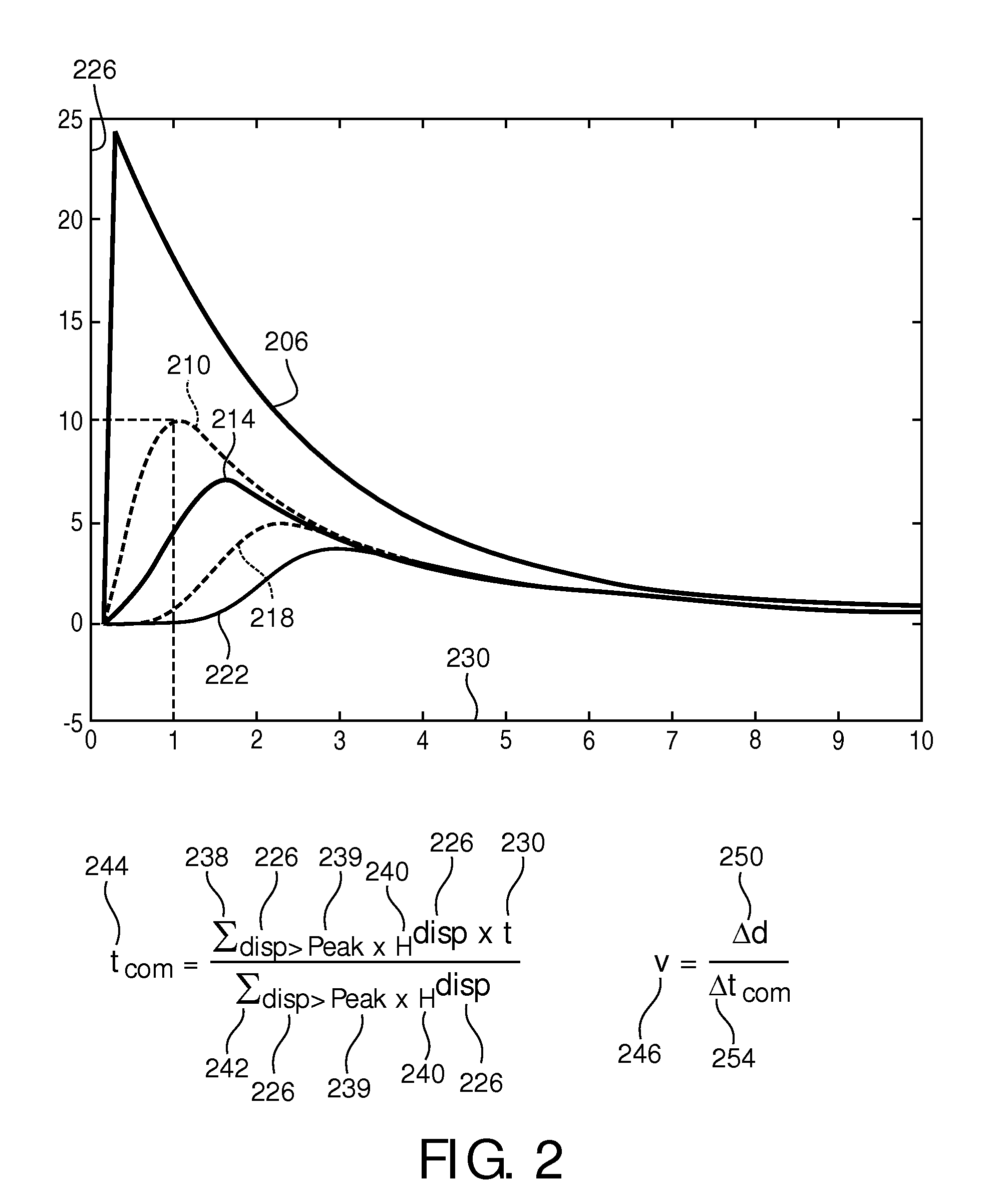Patents
Literature
101results about How to "Less-prone" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Smart tray for dispensing medicaments
ActiveUS7080755B2Less-proneMinimal amountElectrotherapyDrug and medicationsEngineeringBiomedical engineering
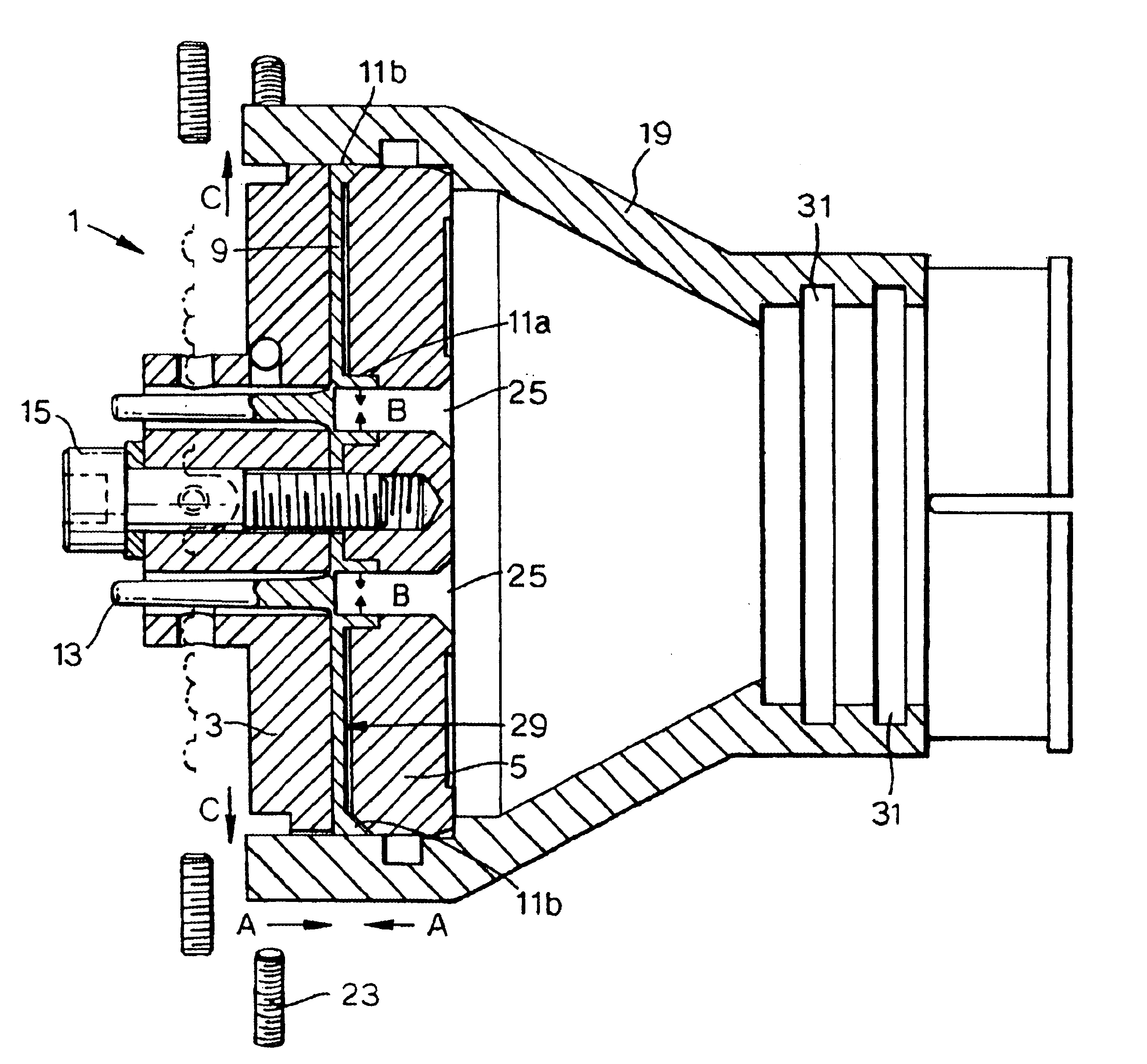
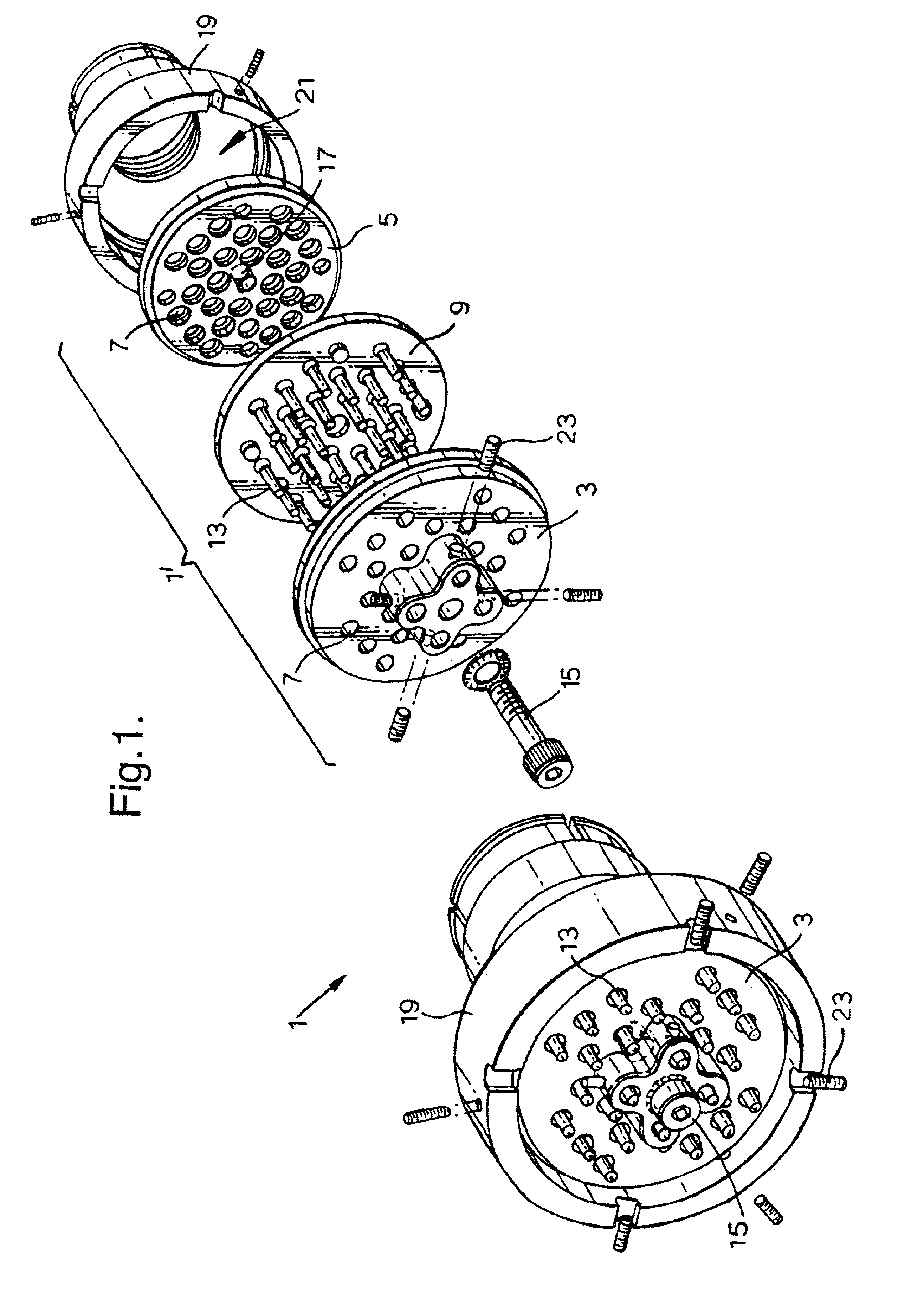
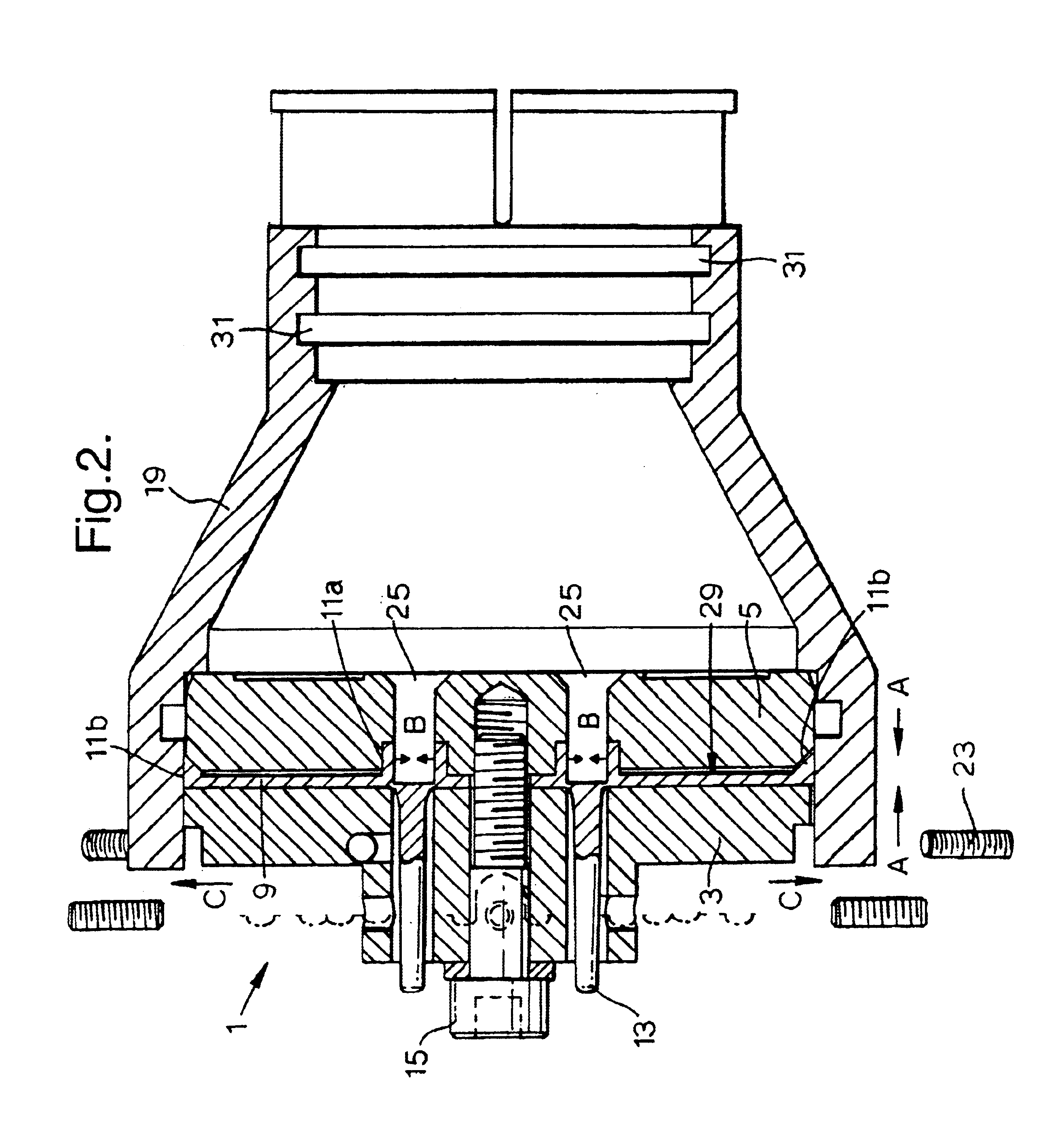
The invention relates to a method and system that utilizes one or more cassettes or trays, which hold one or more types of medicaments, the cassettes or trays being configured for secure and intelligent dispensing of the medicaments. In one embodiment, a smart tray for dispensing medicaments includes: a housing; a chamber within the housing to store the medicament units; an outlet defined in the housing to dispense the medicament units; and a rotatable disk within the housing and defining at least one radial groove configured to hold at least one medicament unit, the rotatable disk being positioned between the storage chamber and the outlet whereby when the rotatable disk rotates, the at least one radial groove carries the at least one medicament unit from the chamber to the outlet. In a further embodiment, the smart tray includes a memory device within the housing to store information pertaining to the medicament units stored in the tray and / or information pertaining to the status or operation of the tray.
Owner:HANDFIELD MICHAEL +1
Polishing pads and methods relating thereto
InactiveUS6022268AEnhanced interactionLess-proneRevolution surface grinding machinesOther chemical processesEngineeringTopography
This invention describes improved polishing pads useful in the manufacture of semiconductor devices or the like. The pads of the present invention have an advantageous hydrophilic polishing material and have an innovative surface topography and texture which generally improves predictability and polishing performance.
Owner:ROHM & HAAS ELECTRONICS MATERIALS CMP HLDG INC
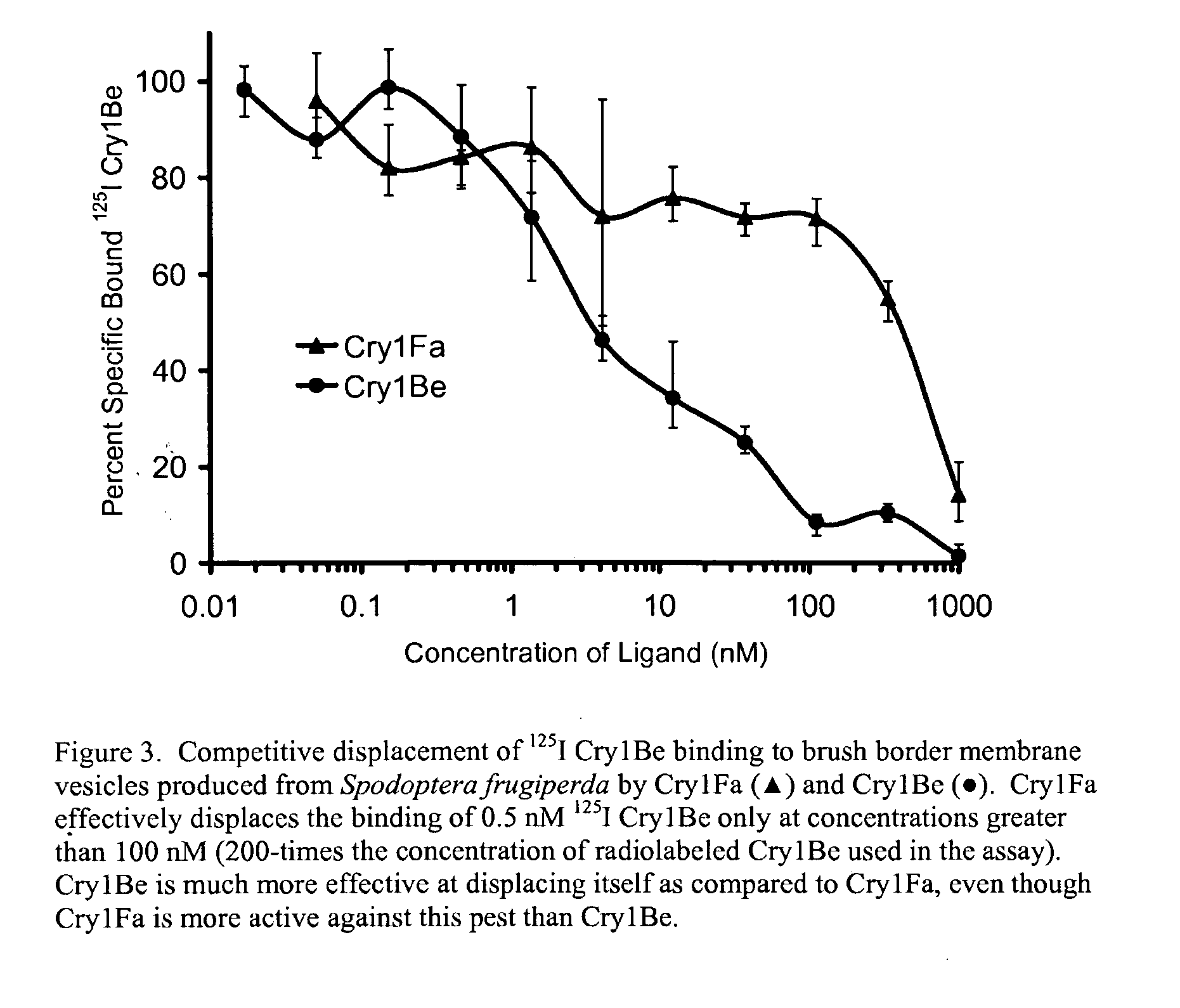
Insect resistance management with combinations of cry1be and cry1f proteins
The subject invention relates in part to stacking Cry1Be toxins along with Cry1Fa toxins to prevent insects from developing resistance towards either toxin by itself. As discussed in more detail herein, the subject pair of proteins is a particularly advantageous combination, as no other pair of proteins is known to provide high levels of control and non-cross-resistant activity against both Spodoptera frugiperda (FAW) and Ostrinia nubilalis (ECB) insects. This dual, non-cross-resistant activity is also advantageous because it can reduce the number of proteins / genes needed to target these insects with multiple, non-cross-resistant proteins. This can reduce or eliminate the need for refuge acreage. Accordingly, the subject invention also relates generally to using four genes to provide three proteins for non-cross-resistant control of a first insect, and three proteins for non-cross-resistant control of a second insect. In preferred embodiments, the targeted insects are FAW and ECB.
Owner:CORTEVA AGRISCIENCE LLC
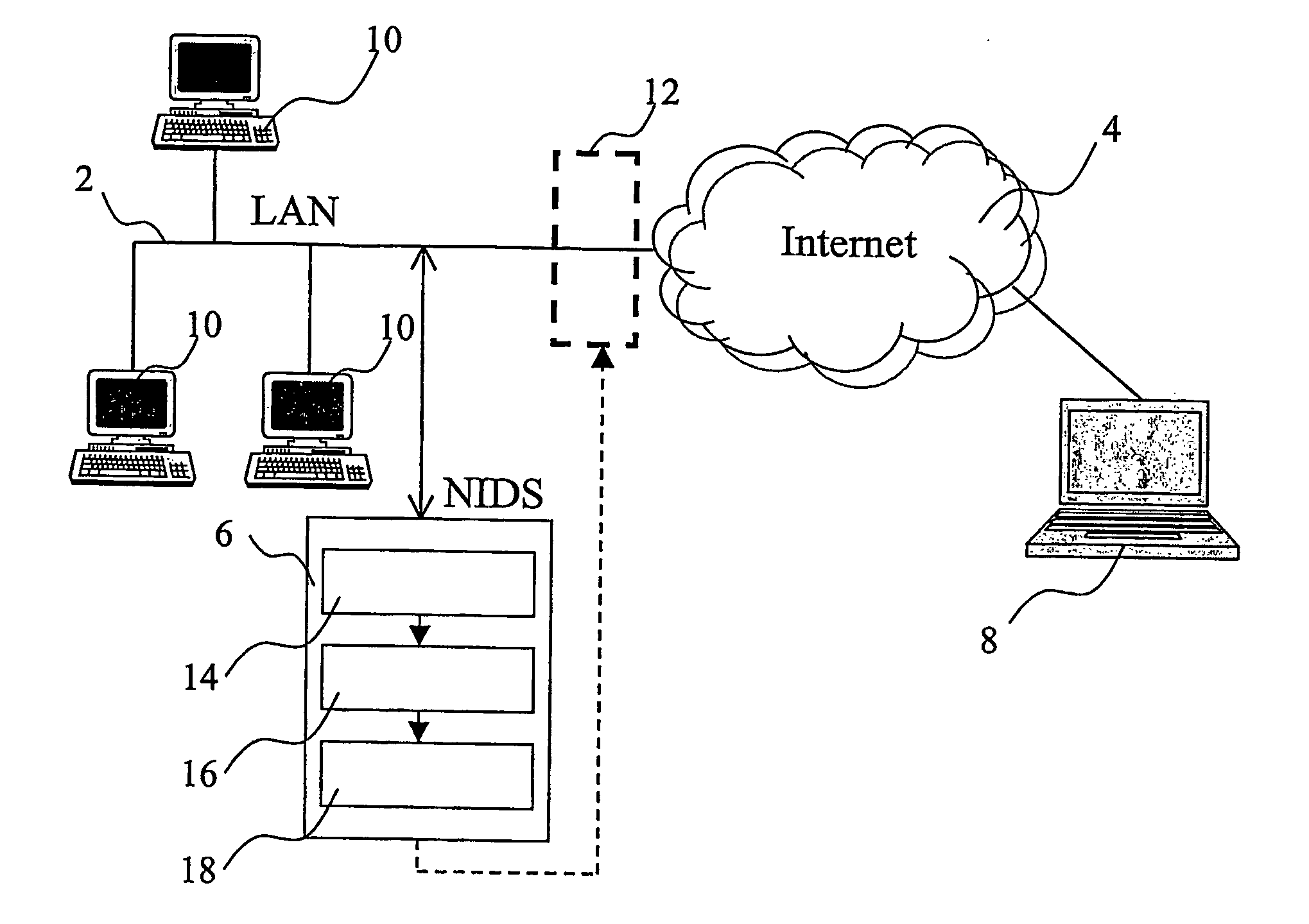
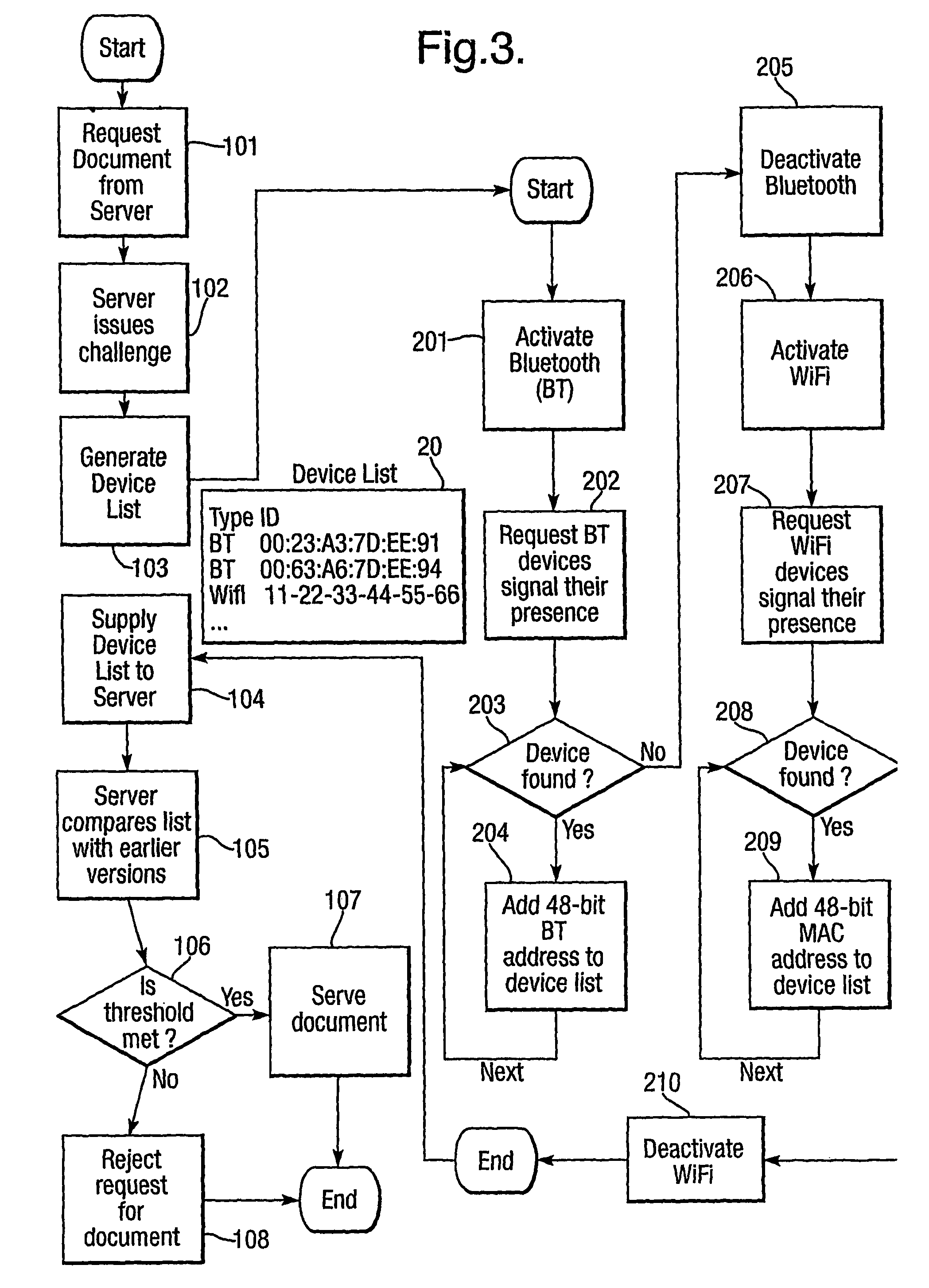
Method and system for detecting unauthorized use of a communication network
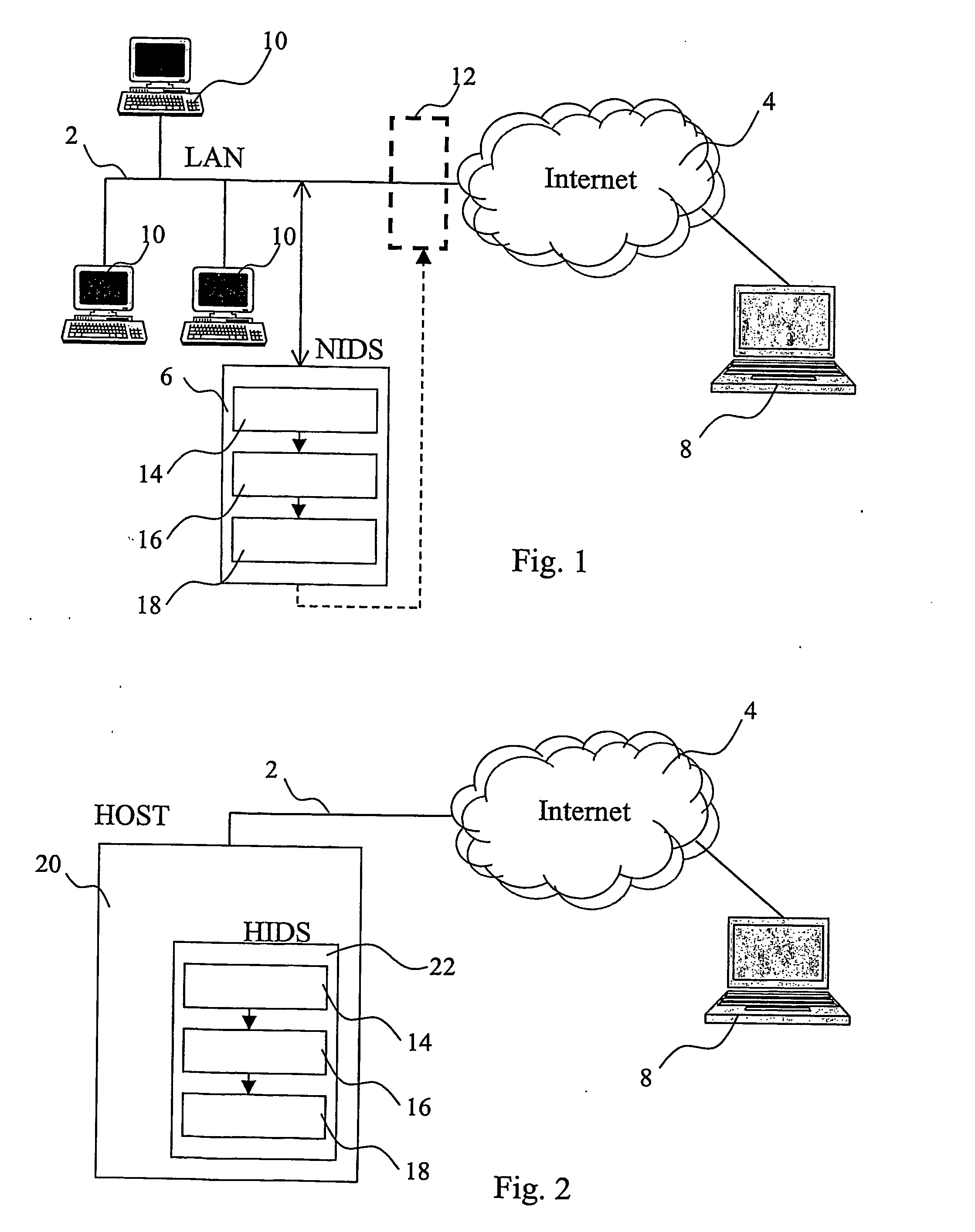
ActiveUS20060242703A1Less proneMemory loss protectionError detection/correctionPattern matchingAlert state
A system for detecting unauthorised use of a network is provided with a pattern matching engine for searching attack signatures into data packets, and with a response analysis engine for detecting response signatures into data packets sent back from an attacked network / computer. When a suspect signature has been detected into a packet, the system enters an alarm status starting a monitoring process on the packets sent back from the potentially attacked network / computer. An alarm is generated only in case the analysis of the response packets produces as well a positive result. Such intrusion detection system is much less prone to false positives and misdiagnosis than a conventional pattern matching intrusion detection system.
