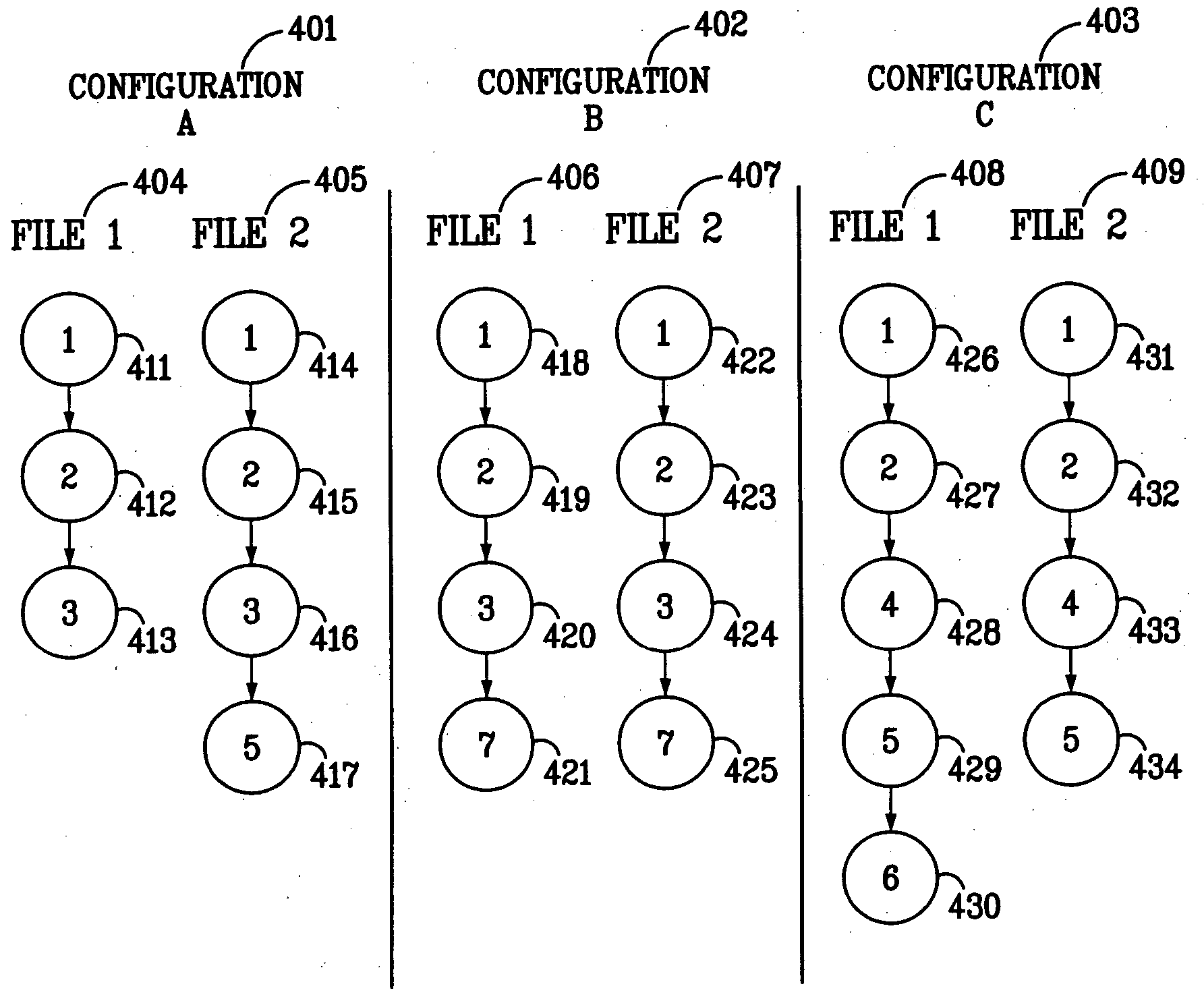
Patents
Literature
1317 results about "User Privilege" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
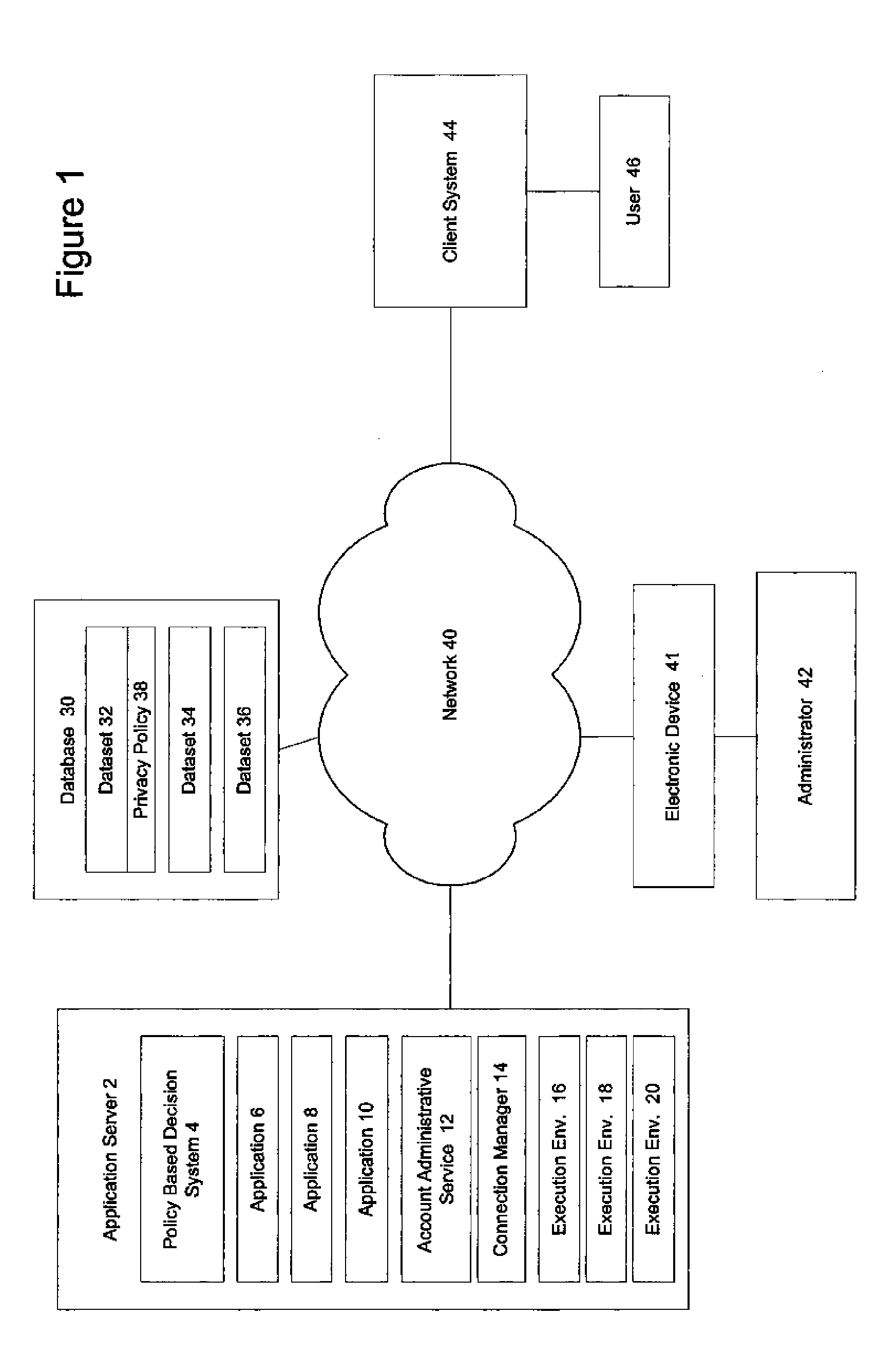
The operations and access levels which are allowed to a user (e.g Create, Read, Update, Delete).
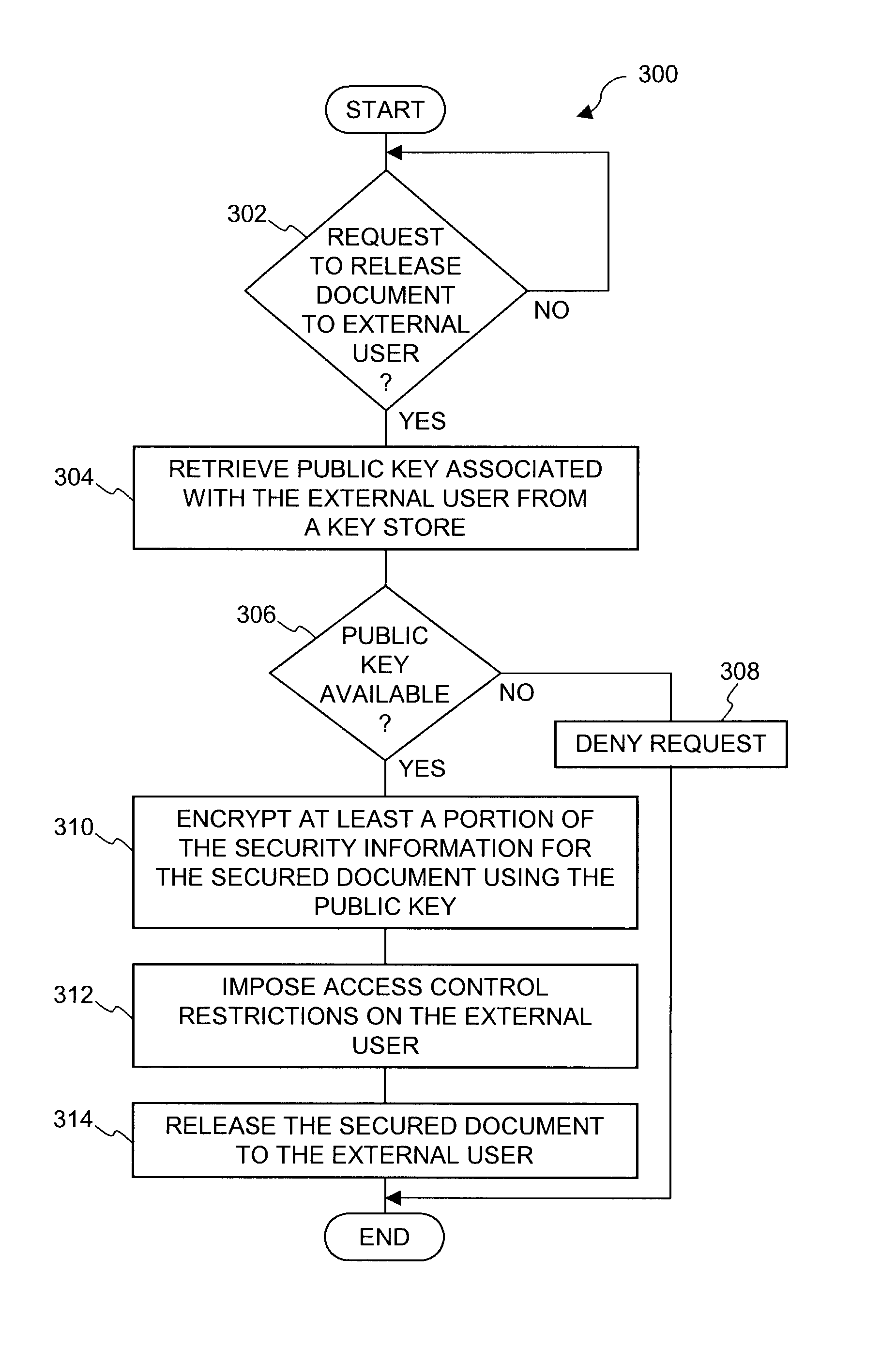
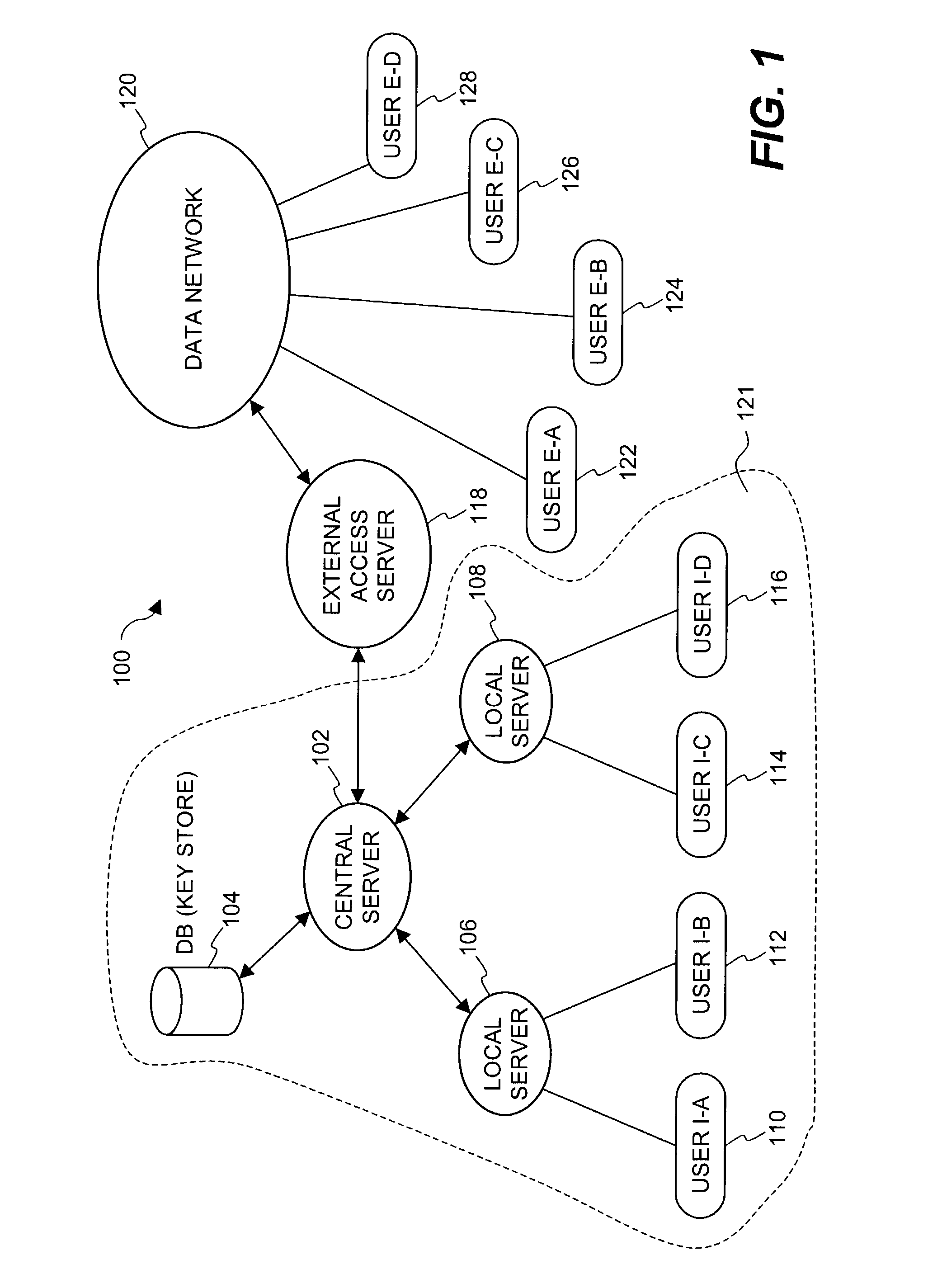
Document security system that permits external users to gain access to secured files
ActiveUS8176334B2Minimal amountLimited accessDigital data processing detailsUser identity/authority verificationUser PrivilegeInternal documentation
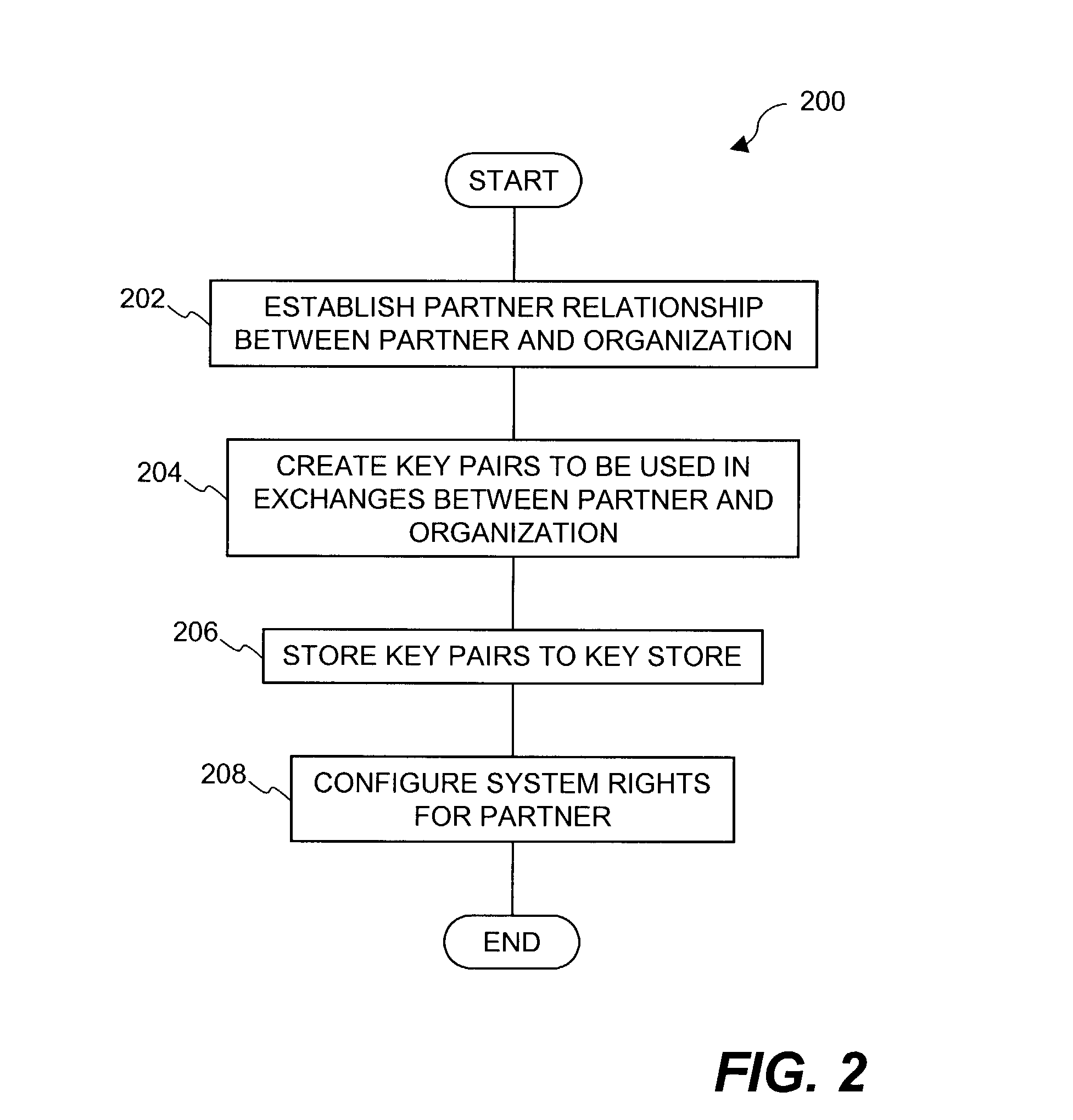
An improved system and approaches for exchanging secured files (e.g., documents) between internal users of an organization and external users are disclosed. A file security system of the organization operates to protect the files of the organization and thus prevents or limits external users from accessing internal documents. Although the external users are unaffiliated with the organization (i.e., not employees or contractors), the external users often have working relationships with internal users. These working relationships (also referred to herein as partner relationships) often present the need for file (document) exchange. According to one aspect, external users having working relationships with internal users are able to be given limited user privileges within the file security system, such that restricted file (document) exchange is permitted between such internal and external users.
Owner:INTELLECTUAL VENTURES I LLC
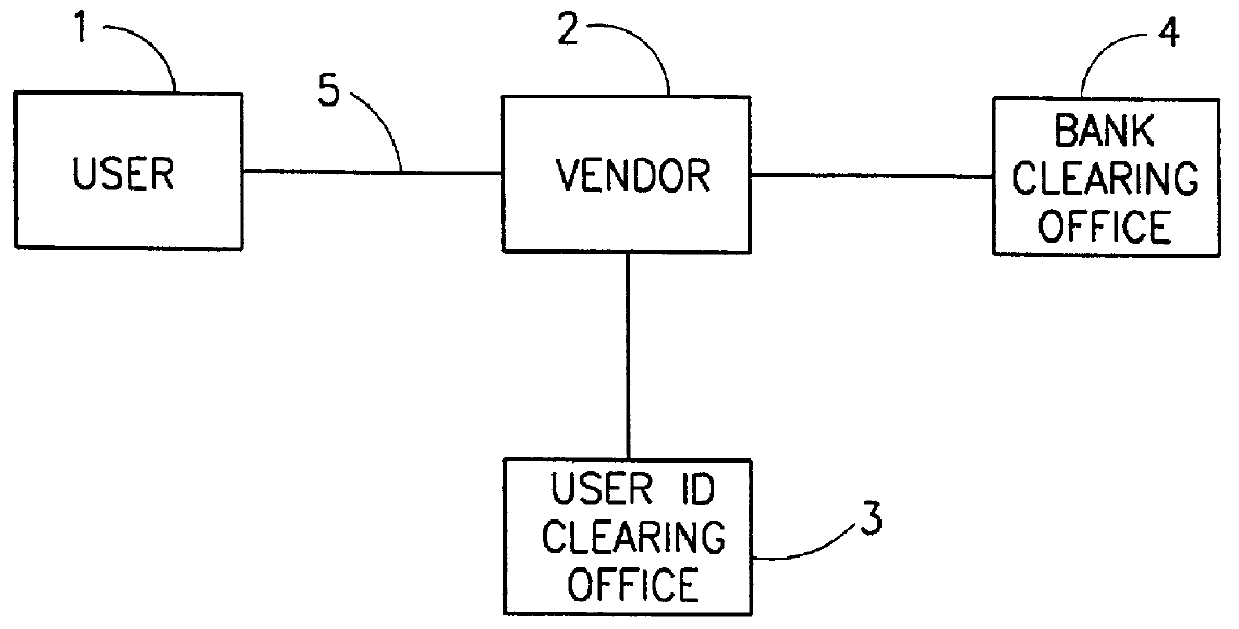
System for transaction over communication network
A method for conducting transaction between first user and a remote second user interlinked through a communication network, by utilizing also a clearing office interlinked to the network. The clearing office storing the user privileged information. The method including the steps of the user and the clearing office establishing a cryptographic secured session, the user transmitting, via the session, a user privileged information and transaction specific data, the transaction specific data being indicative of a transaction identification data. The clearing office activating transaction validity checking procedure by utilizing a user privileged information and the transaction specific data. In response to affirmative result of the transaction validity checking, the clearing office producing a transaction validity indication being indicative of the transaction identification code. The clearing office and the user establishing a communication session and the clearing office transmitting, via the session, the transaction validity indication.
Owner:NUSH MARKETING MANAGEMENT & CONSULTANCE
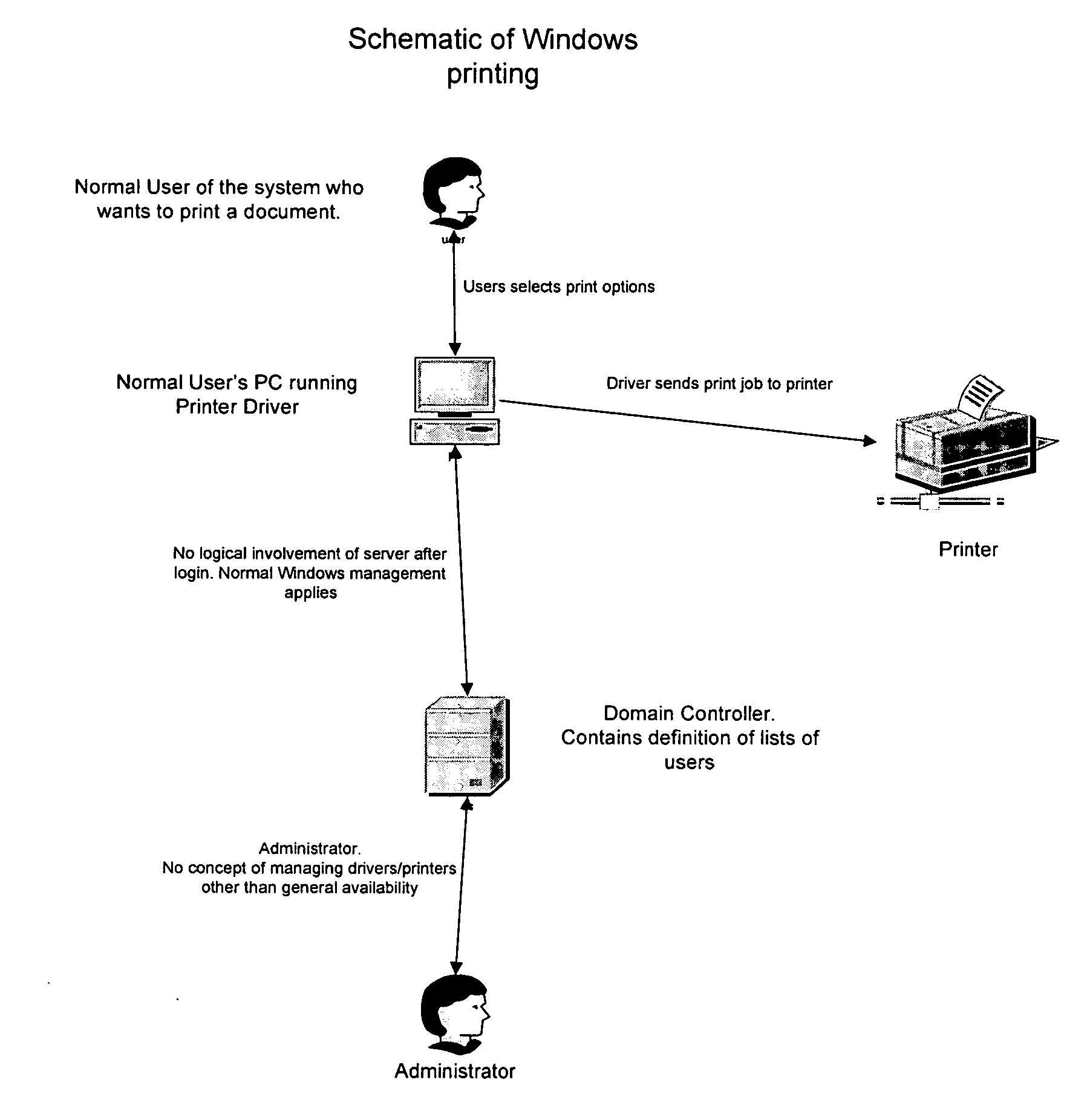
Managing user permissions in a computer system
InactiveUS20070079385A1Digital data processing detailsUser identity/authority verificationOperational systemUser Privilege
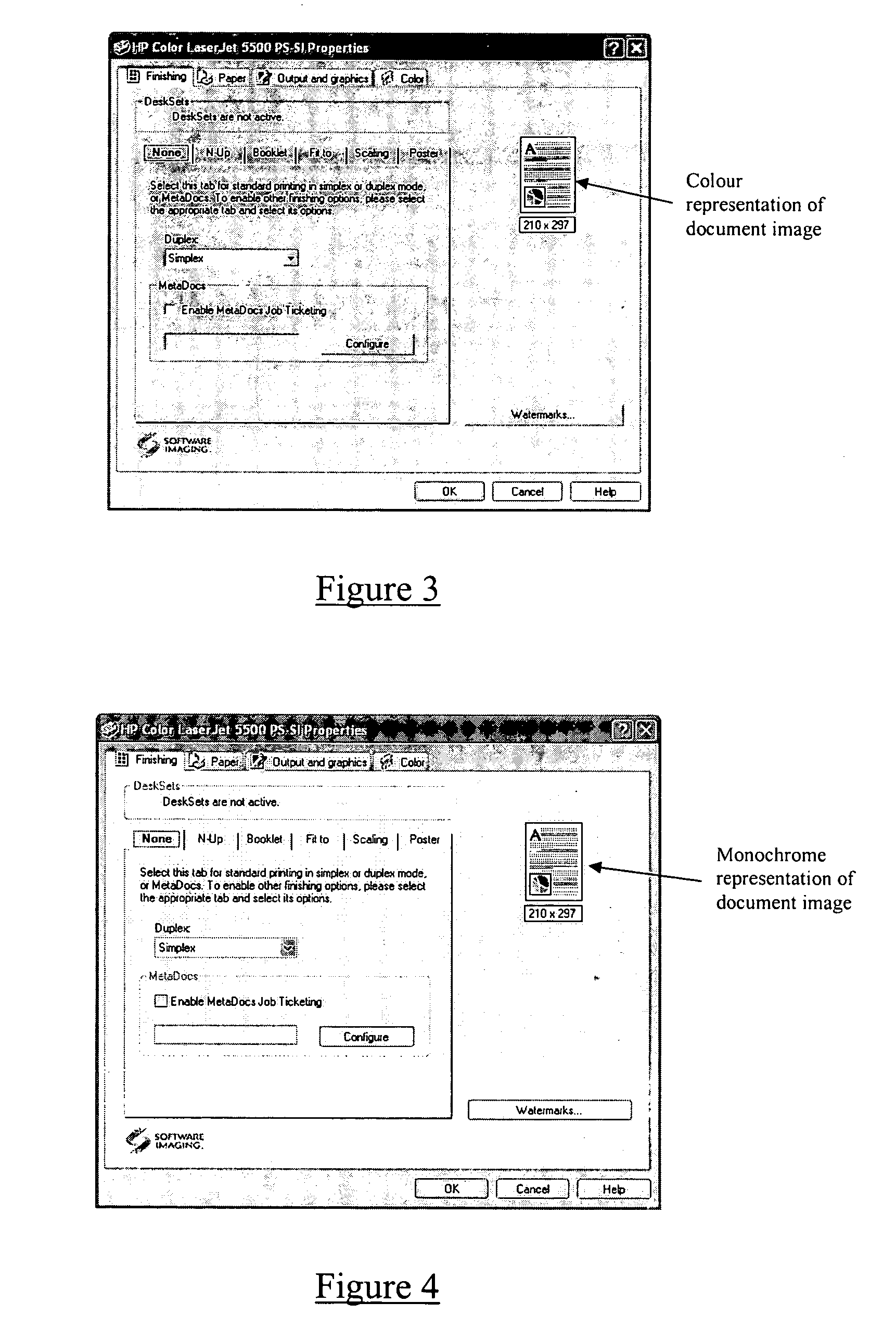
A method of operating a printer coupled to a computer, the method comprising associating one or more permissions of a printer driver resident on the computer with an operating system managed object and, when an attempt is made to print on said print device or a User Interface of the printer driver opened, setting the status of said permissions according to one or more security settings of the operating system managed object.
