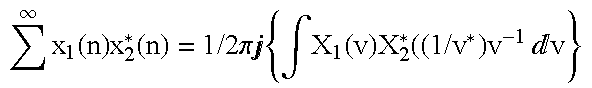Patents
Literature
871 results about "Independent data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Independent Data means, with respect to the Licensed Products, all data, including without limitation, toxicological, pharmaceutical, clinical, non-clinical and medical data, health registration data and marketing data, developed by a Sponsoring Party or its Associates in an Independent Trial in respect...
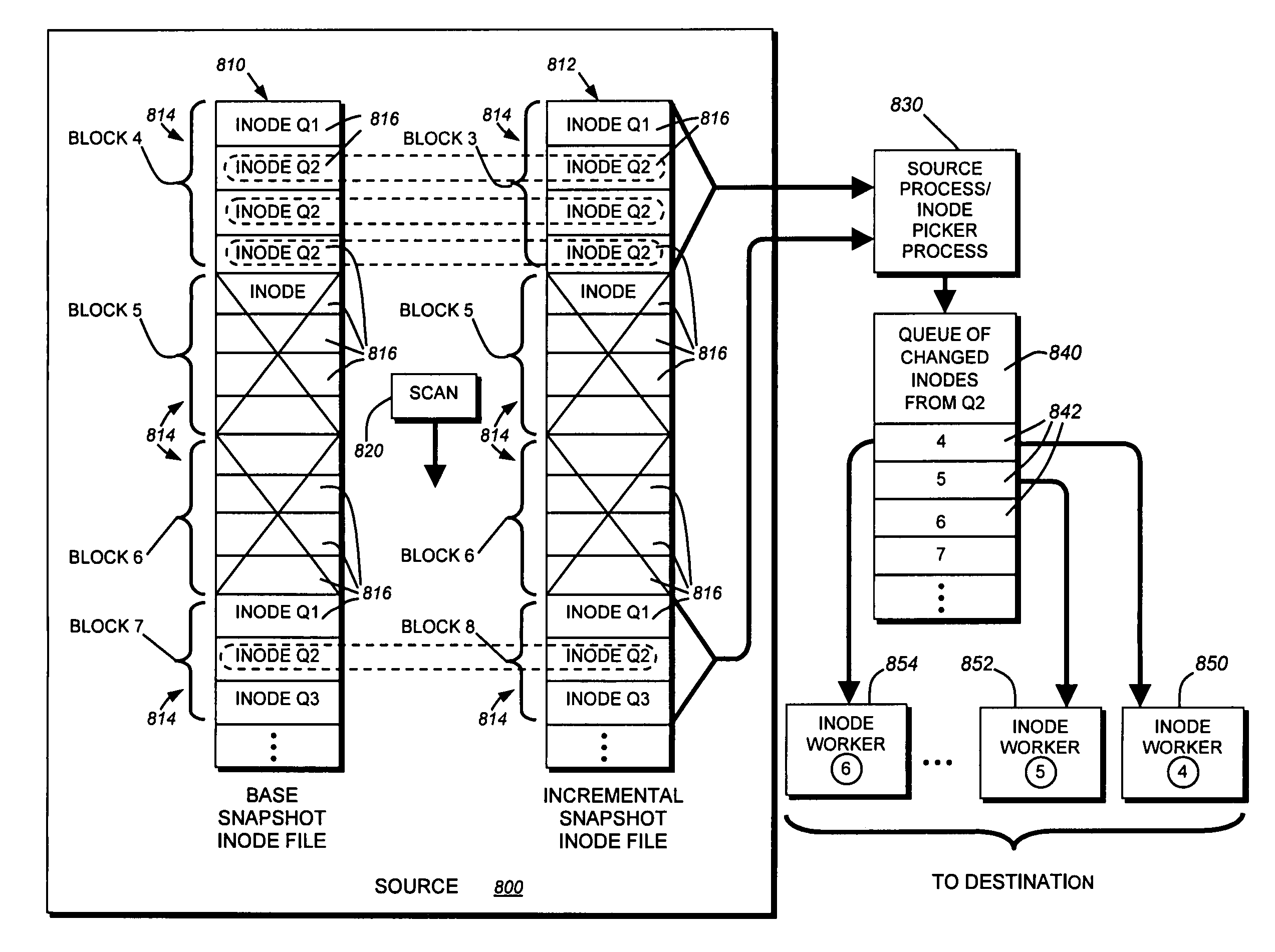
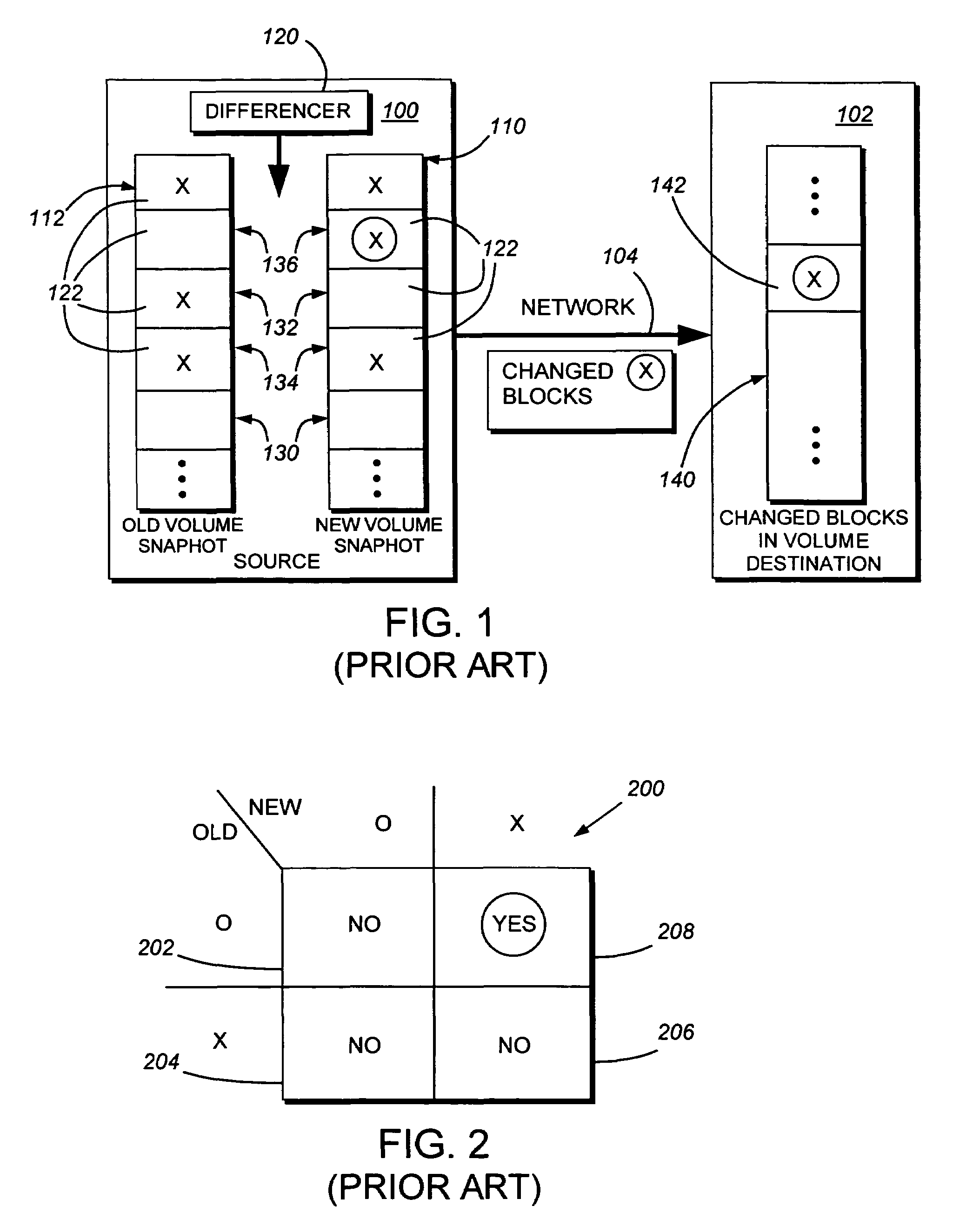
