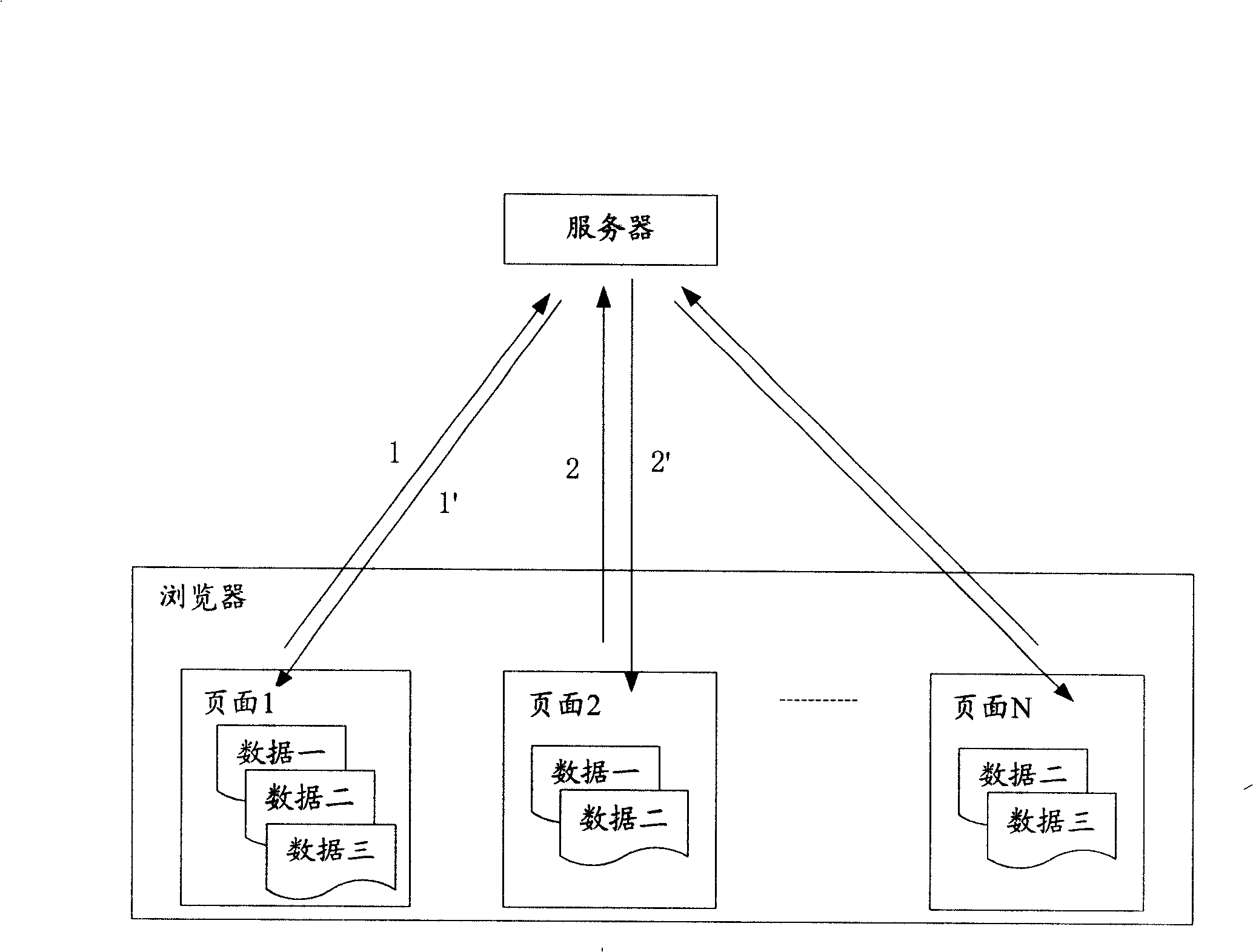
Patents
Literature
956results about How to "Reduce the number of interactions" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
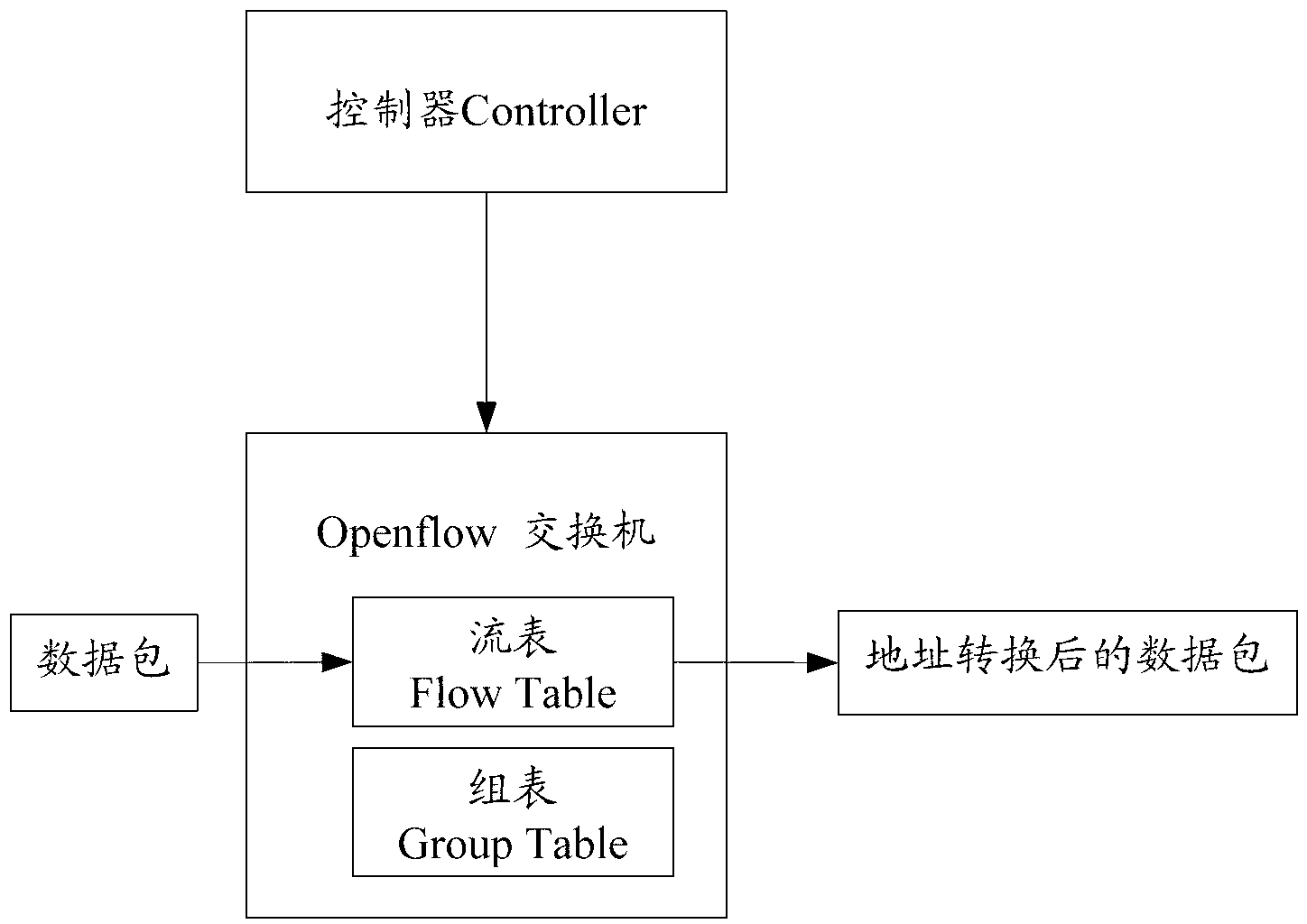
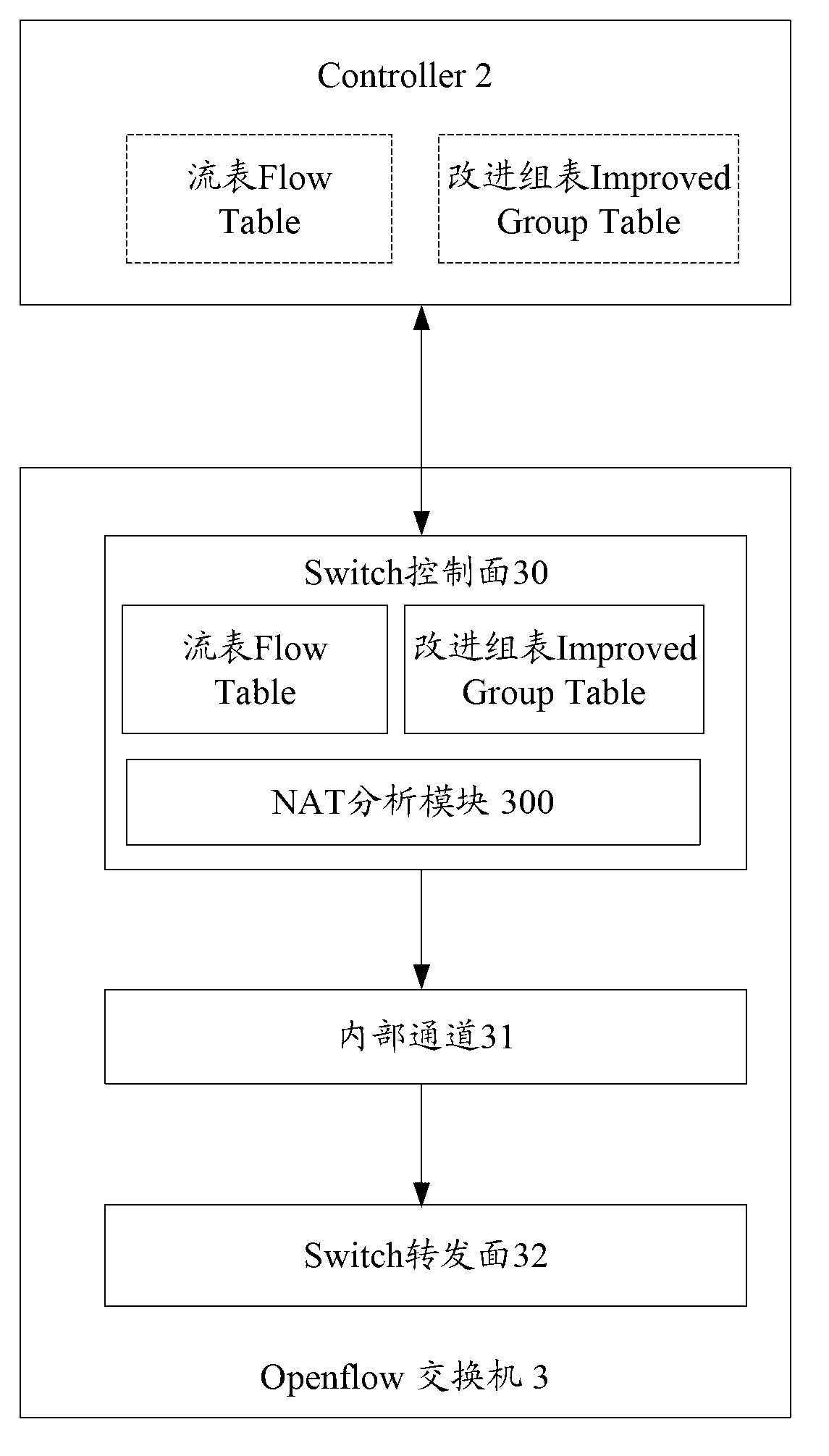
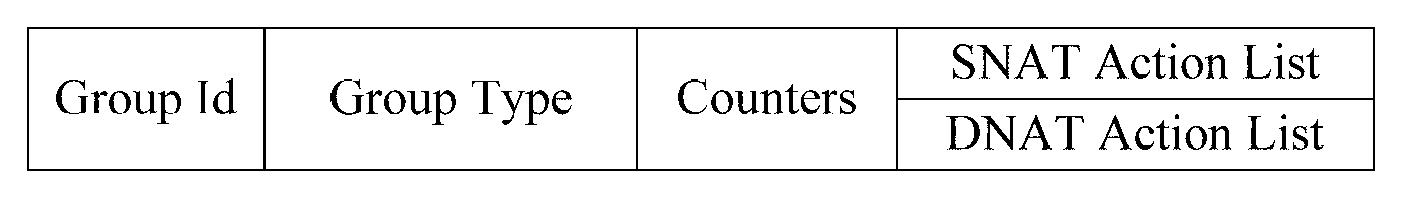
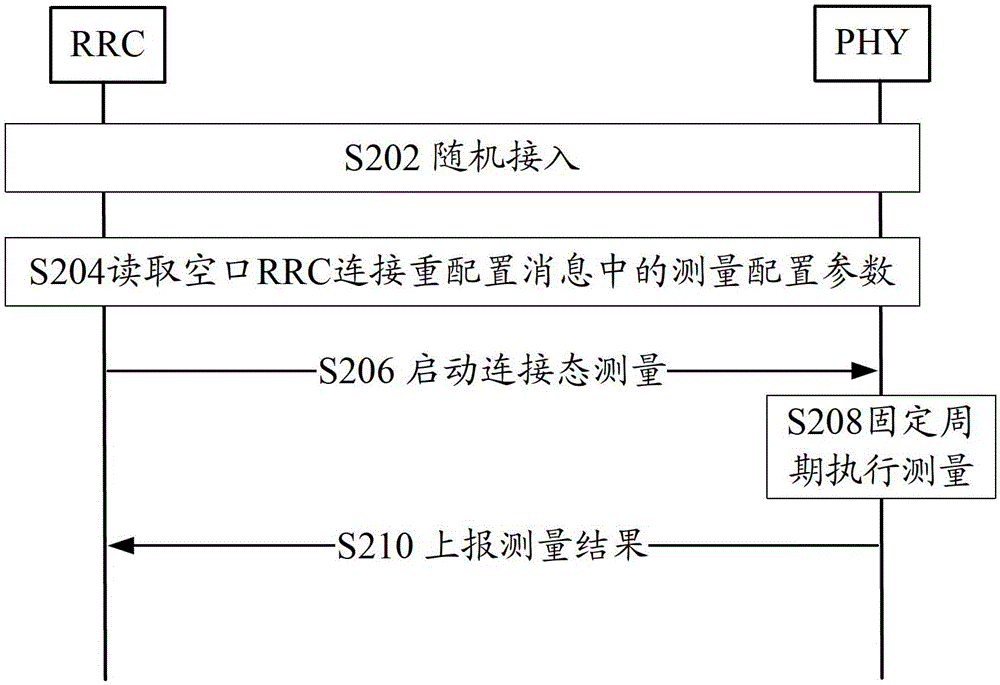
Network address translation (NAT) implementing system, method and openflow switch
ActiveCN103067534AReduce forwarding delayImprove transmission efficiencyHybrid transportNetwork address port translationOpenFlow
The invention discloses a network address translation (NAT) implementing system which comprises a controller and an openflow switch, wherein the controller issues a flow table and an improved group table, the openflow switch receives the flow table and the improved group table, a data package which needs to conduct address translation is matched according to a matching rule of the address translation recorded by the flow table, translation between a private address and a public internet protocol (IP) address is conducted according to a rule of address translation recorded by the improved group table, and the data package is transmitted out through an address which is translated. The invention further discloses an NAT implementing method and the openflow switch. According to the NAT implementing system, only the flow table and the improved group table are transmitted to the openflow switch once, frequent intersection between the openflow switch and the controller is not required, time delay of transmission of the data package is shortened, and transmission efficiency of a network is improved.
Owner:ZTE CORP
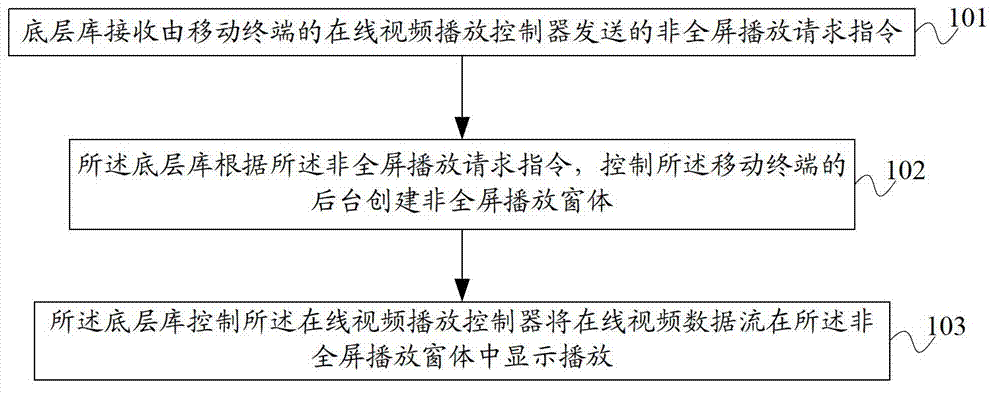
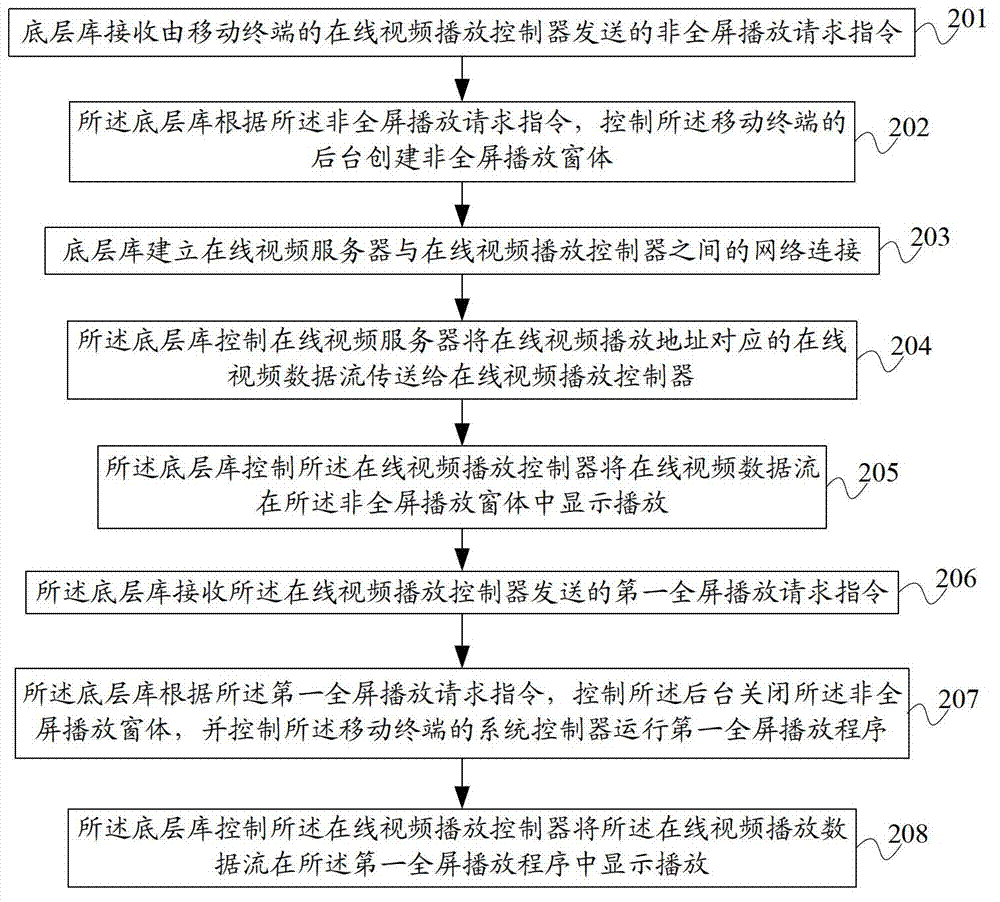
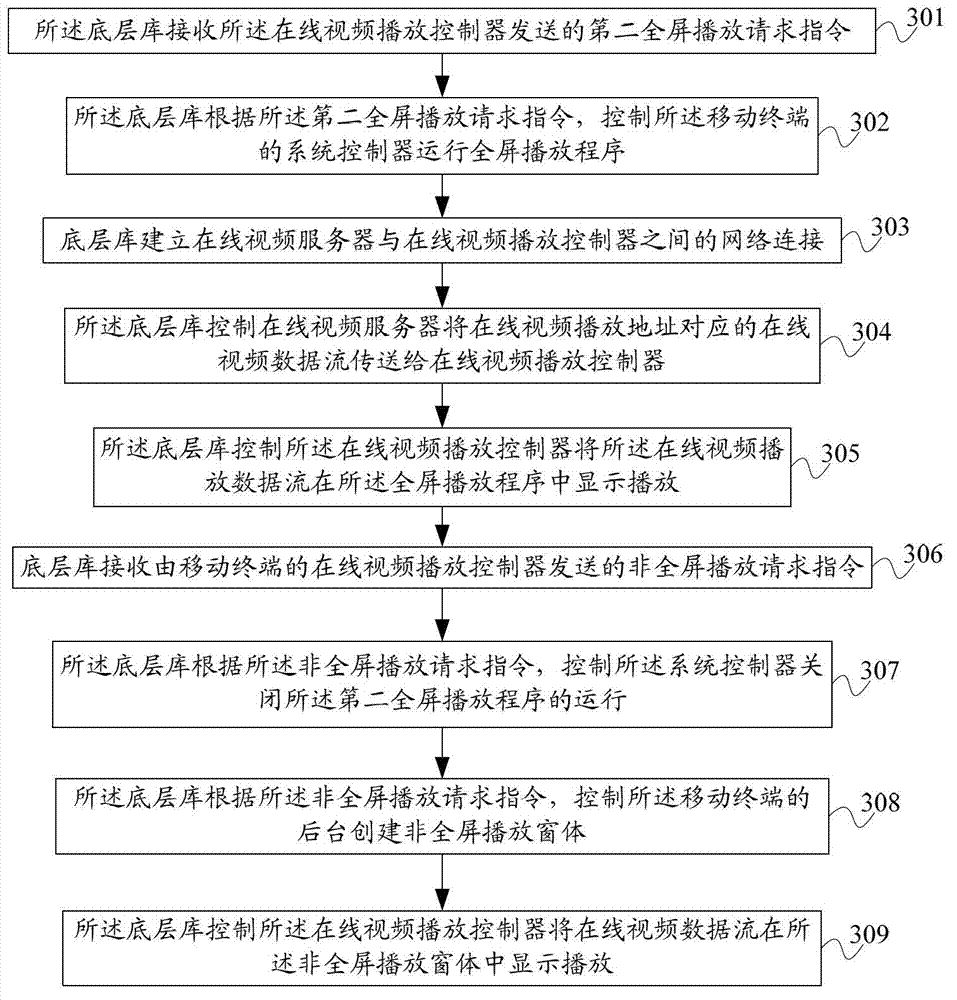
Method for realizing on-line video playing on mobile terminal, underlying library and system
ActiveCN102905181AImprove performanceEasy to operateSubstation equipmentSelective content distributionData streamComputer terminal
The invention provides a method for realizing on-line video playing on a mobile terminal, an underlying library and a system. The method comprises the following steps: the underlying library receives a non-full screen play request instruction transmitted by an on-line video playing controller of the mobile terminal; the underlying library controls a background of the mobile terminal to create a non-full screen play window according to the non-full screen play request instruction; the underlying library controls the on-line video playing controller to display and play on-line video data streams in the non-full screen play window; and the on-line video data streams are on-line video data streams transmitted to the on-line video playing controller by an on-line video server. According to the technical scheme, on-line videos can be played on the mobile terminal in a non-full screen, so that users of the mobile terminal can operate other programs while watching the on-line videos, in this way, not only the system performance of the mobile terminal is improved, but also the operation progress of the users is simpler and more convenient.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
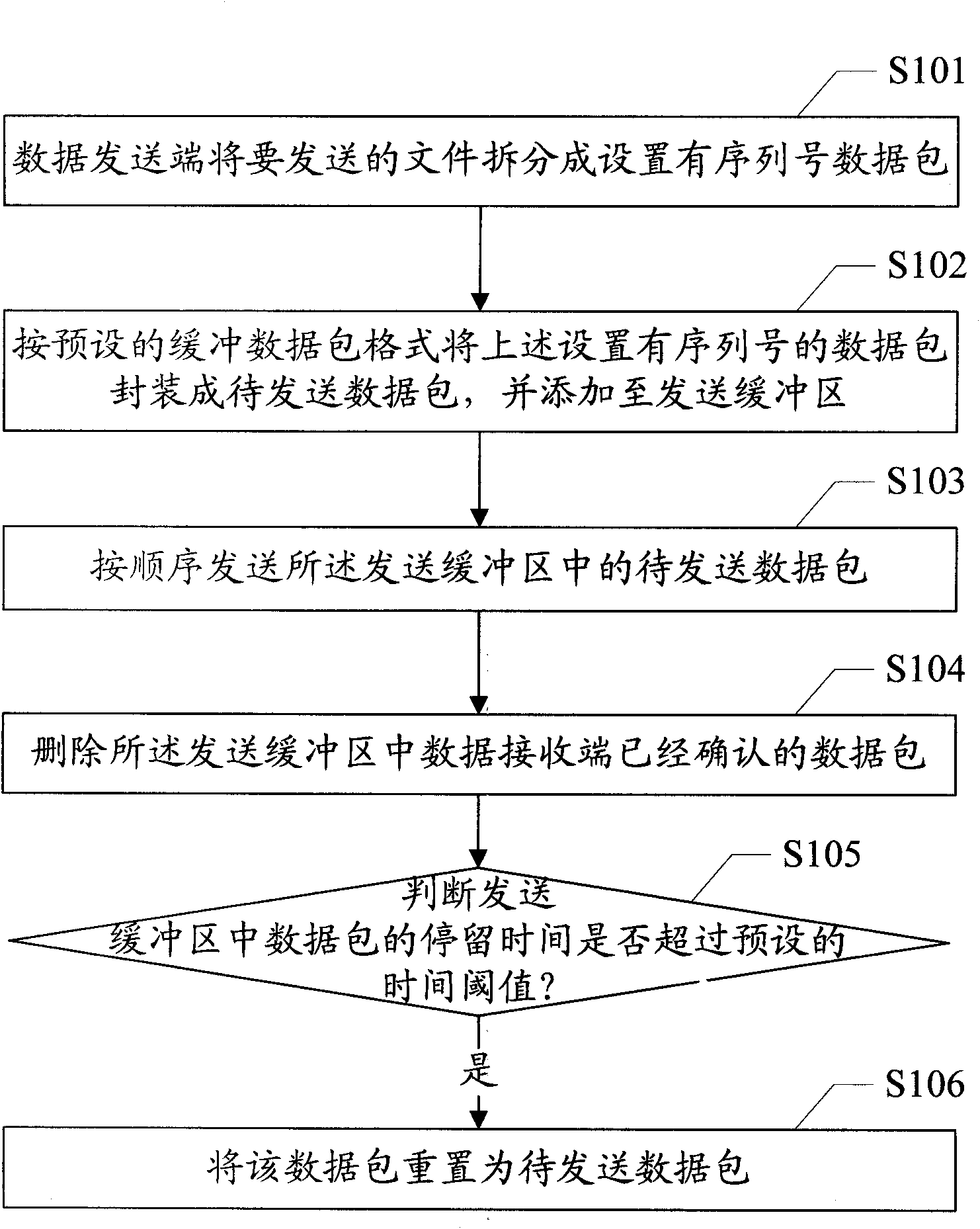
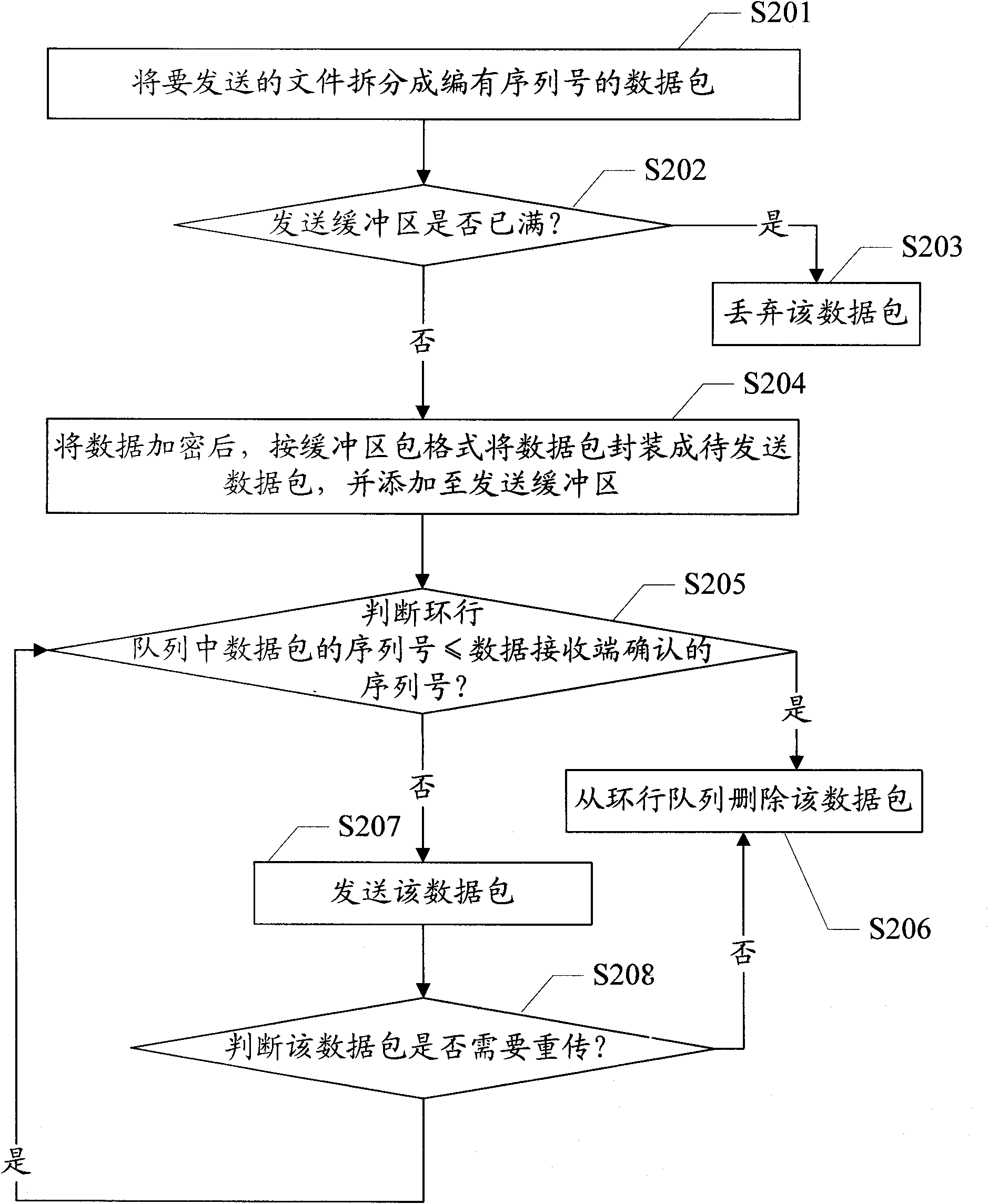
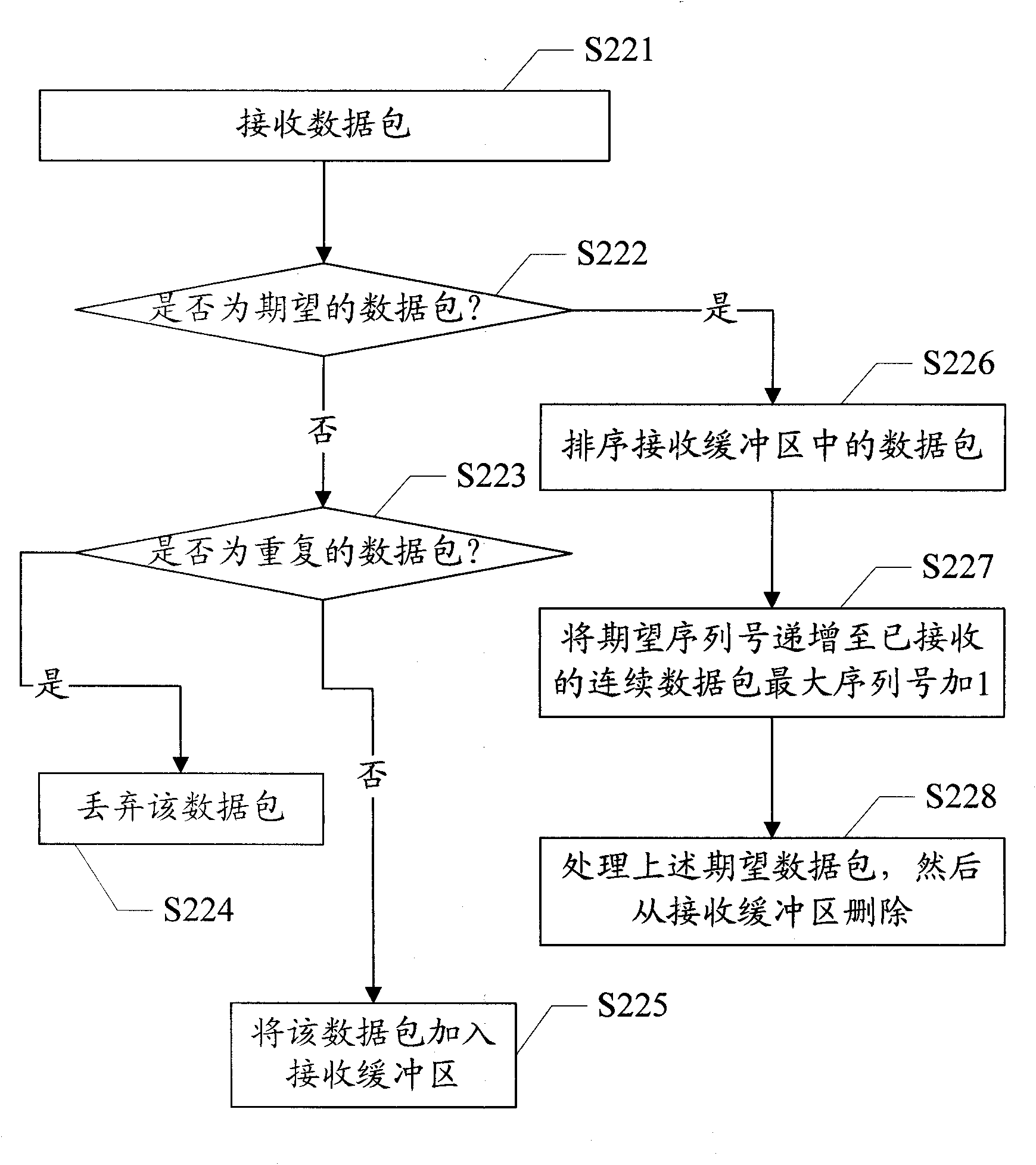
Reliable data transmission method and device thereof
ActiveCN102137027AReduce overheadImprove data transfer efficiencyError prevention/detection by using return channelData switching networksNetwork packetData transmission
