Patents
Literature
469 results about "Trusted Platform Module" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
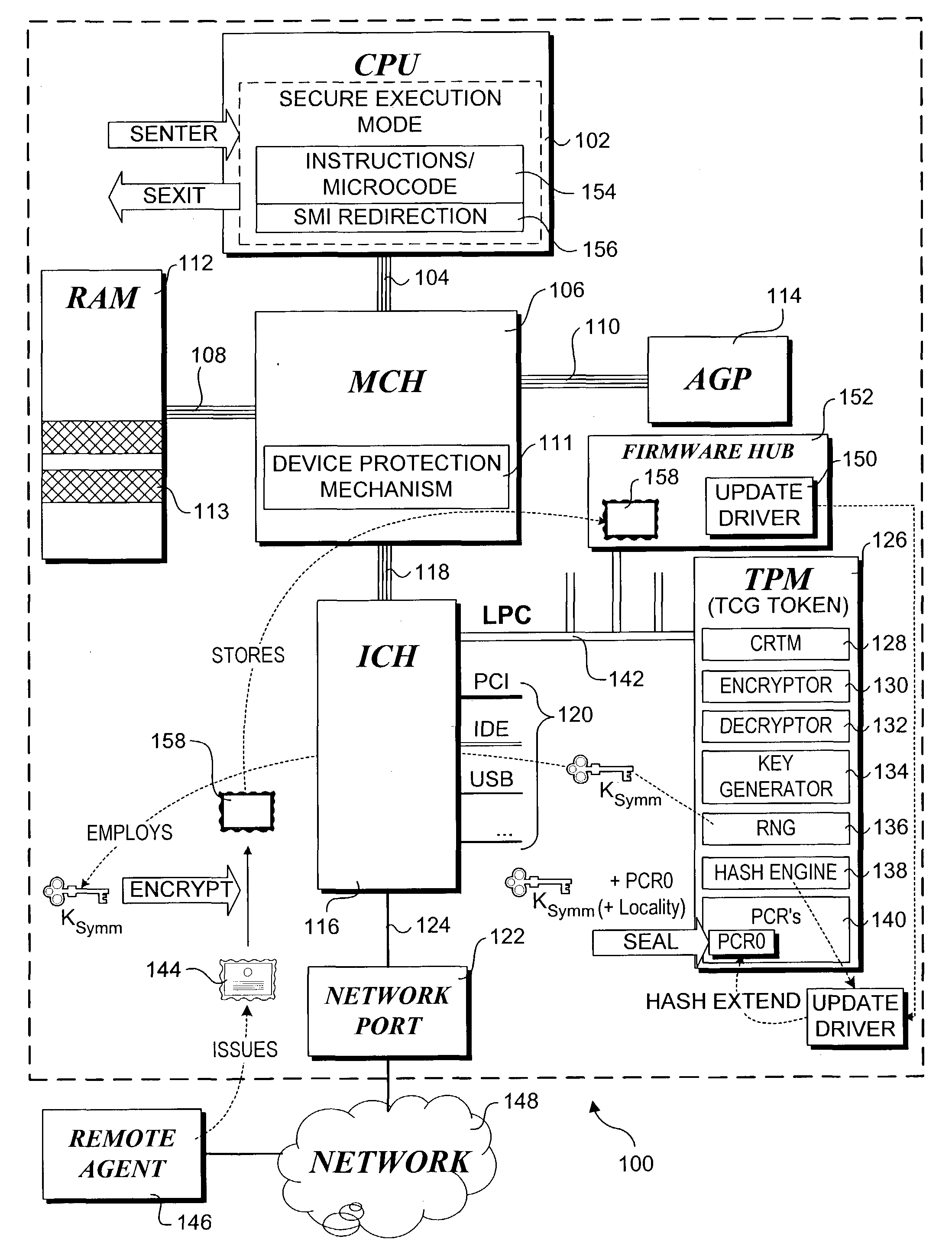
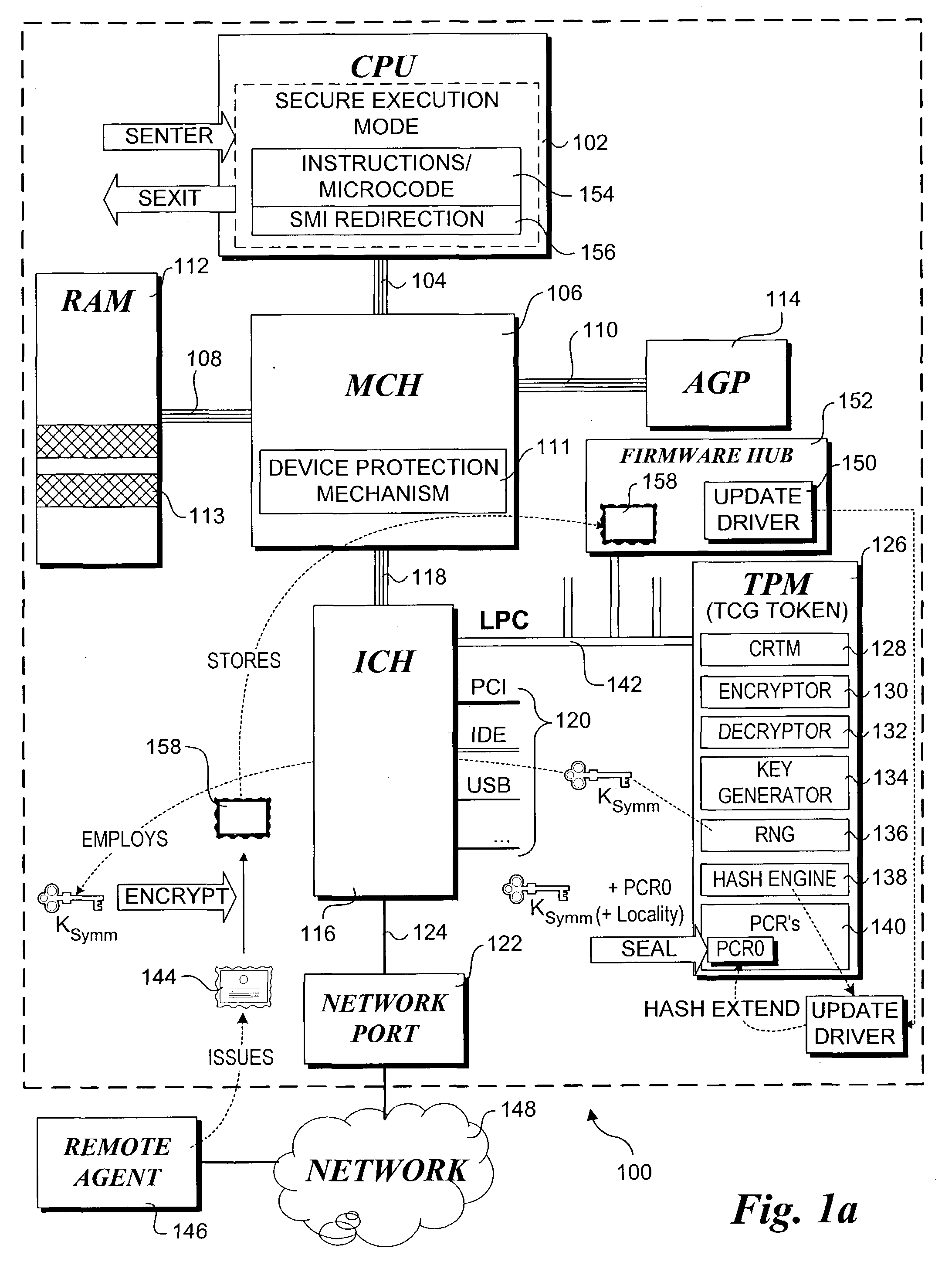
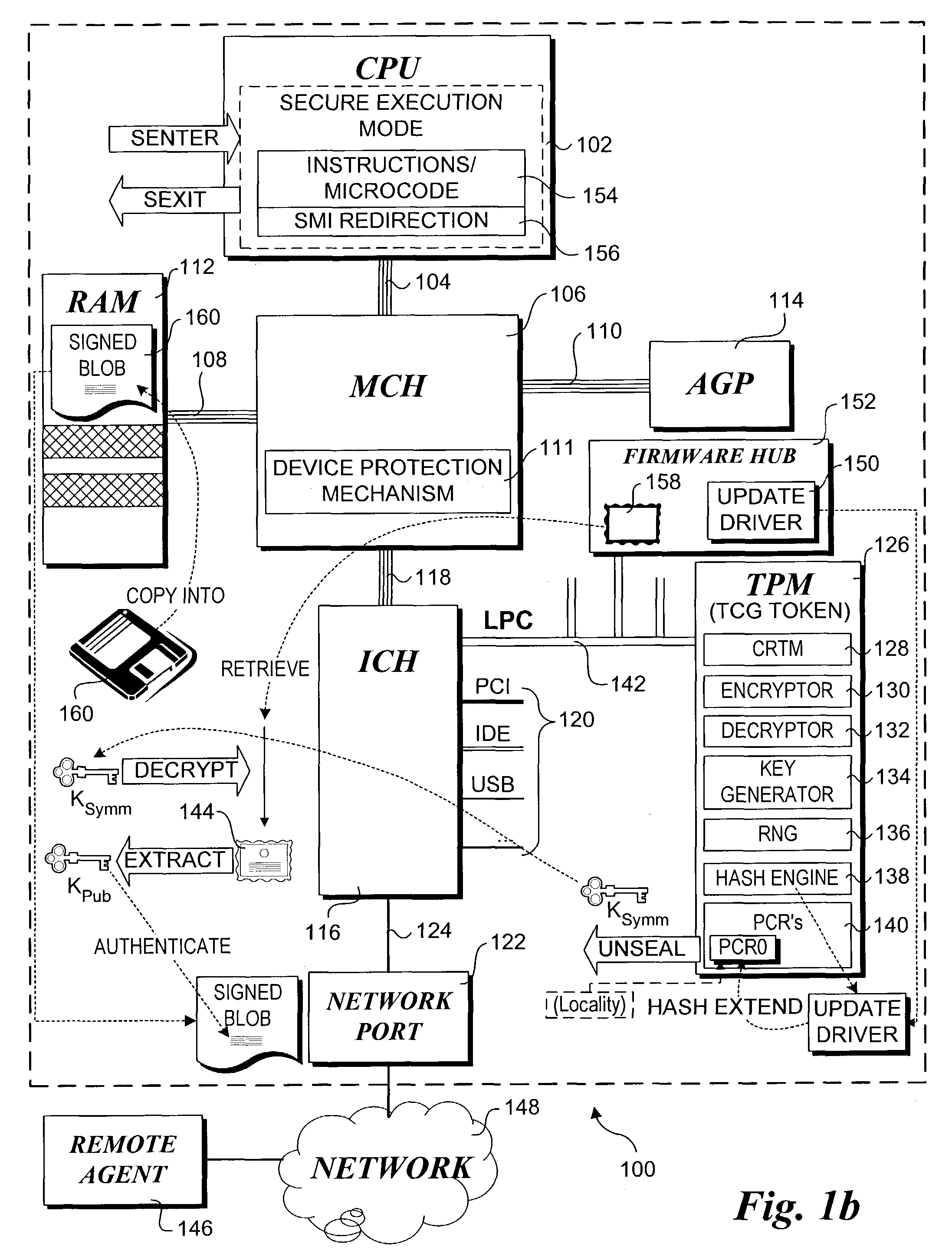
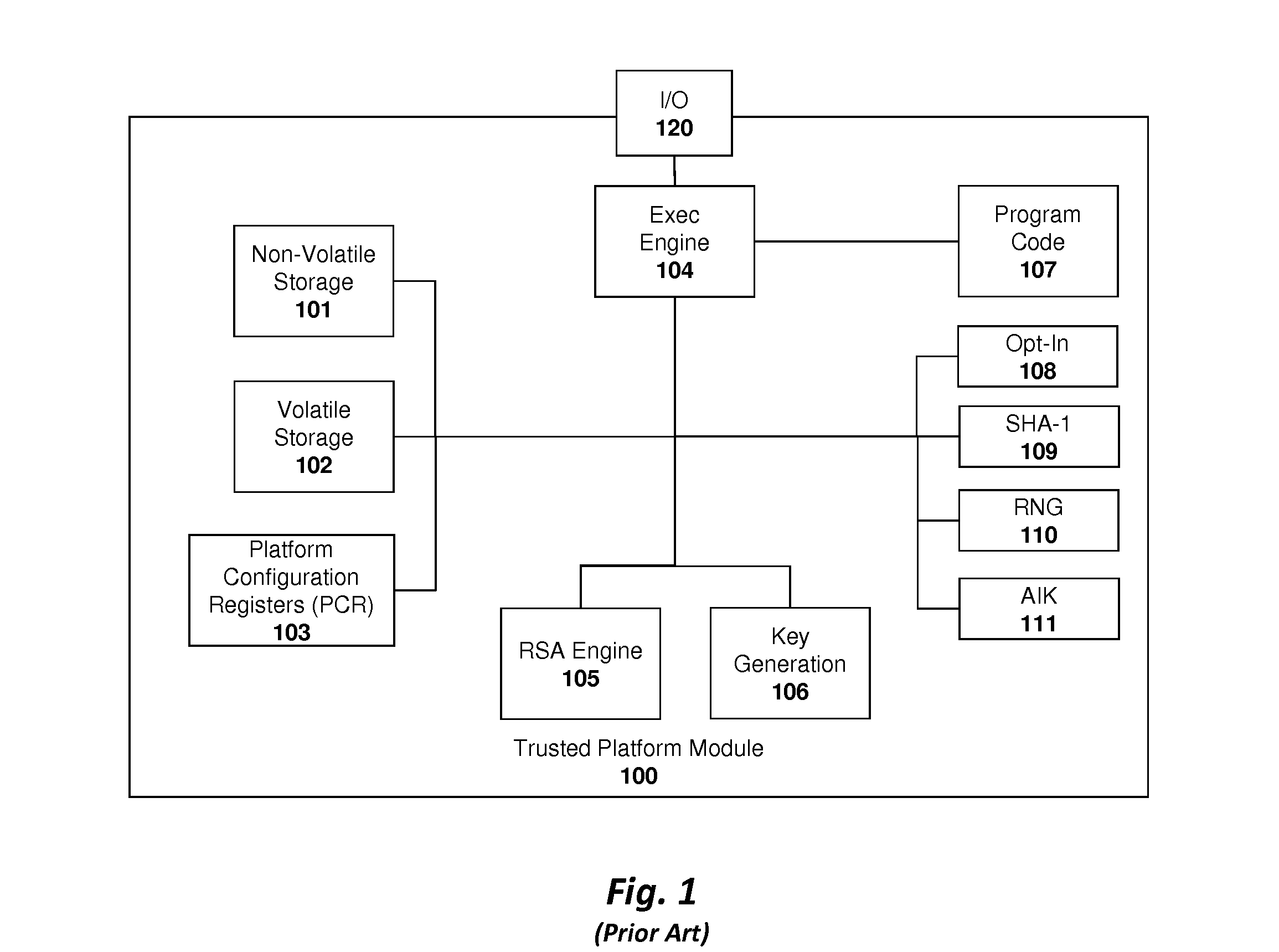
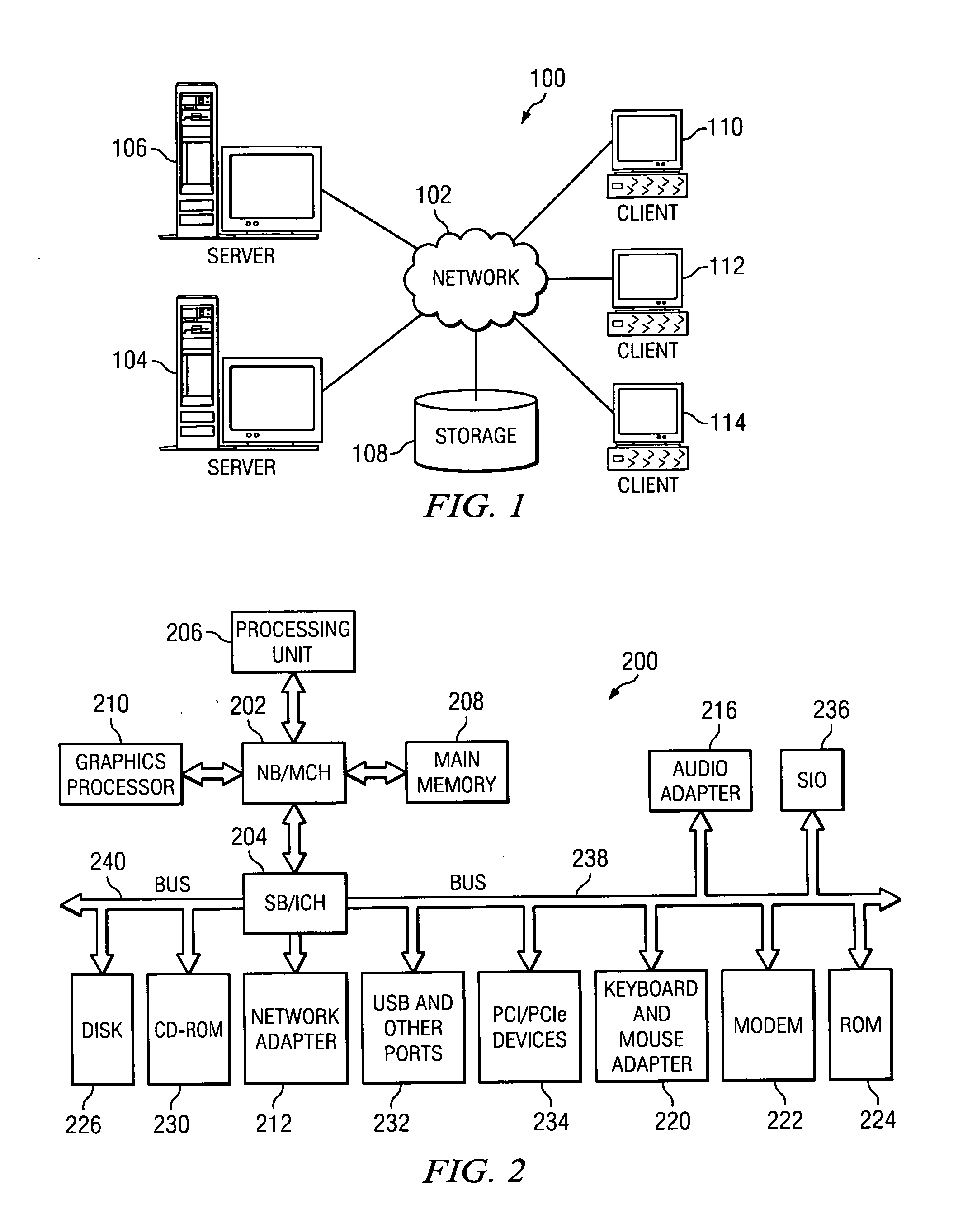
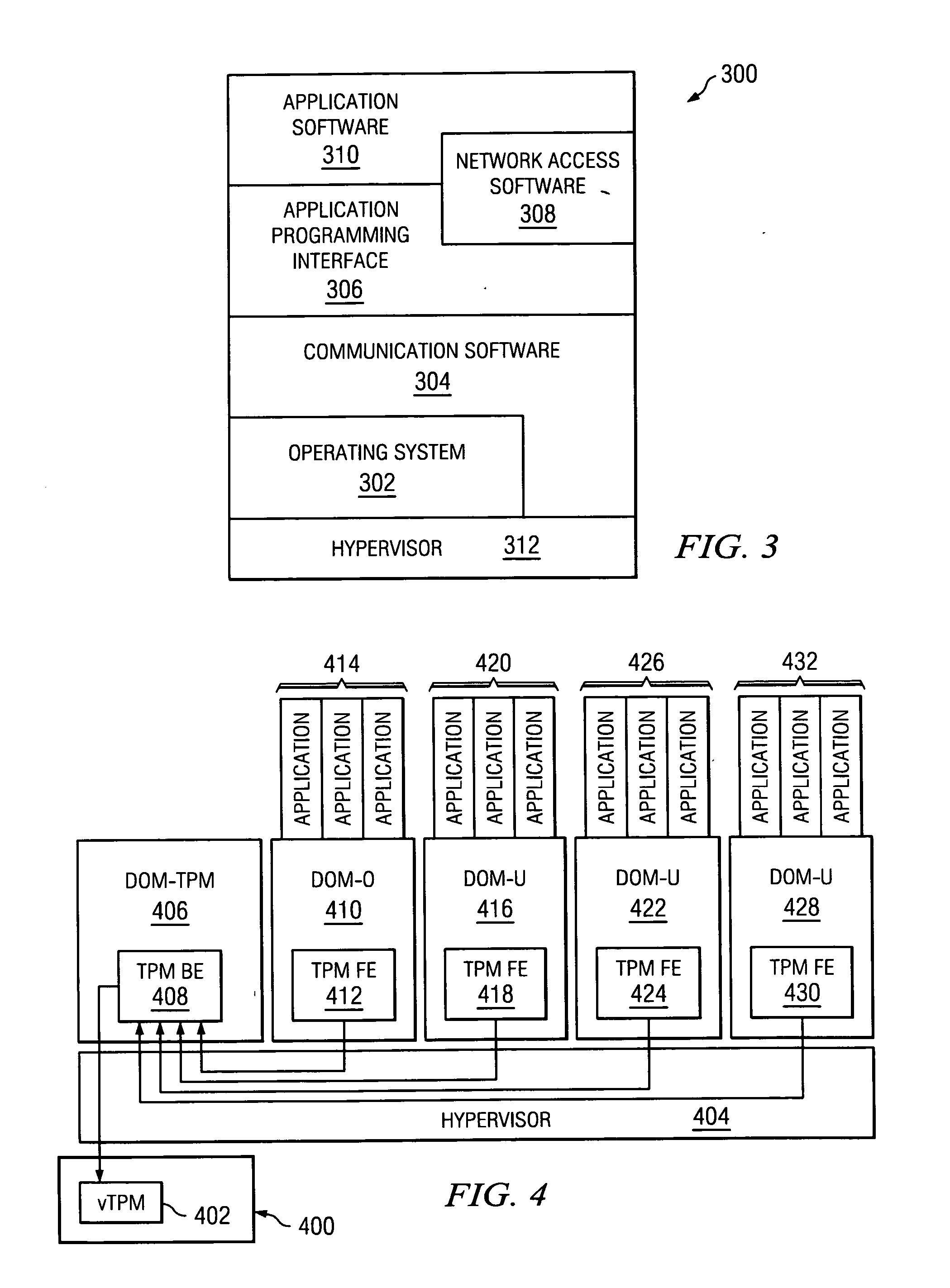
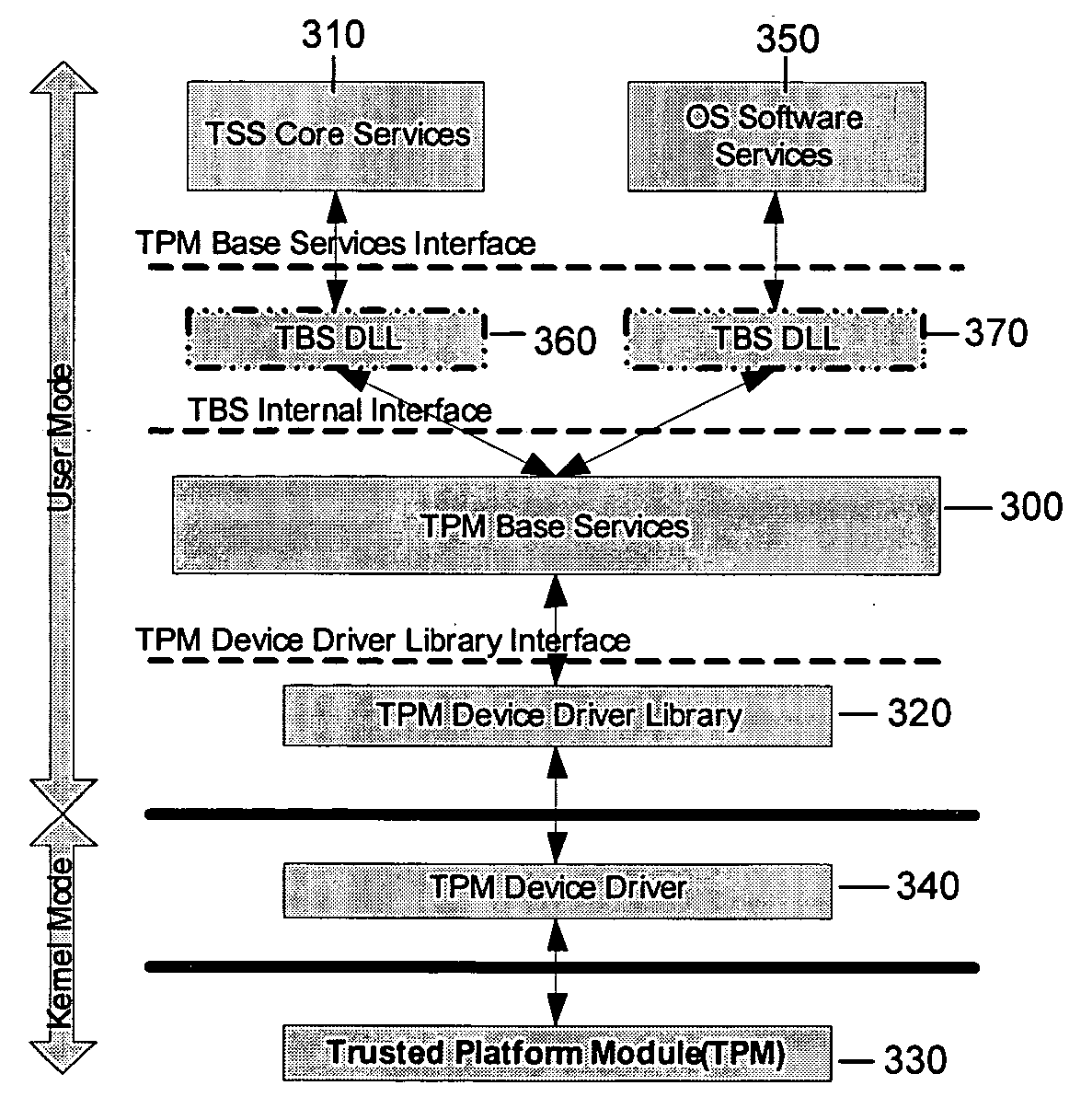
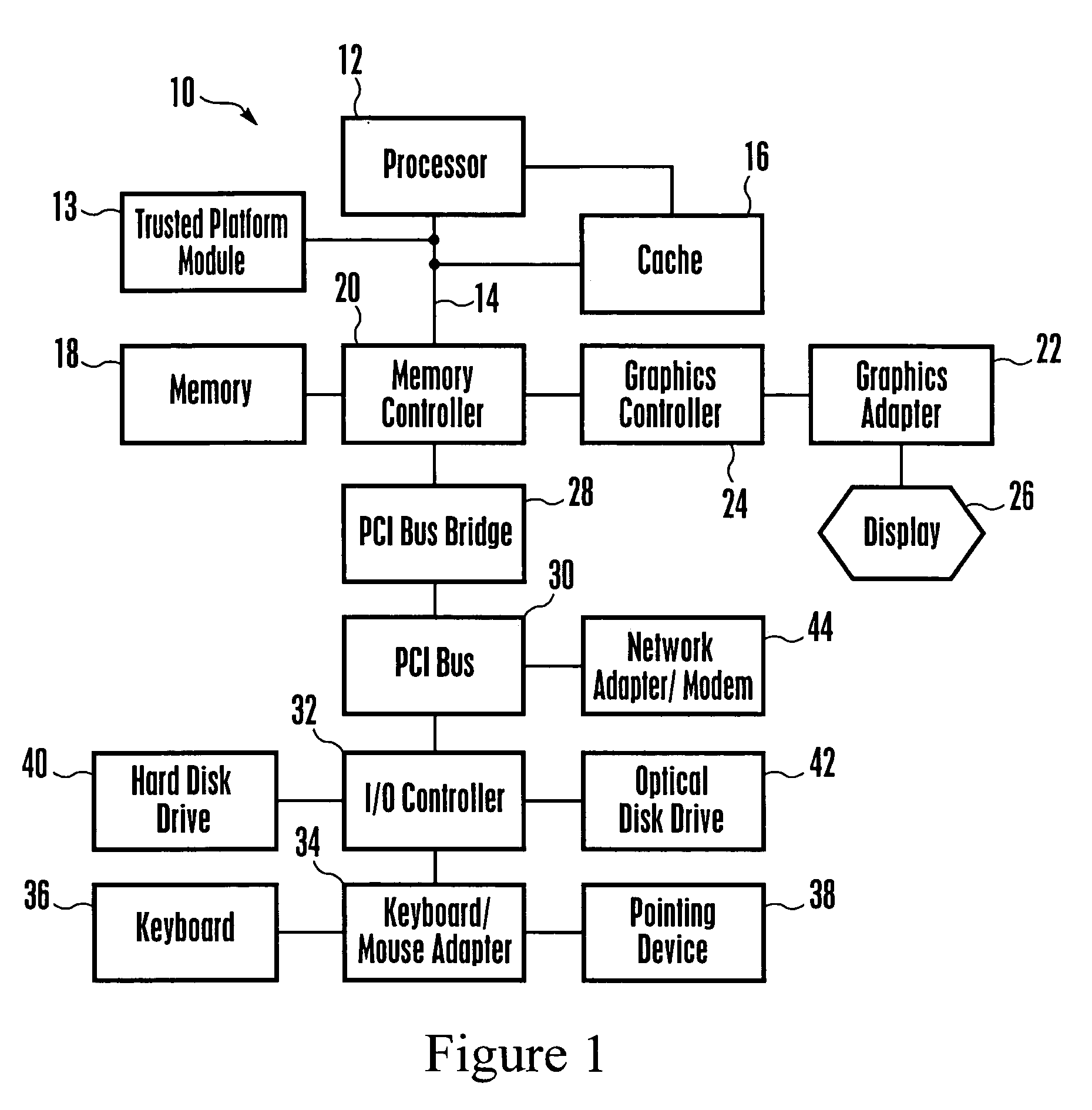
Trusted Platform Module (TPM, also known as ISO/IEC 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated cryptographic keys.
Method for performing a trusted firmware/bios update
InactiveUS20050021968A1User identity/authority verificationComputer security arrangementsTrusted Platform ModuleBIOS
A method for providing a secure firmware update. A first authentication credential is securely stored on a platform in an encrypted form using a key generated by a secure token, such as a trusted platform module (TPM). Typically, the authentication credential will identify a manufacture and the operation will be performed during manufacture of the platform. A configuration of the platform is “imprinted” such that an identical configuration is required to access the key used to decrypt the first authentication credential by sealing the key against the platform configuration. During a subsequent firmware update process, a firmware update image containing a second authentication credential is received at the platform. If the platform configuration is the same as when the key was sealed, the key can be unsealed and used for decrypting the first authentication credential. A public key in the first authentication credential can then be used to authenticate the firmware update image via the second authentication credential.
