Patents
Literature
195 results about "Local variable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
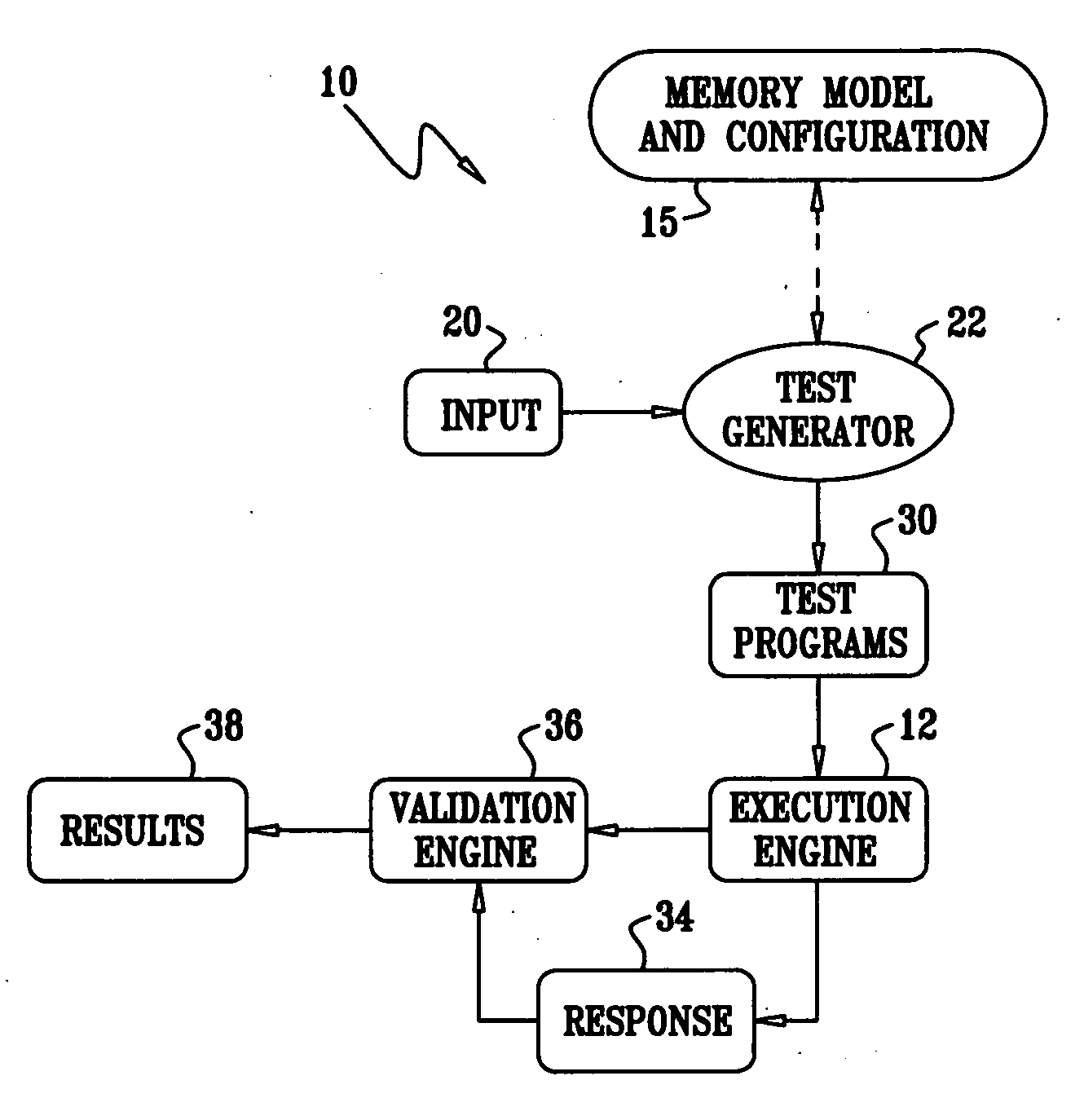
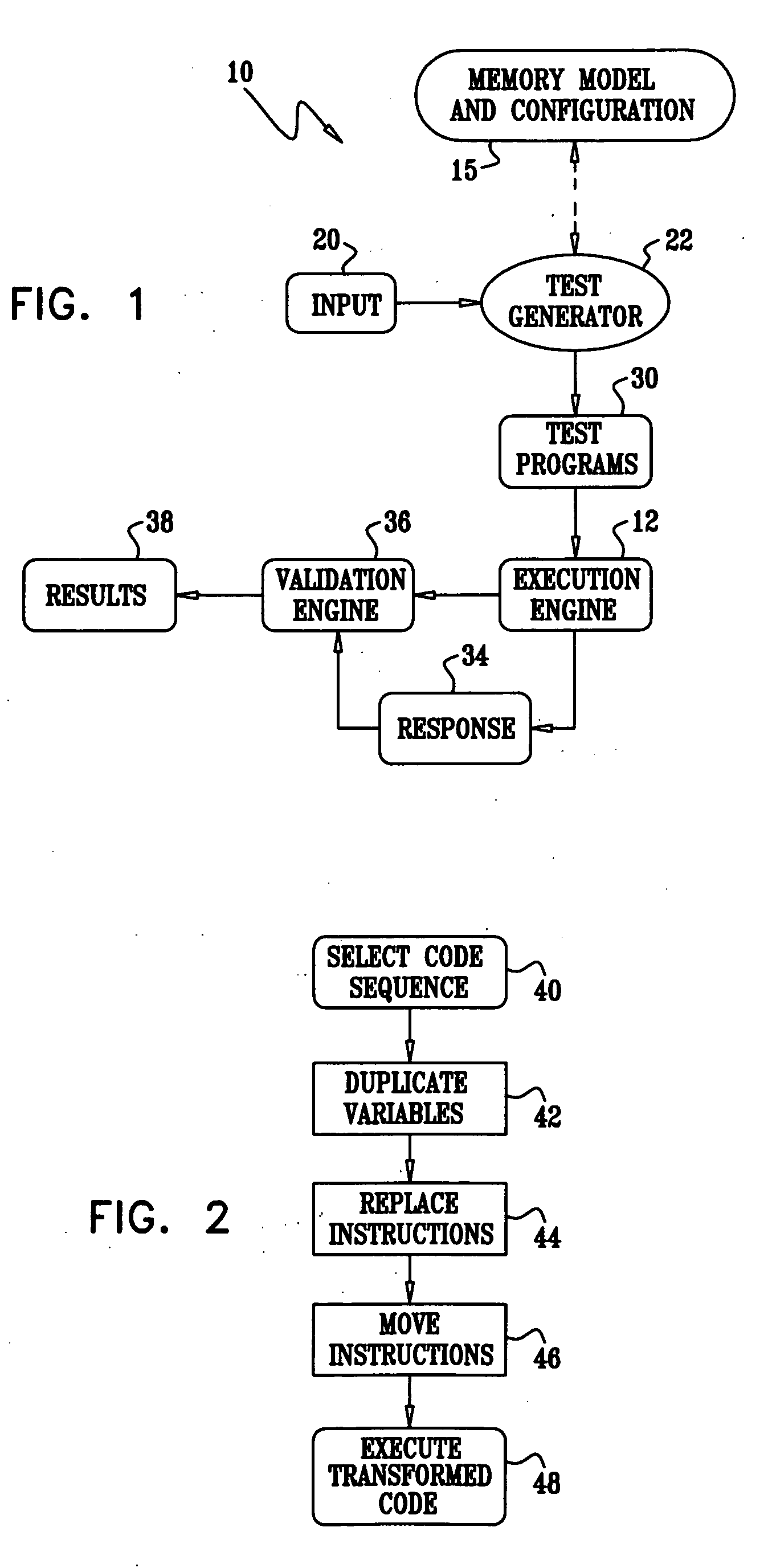
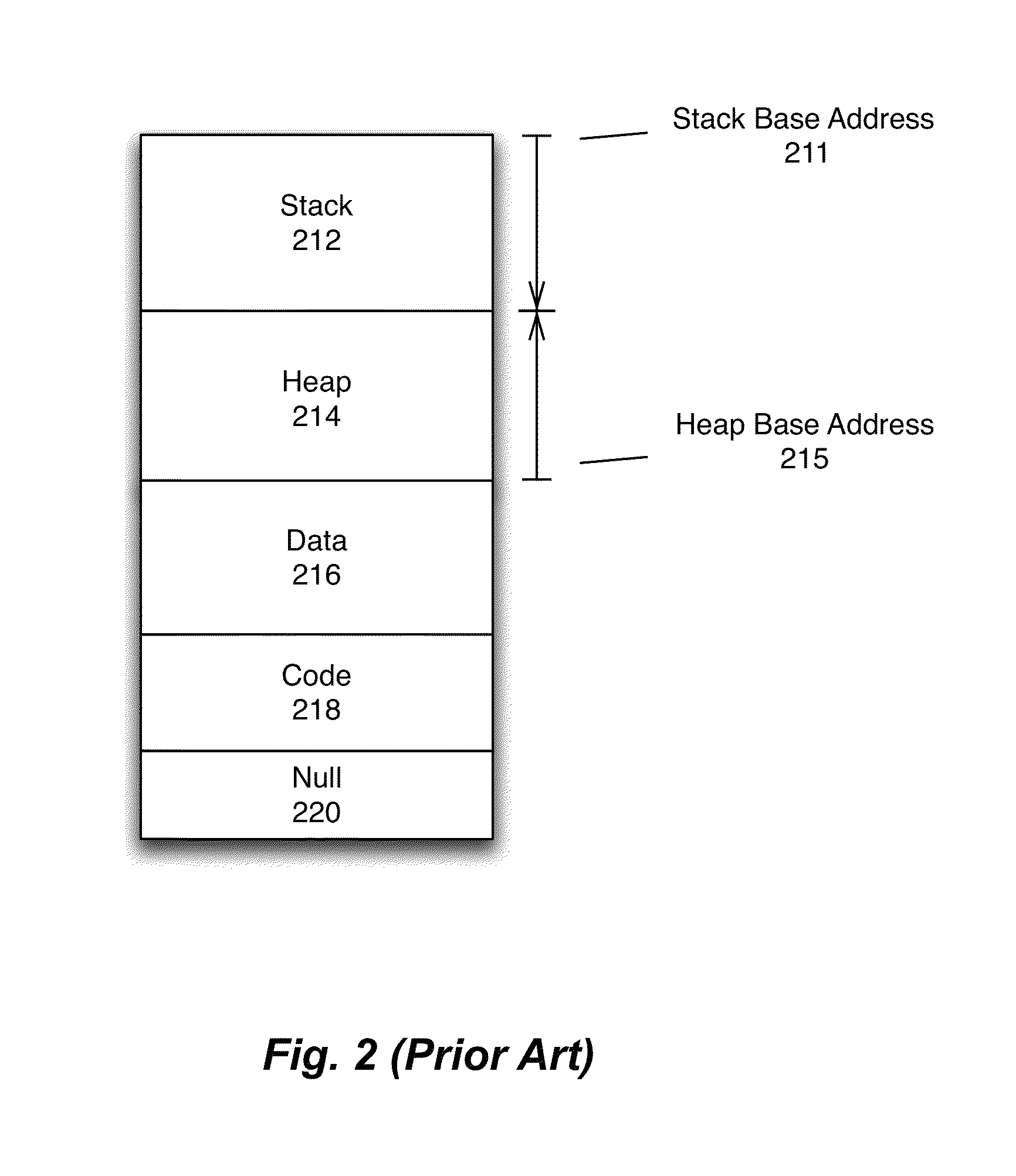
In computer science, a local variable is a variable that is given local scope. Local variable references in the function or block in which it is declared override the same variable name in the larger scope. In programming languages with only two levels of visibility, local variables are contrasted with global variables. On the other hand, many ALGOL-derived languages allow any number of nested levels of visibility, with private variables, functions, constants and types hidden within them, either by nested blocks or nested functions. Local variables are fundamental to procedural programming, and more generally modular programming: variables of local scope are used to avoid issues with side-effects that can occur with global variables.
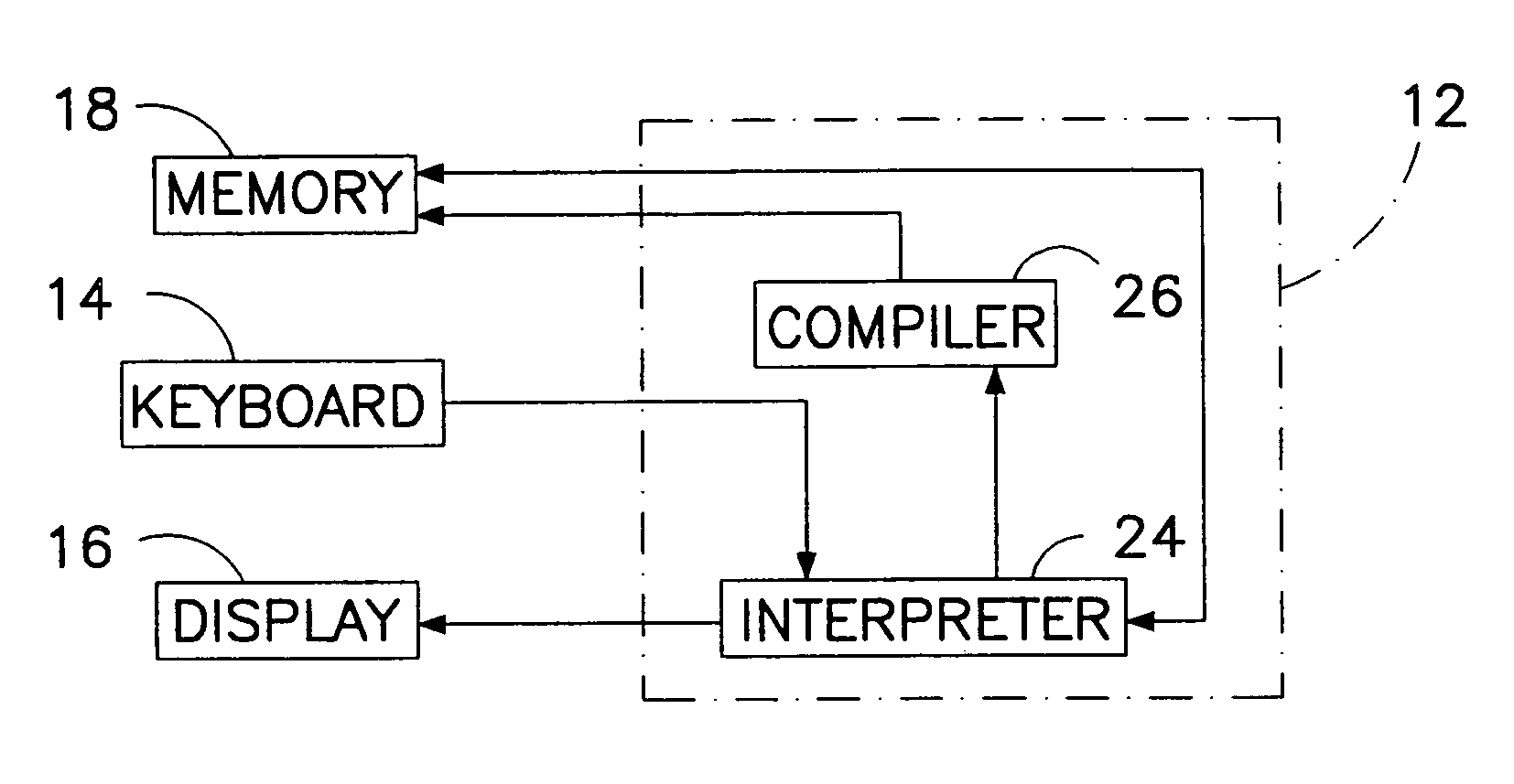
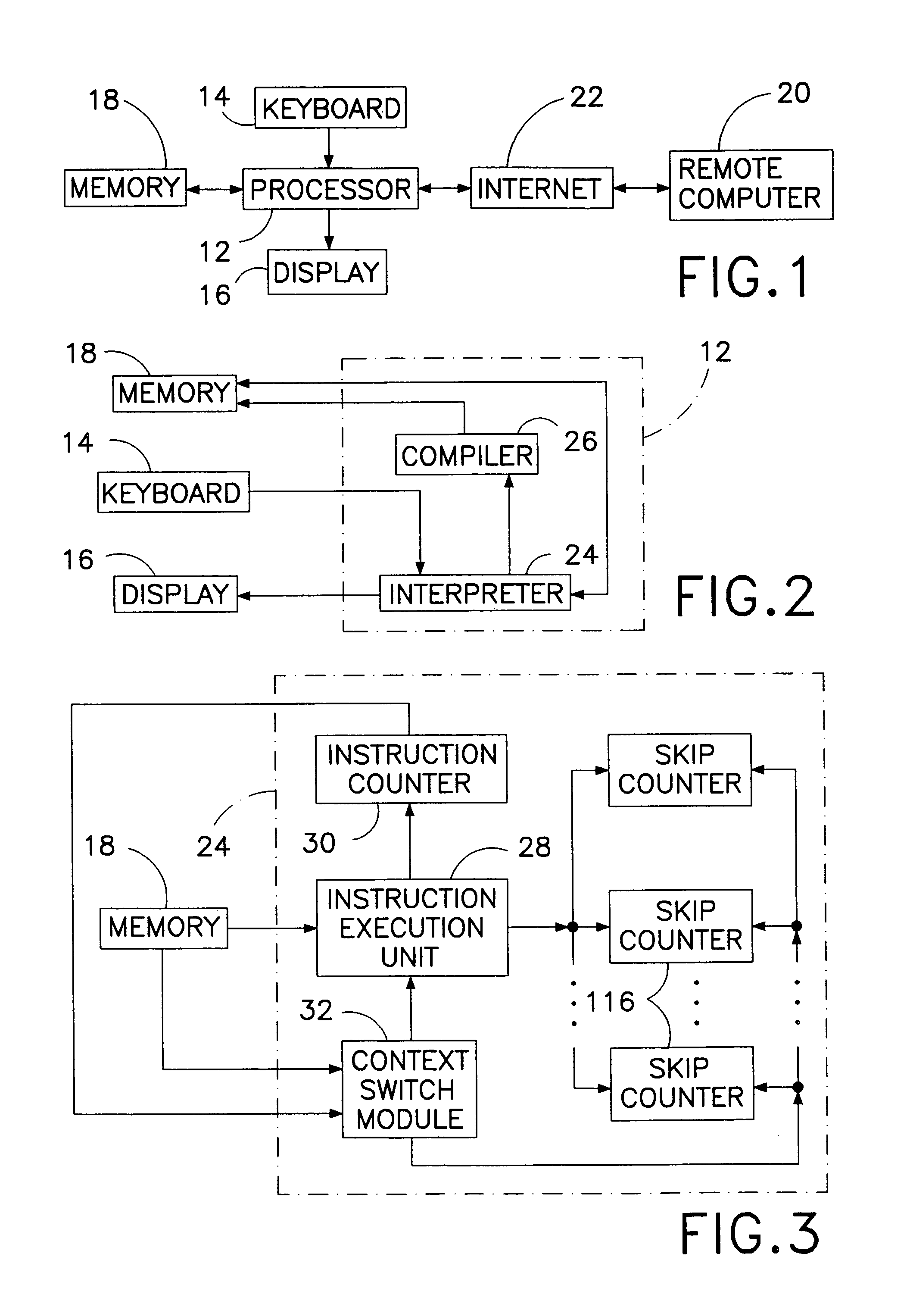
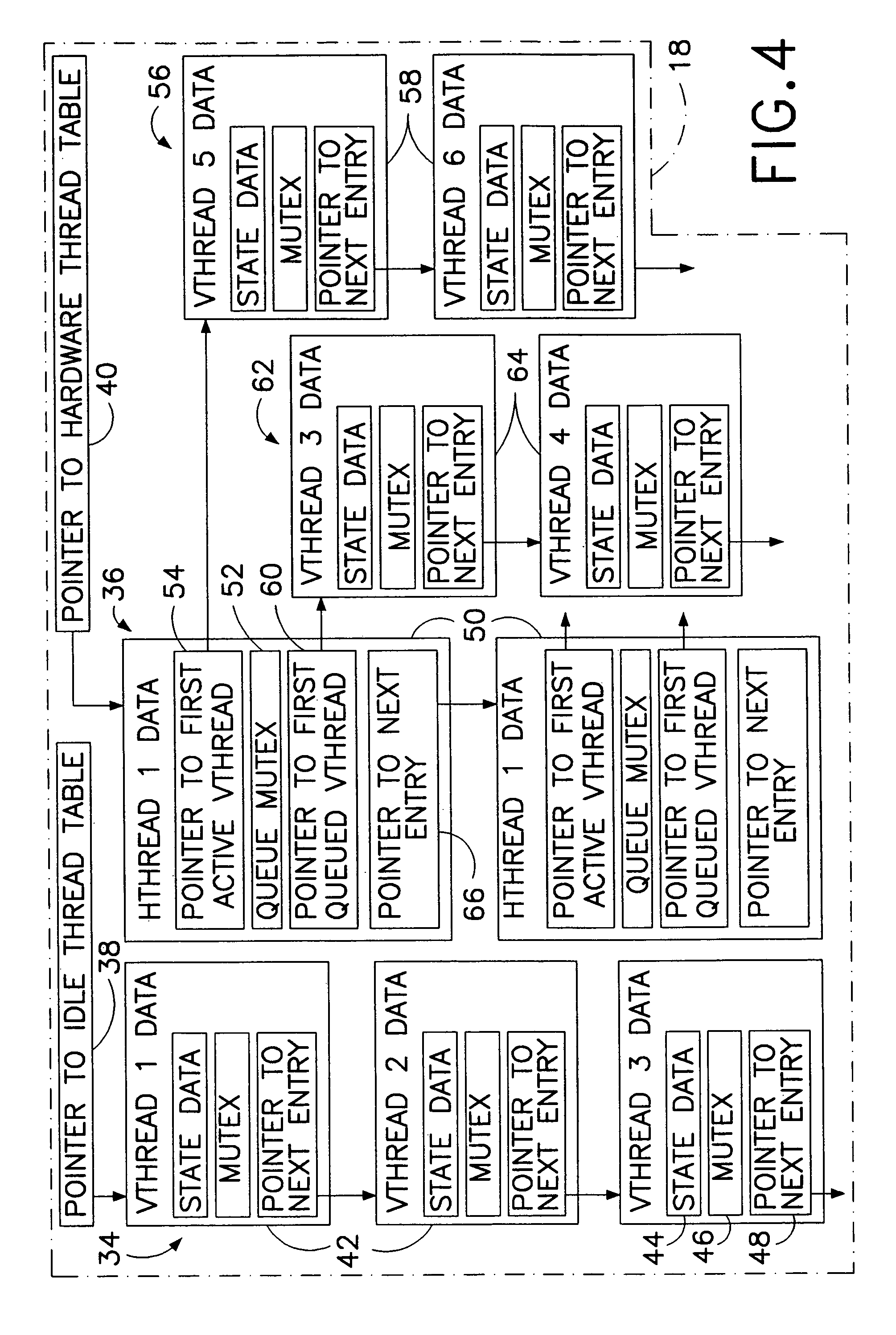
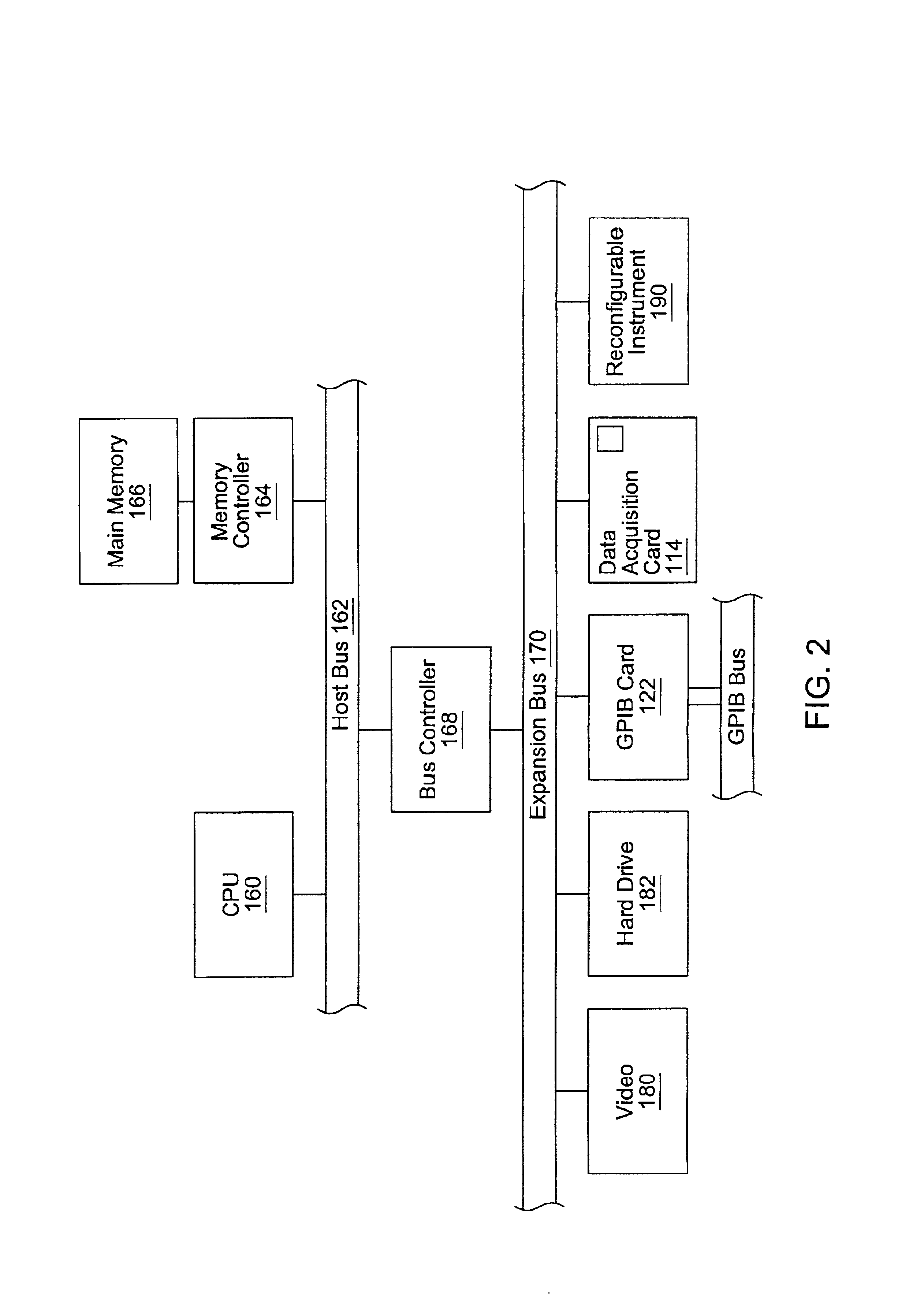
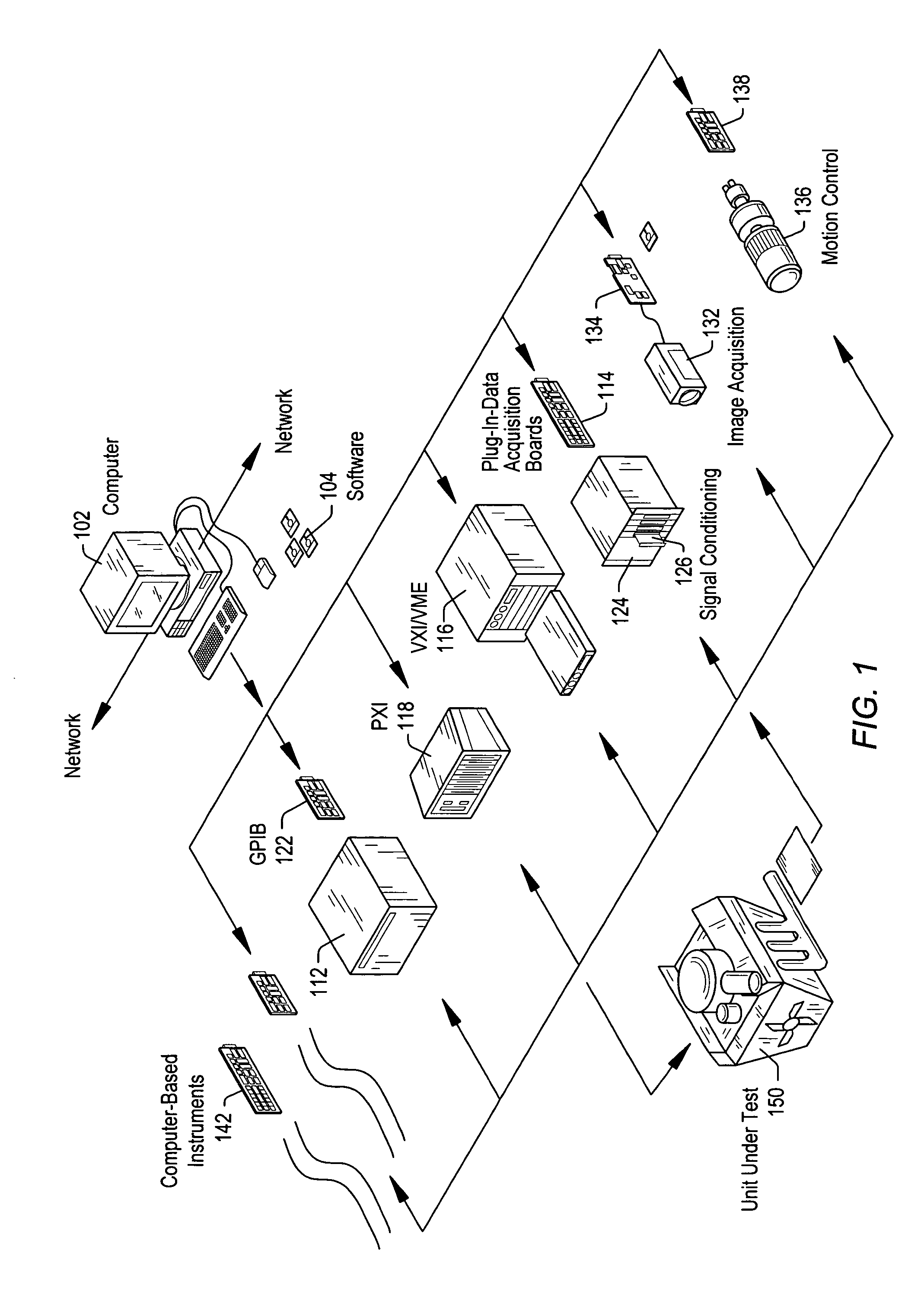
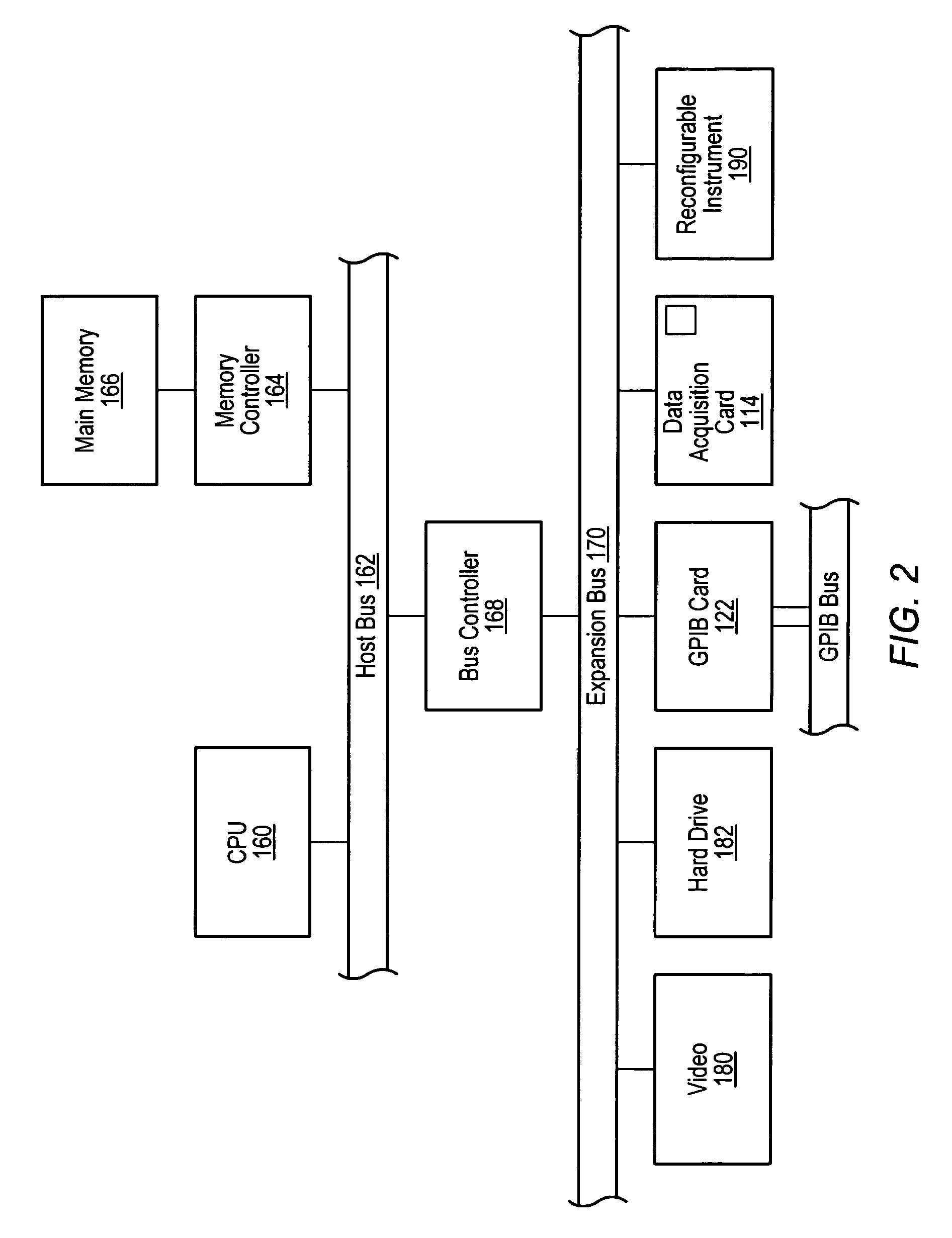
Computer multi-tasking via virtual threading using an interpreter
InactiveUS7234139B1Eliminate dependenciesDifferent operationalProgram initiation/switchingInterprogram communicationLocal variablePseudocode
In the operation of a computer, a plurality of bytecode or pseudocode instructions, at least some of the pseudocode instructions comprising a plurality of machine code instructions, are stored in a computer memory. For each of a plurality of tasks or jobs to be performed by the computer, a respective virtual thread of execution context data is automatically created. The virtual threads each include (a) a memory location of a next one of the pseudocode instructions to be executed in carrying out the respective task or job and (b) the values of any local variables required for carrying out the respective task or job. At least some of the tasks or jobs each entails execution of a respective one of the pseudocode instructions comprising a plurality of machine language instructions. Each of the tasks or jobs are processed in a respective series of time slices or processing slots under the control of the respective virtual thread, and, in every context switch between different virtual threads, such context switch is undertaken only after completed execution of a currently executing one of the pseudocode instructions.
