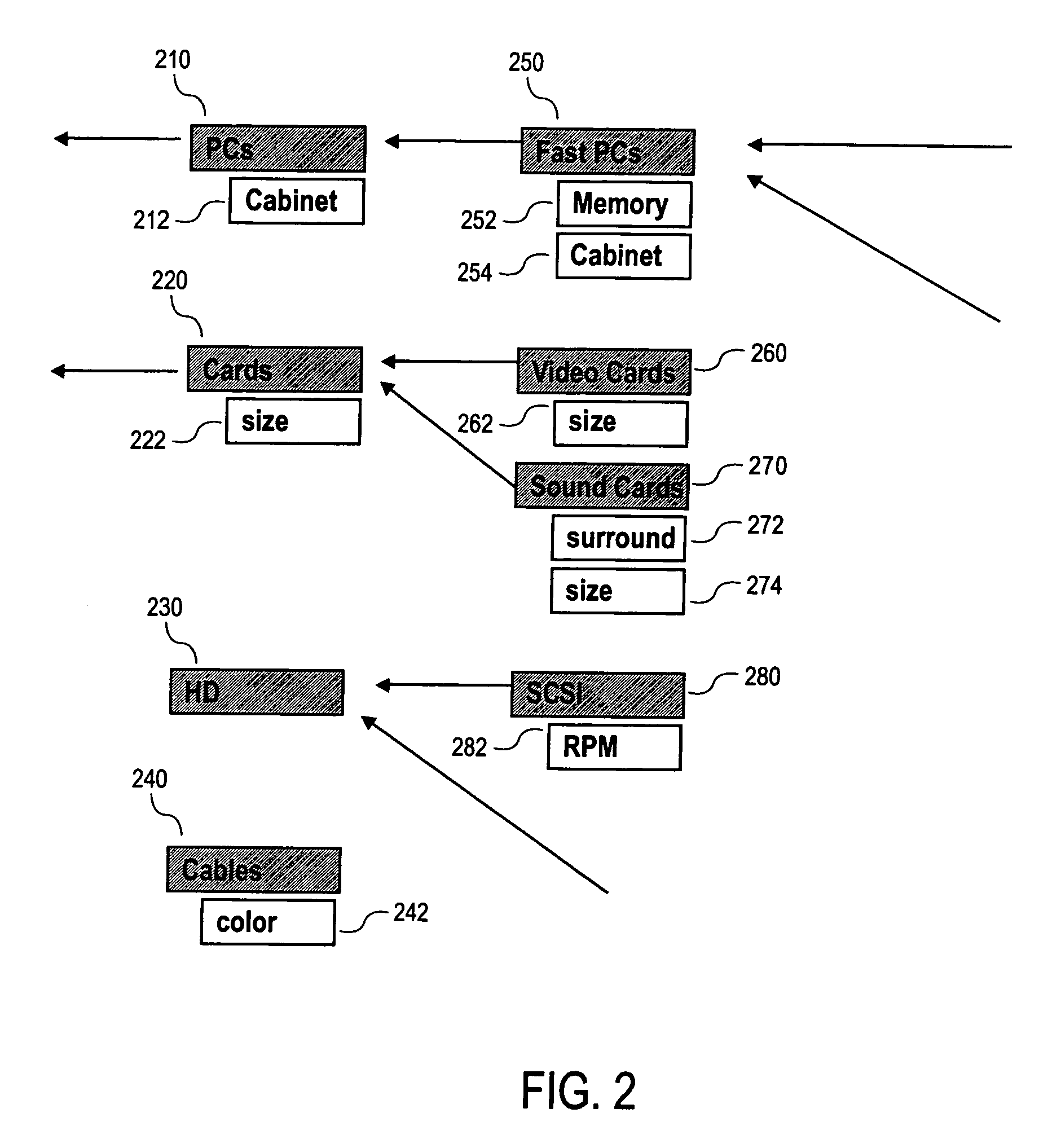
System and method for an online catalog system having integrated search and browse capability
InactiveUS20060095345A1Extend or refine their search or browsing activityCommerceSpecial data processing applicationsLevel of detailSQL
A system and related techniques generate and maintain a unified product index, to perform searching and browsing in an online product, service, content or information catalog. A user investigating, for example, a set of retail offerings of digital cameras may for instance browse through a Web site layout or taxonomy to locate products of interest, such as cameras having resolution in the range of 3-4 megapixels or in the price range of $200-300. Alternatively, the user may input search terms in a search dialogue box to locate those or other features. Unlike conventional e-commerce platforms in which search may be performed against structured databases while browsing may access unstructured HTML or other descriptive material, according to the invention navigation and searching may be integrated and both access a structured index derived from product descriptions as well as traditional SQL or other structured data. A user may thus transparently move between browsing the Web site and searching the Web site, refining their search or browsing activity in a seamless fashion. The HTML or other unstructured data may in one regard be processed by an index engine to identify product attributes such as type (electronics), size, price, weight or other specifications as well as attribute values, which may be sorted or stored in a separate table. A set of results generated by conducting an initial search may thus be continued or refine by further browsing down to a particular product or other level of detail. Conversely a user who has browsed to a given level of detail, such as digital camcorders priced less than $700, may initiate a search through products at that level of the hierarchy without resetting search terms or position in the taxonomy. Greater ease of use, more efficient location of products or services and less dead-end pathways are thus achieved.
Owner:MICROSOFT TECH LICENSING LLC
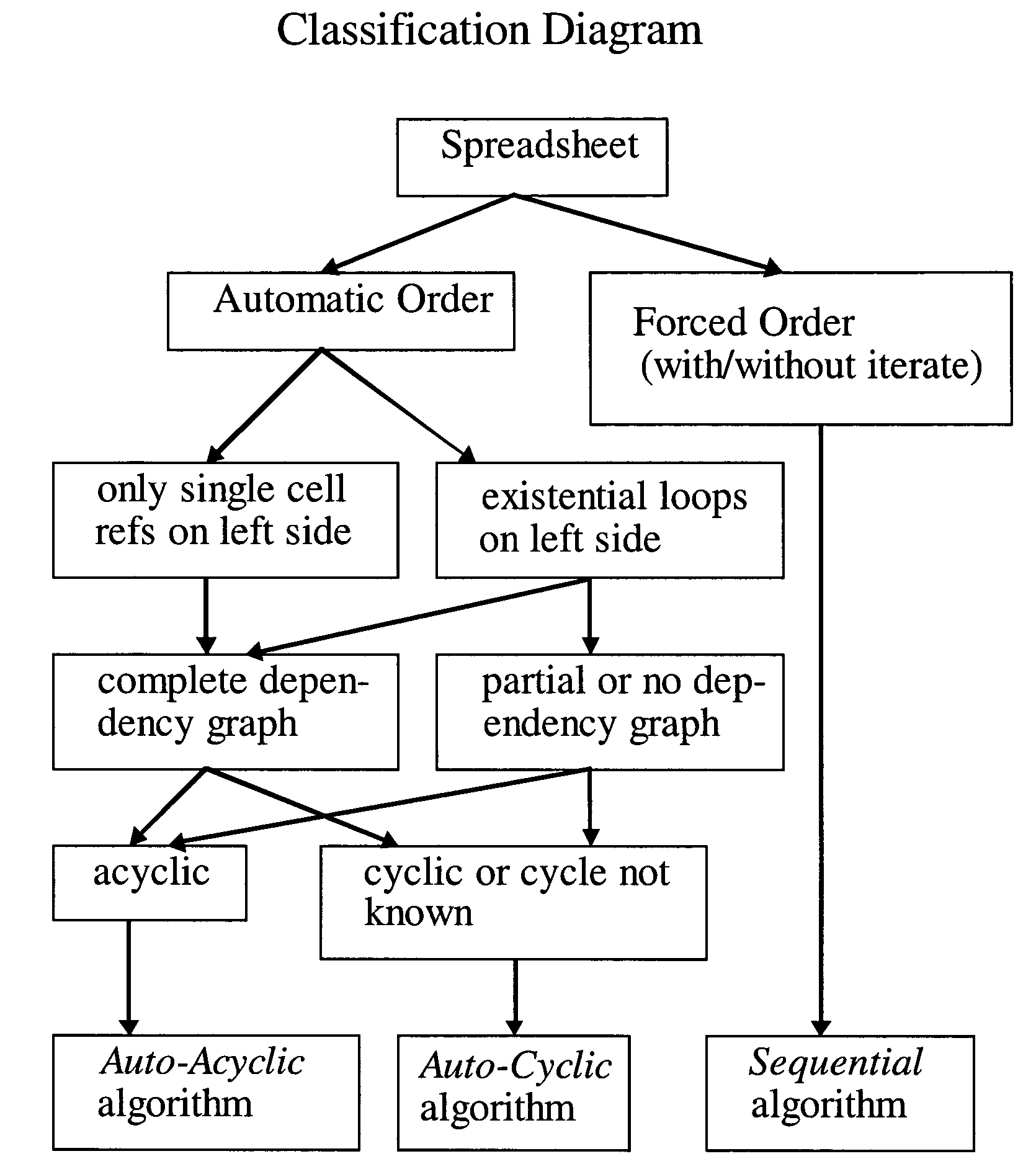
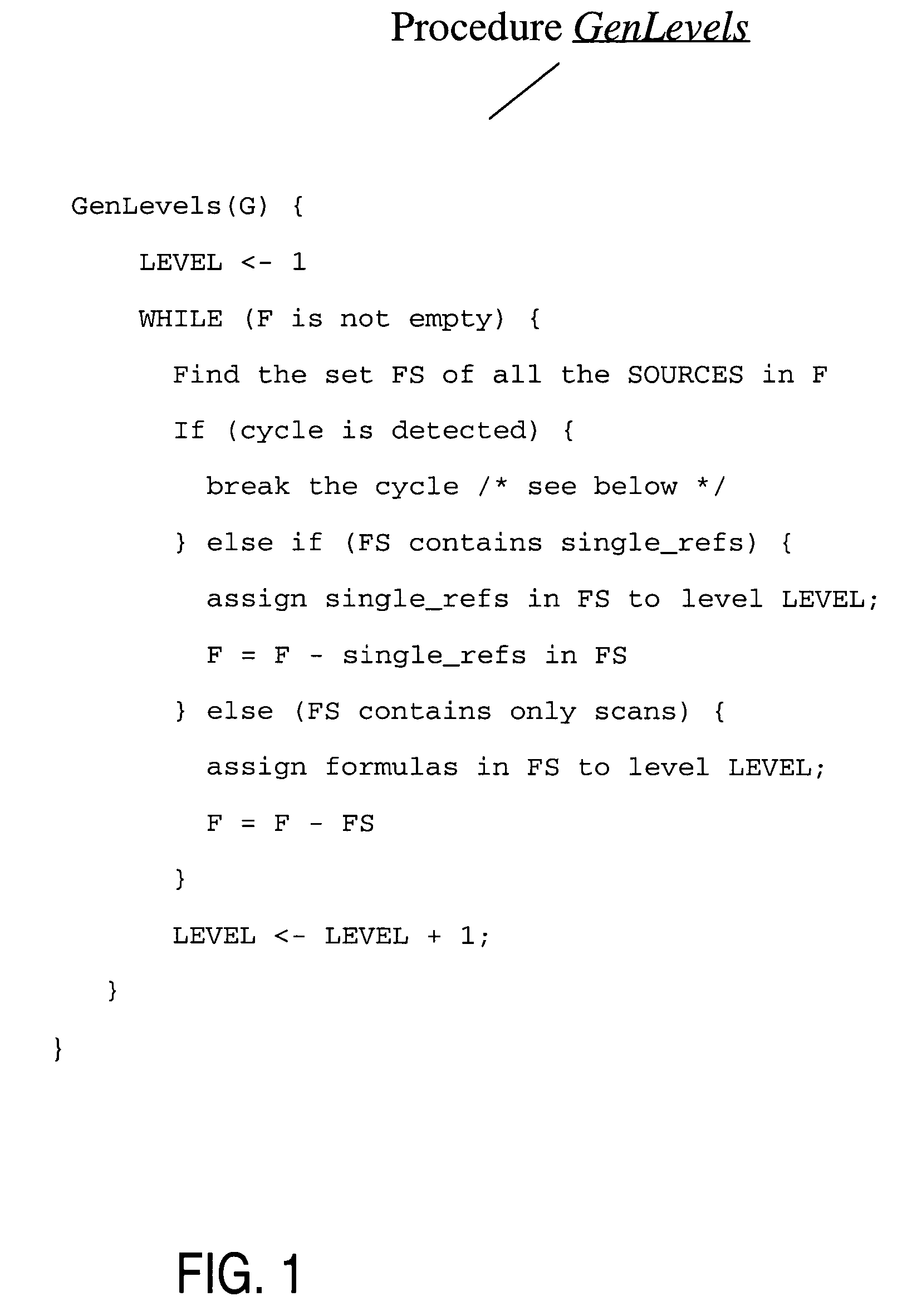
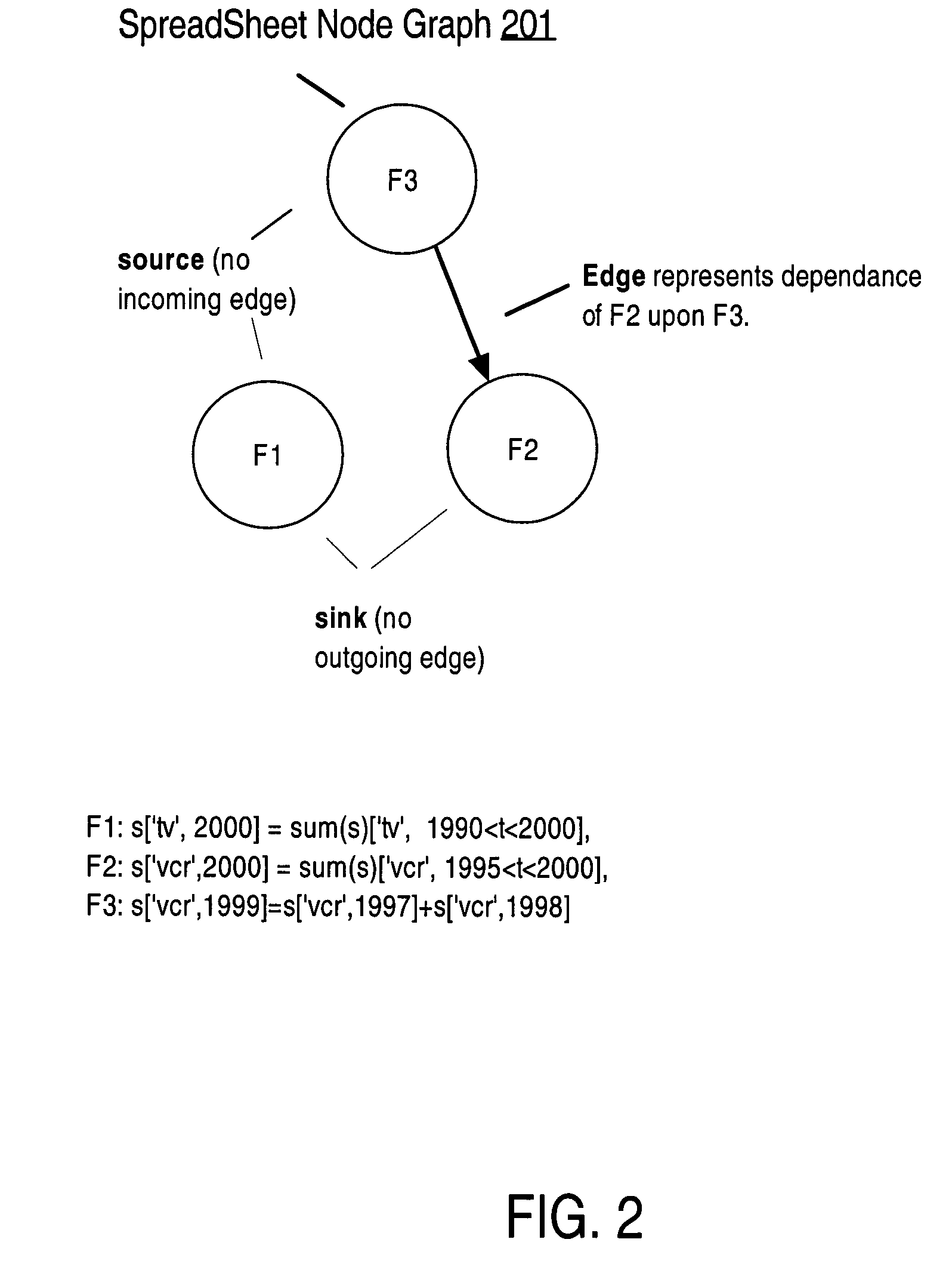
