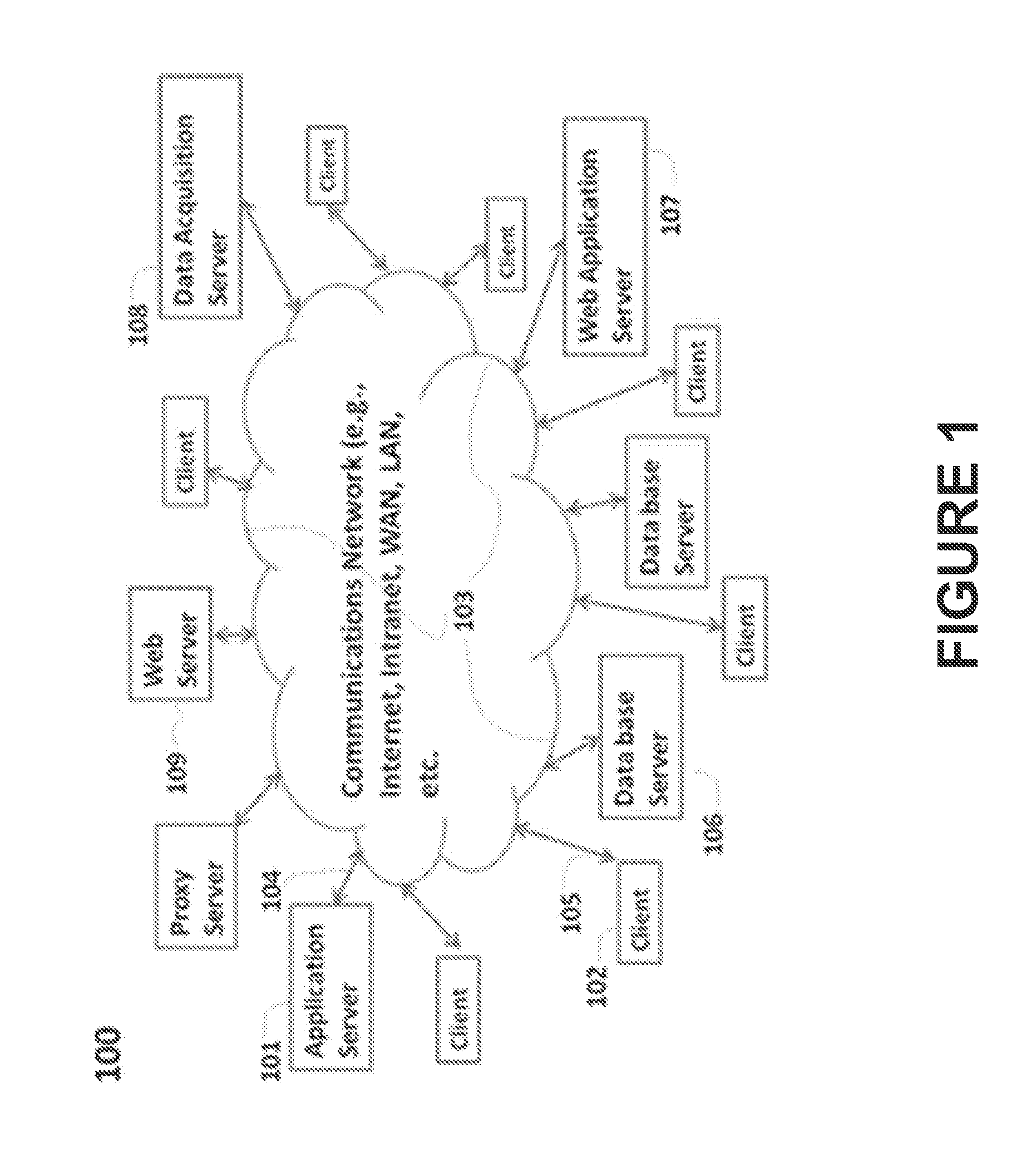
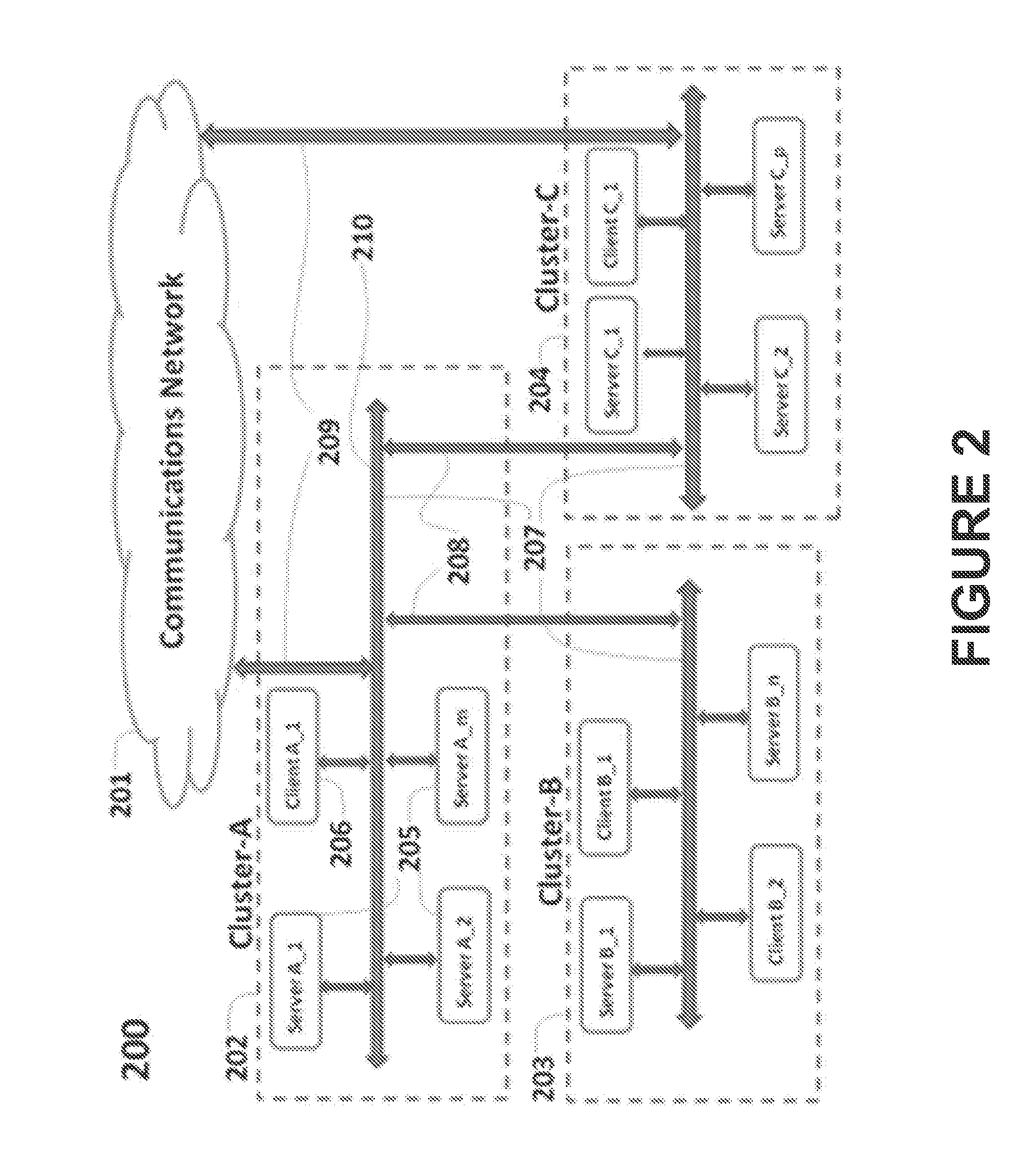
Patents
Literature
6003 results about "Security system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
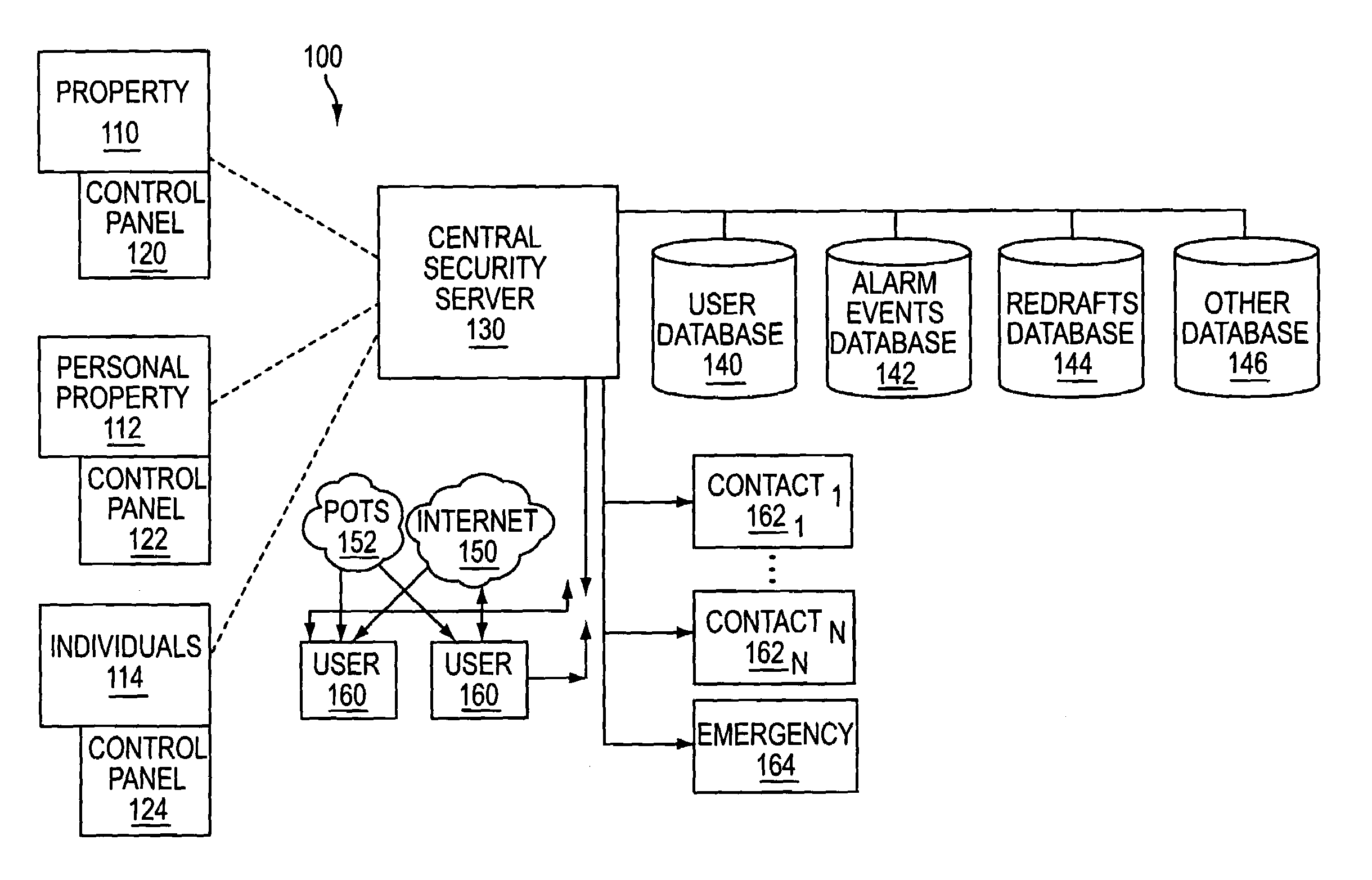
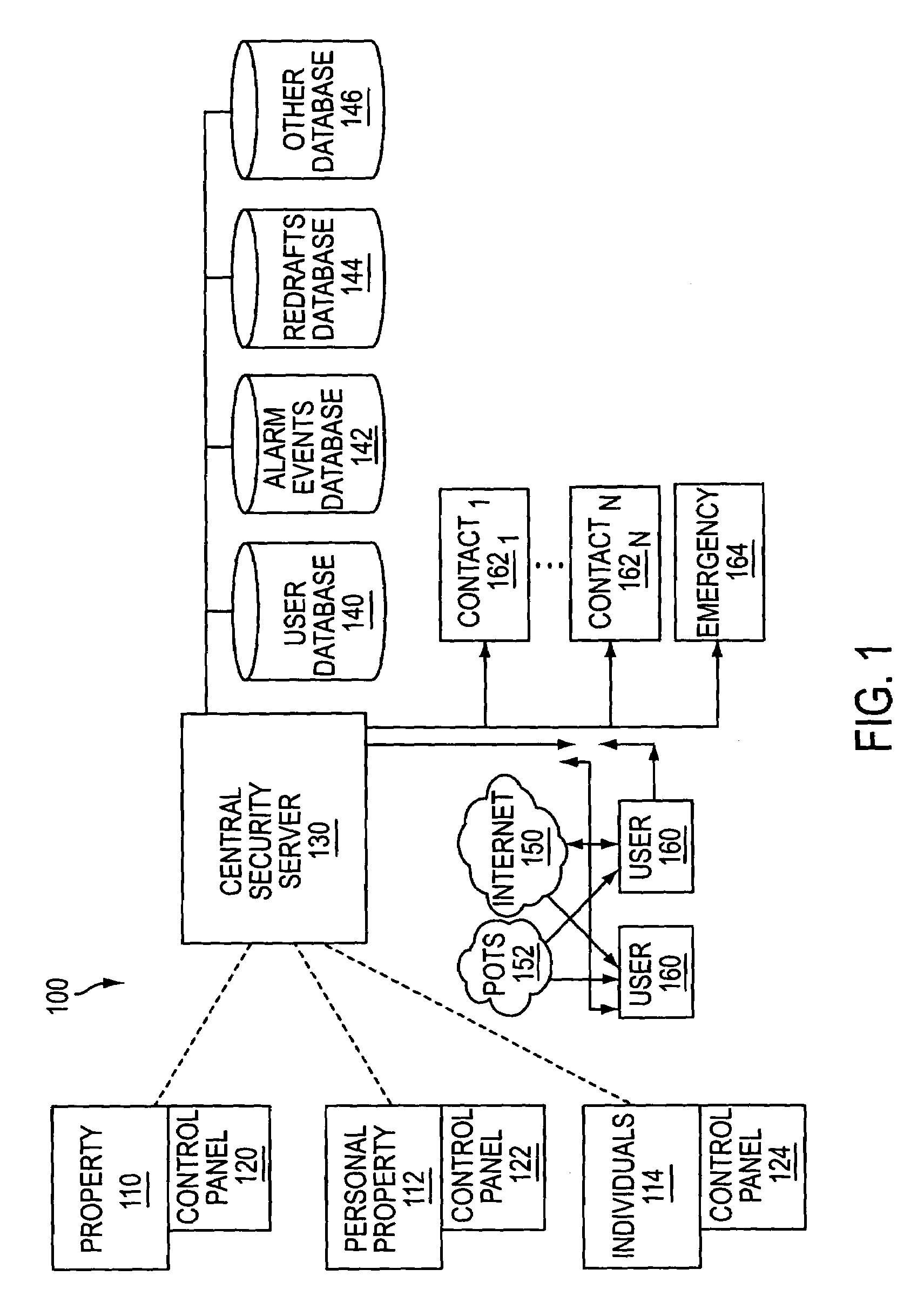
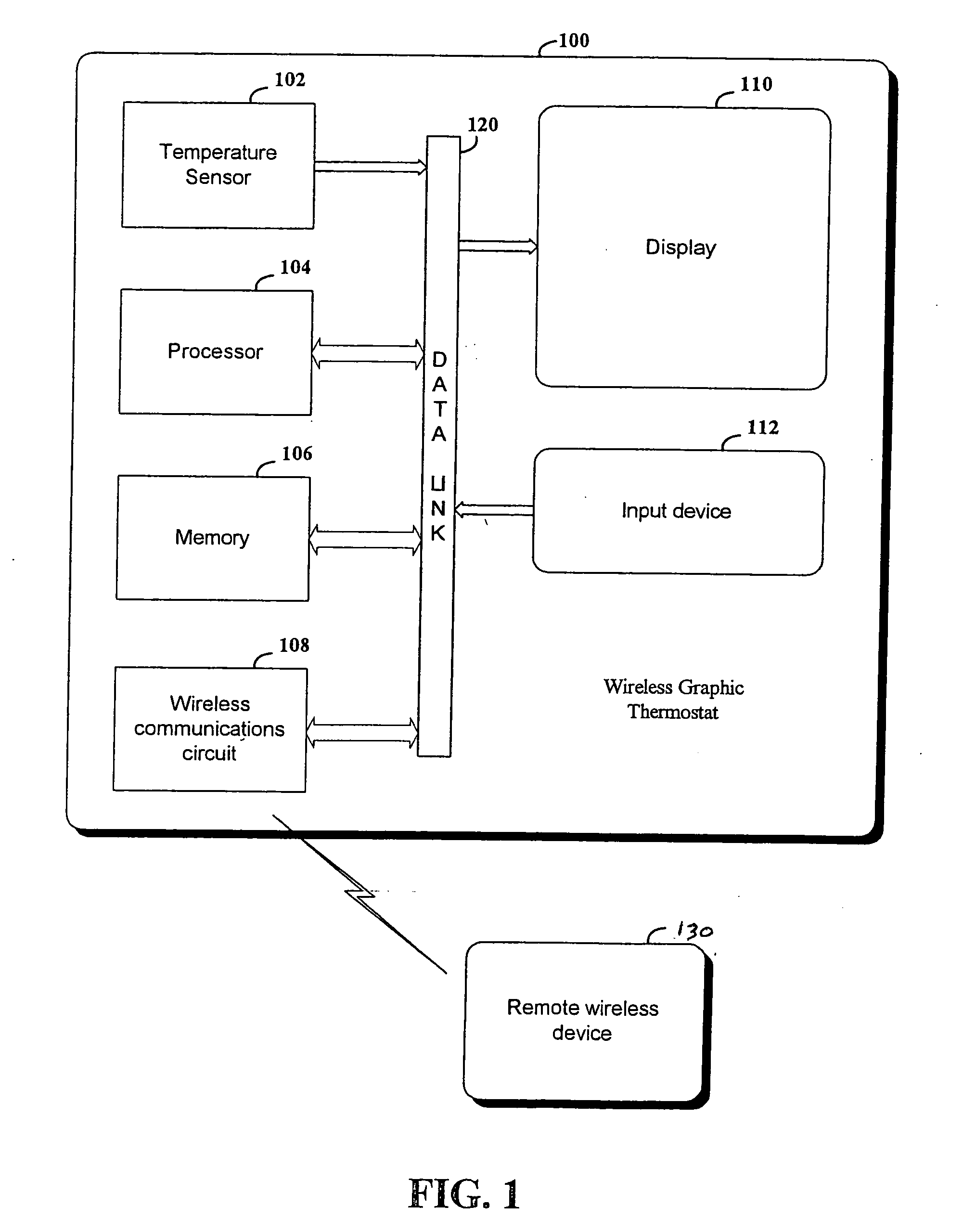
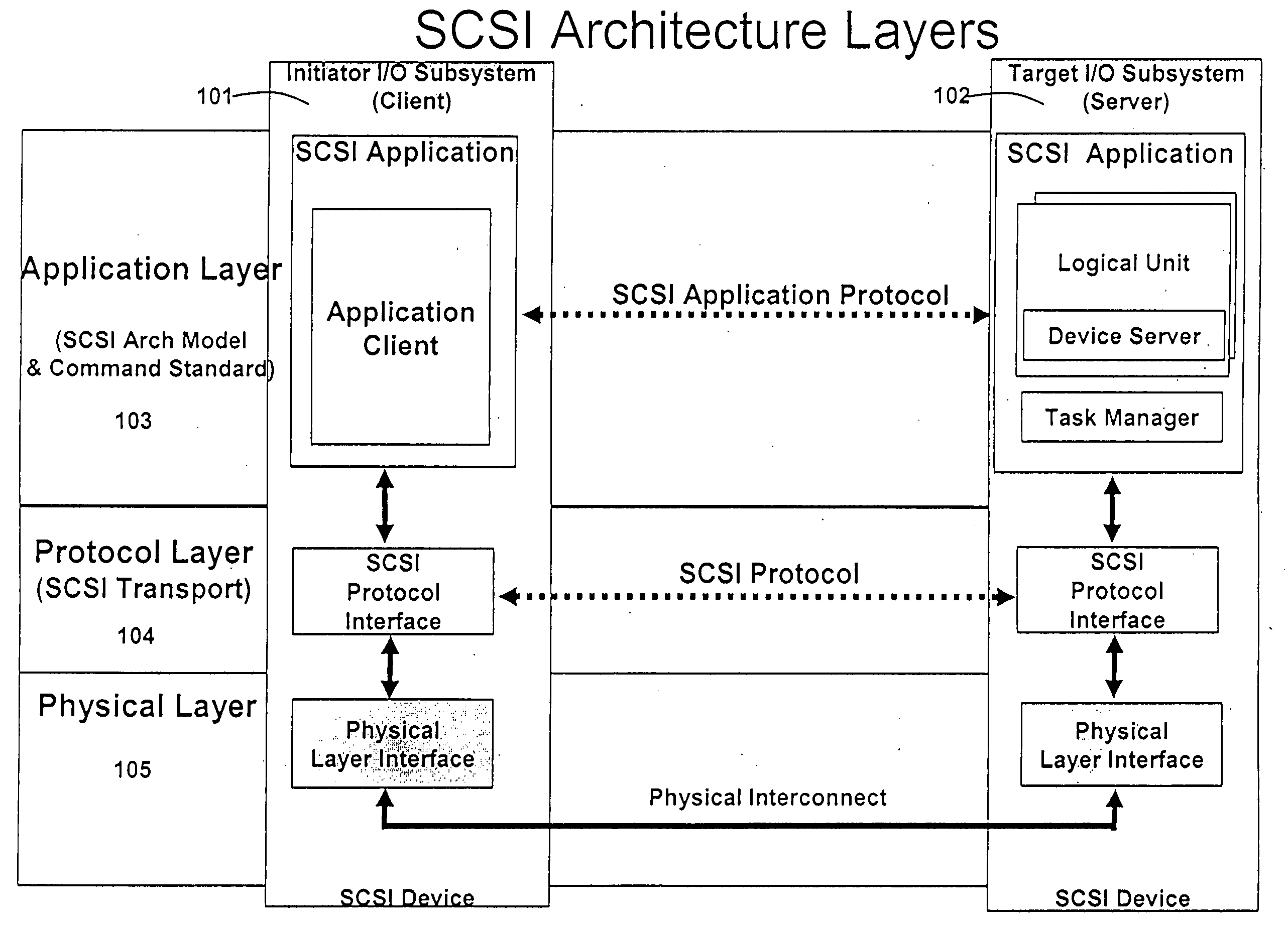
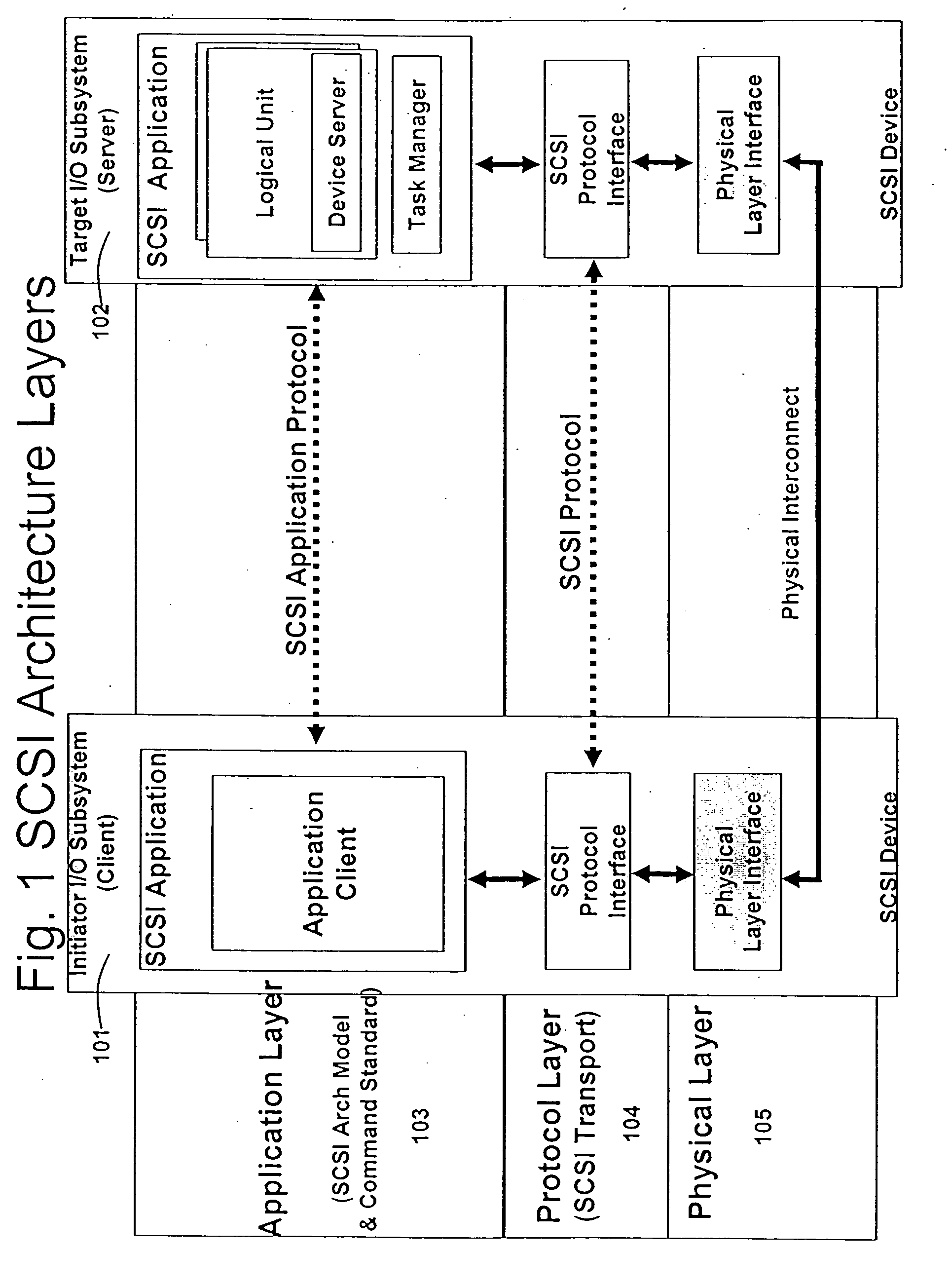
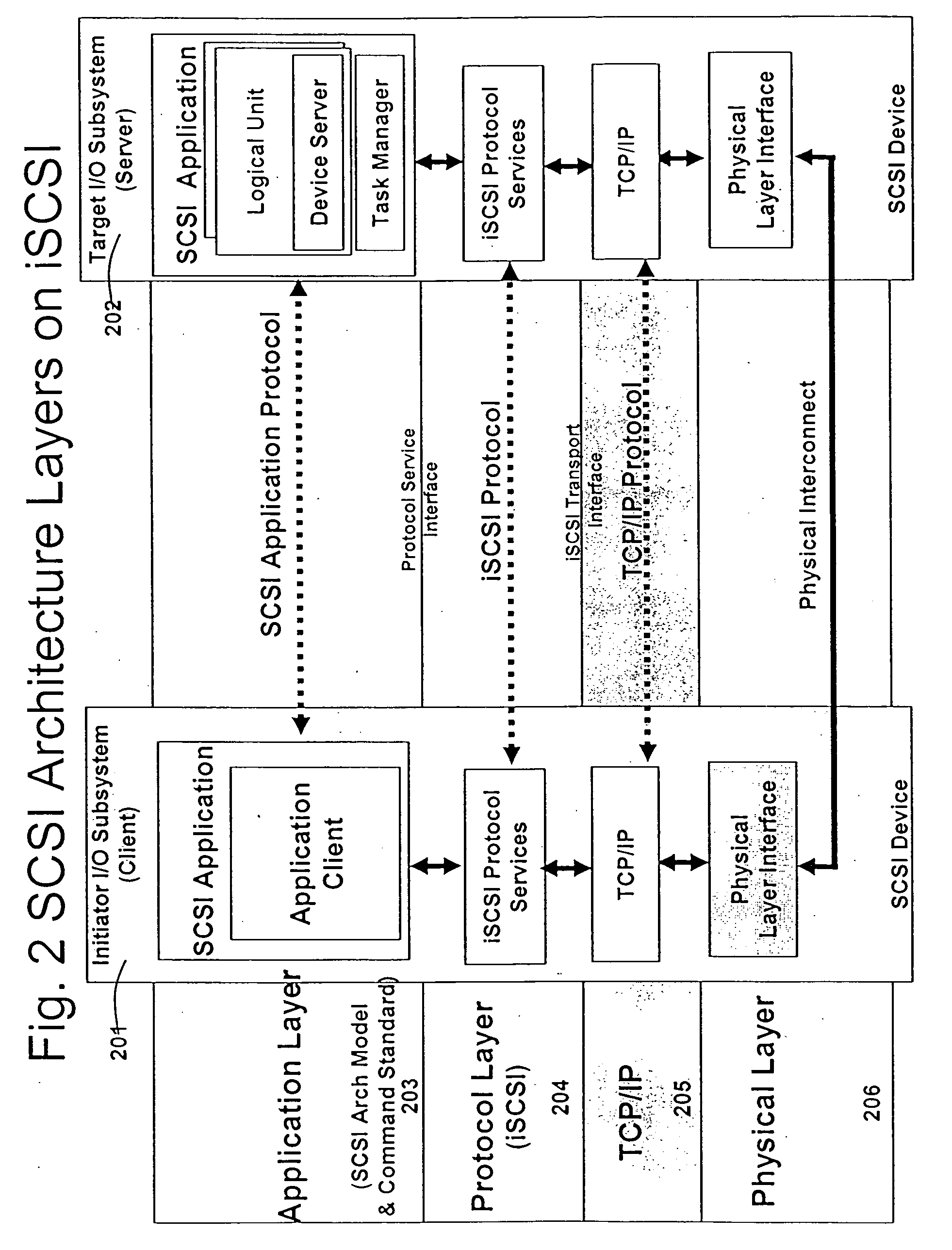
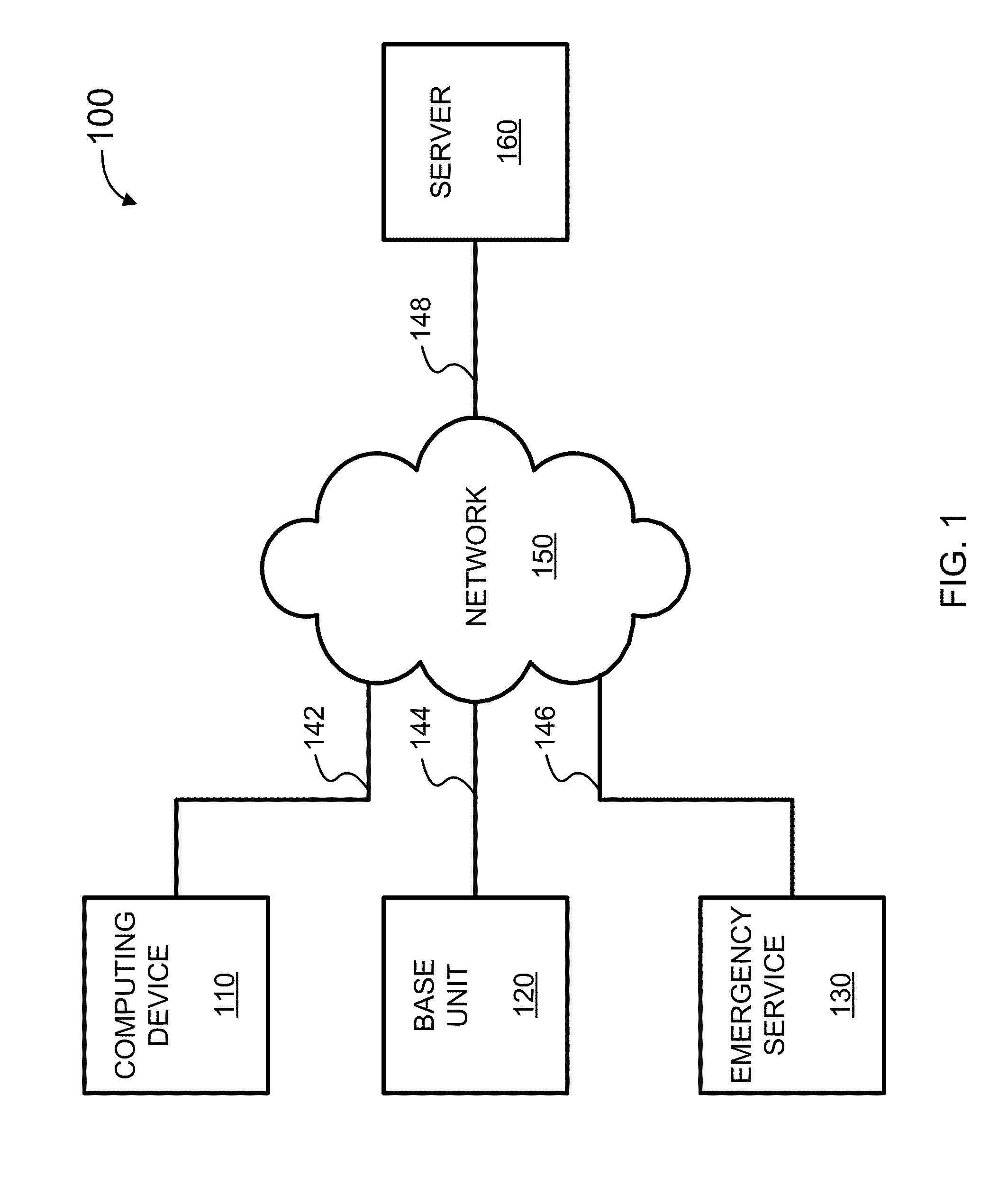
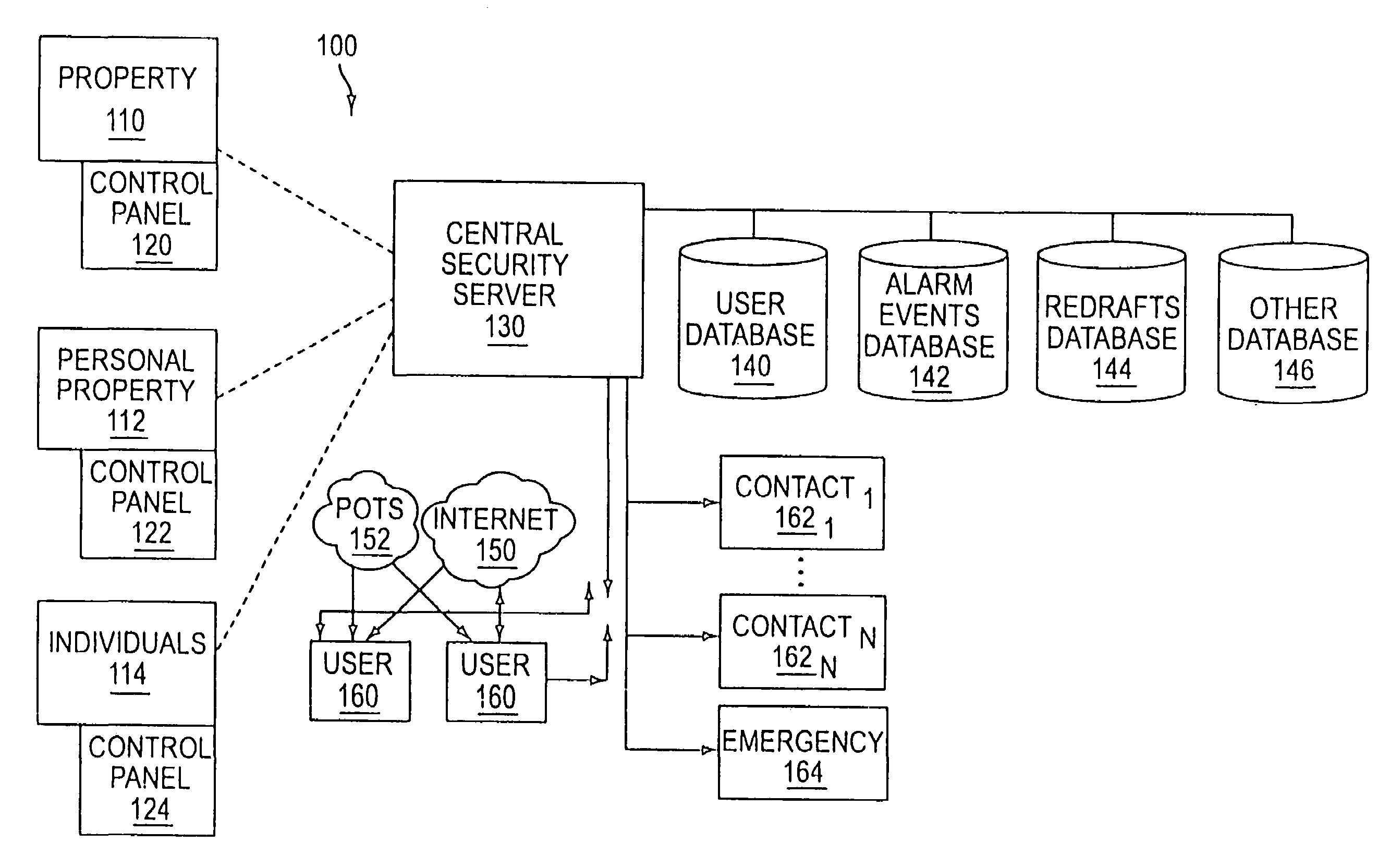
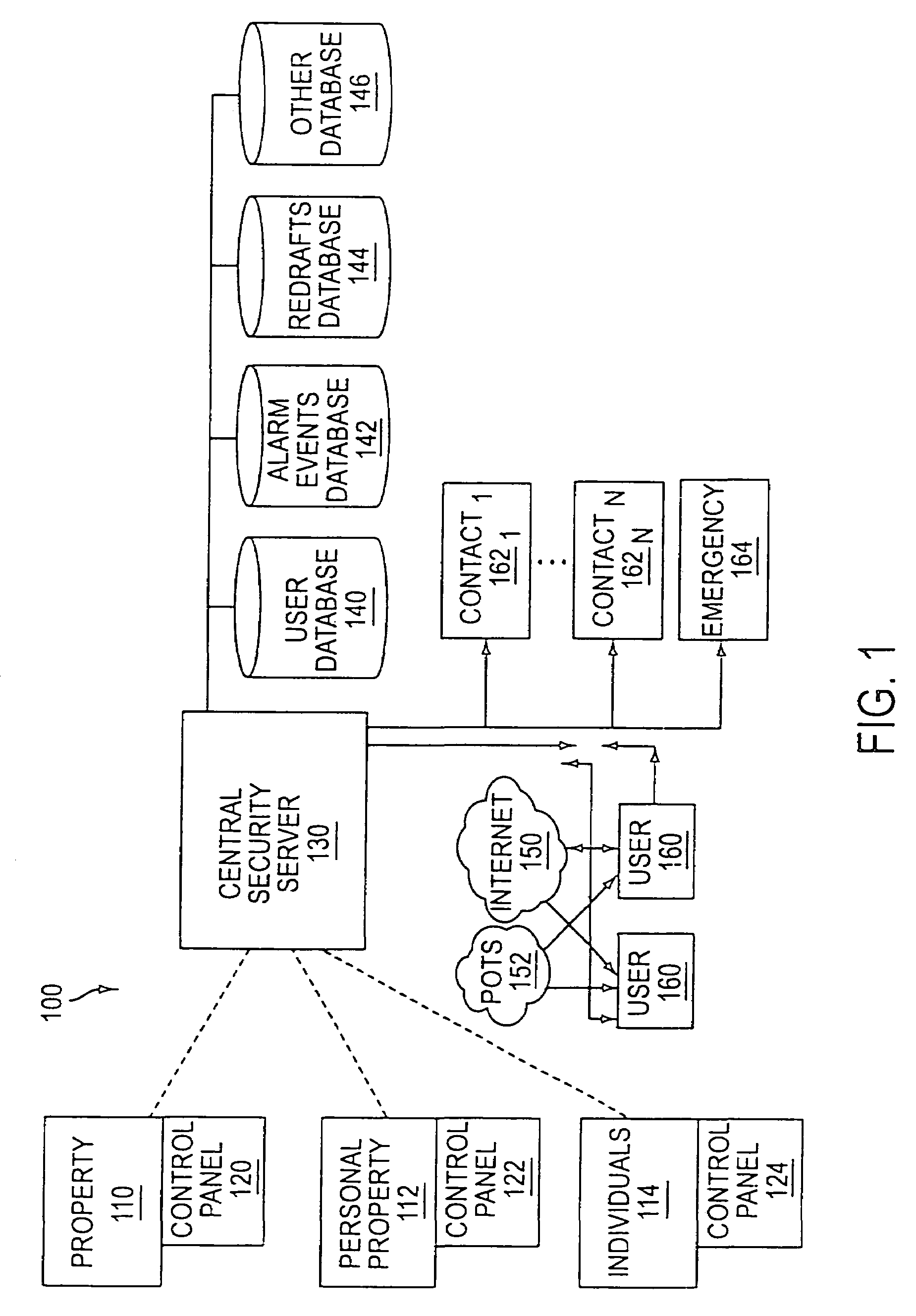
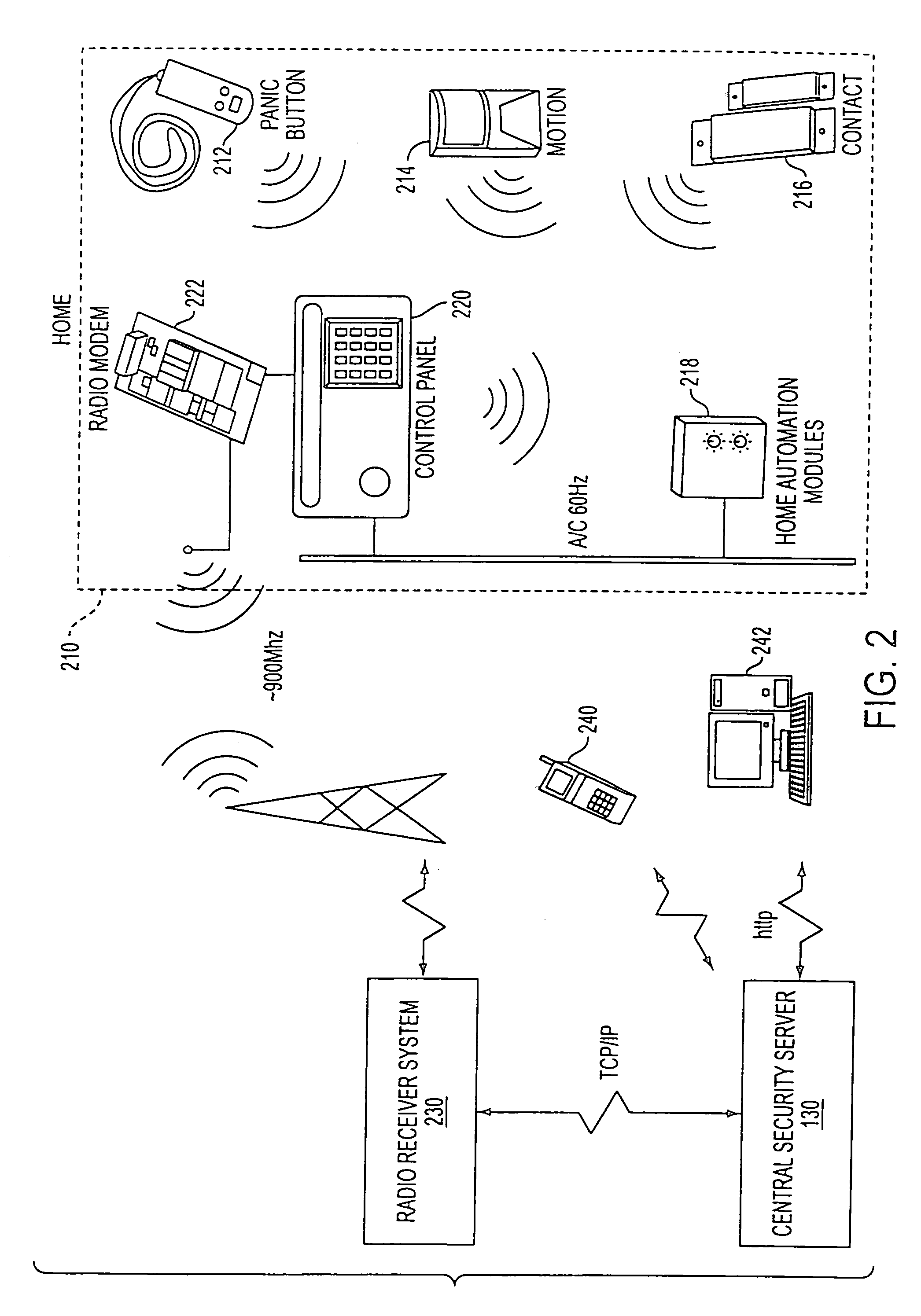
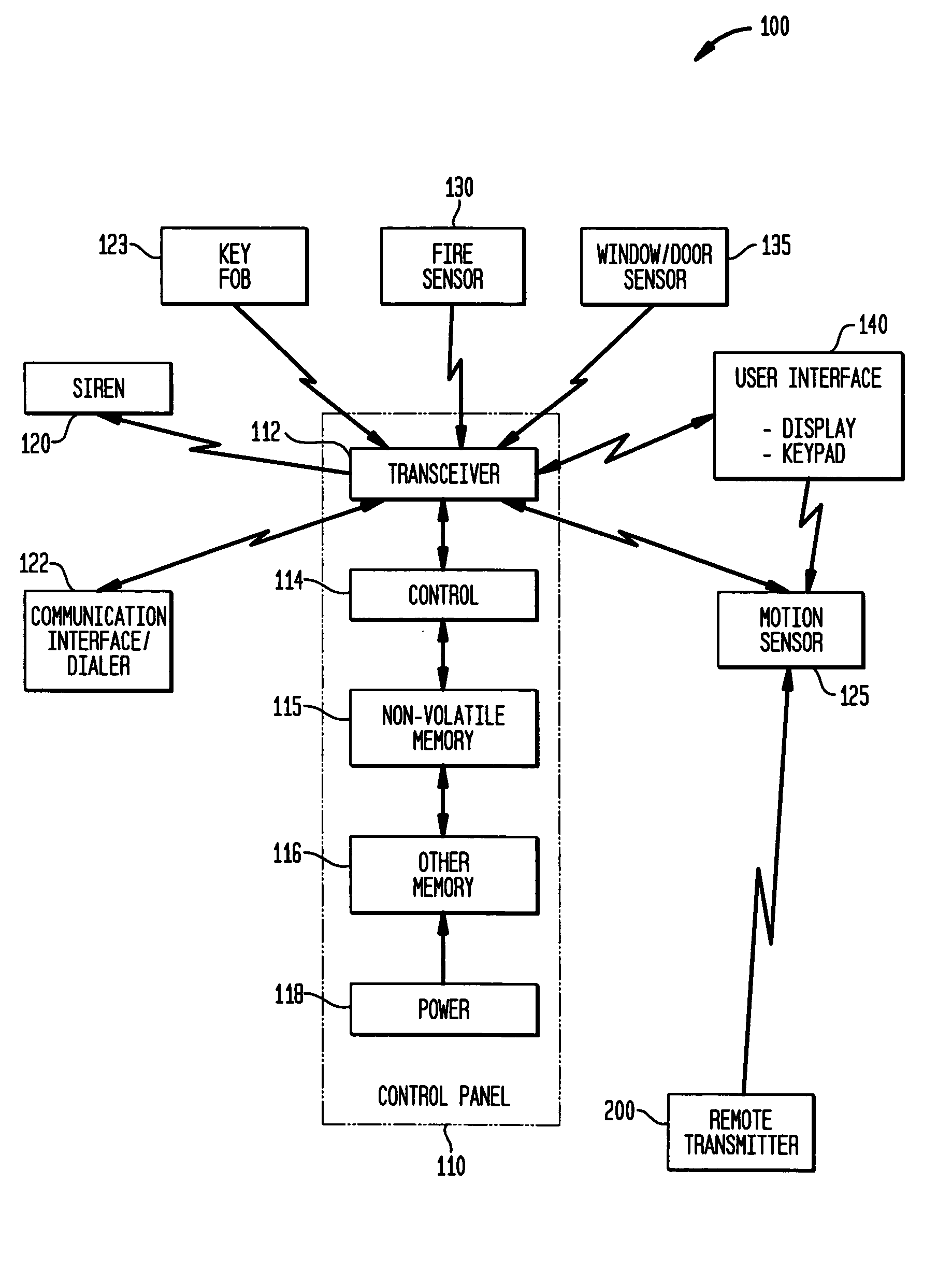
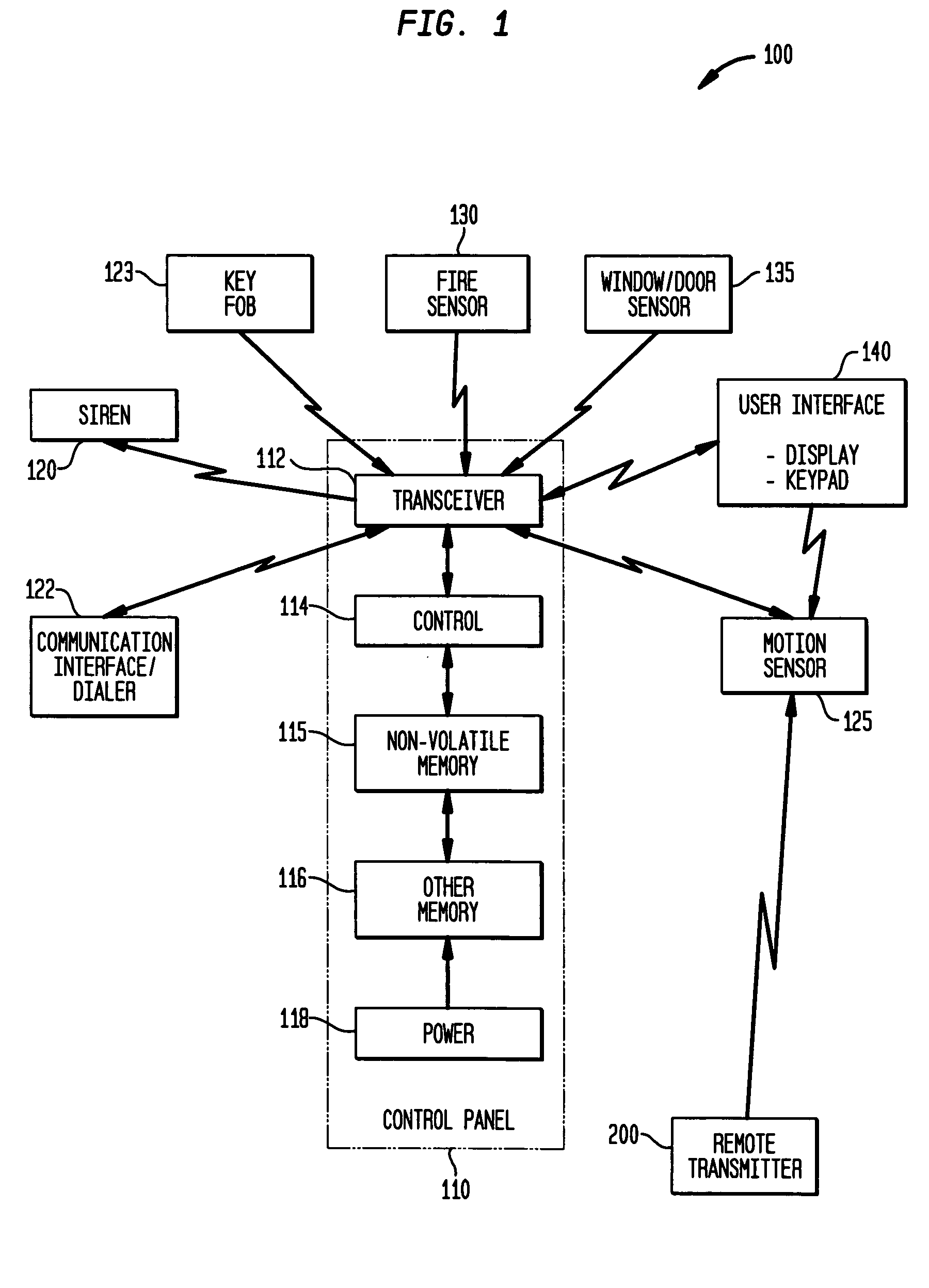
System and method for connecting security systems to a wireless device
InactiveUS7113090B1Electric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
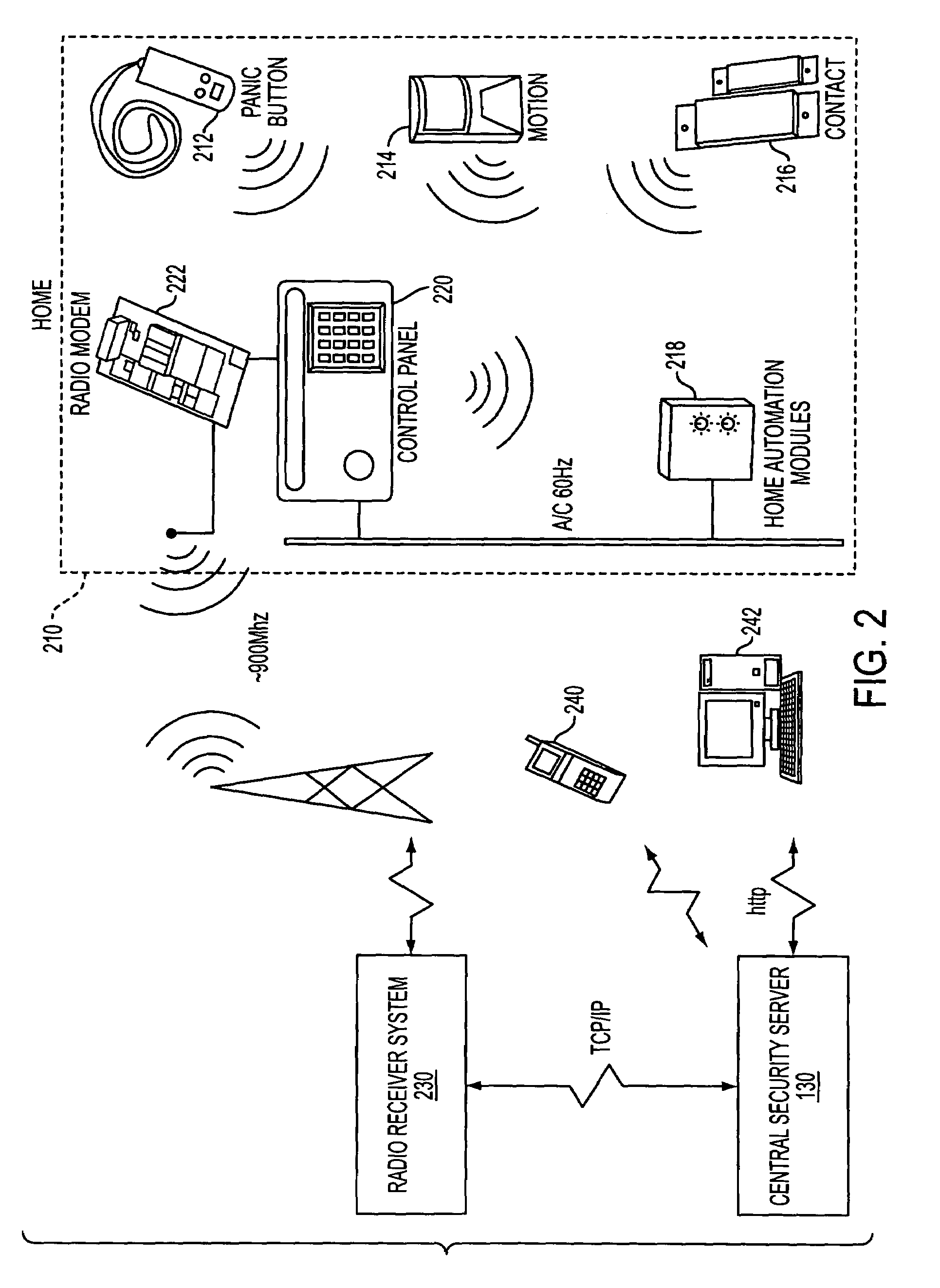
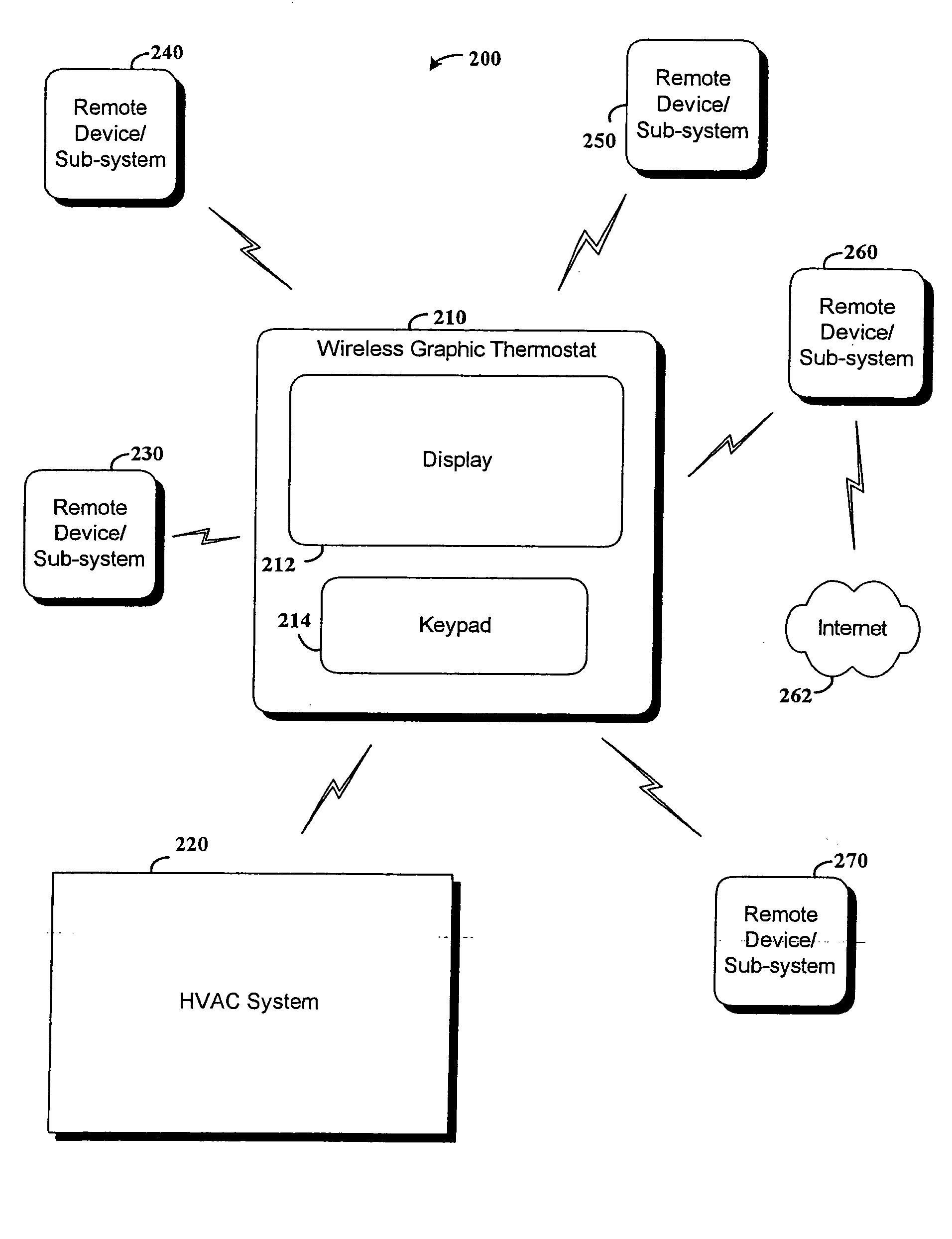
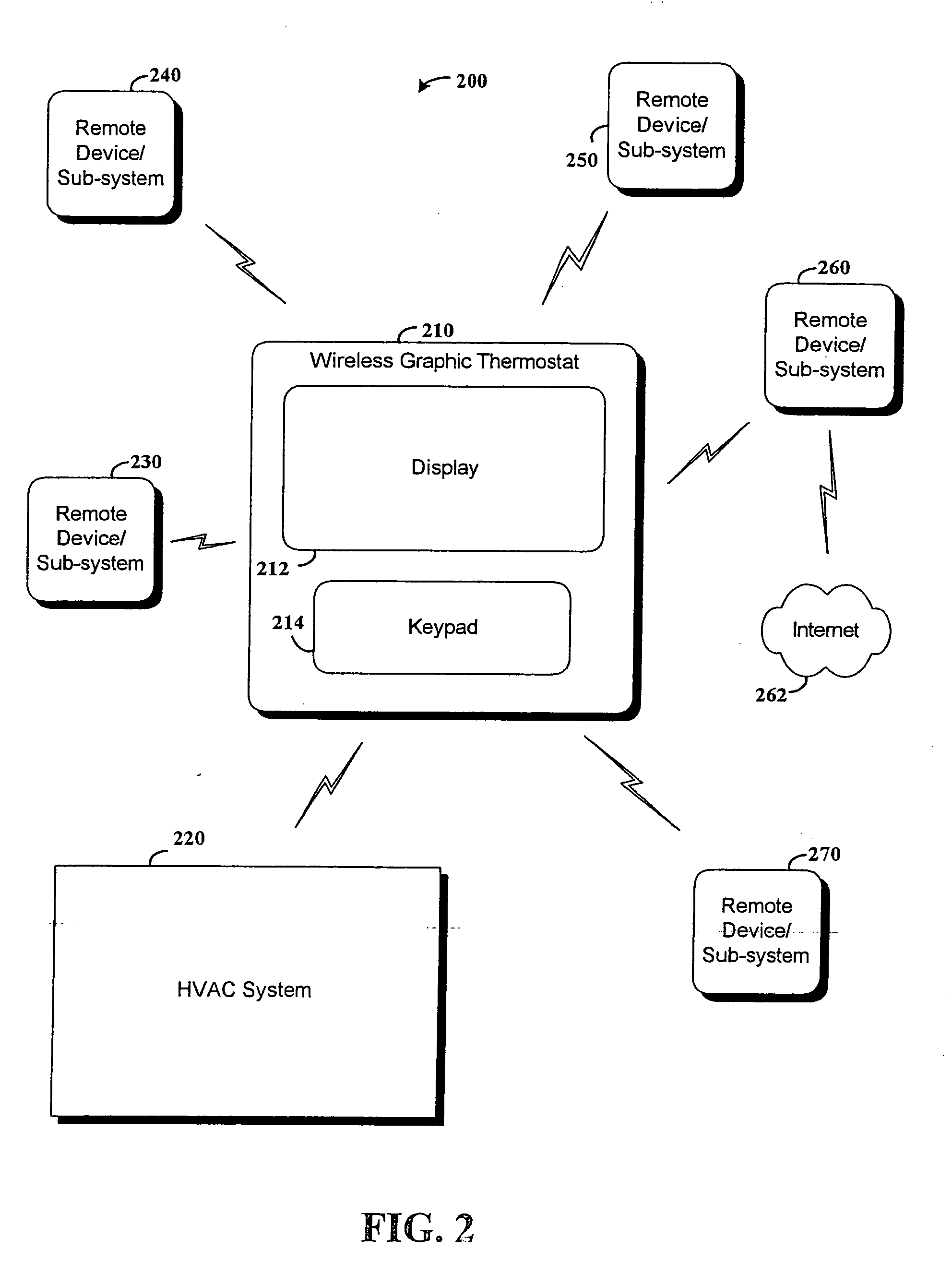
RF interconnected HVAC system and security system
InactiveUS20050270151A1Easy programmingMechanical apparatusSpace heating and ventilation safety systemsWireless controlThermostat
An interconnected wireless HVAC (heating, ventilation, air conditioning) system and wireless security system, which are interconnected and communicate with each other through the use of a common wireless technology, including the same selected frequency, modulation and a set of common protocols. The Wireless HVAC system includes wireless thermostats, which can communicate with and control both the HVAC system and the security system, and the wireless security system includes wireless controls or keypads, which can communicate with and control both the security system and the HVAC system. The universal wireless infrastructure can be expanded to provide communication or control of additional user or manufacturer installed wireless devices or systems through the universal wireless home infrastructure.
