Patents
Literature
81 results about "Referential integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
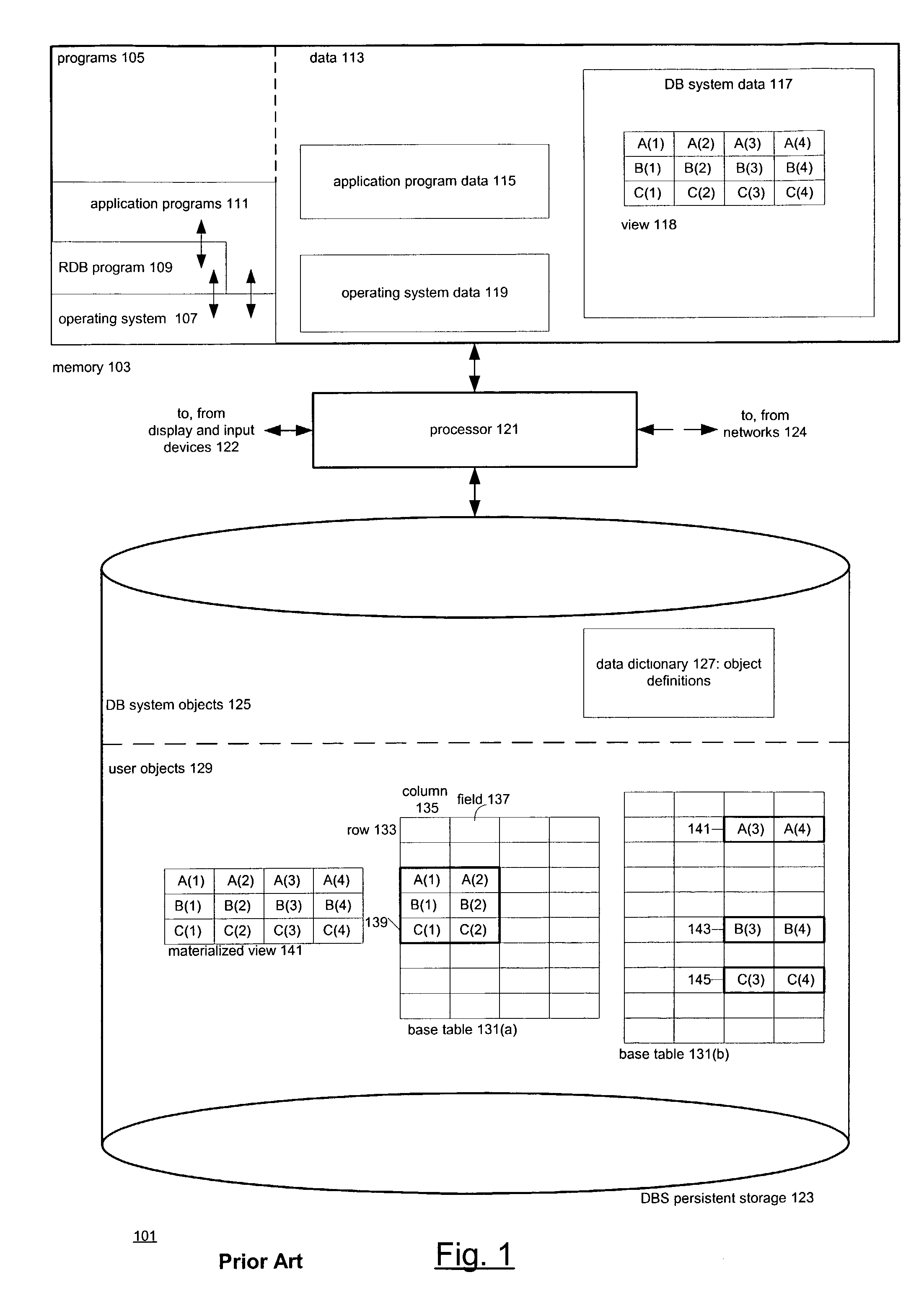
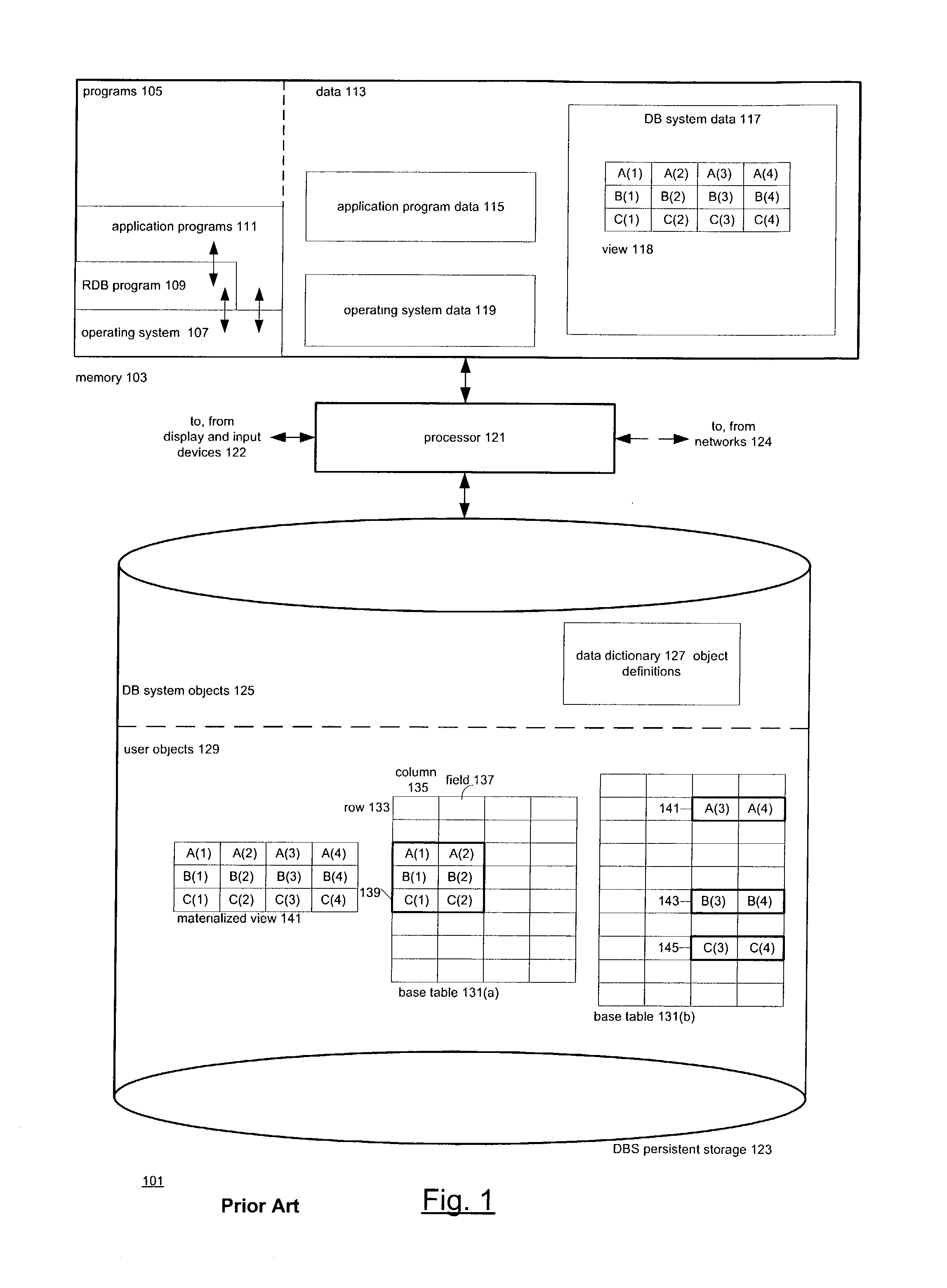
Referential integrity is a property of data stating that all its references are valid. In the context of relational databases, it requires that if a value of one attribute (column) of a relation (table) references a value of another attribute (either in the same or a different relation), then the referenced value must exist.
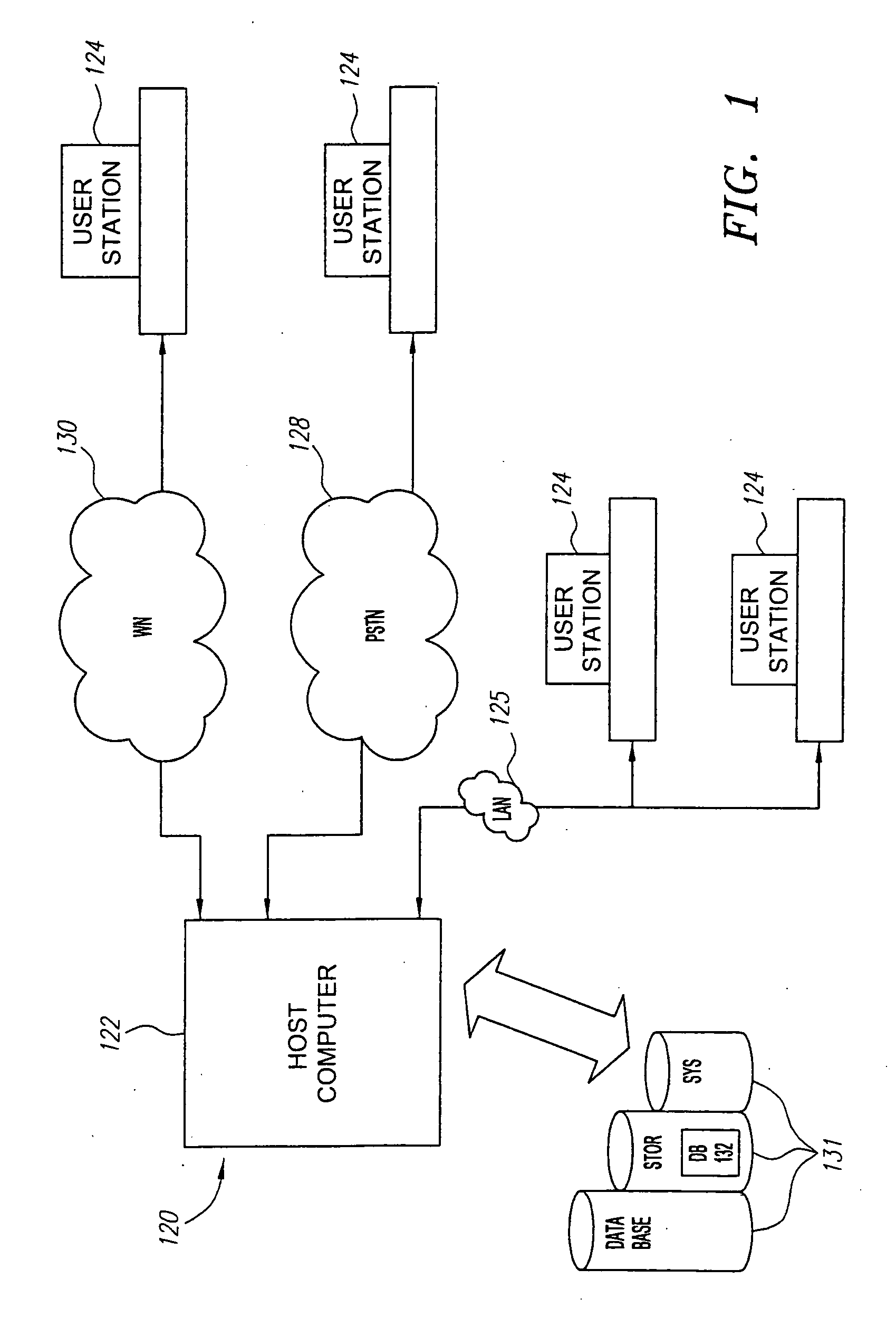
Navigation of view relationships in database system
InactiveUS6609122B1Maintaining correctness and consistency of dataData inconsistencyData processing applicationsDigital data processing detailsOriginal dataApplication software
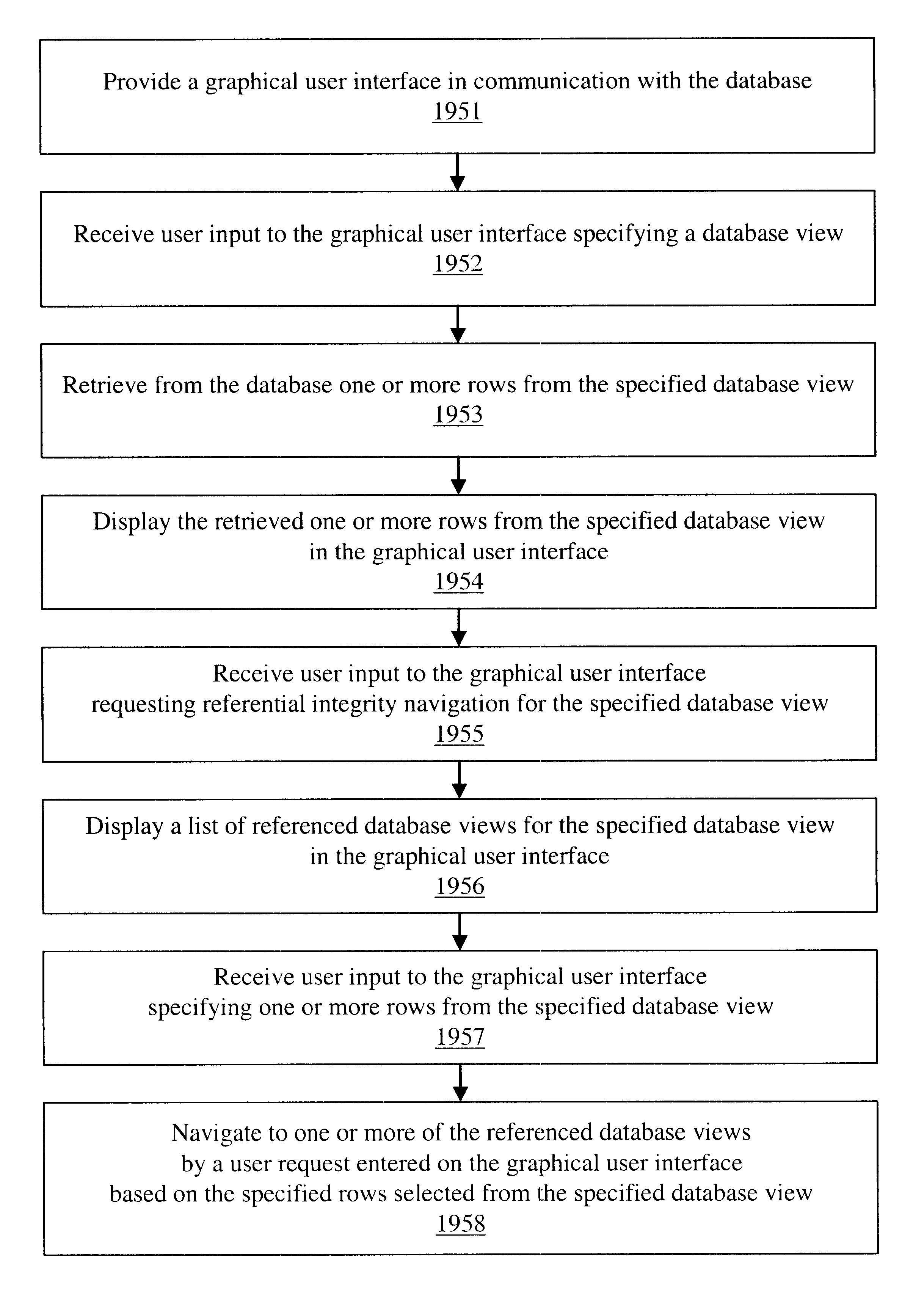
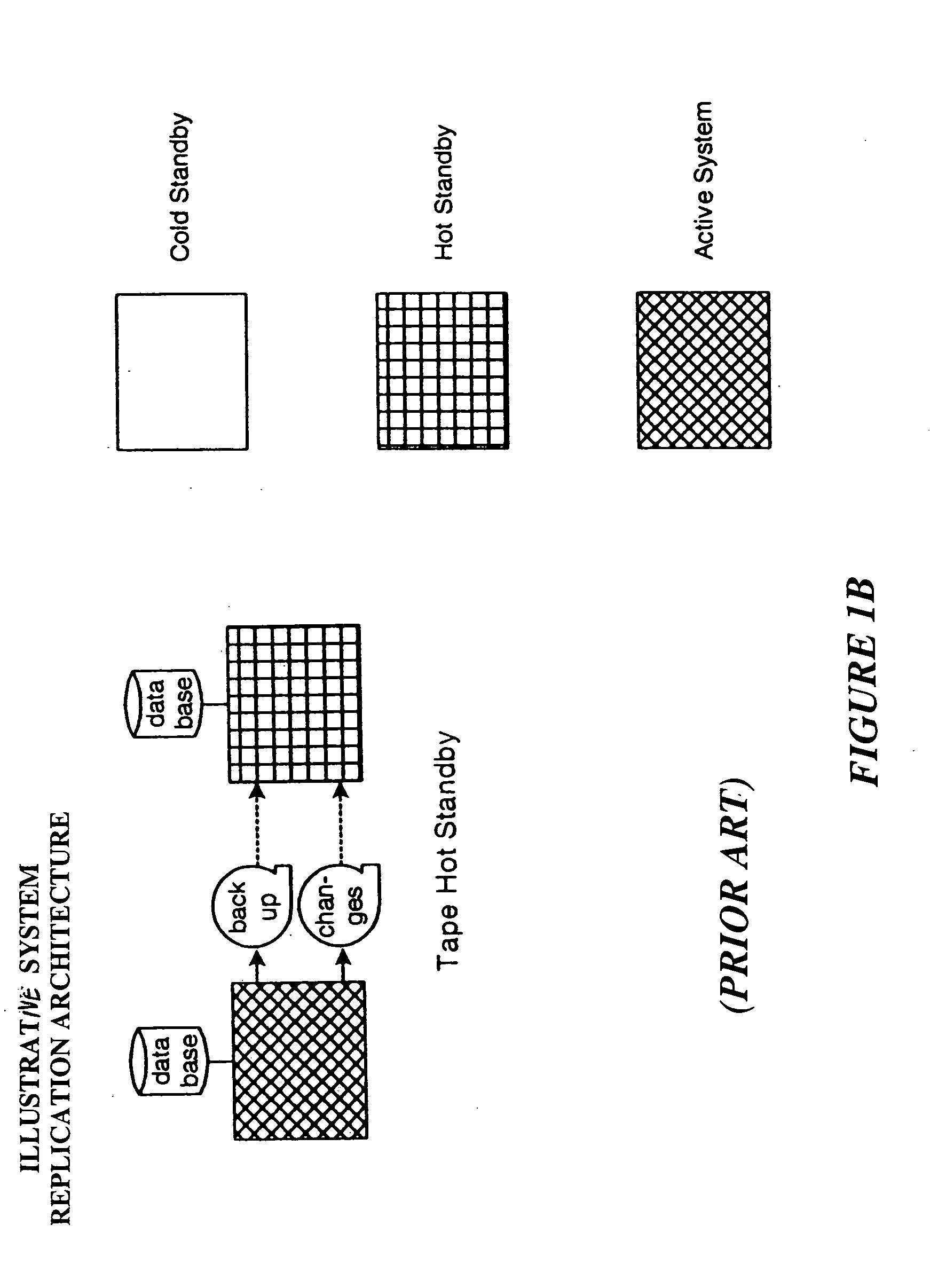
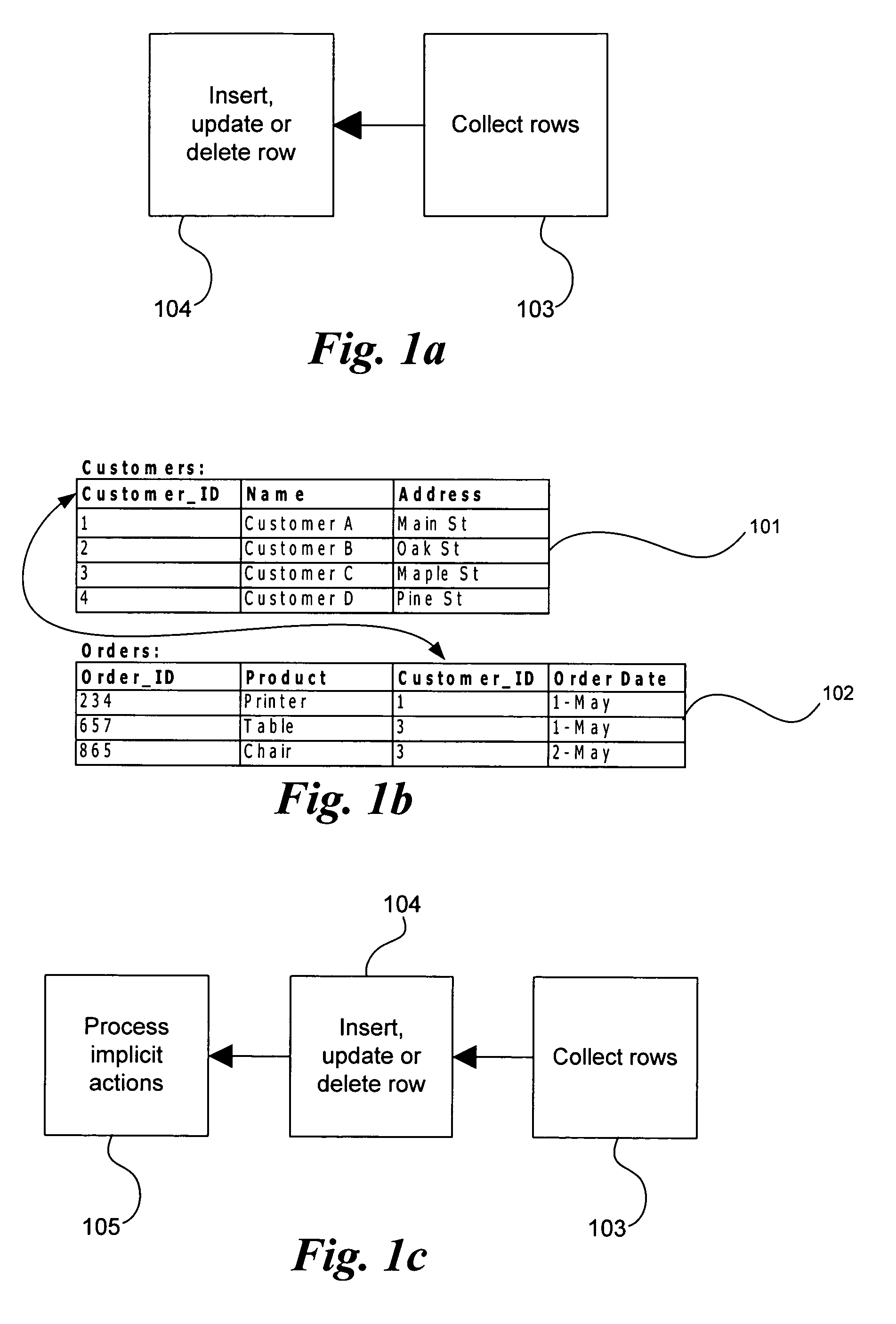
The invention is an improved system and method for browsing and editing data residing in database tables. The method of the present invention includes the steps of providing a graphical user interface in communication with a database, receiving user input to the graphical user interface, retrieving data from the database, displaying the retrieved data in the graphical user interface, and navigating to one or more referenced database tables or views by user request entered on the graphical user interface. The purpose of referential integrity is to prevent database users or applications from entering inconsistent data into a database. The goal of referential integrity navigation is to allow the user, having retrieved one or more rows of data, to navigate easily to the data in other tables that either refers to or is referred to by that data. These relationships are defined by referential integrity constraints, and the data thus retrieved by navigation is then available for all the operations possible on the original data, including data editing and further relational navigation. By storing a catalog of the relationships known to exist between Oracle's V$ views, the same form of navigation can be provided between these data sources.
