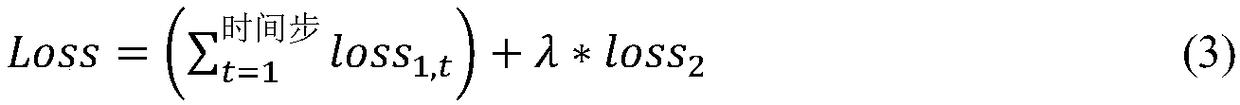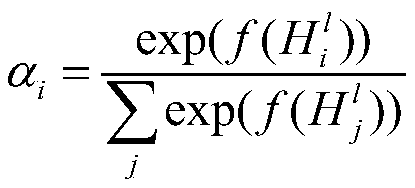Patents
Literature
81 results about "Memory model" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, a memory model describes the interactions of threads through memory and their shared use of the data.
Virtual machine spanning multiple computers
ActiveUS7596654B1Reduce operating costsMemory architecture accessing/allocationMultiprogramming arrangementsOperational systemComputerized system
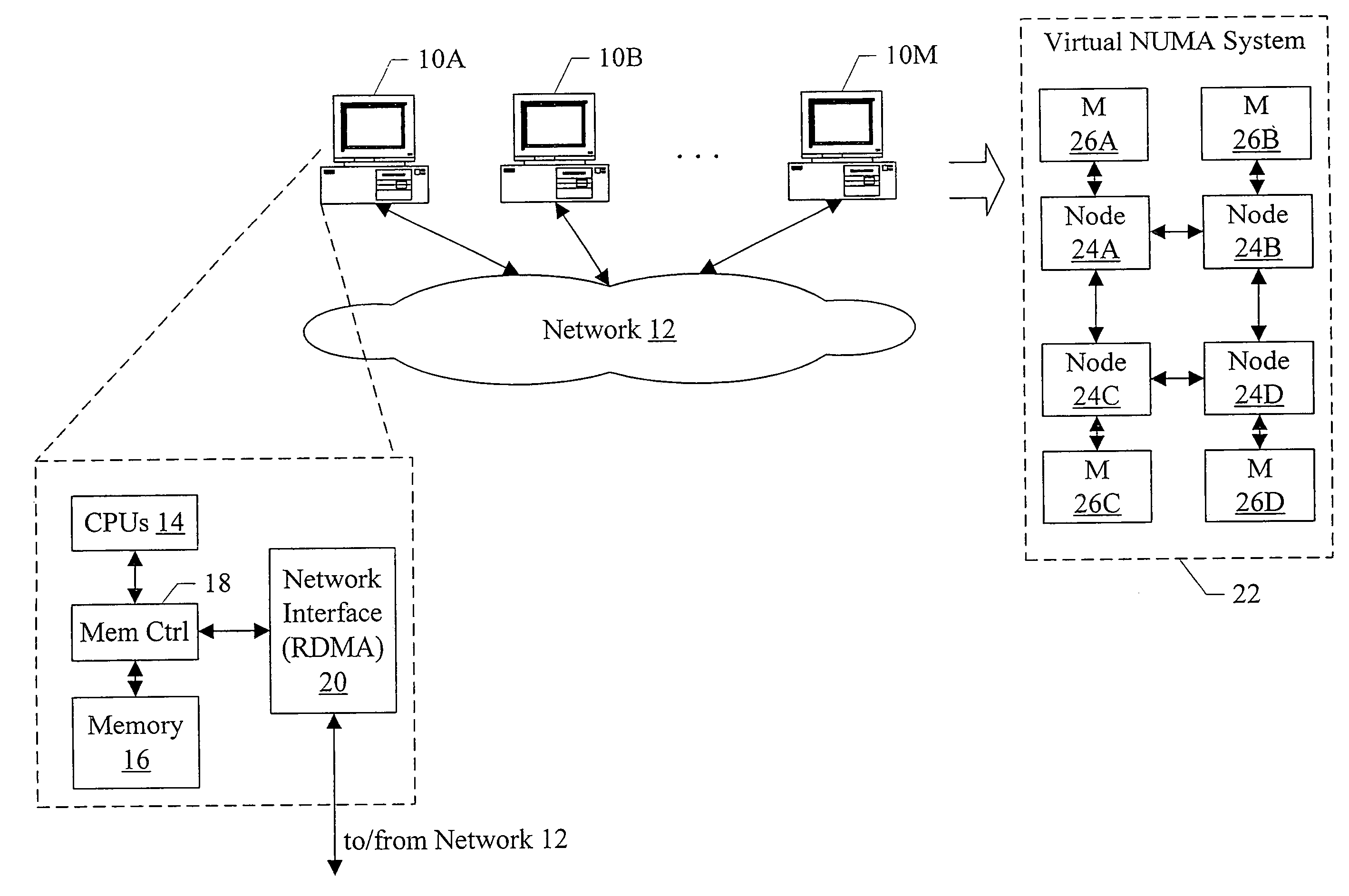
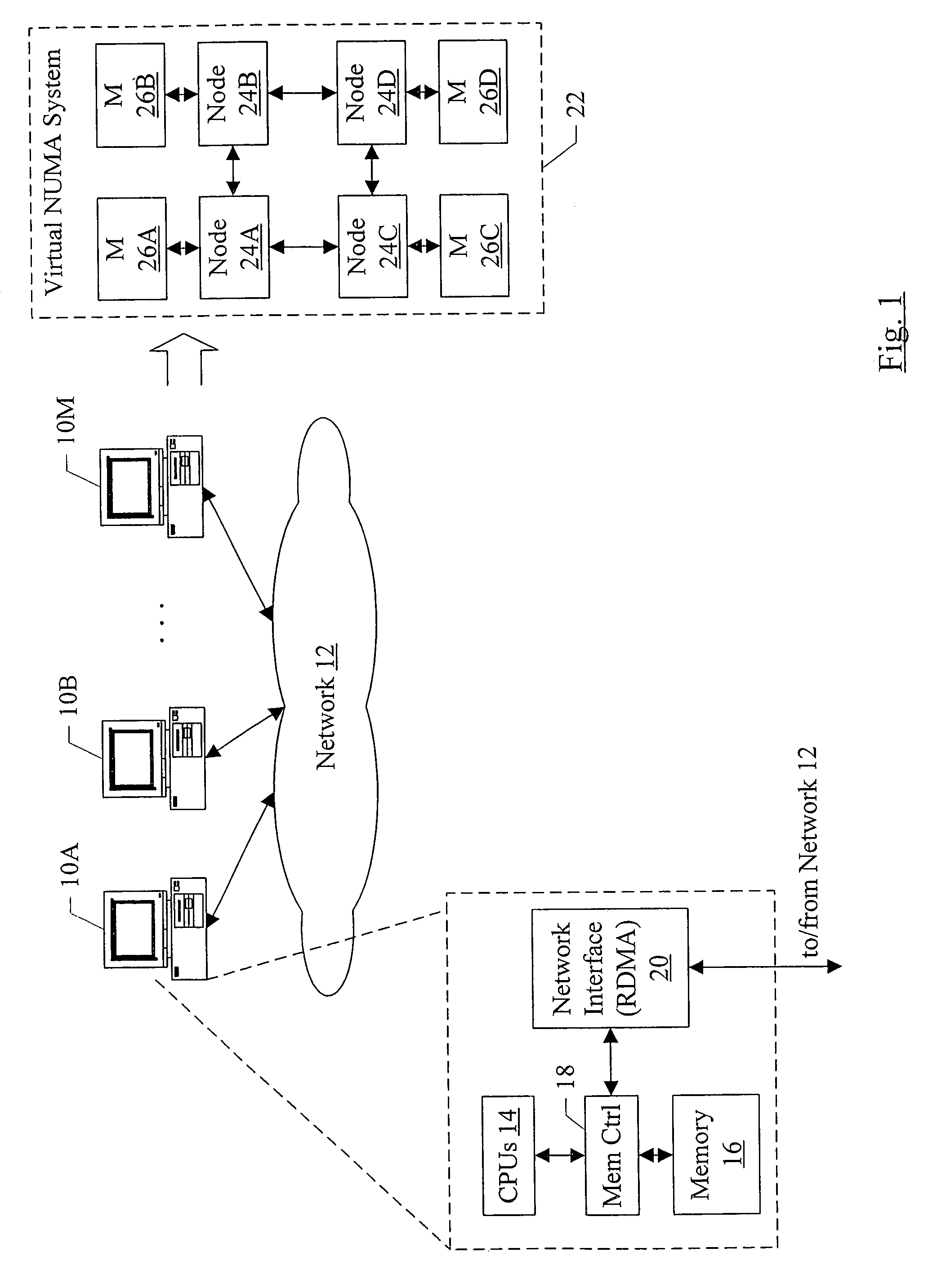
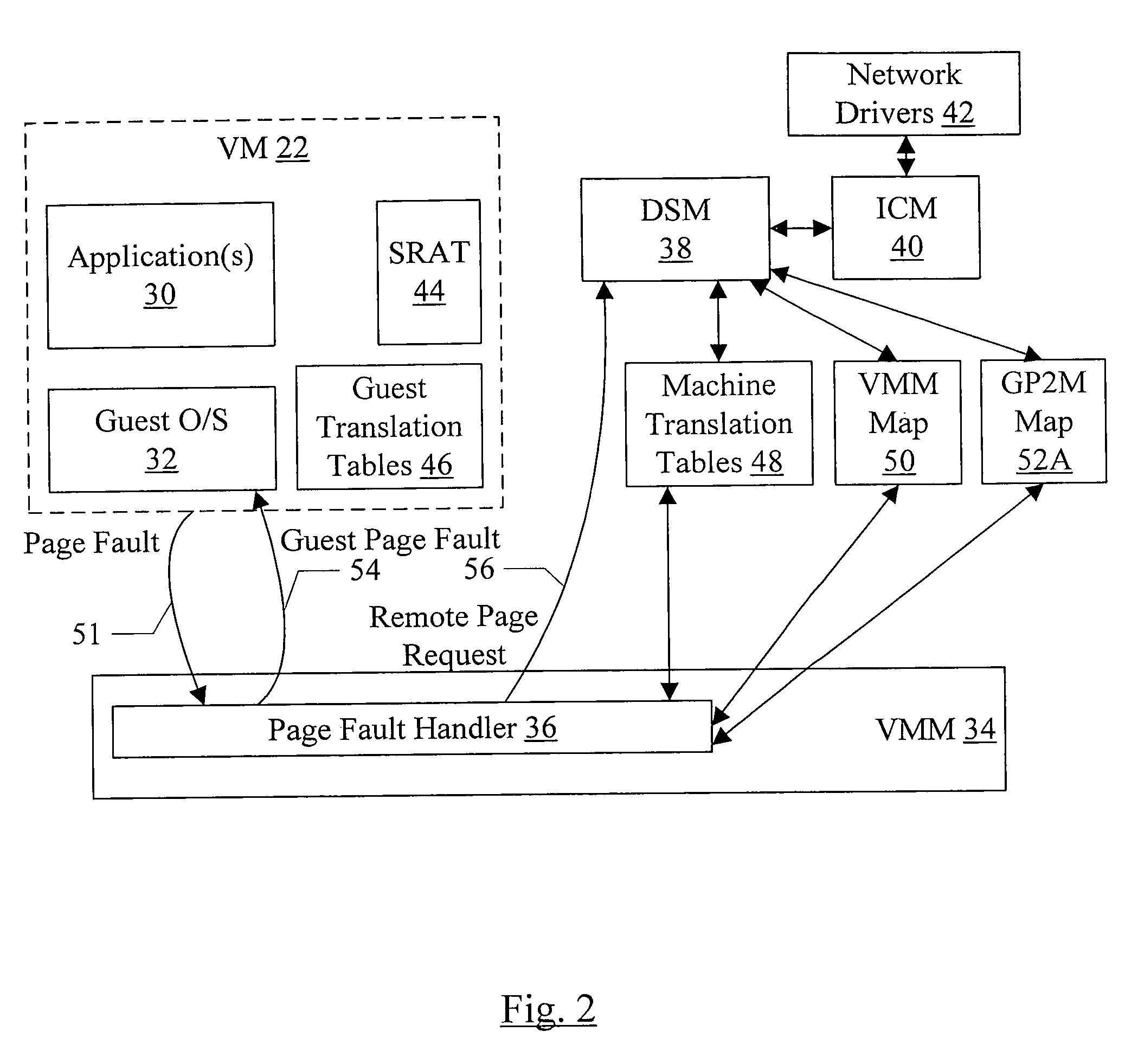
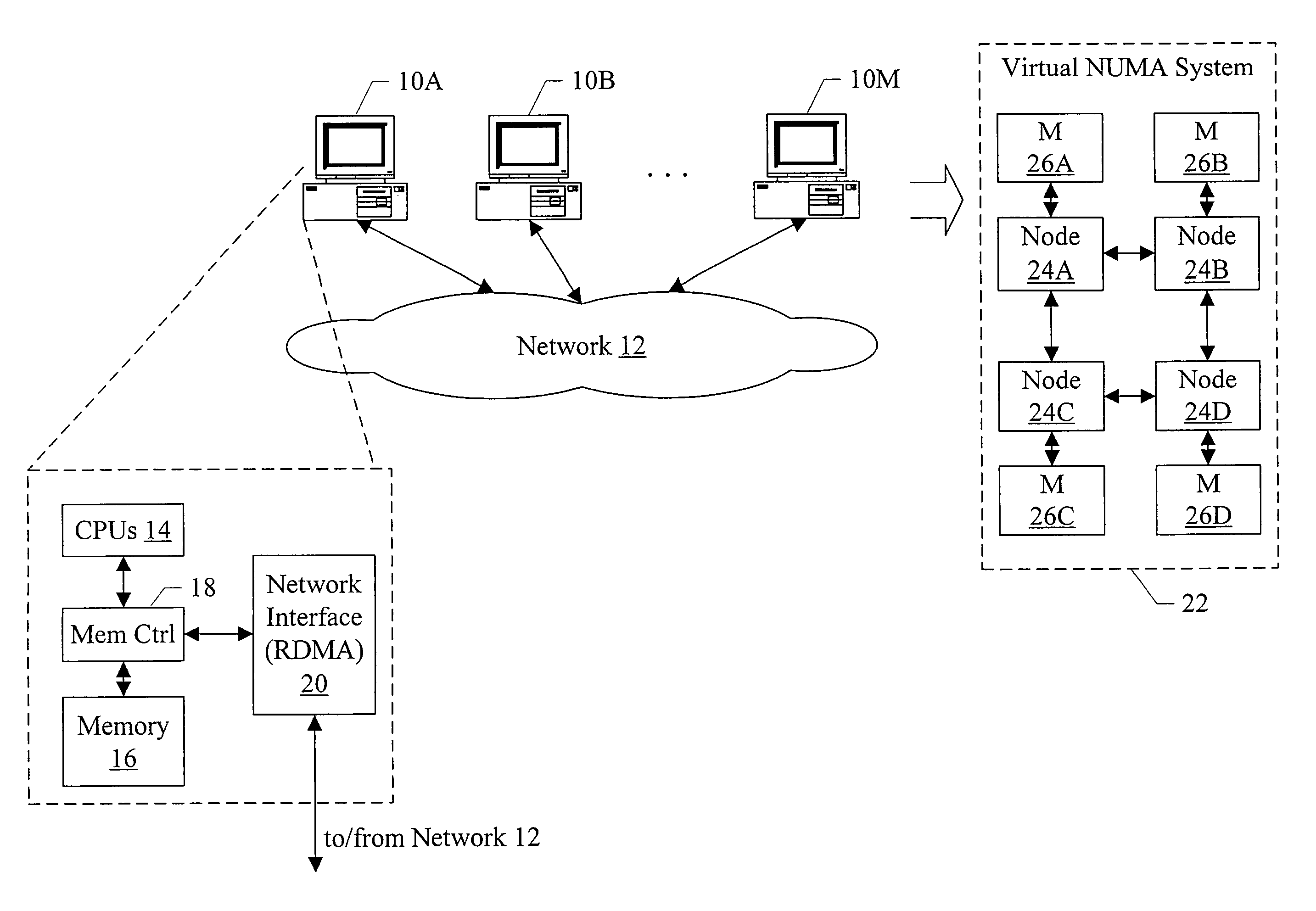
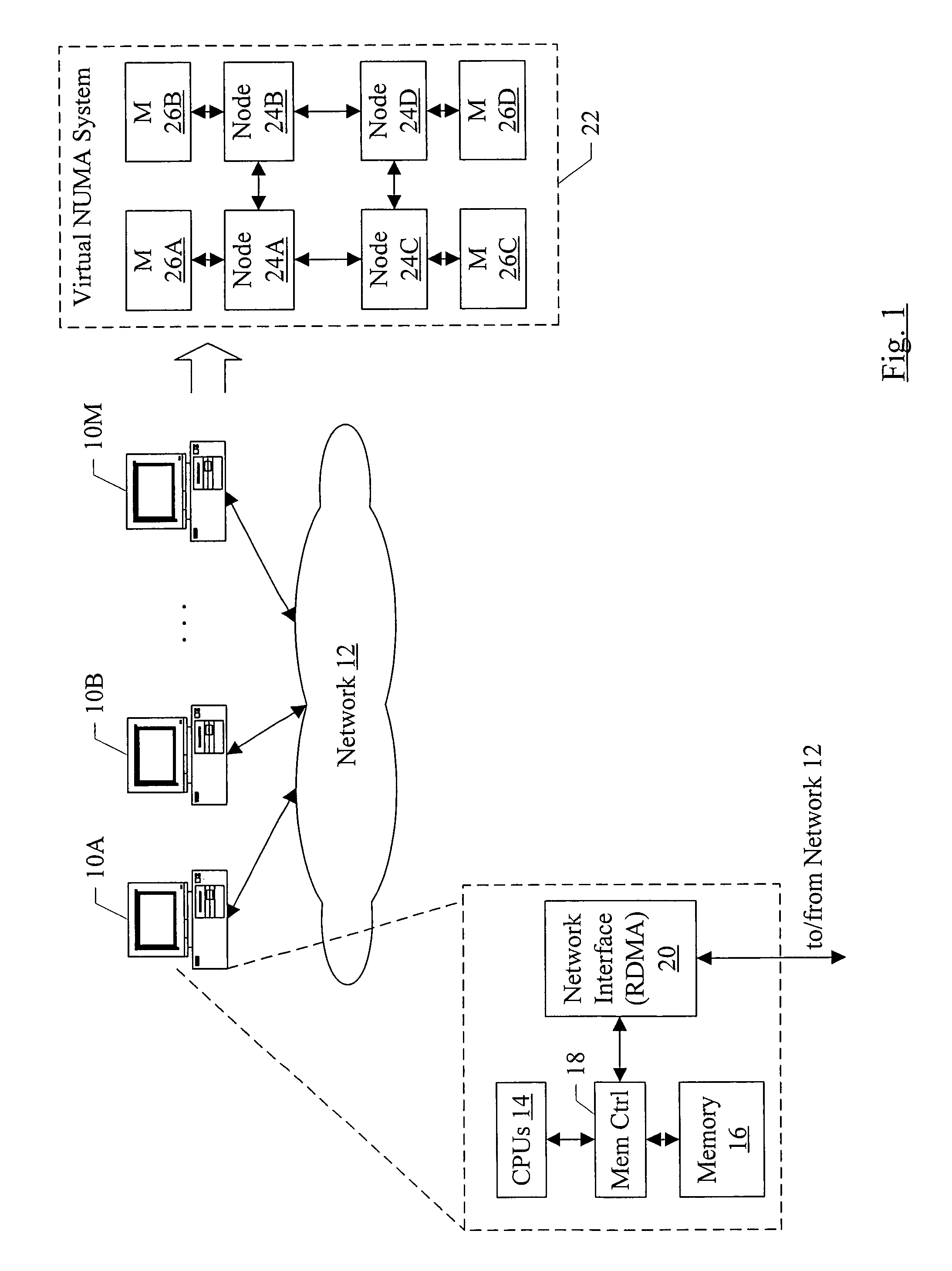
In one embodiment, a virtual NUMA system may be formed from multiple computer systems coupled to a network such as InfiniBand, Ethernet, etc. Each computer includes one or more software modules which present the resources of the computers as a virtual NUMA machine. A single instance of a guest operating system executes on the virtual NUMA machine. The guest operating system is designed to execute on a NUMA system and executes without modification on the virtual machine. The memory model of the virtual NUMA machine includes a single writer, multiple reader memory model.
Owner:SYMANTEC OPERATING CORP
Supporting a weak ordering memory model for a virtual physical address space that spans multiple nodes
InactiveUS7702743B1Memory architecture accessing/allocationDigital computer detailsComputerized systemEthernet
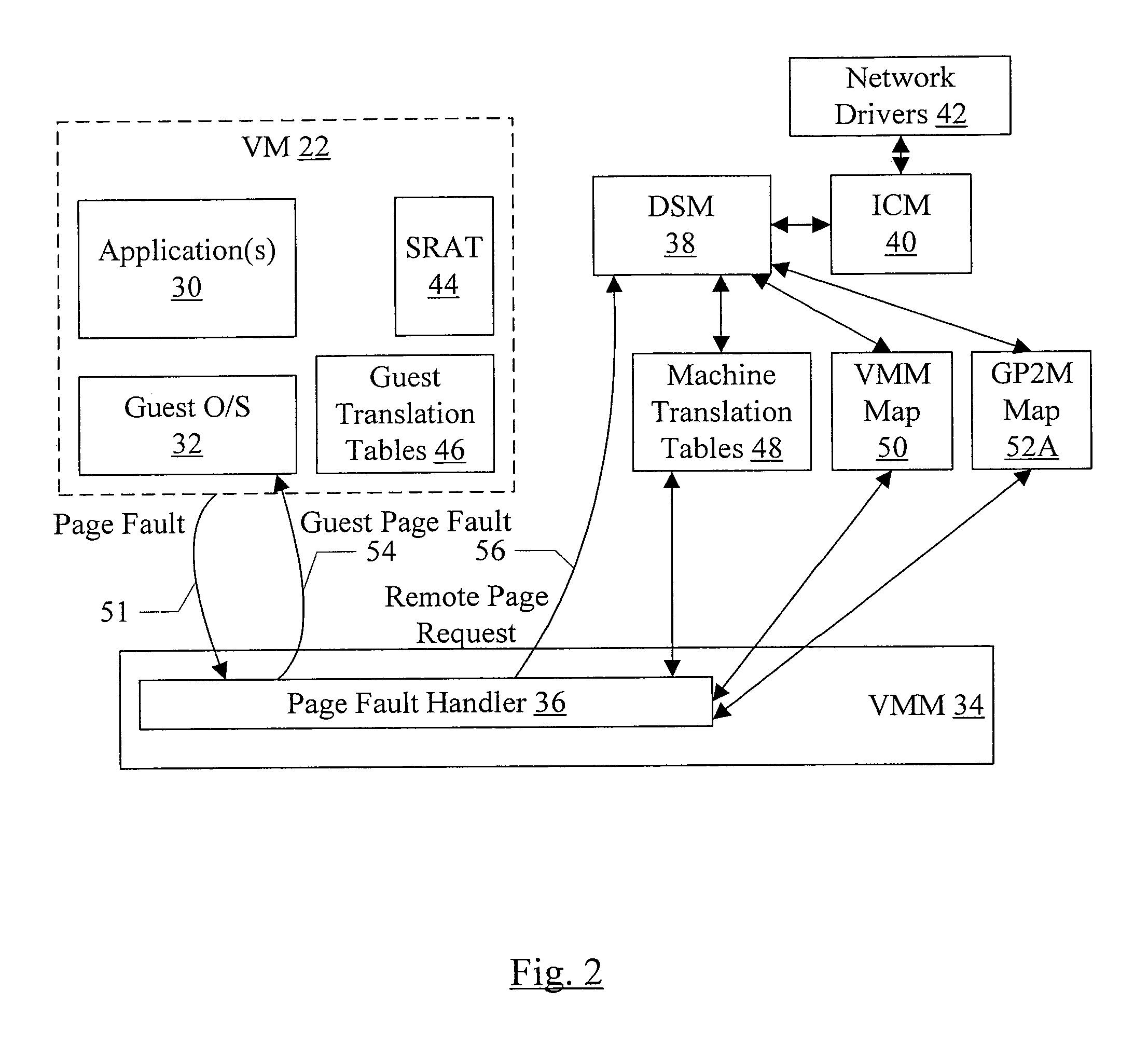
In one embodiment, a virtual NUMA system may be formed from multiple computer systems coupled to a network such as InfiniBand, Ethernet, etc. Each computer includes one or more software modules which present the resources of the computers as a virtual NUMA machine. The virtual machine is a non-uniform memory access (NUMA) machine comprising a plurality of nodes, each node having memory that is part of a distributed shared memory. Additionally, the virtual machine is coherent with a weakly ordered memory model. When executed in a current owner node of a first block in response to an ownership transfer request from a requesting node of the plurality of nodes for the first block, the software modules perform a synchronization operation if the first block has been modified in the current owner node.