Owner:SOFTWARE IMAGING GROUP
Digital rights management system and method
InactiveUS20050229004A1Improve securityCommunication securityProgramme controlComputer controlUser PrivilegeSecure transmission
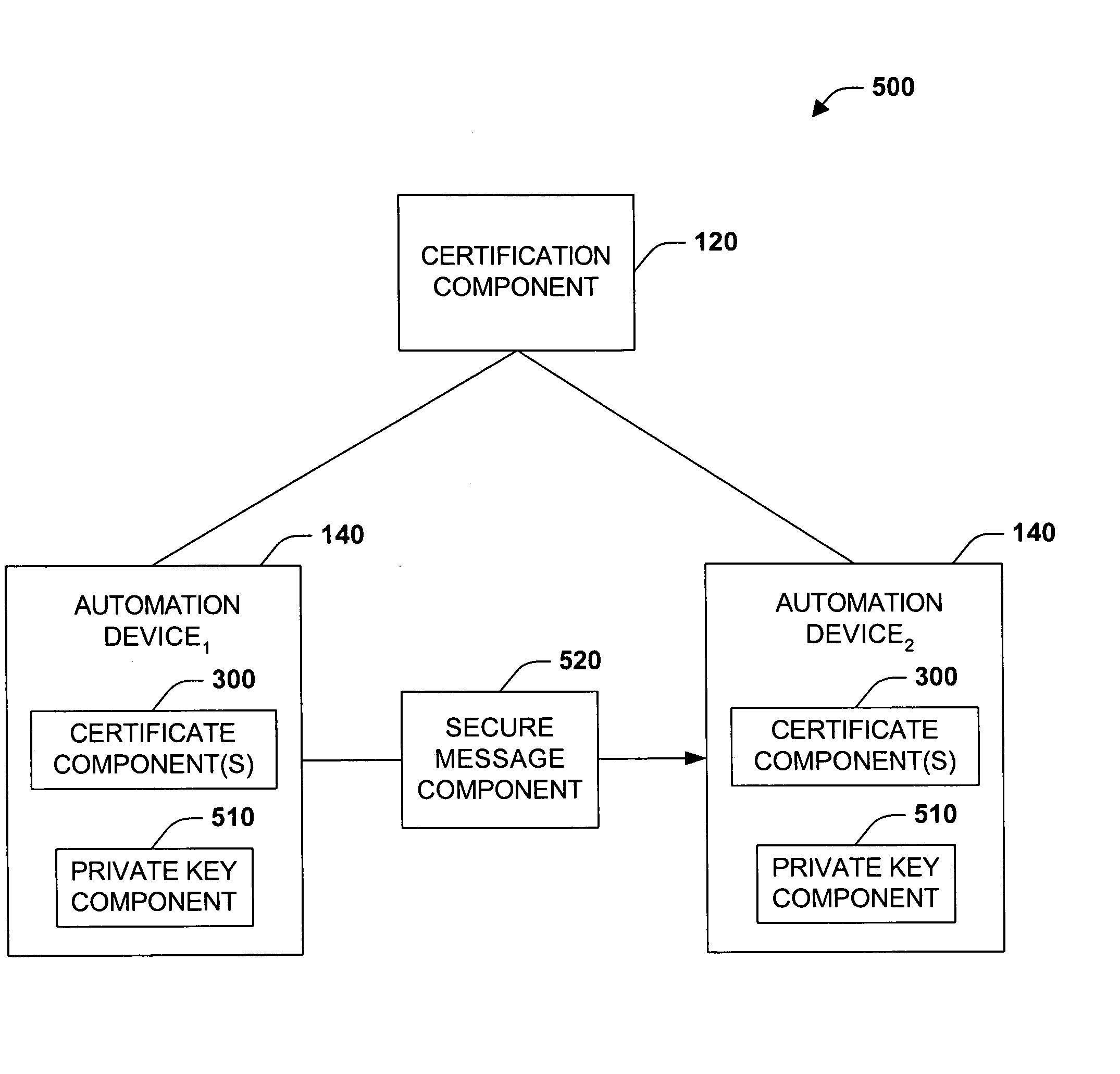
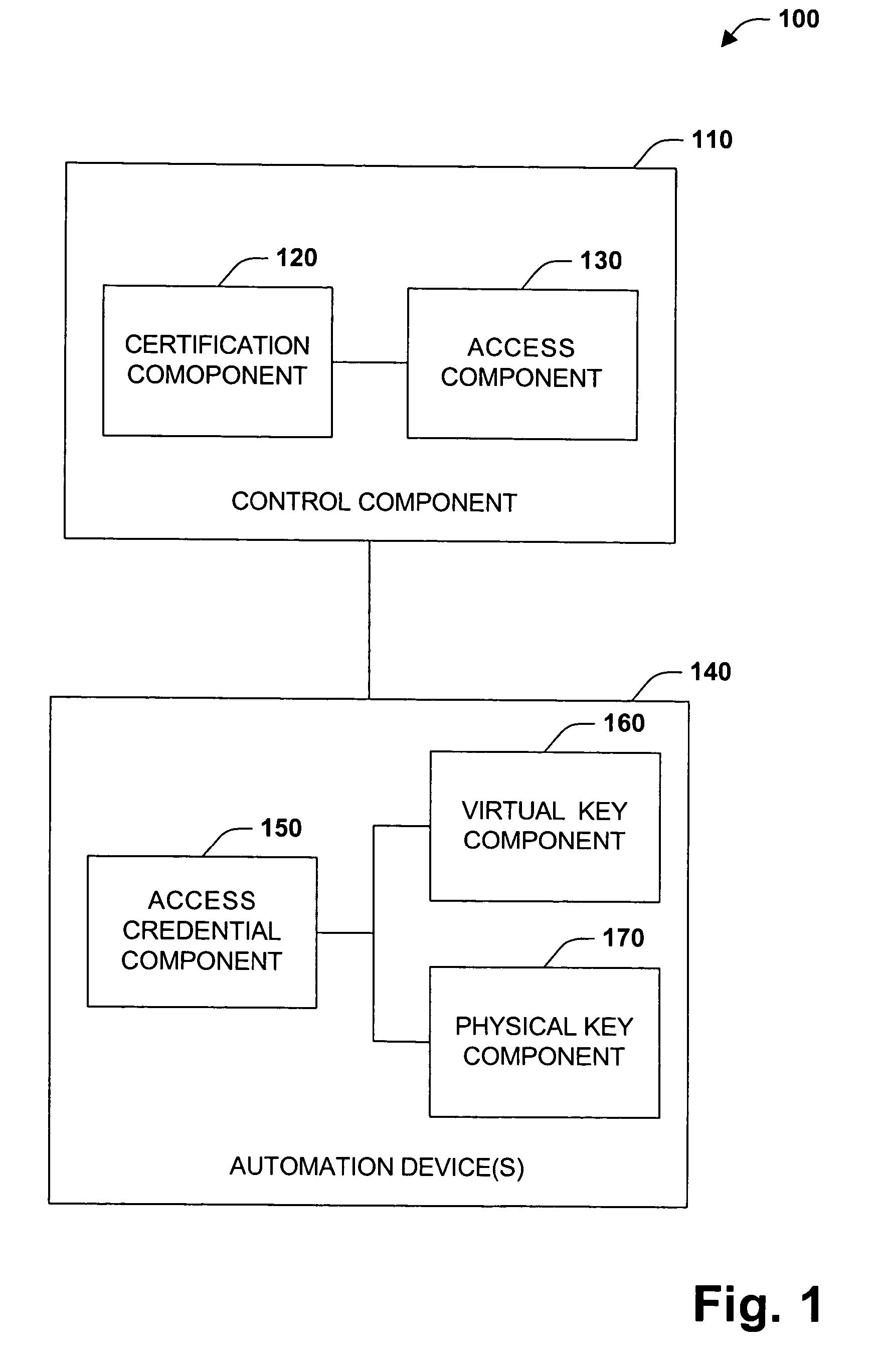
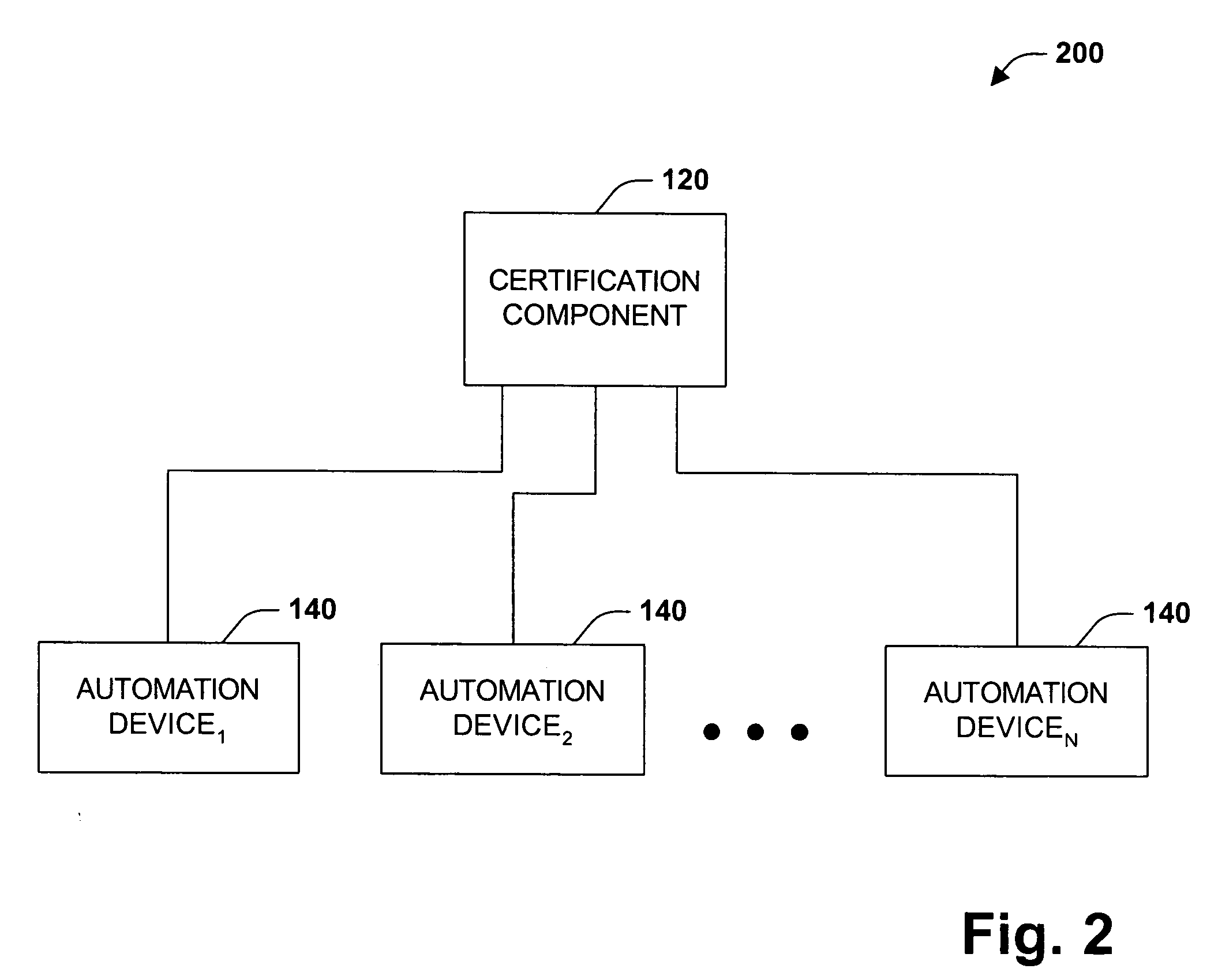
The present invention concerns application of digital rights management to industrial automation devices including programmable logic controllers (PLCs), I / O devices, and communication adapters. Digital rights management involves a set of technologies for controlling and managing access to device objects and / or programs such as ladder logic programs. Access to automation device objects and / or programs can be managed by downloading rules of use that define user privileges with respect to automation devices and utilizing digital certificates, among other things, to verify the identity of a user desiring to interact with device programs, for example. Furthermore, the present invention provides for secure transmission of messages to and amongst automation devices utilizing public key cryptography associated with digital certificates.
Owner:ROCKWELL AUTOMATION TECH
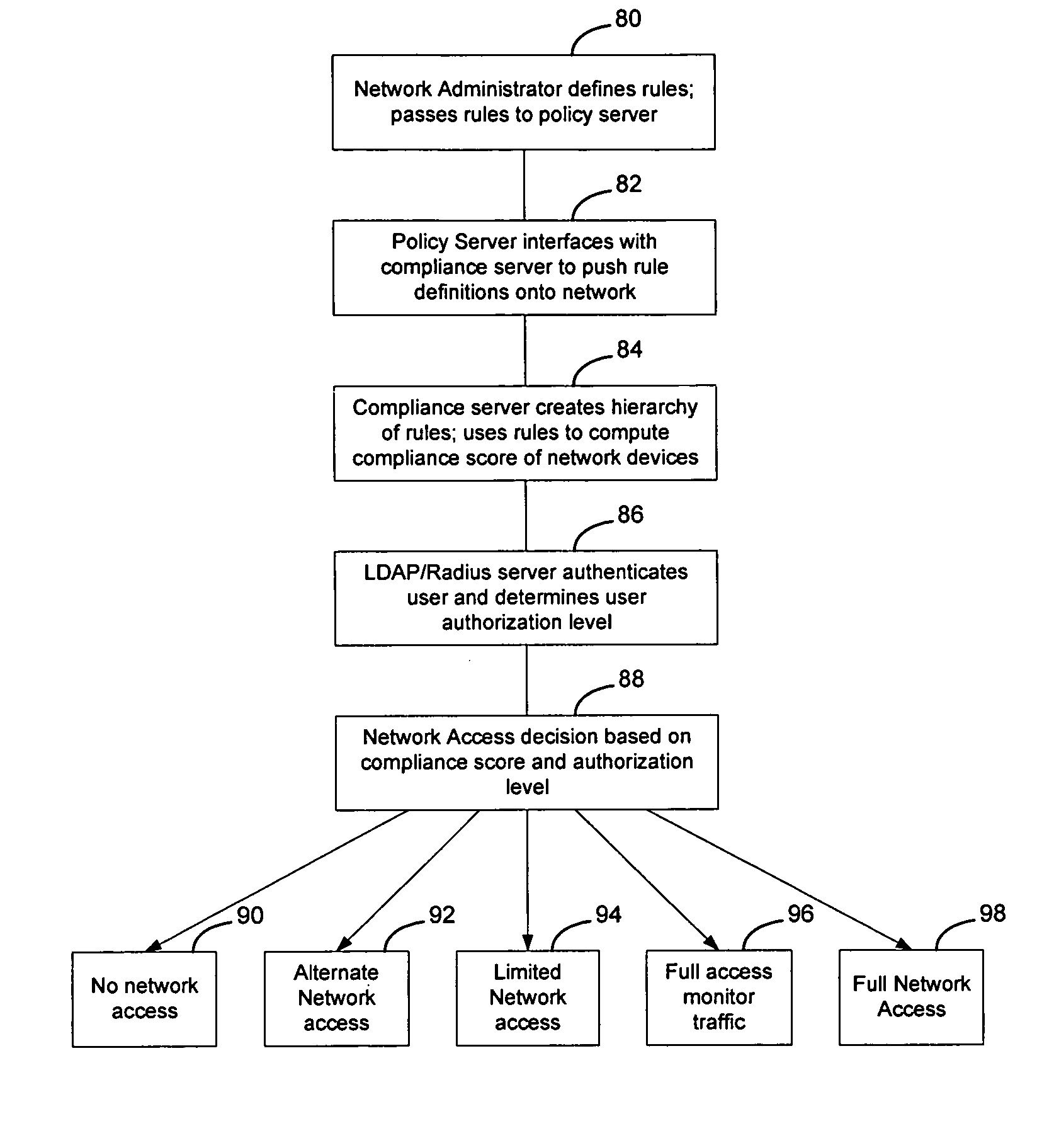
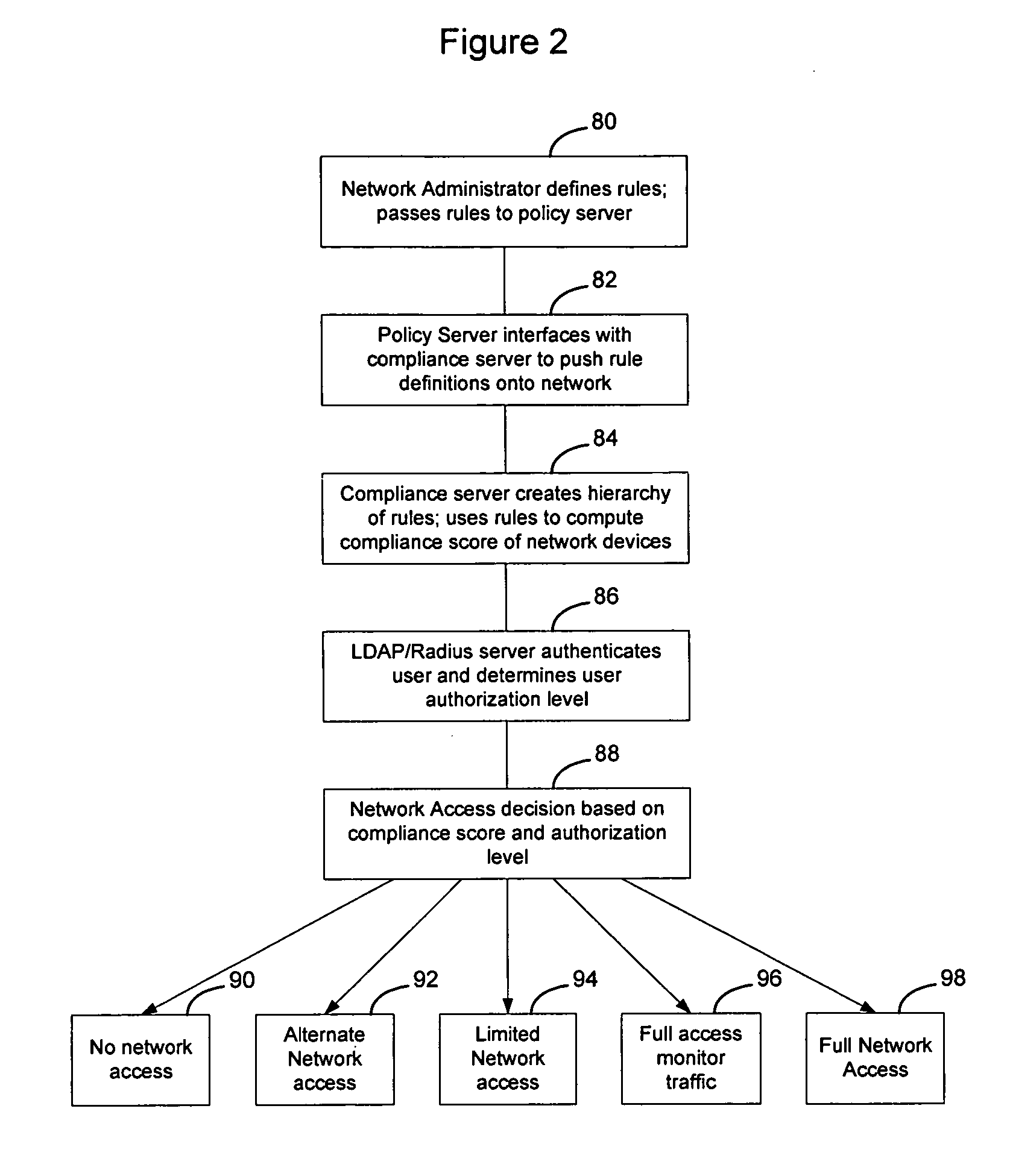
Method and apparatus for rating a compliance level of a computer connecting to a network
InactiveUS20070124803A1MoreOvercomes drawbackRandom number generatorsMemory loss protectionUser PrivilegeCompliance level
Rules are used to determine a compliance level for a computing device attempting to access a network. The compliance level may have multiple categories or facets, that may be determined individually or collectively, to determine a score for the computing device. The score may be used to determine whether the computing device should obtain access to the network, the type of access to be granted, or whether remediation should occur and what type of remediation should occur on the computing device to enable the computing device to enjoy greater network privileges. Optionally, the score may be weighted in connection with the user privileges associated with the user as determined during the authentication process, to enable users with greater network access privileges to access the network in situations where other users may not be able to access the network.
Owner:AVAYA INC
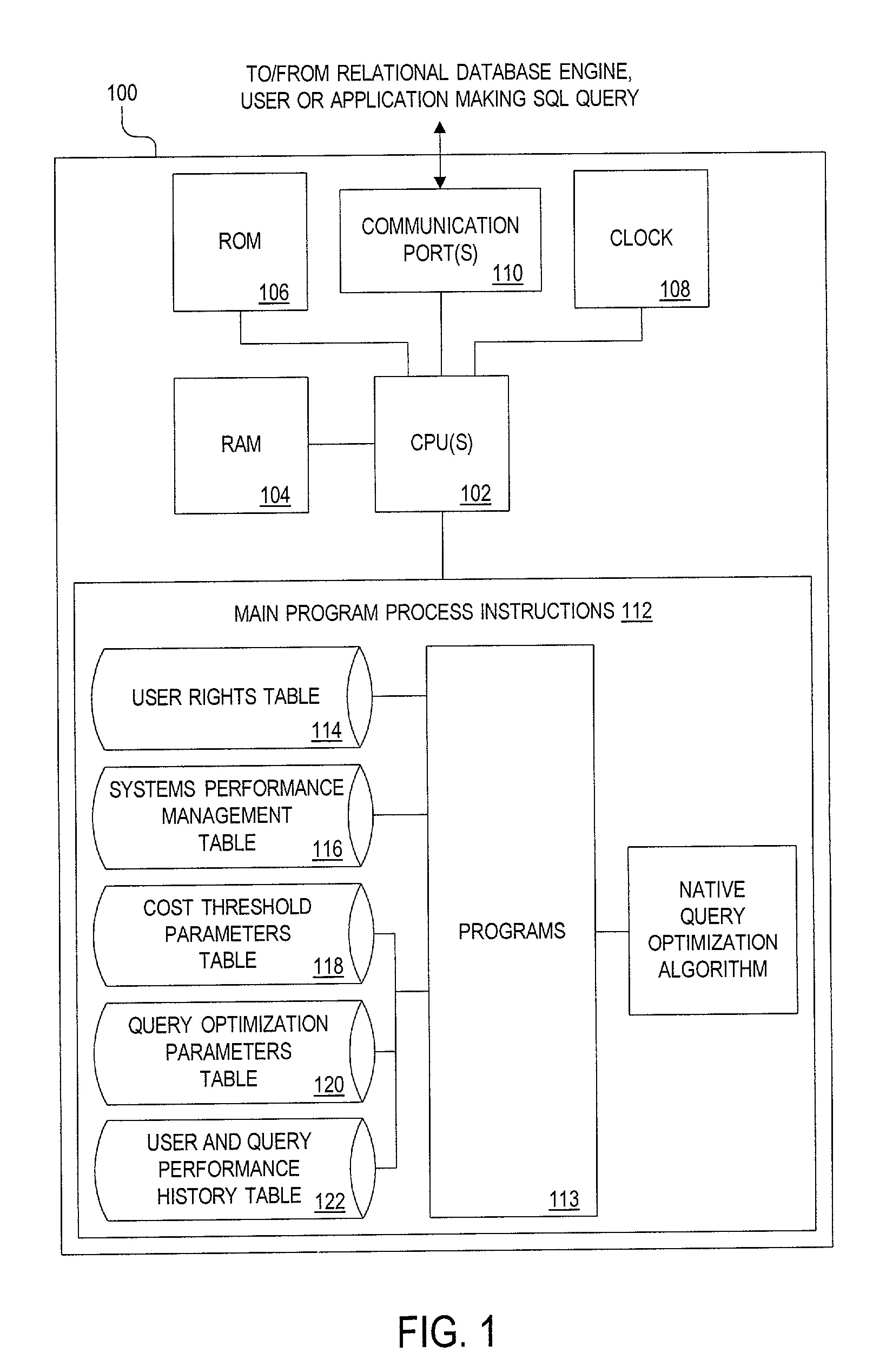
Method, apparatus and system for screening database queries prior to submission to a database
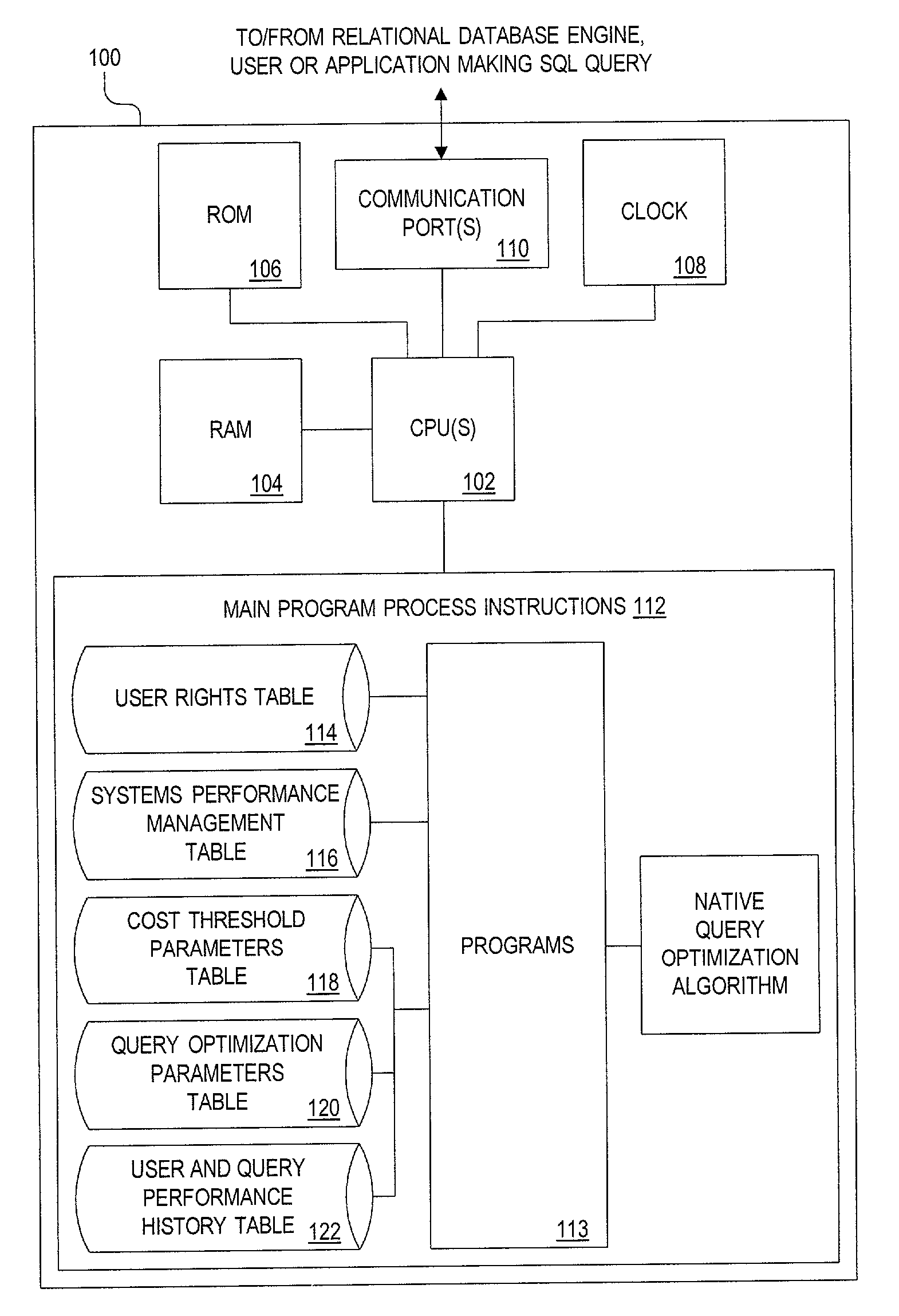
InactiveUS7058622B1Reduce the impactReduce impactData processing applicationsRelational databasesQuery optimizationOperability
To maintain the integrity and operability of enterprise database systems, queries intended for a particular database engine are intercepted, preferably by a separate processing system, prior to being acted upon by the database engine. The query is evaluated to determine its projected impact on available database system resources. The variables evaluated include user rights, administrator-imposed limits to searches, the amount of presently-available system resources, the cost of query and the like. If the query's potential impact does not surpass a predetermined threshold, it is submitted to the search engine. If the query is too resource-intensive or costly, the query may be (i) optimized by a query-optimization system, (ii) stored until more system resources are available, or (iii) rejected.