Owner:INTEL CORP
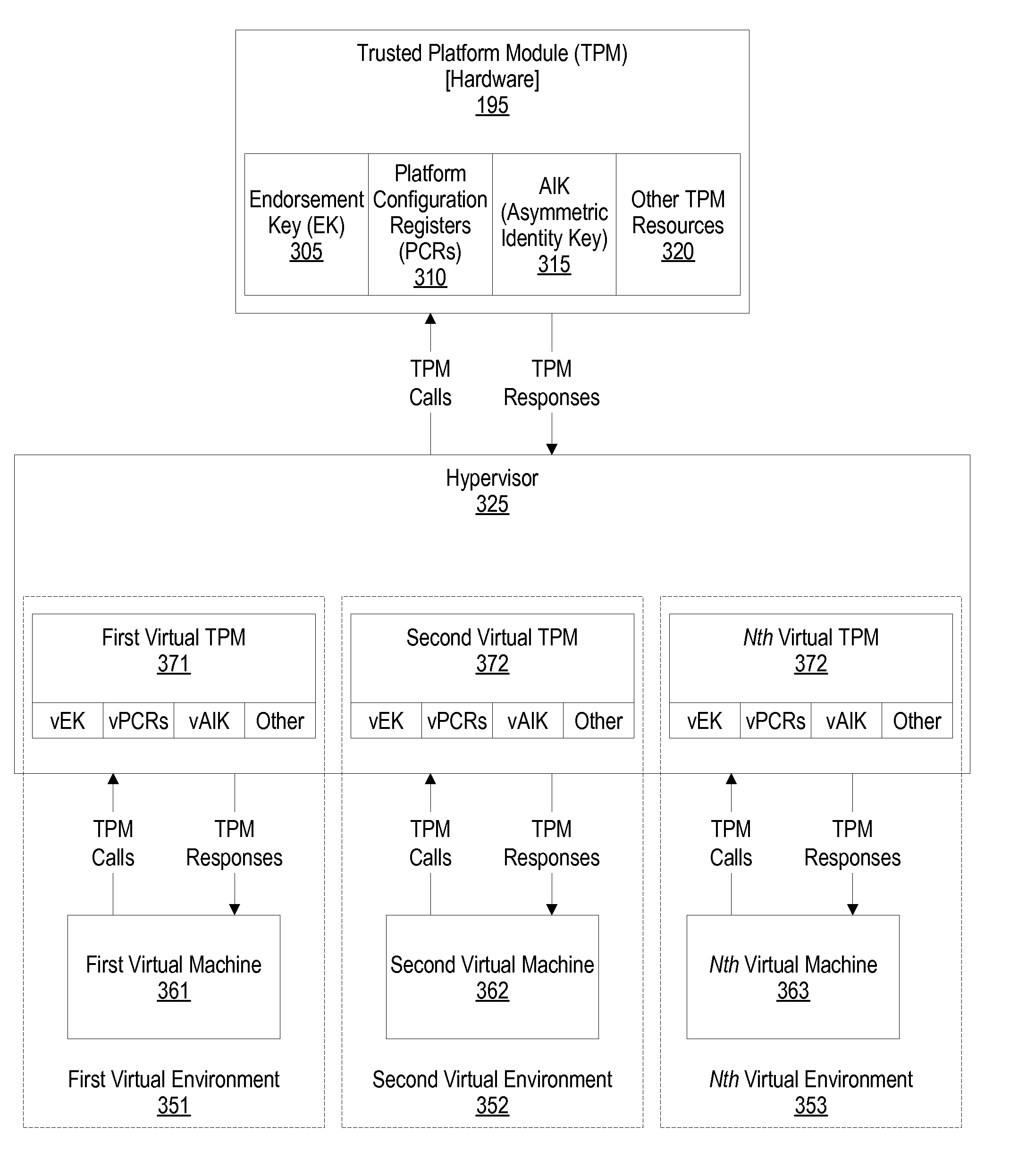
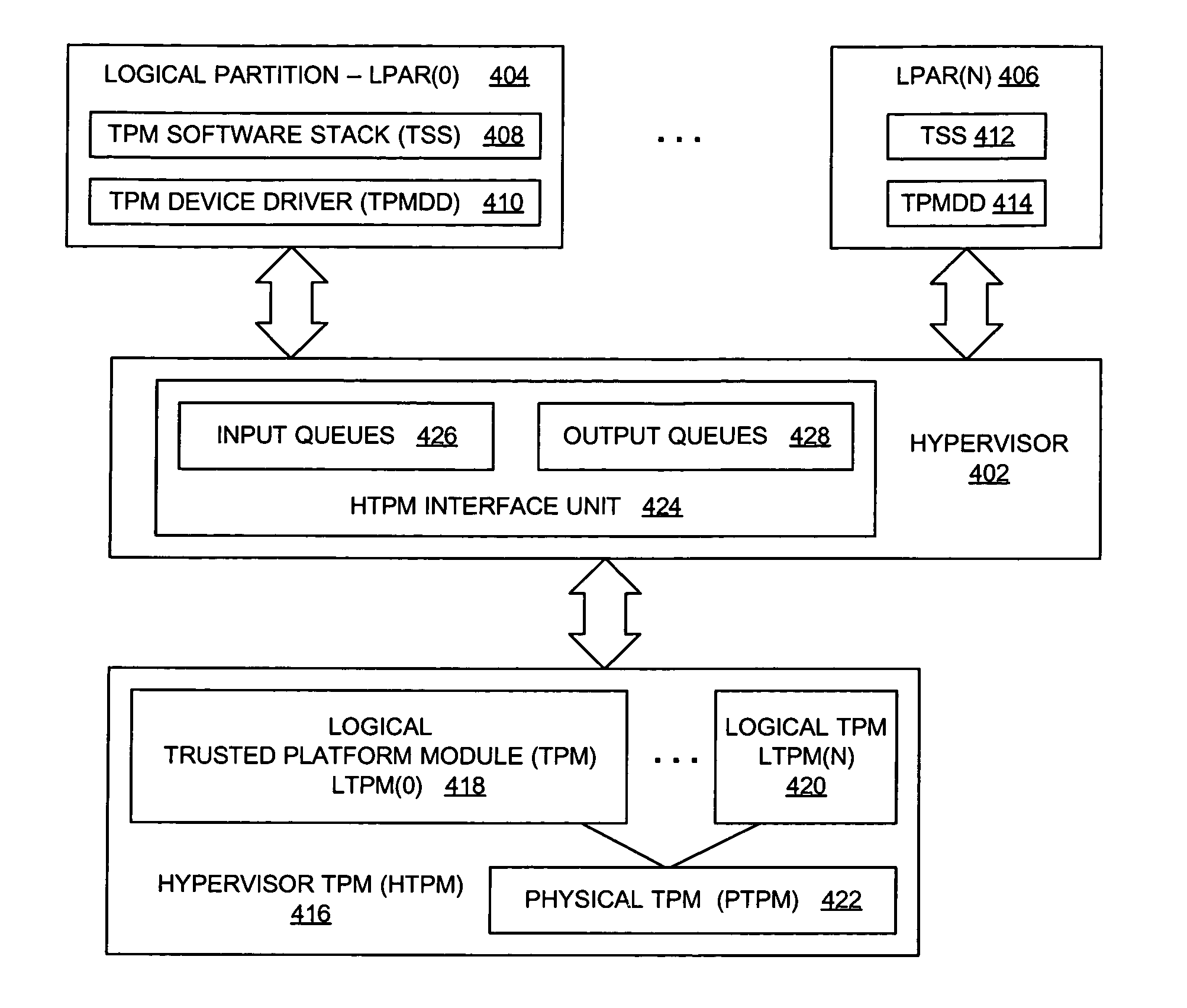
System and Method for Reporting the Trusted State of a Virtual Machine
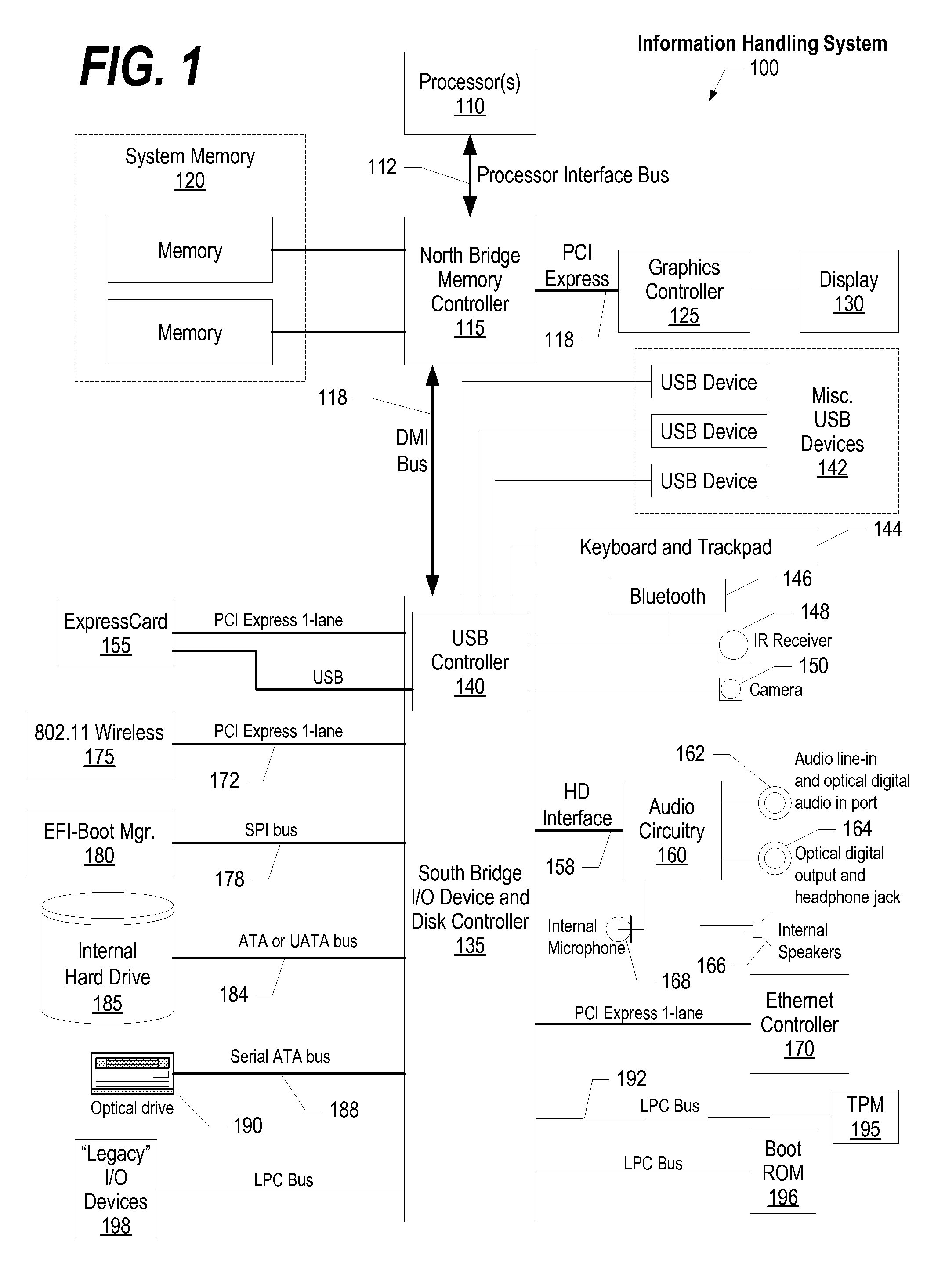
ActiveUS20080244569A1Digital data processing detailsUnauthorized memory use protectionTrusted Platform ModuleHandling system
A system, method, and program product is provided that executes a start sequence of an information handling system that includes a hardware based TPM. Multiple PCRs are stored in the TPM and are initialized to a predetermined state when the start sequence commences. During execution of the start sequence, software modules, including a hypervisor, are loaded the system's memory. PCR values resulting from the loading of the software modules are calculated. The resulting PCR values are compared with expected PCR values. If the PCR values match the expected PCR values, then a virtual environment is created under the hypervisor. The virtual environment includes a VM and a virtual trust platform module (vTPM) that is used by the virtual machine to satisfy the virtual machines TPM requests.
Owner:LENOVO PC INT
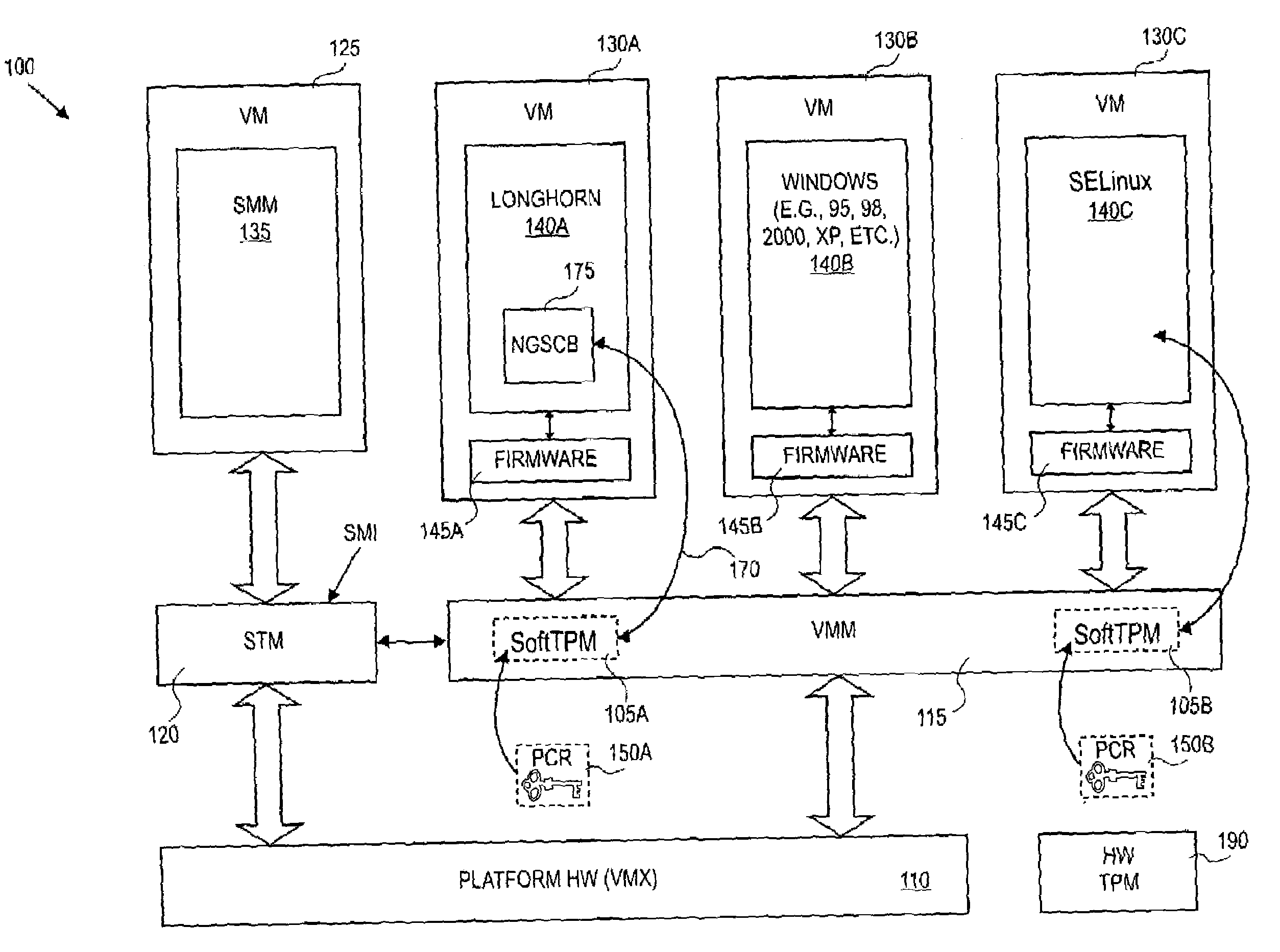
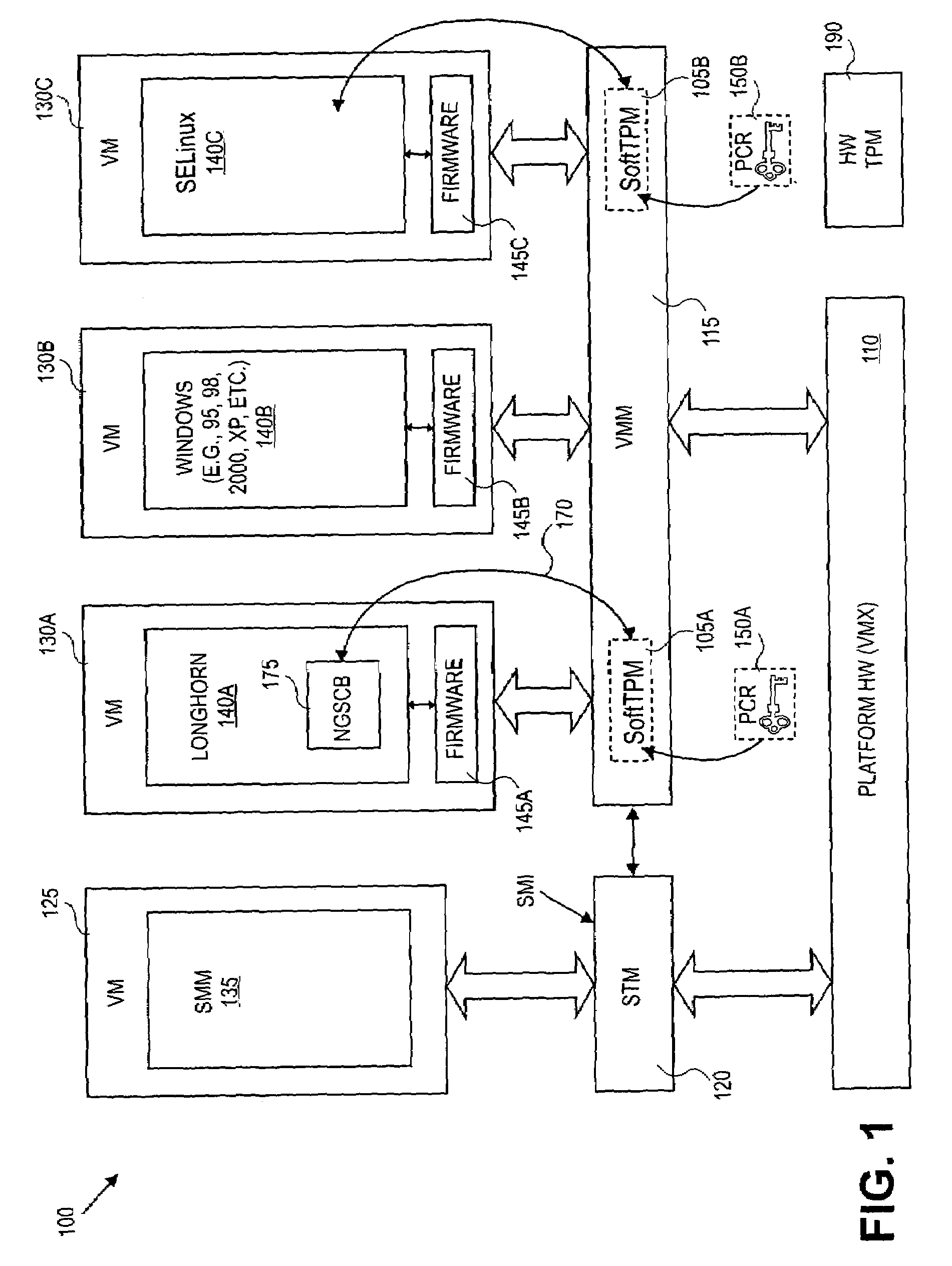
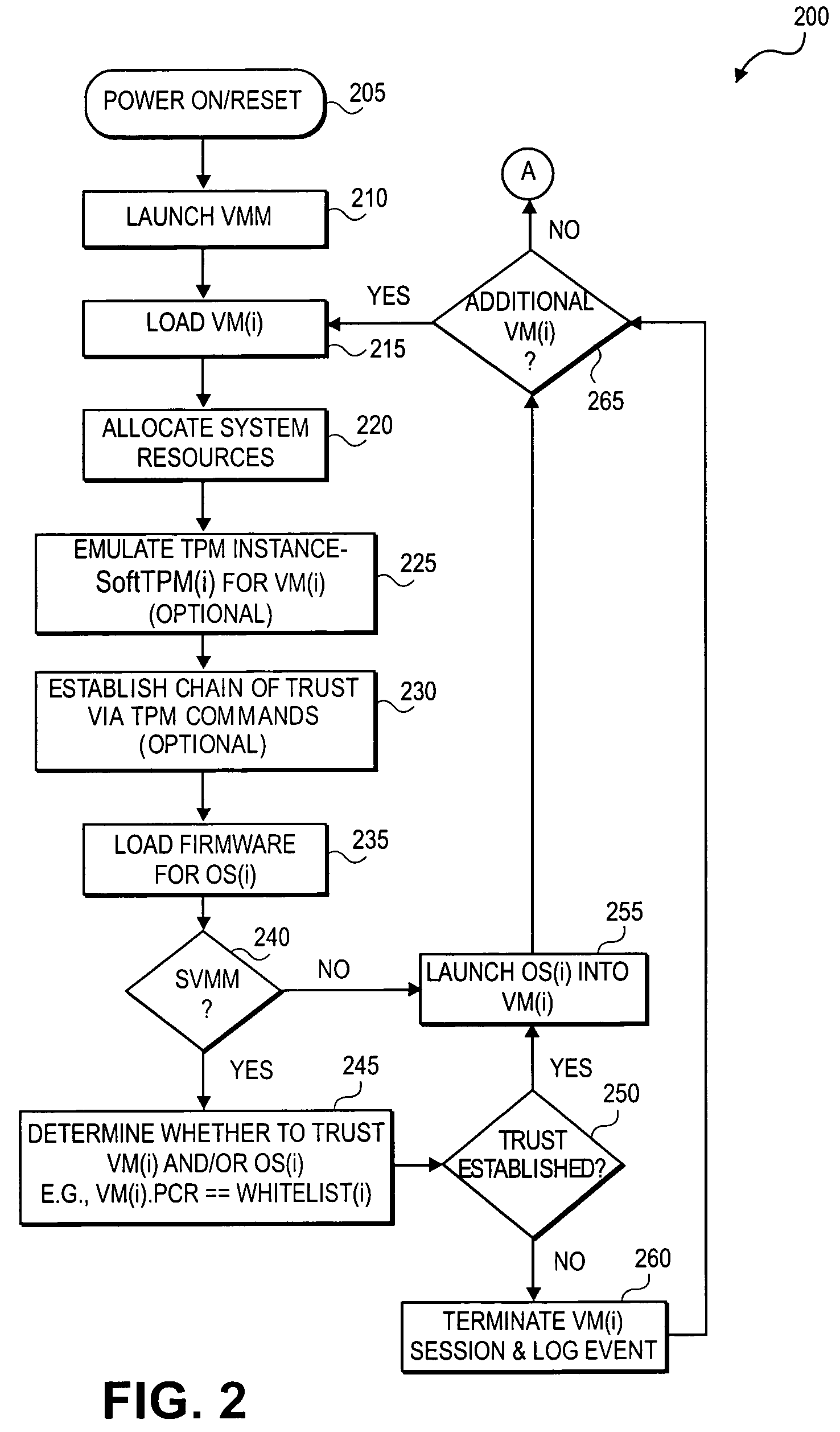
Method and system to support a trusted set of operational environments using emulated trusted hardware
InactiveUS20050138370A1Key distribution for secure communicationUnauthorized memory use protectionComputer hardwareOperational system
A method and system to emulate a trusted platform module to execute trusted operations. A virtual machine monitor is executed to support a virtual machine session. An operating system is loaded into the virtual machine session. The trusted platform module is emulated to hold a key associated with the virtual session and to execute trusted operations.