Owner:BMC SOFTWARE
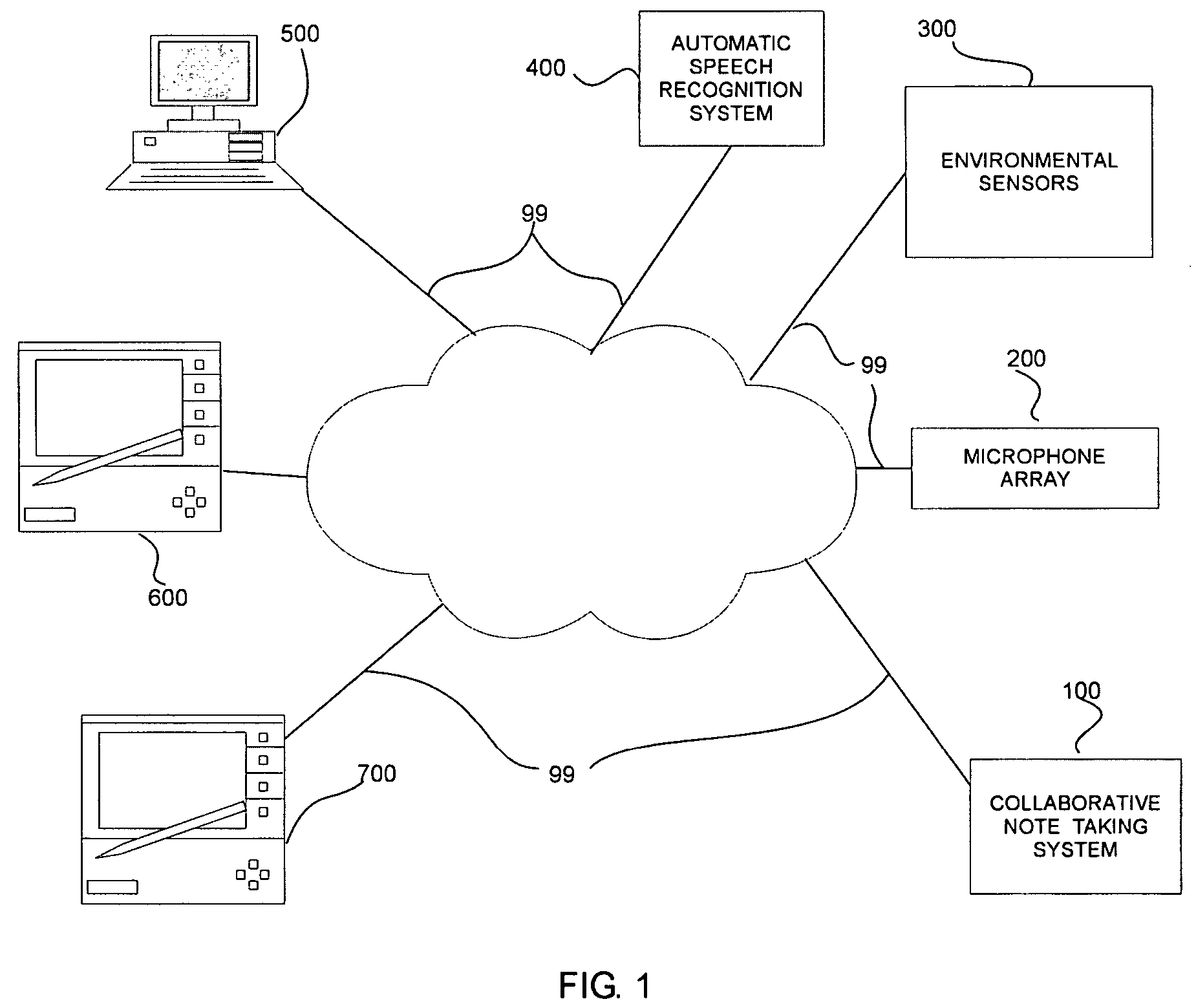
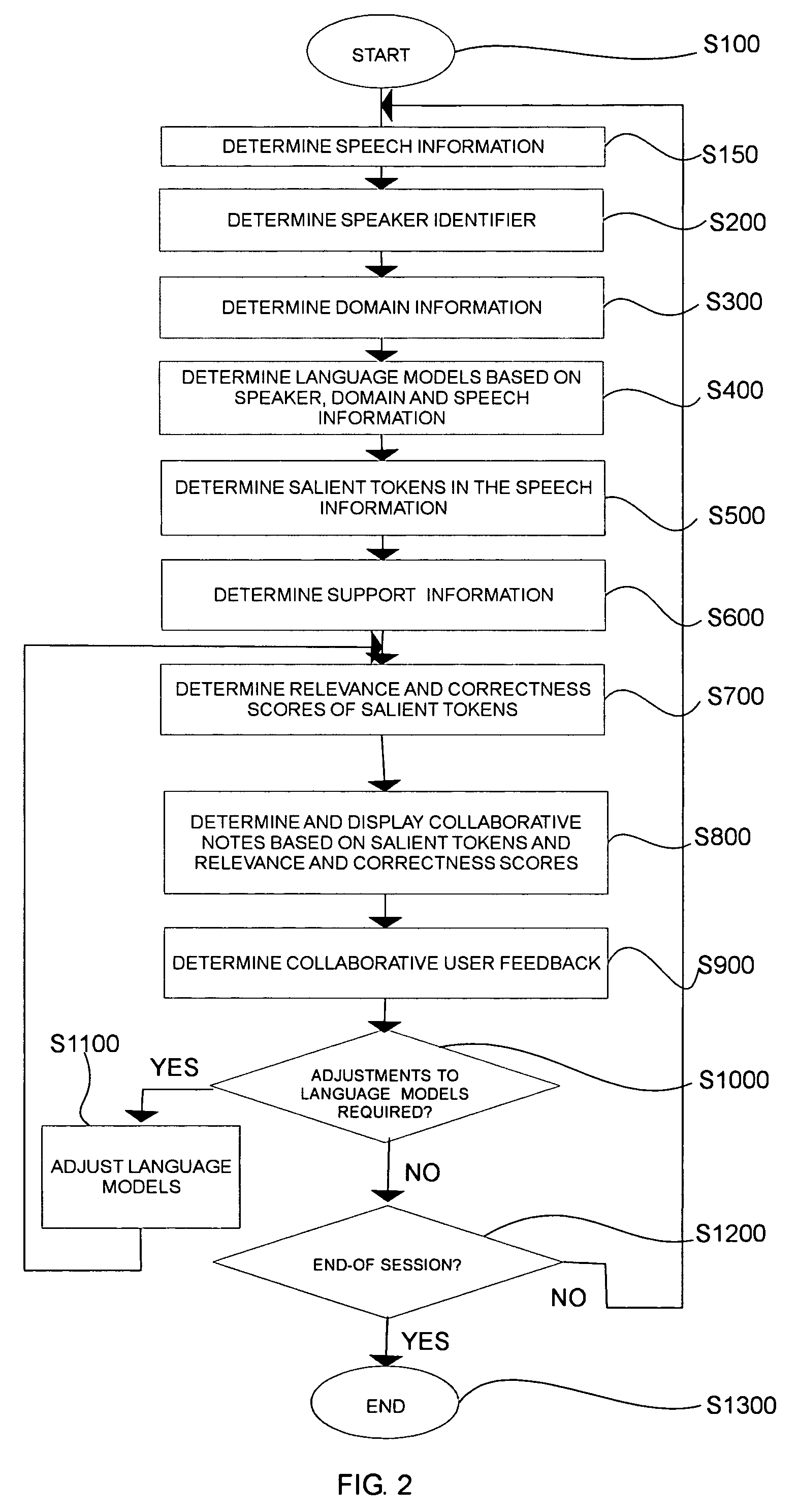
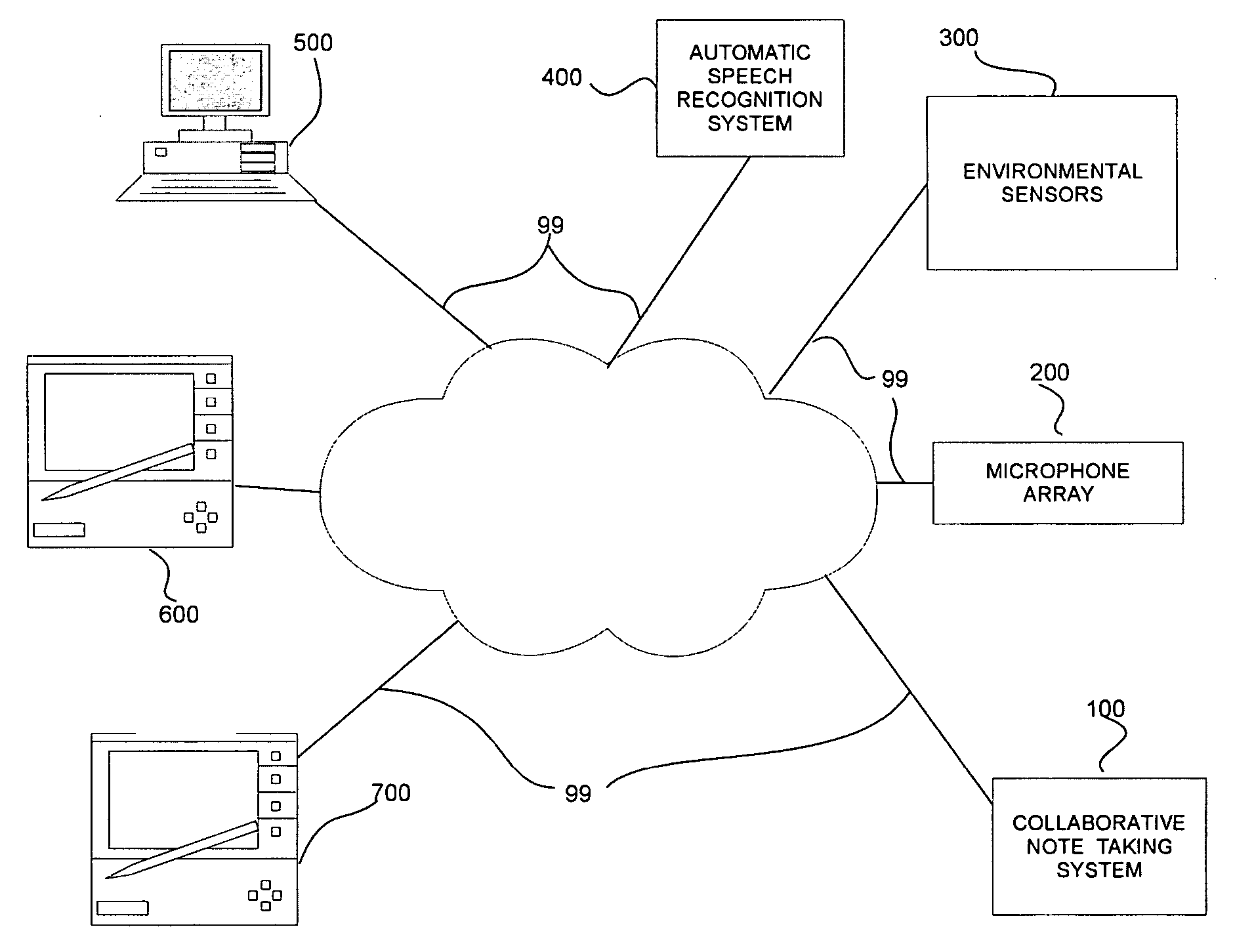
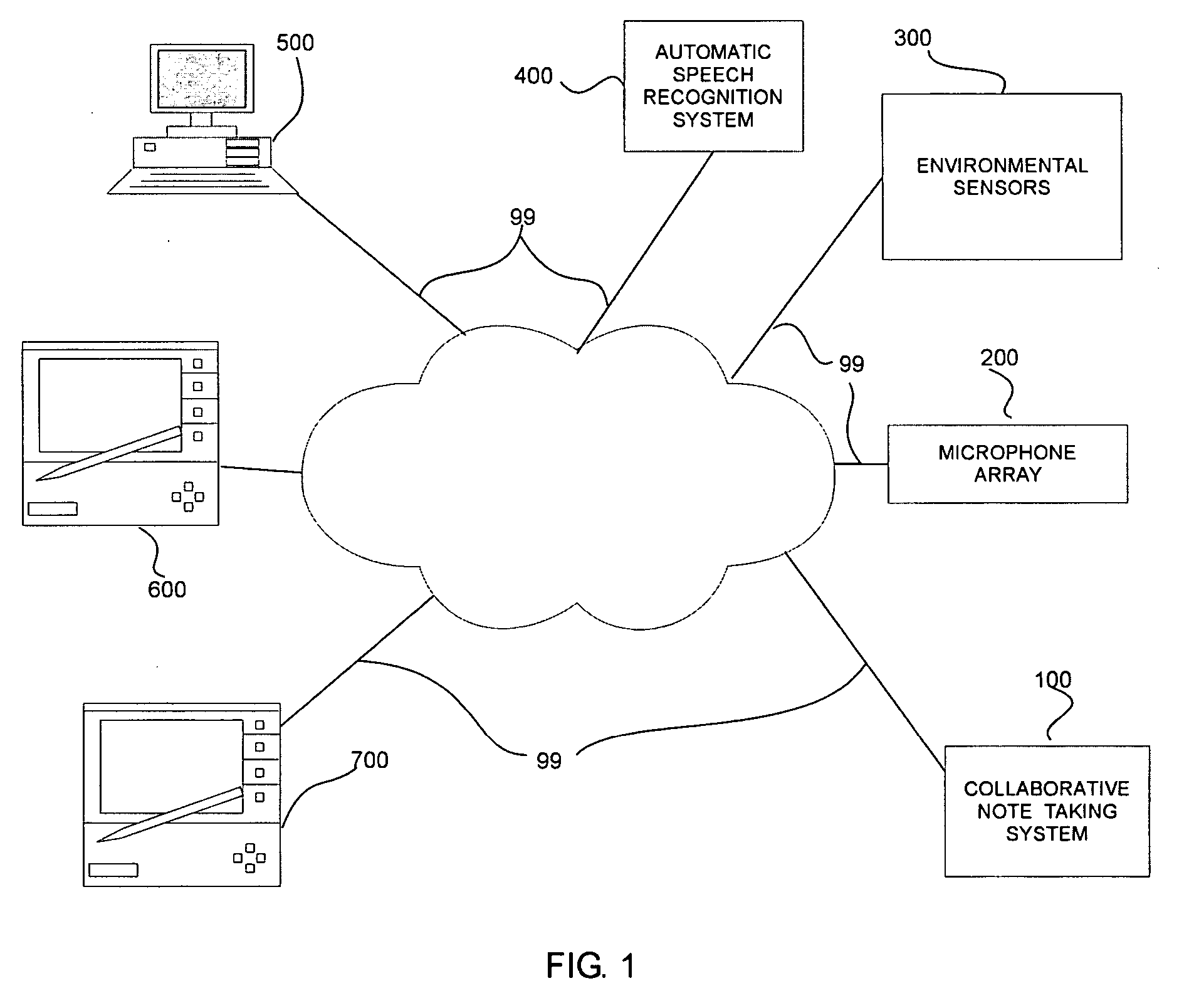
Systems and methods for collaborative note-taking
InactiveUS7542971B2Digital data processing detailsNatural language data processingHandwritingFunction word
Owner:FUJIFILM BUSINESS INNOVATION CORP
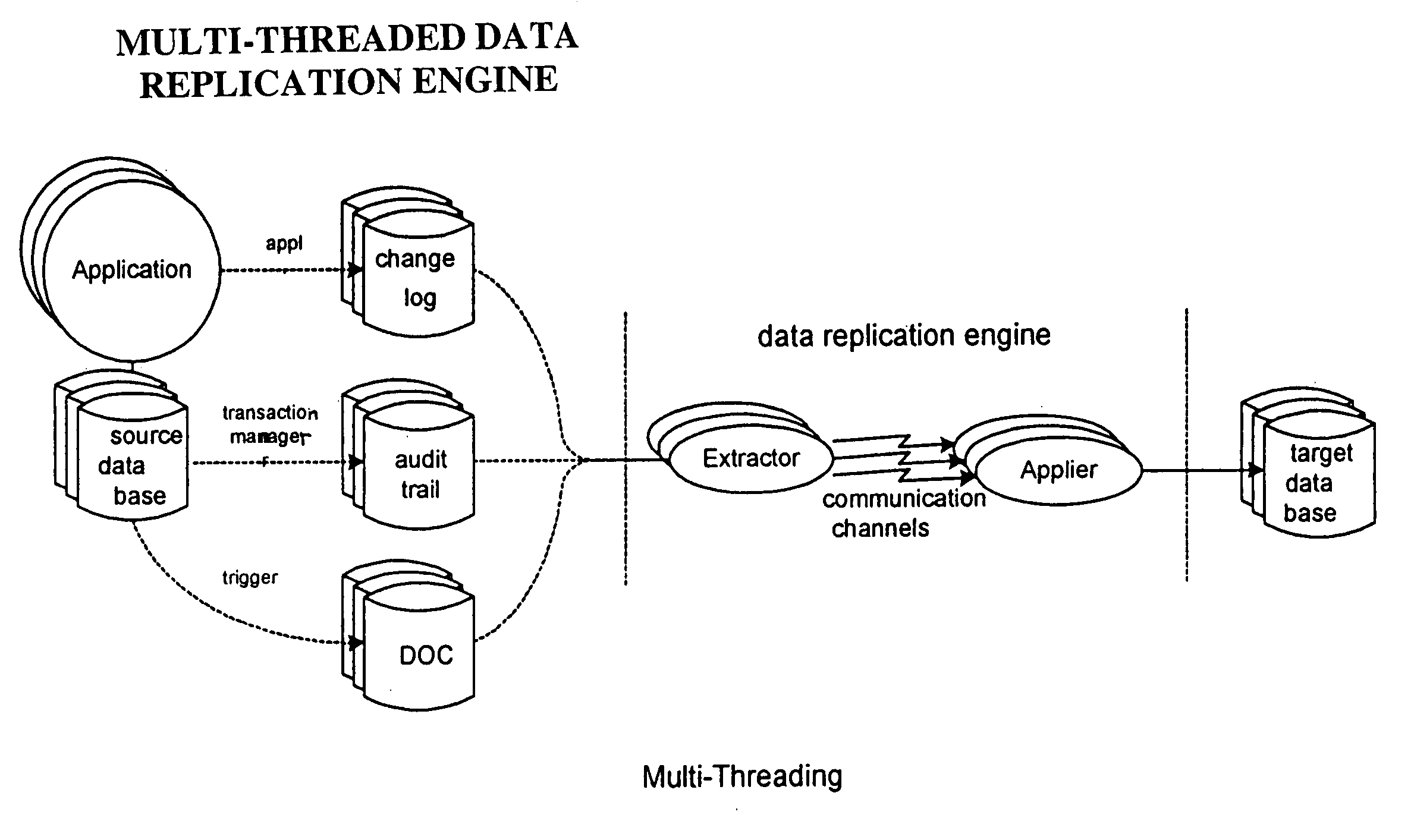
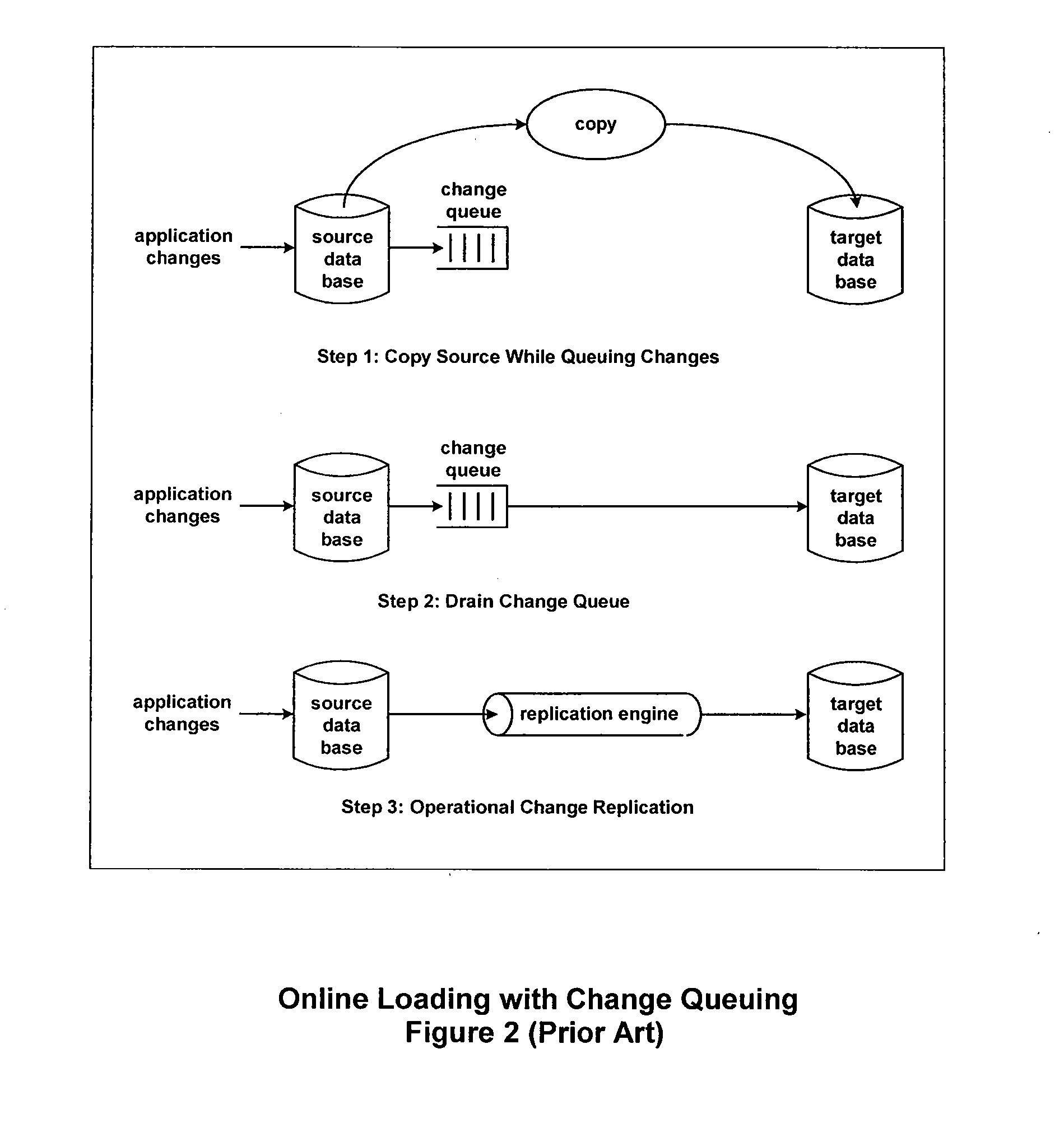
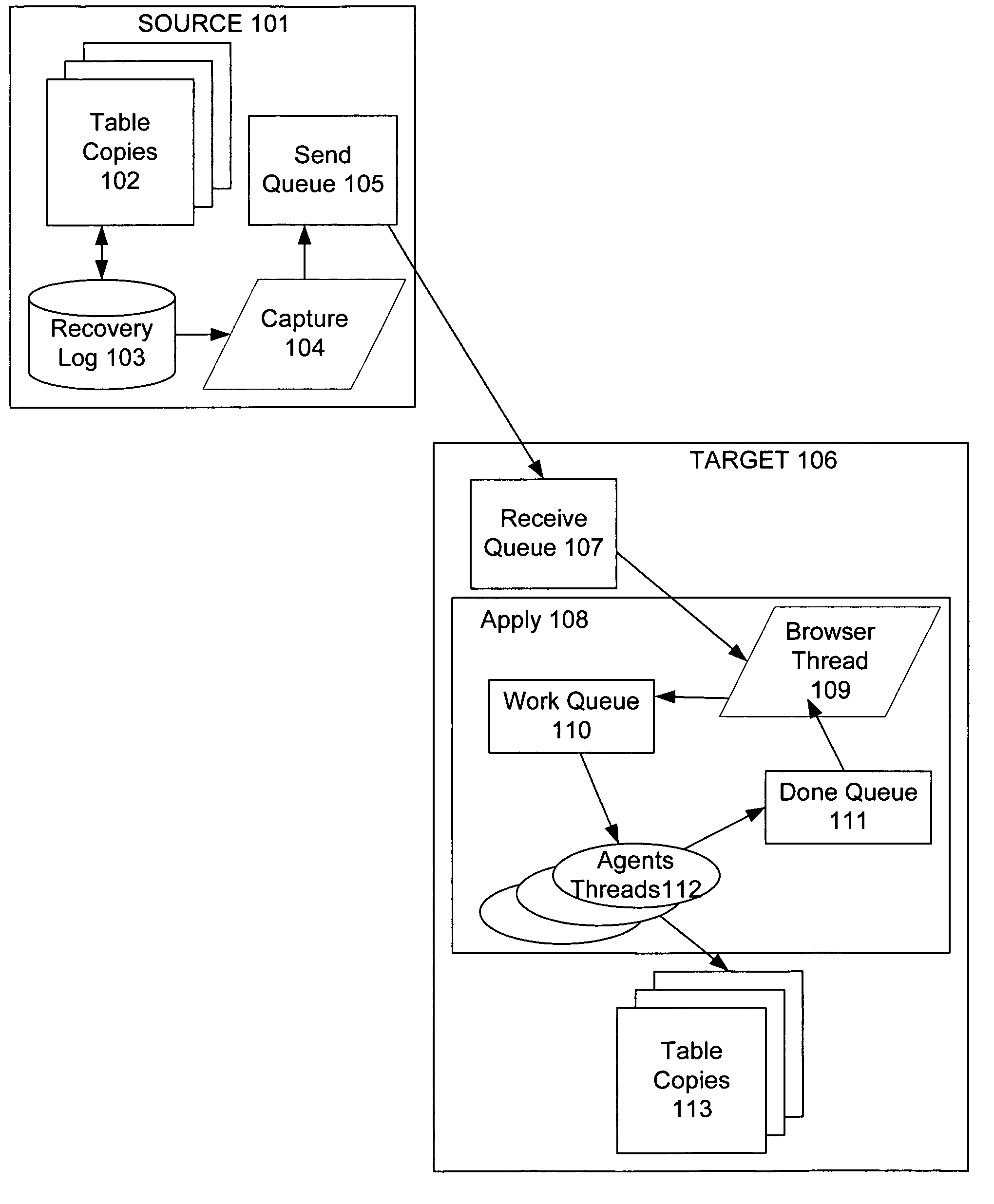
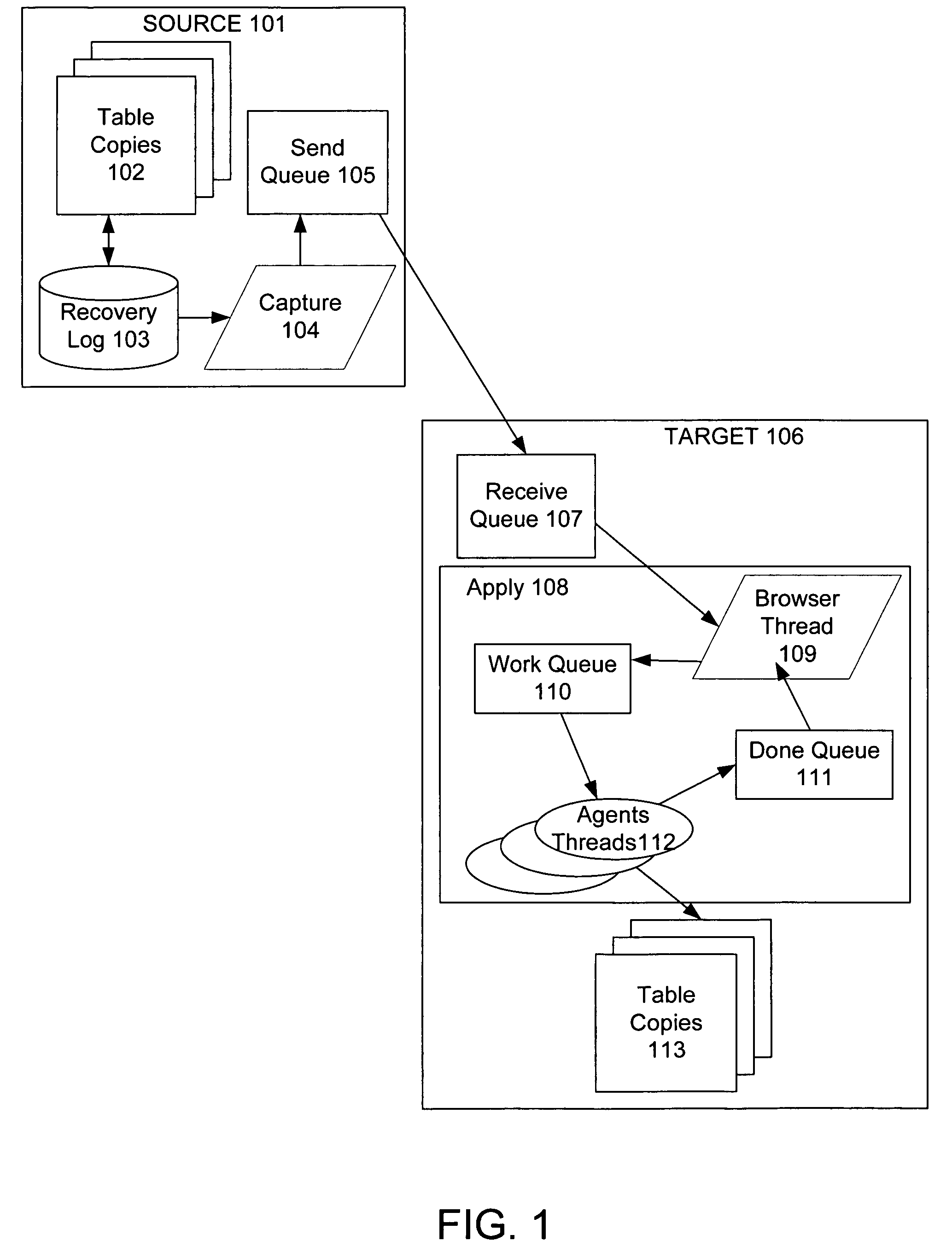
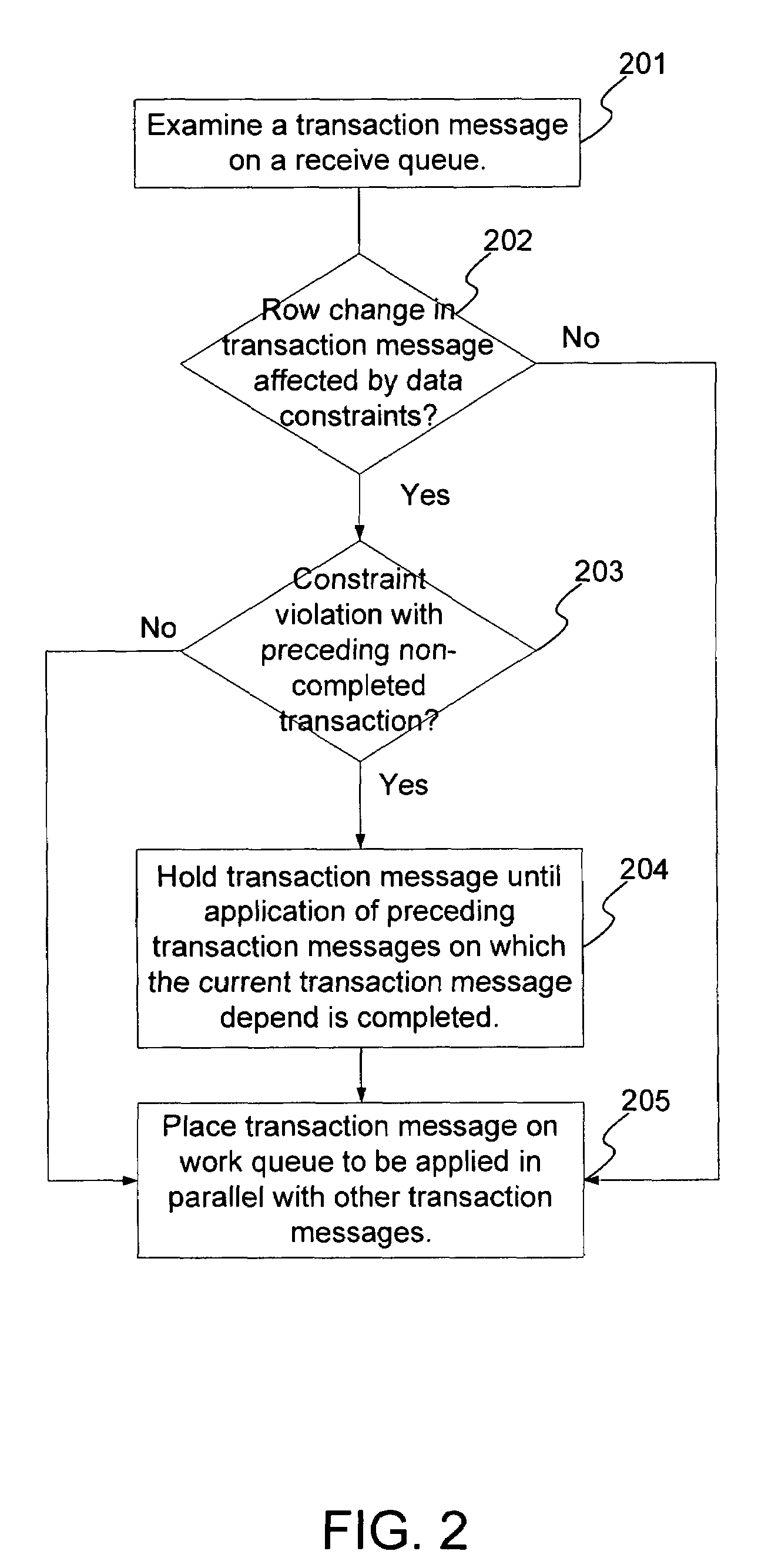
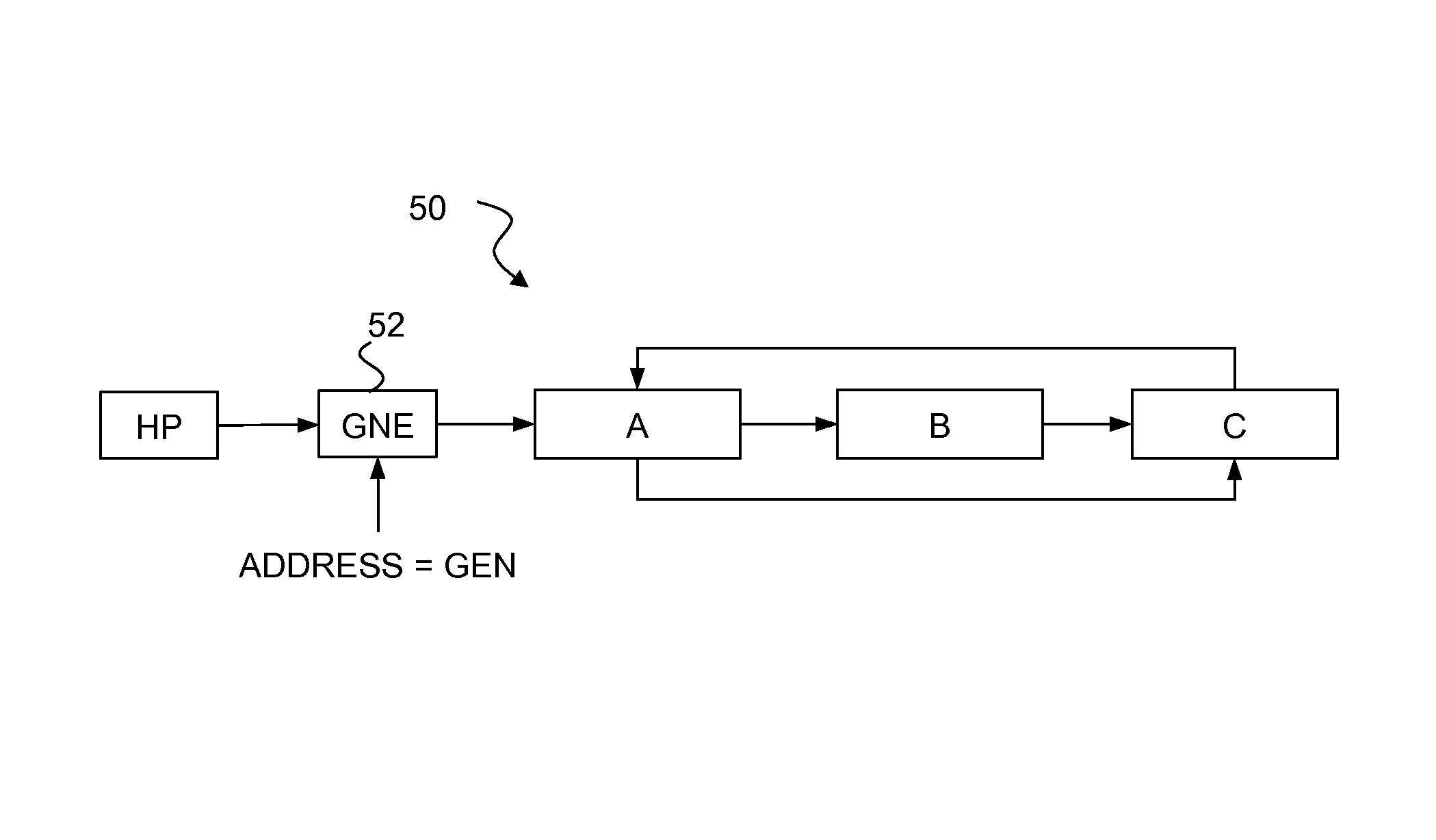
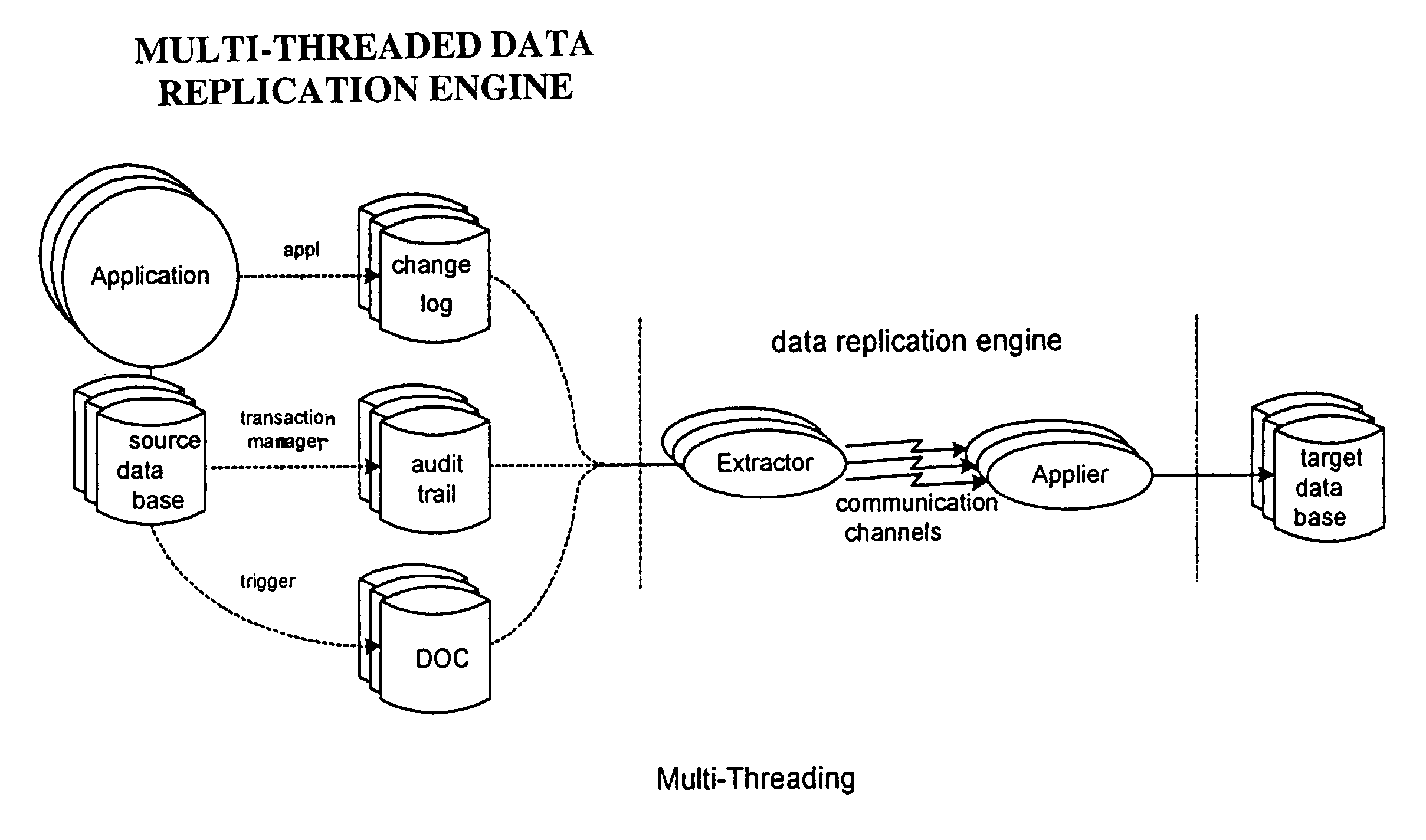
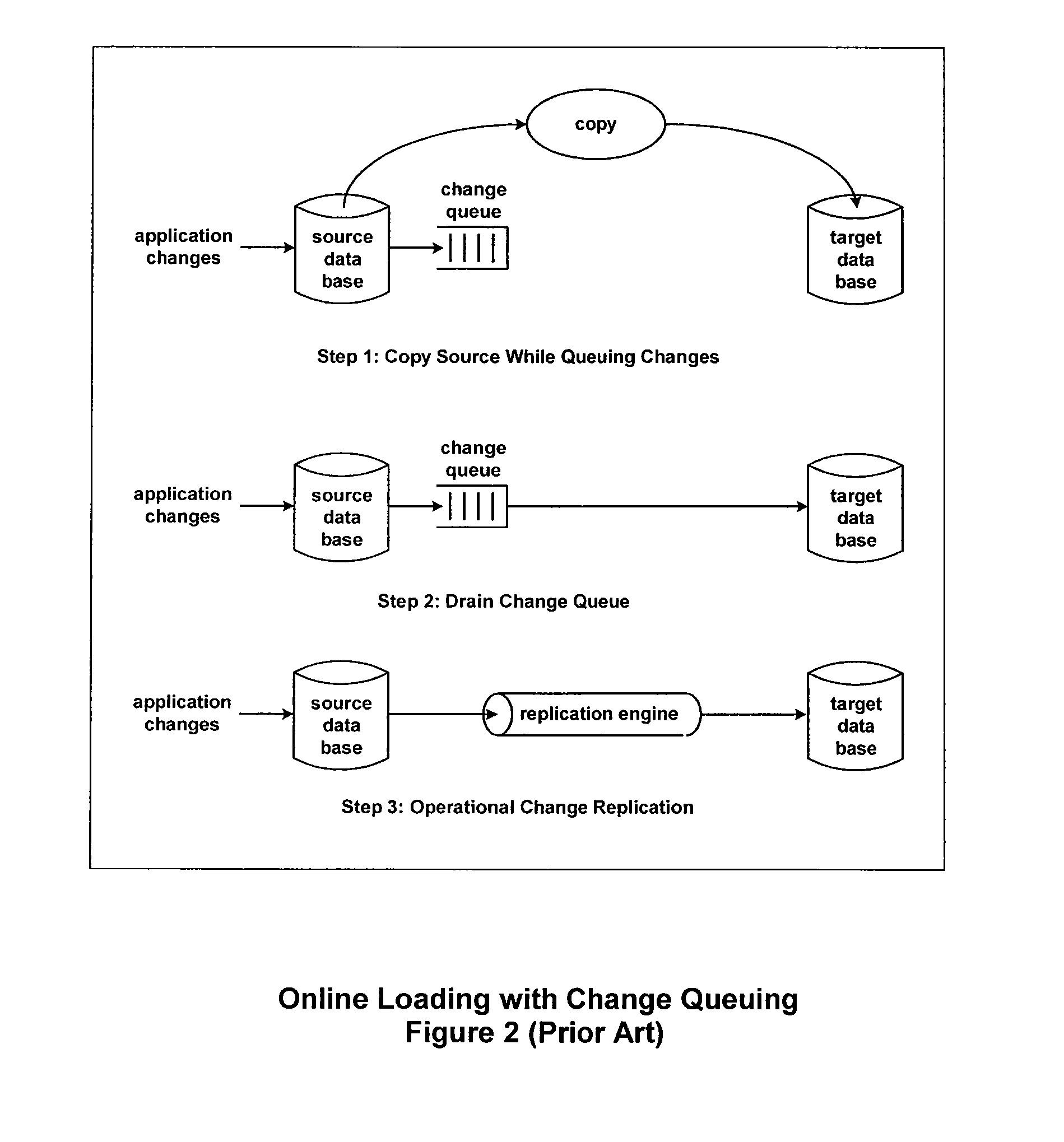
Method for ensuring referential integrity in multi-threaded replication engines
ActiveUS20050021567A1Digital data information retrievalDigital data processing detailsTransaction dataLoad capacity
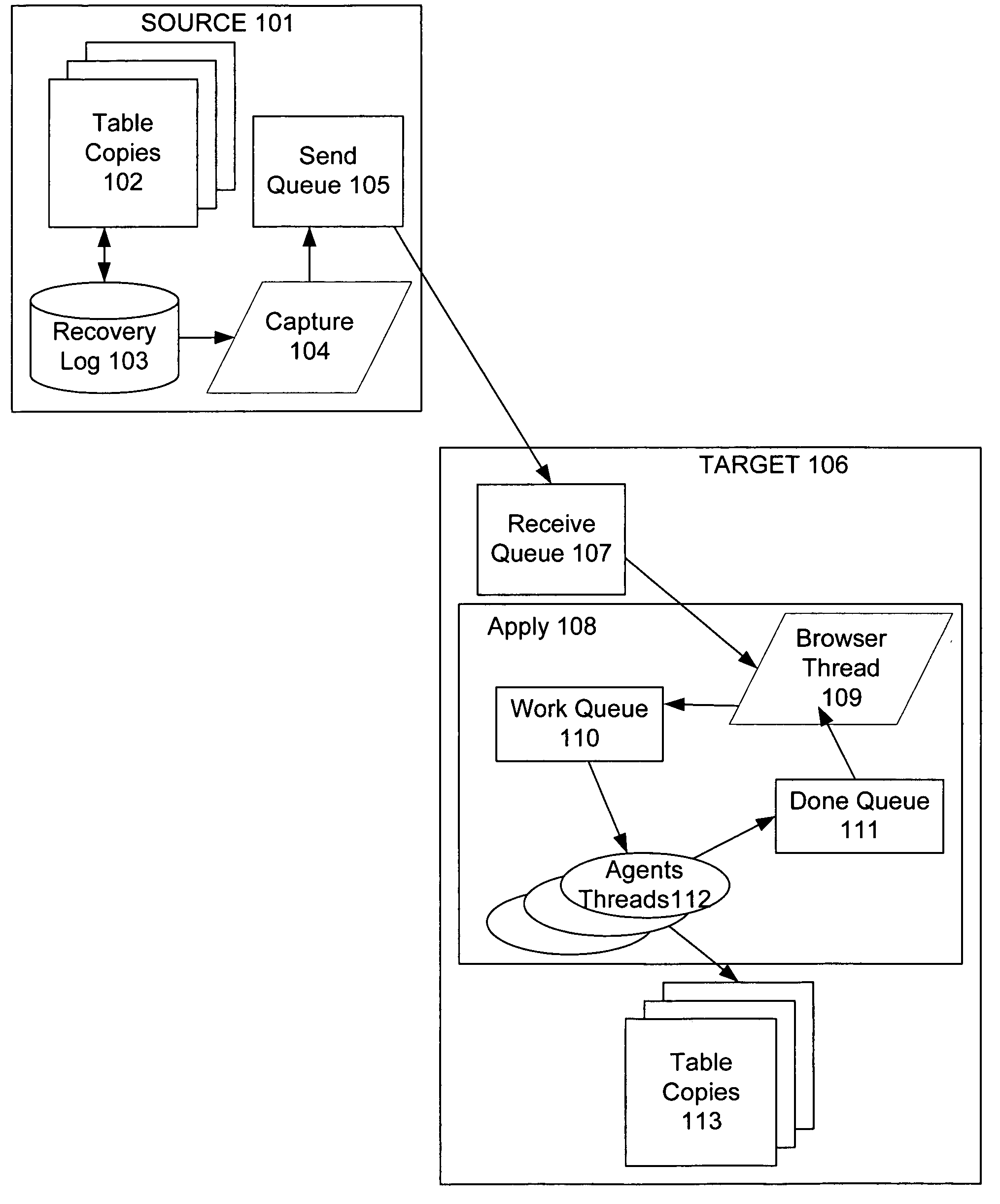
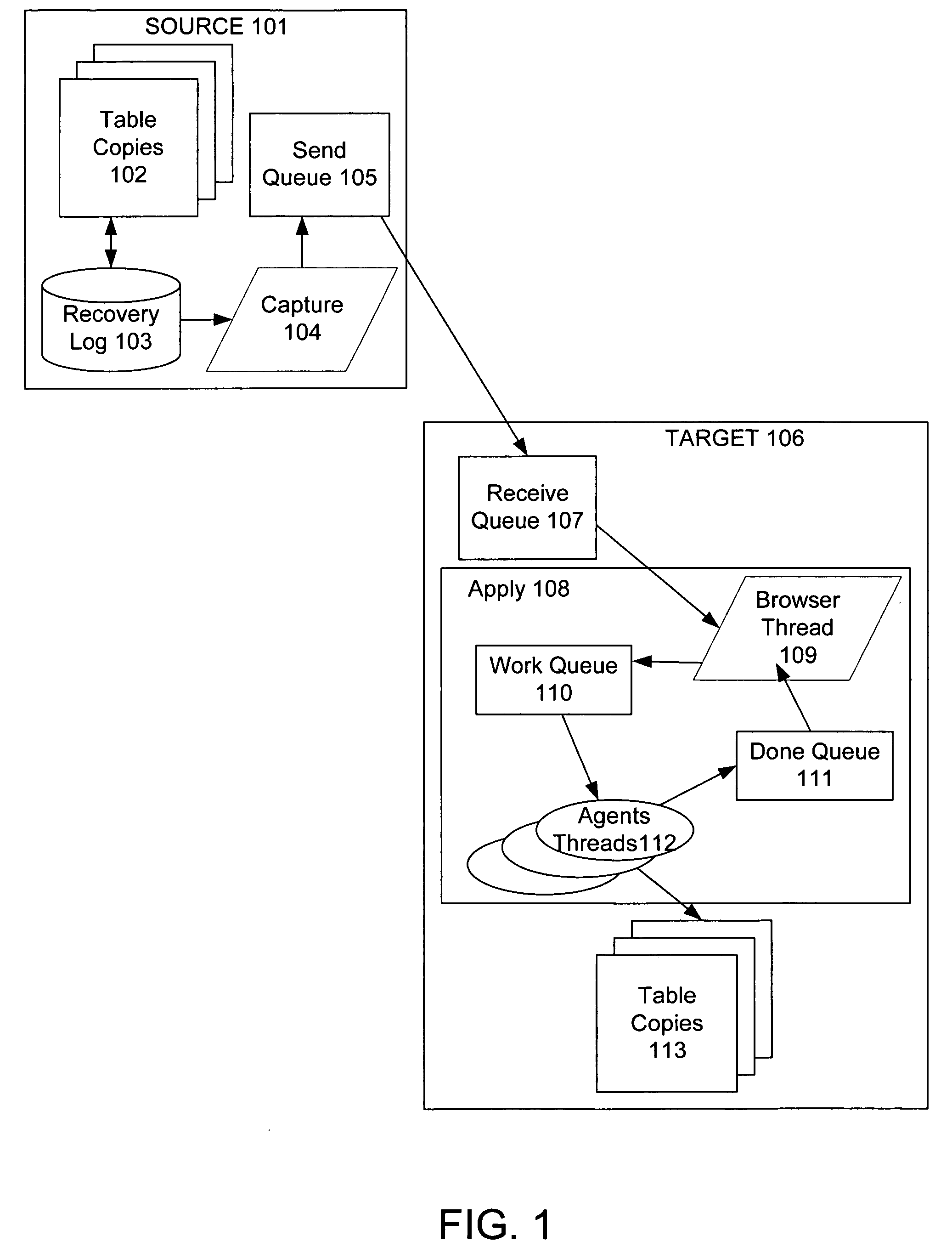
During replication of transaction data from a source database to a target database via a change queue associated with the source database, one or more multiple paths are provided between the change queue and the target database. The one or more multiple paths cause at least some of the transaction data to become unserialized. At least some of the unserialized data is reserialized prior to or upon applying the originally unserialized transaction data to the target database. If the current transaction load is close or equal to the maximum transaction load capacity of a path between the change queue and the target database, another path is provided. If the maximum transaction threshold limit of an applier associated with the target database has been reached, open transactions may be prematurely committed.