Owner:SYMANTEC OPERATING CORP
Integrated software development environments, systems, methods, and memory models
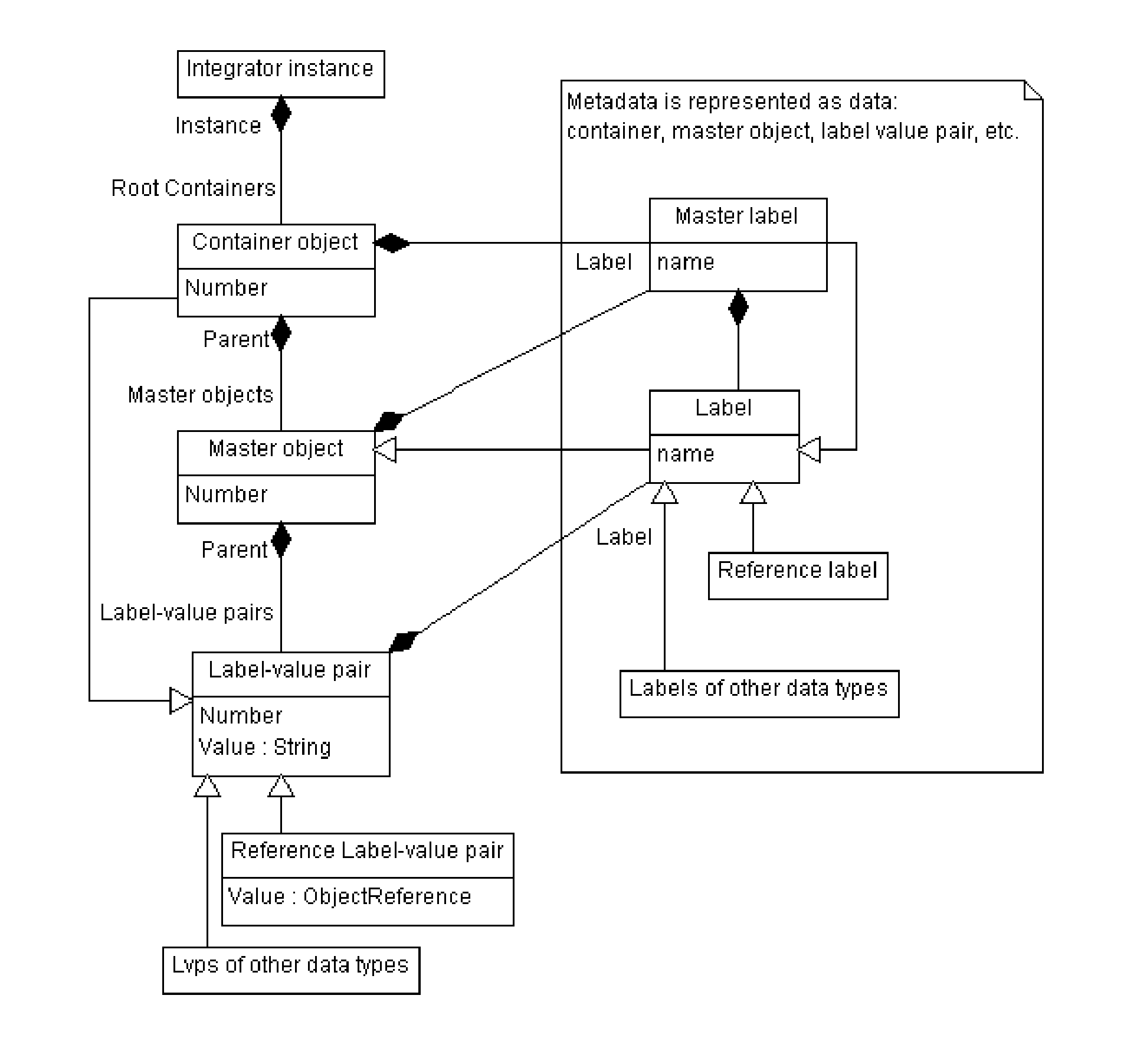
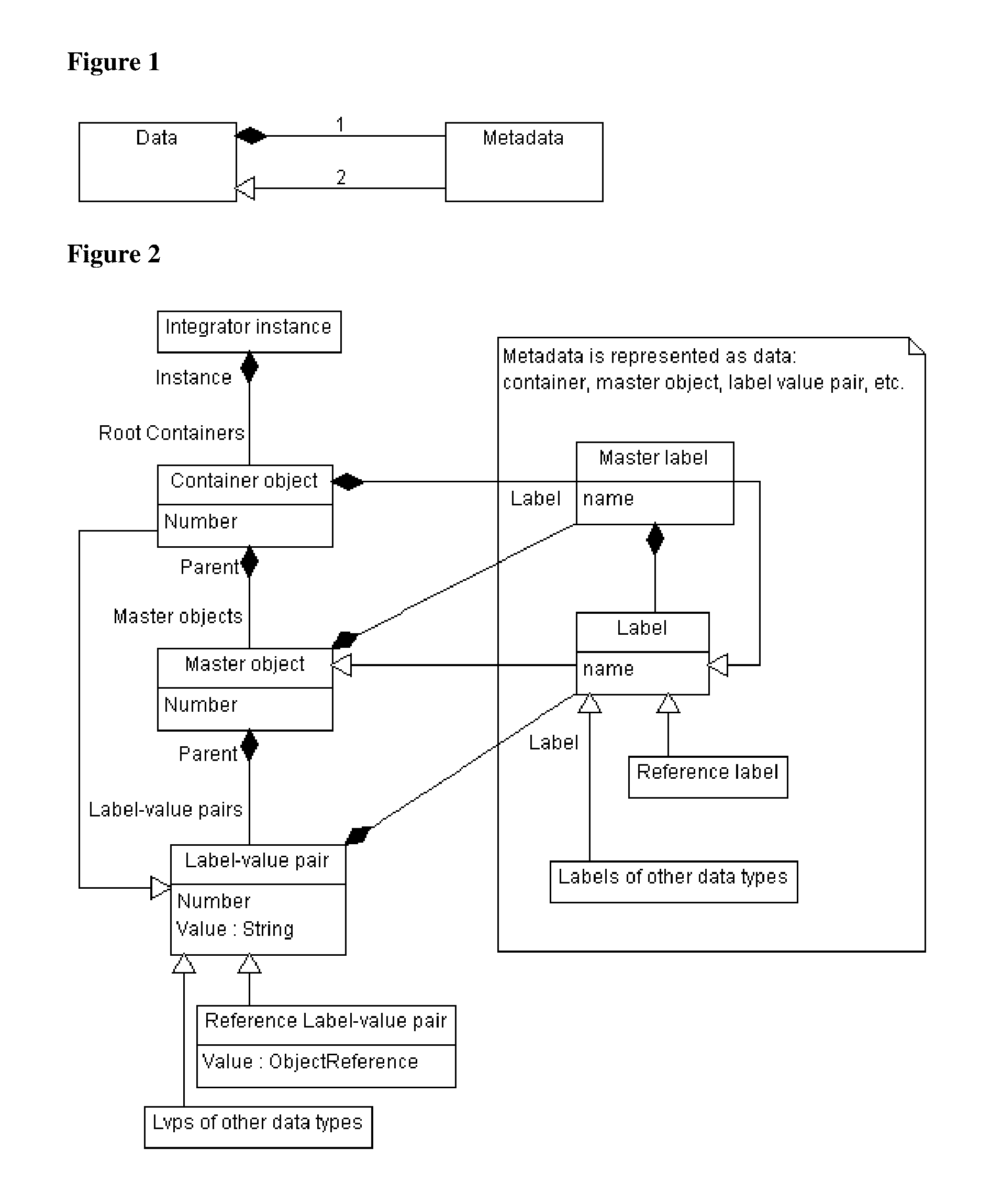
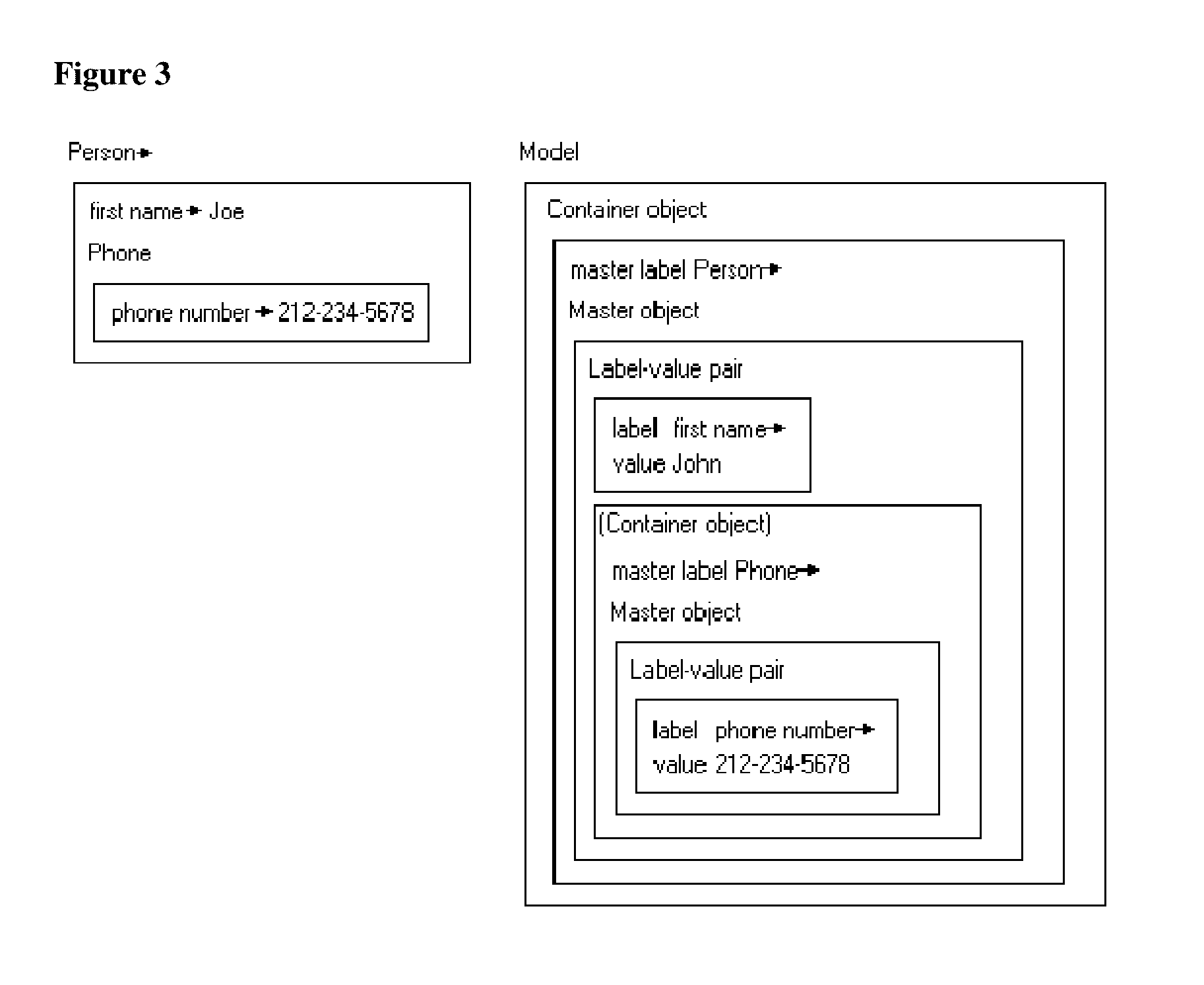
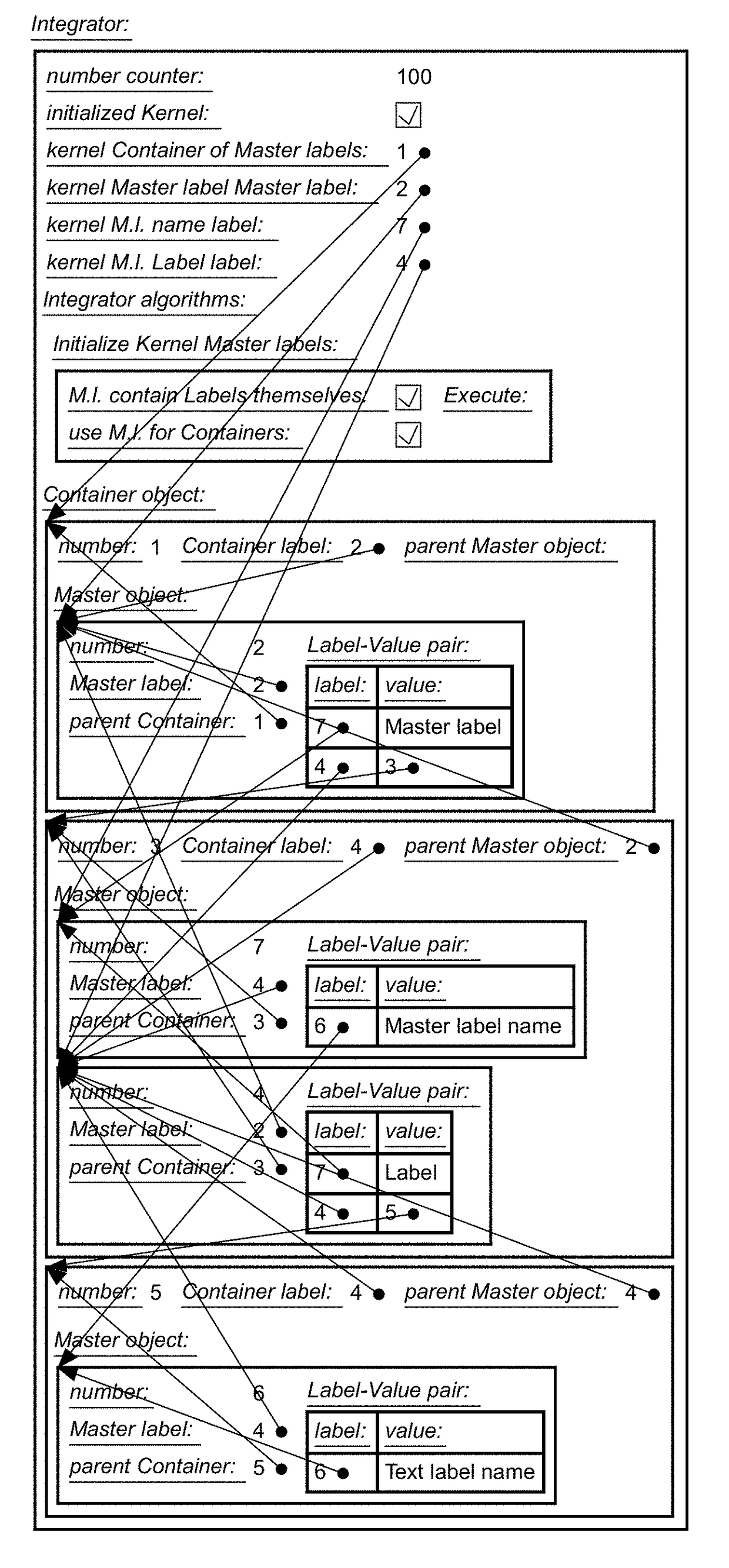
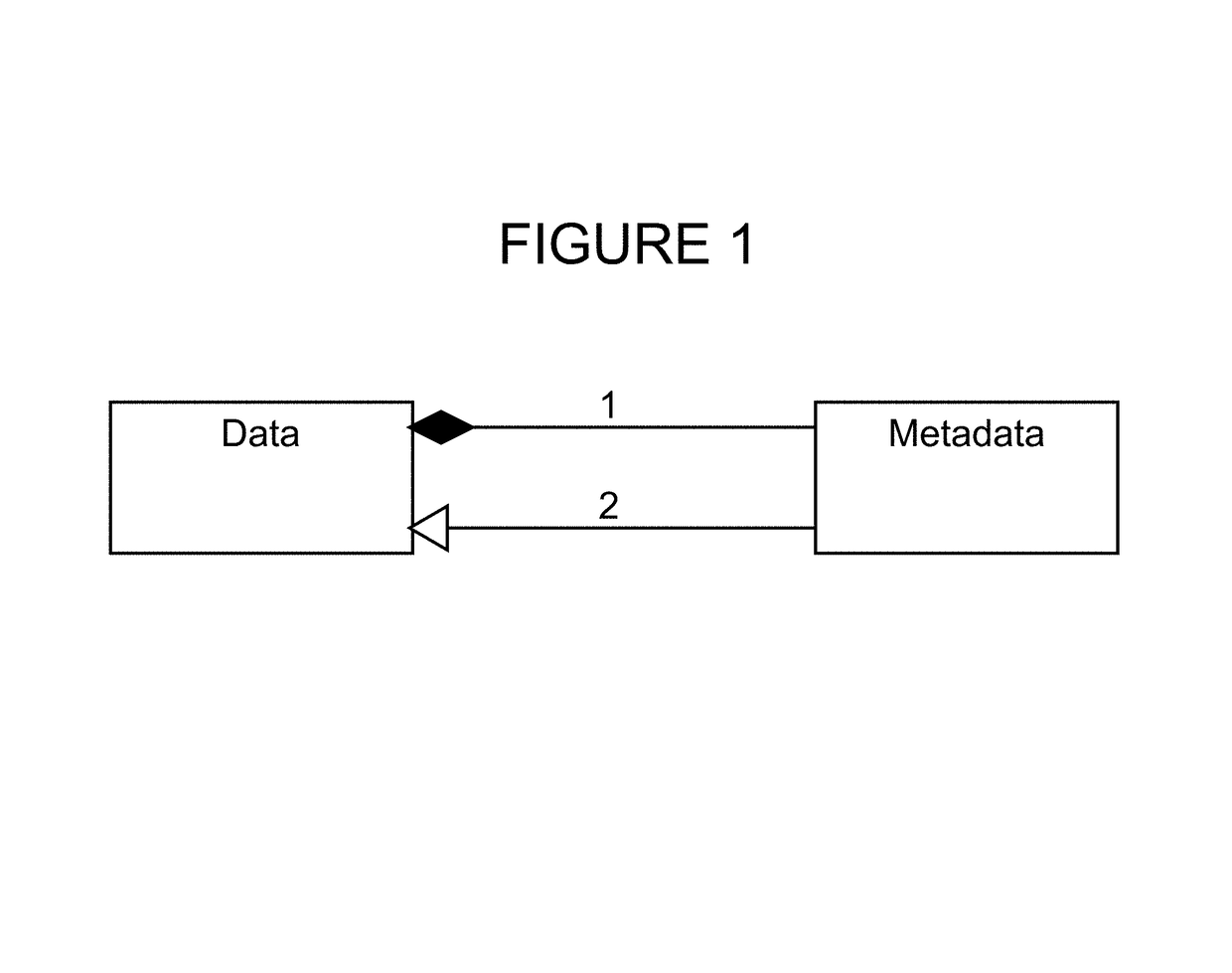
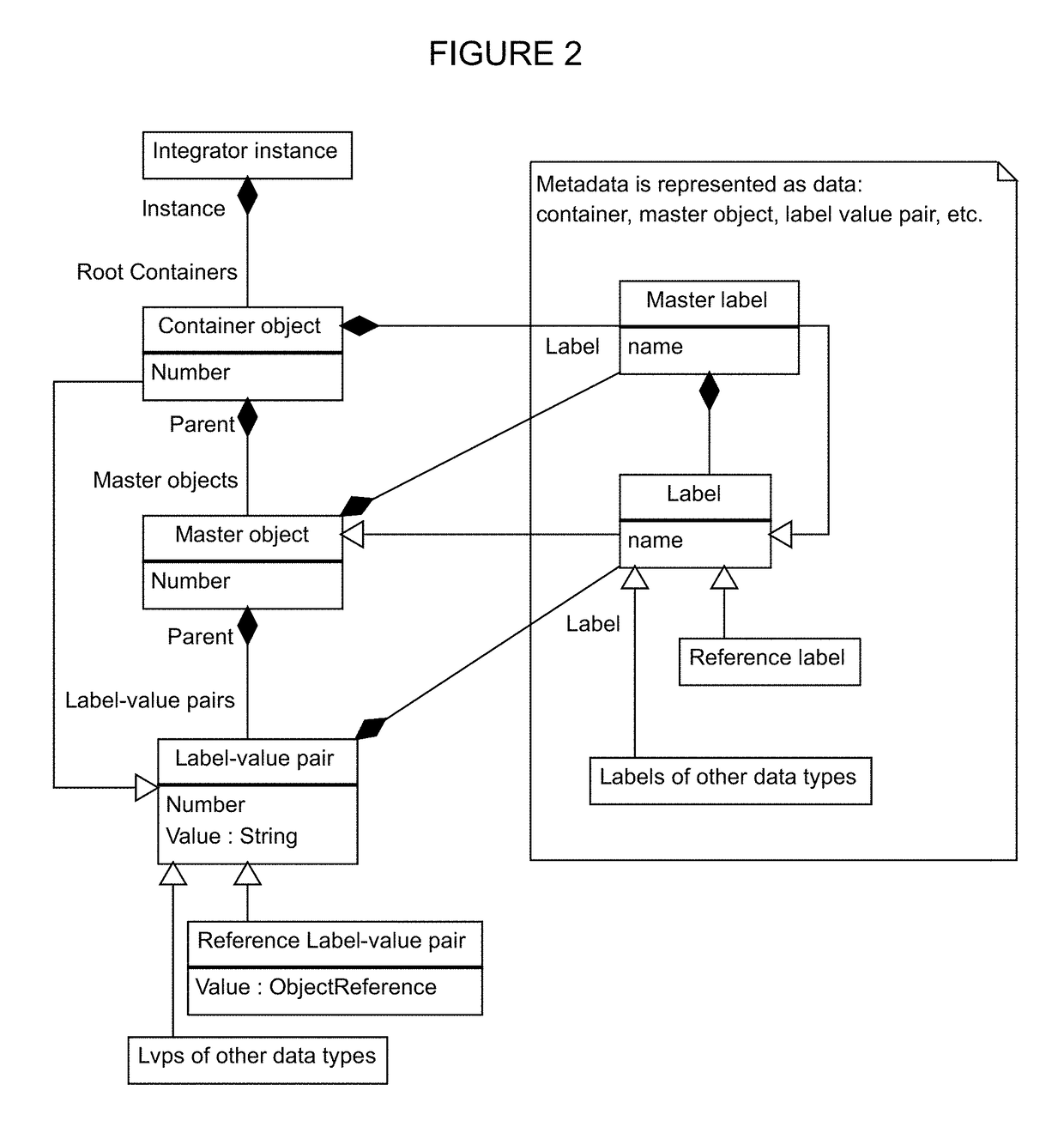
A data schema stores both data and metadata as data in a hierarchical, extensible schema made of three classes of objects. The data schema includes algorithms that generate the data schema and provide the functionality. Container object hold master objects, which represent items in a collection. Master objects hold label-value pairs, having a label portion that provides metadata, and having a value portion that holds the data. The label portion references a second label-value pair, in which the value portion holds the metadata as data, which is retrieved at runtime. Label-value pairs may reference a child container object in master objects to create a hierarchy. The schema can retrieve data and data structures from other databases; multiple databases of different formats can be joined. Software can be stored as data and shown as active flowcharts. A graphical interface can be generated in multiple display modes, including in websites.