Owner:INTEL CORP
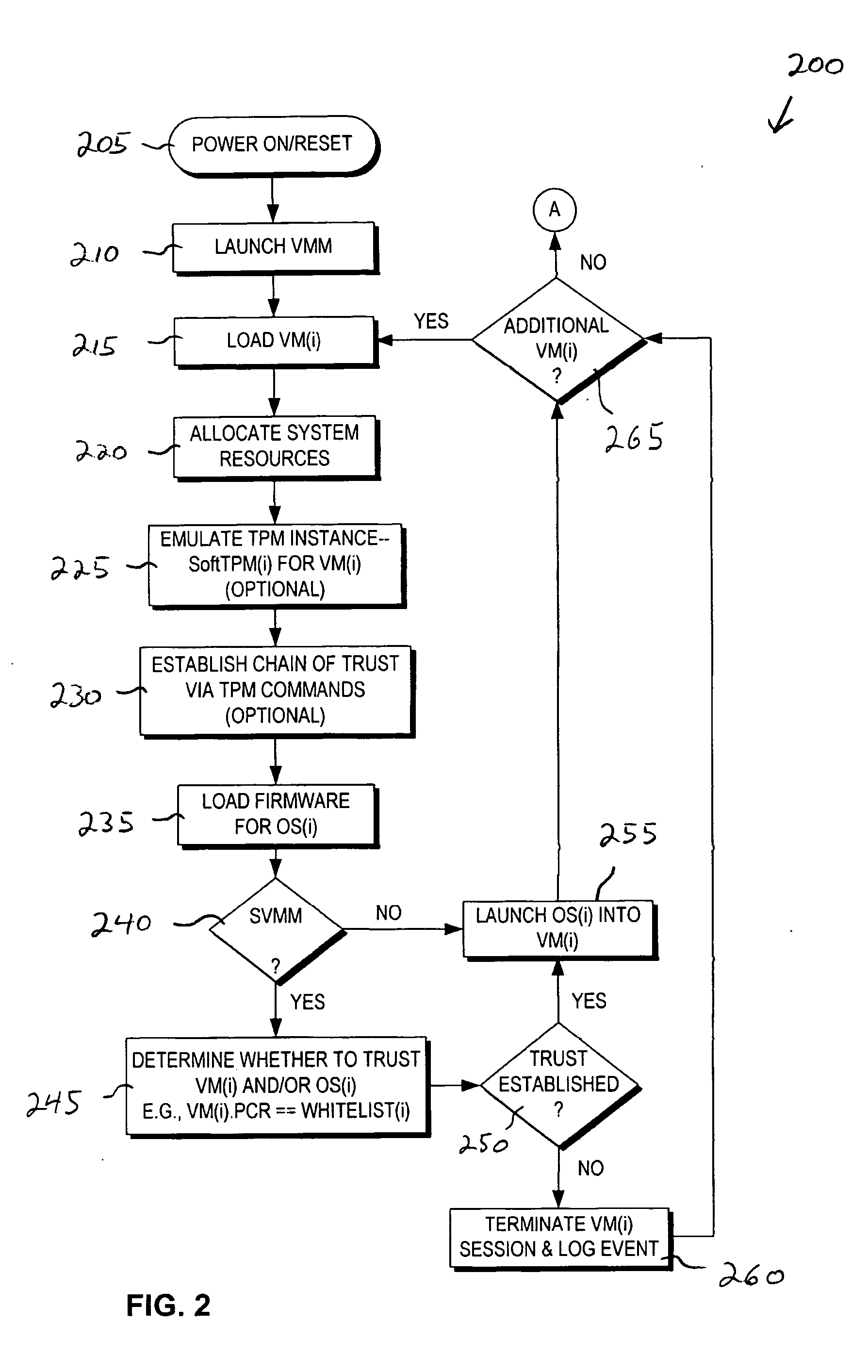
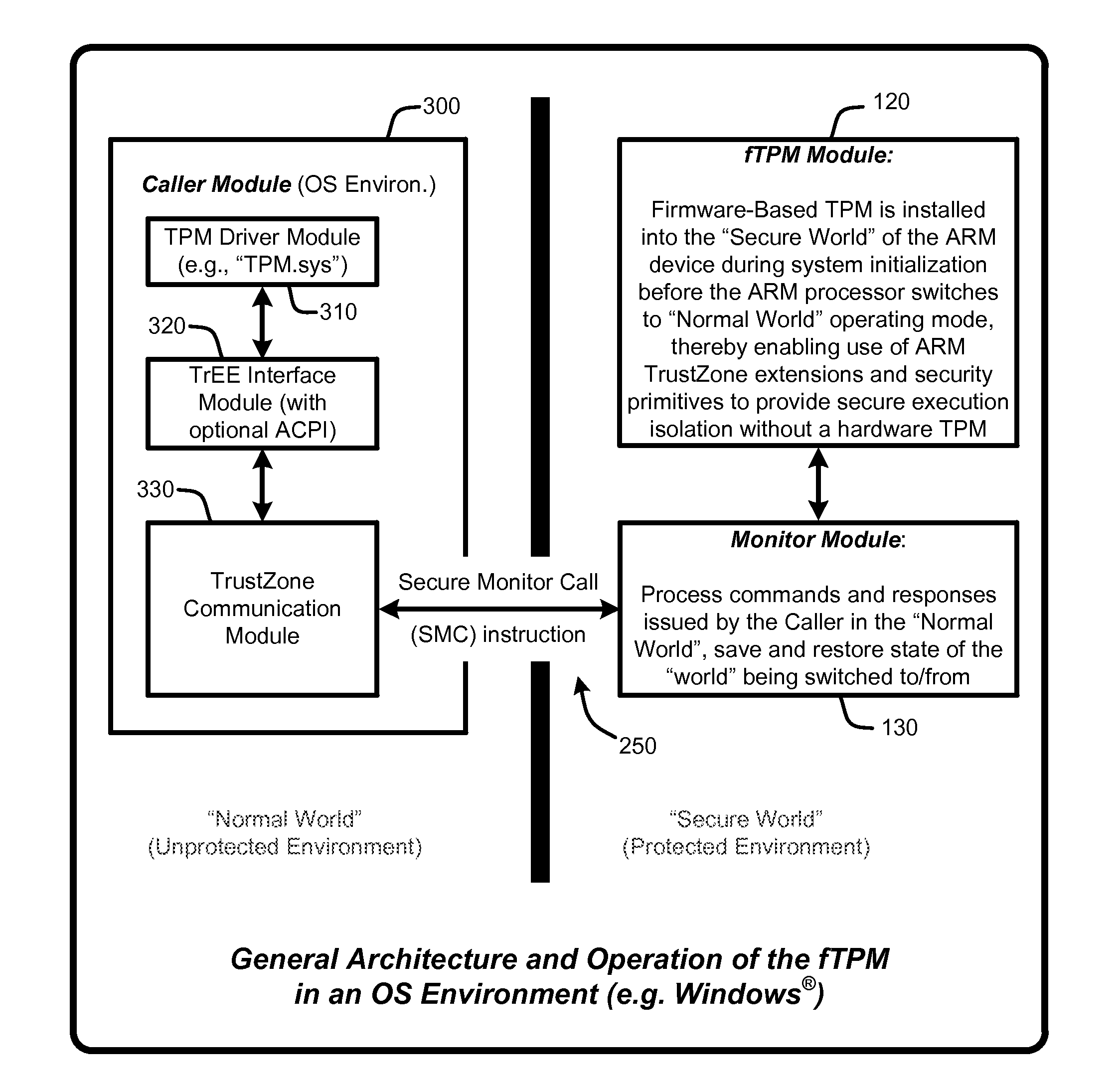
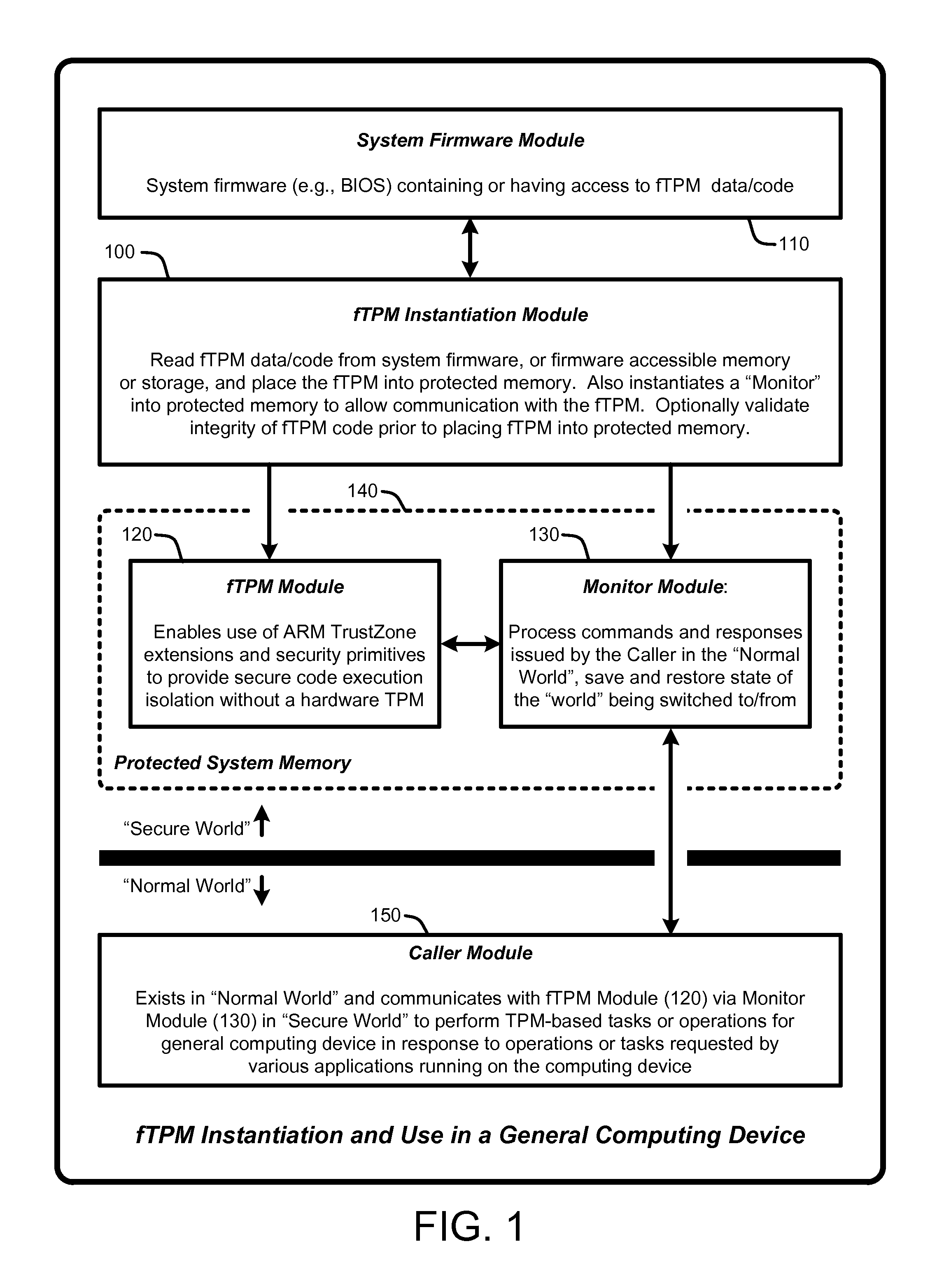
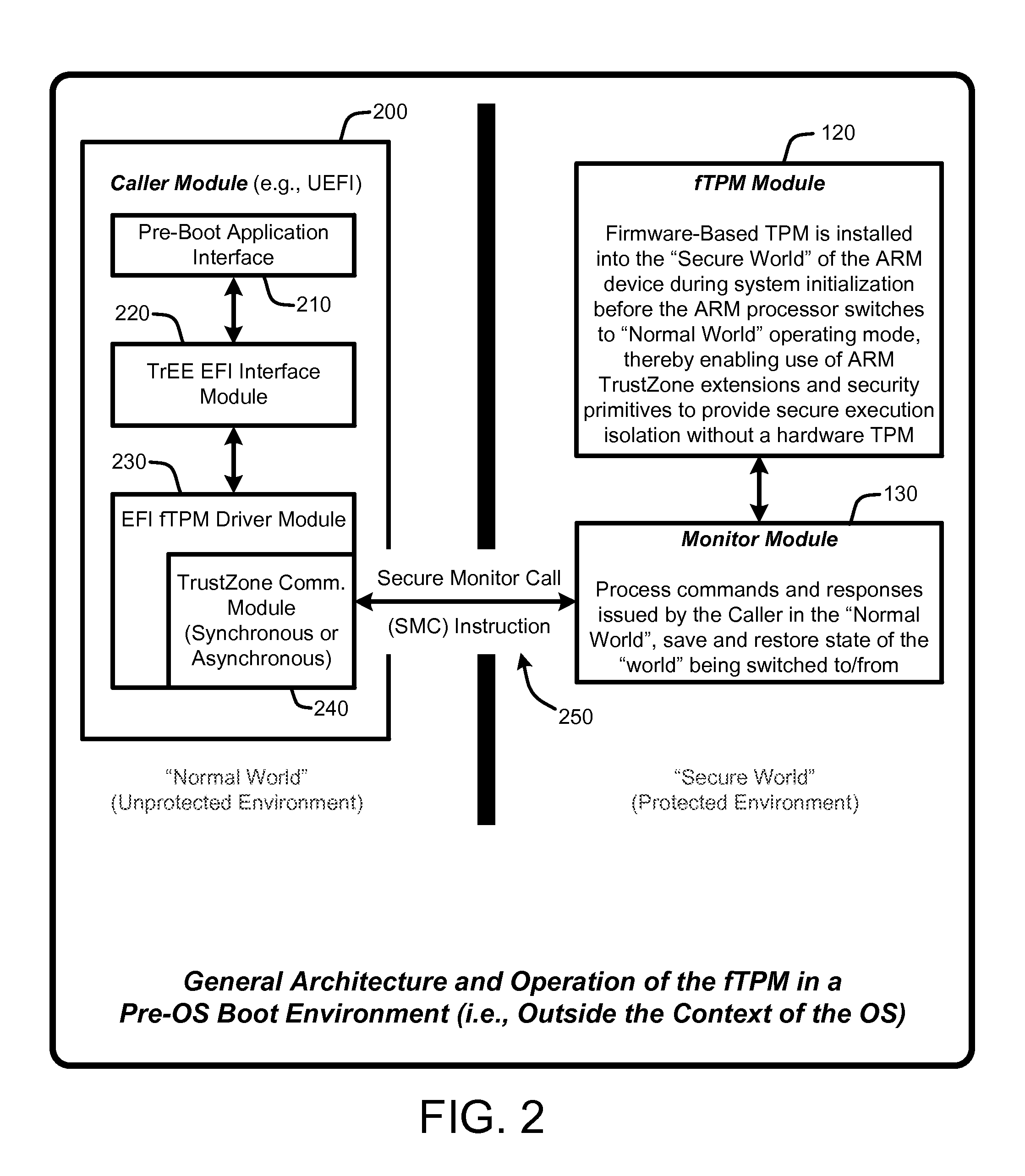
Firmware-based trusted platform module for arm processor architectures and trustzone security extensions
ActiveUS20130031374A1Increase costReduce system costDigital data processing detailsUnauthorized memory use protectionTrusted Platform ModuleSafe handling
A “Firmware-Based TPM” or “fTPM” ensures that secure code execution is isolated to prevent a wide variety of potential security breaches. Unlike a conventional hardware based Trusted Platform Module (TPM), isolation is achieved without the use of dedicated security processor hardware or silicon. In general, the fTPM is first instantiated in a pre-OS boot environment by reading the fTPM from system firmware or firmware accessible memory or storage and placed into read-only protected memory of the device. Once instantiated, the fTPM enables execution isolation for ensuring secure code execution. More specifically, the fTPM is placed into protected read-only memory to enable the device to use hardware such as the ARM® architecture's TrustZone™ extensions and security primitives (or similar processor architectures), and thus the devices based on such architectures, to provide secure execution isolation within a “firmware-based TPM” without requiring hardware modifications to existing devices.
Owner:MICROSOFT TECH LICENSING LLC
Method for securing a computing device with a trusted platform module-tpm
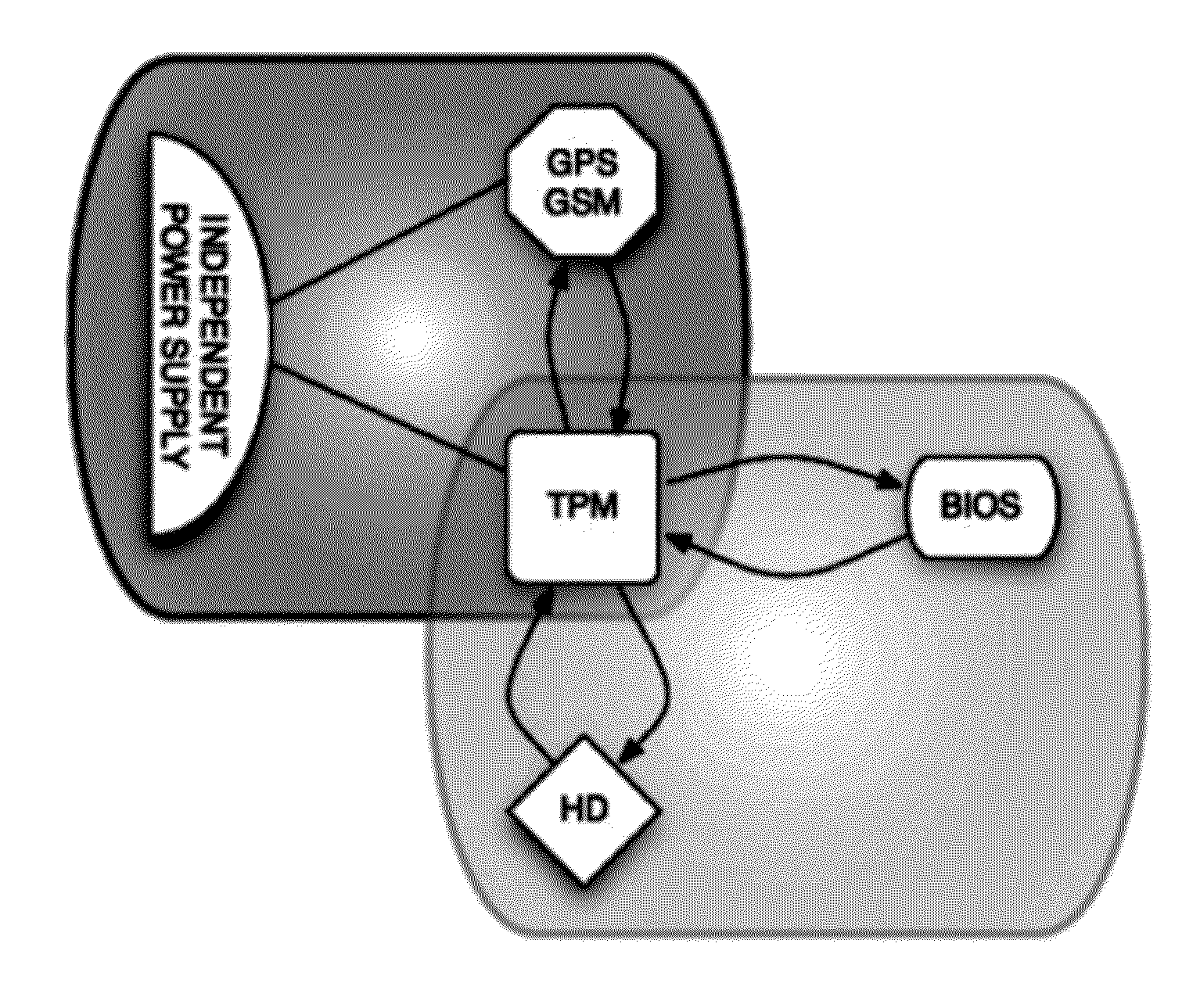
InactiveUS20120151223A1Unauthorized memory use protectionHardware monitoringExternal storageHash-based message authentication code
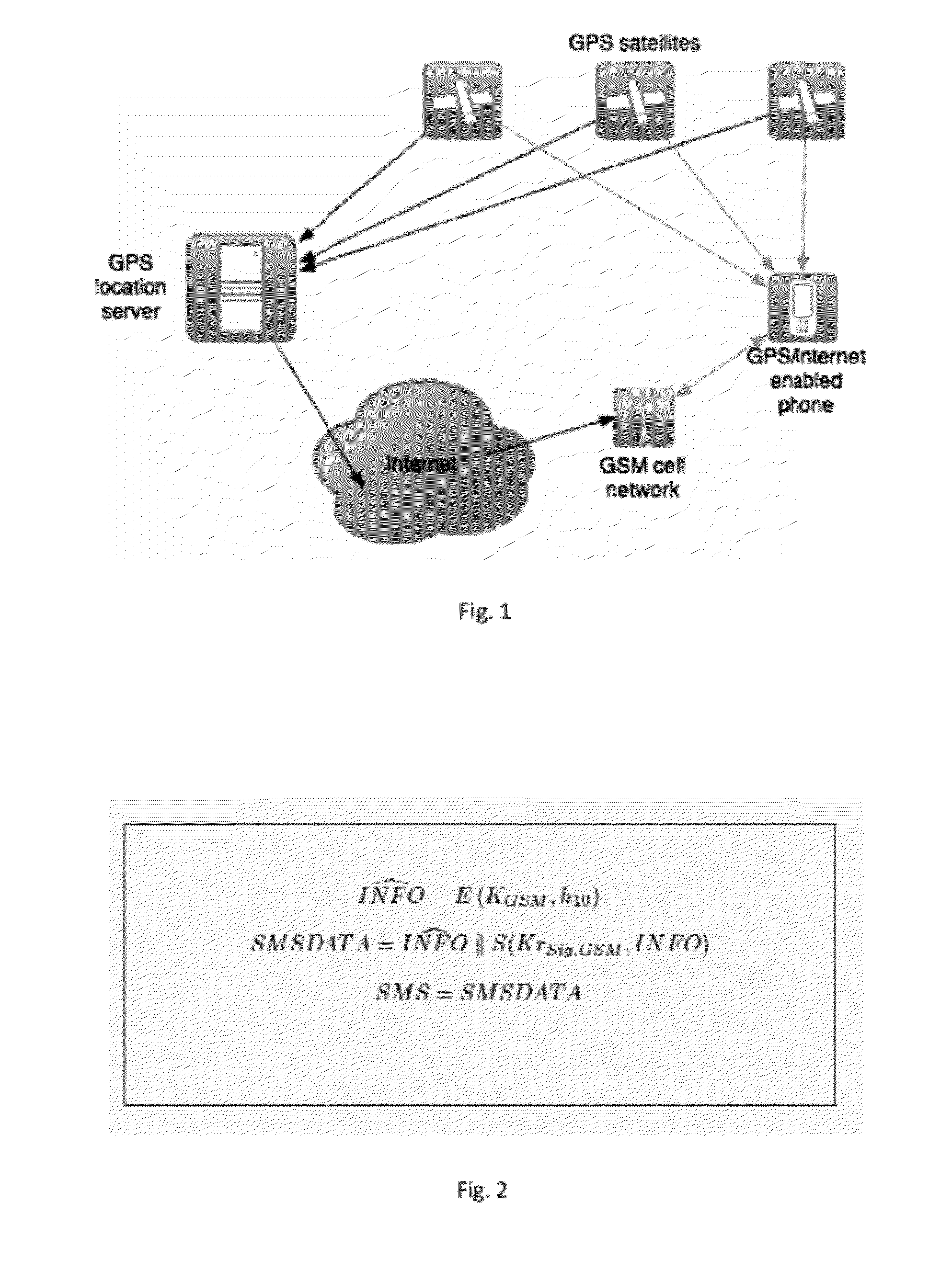
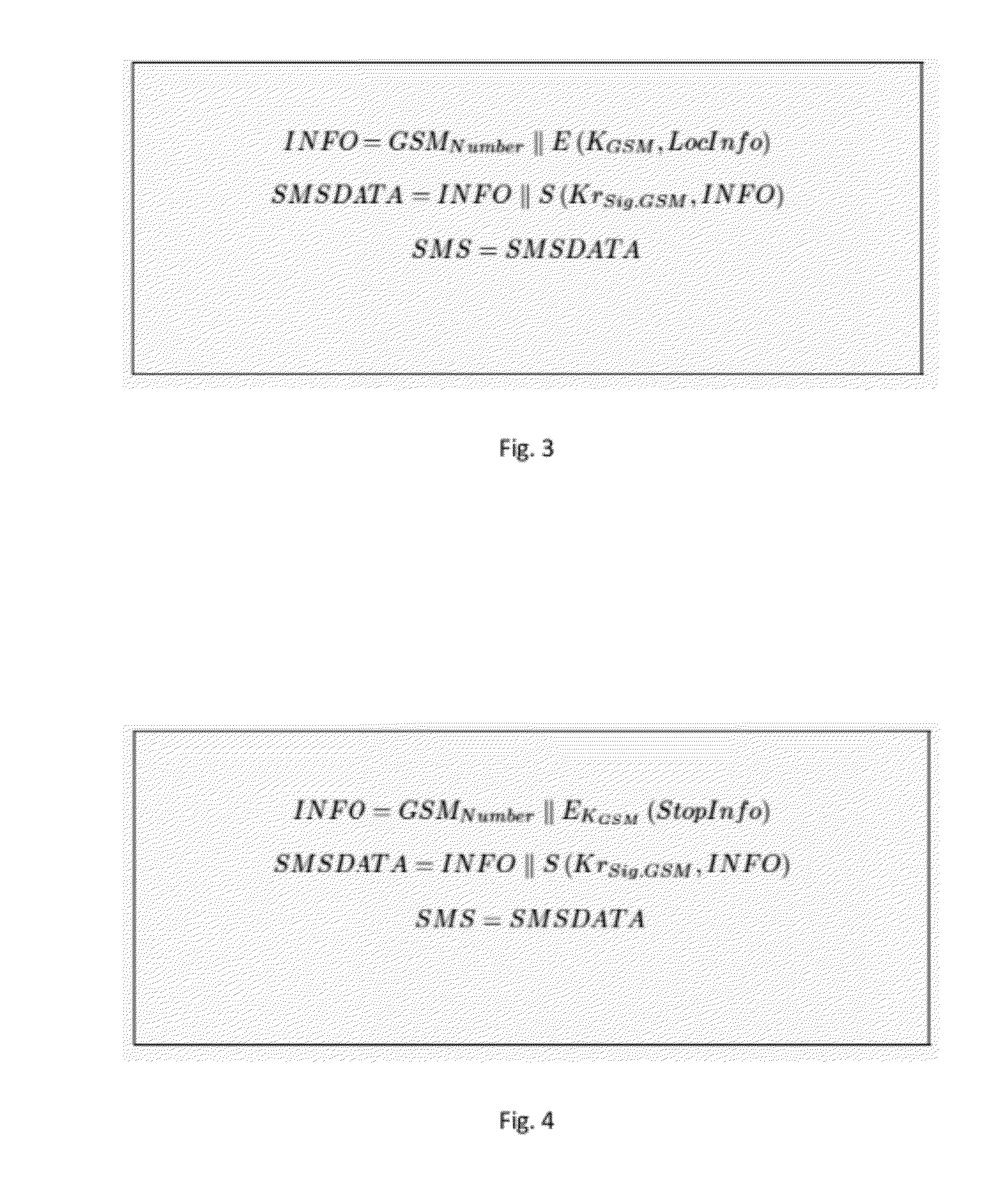
Methods, systems and computer program products for securing a computing device with data storage, power-on firmware—BIOS, geolocation and mobile data module—GPS / GSM, and a Trusted Platform Module—TPM, including establishing a shared-secret between the BIOS and the TPM, requesting the TPM to generate suitable encryption keys, namely for encrypting the data storage, supplying the user of the computing device suitable keys for external storage, calculating a hash-based message authentication codes over the BIOS, MBR, unique ID of the TPM, unique ID of the GPS / GSM module and unique ID of the BIOS; using user provided password and / or token device; using mobile data messages to secure the device if misplaced.
Owner:UNIV DE LISBOA
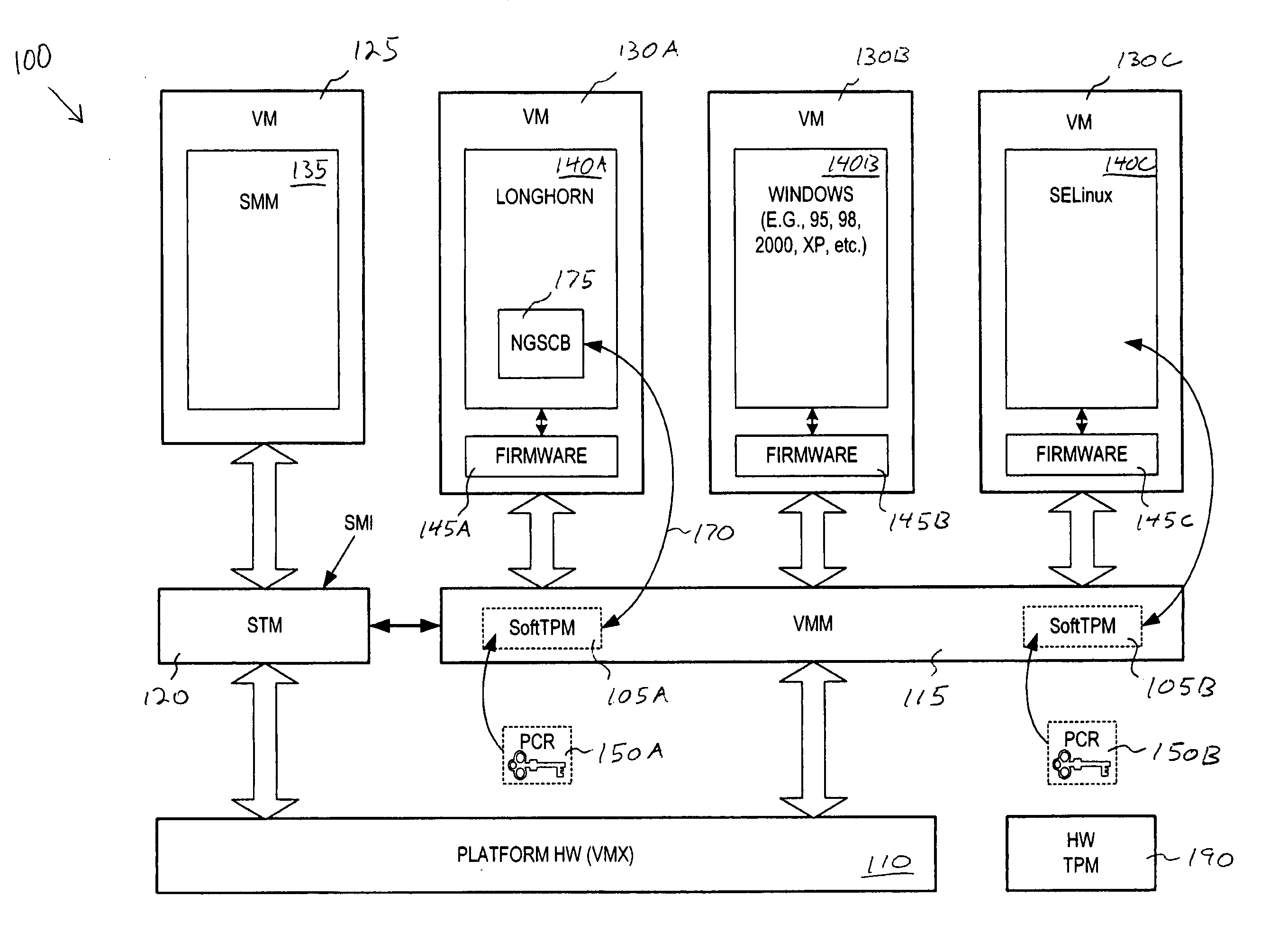
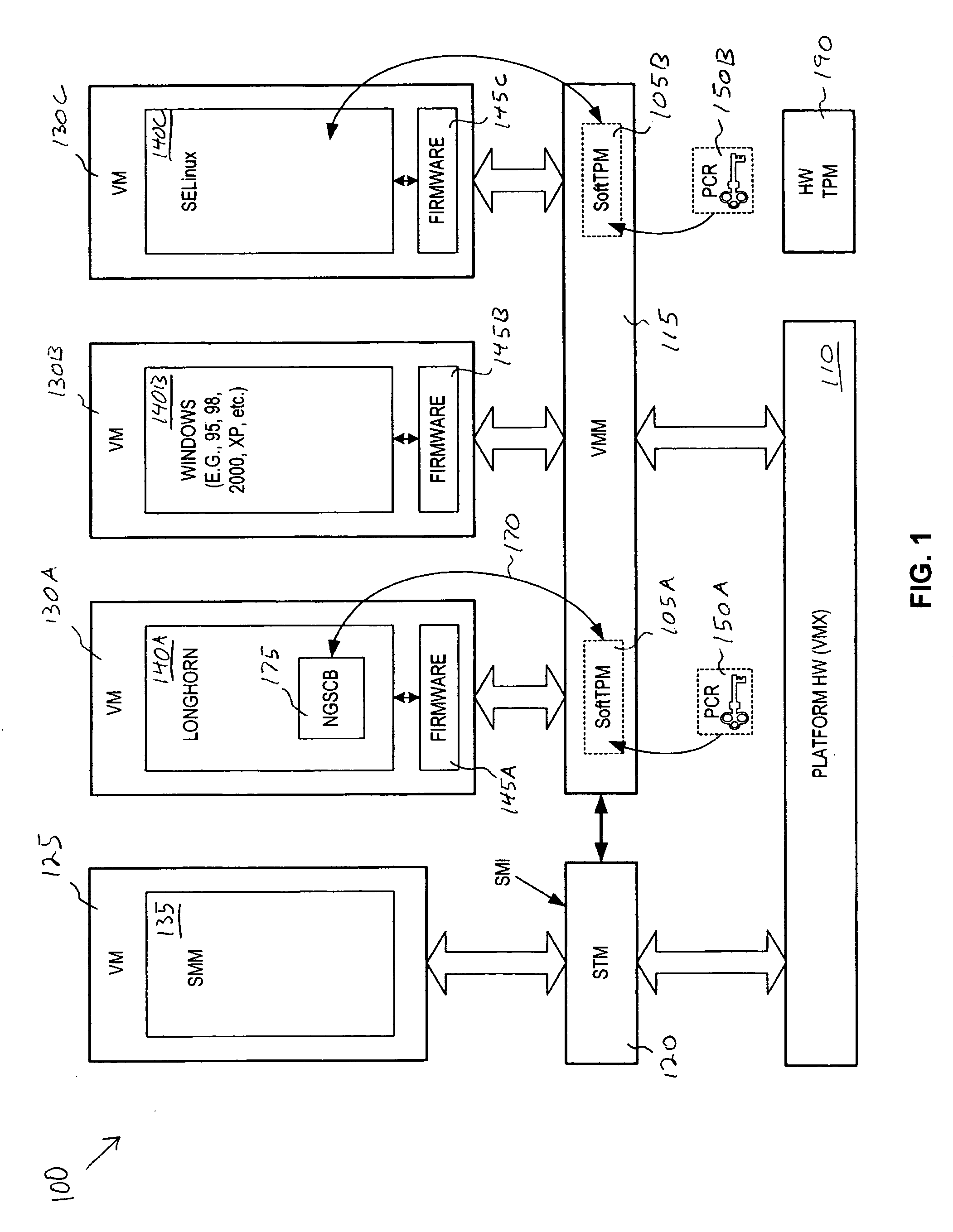
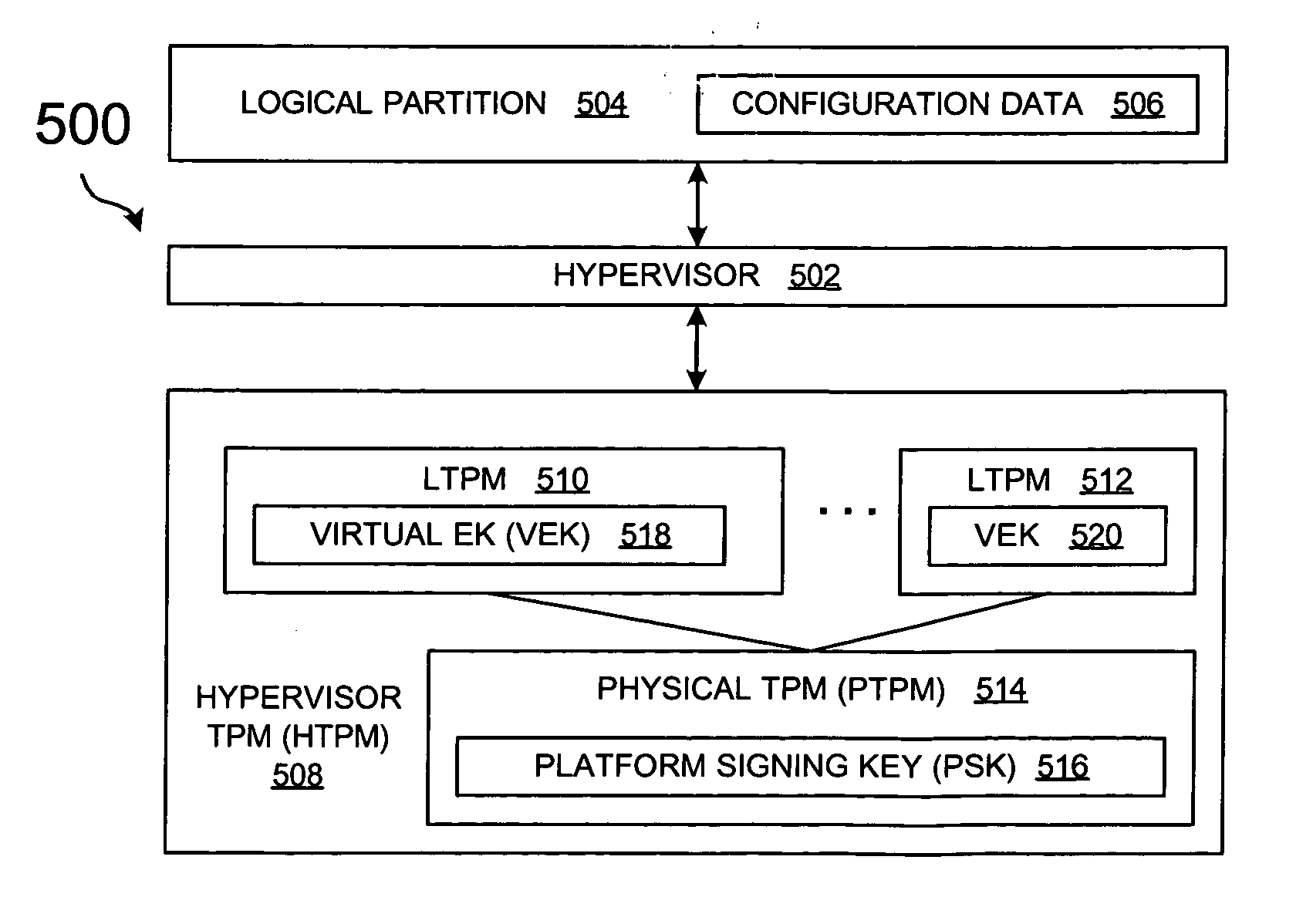
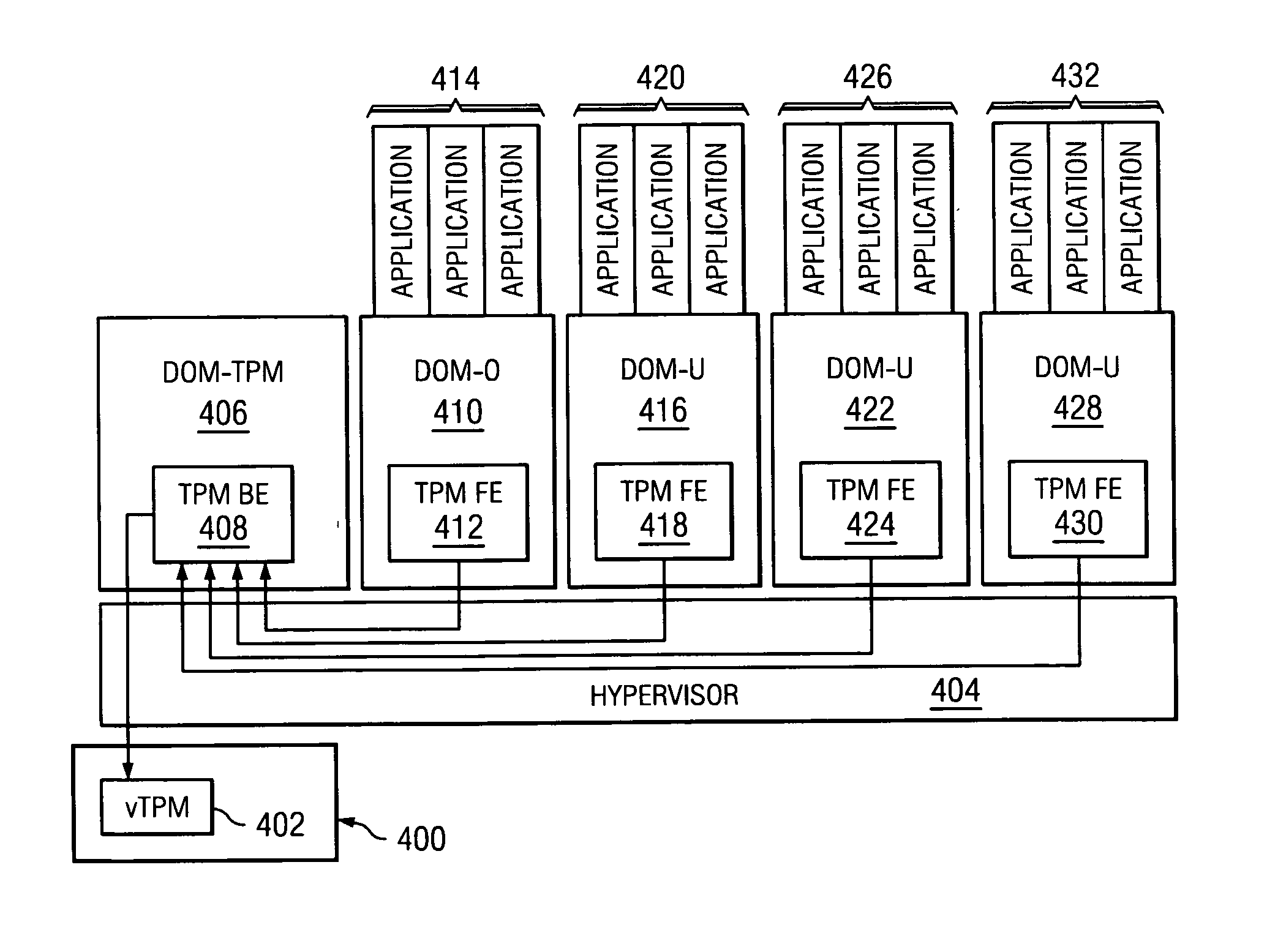
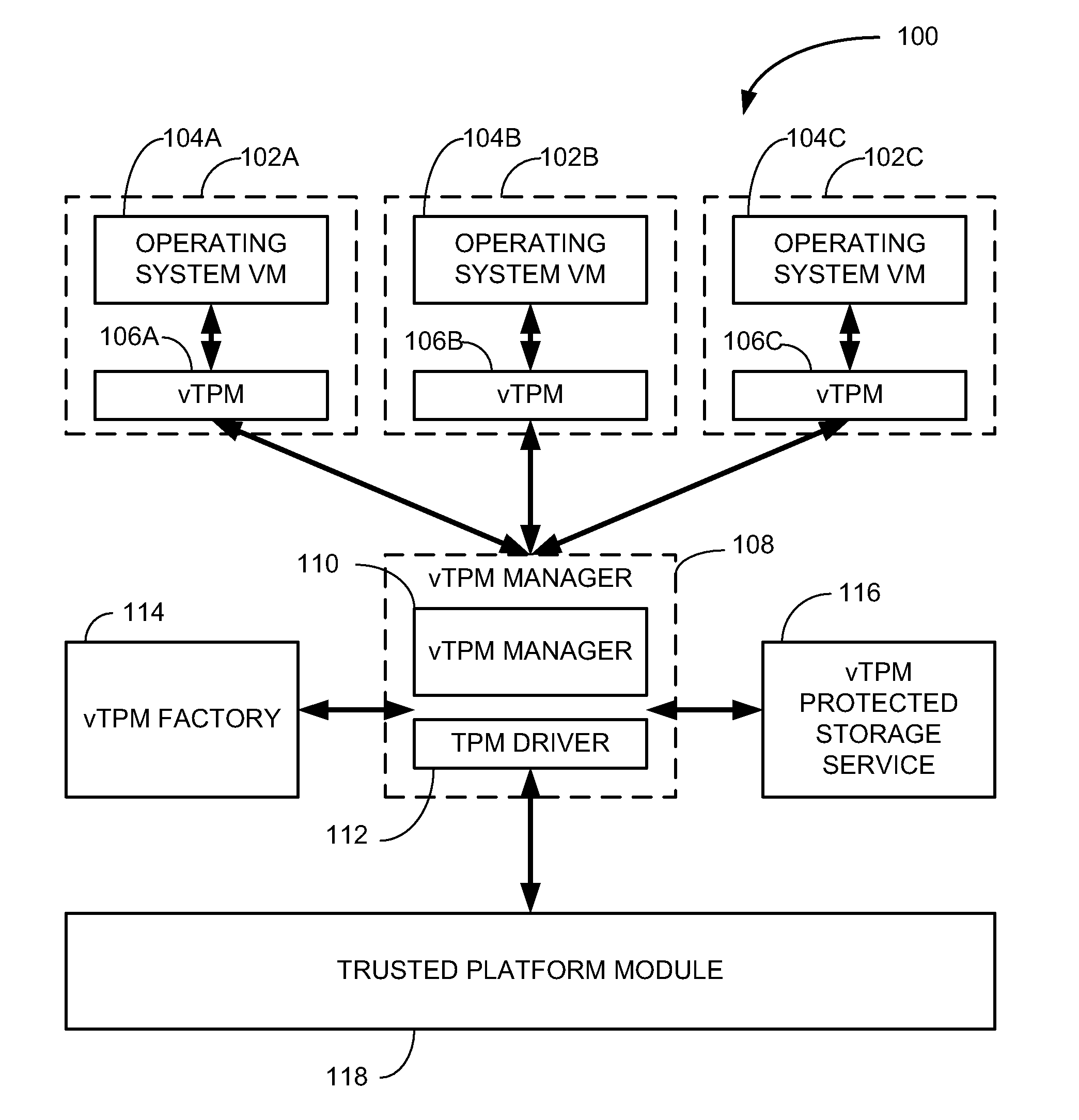
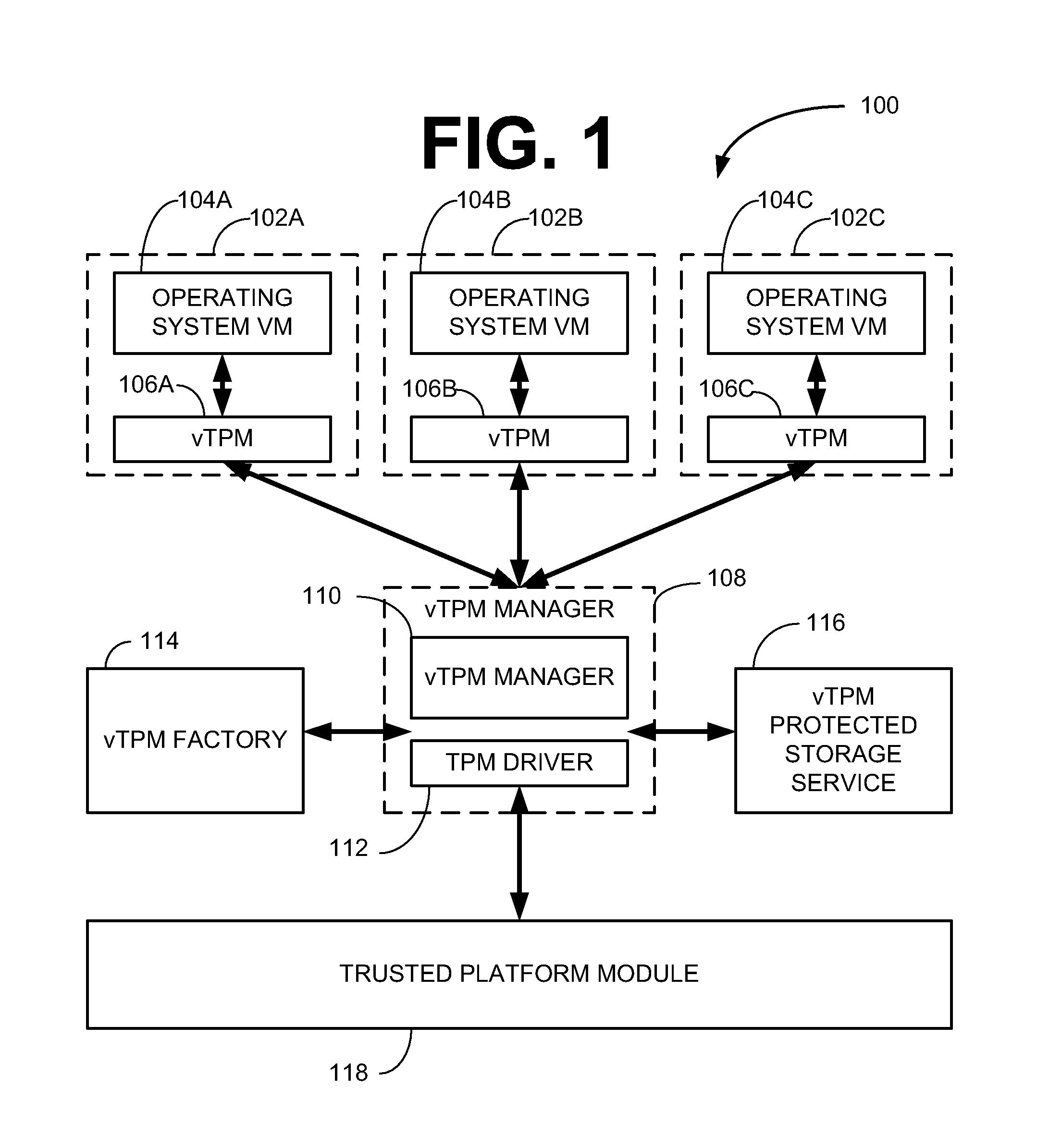
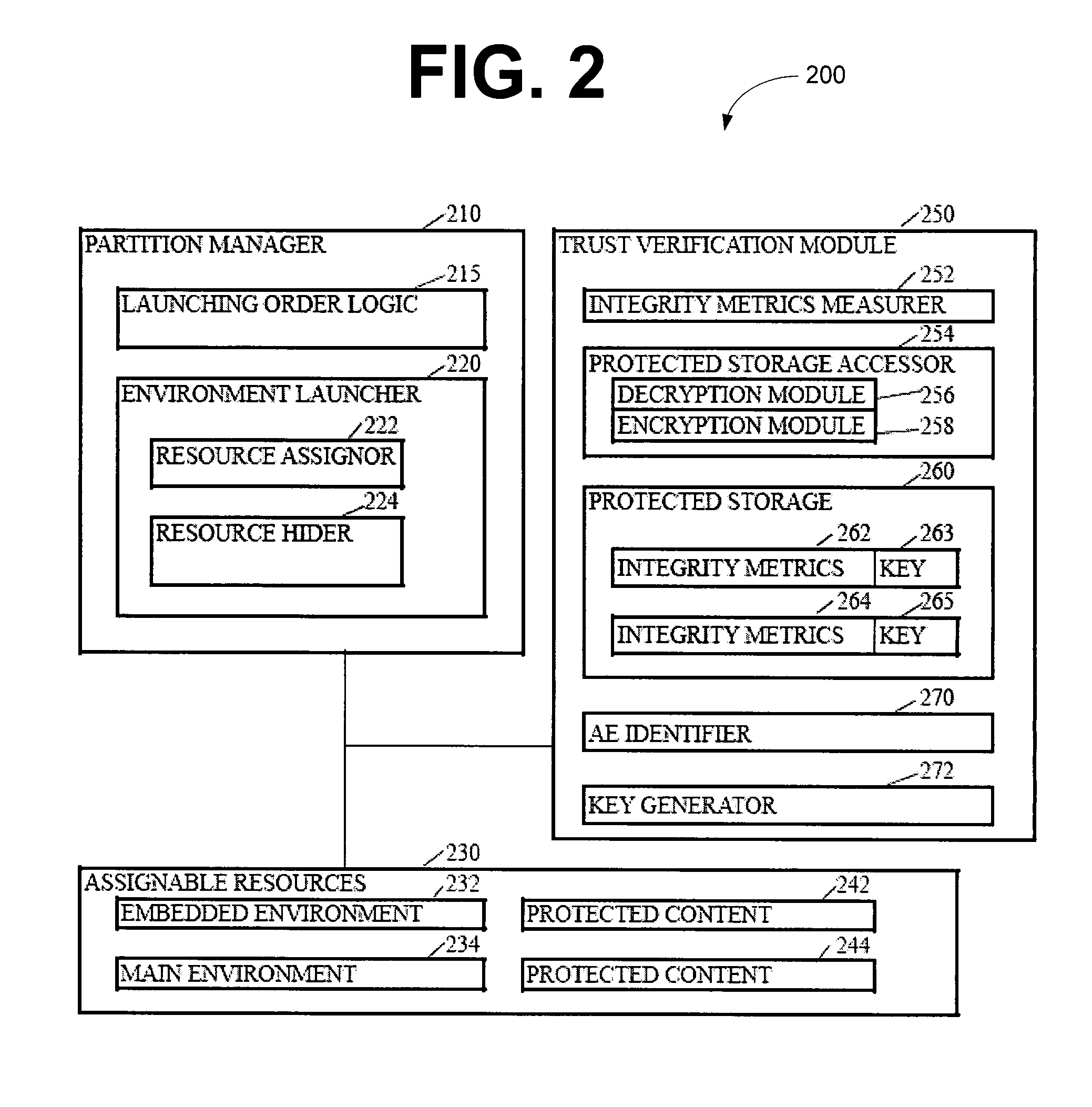
Method and system for virtualization of trusted platform modules
ActiveUS20050246552A1User identity/authority verificationUnauthorized memory use protectionVirtualizationData processing system
A method, an apparatus, a system, and a computer program product is presented for virtualizing trusted platform modules within a data processing system. A virtual trusted platform module along with a virtual endorsement key is created within a physical trusted platform module within the data processing system using a platform signing key of the physical trusted platform module, thereby providing a transitive trust relationship between the virtual trusted platform module and the core root of trust for the trusted platform. The virtual trusted platform module can be uniquely associated with a partition in a partitionable runtime environment within the data processing system.
Owner:IBM CORP
Sharing trusted hardware across multiple operational environments
InactiveUS20050210467A1Platform integrity maintainanceSoftware simulation/interpretation/emulationTrusted hardwareMultiplexer