Owner:INTELLECTUAL VENTURES I LLC
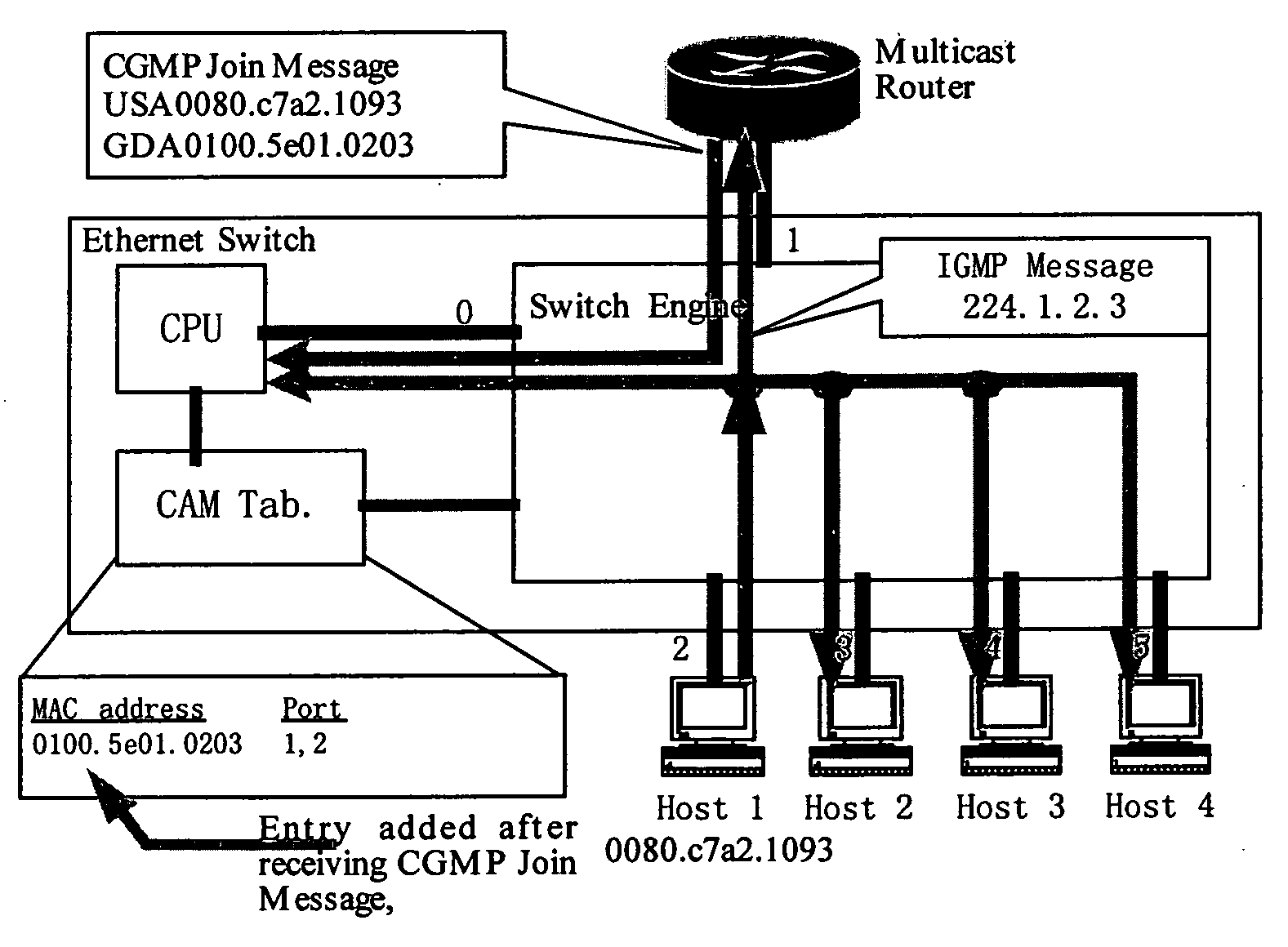
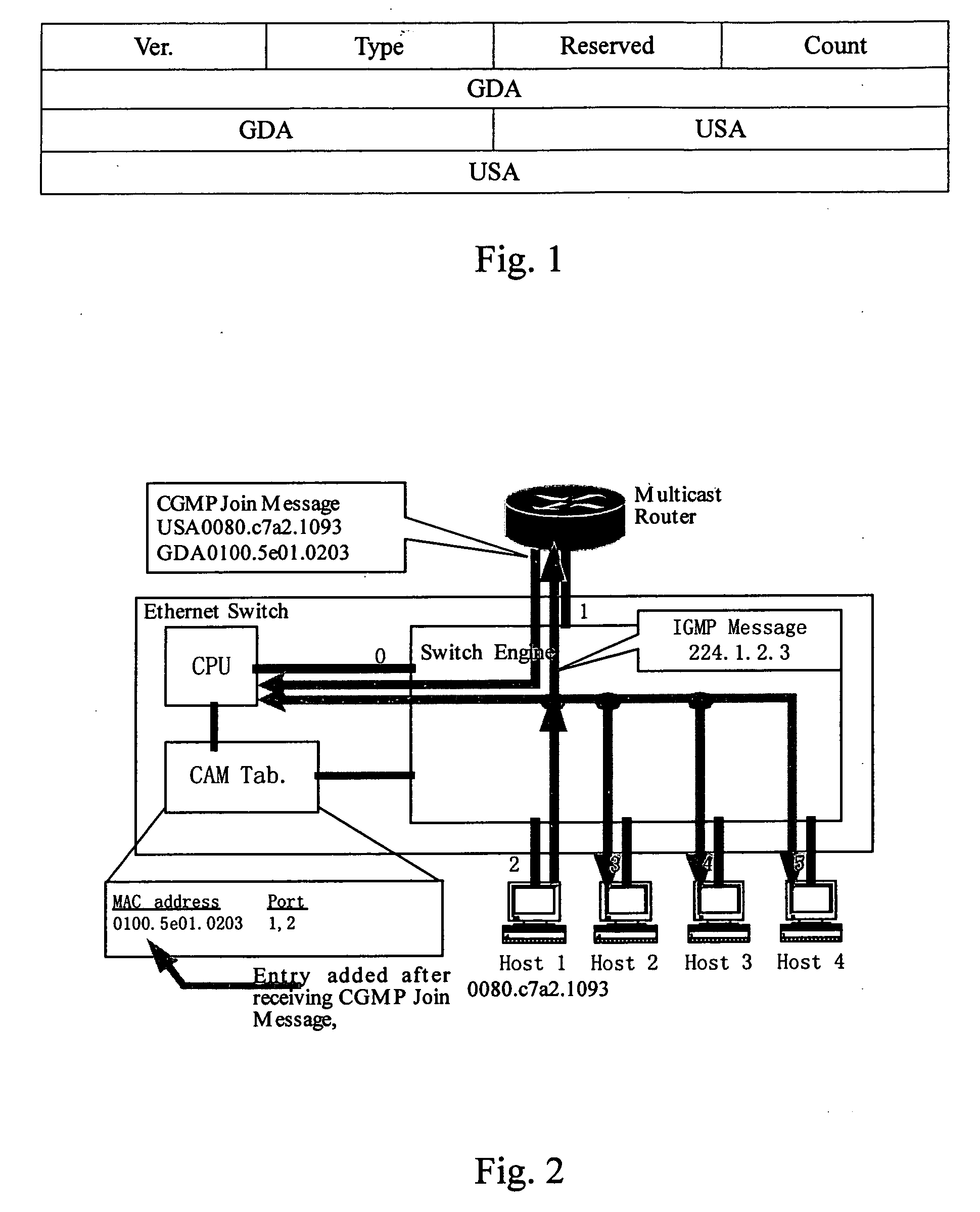
System and implementation method of controlled multicast
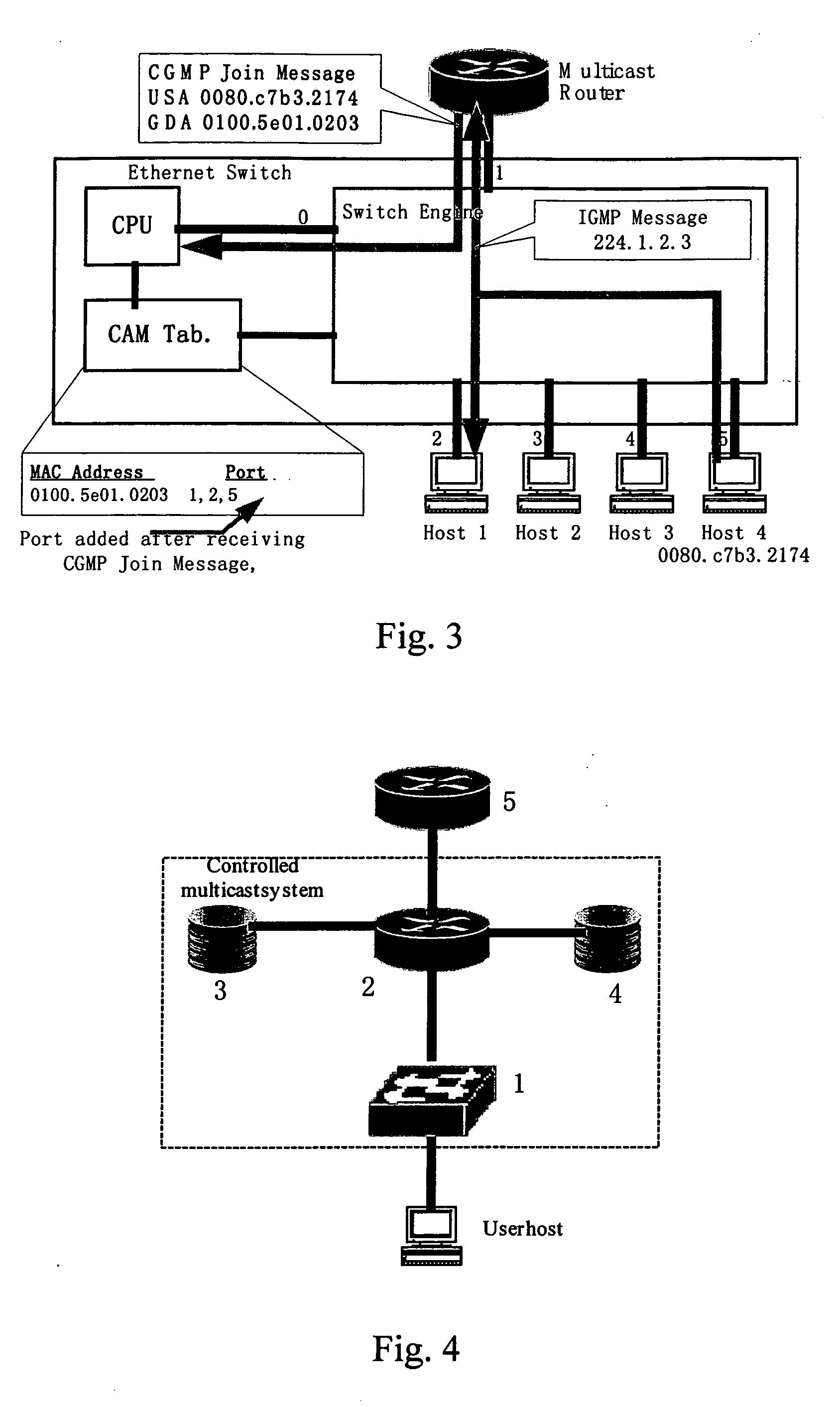
ActiveUS20050091313A1EffectiveSplendid applicationSpecial service provision for substationMultiple digital computer combinationsUser PrivilegeEthernet
A system and method for implementing controlled multicast, wherein comprises Ethernet switch 1, multicast router 2, as well as portal server 3 and AAA server 4 that connect with the multicast router, where Ethernet switch 1 connects with each hosts of user in a downlink, in an uplink connects with multicast router 5 and implements multicast switch of layer 2; portal server 3 is used as an interface for access authentication of the user, AAA server 4 is used to store configuration of user privilege for joining in a multicast group; multicast router 2 connects with multicast router 5 of other systems in the uplink, and cooperates together with AAA server 4 to completes privilege authentication for the user when he joins in the multicast group, distributes a control command according to results of the authentication, and controls forwarding of the multicast made by Ethernet switch 1. The method according to the present invention can resolve better the authenticated authorization and controlled problem of the sender and receiver joining in the multicast, and can identify the host joining in or leaving the multicast group expediently, actively stop the user's group member identification through offline without any influence on the forwarding efficiency.
Owner:CHENGDU HUAWEI TECH
Secured database system with built-in antivirus protection
ActiveUS7844829B2Digital data processing detailsUnauthorized memory use protectionUser PrivilegeEncryption
Owner:SYBASE INC
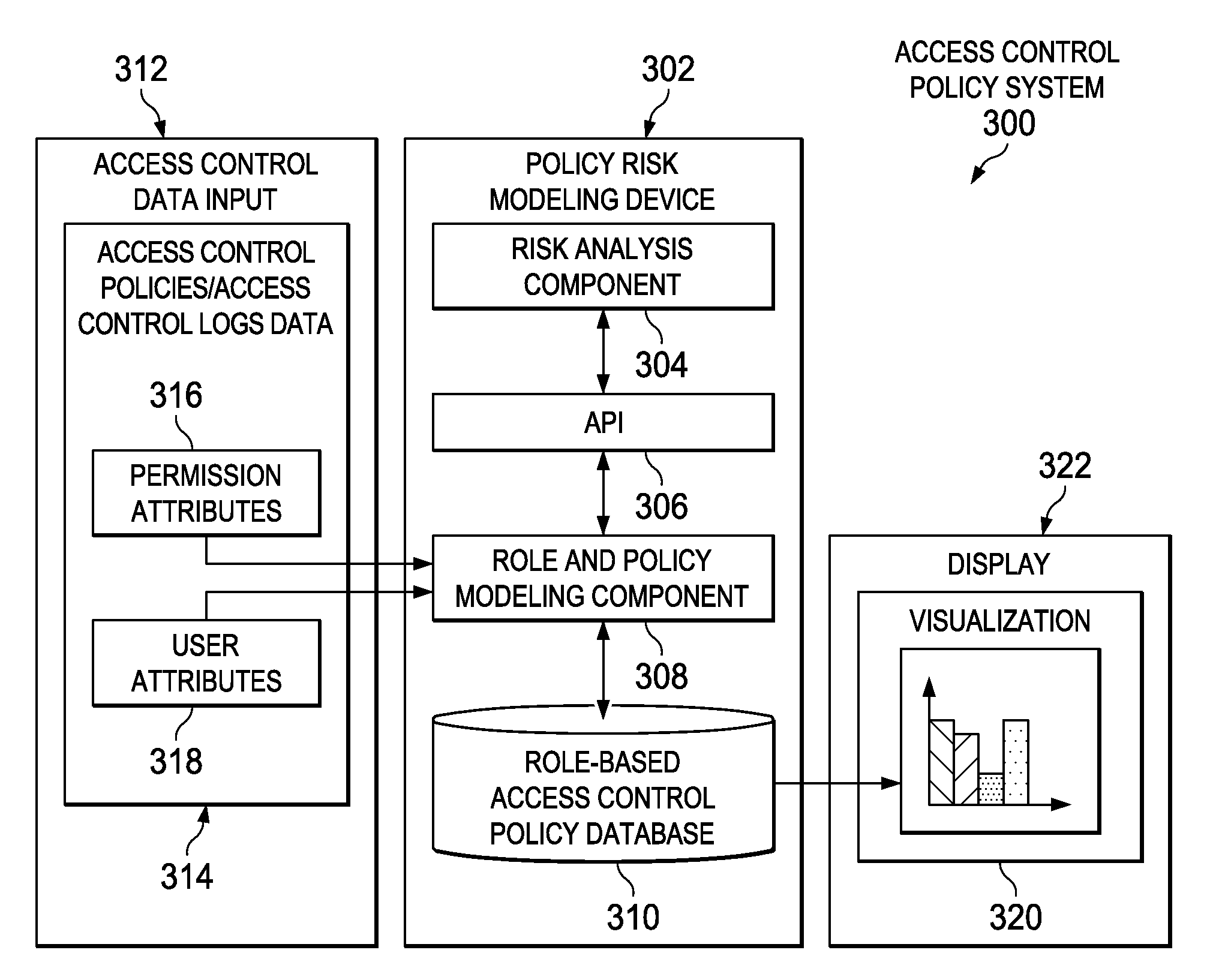
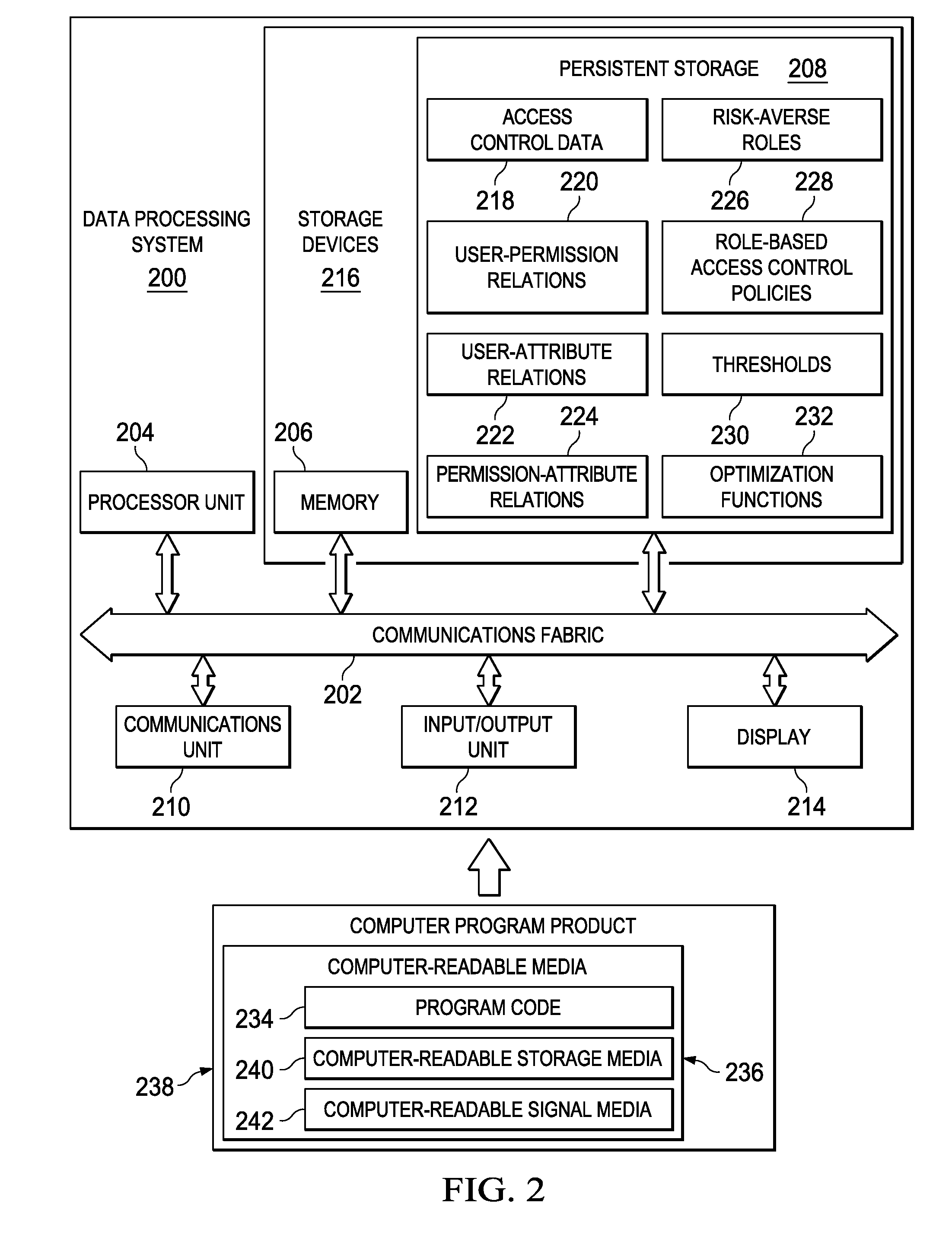
Generating role-based access control policies based on discovered risk-averse roles
InactiveUS20140196104A1Minimize risk profileMinimizes risk profileTransmissionSpecial data processing applicationsUser PrivilegeRisk profiling
Generating role-based access control policies is provided. A user-permission relation is generated by extracting users and permissions assigned to each of the users from a stored access control policy. A user-attribute relation is generated by mapping the users to attributes describing the users. A permission-attribute relation is generated by mapping the permissions to attributes describing the permissions. The set of risk-averse roles, assignment of the set of risk-averse roles to the users, and assignment of the permissions to the set of risk-averse roles are determined based on applying a risk-optimization function to the generated user-permission relation, the generated user-attribute relation, and the generated permission-attribute relation. A role-based access control policy that minimizes a risk profile of the set of risk-averse roles, the assignment of the set of risk-averse roles to the users, and the assignment of the permissions to the set of risk-averse roles is generated.
Owner:IBM CORP
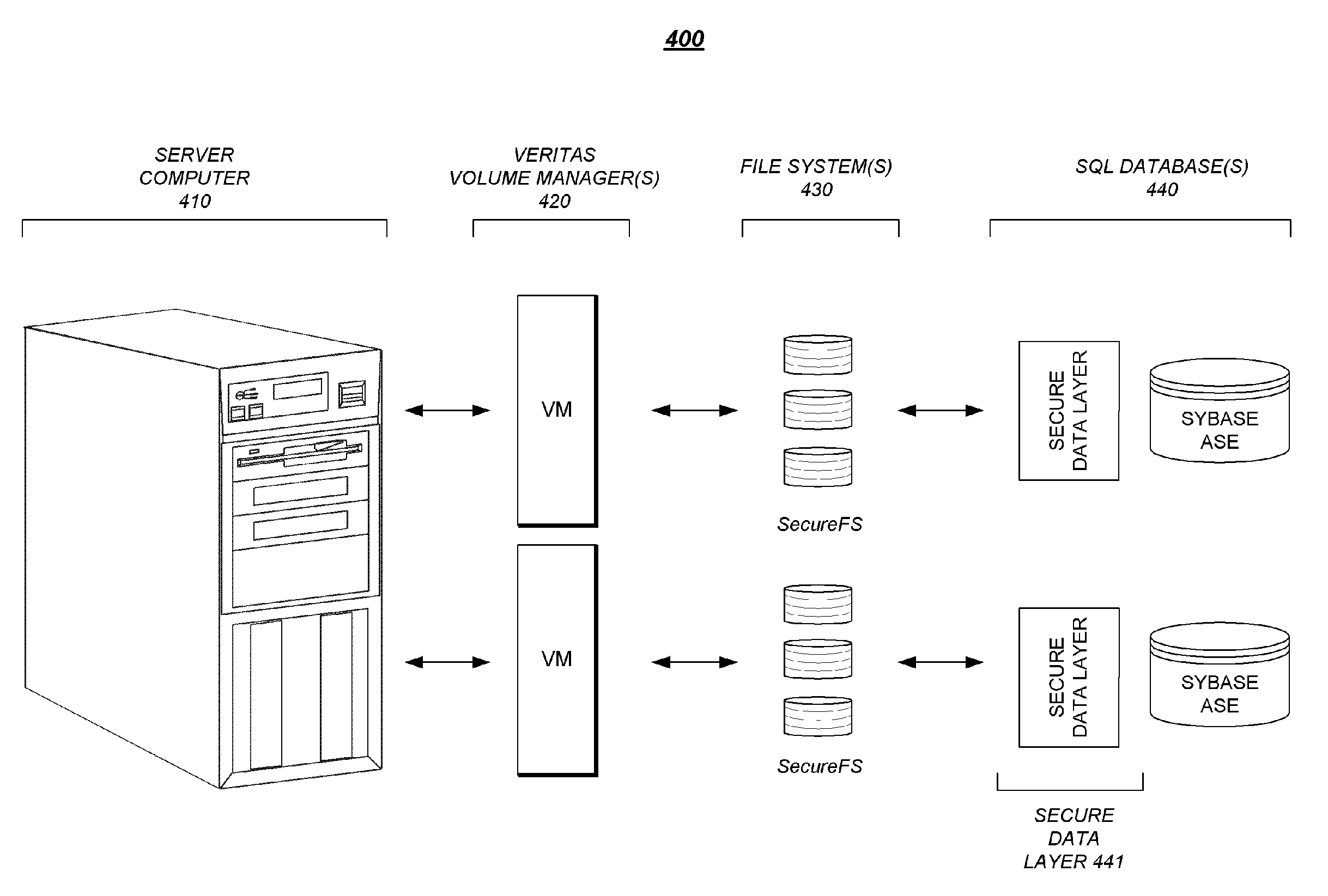
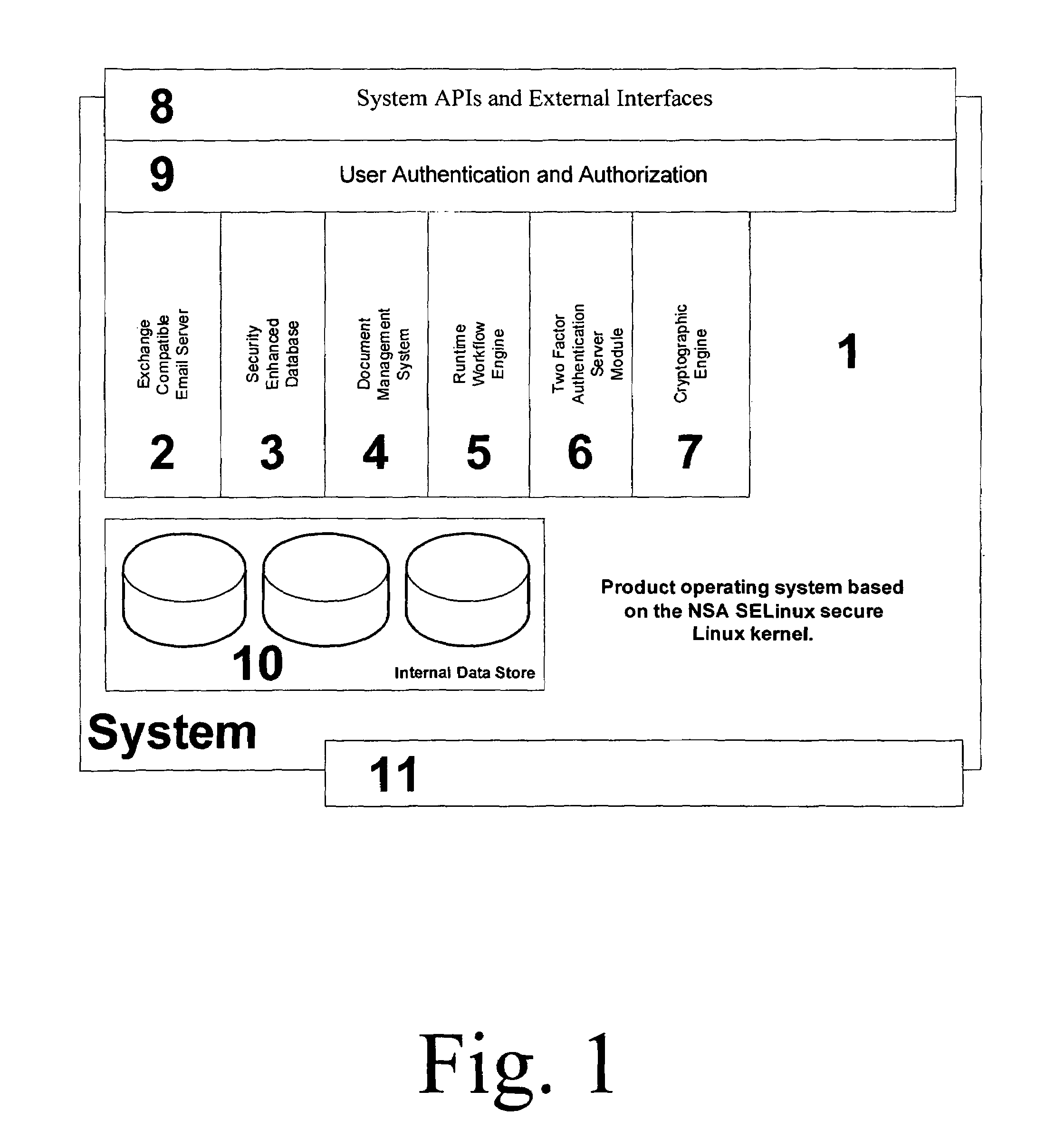
Security Enhanced Data Platform
InactiveUS8161527B2Improve securityConvenient access controlDigital data processing detailsUnauthorized memory use protectionUser PrivilegeInternet privacy
The security enhanced data platform is comprised of two primary subsystems and a host of supporting subsystems. The first primary subsystem is a document management system. A set of client side tools provides the user a way to specify classifications and compartments for selected areas of a document, and a way to save the document in the format required by the system in order to allow the system to enforce the rules and privileges dictated to the system. The second subsystem is a security enhanced database management system. In documents the system allows different user privilege requirements on the document as a whole as well as on pages, paragraphs, sentences, words, and / or letters of a word. A history of document changes is maintained to provide an audit trail after the fact of who did what changes, where those changes were made and when those changes were made.