Owner:INTEL CORP
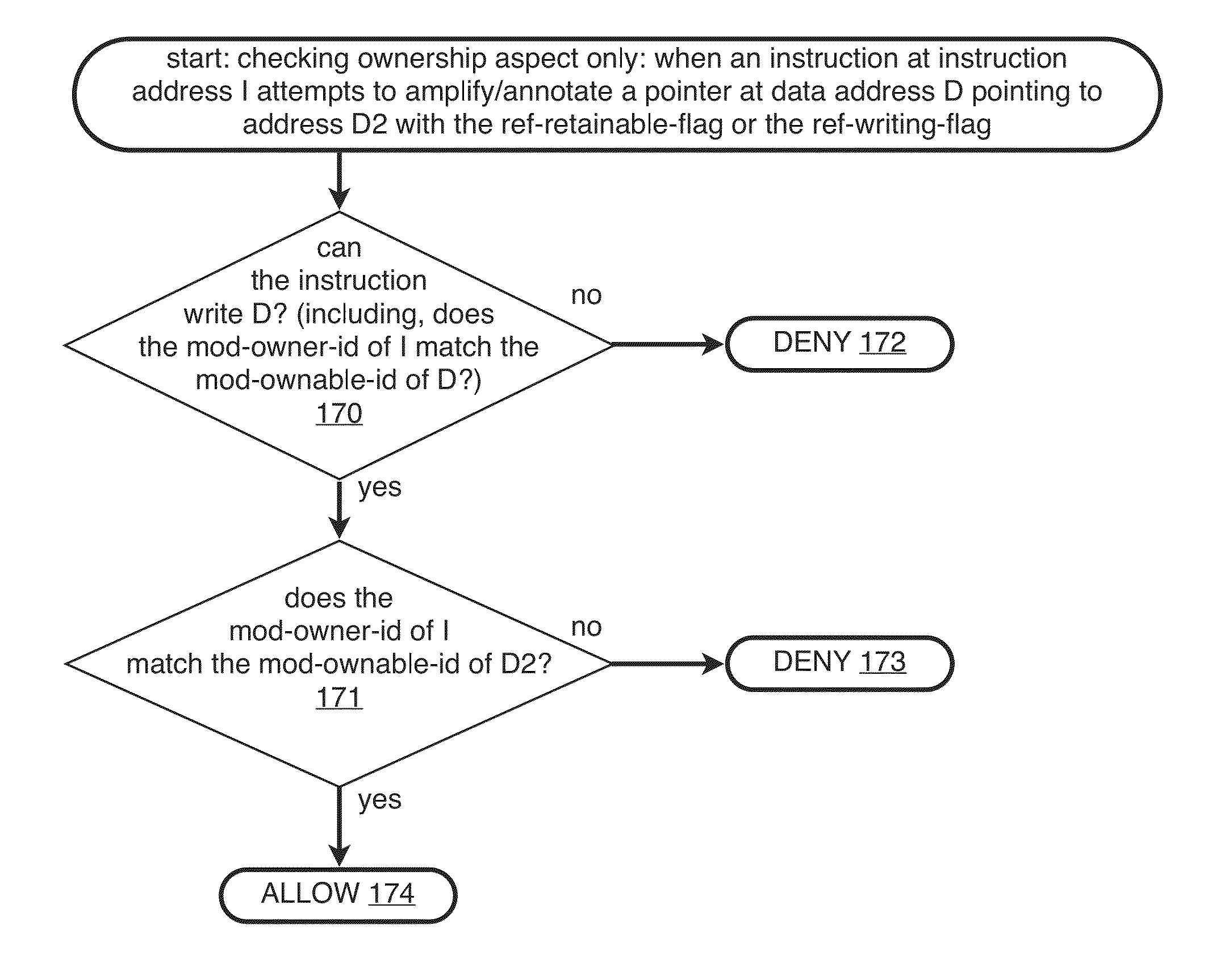
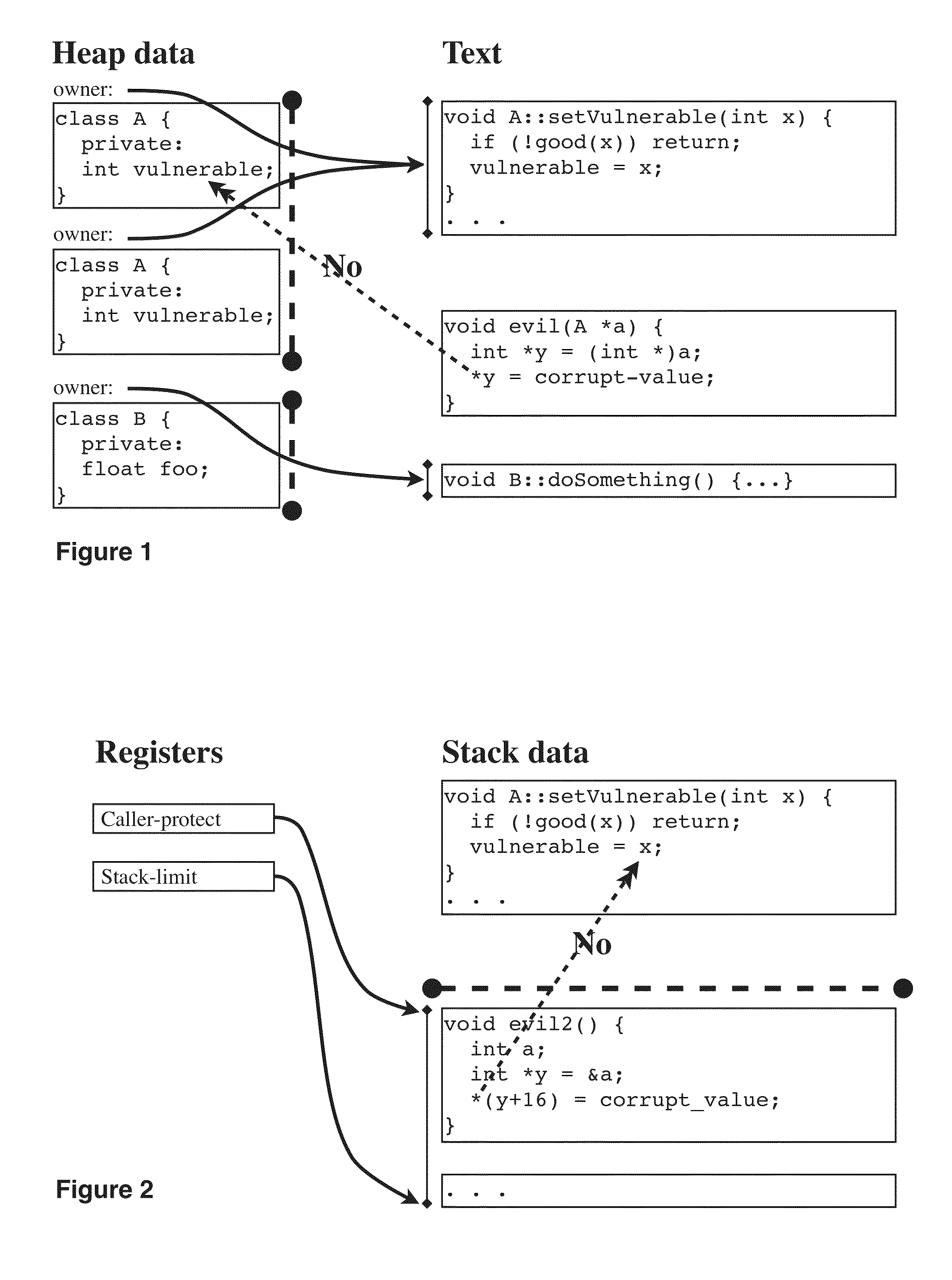
Hard Object: Lightweight Hardware Enforcement of Encapsulation, Unforgeability, and Transactionality
ActiveUS20140283040A1Memory architecture accessing/allocationMemory loss protectionSingle processSoftware correctness
A hardware-implemented method to support three desirable software properties: encapsulation, referential integrity / capabilities, and transactions. These properties in turn may be used to support software correctness, specifically the enforcement of invariants, and computer security, specifically protecting parts of programs from each other within a single process.
Owner:WILKERSON DANIEL SHAWCROSS +1
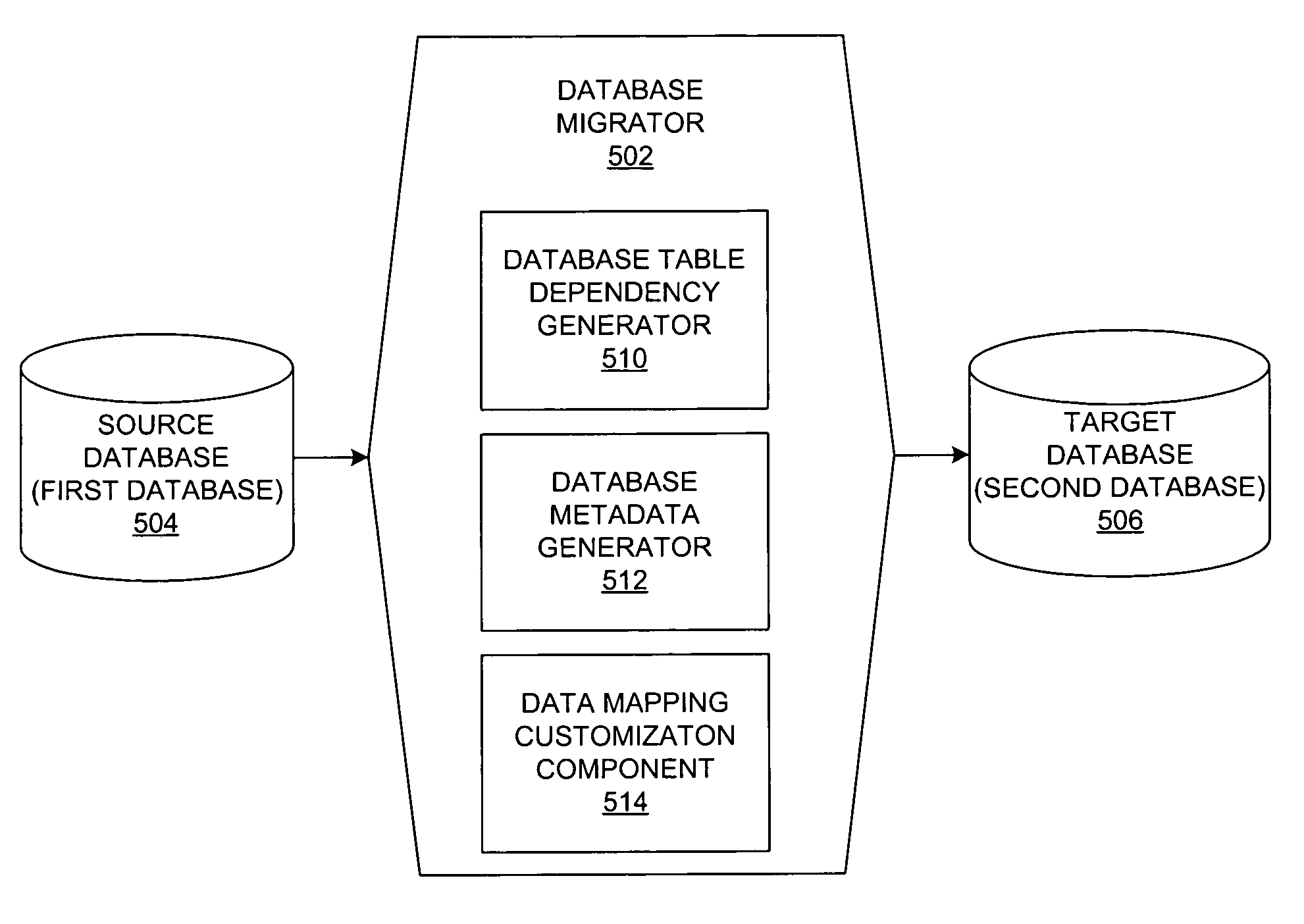
Method and system for a generic metadata-based mechanism to migrate relational data between databases
InactiveUS7620665B1Data processing applicationsDigital data information retrievalTarget databaseMetadata
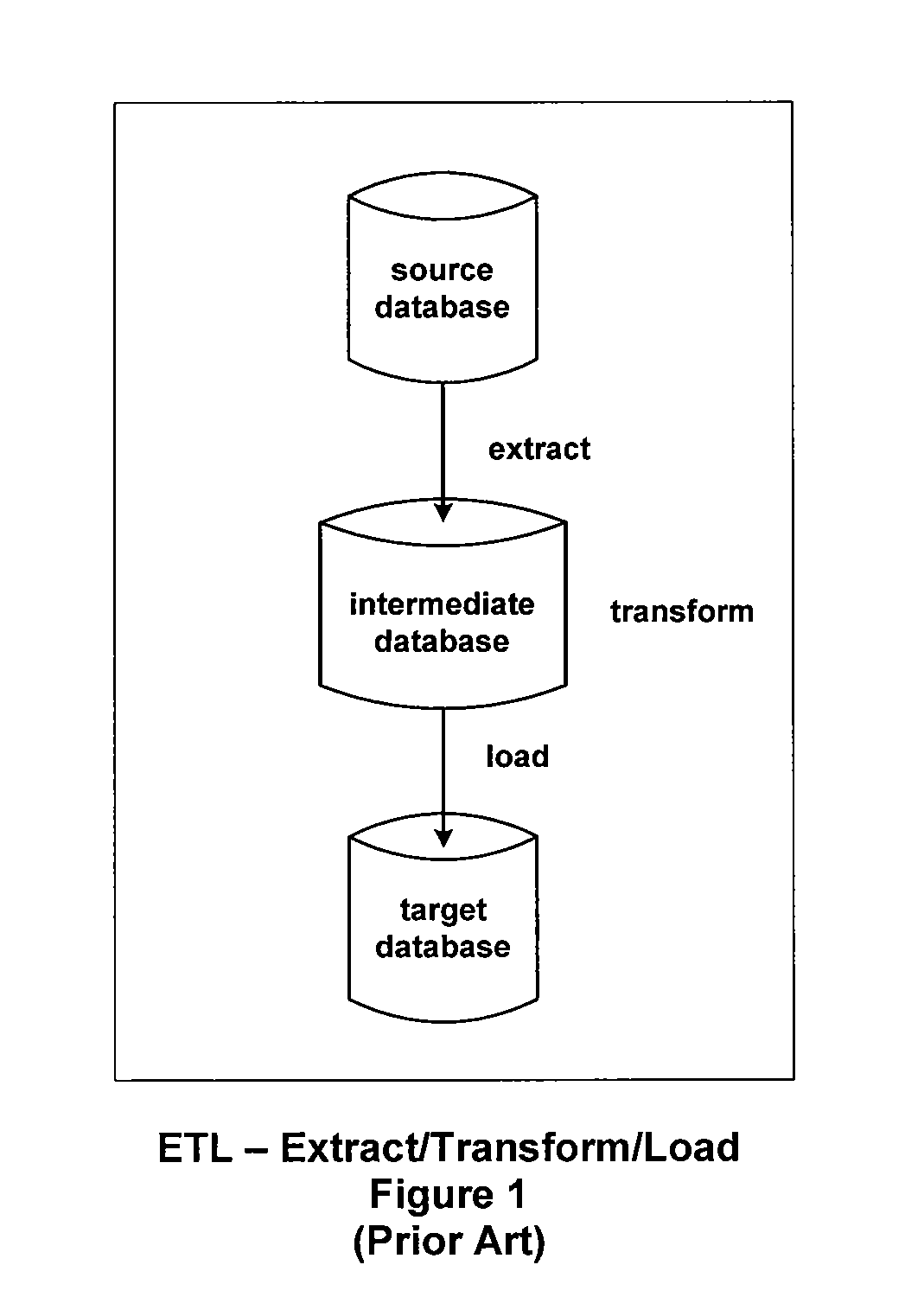
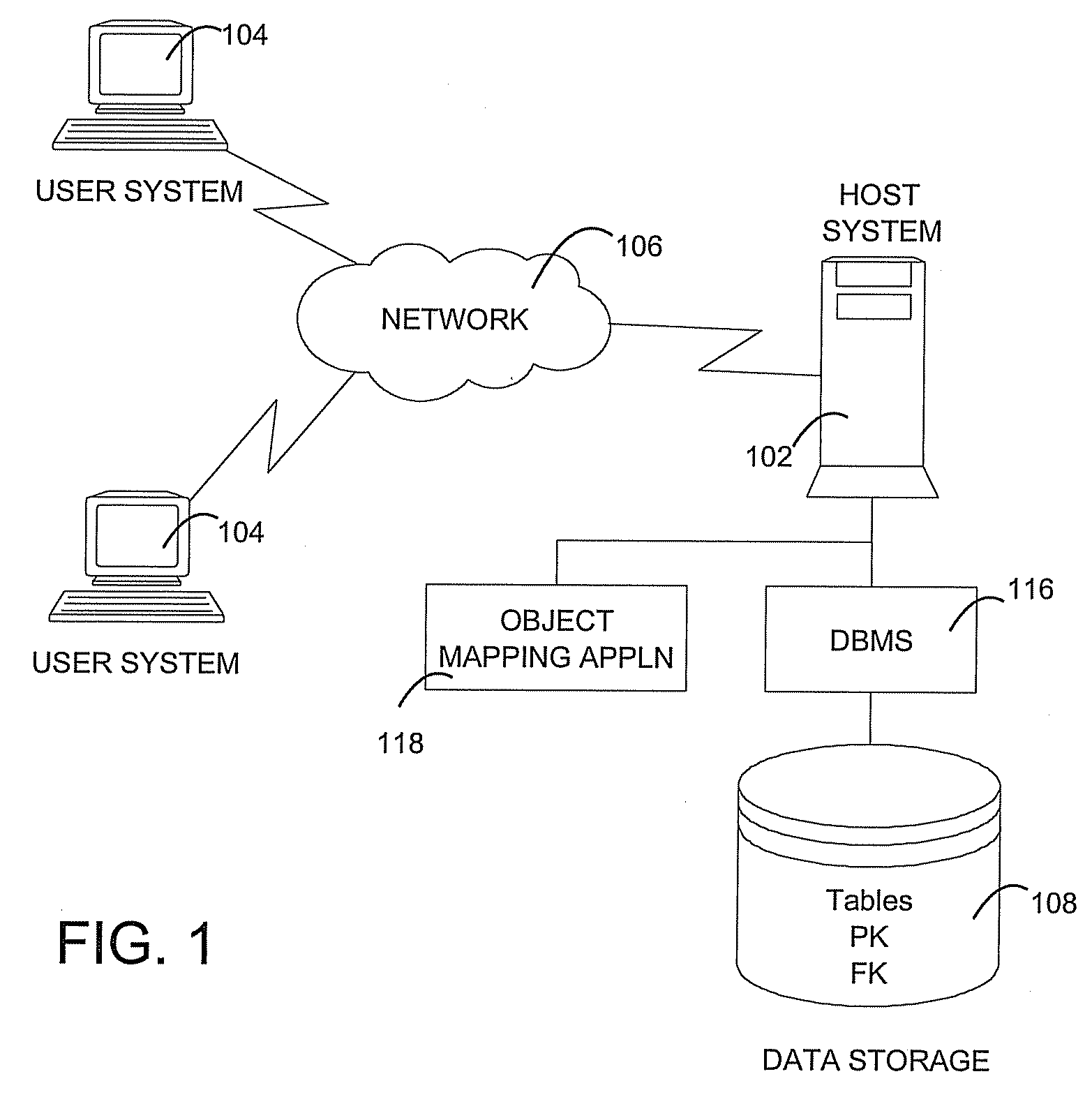
A method and system for migrating data between databases is provided. Metadata is obtained from a source database and used to determine the manner in which the data within the source database should be migrated to a target database. The metadata provides a mechanism for structuring queries to retrieve the data within the source database in a generic manner, thereby providing a generic determination of the structure of the data to be migrated. The dependencies among tables in the source database are discovered, thereby providing an order to the migration operations to be performed when migrating the data. This order ensures that the data can be migrated correctly in the presence of referential integrity (foreign key) constraints. In addition, custom mapping operations may be performed during the migration operations so that the data from the source database is modified before writing the data to the target database.
