Patents
Literature
698results about How to "Improve information security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Voice wake-up method and apparatus, terminal, and processing method thereof
InactiveCN105575395AIncrease wake rateImprove experienceSpeech recognitionSleep stateWord identification
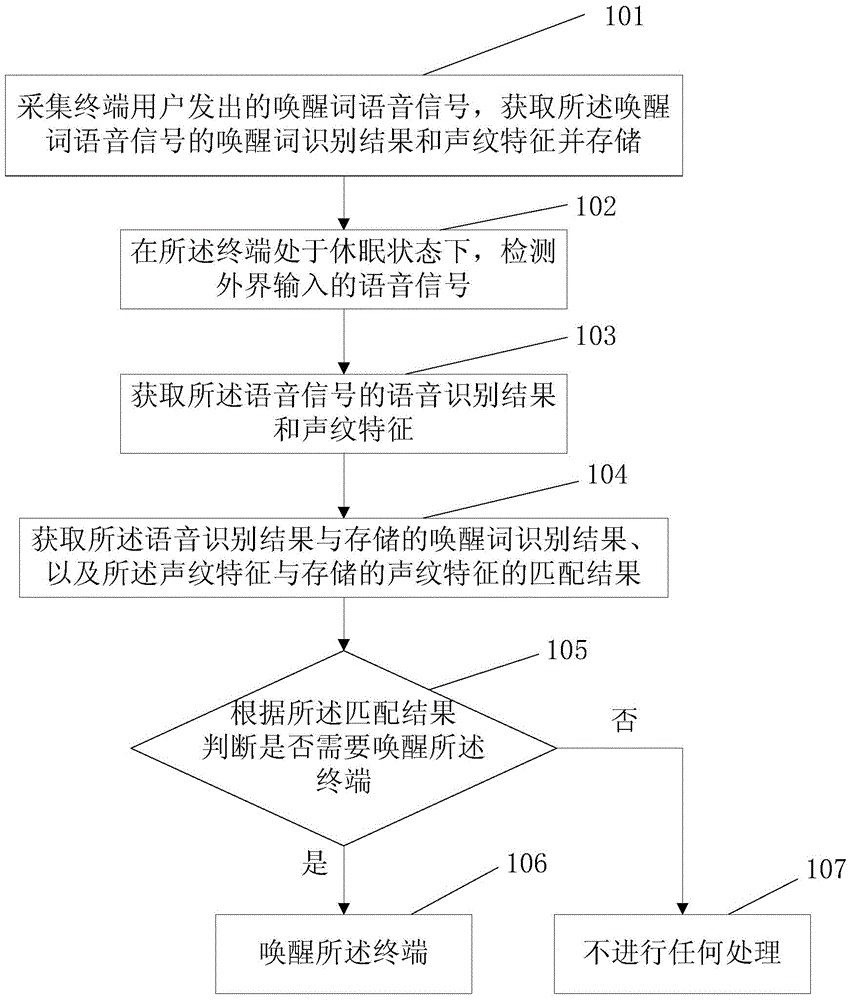
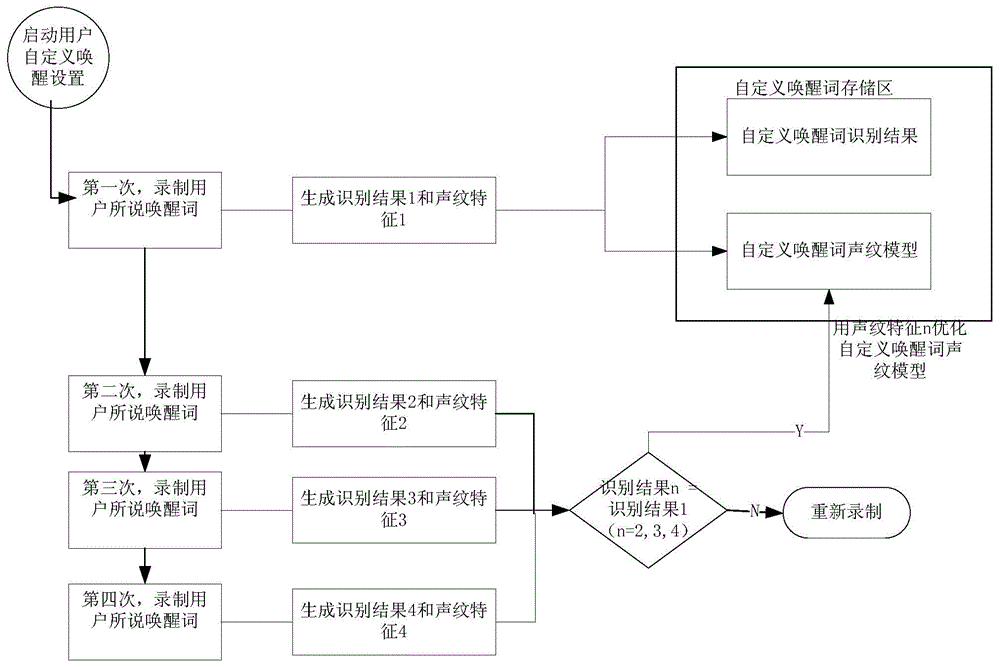
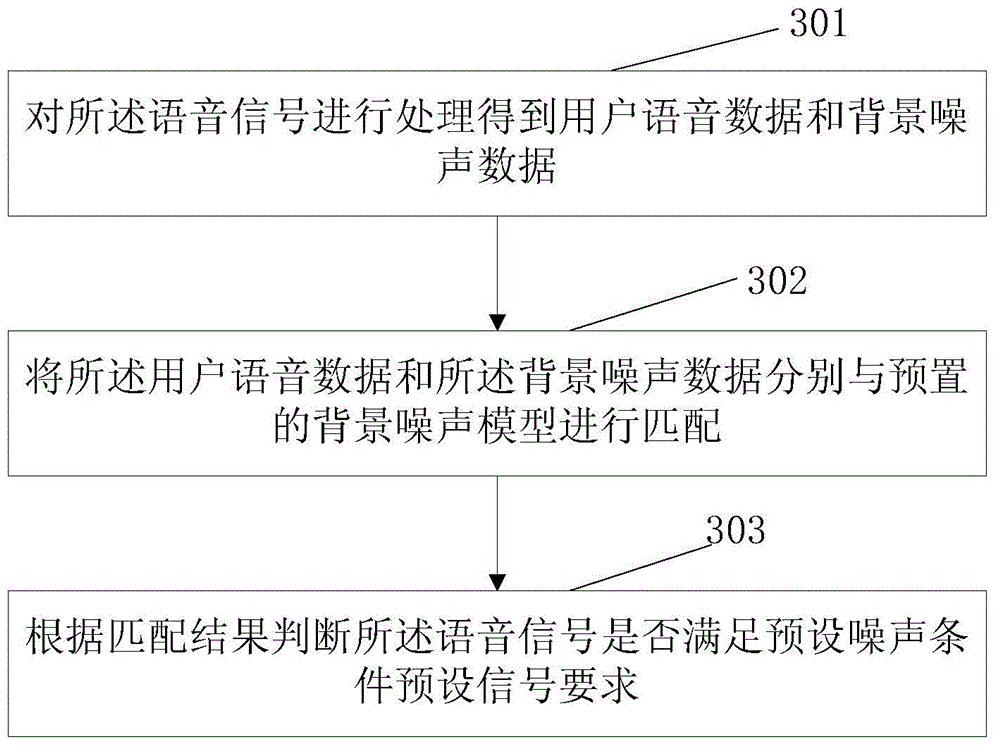
The invention discloses a voice wake-up method and apparatus, a terminal, and a processing method thereof. The voice wake-up method comprises: a wake-up word voice signal sent out by a terminal user is collected and a wake-up word identification result and a vocal print feature of the wake-up word voice signal are obtained and stored; when a terminal is in a sleep state, a voice signal inputted externally is detected; a voice identification result and a vocal print feature of the voice signal are obtained; the voice identification result and the stored wake-up word identification result as well as a matching result of the vocal print feature and the stored vocal print feature are obtained; and according to the matching result, whether the terminal needs to be woken up is determined; and if so, the terminal is woken up. With the method, technical problems of low user wake-up rate, high wrong wake-up rate, and poor user experience according to the existing voice wake-up technology are solved.
Owner:ZTE CORP
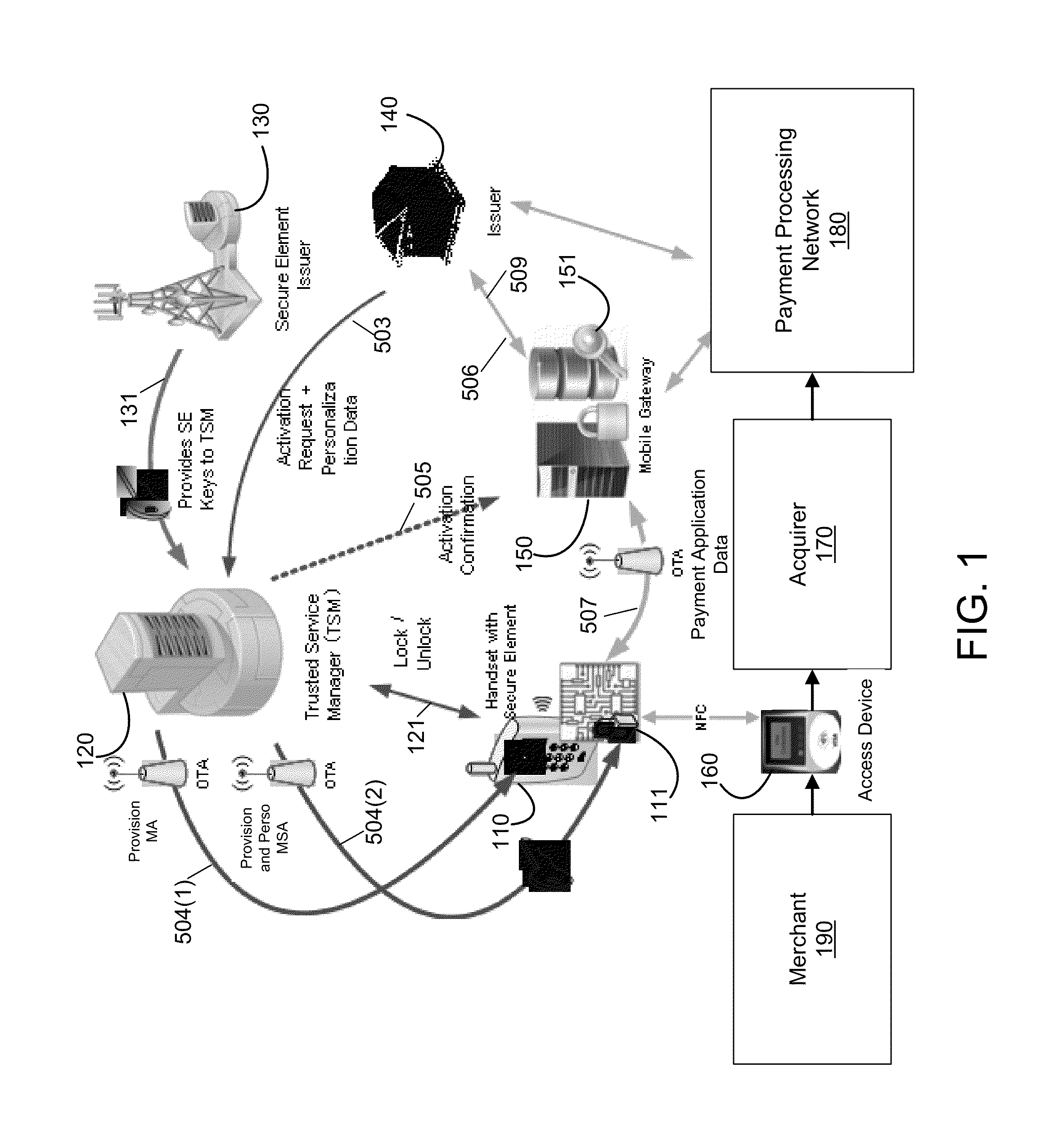
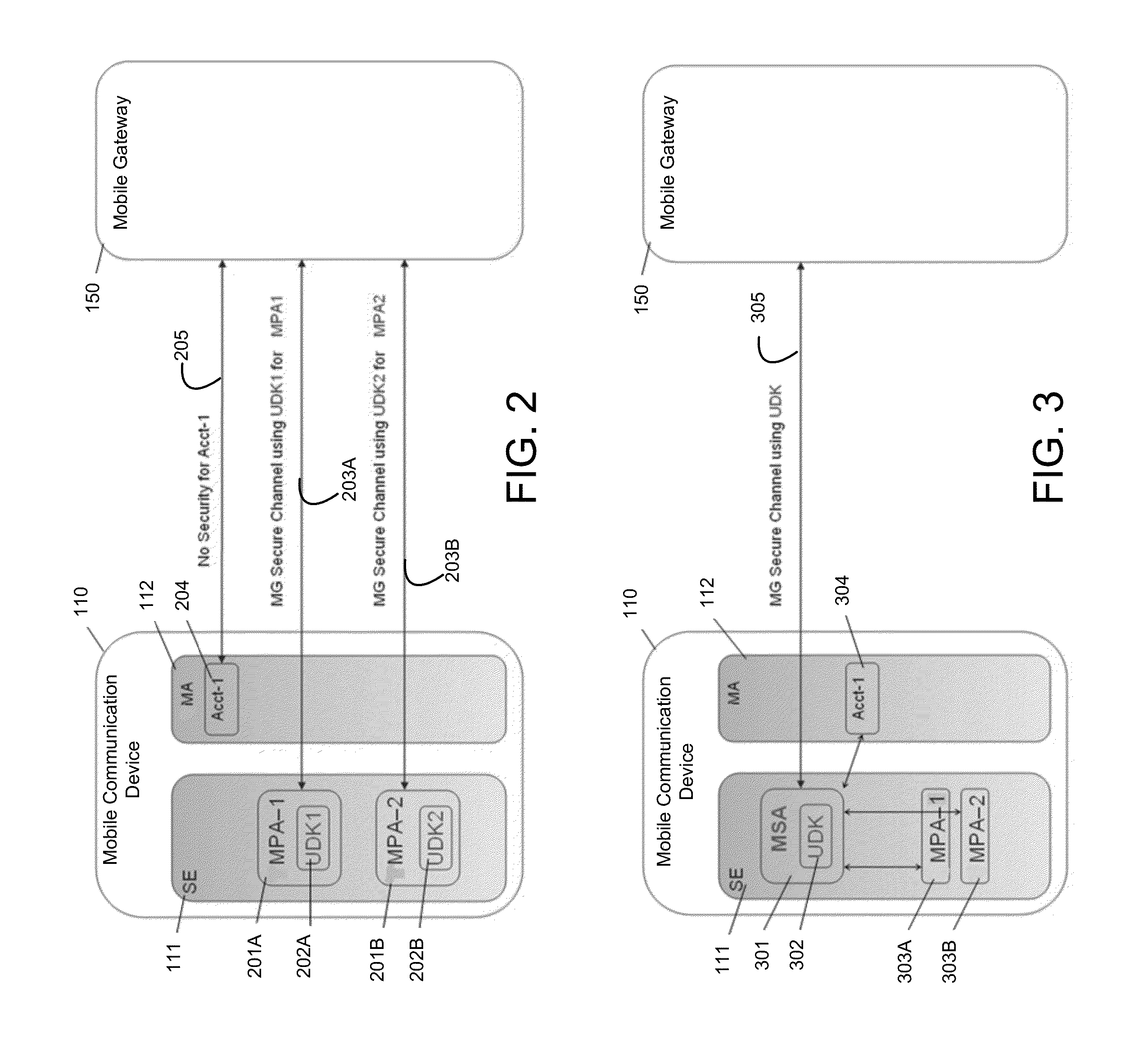
Mobile Device With Secure Element
InactiveUS20130024383A1Improve information securityEfficiently authenticatingSecurity arrangementSecuring communicationUpgradeMobile payment
Embodiments of the present invention are directed to methods, systems, and apparatuses for securely communicating issuer updates, upgrades, and allowing configuration of payment-related applications on a mobile communication device using a mobile security application. One embodiment is directed to a method of using a mobile communication device comprising a mobile security application, a key associated with the mobile security application, a first mobile payment application in communication with the mobile security application and a second mobile payment application in communication with the mobile security application. The method includes communicating, by the first mobile payment application in the mobile communication device with a mobile gateway, in a first communication, wherein the first communication is encrypted using the key and communicating, by the second mobile payment application in the mobile communication device with a mobile gateway, in a second communication, wherein the second communication is encrypted using the key.
Owner:VISA INT SERVICE ASSOC
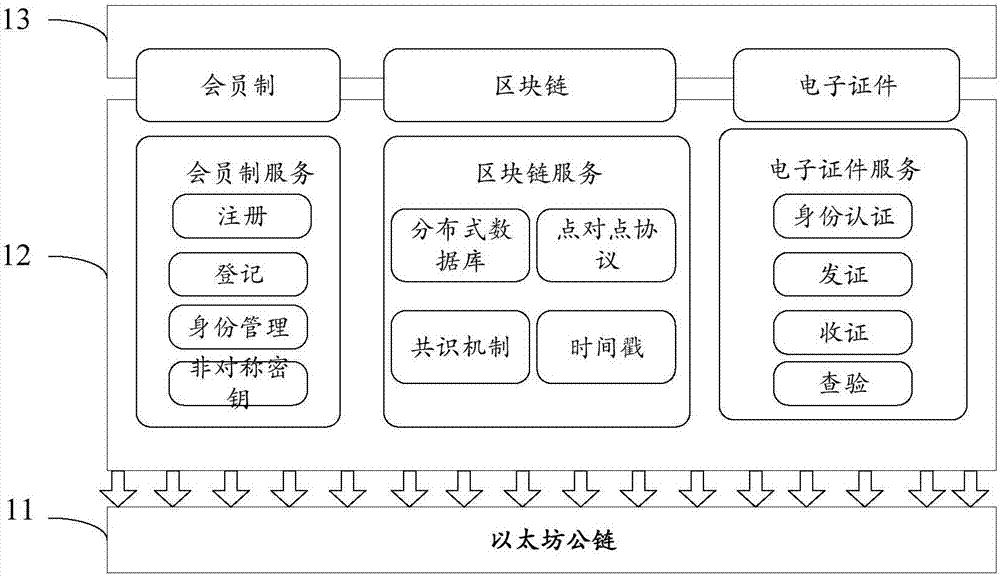
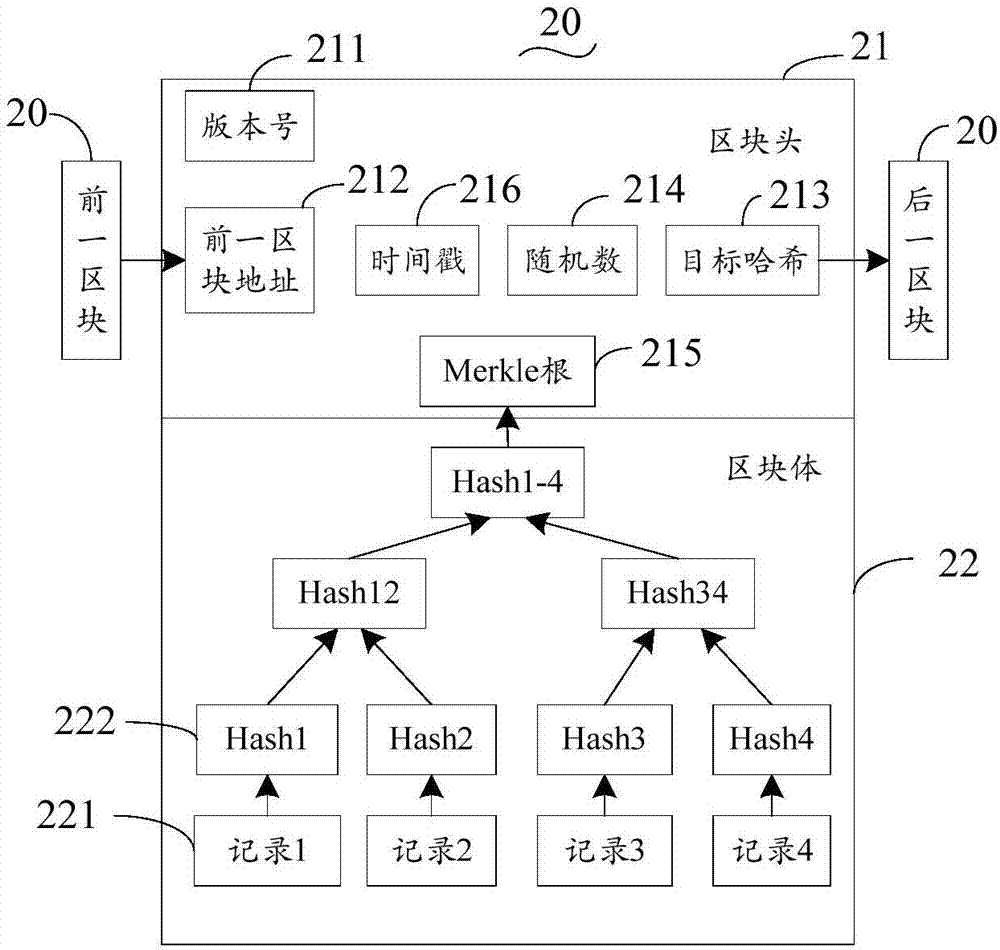
Electronic certificate management method and related equipment
ActiveCN107231351ARealize distributed managementImprove storage reliabilityMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesChain networkInformation security
The invention discloses an electronic certificate management method and related equipment. The method comprises the steps as follows: the electronic equipment processes an electronic certificate in response to a received processing command; an encrypted processing record is broadcasted into a block chain network, thus allowing a node of the block chain network to store the encrypted processing record into a block chain of the block chain network. According to the scheme of the method provided by the invention, distributed management of the electronic certificate is achieved, storage reliability of the electronic certificate is improved, the risk of tampering or leaking certificate information is reduced, and information security and credibility of the electronic certificate are effectively ensured.