The invention provides a reliable data transmission method and a device thereof. The method comprises the following steps: a data transmitting end divides a file to be transmitted into a data packets with serial numbers; according to a preset buffer data packet format, the data packets are packaged into data packets to be transmitted, and then are added to a transmission buffer area: the data packets to be transmitted in the transmission buffer area are transmitted in sequence; the data packets confirmed at a data receiving end in the transmission buffer area are deleted; whether the stoppingtime of the data packets in the transmission buffer area is over a preset time threshold or not is judged, and if so, the data packets are reset to be the data packets to be transmitted; and the transmission process is repeated. In the scheme of the invention, as only the data format and the transmission process at the transmitting end and the receiving of the data packets are controlled, no special data packets are needed to be transmitted between the transmitting end and the receiving end to carry out handshake connection operation, and under the condition that the system expense is less and the data transmission efficiency is high, the problem that the existing UDP (User Datagram Protocol) can not reliably transmit the data can be solved.
Owner:厦门市美亚柏科信息安全研究所有限公司
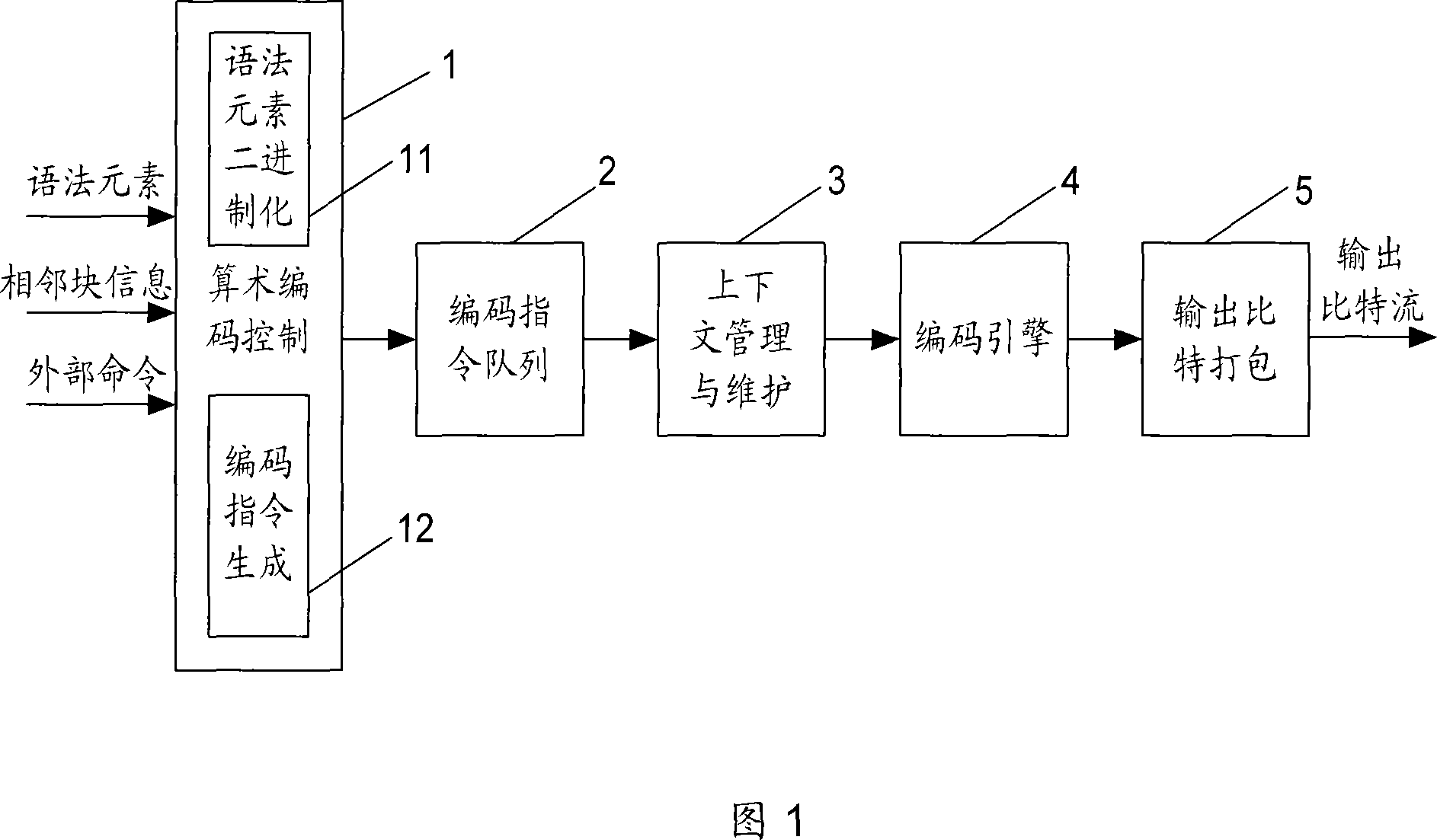
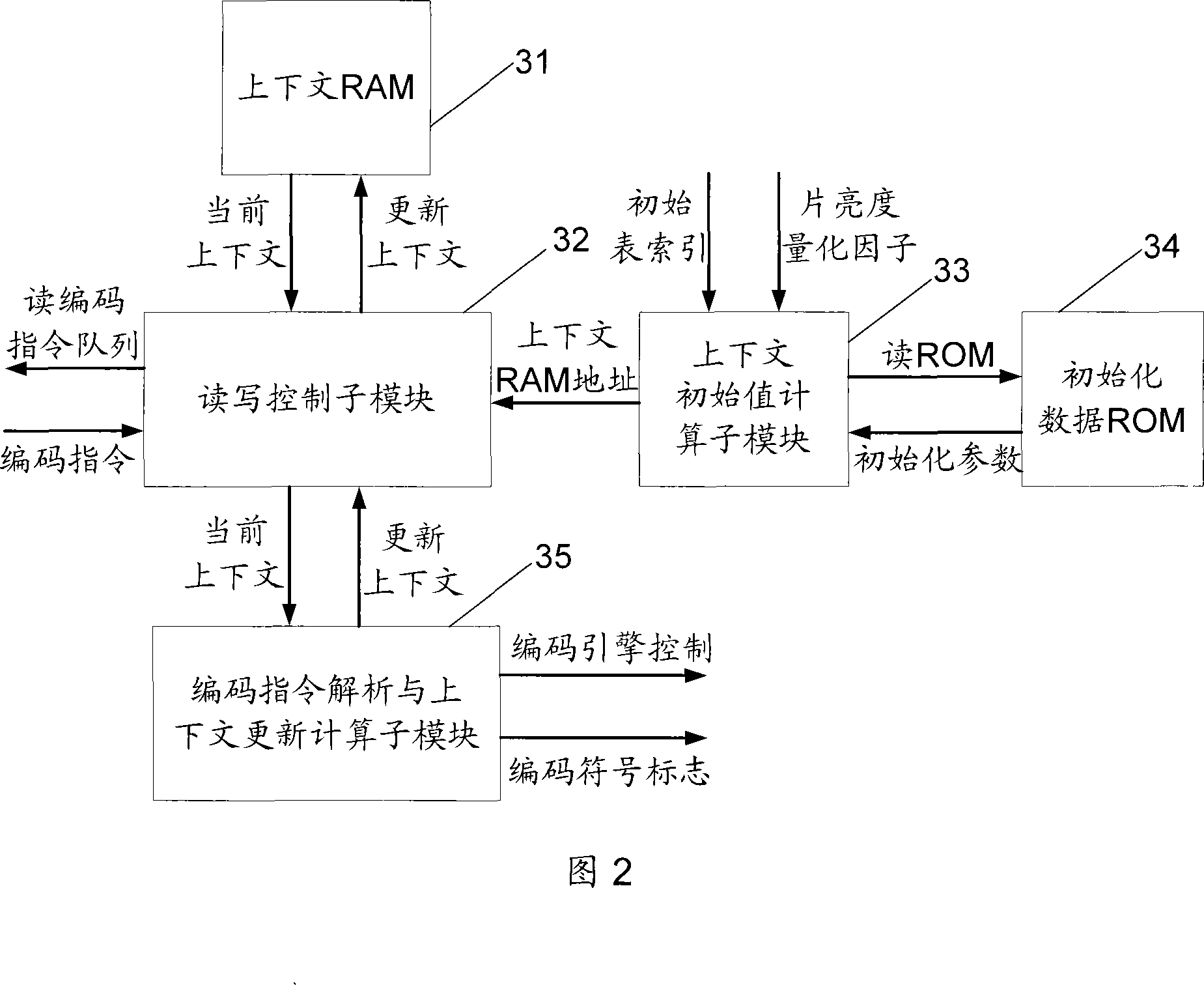
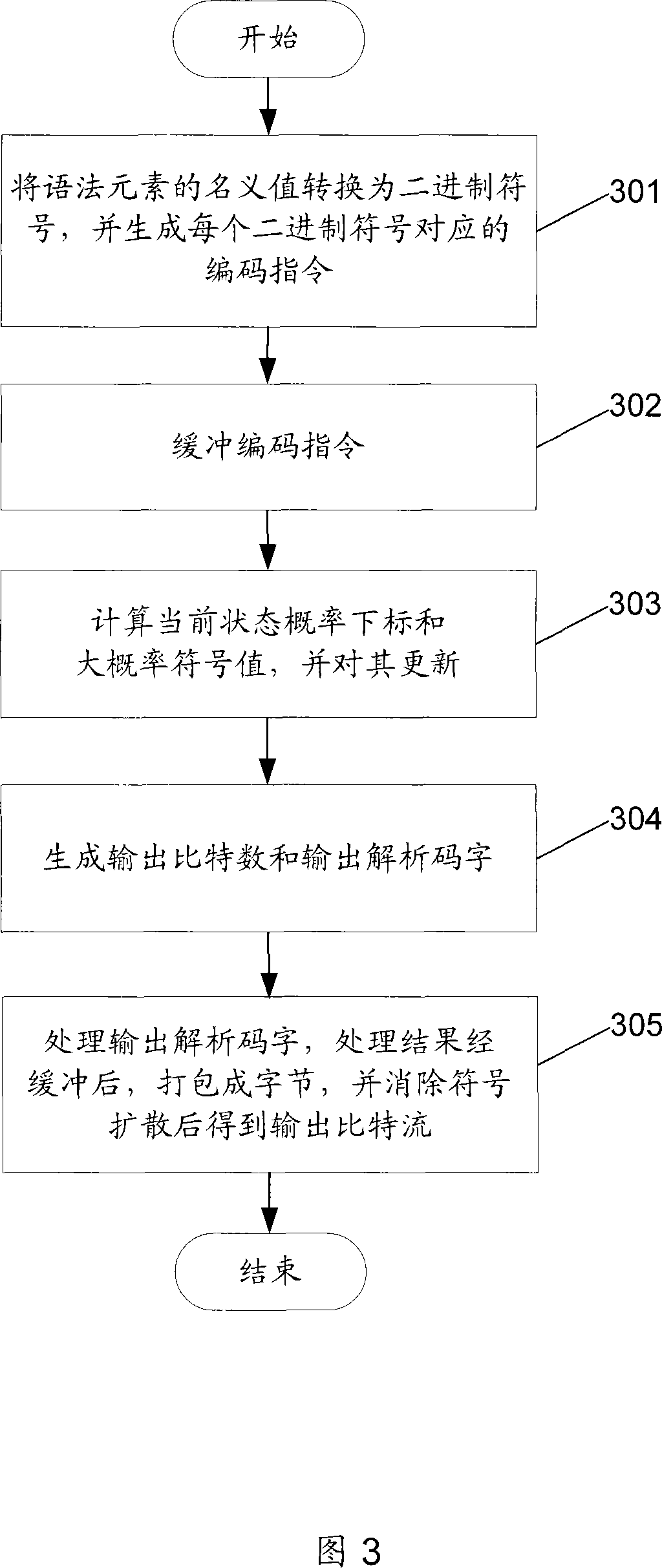
Self-adaptive context binary arithmetic encoder and encoding method
ActiveCN101076114ASimple interfaceFast operationPulse modulation television signal transmissionDigital video signal modificationSelf adaptiveProgramming language
The encode thereof at least comprises: an arithmetic coding control module, an encoding instruction queue module, a context management and maintenances module, an encoding engine module and an outputted bits packaging module. The invention also reveals a context self-adaptive arithmetic encoding method which comprises: processing the external command, syntactic element and adjacent block information to generate an output bit-stream.
Owner:SHANGHAI FULLHAN MICROELECTRONICS
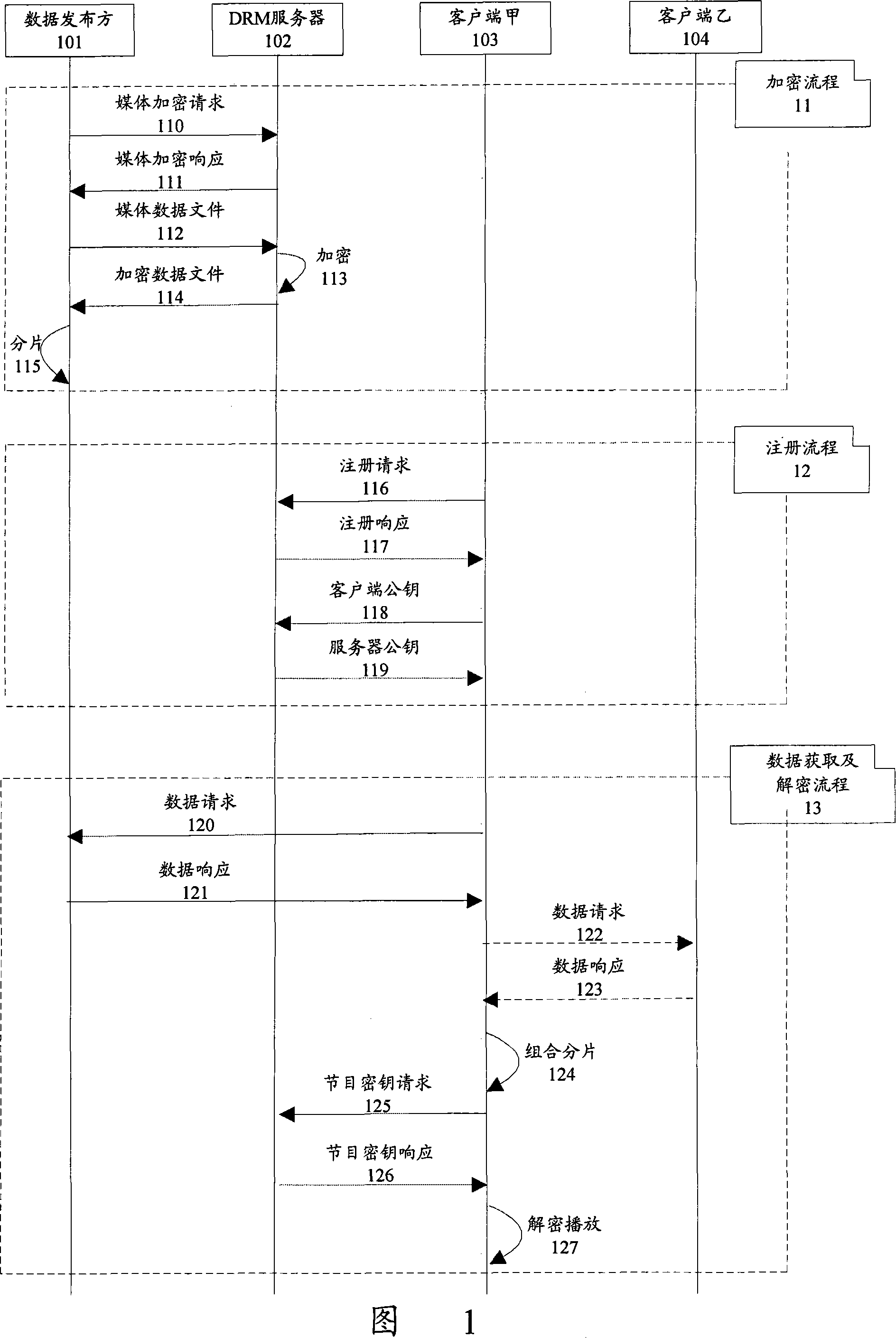
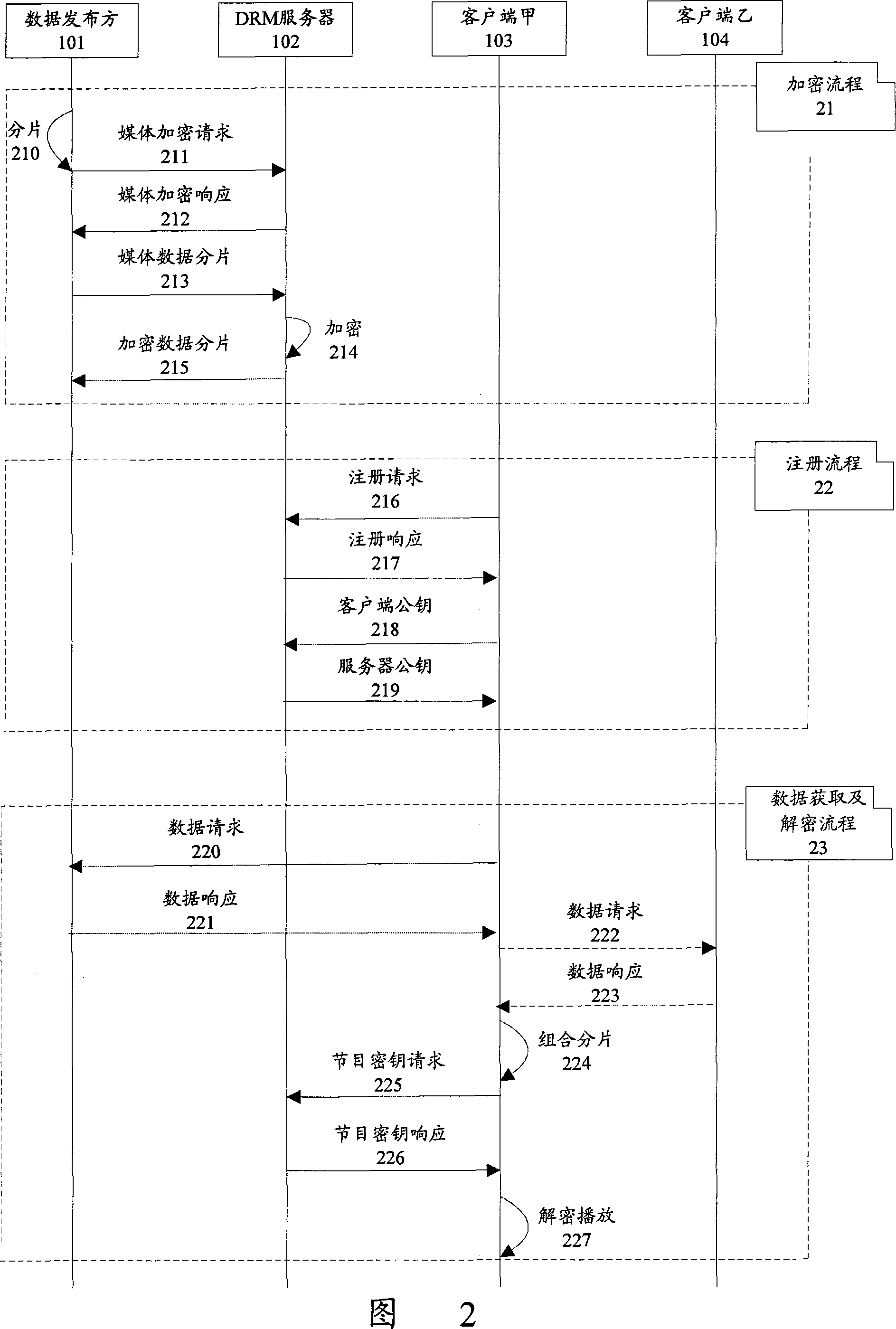
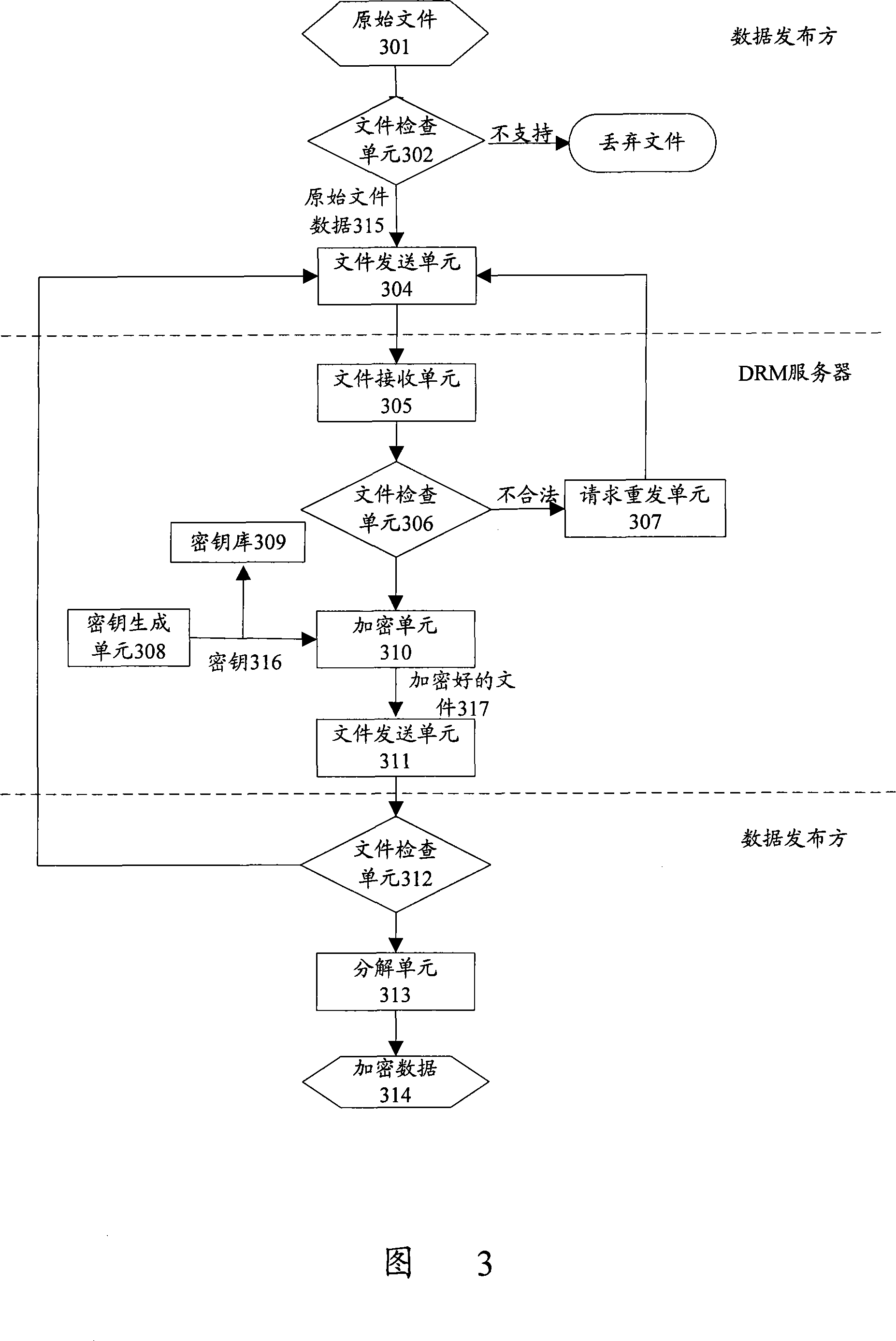
Data protection transmission method of P2P network
The present invention discloses a data protection transmission method for peer-to-peer network. The method has an encryption server arranged in a peer-to-peer network, and comprises following the steps that: A. a data publication party sends data needing to be published to the encryption server; B. the encryption server encrypts the data needing to be published, saves a corresponding key and returns the encrypted data to the data publication party; C. the data publication party publishes the encrypted data in different pieces; D. a data request client collects the published encrypted data pieces through the peer-to-peer network; the data request client acquires the corresponding key from the encryption server and decrypts the collected encrypted data pieces according to the key. The present invention can be applicable to the characteristics of the peer-to-peer network, improve the data transmission security of the peer-to-peer network, prevent hackers from attacking the peer-to-peer network data and guarantee the rights and benefits of data owners and users.
