Patents
Literature
3404 results about "Software modules" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Software modules include a complete range of ETSI / ITU / IEEE compliant algorithms, in addition to many other standard and proprietary algorithms.These libraries are modular and can be executed as a single task under a variety of operating systems or standalone with its own microkernel.
Method and system for enabling connectivity to a data system
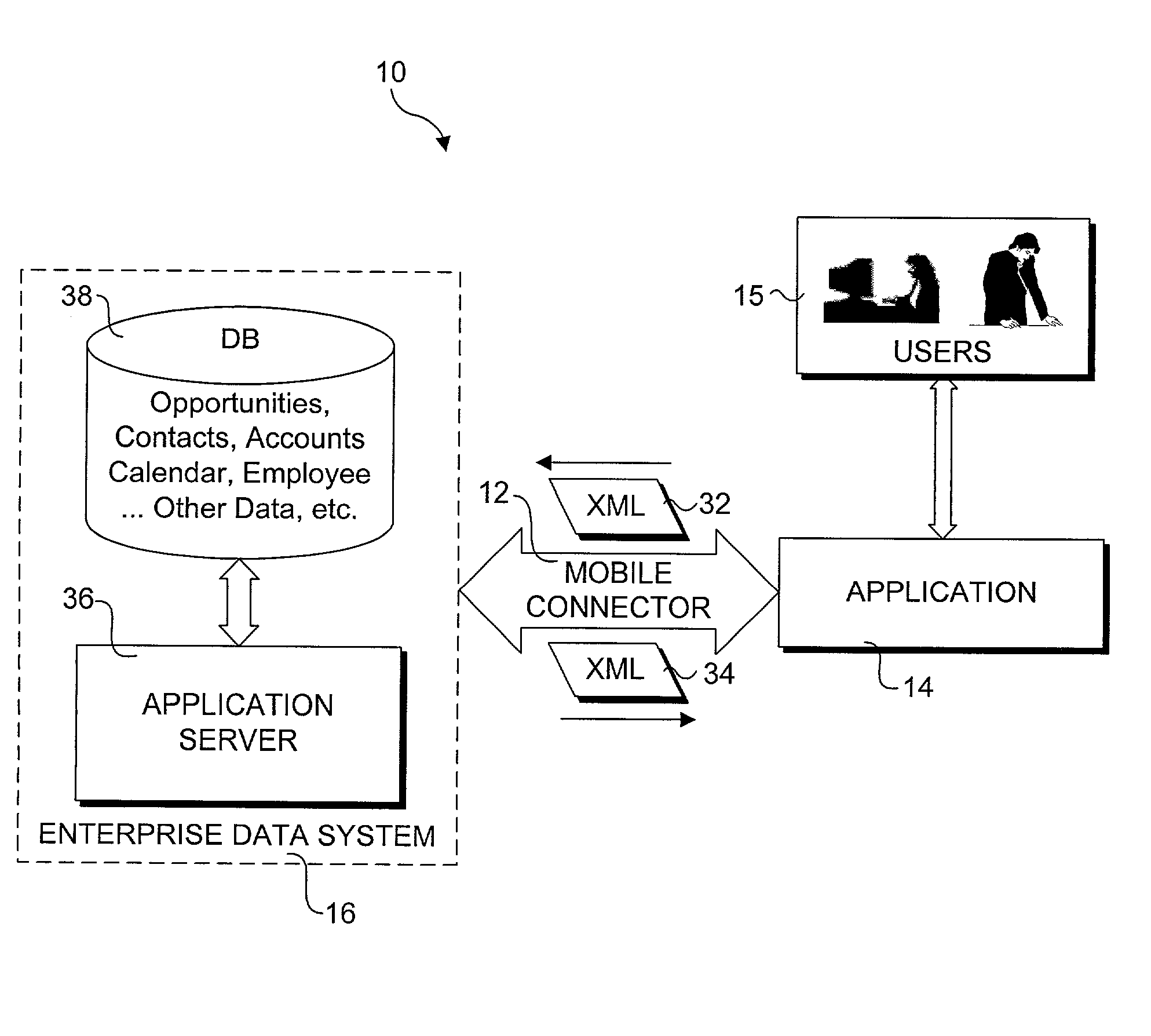
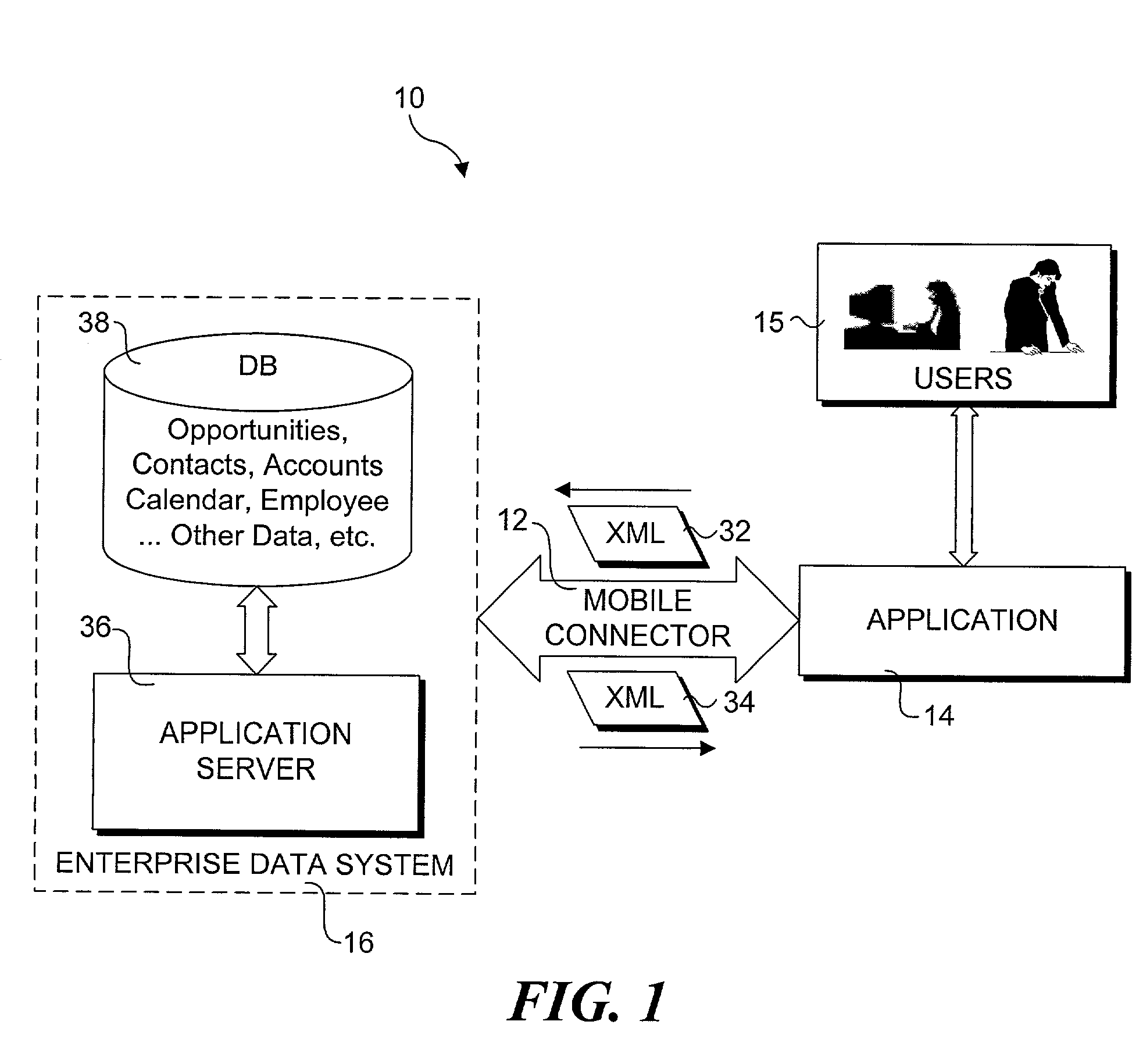
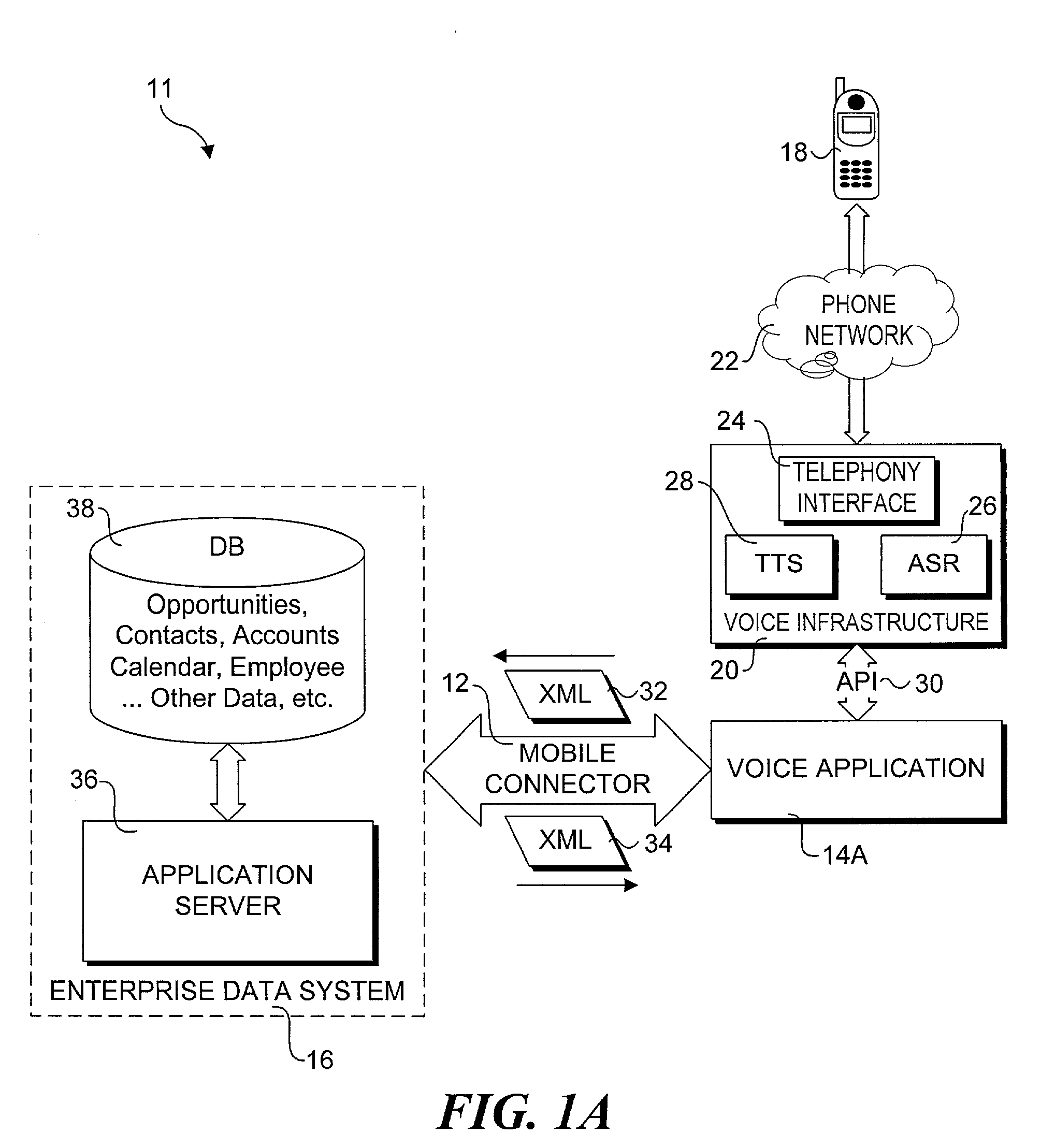
A method and system that provides filtered data from a data system. In one embodiment the system includes an API (application programming interface) and associated software modules to enable third party applications to access an enterprise data system. Administrators are enabled to select specific user interface (UI) objects, such as screens, views, applets, columns and fields to voice or pass-through enable via a GUI that presents a tree depicting a hierarchy of the UI objects within a user interface of an application. An XSLT style sheet is then automatically generated to filter out data pertaining to UI objects that were not voice or pass-through enabled. In response to a request for data, unfiltered data are retrieved from the data system and a specified style sheet is applied to the unfiltered data to return filtered data pertaining to only those fields and columns that are voice or pass-through enabled.
Owner:ORACLE INT CORP
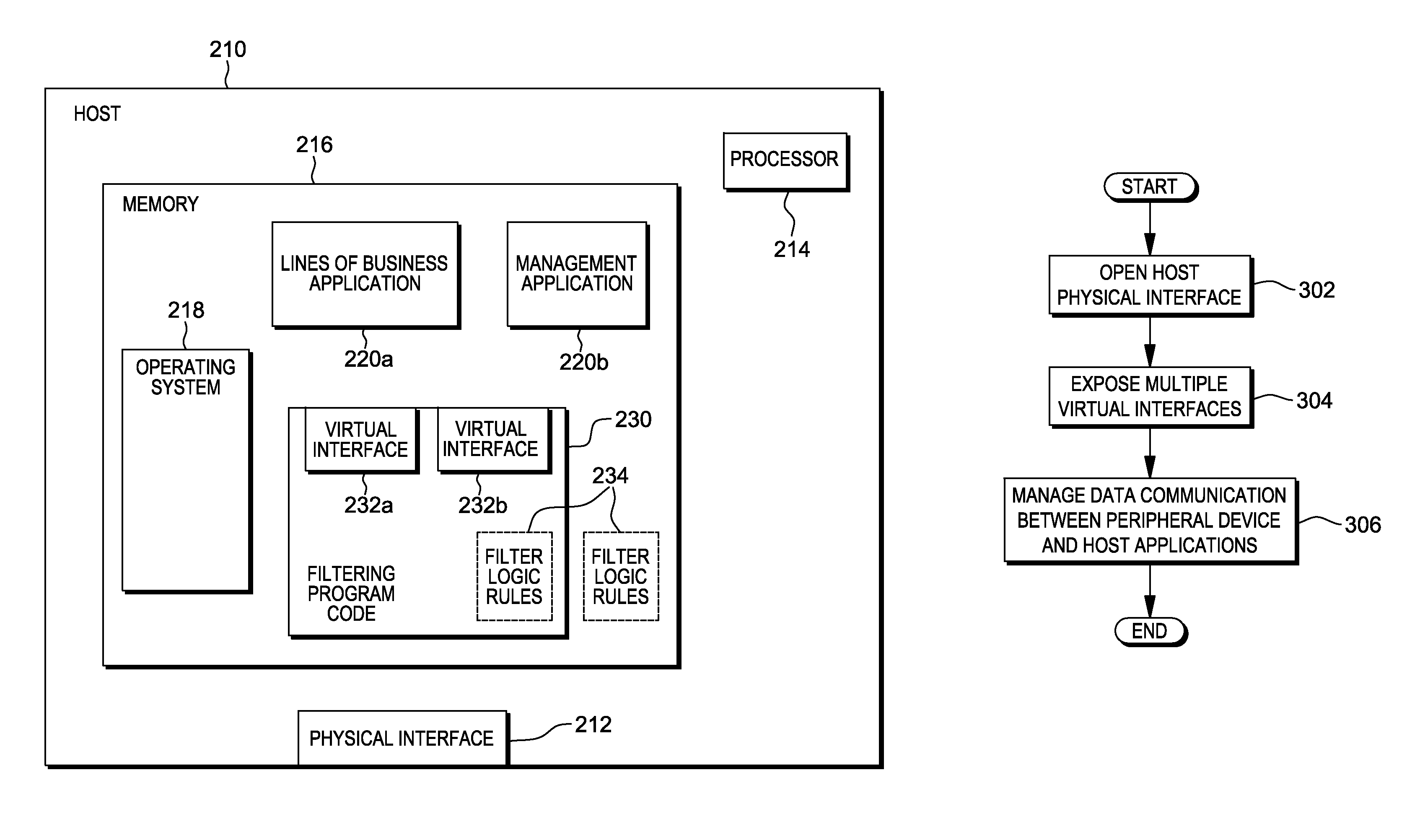
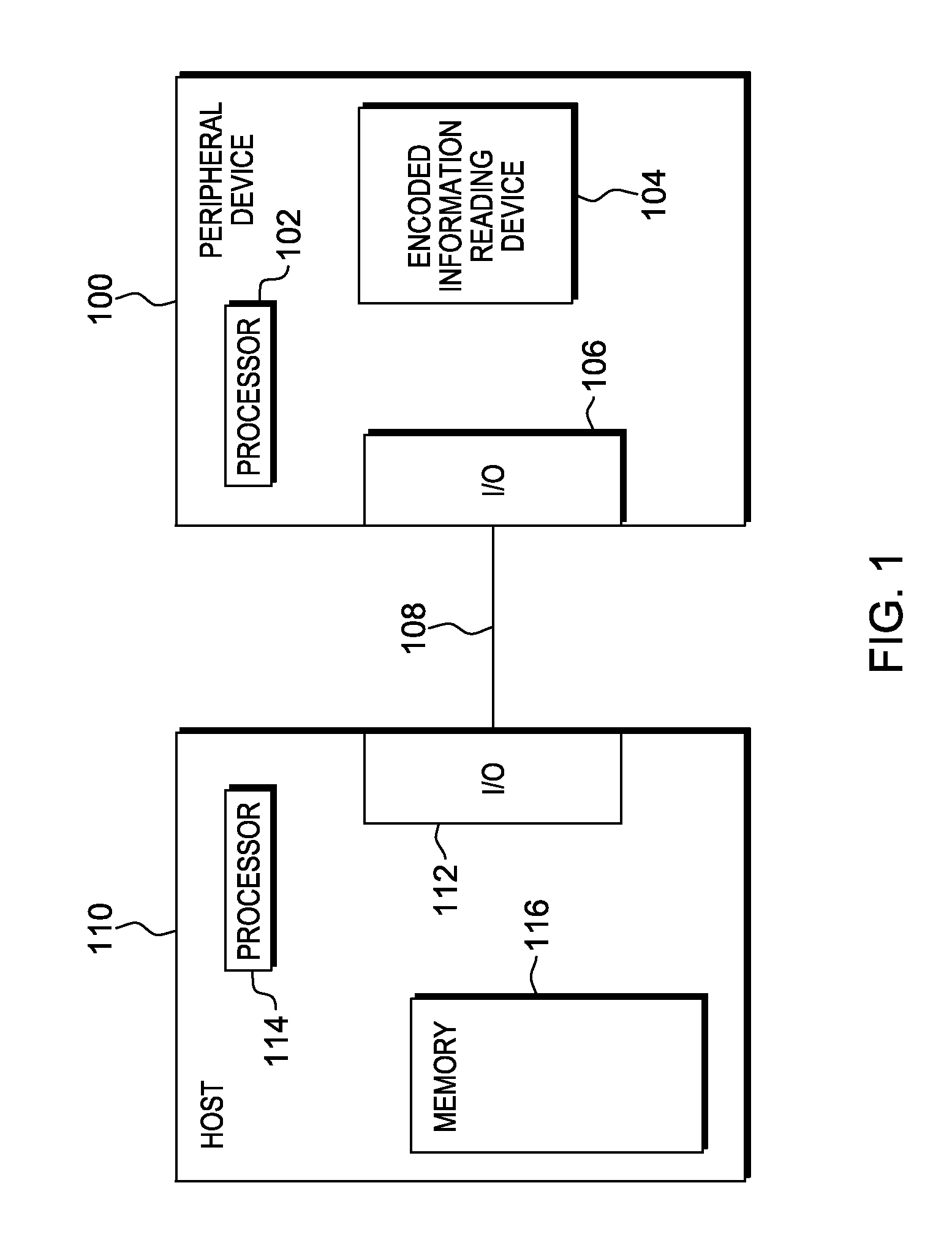
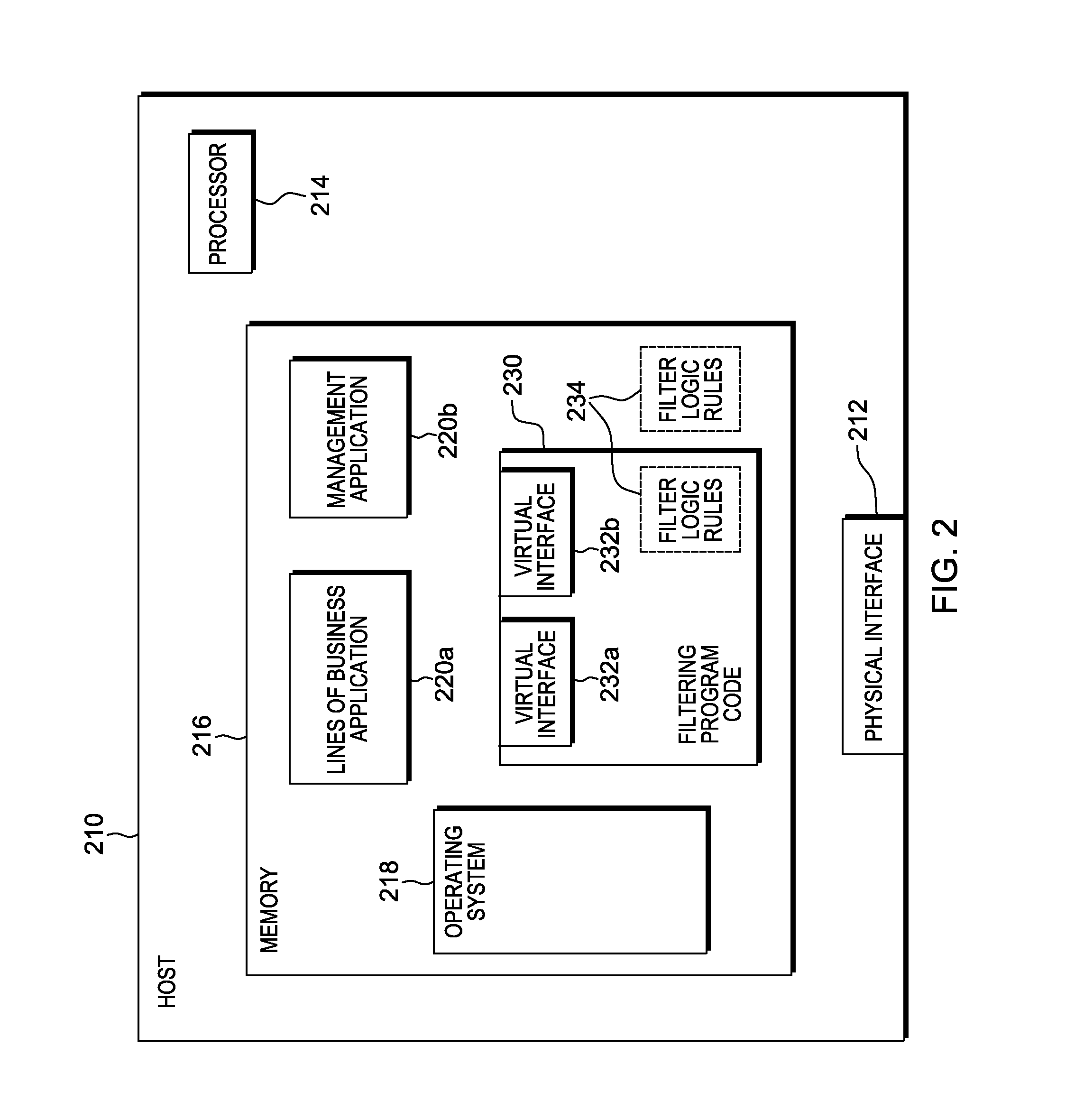
Device management using virtual interfaces
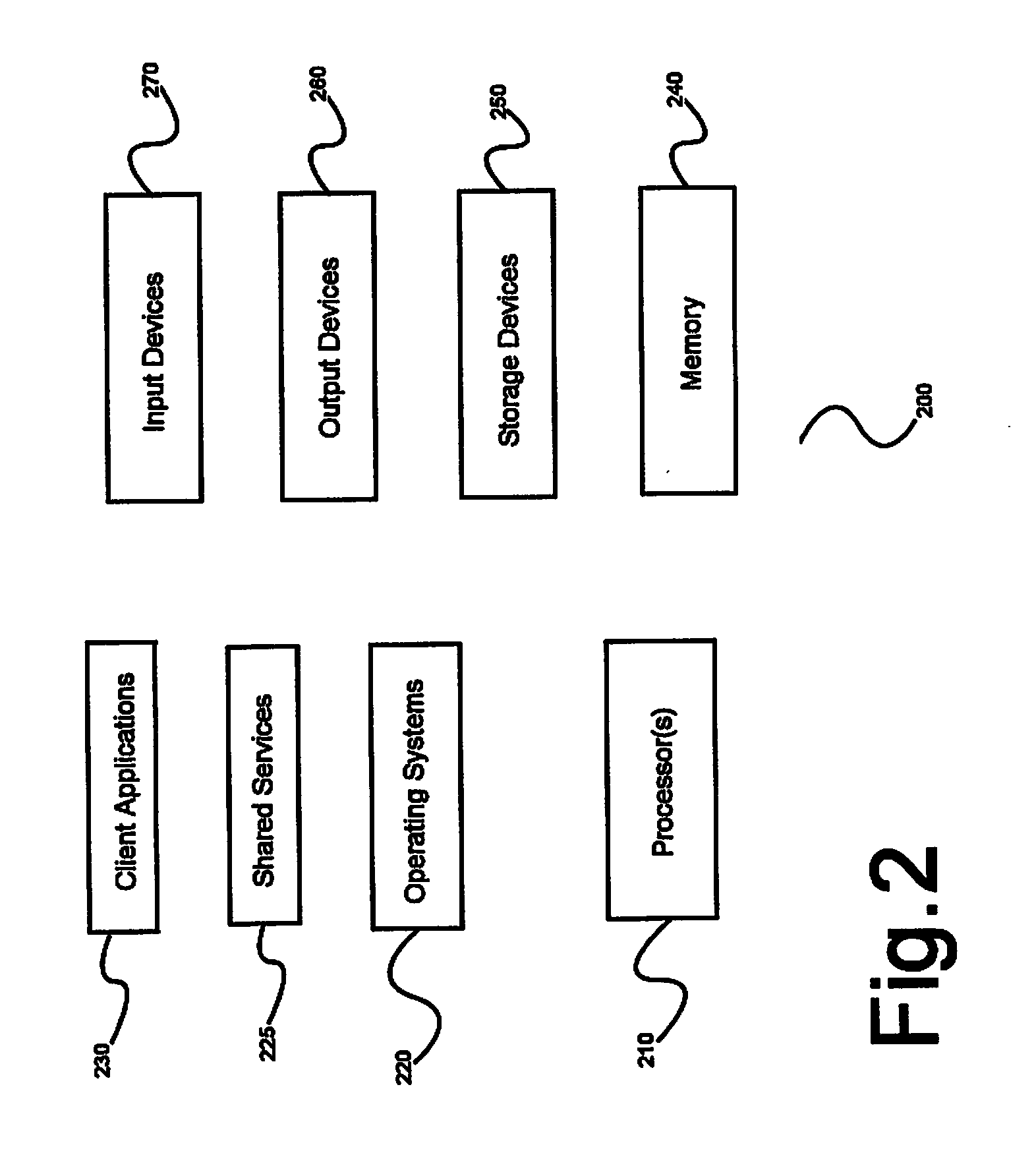
ActiveUS8621123B2Program controlInput/output processes for data processingOperational systemComputerized system
Management of data communication between a peripheral device and host computer system is provided. A physical interface for communicating data between a peripheral device and applications executing on the host is opened and controlled by a software module. First and second virtual interfaces of the software module are exposed to an operating system of the host, and the operating system exposes the first and second virtual interfaces to a first application and a second application executing on the host. The first virtual interface is used for communicating data between the peripheral device and the first application through the physical interface, and the second virtual interface is used for communicating data between the peripheral device and the second application through the physical interface. Management of data communication between the peripheral device and the first application and between the peripheral device and the second application is thereby provided.
