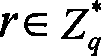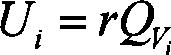Patents
Literature
81results about How to "Simplify the encryption process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data transmission method, device and system
ActiveCN107040369AAvoid the defect of long encryption and decryption timeSimplify the encryption processKey distribution for secure communicationMultiple keys/algorithms usagePaymentCiphertext
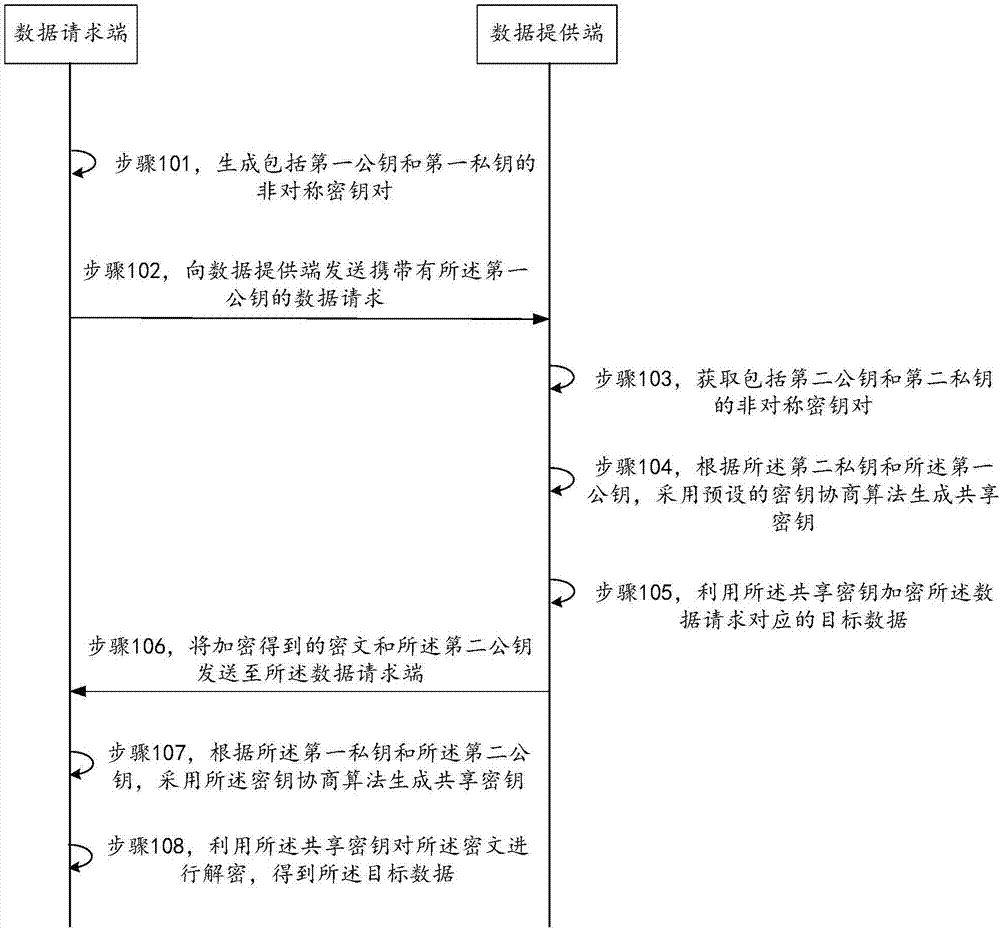
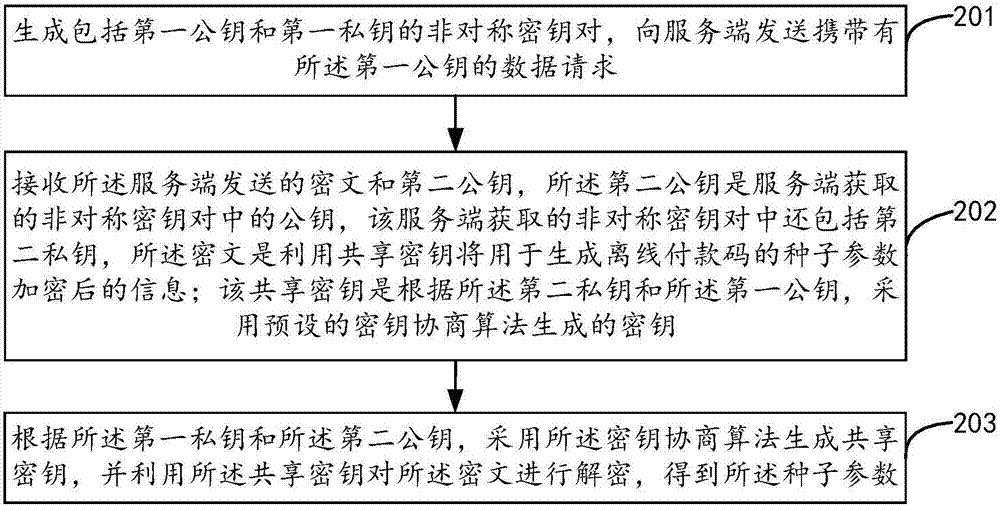
The invention provides a data transmission method, a data transmission device and a data transmission system. The method comprises the steps of generating an asymmetrical secret key pair including a first public key and a first private key, and sending a data request carrying the first public key to a server side; receiving a ciphertext and a second public key sent by the server side, wherein the second public key is the public key in the asymmetrical secret key pair acquired by the server side, the asymmetrical secret key pair acquired by the server side also comprises a second private key, the ciphertext is information generated by encrypting a seed parameter used for generating an offline payment code by using a sharing secret key, and the sharing secret key is the secret key by using a preset secret key negotiation algorithm according to the second private key and the first public key; and generating the sharing secret key by using the secret key negotiation algorithm according to the first private key and the second public key, using the sharing secret key to decrypt the ciphertext, thus acquiring the seed parameter. According to the method, the device and the system provided by the invention, security of the data during a whole transmission process is ensured, and decryption and encryption efficiency is also improved.
Owner:ADVANCED NEW TECH CO LTD
Data protection transmission method of P2P network
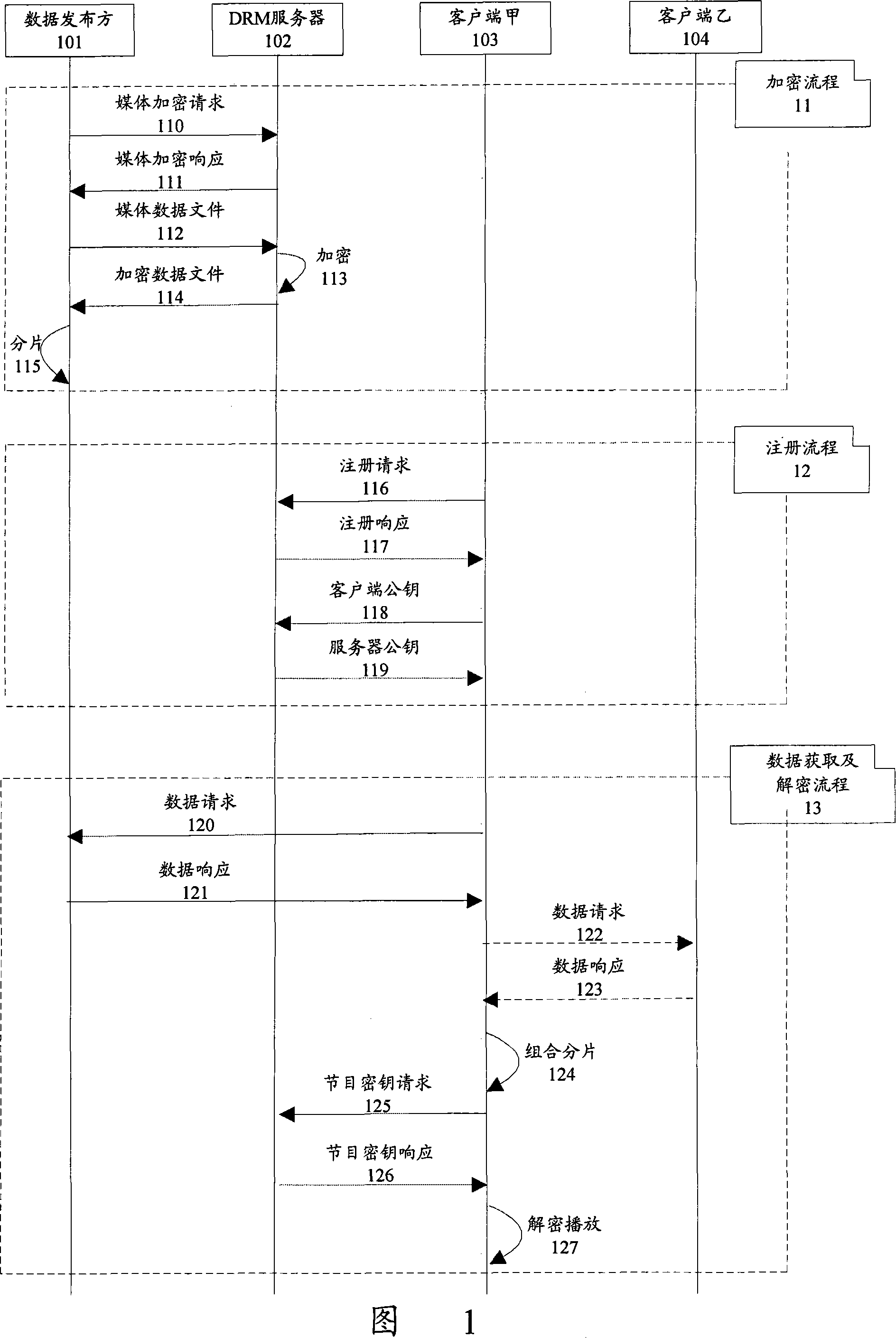
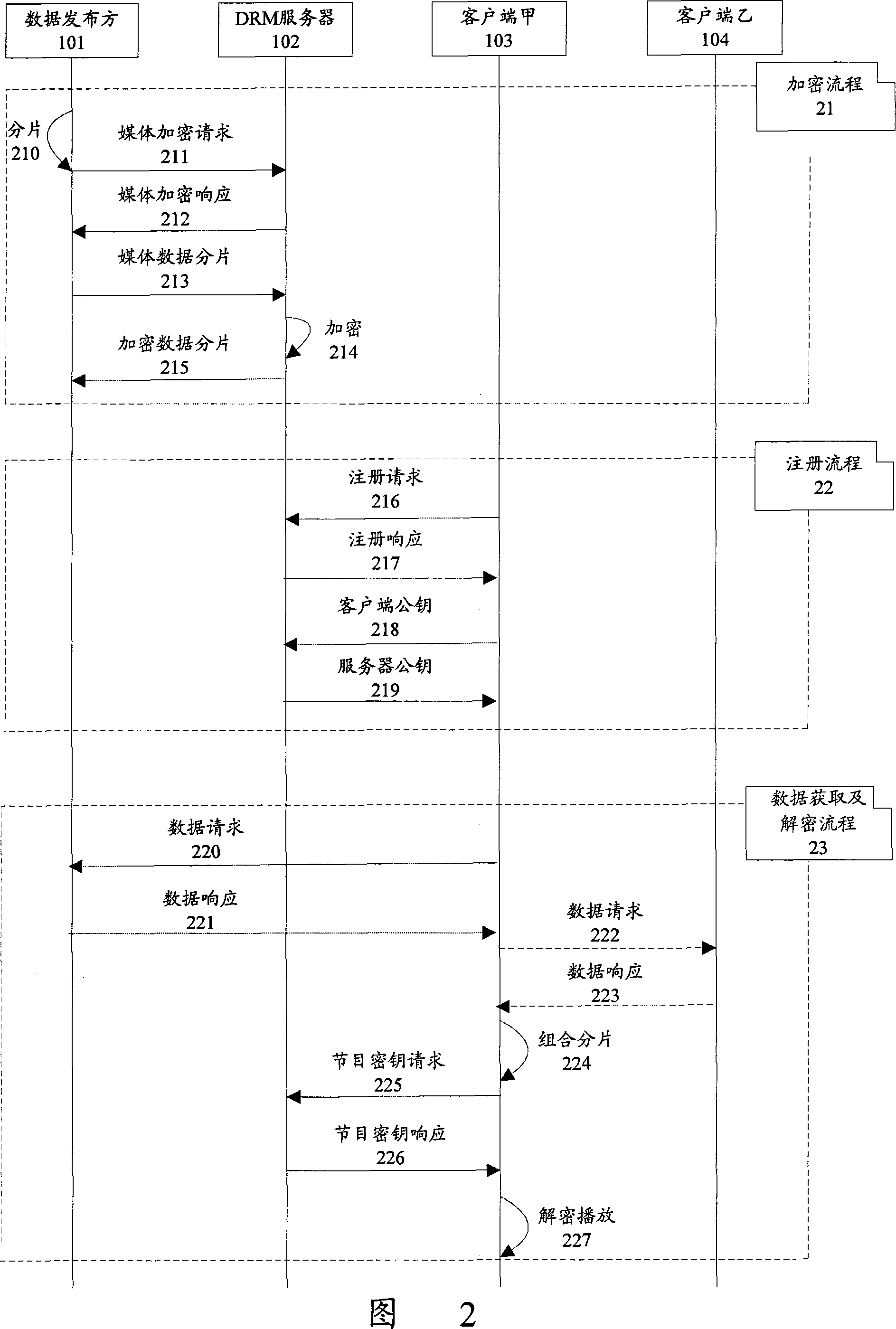
The present invention discloses a data protection transmission method for peer-to-peer network. The method has an encryption server arranged in a peer-to-peer network, and comprises following the steps that: A. a data publication party sends data needing to be published to the encryption server; B. the encryption server encrypts the data needing to be published, saves a corresponding key and returns the encrypted data to the data publication party; C. the data publication party publishes the encrypted data in different pieces; D. a data request client collects the published encrypted data pieces through the peer-to-peer network; the data request client acquires the corresponding key from the encryption server and decrypts the collected encrypted data pieces according to the key. The present invention can be applicable to the characteristics of the peer-to-peer network, improve the data transmission security of the peer-to-peer network, prevent hackers from attacking the peer-to-peer network data and guarantee the rights and benefits of data owners and users.
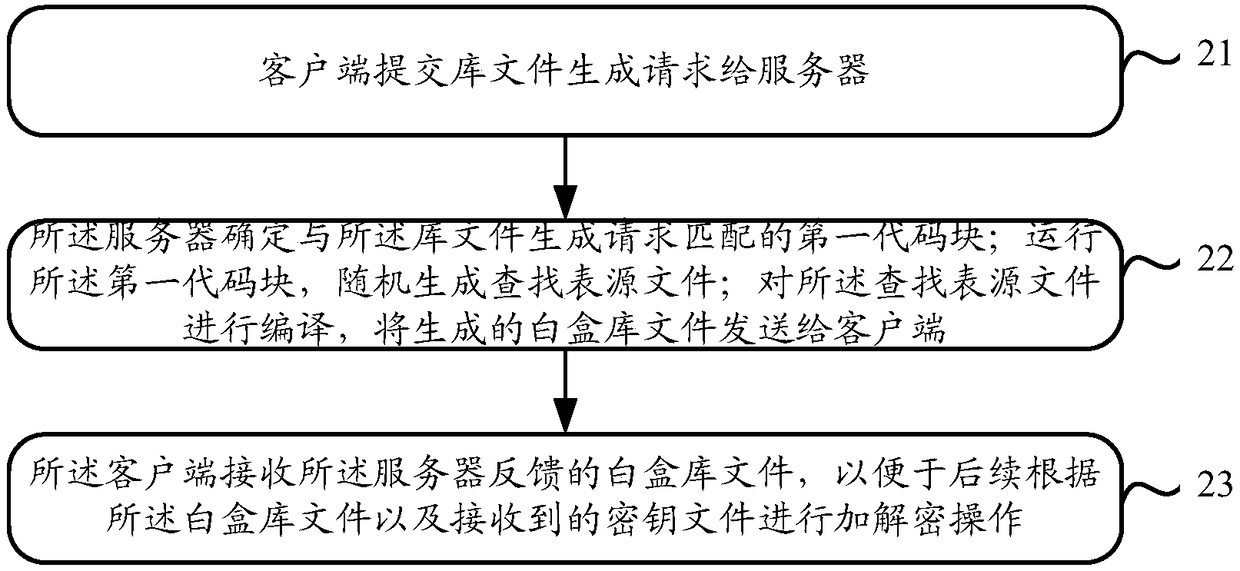
Owner:新疆新颖电子科技有限公司
Secure transmission system for a digital trunked radio system
ActiveUS7203318B2Improve securitySimplify the encryption processKey distribution for secure communicationSynchronising transmission/receiving encryption devicesTrunked radio systemControl signal
A security system for a digital trunked radio system having a digital control channel and a plurality of working channels, wherein said working channels are assigned for temporary use of individual radio units by digital control signals transmitted over said control channel, said control channel carrying digital control signals between a base site and said radio units, comprising a digital key, said key used to limit access to the system equipment and system control channel transmissions.
Owner:EAGLE TECH LLC
System and method for collaboration between regulatory agency and regulated entity
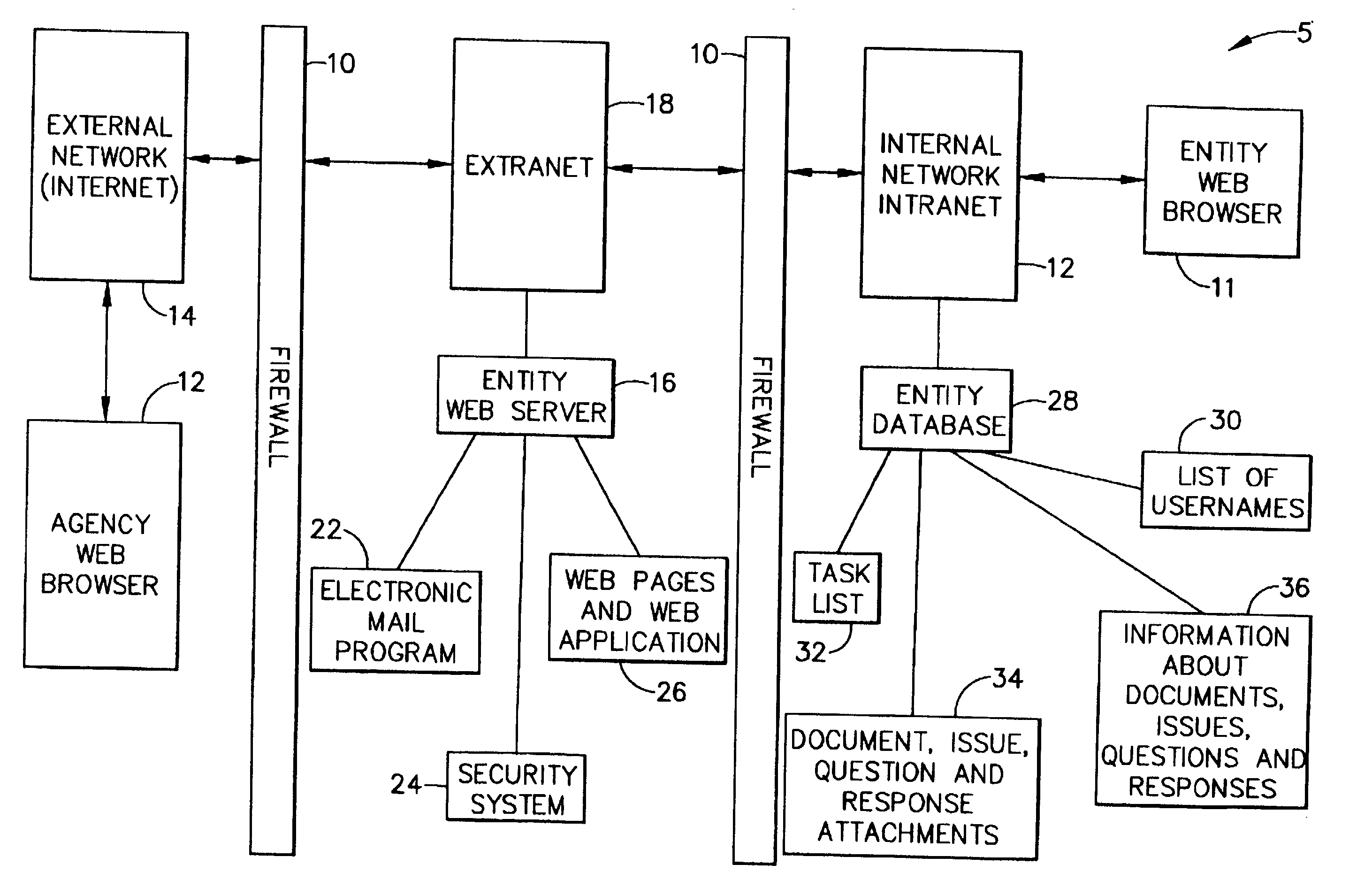
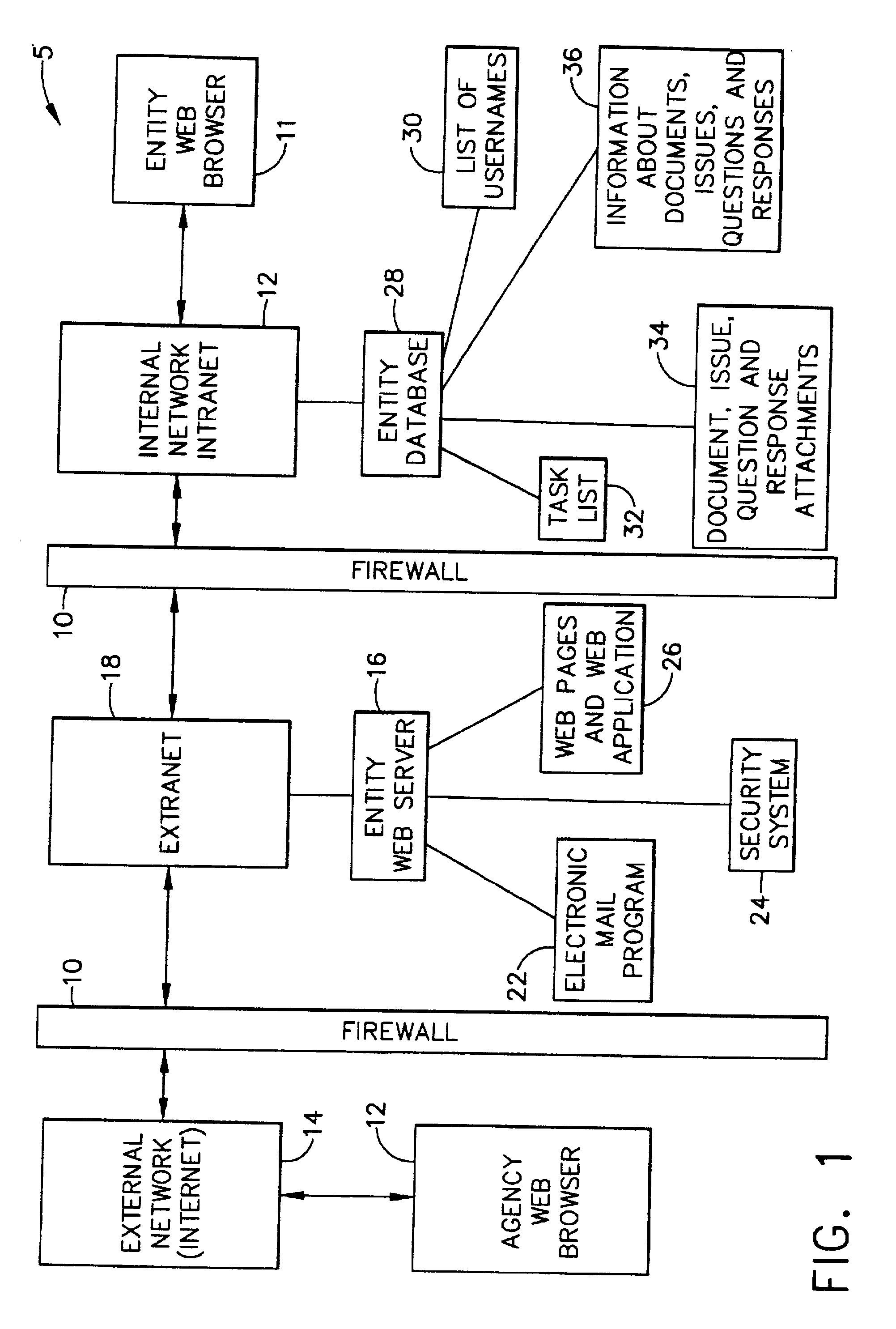
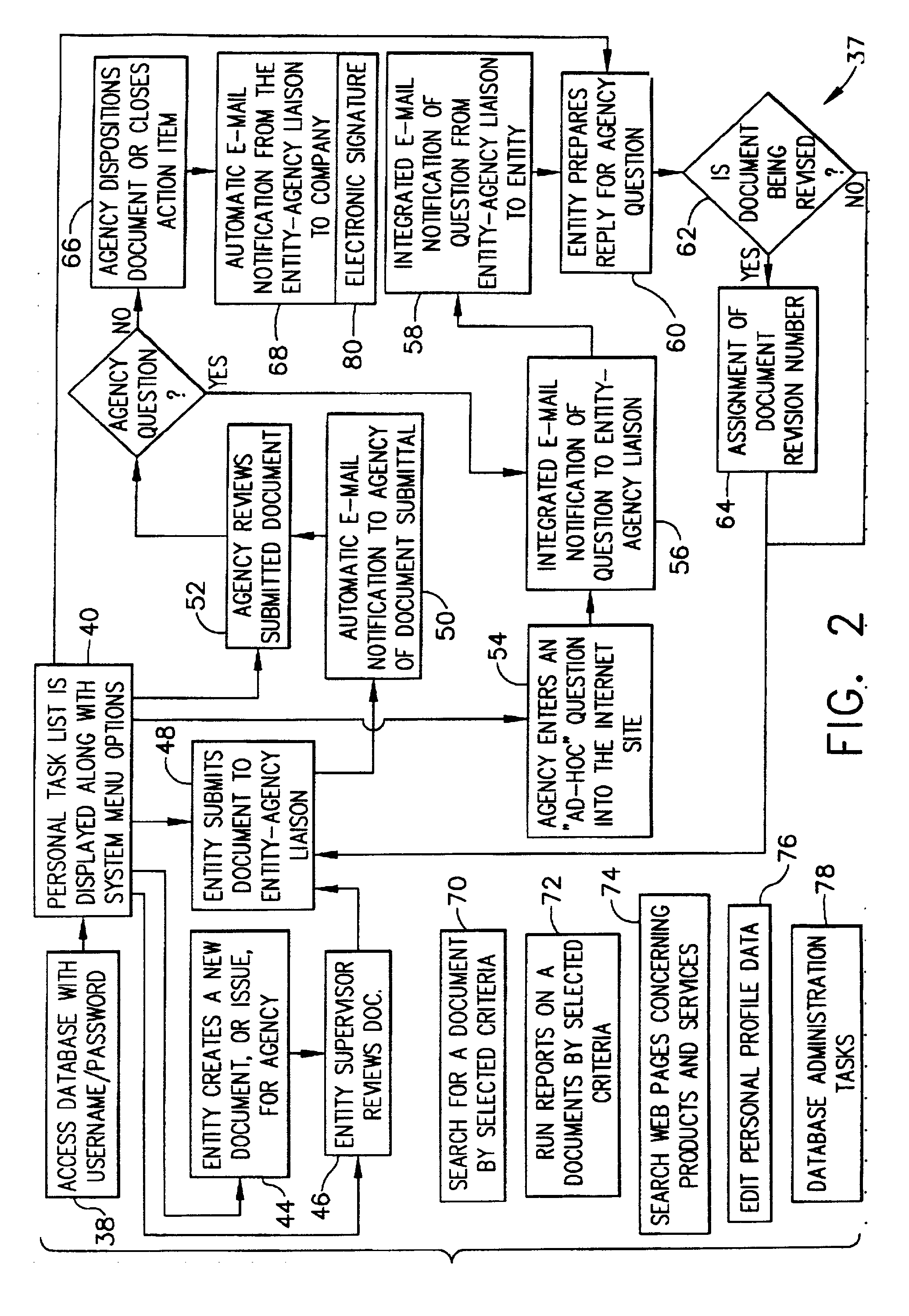
InactiveUS20020116620A1Simplify the encryption processComputer security arrangementsPayment architectureInternet privacySecure transmission
A computer-implemented system and method of secure transmission and collaboration of information between the employees of an entity and a regulator agency for the purpose of obtaining disposition by the regulatory agency. The system consists of a connected web sever and a database, both of which are protected behind at least one firewall. The web server and the multifunctional database are hosted and maintained by the entity for use by the regulatory agency and connects the employees of an agency and employees of the regulatory agency. The web server utilizes a security system to allow access to various functions of the system according to identity of the user.