Owner:III HLDG 1
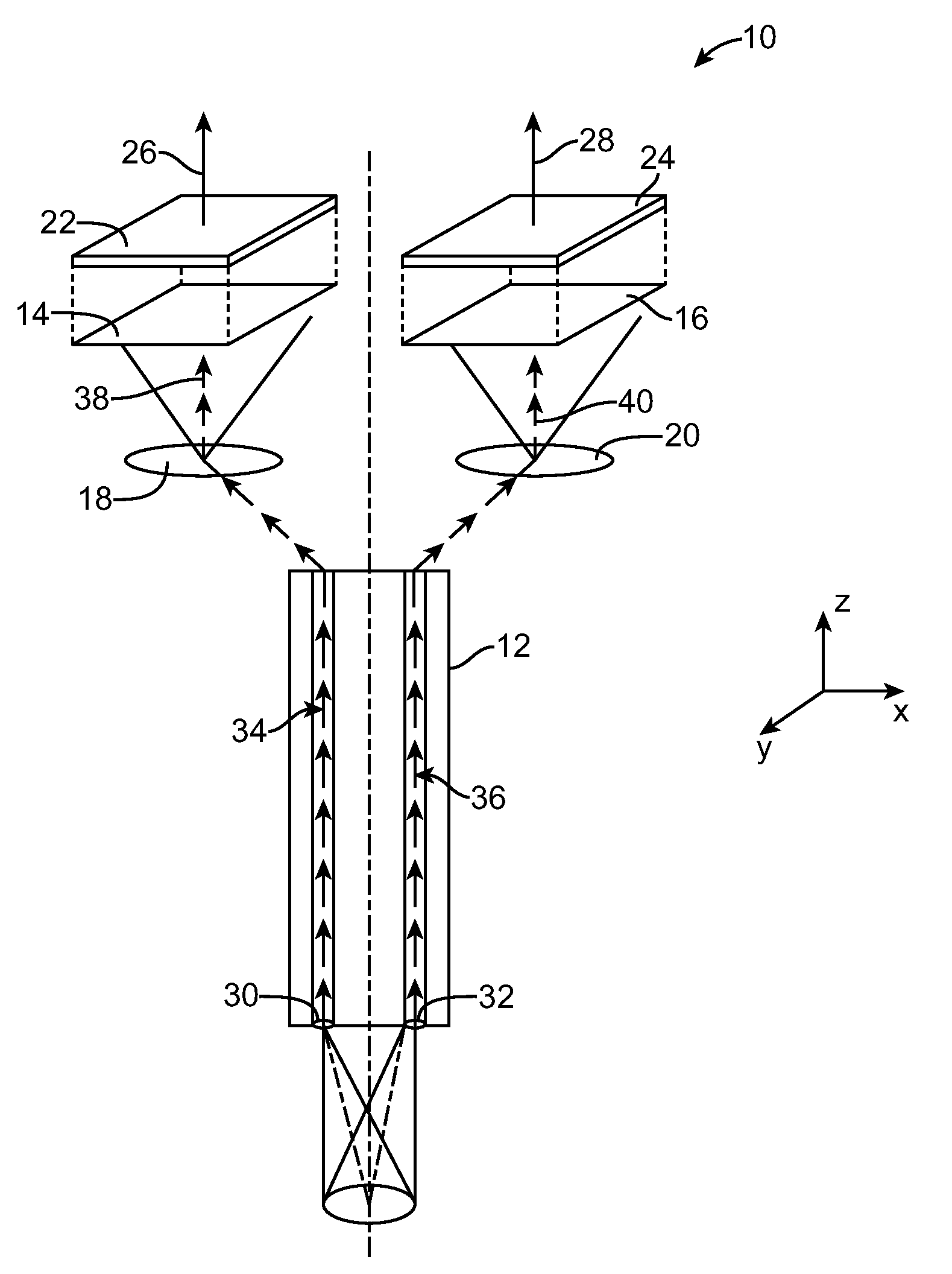
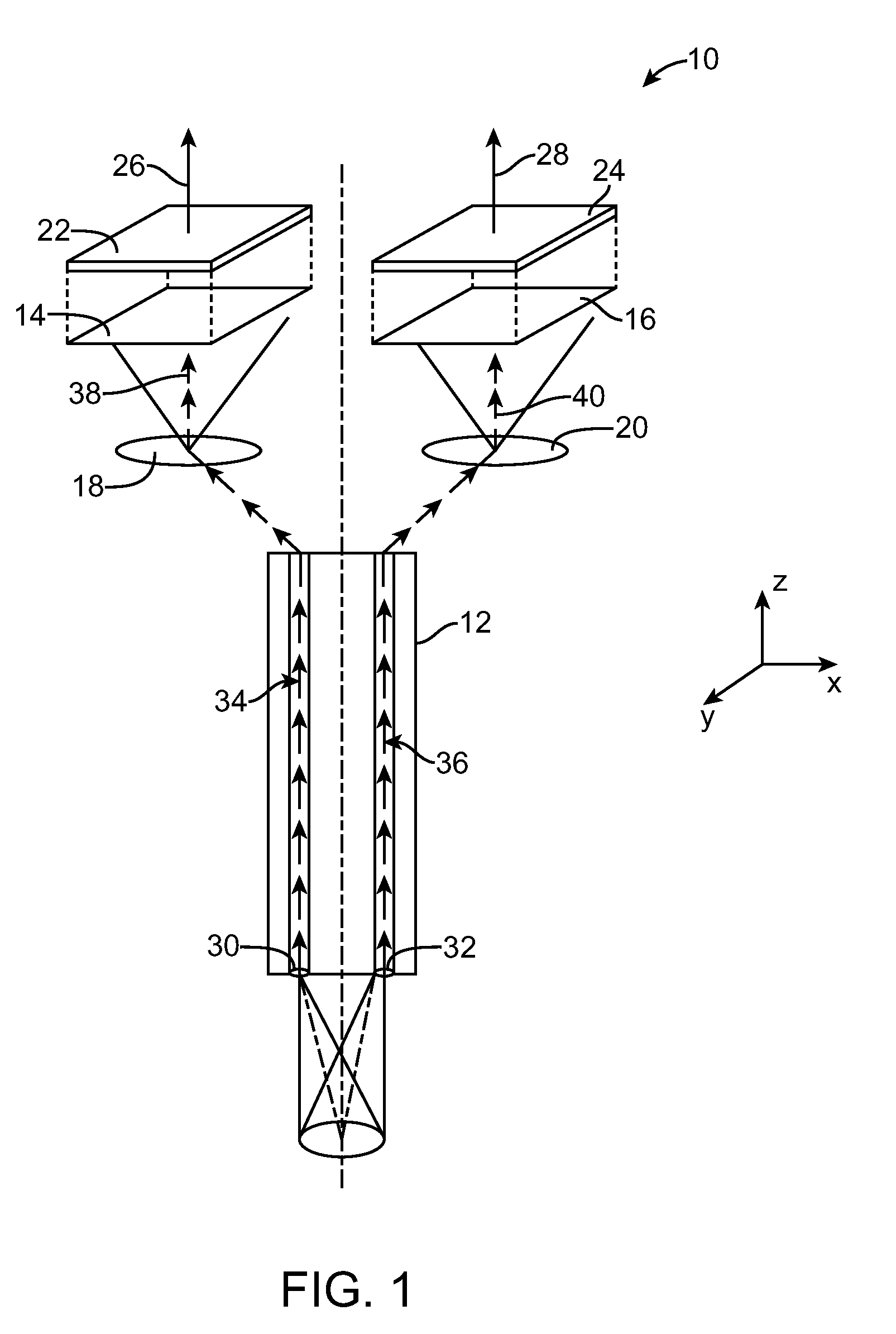
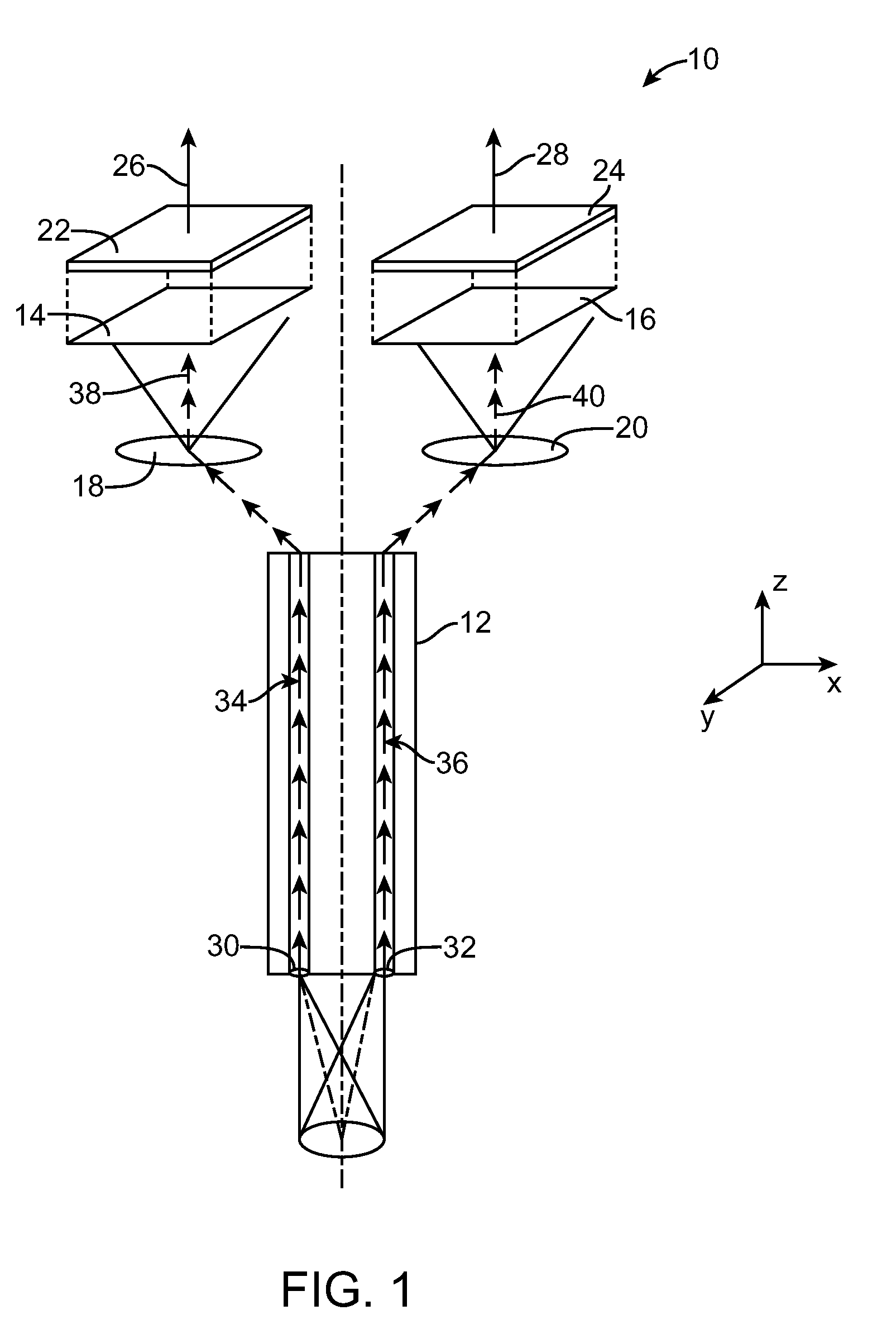
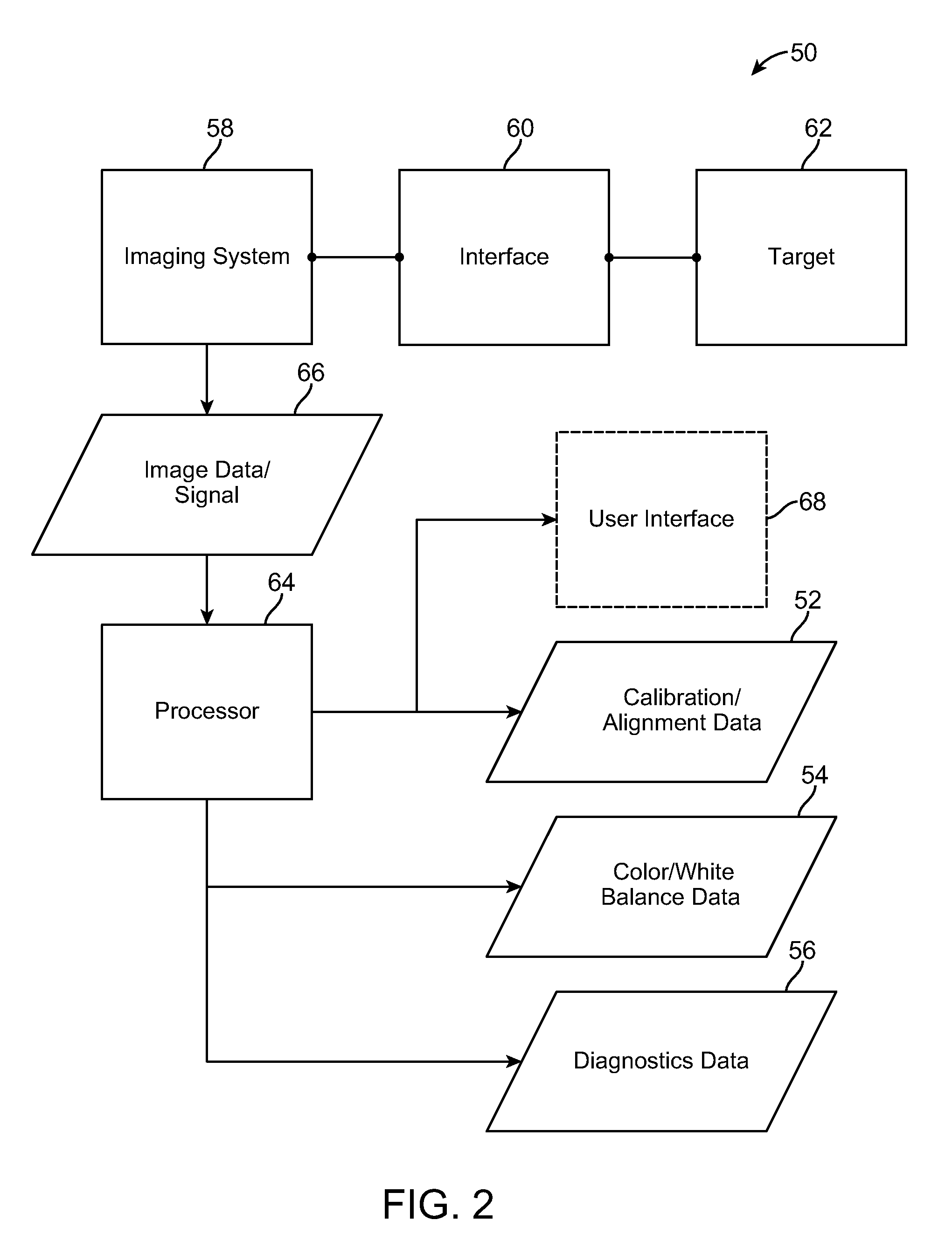
Targets, fixtures, and workflows for calibrating an endoscopic camera
ActiveUS20100245541A1Reduce laborReduce the amount of timeImage enhancementRecording apparatusEndoscopic cameraEndoscope
The present disclosure relates to calibration assemblies and methods for use with an imaging system, such as an endoscopic imaging system. A calibration assembly includes: an interface for constraining engagement with an endoscopic imaging system; a target coupled with the interface so as to be within the field of view of the imaging system, the target including multiple of markers having calibration features that include identification features; and a processor configured to identify from first and second images obtained at first and second relative spatial arrangements between the imaging system and the target, respectively, at least some of the markers from the identification features, and using the identified markers and calibration feature positions within the images to generate calibration data.
Owner:INTUITIVE SURGICAL OPERATIONS INC
Polishing pads and methods relating thereto
InactiveUS6217434B1Improve the level ofLow levelRevolution surface grinding machinesOther chemical processesTopographySemiconductor
This invention describes improved polishing pads useful in the manufacture of semiconductor devices or the like. The pads of the present invention have an advantageous hydrophilic polishing material and have an innovative surface topography and texture which generally improves predictability and polishing performance.