Owner:HONEYWELL INT INC
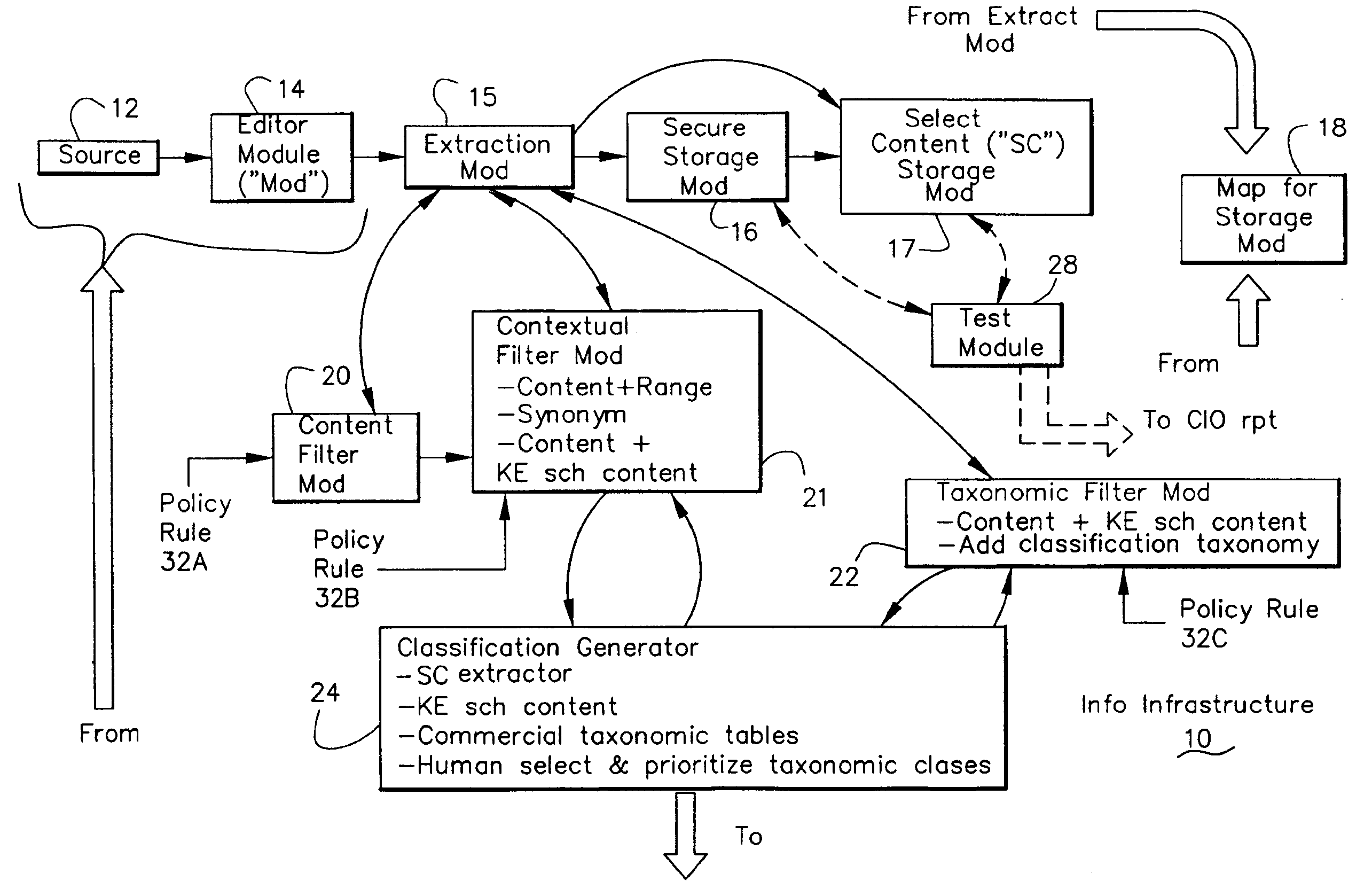
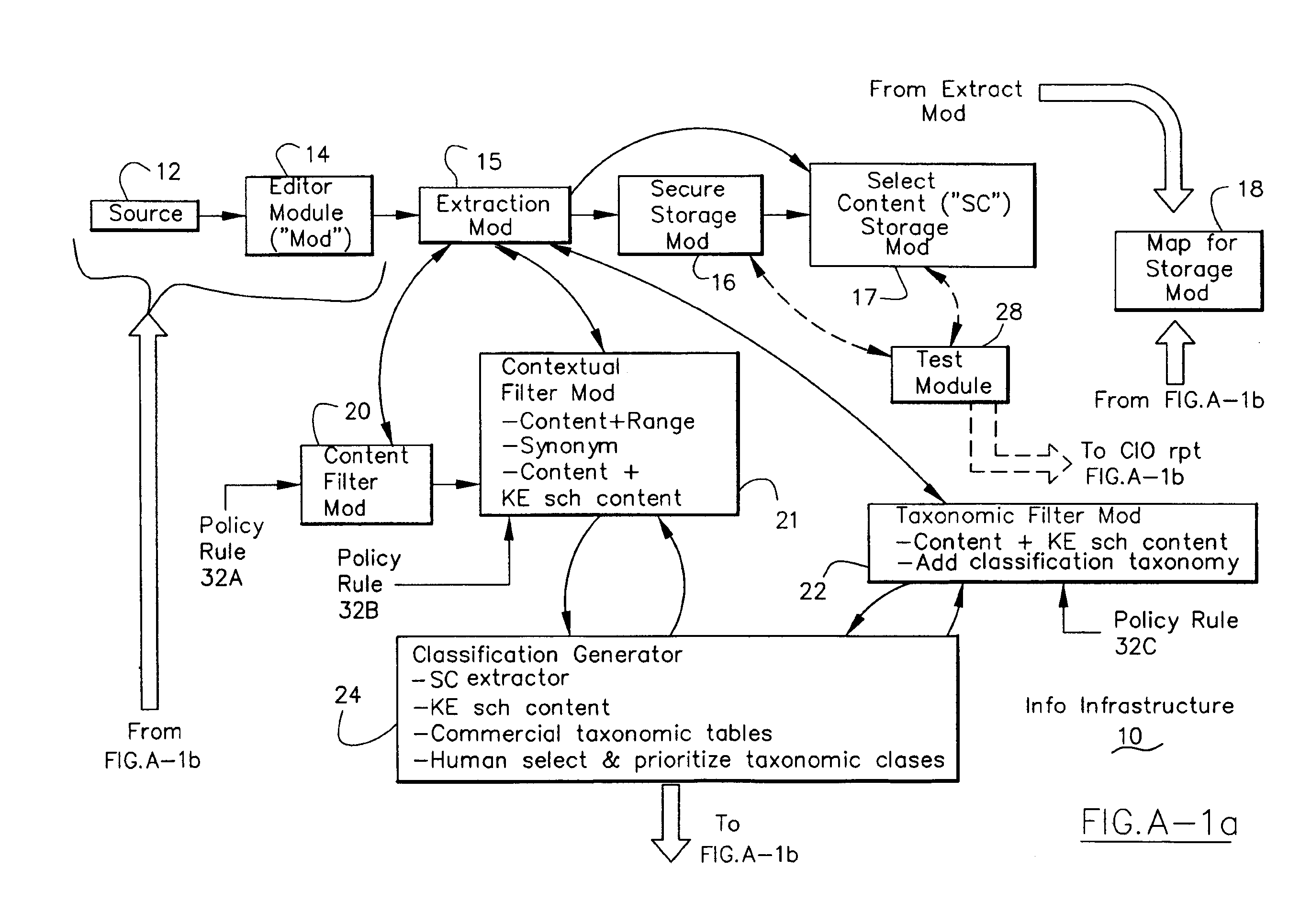
Information Infrastructure Management Tools with Extractor, Secure Storage, Content Analysis and Classification and Method Therefor
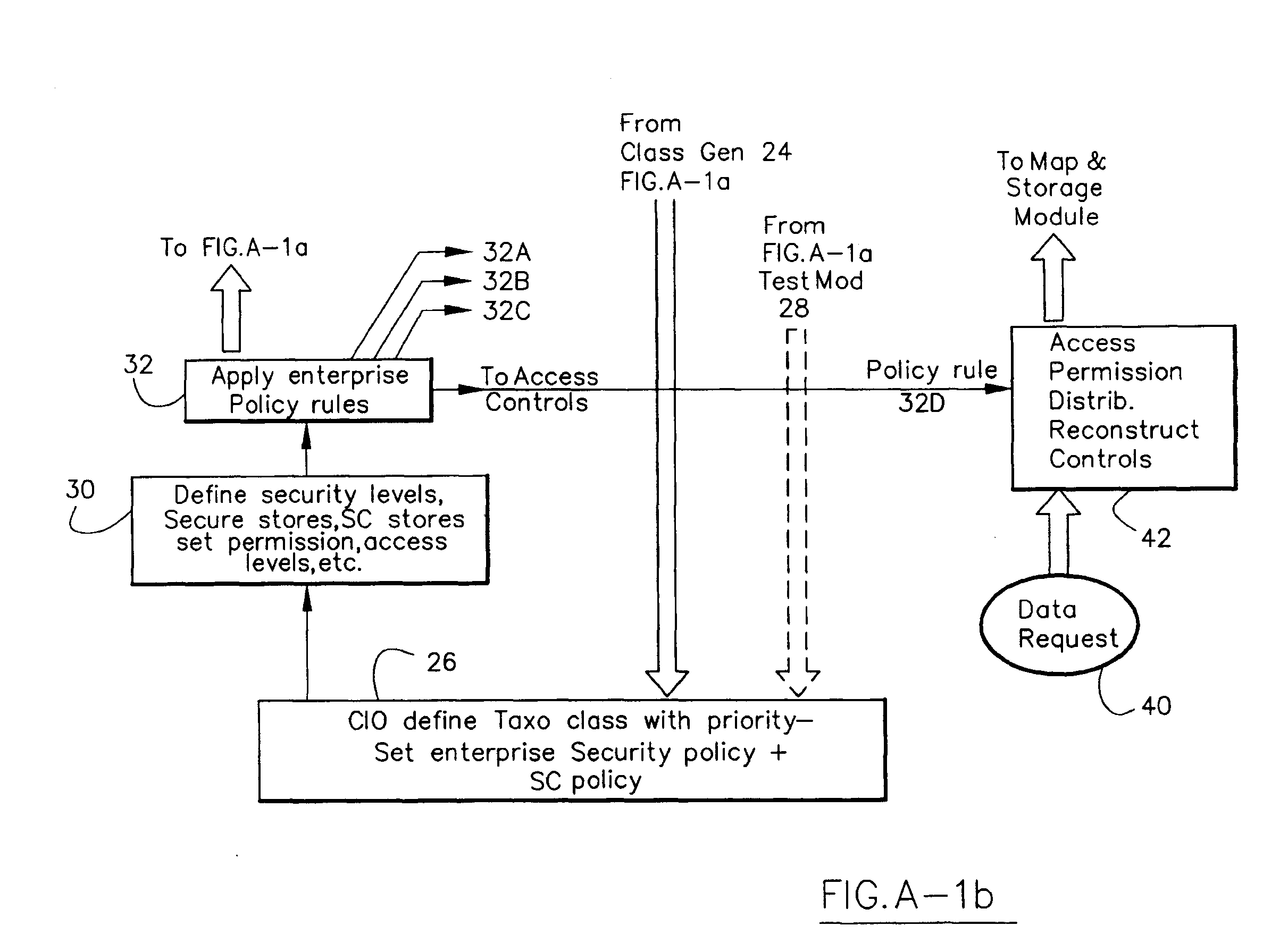
The present invention is a method of organizing and processing data in a distributed computing system. The invention is also implemented as a computer program on a computer medium and as a distributed computer system. Software modules can be configured as hardware. The method and system organizes select content which is important to an enterprise operating said distributed computing system. The select content is represented by one or more predetermined words, characters, images, data elements or data objects. The computing system has a plurality of select content data stores for respective ones of a plurality of enterprise designated categorical filters which include content-based filters, contextual filters and taxonomic classification filters, all operatively coupled over a communications network. A data input is processed through at least one activated categorical filter to obtain select content, and contextually associated select content and taxonomically associated select content as aggregated select content. The aggregated select content is stored in the corresponding select content data store. A data process from the group of data processes including a copy process, a data extract process, a data archive process, a data distribution process and a data destruction process is associated with the activated categorical filter and the method and system applies the associated data process to a further data input based upon a result of that further data being processed by the activated categorical filter utilizing the aggregated select content data.
Owner:DIGITAL DOORS
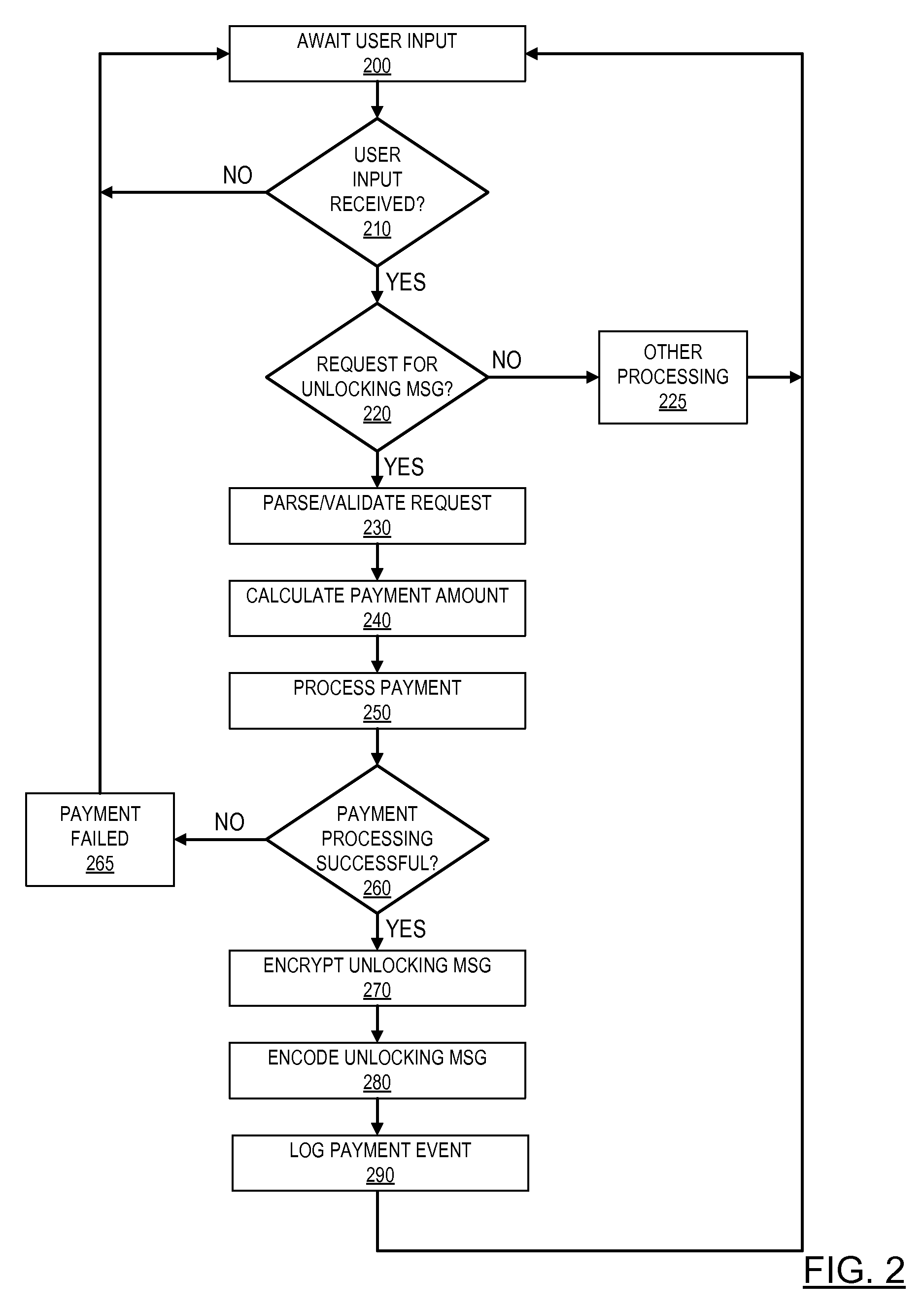
Pre-paid usage system for encoded information reading terminals
A fleet management system for managing a fleet of encoded information reading (EIR) terminals can comprise one or more computers, a fleet management software module, and a payment processing software module in communication with the fleet management software module. The fleet management software module can be configured, responsive to receiving a customer initiated request, to generate an unlocking message upon processing a payment by the payment processing software module. The unlocking message can be provided by a bar code to be read by an EIR terminal, or by a bit stream to be transferred to an EIR terminal via network. Each EIR terminal can be configured to perform not more than a pre-defined number of EIR operations responsive to receiving the unlocking message.
Owner:METROLOGIC INSTR
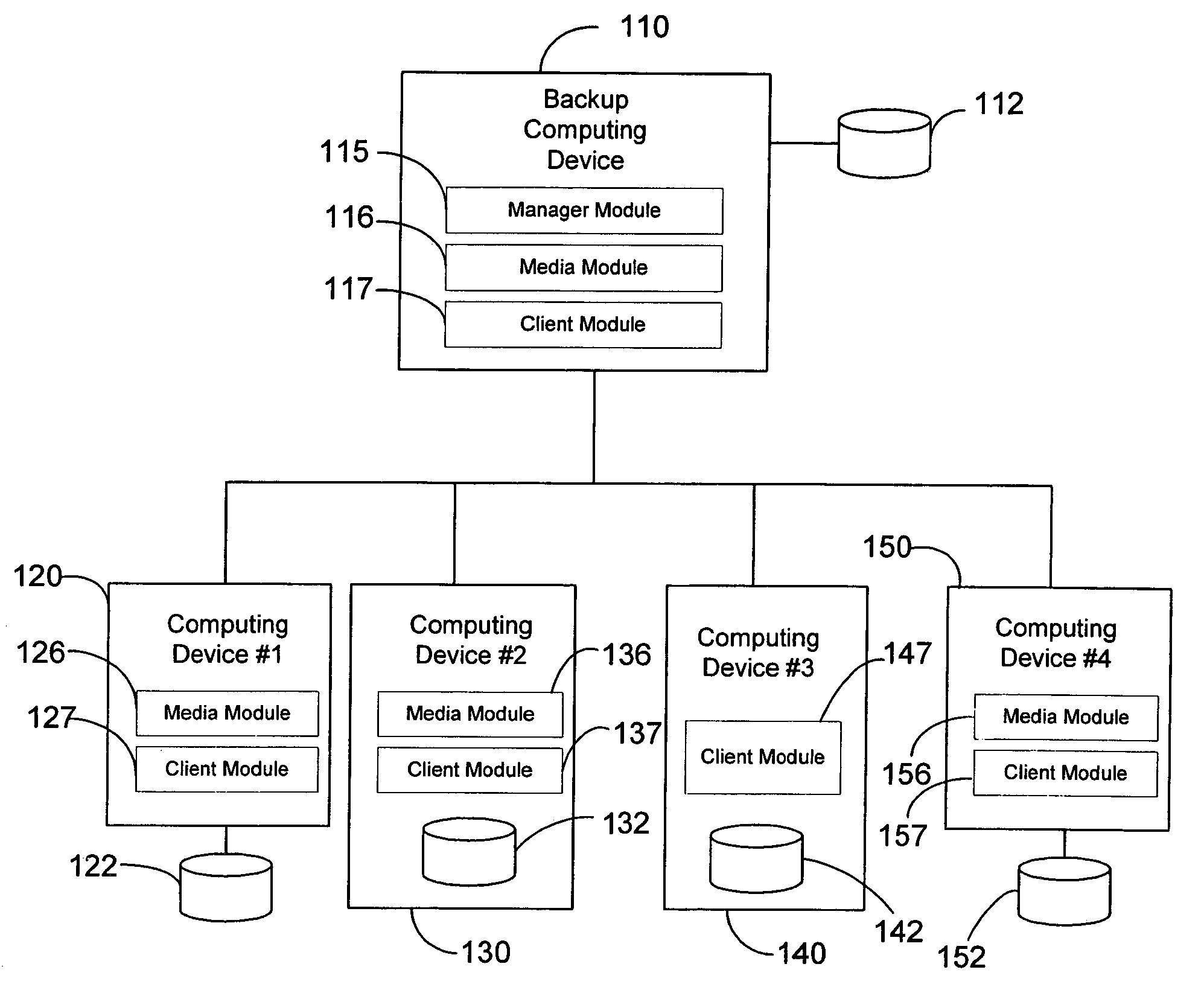
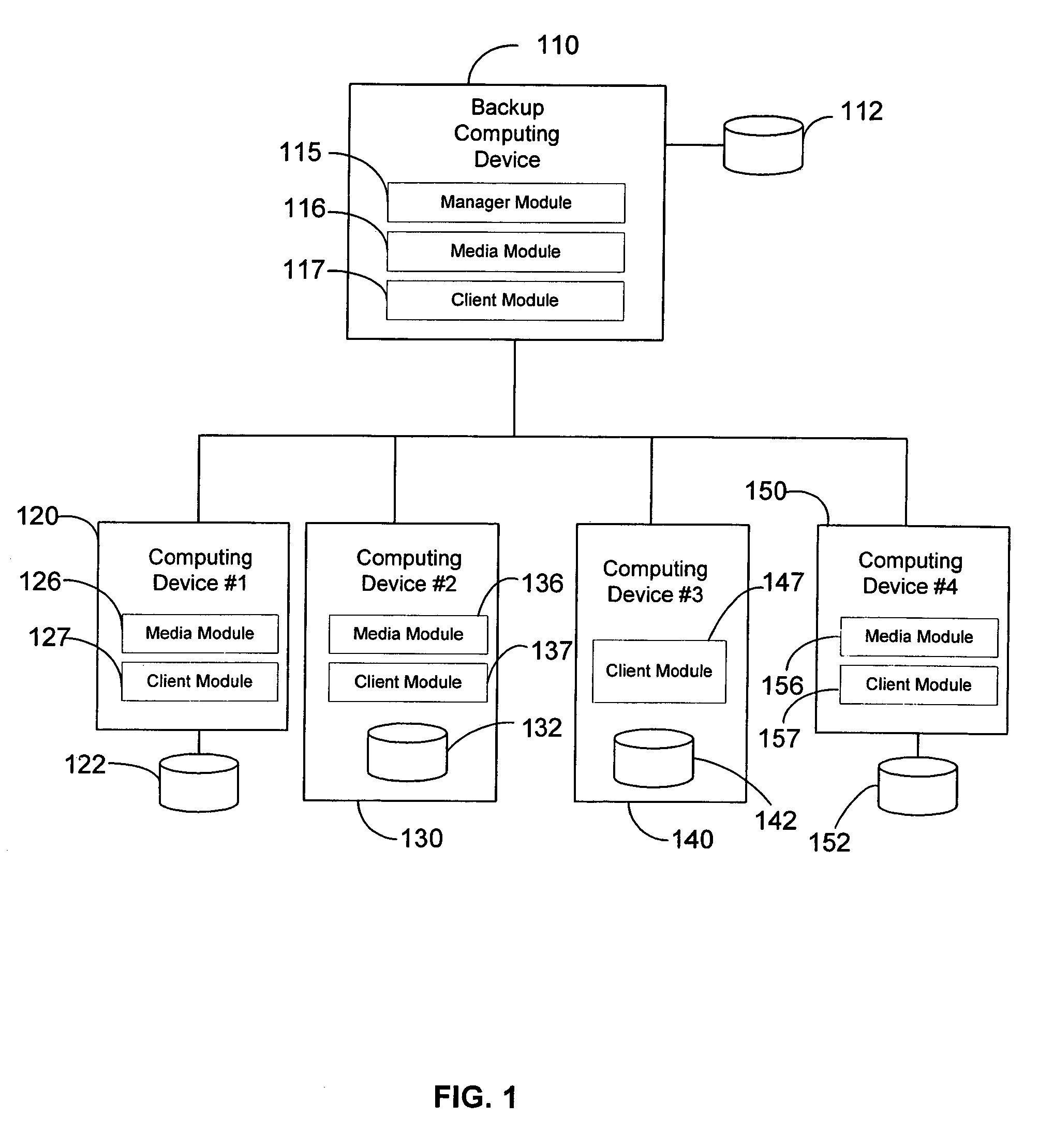
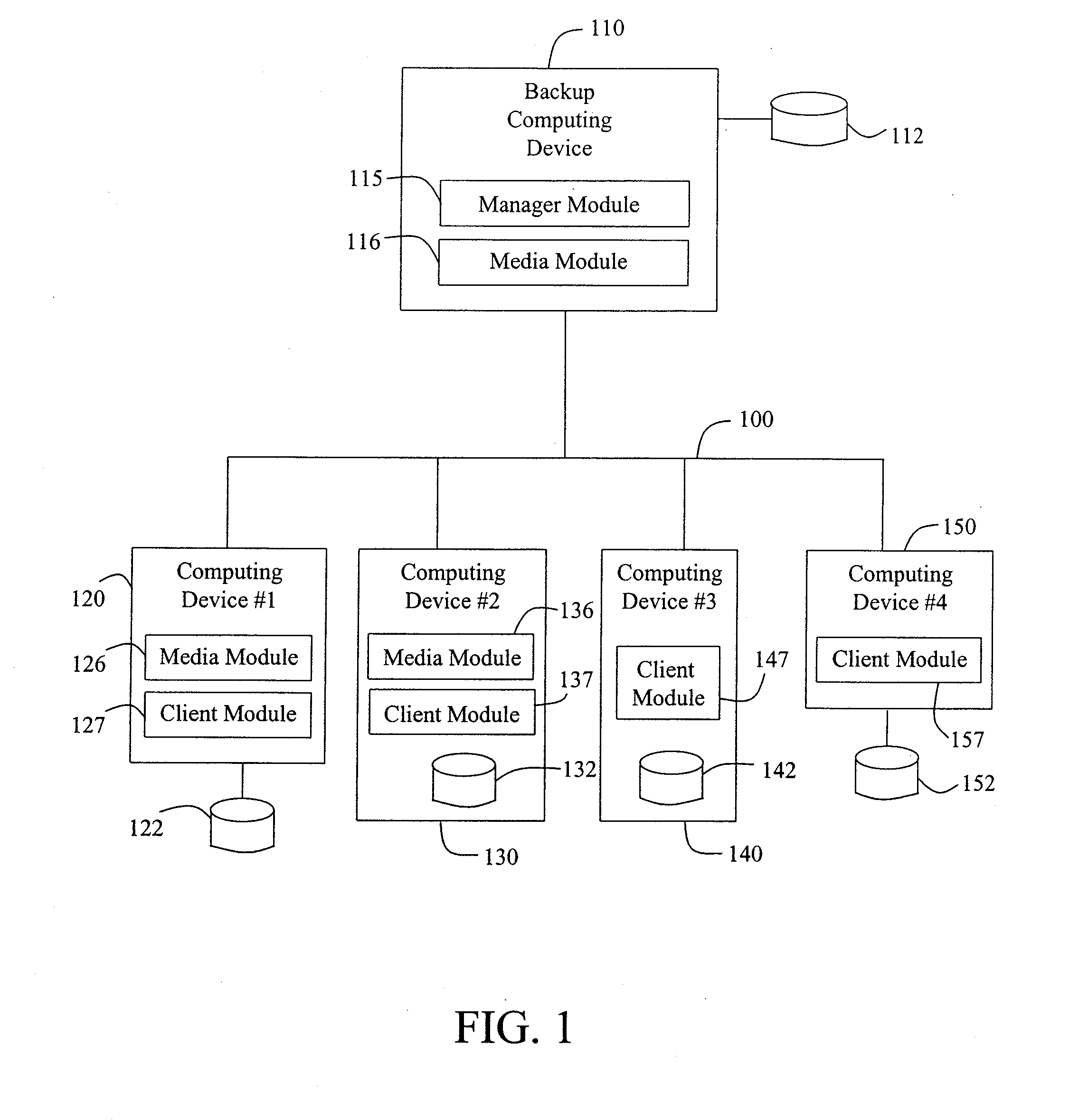
Modular backup and retrieval system
InactiveUS7389311B1Data processing applicationsDigital data processing detailsSystems managementModularity
Owner:COMMVAULT SYST INC
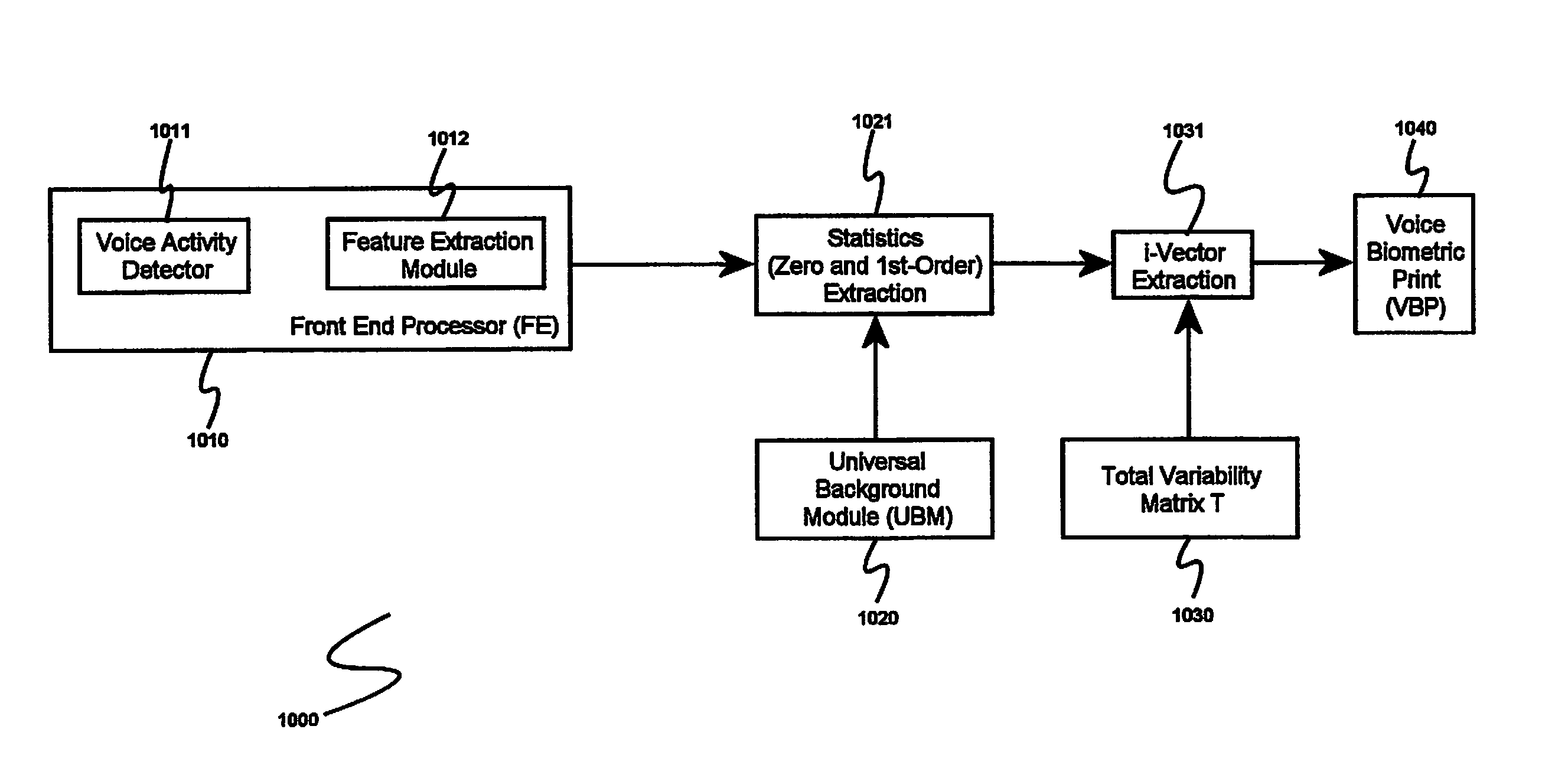
System and method for speaker recognition on mobile devices
InactiveUS20130225128A1Reduce storageReduce processUnauthorised/fraudulent call preventionEavesdropping prevention circuitsSpeaker recognition systemMobile device
A speaker recognition system for authenticating a mobile device user includes an enrollment and learning software module, a voice biometric authentication software module, and a secure software application. Upon request by a user of the mobile device, the enrollment and learning software module displays text prompts to the user, receives speech utterances from the user, and produces a voice biometric print. The enrollment and training software module determines when a voice biometric print has met at least a quality threshold before storing it on the mobile device. The secure software application prompts a user requiring authentication to repeat an utterance based at least on an attribute of a selected voice biometric print, receives a corresponding utterance, requests the voice biometric authentication software module to verify the identity of the second user using the utterance, and, if the user is authenticated, imports the voice biometric print.
Owner:CIRRUS LOGIC INC
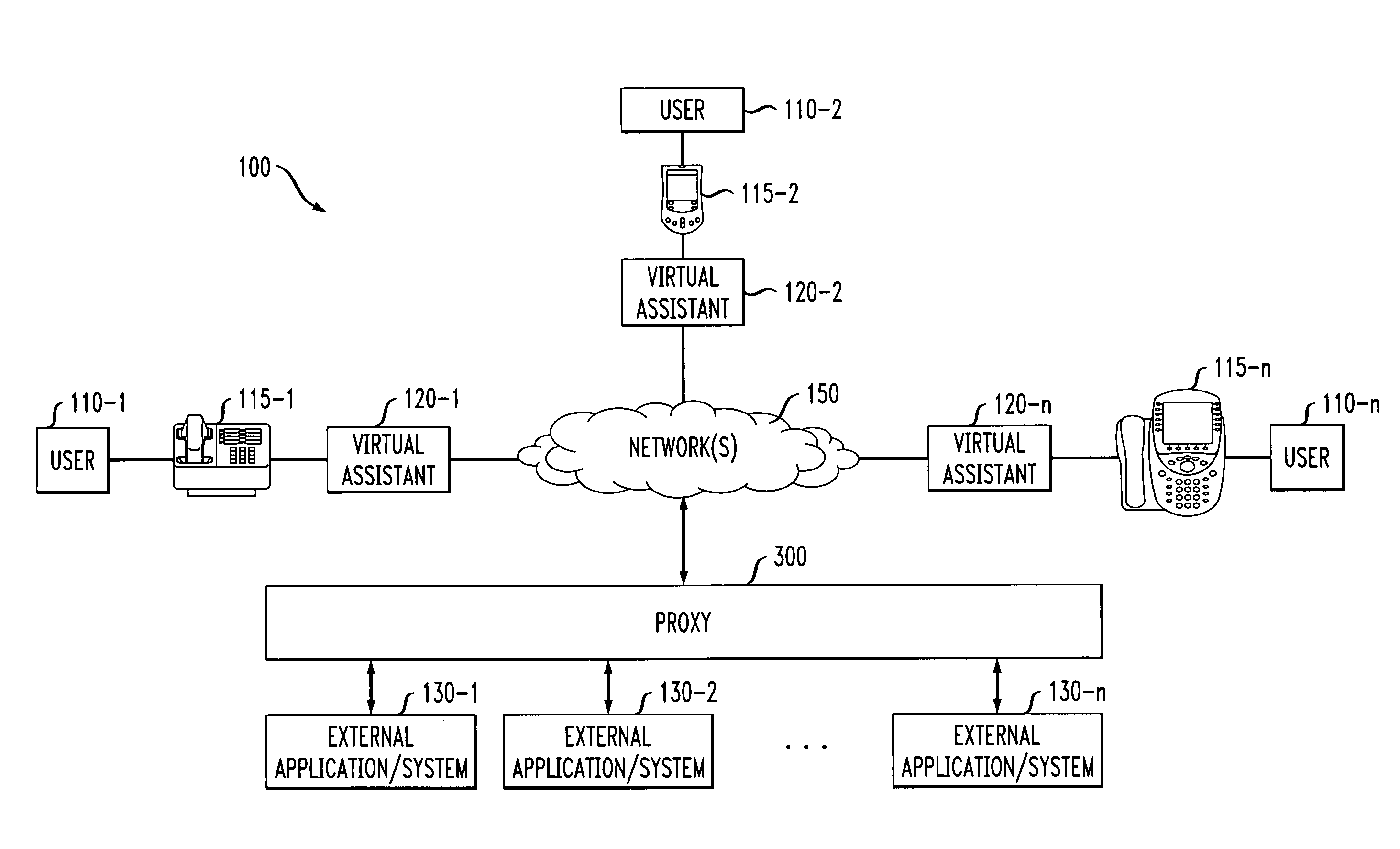
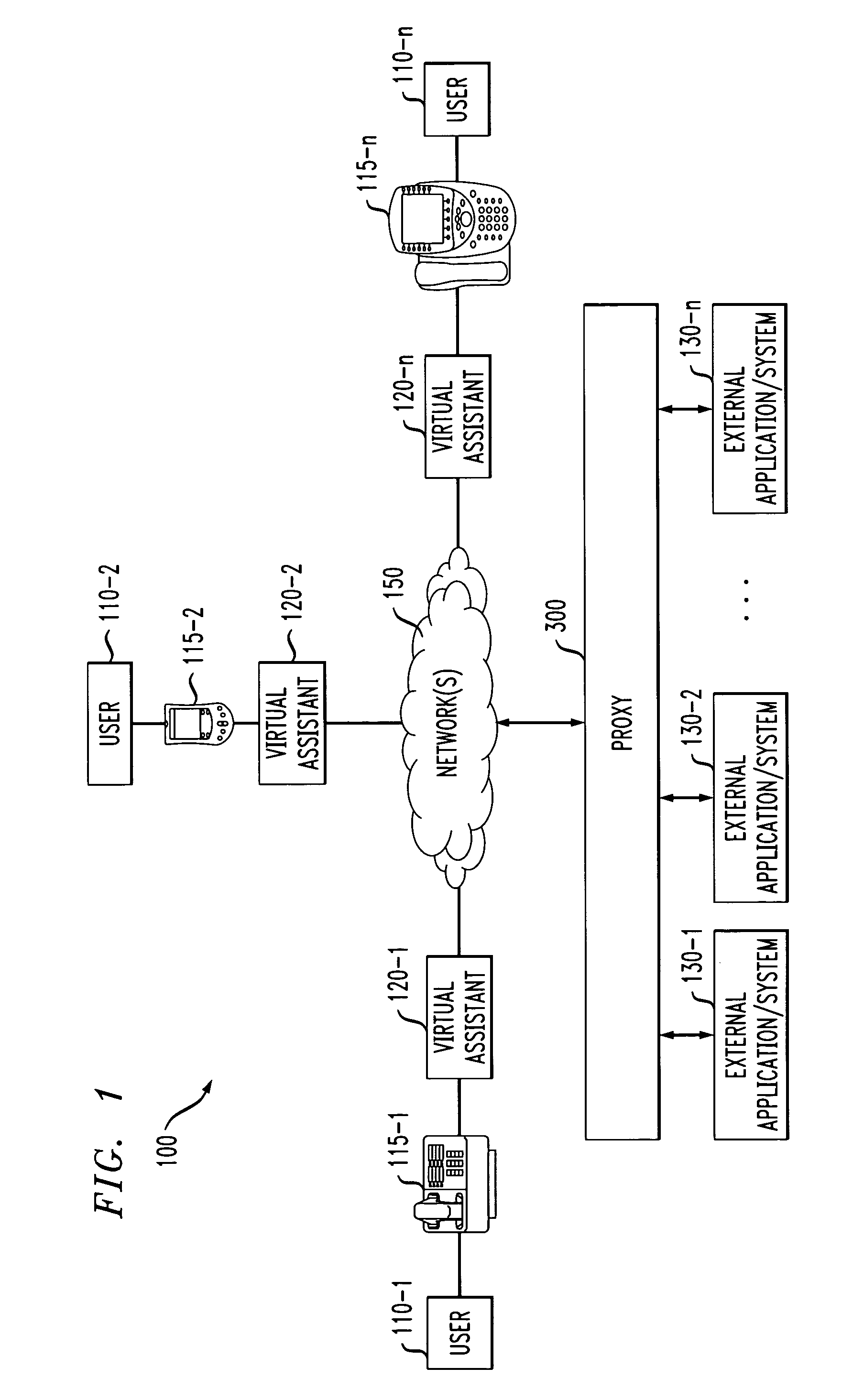
Method and apparatus for providing a virtual assistant to a communication participant
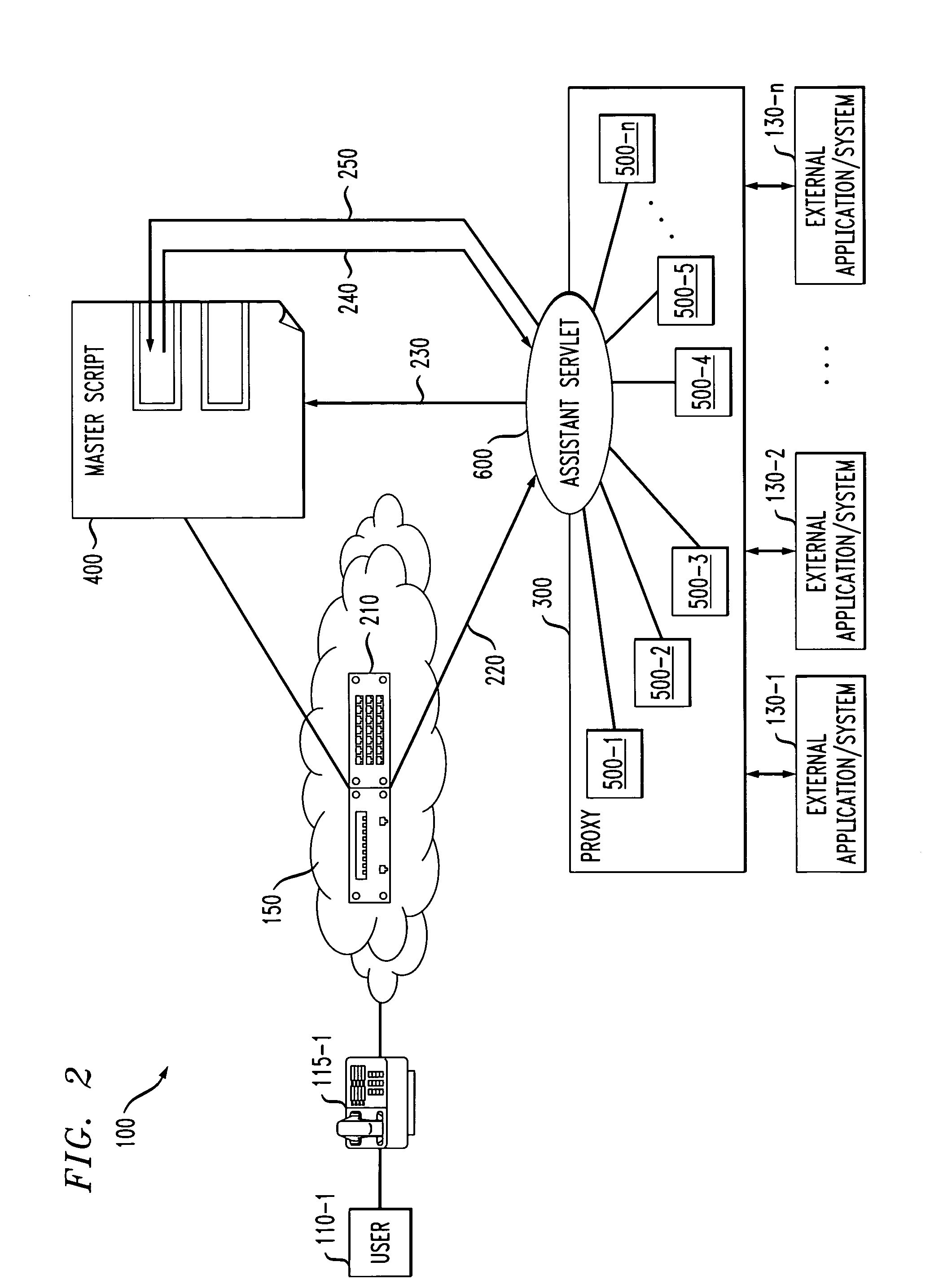
ActiveUS8107401B2Special service provision for substationMultiplex system selection arrangementsExternal applicationComputer module
Methods and apparatus are disclosed for providing a virtual assistant to at least one party of a communication. The virtual assistant is injected into the communication, for example, by a VXML engine. The operation of the virtual assistant is controlled by one or more software modules that are obtained from a proxy node. The software modules allow commands received from or destined for the party to be interpreted. The virtual assistant may optionally be customized based on a selection of the one or more supported external applications. The proxy node provides at least one method for the party that allows the party to access functionality provided by at least one external application. The proxy node interprets signals from the virtual assistant; converts the signals from the virtual assistant into commands for the external application; and converts one or more of commands, messages and data from the external application into signals understood by the virtual assistant.