Compile-time optimizations of queries with SQL spreadsheet
InactiveUS7177855B2Data processing applicationsDatabase queryingAccess structureTheoretical computer science
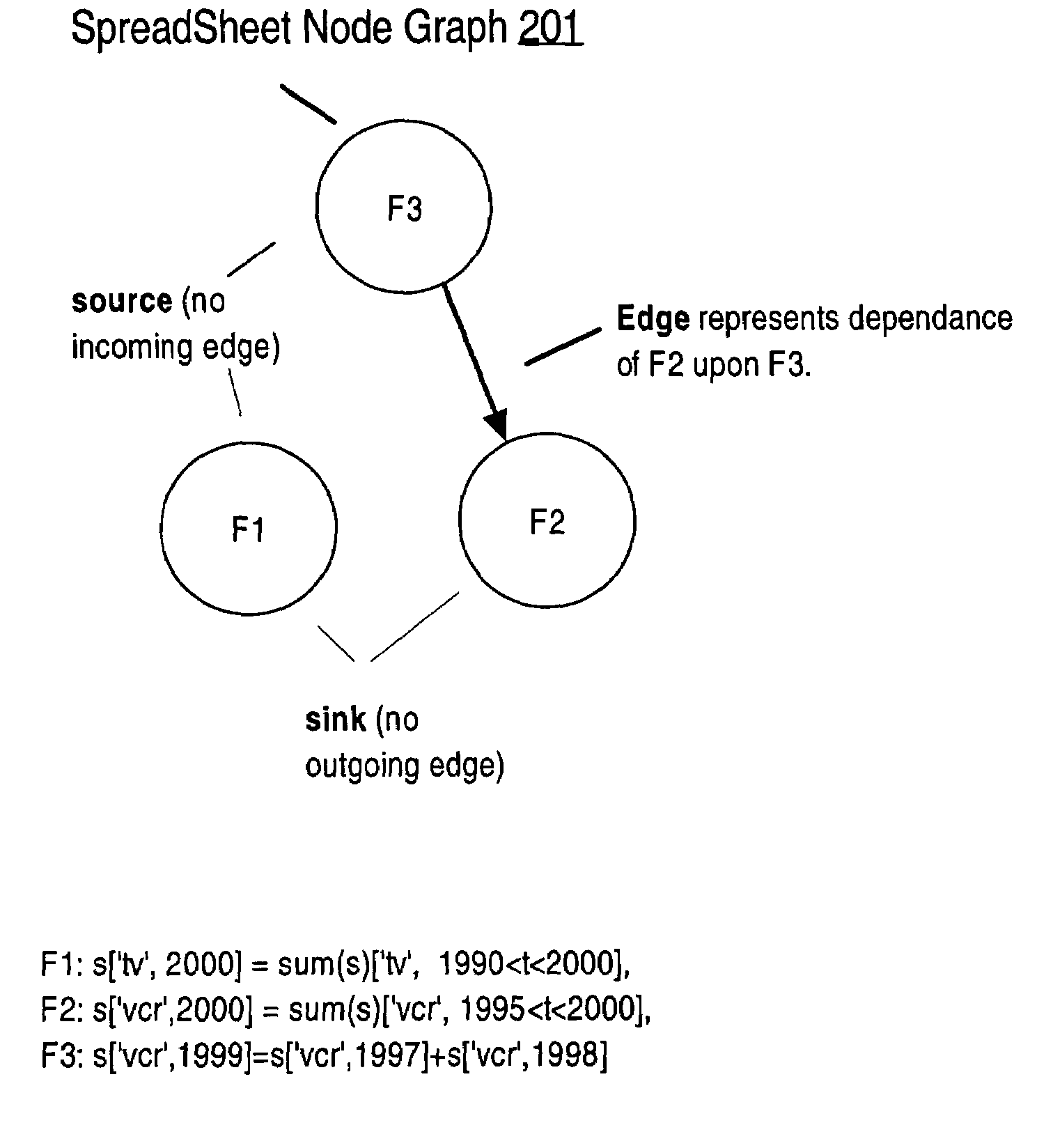
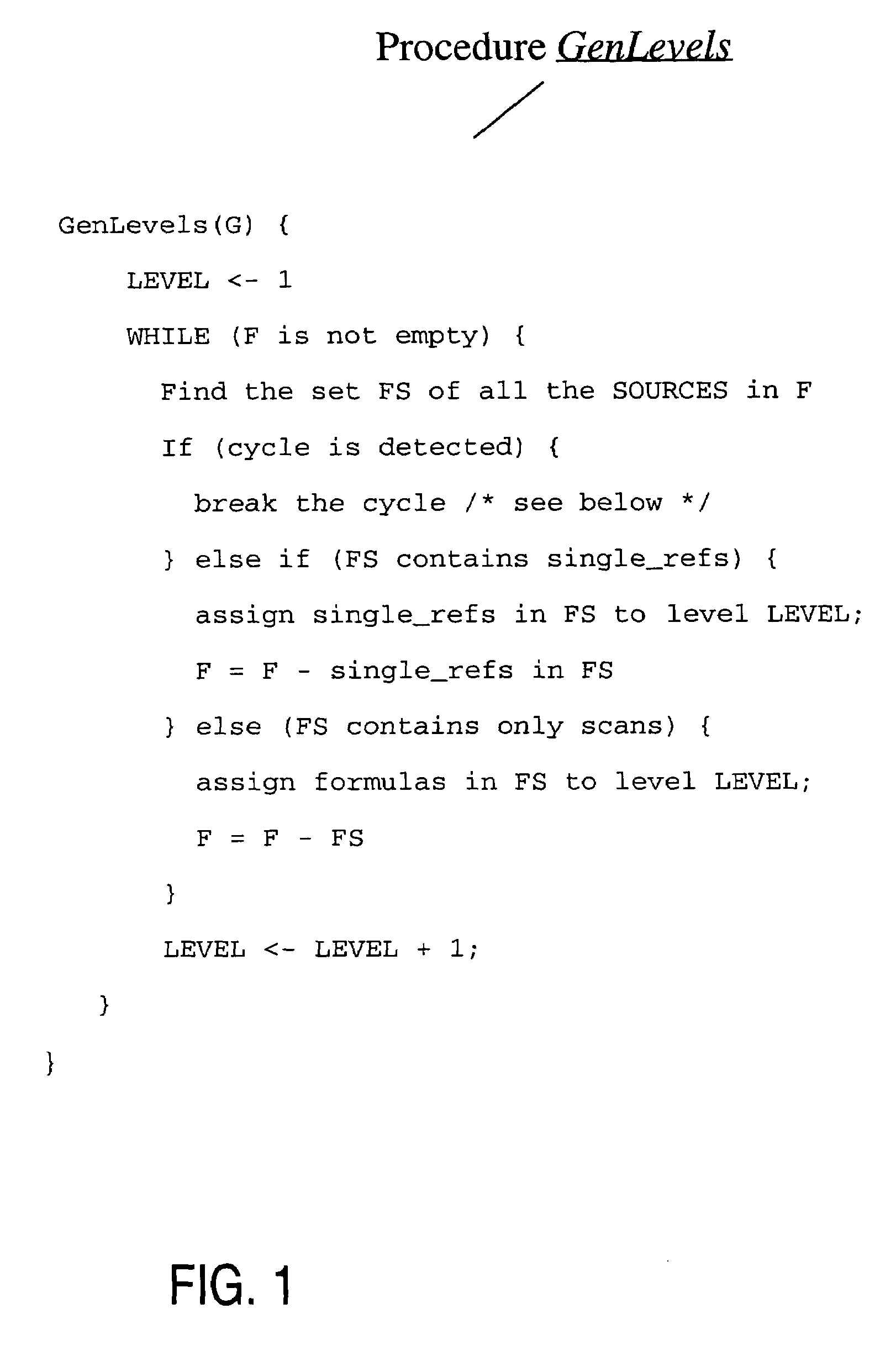
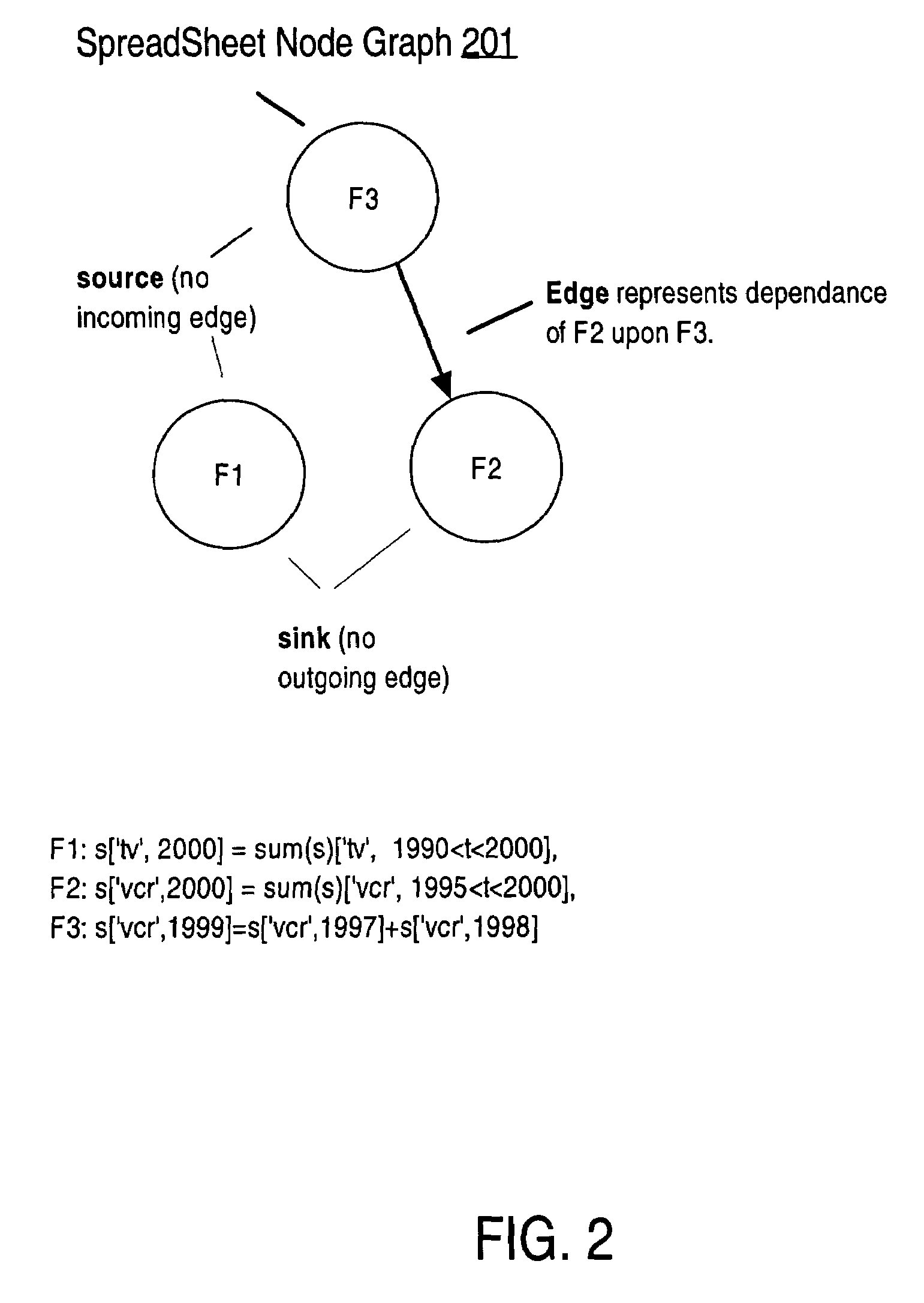
Described herein are optimizations and execution strategies for spreadsheet extensions to SQL. The partitioning of data, as specified in a spreadsheet clause, provides a way to parallelize the computation of spreadsheet and to provide and improve scalability. Even if the partitioning is not explicitly specified in the spreadsheet clause, the database optimizer can automatically infer the partitioning in some cases. Efficient hash based access structures on relations can be used for symbolic array addressing, enabling fast computation of formulas. When rewriting SQL statements, formulas whose results are not referenced in outer blocks can be removed from the spreadsheet clause, thus removing unnecessary computations. The predicates from other query blocks can be moved inside query blocks with spreadsheets clauses, thus considerably reducing the amount of data to be processed. Conditions for validity of this transformation are given.
Owner:ORACLE INT CORP
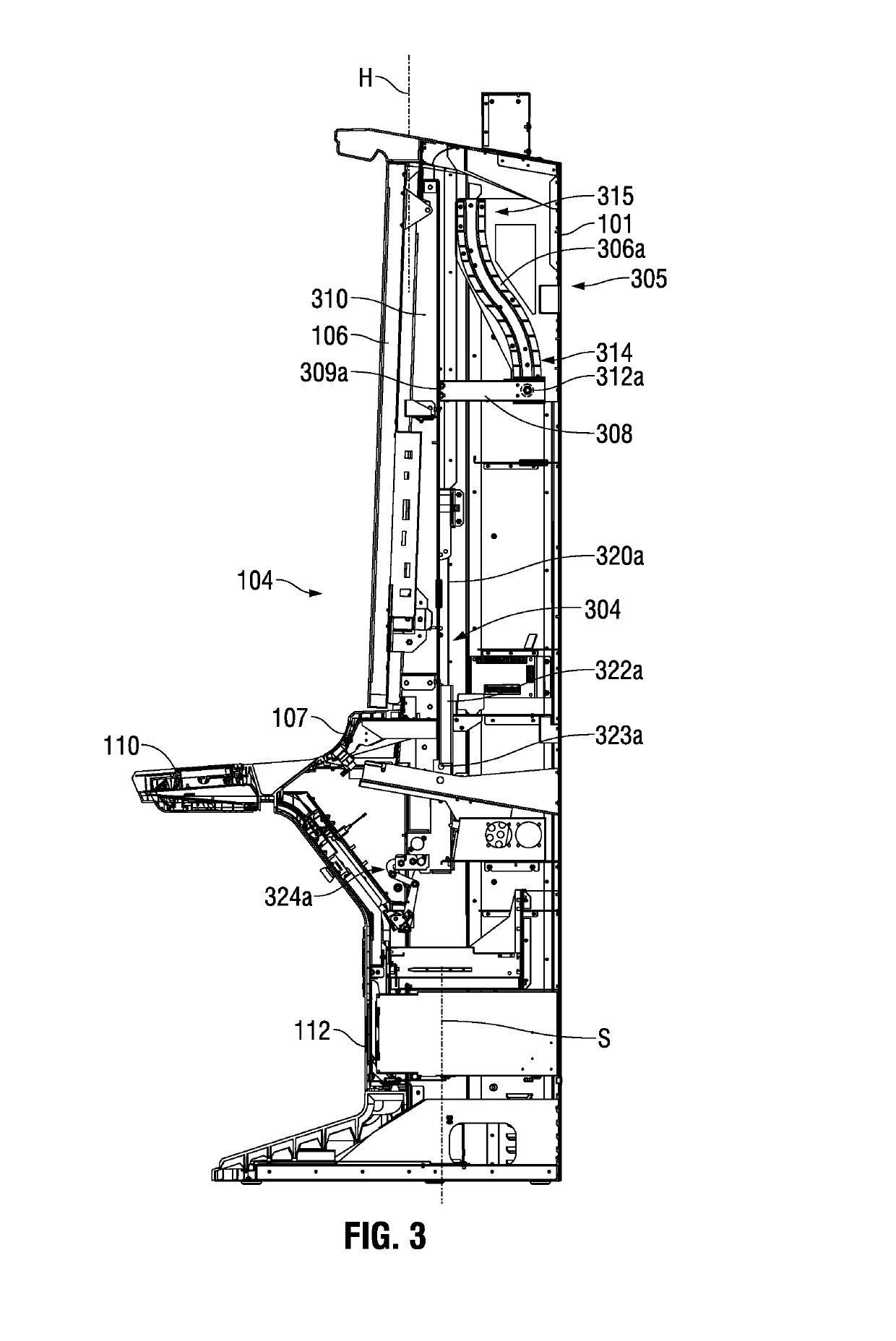
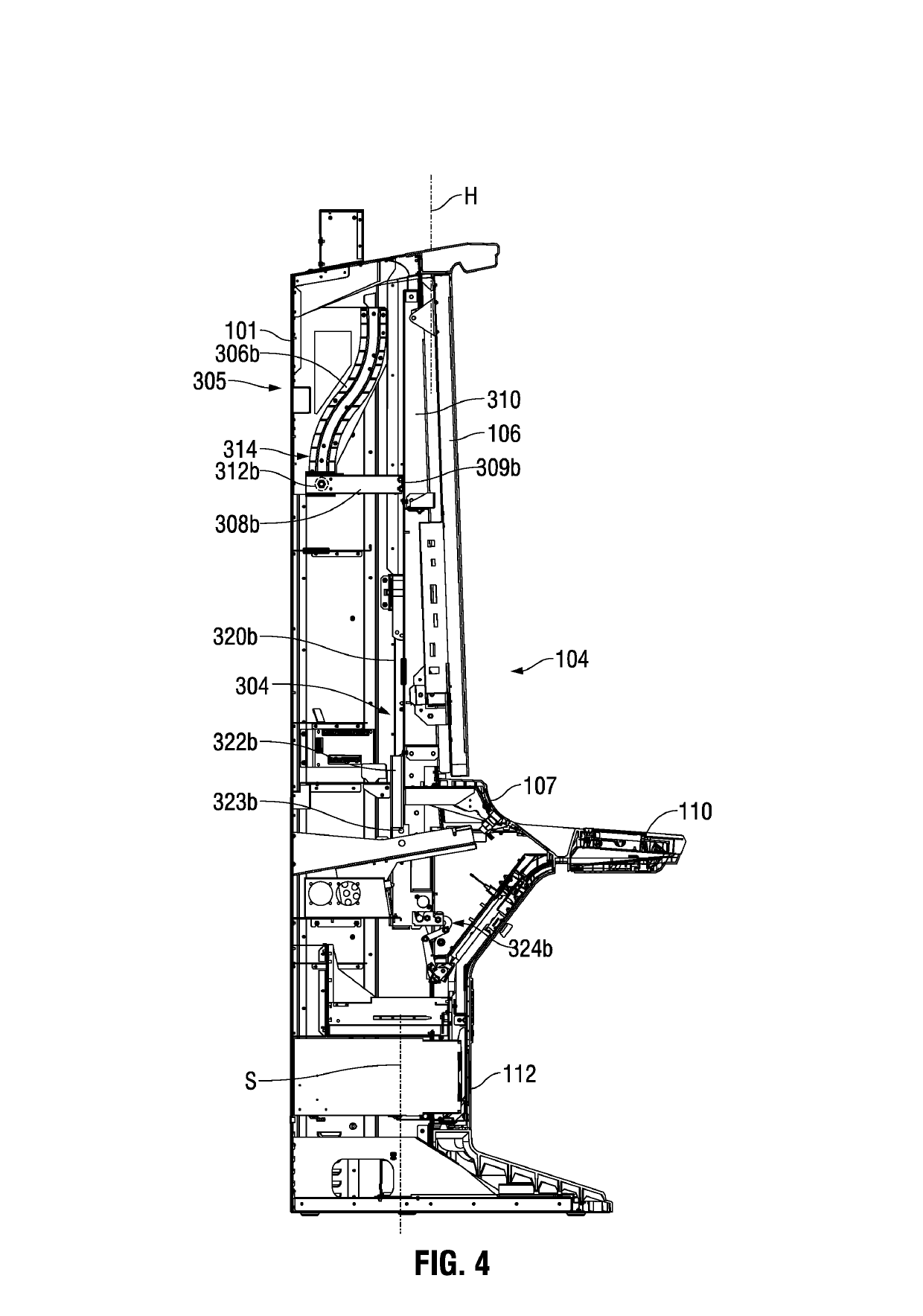
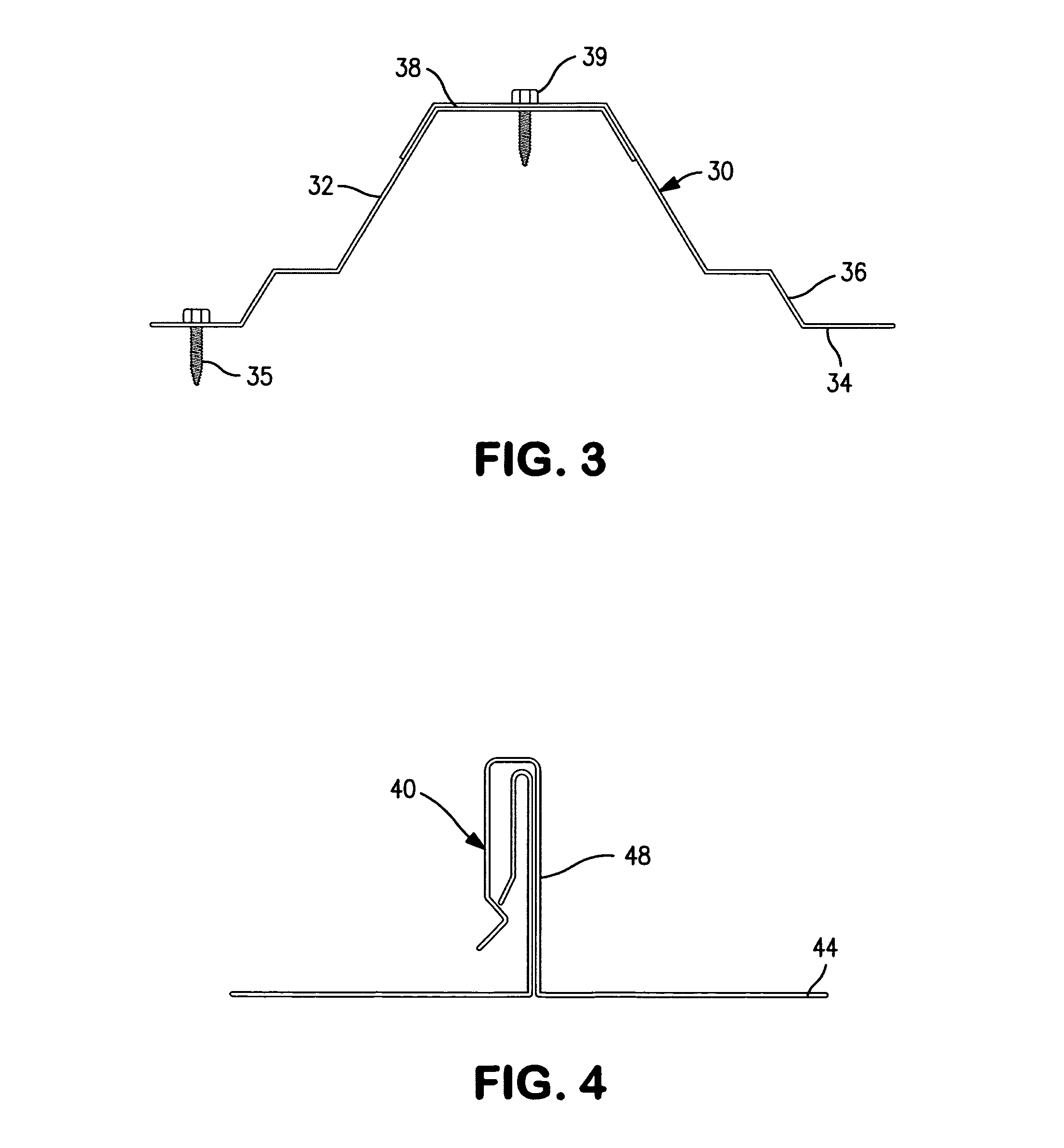
Gaming machine cabinet access structure and method
ActiveUS20190102984A1Prevent tippingSuitable balanceApparatus for meter-controlled dispensingAccess structureEngineering
A gaming machine includes a gaming machine cabinet defining an upper cabinet volume and a cabinet front opening to the upper cabinet volume. A gaming machine panel is mounted on the gaming machine cabinet in a panel operating position in which the gaming machine panel registers with and covers at least a base area of the cabinet front opening. The gaming machine further includes a translation structure connected between the gaming machine panel and the gaming machine cabinet. The translation structure is operable enable the gaming machine panel to be moved from the panel operating position upwardly to a cabinet open position. In this cabinet open position the gaming machine panel remains supported by the gaming machine cabinet and is removed from a base area of the cabinet front opening.