Owner:ROHM & HAAS ELECTRONICS MATERIALS CMP HLDG INC
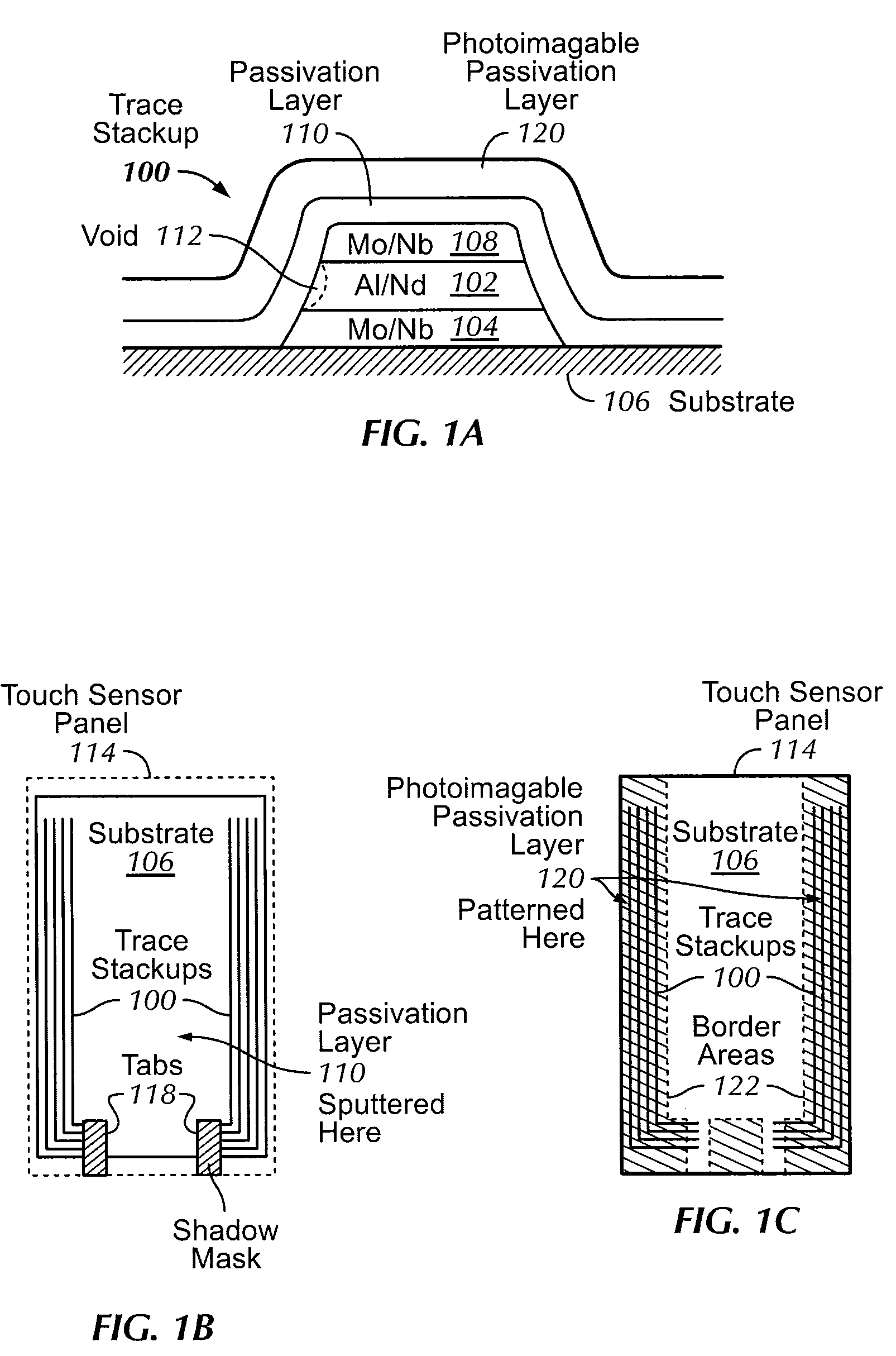
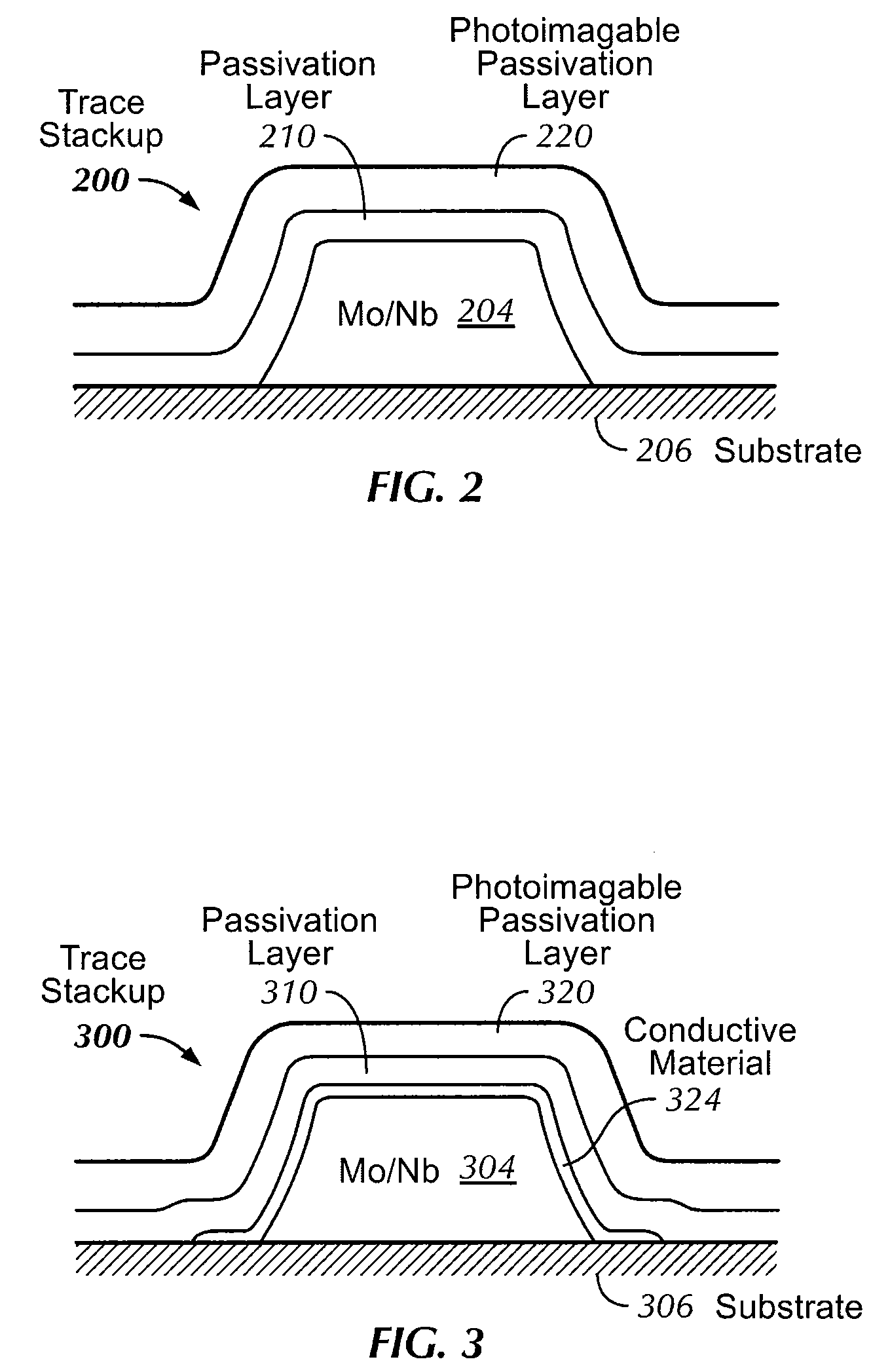
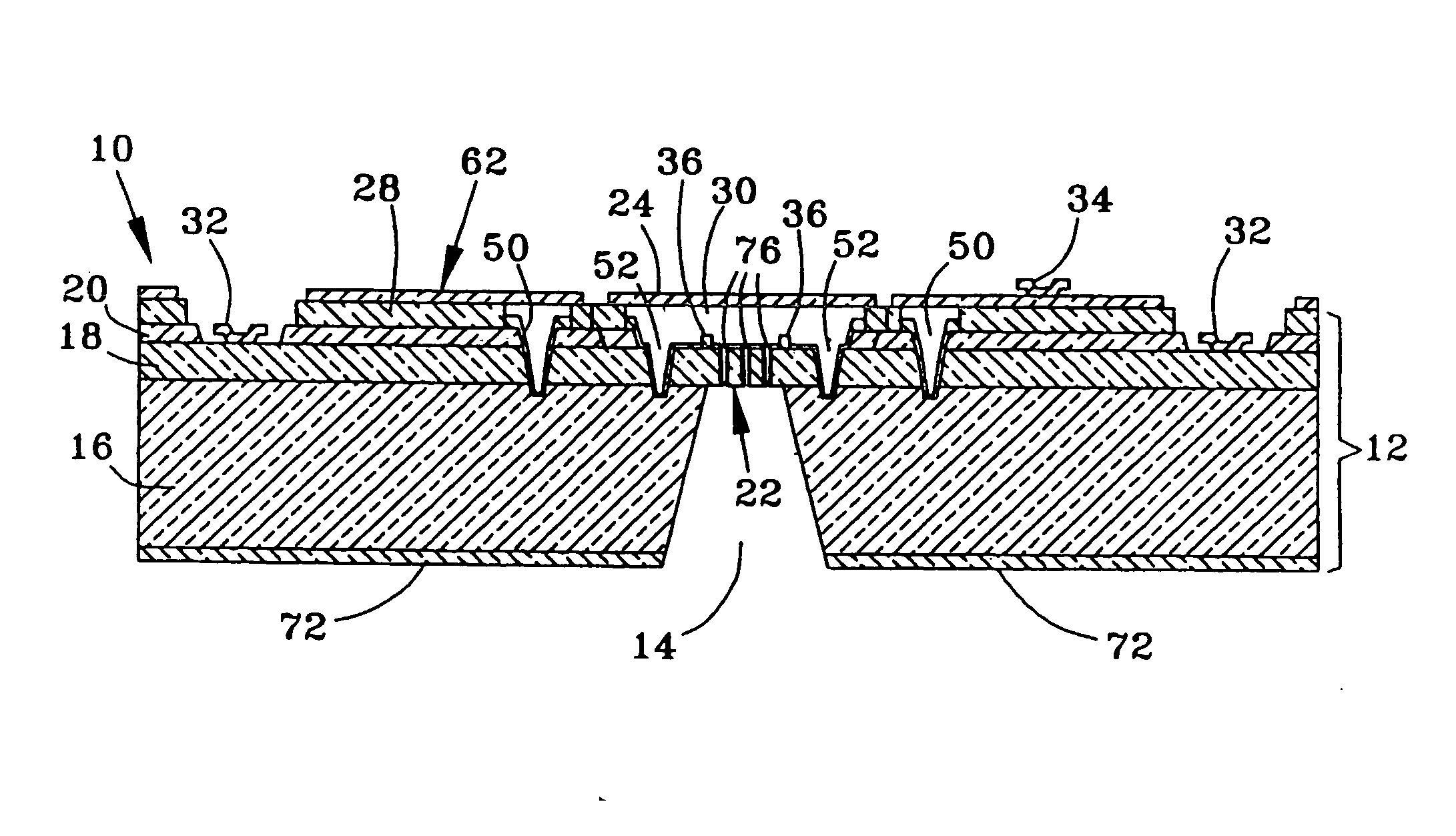
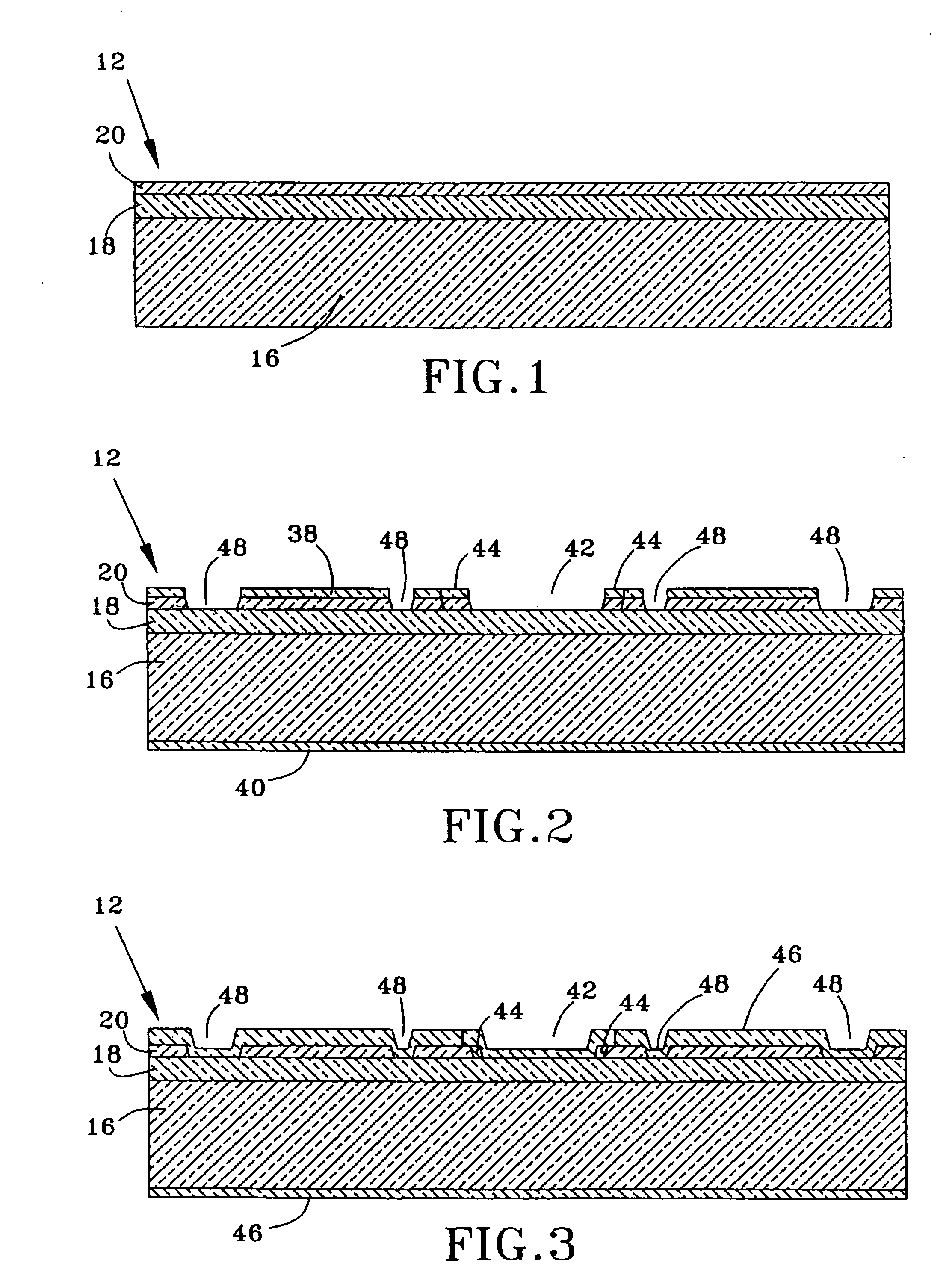
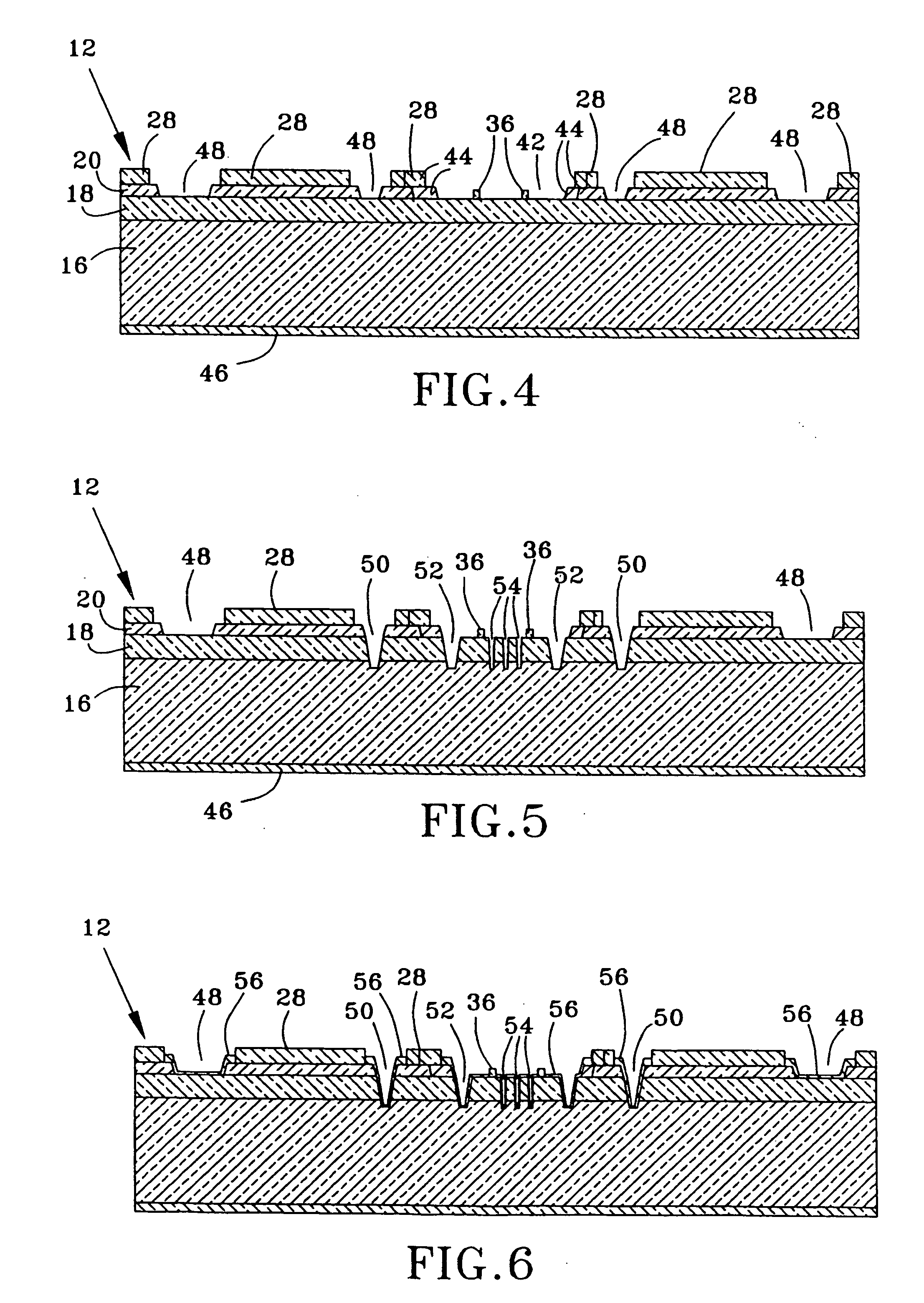
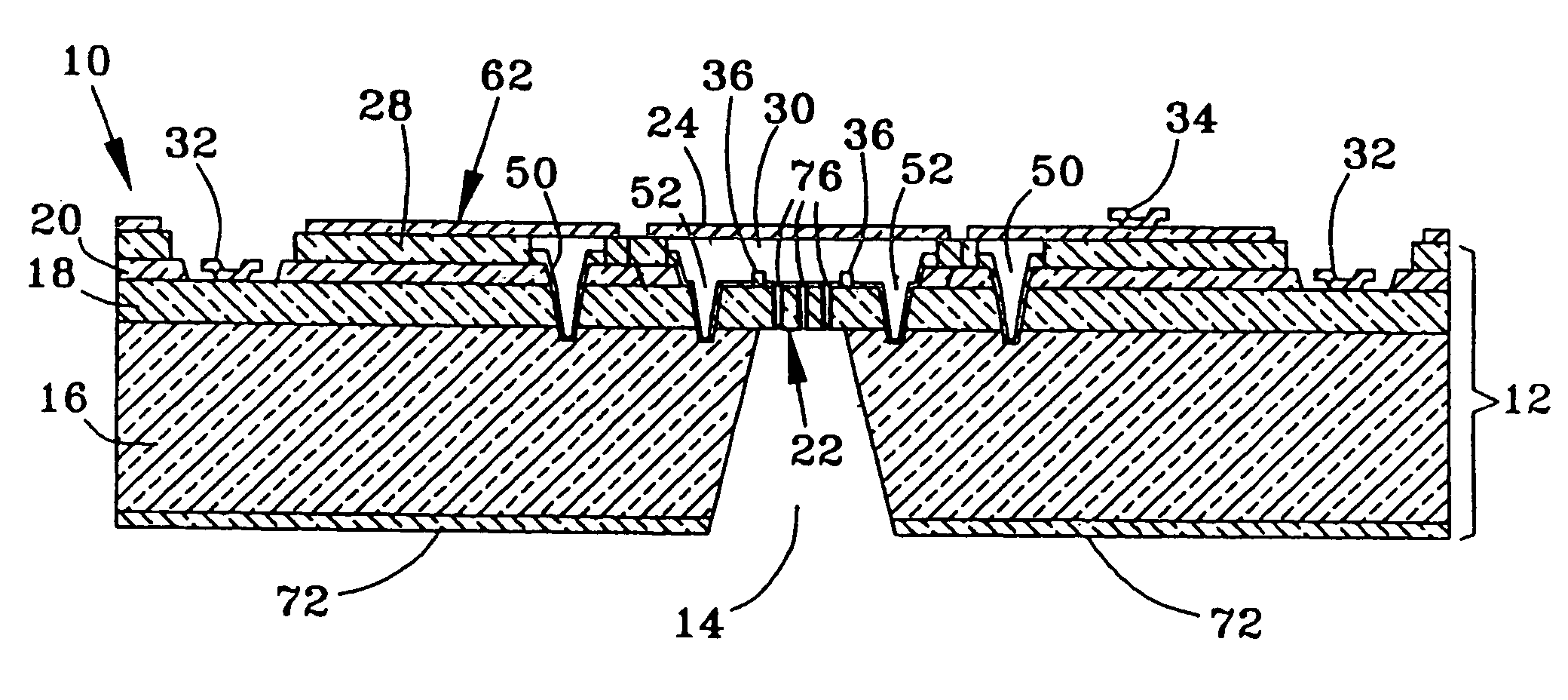
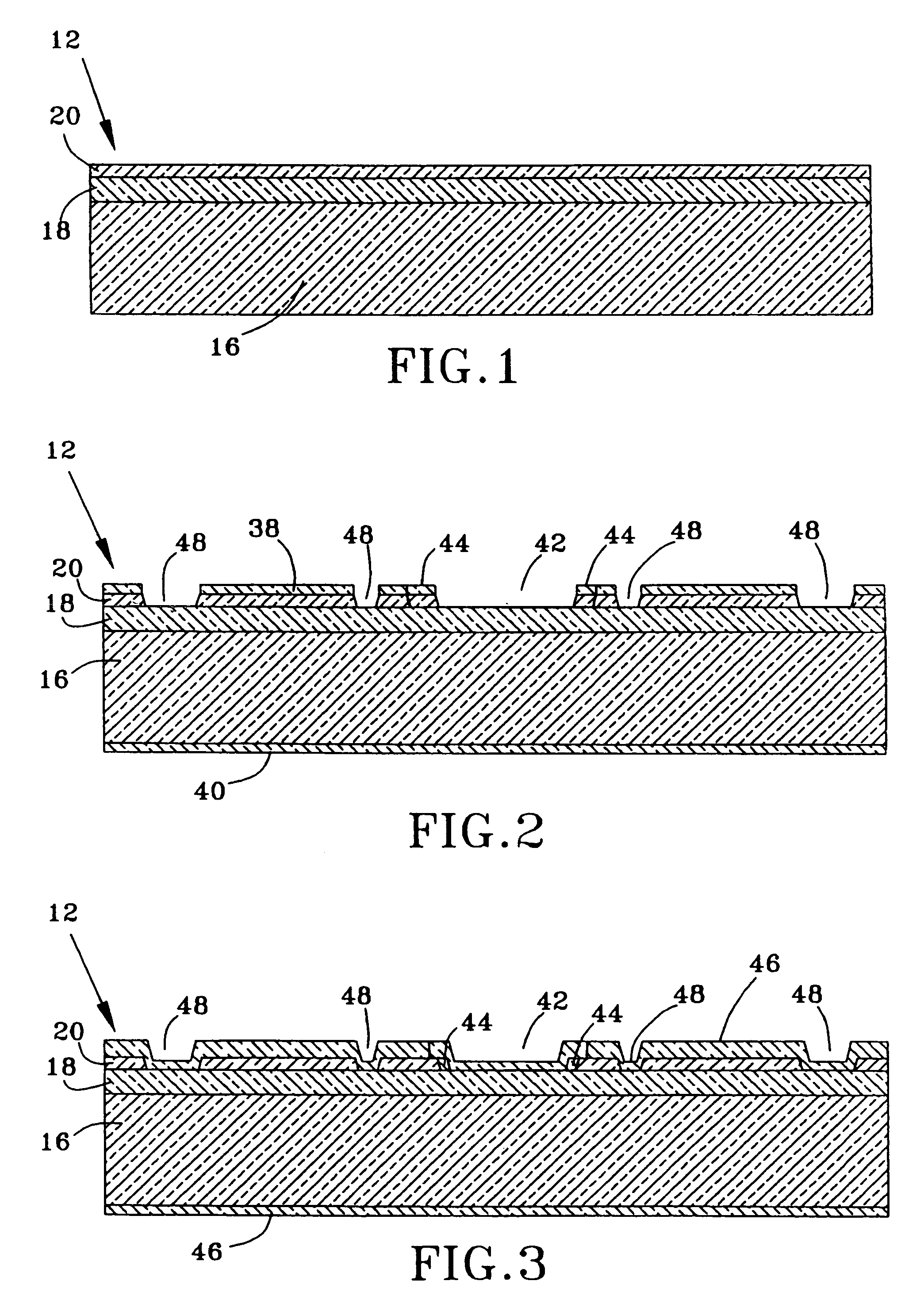
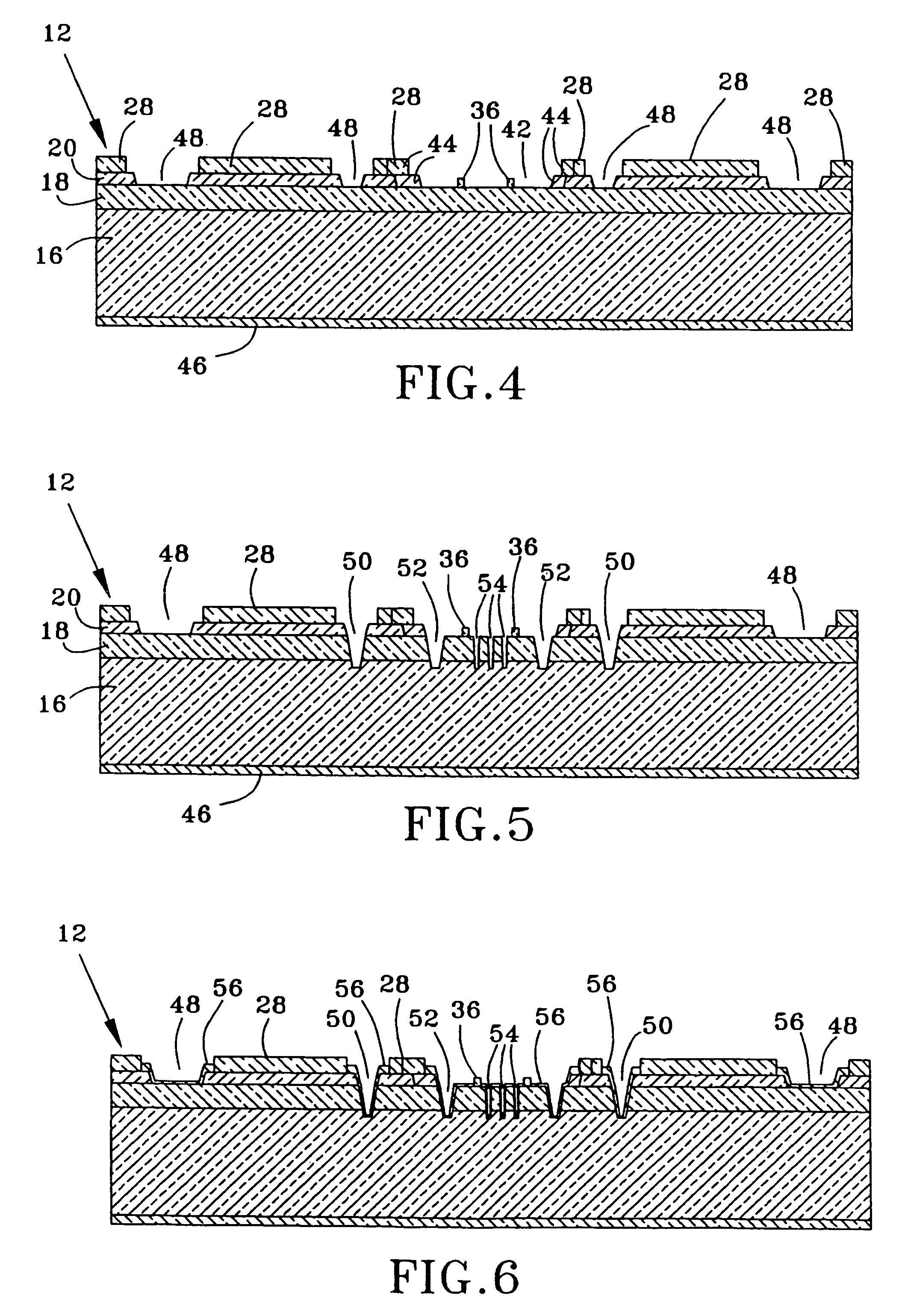
Reliability Metal Traces
ActiveUS20090266621A1Less proneFine toleranceTransmission systemsSemiconductor/solid-state device manufacturingEnvironmental effectEngineering
The formation of improved reliability conductive traces in touch sensor panels that are less prone to failures due to environmental effects is disclosed. Conductive traces, which can be formed from a stackup of metal layers or a single metal layer, can be protected with an additional photoimageable passivation layer of a material such as an organic polymer. This photoimageable coating can be patterned so that it does not appear in the visible area of the touch sensor panel, with much finer tolerances than conventional passivation layers to help keep product dimensions to a minimum.