Owner:AVAYA INC
System and Method for Processor-Based Security
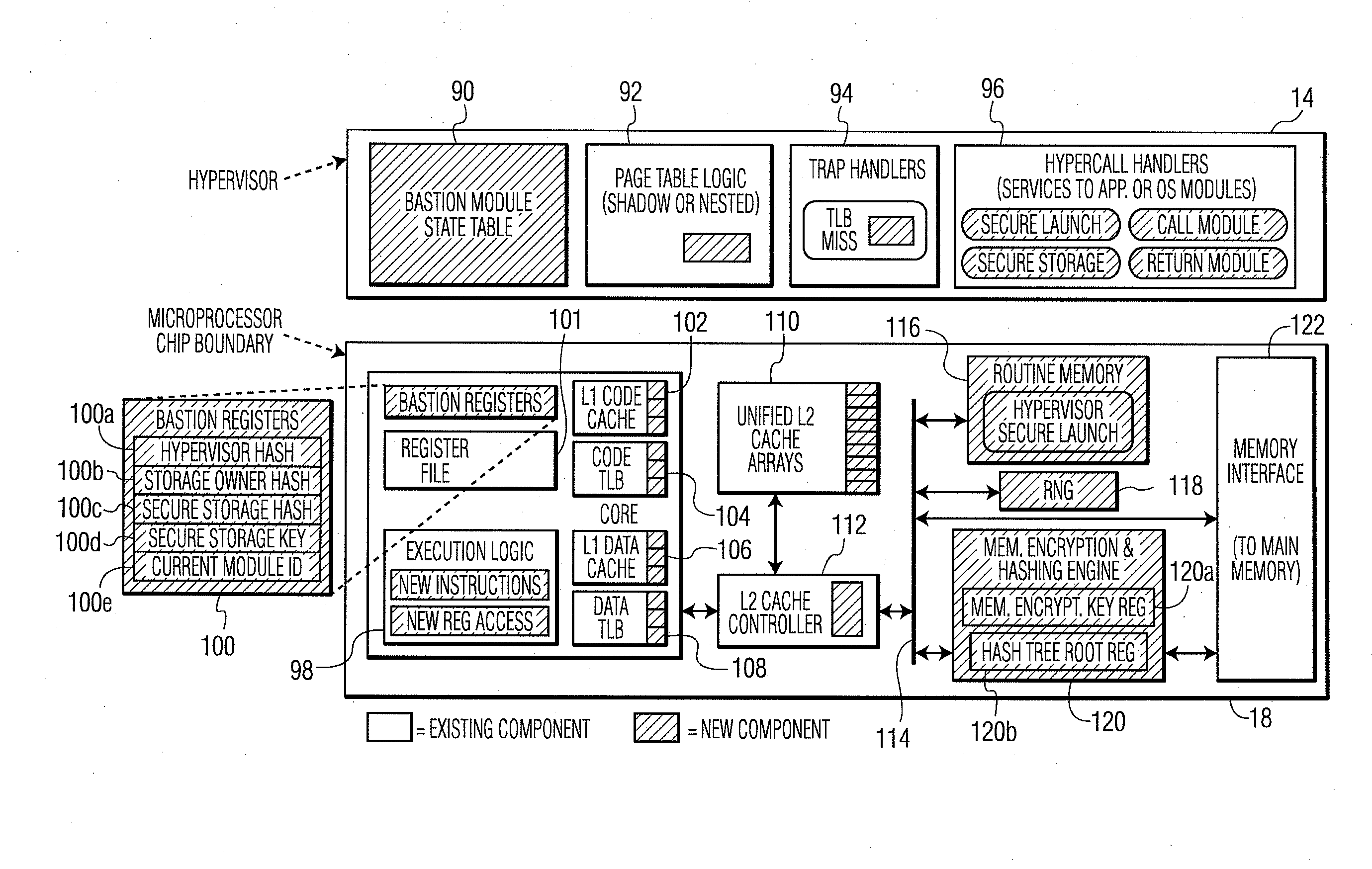
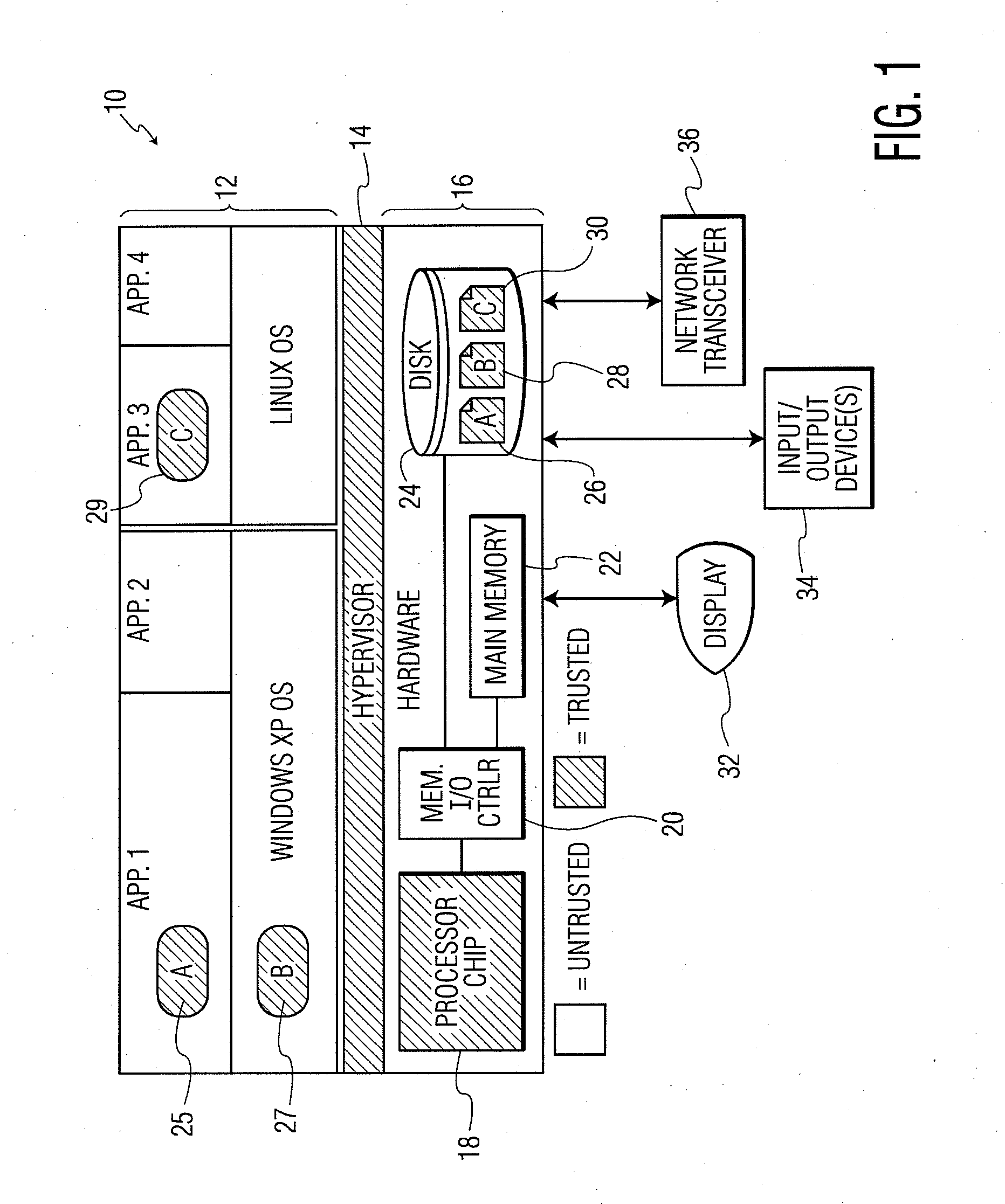
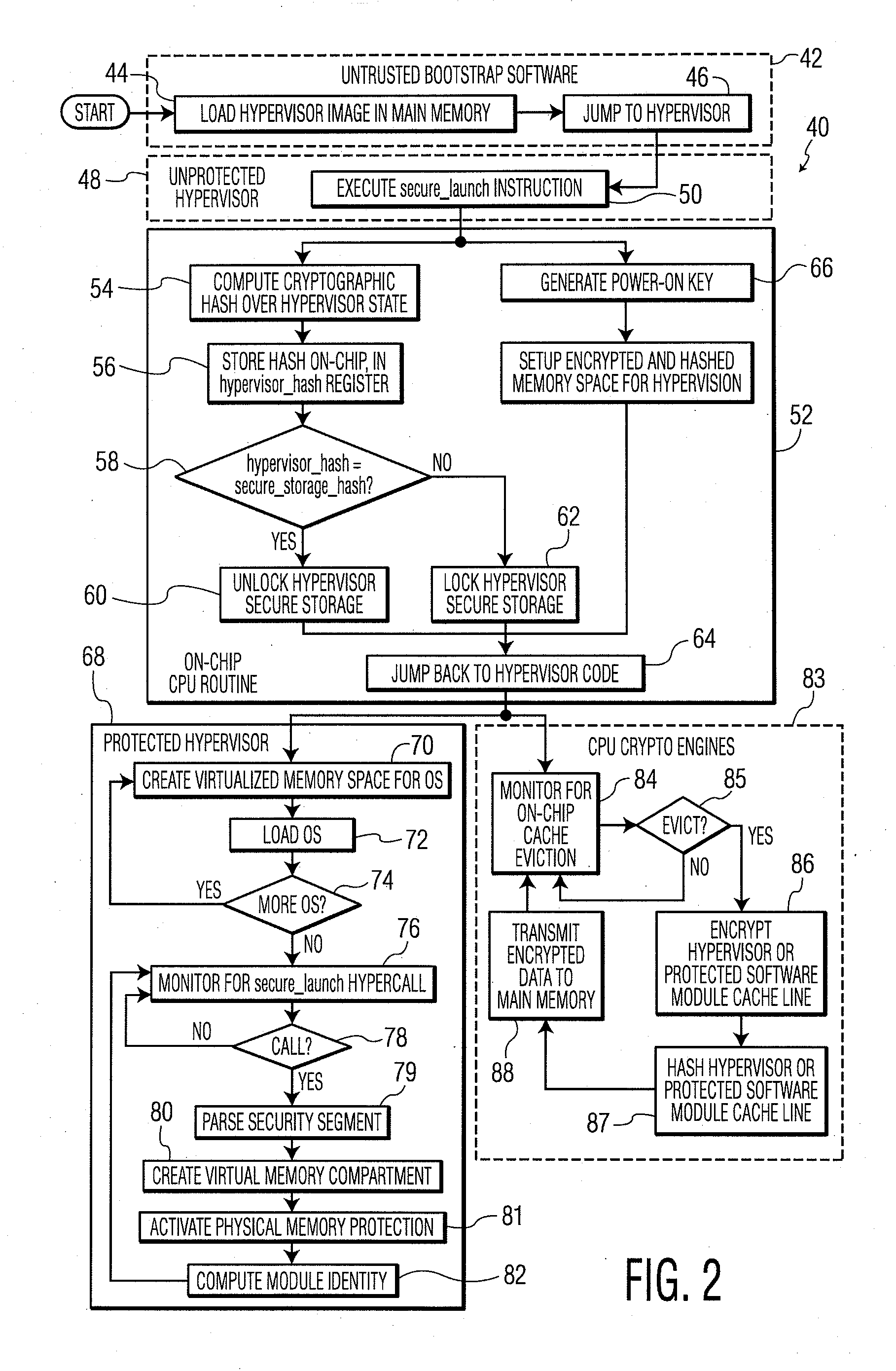
ActiveUS20100281273A1Avoid accessUnauthorized memory use protectionHardware monitoringExternal storageMemory interface
A system and method for processor-based security is provided, for on-chip security and trusted computing services for software applications. A processor is provided having a processor core, a cache memory, a plurality of registers for storing at least one hash value and at least one encryption key, a memory interface, and at least one on-chip instruction for creating a secure memory area in a memory external to the processor, and a hypervisor program executed by the processor. The hypervisor program instructs the processor to execute the at least one on-chip instruction to create a secure memory area for a software area for a software module, and the processor encrypts data written to, and decrypts data read from, the external memory using the at least one encryption key and the verifying data read from the external memory using the at least one hash value. Secure module interactions are provided, as well as the generation of a power-on key which can be used to protect memory in the event of a re-boot event. Lightweight, run-time attestation reports are generated which include selected information about software modules executed by the processors, for use in determining whether the processor is trusted to provide secure services.
Owner:CORESECURE TECH LLC
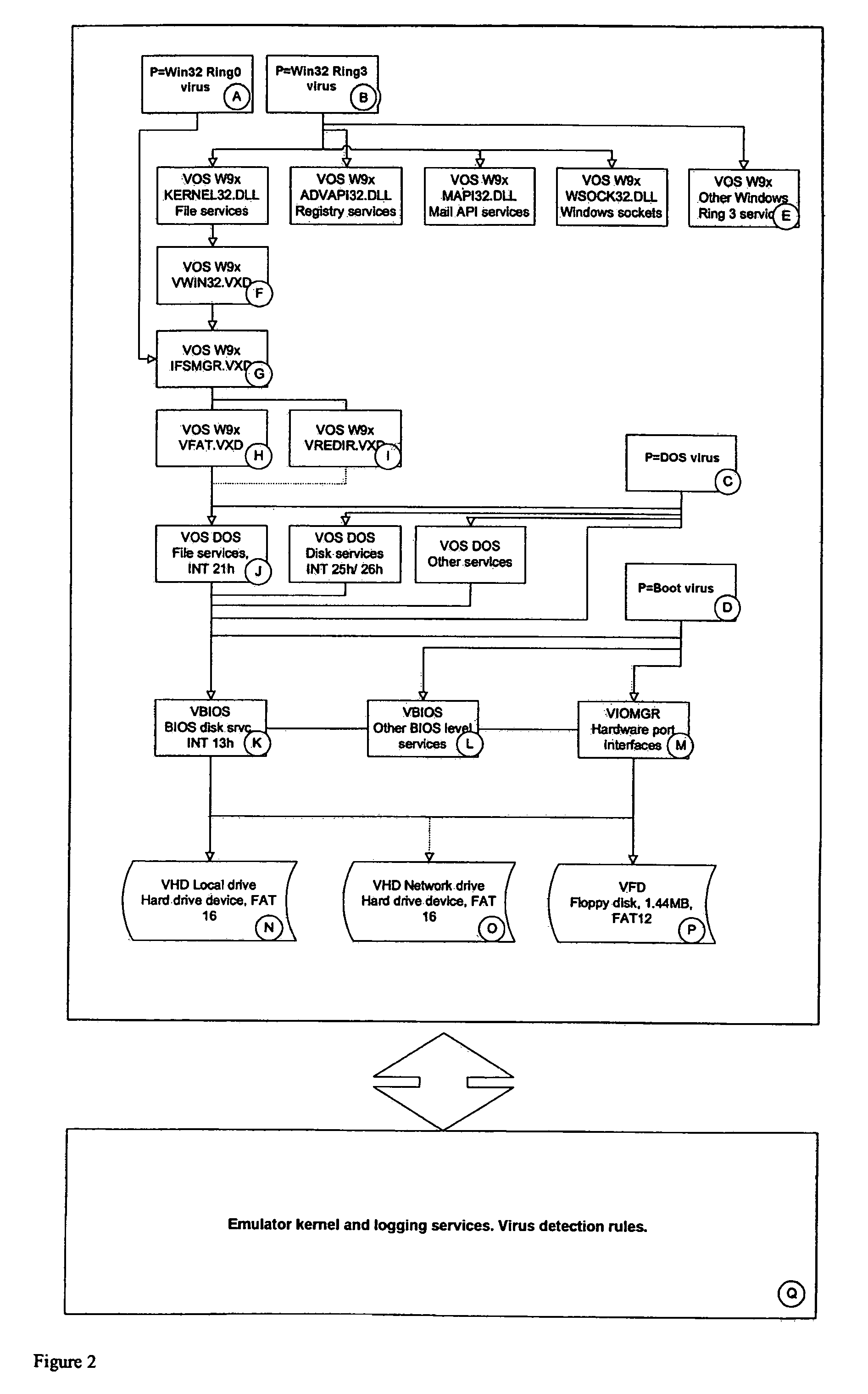
Simulated computer system for monitoring of software performance
InactiveUS7356736B2Reduce riskMemory loss protectionError detection/correctionVery low riskOperational system
A system S is defined which is capable of simulating a computer (virtual computer, VC) for the purpose of software performance monitoring. The system is implemented as a set of software modules (SM) that can be exchanged to change the behavior of the VC. The VC is driven by a CPU emulator, and can run any operating system (virtual operating system, VOS) that is supported by the available SM's. The system is designed to log accesses to system resources and the nature of these accesses. The system is particularly useful for determining whether an executable or file contains an unknown virus, with a very low risk of false positives. Detected viruses include encrypted, polymorphic, metamorphic and other virus types.
Owner:CA TECH INC
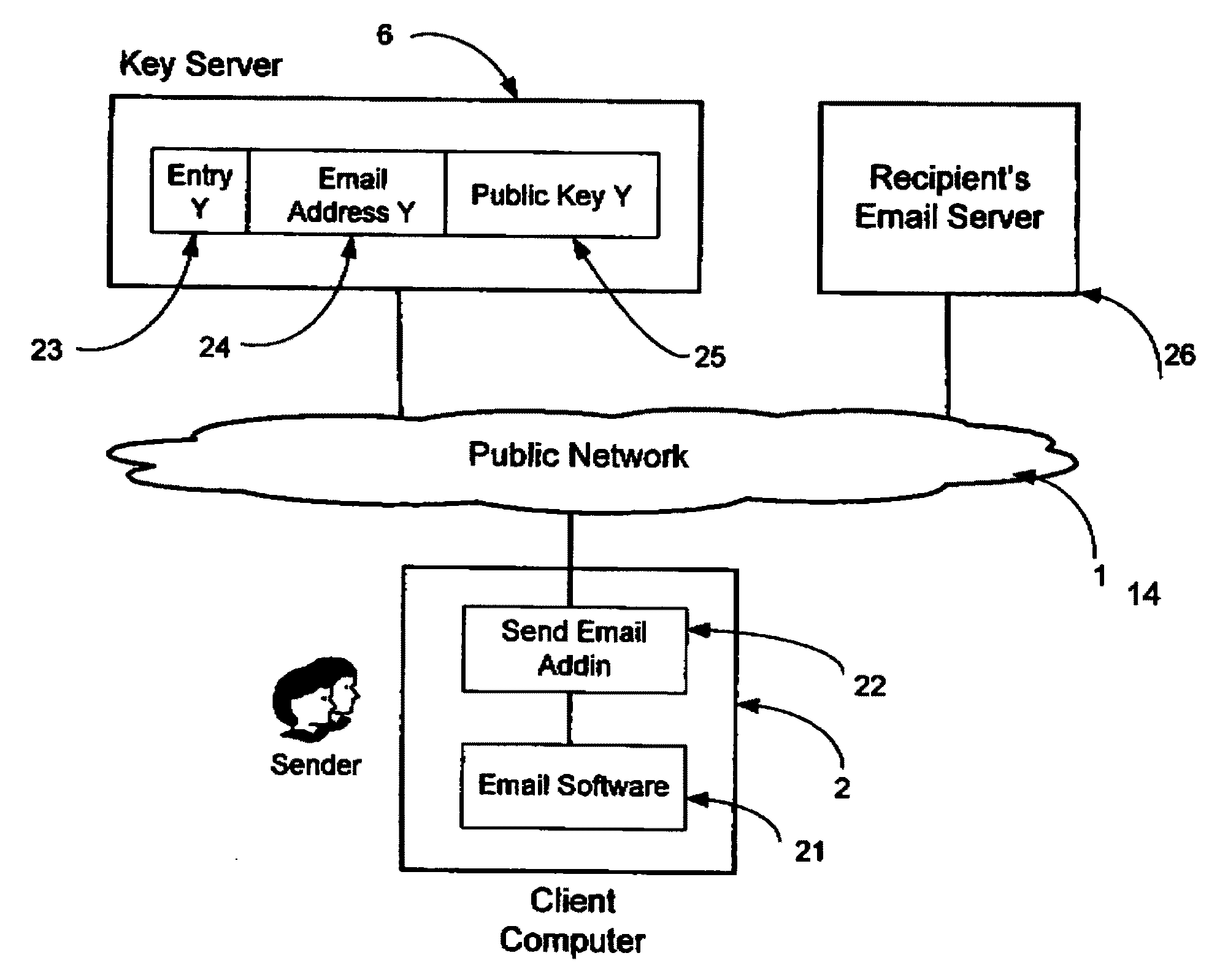
System and method for secure electronic communication services
InactiveUS20090198997A1Easy accessSecure transmissionKey distribution for secure communicationMultiple keys/algorithms usageScalable systemEmail address
A system, method and software module for secure electronic communication services, wherein a public key (25) of private-public-key pair (30,25) is associated with an email address (24), internet name or other registered unique identifier; the registered user of the unique identifier holds the private-key (30) securely, and the respective public-key (25) is made accessible on a key server (6) for look-up and retrieval by other users, for encryption of communications to be sent to the holder of the private-key, and optionally for message confidentiality, message integrity and authentication of sender and recipient, without requiring certificates. A distributed and scalable system is provided by a server network (600; 401, 501) for registration, key distribution and management preferably using a kDNS server hierarchy (601,602,603) or a key-DNS server hierarchy (701,702,) and associated protocols so that public-keys of recipients can be searched and retrieved over the internet based on the recipients email address or other unique identifier, thus facilitating secure communication between users in different network domains and organizations.