Owner:GENERAL ELECTRIC CO
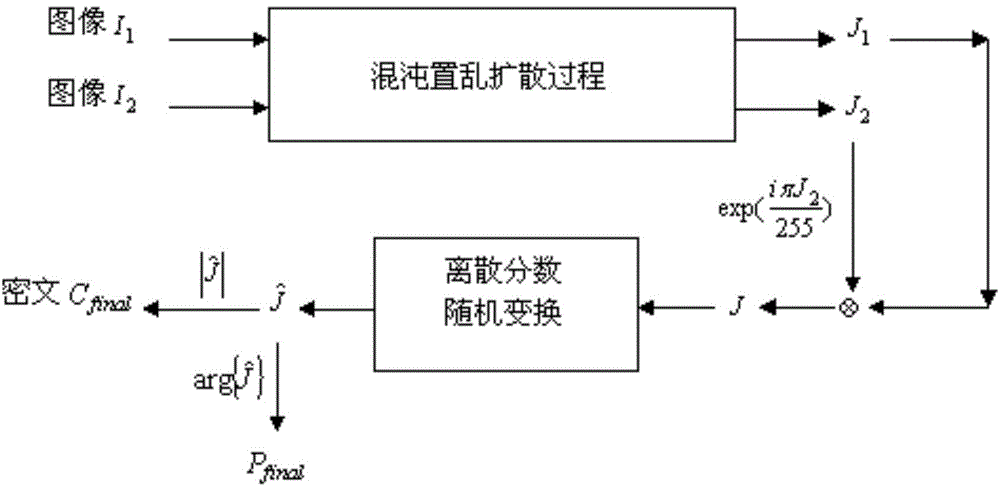
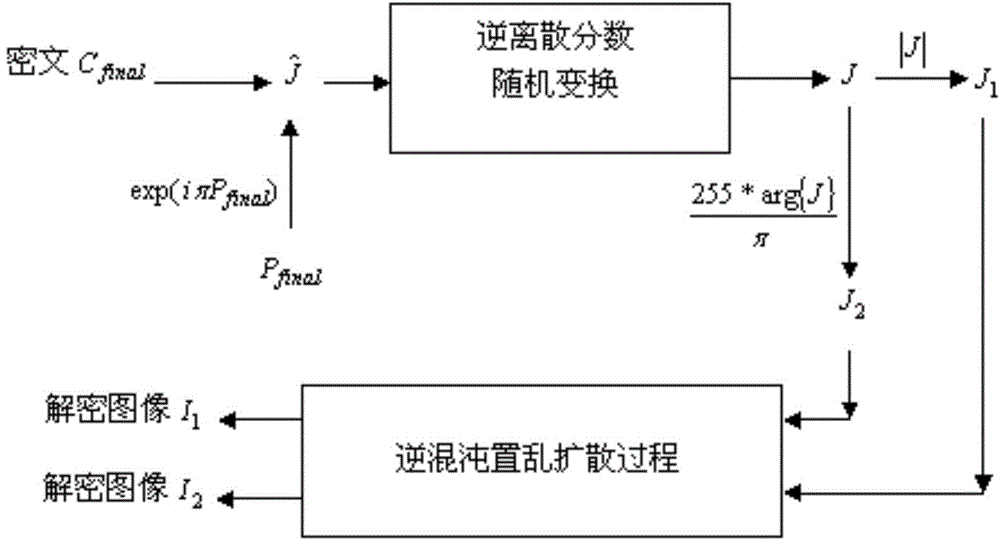
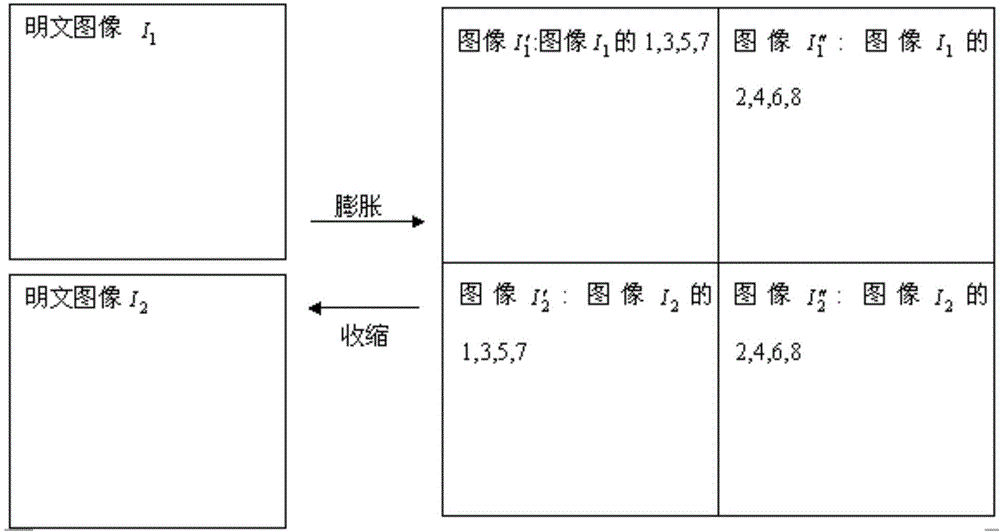
Double-image encryption method based on chaotic and discrete fraction random transform
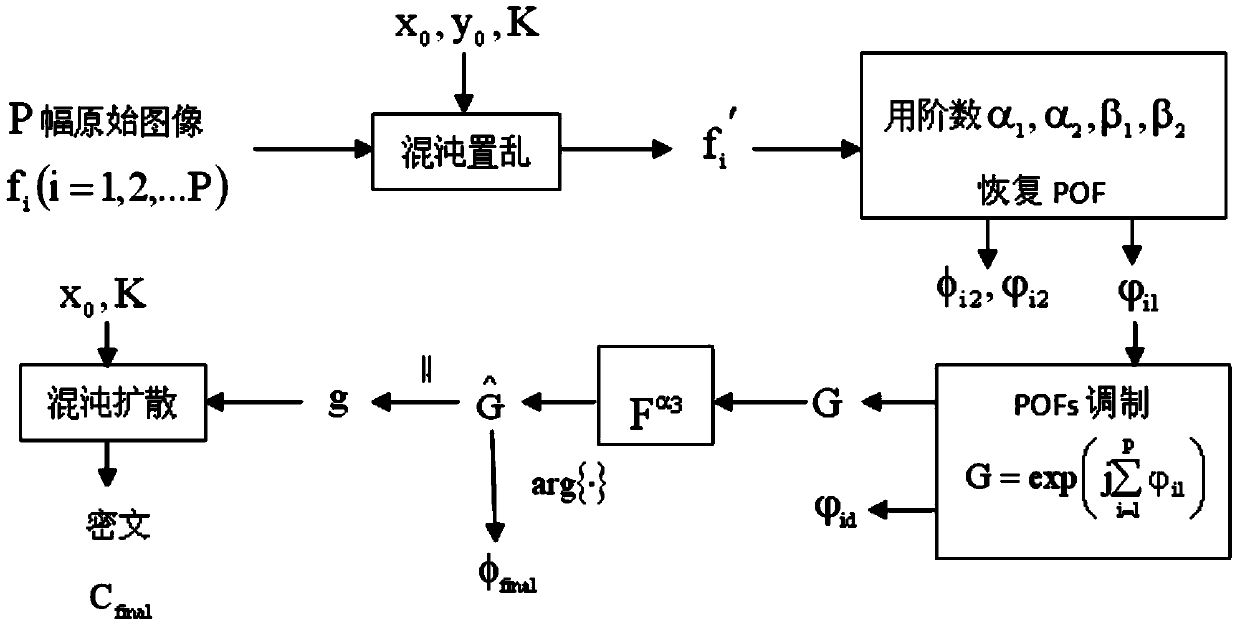
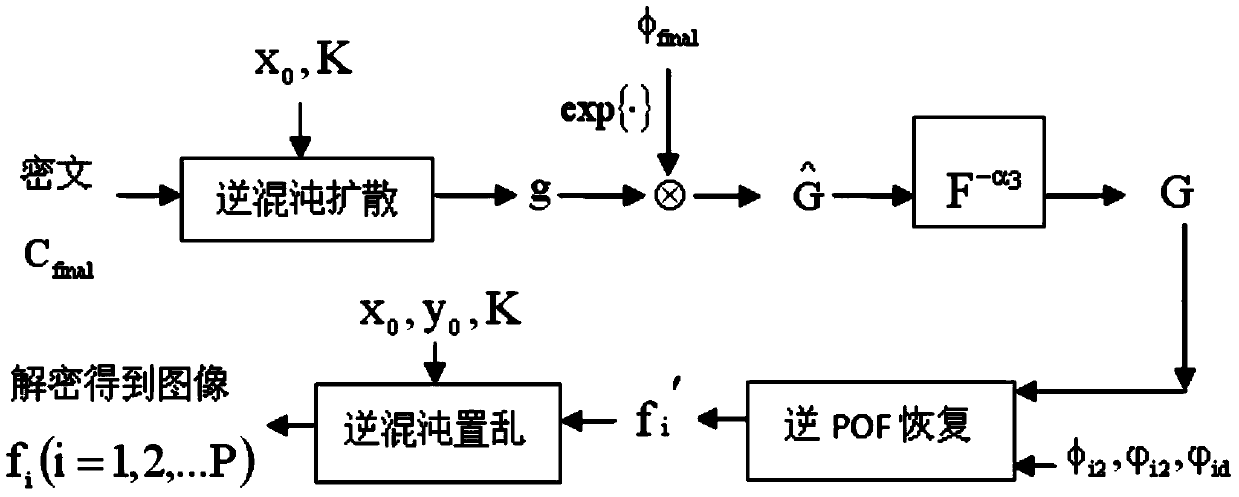
A double-image encryption method based on chaotic and discrete fraction random transform comprises the steps of image expansion, chaotic scrambling, chaotic diffusion, image contraction, image reconstruction and discrete fraction random transform. According to the method, an expanded image is formed by a gray level image I1 and a gray level image I2 through the expansion step, the pixel positions and pixel intensity values are changed through the scrambling and diffusion process based on Logistic chaotic mapping, and then the expanded image is decomposed into a new image J1 and a new image J2 which are stable in white noise distribution through a contraction strategy; the image J2 is normalized and encrypted so as to form a pure phase matrix and a complex matrix J is obtained by multiplying the pure phase matrix and the image J1; finally, the complex matrix encrypted so as to form a temporary image through discrete fraction random transform based on Logistic chaos and the amplitude part is a final ciphertext image. Nonlinearity and randomness of a plaintext image in a spatial domain and a transform domain are enhanced, common attacks can be well resisted, and safety of an encryption system is improved.
Owner:BEIJING YINGPU TECH CO LTD
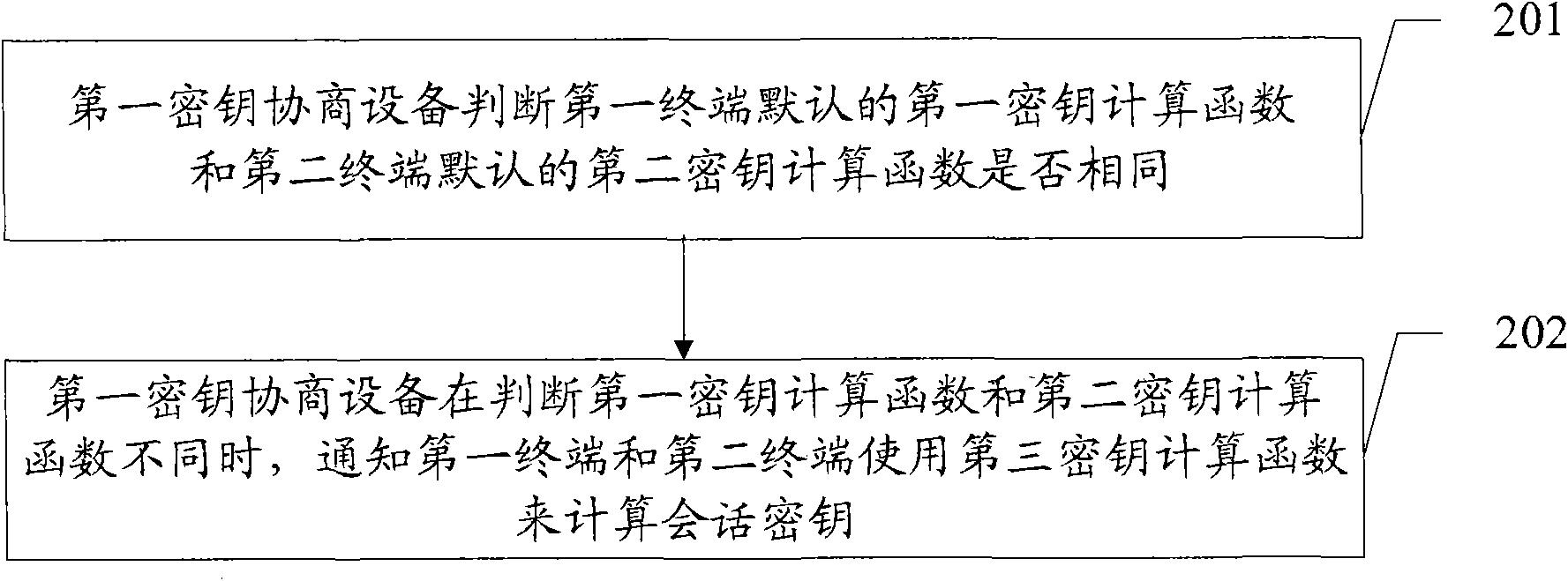
Method, device and system for key agreement
InactiveCN101895877ASimplify the encryption processReduce communication delayConnection managementTransmissionComputer hardwareSession key
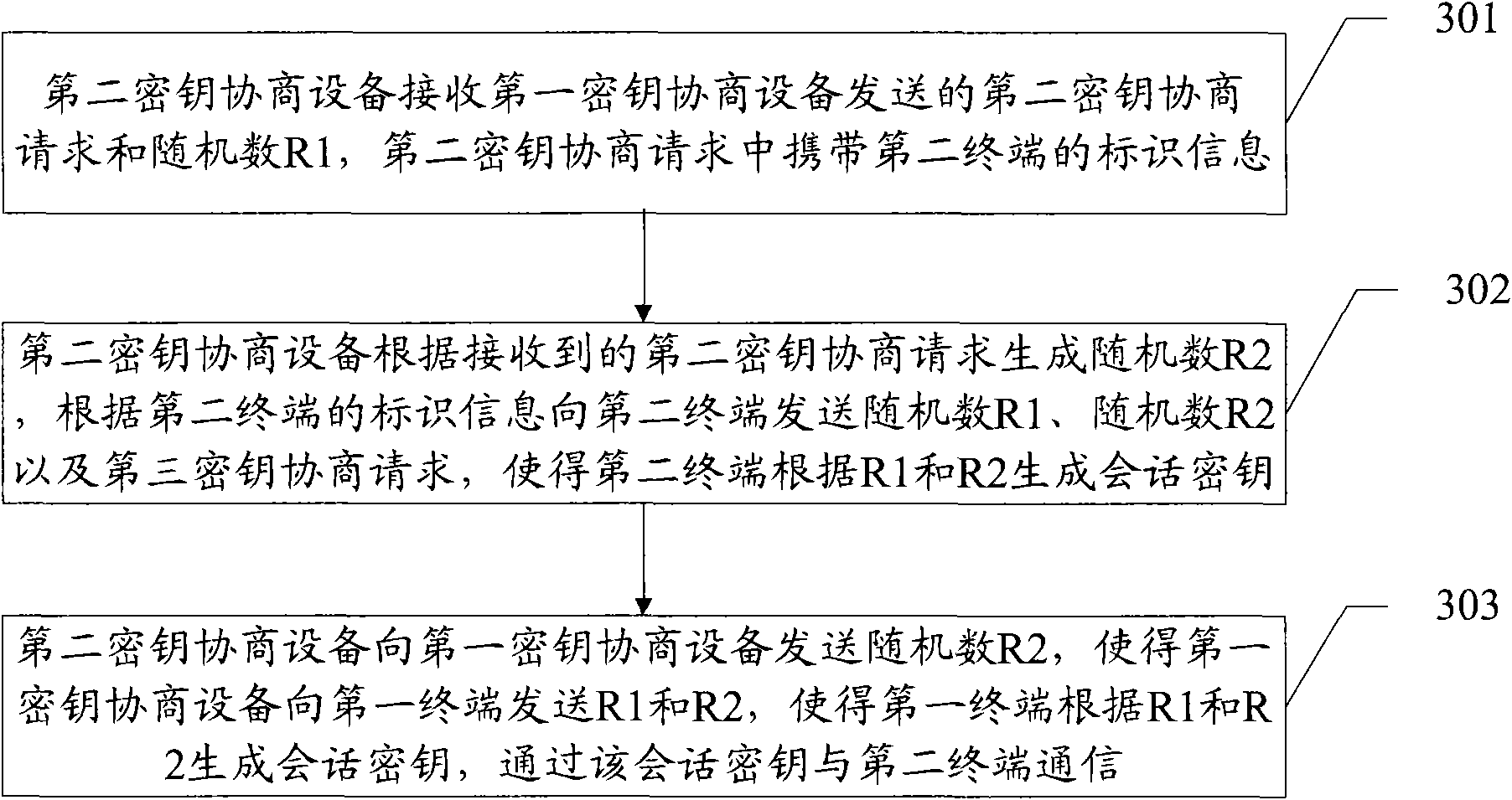
The invention discloses a method, a device and a system for key agreement. The method comprises the following steps: a first key agreement device receives a first key agreement request sent by a first terminal, wherein the identification information of a second terminal is contained in the first key agreement request; the first key agreement device generates a random number R1 according to the received first key agreement request and sends a second key agreement request and the random number R1 to a second key agreement device corresponding to the second terminal according to the identification information of the second terminal; the second key agreement device generates a random number R2 and sends the random numbers R1 and R2 and a third key agreement request to the second terminal; the second terminal generates a session key according to the random numbers R1 and R2; the first key agreement device receives the random number R2 sent by the second key agreement device and sends the random numbers R1 and R2 to the first terminal; and the first terminal generates a session key according to the random numbers R1 and R2 and communicates with the second terminal on the basis of the session key. Accordingly, the invention can achieve the encrypted communication between the first terminal and the second terminal.
Owner:HUAWEI TECH CO LTD
Method of implementing control and management of applied program in terminal apparatus
ActiveCN1863038ASolve the problem that the application is not controllableReduce construction costsDigital data processing detailsSecuring communicationNetwork terminationOperational system
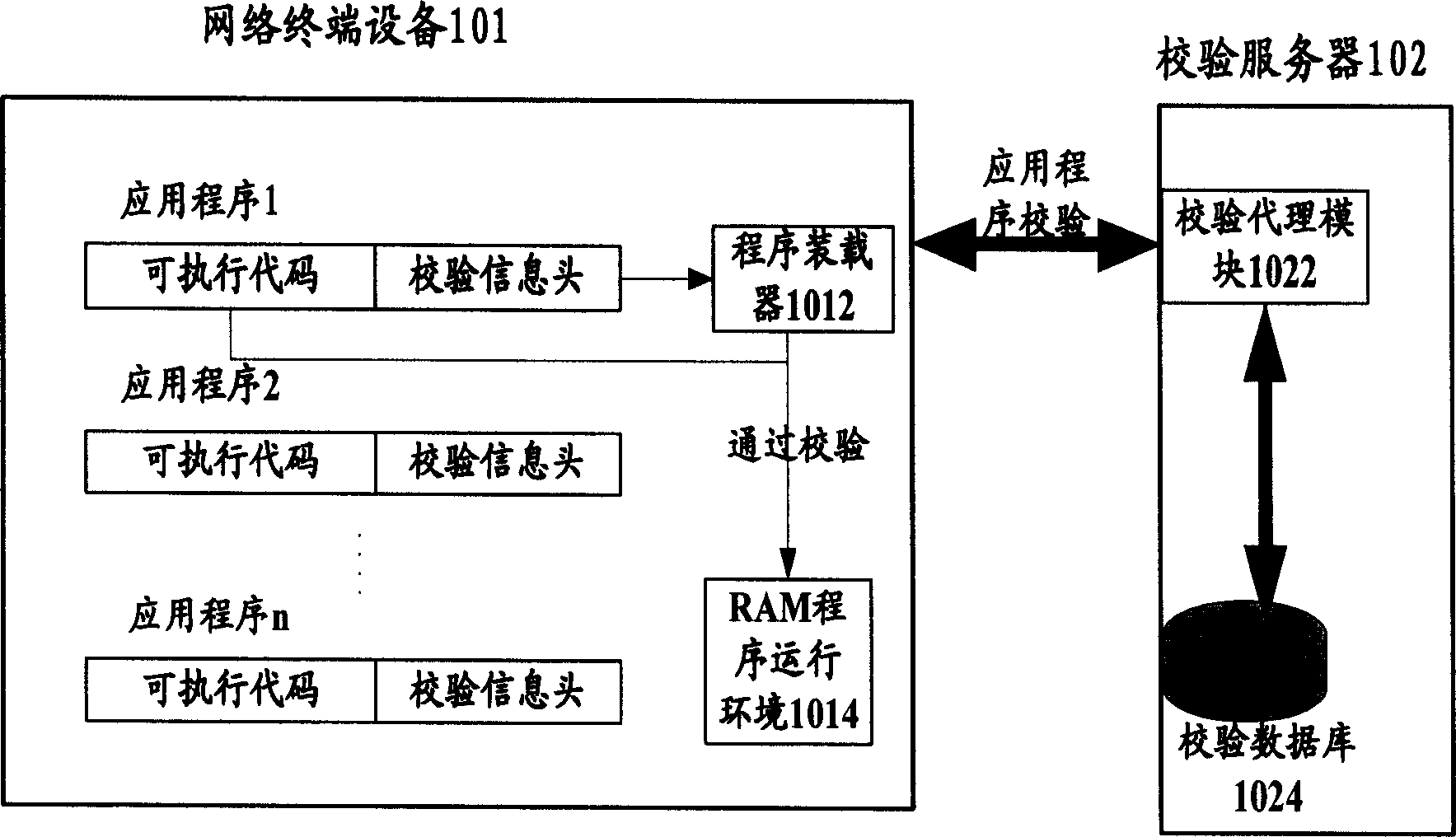
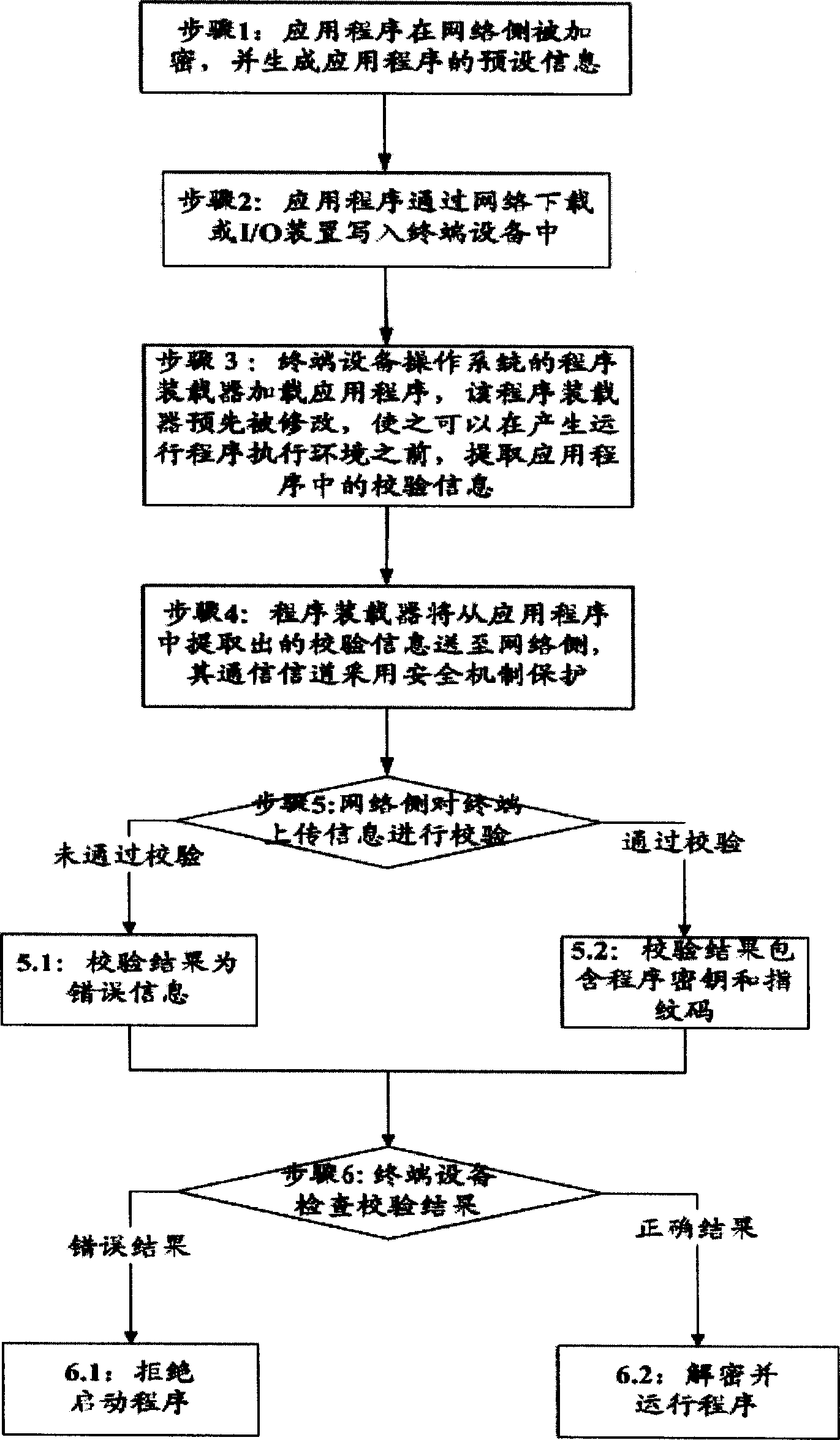
The invention relates to a method to take control and management to the application programs in terminal device that includes PC terminal and non-PC terminal containing network connecting function. The terminal device adopts open source code operation system and setting checking data base in checking server. The application programs only could be run after taking check on checking server. The invention resolves the uncontrollable problem of application programs in network terminal device, and has the advantages of low construction cost, easy to realize and convenience to manage.