Owner:YGSOFT INC
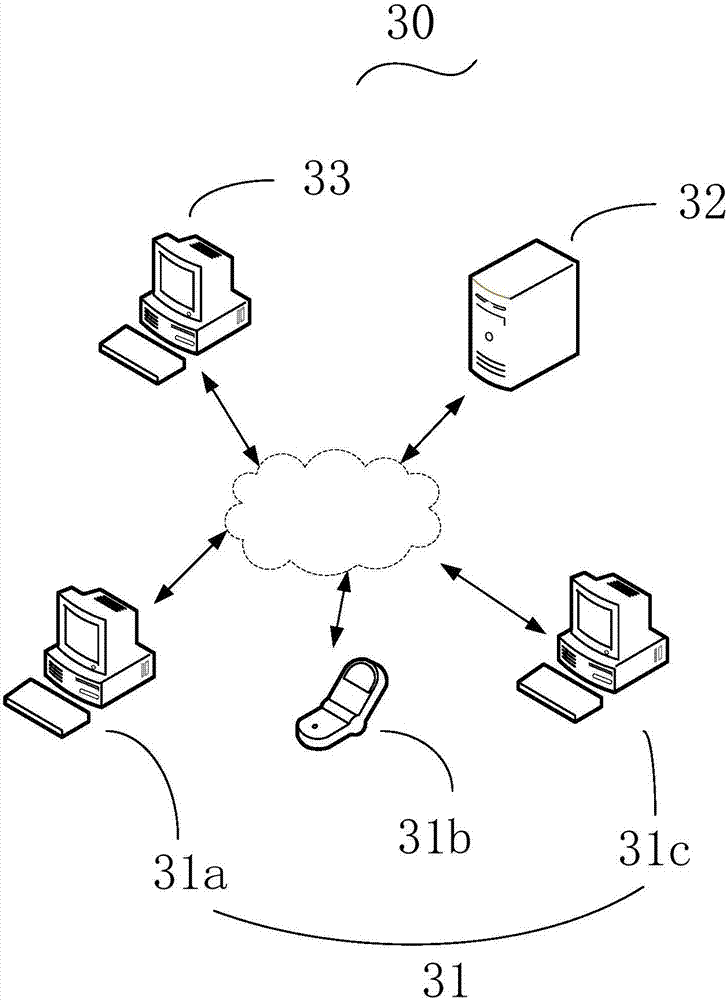
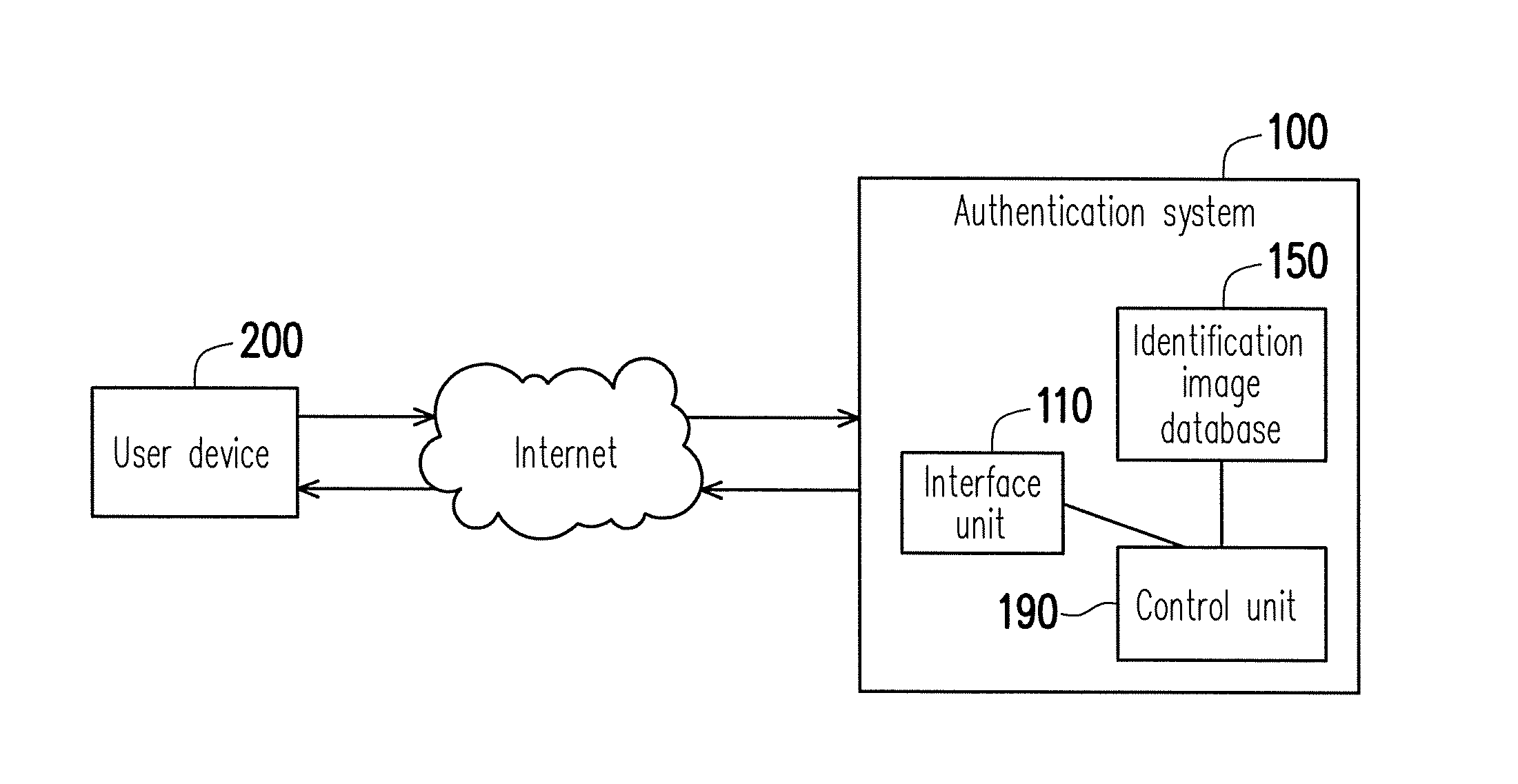
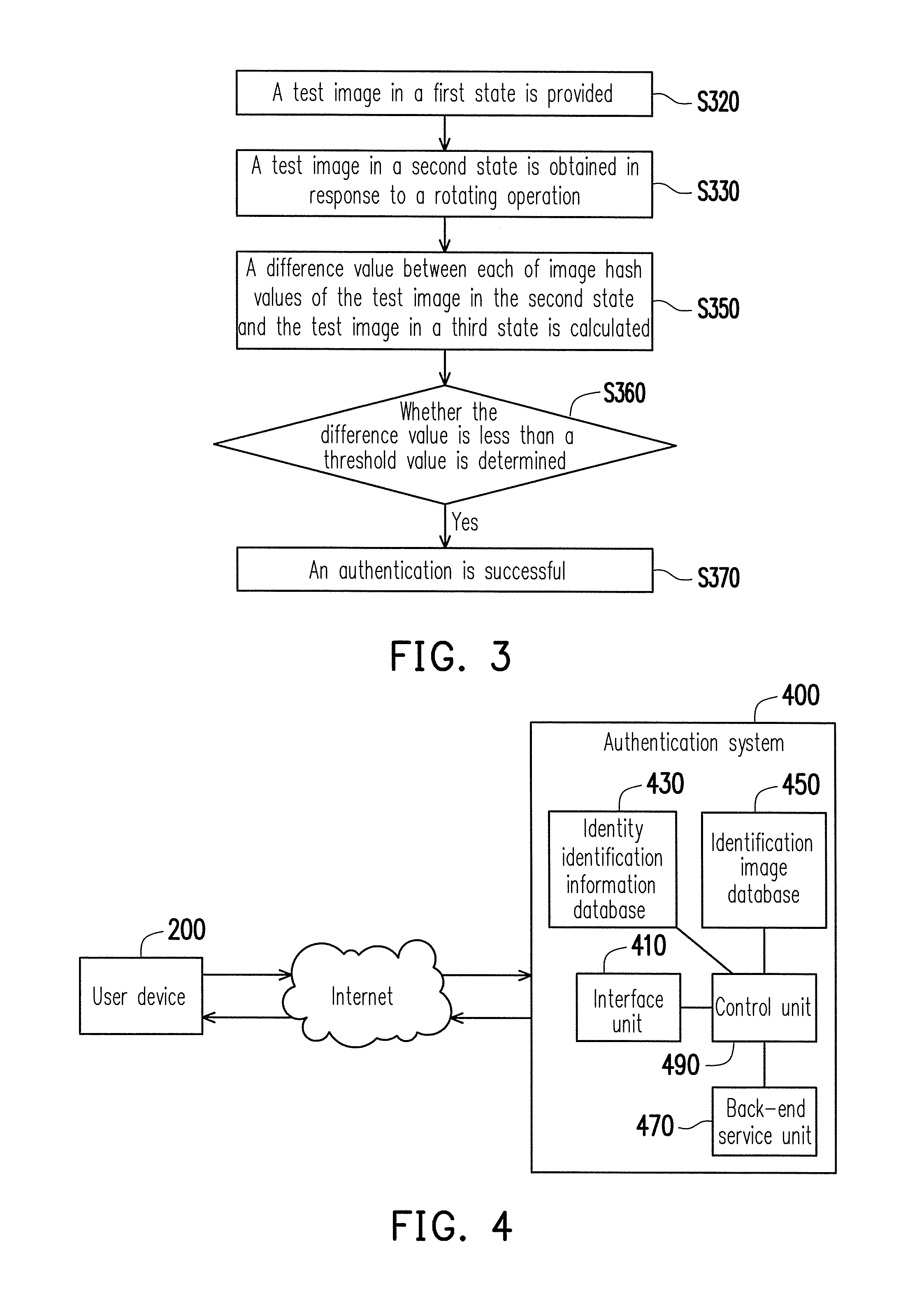
Authentication method and authentication system
InactiveUS20150012988A1Improve information securityDigital data processing detailsMultiple digital computer combinationsComputer hardwareAuthentication system
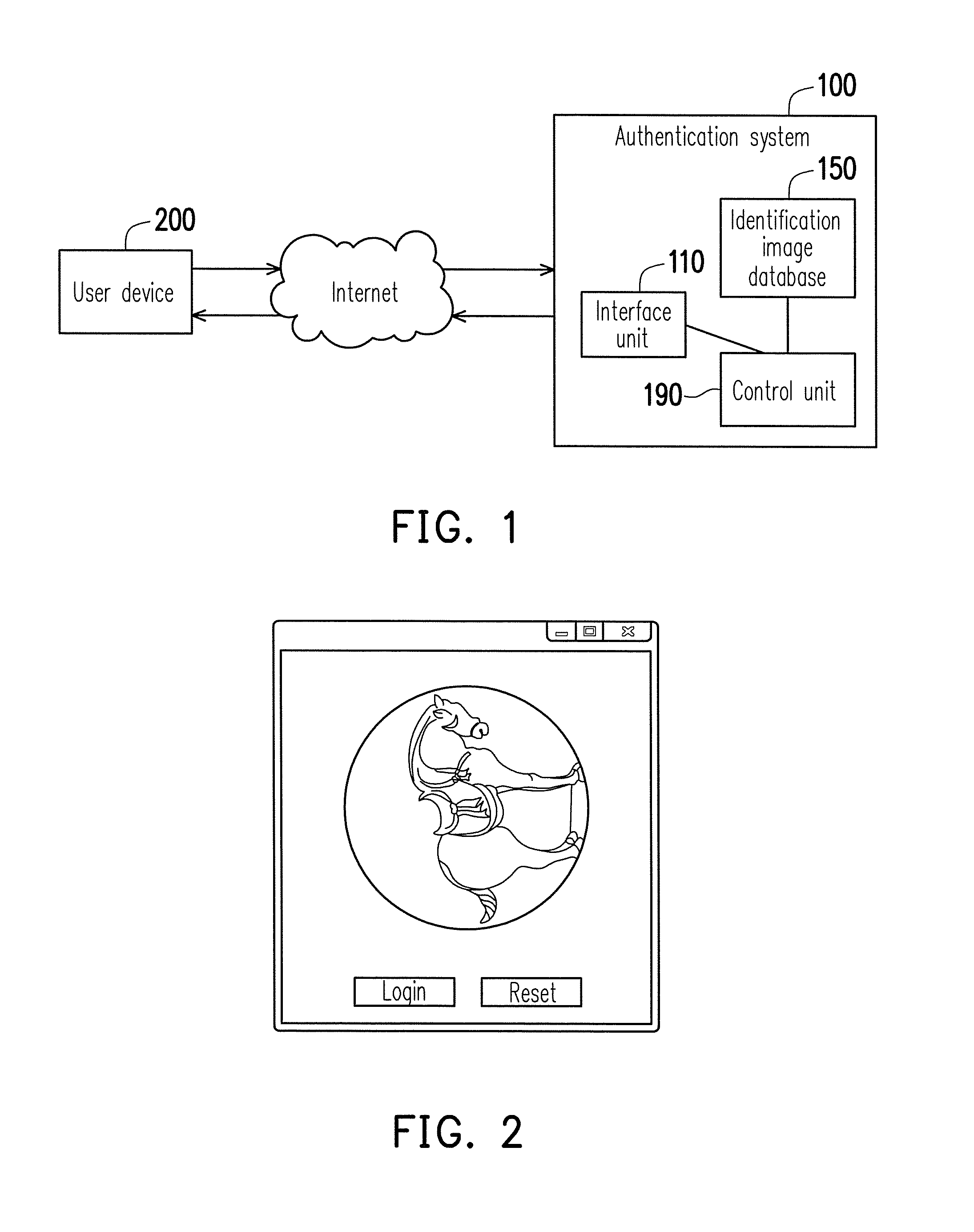
An authentication method and an authentication system are provided. The authentication method includes the following steps. Providing a test image in a first state. Obtaining the test image in a second state in response to a rotating operation. Calculating a difference value between each of image hash values of the test image in the second state and the test image in a third state. Determining that an authentication is successful if the difference value is less than a threshold value, wherein the third state is a state in which the test image is up-right.
Owner:NAT TAIWAN UNIV OF SCI & TECH
Credible government administration data sharing network system and sharing method based on block chain
InactiveCN108234457AIncrease credibilityAchieve comprehensive imputationData processing applicationsTransmissionPublic accountChain network
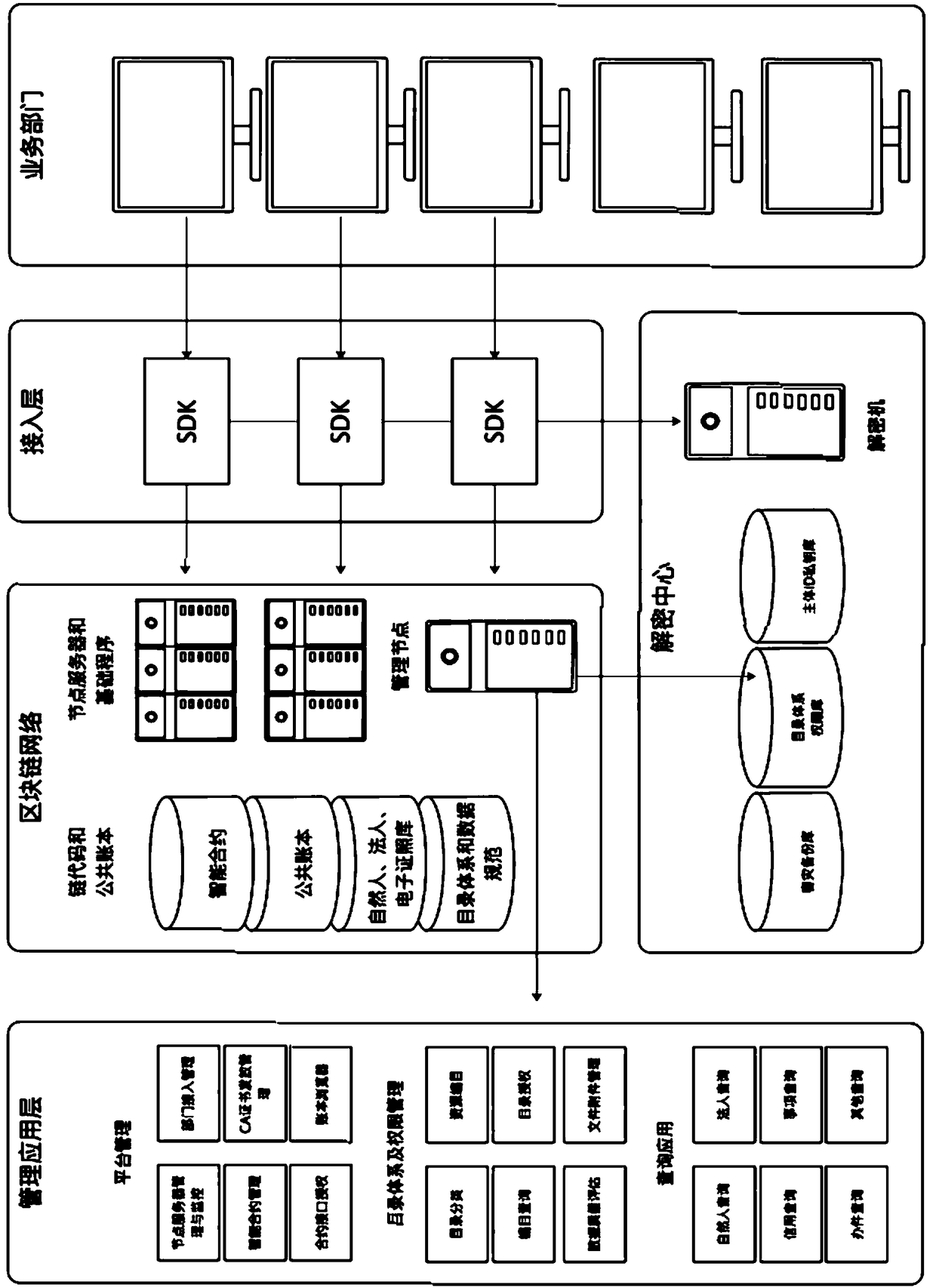
The invention provides a credible government administration data sharing network system based on a block chain. The system comprises service departments, an access layer and a block chain network, wherein the service departments perform information interaction with the block chain network via the access layer; the block chain network comprises a plurality of node servers, and the node servers arecorrespondingly connected with the service departments; the block chain network also comprises chain codes and a public account book based on the chain codes, wherein the public account book is used for dispersedly recording and storing the data of the service departments on the corresponding node servers, and each node server comprises the full amount of service data; the node servers are also separately connected with a management application platform used for interacting the data with the outside and a decryption server used for decrypting the data. The system provided by the invention hasthe advantages of high sate security, strong stability and high degree of opening.
Owner:苏州涞泽信息科技有限公司
Imaging apparatus
ActiveUS20110233383A1Simply manufactureDownsize useSolid-state devicesMaterial analysis by optical meansThin fingersAperture array
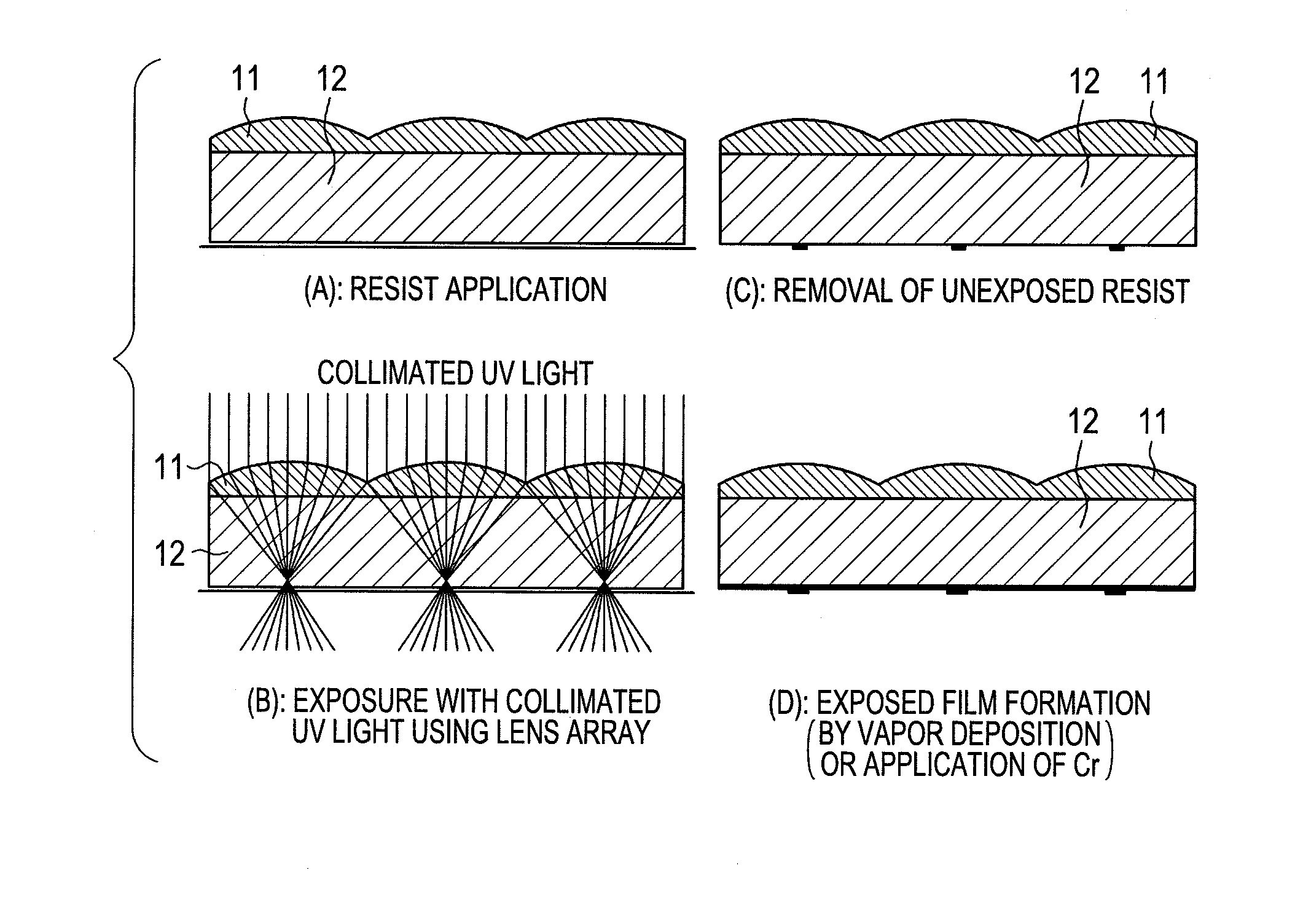
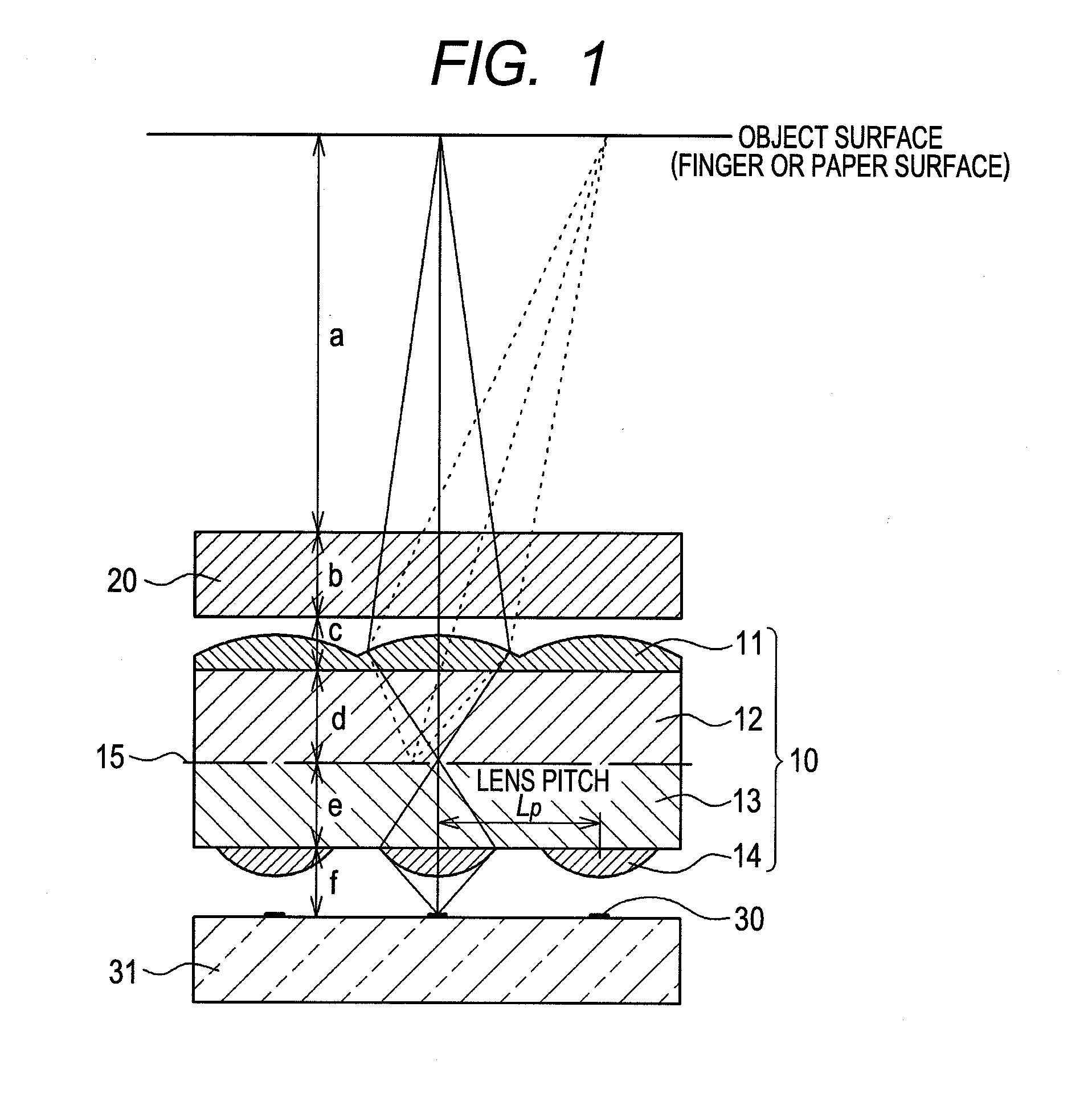
An imaging apparatus is realized which enables a thin finger vein authentication apparatus having a thickness installable in a portable information device. A light beam emitted from an object passes through a visible light cut-off filter 20 and enters a pre-focus lens array 11. The pre-focus lens array 11 focuses the light beam on an opening of a micro aperture array 15. The light beam passed through the micro aperture array 15 diverges, but it is focused with the post-focus lens array 13 on the light detection device 30. With this structure, a thin imaging apparatus can be obtained with maintained resolution, and a finger authentication apparatus installable in a portable information device can be realized.
Owner:PANASONIC LIQUID CRYSTAL DISPLAY CO LTD +1
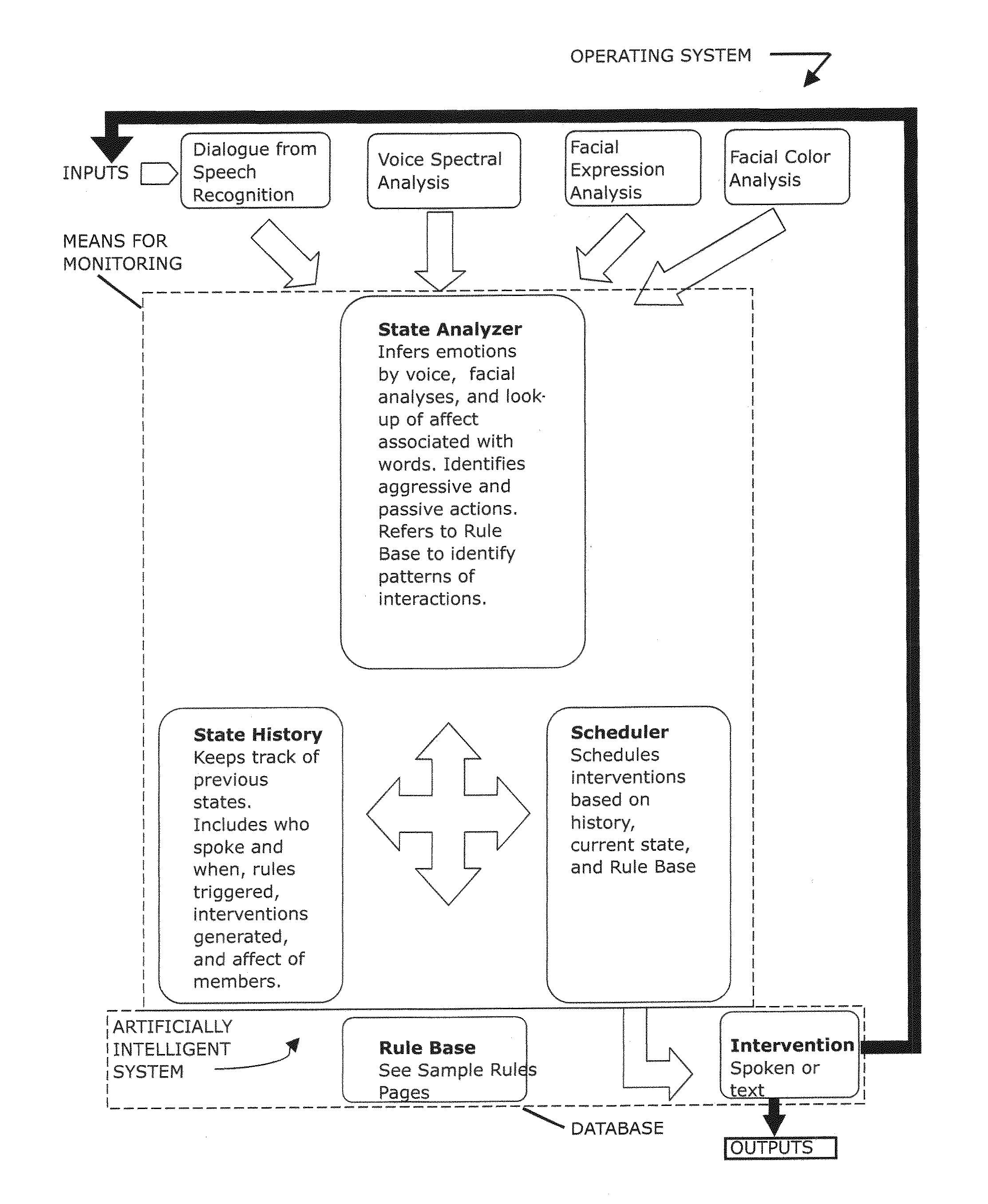
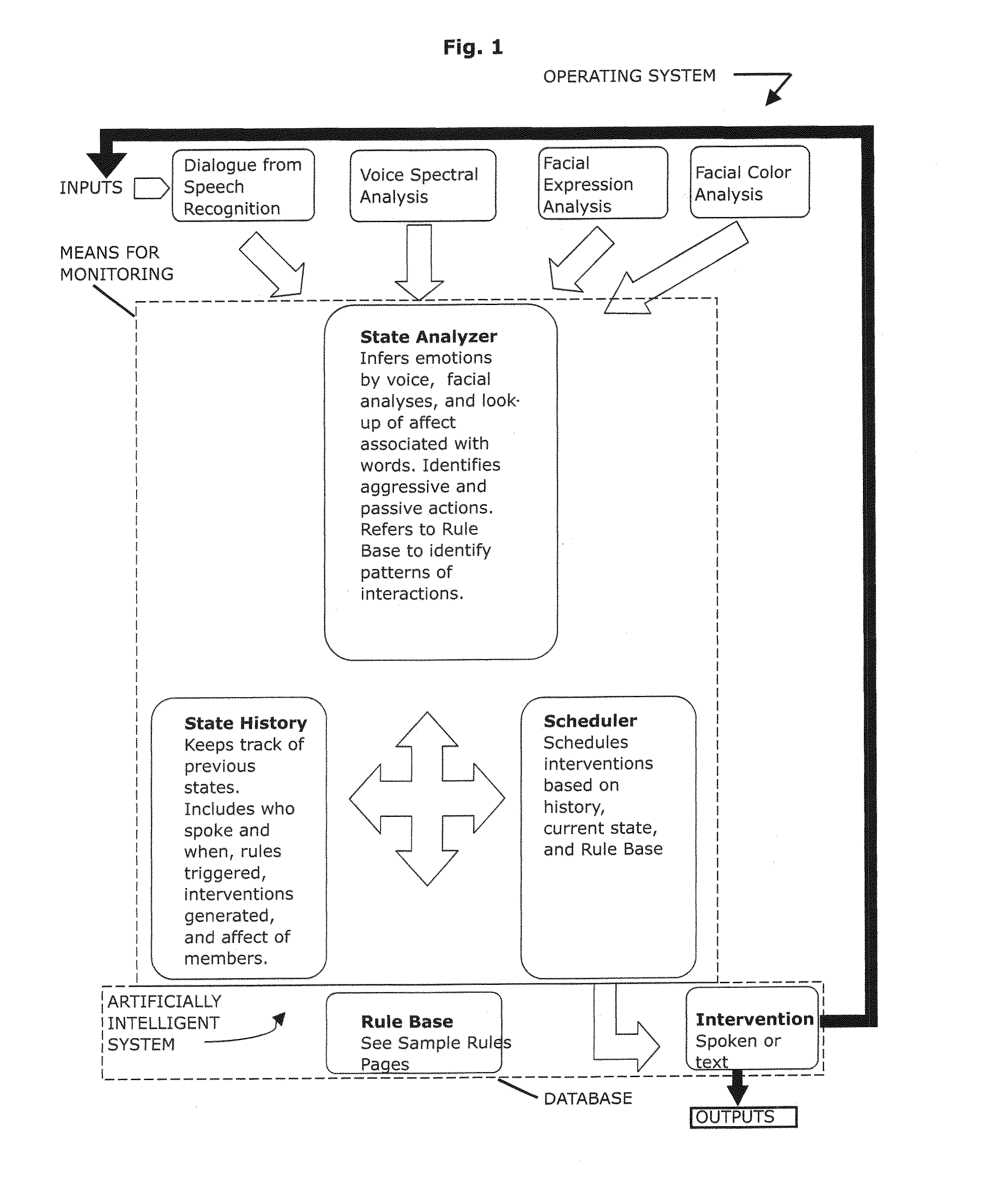
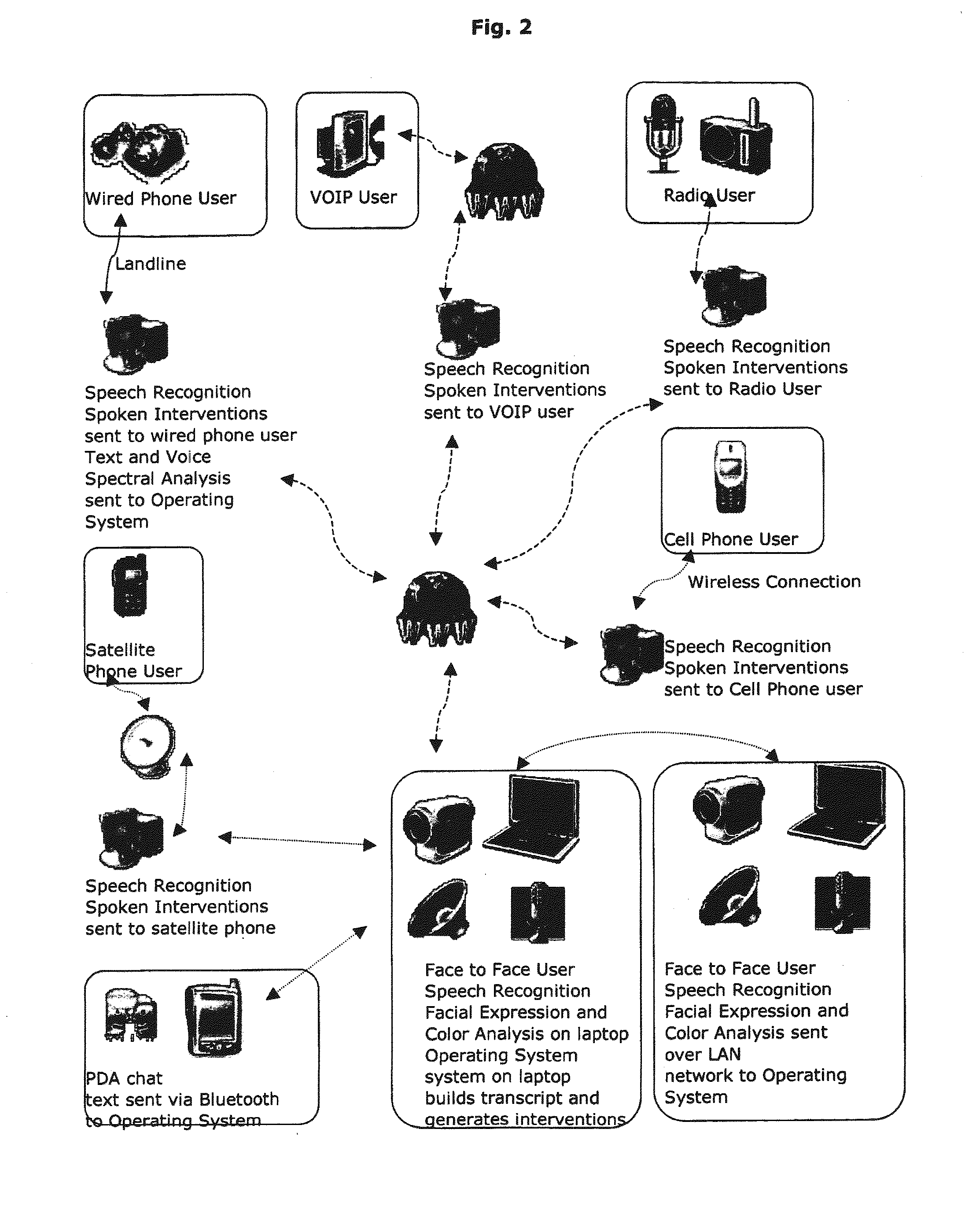
Method, artificially intelligent system and networked complex for facilitating group interactions
ActiveUS8898098B1Facilitate communicationEliminate needDigital computer detailsOffice automationDecision takingRule-based system
An artificially intelligent or rule-based system to assist teams or groups become more effective by improving the communication process between members of the team or group. The system helps members share information, negotiate more effectively and make better group decisions. The system is designed to allow users to provide feedback to the system regarding undetected emotional feelings of any one user to all users of the system.
