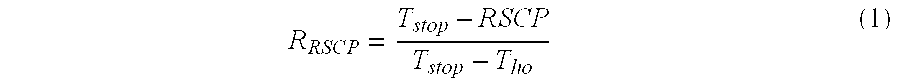Patents
Literature
118 results about "Potential impact" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
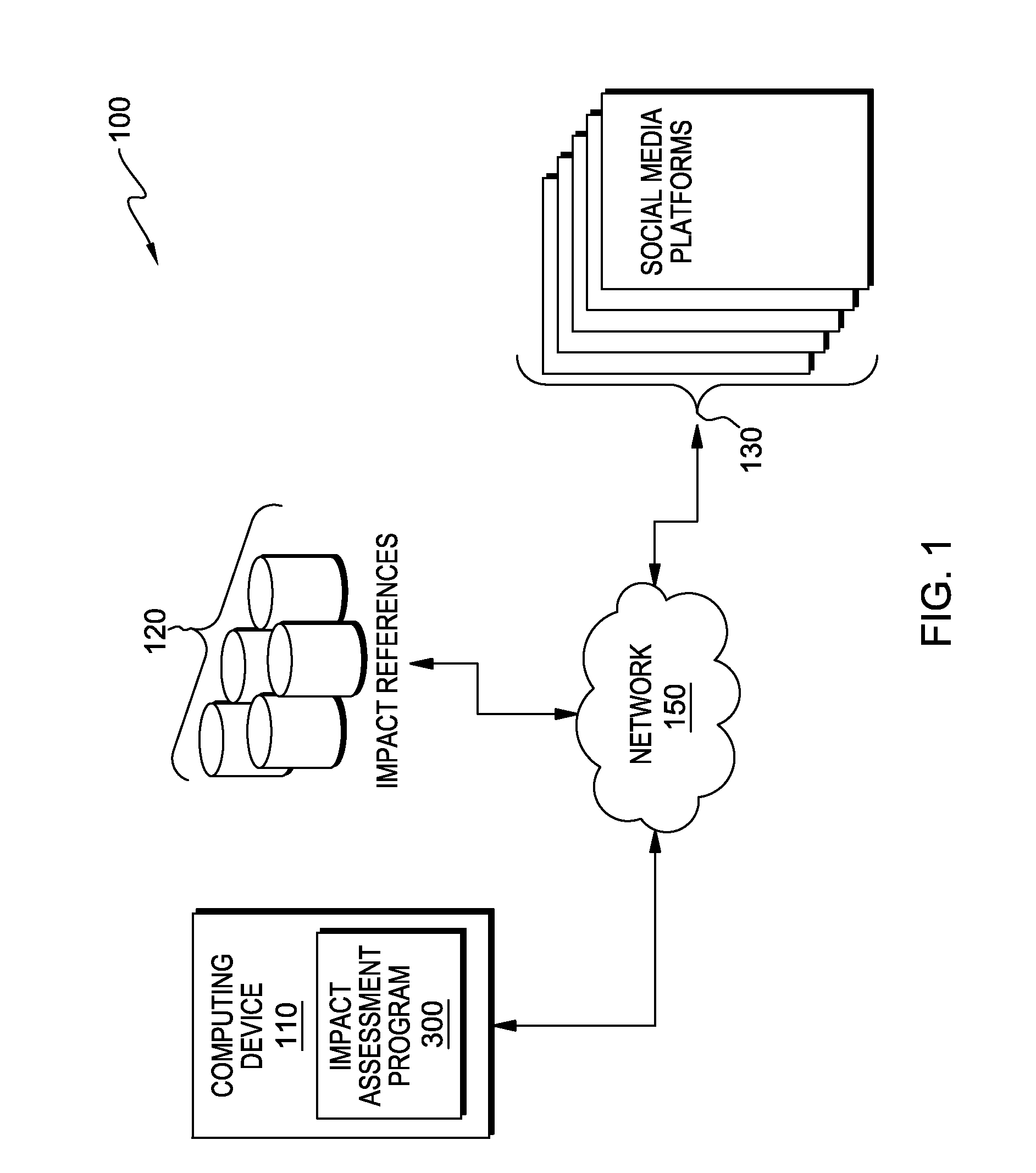
This potential impact is the combination of the previously assessed exposure risk and the sensitivity to those risks of the project’s human beneficiaries, physical assets and resources and related health systems. The potential impact ratings rely on the user’s subject matter expertise and contextual understanding.
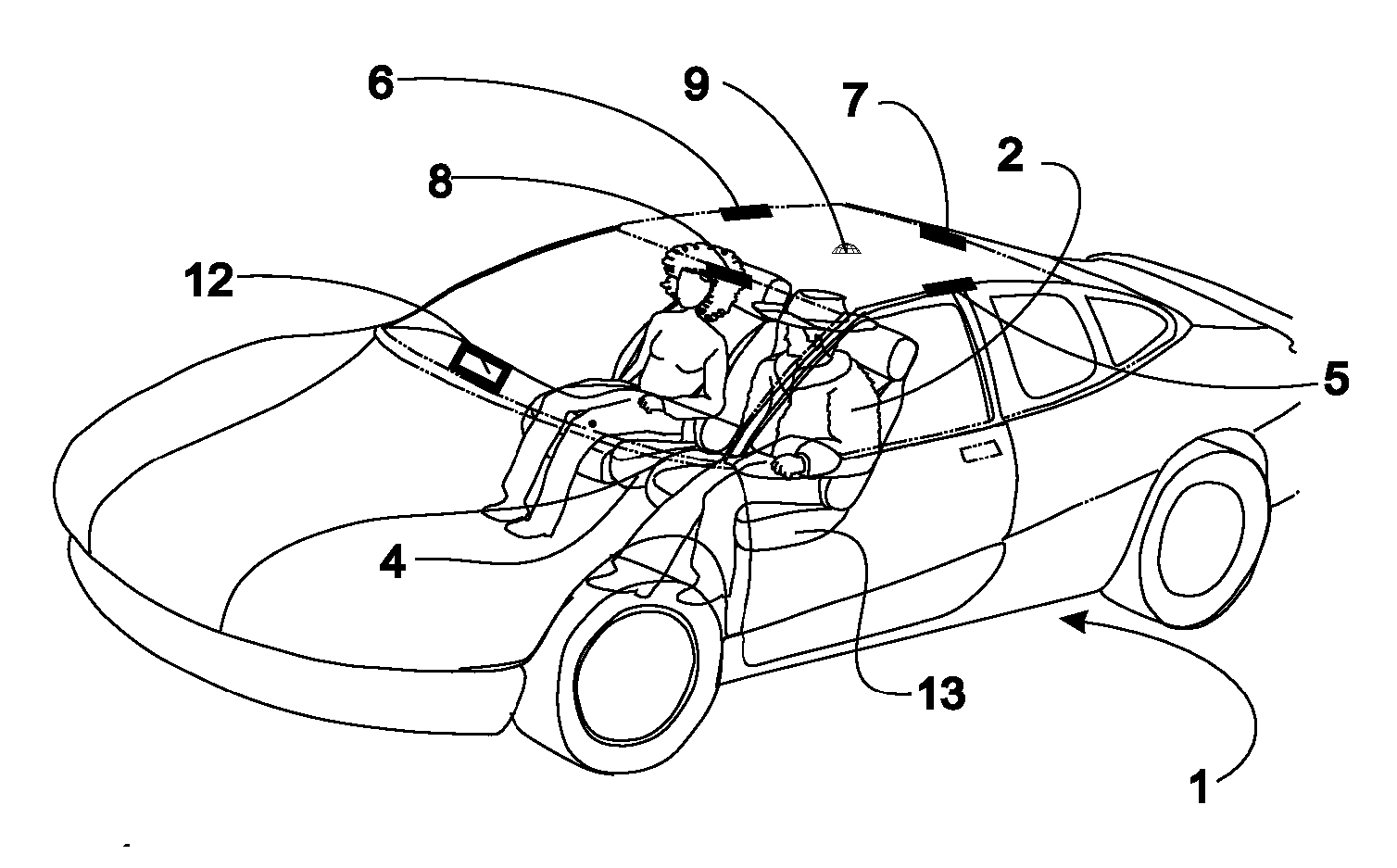
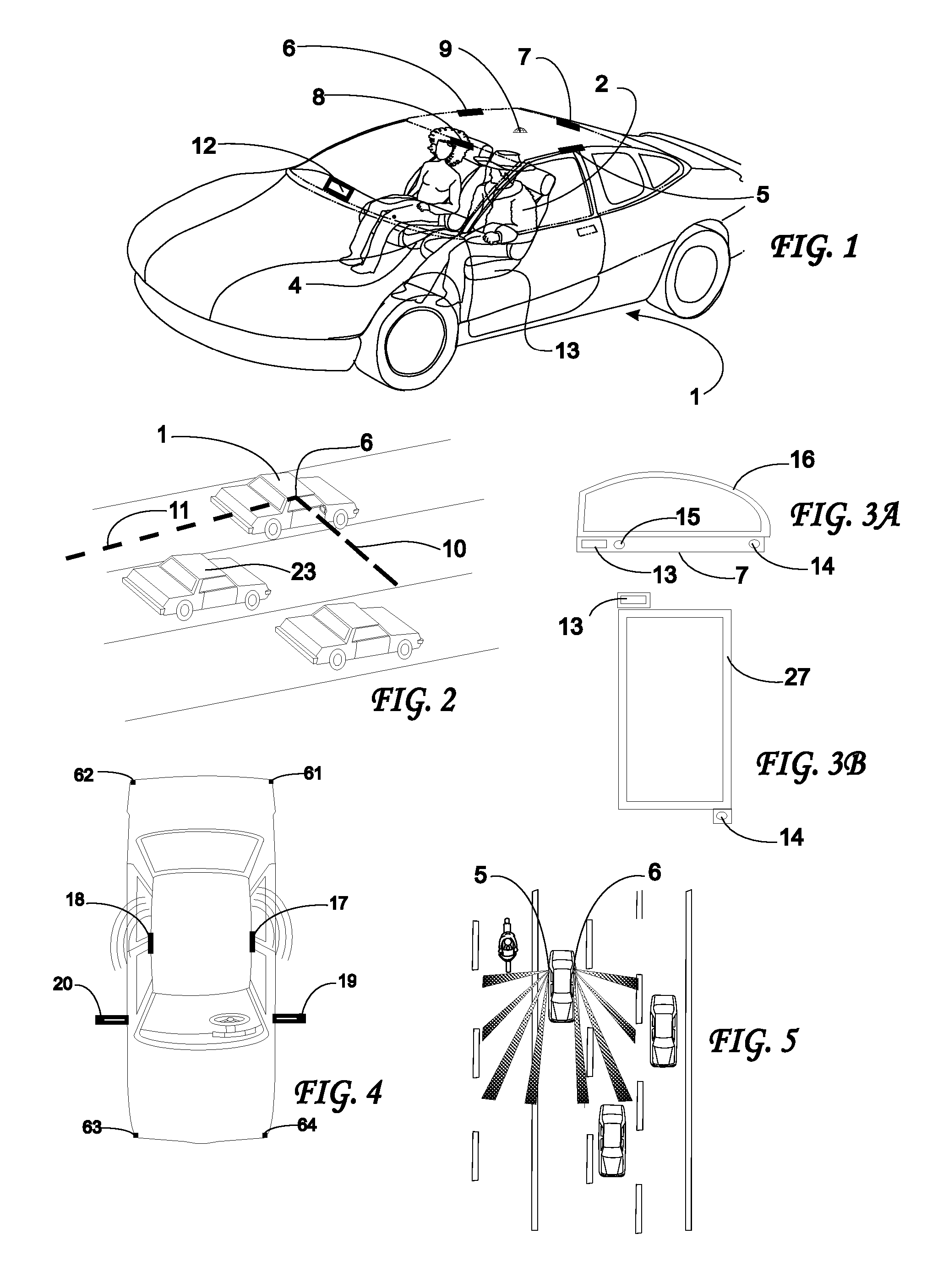
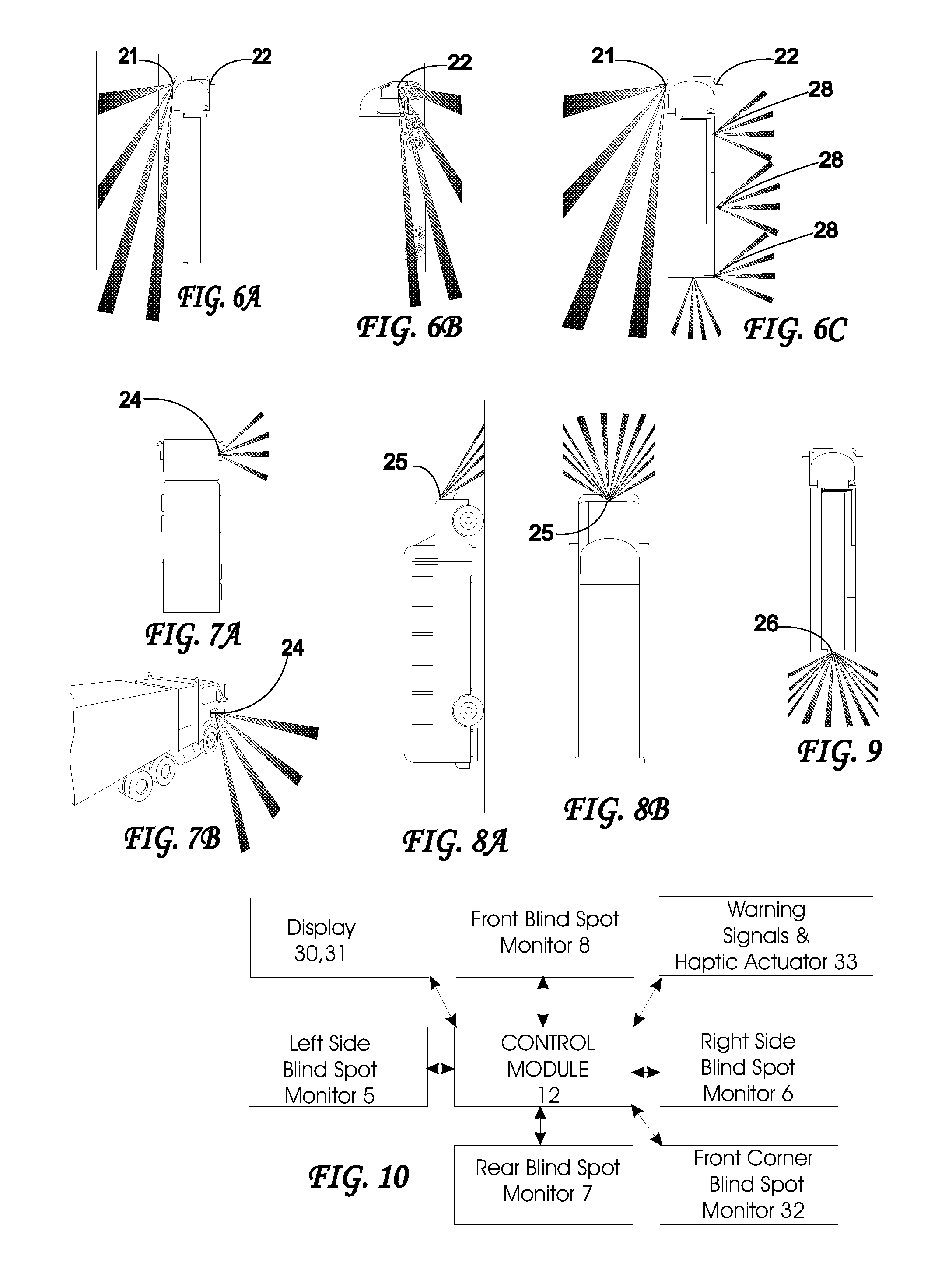
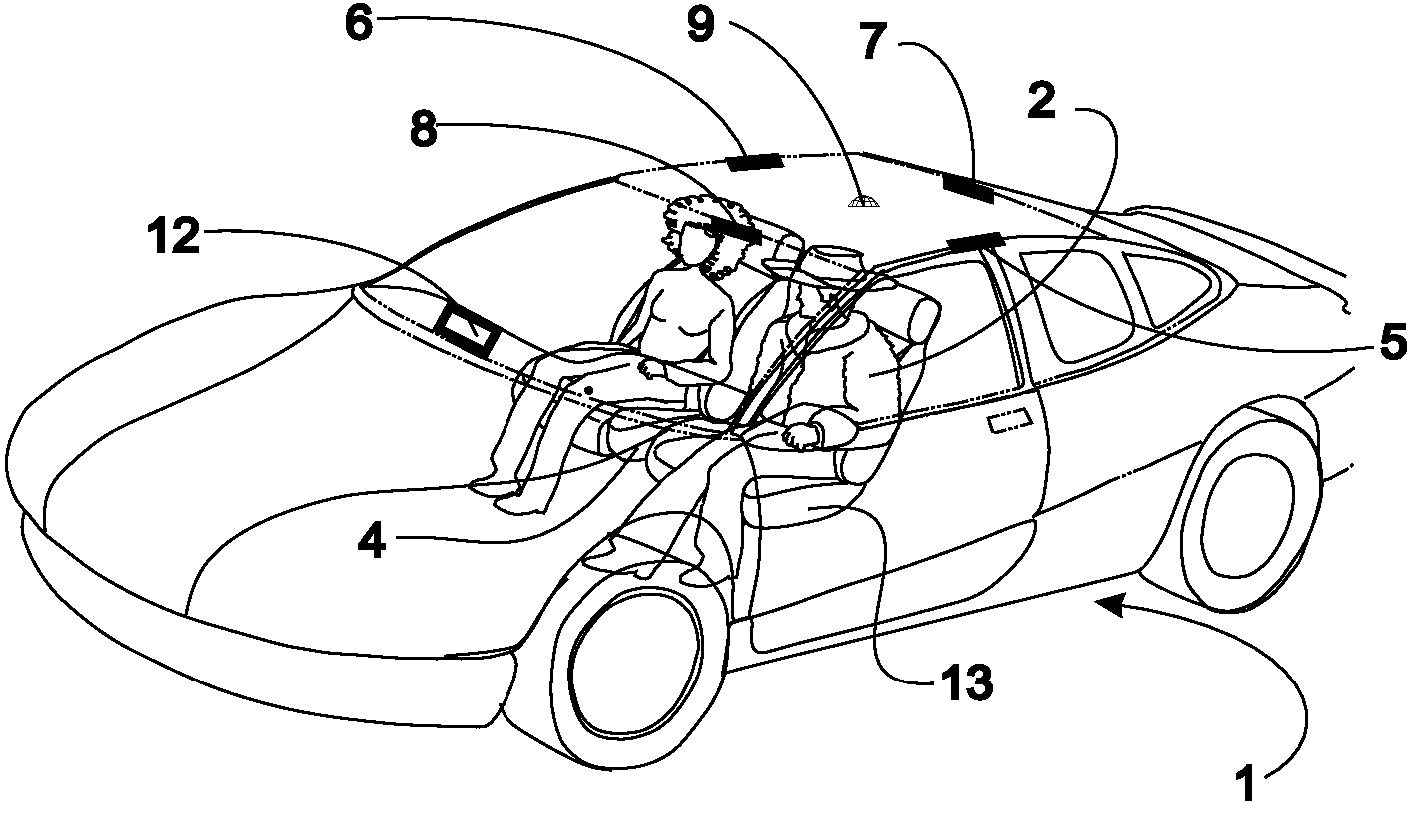
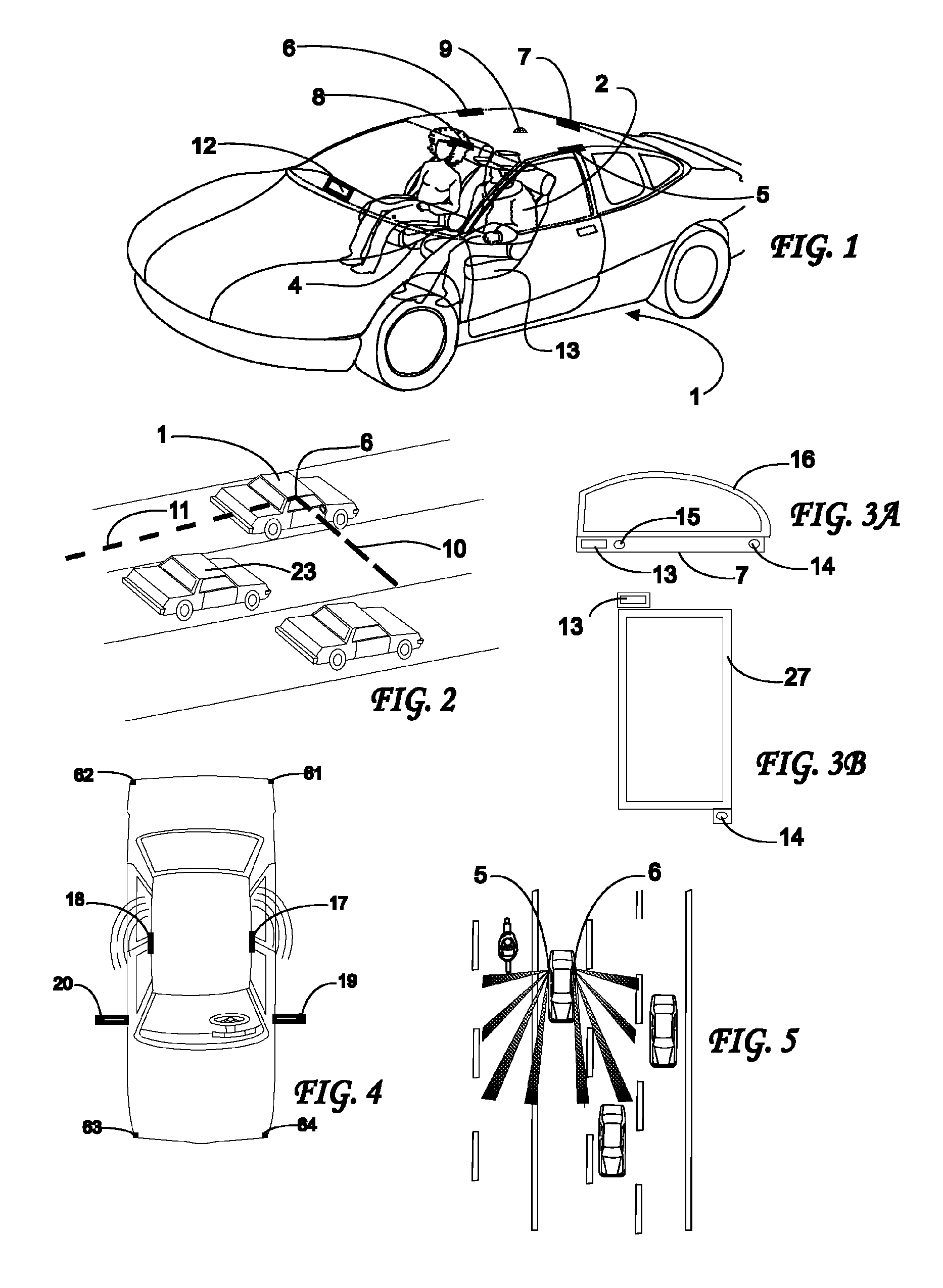
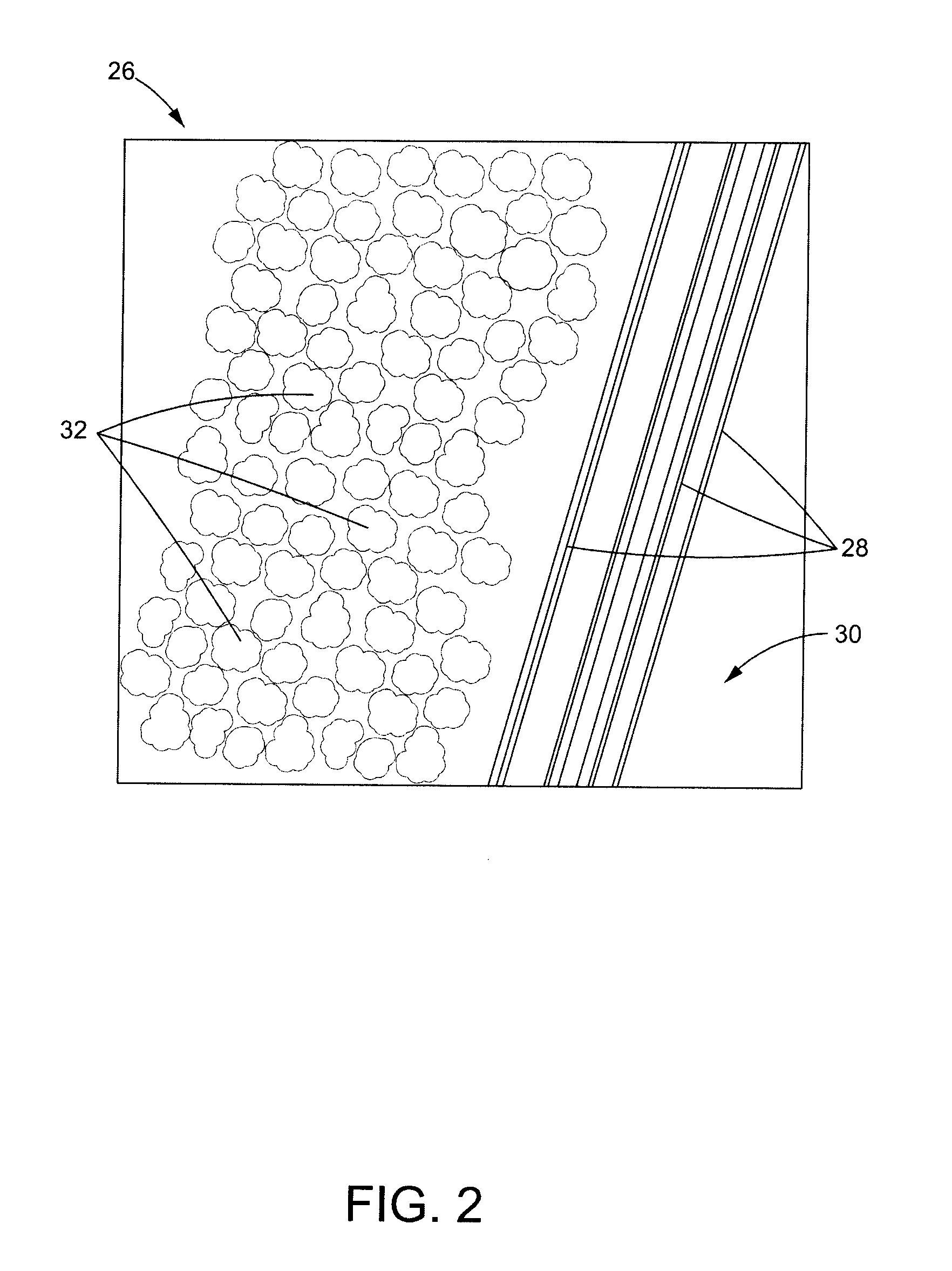
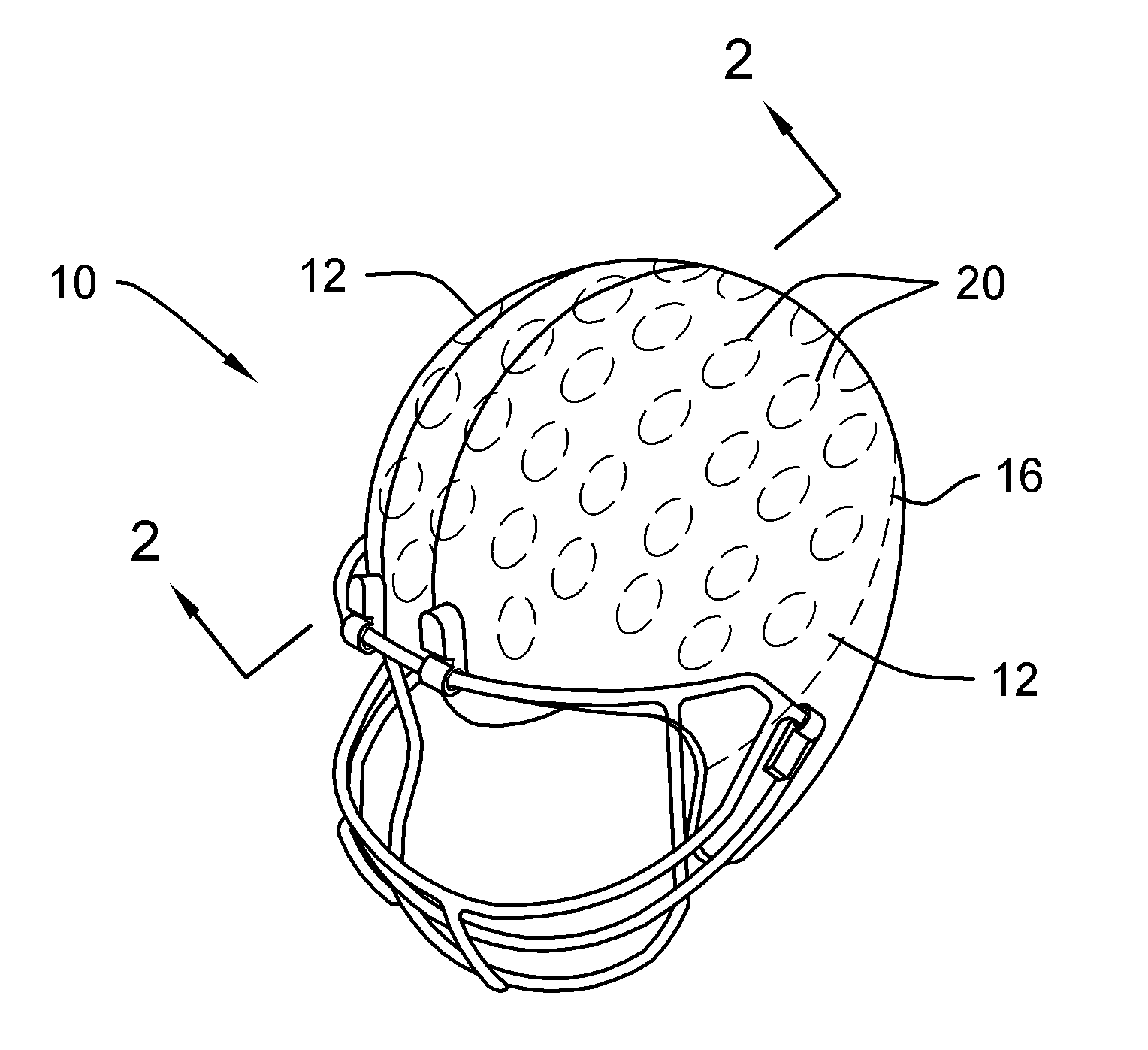
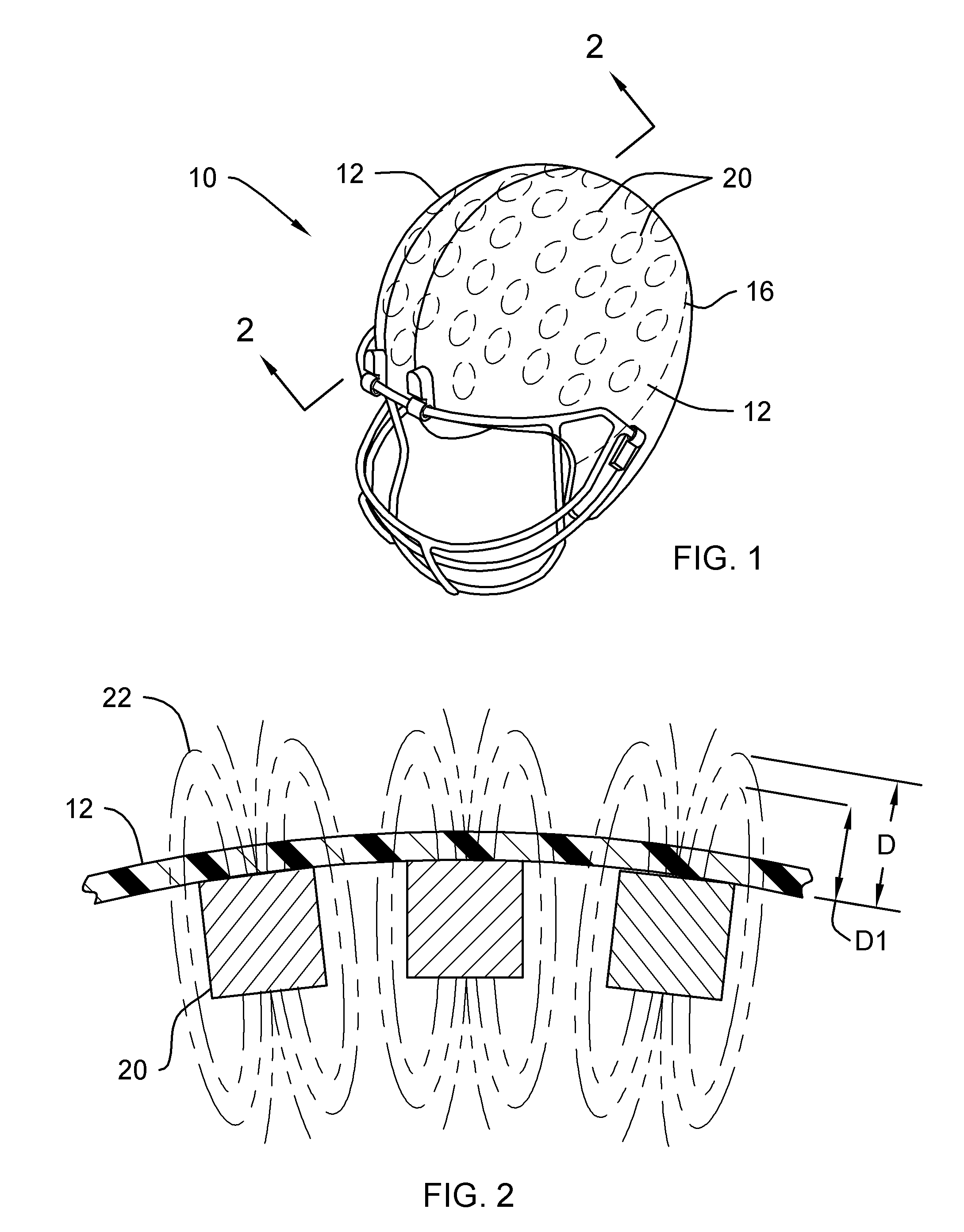
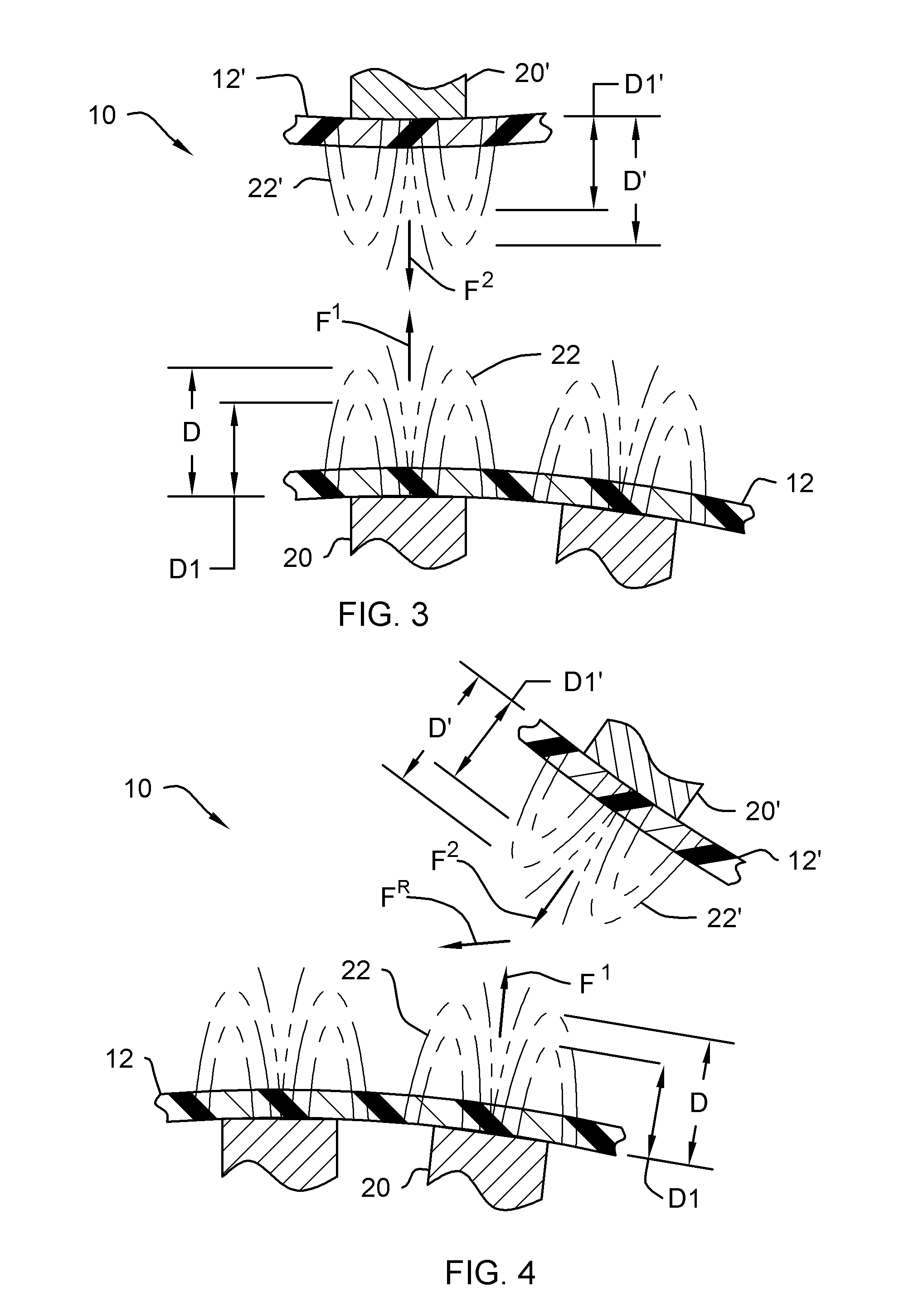
System and Method for Preventing Vehicular Accidents
InactiveUS20080040004A1Reduce the potential harmDigital data processing detailsAnti-collision systemsVehicular accidentEngineering
Vehicle including an anticipatory sensor system for determining that an impact involving the vehicle is about to occur unless a corrective action is taken based on data obtained prior to the impact and determining whether the potential impact requires activation of a reactive system which controls operation of the vehicle. The anticipatory sensor system includes a receiver for receiving waves or energy and a pattern recognition system for analyzing the received waves or energy, or data representative thereof, to determine that an impact is about to occur if corrective action is not taken and whether the potential impact requires activation of the reactive system. The pattern recognition system ascertains the identity of an object from which the waves or energy have been emitted, reflected or generated, so that the determination whether the impact requires activation of the reactive system is based on identification of the object.