Owner:TOPOSIS CORP
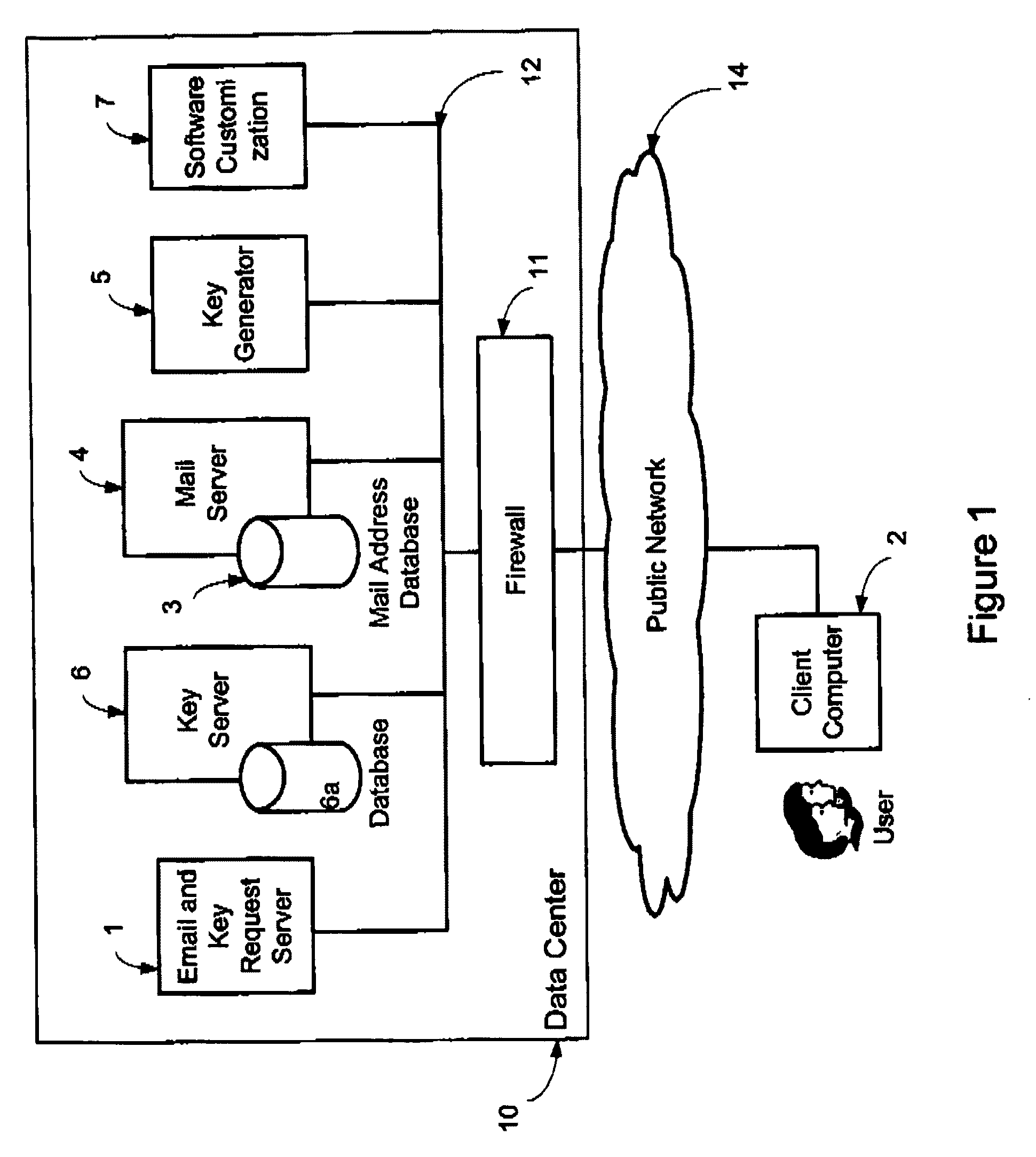
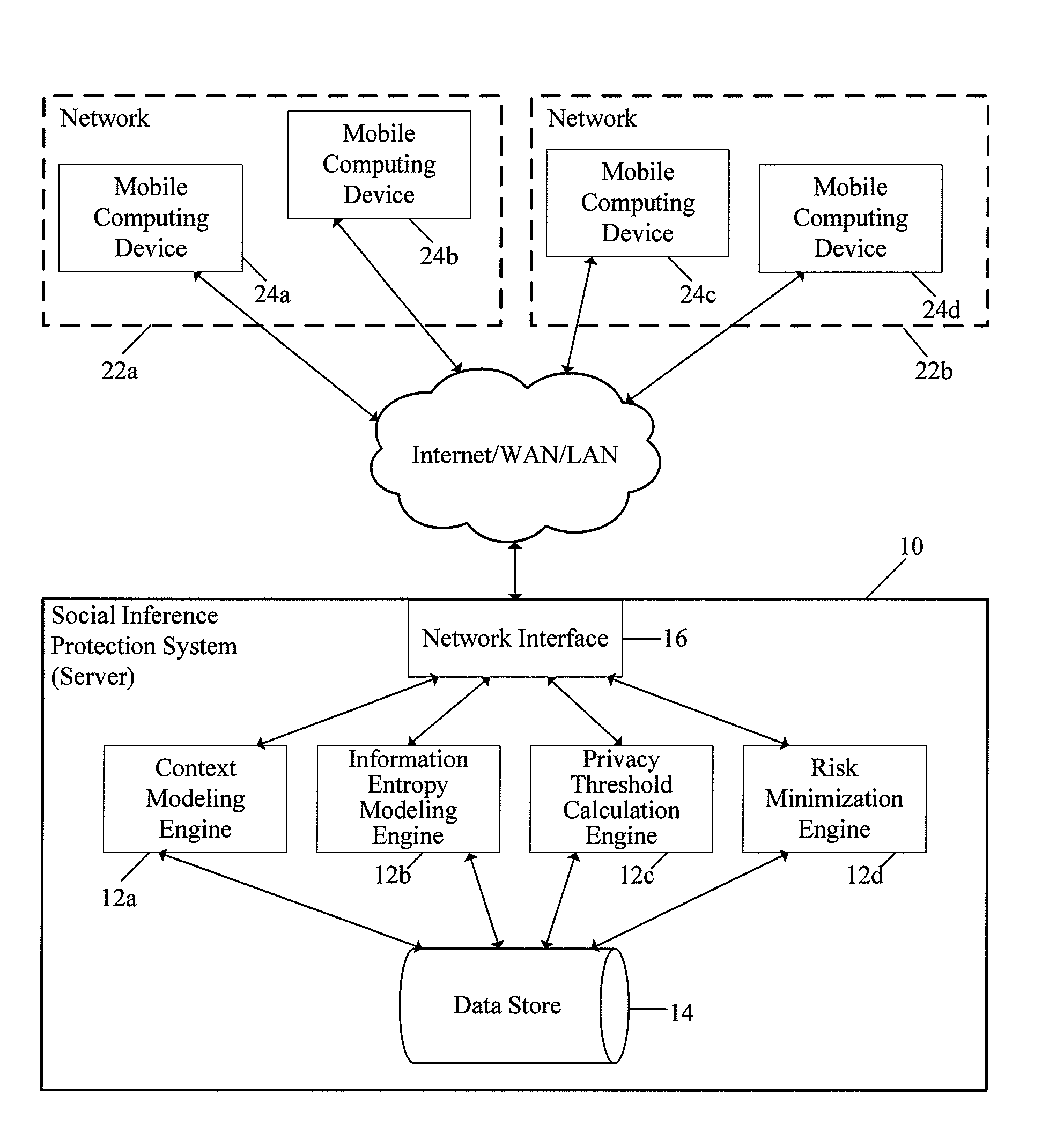
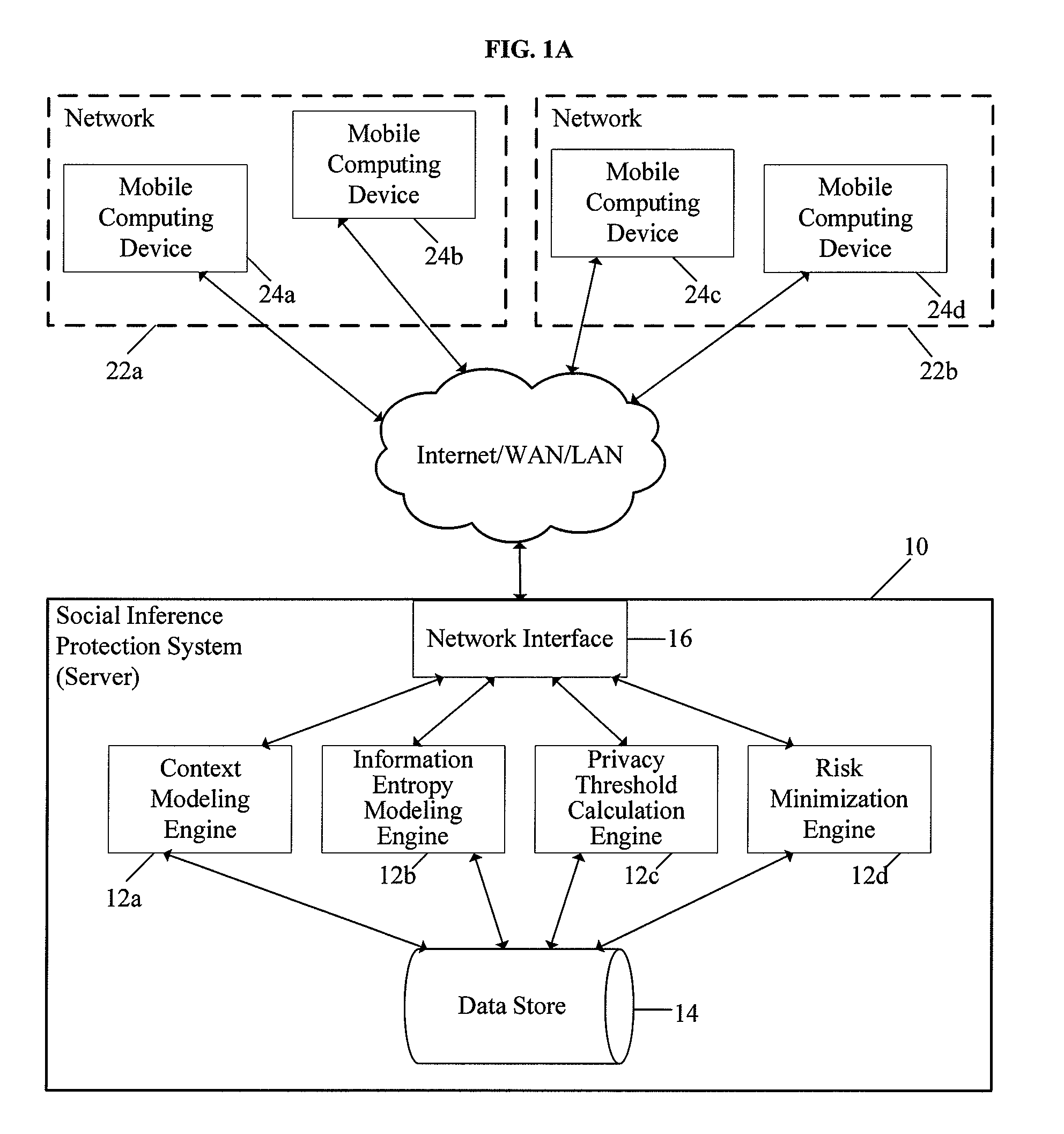
System and method for protecting user privacy using social inference protection techniques
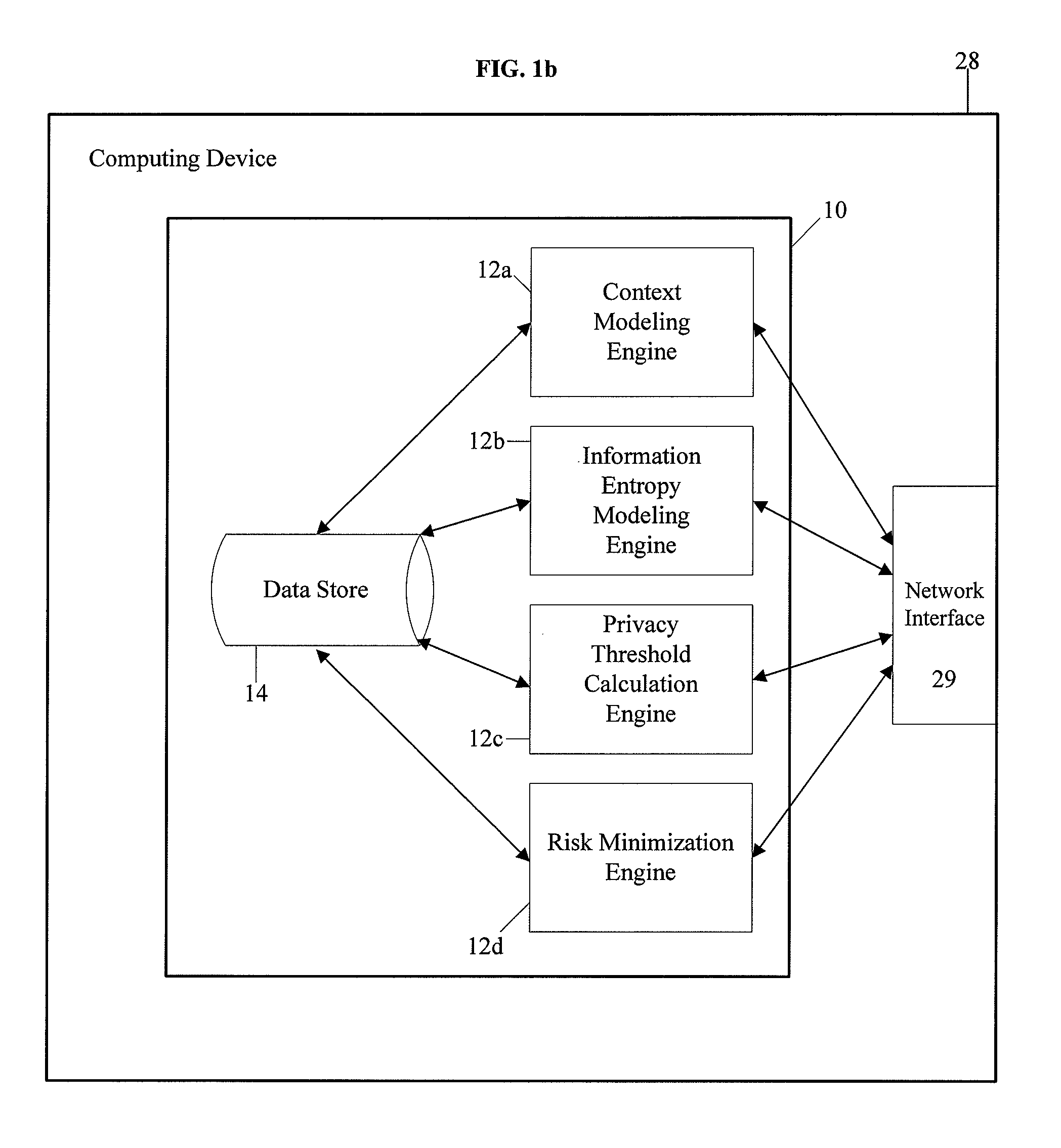
InactiveUS8504481B2Minimize privacy riskInhibit exchangeDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyUser privacy
A system and method for protecting user privacy using social inference protection techniques is provided. The system executes a plurality of software modules which model of background knowledge associated with one or more users of the mobile computing devices; estimate information entropy of a user attribute which could include identity, location, profile information, etc.; utilize the information entropy models to predict the social inference risk; and minimize privacy risks by taking a protective action after detecting a high risk.
Owner:NEW JERSEY INSTITUTE OF TECHNOLOGY
Check21 image based document and processing system
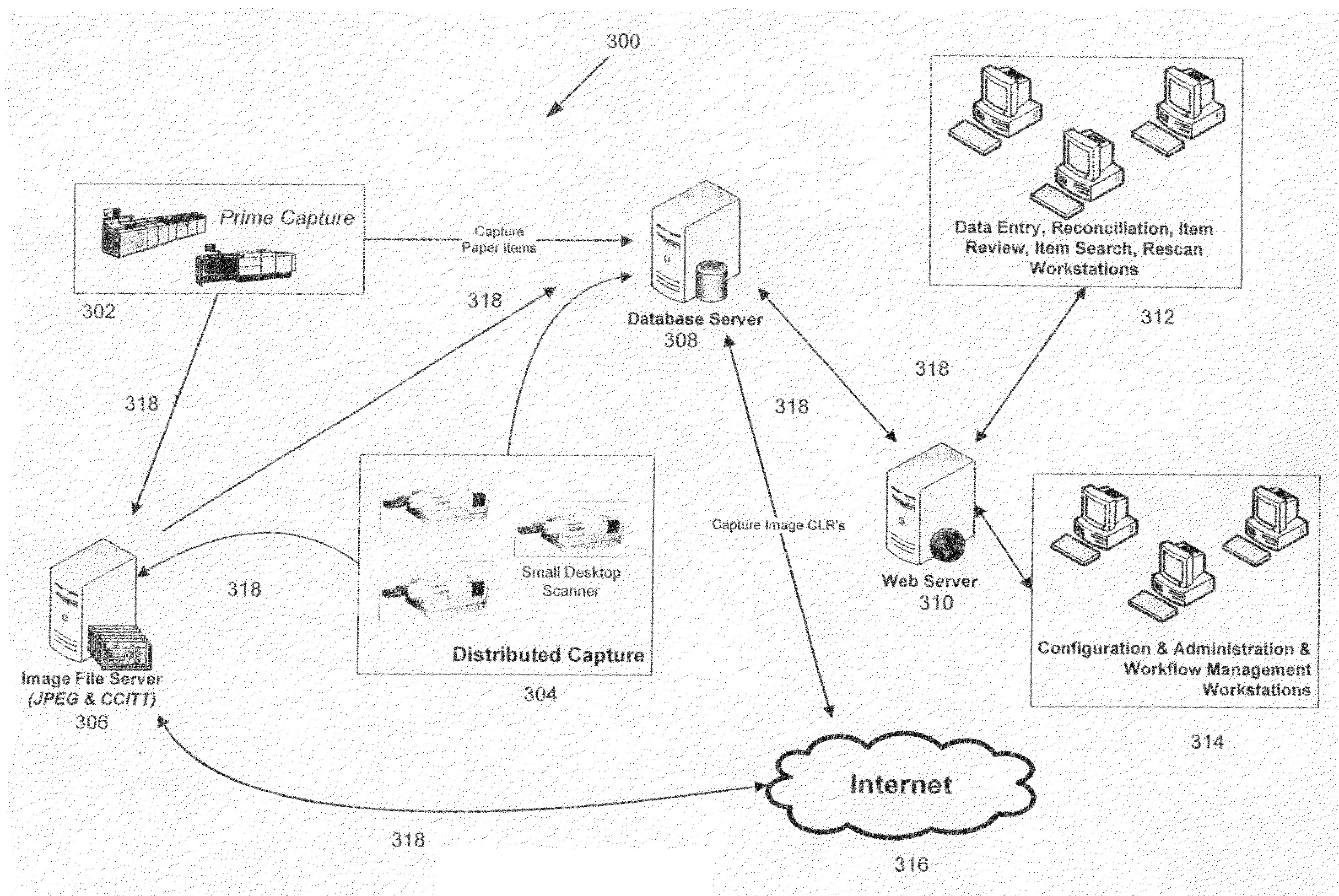
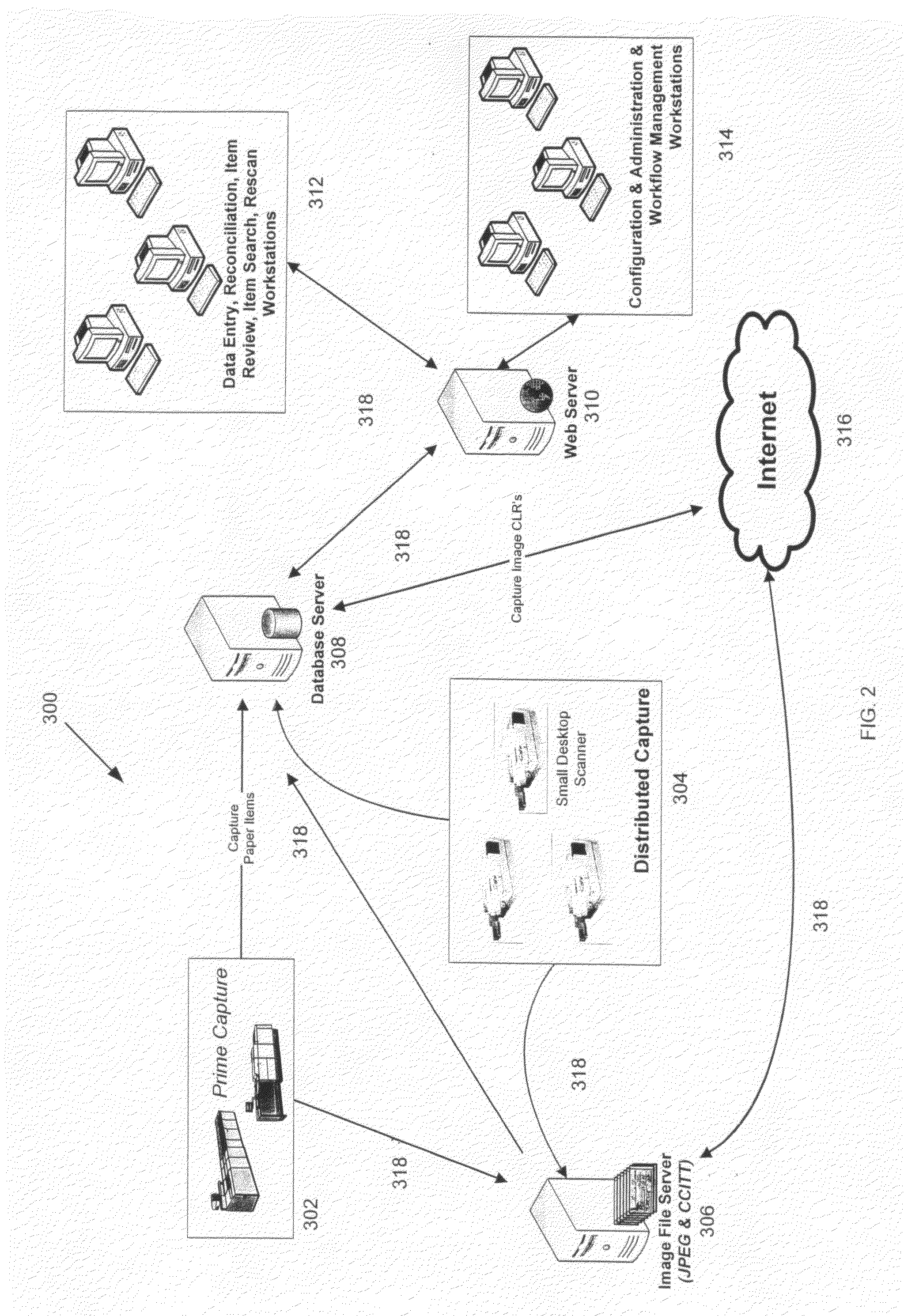
InactiveUS20070288382A1Easy to removeEasy to addFinanceCharacter and pattern recognitionSoftware systemModularity
A Check21 Act image based document and processing system, comprising a modular hardware and software image-based financial processing system with independent software modules supporting specific hardware and or processing applications; thereby, simplifying the process for the removal or addition of support for new computer platforms, components, features, peripherals, applications and / or interoperating with legacy hardware and software systems.
Owner:AVALON INT
Streaming Method and System for Processing Network Metadata
ActiveUS20130117847A1Problem can be addressedEasily correlatedMemory loss protectionError detection/correctionTemplate basedSoftware modules
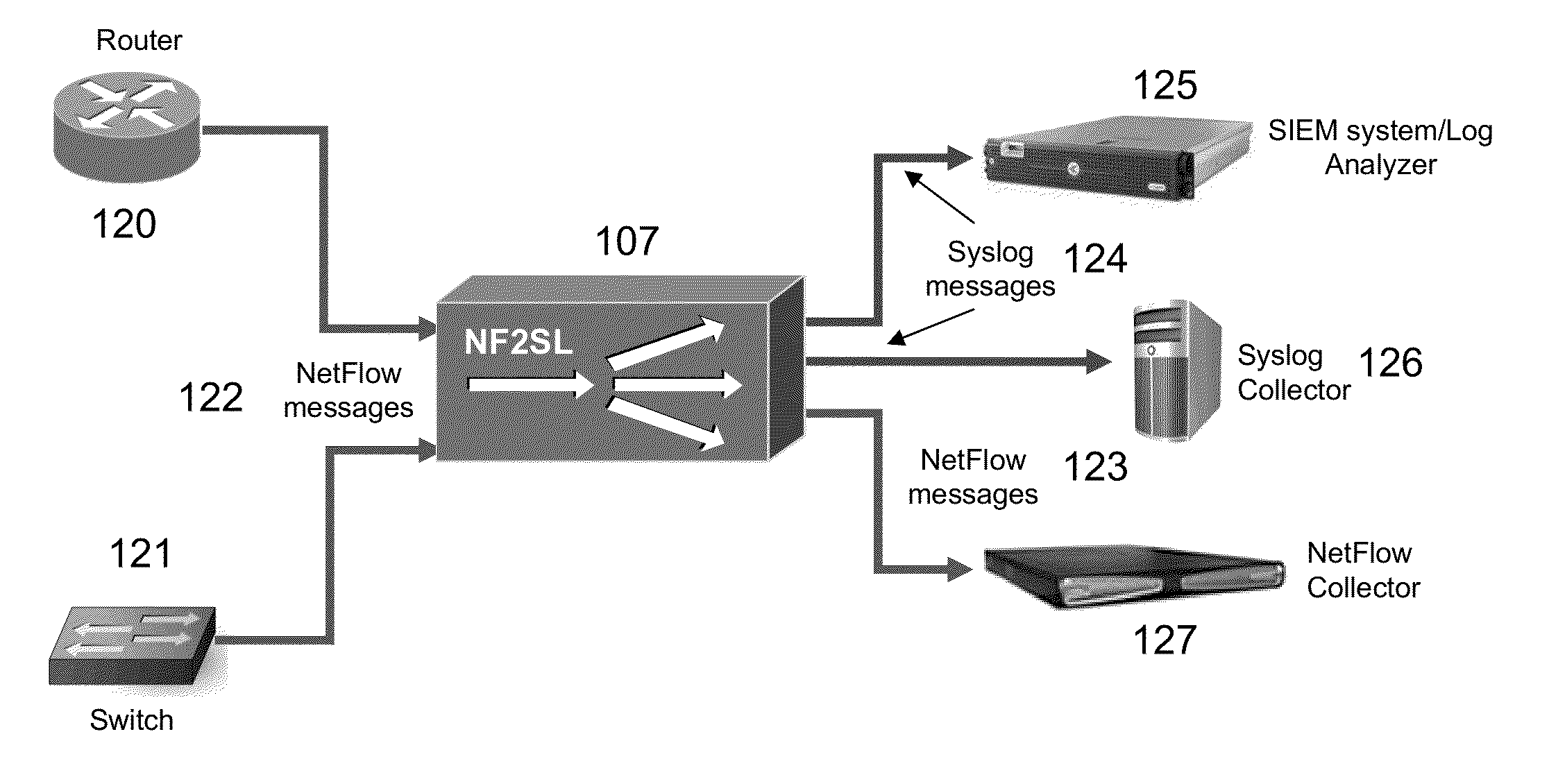
A method and system for processing network metadata is described. Network metadata may be processed by dynamically instantiated executable software modules which make policy-based decisions about the character of the network metadata and about presentation of the network metadata to consumers of the information carried by the network metadata. The network metadata may be type classified and each subclass within a type may be mapped to a definition by a unique fingerprint value. The fingerprint value may be used for matching the network metadata subclasses against relevant policies and transformation rules. For template-based network metadata such as NetFlow v9, an embodiment of the invention can constantly monitor network traffic for unknown templates, capture template definitions, and informs administrators about templates for which custom policies and conversion rules do not exist. Conversion modules can efficiently convert selected types and / or subclasses of network metadata into alternative metadata formats.
Owner:NETFLOW LOGIC
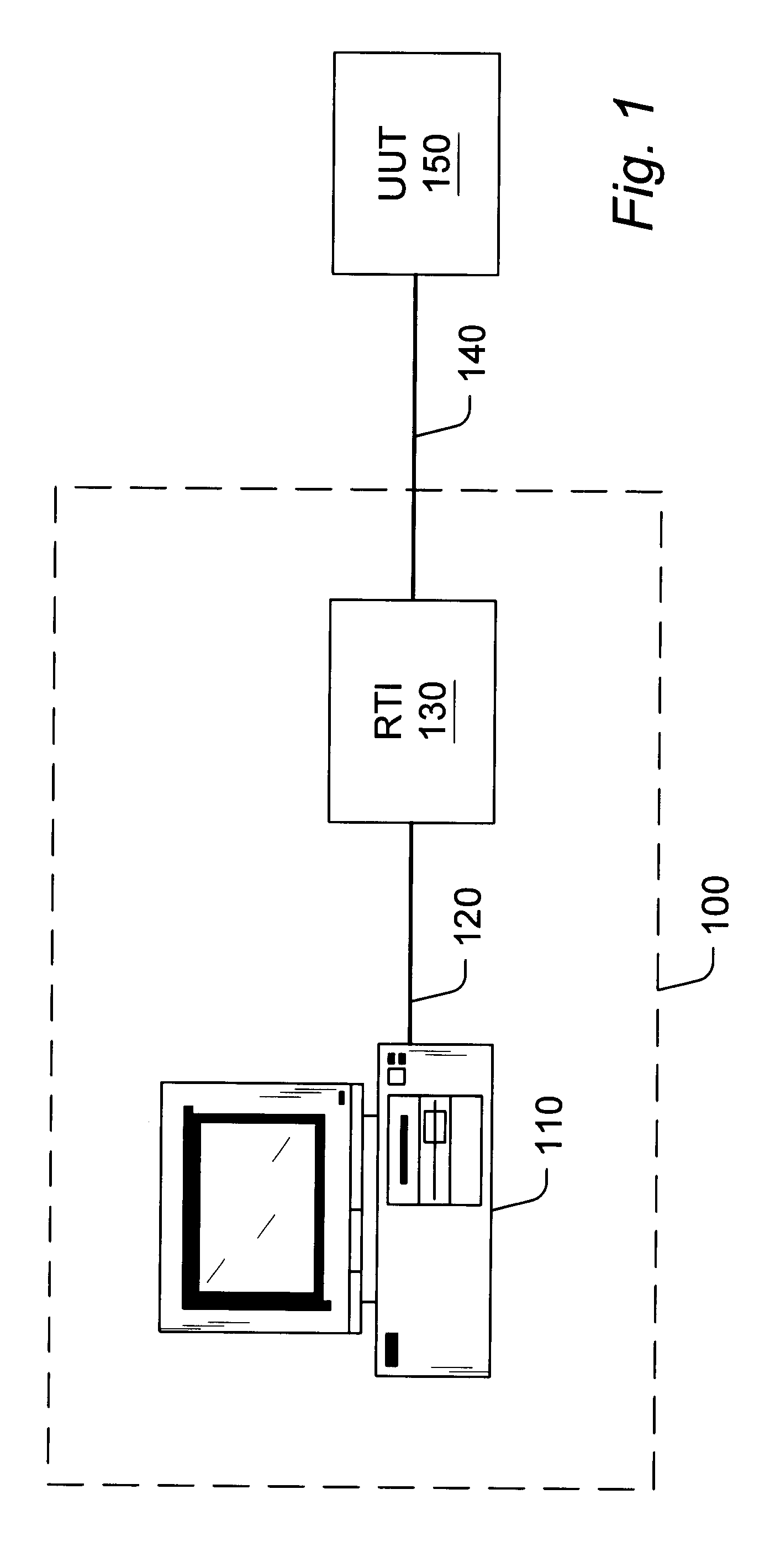
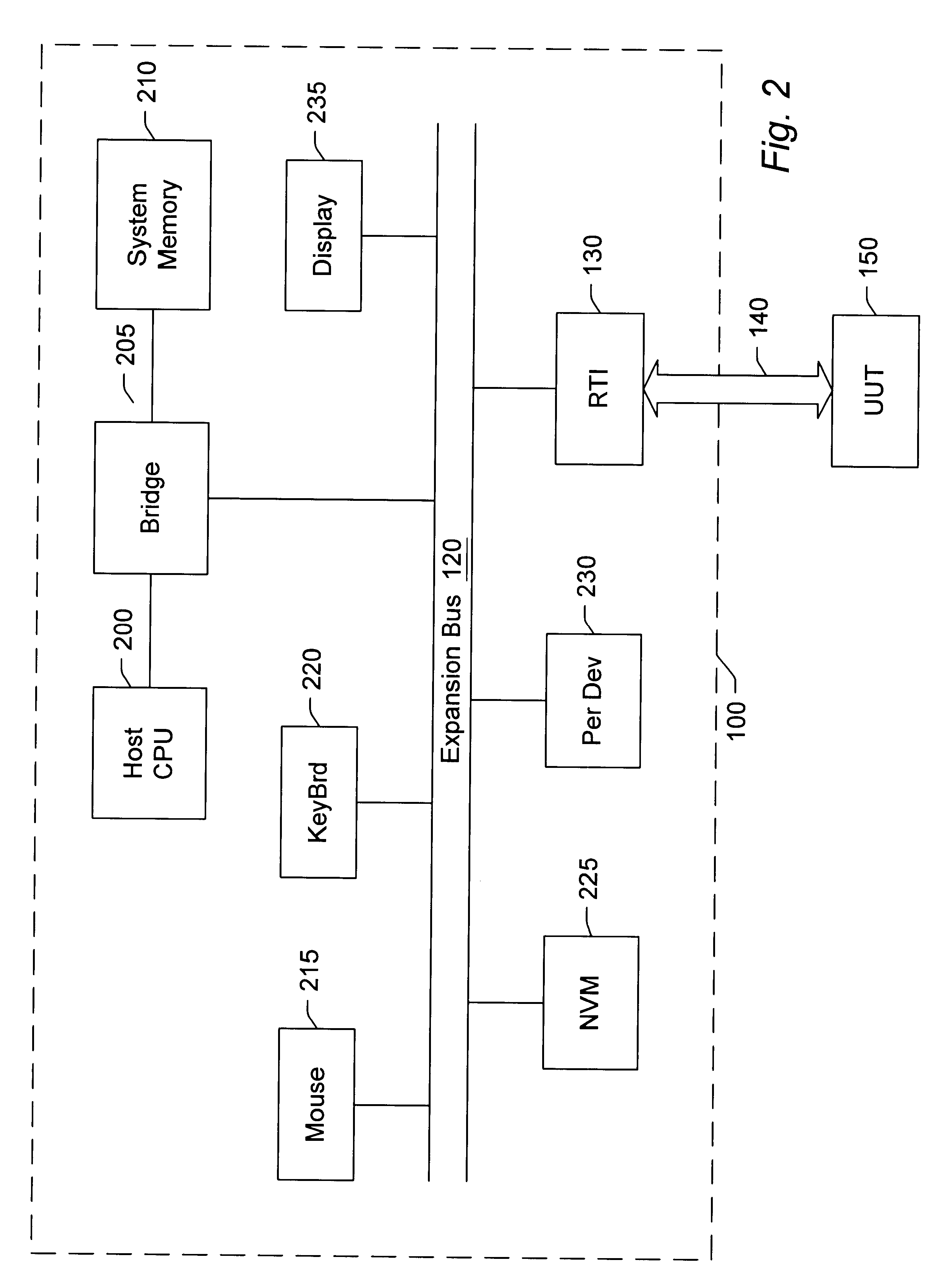
Reconfigurable test system
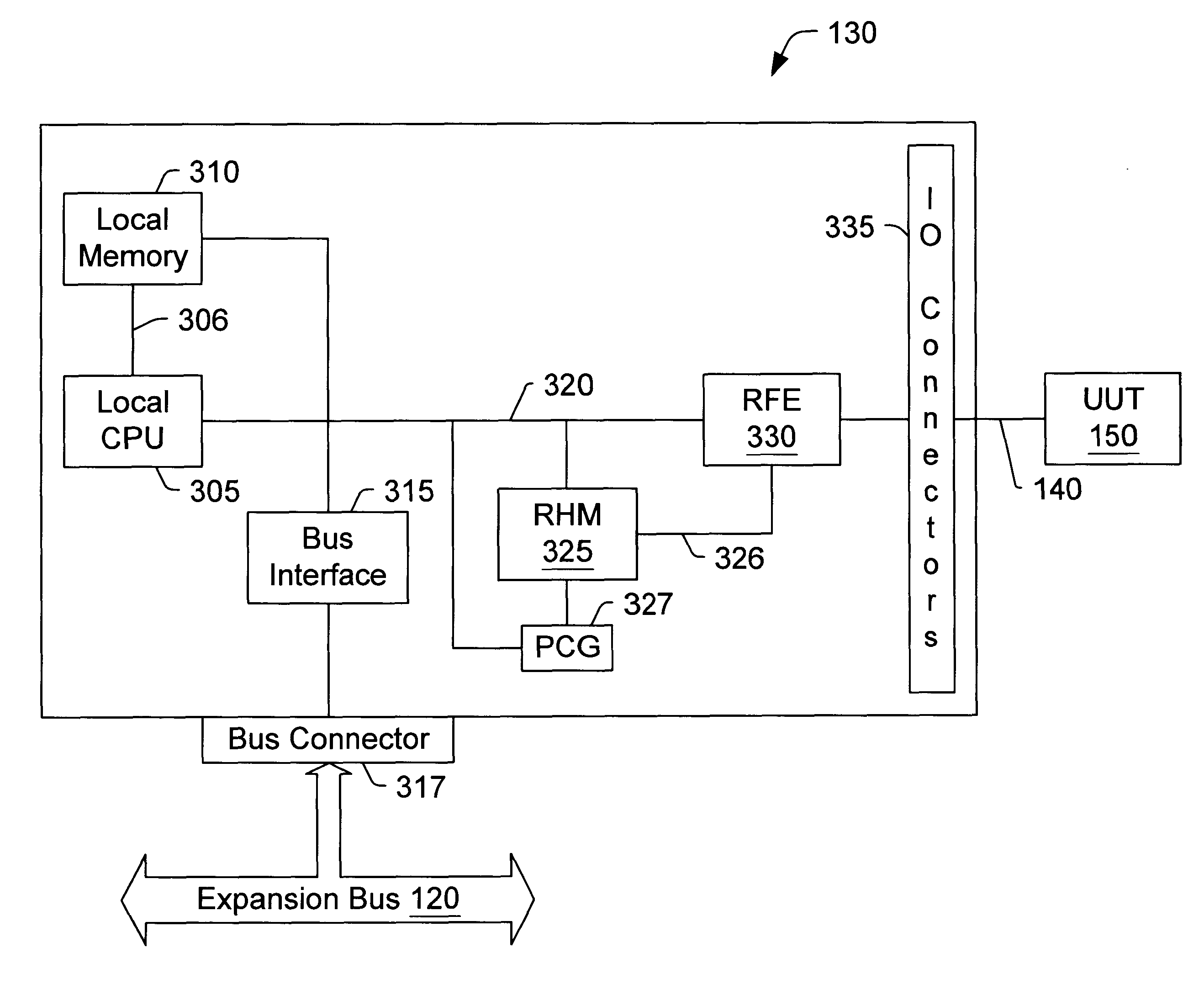
A reconfigurable test system including a host computer coupled to a reconfigurable test instrument. The reconfigurable test instrument includes reconfigurable hardware-i.e. a reconfigurable hardware module with one or more programmable elements such as Field Programmable Gate Arrays for realizing an arbitrary hardware architecture and a reconfigurable front end with programmable transceivers for interfacing with any desired physical medium-and optionally, an embedded processor. A user specifies system features with a software configuration utility which directs a component selector to select a set of software modules and hardware configuration files from a series of libraries. The modules are embedded in a host software driver or downloaded for execution on the embedded CPU. The configuration files are downloaded to the reconfigurable hardware. The entire selection process is performed in real-time and can be changed whenever the user deems necessary. Alternatively, the user may create a graphical program in a graphical programming environment and compile the program into various software modules and configuration files for host execution, embedded processor execution, or programming the reconfigurable hardware.