Owner:LUECHTEFELD RAY ANTHONY
Server, terminal and authority management and permission method
InactiveCN103514397AAvoid cumbersomeImprove experienceDigital data authenticationPlatform integrity maintainanceRights managementApplication software
The invention discloses a server, a terminal and an authority management and permission method. Identification information of an application program to be inquired from the terminal is obtained; an optimal and reasonable permission policy corresponding to the application program to be inquired is inquired and obtained according to the identification information, and the permission policy is sent to the terminal. The tedious process of judging the application software program manually by a user is avoided, and a server sends the optimal permission policy to the terminal directly through inquiring. In addition, the terminal conducts permission limitation on the corresponding application program through the obtained reasonable permission policy, manual permission selection of a user is avoided, the terminal obtains the reasonable permission policy automatically to limit the application program, and user experience is further improved. Meanwhile, the reasonable permission policy is used, inaccurate permission judgment of the user is avoided, and information safety of the user is protected.
Owner:XIAN COOLPAD SOFTWARE TECH CO LTD
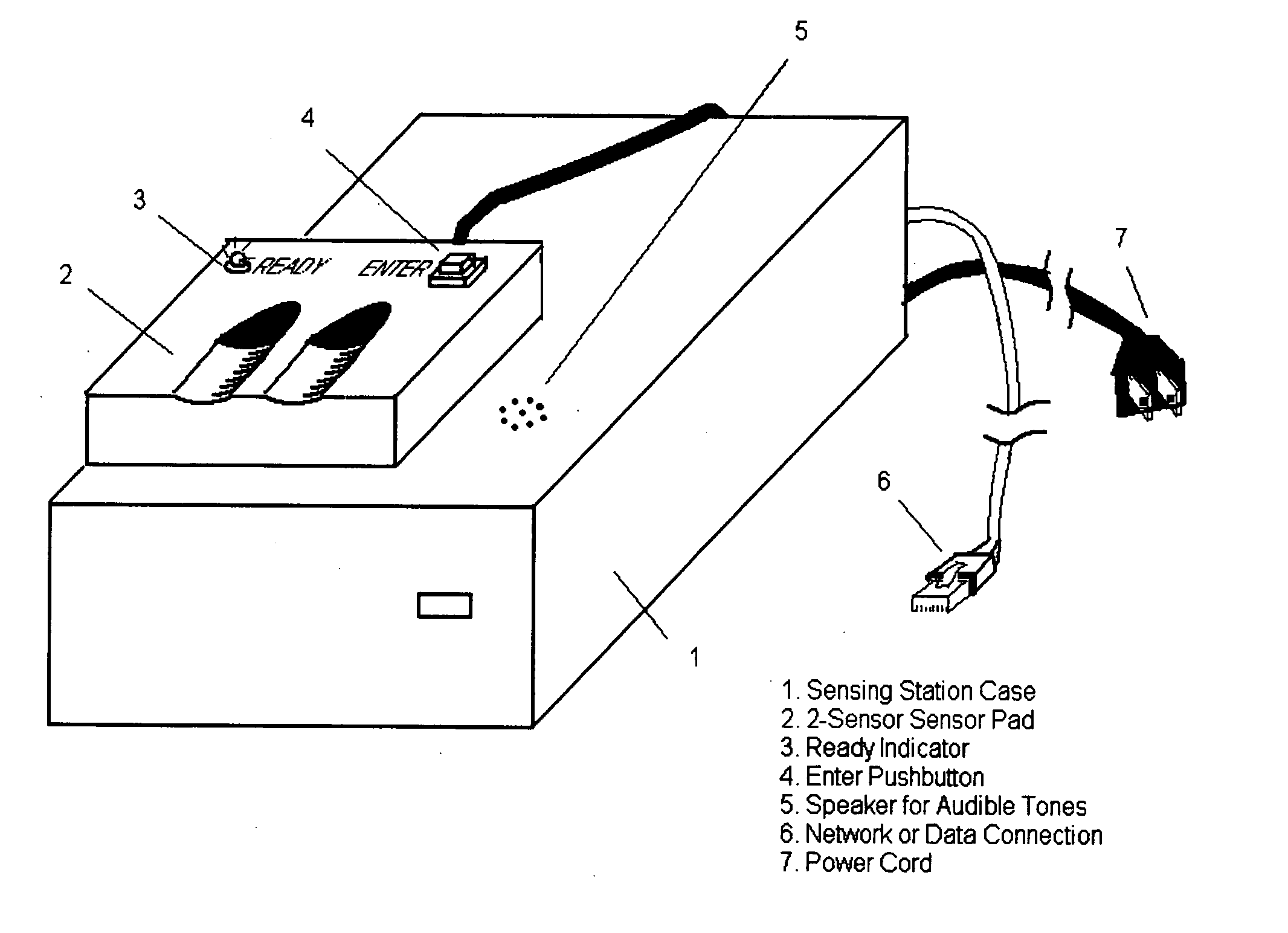
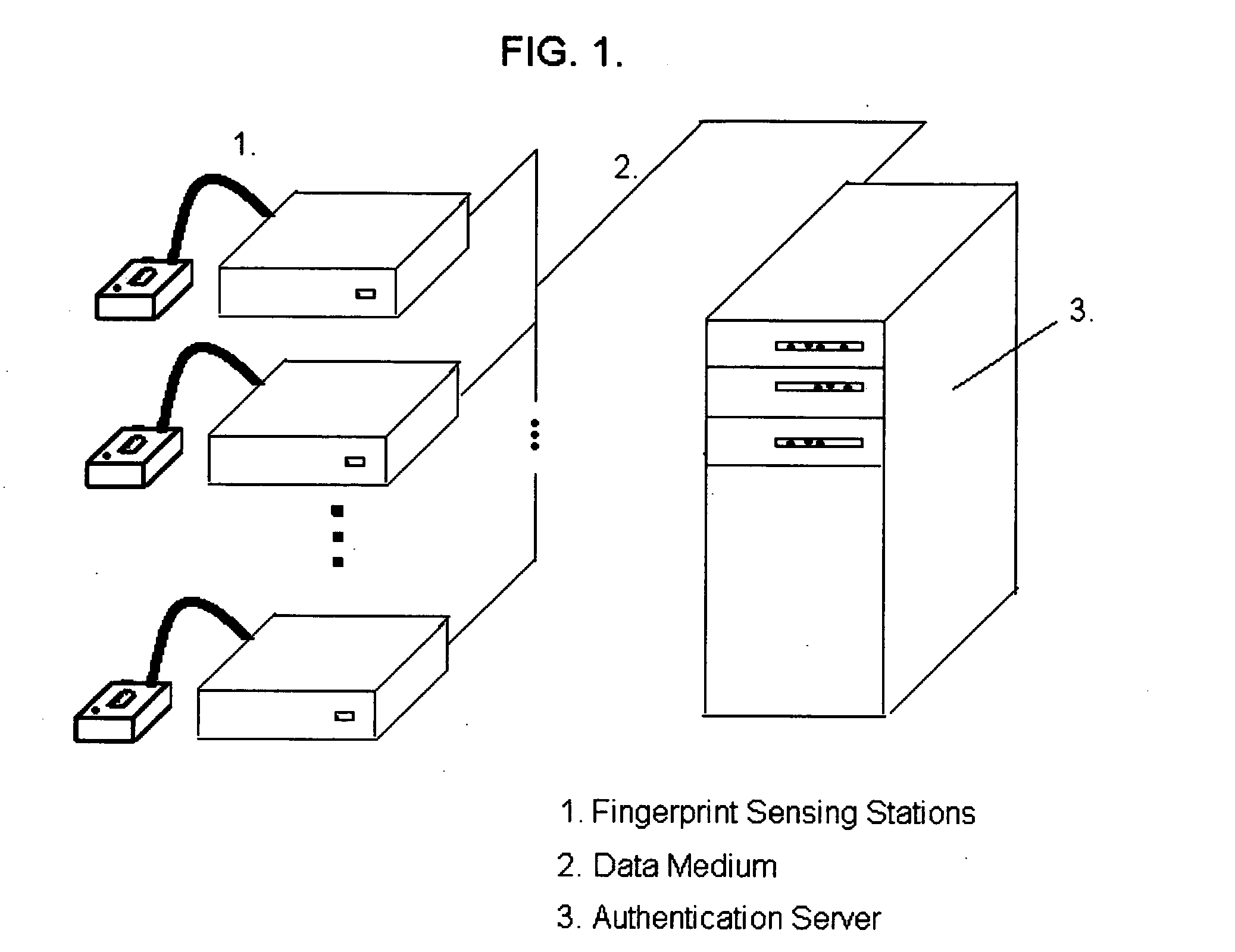
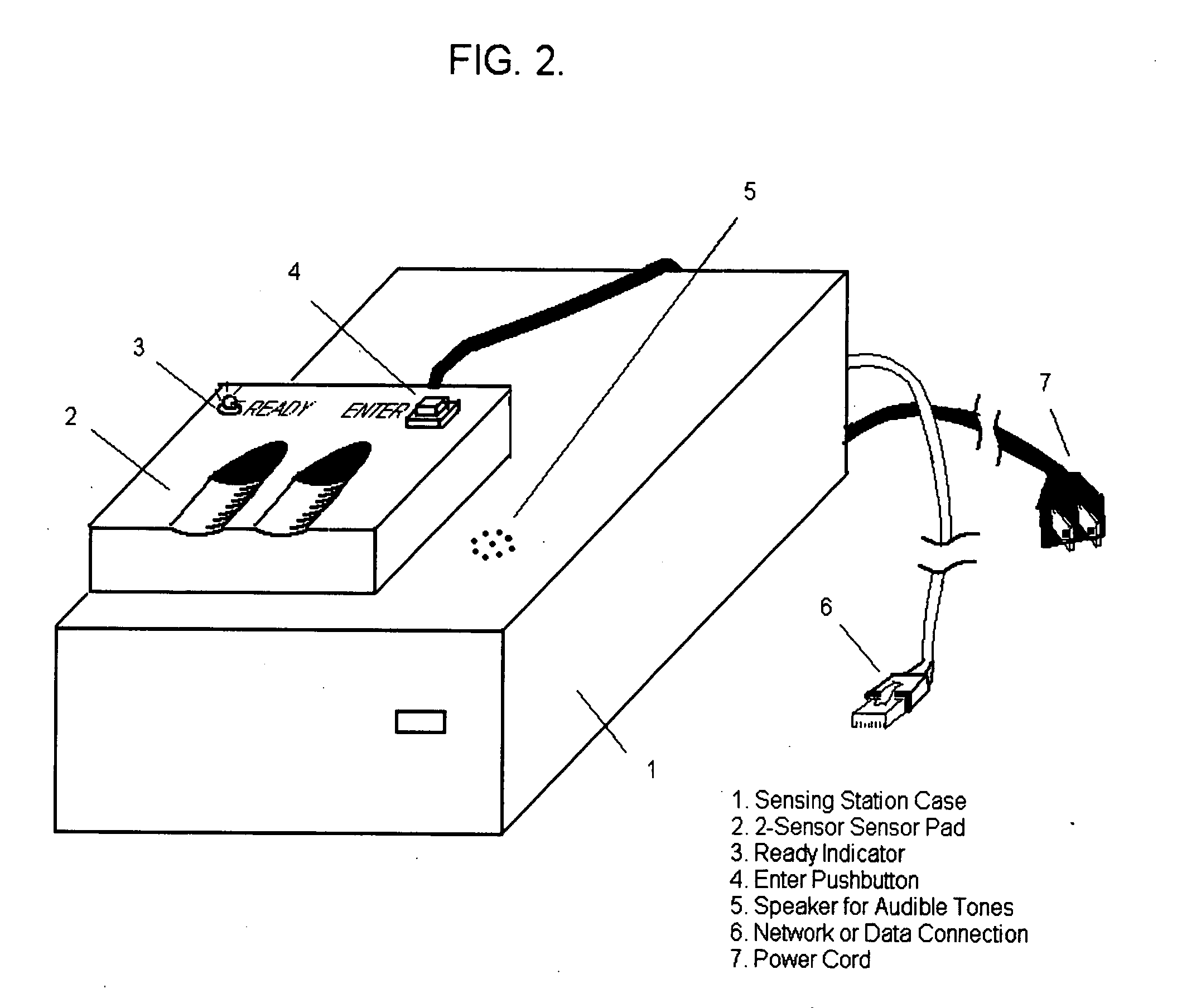
Technique using order and timing for enhancing fingerprint authentication system effectiveness
InactiveUS20050134427A1Increase the number ofAffect the number of potential authentication sequencesElectric signal transmission systemsImage analysisTemporal informationAuthentication server
The invention, which is an embodiment of what the inventor calls, “Active behavior Fingerprint Authentication” is one which employs a sequential reading of fingerprints of various fingers, in a way that may or may not be time constrained, as a means to improve authentication security. Authentication security is strengthened based upon the reduced likelihood that a potential intruder would 1.) Know what the correct sequence of fingerprints were associated with the control authentication template; 2.) Know the correct timing characteristics associated with successive fingerprint readings; 3.) Be able to successfully “hack” the authentication server in order to gain access to minutia or image information, and finger sequence information, and timing information, which would be required in order to fully compromise the authentication system. The technique embodied by the invention represents an overlay of a known, ordered sequence, which may or may not be timed, over the fingerprint authentication process itself.
Owner:HEKIMIAN CHRISTOPHER DAVID
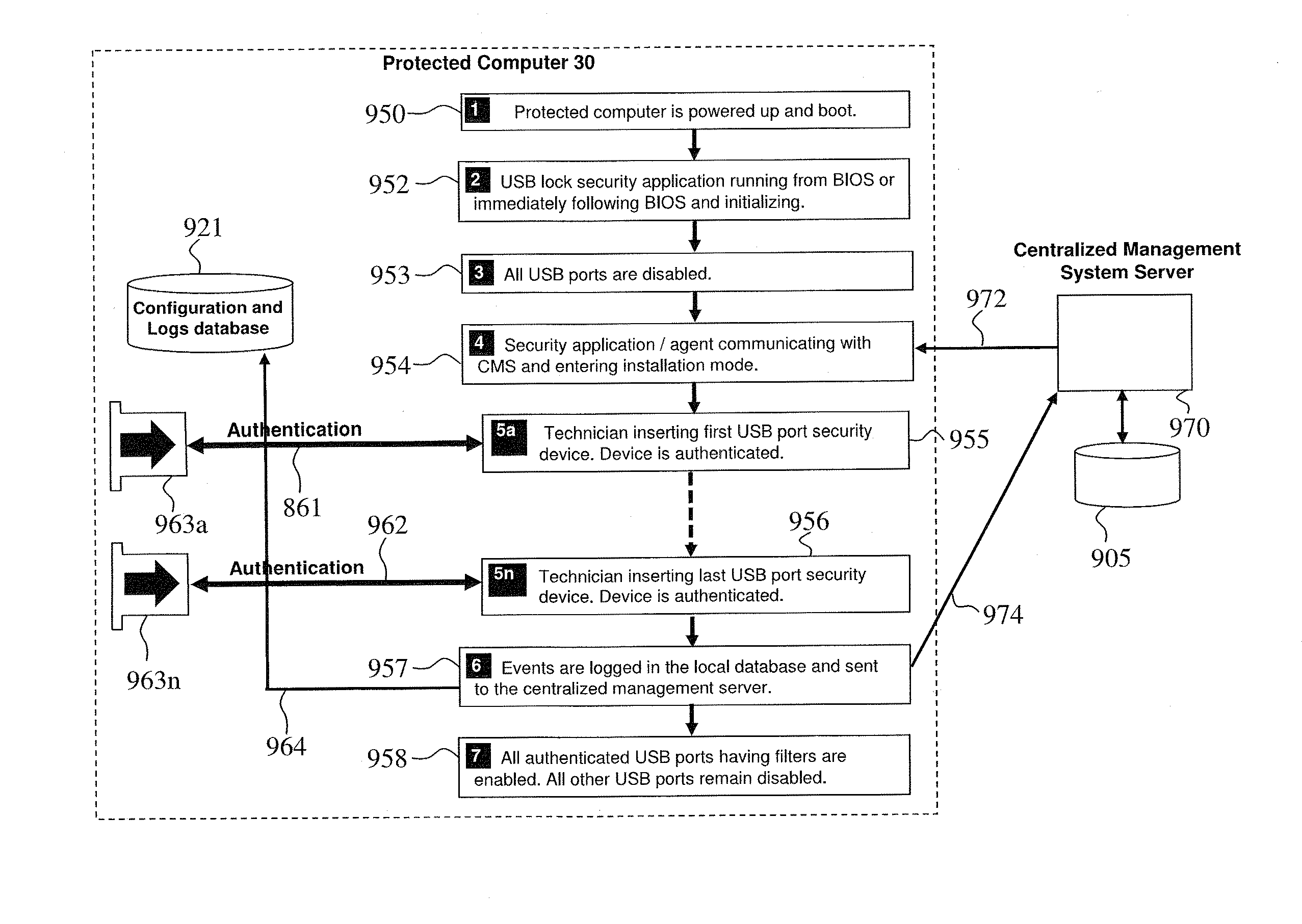
USB security device, apparatus, method and system
ActiveUS20160196454A1Improve information securityAttempt have been hamperedDigital data processing detailsCoupling device detailsEngineeringSelf locking
Methods, devices and system for enhancing computer information security by physically blocking unused USB ports with self-locking devices, or by providing USB port self-locking device with internal circuitry that qualifies and secures user peripheral device attached to the computer, and by continuously communicating with a management software application that provides real-time monitoring and warnings when any USB self-locking device is being removed or tampered. The self-locking devices use a spring loaded teeth in the USB plug that lock into tab spaces in the USB jack. Visual indicator provides positive assurance when all ports are secure. Each self-locking devices include a security circuit which is uniquely paired with the protected port. Some self-locking devices include data filters that only enable connecting authorized peripheral devices.