Owner:新疆新颖电子科技有限公司
Safety data repetition removing method and system applicable to backup system
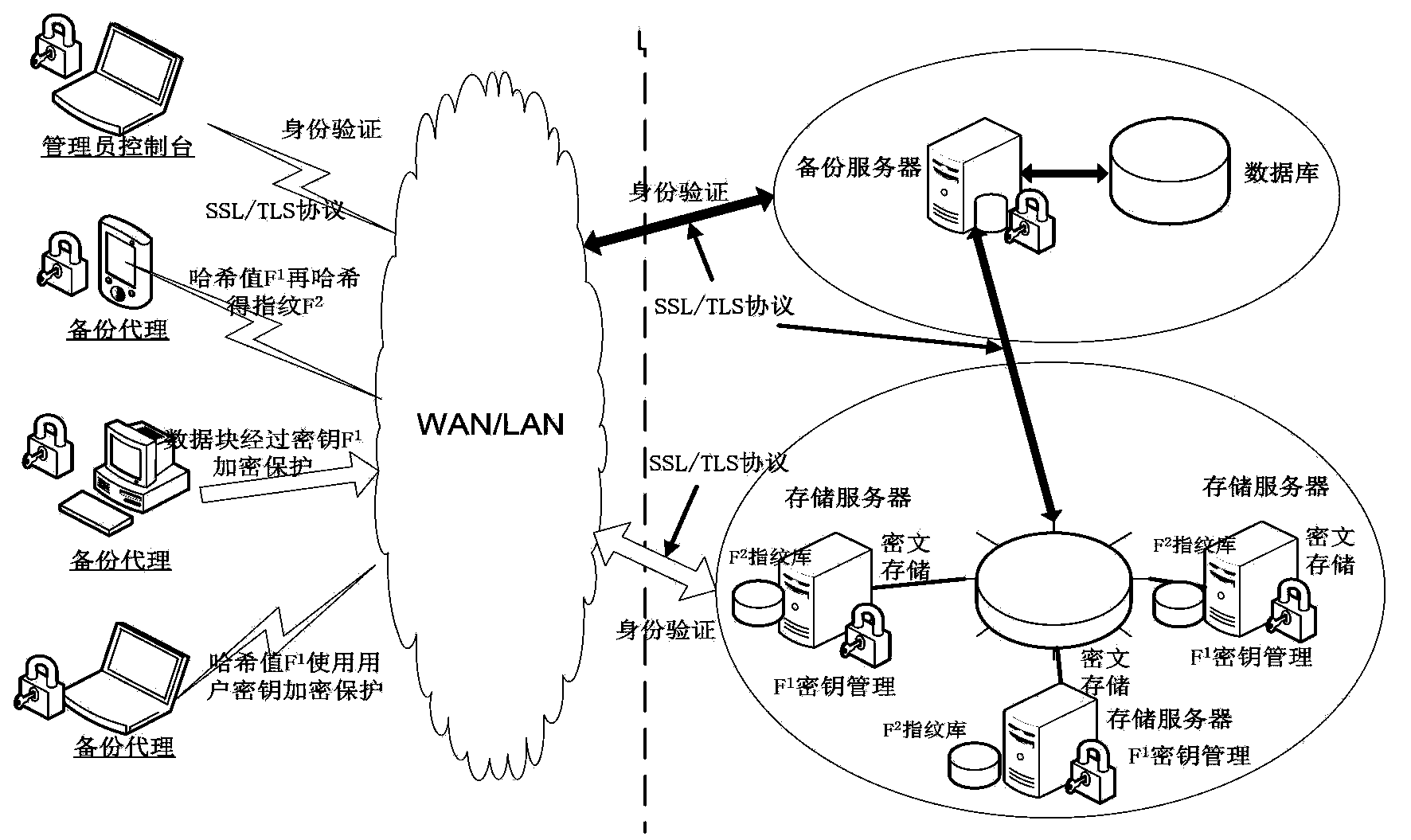
ActiveCN103530201AReduce the burden onImprove performanceUser identity/authority verificationInternal/peripheral component protectionComputer hardwareData loss
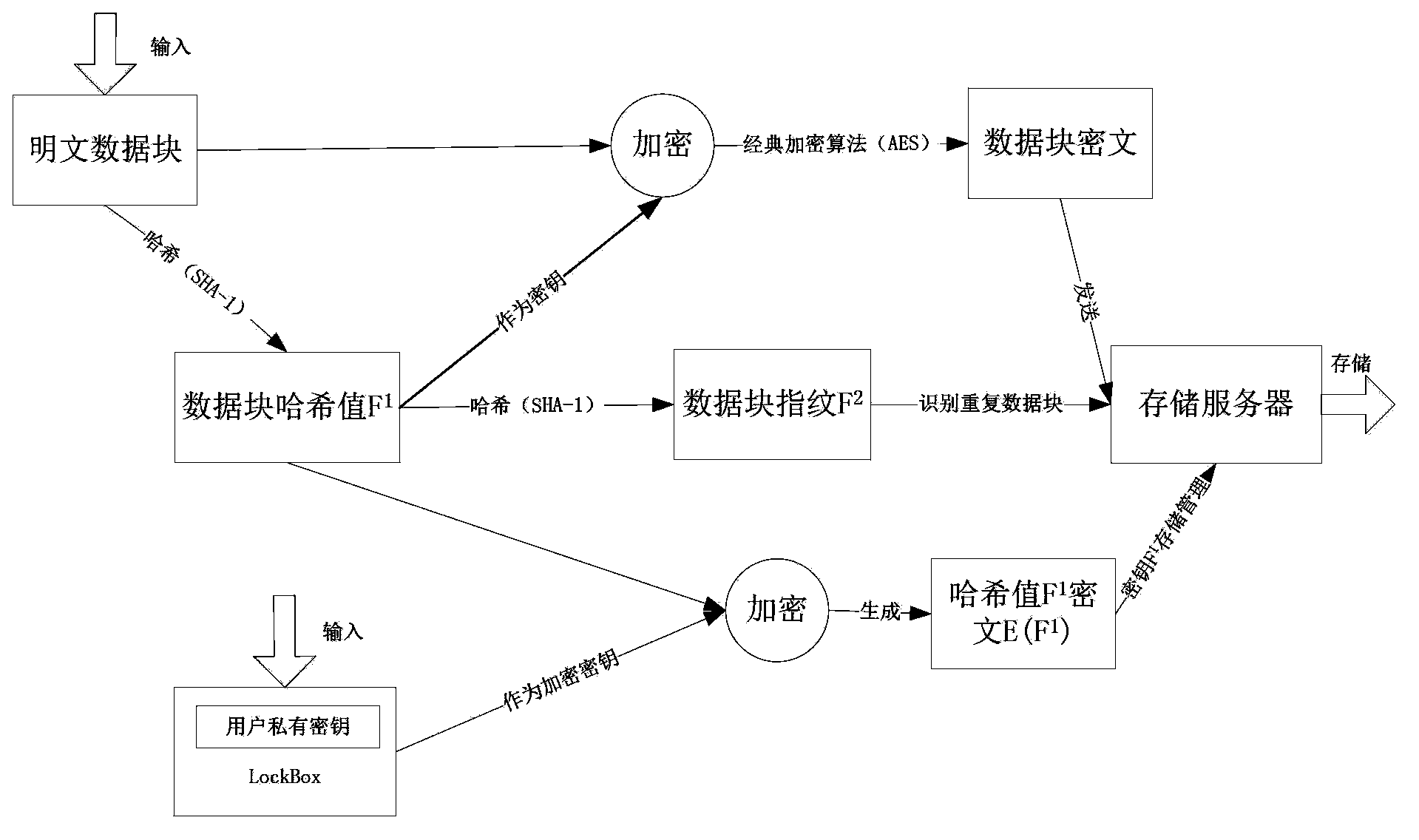
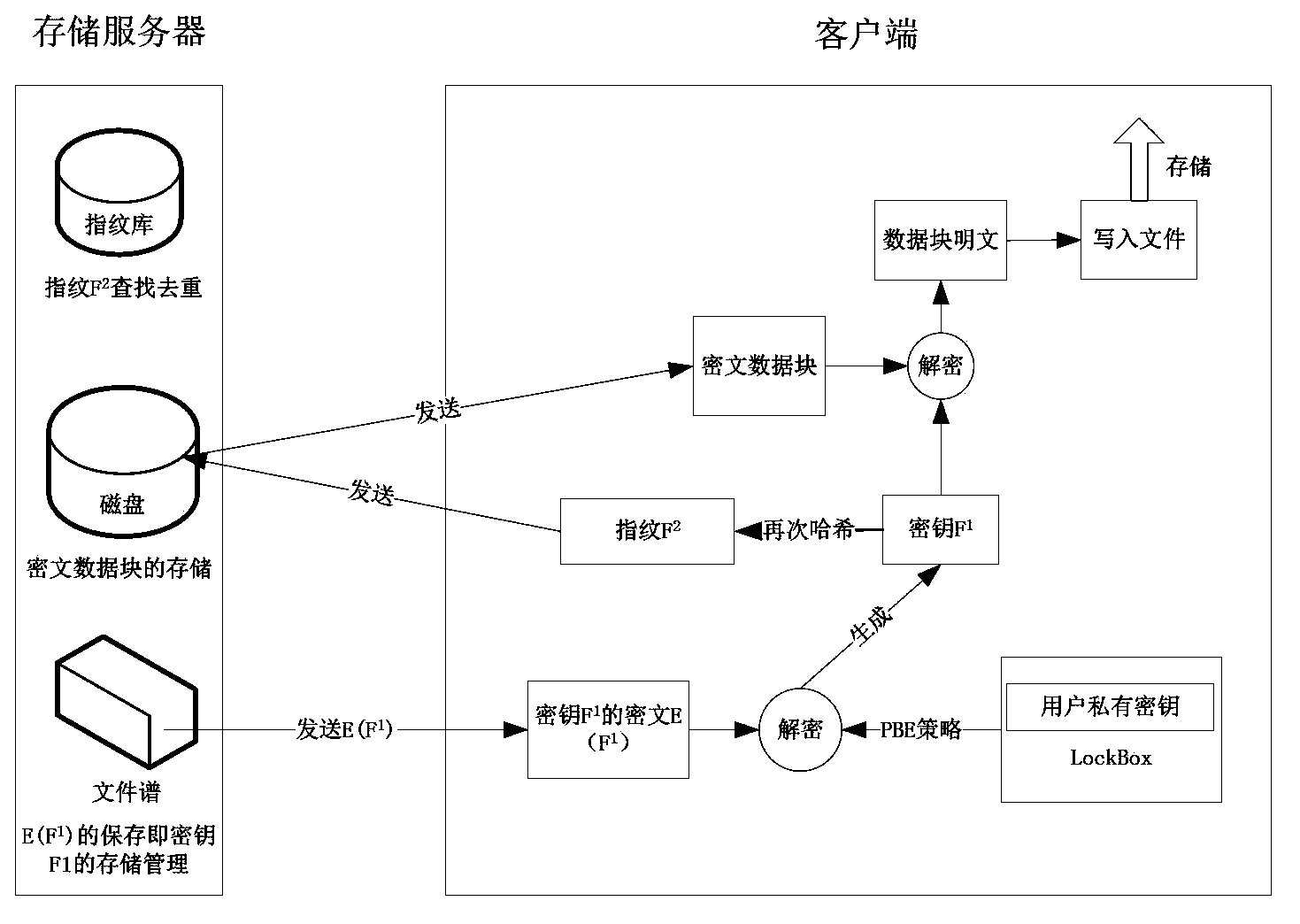
The invention discloses a safety data repetition removing method applicable to a backup system. The method includes the following steps that a backup request submitted by a user is received; all files needing backup are partitioned and multiple data blocks of different sizes are obtained; the Hash algorithm is used for calculating the Hash value F1 of each data block, wherein the Hash values F1 serve as encrypting keys of the data blocks; the Hash algorithm is used again for calculating the Hash value F2 of the Hash value F1 of each data block, wherein the Hash values F2 serve as fingerprints of the data blocks to identify repeated data blocks and the classic encryption algorithm and a private key of the user are used for encrypting the Hash values F1 of the data blocks to obtain ciphertexts E (F1) of the Hash values F1 of the data in order to protect the encrypting keys of the data blocks. All the data block fingerprints F2 and the like are packaged in sequence into fingerprint segments which are transmitted to a storage server. The SSL protocol is adopted in all communication processes. According to the safety data repetition removing method applicable to the backup system, the safety data repetition removing method is adopted to ensure that storage safety problem that data are lost or tampered is solved under the condition that the data repetition removing rate is not changed.
Owner:HUAZHONG UNIV OF SCI & TECH
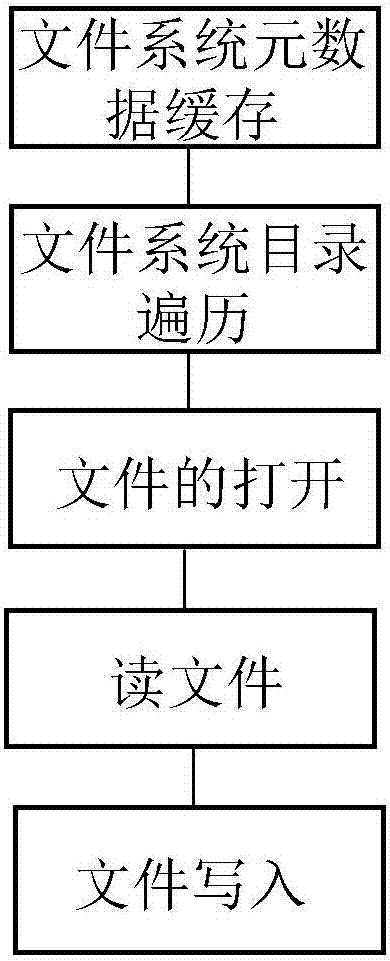
Method for realizing local file system through object storage system
InactiveCN107045530AReduce the number of interactionsImprove the performance of accessing swift storage systemSpecial data processing applicationsApplication serverFile system
The invention discloses a method for realizing a local file system through an object storage system. A metadata cache algorithm of the file system and a memory description structure are adopted, so that the interactive frequency of an application and a background of a swift storage system is reduced and the performance of accessing the swift storage system by the application is improved; a policy of pre-allocating a memory pool and recovering idle memory blocks in batches in a delayed manner is adopted, so that the efficiency of traversing a directory comprising a large amount of subdirectories and files is improved; a memory description structure of an open file handle is adopted, so that the application can efficiently perform file reading-writing operation; a pre-reading policy is adopted, so that the frequency of network interaction between an application server and a swift storage back end is effectively reduced and the reading performance of the file system is improved; and a zero copying and block writing policy is adopted, so that no any data copying and caching exist in a file writing process, system call during each write is a complete block writing operation, and the file writing efficiency is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
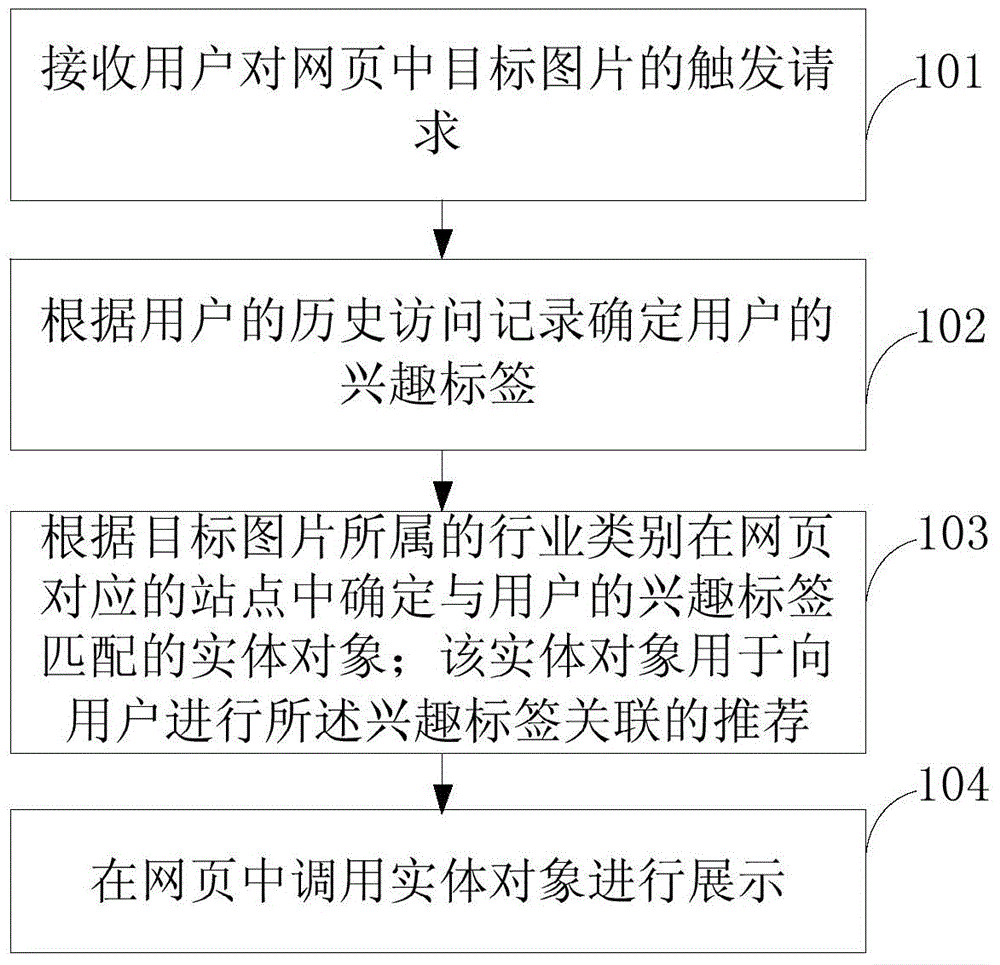
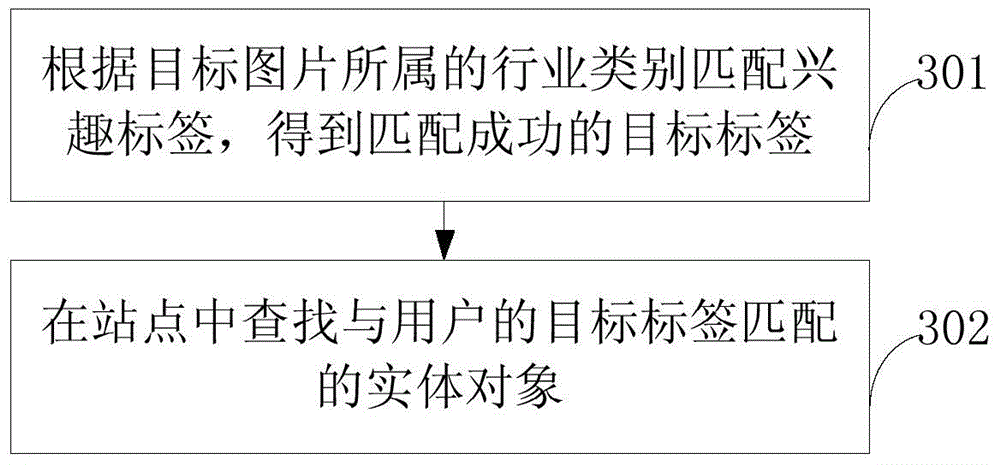
Data processing method and apparatus
InactiveCN105718184AAccurate positioning needsImprove processing efficiencySpecial data processing applicationsInput/output processes for data processingInteraction timeBounce rate
Embodiments of the present invention provide a data processing method and apparatus. The data processing method comprises: receiving a trigger request of a user for a target picture in a webpage; determining a tag of interest of the user according to a historical access record of the user; according to an industry category of the target picture, determining an entity object matched with the tag of interest of the user in a site corresponding to the webpage, wherein the entity object is used for performing recommendation associated with the tag of interest to the user; and calling the entity object in the webpage and displaying the entity object. According to the method and apparatus provided by the embodiments of the present invention, the product matched with the tag of interest of the user can be directly found, so that product information that interests the user can be directly output to the user. The process precisely orients the demand of the user, reduces the number of interaction times obviously compared with the prior art, shortens consumed duration, improves data processing efficiency, provides information desired by the user for the user rapidly and precisely, reduces a website bounce rate and improves a conversion rate of advertisements in the website.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
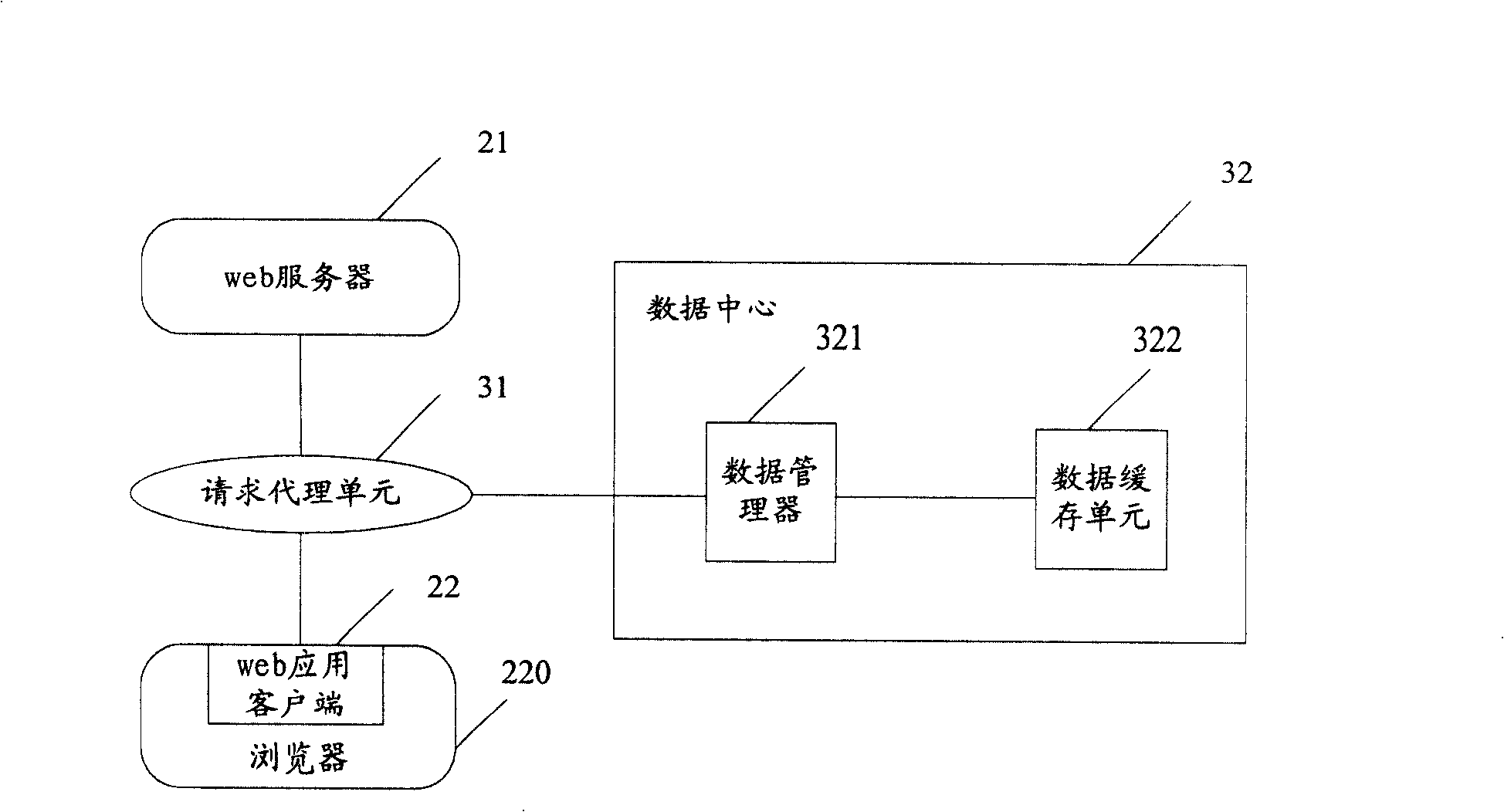
Web applied system and method
InactiveCN101257485AImprove performanceAvoid redundant dataNatural language data processingData switching by path configurationWeb applicationData center
The invention discloses a web application system and a method. The system includes a web server, a browser equipped with web applying client-side, a request agent unit connected with web applying client-side and web server and a data center connected with the request agent unit. The data center is used for buffering the requested data by the web applying client-side through the agent unit in the browser and carrying the centralized management; the request agent unit acquires the required data from the data center according to the request of the web applying client-side, or acquires the required data from the web server through the request, meanwhile the data returned from the web server is provided to the data center, and returned to the web applying client-side. The invention can effectively reduce the alternating times of the client-side and the server, advance the request response speed of the client-side, avoid the redundant data, thereby improving the performance of web application.