Owner:EVERI GAMES
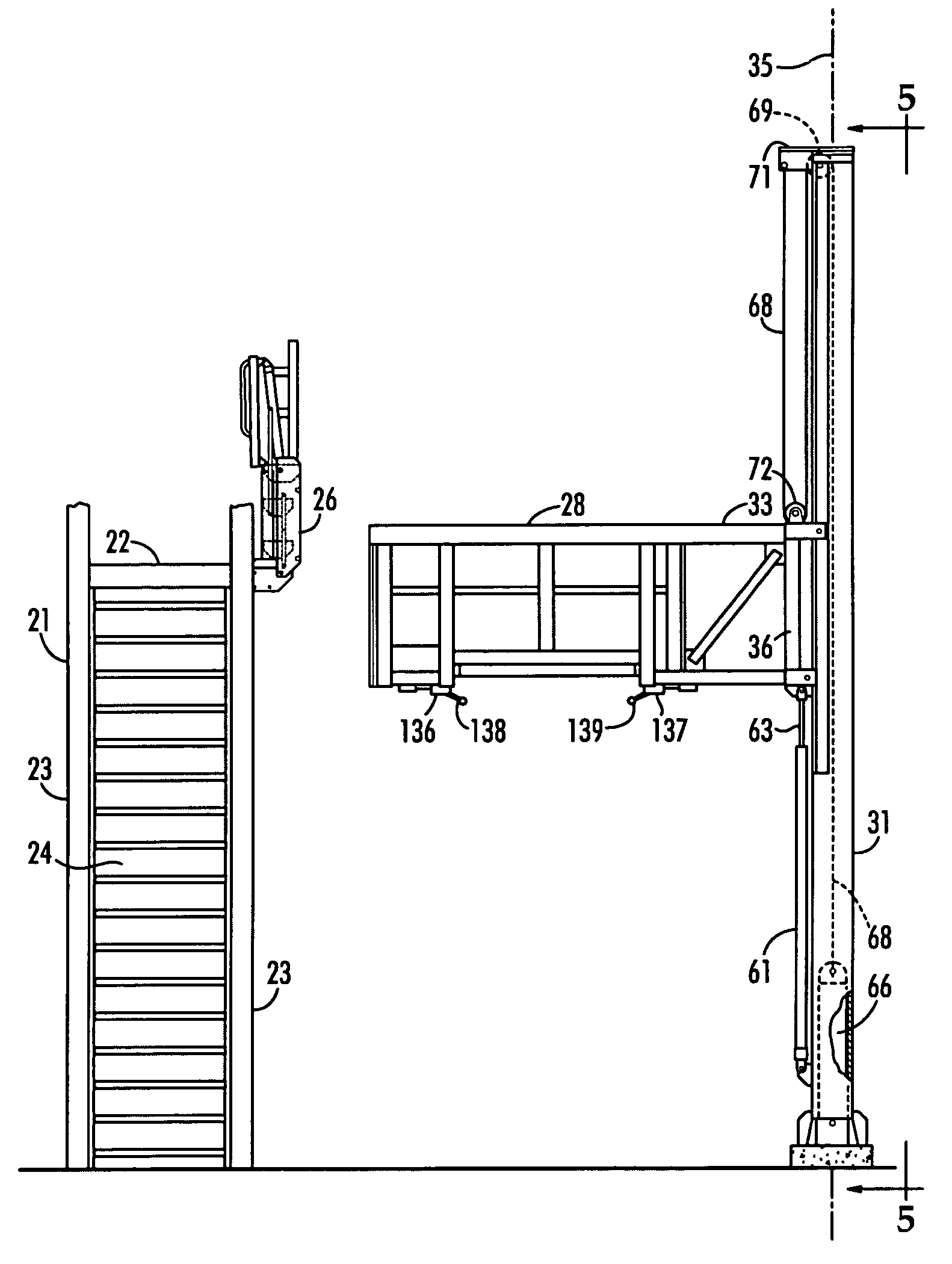
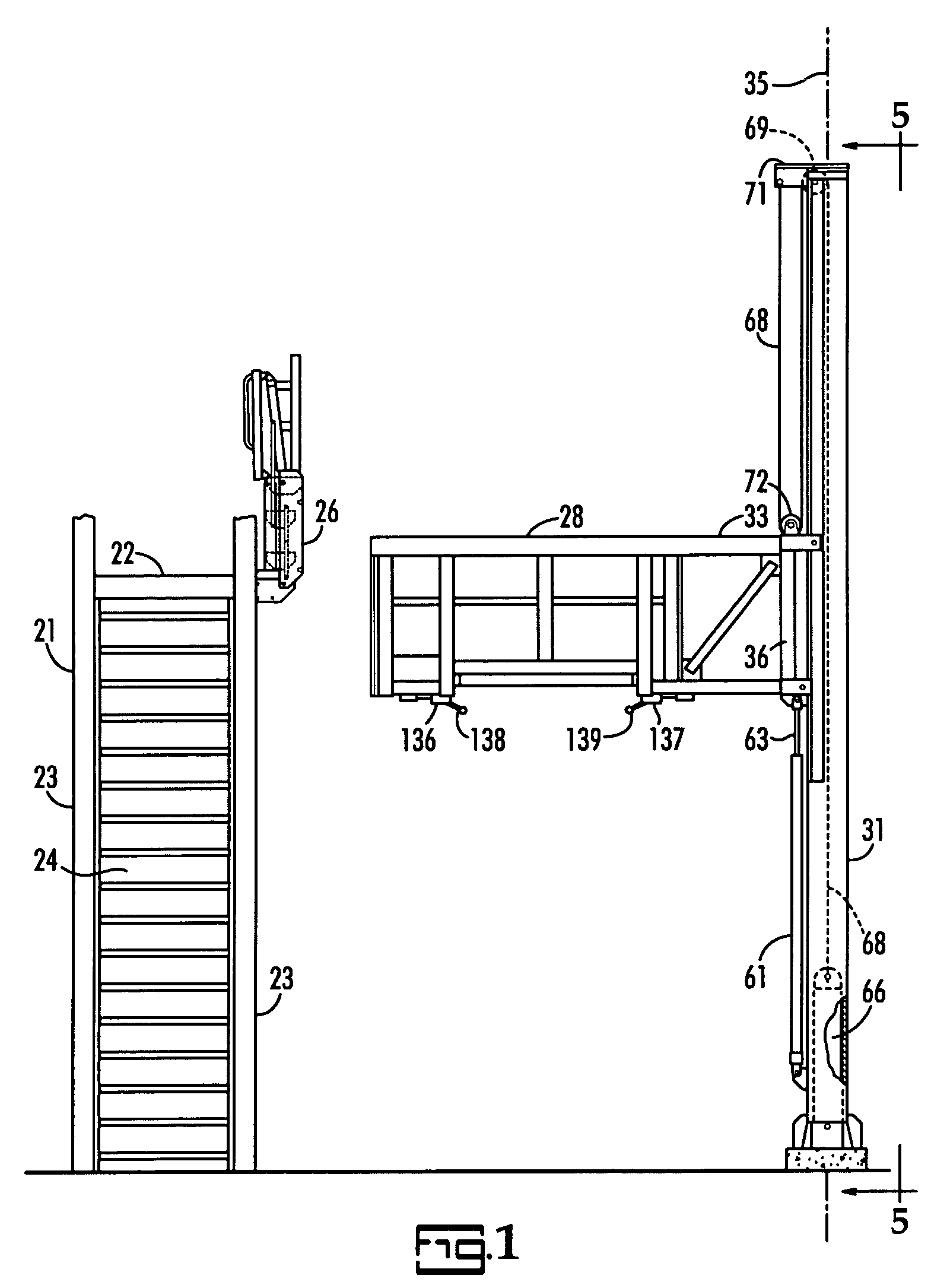
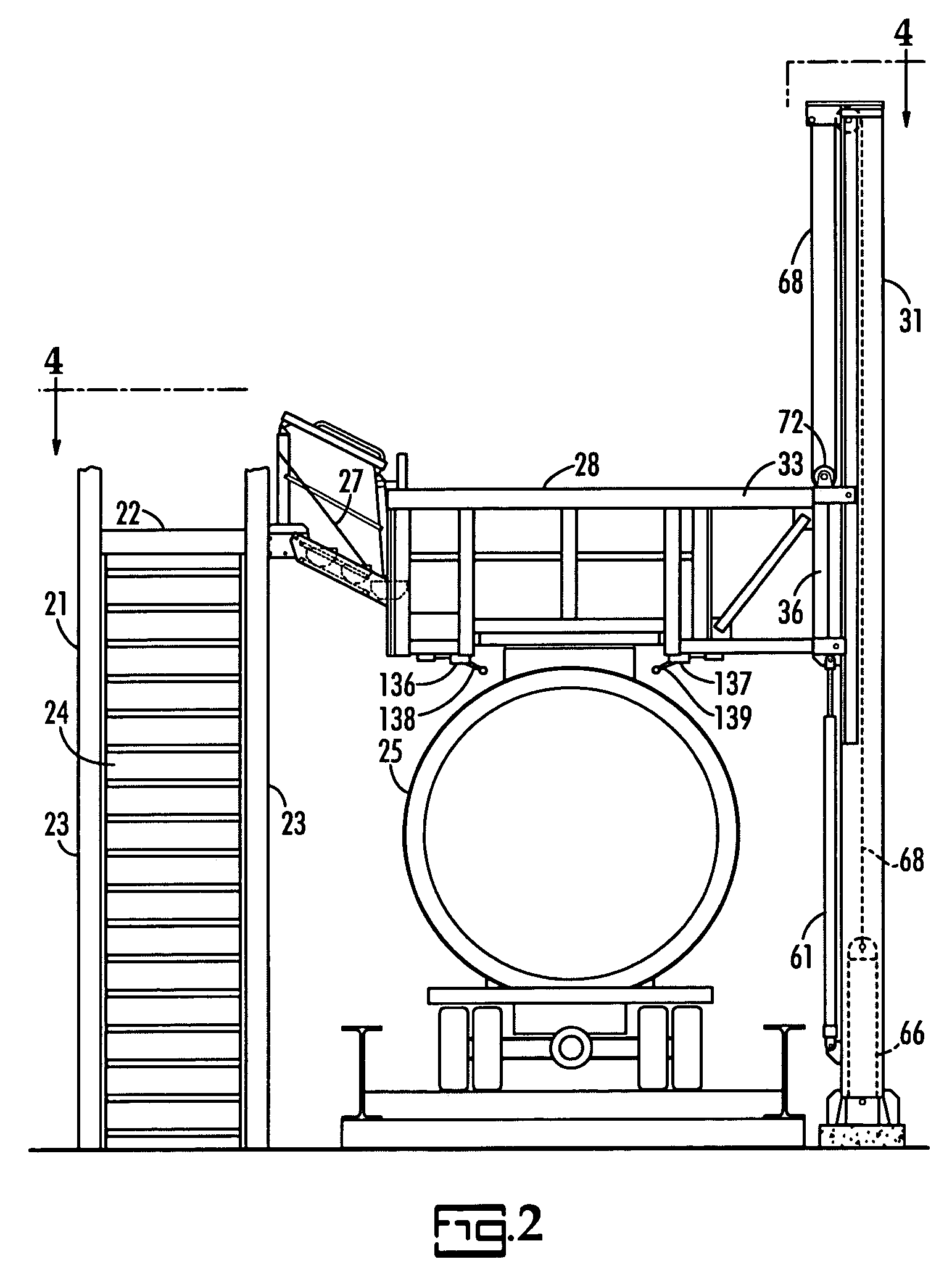
Bulk material transport vehicle access structure
ActiveUS7140467B2Inhibit bindingReduce stepsSteps arrangementBuilding support scaffoldsElectricityAccess structure
A bulk material transport vehicle access structure includes an elongated service platform for workers which is pivotally supported at its opposite ends to cantilever arms on parallel horizontal axes to avoid binding between the roller carriages of the cantilever arms and a pair of support pillars. The floor of the platform includes a walkway and a doorway covered by a plurality of side by side doors which may be selectively opened. Electric controls are provided to automatically stop operation of the power means used to control the elevation of the cantilever arms should the service platform become tilted a predetermined extent. Electric controls are also provided to stop lowering of the service platform when it reaches the top of a bulk material transport vehicle.
Owner:SAM CARBIS ASSET MANAGEMENT
Nanoliter array loading
ActiveUS20070003448A1Additive manufacturing apparatusAnalysis using chemical indicatorsAccess structurePhysics
An interface is provided for storing microfluidic samples in a nanoliter sample chip. A fluid access structure provides a fluid access region to a selected subset of sample wells from an array of sample wells. A fluid introduction mechanism introduces a sample fluid to the fluid access region so that the sample wells in the selected subset are populated with the sample fluid without the unselected sample wells being populated with the sample fluid.
Owner:LIFE TECH CORP
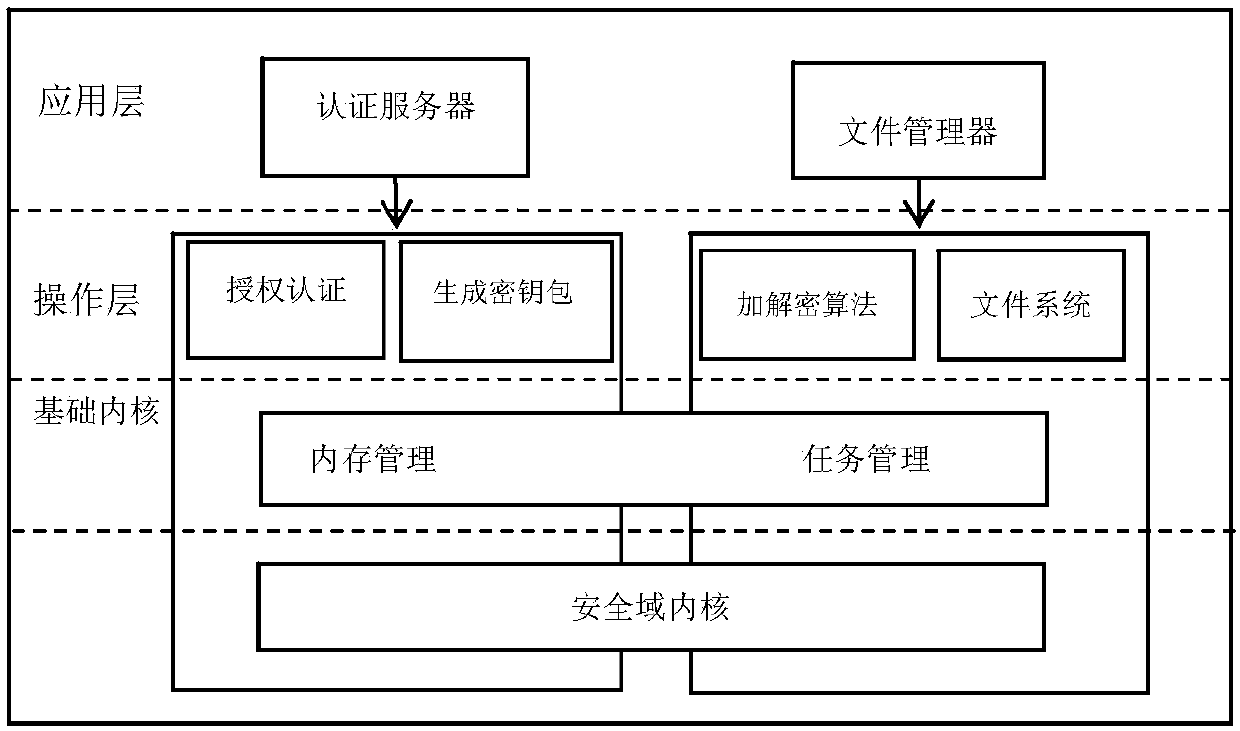
Key encryption method based on file attribution
InactiveCN102624522AEfficient encryptionReduce multiplication (exclusiveSecuring communicationPlaintextAccess structure
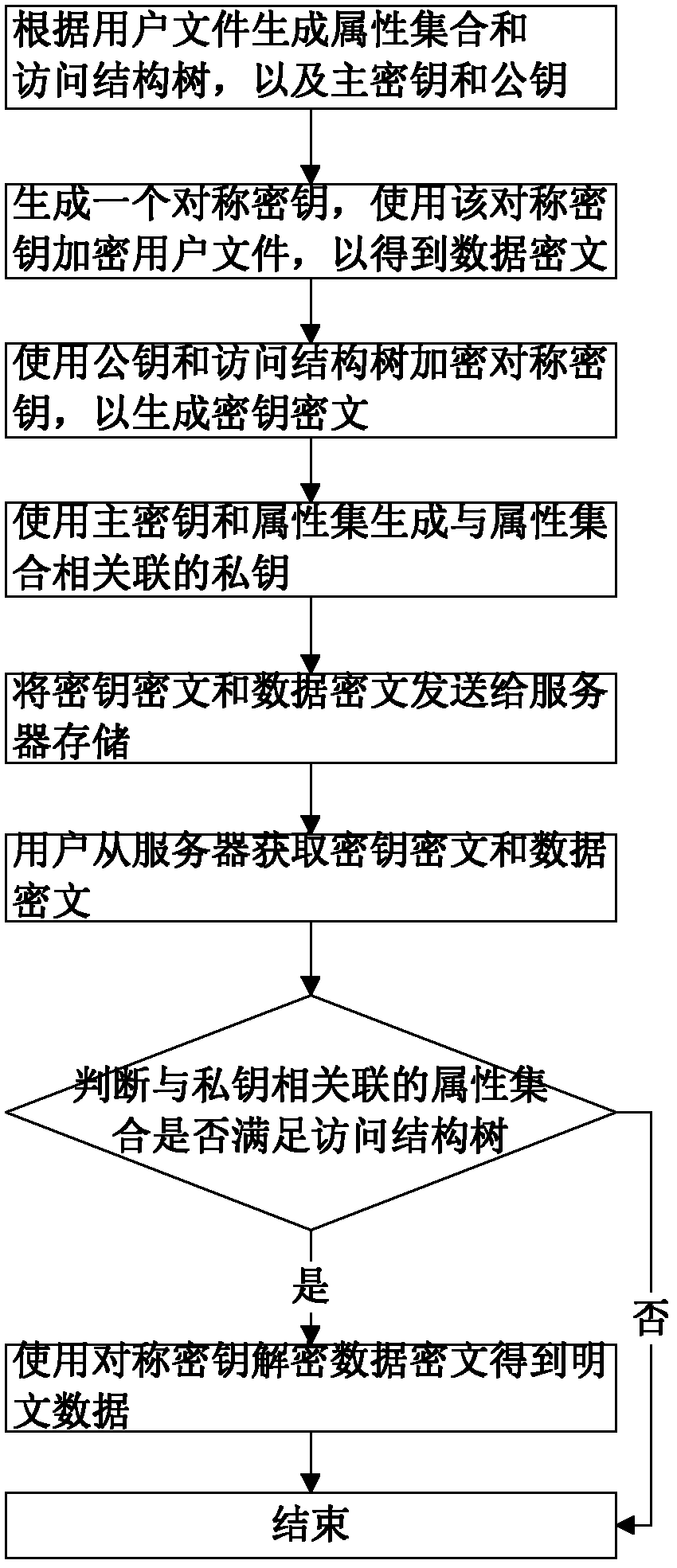
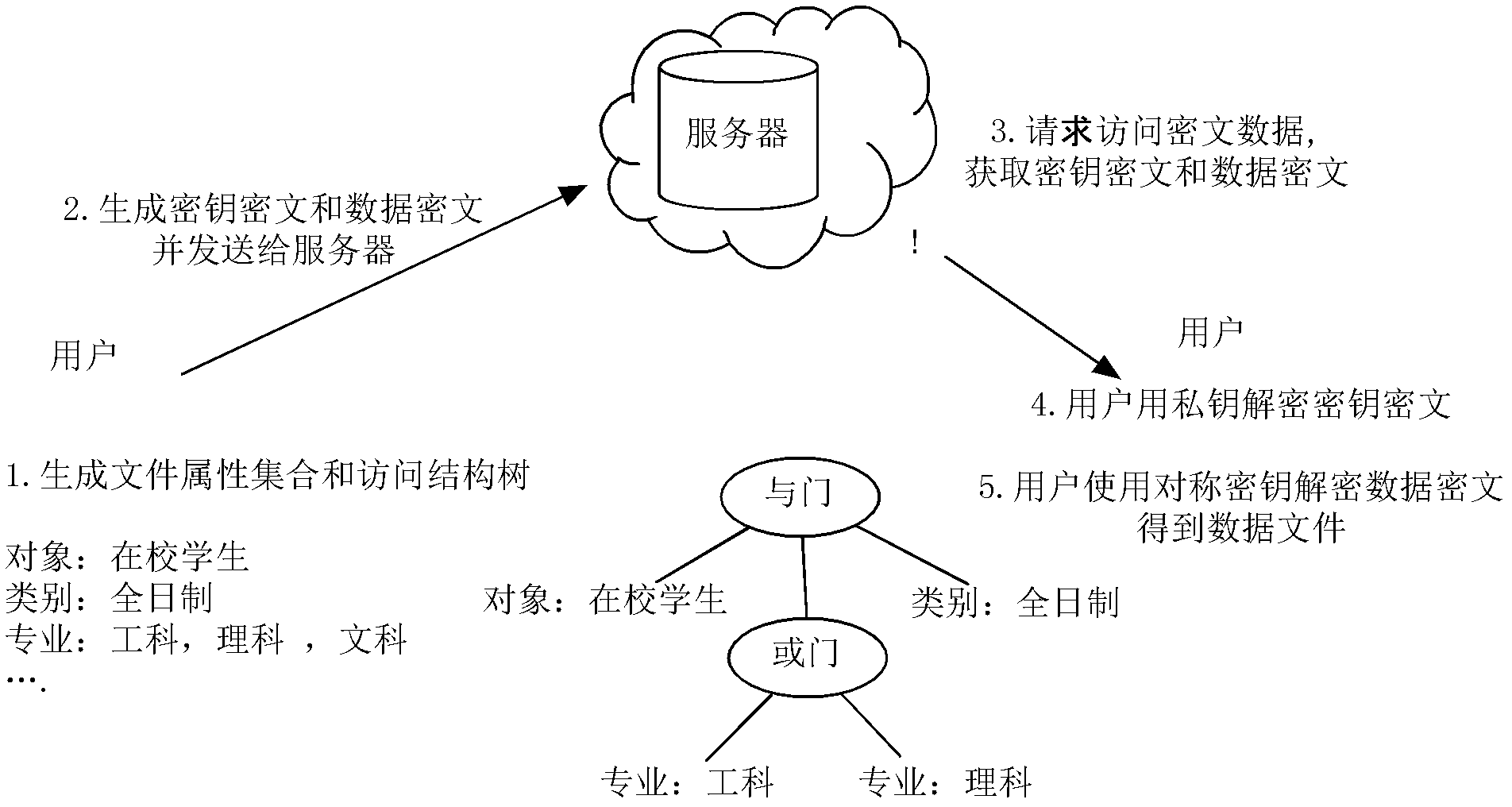
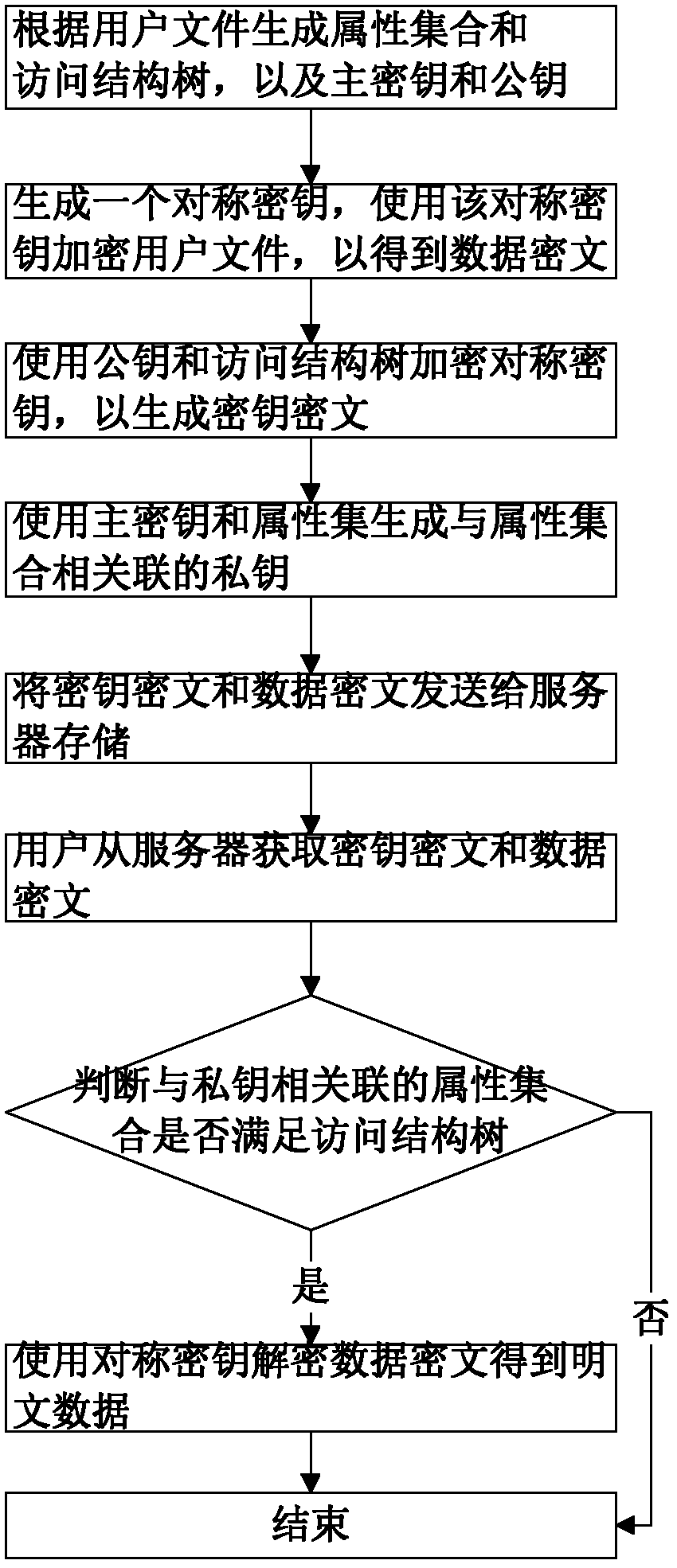
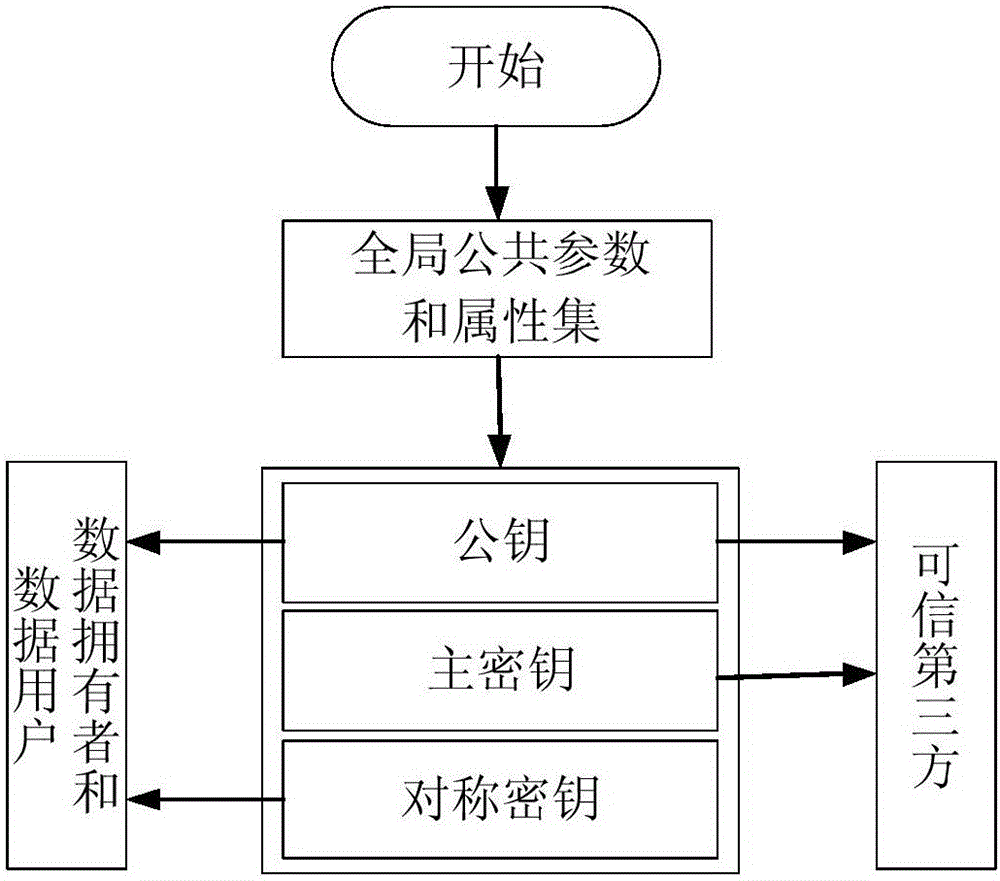
The invention discloses a key encryption method based on file attribution. The key encryption method comprises the following steps of: receiving a user file, generating an attribution aggregate, an access structure tree, a main key and a public key according to the user file, randomly generating symmetric keys, encrypting the user file by using the symmetric keys and a symmetric encryption algorithm to obtain data cipher