Patents
Literature
80 results about "Data in transit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
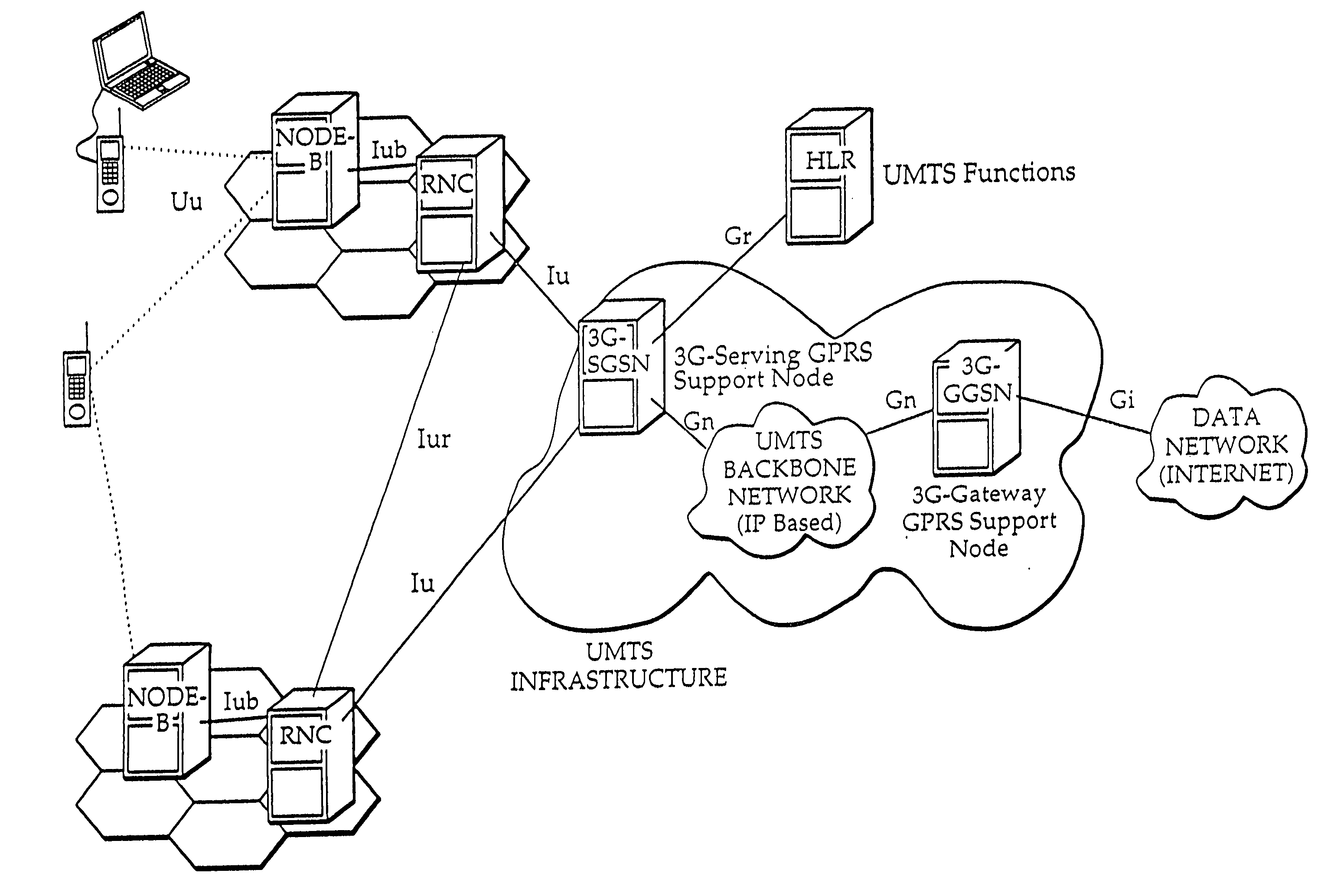
Data in transit is defined into two categories, information that flows over the public or untrusted network such as the Internet and data that flows in the confines of a private network such as a corporate or enterprise Local Area Network (LAN).
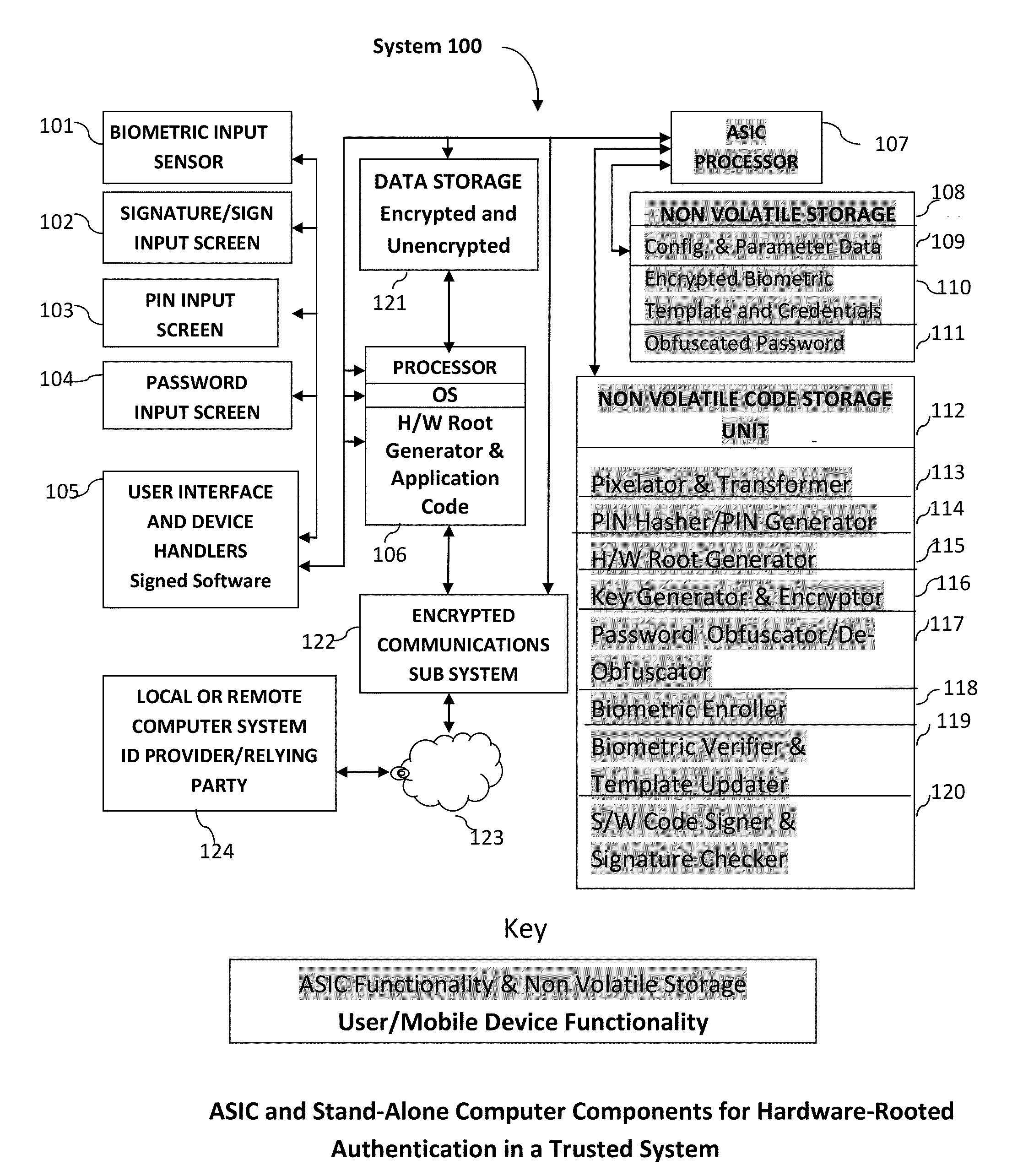
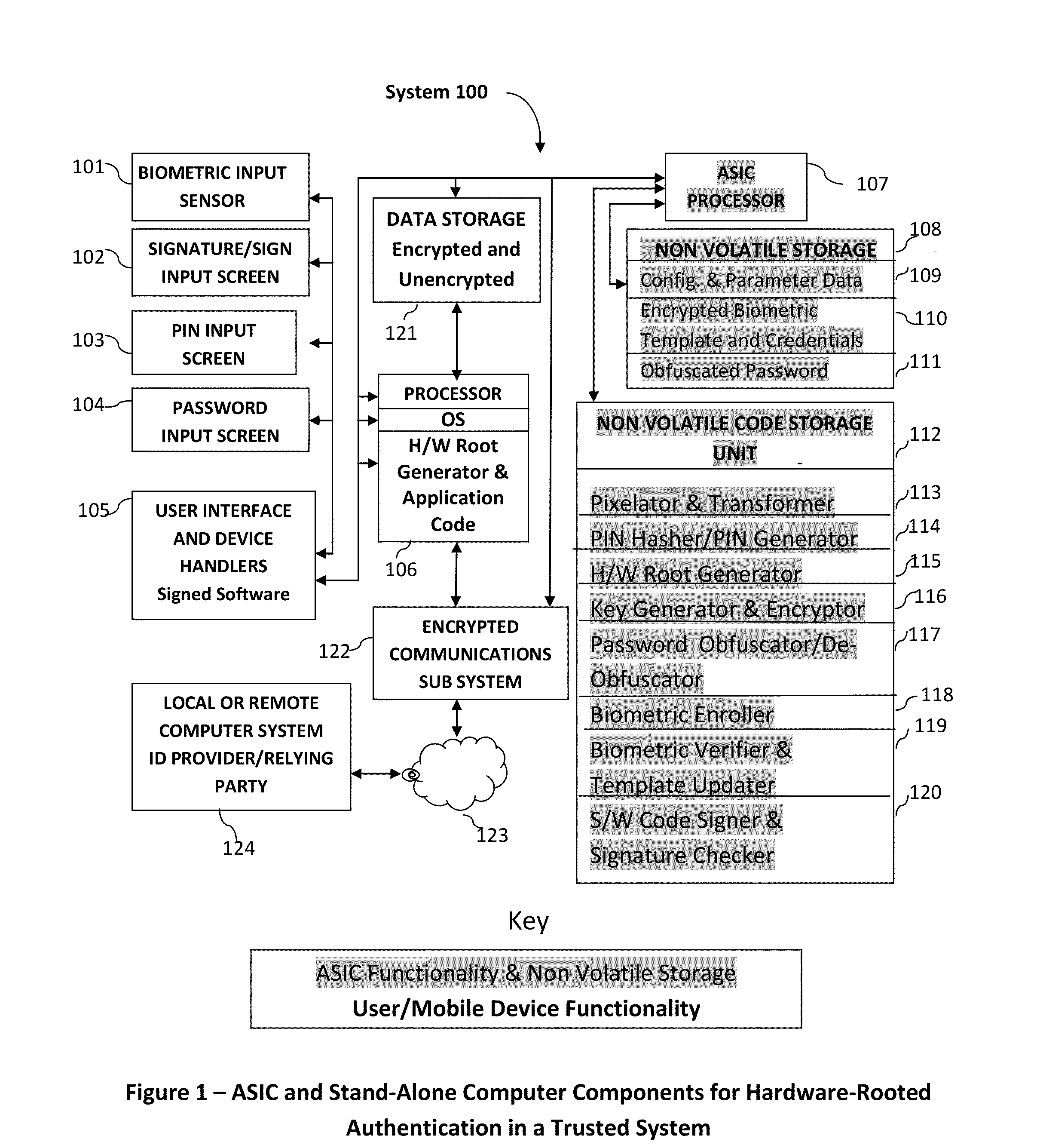
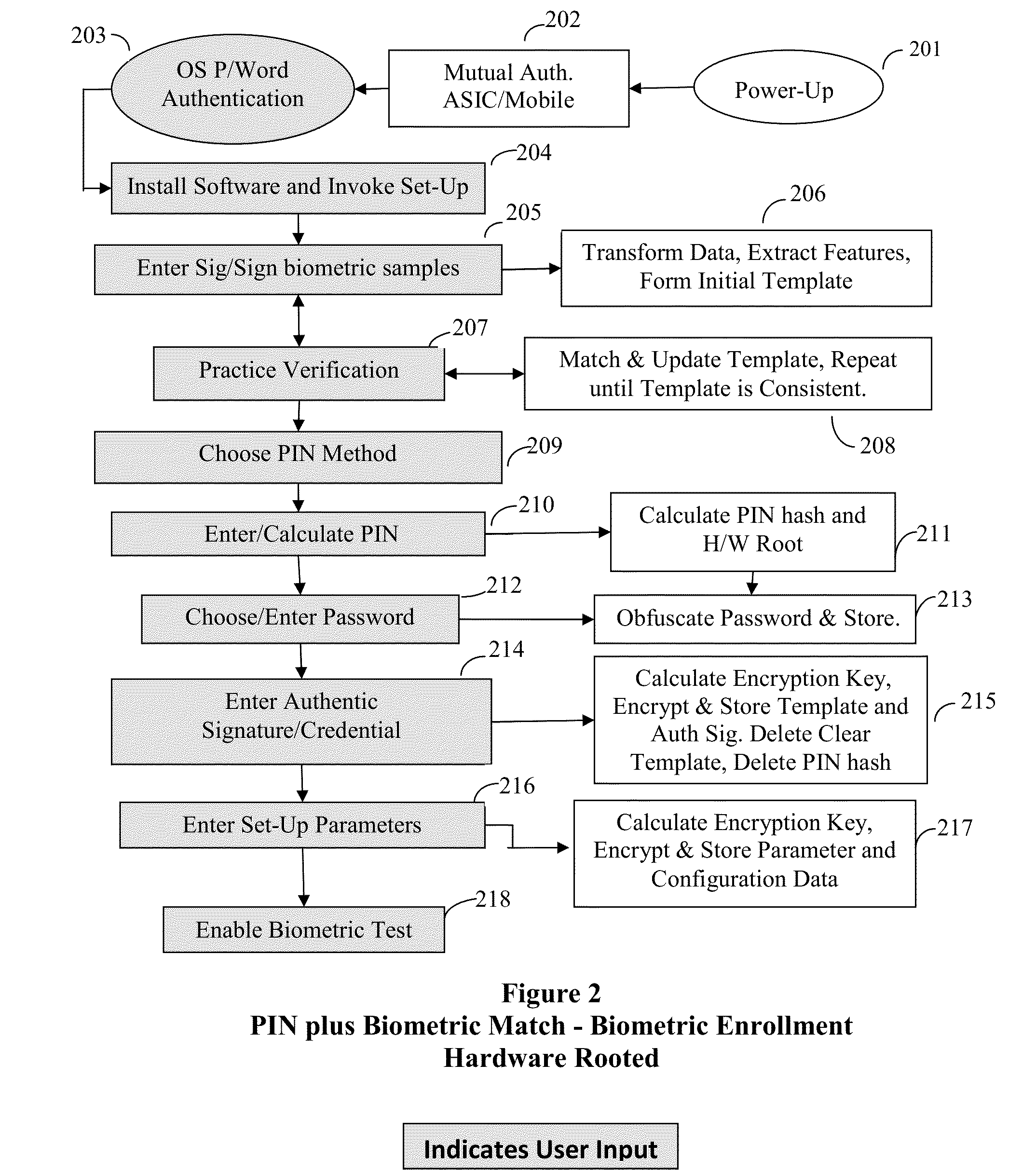
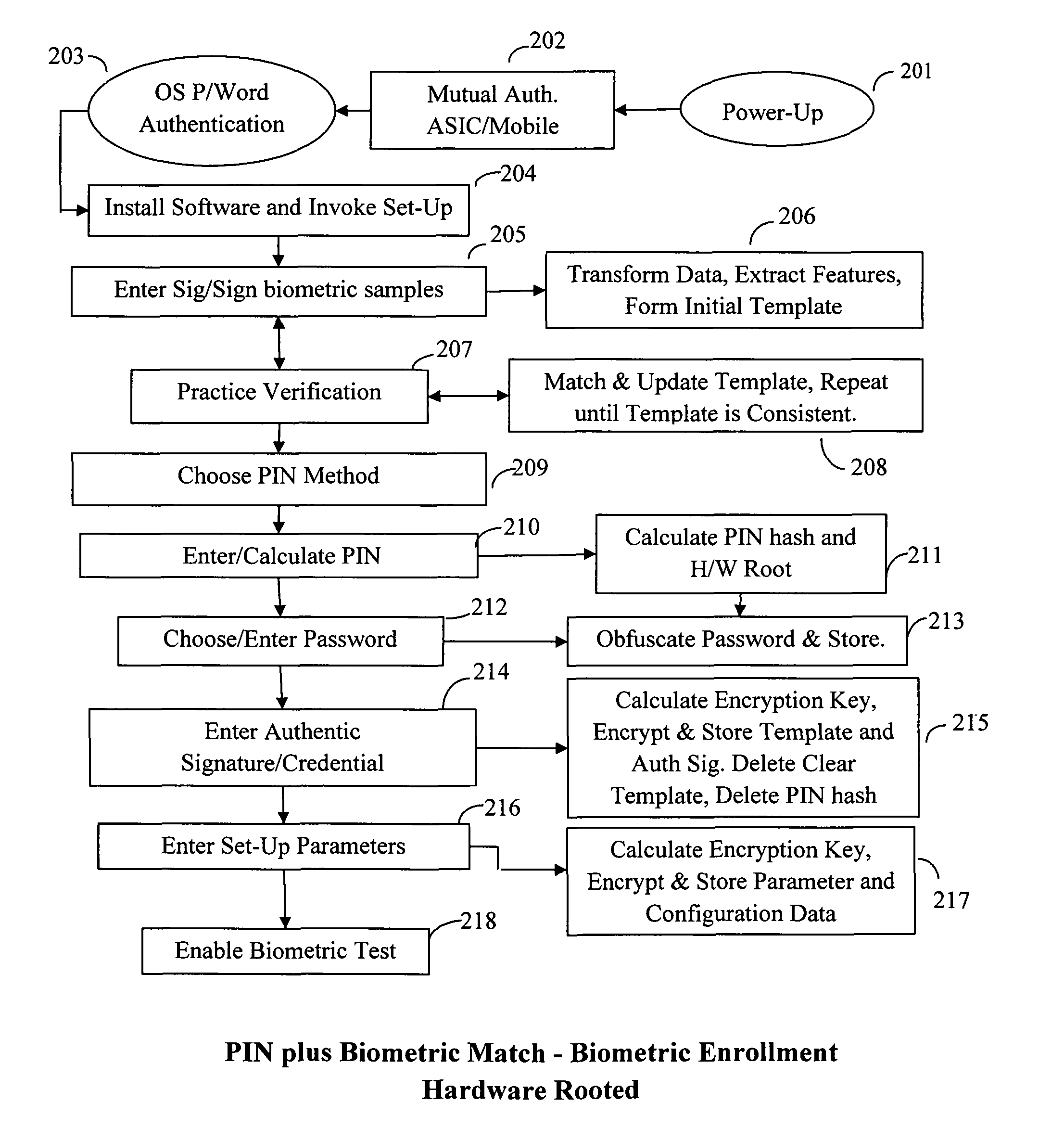
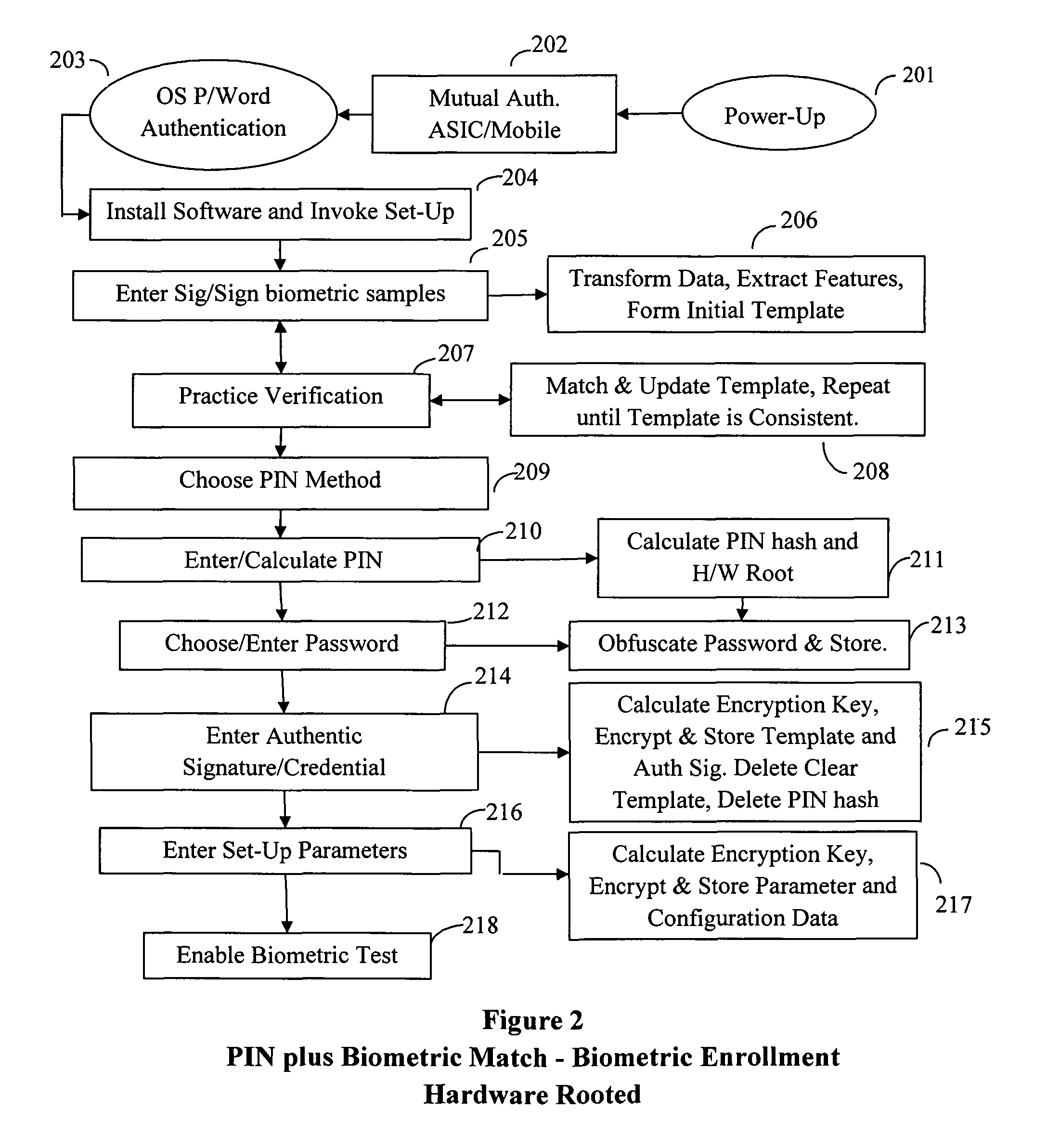
Method and System for Providing Password-free, Hardware-rooted, ASIC-based Authentication of a Human to a Mobile Device using Biometrics with a Protected, Local Template to Release Trusted Credentials to Relying Parties
InactiveUS20140365782A1Significant productivityMaximum safetyUser identity/authority verificationInternal/peripheral component protectionBiometric dataPassword hashing
Biometric data, which may be suitably transformed are obtained from a biometric input device contained within a stand-alone computer or a mobile device, which may contain an ASIC chip connected to or incorporated within the stand-alone computer or mobile device and which includes the capability for capturing one or more biometric samples and for biometric feature extraction, matching and encryption. For extra security, the biometric matching is used in conjunction with a PIN to authenticate the user to the stand-alone computer or mobile device. The biometric template and other sensitive data residing on the mobile device are encrypted using hardware elements of the mobile device (or the ASIC) together with the PIN hash and / or the Password hash. An obfuscated version of the Password, stored on the ASIC or the mobile device is de-obfuscated and released to the mobile device authentication mechanism, including a Trusted Platform Module if present, in response to a successfully decrypted template and matching biometric sample and PIN. A de-obfuscated password is used to authenticate the user to the mobile device and the same or a different de-obfuscated password may be used to authenticate the user to a remote computer using the SSL / TLS or a process based upon a symmetric encryption algorithm. The locally generated password may be used to encrypt data at rest on the mobile device or ASIC and the remote authentication password may be used to encrypt data in transit to and from a remote computer. This creates a trusted relationship between the stand-alone computer or mobile device and the remote computer. The system also eliminates the need for the user to remember and enter complex passwords on the mobile device or for secure transmission of data. A similar method may be used, with the signature / sign biometric modality to determine whether the holder of an IC chip card is, in fact the card owner.