Owner:CHINA TELECOM CORP LTD
Encryption method and device for live and recorded broadcast interaction system
InactiveCN105049877AEnsure safetyImprove securitySelective content distributionComputer hardwareInteraction systems
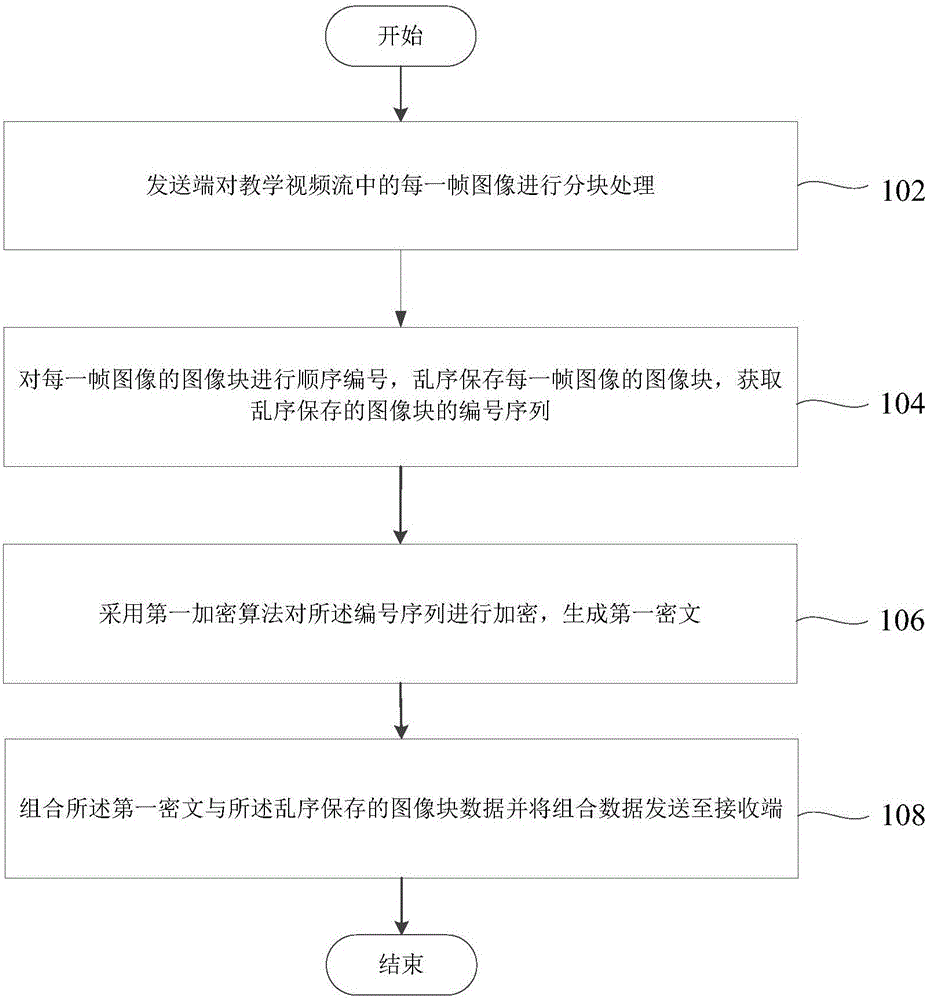
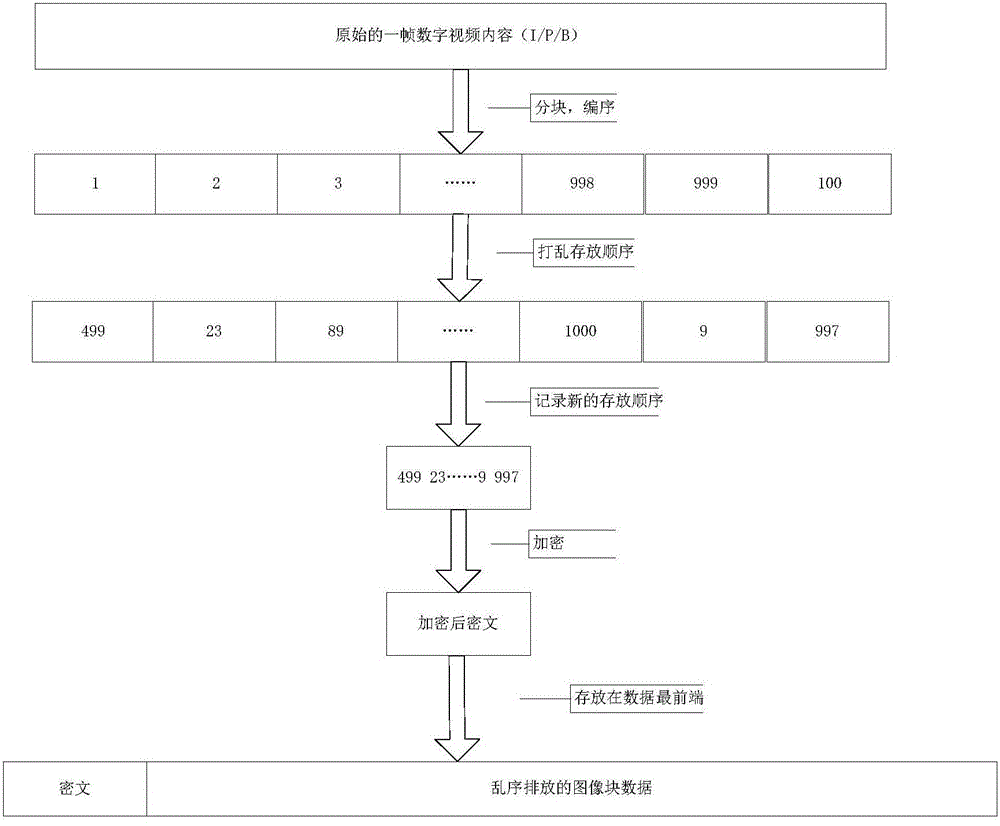
The invention provides an encryption method and device for a live and recorded broadcast interaction system. The method comprises the following steps that a transmitting end divides each frame of image in a teaching video stream into blocks; the image blocks of each frame of image are numbered sequentially, the image blocks are stored in an unordered manner, and a number sequence of the image blocks which are stored in the unordered manner is obtained; a first encryption algorithm is used to encrypt the number sequence and further to generate a first cryptograph; and the first cryptograph is combined with data of the image blocks which are stored in the unordered manner, and combined data is sent to a reception end. The new encryption method is used to encrypt the data, the encryption process is simplified on the premise that the security is ensured, a distributed authentication mechanism is employed, and an un-authorized device is prevented from accessing the live and recorded broadcast interaction system.
Owner:SUZHOU CODYY NETWORK SCI & TECH
Method and apparatus for generating white box key
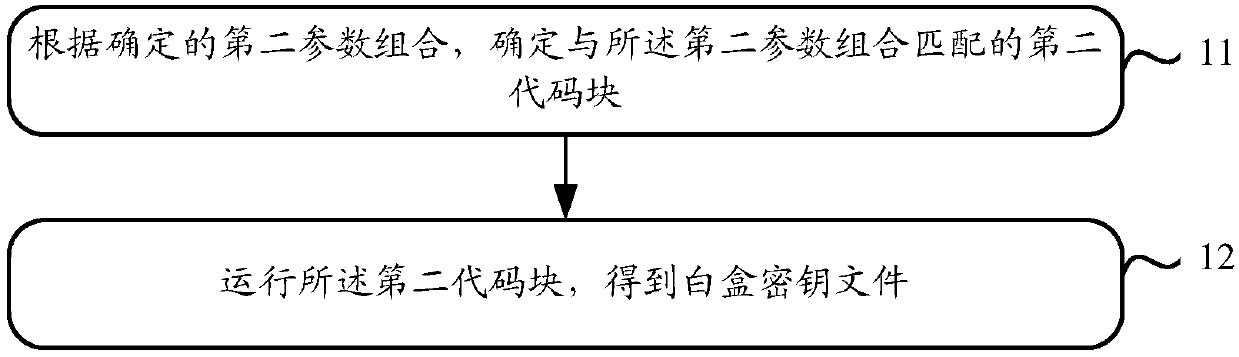
InactiveCN107947917AEasy to updateImprove securityMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesCoding blockPlaintext
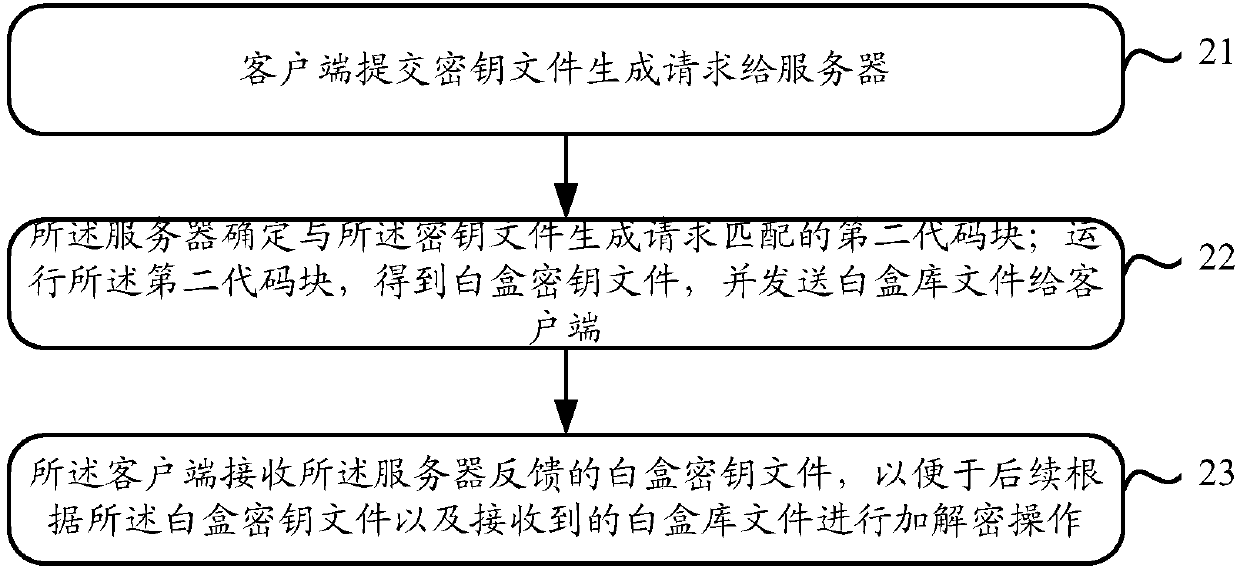
The invention relates to the technical field of terminal security protection, and in particular, to a method and apparatus for generating a white box key for solving the problem of insecure keys in the prior art. The method mainly comprises the following steps: determining a second code block matched with a second parameter combination according to the determined second parameter combination; andrunning the second code block to obtain a white box key, wherein the second parameter combination at least comprises an encryption algorithm identifier, an original key and a target function. Therefore, the key can be conveniently updated, moreover, when the key is updated, a white box library file does not need to be updated, therefore the dynamic white box encryption process can be simplified, and the security of the key can be improved. In addition, the security of the user to decrypt a ciphertext and encrypt the plaintext is improved.
Owner:BEIJING BANGCLE TECH CO LTD
Multi-image encryption method based on chaos and FrFT domain phase retrieval process
InactiveCN103903215AAdd nonlinearityIncrease disorderImage data processing detailsCiphertextPhase retrieval
A multi-image encryption method based on the chaos and FrFT domain phase retrieval process includes the chaos scrambling step, the pure phase extraction step, the phase modulation step and the chaos diffusion step. The method includes the steps of firstly, scrambling multiple original gray level images to be encrypted through paired logistic mapping to obtain scrambled images; secondly, conducting the iterated phase retrieval process on each scrambled image to extract a pure phase function of the scrambled image; thirdly, conducting phase modulation on the pure phase functions on the multiple original gray level images to be encrypted; fourthly, conducting chaos diffusion on the amplitudes of the results obtained through modulation to obtain the final cipher text. According to the multi-image encryption method, nonlinearity and randomness of plaintext images in the spatial domain and the conversion domain are enhanced, the convergence speed of an encryption system is increased, and security of the encryption system is enhanced.
Owner:XIAN UNIV OF TECH
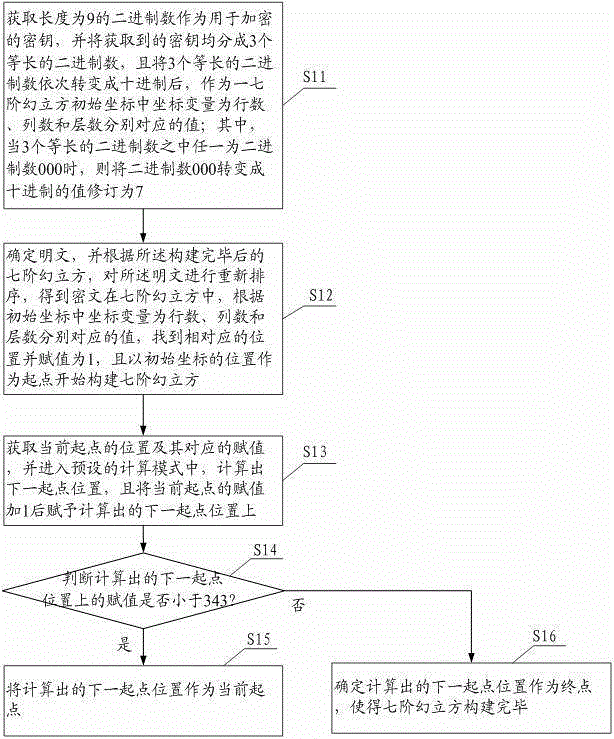
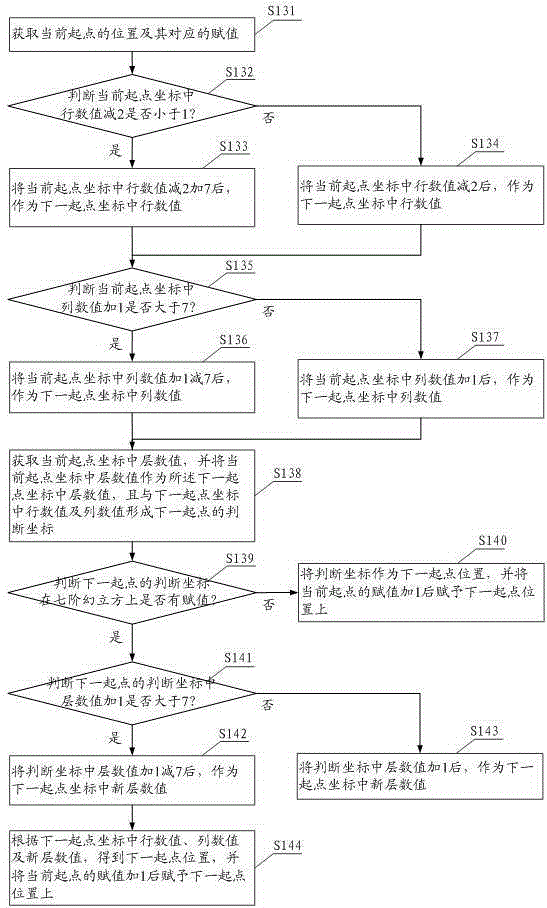
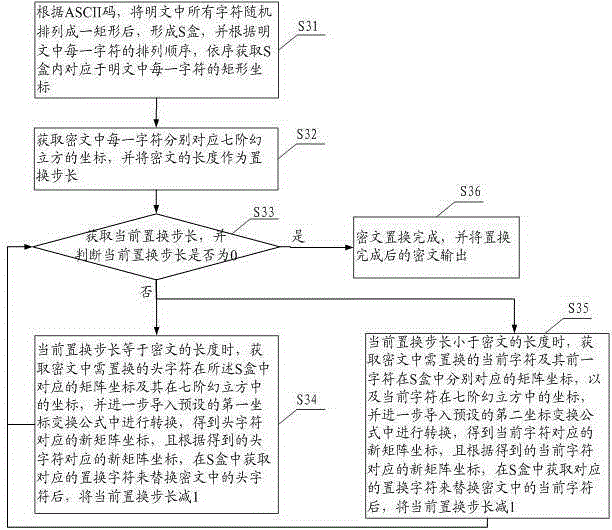
Plaintext encryption method and system based on seven-order magic cube
ActiveCN105281894AOvercoming complexityOvercome the cumbersome processEncryption apparatus with shift registers/memoriesComputer hardwarePlaintext
The invention provides a plaintext encryption method based on a seven-order magic cube, which comprises the steps of obtaining a secret key for encryption; generating an initial coordinate of a seven-order magic cube based on the obtained secret key; and constructing the seven-order magic cube gradually by taking the initial coordinate as the origin, wherein, the secret key is formed of binary numbers in a certain length and the seven-order magic cube comprises a 7*7 matrix with 1 to 7 layers and the coordinate variables comprise rows, columns and layers; determining the plaintext and reordering the plaintext based on the constructed seven-order magic cube to obtain the cryptograph; obtaining an S box by arranging the plaintext into a rectangle in dependence on ASCII codes; and outputting the cryptograph after character displacement for encryption. According to the embodiment, the potential safety trouble brought by character encryption algorithm simply is overcome; the complex and tedious process of image encryption is overcome; and a better encryption effect can be realized.
Owner:SHENZHEN POWER SUPPLY BUREAU
Data processing method and mobile terminal
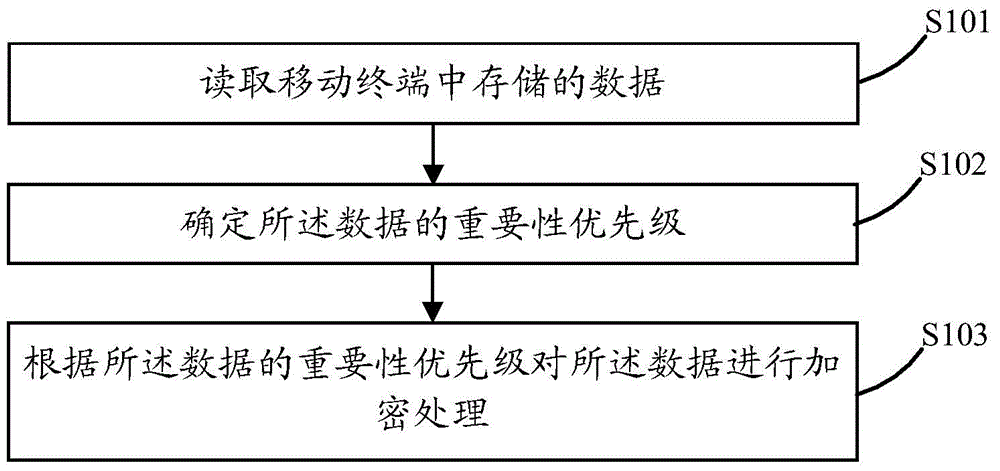
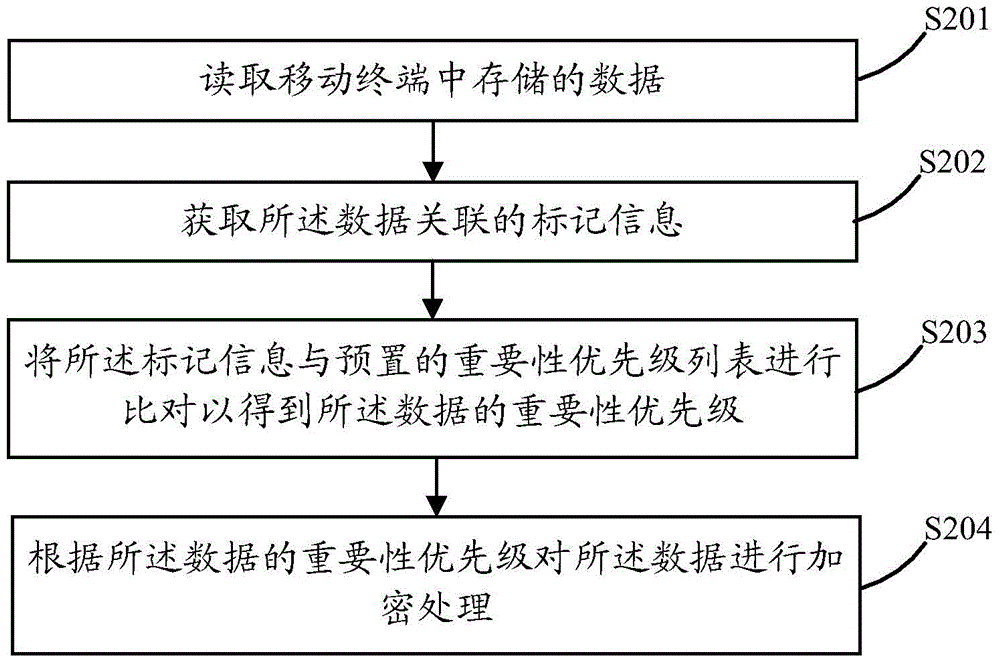
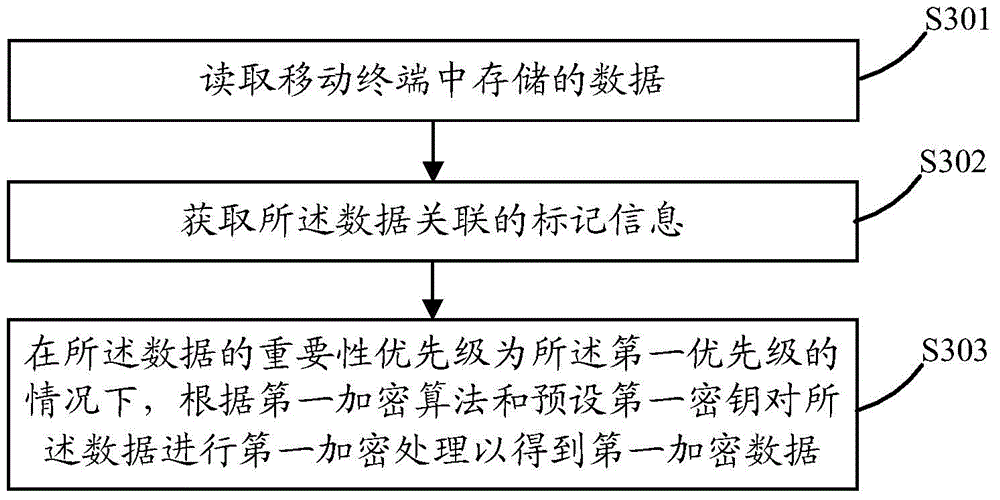
InactiveCN105069365AEasy to rememberReduce in quantityDigital data protectionInternal/peripheral component protectionPasswordComputer terminal
The invention discloses a data encryption method. The data encryption method comprises steps of reading data stored in the mobile terminal; determining the significance priority of the data; and carrying out encryption processing to the data according to the significance priority of the data. The invention also discloses a mobile terminal. In this way, the data can be encrypted according to the determined significance priority of the data, and therefore when a lot of data is encrypted, the lot of data is encrypted by means of the significance priority of the data, the encryption process is simplified, the data having the same significance priority can use the same password, and therefore the number of passwords is reduced, and the passwords used in the encryption process can be remembered easily.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Method and device for encrypting short messages
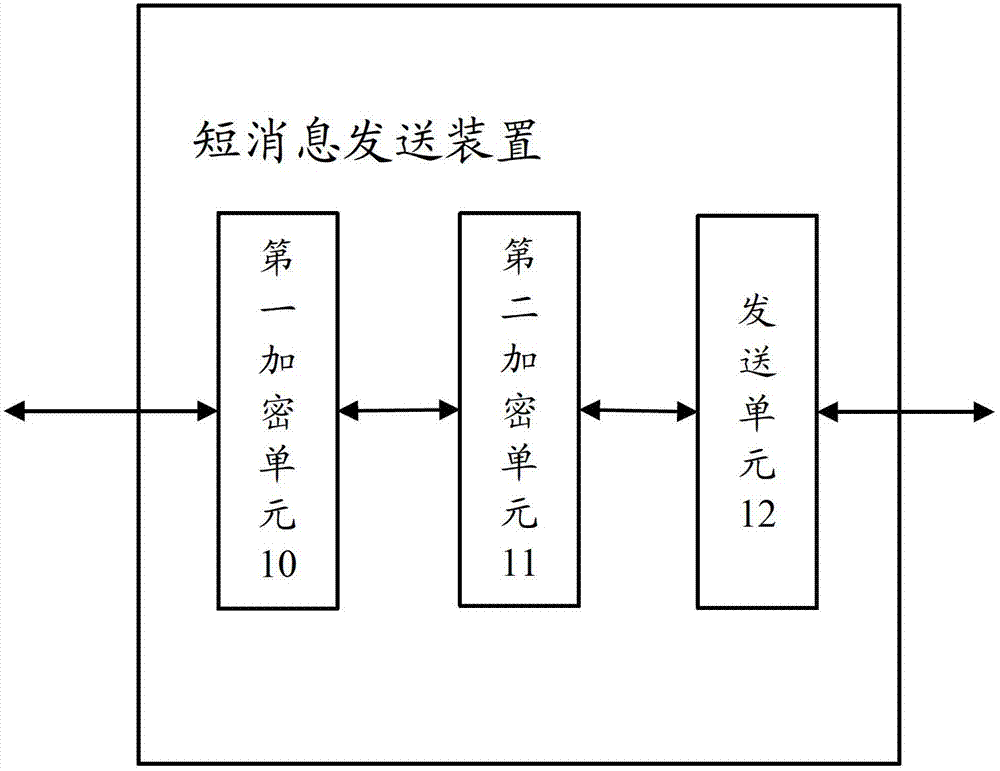
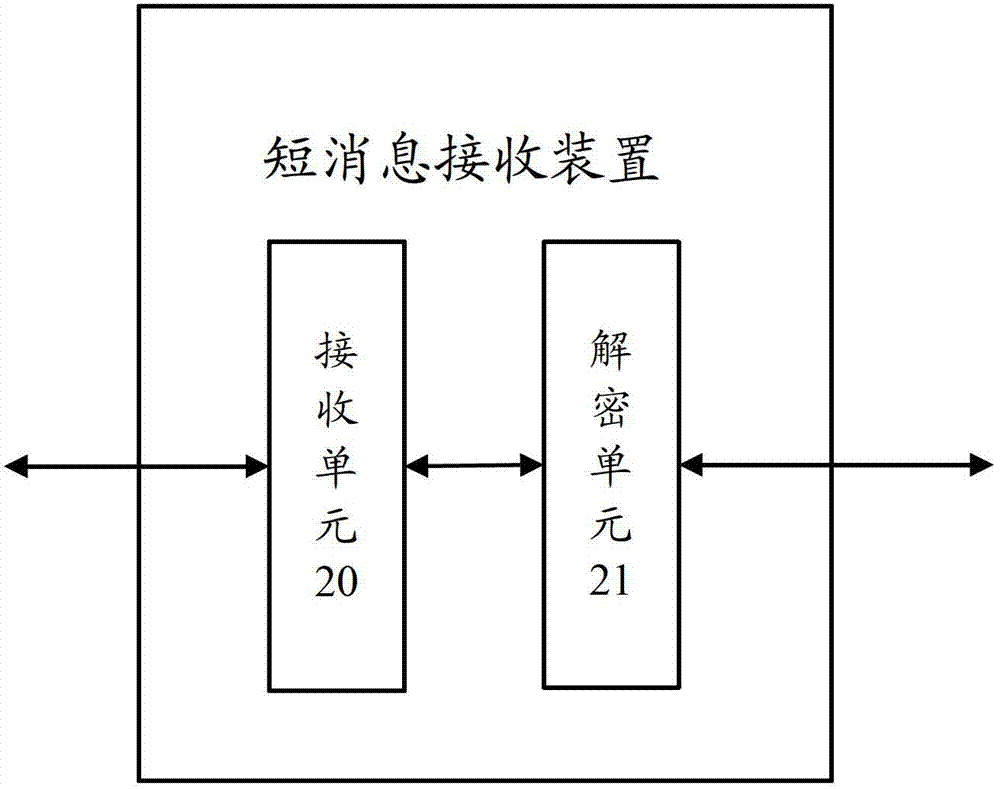
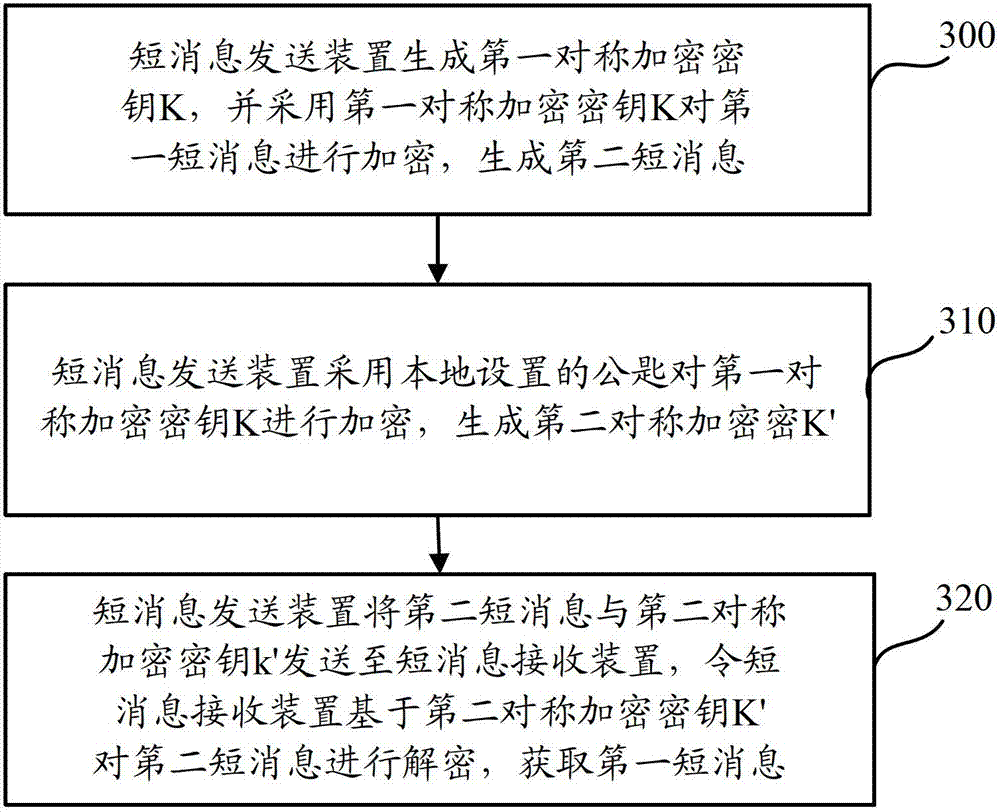
InactiveCN102857889AEnsure safetySimplify the encryption processMessaging/mailboxes/announcementsSecurity arrangementComputer hardwareEncryption
The invention relates to the technical field of communication and particularly relates to a method and a device for encrypting short messages. According to the method and the device, on the premise of ensuring the safety of the short message transmission, the complexity of a short message encryption algorithm is reduced. The method comprises the following steps: generating a first symmetric encryption key by a short message transmitting device; encrypting a to-be-transmitted short message by adopting the first symmetric encryption key; encrypting the first symmetric encryption key to generate a second symmetric encryption key; transmitting a second short message and the second symmetric encryption key to a short message receiving device; and enabling the short message receiving device to decrypt the second short message based on the second symmetric encryption key to acquire a first short message. The realization process of the method is simpler, so that the complexity of the encryption process of short messages interacted between the short message transmitting device and the short message receiving device is effectively avoided.