Owner:HONEYWELL INT INC
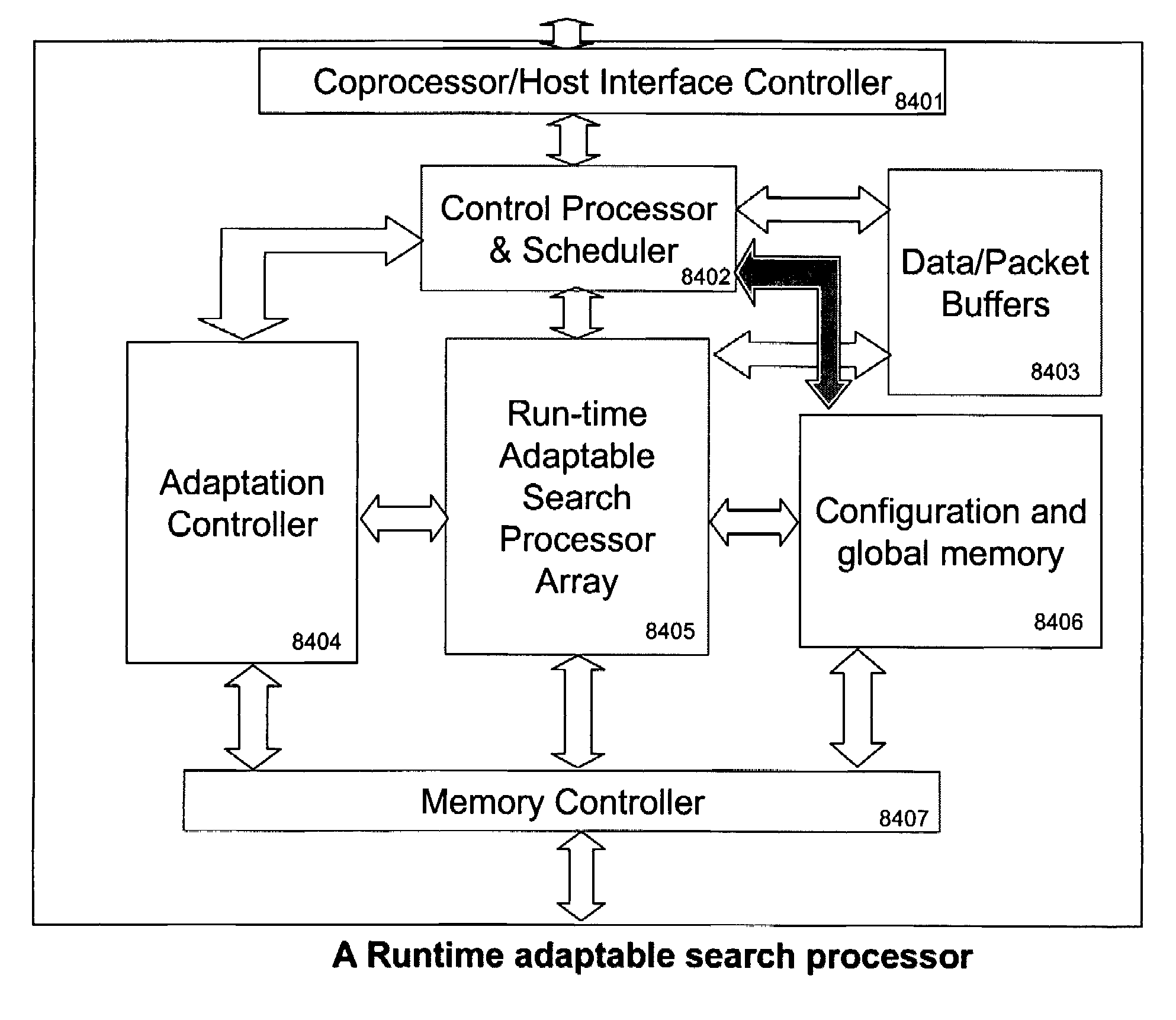
Runtime adaptable search processor
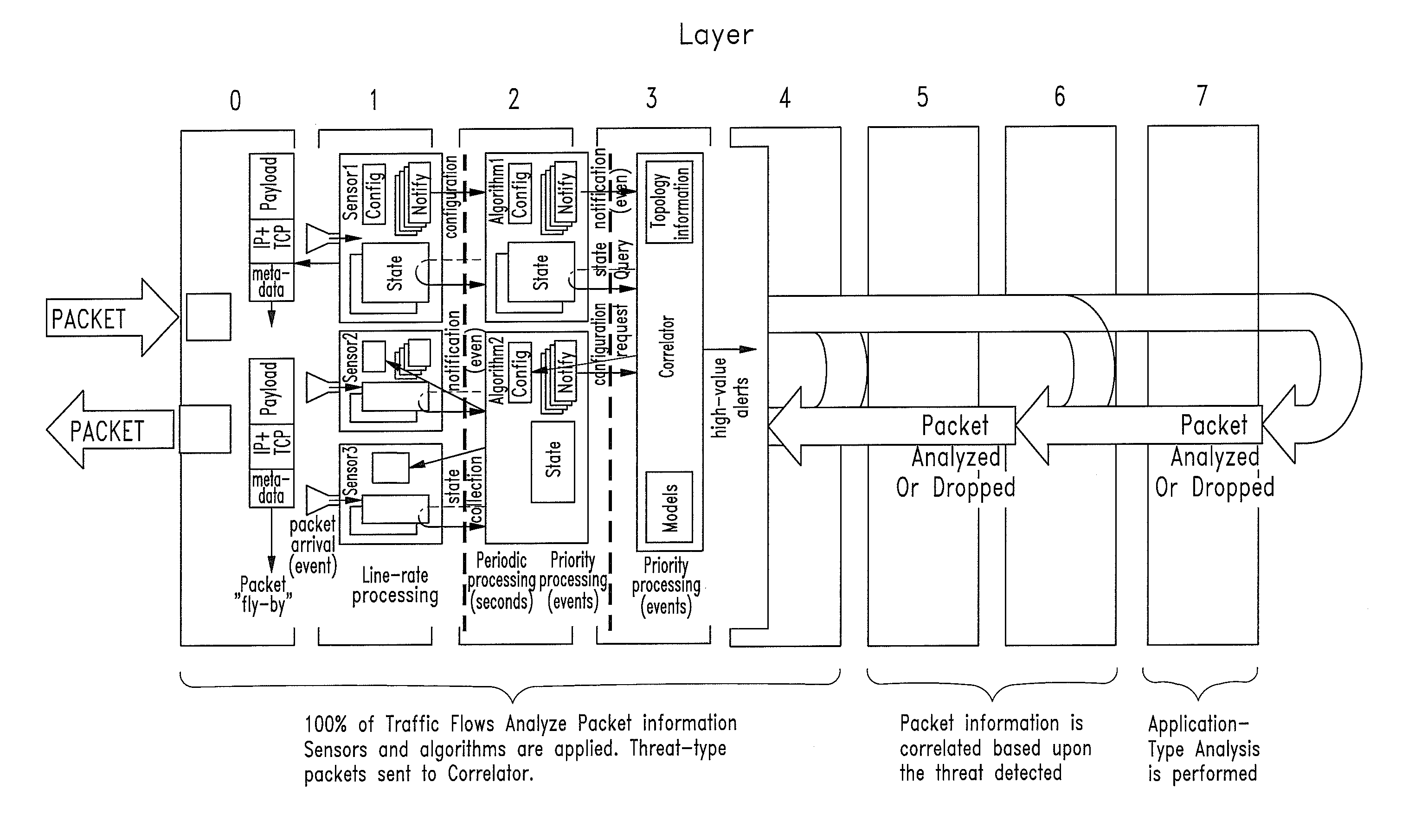
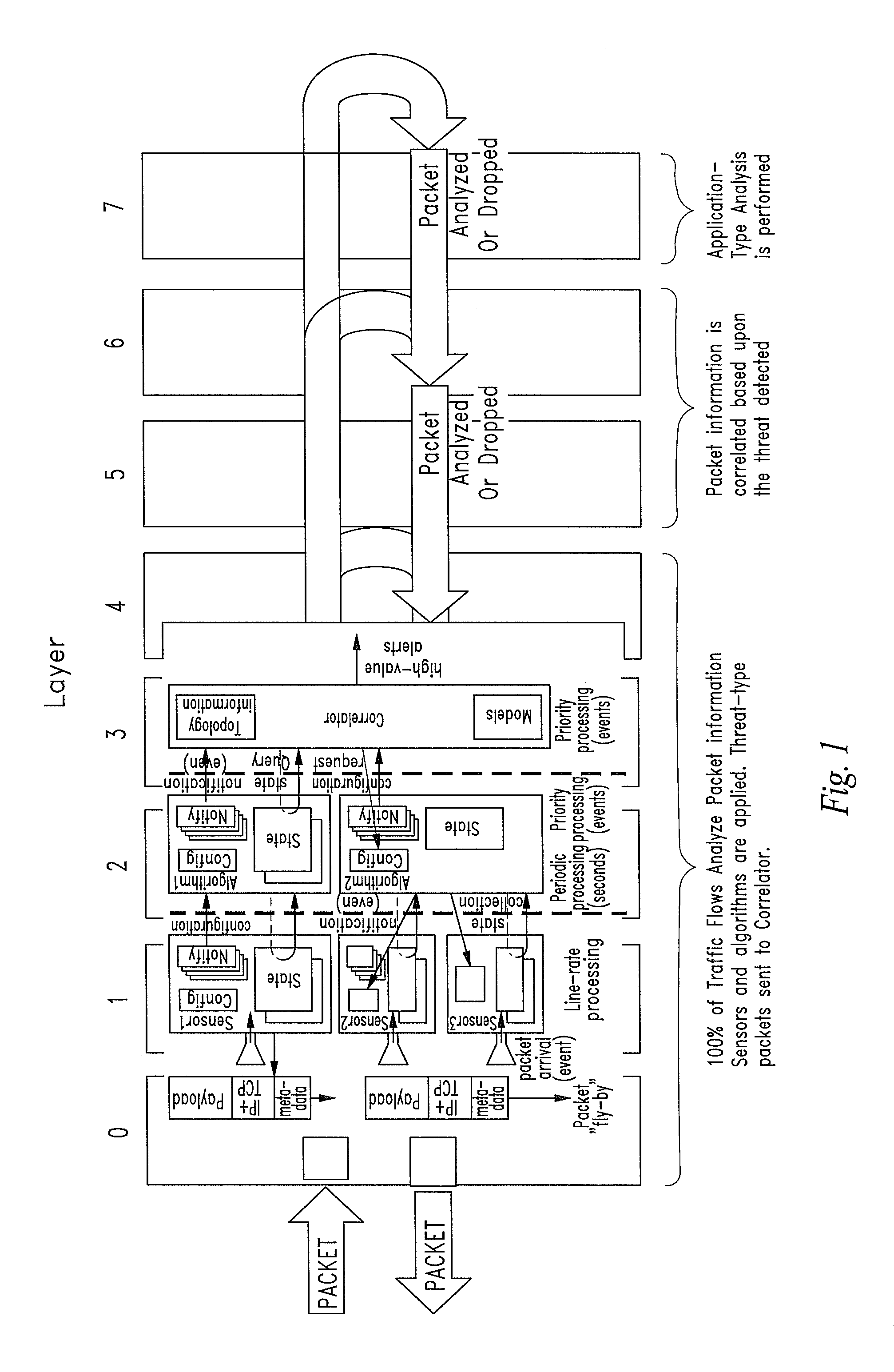
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
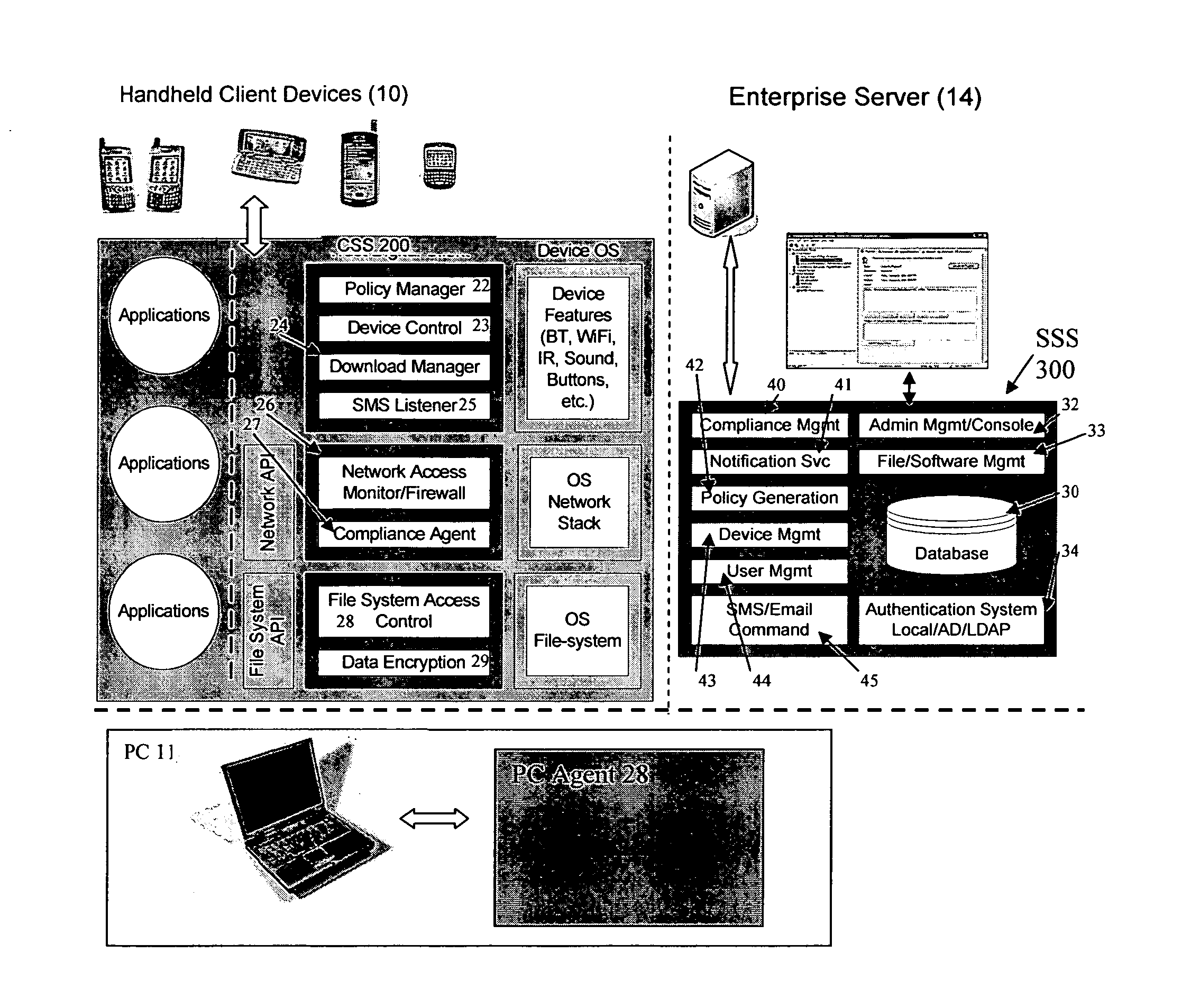
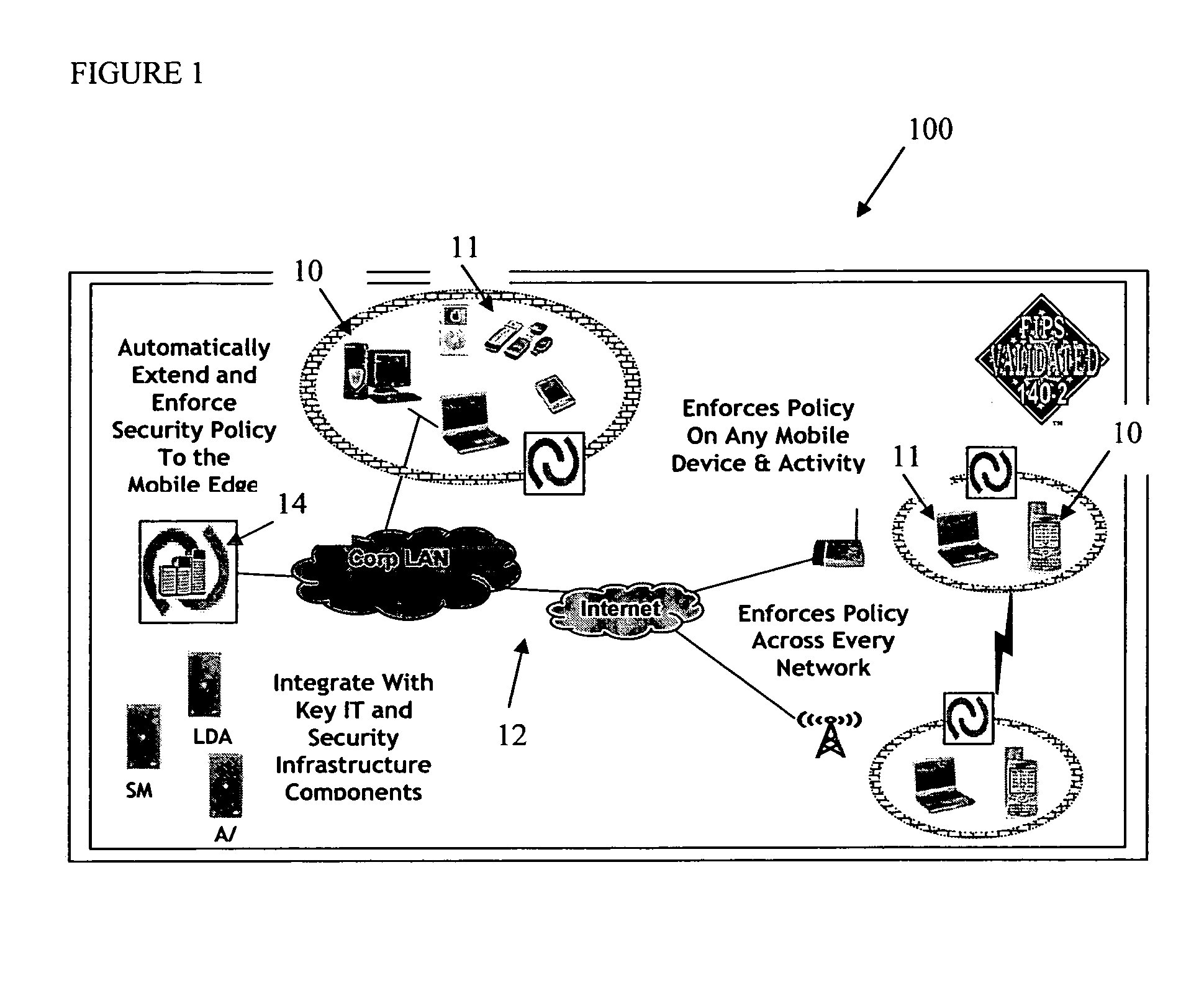
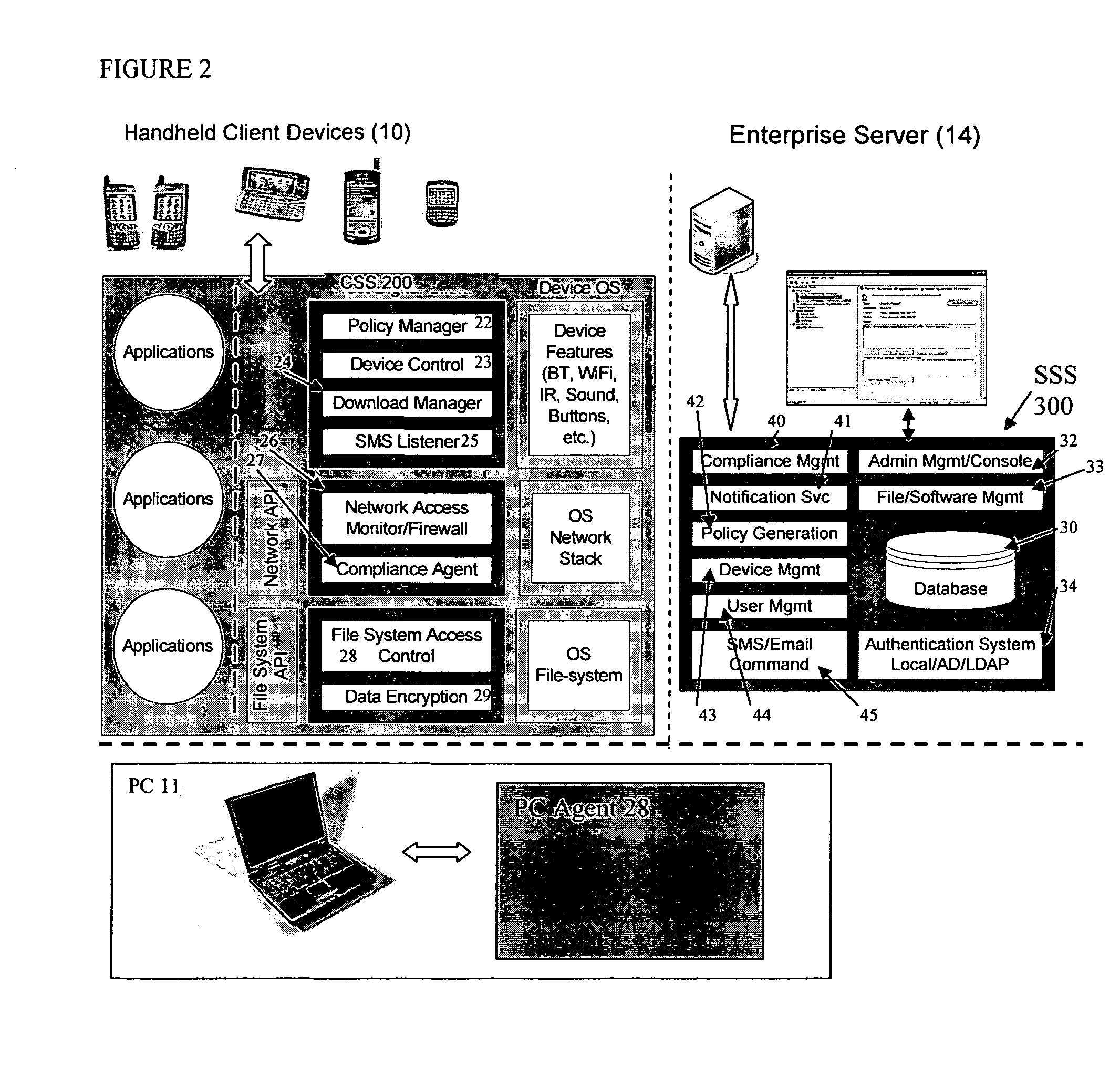
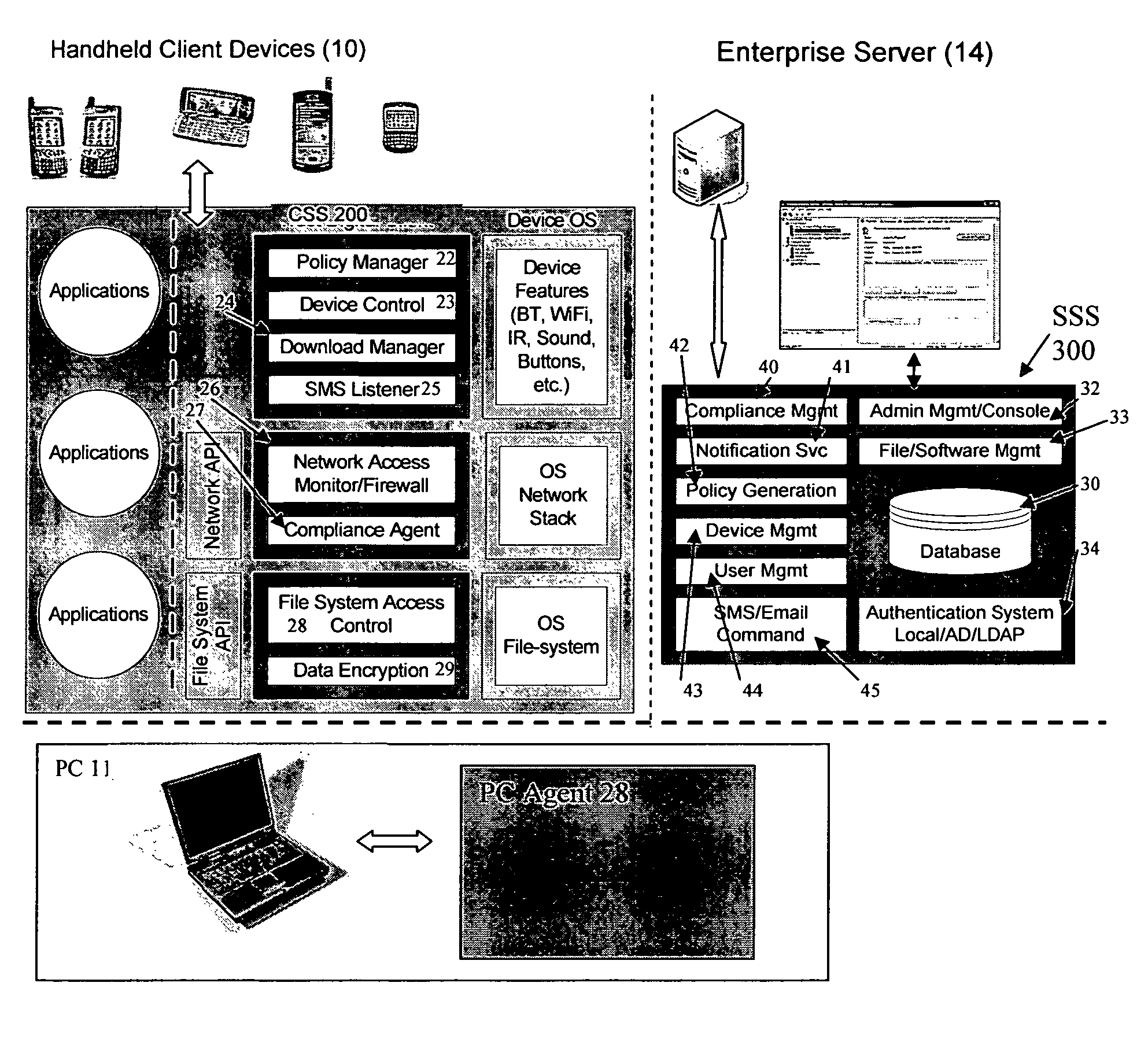
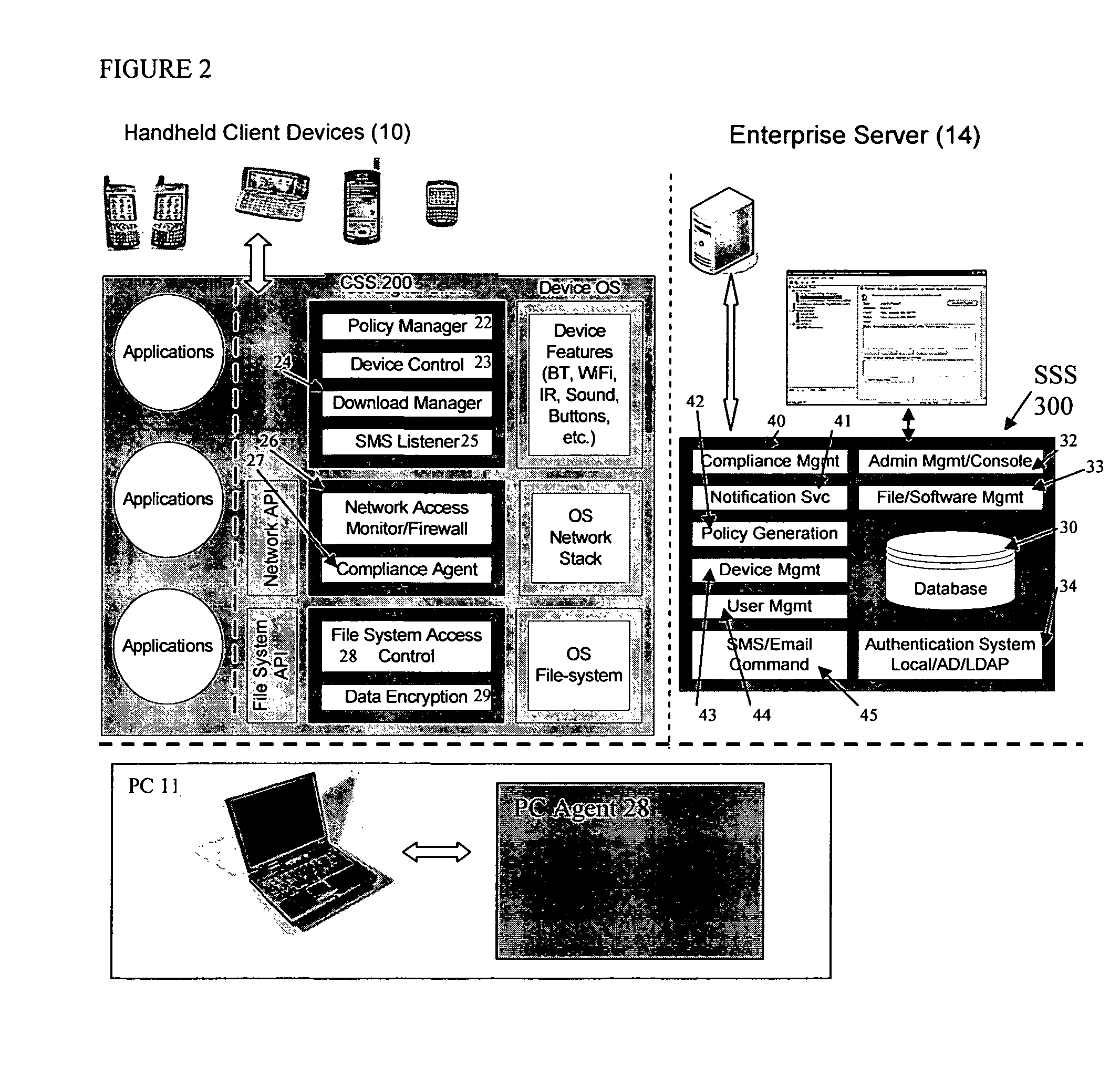
Mobile data security system and methods
ActiveUS20060224742A1Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securitySecurity system
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
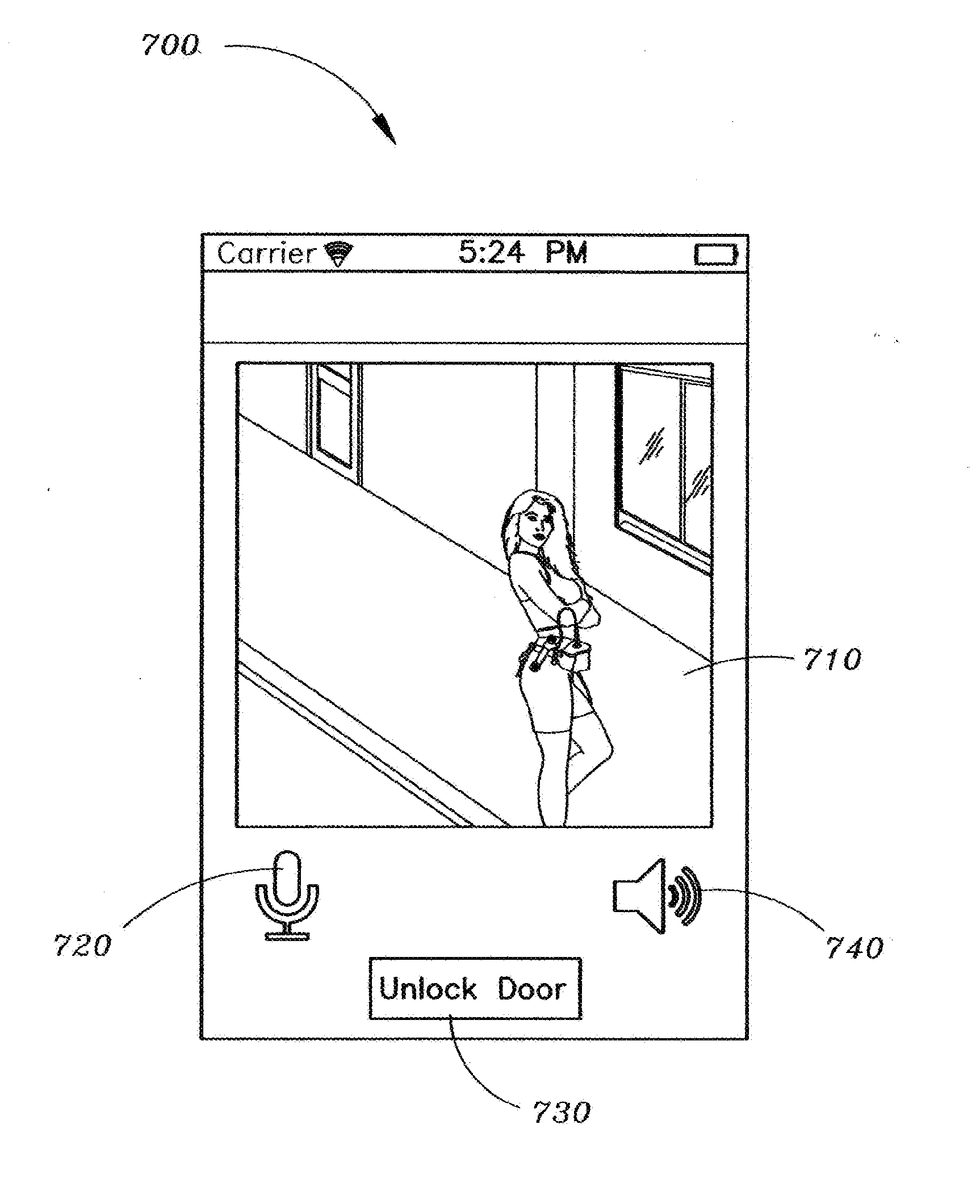
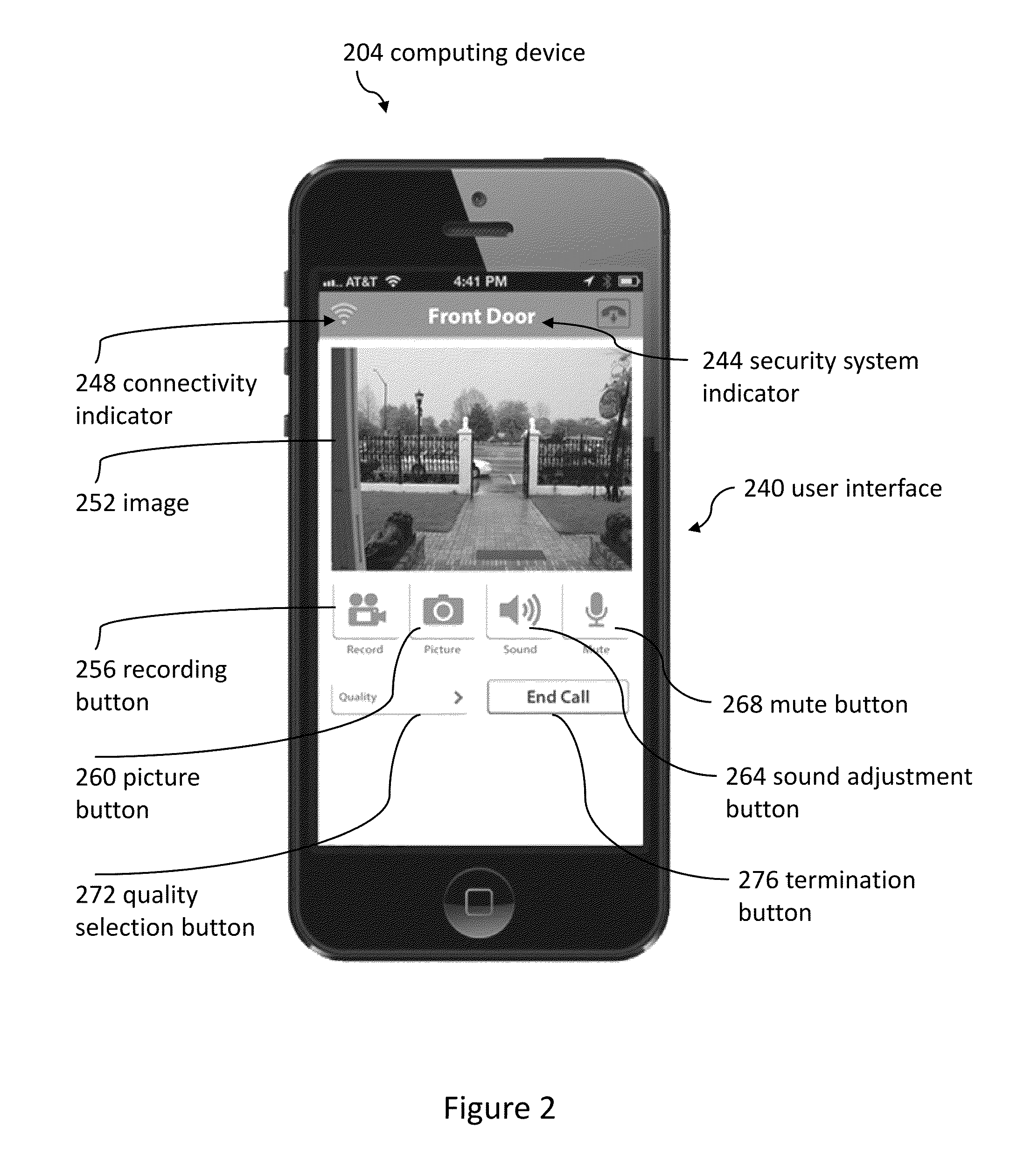
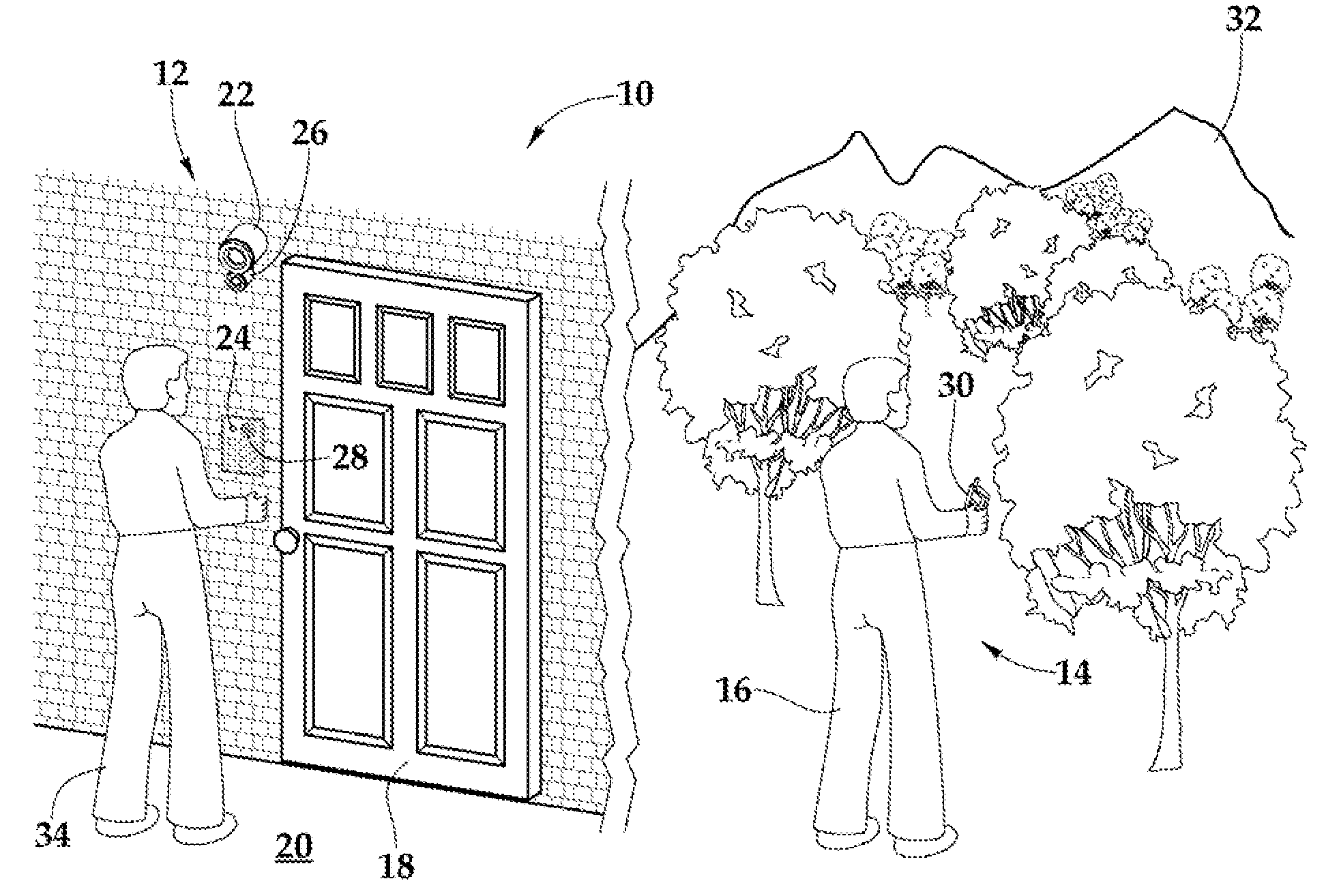
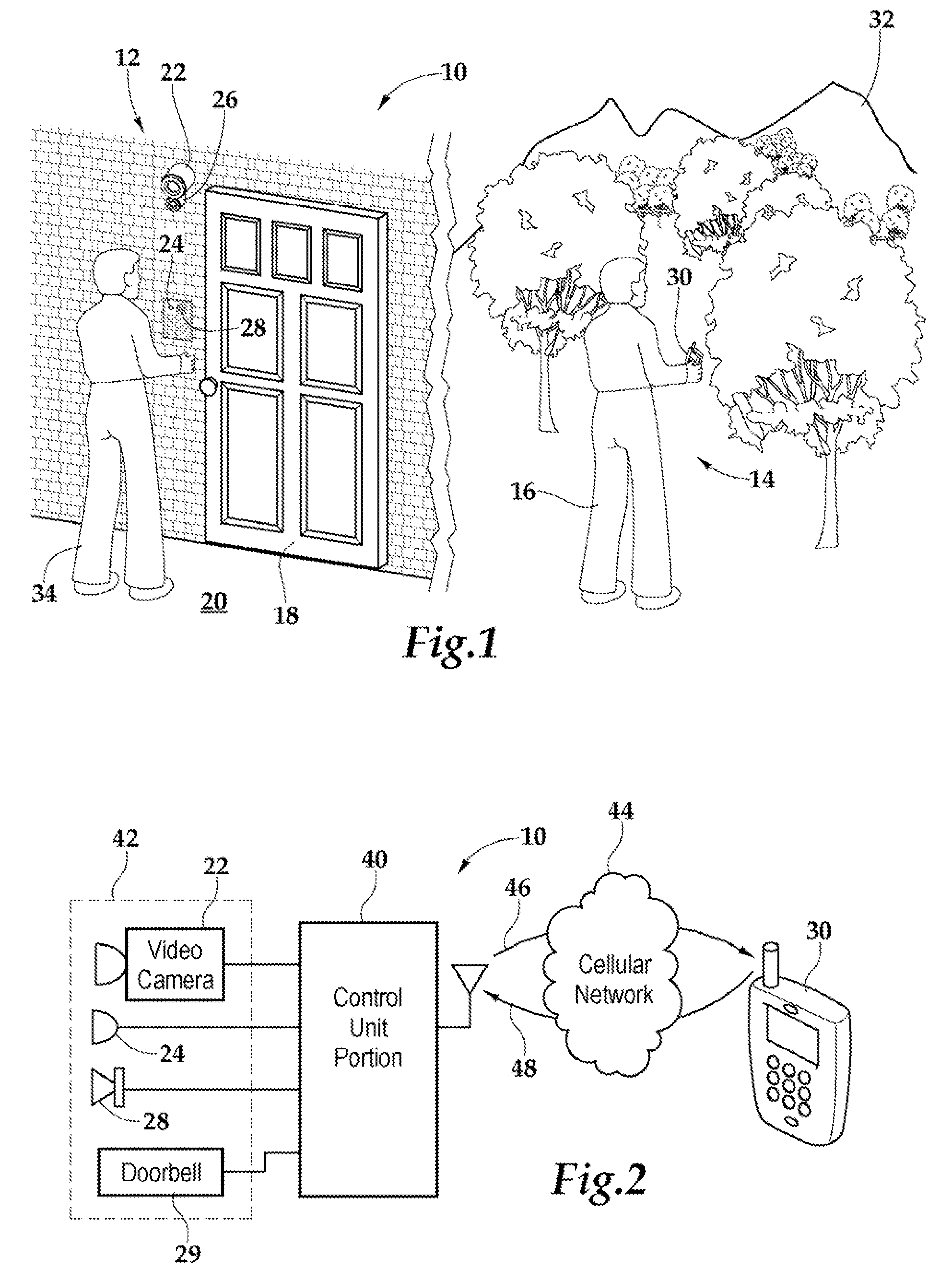
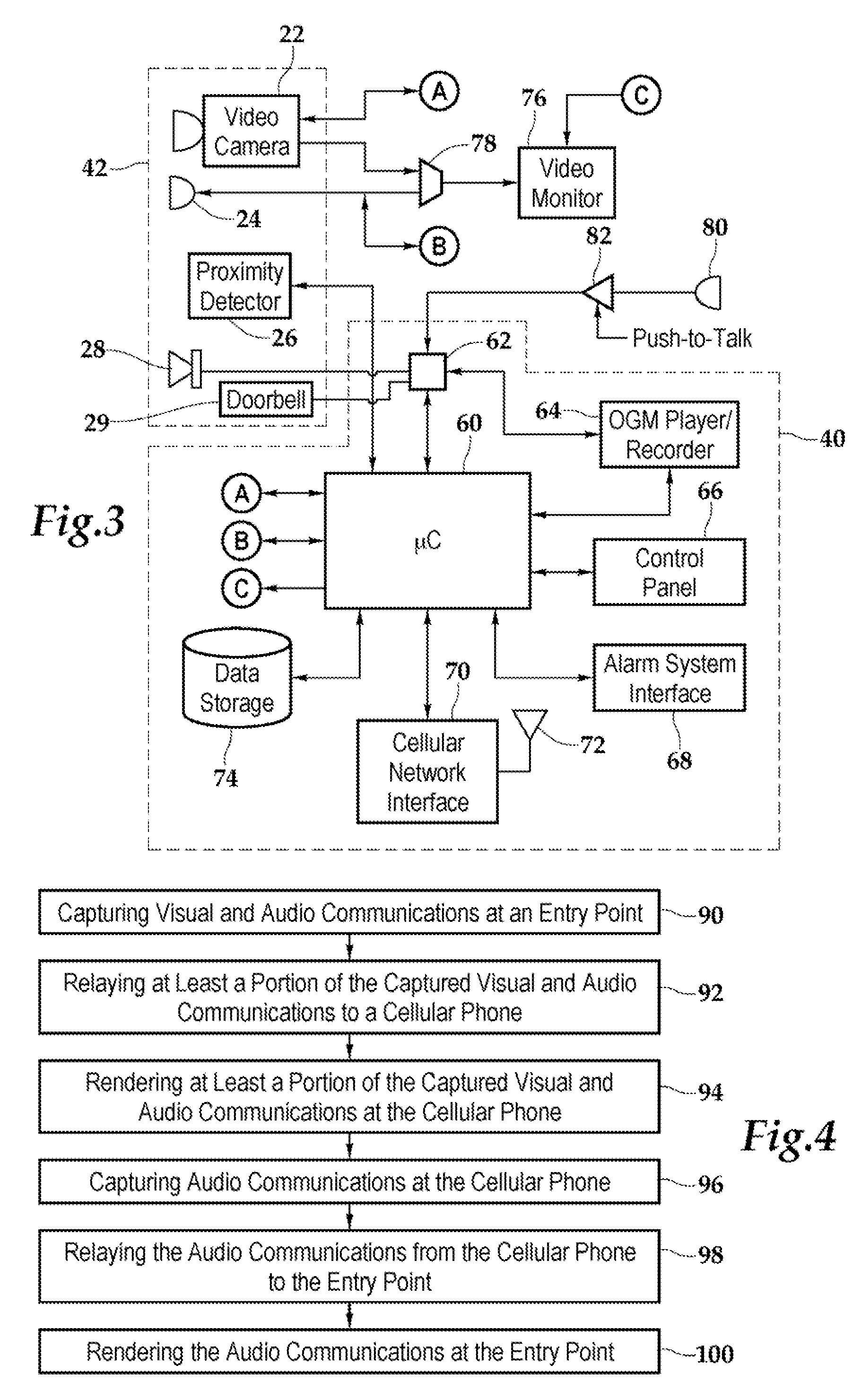
Method and apparatus for unlocking/locking a door and enabling two-way communications with a door security system via a smart phone
A method for operating a doorbell security system. The method may include receiving a doorbell press event signal and sending a doorbell press event notification to at least one mobile computing device. The method may further include receiving an acceptance response from a particular mobile computing device, wherein the acceptance response. The method may include receiving audio from a microphone and video from a camera located in proximity to a doorbell. The method may also include sending the audio from the microphone and the video from the camera to the particular mobile computing device. The method may additionally include receiving a command from the mobile computing device and unlocking, locking, opening, or closing a door.
Owner:HUISKING TIMOTHY J
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
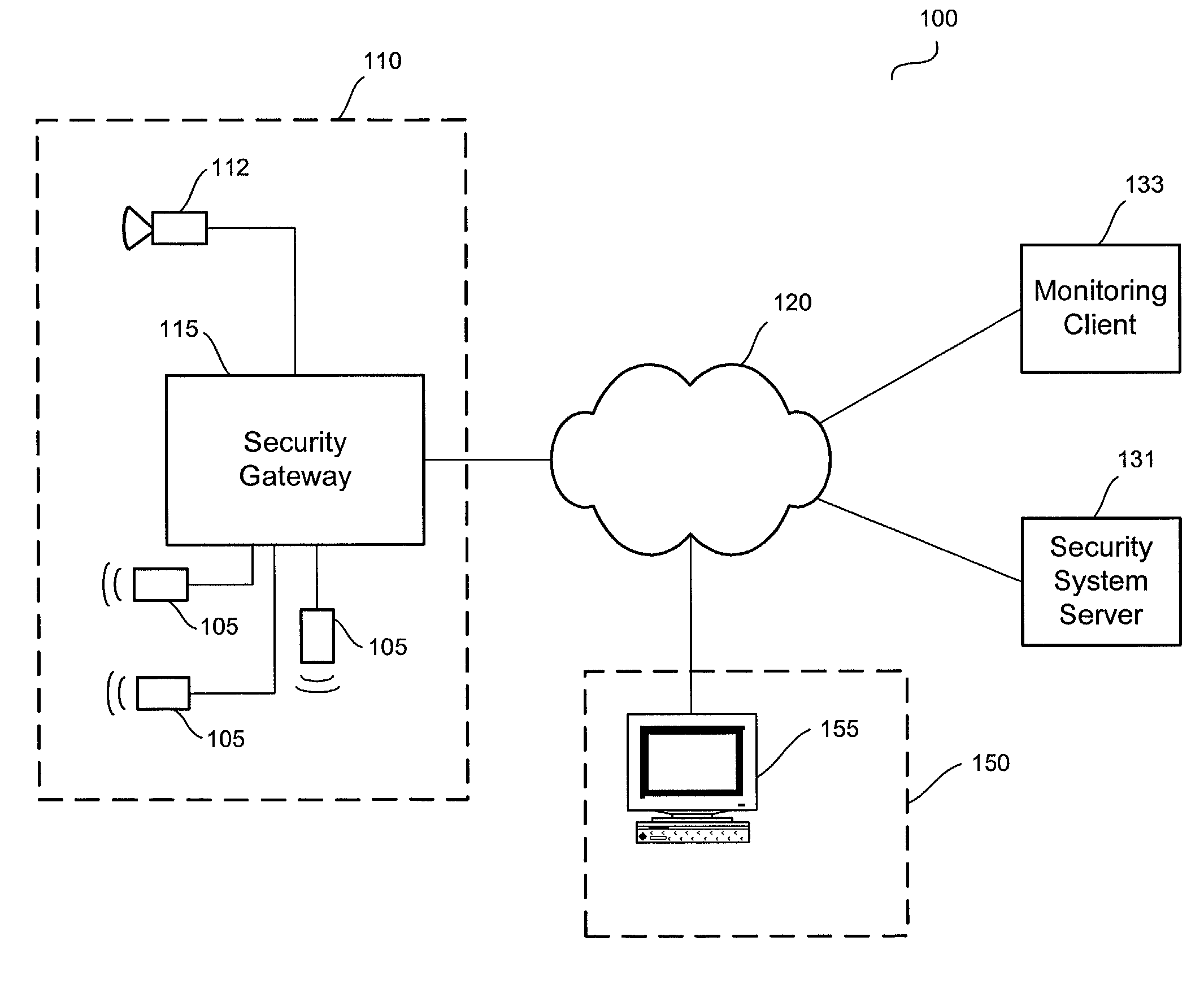
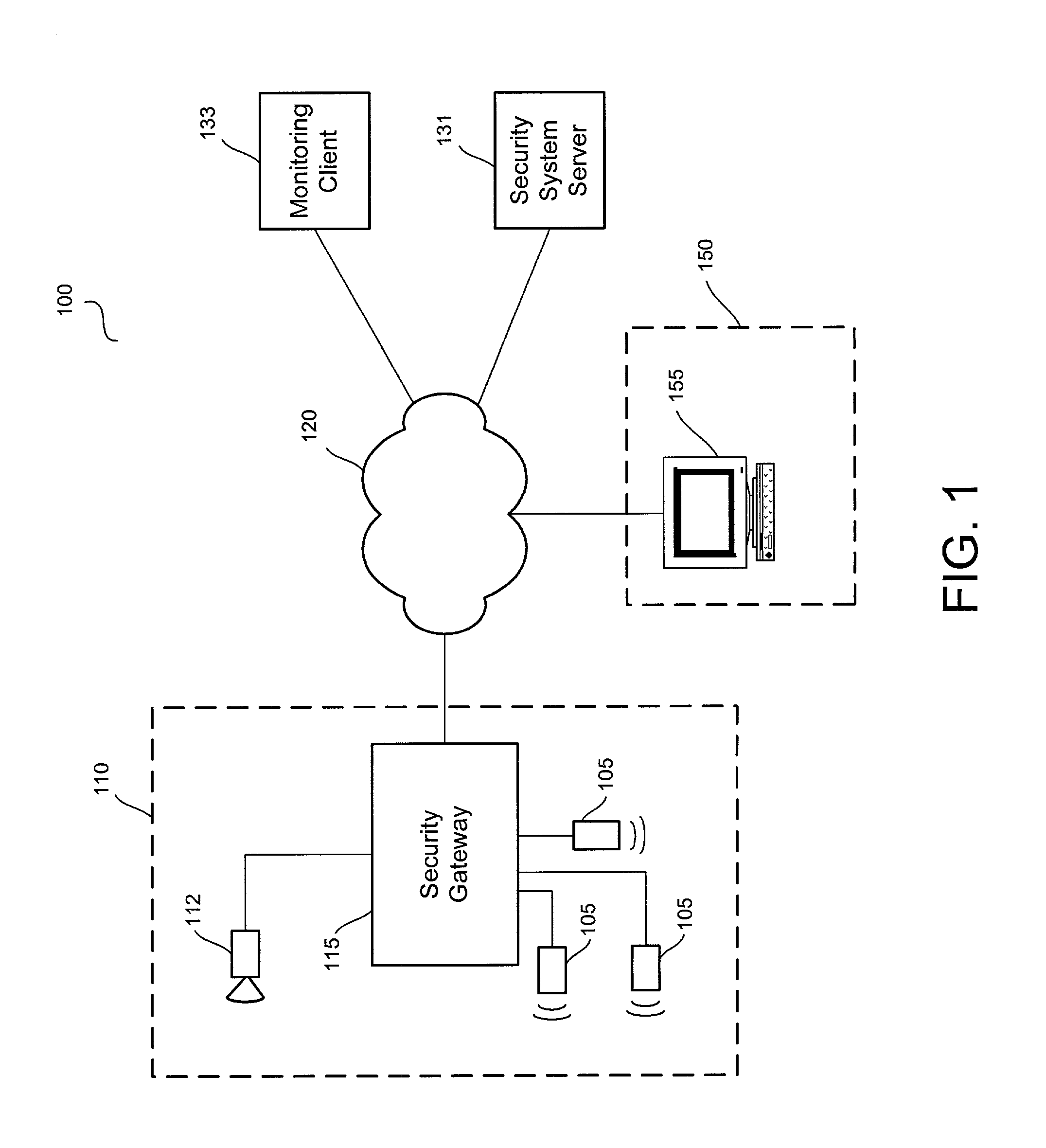
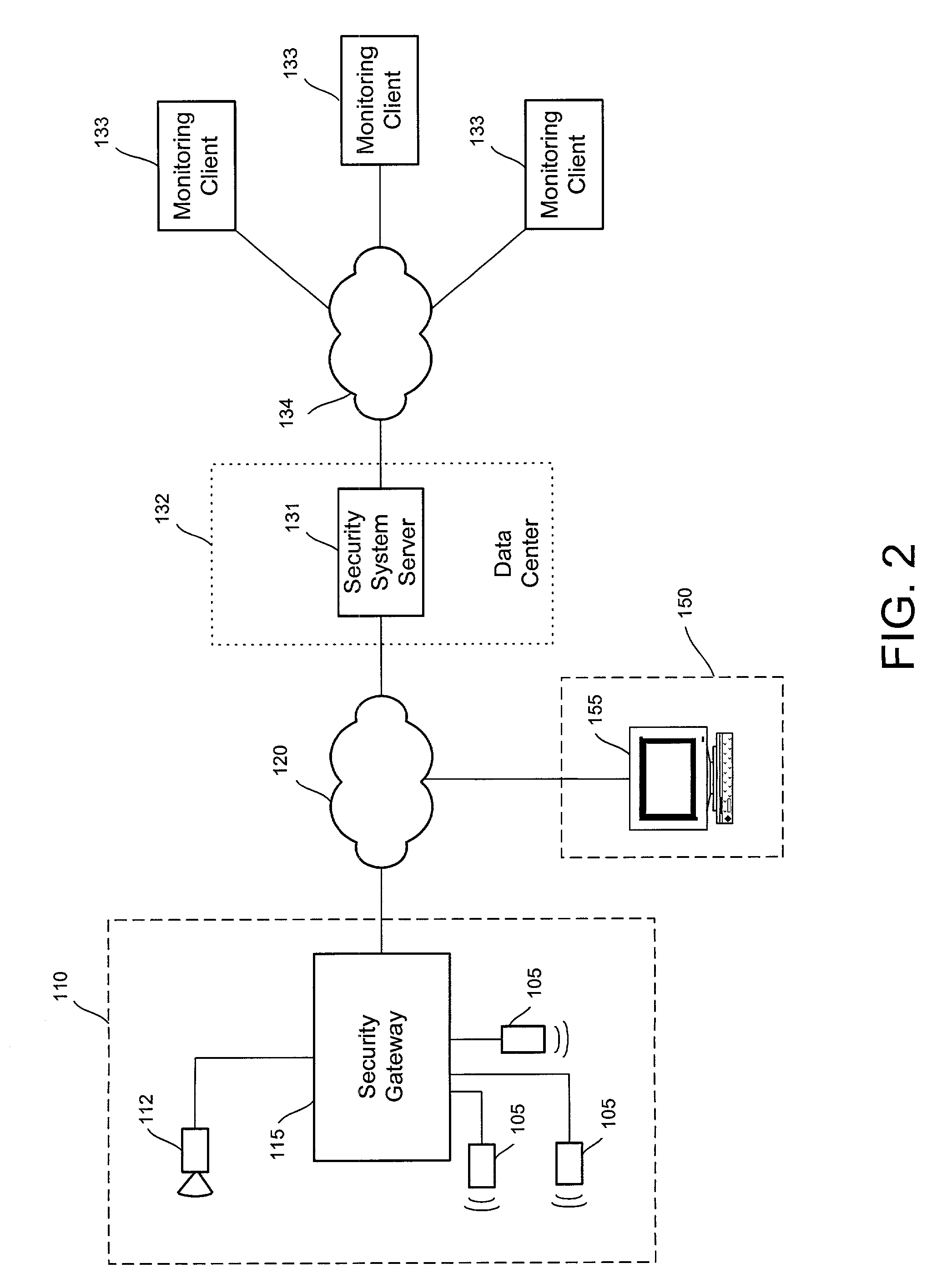
Distributed monitoring for a video security system