Owner:CERINET USA
Determination of local variable type and precision in the presence of subroutines
InactiveUS6442751B1Accurate trackingData processing applicationsSoftware engineeringLocal variableComputer science
A method is provided for tracking the type of at least one local variable after calling a subroutine. The exemplary method associates each one of a plurality of branch instructions calling the subroutine with a first information, which indicates the type of value stored in the local variable when each one of the plurality of branch instructions is executed. The exemplary method associates at least one execution point-of-interest within the subroutine with a second information. The execution point-of-interest is any point within the subroutine where it may be necessary to ascertain the type of each local variable. The second information is a data structure indicating a change in type made to the local variable after entering the subroutine and before the execution point-of-interest. The exemplary method associates the execution point-of-interest with a return address for the subroutine. This return address enables the method to identify the point in the calling program from which the current subroutine was called. When a request is received to identify the type of the local variable at the execution point-of-interest in the subroutine, the exemplary method obtains a second map from the second information using the execution point-of-interest. The second map indicates the change in type of the local variable made within the subroutine. The method also obtains the return address associated with the execution point-of-interest, and obtains a first map from the first information using the return address. The first map indicates the type of value stored in the local variable when one of the branch instructions is executed to call the subroutine. Given the first and second maps, the exemplary method merges the first map with the second map to identify a current type for the local variable. In performing this merge, the method combines the type status of the local variable as modified by the subroutine with the type status of the local variable as it stood before calling the subroutine.
Owner:IBM CORP
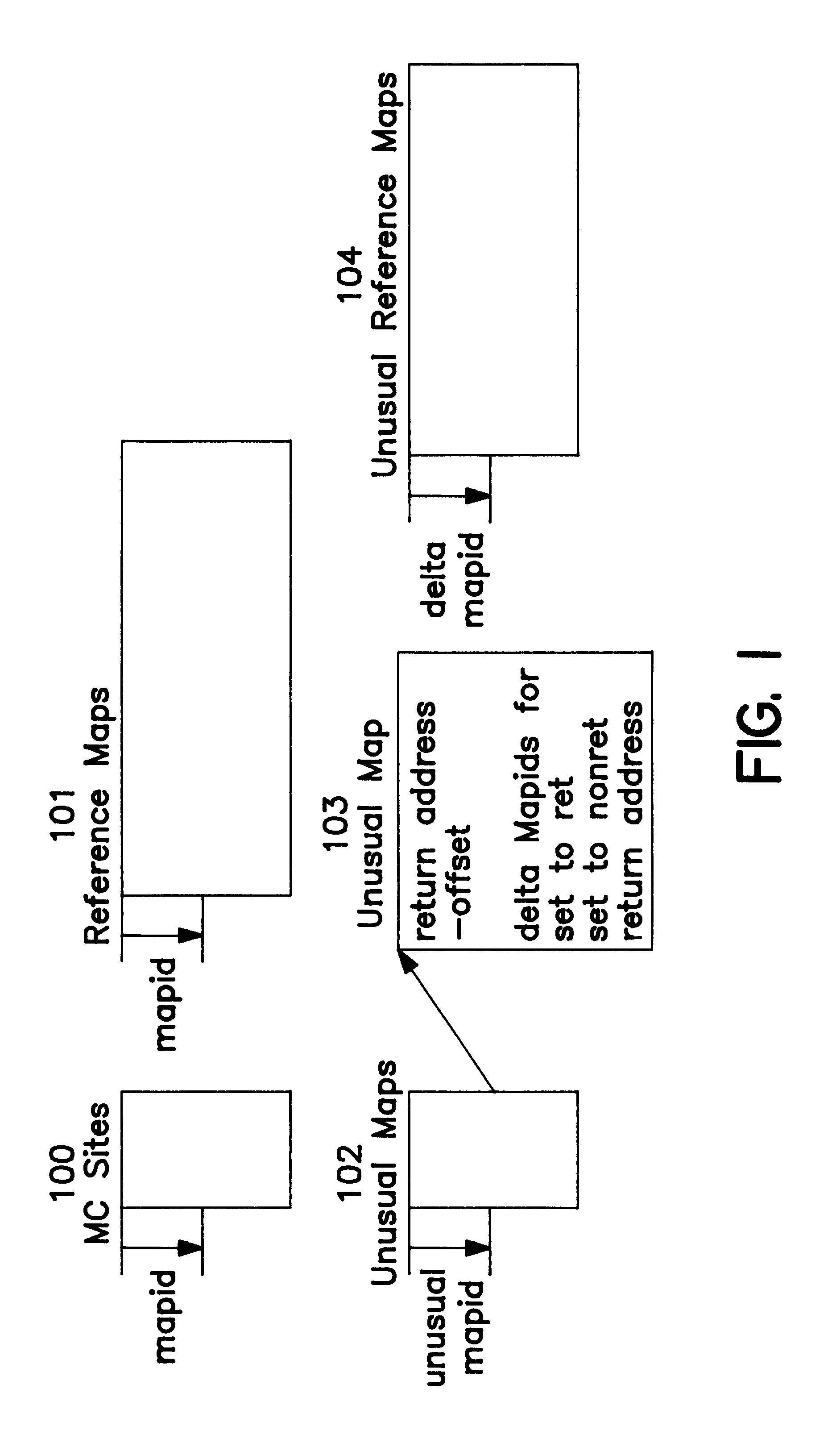
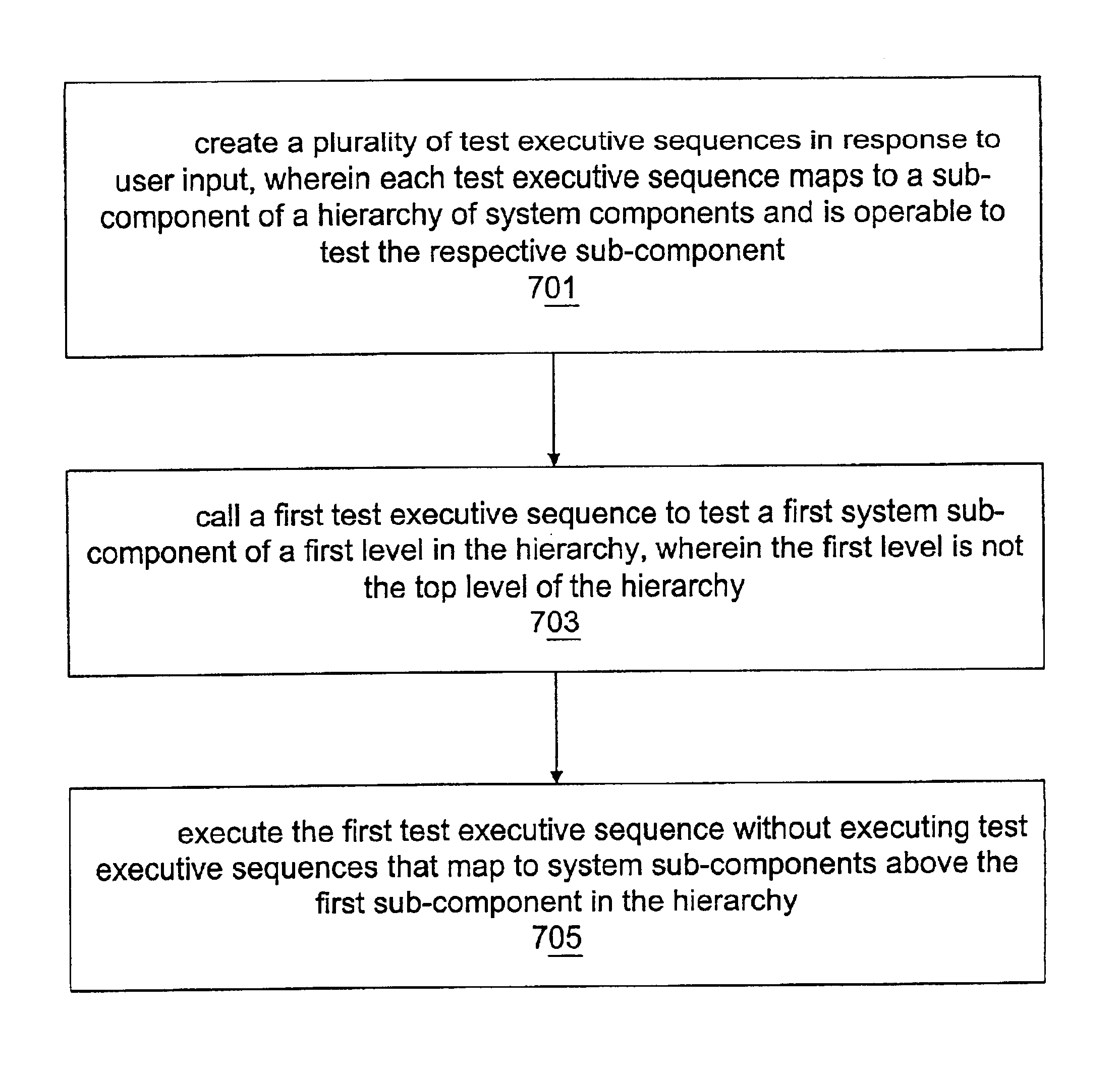
System and method enabling hierarchical execution of a test executive subsequence
InactiveUS6868508B2Resistance/reactance/impedenceElectronic circuit testingLocal variableDirect test
Individual test executive sequences may correspond to individual sub-components of a hierarchical system. To test a system sub-component directly without testing “upper” sub-components in the hierarchy, a first test executive sequence corresponding to that system sub-component may be executed directly, without requiring execution of test executive sequences above the first test executive sequence in the hierarchy, or requiring only partial execution of test executive sequences above the first test executive sequence in the hierarchy. Another embodiment of the invention comprises a system and method for enabling propagation or inheritance of test executive sequence local variables.
Owner:NATIONAL INSTRUMENTS
System, method, and medium for efficiently obtaining the addresses of thread-local variables
InactiveUS20060112374A1Reduce start-up costsReduce performance lossMultiprogramming arrangementsSpecific program execution arrangementsLocal variableParallel computing
A software method for obtaining an address of a thread-local variable while executing a computer program is described. The method designates a memory location to store an address of a function. The method, after the computer program starts to run, obtains the address of the thread-local variable by executing a resolver function whose address is stored in the memory location when a module that references the thread-local variable is loaded. The resolver can be a lazy resolver function or other resolver functions optimized for specific modules or variables.
Owner:RED HAT
Using code motion and write and read delays to increase the probability of bug detection in concurrent systems
InactiveUS20060161897A1Raise the possibilityError detection/correctionSpecific program execution arrangementsLocal variableParallel computing
A tool is provided for modifying the code of a multi-threaded computer program undergoing testing. The program executes in an environment that has a governing memory model. It is assumed that there is a global heap and a thread-local heap, which are synchronized from time to time. The modifications are of two types: (1) code instructions are reordered while remaining in compliance with the memory model; and (2) thread-local variables are added to functions, together with inserted heap synchronizing instructions. The modified programs are then used by a test generator to prepare test cases for execution. The modifications have the effect of changing the interleavings that occur among different threads, and increase the likelihood of exposing flaws that may become evident under different memory models.
Owner:IBM CORP
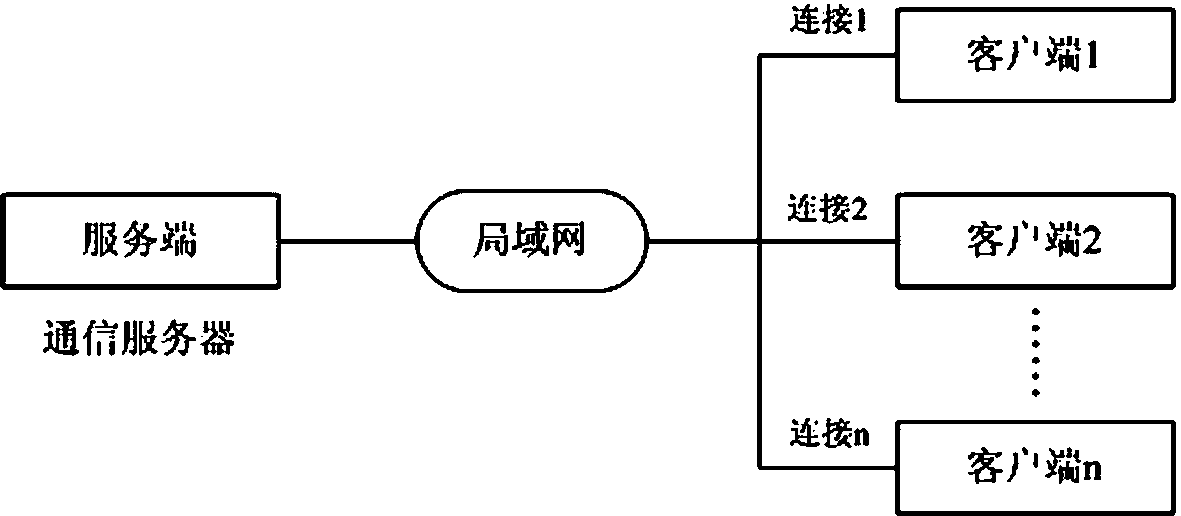
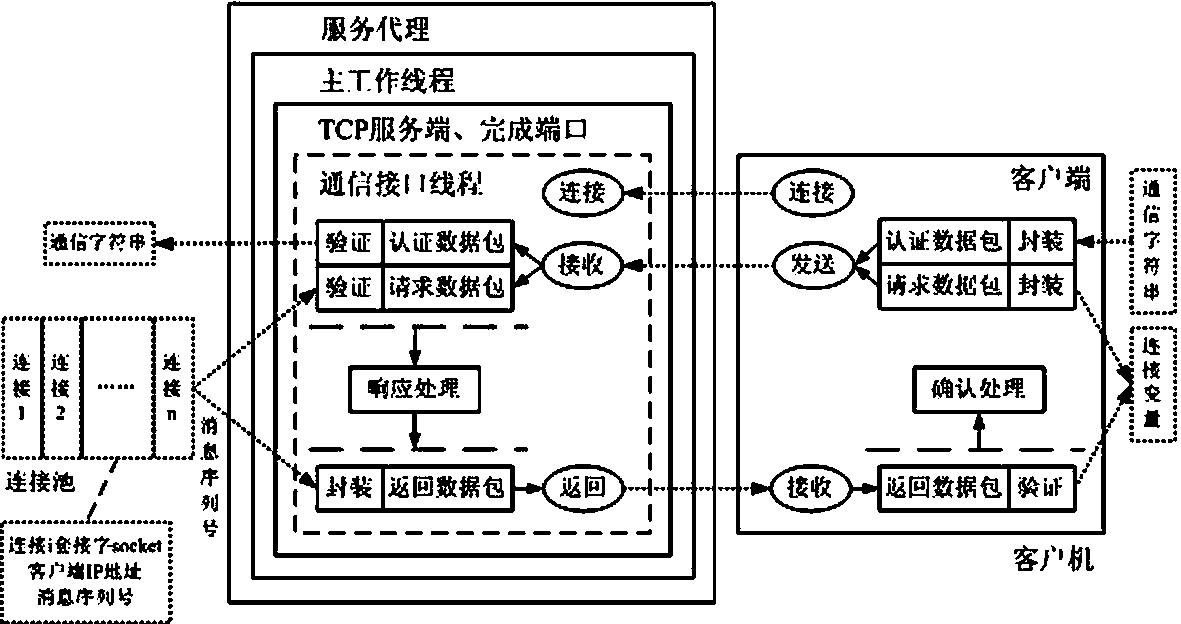
Multilink safety communication method based on completion port model
InactiveCN103391289AImprove scalabilityEasy to implementError preventionSecure communicationCommunication interface
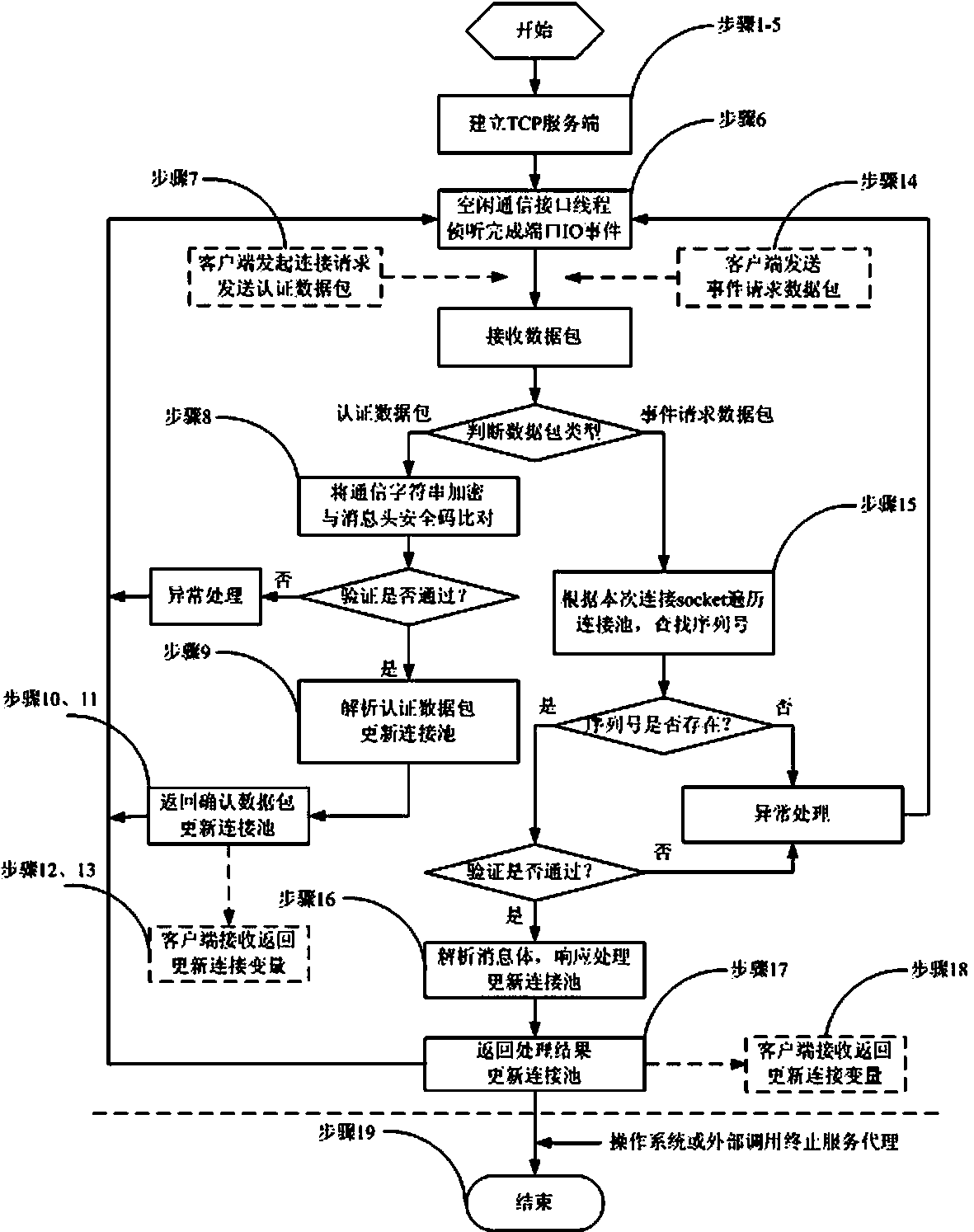
The invention provides a method for supporting multilink concurrence safety communication between a server and multiple clients and relates to a multilink safety communication method based on a completion port model. The method includes that a main worker thread at a communication server is embedded into an application service of a Windows system to run, a transmission control protocol (TCP) communication server is built according to the completion port model, meanwhile a fixed number of communication interface threads are built to conduct communication with the clients in an asynchronous mode, and the parallel processing capability of the server is improved. In an interaction process, after any client builds the TCP connection, two communication parties must adopt a handshake mechanism to ensure connection legality and adopt connection pool queues or local variables to dynamically maintain message serial numbers in the following data receiving and transmitting process, data transmitted by any party on the legal connection are packaged again according to the data package structure definition, and the receiving party adopts a safety verification algorithm to verify the data packages and regroup the plurality of data packages according to the precedence order of the message serial numbers.