Owner:ZTE CORP
Hash ciphertext re-encryption method based on noise and decryption method after re-encryption
InactiveCN103942500ASimple encryption and decryption methodsEasy to implementPublic key for secure communicationDigital data protectionCiphertextPattern recognition
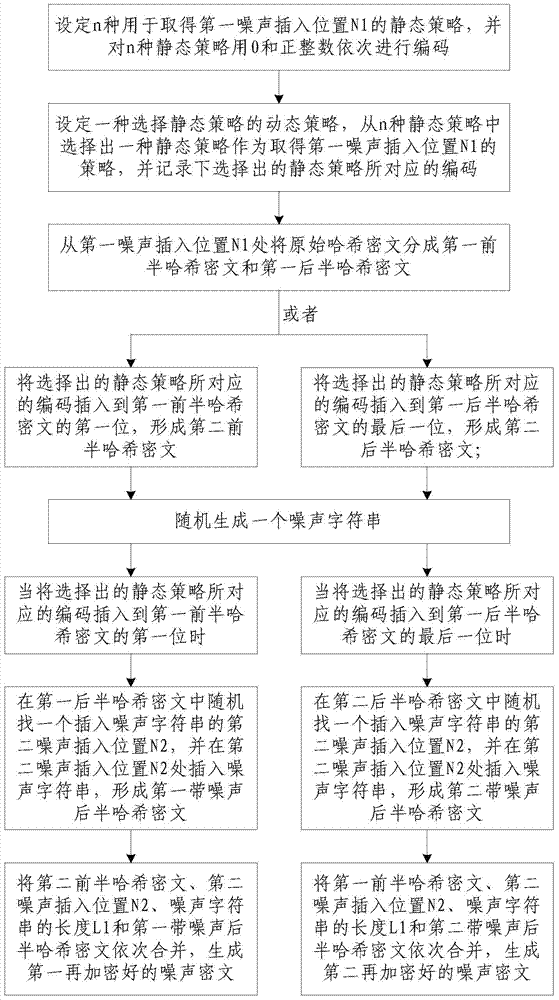
The invention discloses a Hash ciphertext re-encryption method based on noise and a decryption method after re-encryption. The re-encryption method comprises the steps of 1 setting a static strategy; 2 setting a dynamic strategy and selecting the static strategy; 3 dividing original Hash ciphertext into first front half Hash ciphertext and first rear half Hash ciphertext; 4 forming second front half Hash ciphertext or second rear half Hash ciphertext; 5 randomly generating a noise character string; 6 forming first rear half Hash ciphertext with noise or second rear half Hash ciphertext with noise; 7 generating first re-encrypted noise ciphertext or second re-encrypted noise ciphertext. The decryption method comprises the steps of 1 obtaining a first noise inserting position; 2 obtaining a second noise inserting position and the length of the noise character string; 3 forming the first rear half Hash ciphertext with noise; 4 forming first rear half Hash ciphertext; 5 generating decrypted original Hash ciphertext. The safety of the original Hash ciphertext can be improved, and the expenditure is low.
Owner:XIAN UNIV OF SCI & TECH
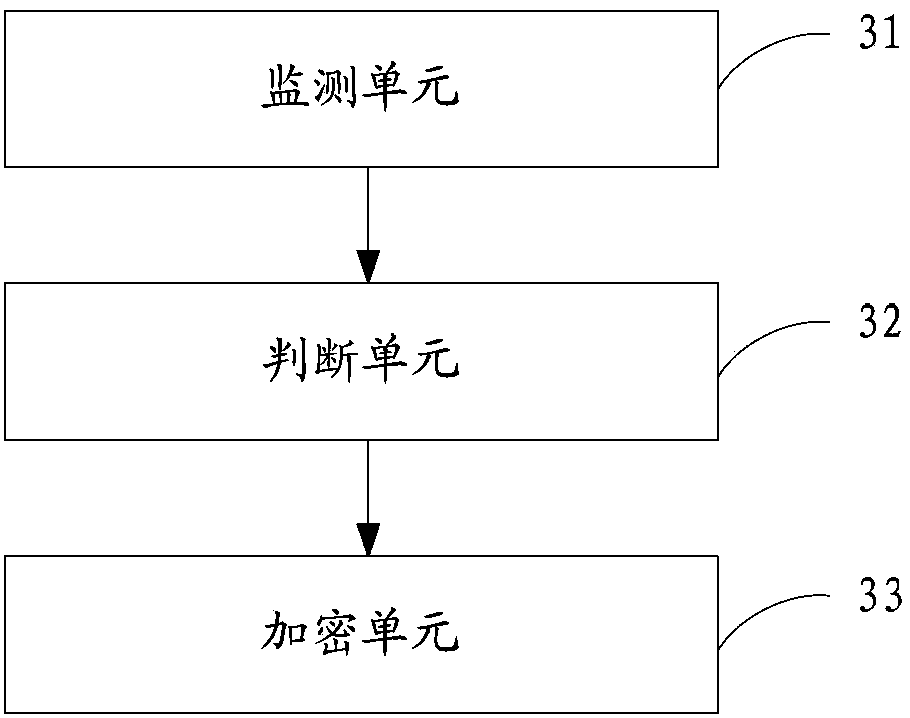
Private file encryption method and private file encryption device
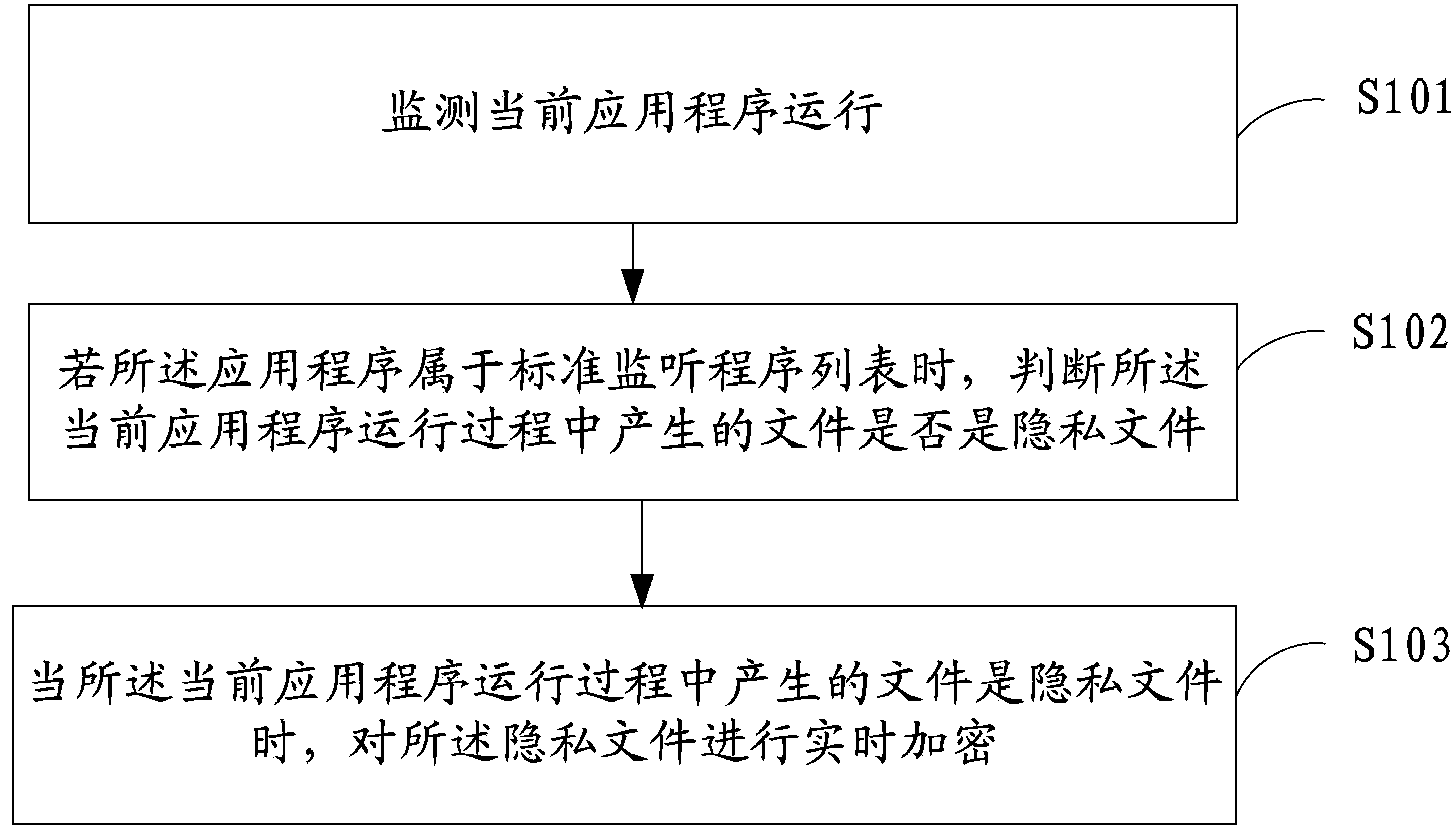
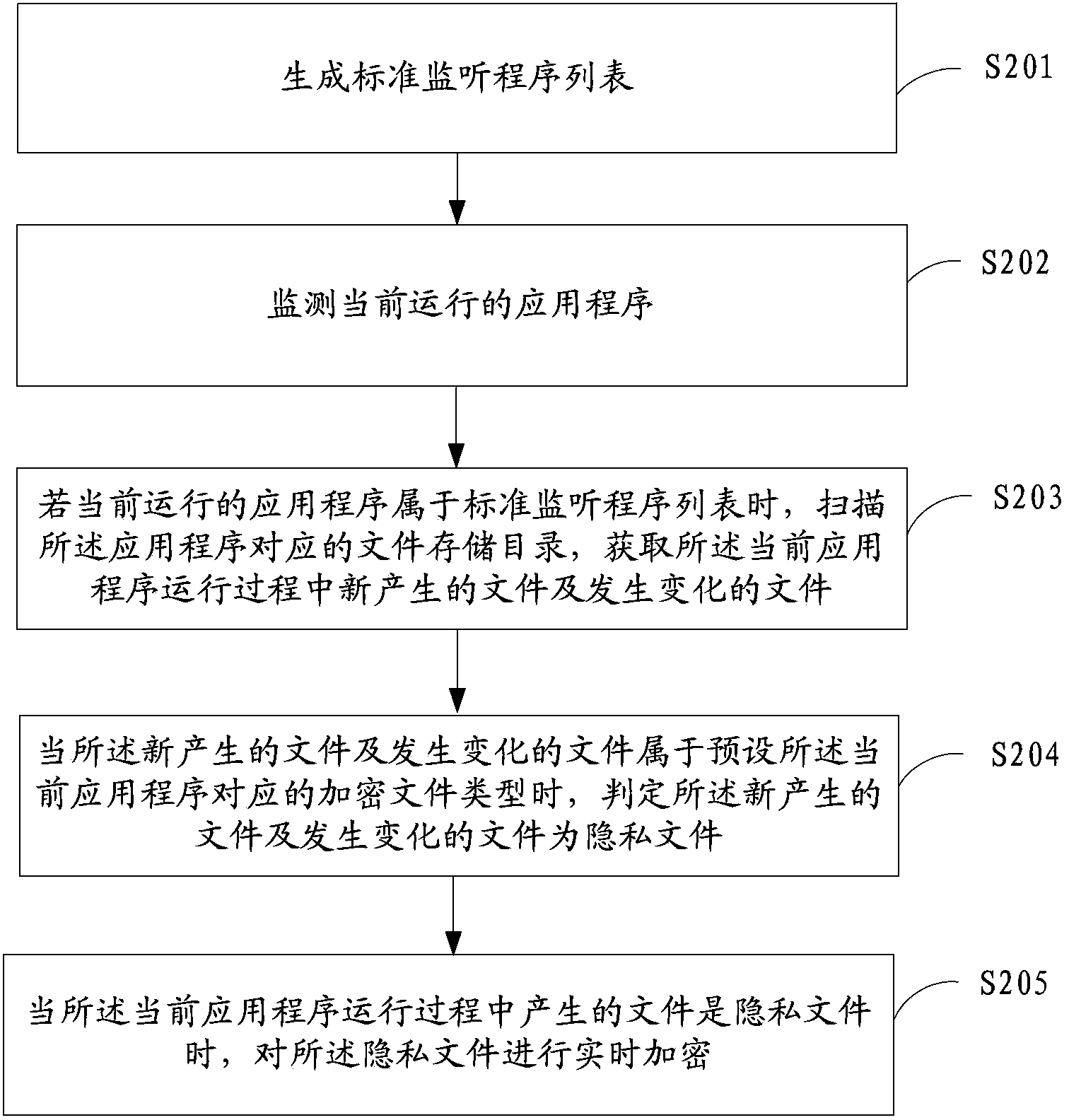
ActiveCN104134042APrevent leakageSimplify the encryption processDigital data protectionSoftware engineeringThe Internet
The invention is applicable to the technical field of Internet, and provides a private file encryption method and a private file encryption device. The private file encryption method comprises the following steps that: a current running application program is monitored; when the application program belongs to a standard monitoring program list, whether a file generated in the current application program running process is a private file or not is judged, and the standard monitoring program list stores application program information to be monitored; and when the file generated in the current application program running process is the private file, the private file is encrypted in real time. The method and the device provided by the invention have the advantages that the real-time encryption on the private file is realized; the manual operation is not needed; the encryption process is simple and convenient; and the private file generated in the application program running process is encrypted in real time, so that the private file leakage due to encryption forgetting can be avoided.
Owner:TENCENT TECH (SHENZHEN) CO LTD
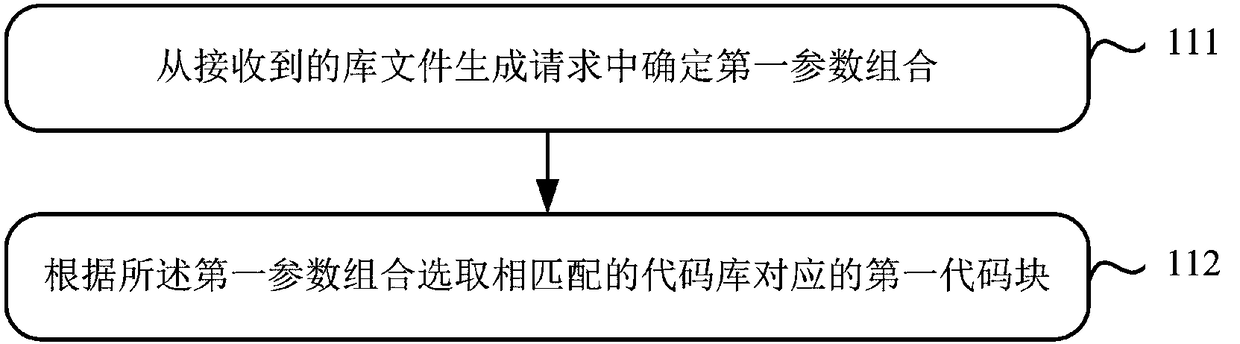
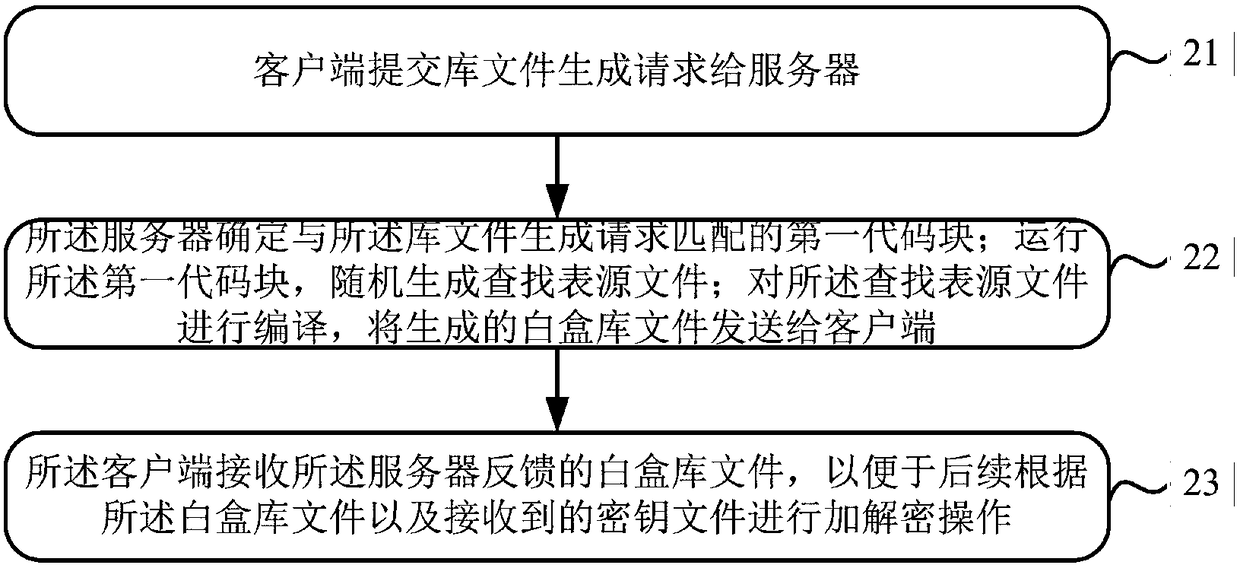
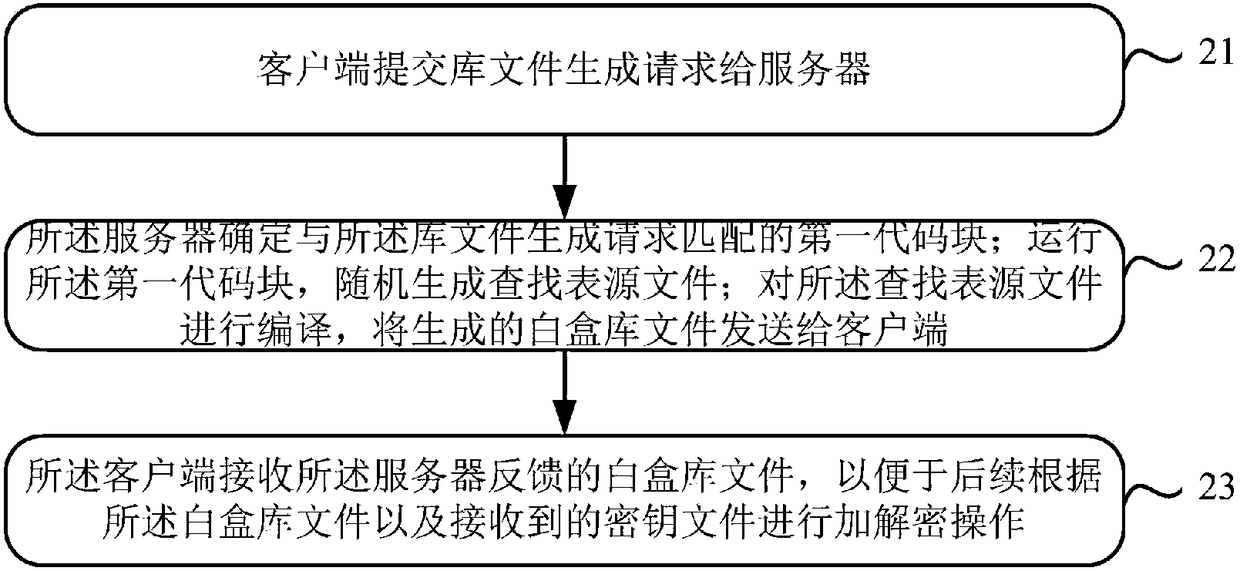
Method, device and system for downloading white-box library file
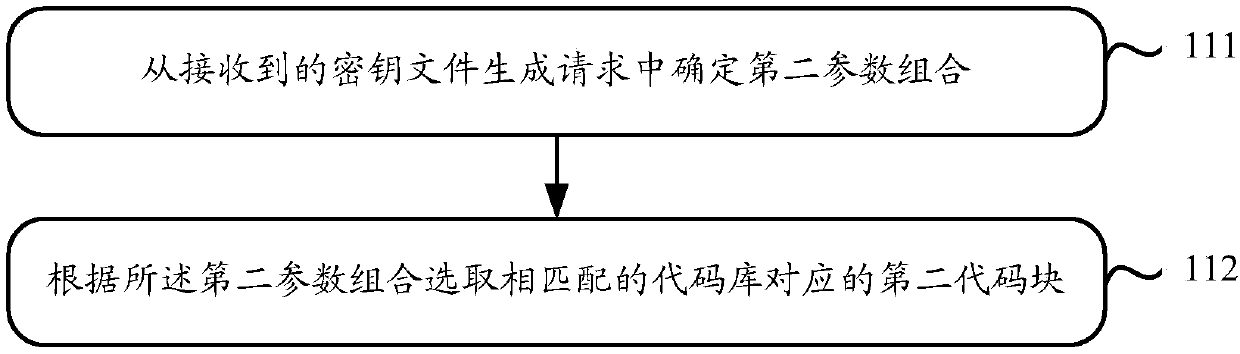
ActiveCN108111622AEasy to updateImprove securityKey distribution for secure communicationPlaintextCiphertext
The application relates to the technical field of terminal security protection, in particular to a method and a device for downloading a white-box library file, and aims to solve the problem of key insecurity in the prior art. The method mainly comprises the following steps: submitting a library file generation request to a server; and receiving a white-box library file fed back by the server according to the library file generation request in order to subsequently perform encryption and decryption operations according to the while-box library file and a received key file. Through the technical scheme, key updating becomes relatively convenient. Moreover, the white-box library file does not need to be updated during key updating, so that a dynamic white-box encryption flow can be simplified, and the security of keys is enhanced. Furthermore, the security in ciphertext decryption and plaintext encryption performed by a user is enhanced.