Owner:AMERICAN VEHICULAR SCI
System and method for preventing vehicular accidents
InactiveUS7783403B2Reduce the potential harmDigital data processing detailsAnti-collision systemsVehicular accidentReactive system
Vehicle including an anticipatory sensor system for determining that an impact involving the vehicle is about to occur unless a corrective action is taken based on data obtained prior to the impact and determining whether the potential impact requires activation of a reactive system which controls operation of the vehicle. The anticipatory sensor system includes a receiver for receiving waves or energy and a pattern recognition system for analyzing the received waves or energy, or data representative thereof, to determine that an impact is about to occur if corrective action is not taken and whether the potential impact requires activation of the reactive system. The pattern recognition system ascertains the identity of an object from which the waves or energy have been emitted, reflected or generated, so that the determination whether the impact requires activation of the reactive system is based on identification of the object.
Owner:AMERICAN VEHICULAR SCI
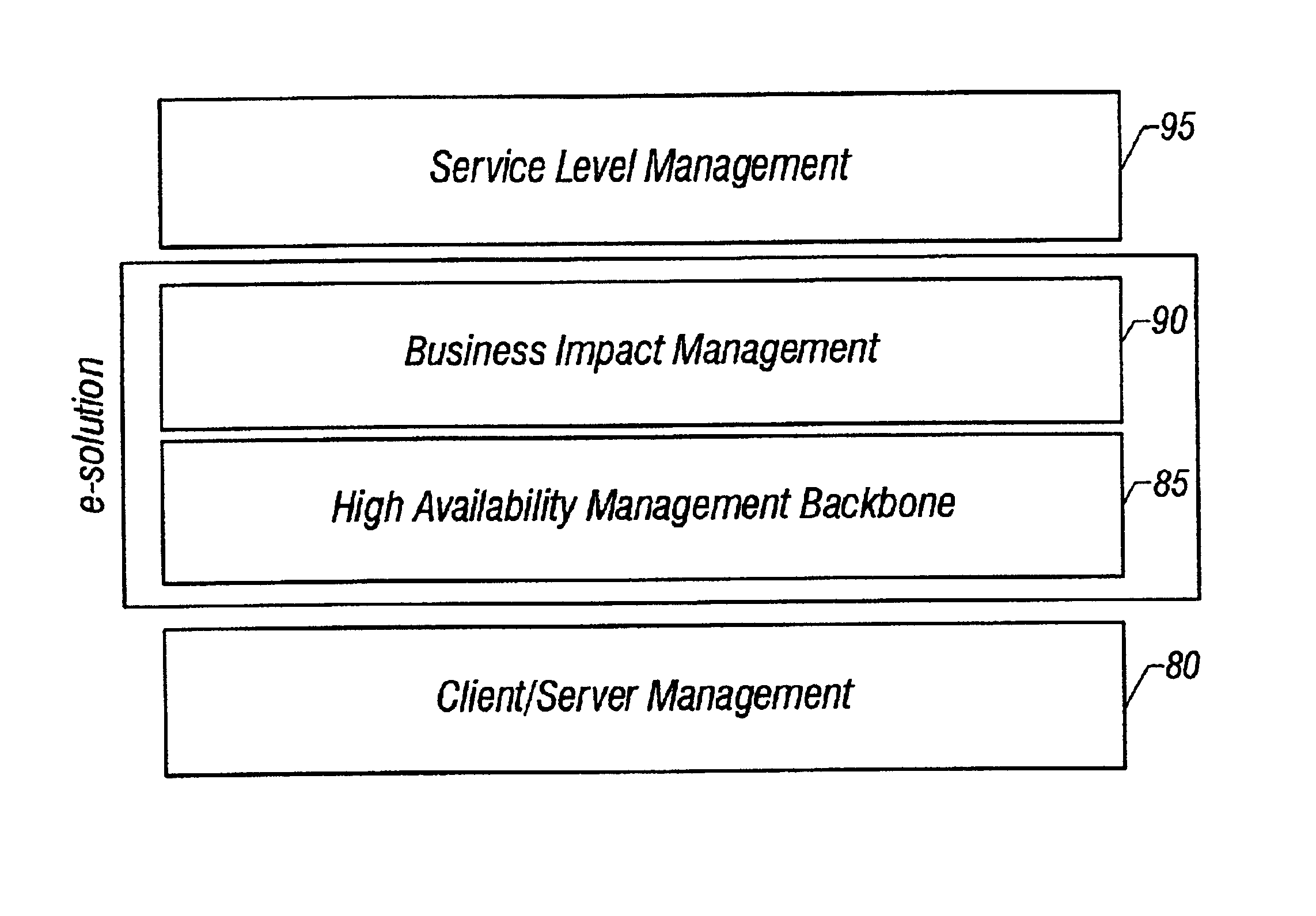
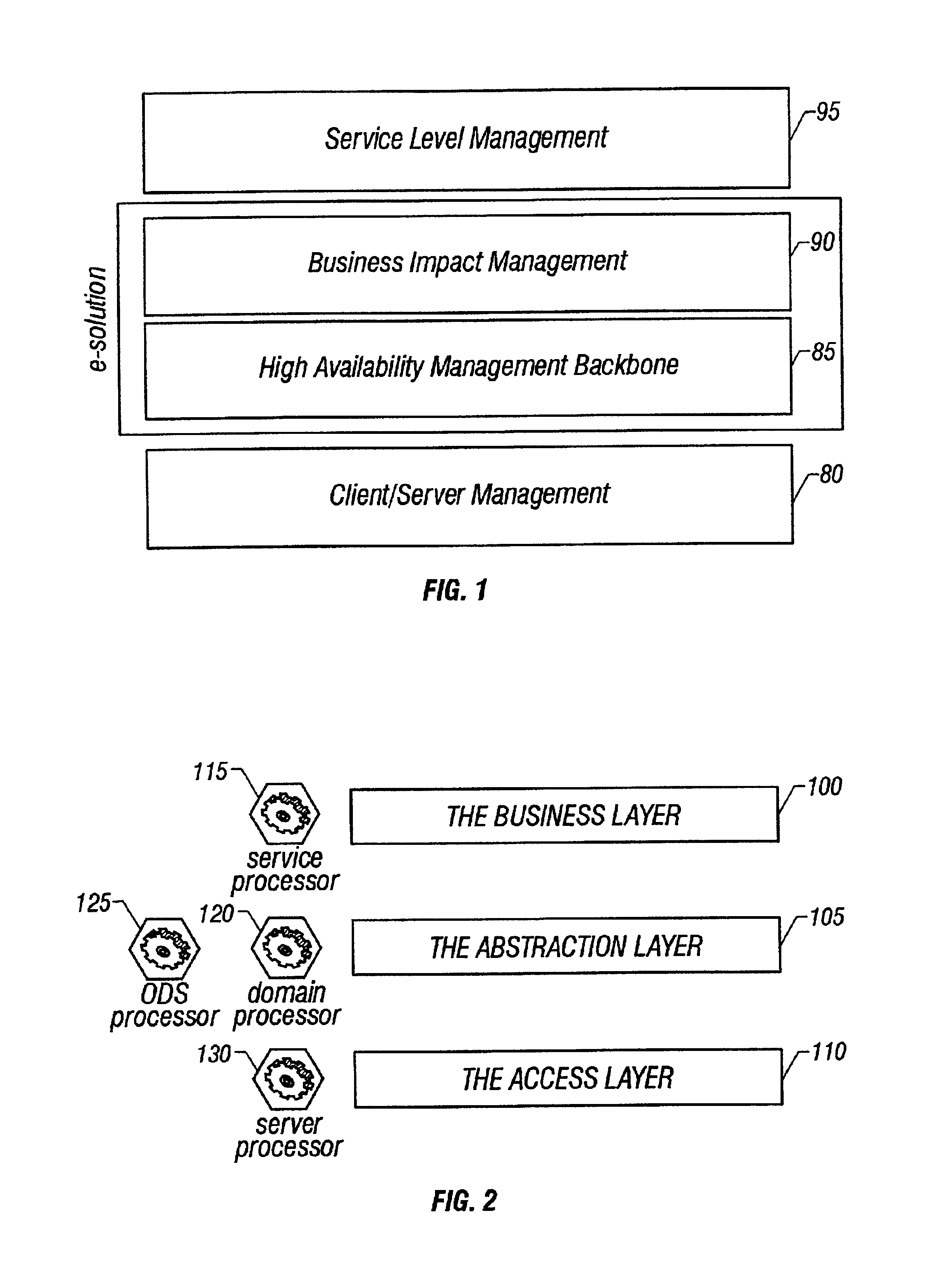
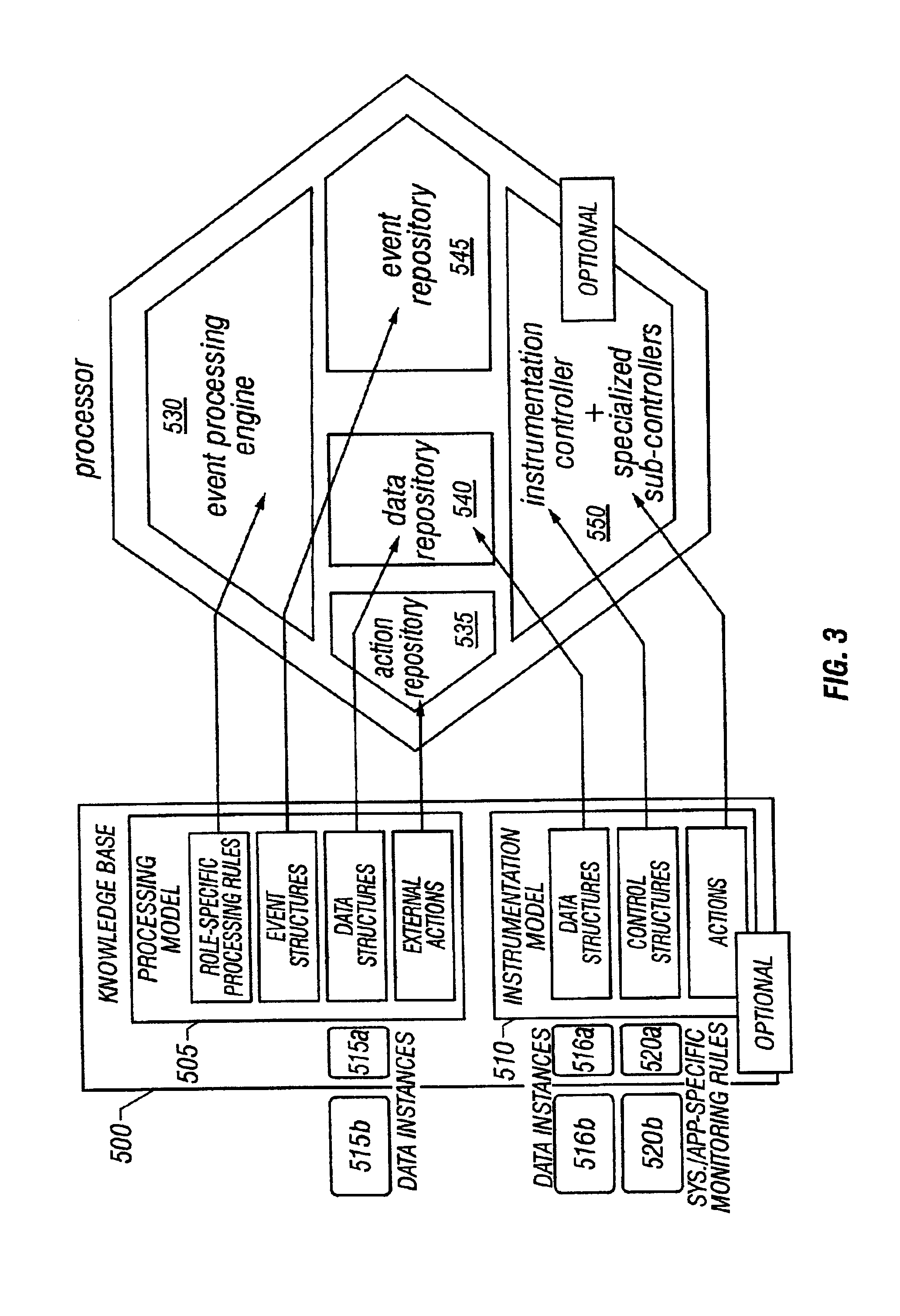
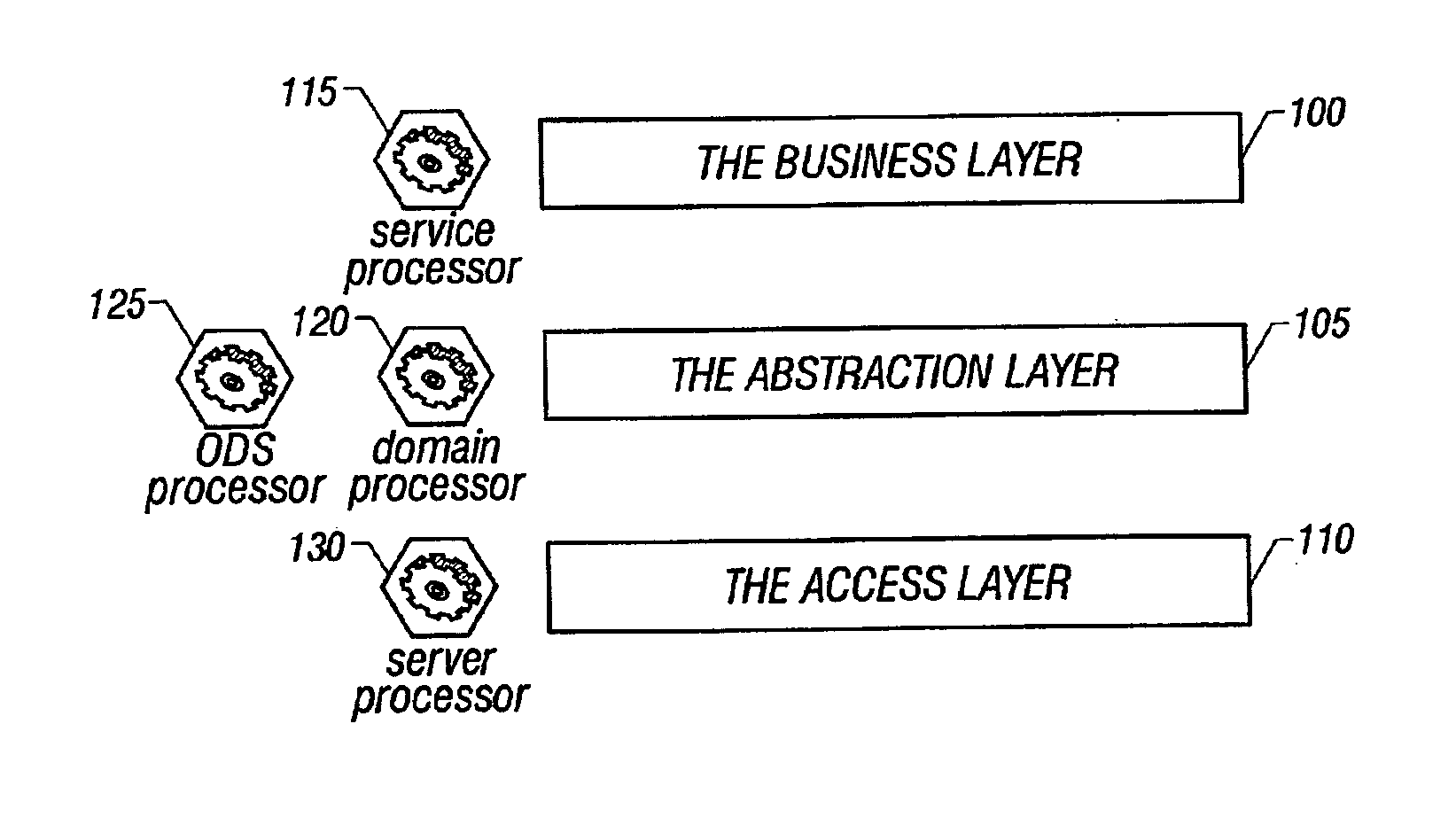
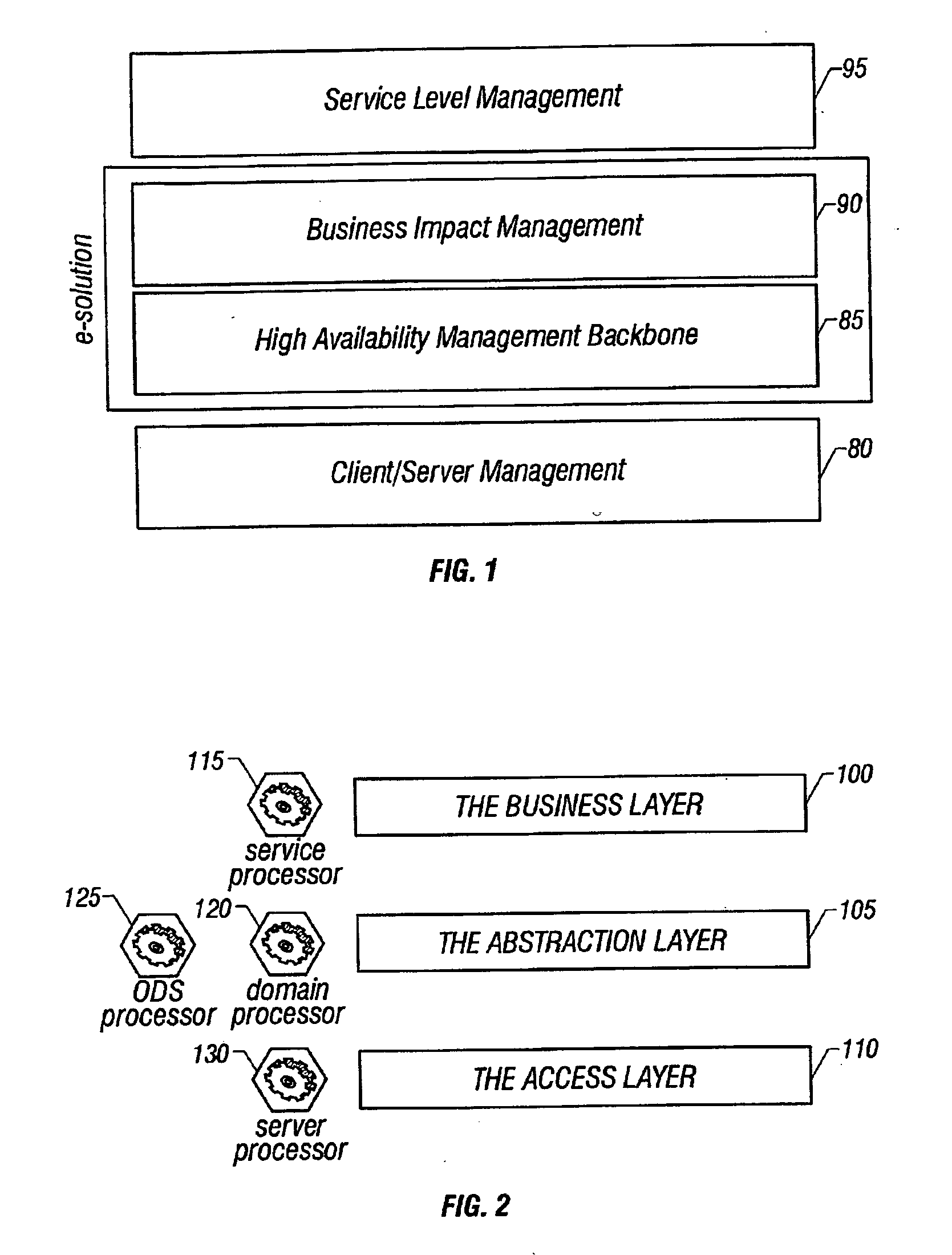
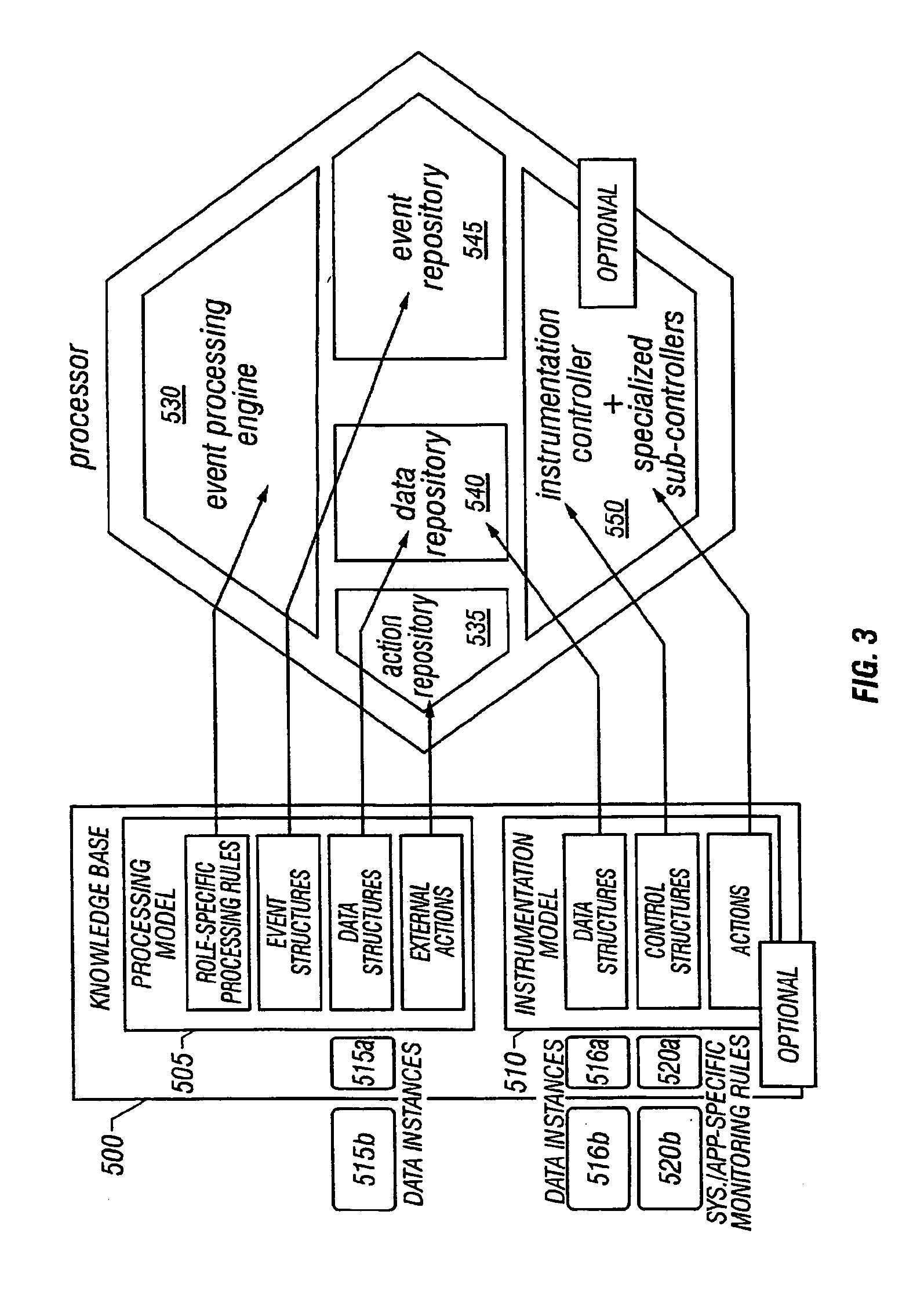
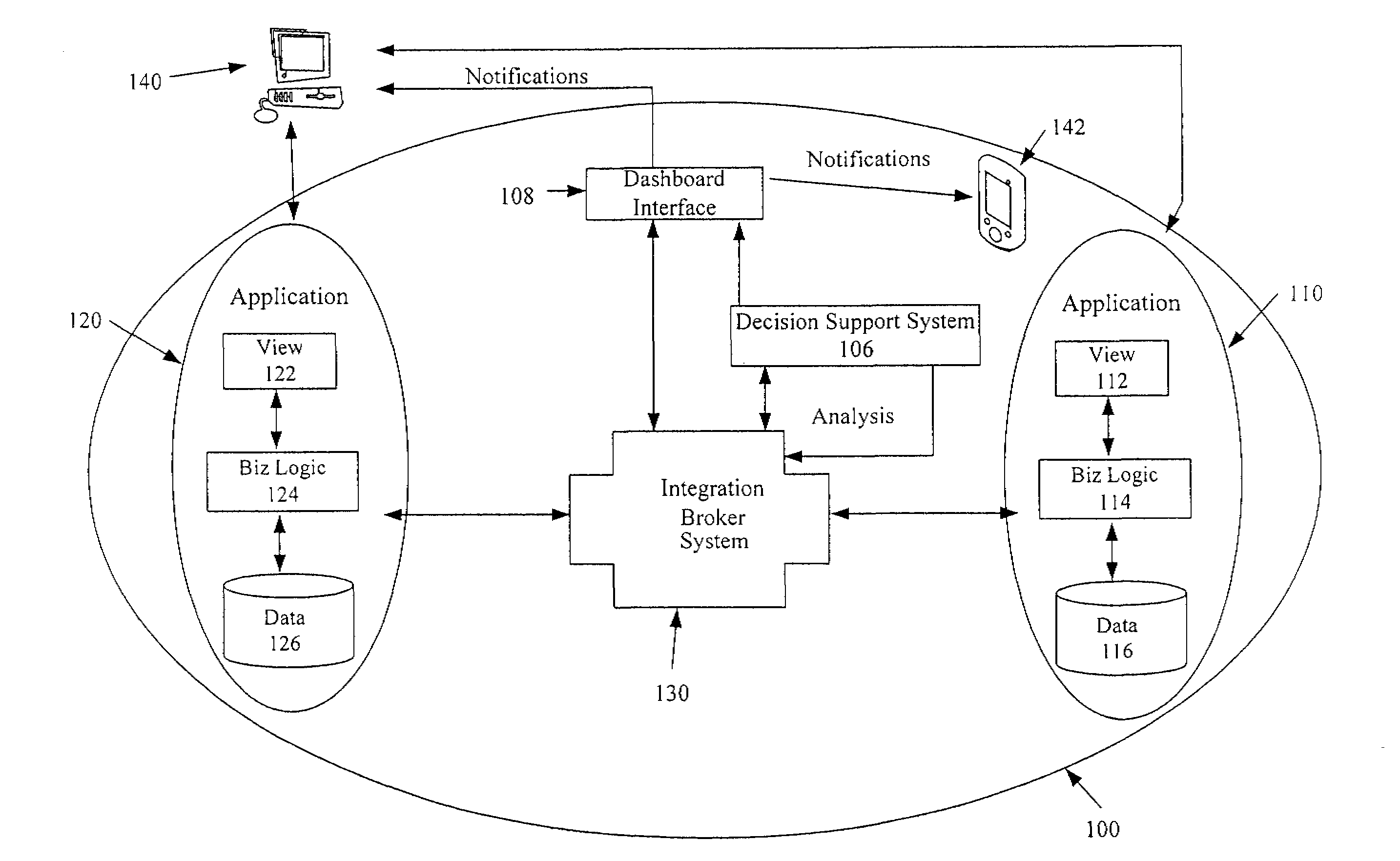
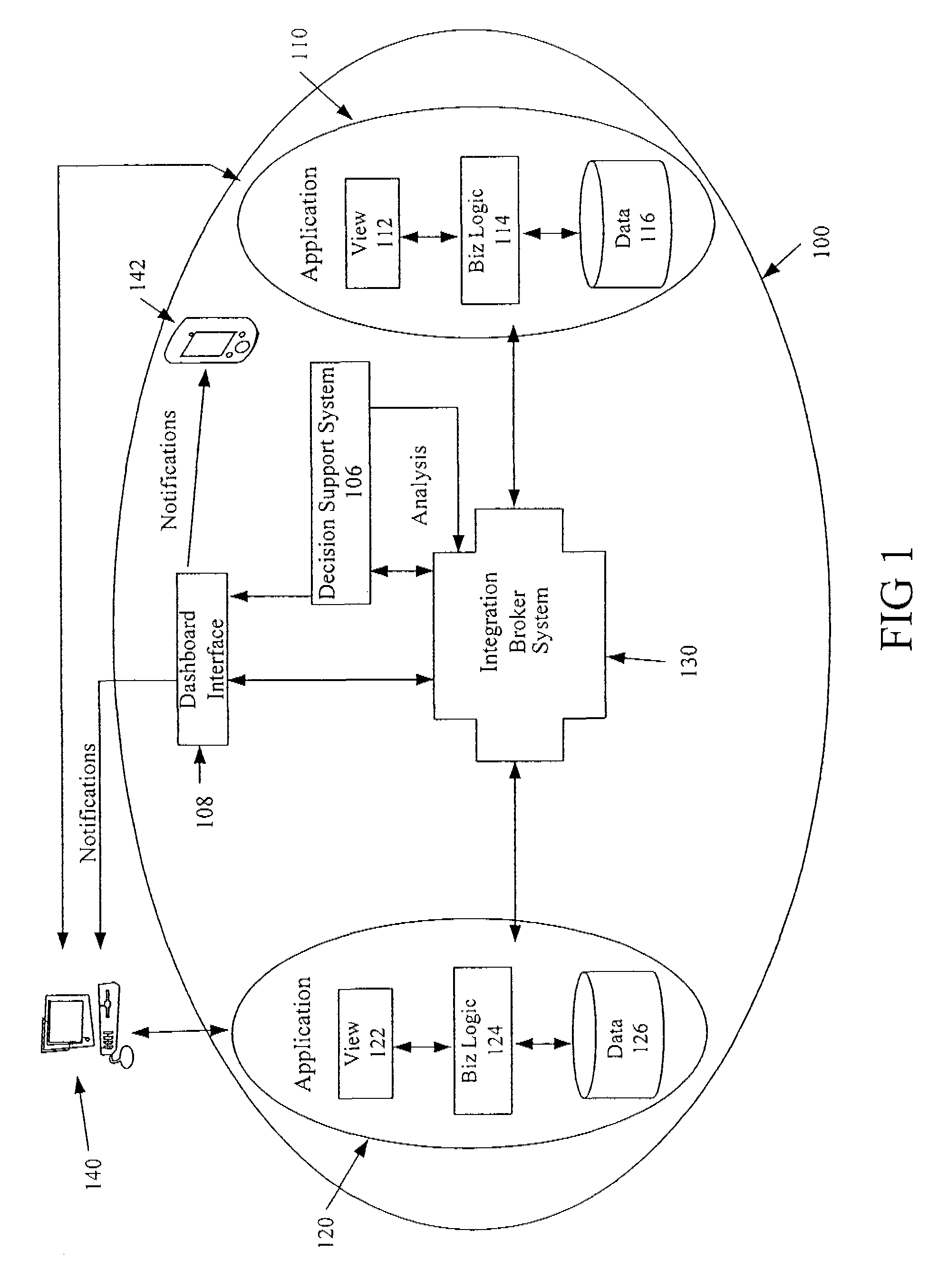
System and method of enterprise systems and business impact management
InactiveUS6983321B2Faster and accurate analysisAvoid lot of costDigital computer detailsPayment architectureBusiness managementPotential impact
A system architecture and a method for management using a cellular architecture to allow multi-tier management of events such as the managing of the actual impact or the potential impact of IT infrastructure situations on business services. A preferred embodiment includes a high availability management backbone to frame monitoring operations using a cross-domain model where IT Component events are abstracted into IT Aggregate events. By combining IT Aggregate events with transaction events, an operational representation of the business services is possible. Another feature is the ability to connect this information to dependent business user groups such as internal end-users or external customers for direct impact measurement. A web of peer-to-peer rule-based cellular event processors preferably using Dynamic Data Association constitutes management backbone crossed by event flows, the execution of rules, and distributed set of dynamic inter-related object data rooted in the top data instances featuring the business services.