Owner:INTEGRATOR SOFTWARE
Systems and methods for backing up computer data to disk medium
InactiveUS20050273650A1Cost reductionDecrease functionMemory loss protectionError detection/correctionData availabilityAddress space
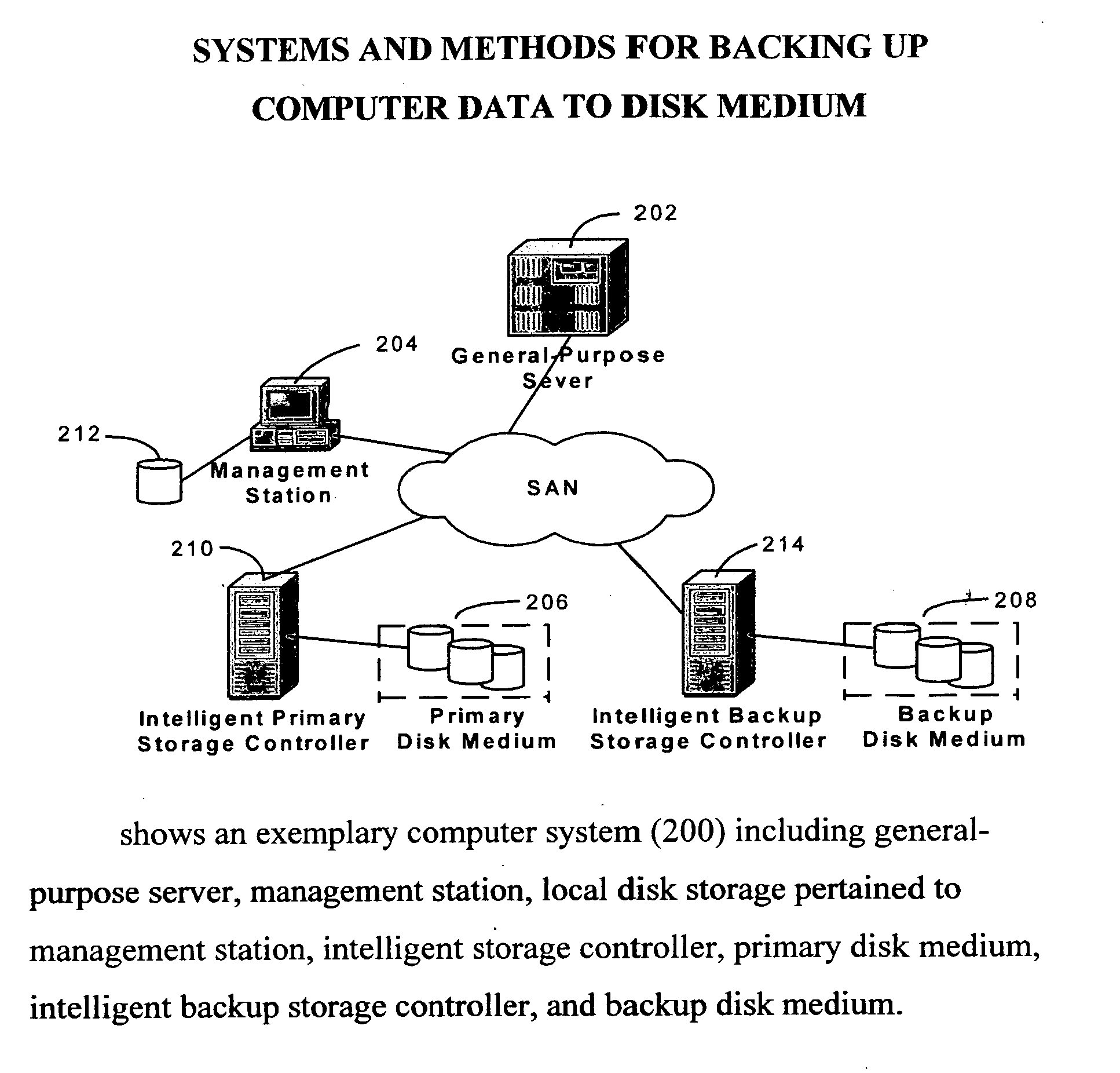
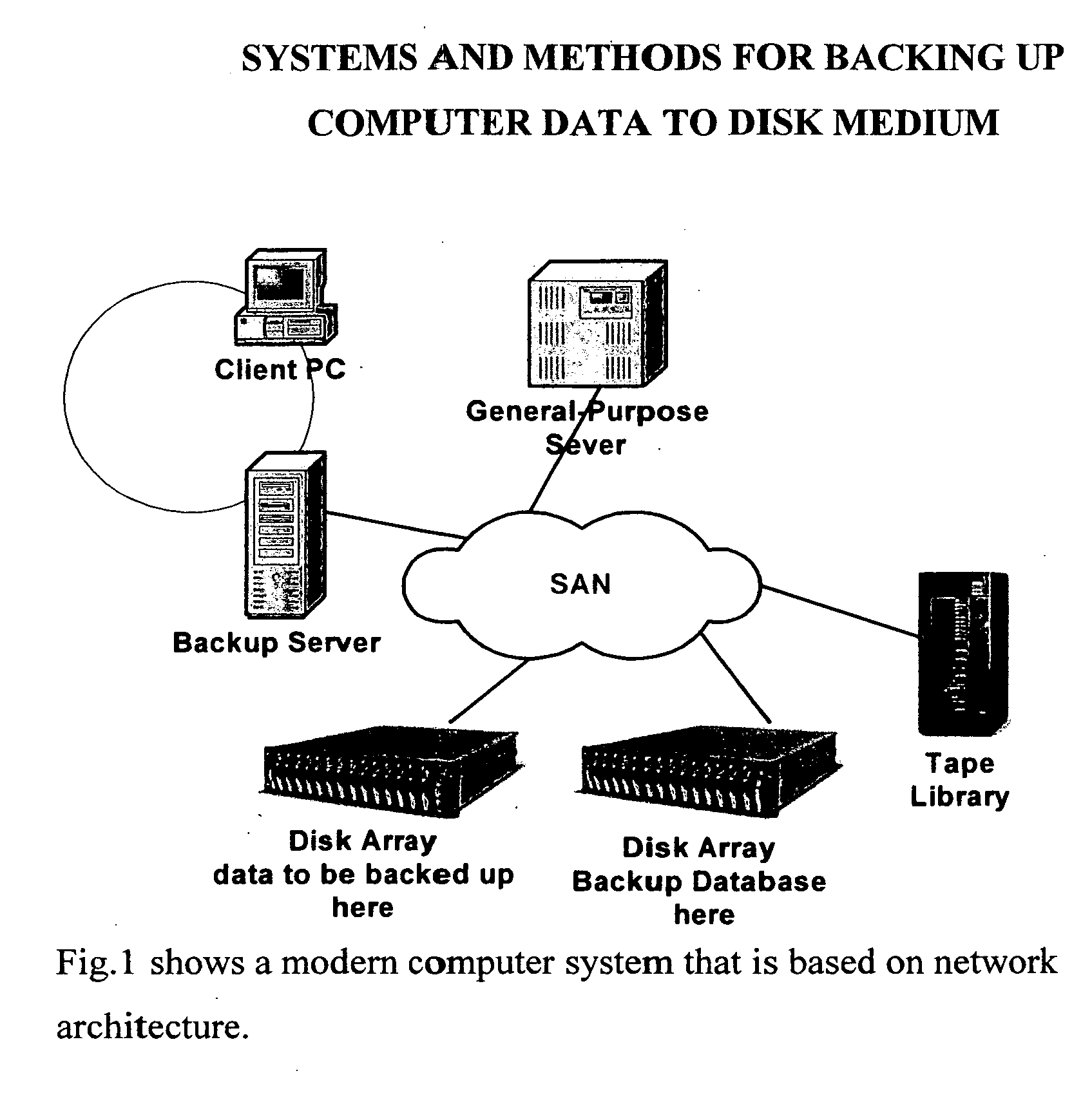
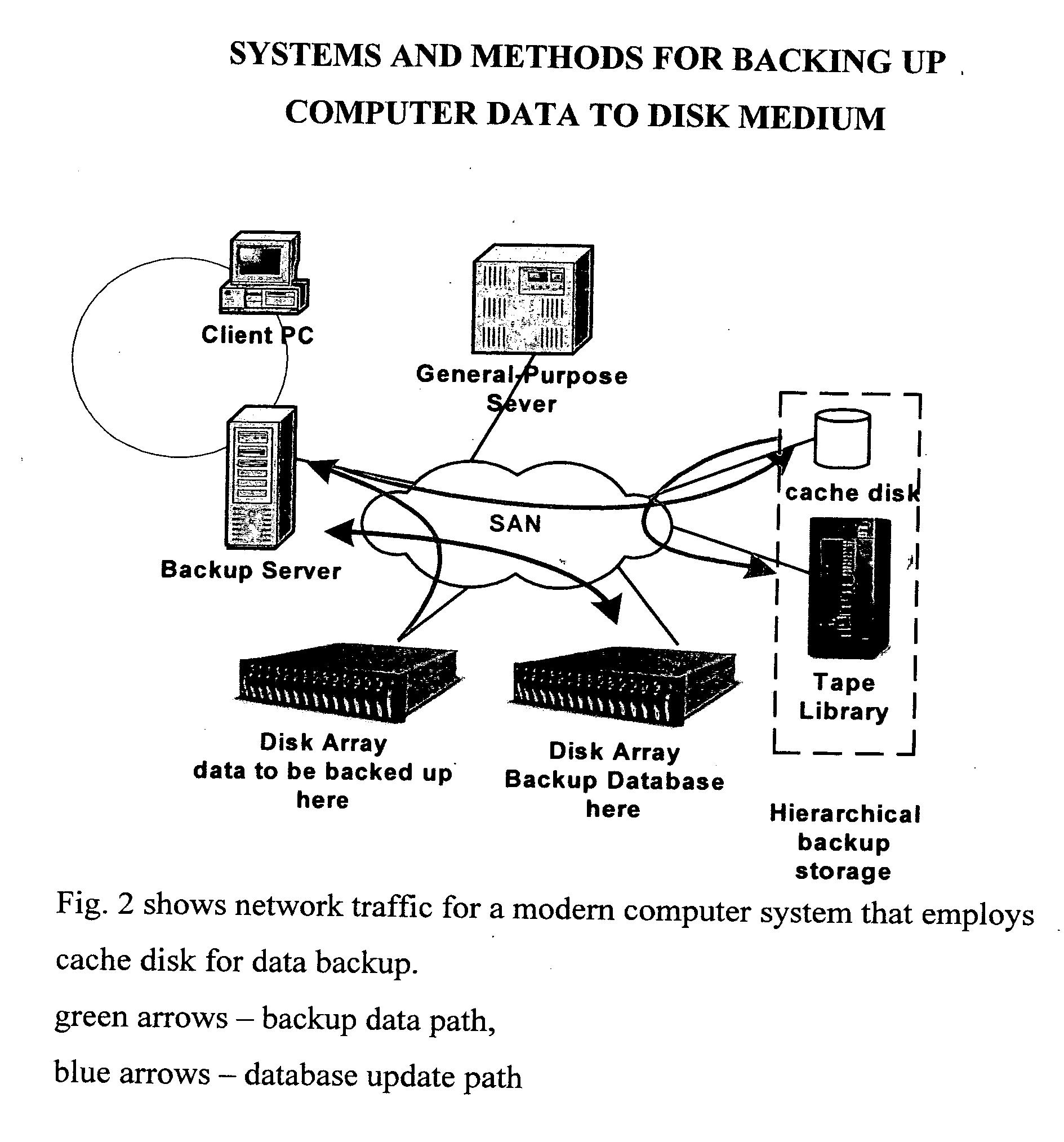
Data Protection on computer data is to insure data availability. The mission critical data has been chronically stored and labeled with version, distinguished in time of stored. In order to save storage of a backup medium, one full backup is stored and then is followed by many differential or incremental backups. The disclosed employs a Direct Access Storage Device (DASD or disk) as a backup medium. Disk provides a memory model with (1) random access attribute and (2) flat address space. Therefore data restoration for a given version can be achieved by an intelligent backup disk device rather than by a backup server. Intelligent backup disk device compares backup data between different versions and eliminates redundant backup data in later version. Presently backup server performs all data protection functions that include data backup and data restoration. An intelligent primary disk device, where the primary data resides, is capable to record all write operations on a write journal continuously between the previous backup and the ensuing backup. Once a backup is requested, the primary intelligent disk device retrieves write data from its disk medium and transfers the write data along with the write journal to the intelligent backup disk device where the second copy is stored. The intelligent primary disk device and the intelligent backup disk device concertedly perform data protection functions. Furthermore, these data protection functions can be located at a SAN (Storage Area network) switch. The switch becomes the center of data protection in networked computer configuration.
Owner:TSOU HENRY HORNGREN
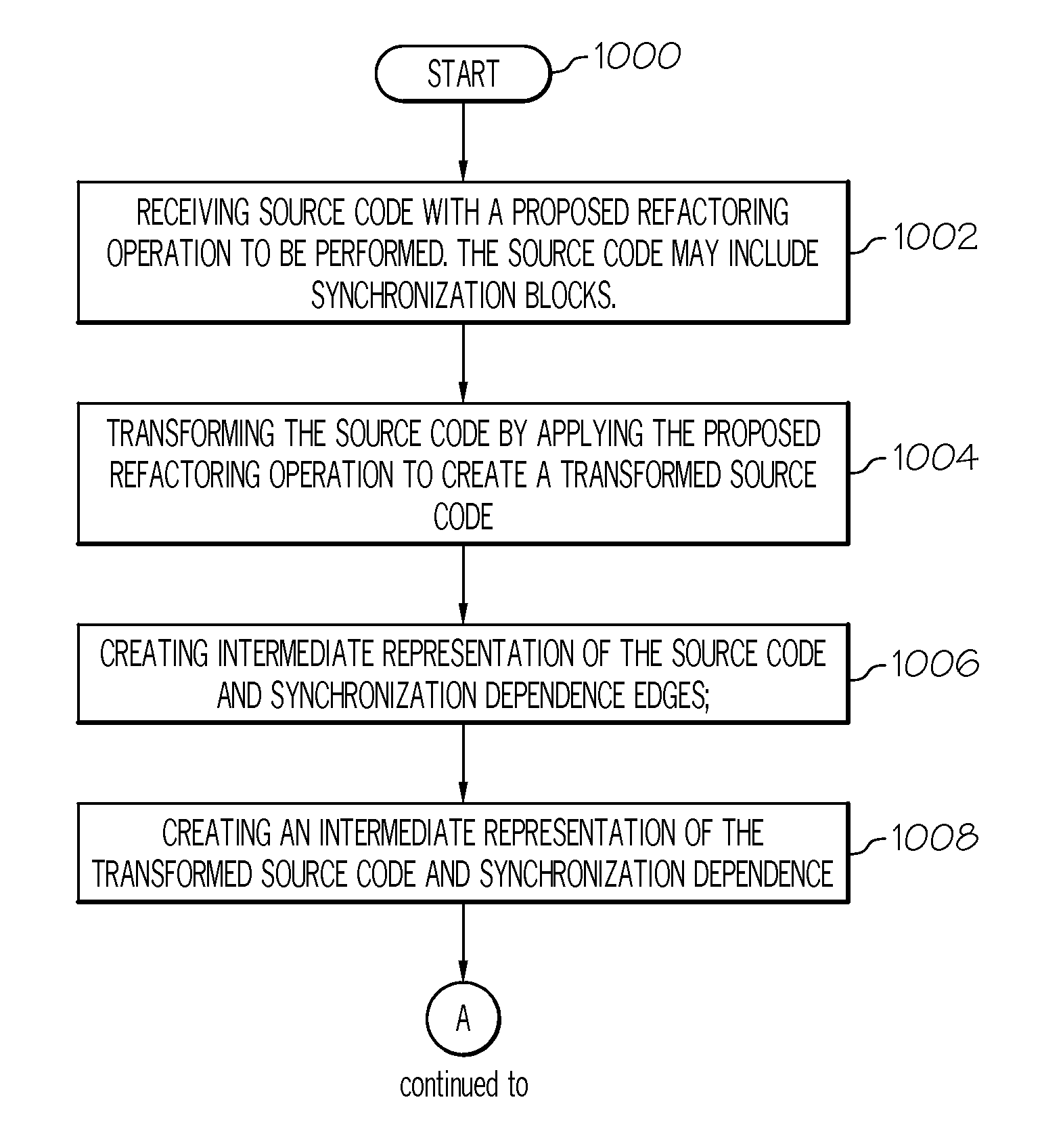
Correct refactoring of concurrent software
InactiveUS20110219361A1Precise correctness resultEasy to implementCode refactoringProgram controlLanguage constructJava Memory Model
Automated refactorings as implemented in modern IDEs for Java usually make no special provisions for concurrent code. Thus, refactored programs may exhibit unexpected new concurrent behaviors. We analyze the types of such behavioral changes caused by current refactoring engines and develop techniques to make them behavior-preserving, ranging from simple techniques to deal with concurrency-related language constructs to a framework that computes and tracks synchronization dependencies. By basing our development directly on the Java Memory Model we can state and prove precise correctness results about refactoring concurrent programs. We show that a broad range of refactorings are not influenced by concurrency at all, whereas other important refactorings can be made behavior-preserving for correctly synchronized programs by using our framework. Experience with a prototype implementation shows that our techniques are easy to implement and require only minimal changes to existing refactoring engines.
Owner:IBM CORP
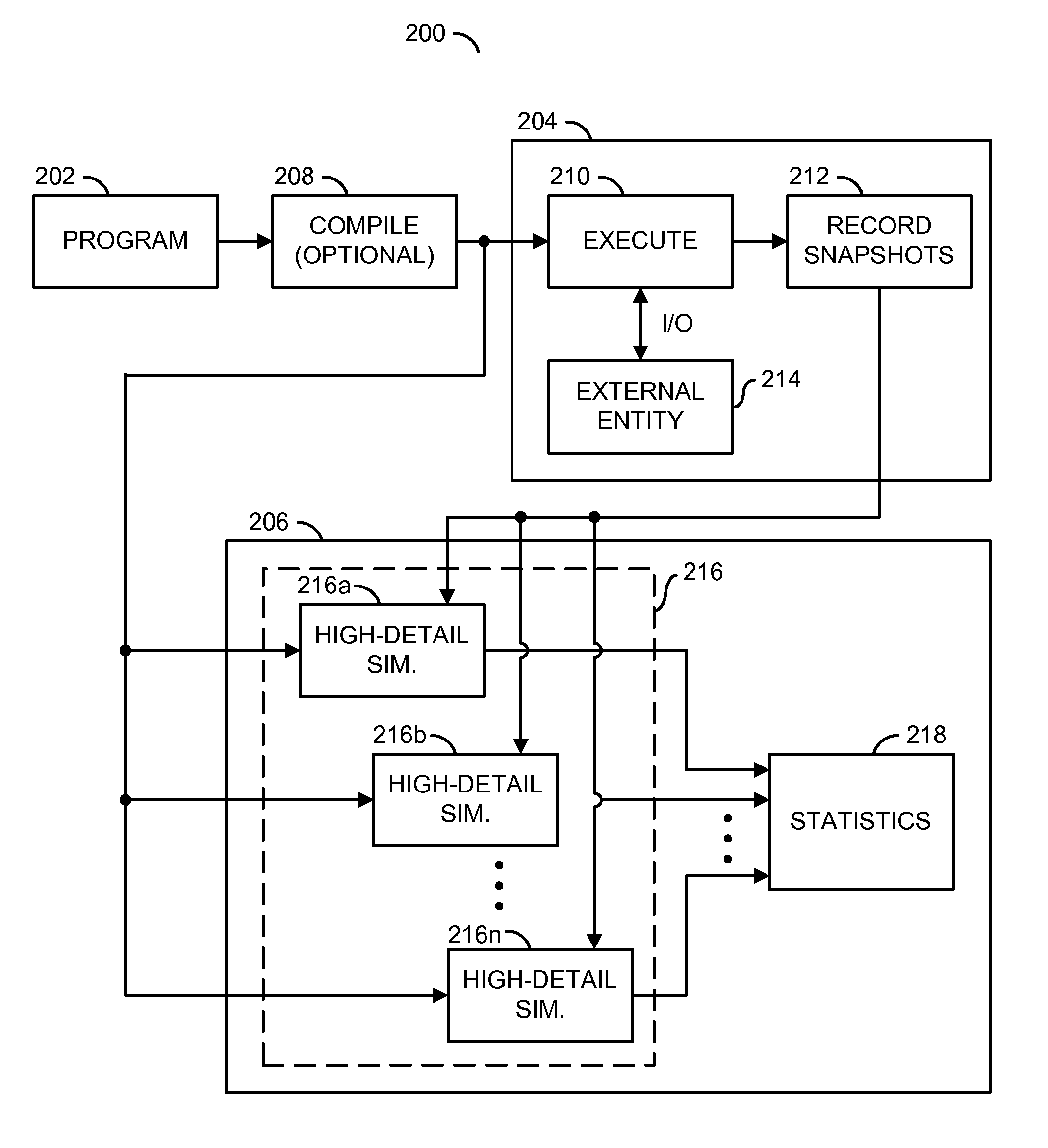
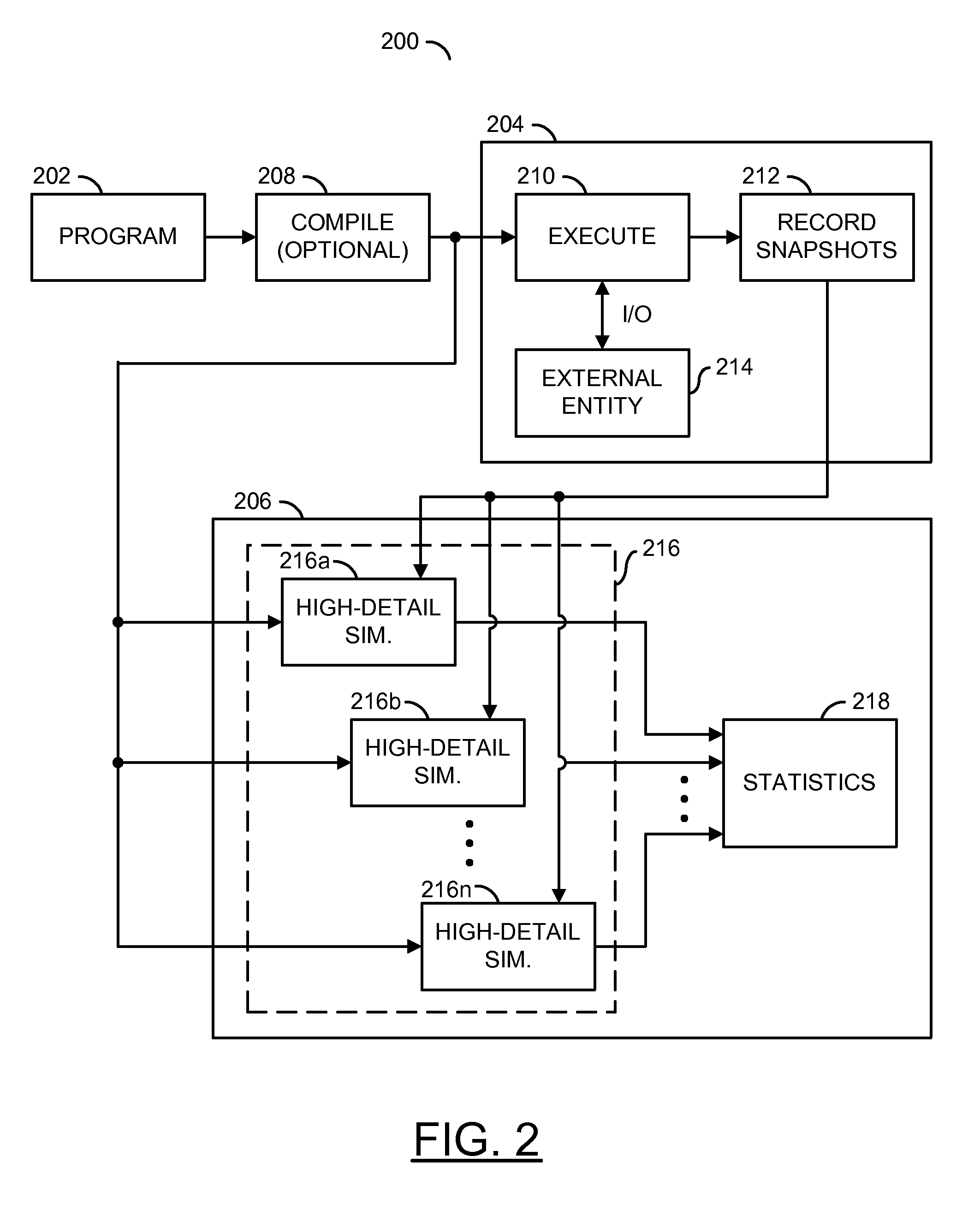
Distributed multi-pass microarchitecture simulation
InactiveUS20130013283A1Loss of precisionReduce running timeAnalogue computers for electric apparatusCAD circuit designProgram instructionInit
A system including a microarchitecture model, a memory model, and a plurality of snapshots. The microarchitecture model is of a microarchitecture design capable of executing a sequence of program instructions. The memory model is generally accessible by the microarchitecture model for storing and retrieving the program instructions capable of being executed on the microarchitecture model and any associated data. The plurality of snapshots are generally available for initializing a number of instances of the microarchitecture model, at least some of which may contain values assigned to one or more registers or memory regions in response to interaction with one or more external entities during a first pass of a simulation of the microarchitecture. The number of instances is generally greater than one and generally perform high-detail simulation. The number of instances, when launched and executed during a second pass of the simulation of the microarchitecture, have run time periods that overlap.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Integrated software development environments, systems, methods, and memory models
A data schema stores both data and metadata as data in a hierarchical, extensible schema made of three classes of objects. The data schema includes algorithms that generate the data schema and provide the functionality. Container object hold master objects, which represent items in a collection. Master objects hold label-value pairs, having a label portion that provides metadata, and having a value portion that holds the data. The label portion references a second label-value pair, in which the value portion holds the metadata as data, which is retrieved at runtime. Label-value pairs may reference a child container object in master objects to create a hierarchy. The schema can retrieve data and data structures from other databases; multiple databases of different formats can be joined. Software can be stored as data and shown as active flowcharts. A graphical interface can be generated in multiple display modes, including in websites.