Owner:BEIJING BANGCLE TECH CO LTD
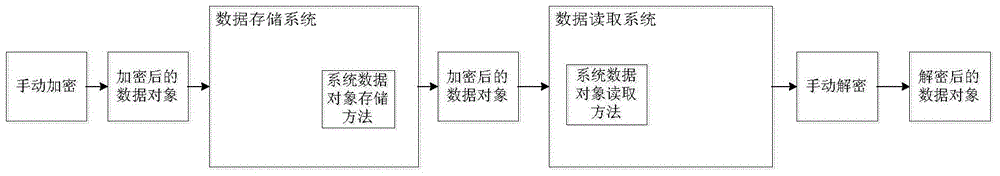
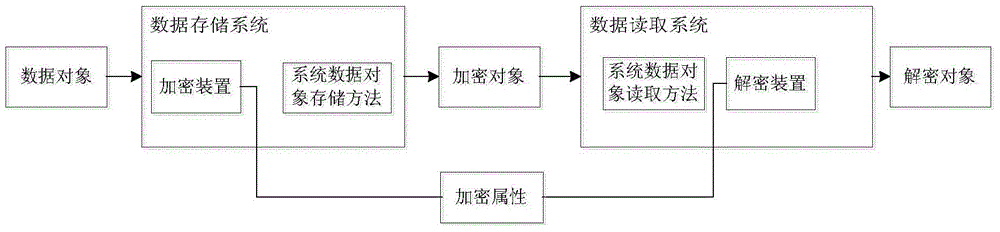
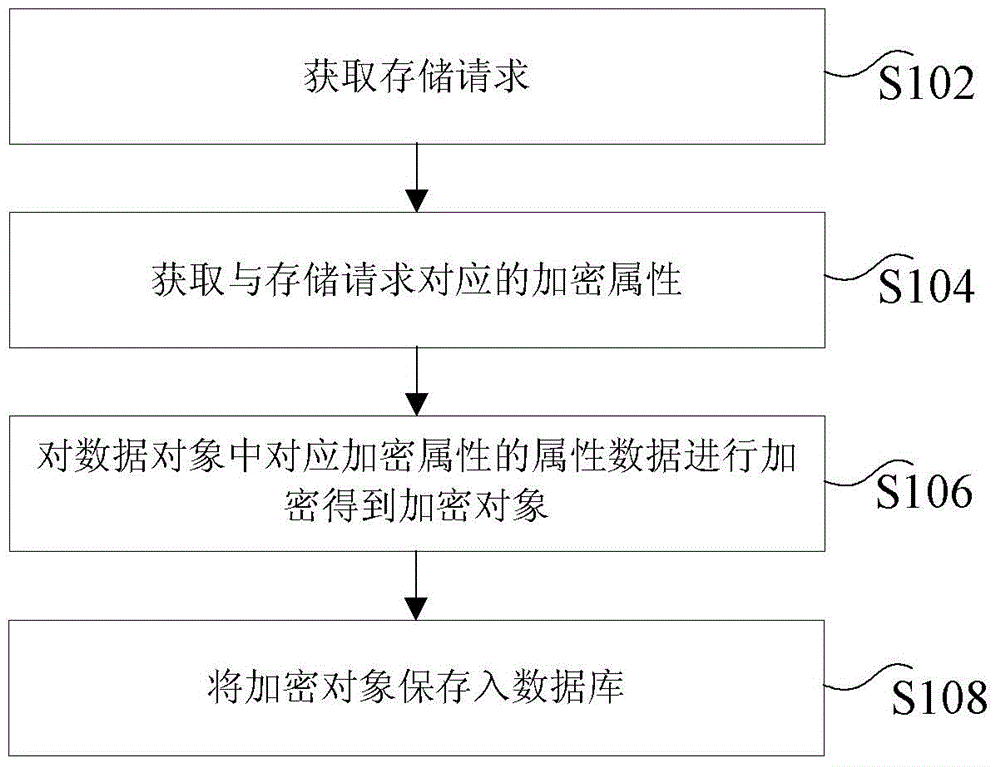
Object encryption storage method, device and system
ActiveCN103605741AImplement automatic encryptionReduce development costsInternal/peripheral component protectionSpecial data processing applicationsComputer hardwareData access
The invention discloses an object encryption storage method, device and system. The method includes: acquiring a storage request which carries a data object; acquiring the encryption attributes corresponding to the storage request; encrypting the attribute data requiring encryption in the data object to obtain the encrypted object; saving the encrypted object in a database. By the method, the problem that the encryption of object data is complex in process and low in development efficiency in the data access system architecture in the prior art is solved, automatic encryption in the data access system architecture is achieved, development cost for manual encryption and decryption is lowered greatly, object data encryption process is simplified, processing speed and development efficiency are increased, and development cost is lowered.
Owner:BEIJING GRIDSUM TECH CO LTD
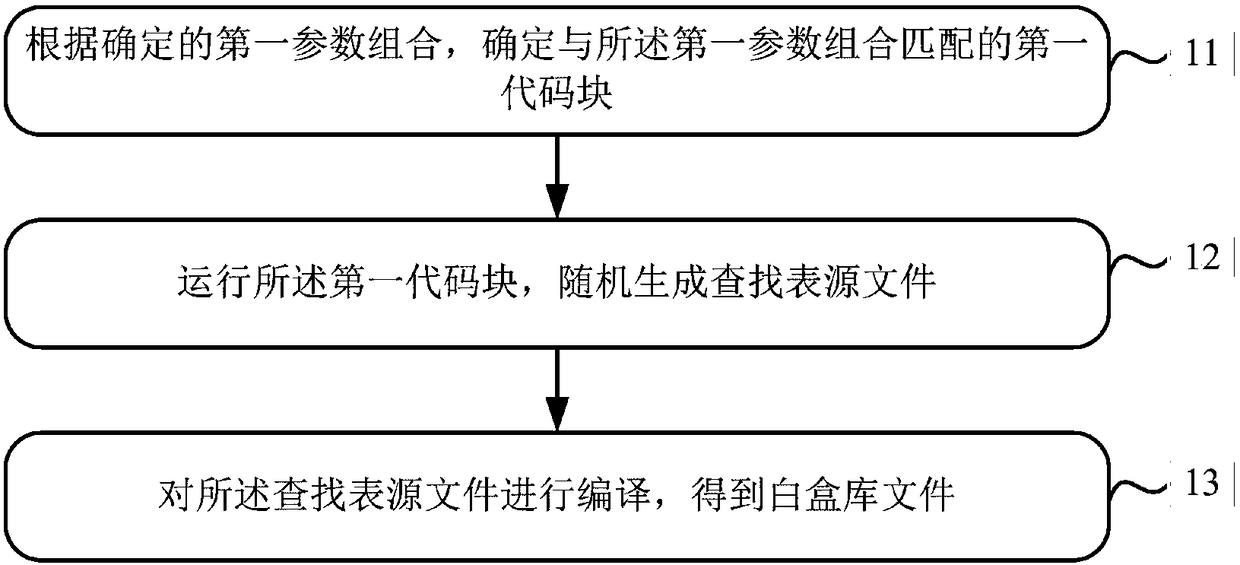
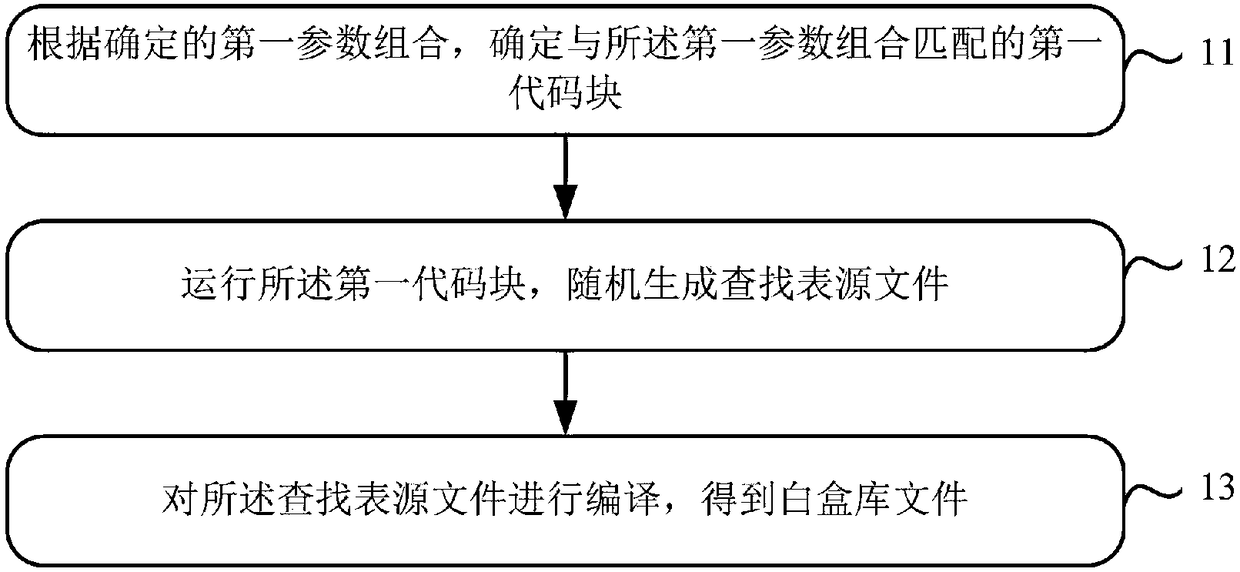
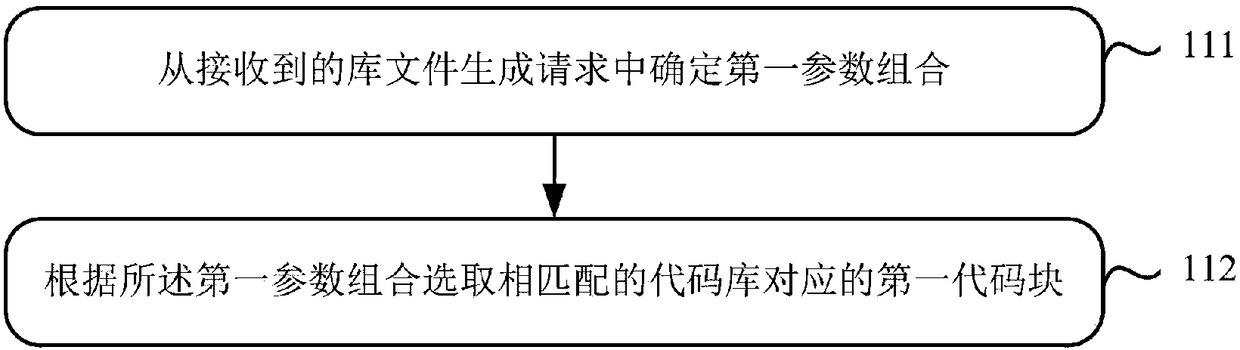
Method and device for generating white box library file
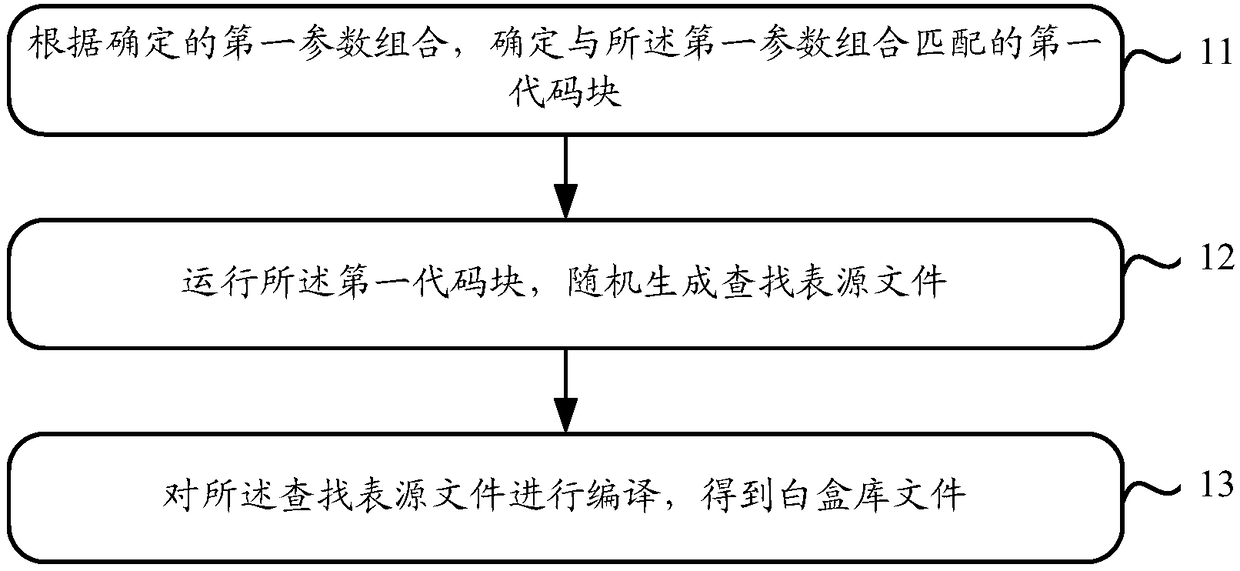
ActiveCN108134673AEasy to updateImprove securityMultiple keys/algorithms usageCryptographic attack countermeasuresPlaintextCoding block
The invention relates to the technical field of terminal security protection, and in particular relates to a method and device for generating a white box library file, used for solving the problem that a key is unsafe in the prior art. The method comprises the steps of: according to a determined first parameter combination, determining a first code block matched with the first parameter combination; running the first code block, and randomly generating a lookup table source file; and, compiling the lookup table source file, so that a white box library file is obtained. Thereby, key updating isrelatively convenient; furthermore, when the key is updated, the white box library file does not need to be updated; therefore, a dynamic white box encryption process can be simplified; furthermore,the security of the key is improved; and thus, the security of decrypting a ciphertext and encrypting a plaintext by a user can be improved.
Owner:BEIJING BANGCLE TECH CO LTD
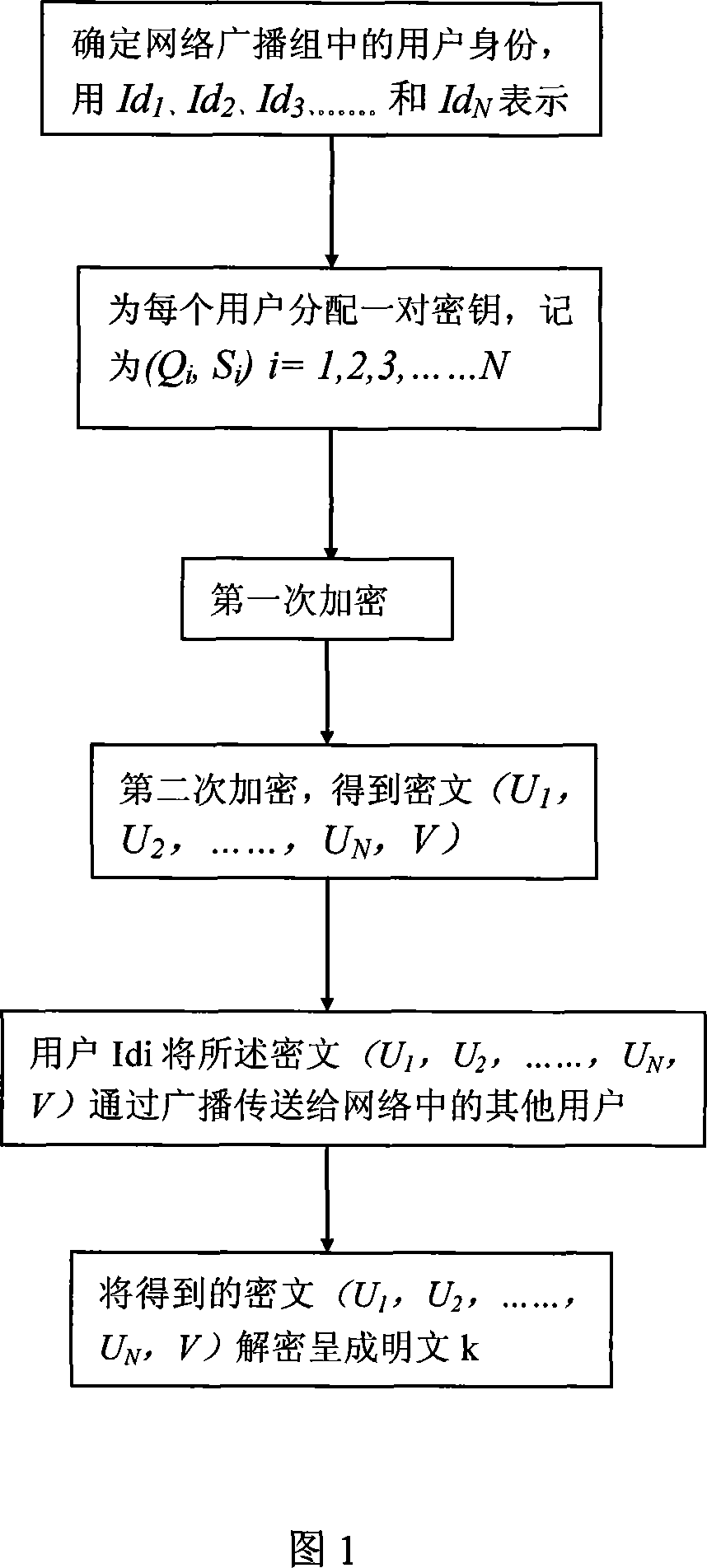
Method for encrypting and decrypting broadcast of network information
InactiveCN101094059AThe encryption algorithm is simpleSimplify the encryption processSecuring communicationHash functionEncryption decryption
The method for encrypting and decrypting a network broadcast comprises: after first encryption, getting n intermediate results QV1,QV2......QVN. Said first encryption comprises: 11) figuring out the value Qi of the hash function H1 of the user Idi in network, namely Qi= H1(Idi); 12) after encryption, figuring out n intermediate results, namely QV1,QV2......QVN; The decryption process is a process of solving a linear equation system.