Owner:中船凌久高科(武汉)有限公司
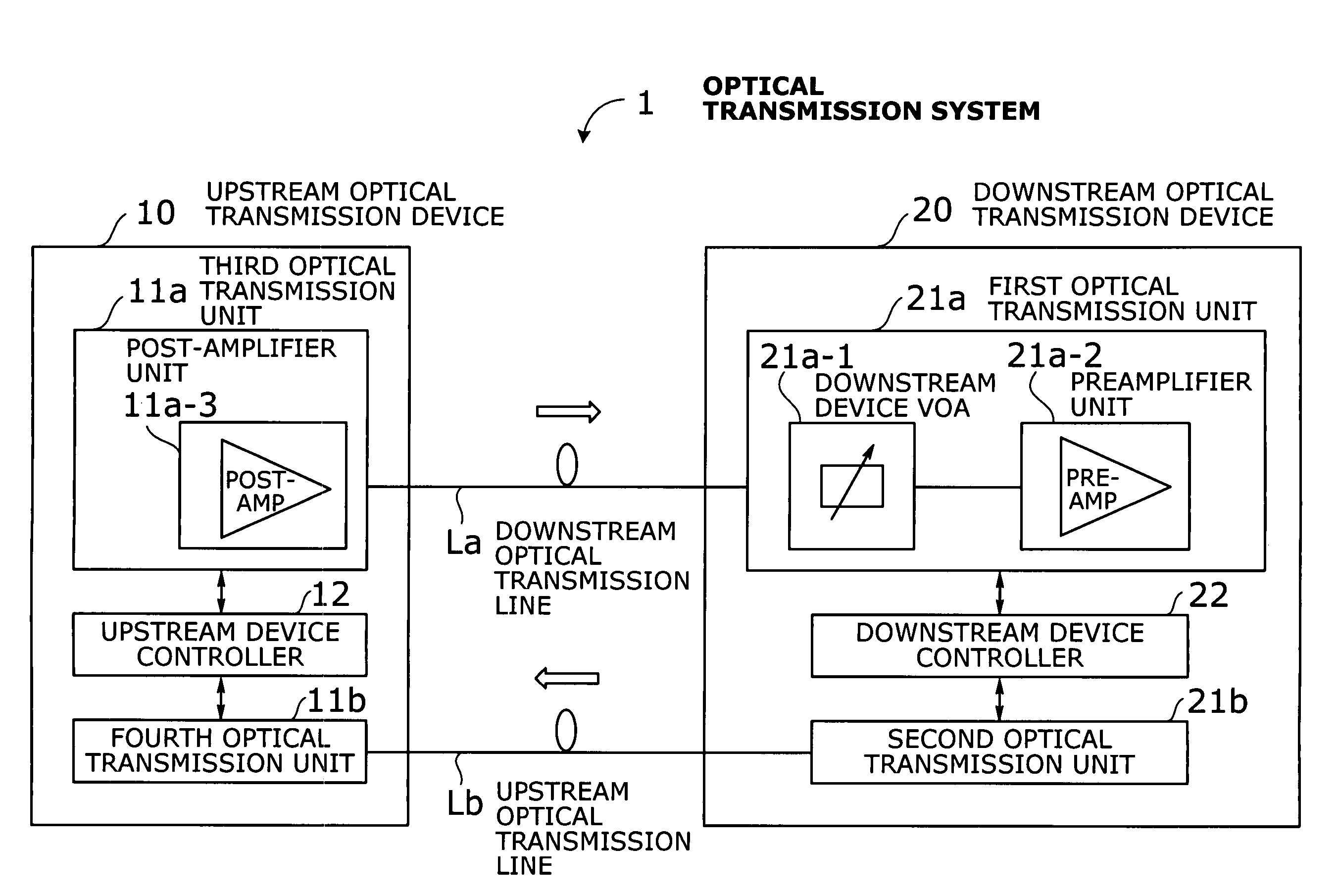
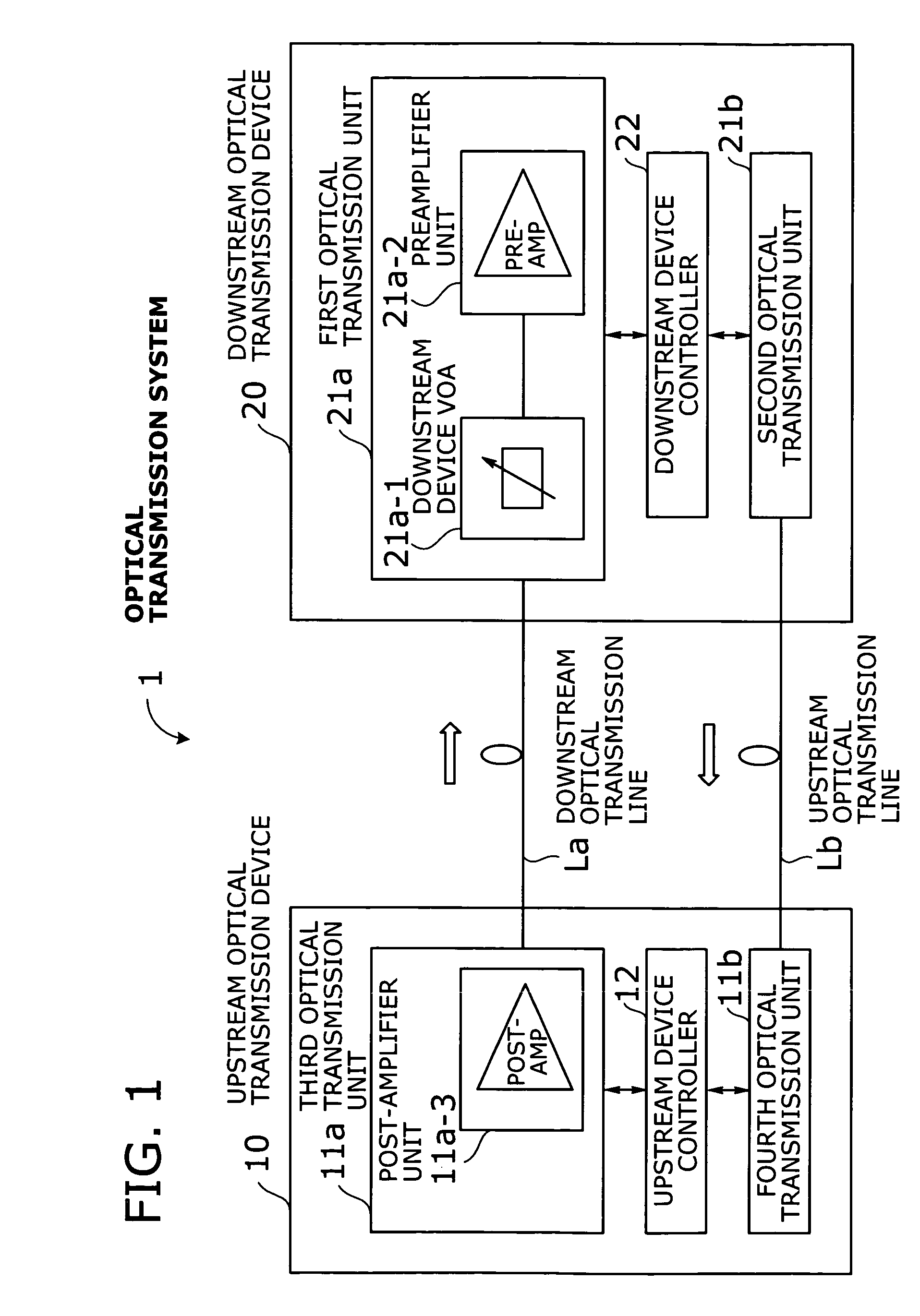
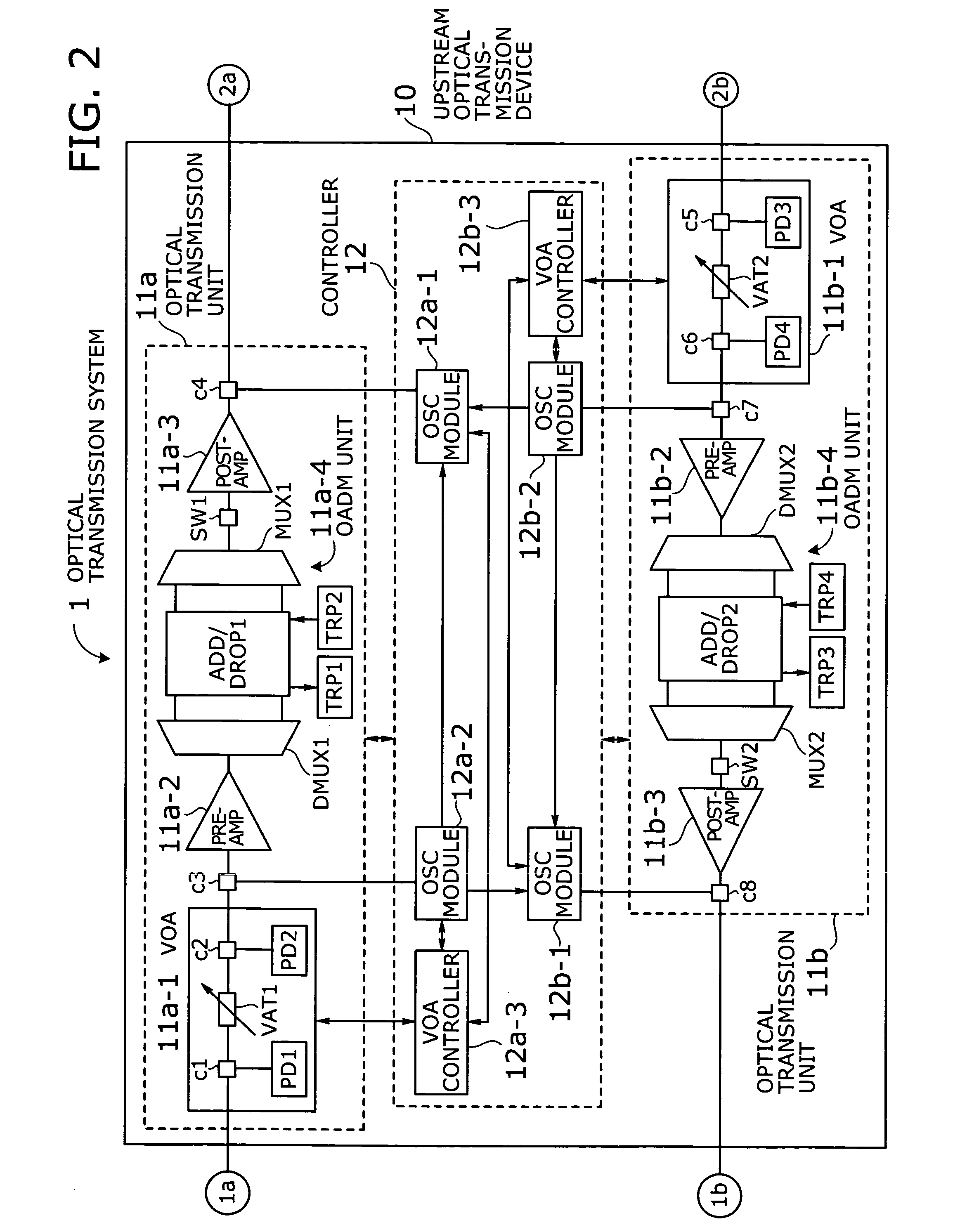
Optical transmission system with automatic signal level adjustment and startup functions
ActiveUS20050158057A1Easy maintenanceEasy to operateWavelength-division multiplex systemsTransmission monitoring/testing/fault-measurement systemsEngineeringOperation mode
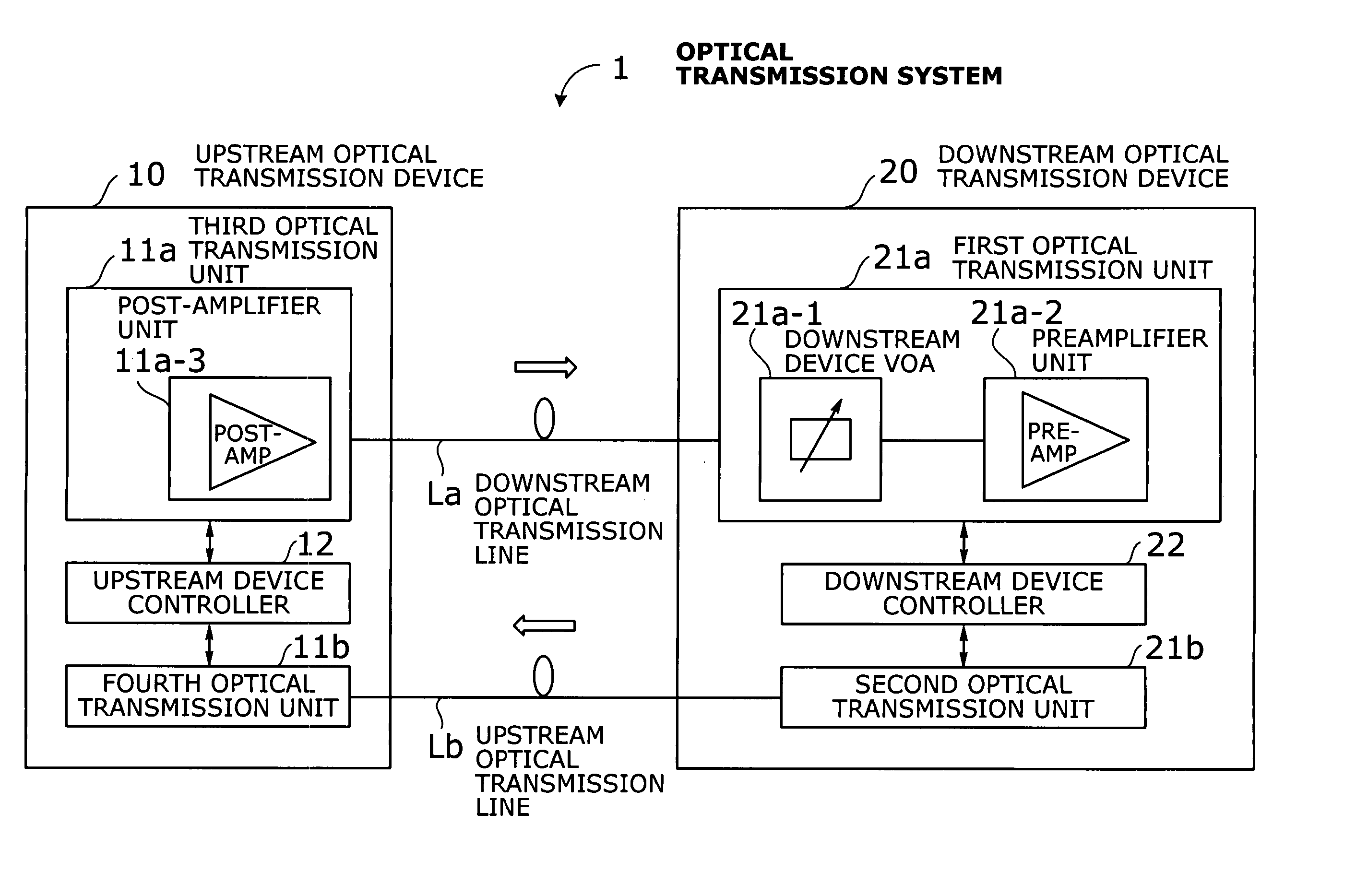
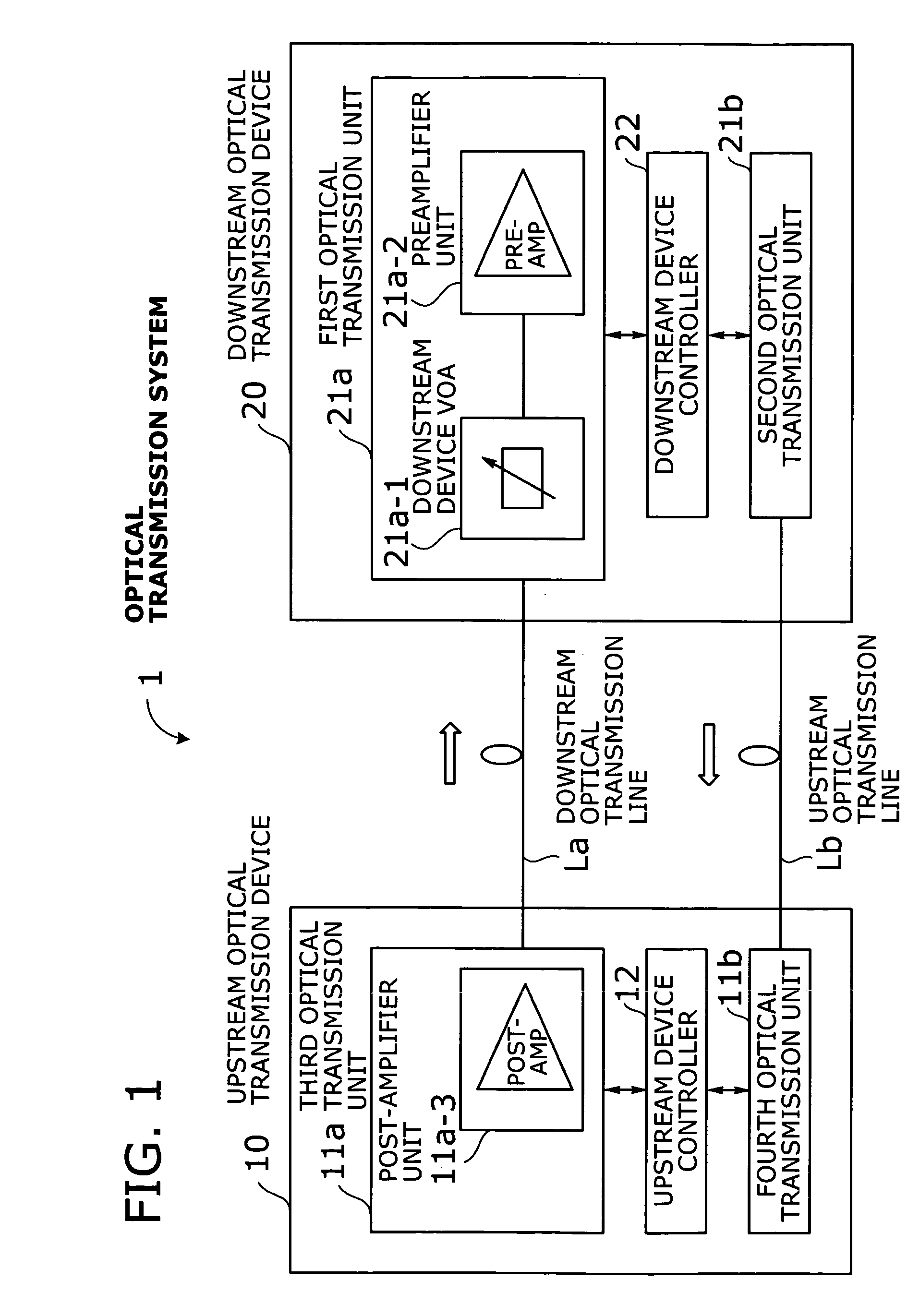
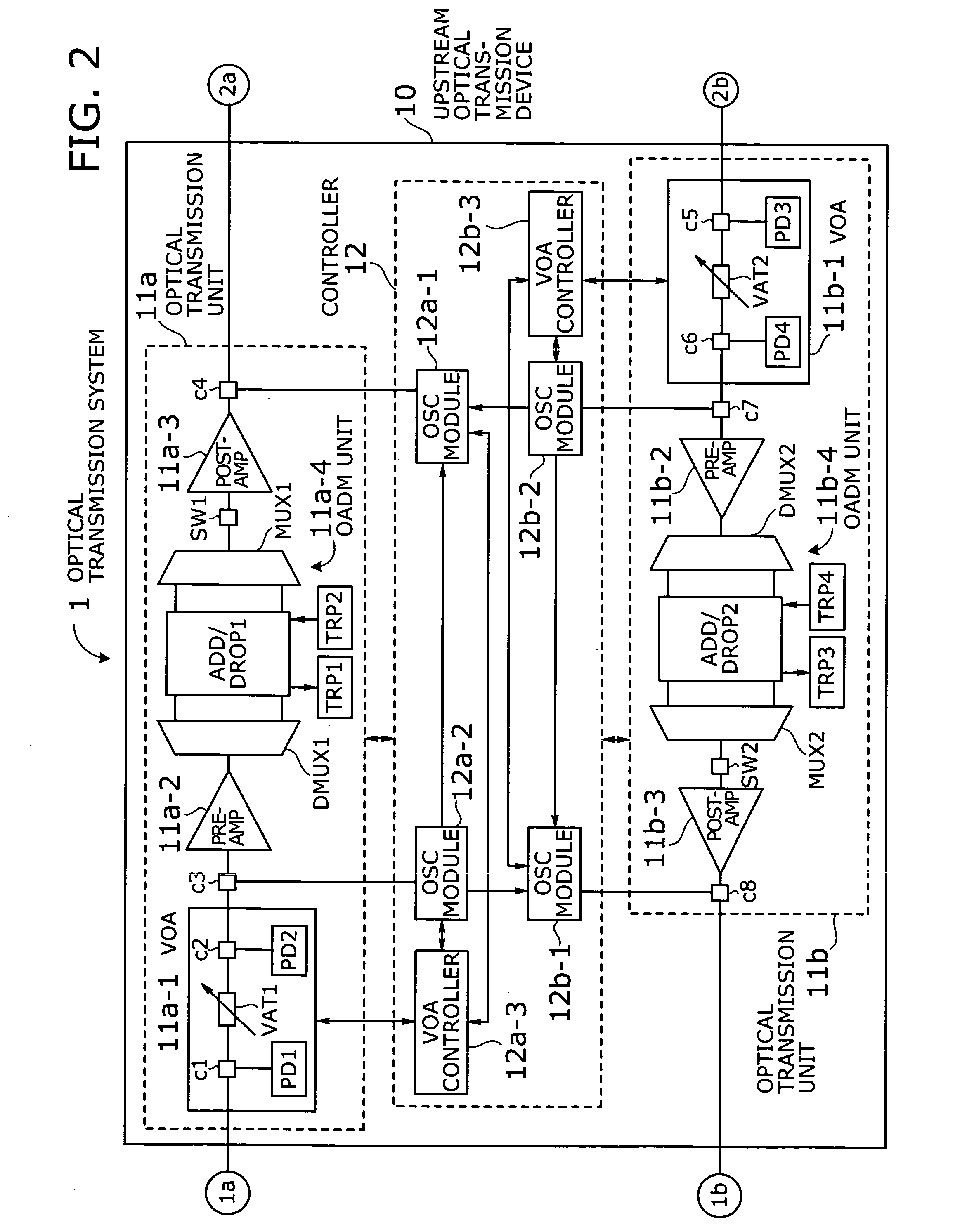
An optical transmission system with automatic startup functions to optimize the power level of optical signals entering each optical amplifier and operate those amplifiers in appropriate mode. In the process of starting up an optical transmission system, upstream and downstream optical transmission devices set up themselves under the coordination of their internal controllers. The downstream device controller adjusts its local variable optical attenuator by utilizing optical noise emission from a post-amplifier in the upstream optical transmission device, and it selects and sets a preamplifier unit to work in appropriate operating mode. The upstream device controller, on the other hand, selects and sets operating mode of its local post-amplifier unit. During this process, the upstream and downstream device controllers exchange messages over supervisory control channels to achieve the purpose.
Owner:FUJITSU LTD
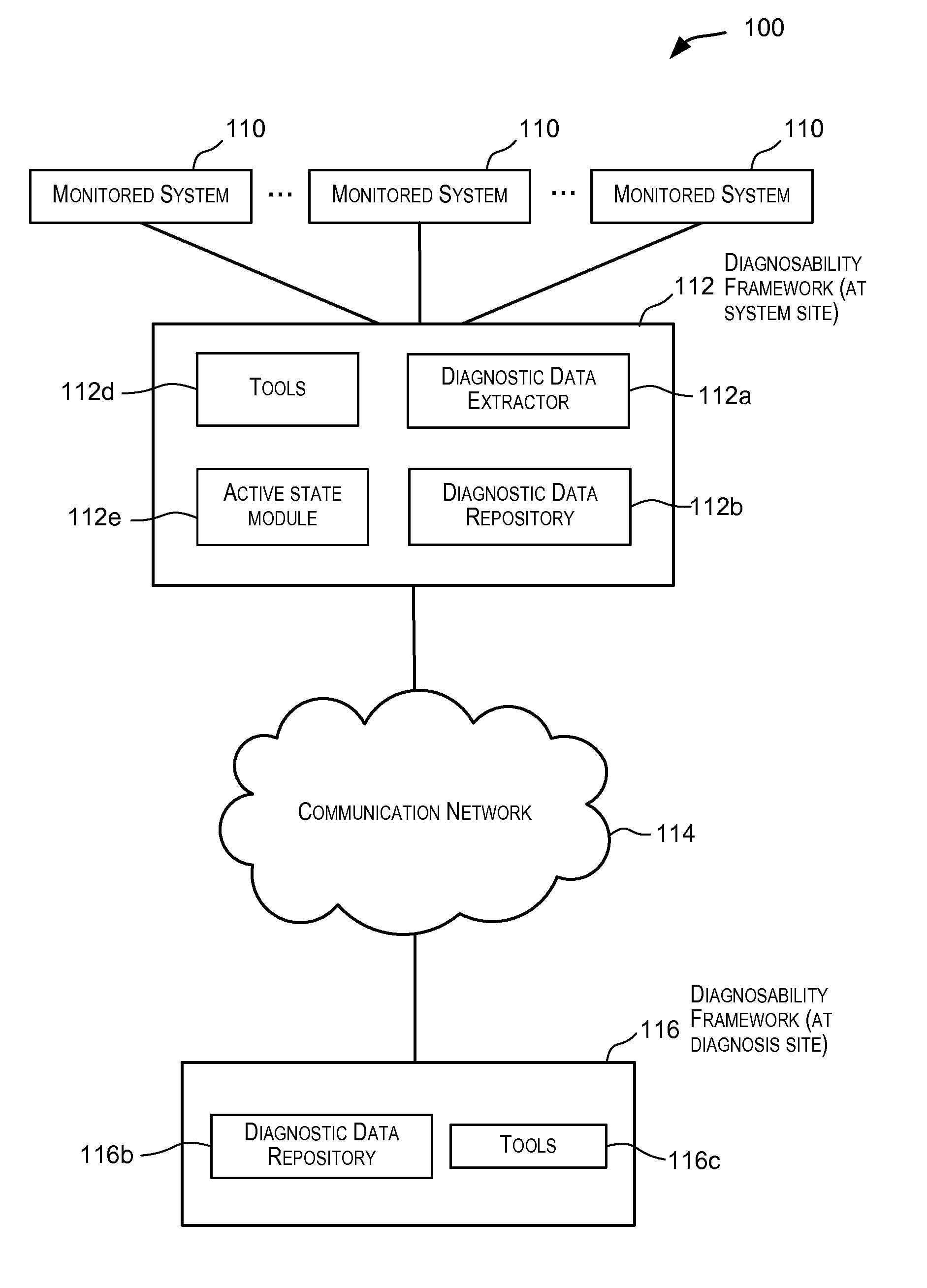
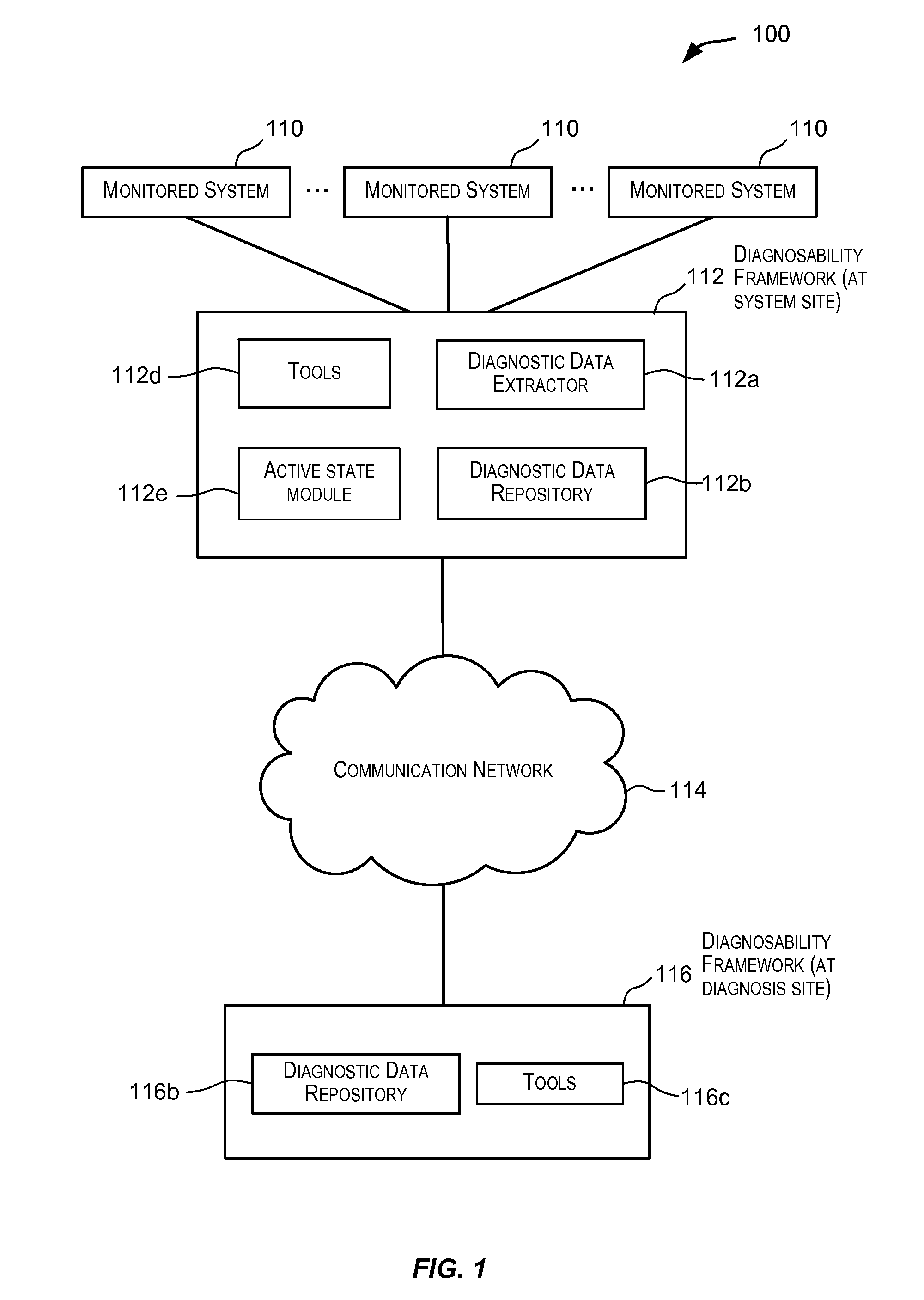
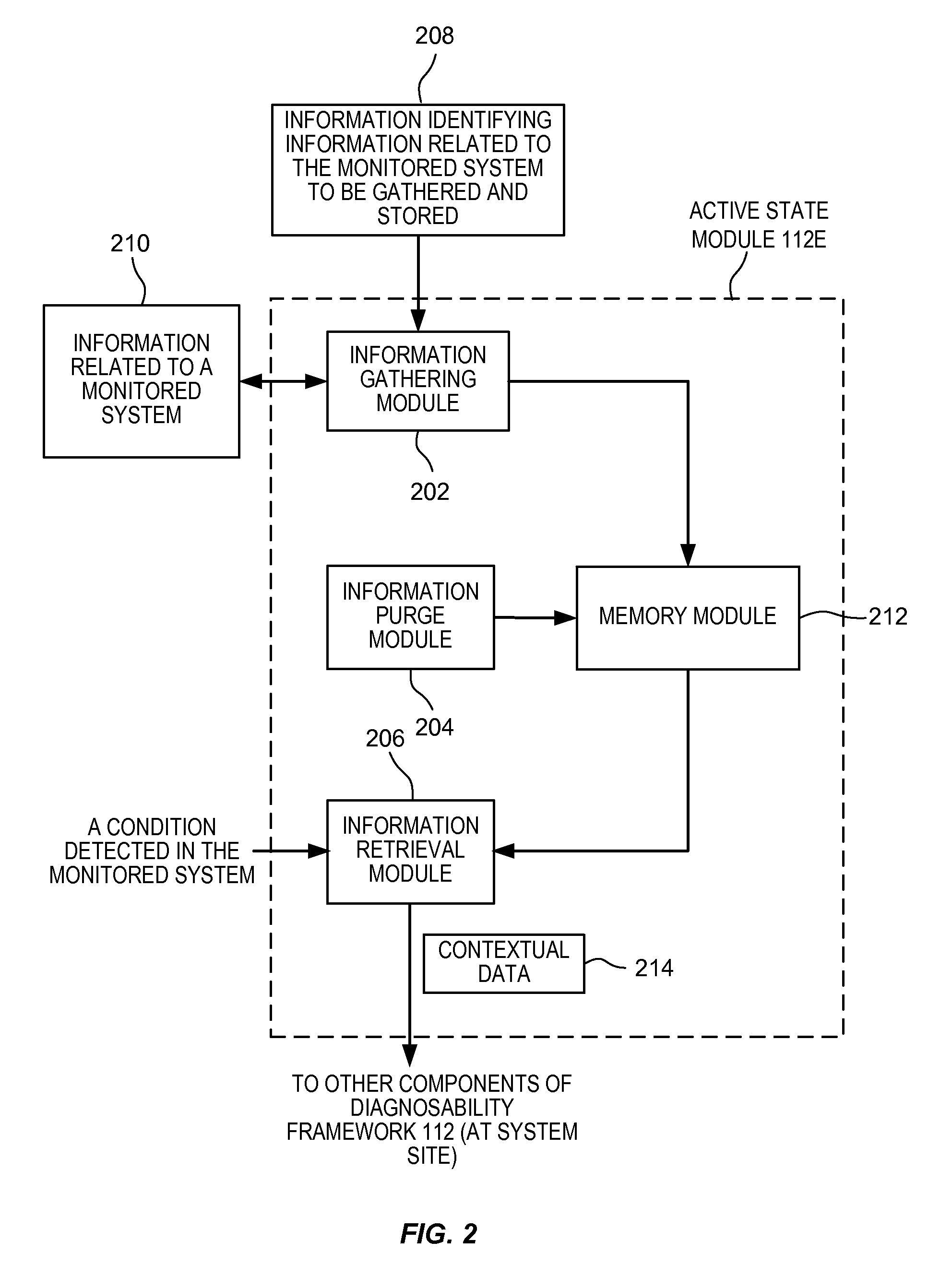
Gathering information for use in diagnostic data dumping upon failure occurrence
ActiveUS20090106595A1Easy to gatherEasy to captureFault responseTransmissionDiagnostic dataLocal variable
Techniques for gathering information during runtime of a monitored system such that the information is available for facilitating diagnostics for the monitored system. In one embodiment, upon detection of a condition (such as an error condition) in the monitored system, a portion of the gathered information provides contextual information that facilitates gathering of diagnostic data that is relevant for the detected condition. This facilitates capturing of diagnostic data that is relevant for diagnosing the detected condition. The information gathered and stored during runtime may include information related to local variables, information related to tagged information (e.g., tagged functions / processes) executing in the monitored system, information related to potential impacts to the monitored system due to failures, metadata information, and other information.