Owner:BMC SOFTWARE
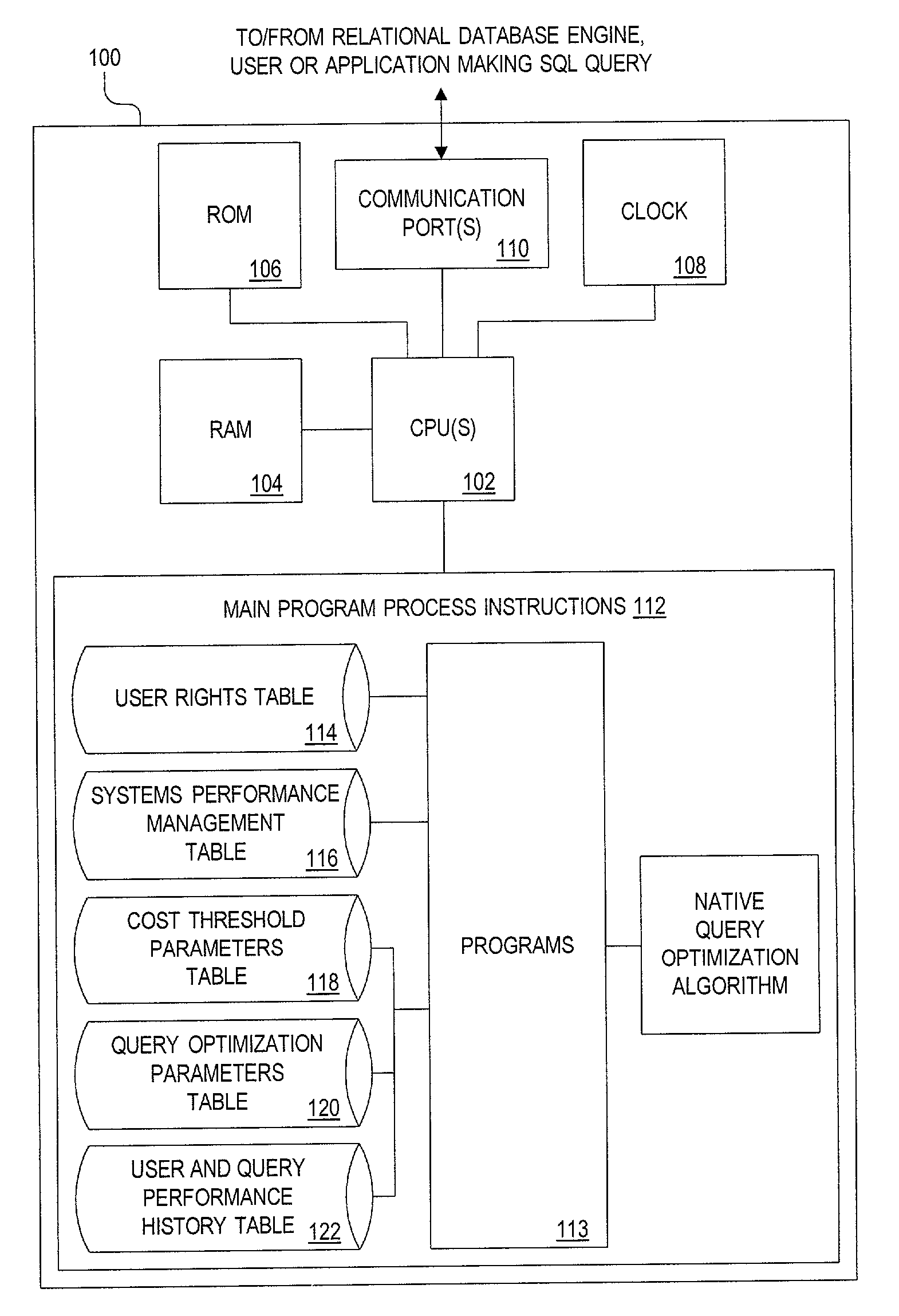
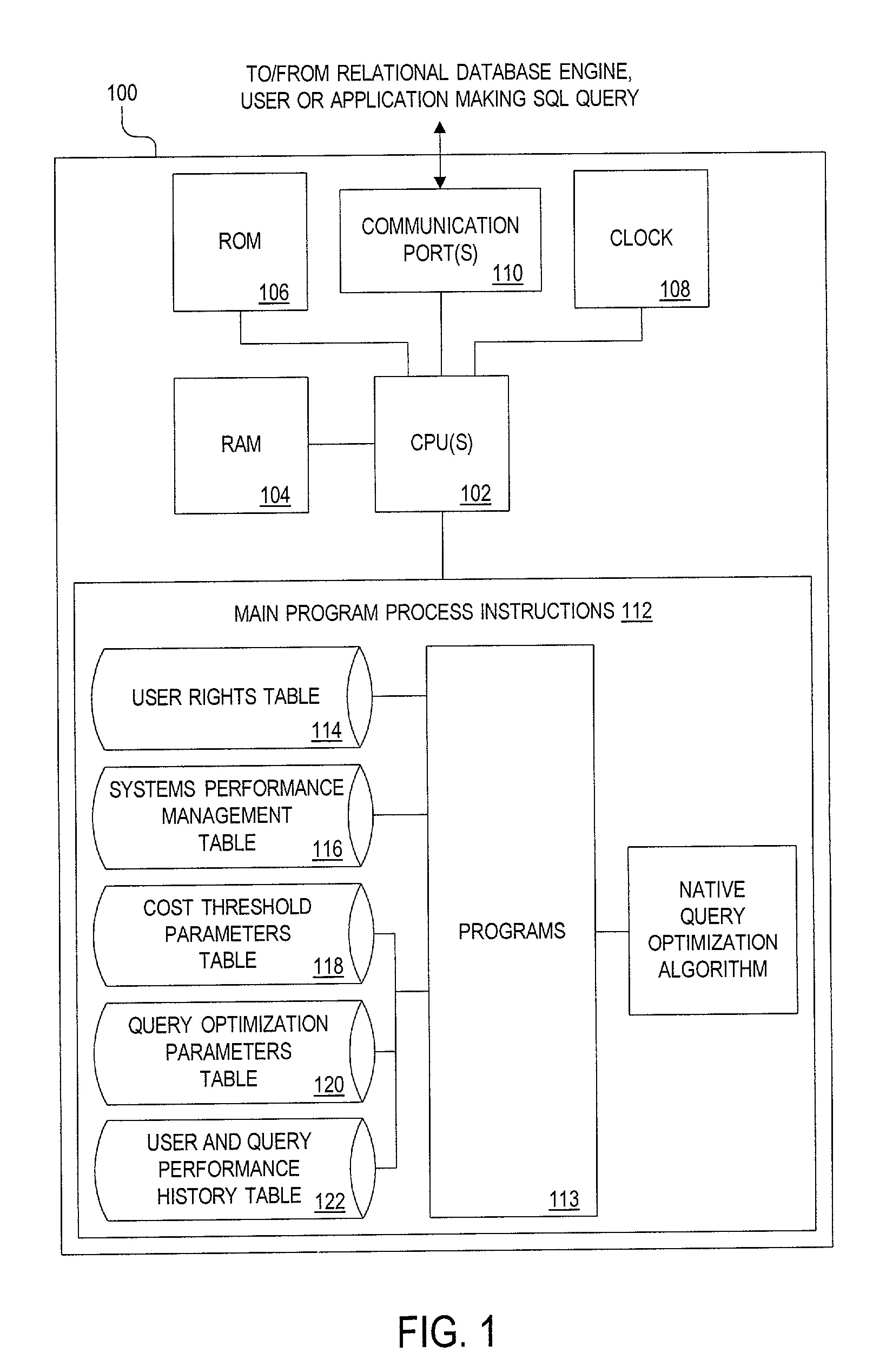
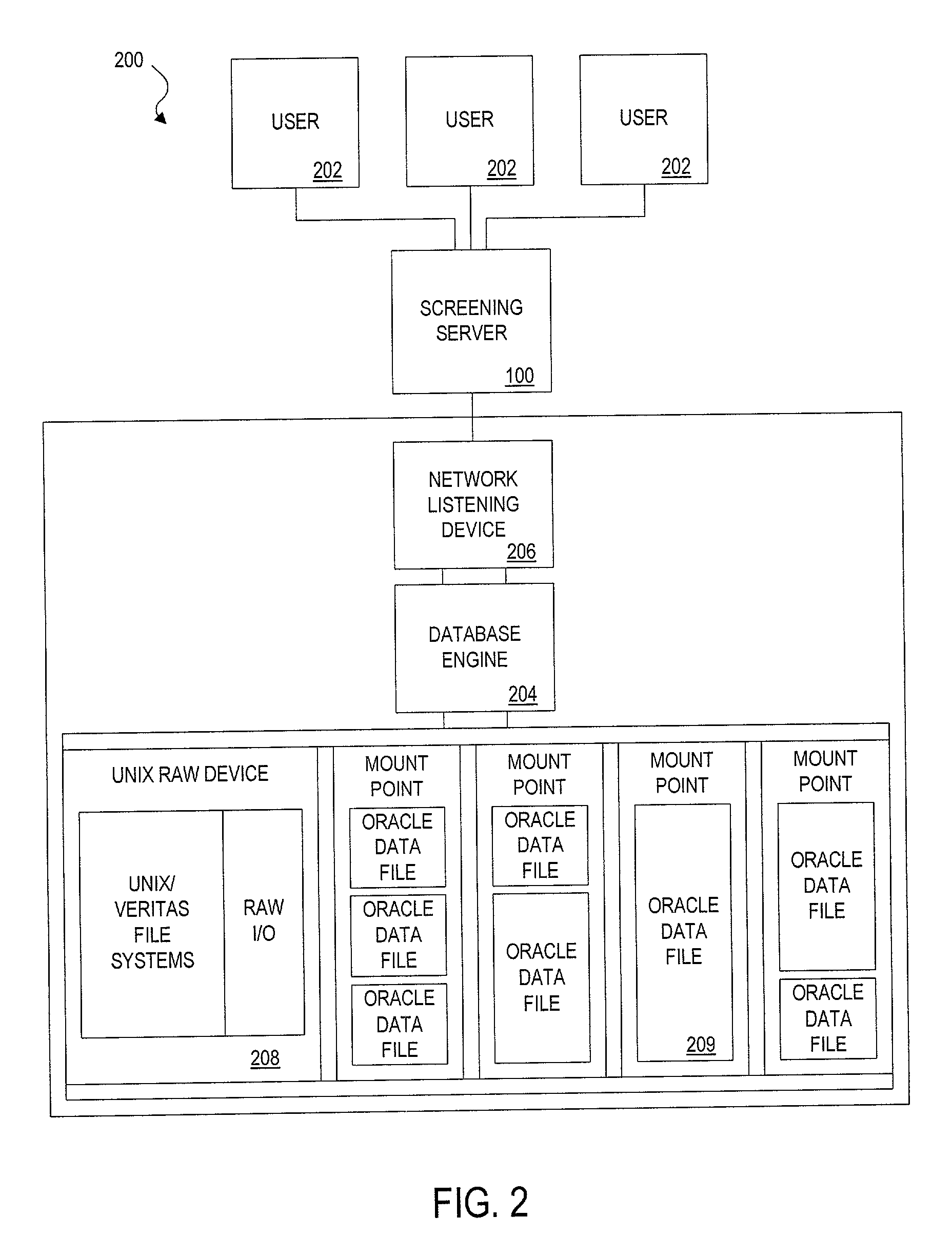
Method, apparatus and system for screening database queries prior to submission to a database
InactiveUS7058622B1Reduce the impactReduce impactData processing applicationsRelational databasesQuery optimizationOperability
To maintain the integrity and operability of enterprise database systems, queries intended for a particular database engine are intercepted, preferably by a separate processing system, prior to being acted upon by the database engine. The query is evaluated to determine its projected impact on available database system resources. The variables evaluated include user rights, administrator-imposed limits to searches, the amount of presently-available system resources, the cost of query and the like. If the query's potential impact does not surpass a predetermined threshold, it is submitted to the search engine. If the query is too resource-intensive or costly, the query may be (i) optimized by a query-optimization system, (ii) stored until more system resources are available, or (iii) rejected.
Owner:INTELLECTUAL VENTURES I LLC
Risk modeling system
InactiveUS20160379326A1Improve accuracyData processing applicationsTransmissionDashboardSocial media
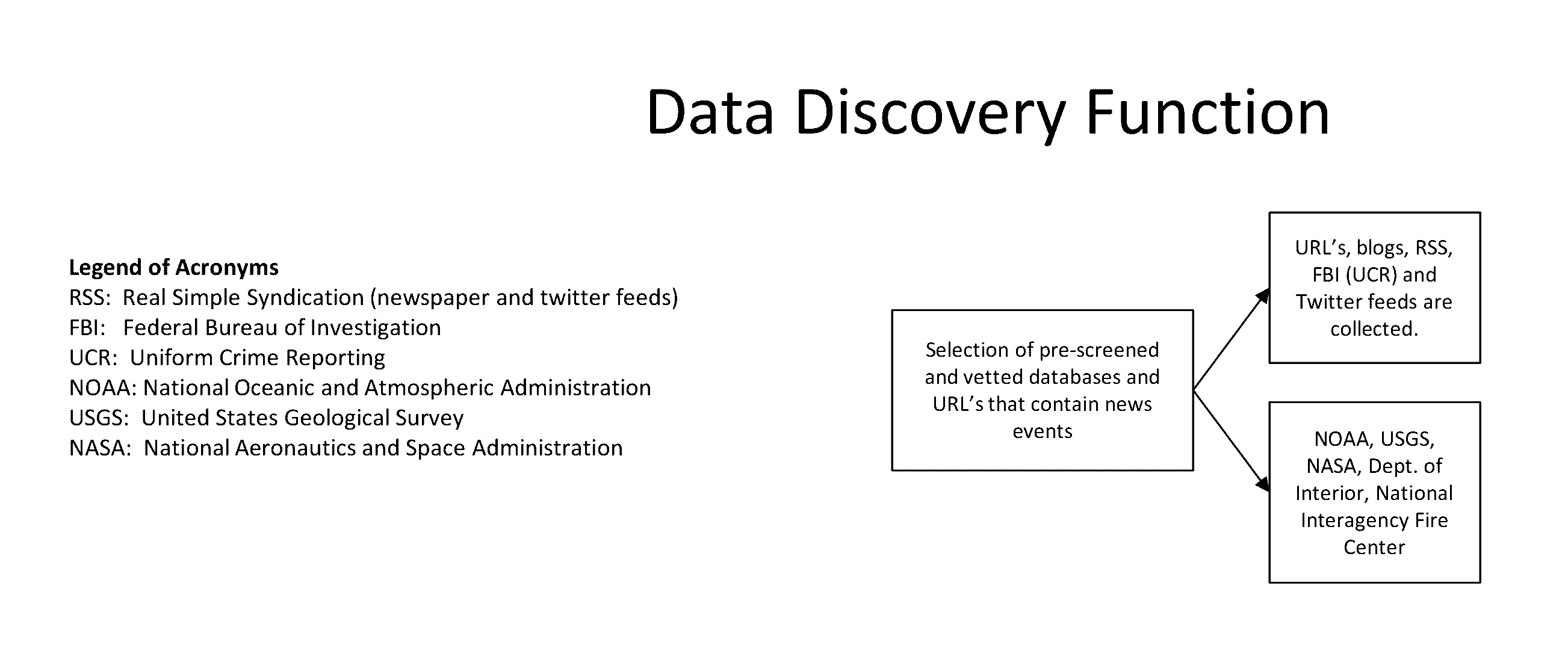
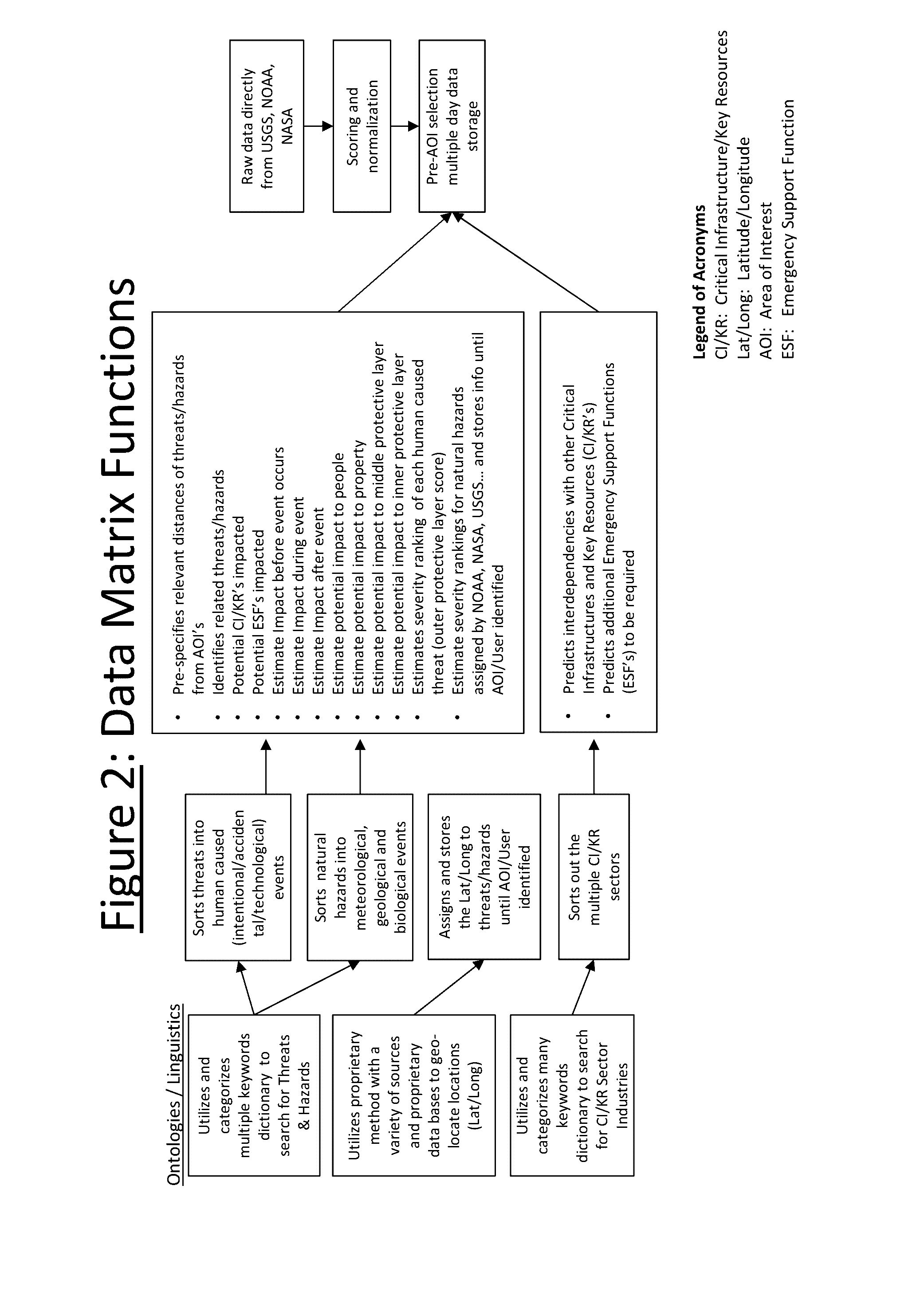
The system provides early warning intelligence feeds which analyze risks of potential human caused threats and naturally caused hazards. It includes data mining functions that autonomously search and categorize threats / hazards from worldwide open source data on a continuing basis. Data comes from many news feeds, social media feeds, government databases, etc. Key word analyses allow potential threats / hazards to be sorted into categories traditionally used by government agencies. Physical and cybersecurity vulnerabilities are analyzed and measured with threats to disclose potential impacts to people, properties, processes, special events, and related critical infrastructures and industries. Overall risk scores are instantly displayed as color coded icons on a worldwide electronic map / dashboard at any geolocation. Daily Intelligence reports and certain immediate alerts are also produced.
Owner:CHAN GOVE MARIE N +1
System and method for managing risk and opportunity
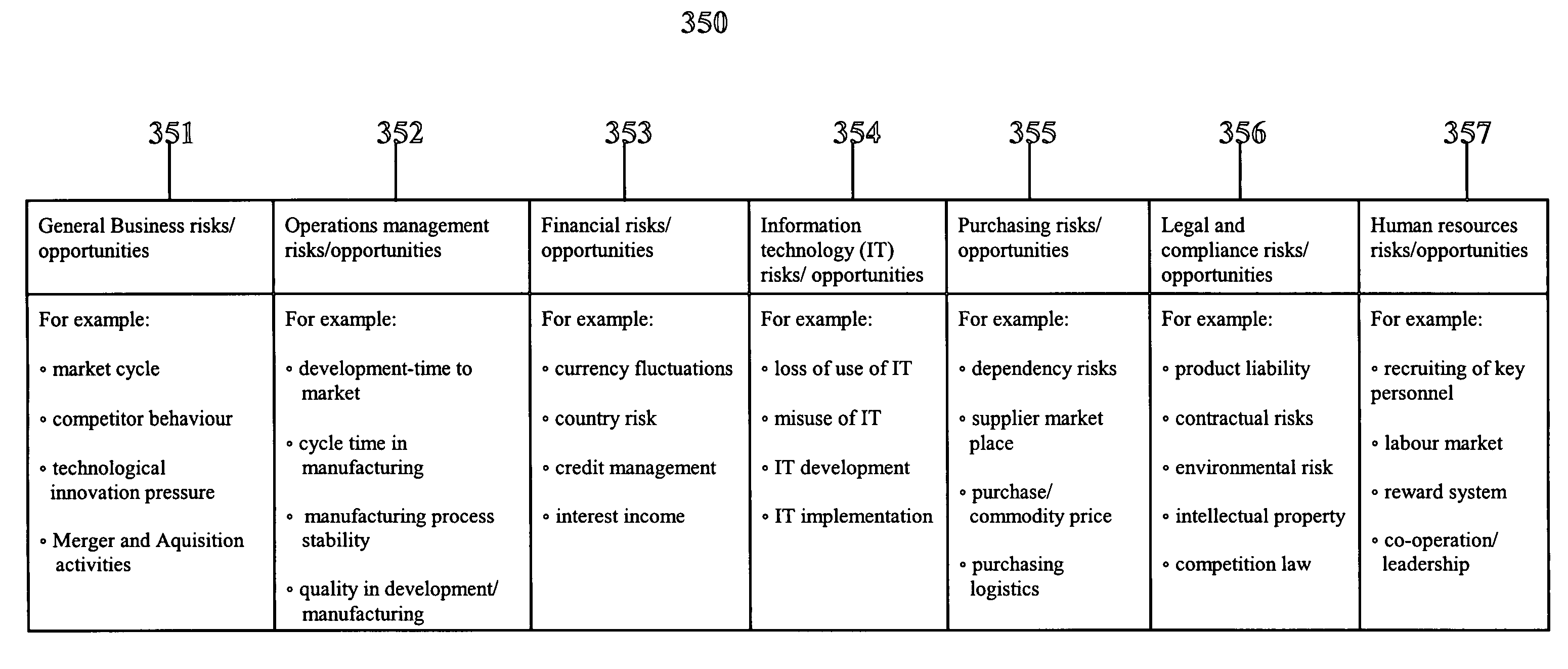
A method of projecting a future condition of a business entity by identifying a plurality of risks and a plurality of opportunities for the business entity and evaluating at predetermined times a potential impact of each of the risks and each of the opportunities on the future condition of the business entity. Determining at each of the predetermined times for each of the risks one of a probability that the risk will come to pass during a predetermined period of time and a frequency at which the risk will come to pass and determining at each of the predetermined times for each of the opportunities one of a probability that the opportunity will become available to the business entity during a predetermined period of time and a frequency at which the opportunity will become available to the business entity. Projecting at each of the predetermined times the future condition of the business entity based on the potential impact of each of the risks and opportunities and based on the determinations with respect to the one of frequency and probability for each of the risks and opportunities.
Owner:SIEMENS AG +1
Compliance workbench
An audit system formally communicates the results of an audit to company officers. The audit system allows company officers to review the audit information in detail to identify specific risks, their associated financial controls, and the potentially impacted financial accounts. The audit system displays a summary of audit results identifying specific financial items, risks, business processes, and organizations that fail to meet audit requirements. The audit system can also summarize audit results by their associated financial items, enabling company officers to see the potential impact of audit results on specific financial items. Similarly, the audit system can summarize audit results by their associated organizations, enabling company officers to see the source of audit shortcomings. If a company officer decides to certify the audit results, the audit system documents the company officers' approval. The audit system can receive an electronic signature to record the company officer's certification of audit results.