Owner:JIANGSU WENTRY TECH
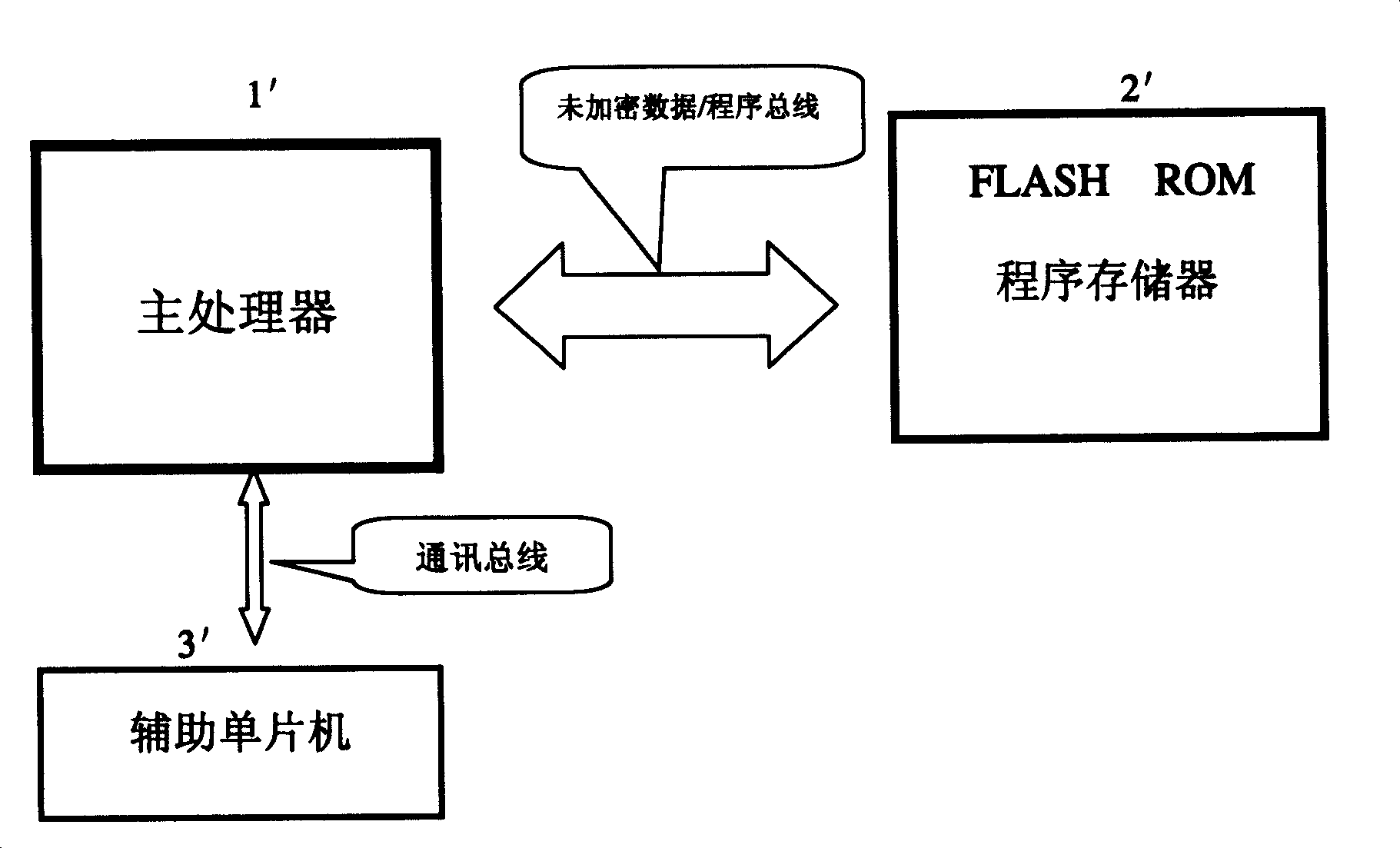
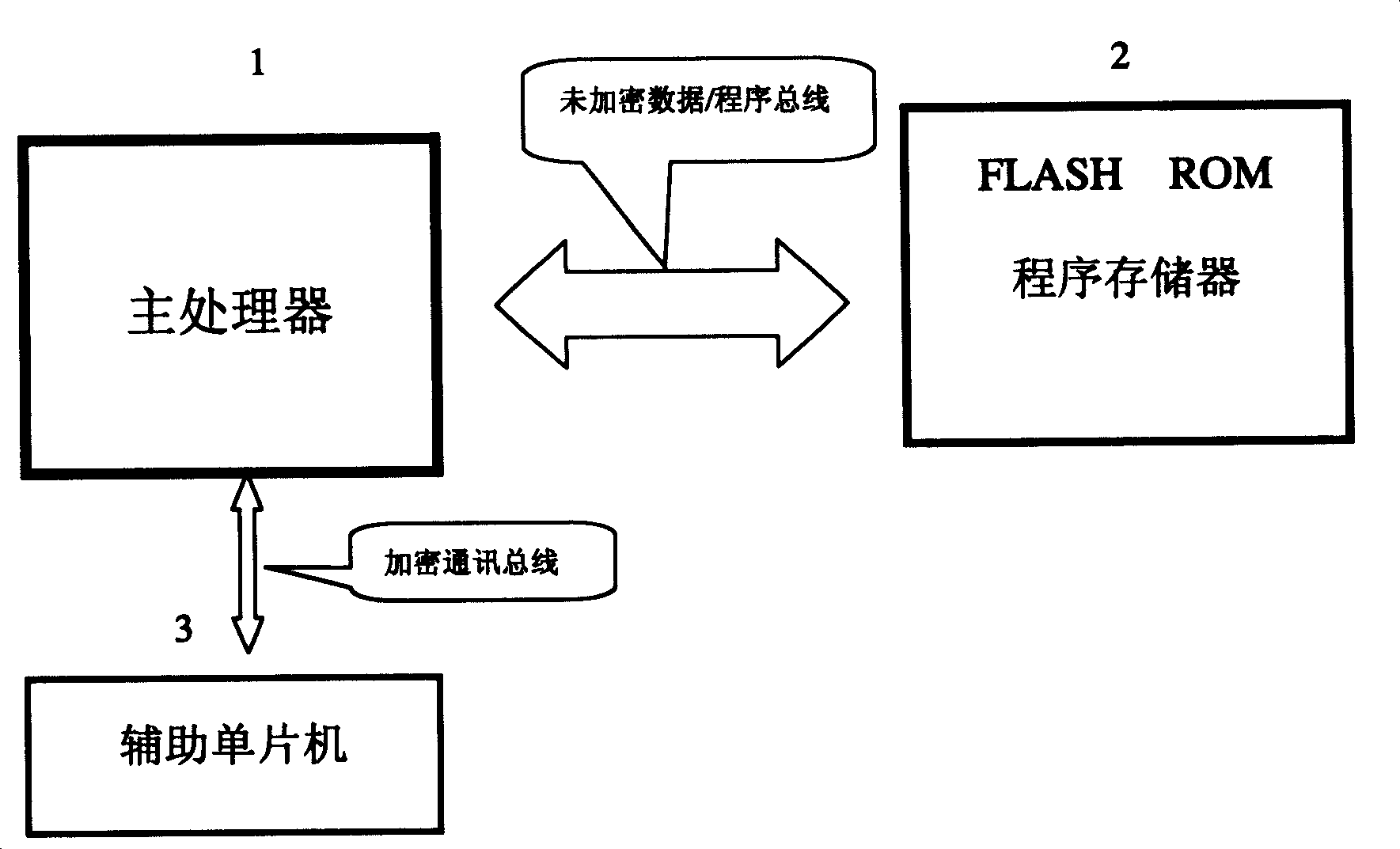
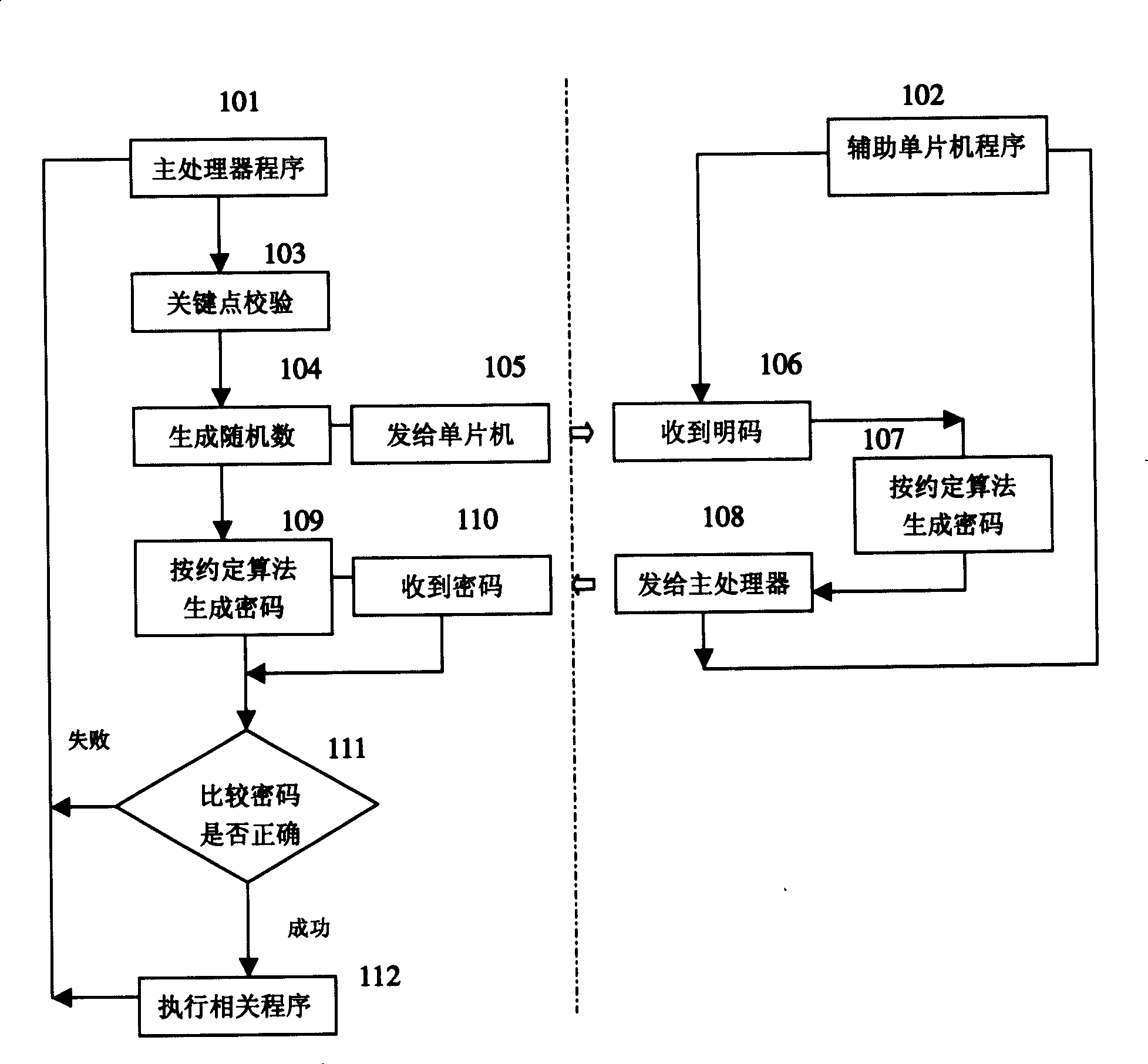
System encrypted method using multifunctional assistant SCM
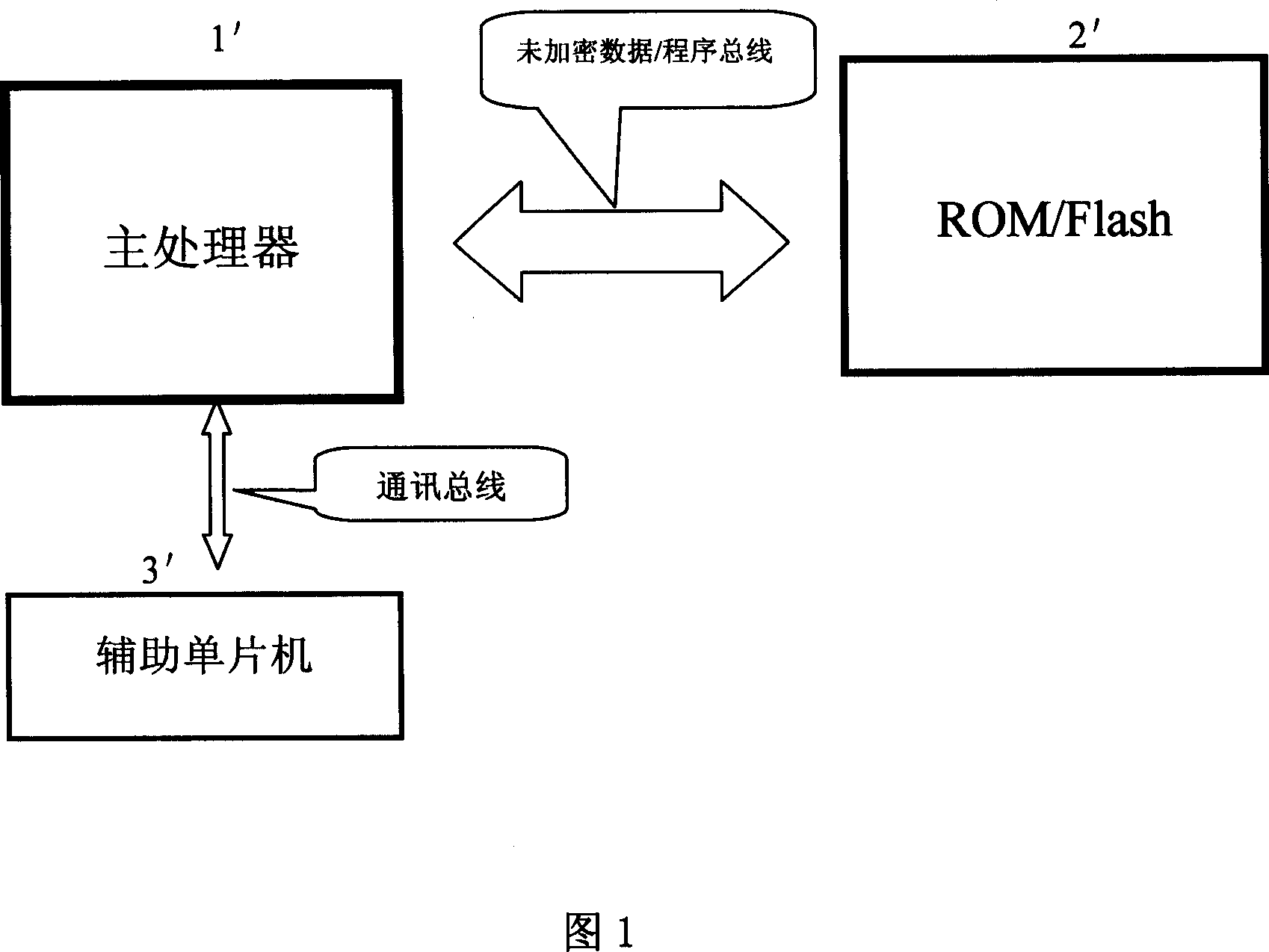
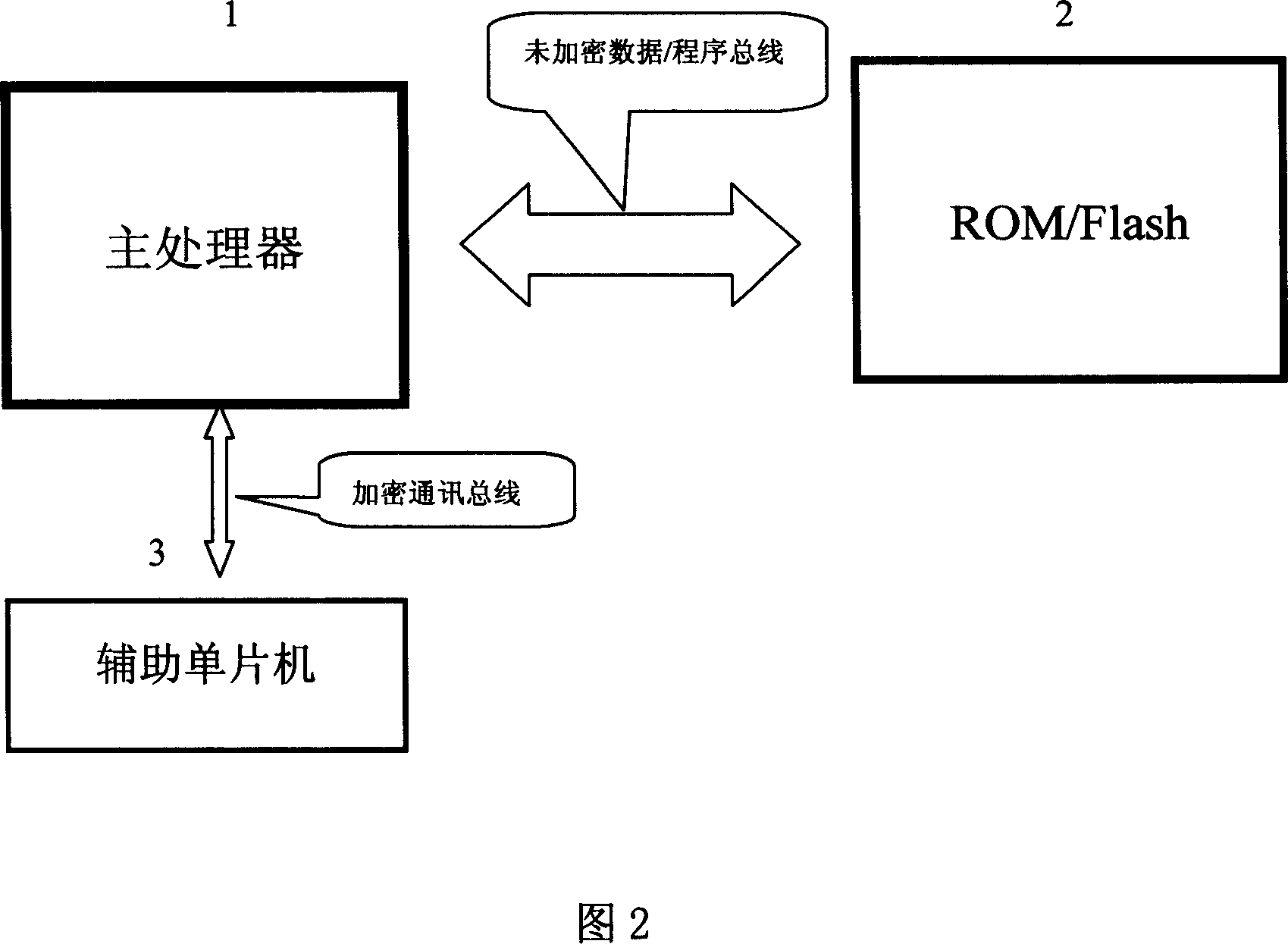
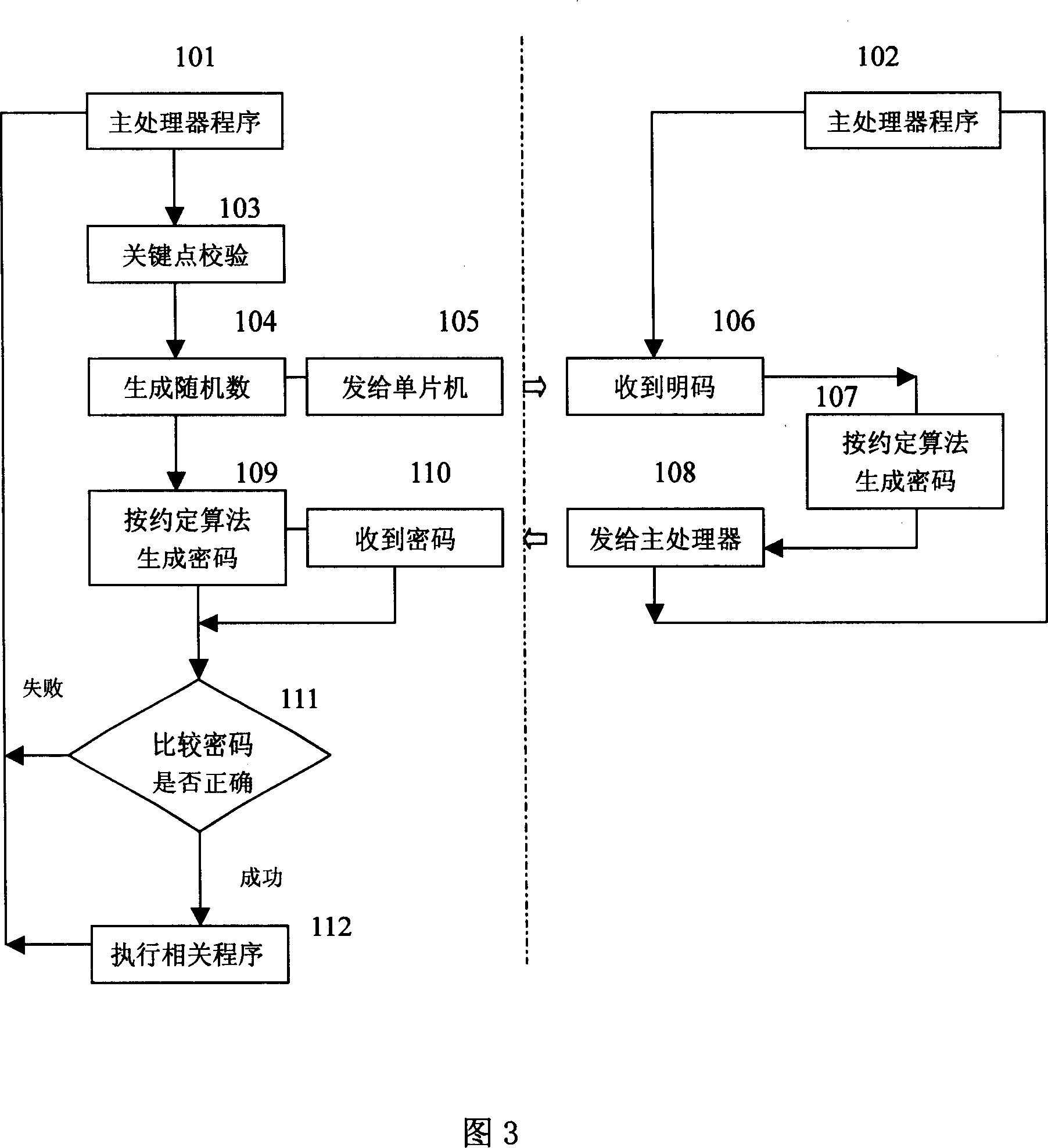
ActiveCN1971470AEasy to modify and upgradeFunction increaseDigital data processing detailsInternal/peripheral component protectionMicrocontrollerCryptography protocols
The invention discloses a system enciphering method adopting multi-purpose auxiliary singlechip, it is in multiple microprocessor system, the support microprocessor (for example power management support microprocessor) that its function is relatively simple and the amount of software programme is few is substituted with singlechip which equipped with inner read only program memory, the code checking of the stipulated enciphering protocol algorithm is added to the program of main processor and auxiliary singlechip to avoid the program to be read out and copied, so the purpose of system encryption can be achieved.
Owner:XIAMEN PRIMA TECH
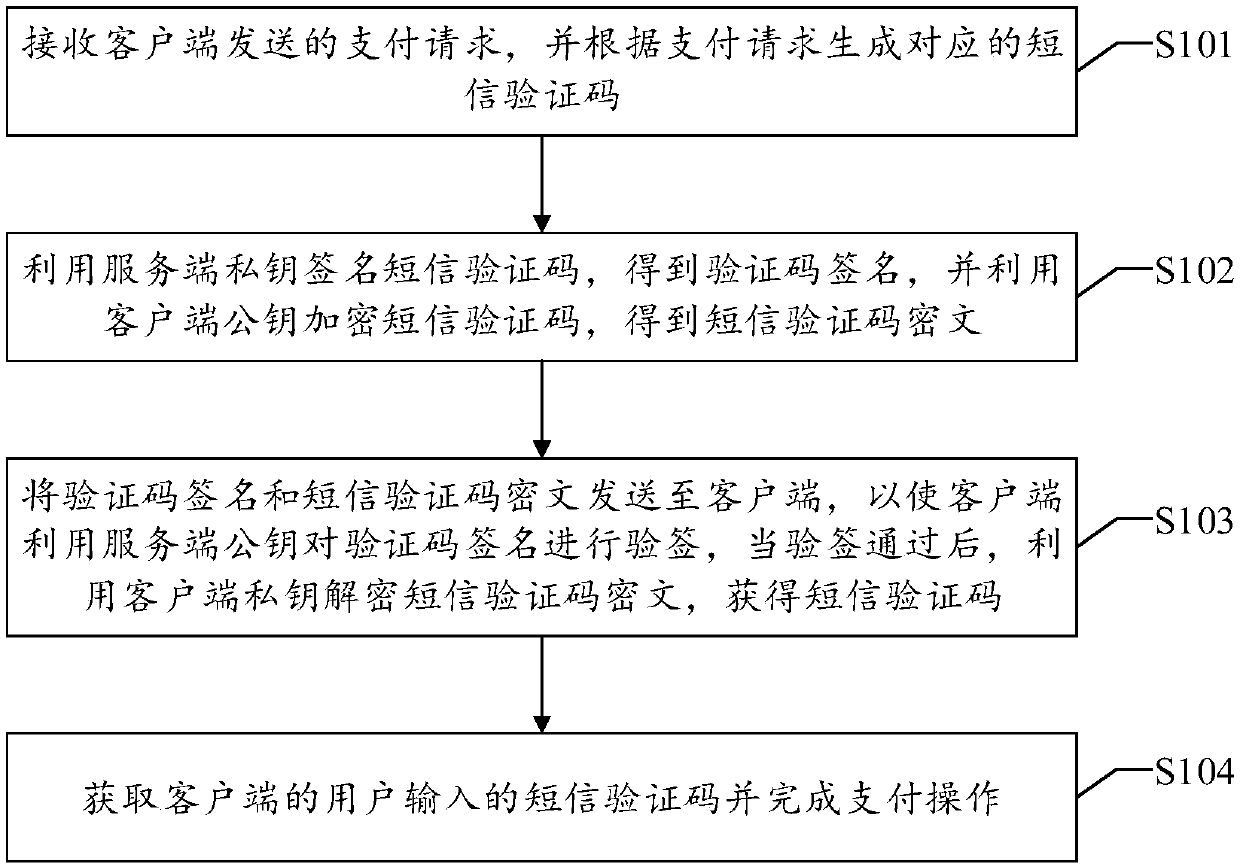
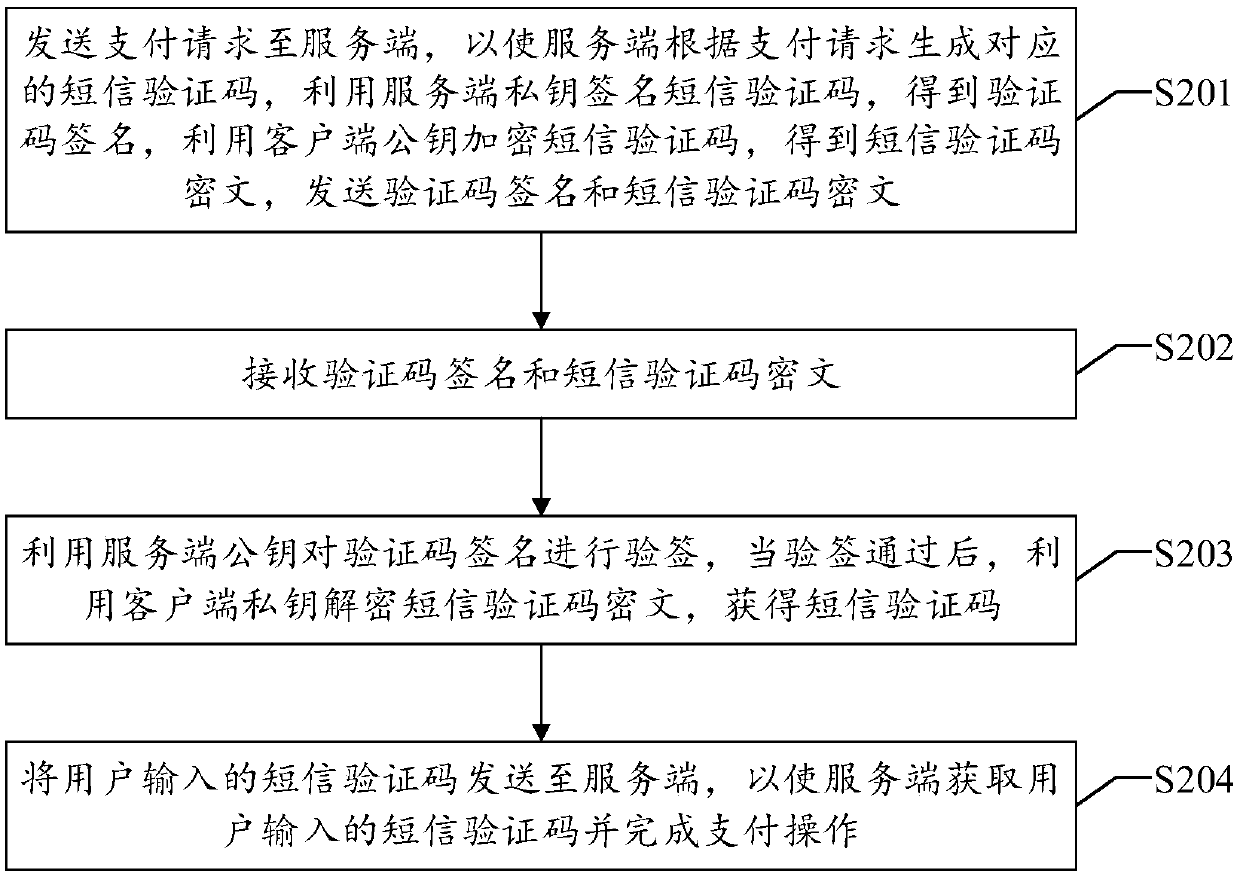
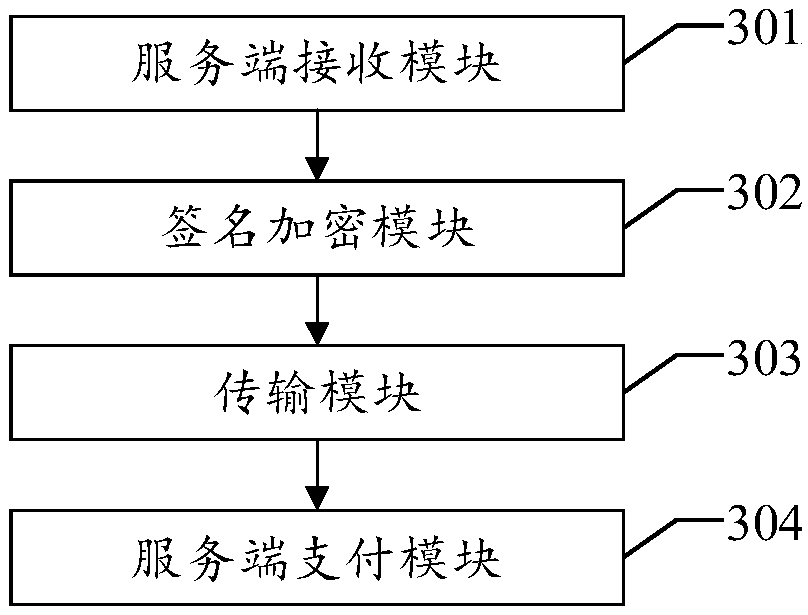
Payment method and apparatus based on short message verification code
ActiveCN108764912AEnsure safetySimplify the encryption processUser identity/authority verificationProtocol authorisationPaymentPassword
The present invention discloses a payment method based on a short message verification code. The method comprises: after receiving a payment request sent by a client, generating a corresponding shortmessage verification code according to the payment request; after encrypting the short message verification code and signing the short message verification code, sending a short message verification code ciphertext and a verification code signature to the client, so that the client can verify the verification code signature; and after the verification is passed, decrypting the short message verification code ciphertext, and obtaining the short message verification code, so that the user can complete the payment operation after inputting the short message verification code. According to the technical scheme of the present invention, the certificateless public key password is used in the whole process to sign the short message verification code, the encryption verification of the short message verification code during transmission is realized, and the security of the short message verification code is ensured; and at the same time, by using the certificateless public key password, the problems of certificate management and key management are not involved, so that the process for processing the short message verification code is simplified, and the costs are saved. Correspondingly, the present invention also discloses a payment apparatus and device based on the short message verification code, and a readable storage medium, which also have the technical effects.
Owner:GUANGDONG UNIV OF TECH
Method and apparatus for performing encryption and decryption by using white box library file and white box key file
InactiveCN108183796AEasy to updateImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPlaintextCiphertext
The invention relates to the technical field of terminal security protection, and in particular, to a method and apparatus for performing encryption and decryption by using a white box library file and a white box key file for solving the problem that the key is insecure in the prior art. The method mainly comprises the following steps: obtaining the white box library file via a first parameter combination carried in a library file generation request; obtaining the white box key file via a second parameter combination carried in a key file generation request; and performing encryption and decryption processing according to the white box library file and the white box key file. By adoption of the technical scheme, the key update is more convenient, when the key is updated, the white box library file does not need to be updated, so that a dynamic white box encryption flow can be simplified, and the security of the key is improved. In this way, the security of decrypting a ciphertext andencrypting a plaintext by a user is improved.