A method, system, and article of manufacture to share trusted hardware across multiple operational environments. A virtual machine monitor (VMM) is loaded to support a plurality of virtual machines in a computer system, the VMM including a VMM multiplexer. A first and a second virtual machine (VM) are loaded. A trusted hardware device is shared between the first VM and the second VM using the VMM multiplexer. In one embodiment, the trusted hardware device includes a trusted platform module (TPM).
Owner:INTEL CORP
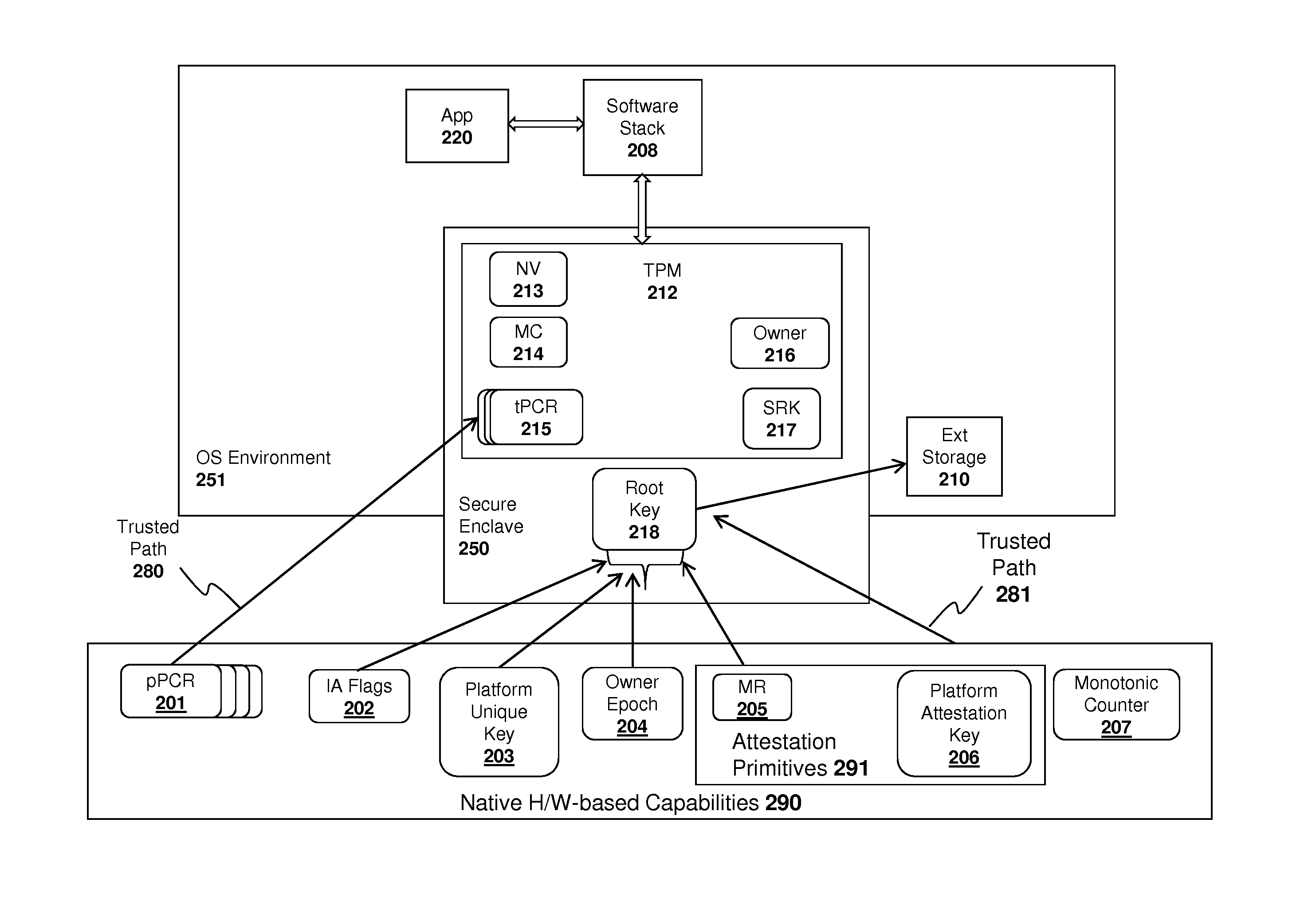
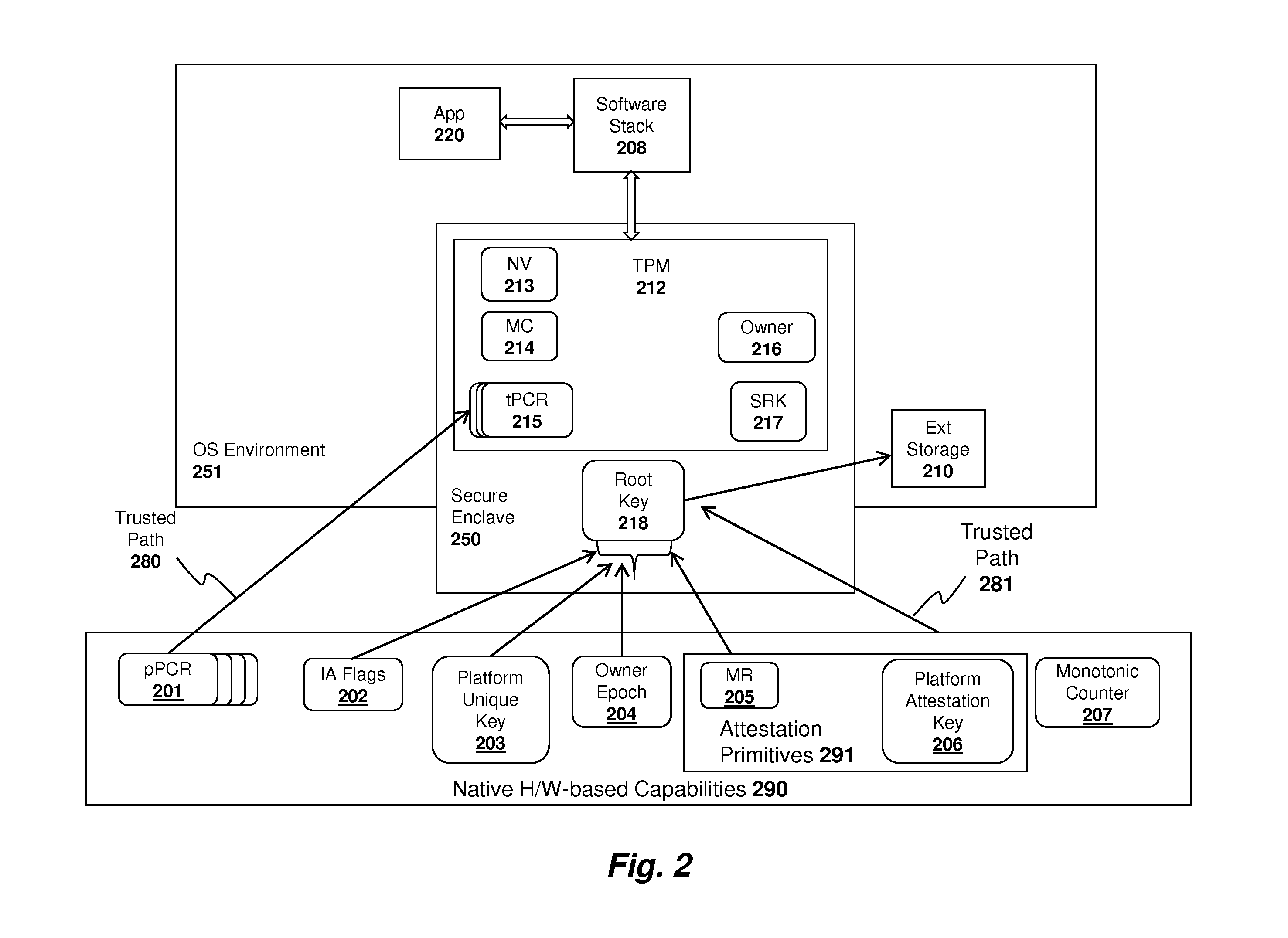
System and method for implementing a trusted dynamic launch and trusted platform module (TPM) using secure enclaves
ActiveUS20120163589A1Public key for secure communicationInternal/peripheral component protectionTrusted Platform ModuleControl register
An apparatus and method are described for implementing a trusted dynamic launch and trusted platform module (TPM) using a secure enclave. For example, a computer-implemented method according to one embodiment of the invention comprises: initializing a secure enclave in response to a first command, the secure enclave comprising a trusted software execution environment which prevents software executing outside the enclave from having access to software and data inside the enclave; and executing a trusted platform module (TPM) from within the secure enclave, the trusted platform module securely reading data from a set of platform control registers (PCR) in a processor or chipset component into a memory region allocated to the secure enclave.
Owner:INTEL CORP
Method and system to support a trusted set of operational environments using emulated trusted hardware
InactiveUS7222062B2Key distribution for secure communicationUnauthorized memory use protectionComputer hardwareTrusted hardware
A method and system to emulate a trusted platform module to execute trusted operations. A virtual machine monitor is executed to support a virtual machine session. An operating system is loaded into the virtual machine session. The trusted platform module is emulated to hold a key associated with the virtual session and to execute trusted operations.
Owner:INTEL CORP
Dynamic creation and hierarchical organization of trusted platform modules
InactiveUS20070079120A1Platform integrity maintainanceSecuring communicationOperational systemTrusted Platform Module
A trusted platform module is presented that is capable of creating, dynamically, multiple virtual trusted platform modules in a hierarchical organization. A trusted platform module domain is created. The trusted platform module creates virtual trusted platform modules, as needed, in the trusted platform module domain. The virtual trusted platform modules can inherit the permissions of a parent trusted platform module to have the ability to create virtual trusted platform modules themselves. Each virtual trusted platform module is associated with a specific partition. Each partition is associated with an individual operating system. The hierarchy of created operating systems and their privilege of spawning new operating systems is reflected in the hierarchy of trusted platform modules and the privileges each of the trusted platform modules has.
Owner:IBM CORP
Virtual tpm key migration using hardware keys
ActiveUS20090169012A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesVirtualizationComputer hardware
The present subject matter is related to trusted computing, and more particularly to migration of virtual trusted platform module keys that are rooted in a hardware trusted platform module. Some embodiments include a trusted platform virtualization module that may perform one or more of inbound and outbound trusted platform module key migrations. Such migrations may be performed between a virtual trusted platform module and either a hardware or a virtual trusted platform module.