Owner:HUAWEI TECH CO LTD
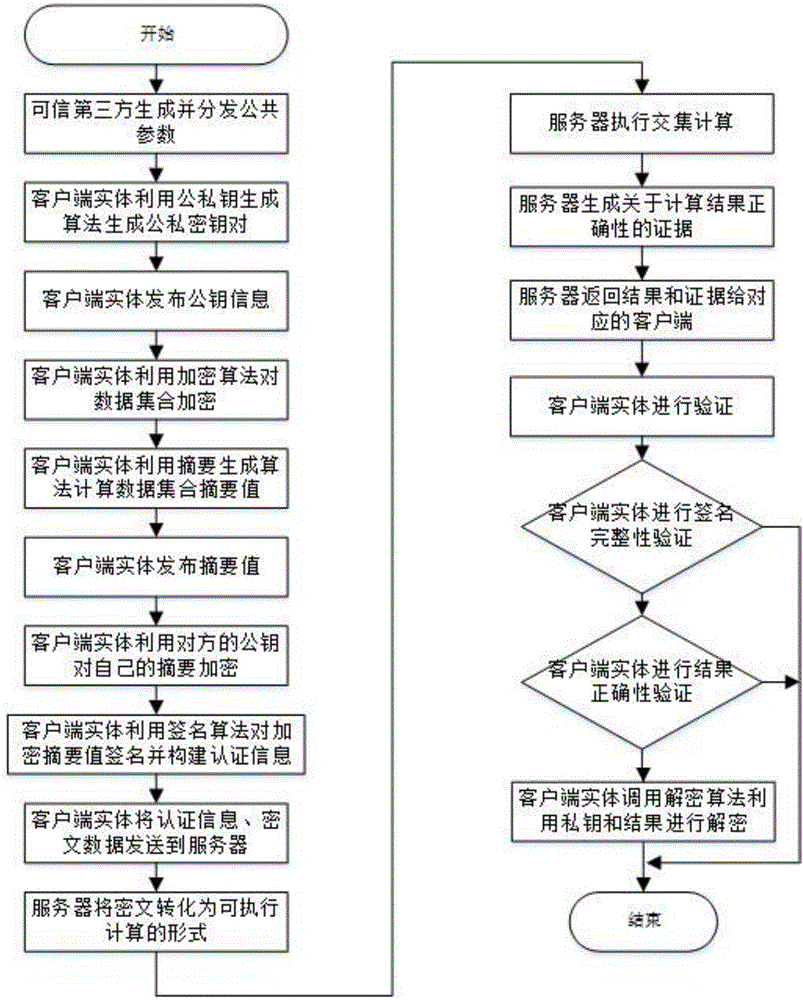
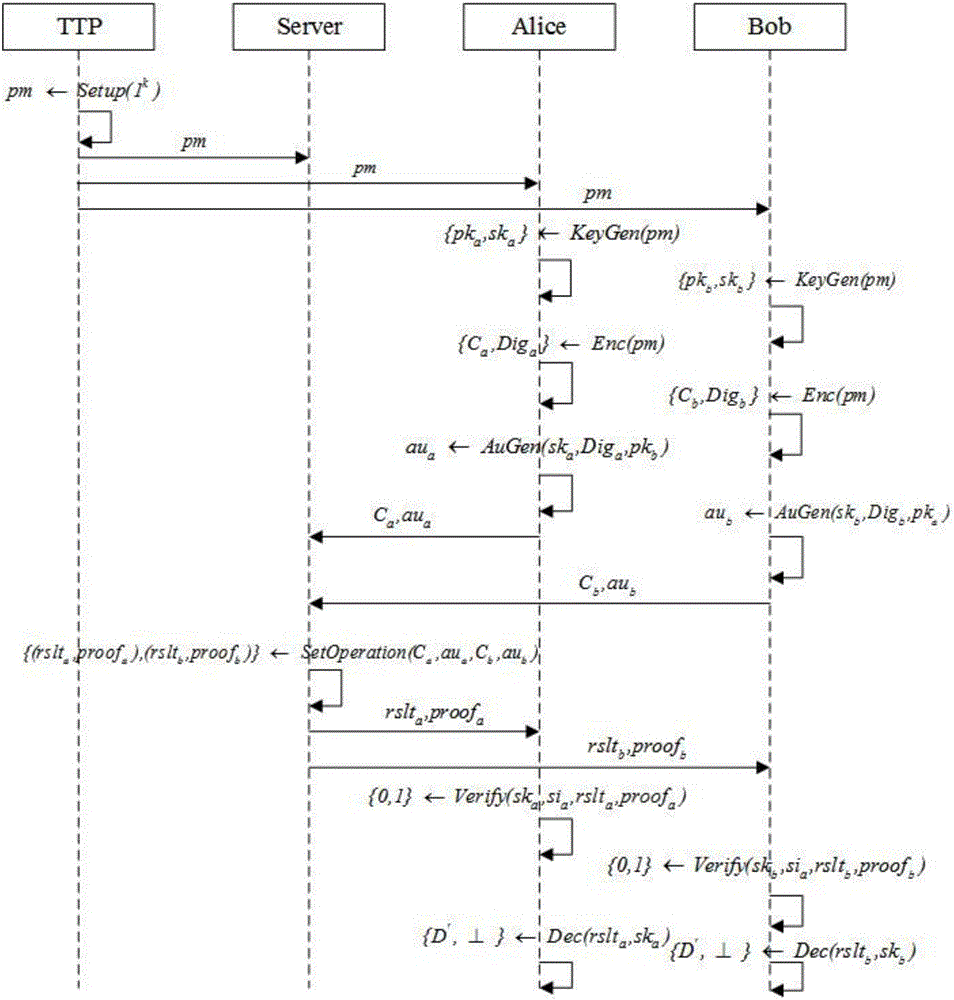
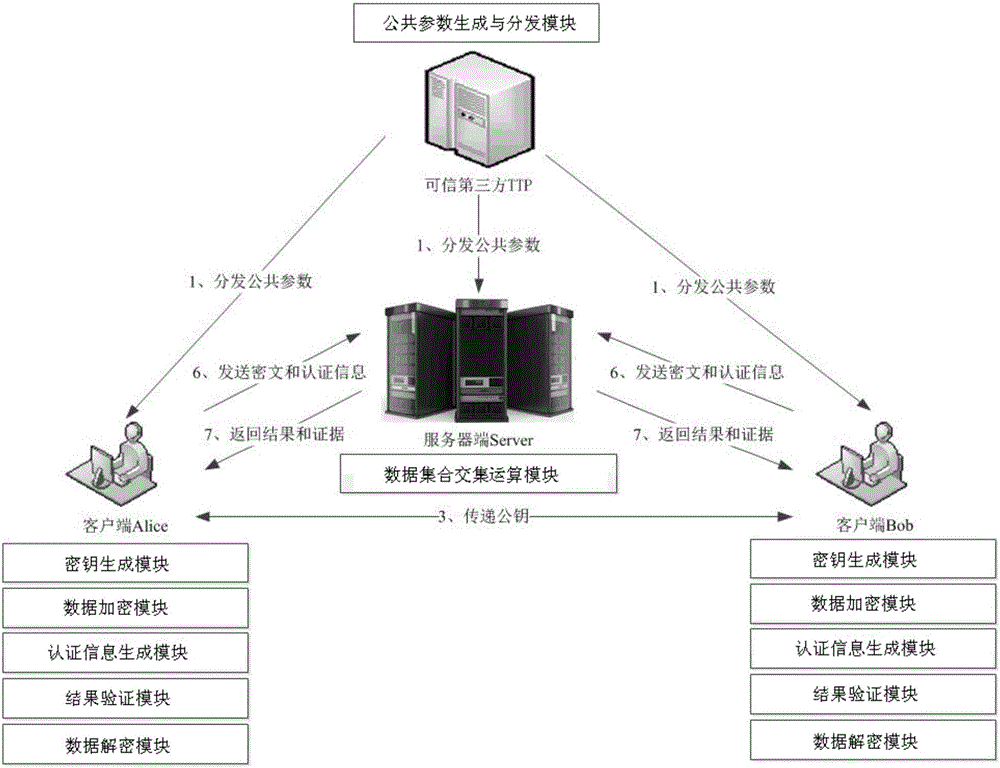
Outsourcing encrypted data-orientated verifiable intersection operation method and system
ActiveCN105812141AGuaranteed privacyReduce the number of interactionsUser identity/authority verificationPlaintextThird party
The invention relates to an outsourcing encrypted data-orientated verifiable intersection operation method and system and belongs to the verifiable outsourcing computation field. The method is carried out among a third-party trusted entity, at least two client entities and an outsourcing server side; the client entities are holders of data sets and requesters of data set intersection operation; the third-party entity is mainly responsible for the initialization and distribution of common parameters; the two client entities are mainly responsible for generating keys, encrypting data sets, calculating authentication information, verifying results and proofs returned by the outsourcing server side and decrypting an ciphertext data set returned by the outsourcing server side; the outsourcing server side is mainly responsible for performing data set intersection operation; and a plaintext data set is not required to be obtained through decryption when the outsourcing server side performs intersection operation, and the outsourcing server performs operation on a ciphertext, and therefore, the privacy of user data can be ensured. The method and system have the advantages of low frequency of interaction among the entities, low communication cost and efficient correctness verification of operation results.
Owner:NORTHEASTERN UNIV
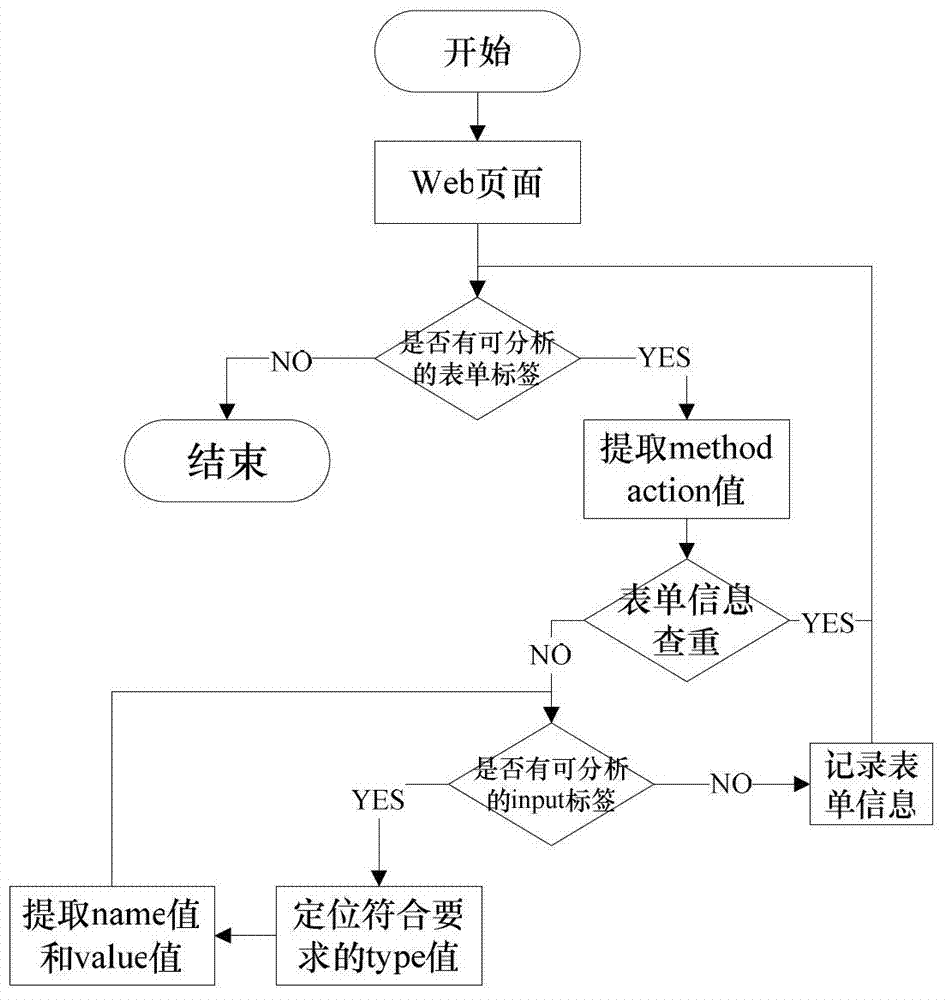
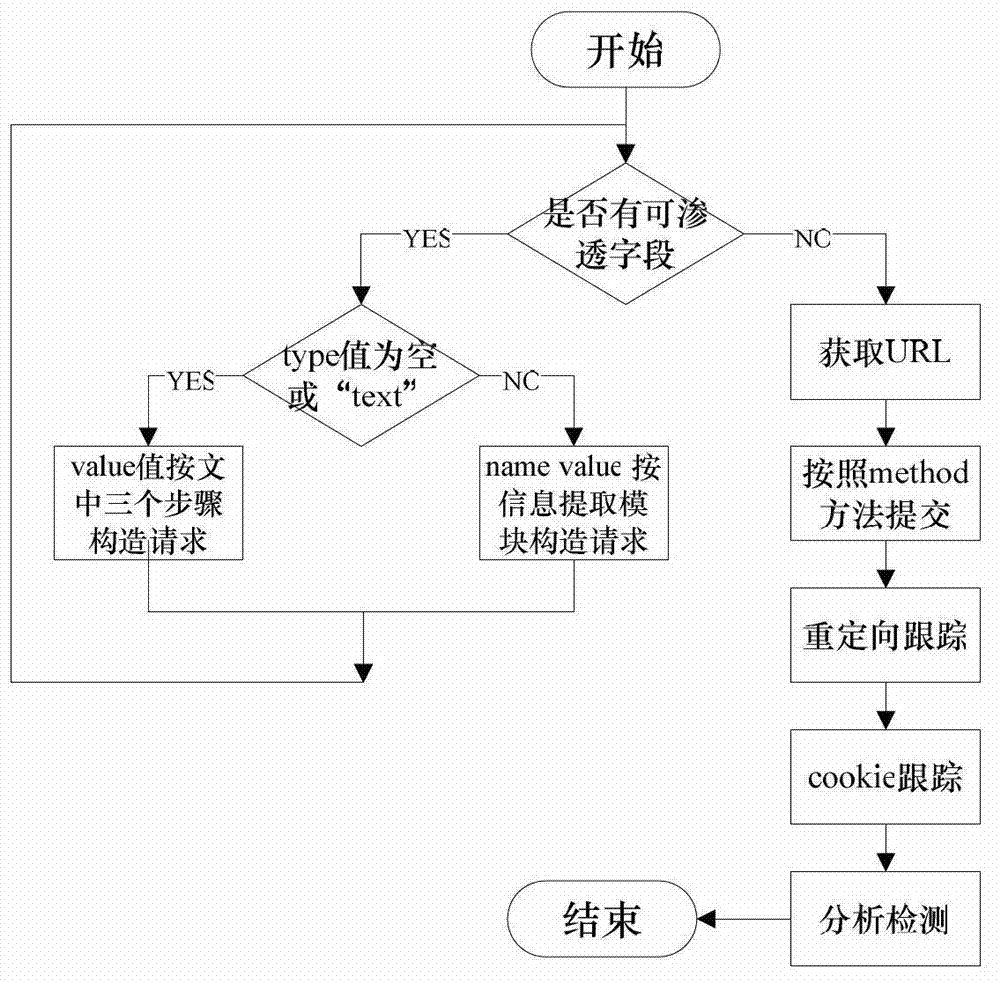
Cross-site script vulnerability detection method based on percolation test
InactiveCN102819710AReduce incomplete analysisImprove detection efficiencyComputer security arrangementsSoftware testing/debuggingWeb siteComputer science
The invention discloses a cross-site script vulnerability detection method based on a percolation test. According to the cross-site script vulnerability detection method, the technical problem of low detection efficiency in a traditional cross-site script vulnerability detection method is solved. The technical scheme provided by the invention is that the cross-site script vulnerability detection method comprises the following steps of: firstly, acquiring a page; secondly, extracting form information and carrying out the percolation test on the extracted form; and finally, carrying out session retaining and redirection tracking. Due to the adoption of a session retaining and redirection tracking method, the conditions that the analysis for Web pages is incomprehensive are reduced, all pages of a Web site are analyzed and detected and further the automatic detection capability is improved. According to a percolation test strategy, the detection range of the XSS (Cross-Site Script) is gradually narrowed and the depth detection for the safe pages is avoided. While test statements are injected, test statements for closing HTML (Hypertext Markup Language) statements are actively constructed according to the returned page information, so that interaction frequencies with a server are reduced and the detection efficiency of the XXS vulnerabilities of large complex Websites is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
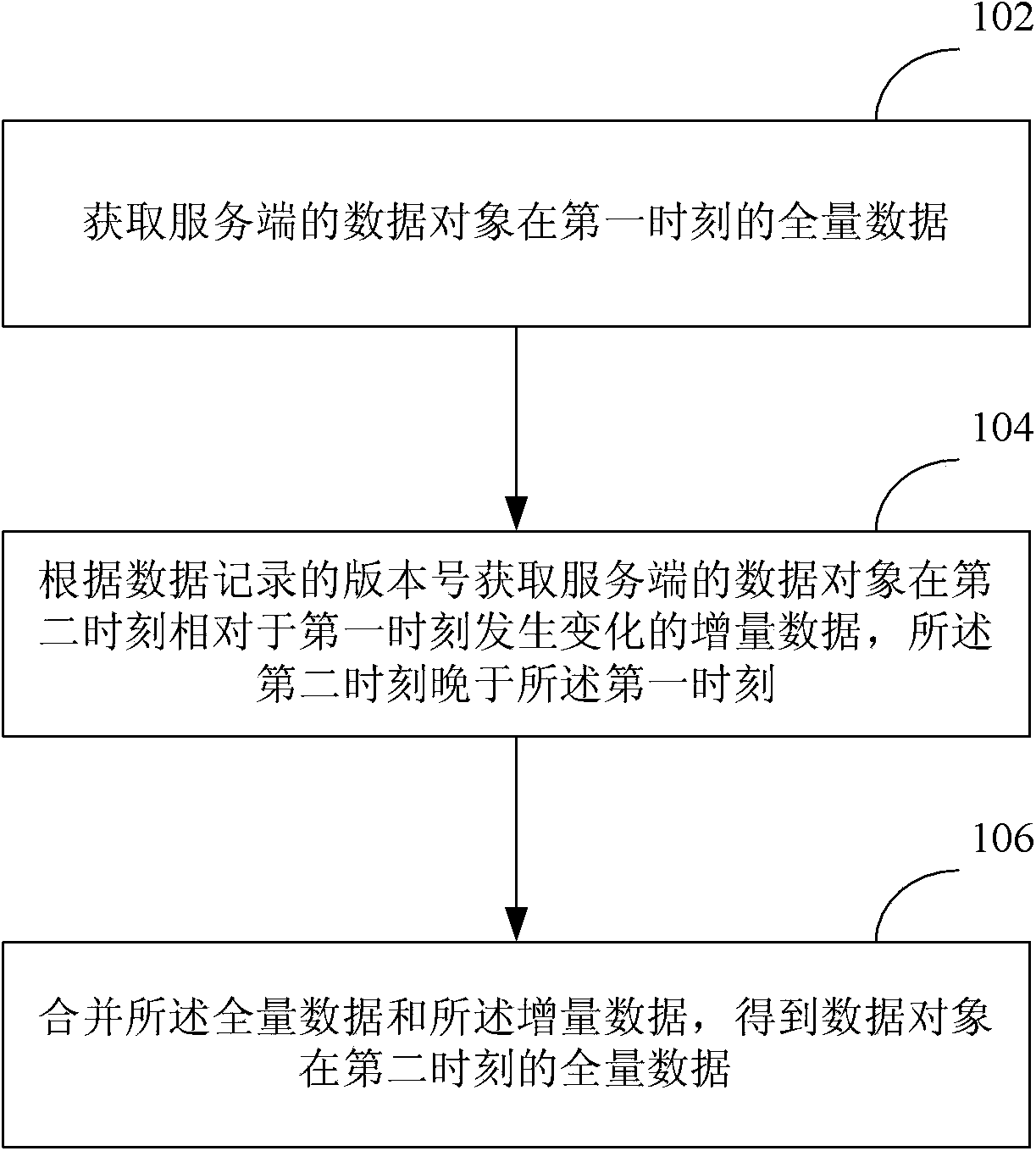
Method and device for client side and server side data synchronization
InactiveCN103678494AReduce complexityReduce the number of interactionsTransmissionSpecial data processing applicationsData synchronizationClient-side
The invention discloses a method and device for client side and server side data synchronization and belongs to the field of database technologies. The method includes the steps that total data of a data object of a server side at a first moment are obtained; according to version numbers of data records, incremental data, changing relative to the first moment, of the data object of the server side at a second moment are obtained, wherein the second moment is later than the first moment; the total data and the incremental data are merged, so that total data of the data object at the second moment are obtained. According to the method and device, the number of times of interaction and the data size of interaction transmission between the client side and the server side can be reduced, and storage consumption of the client side can be reduced.