Owner:INTEGRATOR SOFTWARE
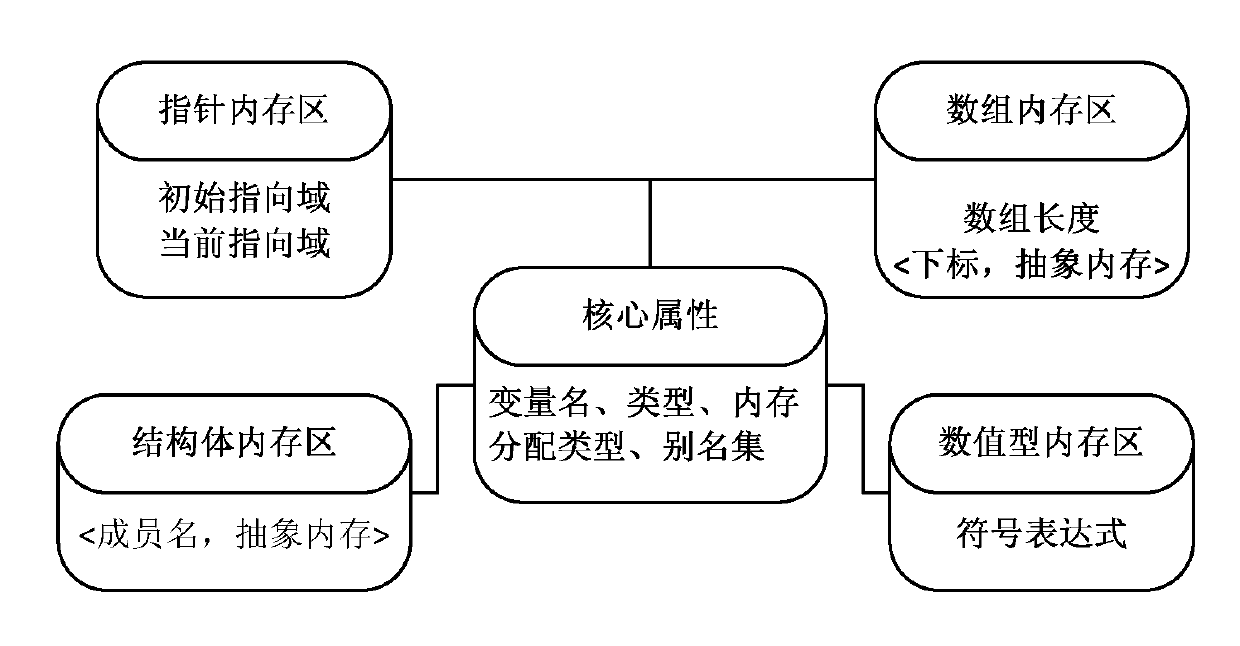
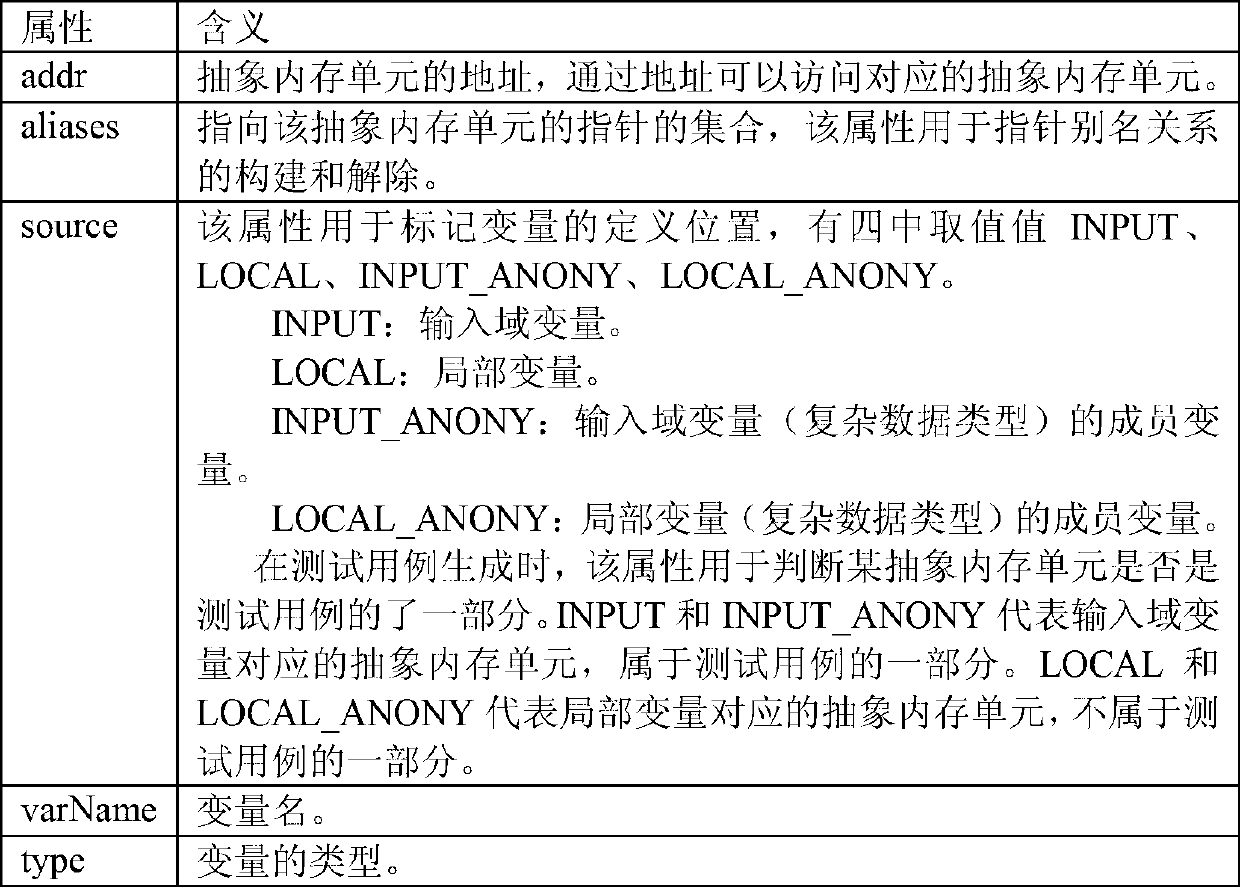
Abstract memory model-based method for calculating non-numerical type data
InactiveCN102999426APrecise record structurePrecise record operabilitySoftware testing/debuggingThird partyNumerical types
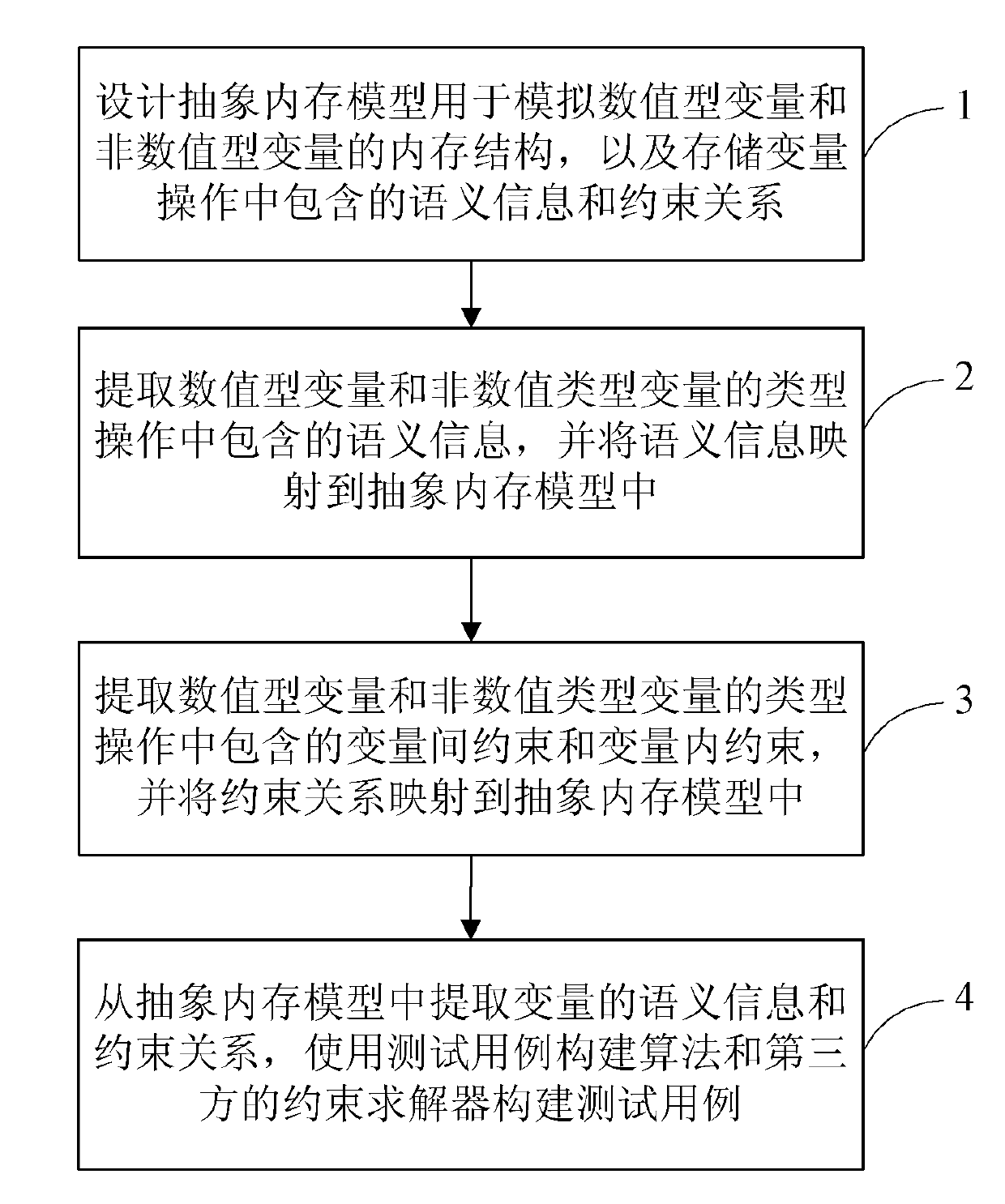
The invention provides an abstract memory model-based method for calculating non-numerical type data. The method comprises the following steps of: A, designing an abstract memory model, wherein the abstract memory model is used for simulating a memory structure of numerical type variants and non-numerical type variants, and storing semantic information and restraint relationship included in the variant operation; B, extracting the semantic information included in the type operation of the numerical type variants and the non-numerical type variants, and mapping the semantic information to an abstract memory model; C, extracting restraint among variants and restraint inside variants included in the type operation of the numerical type variants and the non-numerical type variants, and mapping the restraint relationship to the abstract memory model; and D, extracting the semantic information and the restraint relationship of the variants from the abstract memory model, and establishing a test case by using a test case establishing algorithm and a restraint solver of a third party. By utilizing the method, the defect that in the prior art the non-numerical type variant program semantic cannot be supported is overcome, and the purpose that a program including the non-numerical type automatically generates the test case is realized.
Owner:BEIJING UNIV OF POSTS & TELECOMM
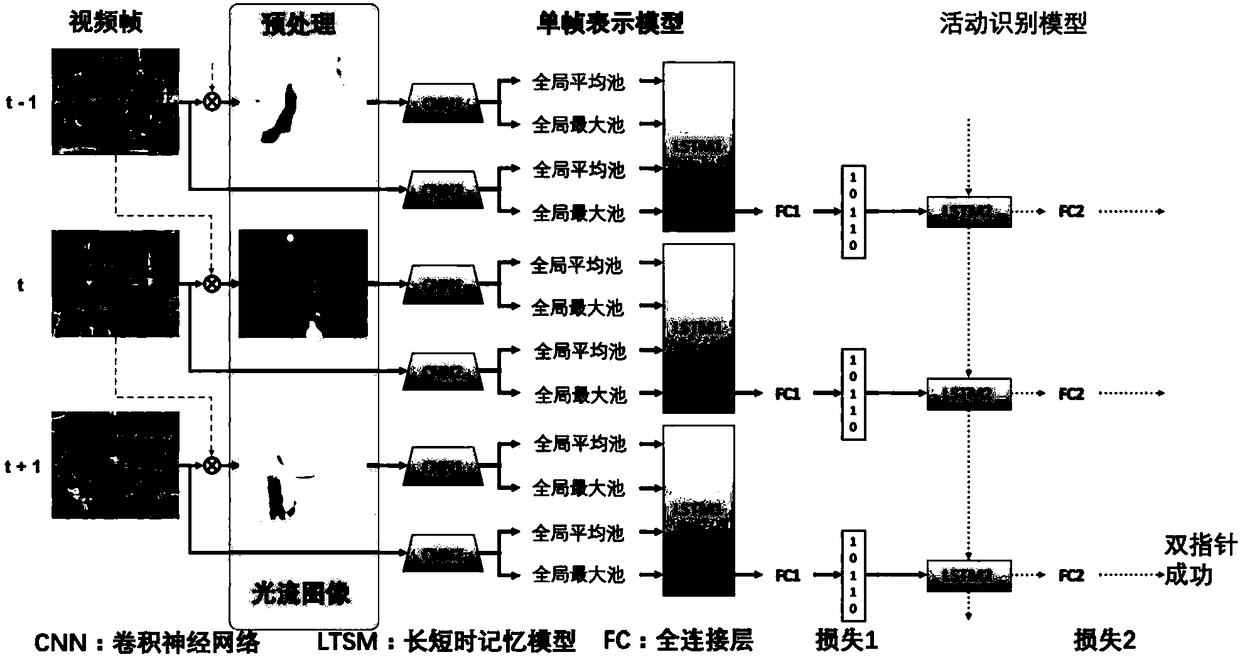
Single frame representation model based human activity identification method
InactiveCN108537195ACharacter and pattern recognitionNeural architecturesActivation functionActivity recognition
The invention provides a single frame representation model based human activity identification method. The single frame representation model based human activity identification method mainly comprisespretreatment, a single frame representation model, an activity identification model, and model optimization and training; the process is as follows: generating a light stream image for each video frame of an inputted video first, then inputting all videos and the corresponding light stream image to one single frame representation model, generating model representation, then using a long and shorttime memory model to generate a predicated final activity label according to the model representation generated in the previous step, and finally determining the final activity label through a full connection layer with a Softmax activation function. The single frame representation model based human activity identification method solves the problems that the previous identification precision of the human activity is not high, the identification requires long computation time and the group activity cannot be accurately identified, the method can identify group activities, the identification precision is relatively high, and the required computation time is less.
Owner:SHENZHEN WEITESHI TECH
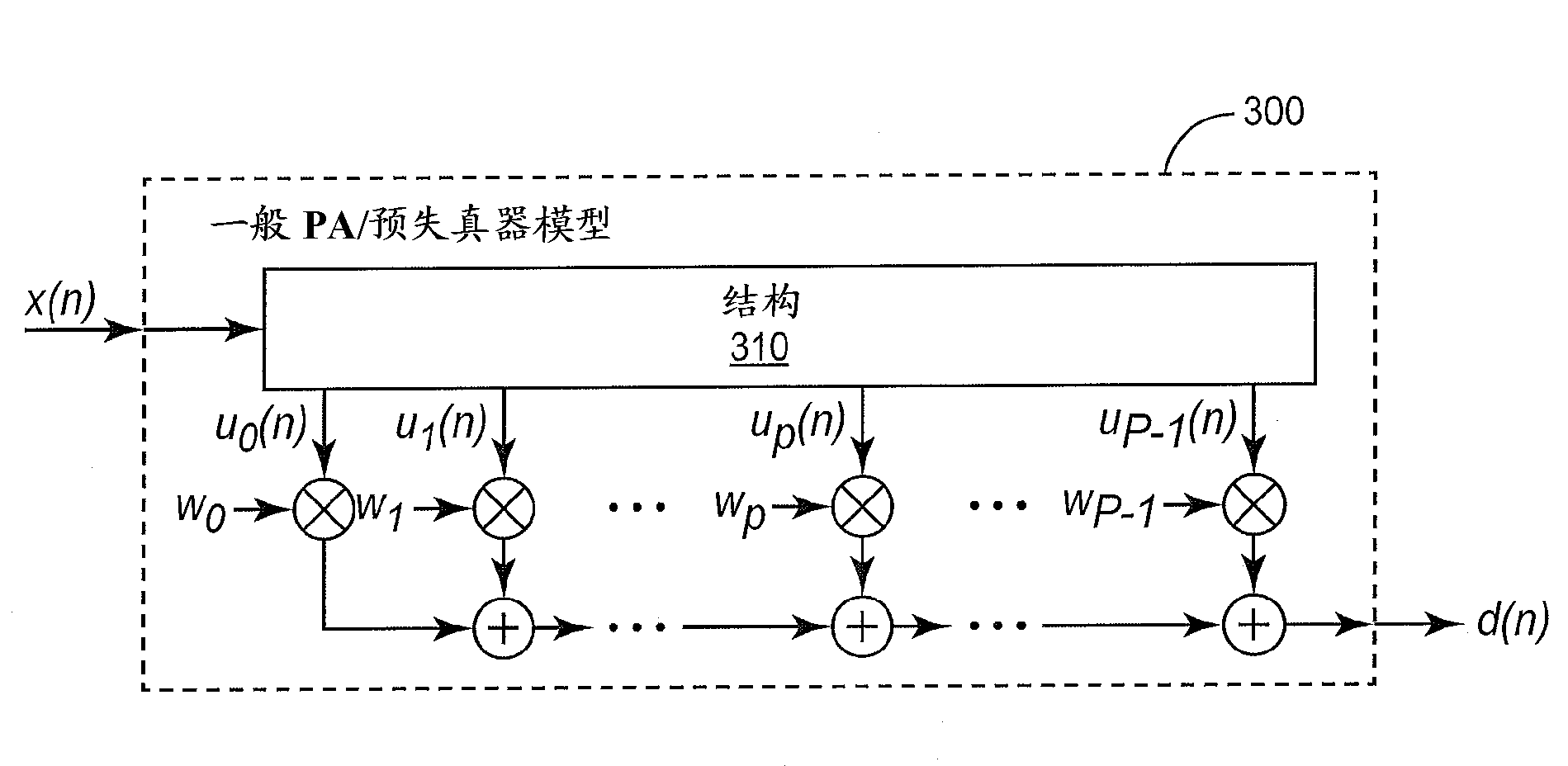
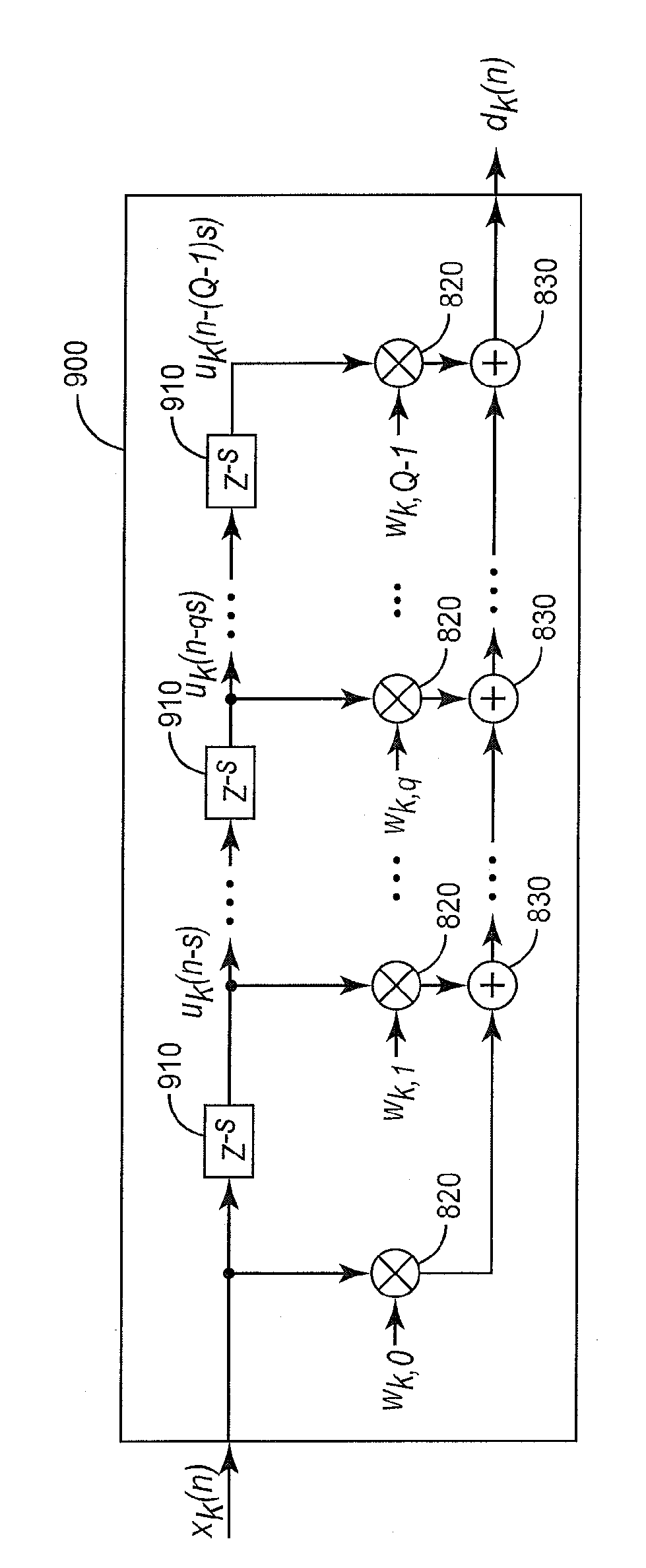
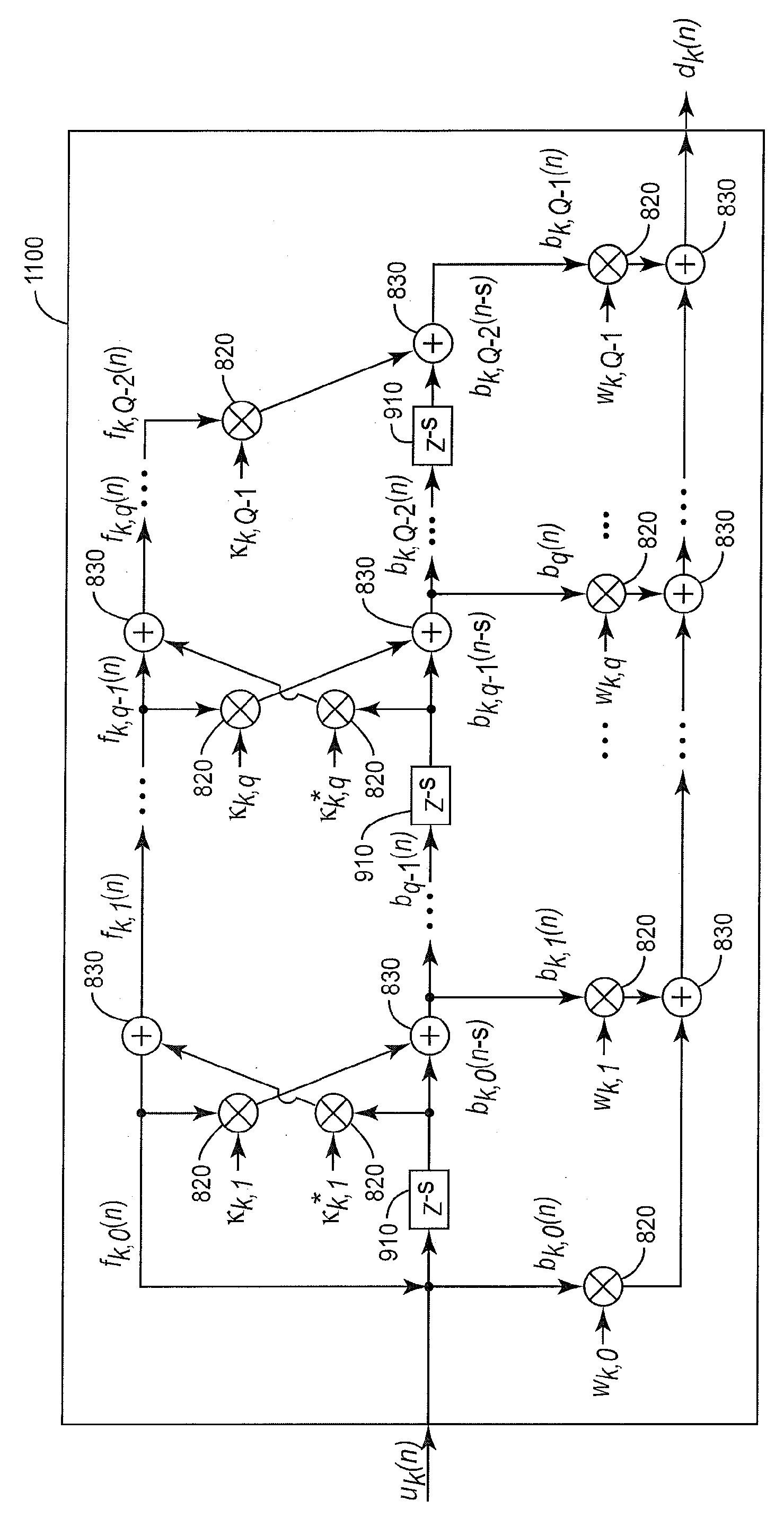
Joint process estimator with variable tap delay line for use in power amplifier digital predistortion
ActiveCN103201950AAmplifier modifications to reduce non-linear distortionAmplifiers with memory effect compensationAudio power amplifierHemt circuits
Methods and circuits for pre-distorting a signal to compensate for distortion introduced by an electronic device operating on the signal. In an example method, first and second signal samples representing the input and output of the electronic device are generated. The first and second signal samples are spaced at unit-delay intervals, and each of the second signal samples corresponds in time to one of the first signal samples. Pre-distortion weights are then calculated from the first and second signal samples, the pre-distortion weights corresponding to a pre-distortion model comprising a lattice-predictor memory model structure having multiple delays and having at least one multi-unit delay interval between adjacent delays. The calculated pre-distortion weights are then applied to the input signal, using a predistorter with a structure corresponding to the lattice-predictor memory model, to produce a pre-distorted input signal for input to the electronic device.
Owner:TELEFON AB LM ERICSSON (PUBL)
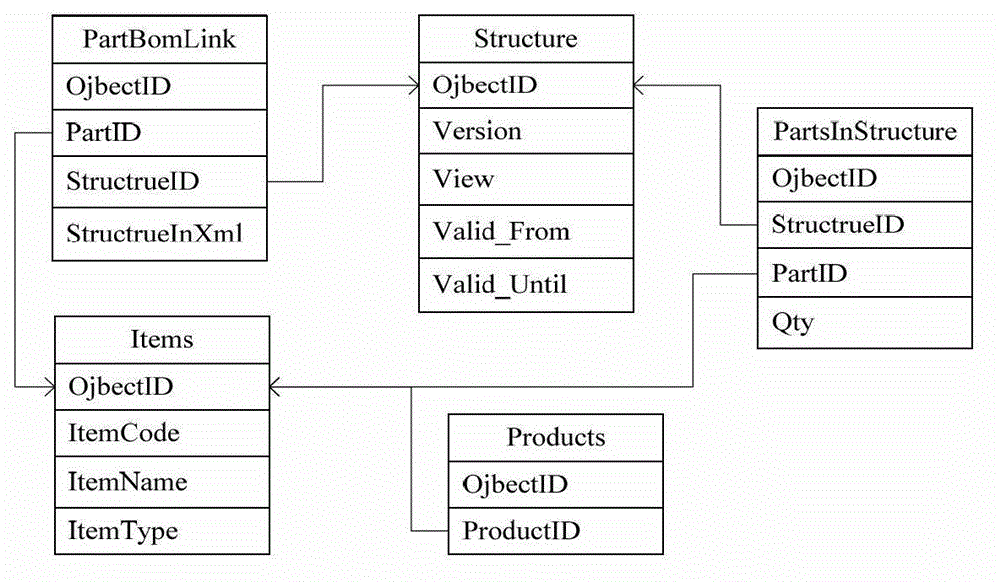
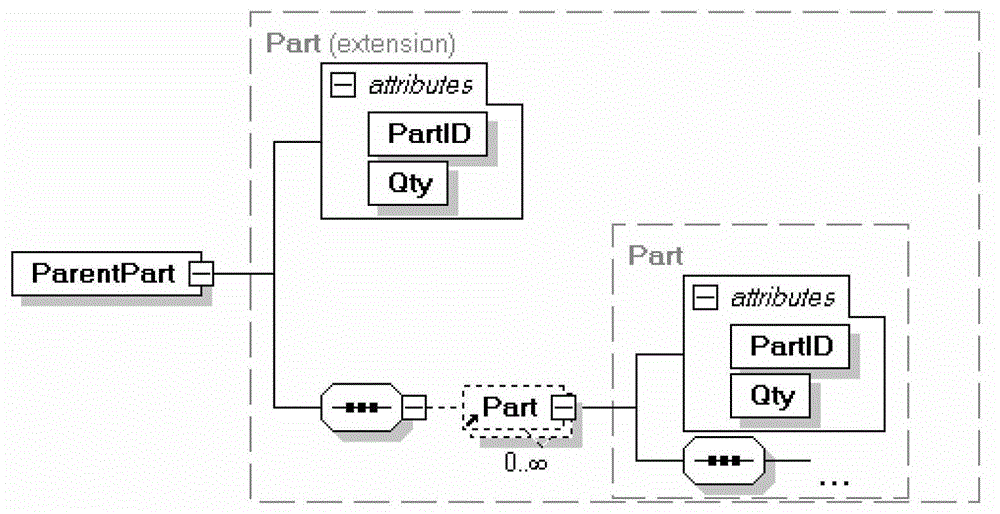
Method for producing BOM (Bill of Material) memory model building based on XML (extensive markup language)
InactiveCN103064877AObvious speed advantageReduce complexitySpecial data processing applicationsBill of materialsSoftware engineering
The invention discloses a method for producing BOM (Bill of Material) memory model building based on XML (extensive markup language). According to the method, BOM aggregation relationship is redefined, BOM memory model building based on XML is innovatively proposed, the problems of high redundancy and low execution efficiency are solved, ideal experimental effects are achieved according to experimental verification, and new methods and thoughts are proposed in terms of BOM memory model building.