Owner:HIGH SEC LABS LTD
Method and system for producing a graphical password, and a terminal device
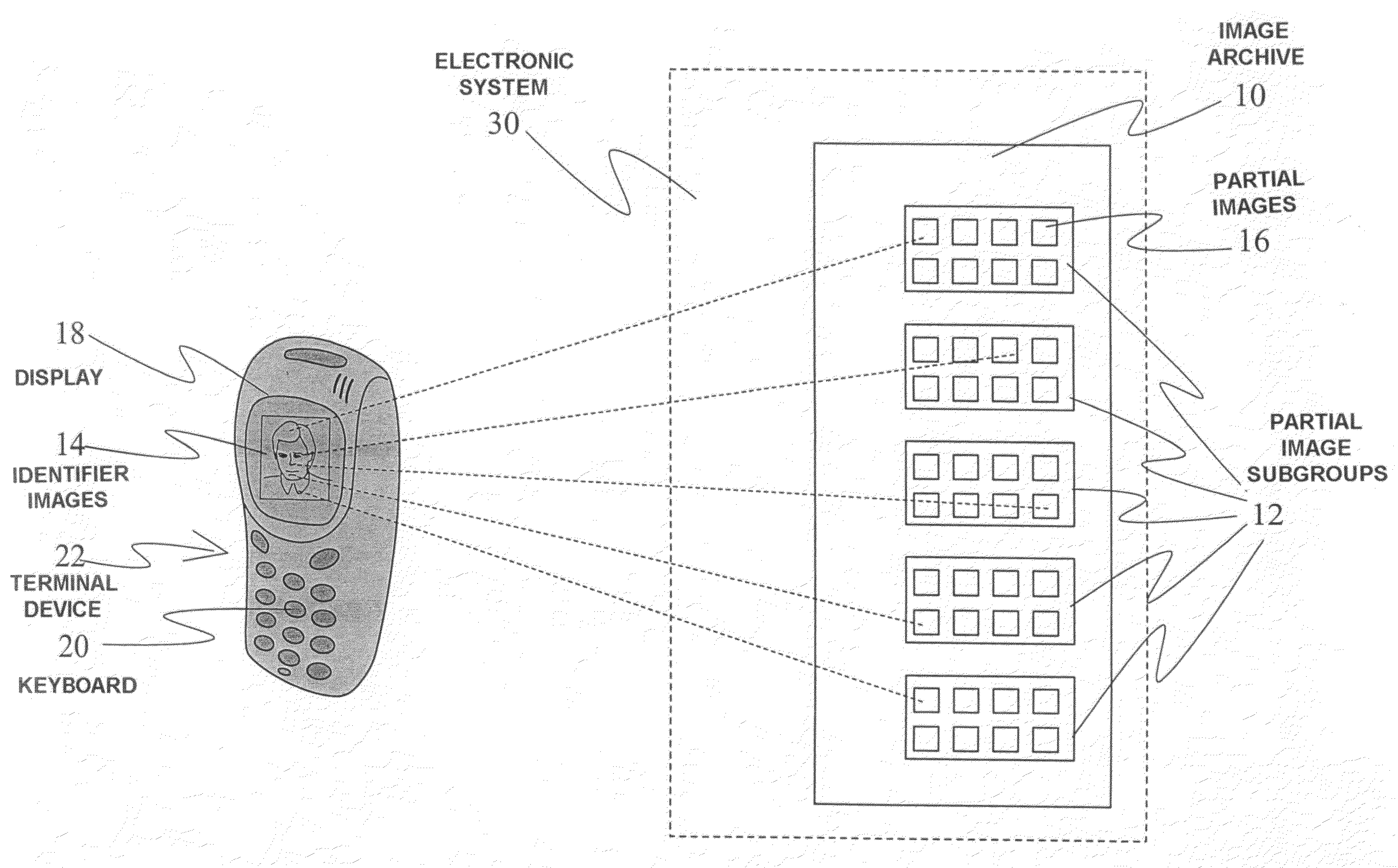
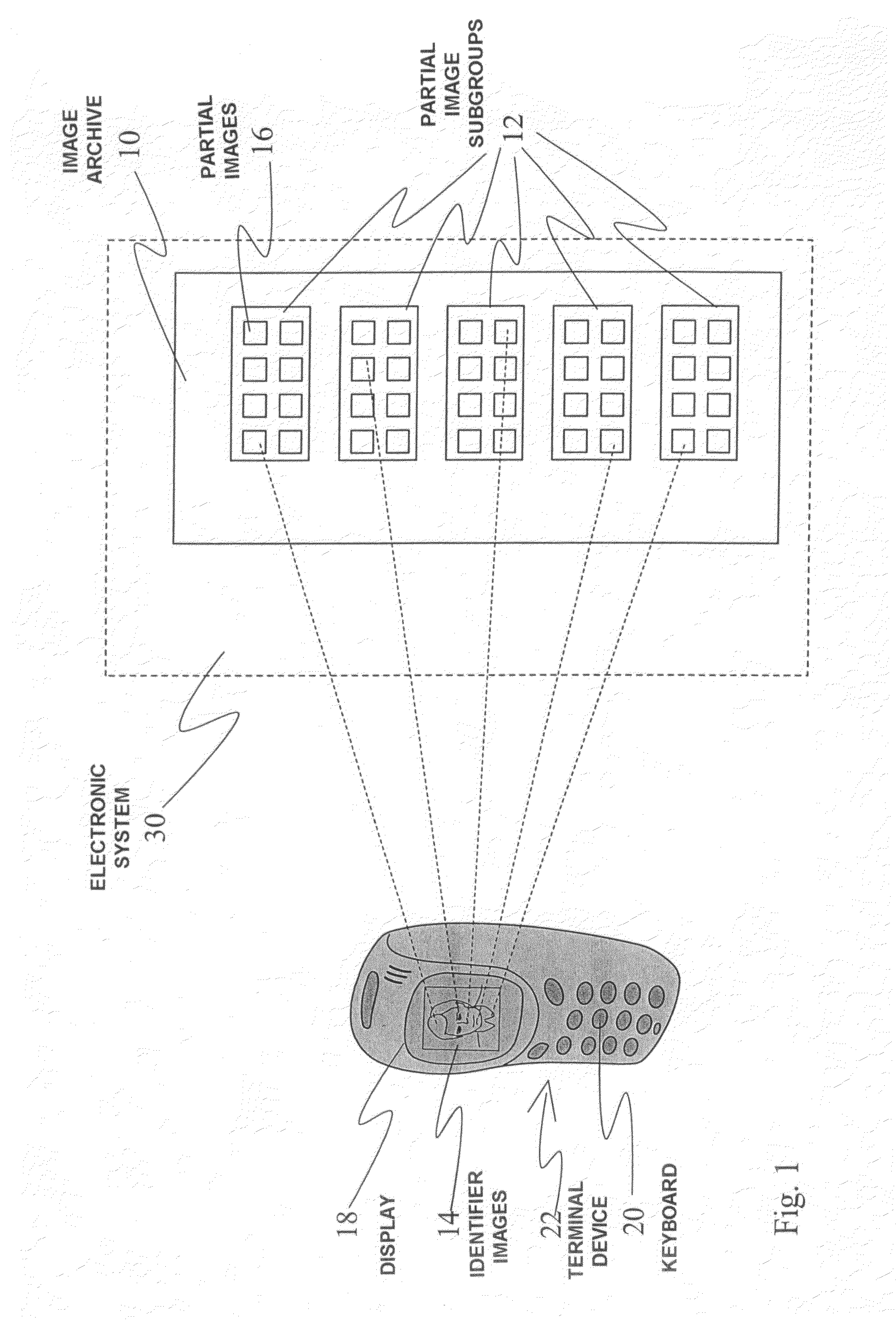
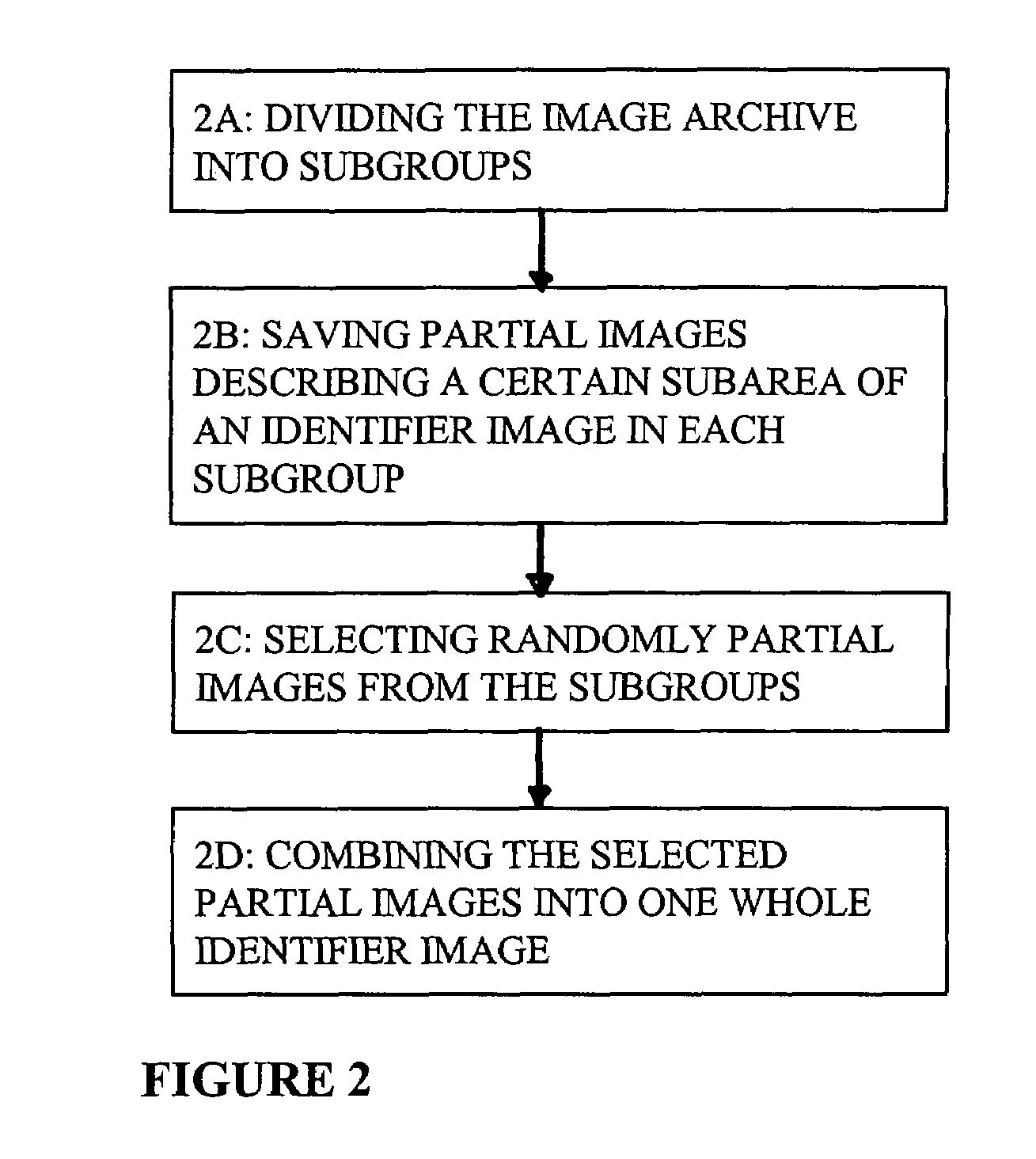
ActiveUS7376899B2Reduce in quantitySmall amountDigital data processing detailsMultiple digital computer combinationsGraphicsElectronic systems
In the method a graphical password is produced for an electronic system, such as a database, a computer program or Internet pages, the password being composed of various identifier images that are clearly distinguishable from each other. The system can be located in a terminal device used by the user, such as a mobile phone or an object separate from the terminal device, to which the user can be connected via the terminal device. For producing the password, the electronic system includes an image archive, in which various partial images representing certain subareas of a whole identifier image have been saved in electronic form. The partial images are divided into subgroups so that the partial images of the same subgroup always represent the same subarea of the identifier image. The identifier images belonging to the graphical password are composed by selecting partial images from different subgroups and by combining the selected partial images into one complete identifier image.
Owner:CONVERSANT WIRELESS LICENSING LTD
Determination method of pseudo base station and mobile terminal
ActiveCN104602241AEasy to identifyReduce signaling burdenLocation information based serviceSecurity arrangementComputer terminalElectric signal
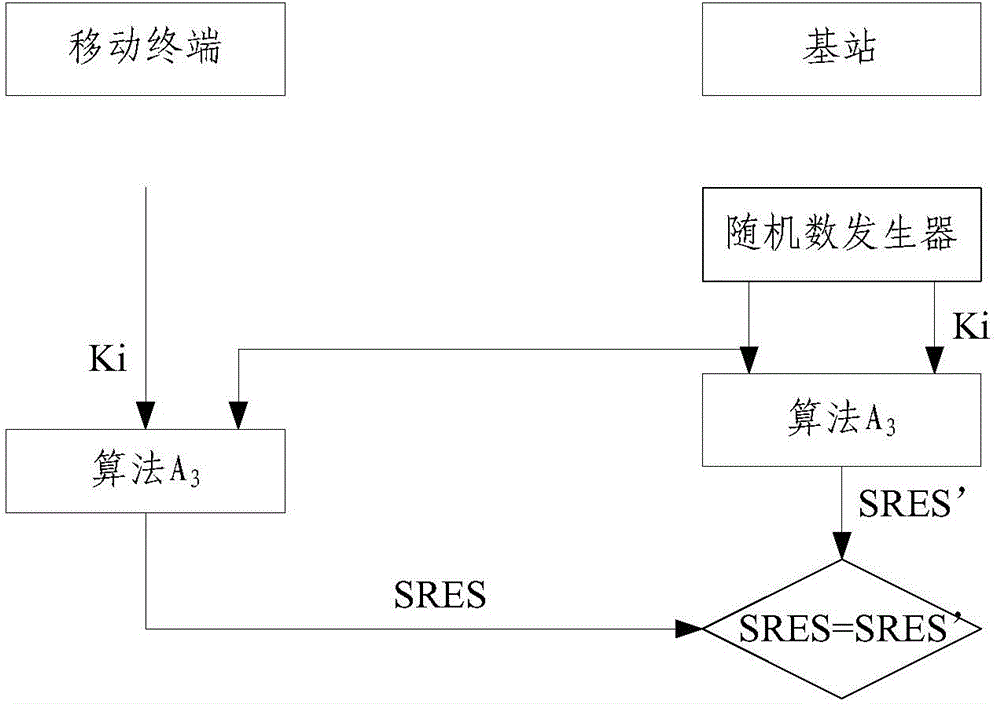
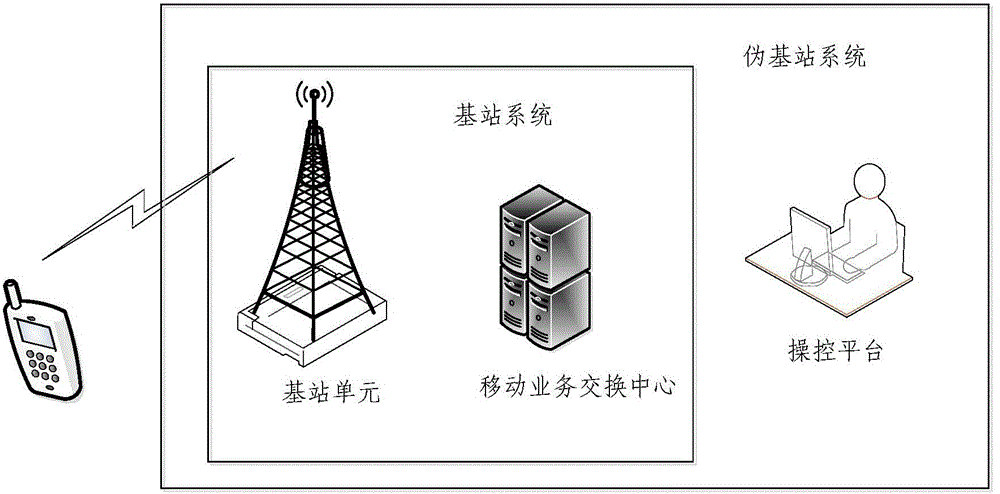
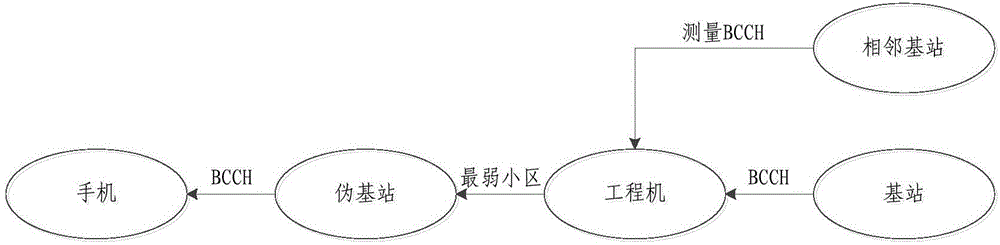
The invention provides a determination method of a pseudo base station and a mobile terminal. The method comprises the steps of sending a base station parameter acquiring request to a base station of the local community through the mobile terminal; receiving the base station parameters from the base station through the mobile terminal; comparing the base station parameters with the preset base station parameters of an operator; if the base station parameters are the same as the base station parameters of the operator, acquiring electric signal strength of the base station; comparing the variable of the electric signal strength of the base station within the preset time quantum with the preset strength variation value; if the variable of the electric signal strength of the base station within the preset time quantum is less than the preset strength variation value, comparing the electric signal strength of the base station with the preset electric signal strength; if the electric signal strength of the base station is more than the preset electric signal strength, determining that the base station is the pseudo base station. With the adoption of the determination method of the pseudo base station and the mobile terminal, the pseudo base station can be quickly and conveniently recognized, and meanwhile, the signaling load of the base station can be reduced; the privacy can be prevented from disclosing; in addition, the pseudo base station can be timely positioned.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Multiuser system privilege management method and instant messaging system applying same
ActiveCN101834878AAchieve sharingEnsure safetyData switching networksAutomatic controlMultiuser system
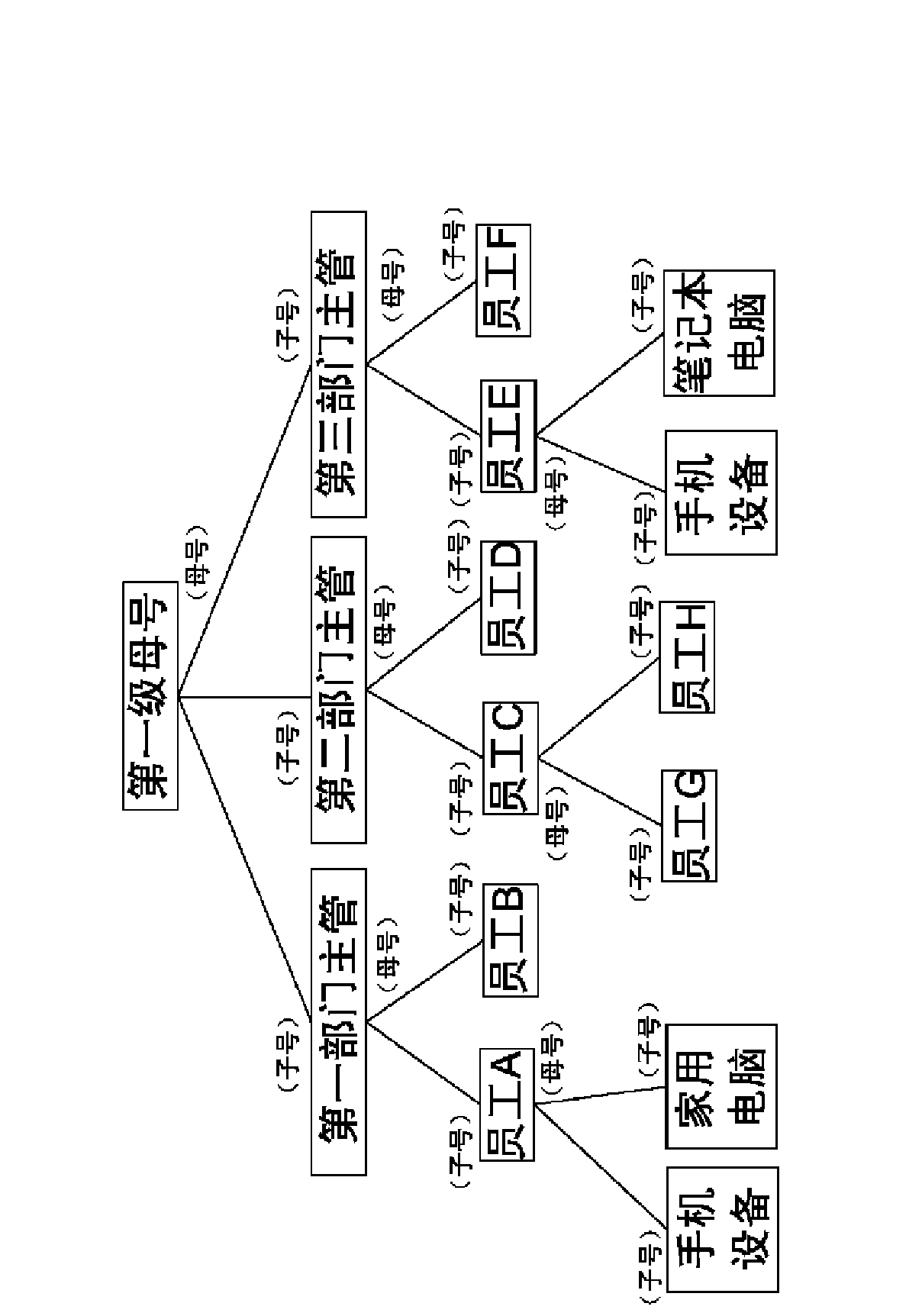
The invention relates to a multiuser system privilege management method which comprises the following steps of: 1, establishing a login account into a mother account; and incorporating the login account except for the mother account by the mother account to enable the login account to be a child account, designating the permission of a holding end of the child account and resources inherited from the holding end of the mother account by the holding end of the mother account. The invention also relates to an instant messaging system for managing function permission and resources of an instant messaging client by applying the multiuser system privilege management method, an instant messaging system which is capable of carrying out inside network communication, outside network communication, private account communication and automatic calling and switching of a communication module according to a sensed network connect state, and a login method for automatically controlling child account, mother account and private account independent login or child account, mother account and private account combined login in a mode of verifying a login device hardware code, a local area network IP address and a special login permission.
Owner:陈时军
Anti-identity theft and information security system
ActiveUS20130201000A1Improve information securityImprove securityElectric signal transmission systemsImage analysisIdentity theftInformation security
The anti-identity theft and information security system process includes storing secure information in association with an electronic device having a communication circuit for sending and receiving data. Biometric information is read with a scanner so that the identity of a user can be authenticating in connection with the supplied biometric information. Once approved, a data communication line is established with a remote device and access to the secure information is unlocked. Thereafter, the secure information may be transmitted between the electronic device and the remote device.
Owner:THE COOPER UNION FOR THE ADVANCEMENT OF SCI & ART
Vehicle attack detection method and device
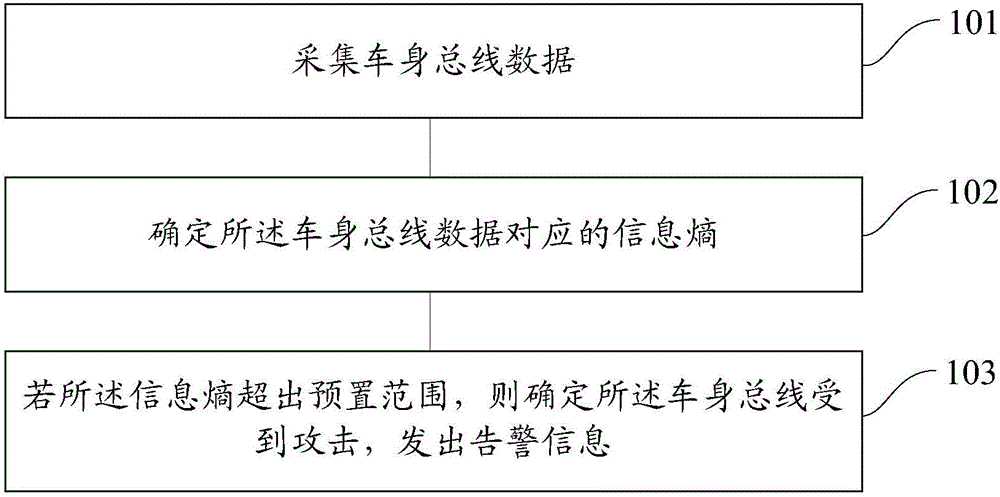
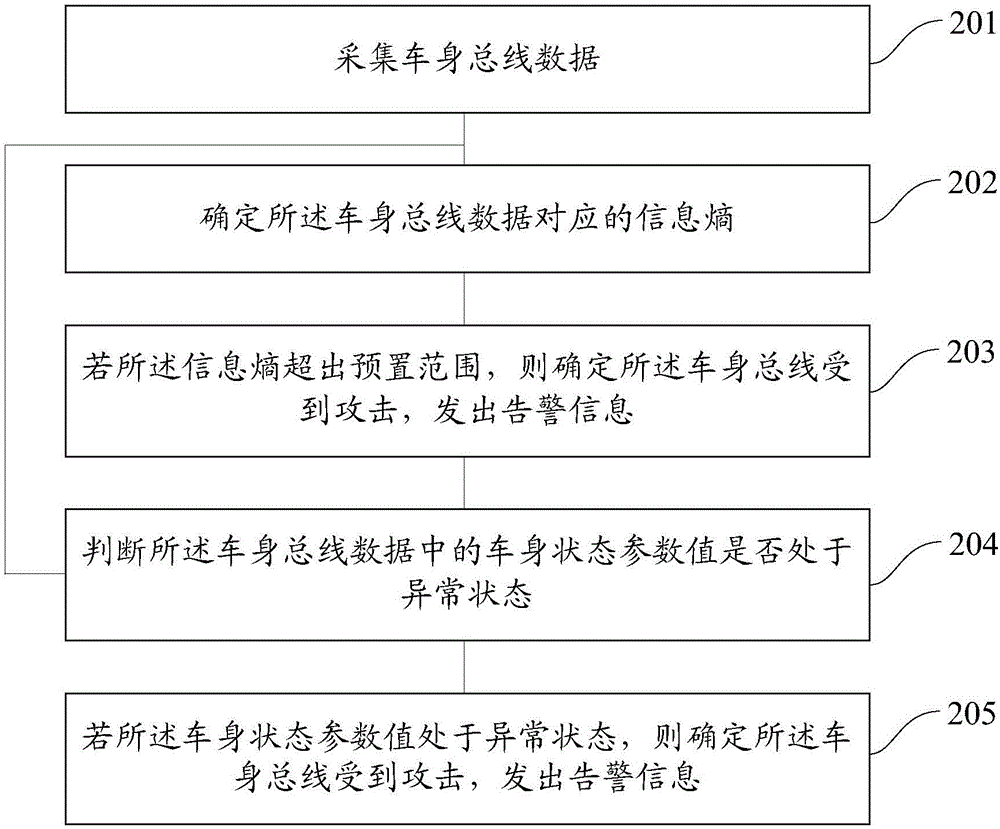
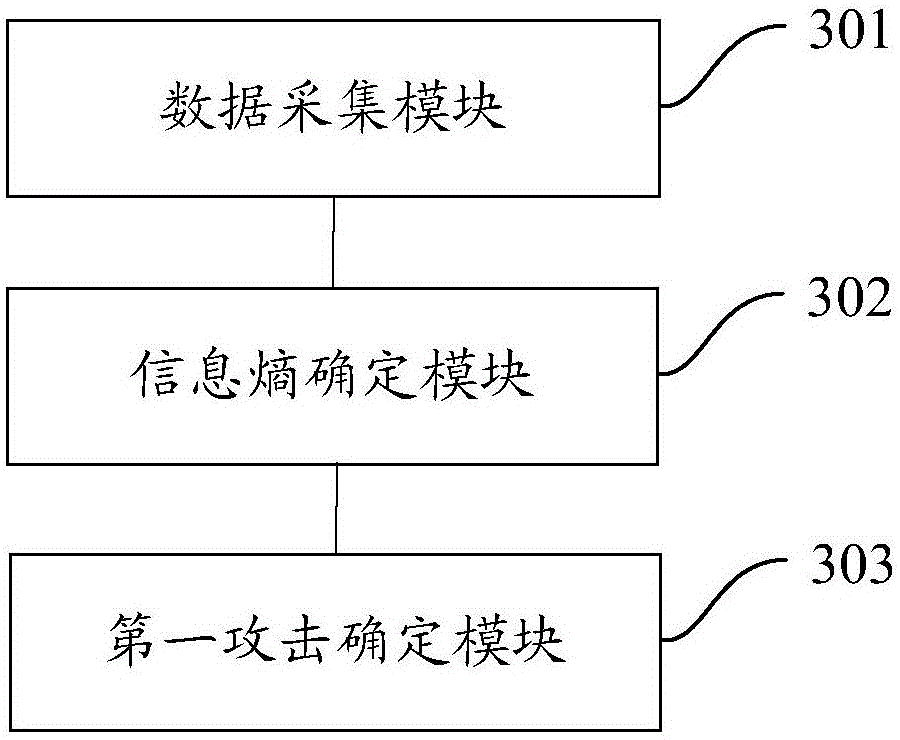
InactiveCN106650505AImprove driving safetyImprove information securityInternal/peripheral component protectionInformation securityReal-time computing
The embodiment of the invention provides a vehicle attack detection method and device. The method specifically comprises the steps of collecting car body bus data; determining information entropy corresponding to the car body bus data; if the information entropy exceeds a preset range, determining that a car body bus is attacked, and sending a warning message. According to the vehicle attack detection method and device, whether the car body bus is attacked or not can be detected, when it is determined that the car body bus is attacked, the warning message can be sent, so that a user takes measures to stop deep development of the attack as soon as possible, and the traffic safety and information safety of the user are accordingly improved.
Owner:BEIJING QIHOO TECH CO LTD
Method, system and apparatus for authenticating user identity
InactiveUS20140351596A1Operational securitySimple software installationDigital data processing detailsUser identity/authority verificationPaymentInternet privacy
The present invention relates to a method and system for authenticating user identity with a user terminal, authentication front-end computer system, and authentication server. In a first scheme, the user terminal transmits an authentication instruction comprising an authentication message to the authentication front-end computer system. Then, the authentication front-end computer system transmits an authentication request comprising the authentication message to a specific authentication server. In a second scheme, the user terminal transmits an authentication request comprising an authentication message to a specific authentication server. In any schemes, after receiving the authentication request, the authentication server authenticates a user's identity according to the authentication message. Preferably, the authentication server transmits an authentication result to the authentication front-end computer system. When a user pays a certain amount of money to an operator, the authentication server transfers the specific amount from a specific user payment account to a specific operator account after successful authentication.