Owner:ORACLE INT CORP
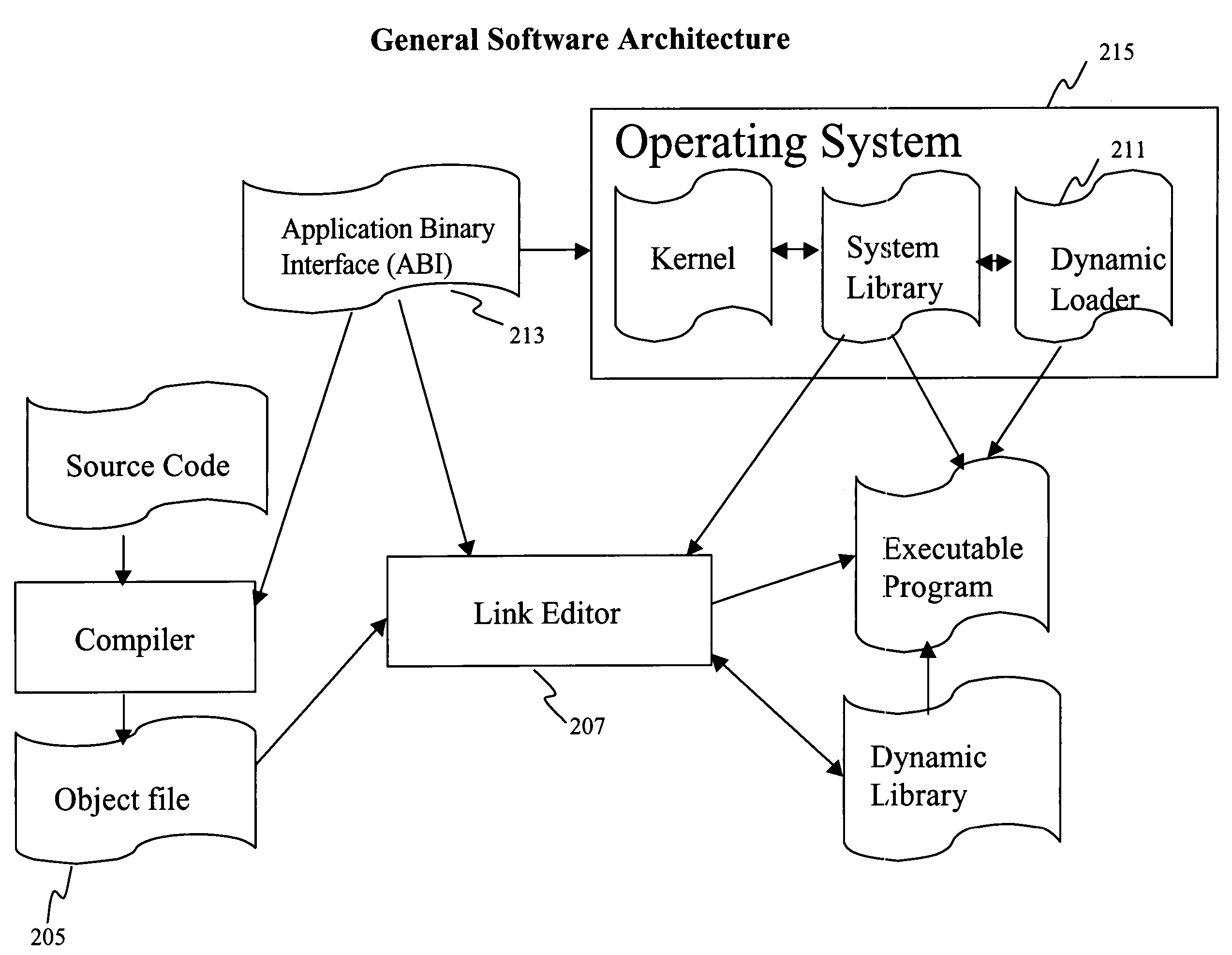
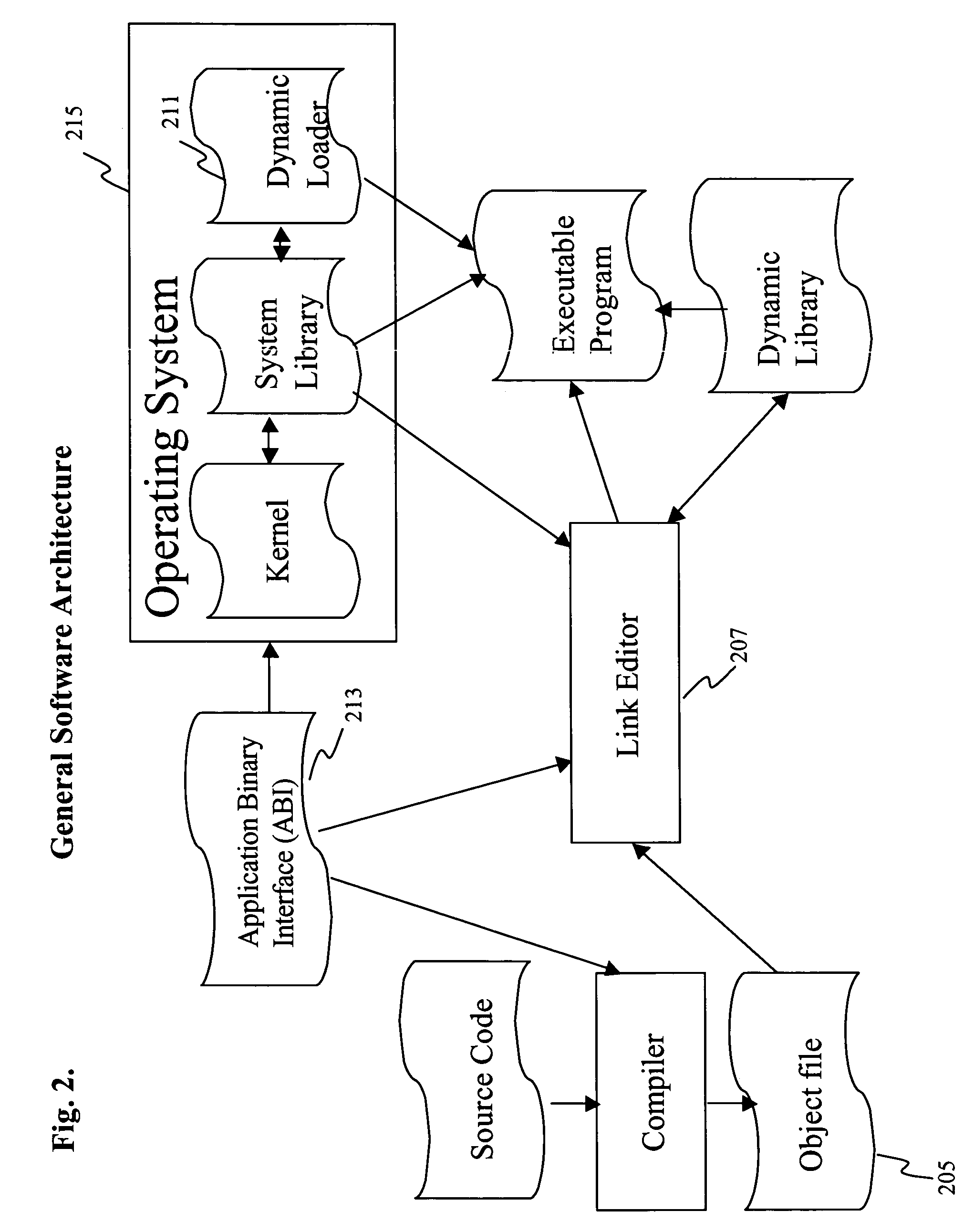
Software development environment with design specification validation tool
InactiveUS20060265690A1Errors can be reduced and avoidedSoftware testing/debuggingRequirement analysisFunction definitionLocal variable
An automated software class specification validation tool automatically determines, for functions defined in a function definition section of a class specification, whether the function is properly declared throughout one or more other sections of the same class specification. Further, it can be determined whether variables, i.e., attributes, parameters, and local variables, associated with respective functions in the function definition section are properly specified throughout one or more other sections of the same class specification. The functions and variables that are validated include attributes and functions that are specified for structures and nested classes defined in a defined type section of the class specification. The validation tool is accessible over a network via a web page, and results of the validation process are also displayed on a web page.
Owner:RICOH KK
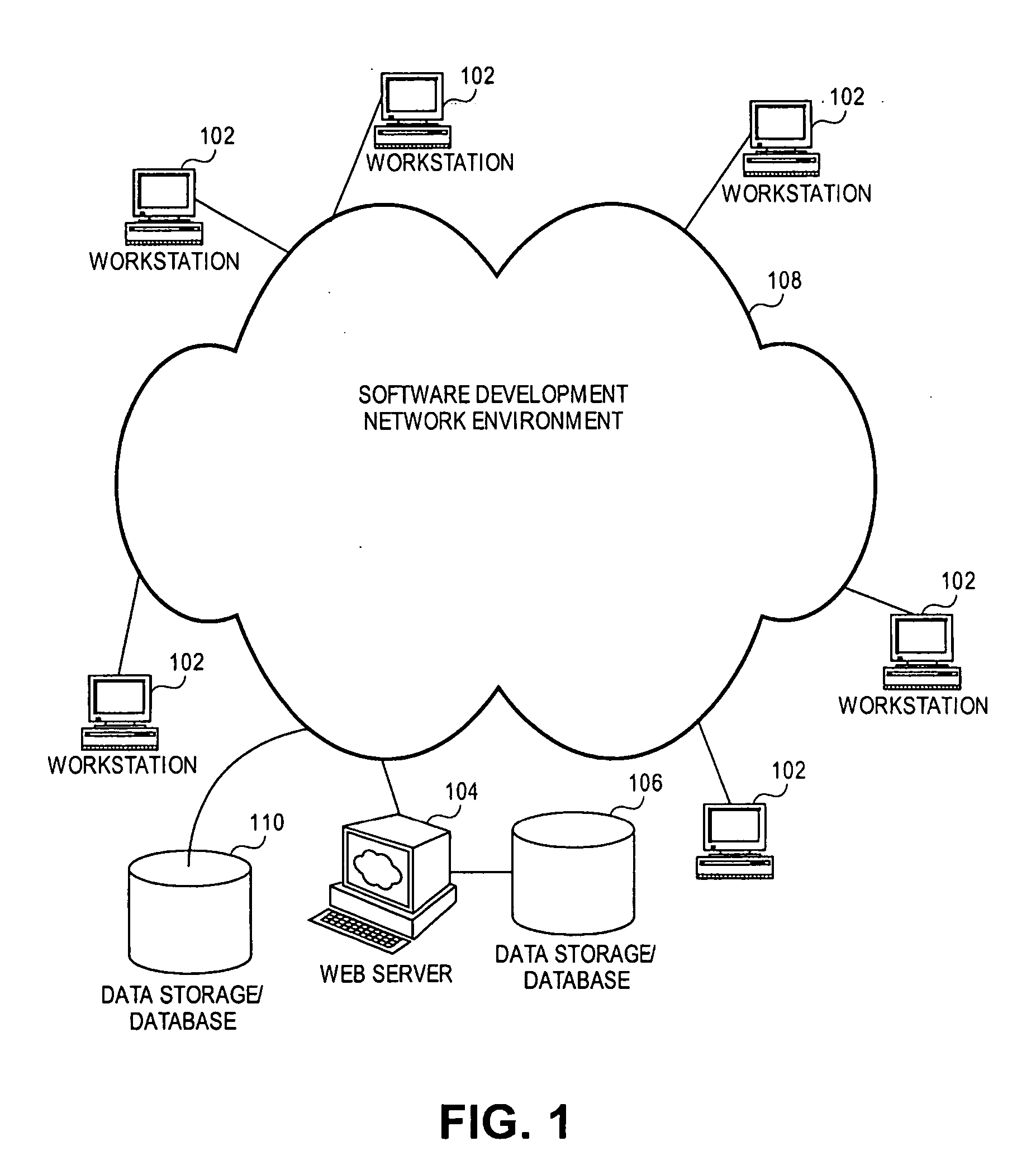
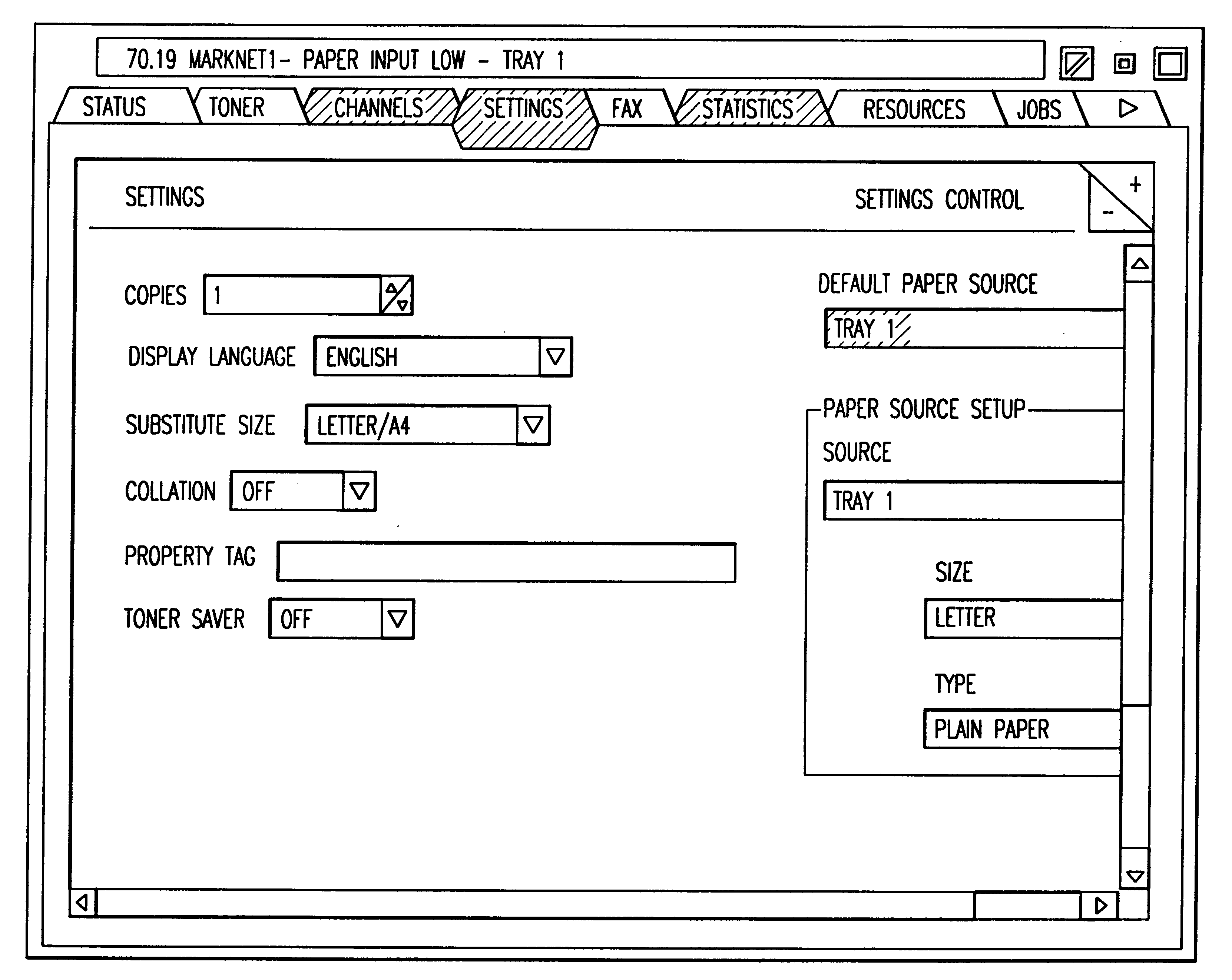
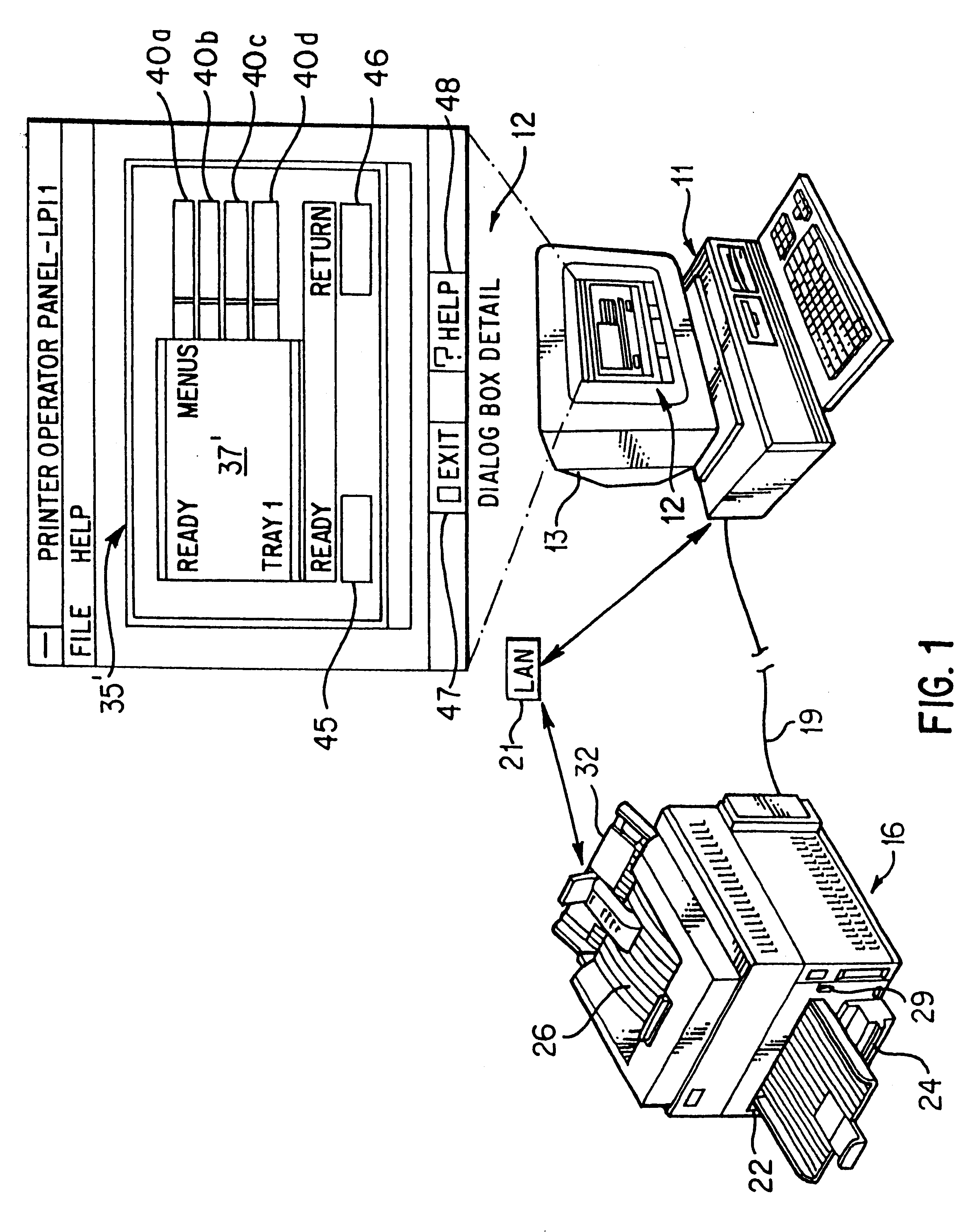
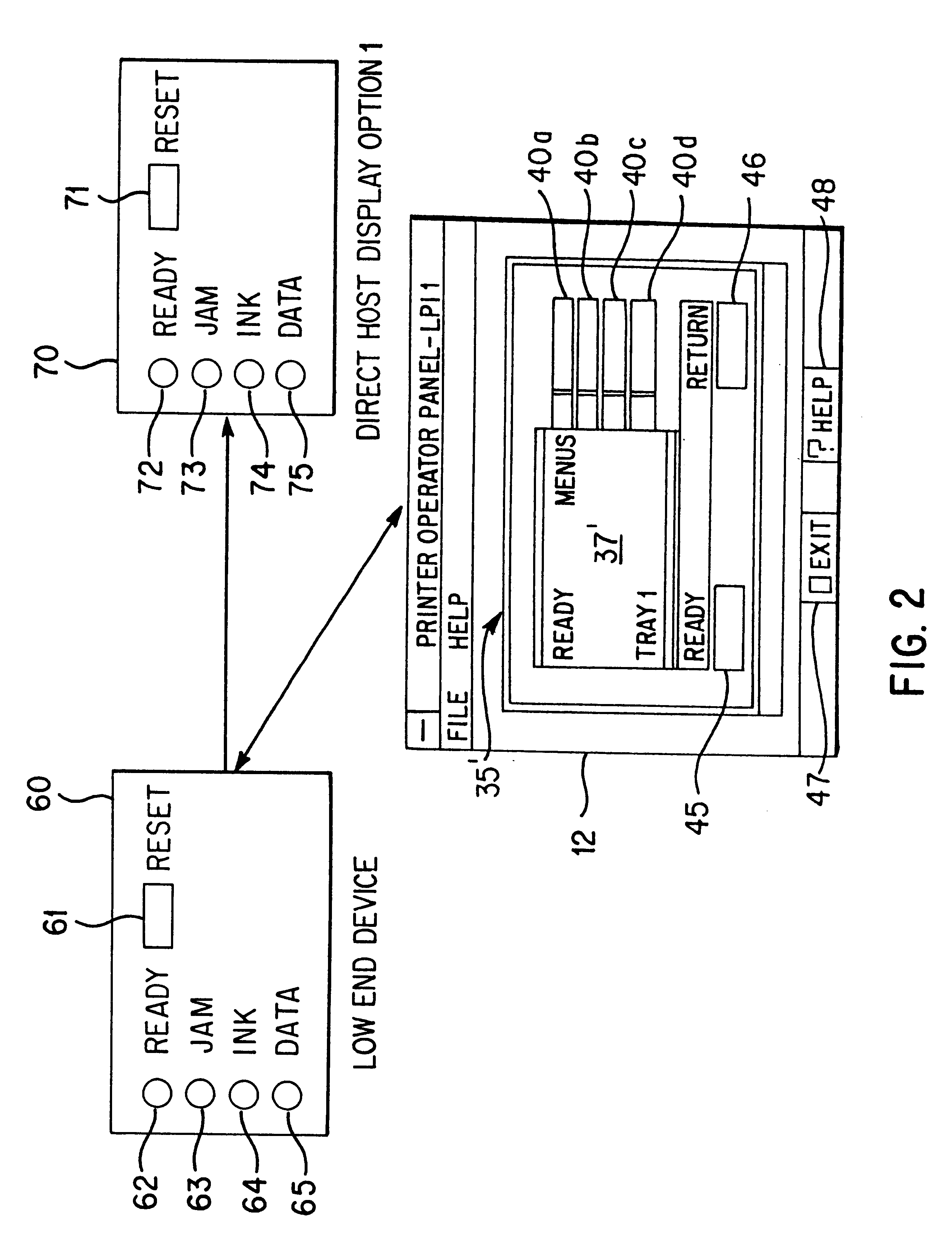
System and method for providing a virtual operator panel for a peripheral device
InactiveUS6498611B1Industrial applicabilityAvoid spreadingProgram controlMemory systemsLocal variableData memory
A system and method for providing a virtual operator panel for a peripheral device where the system includes a peripheral device including a processor and a data store that stores public settings corresponding to private settings of the peripheral device, each public setting indicative of at least one private setting of the peripheral device. The peripheral device has a device process and a host process, or alternately, is in bidirectional communication with at least one host computer including a data store, a display and a processor. The host computer or host process selectively transmits a request to the peripheral device or device process requesting public settings of the peripheral device for the generation of a virtual operator panel for the peripheral device. The peripheral device or device process receives the request for peripheral device settings from the host computer or host process, and transmits a response including at least one public setting from the data store of the peripheral device, and the host computer or host process receives the response from the peripheral device and generates a virtual operator panel based upon the response. In one embodiment, the public setting is a metavariable that implicates one or more local variables of the peripheral device. There is also provided a method for generating a virtual operator panel for a peripheral device including the steps of transmitting a request for peripheral device public settings from a host computer or host process to a peripheral device or device process, receiving the request at the peripheral device or device process, generating a response in the peripheral device or device process that includes at least one public setting of the peripheral device, transmitting the response from the peripheral device or device process to the host computer or host process, receiving the response at the host computer or host process, and generating a functional virtual operator panel based upon the public setting included in the received response.
Owner:LEXMARK INT INC
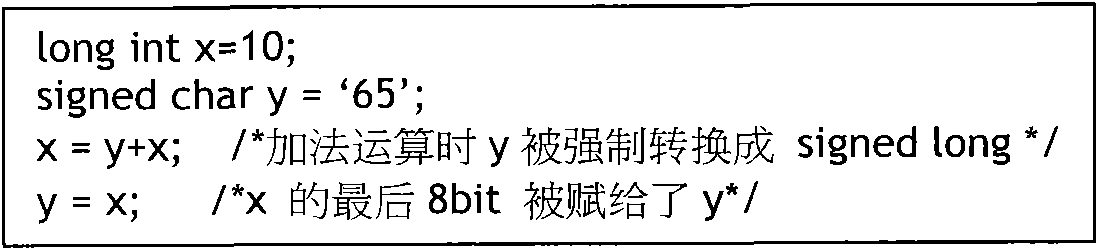
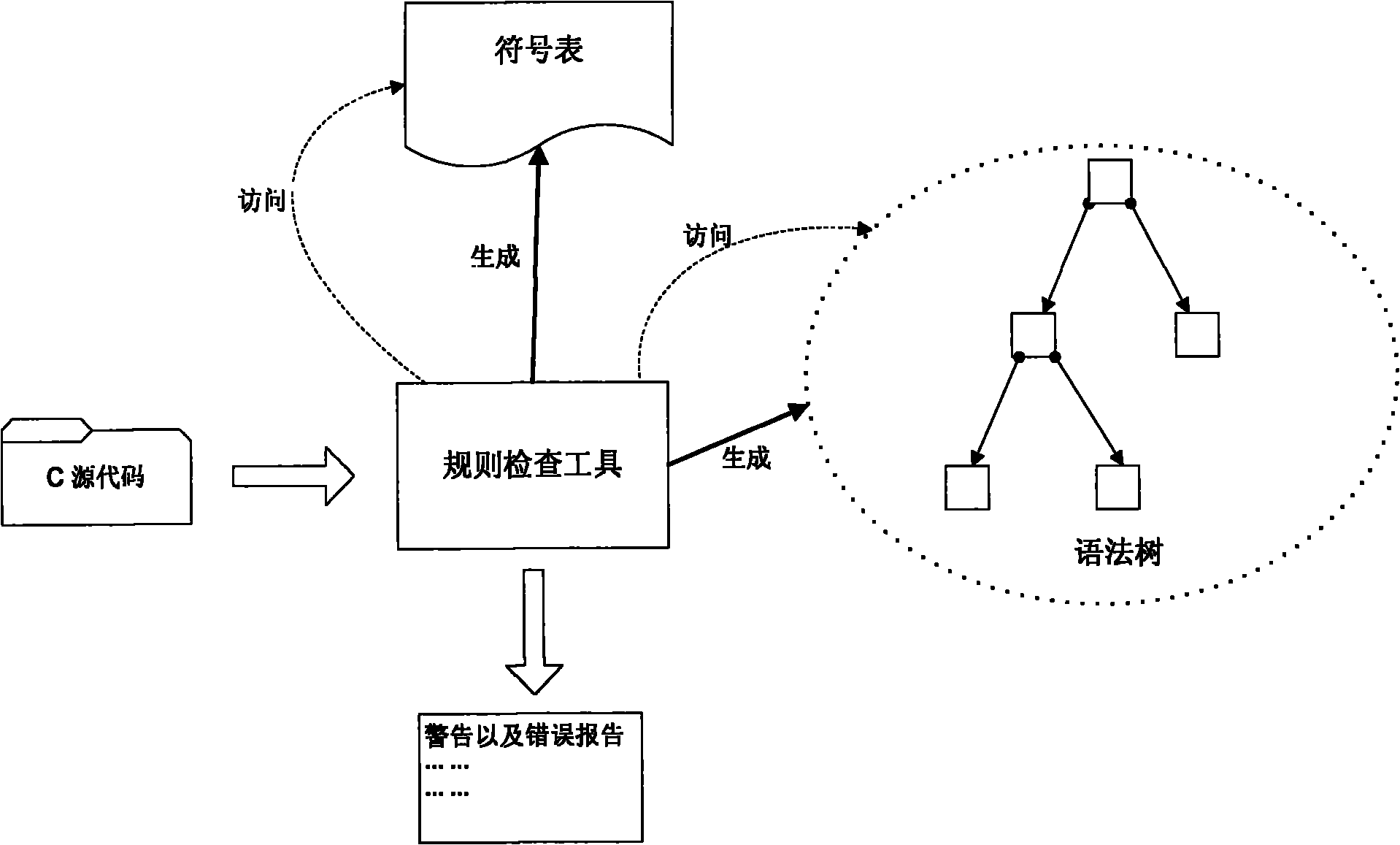
Static analysis-based checking method of safety rules of C language
InactiveCN102012991AMake up for the lack of securityPlatform integrity maintainanceStatic timing analysisType conversion
The invention relates to a static analysis-based checking method of safety rules of C language, which comprises the following steps: 1) checking the type of the C language to avoid the occurrence of compulsory type conversion and prohibiting the declaration of the type of a generic pointer; 2) stipulating that a global variable and a local variable can not be in homonymy, and the global variable and a formal parameter of a function can not be in tautonomy; 3) limiting a cyclic variable of a control flow statement; 4) strengthening the declaration and the definition of the C language; and 5) carrying out analysis of accidence, grammar and semanteme on source codes, and finding out places which do not meet the stipulation from the source codes. The method has the advantages of being capable of finding out possible loopholes on programming of the C language under the premise that the codes do not need to be executed and effectively making up for the deficiency of insufficient safety of the C language in soft engineering.