Owner:北京航天情报与信息研究所
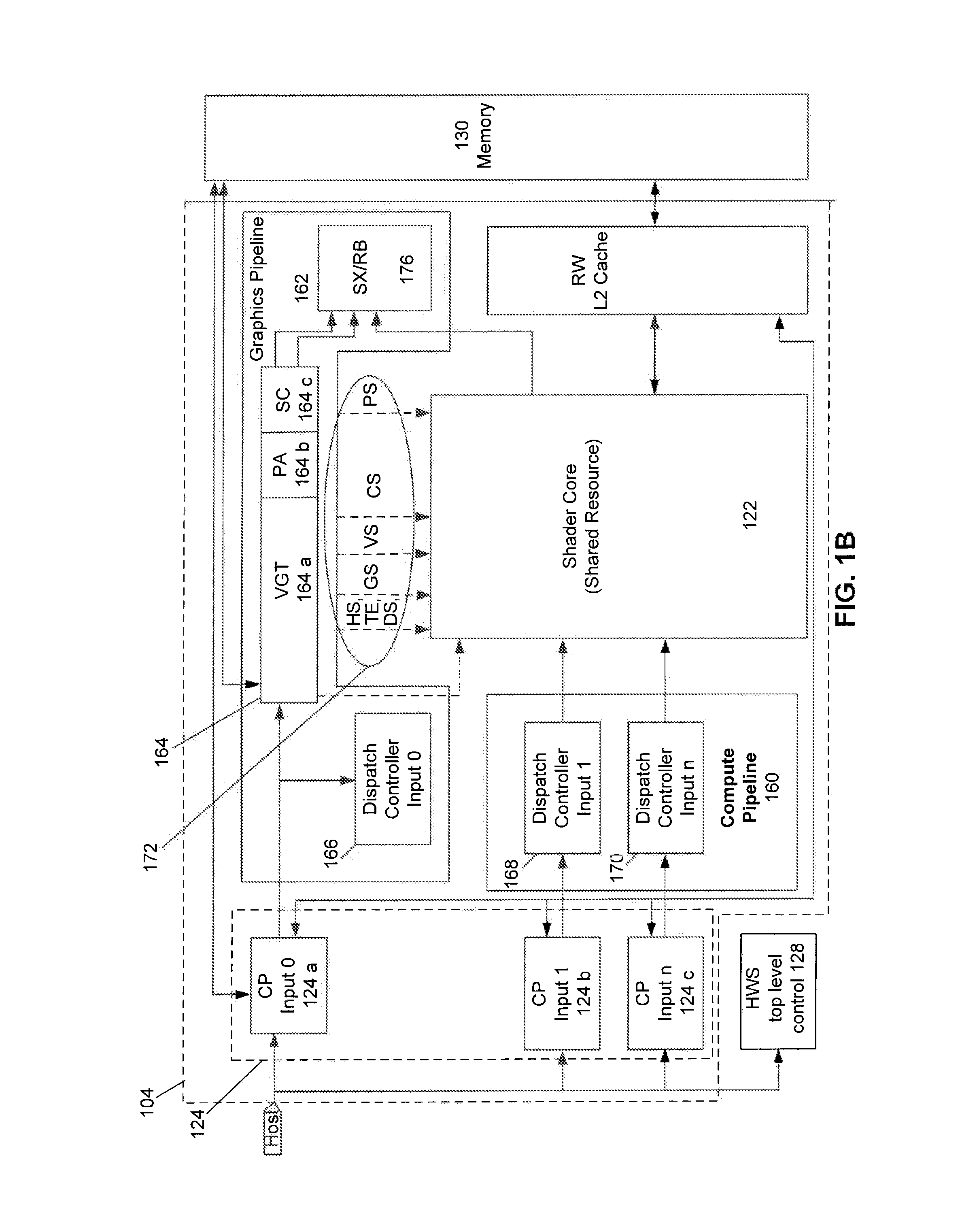
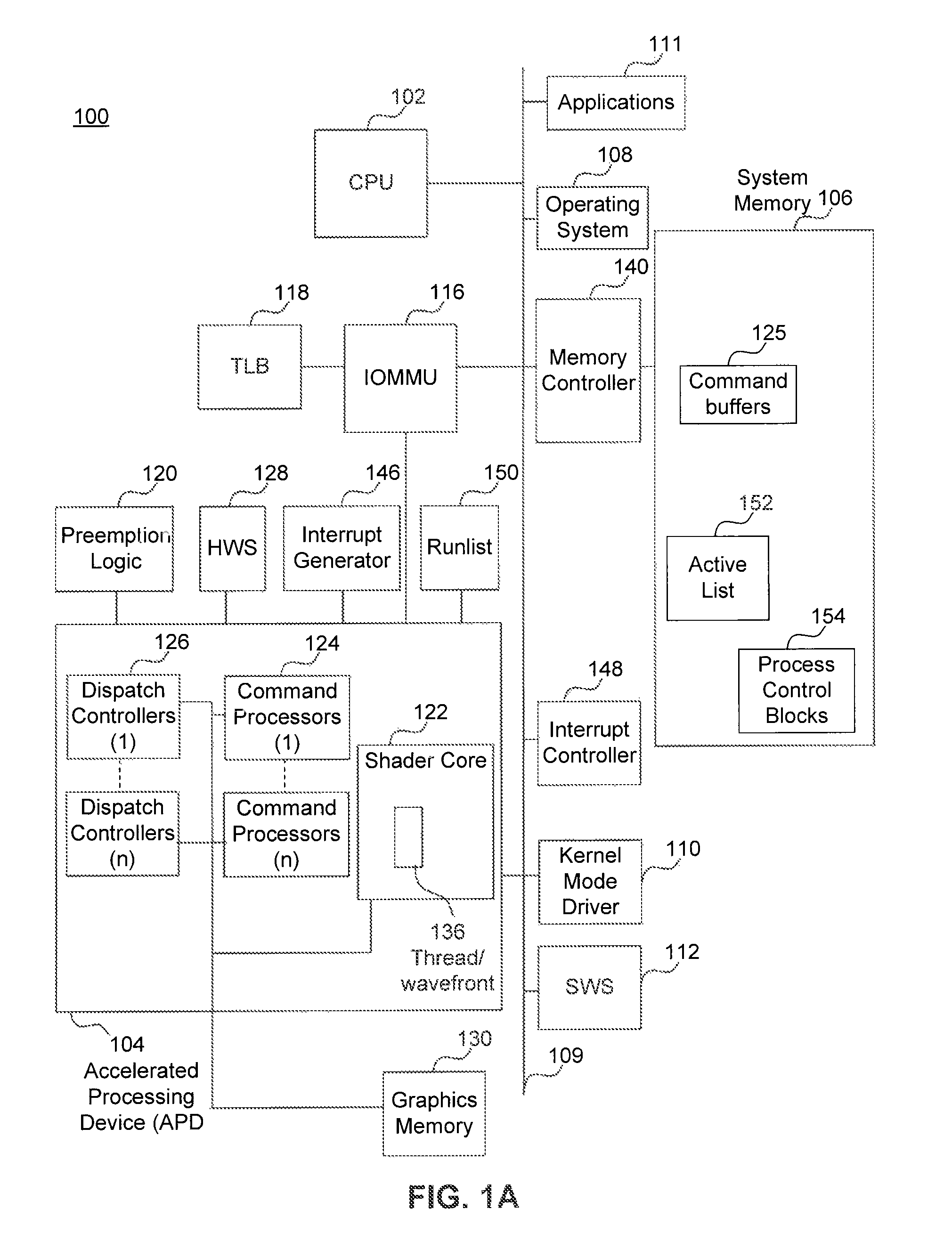
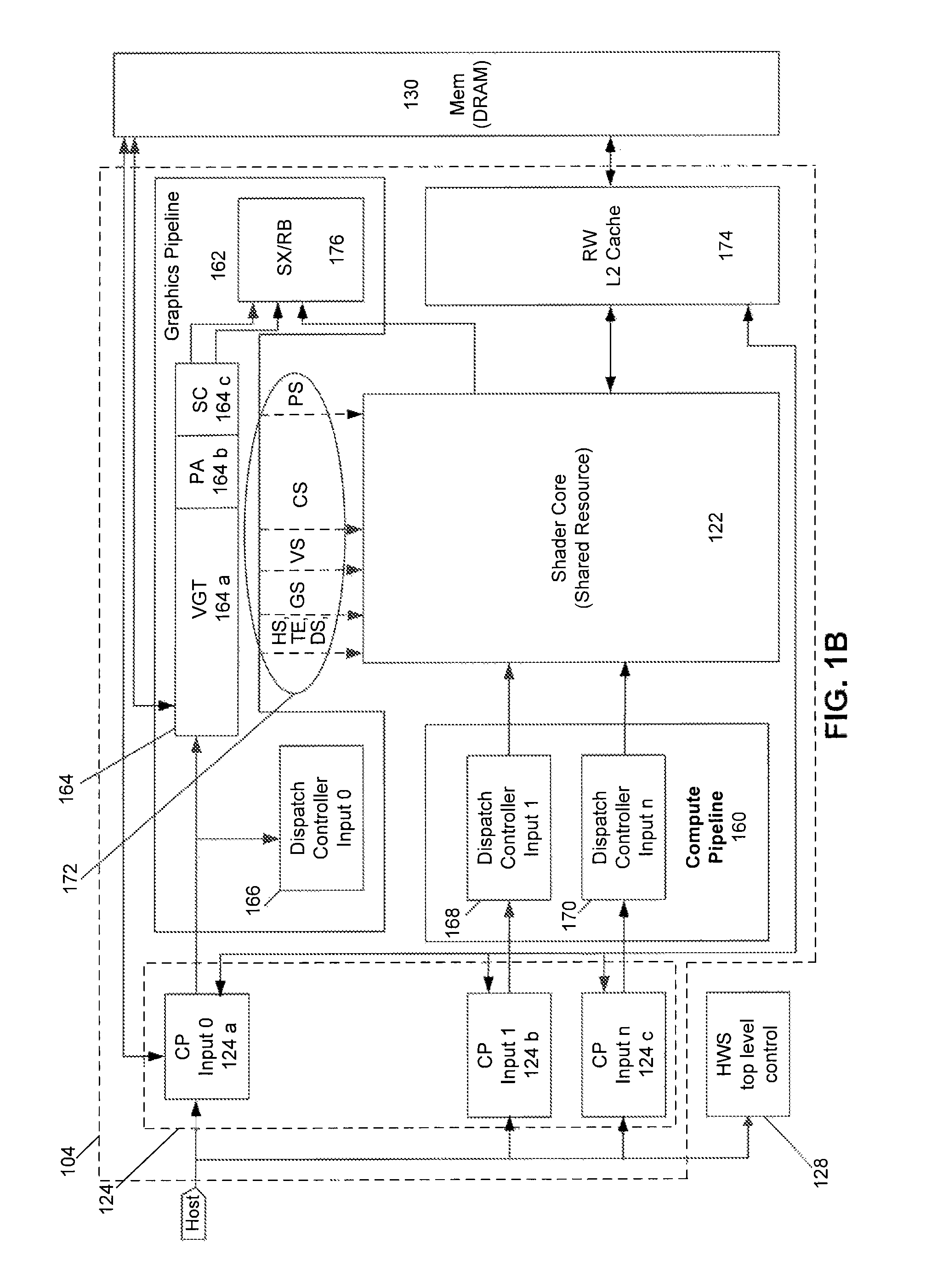
Visibility Ordering in a Memory Model for a Unified Computing System
Provided is a method of permitting the reordering of a visibility order of operations in a computer arrangement configured for permitting a first processor and a second processor threads to access a shared memory. The method includes receiving in a program order, a first and a second operation in a first thread and permitting the reordering of the visibility order for the operations in the shared memory based on the class of each operation. The visibility order determines the visibility in the shared memory, by a second thread, of stored results from the execution of the first and second operations.
Owner:ATI TECH INC +1
Virtual image processor instruction set architecture (ISA) and memory model and exemplary target hardware having a two-dimensional shift array structure
ActiveCN107533750AImage memory managementDesign optimisation/simulationComputer architectureMemory model
A method is described that includes instantiating, within an application software development environment, a virtual processor having an instruction set architecture and memory model that contemplatefirst and second regions of reserved memory. The first reserved region is to keep data of an input image array. The second reserved region is to keep data of an output image array. The method also includes simulating execution of a memory load instruction of the instruction set architecture by automatically targeting the first reserved region and identifying desired input data with first and second coordinates relative to the virtual processor's position within an orthogonal coordinate system and expressed in the instruction format of the memory load instruction.
Owner:GOOGLE LLC
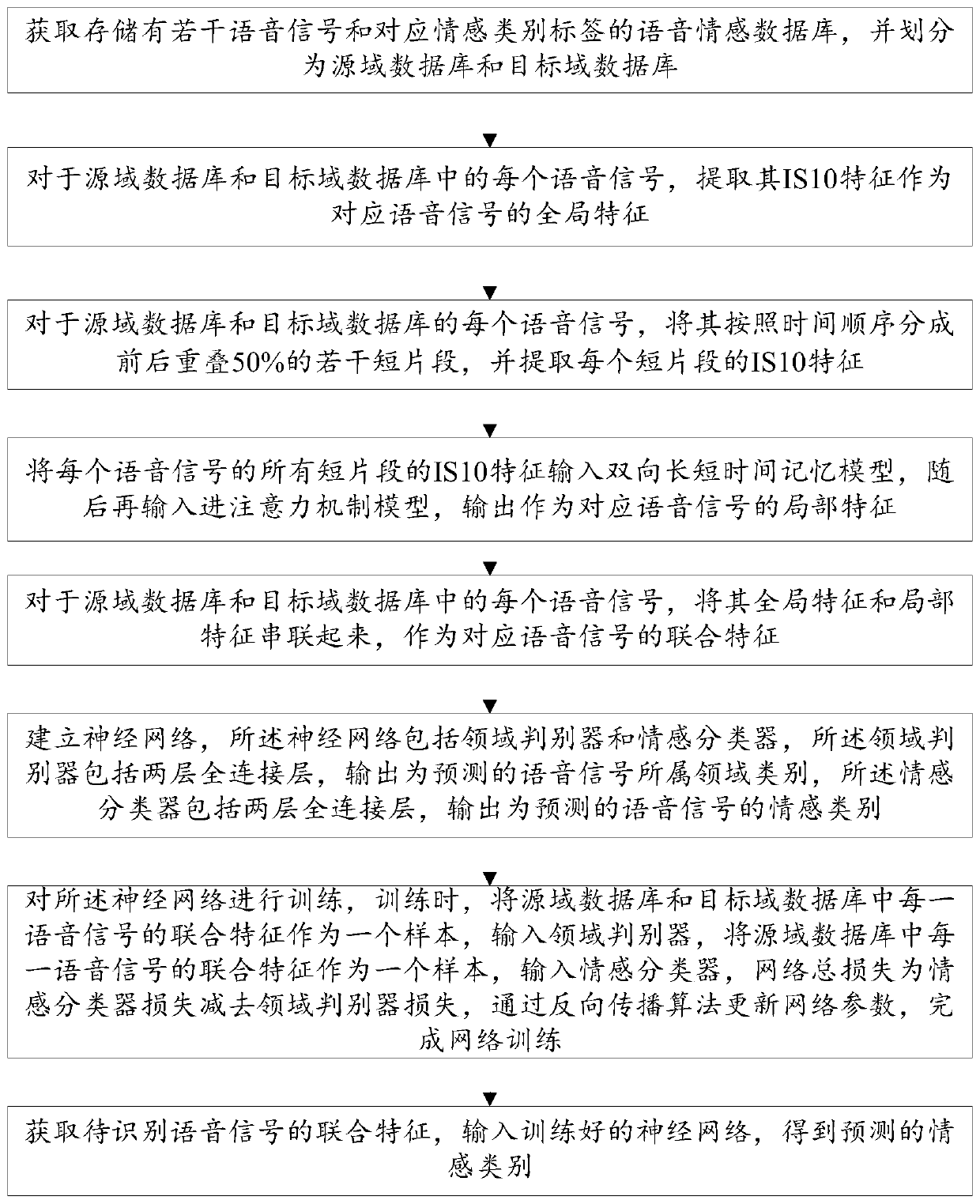
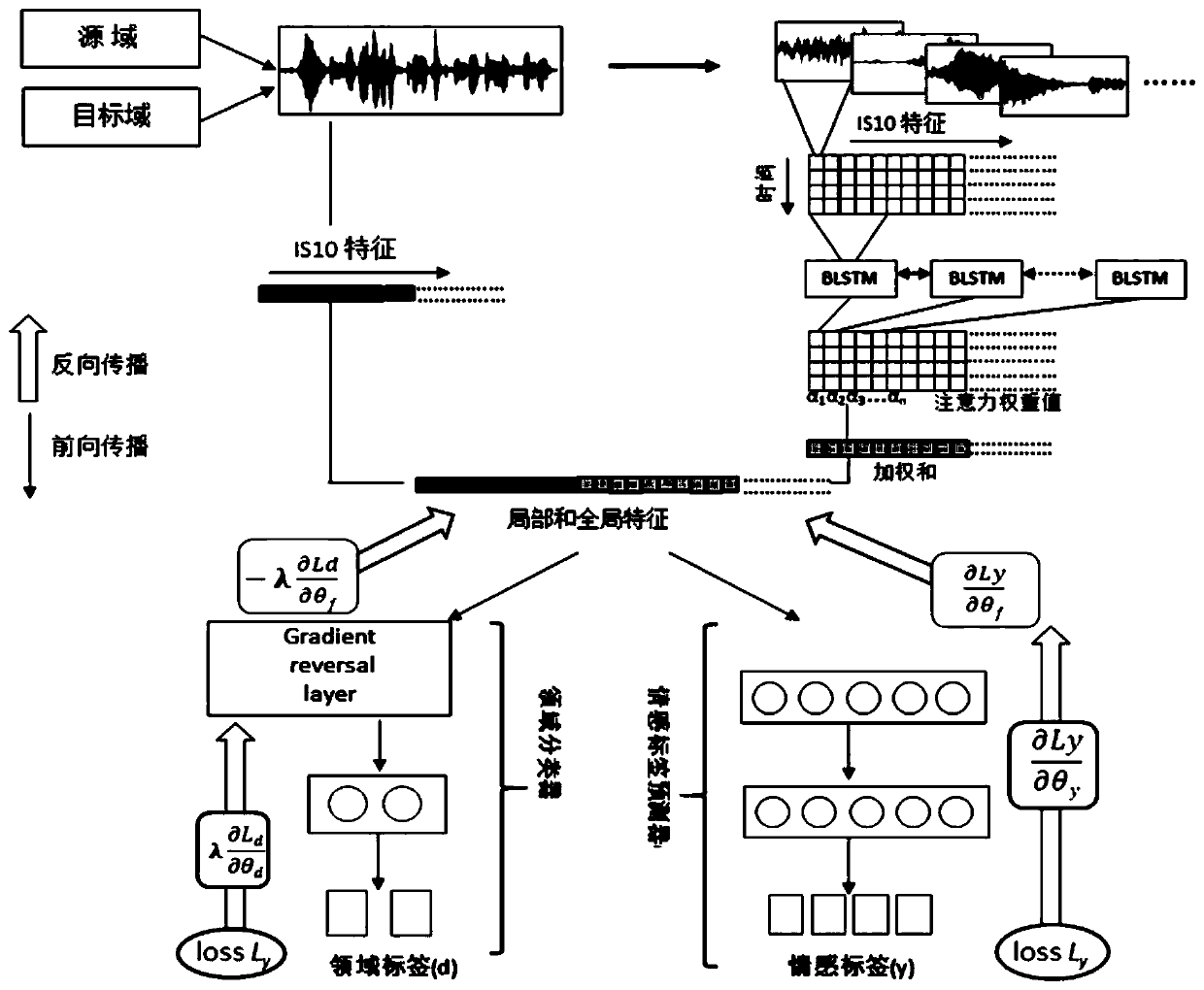
Voice emotion recognition method and device based on domain confrontation
ActiveCN110992988AFeature distribution close toImprove recognition accuracySpeech analysisCharacter and pattern recognitionPattern recognitionMemory model
The invention discloses a voice emotion recognition method and device based on domain confrontation. The method comprises the steps: (1) obtaining a voice emotion database, and dividing the voice emotion database into a source domain database and a target domain database, (2) for each voice signal, extracting IS10 features as global features, (3) dividing the voice signal into a plurality of shortsegments which are overlapped by 50% forwards and backwards according to time, and extracting IS10 features of each short segment, (4) inputting the IS10 features of all the short segments into a bidirectional long-short time memory model, then inputting them into an attention mechanism model, and outputting the IS10 features as local features, (5) connecting the global features and the local features in series to serve as joint features, (6) establishing a neural network which comprises a domain discriminator and an emotion classifier, (7) training the neural network, wherein the total lossof the network is obtained by subtracting the loss of the domain discriminator from the loss of the sentiment classifier, and (8) obtaining the joint features of the speech signals to be recognized, and inputting the joint features into the trained neural network to obtain a predicted emotion category. The method is more accurate in recognition result.