Owner:CHAN KK
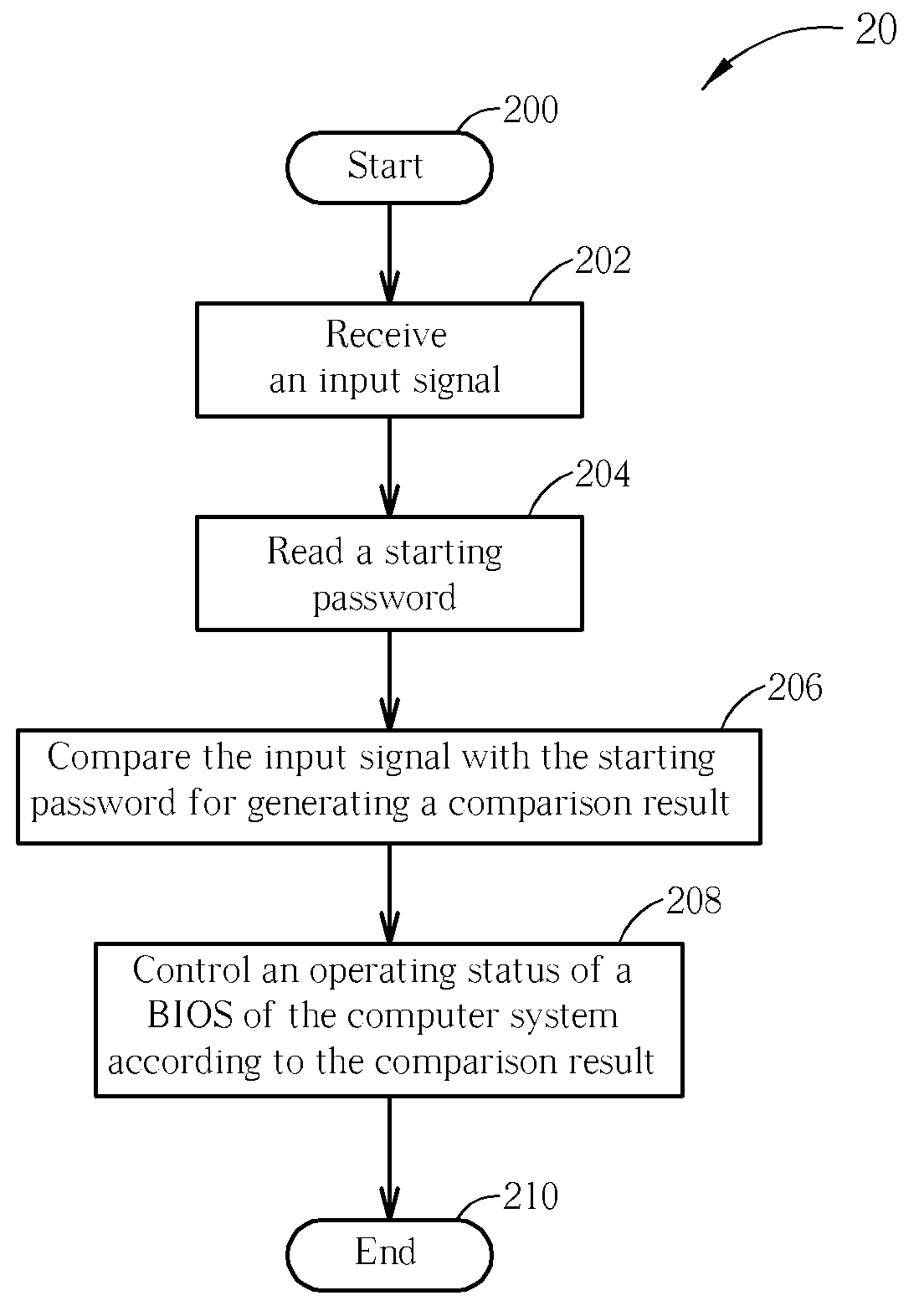
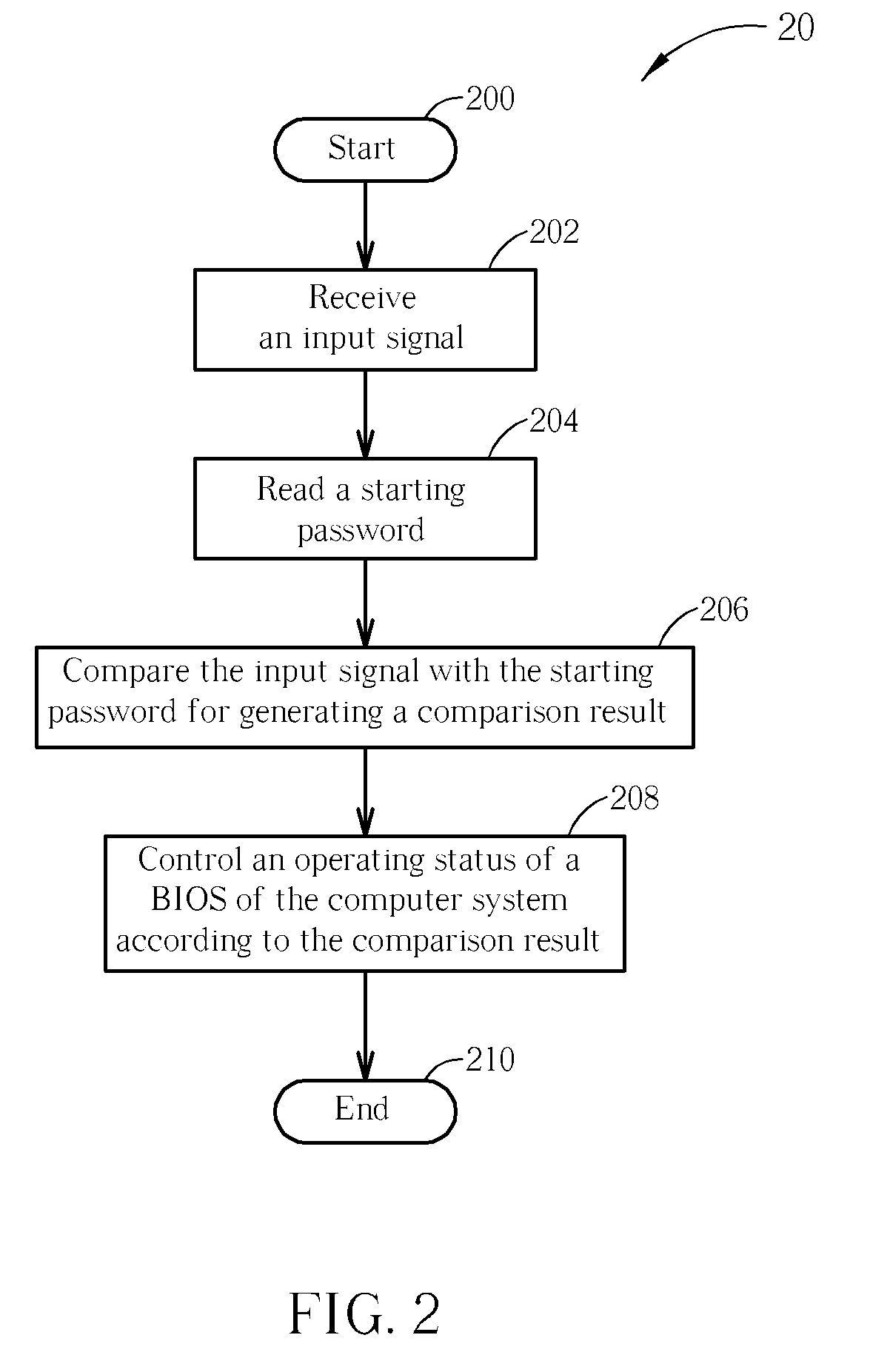
Method and Apparatus for Enhancing Information Security in a Computer System
InactiveUS20090064316A1Improve information securityDigital data processing detailsUnauthorized memory use protectionComputer hardwarePassword
A method of enhancing information security in a computer system comprises receiving an input signal, reading a starting password, comparing the input signal with the starting password for generating a comparison result, and controlling an operating status of a basic input and output system of the computer system according to the comparison result.
Owner:WISTRON CORP
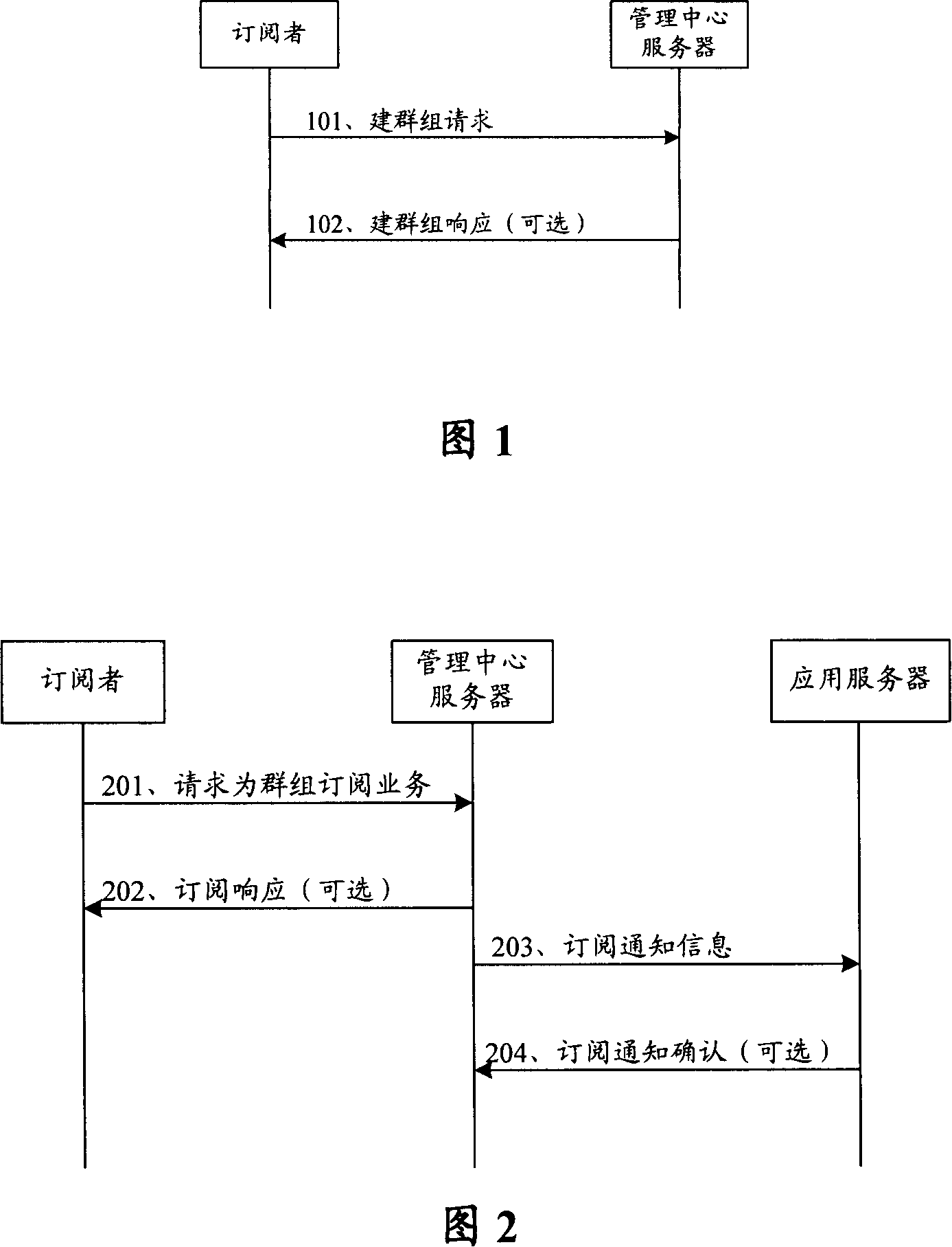
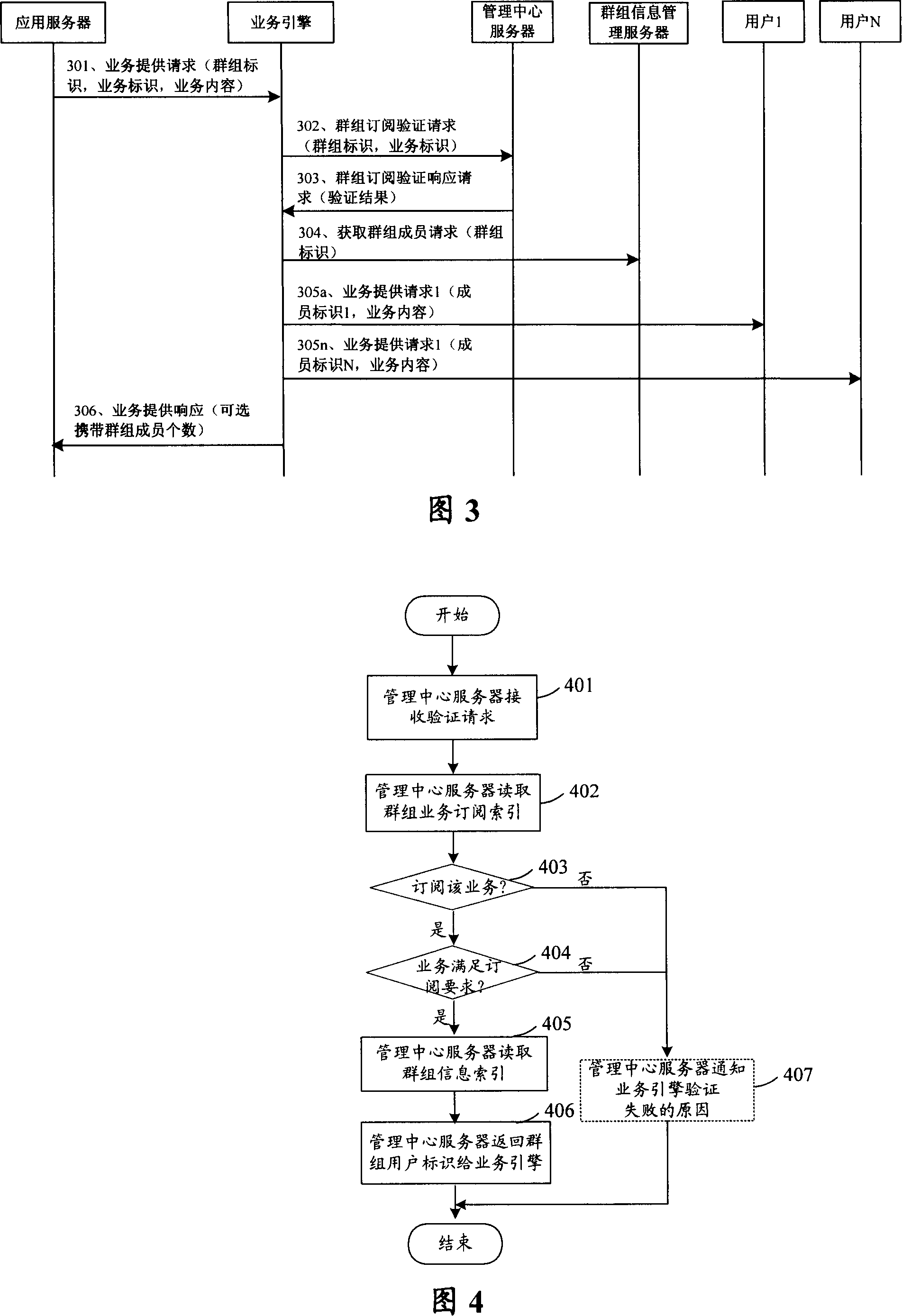
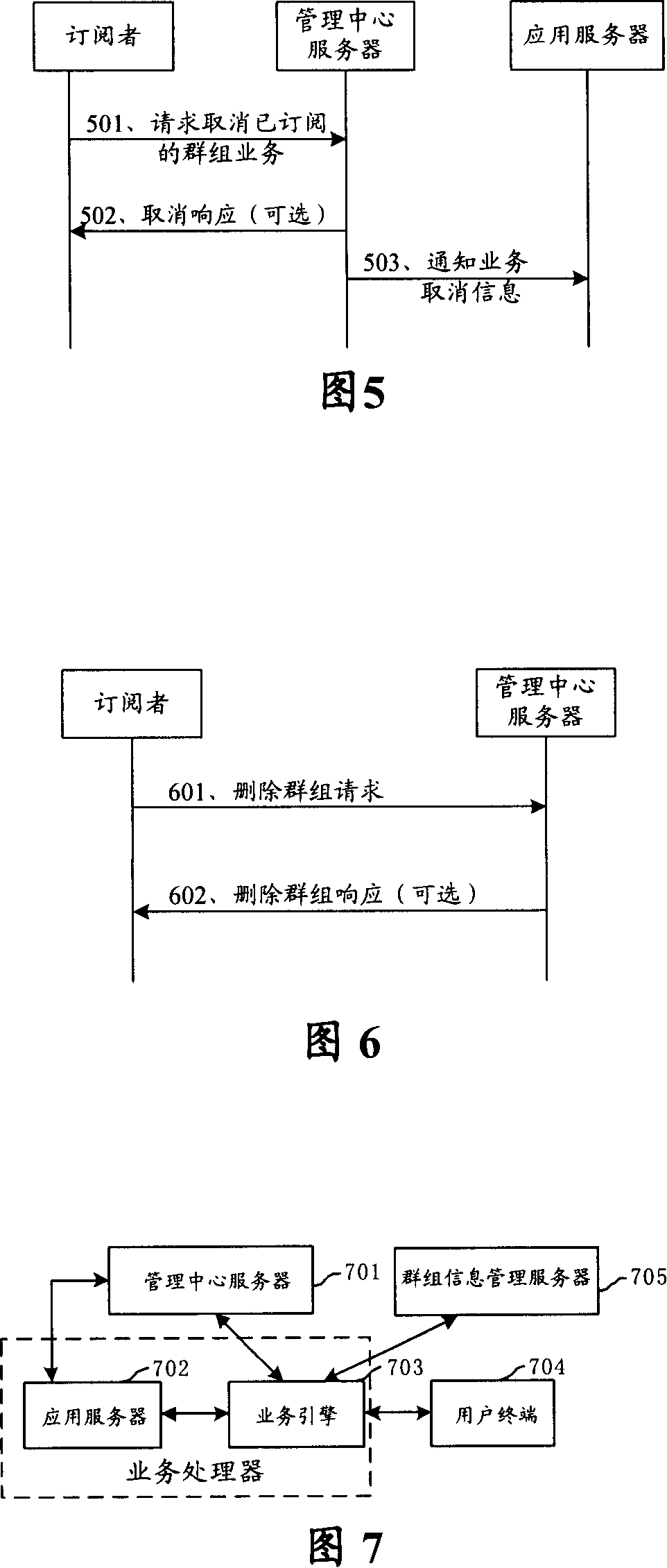
A method and management center server for subscribing mobile service for groups
ActiveCN101127941AReduce the number of interactionsReduce trafficSpecial service provision for substationRadio/inductive link selection arrangementsInteraction timeApplication server
The utility model discloses a method of subscribing mobile business for groups. The utility model is characterized in comprising the following steps: a management center server builds a group business subscription index and informs application server groups of subscribed business information according to received request with a group mark and at least one business mark of subscribing business for groups; the information comprises at least a group mark; the group business subscription index comprises corresponding relationship between the group mark and at least one business mark. The utility model has the advantages of only needing business interaction between the application server and business engine, conveniently and uniformly subscribing mobile business for the group users, decreasing interaction times between the operation business server side and the application server, lowering network traffic, protecting information safety for the groups and the group users. The utility model also provides a management center server.
Owner:HUAWEI TECH CO LTD
Secure access mode for intranet and extranet
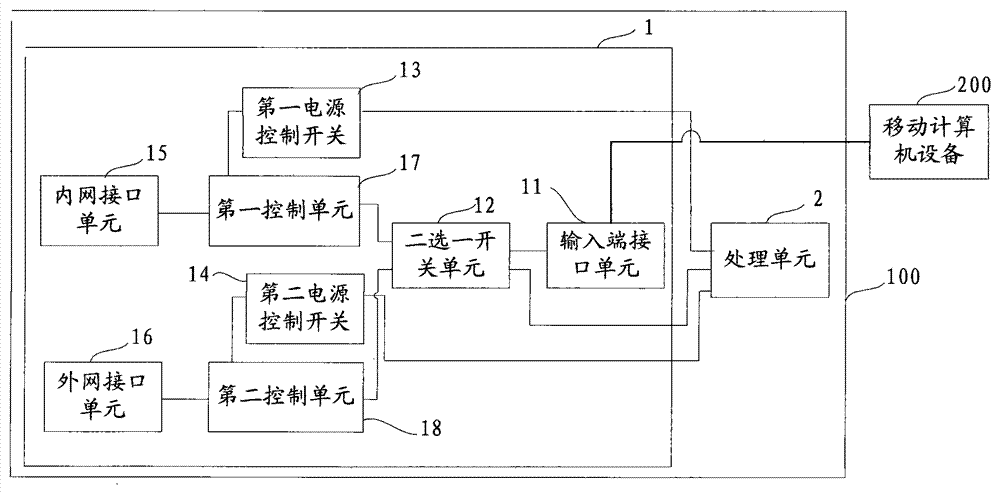
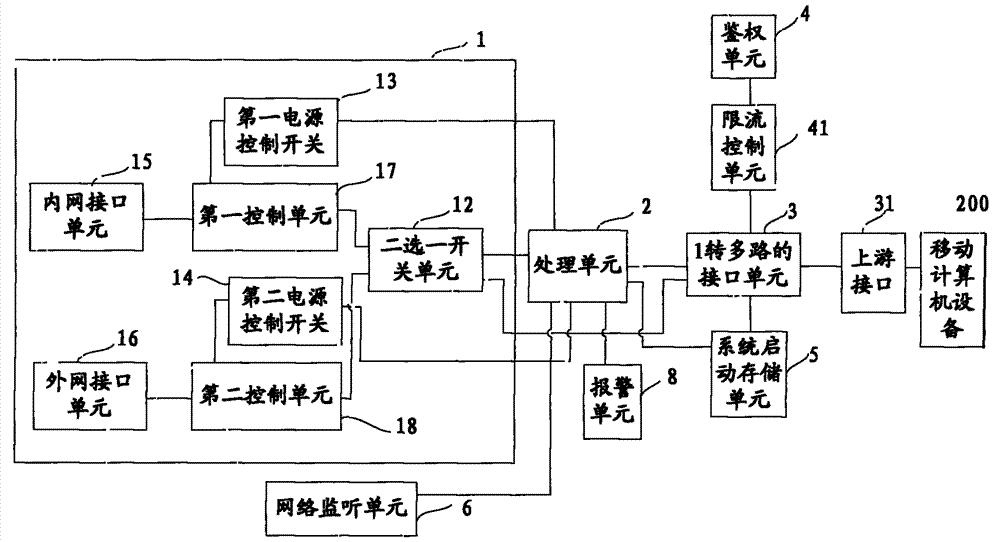
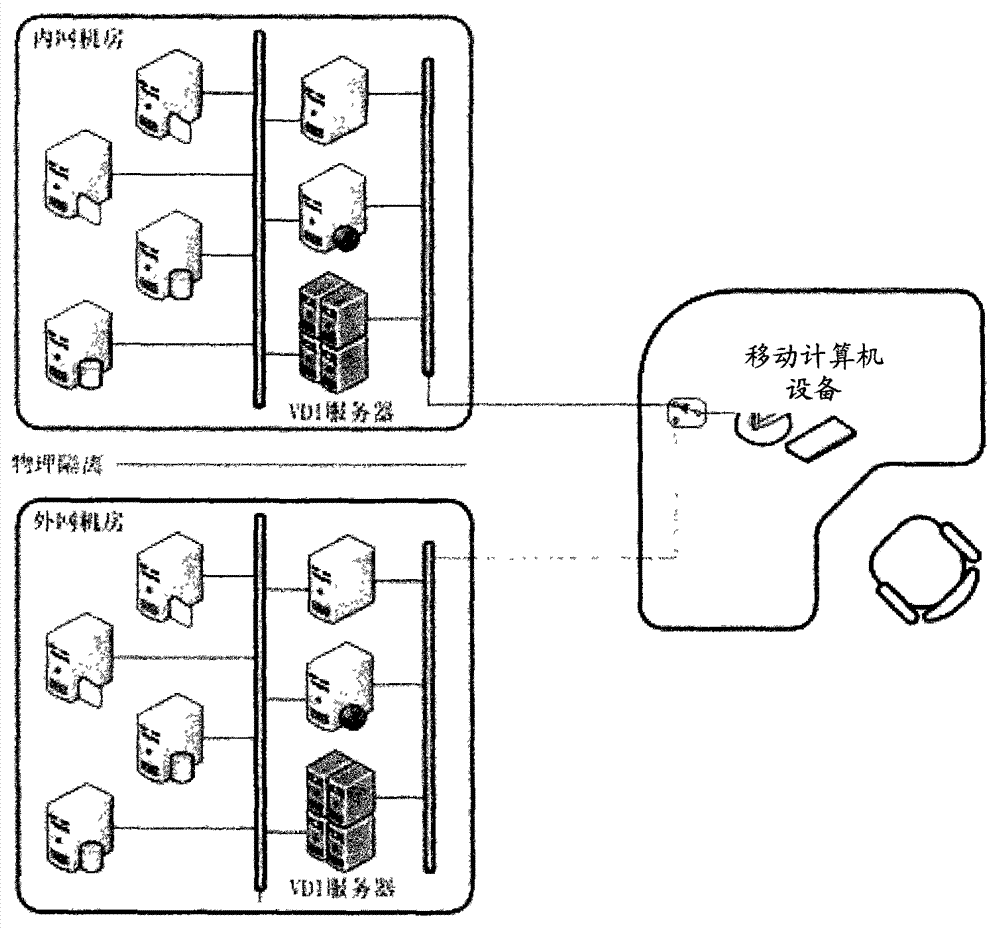
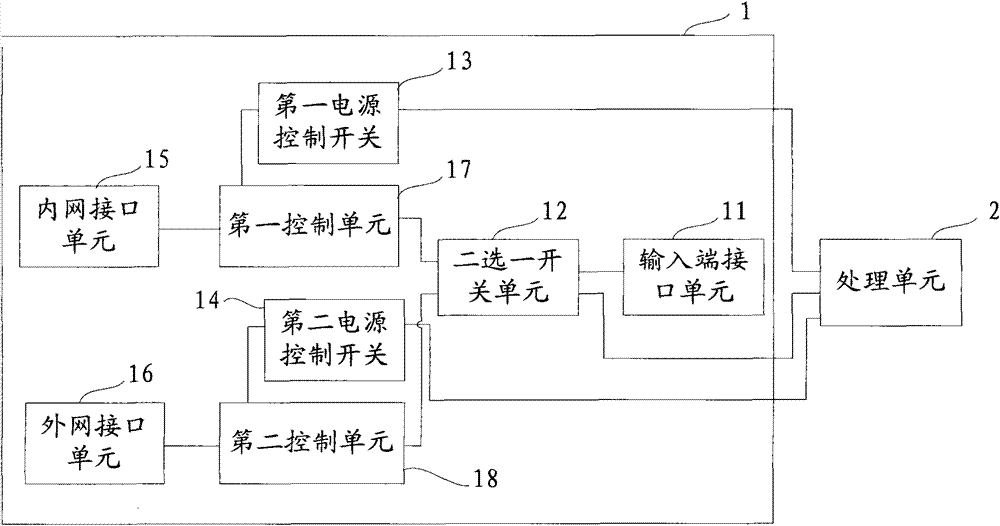
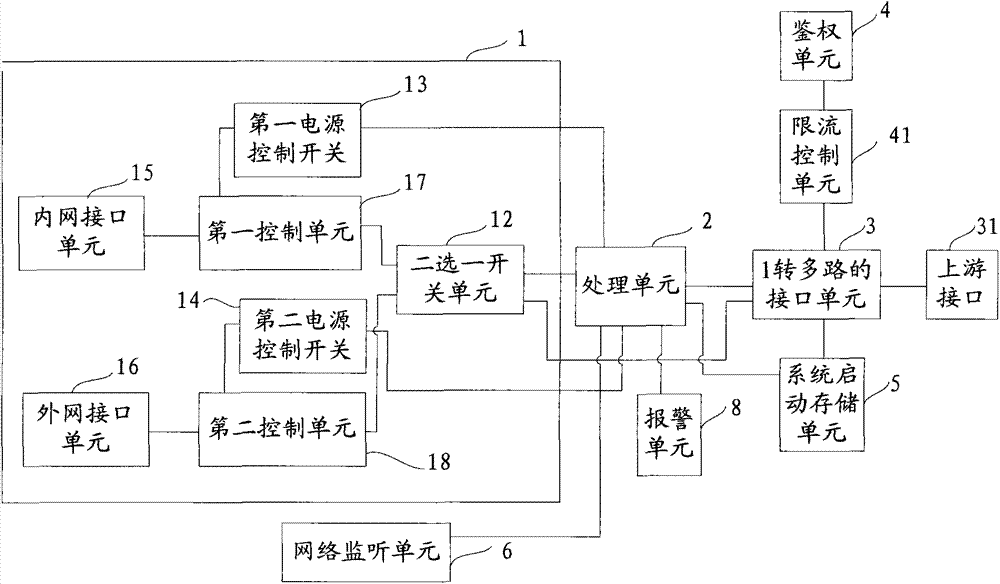
InactiveCN103532978AProtect information securityImprove information securityData switching current supplyPower controlComputer equipment
The invention provides a secure access mode for an intranet and an extranet. An input-end interface unit of intranet and extranet safety equipment is connected with a first control unit and a second control unit respectively through a two-channel switch unit; when mobile computer equipment selects an extranet mode, a processing unit controls the two-channel switch unit to gate the second control unit, switches on a second power control switch to enter an extranet system and switches off a first power control switch to cut off connection with an intranet system at the moment; and when the mobile computer equipment selects an intranet mode, the processing unit controls the two-channel switch unit to gate the first control unit, switches on the first power control switch to enter the intranet system and switches off the second power control switch to cut off connection with the extranet system at the moment. The secure access mode for the intranet and the extranet is used for realizing isolation and safety protection of the intranet and extranet systems, and information security of the intranet system can be protected effectively.
