Data protection transmission method of P2P network
A peer-to-peer network and data protection technology, applied in transmission systems, electrical components, etc., can solve problems such as inappropriate P2P network file transmission methods, achieve simple and effective encryption process, avoid redundant processing, and prevent hacker attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be further described in detail below through specific embodiments and accompanying drawings.
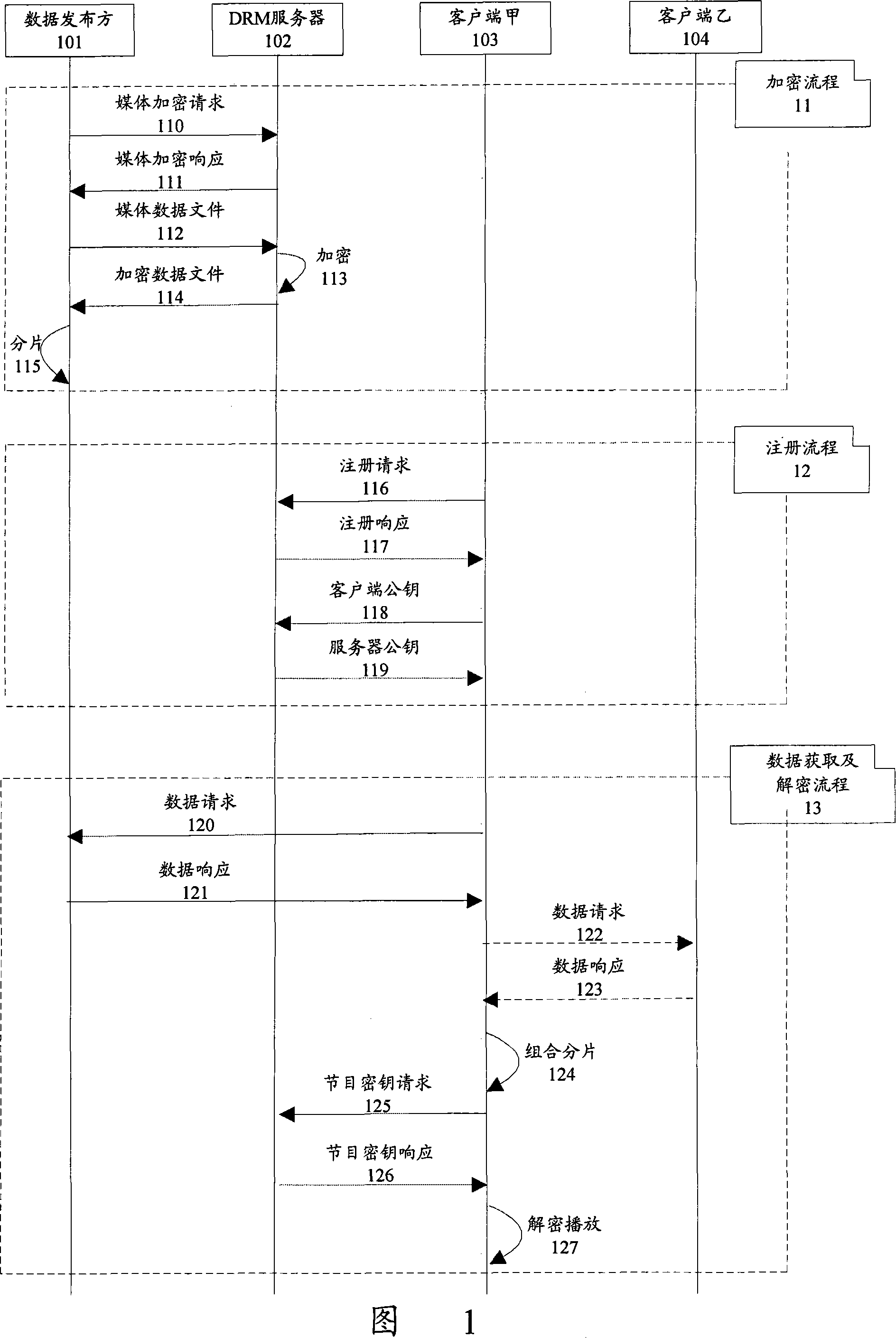
[0044] FIG. 1 is a schematic diagram of a message interaction process according to an embodiment of the present invention. As shown in Figure 1, the data protection method of this embodiment involves four logical entities and three processes:
[0045] The four logical entities are entities that process data based on a point-to-point network. Including: a data publisher 101, an encryption server such as a content digital copyright encryption protection technology (DRM) server 102, a data request client, namely client A 103, and a client B 104 for indirect data transmission in a peer-to-peer network.