Owner:CURREN EDWARD
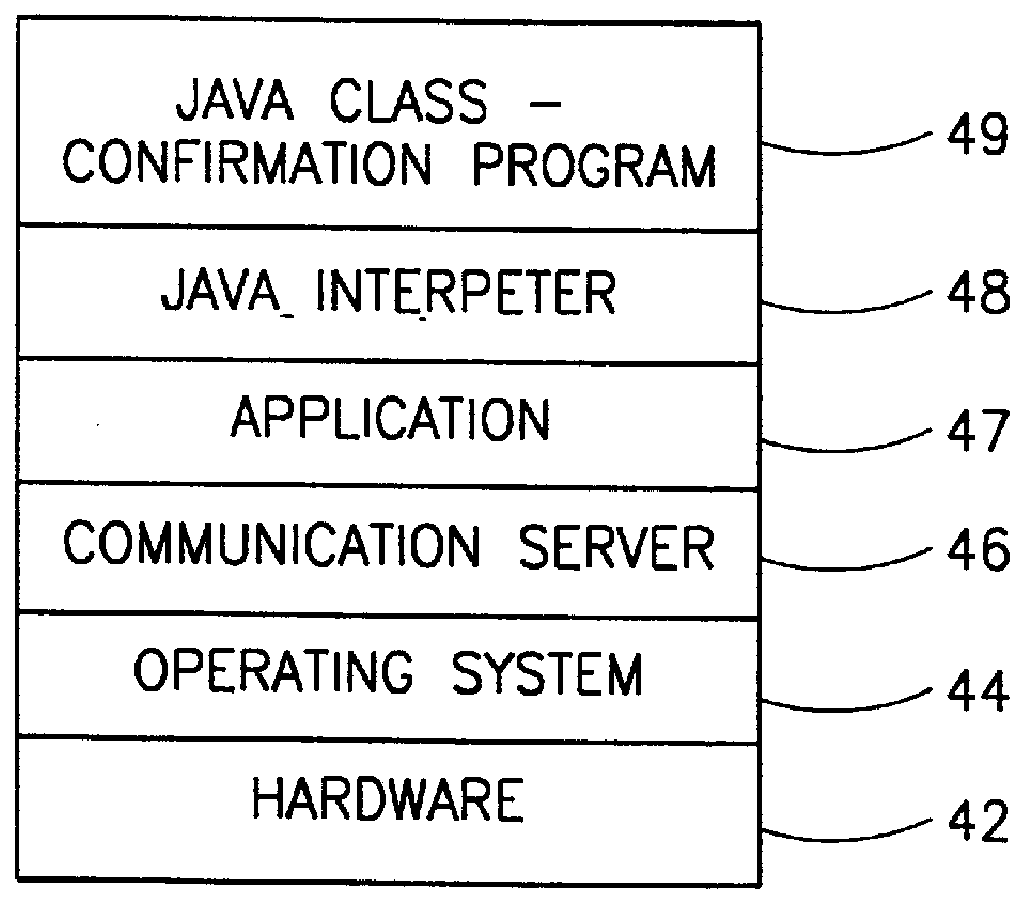
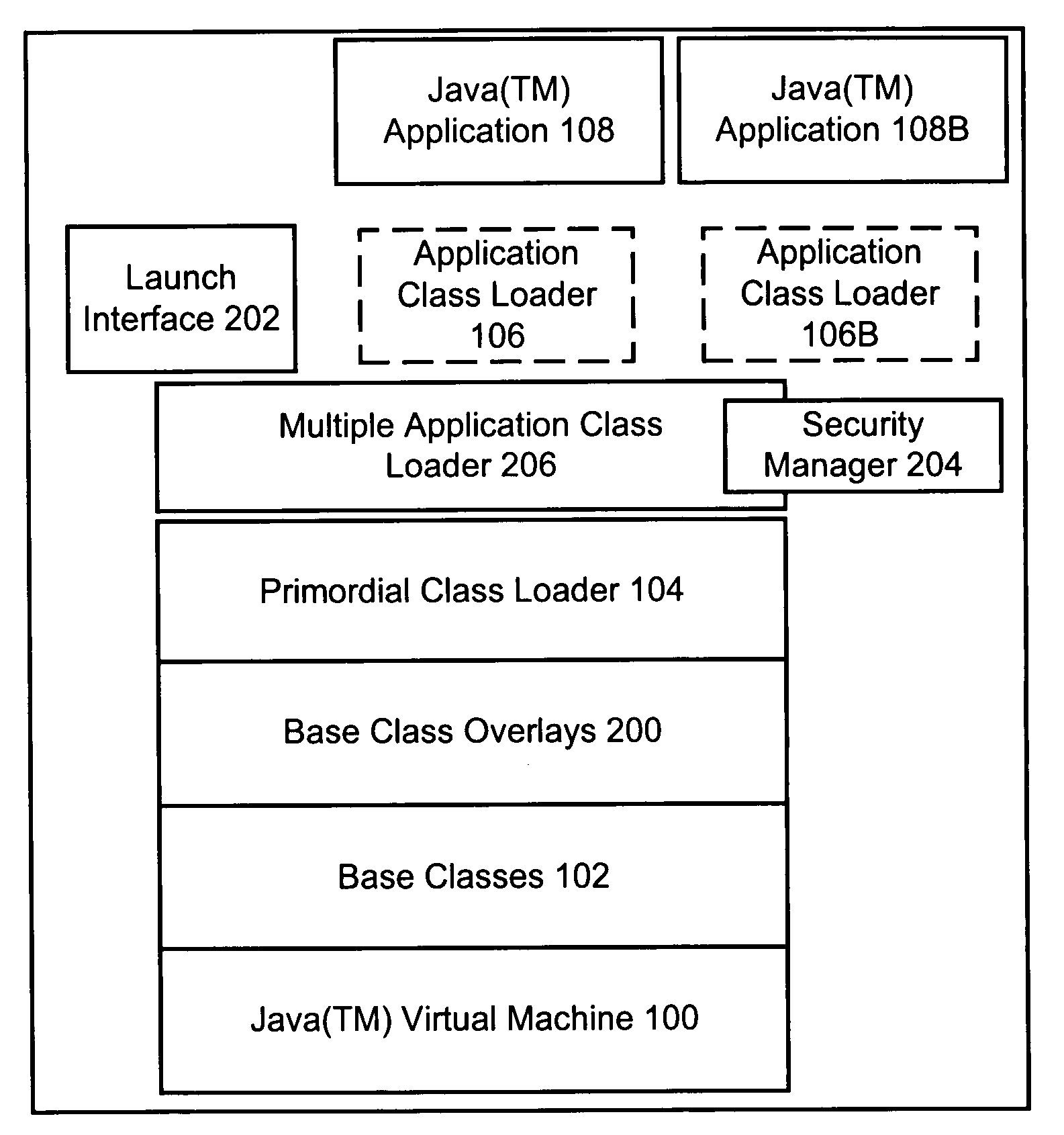
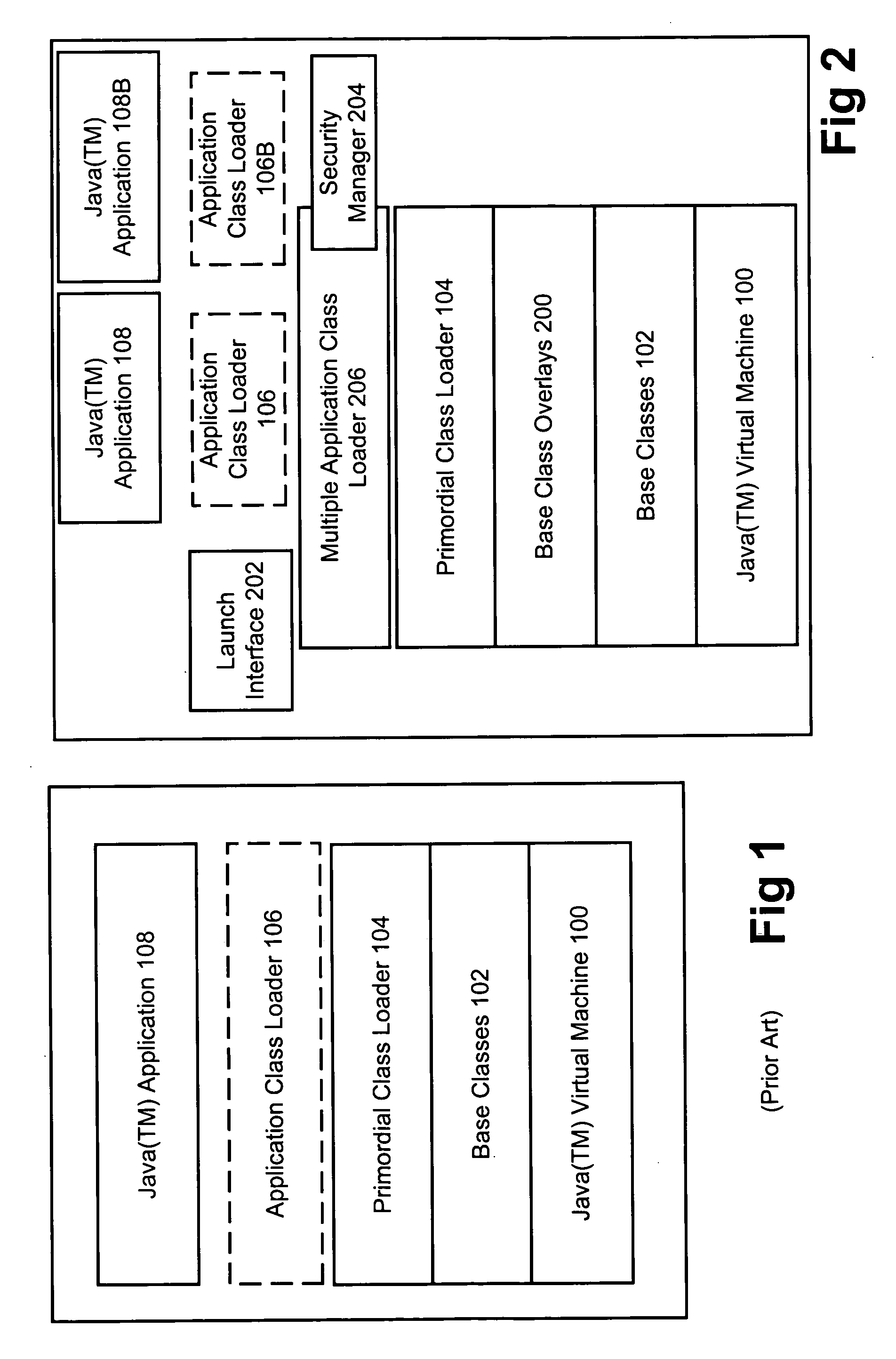
Method and apparatus for executing multiple JAVA((TM)) applications on a single JAVA((TM)) virtual machine
InactiveUS6931544B1Big memorySignificant performance improvementProgram loading/initiatingSoftware simulation/interpretation/emulationOverlayUser Privilege
A modified JAVA(™) execution environment is described. The modified environment supports multiple JAVA(™) applications on a single JAVA(™) virtual machine (JVM). This modified environment provides significant memory and performance improvements when running multiple applications on a single computer system. Notably, no changes are needed to the source code of an application to take advantage of the modified environment. Further, embodiments of the invention may support shared access to base classes through the use of overlays. Additionally, system resource permissions can be enforced based upon the user permissions associated with a running application. Notably, embodiments of the invention allow multiple applications to share the abstract window toolkit (AWT) on a per display basis. Since only a single garbage collection routine is necessary, applications see improved performance relative to running in different JVMs. Further, the shared base classes eliminate significant memory overhead.
Owner:APPLE INC
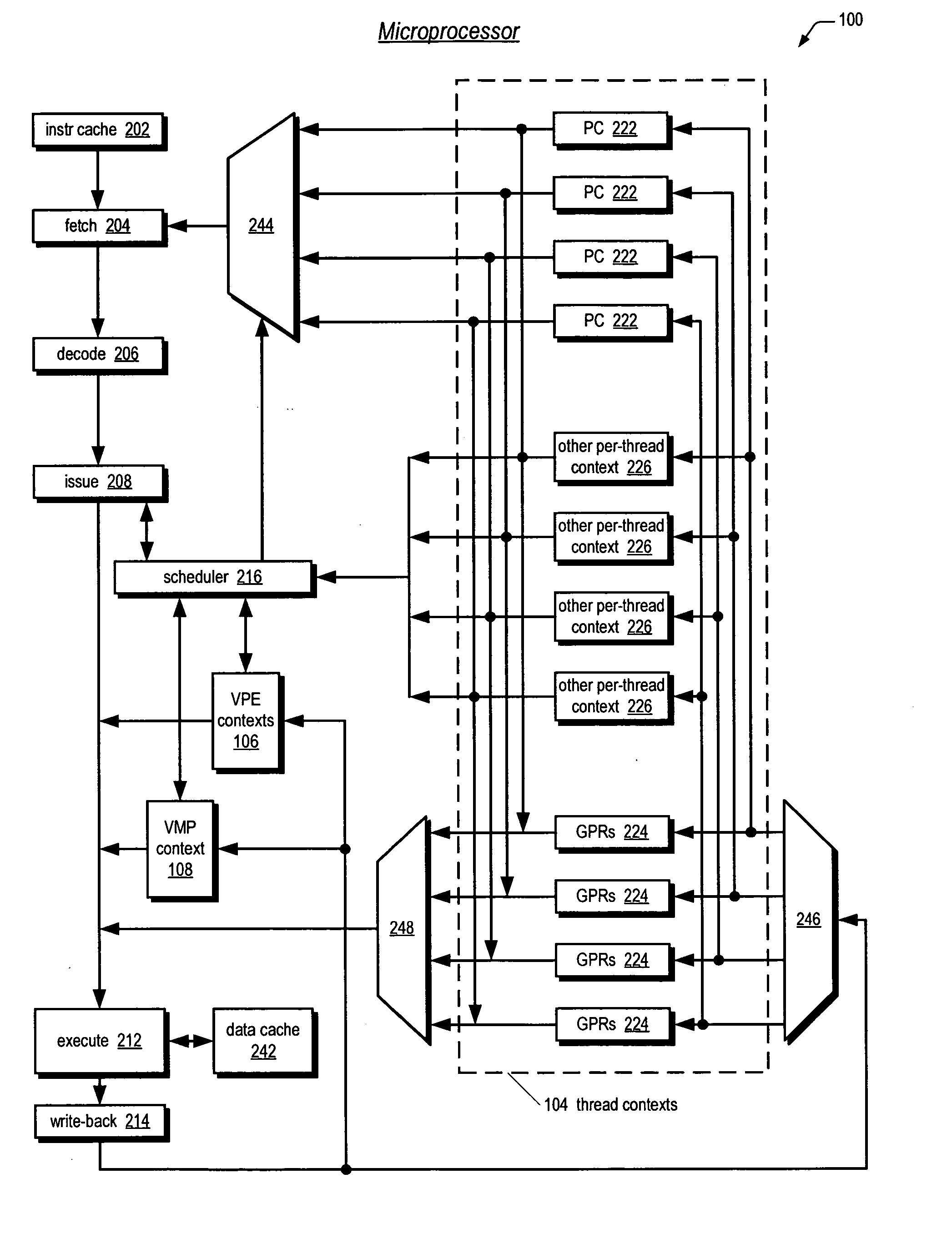
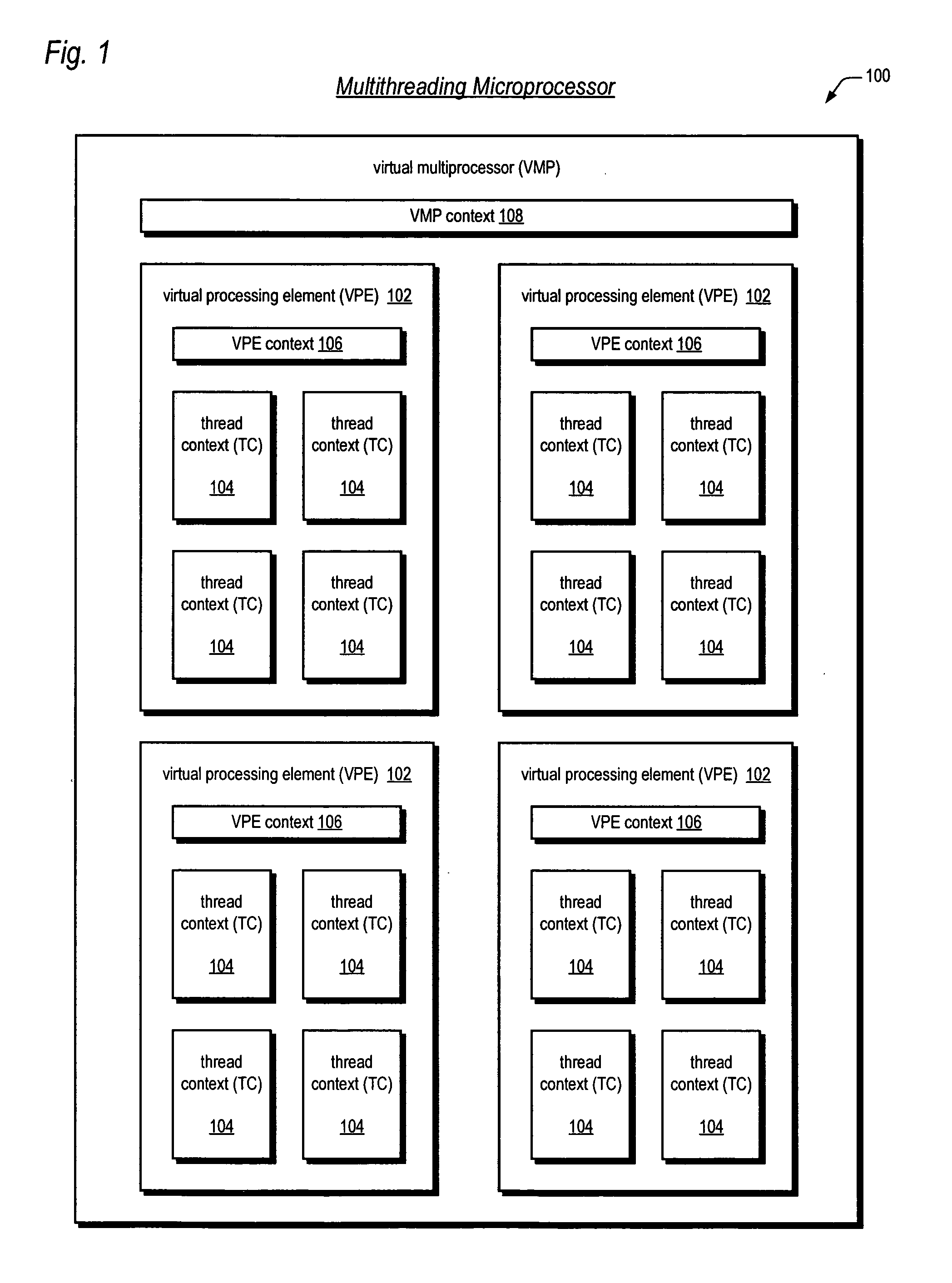
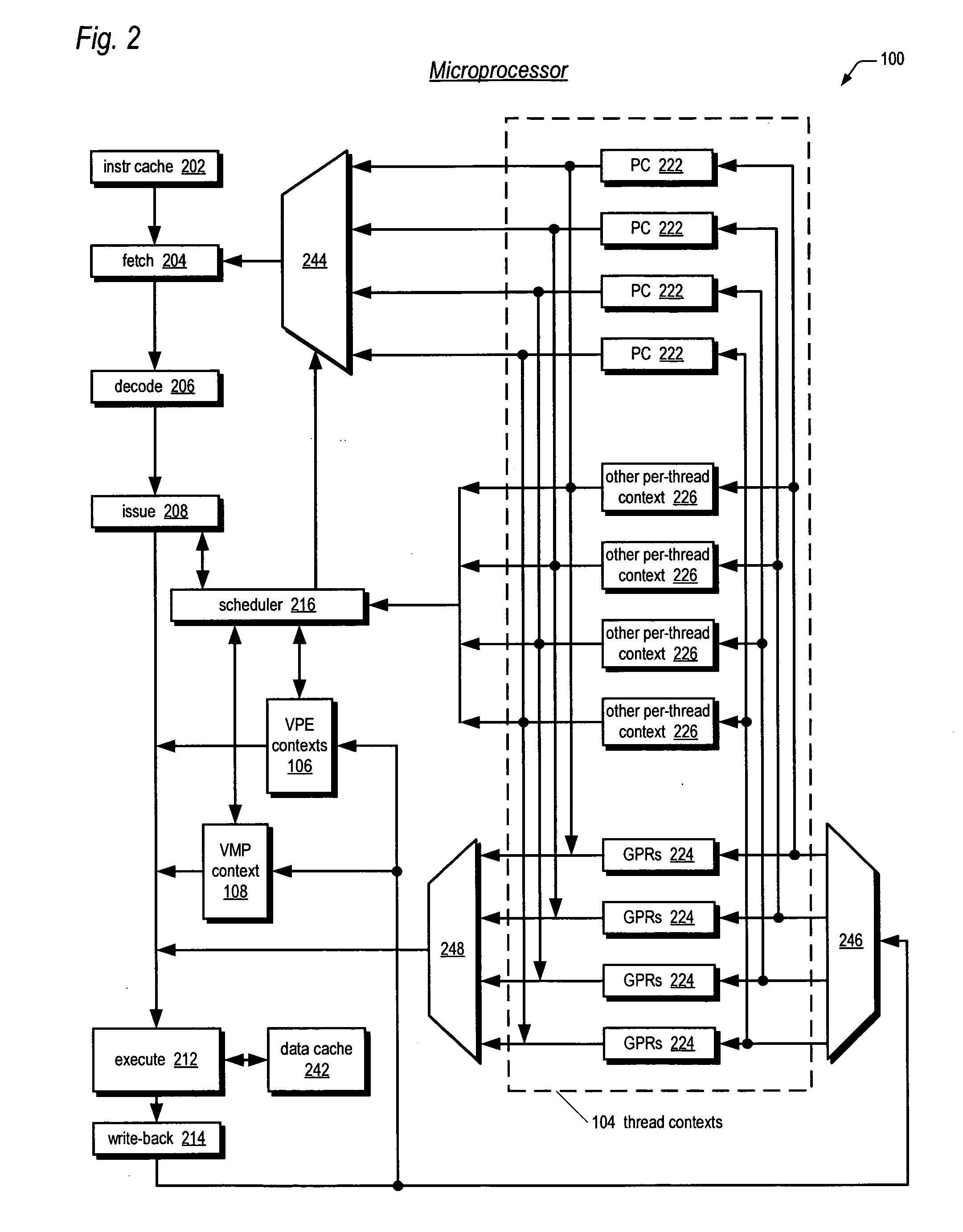
Symmetric multiprocessor operating system for execution on non-independent lightweight thread contexts
InactiveUS20060195683A1Lightweight in of areaLightweight in of powerEnergy efficient ICTDigital computer detailsGeneral purposeUser Privilege
A multiprocessing system is disclosed. The system includes a multithreading microprocessor including a plurality of thread contexts (TCs), each having a program counter and a general purpose register set for executing a thread. The microprocessor also includes a shared privileged resource, shared by the plurality of TCs rather than being replicated for each of the plurality of TCs, and privileged to be managed only by operating system-privileged threads rather than by user-privileged threads. The system also includes a multiprocessor operating system (OS), configured to manage the shared privileged resource, and to schedule execution of both the operating system-privileged threads and the user-privileged threads on the plurality of TCs.