Owner:IBM CORP
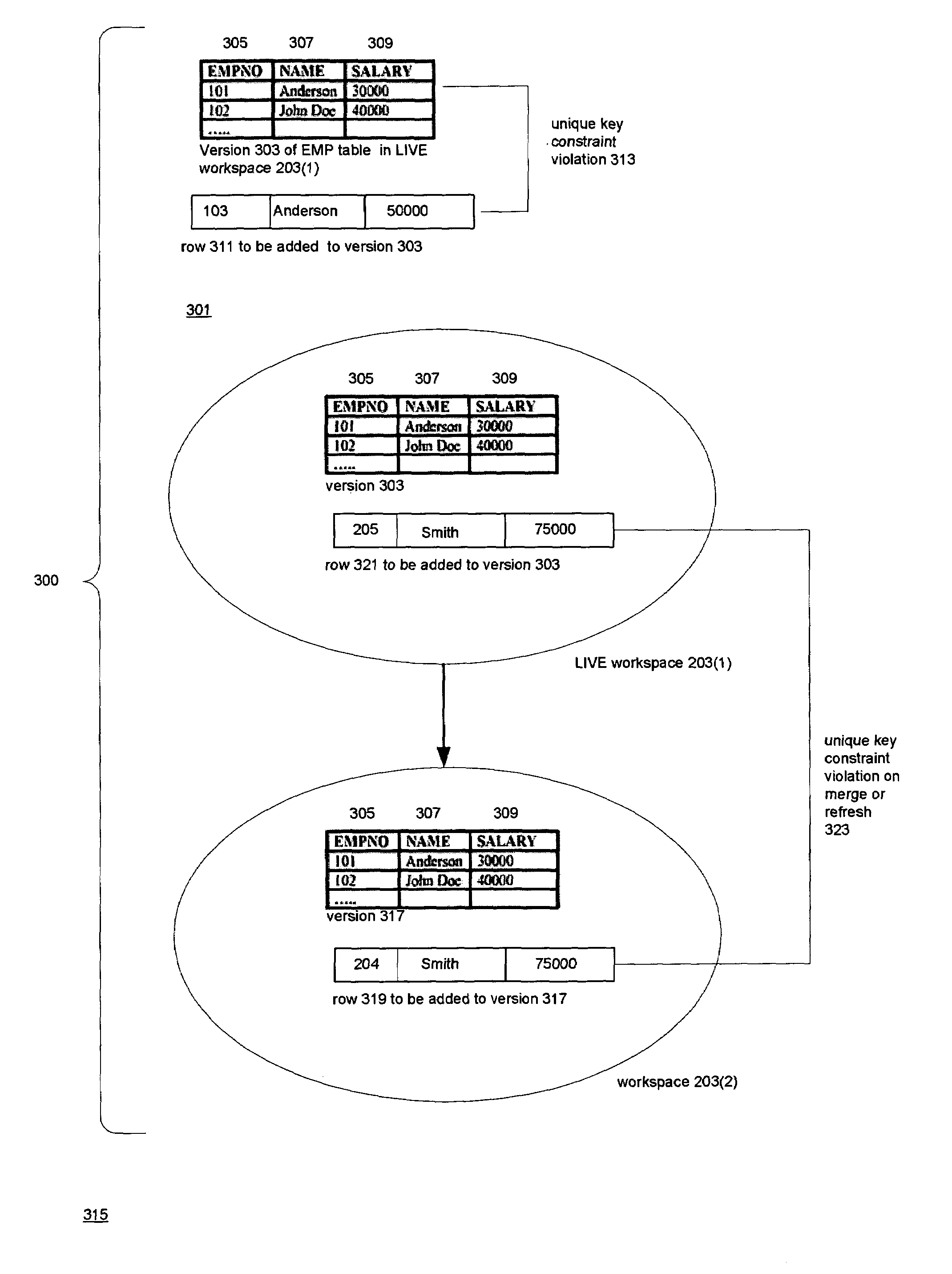
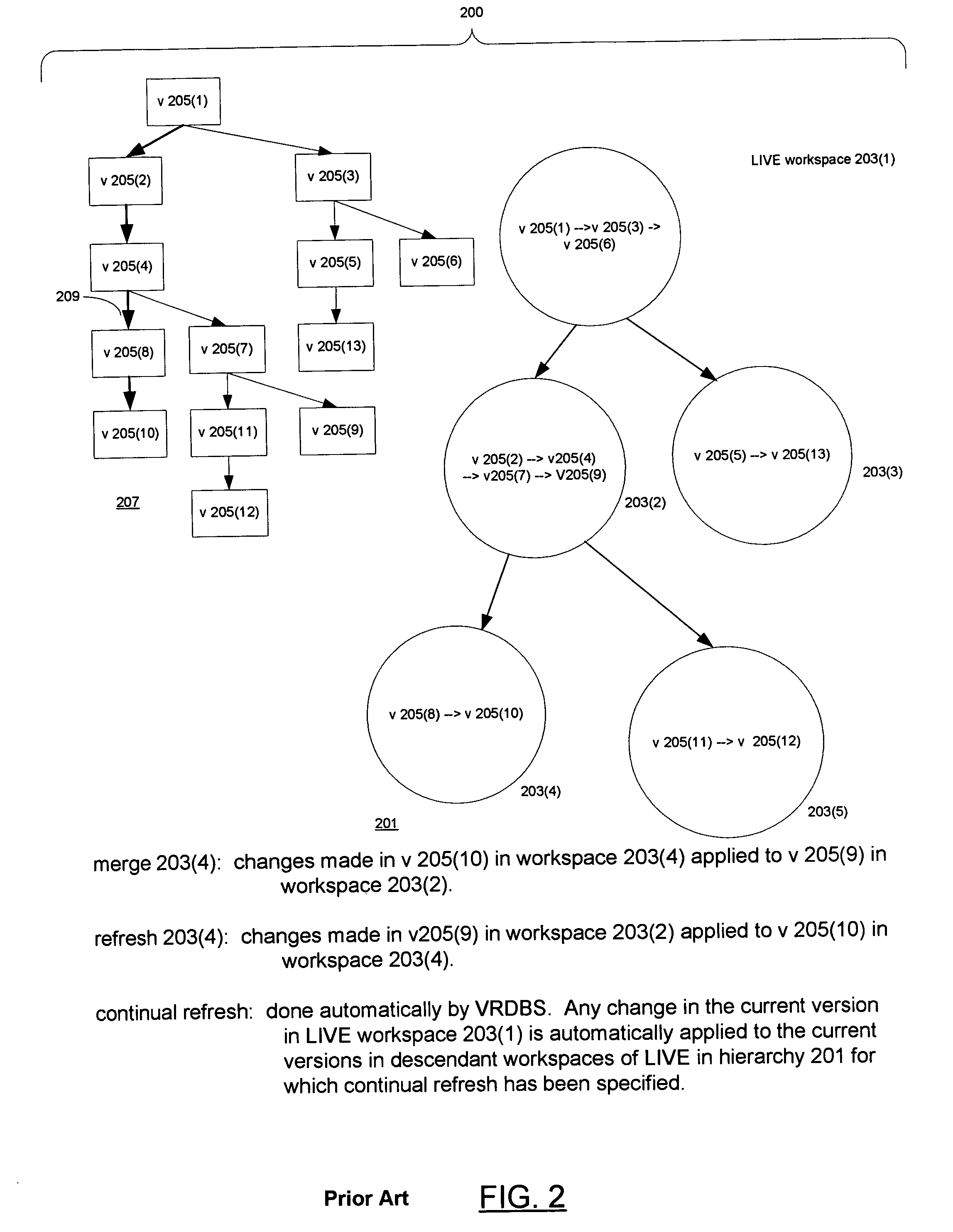
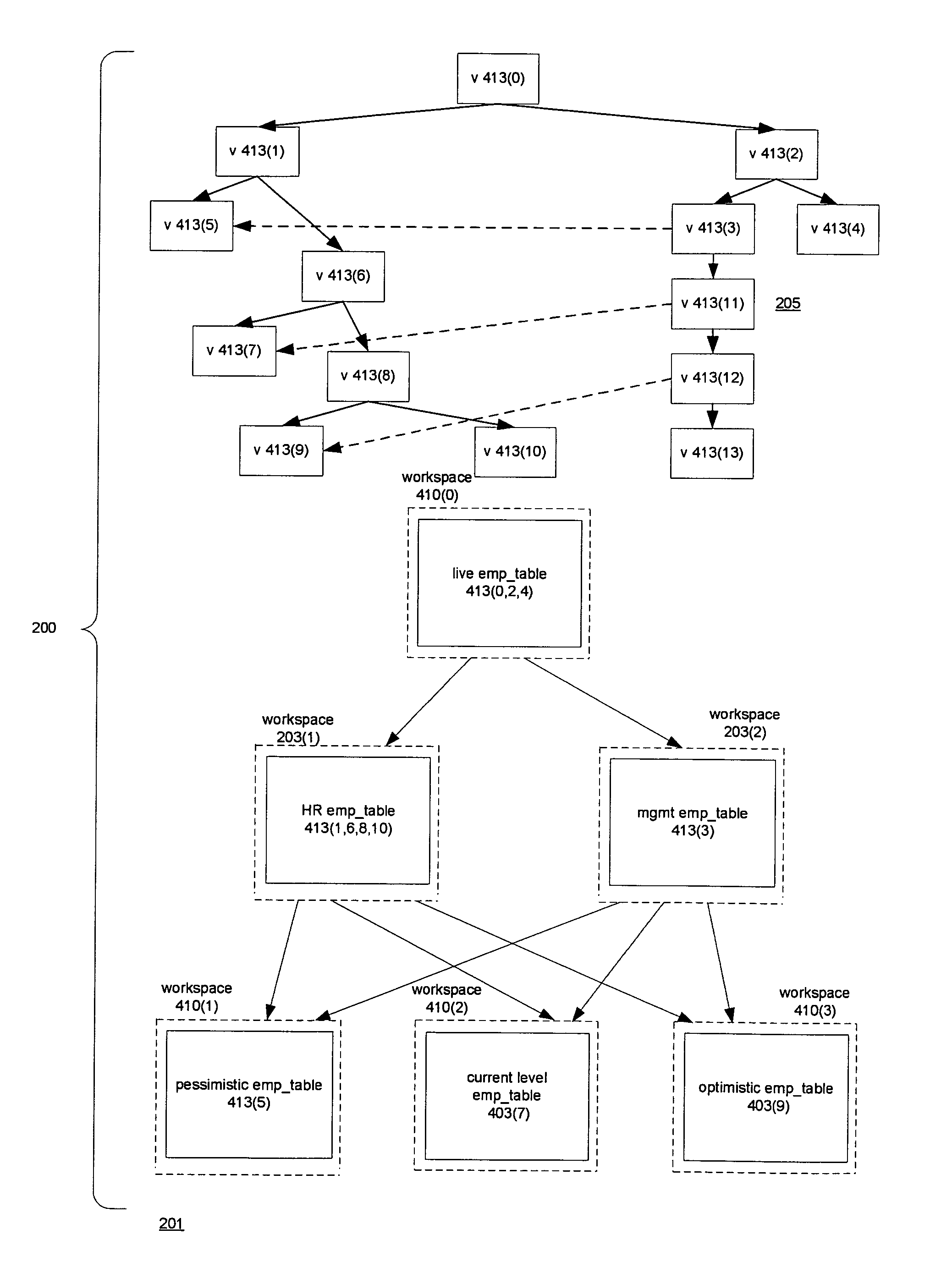
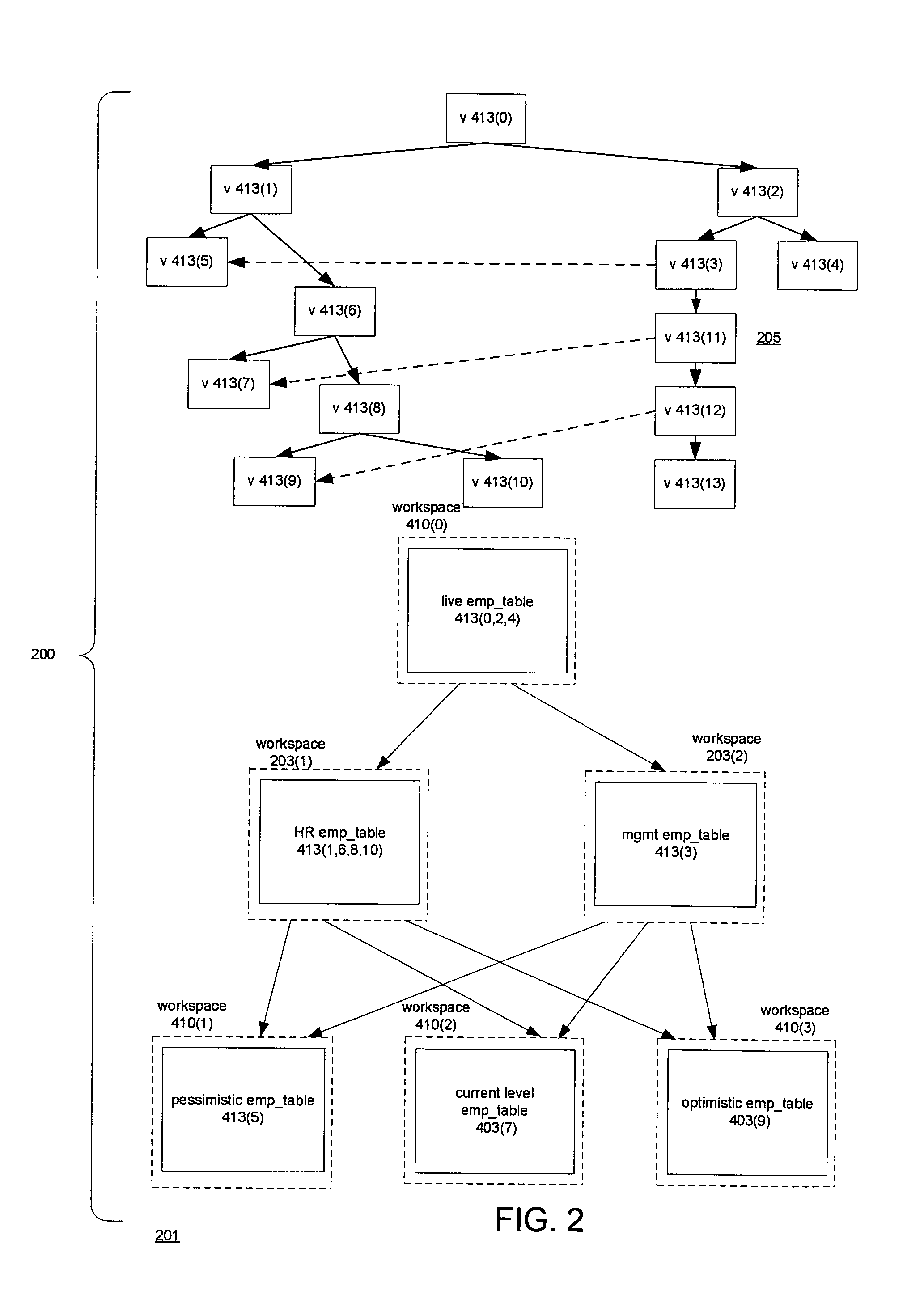
Versioned relational database system with an optimistic constraint model
InactiveUS7028057B1Data processing applicationsDigital data information retrievalTheoretical computer scienceWorkspace
Techniques for doing optimistic constraint checking in a versioned relational database system. The techniques find a subset of the versions of a table that contain all of the rows that need be checked for violation of a constraint when a given version is modified. When the versions of a table are organized into a directed acyclic graph (DAG), the subset for a given version is the ancestry of the given version, that is, the given version plus the ancestors of the given version in the DAG. Within the ancestry, the set of rows that must be checked is termed the version view. A row that belongs to the set has a primary key that is the latest version of the primary key in the given version's ancestry. The technique may be used for constraints including the referential integrity constraint and the unique key constraint. The metadata used to compute the version view is disclosed, as well as the manner in which the constraint checking techniques interact with the workspaces that provide access to the versions. The workspaces may be organized as a DAG. The manner in which the workspaces are organized determines how changes are propagated in the versioned relational database and thus the versions whose ancestry has to be checked for constraint violations.
Owner:ORACLE INT CORP
Systems and methods for collaborative note-taking
InactiveUS20050171926A1Digital data processing detailsNatural language data processingHandwritingFunction word
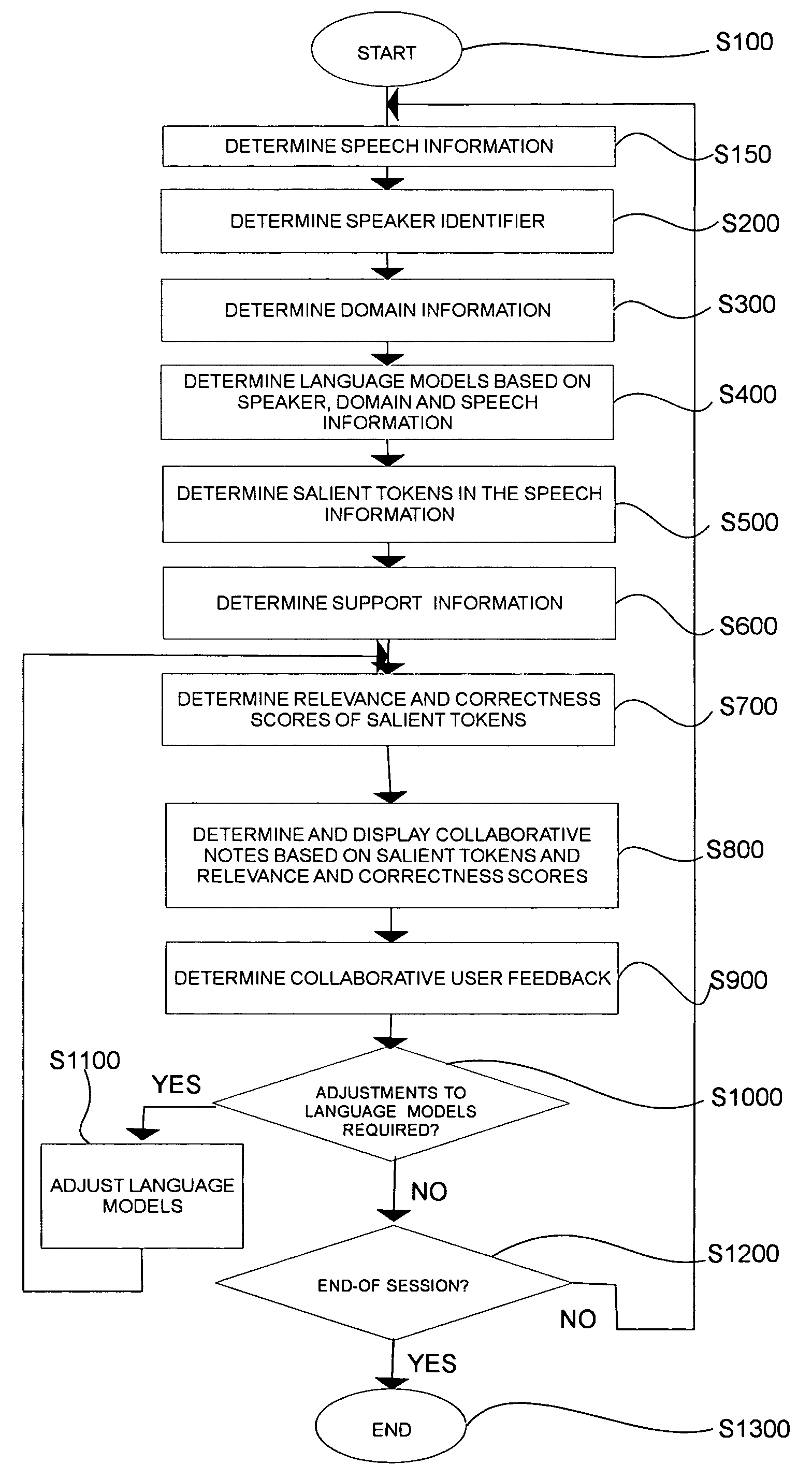
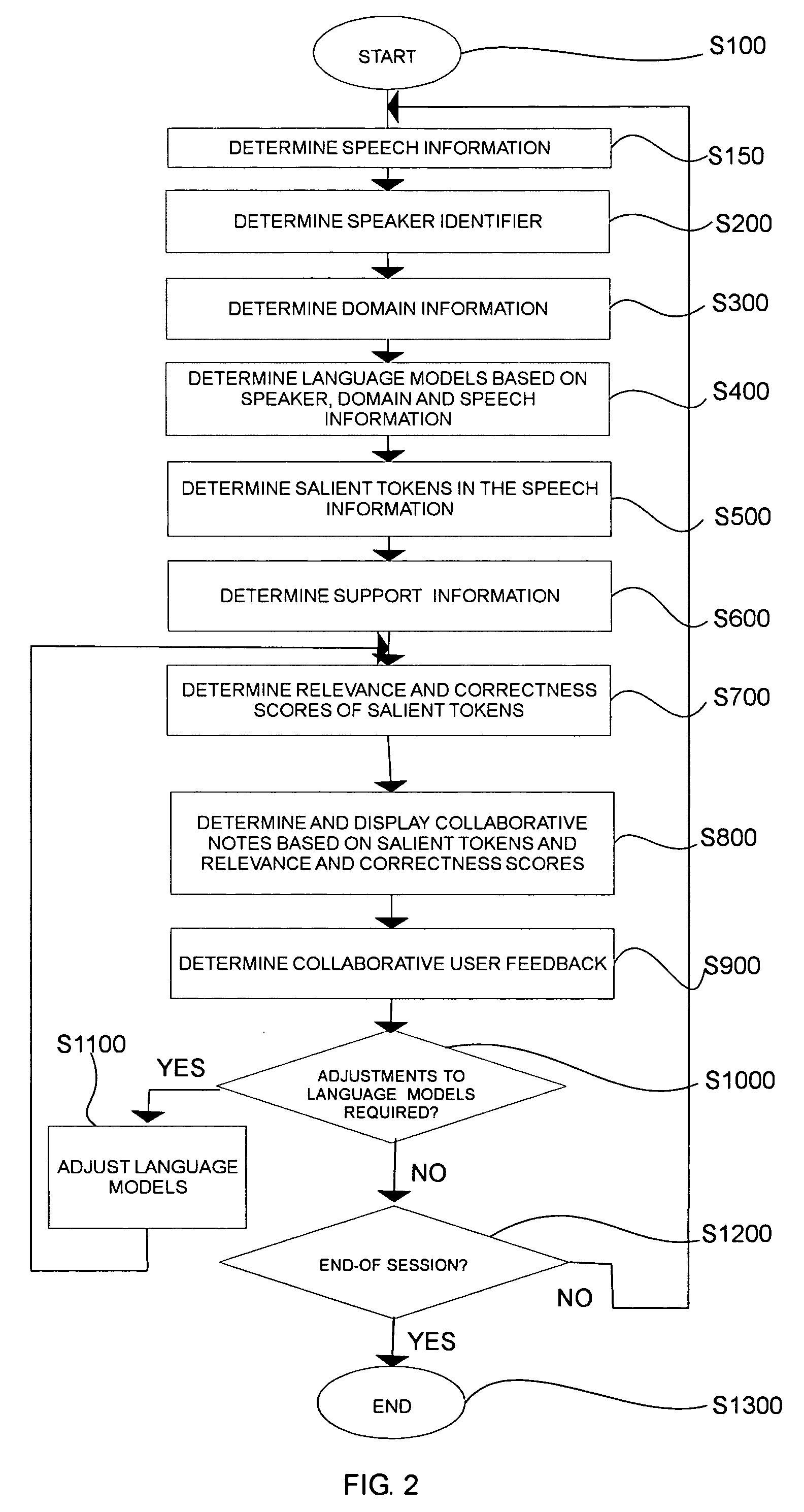
Techniques are provided for determining collaborative notes and automatically recognizing speech, handwriting and other type of information. Domain and optional actor / speaker information associated with the support information is determined. An initial automatic speech recognition model is determined based on the domain and / or actor information. The domain and / or actor / speaker language model is used to recognize text in the speech information associated with the support information. Presentation support information such as slides, speaker notes and the like are determined. The semantic overlap between the support information and the salient non-function words in the recognized text and collaborative user feedback information are used to determine relevancy scores for the recognized text. Grammaticality, well formedness, self referential integrity and other features are used to determine correctness scores. Suggested collaborative notes are displayed in the user interface based on the salient non-function words. User actions in the user interface determine feedback signals. Recognition models such as automatic speech recognition, handwriting recognition are determined based on the feedback signals and the correctness and relevance scores.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Techniques to preserve data constraints and referential integrity in asynchronous transactional replication of relational tables
InactiveUS20050192989A1High degree of parallelismData processing applicationsDigital data information retrievalComputer hardwareImproved method
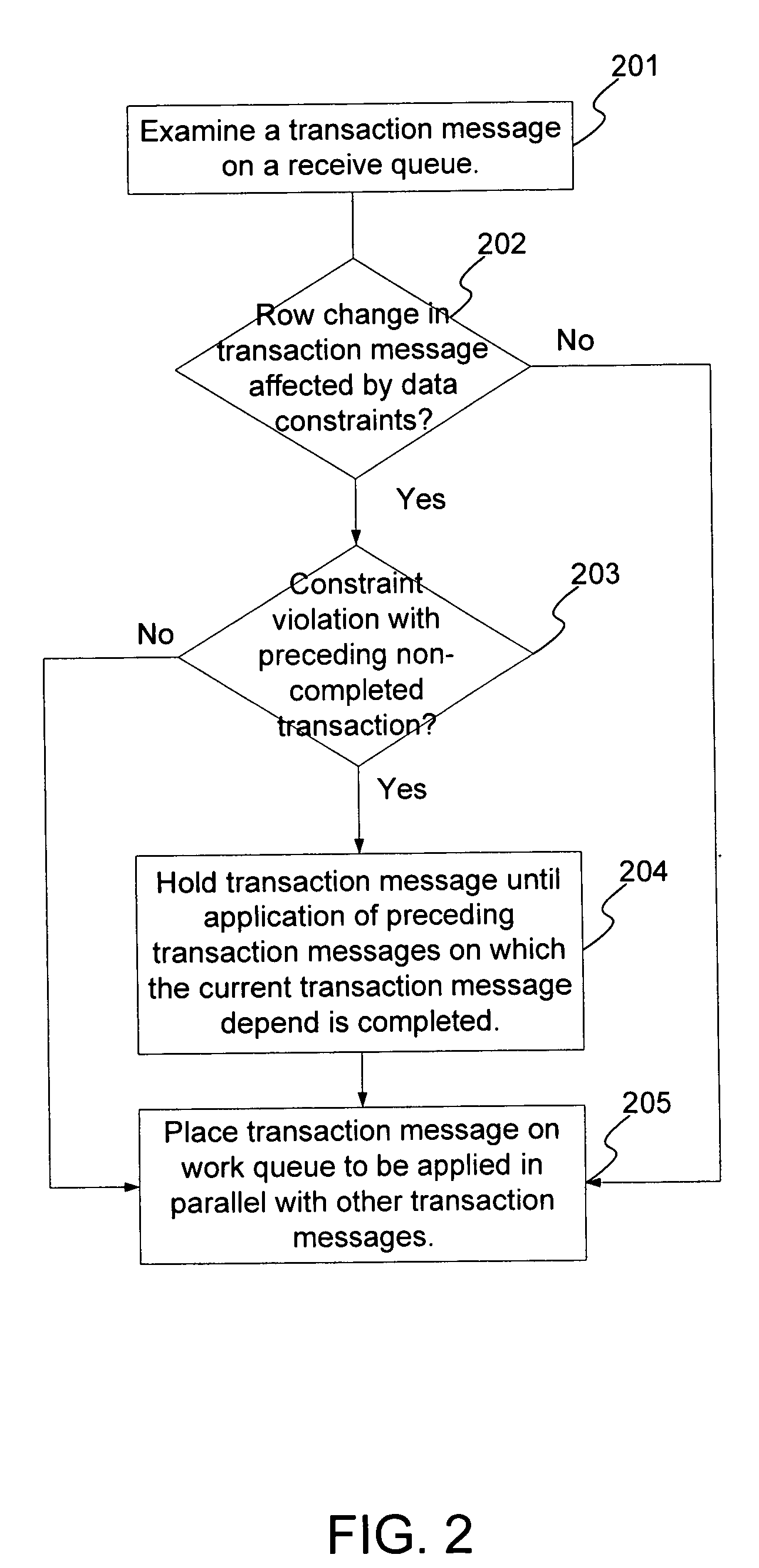
An improved method and system for preserving data constraints during parallel apply in asynchronous transaction replication in a database system have been disclosed. The method and system preserves secondary unique constraints and referential integrity constraints, while also allowing a high degree of parallelism in the application of asynchronous replication transactions. The method and system also detects and resolves ordering problems introduced by referential integrity cascade deletes, and allows the parallel initial loading of parent and child tables of a referential integrity constraint.
Owner:IBM CORP
Method for managing and accessing relational data in a relational cache
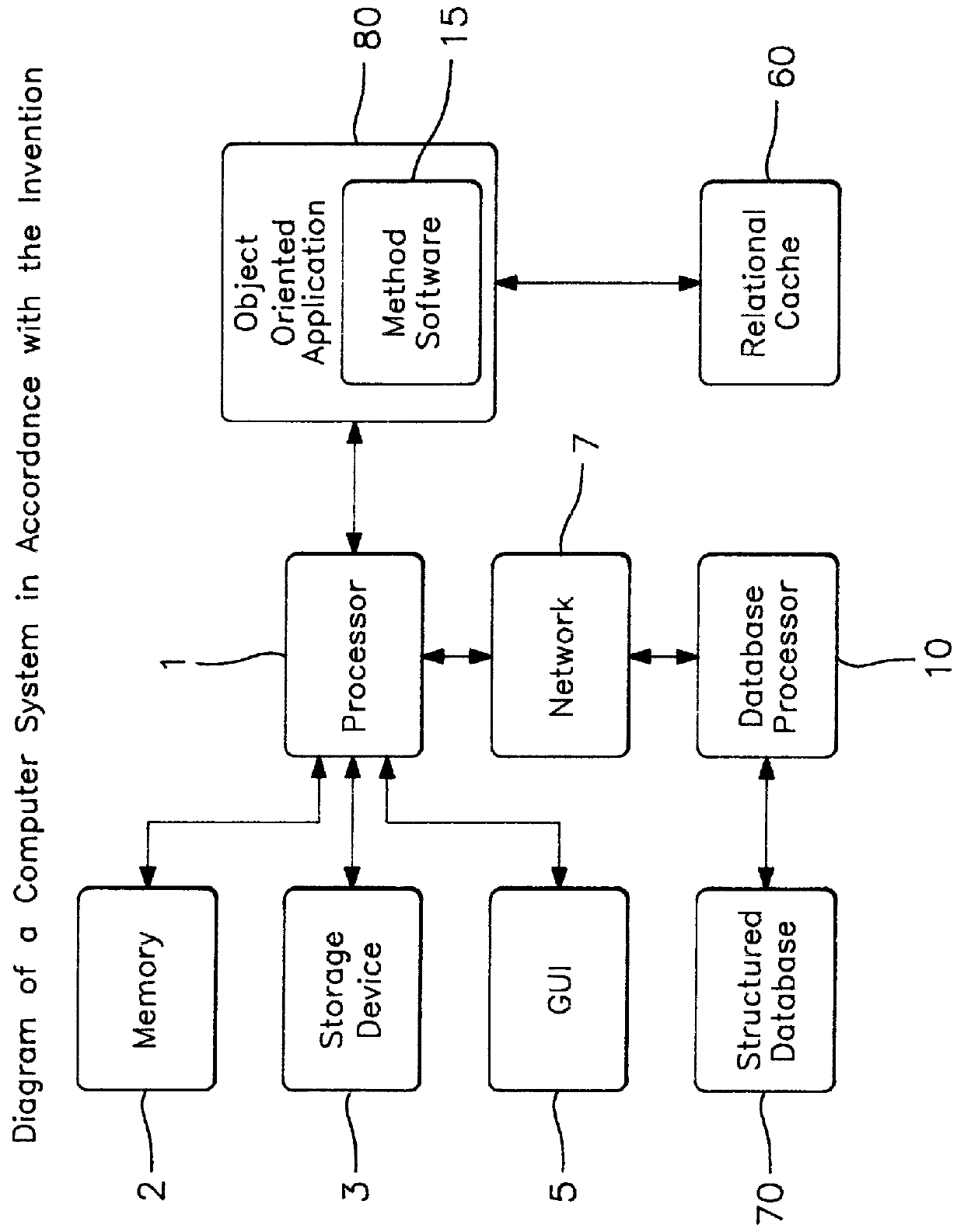
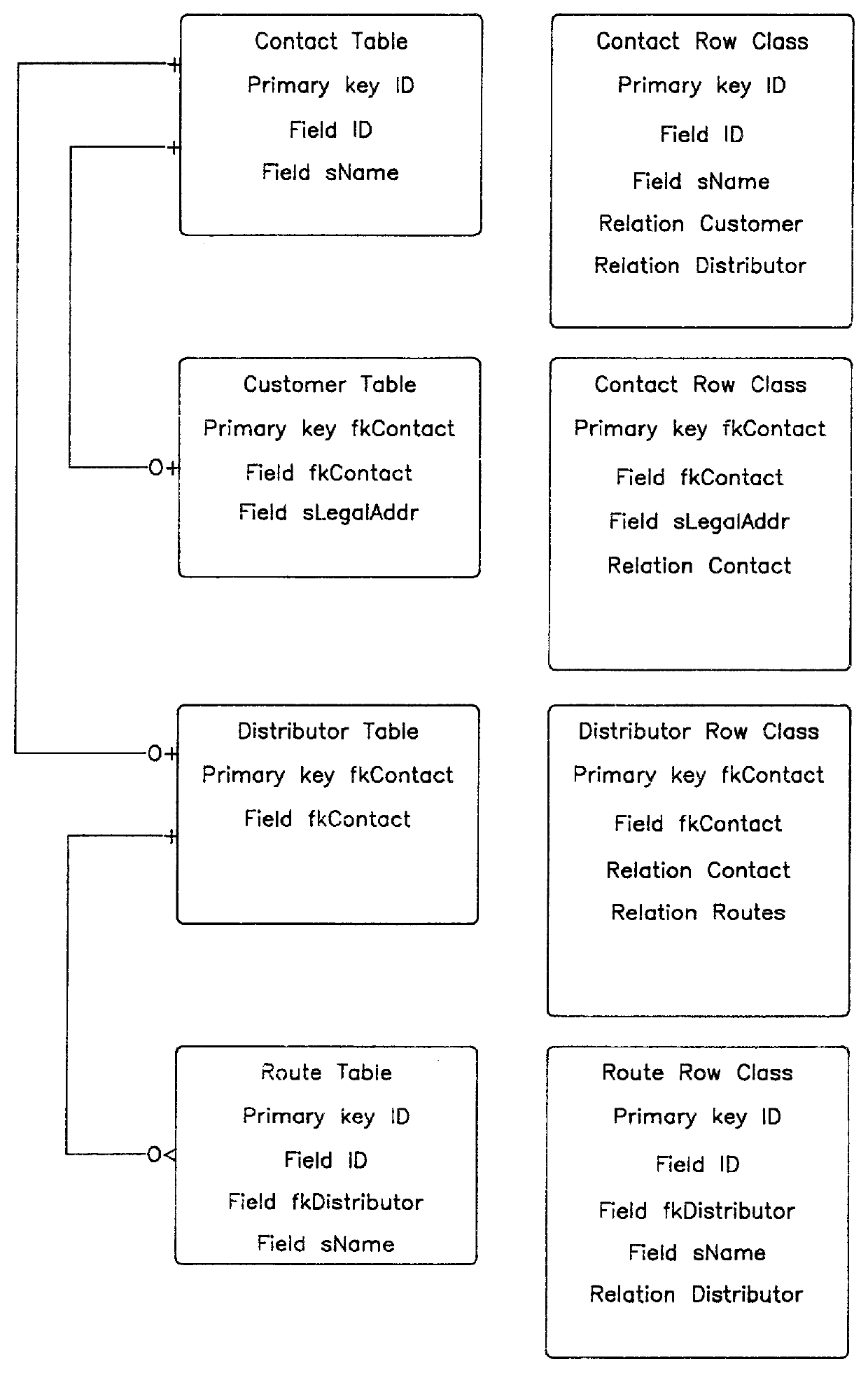
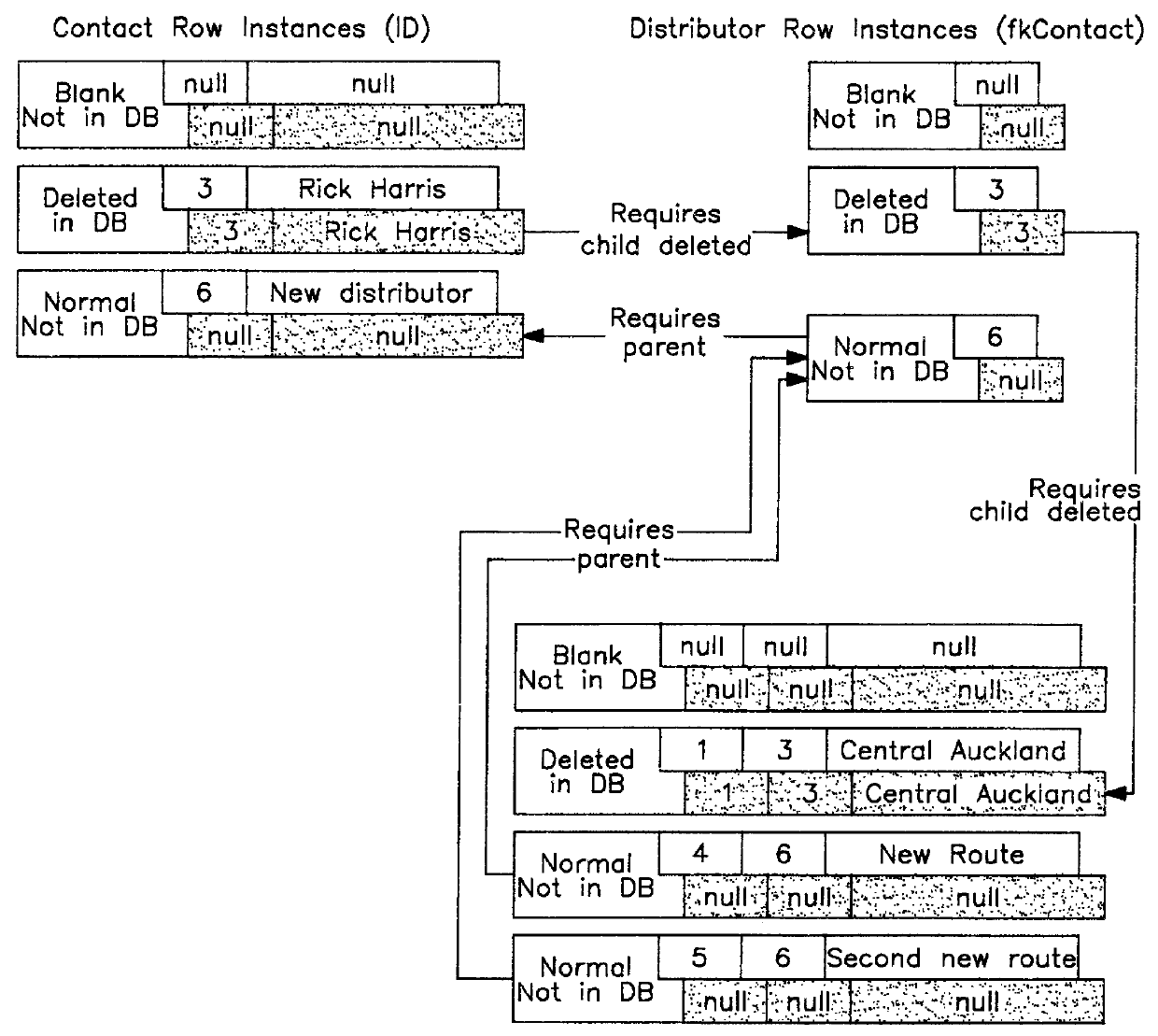
InactiveUS6070165AAvoid repetitionEasy accessData processing applicationsRelational databasesObject basedApplication software
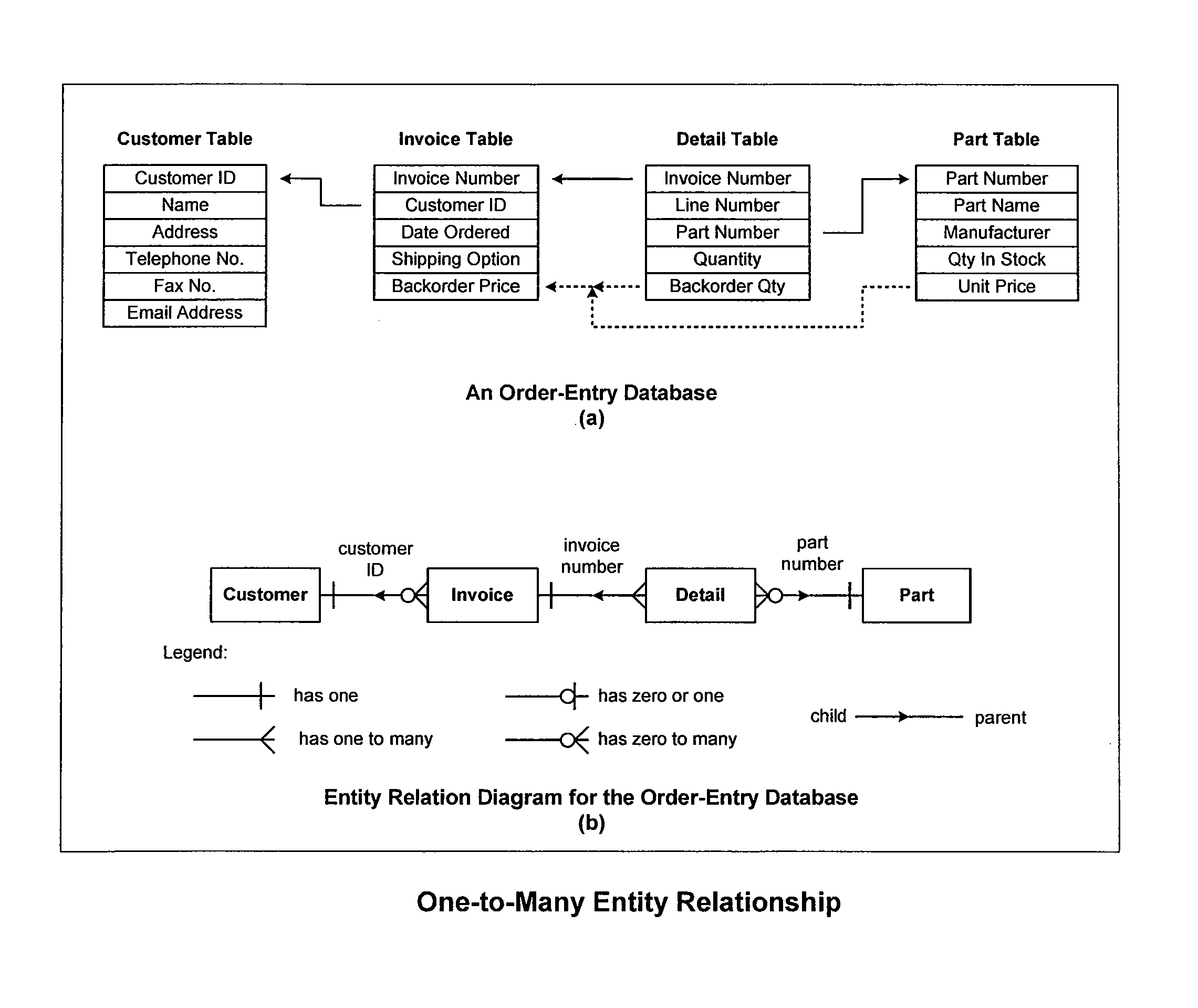
For an object-based application being executed in a digital computing system a framework is provided for managing information retrieved from a structured database, such as a relational database. The processor is used to construct a single cohesive data structure, called a relational cache, that comprises all the row instances and that represents information retrieval from the structured database in a form suitable for use by one or more applications. An application may have several of these relational caches active at any one time, some of which may represent separate user editing sessions, where each session may be saved or discarded independently. The framework ensures that only one copy of a row instance is in a given cache at any given time, even if several different queries return the same information from the database. Row instances within the relational cache may be modified by the application, where the row instances are marked as modified but not saved to the database at that time. The framework ensures all modified row instances within the cache are saved at one time, which are presented to the database as a single transaction, with individual rows ordered so as not to violate database referential integrity rules. Other properties of the framework are disclosed.
