System and method for authorizing software use
a software and authorization technology, applied in the field of system and method for authorizing software use, can solve the problem that licensed items from one smart card cannot be transferred to another smart card, and achieve the effect of facilitating the transfer of licensed items from one smart card to another
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
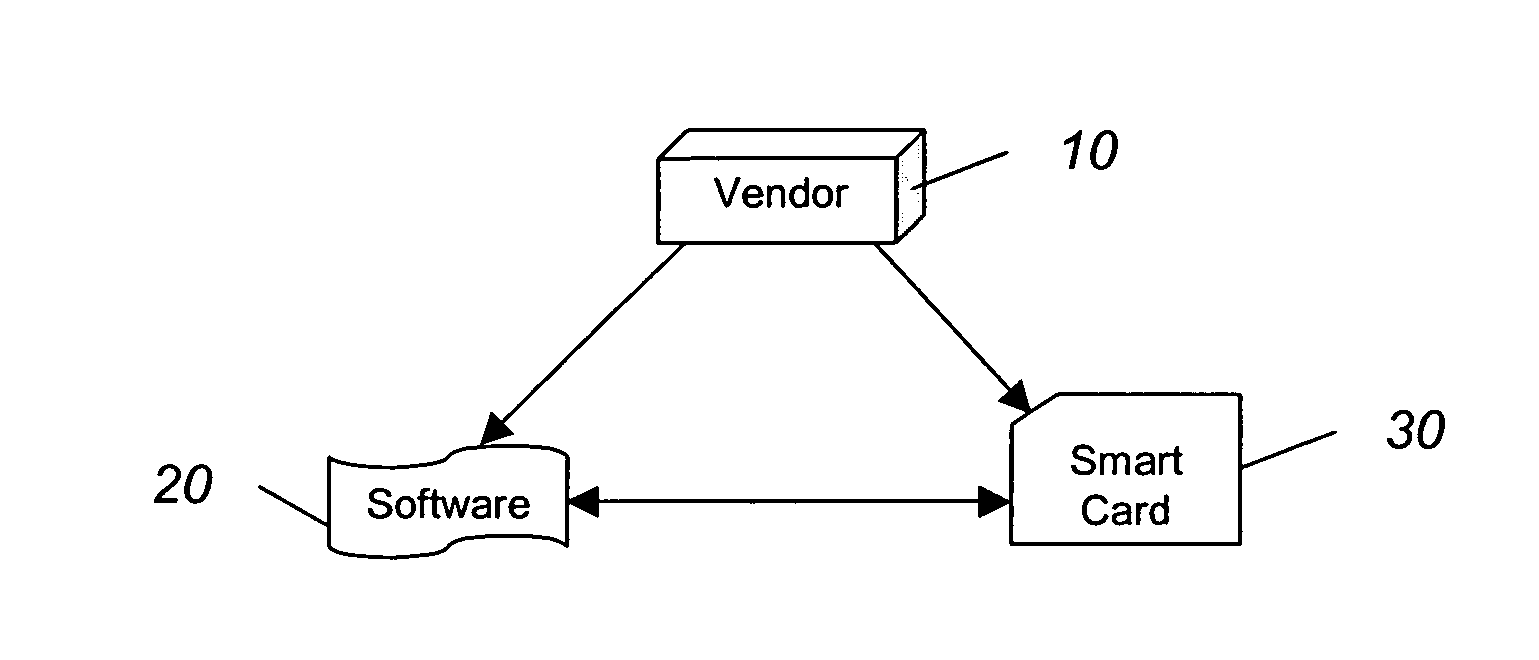
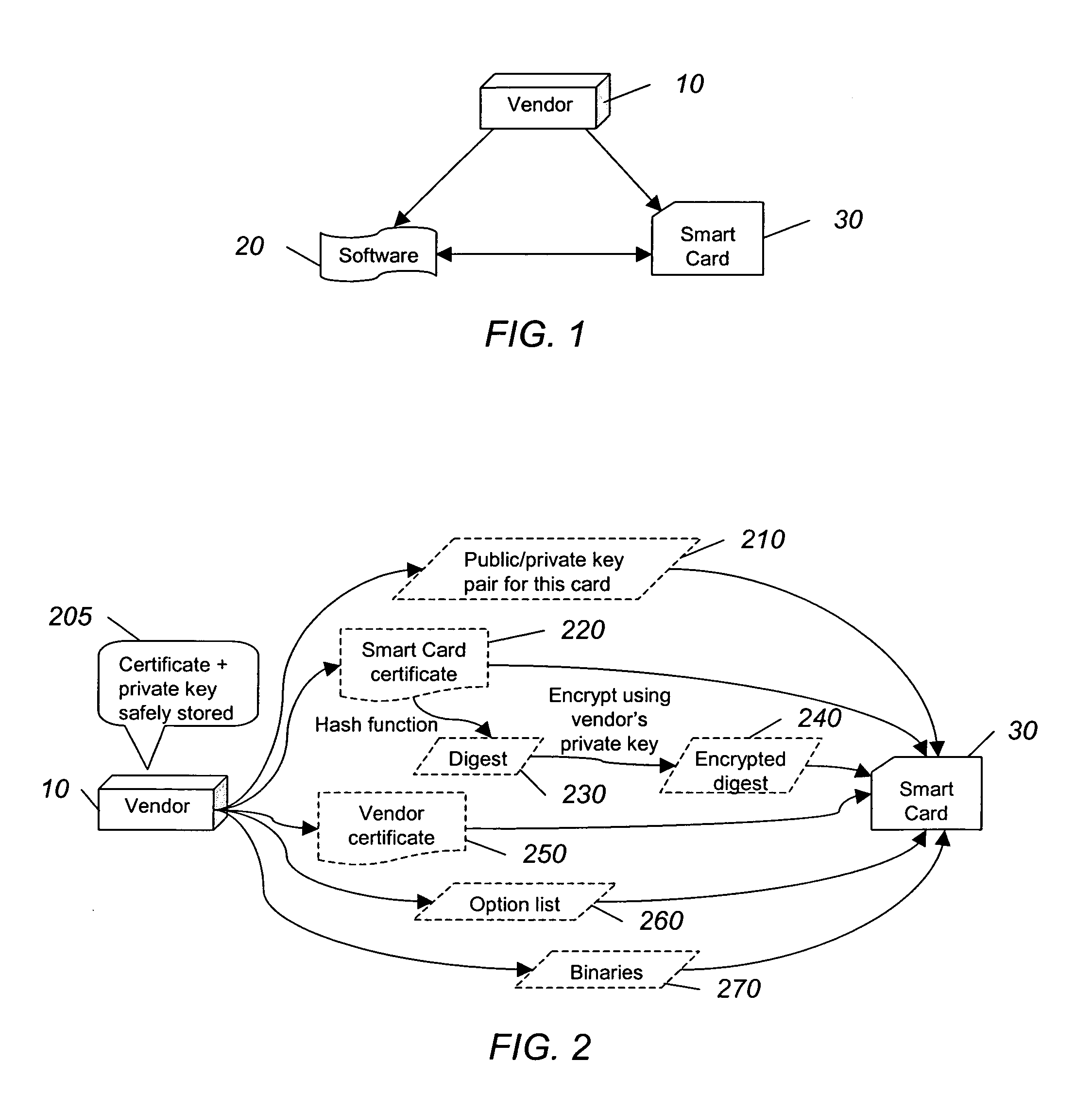
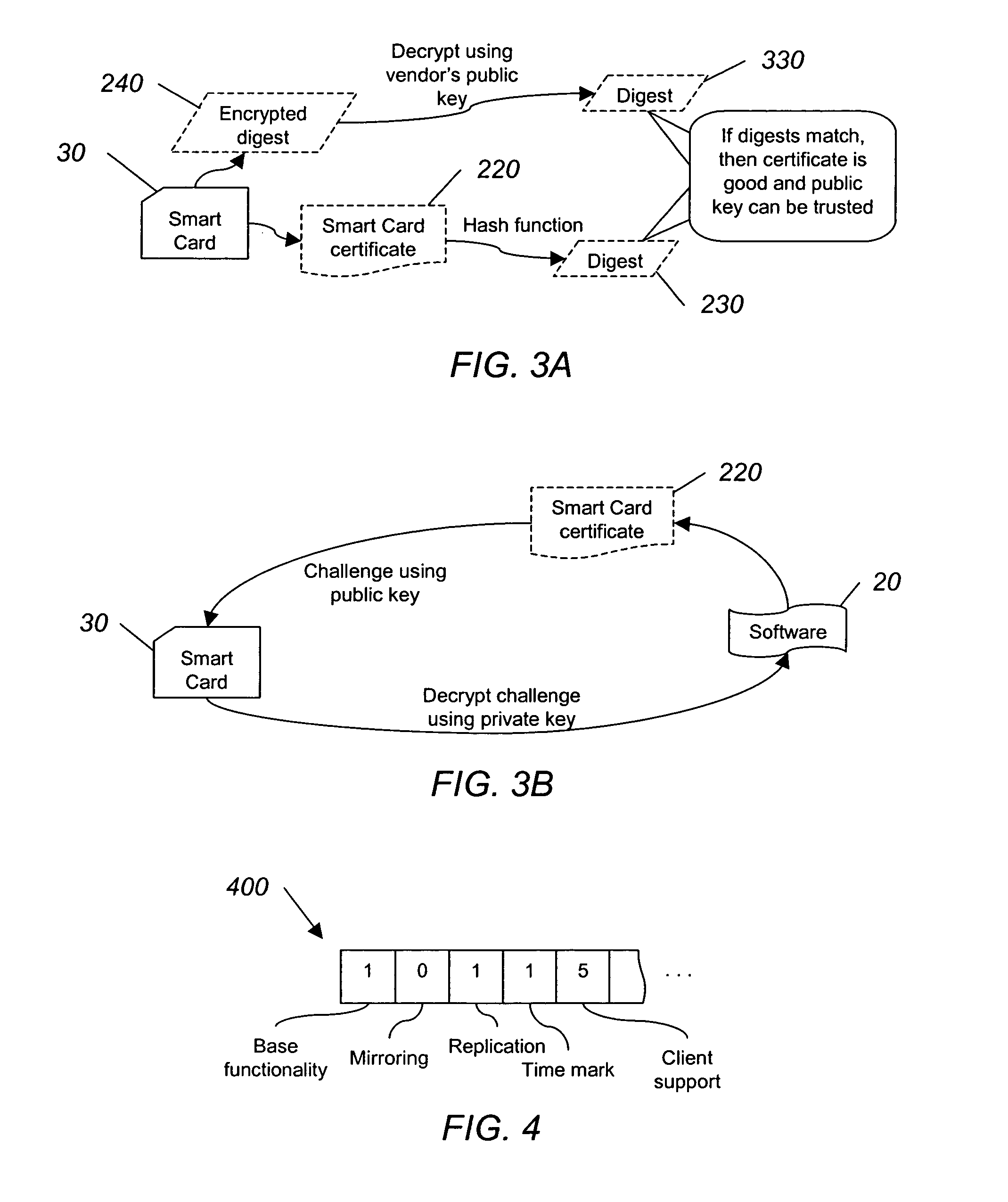
[0017] The present invention uses a smart card in combination with an authentication infrastructure to provide a software licensing system designed to control the distribution of a software package. Smart cards provide a convenient yet secure way of transporting and storing sensitive information used in the authentication infrastructure. The software is freely distributed and copied, but software use is controlled by selling authorized, irreproducible smart cards, and authenticating the smart card before being able to use the software.
[0018] One type of authentication infrastructure is public key infrastructure (PKI), and it will be used to illustrate the principles of the invention. PKI lays the foundation for a well-established system of authentication and authorization. Combining the capabilities of smart cards and PKI produces a new scheme of licensing that provides the level of security and flexibility that is unrealizable in pure software licensing. PKI will be described furt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com