Owner:北京神舟航天软件技术股份有限公司
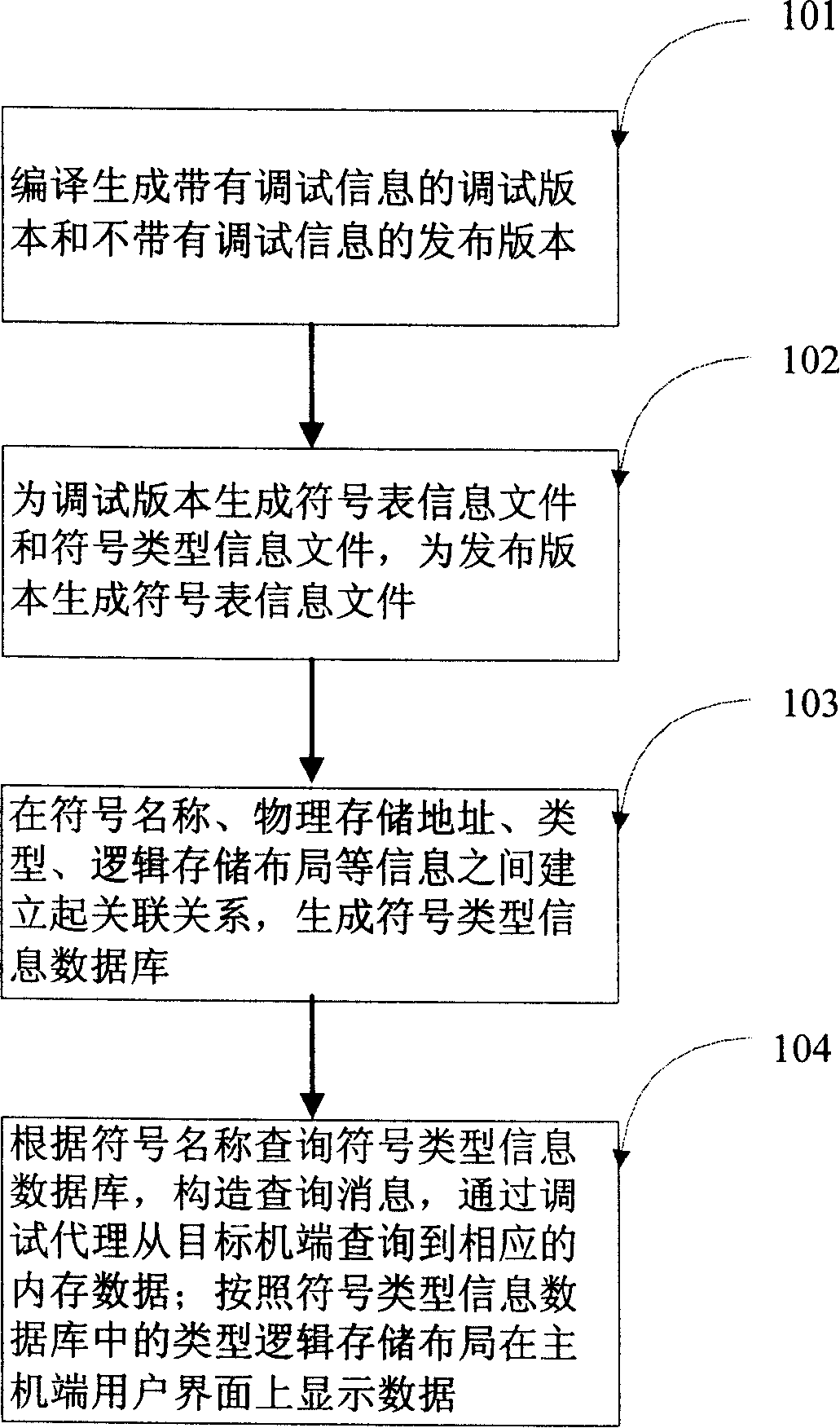
Symbol locating method of embedded system
ActiveCN101178684ARich auxiliary methods for fault locationFlexible choiceSoftware testing/debuggingLocal variableOperational system
The invention relates to a denotation positioning method of an embedding type system which comprises that: (1). the invention creates denotation table information files of debugging version, denotation type information files and denotation table information files of issuing version; (2). the invention creates denotation type information databases with debugging version and issuing version by taking the denotation names as the key words; (3). the invention searches the denotation type information databases according to the denotation names and decomposes the type structures, so as to get the physical positions of the denotation in an object machine. The invention is used for the denotation positioning realizing of various embedding type software versions in the object machine terminals and provides flexible choosing space to the issuing of the embedding type applying system. The invention not only can search and amend the global variable, but also can search and amend information such as the structure, genus, function, partial variable when in use, thereby providing rich failures positioning assisting method to the embedding type applying system. The invention is not limited by any complier, debugger and operation system.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO
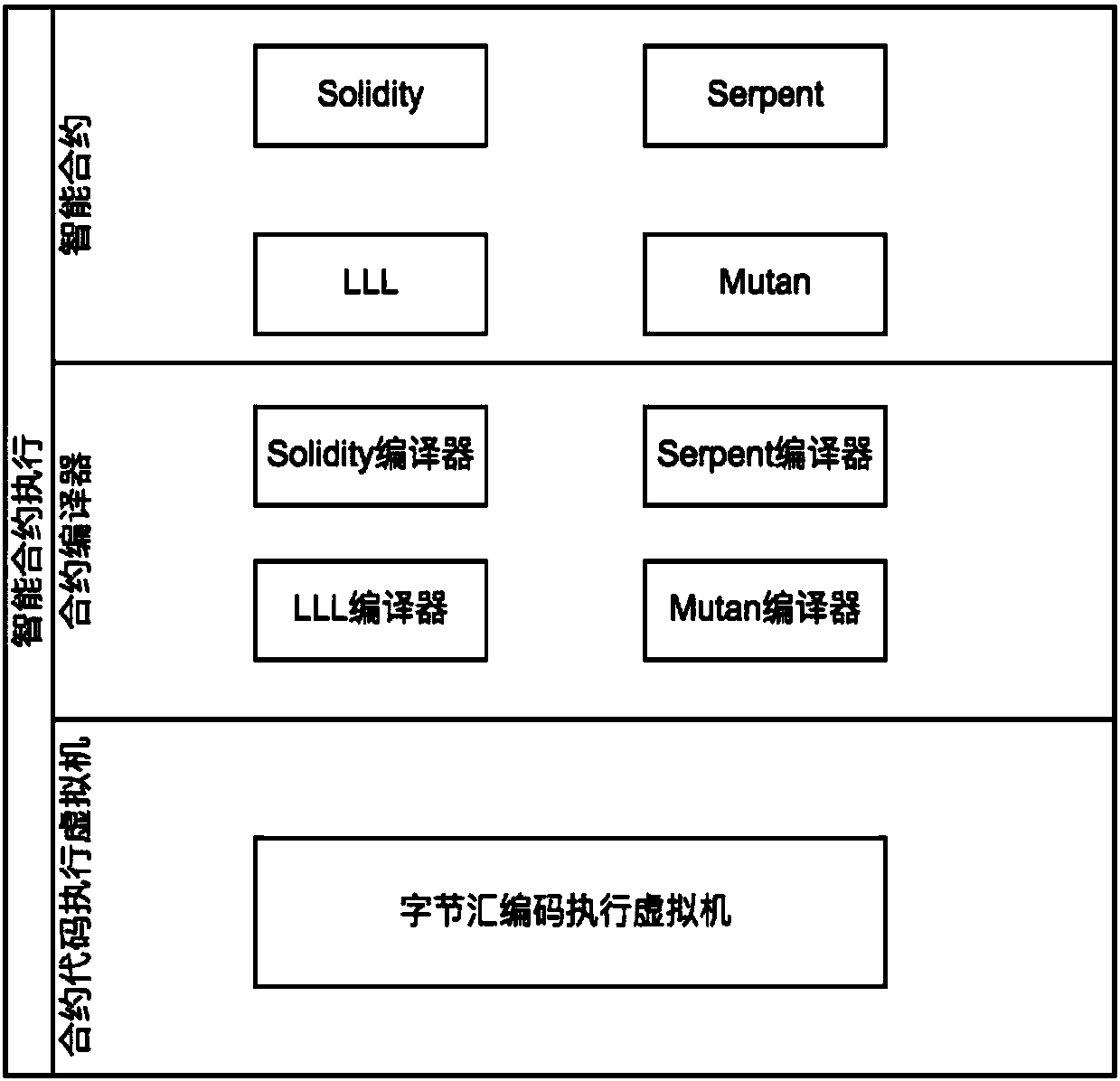
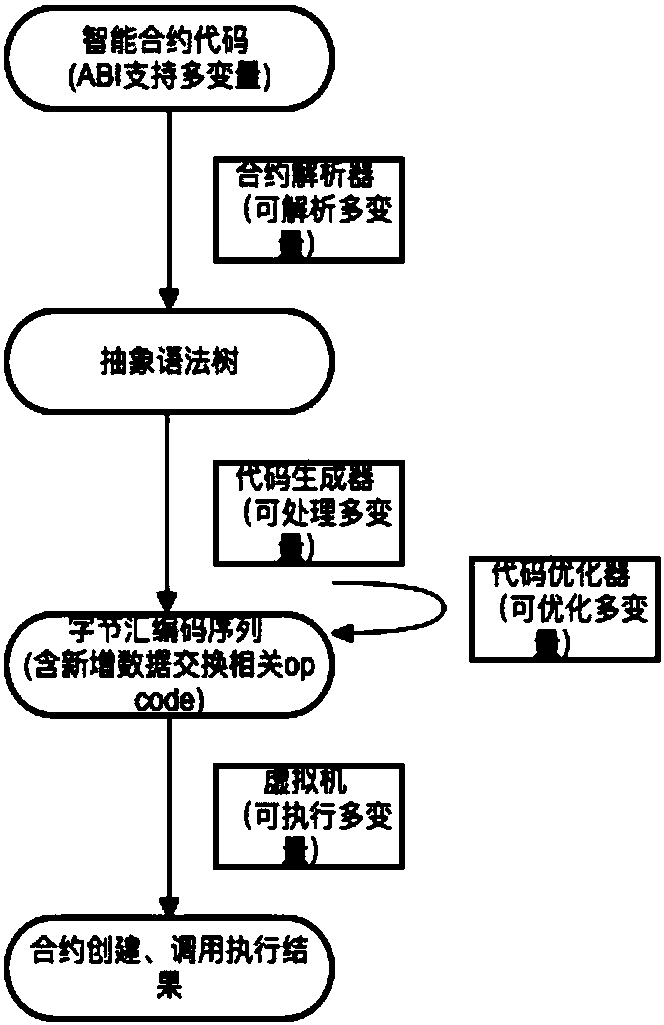
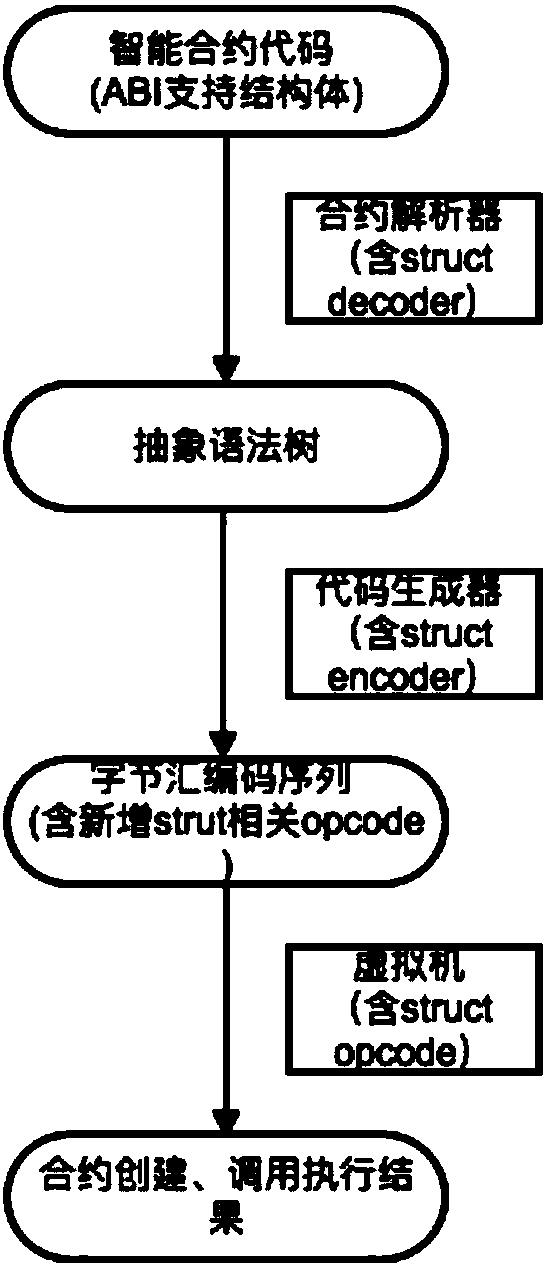
Highly-available contract executing method and system
ActiveCN107844294AReduce writingCompile lowSoftware designCompiler constructionLocal variableTree (data structure)
The invention discloses a highly-available contract executing method, which includes steps of (1), compiling an intelligent contract code according to contract information, wherein the intelligent contract code comprises more than maximum stack depth number of local variables, parameters or structure bodies; (2), performing grammar semantic parsing on the intelligent contract code, and generatinga corresponding abstract grammar tree; (3), converting the abstract grammar tree data structure to be a binary byte assembly code sequence and an related order; (4), explaining and executing the byteassembly code sequence by a contract virtual machine. Specific to the problems that the stack is easy to overflow and a stack element cannot be visited at random, the original intelligent contract design adopts an avoiding plan of small stack depth and exchangeable different storage spaces ordinarily; through the plan of realizing the order visit at random by the contract encoder and the virtual machine, the stack overflow is prevented and the random visit of the stack element can be realized. More complex available intelligent contract can be operated on the system; the cost for contract writing, compilation, and execution is lower.
Owner:HANGZHOU RIVTOWER TECH CO LTD
Declarative pinning
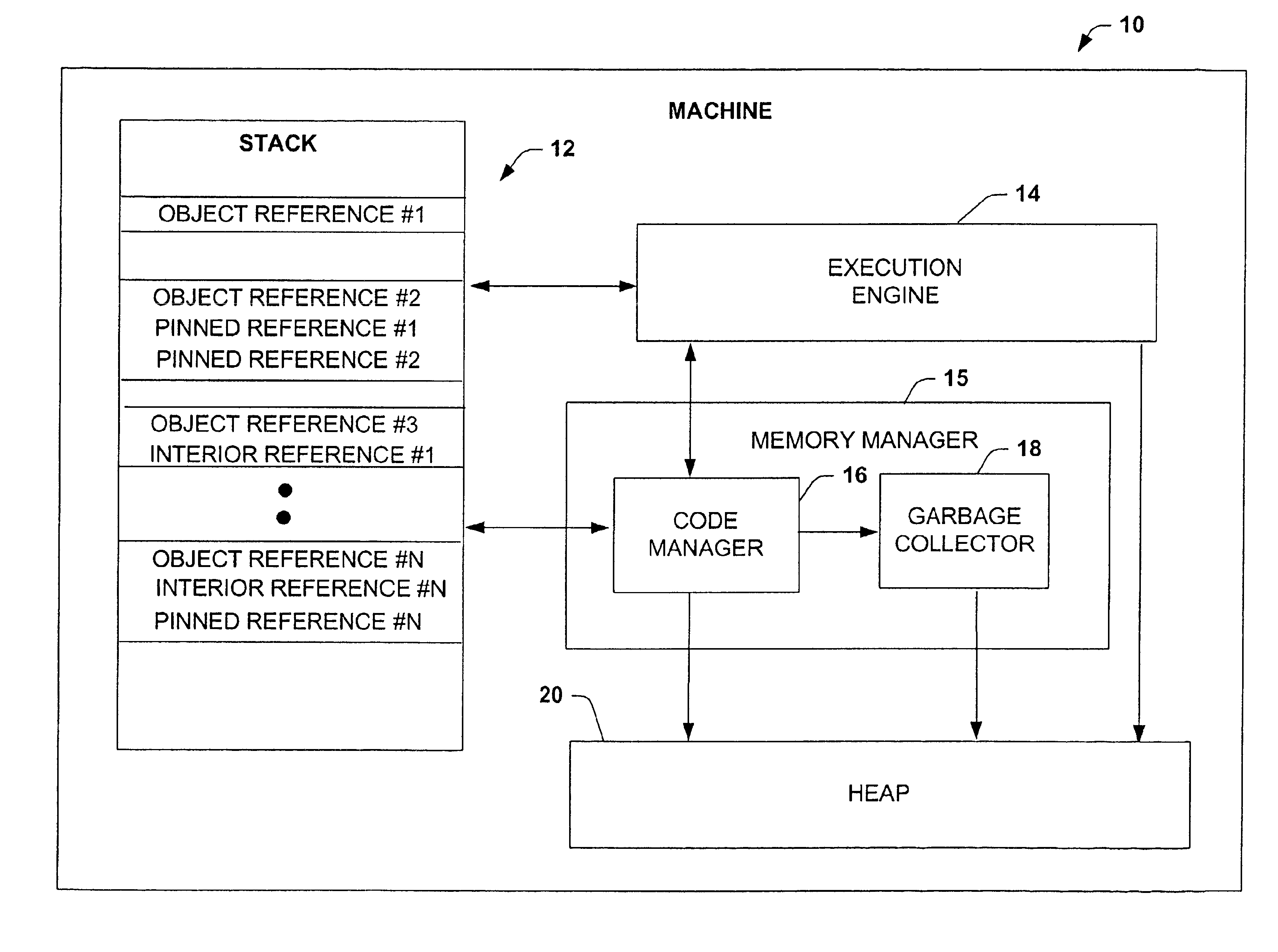
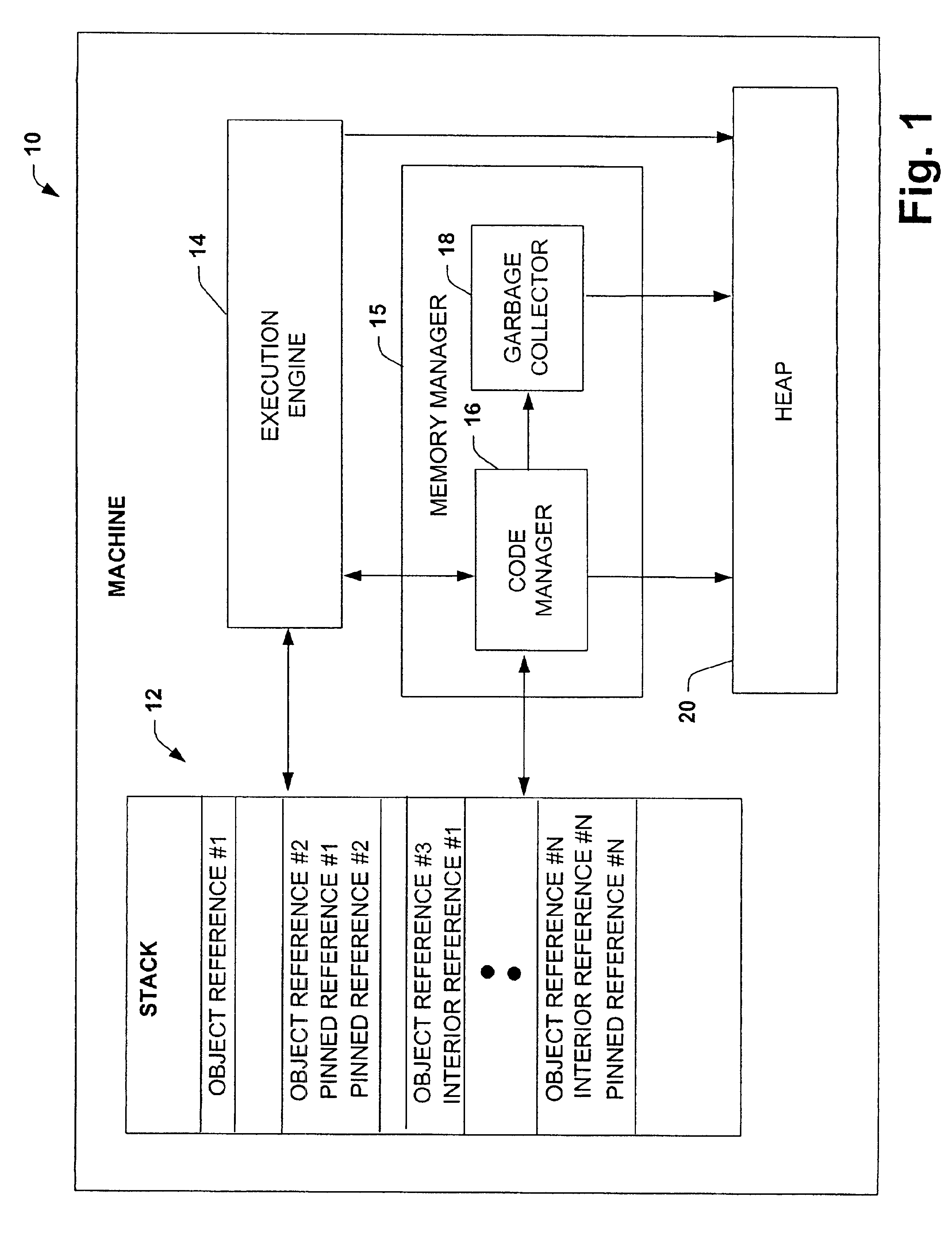
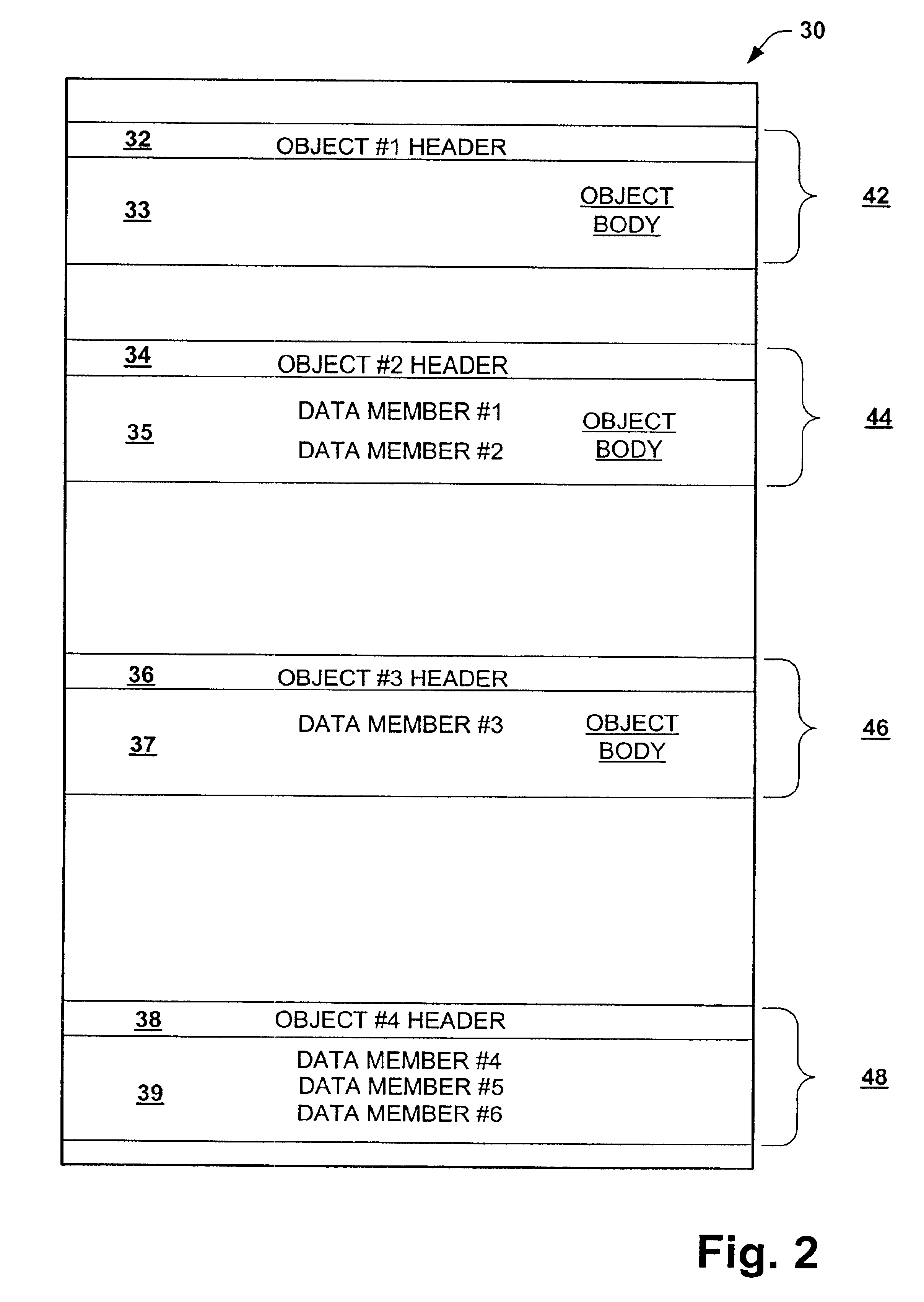
InactiveUS6898611B1Effectively fixedData processing applicationsMemory adressing/allocation/relocationLocal variableUnsafe condition
A system and method is provided for efficiently pinning references to the managed heap. The system and method allow for references to managed objects to be declared as pinned during a call to unmanaged code. The references are then reported as pinned to a garbage collector in response to invocation of a garbage collection service. The reference can be declared as pinned by a programmer within the source code or automatically invoked at run-time based on an unsafe condition. The garbage collection service will not move or relocate objects that are referenced by the active pinned local variables. If a garbage collection does not occur, the fact that the local variables are declared pinned is ignored.