Owner:WHITMORE THOMAS JOHN
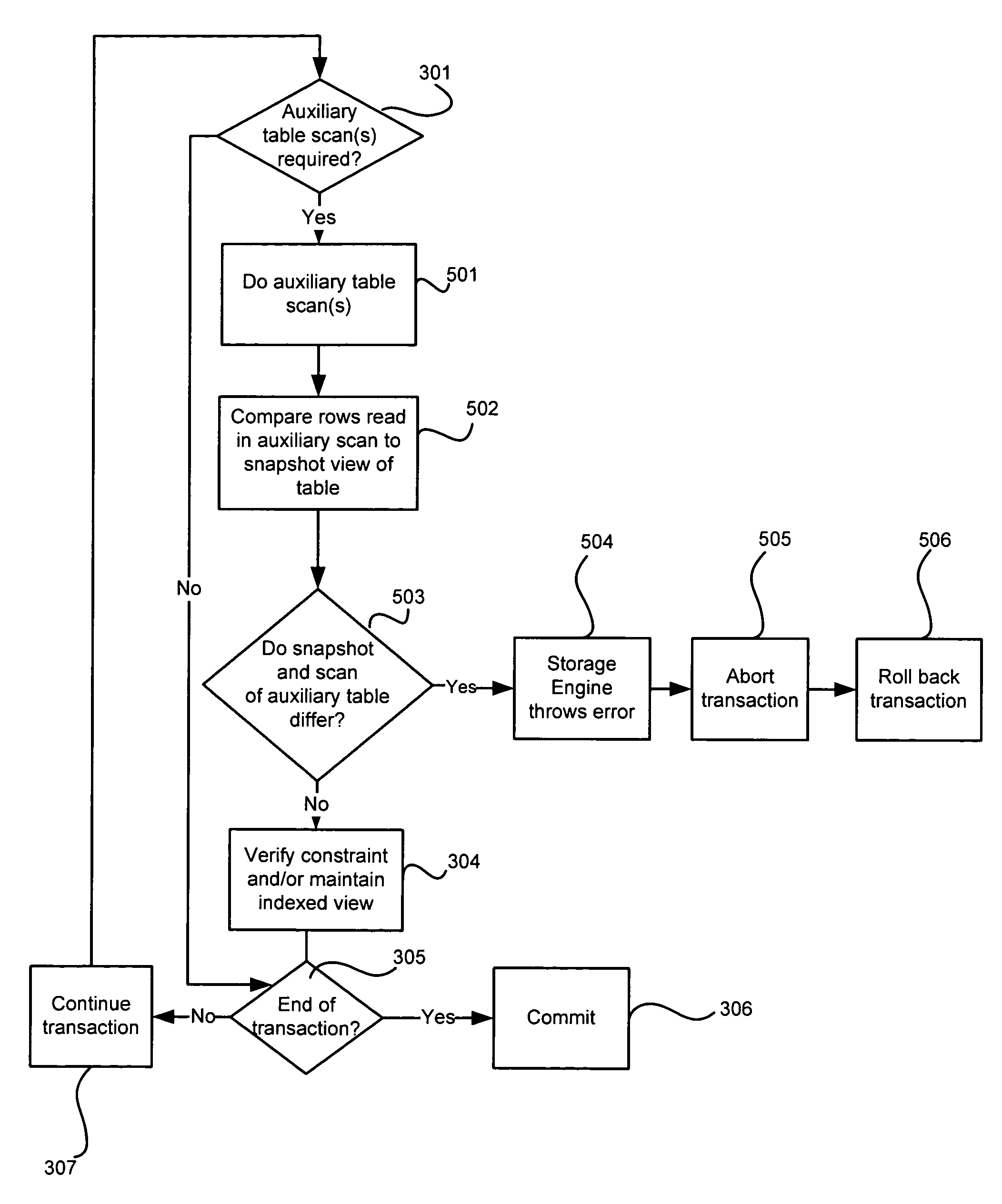
Systems and methods for avoiding database anomalies when maintaining constraints and indexes in presence of snapshot isolation
InactiveUS7653665B1Detecting and avoiding anomalyDigital data information retrievalDigital data processing detailsData validationSource Data Verification
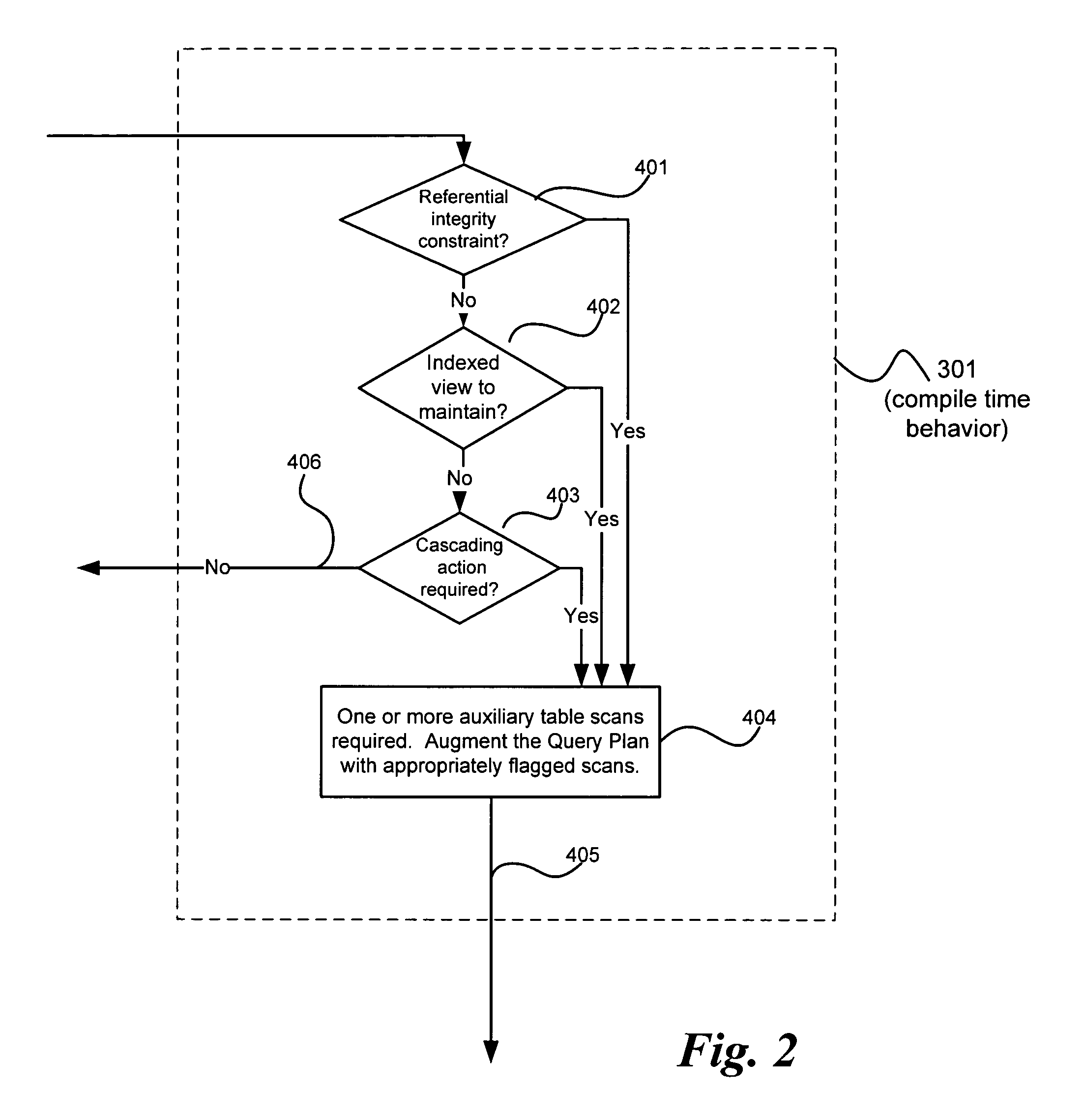
A system and method avoids anomalies in presence of data manipulation language (DML) plans maintaining dependent objects and snapshot isolation. An anomaly due to using a snapshot isolation level within the transaction is detected within a database transaction and the transaction is aborted based upon that detection. Involved in making the anomaly detection is determining whether a view of particular data accessed during the transaction under a snapshot isolation view to ensure read consistency differs from a view of the data under another isolation level, such as the read committed isolation level. Then a detection is made that an anomaly may occur if it is determined that the view of the data accessed during the transaction under the snapshot isolation differs from the view of the data under the other isolation level. Such anomaly avoidance prevents an indexed view being maintained nor a referential integrity constraint validated based on incorrect data.
Owner:MICROSOFT TECH LICENSING LLC
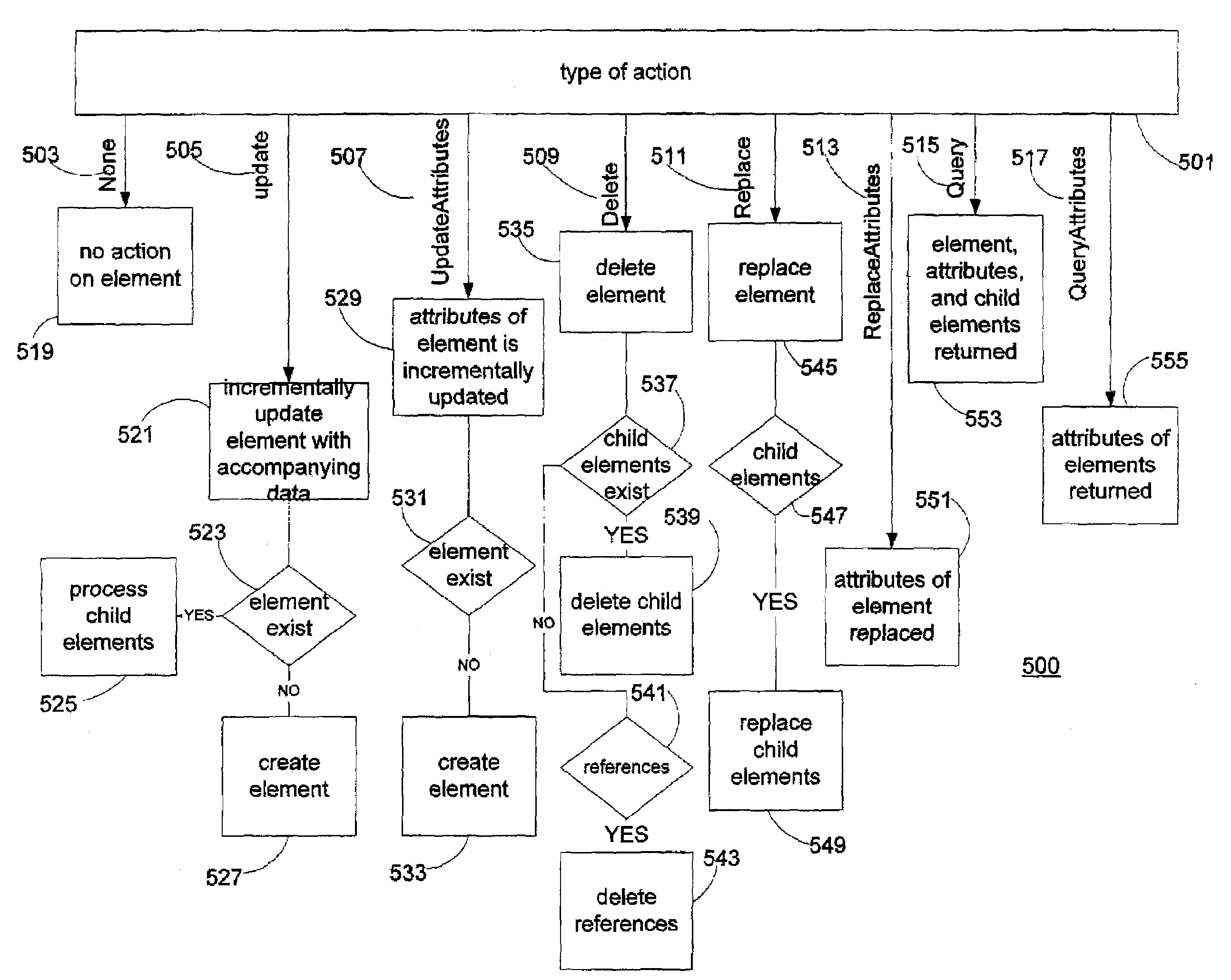
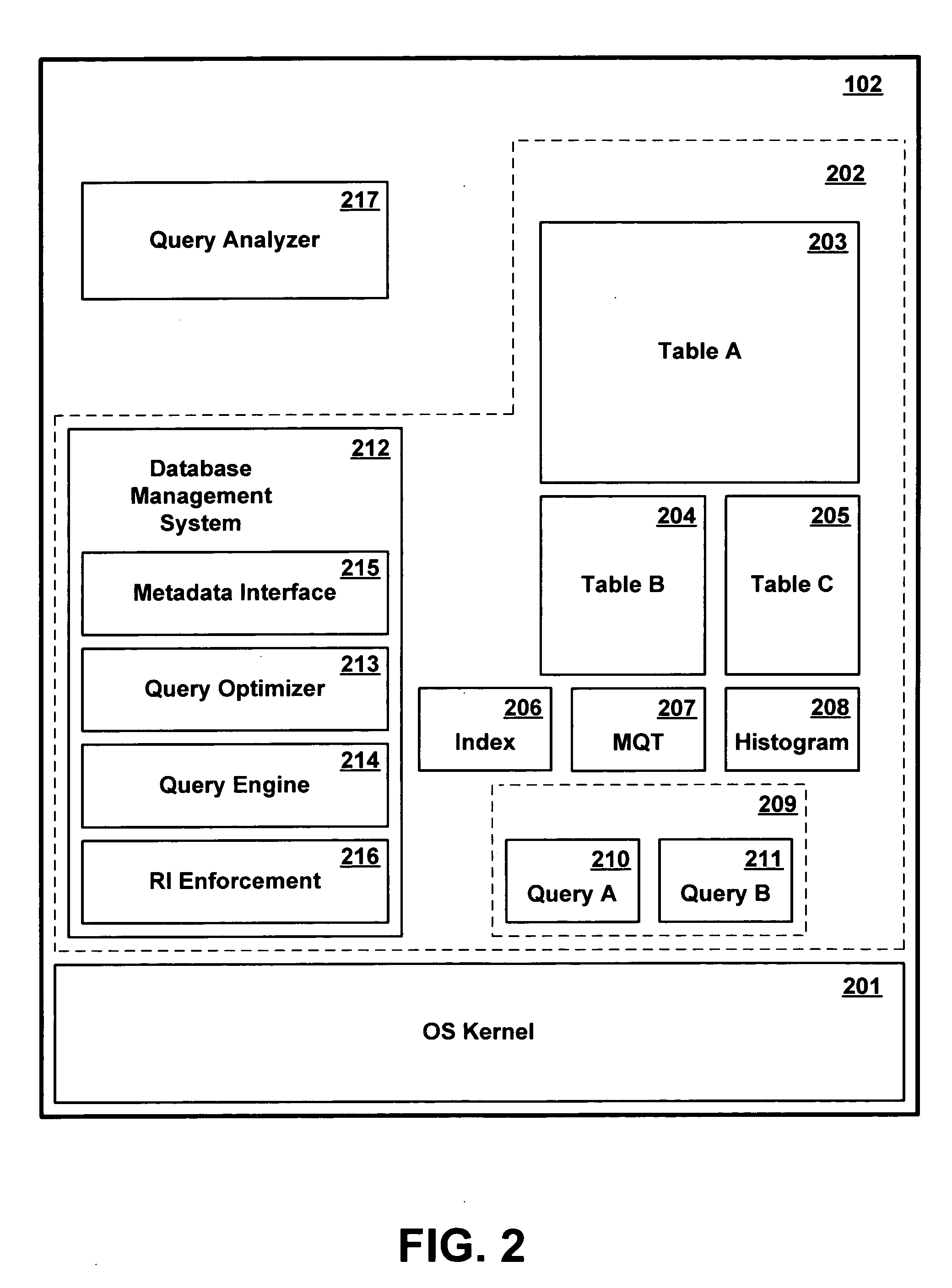
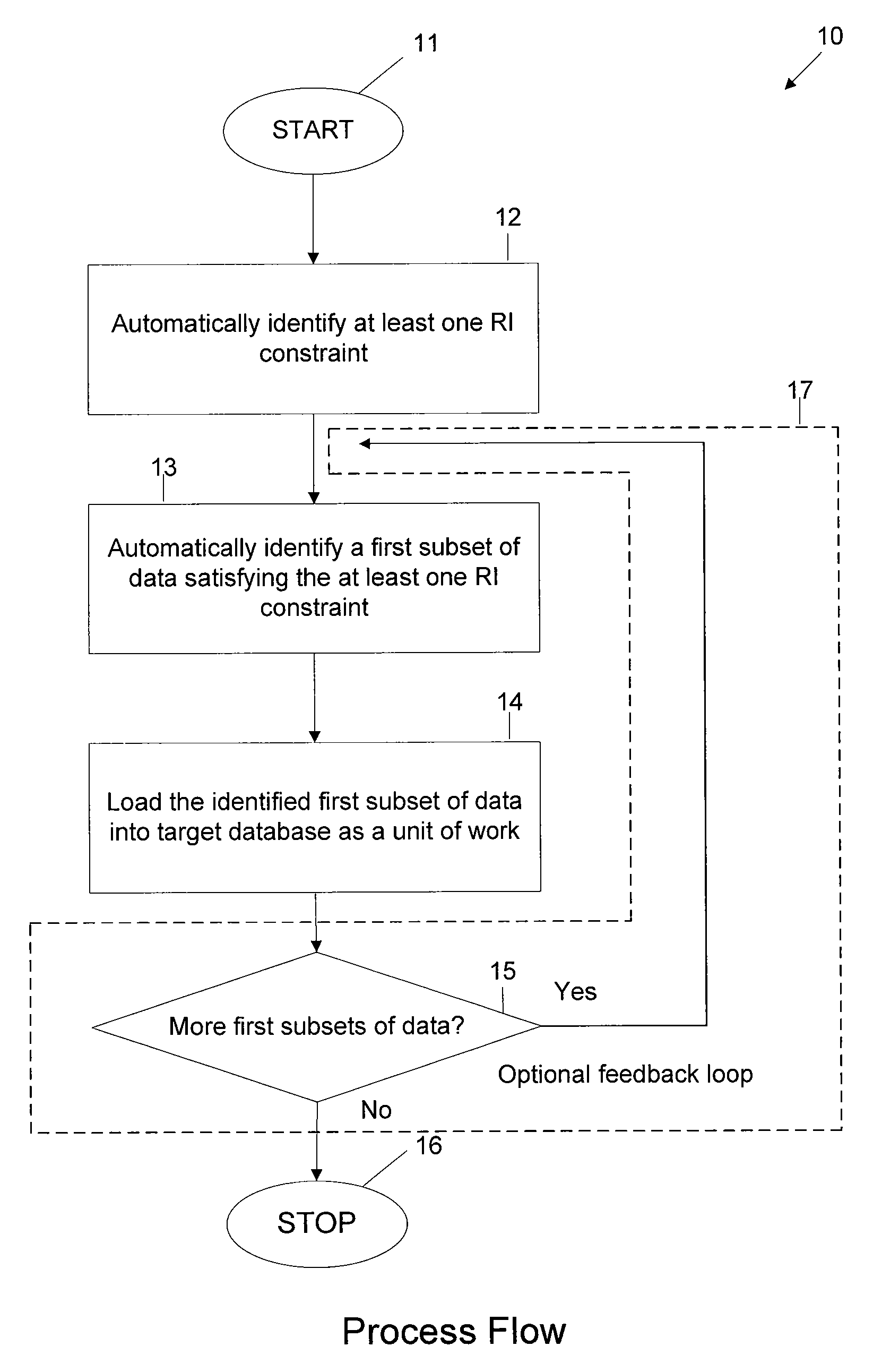
Referential Integrity, Consistency, and Completeness Loading of Databases
InactiveUS20100114841A1Digital data processing detailsSpecial data processing applicationsTarget databaseWork cell
A method is provided for loading data from a source database to a target database that includes at least one table. Prior to loading the data from the source database into the target database, at least one referential integrity constraint and / or at least one consistency requirement regarding the data is automatically identified. A subset of the data that satisfies the at least one referential integrity constraint and / or consistency requirement is then automatically identified. The identified subset of the data is then loaded into the target database as a unit of work.