A system and method for distributed monitoring and remote verification of conditions surrounding an alarm condition in a security system. A security gateway detects alarm conditions at a premises and records video relating to the alarm condition. The security gateway transmits an alarm notification and the video across a network to a security system server in substantially real time. The security system server relays information to one or more distributed monitoring clients using rules-based routines for verification of the alarm condition. An operator at a monitoring client determines whether the alarm condition represents an actual alarm event and activates an appropriate response.
Owner:COMCAST CABLE COMM LLC
Security systems and methods for use with structured and unstructured data
InactiveUS20130104251A1Increase flexibilityEasy accessDigital data processing detailsAnalogue secracy/subscription systemsUnstructured dataDistributed database
Disclosed herein are systems and methods including hardware, software and electronic service components and systems to provide large-scale, reliable, and secure foundations for distributed databases and content management systems combining unstructured and structured data, and allowing post-input reorganization to achieve a high degree of flexibility.
Owner:NEWSILIKE MEDIA GROUP
Runtime adaptable security processor
InactiveUS20050108518A1Improve performanceReduce overheadSecuring communicationInternal memoryPacket scheduling
A runtime adaptable security processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
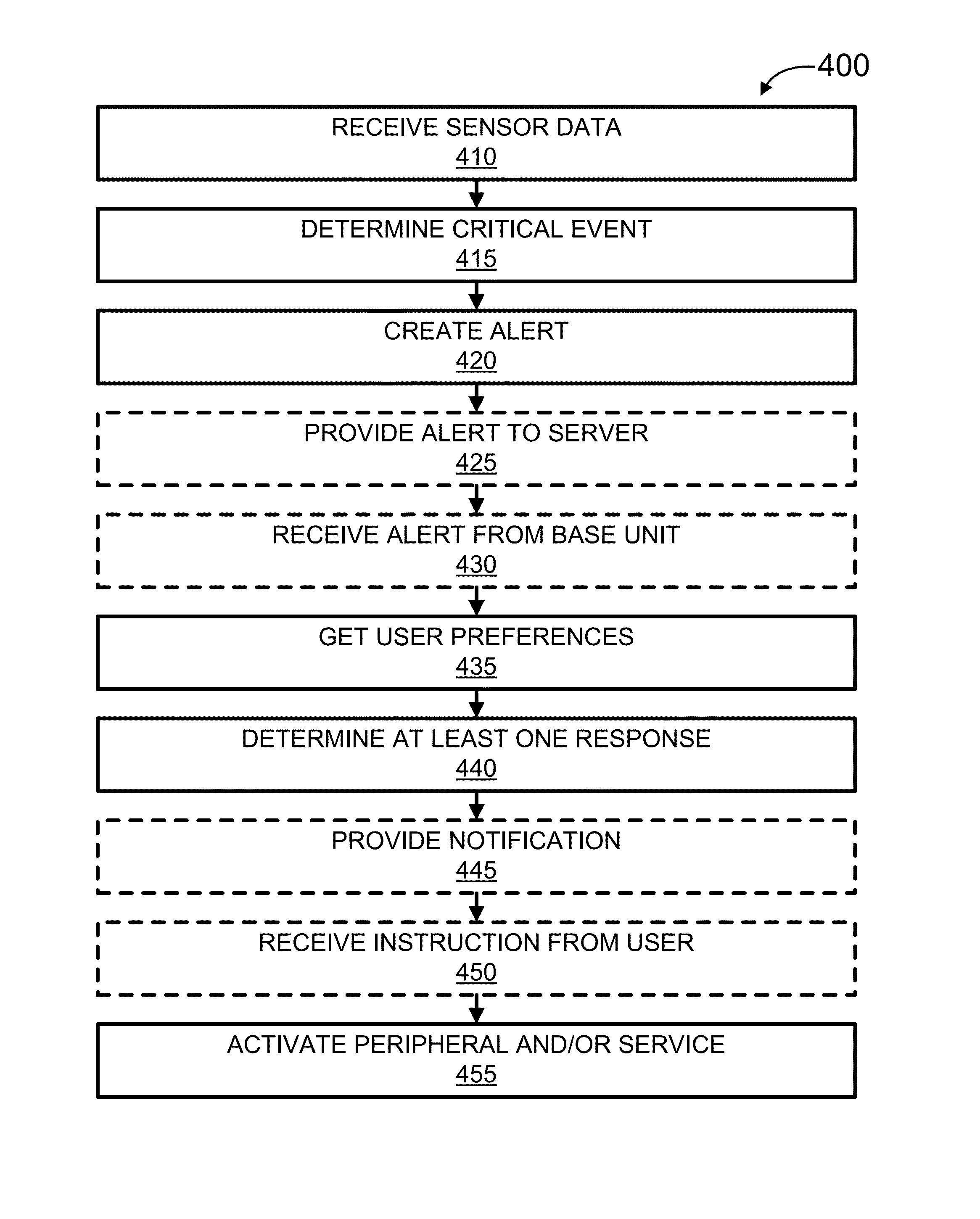
Security Monitoring and Control
ActiveUS20150339912A1Burglar alarm mechanical actuationControl systemStructure of Management Information
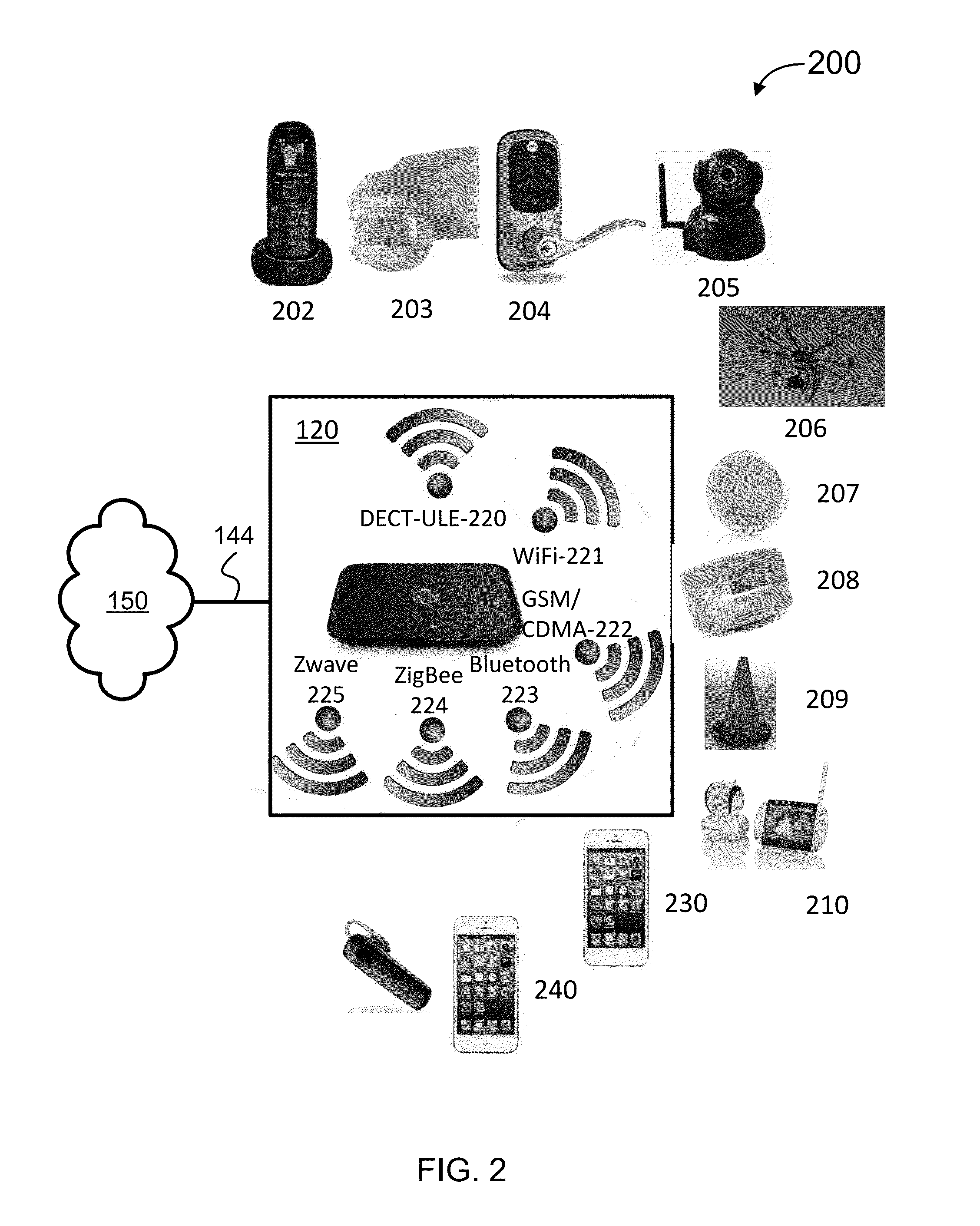
Systems, methods, and software for monitoring and controlling a security system for a structure are provided herein. An exemplary method may include receiving sensor data from at least one first peripheral, the sensor data associated with at least one of activity inside and activity outside of a structure; determining a critical event based in part on the sensor data; creating an alert based in part on the critical event; getting user preferences associated with at least one of a user and a base unit; determining a response based in part on the alert and user preferences; and activating at least one of a second peripheral and a service based in part on the response.