Owner:BEIJING AISIMENG TECH
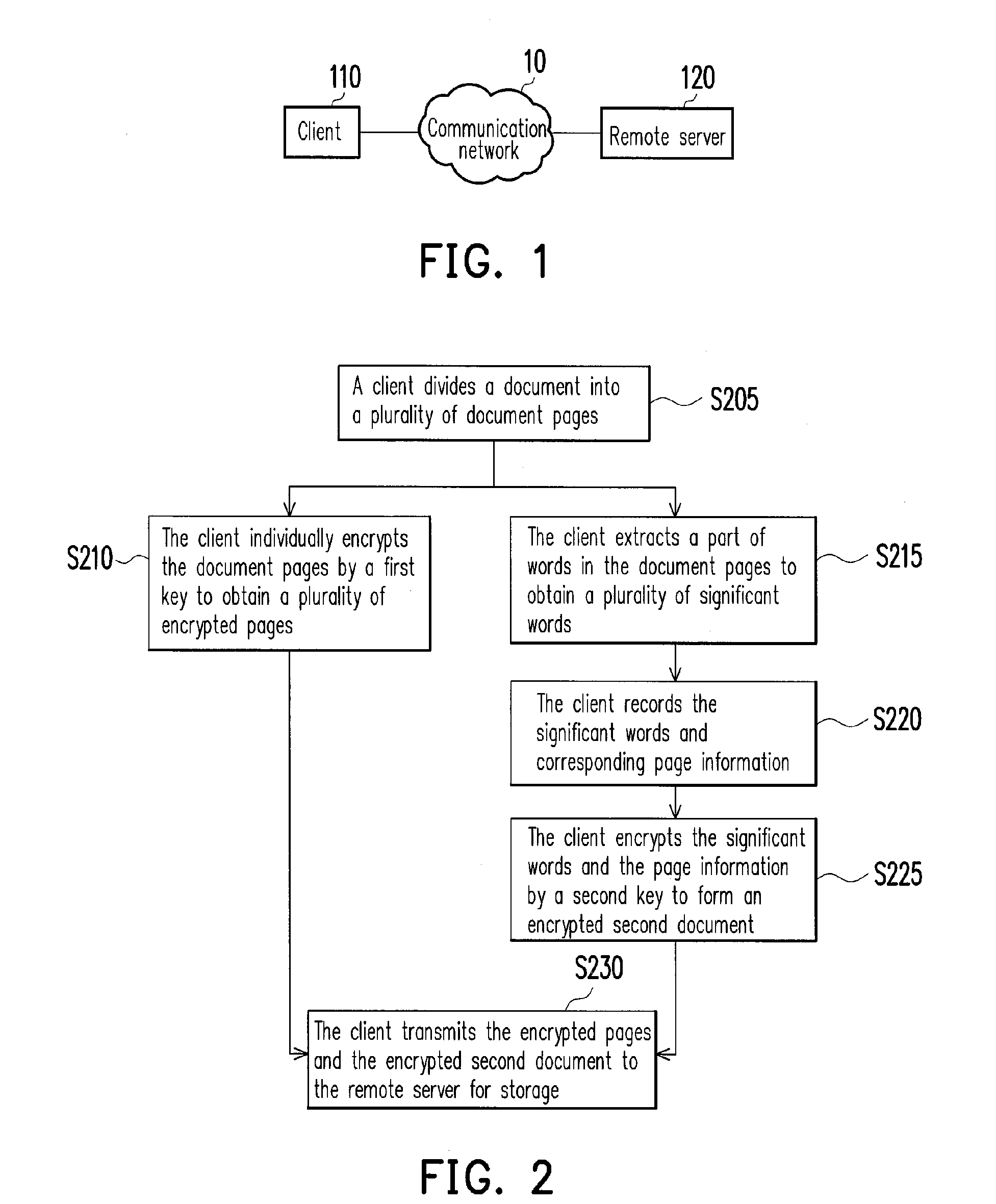
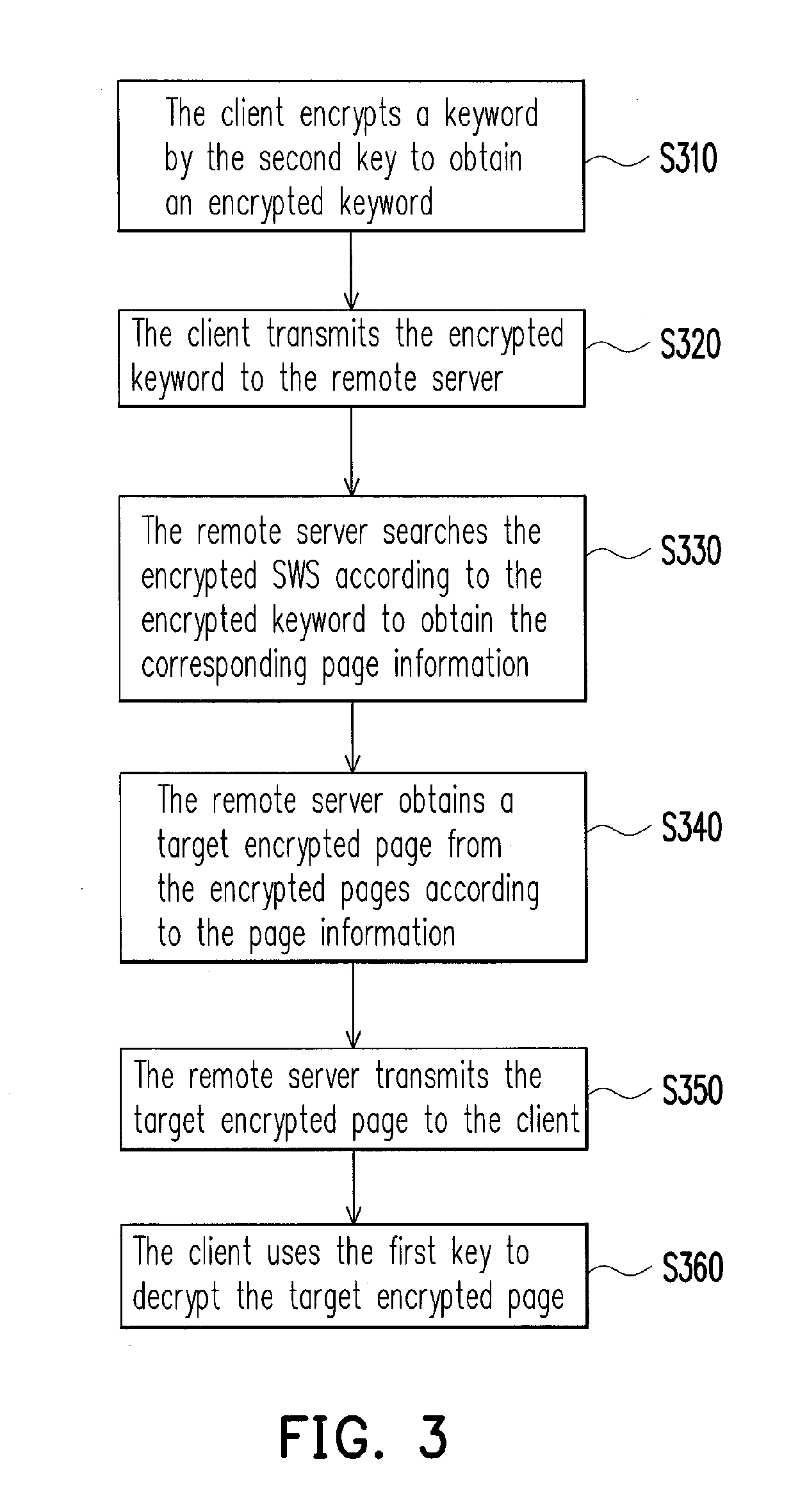
Document processing method and system
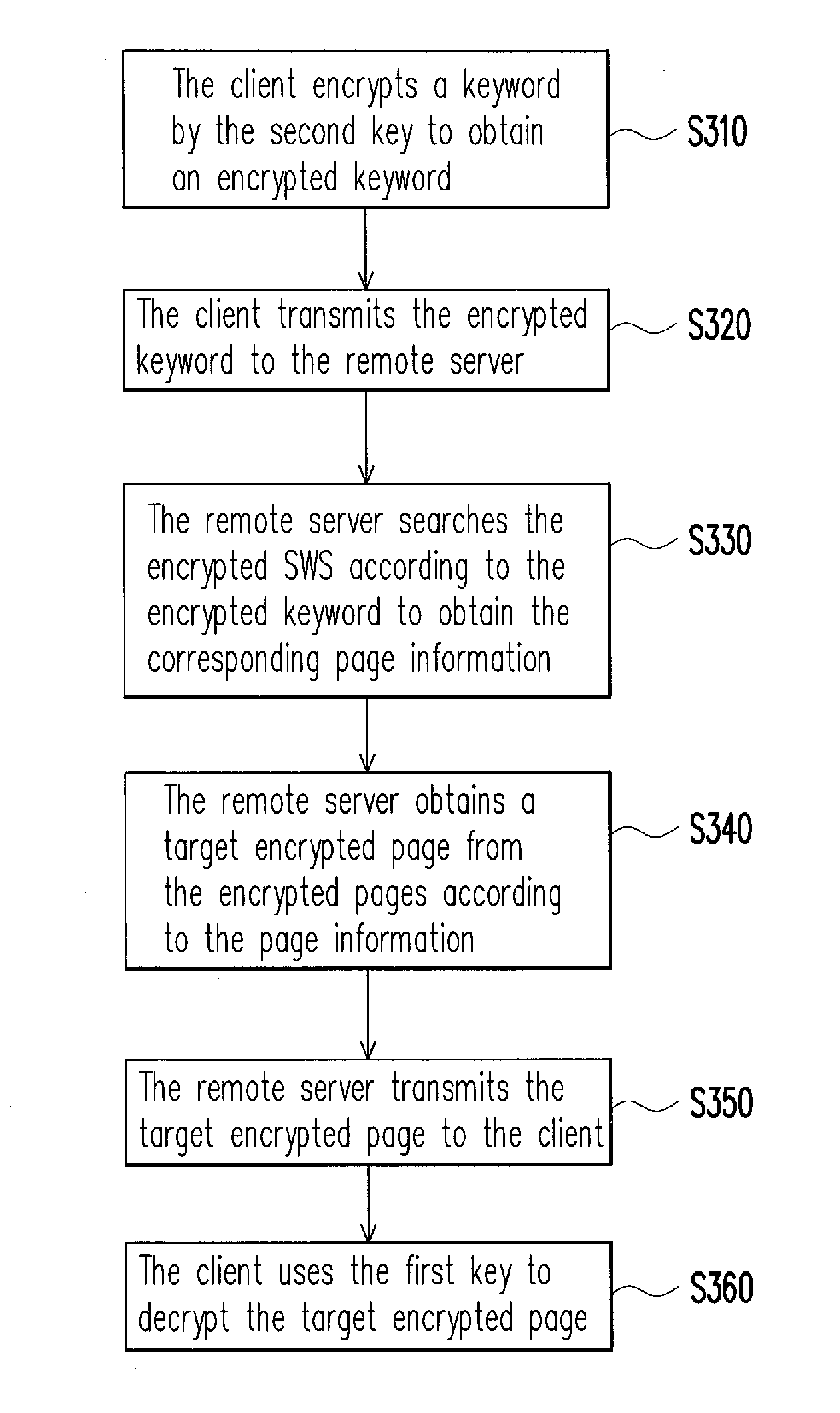
ActiveUS20130159695A1Improve information securityFacilitate a remote server toComputer security arrangementsMultiple digital computer combinationsDocumentationDatabase
A document processing method and system divides a document into document pages, and encrypts the document pages by first key to obtain a plurality of encrypted pages; picks a part of words from the document pages and encrypts them by second key to obtain a Significant Word Set (SWS); picks a part of words from the picked part of words and encrypts them by third key to obtain a Most Relevant Word Set (MRWS). The encrypted pages, the SWS and the MRWS are transmits to a remote server for storage. When user search a keyword in the document, the keyword is encrypted by the second and third keys for performing two query. The first query result is decrypted to obtain the search result. The second query result is decrypted and then checked whether it is a subset of the first decrypted query result for detecting unfaithful execution.
Owner:IND TECH RES INST
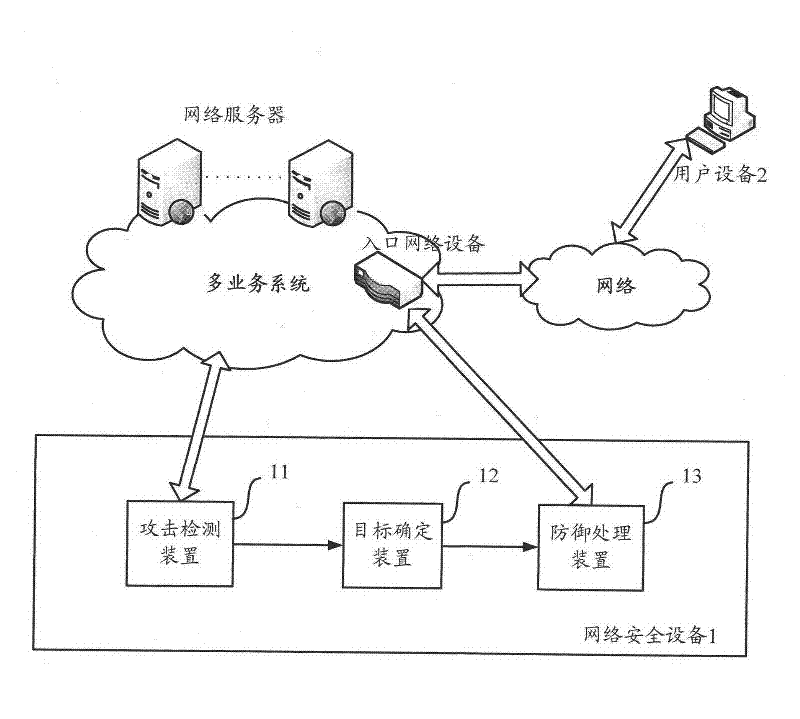
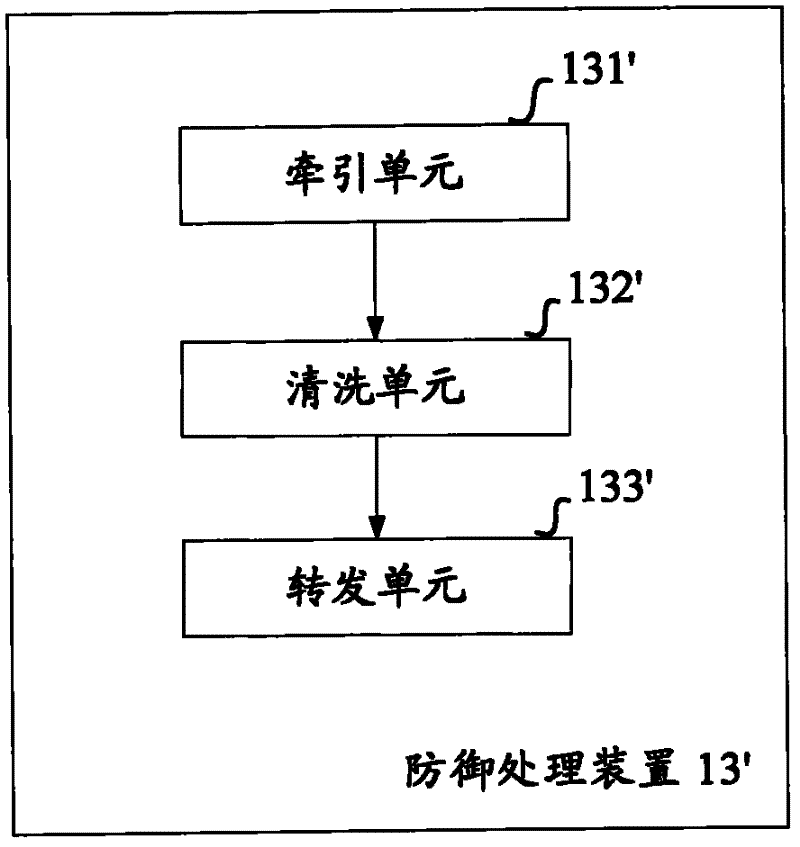
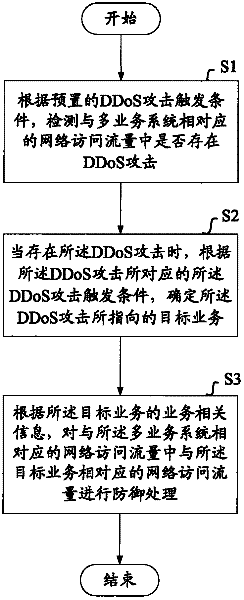
A method and device for defending against ddos attacks directed at multi-service systems
ActiveCN102263788ALimit adverse effectsImprove information securityTransmissionInformation securityTraffic volume
The invention aims to provide a method and equipment for defending against a distributed denial of service (DDoS) attack to a multi-service system. The method comprises the following steps of: detecting whether the DDoS attack exists in network access traffic corresponding to the multi-service system according to preset DDoS attack triggering conditions by using network security equipment; when the DDoS attack exists, determining a target service aimed by the DDoS attack according to the DDoS attack triggering conditions corresponding to the DDoS attack; and protecting the network access traffic, corresponding to the target service, in the network access traffic corresponding to the multi-service system according to the service related information of the target service. Compared with the prior art, the invention not only limits the undesirable impact of the DDoS attack on the whole multi-service system, but also effectively supports access requests for other services in the multi-service system by detecting the target service aimed by the DDoS attack and performing corresponding defense processing according to the service related information of the target service, thereby effectively improving the information security capability of the whole multi-service system in defending against the DDoS attack.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
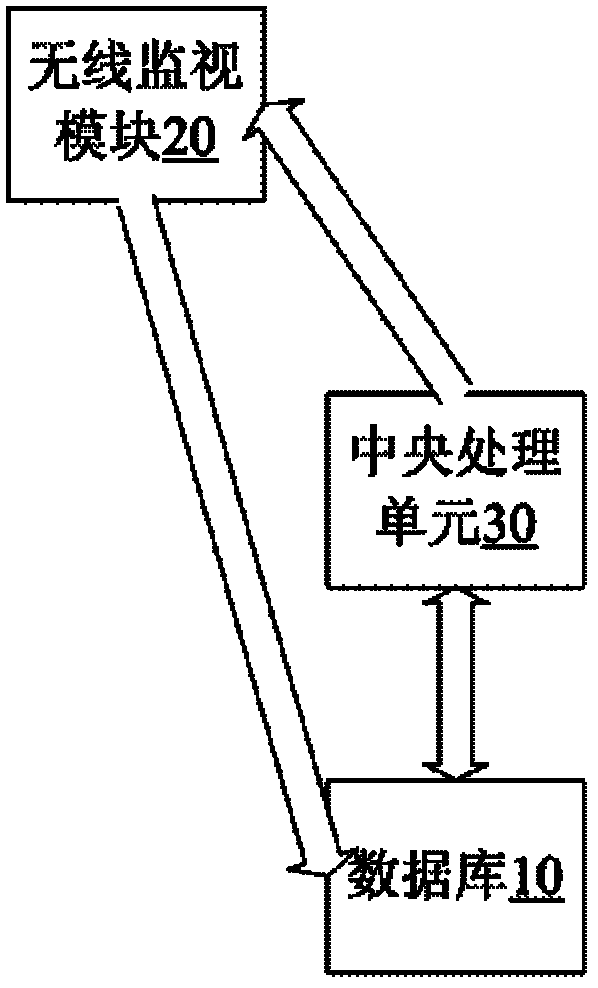
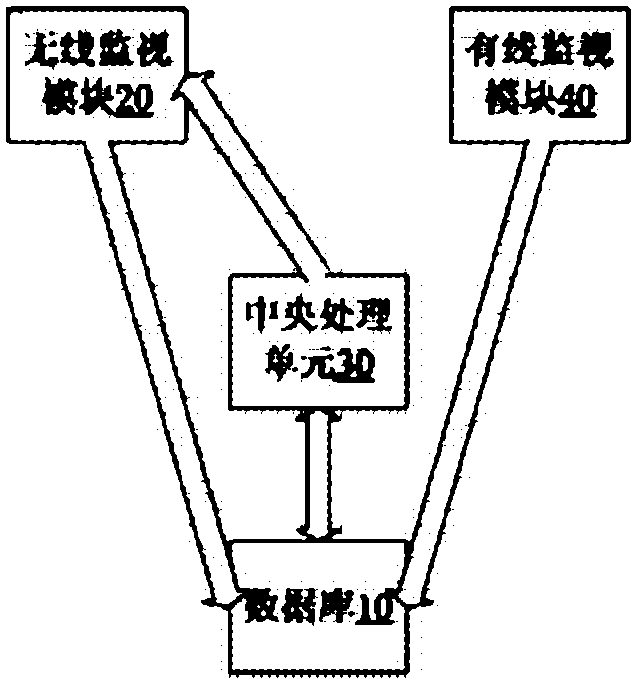
Method and system for detecting rogue wireless access point in local area network
InactiveCN102843684APrevent intrusionAvoid osmosisSecurity arrangementArea networkTelecommunications
The invention discloses a system and a method for detecting a rogue wireless access point in a local area network. The system comprises a database, a wireless monitoring module and a central processing unit, wherein the database is used for storing the corresponding information of a legal wireless access point in the local area network in a legal list; the wireless monitoring module is used for periodically scanning each channel in the local area network to acquire identification information from the channel, and used for testing a suspected wireless access point determined by the central processing unit, trying connecting the suspected wireless access point in a management mode, and further trying connecting a plurality of legal nodes in the local area network by the suspected wireless access point if the connection is successful; and the central processing unit is used for comparing the identification information of an existed access point acquired by the scanning with the corresponding information in the legal list, and listing the wireless access point not occurring in the legal list as the suspected wireless access point and judging that the suspected wireless access point is the rogue wireless access point if successfully receiving the feedback information that the suspected wireless access point is successfully connected with the legal nodes from the wireless monitoring module.
Owner:AEROSPACE INFORMATION
System and method for managing errand and travel
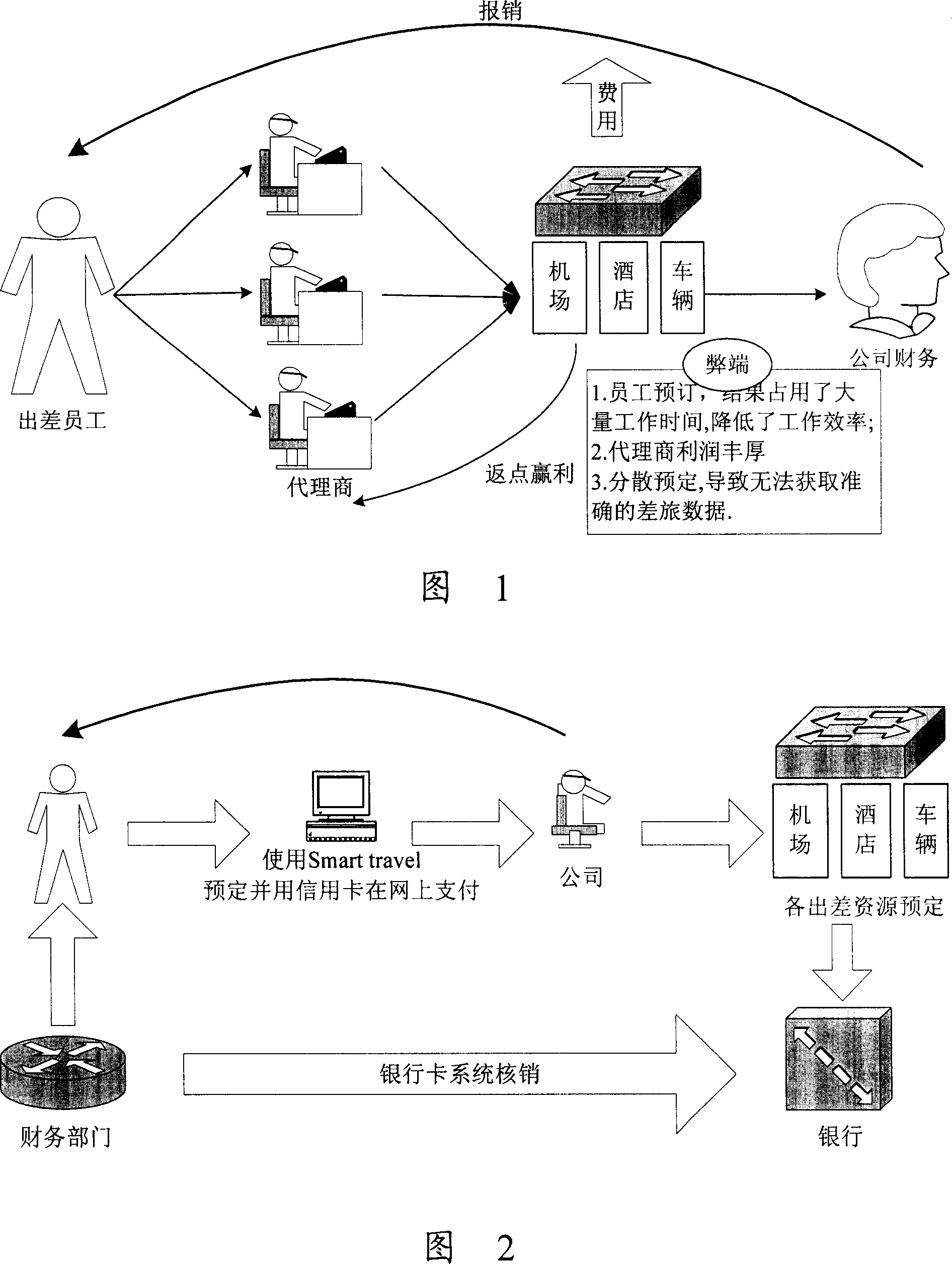
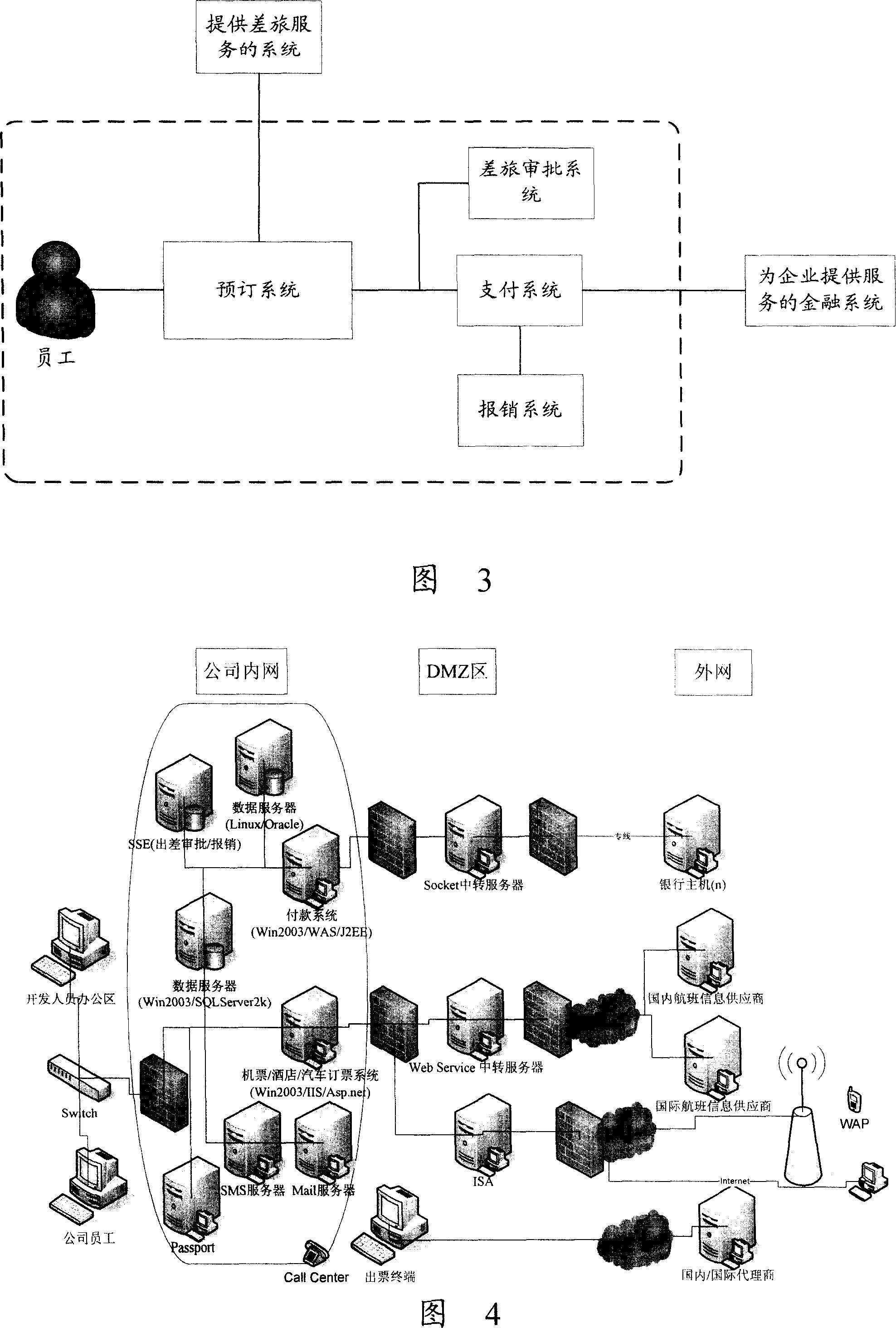
InactiveCN1987915AImprove information securityImprove management abilityPayment architectureResourcesManagement levelManagement system
The invention discloses a system and method of traveling management, including reservation systems and payment system. The reservation system according to the reserved the traveling information can interact information with the system of supplying traveling service to confirm the reserved traveling service, visit the corresponding system of supplying traveling service, reserve, compute fee, sent the fee information to payment system; The payment system can interact the information with the enterprises finance system to receive fee information from reservation system, visit the enterprises finance system, verify the cost. The system and method supplied by the present invention can not only improve the information safety of traveling management, but also integrated analyze the inner traveling data for enterprises and improve the management level of traveling.