Owner:INTEL CORP
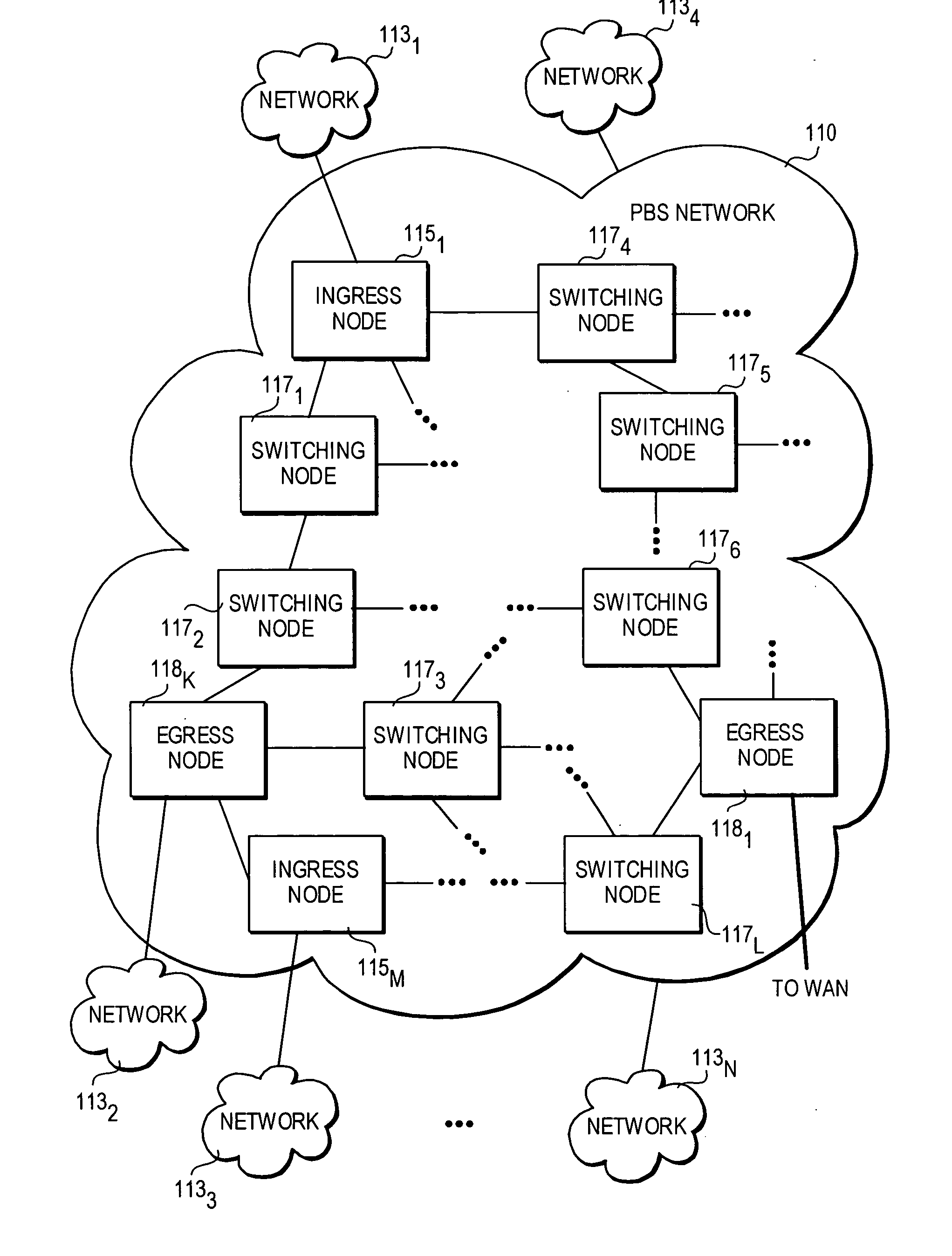
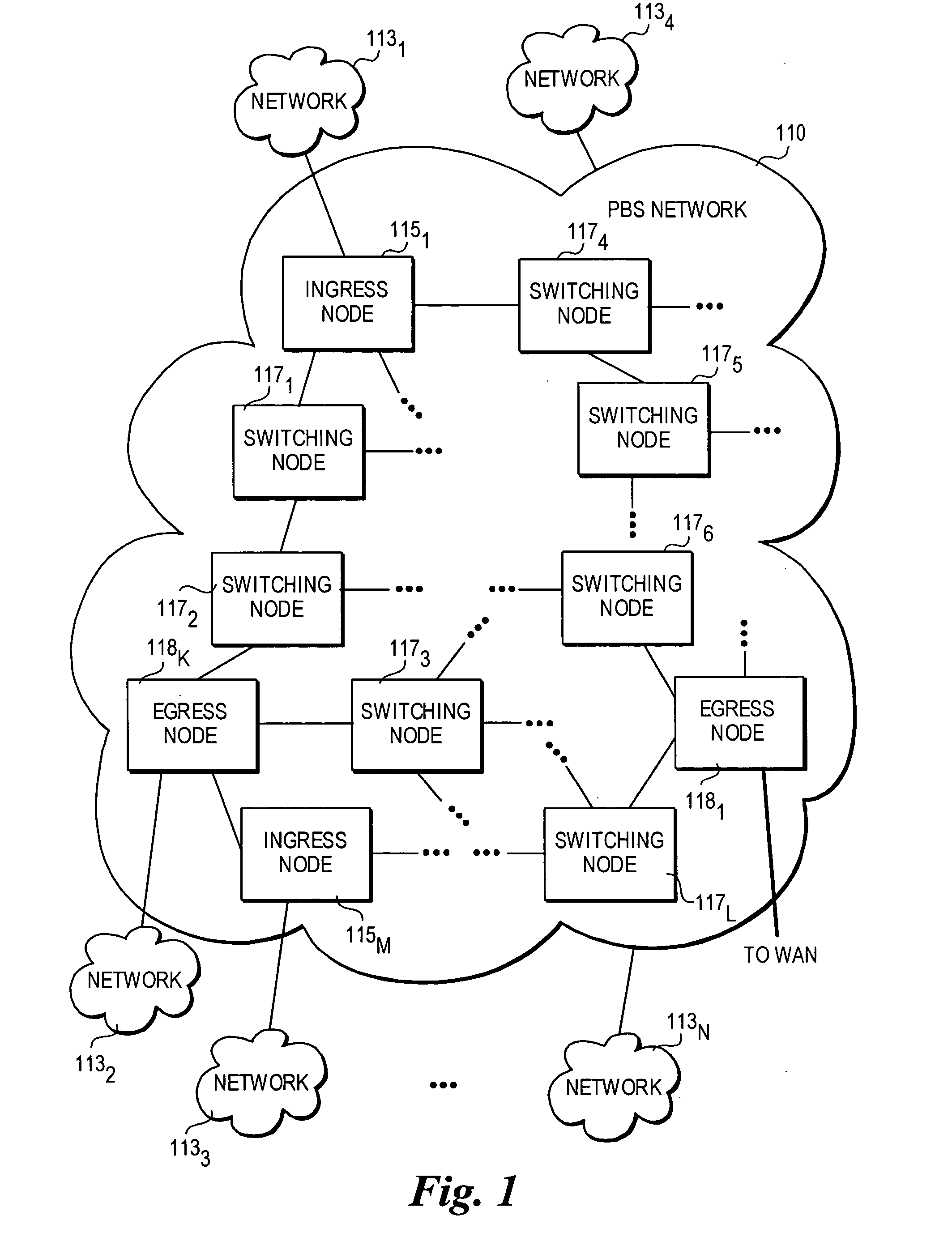
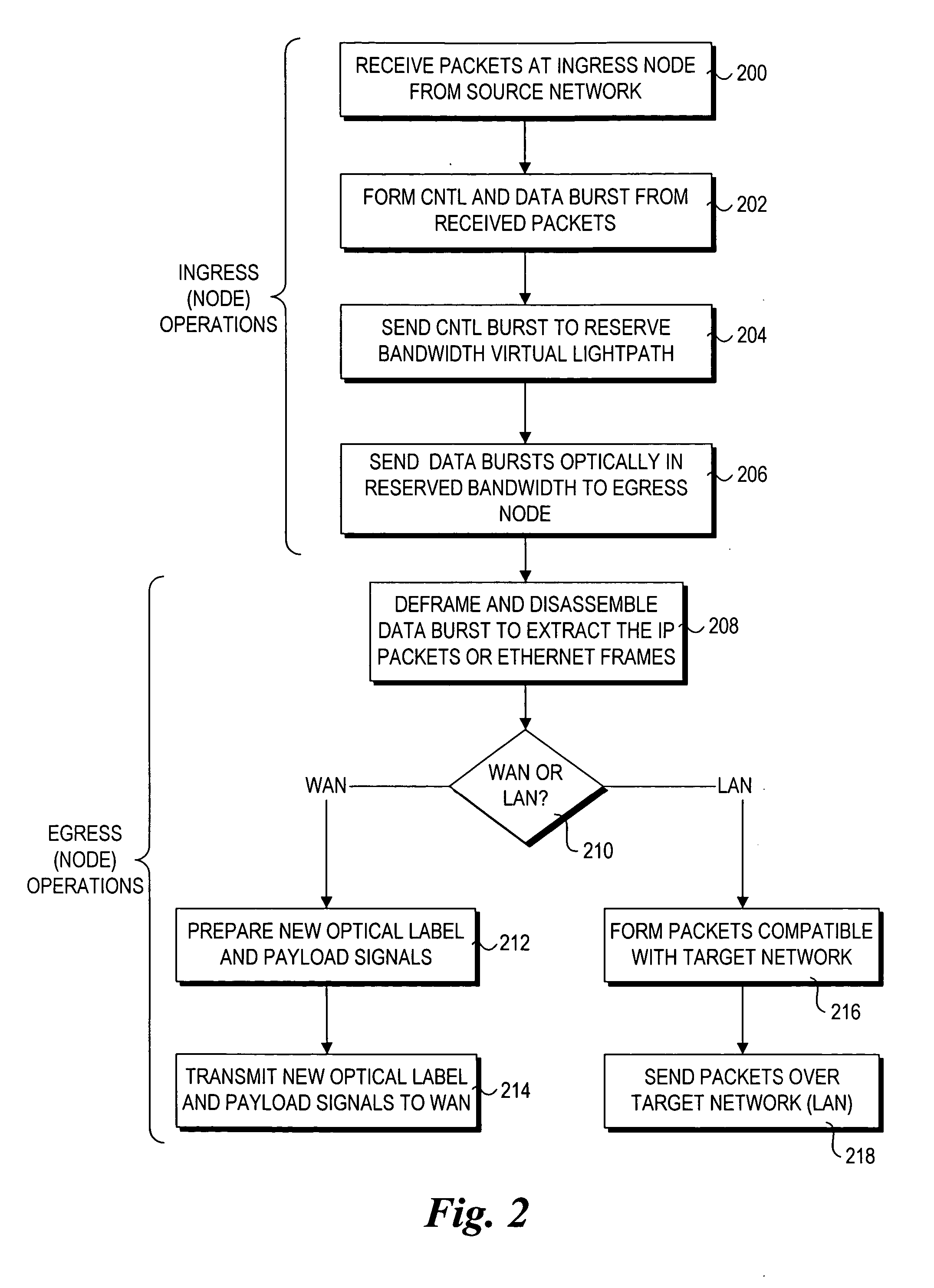
Method and architecture for security key generation and distribution within optical switched networks
InactiveUS20050177749A1Digital data processing detailsUser identity/authority verificationExchange networkEdge node
A method and architecture for secure transmission of data within optical-switched networks. In one embodiment, the optical switched network comprises a photonic burst-switched (PBS) network. Under various schemes, security keys including encryption and decryption keys are generated by edge nodes and the decryption keys are distributed to other edge nodes in a PBS network. In one embodiment, the security keys are dynamically generated by a trusted platform module (TPM). A source edge node uses its encryption key to encrypt selected data bursts to be sent to a destination edge node via a virtual lightpath coupling the source and destination edge nodes. Security data are embedded in a control burst header indicates to the destination node whether corresponding data bursts sent via the virtual lightpath are encrypted. The security data also includes the decryption key and may also identify an encryption / decryption algorithm to be used. In some embodiments, public key infrastructure facilities are used in conjunction with employment of private and public keys and digital certificates.
Owner:TAHOE RES LTD
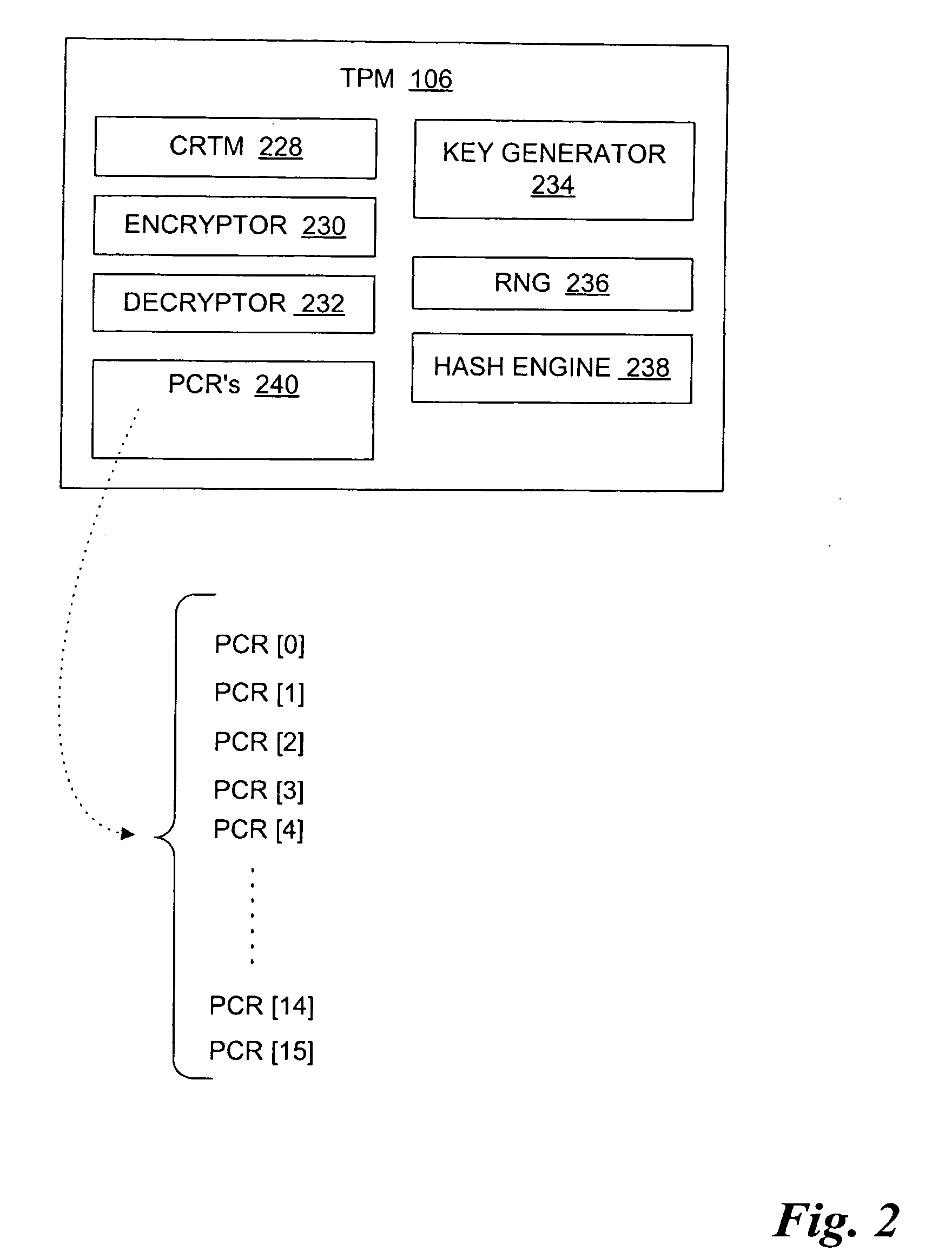
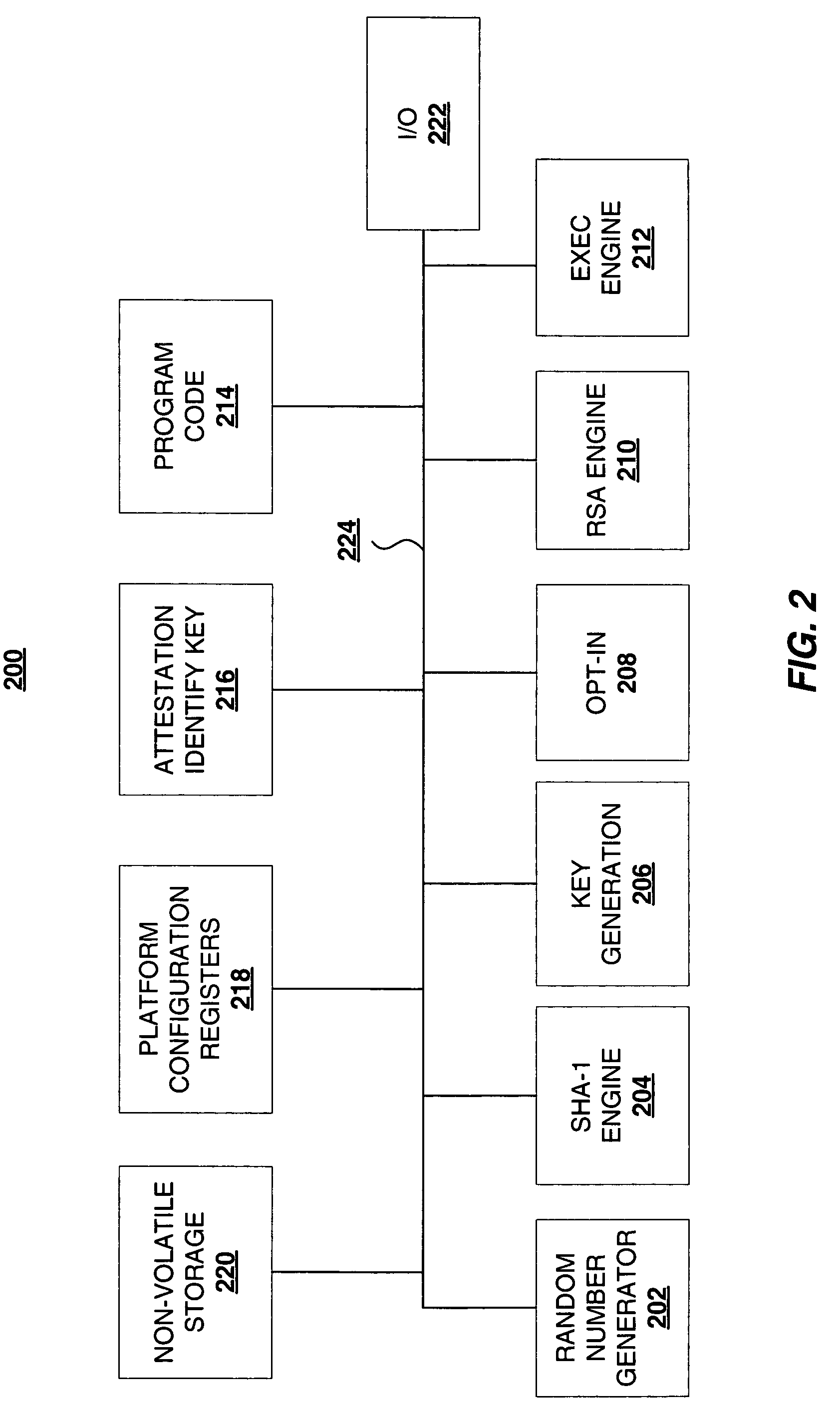
Virtualization of software configuration registers of the TPM cryptographic processor
InactiveUS20060212939A1Direct accessMemory loss protectionUnauthorized memory use protectionComputer hardwareVirtualization
A virtual PCR (VPCR) construct is provided that can be cryptographically tagged as optionally resettable or as enduring for the life of a client (process, virtual machine, and the like) and that can be loaded into a resettable hardware PCR to make use of the functionality of a Trusted Platform Module (TPM). The VPCRs may cryptographically reflect their characteristics (resettable or not) in their stored values. Also, since the PCRs are virtualized, they are (effectively) unlimited in number and may be given general names (UUIDs) that are less likely to collide. The VPCRs can be loaded into a physical PCR as needed, but in a way that stops one piece of software from impersonating another piece of software. The VPCRs thus enable all software using the TPM to be given access to TPM functionality (sealing, quoting, etc.) without security concerns.
Owner:MICROSOFT TECH LICENSING LLC
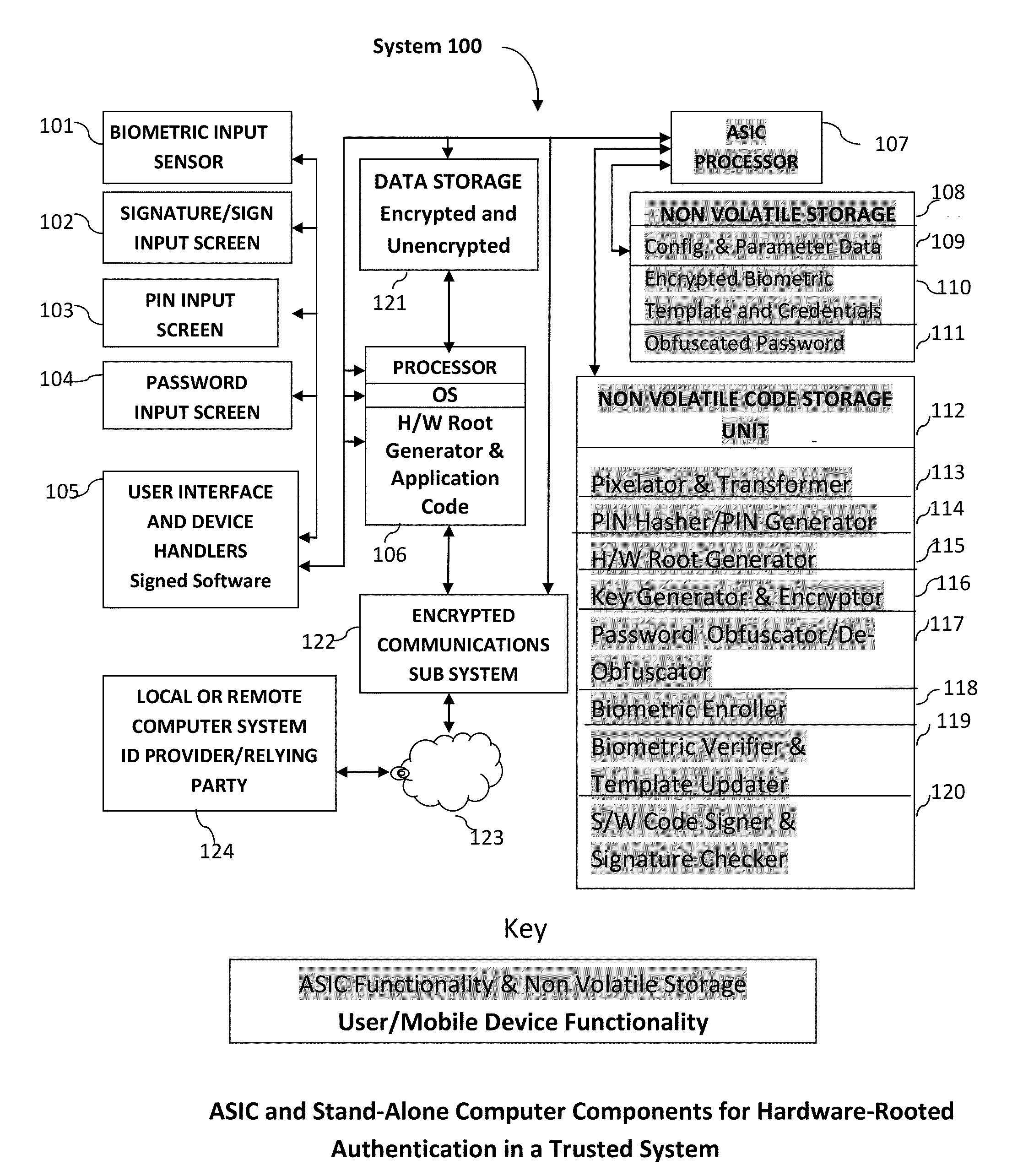
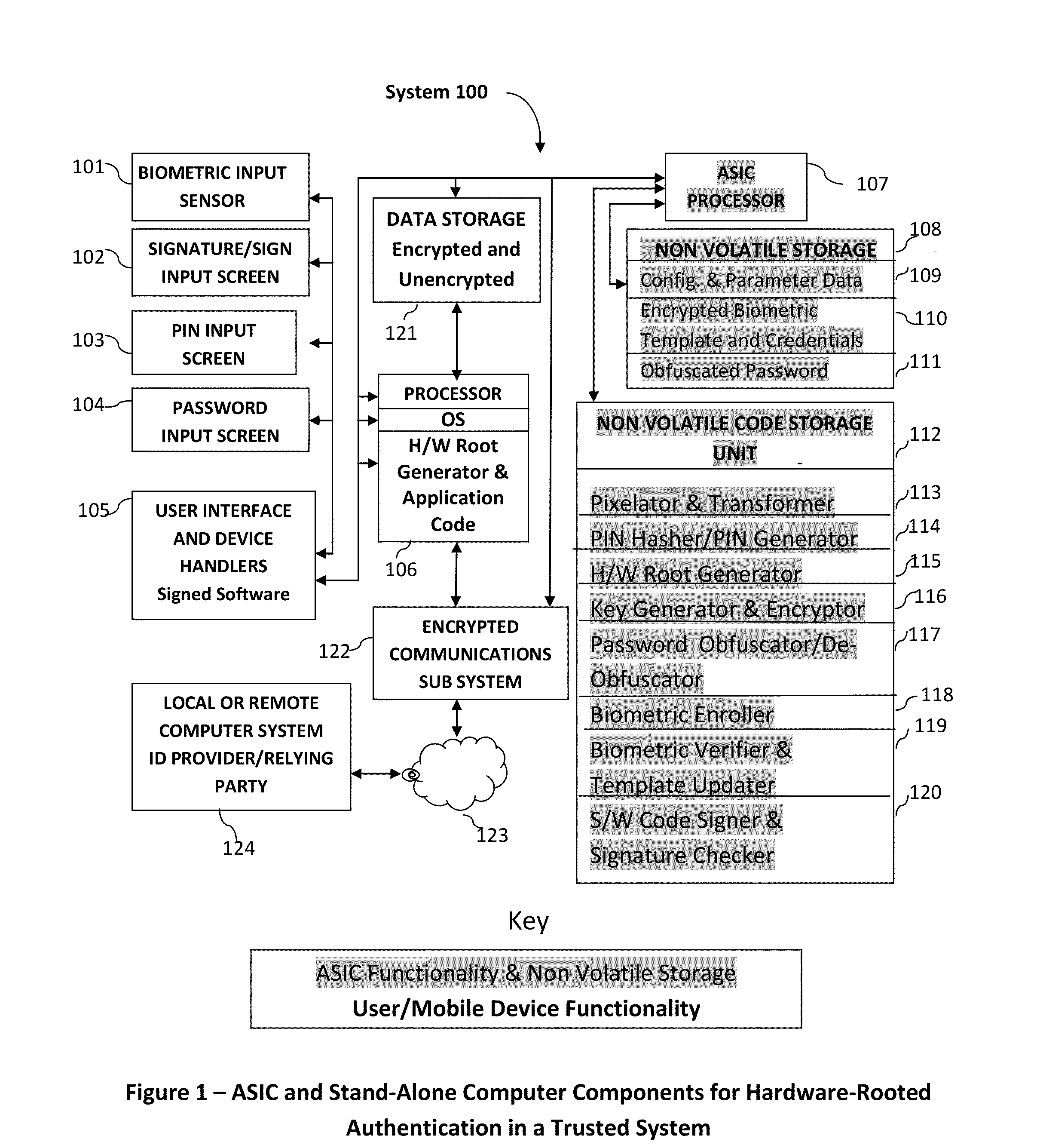
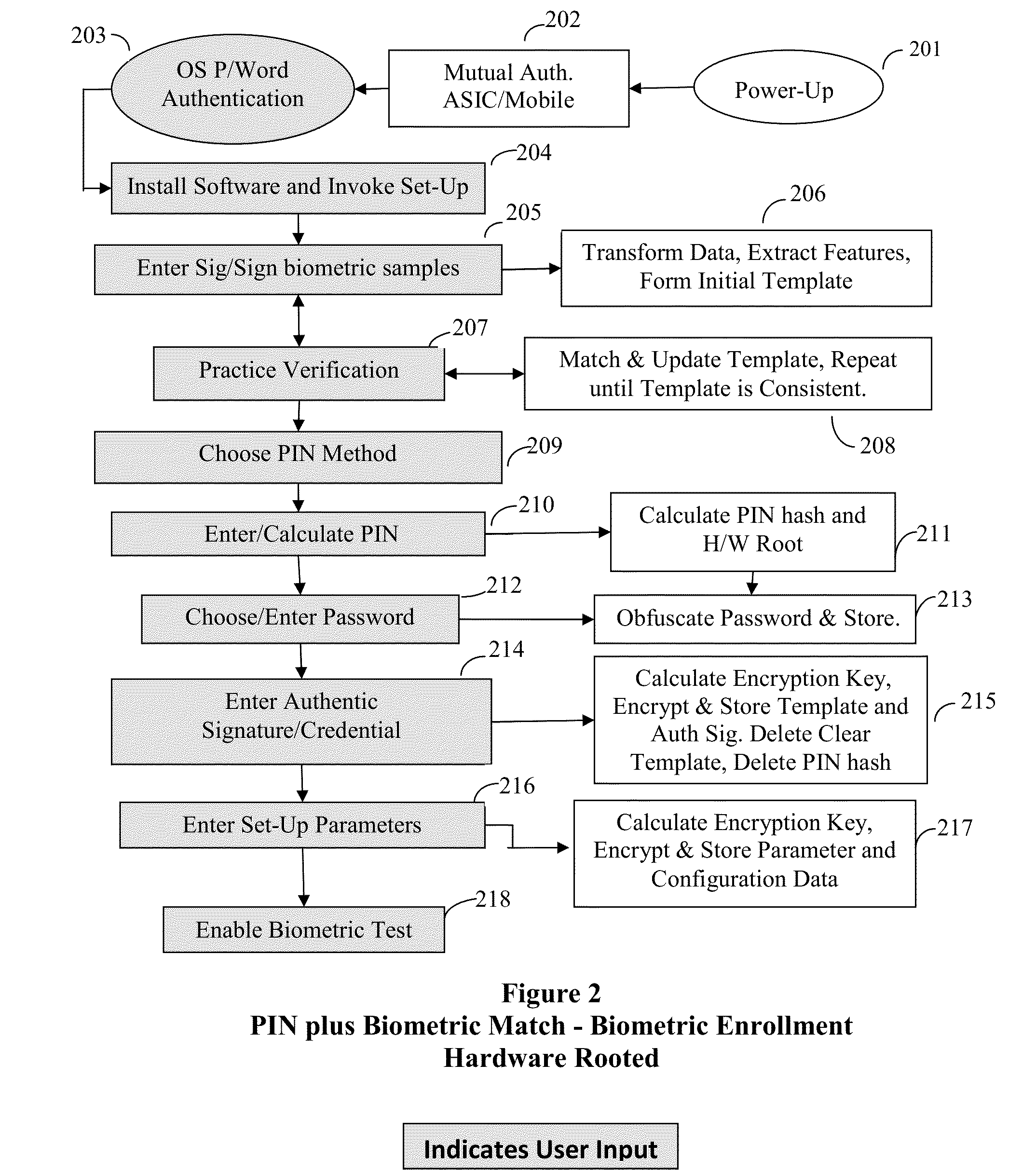
Method and System for Providing Password-free, Hardware-rooted, ASIC-based Authentication of a Human to a Mobile Device using Biometrics with a Protected, Local Template to Release Trusted Credentials to Relying Parties
InactiveUS20140365782A1Significant productivityMaximum safetyUser identity/authority verificationInternal/peripheral component protectionBiometric dataPassword hashing
Biometric data, which may be suitably transformed are obtained from a biometric input device contained within a stand-alone computer or a mobile device, which may contain an ASIC chip connected to or incorporated within the stand-alone computer or mobile device and which includes the capability for capturing one or more biometric samples and for biometric feature extraction, matching and encryption. For extra security, the biometric matching is used in conjunction with a PIN to authenticate the user to the stand-alone computer or mobile device. The biometric template and other sensitive data residing on the mobile device are encrypted using hardware elements of the mobile device (or the ASIC) together with the PIN hash and / or the Password hash. An obfuscated version of the Password, stored on the ASIC or the mobile device is de-obfuscated and released to the mobile device authentication mechanism, including a Trusted Platform Module if present, in response to a successfully decrypted template and matching biometric sample and PIN. A de-obfuscated password is used to authenticate the user to the mobile device and the same or a different de-obfuscated password may be used to authenticate the user to a remote computer using the SSL / TLS or a process based upon a symmetric encryption algorithm. The locally generated password may be used to encrypt data at rest on the mobile device or ASIC and the remote authentication password may be used to encrypt data in transit to and from a remote computer. This creates a trusted relationship between the stand-alone computer or mobile device and the remote computer. The system also eliminates the need for the user to remember and enter complex passwords on the mobile device or for secure transmission of data. A similar method may be used, with the signature / sign biometric modality to determine whether the holder of an IC chip card is, in fact the card owner.
Owner:BIOCRYPT ACCESS LLC
Partitioned scheme for trusted platform module support
InactiveUS20090007104A1Computer security arrangementsSoftware simulation/interpretation/emulationComputer hardwareOperational system
The subject mater herein relates to processing of sensitive data and, more particularly, to a partitioned scheme for trusted platform module support. Various embodiments provide systems, methods, and software that instantiate one or more emulated trusted platform modules in respective sequestered processor cores. In some embodiments, a trusted platform module in instantiated in a processor core, sequestered for the trusted platform module, for each operating system or virtual machine operating on a computing device. The operating system may then communicate with the appropriate trusted platform module over a secure communication channel, such as an interpartition bridge.
Owner:INTEL CORP
Method, apparatus, and product for establishing virtual endorsement credentials for dynamically generated endorsement keys in a trusted computing platform
ActiveUS20070016801A1User identity/authority verificationUnauthorized memory use protectionData processing systemThird party
A method, apparatus, and computer program product are disclosed in a data processing system for establishing virtual endorsement credentials. The data processing system includes a hardware trusted platform module (TPM). Logical partitions are generated in the system. A different virtual TPM is generated for each one of the logical partitions. For each one of the logical partitions, the virtual TPM that was generated for the logical partition then dynamically generates a virtual endorsement credential for use by the logical partition that includes the virtual TPM. The virtual endorsement credential is generated within the data processing system without the data processing system or its devices accessing a trusted third party that is external to the data processing system.