Owner:OOMA
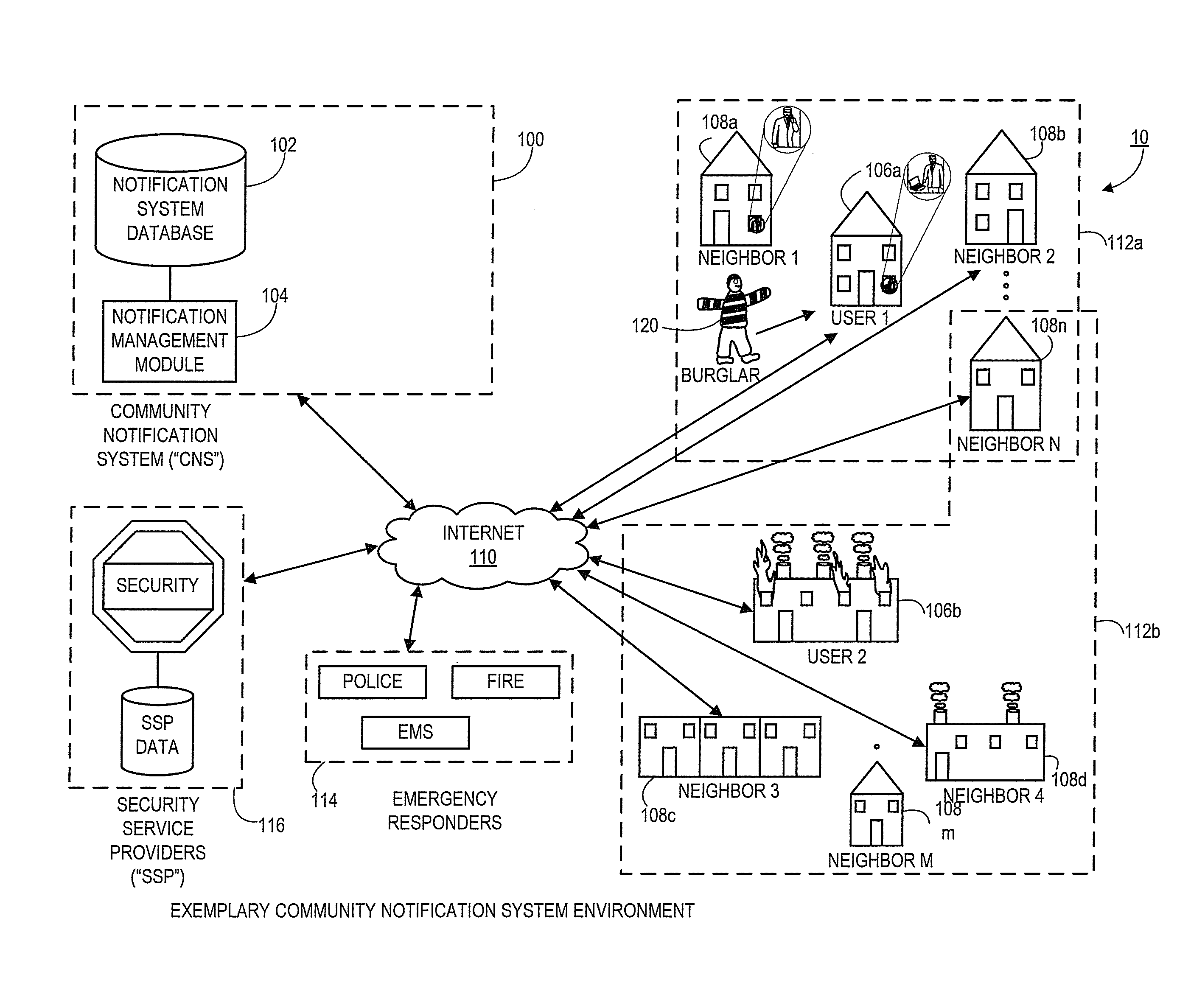
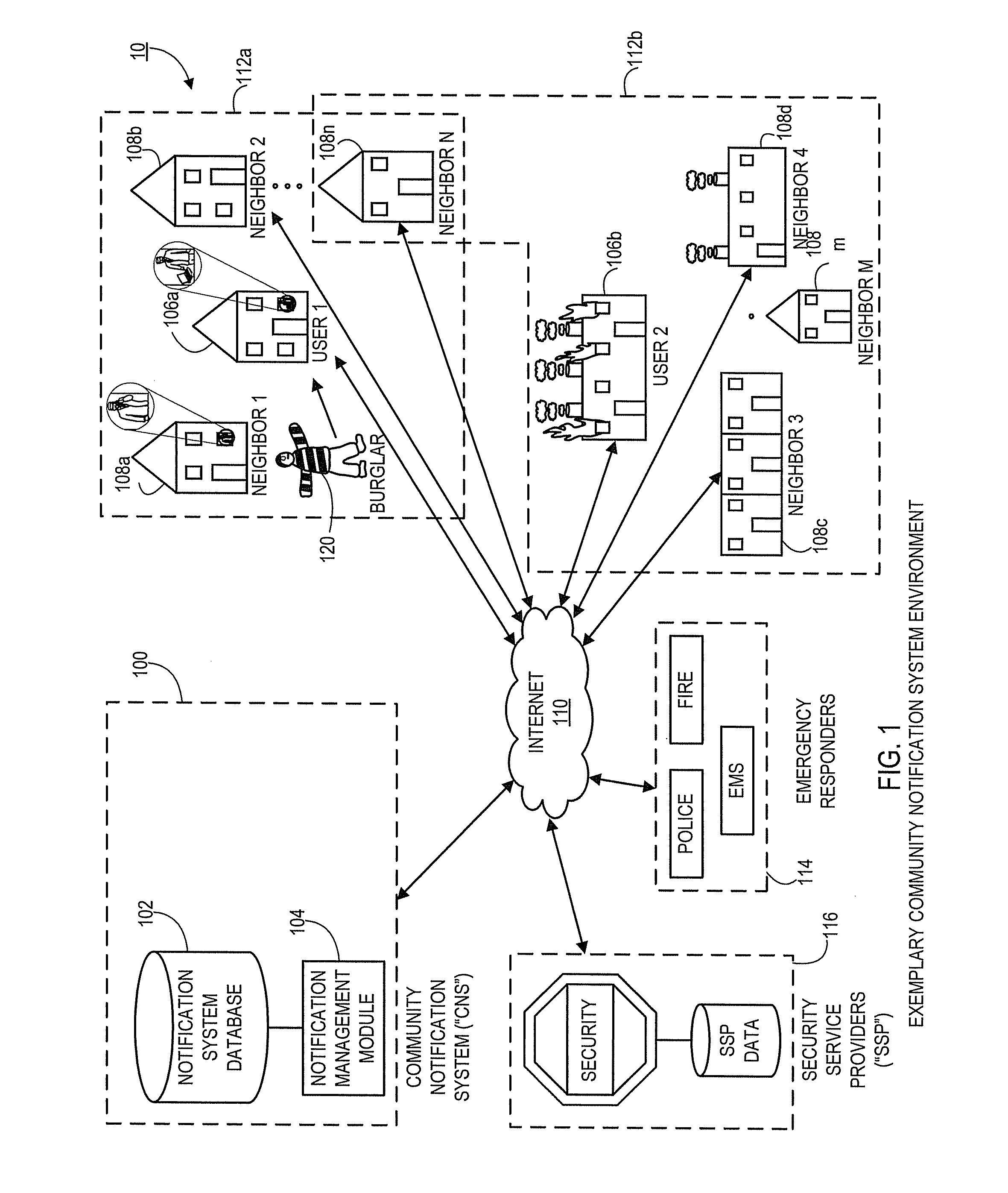
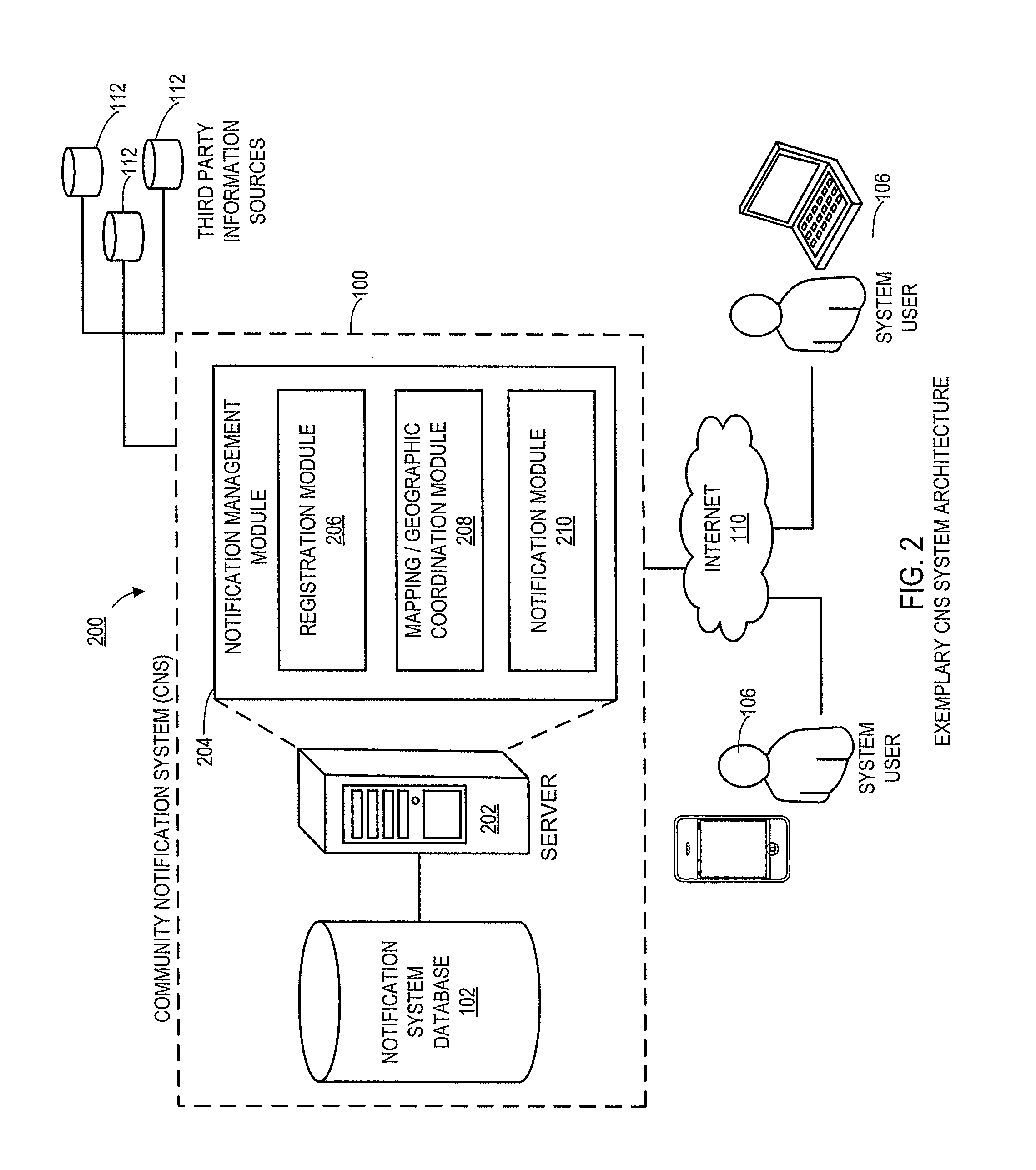
Systems and methods for notifying proximal community members of an emergency or event
Aspects of the present disclosure generally relate to systems and methods for an automated community notification system (“CNS”) that is configured to notify certain individuals with relevant information relating to occurrence of an event or emergency at a given geographical location. Generally, aspects of the system include operative connections to one or more security system providers (“SSPs”) to identify events / emergencies at properties. In alternate embodiments, system users provide event information to the CNS via users' electronic devices. According to one aspect, system users register with the CNS and provide user information, preferences, geographic information, etc., and the CNS subsequently utilizes that information (in connection with other third party information sources) to establish “neighborhood networks” for system users. Typically, members of in the same neighborhood network are notified and provided with relevant information when an emergency occurs at the property or geographic location of another user in the members' network.
Owner:CLIMOTE
Electronic device remote control method and electronic device management facility
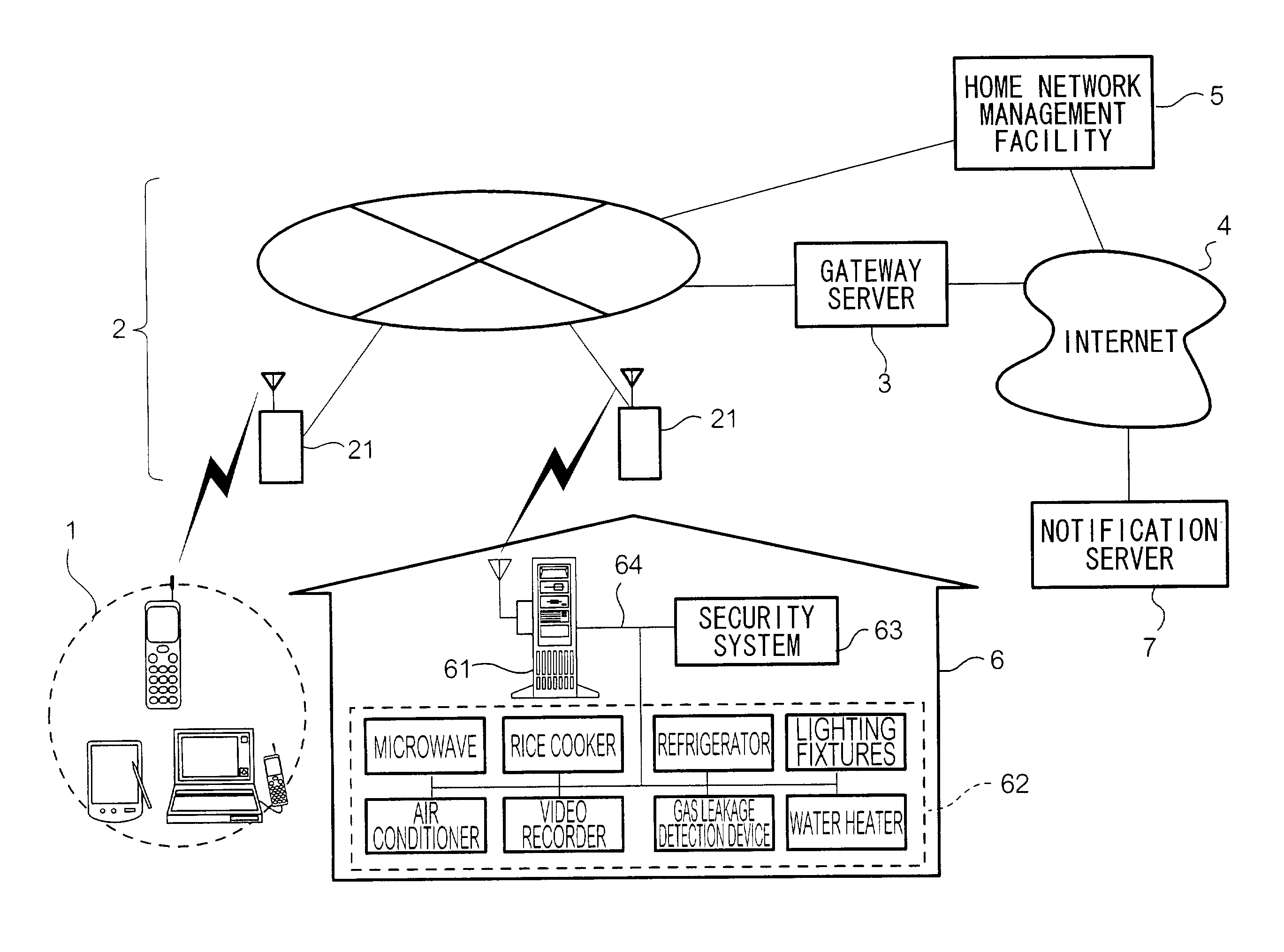
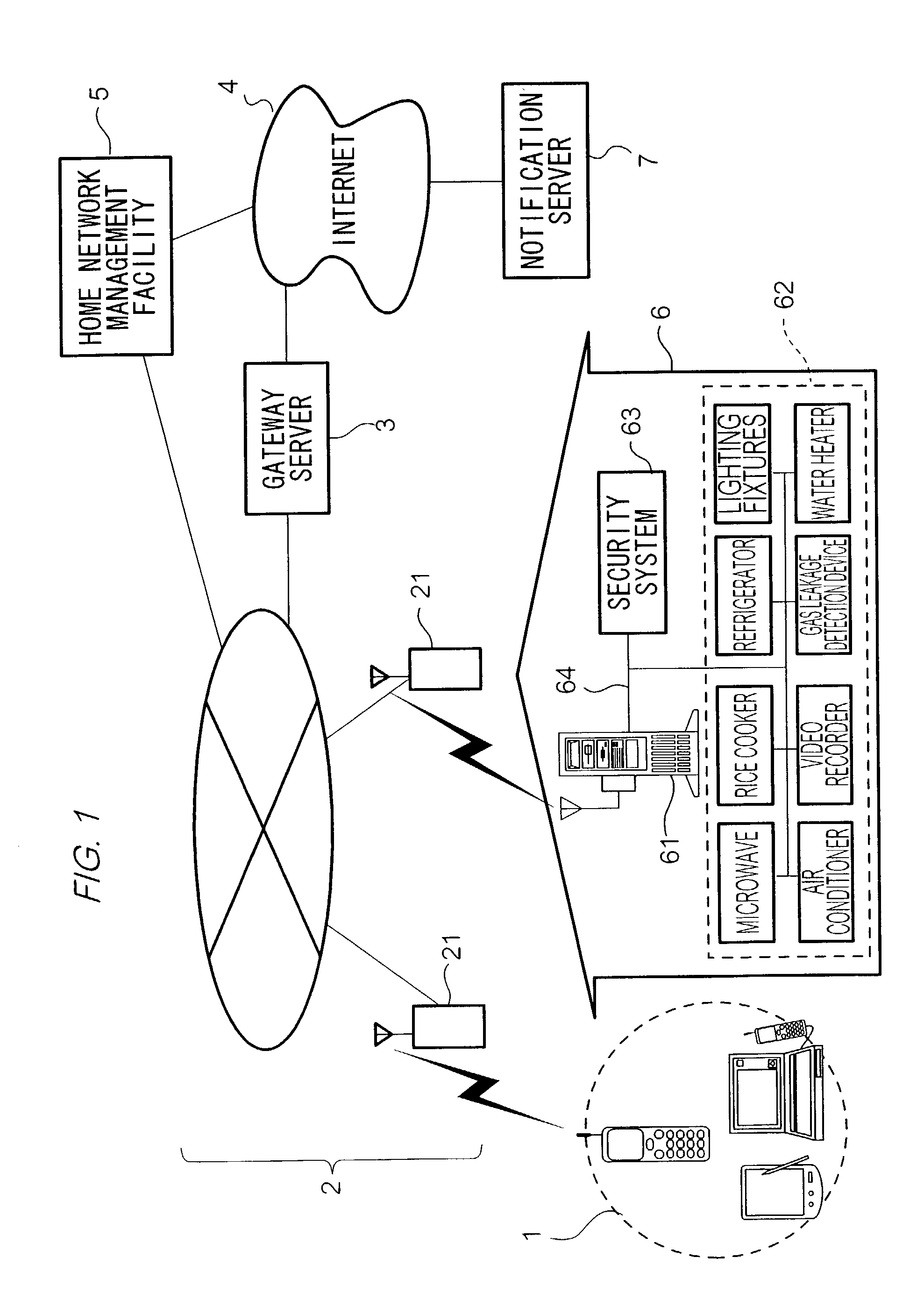
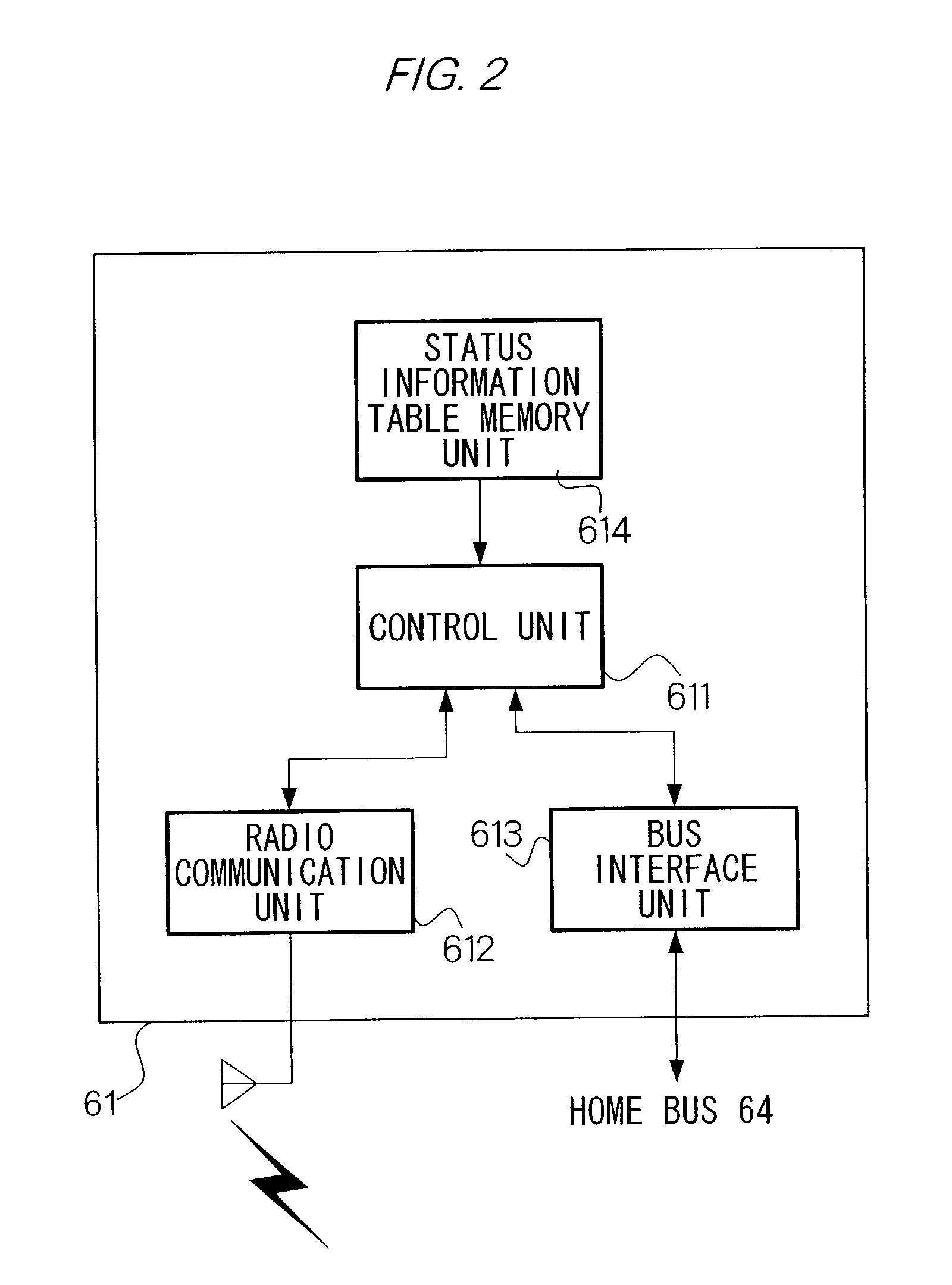
InactiveUS20020180579A1Improve the level ofEasy to handleComputer controlElectric testing/monitoringRemote controlNetwork management
A security system 63 and an electronic group 62 to be stored in a home network 6 are controlled by a home sever 61. A home network management facility 5 obtains status information showing the status of the electronic device group 62 from home server 61 when a user of electronic device group 62 operates a terminal 1 to make a request to home network management facility 5. Next, home network management facility 5 displays a screen for showing the status of electronic device group 62 on a display unit of terminal 1 based on the received status information, generates display information for displaying a screen for prompting input of a control instruction of the home-located electronic devices to the user on the display unit of terminal 1, and transmits the display information to terminal 1. And, home network management facility 5 performs remote control of electronic device group 62 based on the received control instruction via home server 61 when obtaining the control instruction from terminal 1.
Owner:VIVINT INC
System and method for connecting security systems to a wireless device
InactiveUS6965313B1Not be preventElectric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
Casino table game monitoring system
InactiveUS20080113783A1Combination novelData they captureBoard gamesApparatus for meter-controlled dispensingMonitoring systemSecurity system
A networked casino game rules violation alert system that captures game data from numerous game security systems / devices in real time, integrates the data, and compiles the integrated data. The system interprets the compiled data, associates the interpreted data with game rules, analyzes and compares the data to determine if there have been invalid actions (i.e., cheating by the player and / or dealer), detects any game anomalies, categorizes the anomalies, generates alerts based on the anomalies and the priority assigned to the anomaly, and dispatches alerts to various systems and alert mechanisms linked to the network. The system can also be used to collect game statistics, per player and dealer, and can determine and respond to historical anomalies as deemed appropriate.
Owner:SHUFFLE MASTER
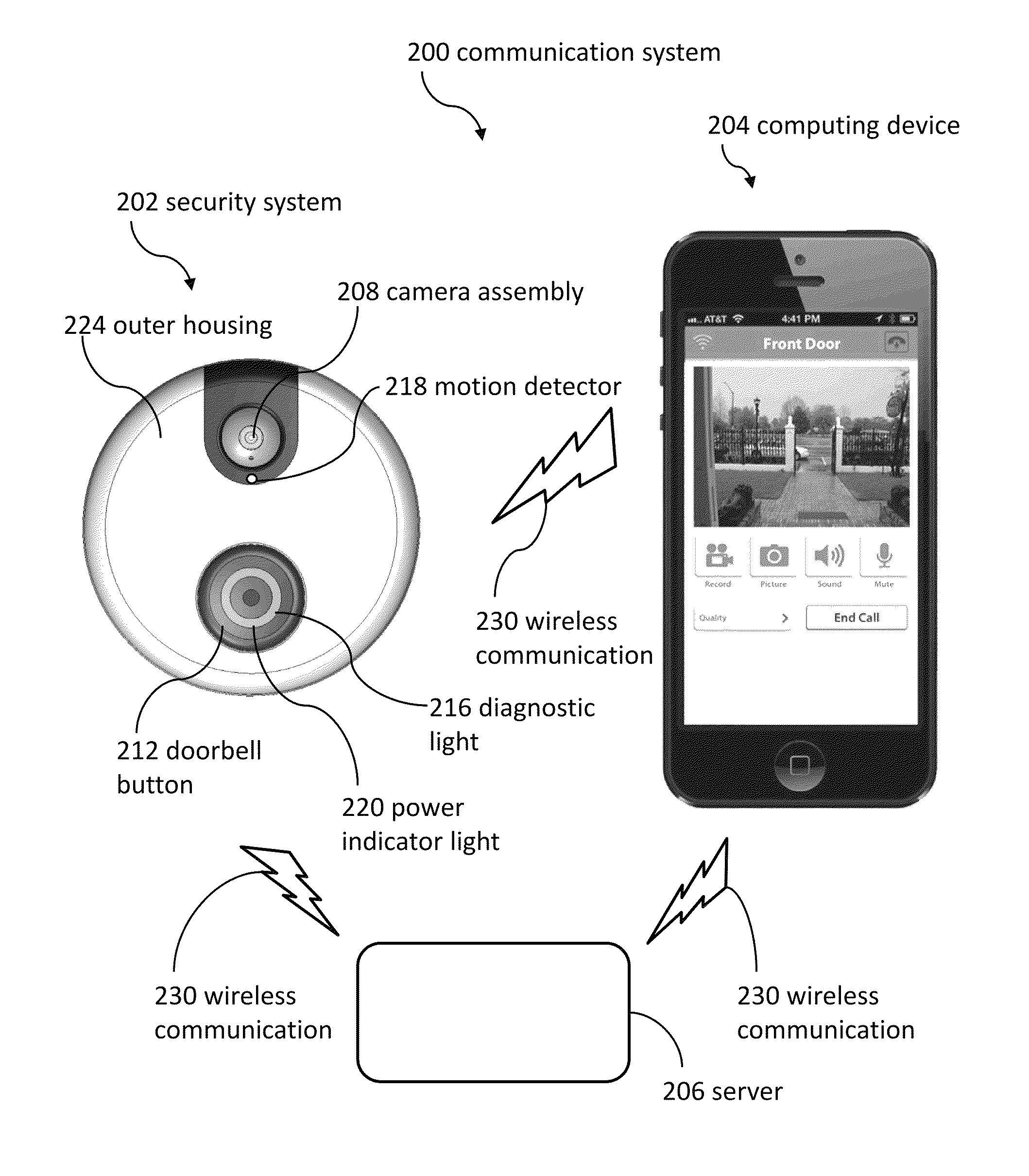
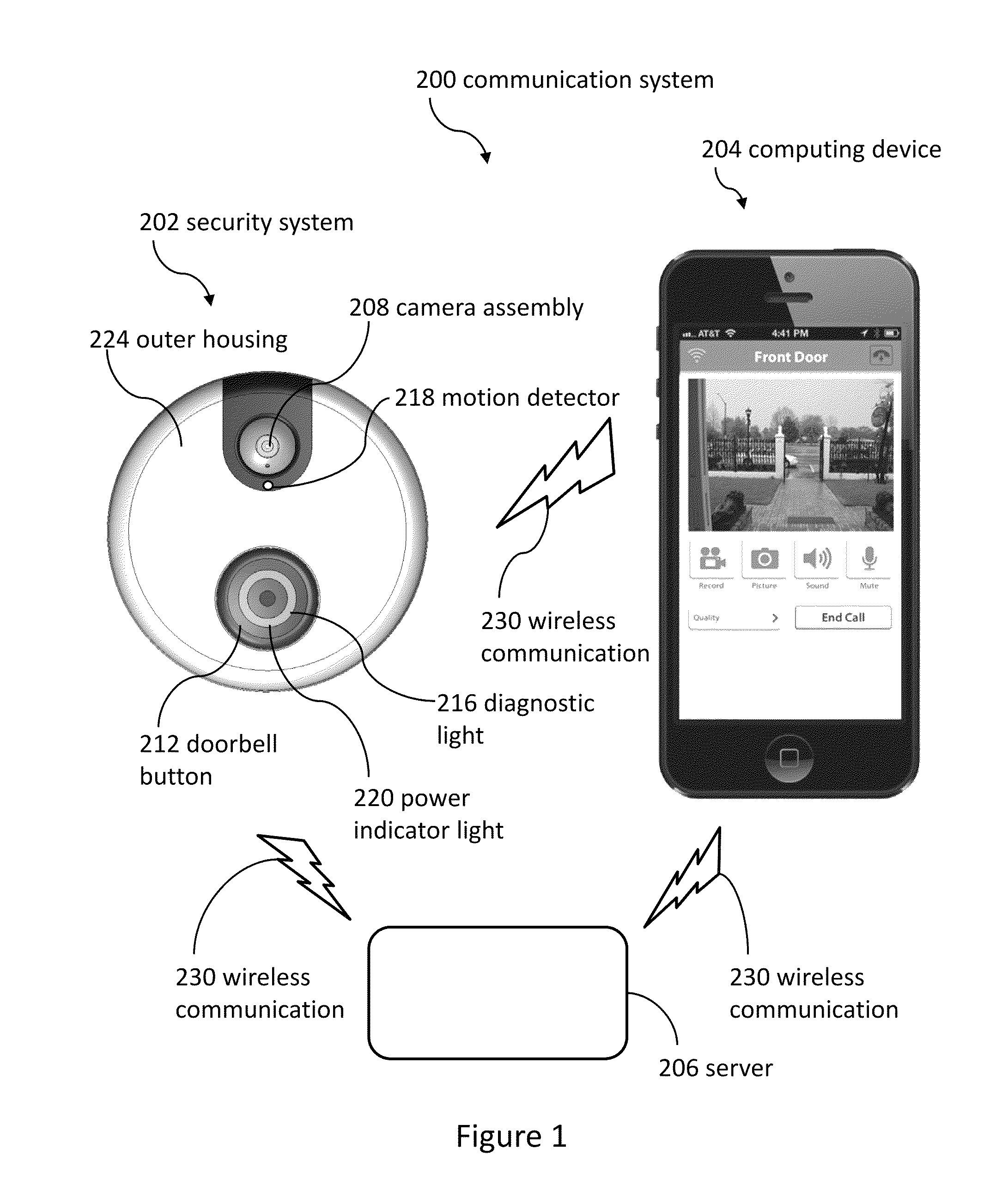
Doorbell communication systems and methods
ActiveUS8823795B1High activityLess powerColor television detailsClosed circuit television systemsDoorbellEntryway
Communication systems configured to monitor an entryway to a building can include a security system configured to wirelessly communicate with a remote computing device. The security system can include a doorbell that comprises a camera, a speaker, and a microphone.