Owner:MIPS TECH INC
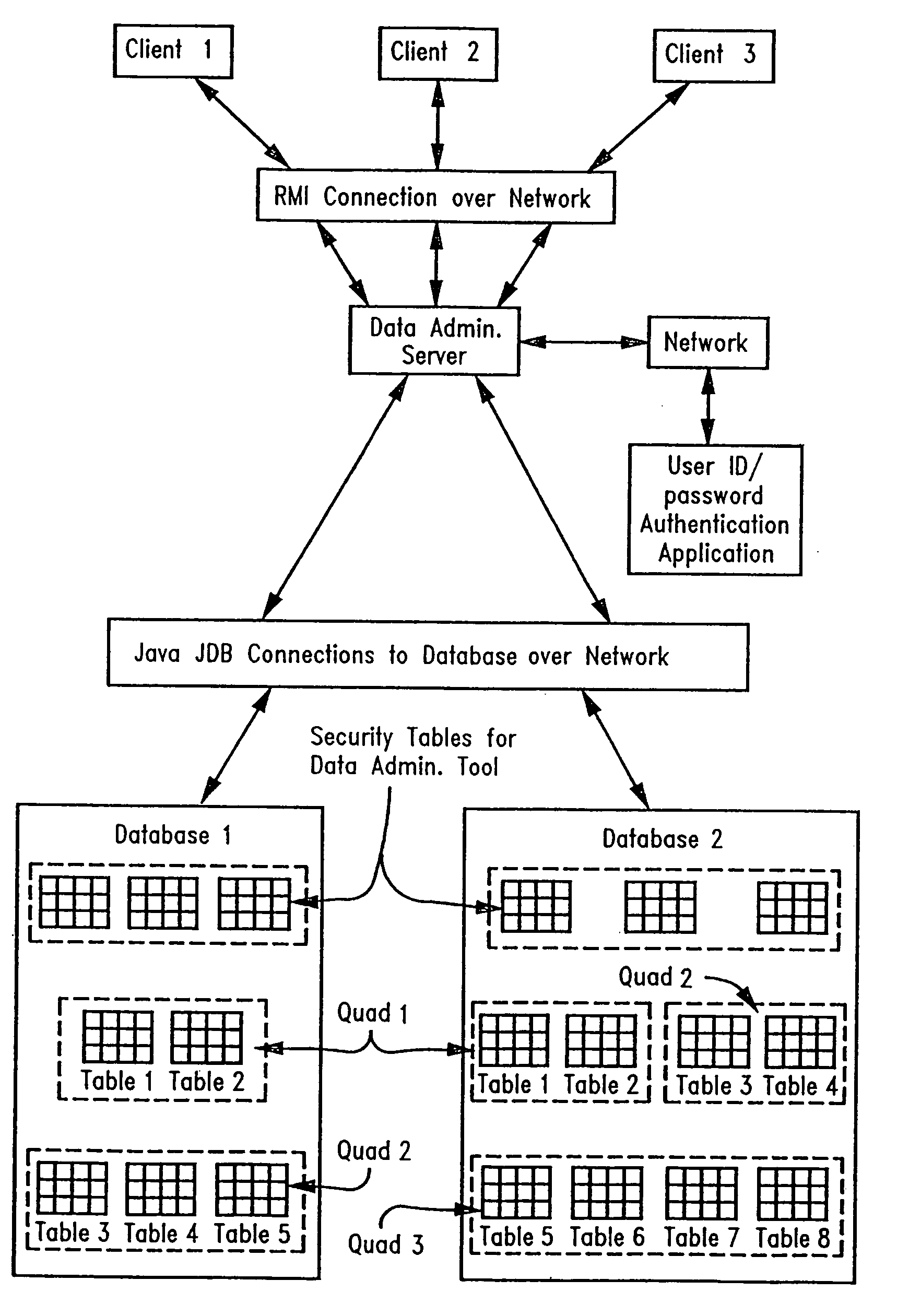
Desktop database data administration tool with row level security
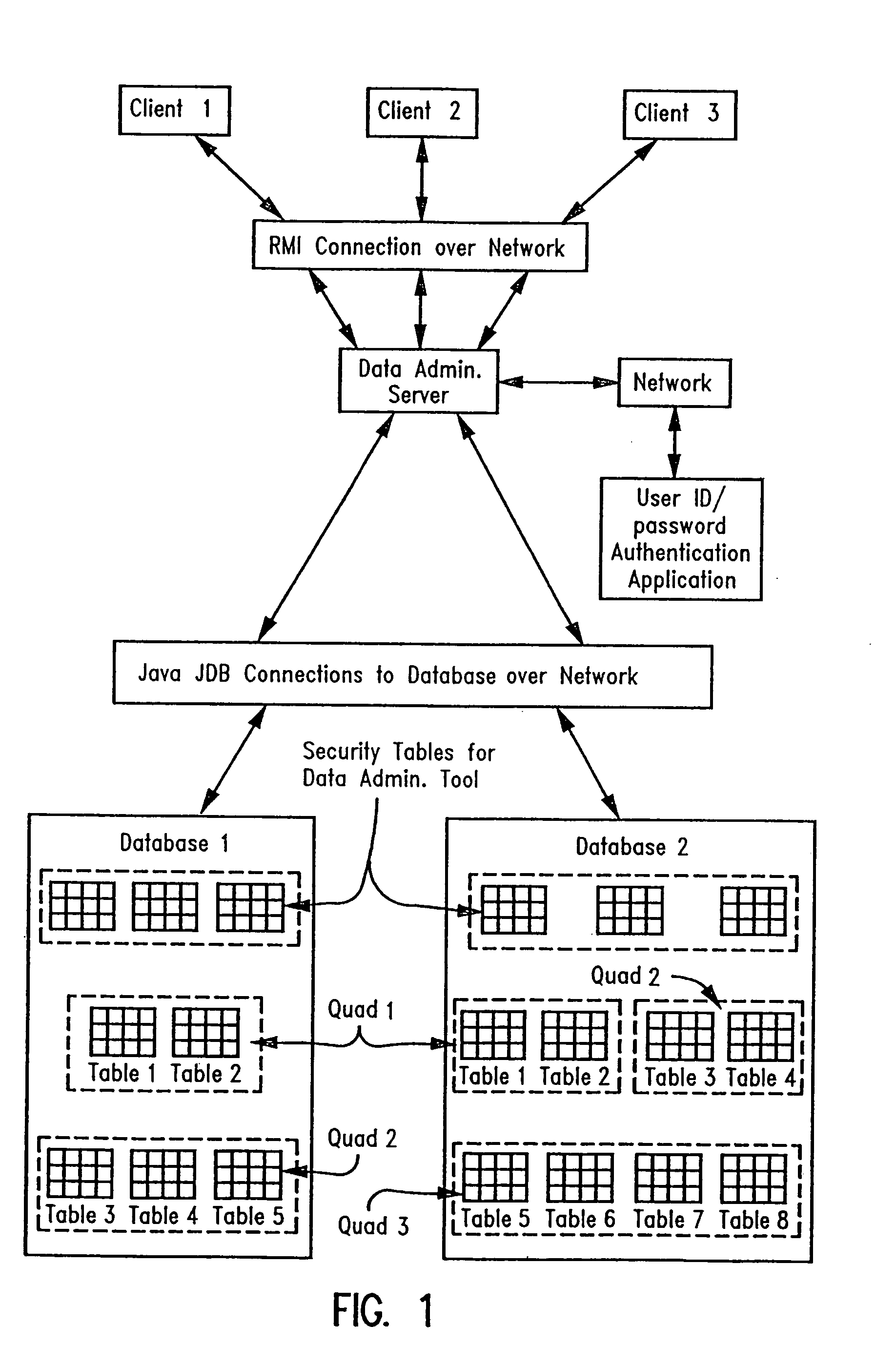
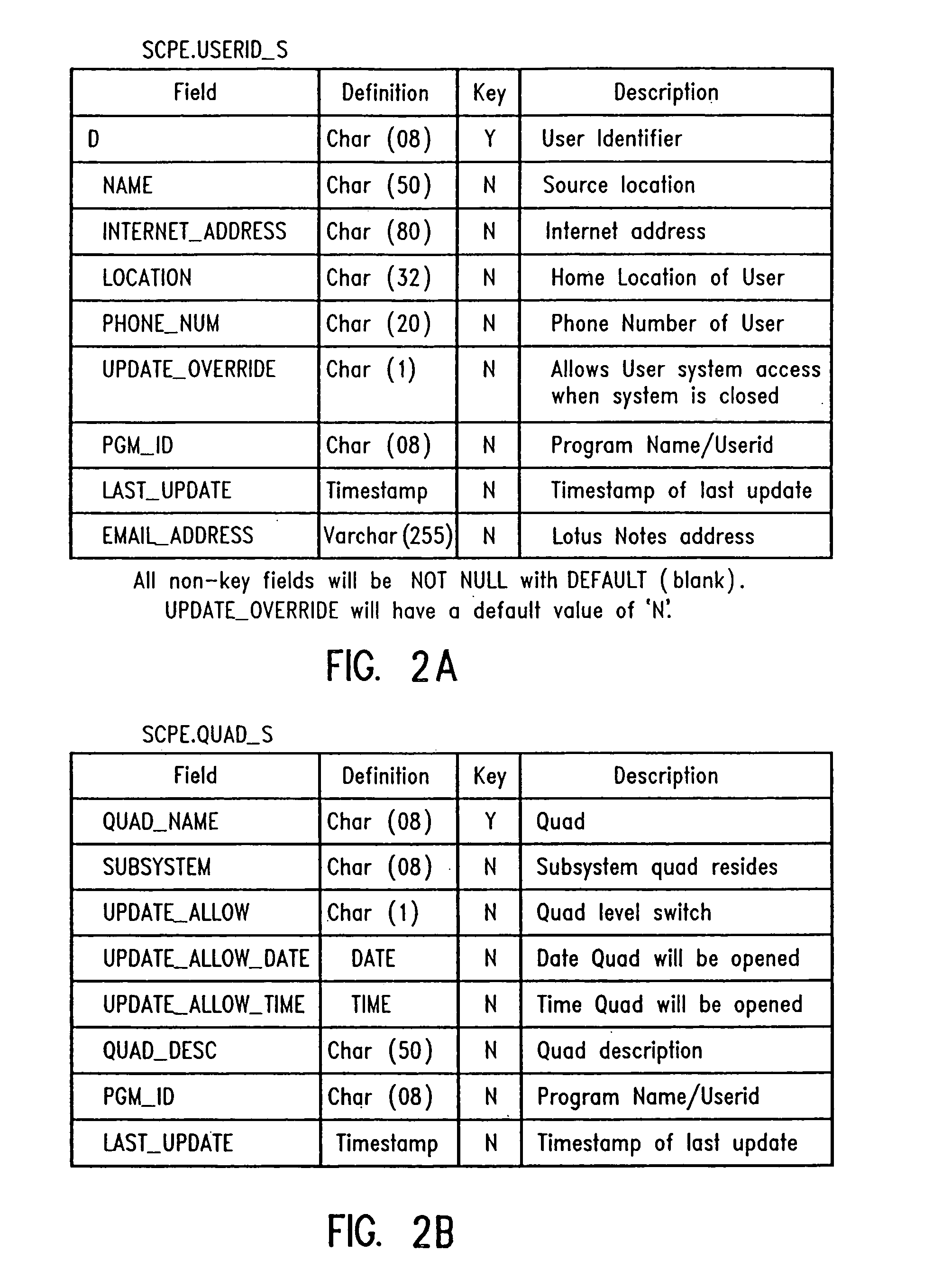
ActiveUS7155612B2Efficient fast effective economicalEasy to set upUnauthorized memory use protectionHardware monitoringManagement toolUser Privilege
A security scheme method and system for authorizing users to access and read data within a table, while only being able to modify selected data rows based on the user's authorities set by a composite of authorities within security tables of the system. Therein, a user of the invention is allowed to retrieve any data from a table while the security scheme limits that data the user is allowed to modify by setting the limit rules within these security tables. These limit rules may simultaneously monitor a plurality of field names existing within selected tables. The security scheme also enables the security tables to automatically open and close access to tables or quads by the security scheme setting flags before, during, after, or combinations thereof, the running of a session for loading tables.
Owner:SERVICENOW INC
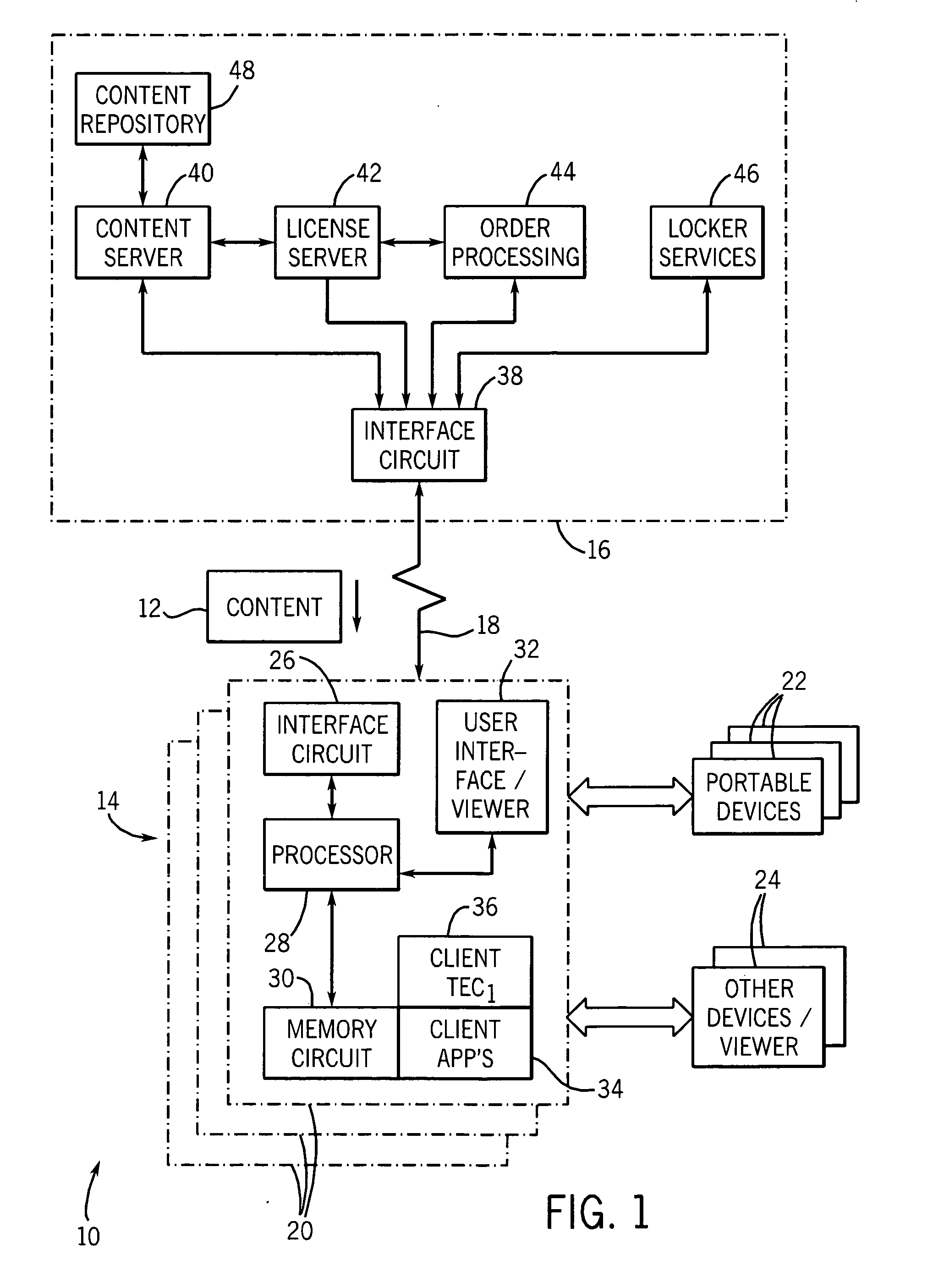
Digital rights management backup and restoration system and method
InactiveUS20080148362A1Satisfy the user experienceMeet user experienceDigital data processing detailsMultiple digital computer combinationsDigital dataUser Privilege
A digital rights management (DRM) system allows for digital data to be delivered to a user, and user rights to be stored by a locker service by the content provider. The rights may be stored in the locker service by request of the user. If the content is then lost, corrupted, or otherwise unavailable or unusable by the user, or in other appropriate circumstances, the user may contact the locker service and obtain authorization to re-access (e.g., download) another copy of the content. The system may verify user compliance with the DRM scheme prior to authorizing re-provisioning of the content.
Owner:NBCUNIVERSAL
Fine-grained access control method for data in cloud storage
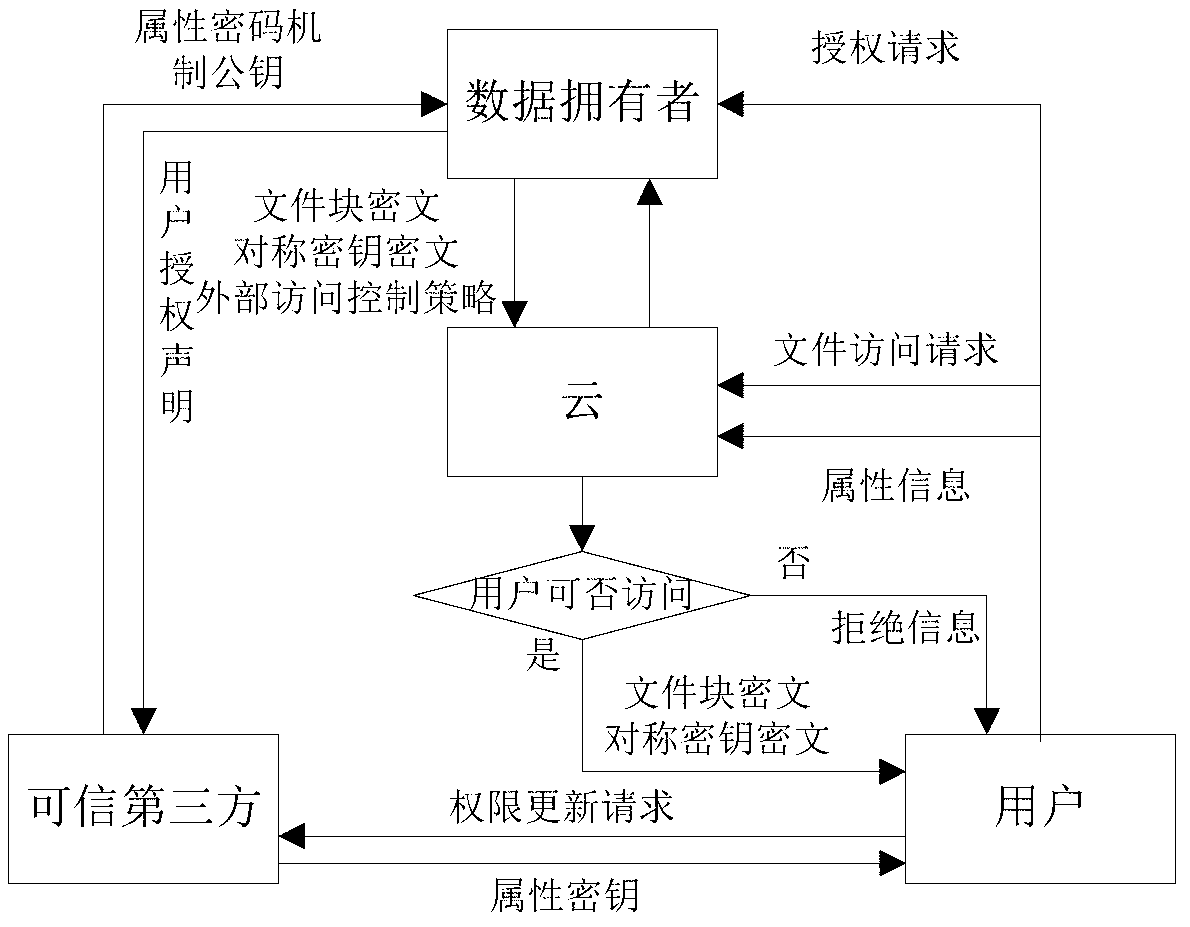
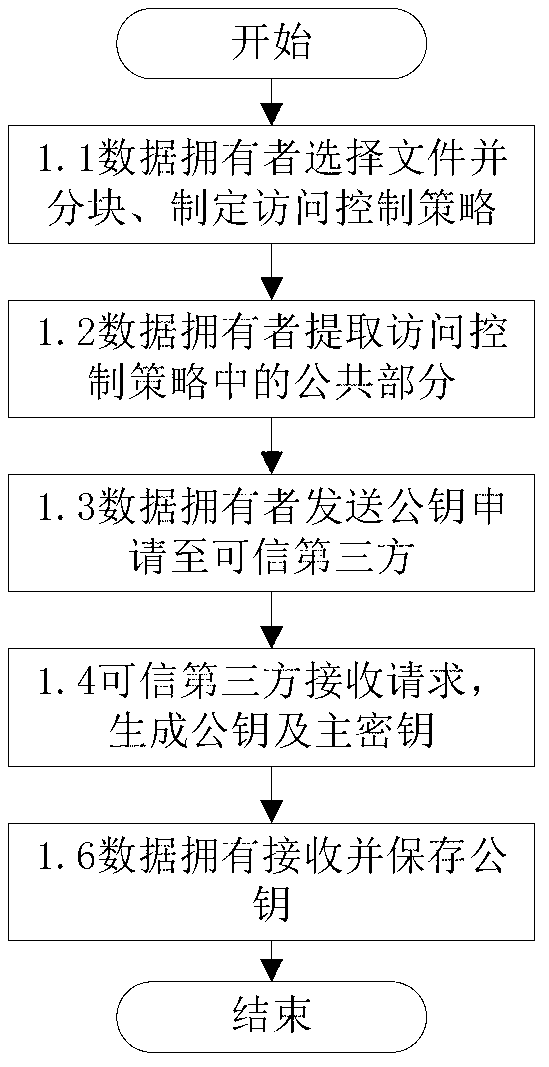
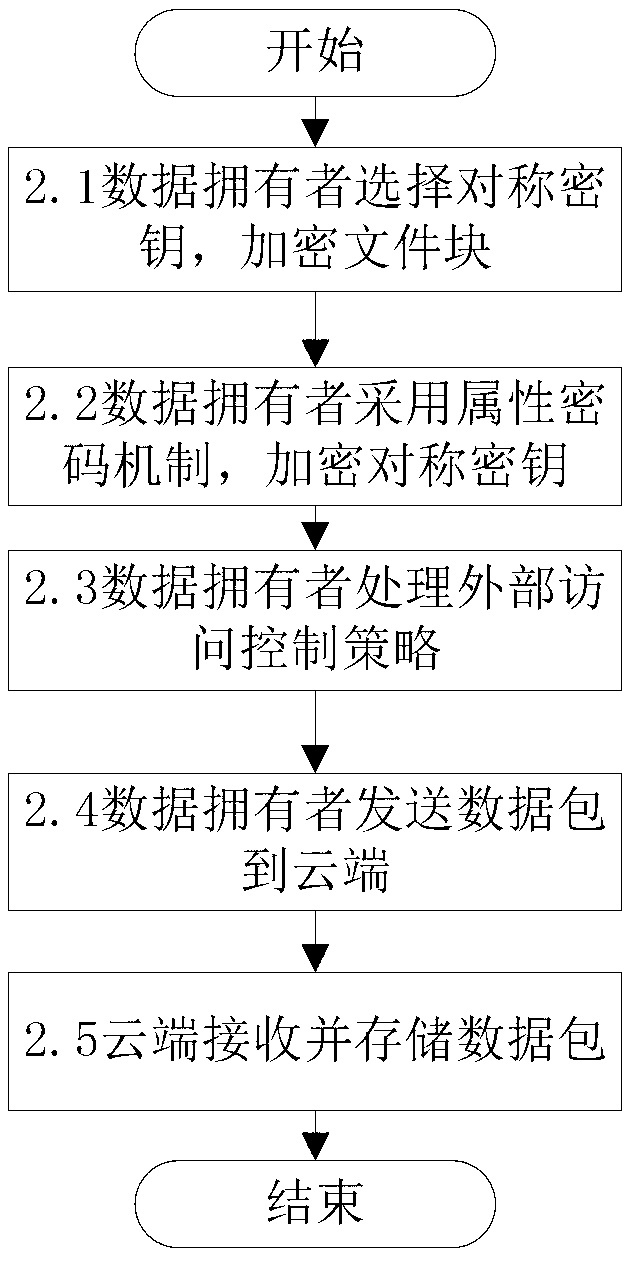
ActiveCN103179114AImplement access controlReduce overheadTransmissionUser PrivilegeAccess control matrix
The invention discloses a fine-grained access control method for data in cloud storage. The method includes the steps: firstly, a data owner blocking files and formulating an external access strategy of file blocks and an internal access strategy of the file blocks according an access control policy, and a trusted third party generating a public key and a master key according to an attribute password mechanism; the data owner utilizing a symmetric password mechanism to encipher the file blocks, utilizing the attribute password mechanism to encipher a symmetric key, and sending a cypher text of the file blocks and a cypher text of a secret key to the cloud; the data owner and the trusted third party utilizing the attribute password mechanism to authorize a user, and generating an attribute key and an attribute processed by an attribute encryption function for each attribute of the user; the data owner sending an user permission change statement to the trusted third party; and the trusted third party judging whether adding or deleting the user permission or not for the user according to the user permission change statement. Compared with the prior art, the method for the fine-grained data access control in the cloud storage has the access control with more fine-grained data under the condition of not increasing additional costs.
Owner:HUAZHONG UNIV OF SCI & TECH
Project-based configuration management method and apparatus
InactiveUS20050091291A1Data processing applicationsDigital data processing detailsUser PrivilegeConfigfs
A configuration management system creates (602) each configuration by assigning a configuration identifier to each configuration. In addition, relational information is computed (706) that indicates the relationships between the configuration and any configurations upon which it is based. The system then tracks (604) changes to files of the configuration by storing information associating each new file version with the configuration identifier. The system also tracks (1210) changes to file properties. A configuration is then reconstructed (608) as of a desired date, by identifying (2104, 2106) the file versions and properties associated with that configuration as of the desired date. A determination is made (2110) whether a user that has requested the file versions has access privileges by first checking a security cache (2600) for the user privileges information. If the information is not on the cache, it is computed from a security table (2800) and stored on the cache. The system automatically compresses (3118) and reconstitutes (3006) file versions that are stored in the version store.
Owner:SZ DJI TECH CO LTD
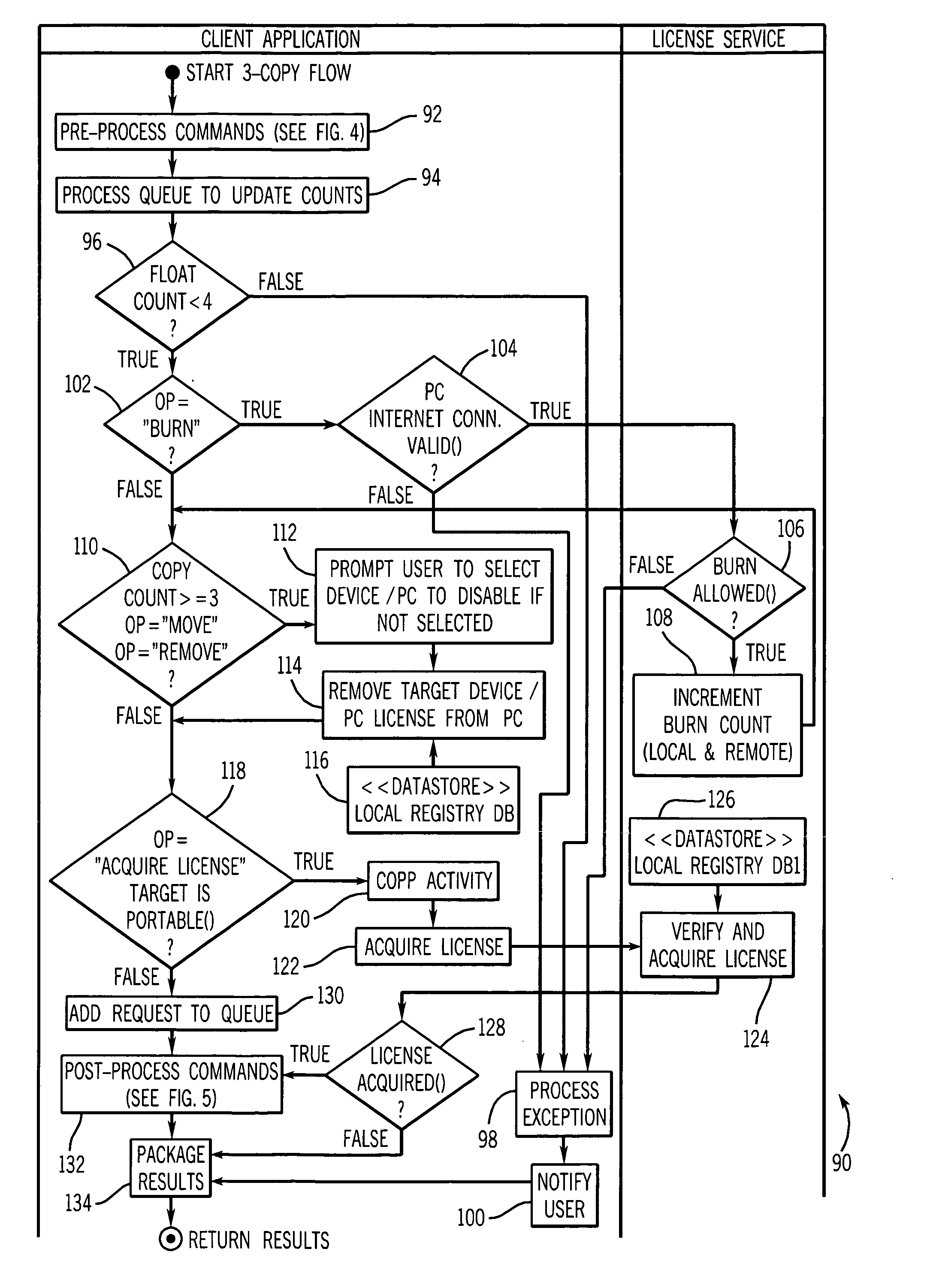
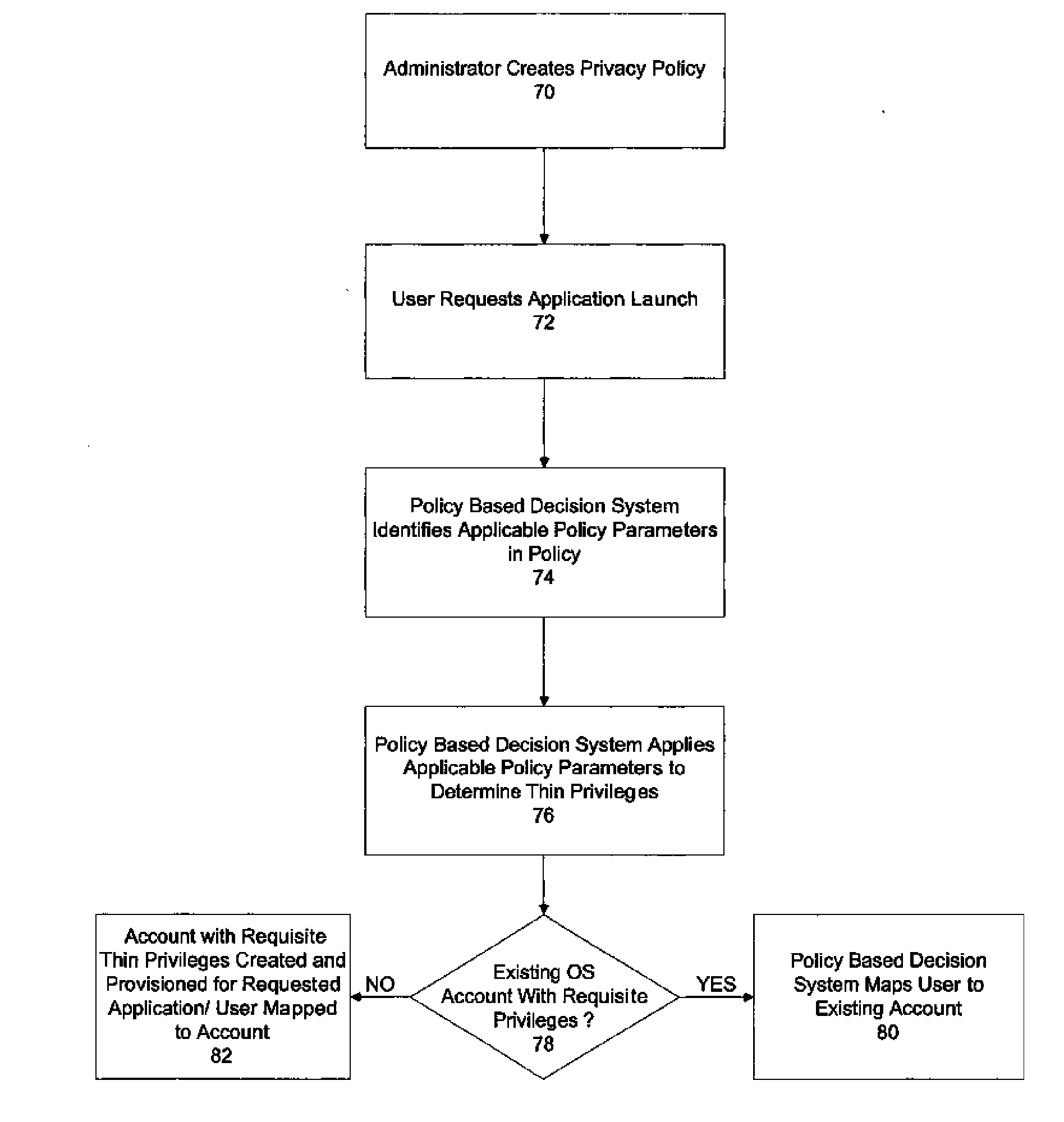
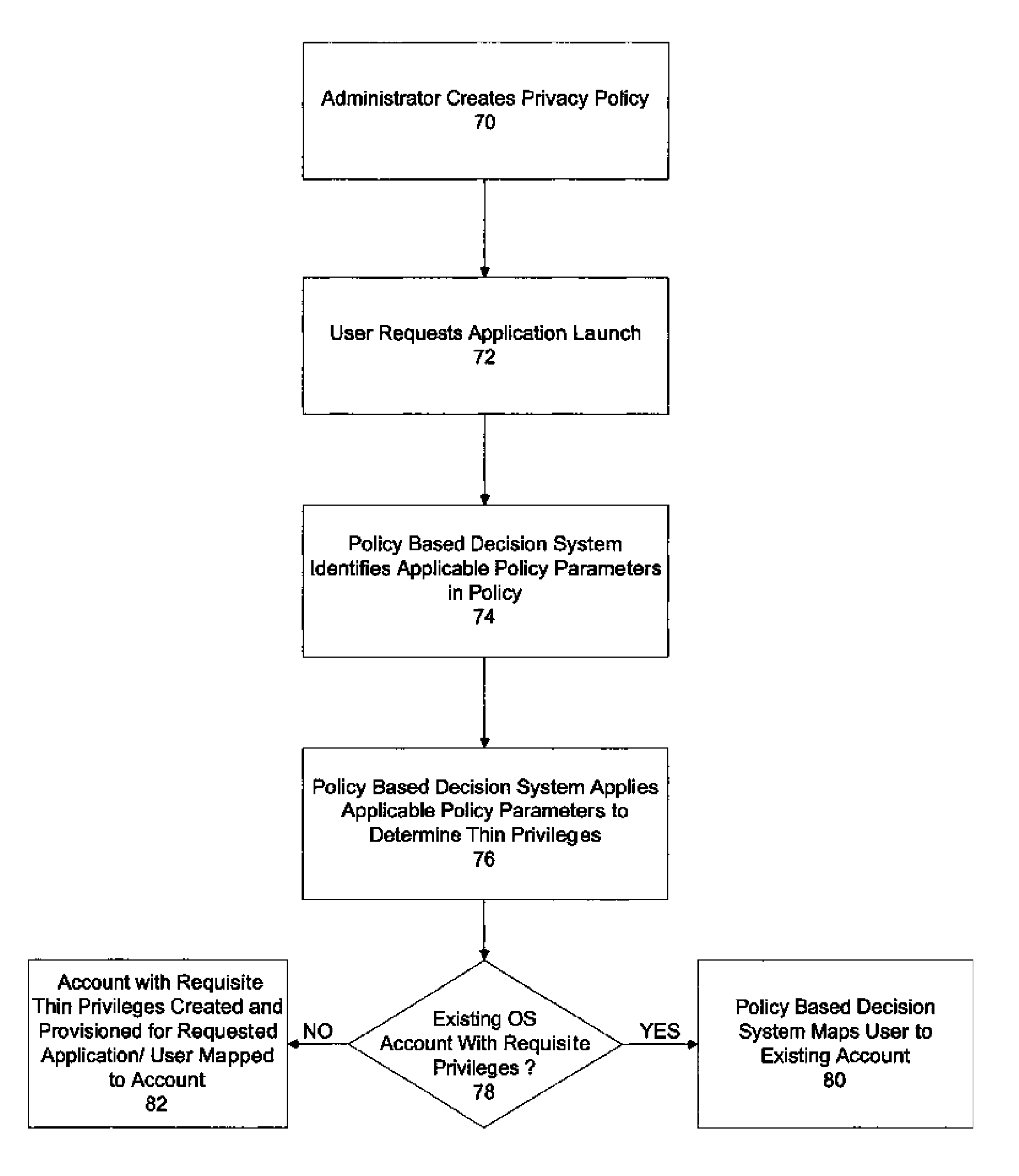
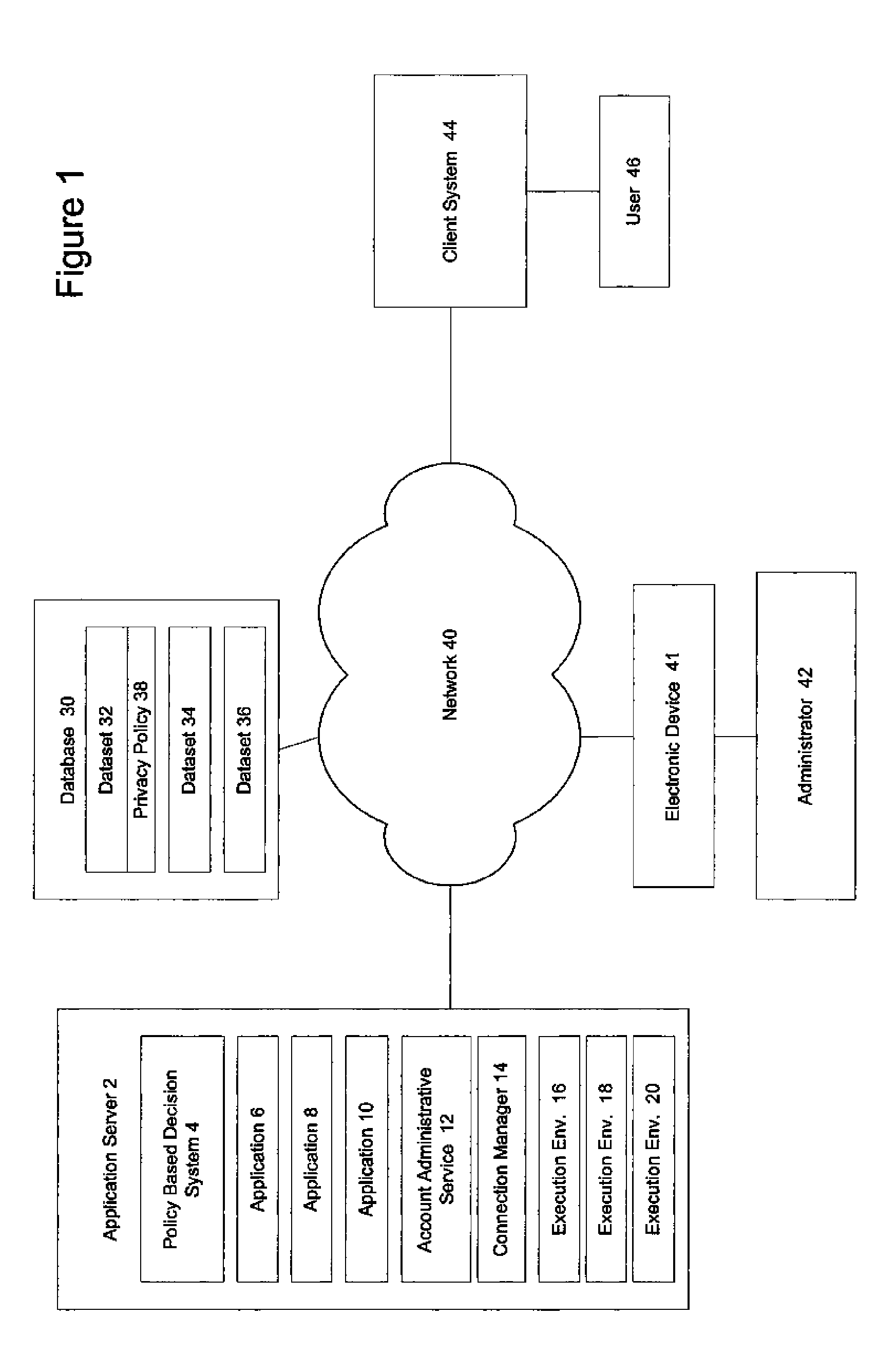
A system and method for executing interactive applications with minimal privileges
ActiveUS20060015740A1Digital data processing detailsMultiple digital computer combinationsOperational systemUser Privilege
A mechanism for running interactive applications with a minimal set of privileges is disclosed. The privileges form a subset of the privileges afforded to the user requesting the application and are allocated consistent with the principle of least privilege. The application runs with the minimal amount of permissions necessary to accomplish its assigned tasks. A new user account is created and provisioned or identified for each application to which a user requests access. The accounts have a subset or superset of the access rights and operating system privileges that the user who is logged on to the system and requesting access to the application ordinarily enjoys. The subset / superset of the user's privileges is determined by a policy-based decision system. The policy-based decision system makes its determination based on an analysis of the application requirements, an analysis of the data security and privacy concerns associated with the execution of the application, the identity of the user and user's role and any other policy considerations previously specified by an administrator. Once the determination as to the appropriate set of privileges to be afforded in the execution environment has been made, the execution environment is created and provisioned or a pre-existing execution environment possessing the requisite privileges is identified and the remote user is logged into the server-side account. The application-specific accounts may be audited by audit trail tools that provide evidence of policy enforcement.