Owner:HUAWEI TECH CO LTD
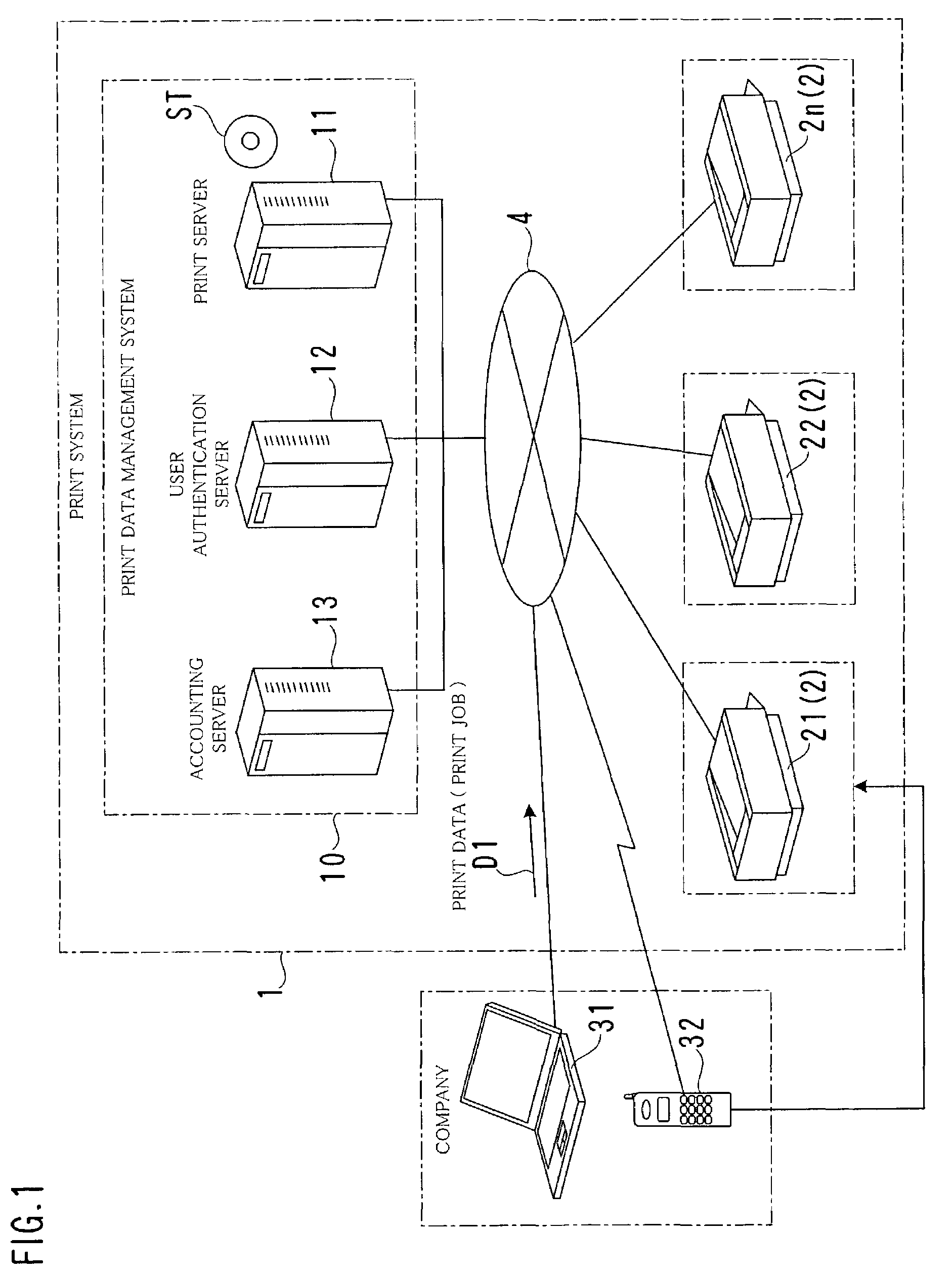
Print system, print data management system and printer
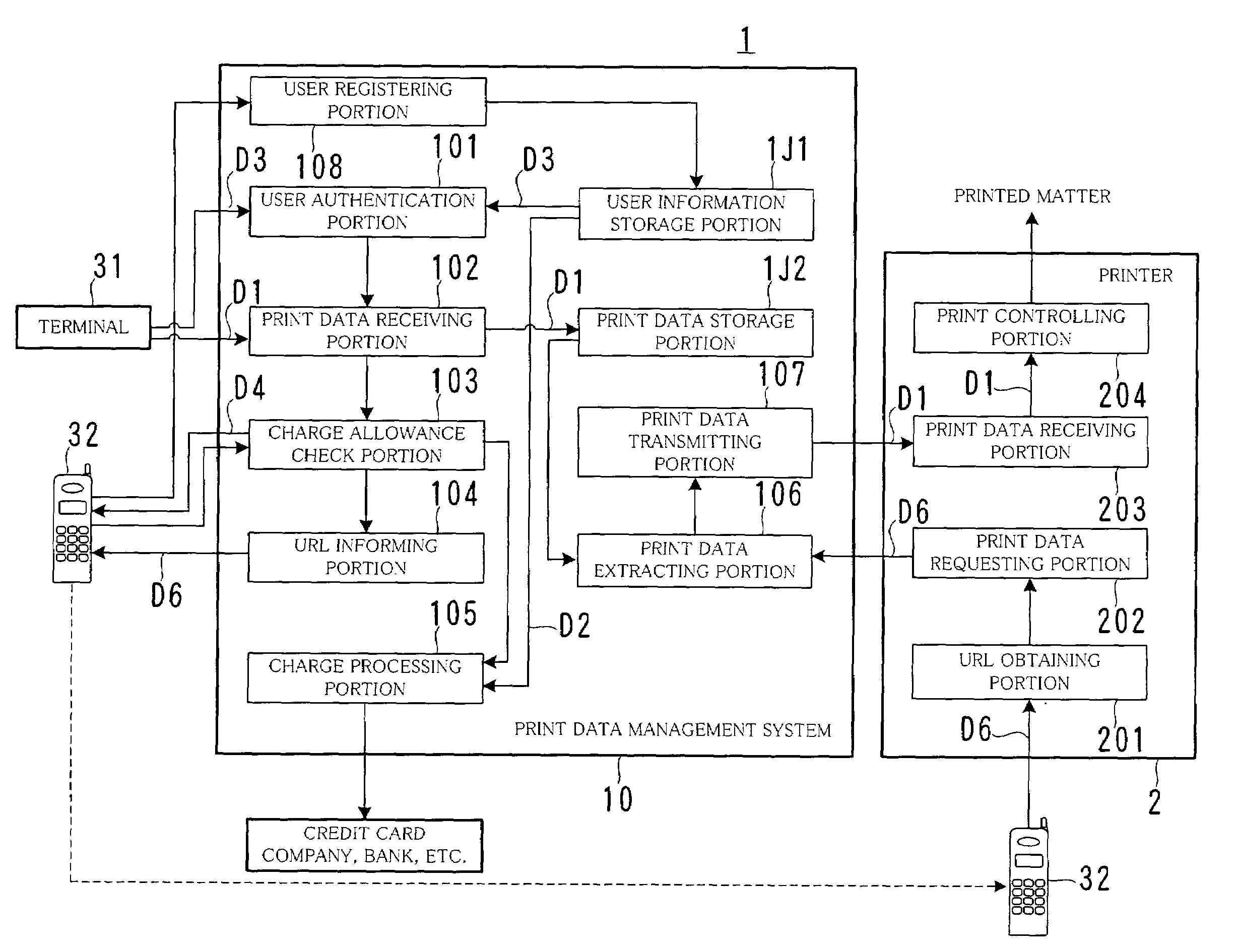
InactiveUS7079276B2Improve information securityReduce wasteData processing applicationsDigital computer detailsComputer terminalData management
A print system is provided in which security of information is enhanced, and waste of print is reduced. The print system comprises a print data management system and a printer. The print data management system includes a print data receiving portion for receiving print data from a terminal, a print data storage portion for storing the received print data, a URL informing portion for informing the storage location information of the print data to a user of a terminal, an extraction portion for extracting print data requested by the printer from the print data storage portion, and a transmission portion for transmitting the extracted print data to the printer. The printer includes a URL obtaining portion for obtaining storage location information from the user who came to the place where the printer is installed, a print data requesting portion for requesting the print data management system for print data of the obtained storage location information, and a print controlling portion for printing in accordance with the print data received from the print server.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Secure access terminal for intranet and extranet
InactiveCN103532980AImprove information securityAchieve isolationTransmissionControl switchClient-side
The invention provides a secure access terminal for an intranet and an extranet. The secure access terminal comprises intranet and extranet safety equipment and a processing unit, wherein an input-end interface unit of the intranet and extranet safety equipment is connected with a first control unit and a second control unit respectively through a two-channel switch unit; when a client selects an extranet mode, the processing unit controls the two-channel switch unit to gate the second control unit, switches on a second power control switch to enter an extranet system and switches off a first power control switch to cut off connection with an intranet system at the moment; and when the client selects an intranet mode, the processing unit controls the two-channel switch unit to gate the first control unit, switches on the first power control switch to enter the intranet system and switches off the second power control switch to cut off connection with the extranet system at the moment. The secure access terminal for the intranet and the extranet is used for realizing isolation and safety protection of the intranet and extranet systems, and information security of the intranet system can be protected effectively.
Owner:国家信息中心 +1
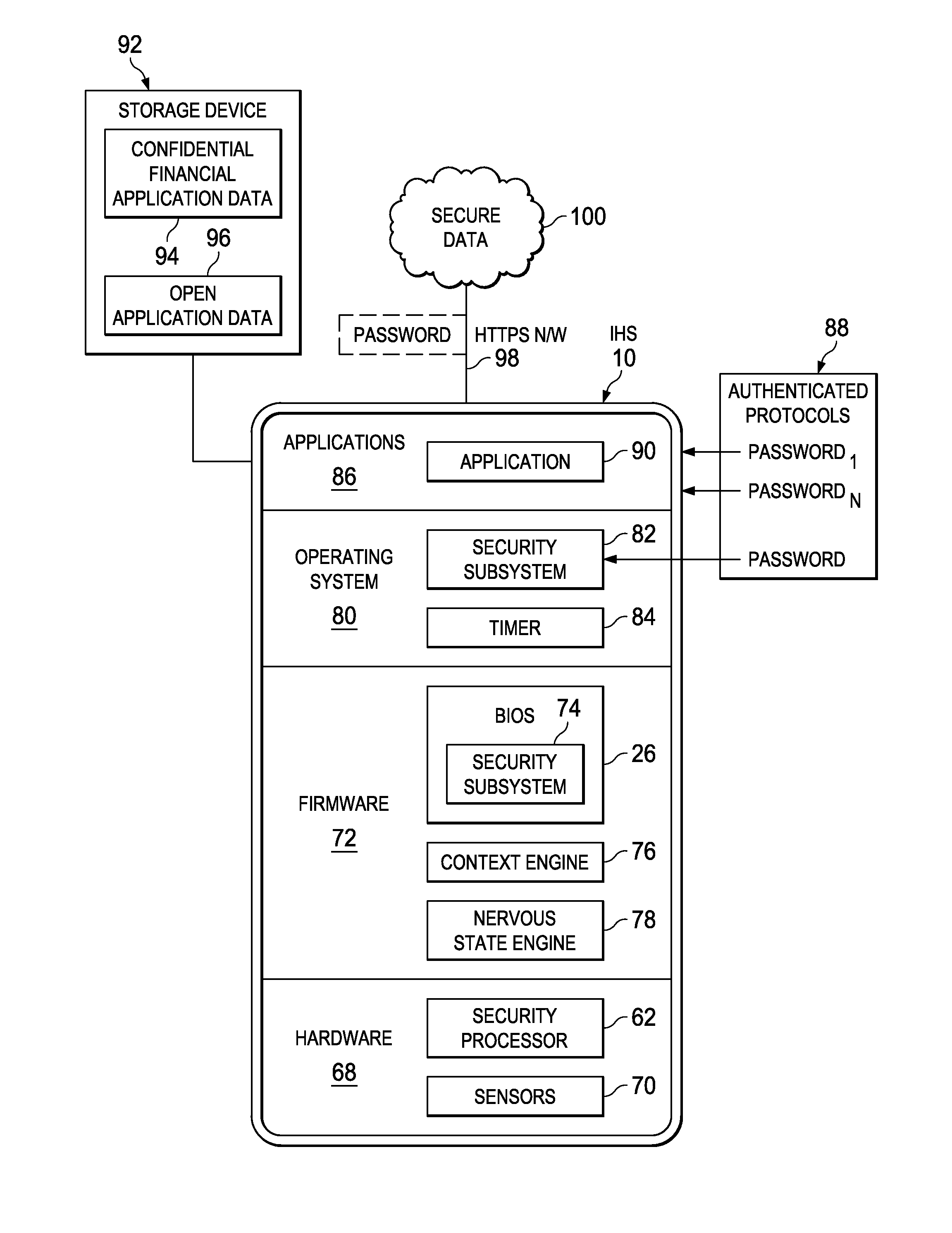
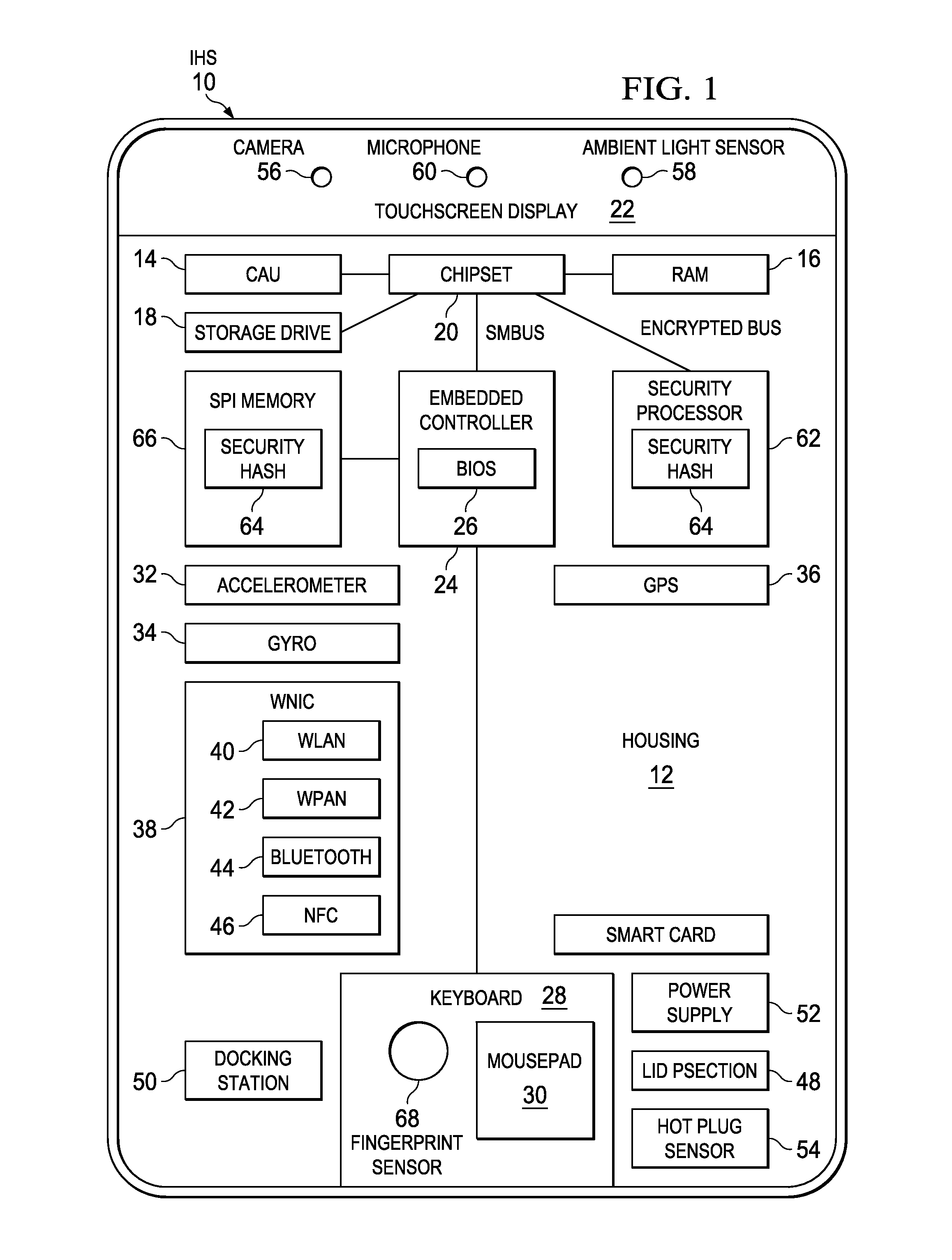
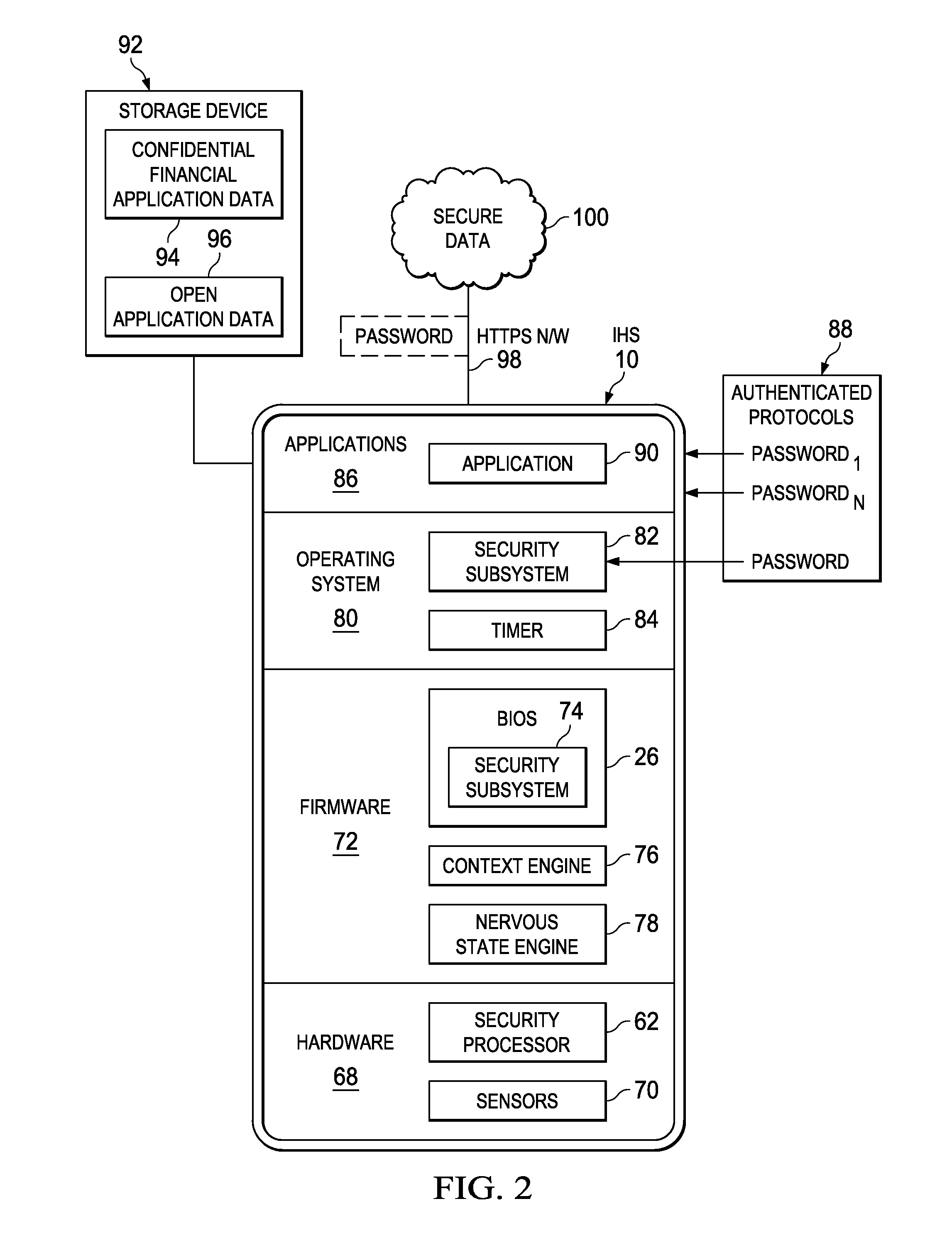
Context Analysis at an Information Handling System to Manage Authentication Cycles
ActiveUS20150135298A1Various levelReduce disadvantagesDigital data processing detailsUnauthorized memory use protectionContext basedHandling system
Context captured with sensors of an information handling system is applied to selectively lock access to currently unlocked information, with conditions for locking access based upon the context. Nervous states enforce locking of selected information based upon the confidence of the security of the information under sensed external conditions. Increased sensitivity for locking access includes reduced timeouts to a lock command, increased response to sensed conditions, and more rapid response where unlocked access is to sensitive information.