Owner:APPLE INC
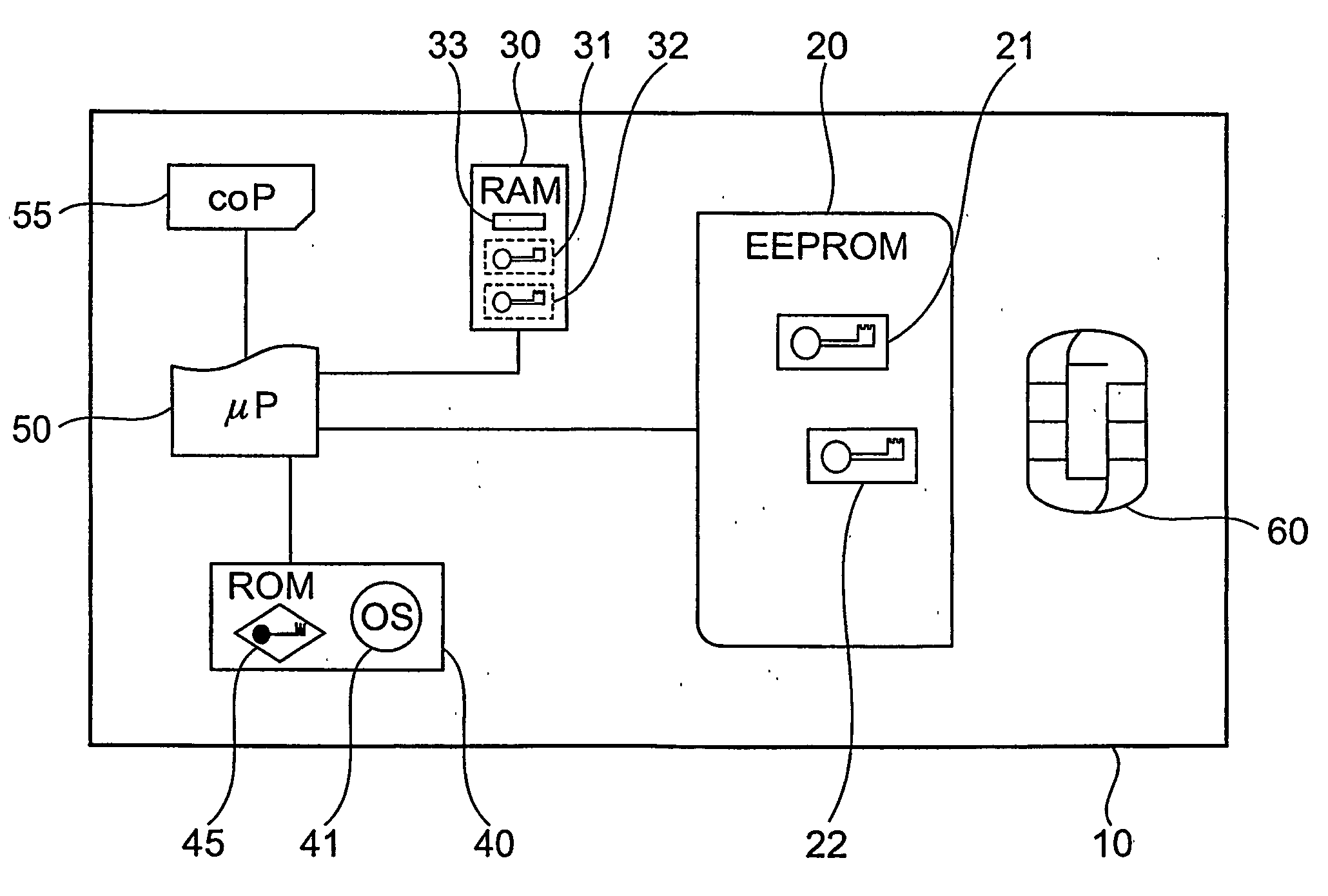
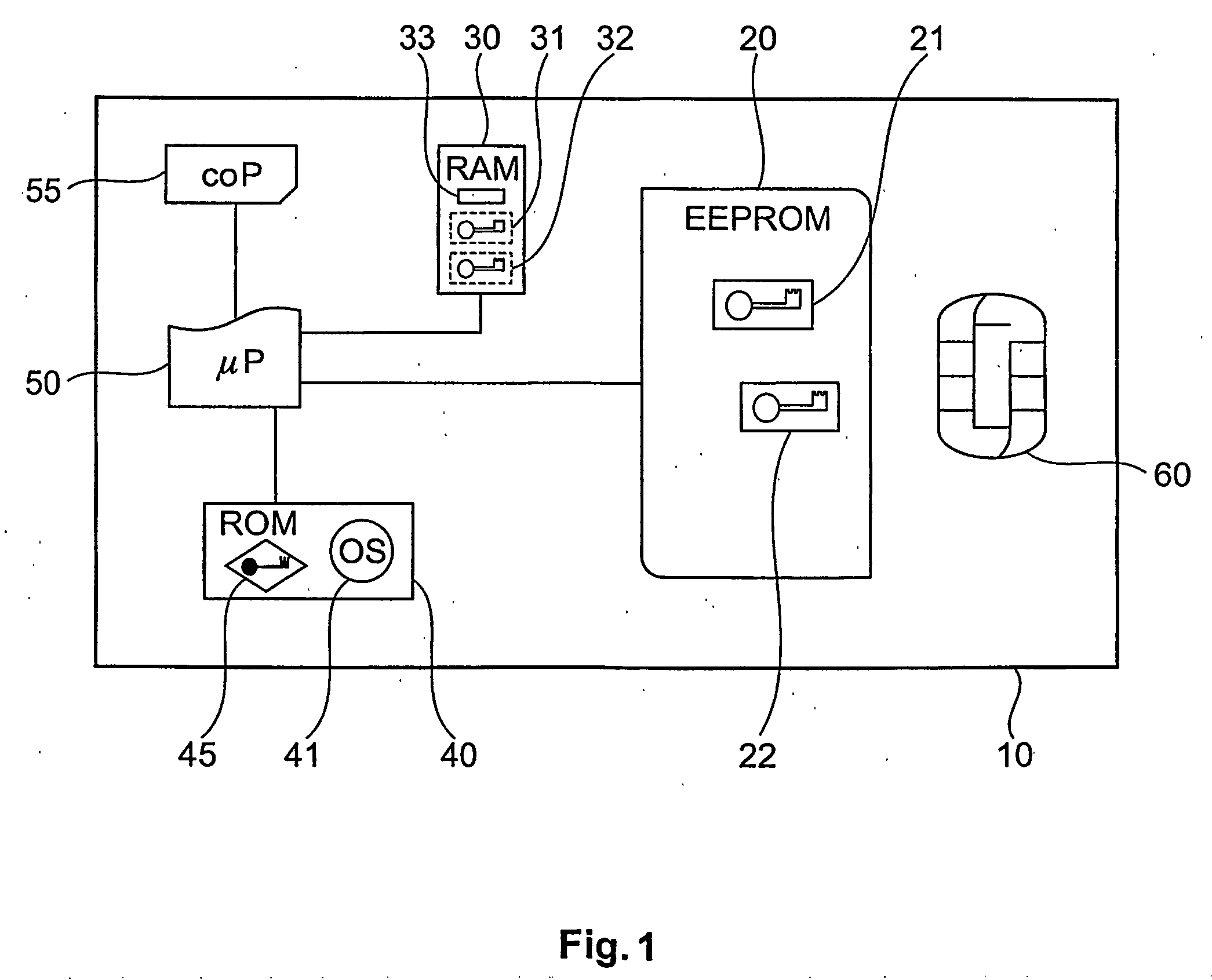
Device and method with reduced information leakage
InactiveUS20060090081A1Low level of information leakageLess-proneKey distribution for secure communicationDigital data processing detailsComputer hardwareData processing system
The invention is directed to a data-processing system comprising a processor and first encrypted information in a first persistent memory whose level of information leakage is higher than that of a second persistent memory. In the second persistent memory is stored a first cryptographic key for decrypting the first encrypted information, thereby generating therefrom first unencrypted information that is usable by the processor for executing an operation. The same cryptographic key may also be used for encrypting the first unencrypted information, thereby generating the first encrypted information. It is also directed to a method of processing such a data-processing system with an operating system, comprising a writing step for writing first unencrypted information into the first persistent memory, an encryption step for encrypting the first unencrypted information under use of the first cryptographic key, creating therefrom first encrypted information in the first persistent memory, and an access-limitation step for setting the data-processing system to a state in which writing into the first persistent memory is controlled by the operating system. It also relates to a method of executing an operation on such a data-processing system comprising a decryption step for decrypting the first encrypted information under use of the first cryptographic key, thereby generating therefrom first unencrypted information and an execution step for executing an operation by the processor, using the first unencrypted information.
Owner:IBM CORP
Longitudinally activated compression sealing device for elongate members and methods for using the same
ActiveUS6875926B2Reduce compressionMore reliableFlexible elementsFibre mechanical structuresEngineeringLateral expansion
A compression-expandable plug provides lateral expansion of an elastomeric gasket to seal around mini-tubes within an optical fiber duct, the mini-tubes containing optical fibers. The compression-expandable plug includes an elastomeric gasket having longitudinal passages configured to be positioned around optical-fiber-containing mini-tubes in an optical fiber duct and means for longitudinally compressing the gasket thereby laterally expanding it to exert sealing pressure around the mini-tubes and between the mini-tubes and the duct. A means for limiting the longitudinal compression applied to the gasket to limit the sealing pressure to a level selected to limit damage to the optical fibers may be provided.
Owner:COMMSCOPE CONNECTIVITY BELGIUM BVBA
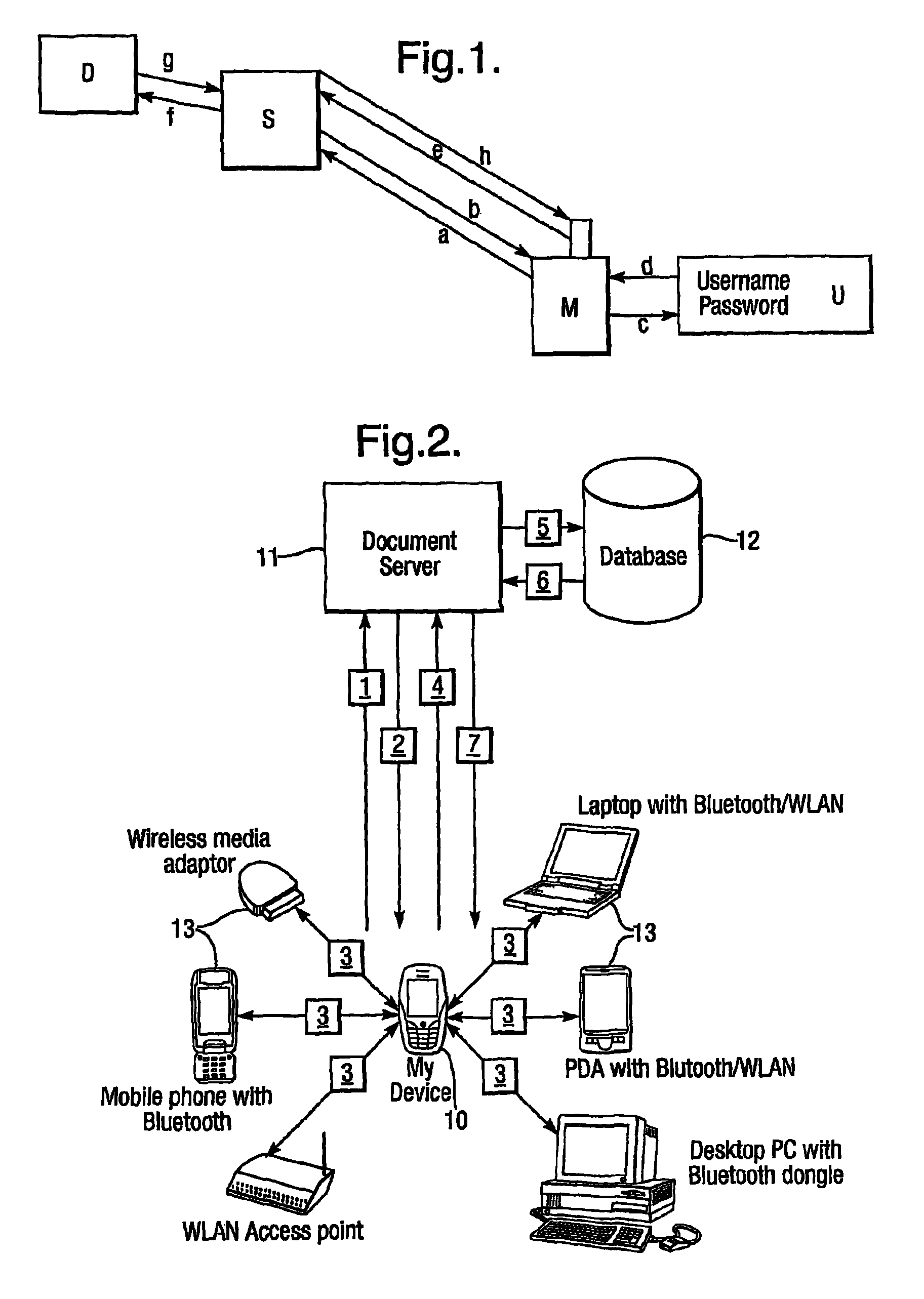
Location based authentication
ActiveUS8321913B2Less-proneMore useableDigital data processing detailsNetwork topologiesUser devicePosition dependent
The present invention relates to authenticating a mobile device using logical location information associated with the device which provides an indication of the proximity of the device to other devices. The present invention provides a mechanism for authenticating a mobile device based on location related information or a “logical location”, but without requiring an actual location. The mobile user device identifies or discovers other devices, using direct wireless communication, within its vicinity and forwards this information to the authenticating authority. If this information matches previous or otherwise predetermined information, then the device is authenticated.
Owner:BRITISH TELECOMM PLC
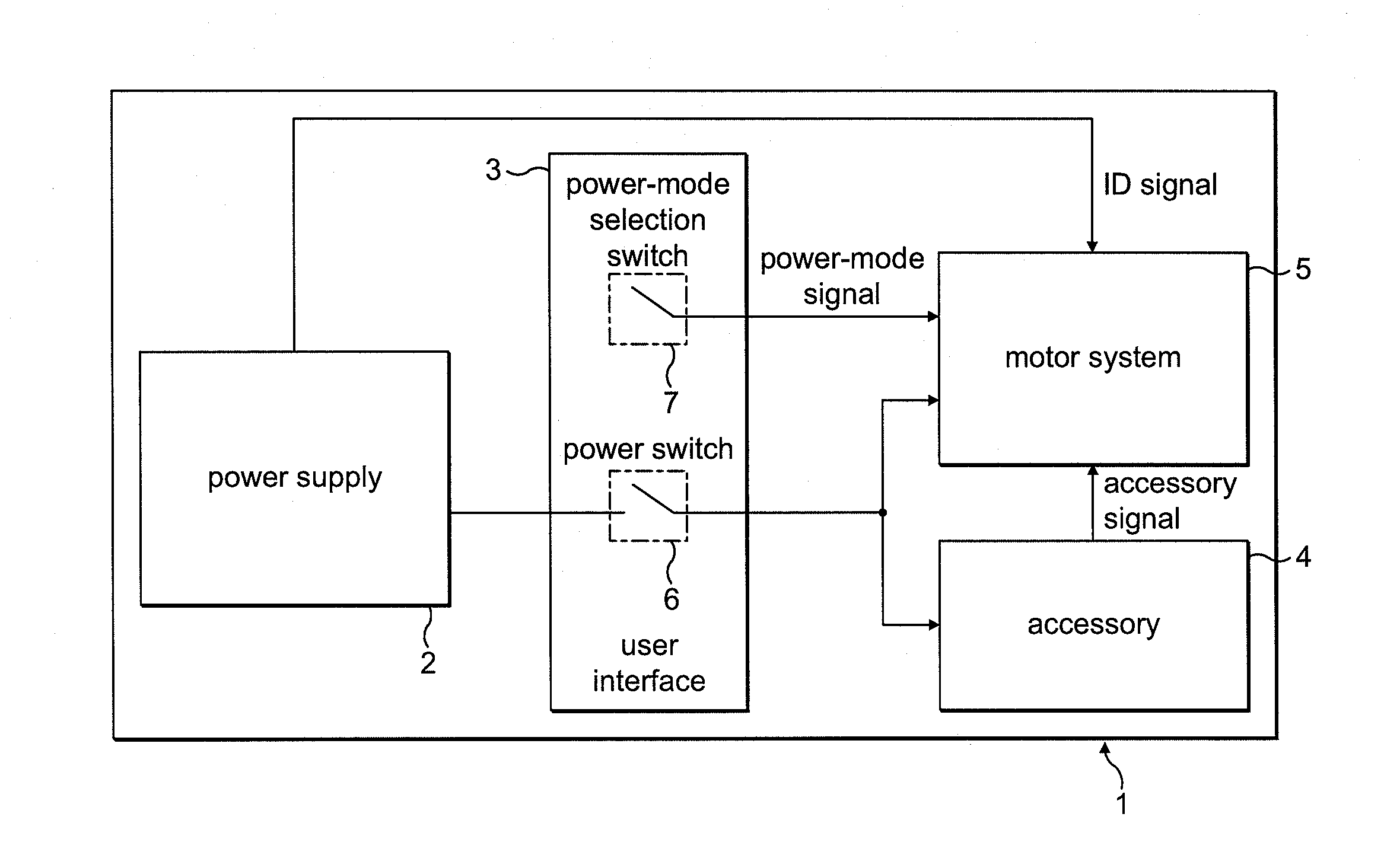
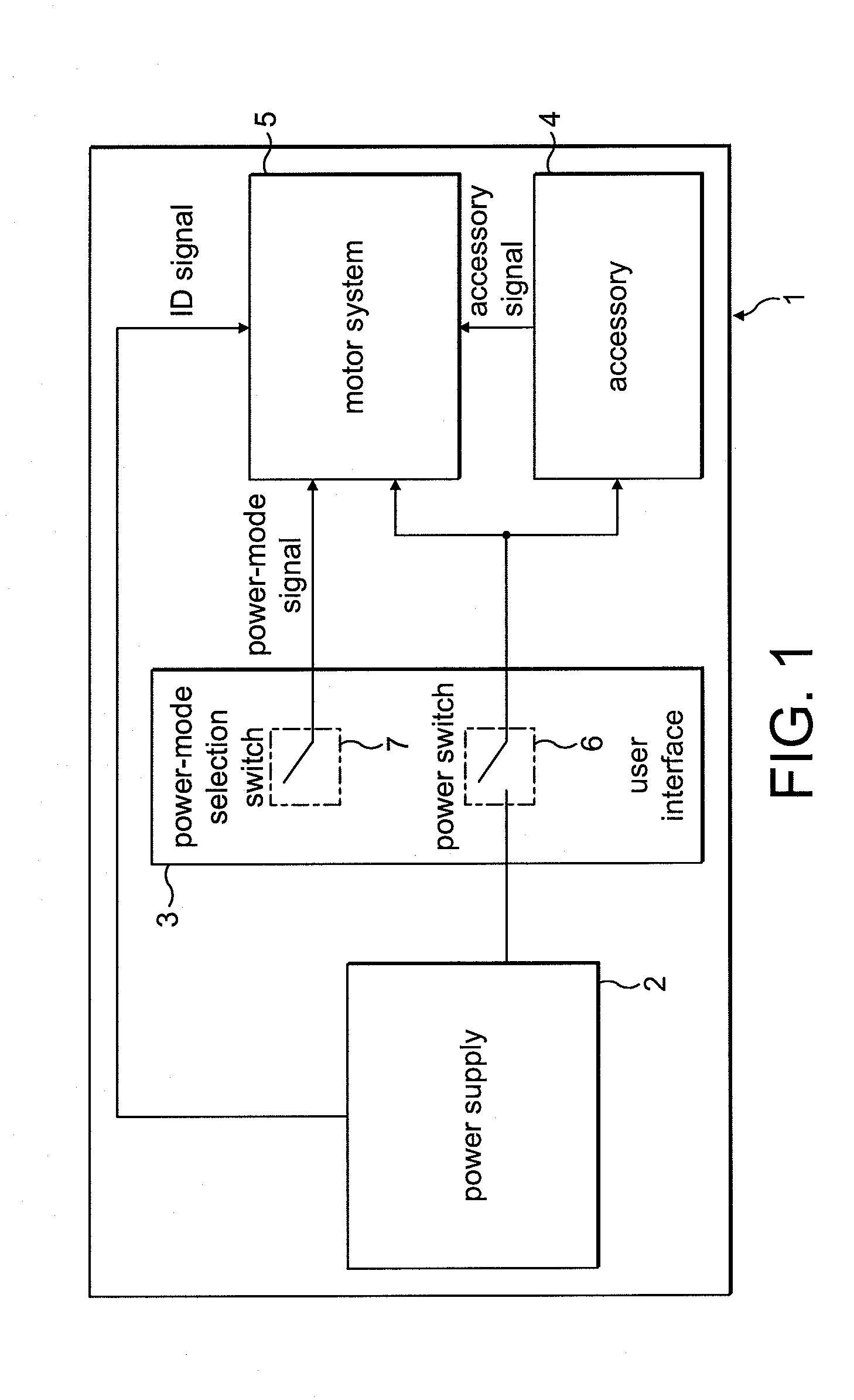
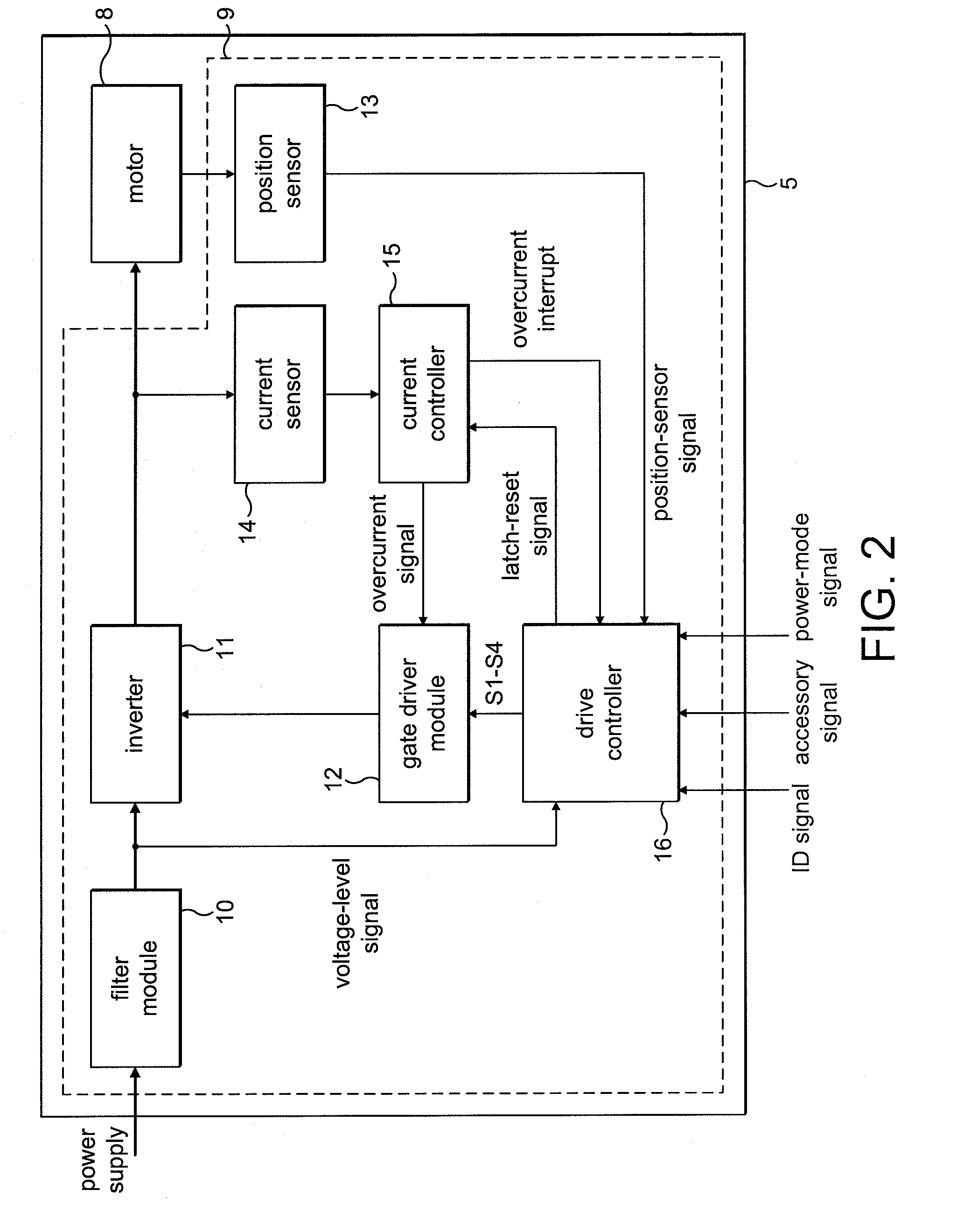
Control system for an electric machine
InactiveUS20100256782A1High speed rangeImprove electrical performanceAC motor controlElectric controllersControl systemElectric machine
A control system for an electric machine, the control system including a position sensor and a drive controller. The drive controller generates one or more control signals for exciting a winding of the electric machine in response to edges of a signal output by the position sensor. Moreover, the drive controller generates control signals in response to an edge that occurs within a time window. The time window starts at a time when control signals are generated and has a length less than the electrical half-cycle period.