Owner:BEIJING QIHOO TECH CO LTD +1
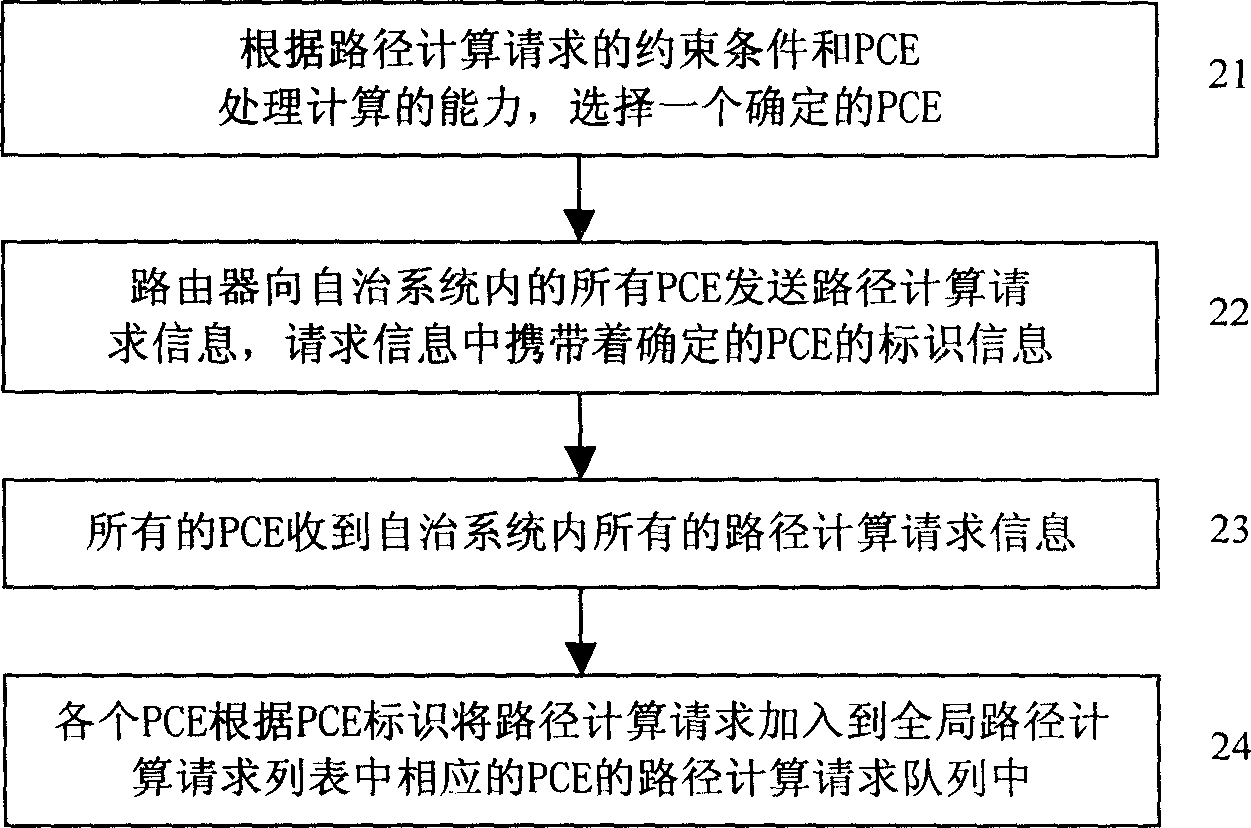
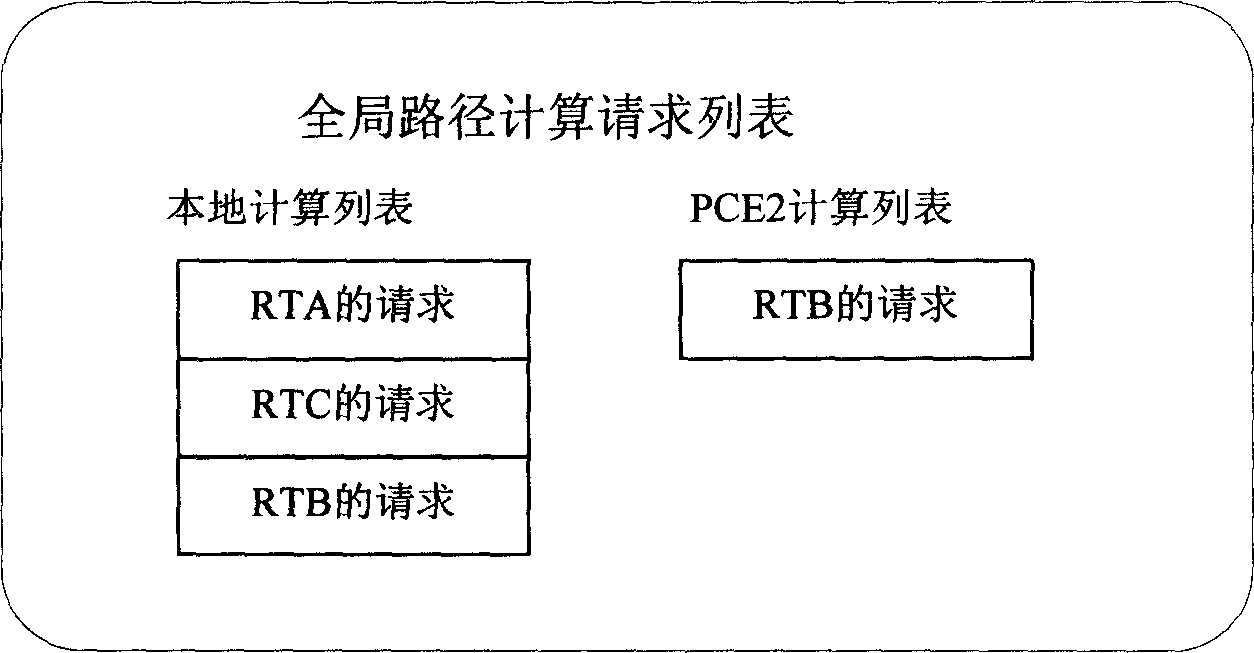
Method for realizing path computation in network domain
ActiveCN1866852AImprove efficiencyImprove accuracyData switching networksResource informationPath computation element
The invention discloses a route calculating method of network area, which is characterized by the following: the route calculation network entity saves global route calculating information for route calculating in the network area; the global route calculating information is composed of the following information: all current route calculating request information, current network resource information for distributing and current occupying resource;the route calculation network entity calculates the route according to the saved global route calculation information. The invention improves the efficiency and correctness of treating route calculation task, which improves the whole protocol operation efficiency.
Owner:HUAWEI TECH CO LTD
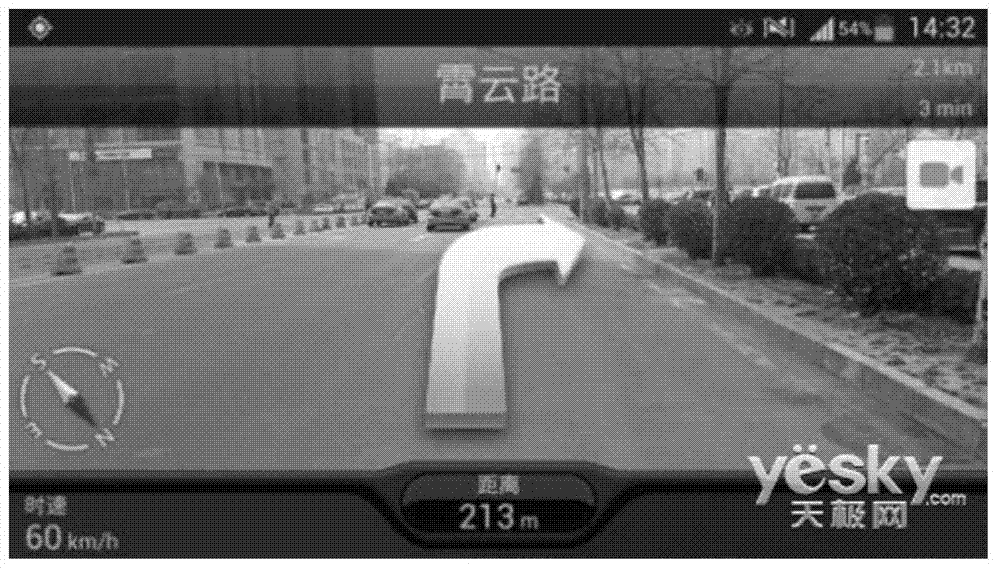
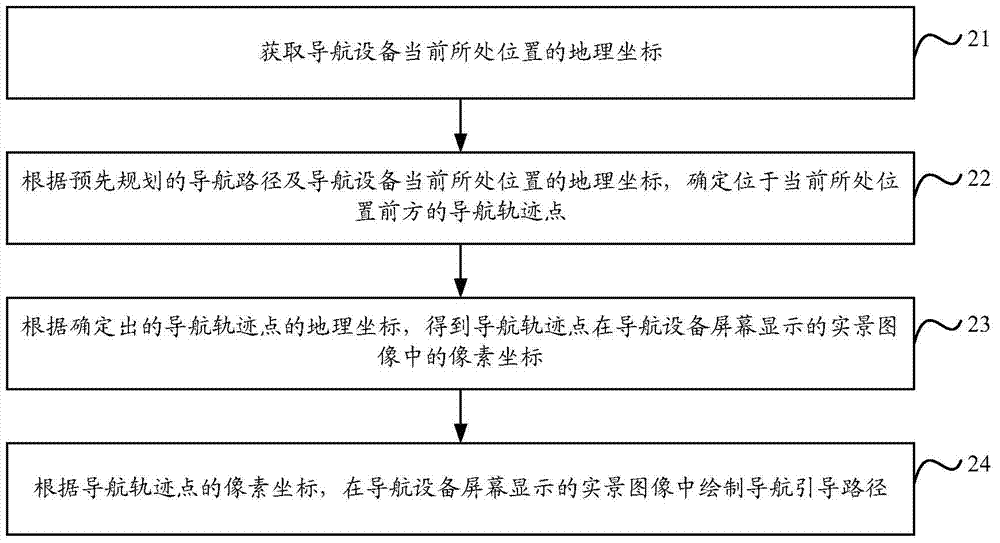
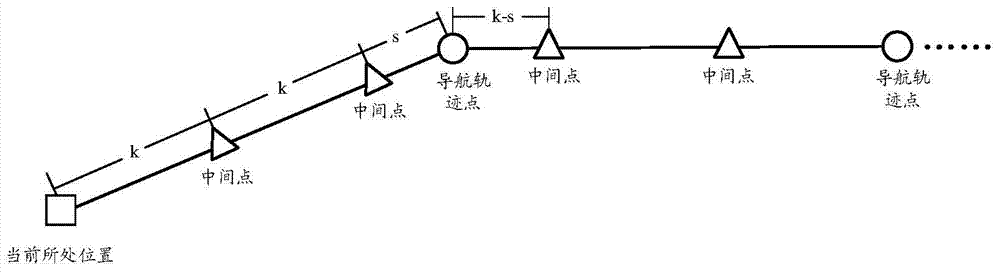
Real-scenery navigation method and navigation equipment
InactiveCN104515529AAccurately determineAvoid issues with incomplete navigation promptsInstruments for road network navigationSatellite radio beaconingComputer scienceMarine navigation
The invention discloses a real-scenery navigation method and navigation equipment. The method comprises: acquiring a geographical coordinate of the navigation equipment present position; determining a navigation tracing point at the front of the present position according to a pre-programmed navigation path and the geographical coordinate of the navigation equipment present position; obtaining a pixel coordinate of the navigation tracing point in a real-scenery image displayed on a navigation equipment screen according to the determined geographical coordinate of the navigation tracing point; and drafting a navigation guiding path in the real-scenery image displayed the navigation equipment screen according to the pixel coordinate of the navigation tracing point. By employing the technical scheme, the problem that navigation prompt is incomplete during real-scenery navigation in the prior art is solved.
Owner:AUTONAVI
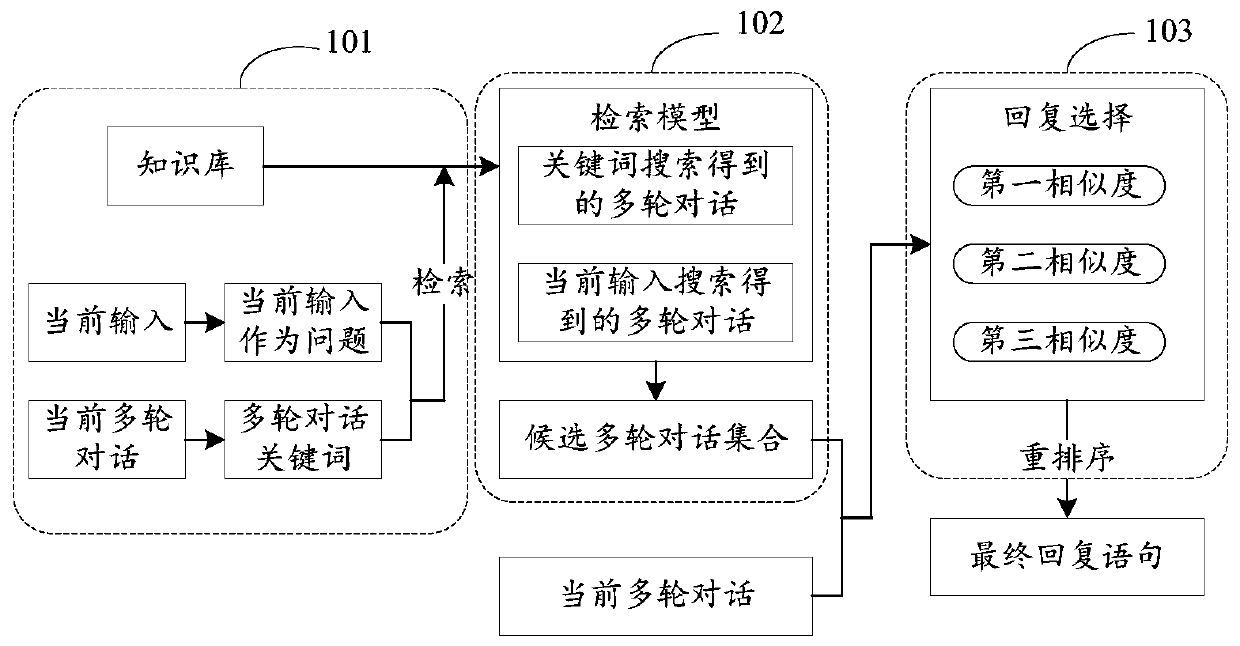
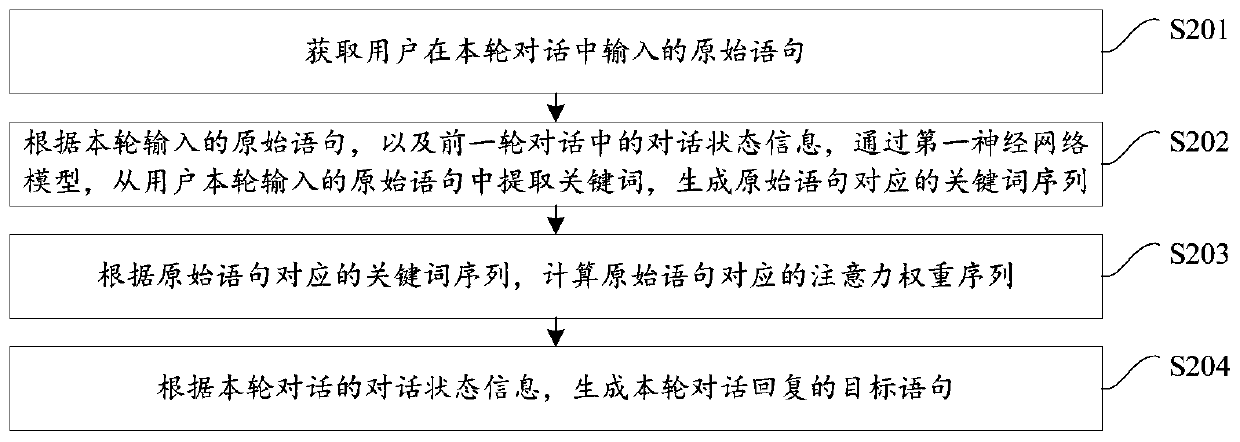
Voice interaction method and device and terminal equipment
ActiveCN111428483AMeet interaction needsImprove accuracyMetadata text retrievalNatural language data processingDialog systemTerminal equipment
The invention is suitable for the technical field of artificial intelligence, and provides a voice interaction method and device and terminal equipment, and the method comprises the steps of obtaininghistorical dialogue data when a to-be-replied user statement is received; identifying target entity information in the user statement, and identifying historical entity information in the historicaldialogue data; extracting key entity information associated with the user statement from the historical entity information; generating a target interaction statement according to the target entity information and the key entity information; and outputting a reply statement corresponding to the target interaction statement. By adopting the method, the accuracy of dialogue state tracking and user intention recognition can be improved, the natural language processing capacity of the dialogue system is improved, and the reply rationality of the dialogue system in the multi-round dialogue process is enhanced.
Owner:HUAWEI TECH CO LTD
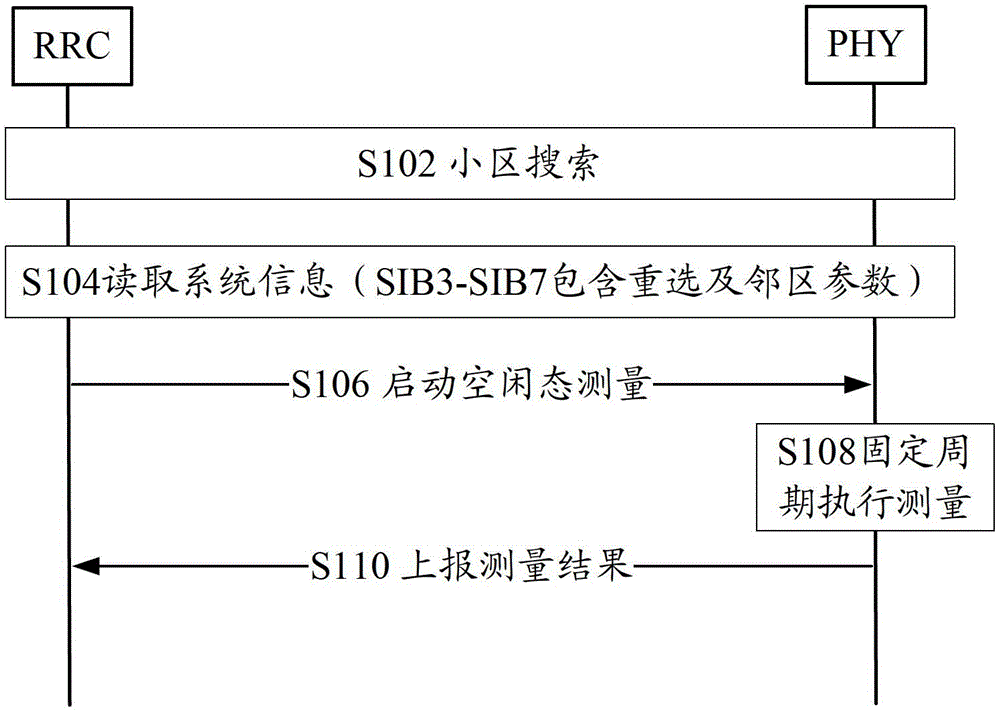
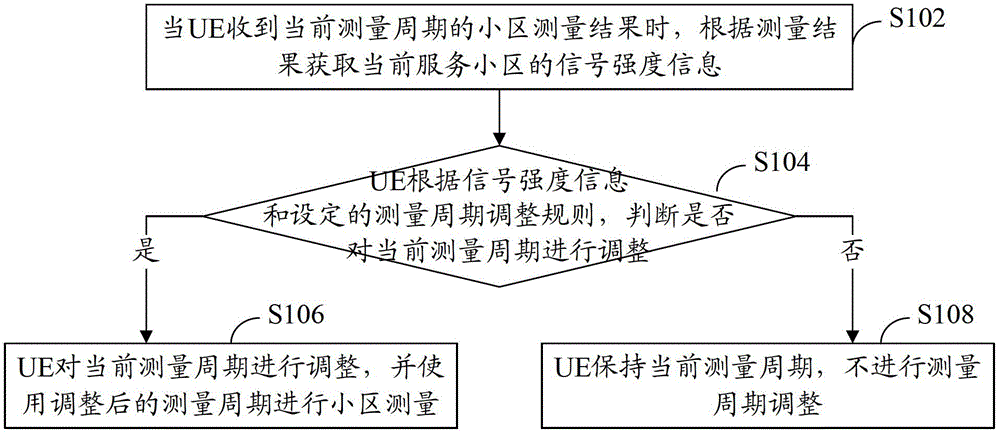
Cell measurement method and device
ActiveCN102917380ARealize dynamic adjustmentReduce consumptionEnergy efficient ICTPower managementUltimate tensile strengthUser equipment
The invention provides a cell measurement method and device. The cell measurement method comprises the following steps: when receiving a cell measurement result in a current measurement cycle, user equipment (UE) acquires signal strength information of a current serving cell according to the measurement result; the UE determines whether regulation of the current measurement cycle is carried out or not according to the signal strength information and a set regulation rule for measurement cycles; and if yes, regulation of the current measurement cycle is carried out and using the regulated current measurement cycle to measure the cell. According to the invention, power consumption and CPU (Central Processing Unit) consumption brought by measurement can be effectively reduced, the number of message interaction generated by the measurement is reduced, and the measurement consumption is reduced on the premise of not influencing the measurement performance.
Owner:DATANG MOBILE COMM EQUIP CO LTD
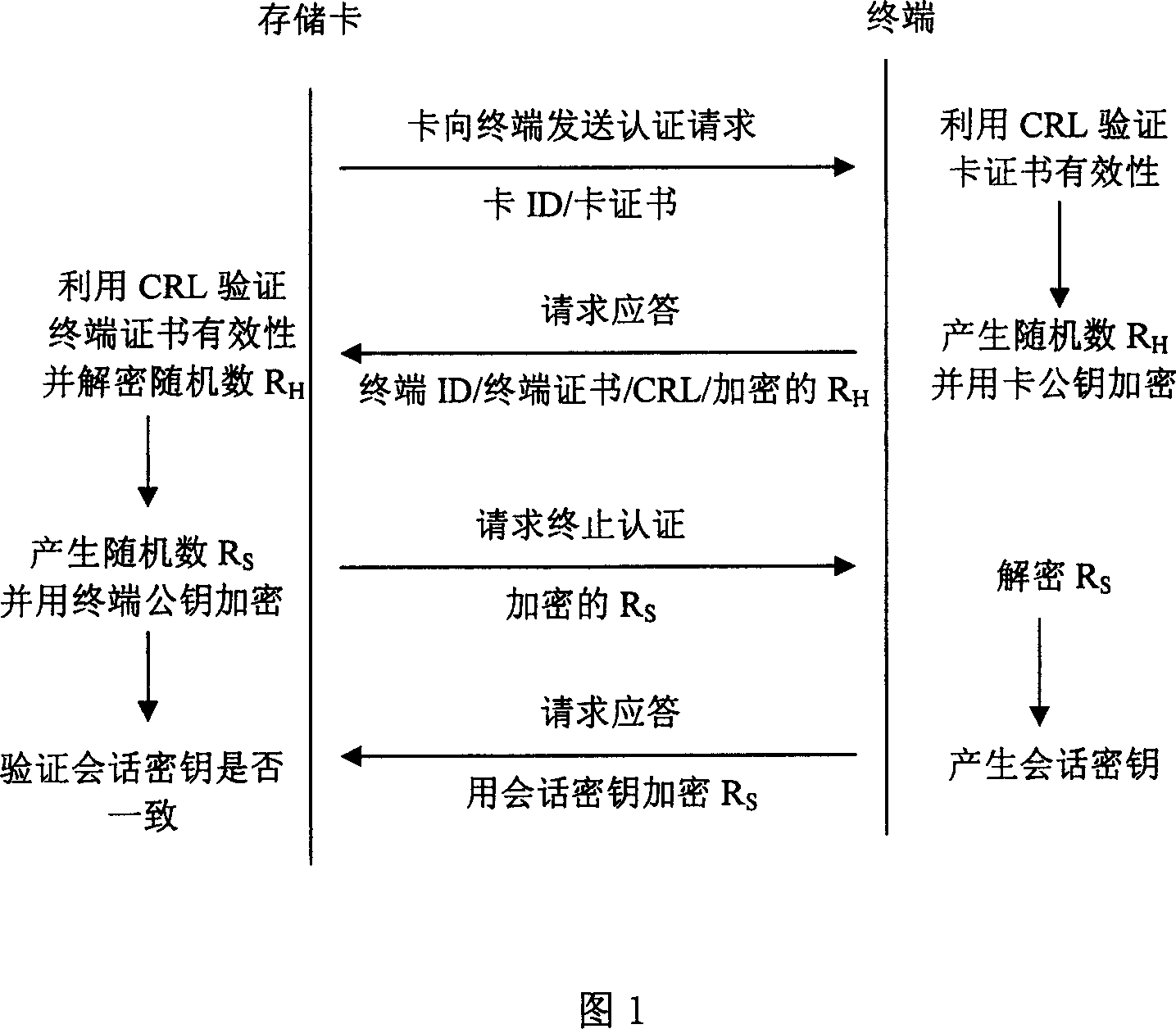
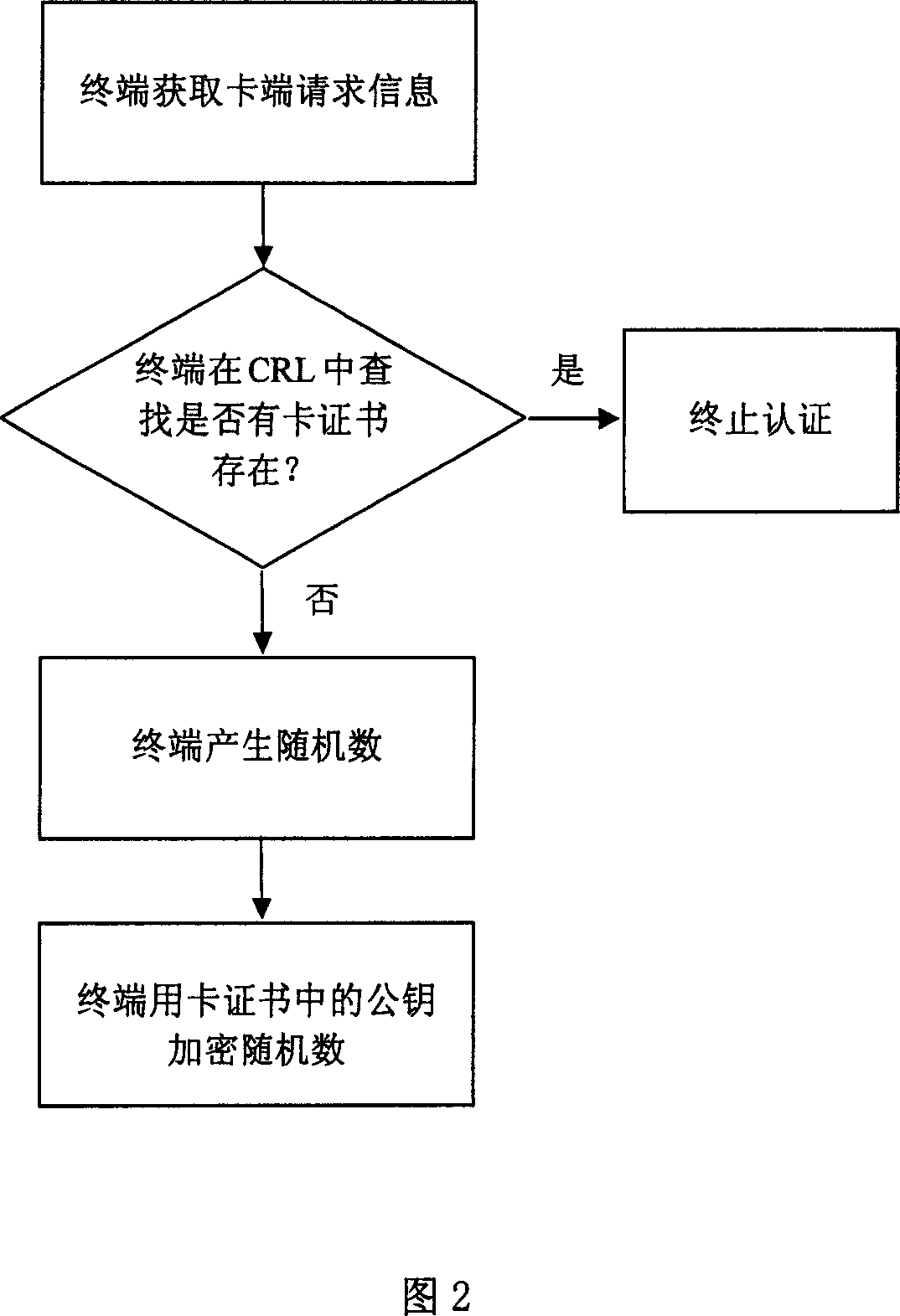
Identify authorization method between storage card and terminal equipment at off-line state
InactiveCN101090316ASimple and effective authentication methodQuick responsePublic key for secure communicationUser identity/authority verificationComputer hardwareTerminal equipment
This invention discloses an identity authentication method between storage cards and a terminal device at the off-line state including: a storage card sends an authentication request to a terminal device including the identity number of the card and the card certificate, the terminal processes the request and sends a response to the card including the identity number of the terminal, a certificate, a list for certificate revoking and a random number of the card ciphered public key, the storage card sends a request for stopping the authentication to the terminal with the random number of the ciphered terminal public key, the terminal sends a stopping request response to the card with the session secret key encryption random number generated by the card, which processes the response request to verify the exclusiveness of the session key.