Owner:BIOCRYPT ACCESS LLC
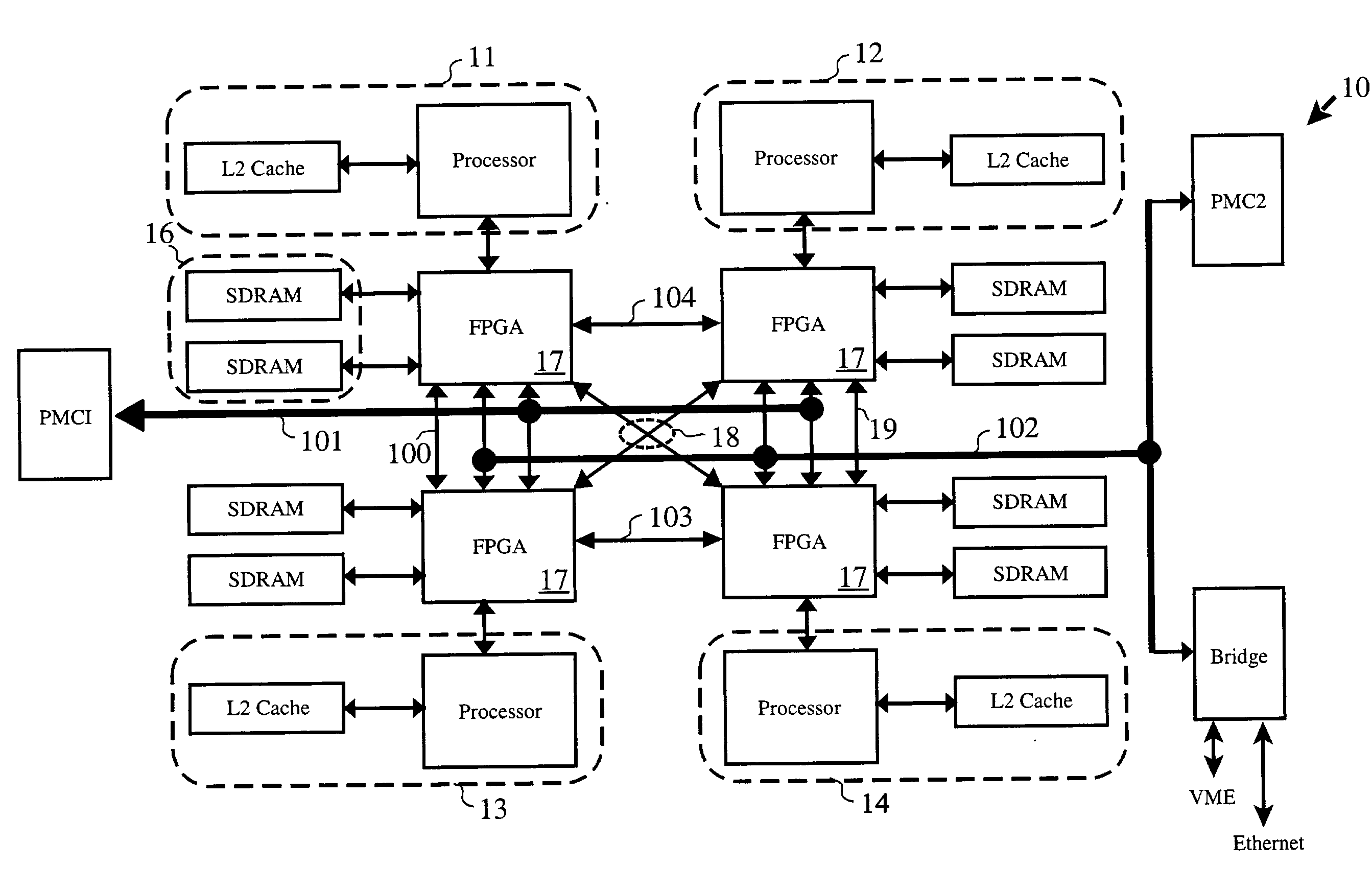
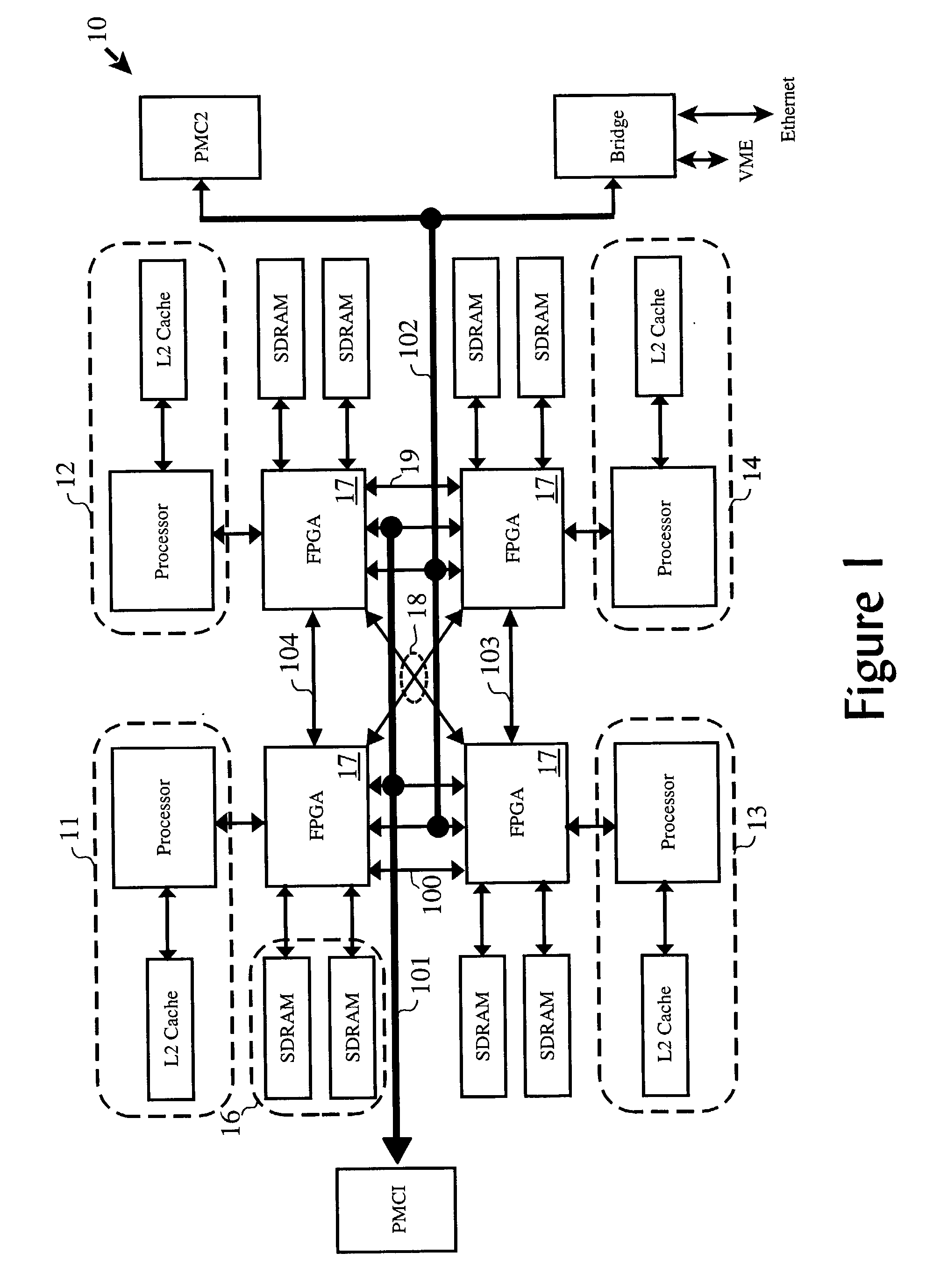
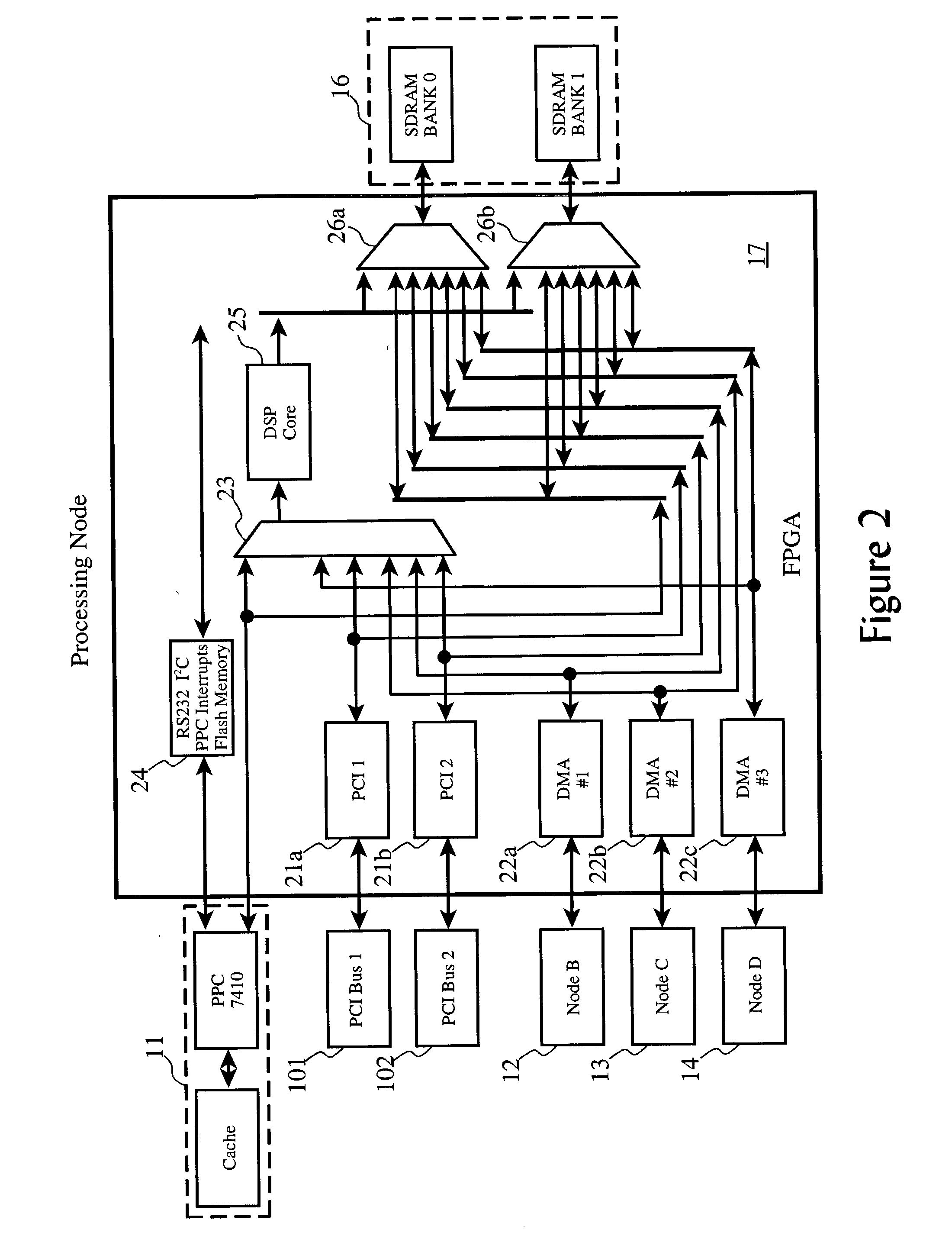
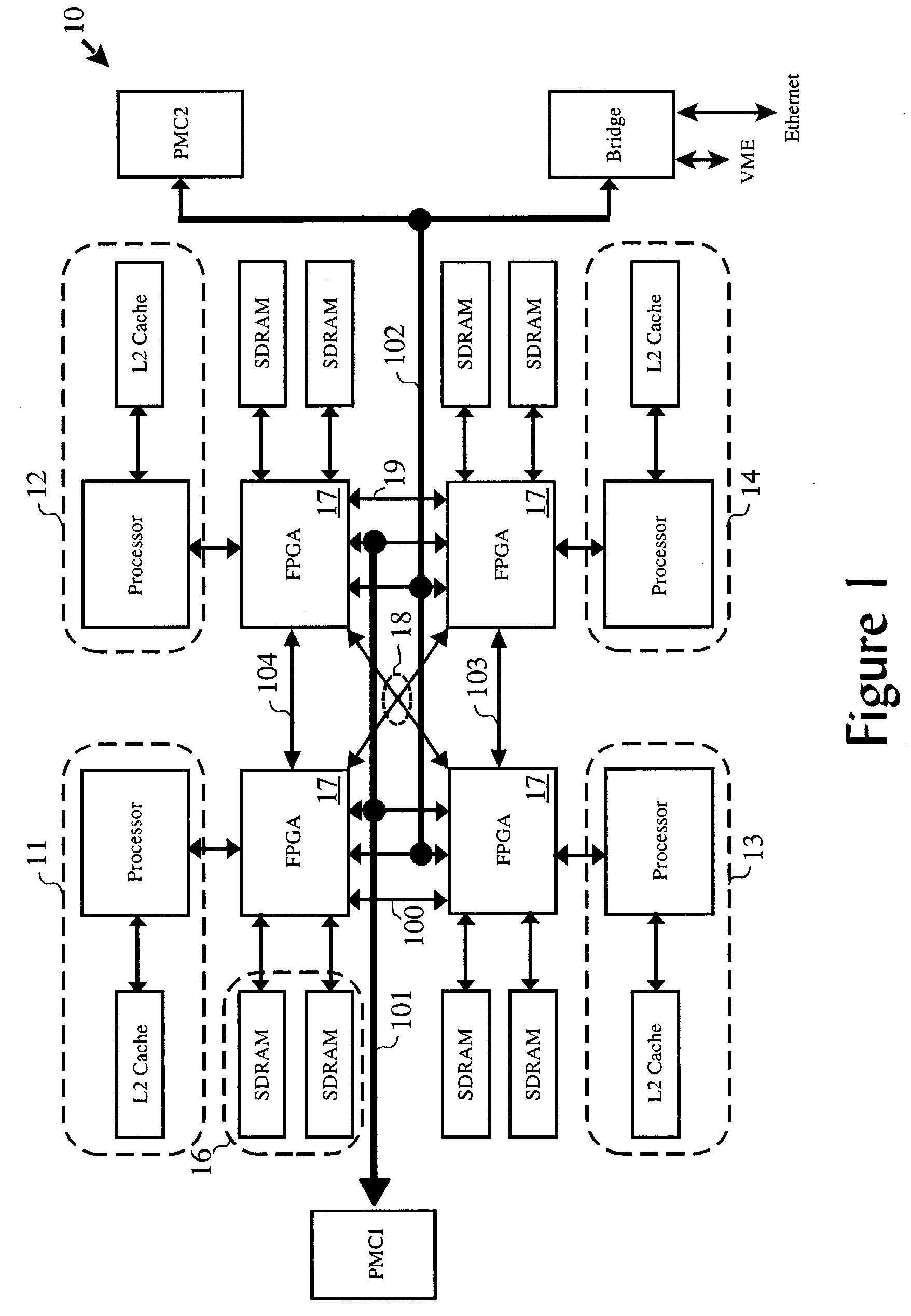
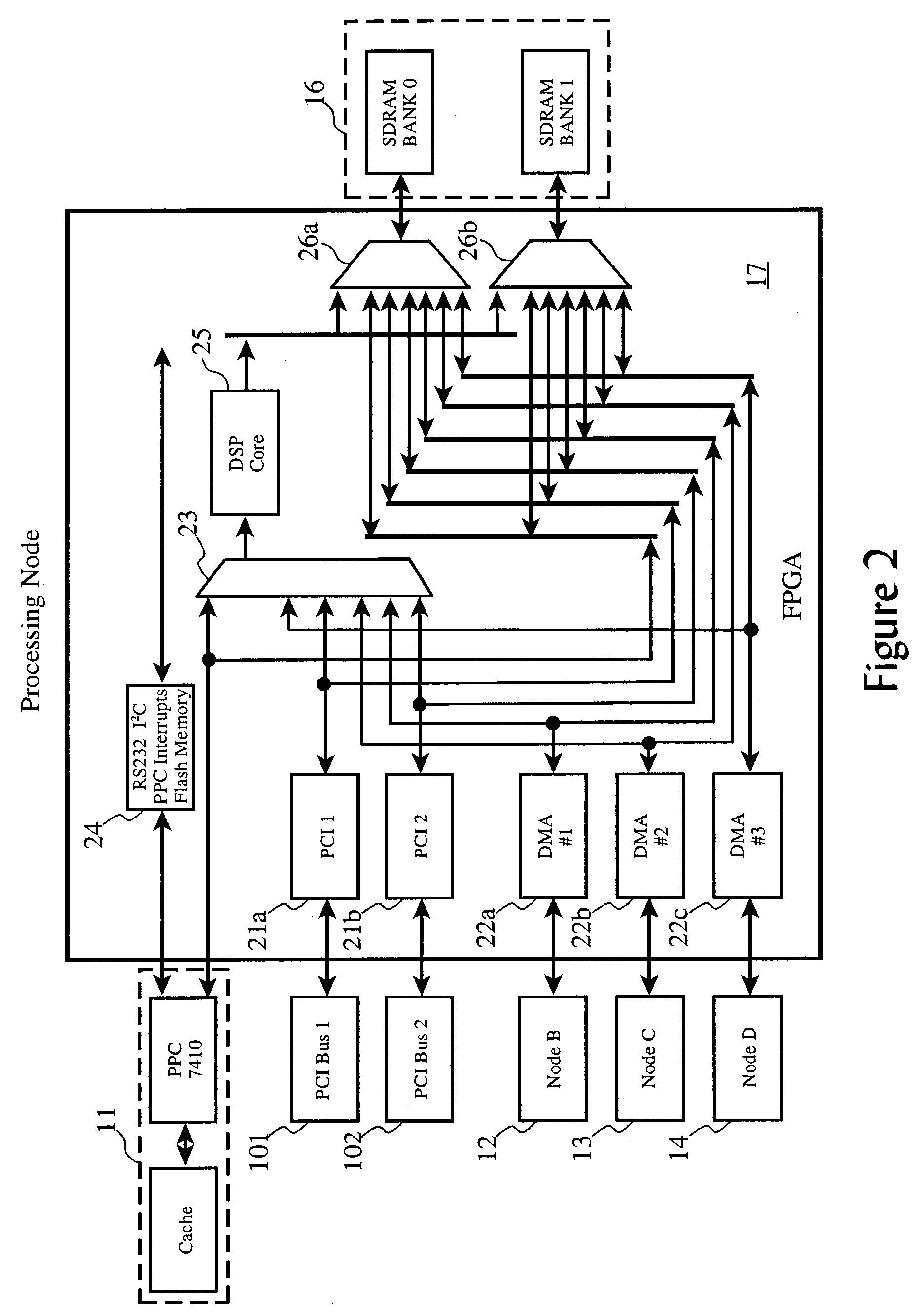
Signal processing resource for selective series processing of data in transit on communications paths in multi-processor arrangements
InactiveUS20040015633A1General purpose stored program computerElectric digital data processingMulti processorInterprocessor communication
A multi-processor arrangement having an interprocessor communication path between each of every possible pair of processors, in addition to I / O paths to and from the arrangement, having signal processing functions configurably embedded in series with the communication paths and / or the I / O paths. Each processor is provided with a local memory which can be accessed by the local processor as well as by the other processors via the communications paths. This allows for efficient data movement from one processor's local memory to another processor's local memory, such as commonly done during signal processing corner turning operations. The configurable signal processing logic may be configured to host one or more signal processing functions to allow data to be processed prior to its deposit into local memory.
Owner:GE FANUC EMBEDDED SYST
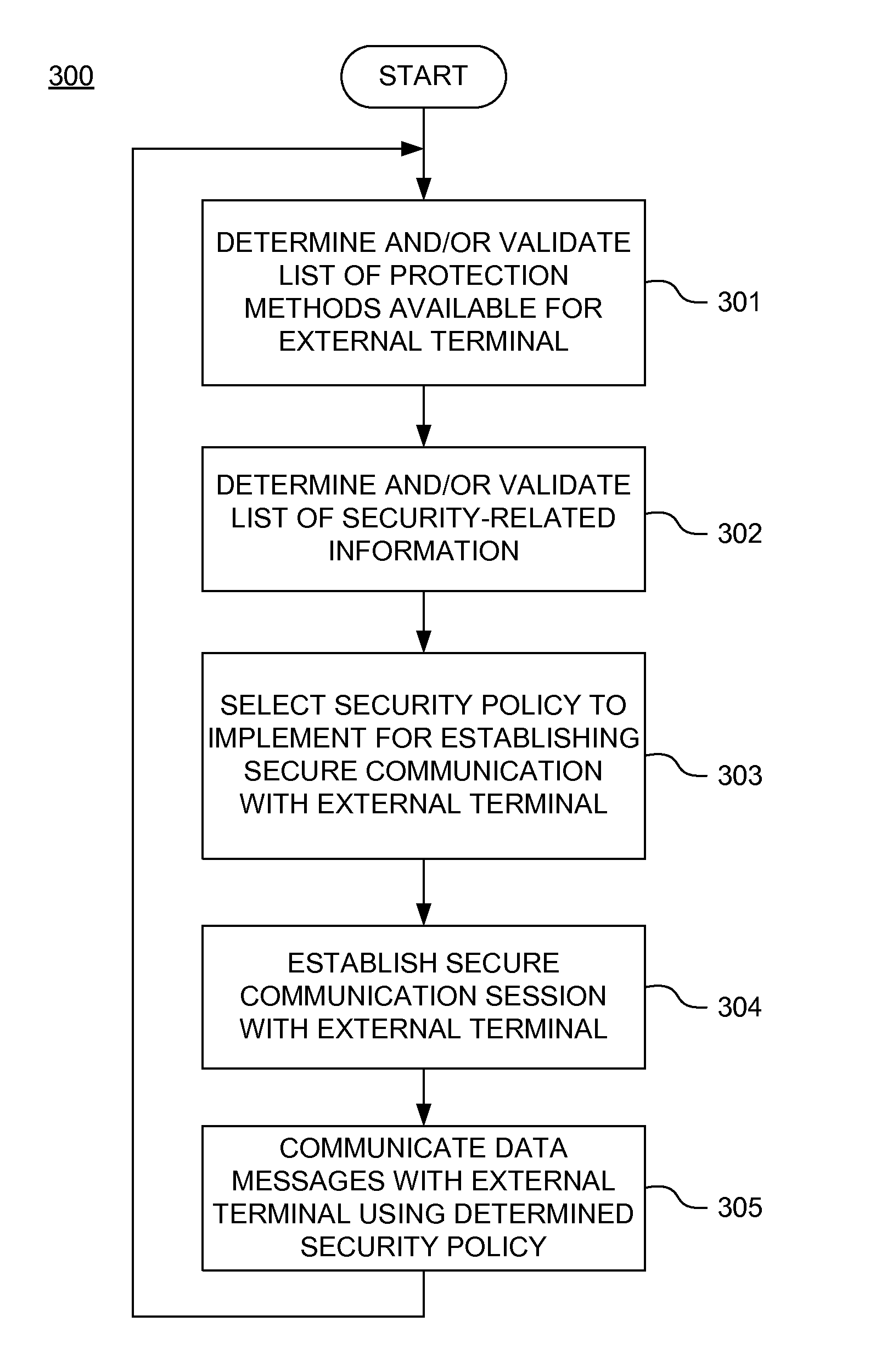
Dynamically reacting policies and protections for securing mobile financial transaction data in transit
ActiveUS20110178933A1Shorten the time to marketAcceptable levelFinanceMemory loss protectionEngineeringFinancial transaction
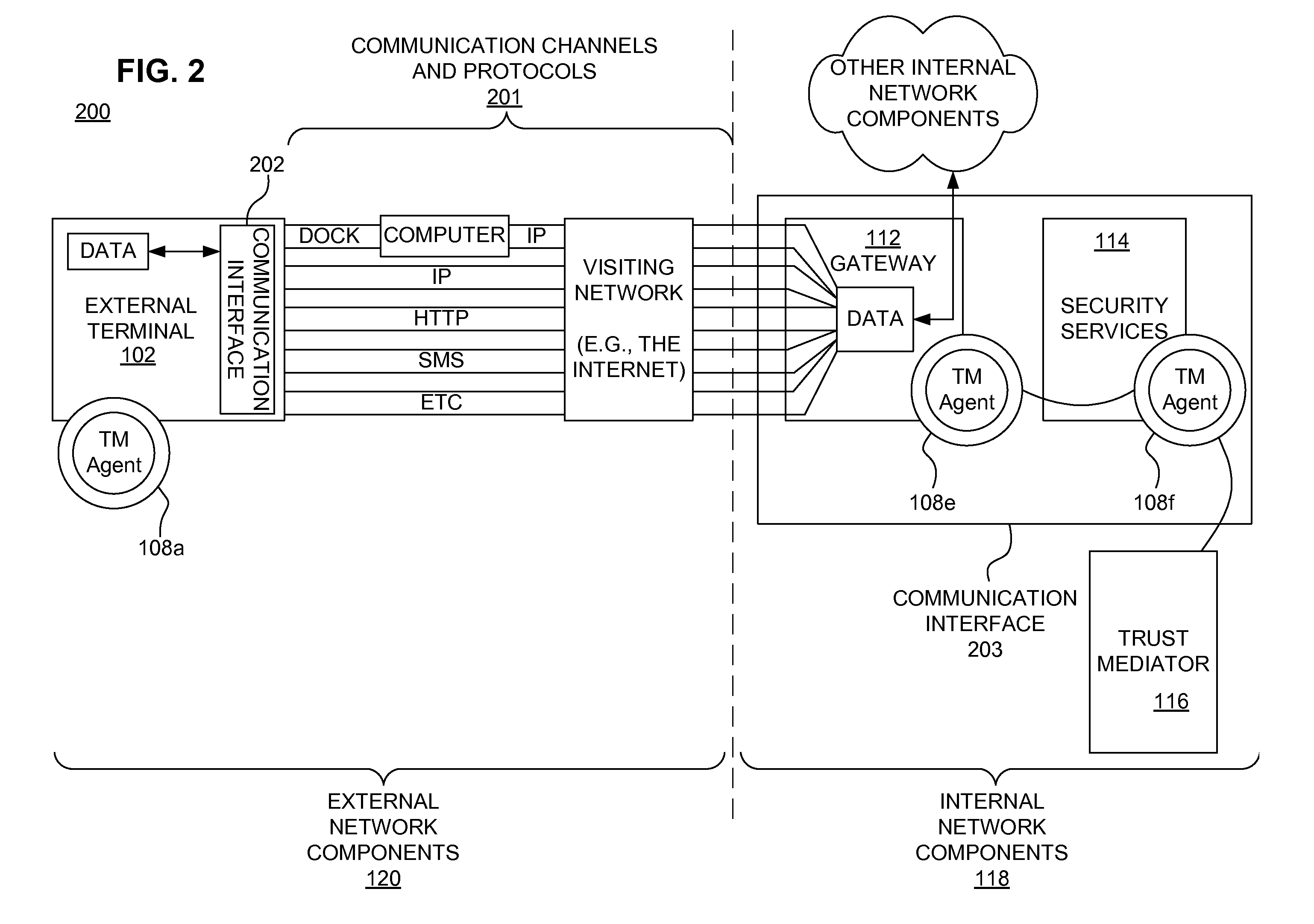
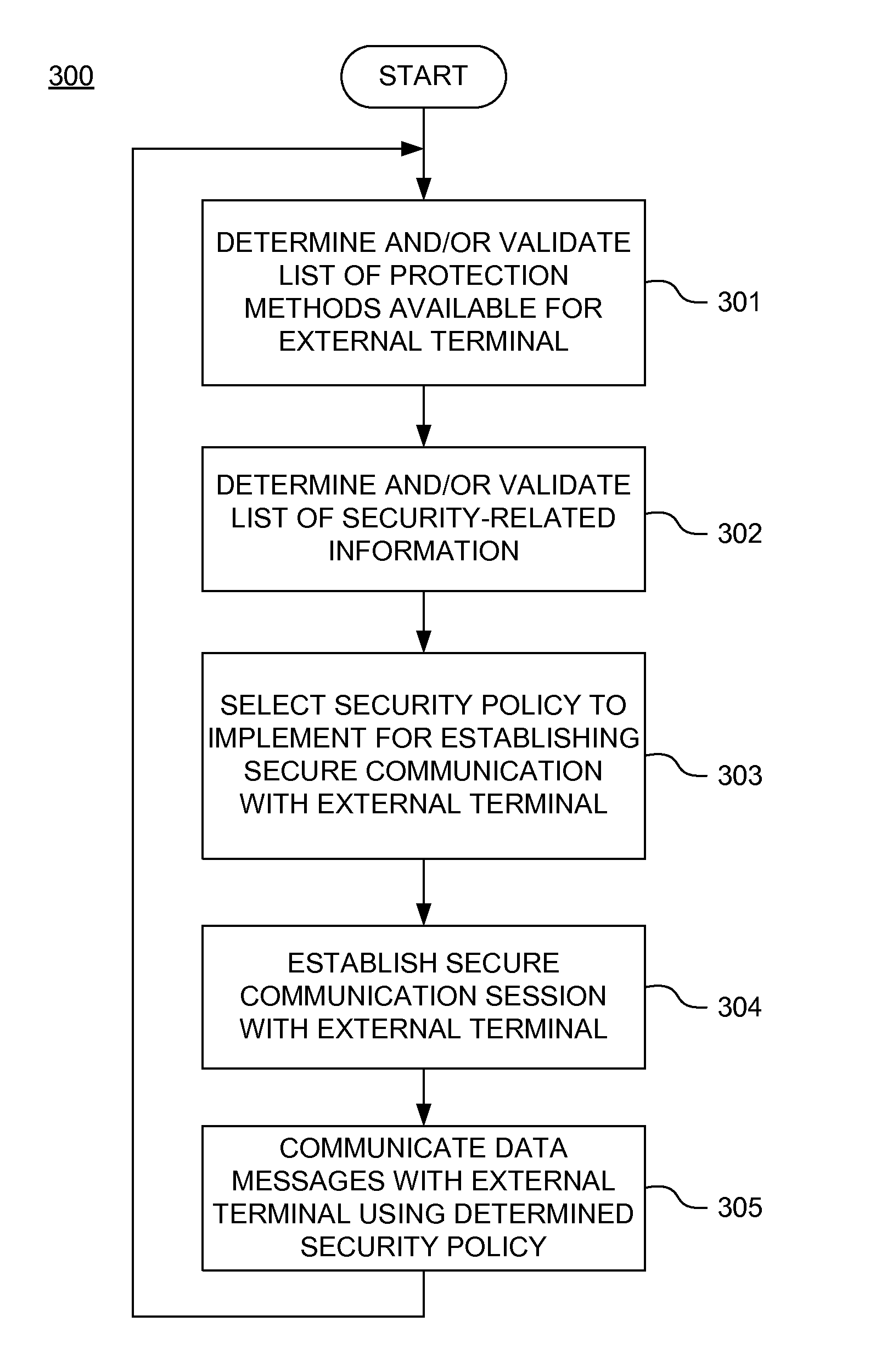
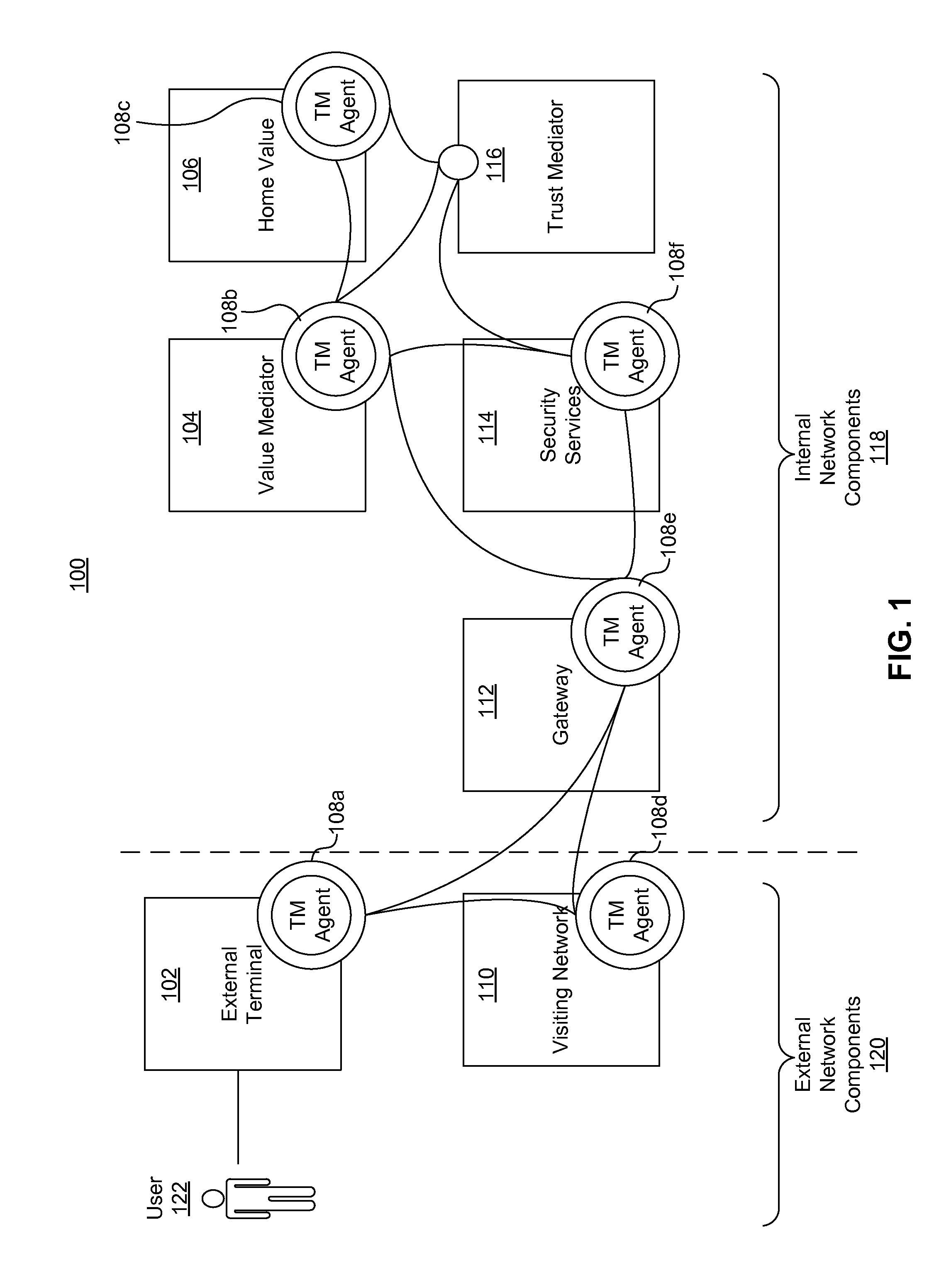
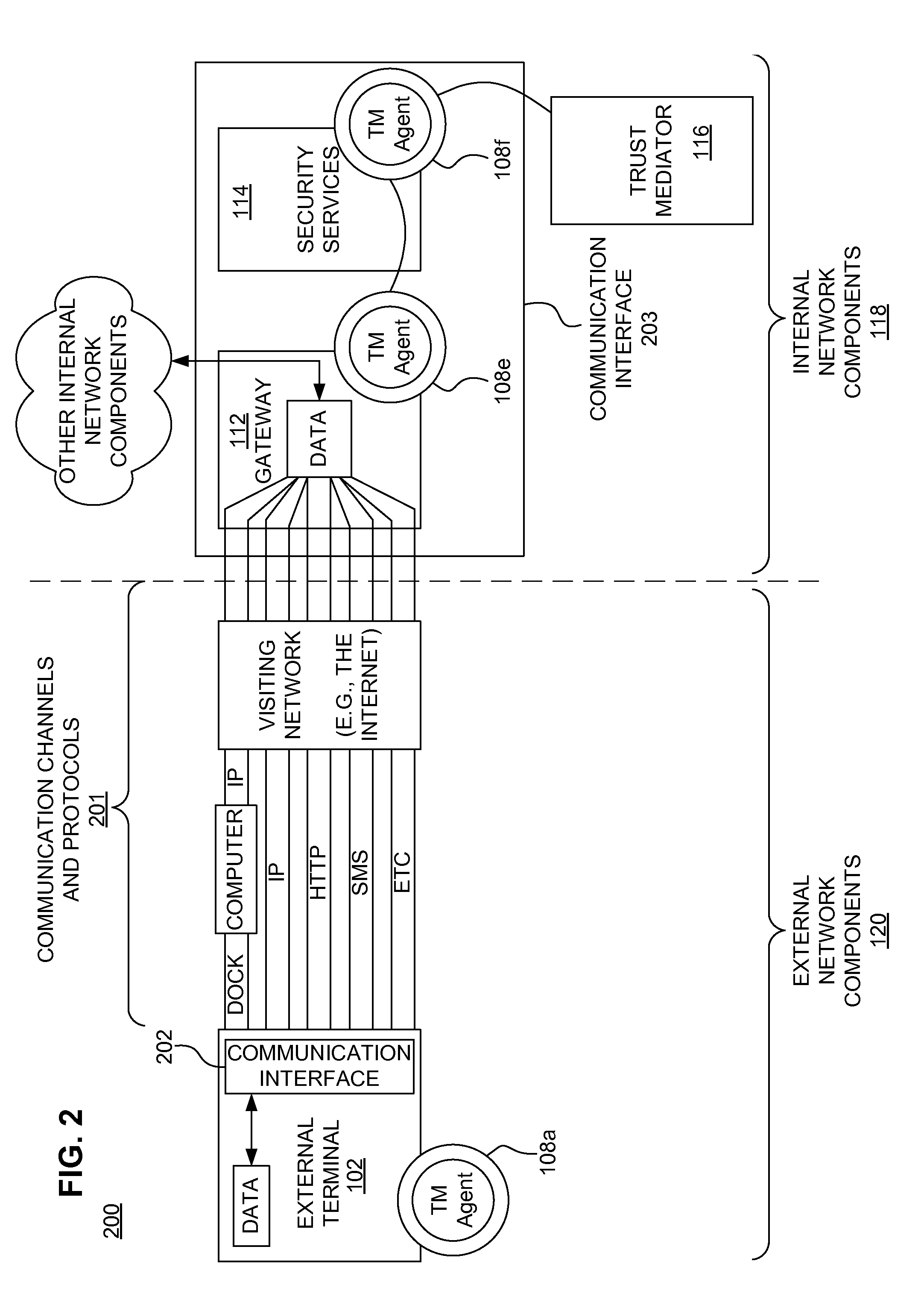
A secure mobile financial transaction is provided by receiving, over a communication network, a list of protection mechanisms available for implementation by an external terminal. Security-related data is received from one or more sensors and an attack signature is computed based on the security-related data. An appropriate security policy is selected from multiple security policies stored in a database based on the list of protection mechanisms and the attack signature. A secure communication session is established between the external terminal and an internal network component according to the selected security policy. A data message associated with a mobile financial transaction is communicated over the communication network during the communication session.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
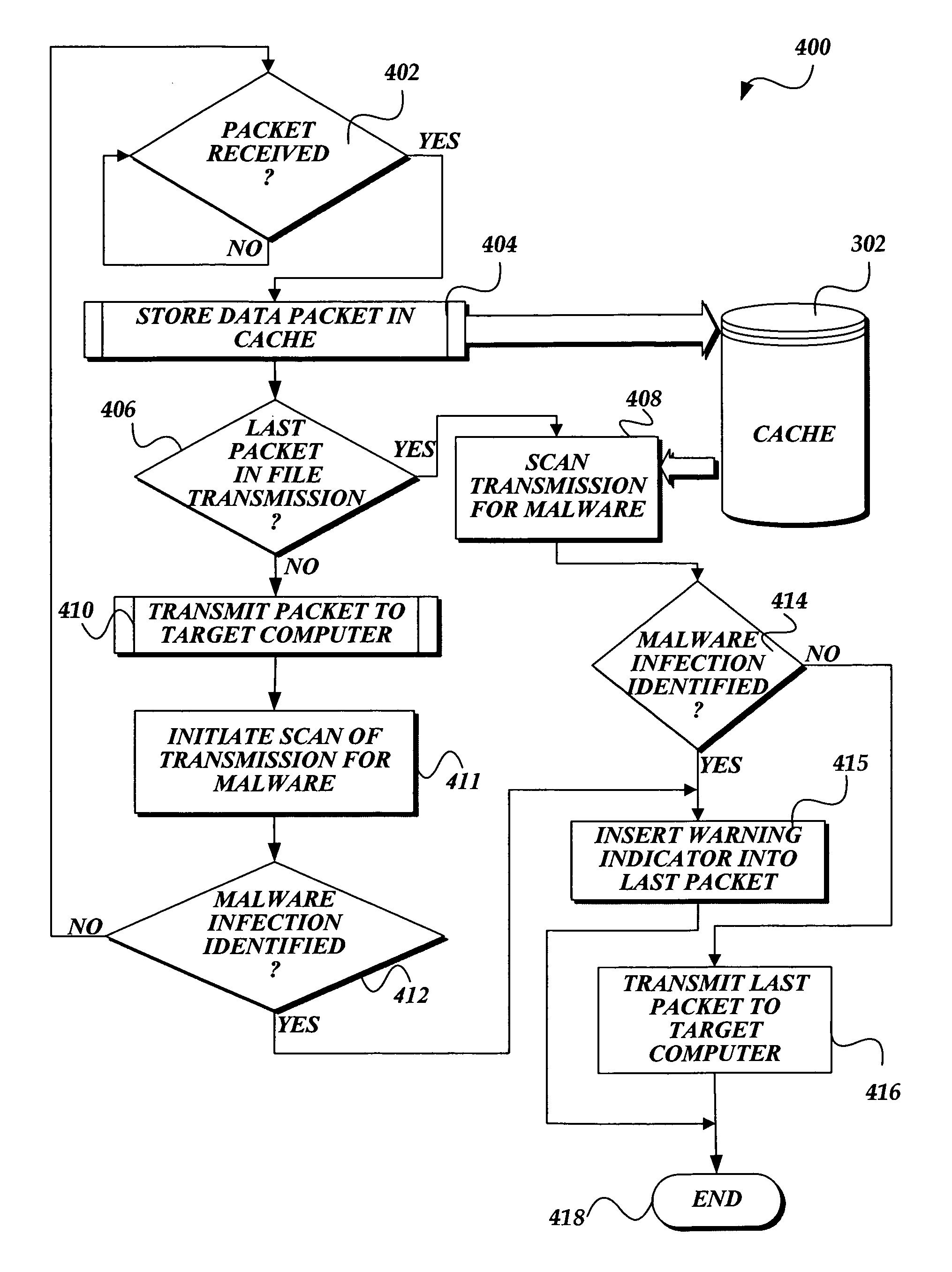
Latency free scanning of malware at a network transit point
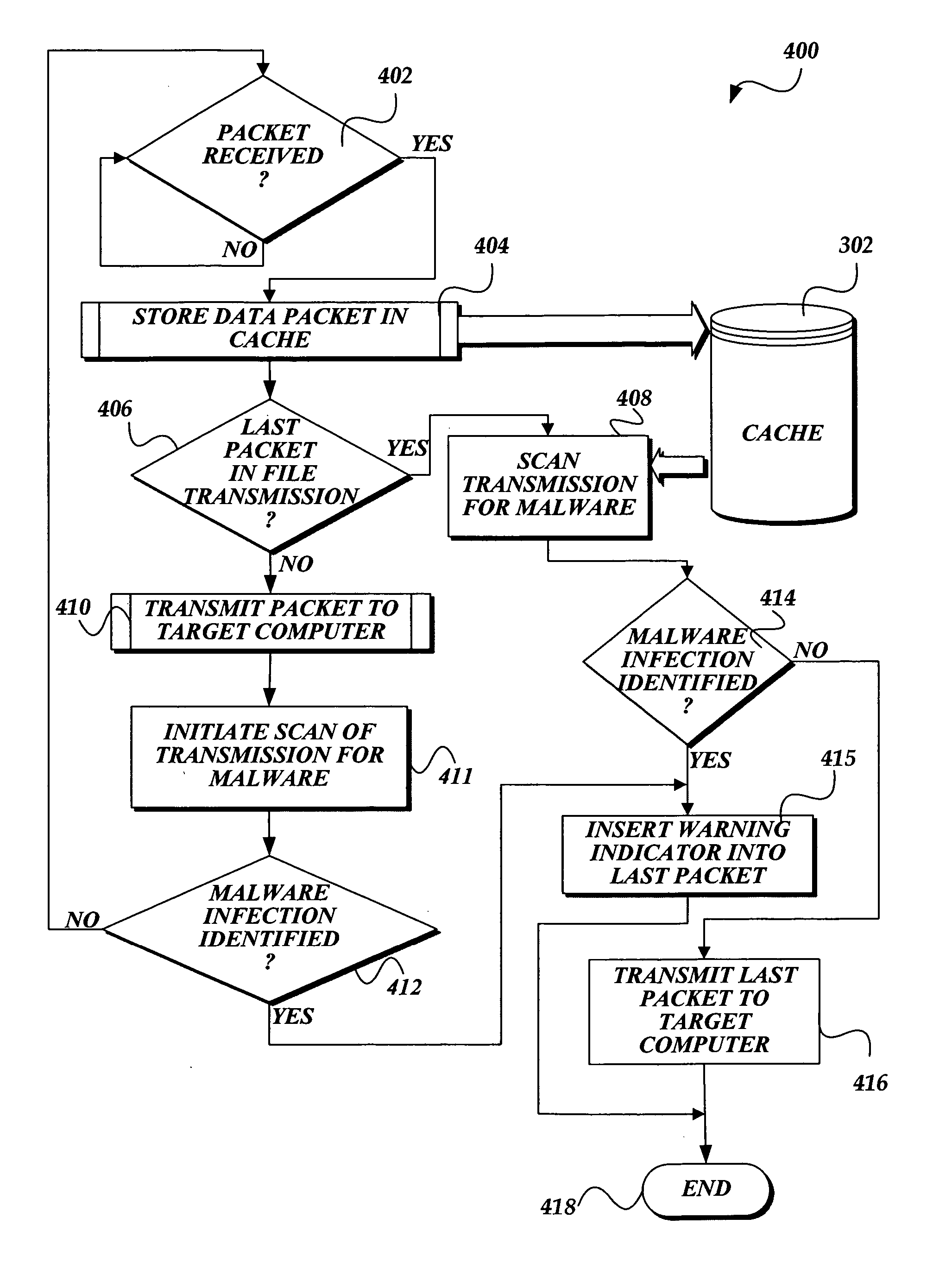
In accordance with the present invention, a system, method, and computer-readable medium for identifying malware at a network transit point such as a computer that serves as a gateway to an internal or private network is provided. A network transmission is scanned for malware at a network transit point without introducing additional latency to the transmission of data over the network. In accordance with one aspect of the present invention, a computer-implemented method for identifying malware at a network transit point is provided. More specifically, when a packet in a transmission is received at the network transit point, the packet is immediately forwarded to the target computer. Simultaneously, the packet and other data in the transmission are scanned for malware by an antivirus engine. If malware is identified in the transmission, the target computer is notified that the transmission contains malware.