Owner:DYSON TECH LTD
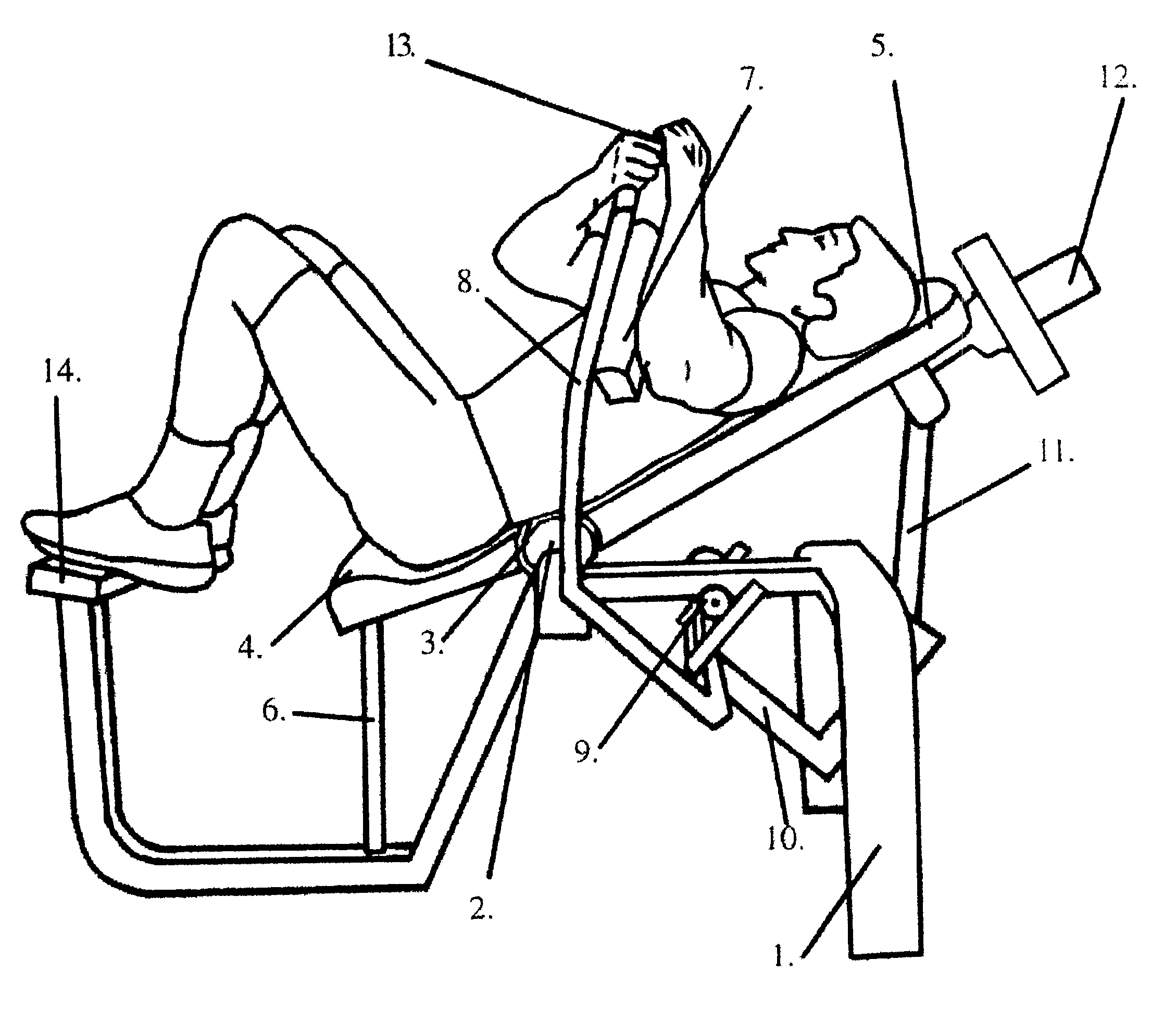
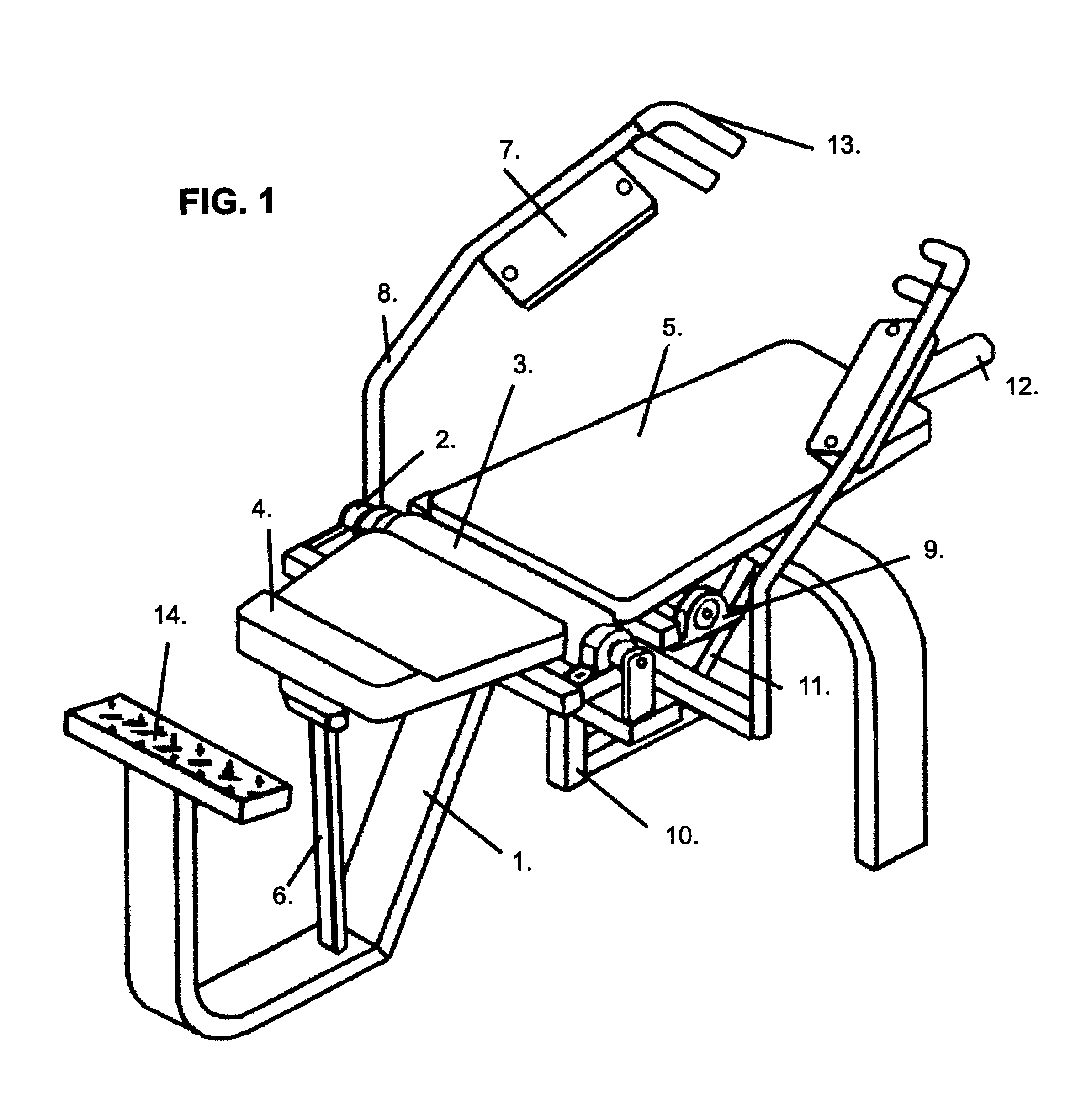
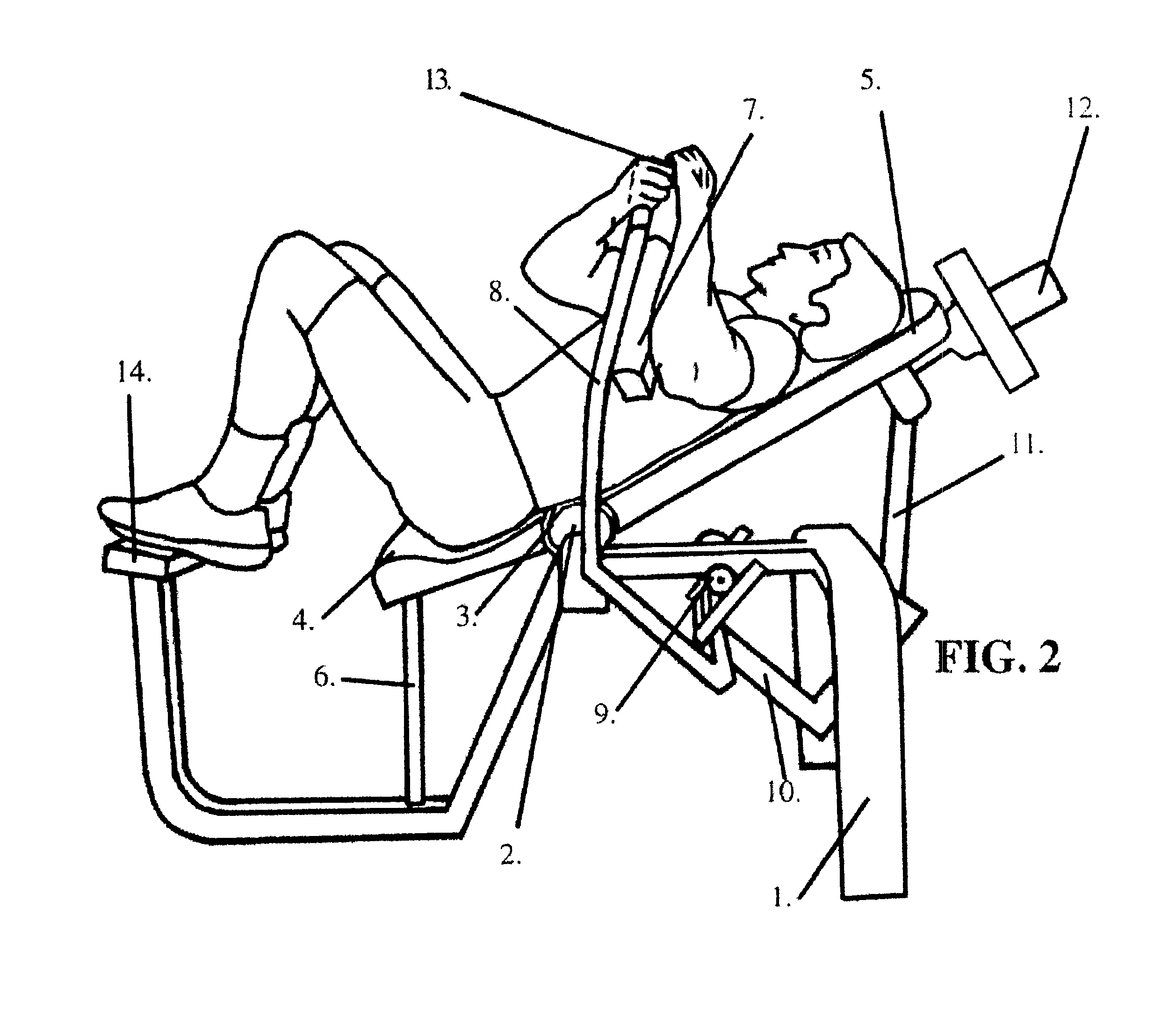
Abdominal weight lifting apparatus and method
InactiveUS6475123B1Need can be providedNo excess bendingLayered productsStiltsPhysical exerciseLumbar
A method and apparatus for exercising the abdominal muscles where the exerciser is laying on his backside and the exercisers middle and upper spine as well as head are dynamically supported when exercising. The exercise is accomplished as the upper-torso support moves forward and upward, then rearward and downward through exertion of the abdominal muscles. The lumbar-end of the upper-torso support is secured to a pivot-point. This axis is directly supporting the center of the lumbar region. Resistance is provided by weight plates mounted on the head-end of the support for the upper-torso. The upper-torso support at the head-end is connecting to a lever. The lever is connected to handles and resistance pads engageable by the exerciser's hands and forearms respectively. The upper-torso support and the exerciser's upper-torso move forwardly and upwardly to perform positive work and rearwardly and downwardly to perform negative work. Respectively, the handles and resistance pads move forward and toward the exercisers lower-body during positive work and rearward and away from the exercisers lower-body during negative work.
Owner:EVANS LAYNE W
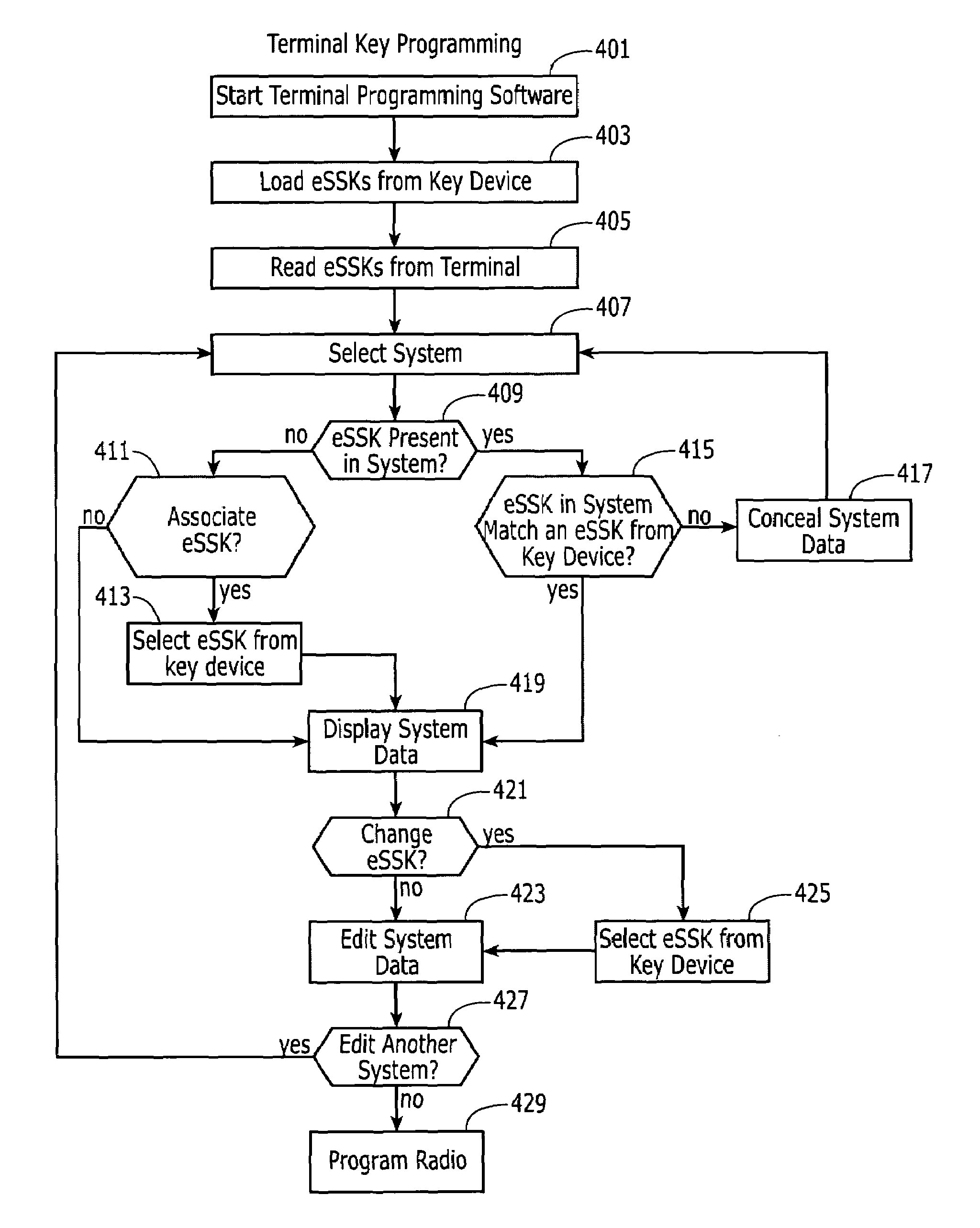
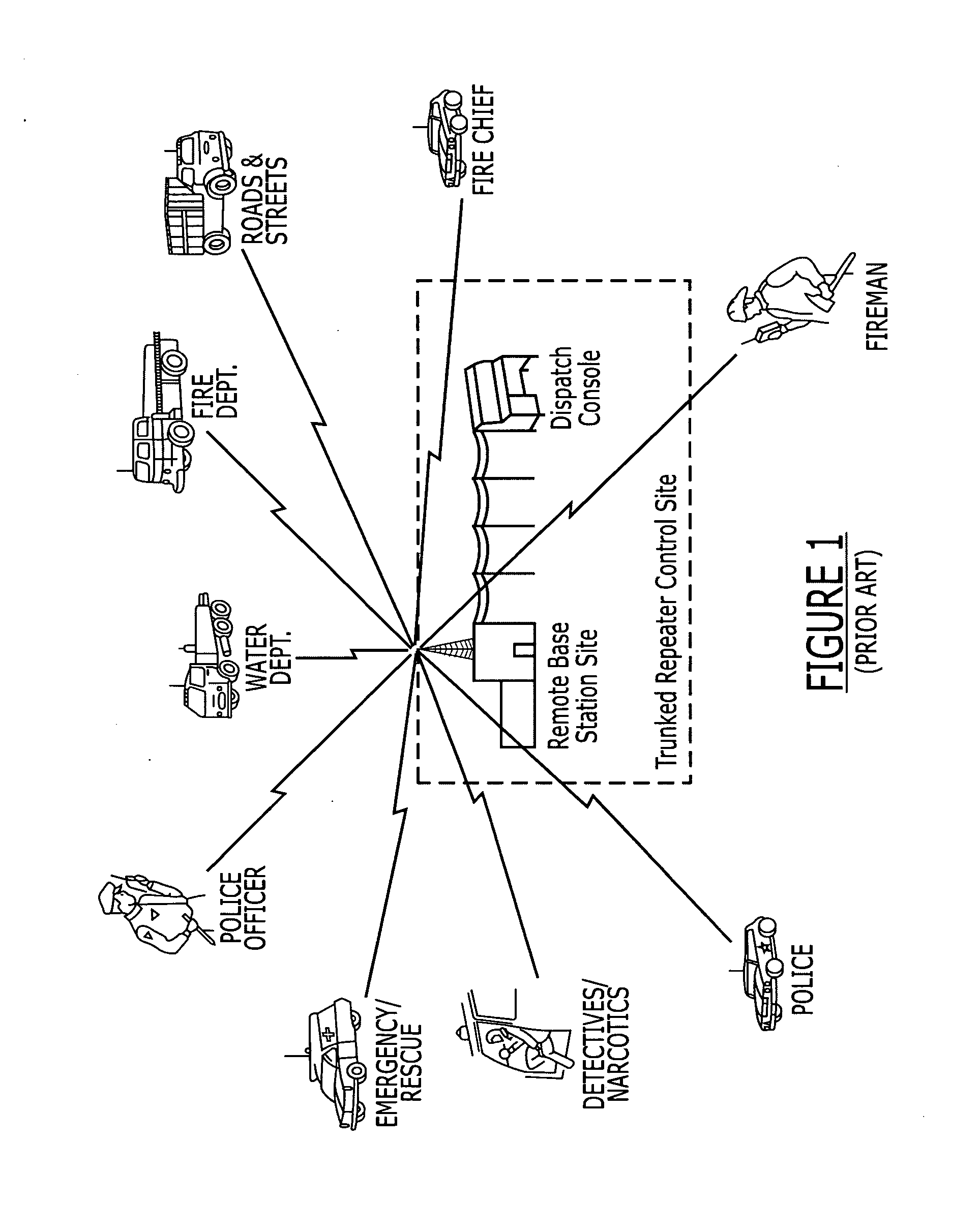
Secure transmission system for a digital trunked radio system
ActiveUS7203318B2Improve securitySimplify the encryption processKey distribution for secure communicationSynchronising transmission/receiving encryption devicesTrunked radio systemControl signal
A security system for a digital trunked radio system having a digital control channel and a plurality of working channels, wherein said working channels are assigned for temporary use of individual radio units by digital control signals transmitted over said control channel, said control channel carrying digital control signals between a base site and said radio units, comprising a digital key, said key used to limit access to the system equipment and system control channel transmissions.
Owner:EAGLE TECH LLC
Targets, fixtures, and workflows for calibrating an endoscopic camera
ActiveUS8223193B2Reduce the amount requiredReduce laborRecording apparatusImage enhancementEndoscopic cameraEndoscope
The present disclosure relates to calibration assemblies and methods for use with an imaging system, such as an endoscopic imaging system. A calibration assembly includes: an interface for constraining engagement with an endoscopic imaging system; a target coupled with the interface so as to be within the field of view of the imaging system, the target including multiple of markers having calibration features that include identification features; and a processor configured to identify from first and second images obtained at first and second relative spatial arrangements between the imaging system and the target, respectively, at least some of the markers from the identification features, and using the identified markers and calibration feature positions within the images to generate calibration data.
Owner:INTUITIVE SURGICAL OPERATIONS INC
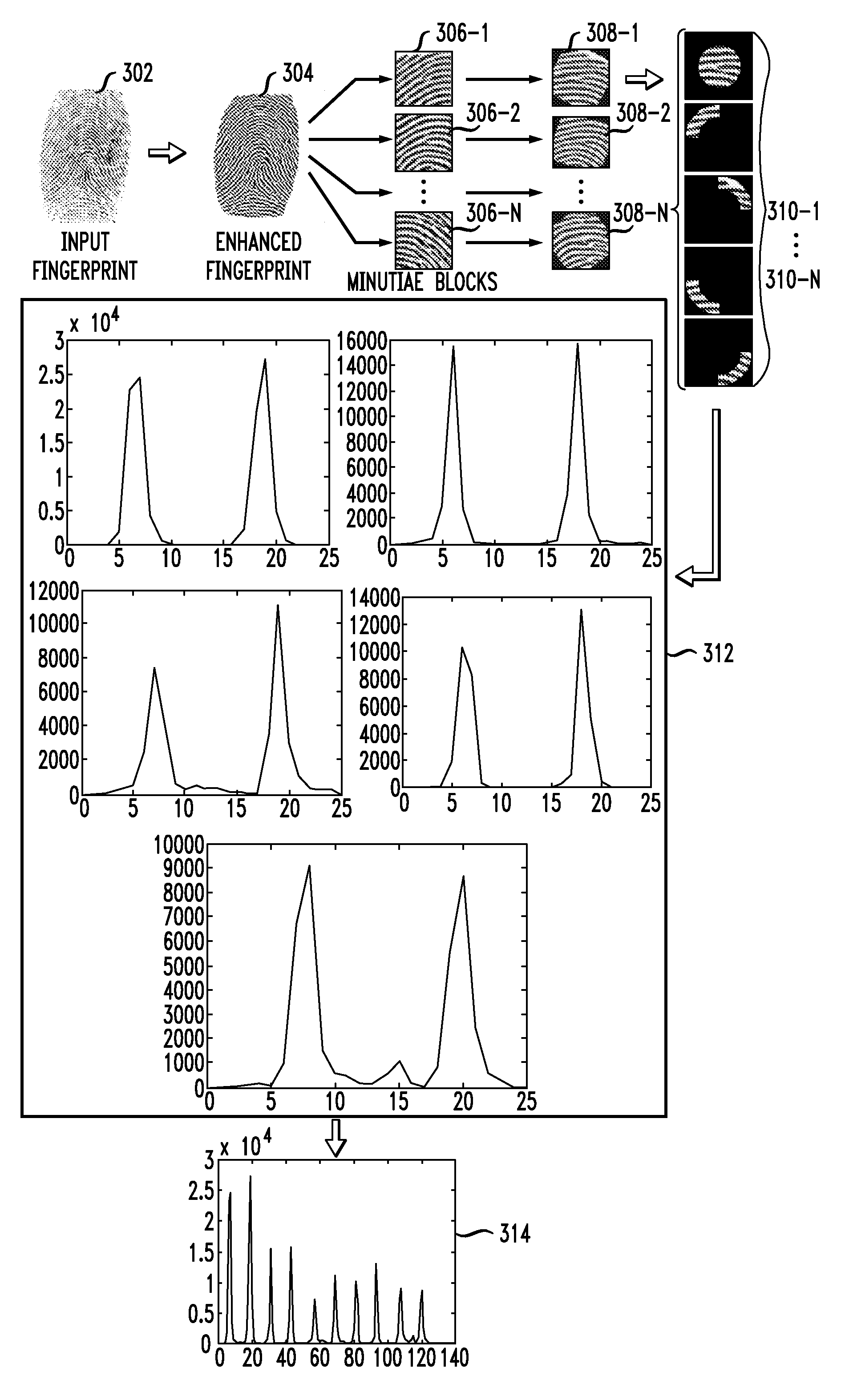
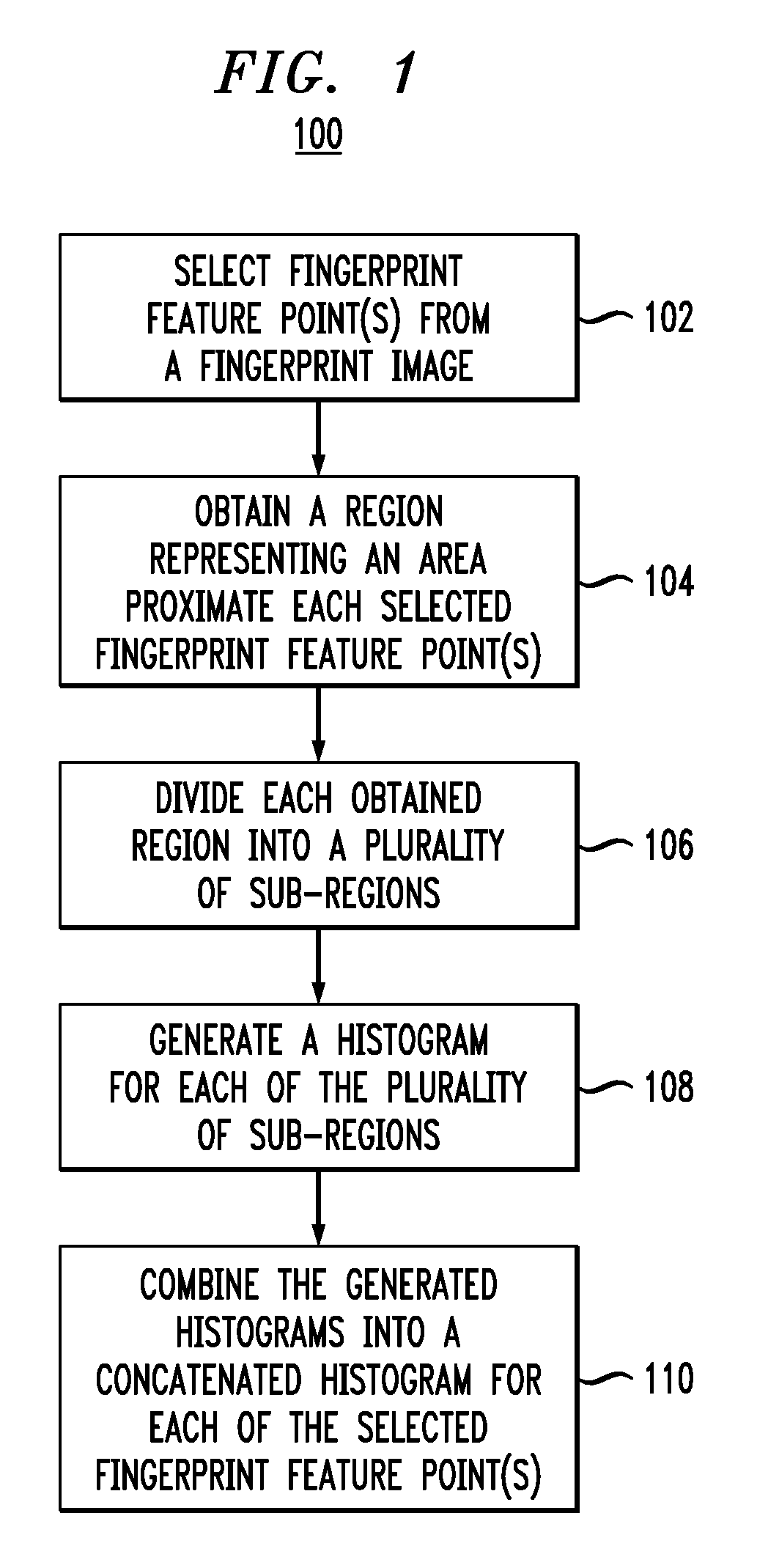
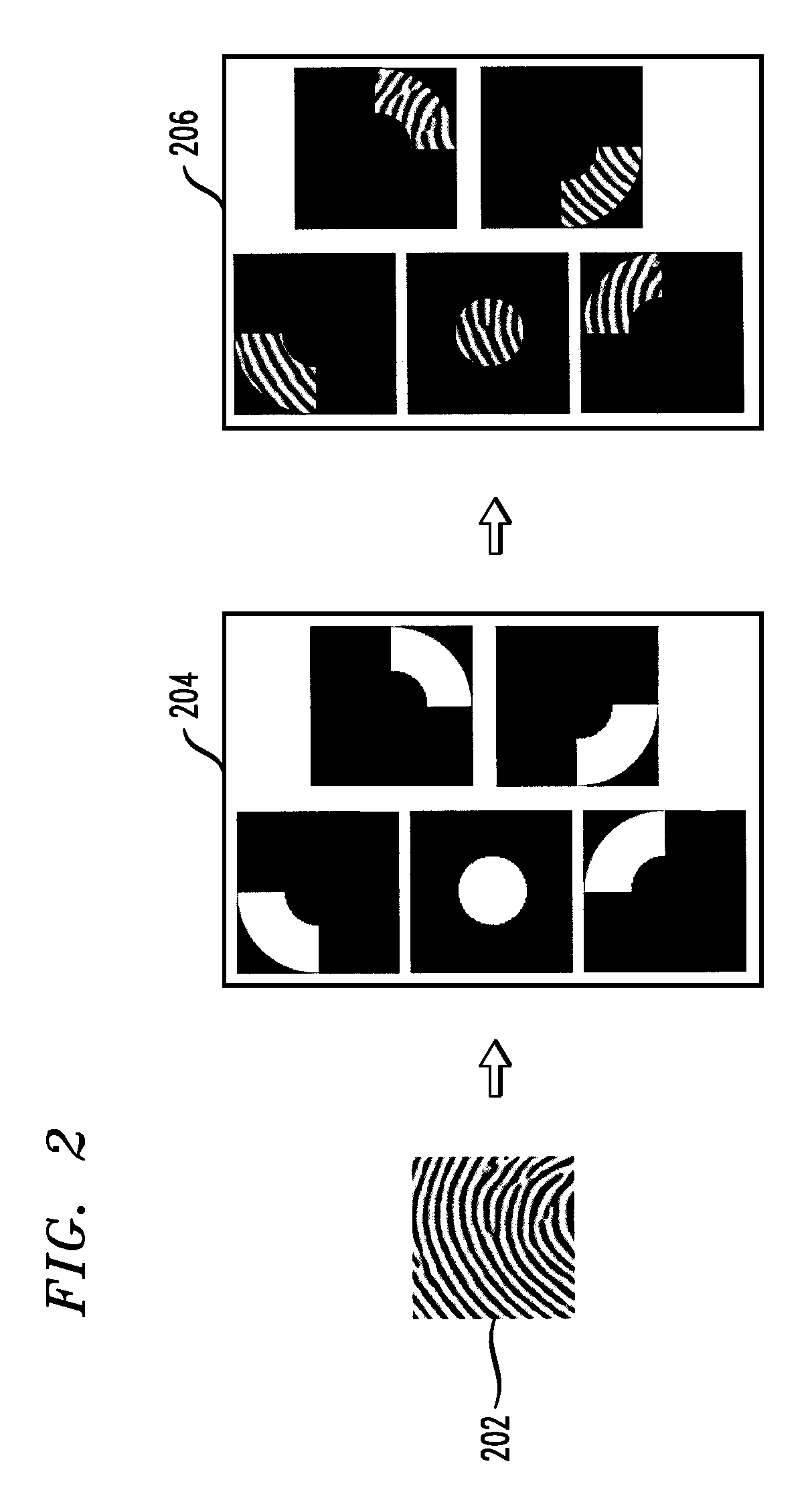
Fingerprint representation using gradient histograms
Techniques for generating a gradient characterization for a first fingerprint image are provided. One or more fingerprint feature points are selected from the first fingerprint image. A region is obtained for each of the one or more selected fingerprint feature points. The region is a representation of an area proximate a given fingerprint feature point. Each of the obtained regions is divided into a plurality of sub-regions. A histogram is generated for each of the plurality of sub-regions. For each of the one or more selected fingerprint feature points, the one or more generated histograms are combined into a concatenated histogram. The concatenated histogram is used for identification purposes.