Owner:NATIONAL INSTRUMENTS
System and methods for semiautomatic generation and tuning of natural language interaction applications
ActiveUS20140019116A1Natural language translationSemantic analysisIdentifying problemsSemi automatic
A system for supervised automatic code generation and tuning for natural language interaction applications, comprising a build environment comprising a developer user interface, automated coding tools, automated testing tools, and automated optimization tools, and an analytics framework software module. Text samples are imported into the build environment and automated clustering is performed to assign them to a plurality of input groups, each input group comprising a plurality of semantically related inputs. Language recognition rules are generated by automated coding tools. Automated testing tools carry out automated testing of language recognition rules and generate recommendations for tuning language recognition rules. The analytics framework performs analysis of interaction log files to identify problems in a candidate natural language interaction application. Optimizations to the candidate natural language interaction application are carried out and an optimized natural language interaction application is deployed into production and stored in the solution data repository.
Owner:ARTIFICIAL SOLUTIONS
Reconfigurable service provision via a communication network
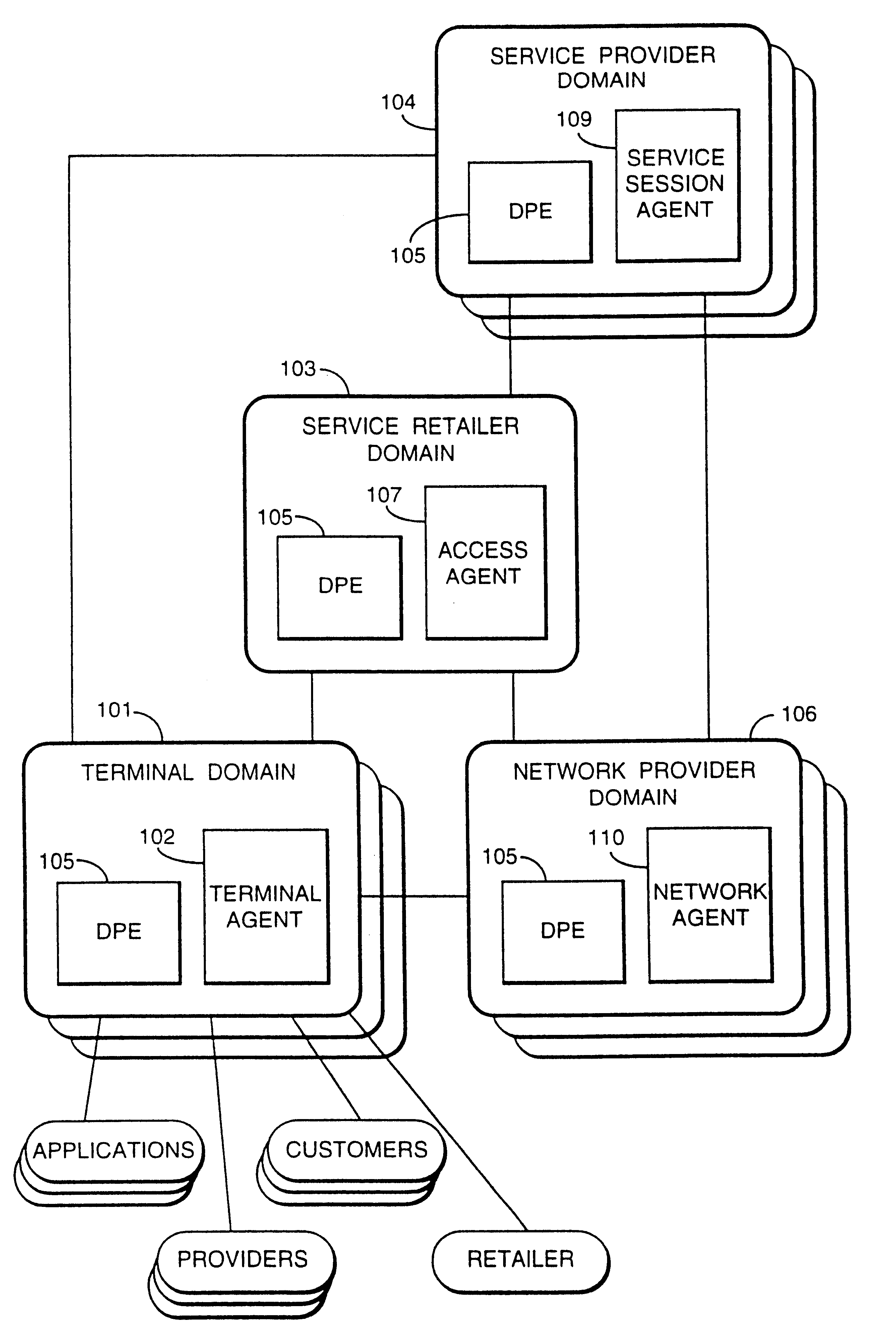
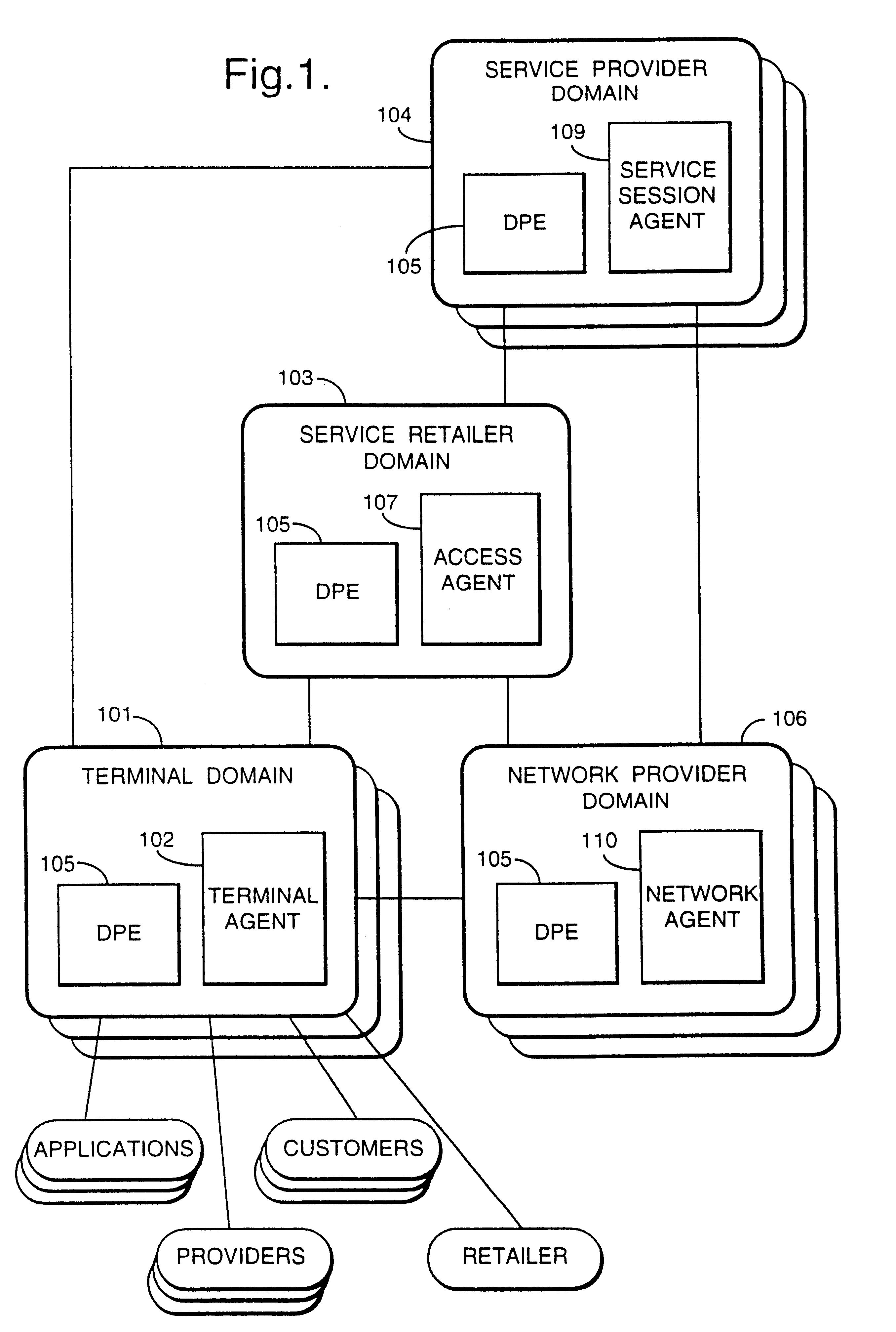
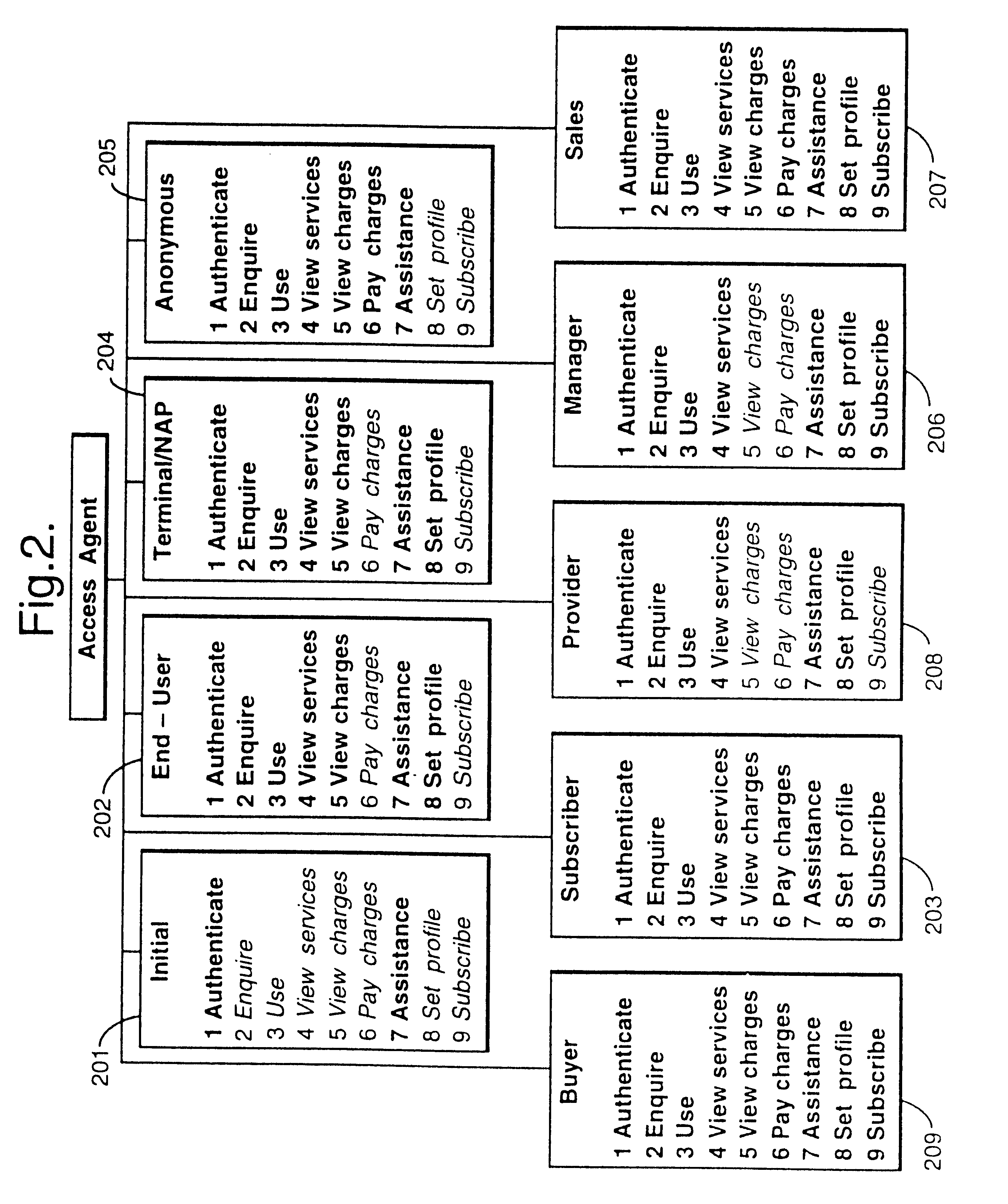
InactiveUS6330586B1Customer base for information services is particularly wideLarge capacityMultiplex system selection arrangementsData processing applicationsReconfigurabilityReusable software
A services provision system provides information services over one or more communications networks and has a software infrastructure divided into domains. Each domain has an intelligent software agent and this community of agents sits in a computing environment represented in each domain by a DPE kernel. The community of agents co-operates to provide service and service management functionality to a user. At least one of the agents is reconfigurable to change the functionality the system makes available. Reconfigurability is based on the use of a plurality of reusable software modules, the agent reconfiguring by selecting a new combination of modules. The software modules themselves incorporate rules, or policies, which determine process steps offered by the modules at run-time. These policies are external to the modules and may be loaded at run-time, allowing dynamic modification to functionality of the system. The system as a whole offers functionality associated with using services, providing them and managing them and the reconfigurability allows it to offer the different types of functionality in an efficient way. It also allows access control to functionality at different levels with particularly good security against fraudulent use.
Owner:BRITISH TELECOMM PLC
Biometric-based system and method for enabling authentication of electronic messages sent over a network
InactiveUS7689832B2Digital data processing detailsUser identity/authority verificationReal time validationData authenticity
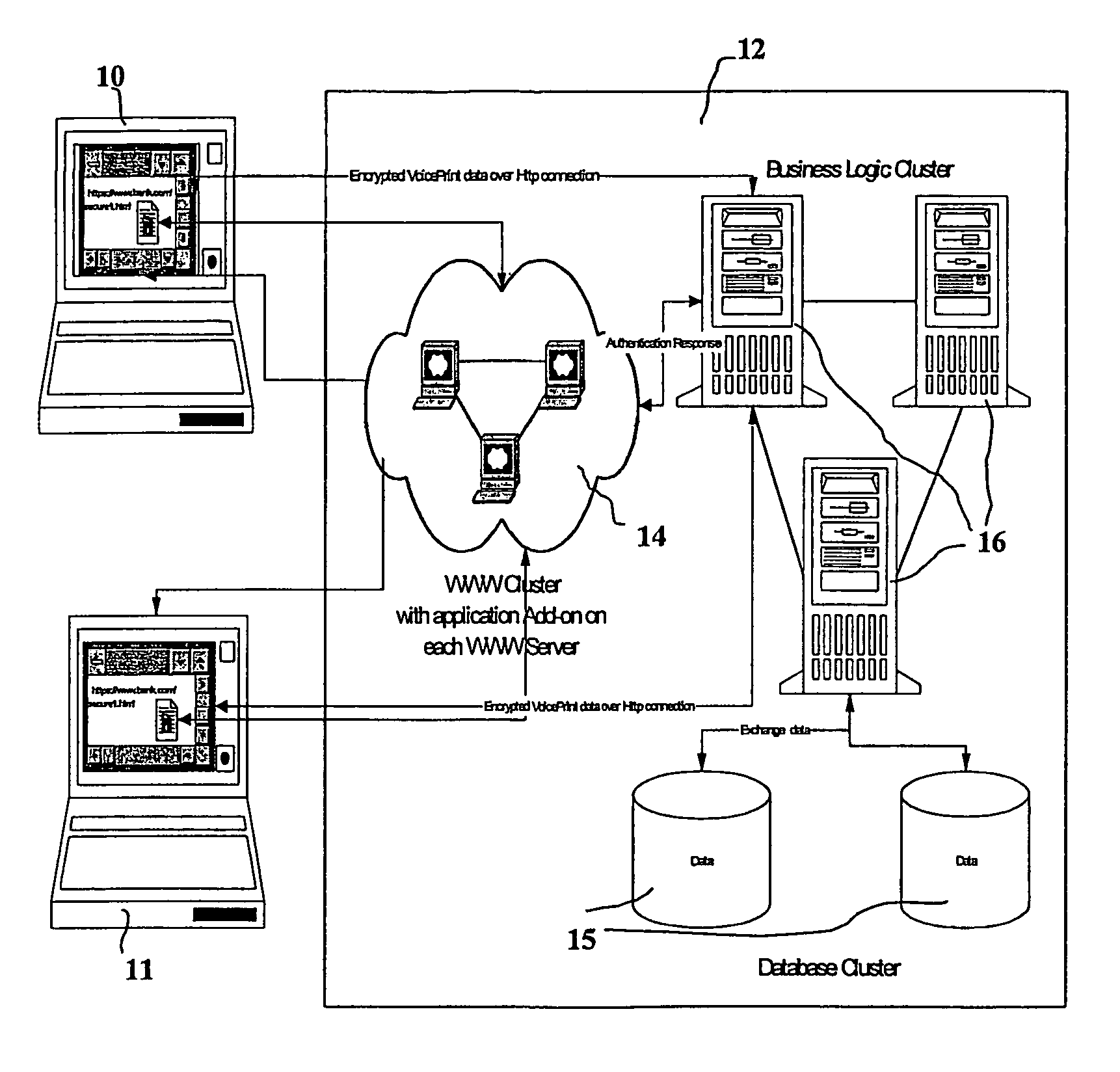
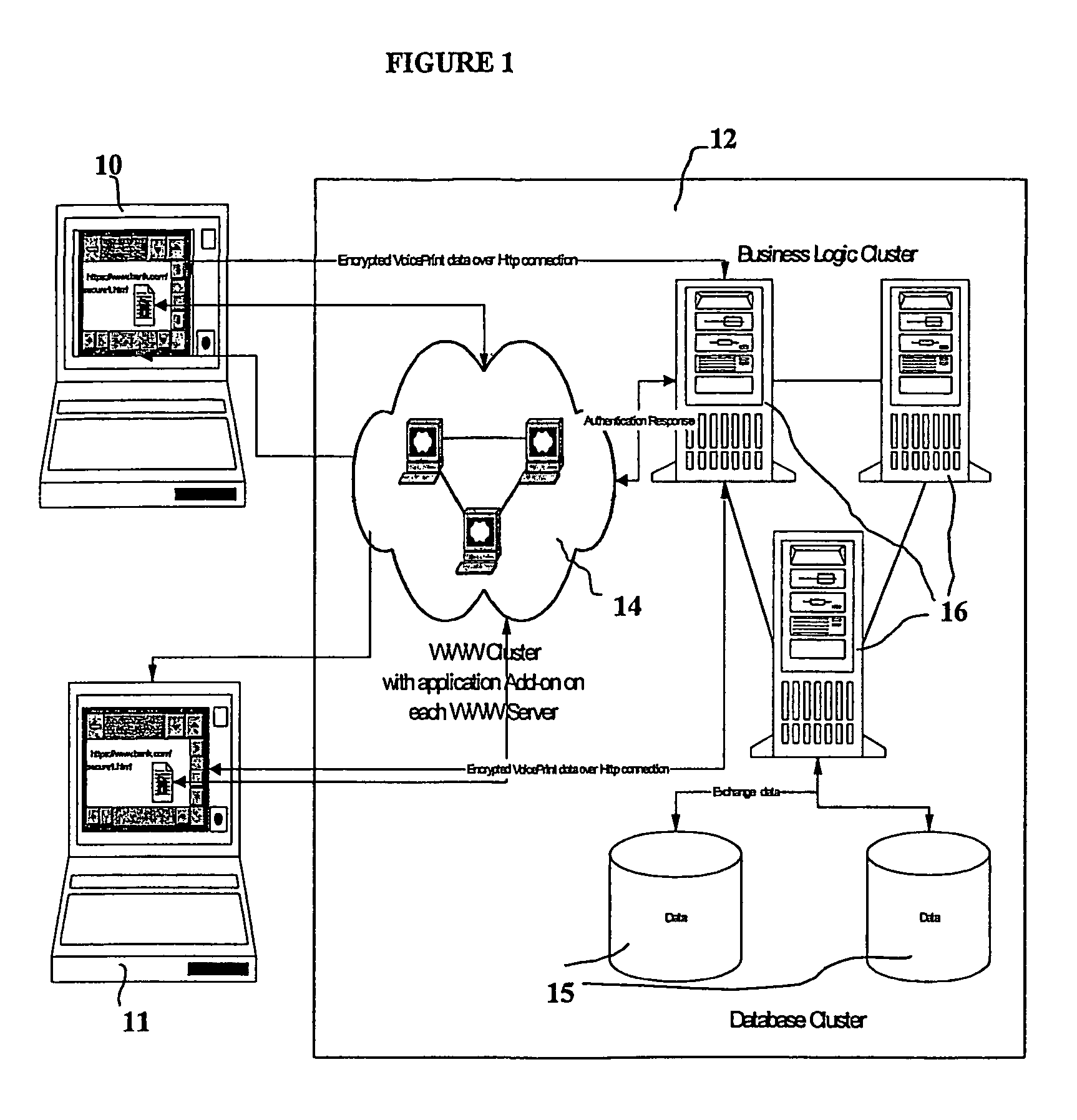
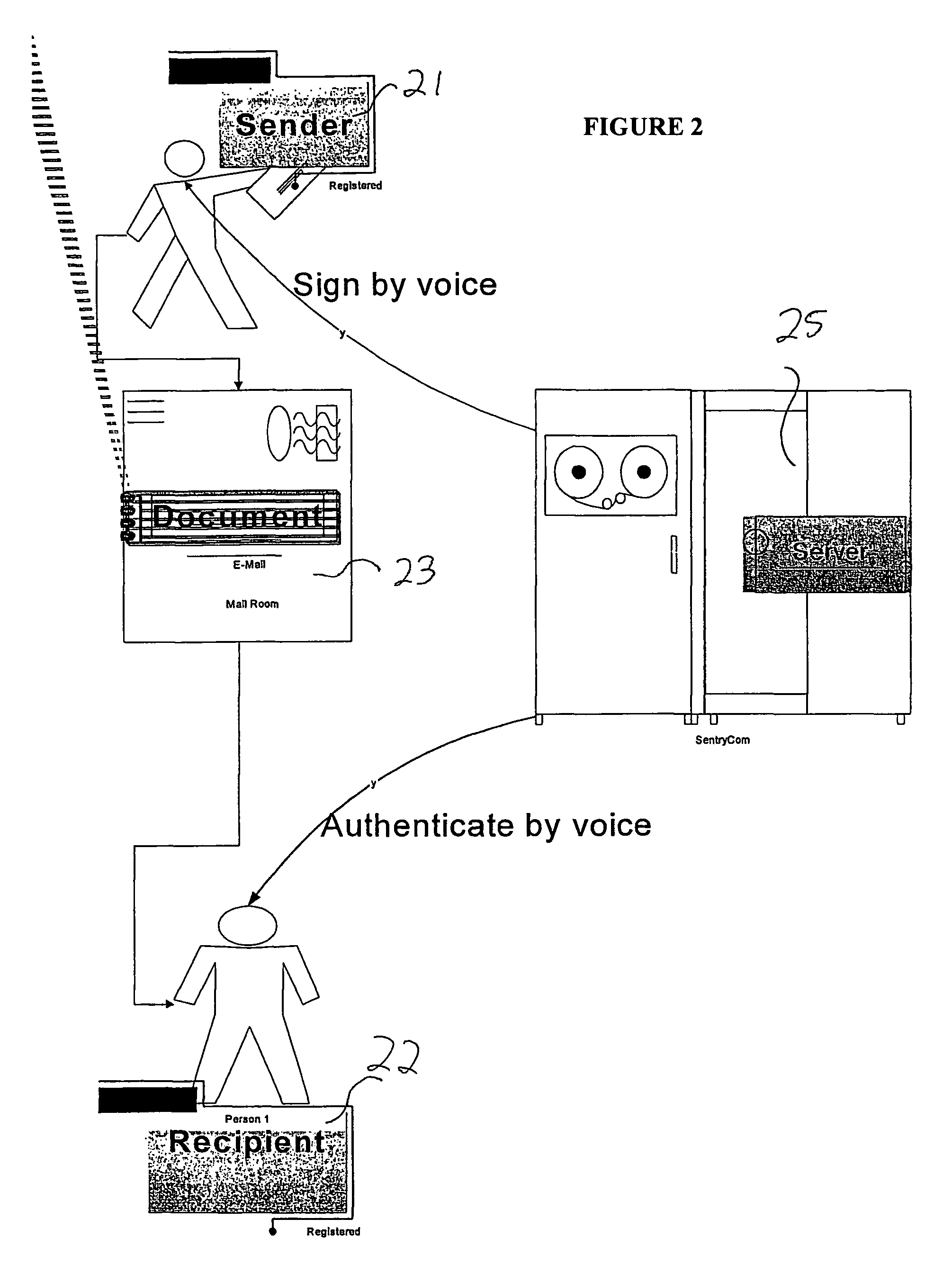
A network based mechanism for real time verification and authentication of data and user identities. The present invention enables a method whereby biometric elements, such as voice prints, are utilized to enhance the Public Key Infrastructure as a means to decrypt data and verify data authenticity, such that the user's private key is authenticated remotely on a one-time basis. The present invention comprises an authentication server (25) with various software modules that enable authentication of user identity, secure user access to data, digital signatures, secure messaging and secure online transactions.
Owner:SENTRYCOM
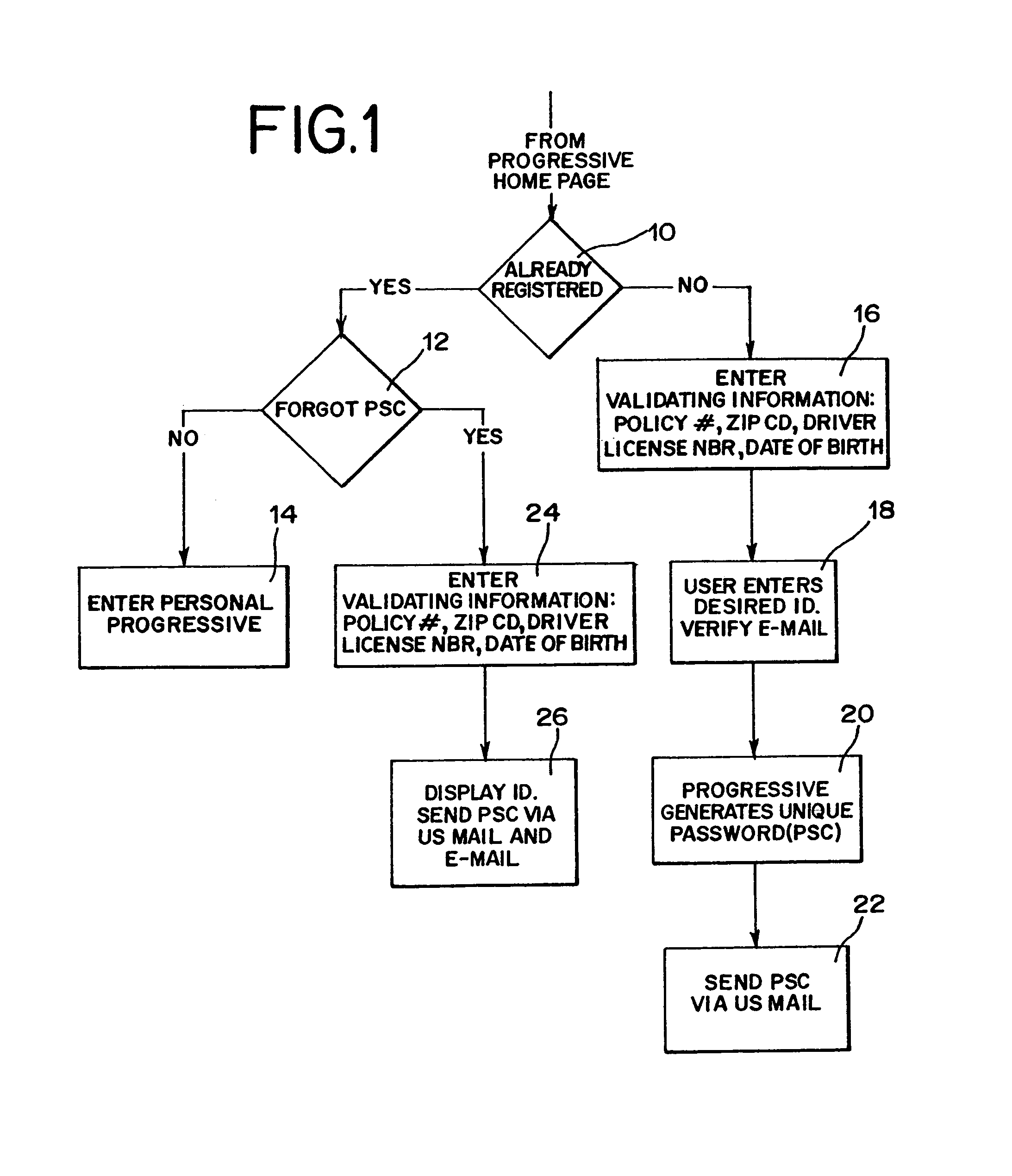
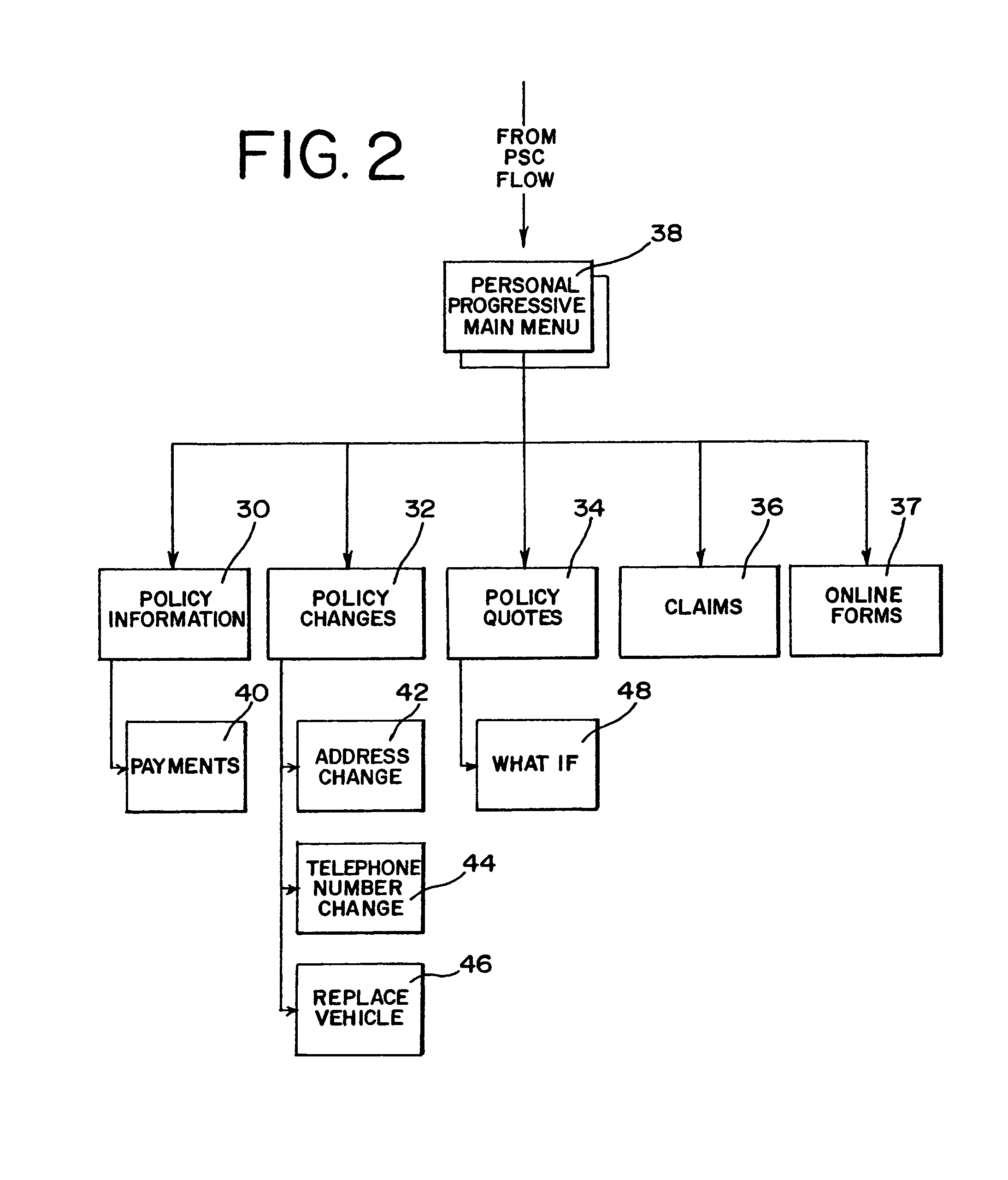
Apparatus for internet on-line insurance policy service
InactiveUS7124088B2Easy to handleReduce management costsFinanceOffice automationThe InternetComputer science
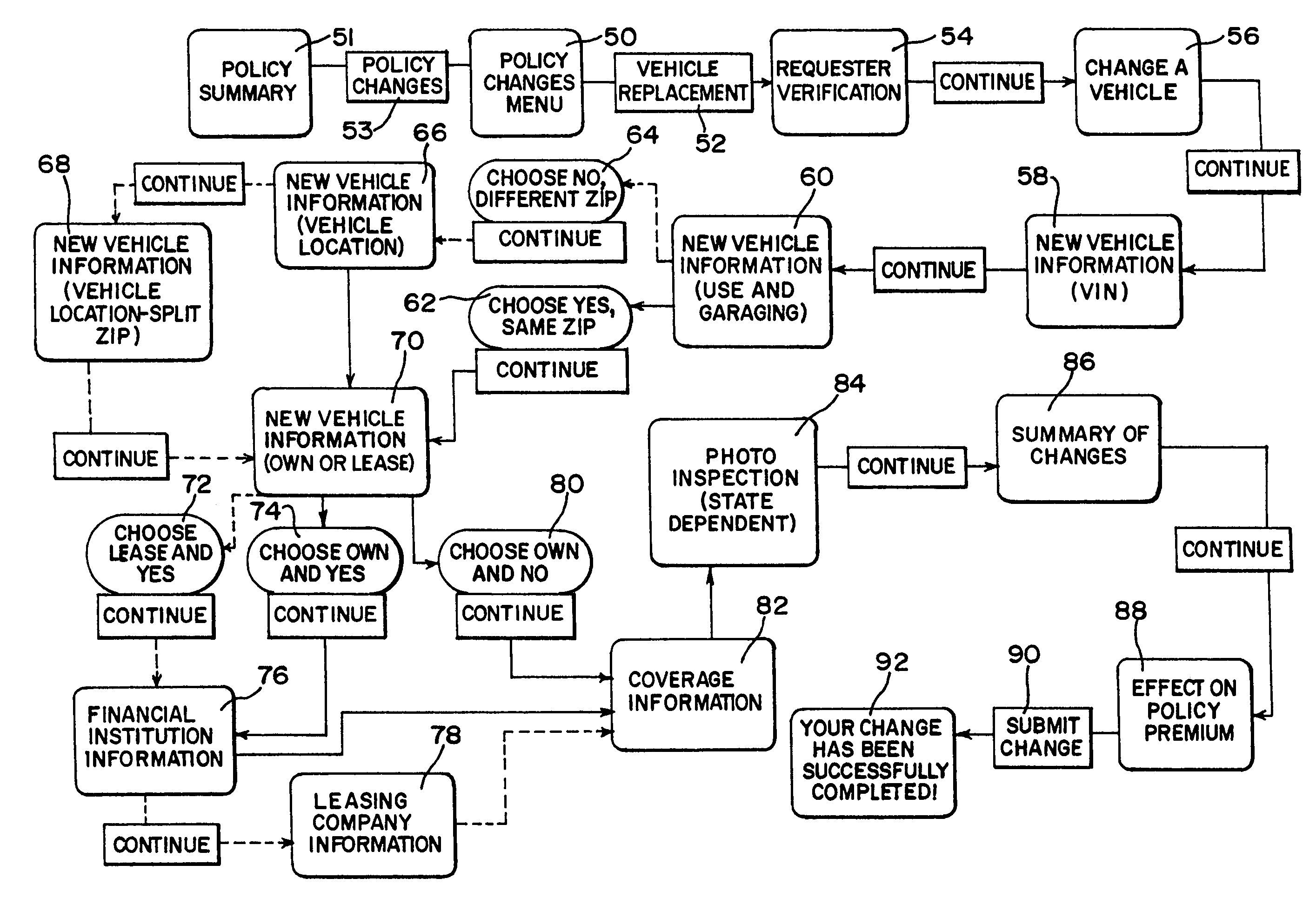
An Internet on-line insurance policy service system that facilitates real-time automated communication of policy information, adjustment of policy parameters, calculation and communication of resulting policy quotes, and implementation of policy changes, while obviating insurer personnel involvement and supervision of the communication. The system comprises a plurality of software modules relating to on-line real-time communication of existing policy information, testing of a wide range of variations in policy parameters, computing and communicating changes in policy premiums that would result from such variations, communicating desired changes in policy parameters and implementing desired policy changes. Other modules relate to communication of claims information and the providing of on-line forms.