Owner:MICROSOFT TECH LICENSING LLC
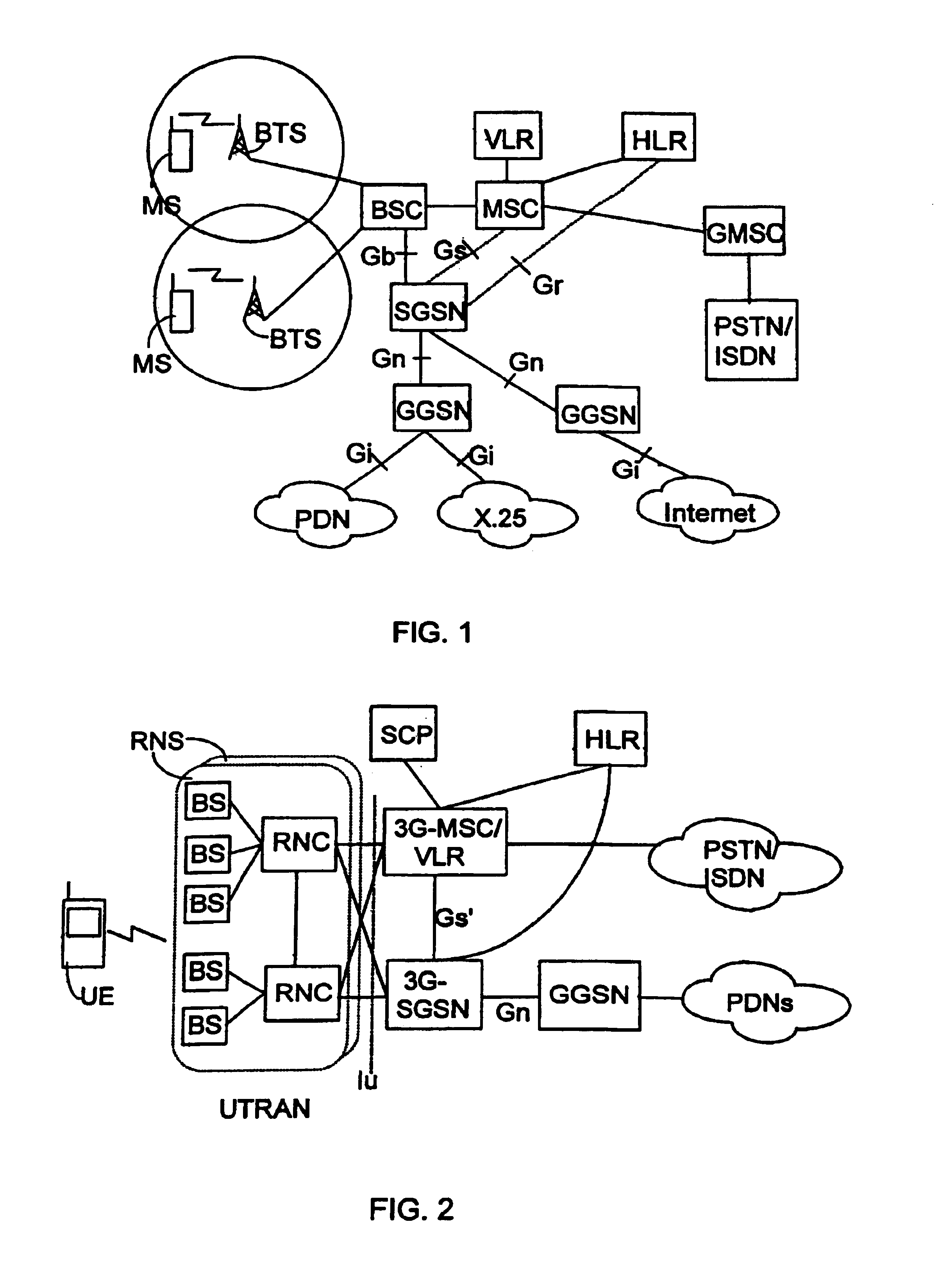
Method, apparatus, data structure, computer program, and system for providing appropriate QoS end-to-end for data crossing network boundaries
InactiveUS20050185651A1Network traffic/resource managementData switching by path configurationQuality of serviceComputer science
Data is structured with information indicative of time-related, bandwidth-related, or class-related quality-of-service (QoS) required for sending the data so that a receiving terminal or any network element processing the data in transit over a network is able to determine whether the required quality-of-service has actually been uniformly experienced by the data and, in case the quality-of-service is degraded in any section of the network, the receiving terminal or the network element is able to cause the network to either uniformly accord to the data a degraded quality-of-service corresponding to that actually experienced or to actually uniformly provide the required quality-of-service between the sending and receiving terminals by improving the processing of the data by the network element or elements. A corresponding method, apparatus, system and computer programs are shown.
Owner:NOKIA CORP
Systems and methods for security hardening of data in transit and at rest via segmentation, shuffling and multi-key encryption
ActiveUS20150310219A1Hardening securityHardening confidentialityKey distribution for secure communicationMultiple keys/algorithms usageContextual integrityComputerized system
Systems and methods for security hardening of a file in transit and at rest via segmentation, shuffling and multi-key encryption are presented. The method including segmenting at a first computer system a file into a plurality of file segments, and encrypting the plurality of file segments using a plurality of encryption keys in order to generate a corresponding plurality of encrypted file segments, wherein each file segment of the plurality of file segments is encrypted using a respective encryption key of the plurality of encryption keys. Additionally included is bidirectional data transformation of a file by obfuscating at a first computer system digital values of the file in order to generate corresponding obfuscated digital values of the file, wherein the obfuscated digital values of the file retain their contextual integrity and referential integrity
Owner:TOPIA TECH
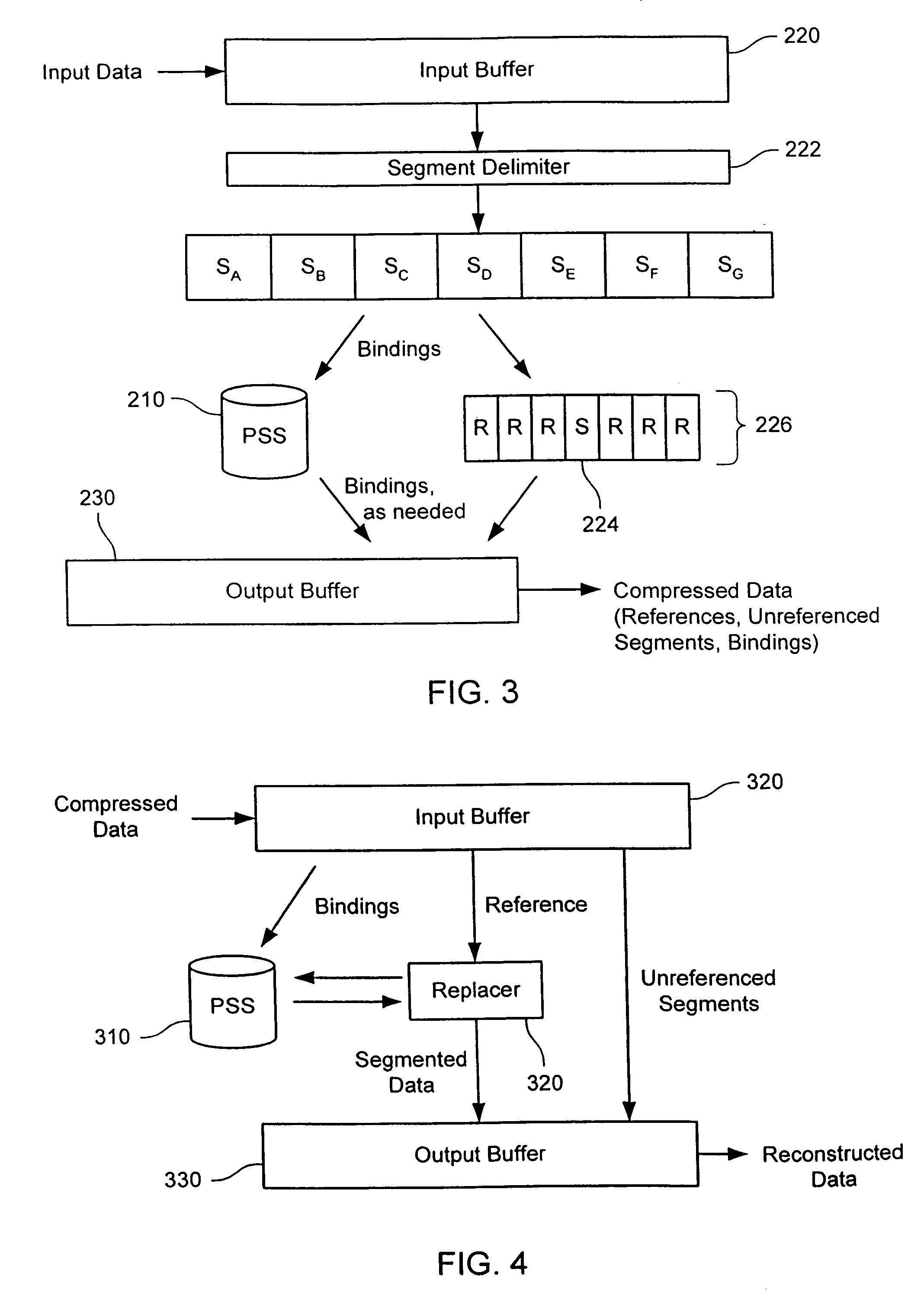
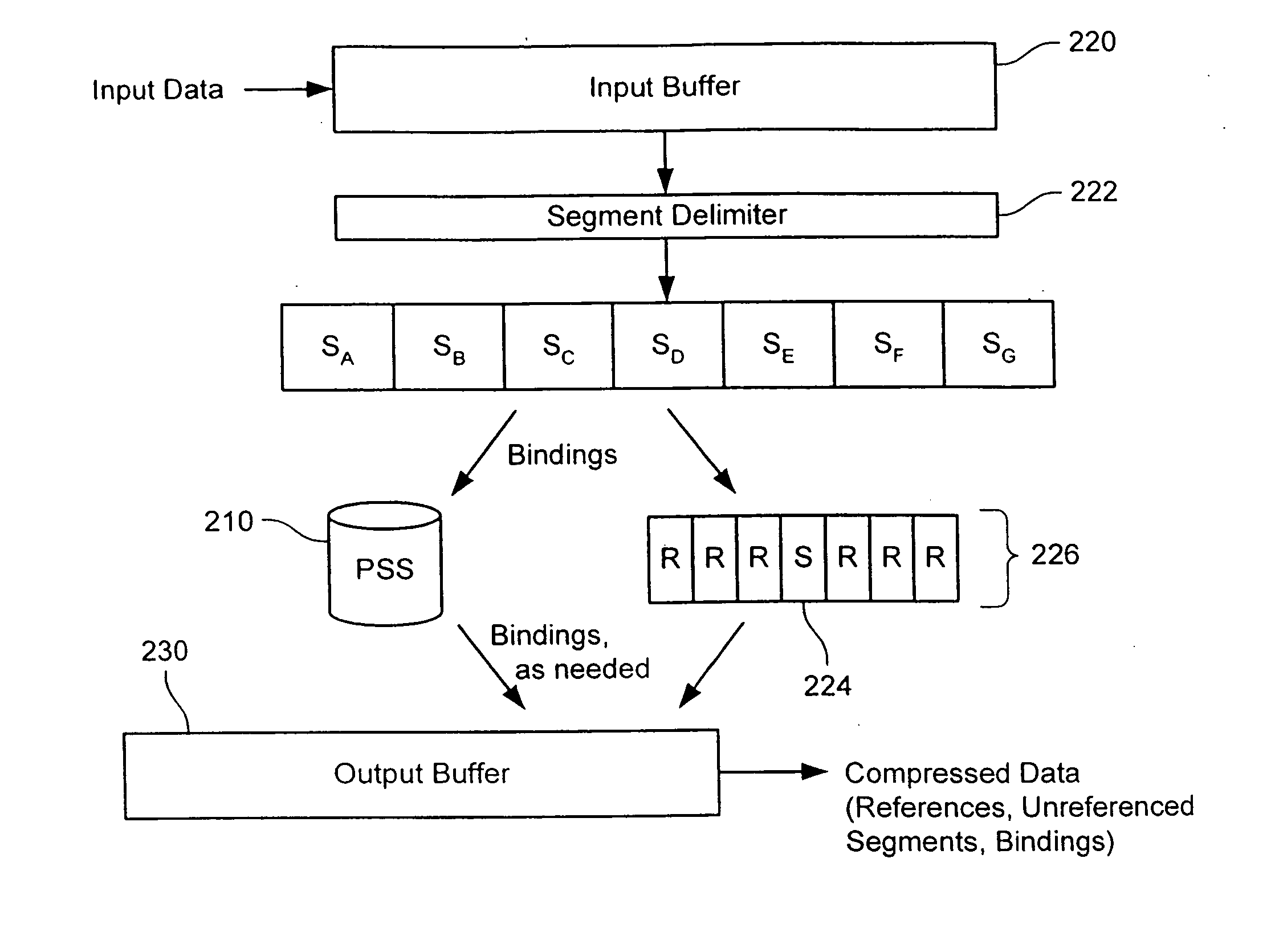
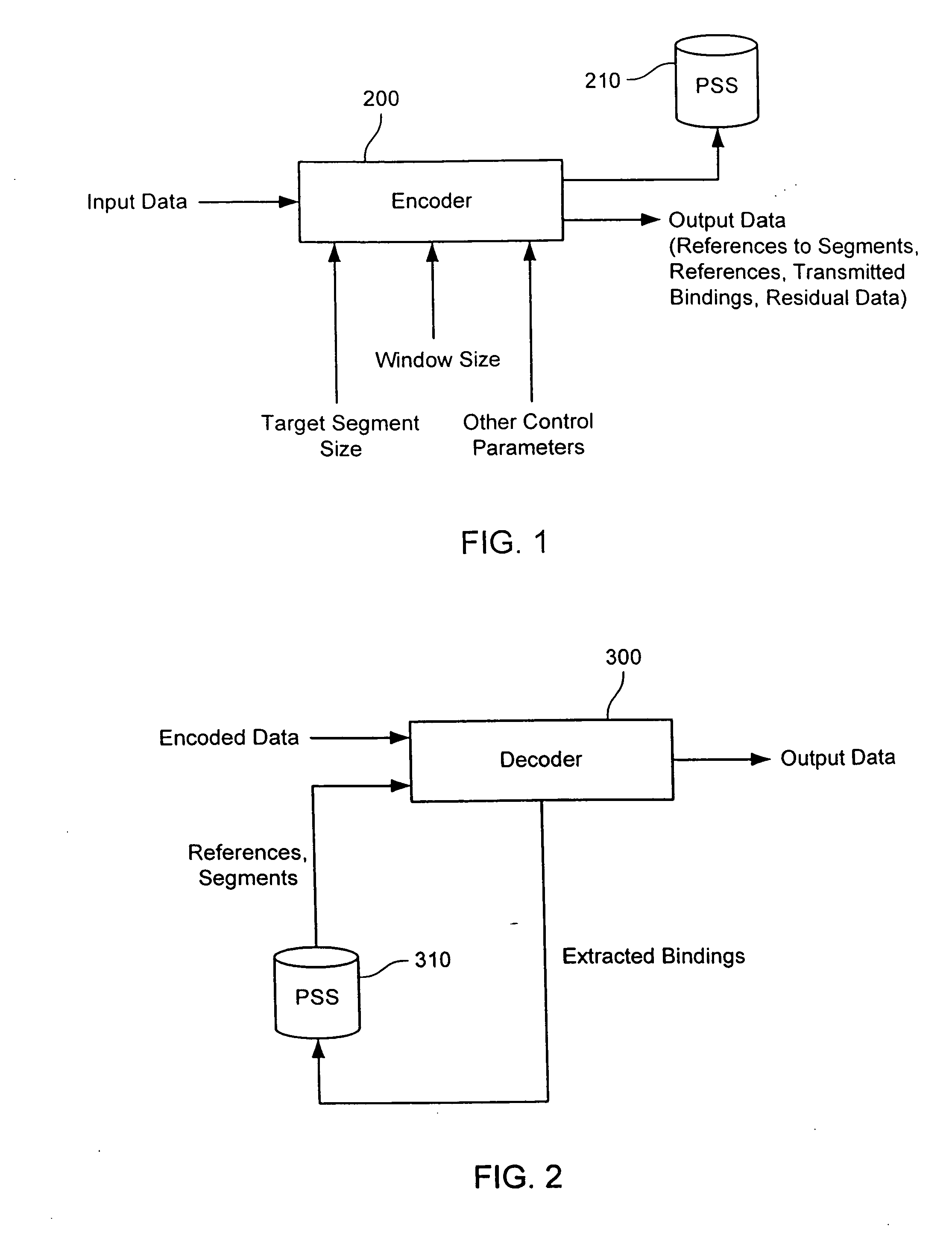
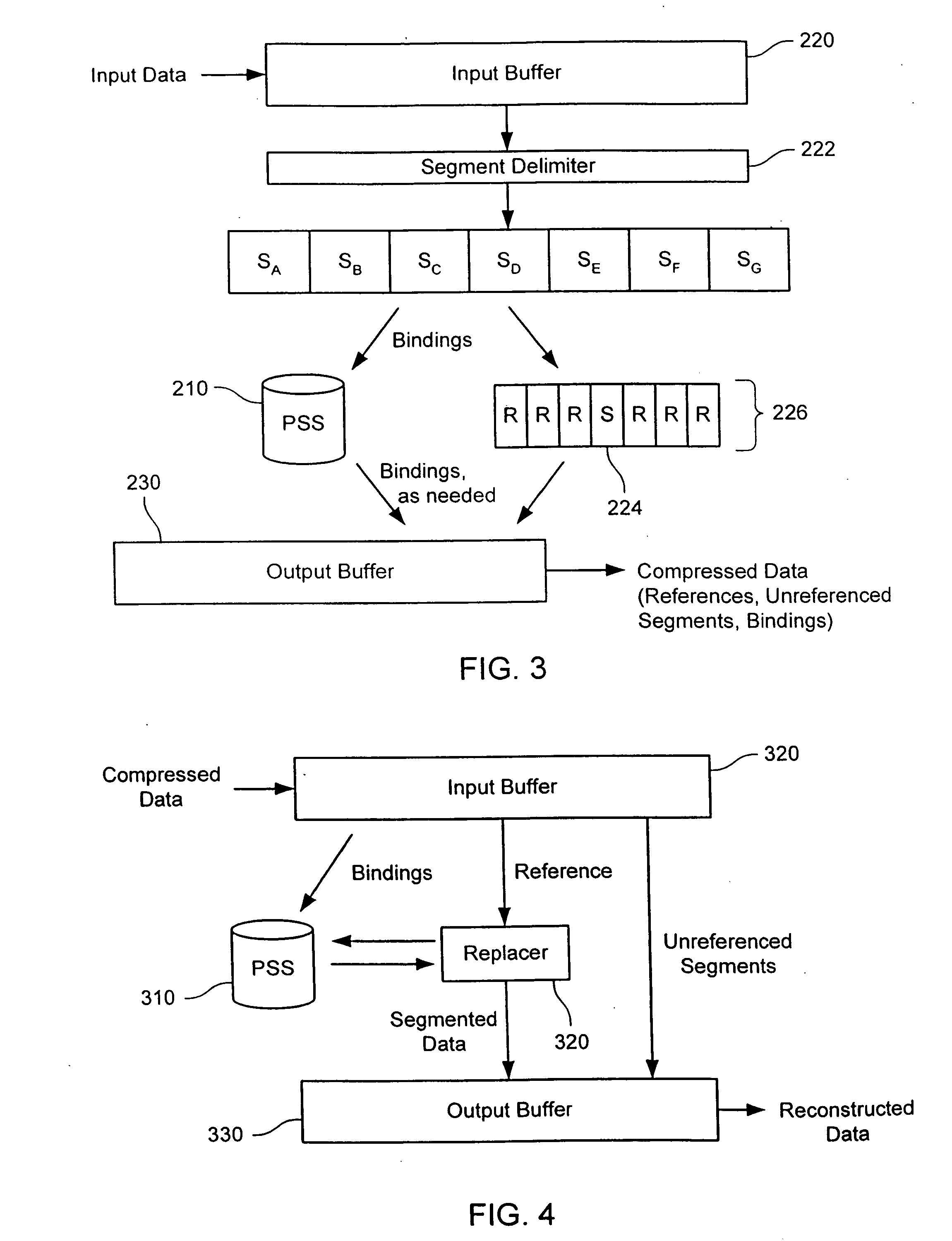
Content-based segmentation scheme for data compression in storage and transmission including hierarchical segment representation
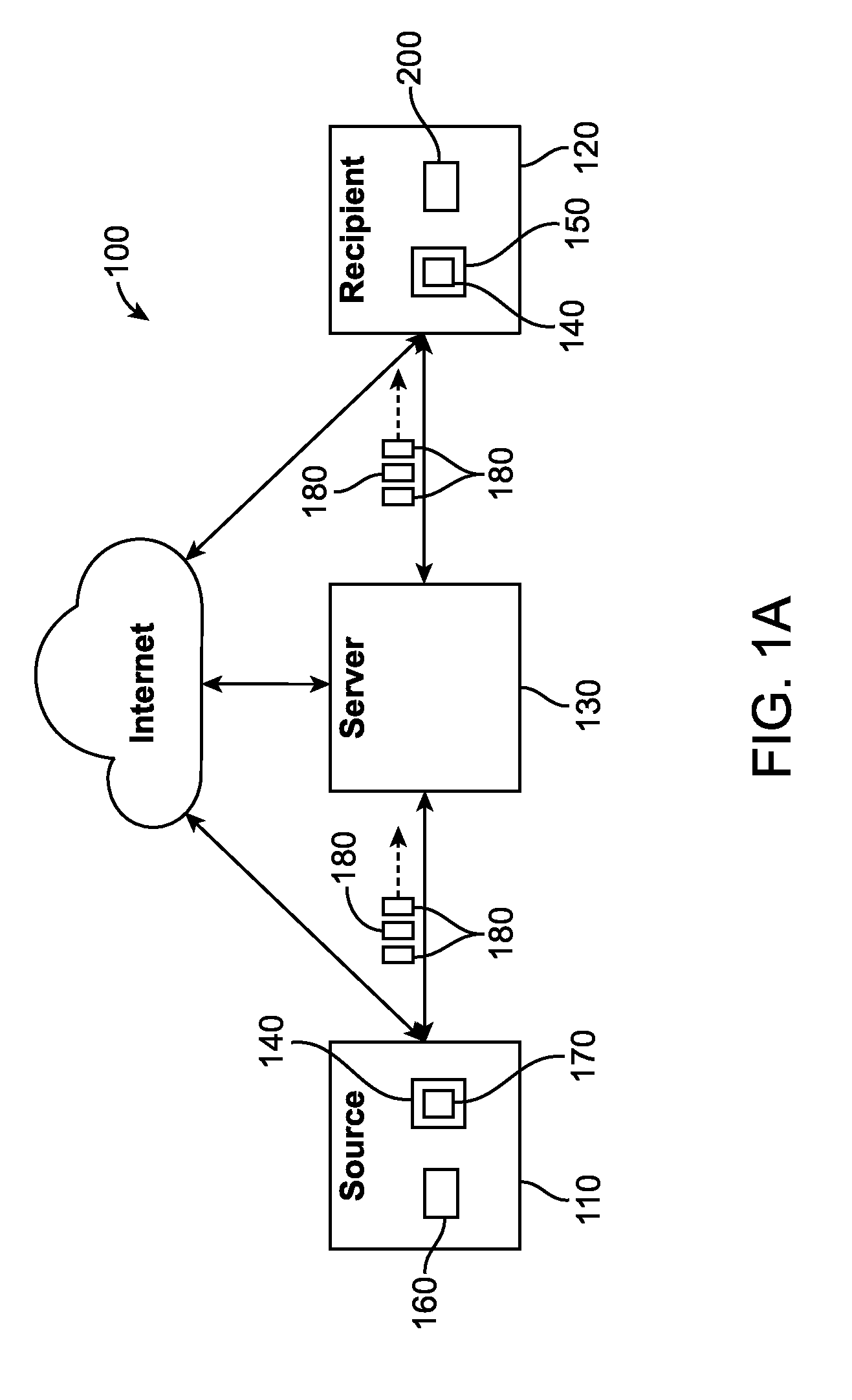
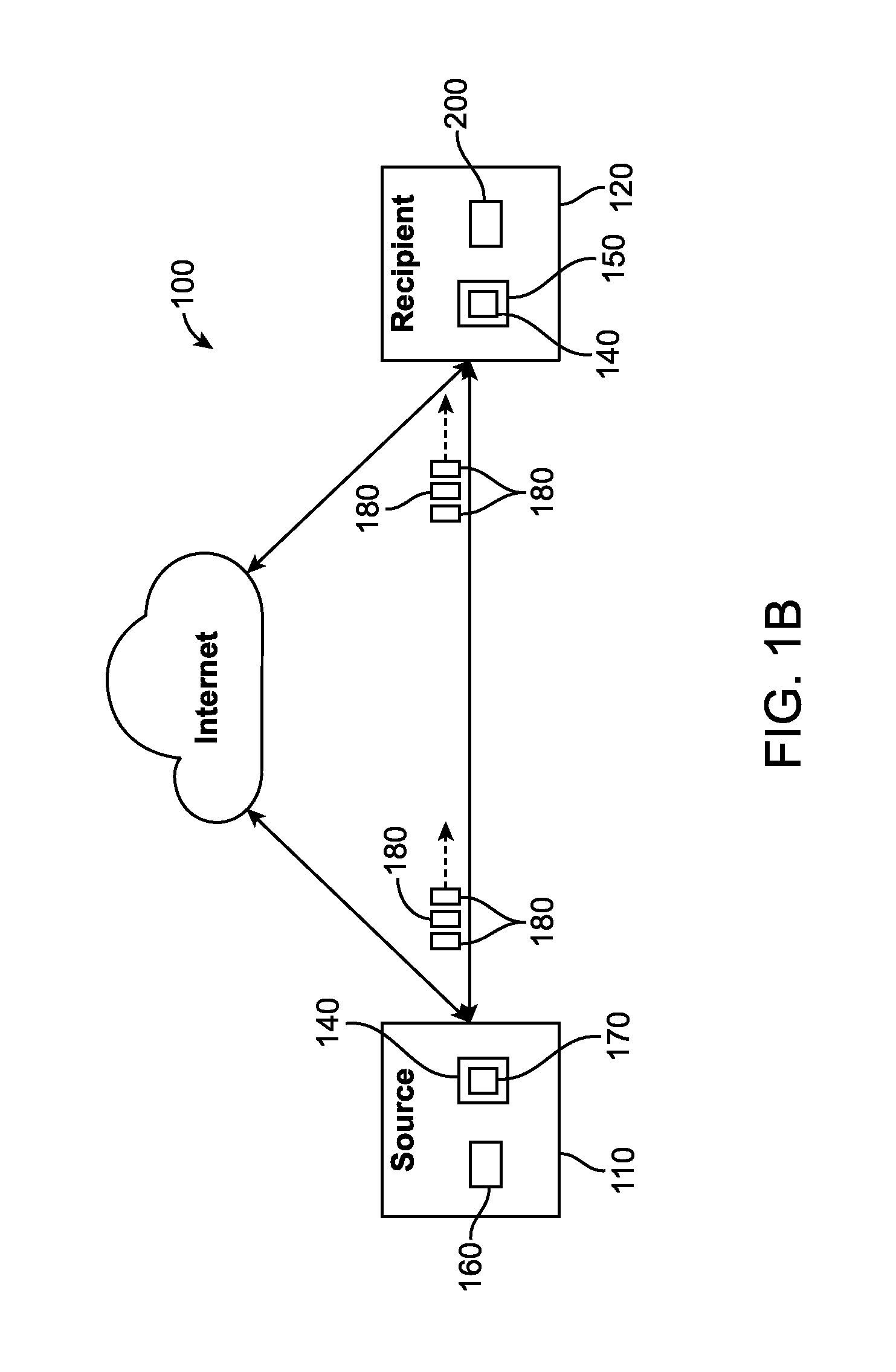
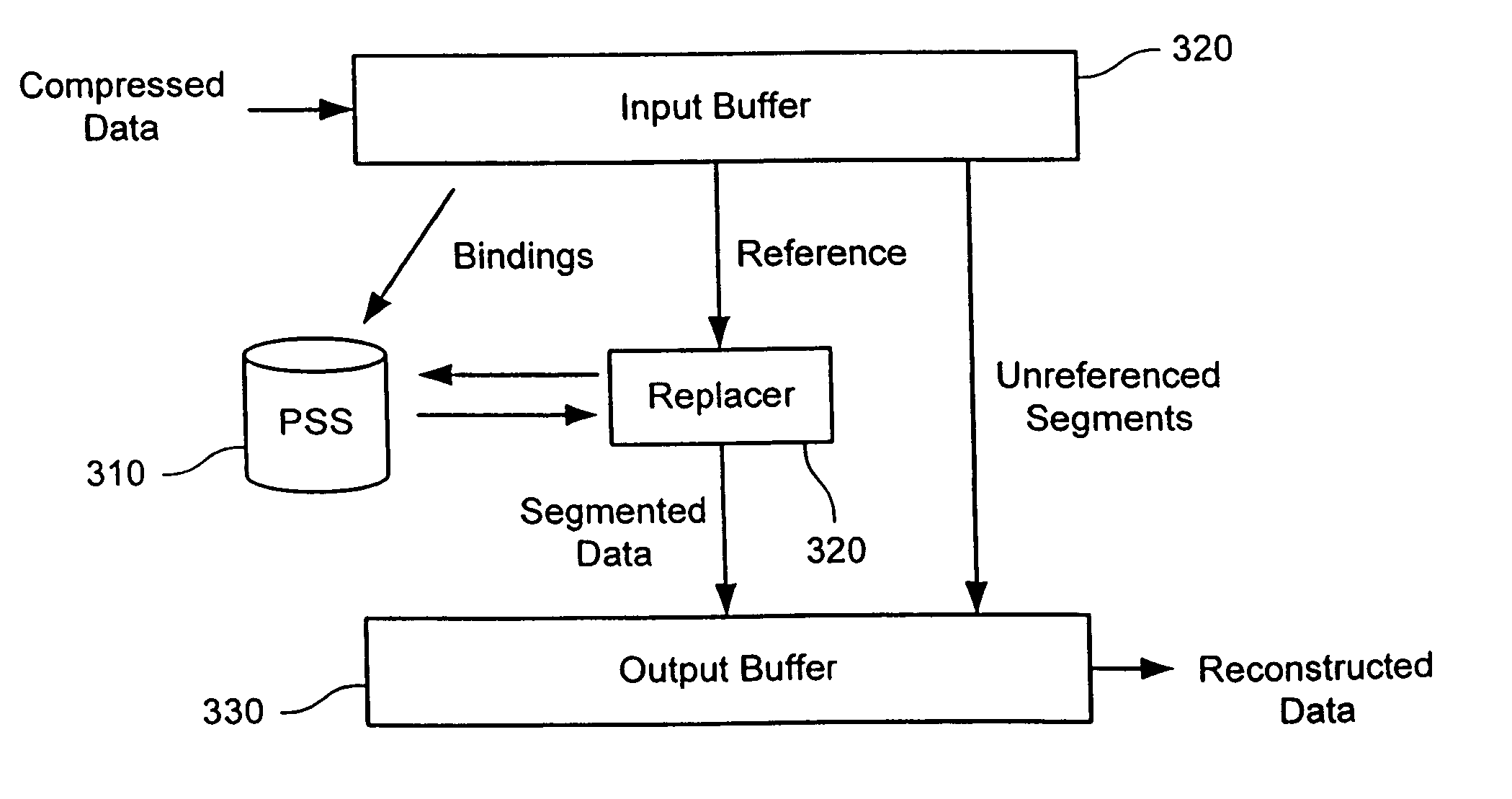
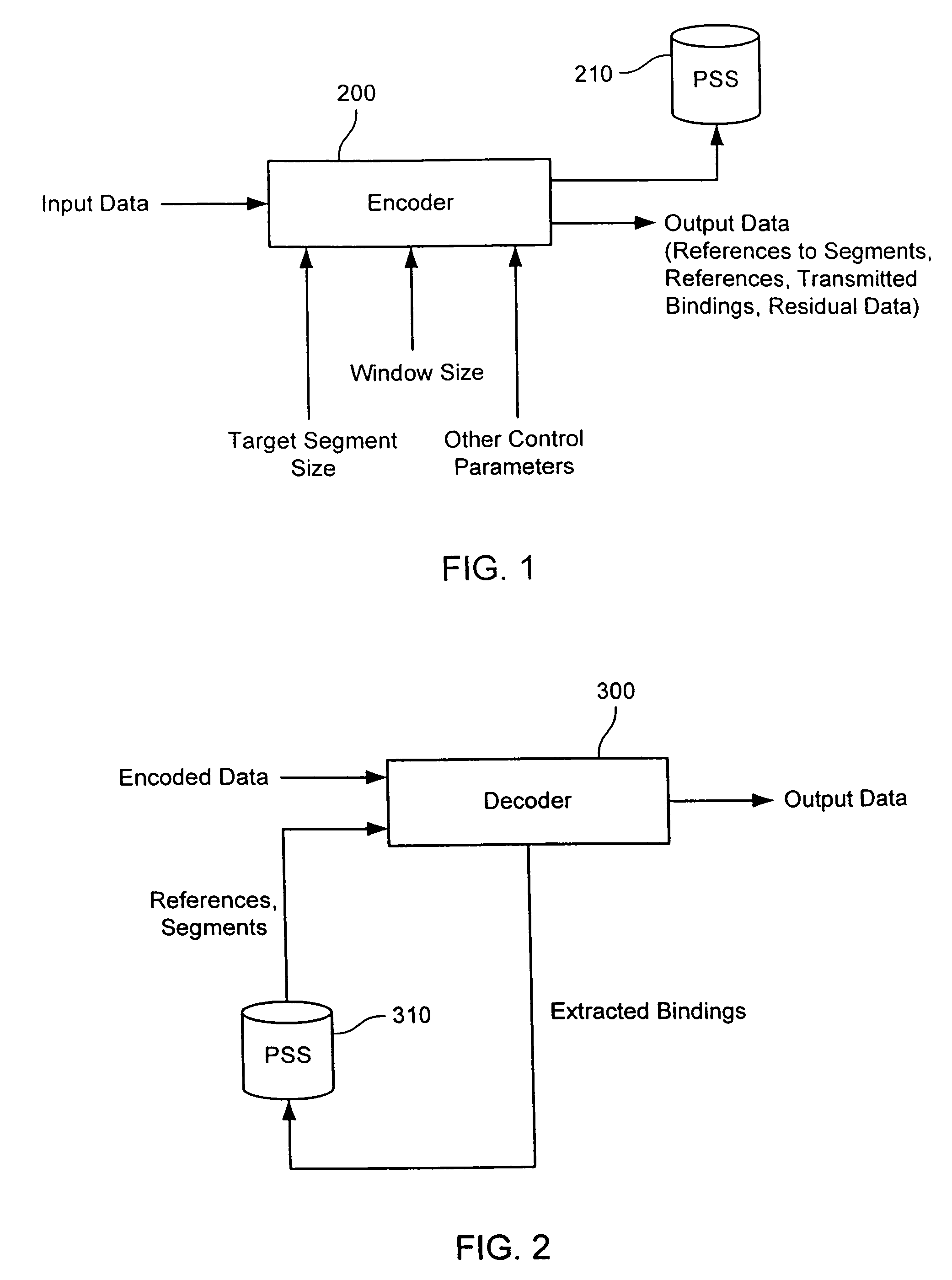
In a coding system, input data within a system is encoded. The input data might include sequences of symbols that repeat in the input data or occur in other input data encoded in the system. The encoding includes determining a target segment size, determining a window size, identifying a fingerprint within a window of symbols at an offset in the input data, determining whether the offset is to be designated as a cut point and segmenting the input data as indicated by the set of cut points. For each segment so identified, the encoder determines whether the segment is to be a referenced segment or an unreferenced segment, replacing the segment data of each referenced segment with a reference label and storing a reference binding in a persistent segment store for each referenced segment, if needed. Hierarchically, the process can be repeated by grouping references into groups, replacing the grouped references with a group label, storing a binding between the grouped references and group label, if one is not already present, and repeating the process. The number of levels of hierarchy can be fixed in advanced or it can be determined from the content encoded.