Owner:BEIJING BANGCLE TECH CO LTD
Sliding type capacitance fingerprint identification method and system and unblocking method of system
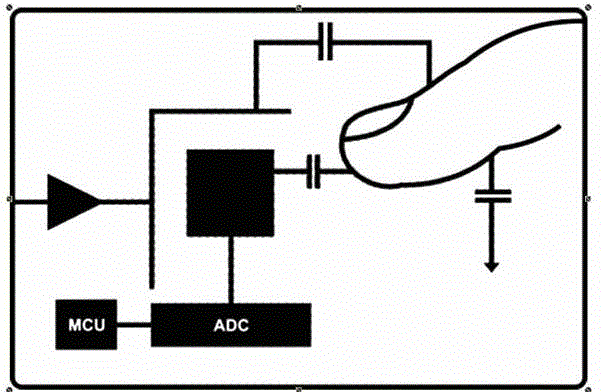
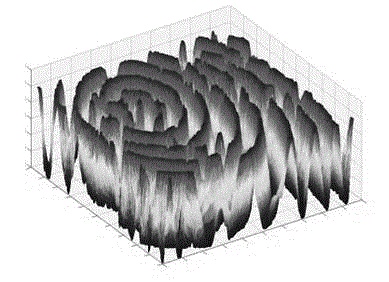
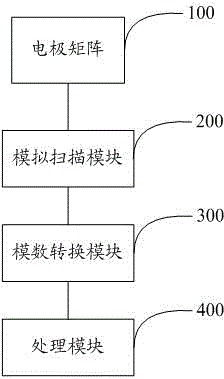
InactiveCN104636650ASufficient encryptionSimple structureDigital data authenticationPrint image acquisitionCapacitancePressure sense
The invention provides a sliding type capacitance fingerprint identification method and system and an unblocking method of the sliding type capacitance fingerprint identification system. The sliding type capacitance fingerprint identification system comprises an electrode matrix, multiple analog scanning modules, an analog-digital conversion module and a processing module, wherein the electrode matrix is composed of multiple electrodes, the analog-digital conversion module is used for converting analog signals into digital signals, and the processing module is used for receiving the digital signals and identifying a formed code series. Each electrode is independently connected with the corresponding analog scanning module, and user fingerprint analog signals are obtained according to the changes of capacitance signals of the electrodes. The analog scanning modules, the analogue-digital conversion module and the processing module are connected in sequence. According to the sliding type capacitance fingerprint identification system, sliding type pressure sense and touch type capacitance identification are combined, it is guaranteed that the encryption effect is good enough, the system is simpler in structure and smaller in size, encryption methods and decryption methods are simple, and the encryption cost is effectively reduced.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
Encrypting method and system, decrypting method and system, encryption and decryption method and system for photo album of mobile terminal
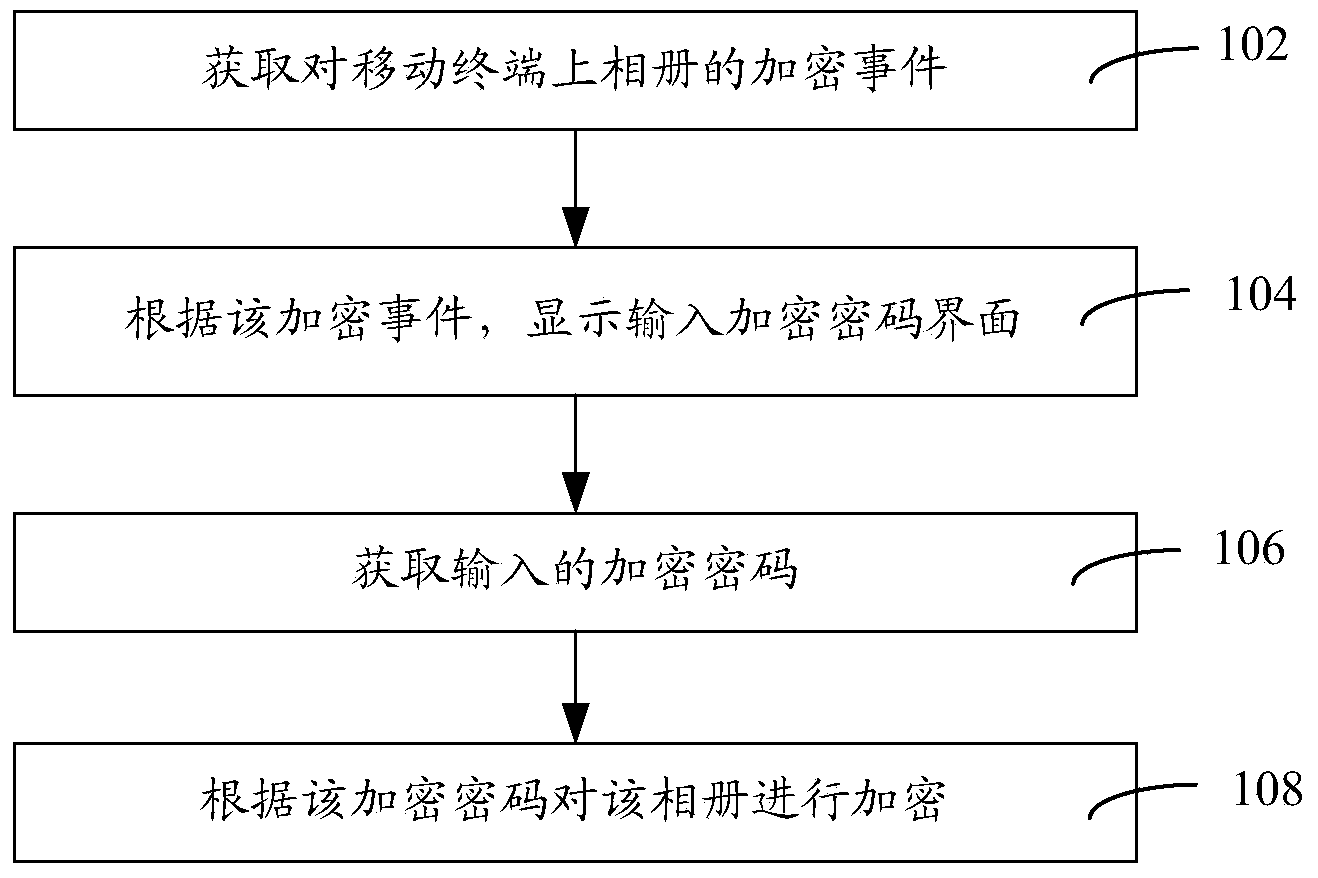
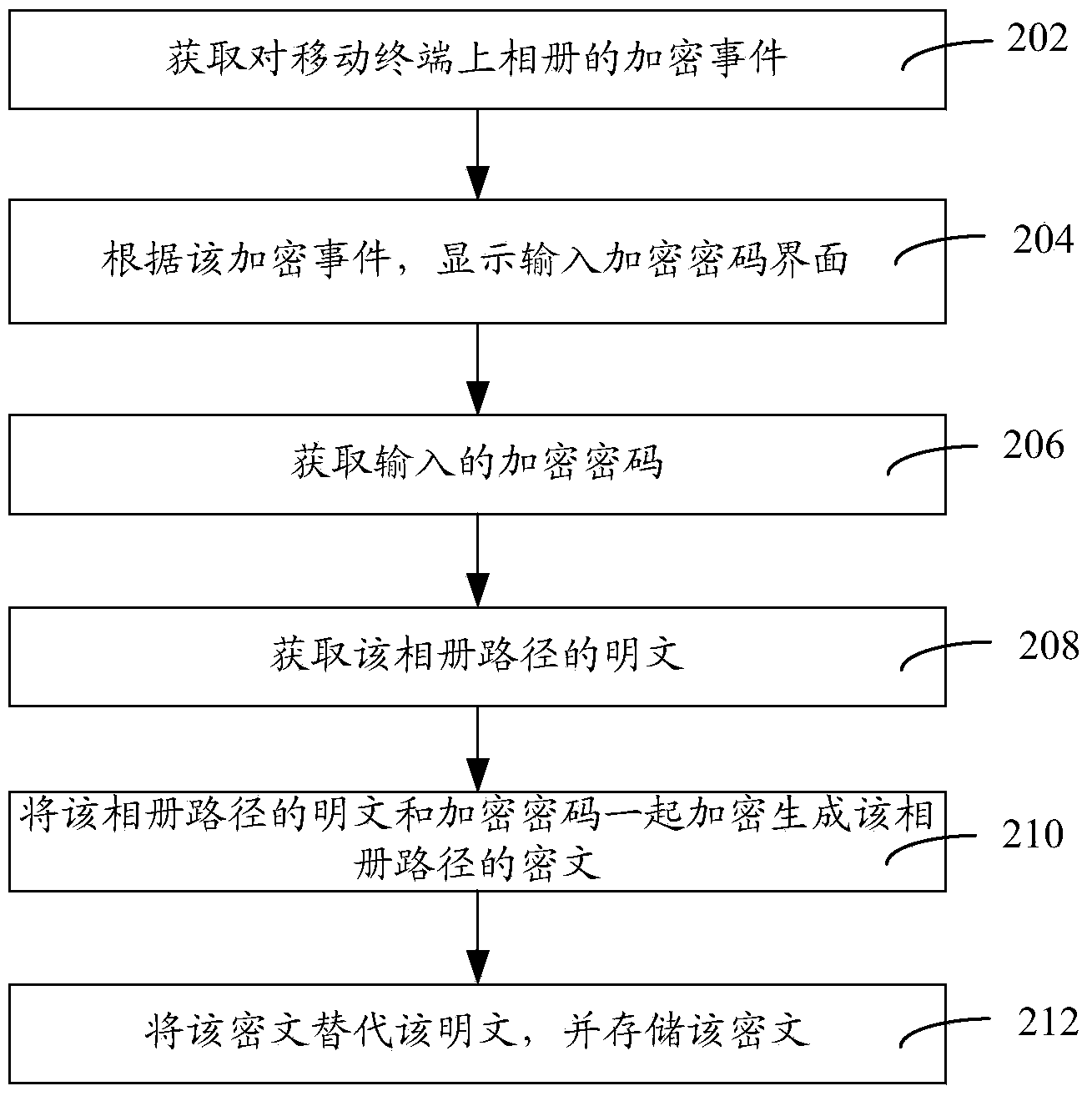
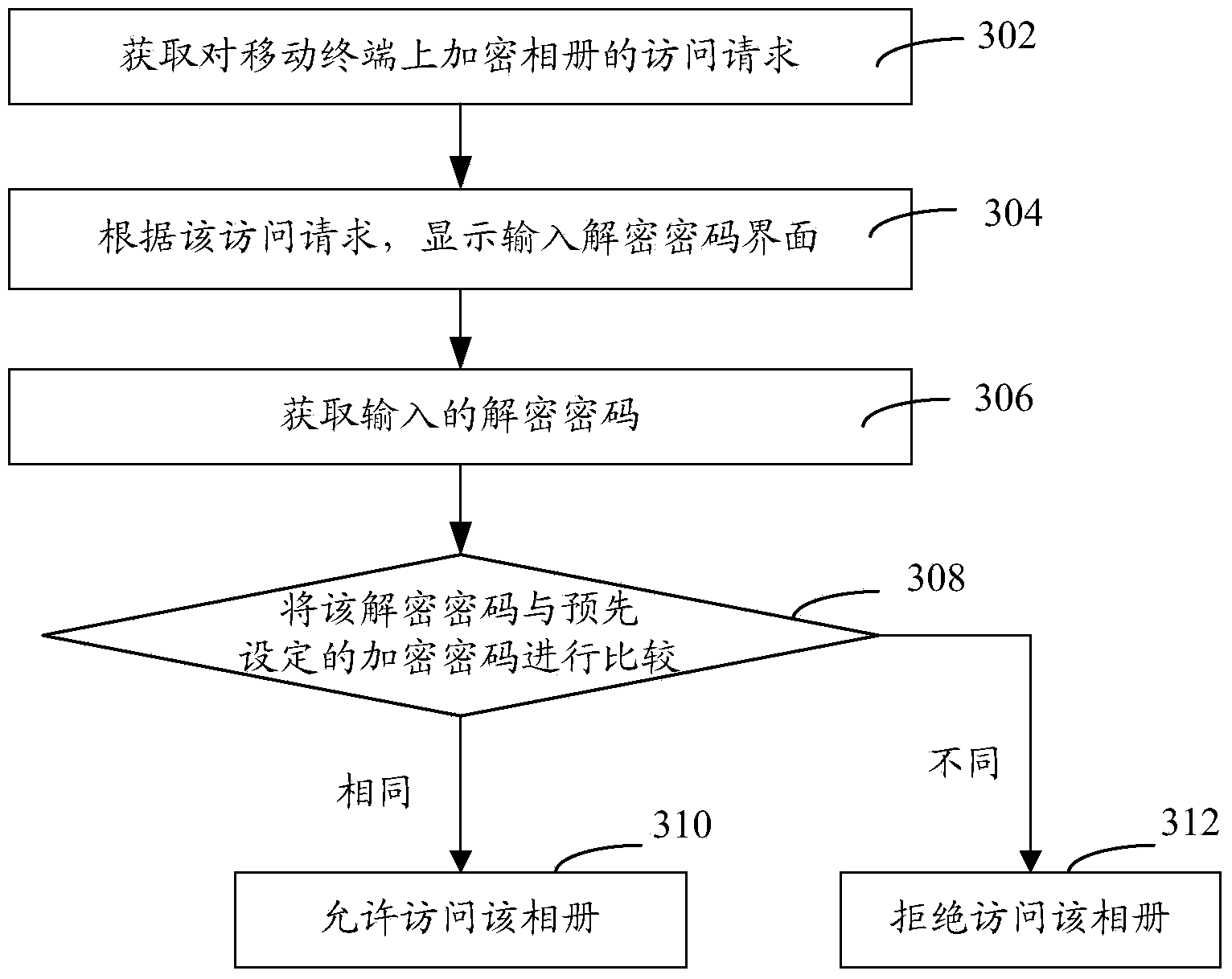
InactiveCN103684740AImprove securityThe encryption process is simpleSecuring communicationPasswordCipher
The invention relates to encrypting method and system, decrypting method and system and encryption and decryption method and system for a photo album of a mobile terminal. The encrypting method for the photo album of the mobile terminal includes the steps of acquiring encrypted events of the photo album on the mobile terminal, displaying an interface for inputting encrypted password according to the encrypted events, acquiring the inputted encrypted password, and encrypting the photo album by the encrypted password. By the encrypting method and system, the decrypting method and system and the encryption and decryption method and system, the photo album of the mobile terminal is encrypted, other people cannot acquire the encrypted password and cannot check the content of the photo album, the photo album can be accessed only when verification is passed by inputting the encrypted password, and safety to the information of the photo album is improved.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
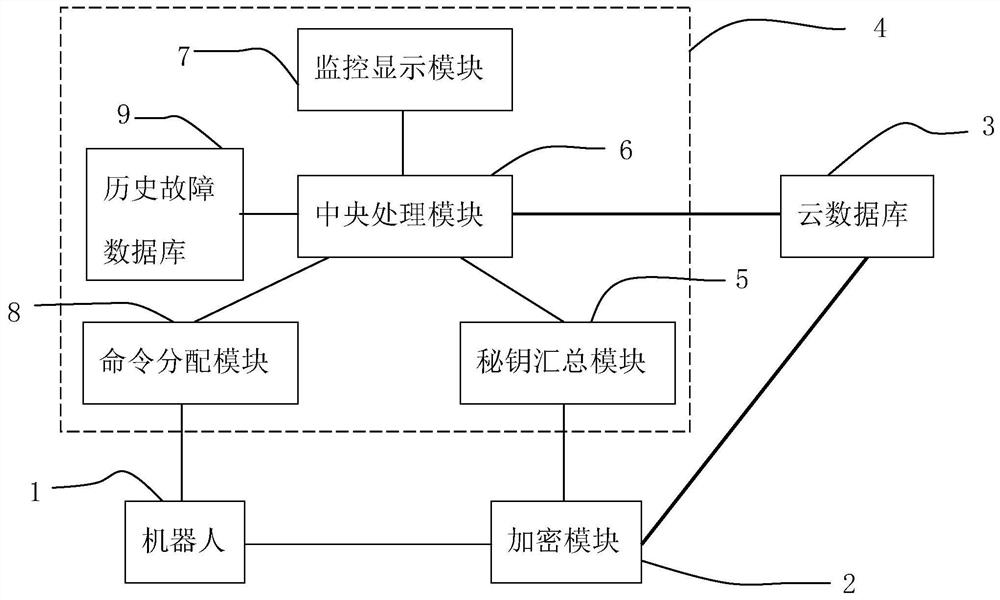
Intranet and extranet integrated power grid data communication system and method
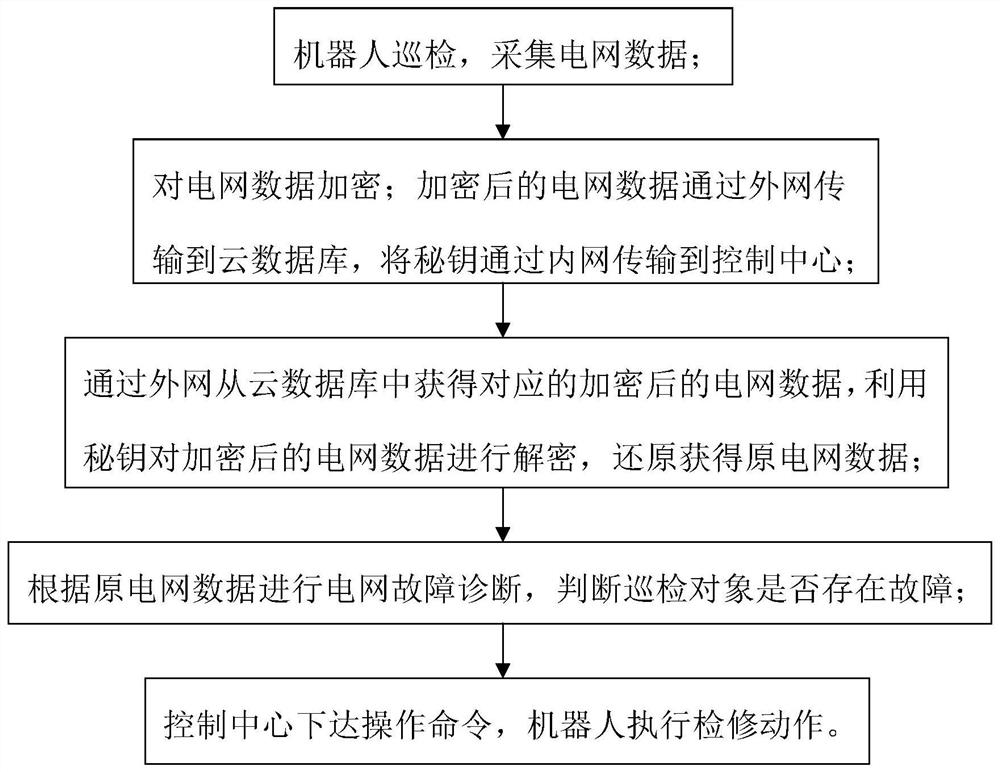
PendingCN113395254AEnsure safetyReduce data volumeKey distribution for secure communicationUser identity/authority verificationGrid faultCommunications system
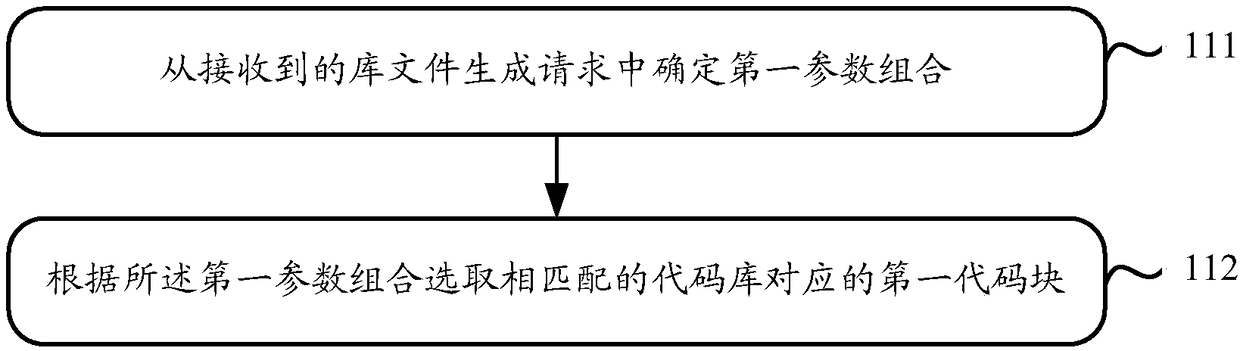
The invention discloses an internal and external network integrated power grid data communication system and method. The problems that in the prior art, a power grid independently uses a private network for communication, huge information amount interaction cannot be met, and data communication safety cannot be guaranteed when an external network is used are solved. The method comprises the following steps: S1, robot inspection: collecting power grid data; S2, encrypting the acquired power grid data; transmitting the encrypted power grid data to a cloud database through an external network, and transmitting a secret key to a control center through an internal network; S3, the control center obtaining the corresponding encrypted power grid data from the cloud database through the external network, decrypting the encrypted power grid data by using the secret key, and restoring the encrypted power grid data to obtain the original power grid data; and S4, the control center performing power grid fault diagnosis according to the original power grid data and judging whether the inspection object has a fault or not. Encrypted data is transmitted through the extranet, and a secret key is transmitted through the intranet, so that huge information interaction can be met, and meanwhile, the security of data transmission can be ensured.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD JIAXING POWER SUPPLY CO
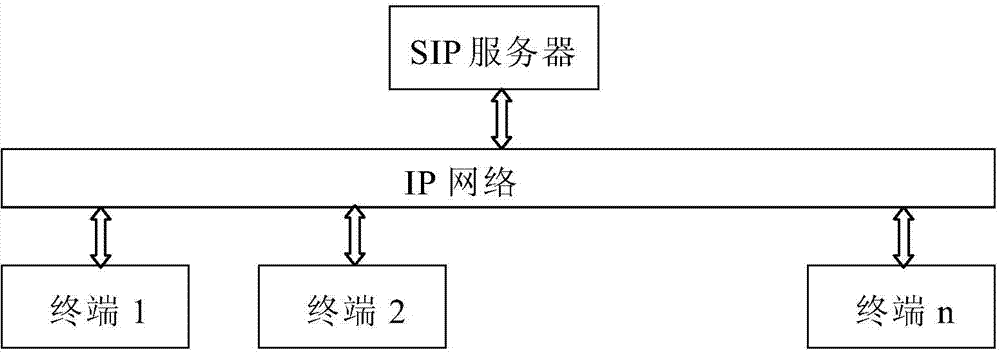
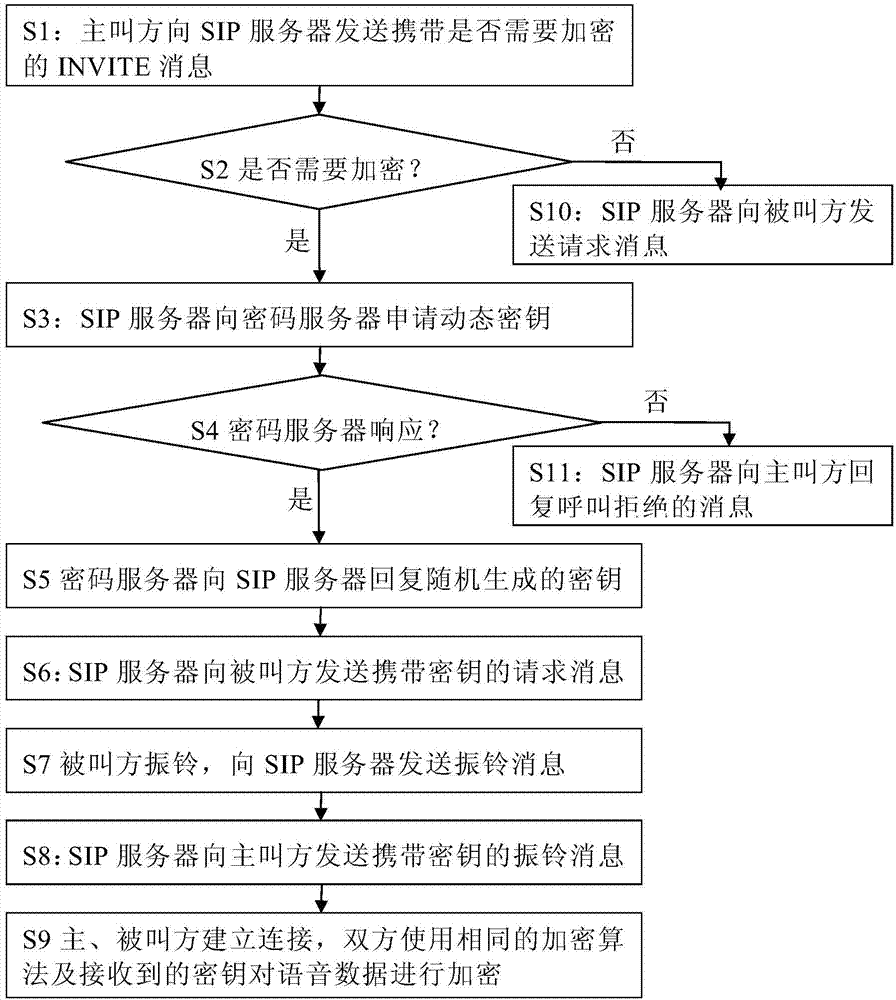
Flexible and controllable session encryption method
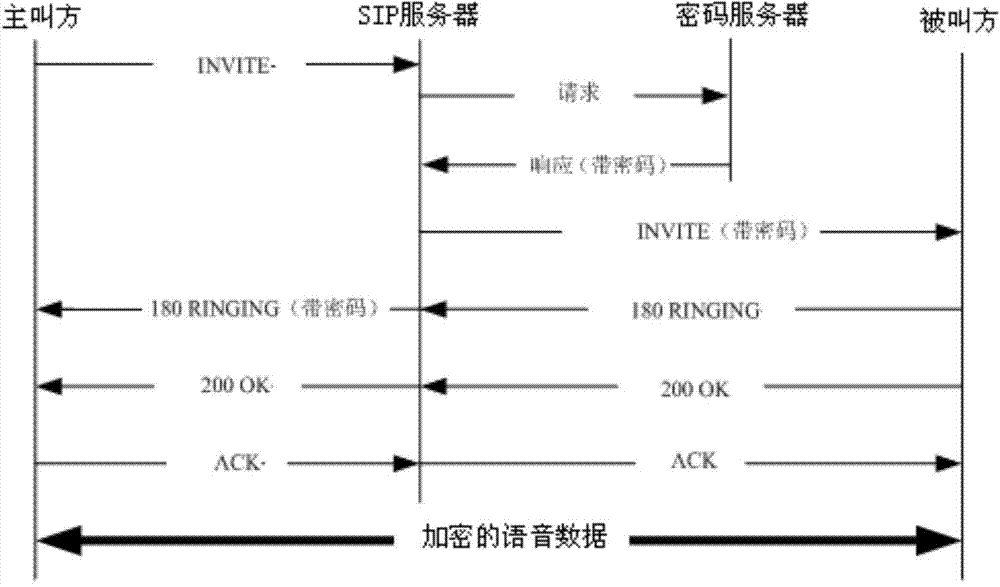
InactiveCN104753876ASimplify the encryption processReduce complexityKey distribution for secure communicationVoice dataSpeech sound
The invention discloses a flexible and controllable session encryption method. An SIP server in the calling direction sends a connection establishment request message carrying an identification indicating whether session contents during connection are needed to be encrypted or not, the SIP server obtains a randomly-generated secret key through a password server if encryption is needed, the secret key is sent to two communicated parties by utilizing messages interacted by the two communicated parties, and follow-up voice data of the two parties are encrypted by adopting a encrypted and the secret key; if the encryption is not needed, the SIP server directly sends a connection establishment request message to a called party. The IP voice encryption processing process can be simplified. Compared with secret keys configured and fixed in advance, configuration work is omitted, communicated-connected secret keys each time are different, and even if the secret keys are cracked, session contents after connection is re-established cannot be obtained.