Owner:IBM CORP
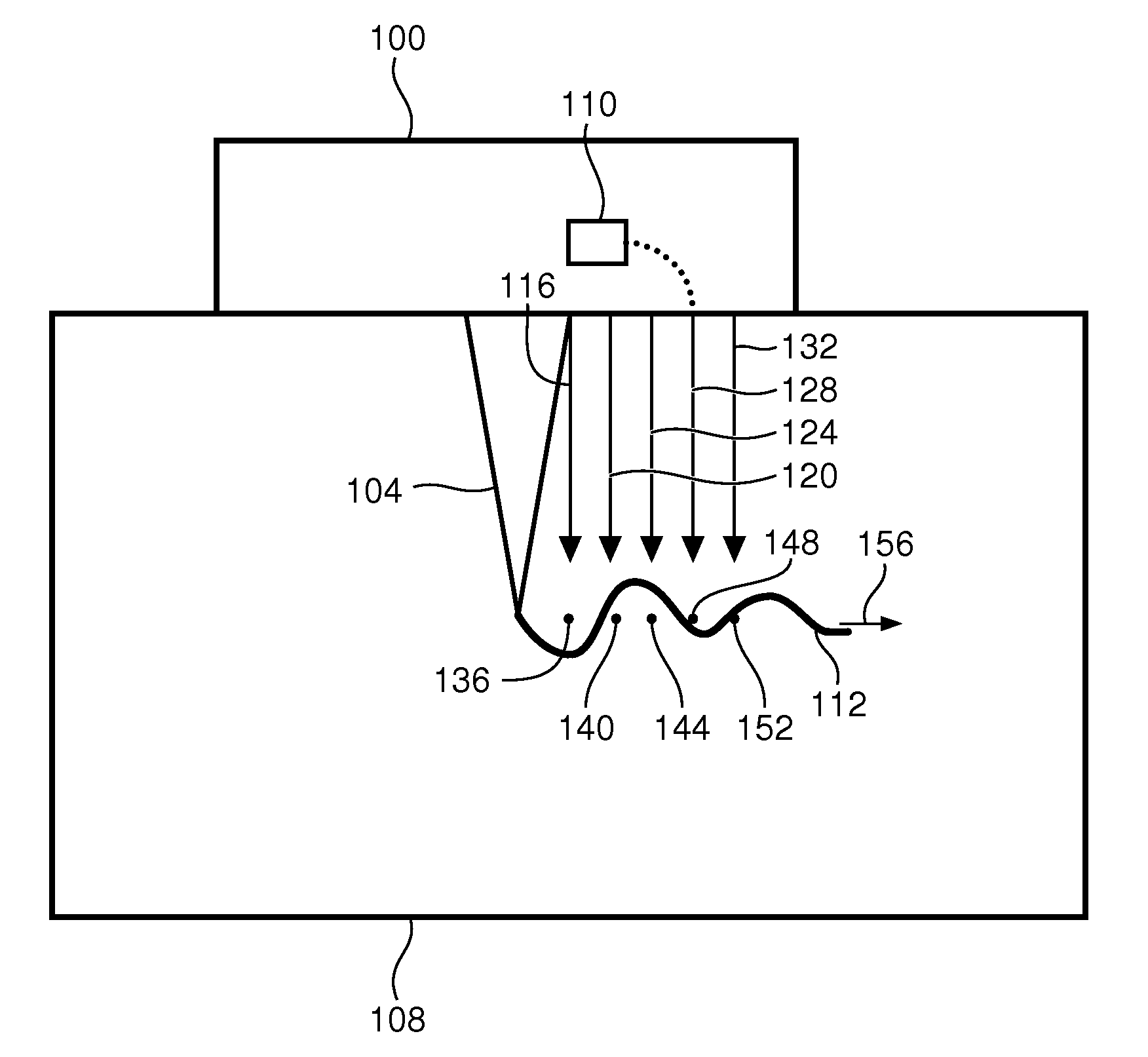
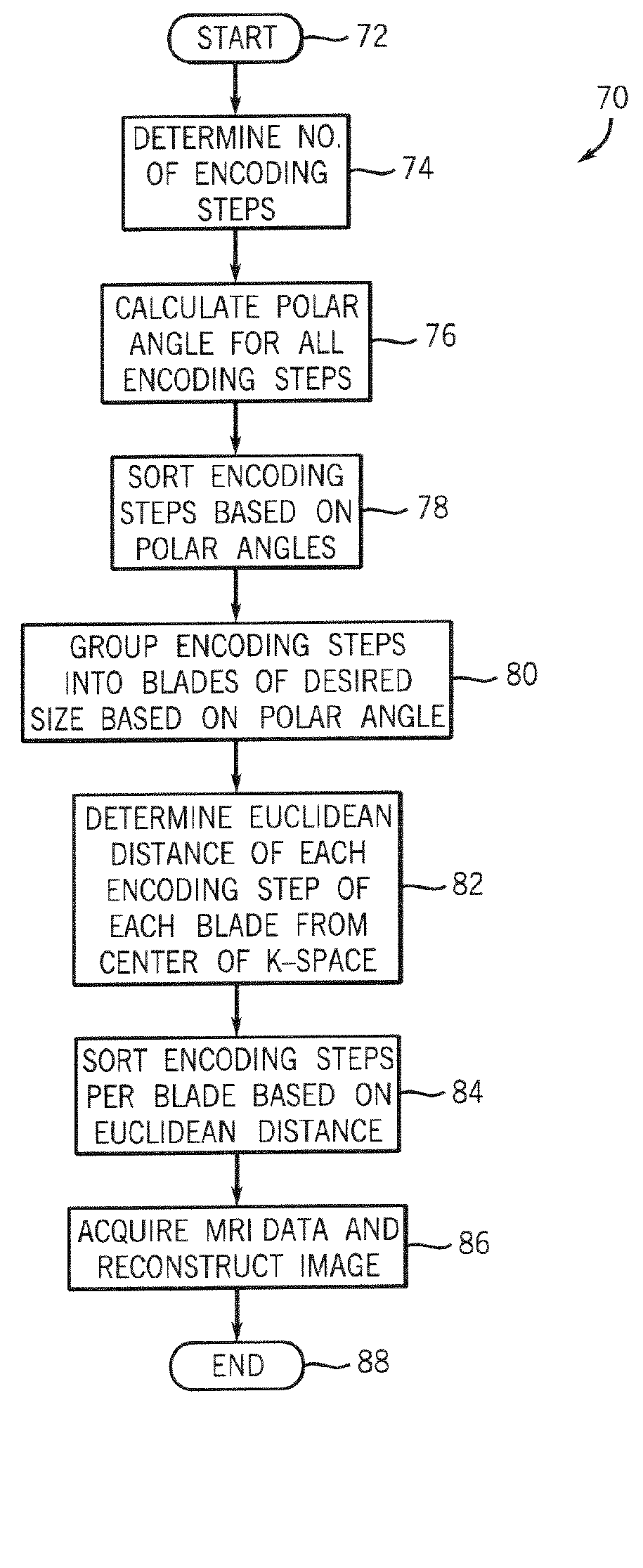
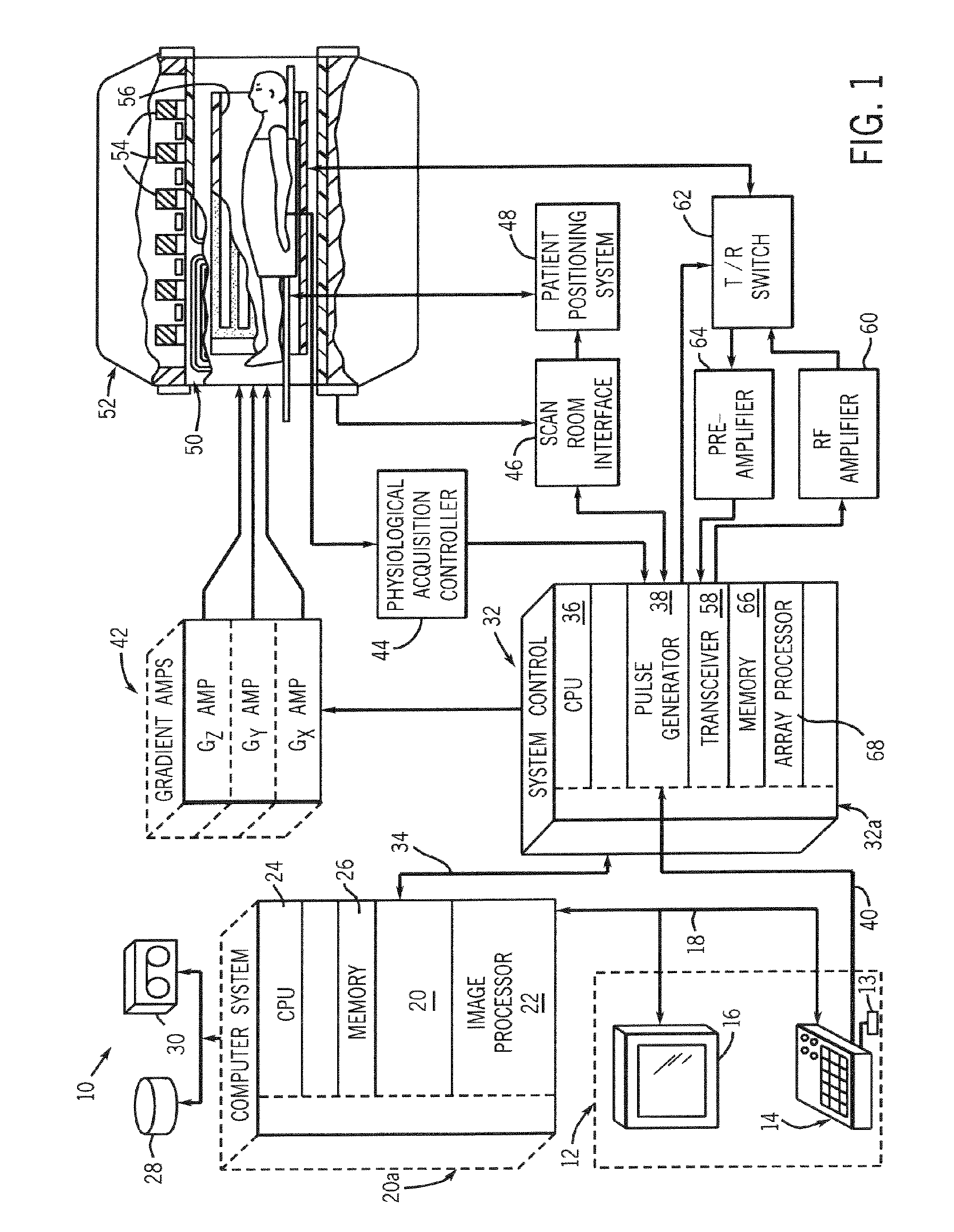
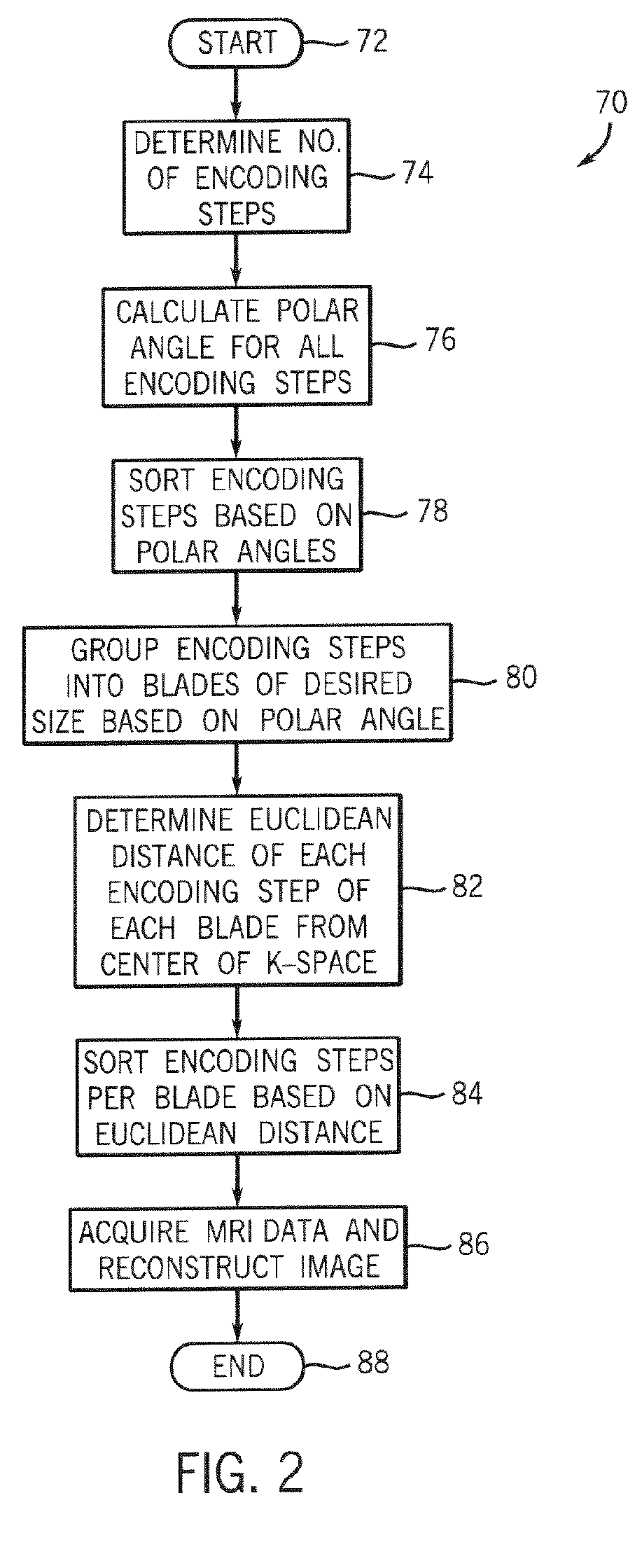
Method and apparatus for acquiring mr data with a segmented multi-shot radial fan beam encoding order
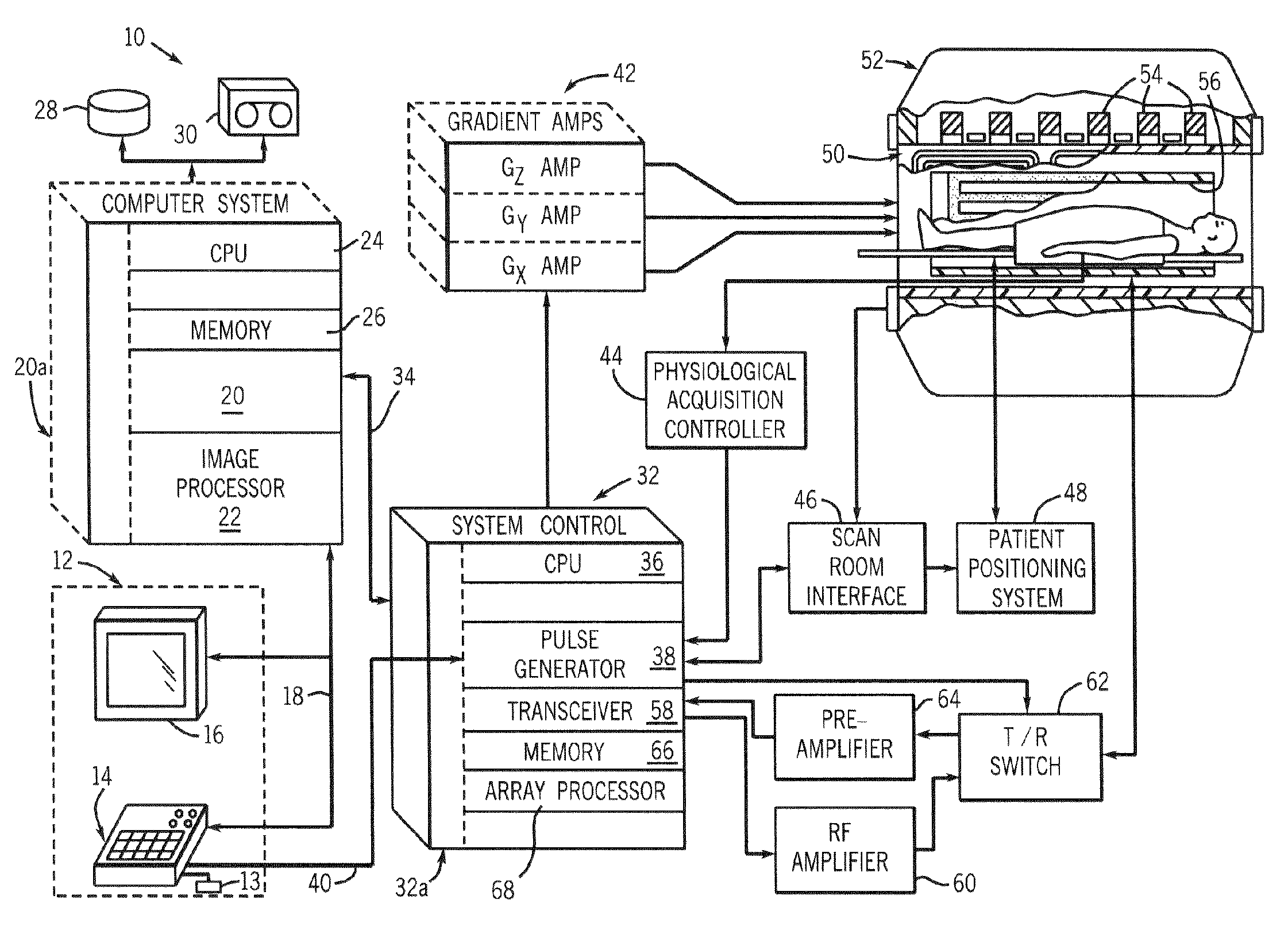
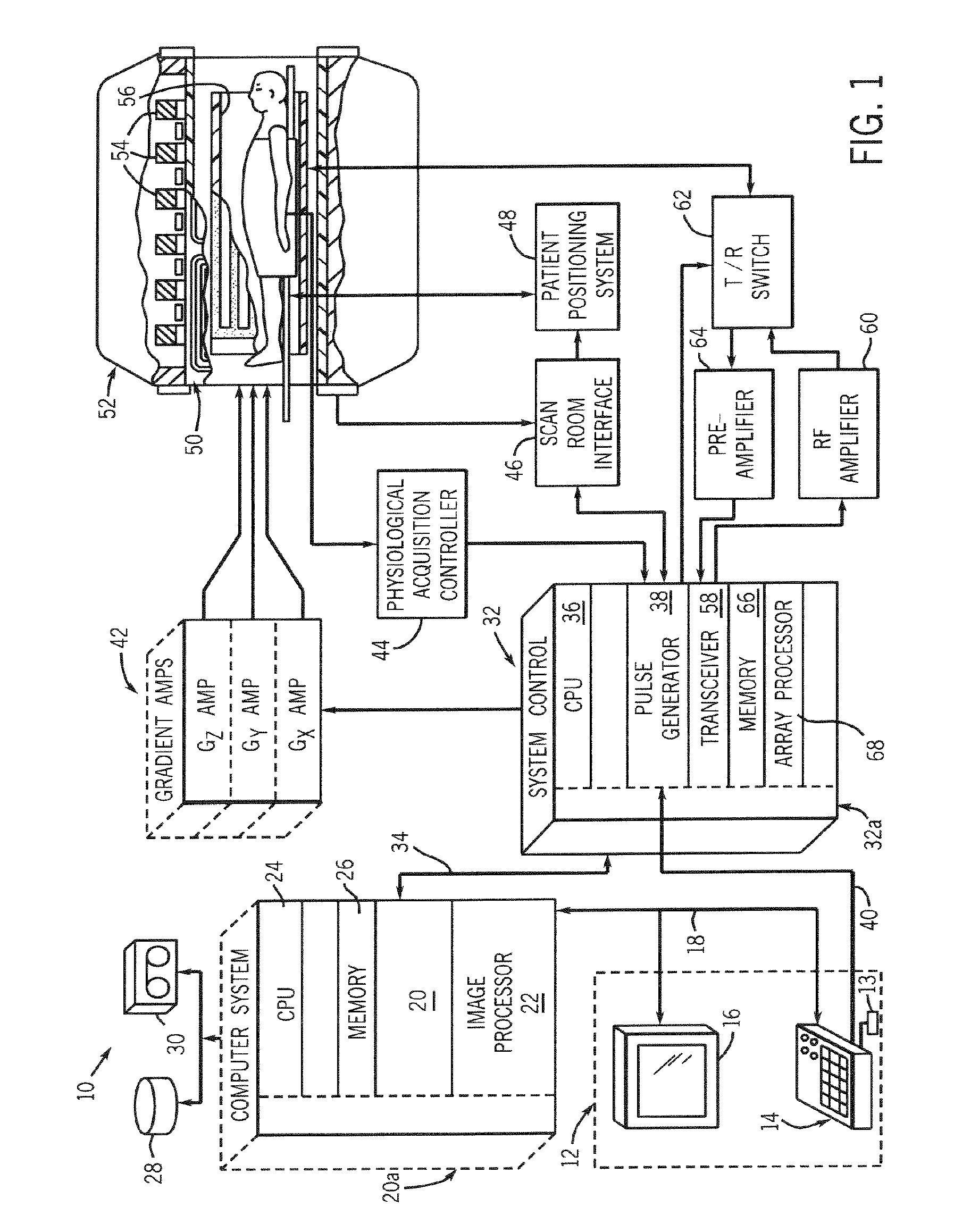
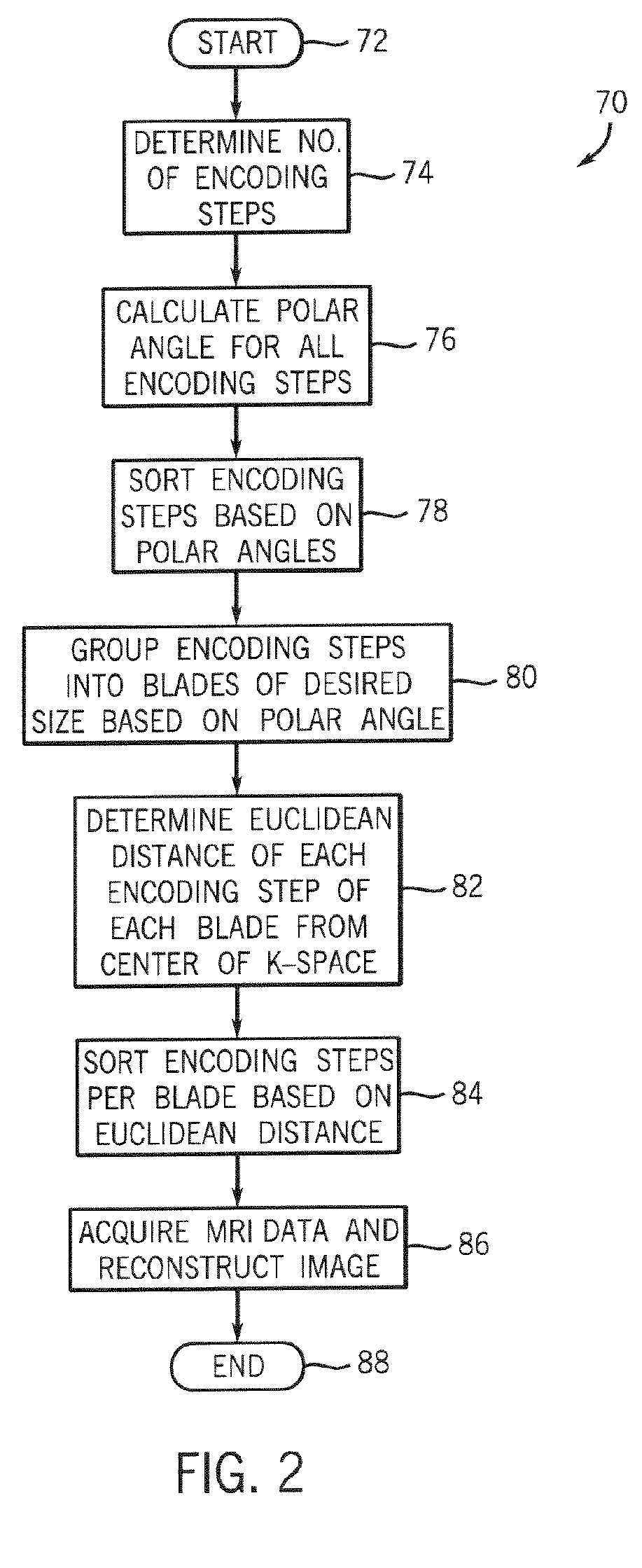
ActiveUS20070063701A1Avoid excessive currentGreat and uniform centric weightingMagnetic measurementsDiagnostic recording/measuringTransceiver3d image
An MR imaging apparatus is presented and includes a plurality of gradient coils positioned about a bore of a magnet to impress a polarizing magnetic field. An RF transceiver system and an RF switch are controlled by a pulse module to transmit and receive RF signals to and from an RF coil assembly to acquire MR images. The MR imaging apparatus also includes a computer programmed to apply a 3D imaging sequence and acquire MR data using a segmented acquisition. The computer is further programmed to reconstruct an image from the MR data that is substantially free of eddy current induced artifacts.
Owner:GENERAL ELECTRIC CO
Process of making an all-silicon microphone
InactiveUS20050101047A1Easy to characterizeImprove performanceDecorative surface effectsSemiconductor electrostatic transducersCapacitanceHigh volume manufacturing
A process of forming a capacitive audio transducer, preferably having an all-silicon monolithic construction that includes capacitive plates defined by doped single-crystal silicon layers. The capacitive plates are defined by etching the single-crystal silicon layers, and the capacitive gap therebetween is accurately established by wafer bonding, yielding a transducer that can be produced by high-volume manufacturing practices.