Owner:RIVERBED TECH LLC
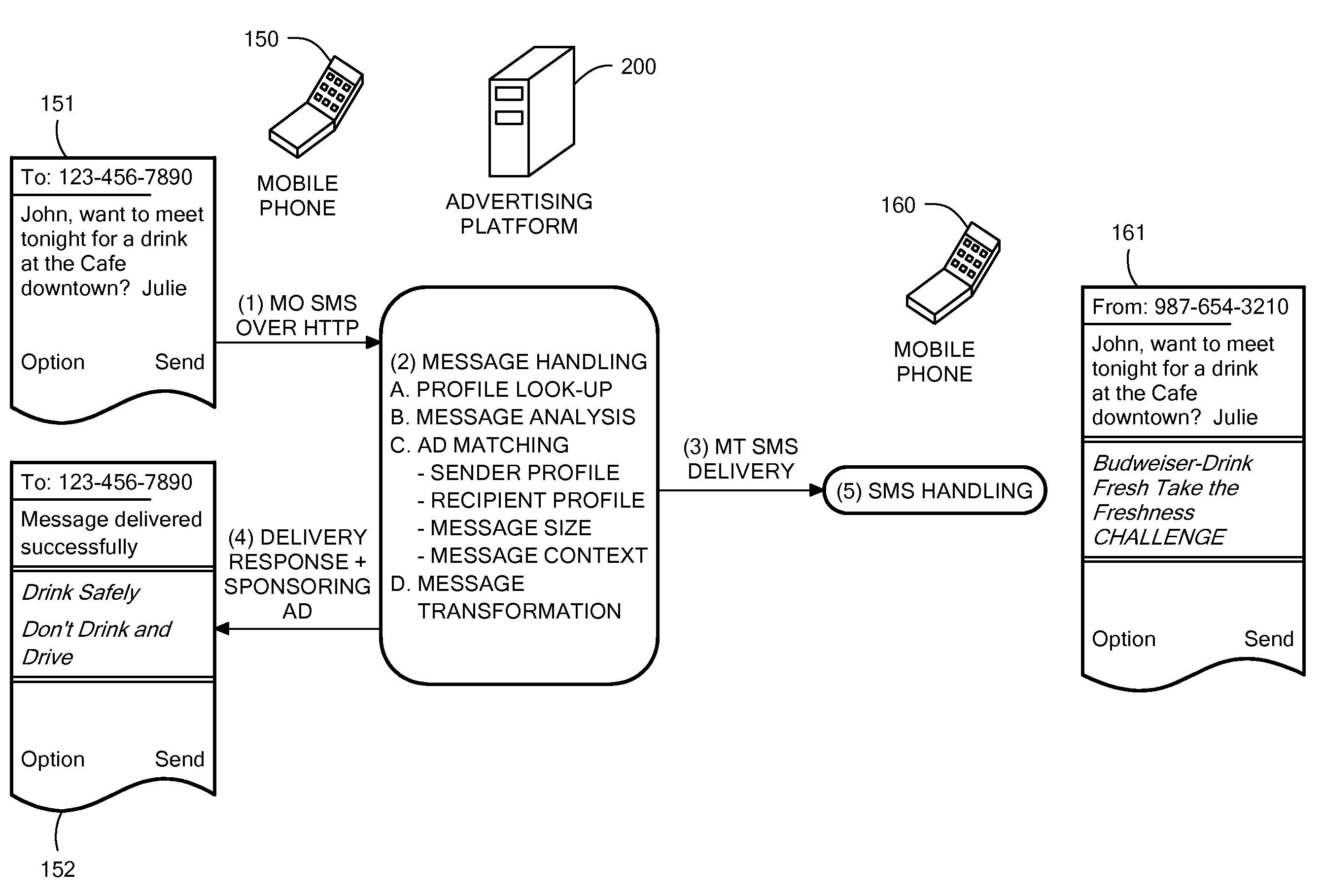
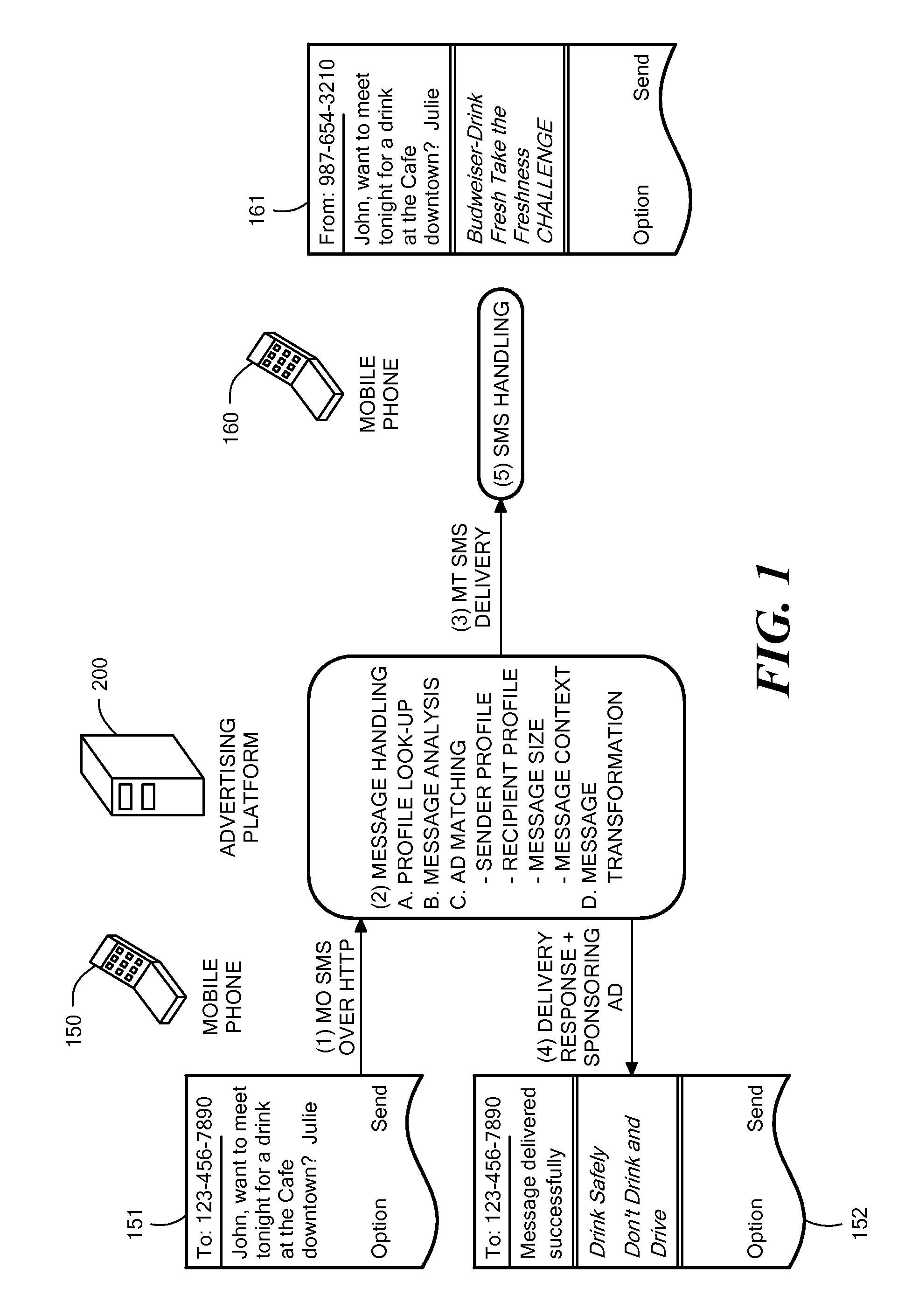
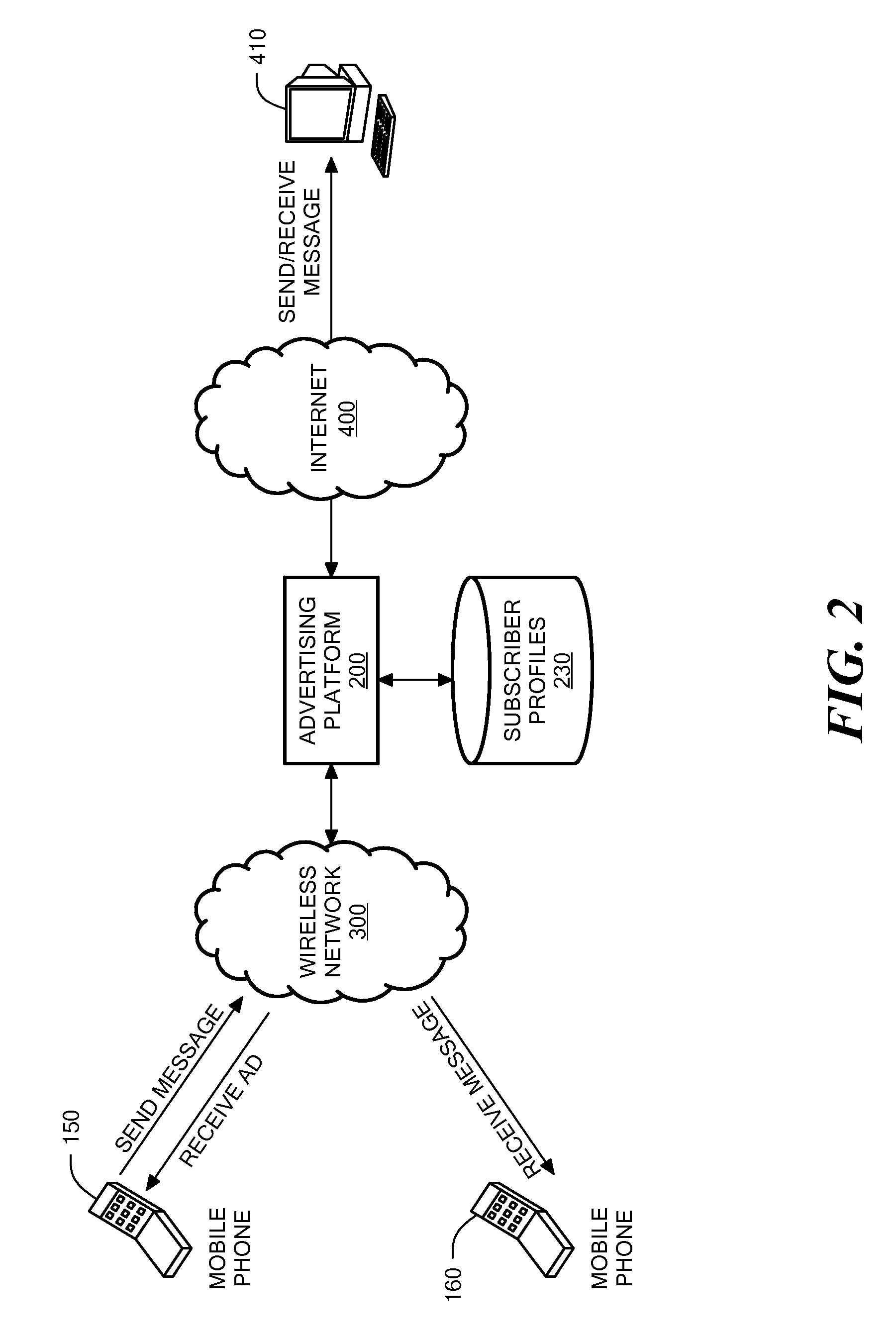
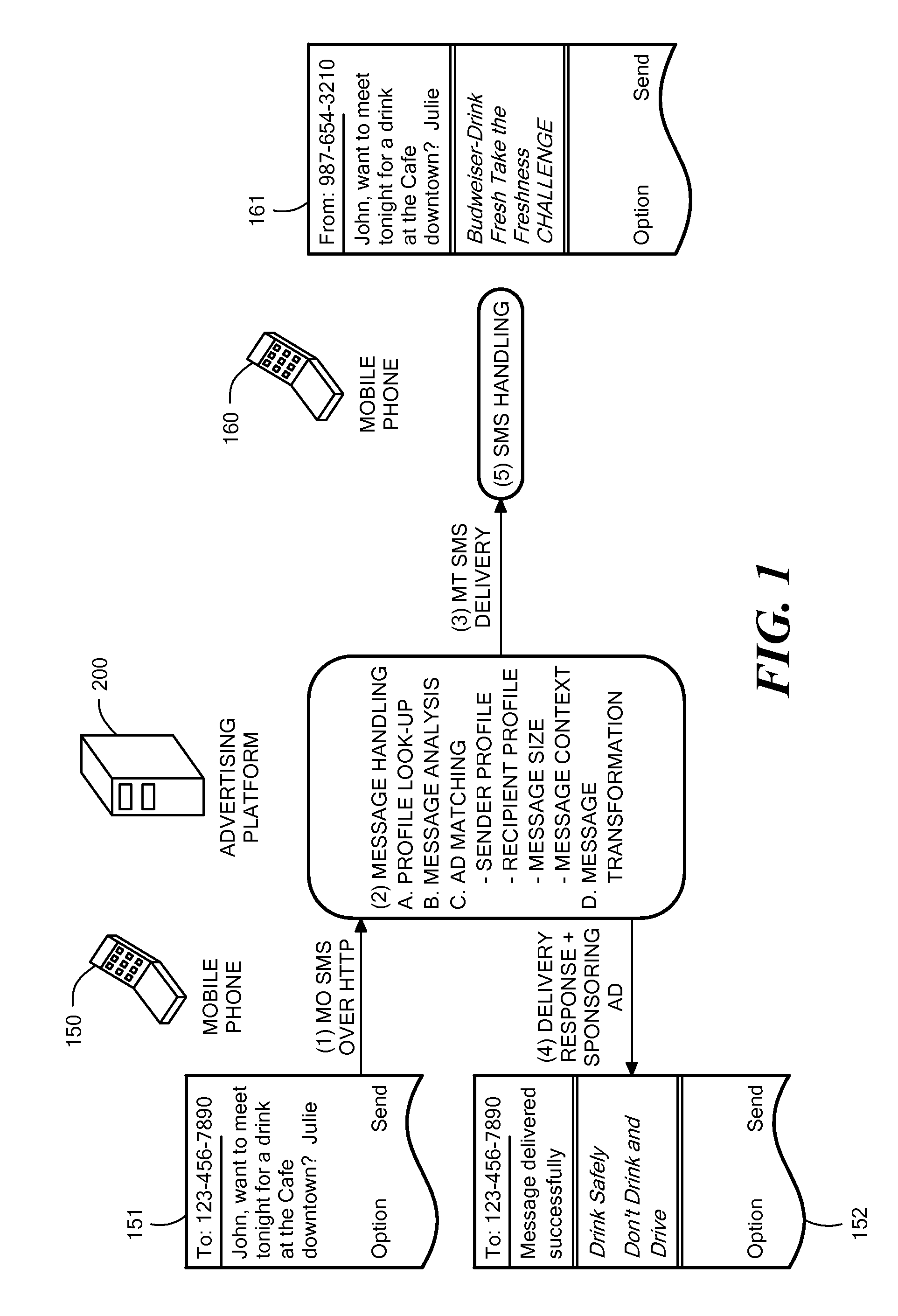
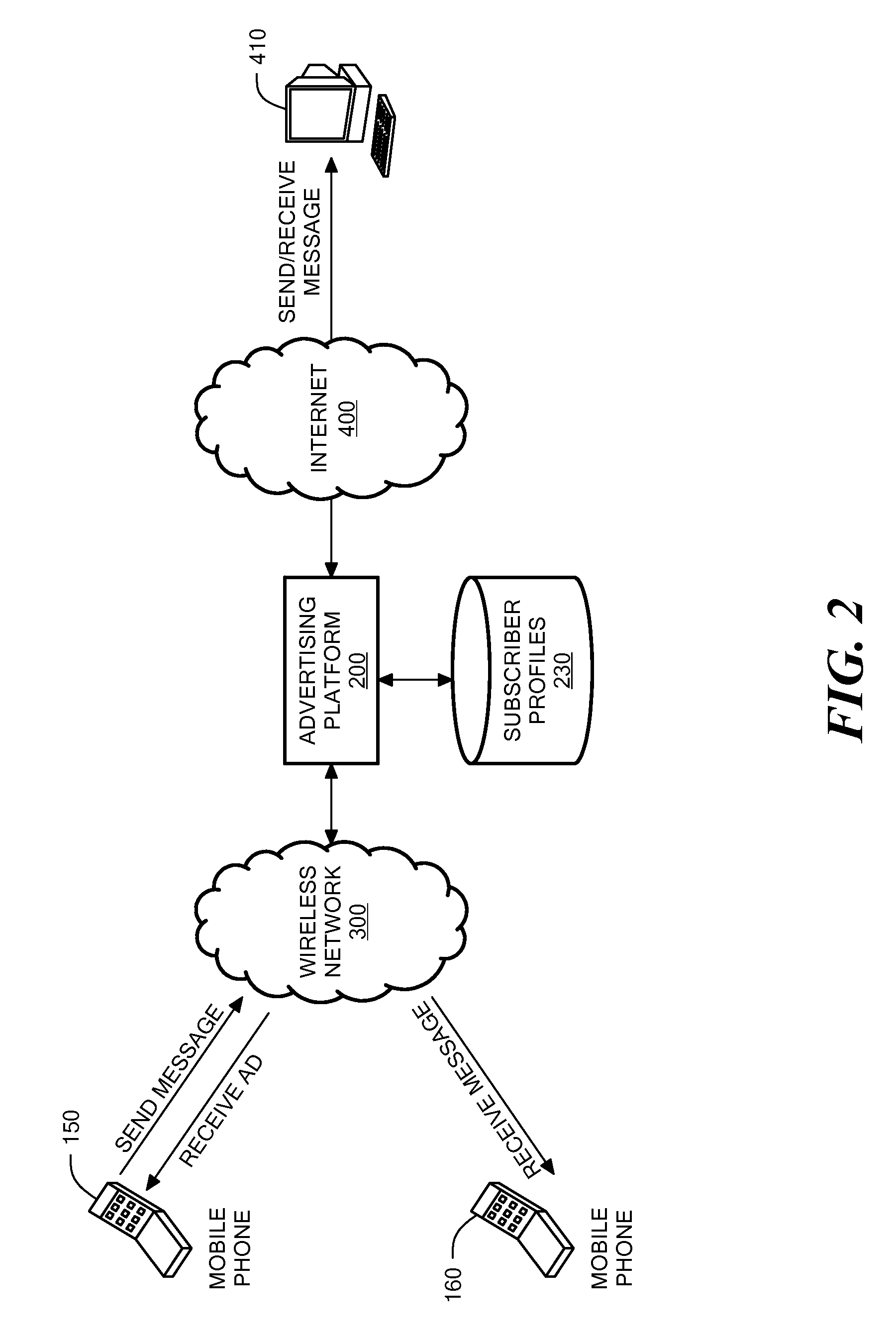
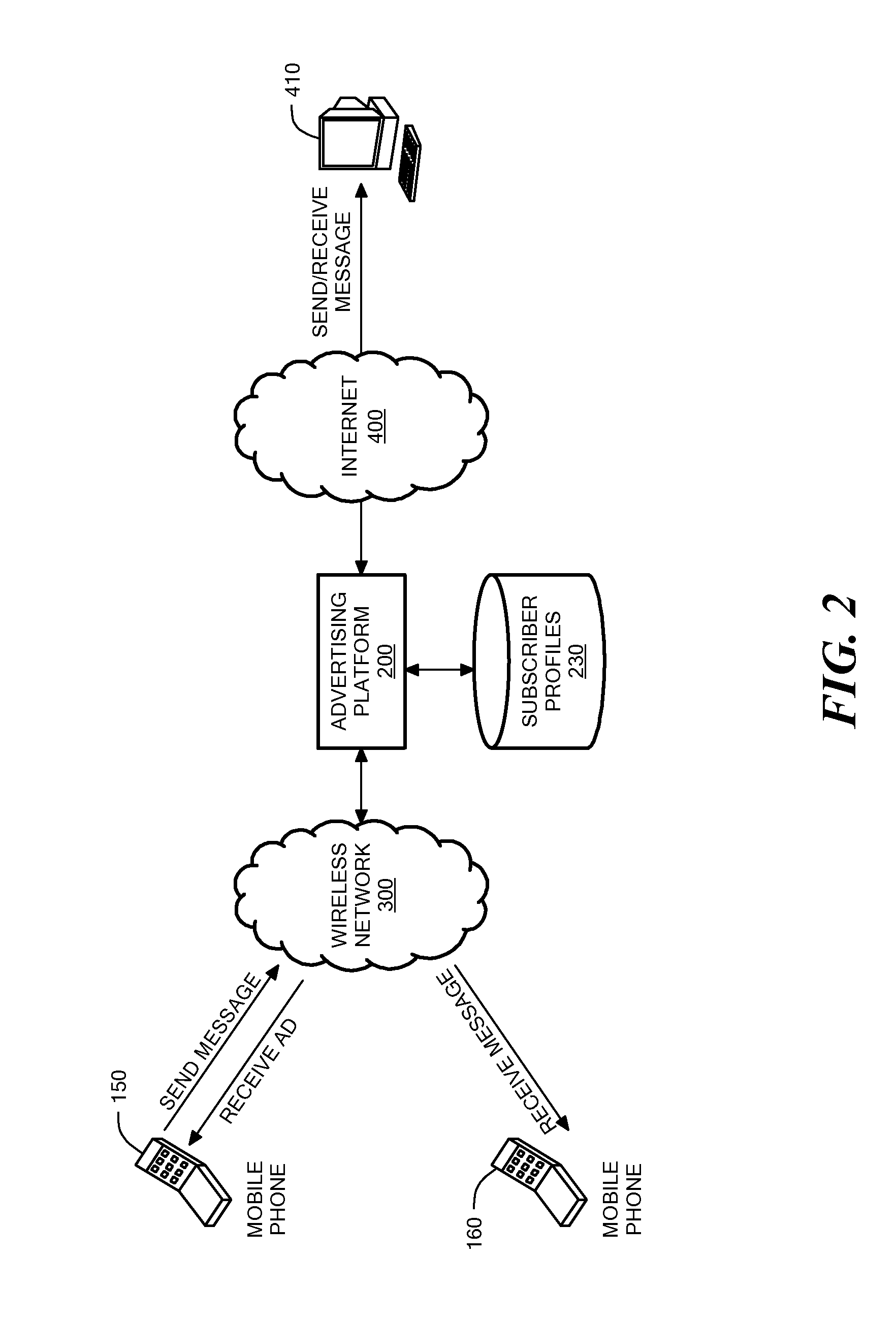
Method and System for Wireless Message-Based Advertising
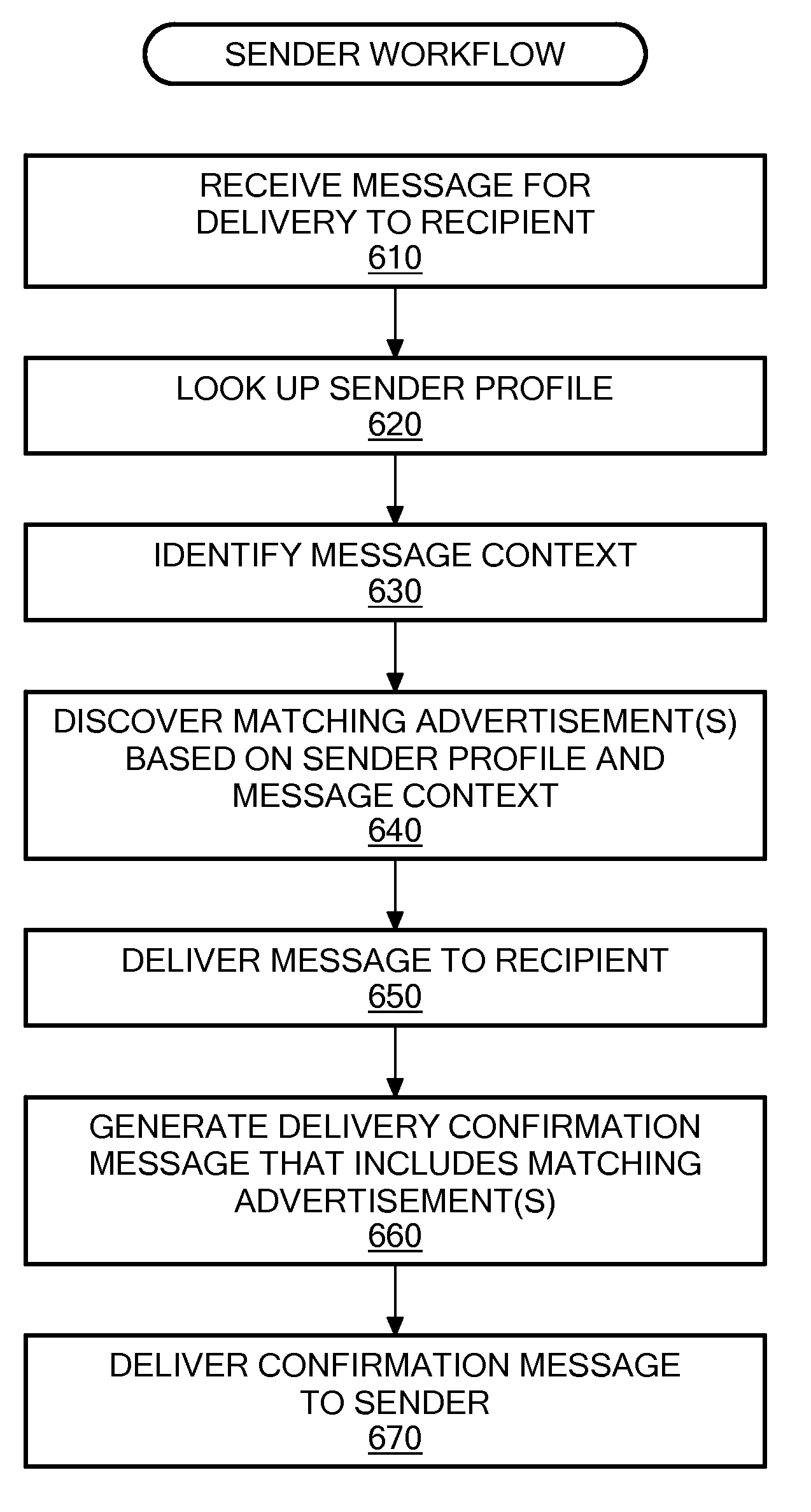
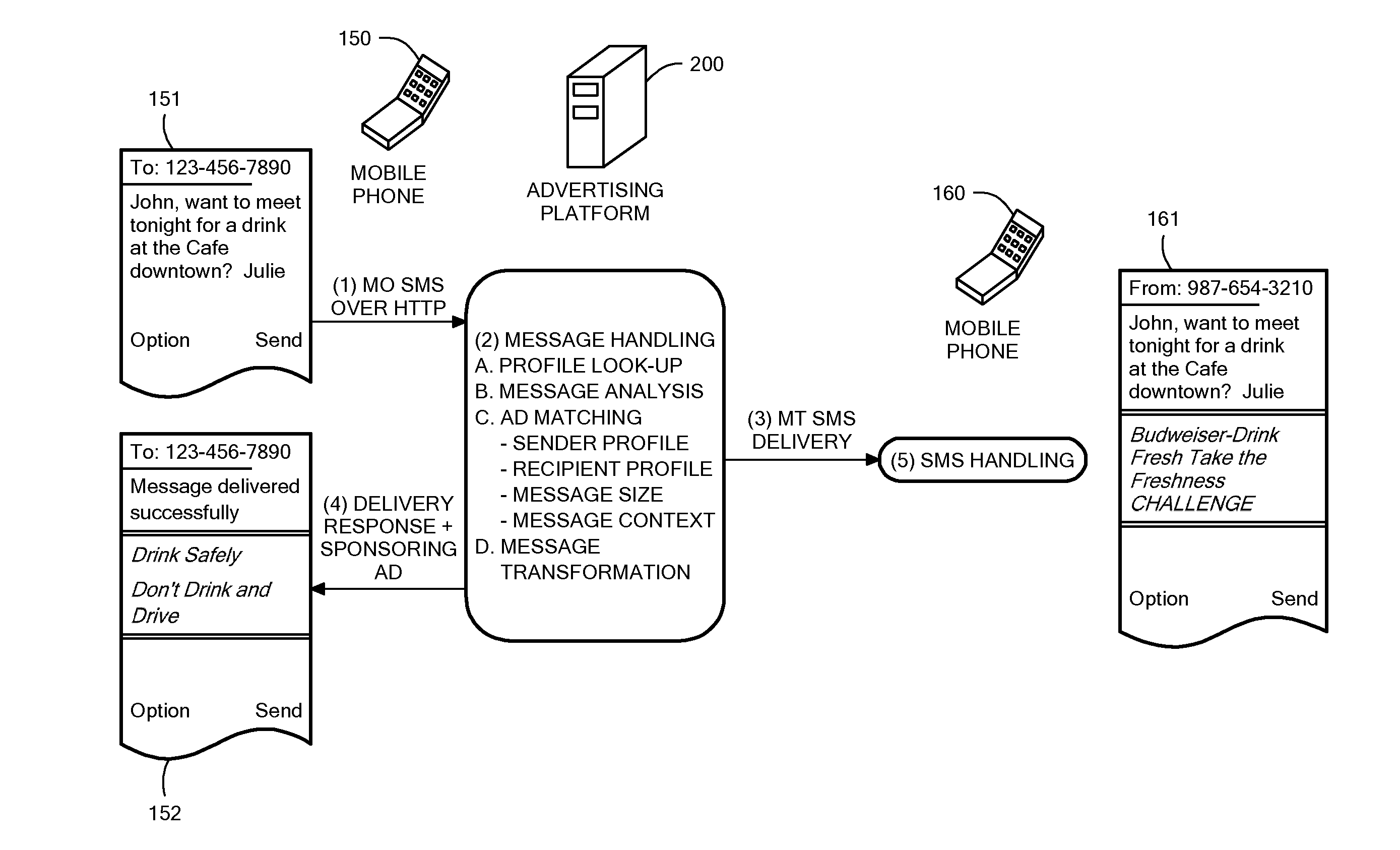
Systems and methods for message-based advertising in a wireless communications network are described. A digital message is contained in a data packet set in transit from a terminal of a sender to a terminal of a recipient. At least one of the terminals is implemented as a mobile telephone. The digital message is received through a network connection. A processor determines a context for the digital message and matches the message context to content of advertisements stored in an advertisement database in order to identify at least one relevant advertisement. The data packet set is transmitted to the terminal of the recipient. A processor retrieves the relevant advertisement(s) from the advertisement database and generates a confirmation message containing a delivery status of the data packet set. The confirmation message includes the relevant advertisement and is transmitted to the terminal of the sender.