Owner:MICROSOFT TECH LICENSING LLC
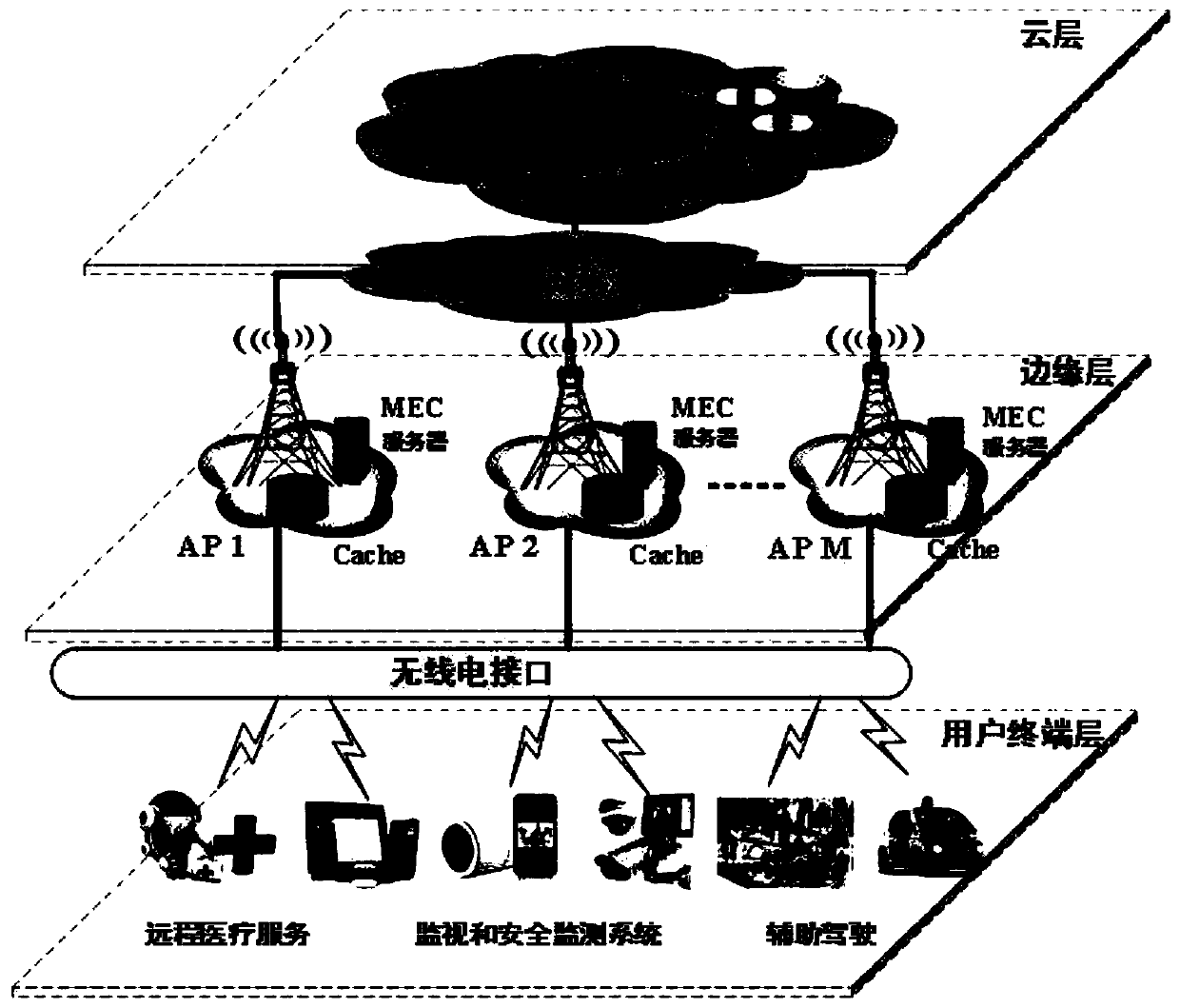
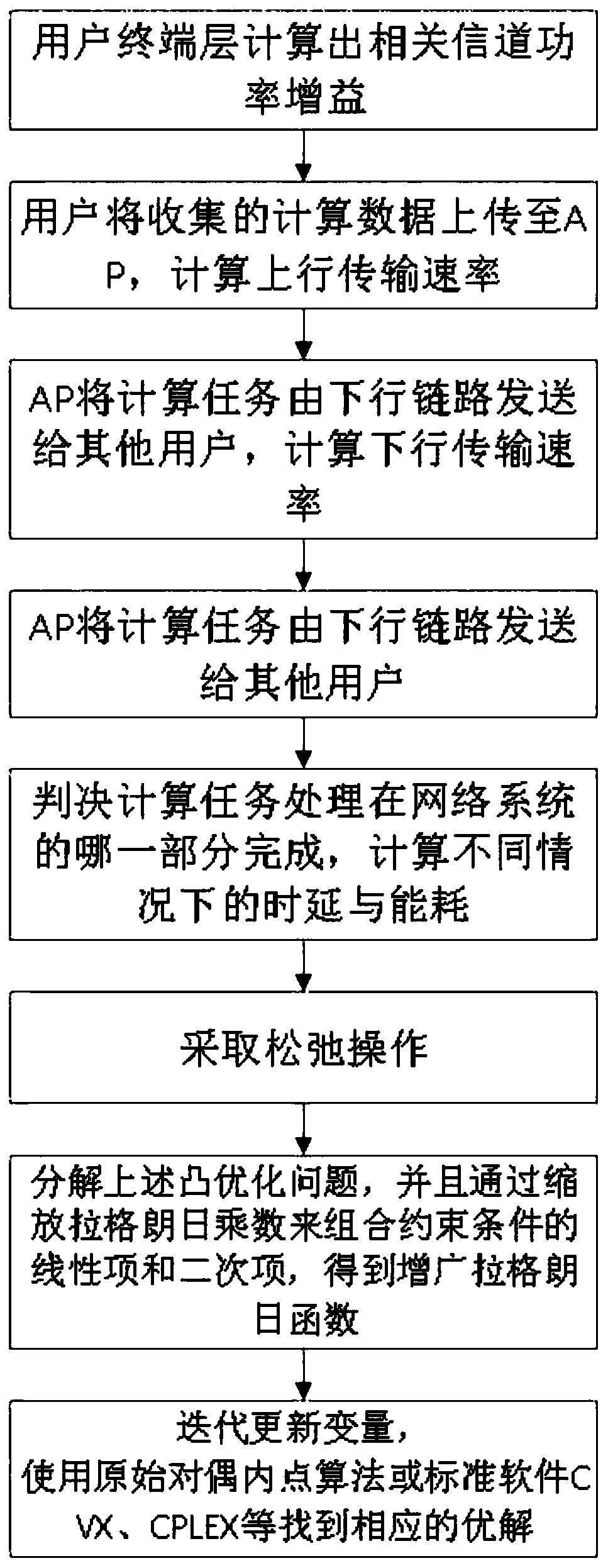
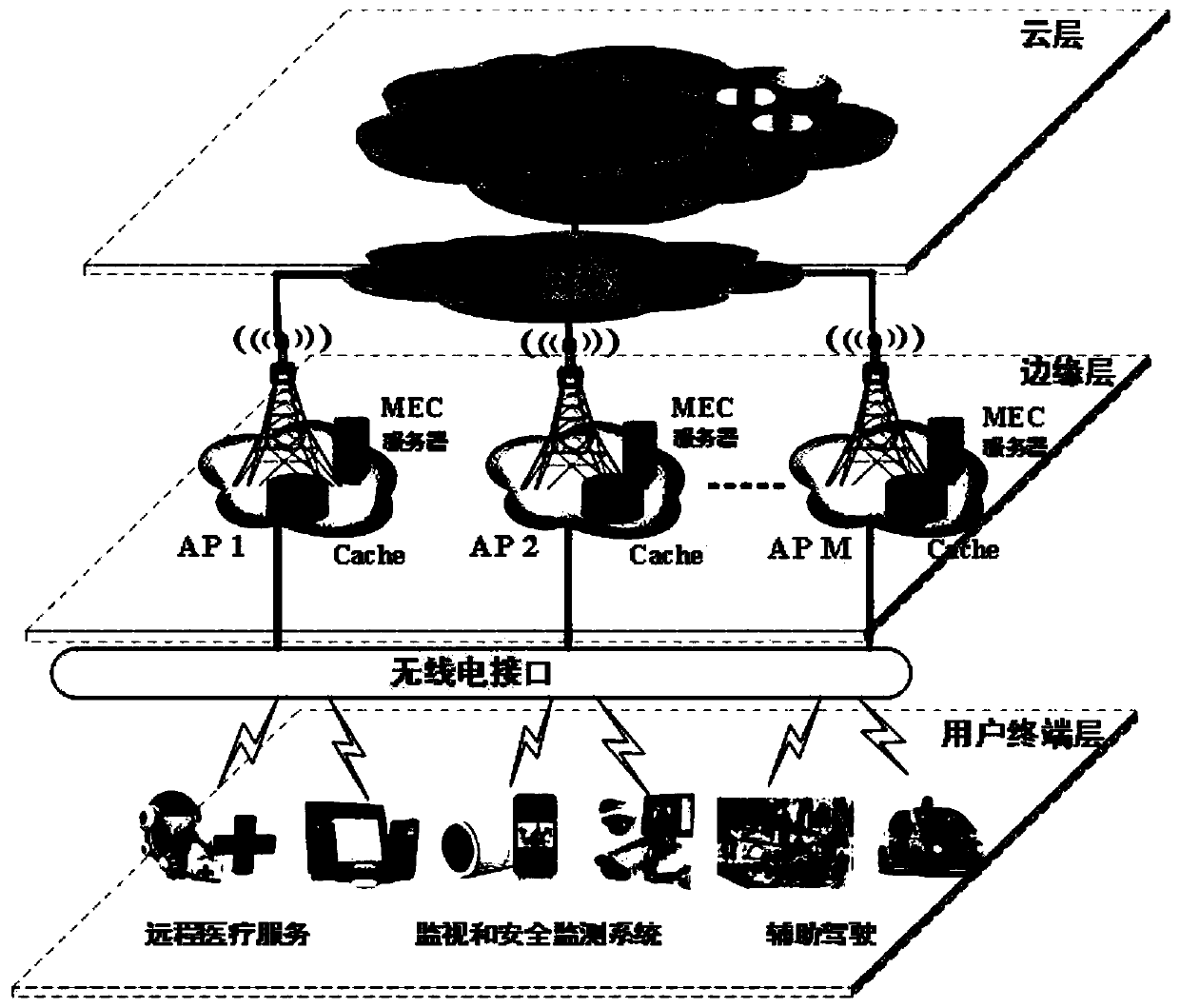
Task unloading and data caching method for hybrid mobile cloud/edge computing
PendingCN110018834APowerful computing cacheTake advantage ofResource allocationEnergy efficient computingChannel powerComputer architecture
The invention discloses a task unloading and data caching method for hybrid mobile cloud / edge computing, and belongs to the technical field of decision optimization and multi-user resource allocation.The method comprises the following steps: 1) calculating channel power gain; 2) uploading the calculation data to an AP, and calculating uplink and downlink transmission rates; 3) judging which partof the user of the user terminal layer, the MEC server of the edge layer or the cloud server in the cloud layer the task processing is completed, and calculating task processing time delay and energyconsumption which are completed according to corresponding conditions after judging; 4) obtaining a minimization optimization problem of the task processing process delay; 5) copying a local variableand storing the local variable in the MEC server; 6) using an alternating direction multiplier method to obtain an augmented Lagrangian function, and 7) performing iteratively updating to obtain a final expression form of the optimized objective function, and finding out the minimization of the task processing process delay. The method satisfies the energy consumption of the user, and minimizes the total user delay while constraining the storage and calculation capability of the AP.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
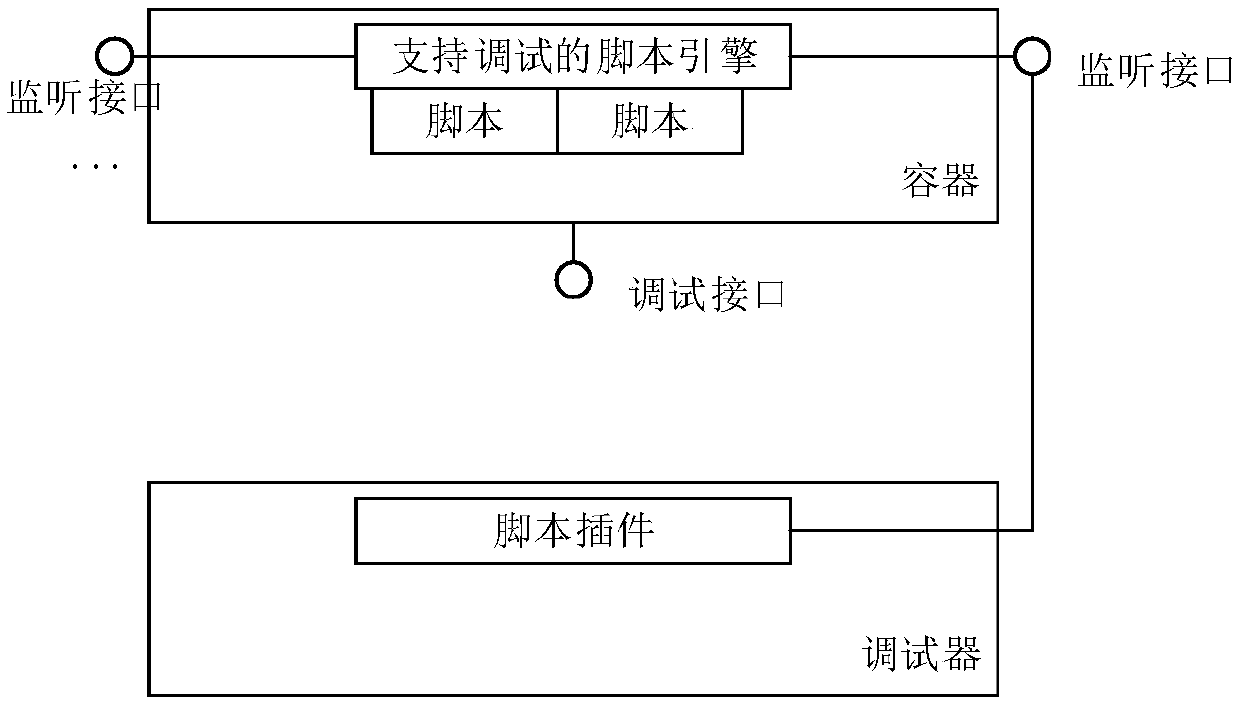
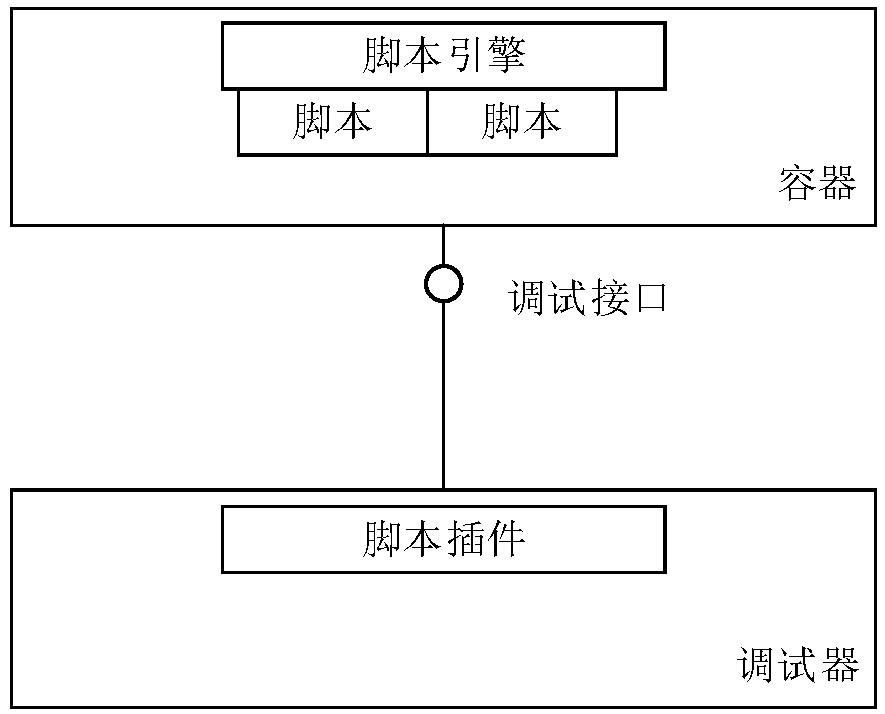
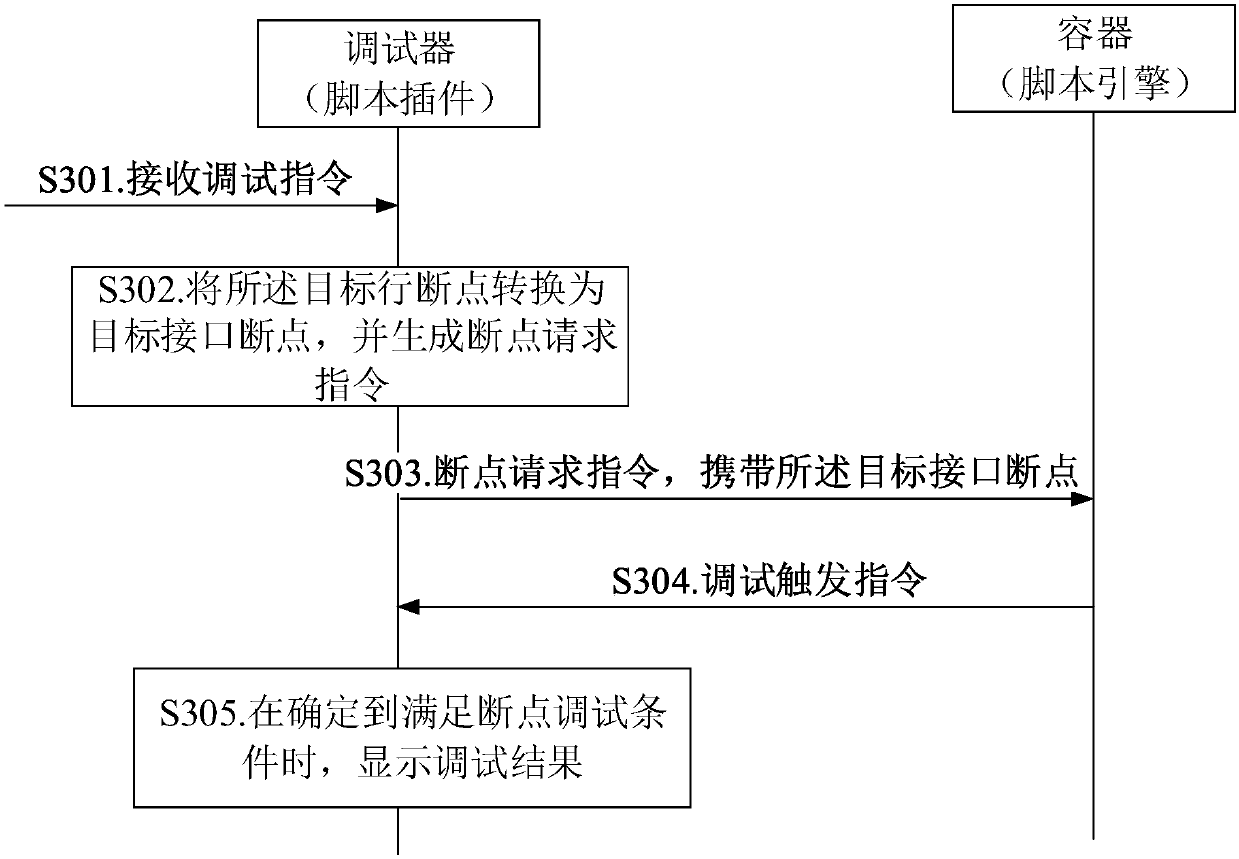
Script debugging method and device and computer storage medium
The embodiment of the invention discloses a script debugging method and device and a computer storage medium, and the method comprises the steps that the device obtaining a debugging instruction, thedebugging instruction carrying a to-be-debugged target row breakpoint, and the target row breakpoint at least comprising row information used for indicating a row code where a script file interrupt point position is requested to be debugged; when it is determined that breakpoint debugging conditions are met, displaying a debugging result, wherein the debugging result comprises information obtainedwhen the equipment executes breakpoint processing on row codes corresponding to the target row breakpoints, and the breakpoint debugging conditions at least comprise that identification information corresponding to the target interface breakpoints is consistent with identification information corresponding to target local variables. By adopting the embodiment of the invention, the functions of script debugging, quick positioning of problem positions and the like can be realized under the condition of not modifying the debugging function of the script engine.
Owner:HUAWEI TECH CO LTD
Method for sharing stream memory of heterogeneous multi-processor
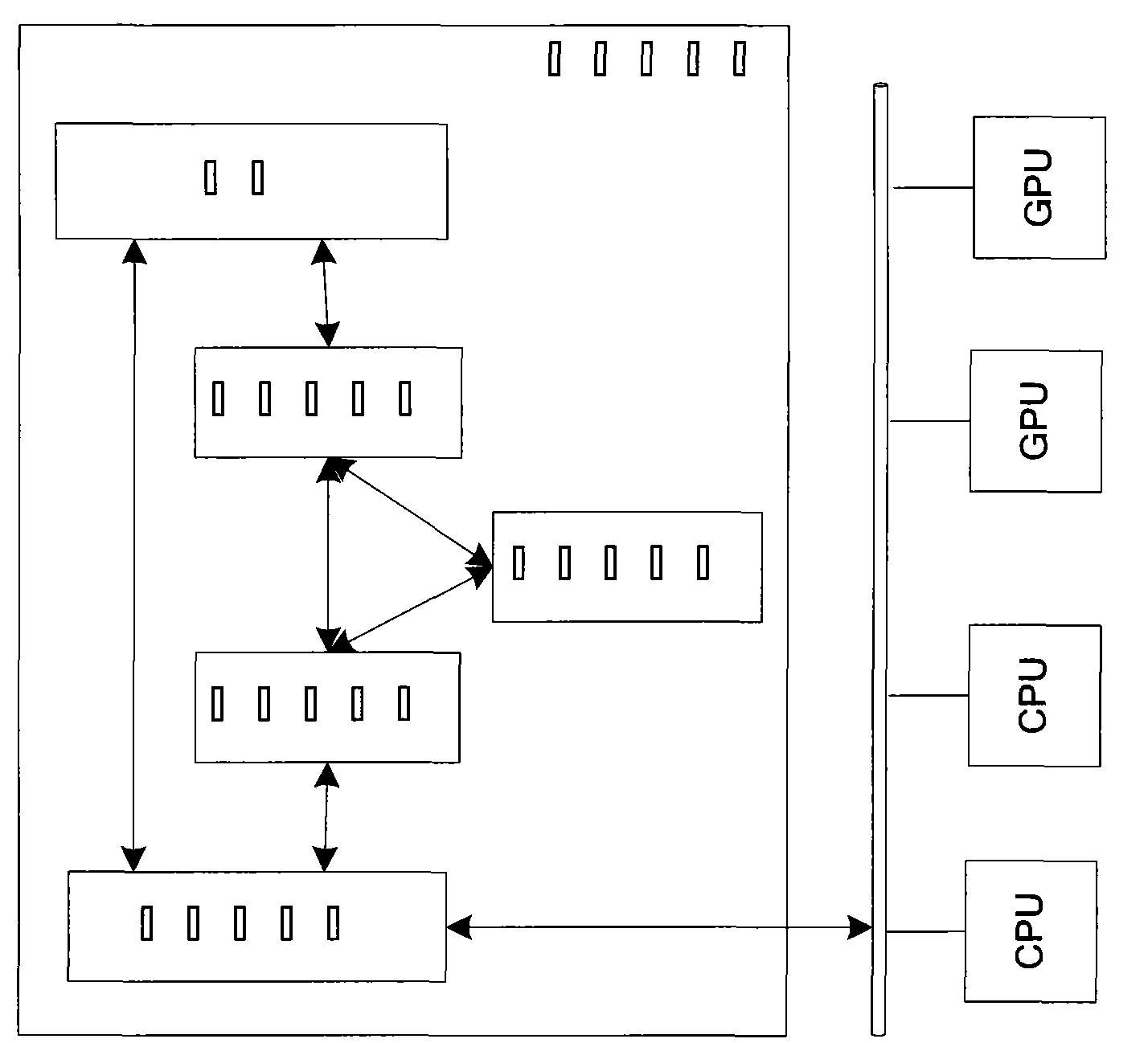
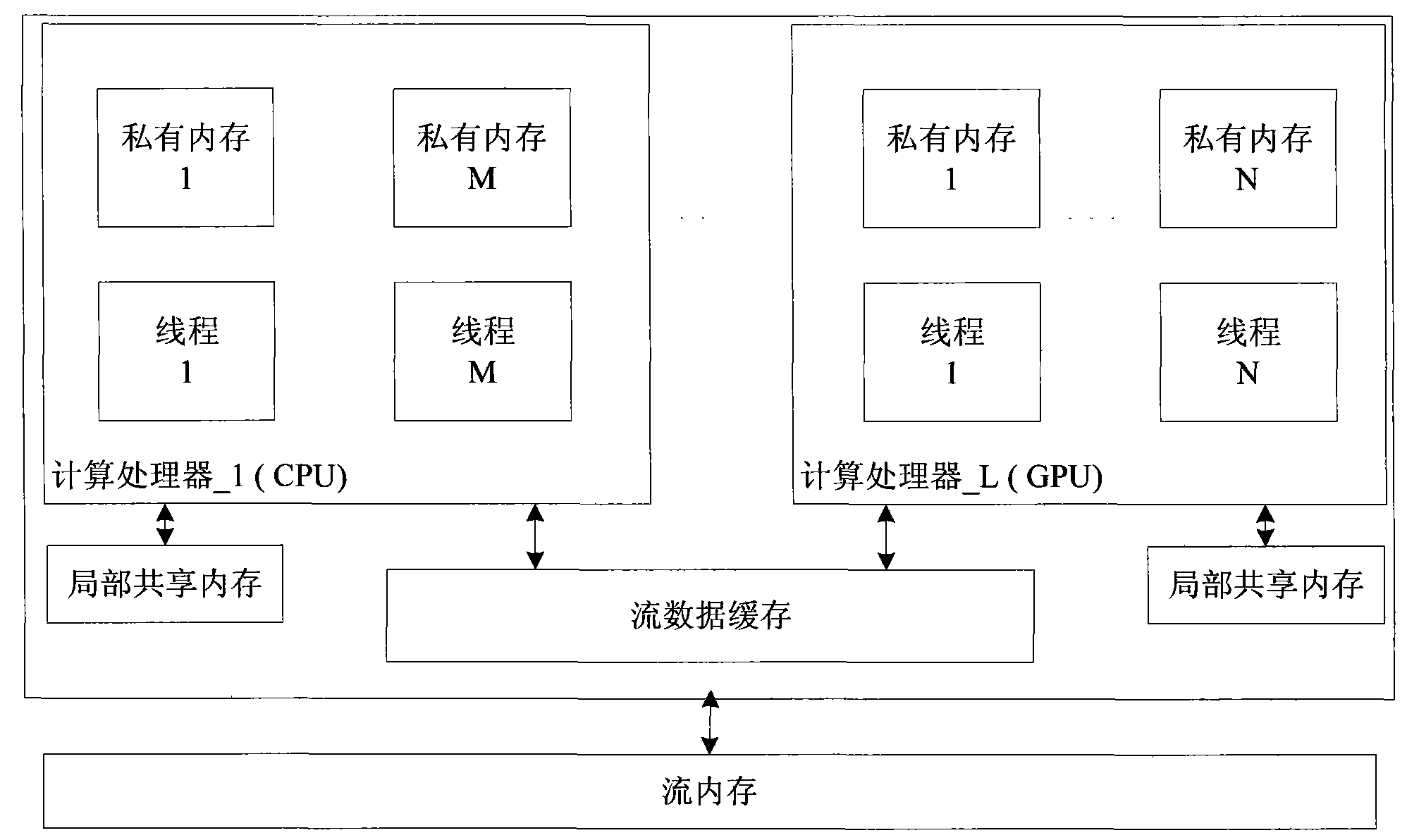
InactiveCN101551761AImprove the ability to handle massive amounts of dataResource allocationConcurrent instruction executionLocal variableMulti processor
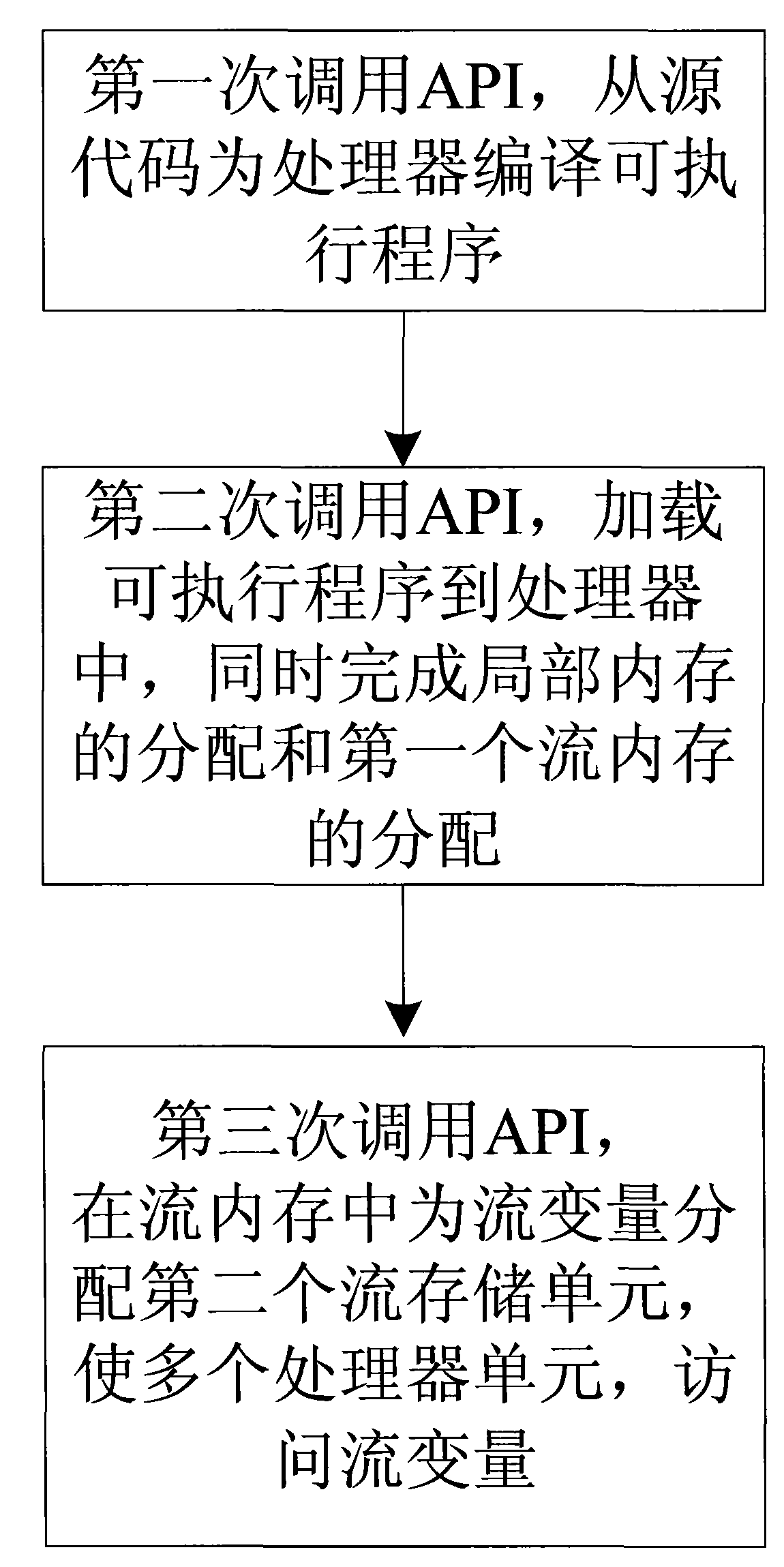
The invention provides a method for sharing the stream memory of a heterogeneous multi-processor. The method comprises the following steps: an application program runs on a master processor and an API is called for the first time, and one or more executable programs are encoded from the source code containing local variables for a plurality of processor units with stream memory; and then the API is called for the second time so as to load one or more executable programs to a plurality of processor units; collateral execution is conducted on a plurality of treads; when in loading, local storage units are allocated from the local storage of a processor; in addition, when in loading, a first stream storage unit is allocated from the stream memory; when a processing unit executes a plurality of treads simultaneously, the threads access to the values of the variables on the basis of the storage units of the stream memory; the source program containing stream variables further comprises the following steps: the API is called for the third time; in the stream memory, a second stream storage unit is allocated for the stream variables; based on the second stream storage unit, the variable values of the stream variables are accessed through a plurality of processor units.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Dynamic stacking memory management method for preventing buffering area from overflow attacking
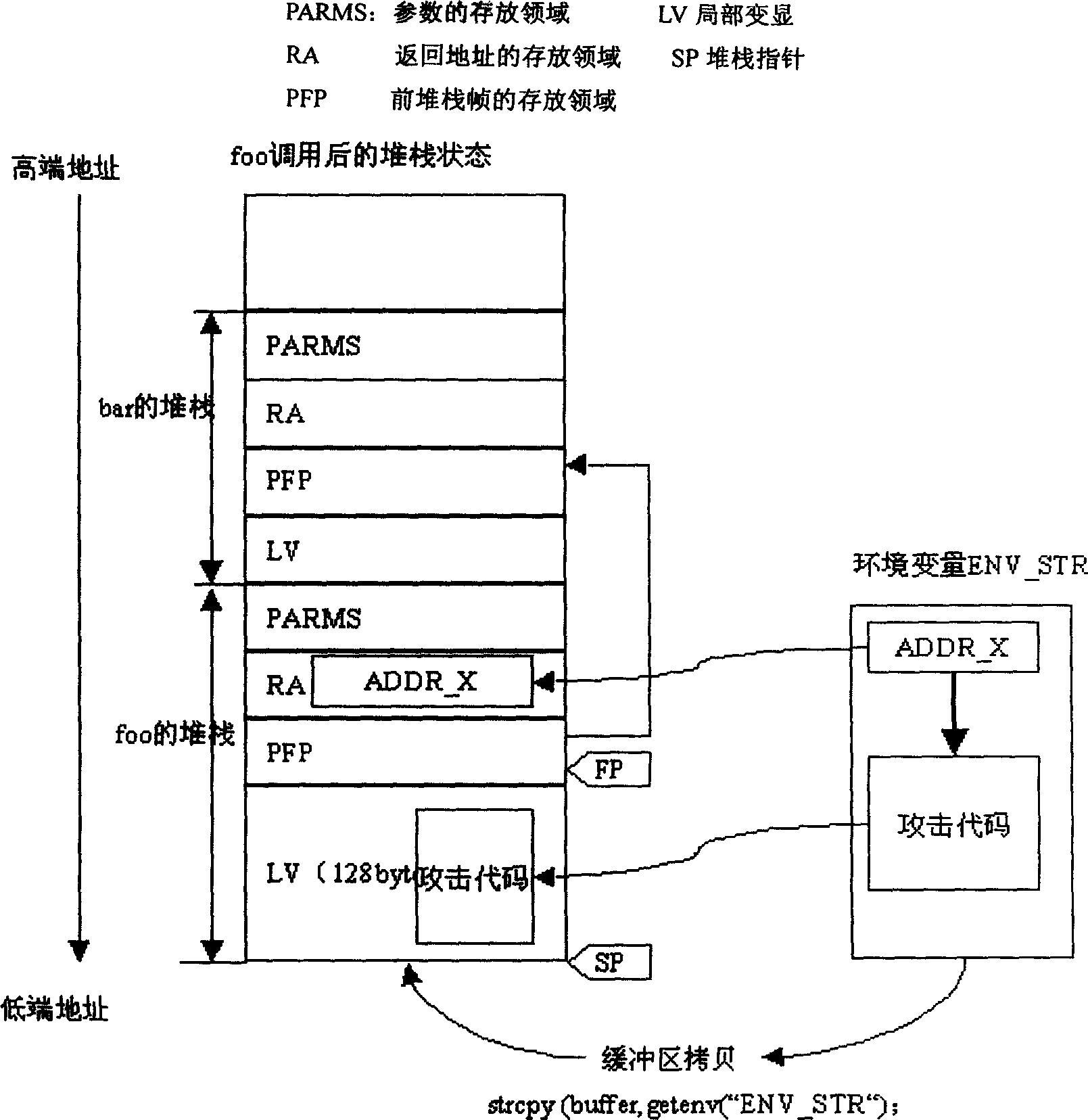
InactiveCN1564098APrevent overflowAvoid attackDigital data processing detailsPlatform integrity maintainanceLocal variableBuffer overflow
Since relative position between return address and local variable is changed in dynamic random, return address is not possible to be rewritten so as to prevent attacking computer by using buffer flood. The invention includes following claim of rights: method of dynamic stack memory management including object program, compiler, memory device and computer system, which possesses characters of the method.