Owner:POTEVIO INFORMATION TECH
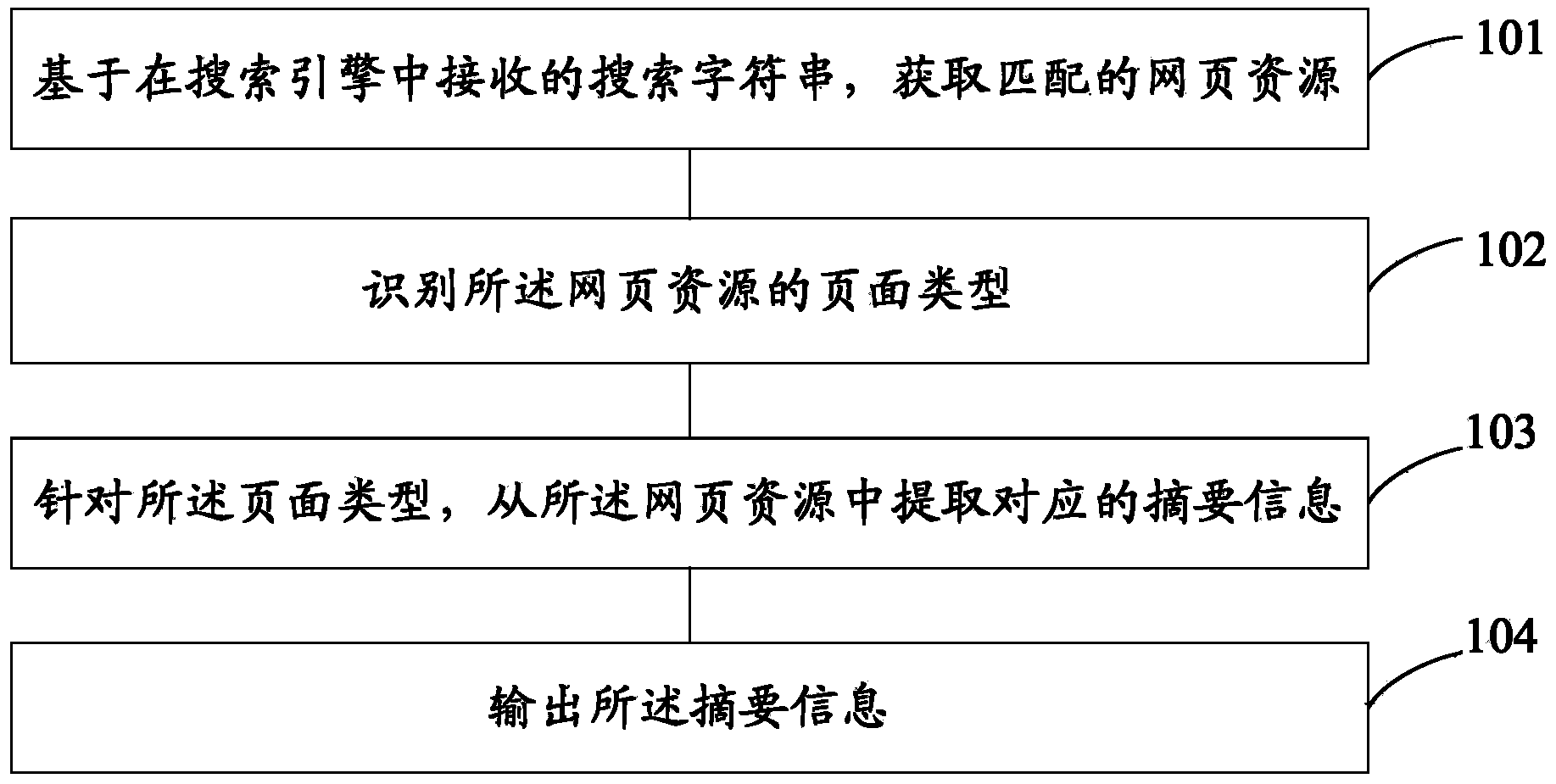
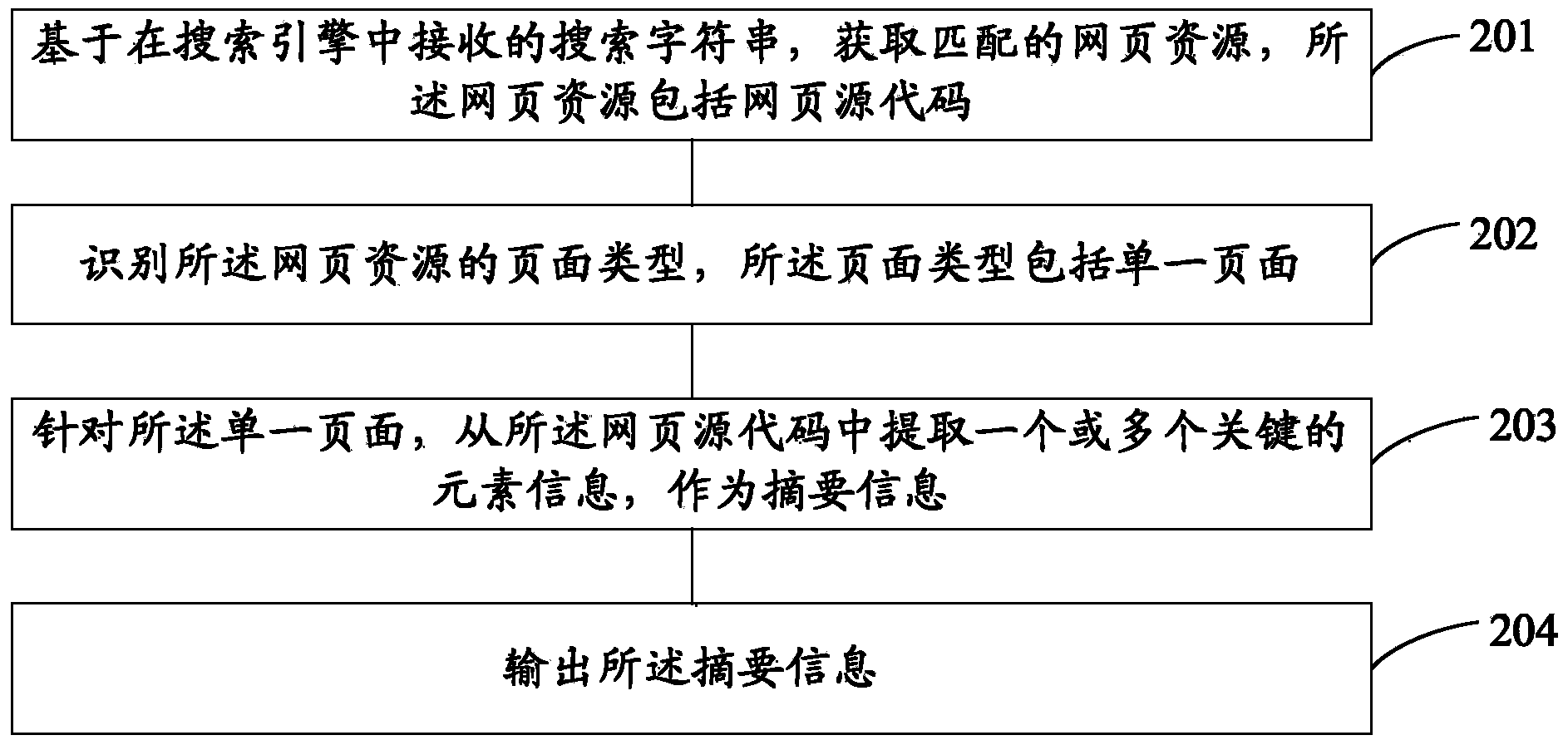
Summary information extraction method and device based on search engine and search engine
InactiveCN104077388AReduce the number of interactionsFewer instances of finding the information you needWeb data indexingSpecial data processing applicationsInteraction timeResource based
The invention discloses a summary information extraction method and device based on a search engine and the search engine. The method comprises: obtaining matched webpage resources based on a search character string received by the search engine; identifying the webpage types of the webpage resources; extracting corresponding summary information from the webpage resources aiming at the webpage types; and outputting the summary information. According to the summary information extraction method and device based on the search engine, the situation that a user may frequently click pages corresponding to search results to find required information can be reduced, and thereby retrieval speed is improved, interaction times of the search engine are reduced, and date processing speed is enhanced.
Owner:BEIJING QIHOO TECH CO LTD +1
Method for discovering PMTU (Path Maximum Transfer Unit) and node
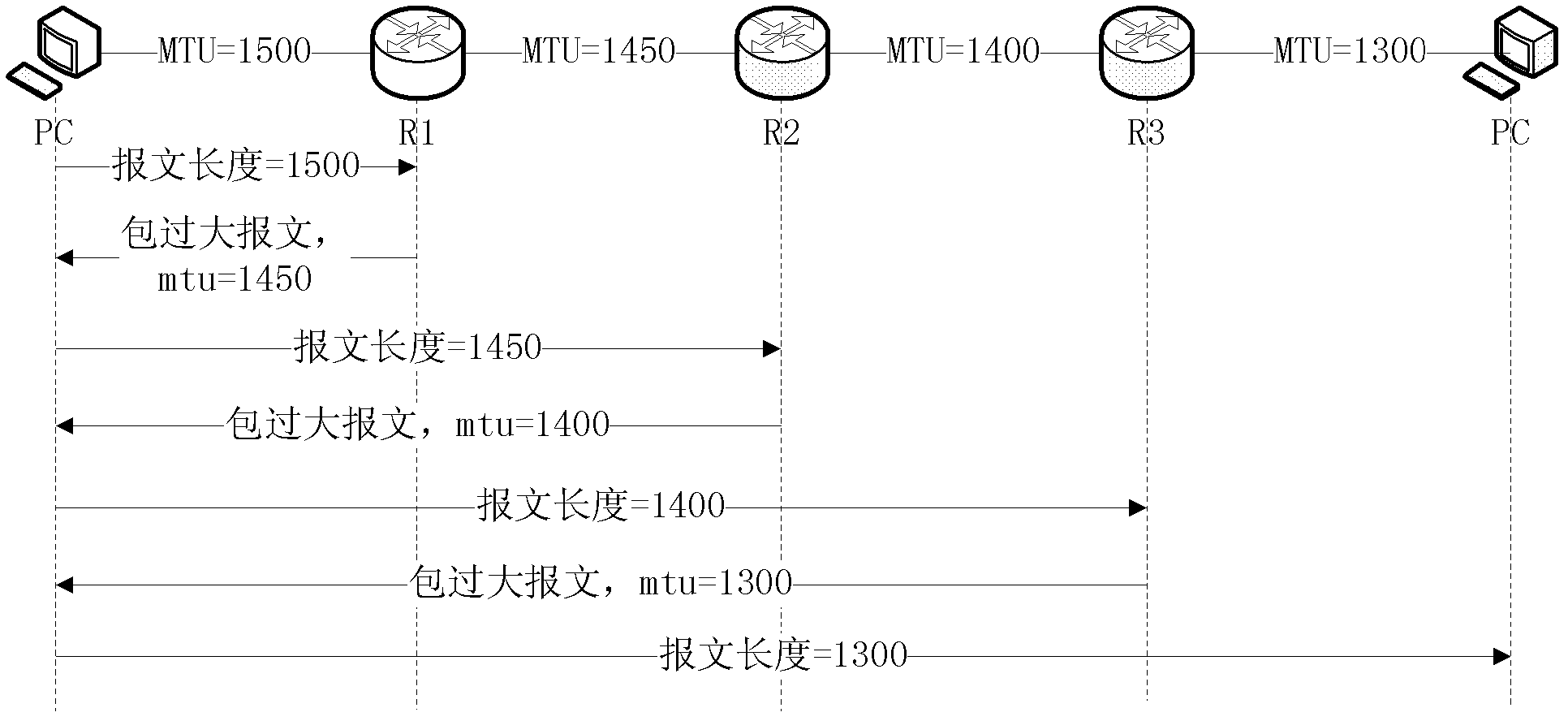
ActiveCN102325076AAvoid security issuesImprove efficiencyData switching networksData messagesDistributed computing
The invention provides a method for discovering a PMTU (Path Maximum Transfer Unit). The method comprises the following steps that: a source node searches whether PMTU routes corresponding to messages to be sent exist or not, creates or updates MTU (Maximum Transfer Unit) values of the PMTU routes to be specified values which are not more than the minimal MTU value of a system if the PMTU routes corresponding to the messages to be sent do not exist or the MTU values of the searched PMTU routes are invalid, carries out fragmentation treatment the messages to be sent by using the specified values, and sends the messages which carry PMTU detection indication; each intermediate node forwards the messages when each intermediate node receives the messages which carry the PMTU detection indication, and sends the packet-too-big messages to the source node, and carries an MTU of an output interface; and the source node receives the packet-too-big messages returned by each intermediate node, and determines the MTU values of corresponding PMTU routes according to the MTU values carried by the packet-too-big messages. The invention further provides a node. With the adoption of the method and the node provided by the invention, the problem of the loss of data messages in a PMTU learning process is solved, and the number of message interaction in the PMTU learning process is reduced.
Owner:ZTE CORP
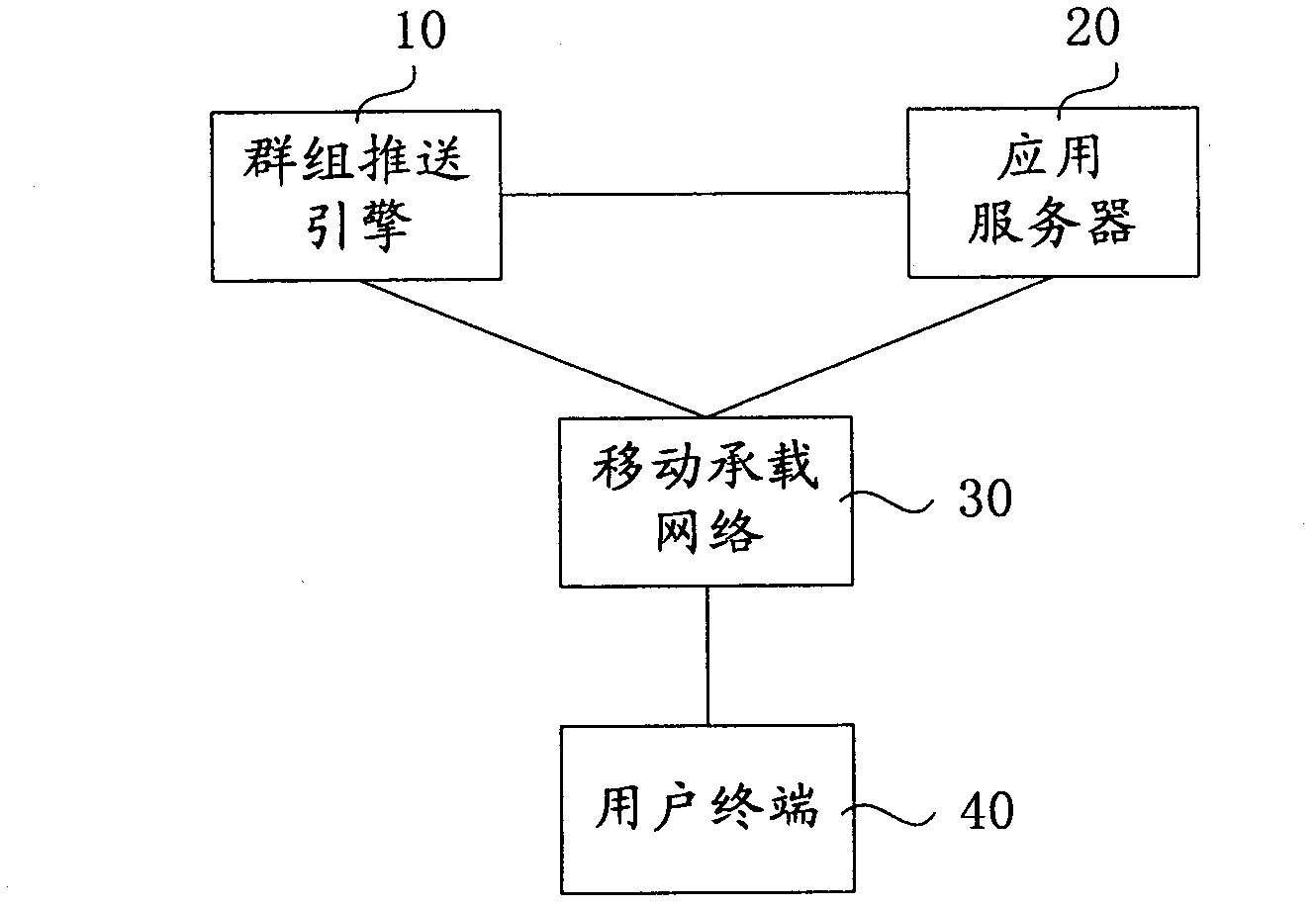
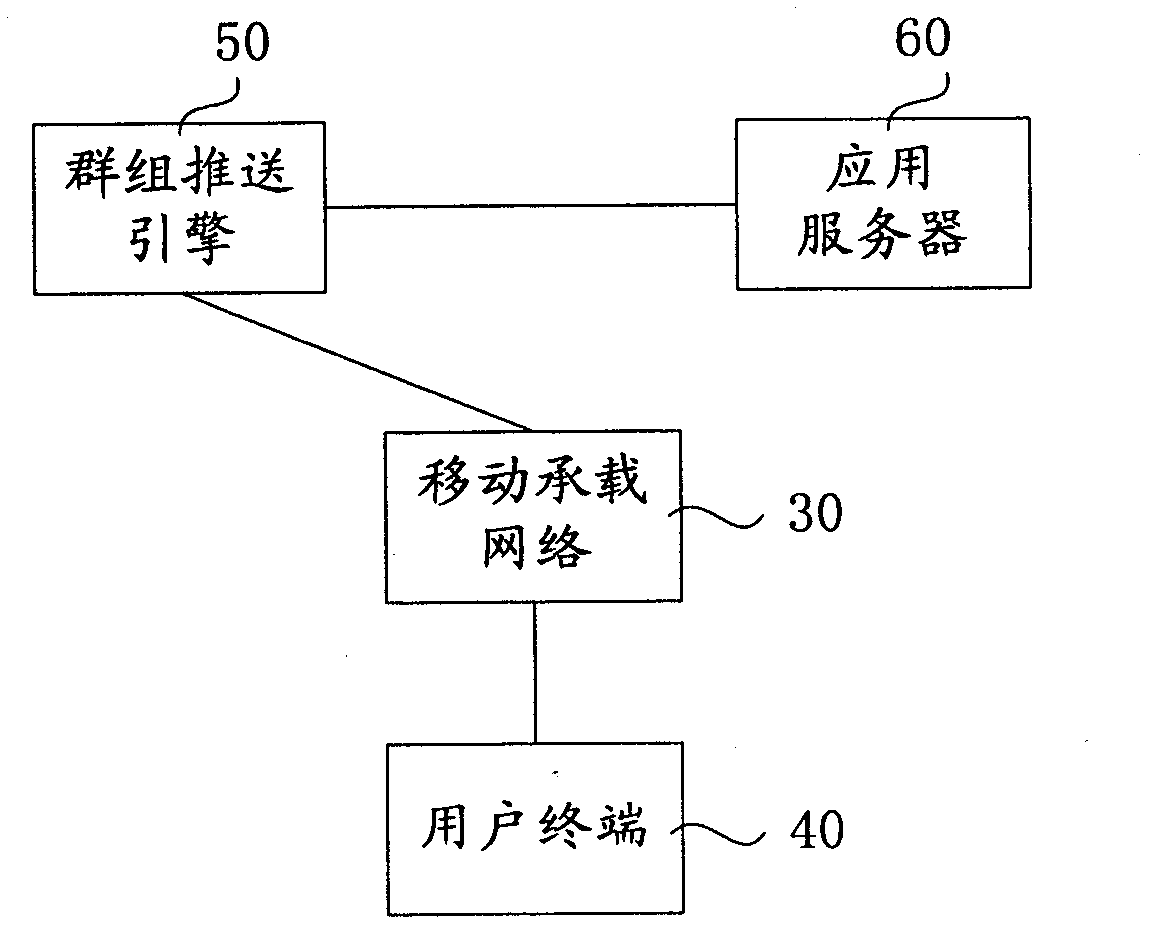
Business push system and method
ActiveCN103036926AReduce the number of interactionsEasy to handleSpecial service provision for substationApplication serverComputer science
The invention relates to a business push system which comprises an application server for sending a push group build request including identification information of a user member, sending a group push business request and pushing data to client ends corresponding to user members of a push group through a mobile hosted network, and a group push engine for creating push groups, distributing corresponding group identification of the push groups, returning the group identification to a request party, determining the push groups according to the group identification to be pushed in the group push business request and the members complying with push conditions in the push groups and sending push notice to the client ends corresponding to user members complying with the push conditions. The invention further relates to a business push method. The business push system is capable of greatly reducing times of interactions between the application server and the push engine, achieving push business of a plurality of users through one interaction, and obviously improving processing capacity and efficiency of the push system.
Owner:CHINA TELECOM CORP LTD
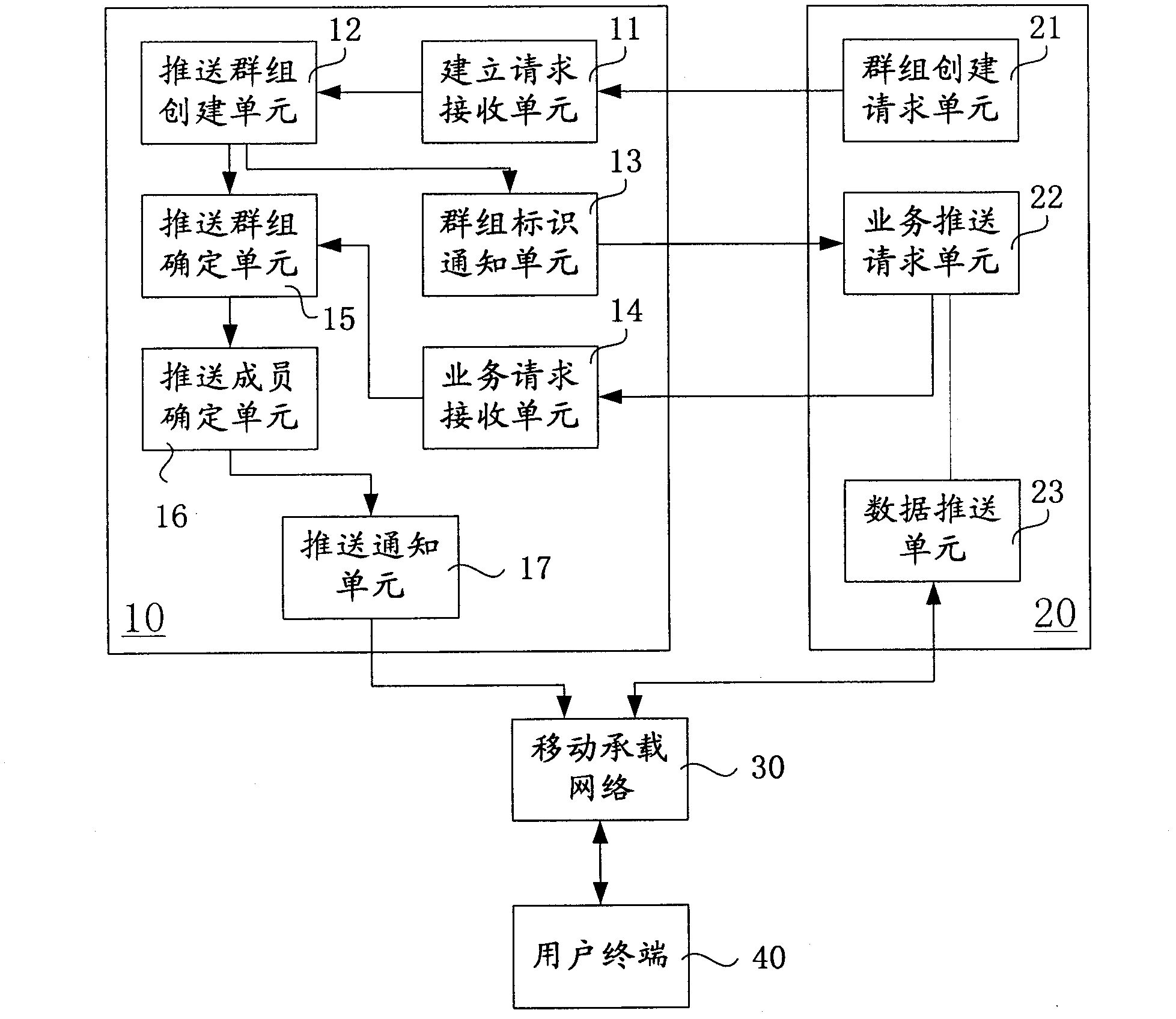
A method and management center server for subscribing mobile service for groups
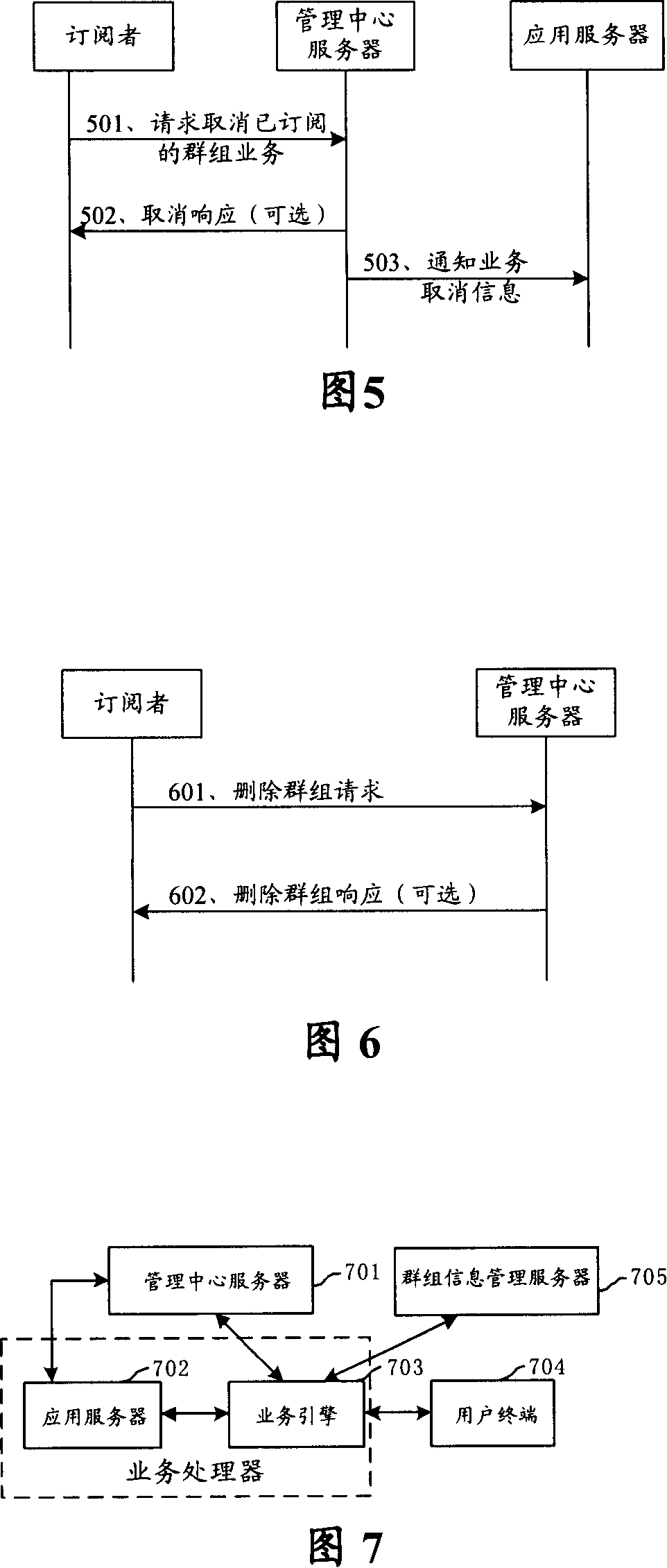
ActiveCN101127941AReduce the number of interactionsReduce trafficSpecial service provision for substationRadio/inductive link selection arrangementsInteraction timeApplication server
The utility model discloses a method of subscribing mobile business for groups. The utility model is characterized in comprising the following steps: a management center server builds a group business subscription index and informs application server groups of subscribed business information according to received request with a group mark and at least one business mark of subscribing business for groups; the information comprises at least a group mark; the group business subscription index comprises corresponding relationship between the group mark and at least one business mark. The utility model has the advantages of only needing business interaction between the application server and business engine, conveniently and uniformly subscribing mobile business for the group users, decreasing interaction times between the operation business server side and the application server, lowering network traffic, protecting information safety for the groups and the group users. The utility model also provides a management center server.