Owner:SKYBELL TECH IP LLC
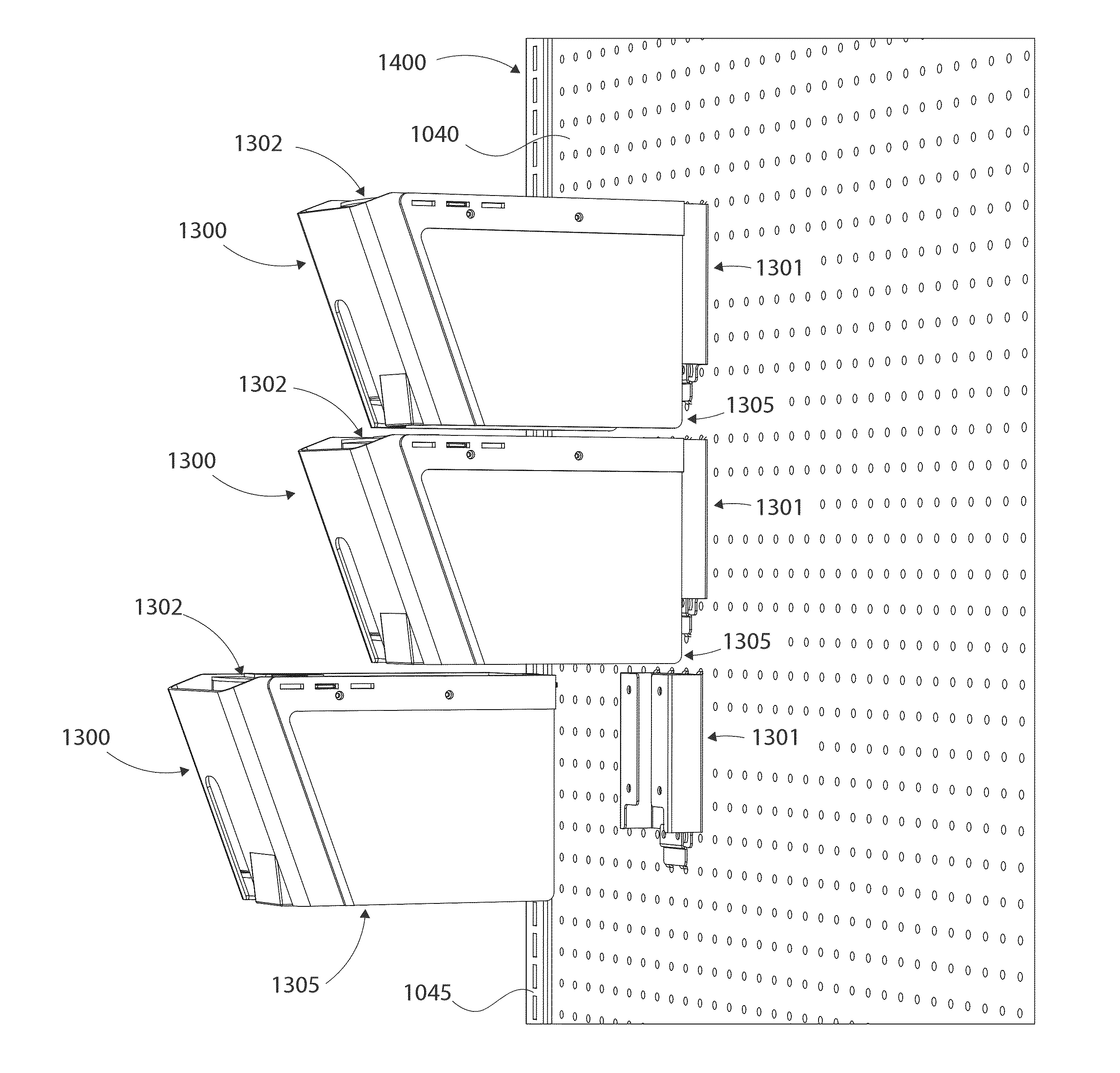
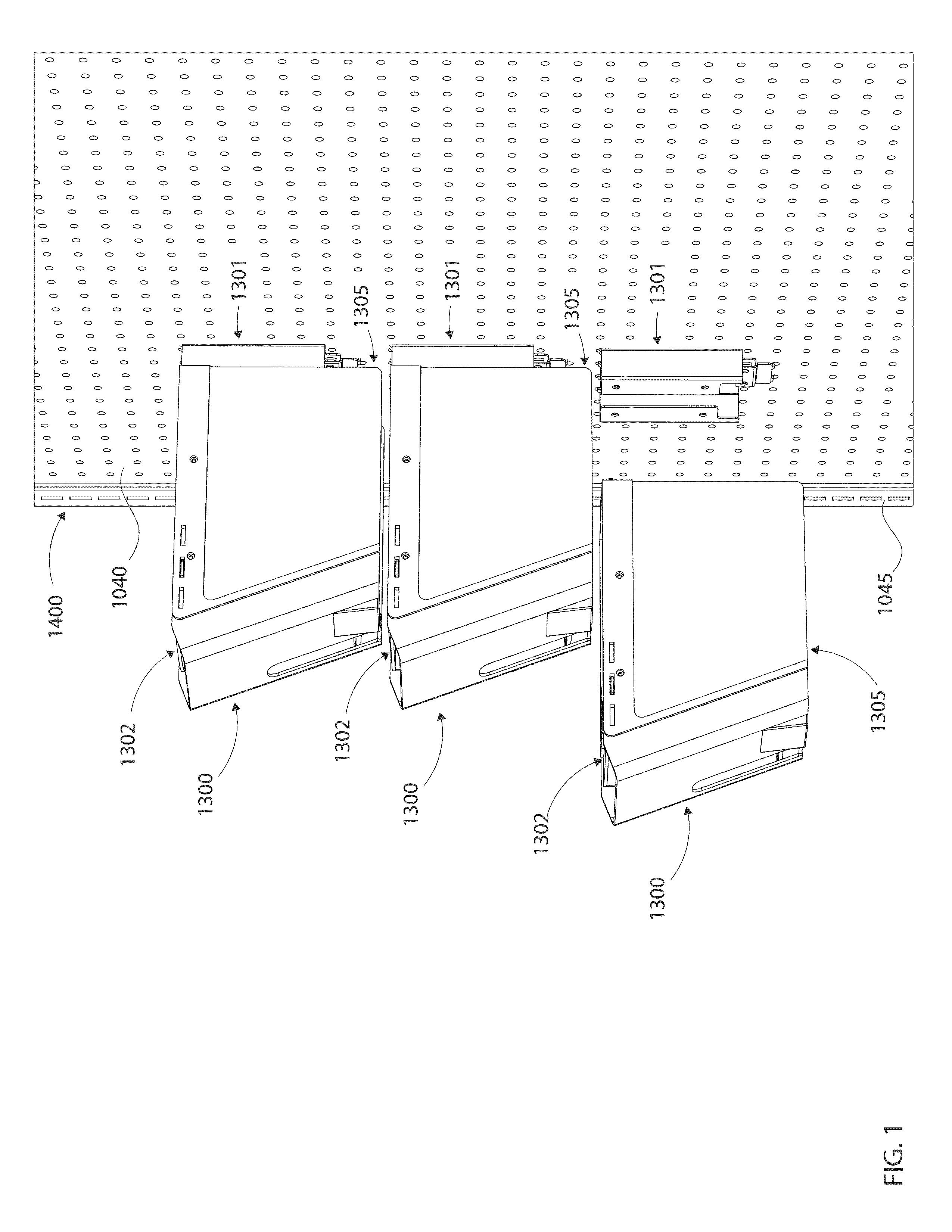
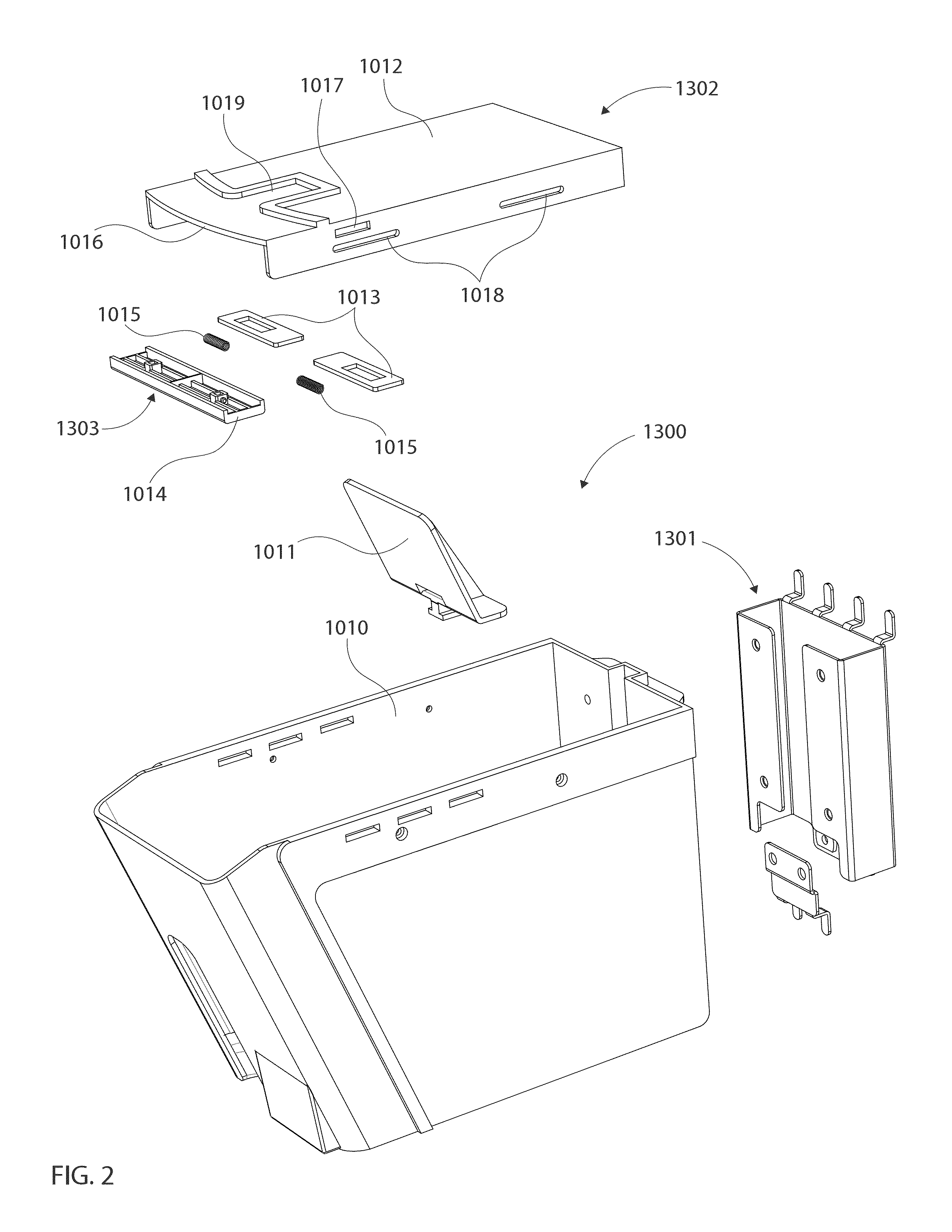
Modular manual lift dispenser security systems and methods for assembling, manufacturing and/or utilizing said security systems
Modular manual lift dispenser security systems and methods store and dispense at least one retail product. The systems and methods have a dispenser body having a floor and walls extending above the floor, wherein the walls of the dispenser body define an interior of the dispenser body that is sized to receive one or more retail products. Further, the systems and methods have a locking lid assembly slidably connected to a top edge of each side wall of the dispenser body via at least one fastener and a pusher paddle located within the interior of the dispenser body, wherein the pusher paddle is spring-loaded and configured to move one or more retail products towards the front wall of the dispenser body. Still further, the systems and methods have a first opening between a lip of the front wall of the dispenser body and a front edge of the locking lid assembly that is located adjacent to the front wall of the dispenser body, wherein the first opening is sized such that a leading retail product is passable through the opening between the lip of the front wall and the front edge of the locking lid assembly. Moreover, the systems and methods have a recess formed in the floor of the dispenser body and a lift slot formed in the front wall of the dispenser body, wherein the recess and lift slot are at least one of sized and shaped such that a leading retail product is accessible through the recess and lift slot.
Owner:MARKETING IMPACT
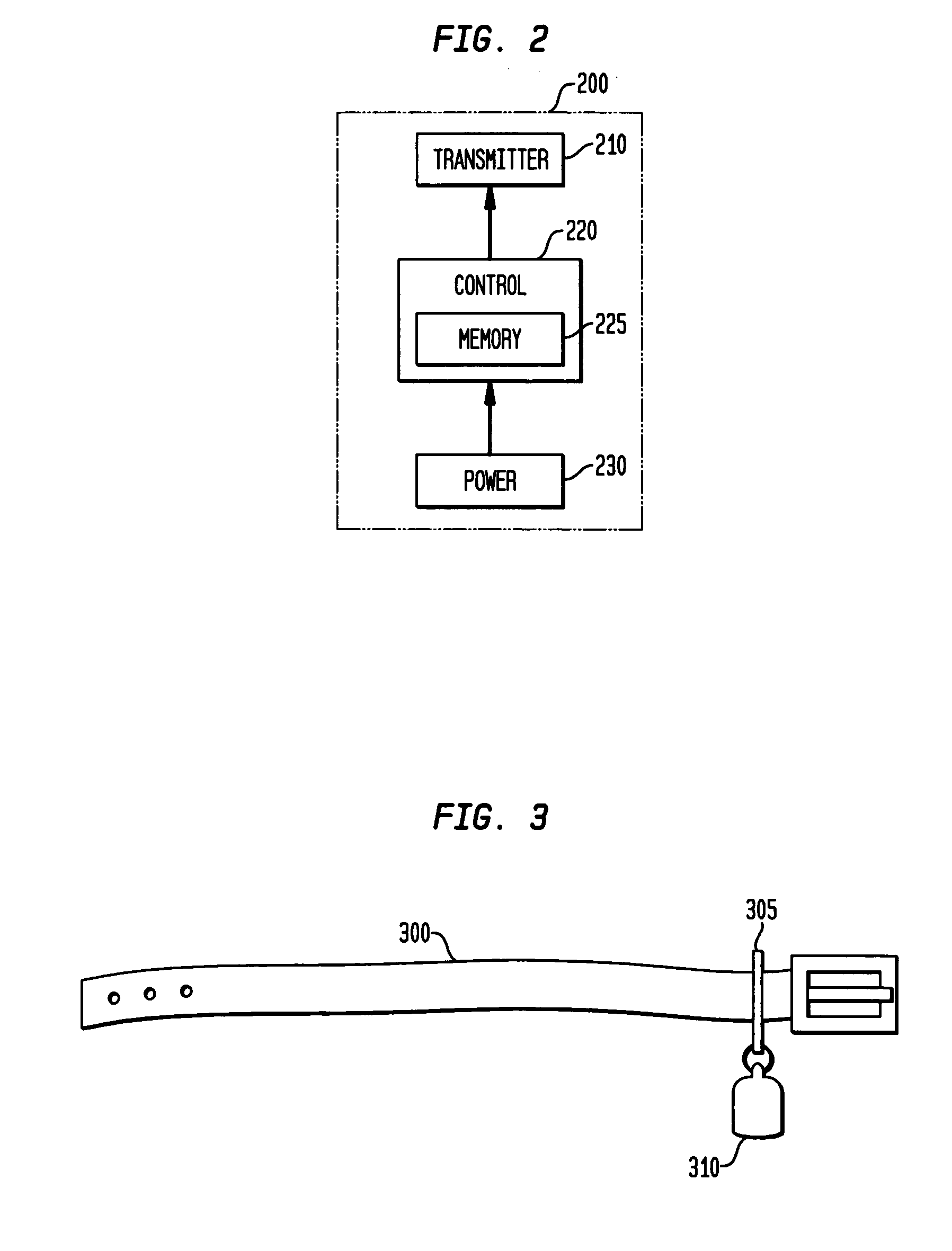
Automatic sensitivity adjustment on motion detectors in security system
InactiveUS20050128067A1Sensitivity adjustableSignalling system detailsAlarmsMotion detectorEngineering
The sensitivity of a motion sensor or detector in a security system is adjusted by a remotely-transmitted signal, such as from a user interface device in the security system. In another approach, a pet wears a transmitter on its collar that transmits a wireless signal to command the motion sensor to adjust its sensitivity, e.g., by entering a pet immune mode, when the pet is in the room that is protected by the motion sensor. In another approach, a remote monitoring site sends instructions to the motion sensor via a communication interface. The sensitivity can be adjusted by adjusting a pulse count, optical gain, or electrical or optical sensitivity of the motion sensor.
Owner:HONEYWELL INT INC
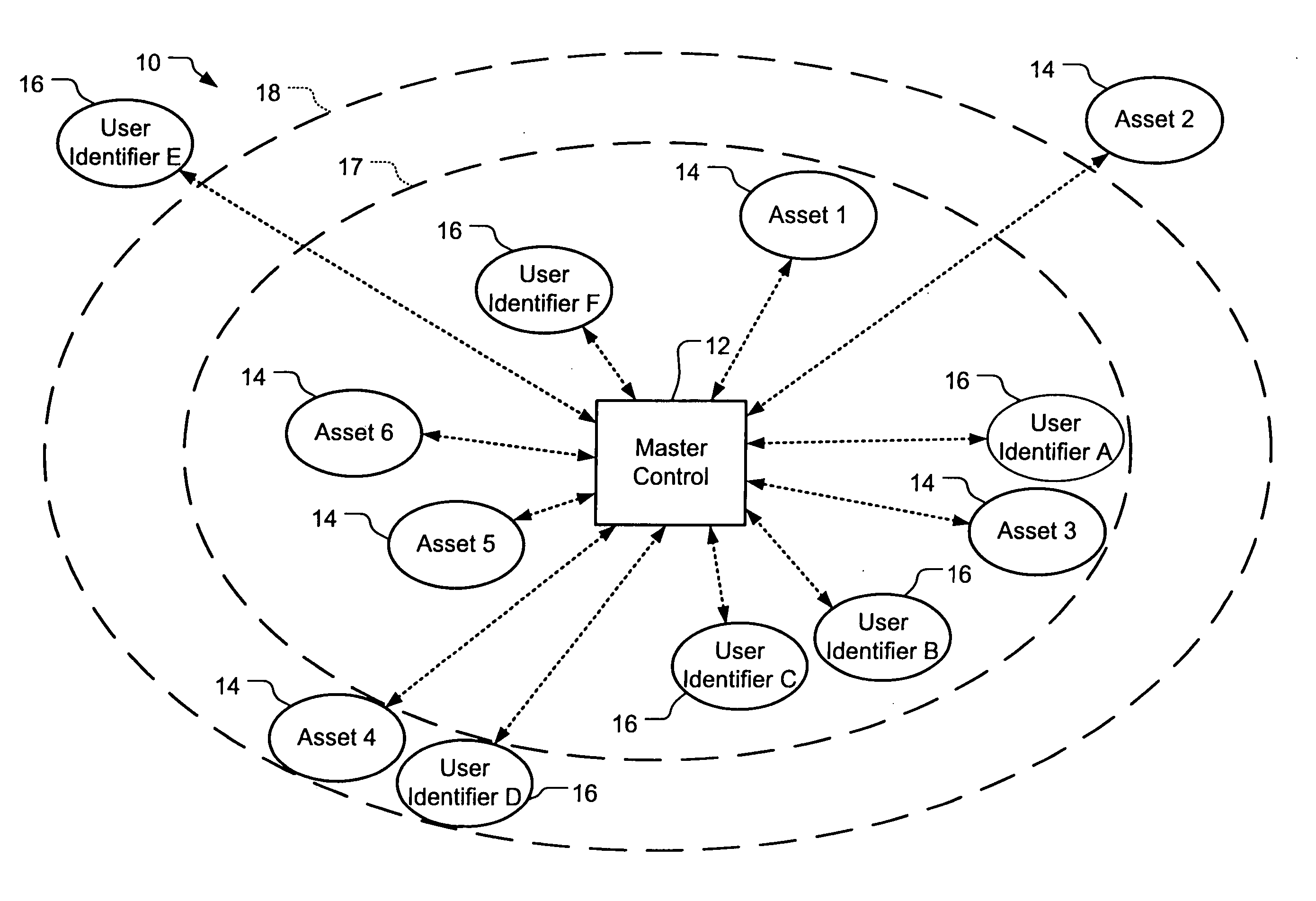
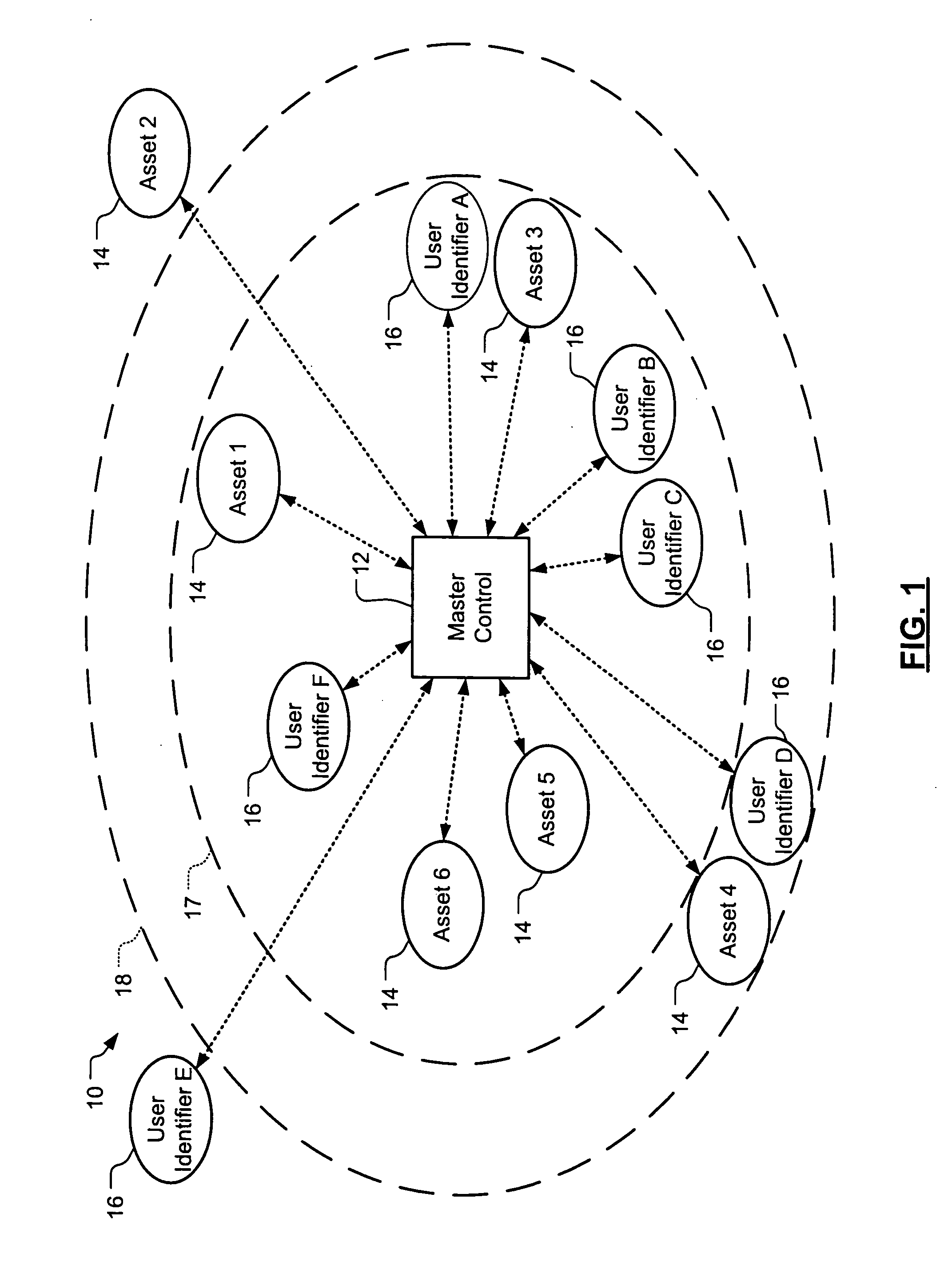
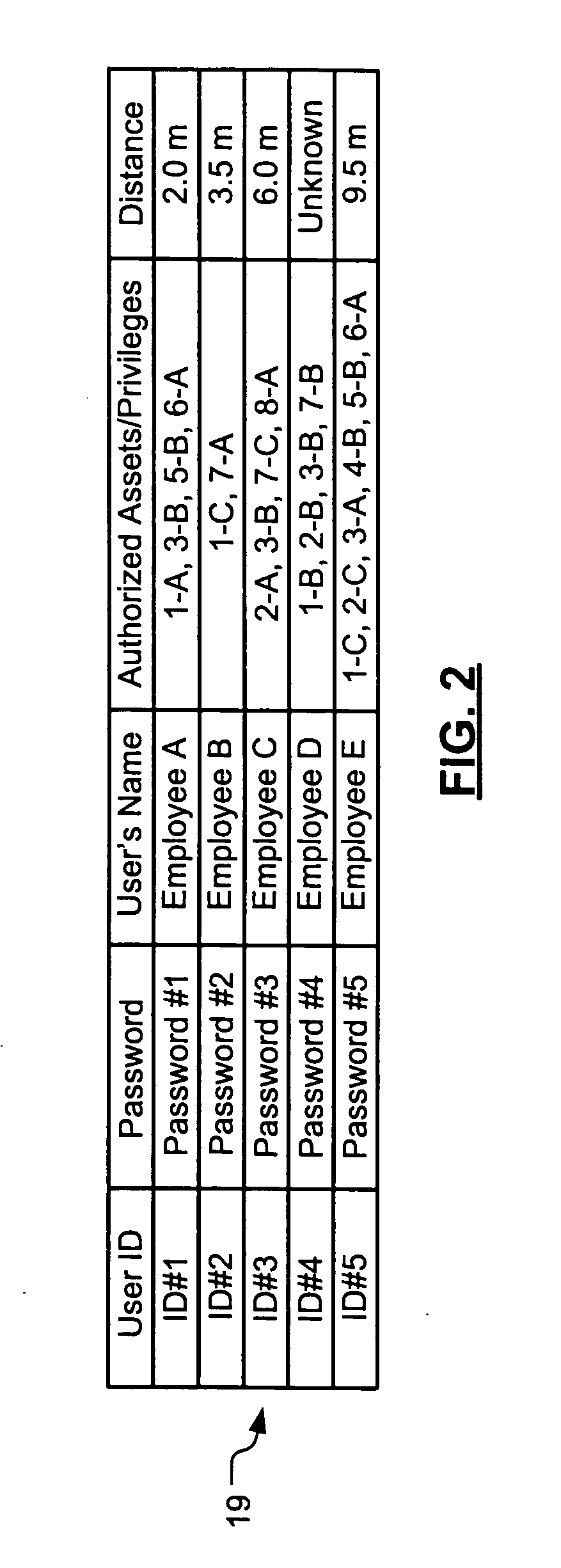
Wireless asset monitoring and security system
InactiveUS20050128083A1Electric signal transmission systemsMultiple keys/algorithms usageLocking mechanismUnique identifier
An asset monitoring and security system includes at least one asset assigned a unique identifier and operable wirelessly transmit an identification signal embodying the identifier. A data store maintains a list of the assets and privileges associated with the assets for authorized users of the assets. A control unit is adapted to receive identification signals from the assets and monitor positions of the assets within a defined area. The control unit communicates with the data store and is further operable to initiate an alarm event when privileges associated with a given asset for authorized users of the asset are exceeded. Each of the assets includes a lock-out mechanism that impedes use of the asset when the lock-out mechanism is activated. The control unit activates the lock-out mechanism of a given asset when the privileges associated with the asset for authorized users of the asset are exceeded.
Owner:BLACK & DECKER INC
Mobile data security system and methods
ActiveUS8495700B2Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securityMobile Web
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
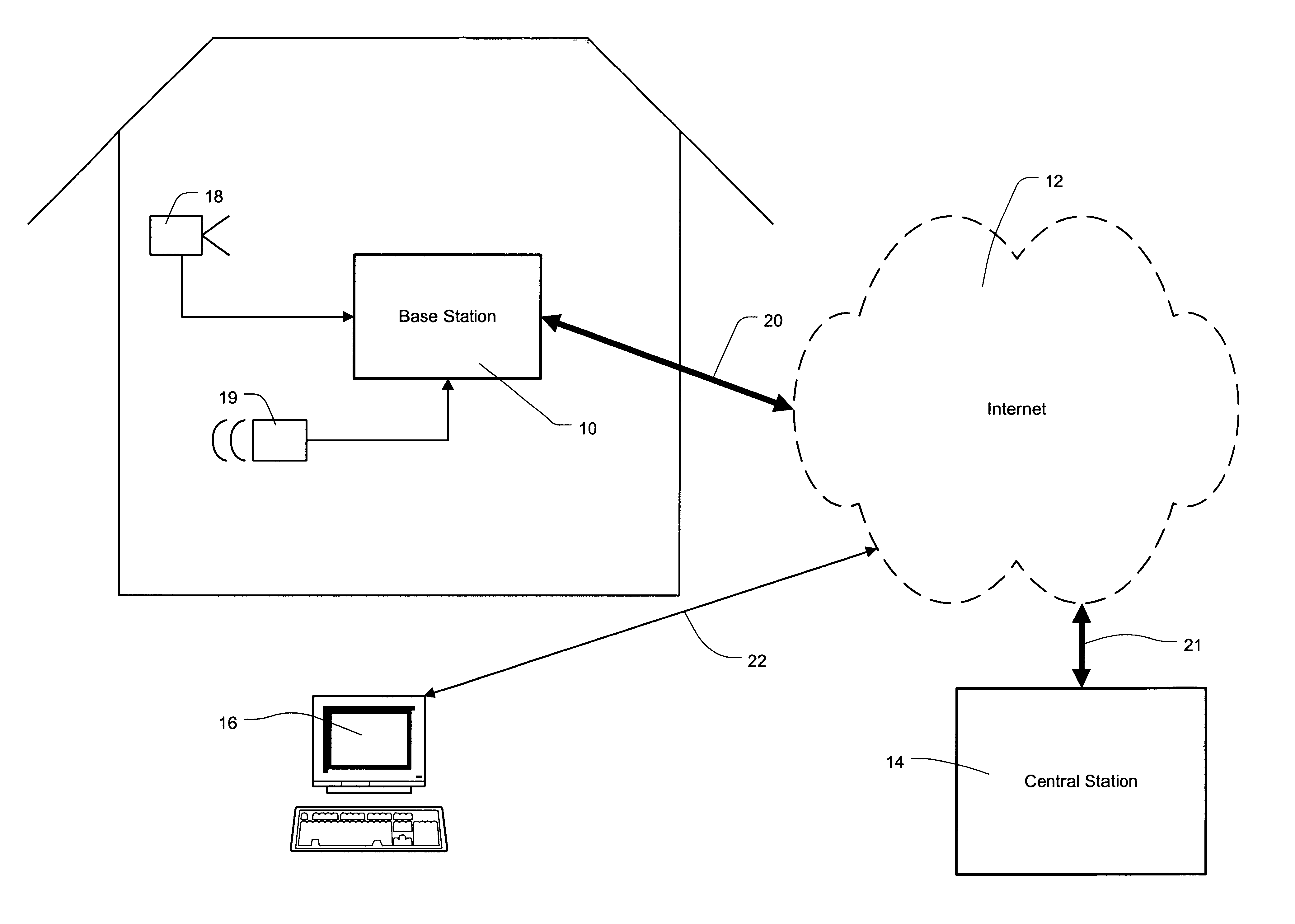
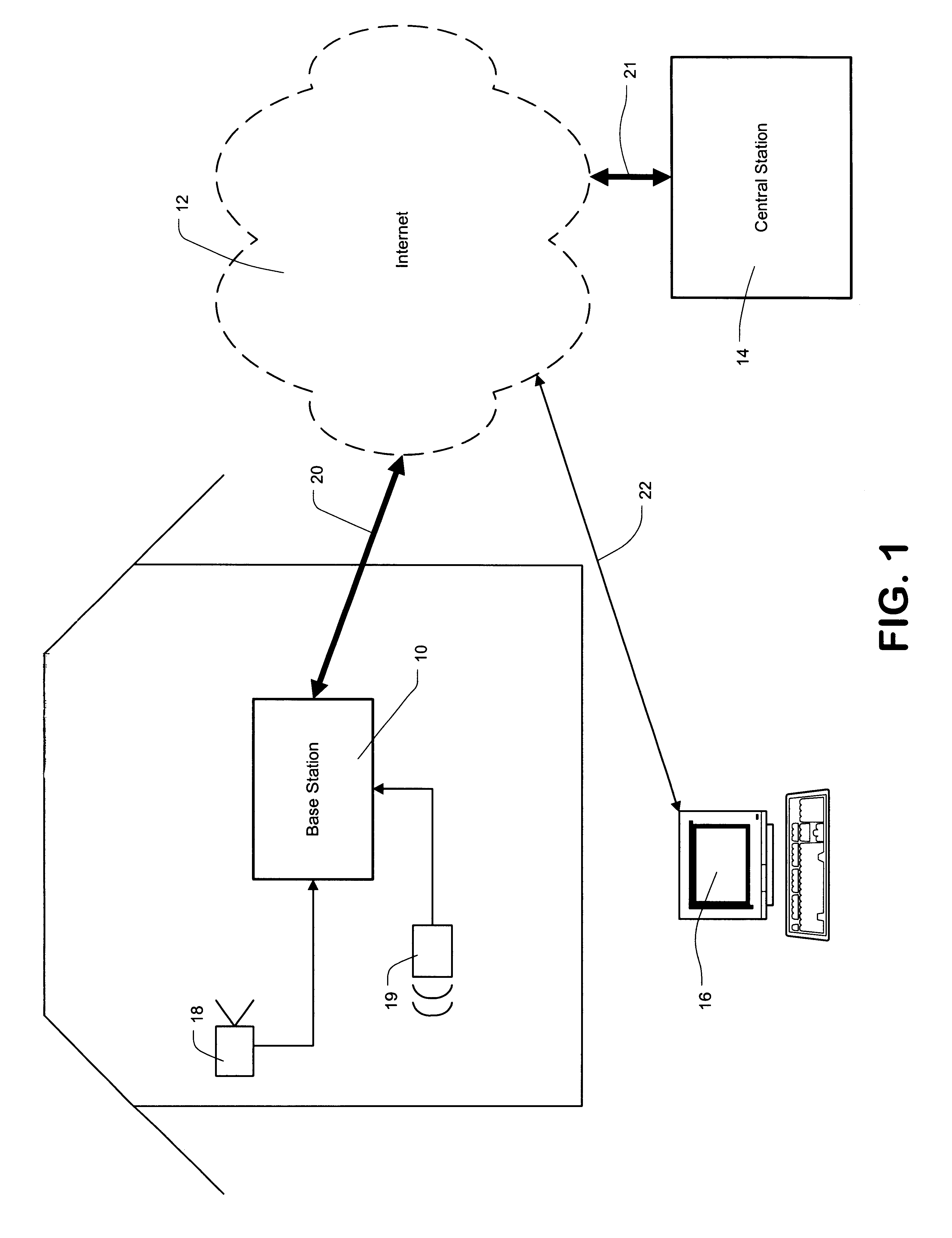
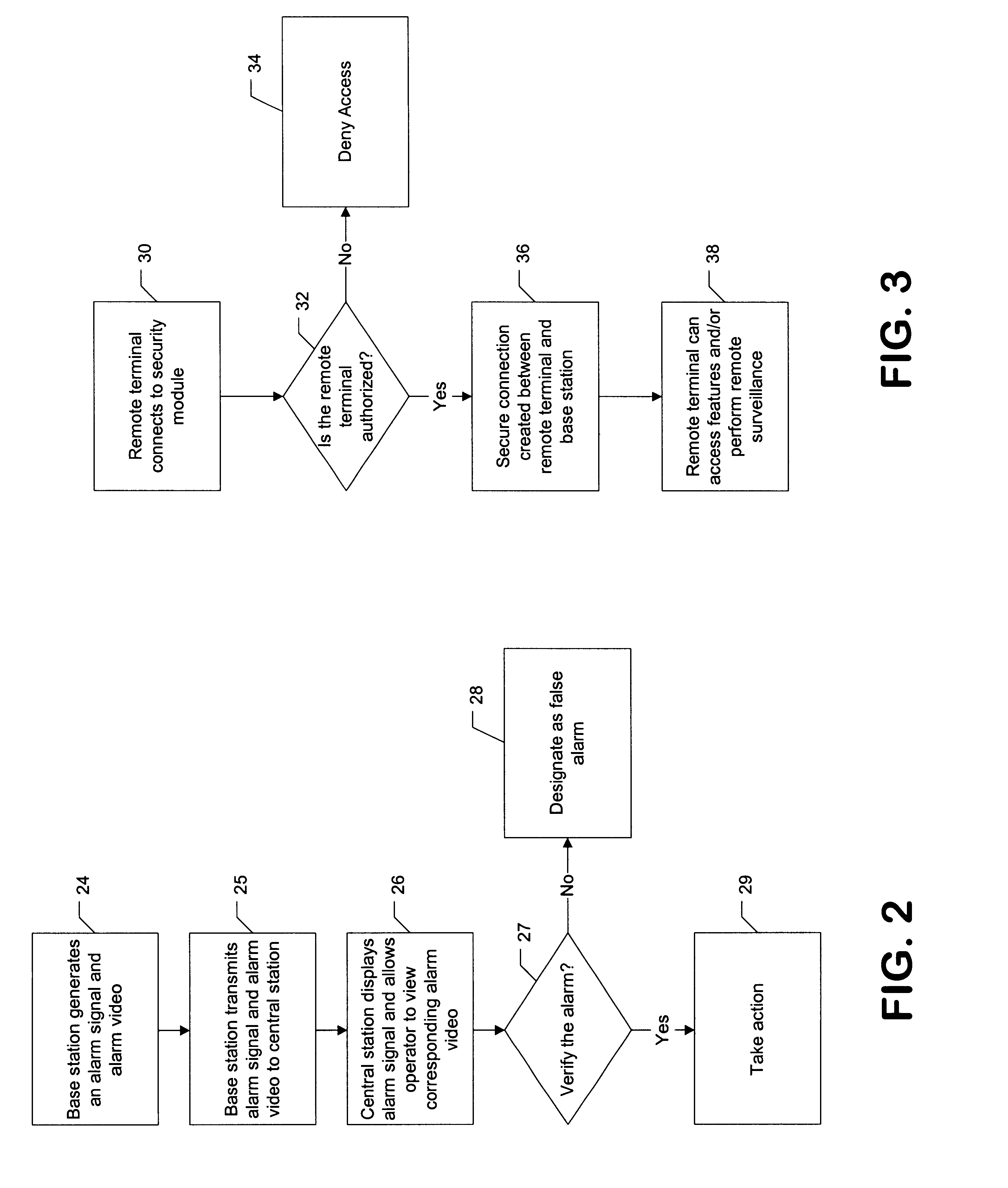
Security system
InactiveUS6690411B2Color television detailsClosed circuit television systemsGuard - securityEngineering
A system and method for enabling a central station to accurately verify in real-time whether an alarm signal generated by a security base station is a false alarm, and for enabling remote users to securely access features of the security base station such as remote surveillance, activating and deactivating the system, and adjusting alarm sensitivities.