text, encrypting the symmetric keys by utilizing the public key and the access structure tree to generate a key cipher text, generating a private key associated with the attribution aggregate by utilizing the main key and the attribution aggregate, transmitting the key cipher text and the data cipher text to a server to store, obtaining the key cipher text and the data cipher text from the server by a user, decrypting the key cipher text by using the private key by the user to judge whether the attribution aggregate associated with the private key meets the access structure tree or not, and if meeting the access structure tree, decrypting the symmetric key and decrypting the data cipher text by utilizing the symmetric key through the user to obtain plaintext data. According to the key encryption method based on the file attribution, disclosed by the invention, data is encrypted by the symmetric encryption algorithm, the safety of the symmetric key is protected based on attribution encryption, and the high-efficiency safe access of encrypted data is realized.
Owner:HUAZHONG UNIV OF SCI & TECH
Logic Chip, Logic System and Method for Designing a Logic Chip
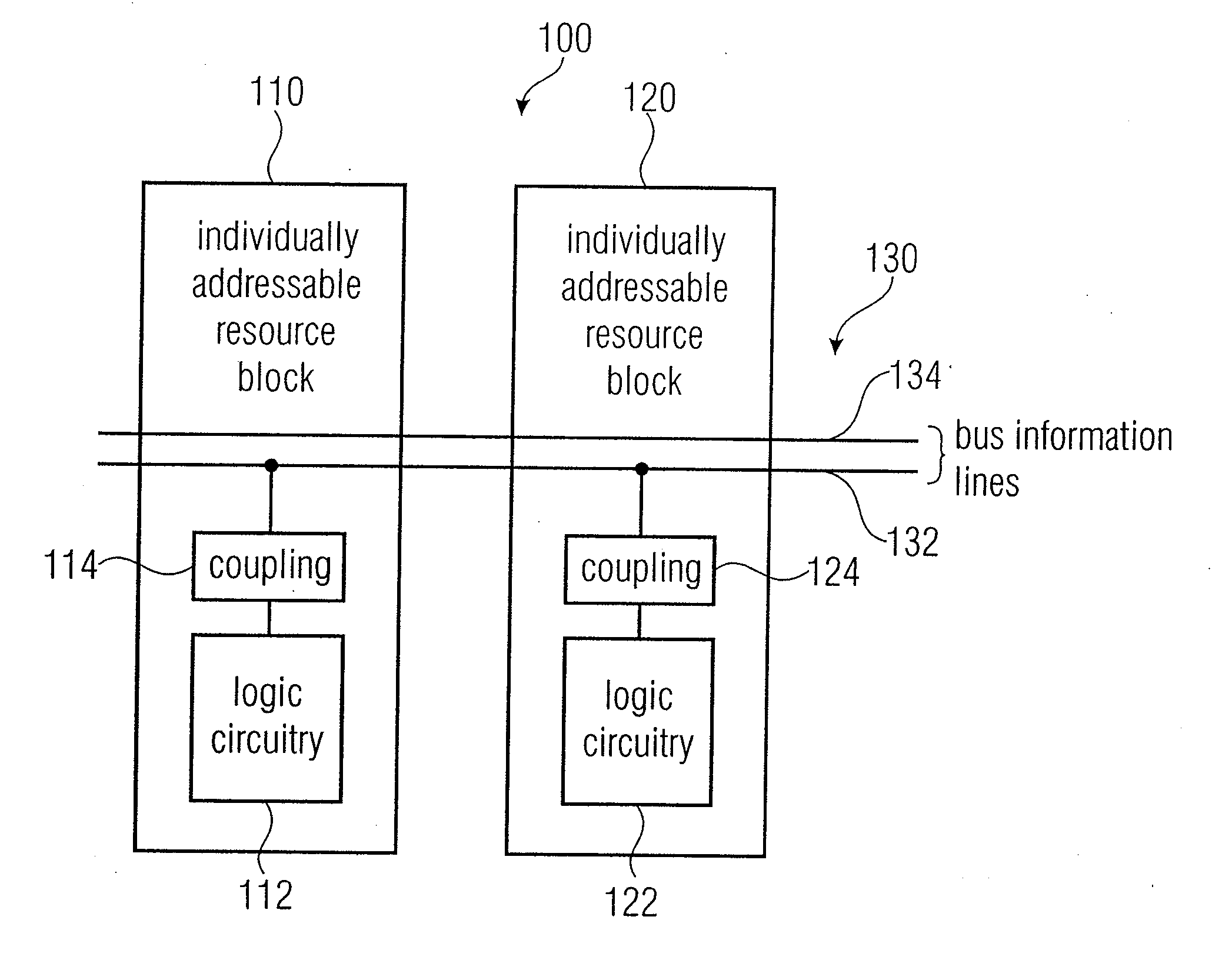
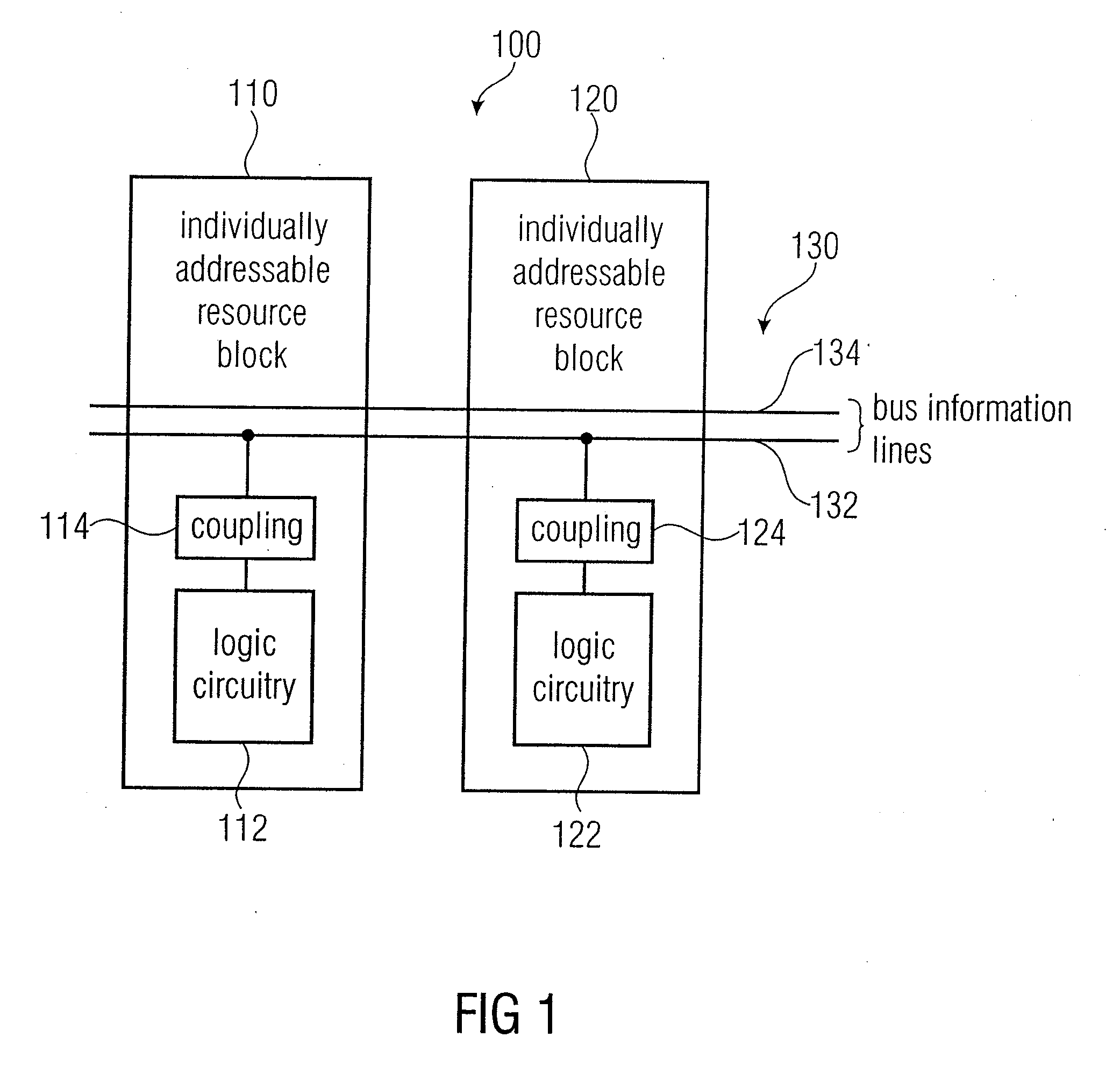
ActiveUS20100283505A1Efficiently establishedFlexible communicationSingle instruction multiple data multiprocessorsSolid-state devicesAccess structureResource block
A logic chip has a plurality of individually addressable resource blocks each of the resource blocks having logic circuitry, and a communication bar extending across a plurality of the individually addressable resource blocks. The communication bar has a plurality of communication bar segments associated with the resource slots. The communication bar segments of the individually addressable resource blocks have identical interface locations with respect to boundaries of the resource blocks, such that an input interface location of a first resource block matches an output interface location of an adjacent second resource block. At least one of the individually addressable resource blocks has a bypass segment of the communication bar. At least one of the individually addressable resource blocks has an access segment of the communication bar. The access segment has an access structure inserted between a first communication bar interface location and a second communication bar interface location, to allow for a read access or a write access or a combined read / write access to the communication bar.