Owner:CITRIX SYST INC
Method and apparatus for restricting access to a database according to user permissions
InactiveUS20030187848A1Easy to implementEasy maintenanceDigital data information retrievalDigital data processing detailsUser PrivilegeRights management
A method and apparatus for restricted access to a database according to user permissions are described. A user permissions file residing on a server includes information of permissions related to database records, and which of those permissions are associated with individual users. A permissions manager also residing on the server manages user queries either directly by generating restricted queries that reflect only authorized access to database records for the user generating the query, or indirectly by downloading a permissions filter or information for a restricted parameters screen to the user's client, so as to generate the restricted query on the client. In any case, a database management system residing on the server receives the restricted query and generates a result by accessing only authorized database records for the user, and communicates the result back to the user's client.
Owner:GHUKASYAN HOVHANNES +1
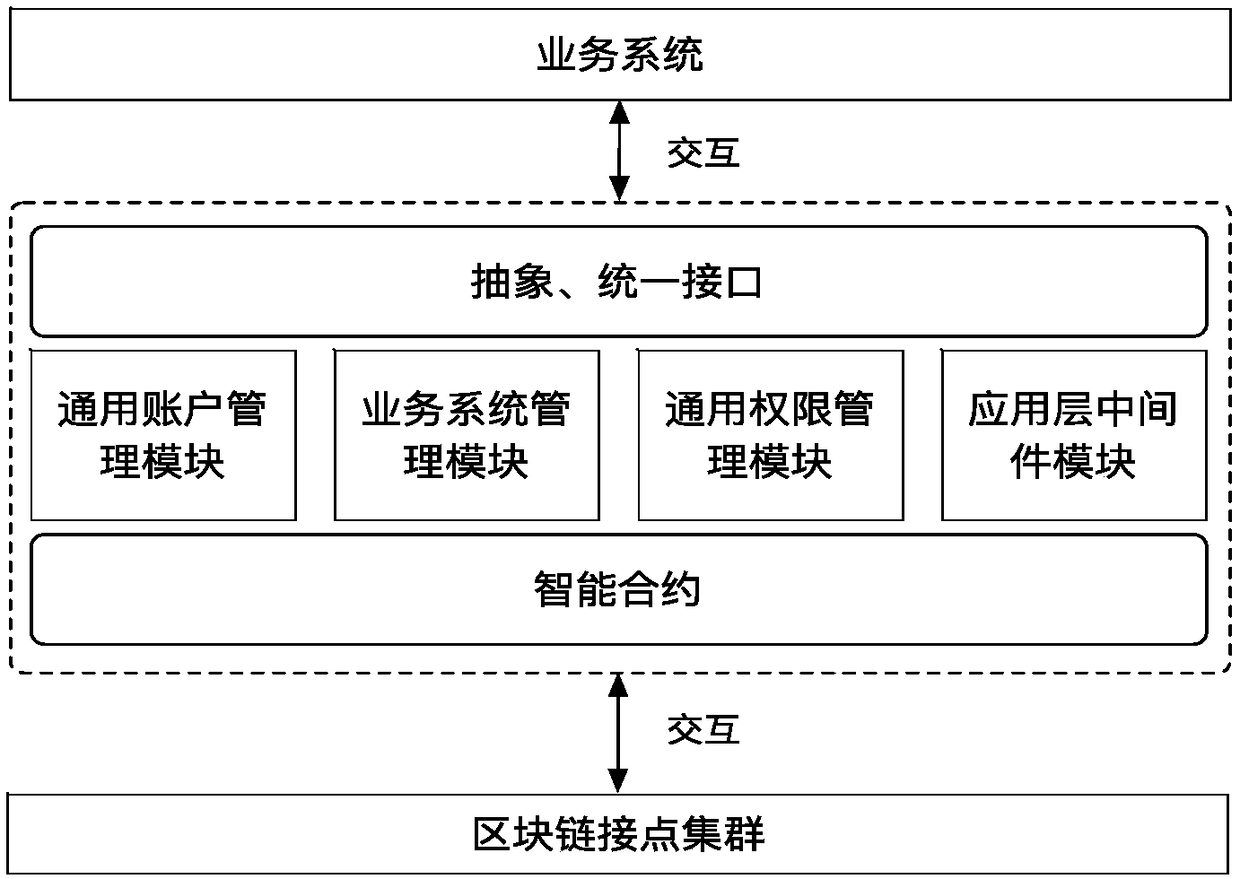
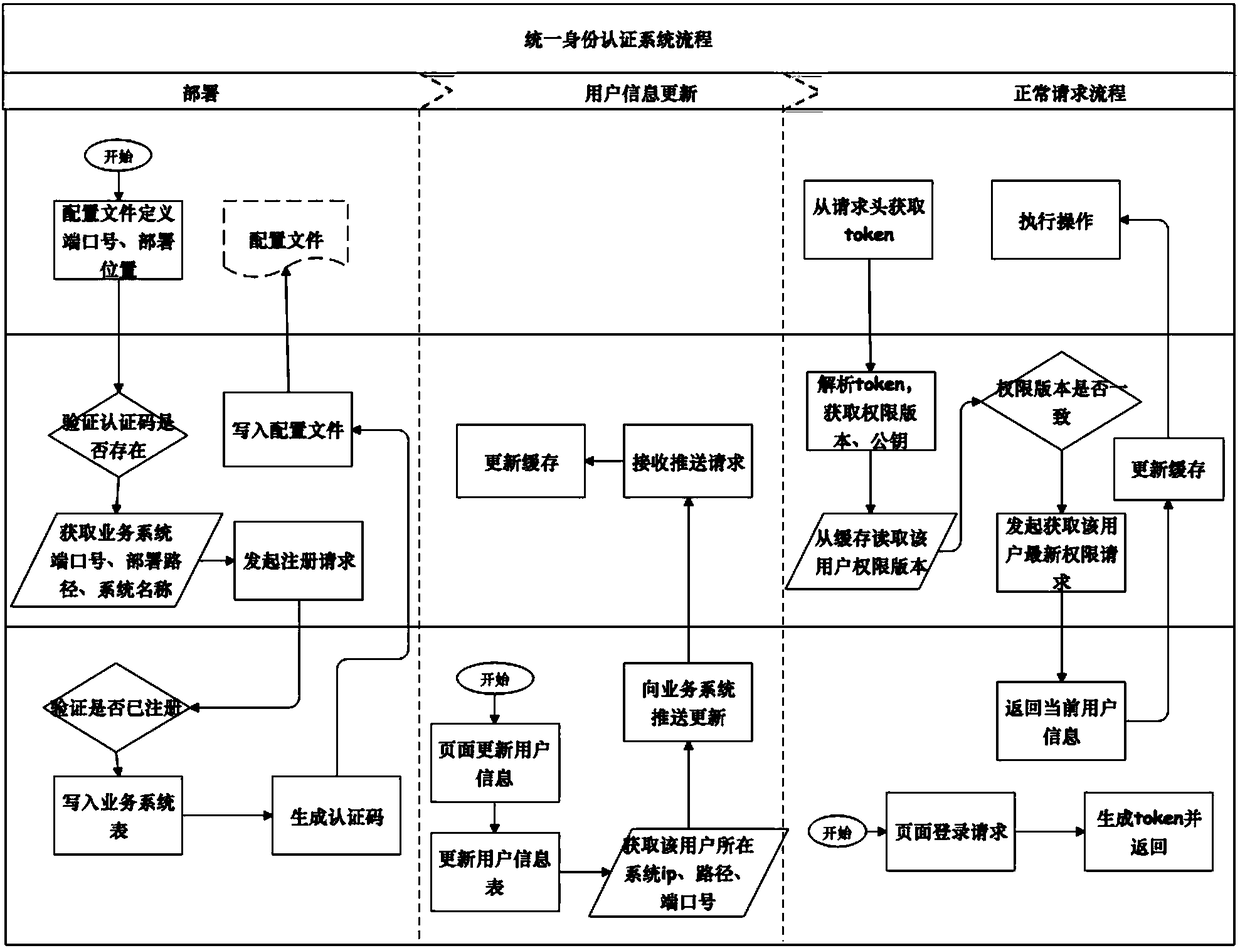
Identity authentication system and identity authentication method based on block chain smart contract
The invention discloses an identity authentication system based on a block chain smart contract. An application layer middleware module provides a universal unified external interface; a universal authority management module manages a user role authority of the identity authentication system and verifies the user authority according to specified rules and policies; a general account management module manages a relevant operation of a user on account information in the identity authentication system, verifies the validity of an access account, and meanwhile, provides an asynchronous message push service to complete real-time updating of the account cache information; and a service system management module manages a service system, completes the registration of an access service system, stores relevant information and an identifier of the service system in the block chain smart contract, and provides a single sign-on scheme for the service system. The identity authentication system provided by the invention has very good reliability, stability and safety.
Owner:HANGZHOU QULIAN TECH CO LTD
System for automatic connection to a network
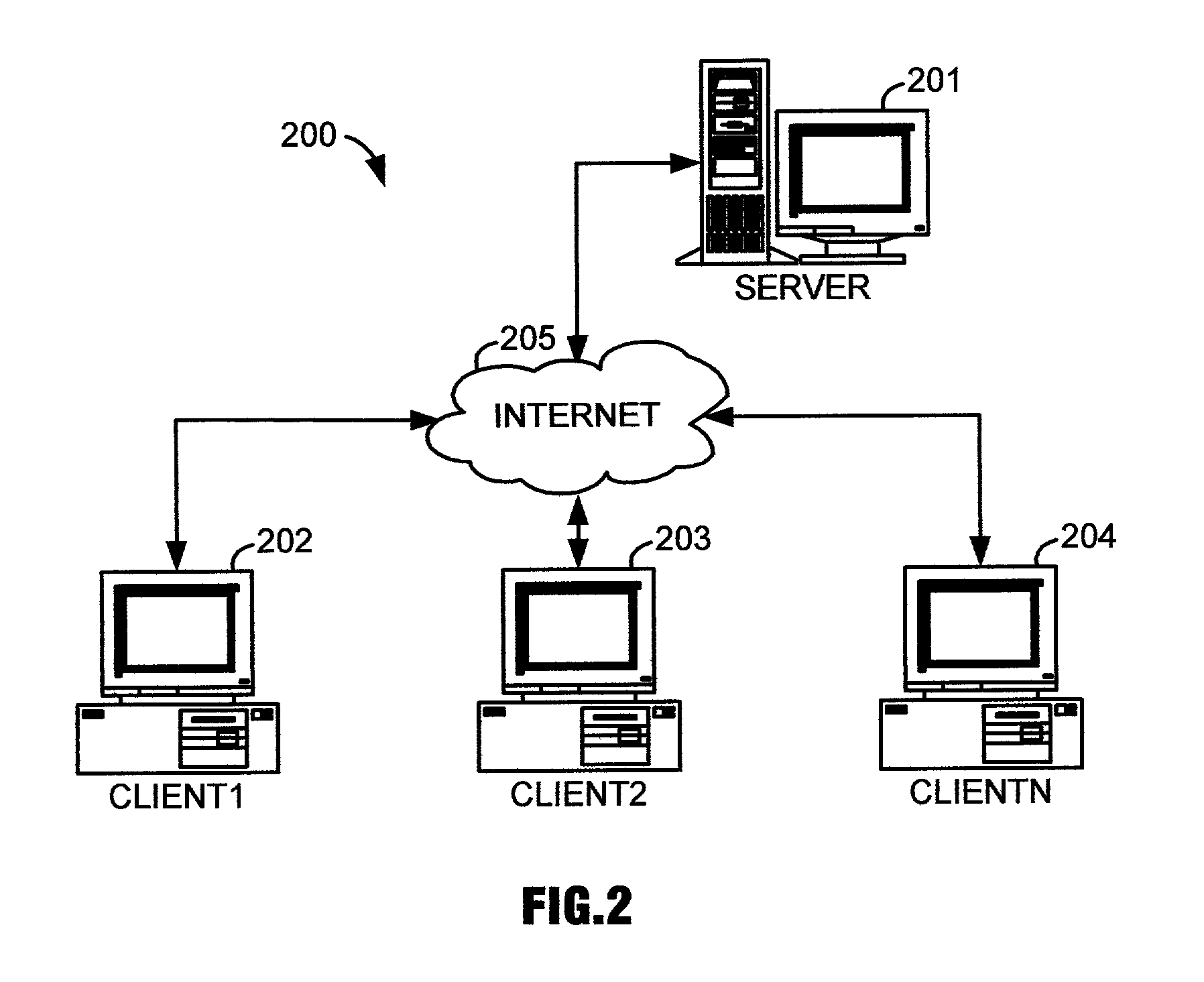
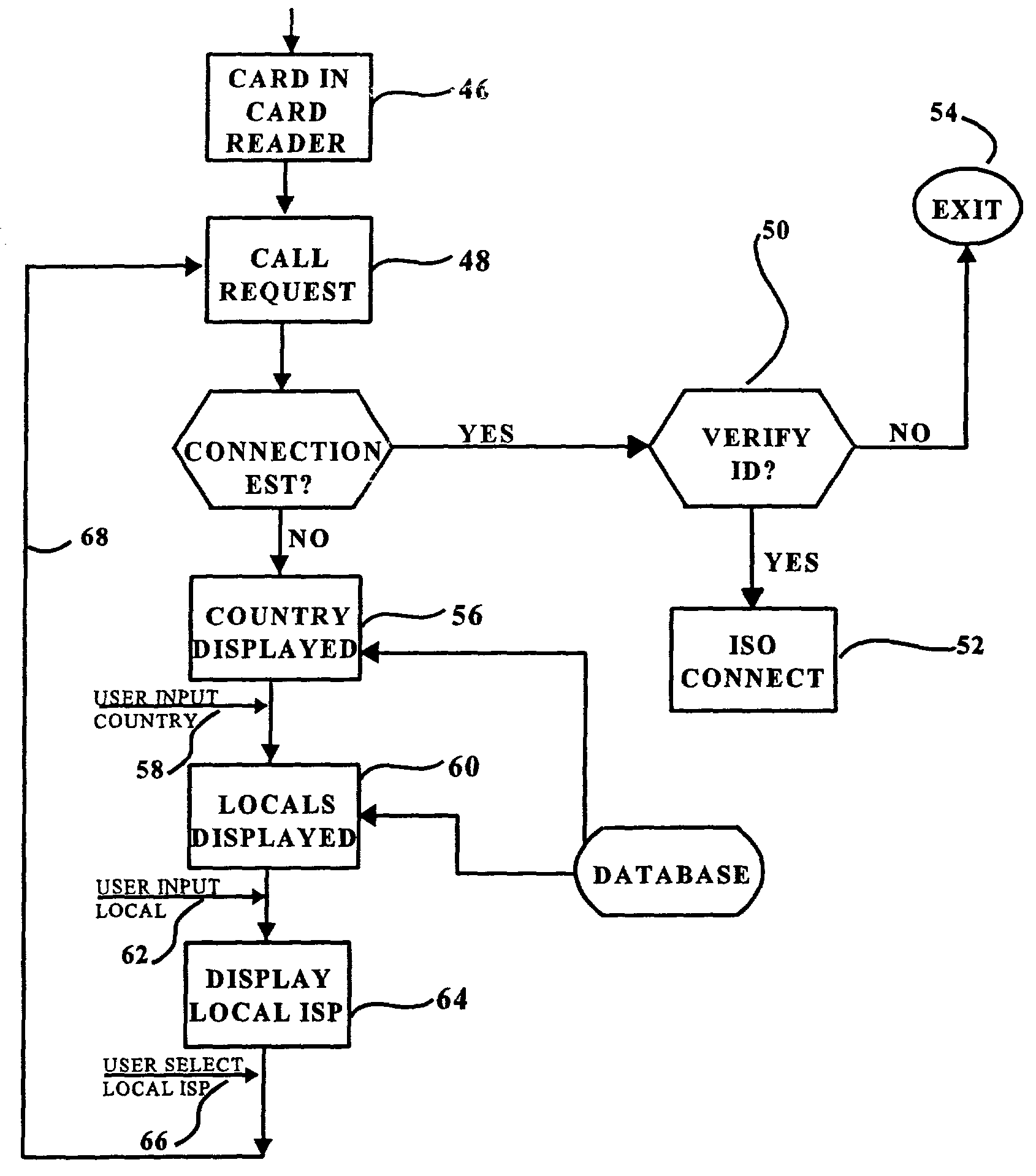
InactiveUS7083095B2Increase costShorten the timeConveying record carriersDigital data processing detailsUser PrivilegeDigital content
A system for managing digital rights of digital content over a network. A data card contains user information including digital rights information specific to a user, the data card having a memory component for enabling information to be stored within the data card. A data card reader is adapted to access the user information contained on the data card when the data card is in communication therewith. A data processor in communication with the data card reader is adapted to be connected to the network. An application program resides on the memory component of the data card, the application program being configured to operate in conjunction with a universal language for creating and controlling digital rights, to manage user rights of the digital content available on the network based on the digital rights information specific to the user which is contained on the data card.