Owner:UNOMOBI
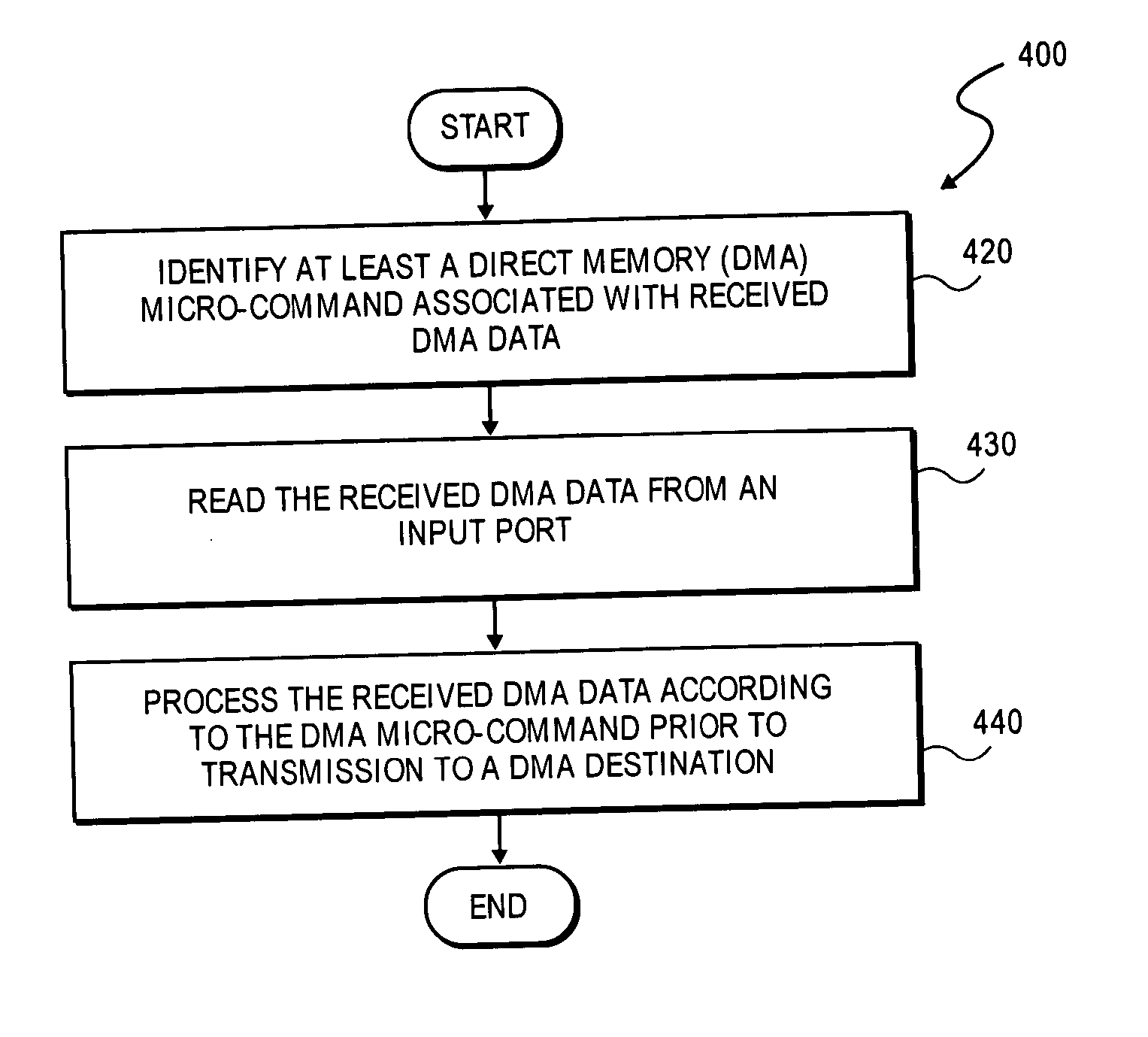
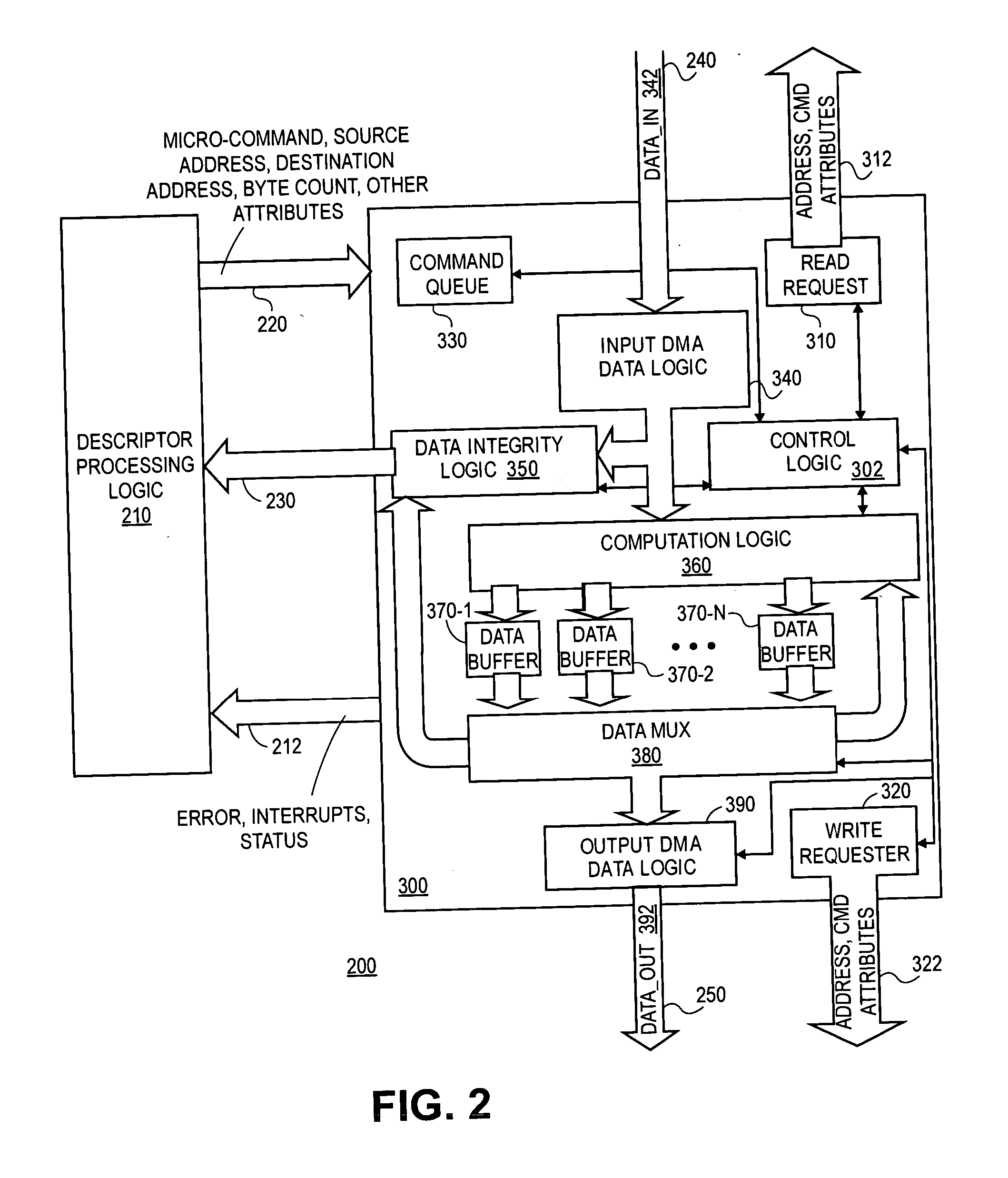
Apparatus and method for a multi-function direct memory access core
A method and apparatus for a multi-function direct memory access core are described. In one embodiment, the method includes the reading of a direct memory access (DMA) descriptor having associated DMA data to identify at least one micro-command. Once the micro-command is identified, the DMA data is processed according to the micro-command during DMA transfer of the data. In one embodiment, a DMA engine performs an operation on the DMA data in transit within the DMA controller according to the identified micro-command. Hence, by defining a primitive set of micro-commands, the DMA engine within, for example, an input / output (I / O) controller hub (ICH), can be used to perform a large number of complex operations on data when data is passing through the ICH without introducing latency into the DMA transfer. Other embodiments are described and claimed.
Owner:INTEL CORP
Autonomous signal processing resource for selective series processing of data in transit on communications paths in multi-processor arrangements
InactiveUS20040117519A1General purpose stored program computerElectric digital data processingMulti processorInterprocessor communication
A multi-processor arrangement having an interprocessor communication path between each of every possible pair of processors, in addition to I / O paths to and from the arrangement, having signal processing functions configurably embedded in series with the communication paths and / or the I / O paths. Each processor is provided with a local memory which can be accessed by the local processor as well as by the other processors via the communications paths. This allows for efficient data movement from one processor's local memory to another processor's local memory, such as commonly done during signal processing corner turning operations. Configurable signal processing logic may be configured to host one or more signal processing functions which allow data to be autonomously accessed from the processor local memories, processed, and re-deposited in a local memory.
Owner:GE FANUC EMBEDDED SYST
Latency free scanning of malware at a network transit point
In accordance with the present invention, a system, method, and computer-readable medium for identifying malware at a network transit point such as a computer that serves as a gateway to an internal or private network is provided. A network transmission is scanned for malware at a network transit point without introducing additional latency to the transmission of data over the network. In accordance with one aspect of the present invention, a computer-implemented method for identifying malware at a network transit point is provided. More specifically, when a packet in a transmission is received at the network transit point, the packet is immediately forwarded to the target computer. Simultaneously, the packet and other data in the transmission are scanned for malware by an antivirus engine. If malware is identified in the transmission, the target computer is notified that the transmission contains malware.
Owner:MICROSOFT TECH LICENSING LLC
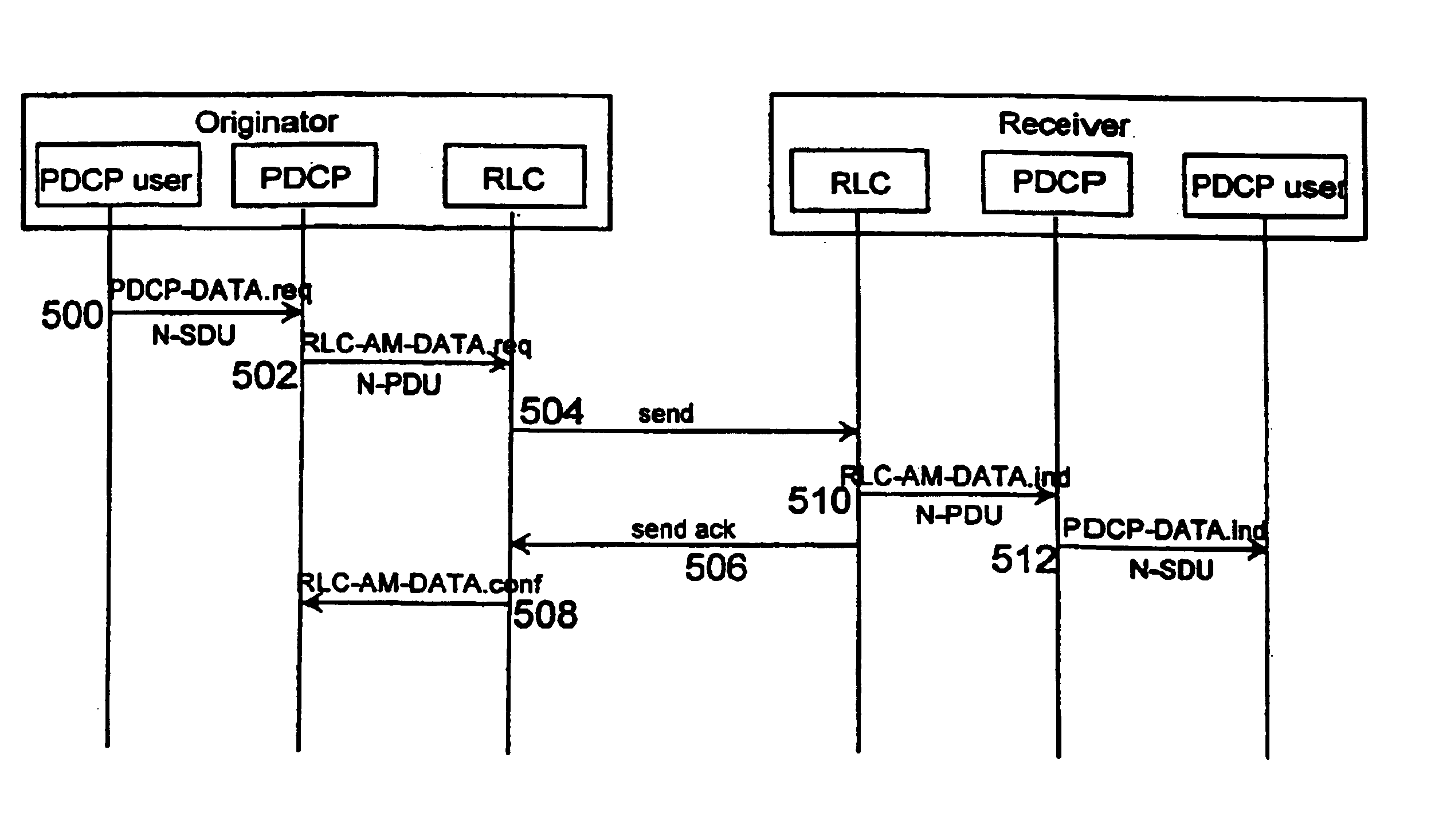
Data packet numbering in packet-switched data transmission
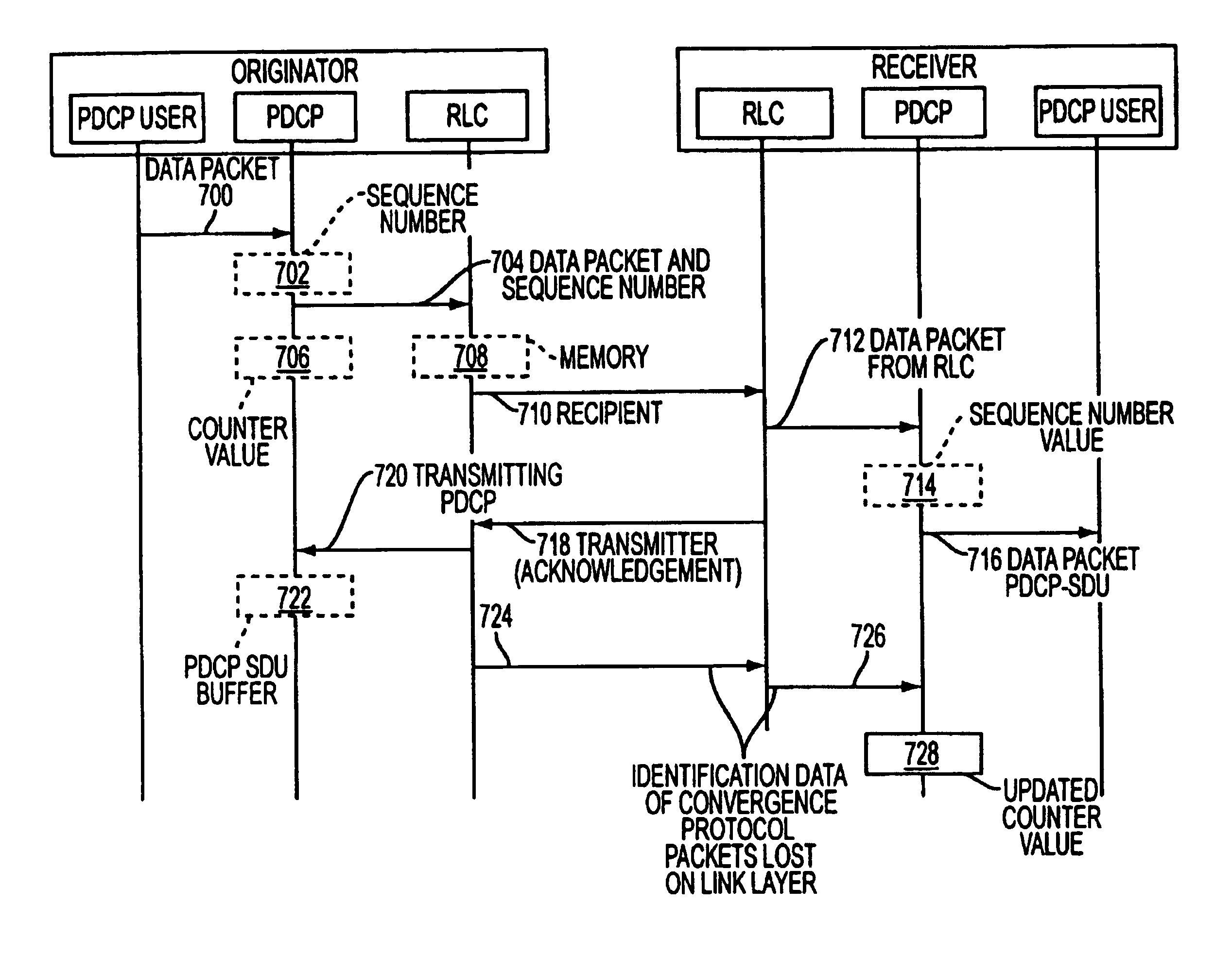
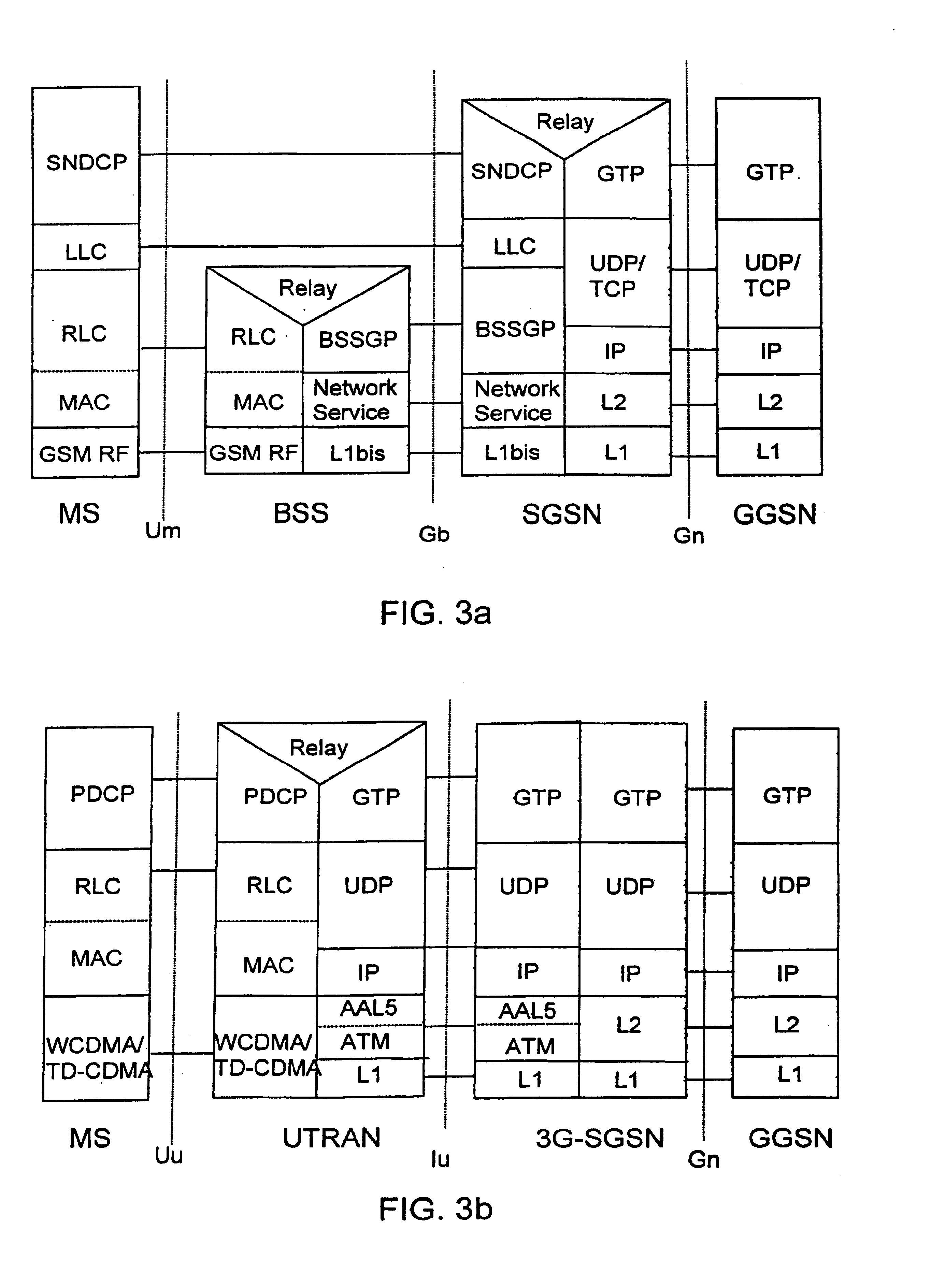
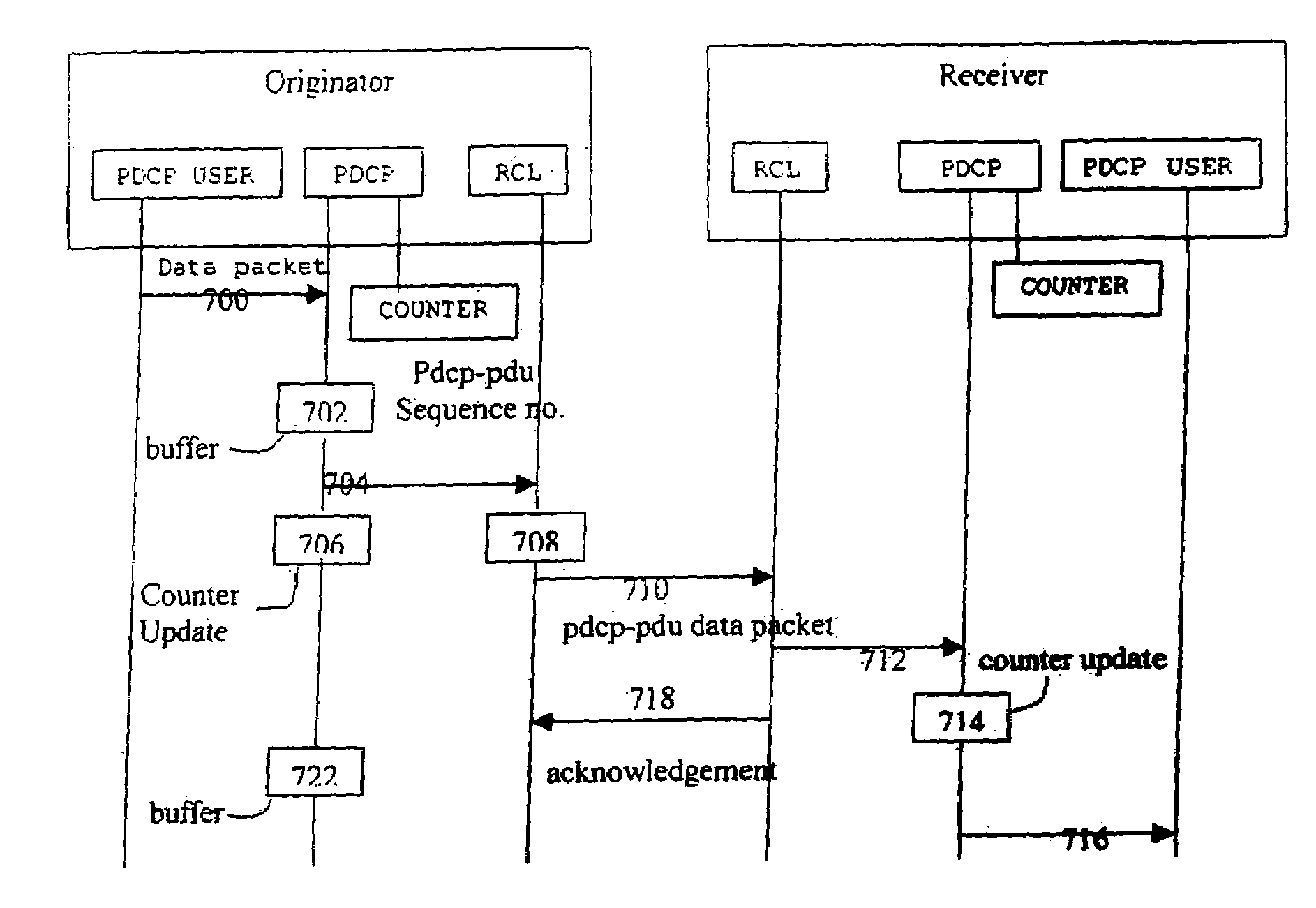
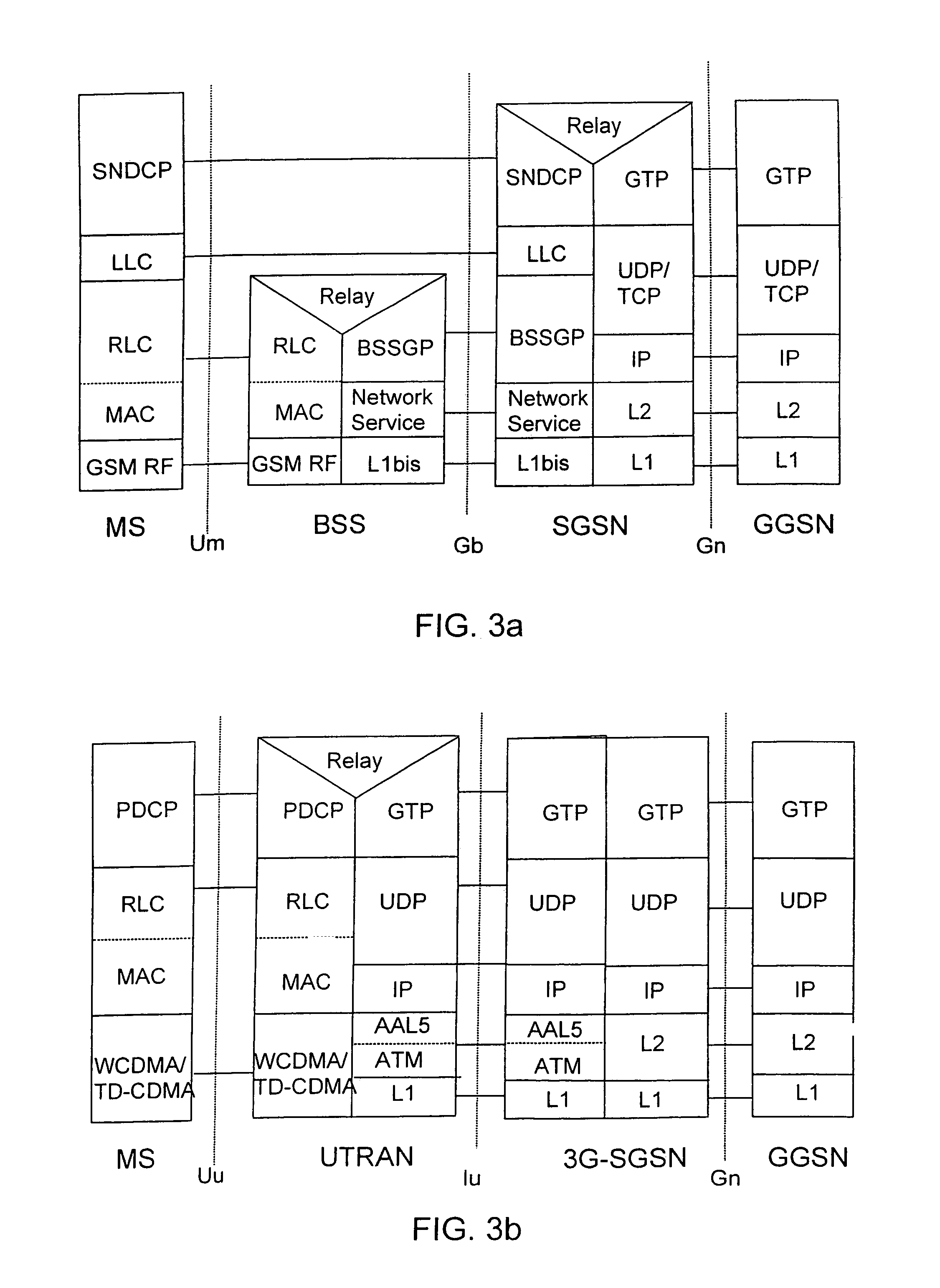
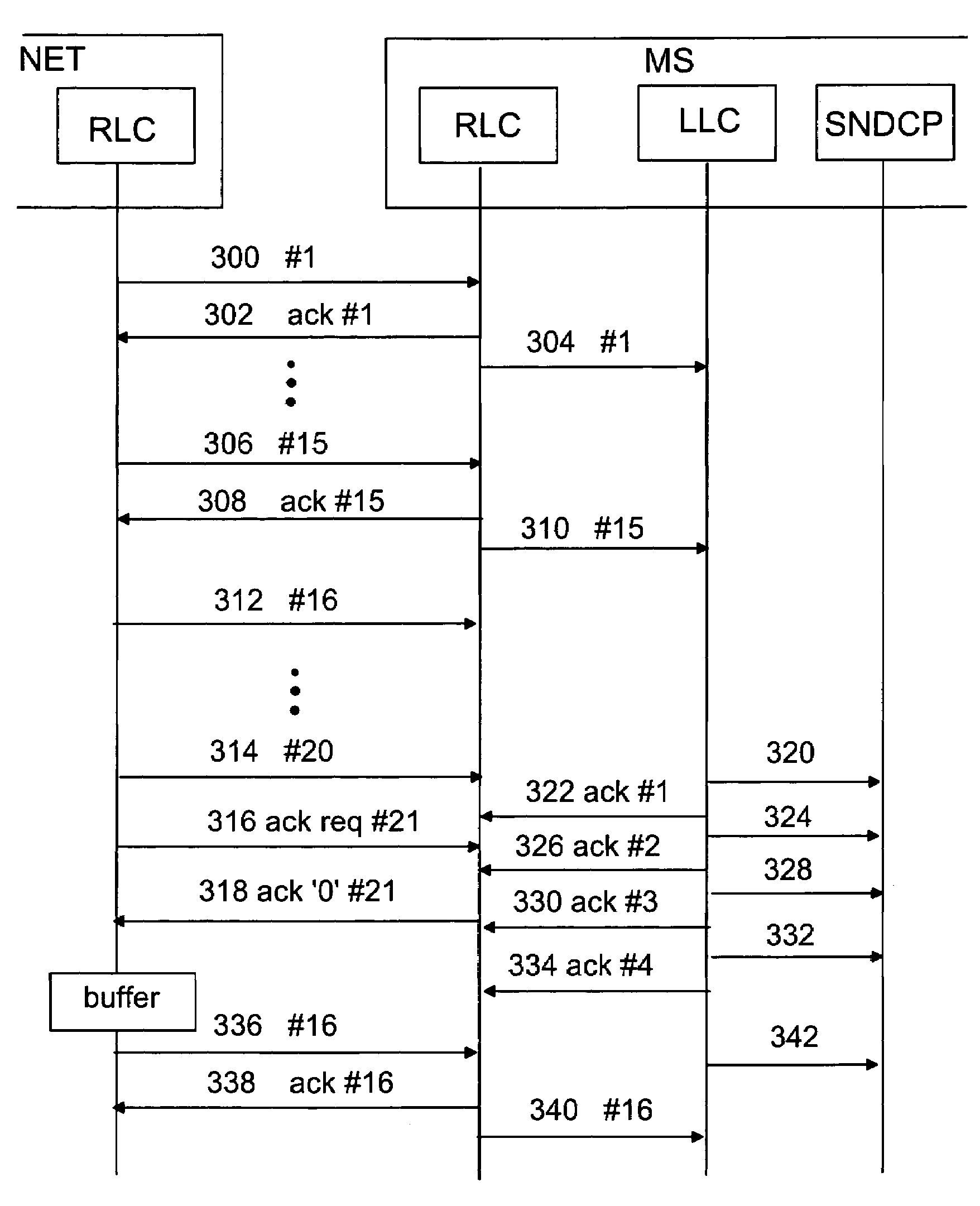
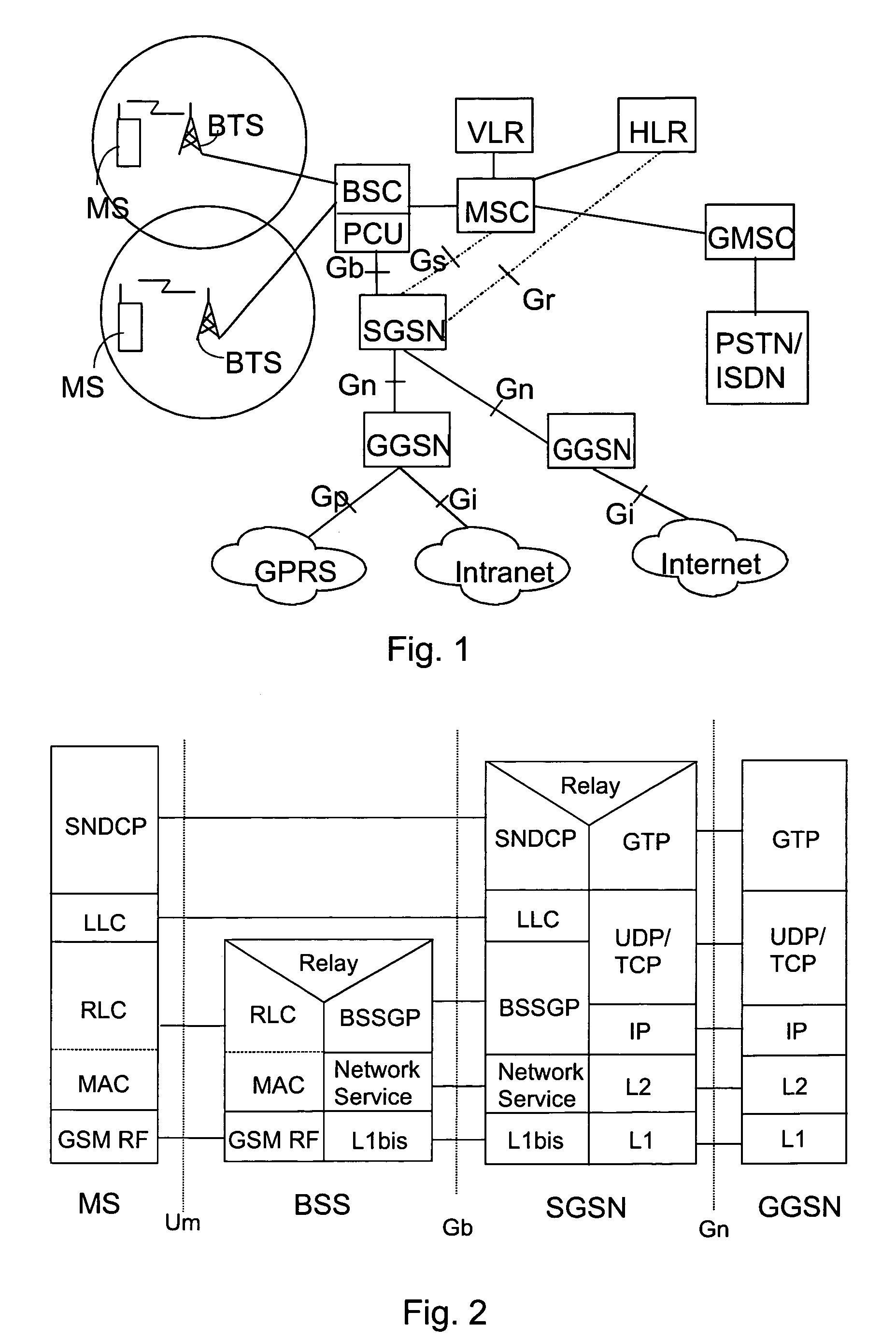
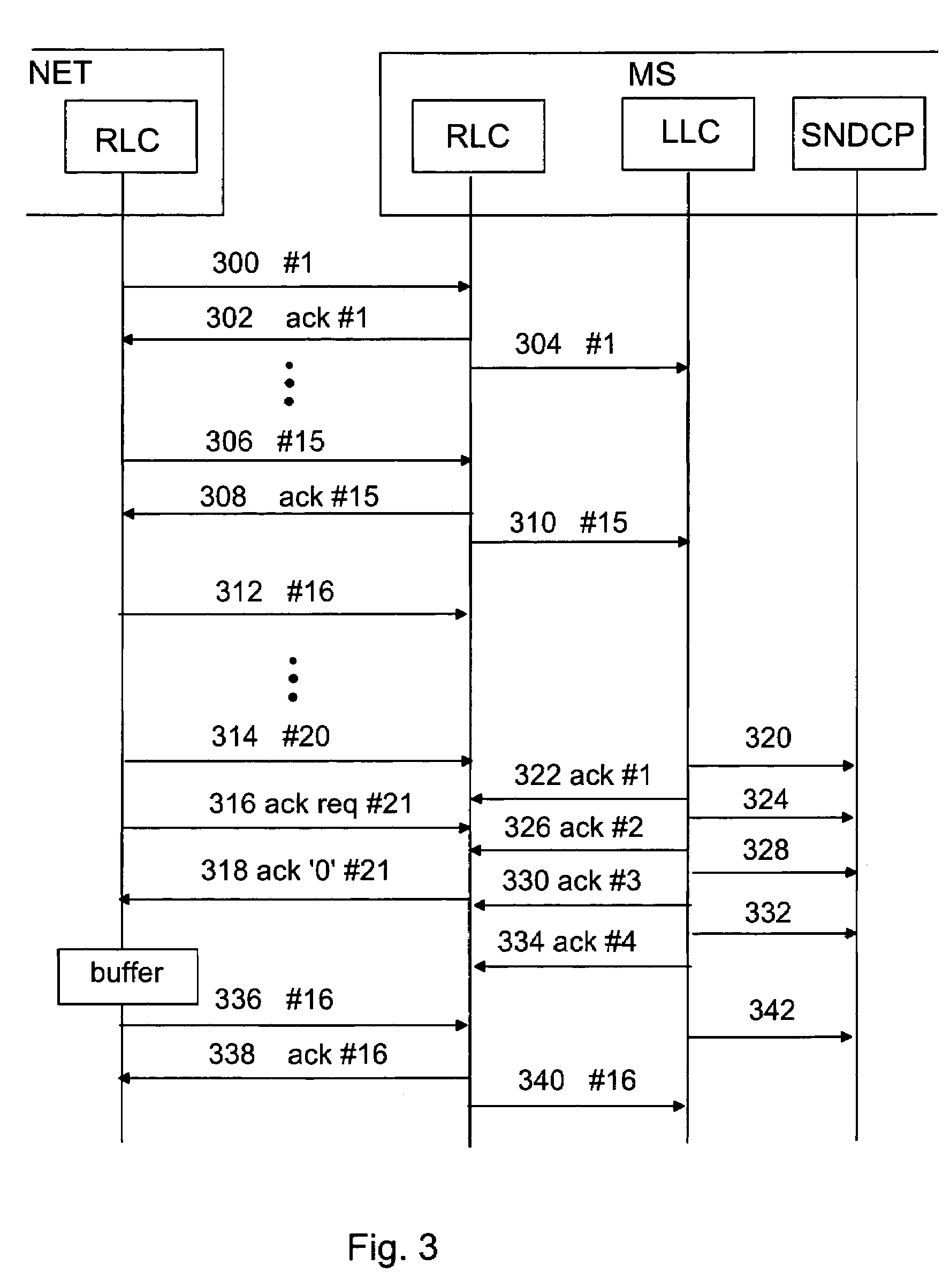
ActiveUS7167475B2Reliable data transmissionError prevention/detection by using return channelNumber-allocation/character-counting for messagesData transmissionTransmitter
A data packet transmission method in a packet-switched telecommunication system. A telecommunication protocol comprises a convergence protocol layer for adapting user data packets to convergence protocol packets and a link layer for transmitting the convergence protocol packets as data units and for acknowledging the transmission. A data packet number is defined for the convergence protocol packets to be transmitted. The convergence protocol packets are transferred to the link layer to be transmitted. A data packet number is defined for the received convergence protocol packets and the received convergence protocol packets are acknowledged to the transmitter. The identification data of any convergence protocol packets lost on the link layer are transmitted to the recipient. The counter value of the recipient is updated to correspond to the counter value of the transmitter, to take into account the lost convergence protocol packets.
Owner:QUALCOMM INC
Dynamically reacting policies and protections for securing mobile financial transaction data in transit
ActiveUS8650129B2Shorten the time to marketIncrease propensityFinanceCryptography processingSecure communicationProtection mechanism
A secure mobile financial transaction is provided by receiving, over a communication network, a list of protection mechanisms available for implementation by an external terminal. Security-related data is received from one or more sensors and an attack signature is computed based on the security-related data. An appropriate security policy is selected from multiple security policies stored in a database based on the list of protection mechanisms and the attack signature. A secure communication session is established between the external terminal and an internal network component according to the selected security policy. A data message associated with a mobile financial transaction is communicated over the communication network during the communication session.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Method and system for wireless message-based advertising
Systems and methods for message-based advertising in a wireless communications network are described. A digital message is contained in a data packet set in transit from a terminal of a sender to a terminal of a recipient. At least one of the terminals is implemented as a mobile telephone. The digital message is received through a network connection. A processor determines a context for the digital message and matches the message context to content of advertisements stored in an advertisement database in order to identify at least one relevant advertisement. The data packet set is transmitted to the terminal of the recipient. A processor retrieves the relevant advertisement(s) from the advertisement database and generates a confirmation message containing a delivery status of the data packet set. The confirmation message includes the relevant advertisement and is transmitted to the terminal of the sender.
Owner:UNOMOBI
Data packet numbering in packet-switched data transmission
InactiveUS6930980B2Reliable data transmissionError preventionFrequency-division multiplex detailsTelecommunications networkNetwork packet