Owner:KOCH DIRK DR
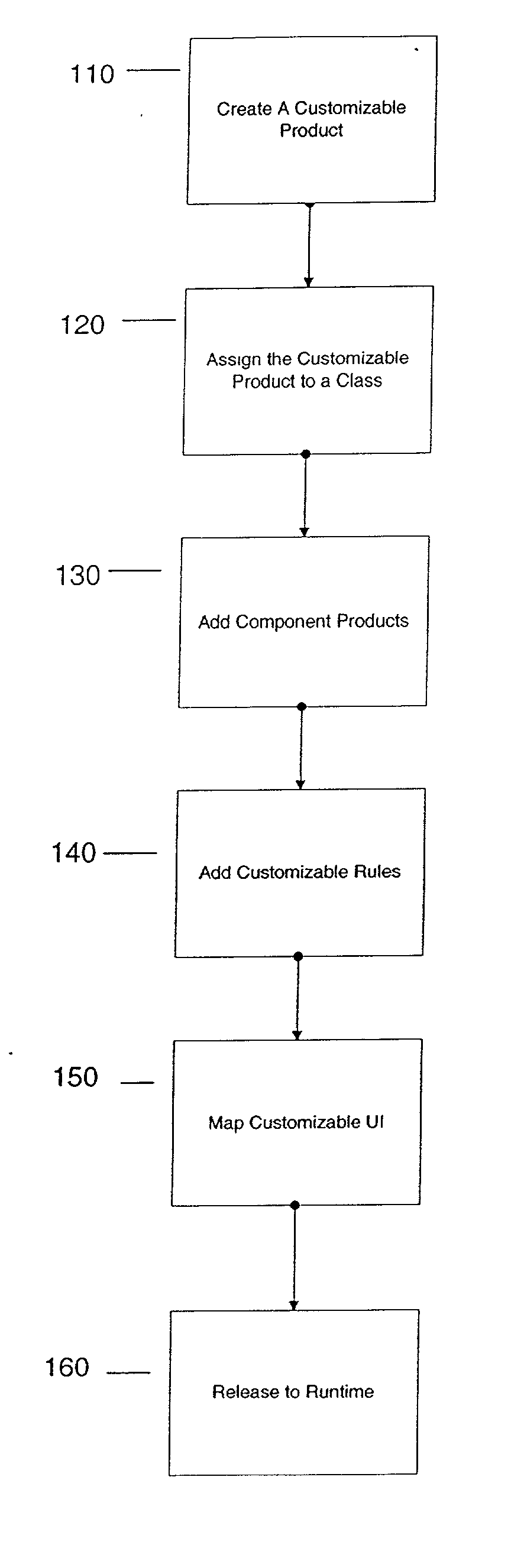
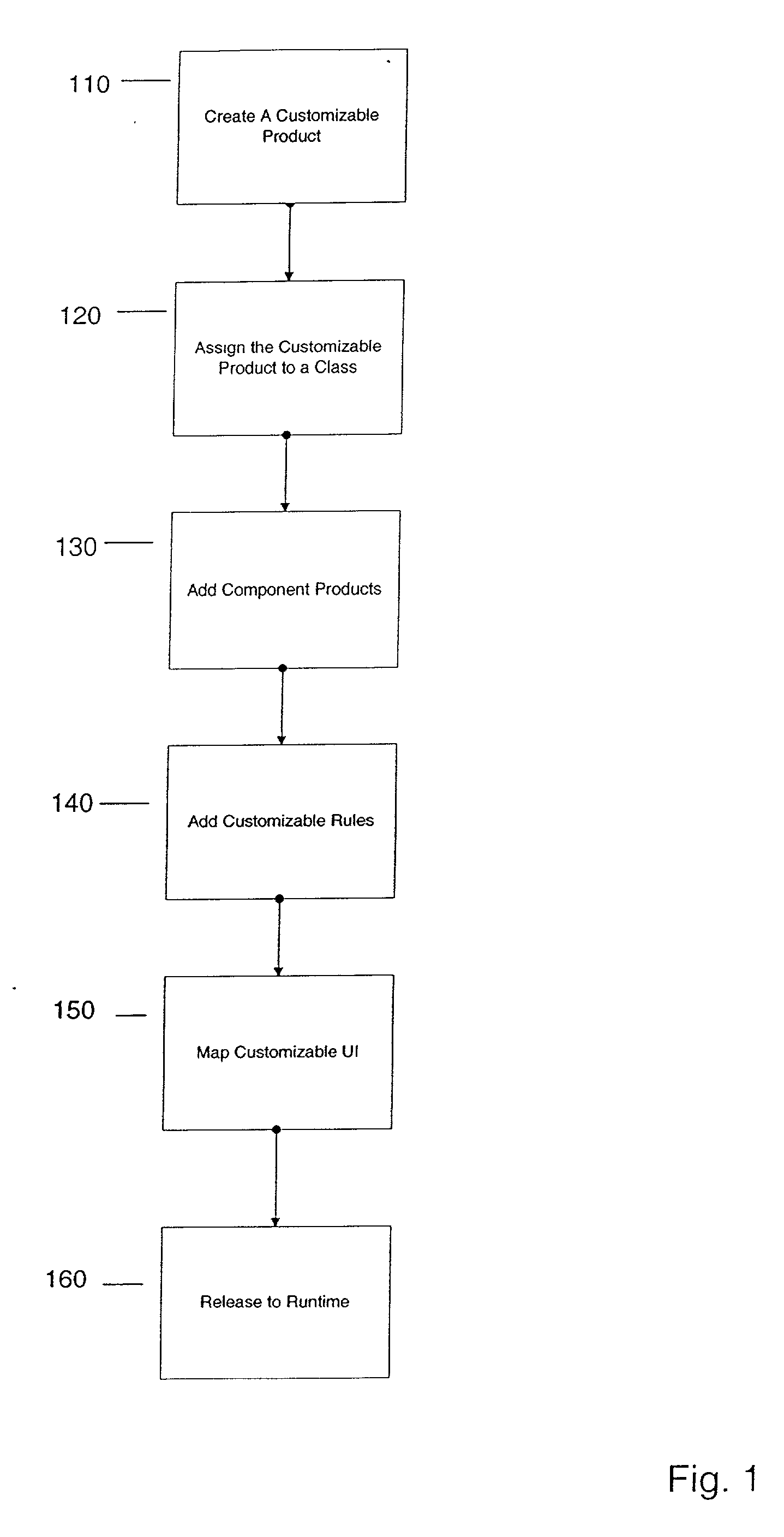
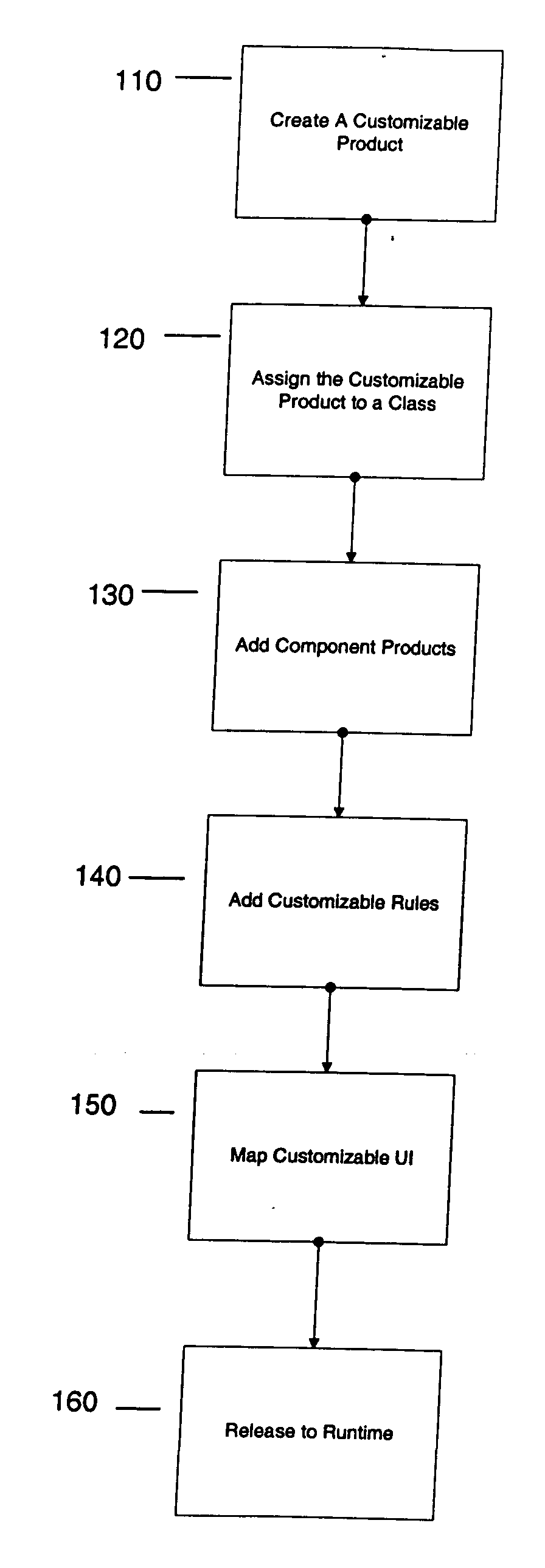
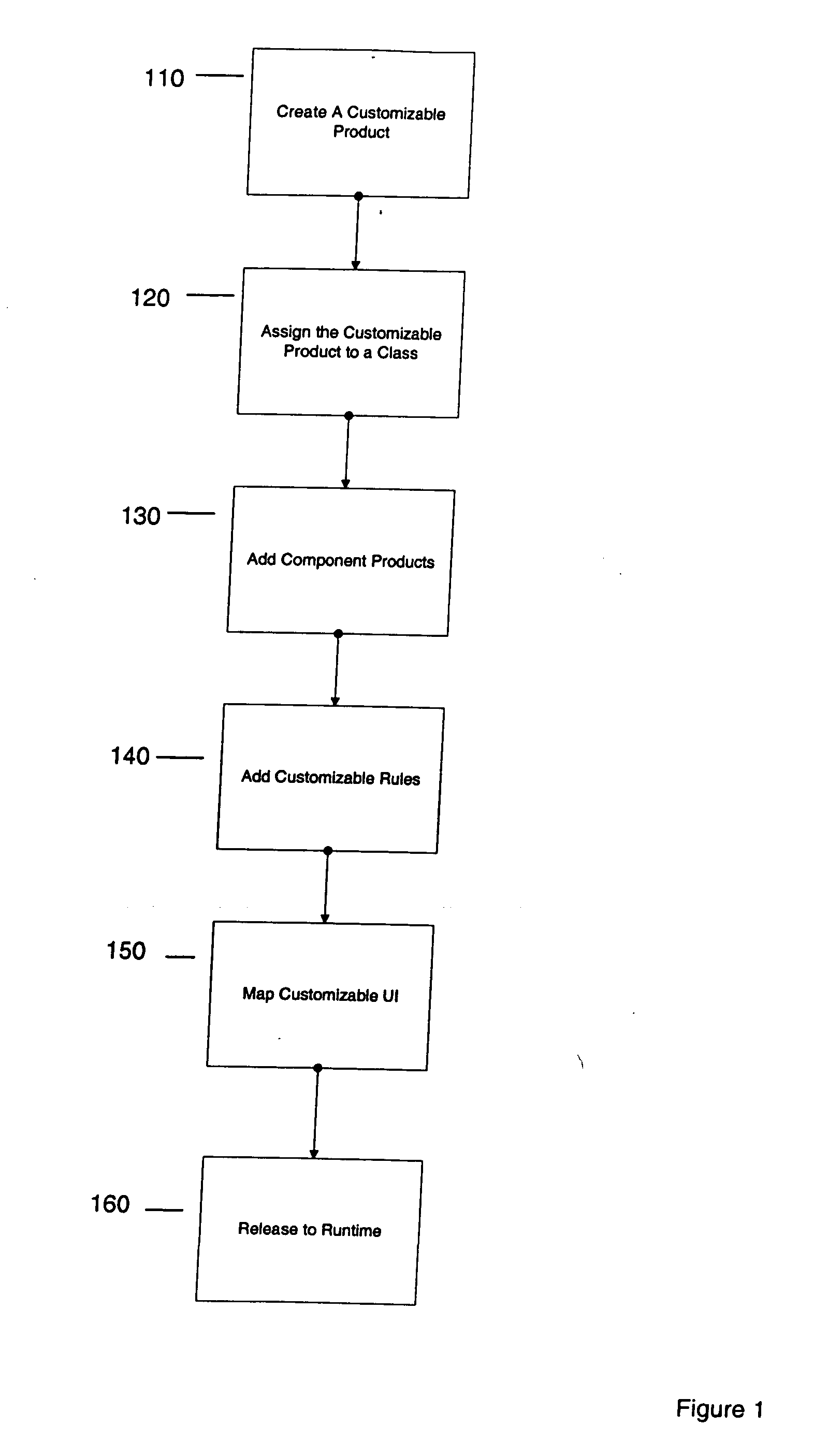
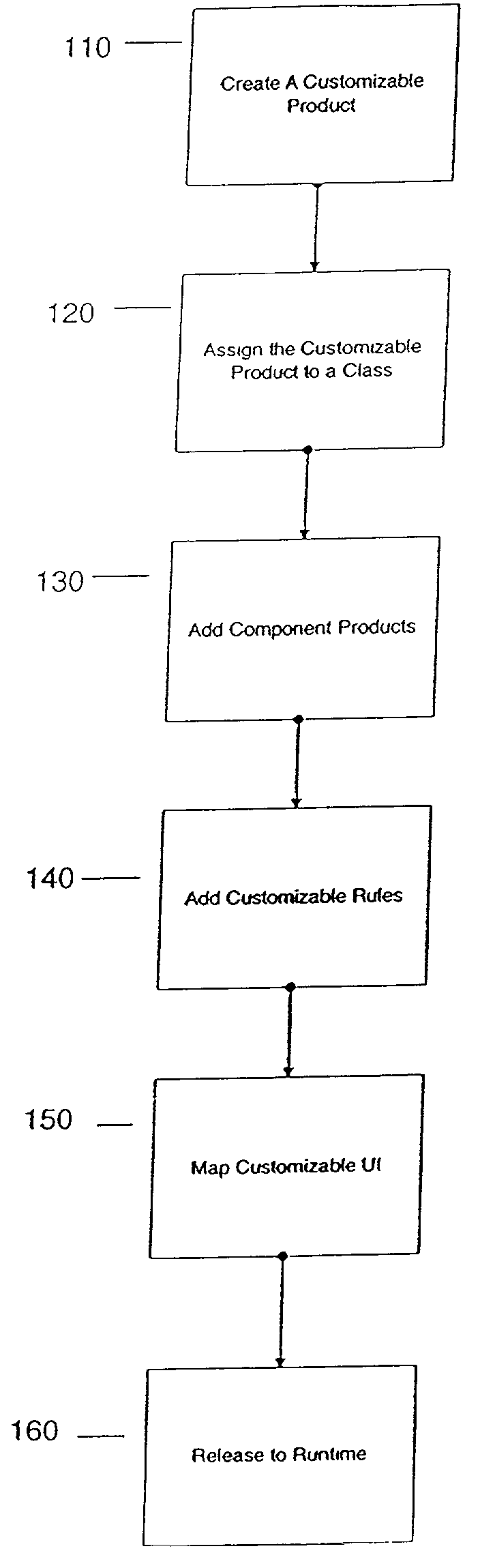
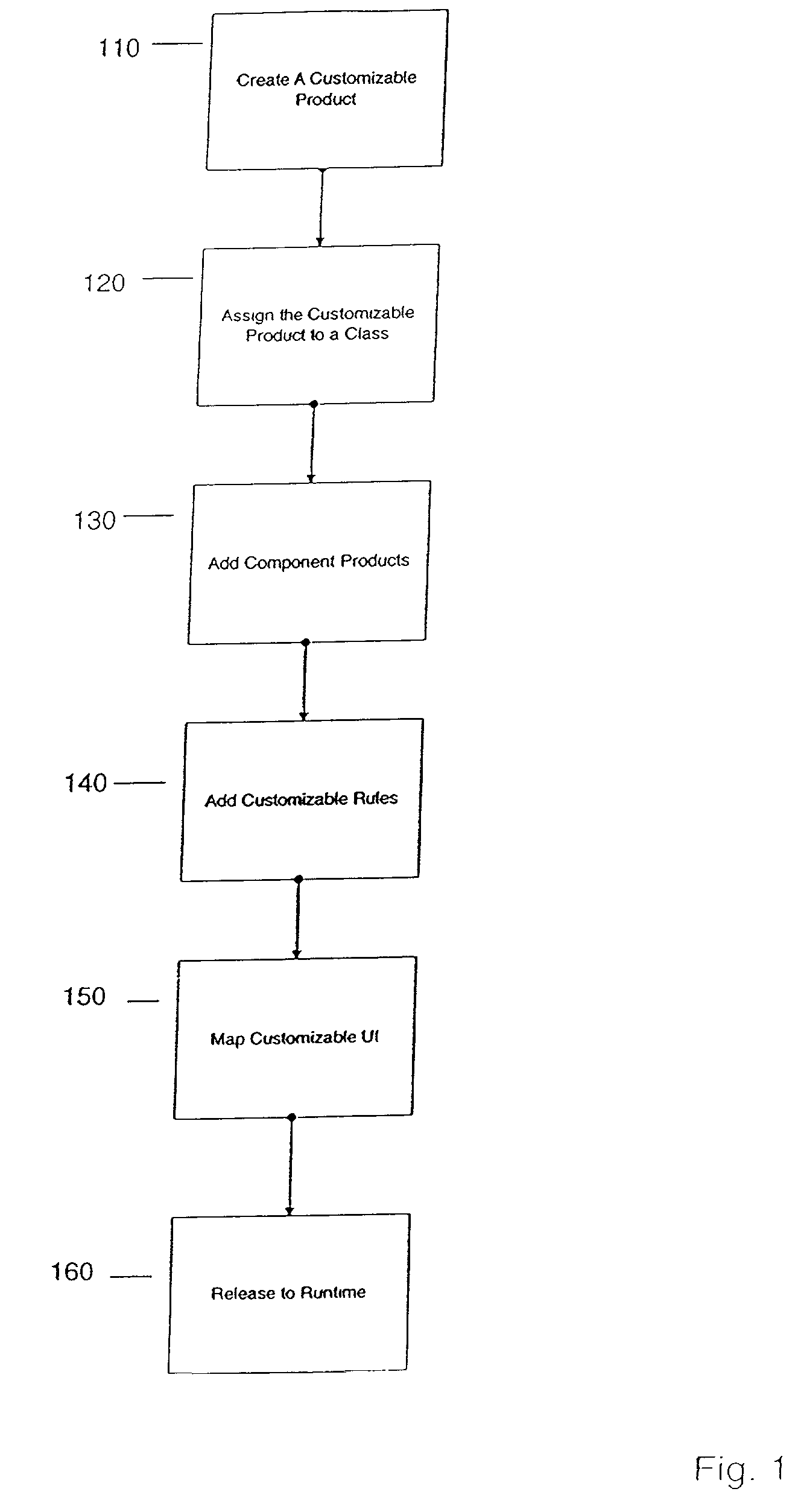
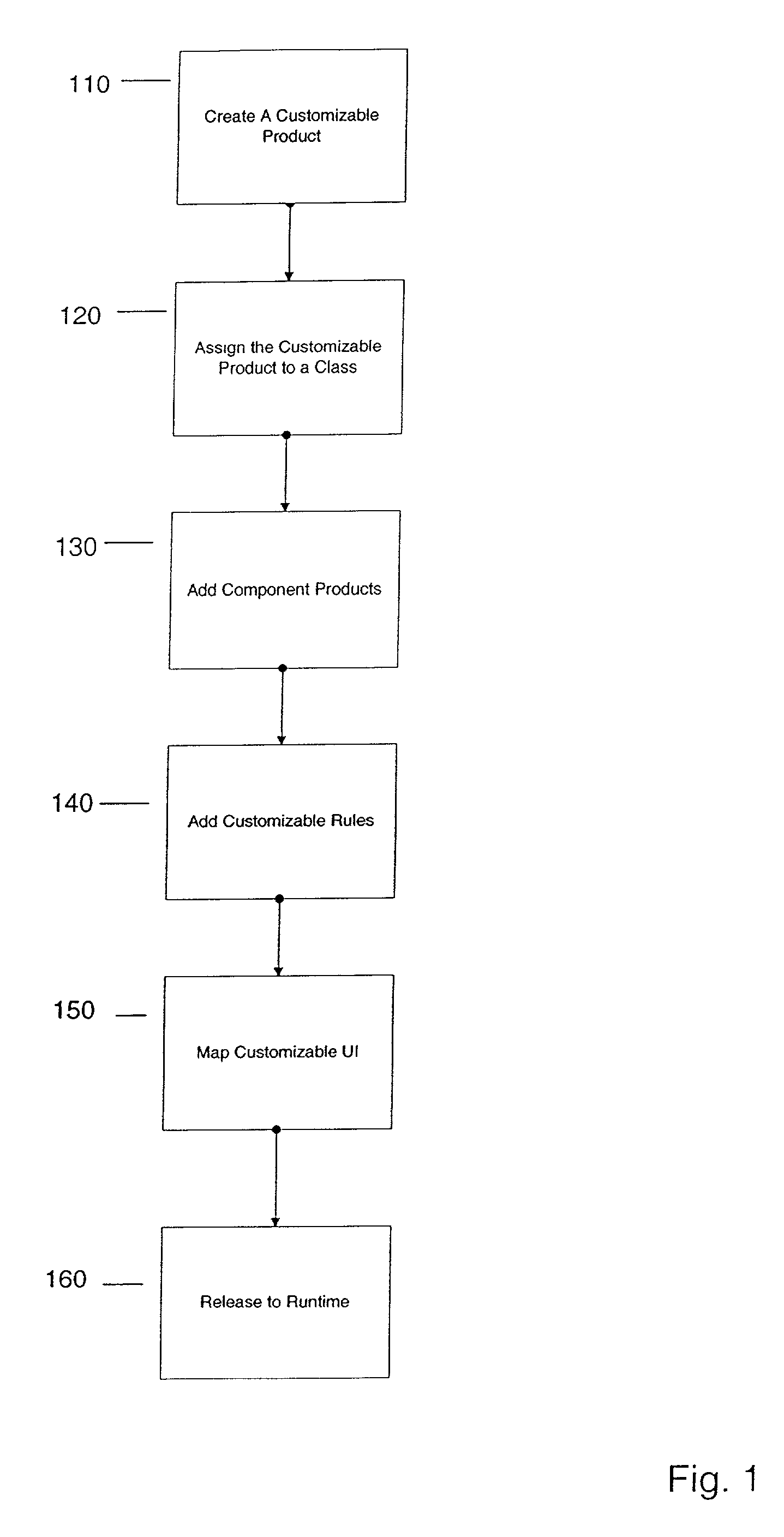
Configurator using structure to provide a user interface
A method and apparatus system for generating a configurator. According to one embodiment of the invention, a customizable product class is created. The customizable product class includes a set of one or more attributes to define the customizable product class. A component product class is added to the customizable product class, where the component product class is a subclass of the customizable product. A customizable UI is mapped to the customizable product class, where the customizable UI provides access structure to the configurator.