Owner:BEIJING DATANG GOHIGH DATA NETWORKS TECH CO LTD
Method and device for implementing file manager confidentiality box and mobile terminal
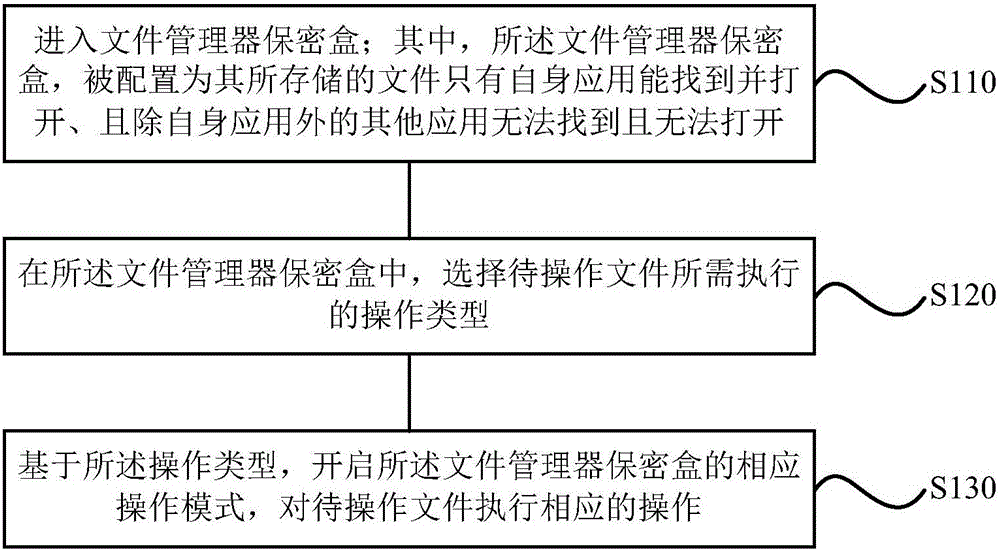
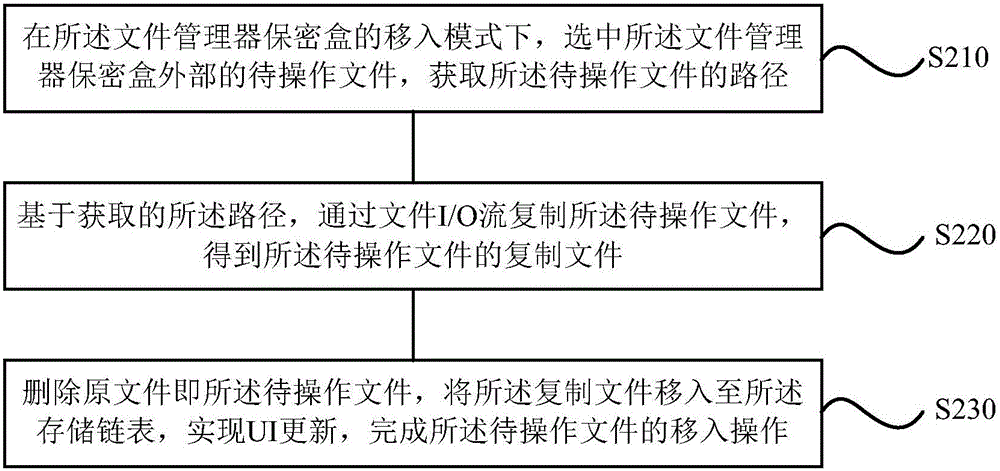
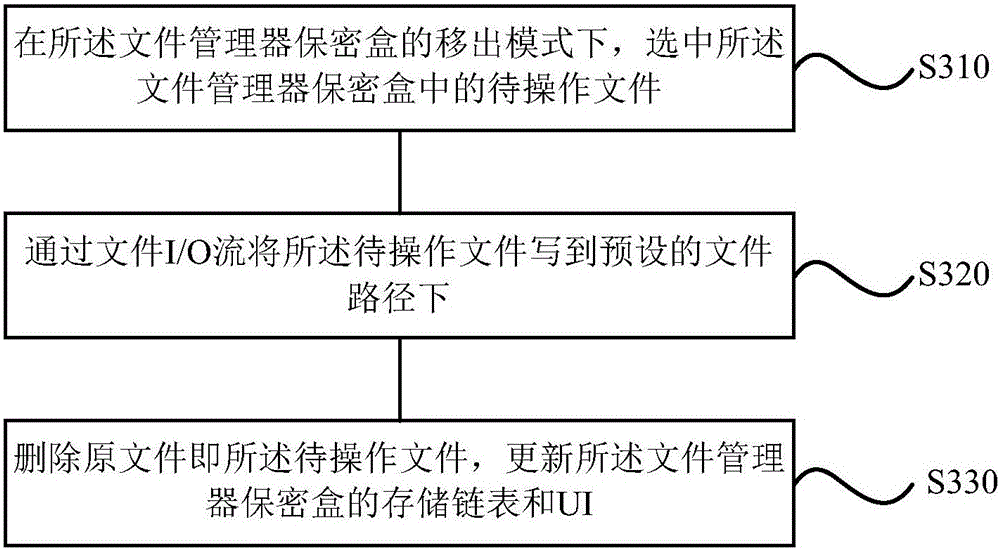
ActiveCN105787385AImprove efficiencyReduce the process of file encryptionDigital data protectionFile managerConfidentiality
The invention discloses a method and device for implementing a file manager confidentiality box and a mobile terminal.The method for implementing the file manager confidentiality box comprises the steps of entering the file manager confidentiality box, wherein the file manager confidentiality box is configured to achieve the effect that each file stored in the file manager confidentiality box can only be found and opened through an application of the corresponding file and cannot be found and opened through other applications other than the application of the corresponding file; in the file manager confidentiality box, selecting the operation type which the file to be operated needs to implement; based on the operation type, starting a corresponding operation mode of the file manager confidentiality box, and executing corresponding operation on the file to be operated.By means of the method and device for implementing the file manager confidentiality box and the mobile terminal, the defects that in the prior art, the encryption process is complex, consumed time is long, and user experience is poor are overcome, and the method and device for implementing the file manager confidentiality box and the mobile terminal have the advantages of being simple in encryption process, short in consumed time and good in user experience.
Owner:GREE ELECTRIC APPLIANCES INC
Data security system and data security method of slimming data sharing cloud platform
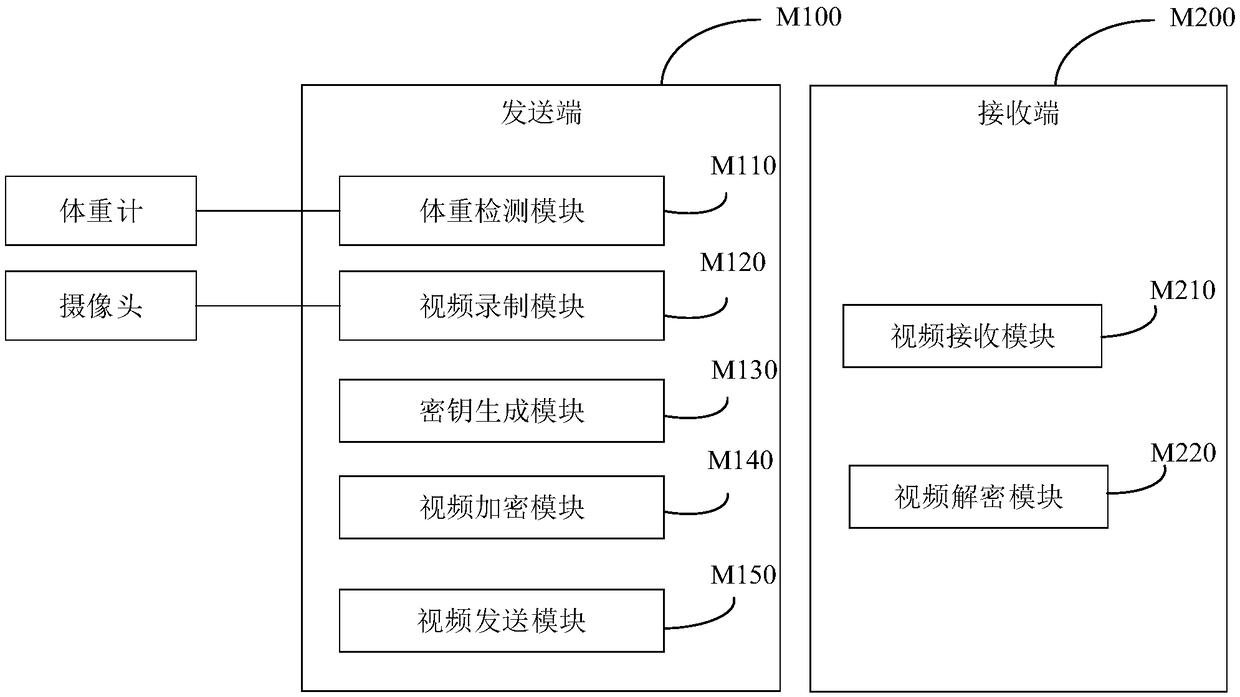
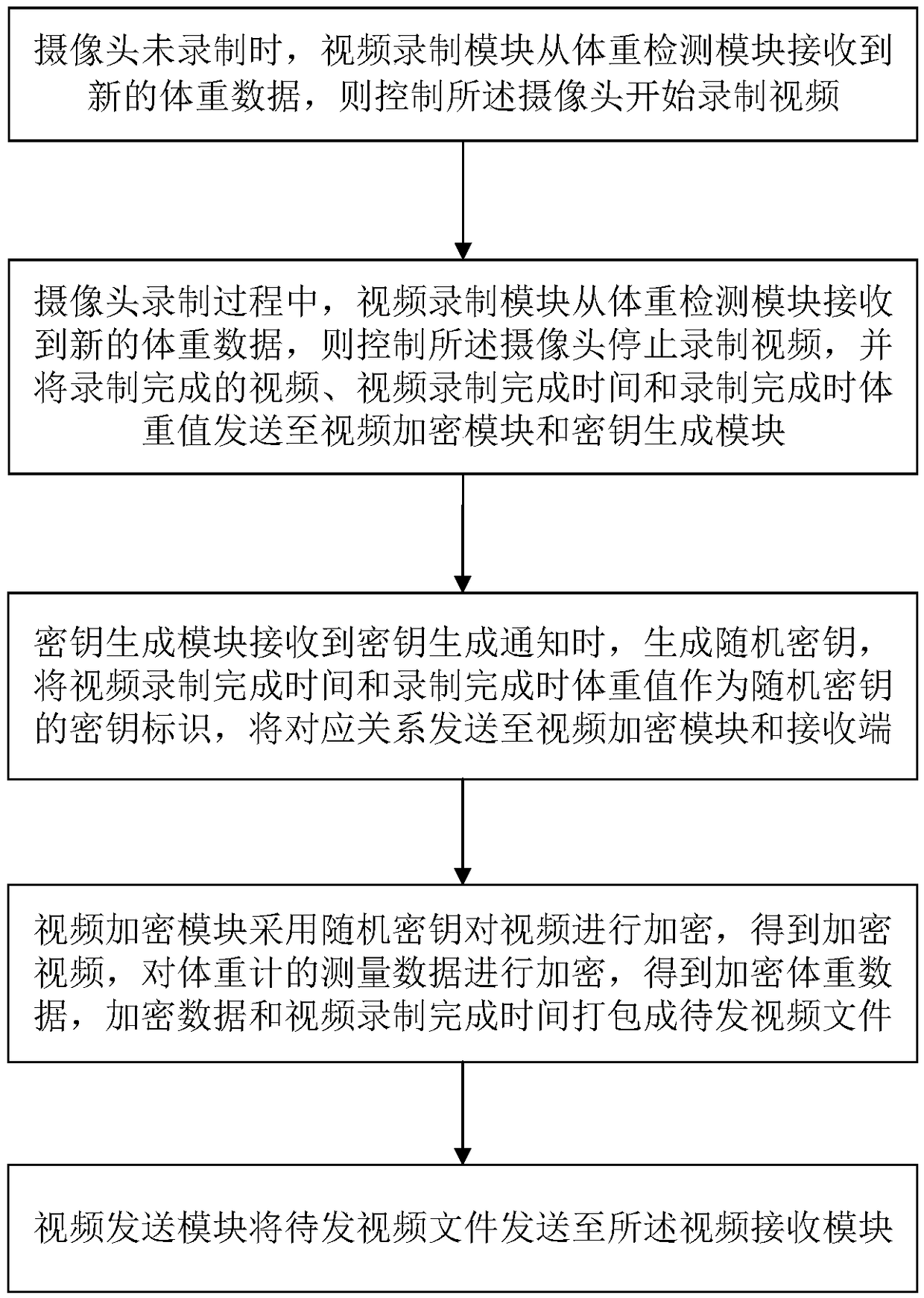
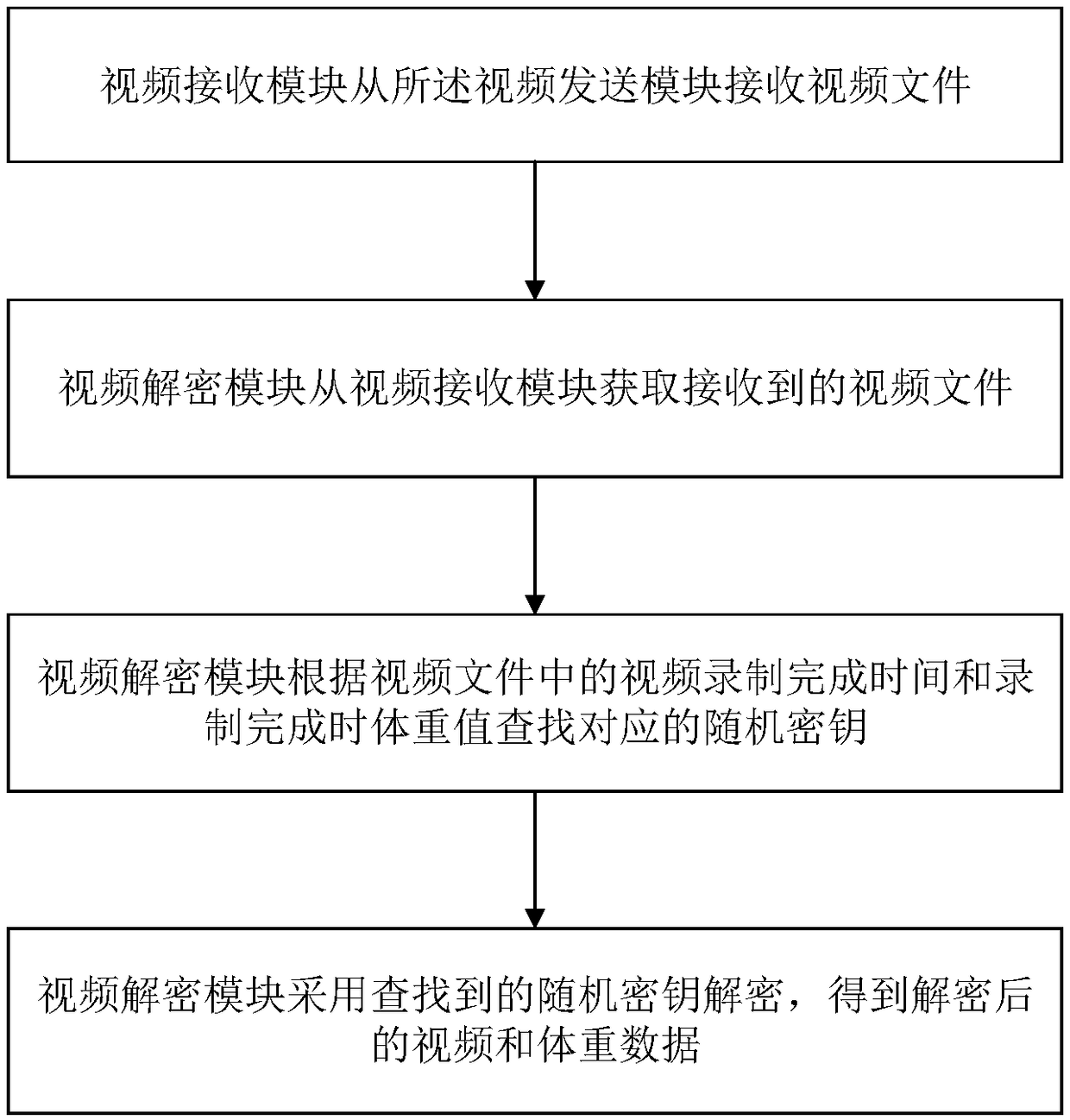
ActiveCN109274917AEnsure safetyDoes not affect the efficiency of normal transmissionTelevision system detailsColor television detailsComputer hardwareAutomatic control
The invention relates to a data secrecy system and a data secrecy method of a slimming data sharing cloud platform, wherein the sending end comprises a weight detection module, a video recording module, a key generation module, a video encryption module and a video sending module, and the receiving end comprises a video receiving module and a video decryption module. The invention adopts the weight detection result of the weight detection module as a signal for a user to start and stop fitness, if the video recording module detects that the camera does not record, the weight detection result is detected, the user starts to exercise and starts to record video; if the video recording module detects that the weight detection result is detected during the camera recording, the user stops the exercise and automatically controls the video recording start and end process. Encrypt the fitness video and weight data to ensure the security of video and weight data transmission, avoid being obtained by other non-designated receiver video content, and ensure the security of user privacy data.
Owner:苏州东巍网络科技有限公司
System encrypting method using multifunctional assistant SCM
ActiveCN100461063CImprove securityHigh costDigital data processing detailsInternal/peripheral component protectionMicrocontrollerMaster processor
Owner:XIAMEN PRIMA TECH
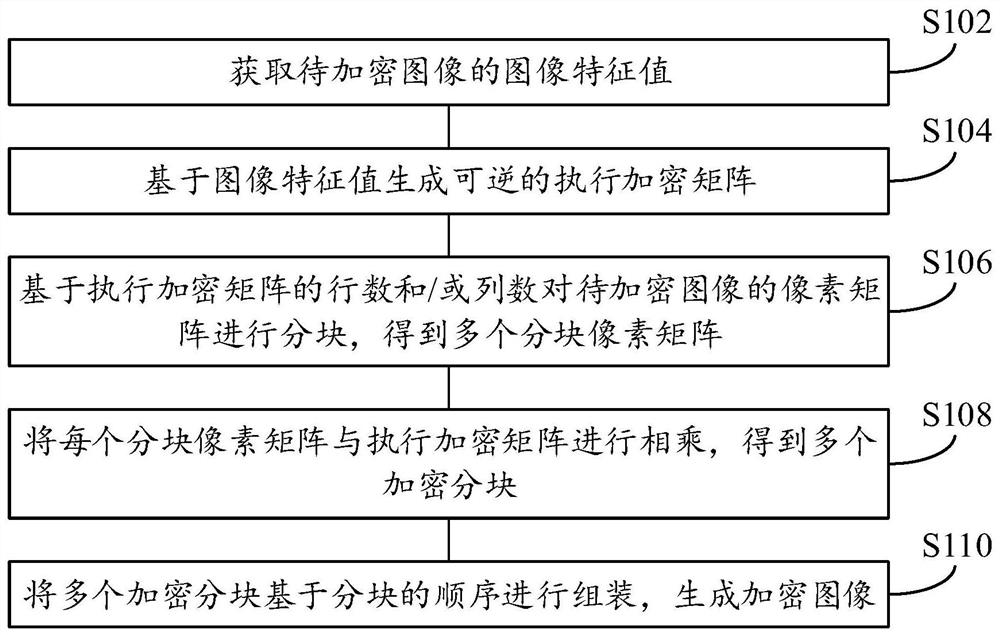
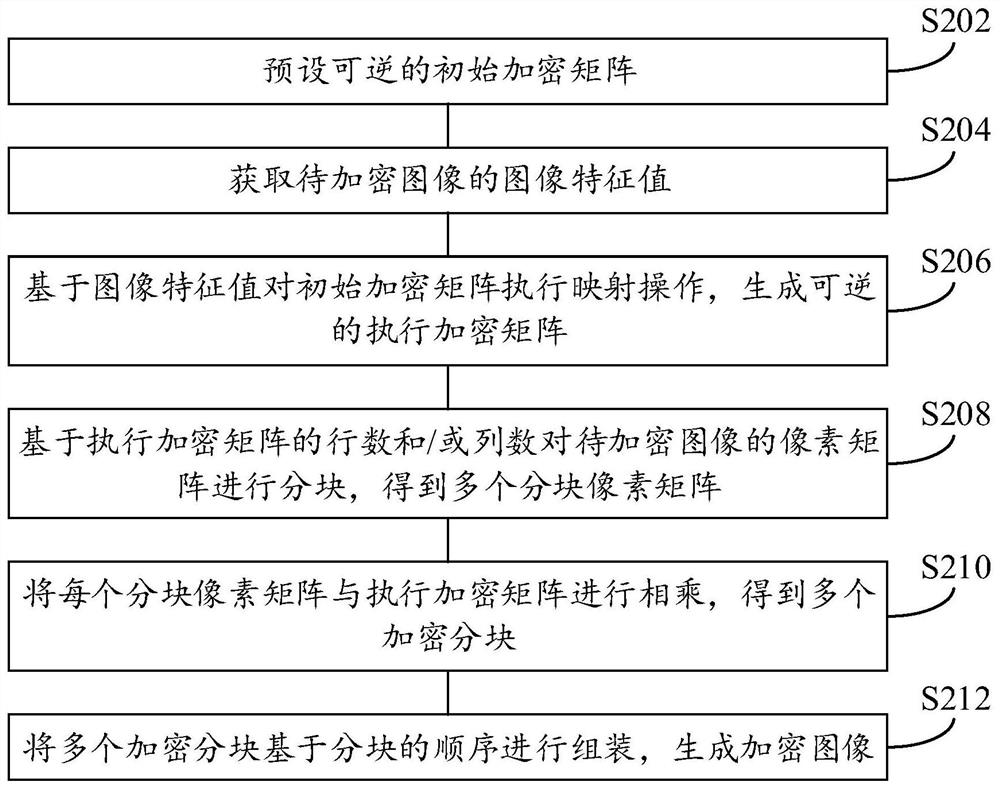
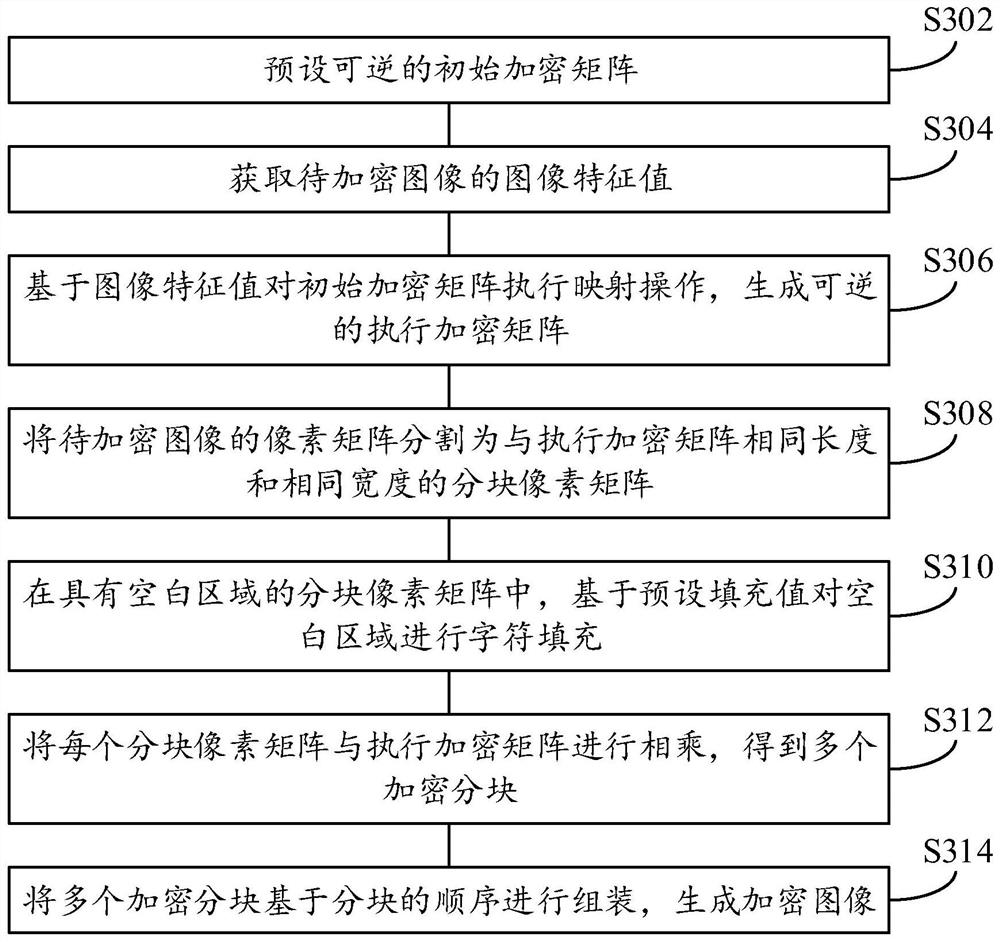
Image encryption method and device, image decryption method and device, electronic equipment and medium
PendingCN113793245ARealize dynamic generationImplement Block EncryptionDigital data protectionImage data processing detailsComputer hardwareEmbedded system
The invention provides an image encryption method and device, an image decryption method and device, electronic equipment and a medium, and relates to the technical field of image encryption. The image encryption method comprises the following steps: acquiring an image feature value of a to-be-encrypted image; generating a reversible execution encryption matrix based on the image feature value; partitioning a pixel matrix of the to-be-encrypted image based on the number of rows and / or the number of columns of the encryption execution matrix to obtain a plurality of partitioned pixel matrixes; multiplying each block pixel matrix by the encryption execution matrix to obtain a plurality of encryption blocks; and assembling the plurality of encrypted blocks based on the sequence of the blocks to generate an encrypted image. According to the technical scheme, the reliability of encryption operation and the security of the encrypted image are ensured, the implementation process of encryption is simplified, and operation is easy.
Owner:CHINA TELECOM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com