Owner:ORACLE INT CORP
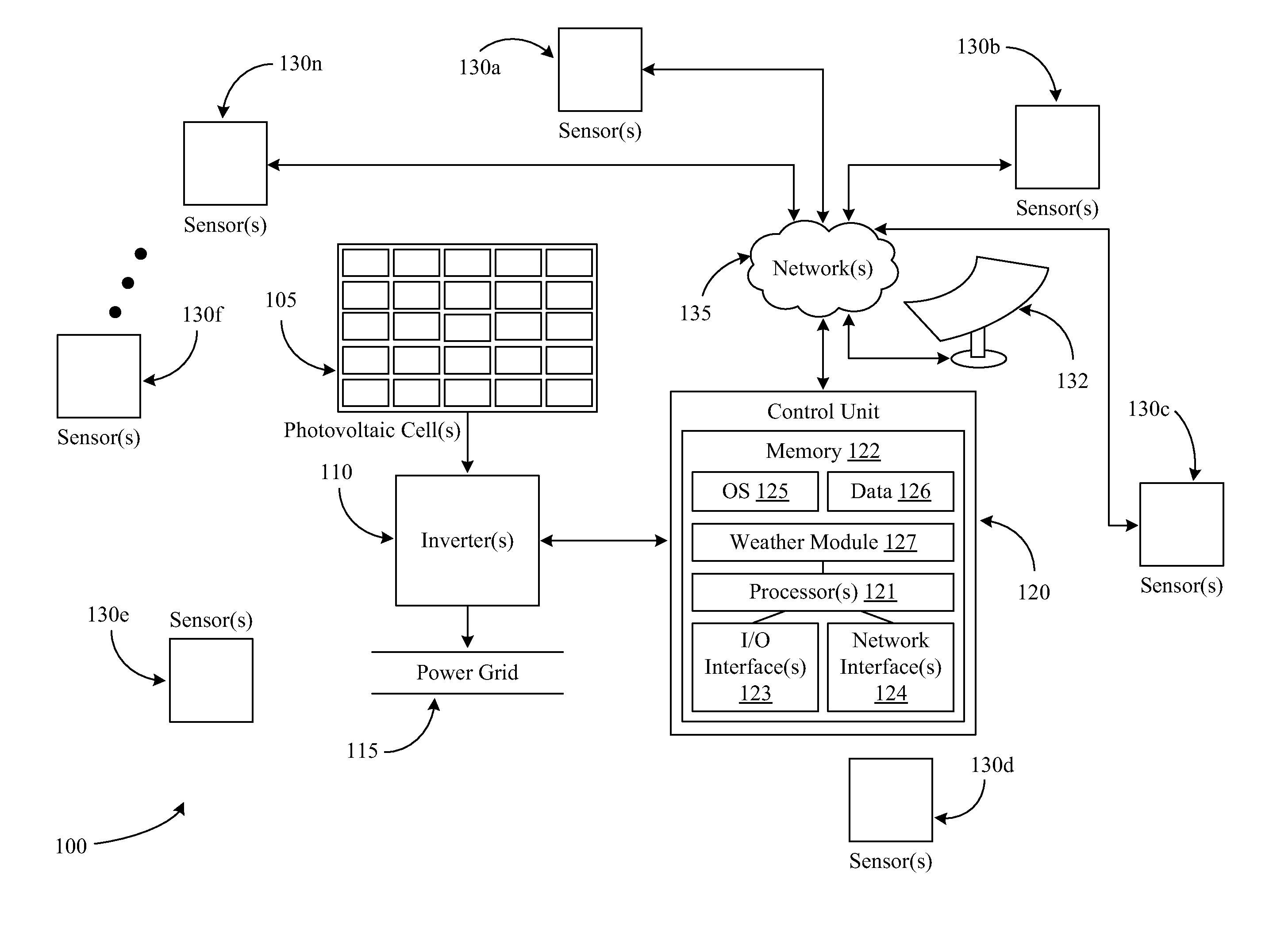
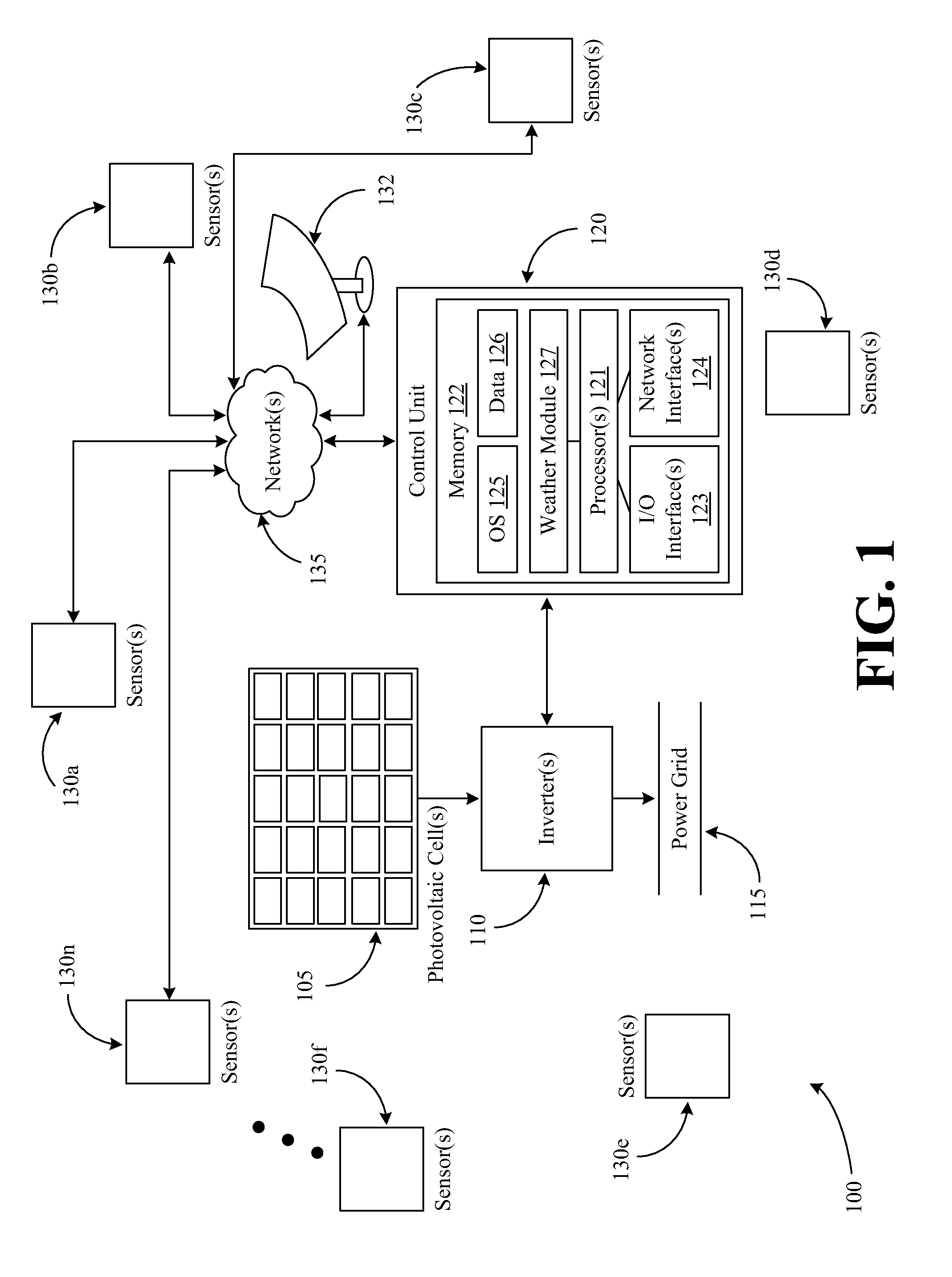
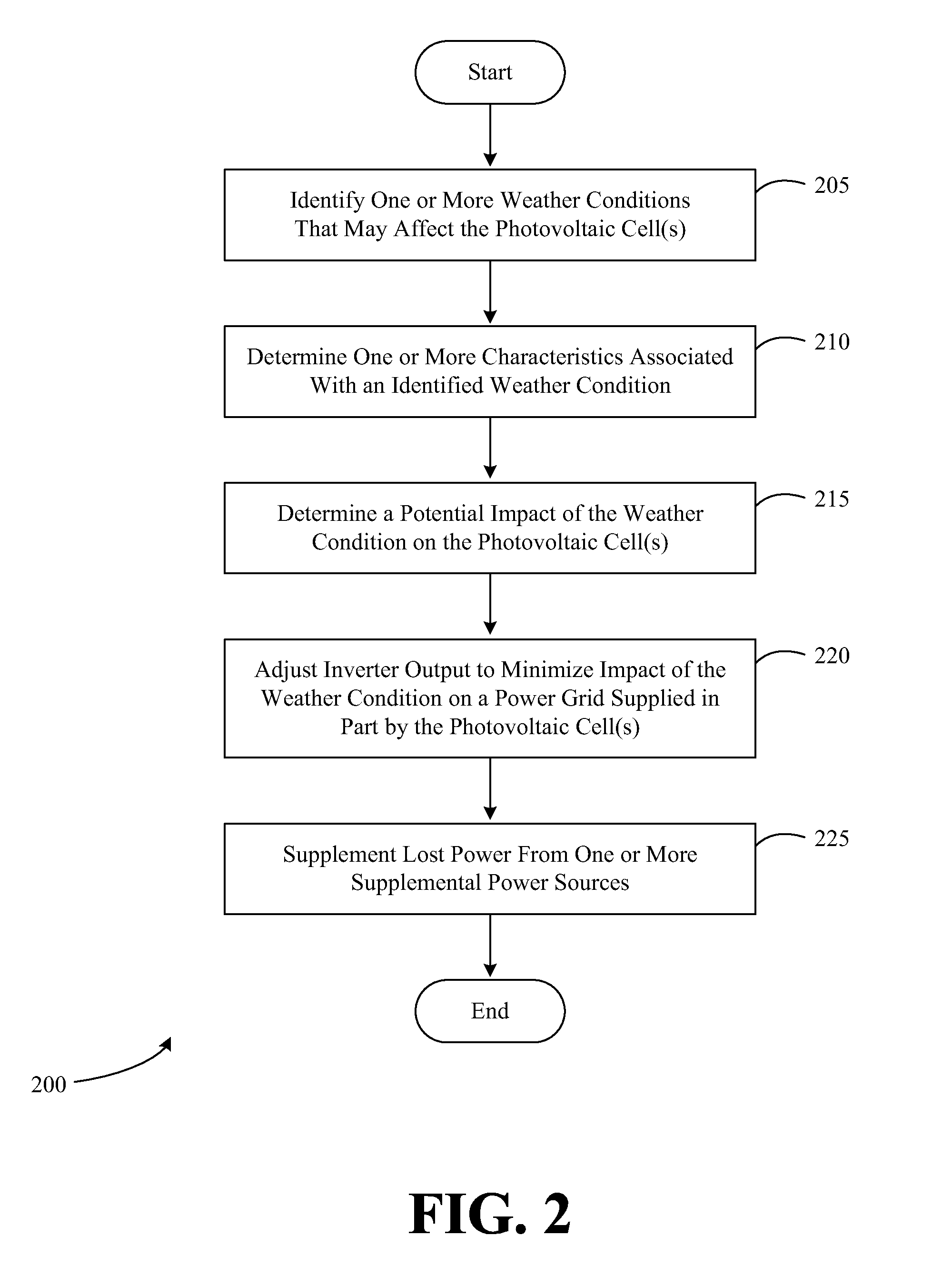
Systems and methods for interfacing renewable power sources to a power grid
Systems and methods for interfacing renewable power sources to a power grid are provided. In certain systems and methods, at least one weather condition that may affect the power output of a renewable power source is identified. A potential impact of the identified at least one weather condition on the renewable power source is determined. Historical data associated with the impact of at least one prior weather condition on the renewable power source is accessed. An output of the renewable power source that is supplied to the power grid is adjusted based at least in part on the determined potential impact and the historical data.
Owner:GENERAL ELECTRIC CO
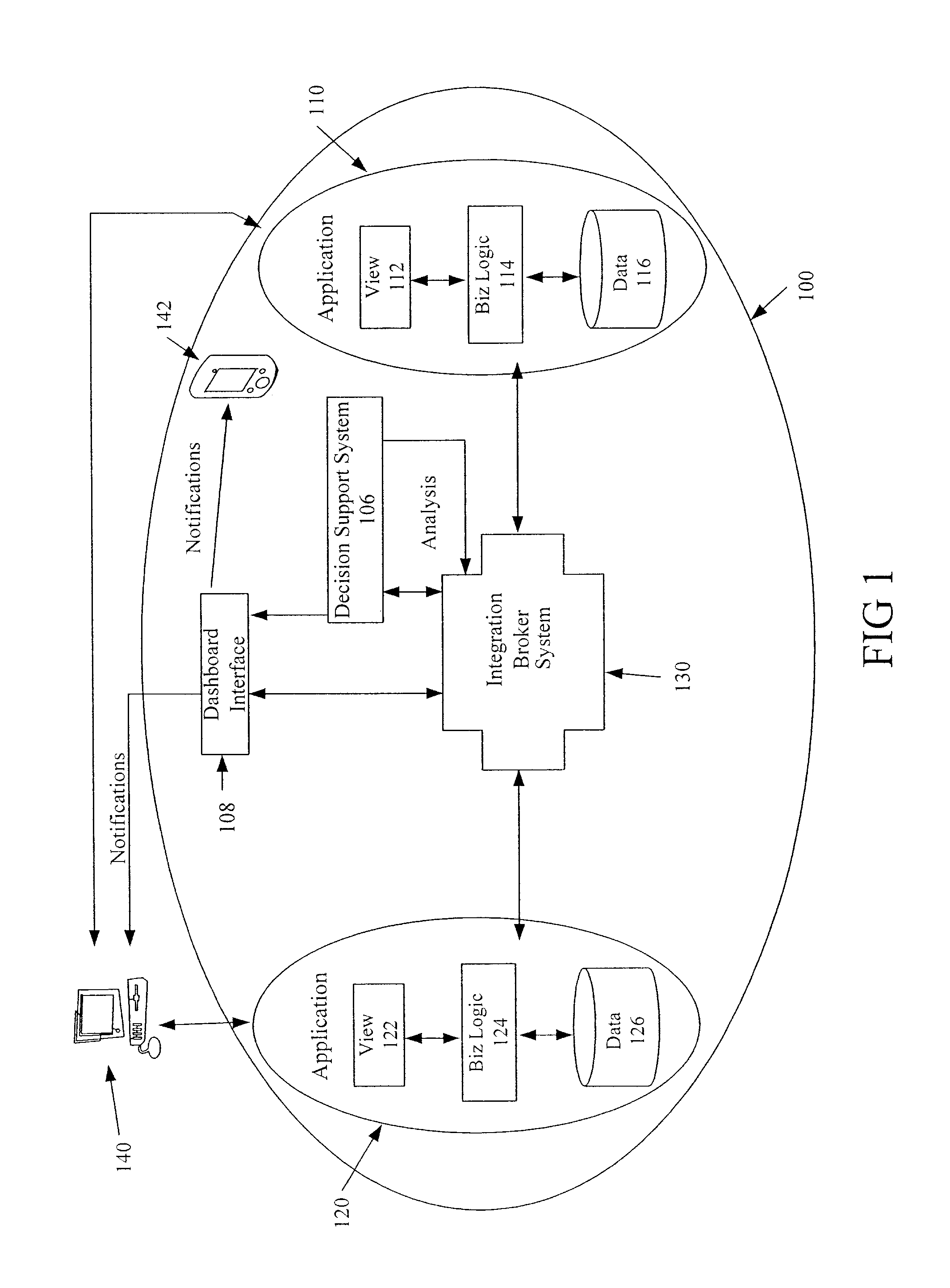
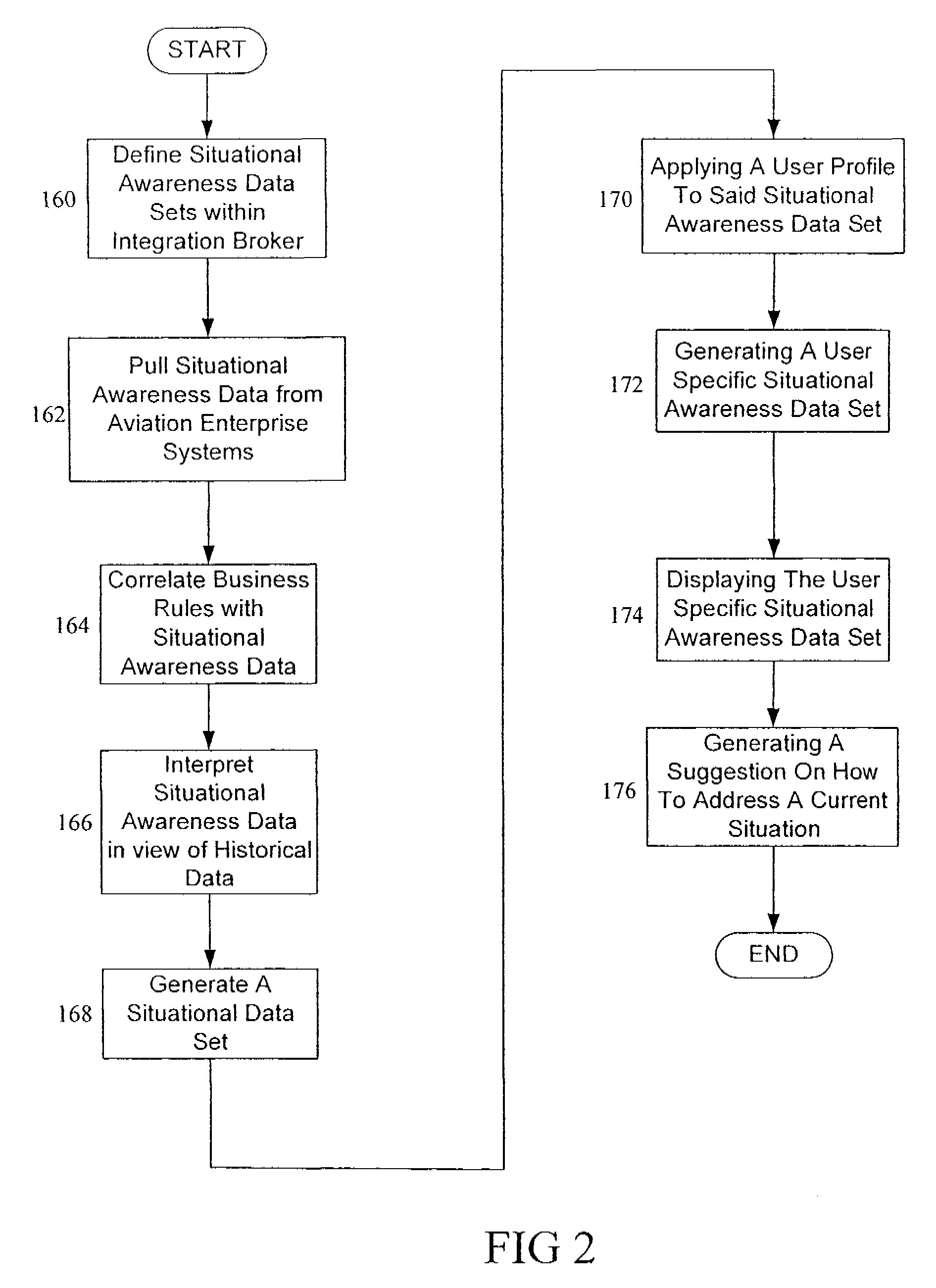
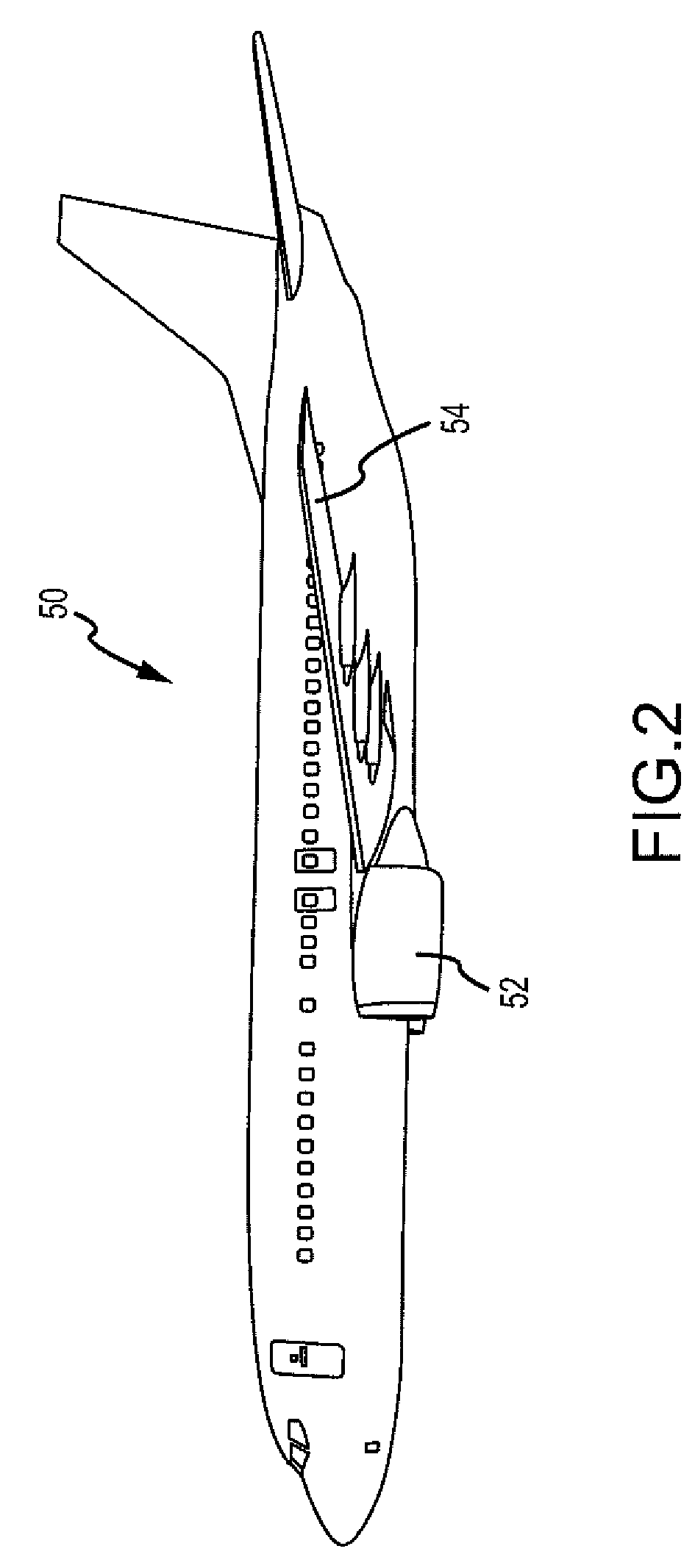
Methods and systems for providing a global view of airline operations
InactiveUS20080010107A1Digital computer detailsMultiprogramming arrangementsTime scheduleData source
A method for providing an airline a global view of asset management is described. The method includes receiving data relating to aircraft positions from at least one data source, receiving data relating to flight and maintenance schedules for the aircraft from at least one other data source, correlating the received data in accordance with one or more business rules, interpreting the correlated data to determine potential impacts to assets and resources from an airline system perspective, and presenting the interpretation of the correlated data in a single format to a user.
Owner:THE BOEING CO
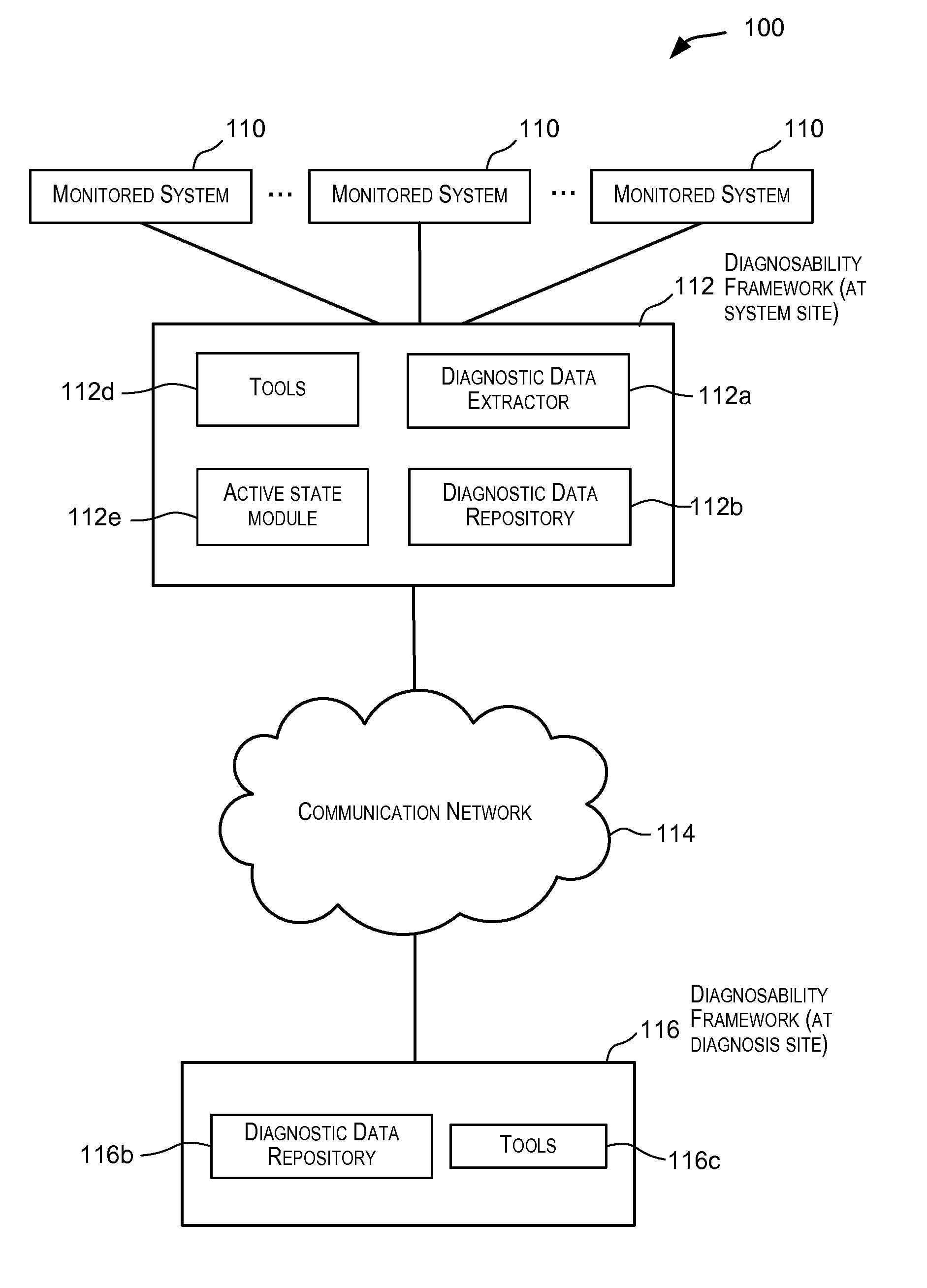
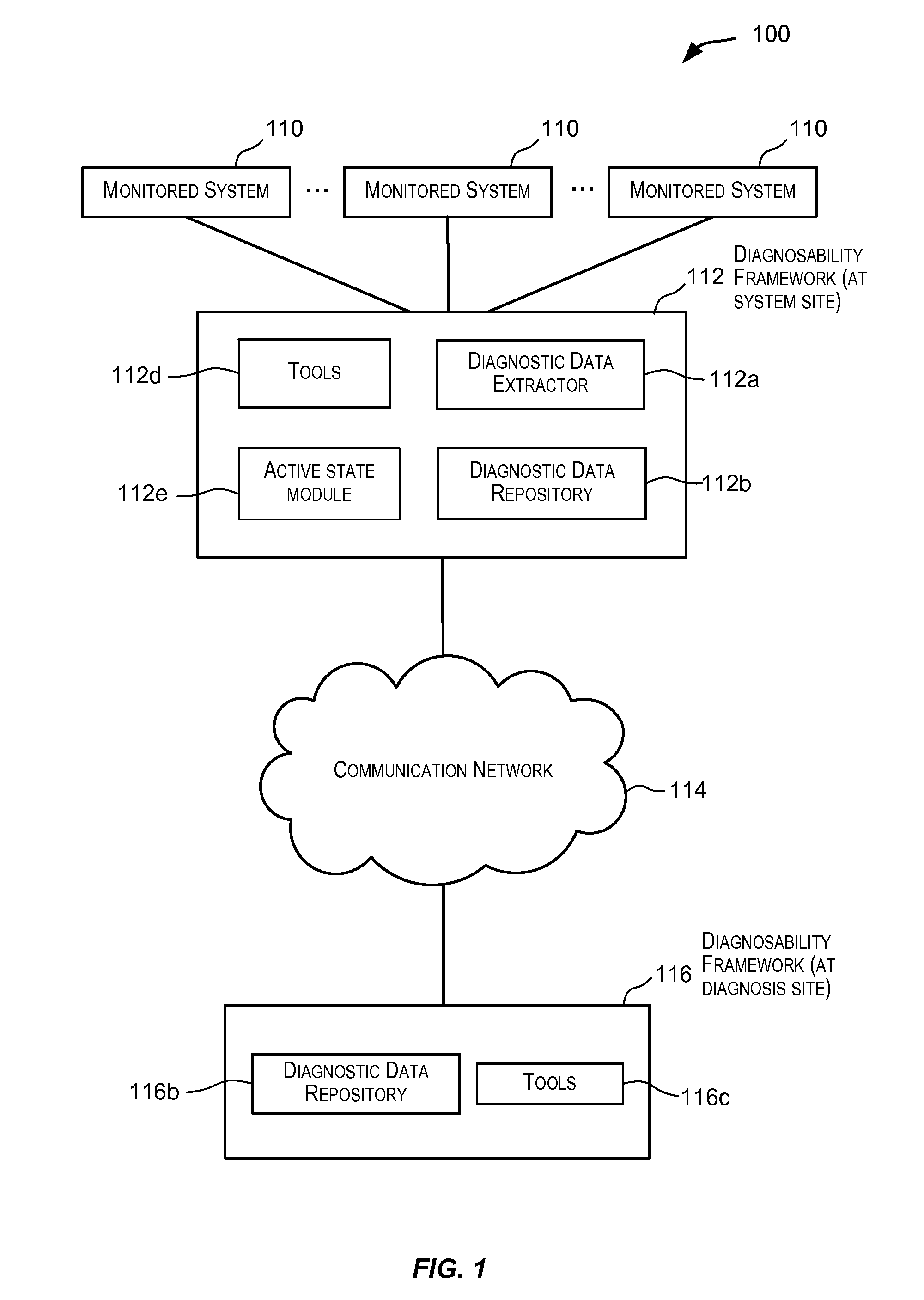
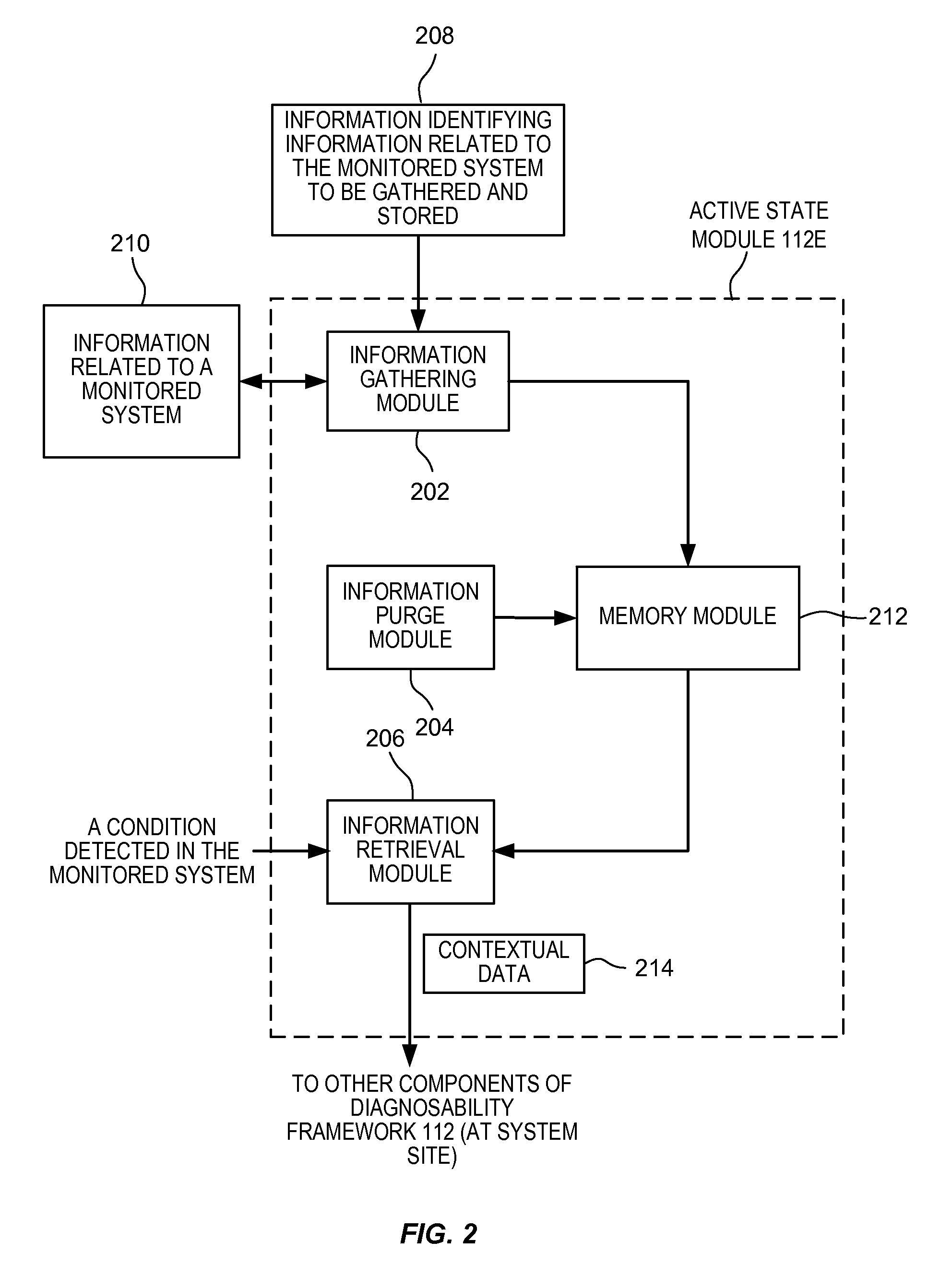
Gathering information for use in diagnostic data dumping upon failure occurrence
ActiveUS20090106595A1Easy to gatherEasy to captureFault responseTransmissionDiagnostic dataLocal variable
Techniques for gathering information during runtime of a monitored system such that the information is available for facilitating diagnostics for the monitored system. In one embodiment, upon detection of a condition (such as an error condition) in the monitored system, a portion of the gathered information provides contextual information that facilitates gathering of diagnostic data that is relevant for the detected condition. This facilitates capturing of diagnostic data that is relevant for diagnosing the detected condition. The information gathered and stored during runtime may include information related to local variables, information related to tagged information (e.g., tagged functions / processes) executing in the monitored system, information related to potential impacts to the monitored system due to failures, metadata information, and other information.
Owner:ORACLE INT CORP
System and method of enterprise systems and business impact management
ActiveUS20050283445A1Faster and accurate analysisAvoid lot of costDigital computer detailsPayment architectureDomain modelCellular architecture
A system architecture and a method for managing using a cellular architecture to allow multi-tier management of events such as the managing of the actual impact or the potential impact of IT infrastructure situations on business services. A preferred embodiment includes a high availability management backbone to frame monitoring operations using a cross-domain model where IT component events are abstracted into IT Aggregate events. By combining IT Aggregate events with transaction events, an operational representation of the business services is possible. Another feature is the ability to connect this information to dependent business user groups such as internal end-users or external customers for direct impact measurement. A web of peer-to-peer rule-based cellular event processors preferably using Dynamic Data Association constitutes management backbone crossed by event flows, the execution rules, and distributed set of dynamic inter-related object data rooted in the top data instances featuring the business services.