Owner:HENDRICK COLIN
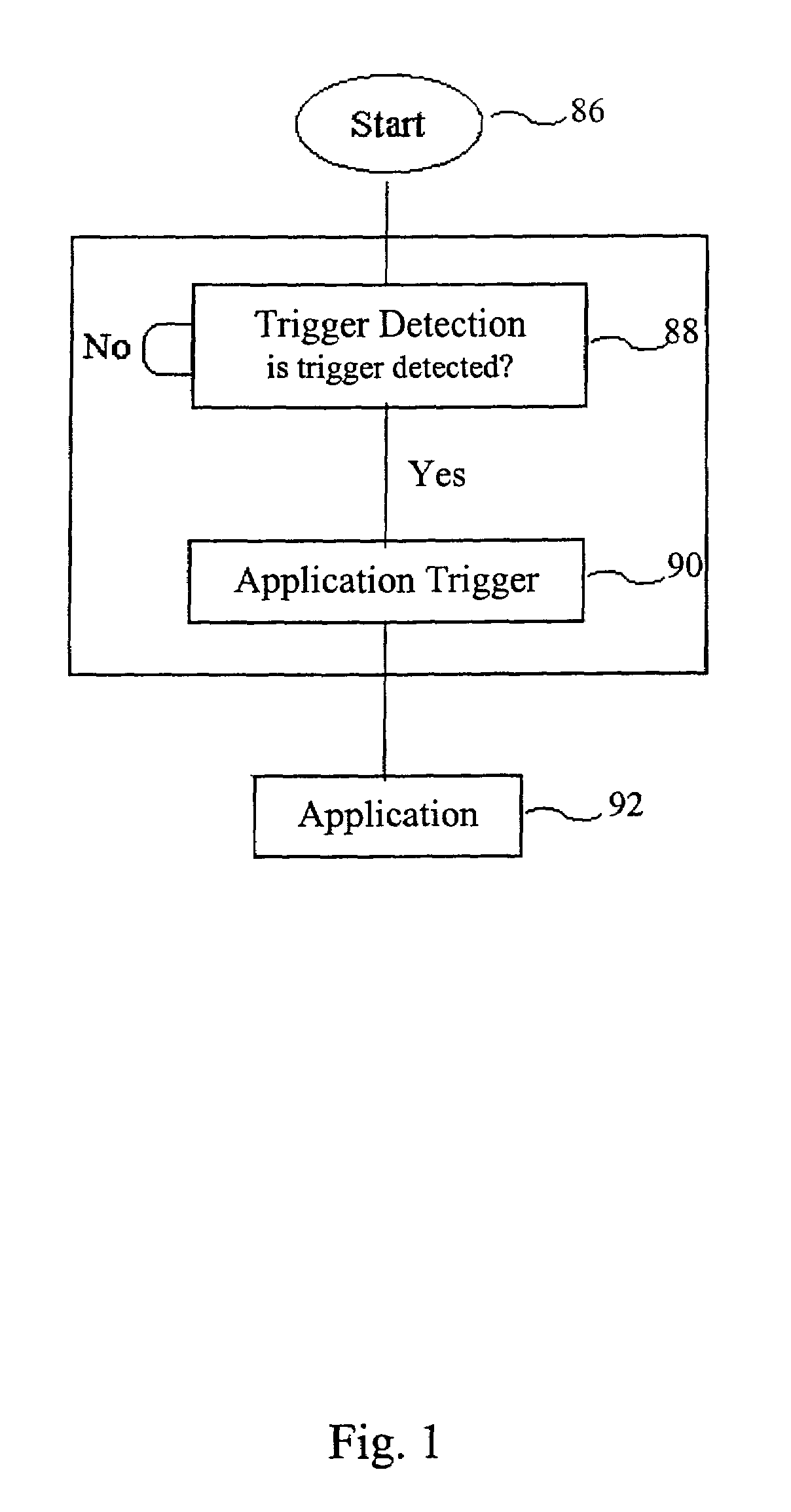
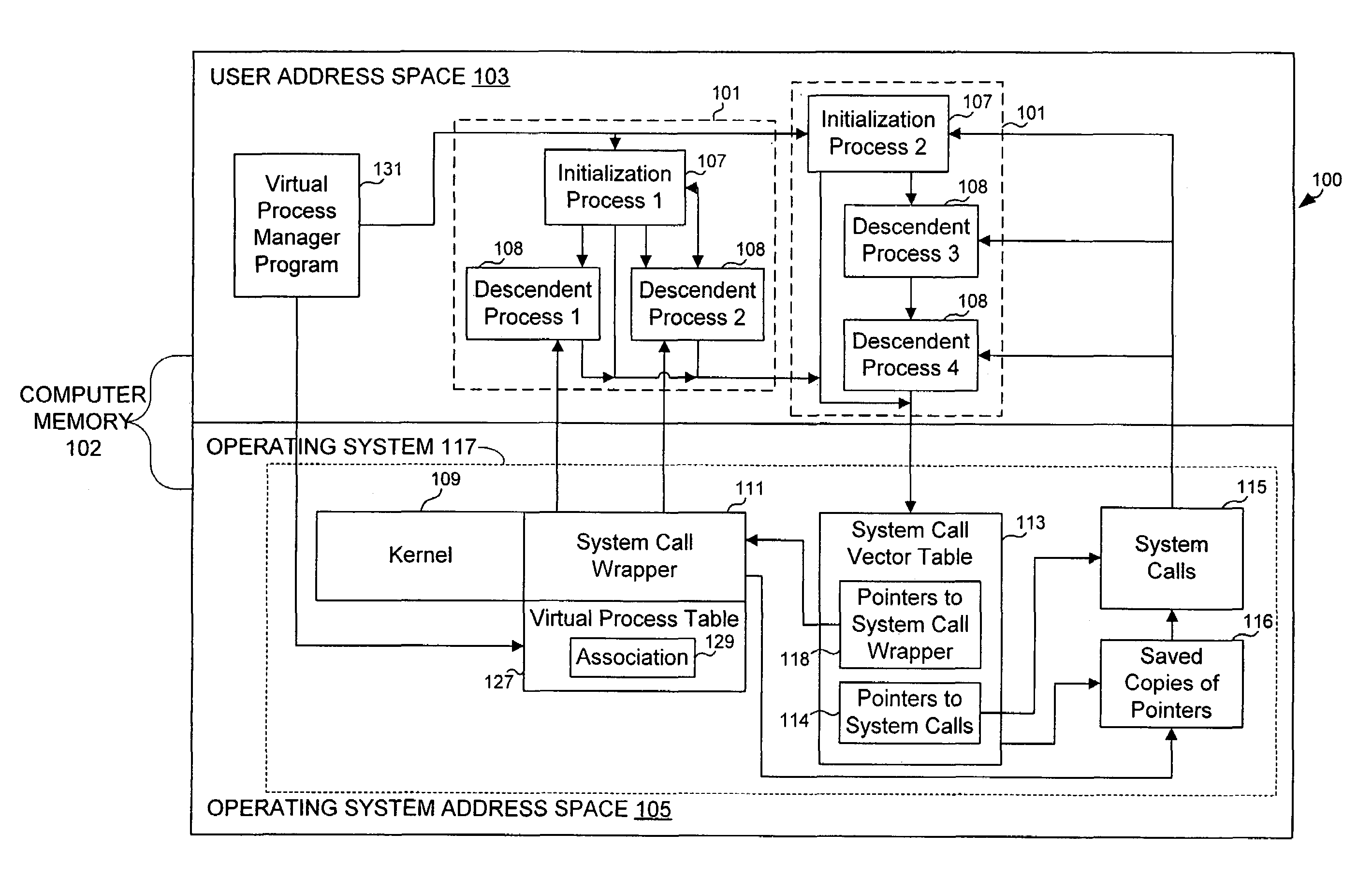
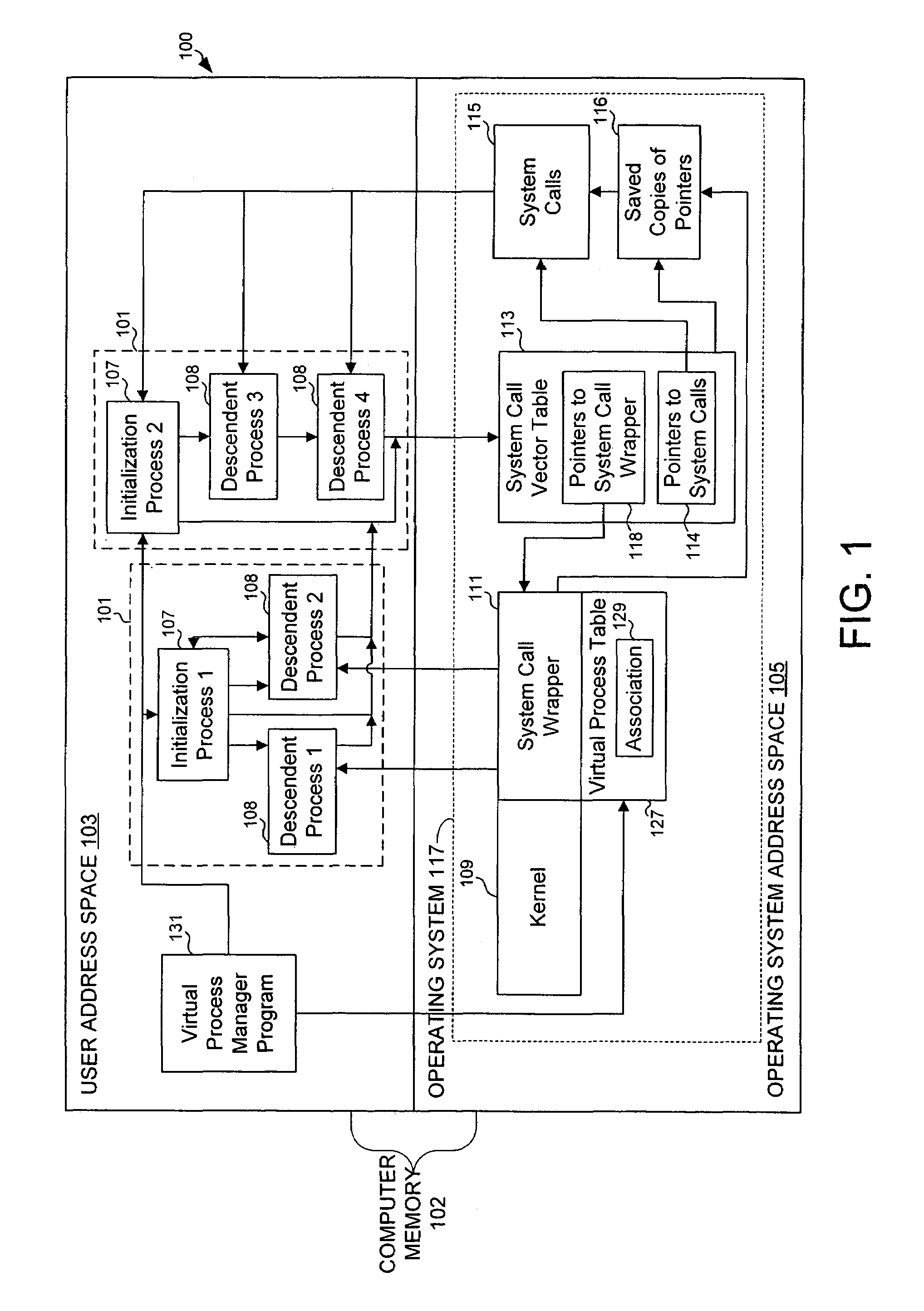
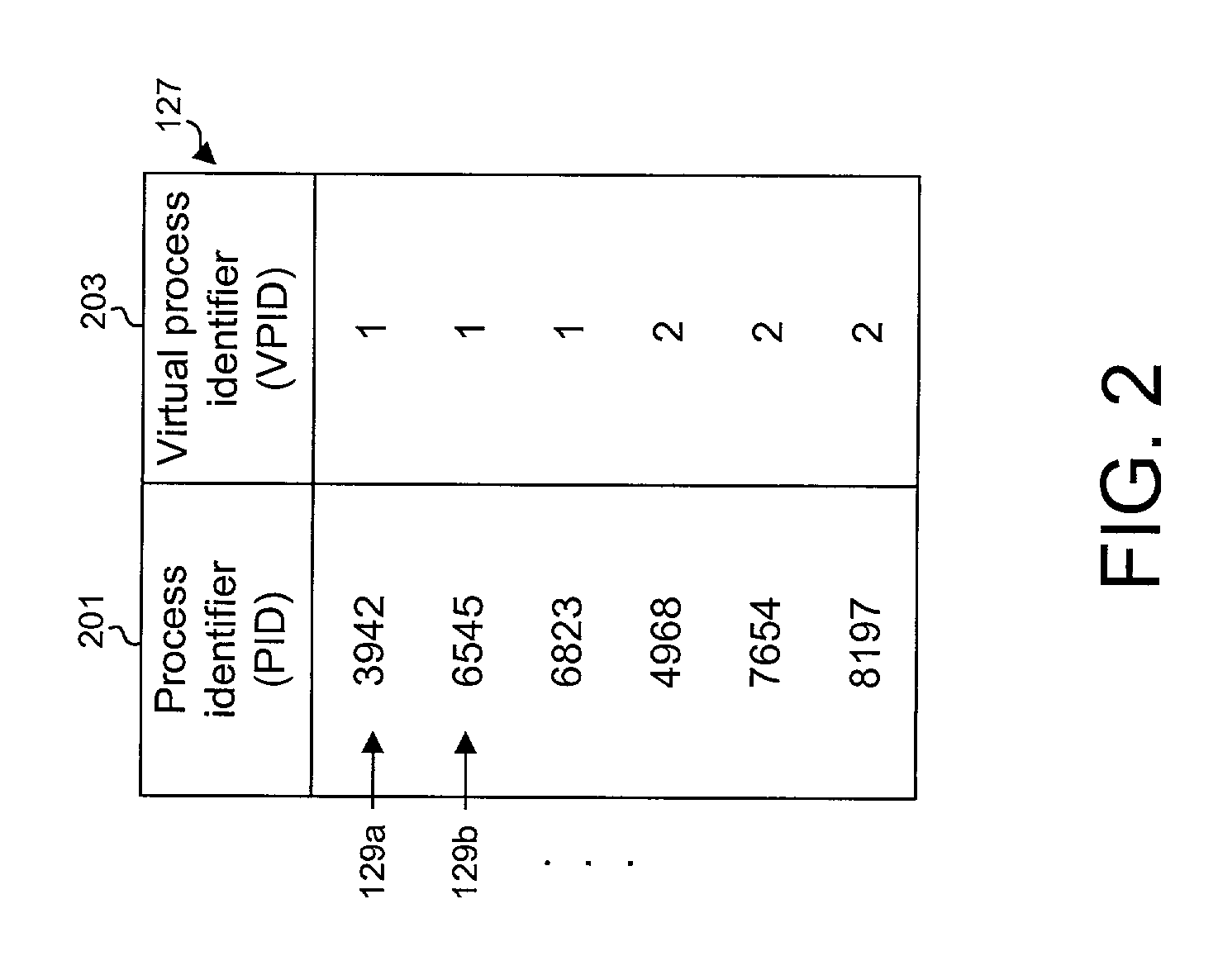
Virtualizing super-user privileges for multiple virtual processes
Super-user privileges are virtualized by designating a virtual super-user for each of a plurality of virtual processes and intercepting system calls for which actual super-user privileges are required, which are nevertheless desirable for a virtual super-user to perform in the context of his or her own virtual process. In one embodiment, a computer operating system includes multiple virtual processes, such as virtual private servers. Each virtual process can be associated with one or more virtual super-users. When an actual process makes a system call that requires actual super-user privileges, the call is intercepted by a system call wrapper.
Owner:CUFER ASSET LTD LLC +1
System and method for executing interactive applications with minimal privileges
ActiveUS7587755B2Digital data processing detailsUnauthorized memory use protectionOperational systemUser Privilege
A mechanism for running interactive applications with a minimal set of privileges is disclosed. The privileges form a subset of the privileges afforded to the user requesting the application and are allocated consistent with the principle of least privilege. The application runs with the minimal amount of permissions necessary to accomplish its assigned tasks. A new user account is created and provisioned or identified for each application to which a user requests access. The accounts have a subset or superset of the access rights and operating system privileges that the user who is logged on to the system and requesting access to the application ordinarily enjoys. The subset / superset of the user's privileges is determined by a policy-based decision system. The policy-based decision system makes its determination based on an analysis of the application requirements, an analysis of the data security and privacy concerns associated with the execution of the application, the identity of the user and user's role and any other policy considerations previously specified by an administrator. Once the determination as to the appropriate set of privileges to be afforded in the execution environment has been made, the execution environment is created and provisioned or a pre-existing execution environment possessing the requisite privileges is identified and the remote user is logged into the server-side account. The application-specific accounts may be audited by audit trail tools that provide evidence of policy enforcement.
Owner:CITRIX SYST INC
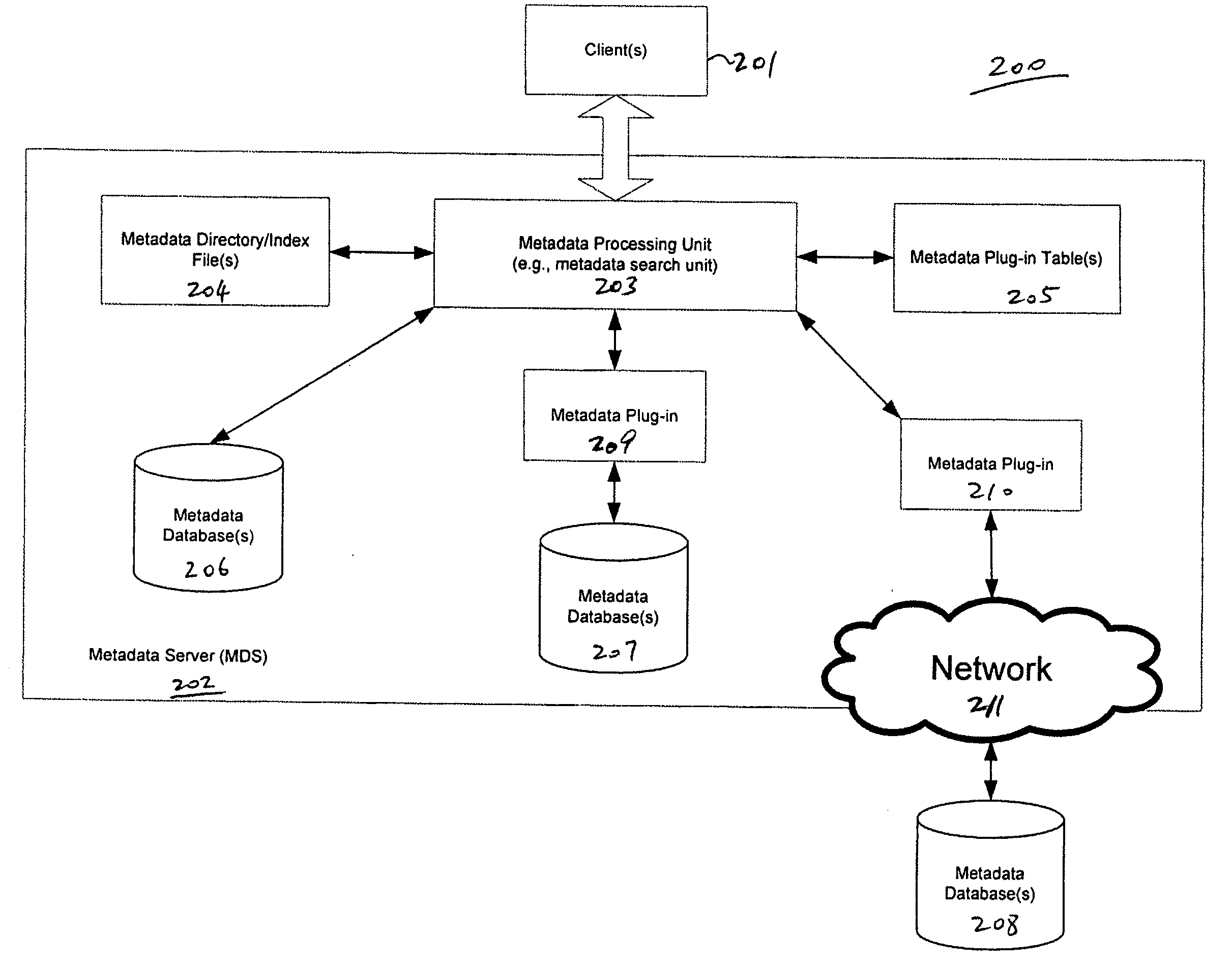
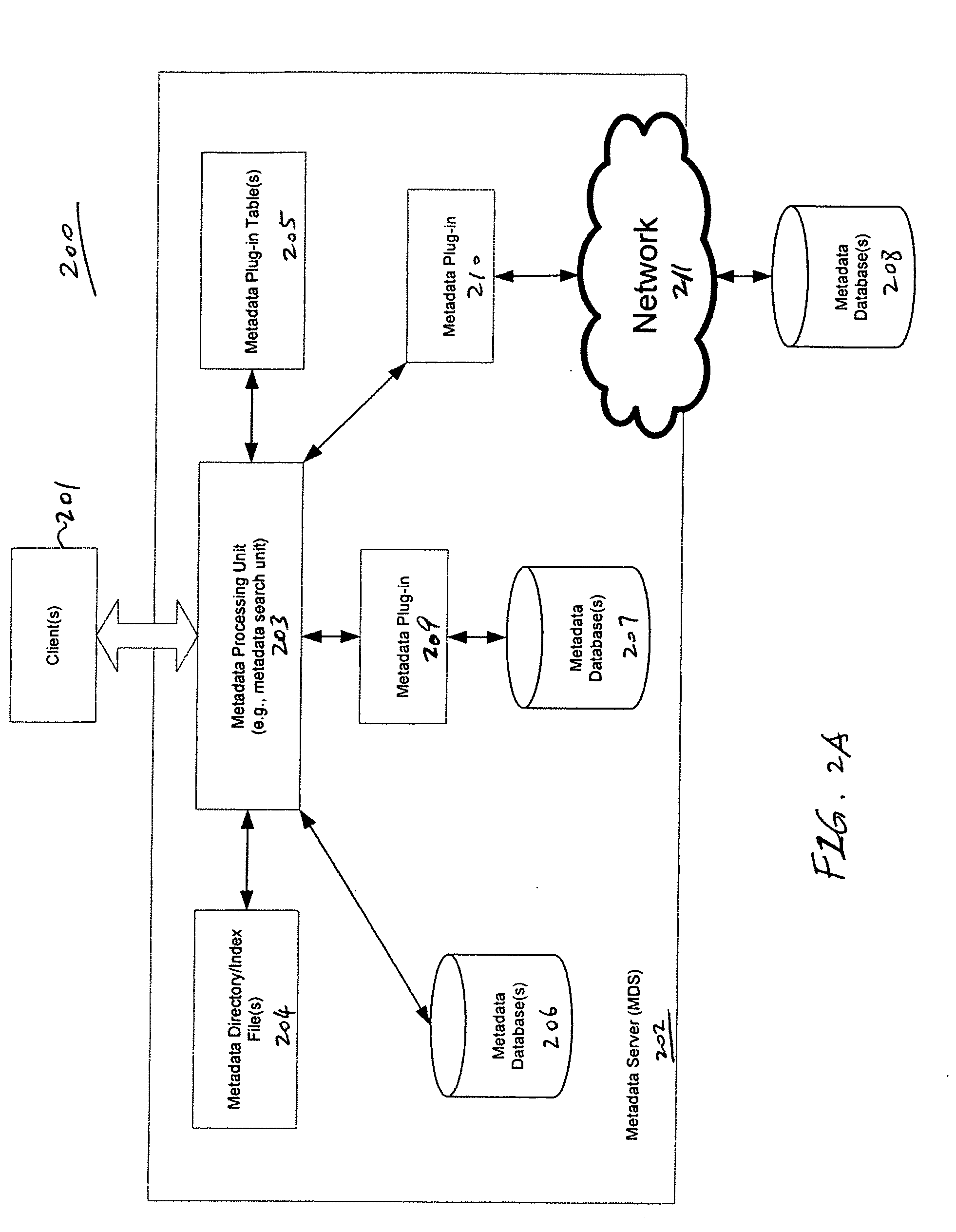
Method and apparatus for processing metadata
InactiveUS20080033921A1Digital data processing detailsSpecial data processing applicationsUser PrivilegeApplication software
A method and apparatus for processing metadata search with plug-in applications is disclosed. In one embodiment, in response to a search request for metadata stored in a metadata store, a plug-in associated with the metadata store is invoked to perform the request search within the metadata store. In addition, according to another embodiment, a search result of the metadata search may be filtered based on user privileges of a client initiating the search request, and some or all of the metadata from the search result may be returned to the client dependent upon the user privileges of the client. Other methods and apparatuses are also described.
Owner:APPLE INC
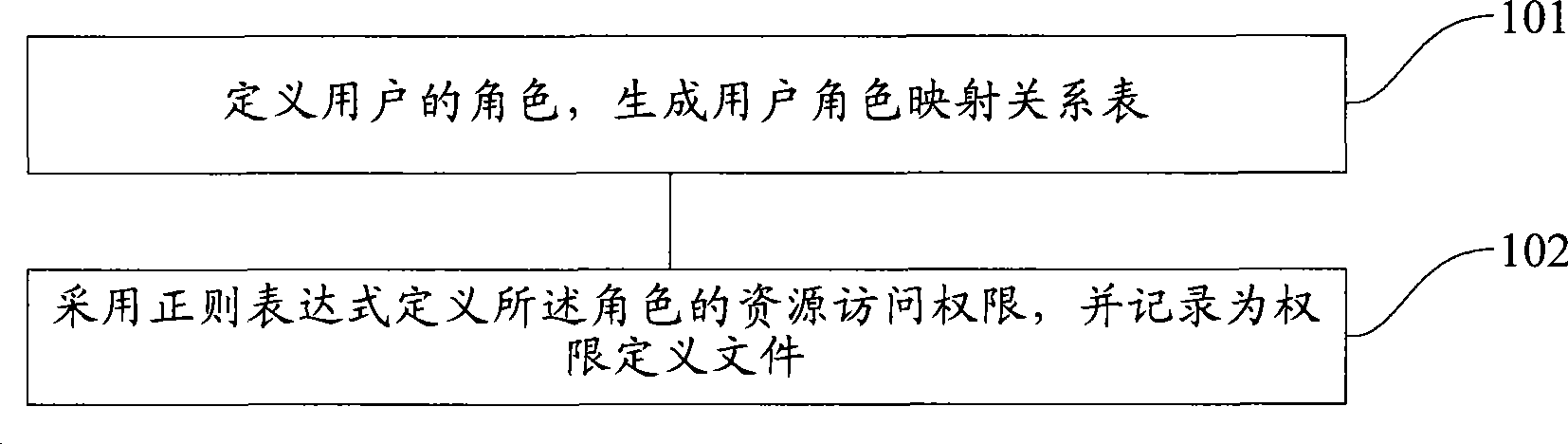
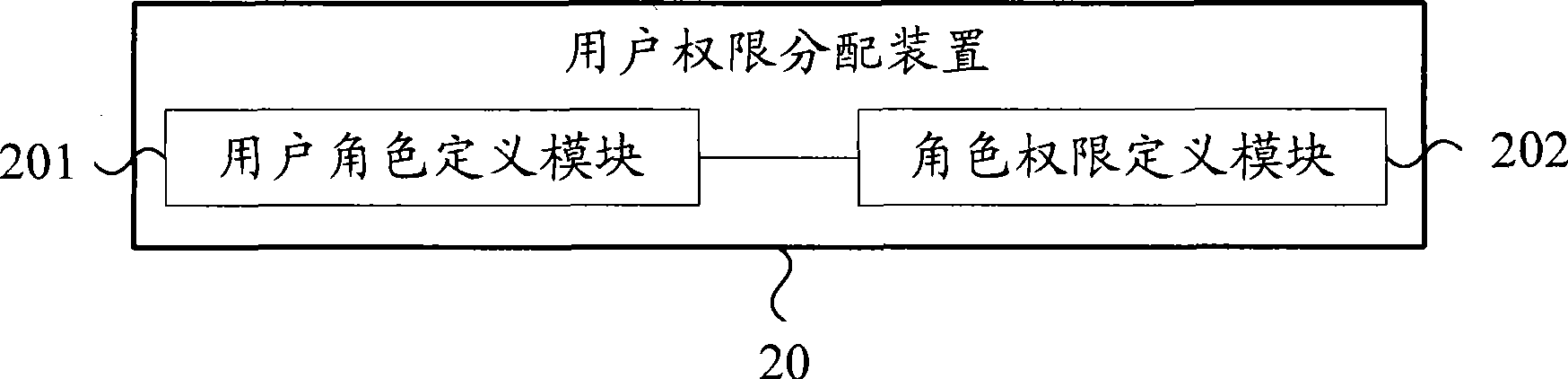
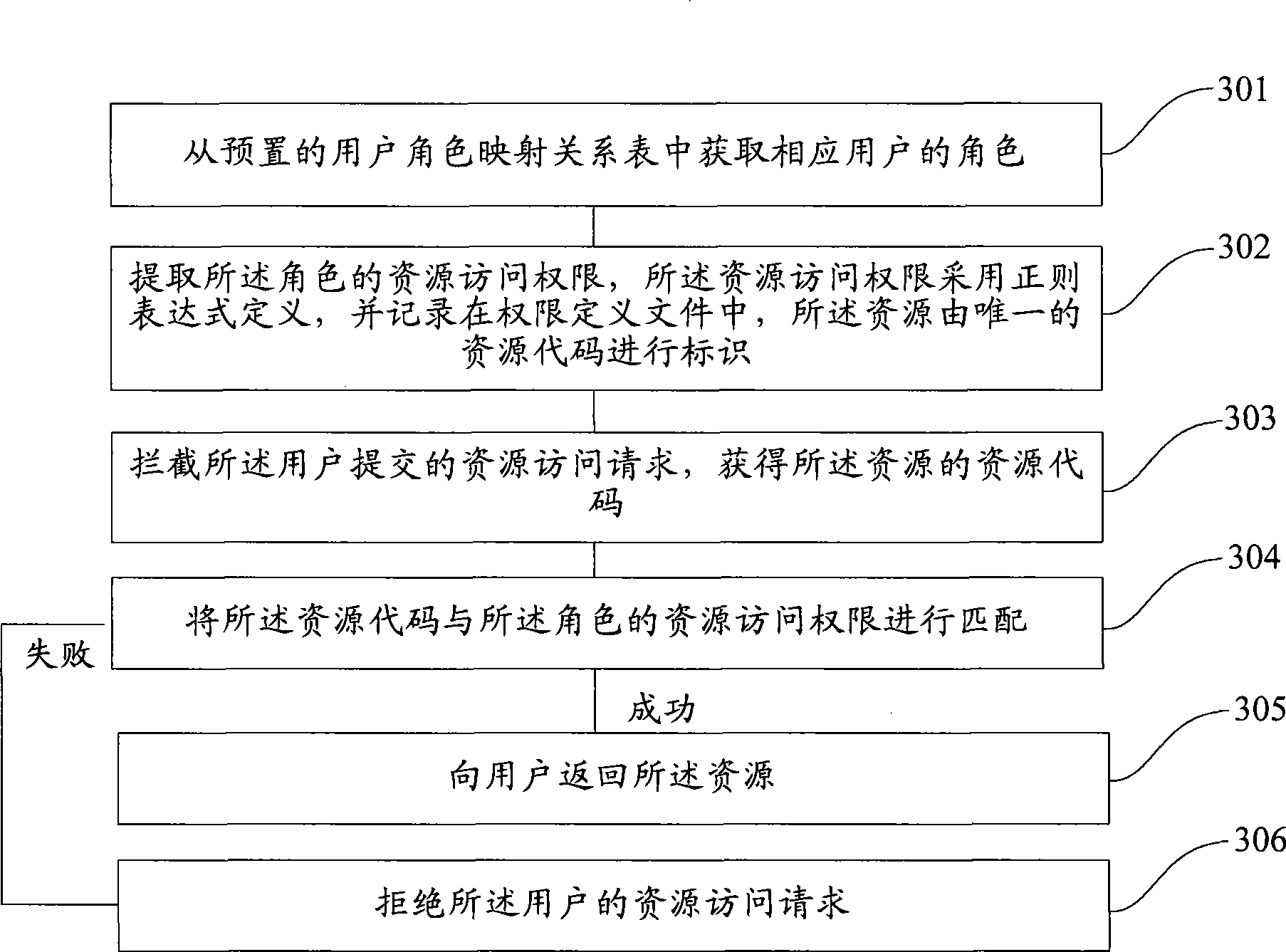
User authority allocation method and user authority control method
ActiveCN101441688APermission definitions are highly descriptiveSupport access controlDigital data authenticationUser PrivilegeSystem development
The invention provides a method for controlling user rights. The method comprises the following steps: a user role is correspondingly acquired from a preset user role mapping relational table; the resource access right of the role is picked up, and the resource access right is defined by a regular expression, recorded in a right definition file, and marked by an exclusive resource code; the resource access request from the user is intercepted, and the resource code of the resource is acquired; by matching the resource code with the resource access right of the role, if matched, the resource is returned to the user; and if not matched, the resource access request from the user is refused. In the inserting mode, the method can be applied to e various system structural frames; moreover, the method also has the advantages of wide application range, flexible definition, and obvious lowering of system development and operation costs.
Owner:ALIBABA GRP HLDG LTD
Secured Database System with Built-in Antivirus Protection
ActiveUS20070168678A1Digital data processing detailsUnauthorized memory use protectionUser PrivilegeEncryption
A secured database system with built-in antivirus protection is described. In one embodiment, for example, a method of the present invention is described for securing a database system, the method comprises steps of: provisioning storage from a storage device, for storing database information; generating an encryption key so that the database information is stored on the storage device in an encrypted manner; generating a decryption key for decrypting the database information stored on the storage device, wherein access to the decryption key is controlled by the database system based on user privileges; receiving a request from a user for access to the database information; determining whether the user has been granted sufficient privileges to access the database information; if the user has been granted sufficient privileges, automatically decrypting the database information to provide the access; and otherwise denying the request if the user has not been granted sufficient privileges.