Owner:ORACLE INT CORP
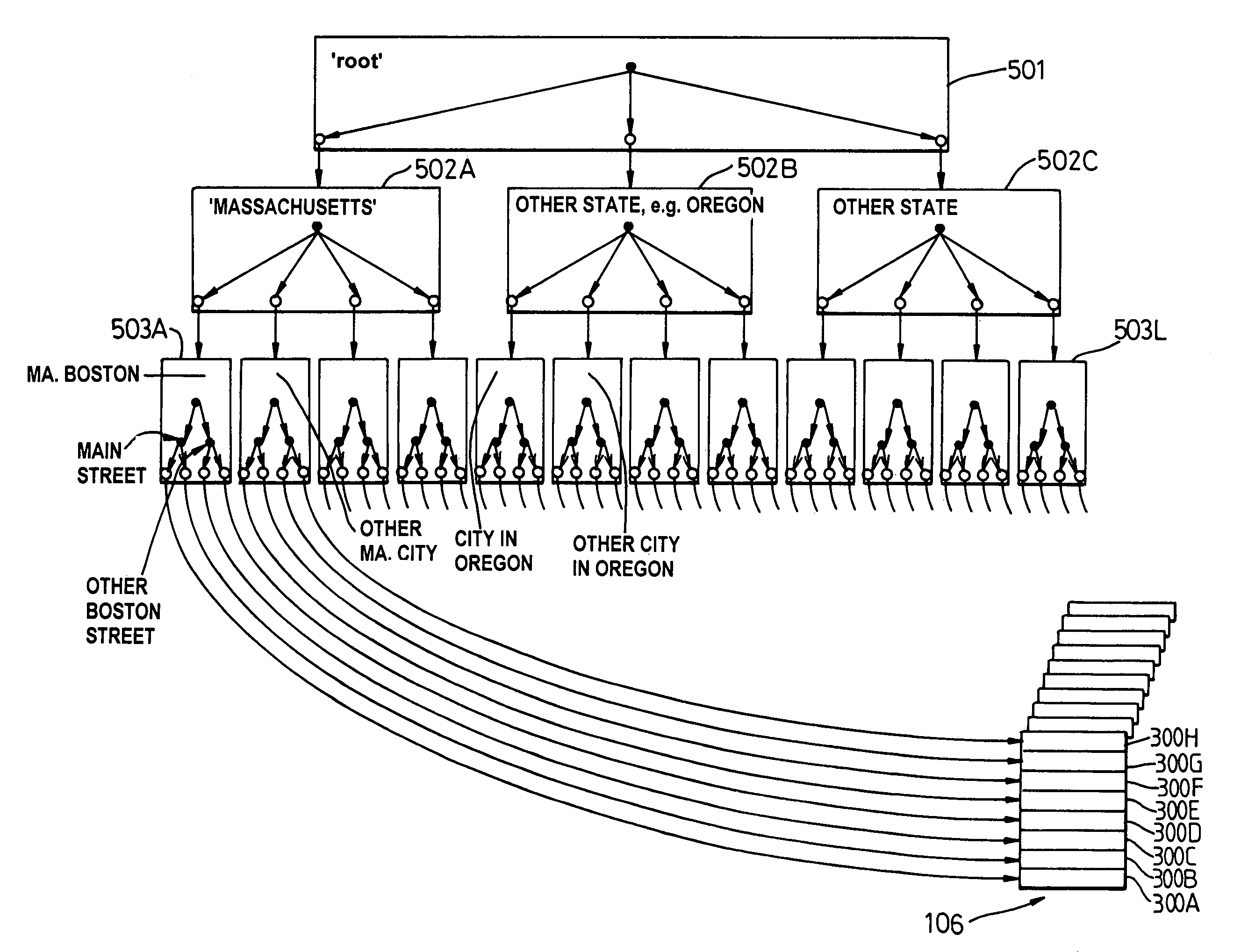
System, method and technique for searching structured databases
ActiveUS20060004721A1Data processing applicationsDigital data information retrievalAccess structureTree (data structure)
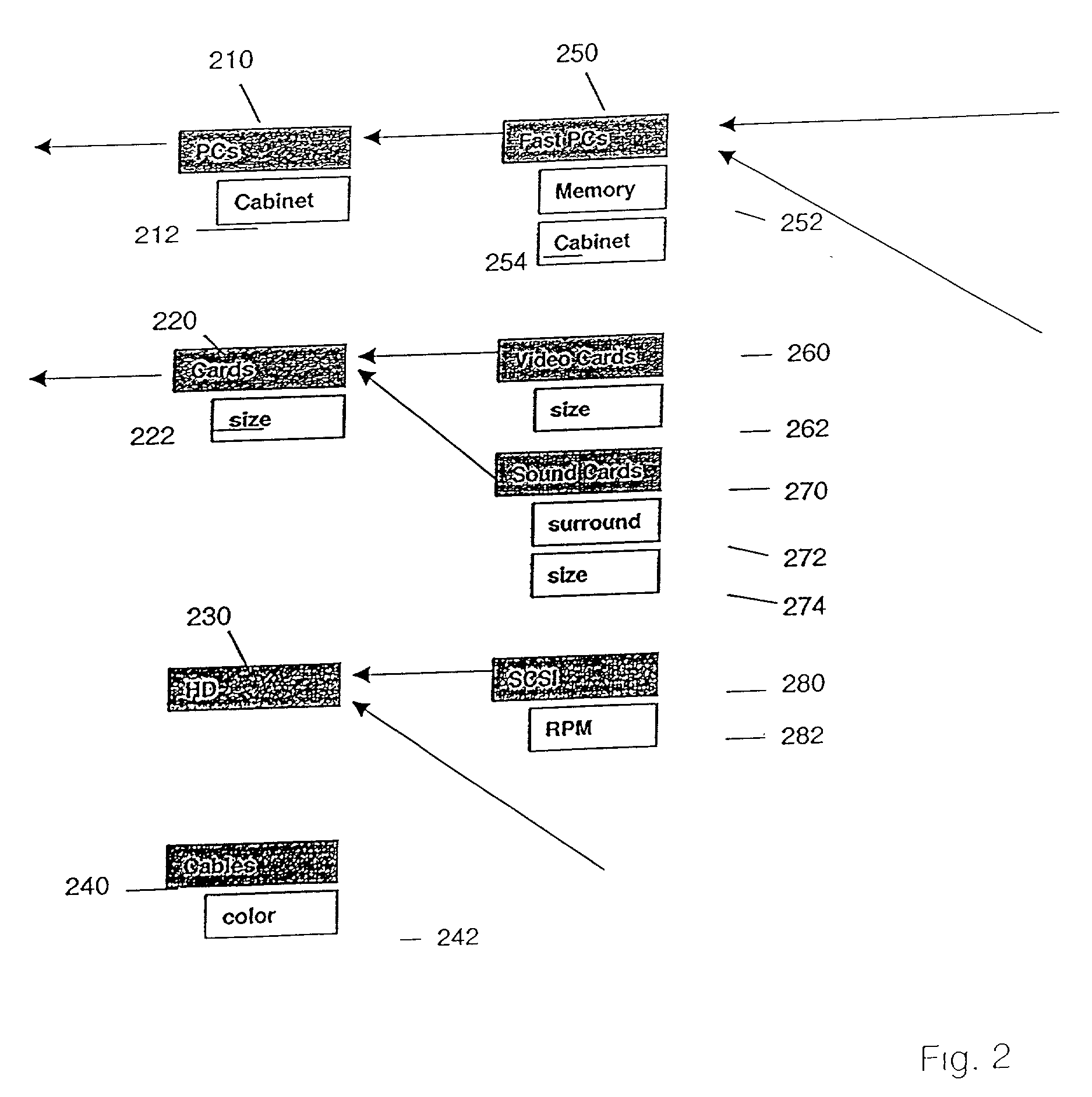
Searching a database (106) involves creating an access structure including a first tree data structure (501) having a root node (5011) and at least one child node (5012). Each child node is associated with match data corresponding to a data value of a field of a database record (300). Leaf child nodes of the first tree data structure include a link (704) to another tree data structure in the access structure. Leaf child nodes (5033) of a further tree data structure include a link (718) to a database record. The tree structures are traversed and scores are computed for the paths traversed that reflect the level of matching between the match pattern data of the nodes in a path and a search request to identify a database record that best matches the request.
Owner:APPLE INC
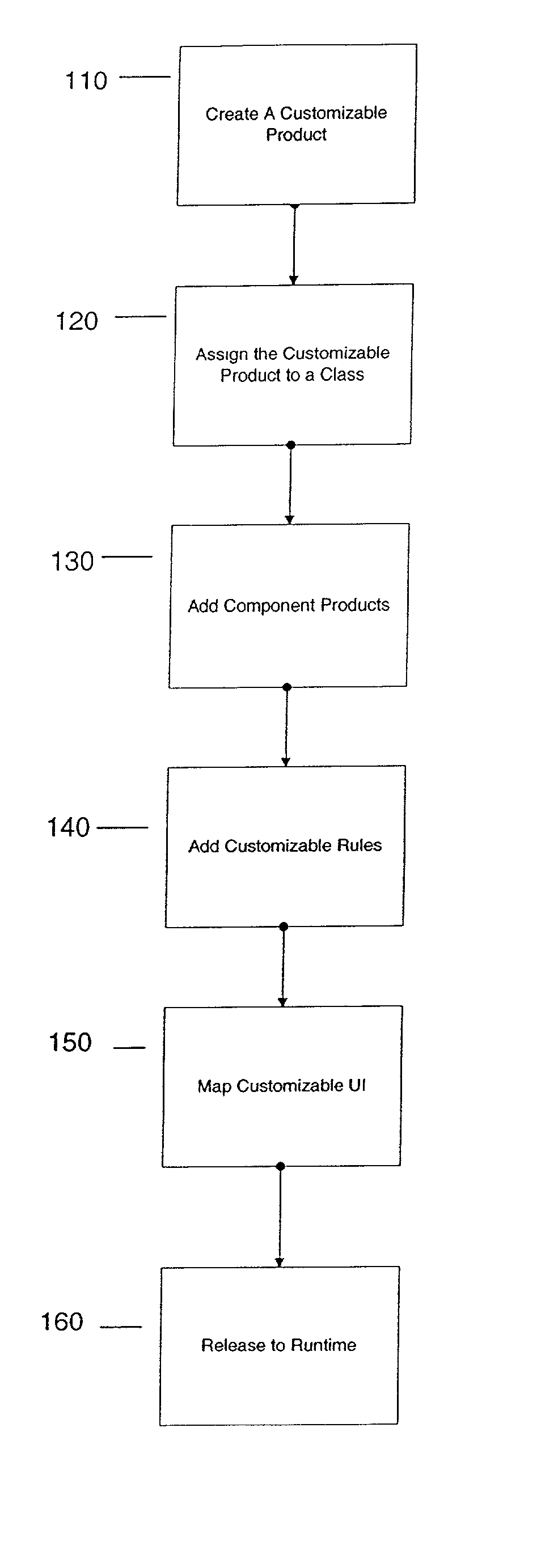
Configurator using structure and rules to provide a user interface
InactiveUS20070226066A1Buying/selling/leasing transactionsSpecial data processing applicationsAccess structureWorld Wide Web
A configurator using structure and rules to provide a user interface. According to one embodiment of the invention, a customizable product class is created. The customizable product class includes a set of one or more attributes to define the customizable product class. A component product class is added to the customizable product class, where the component product class is a subclass of the customizable product. A customizable class rule is associated to the customizable product class, the customizable class rule including expressions which provide conditions on component products added to the customizable product. A customizable UI is mapped to the customizable product class, where the customizable UI provides access structure to the configurator.
Owner:SIEBEL SYST INC
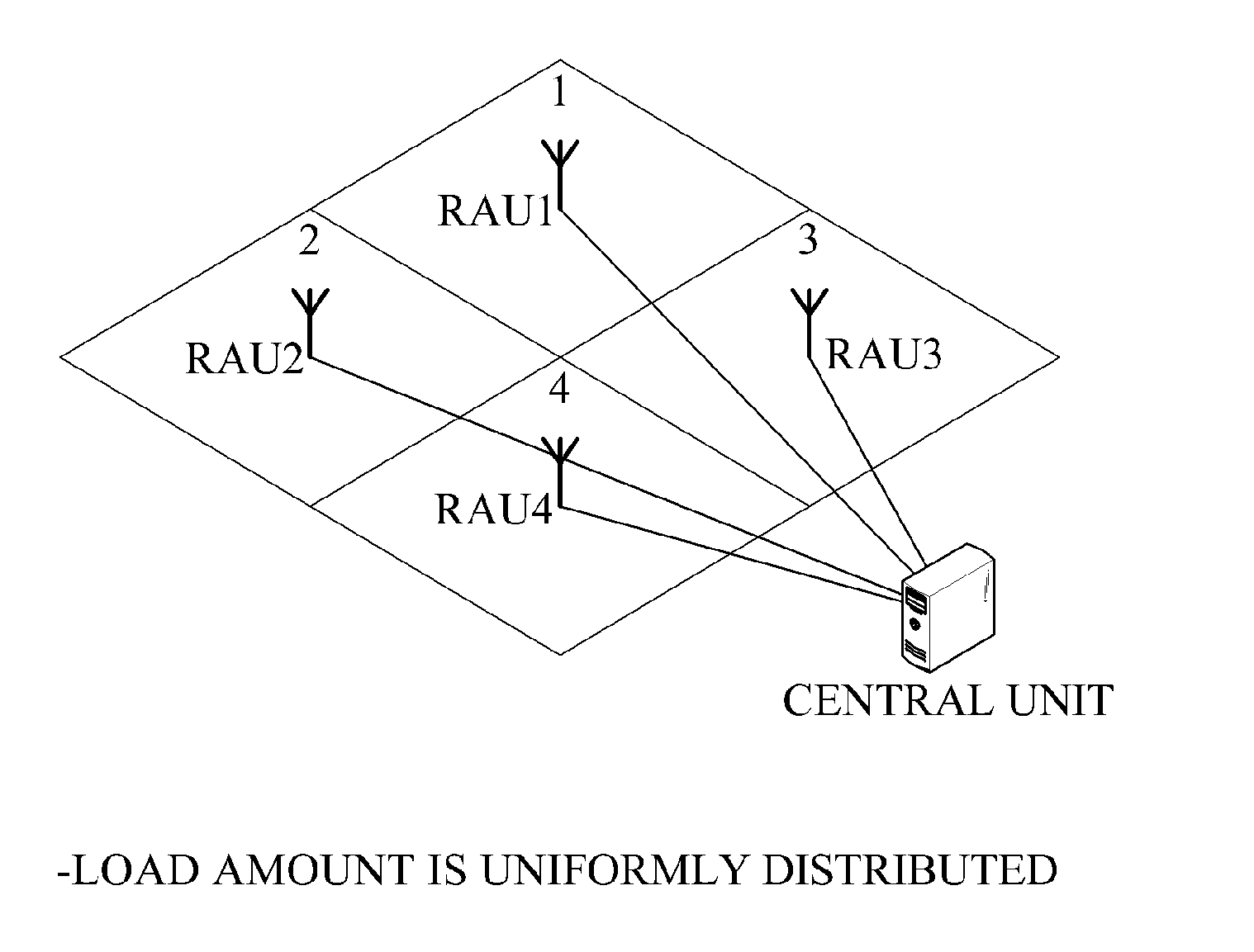
Communication system having network access structure
ActiveUS20110096736A1Decrease frequency of handoverReduce frequencyWireless commuication servicesNetwork planningAccess structureCommunications system
A communication system with an improved network access structure for inter-cell cooperation is provided. The communication system includes a central unit and at least one radio access unit. The at least one radio access unit may form at least one virtual cell by merging or separating cells of radio access units according to a distribution of terminals, statuses of channels, an amount of traffic, and the like.