Owner:DELL PROD LP
Security authentication method and terminal
InactiveCN105959317AImprove information securityMeet information security needsTransmissionSecurity authenticationInformation security
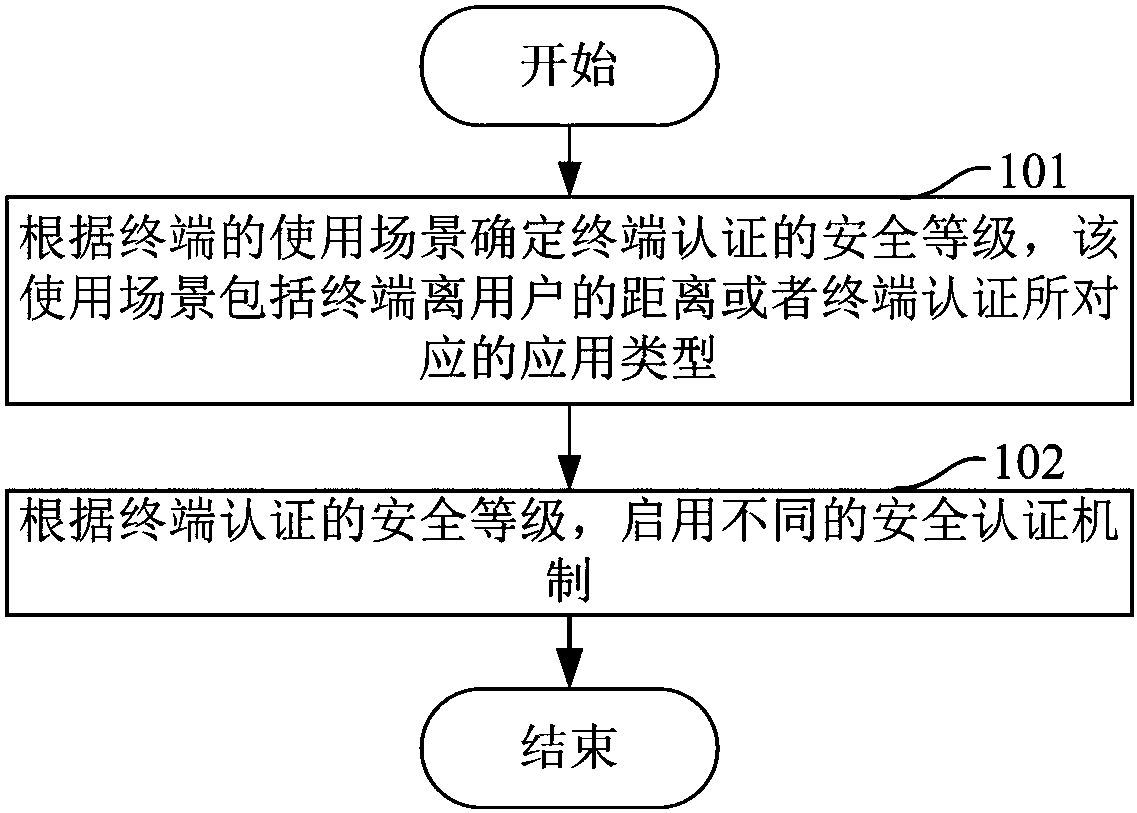
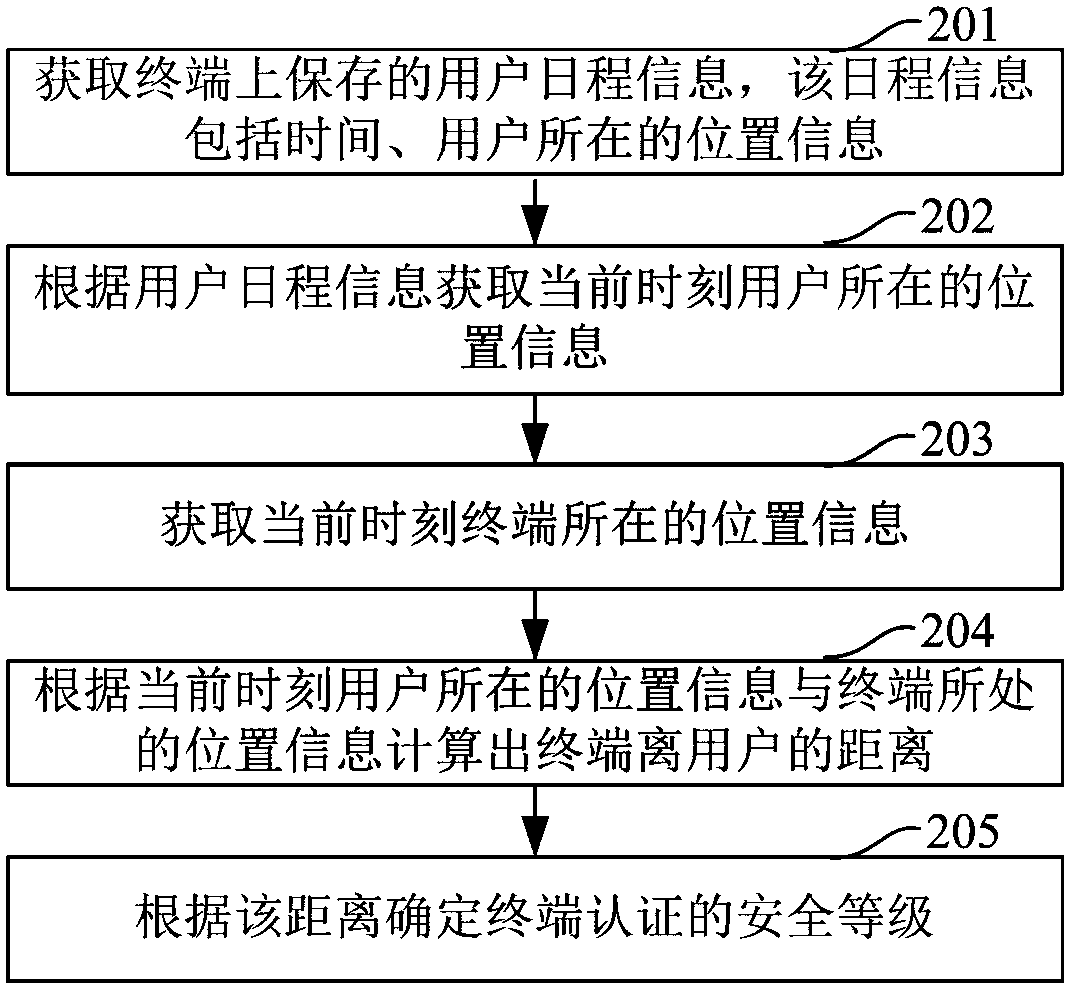
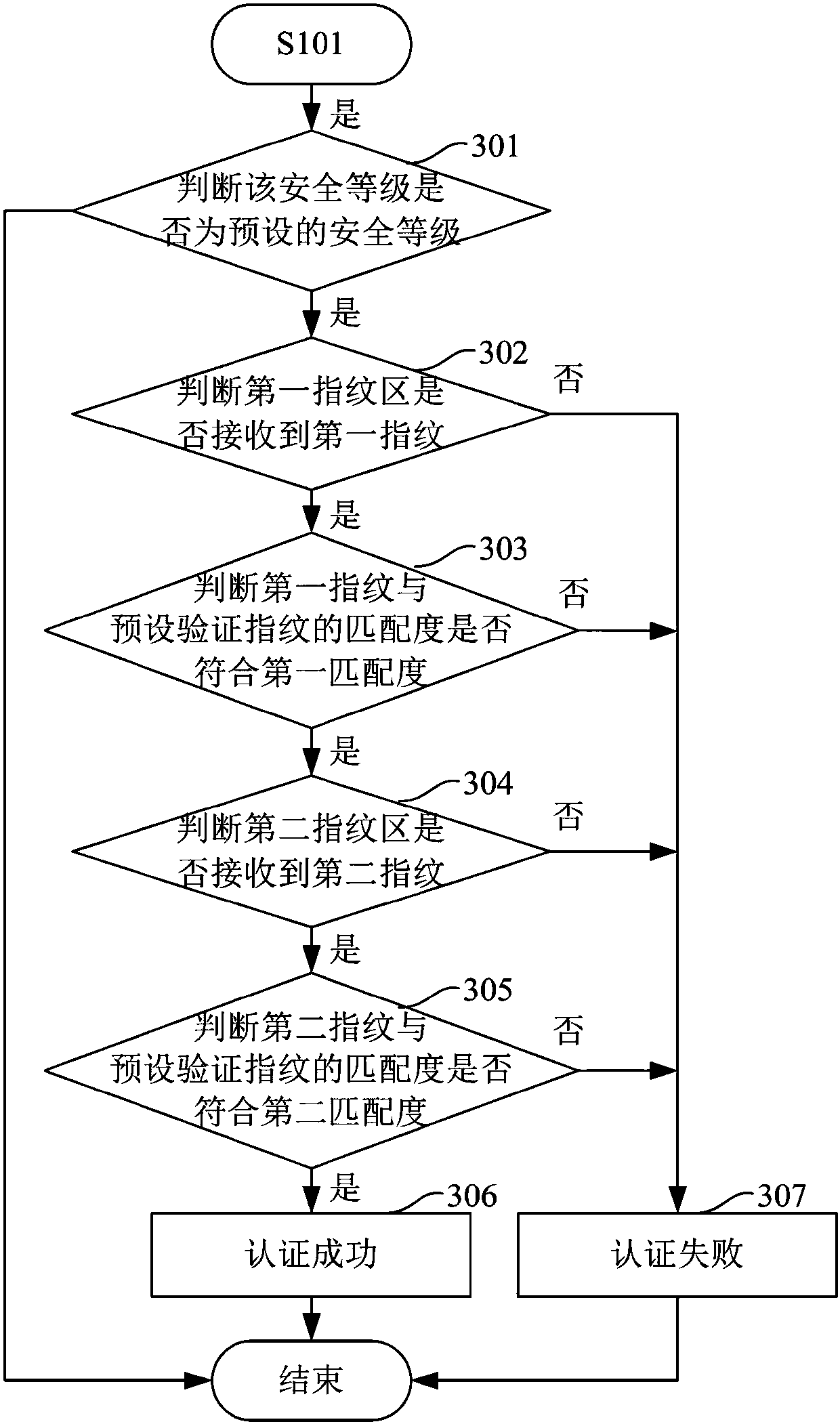
The embodiment of the invention discloses a security authentication method and a terminal. The method comprises the steps of determining a security level of terminal authentication according to usage scenario of the terminal, wherein the usage scenario comprises the distance between the terminal and a user or an application type corresponding to the terminal authentication; and starting different security authentication mechanisms according to the security level of the terminal authentication. The terminal comprises a determining unit for determining the security level of the terminal authentication according to the usage scenario of the terminal, wherein the usage scenario comprises the distance between the terminal and the user or the application type corresponding to the terminal authentication; and an authentication unit for starting different security authentication mechanisms according to the security level of the terminal authentication. According to the method and the terminal provided by the embodiment of the invention, the information security of the user can be improved, and the information security demand of the user can be satisfied.
Owner:SHENZHEN GIONEE COMM EQUIP
Safety intelligent terminal equipment and information processing method
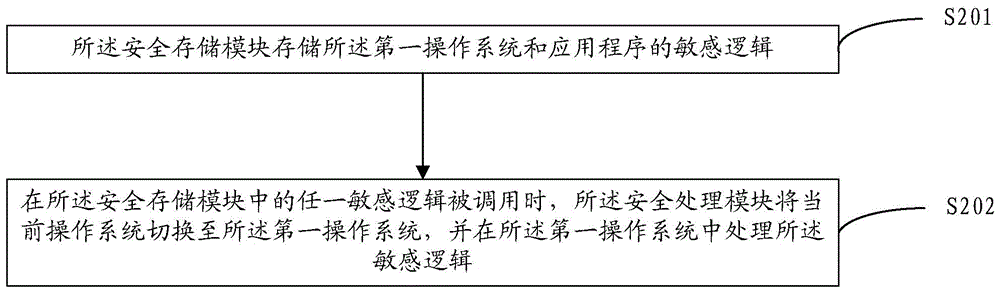
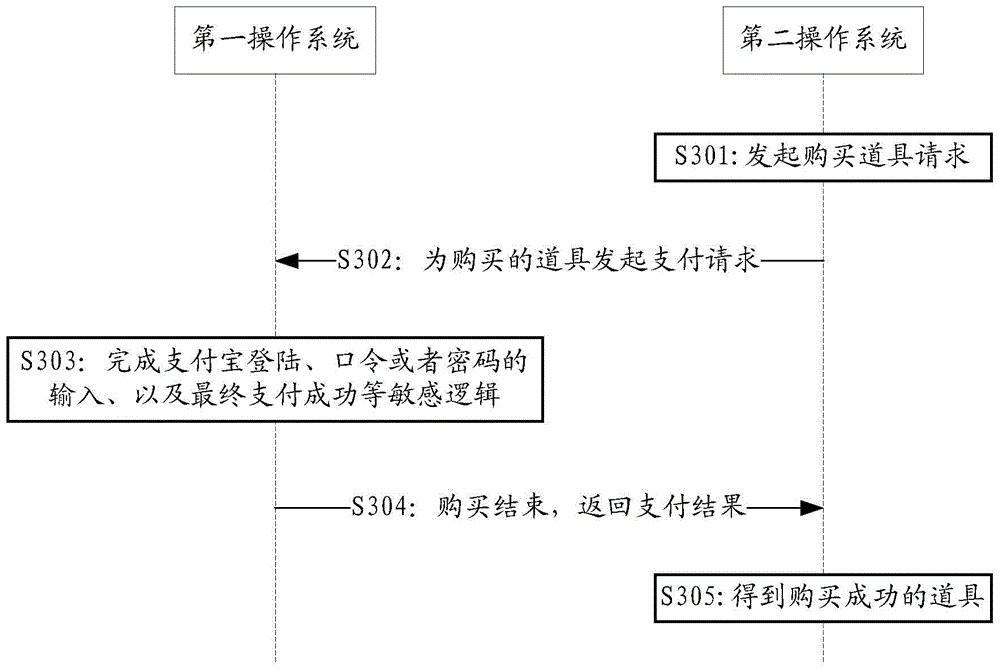
InactiveCN104143065AProtection securityImprove information securityInternal/peripheral component protectionPayment architectureInformation processingTerminal equipment
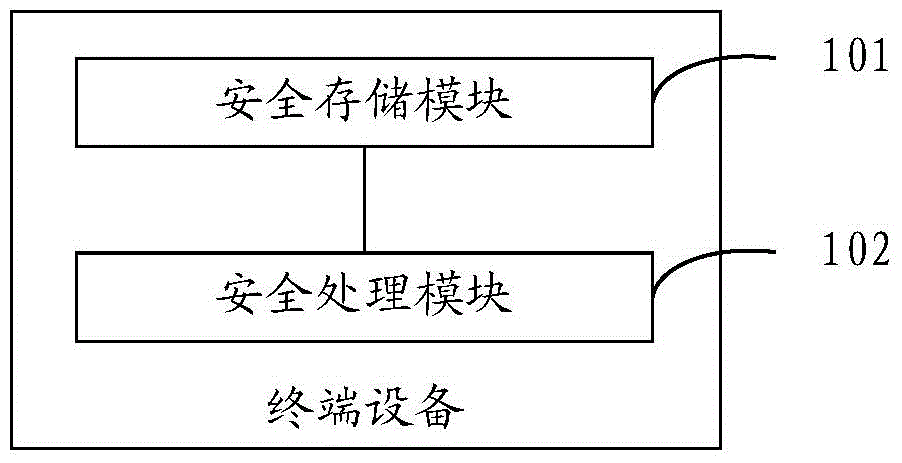
The embodiment of the invention discloses safety intelligent terminal equipment and an information processing method. The terminal equipment comprises a first operating system, wherein the first operating system is used for processing a sensitive logic. The terminal equipment comprises a safety storage module and a safety processing module, wherein the safety storage module is used for storing sensitive logics of the first operating system and an application program; and the safety processing module is used for switching a current operating system to the first operating system when any sensitive logic in the safety storage module is called, and processing the sensitive logic in the first operating system. According the safety intelligent terminal equipment, the first operating system has a function of protecting the safety of user information to prevent the user information from being invaded by malicious software and the like. Thus, by using the terminal equipment provided by the invention, the safety of the user information can be improved.
Owner:WATCHDATA SYST
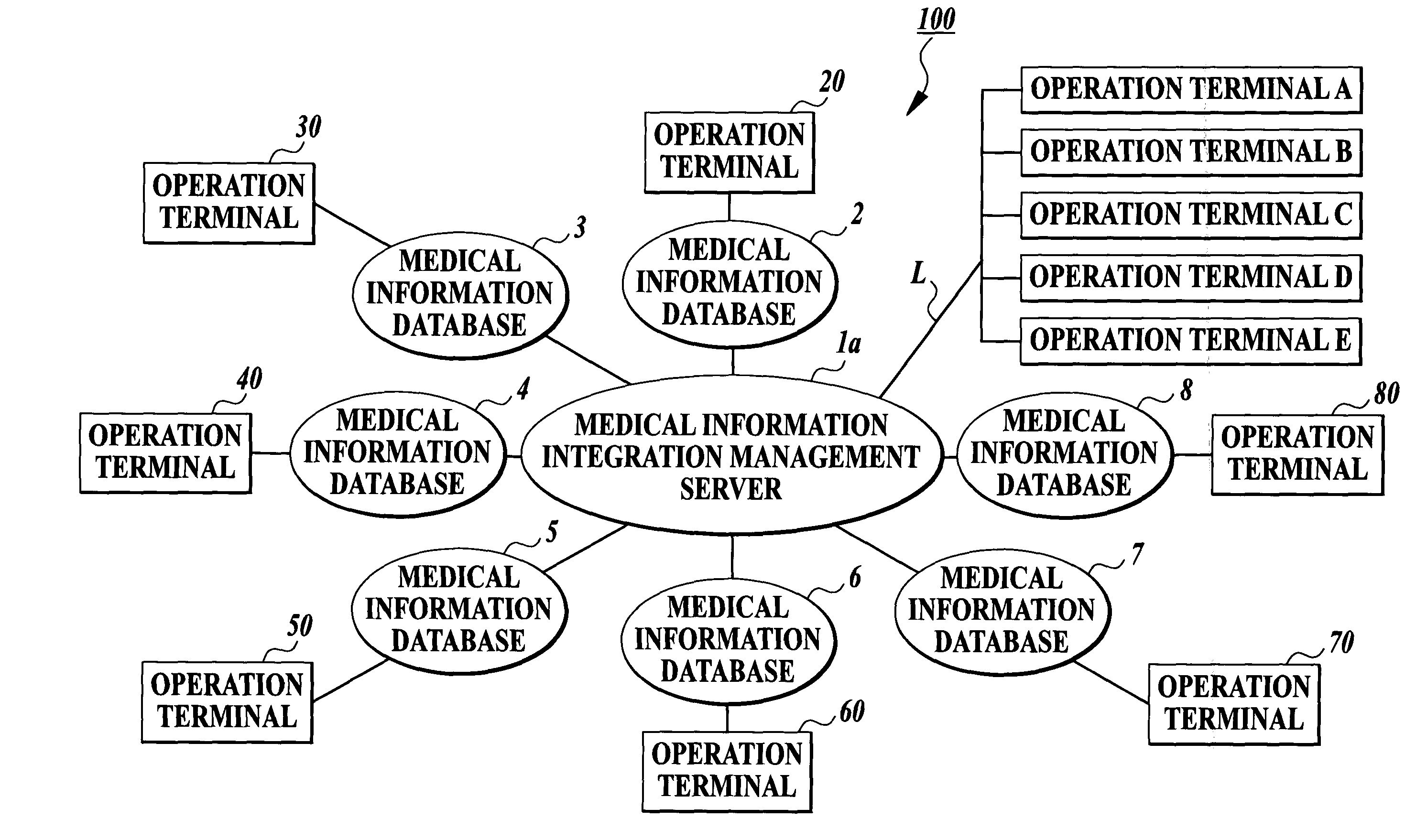
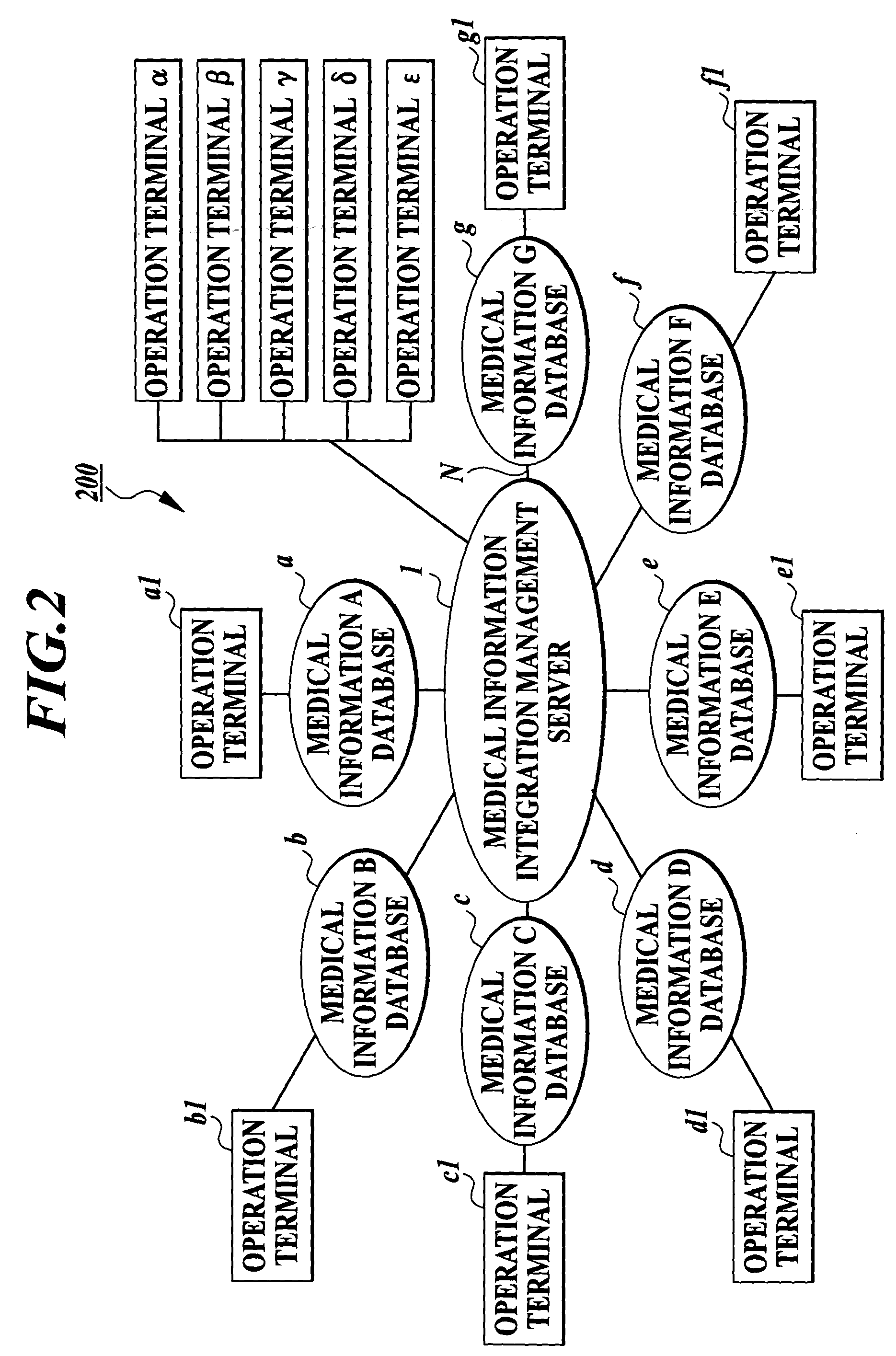
Medical information management system
InactiveUS20040054657A1Improve information securityImproper operationDigital data processing detailsDigital data protectionAutomatic transmissionData access
A medical information management system including: plural database devices for storing medical information in a database; a management device for managing the medical information integrally; and an operation terminal for operating at least one of the database and management devices, database devices having an automatic transmission section for extracting necessary information from the medical information stored in the database and sending the necessary information to the management device. The management device includes a reception section for receiving the medical information sent from the transmission section; a storage section for storing integrally the medical information received by the reception section based on predetermined information included in the medical information; an individual verification section for verifying whether an operator of the terminal is an individual registered beforehand; and a data access authentication section for judging whether medical information instructed to be operated by the terminal is information capable of being operated.
Owner:KONICA MINOLTA INC
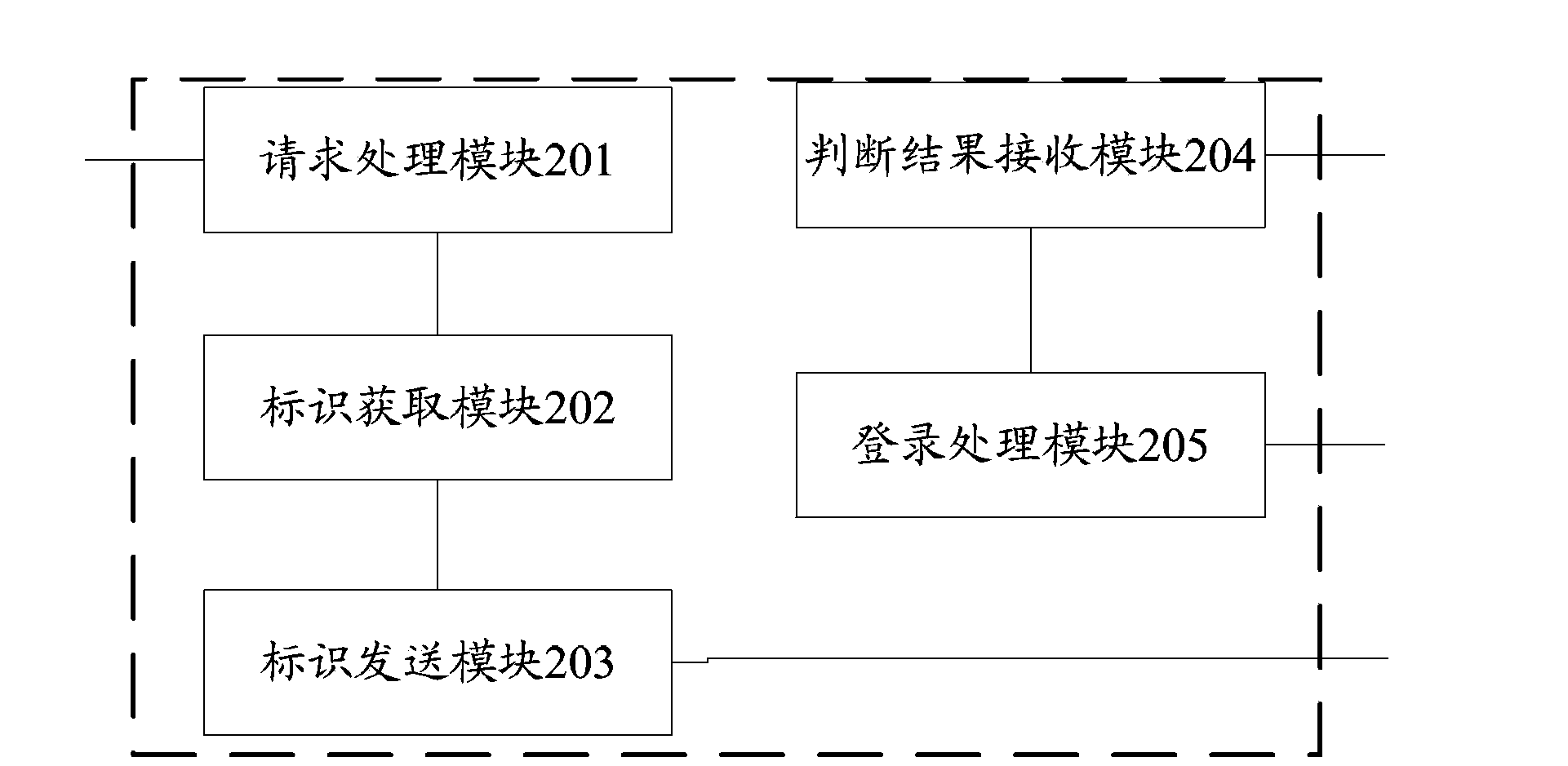
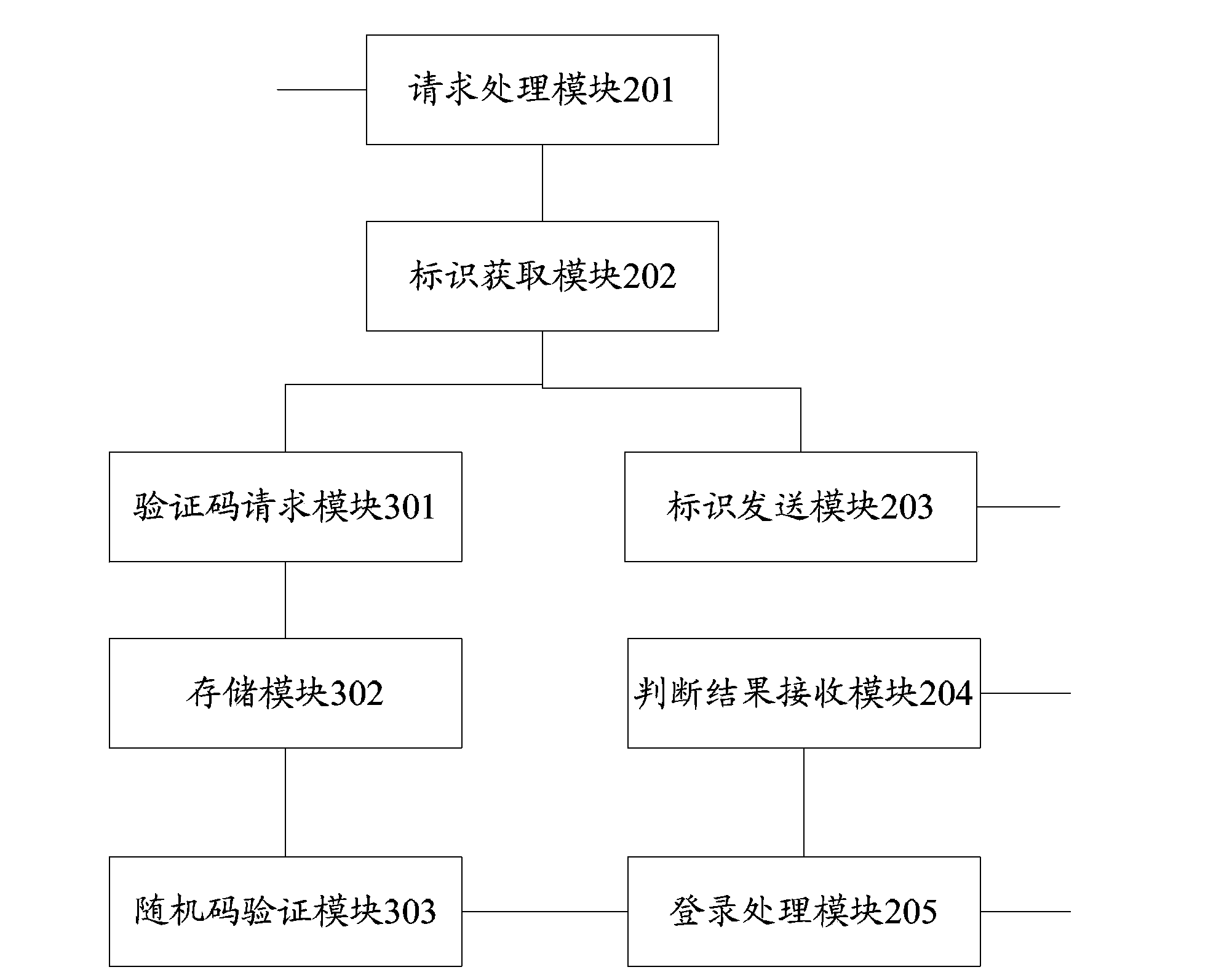
Login method, maintenance terminal, data management service equipment and login system
The invention provides a login method, a maintenance terminal, data management service equipment and a login system. In the method, the maintenance terminal receives a login request and transmits user authentication information contained in the login request to the data management service equipment; after the data management service equipment returns a verification result that the user identity is legitimate, the maintenance terminal obtains identification information of a server to be logged and transmits the identification information to the data management service equipment which determines whether a user has the authority to manage the server to be logged; and according to a determination result which shows that the user has the authority, the maintenance terminal requests login information for logging on to the server from the data management service equipment and transmits the received login information to the server to be logged, and the user is logged in when the login information is verified by the server to be logged server. The technical scheme of the invention can effectively improve the information security of a data center, reduce the workload to find out login information and improve the information maintenance efficiency of the data center.
Owner:CHINA MOBILE COMM GRP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com