Owner:COMCAST CABLE COMM LLC
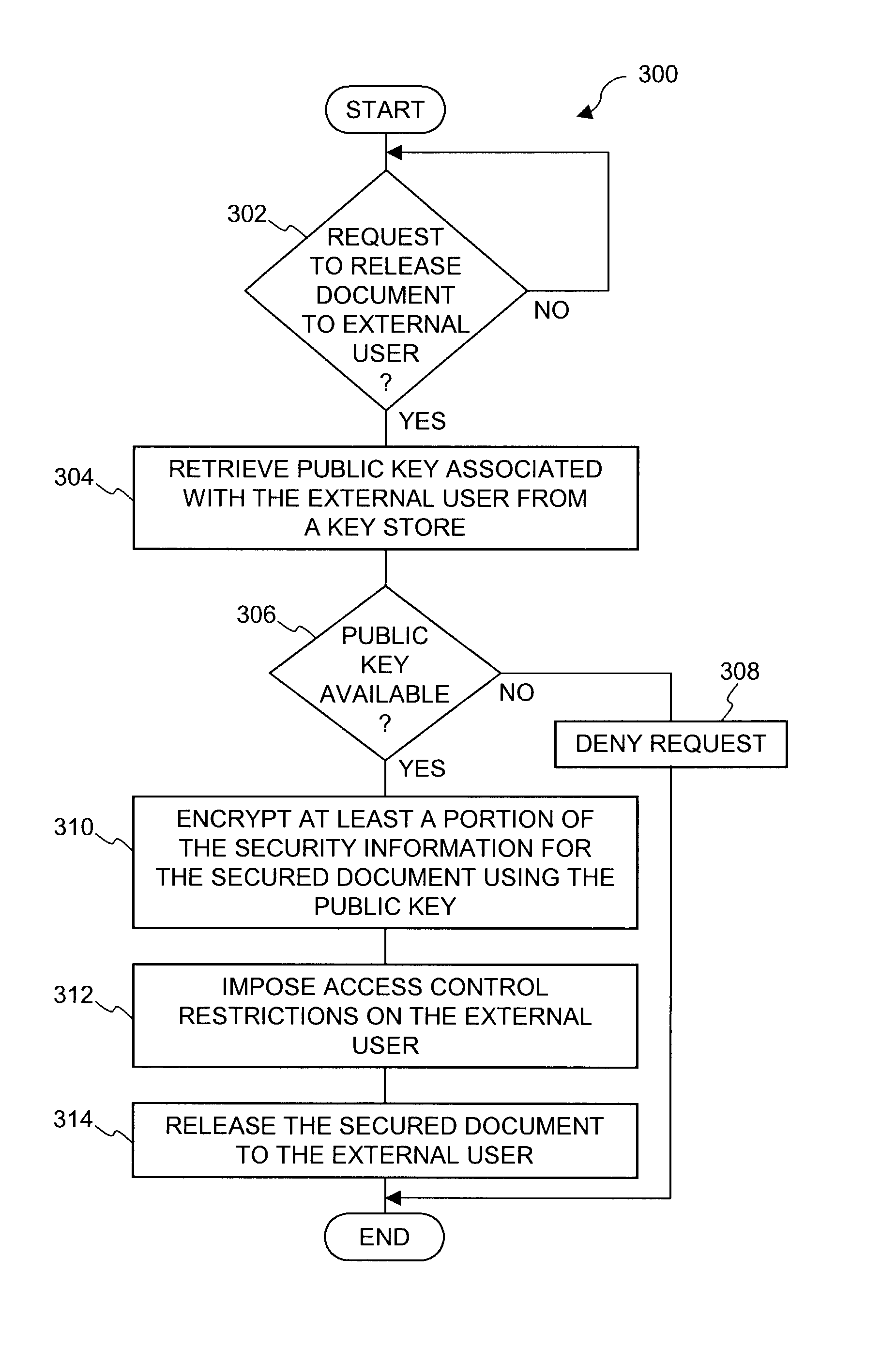
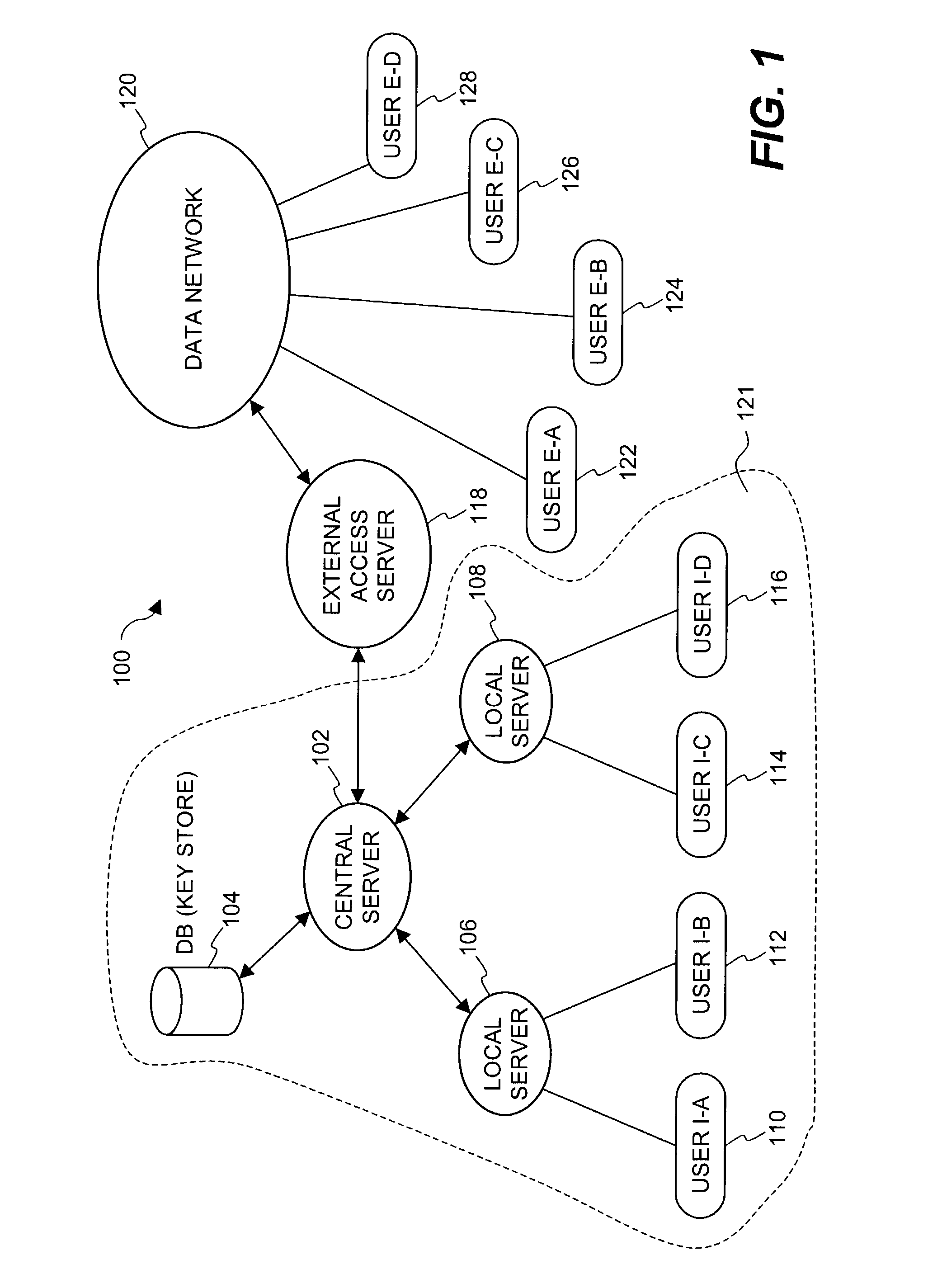
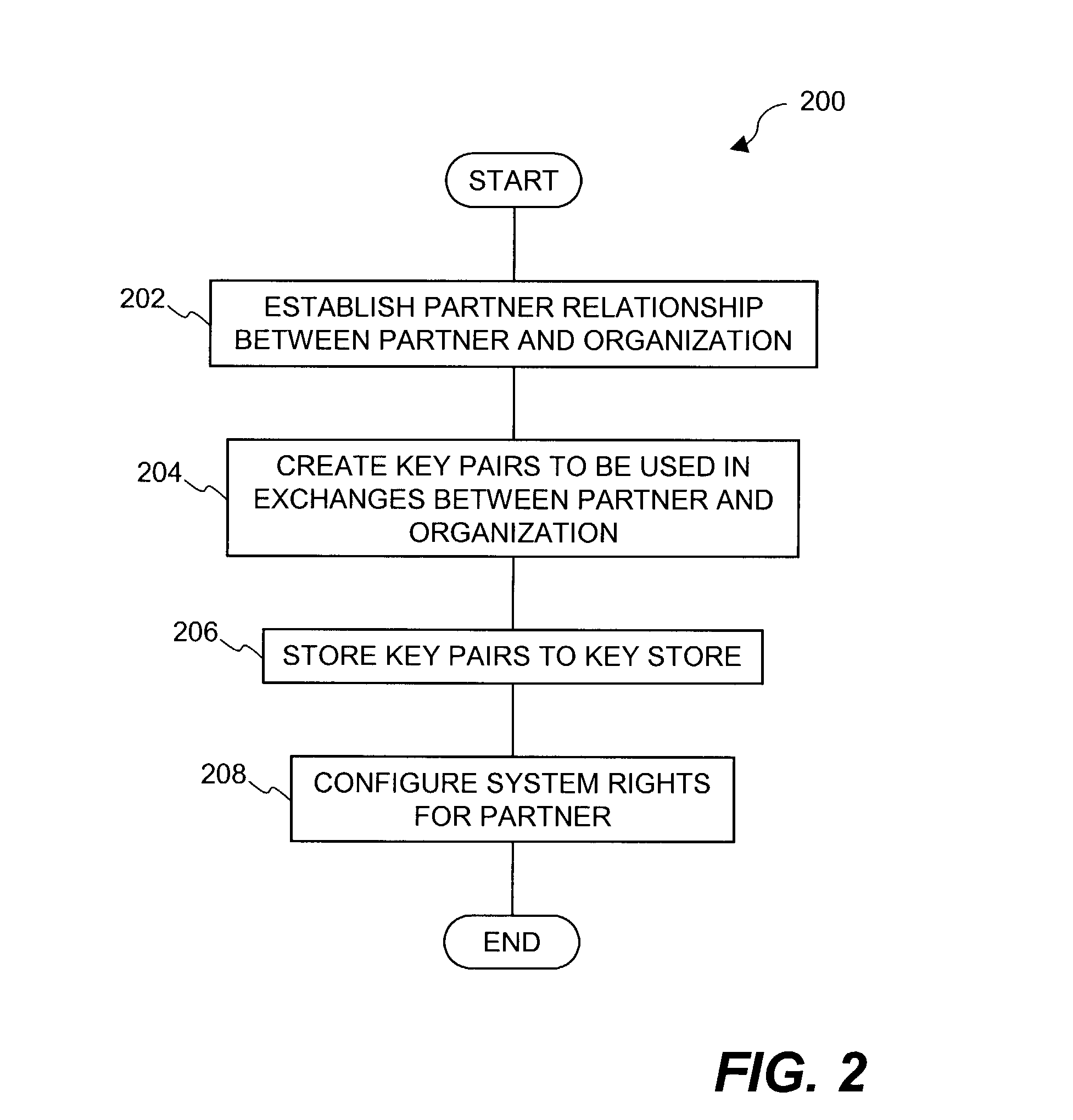
Document security system that permits external users to gain access to secured files
ActiveUS8176334B2Minimal amountLimited accessDigital data processing detailsUser identity/authority verificationUser PrivilegeInternal documentation
An improved system and approaches for exchanging secured files (e.g., documents) between internal users of an organization and external users are disclosed. A file security system of the organization operates to protect the files of the organization and thus prevents or limits external users from accessing internal documents. Although the external users are unaffiliated with the organization (i.e., not employees or contractors), the external users often have working relationships with internal users. These working relationships (also referred to herein as partner relationships) often present the need for file (document) exchange. According to one aspect, external users having working relationships with internal users are able to be given limited user privileges within the file security system, such that restricted file (document) exchange is permitted between such internal and external users.
Owner:INTELLECTUAL VENTURES I LLC
Pervasive, domain and situational-aware, adaptive, automated, and coordinated analysis and control of enterprise-wide computers, networks, and applications for mitigation of business and operational risks and enhancement of cyber security
ActiveUS20130104236A1Reduce analysisLower control priorityMemory loss protectionError detection/correctionApplication softwareBusiness process
Real time security, integrity, and reliability postures of operational (OT), information (IT), and security (ST) systems, as well as slower changing security and operational blueprint, policies, processes, and rules governing the enterprise security and business risk management process, dynamically evolve and adapt to domain, context, and situational awareness, as well as the controls implemented across the operational and information systems that are controlled. Embodiments of the invention are systematized and pervasively applied across interconnected, interdependent, and diverse operational, information, and security systems to mitigate system-wide business risk, to improve efficiency and effectiveness of business processes and to enhance security control which conventional perimeter, network, or host based control and protection schemes cannot successfully perform.
Owner:ALBEADO
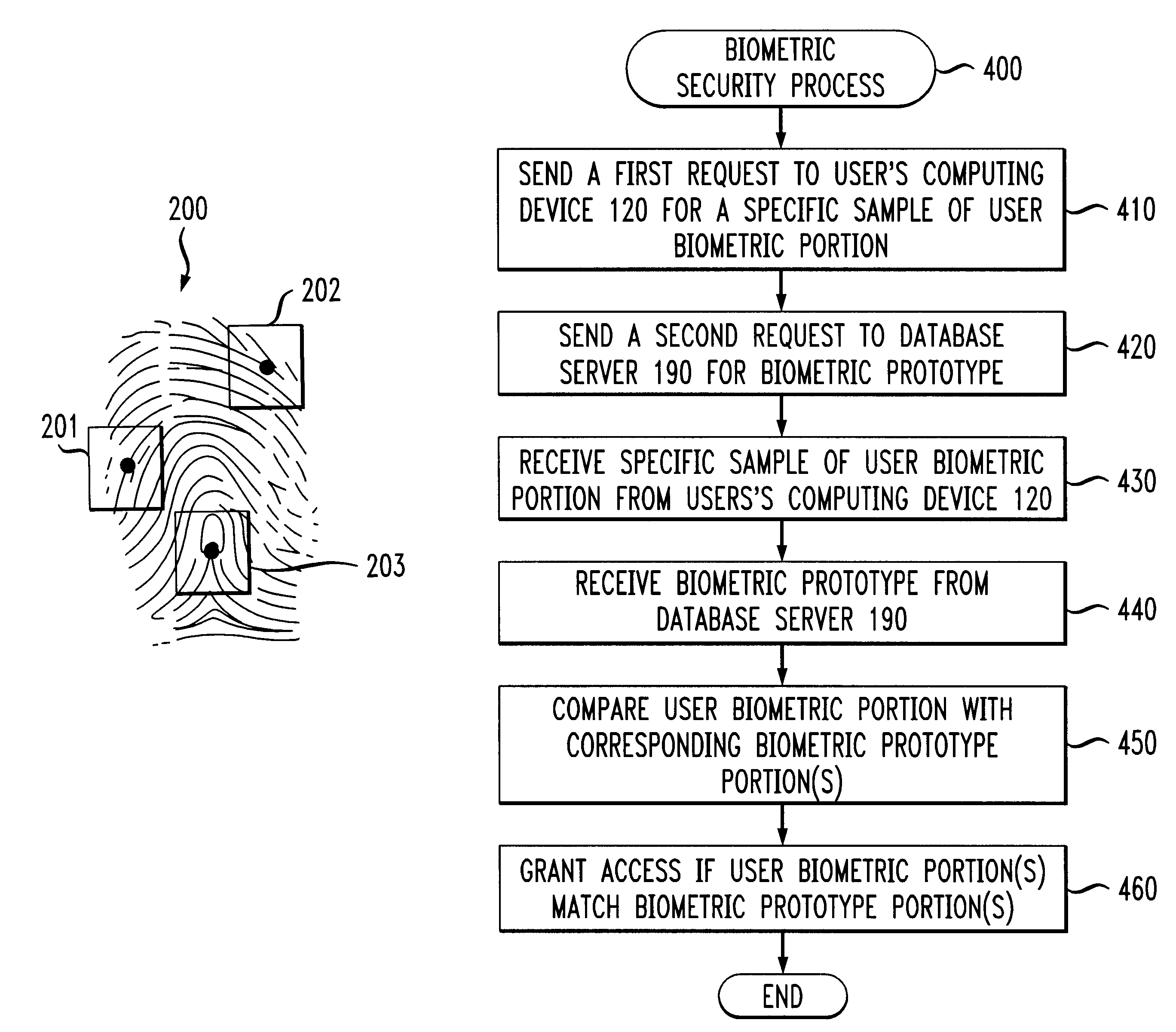
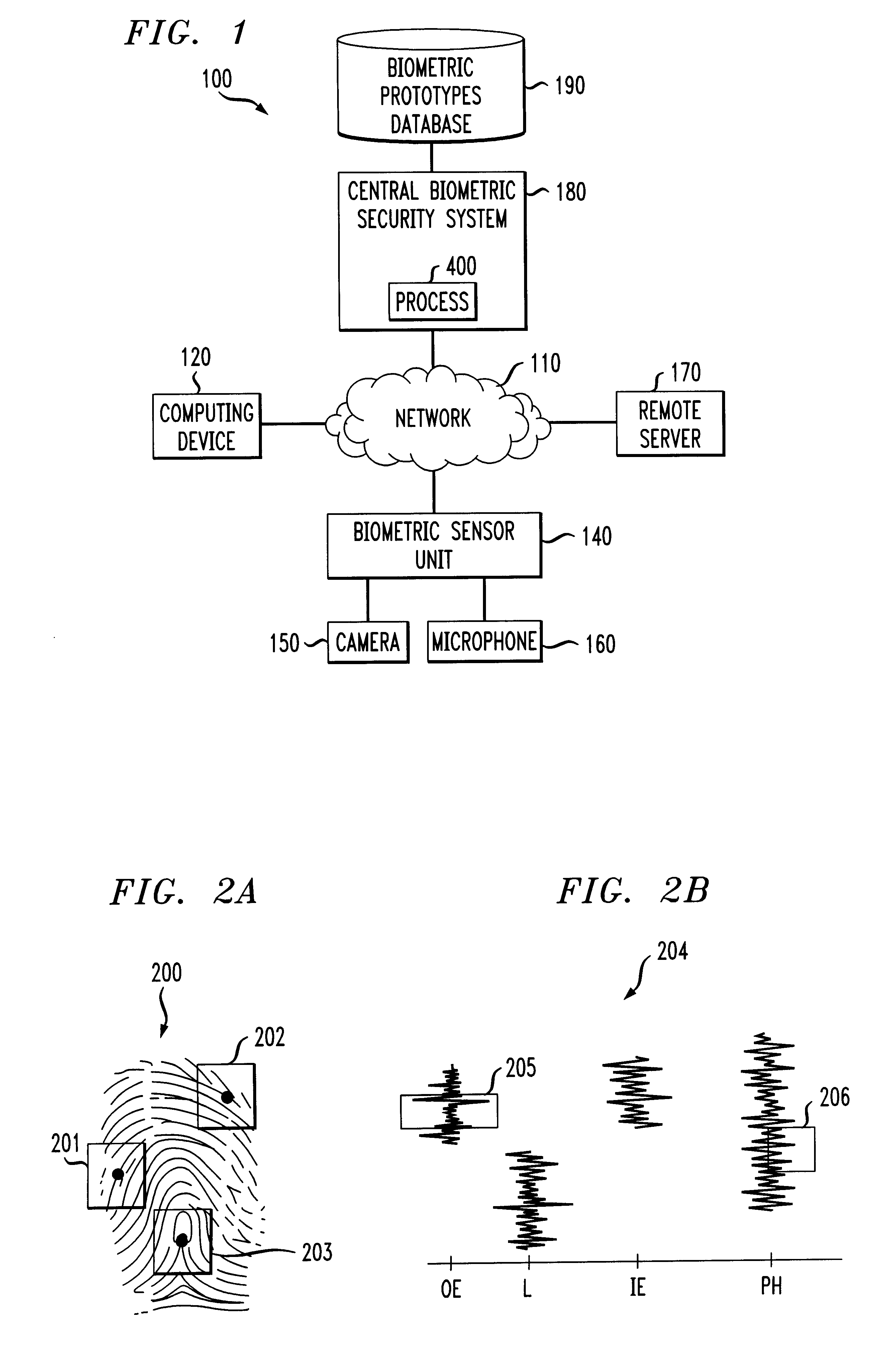
Methods and apparatus for restricting access of a user using random partial biometrics
InactiveUS6735695B1Reduce riskDigital data processing detailsUser identity/authority verificationBiometric dataSecurity system
A biometrics security method and apparatus are disclosed that restrict the ability of a user to access a device or facility using a portion of biometric data to validate the user's identity. Upon a user request to access a secure device or facility, the central biometric security system initially sends a first request for a specific sample of a portion of the user's biometric information. The specific sample may be identified, for example, using a set of image coordinates. A second request is also sent to retrieve the biometric prototype from a database of registered users. The central biometric security system then compares the user biometrics portion with the corresponding biometrics prototype portions. The user receives access to the requested device if the user biometrics portion(s) matches the corresponding biometrics prototype portions. In one variation, the biometric security system transmits a security agent to the user's computing device upon a user request to access a remote device. The security agent serves to extract user biometric portions in accordance with the sampling request from the central biometric security system. In another variation, a local recognition is performed before a remote recognition to reduce the risk of a failed server side recognition due to a poor biometrics feature.
Owner:IBM CORP
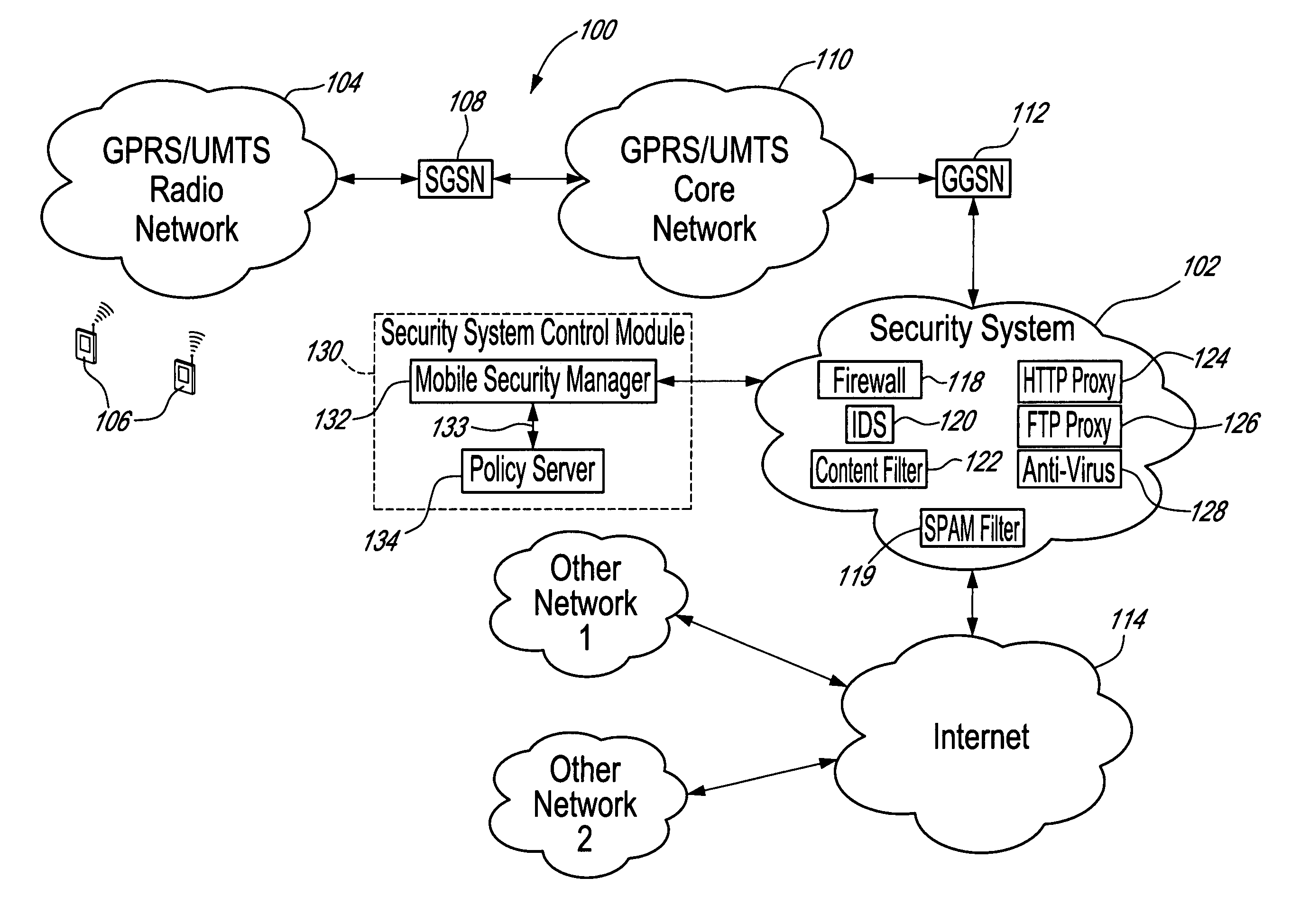
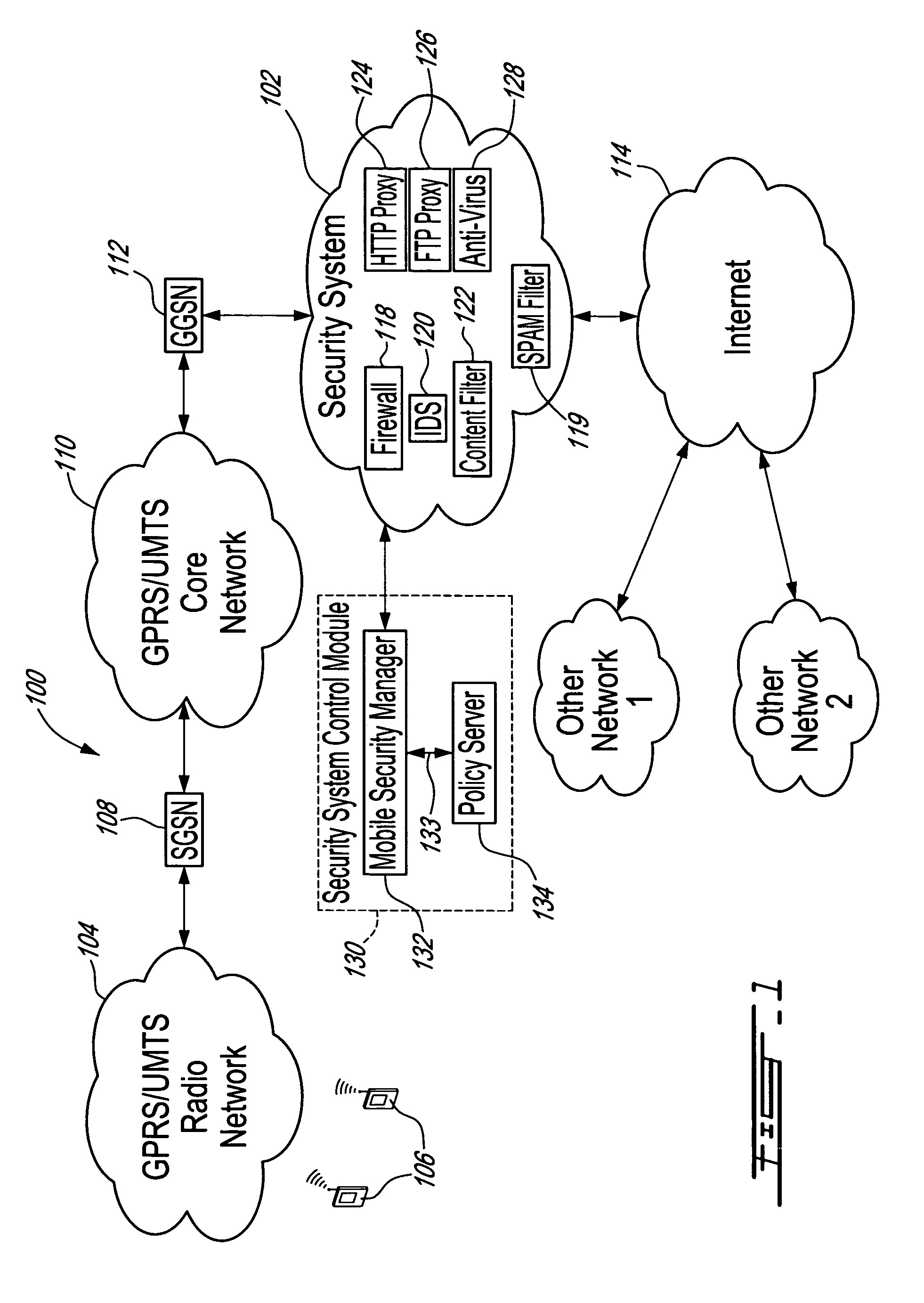
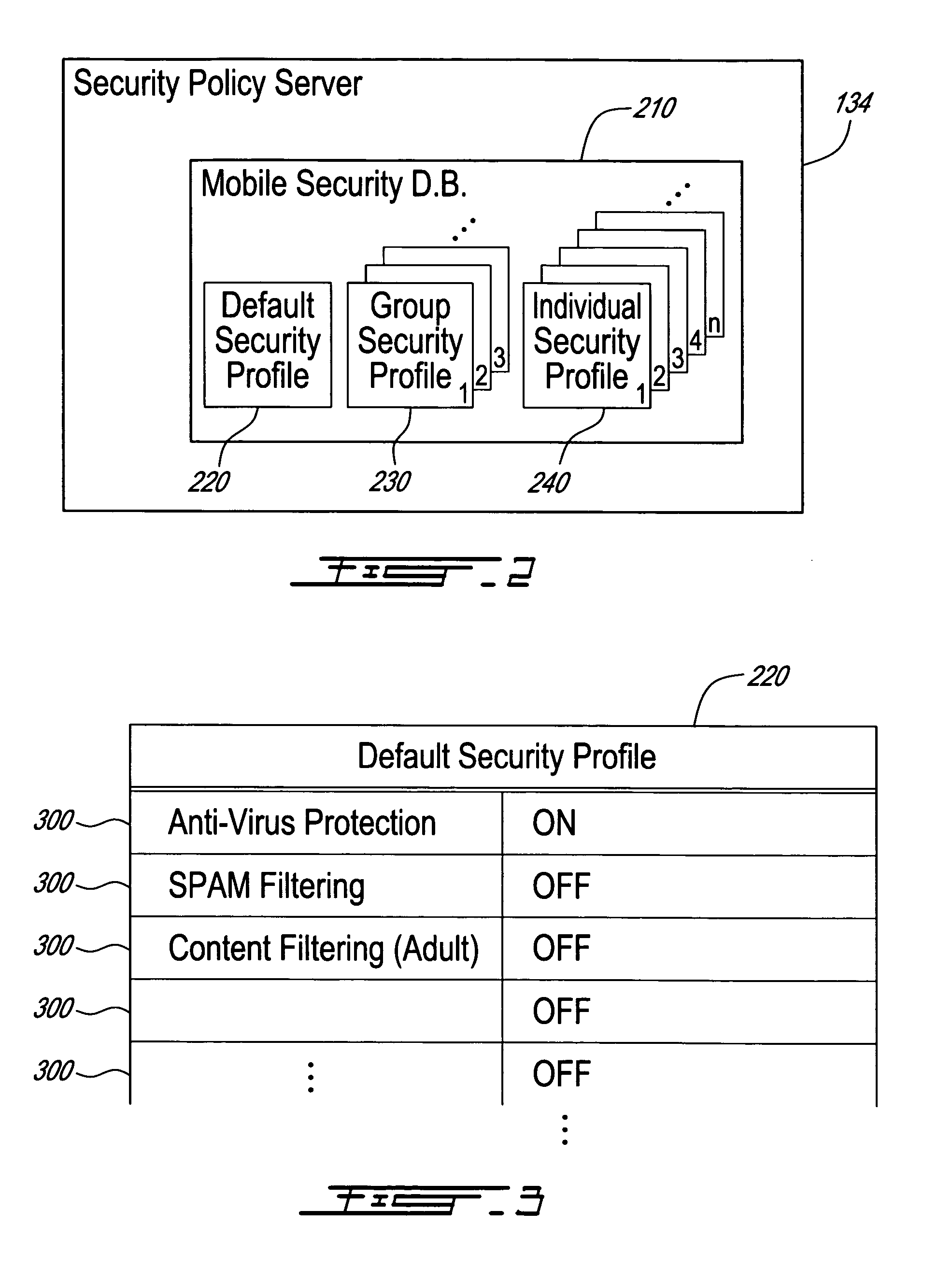
Method, security system control module and policy server for providing security in a packet-switched telecommunications system
ActiveUS7418253B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securityMobile station
A method, security system control module and policy server for providing security for Mobile Stations (MSs) in a Packet-Switched Telecommunications System. When an MS accesses the system, its identity is sent to a security system control module that retrieves a security profile associated with the MS. A policy server of the security system control module stores individual security profiles, default security profiles and group security profiles for registered subscribers. Security settings associated with the MS security profile are returned from the policy server to a mobile security manager of the control module, which then determines if they should be propagated in the system. When no previous network access was made in a given time period by an MS having similar security settings, i.e. belongs to the same group security profile, the settings are propagated in the system in order to be enforced, for providing security protection for the MS.