Owner:SAMSUNG ELECTRONICS CO LTD +1
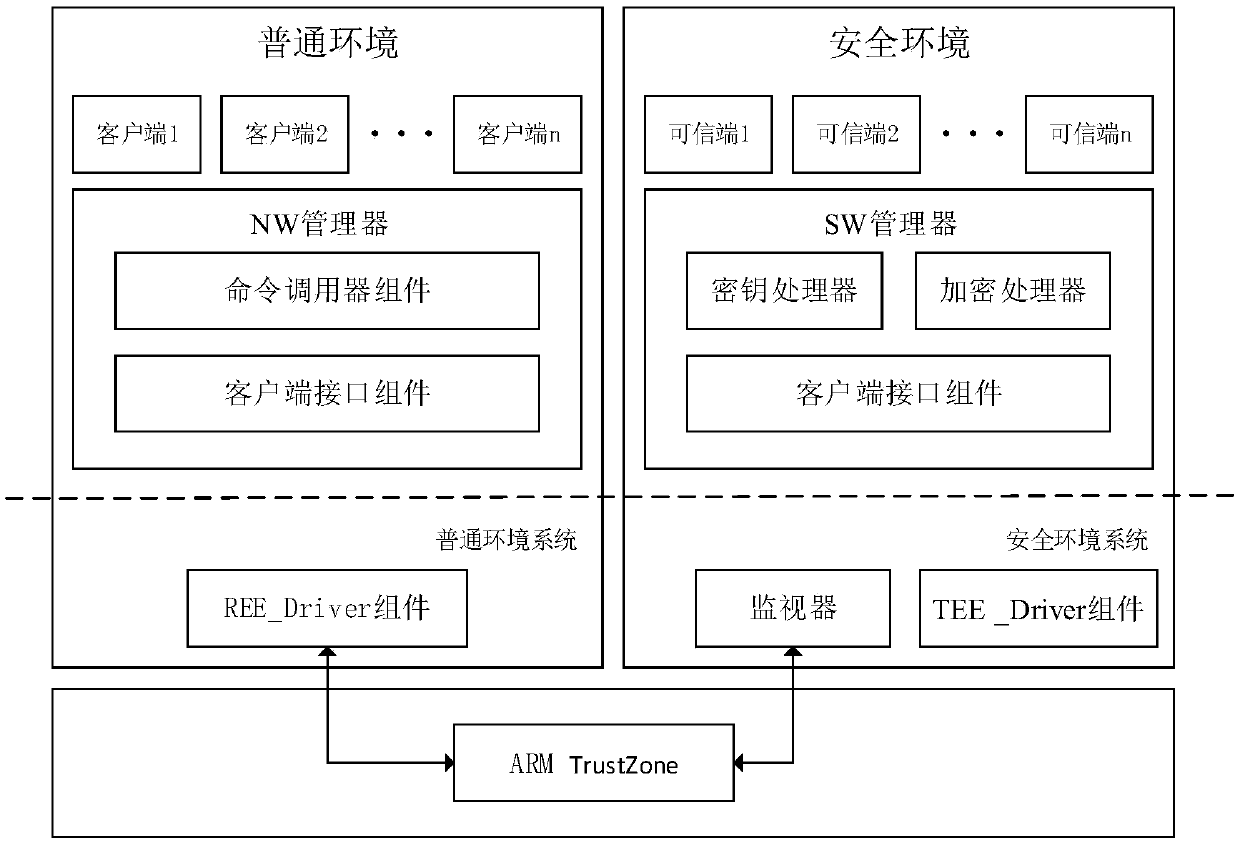
Mobile terminal and access control method and system based on trusted security environment
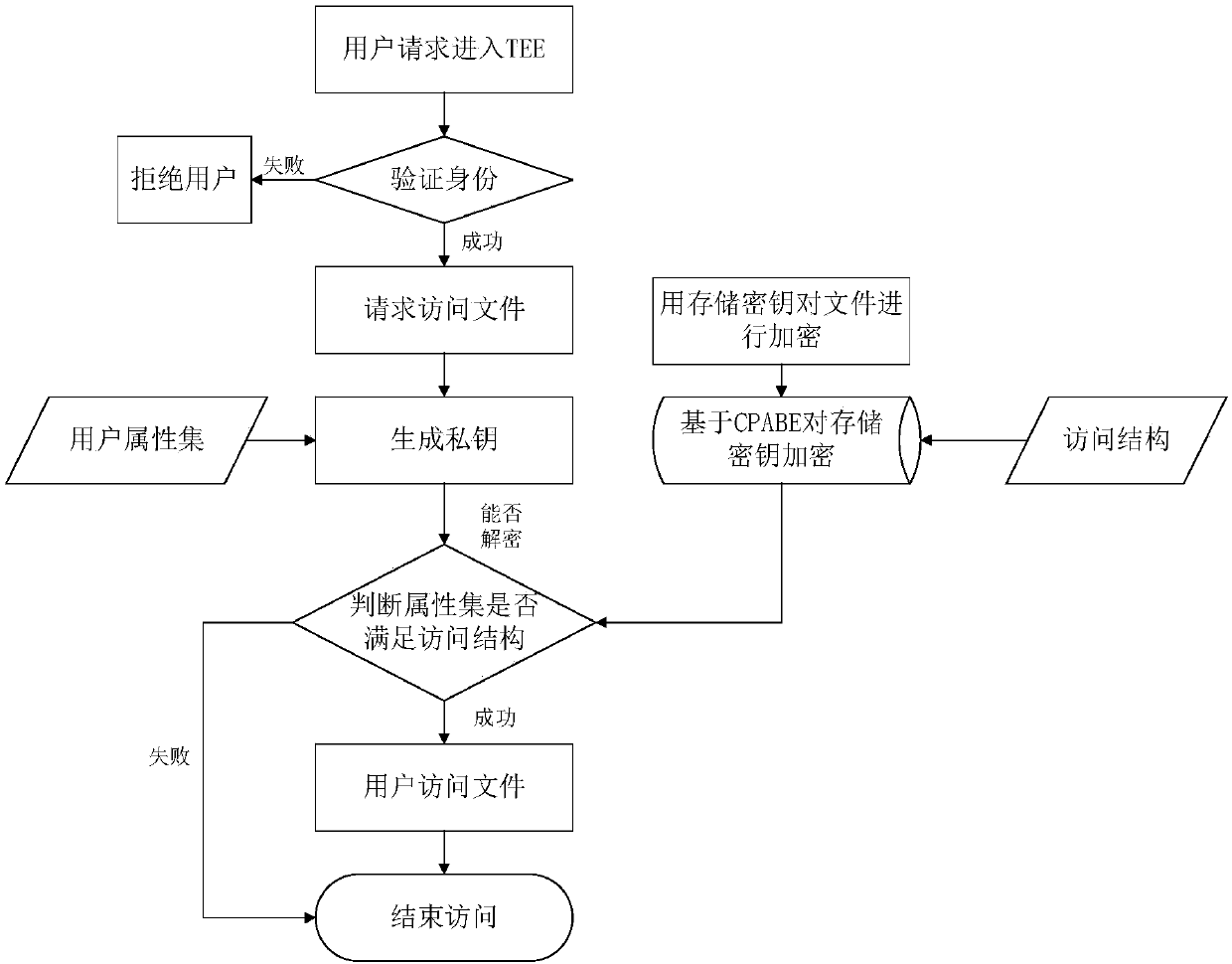
InactiveCN107743133AImprove information securityKey distribution for secure communicationAccess structureCiphertext
The embodiment of the application provides a mobile terminal and an access control method and system based on a trusted security environment. The access control method based on the trusted security environment comprises the following steps: encrypting a private file with a storage key in advance in the trusted security environment, and encrypting the storage key with CPABE and the access structureof the private file; verifying the identity of a client when receiving a trusted security environment access request initiated by the client in an ordinary execution environment; generating the CPABEprivate key of the client according to the client attribute set carried by a file access request when receiving the file access request initiated by the client after passing the identity verification; obtaining the corresponding private file according to the CPABE private key when the client attribute set satisfies the access structure of the corresponding file ciphertext; and returning the private file to the client. The embodiment of the application can improve the information security of the mobile terminal.
Owner:CHINA UNIV OF PETROLEUM (BEIJING)
Attribute-based multi-keyword ciphertext retrieval method under background of multiple data owners
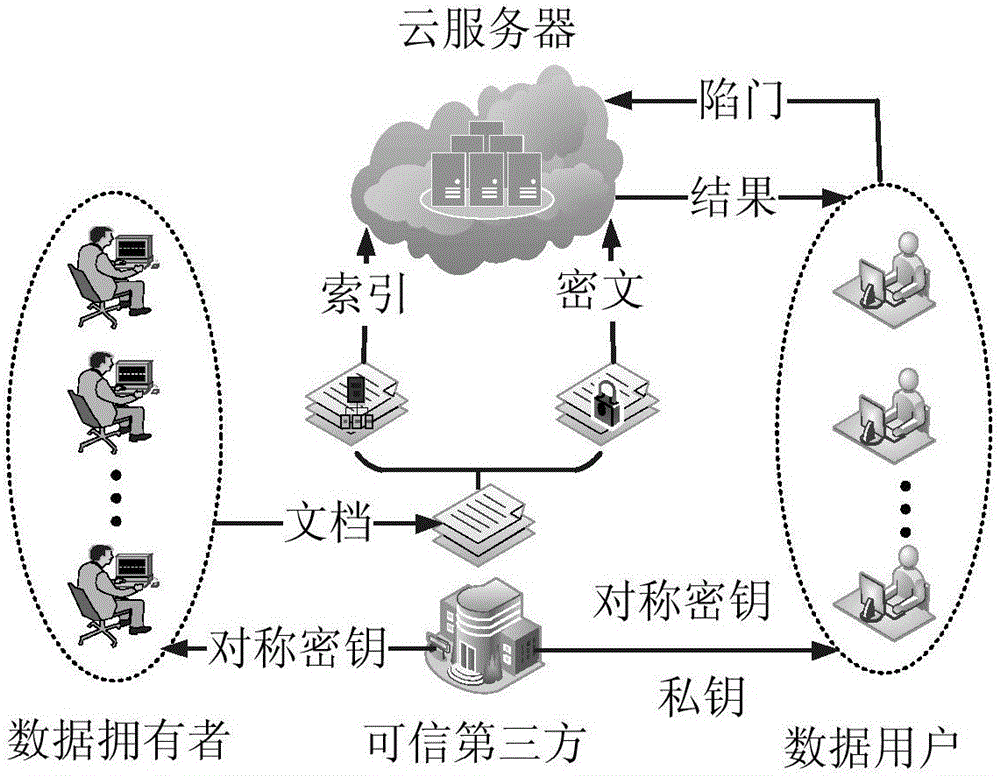
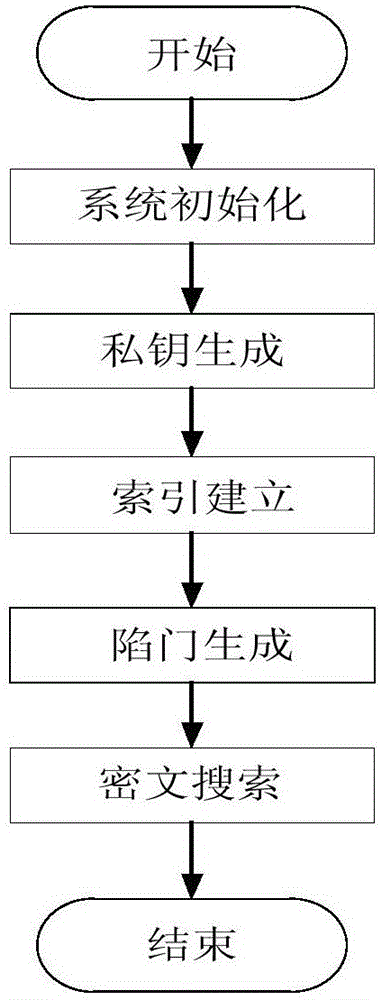
ActiveCN105871543ARapid positioningReduce the burden onKey distribution for secure communicationCloud storageAccess structure
The invention discloses an attribute-based multi-keyword ciphertext retrieval method under the background of multiple data owners and mainly solves a problem that the existing technology only supports single-keyword ciphertext retrieval. A technical scheme of the method comprises the following steps that a searchable encryption technology and an encryption strategy based on the ciphertext attribute are combined, and a keyword set index is established under the scene of multiple data owners according to access structures of the data owners and a keyword set of the ciphertext; a data user generates a trap door according to a query keyword set; and the data user utilizes the trap door to realize multi-keyword query of the ciphertext. According to the method, the load of local data storage and management of the data owners is relieved, and the method supports the data user to carry out multi-keyword precise query on the ciphertext and can be used for realizing fine-grained access control and safe and efficient retrieval of the ciphertext data under the cloud storage background.
Owner:XIDIAN UNIV
Nanoliter array loading
ActiveUS8105554B2Analysis using chemical indicatorsAdditive manufacturing apparatusAccess structurePhysics
An interface is provided for storing microfluidic samples in a nanoliter sample chip. A fluid access structure provides a fluid access region to a selected subset of sample wells from an array of sample wells. A fluid introduction mechanism introduces a sample fluid to the fluid access region so that the sample wells in the selected subset are populated with the sample fluid without the unselected sample wells being populated with the sample fluid.
Owner:LIFE TECH CORP
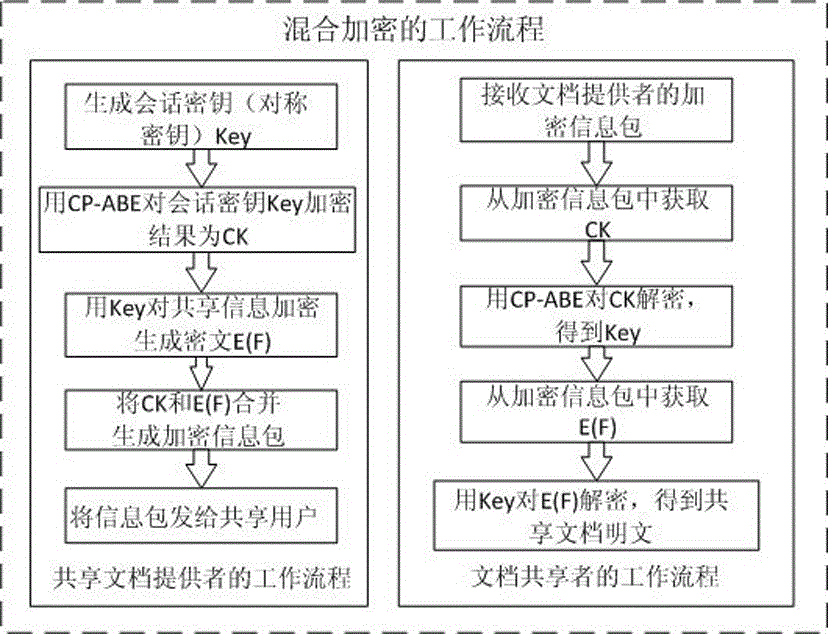
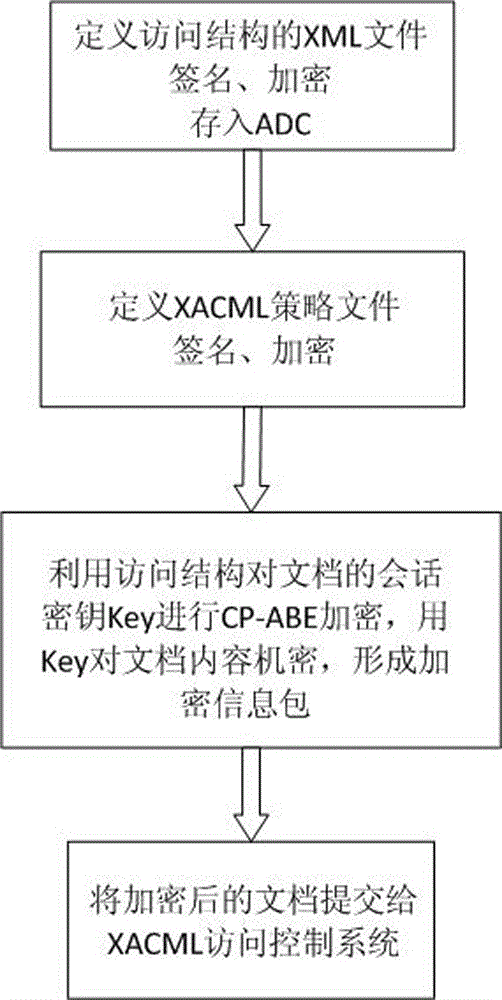
Ciphertext access control method based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption)
ActiveCN105991278AEnsure safetyKey distribution for secure communicationAccess structureControl system
The invention discloses a ciphertext access control method based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption), which belongs to the field of information security. The method comprises the following steps: preparation and maintenance work which comprises initialization of CP-ABE (Ciphertext-Policy Attribute-Based Encryption), user registration and auditing, generation of an asymmetric key pair for signature and encryption by the system and the user, generation of a CP-ABE attribute key SK for the user and key and attribute certificate management is carried out; 2, and file sharing requires a file provider, an extensible access control markup language (XACML) access control system and a sharing user to work cooperatively. The attribute certificate in a PMI system is used as an expression document for a CP-ABE attribute set and the access structure, the XACML expresses the CP-ABE policy, and security of the attribute set and the access control structure description is ensured. A hierarchical structure with an inheritance relationship is introduced, features such as distribution, authorization and calculability are supported, the attribute authorization ability needs to comply with constraints, and the method is applicable to a distributed and open network application environment.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
Carton and carton blank
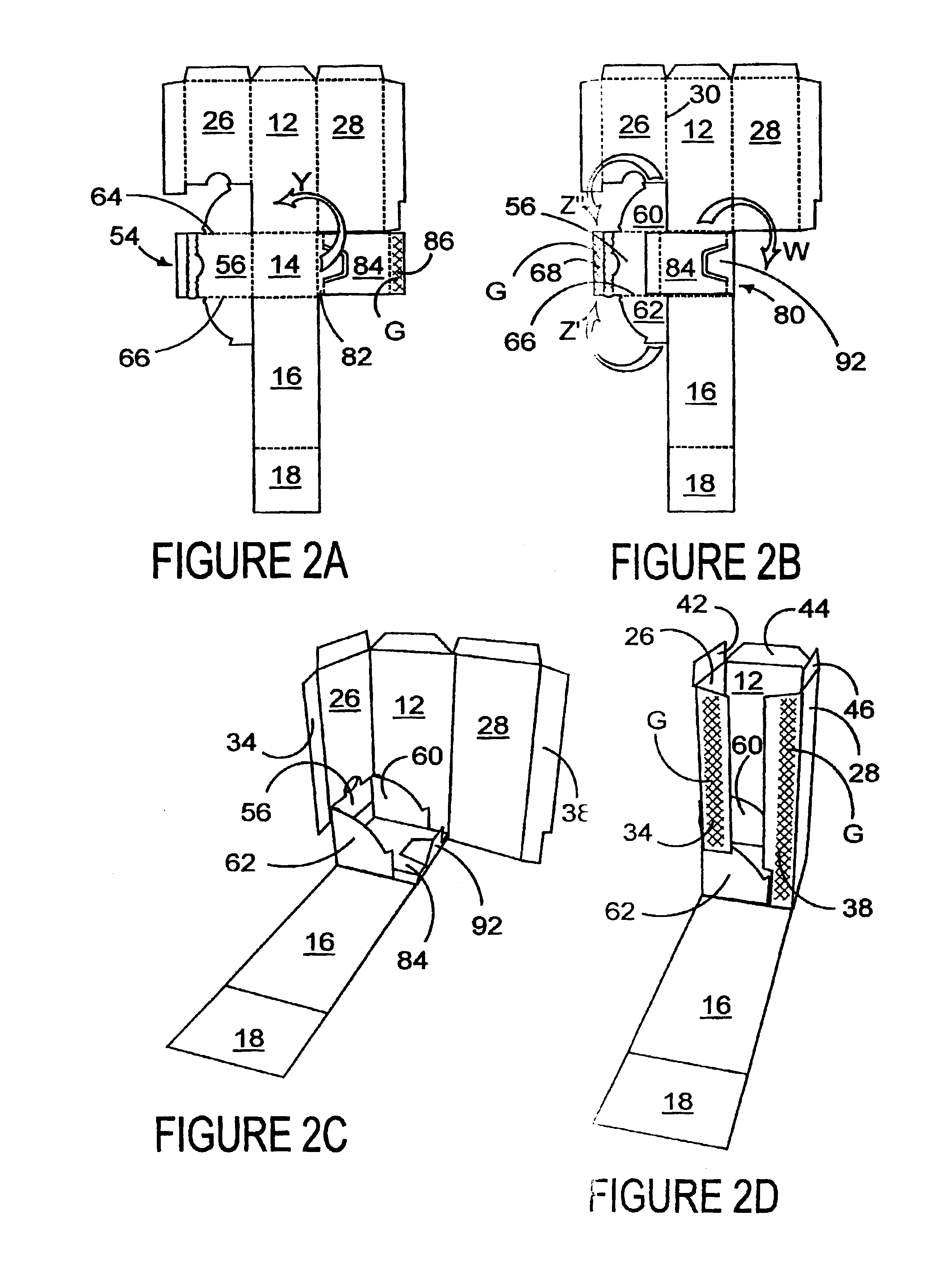
A carton and blank for forming a carton for accommodating one or more articles which carton is provided with an access structure for the removal of articles from within the carton. The access structure comprises a closure panel hinged to a carton wall for forward and backward pivotal movement and a movable platform hinged to the closure panel for moving the contents of the carton forward for their removal in response to the forward pivotal movement of the closure panel.