Owner:INTEL CORP
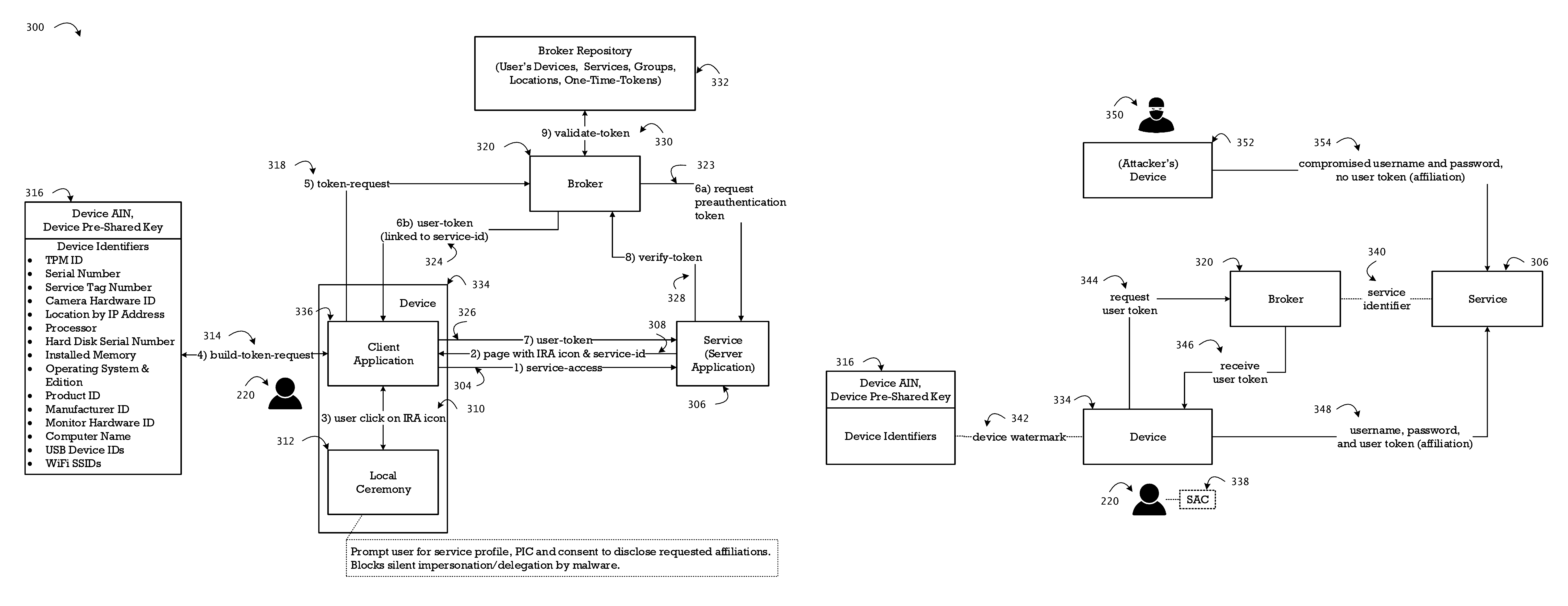
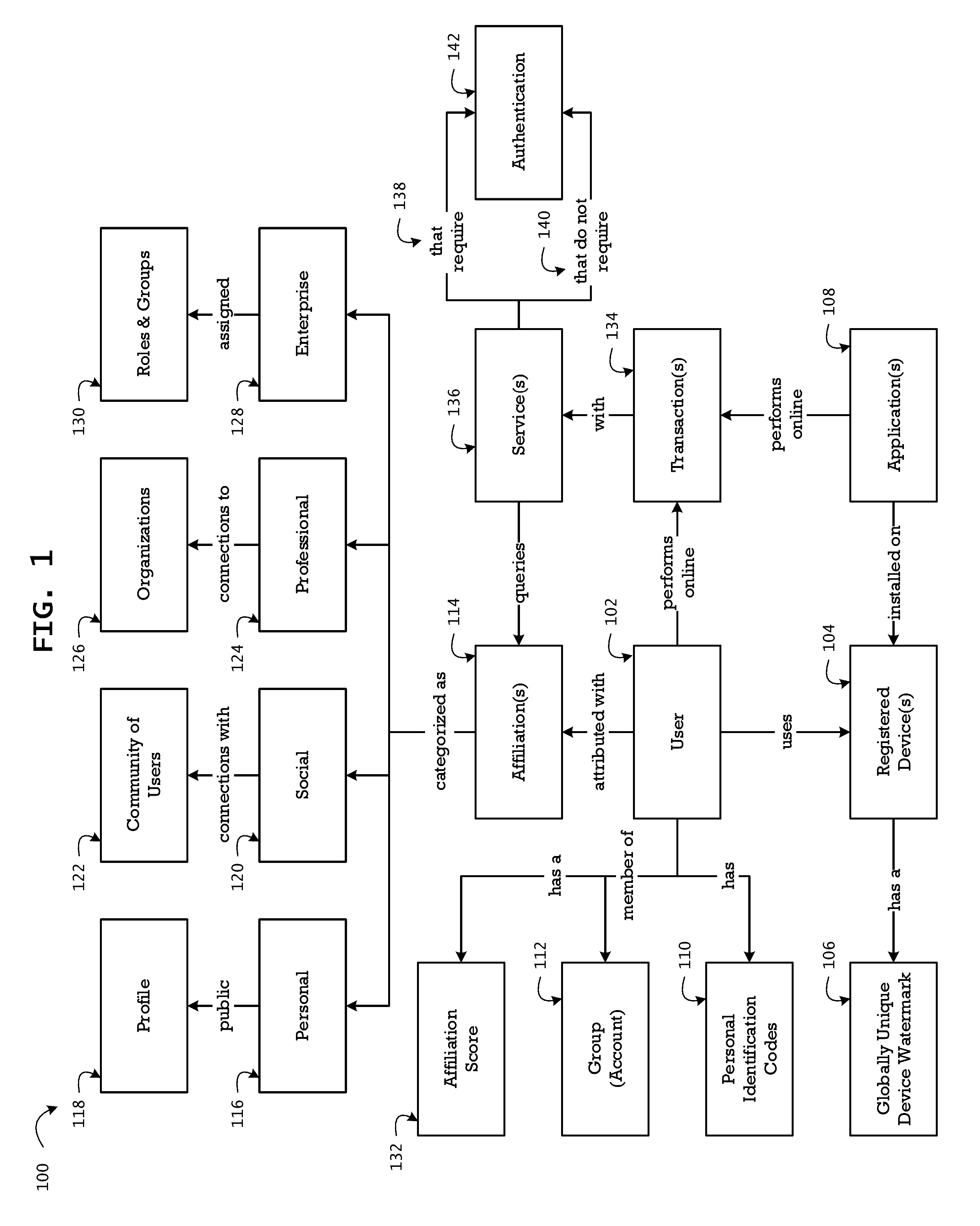
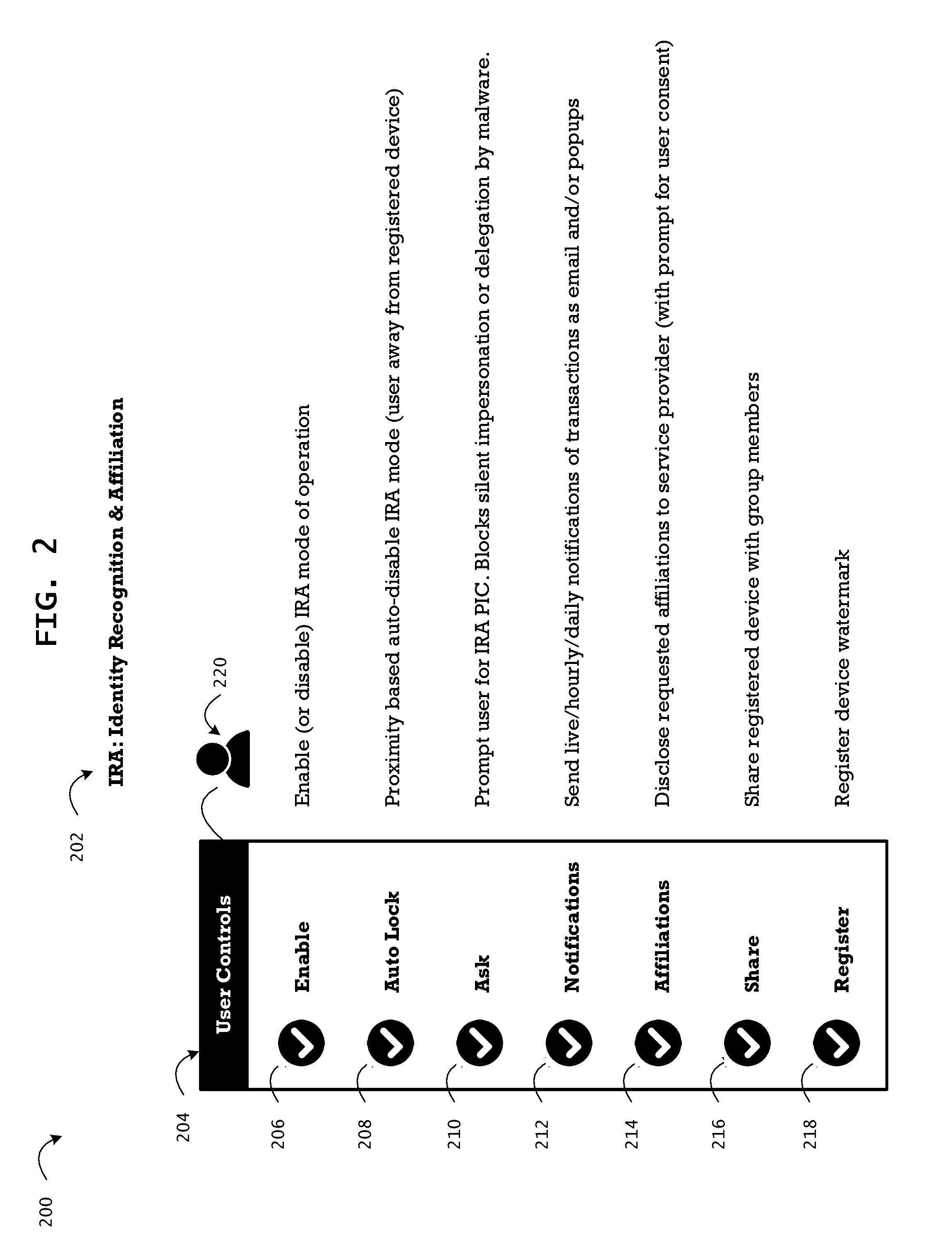
System and method for identity recognition and affiliation of a user in a service transaction
The method integrates the dynamic and authoritative posture of an authenticated user, a registered device, and a registered service provider as a conclusive proof of identity recognition for affiliation of associated contextual attribution and referential integrity. In addition to relieving the user of the burden of remembering multiple passwords for a plurality of services, the method provides a means to facilitate an affiliation oriented architecture for a broad spectrum of web and cloud based services with affiliation aware content streaming, leveraging the affiliation score as a key trust metric. The method provides protection from user-agnostic delegation and impersonation of identity, social engineering, and compromised passwords, which are exploited by numerous strains of landed malware to launch multi-stage coordinated cyber-attacks on consumer accounts and enterprise systems. The method of affiliation based on identity recognition provides authoritative, contextual, and consensual user information, of relevance in a live transaction, to the service provider.
Owner:KUMAR SRINIVAS +2
Techniques to preserve data constraints and referential integrity in asynchronous transactional replication of relational tables
InactiveUS7240054B2High degree of parallelismData processing applicationsDigital data information retrievalComputer hardwareImproved method
An improved method and system for preserving data constraints during parallel apply in asynchronous transaction replication in a database system have been disclosed. The method and system preserves secondary unique constraints and referential integrity constraints, while also allowing a high degree of parallelism in the application of asynchronous replication transactions. The method and system also detects and resolves ordering problems introduced by referential integrity cascade deletes, and allows the parallel initial loading of parent and child tables of a referential integrity constraint.
Owner:IBM CORP
Systems and methods for security hardening of data in transit and at rest via segmentation, shuffling and multi-key encryption
ActiveUS20150310219A1Hardening securityHardening confidentialityKey distribution for secure communicationMultiple keys/algorithms usageContextual integrityComputerized system
Systems and methods for security hardening of a file in transit and at rest via segmentation, shuffling and multi-key encryption are presented. The method including segmenting at a first computer system a file into a plurality of file segments, and encrypting the plurality of file segments using a plurality of encryption keys in order to generate a corresponding plurality of encrypted file segments, wherein each file segment of the plurality of file segments is encrypted using a respective encryption key of the plurality of encryption keys. Additionally included is bidirectional data transformation of a file by obfuscating at a first computer system digital values of the file in order to generate corresponding obfuscated digital values of the file, wherein the obfuscated digital values of the file retain their contextual integrity and referential integrity
Owner:TOPIA TECH
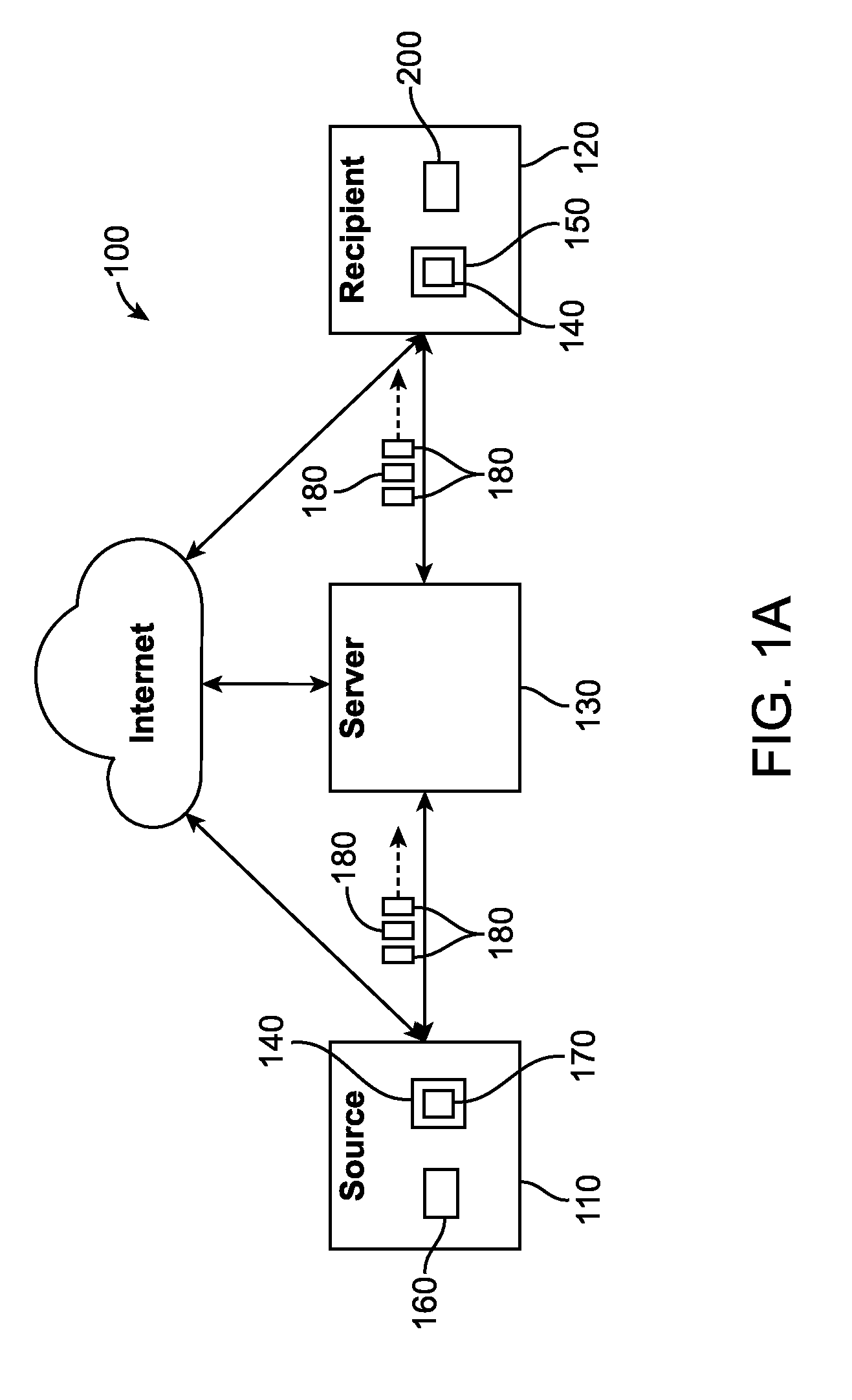
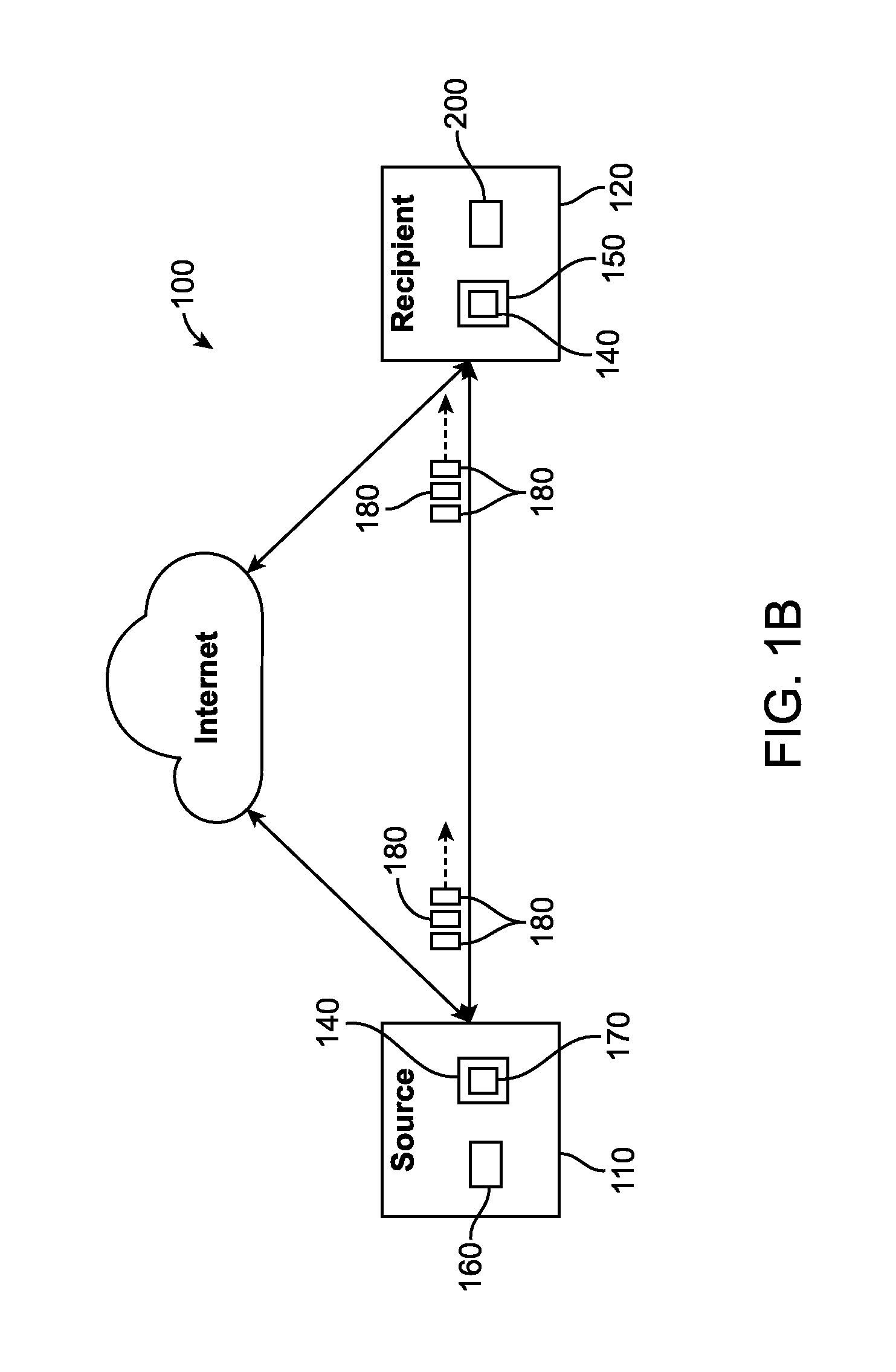
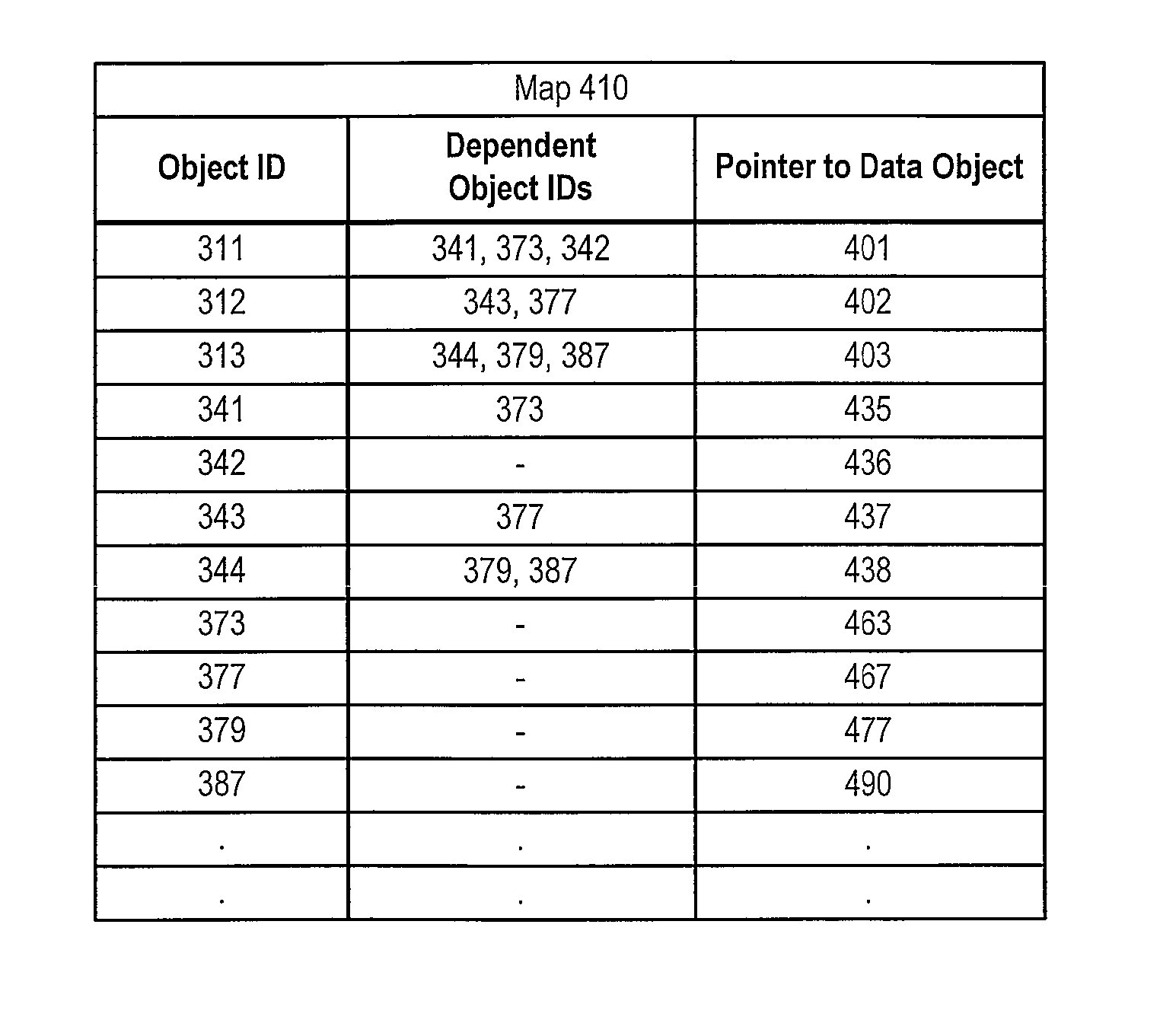
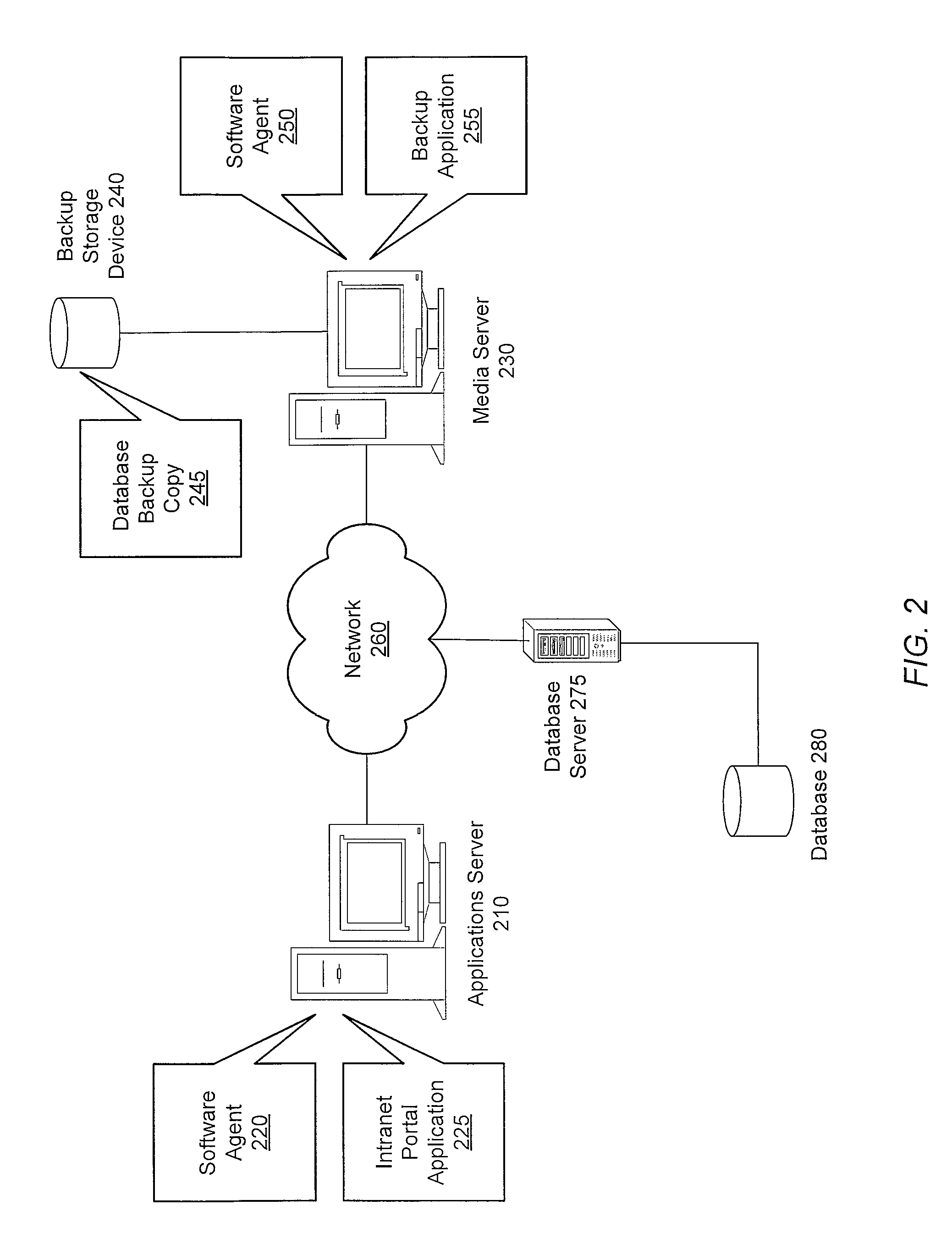
Method and system of restoring items to a database while maintaining referential integrity
ActiveUS8606752B1Digital data information retrievalDigital data processing detailsDatabaseReferential integrity
A system and method for restoring list items to a database while maintaining the referential integrity of the list items. Before requested list items are restored to a database, a dependencies tablemetadata is read to determine the links between list items of the database. A map is created, and the links between list items are stored in the map. When the requested list items are restored to the database, the requested items and any dependent items are identified from the map and restored to the database. By restoring the dependent items of the selected item to be restored, referential integrity of the database is maintained.
Owner:VERITAS TECH
Safe computer code formats and methods for generating safe computer code
InactiveUS7117488B1Preventing executionExpending valuable timePlatform integrity maintainanceSpecific program execution arrangementsType safetySource code
An inherently safe code format for representing computer programs is disclosed. The format provides incorruptible referential integrity and uses type separation to achieve intrinsic type safety. The format preserves a safety guarantee found in a source code language representation of the computer program while the computer program proceeds through various stages of the code compilation process.
Owner:RGT UNIV OF CALIFORNIA
Synchronizing centralized data store from distributed independent data stores using fixed application programming interfaces
InactiveUS7484219B2Provide flexibilityData processing applicationsDigital data information retrievalApplication programming interfaceSemantics
A data transfer protocol utilizes a set of actions for affecting different objects that are stored in a data store. The data transfer protocol supports a set of application programming interfaces (APIs) that are applicable to the different objects. With the APIs, the data transfer protocol may synchronize a centralized data store with independent data stores. The data transfer protocol may support data that is hierarchical while maintaining referential integrity. Node objects may vary from nightly bulk uploads to interactive users uploading or querying smaller portions of the database. The data transfer protocol provides the semantics to carry out these operations with a fixed number of APIs for any arbitrary database. The data uploads may be sparse depending on what the remote data store holds and need not be in serial order.
Owner:MICROSOFT TECH LICENSING LLC
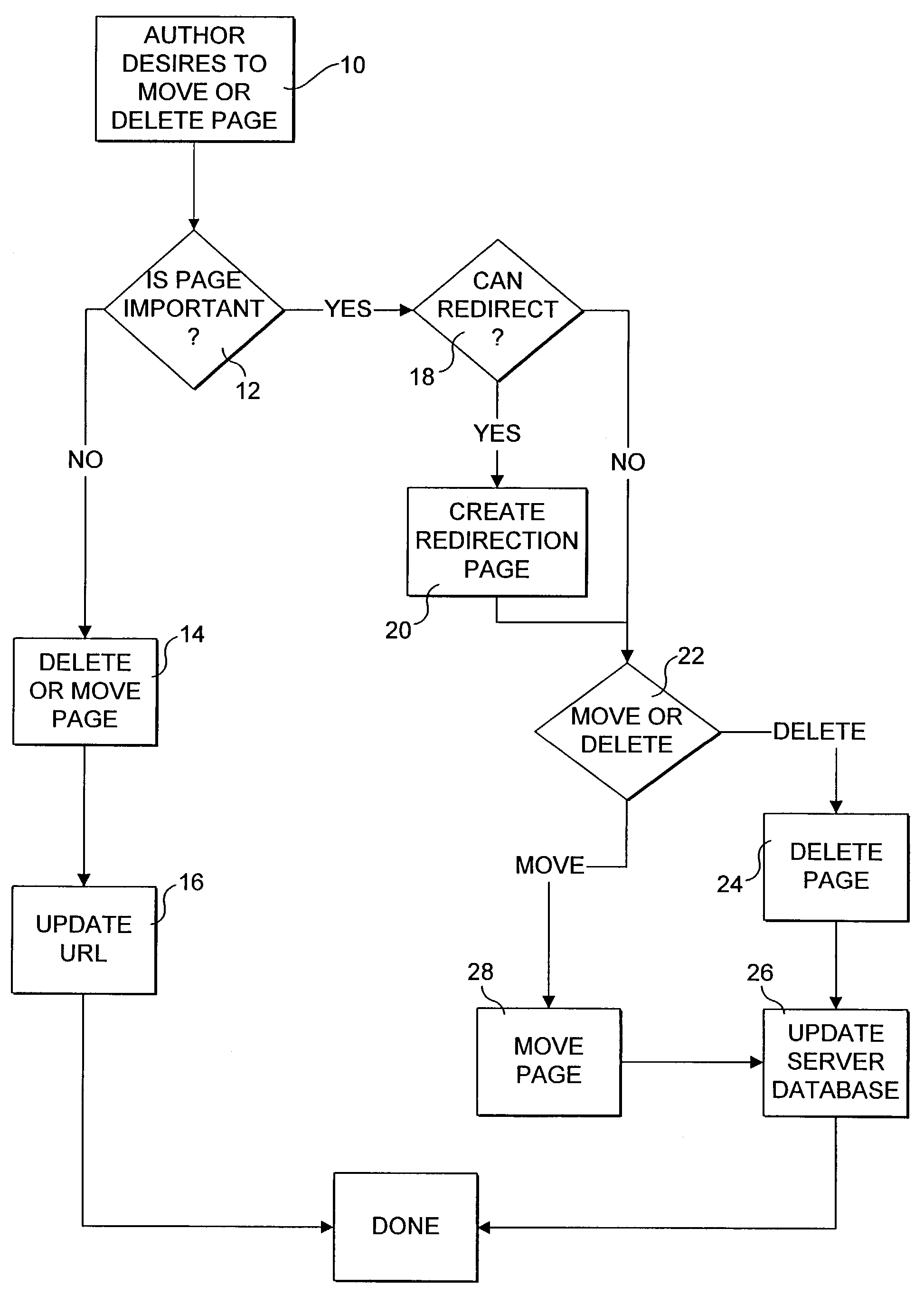
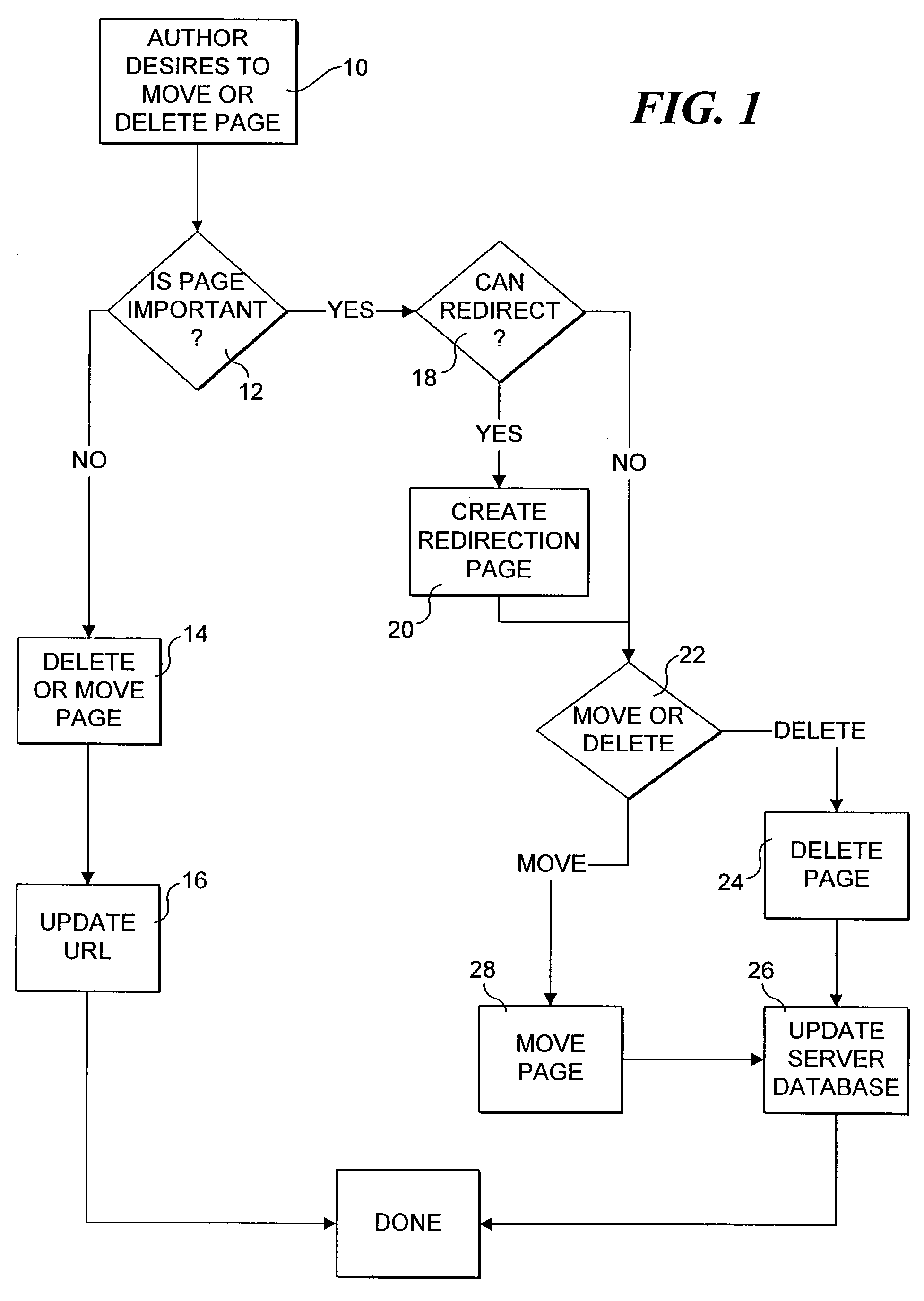
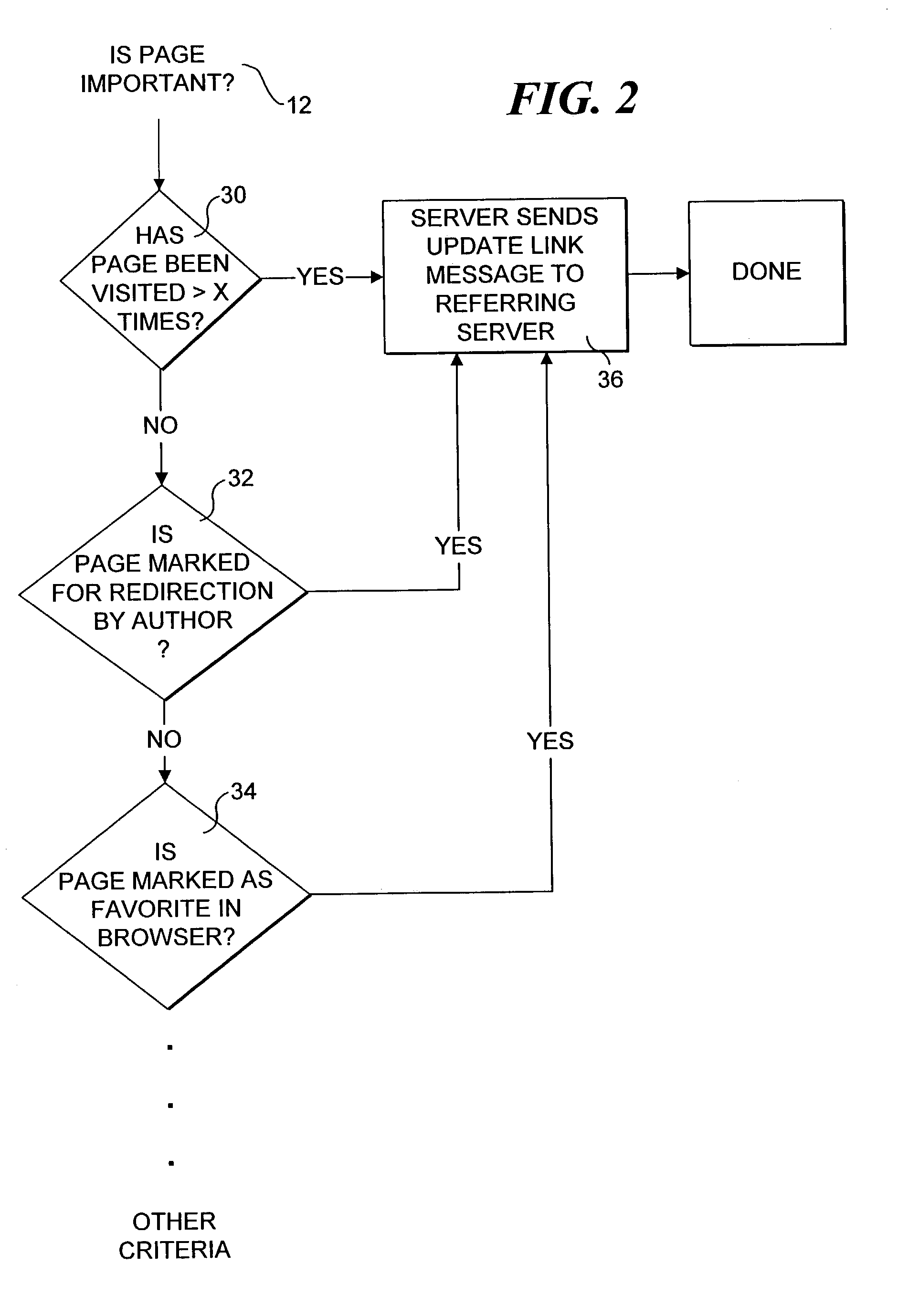
Method for preserving referential integrity within web sites
InactiveUS7392303B2Maintain integrityMultiple digital computer combinationsWebsite content managementHyperlinkWeb site
The integrity of uniform resource locator (URL) references within web sites are maintained when changes occur in the locations where resources referenced by URLs are stored. A Referential Preservation Engine (RPE) maintains a database in which the location of web site documents and reference information are stored and updates various URL hyperlink references contained in the web pages on the site so that users can locate documents that have been moved to new storage locations. The RPE can also update links to external web sites by communicating with an RPE running on each external site. The RPE on the external site keeps track of the movement of linked documents on the sites and passes information pertaining to the new location of the linked documents to the local site, whereupon the links on the local web site pages are updated to reflect the new storage locations. The RPE also can track usage of a user's favorite sites and / or documents that are stored in an Internet browser and update the URL references for these favorites when the resources they are mapped to are moved (or renamed).