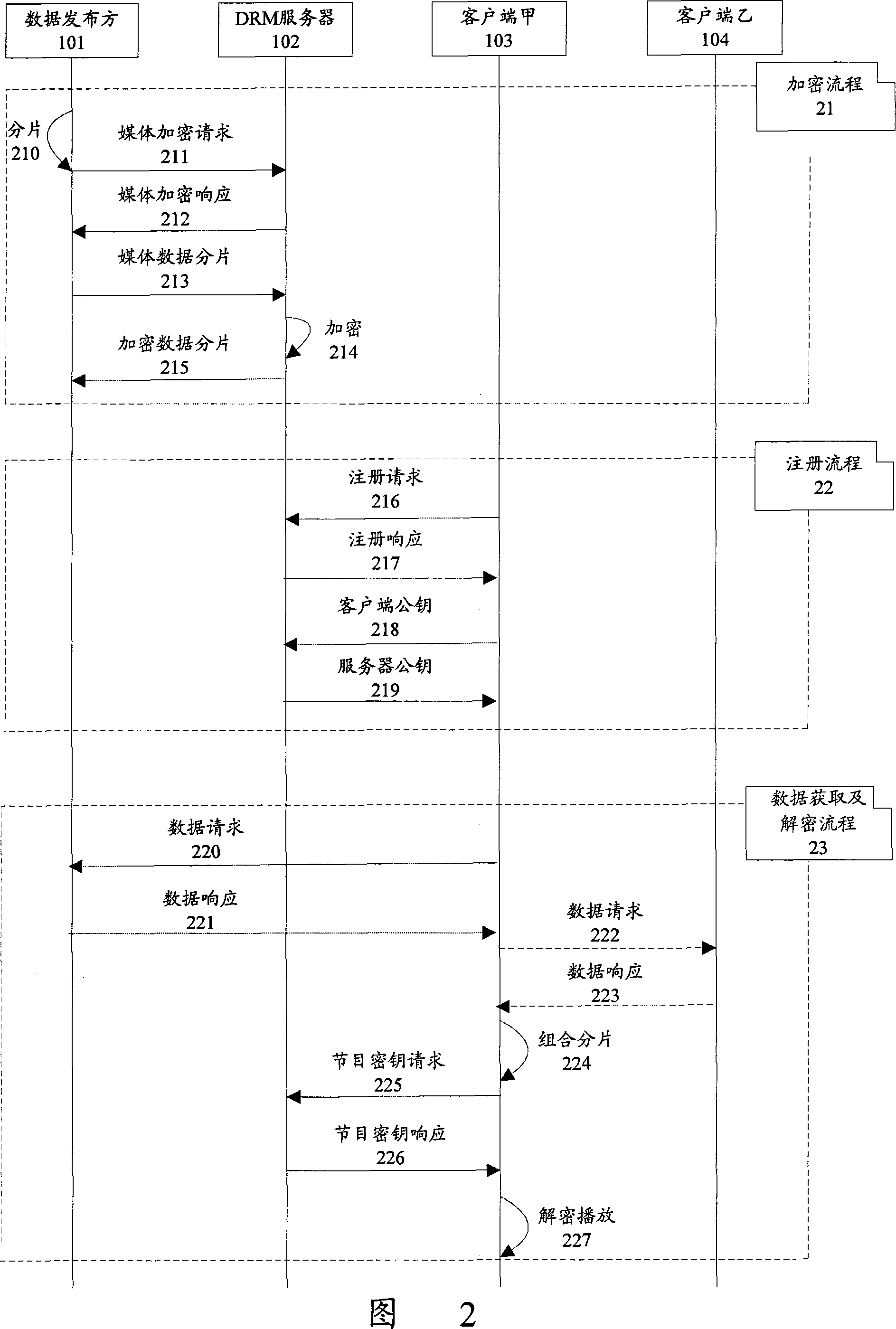
[0046] The three processes mainly include an encryption process 11 , a registration process 12 , and a data acquisition and decryption process 13 .