Owner:IBM CORP
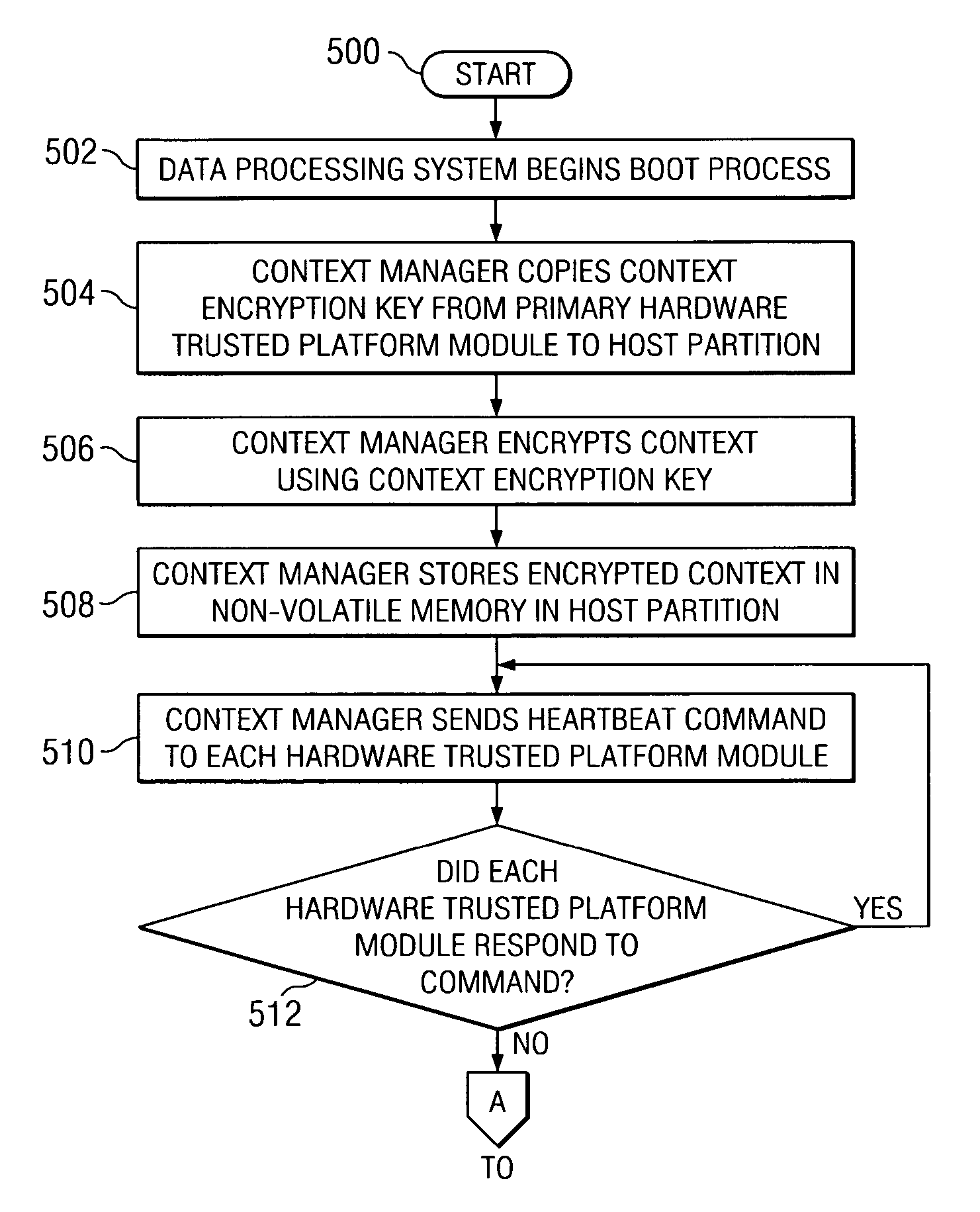
Method, apparatus, and product for providing a backup hardware trusted platform module in a hypervisor environment
A method, apparatus, and computer program product are described for implementing a trusted computing environment within a data processing system. The data processing system includes a primary hardware trusted platform module (TPM) and a secondary hardware backup TPM. The data processing system also includes multiple logical partitions. The primary hardware TPM is used to provide trusted computing services to the logical partitions. A determination is made as to whether the primary hardware TPM is malfunctioning. If a determination is made that the primary hardware TPM is malfunctioning, the secondary hardware TPM is designated as a new primary hardware TPM and is utilized instead of the primary TPM to provide trusted computing services to the logical partitions.
Owner:IBM CORP
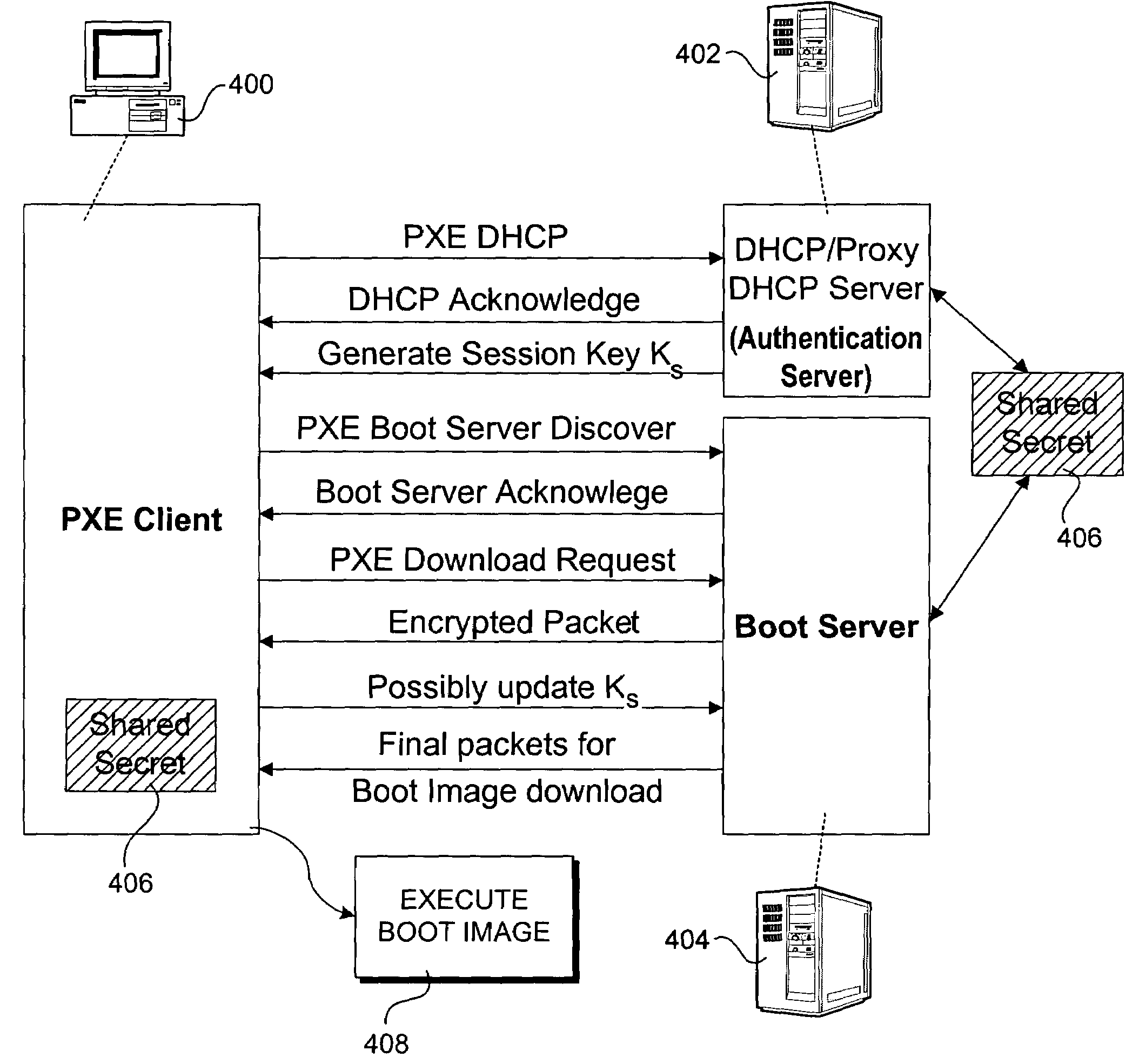
Method to authenticate clients and hosts to provide secure network boot
InactiveUS7299354B2Key distribution for secure communicationDigital data processing detailsTrusted Platform ModuleAuthentication server
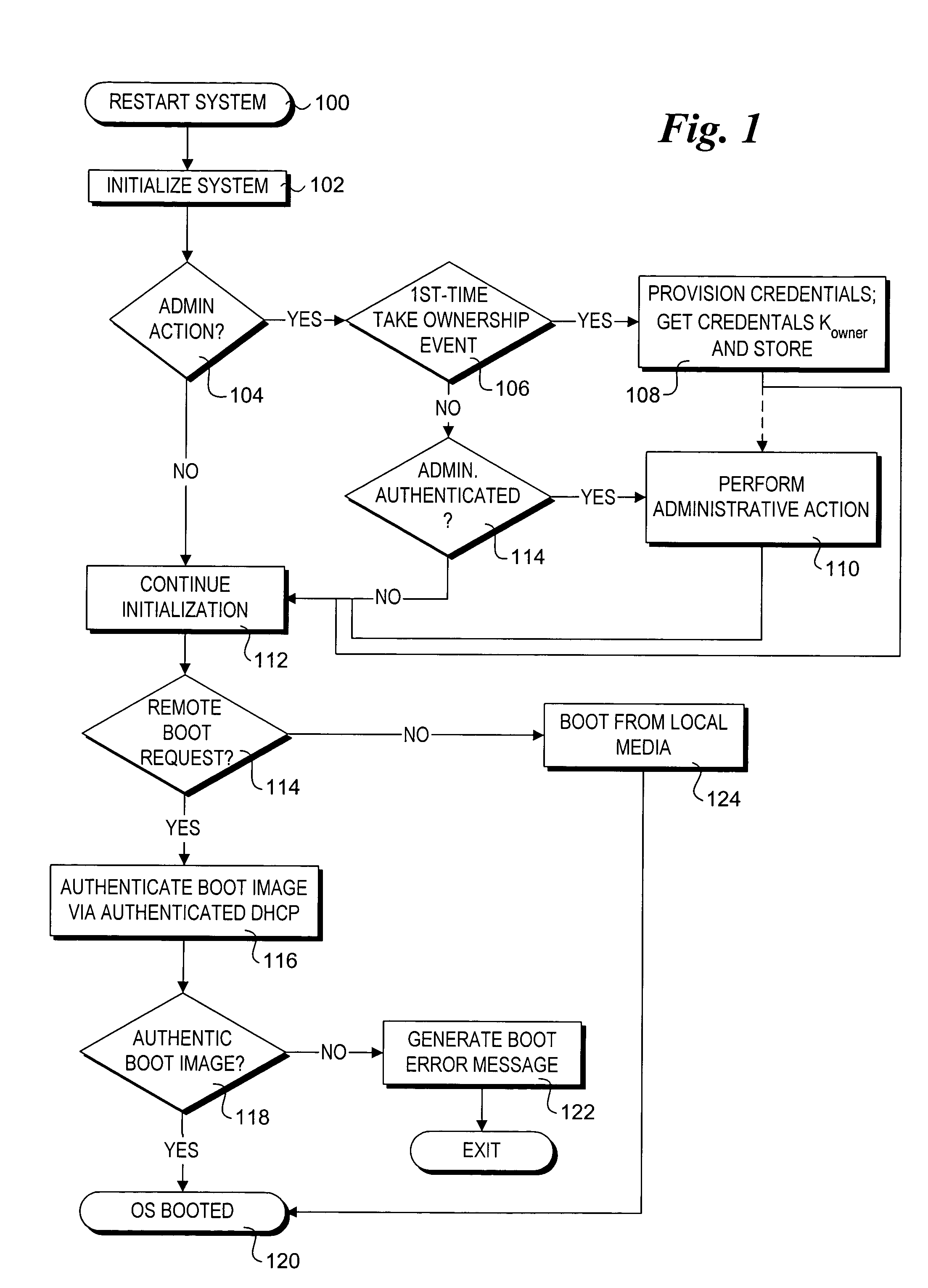
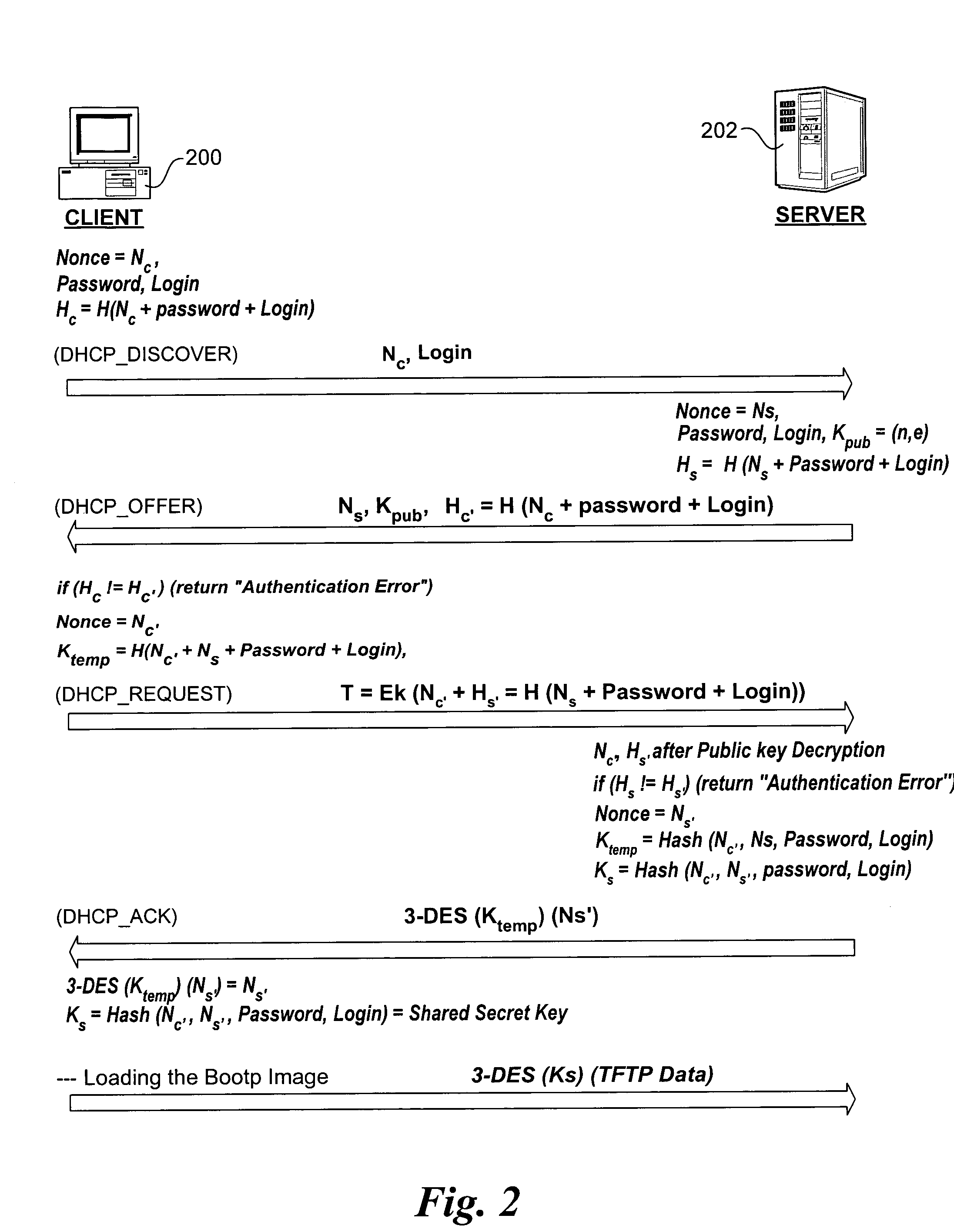
A method for authenticating clients and boot server hosts to provide a secure network boot environment. Messages are exchanged between a client and a boot server or authentication server proxy for the boot server during pre-boot operations of the client to authentic the boot server and the client. In one embodiment, authentication is performed by comparing shared secrets stored on each of the client and the boot server or authentication proxy. The shared secret comprises authentication credentials that may be provisioned by an administrator, user, or by the client itself via a trusted platform module. Authentication provisioning schemes include an Extensible Authentication Protocol (EAP) exchange. In one embodiment, authentication is performed during the pre-boot via an authenticated Dynamic Host Configuration Protocol (DHCP) process. The scheme provides a faster and more simplified authentication mechanism, without requiring extensive set-up for IT administrators or significantly changing the login and OS boot user experience.
Owner:INTEL CORP
Scalable paging of platform configuration registers
ActiveUS20060075223A1Prevent breachUser identity/authority verificationDigital computer detailsComputer hardwareProcessor register
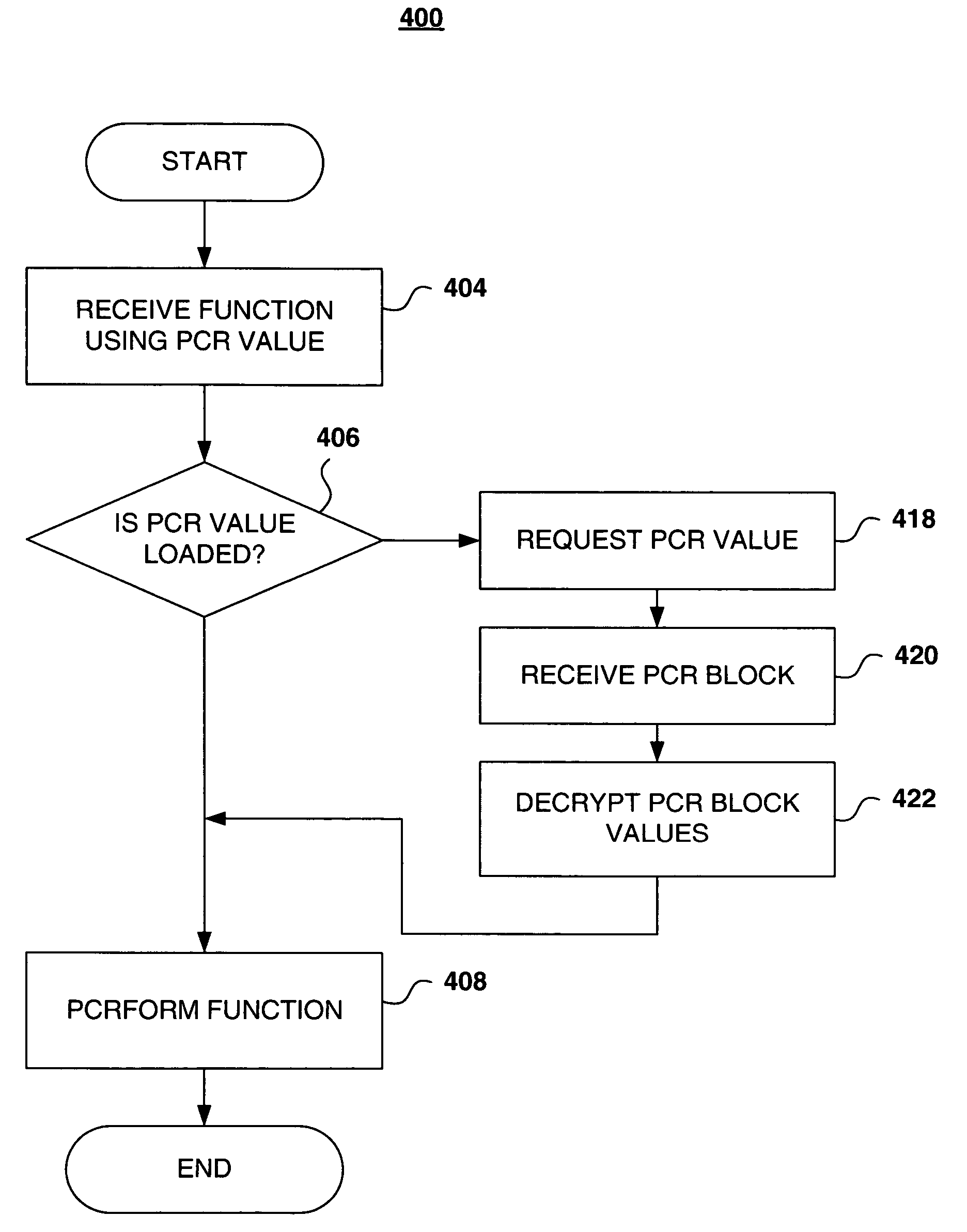
A method, computer program, and system for paging platform configuration registers in and out of a trusted platform module. In a trusted computing platform, an unlimited number of platform configuration registers can be obtained through paging. The trust platform module encrypts and decrypts platform configuration registers for storage outside the trusted platform module.
Owner:LENOVO PC INT
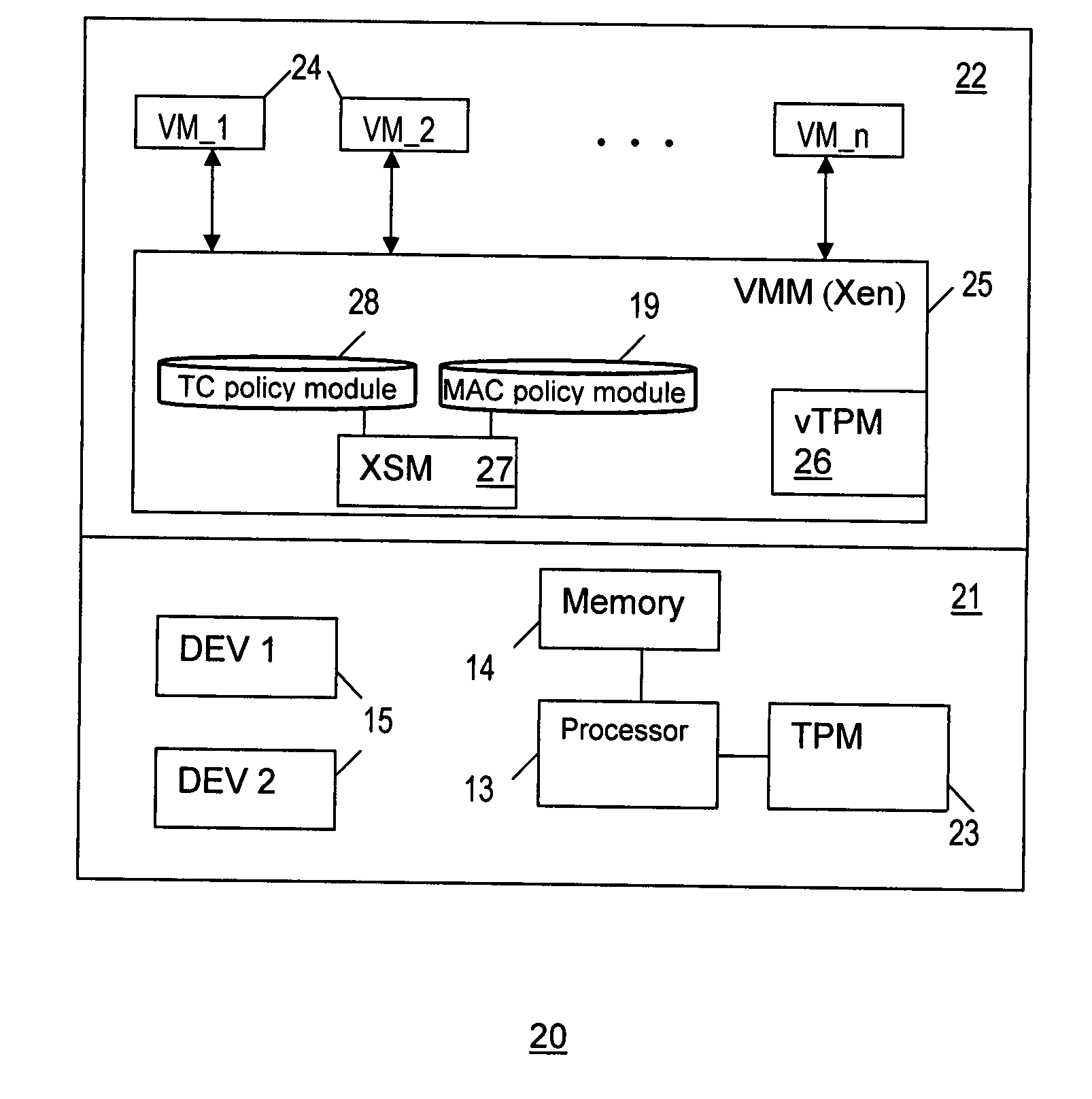
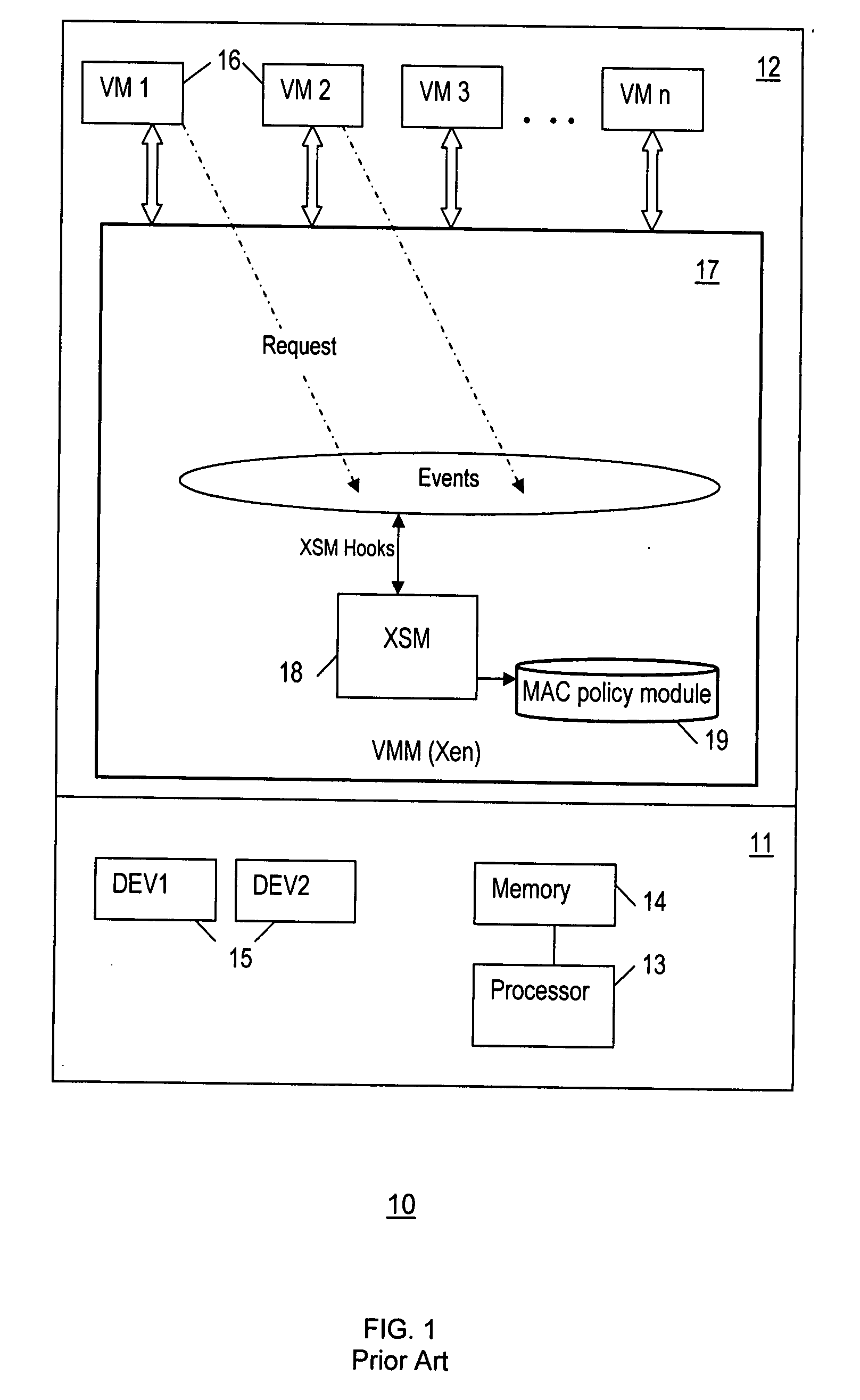
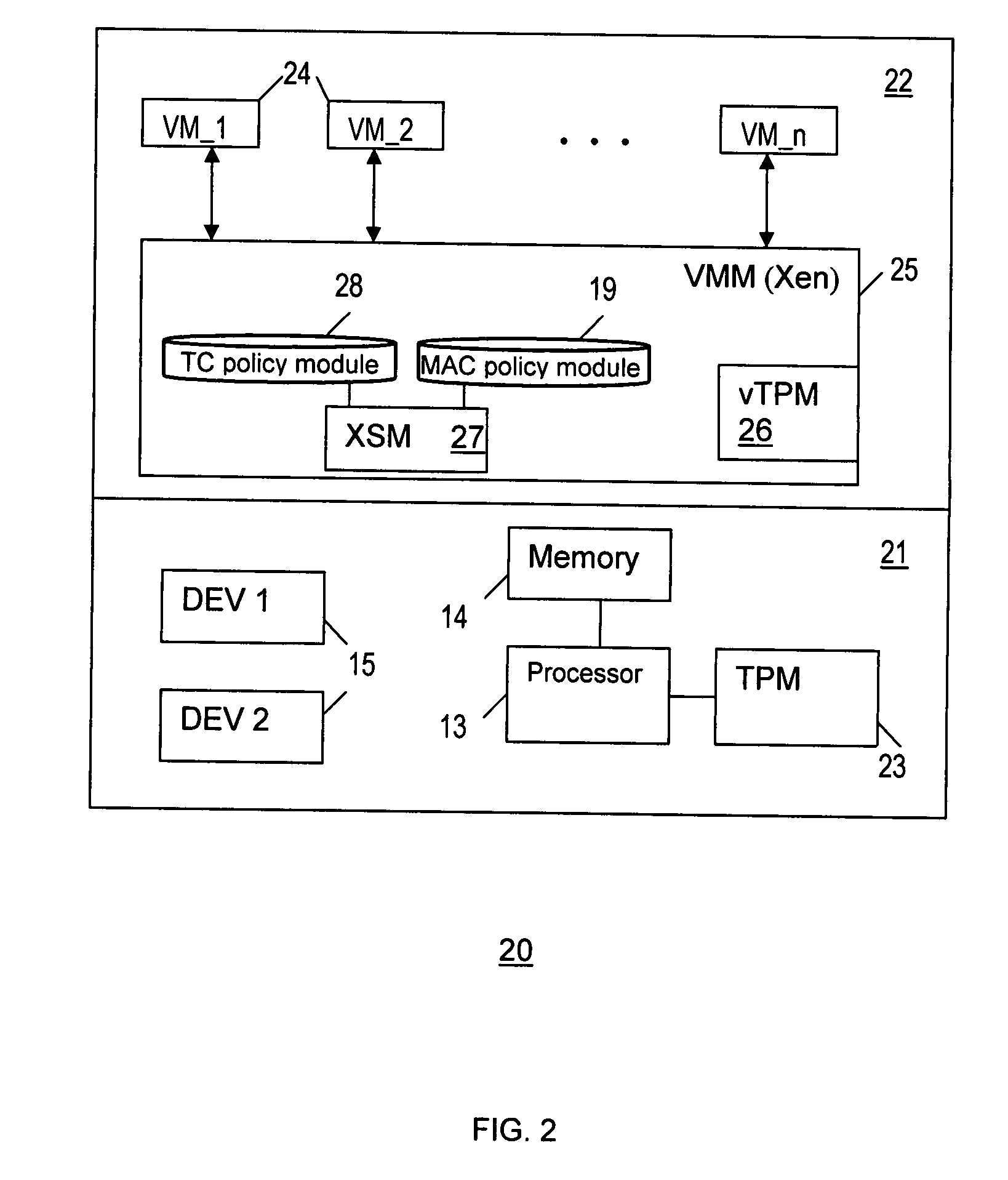
Method and system for enforcing trusted computing policies in a hypervisor security module architecture
InactiveUS20090125974A1Platform integrity maintainanceTransmissionObject basedTrusted Platform Module
A method and system for enforcing trusted computing (TC) policies in a security module architecture for a hypervisor. Upon receiving a request from a subject for access to an object, TC-related attribute values are obtained for the subject and the object based on a virtualized trusted platform module (vTPM). Access control decisions are the made based at least on the TC-related attribute values and TC-related policies.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system for virtualization of trusted platform modules
ActiveUS7380119B2User identity/authority verificationUnauthorized memory use protectionData processing systemVirtualization
A method, an apparatus, a system, and a computer program product is presented for virtualizing trusted platform modules within a data processing system. A virtual trusted platform module along with a virtual endorsement key is created within a physical trusted platform module within the data processing system using a platform signing key of the physical trusted platform module, thereby providing a transitive trust relationship between the virtual trusted platform module and the core root of trust for the trusted platform. The virtual trusted platform module can be uniquely associated with a partition in a partitionable runtime environment within the data processing system.