Owner:BMC SOFTWARE
Security control verification and monitoring subsystem for use in a computer information database system
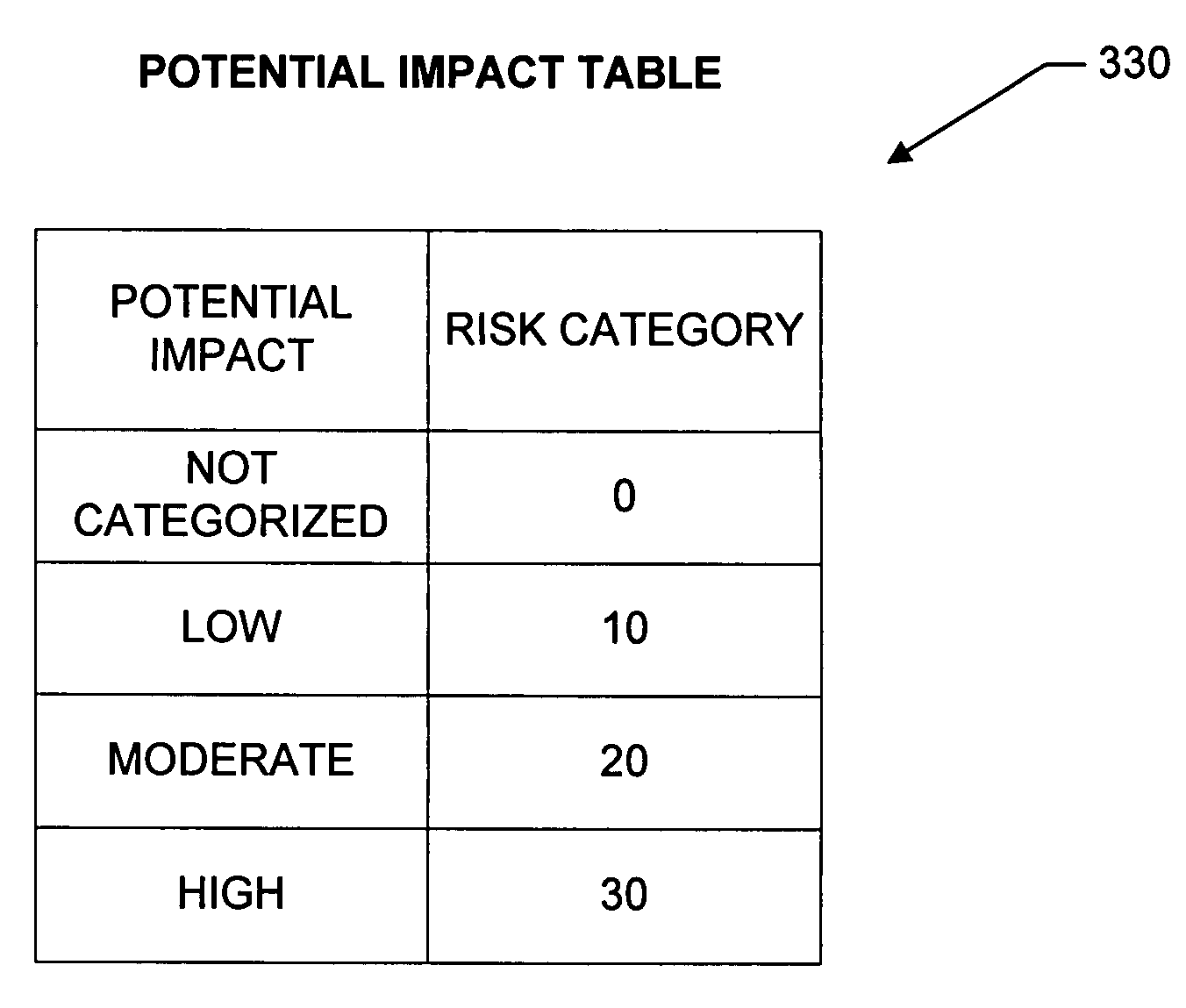
A security control verification and monitoring subsystem of a managed computer system performs security control verification operations regularly and for each security control verification operation determines the applicable security benchmark level for use by a given computer. The subsystem assigns security risk categories to groups of computers based, for example, on overall system or group administrator supplied potential impact settings and / or system type and business or information type selections. The subsystem further associates the security risk categories with security benchmark levels based on mapping information supplied by the overall system or group administrator. The subsystem then directs the computer to benchmark definition files based on the assigned security risk category, the associated security benchmark level and attributes of the computer. The subsystem performs the security control verification operations whenever the computer performs computer profile data update operations, and thus, monitors essentially continuously the security control compliance of the computer. The subsystem stores the results of the security verification operations and includes the results in reports for the system, group or computer.
Owner:BELARC
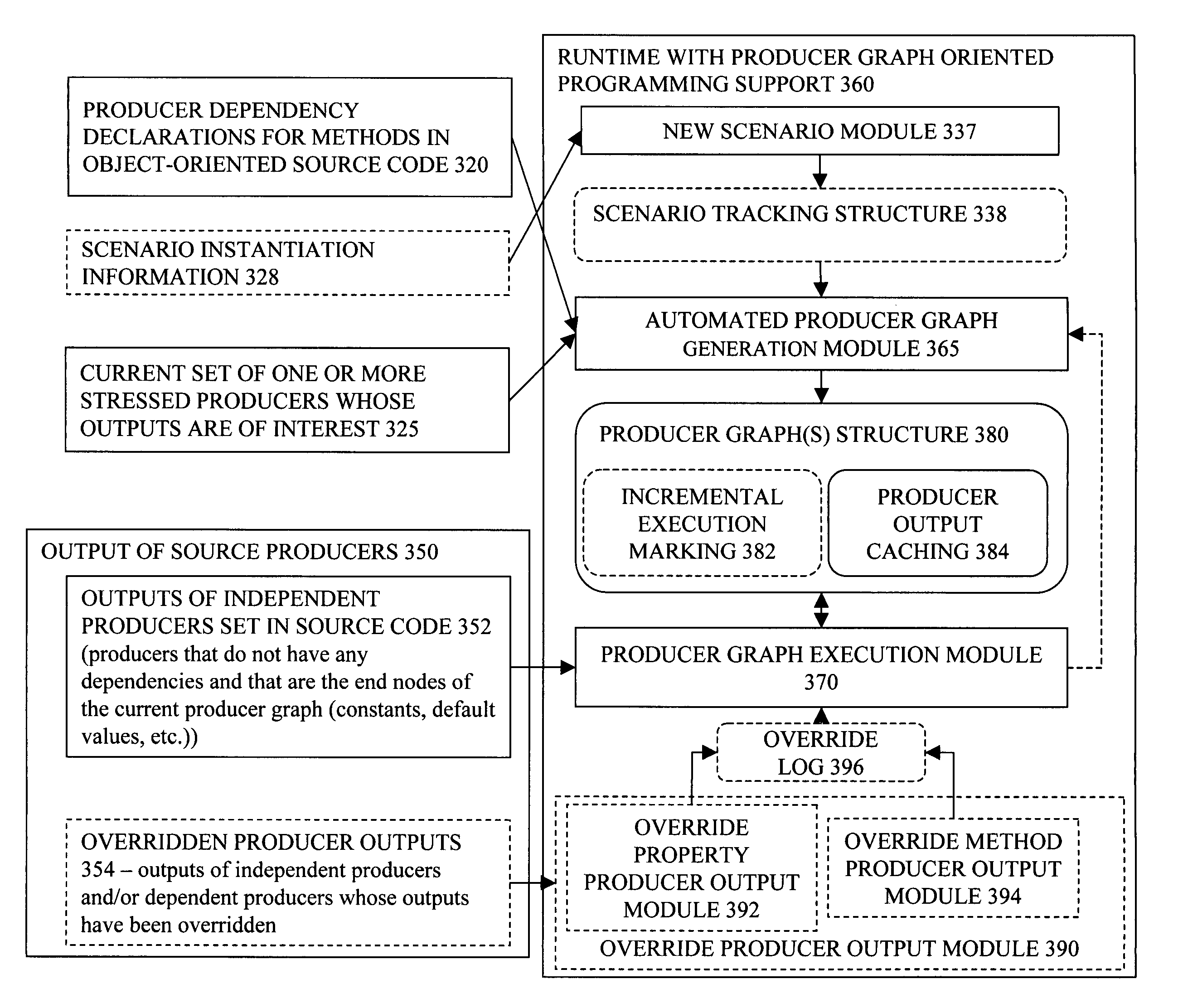
Produce graph oriented programming framework with scenario support
ActiveUS8332827B2Software testing/debuggingSpecific program execution arrangementsGraphicsSoftware engineering
Owner:MUREX
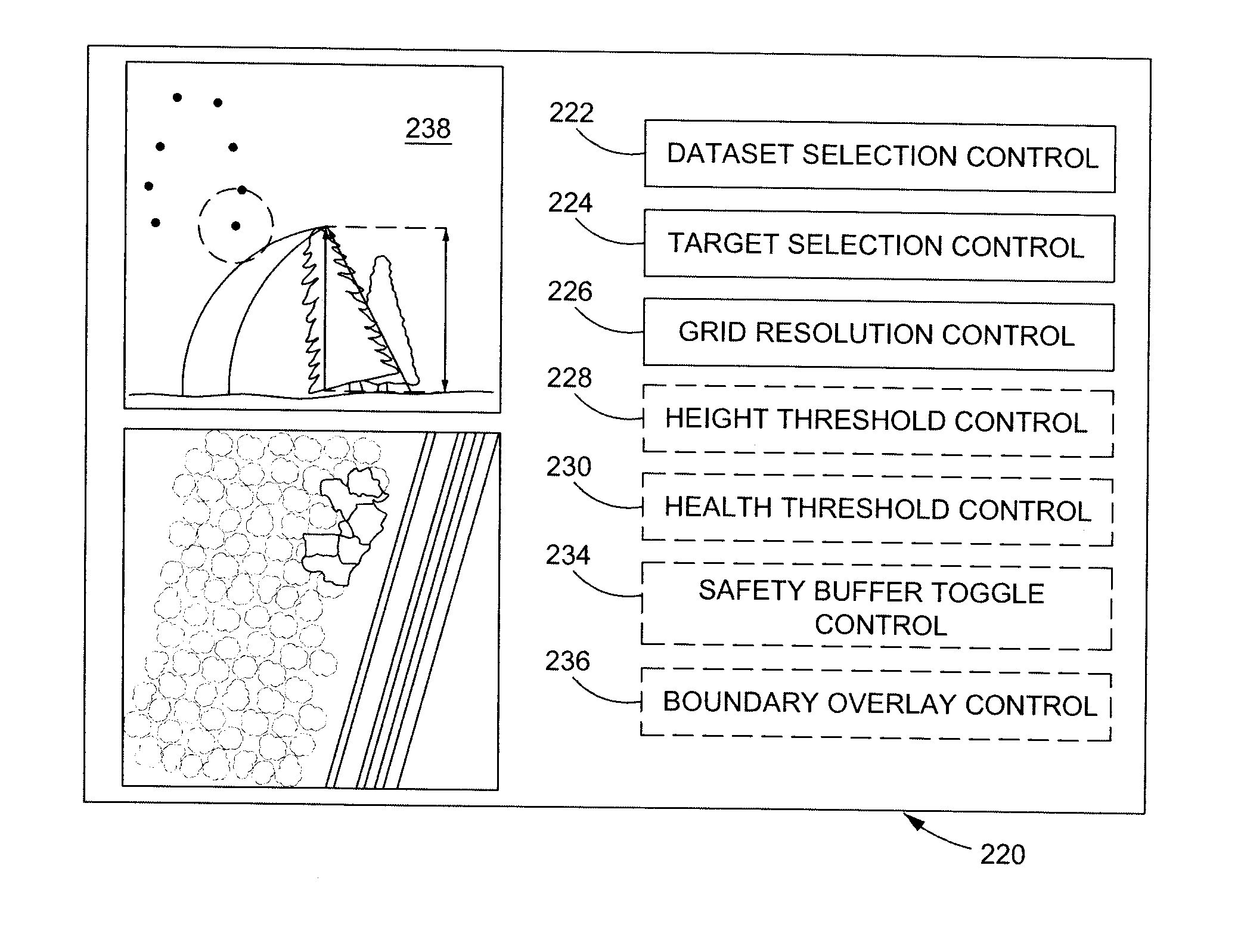
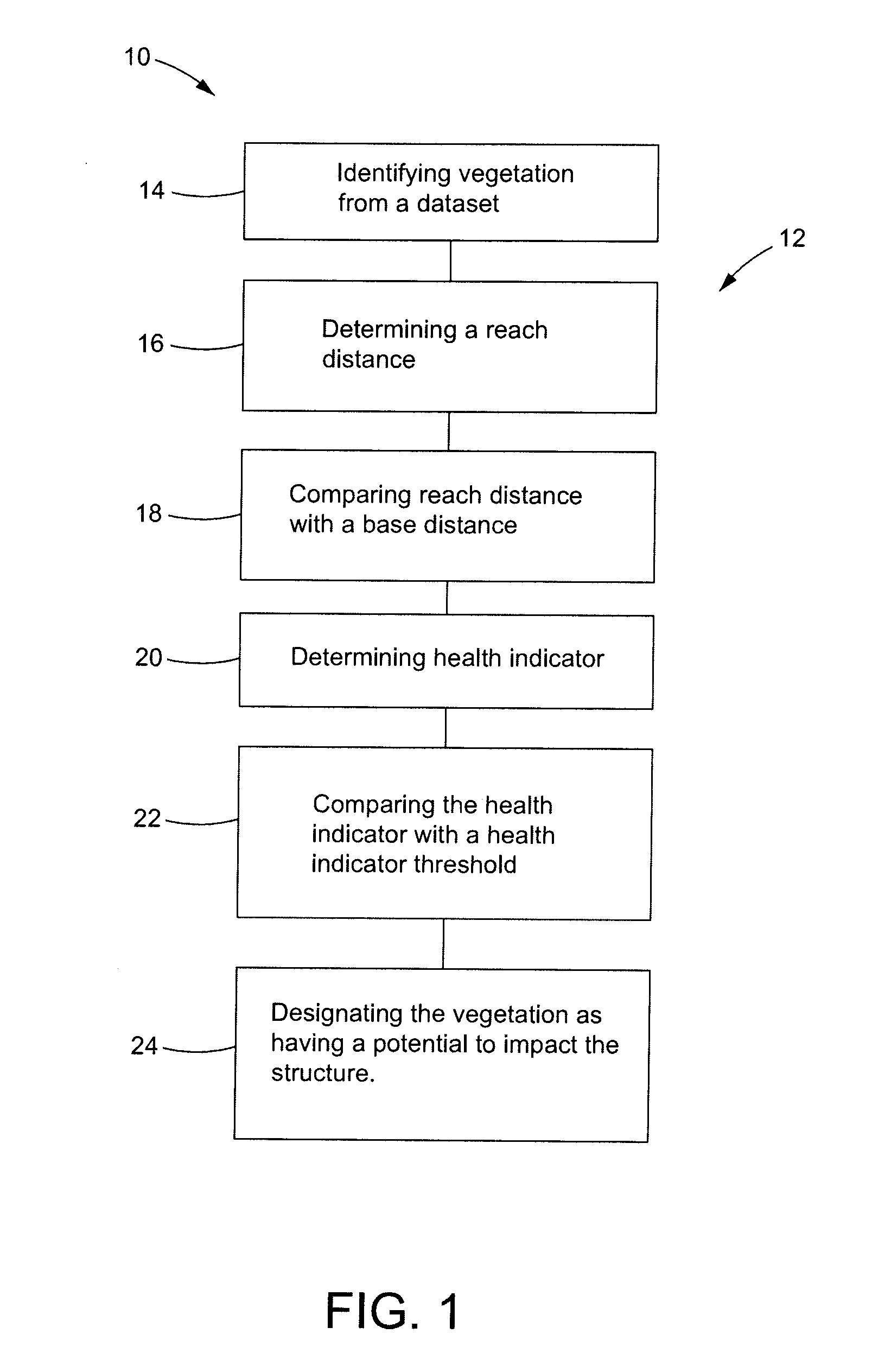
Method for locating vegetation having a potential to impact a structure
A method for designating vegetation as potential impact vegetation includes identifying data relating to target vegetation from a dataset and determining a reach distance of the target vegetation. The reach distance includes a distance from a point on a ground to a point of the target vegetation that is farthest from the point on the ground. The method also includes comparing the reach distance of the target vegetation with a closest distance between the point on the ground and a structure to produce a compared reach distance value and determining a health indicator value for the target vegetation. The method further includes comparing the health indicator value of the target vegetation to a health indicator threshold value and designating the target vegetation as having a potential to impact the structure based on the compared reach distance value and the comparison of the health indicator to the health indicator threshold.
Owner:HUDSON POWER TECH LLC
Methods and systems for providing a resource management view for airline operations
InactiveUS20080046167A1Analogue computers for vehiclesAnalogue computers for trafficTime scheduleData source
A method for providing an airline a global view of resource management is described. The method includes receiving data relating to aircraft positions from at least one data source, receiving data relating to flight and maintenance schedules for the aircraft from at least one other data source, correlating the received data in accordance with one or more business rules, interpreting the correlated data to determine potential impacts to resources from an airline system perspective, and presenting the interpretation of the correlated data in a single format to a user.
Owner:THE BOEING CO
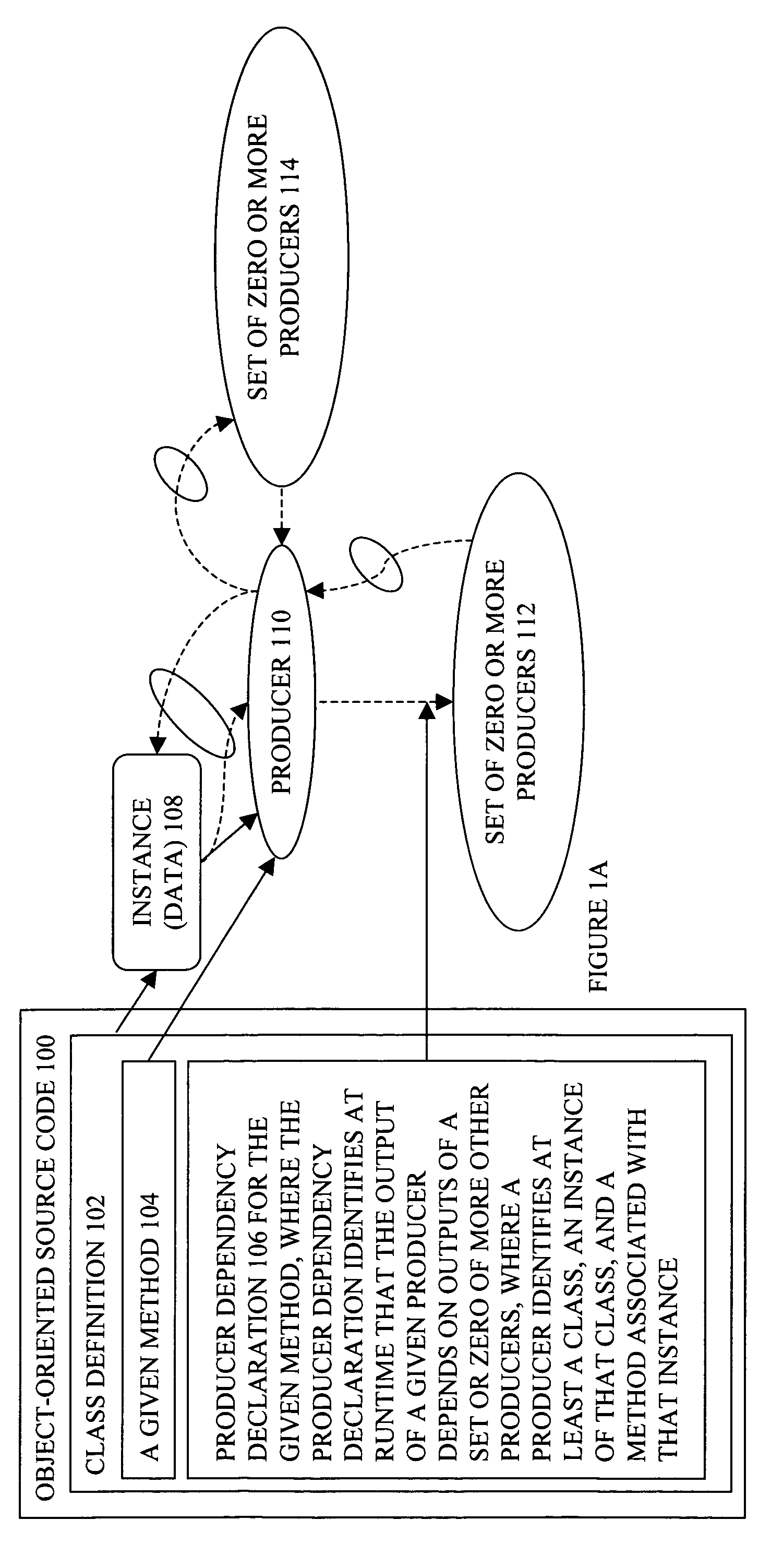
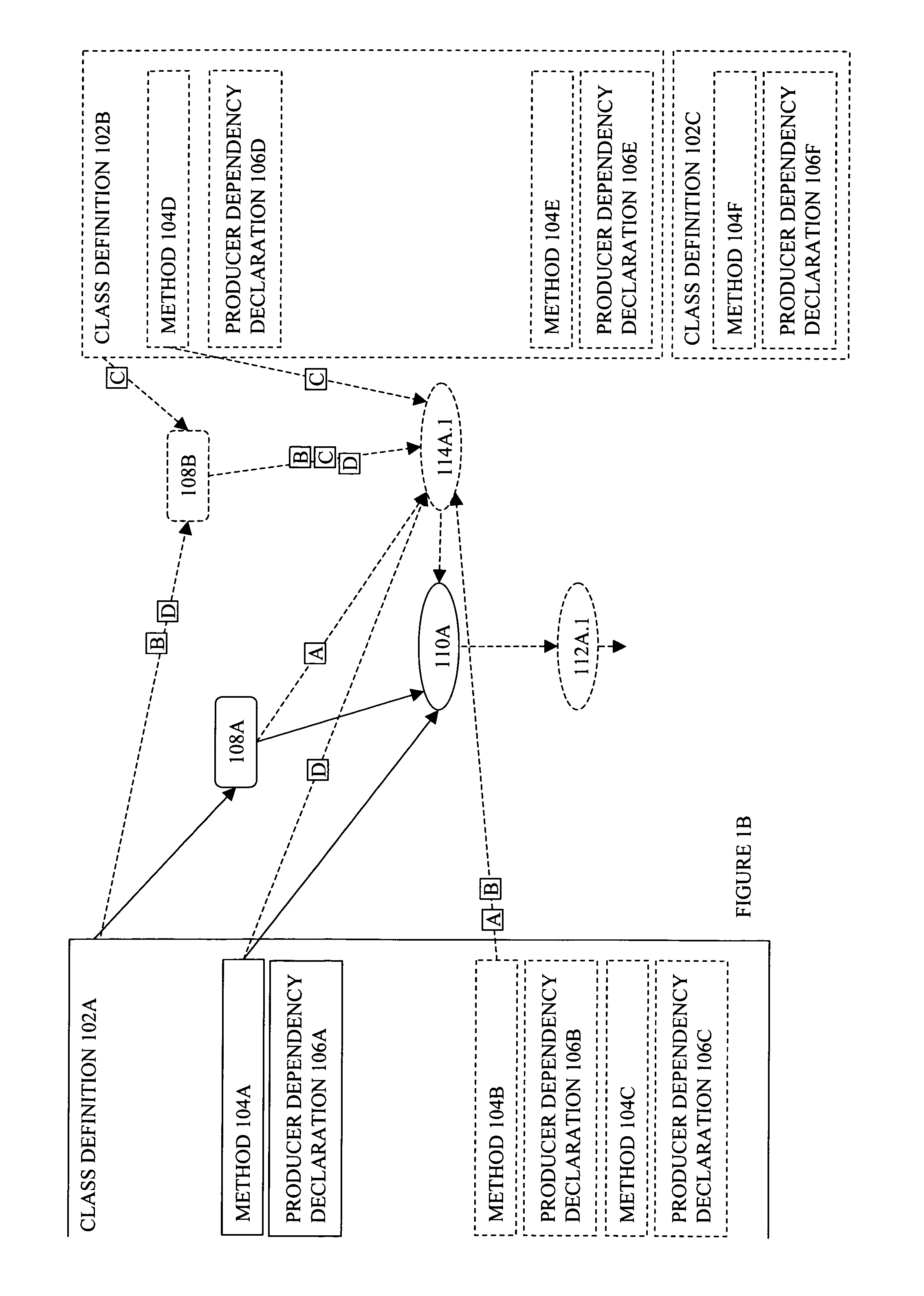
Producer graph oriented programming framework with scenario support
ActiveUS20080134152A1Software testing/debuggingSpecific program execution arrangementsGraphicsSoftware engineering
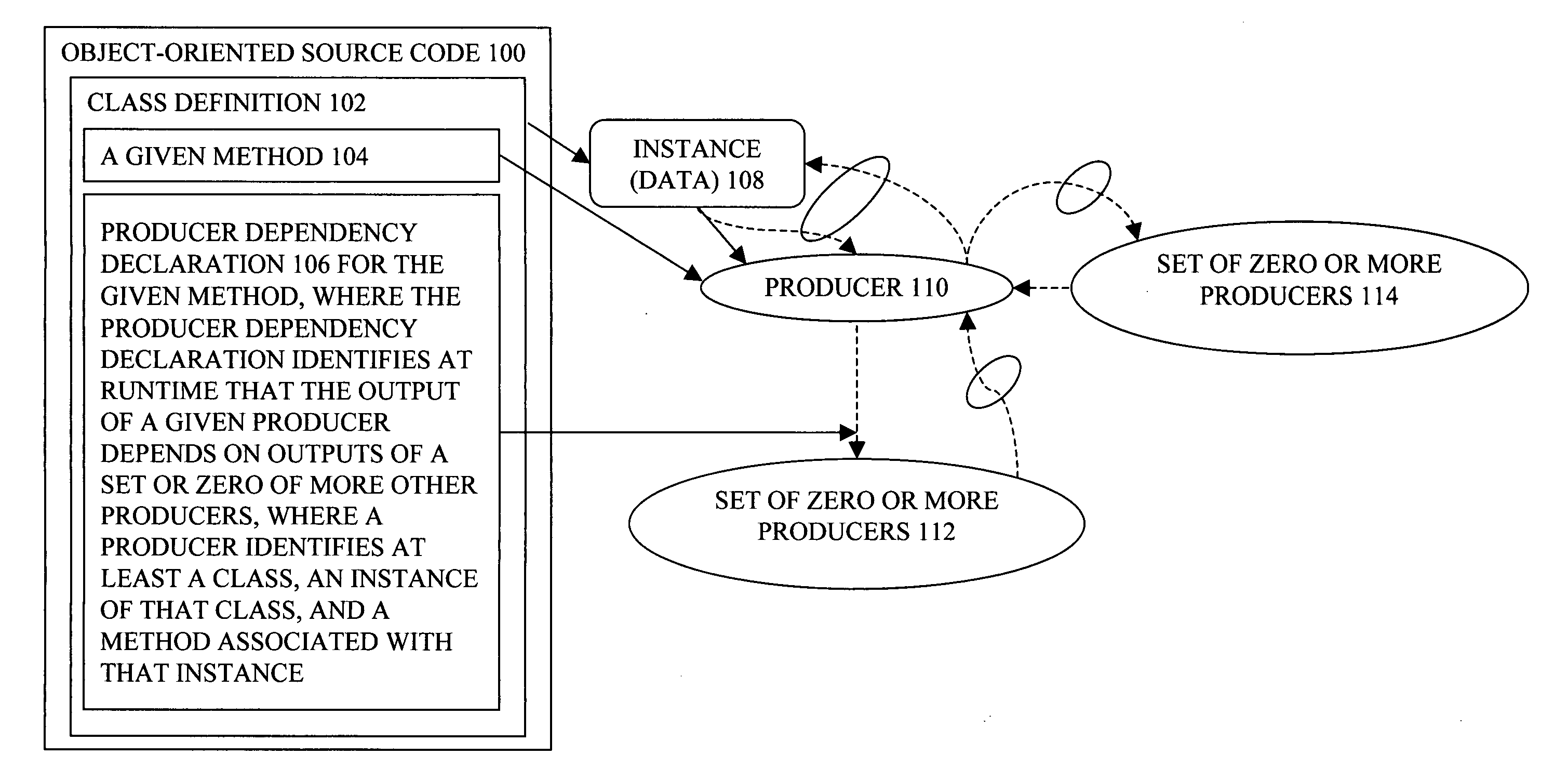
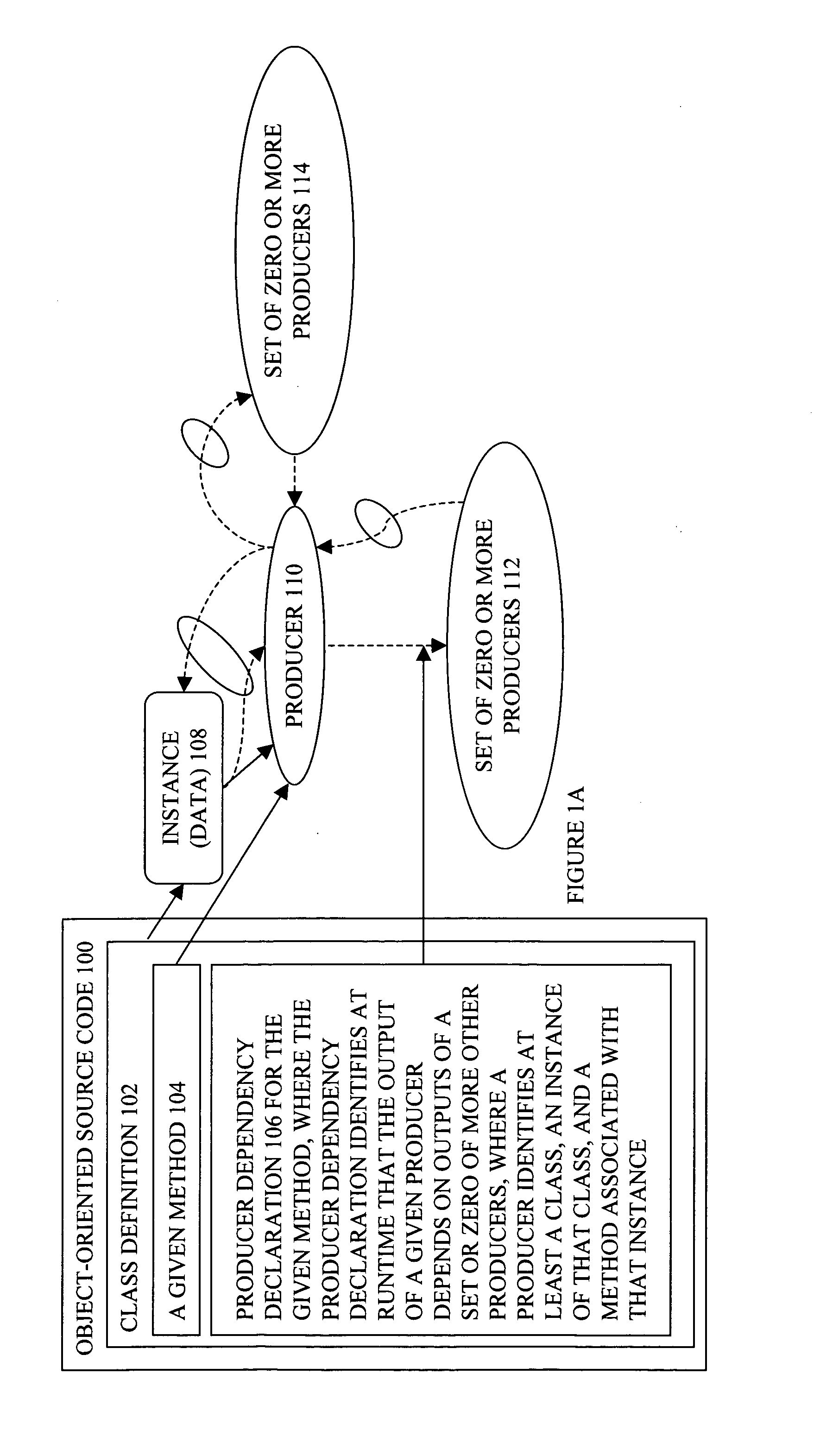
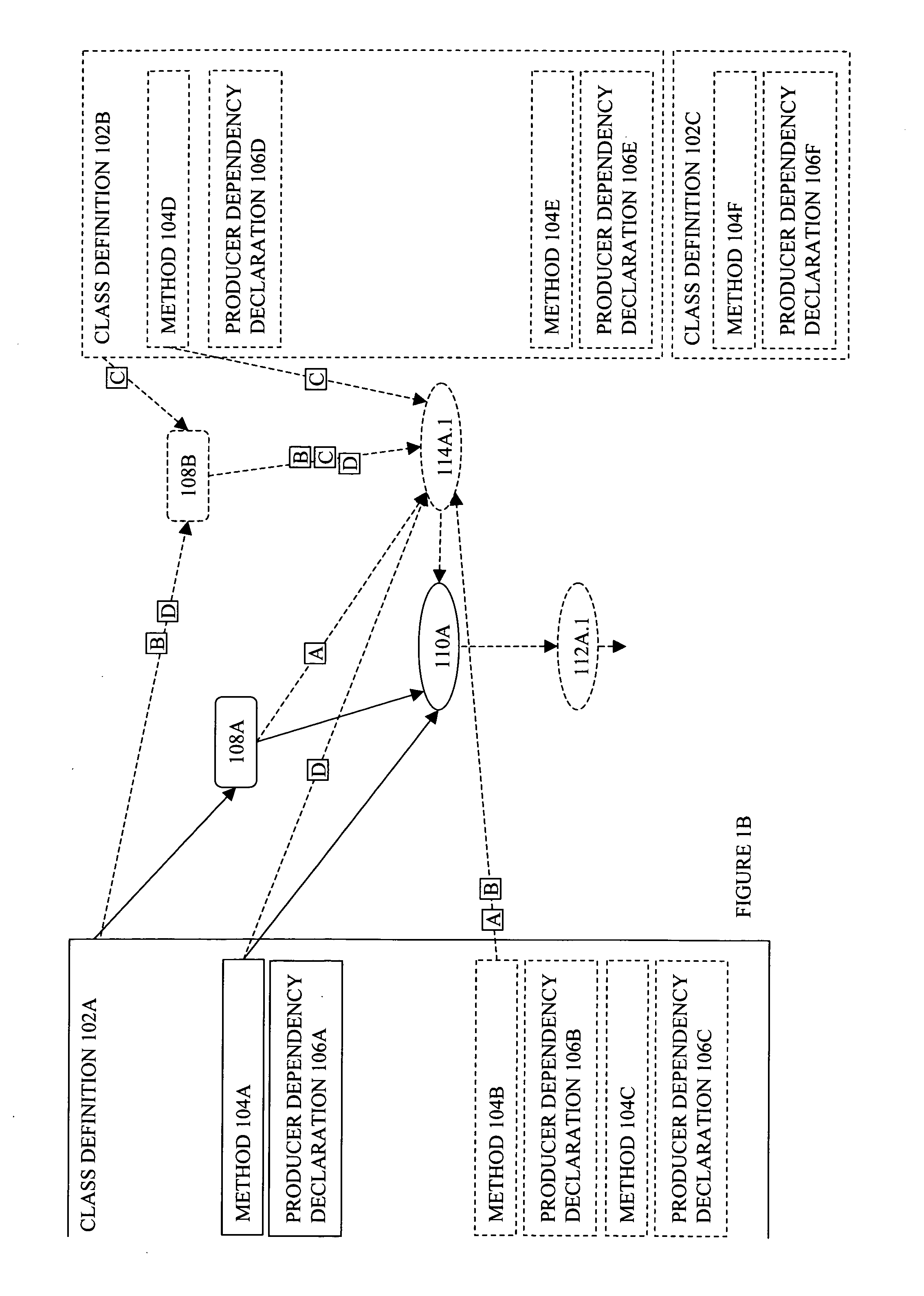
Embodiments of a producer graph oriented programming framework with scenario support have been presented. In one embodiment, a request to evaluate potential impacts by a change on an application program is received. The application program includes a set of producers, each having at least an instance and a method associated with the instance. Responsive to the request, the application program may be simulated with the change while the existing states and existing outputs of the producers are preserved.