Owner:TELEFON AB LM ERICSSON (PUBL)
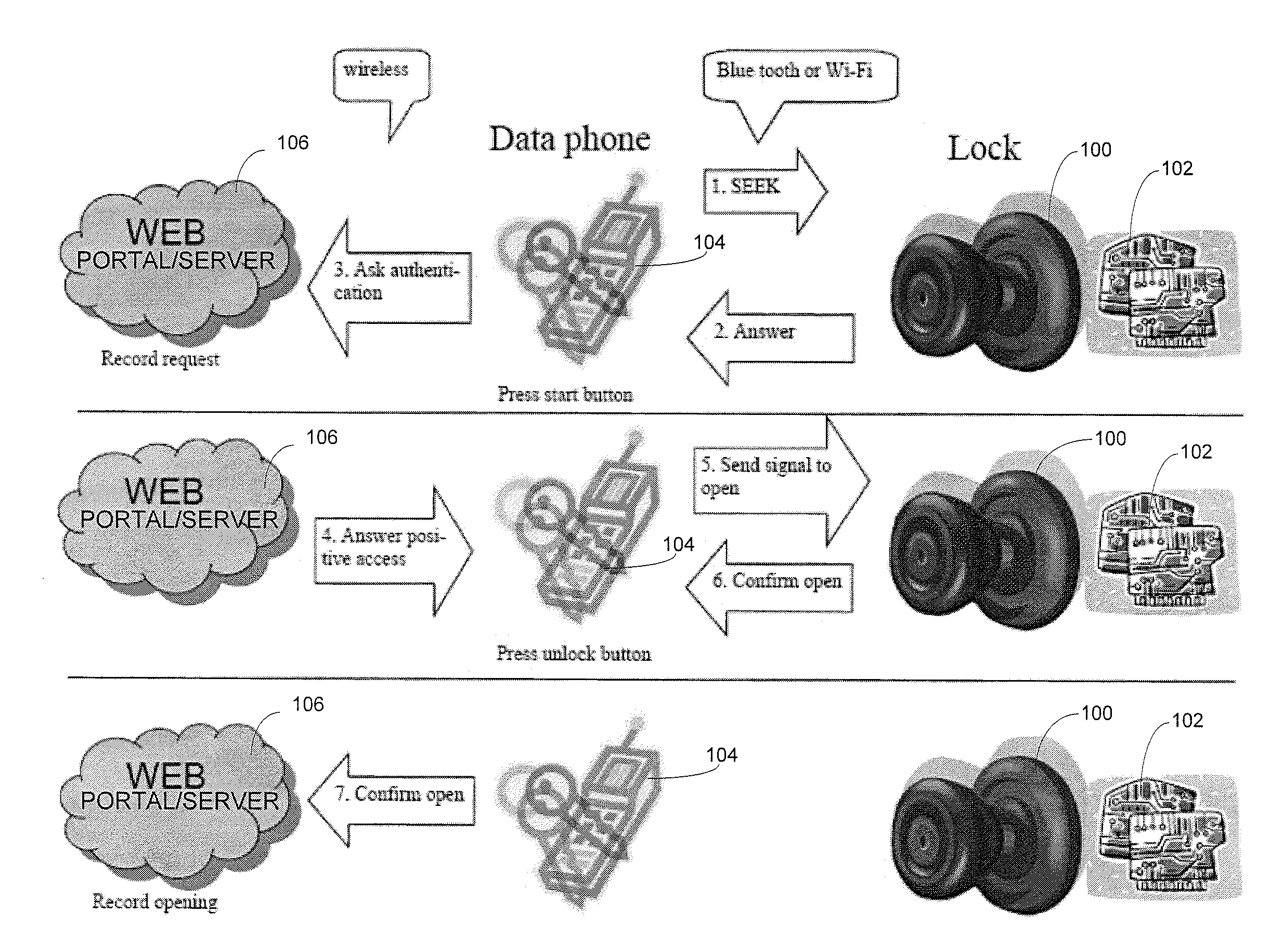
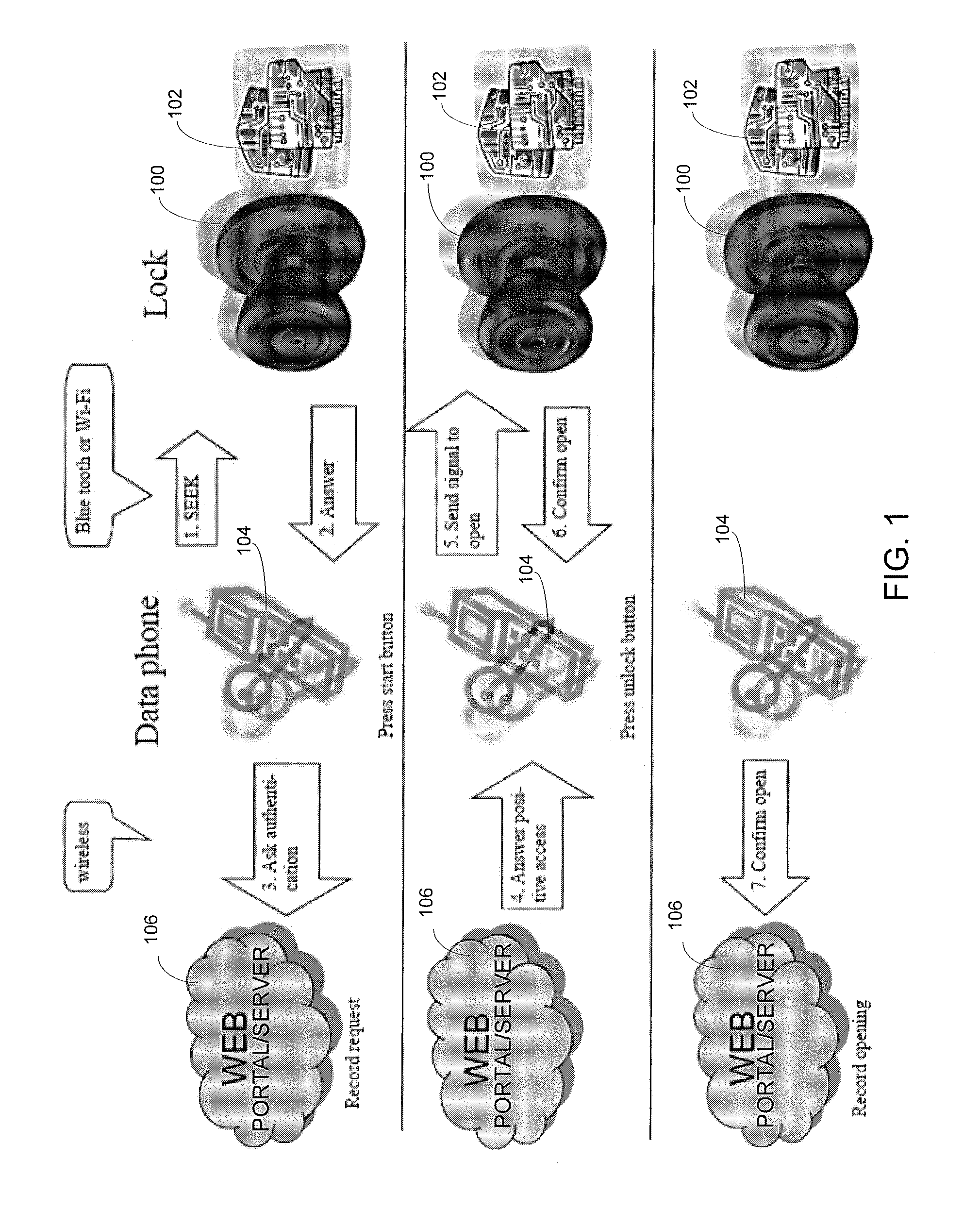
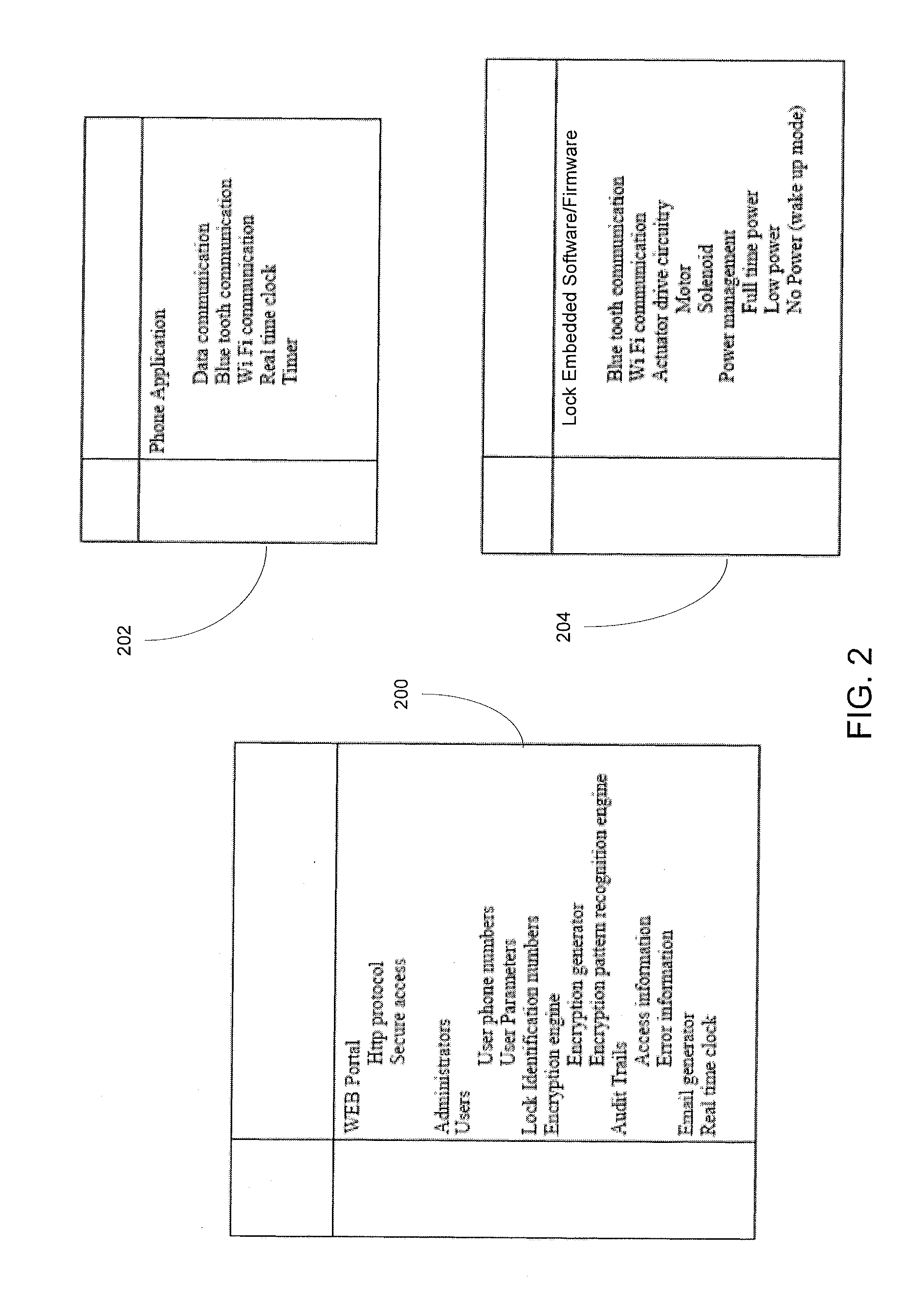
Wireless Device Enabled Locking System
ActiveUS20110311052A1Provide securityDigital data authenticationSecret communicationUnique identifierMobile device
An encrypted security system and associated methods for controlling physical access. The system includes a security server configured to receive a request for authentication from a mobile device, the request comprising information identifying the mobile device and a physical access control device. The security server forwards an encryption message comprising a plurality of unique identifiers to the physical access control device via the mobile device. The physical access control device is configured to authenticate the plurality of unique identifiers in the encryption message and operate an access control mechanism.
Owner:DELPHIAN SYST
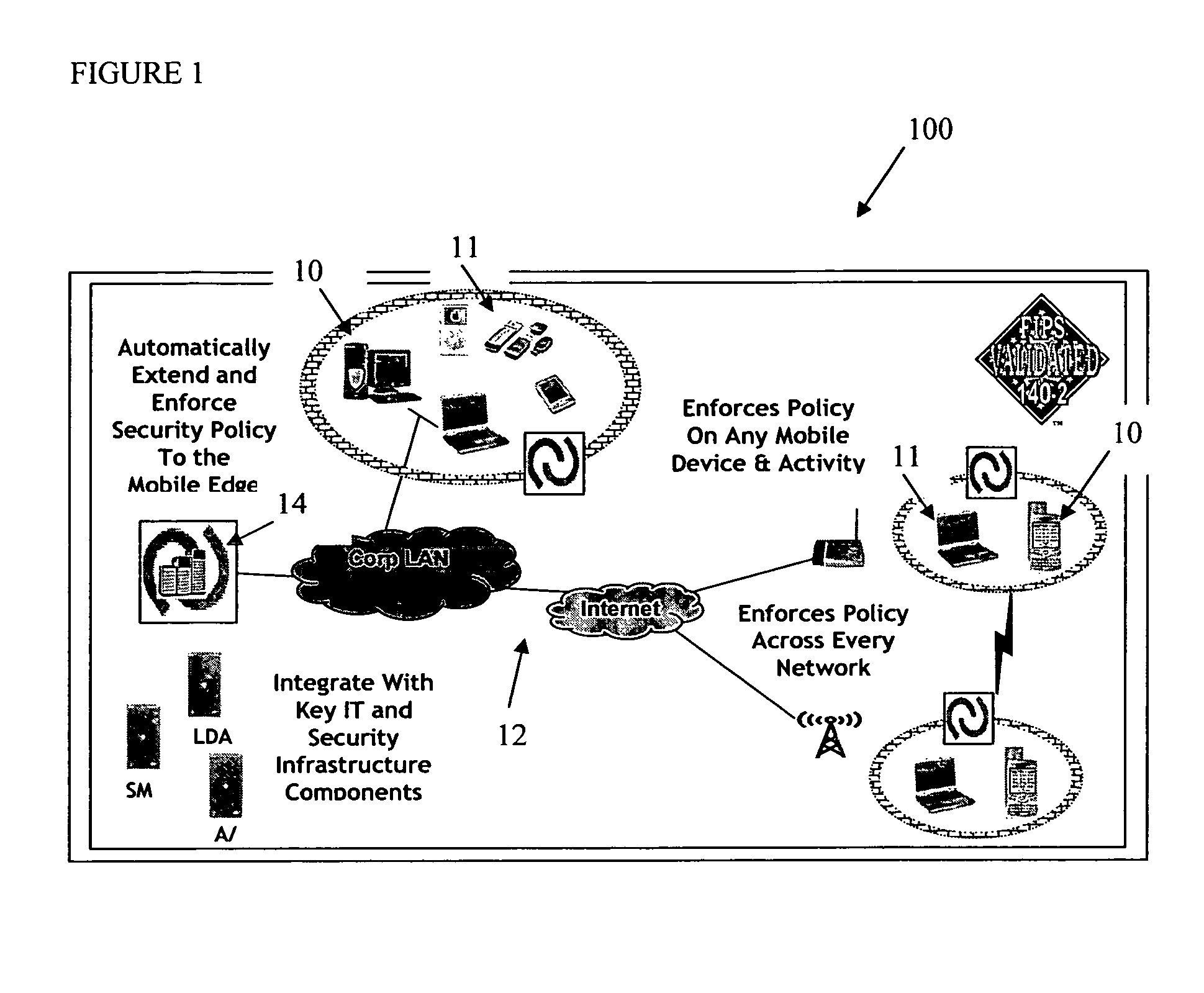
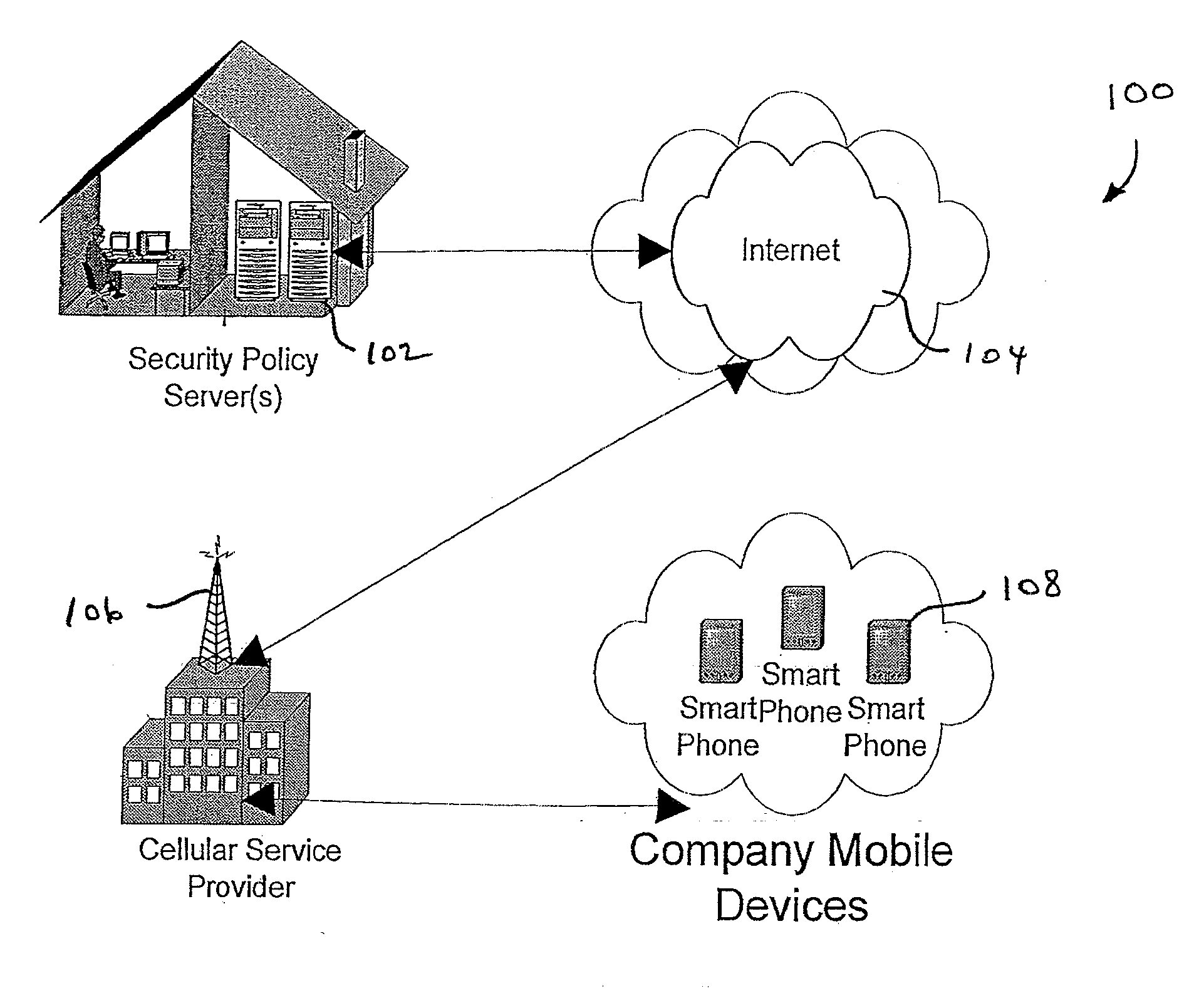
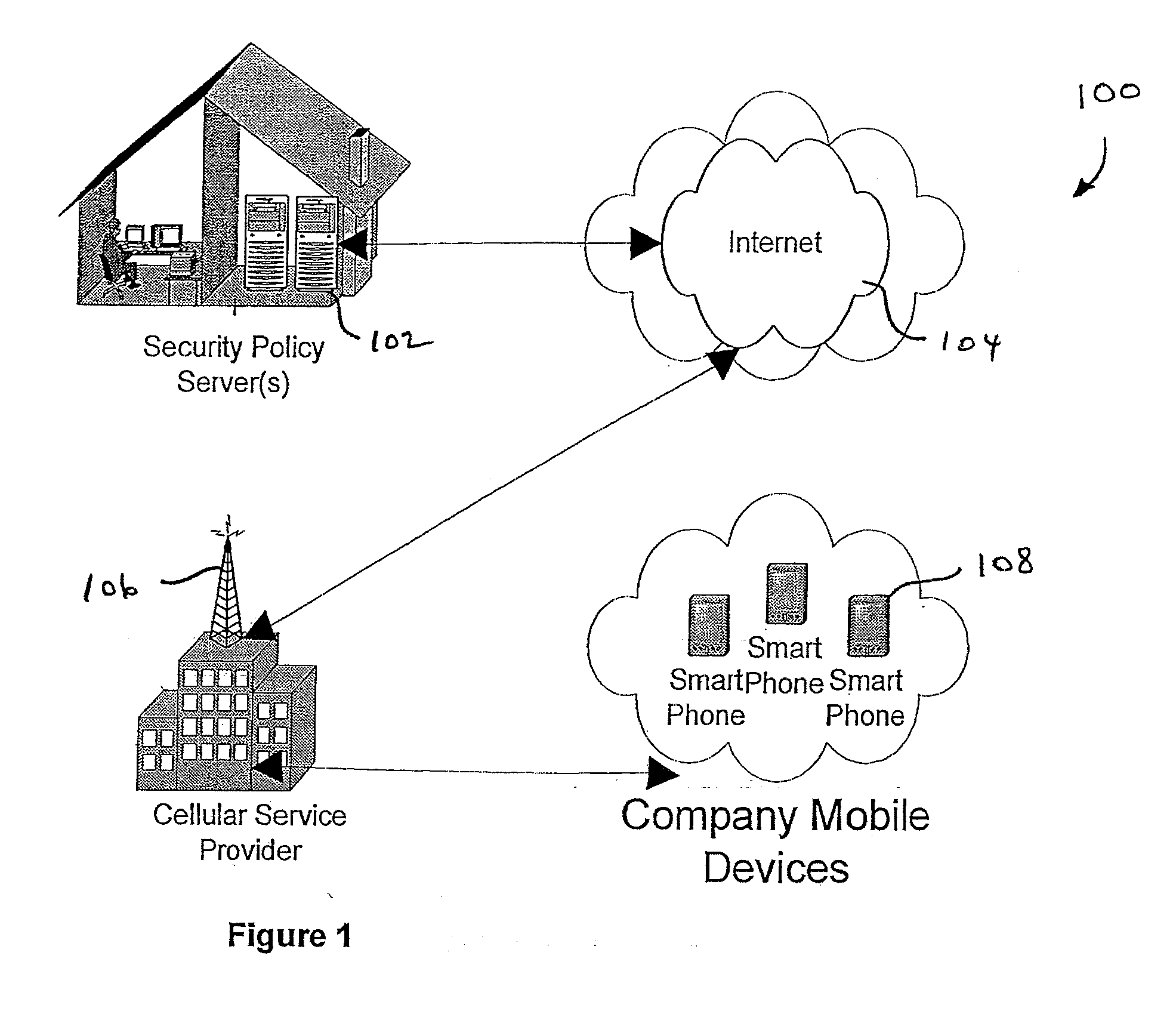
Centralized Dynamic Security Control for a Mobile Device Network
InactiveUS20070266422A1Well formedSecurity arrangementSpecial data processing applicationsTimerSecurity system
An security system for an enterprise network and data automates the revision, deployment, enforcement, auditing and control of security policies on mobile devices connected to said enterprise network, through automated communication between a security policy server and the mobile device. Control of the security system is centralized through administrative control of security policies stored on the security policy server. Automation of deployment of security policies to mobile devices occurs through transparent background communication and transfer of updated policies either triggered by a change in a security policy within the central repository of security policies or upon the expiration of a certain time period during which no policies were downloaded to the mobile device. When the mobile device is not in compliance with a security policy, a software security agent operating thereon limits access to said enterprise network and enterprise data. To aid in preventing the overwhelming of the enterprise network and the security policy server as a result of to many synchronization communications coming from too many mobile devices, a randomized timer is set by the software security agent upon receipt by the mobile device of a synchronization command from the security policy server.
Owner:SQUARE 1 BANK
Security system and method for use of same
A security system and method for use of the same are disclosed that provide for remote surveillance. In one embodiment, a property's entry point such as a doorway is equipped with a video camera, an external microphone, and an external speaker. An individual, such as an owner of the property, is away from the property and equipped with a cellular telephone. When a person arrives at the entry point, a control unit relays audio and visual data captured by the video camera and the external microphone to the individual's cellular telephone. Similarly, the control unit relays audio data from the owner to the person at the entry point.
Owner:ZINSER DUKE W
Security System with Methodology for Defending Against Security Breaches of Peripheral Devices
ActiveUS20050138433A1Digital data processing detailsAnalogue secracy/subscription systemsAuthorizationSecurity system
A security system with methodology for defending against security breaches of peripheral devices is described. In one embodiment, for example, a method is described for protecting a computer from security breaches involving devices that may be attached to the computer, the method comprises steps of: when a device is first attached to the computer, specifying authorization information indicating that the device is allowed to communicate with the computer; detecting detachment of the device from the computer; updating the authorization information to indicate that the device is no longer authorized to communicate with the computer; and upon reattachment of the device, blocking communication with the device while the device remains unauthorized, thereby preventing a security breach involving the device.
Owner:CHECK POINT SOFTWARE TECH INC
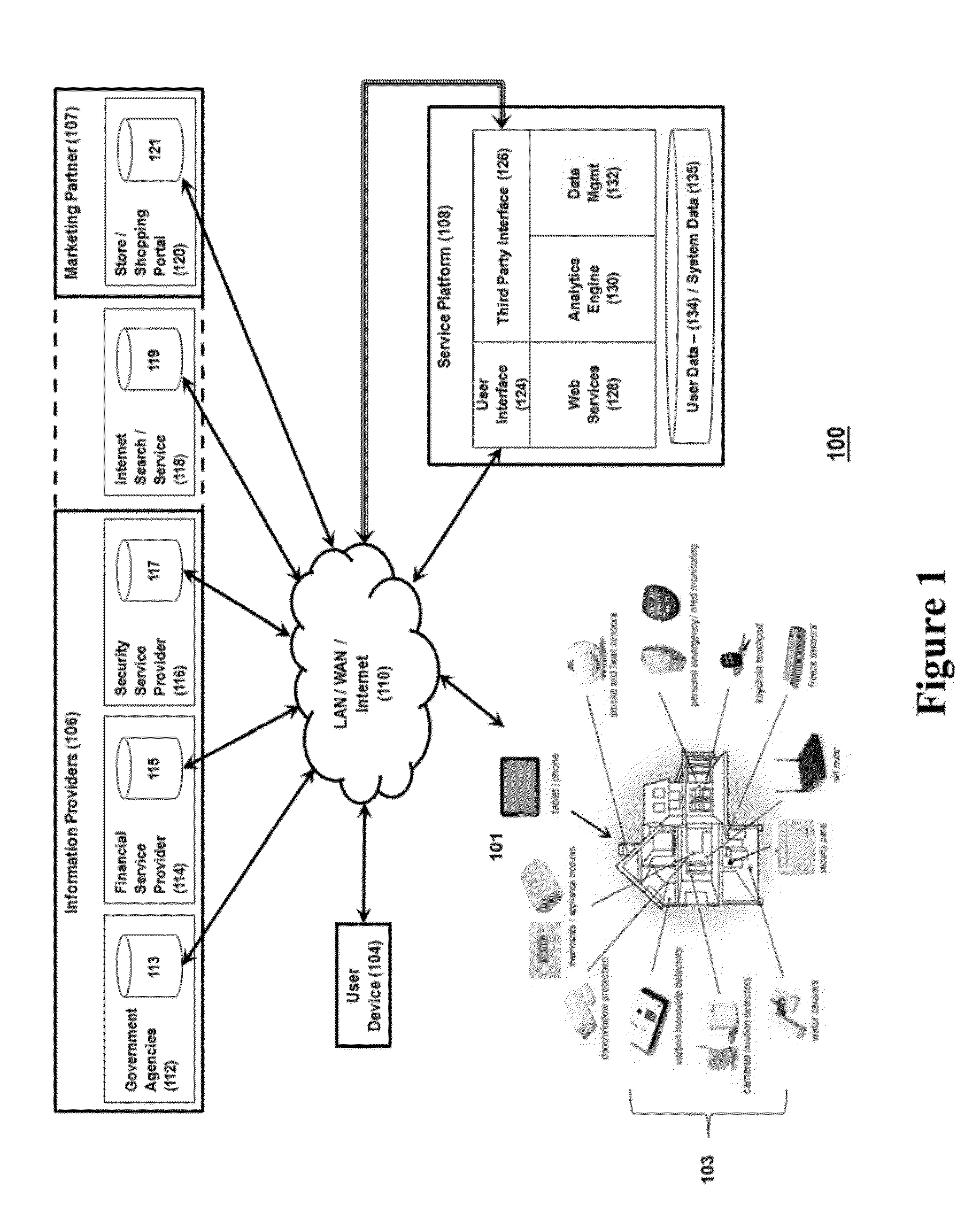
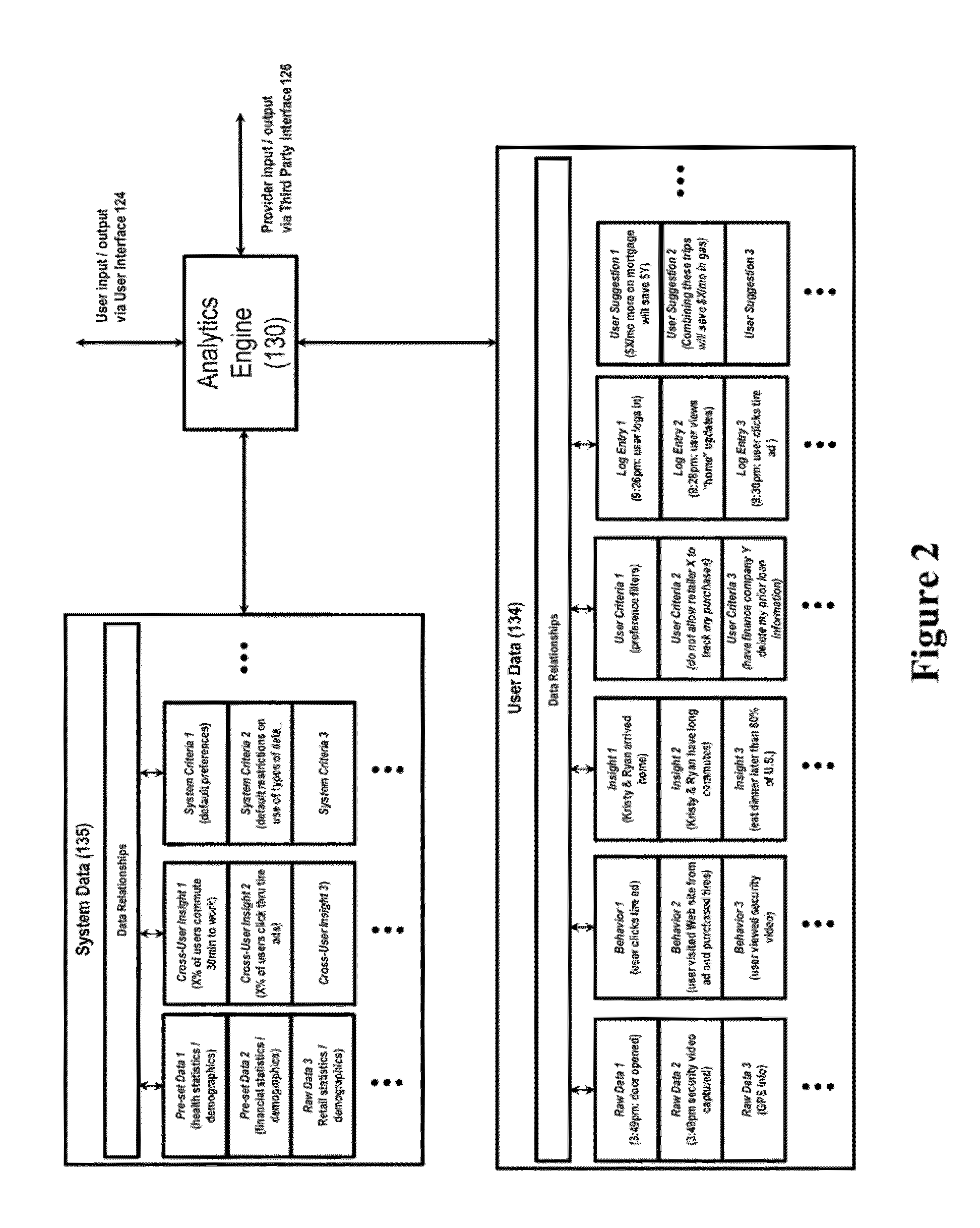
System for controlling use of personal data
InactiveUS20140244399A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyPersonal details
The invention relates to a system configured to enable a user to track how his or her personal data is being used, and to control its collection, storage, and / or use, and delete certain personal data across information providers. A user may establish criteria regarding such collection, use, and storage of personal data generated by a security system device, capture the personal data at a control gateway before it is provided to an information provider; and applying the criteria to the personal data. The invention also relates to a system to present additional information to the user that is relevant to both the user and at least one marketing partner (such as targeted advertising); and to provide data to enable at least one marketing partner to provide value (a “reward”) to the user in exchange for the user allowing an information provider to collect and use personal data of the user.
Owner:ADT US HLDG INC
Cyber Behavior Analysis and Detection Method, System and Architecture
A scalable cyber-security system, method and architecture for the identification of malware and malicious behavior in a computer network. Host flow, host port usage, host information and network data at the application, transport and network layers are aggregated from within the network and correlated to identify a network behavior such as the presence of malicious code.
Owner:CYBER ADAPT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com