Owner:INT BUSINESS MASCH CORP
Systems and methods for securely booting a computer with a trusted processing module
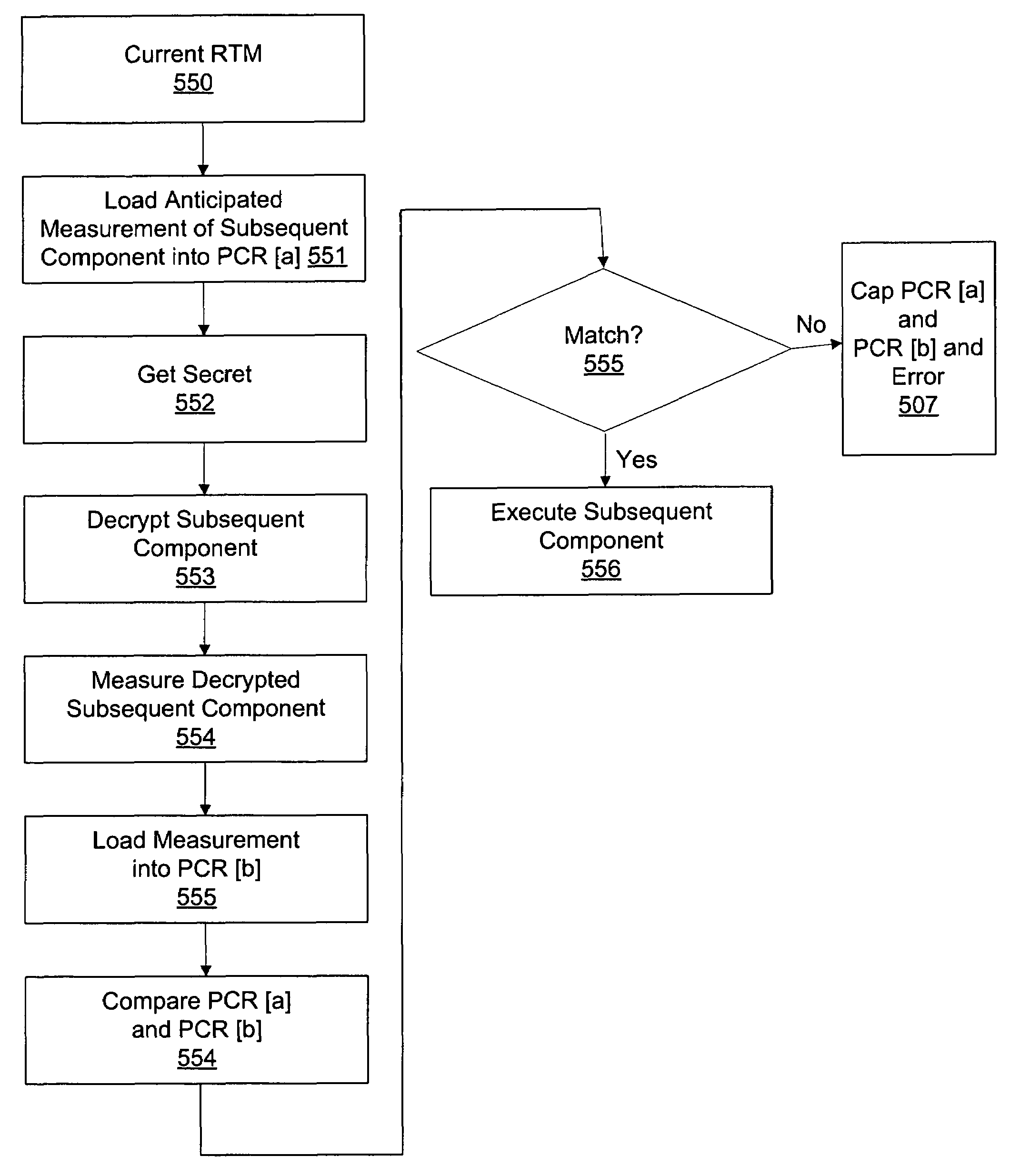
ActiveUS7725703B2Volume/mass flow measurementUser identity/authority verificationComputer hardwareTrusted Platform Module
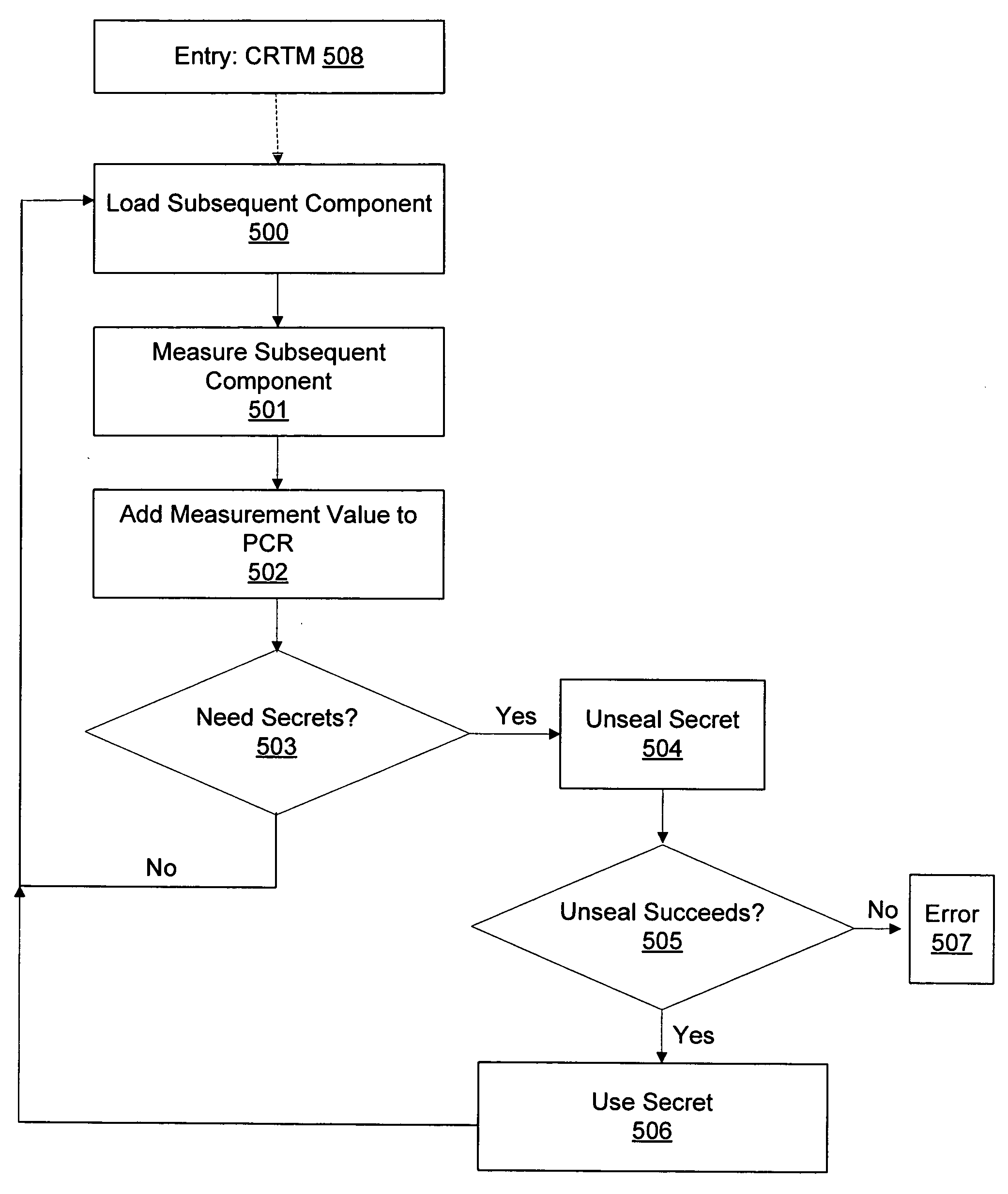
In a computer with a trusted platform module (TPM), an expected hash value of a boot component may be placed into a platform configuration register (PCR), which allows a TPM to unseal a secret. The secret may then be used to decrypt the boot component. The hash of the decrypted boot component may then be calculated and the result can be placed in a PCR. The PCRs may then be compared. If they do not, access to the an important secret for system operation can be revoked. Also, a first secret may be accessible only when a first plurality of PCR values are extant, while a second secret is accessible only after one or more of the first plurality of PCR values has been replaced with a new value, thereby necessarily revoking further access to the first secret in order to grant access to the second secret.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for updating a secure boot process on a computer with a hardware security module
ActiveUS20060161784A1Unauthorized memory use protectionHardware monitoringComputer hardwareTrusted Platform Module
Systems and methods are provided for maintaining and updating a secure boot process on a computer with a trusted platform module (TPM). A boot process may be maintained by inspecting a log of TPM activity, determining data that prevented a secret to unseal, and returning the data to an original state. In situations where this type of recovery is not workable, techniques for authenticating a user may be used, allowing the authenticated user to bypass the security features of the boot process and reseal the boot secrets to platform configuration register (PCR) values that may have changed. Finally, a secure boot process may be upgraded by migrating TPM sealed secrets to a temporary storage location, updating one or more aspects of a secure boot process, and resealing the secrets to the resulting new platform configuration. Other advantages and features of the invention are described below.
Owner:MICROSOFT TECH LICENSING LLC
Apparatus and method for a direct anonymous attestation scheme from short-group signatures
InactiveUS20090129600A1Key distribution for secure communicationPublic key for secure communicationDigital signatureTrusted Platform Module
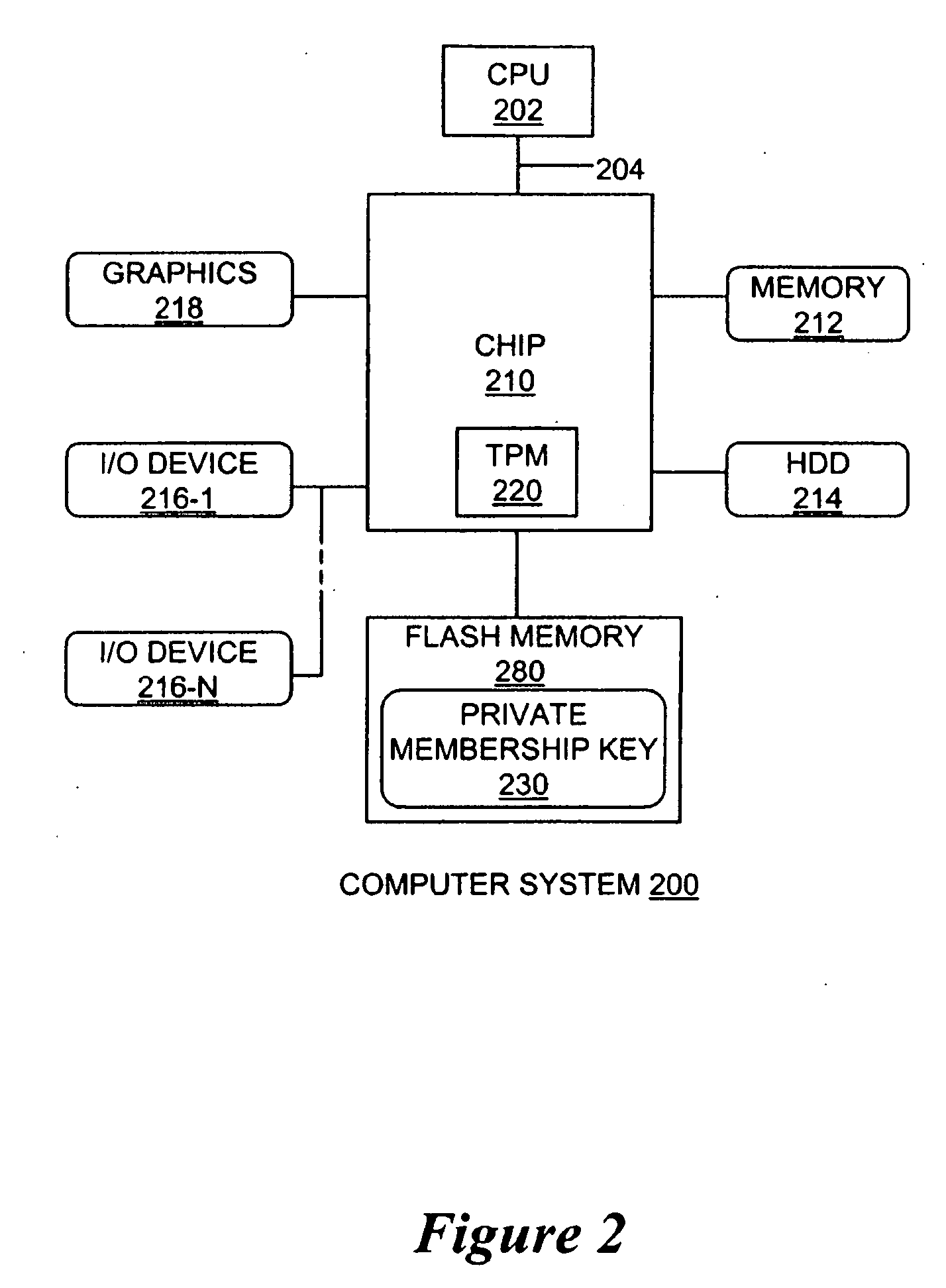
An apparatus and method is provided for a direct anonymous attestation scheme from short-group signatures. The method may include the creation of a group public / private key pair for a trusted membership group defined by an issuer; and assigning a cryptographic pair that is combined with a unique private member value to form a private membership key. A trusted member device generates the unique private member value during a join procedure of a trusted membership group. In one embodiment, the private member value of the private membership key is unknown to the issuer. A member may sign a message with the private membership key to form a short-group digital signature that is verified using a public key of the trusted membership group to maintain anonymity of trusted member devices. A size of the private membership key may be reduced to enable storage within a trusted platform module. Other embodiments are described and claimed.
Owner:INTEL CORP
Systems, methods and computer program products for high availability enhancements of virtual security module servers
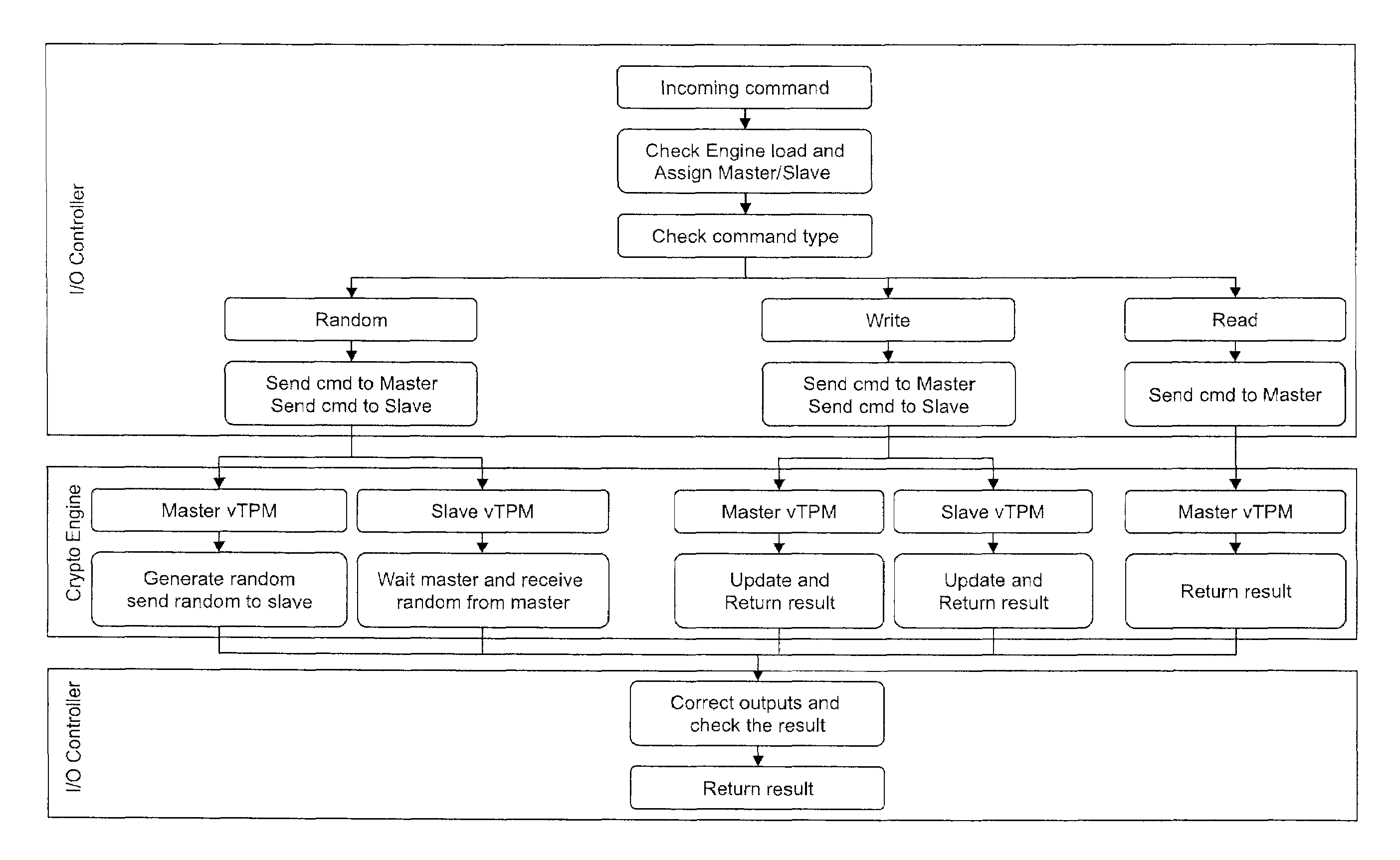
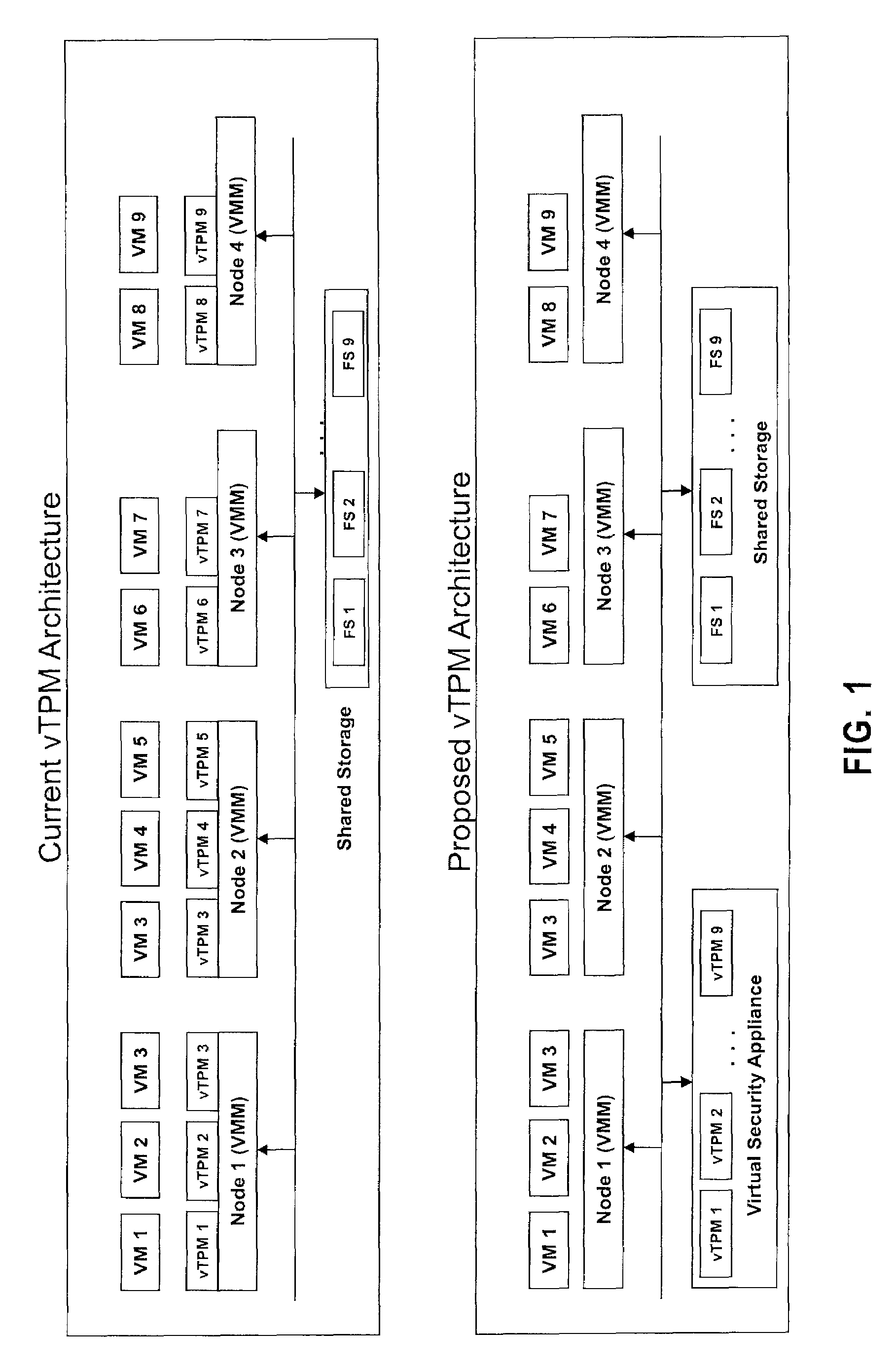
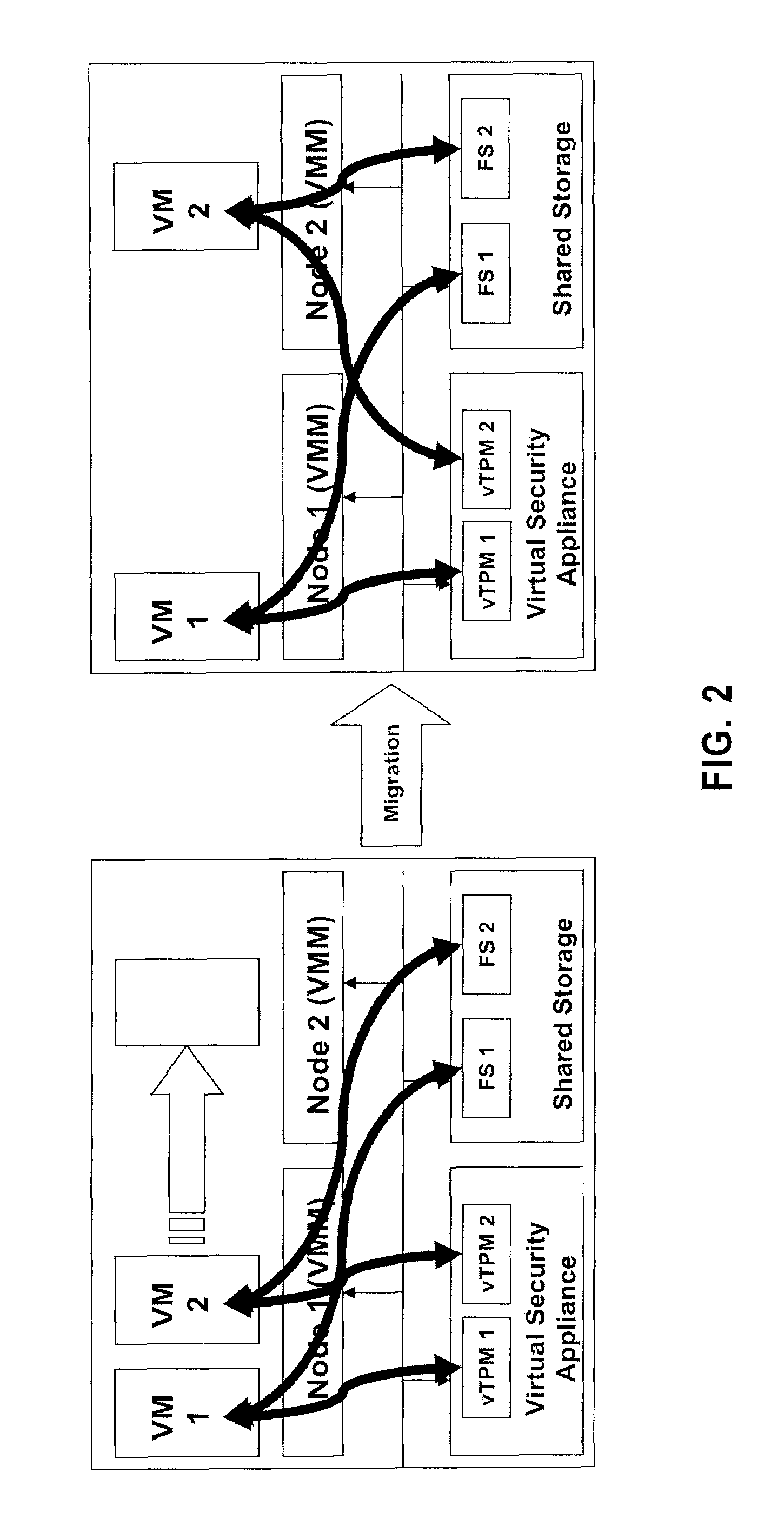
ActiveUS7512815B1User identity/authority verificationUnauthorized memory use protectionTrusted Platform ModuleComputer module
Systems, methods and computer program products for high availability enhancements of virtual security module servers. Exemplary embodiments include a virtual security appliance system, including a recipient Virtual Security Appliance having an I / O controller configured to received commands from a Virtual Machine Monitor and a crypto engine of the recipient virtual security appliance configured to assign a master / slave flag, the crypto engine having a master virtual Trusted Platform Module and a slave virtual Trusted Platform Module, wherein the crypto engine includes an appliance endorsement key configured to provide an identification and to pair with an additional recipient virtual security appliance in the virtual security appliance system, the additional recipient virtual security appliance including an additional crypto engine having an additional appliance endorsement key.