Owner:MUREX
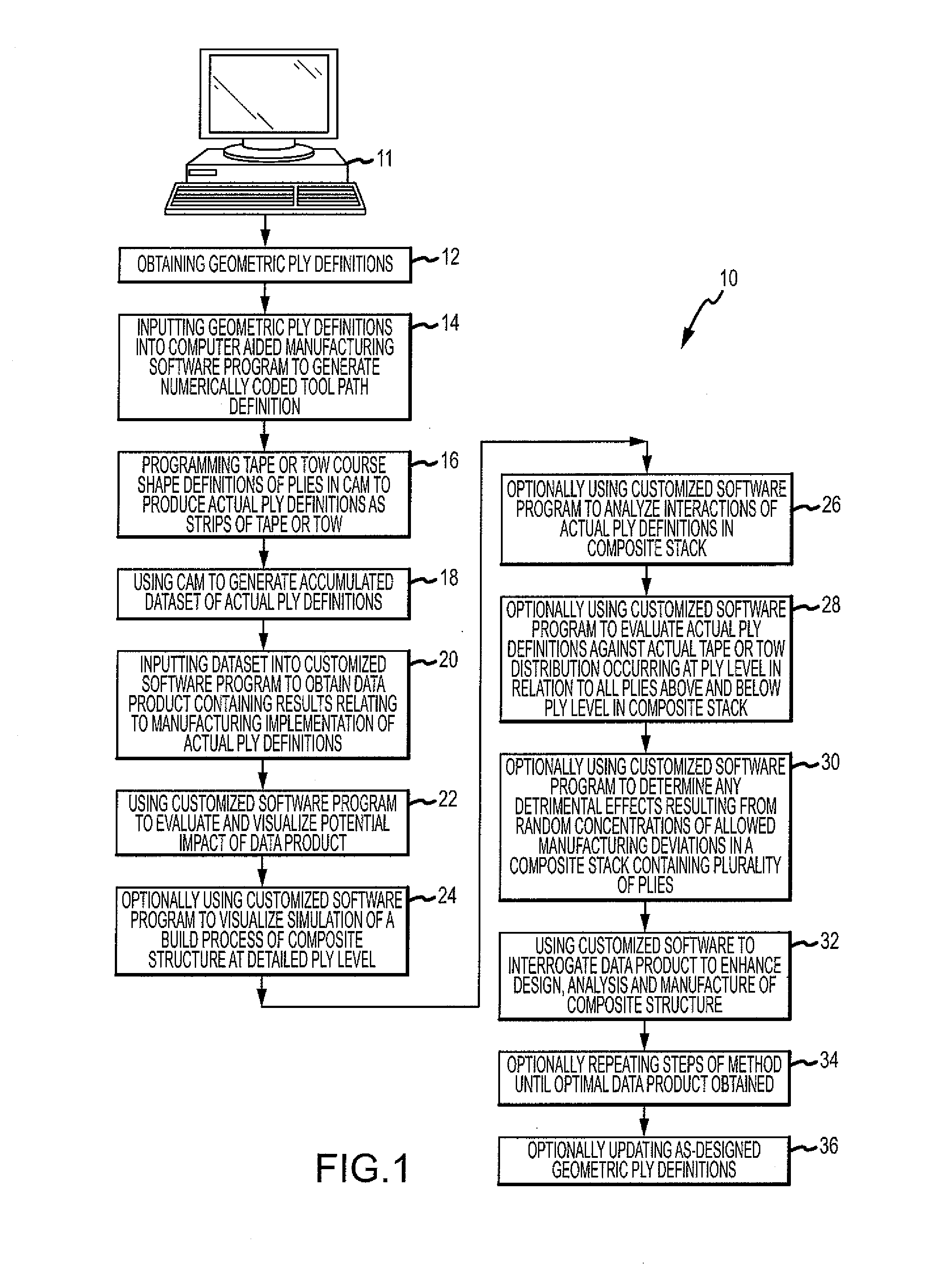
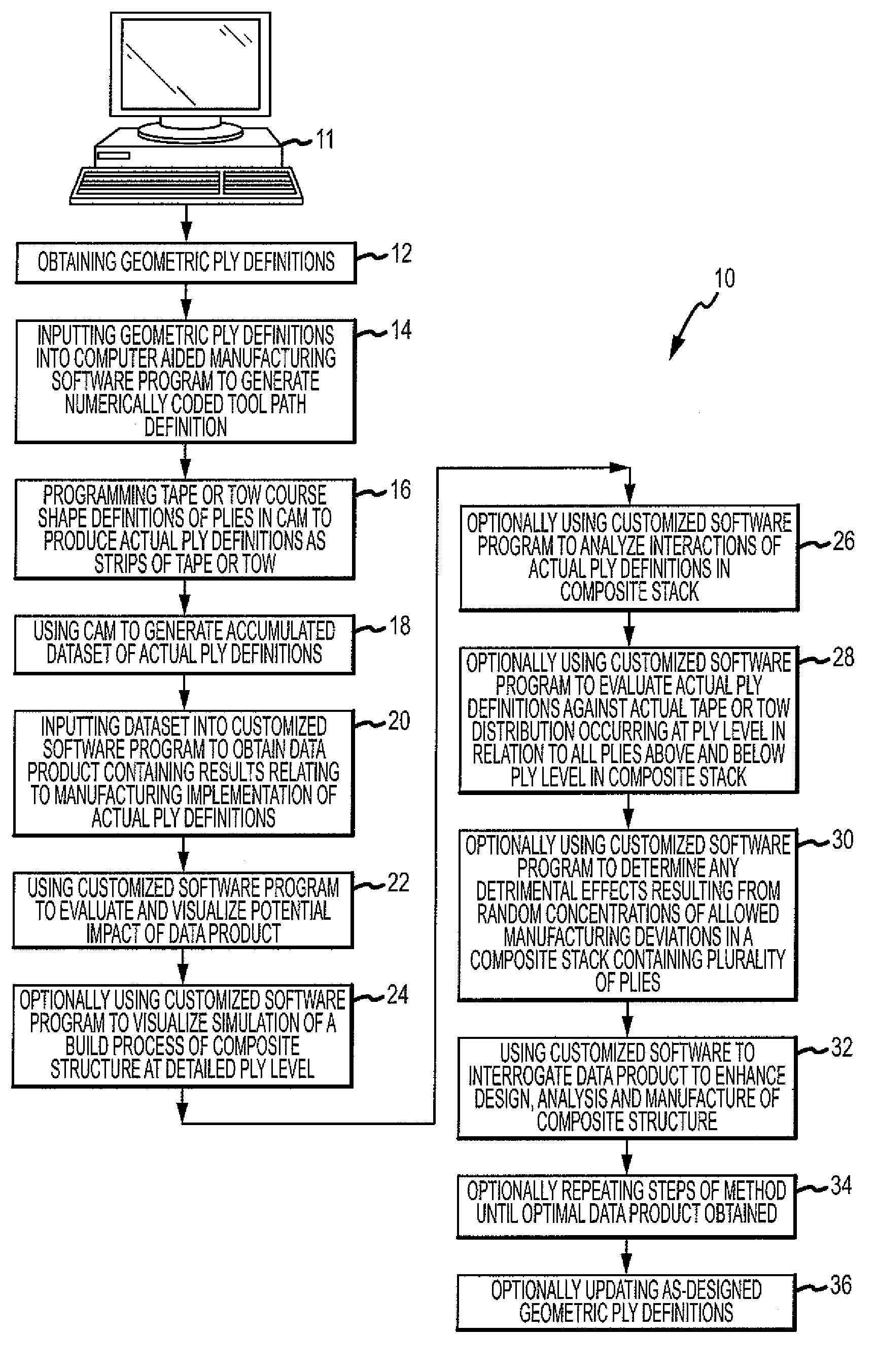
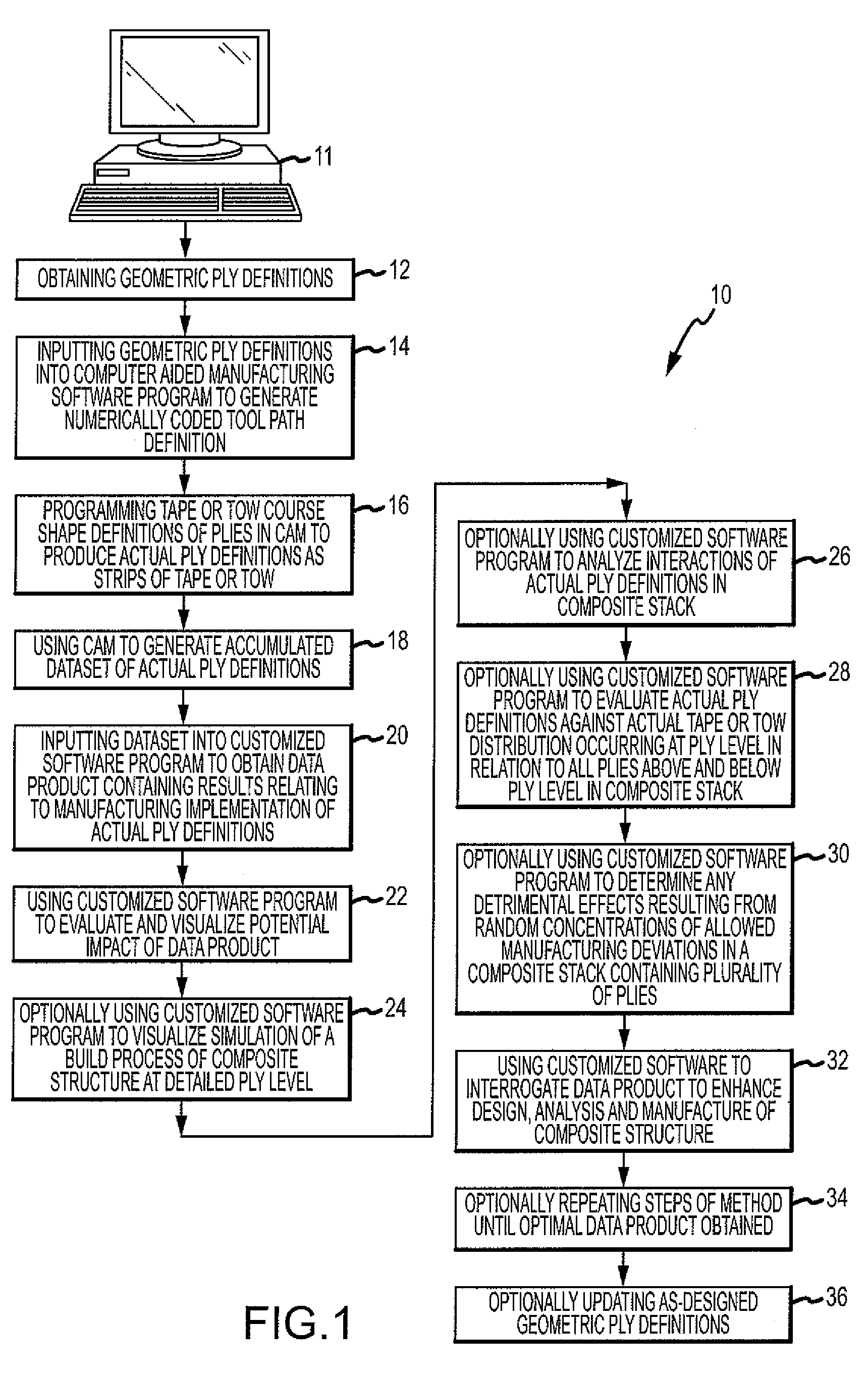
Composite stack analysis method
ActiveUS20100204815A1Improve manufactureStructural Design ImprovementProgramme controlComputer controlData setAnalysis method
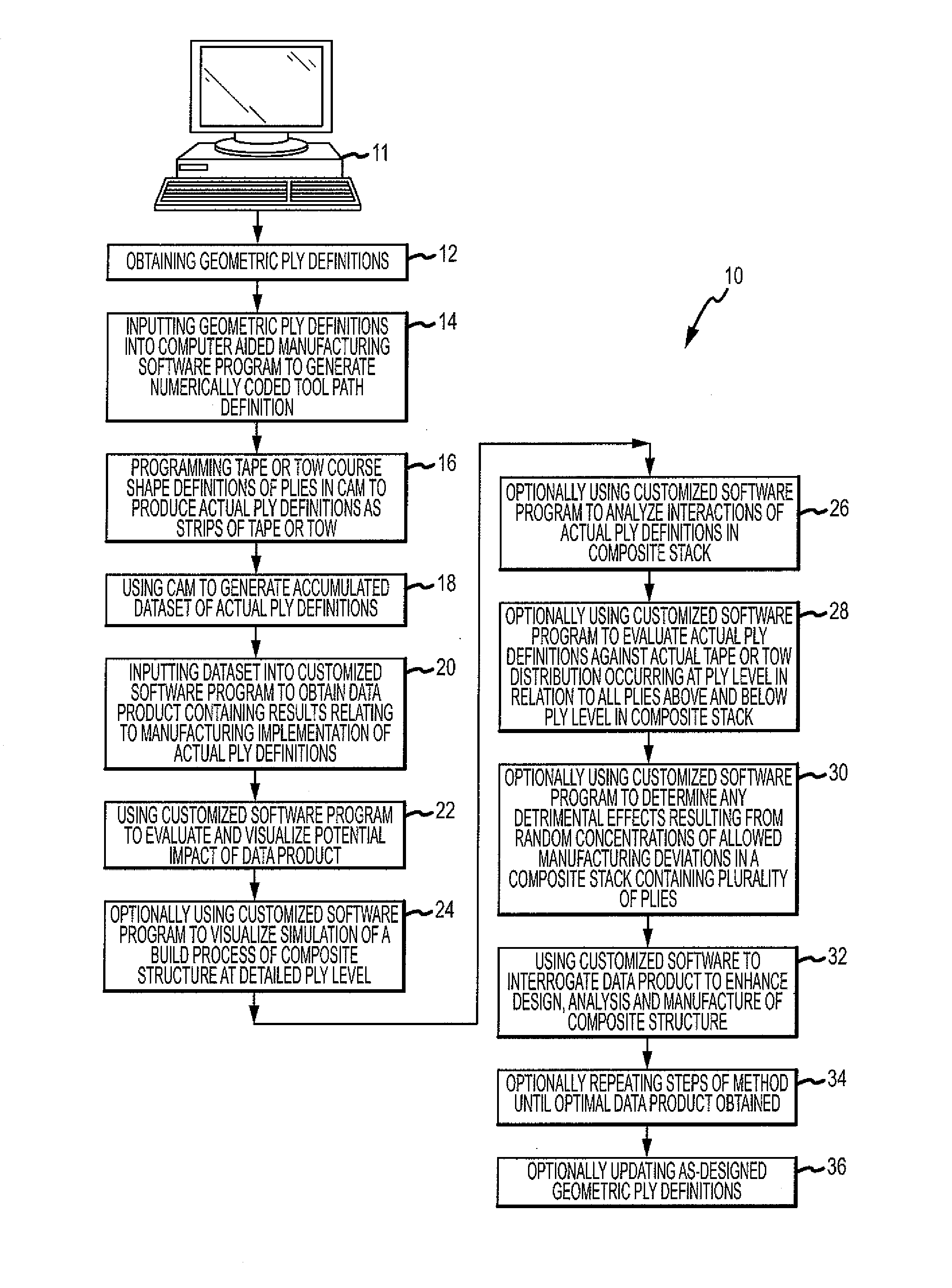
A method is provided for generating a data product that allows for enhanced design, analysis and manufacture of a composite structure comprising a plurality of plies. The method comprises the steps of obtaining geometric ply definitions, inputting the geometric ply definitions into a computer aided manufacturing (CAM) software program to generate a numerically coded tool path definition containing centerline data for each tape or tow comprising a ply, programming tape or tow course shape definitions of a plurality of plies in CAM to produce actual ply definitions, using CAM to generate an accumulated dataset of actual ply definitions, using a customized software program to analyze the dataset to obtain a data product containing results relating to manufacturing implementation of the actual ply definitions, and using the customized software program to evaluate and visualize potential impact of the data product and to interrogate the data product.
Owner:THE BOEING CO
Method of analyzing composite structures
ActiveUS8108058B2Simple designImprove manufactureProgramme controlTotal factory controlData setPotential impact
A method is provided for generating a data product that allows for enhanced design, analysis and manufacture of a composite structure comprising a plurality of plies. The method comprises the steps of obtaining geometric ply definitions, inputting the geometric ply definitions into a computer aided manufacturing (CAM) software program to generate a numerically coded tool path definition containing centerline data for each tape or tow comprising a ply, programming tape or tow course shape definitions of a plurality of plies in CAM to produce actual ply definitions, using CAM to generate an accumulated dataset of actual ply definitions, using a customized software program to analyze the dataset to obtain a data product containing results relating to manufacturing implementation of the actual ply definitions, and using the customized software program to evaluate and visualize potential impact of the data product and to interrogate the data product.
Owner:THE BOEING CO
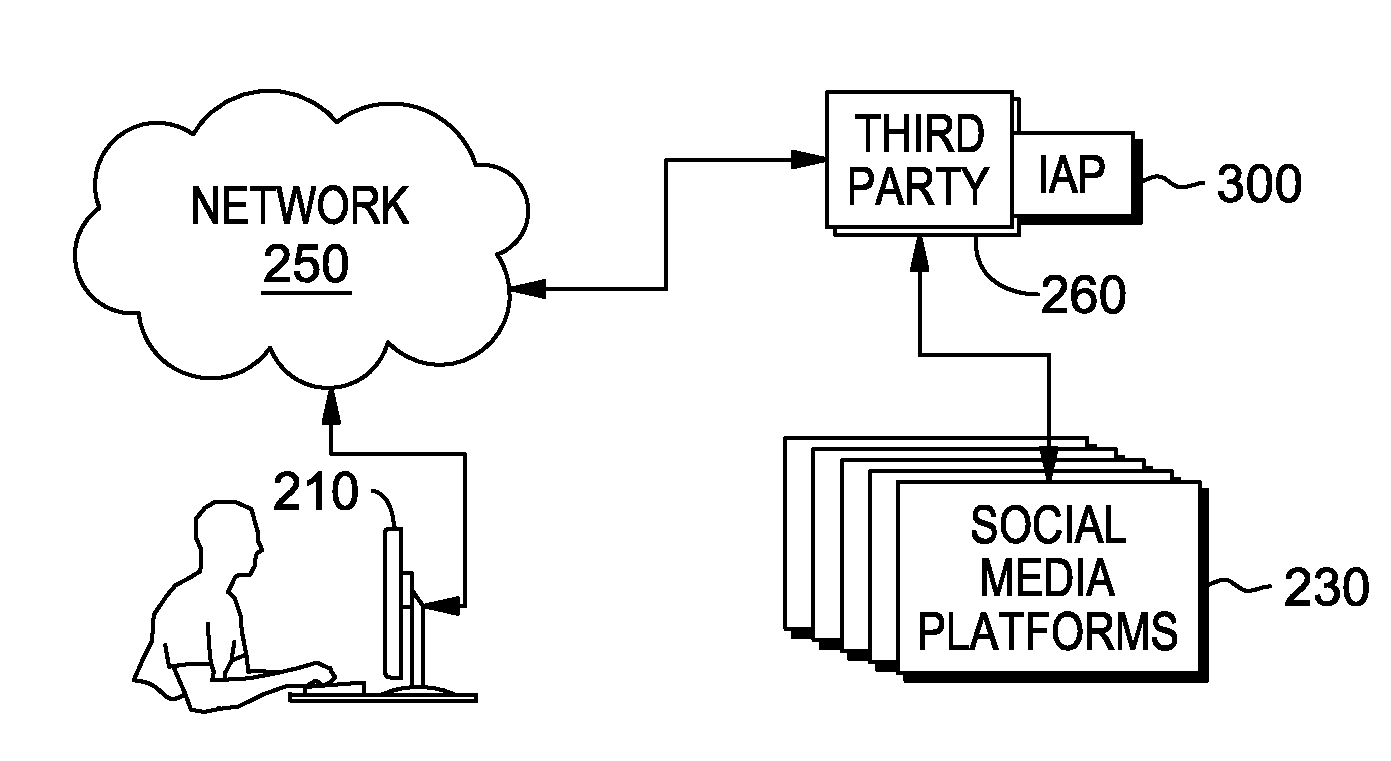
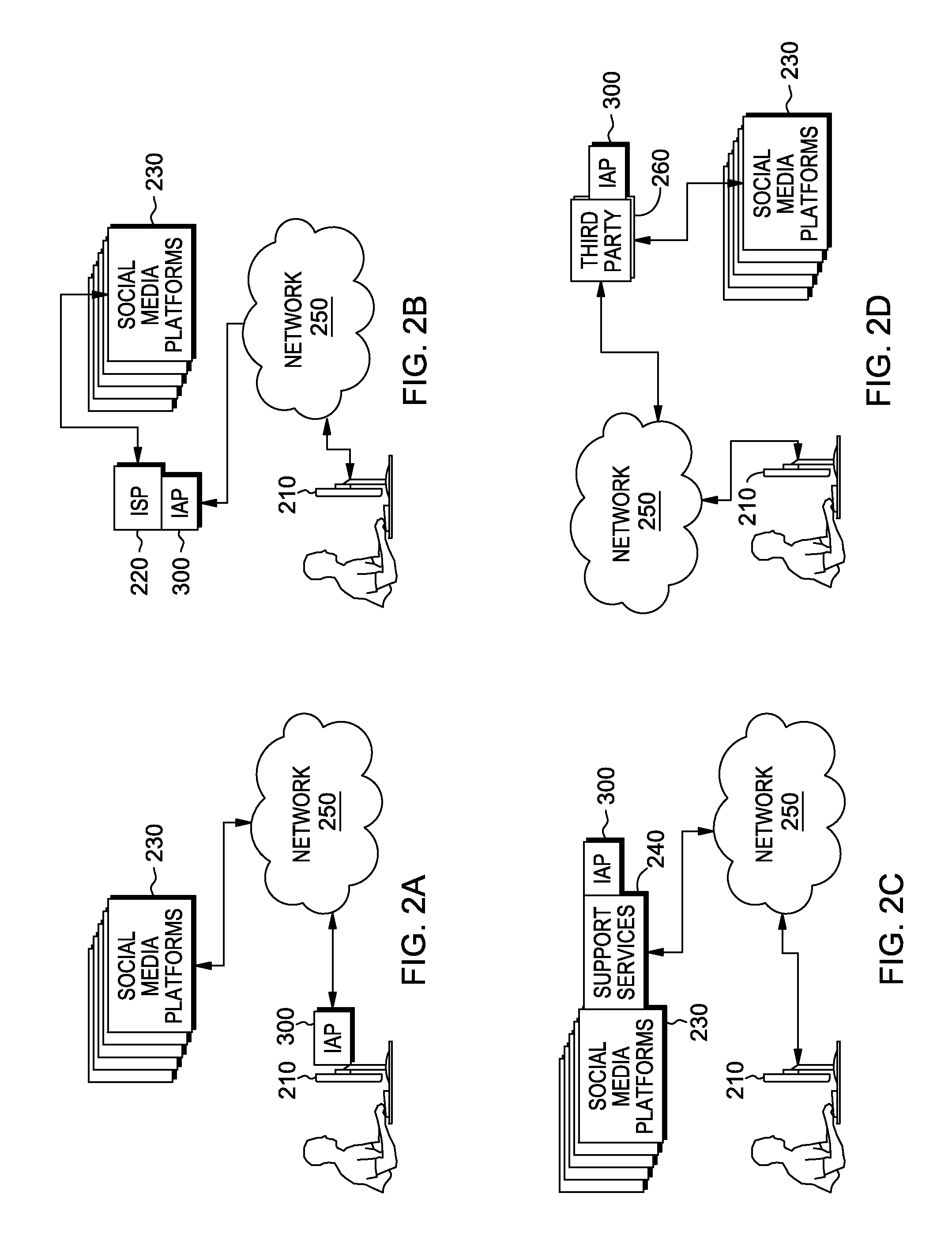
Impact assessment for shared media submission
InactiveUS20150229531A1Data processing applicationsDigital computer detailsSocial mediaPotential impact
A processor receives a submission to post to a social media platform, wherein the submission includes content. The processor analyzes the content of the submission. The processor determines an impact of the content of the submission. The processor determines one or more objectives of an impact assessment, wherein each of the one or more objectives is associated with a potential impact. The processor compares the impact of the submission to the one or more objectives, based on the content of the submission which is analyzed. The processor determines an impact assessment, wherein the impact assessment is based on whether the impact meets the one or more objectives, and the processor performs an action based on the impact assessment.
Owner:IBM CORP
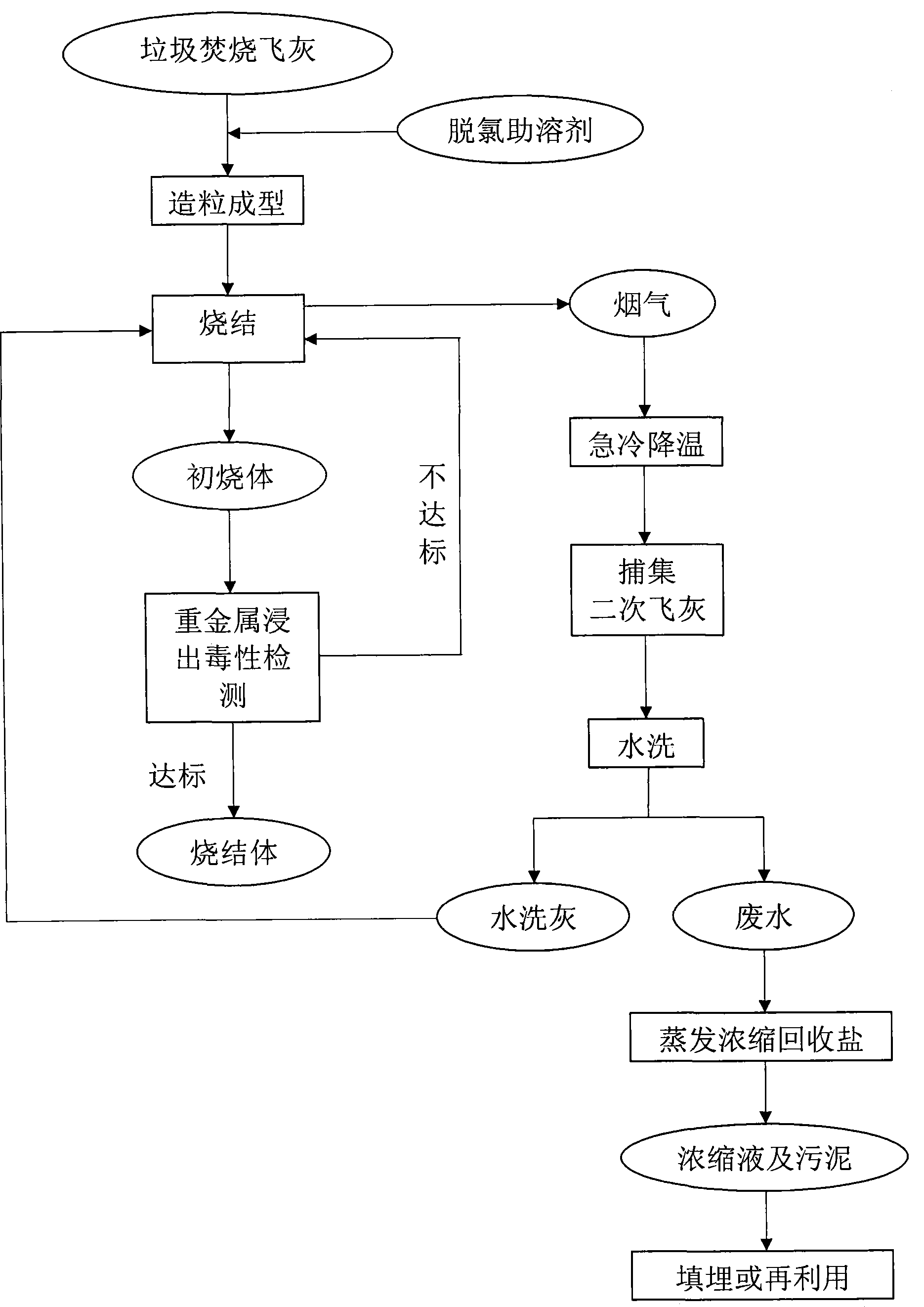
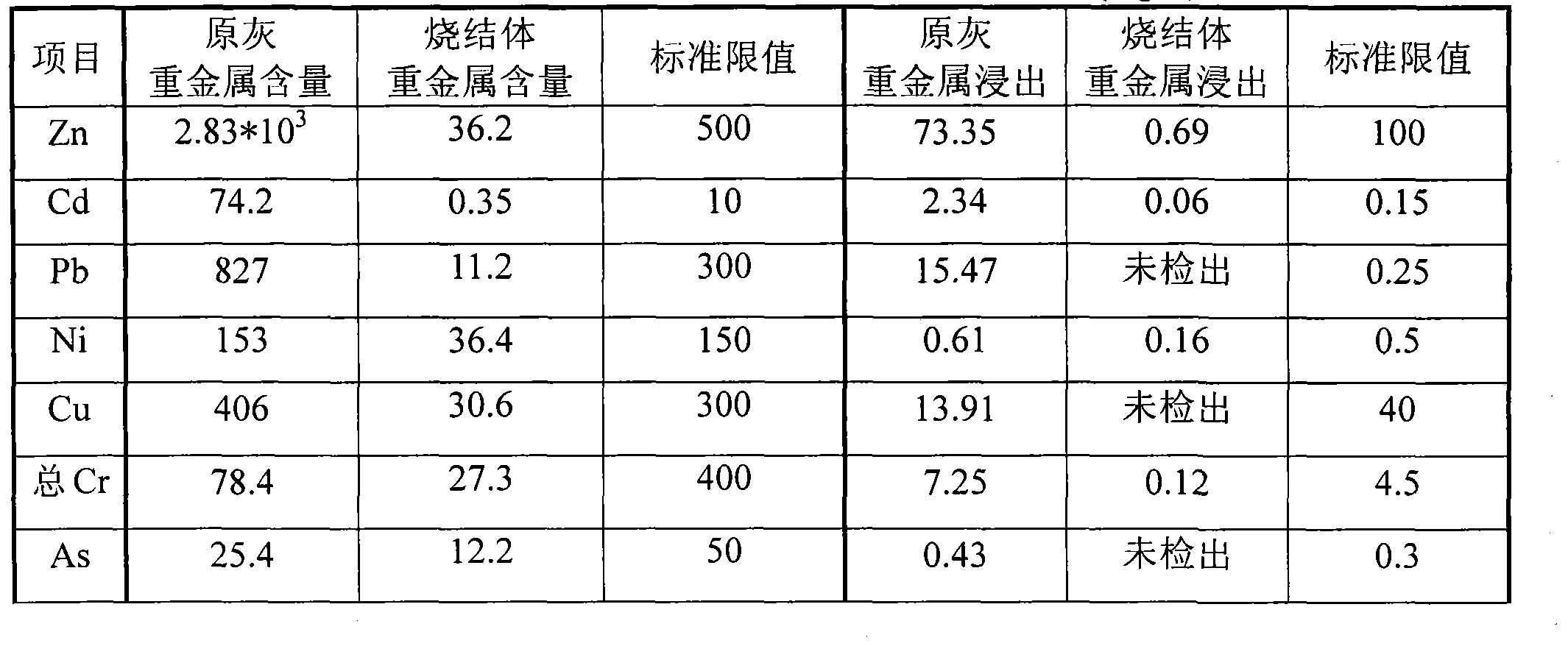
Waste incineration fly ash sintering reduction treatment technique
ActiveCN104070054AAccelerate evaporationPromote decompositionSolid waste disposalReduction treatmentDecomposition
The invention relates to a waste incineration fly ash sintering reduction treatment technique which is especially applicable to treatment and disposition of waste incineration fly ash of which the salt content is lower than 20%. The fly ash is added with a dechloridation fusing assistant to intensify the volatilization of heavy metals and the decomposition of dioxin, heavy metals and chlorine salt are intensively concentrated in secondary fly ash within a relatively low temperature range, and then the secondary fly ash is washed by water so as to further realize concentration of pollutants and reduction of the fly ash. The water-washed fly ash is returned to a rapid sintering device so as to completely degrade dioxin type pollutants; water-washing liquid is evaporated and concentrated to recycle the salt by using the afterheat of a sintering system, the concentrated liquid and mud obtained by evaporation and the obtained sintered body are safely buried or recycled. The treatment technique disclosed by the invention is relatively simple in overall process and equipment, the energy consumption and the treatment cost are relatively low, the environmental friendliness of the obtained end product is improved, and the long-term potential impacts of the fly ash on the environment are minimized.