Owner:SOUTHEAST UNIV
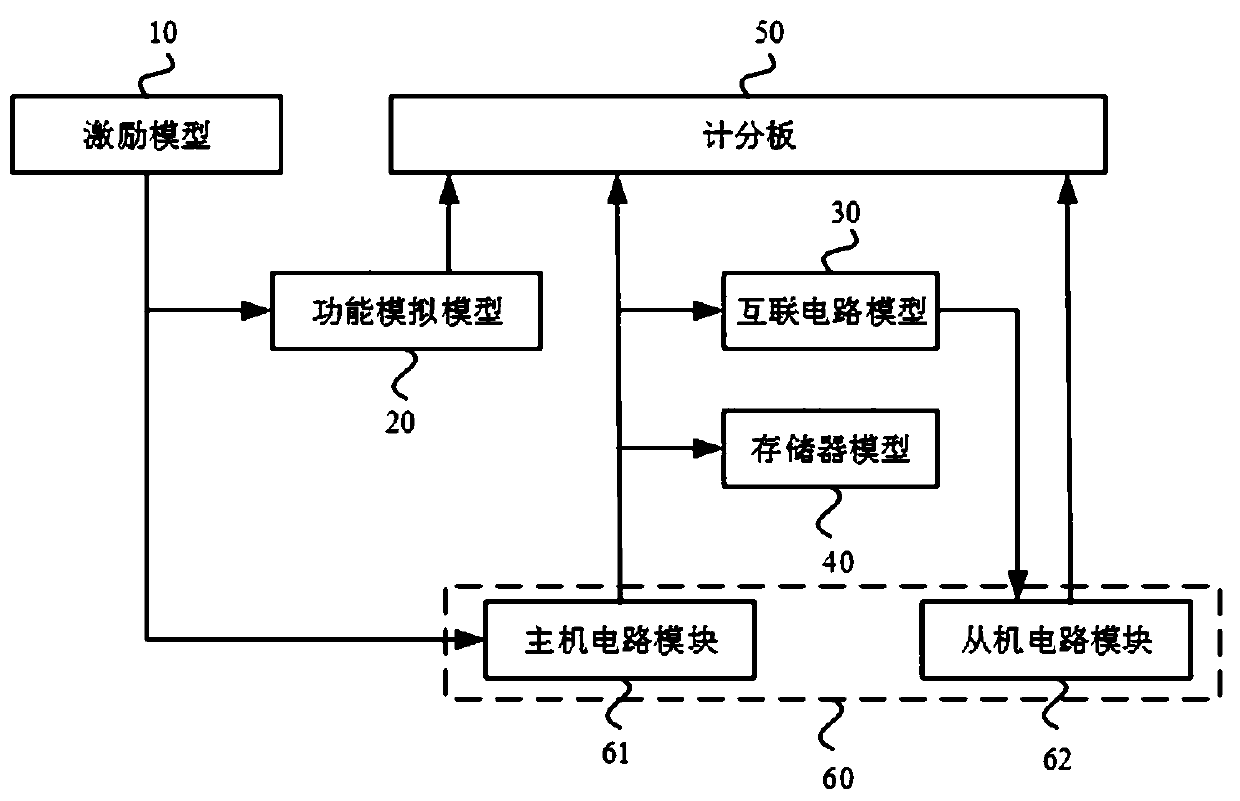
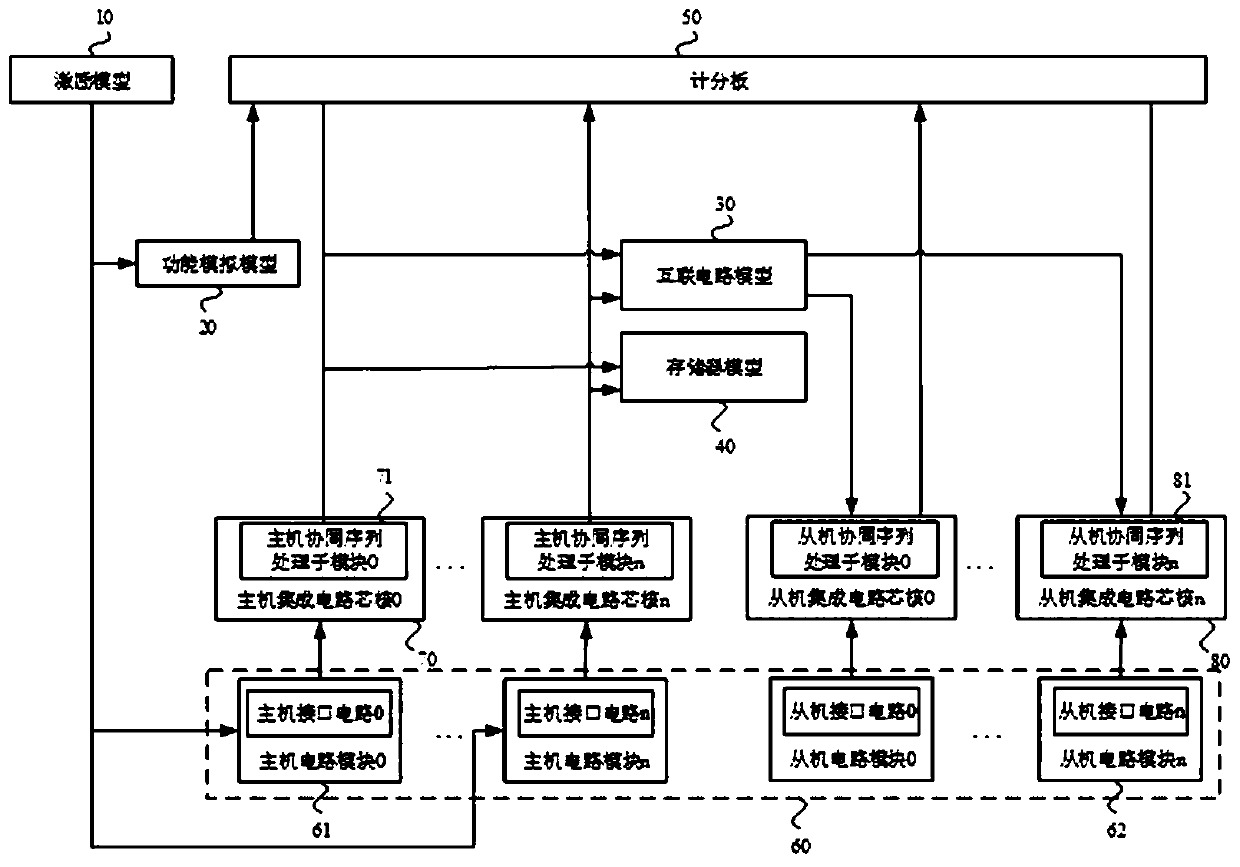
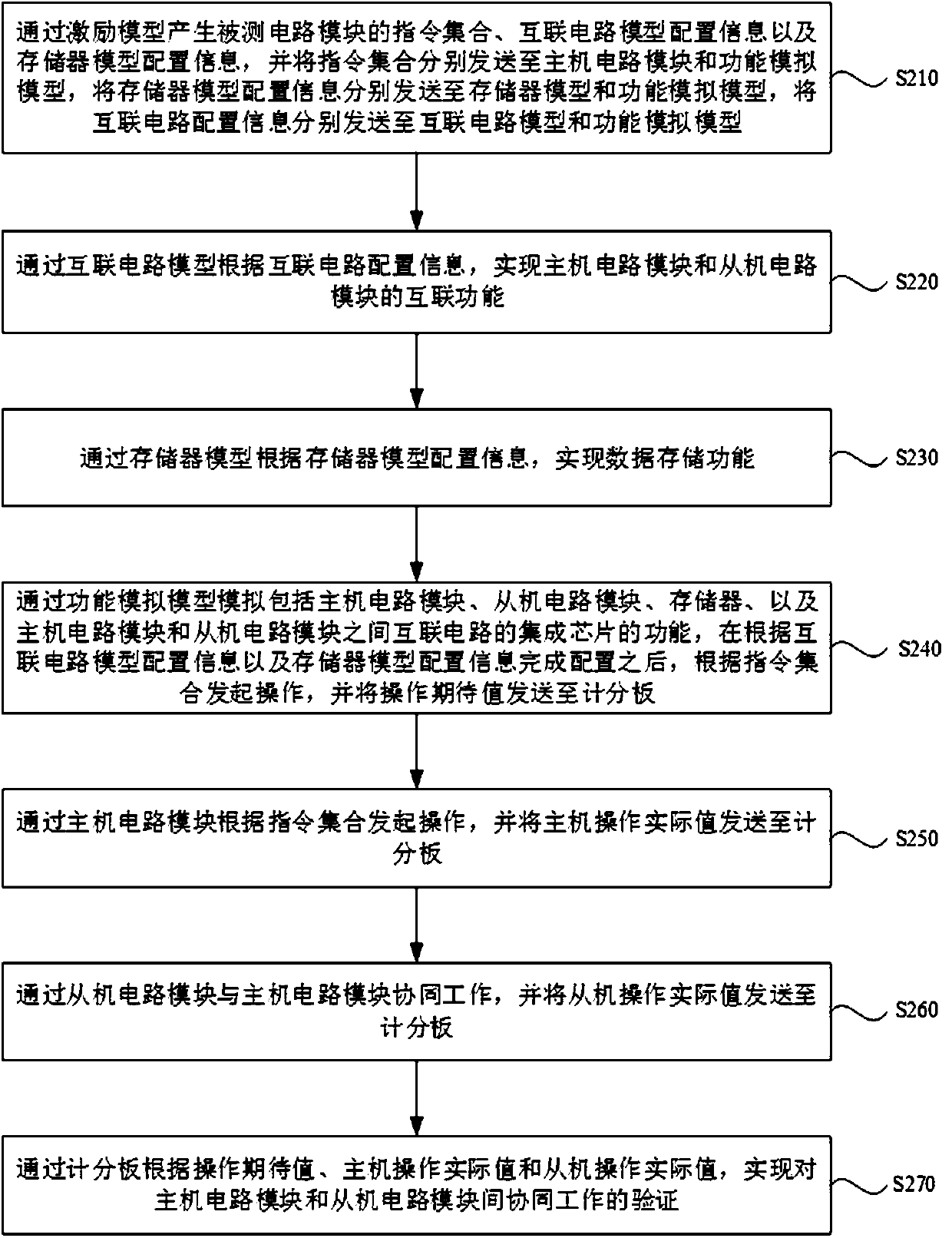
Verification system and method for cooperative work between integrated circuit modules
ActiveCN111353266AProblem discovery and resolutionSolve the real problemComputer aided designSpecial data processing applicationsSoftware engineeringCircuit under test
The embodiment of the invention discloses a verification system and method for cooperative work between integrated circuit modules. The verification system comprises an excitation model, a function simulation model, an interconnection circuit model, a memory model and a scoreboard, and the interconnection circuit model is used for realizing an interconnection function of a host circuit module anda slave circuit module in a tested circuit according to interconnection circuit configuration information; and the scoreboard is used for realizing verification of cooperative work between the host circuit module and the slave circuit module according to the operation expectation value, the host operation actual value and the slave operation actual value. By adopting the verification system for cooperative work between the integrated circuit modules, the interconnection function of the tested circuit and the verification of the cooperative work capability of multiple modules can be completed with high quality under the condition of no interconnection circuit, memory and upper-layer integrated connecting wire, so that the problem of the tested circuit can be found and solved earlier.
Owner:北京燧原智能科技有限公司
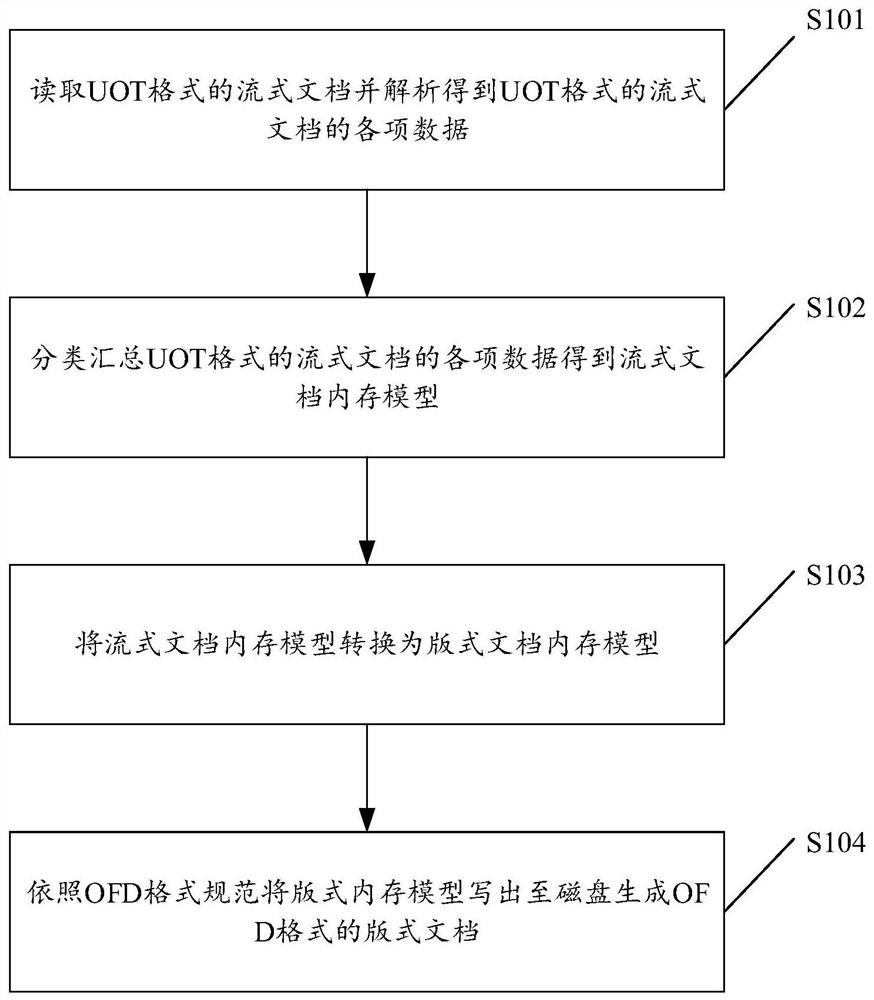
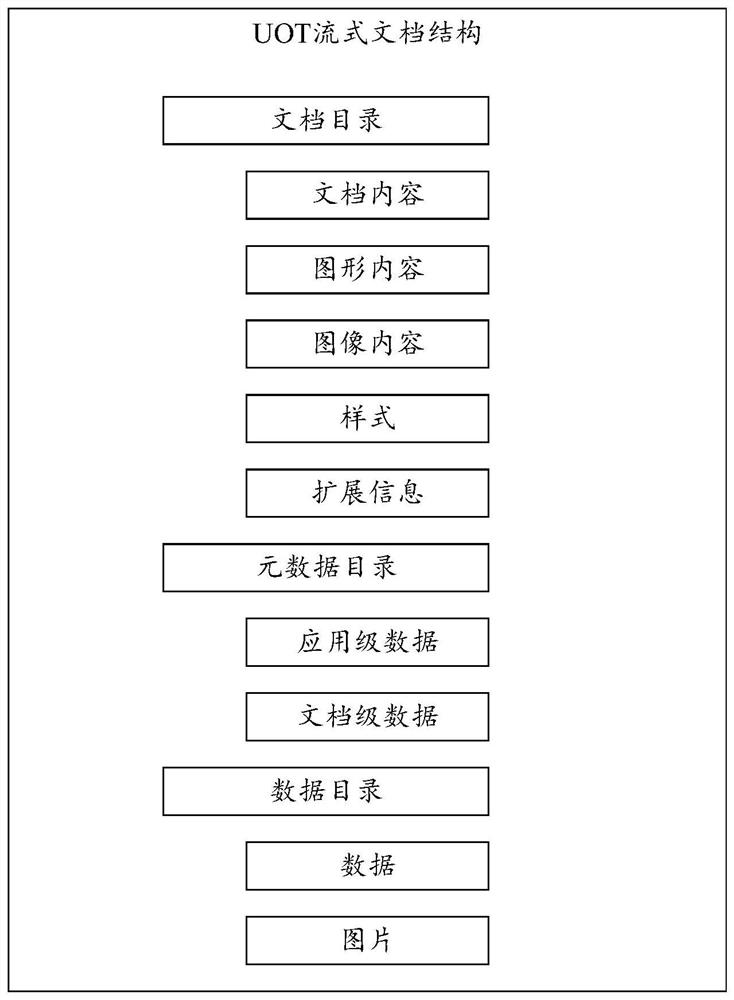
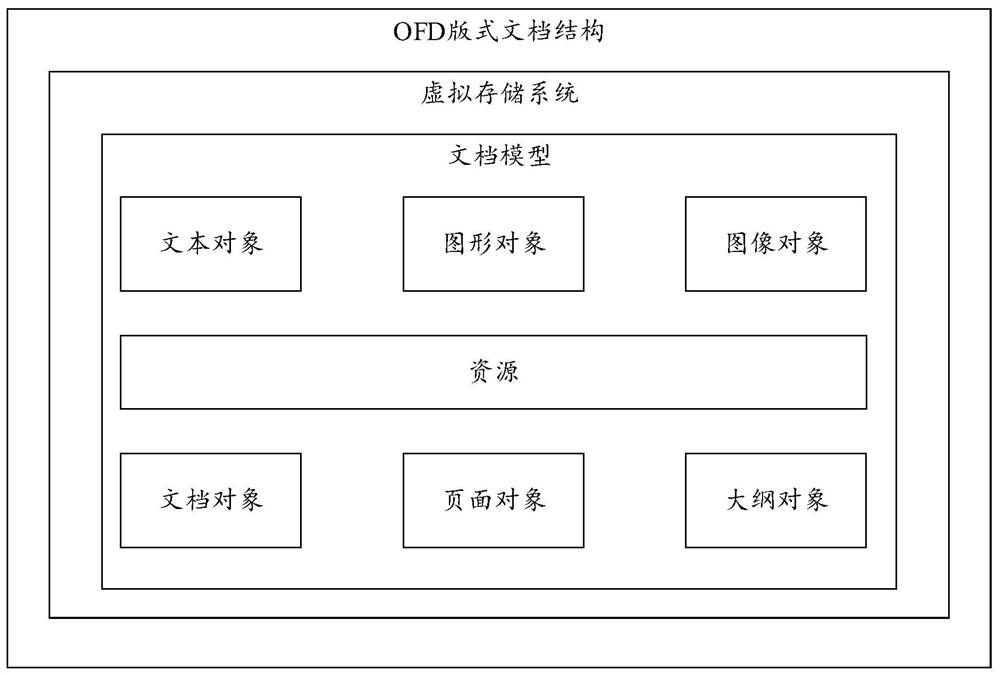
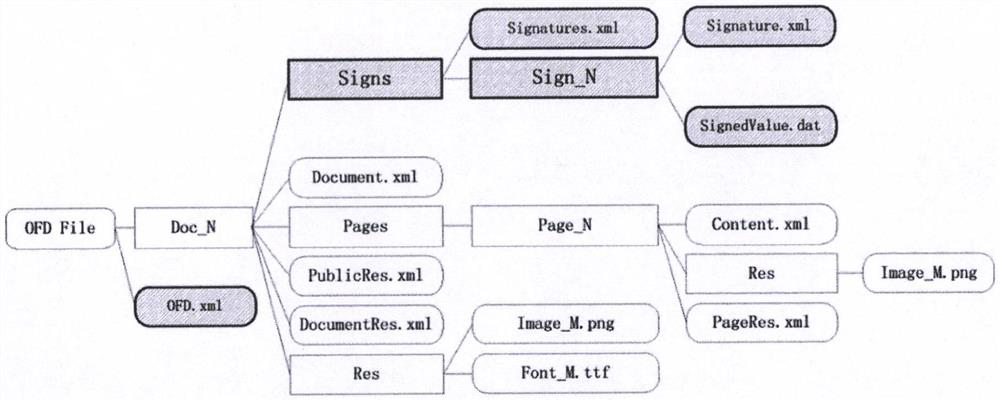
Method for converting UOT streaming document into OFD format document
PendingCN111881651AClear structureEnsure consistencyNatural language data processingMemory modelTerm memory
The invention discloses a method for converting a UOT streaming document into an OFD format document. The method comprises the steps: reading and analyzing the streaming document in the UOT format toobtain various data of the streaming document in the UOT format; summarizing various data of the streaming document in the UOT format in a classified manner to obtain a streaming document memory model; converting the streaming document memory model into a format document memory model; and writing the layout memory model to a disk according to an OFD format specification to generate a layout document in an OFD format. According to the method, the streaming document in the UOT format can be converted into the layout document in the OFD format. The invention also discloses a device and equipmentfor converting the UOT streaming document into the OFD format document, and a computer readable storage medium, which all have the above technical effects.
Owner:泰山信息科技有限公司
Mouse hearing and vision memory model and intelligent action inspecting system
InactiveCN100471465CInconsistent dwell timeKeep awayEducational modelsVeterinary instrumentsSimulationData acquisition
Owner:SHENYANG MEDICAL COLLEGE
Dimension reduction-based layered time memory industrial anomaly detection method and device
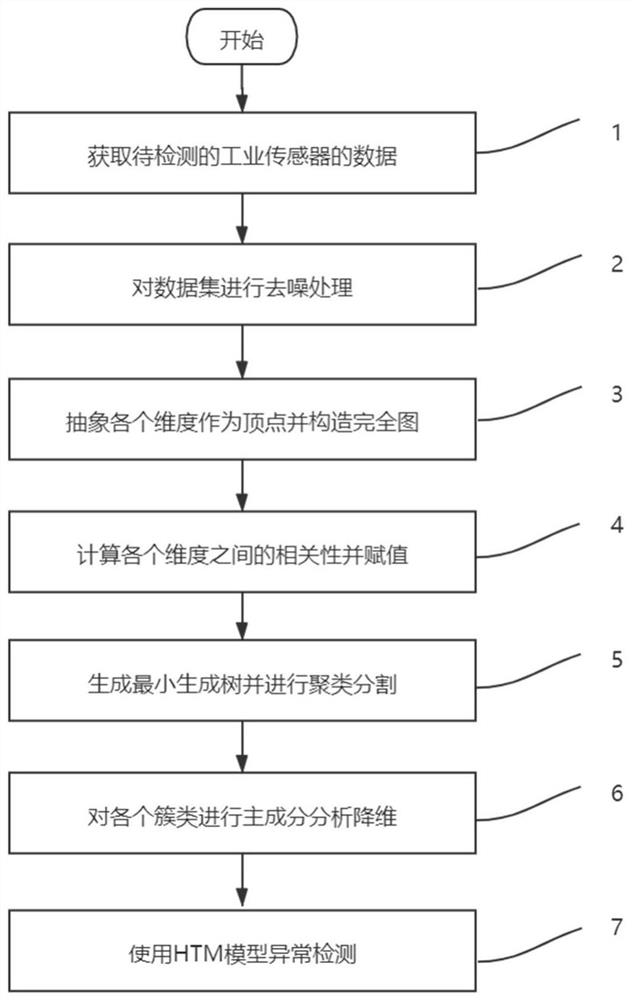
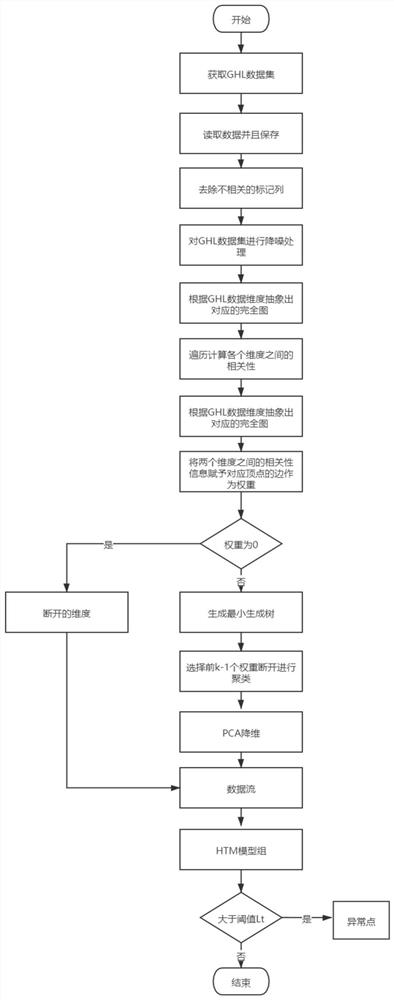
ActiveCN111898639AAvoid direct detectionFacilitates anomaly detectionDigital data information retrievalMeasurement devicesData setData stream
The invention provides a dimension reduction-based layered time memory industrial anomaly detection method and device. The method comprises the steps of obtaining a data set corresponding to a multi-dimensional time sequence generated by a to-be-detected industrial sensor; performing denoising processing on the original data; abstracting the number of dimensions of the data set into the corresponding number of dimension information vertexes; calculating a correlation numerical value between the dimensions and endowing the correlation numerical value to a corresponding edge in the graph as a weight value; performing minimum spanning tree selection clustering according to the relevancy between the dimensions; performing PCA dimension reduction on the formed block cluster; and carrying out layered time memory model abnormality judgment on the obtained feature data after dimension reduction. According to the invention, dimensionality reduction is carried out through correlation dimensionality selection, redundant features are removed, the calculated amount is reduced, the time point abnormity in the industrial sensor time sequence data flow can be found in time, and the trouble that anormal data set in the industry is collected to train the model is avoided.
Owner:HOHAI UNIV
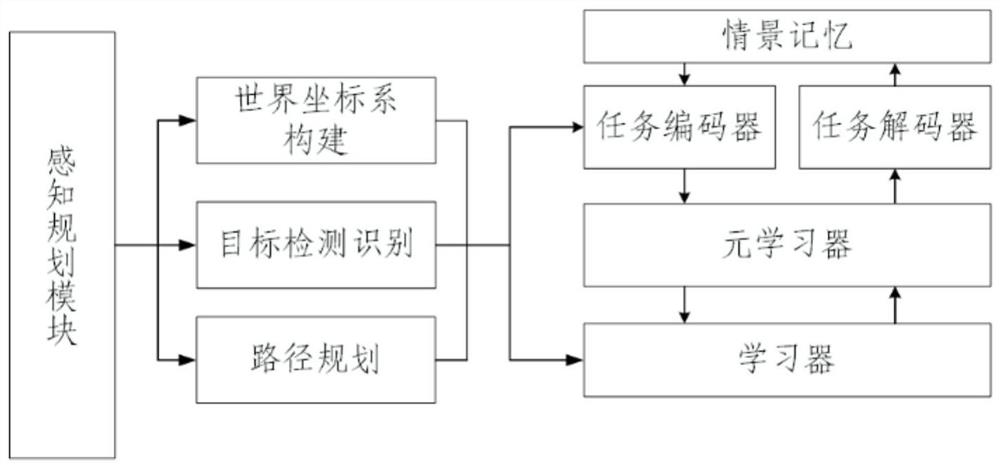
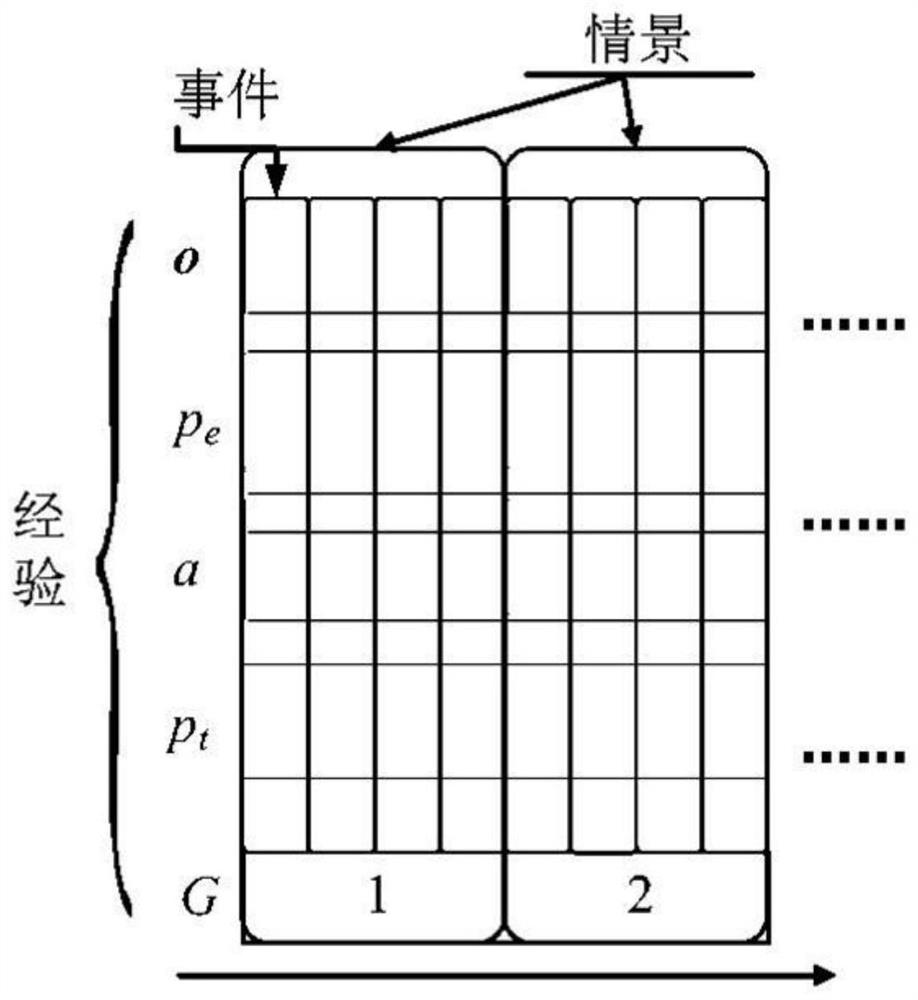
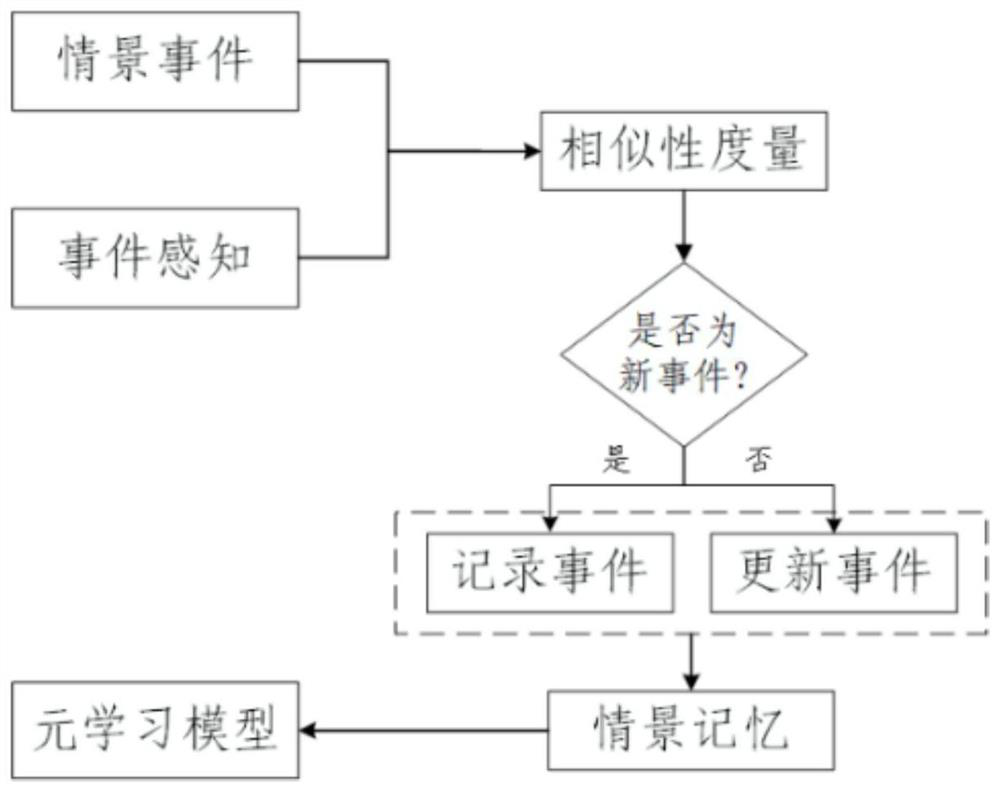
Robot skill acquisition method based on meta-learning under guidance of scene memory
PendingCN113657573ASolve the need for a large amount of data trainingSolve the repeatabilityCharacter and pattern recognitionArtificial lifeMemory modelMachine learning
The invention provides a robot skill acquisition method based on meta-learning under the guidance of scene memory. The method comprises the following steps: firstly, establishing a robot learning system scene memory model, and constructing a robot perception and memory similarity measurement algorithm to realize event and scene information retrieval matching and event update calling in scene memory; and constructing a robot operation skill meta-learning algorithm guided by scene memory, obtaining knowledge from the independent tasks and all the tasks, and performing skill learning. According to the method for guiding the robot to learn new skills by using the existing experience, the learning efficiency of the robot on the operation skills is improved, and the problems that in the robot operation skill learning process, the data size is too large, and similar tasks need to be trained repeatedly are solved.