A method and a telecommunication system for data packet numbering in packet-switched data transmission in connection with a handover, in which the responsibility for a connection is transferred from the connection between a mobile station and a first wireless telecommunication network to the connection between said mobile station and a second wireless telecommunication network. In the first wireless telecommunication network a data packet number space available for data packet numbering is bigger than a data packet number space of the second wireless telecommunication network. Data packet numbering is restricted in the first wireless telecommunication network such that the numbers of the data packets of the first wireless telecommunication network do not exceed the maximum value of the data packet number space of the second wireless telecommunication network.
Owner:CORE WIRELESS LICENSING R L
Data packet numbering in mobile packet switched data transmission
InactiveUS7009951B2Guaranteed data transferError prevention/detection by using return channelNumber-allocation/character-counting for messagesData transmissionTransmitter
A method of numbering data packets in a packet-switched telecommunications system which utilizes acknowledged transmission and the telecommunications protocol of which comprises a convergence protocol layer for converting user data packets into convergence protocol packets, and a link layer for transmitting convergence protocol packets as data units and for acknowledging the transmission. A data packet number is defined for the convergence protocol packets to be sent by a counter and the convergence protocol packets to be sent are transmitted to the link layer for transmission without the data packet number. A data packet number is also defined for received convergence protocol packets by means of the counter and an acknowledgement of received convergence protocol packets is transmitted to the transmitter.
Owner:NOKIA TECHNOLOGLES OY
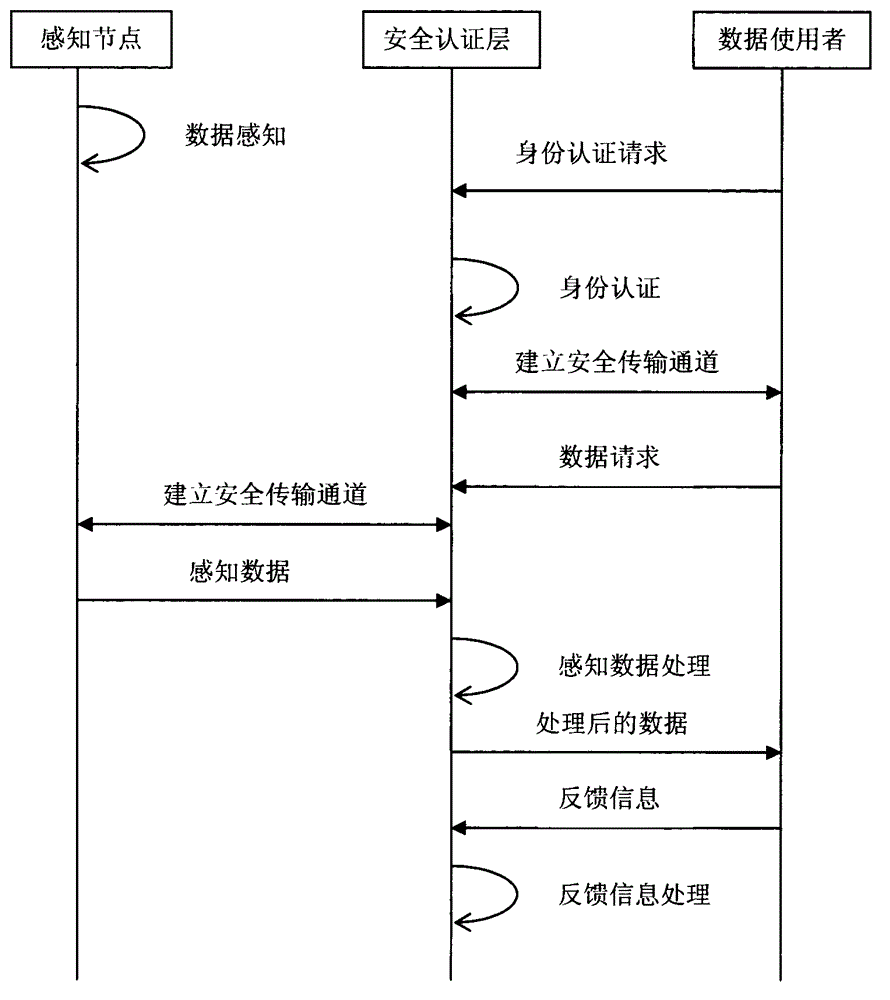
Internet of things data security method based on security certificate
InactiveCN103067171AImprove securityEnsure safetyUser identity/authority verificationUser needsIdentity recognition
The invention discloses an Internet of things data security method based on security certificate. The method includes the following steps: (1) sending an identity authentication request to a security certificate layer when a data user needs to perceive data; (2) establishing secure transmission channel between the security certificate layer and the data user through the certificate to receive a data request from the data user; and (3) obtaining perception data from a perception node by the security certificate layer, processing the perception data, and sending the processed data to the data user. According to the Internet of things data security method based on the security certificate, the security certificate layer is added between the perception node and the user, the purpose of user identity recognition is achieved, and the fact that important Internet of things data are accessed illegally by the user can be effectively avoided. Meanwhile, the perception data can also be encrypted in the transmitting process, and thus data security in the transmitting process is ensured.
Owner:WUXI CINSEC INFORMATION TECH
Content-based segmentation scheme for data compression in storage and transmission including hierarchical segment representation
In a coding system, input data within a system is encoded. The input data might include sequences of symbols that repeat in the input data or occur in other input data encoded in the system. The encoding includes determining a target segment size, determining a window size, identifying a fingerprint within a window of symbols at an offset in the input data, determining whether the offset is to be designated as a cut point and segmenting the input data as indicated by the set of cut points. For each segment so identified, the encoder determines whether the segment is to be a referenced segment or an unreferenced segment, replacing the segment data of each referenced segment with a reference label and storing a reference binding in a persistent segment store for each referenced segment, if needed. Hierarchically, the process can be repeated by grouping references into groups, replacing the grouped references with a group label, storing a binding between the grouped references and group label, if one is not already present, and repeating the process. The number of levels of hierarchy can be fixed in advanced or it can be determined from the content encoded.
Owner:RIVERBED TECH LLC
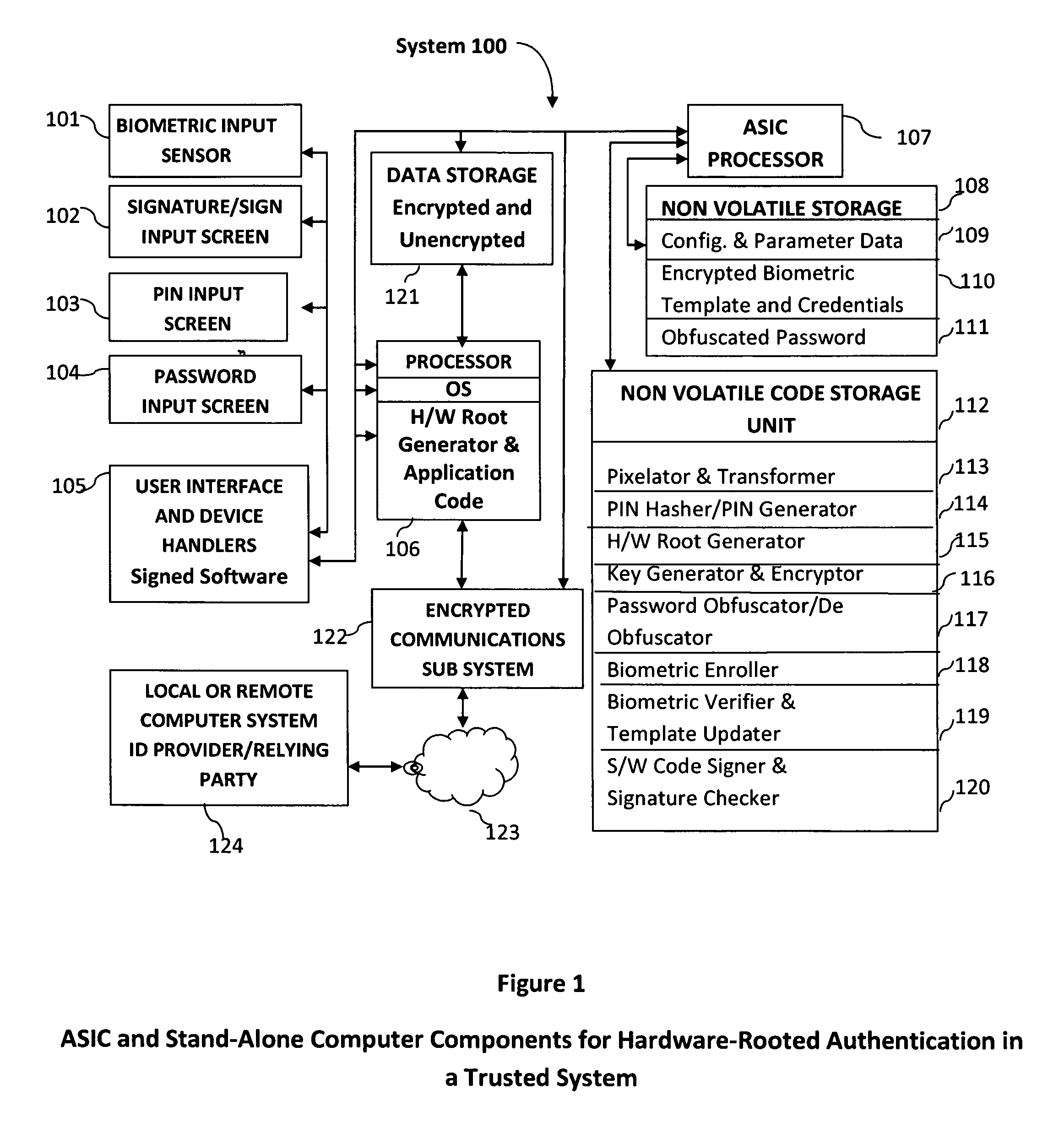
Method and system for providing password-free, hardware-rooted, ASIC-based authentication of a human to a mobile device using biometrics with a protected, local template to release trusted credentials to relying parties
InactiveUS9286457B2Significant productivityMaximum safetyKey distribution for secure communicationUser identity/authority verificationBiometric dataPassword
Biometric data are obtained from a biometric sensor on a mobile device, containing an ASIC, which is connected to or incorporated within it. The mobile device and ASIC, in combination or individually, capture biometric samples, extract biometric features and match them to a locally stored, encrypted template. For extra security, the biometric matching may be enhanced by the use of an entered PIN. The biometric template and other sensitive data are encrypted using hardware elements of the mobile device and ASIC, together with a PIN hash. A stored obfuscated Password is de-obfuscated and released to the mobile device authentication mechanism in response to a successfully decrypted template and matching biometric sample. A different de-obfuscated password may be released to authenticate the user to a remote computer and to encrypt data in transit. The system eliminates the need for the user to remember and enter complex passwords on the mobile device.
Owner:BIOCRYPT ACCESS LLC
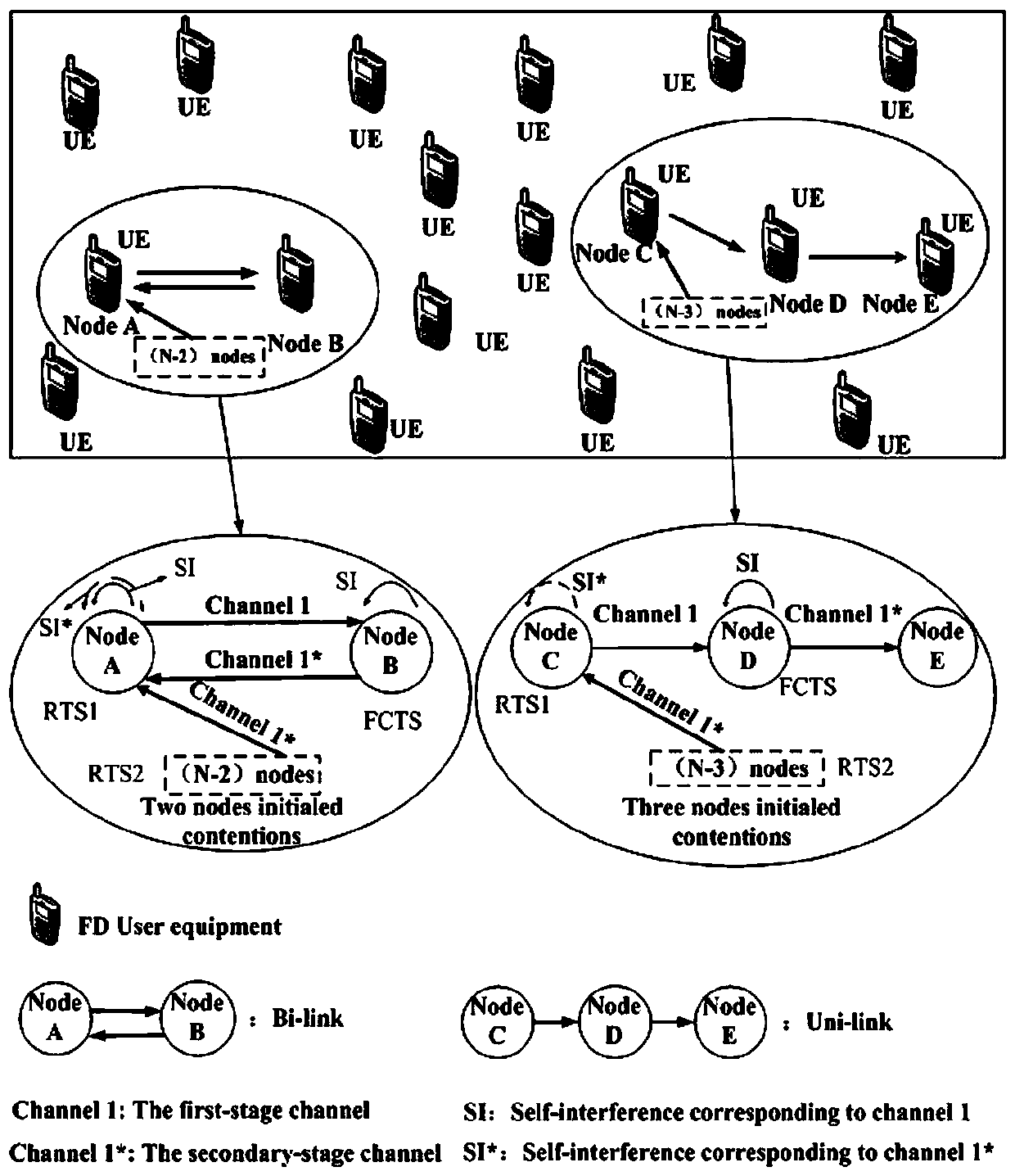
Two-stage competition-based MAC (media access control) protocol method in full duplex wireless network
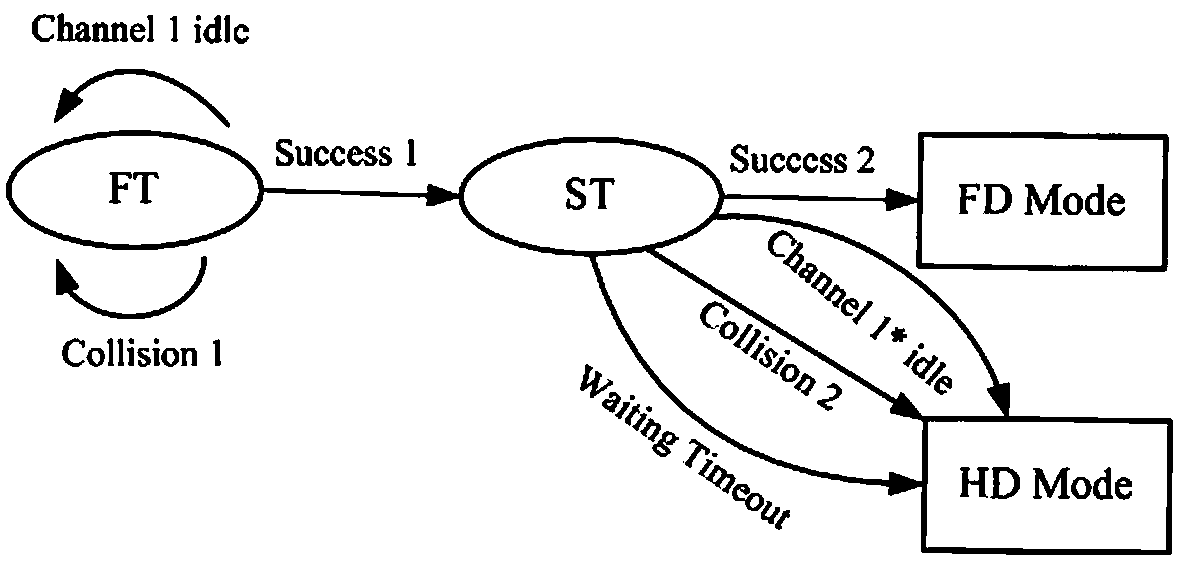
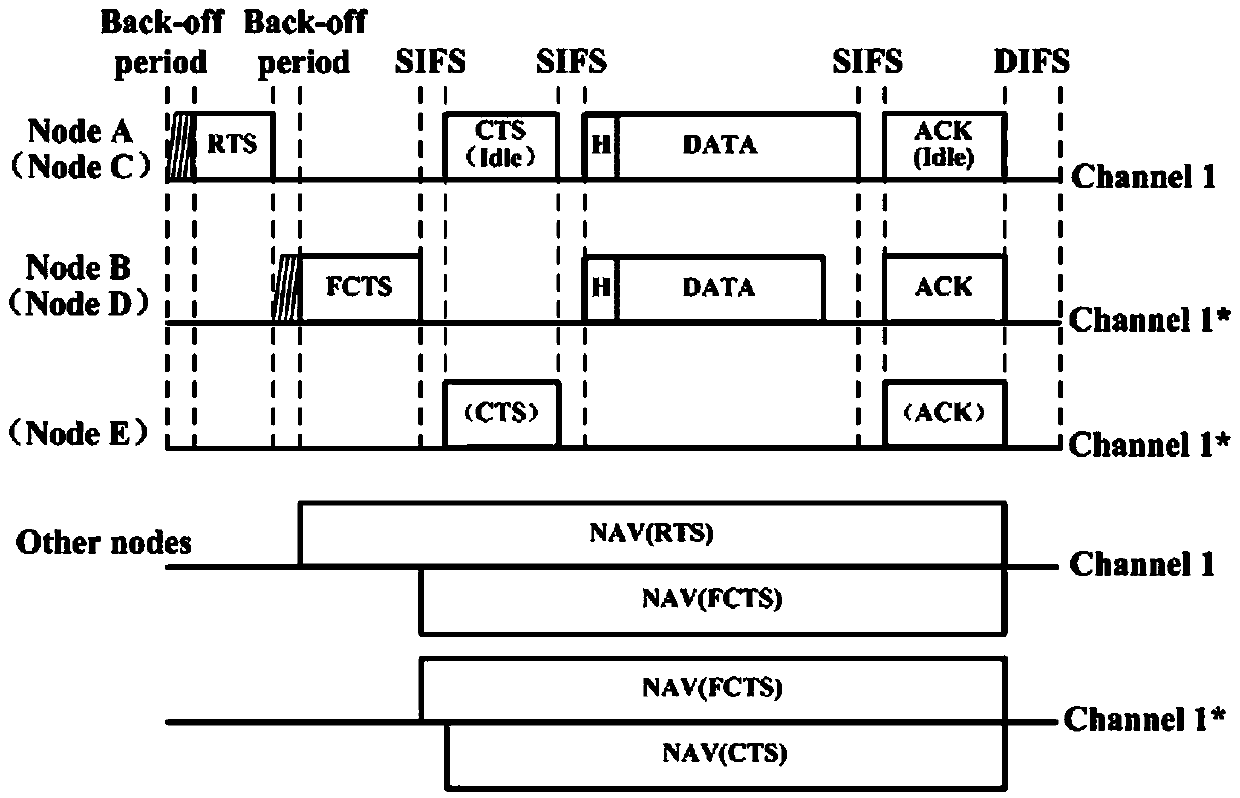
ActiveCN107666489ASolve the problem of hidden nodesExcellent throughputDuplex signal operationMarkov chainHidden node problem
The invention discloses a two-stage competition-based MAC (media access control) protocol method in a full duplex wireless network, and proposes a method using a two-stage competition-based TF-MAC protocol to optimize the full duplex wireless network throughput; the control protocol comprises a RTS / FCTS / CTS handshake mechanism and a full duplex back off algorithm, thus solving the hidden node problems in the full duplex network, and reducing data frame bumping in the first stage transmission and the second node transmission; the method is suitable for a two-node symmetrical full duplex link and a three-node asymmetric full duplex link; the method can select three types of competition node transmission probabilities so as to obtain the optical throughput of the full duplex wireless network;the method uses a cascade two dimensional Markov chain model to analyze the performance of the full duplex wireless network employing the TF-MAC protocol, thus obtaining a full duplex wireless network throughput enclosed expression, and using the simulation result to verify the validity of the proposed TF-MAC protocol.