Owner:META PLATFORMS INC
Trusted bootstrap method and system thereof
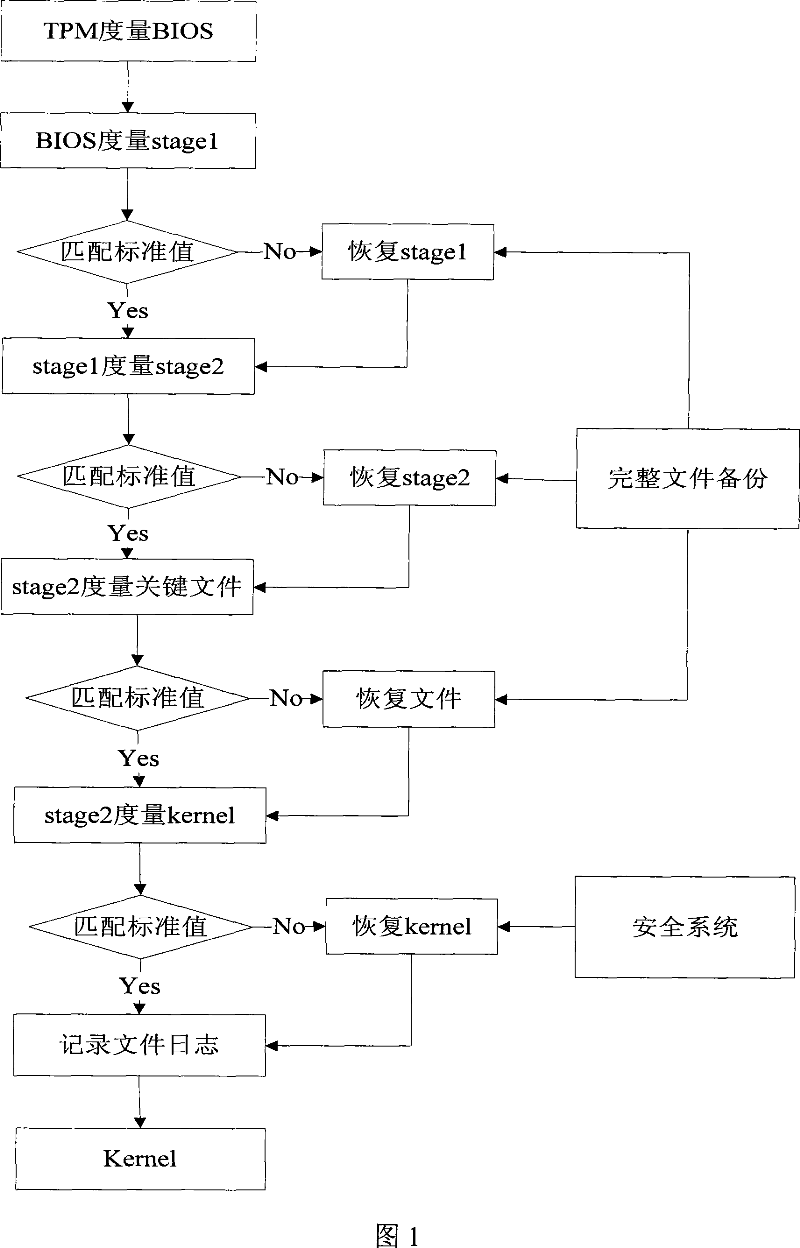
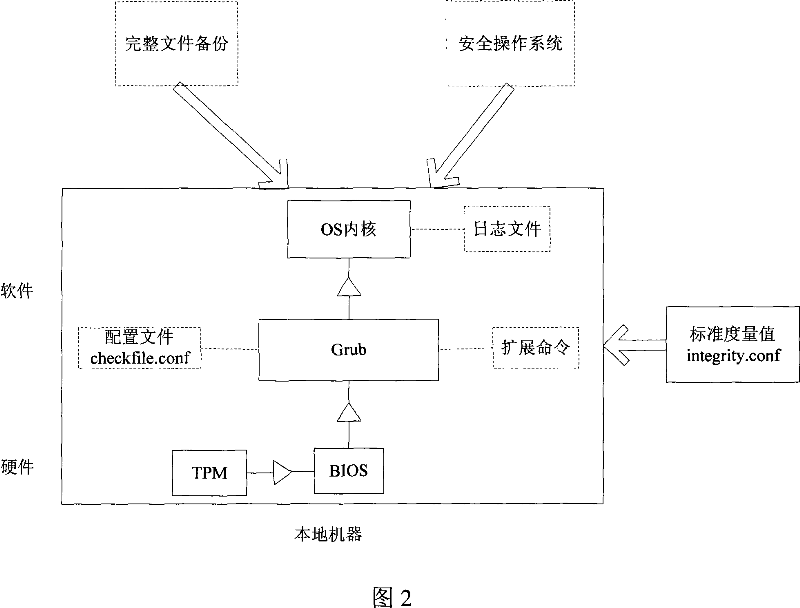
The invention provides a method and system for improving the system booting process via a trusted platform module, wherein he booting process for starting the internal kernel of the operation system are divided into a plurality of interdependent layers, the integrity of the upper layer is verified by the lower layer by using the trusted platform module as the trust root, the system operation control right is transmitted layer upon layer till to the operation system kernel to form an integral trusted chain, and if the integrity verification fails, a correspondent restore scheme will be provided, the boot log is recorded into the file system before entering the operation system. The invention takes into account of the situations such as integrity verification, verification failure restore, and the interaction of the starting log and the operation system so as to form an integral booting system, the initial circumstance is considered as safe and trusted, and the operation system can also proves the safety of its starting circumstances to other platforms by using the log file of the booting process.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
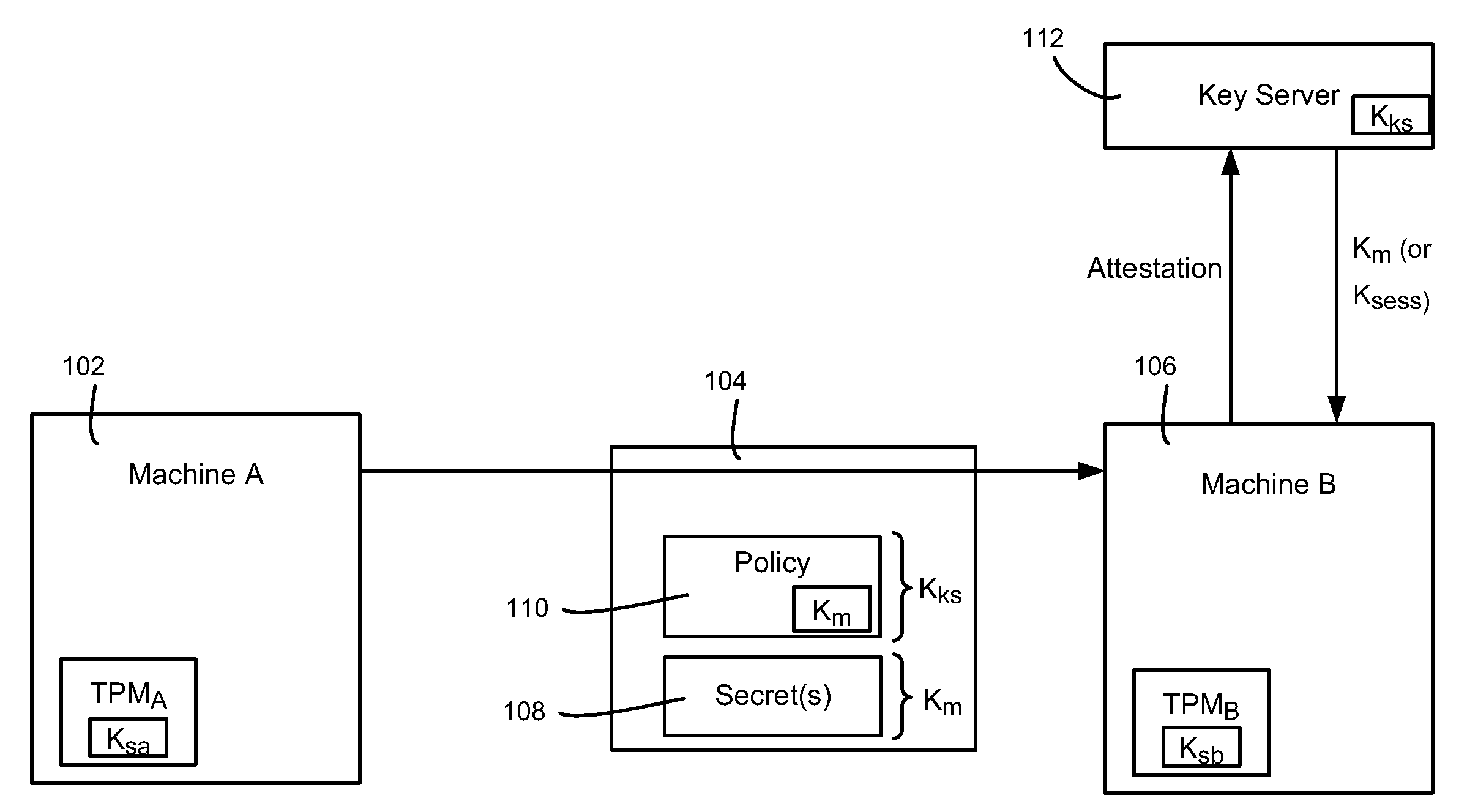
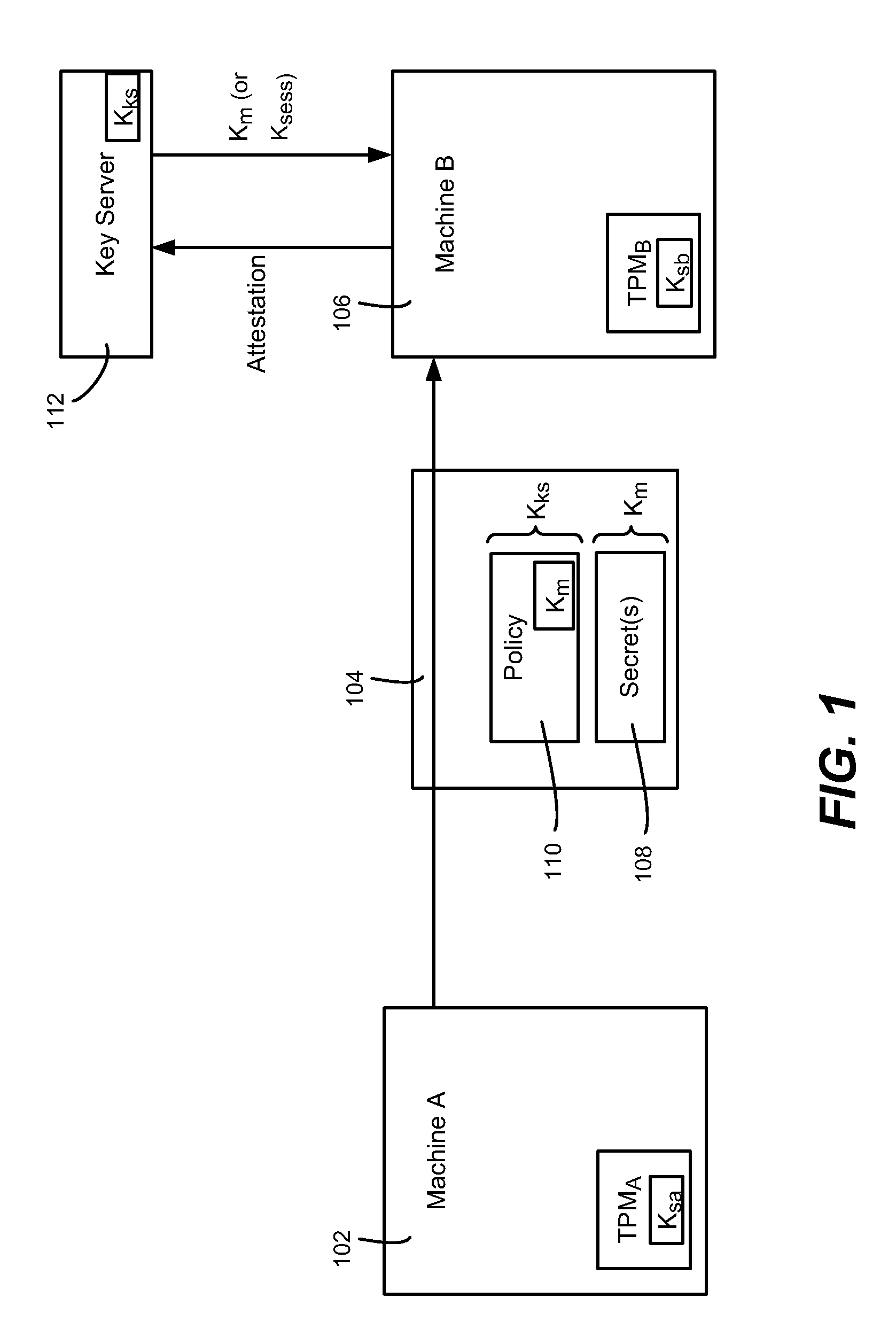
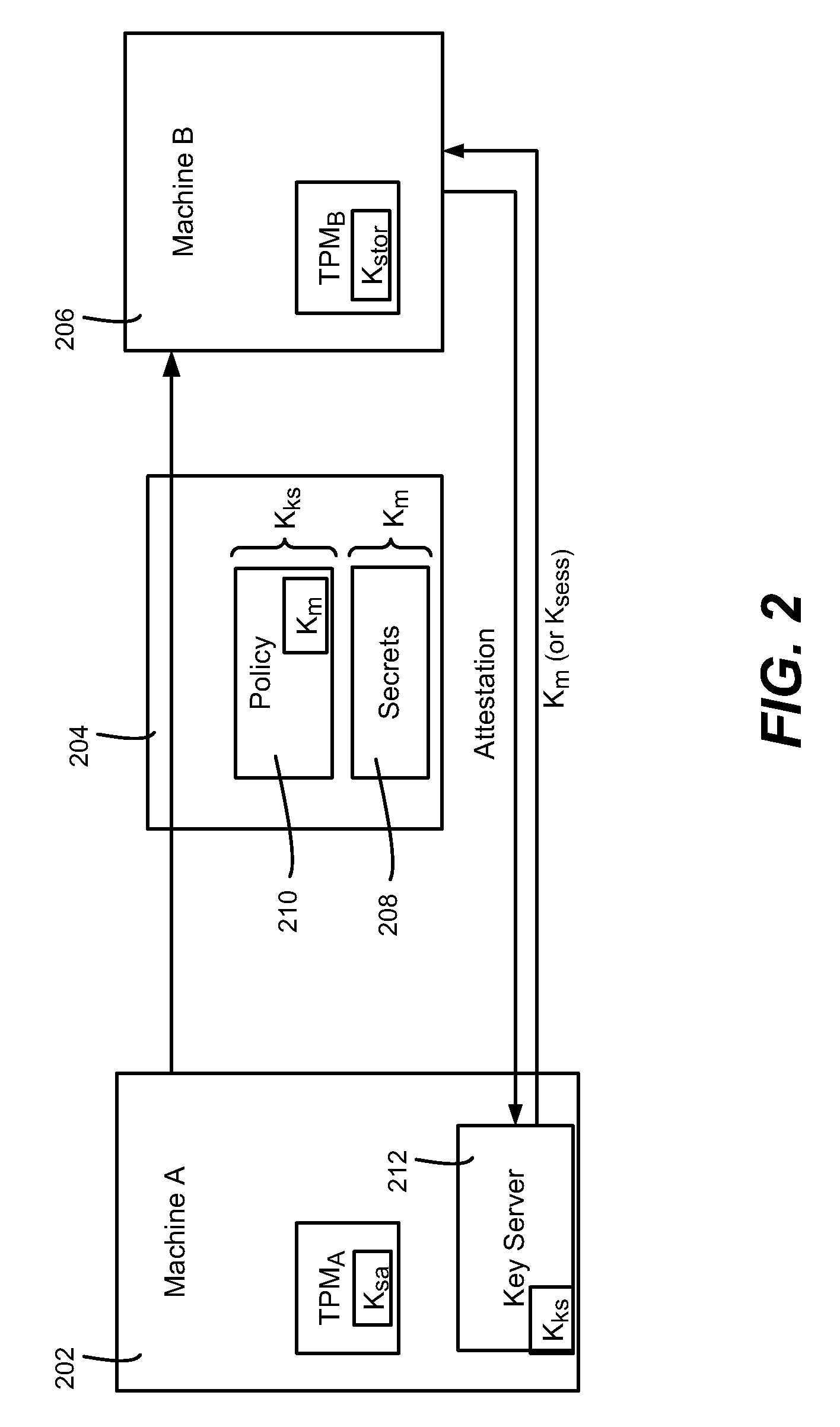
Migration of computer secrets
ActiveUS20090154709A1Well formedKey distribution for secure communicationUser identity/authority verificationComputer hardwareTrusted Platform Module
Described is a technology by which computer data secrets sealed by a trusted platform module (TPM) or like device may be securely migrated from a physical source computing machine to a physically different destination machine. For example, migration of TPM secrets allows migration of a virtual machine from one physical machine to another. A destination machine receives a set of data sealed at a source machine. The set of data includes a migration key and a secret sealed by the migration key. The destination machine performs attestation with a key server to attest that the destination machine is entitled to access the sealed secret, via credentials, known good configuration and / or other policy compliance. The key server unseals the migration key, and provides a returned key (e.g., the migration key or a session key) to the destination machine for unsealing the secrets.
Owner:MICROSOFT TECH LICENSING LLC
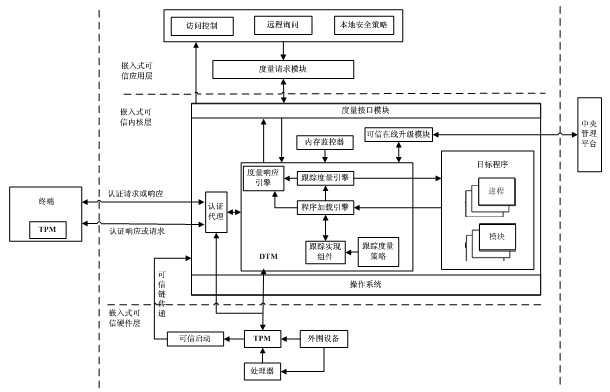
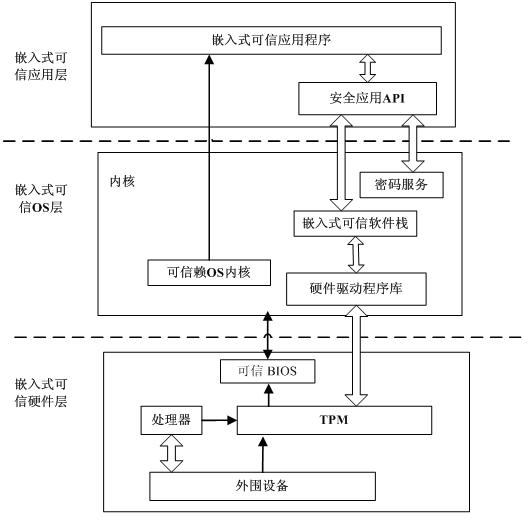
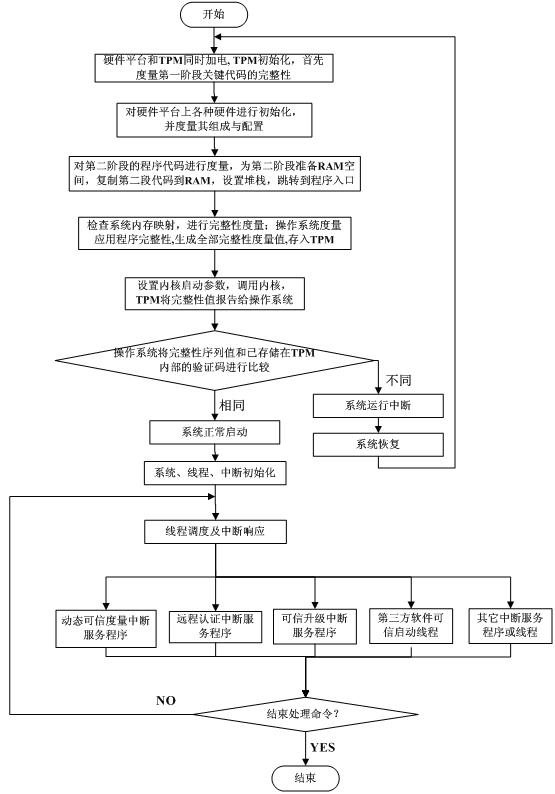
Dynamic trusted measurement method and safe embedded system
InactiveCN102436566AEnsure safetyEffective defenseInternal/peripheral component protectionAttackTrusted Platform Module
The invention discloses a dynamic trusted measurement method and a safe embedded system. The method comprises the following steps that: S1. a hardware layer redesigns a trusted BIOS (Basic Input Output System) by a TPM (Trusted Platform Module) chip and traditional hardware, a trust chain is transferred to an application program from the TPM security chip, trusted BISO, a trusted OS (Operating System) kernel and an embedded software stack to realize the trusted starting of a dynamic trusted measurement module (DTM); S2. an application layer measurement request module generates measurement request information according to a suspicious event from safety equipment and a local security strategy requirement, the measurement request information is formatted, and the measurement request is sent to the DTM of a kernel layer to activate the DTM; and S3. the DTM carries out trusted measurement to a system progress or module and responds. According to the dynamic trusted measurement method, the complex real-time attack can be effectively detected and defended, the attack on an internal physical layer can be actively detected and defended, and a safe embedded system platform can be realized.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
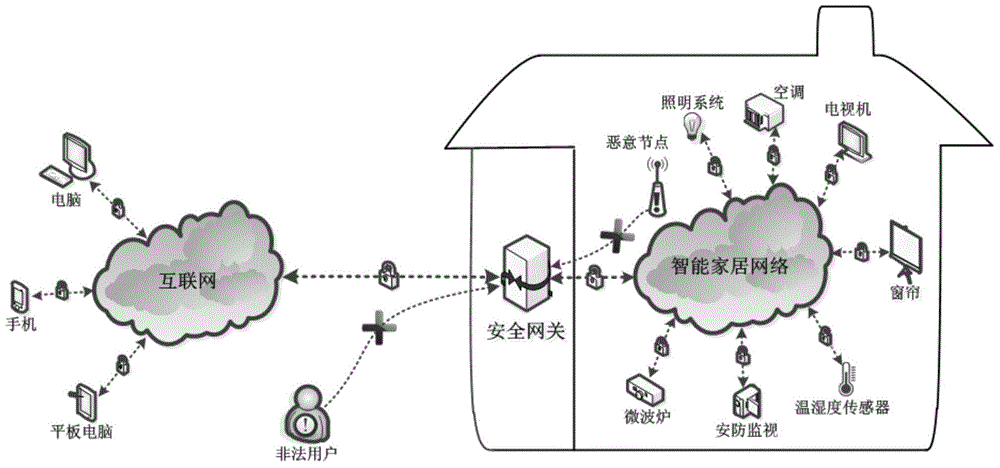
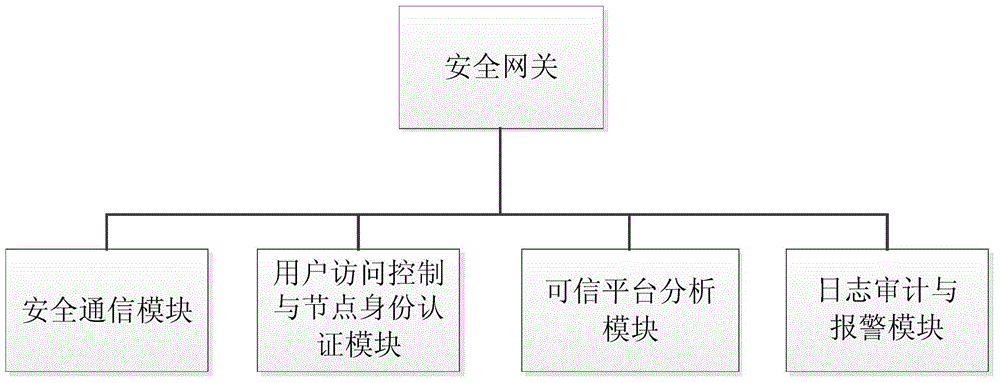
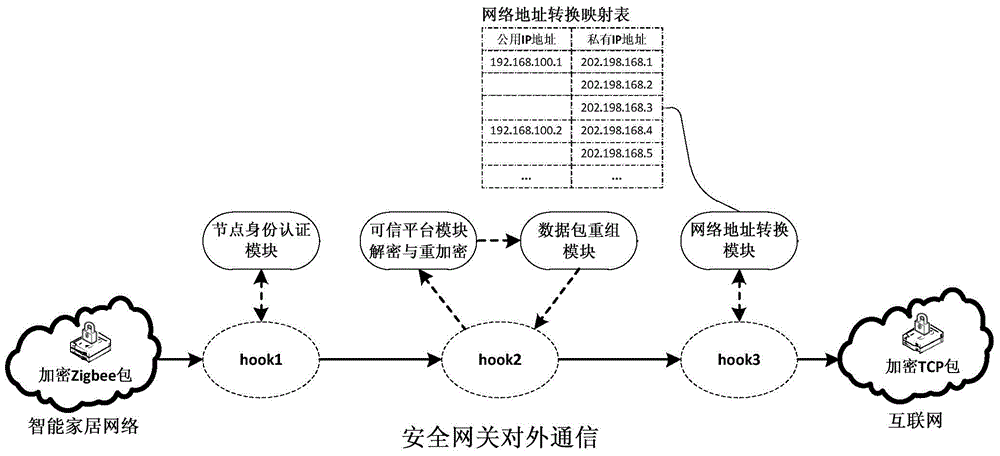
Internet of Things smart home security gateway system
ActiveCN104580233AEnhanced defense against attacksRealize free decouplingUser identity/authority verificationNetwork connectionsThe InternetSecure authentication
The invention relates to an Internet of Things smart home security gateway system. The system comprises a user side, a security gateway and a terminal node. The user side and the terminal node each comprise a data encrypting / decrypting module used for encrypting / decrypting a sent control order and received data through a preset encrypting program on a remote client side or the terminal node; the security gateway comprises a safety communication module, a user access control and node identity authentication module, a credible platform module and a log audit and alarm module; the safety communication module achieves data safety filtering, reconstructing and forwarding and guarantees safety of the bi-direction transmission; the credible platform module is used for achieving system safety authentication, user behavior credibility analysis, data sealing storage and free decoupling and can be independently maintained and upgraded; the log audit and alarm module is used for recording user access and node authentication behaviors, carrying out safety audit on the operation of viewing logs and giving a timely alarm for an abnormal phenomenon found in the gateway system safety monitoring process. By means of the Internet of Things smart home security gateway system, the safety performance of a smart home system and the running efficiency of a gateway can be improved, and a safety guarantee is provided for Internet of Things smart home.
Owner:重庆中邮信科集团股份有限公司
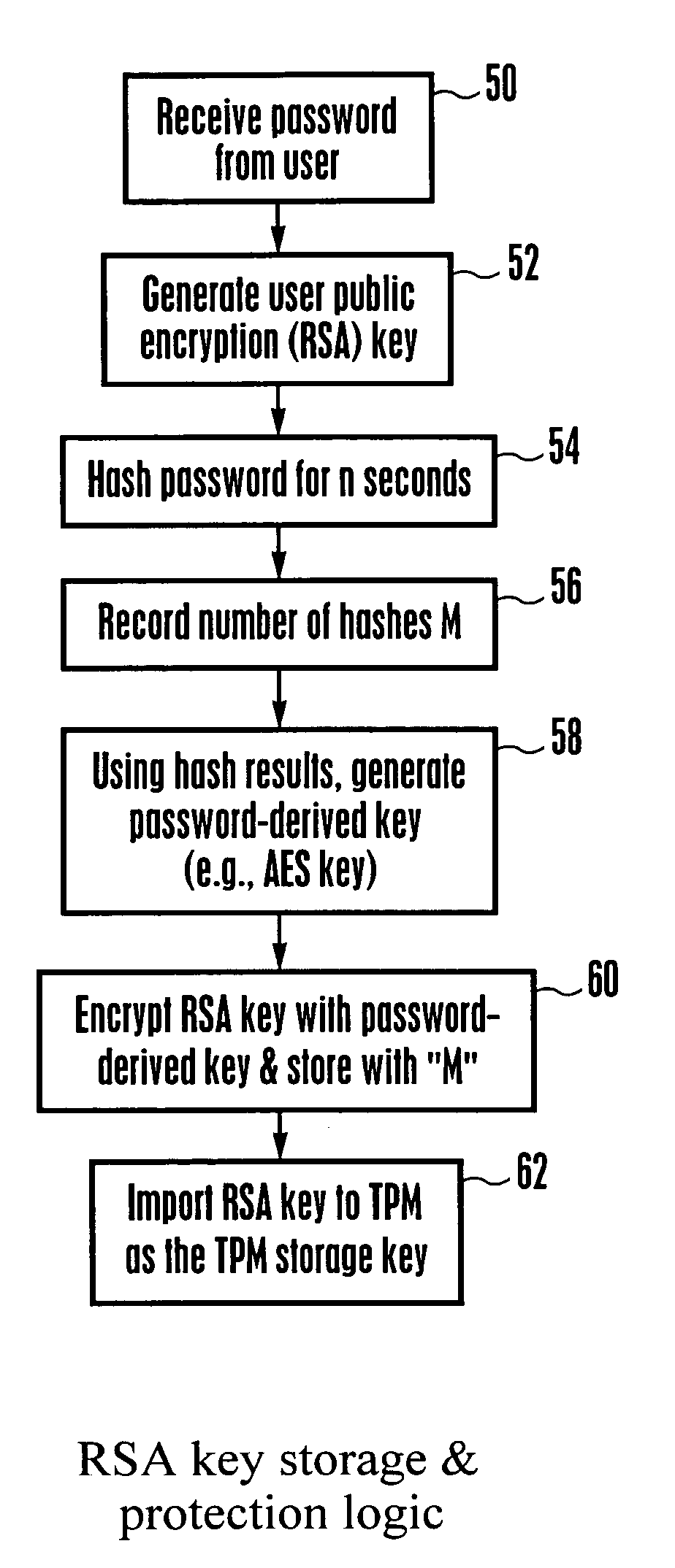
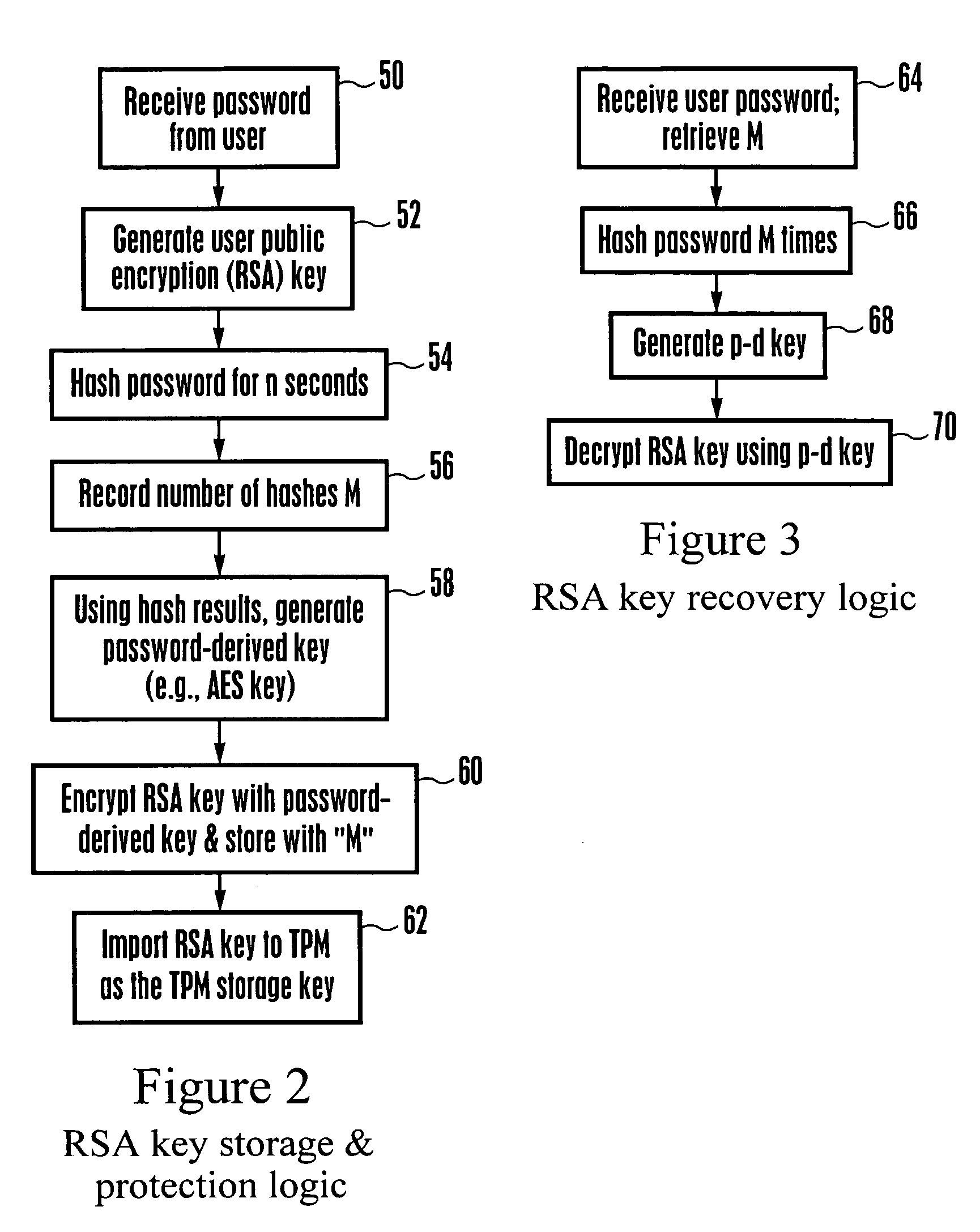
System and method for protecting against dictionary attacks on password-protected TPM keys
InactiveUS20070014416A1Key distribution for secure communicationCryptographic attack countermeasuresTrusted Platform ModuleUser input
A computer system that may include a trusted platform module (TPM) along with a processor hashes a user-supplied password for a predetermined time period that is selected to render infeasible a dictionary attack on the password. The results of the hash are used to render an AES key, which is used to encrypt an RSA key. The encrypted RSA key along with the total number of hash cycles that were used is stored and the RSA key is provided to the TPM as a security key. In the event that the RSA key in the TPM must be recovered, the encrypted stored version is decrypted with an AES key that is generated based on the user inputting the same password and hashing the password for the stored number of cycles.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com