Owner:HUAWEI TECH CO LTD
Method for mutual authentication of user identities based on elliptic curve passwords
ActiveCN104639329AReduce verification timesReduce storage overheadPublic key for secure communicationUser identity/authority verificationInteraction timeMan-in-the-middle attack
The invention relates to a method for mutual authentication of user identities based on elliptic curve passwords. The characteristics of storage capability, calculation capability and limited bandwidth of an Ad Hoc network are considered, and a self-authentication public key system and the intractability of an elliptic curve discrete logarithm problem are utilized, so as to reduce the interaction times of the user identity authentication process, and accelerate the authentication speed. The method comprises the following steps of system initializing, user registering, and mutual authentication of the user identities. The method has the advantages that while the mutual authentication of the user identities is guaranteed, the function of session key negotiation is realized, the storage expense, communication expense and calculation expense are all less, the replay attack, man-in-the-middle attack, counterfeiting and tampering attack, and key disclosure counterfeiting attack can be resisted, a generated one-time session key has the advancing security and backward security, and the security is higher.
Owner:ZHEJIANG UNIV
Communication method, device and system based on combined public key cryptography system
InactiveCN103825733AReduce the number of interactionsImprove authentication efficiencyKey distribution for secure communicationPublic key for secure communicationKey generation centerComputer security
The invention provides a communication method, device and system based on a combined public key cryptography system. The method includes the steps of obtaining a private key of a first node from a secret key generating center through the first node, obtaining identification of a second node according to an adjacent node identification list, calculating a public key of the second node according to the identification of the second node, calculating a shared secret key parameter of the first node according to the secret key of the first node and the public key of the second node, then, calculating a shared secret key of the first node according to the shared secret key parameter of the first node, generating a first secret key verification code corresponding to the shared secret key of the first node, sending shared secret key verification information with the first secret key verification code to the second node, and receiving shared secret key response information from the second node. The calculation steps can be completed offline, the number of times of interaction between the nodes is lowered, and therefore when the first node starts verification, verification can be completed in a quite short period of time, and verification efficiency is improved.
Owner:HUAWEI TECH CO LTD
Resource allocation method and apparatus
ActiveCN106550457AImprove efficiencyReduce the number of interactionsConnection managementData transmissionRadio Resource Control
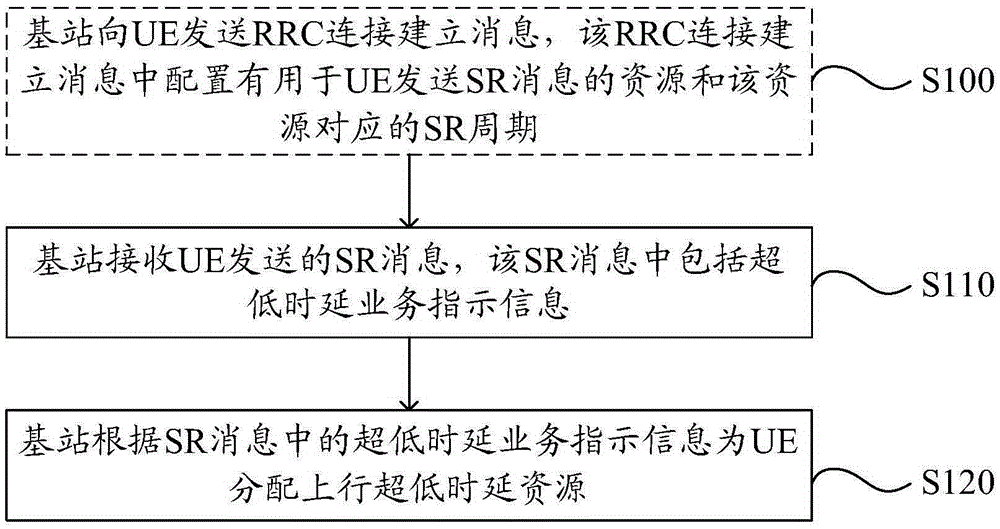
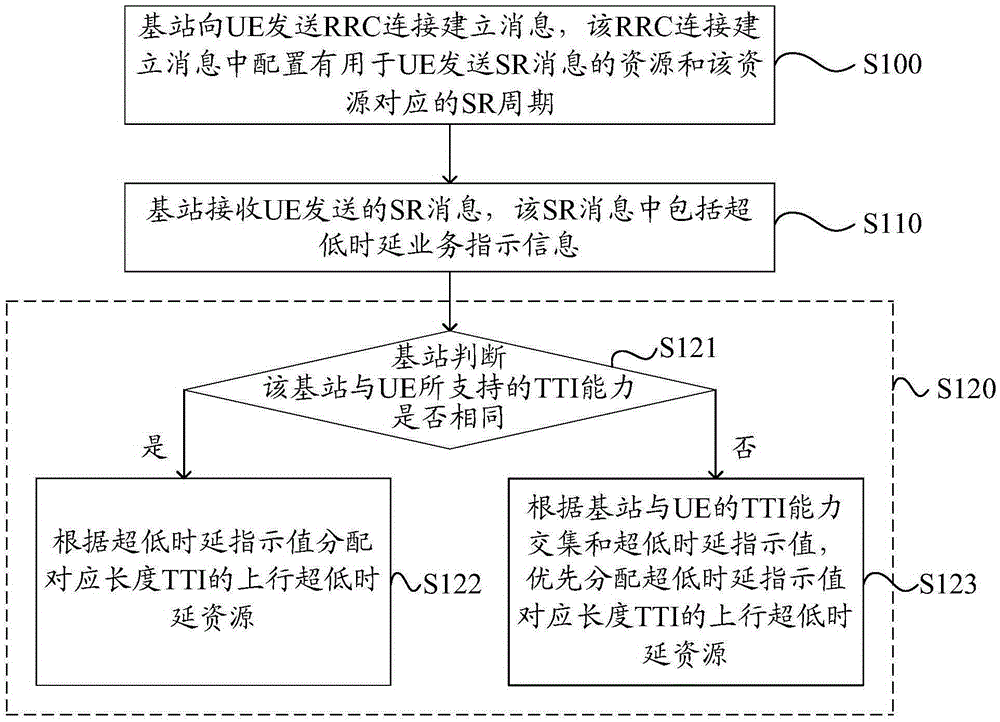
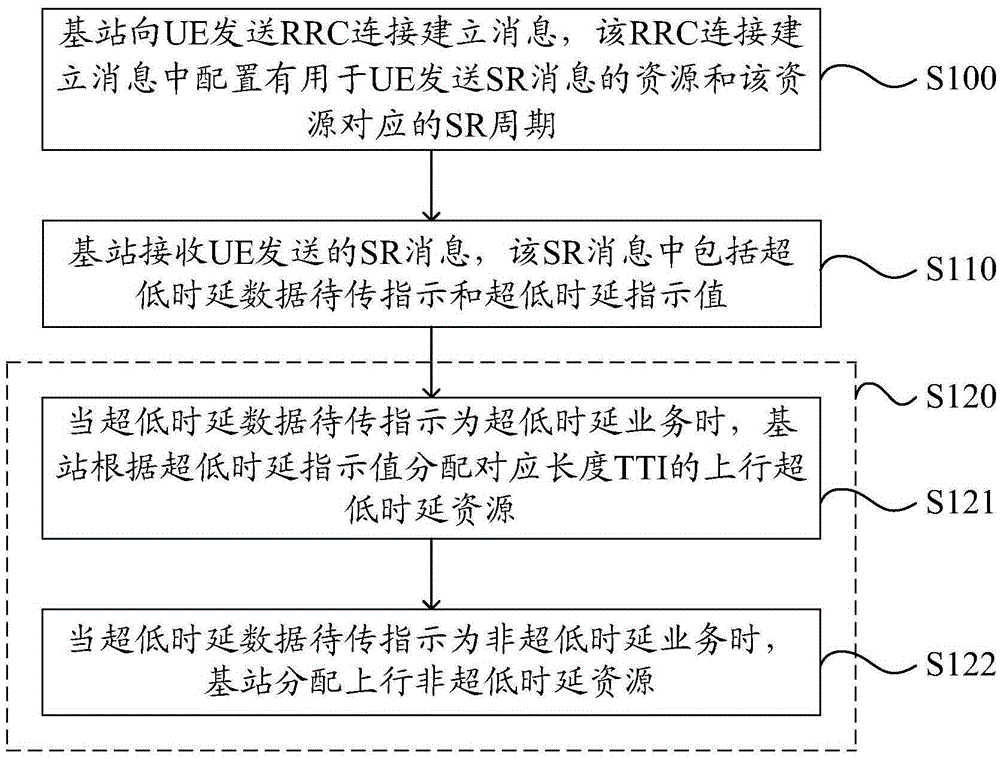
The present invention discloses a resource allocation method and apparatus. The resource allocation method in the invention includes the following steps that: a base station receives an uplink scheduling request (SR) message sent by user equipment (UE), wherein the SR message contains ultra-low delay service indication information; and the base station allocates uplink ultra-low delay resources to the UE according to the ultra-low delay service indication information in the SR message. With the method and apparatus of the present invention adopted, the problem that a conventional SR message cannot indicate ultra-low delay service demand information when UE in an RRC (radio resource control) connection state requests data transmission can be solved.
Owner:ZTE CORP
Method and device for generating searching result
ActiveCN103186574ABoost Relevance RankingFind quicklySpecial data processing applicationsInteraction timeLexical item
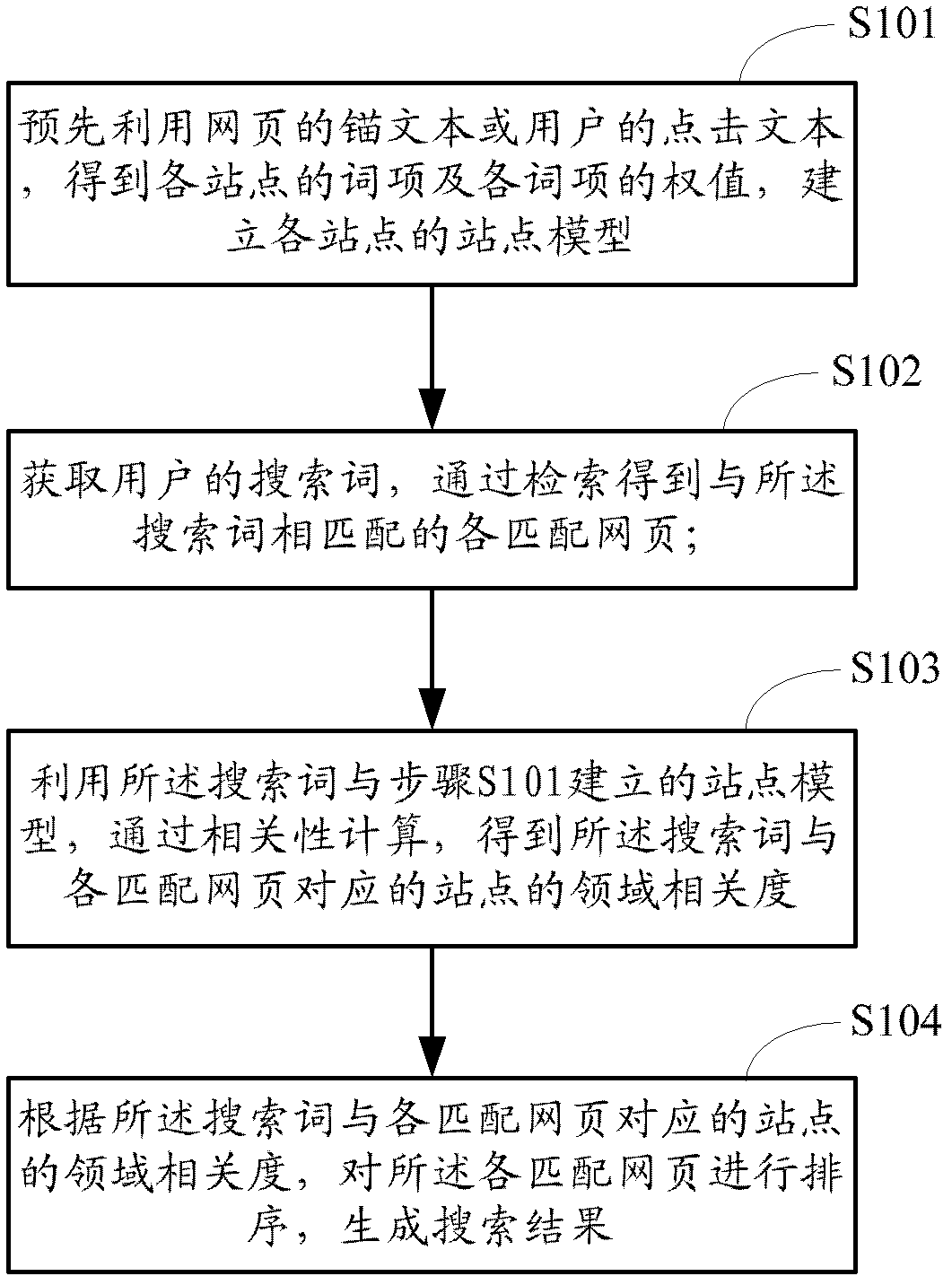
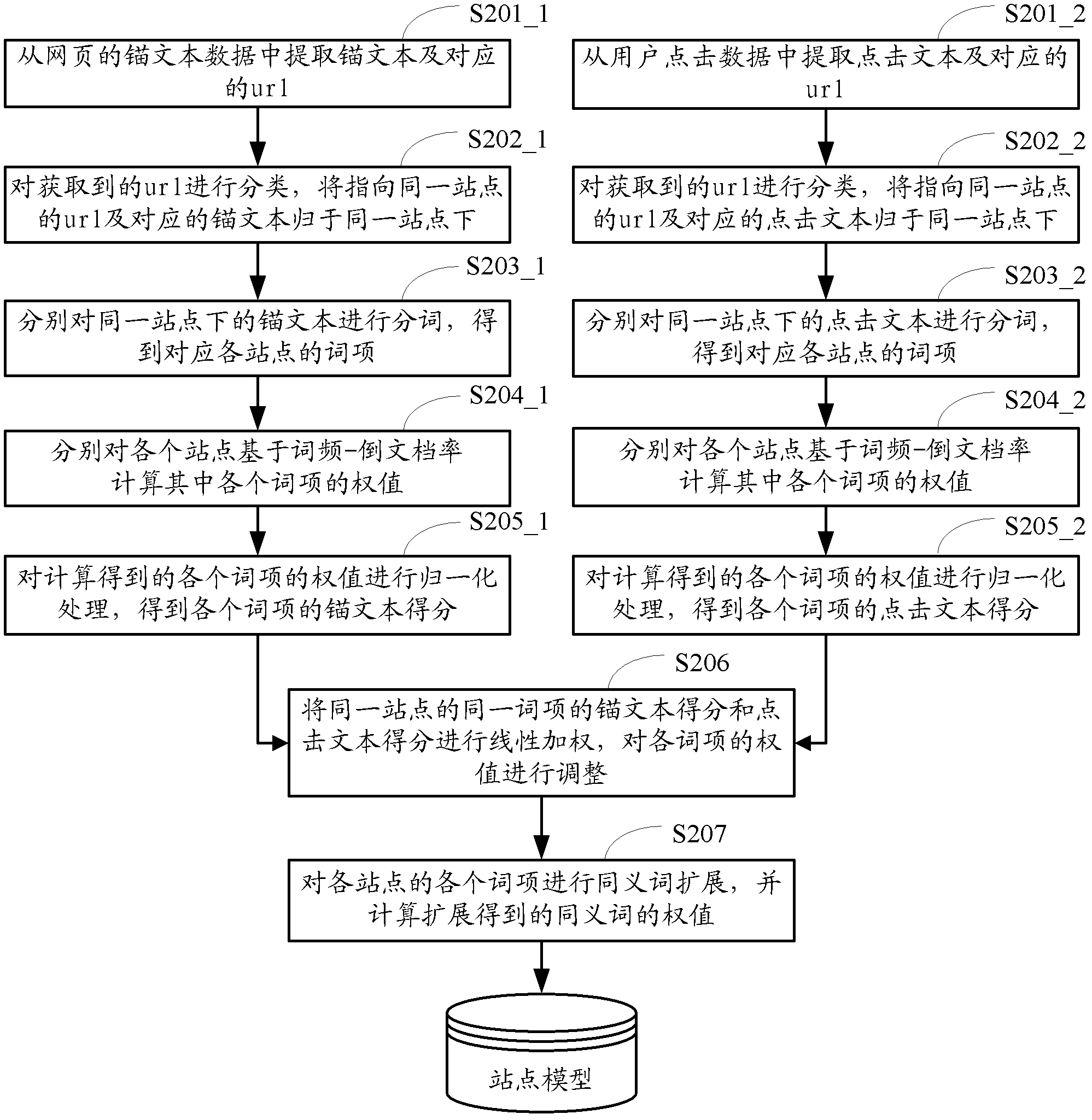
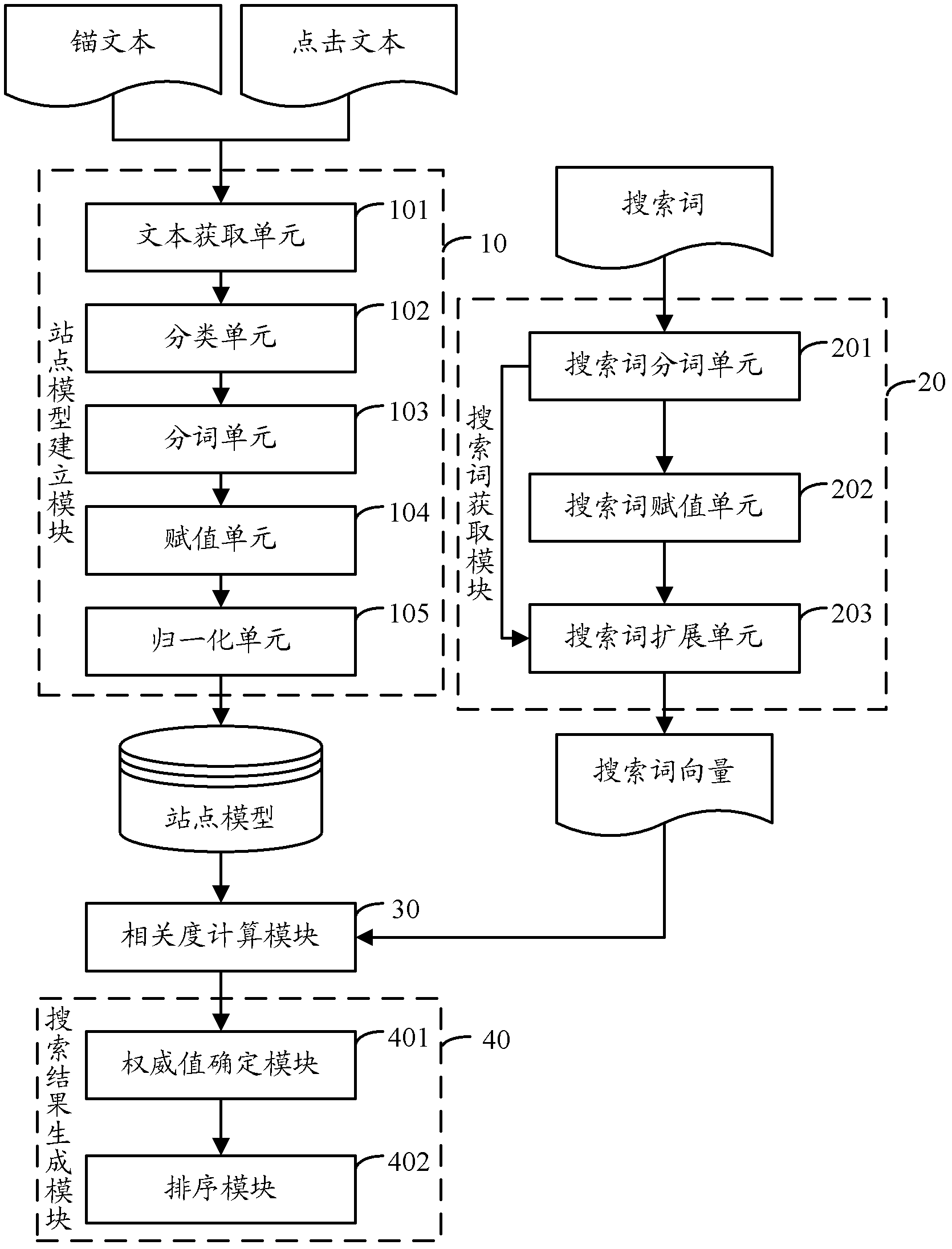
The invention provides a method and a device for generating a searching result. The method comprises the following steps of S1, using an anchor text of a webpage or a click text of a user in advance to obtain a lexical item of each website and the weight of each lexical item, and establishing the website model of each website; S2, acquiring a search term of the user, and obtaining each matched webpage matched with the search term through retrieval; S3, obtaining the domain relevance between the search term and the website corresponding to each matched webpage through correlation calculation by using the search term and the website model established in the step S1; and S4, according to the domain relevance between the search term and the website corresponding to each matched webpage, sequencing each matched webpage to generate the searching result. Compared with the prior art, the method has the advantages that the domain relevance sequencing of the searching result can be improved, the user is facilitated to quickly find the searching result, meanwhile, the efficiencies of the user and a system are improved, the interaction times are reduced, and the burden of a server is mitigated.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Method for triggering co-registration of long term evolution (LTE) single-card dual-standby multimode terminal and terminal
InactiveCN102497629AReduce the number of interactionsReduce power consumptionEnergy efficient ICTPower managementTelecommunicationsAir interface
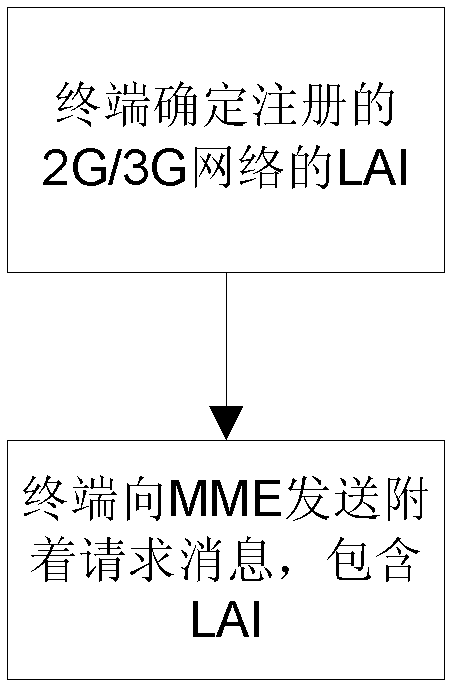
The embodiment of the invention relates to a method for triggering the co-registration of a long term evolution (LTE) single-card dual-standby multimode terminal and the LTE single-card dual-standby multimode terminal, and aims to solve the technical problems of increasing of network signaling interaction times and power consumption of the terminal and air interface resource waste caused by respective registration in an LTE network and a second-generation (2G) / third-generation (3G) network, realize the co-registration in the LTE network and the 2G / 3G network, reduce air interface signaling consumption, reduce the power consumption of the terminal and prolong the standby time of the terminal. The method for the co-registration comprises the following steps that: the terminal determines a location area identifier of the 2G / 3G network in which the terminal is to be registered; and the terminal transmits an attach request message comprising the location area identifier to a mobile management entity of the LTE network to trigger the co-registration of the terminal and the mobile management entity of the LTE network in the LTE network and the 2G / 3G network.