Owner:TIANJIN YIMING ENVIRONMENTAL TECH CO LTD
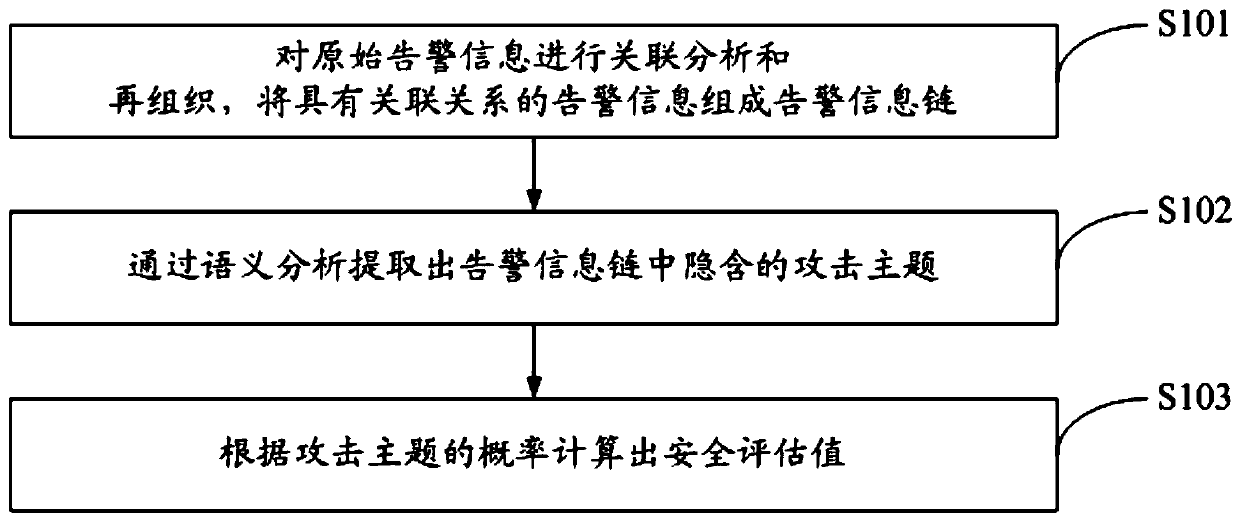
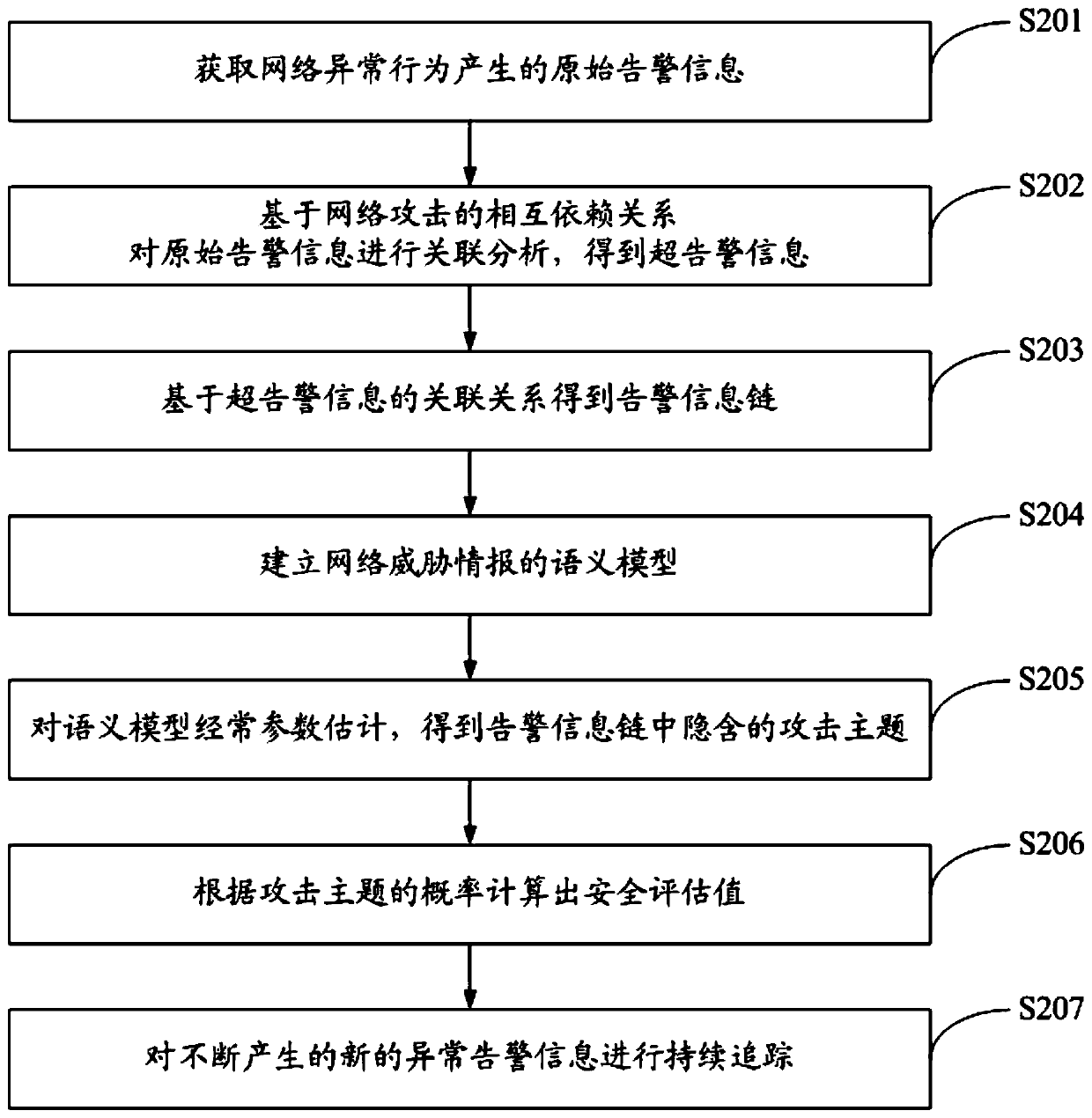
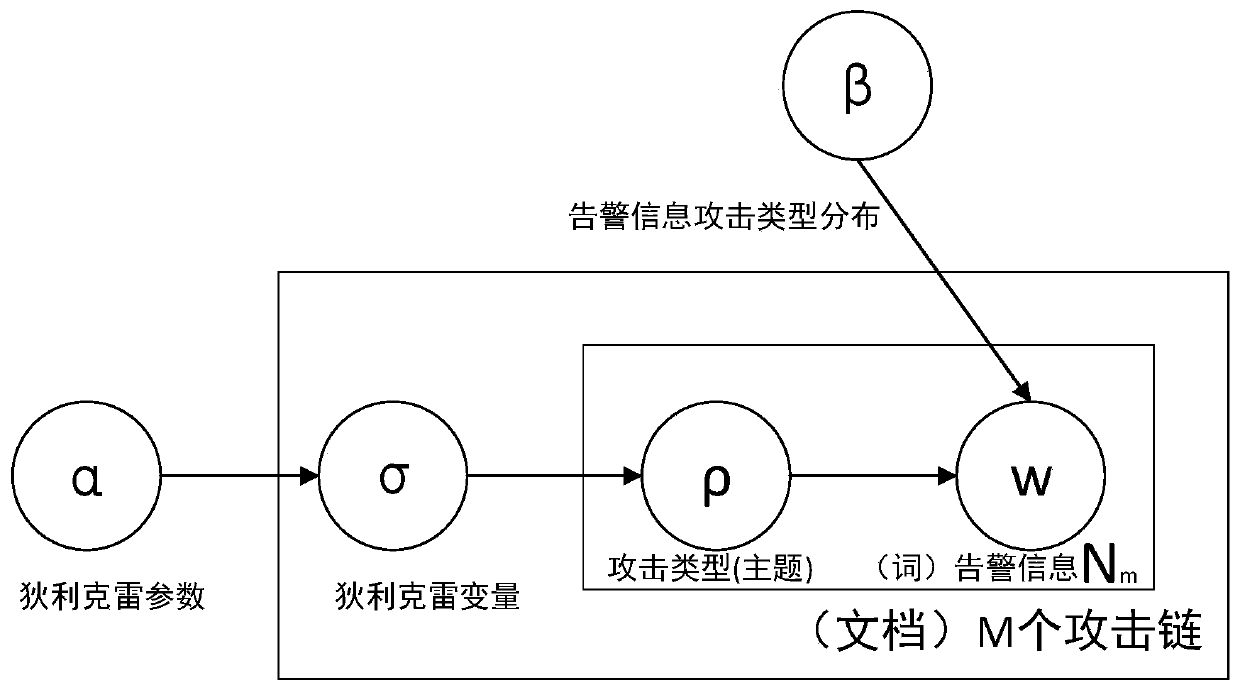
A multidimensional association analysis method and system for advanced persistent threats
ActiveCN109922069AEnable security posture assessmentImplement attack correlation assessmentData switching networksSpecial data processing applicationsPotential impactData mining
The invention discloses a multidimensional association analysis method and system for advanced persistent threats, and the method comprises the steps: carrying out the association analysis and reorganization of original alarm information, and enabling the alarm information with an association relationship to form an alarm information chain; extracting an attack theme hidden in the alarm information chain through semantic analysis; and calculating a security evaluation value according to the probability of the attack theme. According to the invention, attack correlation assessment can be realized, and potential influence of each attack stage of network threats on the security situation is discovered, so that the whole network security situation assessment is realized.
Owner:UNIV OF SCI & TECH OF CHINA
Estimating impact of property on individual health - property score
Embodiment of the invention provide a method for determining a health index of a property area. The method comprises acquiring property data associated with a property area from a data source, and extracting a first property attribute data from the property data acquired. The first property attribute data extracted is used to determine presence or movement of a first pollutant data within the property area. The method further comprises determining a first potential impact data the first pollutant data may have on individual health based in part on the first property attribute data extracted, and computing a property score representing a health index of the property area based in part on the first potential impact data determined.
Owner:HAYWARD WILLIAM E
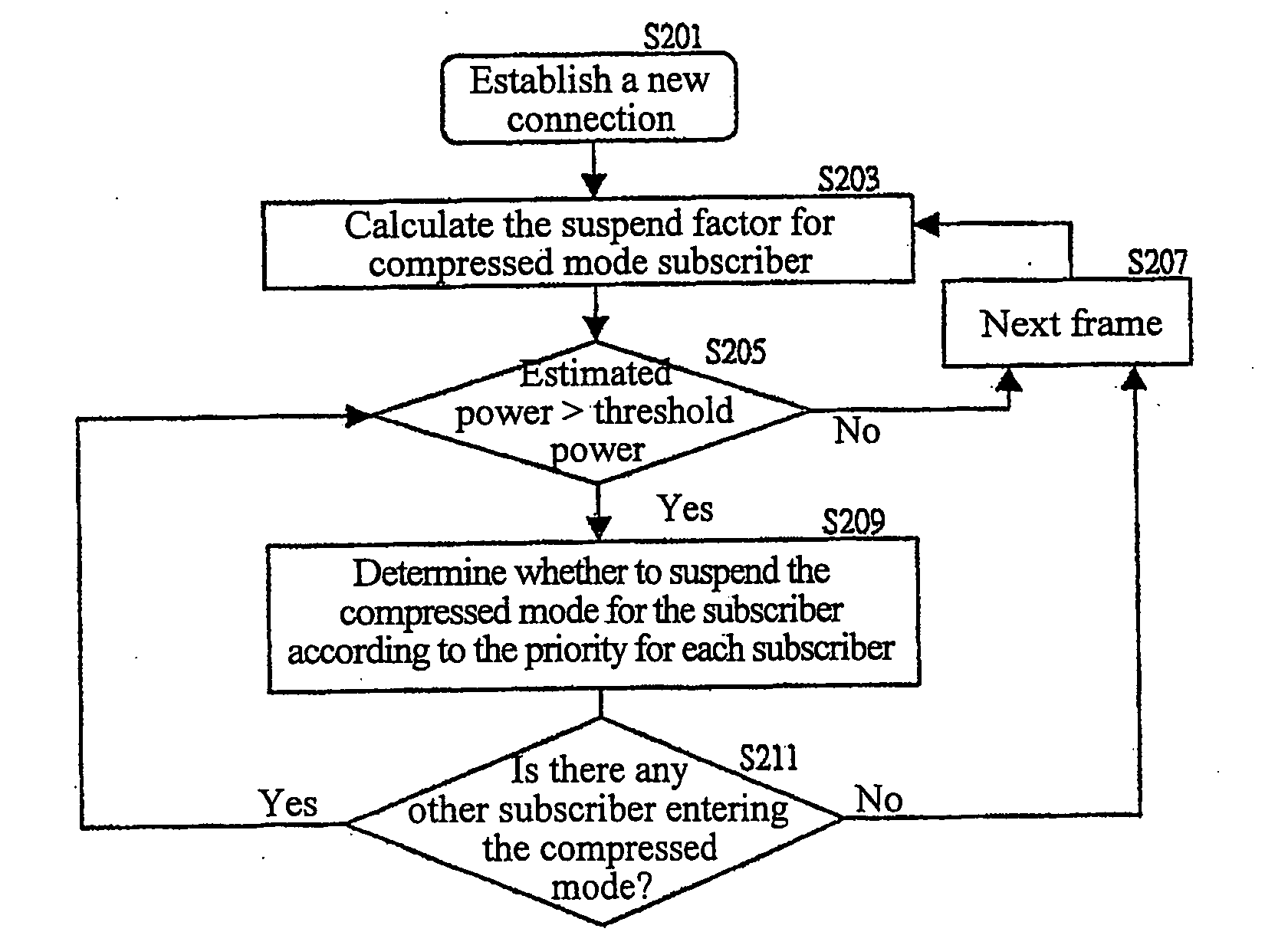
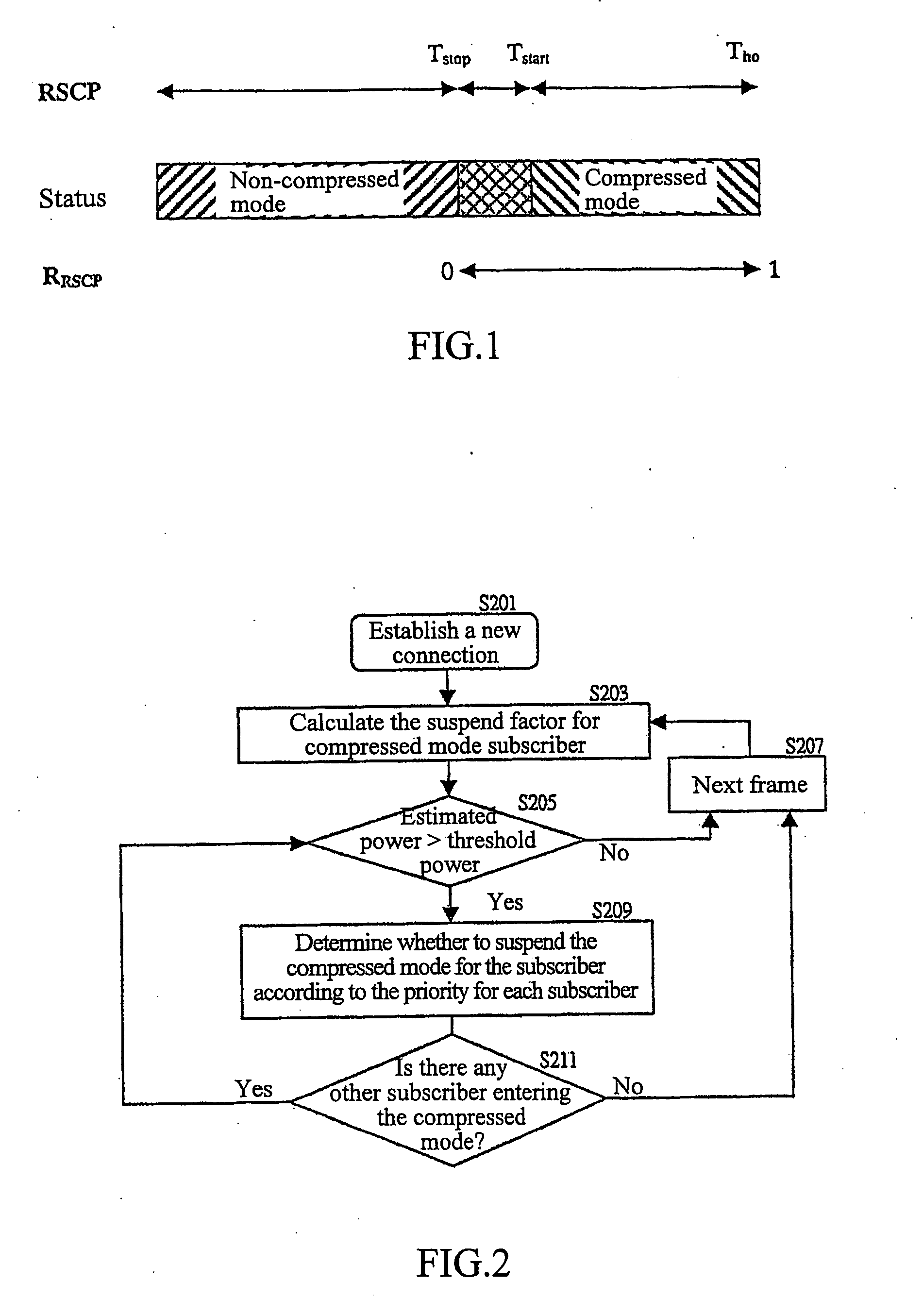
Capacity-based compressed mode control method for inter-system handover in universal mobile telecommunication system
InactiveUS20070258410A1Keep system capacityReduce power consumptionNetwork traffic/resource managementRadio/inductive link selection arrangementsCommunication qualityMode control
The Inter-System handover is one of the key features in the third generation cellular systems. The compressed mode, with variable transmission gaps and power levels, is standardized to support the inter-frequency system handover. To minimize the use of system resources while maintaining the border-cell handover quality, a capacity-based compressed mode control method of the present invention is proposed. Considering the tradeoff between the capacity and the communication quality, the control method can adaptively manage the compressed mode operation based on the potential impacts on the capacity and the effectiveness of the compressed mode measurement. The present invention will improve the effectiveness and performance of the compressed mode operation.
Owner:NAT CHIAO TUNG UNIV
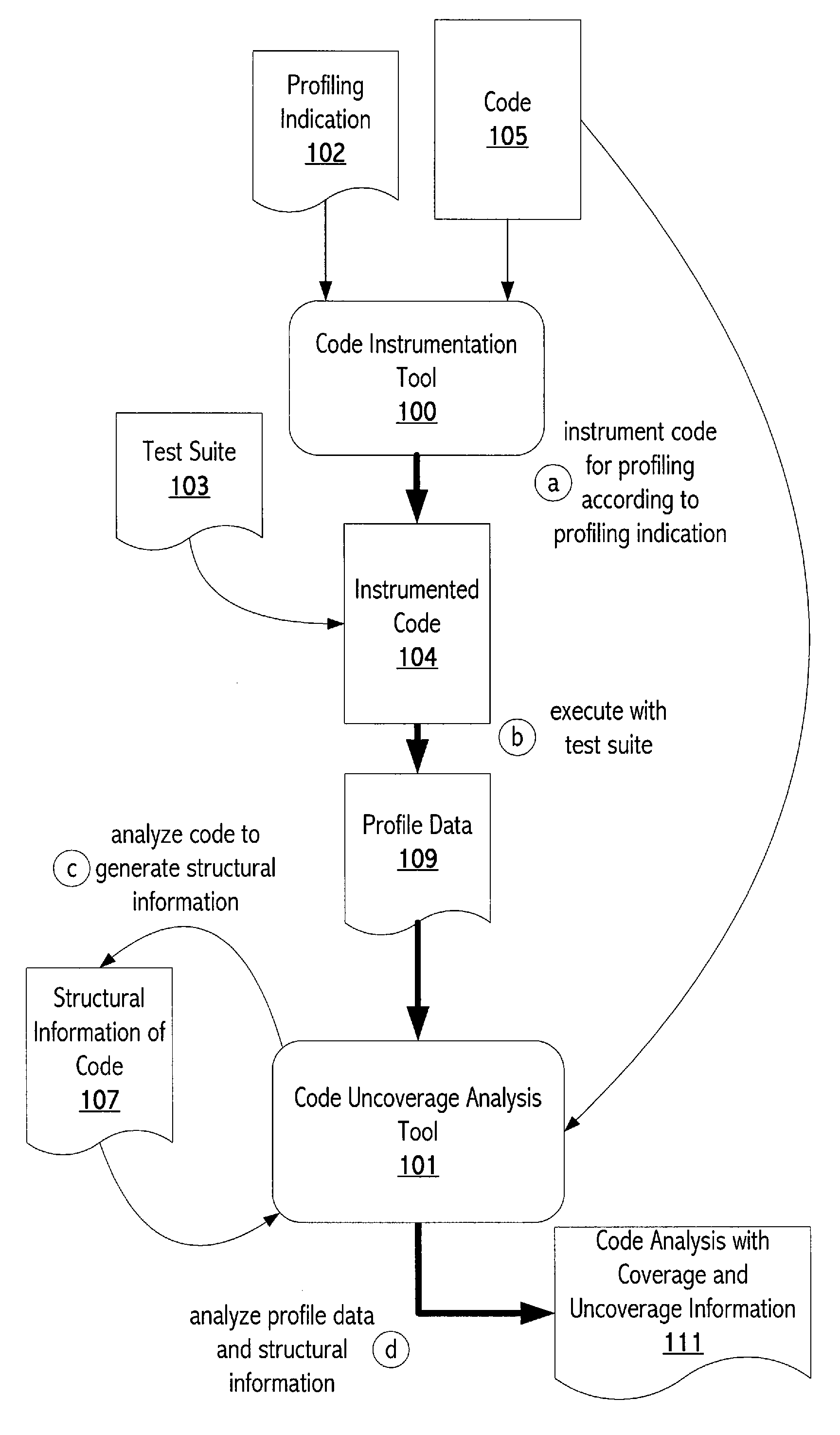
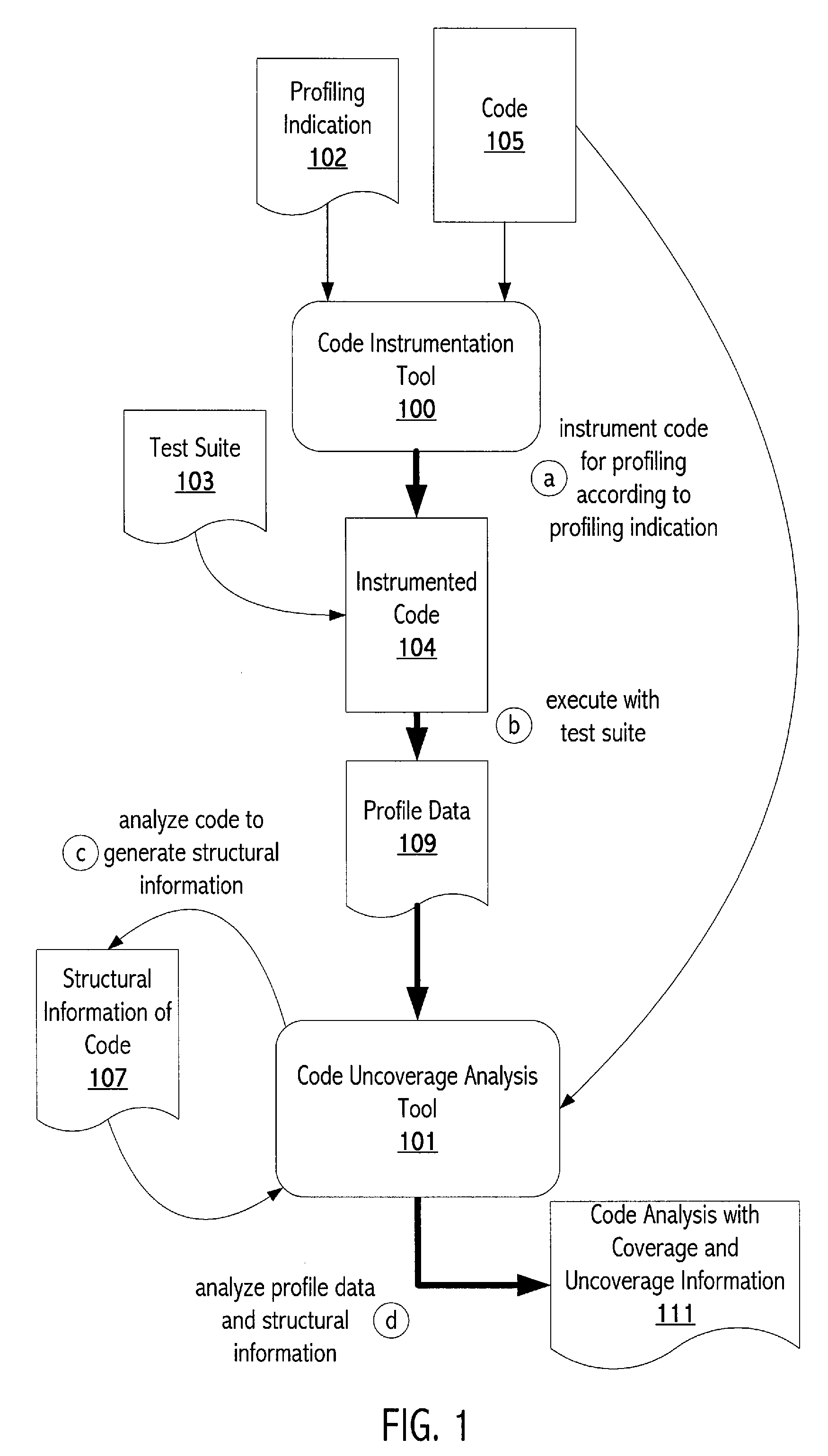
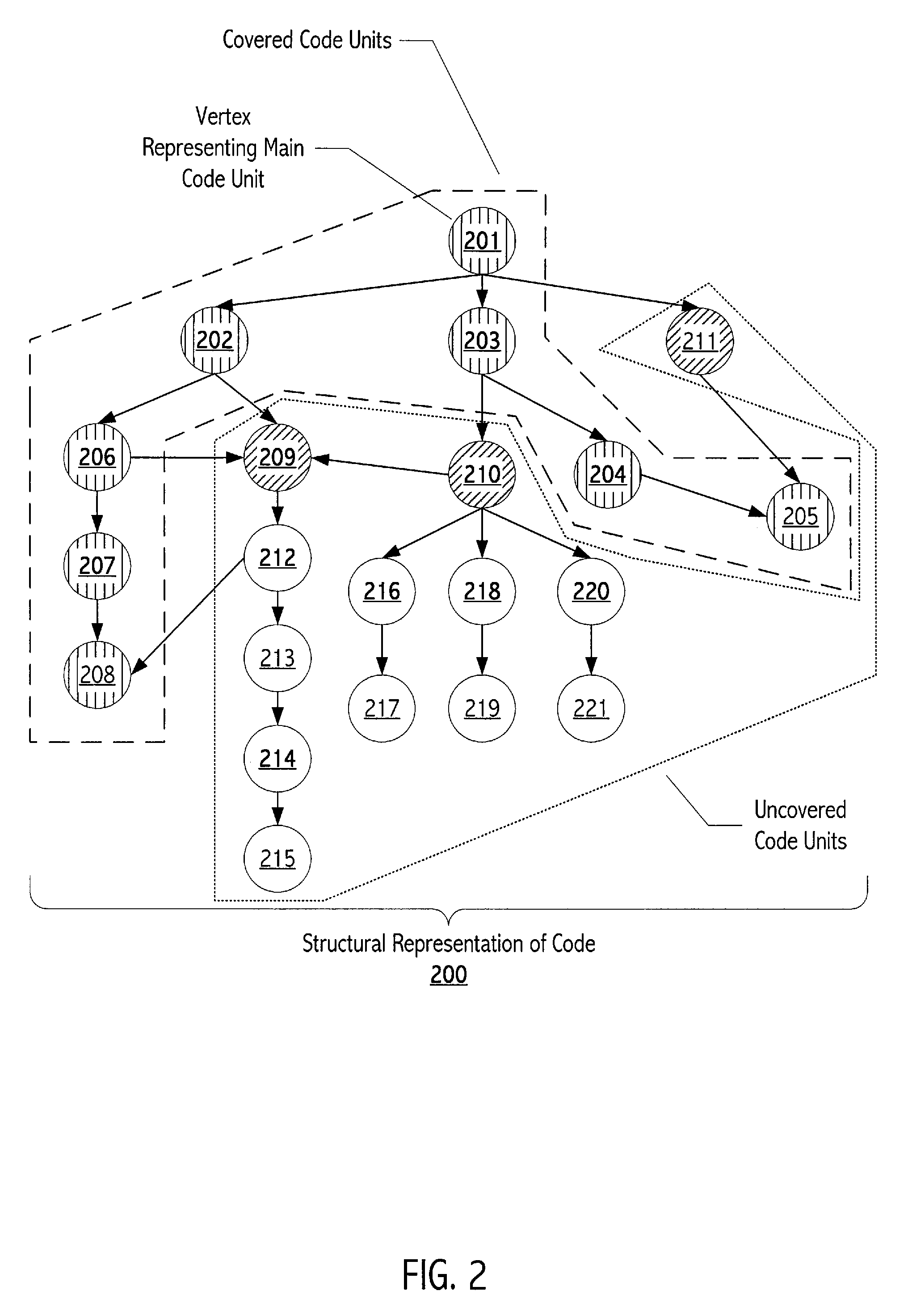
Uncoverage tool
ActiveUS20080022262A1Expand coverageEfficient targetingError detection/correctionSpecific program execution arrangementsControl flowParallel computing
Indication of uncoverage information allows tests to be tailored to target those uncovered code units with the most potential to increase coverage of a program. A tool examines coverage information of a program to identify code units of the program that were not covered by test data used to exercise the program. The tool also examines structural information (e.g., control flow) for the program to identify those of the uncovered code units that have direct control flow from a corresponding covered code unit (“root level uncovered code units”). The coverage tool then measures potential impact on coverage for each of the root level uncovered code units.