Owner:MICROSOFT TECH LICENSING LLC
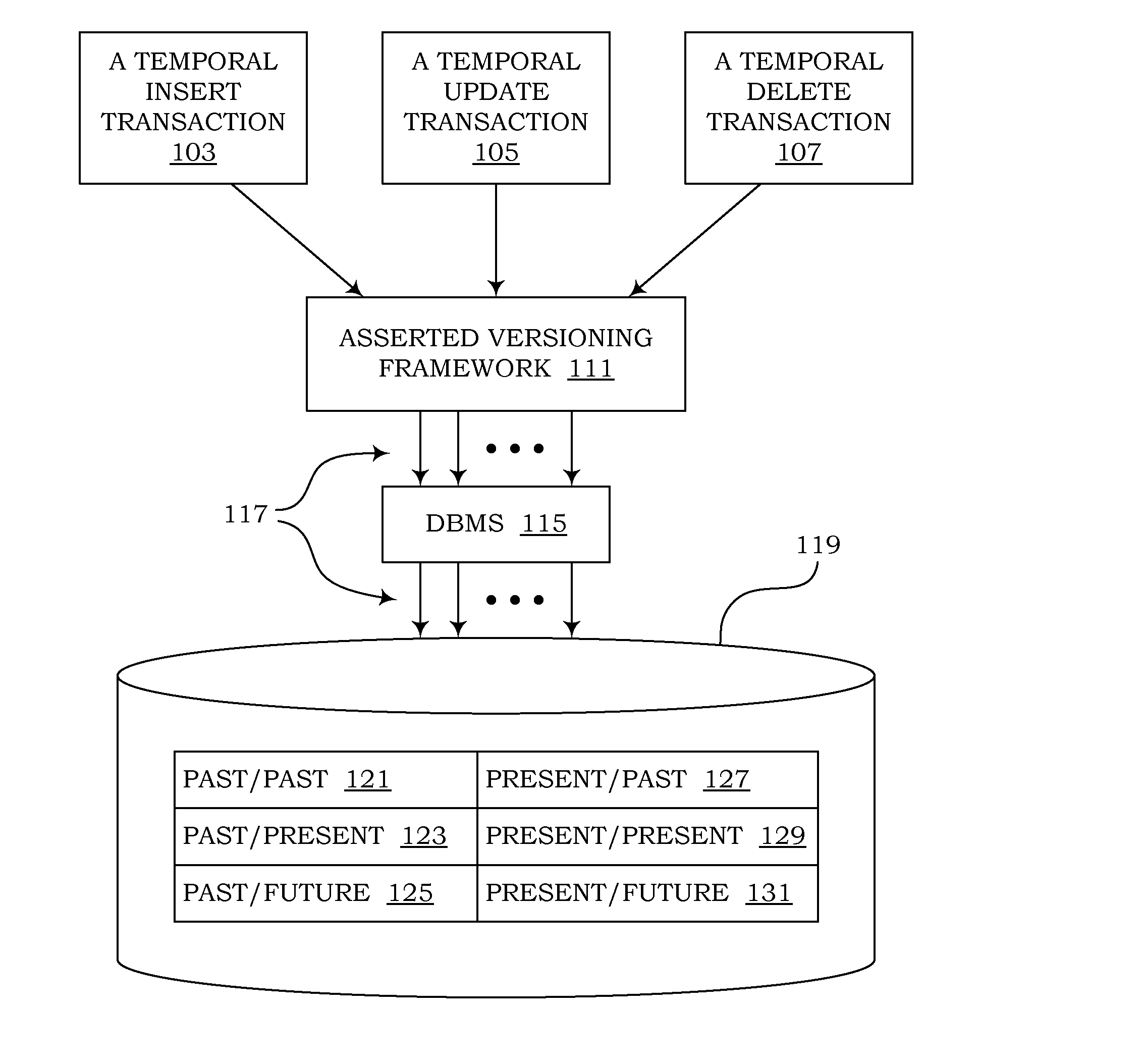
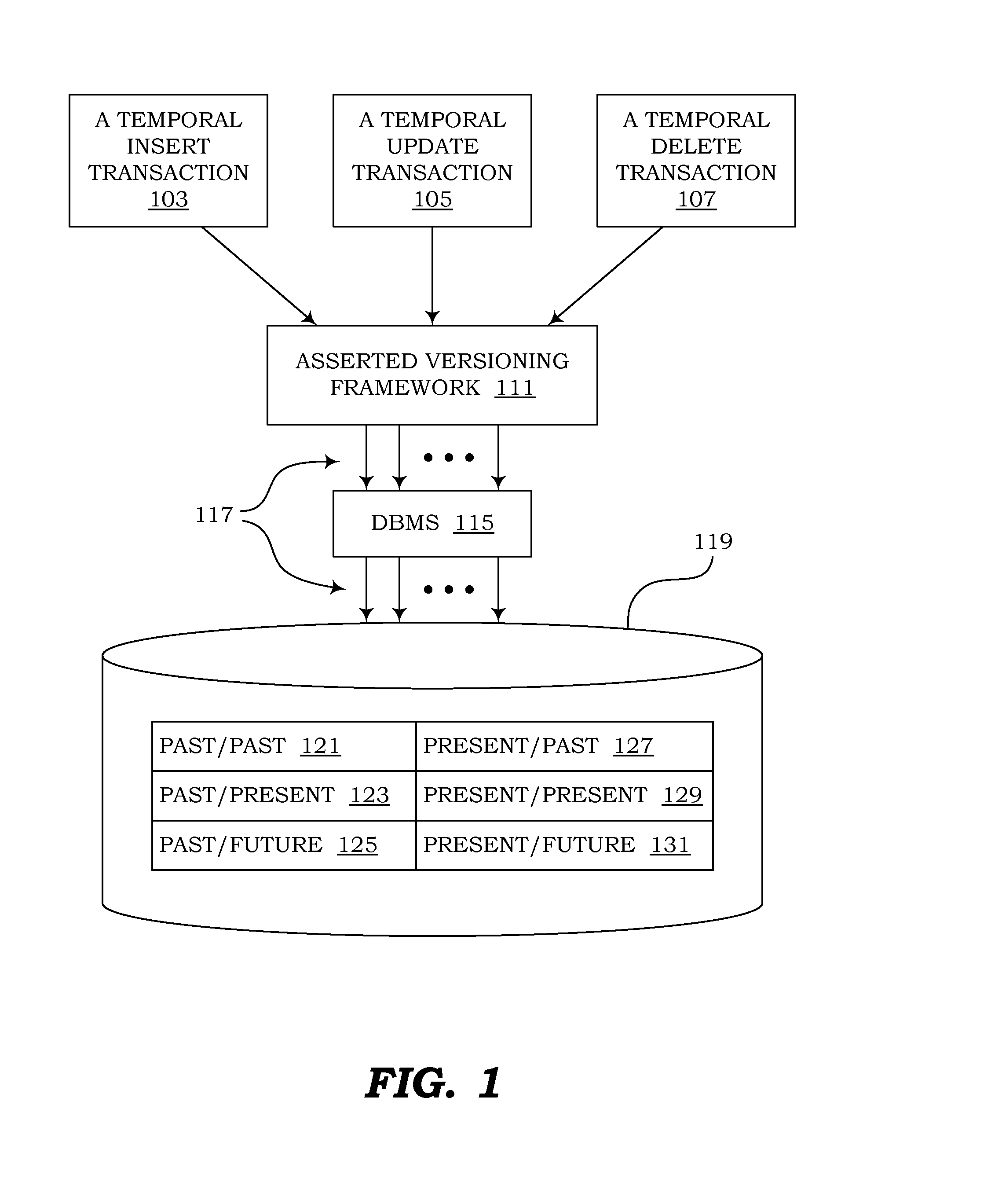
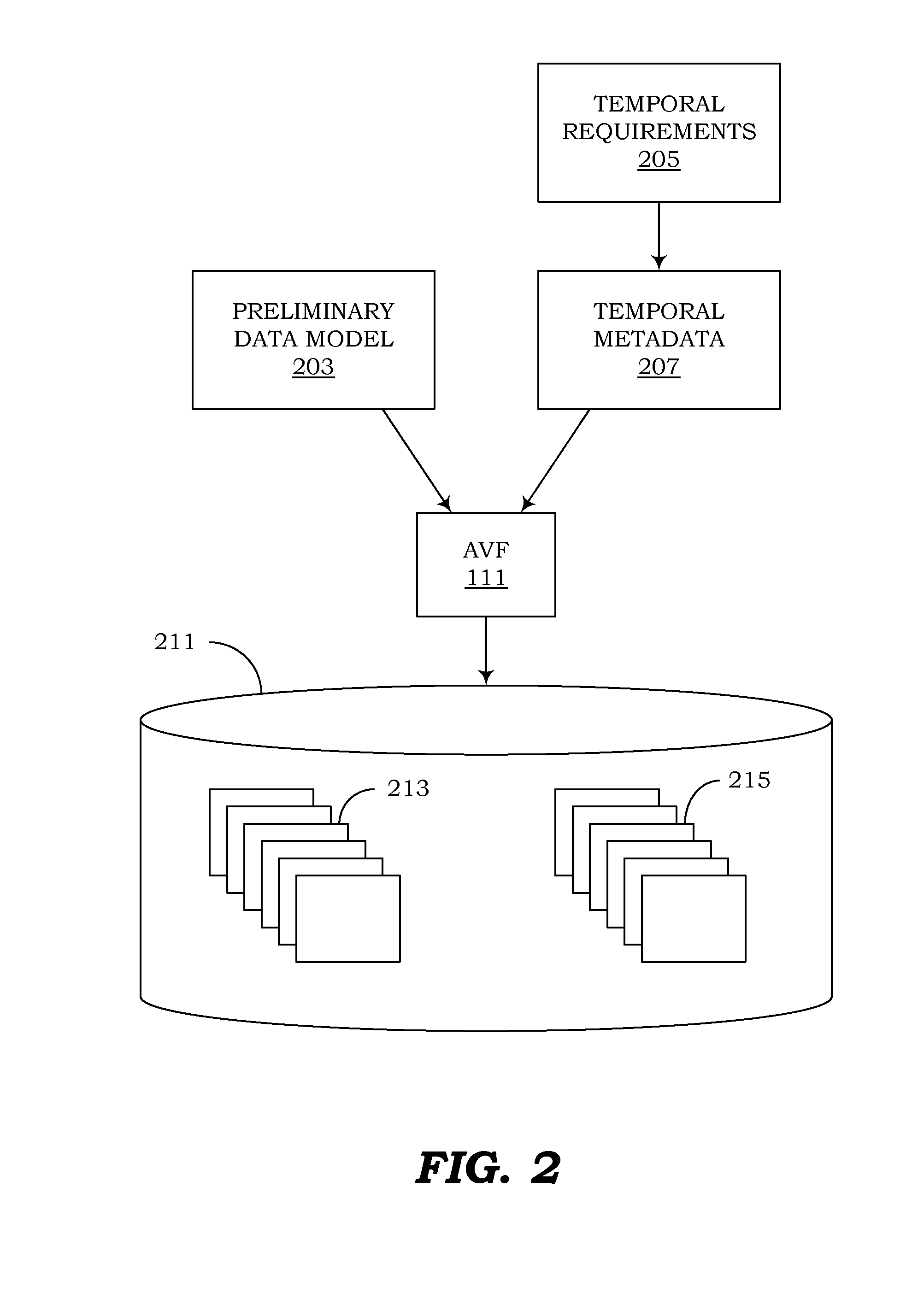
Management of temporal data by means of a canonical schema
ActiveUS20130018849A1Eliminate needSimplifying codebaseDigital data information retrievalDigital data processing detailsEffective timeSpecification pattern
Computer programs embodied in computer-readable media that can use canonical schemas to persist data from non-temporal tables, effective-time tables, assertion-time tables, and bitemporal tables, and that can enforce temporal integrity constraints on those tables, are provided. In one embodiment, the canonical schemas are used by database tables. In another embodiment, they are used by the physical files which persist data from those tables. Temporal metadata is used to express temporal requirements. Thus, uni-temporal, bitemporal, and temporally-enabled non-temporal tables can be generated without altering existing data models or designing temporal features into new data models. Support is also provided for managing temporal data that exists in future assertion time, and for using episodes to enforce temporal referential integrity.
Owner:JOHNSTON THOMAS DR +1
Versioned database system with multi-parent versions
InactiveUS7836028B1Digital data information retrievalDigital data processing detailsWorkspaceMetadata
A versioned relational database system (VRDBS) in which versions of data contained in a relational database system are accessed by means of workspaces. Metadata in the VRDBS permits a workspace to have multiple parents. The multi-parented VRDBS performs operations including specifying that a workspace be made an additional parent of another workspace or that an additional parent be removed as a parent of the other workspace. The fact that a workspace may have multiple parents affects the manner in which merge and refresh operations are performed and the manner in which system-enforced constraints such as primary key constraints, unique key constraints, and referential integrity constraints are handled. The metadata for the VRDBMS includes a multi-parent graph for each workspace that has multiple parents. The multi-parent graph is used in the performance of the merge and refresh operations and in determining constraint violations.
Owner:ORACLE INT CORP
Performance of RCU-based searches and updates of cyclic data structures
InactiveUS8874535B2Improve performanceProgram initiation/switchingDigital data processing detailsTheoretical computer scienceEngineering
A technique for improving the performance of RCU-based searches and updates to a shared data element group where readers must see consistent data with respect to the group as a whole. An updater creates one or more new group data elements and assigns each element a new generation number that is different than a global generation number associated with the data element group, allowing readers to track update versions. The updater links the new data elements into the data element group and then updates the global generation number so that referential integrity is maintained. This is done using a generation number element that is referenced by a header pointer for the data element group, and which in turn references or forms part of one of the data elements. After a grace period has elapsed, the any prior version of the generation number element may be freed.
Owner:INT BUSINESS MASCH CORP
Method for ensuring referential integrity in multi-threaded replication engines
ActiveUS7801851B2Digital data information retrievalDigital data processing detailsTransaction dataApplication software
Owner:INTEL CORP
Method and apparatus for automatically detecting a latent referential integrity relationship between different tables of a database
InactiveUS20070156736A1Improve performanceDigital data information retrievalDigital data processing detailsTable (database)Query analysis
In one aspect, a database analytical tool or function analyzes join queries to detect queries which could be reduced if a referential integrity relationship were known. In another aspect, a probable latent referential integrity relationship is detected using one or more heuristics. Preferably, a join query is analyzed to detect a joined table which has no other conditions placed on it, and no referential integrity relationship already defined. For any such query, the analysis attempts to verify a probable latent referential integrity relationship using at least one heuristic, such as comparing cardinality of the potential primary key with the size of the table and / or with the cardinality of the foreign key. It is further possible to execute the join for some sample of records, and determine whether any records were found which did not conform to referential integrity constraints.
Owner:IBM CORP
Referential integrity, consistency, and completeness loading of databases
InactiveUS7949640B2Digital data information retrievalDigital data processing detailsTarget databaseWork cell
A method is provided for loading data from a source database to a target database that includes at least one table. Prior to loading the data from the source database into the target database, at least one referential integrity constraint and / or at least one consistency requirement regarding the data is automatically identified. A subset of the data that satisfies the at least one referential integrity constraint and / or consistency requirement is then automatically identified. The identified subset of the data is then loaded into the target database as a unit of work.
Owner:INTEL CORP
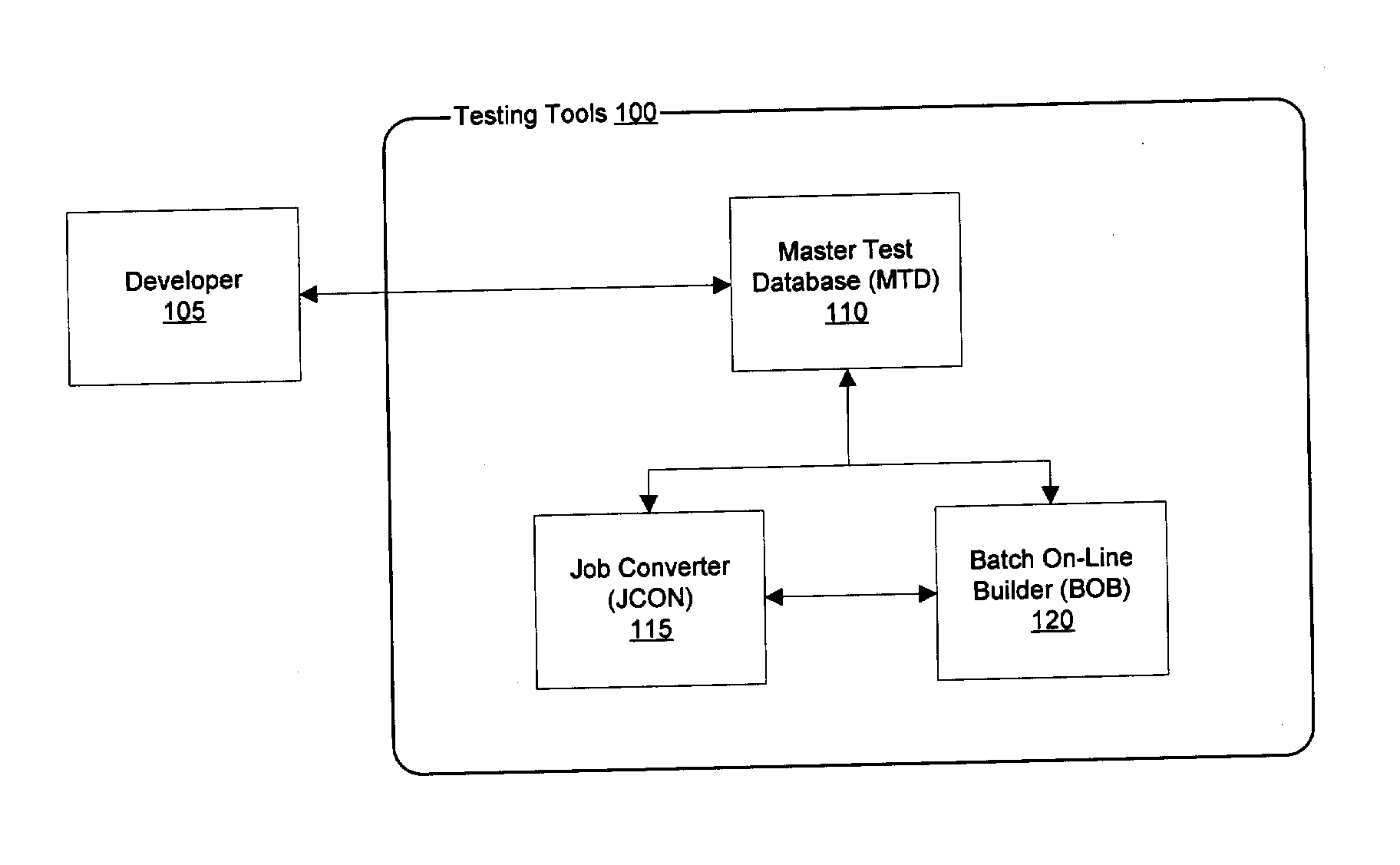
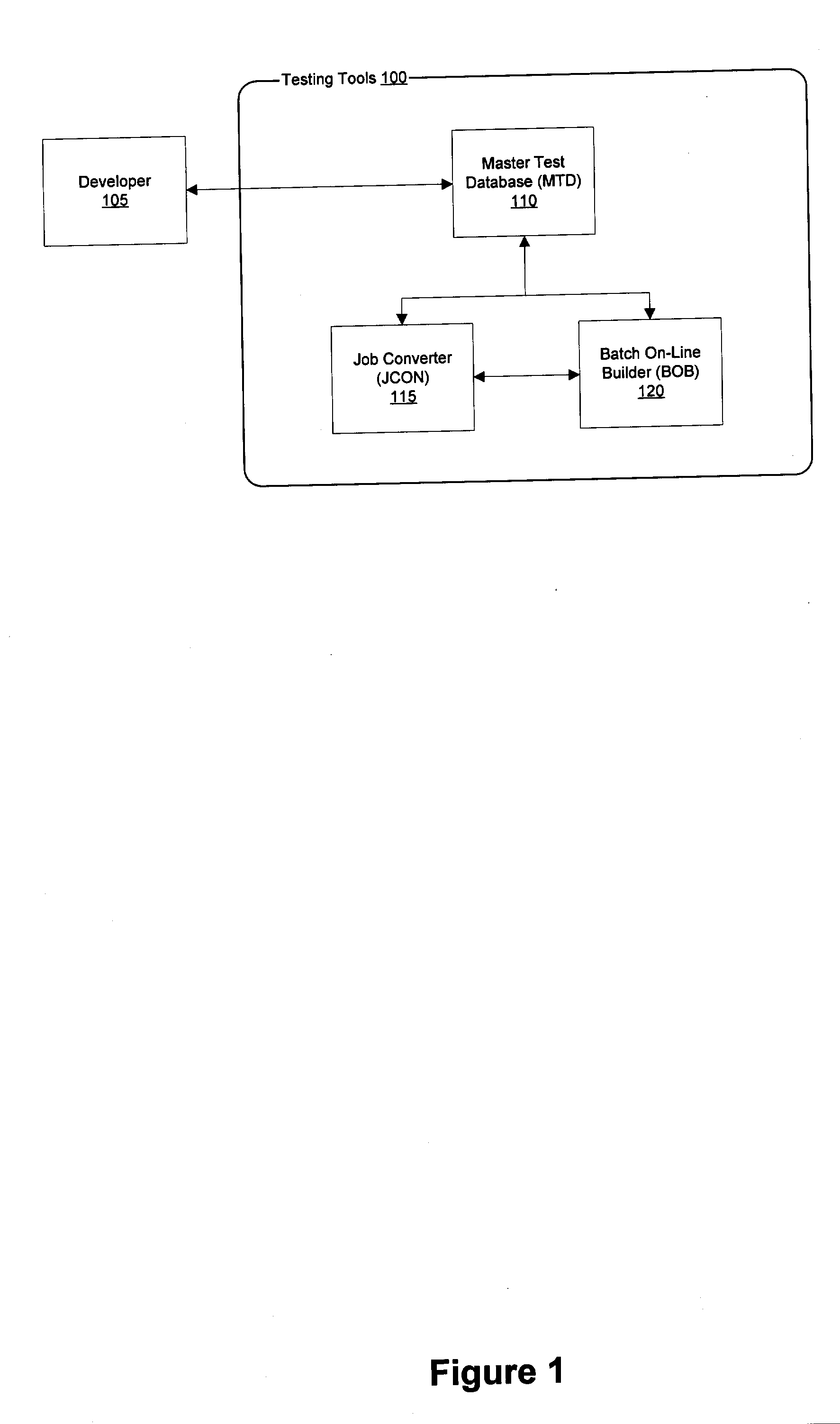
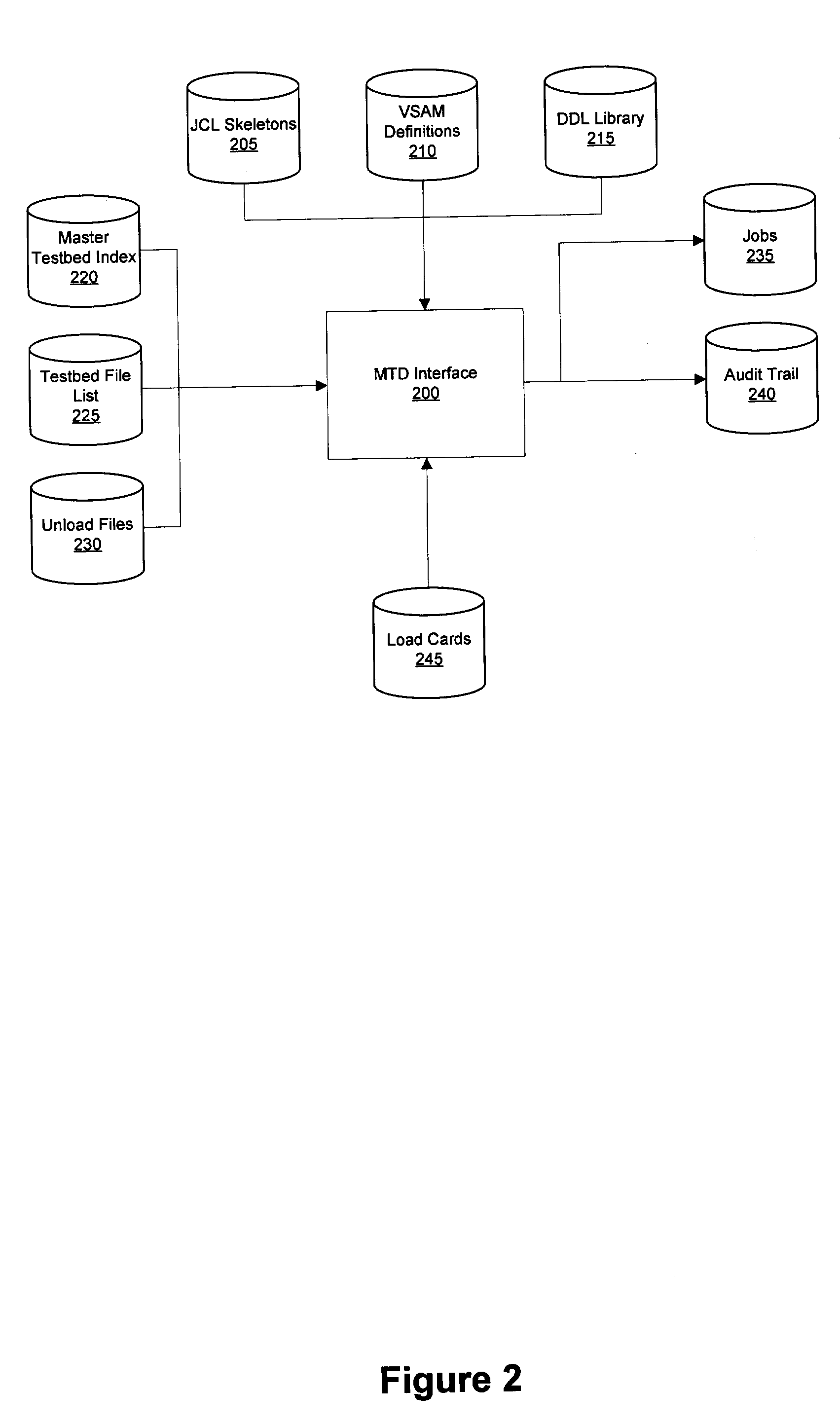
System and method for building full batch test environments
InactiveUS20050283667A1Easy loadingEnsure data integrityError detection/correctionSpecific program execution arrangementsComputer hardwarePersonalization
The invention includes an integrated toolset of software development aids for testing of software systems directed toward the production, access, management, and retrieval of stored data by providing a fast and efficient means for a developer to recreate production data within a testing environment. The toolset consists of components which, when combined, provide an interactive on-line system where a developer is provided with access to low volume, high-quality, depersonalized, and targeted data with referential integrity and is suitable for most testing needs.