Owner:DELPHI TECH IP LTD
Shear wave velocity estimation using center of mass
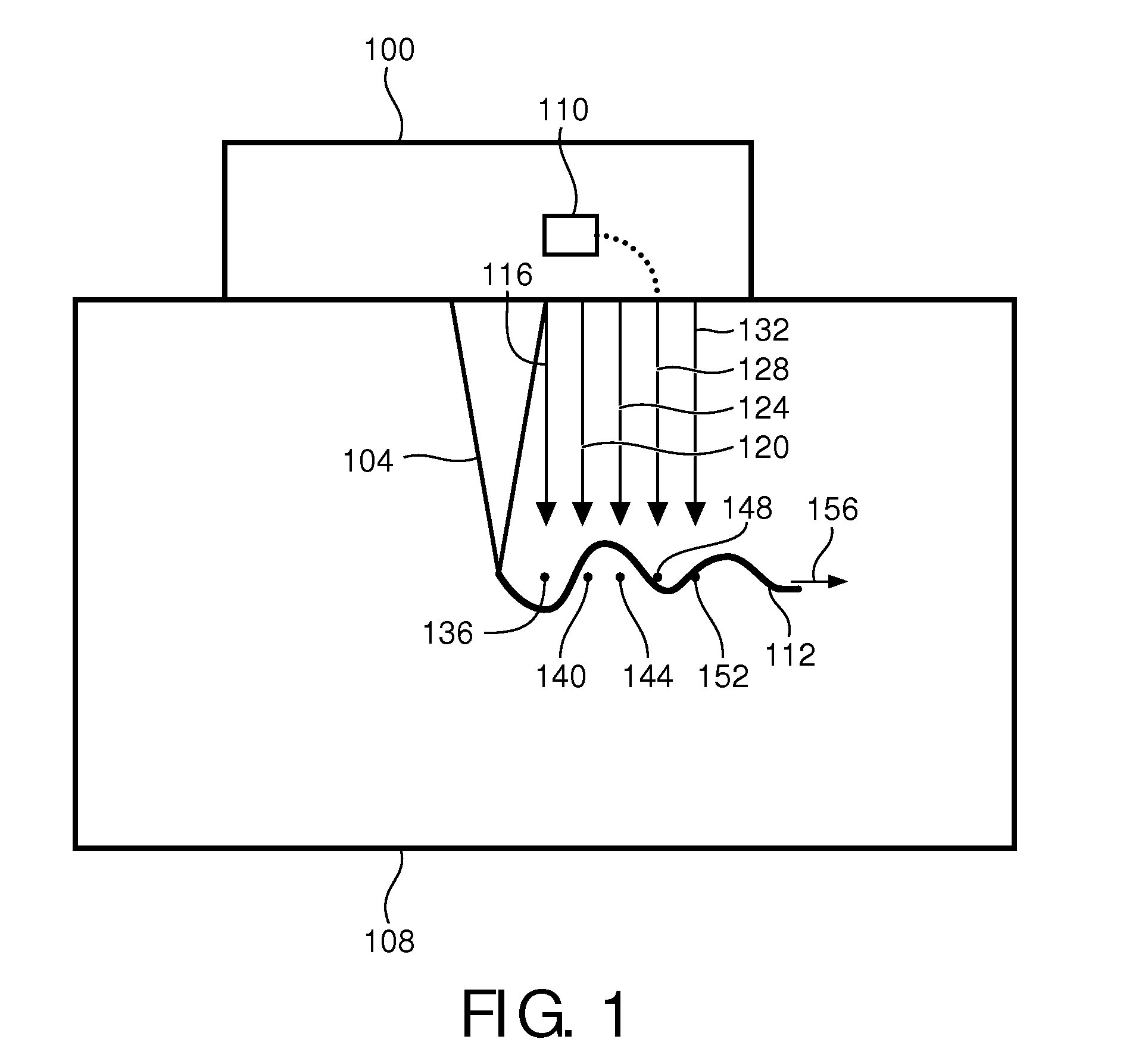
ActiveUS20130317362A1Improve accuracyReduce signal to noise ratioDiagnostics using vibrationsOrgan movement/changes detectionTime domainTherapy Evaluation
The weighted-average-based position (244) in the temporal domain is computed based on the sampling of shear wave displacement (226) along the propagation path. The weighting is, for example, by displacement observed at times (230) corresponding to sampling and represents the time of arrival of the shear wave at the shear-wave propagation path location being sampled. In some embodiments, the computed shear-wave times of arrival at respective locations are functionally related to known inter-location distances (250) to derive shear-wave group velocity. The derived velocity can serve as input into known algorithms for estimating shear elasticity of the medium, such as body tissue, for purposes of clinical diagnosis and therapy assessment.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
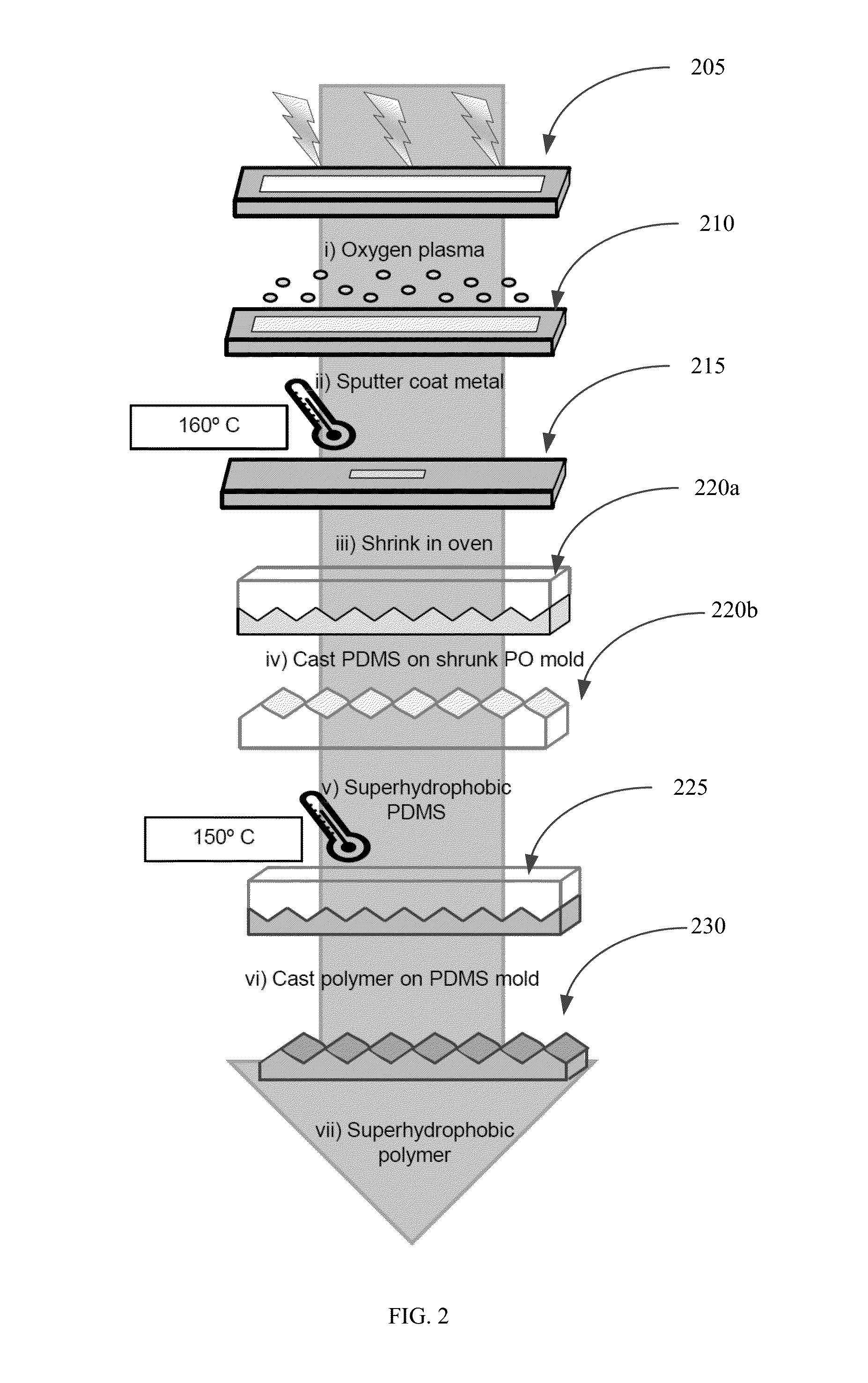
Evaporation on superhydrophobic surfaces for detection of analytes in bodily fluids
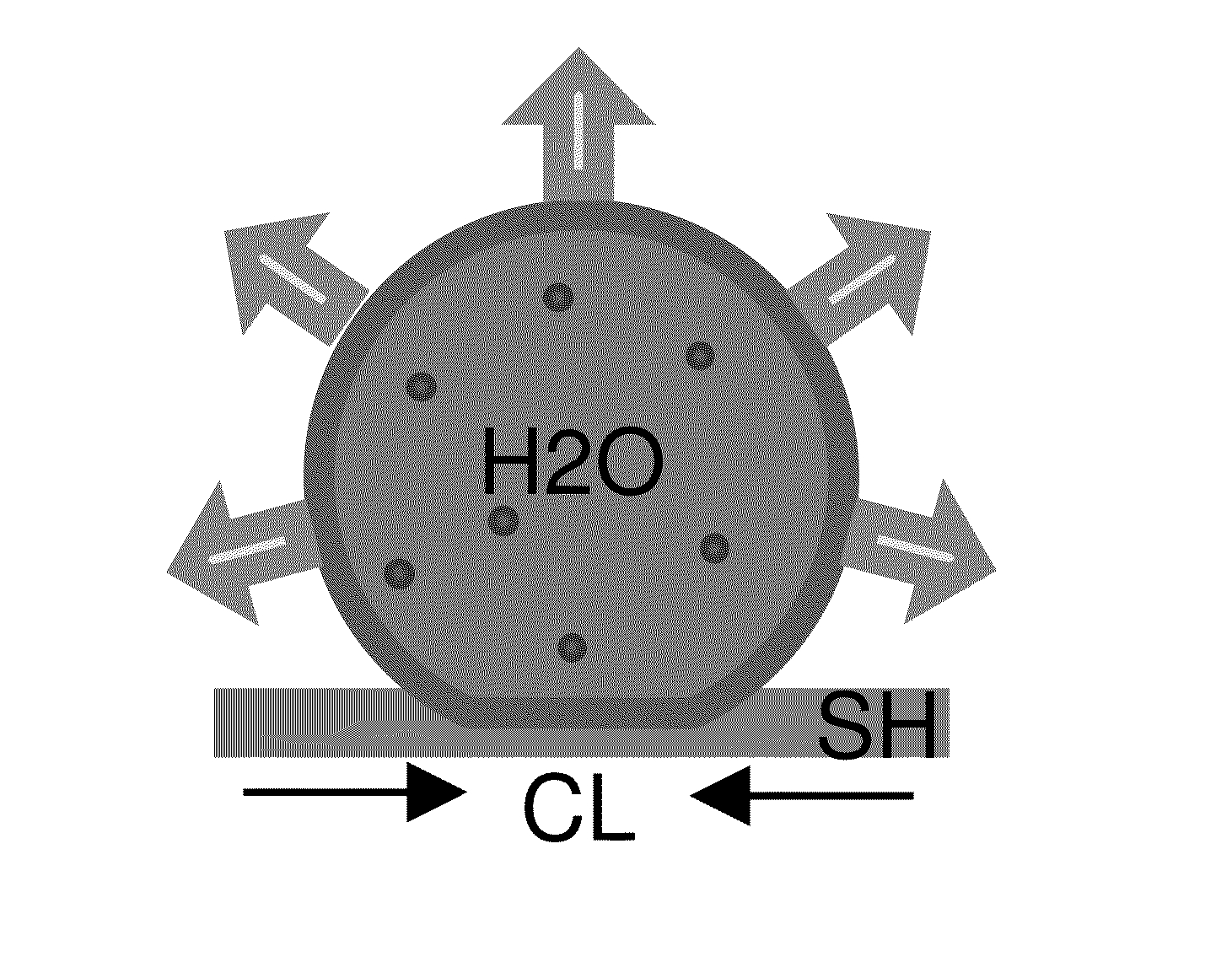
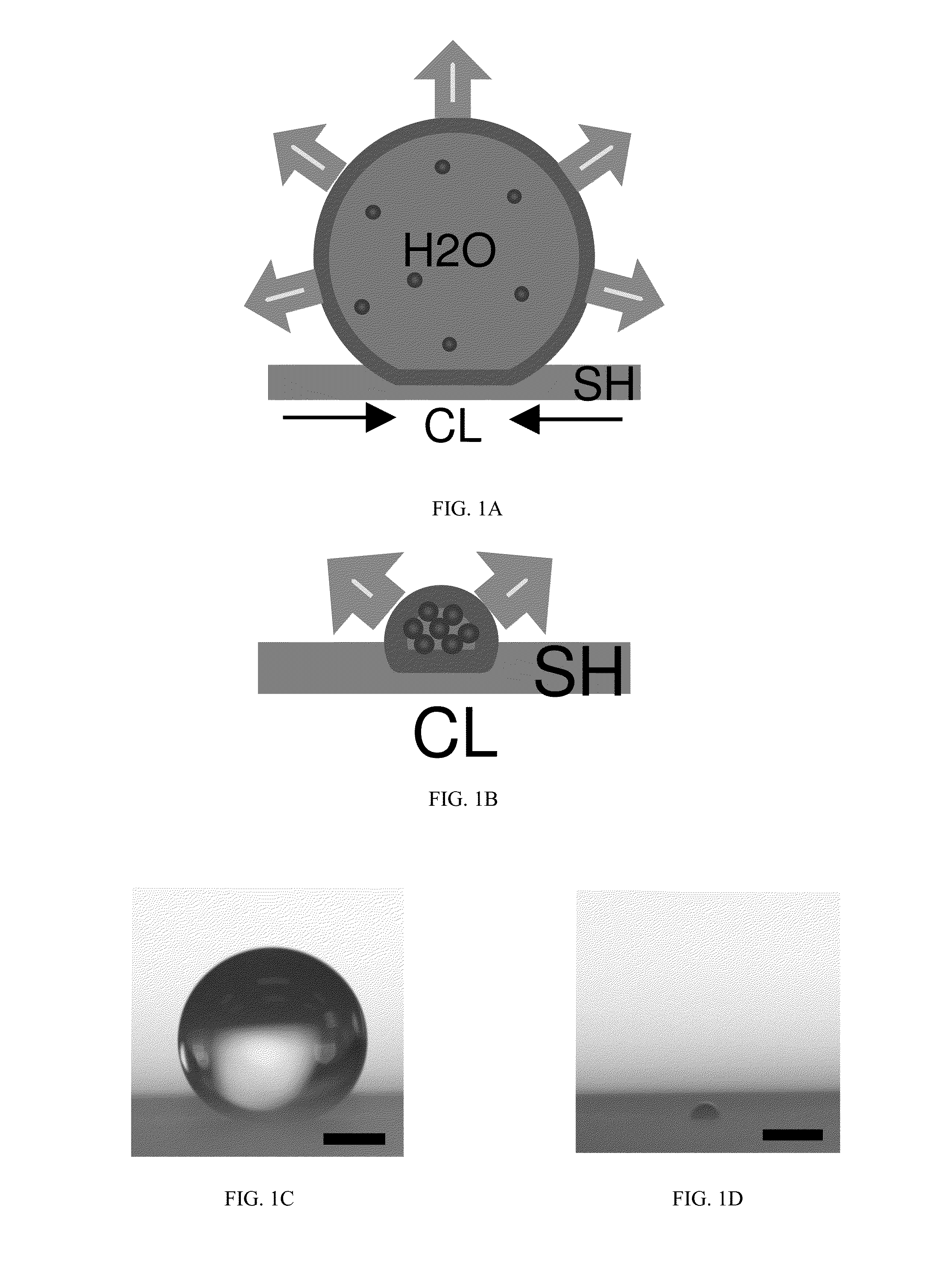
InactiveUS20160169867A1Enhance concentrationWeak adhesionLaboratory glasswaresColor/spectral properties measurementsMicrofluidic channelBiological fluid
This disclosure provides a diagnostic system including a detection zone adapted to receive a volume of biological fluid. The detection zone includes a plurality of micro-scale and nano-scale features that render the detection zone superhydrophobic. Analytes (e.g., proteins and / or other molecules) are concentrated when the volume of biological fluid is allowed to evaporate on the detection zone. Concentrating the analytes in the detection zone by evaporation can advantageously increase the sensitivity of detection of the analyte. In various implementations, microfluidic channels can be integrated with the diagnostic system to convey the volume of biological fluid to the detection zone. In various implementations, the microfluidic channels can have a lower hydrophobic characteristic than the surrounding to realize self-driven microfluidic channels that convey the biological fluid to the detection zone without using any external devices.
Owner:RGT UNIV OF CALIFORNIA
Method for making automotive headliners
InactiveUS8133419B2Less susceptible to degassingFaster demold timeLamination ancillary operationsSynthetic resin layered productsFiberPolyol
Vehicle headliners are prepared with a core layer of a fiber-reinforced polyurethane foam. The polyurethane foam is prepared from a polyurethane-forming composition that uses water as a blowing agent and polyol or polyol mixture that has a high functionality and an average hydroxyl equivalent weight of 100-130. The selection of polyols permits cycle times to be reduced by allowing for faster demolding and shortened aging times before post-molding heat lamination steps can be performed.
Owner:THE DOW CHEM CO
Method and apparatus for acquiring MR data with a segmented multi-shot radial fan beam encoding order
ActiveUS7265547B2Avoid excessive currentLess-proneMagnetic measurementsDiagnostic recording/measuringTransceiver3d image
An MR imaging apparatus is presented and includes a plurality of gradient coils positioned about a bore of a magnet to impress a polarizing magnetic field. An RF transceiver system and an RF switch are controlled by a pulse module to transmit and receive RF signals to and from an RF coil assembly to acquire MR images. The MR imaging apparatus also includes a computer programmed to apply a 3D imaging sequence and acquire MR data using a segmented acquisition. The computer is further programmed to reconstruct an image from the MR data that is substantially free of eddy current induced artifacts.
Owner:GENERAL ELECTRIC CO
Antigenic modulation of cells
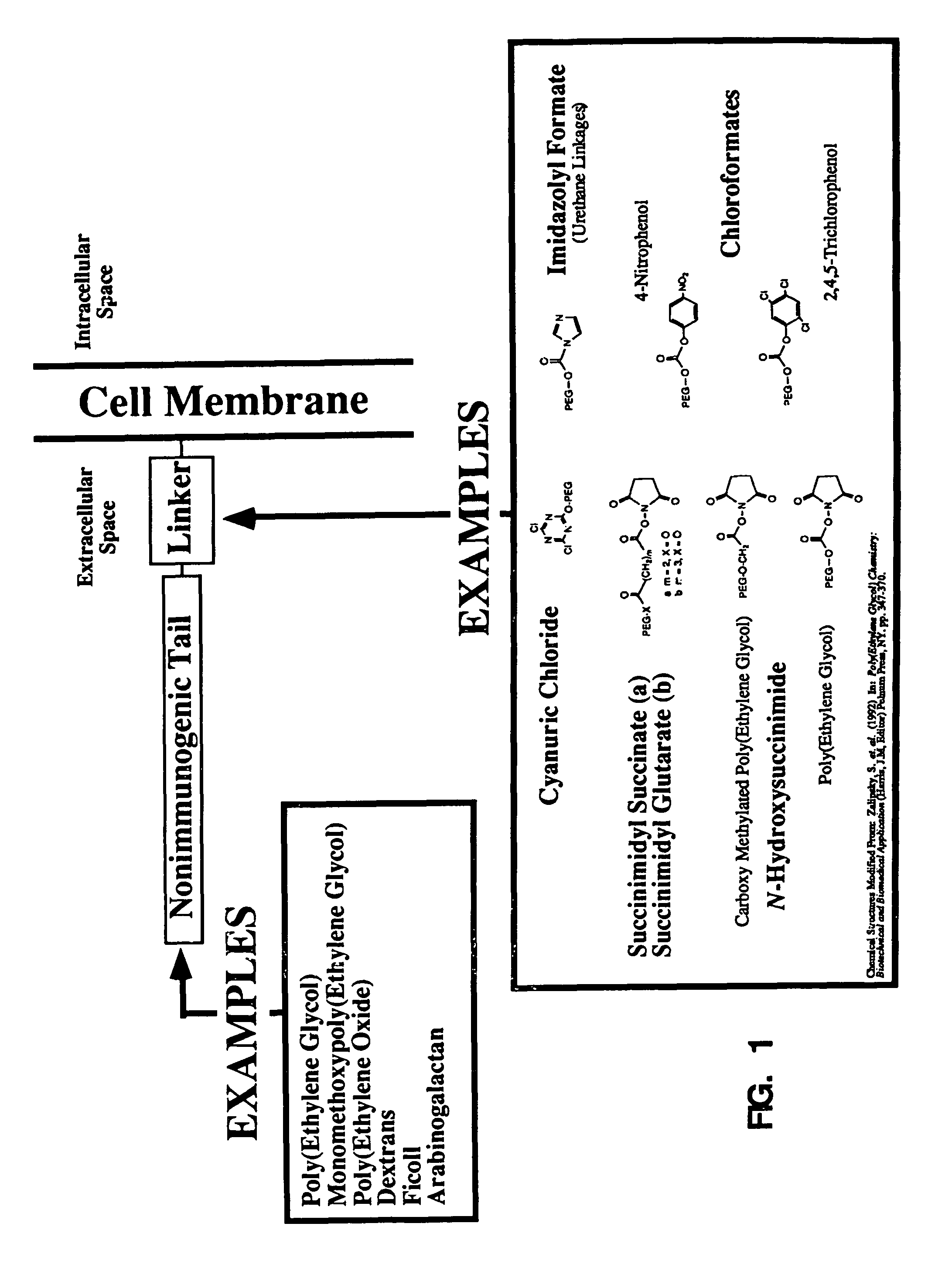
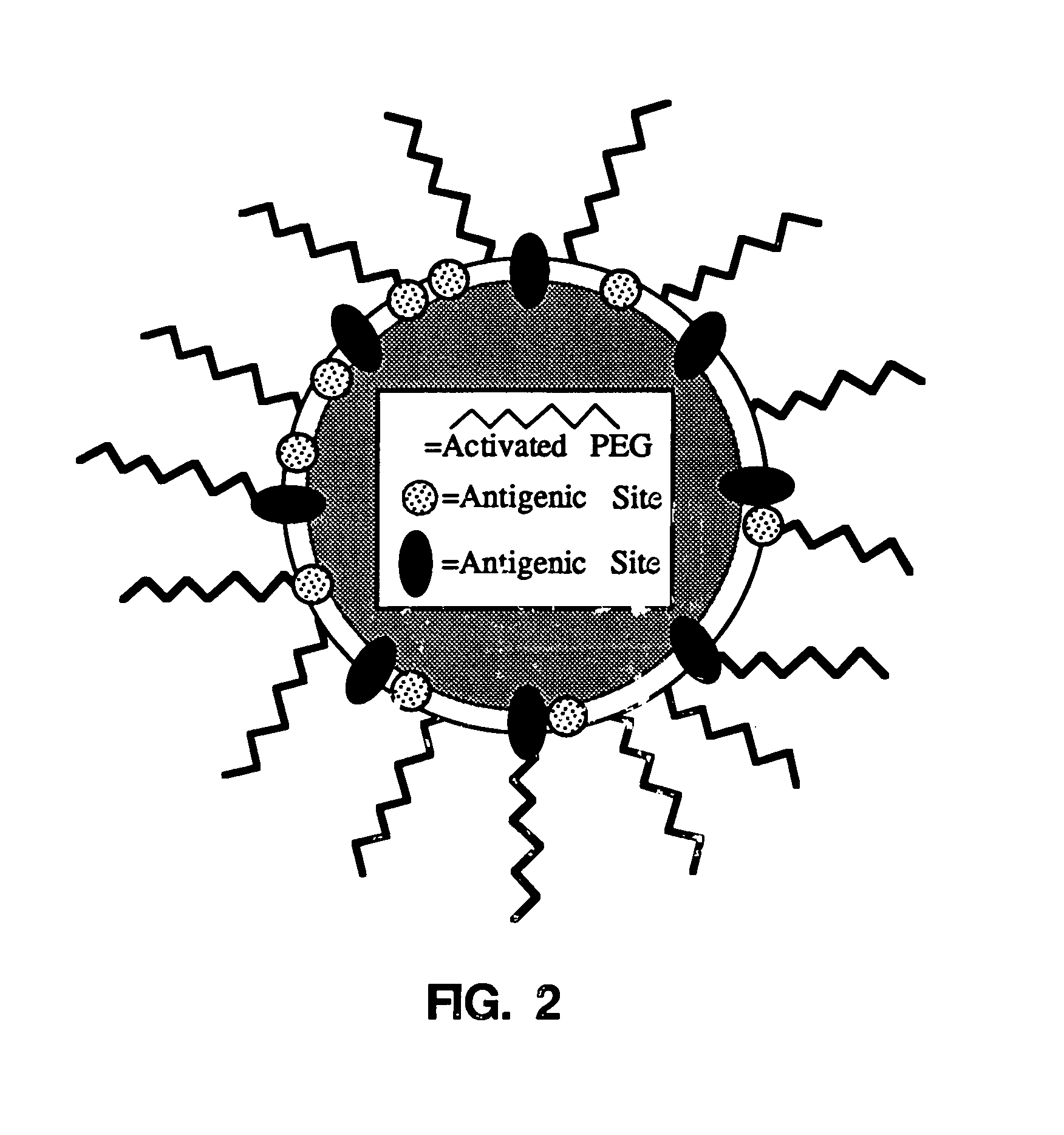
InactiveUS8007784B1Less anti-ALess-proneBiocideSnake antigen ingredientsPolyethylene glycolDecreased Phagocytosis
The present invention is directed to a non-immunogenic cellular composition comprising: a cell having a cell surface and antigenic determinants on the cell surface; an optional linker molecule covalently attached to the cell surface; and a hydrophilic, biocompatible, non-immunogenicity providing compound or polymer (e.g., polyethylene glycol or a derivative thereof) covalently attached to the linker molecule or directly to the cell. In one embodiment, the linker molecule is covalently attached directly to the antigenic determinant on the cell surface. In an alternate embodiment, the linker molecule may be covalently attached to a non-antigenic site on the cell surface, but will camouflage the antigenic determinant on the cell surface. Various uses of the resulting non-immunogenic cell are also provided, including a method of decreasing phagocytosis of a cell, a method of decreasing an adverse reaction to a transfusion, a method of decreasing rejection of a transplanted cell, tissue or organ, and a method of decreasing antibody-induced aggregation of cells.