Owner:NANJING UNIV
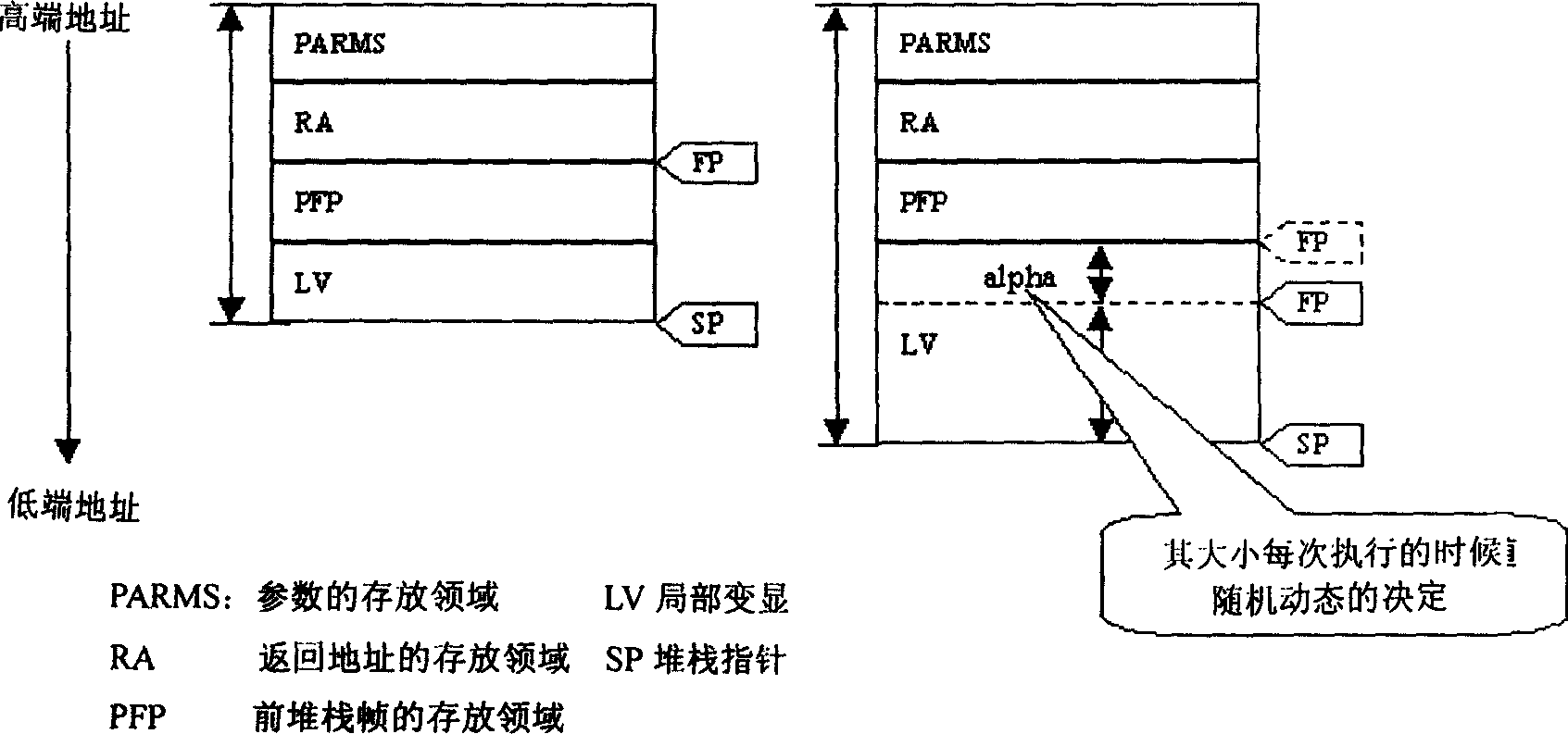
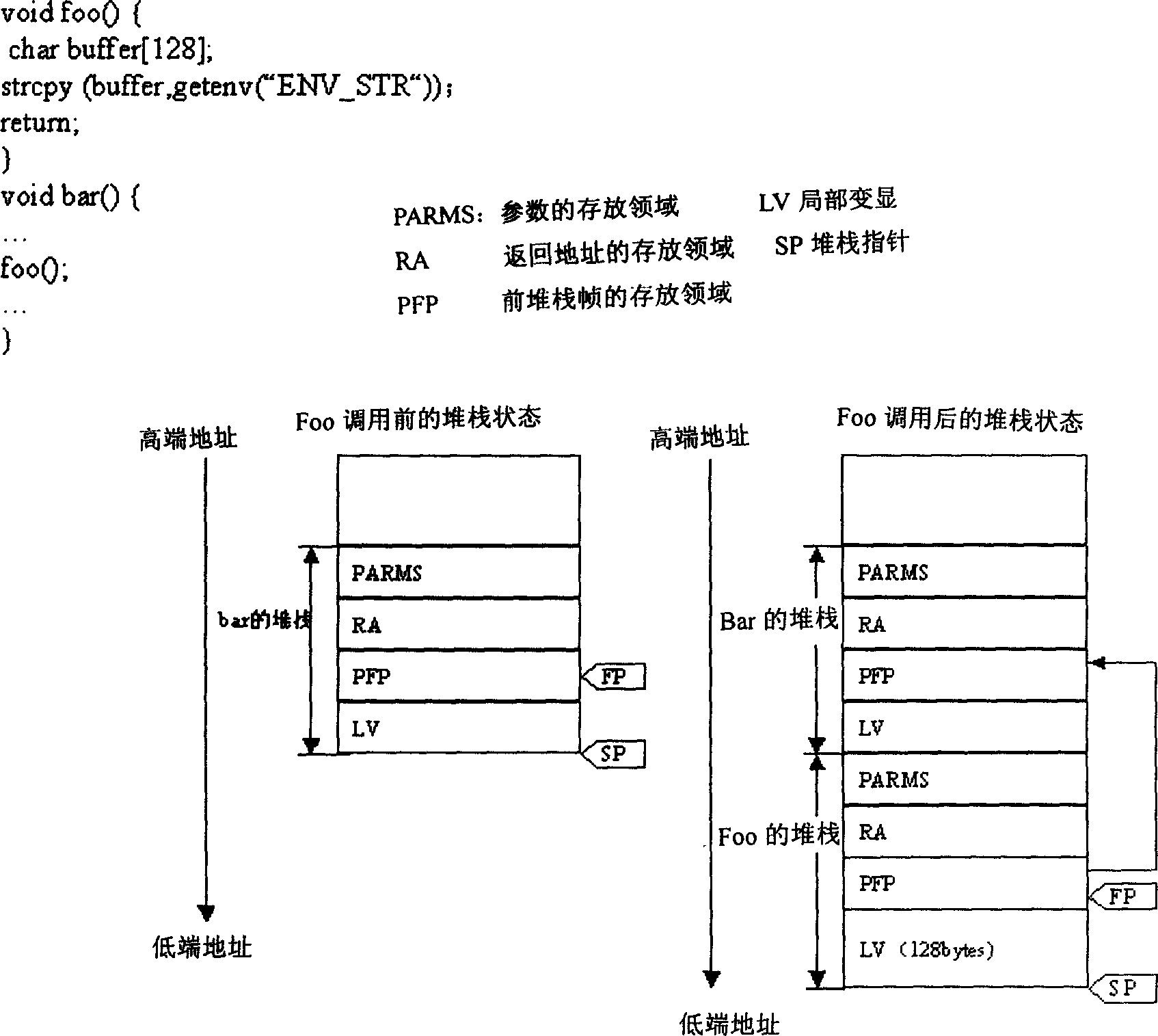
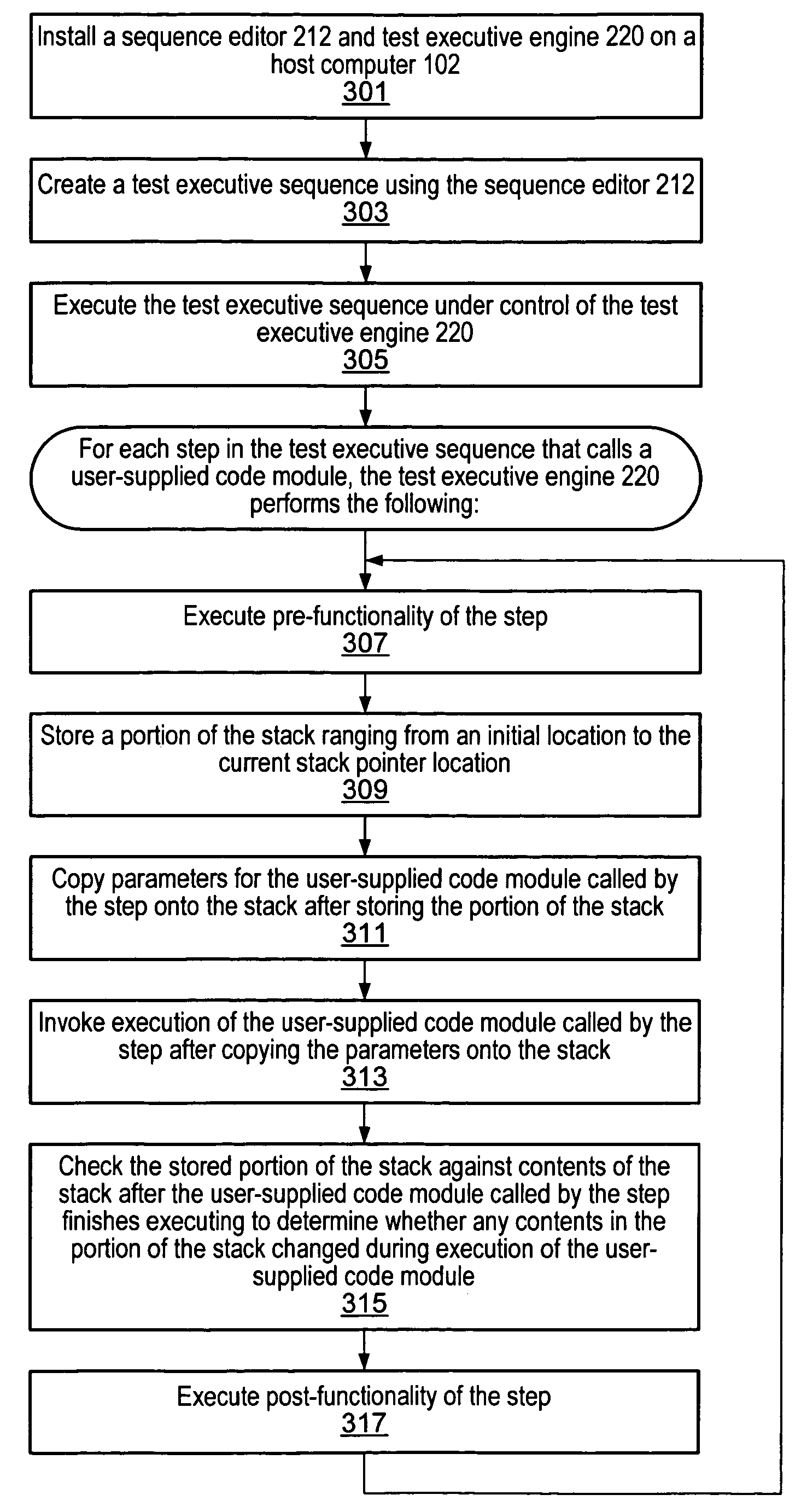
Test executive with stack corruption detection, stack safety buffers, and increased determinism for uninitialized local variable bugs
A system and method for detecting and / or preventing execution problems caused by user-supplied code modules that are called by steps of a test executive sequence. The test executive sequence may include a plurality of test executive steps. At least a subset of the steps may be configured to call user-supplied code modules. The test executive sequence may be executed on a host computer under control of a test executive engine. For each step that calls a user-supplied code module, the test executive engine may perform certain actions to detect and / or prevent execution problems caused by the user-supplied code module. For example, the test executive engine may be operable to automatically detect stack corruption caused by the user-supplied code module, may be operable to utilize stack safety buffers to avoid stack corruption problems caused by the user-supplied code module, and / or may include features for aiding a user in determining whether the user-supplied code module contains an uninitialized local variable.
Owner:NATIONAL INSTRUMENTS
Method and system for dynamic loop transfer by populating split variables
InactiveUS20090064113A1Performing codeIncrease flexibilitySoftware engineeringProgram controlLocal variableParallel computing
A method that provides for dynamic loop transfer for a method having a first set of instructions being executed by an interpreter is provided. An execution stack includes slots for storing a value of each local variable known to each subroutine while the subroutine is active. The method comprises suspending execution at a point for which a current execution state can be captured from the execution stack; assigning the value in each slot of the execution stack to a corresponding slot of an array of values; scanning the first set of instructions to identify a data type for local variable that is not known in the current execution state and shares a slot in the execution stack with a local variable that is known; and generating a second set of instructions for the method coded to be initially executed to declare each local variable that is known in the current execution state and each local variable for which a data type was identified, assign each declared variable with the value assigned to the slot in the array that corresponds to the slot of the execution stack in which the value of the variable is stored during execution of the first set of instructions, and branch to a target point in the second set of instructions that corresponds to the point at which execution was suspended.
Owner:IBM CORP
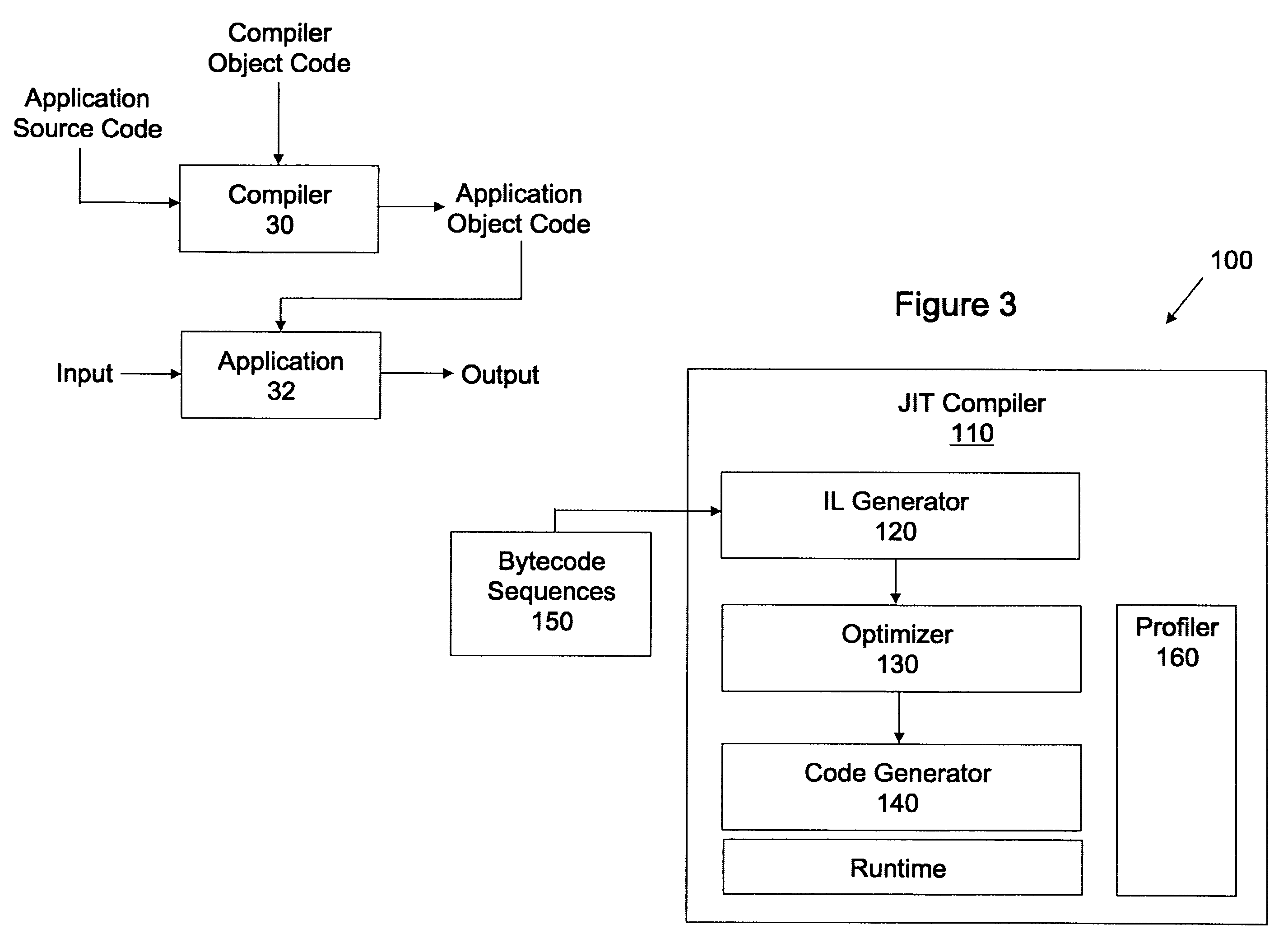
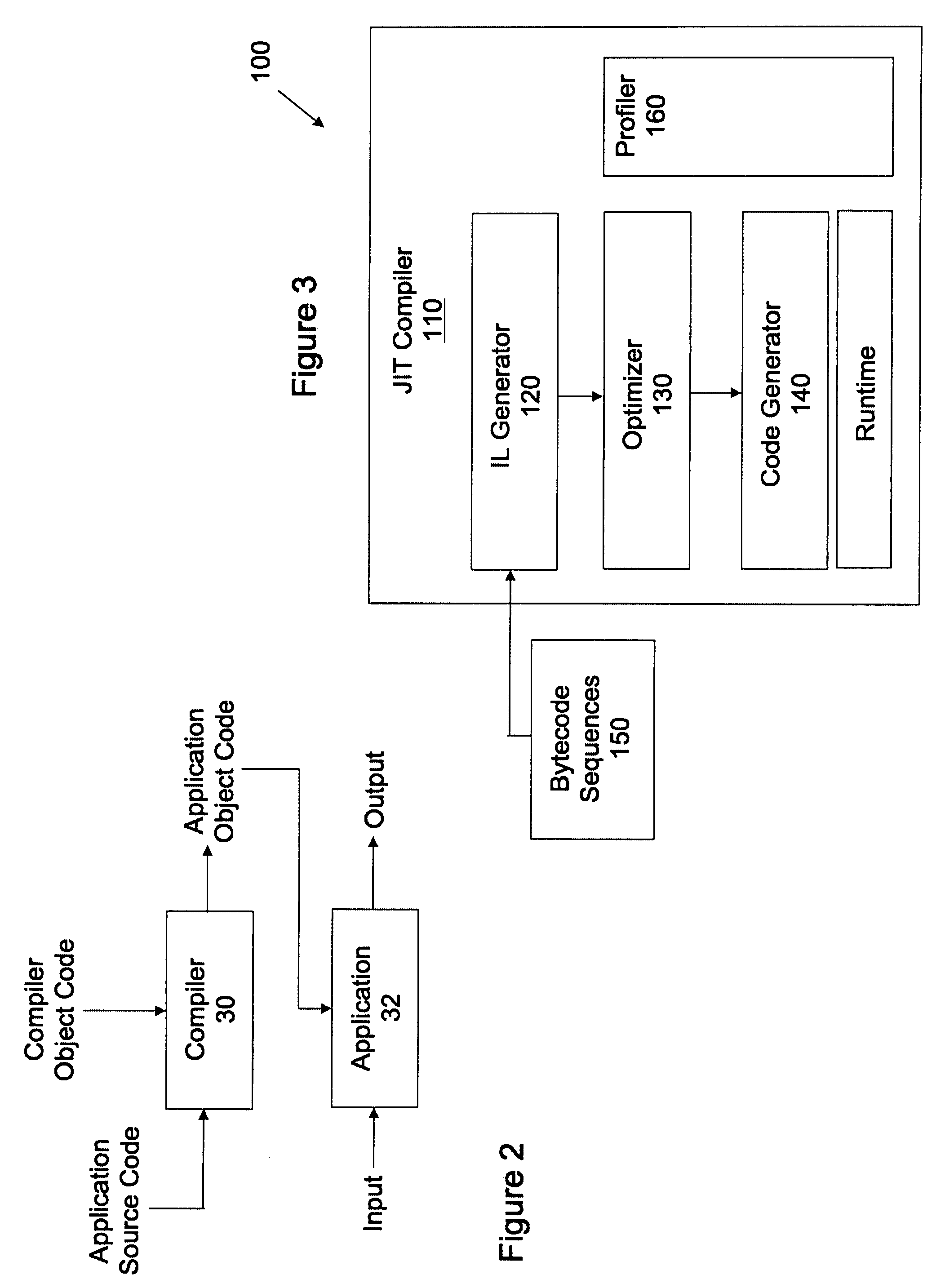
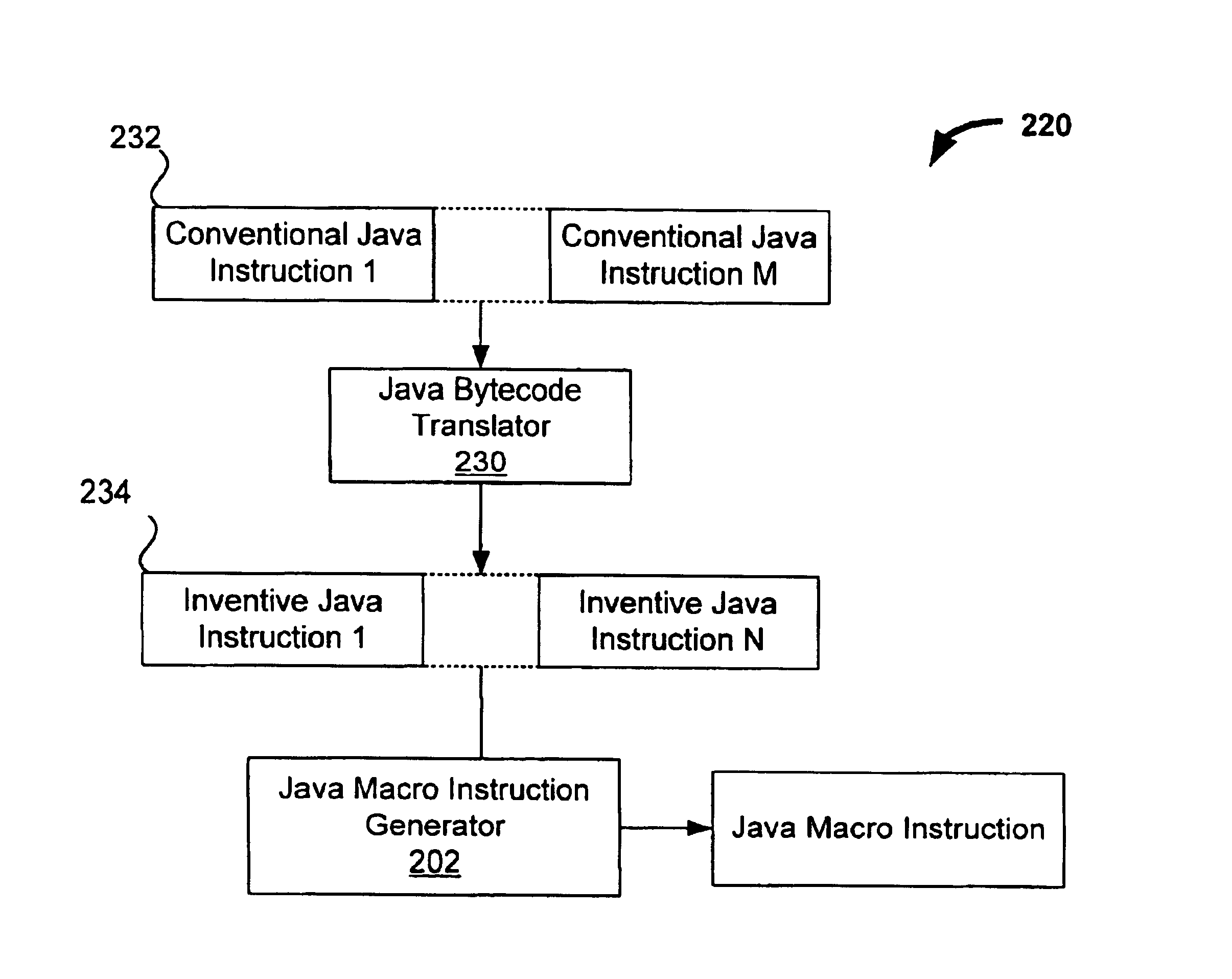
Frameworks for generation of Java macro instructions in Java computing environments
InactiveUS6988261B2Efficient executionReduce in quantitySoftware engineeringSpecific program execution arrangementsLimited resourcesLocal variable
Techniques for generation of Java™ macro instructions suitable for use in Java™ computing environments are disclosed. As such, the techniques can be implemented in a Java™ virtual machine to efficiently execute Java™ instructions. As will be appreciated, a Java™ macro instruction can be substituted for two or more Java™ Bytecode instructions. This, in turn, reduces the number of Java™ instructions that are executed by the interpreter. As a result, the performance of virtual machines, especially those operating with limited resources, is improved. A Java™ macro instruction can be generated for conventional Java™ instruction sequences or sequences of Java™ instruction that are provided in a reduced set of instruction. In any case, sequences that are frequently encountered can be replaced by a Java™ macro instruction. These sequences are typically encountered when Java™ objects are instantiated, during programming loops, and when a local variables are assigned a value.
Owner:ORACLE INT CORP
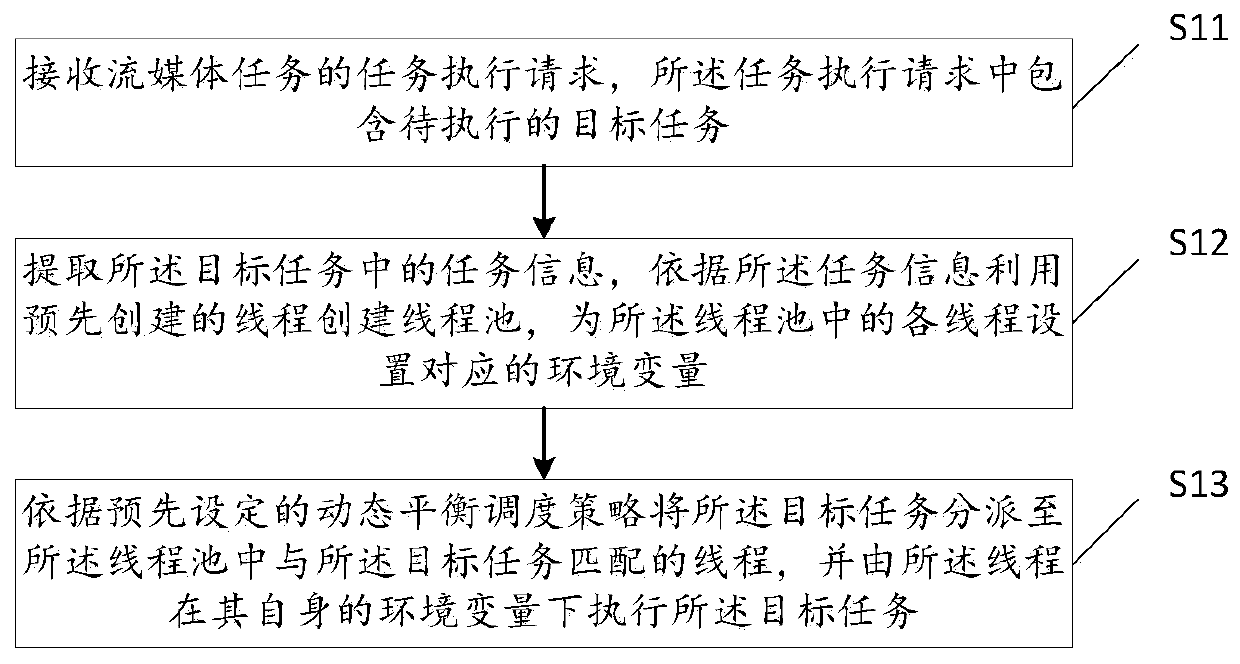
Streaming media task processing method and device based on multiple threads, and computer device
PendingCN109753354AImprove performanceImprove stabilityResource allocationLocal variableDynamic balance
The invention provides a streaming media task processing method and device based on multiple threads, and the method comprises the steps: receiving a task execution request of a streaming media task,and enabling the task execution request to comprise a to-be-executed target task; Extracting task information in the target task, creating a thread pool by utilizing a pre-created thread according tothe task information, and setting a corresponding environment variable for each thread in the thread pool; and allocating the target task to a thread matched with the target task in the thread pool according to a preset dynamic balance scheduling strategy, and executing the target task by the thread under the environment variable of the thread. A multi-thread task processing mode is adopted, a dynamic balance scheduling strategy is used for achieving reasonable distribution of target tasks, environment variables are local variables, possibility is provided for packaging use of a Dll library, the performance and stability of simultaneous multi-path data processing are improved, and the client experience is better.
Owner:PING AN TECH (SHENZHEN) CO LTD
Test executive with stack corruption detection, stack safety buffers, and increased determinism for uninitialized local variable bugs
A system and method for detecting and / or preventing execution problems caused by user-supplied code modules that are called by steps of a test executive sequence. The test executive sequence may include a plurality of test executive steps. At least a subset of the steps may be configured to call user-supplied code modules. The test executive sequence may be executed on a host computer under control of a test executive engine. For each step that calls a user-supplied code module, the test executive engine may perform certain actions to detect and / or prevent execution problems caused by the user-supplied code module. For example, the test executive engine may be operable to automatically detect stack corruption caused by the user-supplied code module, may be operable to utilize stack safety buffers to avoid stack corruption problems caused by the user-supplied code module, and / or may include features for aiding a user in determining whether the user-supplied code module contains an uninitialized local variable.
Owner:NATIONAL INSTRUMENTS
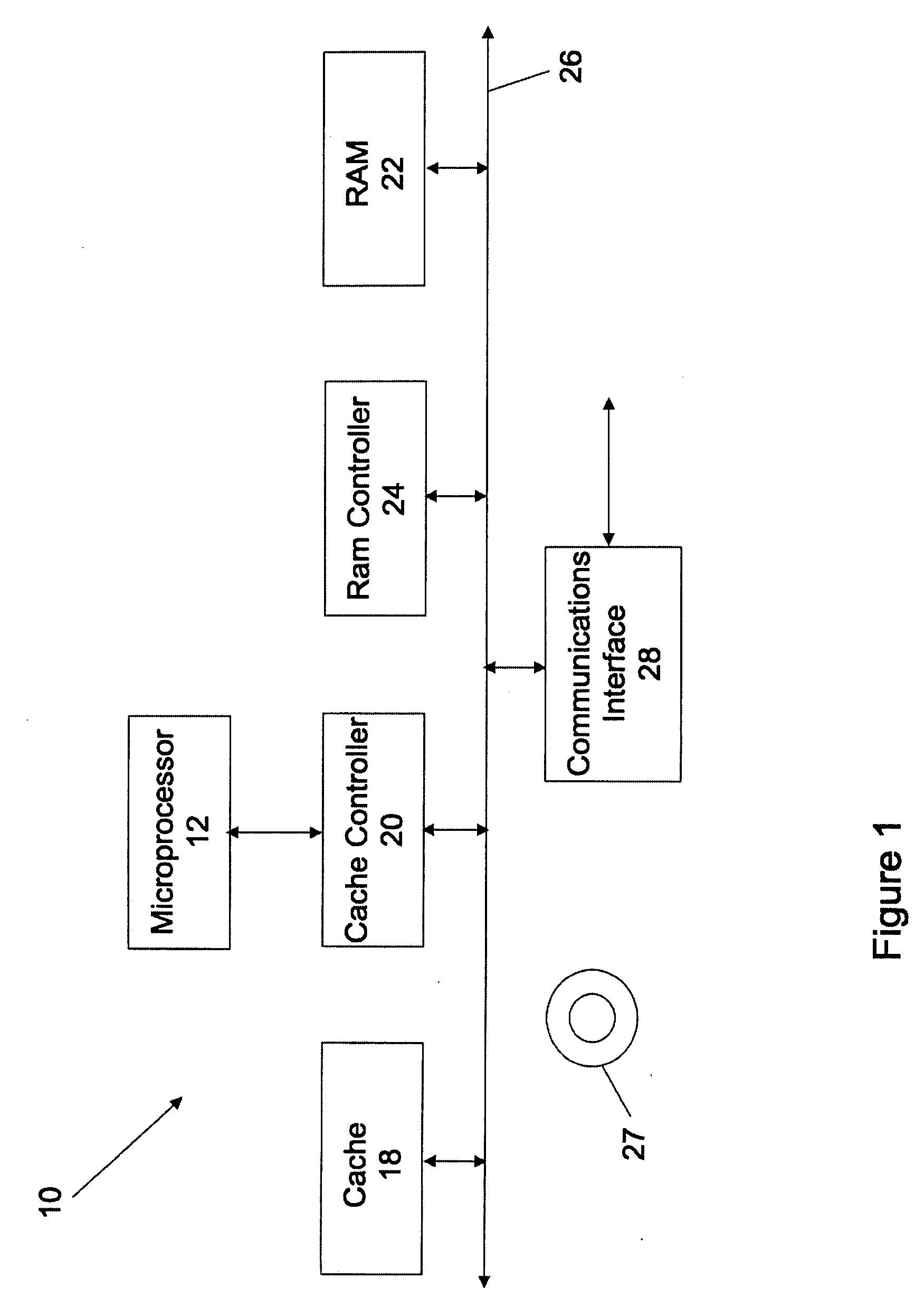
Obfuscating function resources while reducing stack consumption
ActiveUS20140095812A1Reducing stack consumptionMemory architecture accessing/allocationMemory adressing/allocation/relocationArray data structureStatic random-access memory
In one embodiment, a system wide static global stack pool in a contiguous range of random access memory is generated, a block of memory in the system global pool is assigned to a thread of a running process, and the thread stores local variable information in static global stack pool, such that the local variable is hidden from a stack frame back-trace. In one embodiment, a dynamically allocated data structure in system heap memory is generated, the data structure is locked to ensure atomic access, a block of memory in the data structure is assigned to a thread of a process, the data structure is unlocked, and the thread stores local variable information in static global stack pool, such that the local variable is hidden from a stack frame back-trace.