Owner:CHANGZHOU INST OF DALIAN UNIV OF TECH
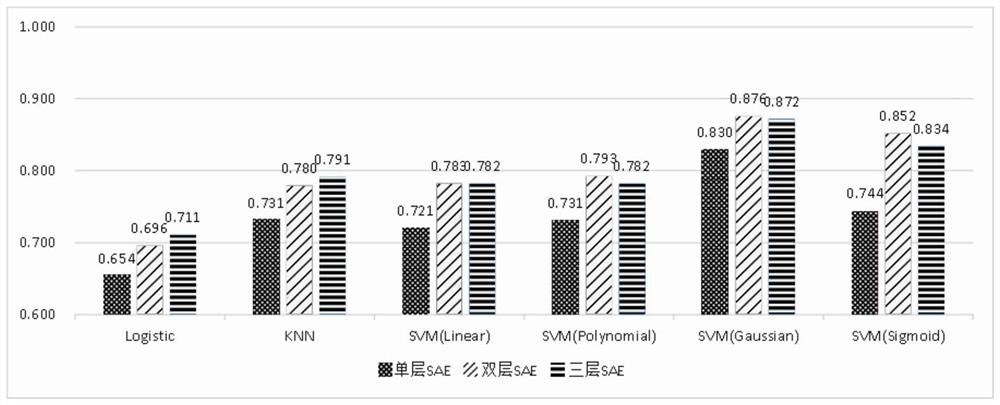
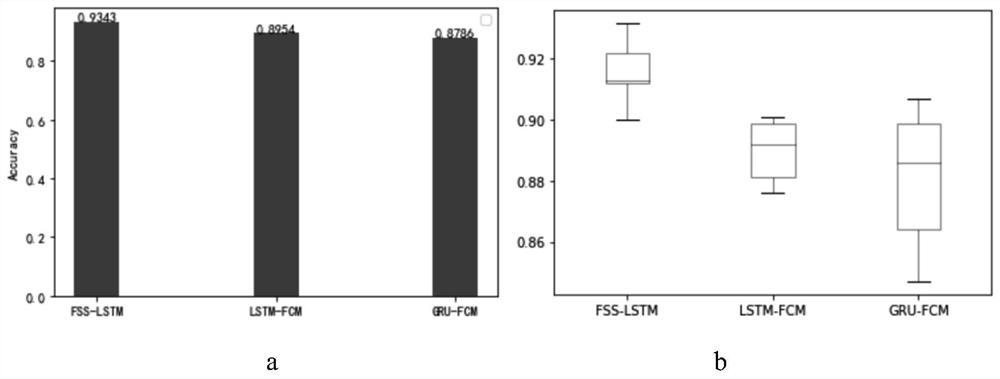
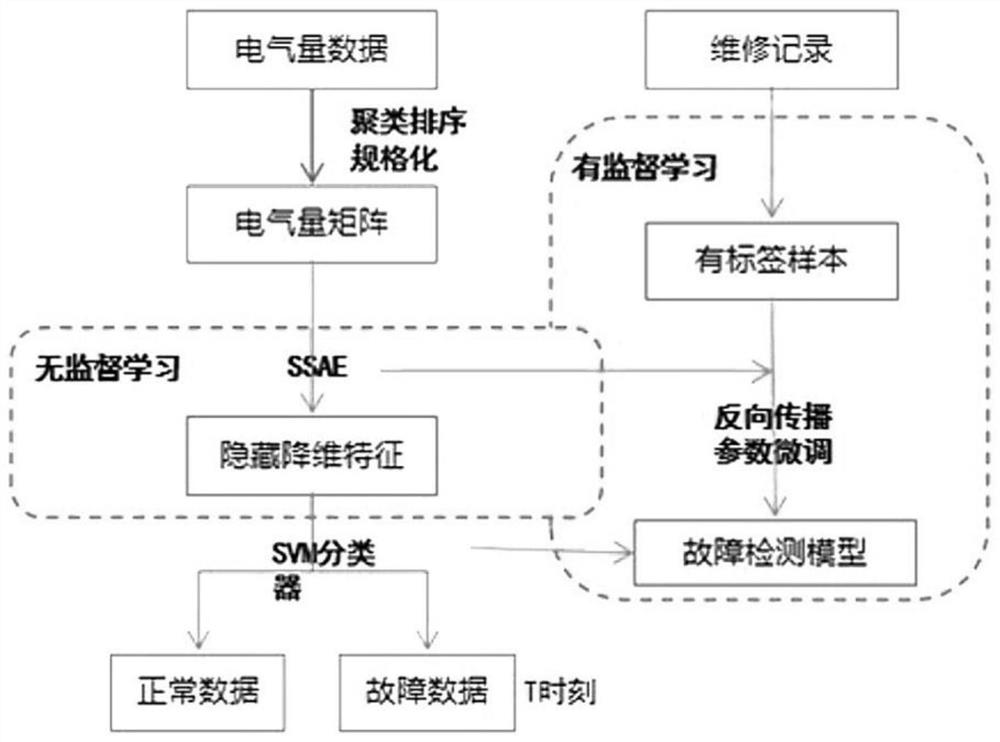
Highway electromechanical system fault classification method based on deep sparse memory model
PendingCN113743537AIncrease the number of layersIncrease sparse dimensionCharacter and pattern recognitionNeural architecturesSparse learningMemory model
The invention discloses a highway electromechanical system fault classification method based on a deep sparse memory model. The method comprises the steps: acquiring data collected by a data collection and monitoring system SCADA of an expressway electromechanical system, and carrying out the data preprocessing; constructing a tripping fault detection model based on a double-layer stack type sparse auto-encoder and an SVM, performing feature extraction and fault detection on the electrical quantity parameters of the highway electromechanical system, and outputting a fault moment; and constructing an improved FSS-LSTM network model, performing fault state classification on the fault moment data of the system, and outputting fault classes. Through close combination of sparse learning and the deep neural network, classification efficiency is improved, classification of various faults is realized more accurately, and technical support is provided for operation and maintenance of an electromechanical system in a highway scene.
Owner:SOUTHEAST UNIV
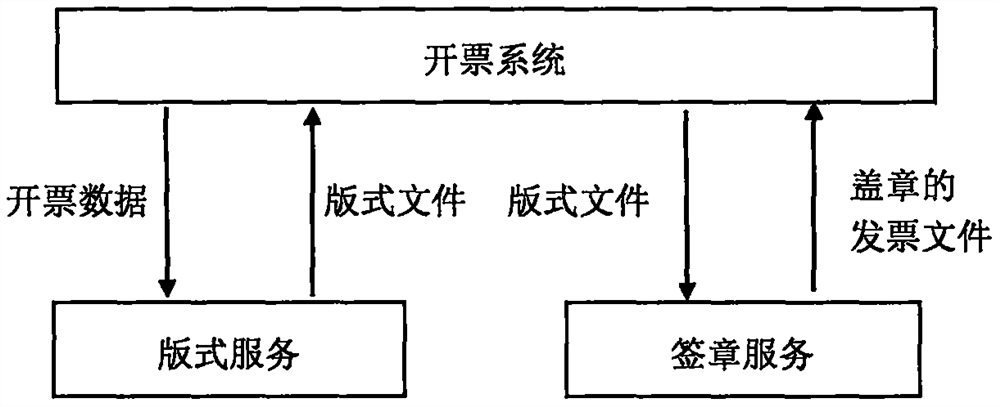
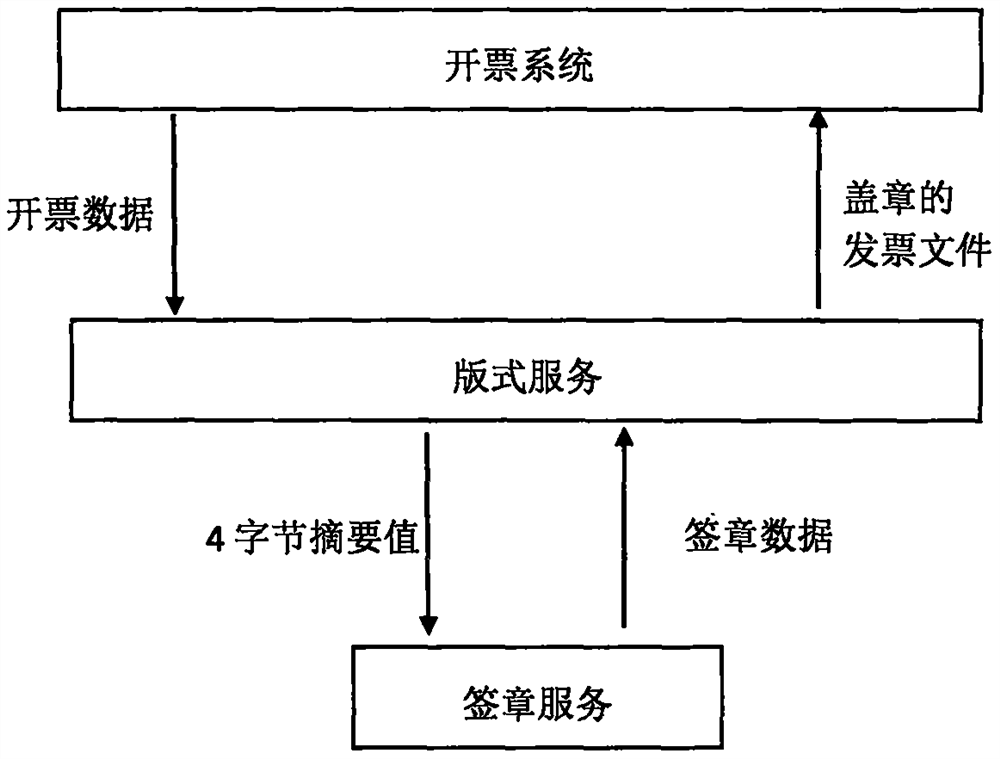
Electronic invoice generation method
PendingCN111898982AReduce the amount of calculationReduce transmission overheadDigital data protectionOffice automationMemory modelInvoice
The invention discloses an electronic invoice generation method. The method comprises the steps of generating an electronic invoice layout file; creating a thread; analyzing the invoicing data; filling in part of signature structure information; serializing the OFD data model; calculating an OFD internal file abstract; serializing the memory model of the signature structure into a Sigatore.xml file, and calculating a Sigatore.xml abstract value; calling a signature service, and sending an abstract value to request signature data; and calling a cipher machine to calculate a signature value andpackaging the signature value into signature data to return to the format service. The invention discloses an electronic invoice generation method. A signature data structure is directly generated through a format service; the signature service does not need to analyze the OFD file again; the signature service only calculates the signature data, only the abstract value and the signature data are transmitted between the format service and the signature service, and the format service simplifies the dynamic calculation step by adopting a set table technology, so that the calculation amount of the format service and the signature service can be reduced at the same time, the network transmission overhead is reduced, the resource occupation is greatly reduced, and the processing efficiency is improved.
Owner:百望股份有限公司
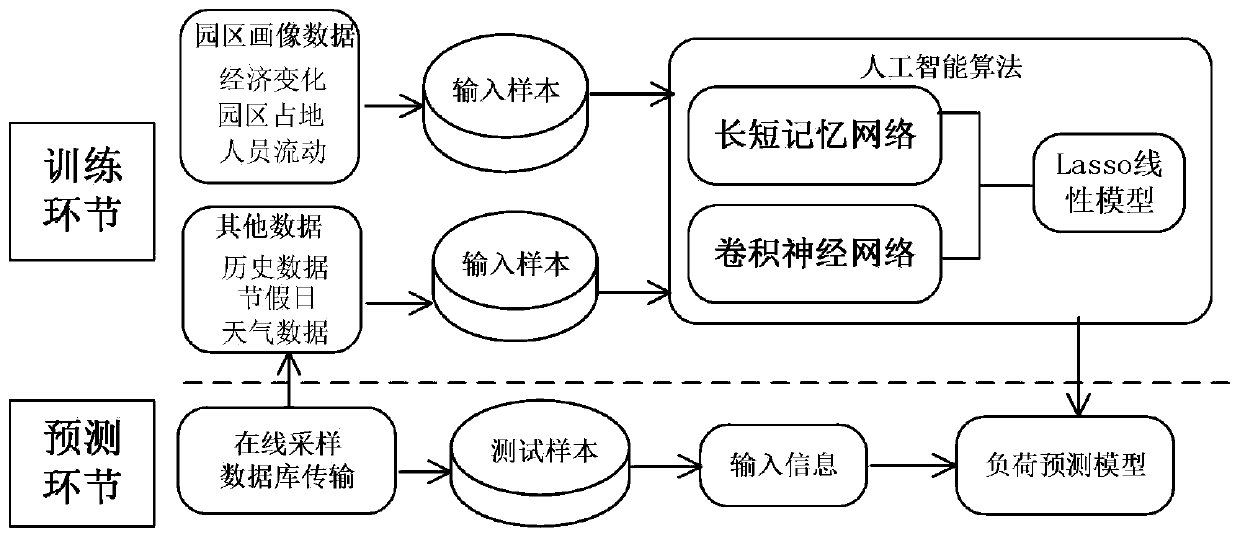
Park load prediction method and system based on park portrait
PendingCN111292121AHigh precisionAvoid the risk of getting stuck in local minimaResourcesNeural architecturesLoad forecastingAlgorithm
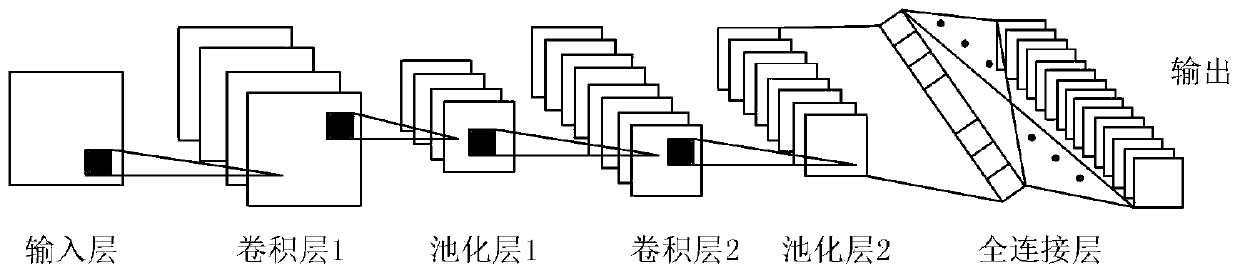
The invention provides a park load prediction method and system based on a park portrait. The park short-term load prediction model combining a convolutional neural network model and a long-short memory model is adopted, the risk that a single model falls into a local minimum value in the training process is effectively avoided, the combined models can give full play to respective advantages, andthe load prediction precision is improved.
Owner:STATE GRID CORP OF CHINA +2
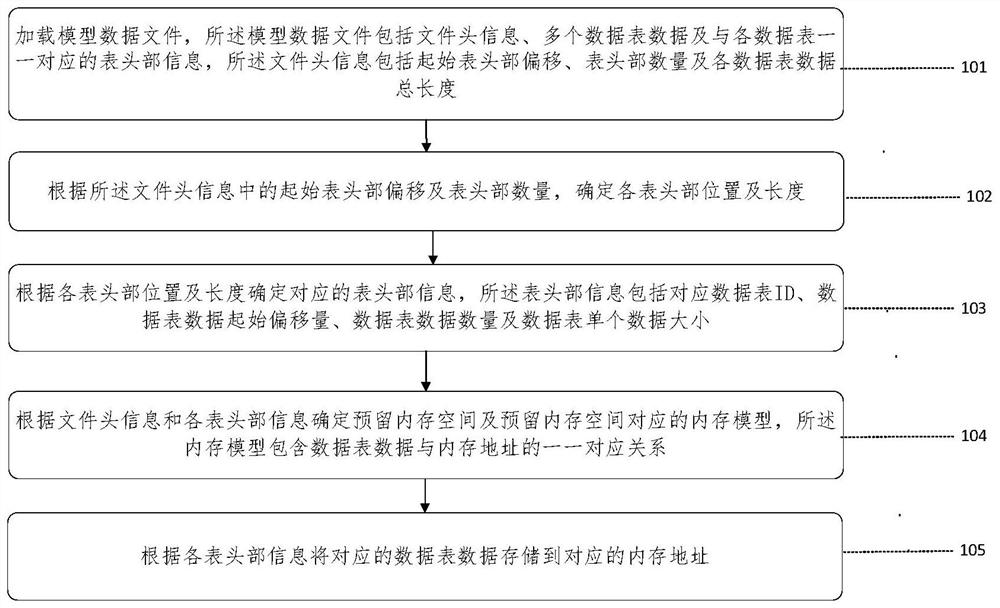
Embedded device model data management method and device
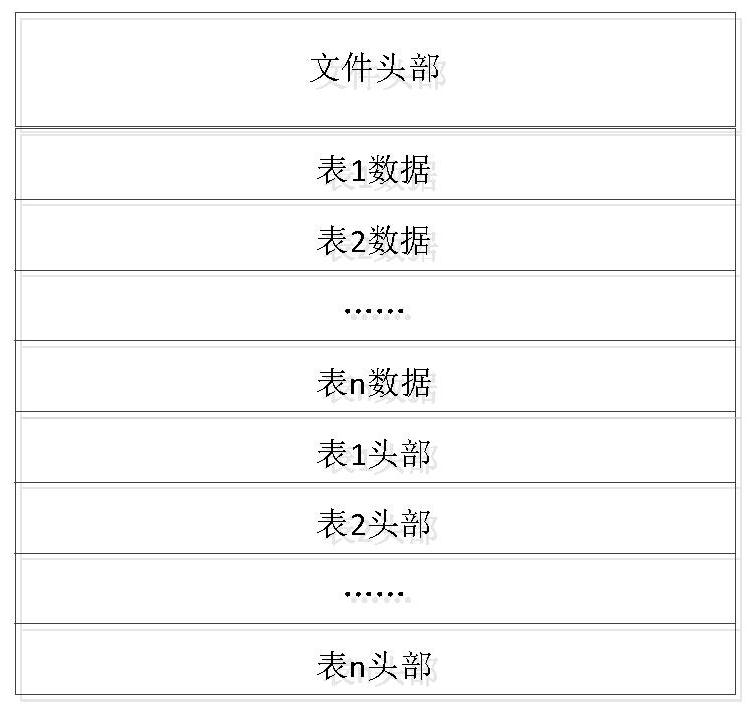
PendingCN112328594AImprove loading efficiencyImprove storage efficiencyDatabase management systemsSpecial data processing applicationsComputer hardwareMemory address
The invention discloses an embedded device model data management method and device, and the method comprises the steps: loading a model data file which comprises file header information, a plurality of pieces of data table data and table header information in one-to-one correspondence with all data tables, and the file header information comprises initial table header deviation, the number of table headers, and the total length of all data table data; determining the position and the length of each header according to the initial header offset and the number of headers in the file header information; determining corresponding header information according to the position and length of each header; determining a reserved memory space and a memory model corresponding to the reserved memory space according to the file header information and the header information, wherein the memory model comprises a one-to-one correspondence relationship between data table data and a memory address; and storing the corresponding data table data to the corresponding memory address according to the header information of each table. The problems of storage, sharing, quick loading and conversion of modeldata between embedded devices or between the device and a computer are solved, and the storage efficiency is improved.
Owner:XUJI GRP +2
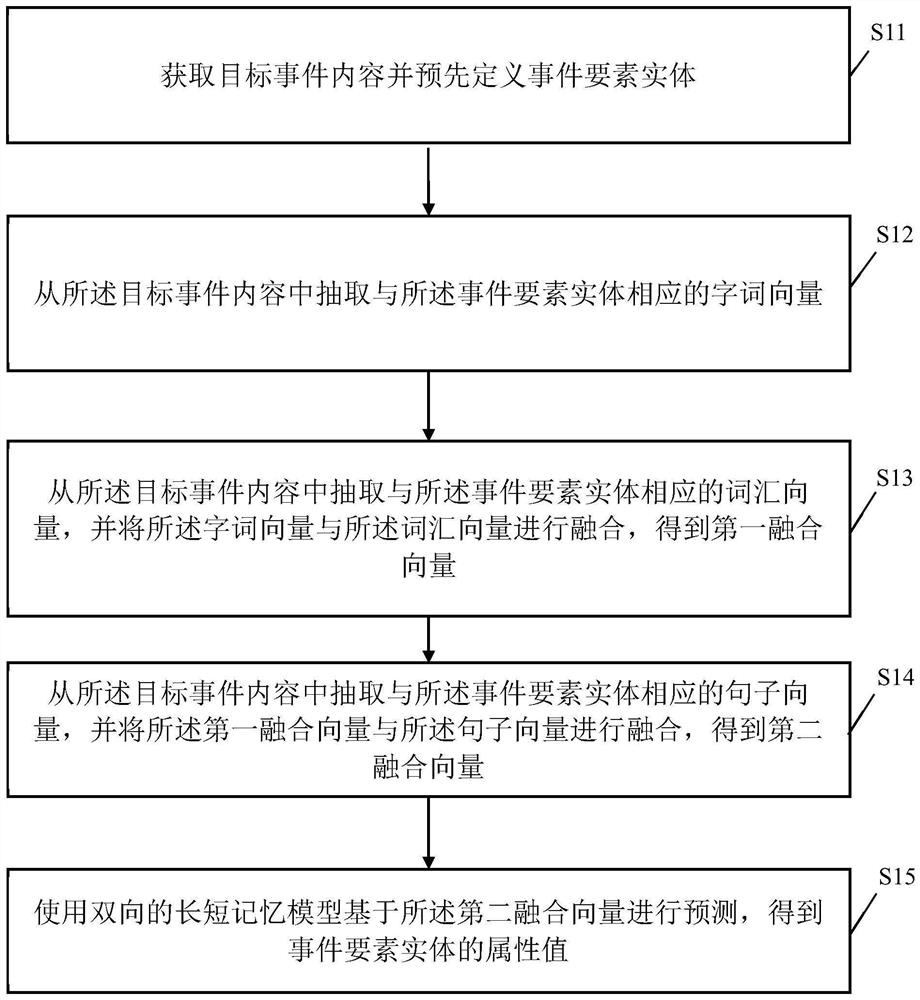
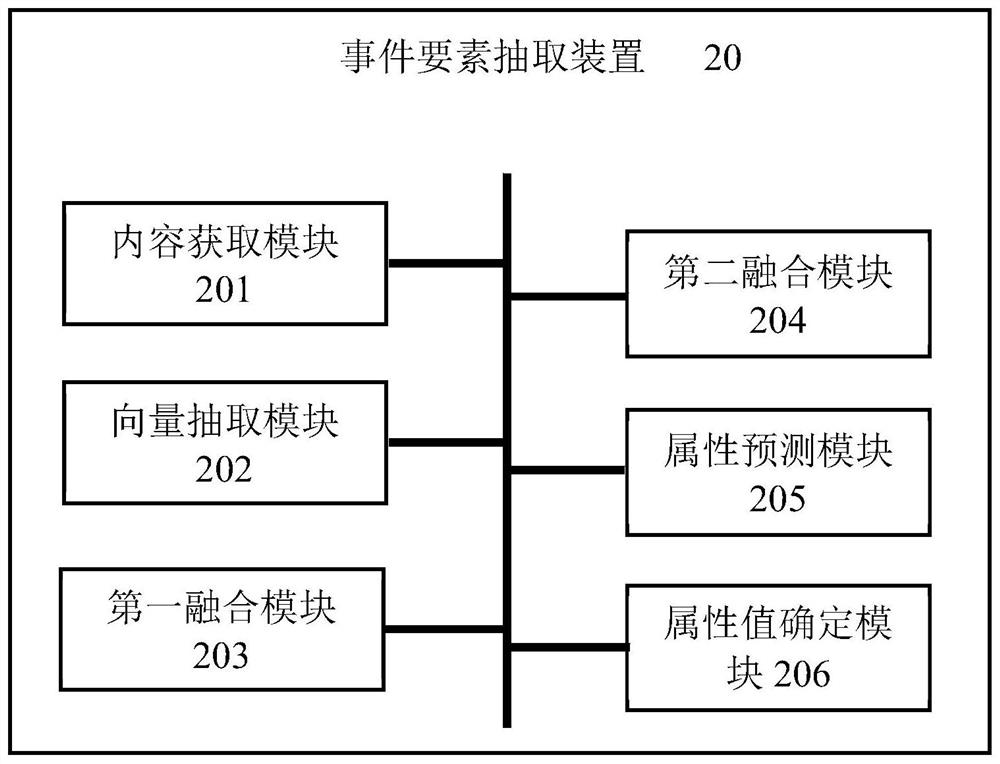
Event element extraction method, computer equipment and storage medium
PendingCN113434697AImprove extraction accuracyEnhance feature expressionNatural language data processingNeural architecturesMemory modelEngineering
The invention relates to the technical field of artificial intelligence, and provides an event element extraction method, computer equipment and a storage medium. After an event element entity is defined, a word vector and a vocabulary vector corresponding to the event element entity are extracted from target event content and are fused to obtain a first fusion vector, extracting a sentence vector, fusing the sentence vector, with the first fusion vector to obtain a second fusion vector, and finally performing prediction based on the second fusion vector by using a bidirectional long-short memory model to obtain an attribute value of the event element entity, thereby completing the extraction of the event element. As the first fusion vector combines the word vector and the vocabulary vector, the feature expression ability of the word vector is enhanced, extraction of the attribute value of the event element entity is facilitated, the second fusion vector fuses the sentence vector on the basis of the first fusion vector, the feature expression ability of the word vector is further enhanced, extraction of the attribute value of the event element entity is further improved, and the extraction accuracy of the event elements is high.