Owner:HUAWEI DEVICE CO LTD
Method and system for realizing remote configuration of customer premises equipment (CPE) service parameters by TR069
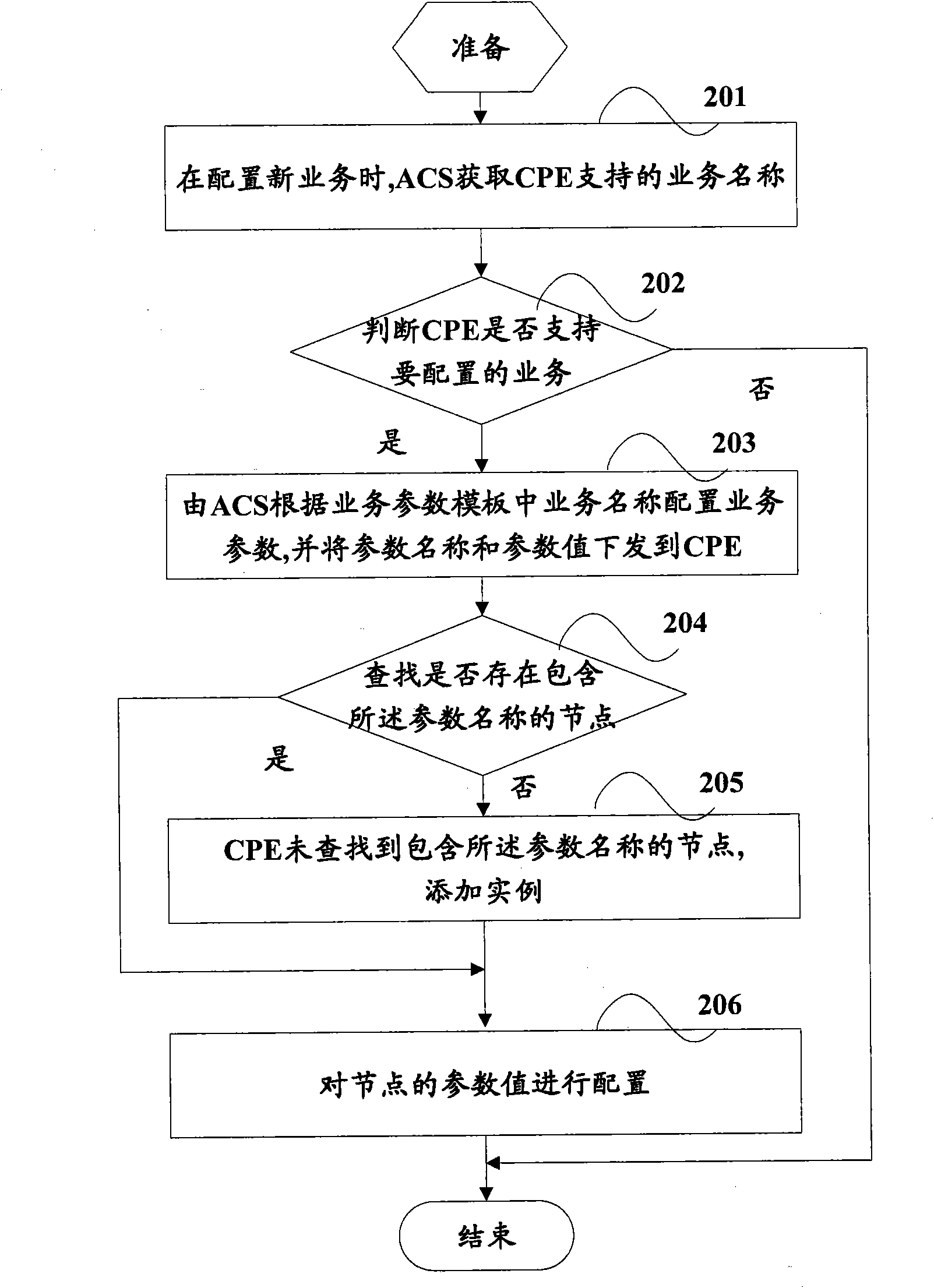
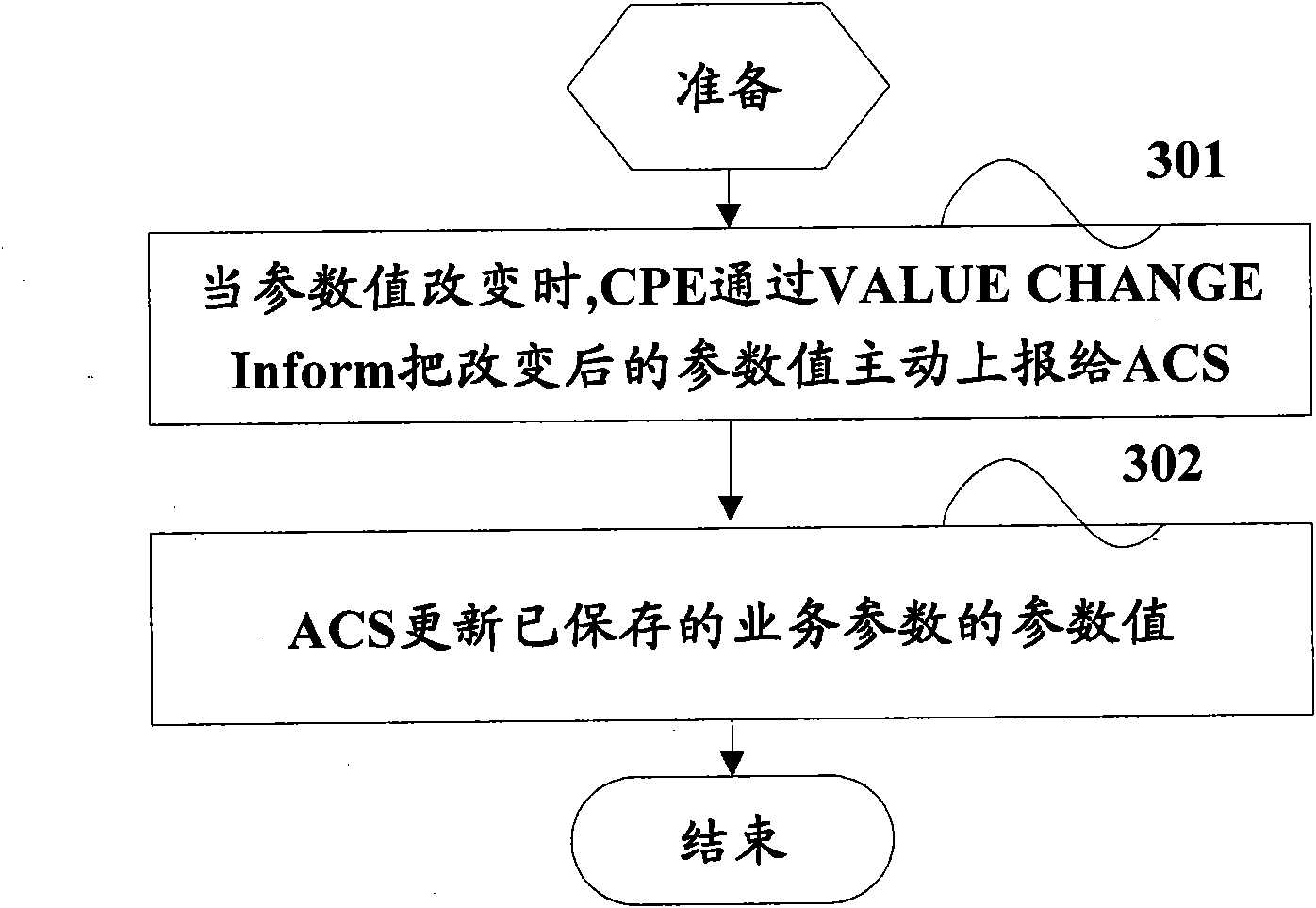
ActiveCN102082676AConfiguration highReduce the number of interactionsData switching networksCommunications systemService configuration
The invention provides a method and system for realizing remote configuration of customer premises equipment (CPE) service parameters by TR069. The method comprises the following steps: acquiring a service name supported by CPE via an audio communications system (ACS); when the service name shows that the CPE supports the services to be configured by the ACS, configuring service parameters by the ACS in accordance with the service name in a service parameter template, and sending the parameter name and parameter values to the CPE; and when the CPE receives the sent parameter name and the parameter values, searching a node containing the parameter name, and configuring the parameter value of the node. According to the method and system, a service configuration process is accelerated and the bandwidth use ratio is effectively improved by reducing the interactive times between the ACS and the CPE.
Owner:CHINA TELECOM CORP LTD
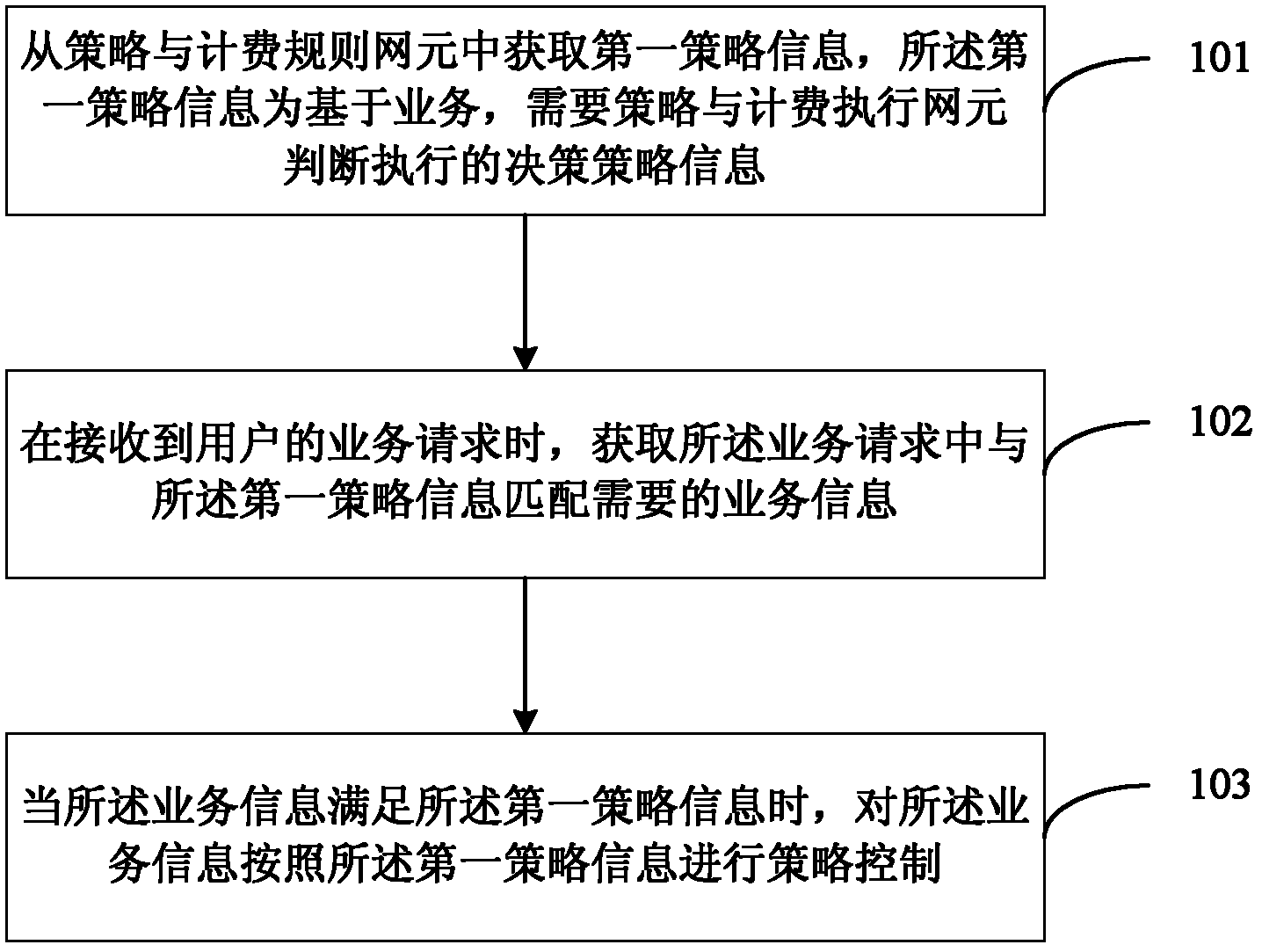
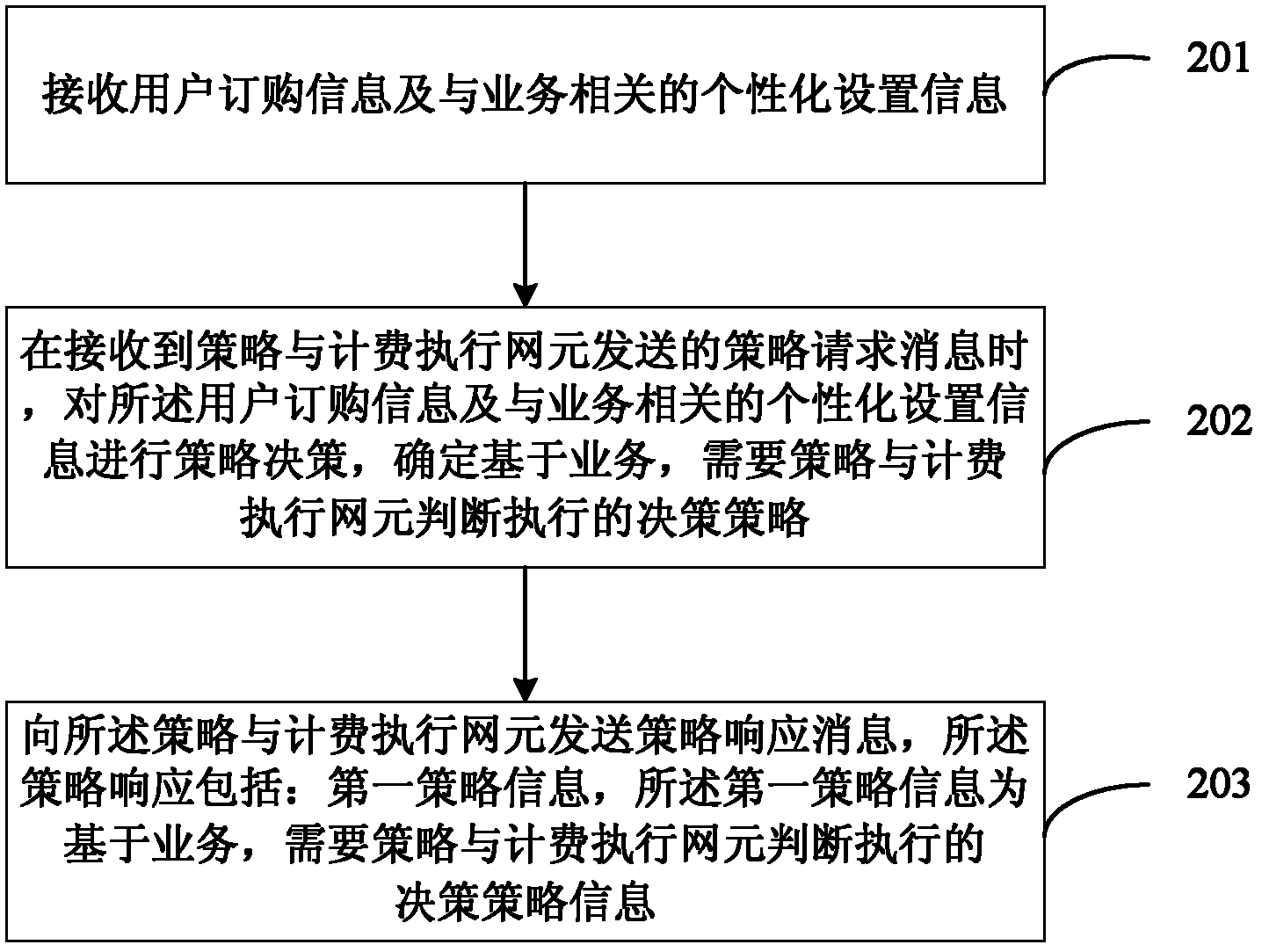
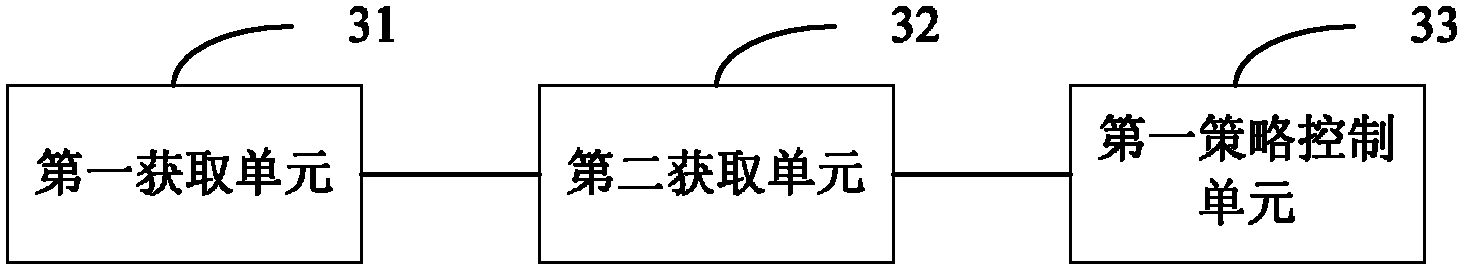
Policy control method, policy control device and policy control system for data services
ActiveCN102665191AReduce the number of interactionsReduce performance overheadTransmissionNetwork data managementControl systemDecision strategy
An embodiment of the invention provides a policy control method, a policy control device and a policy control system for data services. The method includes: acquiring first policy information from a policy and charging rule function network element, wherein the first policy information is decision policy information needing to be judged and enforced by a policy and charging enforcement function network element based on the services; when a service request is received from a user, acquiring service information needed in match with the first policy information from the service request; and when the service information satisfies the first policy information, performing policy control for the service information according to the first policy information. The method, the device and the system in the embodiment solve the technical problem of more interactive times between the PCRF (policy and charging rule function) network element and the PCEF (policy and charging enforcement function) network element in policy control of frequently modified service request information or result associated policy control in the prior art.
Owner:HUAWEI TECH CO LTD
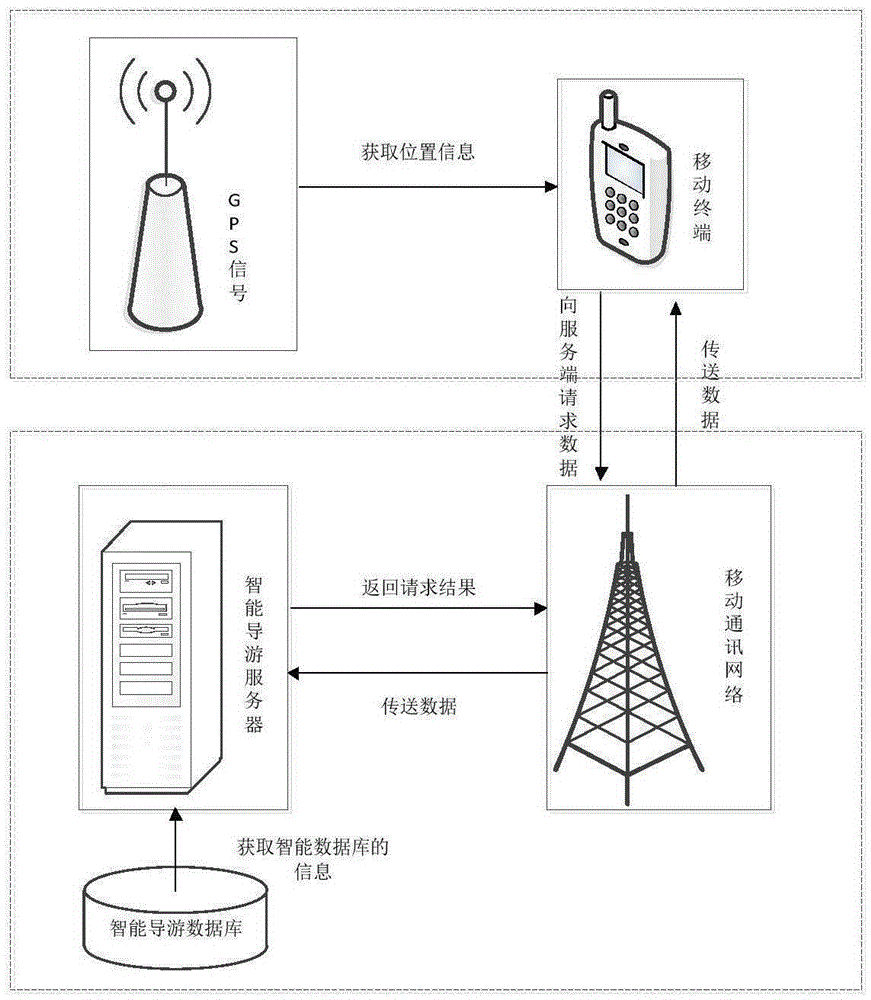
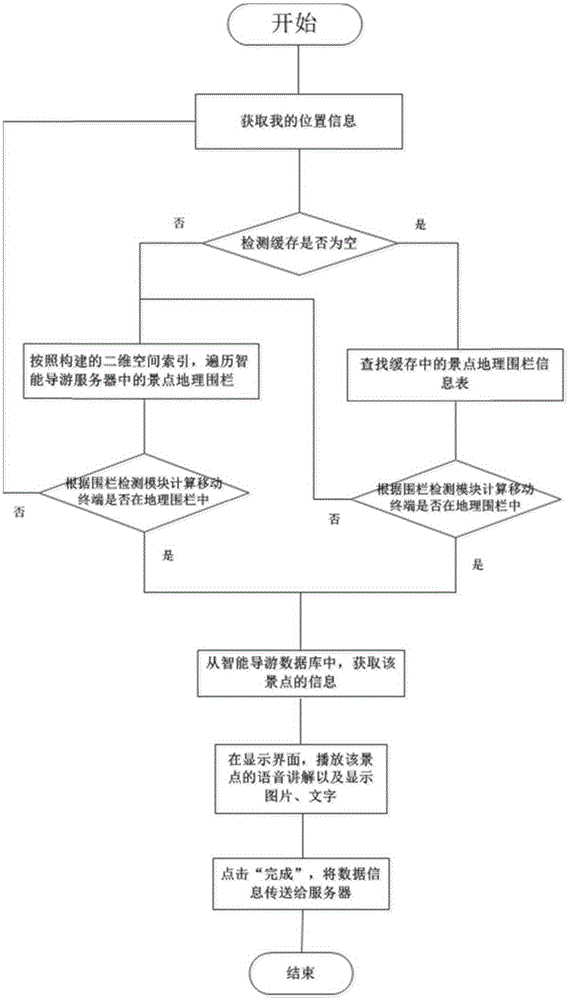
Intelligent electronic tourist guide system based on geographic fencing technology
ActiveCN105338492AImprove experienceFast response timeLocation information based serviceNetwork communicationSpeech sound
The invention discloses an intelligent electronic tourist guide system based on a geographic fencing technology. The system comprises a mobile terminal, an intelligent tourist guide server and an intelligent tourist guide database. A method for realizing the system comprises the steps: firstly, locating data are received by the mobile terminal and are sent to the intelligent tourist guide server through a network communication module; then, a scenic region where the mobile terminal is located is calculated by the intelligent tourist guide server through a geographic fencing technology according to the locating data, and information of the scenic region is found from the intelligent tourist guide database; finally, the information of the scenic region is sent to the mobile terminal by the intelligent tourist guide server through the network communication module, the a multimedia module of the mobile terminal is triggered to play voice, and meanwhile pictures, characters and voice playing states are displayed on the mobile terminal.
Owner:NANJING UNIV +2
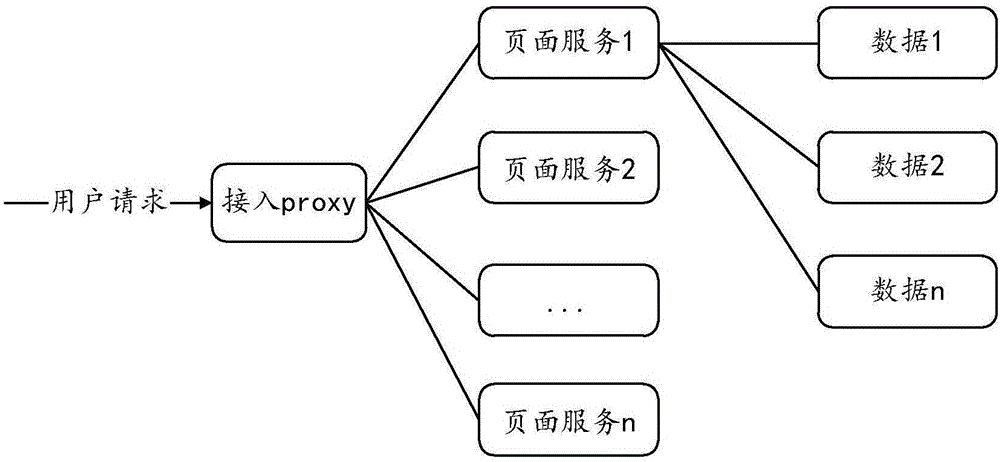
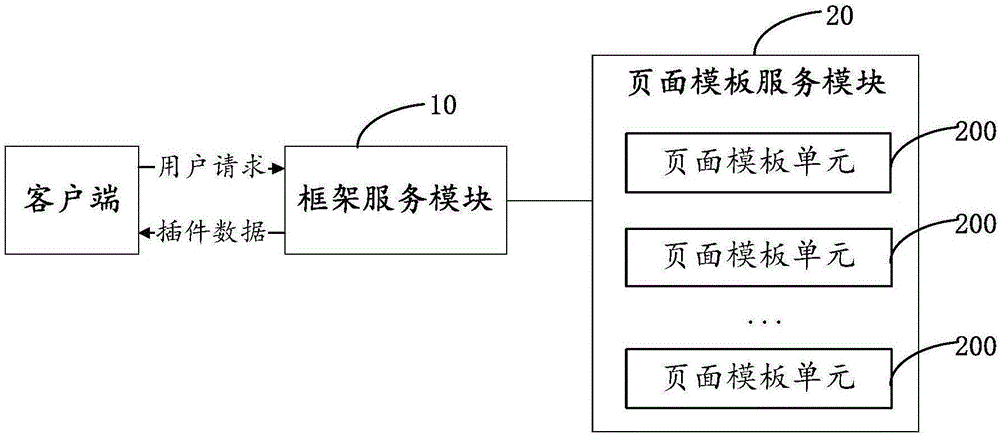
Page data interaction apparatus and method
ActiveCN106446049AImprove loading speedAchieve decouplingWebsite content managementProgram loading/initiatingData displayApplication software
The invention discloses a page data interaction apparatus and method. The apparatus comprises a framework service module and a page template service module; a page template unit is used for decomposing a page corresponding to a request into a plurality of modules, obtaining plug-in information corresponding to the modules, generating a plug-in information list according to the plug-in information, and sends the plug-in information to the framework service module; and the framework service module is used for analyzing the request sent by a client, sending the request to the page template unit corresponding to the request, obtaining corresponding plug-in data according to the plug-in information list, and returning the plug-in data to the client. A client application only needs to interact with a framework service, and all data required for performing data display and UI rendering by the client can be obtained through one-time interaction, so that background inter-logic decoupling is achieved, the interactive frequency of the client and a background is reduced, the page loading speed is increased, and the efficiency of the client and a server is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com