Owner:APPLE INC
Stack tracing method and device in decompilation process and decompiler
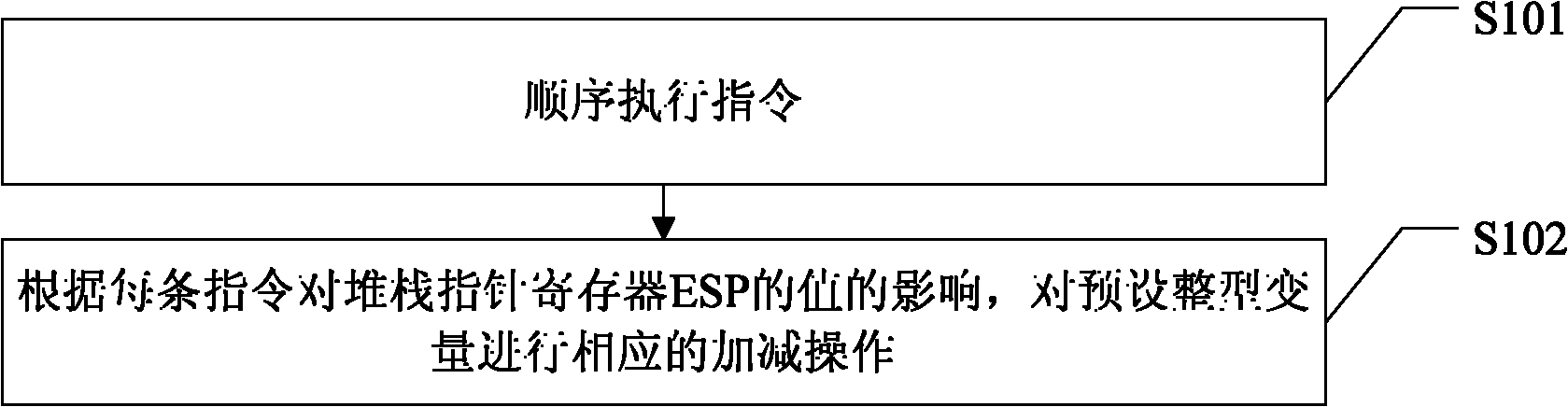
ActiveCN101976187AImprove accuracyImprove readabilityMemory systemsMachine execution arrangementsLocal variableParallel computing
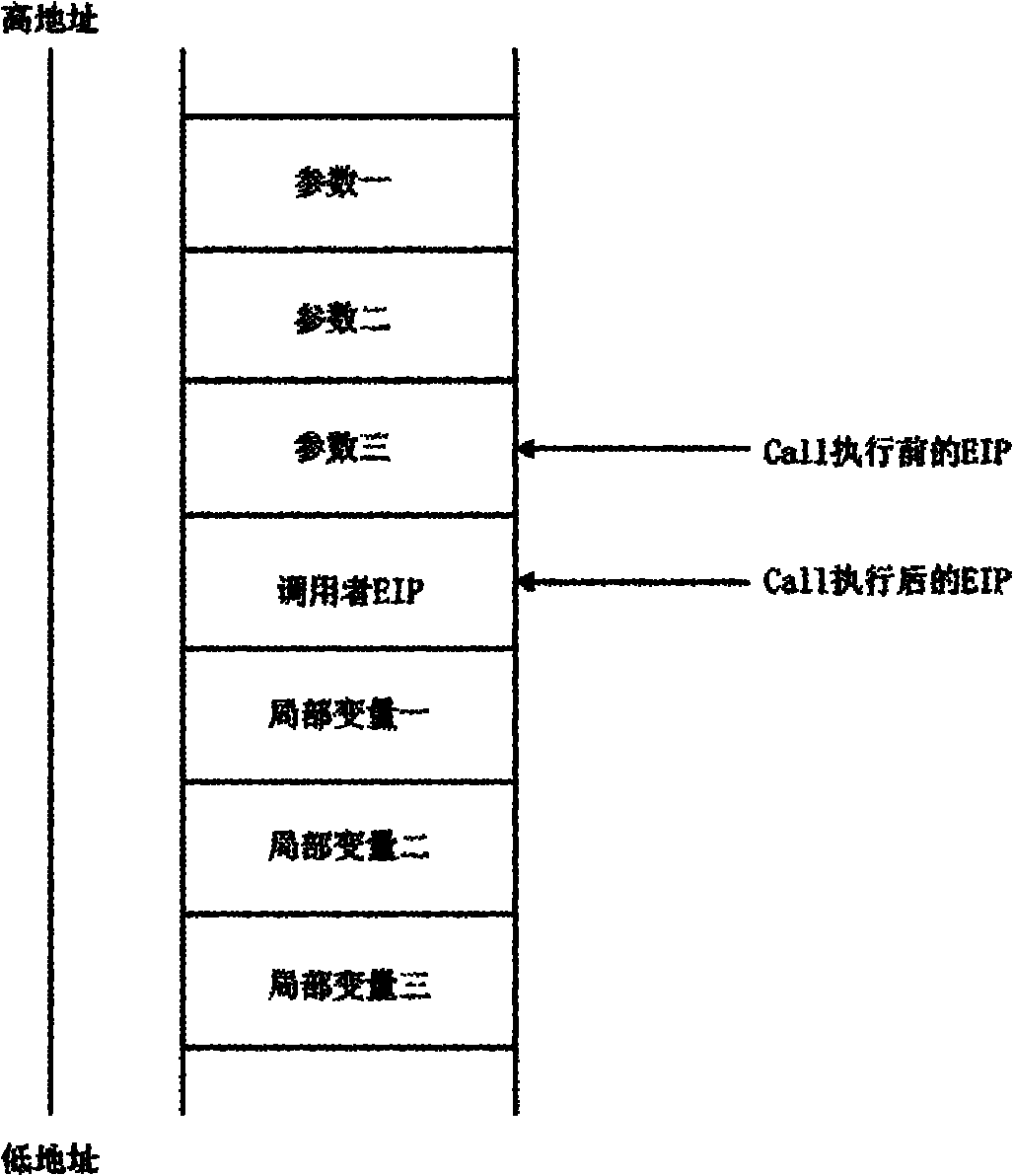
The invention relates to a stack tracing method and device in a decompilation process and a decompiler. The method comprises the steps of sequentially executing commands, carrying out corresponding addition and subtraction operations on a preset integer variable according to the influence of each command to a stack pointer register (ESP), wherein the preset integer variable is used for presentingan offset between a value of the current ESP register and a value of a system ESP register at a function inlet. The behavior of the ESP register is simulated through the preset integer variable, and the corresponding add and subtract operations are executed on the preset integer variable according to the influence of each command to the ESP register, thus stack operation behaviors of pushing stack and entering stack of a CPU are simulated, parameters and local variables in the function executing process are accurately recognized according to the preset integer variables, more accurate information can be provided for the decompilation process, and finally the exactness and the readability of a decompilation result are improved.
Owner:GUANGZHOU DIQING ELECTRONICS TECH
Internet of things information processing method
ActiveCN102523200ATroubleshoot integration issuesData switching networksDescription formatInformation processing
The invention discloses an internet of things information processing method, which comprises describing processed internet of things information with a describing structure comprising statements, sentences and expression; and using electronics control assembly (ECA) rules to obtain description of relational models of the information and description including conditional description and description with movement decisions on a processing procedure of the information according to description of the information. The statement is used for defining port arrangement, information description and a plurality of local variables which are needed in an information processing procedure, the port arrangement indicates various message sources in different types, the information description provides universal description formats for information in each type, the local variables are variables needed for meeting information changes in the information processing procedure, the sentences are used for describing transmission and transition of the information between various different message sources, and the expression is description of limitation conditions, namely judging whether certain attributes of the information meet condition definitions or not.
Owner:SHANGHAI DEV CENT OF COMP SOFTWARE TECH
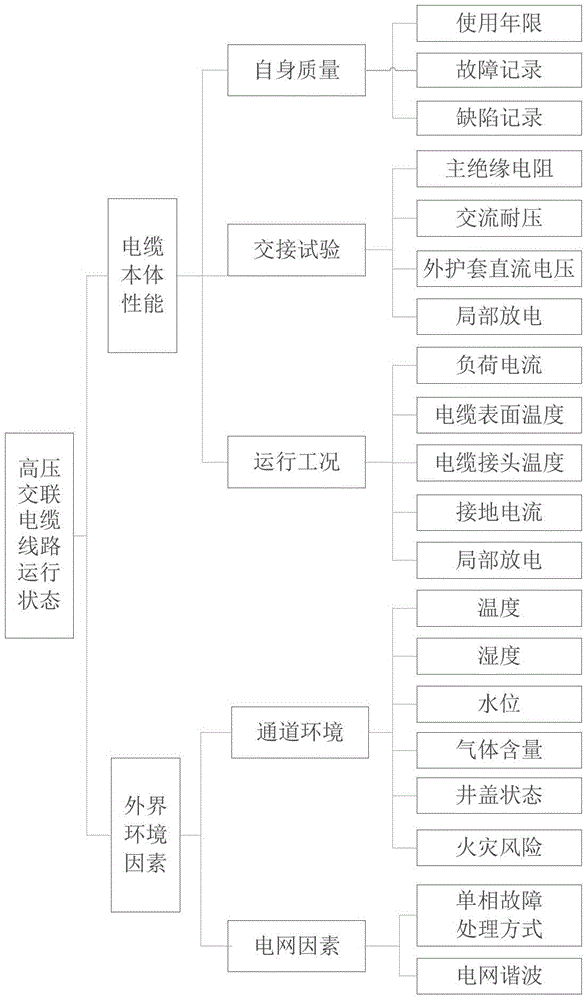
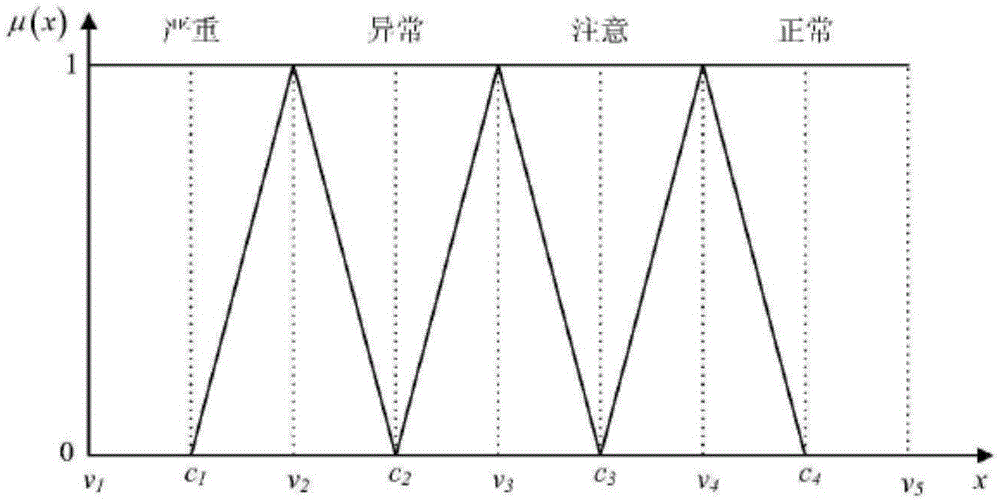
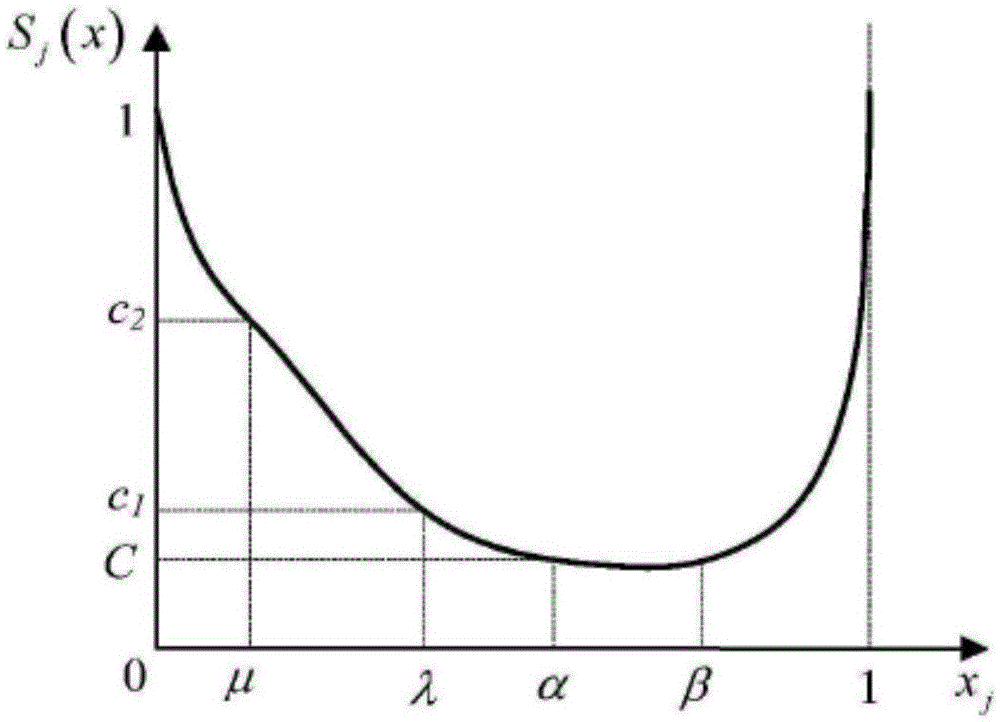
Variable weight function-based multi-parameter cable state evaluation method
InactiveCN105631771AIn line with the actual state of production and operationStatus Evaluation Production ActualData processing applicationsEvaluation resultLocal variable
The invention discloses a variable weight function-based multi-parameter cable state evaluation method. The method comprises steps: a cable state evaluation index set is built; a judgment matrix A is built; normalization processing is carried out on evaluation indexes; a comment set for fuzzy evaluation is built; a membership function corresponding to the evaluation state is set, and a fuzzy judgment matrix R is obtained; an evaluation index variable weight vector W is built; a local variable weight function S is built; and a high-voltage crosslinked cable line comprehensive state evaluation model is built for evaluating the cable state. According to the method of the invention, the index weight changes along with changes of the index value, the problem that the constant weight evaluation method can not present influences on an evaluation target by deterioration of a small weight value state amount can be effectively solved, and the evaluation result is more in line with the actual production and operation state of the cable and even the power grid equipment state.
Owner:STATE GRID CORP OF CHINA +1
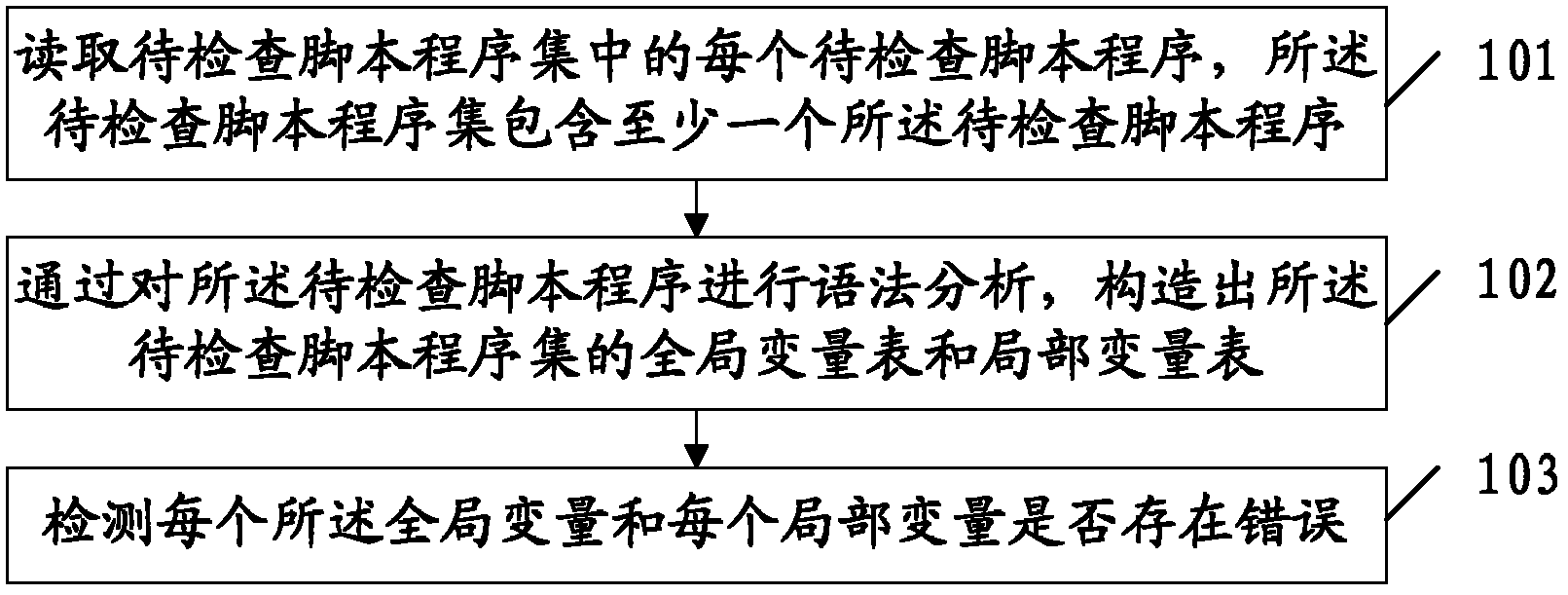
Inspection method and device for script programs
An embodiment of the invention discloses an inspection method and device for script programs and relates to the technical field of software inspection. According to the inspection method and device, variables can be inspected before a script program set is executed, and probabilities of errors of script programs during operation are reduced. The method comprises reading each script program to be inspected in the script program set to be inspected, wherein the script program set to be inspected contains at least one of the script program to be inspected; performing grammatical analysis on the script programs to be inspected and constructing a global variable table and a local variable table of the script program set to be inspected; and inspecting whether each global variable and each local variable has errors. The inspection method and device are mainly used for inspecting variables in script programs.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Optical transmission system with automatic signal level adjustment and startup functions
ActiveUS7343102B2Easy maintenanceEasy to operateWavelength-division multiplex systemsTransmission monitoring/testing/fault-measurement systemsTransport systemEngineering
An optical transmission system with automatic startup functions to optimize the power level of optical signals entering each optical amplifier and operate those amplifiers in appropriate mode. In the process of starting up an optical transmission system, upstream and downstream optical transmission devices set up themselves under the coordination of their internal controllers. The downstream device controller adjusts its local variable optical attenuator by utilizing optical noise emission from a post-amplifier in the upstream optical transmission device, and it selects and sets a preamplifier unit to work in appropriate operating mode. The upstream device controller, on the other hand, selects and sets operating mode of its local post-amplifier unit. During this process, the upstream and downstream device controllers exchange messages over supervisory control channels to achieve the purpose.
Owner:FUJITSU LTD
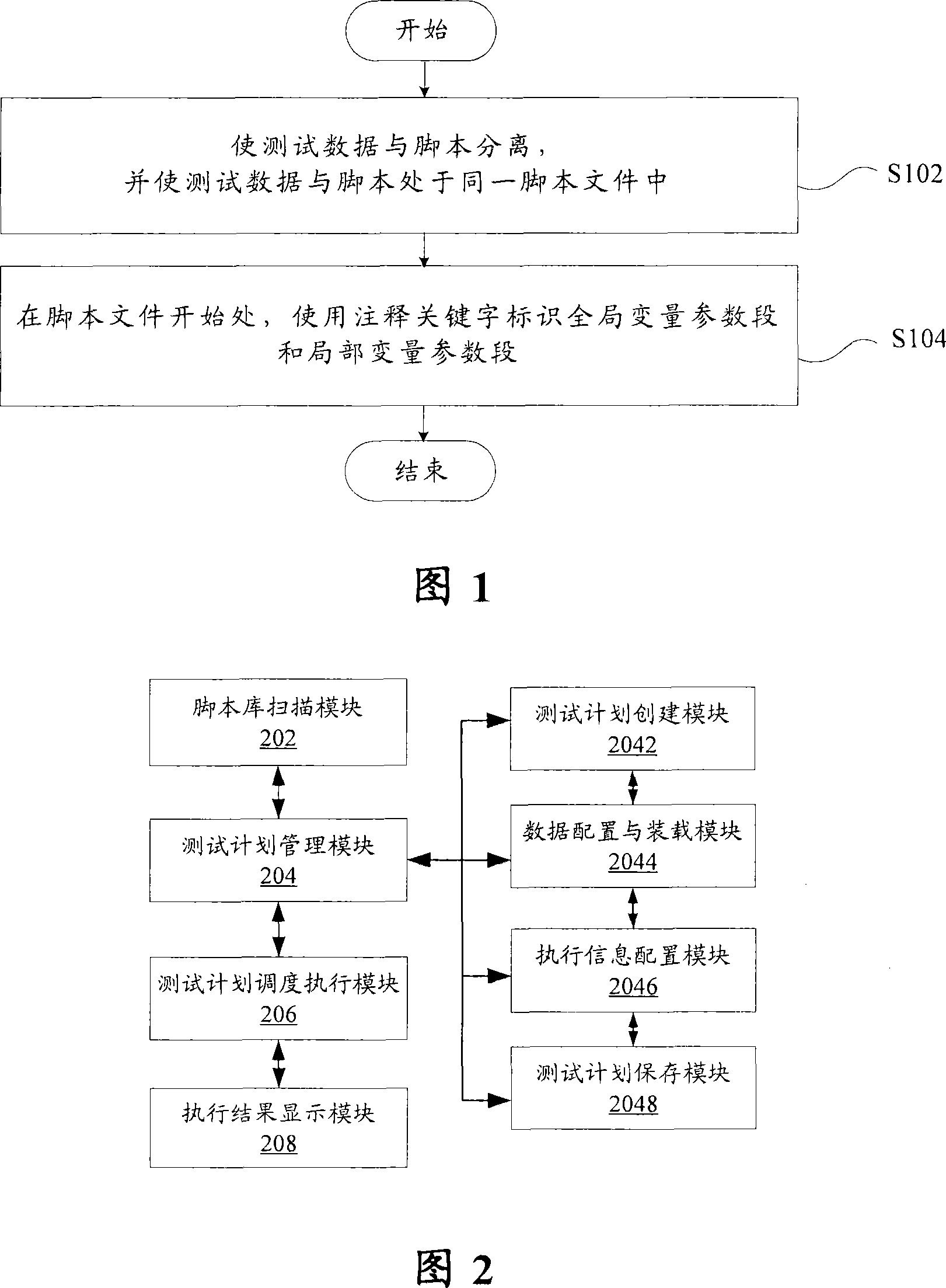
Test script processing method and its scheduling and executing system
InactiveCN101221504AEasy to configureReduce duplicationError detection/correctionSpecific program execution arrangementsTest scriptLocal variable
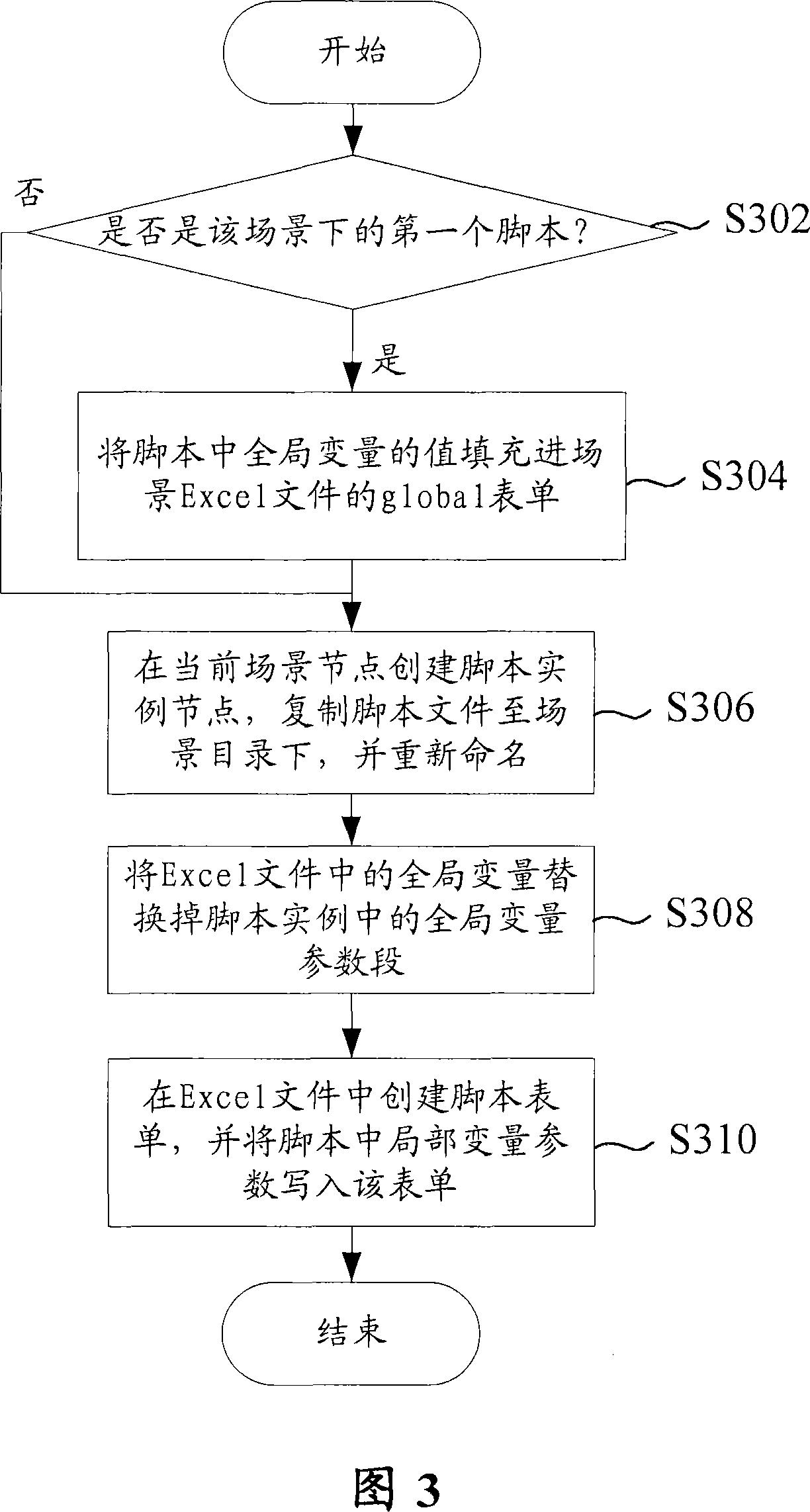
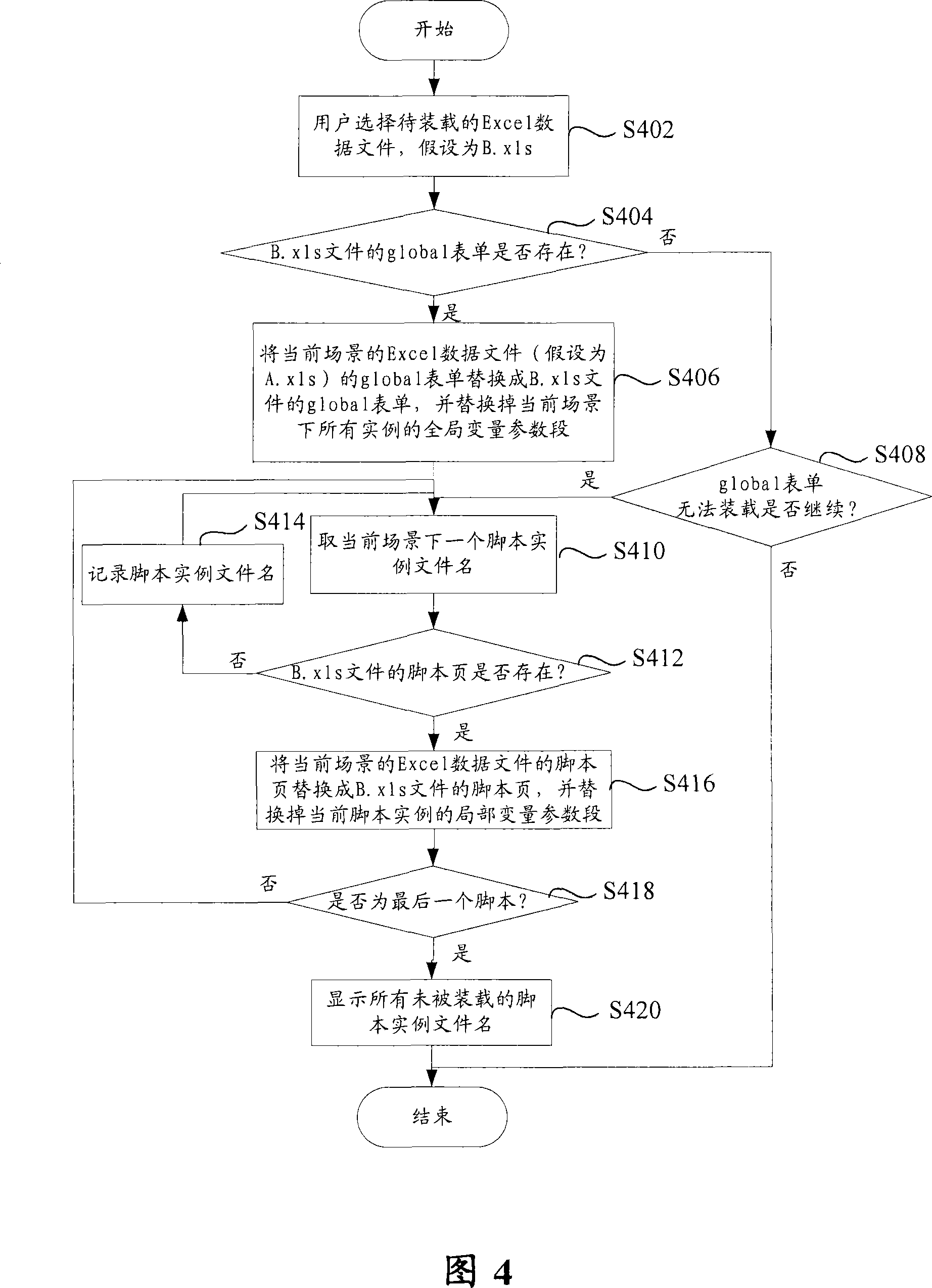
The invention discloses a test script processing method and a dispatching executive system thereof. The method of the invention comprises the following steps: test data is separated from a script, and the test data and the script are in the same script file; moreover, global variable parameter sections and local variable parameter sections are marked by annotating keywords on beginning parts of the script file. The invention allows creation of a plurality of script examples for the same test script when a test plan is established, and a plurality of sets of data are configured for execution of a test.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com