Owner:PING AN TECH (SHENZHEN) CO LTD
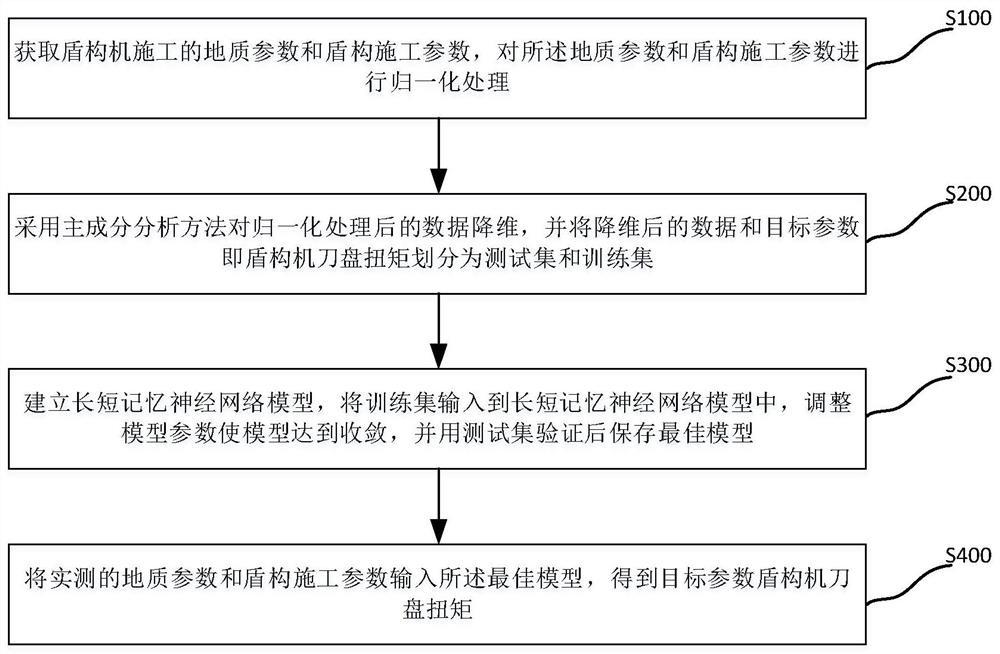
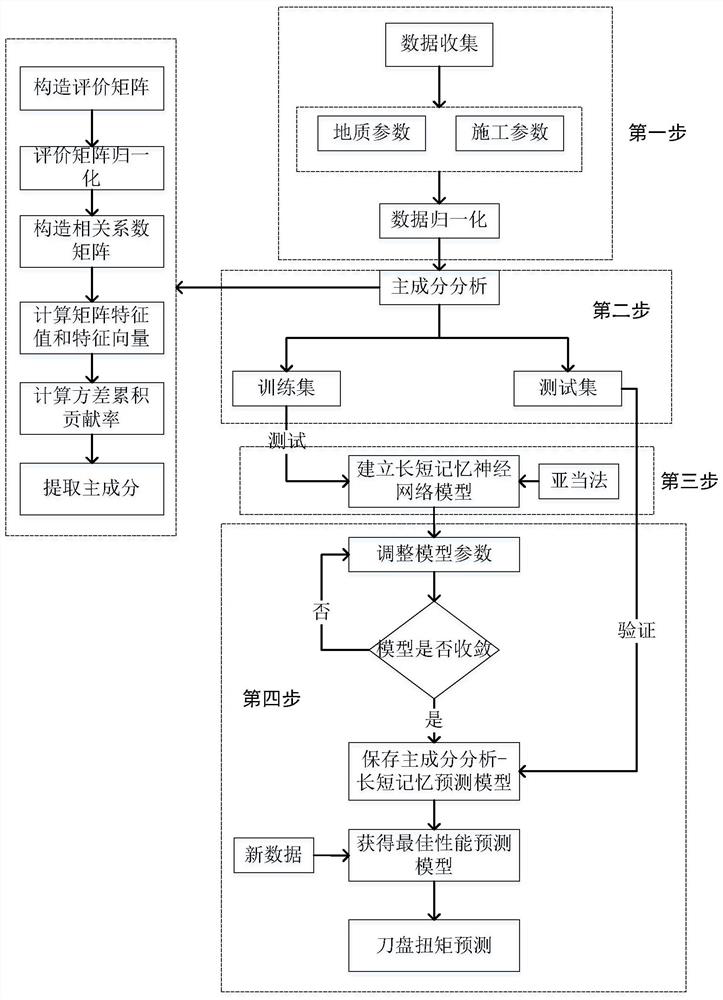
Method for determining torque of cutter head of shield tunneling machine by using principal component analysis-long-short memory model
PendingCN113323676ACause subsidenceCause bulgeMining devicesDesign optimisation/simulationComputational scienceAlgorithm
Owner:SHANGHAI TUNNEL ENGINEERING RAILWAY TRANSPORTATION DESIGN INSTITUTE +1
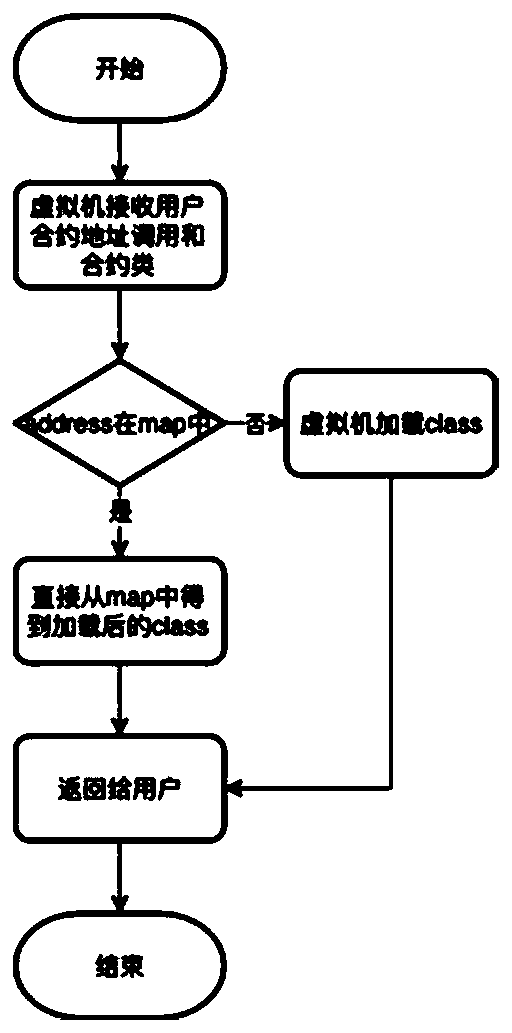
Memory management method for intelligent contract based on JAVA
InactiveCN110908771AImprove execution efficiencyPrevent overflowSoftware simulation/interpretation/emulationSoftware engineeringMemory model
The invention discloses a memory management method for an intelligent contract based on JAVA. According to the method, a JAVA virtual machine is modified, the contract class of the user is cached in the memory, the function that the contract byte code does not need to be repeatedly analyzed when the user sends the request every time is achieved, and meanwhile by modifying a junk collector mechanism of the JAVA virtual machine, management of the life cycle of the contract class is achieved, and the recovery mechanism of the contract class is controlled. According to the method, the memory modeland the garbage collection mechanism of the JAVA virtual machine are modified, so that the virtual machine is more efficient when processing JAVA contract codes, and the processing efficiency of thevirtual machine is improved.
Owner:HANGZHOU QULIAN TECH CO LTD
Verification method and system for second-level cache interface protocol
PendingCN114153680ARapid positioningImprove debugging efficiencyFunctional testingChannel dataInterface protocol
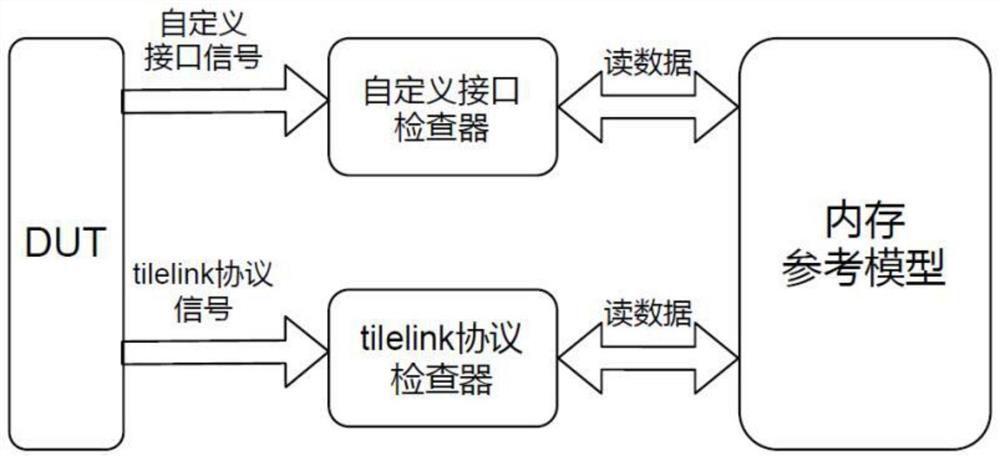
The invention relates to the technical field of multi-core verification, in particular to a verification method and system for a second-level cache interface protocol, and the method comprises the steps: recording key information of each read request when read data is checked, comparing data of a memory model with DUT data when the read data is returned, and checking through protocol agreement when a wake-up request is checked; according to the method, when D or C channel data are checked, data of a memory model is compared with DUT data, and when B / C channels are subjected to rationality check, judgment is carried out according to second-level cache content. According to the method, the second-level cache interface protocol is verified, when data in the protocol goes wrong, error information is reported in real time, it is not needed to wait for a global checker to report errors, error codes can be more effectively and rapidly positioned, and the debugging efficiency is improved.
Owner:GUANGDONG STARFIVE TECH LTD
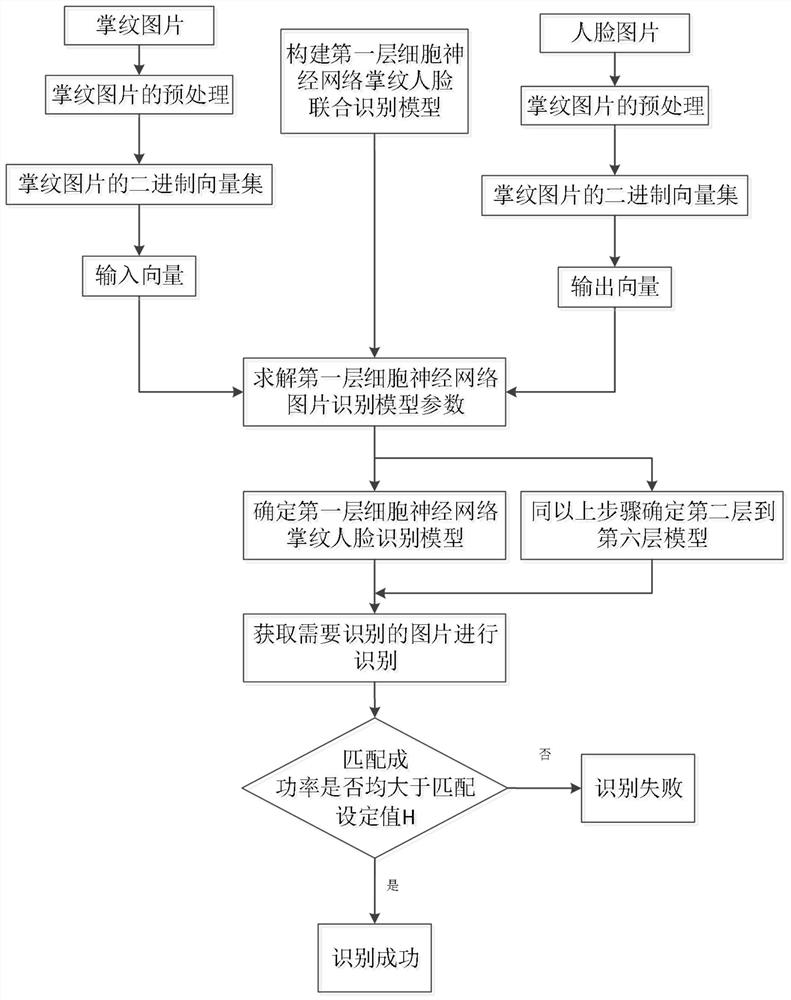
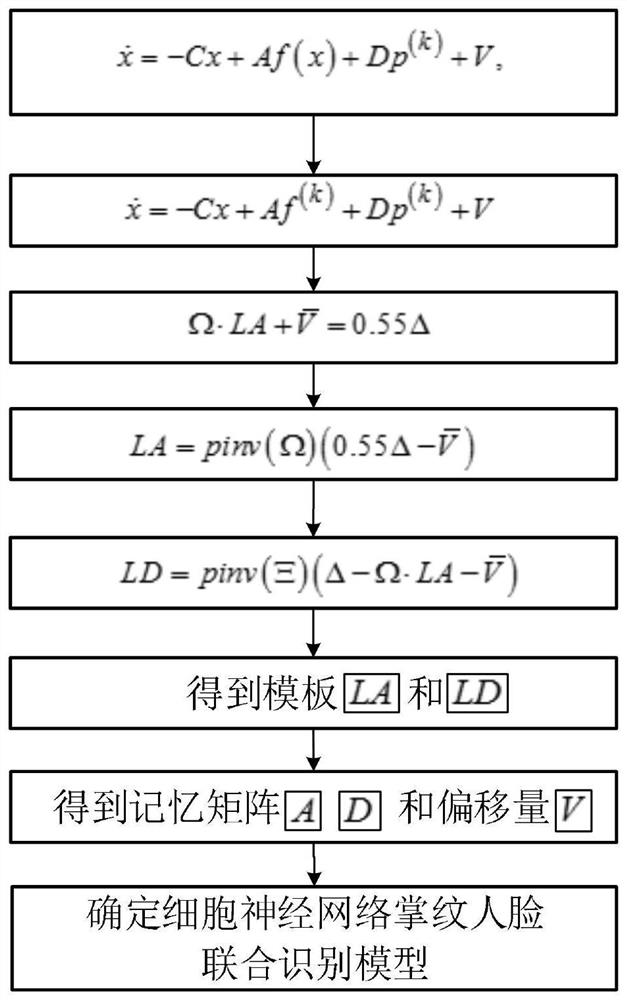
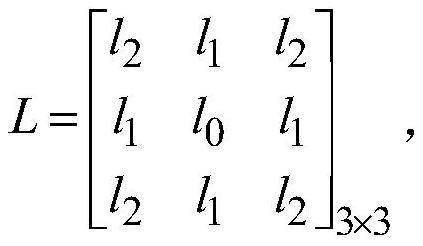
Identity identification method based on cell neural network self associative memory model
InactiveCN107330404AImprove securityPrevent leakageBiometric pattern recognitionMatching and classificationPattern recognitionTransfer procedure
The invention discloses an identity identification method based on a cell neural network self associative memory model. The method includes the steps of acquiring m fingerprint pictures and face pictures, grouping and numbering the pictures, setting the binary image luminance threshold for the fingerprint picture groups and face picture groups, obtaining a binary fingerprint picture set and a binary face picture set, establishing a fingerprint association memory input matrix and output matrix and a face association memory input matrix and output matrix, establishing a cell neural network fingerprint picture identification model with unknown fingerprint model parameters and a cell neural network face picture identification model with unknown face model parameters, determining the cell neural network fingerprint picture identification model, determining the cell neural network face picture identification model, and conducting identification and matching. Trough a data form, leakage during a transmission process is impossible, and the safety is high. The storage volume is small, and the identity identification effect is good.
Owner:CHONGQING UNIVERSITY OF SCIENCE AND TECHNOLOGY
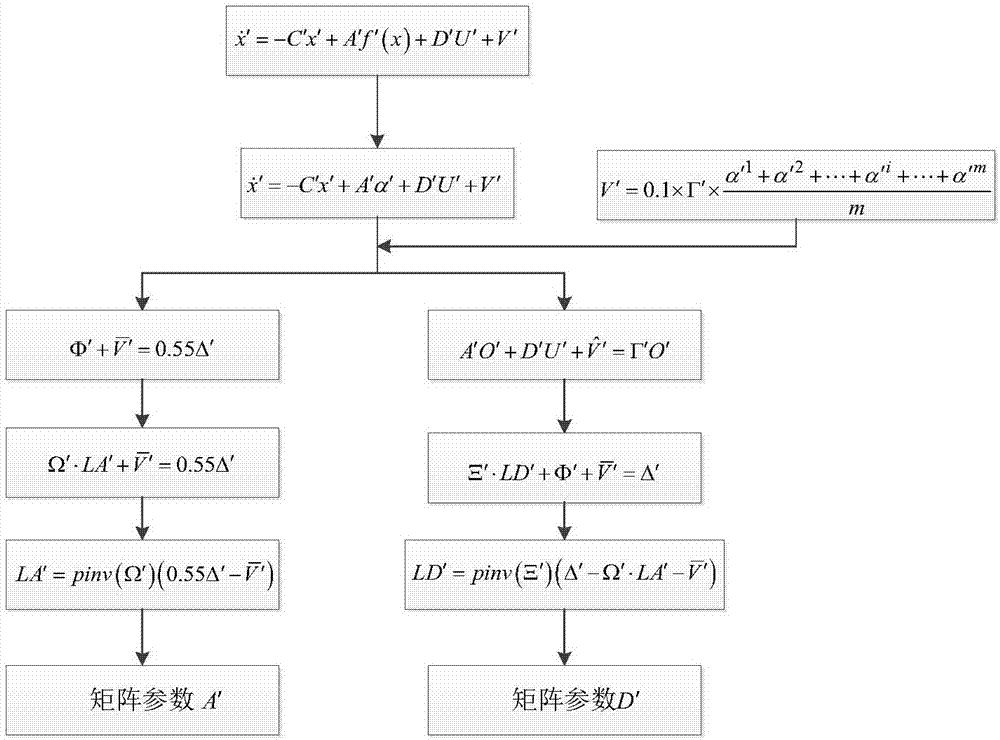
Palmprint and face recognition method based on cellular neural network hetero-associative memory model
ActiveCN111652166AImprove protectionHigh verification reliabilityNeural architecturesMatching and classificationPattern recognitionPalm print
The invention relates to a palmprint and face recognition method based on a cellular neural network hetero-associative memory model, and belongs to the technical field of intelligent recognition. Themethod comprises registration and identification. According to the method, the hetero-associative memory and the cellular neural network model are combined; palm print picture data and face picture data are converted into a series of parameters to be stored, identity information, namely the palm print picture data and the face picture data, is high in verification reliability, the picture storagemode is high in confidentiality and safety coefficient, and the identity information of people is effectively prevented from being leaked. The mode of converting the picture into the parameter throughthe model is adopted, and the method is simple, convenient, good in practicability, good in picture recognition effect and good in face picture data protection effect.
Owner:CHONGQING UNIVERSITY OF SCIENCE AND TECHNOLOGY
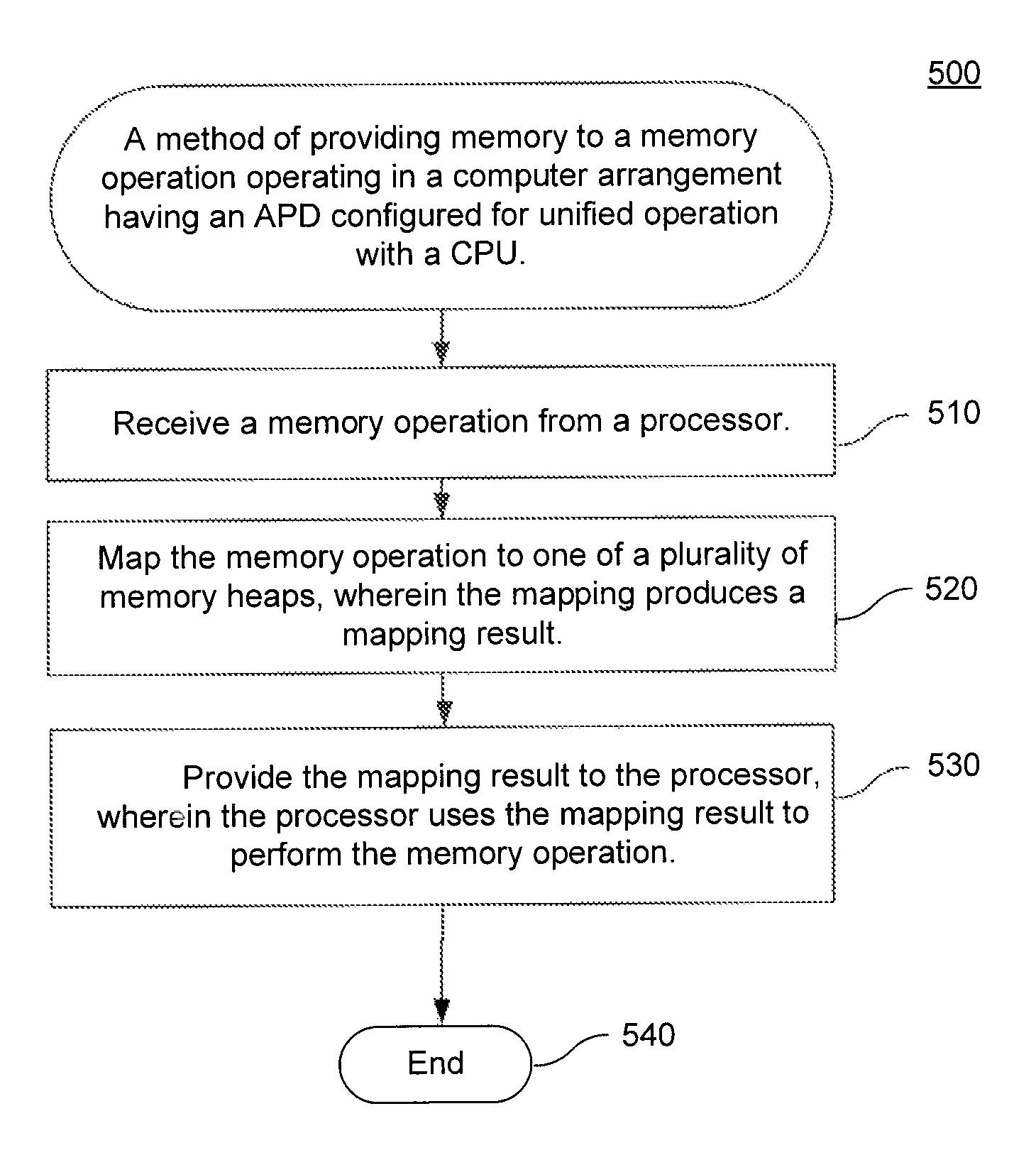
Memory heaps in a memory model for a unified computing system
ActiveUS9116809B2Memory architecture accessing/allocationMemory adressing/allocation/relocationMemory modelTerm memory
A method and system for allocating memory to a memory operation executed by a processor in a computer arrangement having a first processor configured for unified operation with a second processor. The method includes receiving a memory operation from a processor and mapping the memory operation to one of a plurality of memory heaps. The mapping produces a mapping result. The method also includes providing the mapping result to the processor.
Owner:ATI TECH INC +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com