Owner:SYBASE INC
System and Method for Reconciling One or More Financial Transactions
InactiveUS20080103949A1Reduce effortProvide capabilityComplete banking machinesFinanceUser PrivilegeTransaction data
A system, method and computer program product for reconciling one or more financial transactions of one or more business units. The method includes capturing transaction data from the financial transactions using a first set of data logics. The capturing further includes extracting the transaction data from the financial transactions using import templates and transforming the extracted transaction data to a predefined format, using a first set of validations. The captured transaction data is then auto-matched with master data as reference, using one or more auto-match logics and a second set of validations. One or more reports are then generated on the auto-matched transaction data. The method further includes providing user privileges for controlling the capturing, the auto-matching, and the generation of the one or more reports according to a first predefined criterion.
Owner:LIBERTY PEAK VENTURES LLC
Access control system
InactiveUS7035850B2Technique be restrictAvoid accessData processing applicationsDigital data protectionUser PrivilegeControl system
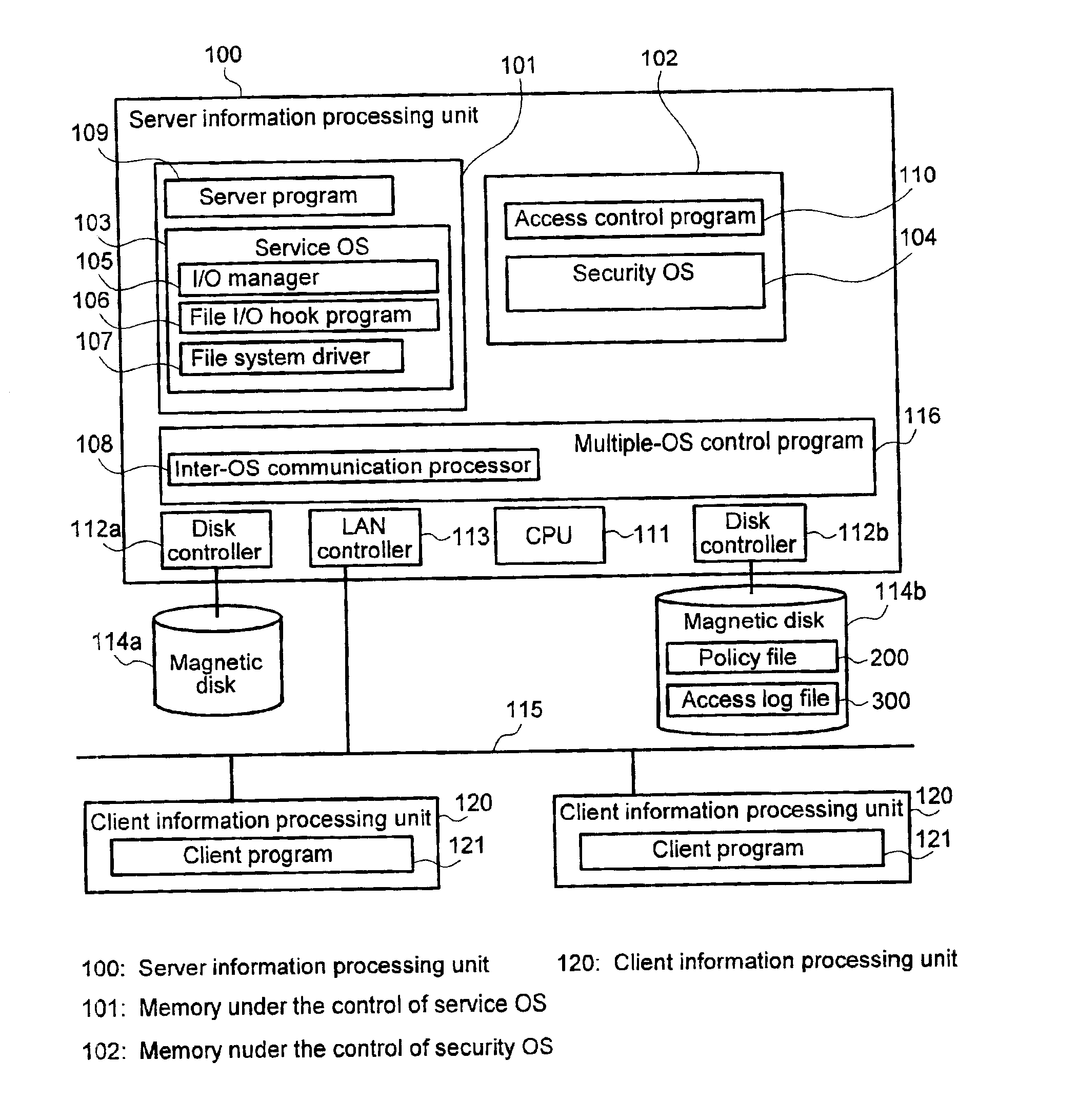
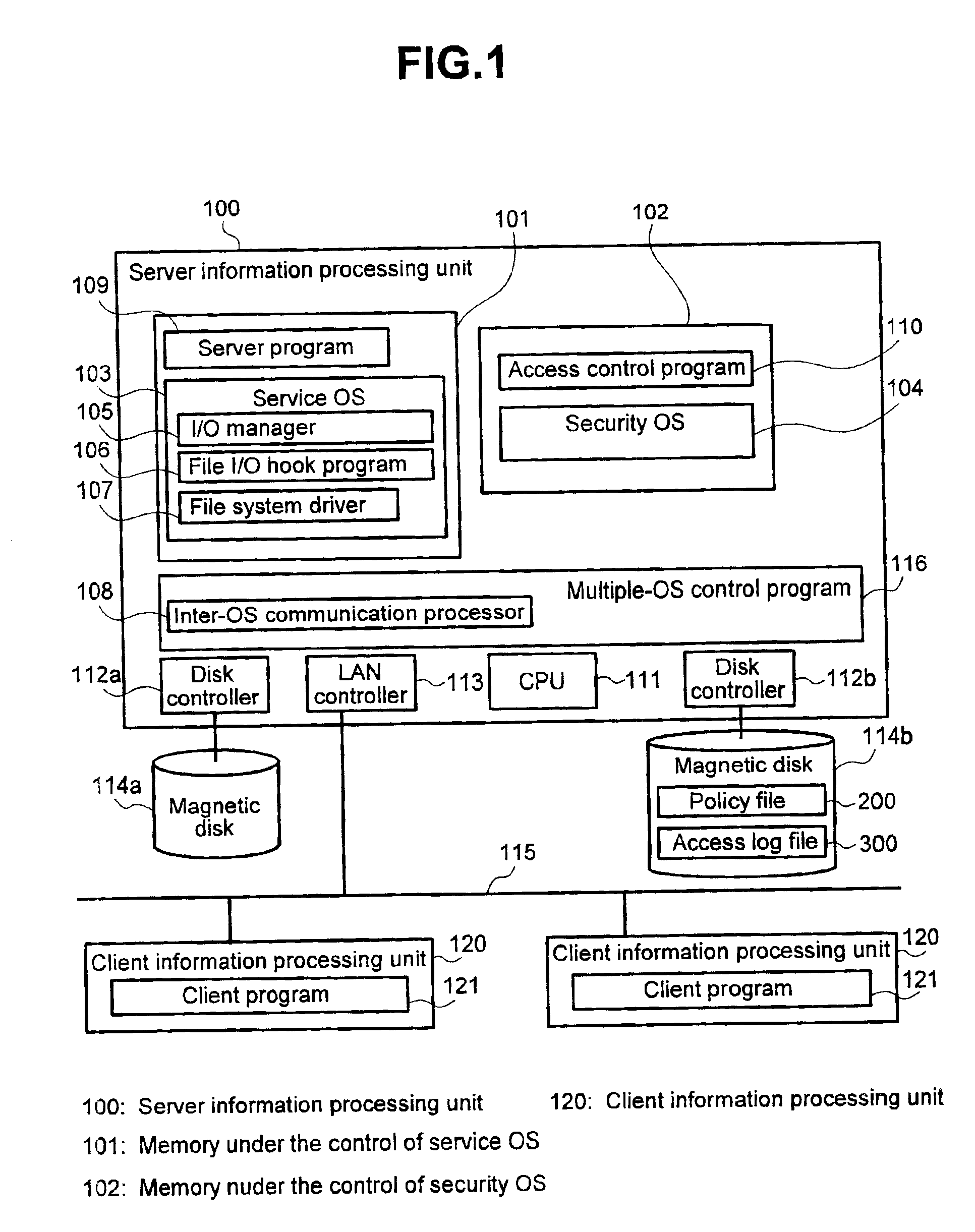
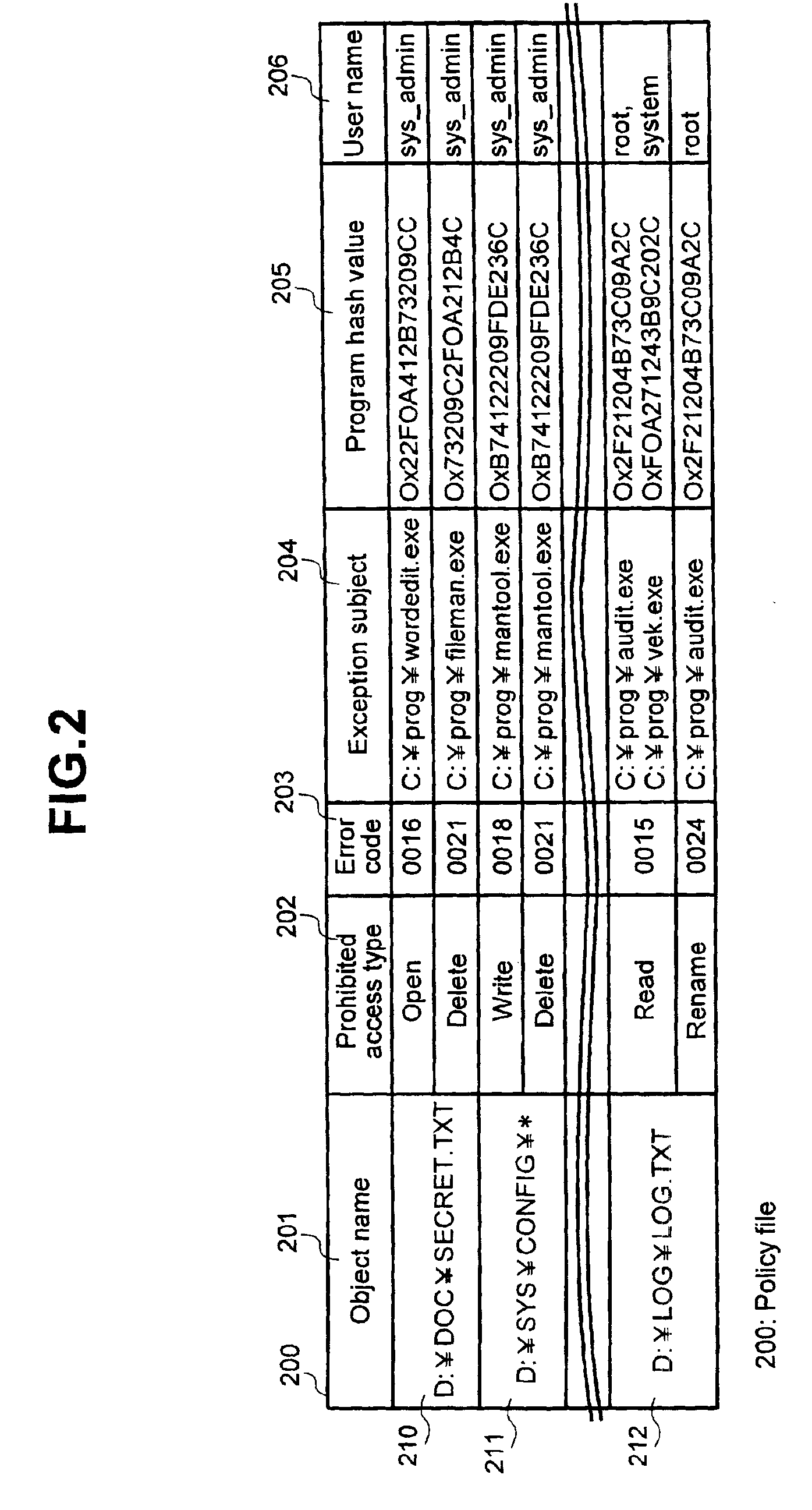
An access control system and its method that can prevent access to read or write into a file, no matter what user right the access request source uses to attempt an unauthorized access. This invention uses a policy that access to a specific file is authorized only when it is made by a specific user using a specific program. In addition, the policy is registered in a policy file 200 and the access information hooked by a file I / O hook program 106 is transmitted through an inter-OS communication processor 108 to an access control program 110 for a security OS 104 in order to perform access control according to said policy.
Owner:HITACHI LTD
Authority delegate system, authorization server system, control method, and program
ActiveUS20140380429A1Digital data processing detailsMultiple digital computer combinationsManagement unitUser Privilege
An authority delegate system, including a server system which provides a service to a device having an application, and an authorization server system which performs authorization processing to delegate user authority in the service to a usage source of the service, includes a management unit, and a providing unit. The management unit identifies authority of the application, in accordance with having received a request to register the application as the usage source, and manages the identified authority, and an identifier of the application, in an associated manner. The providing unit provides the service, in a case where an authorization operation has been performed to permit delegating of the user authority to the application transmitting a request to use the service, and an authority which the application uses is included in authorities associated with the identifier of the application.
Owner:CANON KK
Dynamic digital copyright protection method based on dual identity authentication
InactiveCN101872399AReduce stepsRealize online downloadUser identity/authority verificationDigital data authenticationClient-sideUser Privilege
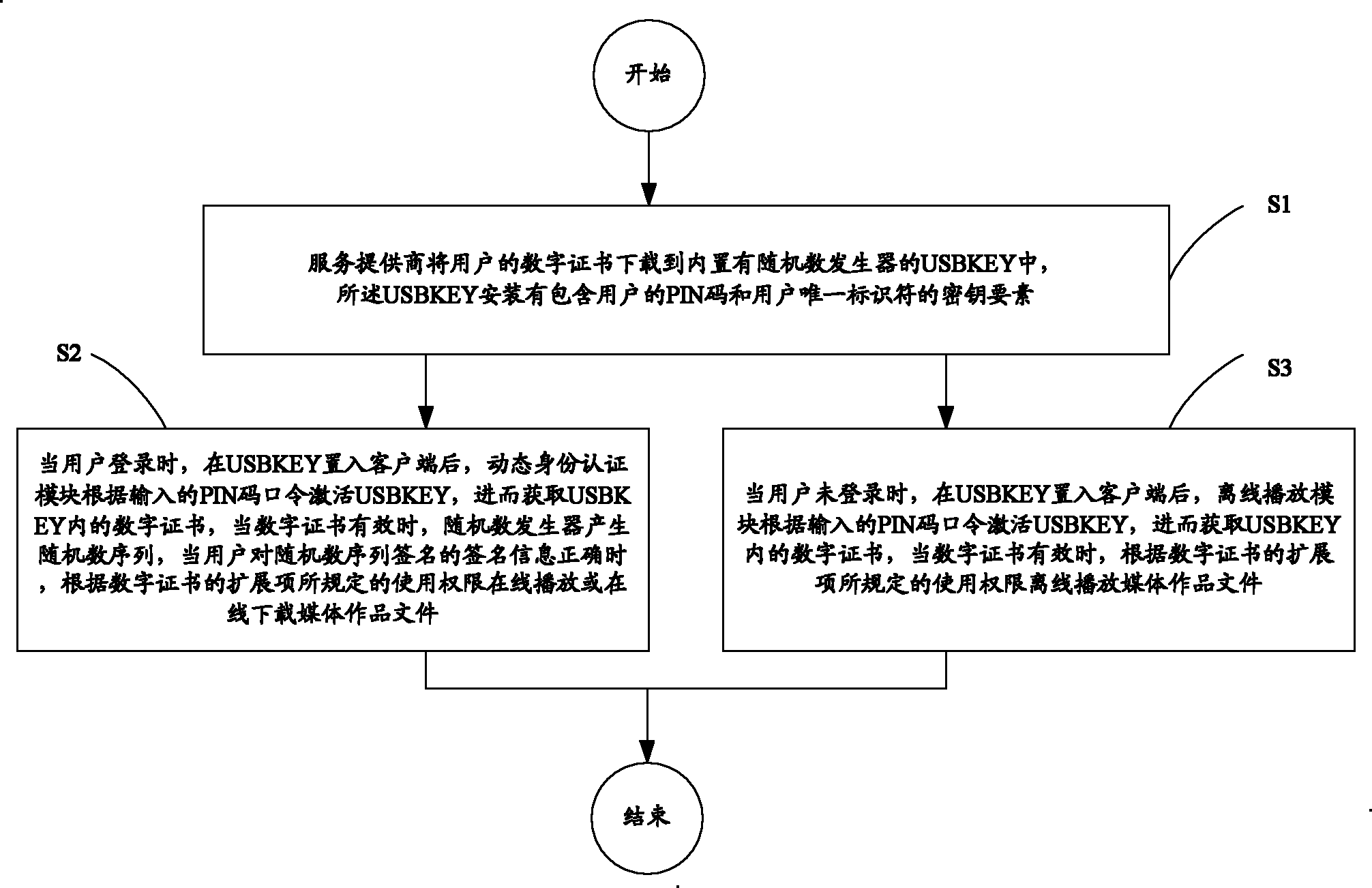
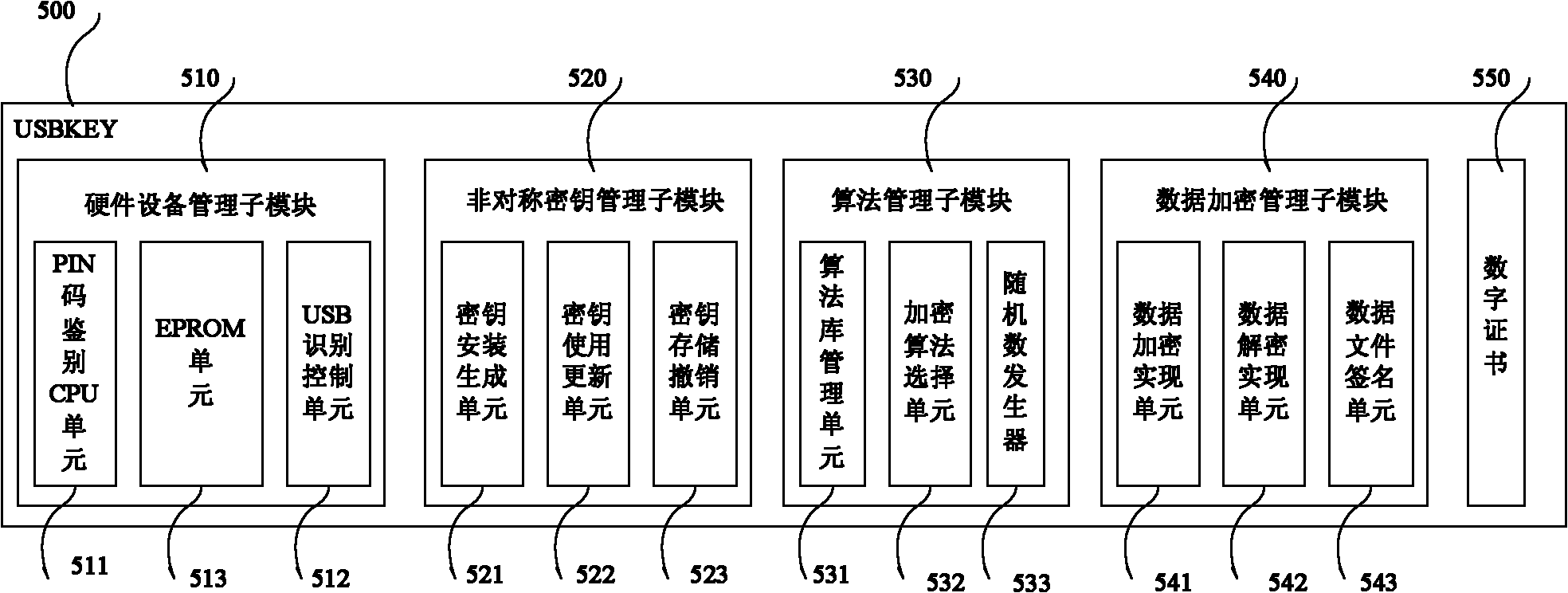
The invention discloses a dynamic digital copyright protection method based on dual identity authentication, comprising the following steps of: downloading a digital certificate of a user into a USBKEY internally provided with a random number generator; when a user logins, after placing the USBKEY into a client end, activating the USBKEY according to the input PIN code command, acquiring the digital certificate in the USBKEY, when the digital certificate is valid, generating a random number sequence by the random number generator, when the signature information of a signature of the user to the random number sequence is right, playing or downloading media works files on line according to the user right specified by an expansion item of the digital item; and when the user does not login, after placing the USBKEY into the client end, activating the USBKEY according to the input PIN code command, acquiring the digital certificate in the USBKEY, and when the digital certificate is valid, playing media works files off line according to the user right specified by the expansion item of the digital item. The method can restrict the user use right and divide the user right range and is used for authenticating the off-line state user identity to prevent off-line diffusion.
Owner:WUHAN UNIV OF TECH
Time management system for mobile employees
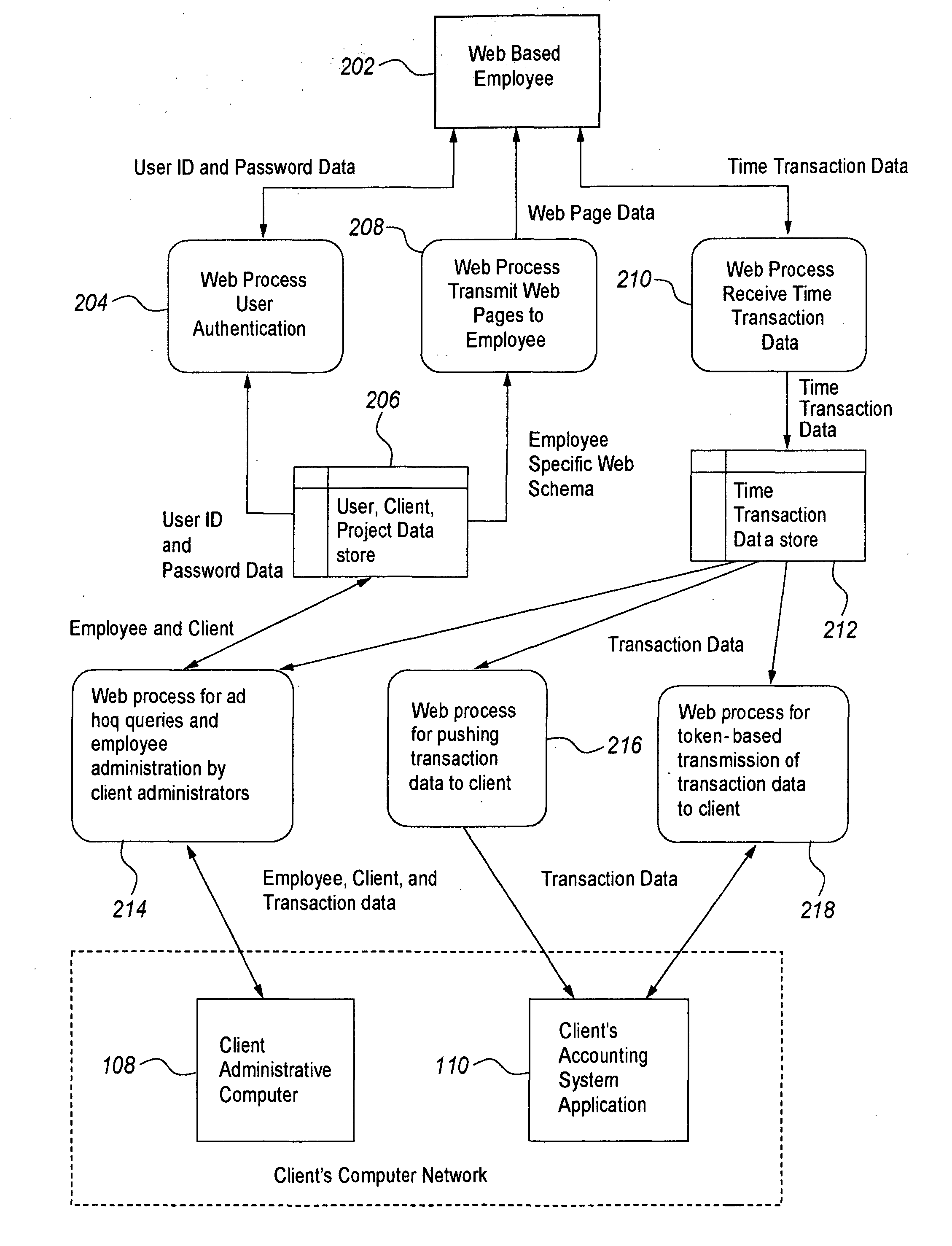
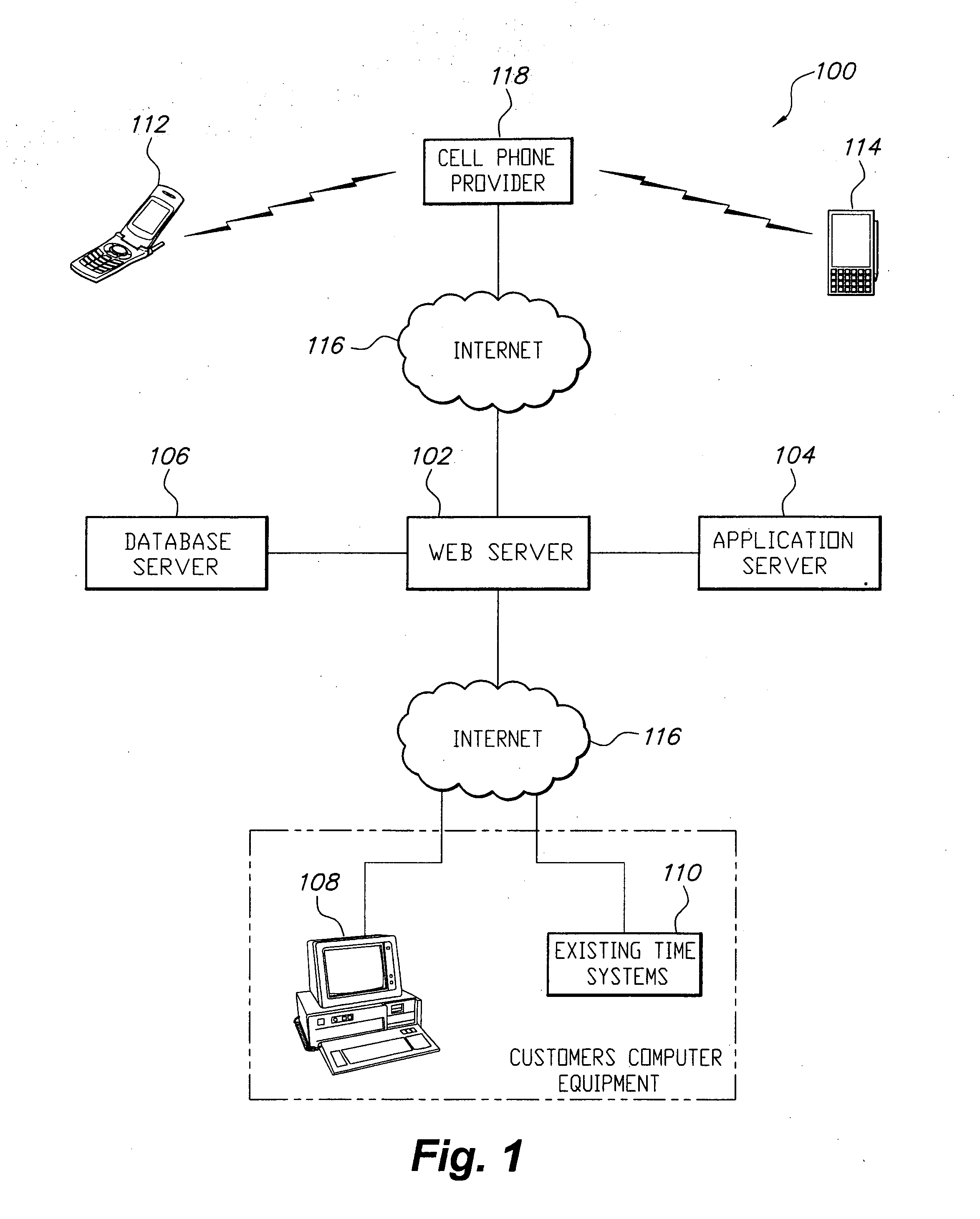
InactiveUS20050021428A1Registering/indicating time of eventsDigital computer detailsUser PrivilegeData access
The time management system for mobile employees is a telecommunications system allowing a company client to manage their off-site employees efficiently and effectively. Mobile employees, in communication with the system Web server via a cell phone or PDA, enter time transaction data using the mobile computing device's Web browser. Based upon the employee's predefined profile, custom Web pages are presented requesting employee specific time transaction information. Once received, time transaction data may be forwarded to the company client's computer directly or downloaded to client computers upon request or based upon a predetermined schedule. Having at least one Web server and application / database server, the system maintains employee data, client data, project data, and transaction data. The system protects against unauthorized access of data by having defined administrative user privileges.
Owner:COSTELLO CHARLES T
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com