Owner:PROGRESSIVE CASUALTY INSURANCE
System and methods for semiautomatic generation and tuning of natural language interaction applications
ActiveUS20130268260A1Natural language translationSemantic analysisIdentifying problemsApplication software
A system for supervised automatic code generation and tuning for natural language interaction applications, comprising a build environment comprising a developer user interface, automated coding tools, automated testing tools, and automated optimization tools, and an analytics framework software module. Text samples are imported into the build environment and automated clustering is performed to assign them to a plurality of input groups, each input group comprising a plurality of semantically related inputs. Language recognition rules are generated by automated coding tools. Automated testing tools carry out automated testing of language recognition rules and generate recommendations for tuning language recognition rules. The analytics framework performs analysis of interaction log files to identify problems in a candidate natural language interaction application. Optimizations to the candidate natural language interaction application are carried out and an optimized natural language interaction application is deployed into production and stored in the solution data repository.
Owner:ARTIFICIAL SOLUTIONS
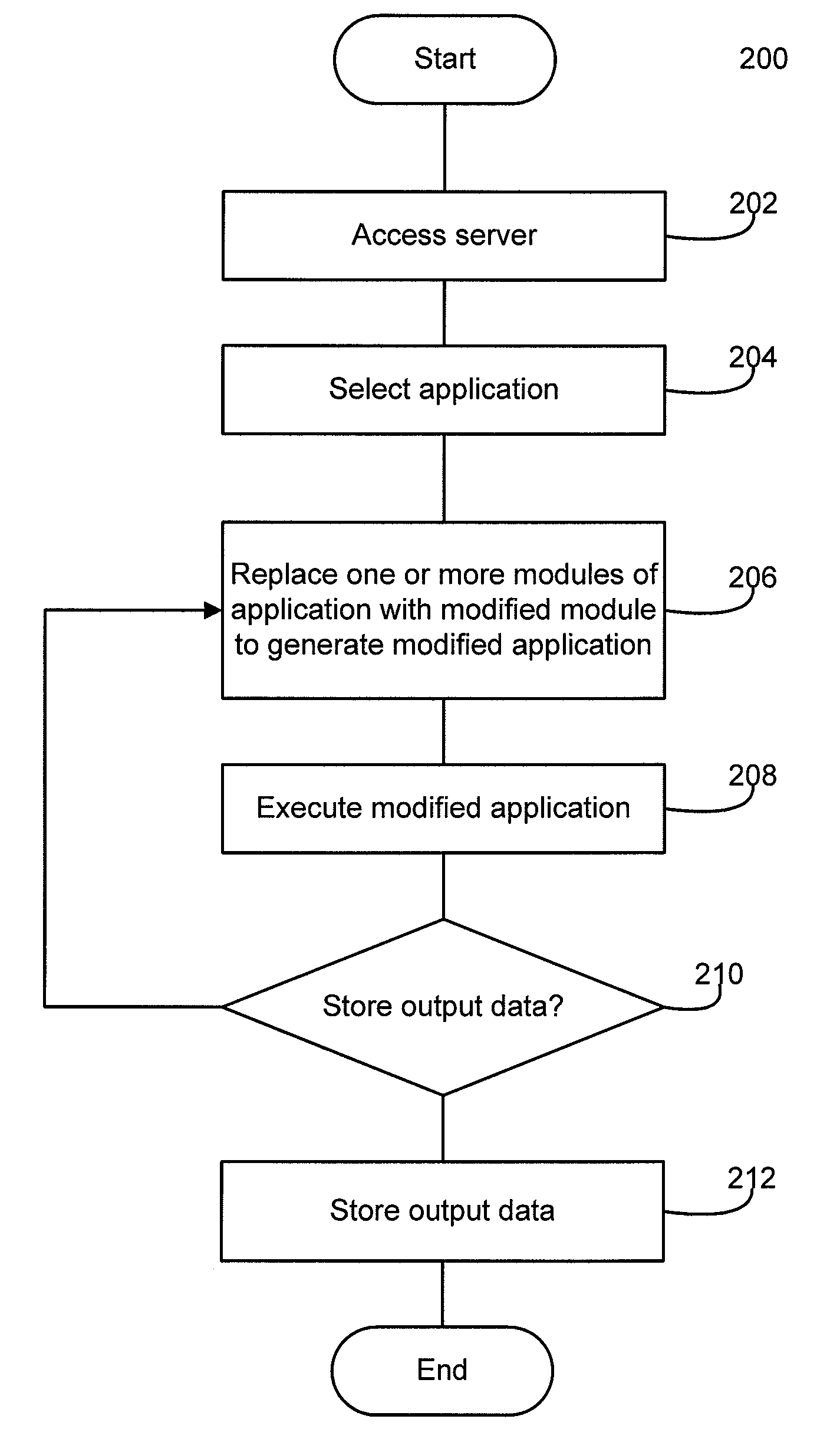
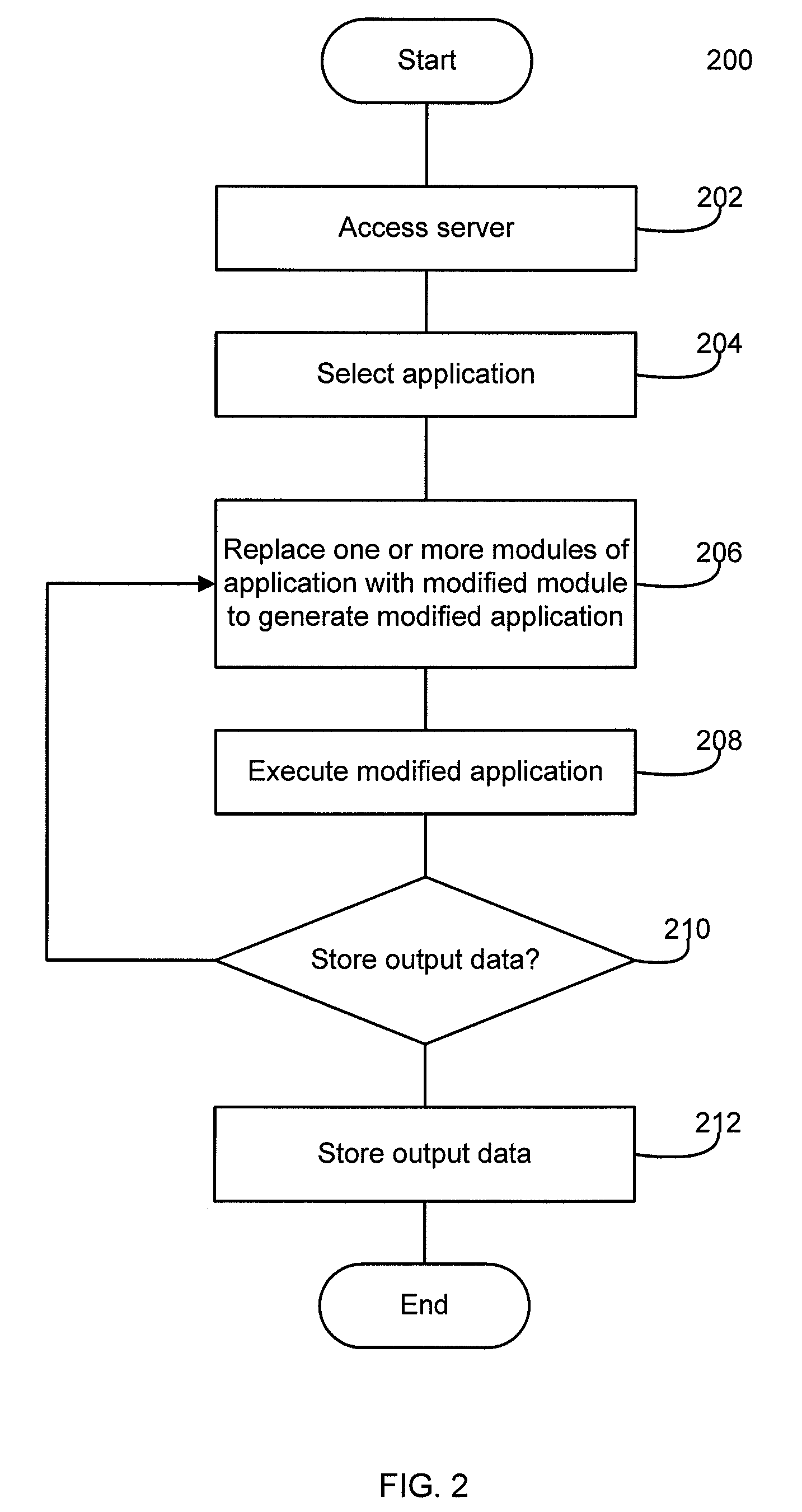
System and method for testing a software module
InactiveUS20090158249A1Error detection/correctionVersion controlSoftware engineeringApplication software
Systems and methods are described for testing a software module. The method comprises receiving a modified software module for use as part of a software application which includes a plurality of constituent software modules, replacing at least one of the constituent software modules with the modified software module to generate a modified software application, generating output data as a function of execution of the modified software application, and storing the output data.
Owner:OATH INC
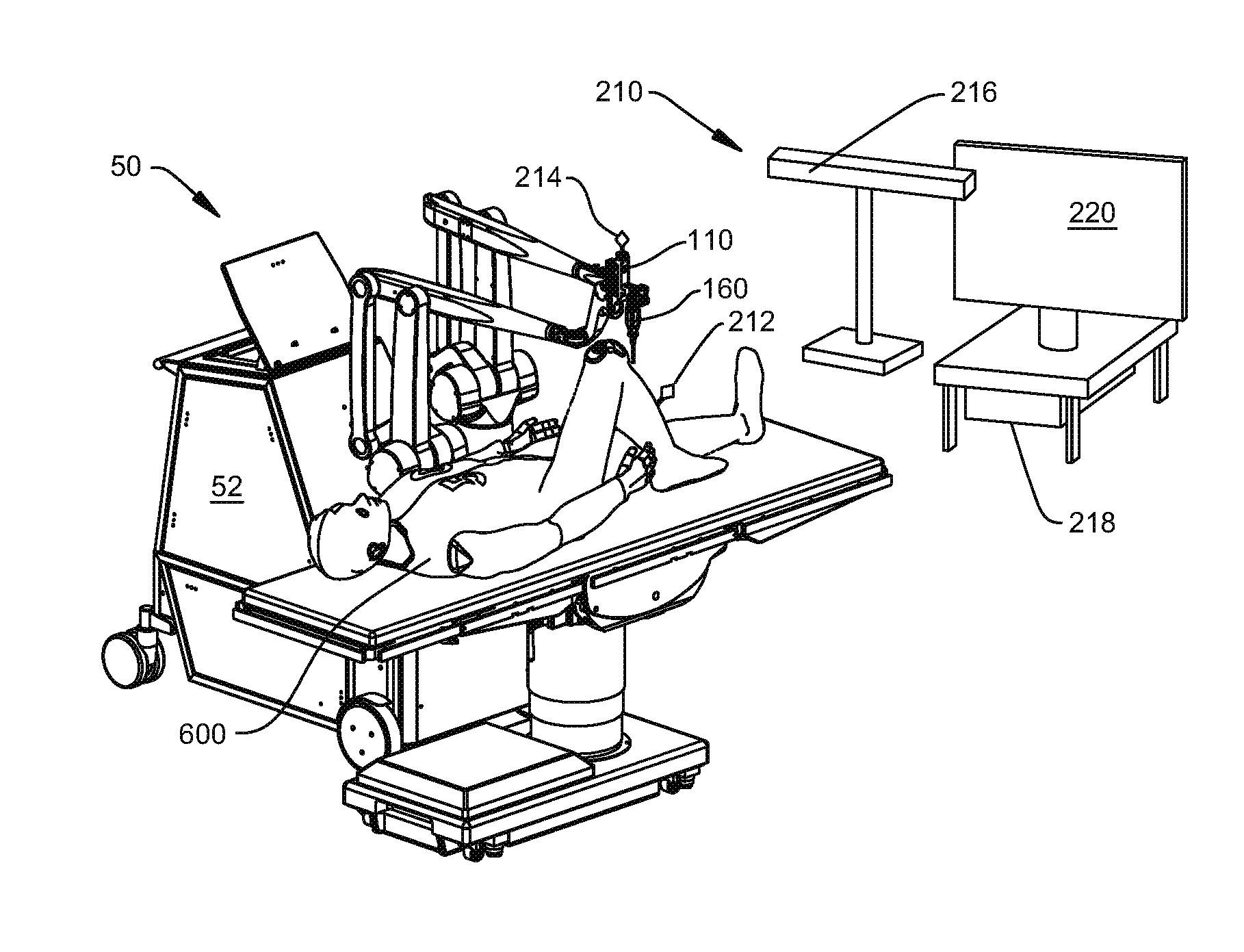
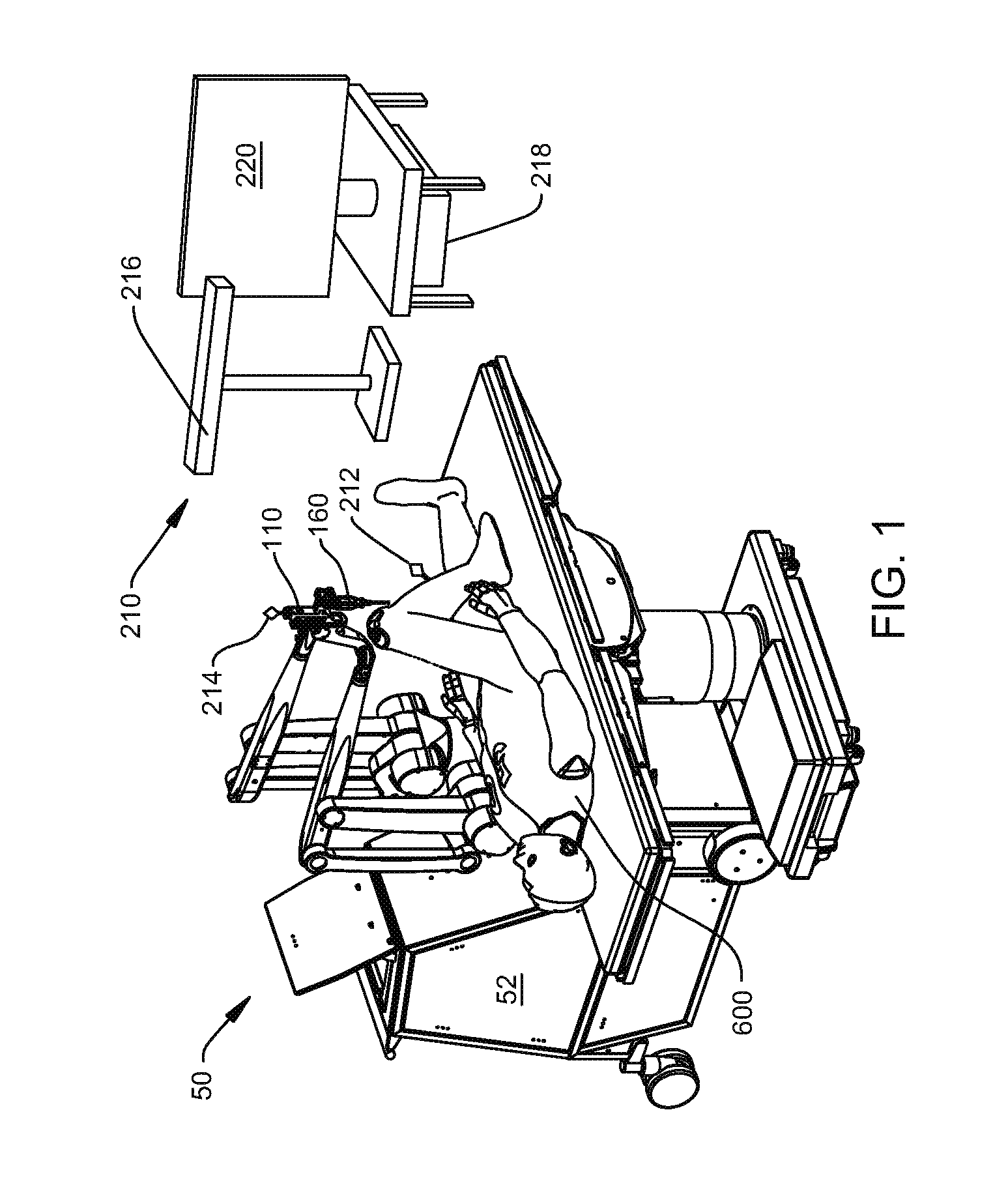
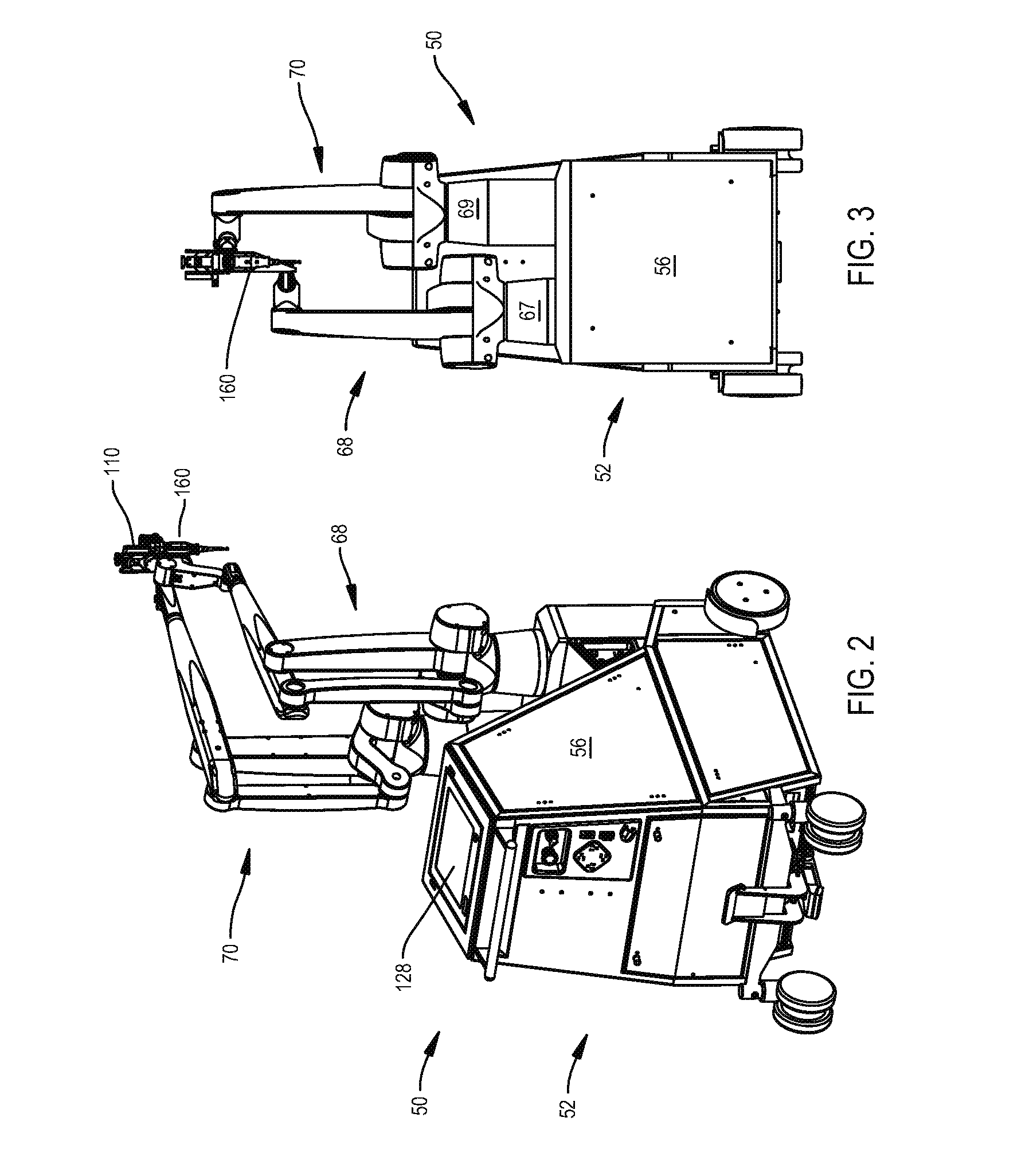
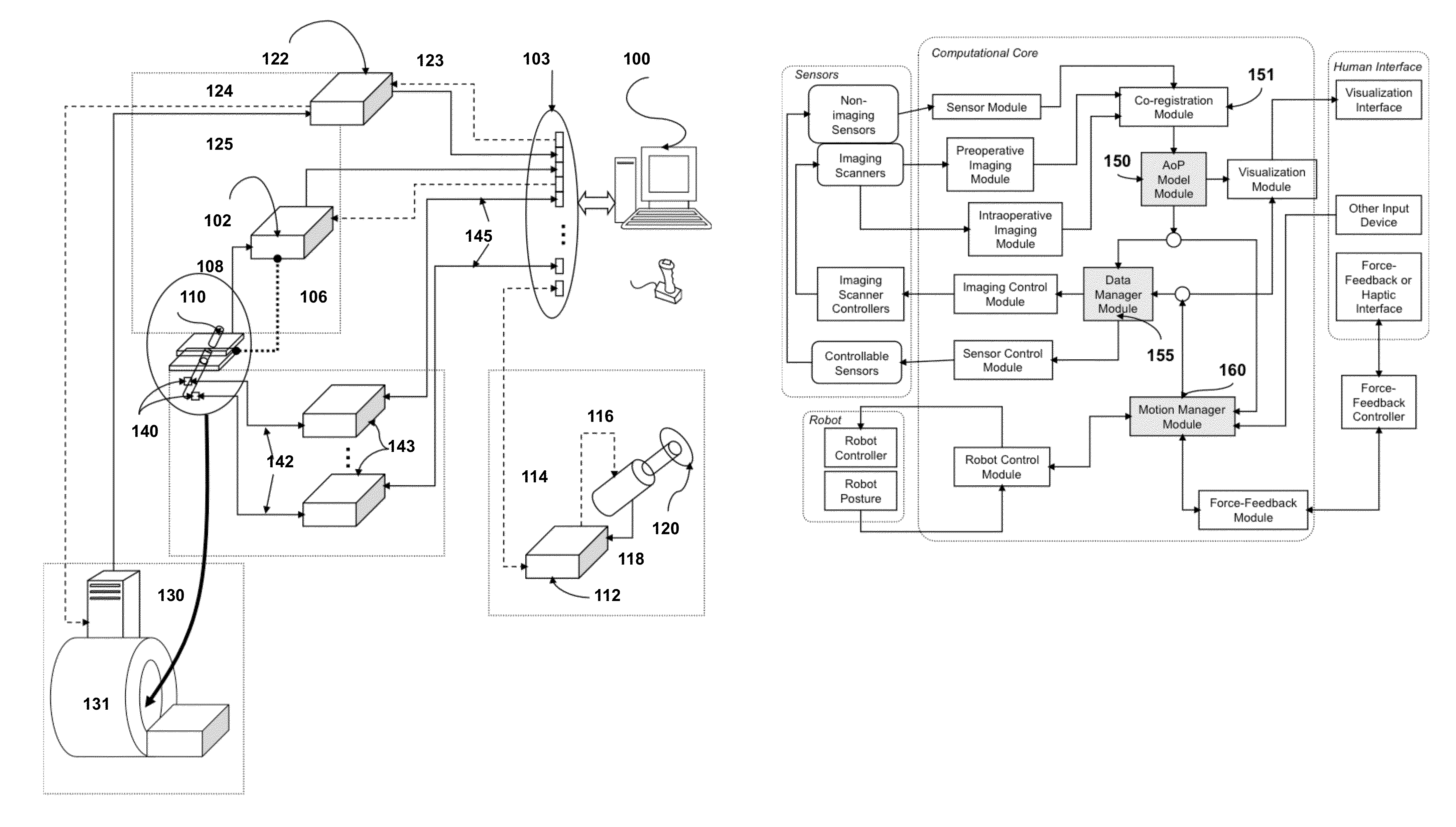
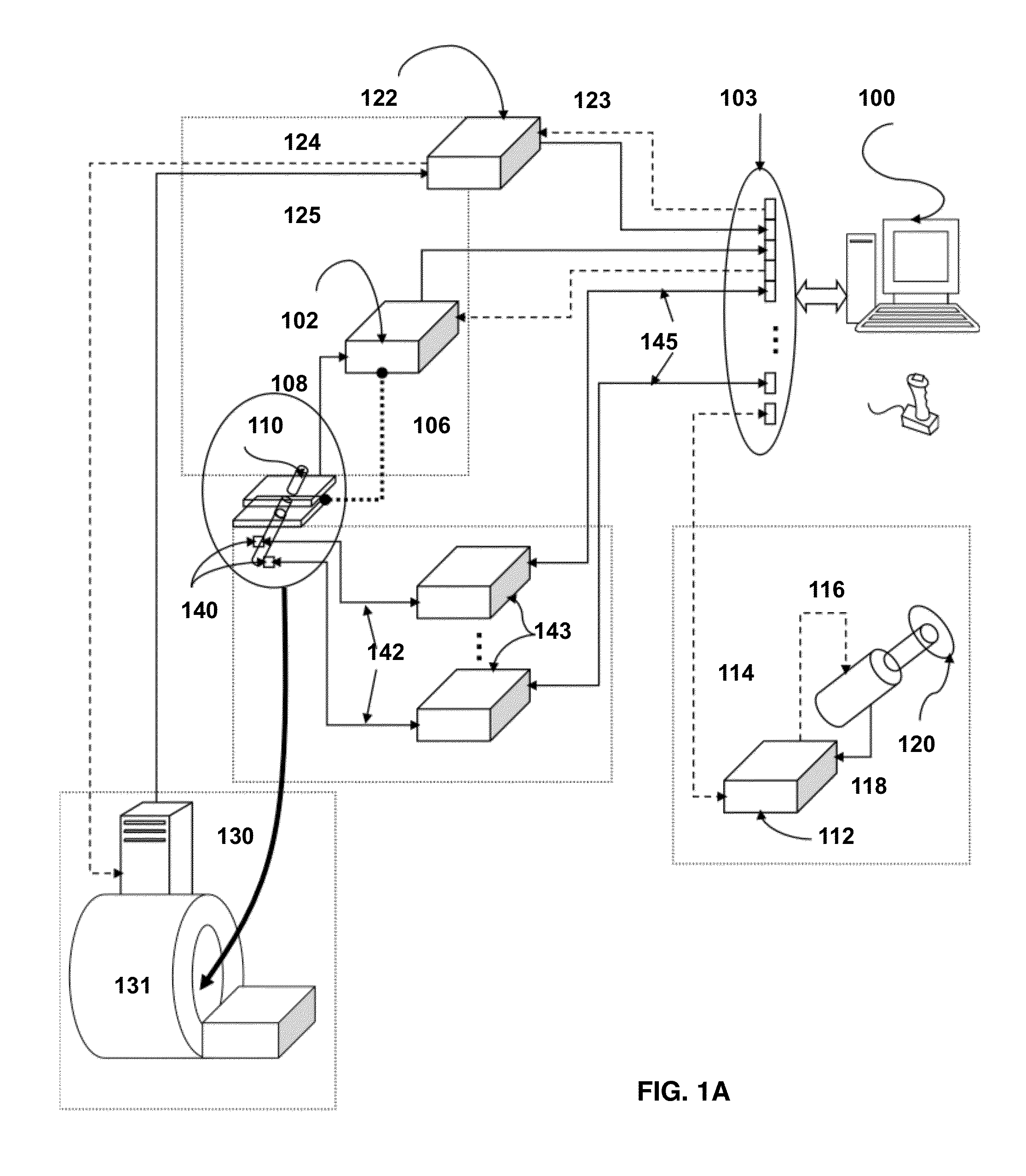
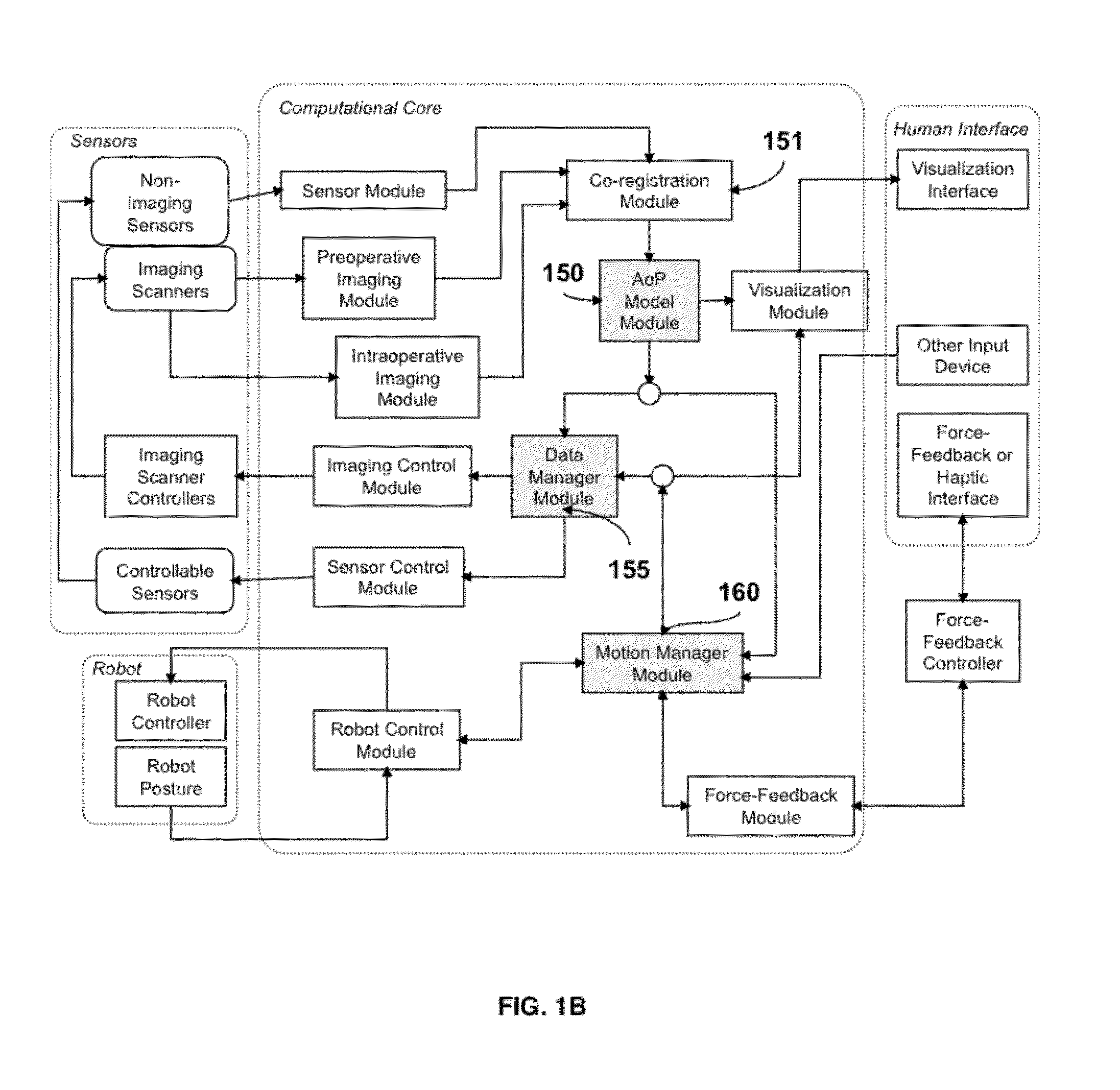
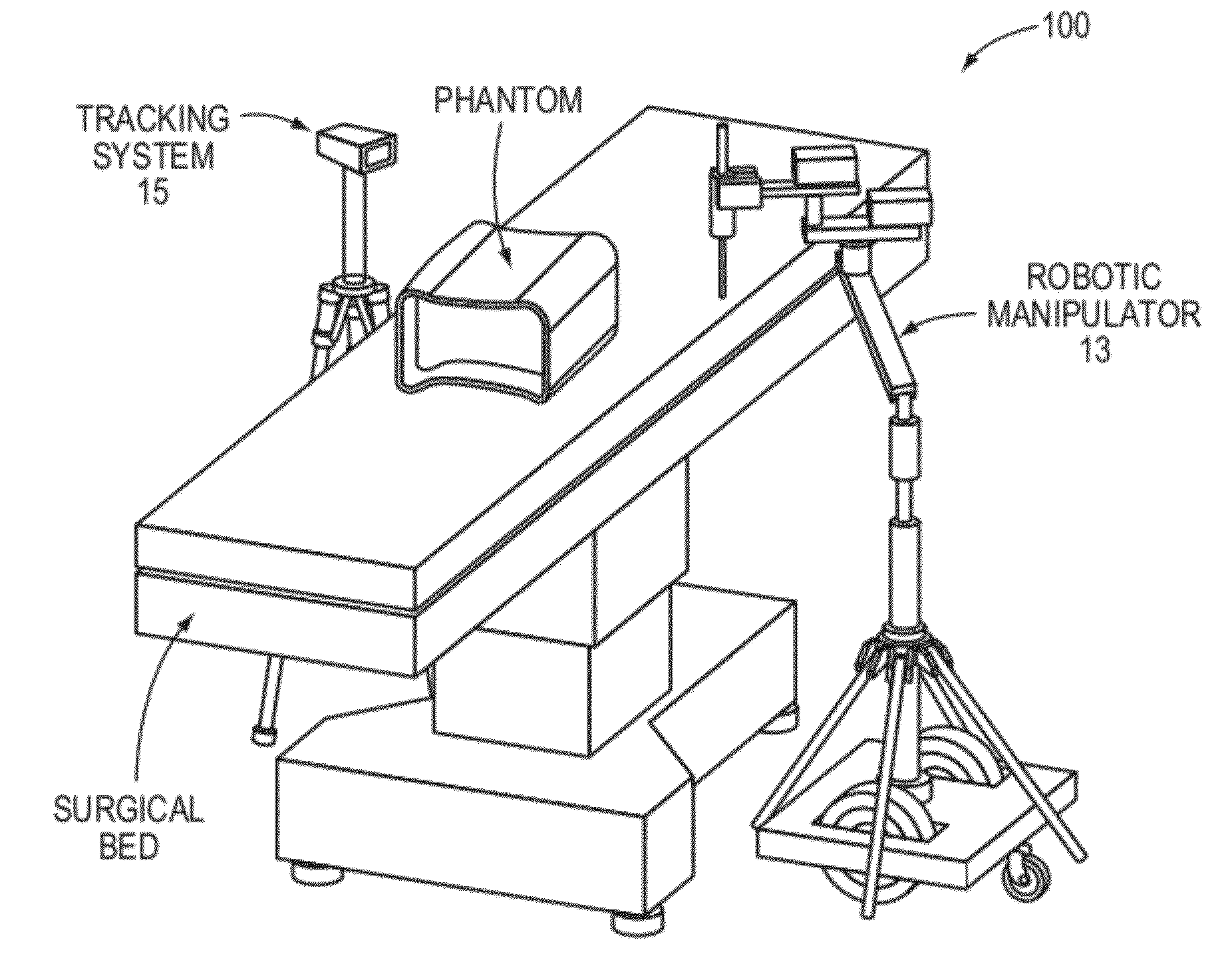
Navigation System for use with a Surgical Manipulator Operable in Manual or Semi-Autonomous Modes
A navigation system for use with a surgical manipulator operable in manual or semi-autonomous modes. The navigation system includes a tracker for attaching to the patient and a localizer to receive signals from the tracker or transmit signals to the tracker. The navigation system includes a navigation processor that runs a plurality of software modules.