Owner:XIDIAN UNIV
Method and System for Wireless Message-Based Advertising
Systems and methods for message-based advertising in a wireless communications network are described. A digital message is contained in a data packet set in transit from a terminal of a sender to a terminal of a recipient. At least one of the terminals is implemented as a mobile telephone. The digital message is received through a network connection. A processor determines a context for the digital message and matches the message context to content of advertisements stored in an advertisement database in order to identify at least one relevant advertisement. The data packet set is transmitted to the terminal of the recipient. A processor retrieves the relevant advertisement(s) from the advertisement database and generates a confirmation message containing a delivery status of the data packet set. The confirmation message includes the relevant advertisement and is transmitted to the terminal of the sender.
Owner:UNOMOBI
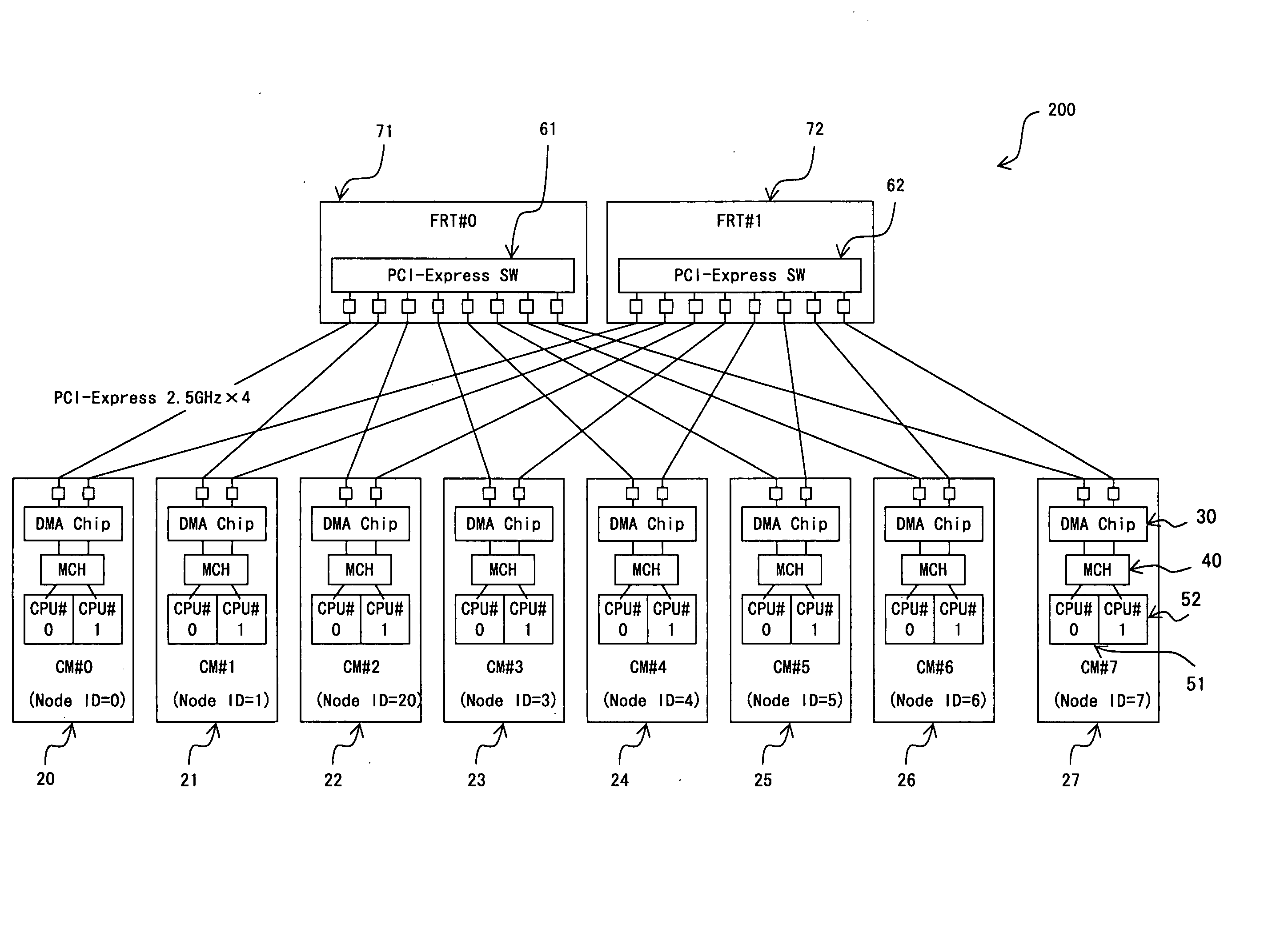
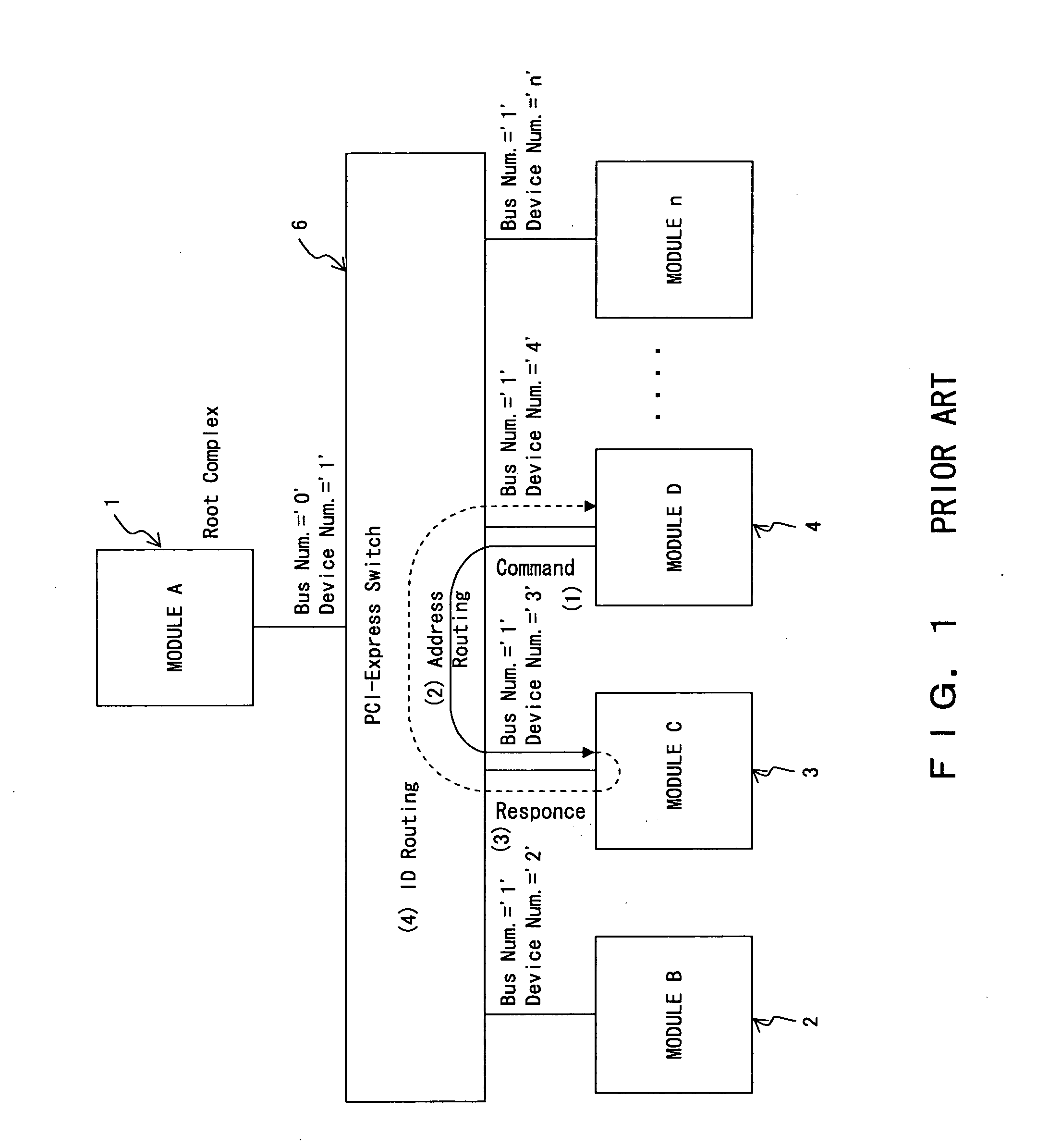
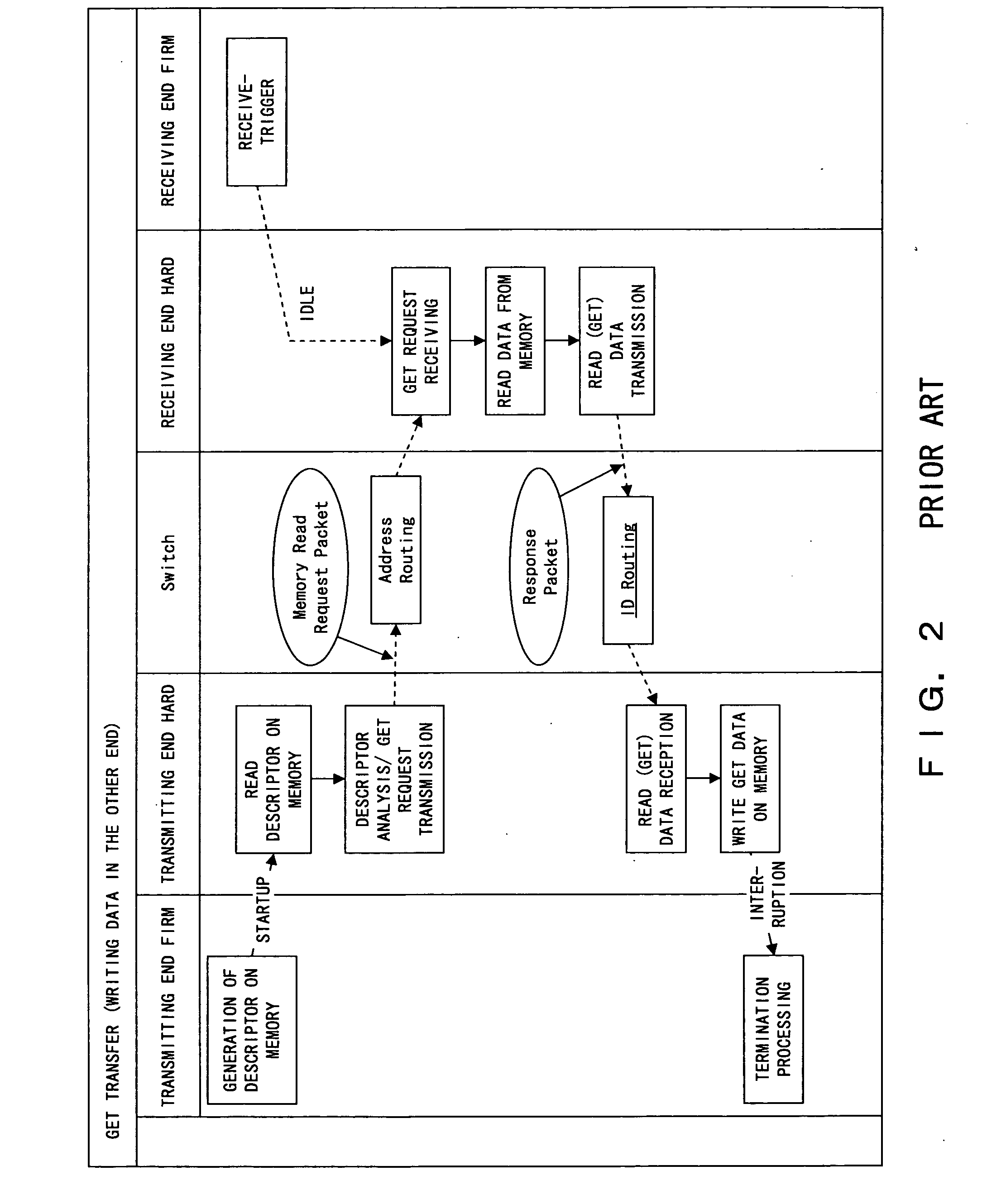
PCI-Express communications system
ActiveUS20070073960A1Digital computer detailsElectric digital data processingCommunications systemPCI Express
To be able to transmit a response packet to the original request node after a bus ID / a device ID is replaced in the PCI-Express switch for a PCI-Express communication system, a unique node ID for indicating each node is set to the nodes. Additionally, it is confirmed whether or not the packet is transferred in the correct order in a series of packet transfers. For that purpose, a sequence code indicating the sequence number of a packet in a series of packet transfer is set in an address field of a packet of data transfer.
Owner:FUJITSU LTD
Device and method of recognizing at least one individual, the corresponding access control device and system and applications thereof
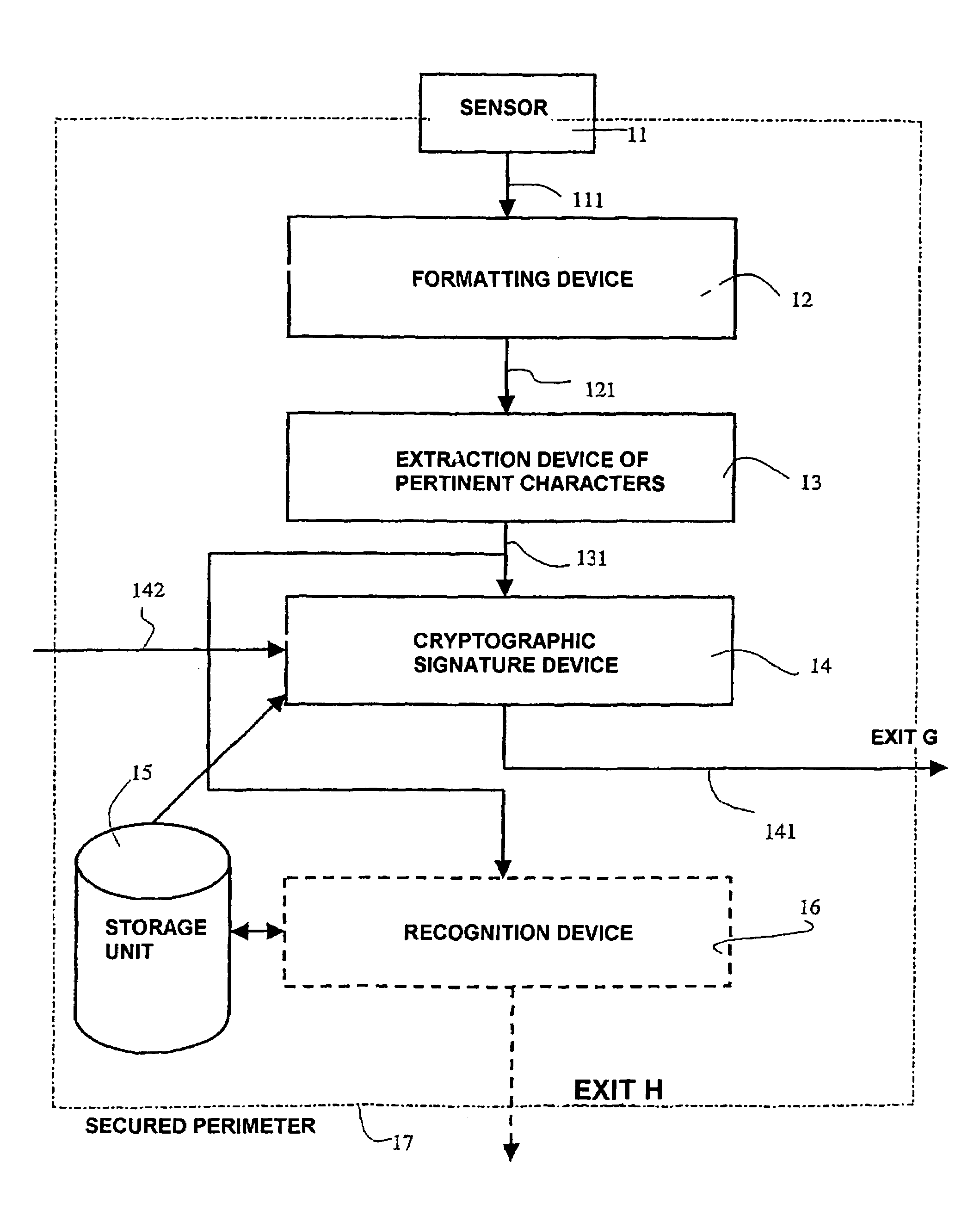
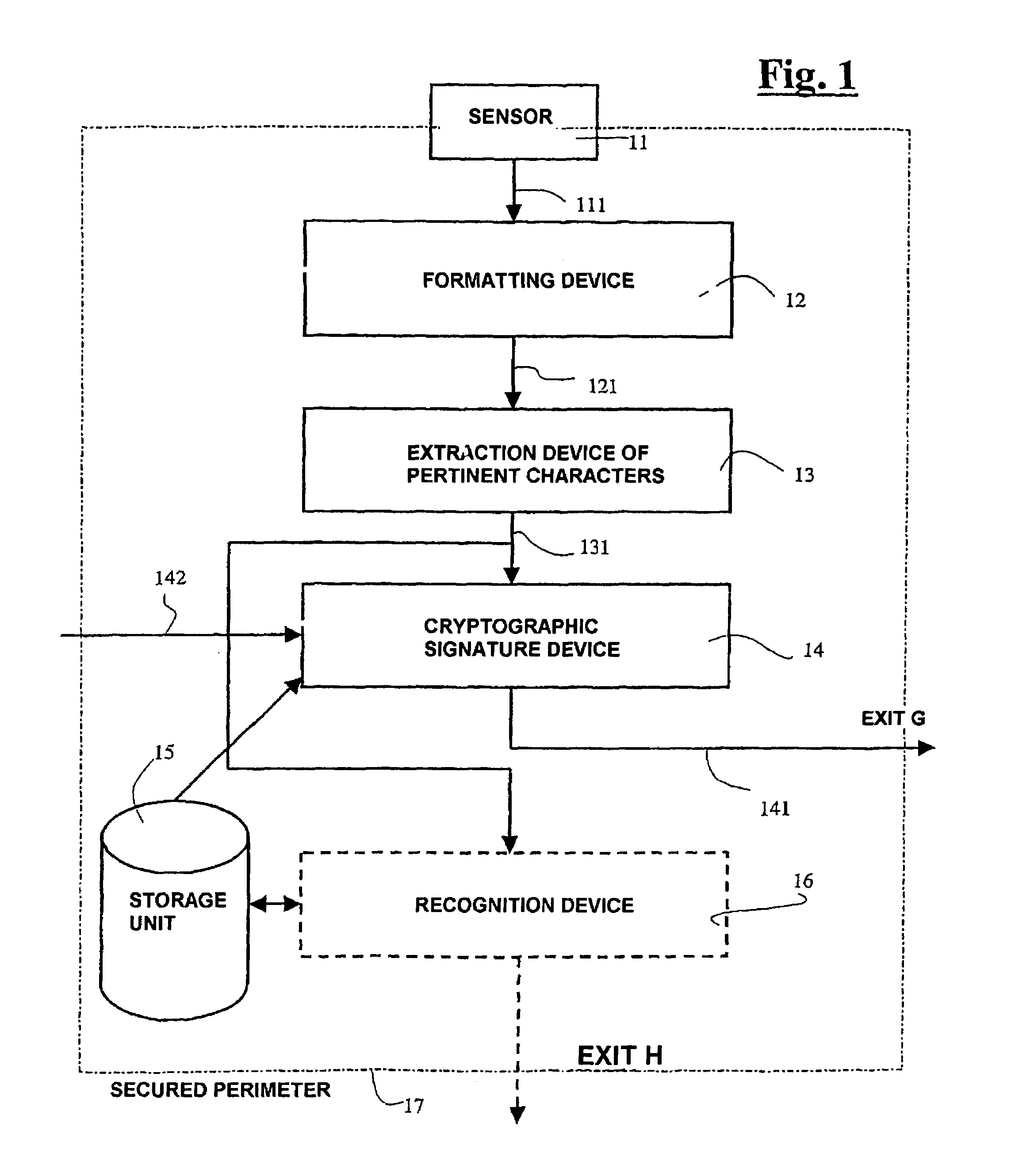
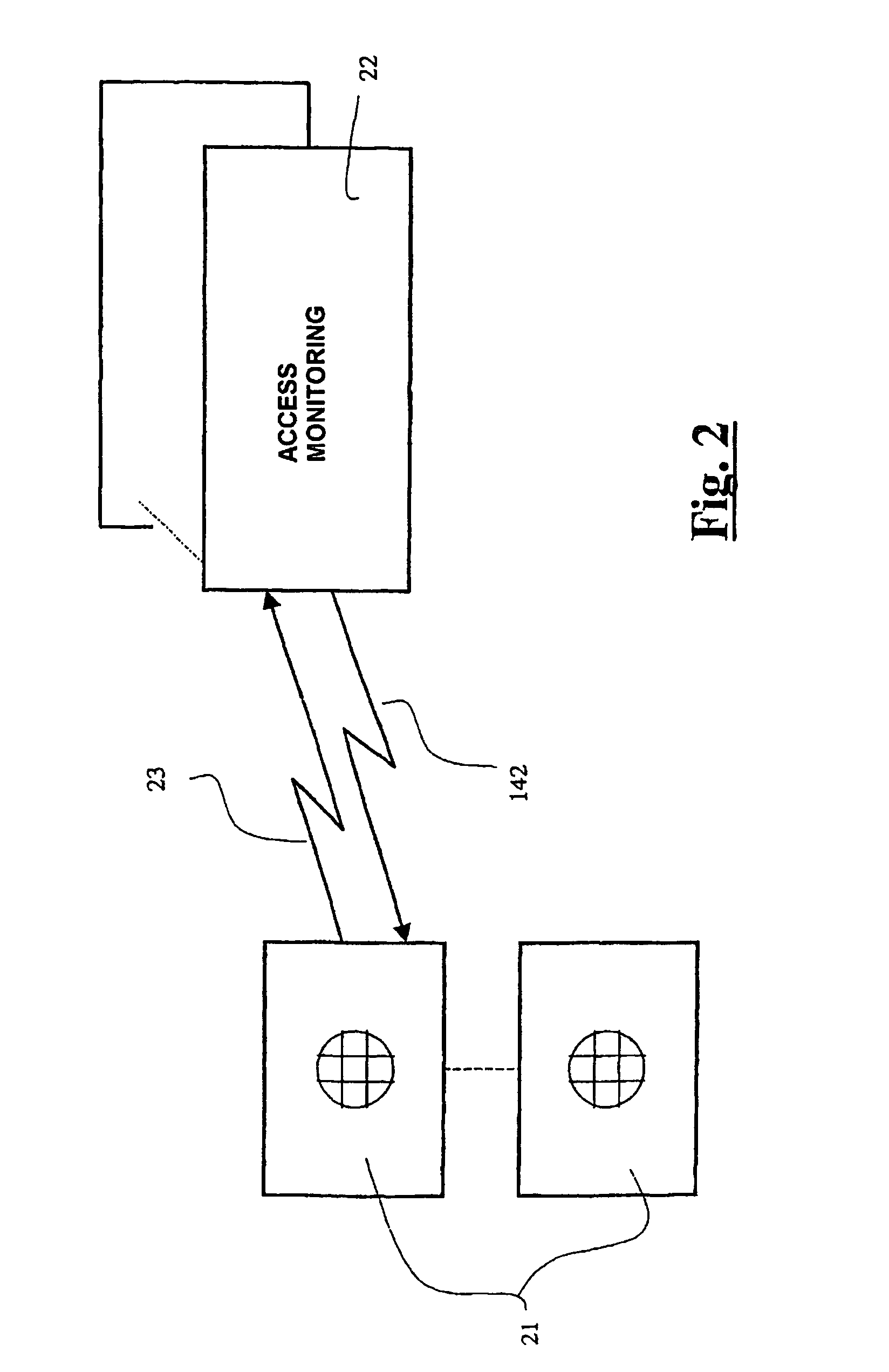
InactiveUS7255269B2Guaranteed efficiencyEasy to implementElectric signal transmission systemsDigital data processing detailsIdentification deviceSilicon
The invention relates to a device and method for the recognition of at least one individual and to the corresponding access control device and system and application thereof. The inventive recognition device comprises a one-piece integrated circuit which is produced by integrating the following elements on a silicon substrate: at least one biometric information sensor; means of processing said biometric information; cryptographic means which deliver at least one piece of encrypted data that is representative of at least one part of said biometric information and / or a corresponding piece of recognition information; and protection means that block access to data in transit, stored and / or processed in said one-piece integrated circuit in order to create a secure perimeter. In this way, the data exchanged by said sensor(s), processing means and cryptographic means, and particularly the aforementioned biometric information, are only saved in the one-piece integrated circuit and cannot be accessed from outside. Moreover, only encrypted data are delivered to the outside from said one-piece integrated circuit.