Owner:ALBANY MEDICAL COLLEGE
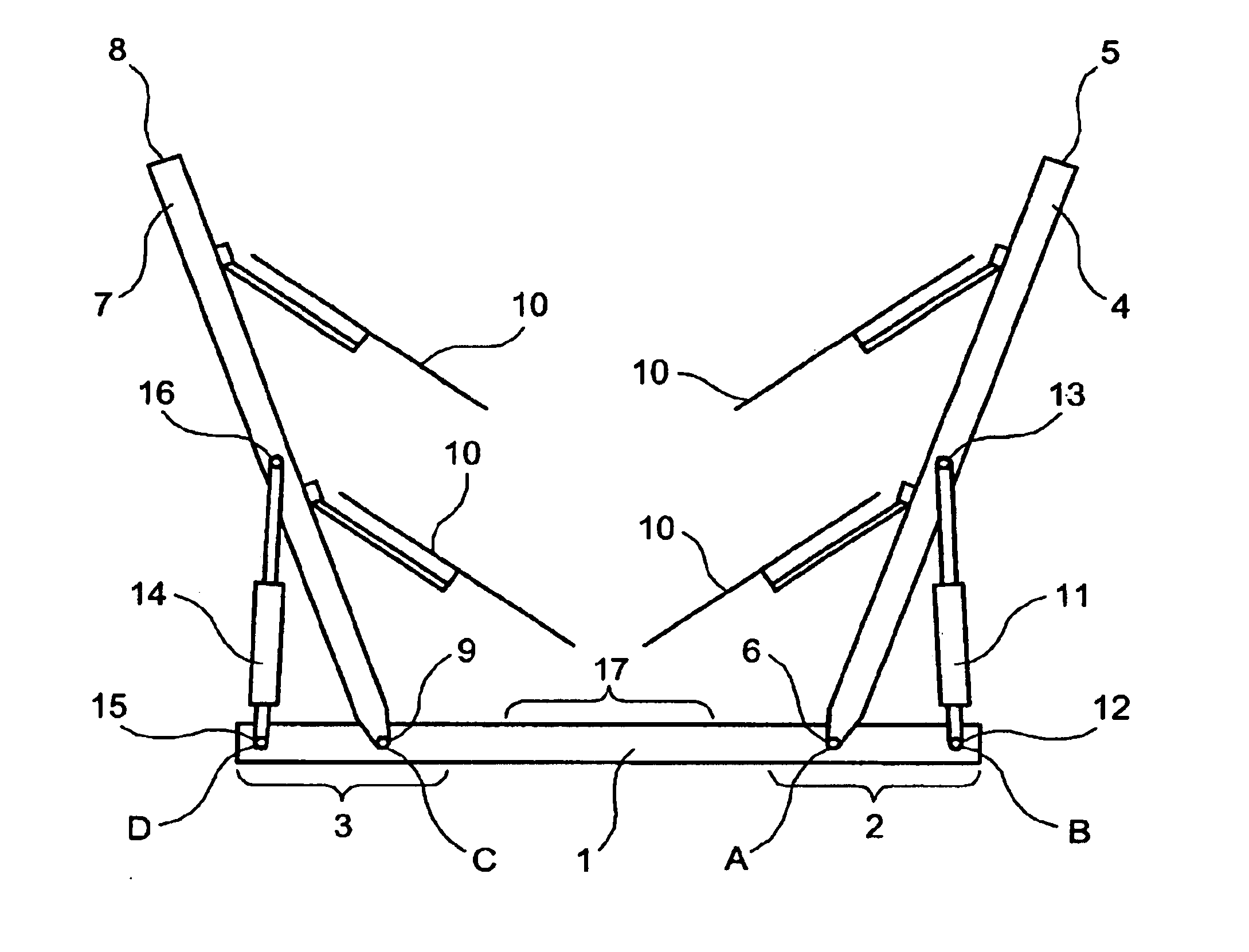
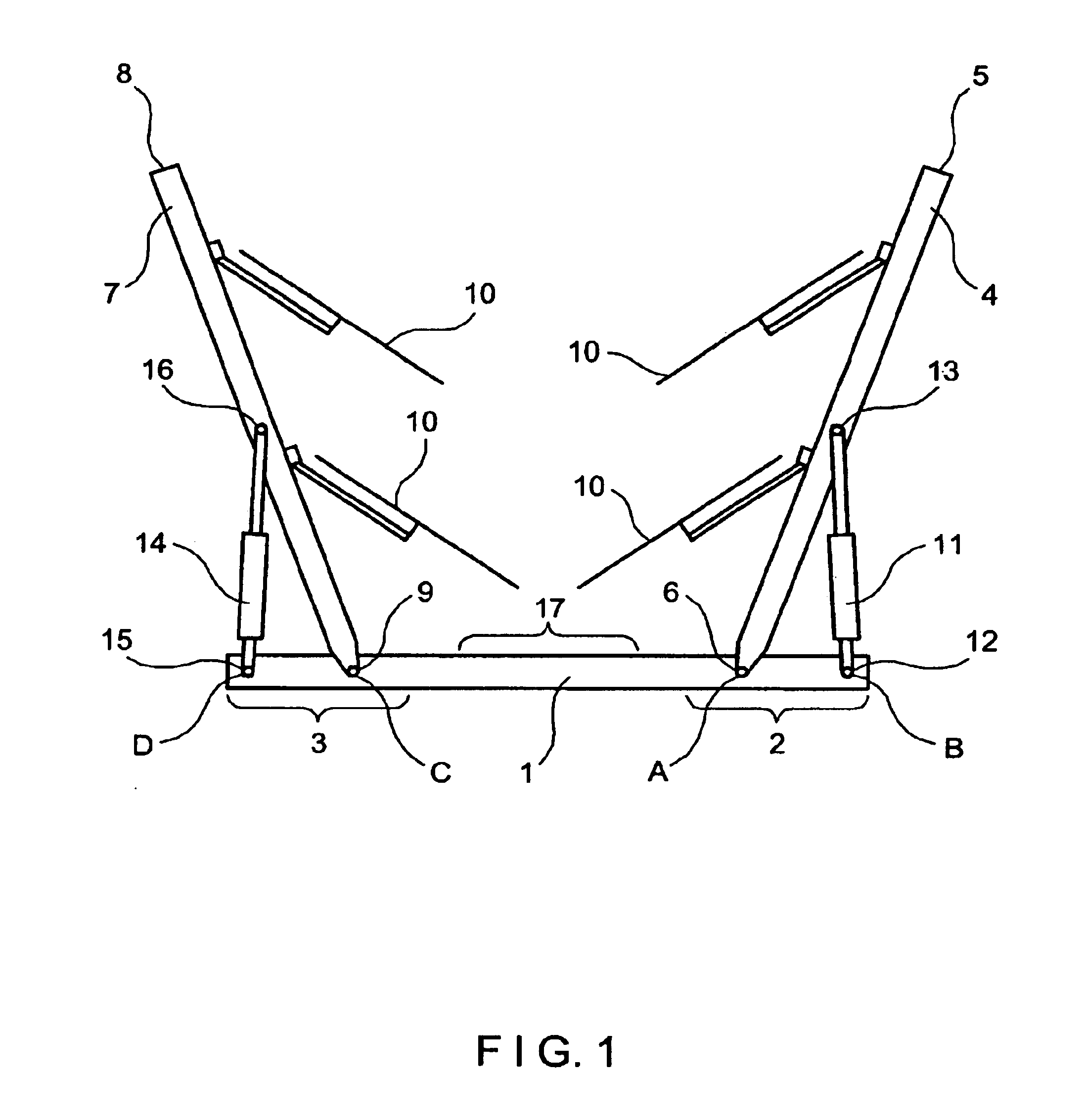
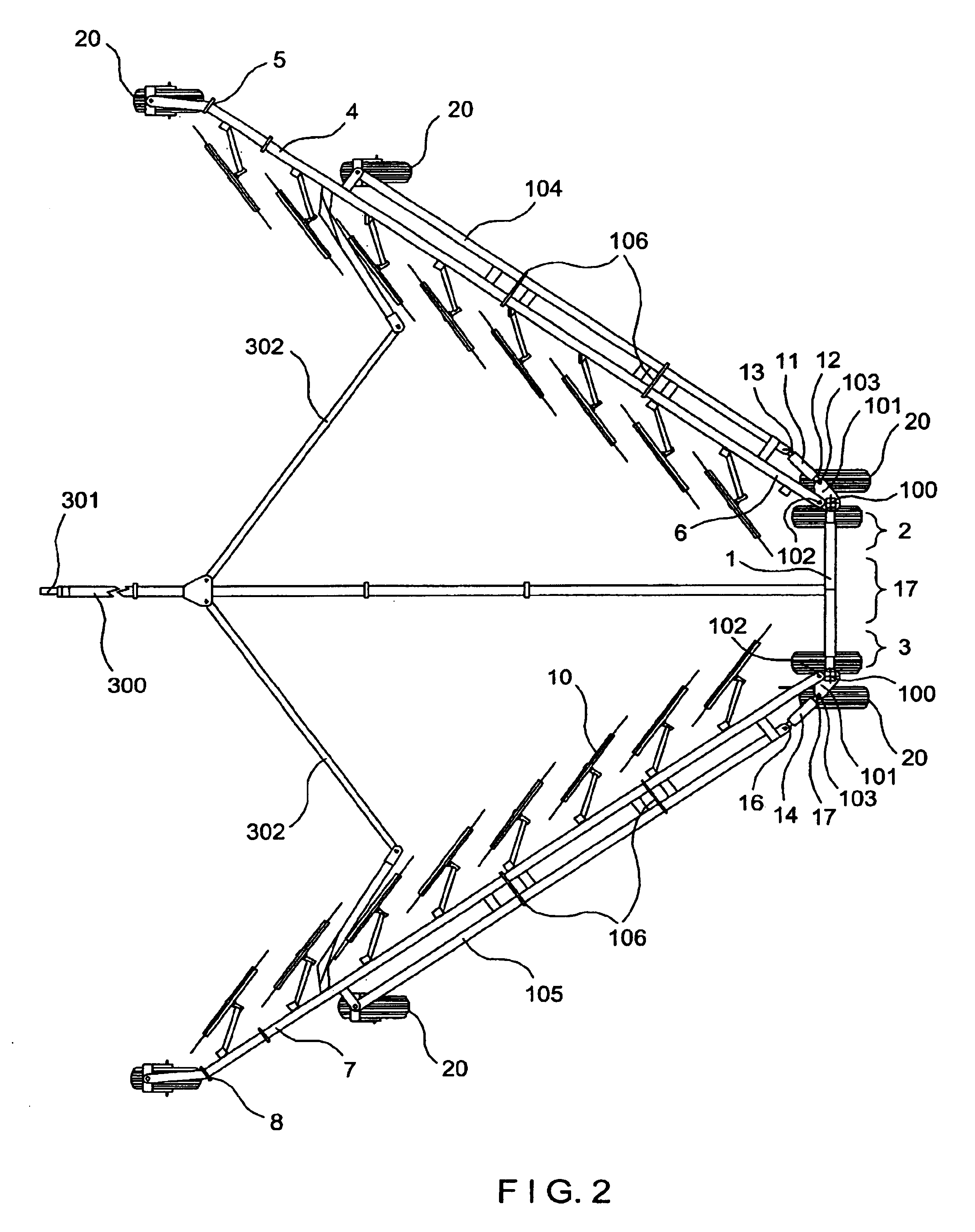
Pull type V-shaped hay rake
A hay rake includes a crosswise member having a right section and a left section. A first rake arm has a front end and a back end, the first rake arm being pivotably mounted at its back end to the right section of the crosswise member so as to be moveable between an open position and a closed position. A second rake arm has a front end and a back end, the second rake arm being pivotably mounted at its back end to the left section of the crosswise member so as to be moveable between an open position and a closed position. A plurality of rotatable rake wheels are mounted on each of the first and second rake arms. The hay rake also includes first and a second actuators. The first actuator has a first section connected to the right section of the crosswise member and a second section connected to the first rake arm. The second actuator has a first section connected to the left section of the crosswise member and a second section connected to the second rake arm. Each actuator operates to move the rake arm to which it is connected between the open position and the closed position.
Owner:SITREX
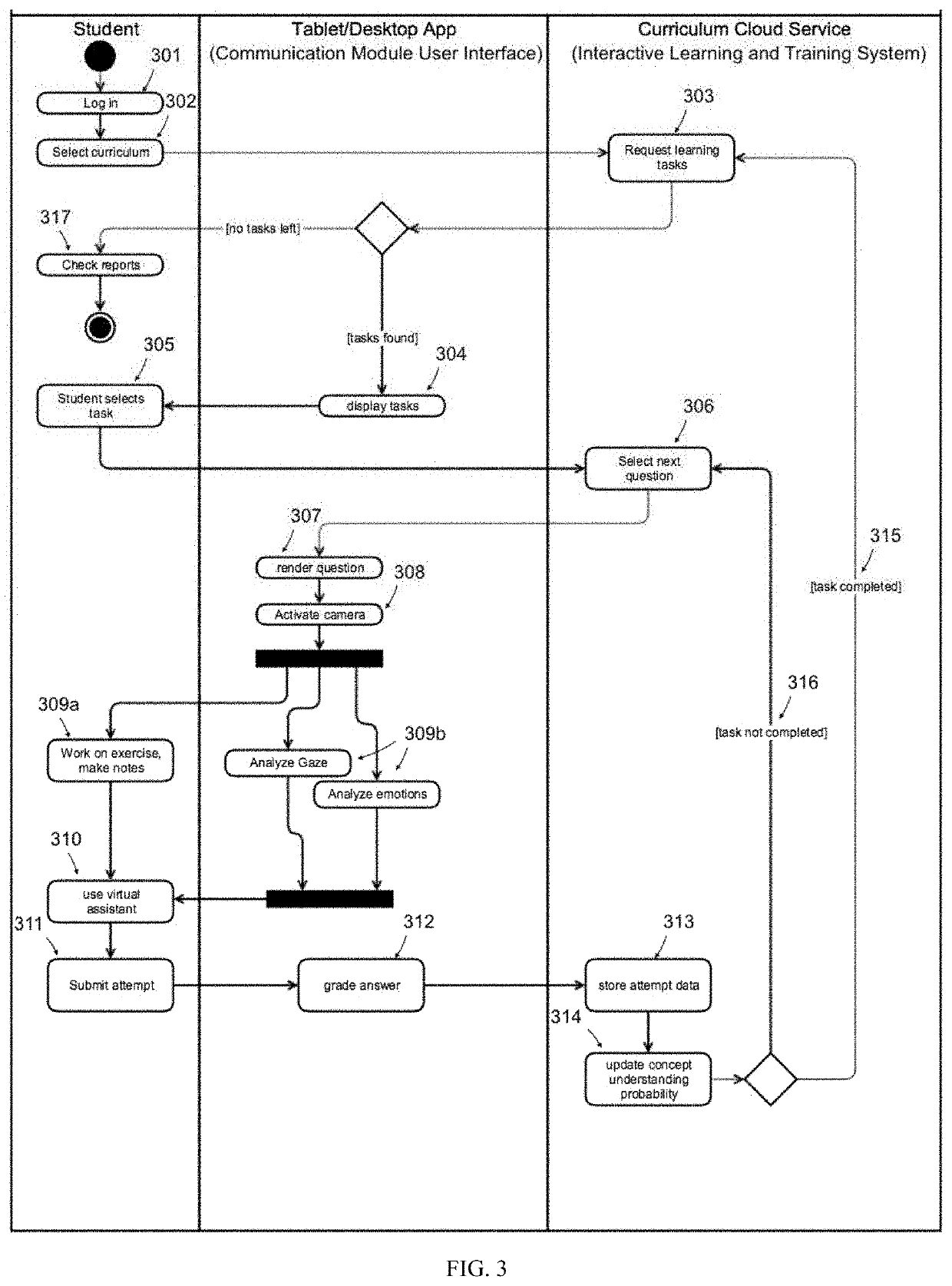
Interactive and adaptive learning, neurocognitive disorder diagnosis, and noncompliance detection systems using pupillary response and face tracking and emotion detection with associated methods
InactiveUS20200178876A1High precision estimationLess-proneHealth-index calculationAcquiring/recognising eyesSubstance abuserAdaptive learning
A system for detection of noncompliance including substance abuse, driving under influence, and untruthful testimony giving under law enforcement setting, comprising optical sensors for capturing a subject's pupillary responses, blinking eye movements, point-of-gaze, facial expression, and head pose during a compliance test session. The system can also be applied in neurocognitive disorder diagnosis. The subject's affective and cognitive states estimation based on the captured sensory data during a diagnosis test is feedback to the system to drive the course of the compliance or cognitive test, adaptively change the test materials, and influence the subject's affective and cognitive states. The estimated affective and cognitive states in turn provide a more accurate reading of the subject's condition.
Owner:LAM YUEN LEE VIOLA
Compacting device and a system and a method for compacting a material
InactiveUS6869250B2Withstand deteriorationLess proneRoads maintainenceSoil preservationBiomedical engineering
A compacting device and a system and a method for compacting a material are provided. The compacting device may have a base and a column which extends from the base. A sleeve may be fitted and secured around the column. The sleeve may have a length which is greater than a length of the column. Material may be collected within the sleeve and may be used for compaction.
Owner:CATERPILLAR INC
Thin concrete repair composition for alkali-aggregate reaction affected concrete
A cement repair composition is provided for repairing thin concrete. The composition comprises, in weight percentages: fine aggregates, 50-80%; Portland cement, 10-20%; reinforcing fibers such as polyethylene, steel and fiberglass fibers, 0-5%; and a plurality of further additives. The additives preferably include a lithium admixture, an air entraining admixture and a water reducing chemical additive, and a shrinkage compensating chemical additive, in a combined weight percentage of 0.01 to 5%.
Owner:US DEPT OF THE INTERIOR
Process of forming a capacitative audio transducer
InactiveUS7134179B2Easy to characterizeImprove performanceDecorative surface effectsSemiconductor electrostatic transducersHigh volume manufacturingTransducer
A process of forming a capacitive audio transducer, preferably having an all-silicon monolithic construction that includes capacitive plates defined by doped single-crystal silicon layers. The capacitive plates are defined by etching the single-crystal silicon layers, and the capacitive gap therebetween is accurately established by wafer bonding, yielding a transducer that can be produced by high-volume manufacturing practices.
Owner:DELPHI TECH IP LTD
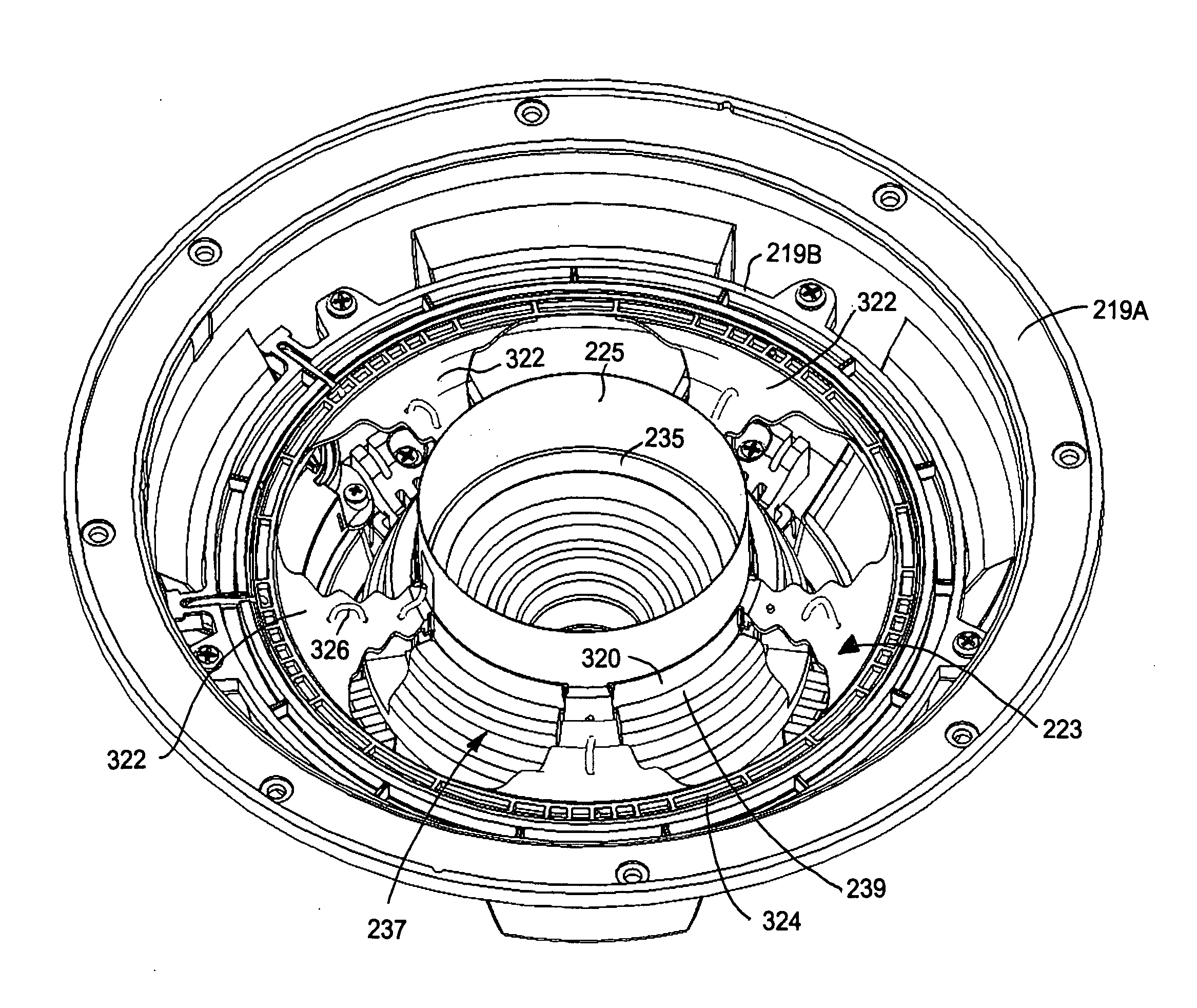
Structure of loudspeaker for reducing thickness and mounting depth
A structure of a loudspeaker is designed to decrease a thickness or height thereof, thereby reducing a mounting depth of the loudspeaker on a mounting panel or wall. The loudspeaker includes a speaker frame, a diaphragm connected to the speaker frame in a manner capable of vibration, a voice coil connected to the diaphragm through a coil bobbin to receive an electric signal to vibrate the diaphragm, a spider connected to the speaker frame and to the diaphragm for supporting the diaphragm and the voice coil in a flexible manner, a magnetic assembly including a top plate, a permanent magnet and a pole piece for creating a magnetic circuit for interaction with the voice coil inserted in an air gap, and a plurality of cut-outs formed on a top of the magnetic assembly at an outside thereof to receive therein corresponding suspension elements of the spider.
Owner:ALPINE ELECTRONICS INC
Glass and glass-ceramics
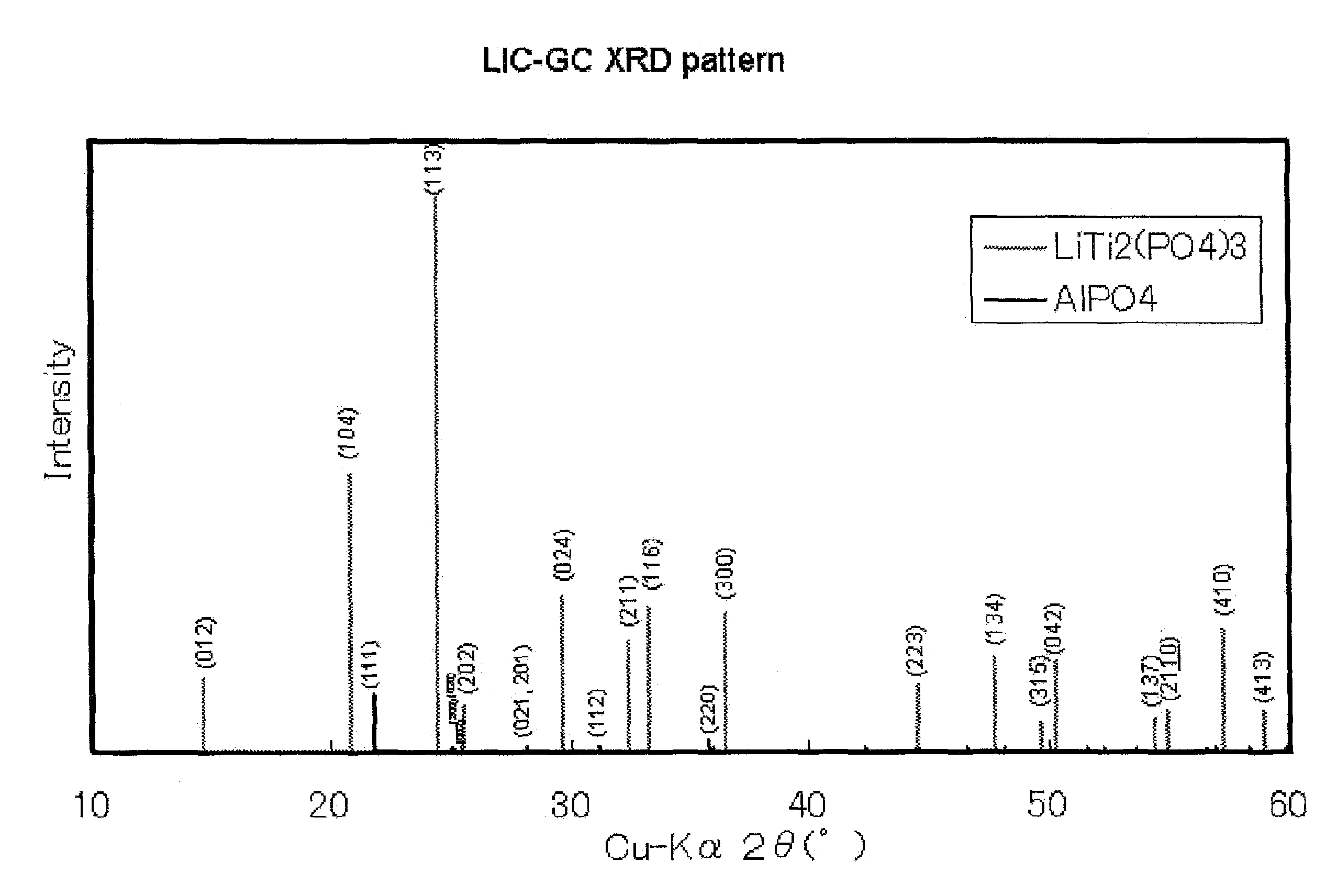
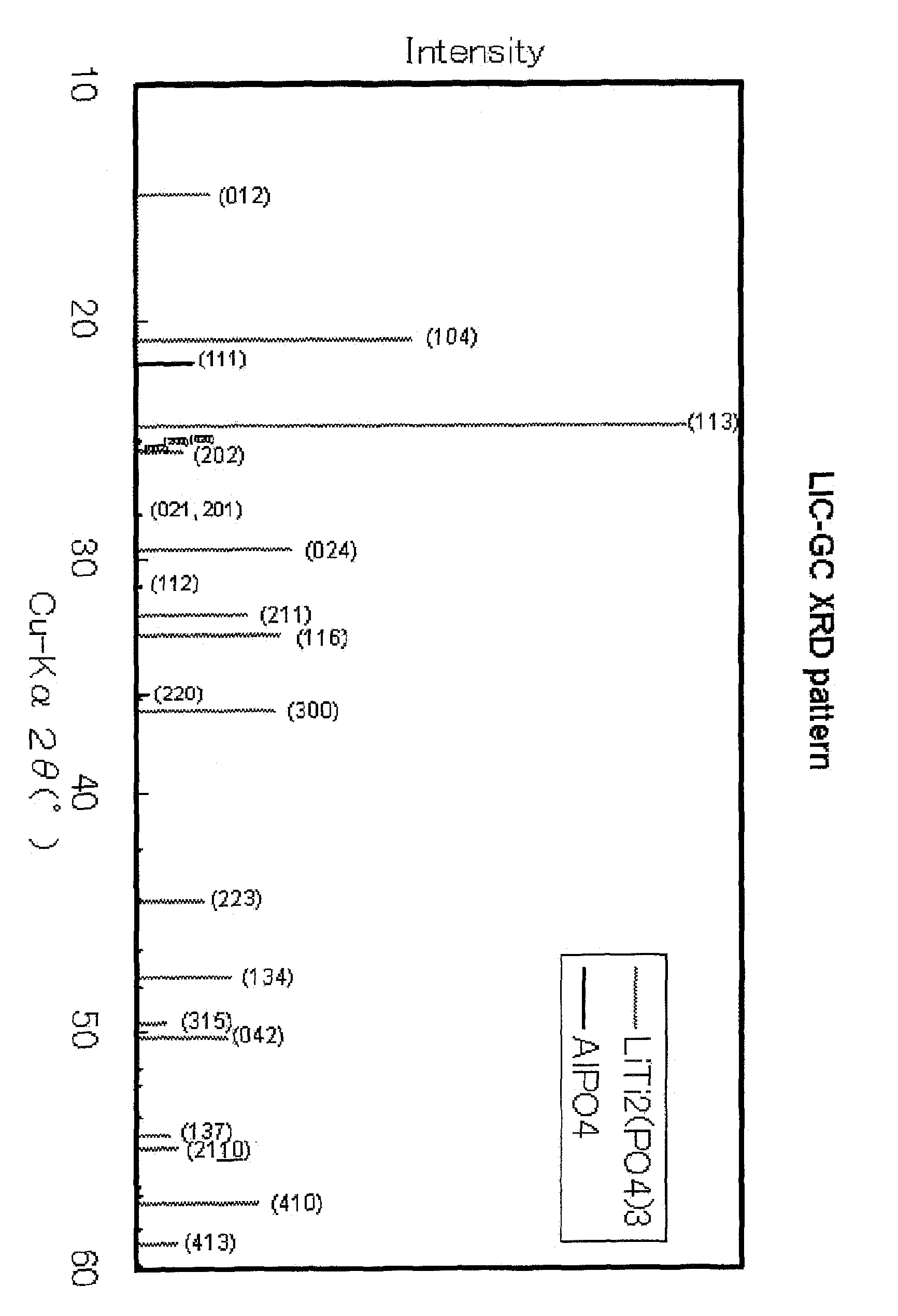
ActiveUS8476174B2High densityImprove lithium ion conductivitySecondary cellsSolid electrolyte cellsLithiumX-ray
There is provided a lithium ion conductive glass-ceramics which is dense, contains few microvoids causing the decrease in lithium ion conductivity, and achieves good lithium ion conductivity. A glass-ceramics which comprises at least crystallines having an LiTi2P3O12 structure, the crystallines satisfying 1<IA113 / IA104≦2, wherein IA104 is the peak intensity assigned to the plane index 104 (2θ=20 to 21°), and IA113 is the peak intensity assigned to the plane index 113 (2θ=24 to 25°) as determined by X-ray diffractometry.
Owner:OHARA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com