Owner:LIBERTY PEAK VENTURES LLC
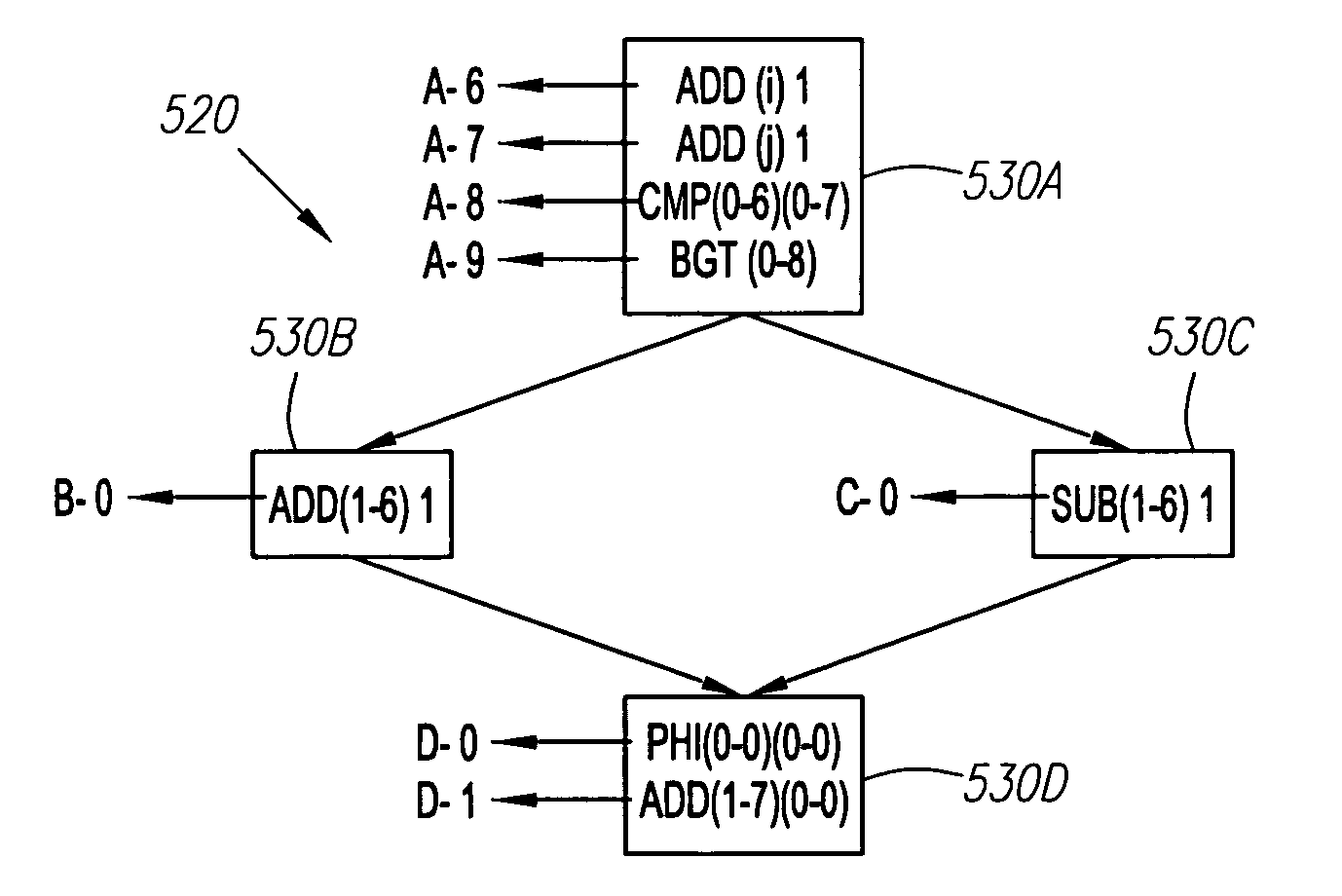
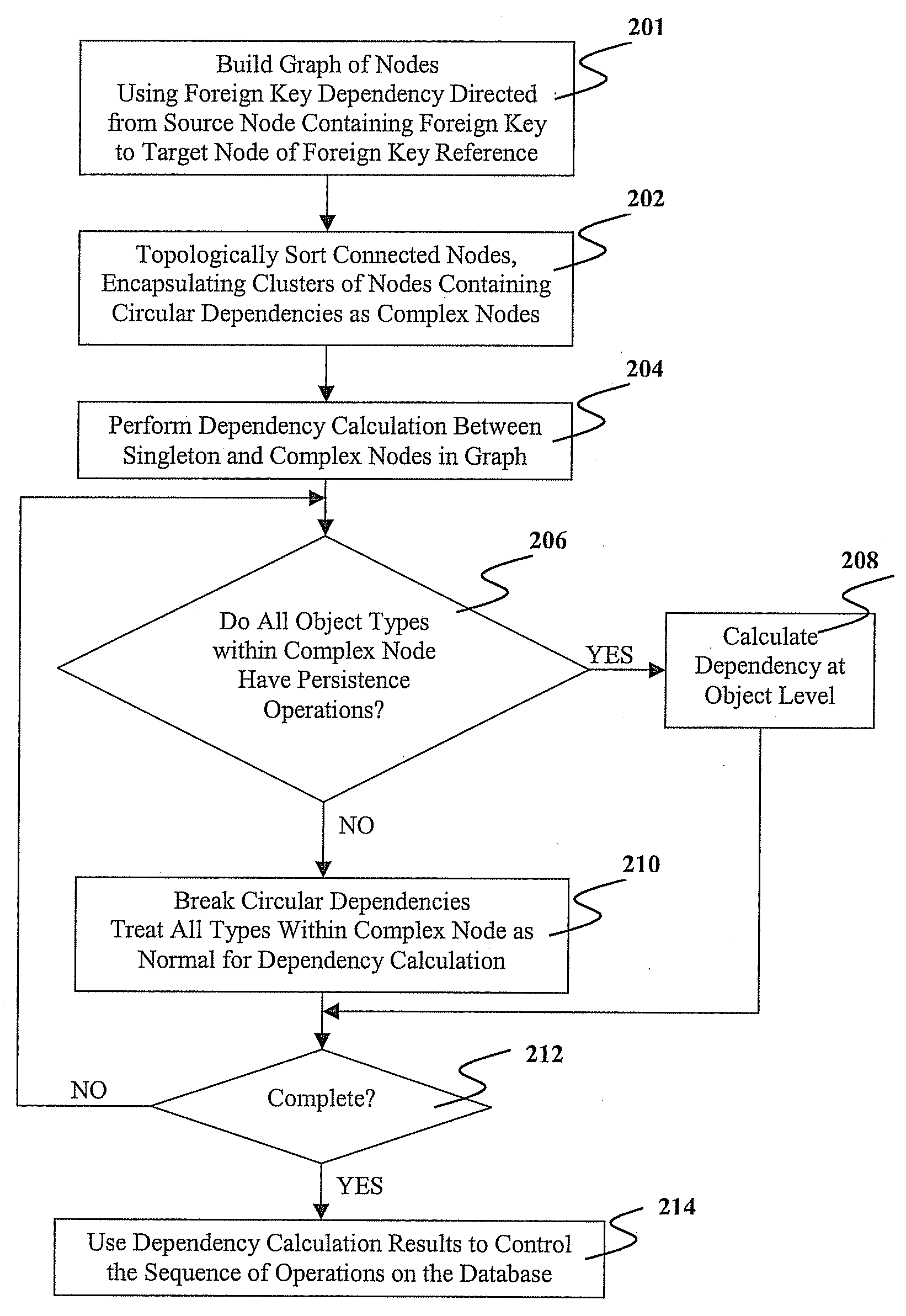
Methods, systems, and computer program products for using graphs to solve circular dependency in object persistence
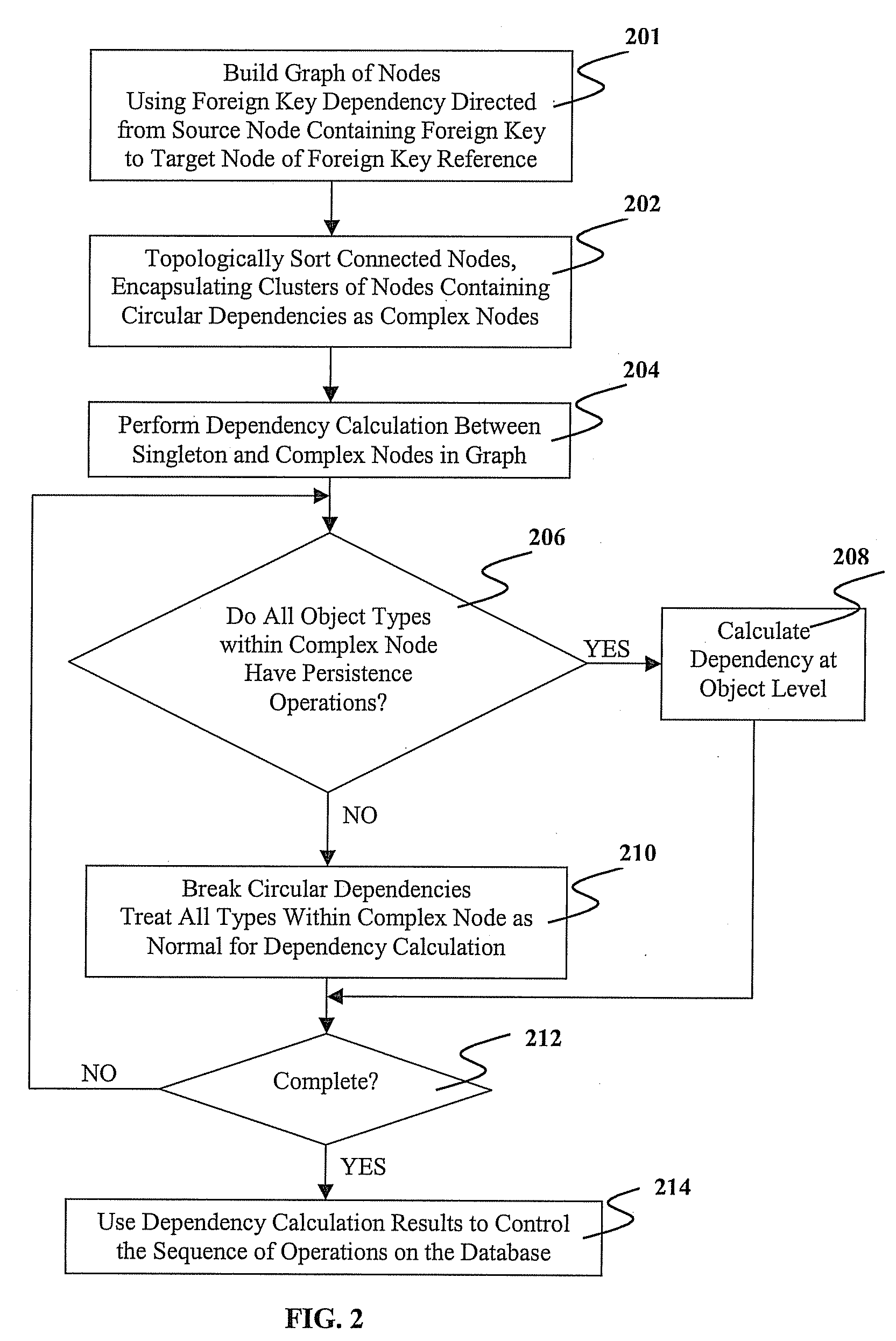
ActiveUS20080040367A1Minimizes object level calculation timeData processing applicationsDigital data processing detailsGraphicsTheoretical computer science
A method, system, and computer program product for reducing dependency calculation time in object persistence with circular referential integrity dependency is provided. The method includes building a graph using foreign key dependency from object to relational mapping, where nodes of the graph are object types and connected directionally from a source containing a foreign key to a target of a foreign key reference. The method further comprises topologically sorting the graph to order dependencies among the nodes including circular dependencies. The method also includes encapsulating the circular dependencies as a complex node. Furthermore, the method comprises performing object dependency calculations on the nodes and the complex node in the graph. The results of the object dependency calculations are used to generate a sequence in which the objects can be modified in a relational database.
Owner:SAP AG
System and method of data movement between a data source and a destination
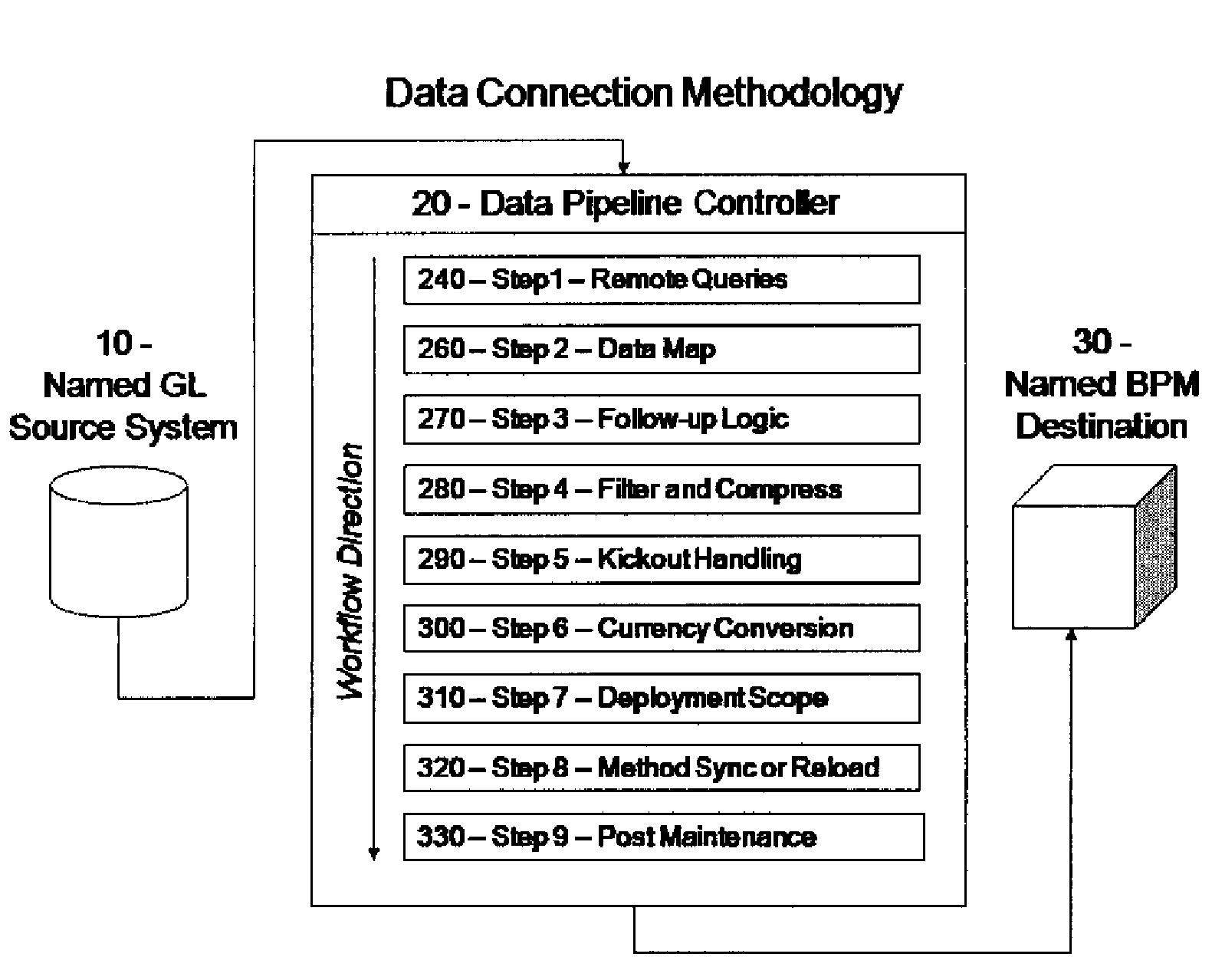
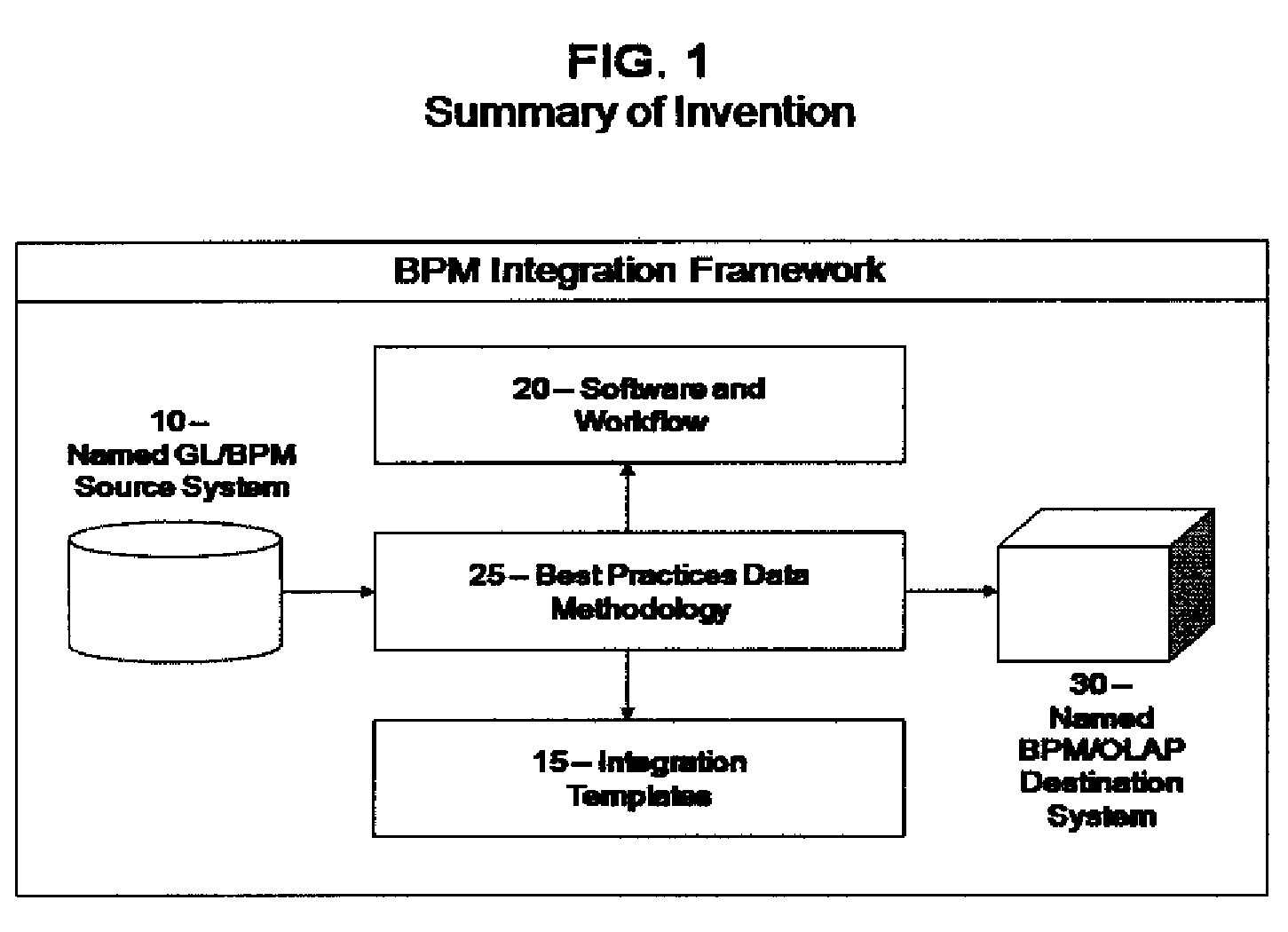
ActiveUS7747563B2Easy to deployImprove functionalityDigital data information retrievalDigital data processing detailsData streamFiltration
A method of data migration and integration with a data load mechanism. The first primary step is to extract the data from a named source by remote queries. The follow-up logic is used for any miscellaneous or supplemental transformations to inbound data for data renaming, null scrubbing, and data polishing. The filtration step allows for any extraneous data to be filtered out. The compression step consolidates any fragmented balances residual in the remote queries, localize remote data, data map, or follow-up logic. As a part of the compression process, the result set table signature is explicitly cast to that of the destination fact table. The result of this is an exact replica of the destination fact table format, data types and column order. The kickout handling provides referential integrity of the inbound data flow against the named BPM Destination System. Finally, the deployment step limits the dynamic reload or sync determination to certain fields.
Owner:BREAKAWAY TECH
Method and Apparatus for Loading Data Files into a Data-Warehouse System
InactiveUS20090172047A1Improve reliabilityEffective applicationDigital data information retrievalDigital data processing detailsData warehouseData file
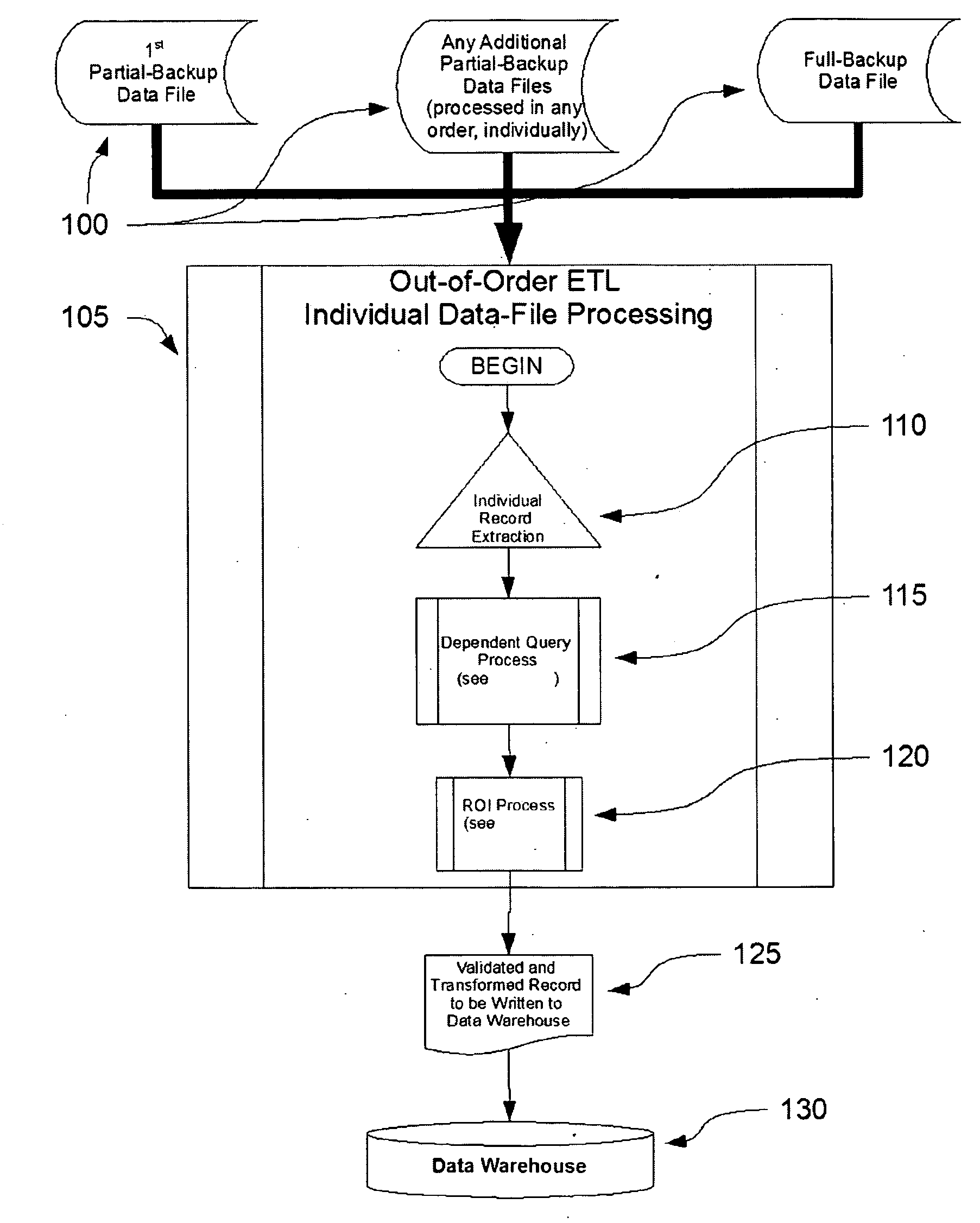
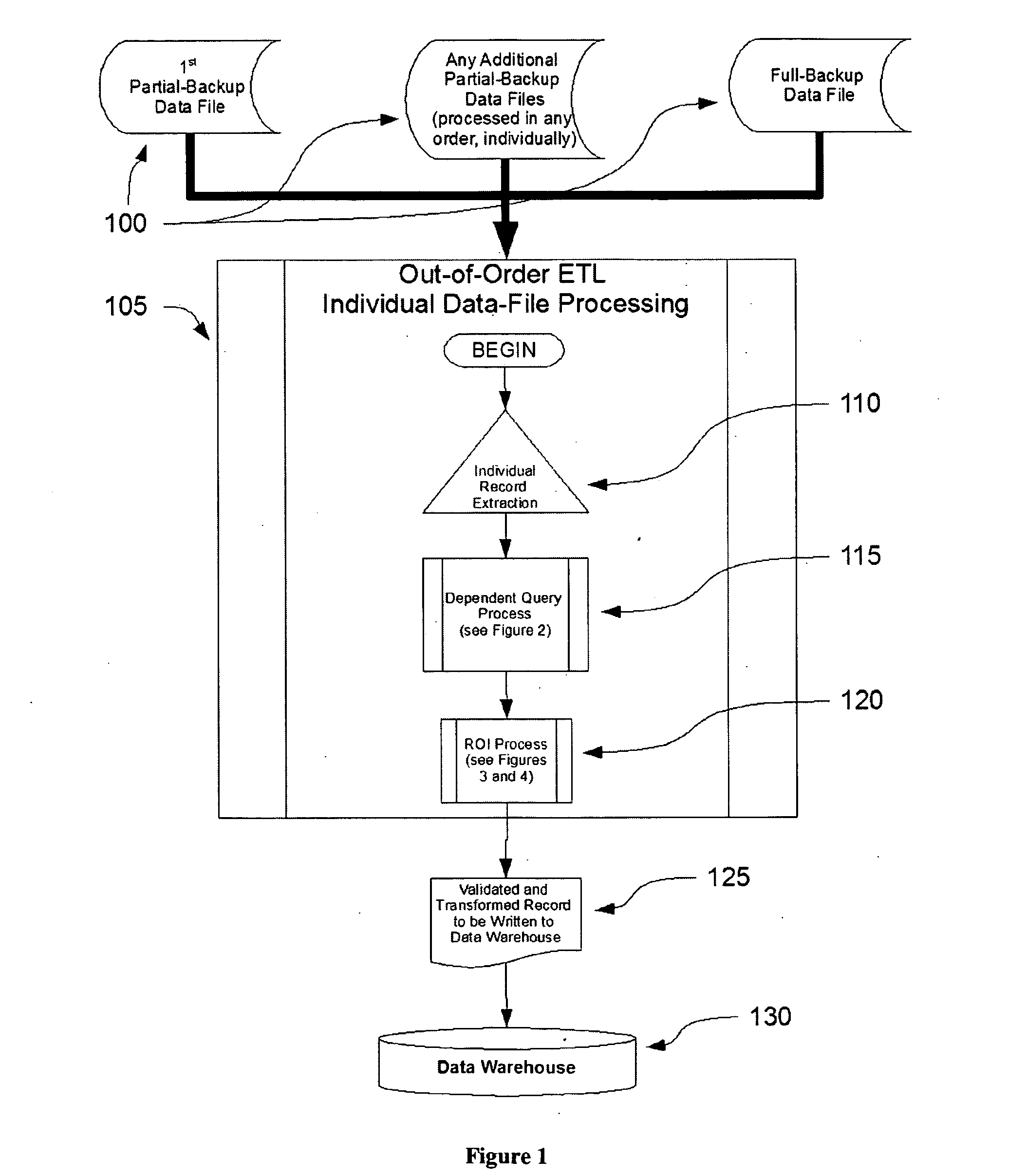
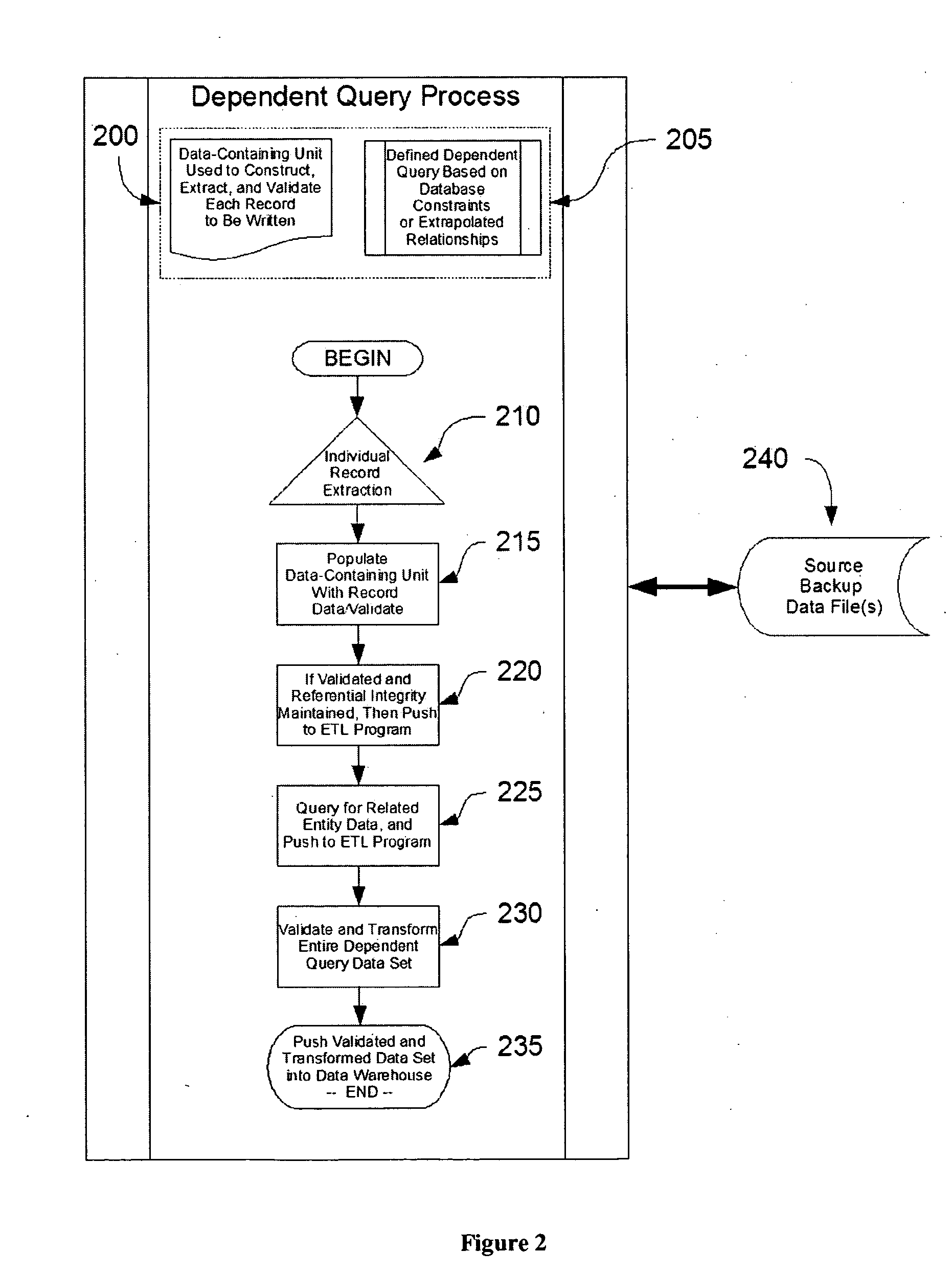
Date-warehouse systems are populated using an enhanced Extraction-Load-Transform (ETL) process and system by employing three ideas: Out-of-order-fill ETL, relative-ordering index (ROI), and dependent queries. Out-of-order-fill ETL allows a data warehouse to accept the loading of data files in any order, and does not require the loading of any previous backup data files in order to provide some functionality to end users under the view that some functionality or data access is better than none at all. Dependent queries are processes that use defined data structures for use in constructing, extracting, and validating each record to be written in said data-warehouse system in order to ensure that referential integrity is maintained and that no orphaned data is pushed into the data warehouse. Finally, ROI is a process wherein a value is determined, based on the constraints of the source data, which indicates the relative newness of the data.
Owner:I2MERGER SUB TWO INC +1
Methods of exposing a missing collection of application elements as deprecated
InactiveUS20060242188A1Digital data processing detailsCode refactoringSoftware engineeringReferential integrity
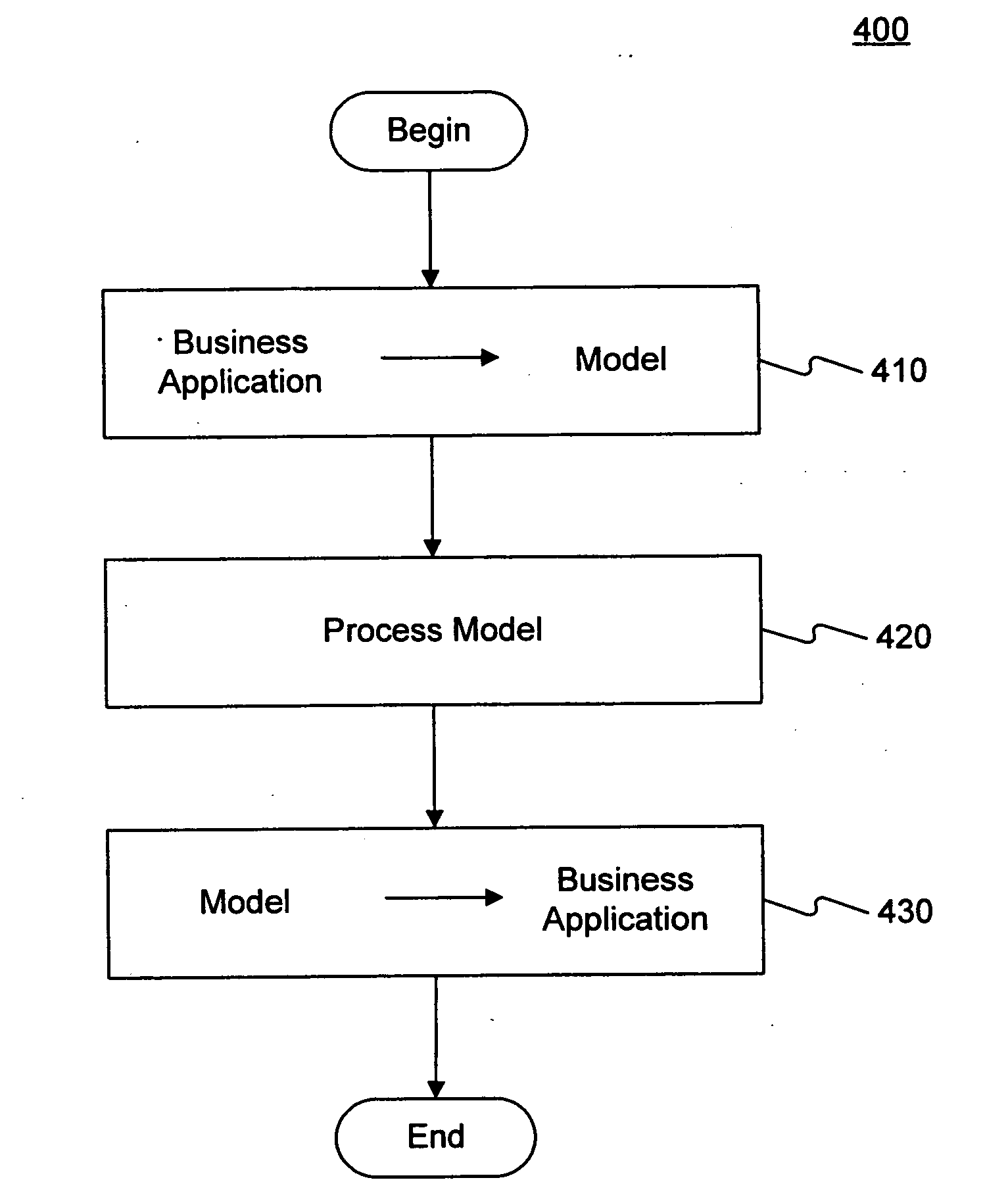
Using methods and systems consistent with the present invention, deprecated logic entities of a business application may be identified using an object-oriented model of the business application. By transforming business application structures into object-oriented structures, deprecated logic entities in the business application may be exposed using object-oriented referential integrity checking.
Owner:SAP AG
Safe computer code formats and methods for generating safe computer code
ActiveUS20070006191A1Preventing executionFacilitates prevention from executionPlatform integrity maintainanceSpecific program execution arrangementsType safetySource code
An inherently safe code format for representing computer programs is disclosed. The format provides incorruptible referential integrity and uses type separation to achieve intrinsic type safety. The format preserves a safety guarantee found in a source code language representation of the computer program while the computer program proceeds through various stages of the code compilation process.
Owner:RGT UNIV OF CALIFORNIA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com