Owner:MEADWESTVACO PACKAGING SYST LLC
Hydrocarbon well information portal
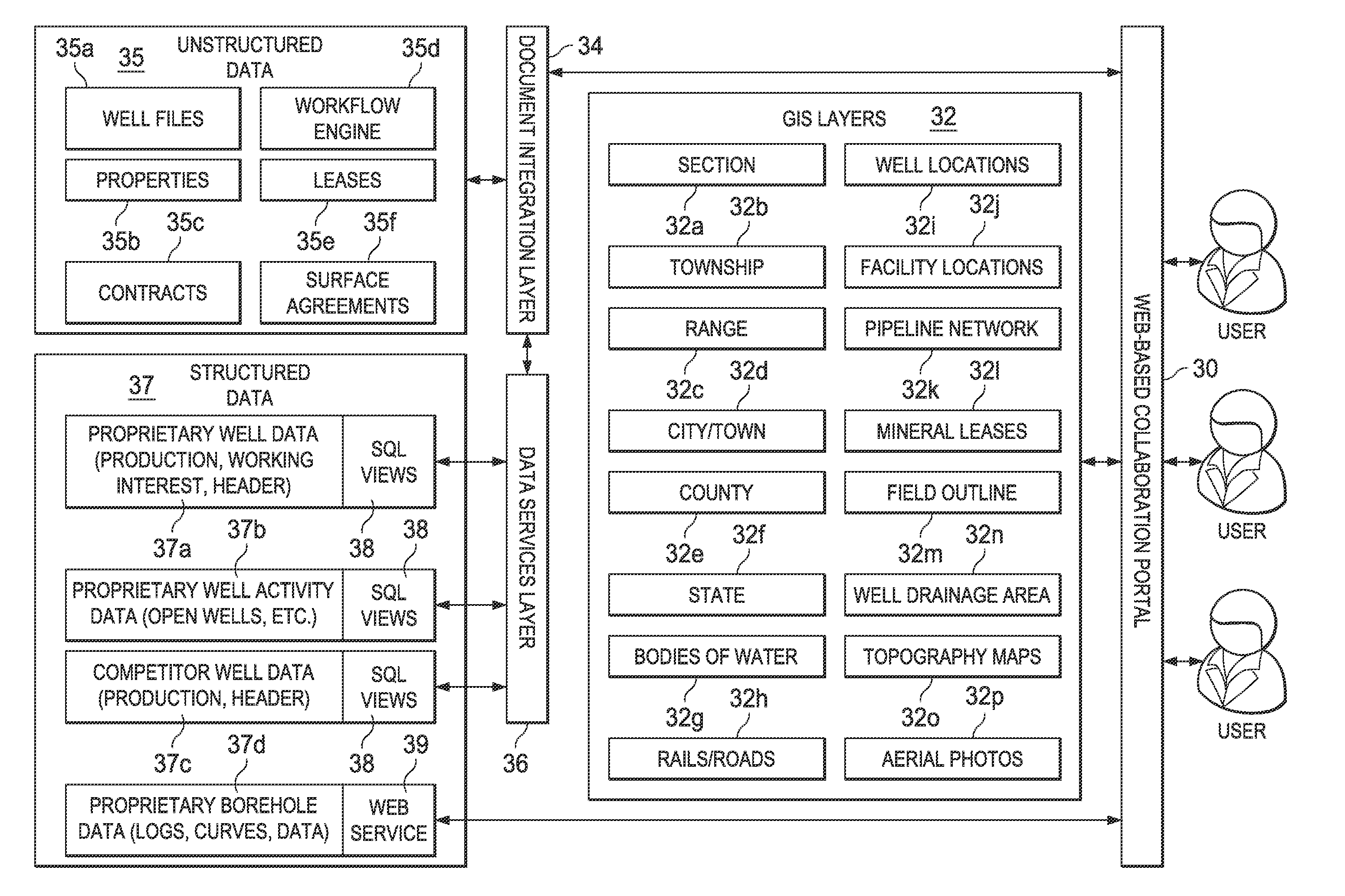
ActiveUS20120054270A1Easy accessEasy to manufactureMultiple digital computer combinationsOffice automationAccess structureUnstructured data
A networked information management system and architecture for managing files and documents pertaining to oil and gas wells and properties. On request by an authenticated user, a client workstation displays geographical information system (GIS) layers, via a web collaboration portal, for a region of the earth at which wells or properties may be located. The wells or properties within the displayed region enable links to documents or files associated with those wells and properties, and by way of which the system user can access the documents and files. Both structured and unstructured data elements can be accessed by the system. A collaboration portal allows for standardized access to the data, and also for simultaneous or collaborative access to the data. Workflow management capability is also implemented.
Owner:BP CORP NORTH AMERICA INC
Run-time optimizations of queries with SQL spreadsheet
ActiveUS7761403B2Digital data processing detailsText processingAccess structureTheoretical computer science
Described herein are optimizations and execution strategies for spreadsheet extensions to SQL. The partitioning of data, as specified in a spreadsheet clause, provides a way to parallelize the computation of spreadsheet and to provide and improve scalability. Even if the partitioning is not explicitly specified in the spreadsheet clause, the database optimizer can automatically infer the partitioning in some cases. Efficient hash based access structures on relations can be used for symbolic array addressing, enabling fast computation of formulas. When rewriting SQL statements, formulas whose results are not referenced in outer blocks can be removed from the spreadsheet clause, thus removing unnecessary computations. The predicates from other query blocks can be moved inside query blocks with spreadsheets clauses, thus considerably reducing the amount of data to be processed. Conditions for validity of this transformation are given.
Owner:ORACLE INT CORP
Substrate container with fluid-sealing flow passageway
ActiveUS7328727B2Efficiently provideAvoid insufficient lengthLiquid fillingSemiconductor/solid-state device manufacturingAccess structureEngineering
A substrate container includes an enclosure and an access structure formed in the enclosure and providing fluid access through the enclosure to an interior of the substrate container. The access structure includes an opening and an inner surface. A grommet is situated against the inner surface of the access structure.
Owner:ENTEGRIS INC
Roof penetrating closure structures and systems
The invention provides an environment-accessing structure for providing environmental access to the interior of a building through an aperture in the roof. The environment-accessing structure can provide natural day-lighting by use of a skylight lens as the closure member, or a smoke vent which can be opened and closed. Such smoke vent can be transparent or translucent to natural sunlight, or can be opaque. Such environment-accessing structure is installed in an aperture in a metal roof. The system limits opportunity for water leakage from the outside environment. The environment-accessing structure includes a rail and closure structure adapted to be supported by adjacent rib elevations of adjacent roof panels, a closure panel adapted to be supported on the rail and closure structure, and a diverter which seals a cut away portion of the rib structure and diverts water laterally away from the rail and closure structure.
Owner:T&M INVENTIONS
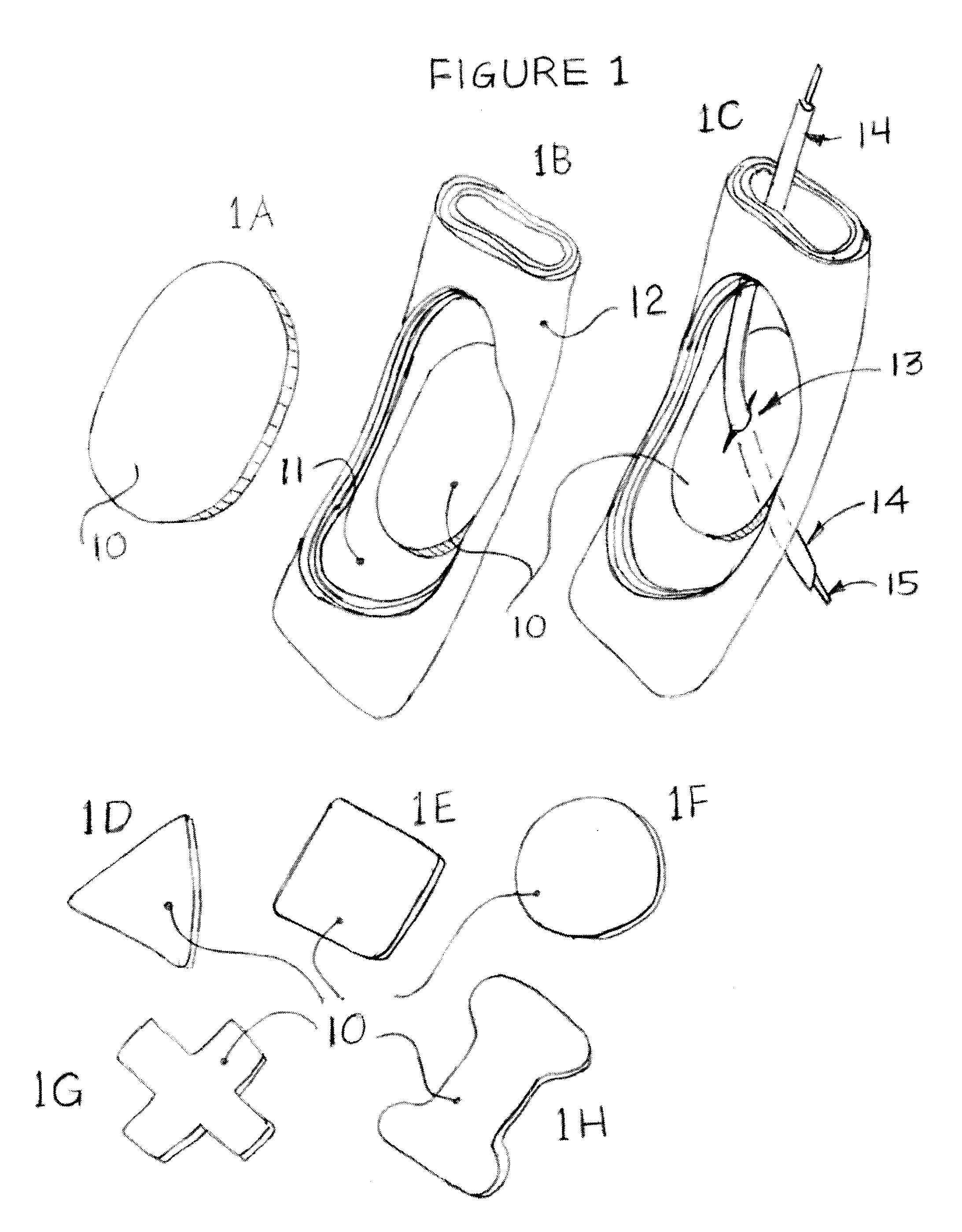
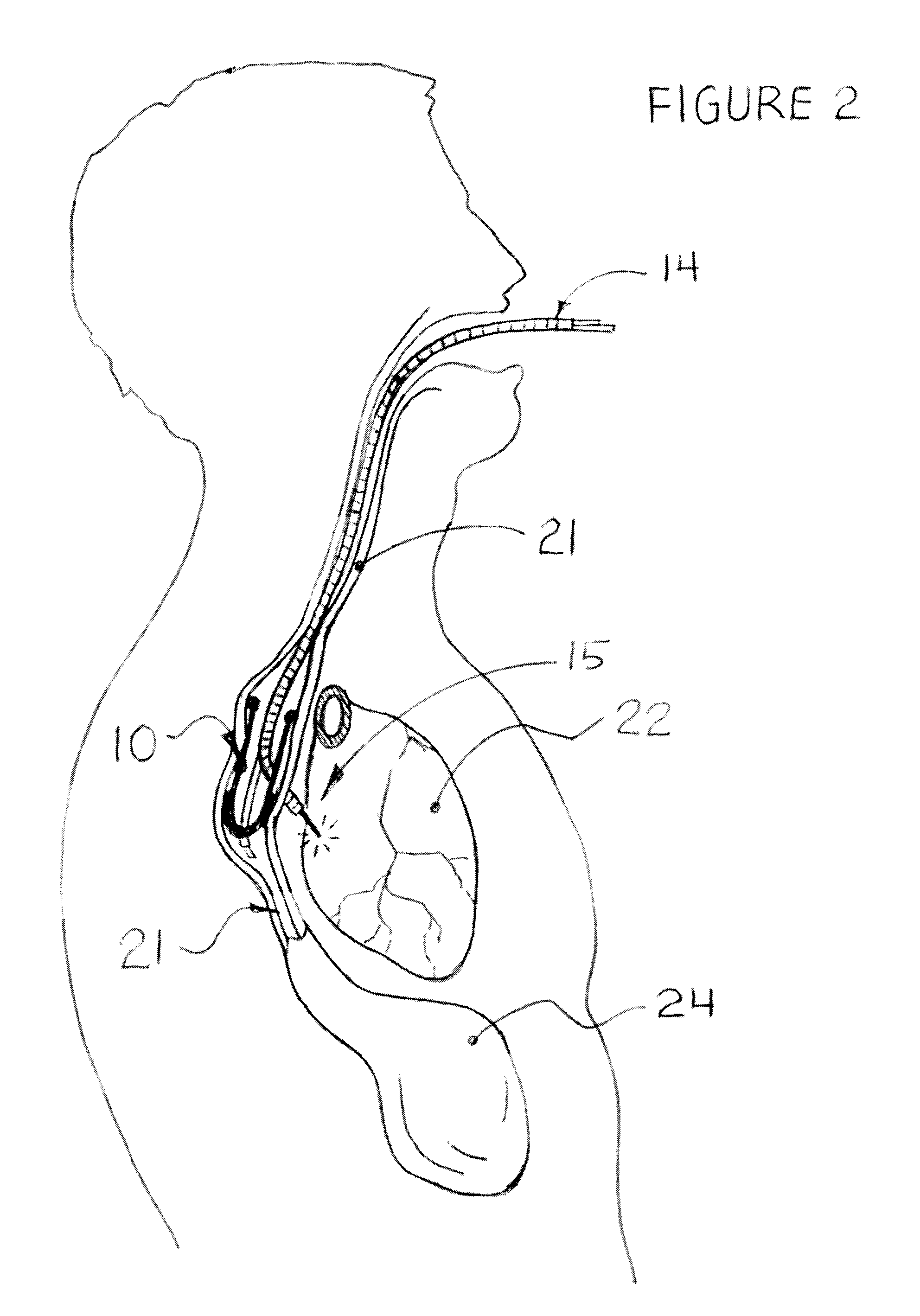
Methods and apparatus for transesophageal microaccess surgery
InactiveUS20100036197A1Avoid pollutionPrecise positioningBronchoscopesLaryngoscopesNODALOesophageal tube
The current invention describes methods of transesophageal access to the neck and thorax to perform surgical interventions on structures outside the esophagus in both the cervical and the thoracic cavity. It describes a liner device made of a complete or partial tubular structure, or a flat plate, the liner having means to facilitate creation of a side opening, which may include a valve. The liner with its side opening form a port structure inside the esophageal lumen. The port structure allows elongated surgical devices to pass through a perforation across the full thickness of the esophageal wall to outside location, in a controlled way. The elongated surgical devices can be diagnostic scopes, therapeutic scopes, manual elongated surgical devices, robotic arms or the like. After being deployed outside the esophagus, the surgical devices can access structures outside the esophagus, in the neck and thorax in 360 degrees of freedom around the esophageal circumference. These structures can be bony, cartilaginous, spinal, vascular, soft tissue, deep tissues, lymph nodal, cardiac, pulmonary, tracheal, nervous, muscular or diaphragmatic, skin and subcutaneous tissues of the neck, skin and subcutaneous tissues of the anterior chest wall, skin and subcutaneous tissues of the skin of the back, and skin and layers of the breast.
Owner:MICROACCESS
Configurator using structure and rules to provide a user interface
ActiveUS7650296B1Buying/selling/leasing transactionsSpecial data processing applicationsAccess structureWorld Wide Web
A configurator using structure and rules to provide a user interface. According to one embodiment of the invention, a customizable product class is created. The customizable product class includes a set of one or more attributes to define the customizable product class. A component product class is added to the customizable product class, where the component product class is a subclass of the customizable product. A customizable class rule is associated to the customizable product class, the customizable class rule including expressions which provide conditions on component products added to the customizable product. A customizable UI is mapped to the customizable product class, where the customizable UI provides access structure to the configurator.
Owner:ORACLE INT CORP
Configurator using structure to provide a user interface
A method and apparatus system for generating a configurator. According to one embodiment of the invention, a customizable product class is created. The customizable product class includes a set of one or more attributes to define the customizable product class. A component product class is added to the customizable product class, where the component product class is a subclass of the customizable product. A customizable UI is mapped to the customizable product class, where the customizable UI provides access structure to the configurator.
Owner:ORACLE INT CORP
Multi-mechanism encryption method used in lattices for supporting strategy hiding
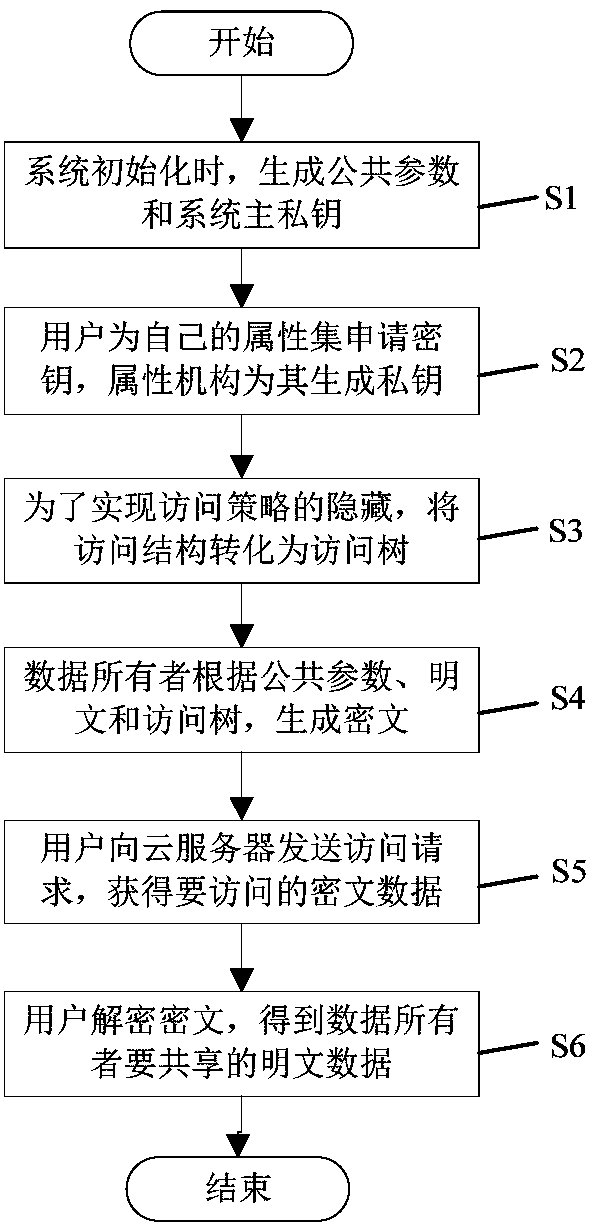
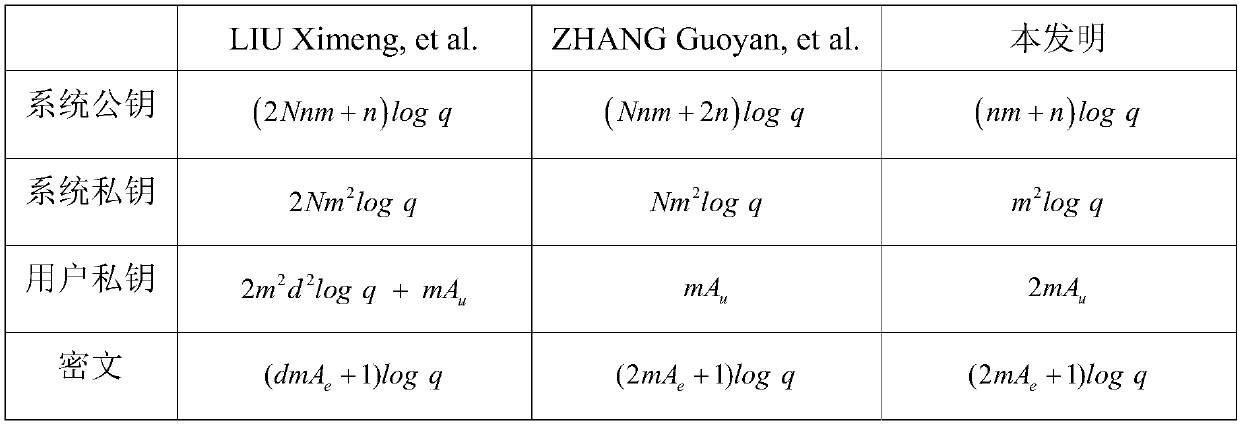
InactiveCN108512662AImprove efficiencyResistant to Quantum AttacksKey distribution for secure communicationPlaintextAccess structure
The invention discloses a multi-mechanism encryption method used in lattices for supporting strategy hiding. The multi-mechanism encryption method comprises steps that S1, during system initialization, a public parameter and a system main private key are generated; S2, a user applies for a cipher key for own attribute, and an attribute mechanism is used to generate a private key according to the public parameter, the system main private key, and the attribute set of the user; S3, an access structure is converted into a corresponding access tree to realize complete hiding of an access strategy;S4, a data owner is used to generate the ciphertext data according to the public parameter, a plain text, and the converted access tree, and the ciphertext data is uploaded to a cloud server for storage; S5, the user transmits an access request to the cloud server to acquire the ciphertext data stored in the cloud server; S6, the user uses the private key acquired from the attribute mechanism todecrypt the ciphertext data acquired from the cloud server, and the plaintext of the data owner is acquired, and related subsequent operations are carried out. The multi-mechanism encryption method isadvantageous in that the efficiency of the system is improved, and quantum attacks are prevented, and user privacy is effectively improved.
Owner:SHANGHAI MARITIME UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com