Owner:STRYKER CORP
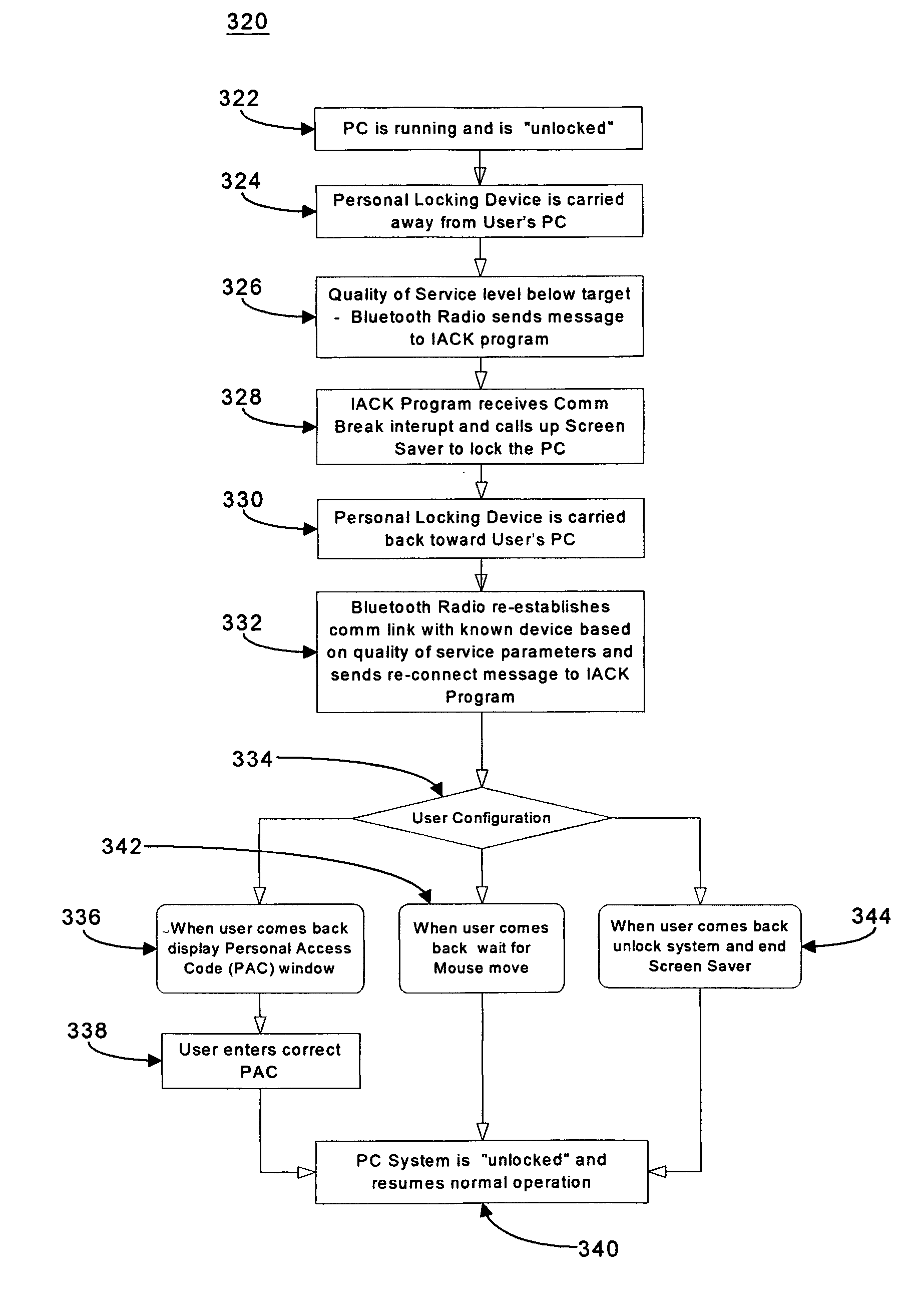
Wireless access management and control for personal computing devices
InactiveUS20050076242A1Monitoring quality of serviceDigital data processing detailsNetwork topologiesQuality of serviceControl system
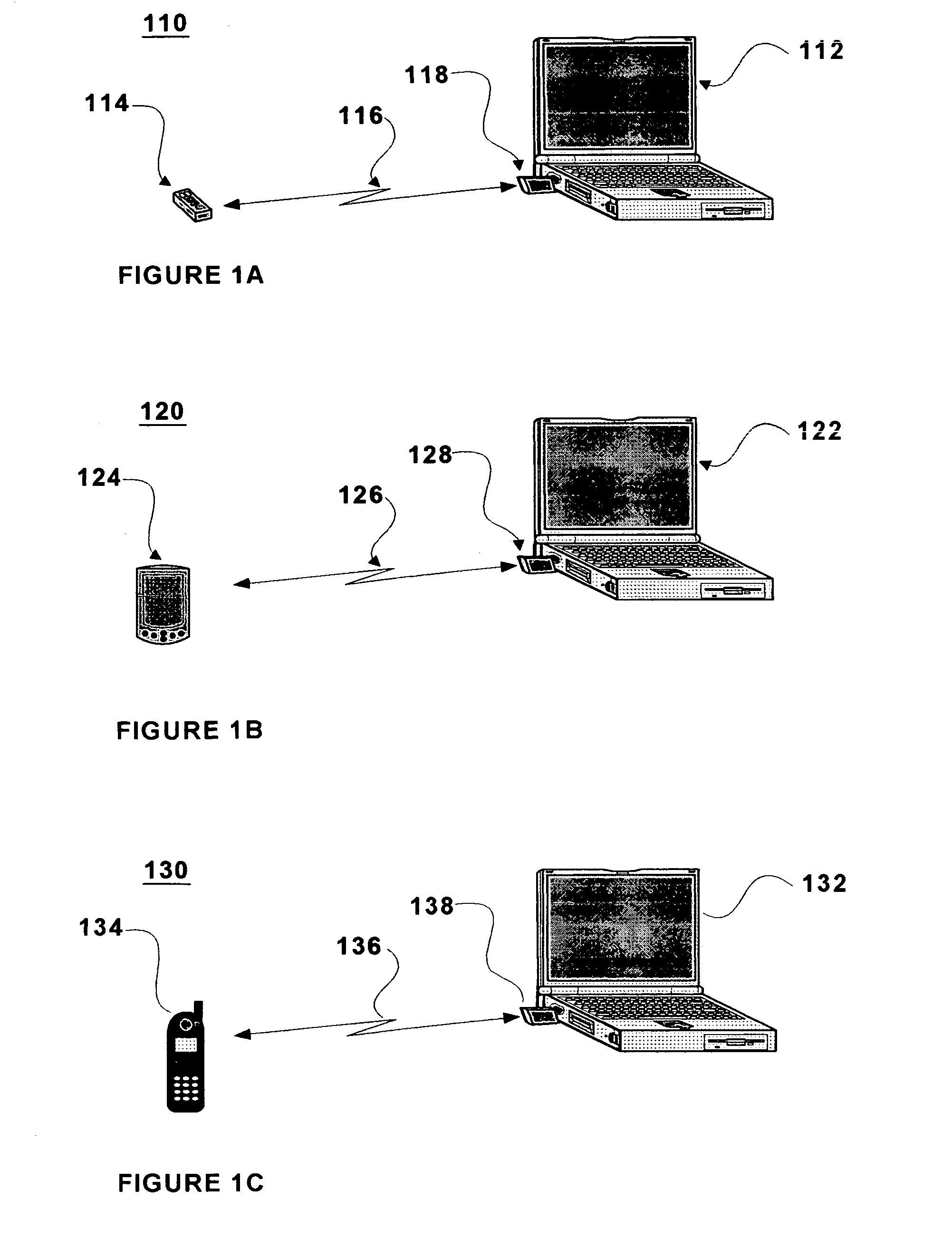
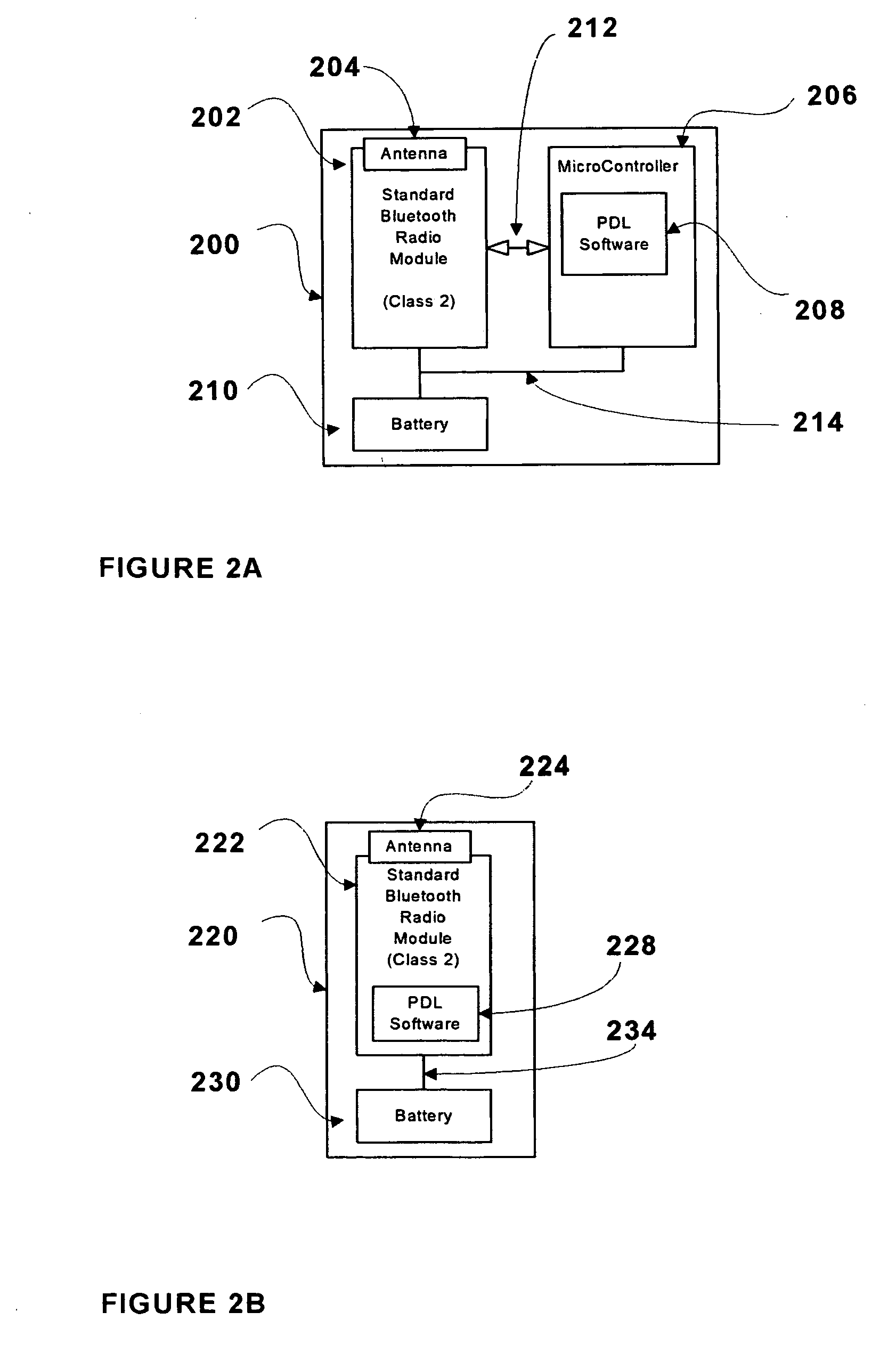
A wireless access control system for an electronic device comprises a personal locking device and an access control software module. The electronic device and personal locking device are Bluetooth-enabled and use Bluetooth to communicate with each other. The access control software is used to establish a Bluetooth link between these devices, based on the unique Bluetooth identifiers of the personal locking device and the electronic device. The personal locking device is preferably portable and is carried by the user at all times. Examples of preferred personal locking devices are cellular telephones, personal digital assistants, and pocket PCs. The Bluetooth radio chip and the Bluetooth communications protocol monitor the quality of service of the Bluetooth link between the devices. When the quality of service falls below a predetermined threshold, the access control software may switch the electronic device from an unlocked state to a locked state. When the quality of service rises above a predetermined threshold from below the threshold, the software may switch the electronic device from a locked state to an unlocked state.
Owner:BREUER ROLF
Targeted delivery of informational content with privacy protection
InactiveUS7472093B2Privacy protectionHigh degreeFinanceComputer security arrangementsThird partyObjective information
A system and method for enabling use of detailed consumer profiles for the purposes of targeted information delivery while protecting these profiles from disclosure to information providers or hostile third parties are disclosed herein. Rather than gathering data about a consumer in order to decide which information to send her, an information provider makes use of a client-side executable software module called a negotiant function. The negotiant function acts as a client-side proxy to protect consumer data, and it also directs the targeting of information, requesting items of information from the information provider that are tailored to the profile provided by the consumer.
Owner:RSA
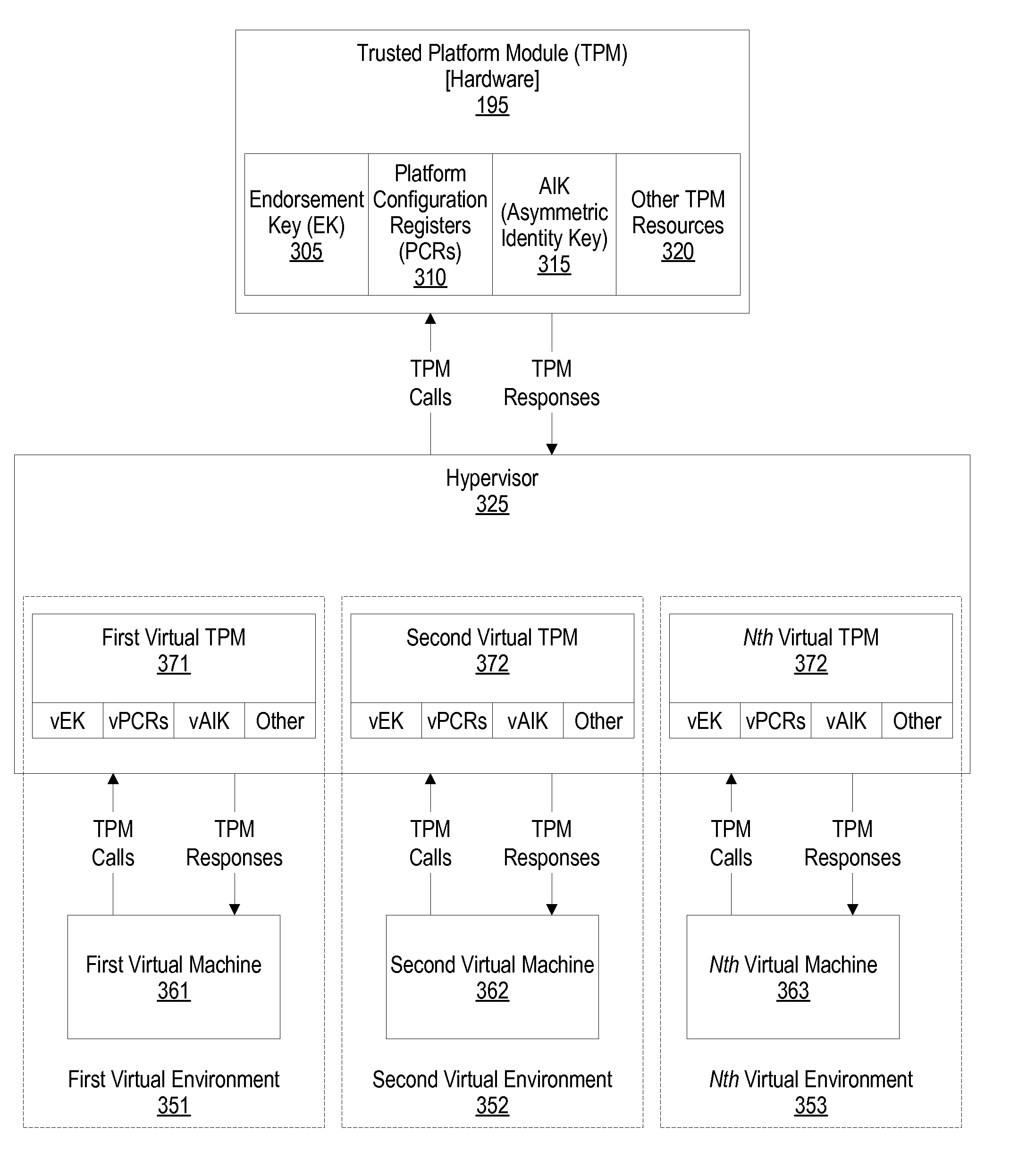
System and Method for Reporting the Trusted State of a Virtual Machine
ActiveUS20080244569A1Digital data processing detailsUnauthorized memory use protectionTrusted Platform ModuleHandling system
A system, method, and program product is provided that executes a start sequence of an information handling system that includes a hardware based TPM. Multiple PCRs are stored in the TPM and are initialized to a predetermined state when the start sequence commences. During execution of the start sequence, software modules, including a hypervisor, are loaded the system's memory. PCR values resulting from the loading of the software modules are calculated. The resulting PCR values are compared with expected PCR values. If the PCR values match the expected PCR values, then a virtual environment is created under the hypervisor. The virtual environment includes a VM and a virtual trust platform module (vTPM) that is used by the virtual machine to satisfy the virtual machines TPM requests.
Owner:LENOVO PC INT
Robotic Device and Systems for Image-Guided and Robot-Assisted Surgery
Provided herein are robotic systems, for example, MRI guided robots, for image-guided robot-assisted surgical procedures and methods for using the same to perform such surgical procedures on a patient. The robotic systems comprise a robotic manipulator device or global positioner, means for actuating the robotic manipulator or global positioner that is mechanically linked thereto and a computer having a memory, a processor and at least one network connection in electronic communication with the robotic system. The actuating means comprises at least one transmission line having a flexible component comprising a displaceable medium, a rigid component comprising rigid pistons or a combination through which actuation is transmitted to the robotic manipulator or global positioner. The computer tangibly stores in memory software modules comprising processor-executable instructions to provide interfaces between the robotic system, an imaging system and an operator and to control operation thereof.
Owner:UNIV HOUSTON SYST
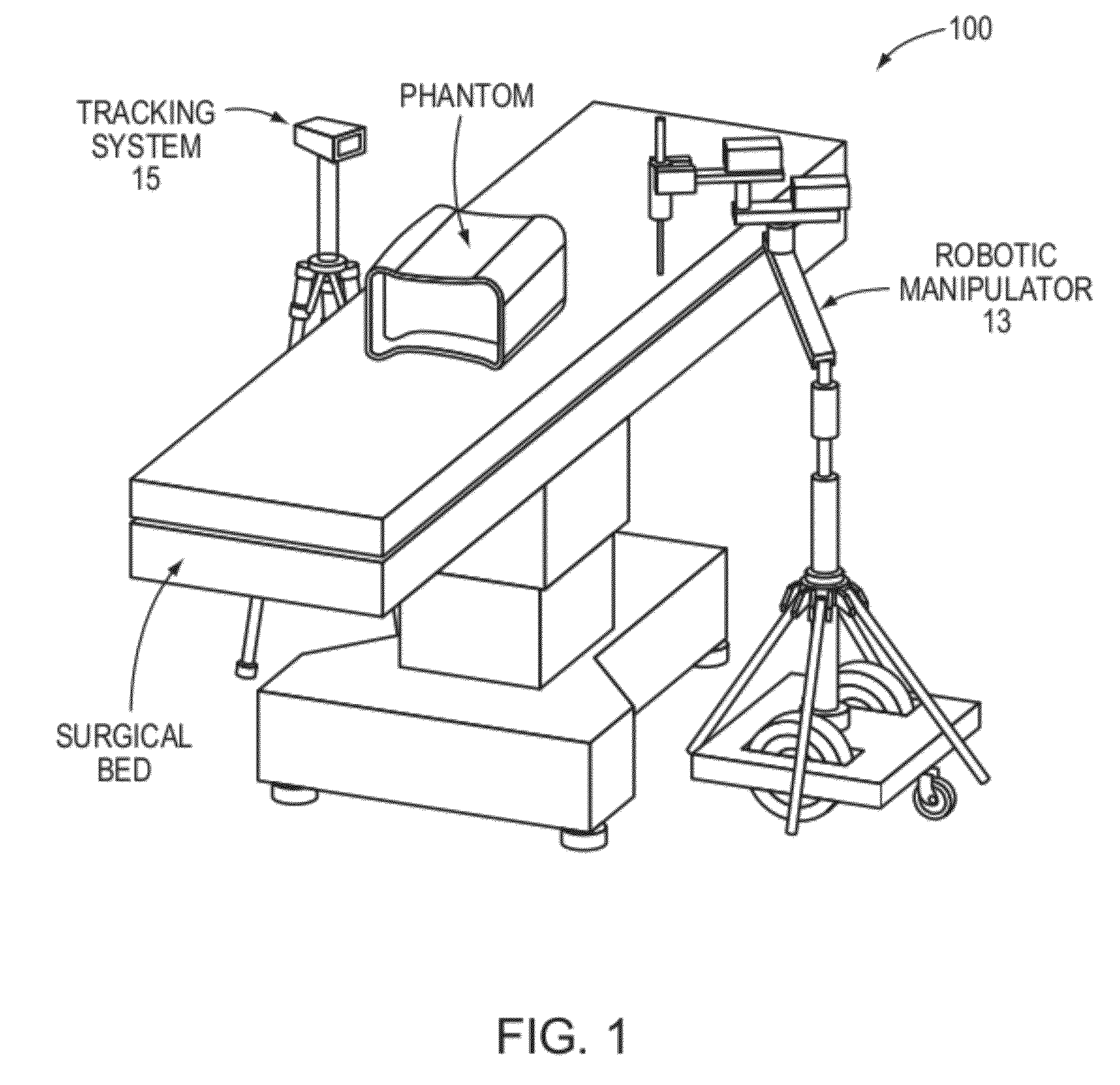
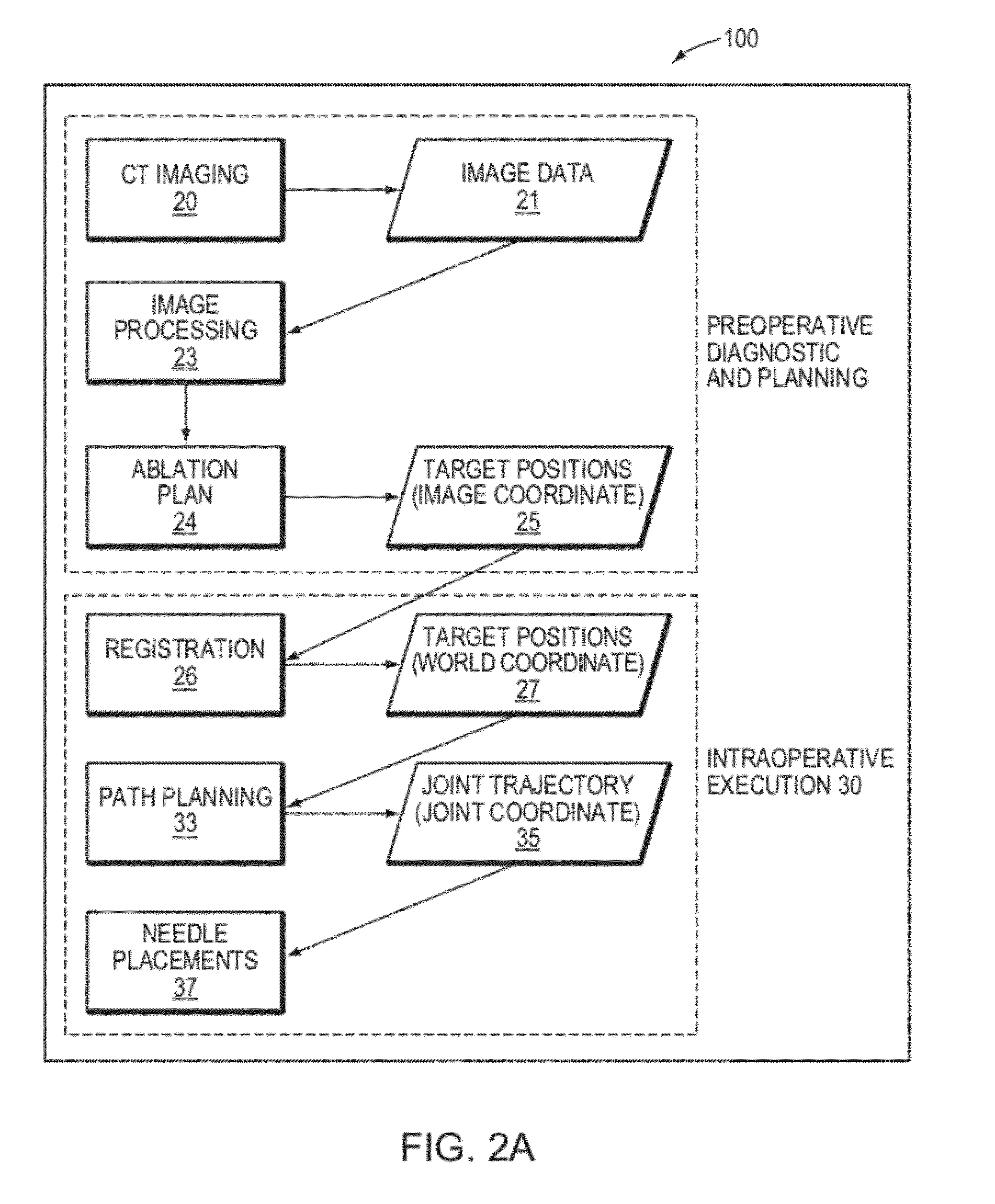
Transcutaneous robot-assisted ablation-device insertion navigation system
InactiveUS20120226145A1Easy to operateFacilitates potential expansionUltrasonic/sonic/infrasonic diagnosticsSurgical needlesRadiofrequency ablationControl system design
A robotic system for overlapping radiofrequency ablation (RFA) in tumor treatment is disclosed. The robot assisted navigation system is formed of a robotic manipulator and a control system designed to execute preoperatively planned needle trajectories. Preoperative imaging and planning is followed by interoperative robot execution of the ablation treatment plan. The navigation system combines mechanical linkage sensory units with an optical registration system. There is no requirement for bulky hardware installation or computationally demanding software modules. Final position of the first needle placement is confirmed for validity with the plan and then is used as a reference for the subsequent needle insertions and ablations.