Owner:APPLE INC
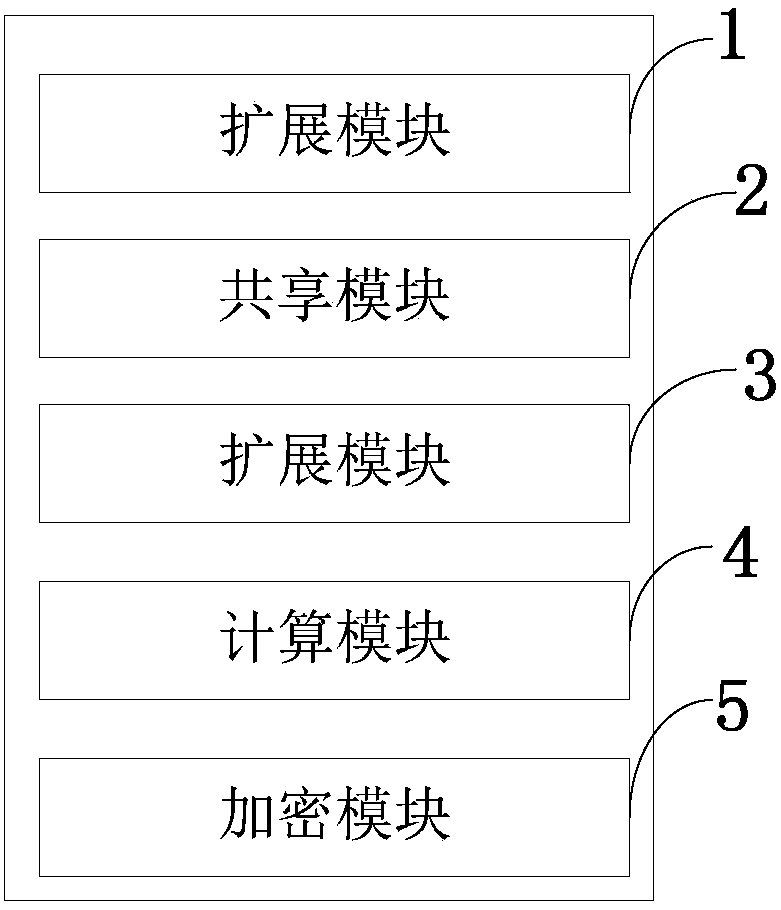
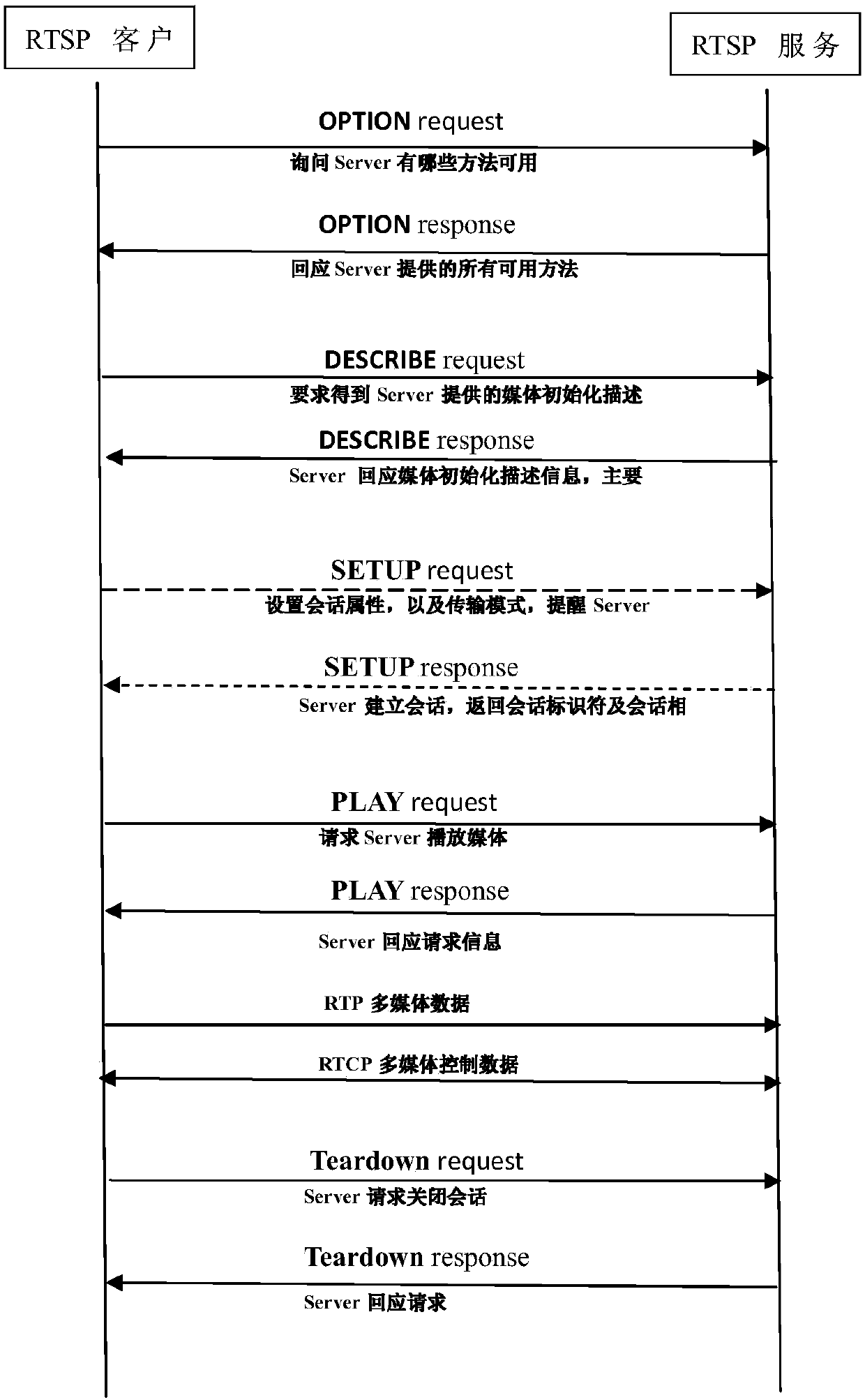
Key negotiation method and system for video surveillance system and computer
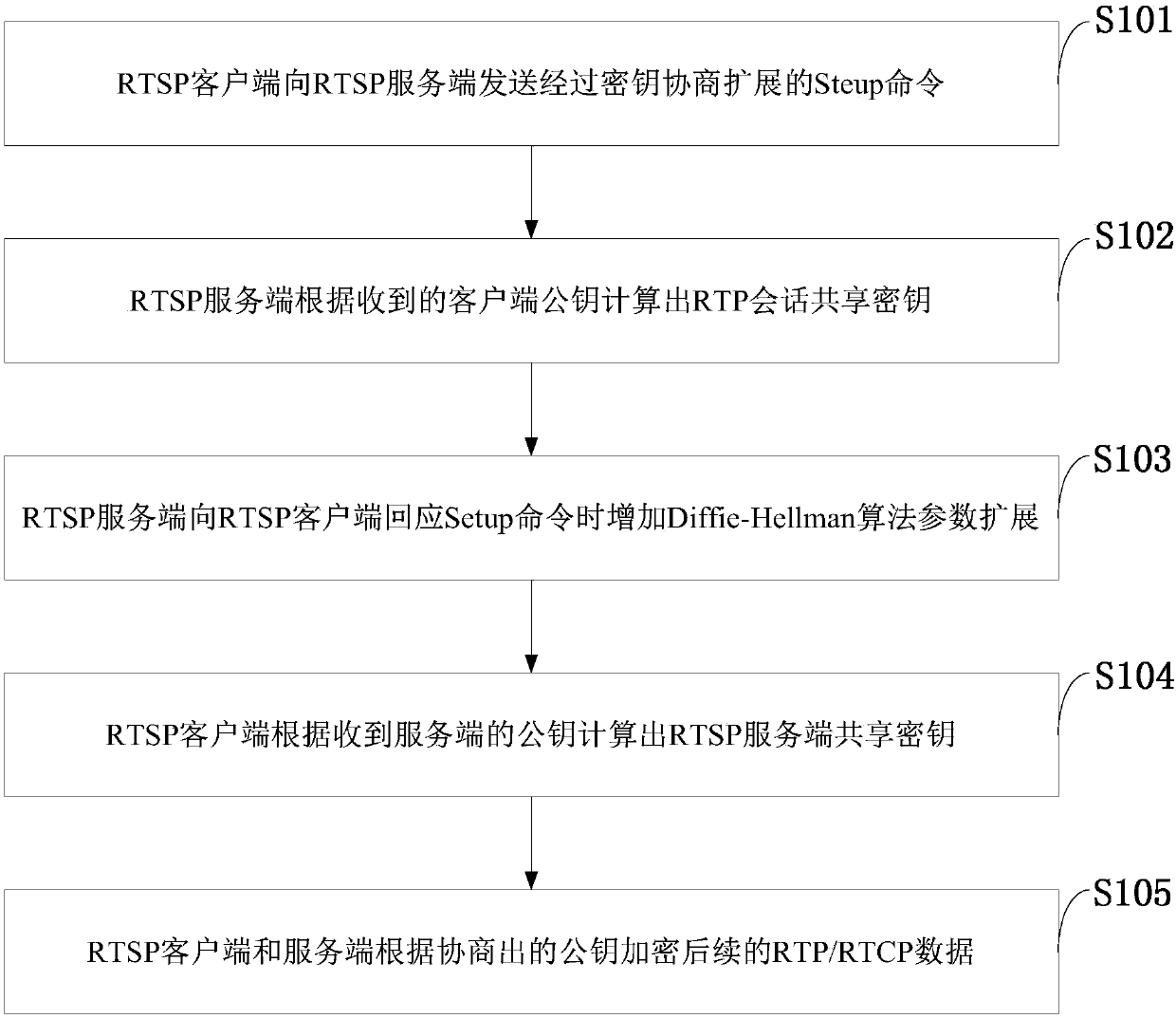
InactiveCN108040269AReduce the impactEasy to implementKey distribution for secure communicationPublic key for secure communicationVideo monitoringControl data
The invention belongs to the technical field of audio / video data processing and discloses a key negotiation method and system for a video surveillance system and a computer. An RTSP signal is expanded, when an RTSP session is established, a key employed by an RTP / RTCP message is negotiated, and the negotiated key is used for encrypting audio / video and control data in RTP / RTCP data transmission. According to the method, the system and the computer, the RTSP signal is expanded, when the RTSP session is established, a shared key required for encrypting and decrypting a follow-up RTP / RTCP messageis negotiated, and the key is used for encrypting and decrypting the data in whole RTP / RTCP data transmission. For an existing system, only newly increased expansion parameter processing needs to be carried out, and the shared key can be calculated based on public key information exchanged from signal interaction between an RTSP client and a server through utilization of a Diffie-Hellman algorithm. The existing system is influenced a little. The realization is easy. The negotiated key is used for encrypting the RTP / RTCP data in transmission.
Owner:XIAN UNIV OF POSTS & TELECOMM
Operation interruption control system for a communication network router
A system is dedicated to controlling interruption of the operation of a router of an Internet protocol communication network. The system comprises observation means which, in the event of reception of an instruction to observe IP datagrams in transit received by the router, deliver an alert signal in case of absence of detection of IP datagrams during a first selected time period. It further comprises control means which, if it is required to interrupt the operation of the router, instruct processing means to generate outgoing warning messages to other routers reporting the withdrawal of routes for routing of IP datagrams by the router, instruct the observation means to commence an observation, and authorize interruption of the operation of the router in the event of reception of an alert signal from the observation means.
Owner:ALCATEL LUCENT SAS
Data packet transfer restrictions in packet-switched data transmission
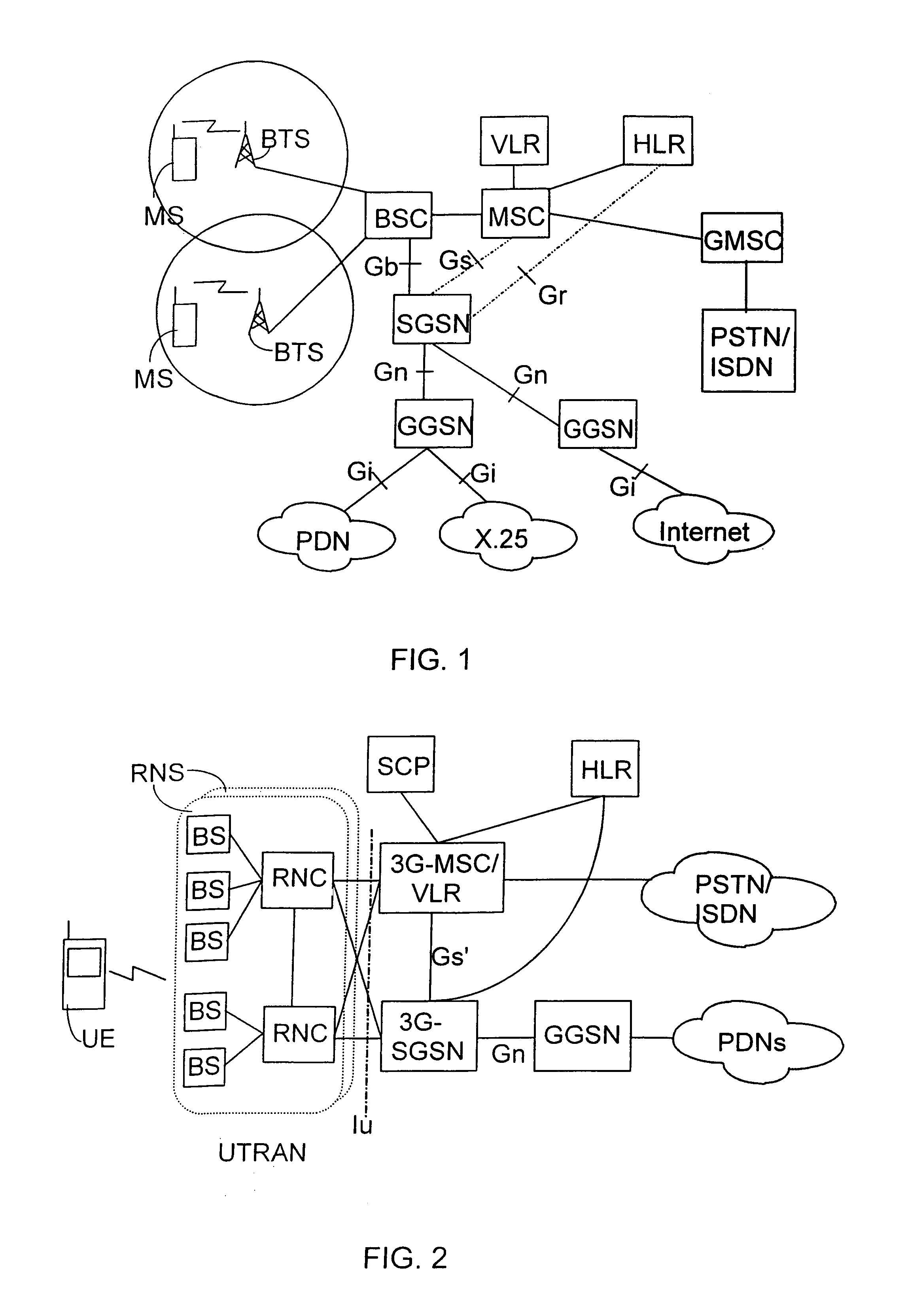
InactiveUS7321574B2Less processing capacityThe right amountError prevention/detection by using return channelTransmission systemsTelecommunications networkMobile station
A method of data packet handling in data transmission between a mobile station and a wireless telecommunication network, comprising protocol layers of a LLC layer for handling control information of data packet transmission and a RLC layer for transmitting the data packets between the mobile station and the network. A plurality of the RLC data units, received from the network, are transferred to the LLC as LLC PDUs and if a high load situation caused by the transfer of the LLC PDUs to the LLC layer is detected, the operation of the RLC layer is intermitted until a number of LLC PDUs has been acknowledged by the LLC layer. When the transfer of the LLC PDUs to the LLC layer is intermitted, also the acknowledgements of RLC PDUs on RLC layer between the mobile station and the wireless telecommunication network are intermitted.
Owner:NOKIA CORP
Wireless remote control smart ball
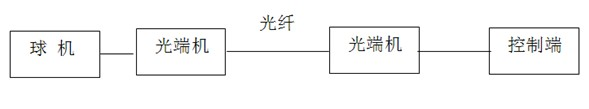
InactiveCN102291535AAvoid lossEasy to controlTelevision system detailsTransmission systemsMicrocontrollerMonitoring site
A wireless remote control smart ball, including: a dome camera, referred to as a dome machine, installed on the monitoring site, collecting video signals in the area, and transmitting the collected signals back to the monitoring system in the background; In the camera, according to the external control command, it sends an execution command to the spherical camera, and also includes a short message sending and receiving module and a data analysis module, wherein the short message sending and receiving module sends and receives short messages through the wireless communication network and the user's mobile phone; Connect with the microcontroller MCU separately, convert and parse the received text messages into control instructions, and control the work of the dome camera. The wireless remote control smart ball of the present invention realizes the control of the ball machine in the ultra-long-distance environment through the public wireless communication network, avoids the loss of data in the long-distance wired transmission, improves the reliability of the ball machine operation, and reduces the The cost of ultra-long distance wireless remote control ball machine.
Owner:TIANJIN TIANDY DIGITAL TECH
Packet sticking and splicing method based on protocol transmission
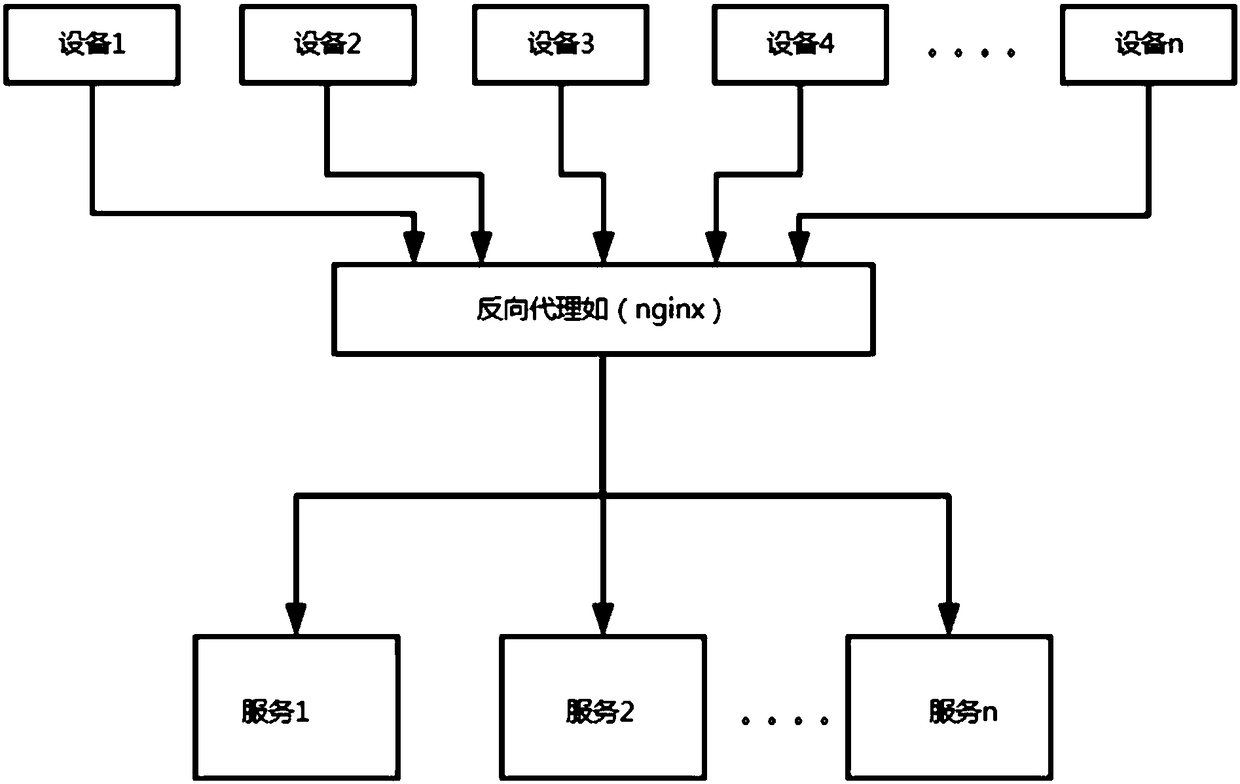
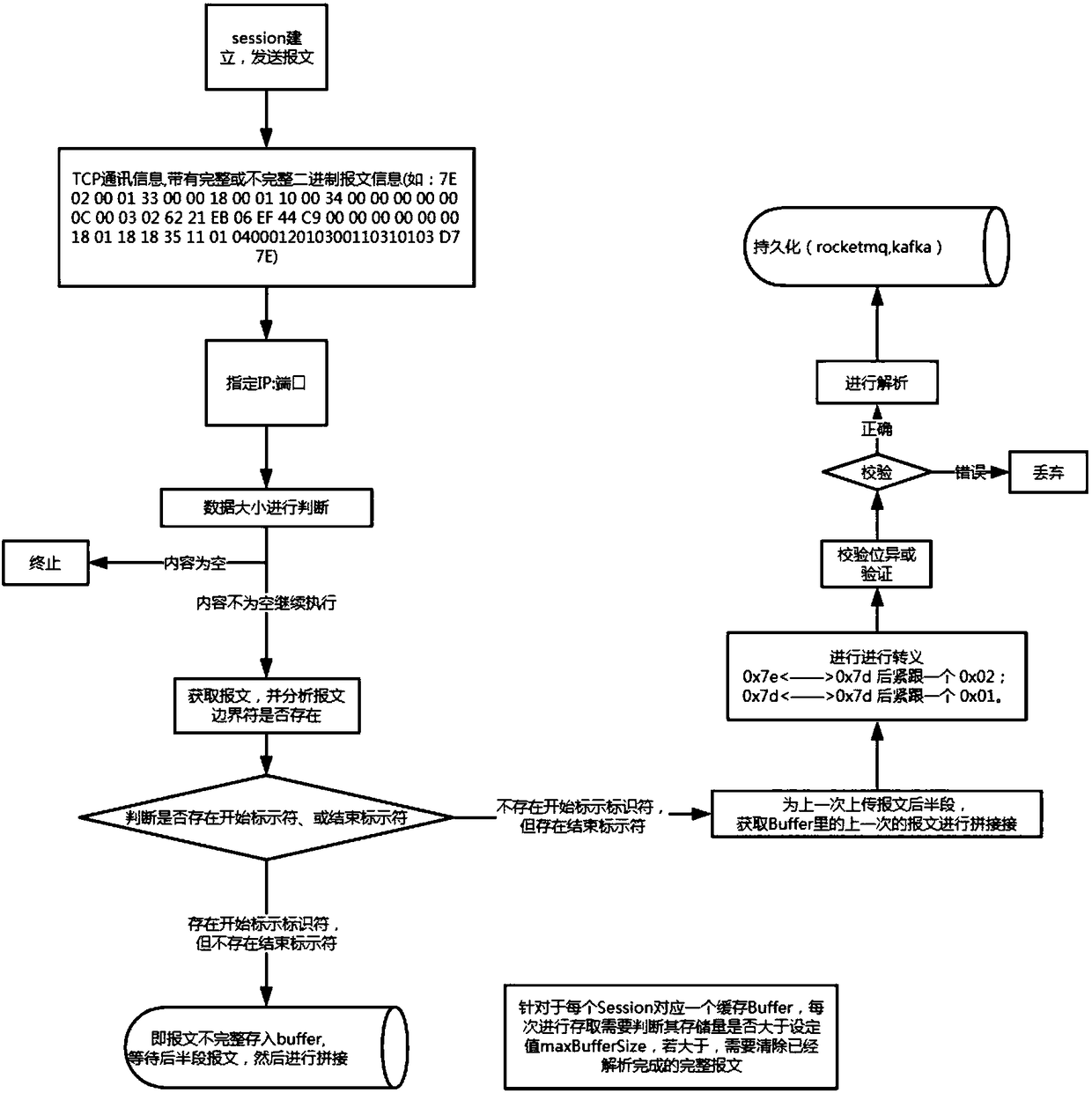
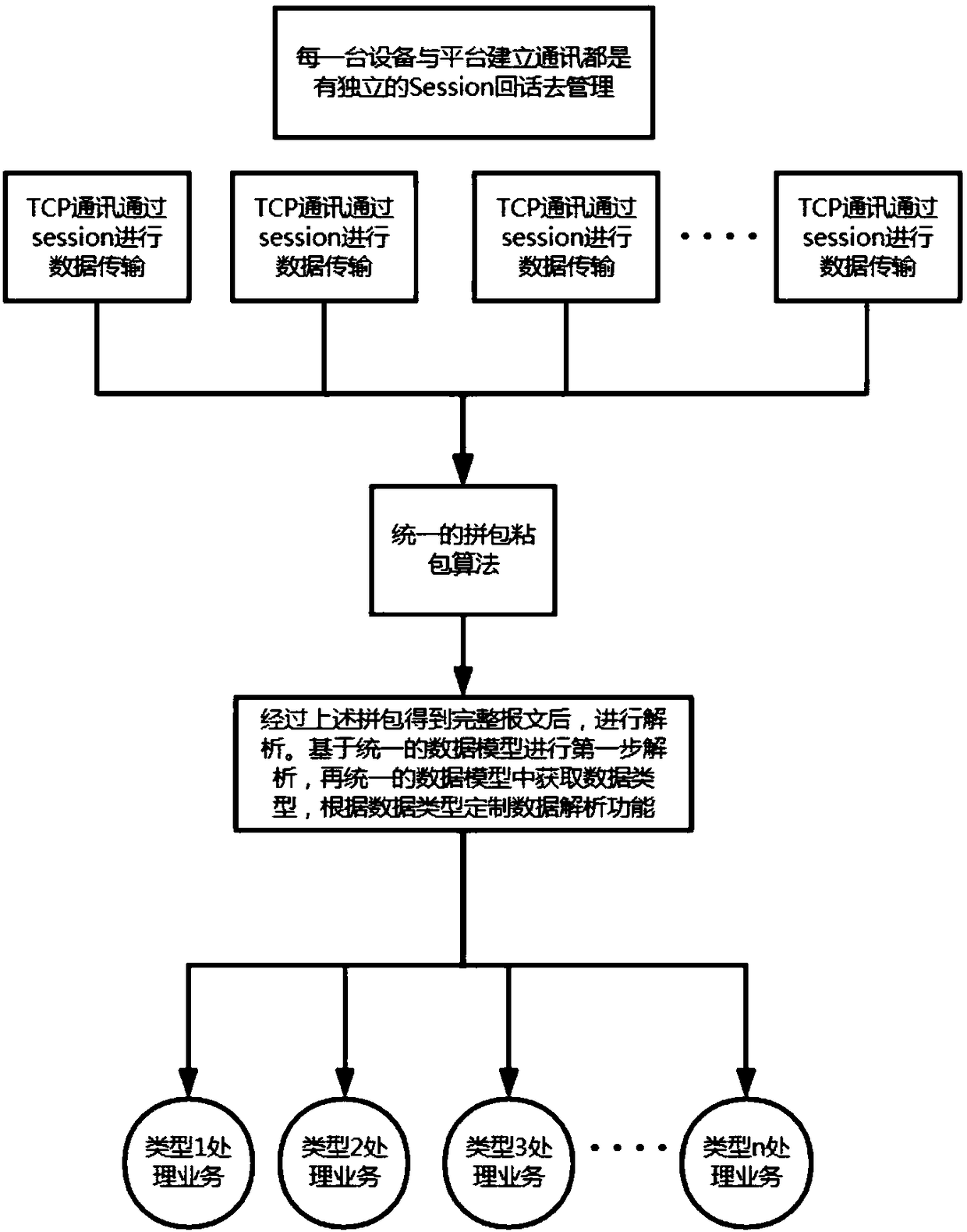
The invention discloses a packet sticking and splicing method based on protocol transmission. The scheme of the invention is mainly based on a framework of an Apache MINA high-performance and high-scalability network application, aims at network data communication in a transmission control protocol (TCP) communication mode between equipment and equipment, the equipment and platforms, and the platforms and the platforms in the field of Internet of Things that is rapidly developed at present, and performs strict processing on packet sticking and splicing and other operations of data packets during transmission by using a mode of specifying communication protocol rules. Thereby, the problem of integrating data packet sticking and splicing schemes in the process of performing data packet transmission based on a certain communication protocol in the Internet of Things industry can be solved, and the relatively strict data packet sticking and splicing can be achieved on the basis of ensuringhigh efficiency and low resource consumption.
Owner:JIQI CHENGDU TECH CO LTD
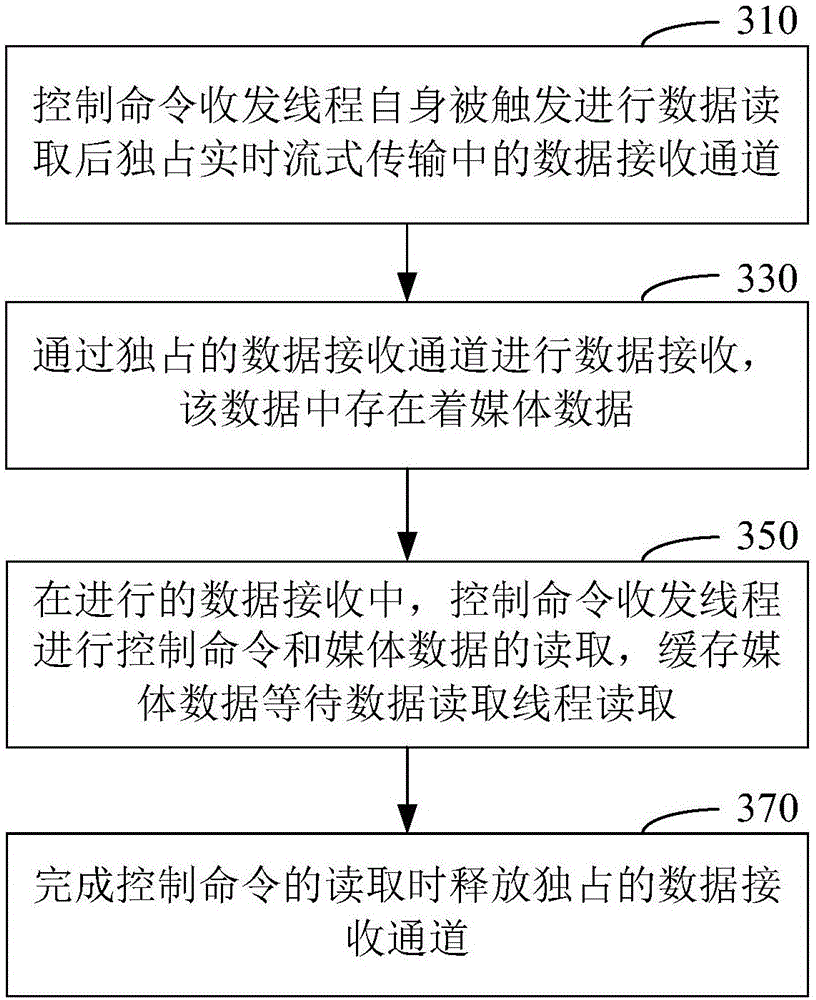
Real-time stream transmission receiving control method and device
ActiveCN106230839AAvoid data corruptionTransmissionMachine execution arrangementsComputer hardwareData in transit
The invention discloses a real-time stream transmission receiving control method and device. The method comprises the steps that a control command receiving and transmitting thread is triggered to read row data and monopolizes a data receiving channel in real-time stream transmission; data is received through the monopolized data receiving channel, wherein the data comprises multimedia data; during the data reception, the control command receiving and transmitting thread reads a control command and the multimedia data, and caches the multimedia data for the reading of a data reading thread; and the monopolized data receiving channel is released after the control command is read. The control command receiving and transmitting thread reads the control command and the multimedia data, and caches the multimedia data for the reading of the data reading thread, so that the situation that the same data receiving channel reads the data when receiving the multimedia data and the control command to cause data chaos in a multi-thread mechanism can be avoided, and the data reading thread and the control command receiving and transmitting thread are guaranteed to read respective necessary data.
Owner:HISENSE BROADBAND MULTIMEDIA TECH
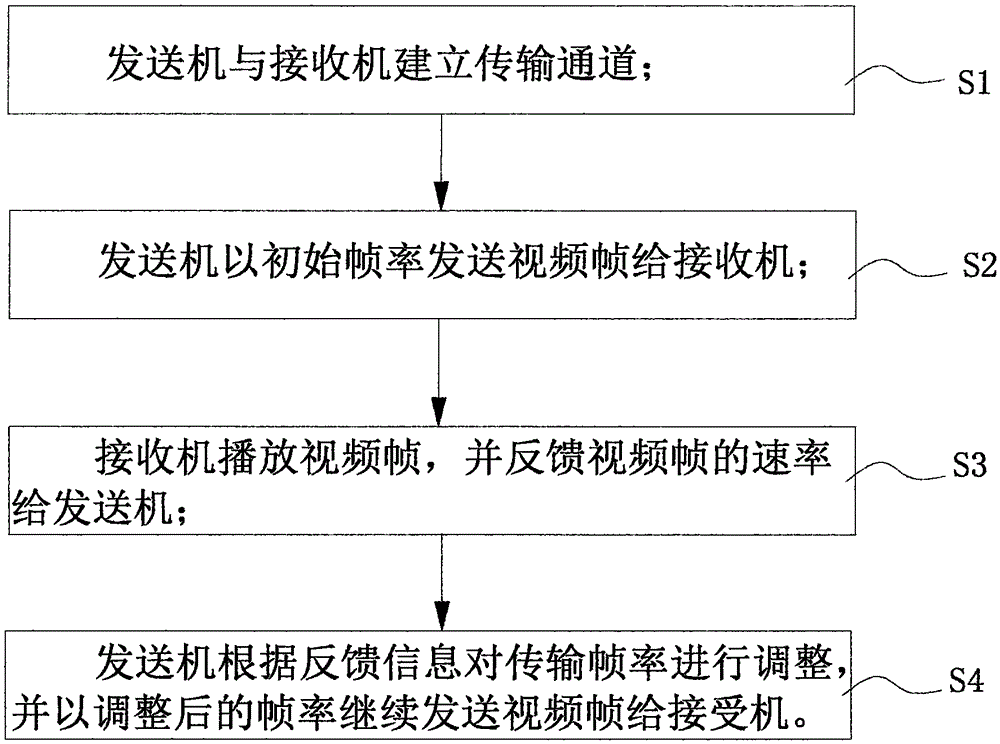
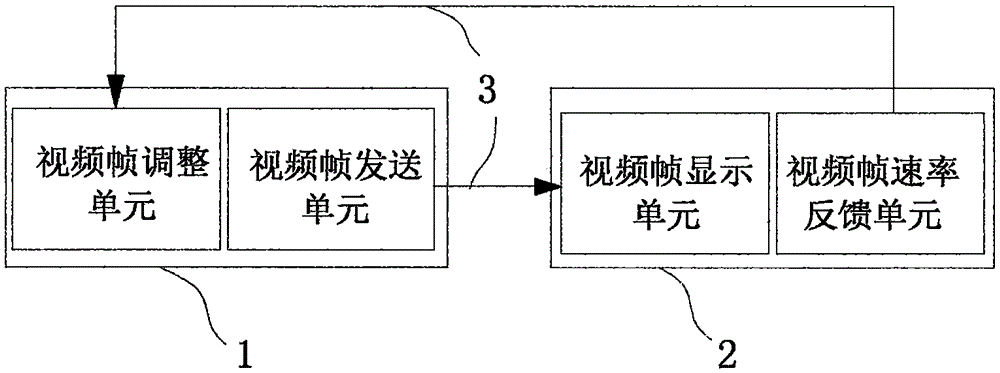
Video transmission method and system
InactiveCN106534055AGuaranteed normal transmissionReduce wasteTransmissionNetwork packetTransfer procedure
The invention discloses a video transmission method and system. The video transmission method comprises the steps of establishing a transmission channel between a transmitter and a receiver; transmitting video frames to the receiver at an initial frame rate by the transmitter; playing the video frames and feeding back the rate of the video frames to the transmitter by the receiver; and adjusting the transmission frame rate based on the feedback information and carrying on transmitting the video frames to the receiver at the adjusted frame rate by the transmitter. Through real-time feedback of the video frame rate in the transmission process, and real-time judgment and adjustment for the transmission frame rate, the discarding problem of data packets in the video transmission is greatly reduced, and video transmission via a small data volume can be realized.
Owner:GUANGZHOU SHIRONG ELECTRONICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com