Owner:SUN MICROSYSTEMS INC
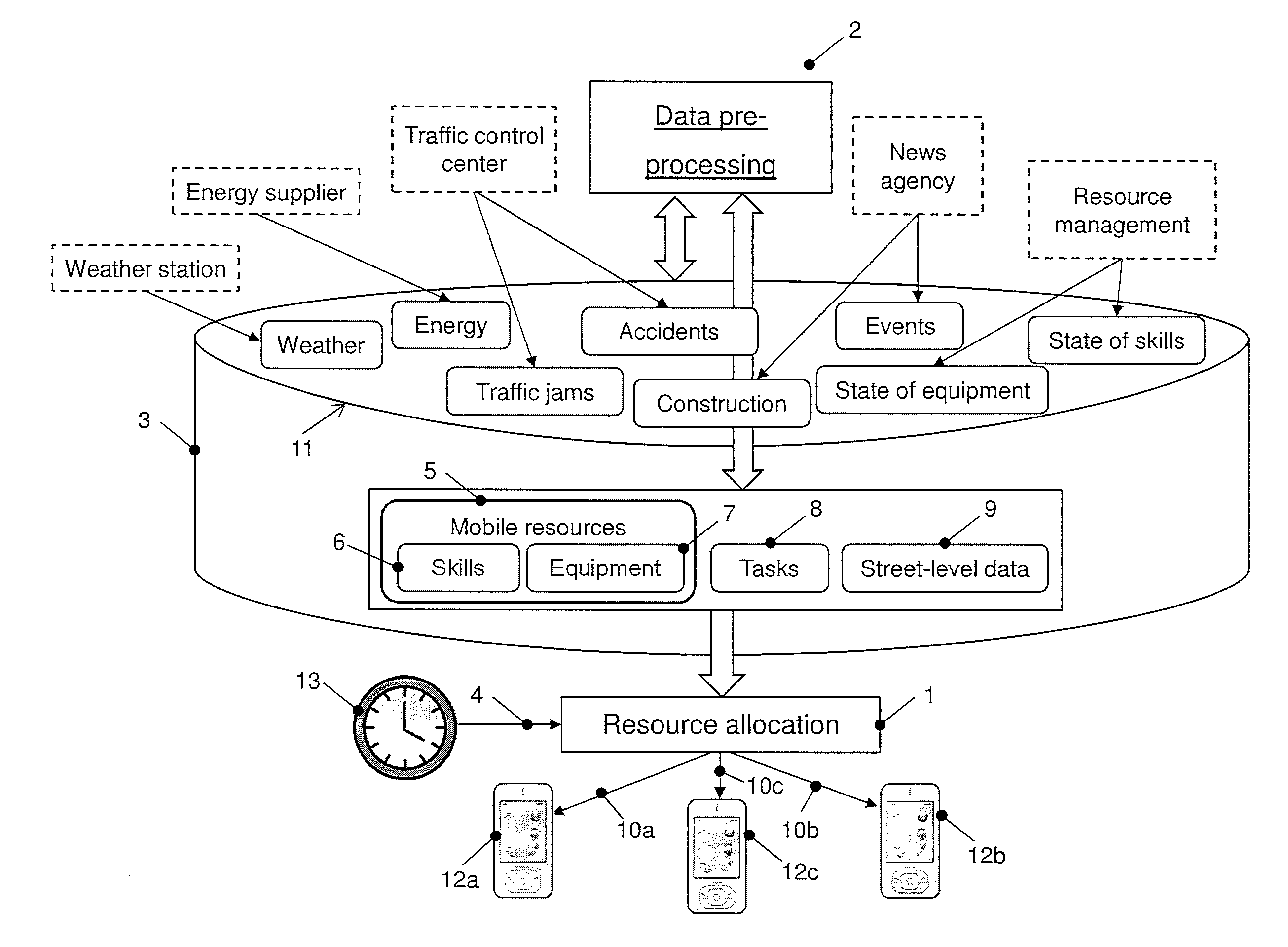
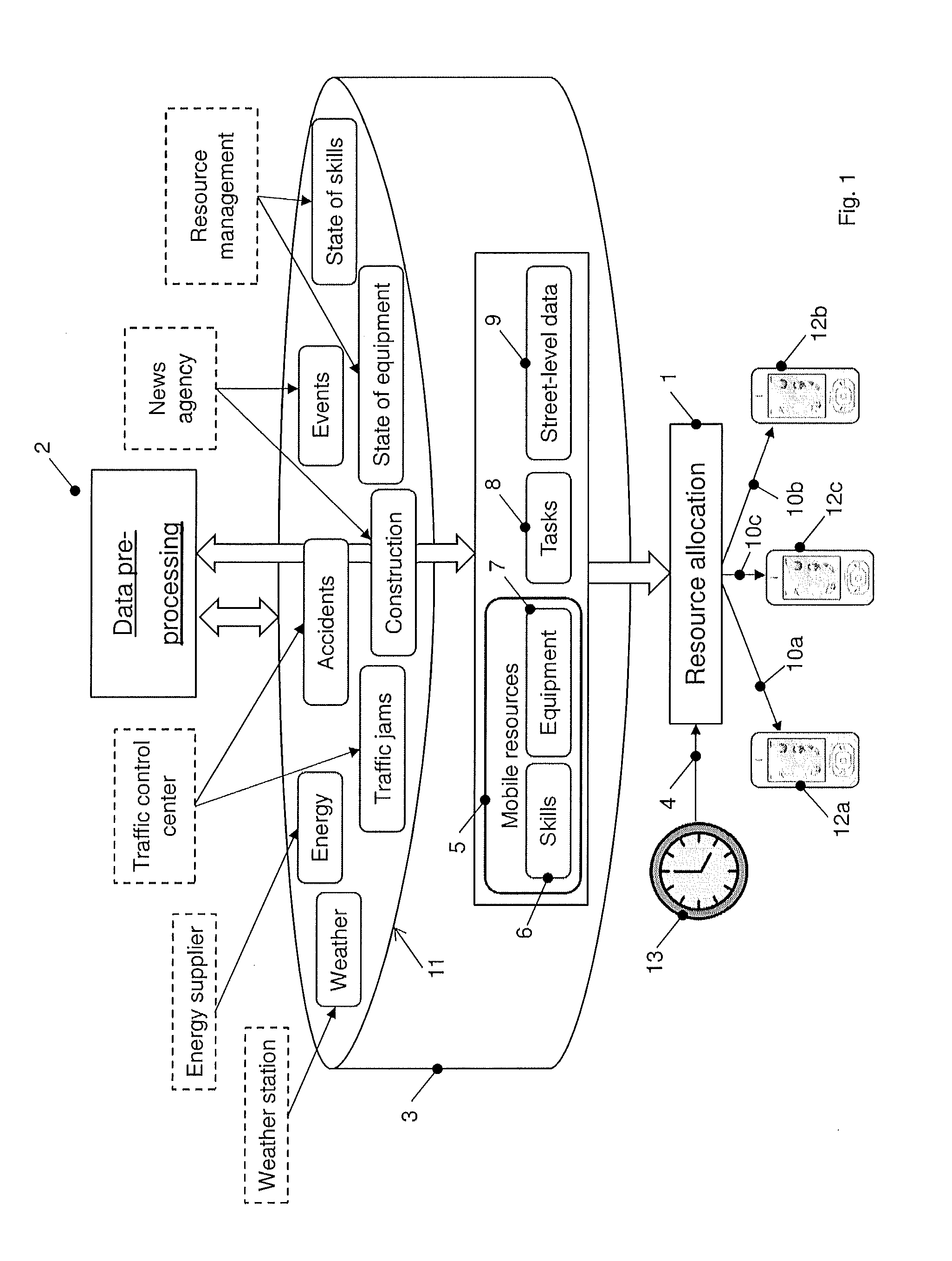
System and method for automatic allocation of mobile resources to tasks
A system for automatic allocation of mobile resources to tasks includes at least one database which stores for each mobile resource at least one corresponding skill and equipment as well as street-level data defining roads between a current location of the mobile resources and the distant locations of the tasks, and dynamic data which have a potential impact on performance of the tasks. A first data processing unit allocates the mobile resources to the tasks by allocating the skills to the tasks and the equipment, and generates for at least one of the mobile resources an individual schedule including a street-by-street route along the roads to the respectively allocated tasks. A second data processing unit continuously pre-processes the dynamic data to determine which of the street-level data, the mobile resources and the tasks are affected by the dynamic data and to what extent, and to amend the affected data accordingly.
Owner:ABB POWER GRIDS SWITZERLAND AG
Method and device for automatic gain control in wireless communication system
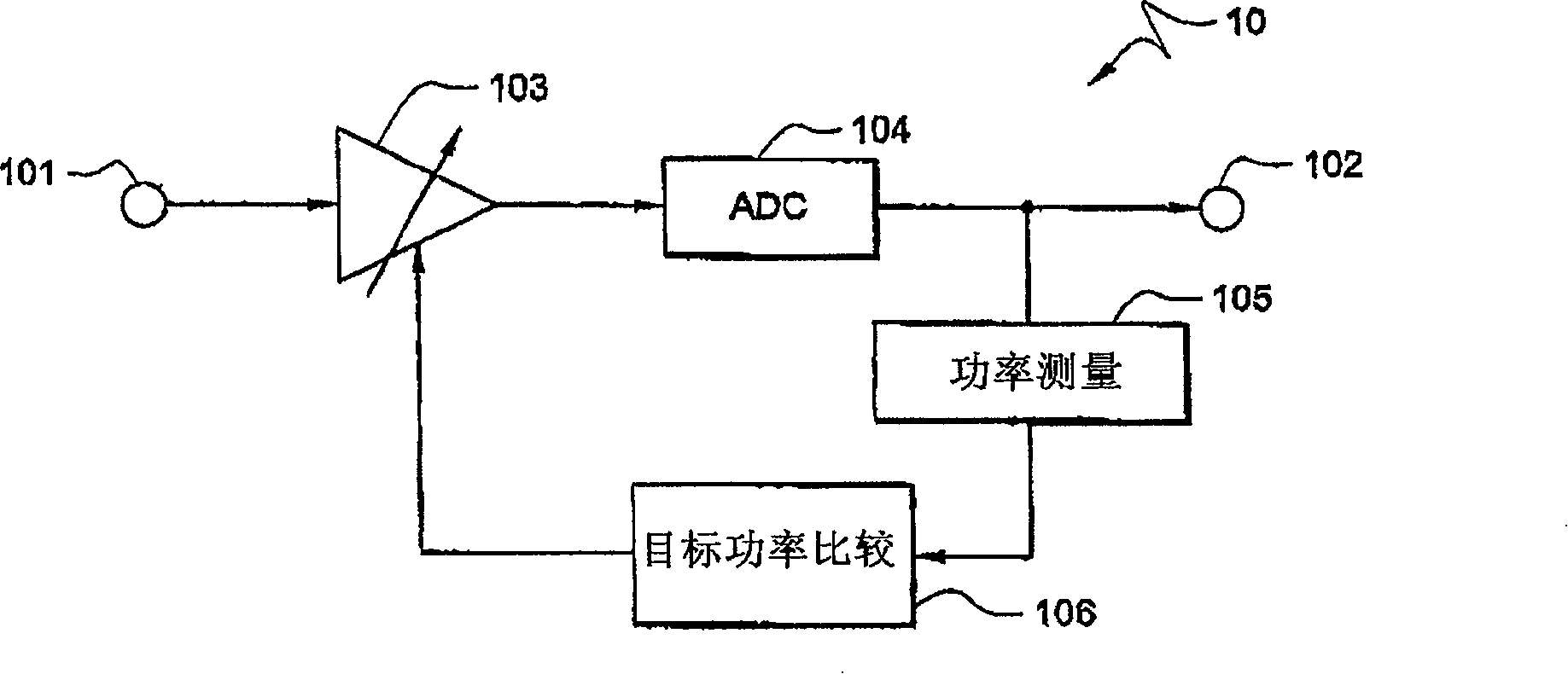
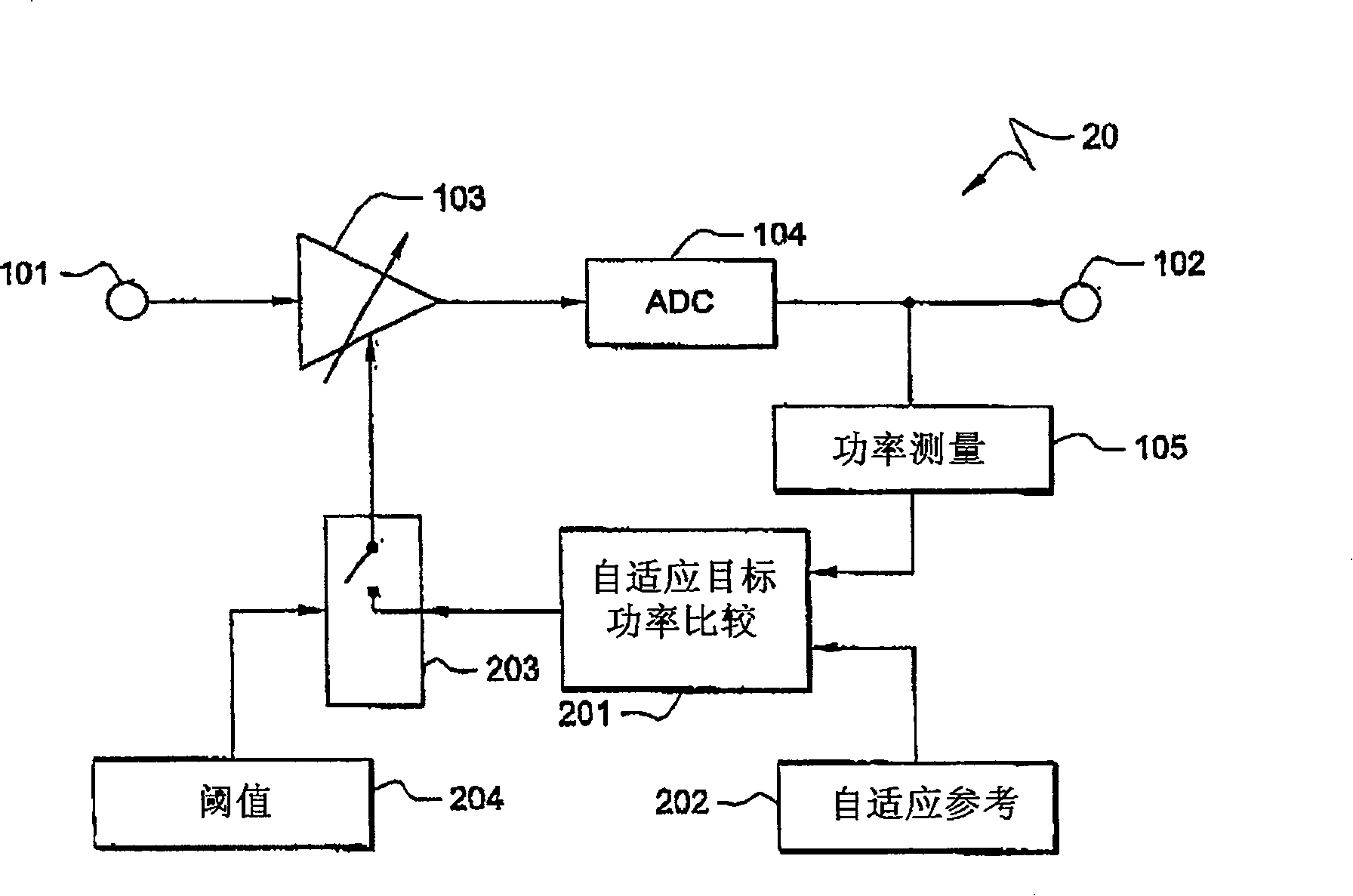
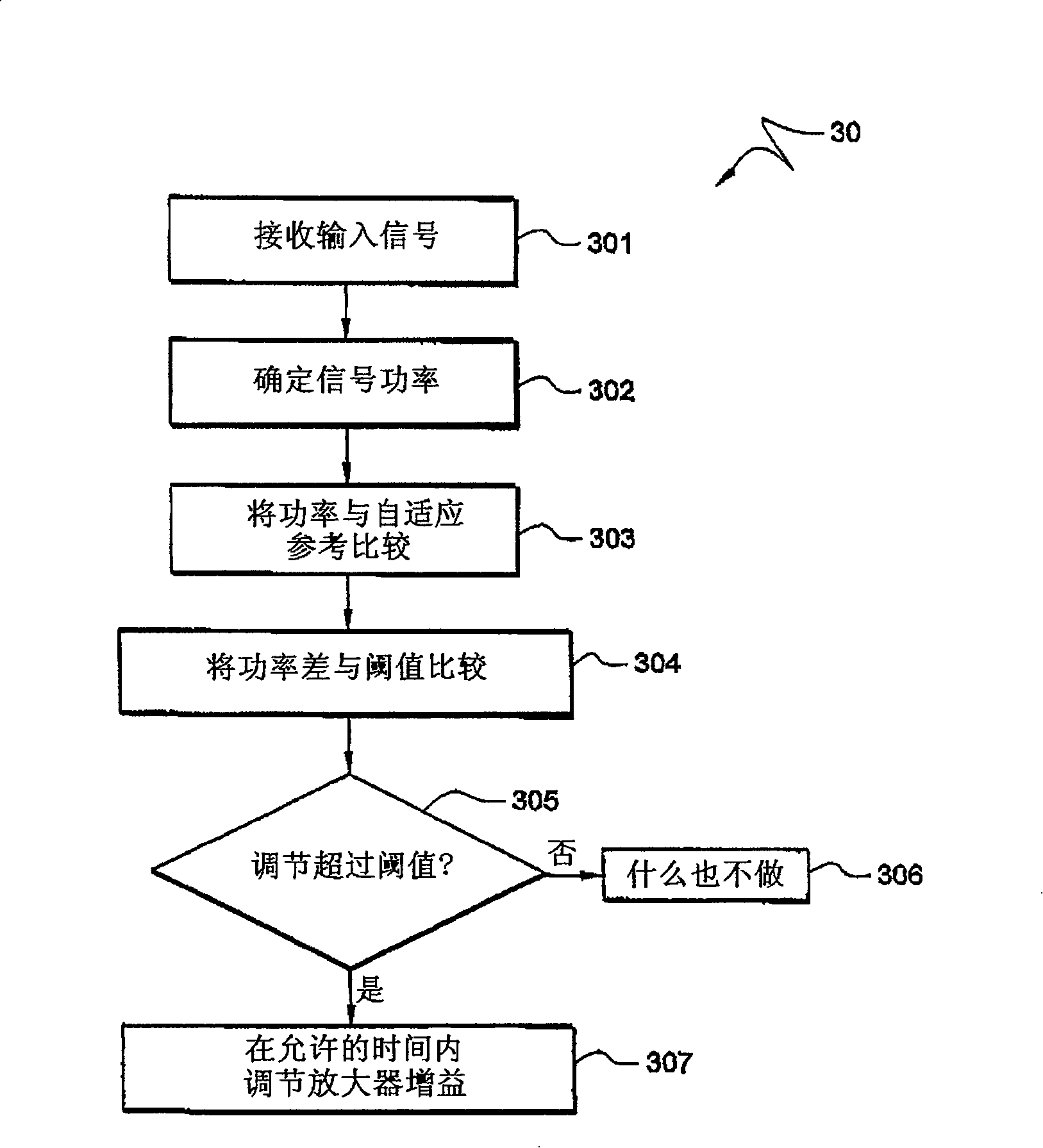
InactiveCN101192862AReduce oscillationReduce the ping-pong effectTransmission control/equalisingGain controlCommunications systemSignal-to-noise ratio (imaging)
The invention provides an automatic gain control (AGC) system and a method which has an adaptive reference and an adaptive threshold value. The adaptive reference allows the target power to be adjusted according to variation of the operation parameter and condition, such as the modulation mode changing for sustaining the performance with different Signal to Noise Ratio (SNR), while the adaptive threshold value allows a fast AGC response and reduces the delayed and potential impact. The invention has the advantage that the AGC level can be changed between the symbol prefix and the symbol suffix, but can not be changed during the data part of the signal. The embodiment provided allows the AGC to be changed according to each symbol in OFDM, OFDMA and TDD systems.
Owner:ADAPTIX
Magnetically repulsive sport equipment
InactiveUS20140283286A1Reduce impactEasy and efficient to manufactureChemical protectionHeat protectionSports equipmentEngineering
The present invention is a sport equipment system for reducing the impact force on sport equipment using magnetic repulsion. The sport equipment system includes sport equipment that is worn by a wearer. The sport equipment has a body, at least one magnetic element associated with the body, and an impact absorbing member configured to receive at least a portion of the magnetic element. The magnetic element has a first pole orientated in a direction exterior of the sport equipment, and is configured to produce a repulsive magnetic force when a second magnetic element of a second sport equipment is at a predetermined distance from the sport equipment prior to the sport equipment contacting the second sport equipment. The magnetic element reduces the impact force prior to a potential impact, and the impact absorbing member reduces the impact force after any impact.
Owner:YOON SEBASTIAN
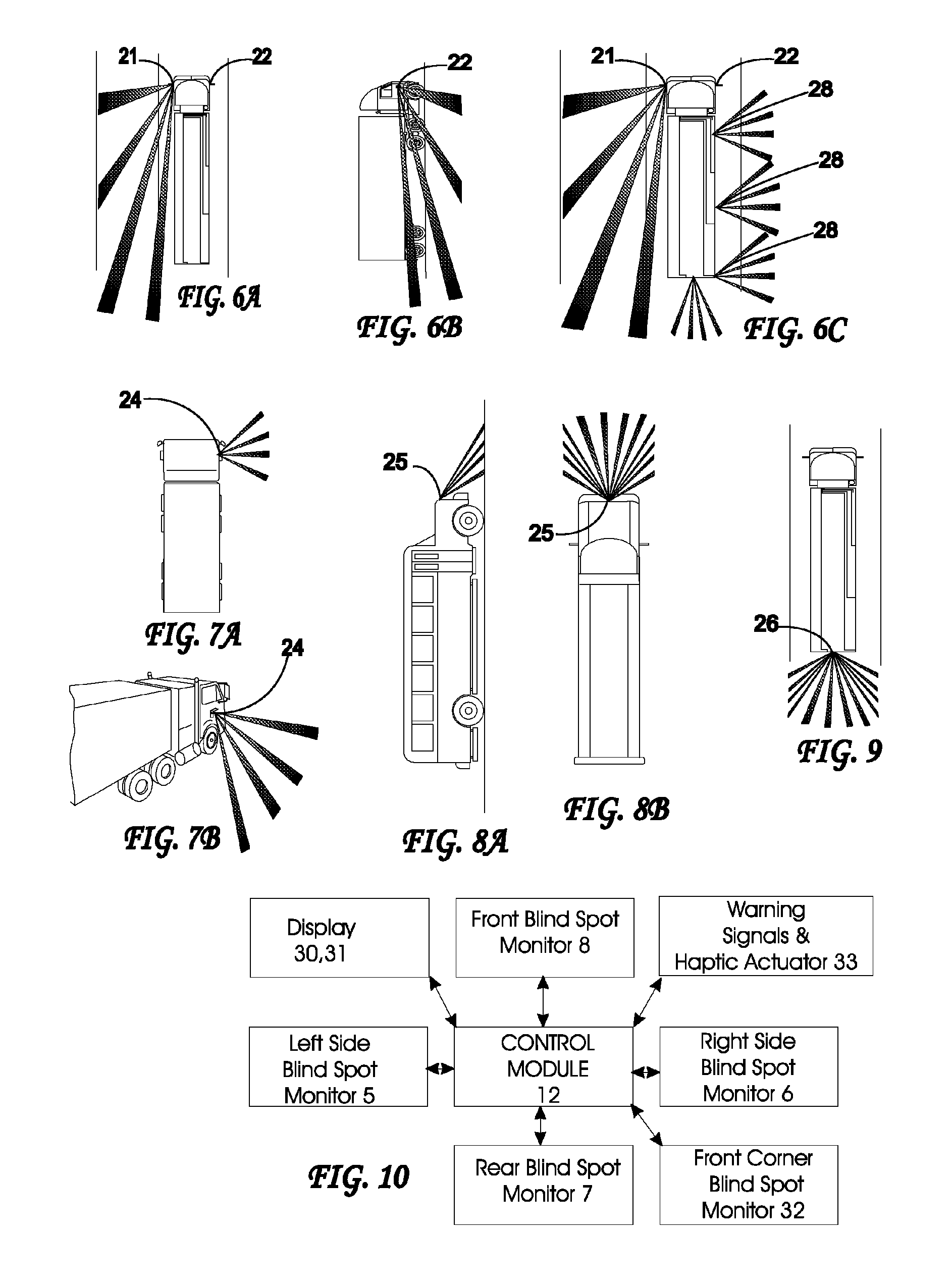
System and method for impact prediction and proximity warning
InactiveUS9384645B1Road vehicles traffic controlVisible signalling systemsObject basedPotential impact
A system for predicting and warning of impacts includes a sensor located remote from a user and configured to acquire user data regarding motion of the user and object data regarding motion of the object; and a processing circuit configured to predict a potential impact between the user and the object based on the user data and the object data; and control operation of a user-wearable warning device to provide a warning output to the user in advance of a predicted time of the potential impact.
Owner:ELWHA LLC
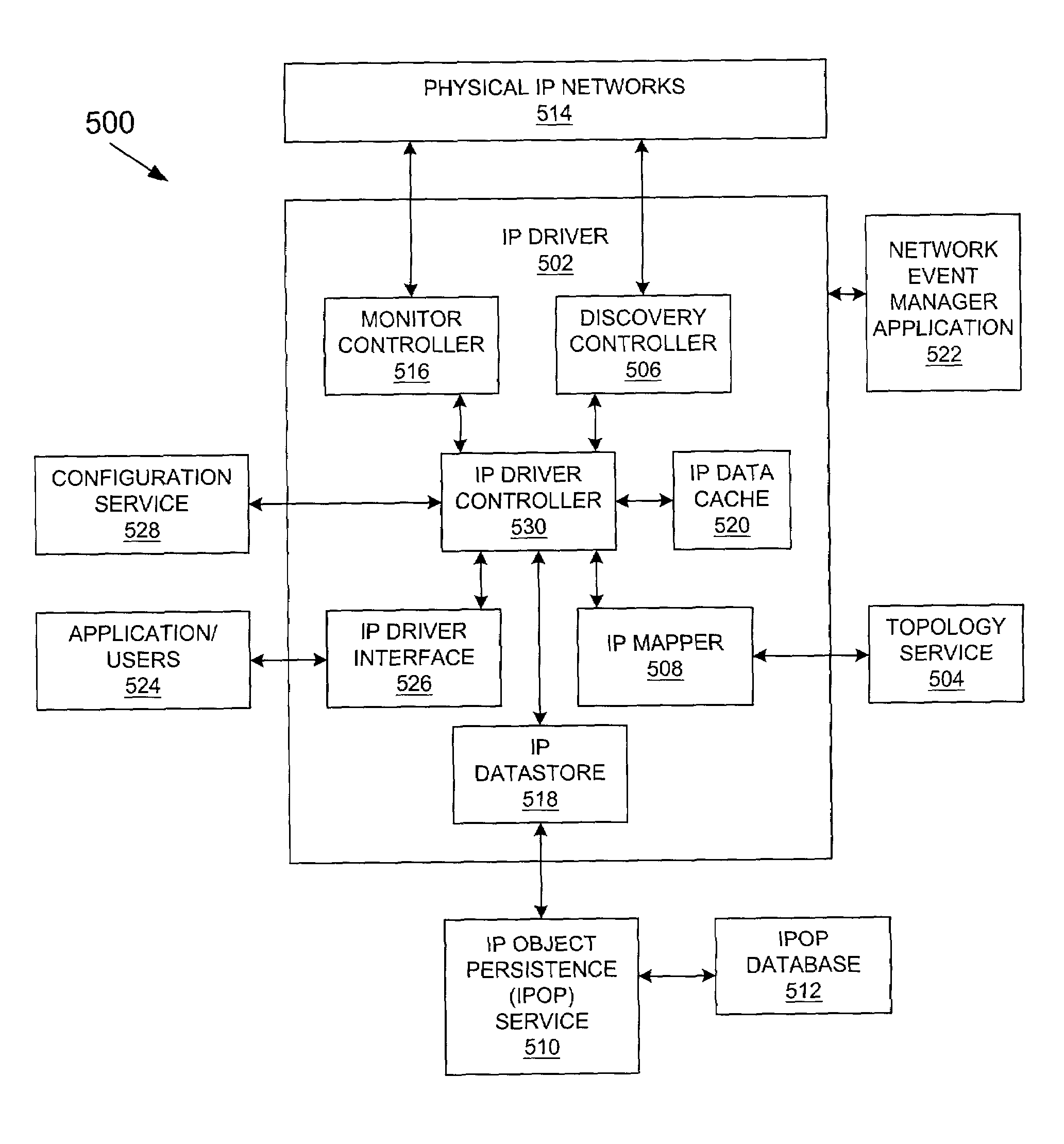
Method and system for network management with per-endpoint adaptive data communication based on application life cycle
A method, system, apparatus, and computer program product is presented for management of a distributed data processing system. The present invention uses an improved iterator methodology to dynamically adapt the administrative communication operations of the network management system so as to minimize the potential impact on system performance, including customer applications, that might be caused by system management operations. In particular, the adjustments to the operations occur in accordance with a phase or life cycle state of system management applications.
Owner:GOOGLE LLC
Supplemental side impact protection system for automotive vehicle
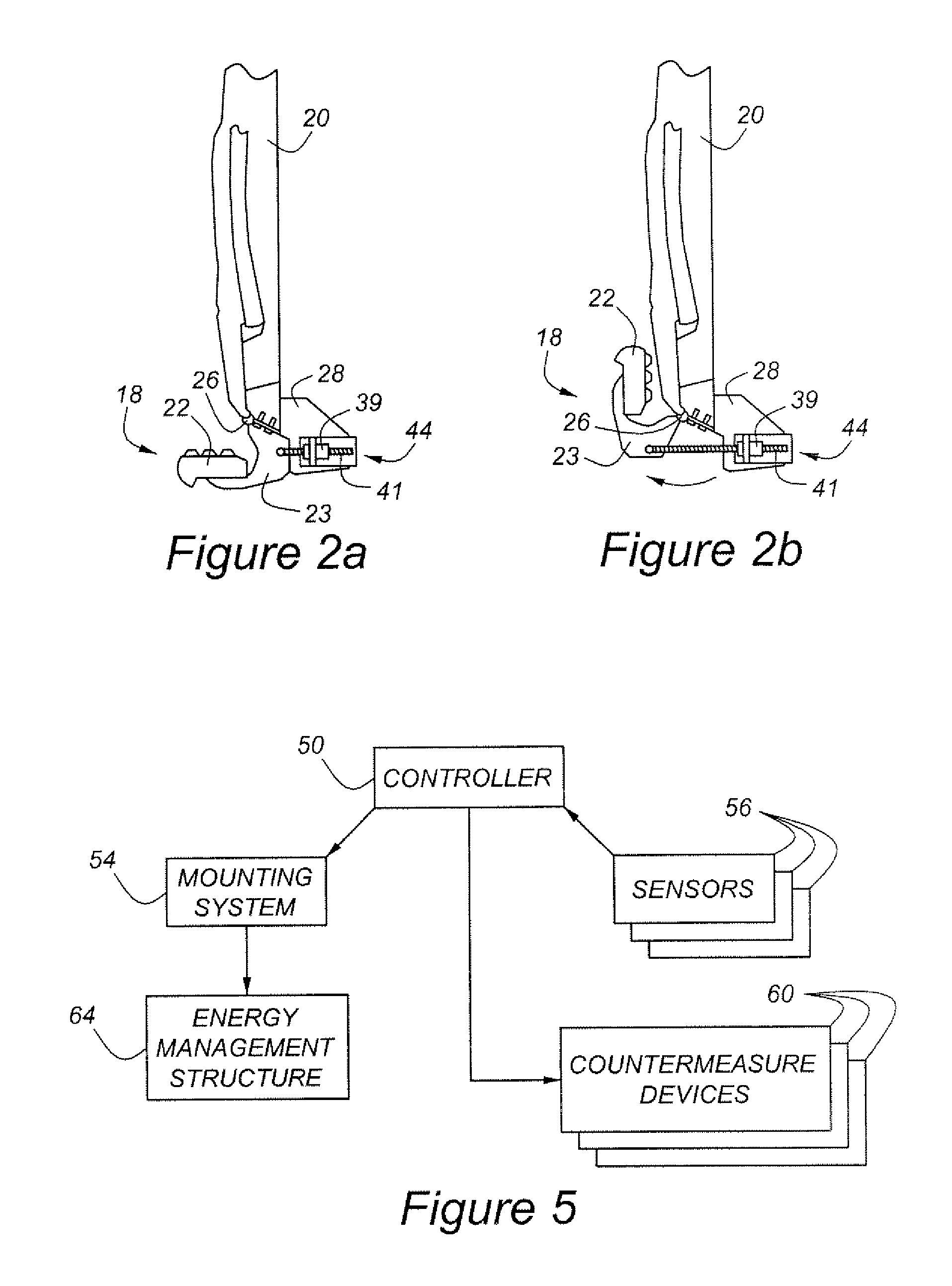
A supplemental impact protection system for an automotive vehicle includes an external energy management structure having a first position for normal vehicle operation and a second position for deployment during an impact event. A mounting system allows selective positioning of the energy management structure in either the first or second position, as determined by a controller which assesses an impact potential of the vehicle and operates the mounting system to move the energy management structure to the second, or deployed, position in the event that the assessed impact potential satisfies a predetermined threshold.
Owner:FORD GLOBAL TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com