Owner:NAT UNIV OF SINGAPORE
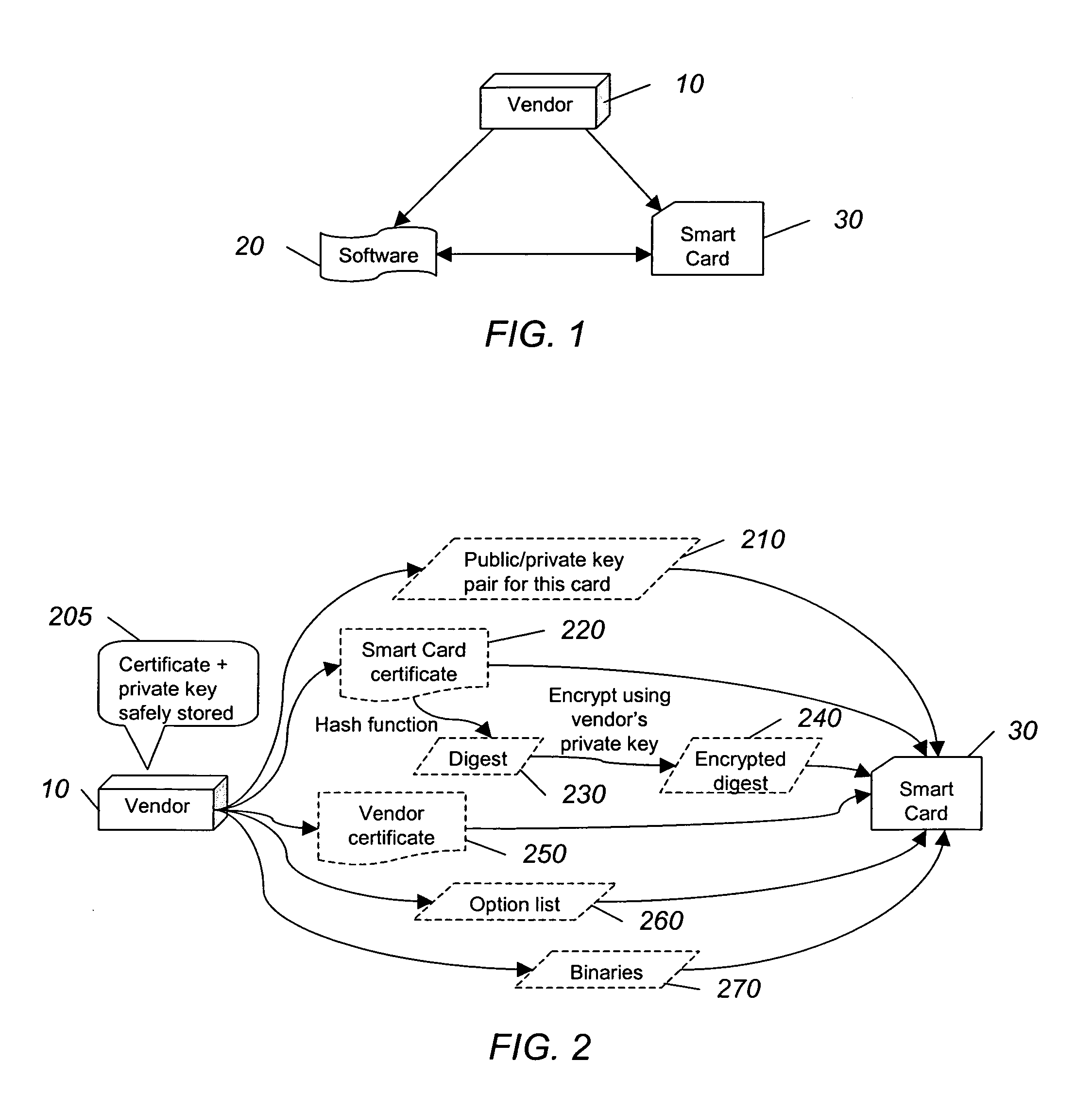
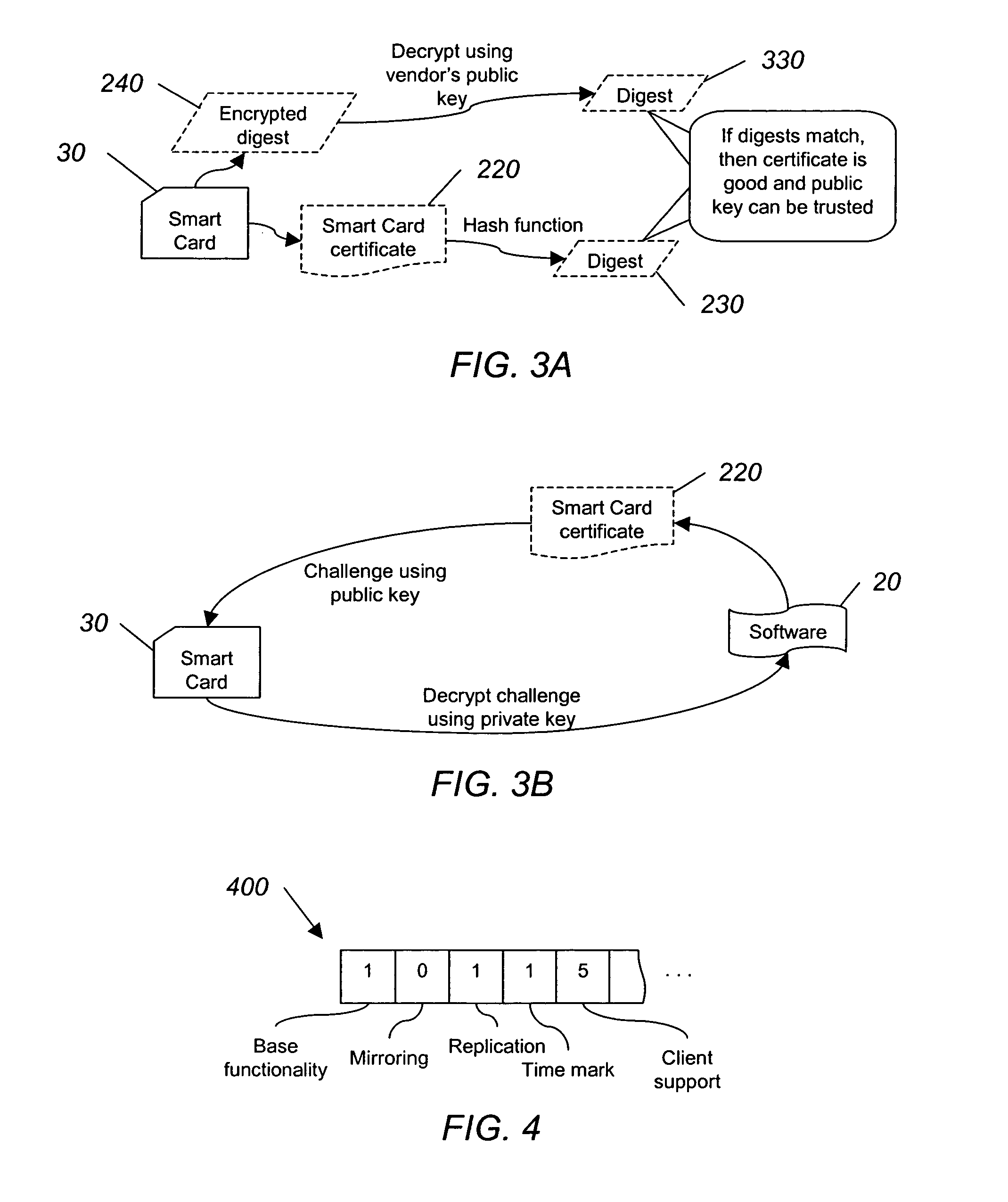
System and method for authorizing software use
InactiveUS20050138387A1User identity/authority verificationComputer security arrangementsSmart cardSoftware vendor
A software vendor freely distributes software to users and issues smart cards to be used with the software. The smart card includes at least one software module missing from the software package and a list of allowed functionality dictating the capabilities of the software package. A user authenticates, using, e.g., public key cryptography, the smart card, which authorizes the use of the software. Once authorized, the module missing from the software is reunited with the rest of the software package. The software can be used limited to the allowed functionality included with the card. If more or different functionality is needed, the user can purchase another card authorizing such additional functionality, and then transfer the new functionality to the old smart card.
Owner:FALCONSTOR
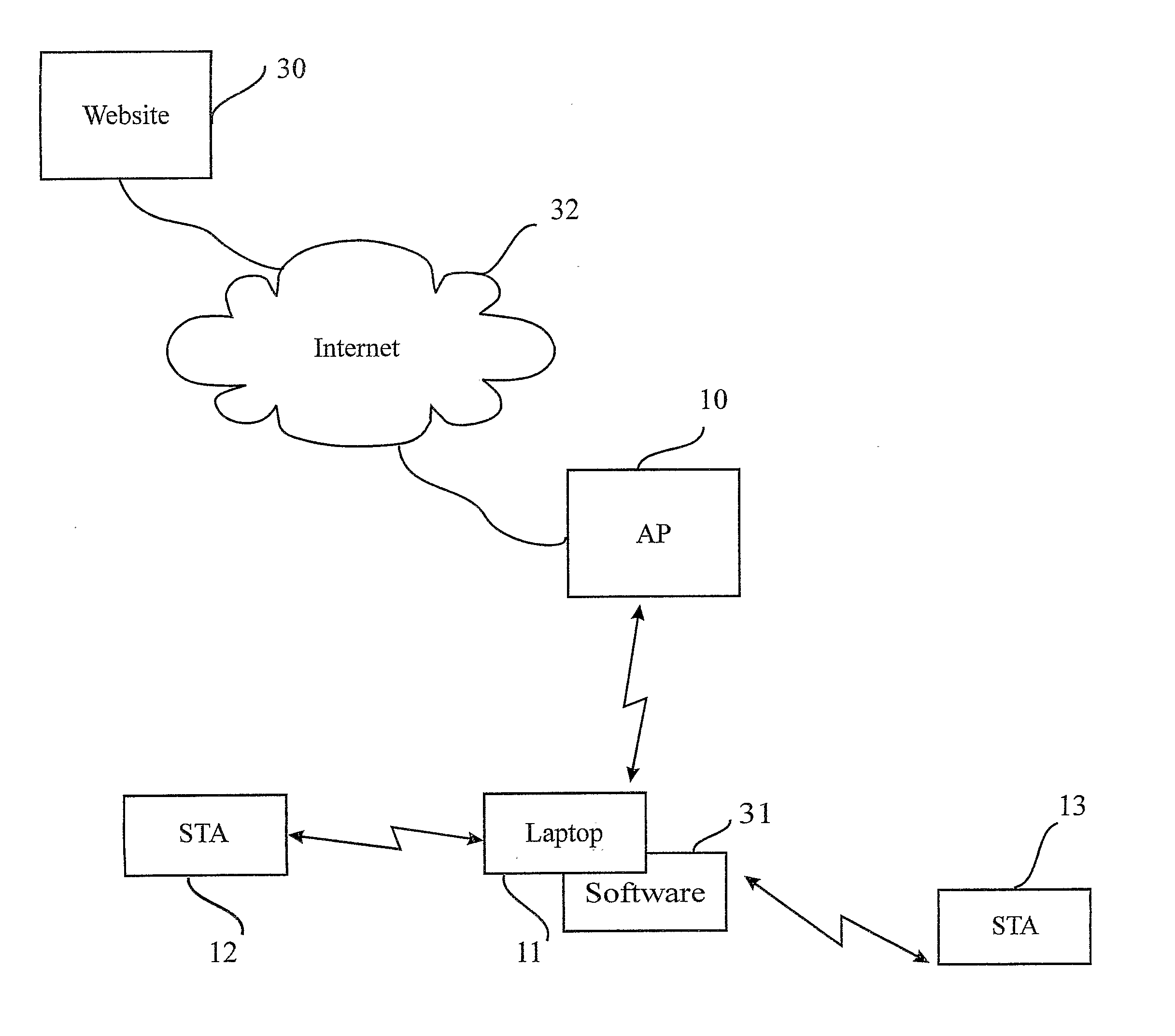
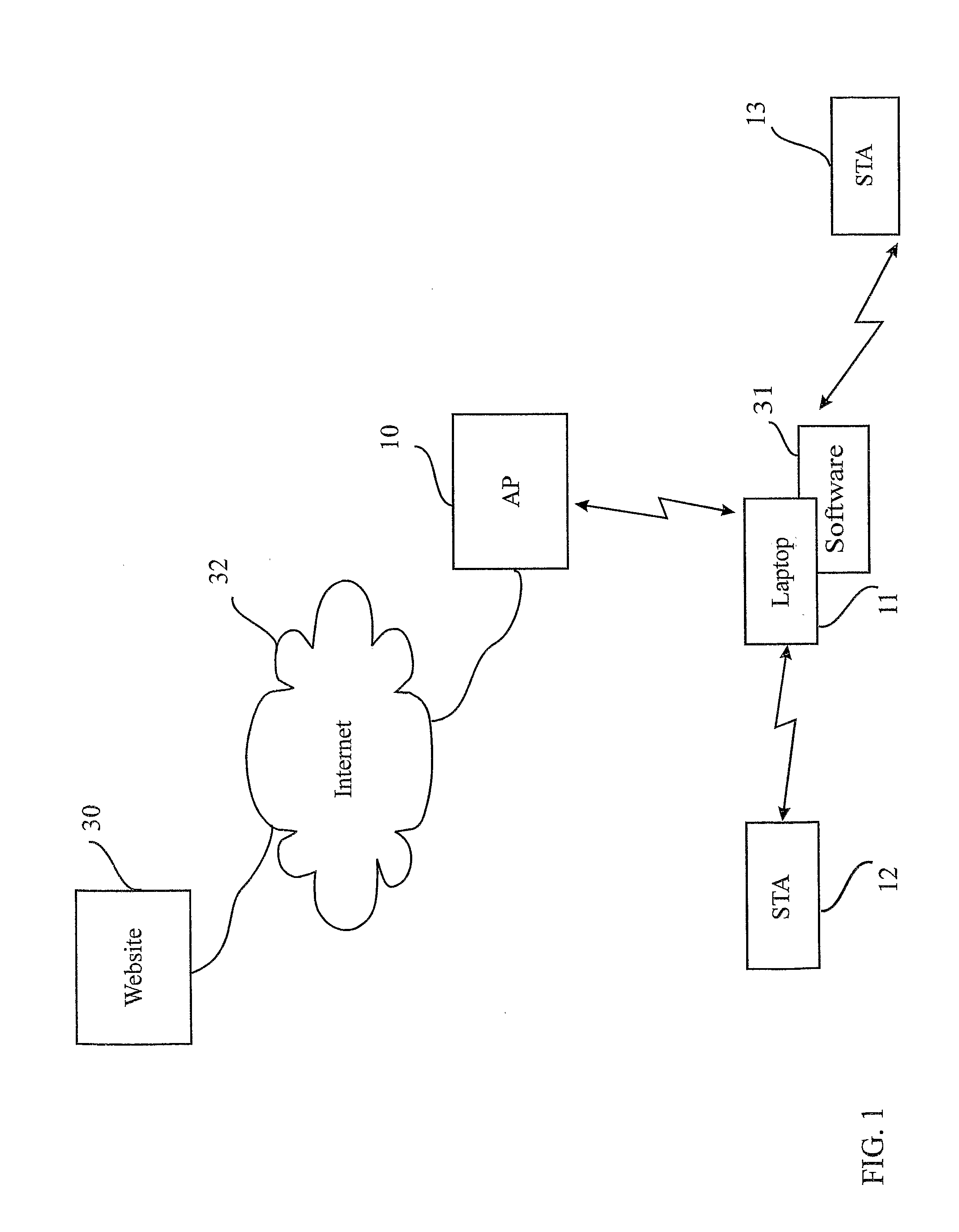
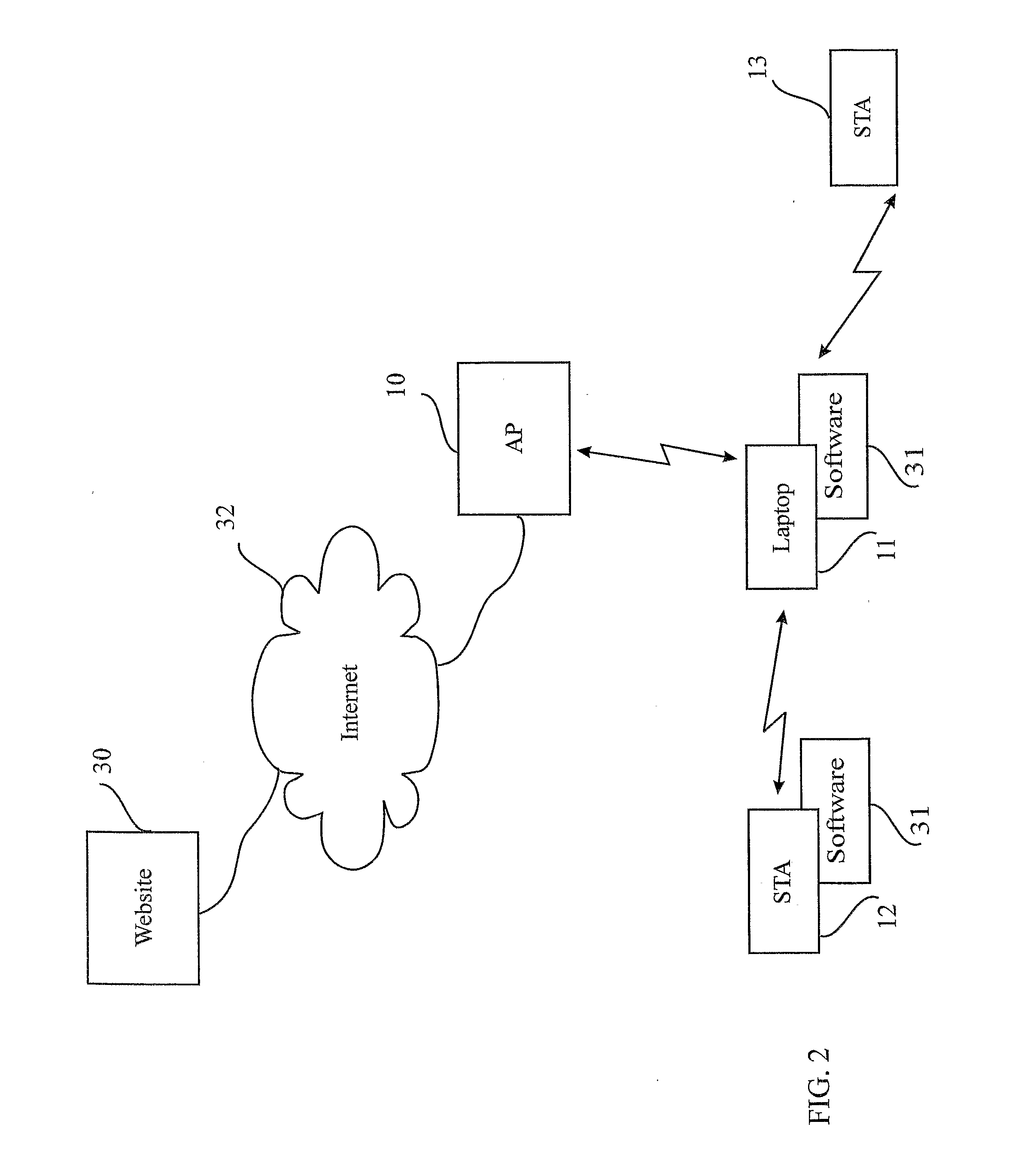
Wireless internet system and method
ActiveUS20100296441A1Light burdenFirmly connectedNetwork topologiesConnection managementSecurity parameterSecurity information
A method for providing a wireless Internet connection to WiFi-enabled devices (STAs) comprising: wirelessly connecting a first STA to the Internet through a first AP with a first SSID; remaining connected to the first Access Point (AP), the first STA creates a software-based wireless AP with a second SSID for wirelessly connecting other STAs to the Internet through the first STA. A software module running on the first STA allows a second STA a wide access to the Internet only if the second STA has a copy of the software module running installed and active therein. A method for configuring STAs to connect to a wireless network, comprising: a customer first connects a STA by wire to its network; a software on the STA copies to the STA the security information gained through the wired connection, thus setting the security parameters for the STA.
Owner:BARKAN WIRELESS ACCESS TECH
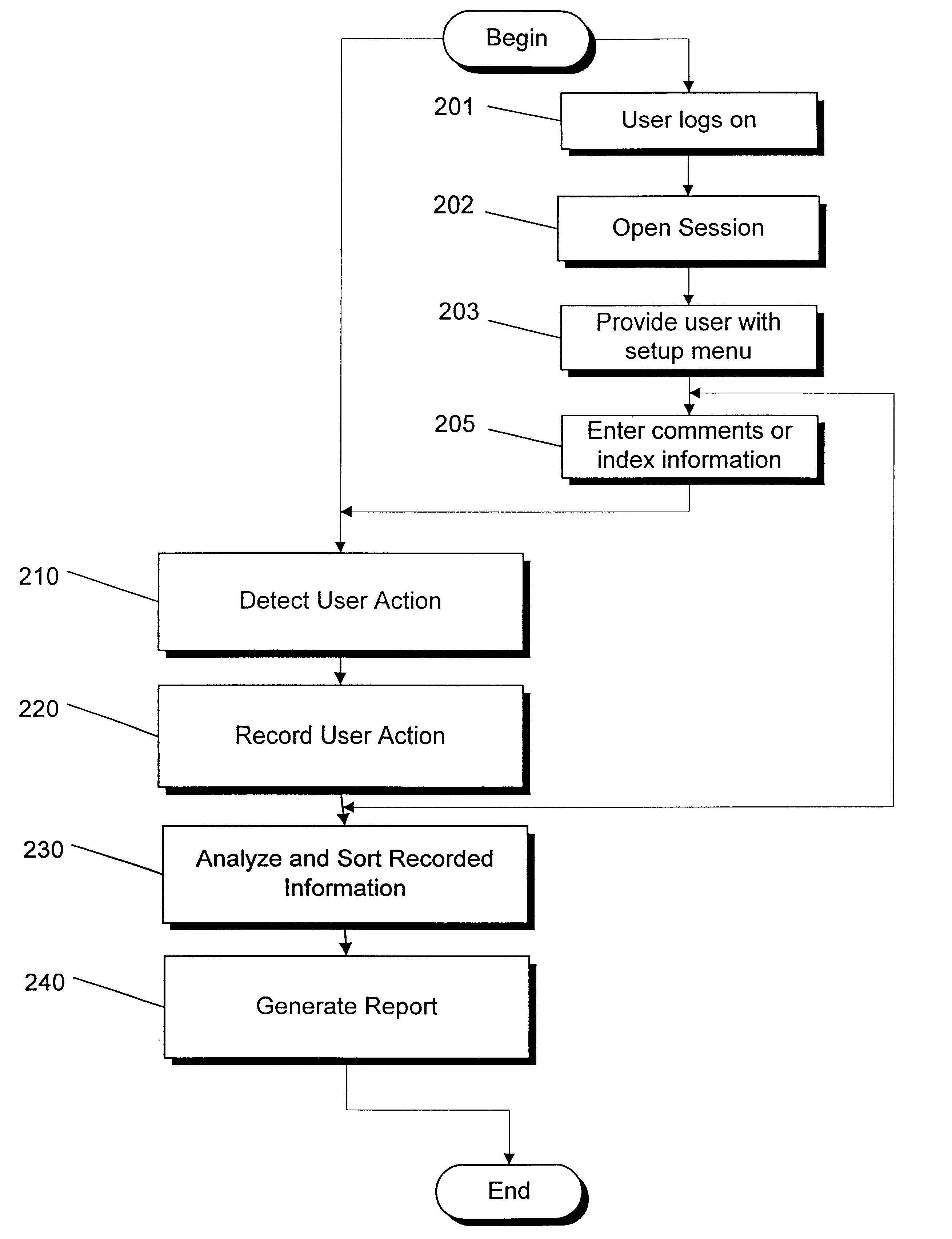
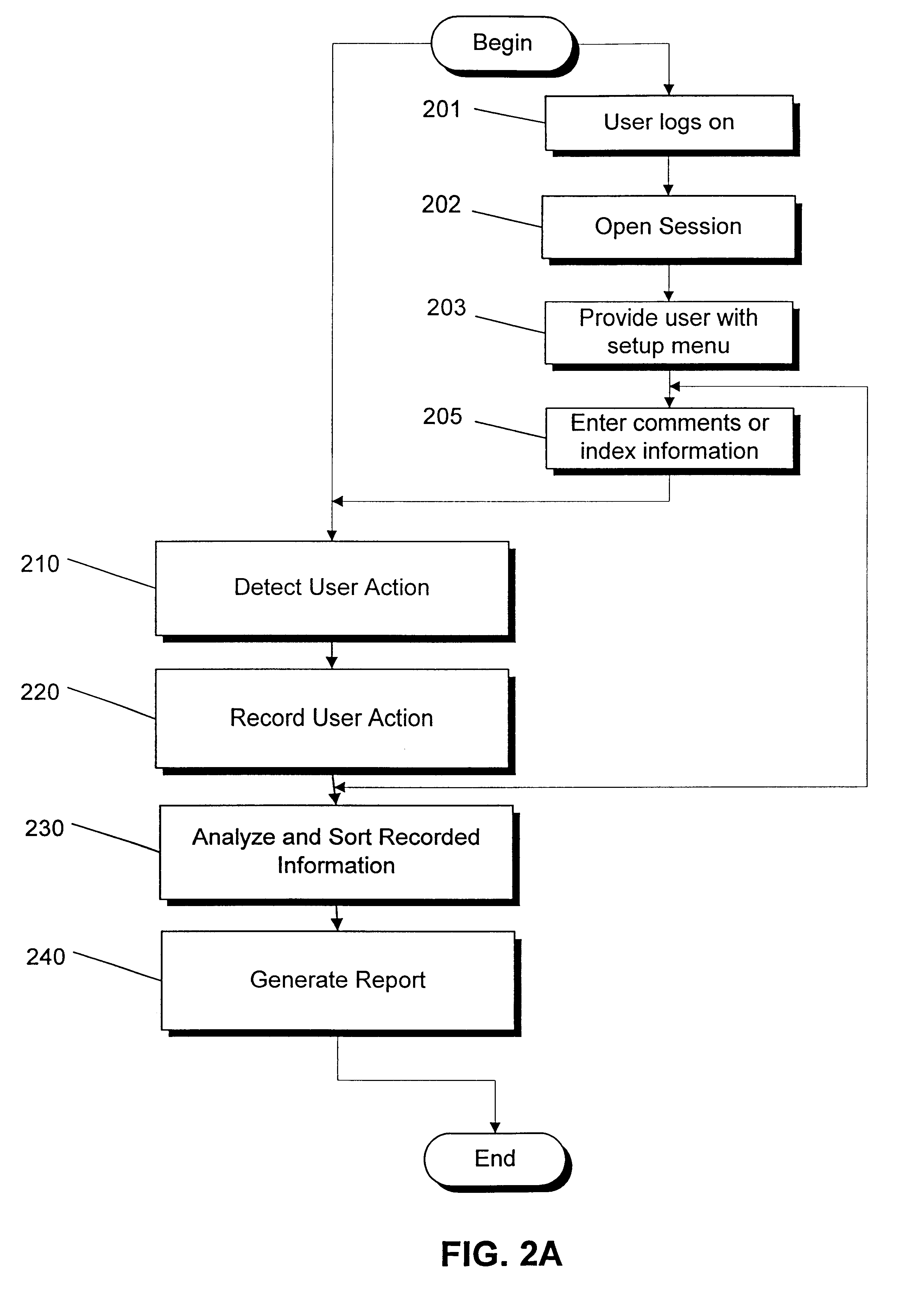
Real time monitoring system for tracking and documenting changes made by programmer's during maintenance or development of computer readable code on a line by line basis and/or by point of focus
InactiveUS6698013B1Version controlSpecific program execution arrangementsMonitoring systemComputer software
A method and system for documenting and tracking user interaction with computer readable code during modification or development of computer software is described. The invention provides a controlled environment for recording detailed information about user actions and events that occur during the maintenance and development of computer readable code. Features of the invention facilitate the entry of comments, review, and modification of the computer readable code. Embodiments of the invention, in real time, monitor, record, and report changes made to software modules at a line-by-line level. The nature and context of changes made to lines of code and any search requests are identified and recorded in one or more databases for review and reporting.
Owner:MINTAKA TECH GROUP
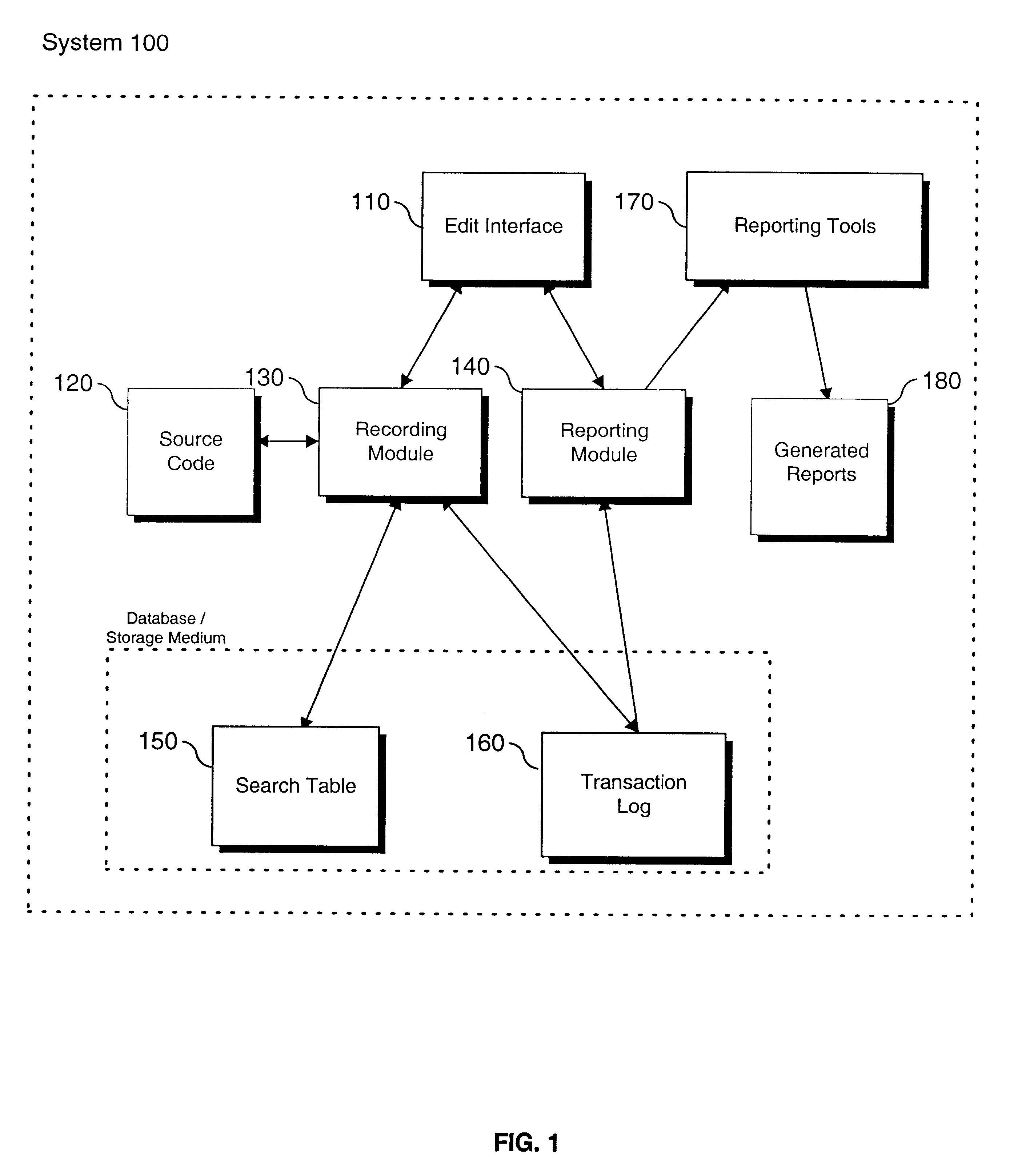
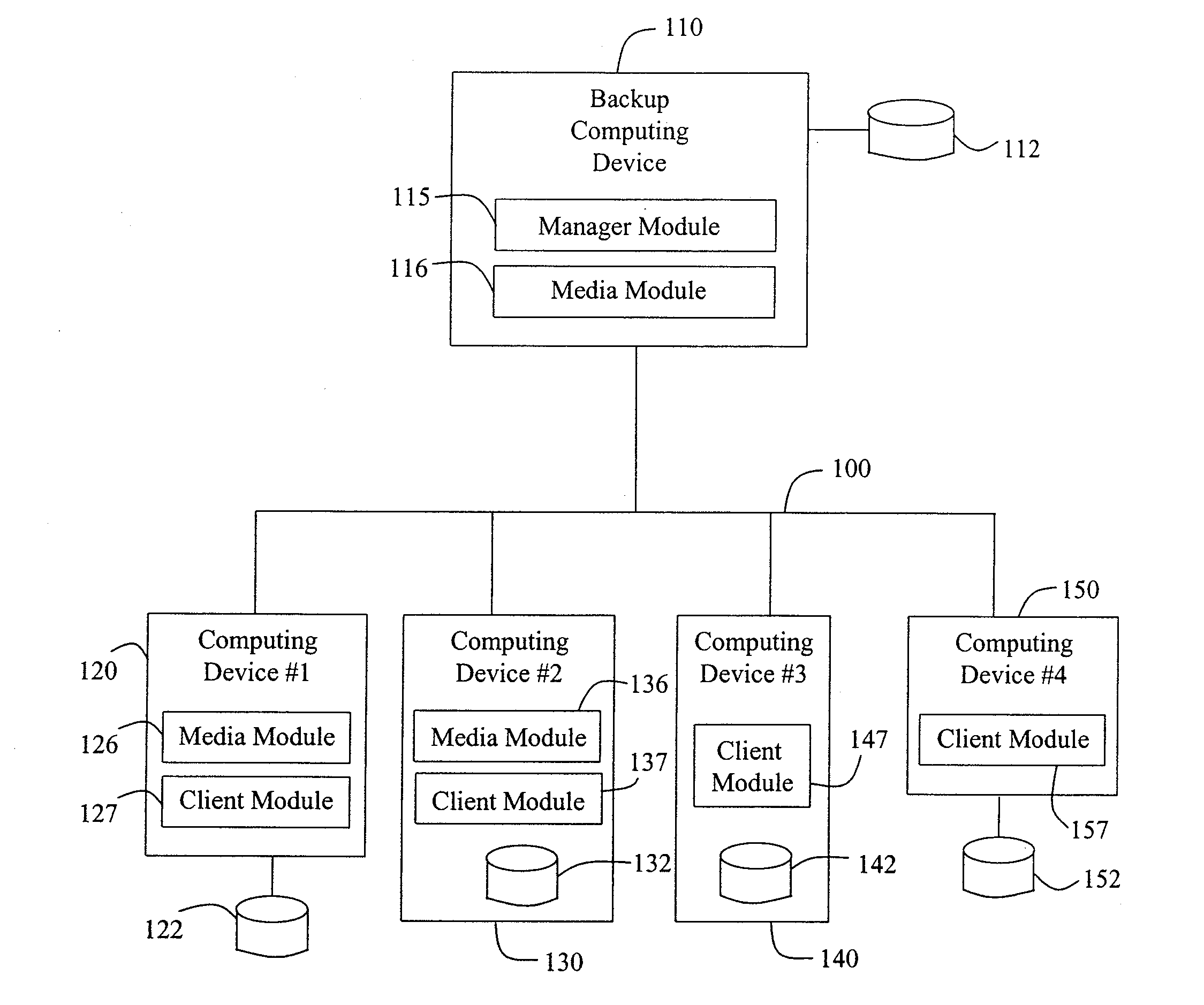
Modular systems and methods for managing data storage operations
InactiveUS20080244177A1Data processing applicationsDigital data processing detailsRegimenSystems management
The invention is a modular backup and retrieval system. The software modules making up the backup and retrieval system run independently, and can run either on the same computing devices or on different computing devices. The modular software system coordinates and performs backups of various computing devices communicating to the modules. At least one module on one of the computing devices acts as a system manager for a network backup regimen. A management component acts as a manager for the archival and restoration of the computing devices on the network. It manages and allocates library media usage, maintains backup scheduling and levels, and supervises or maintains the archives themselves through pruning or aging policies. A second software module acts as a manager for each particular library media.
Owner:COMMVAULT SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com