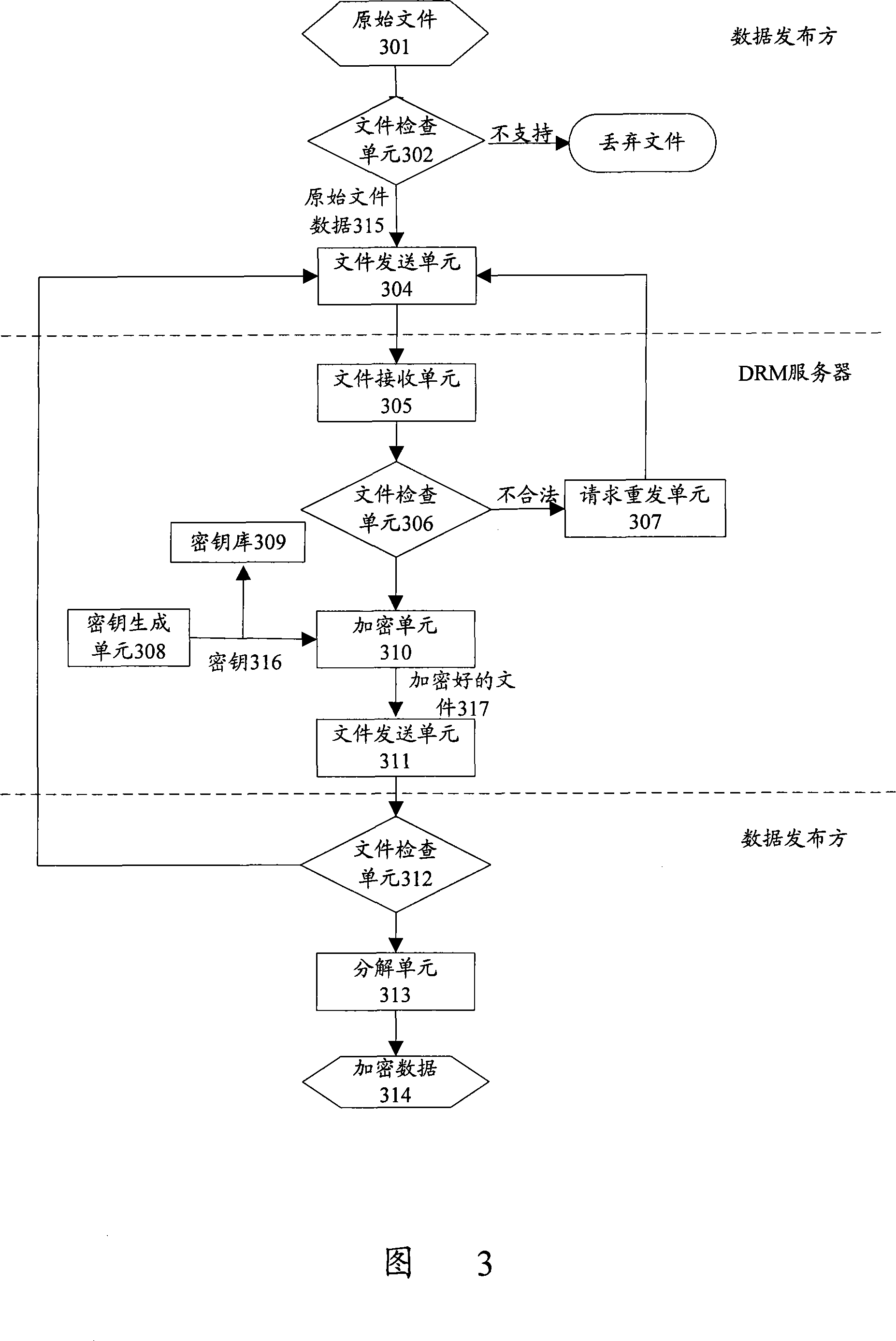
[0047] Encryption process 11, through which the data publisher 101 completes fragmentation and encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com