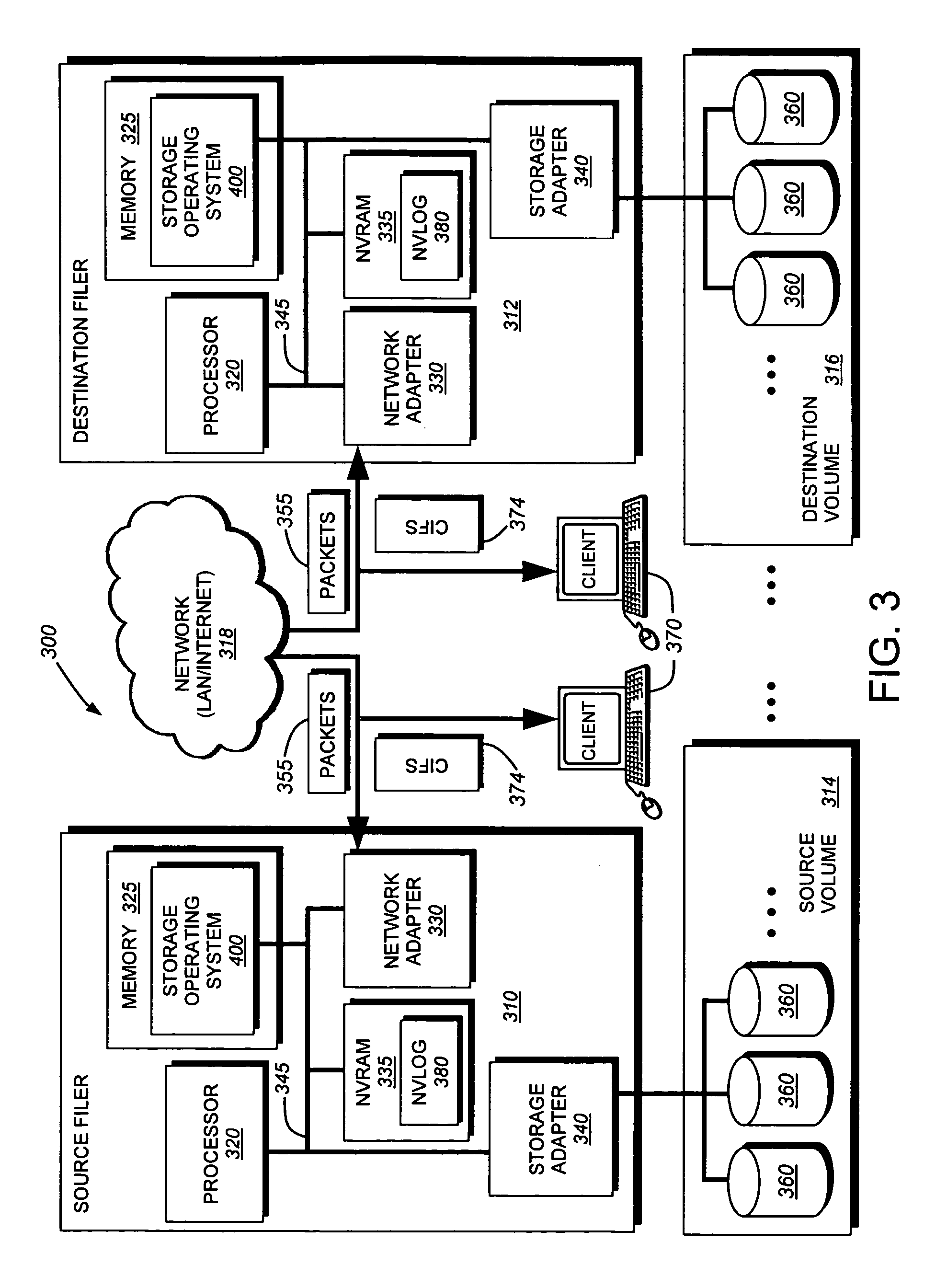
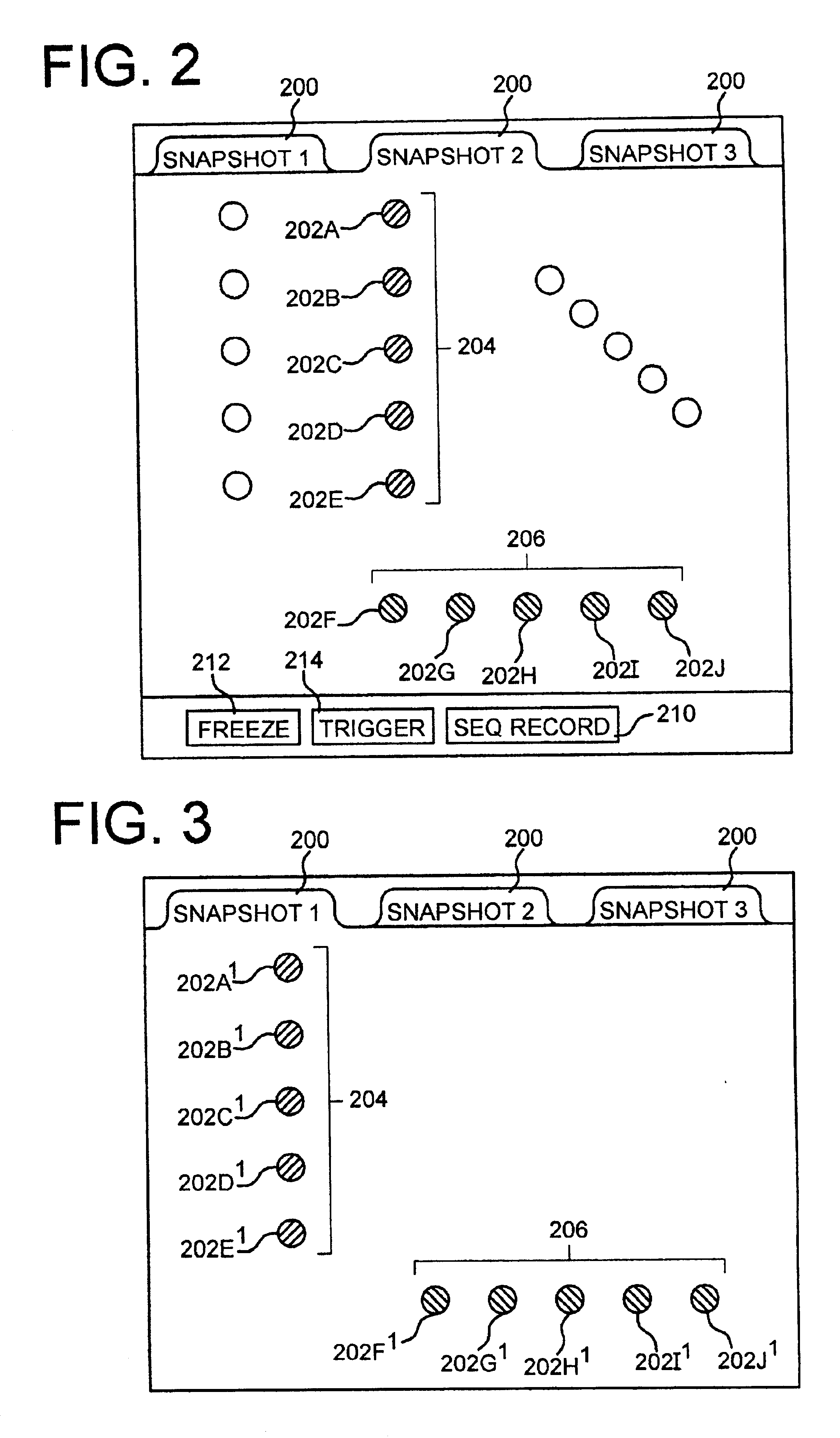
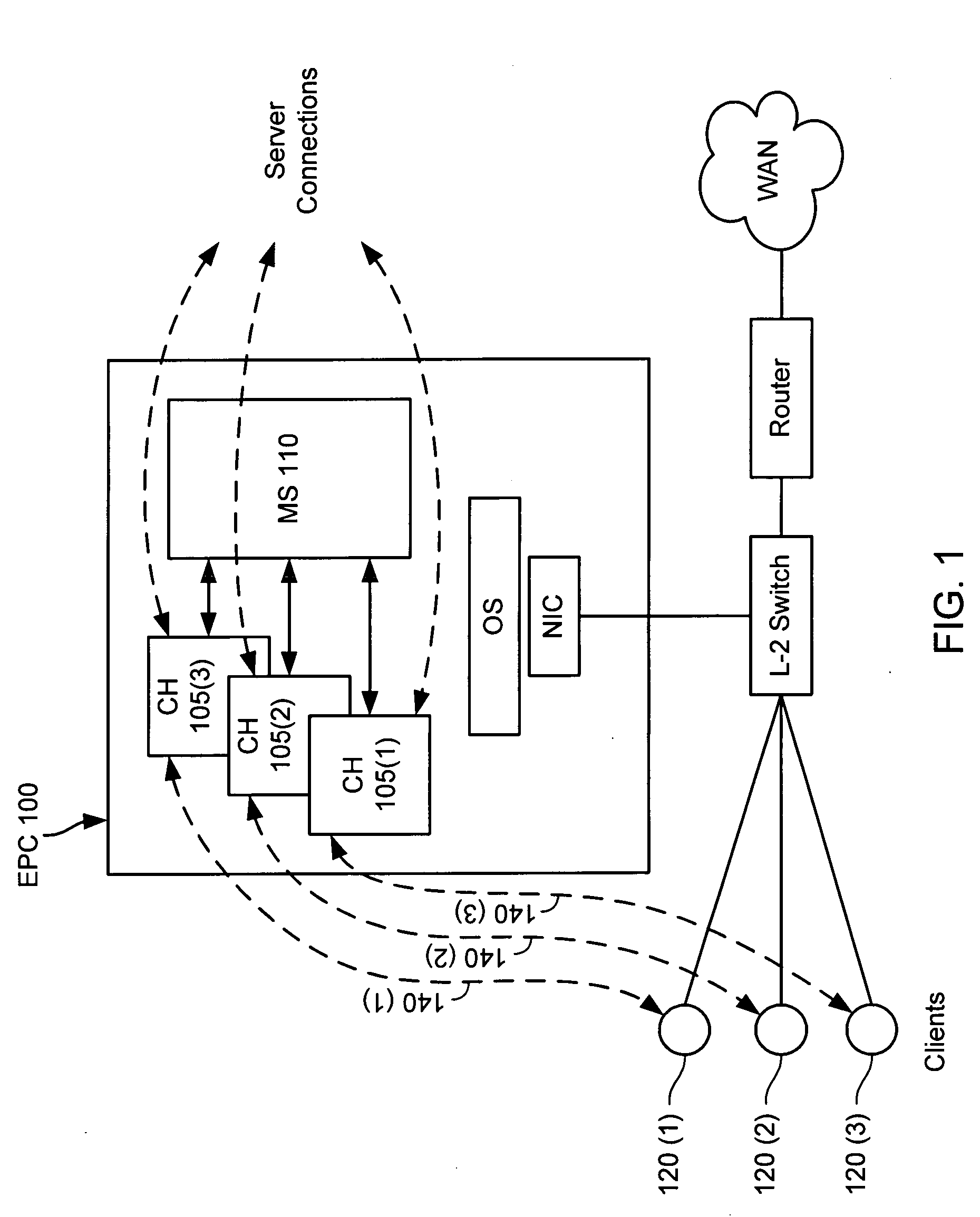
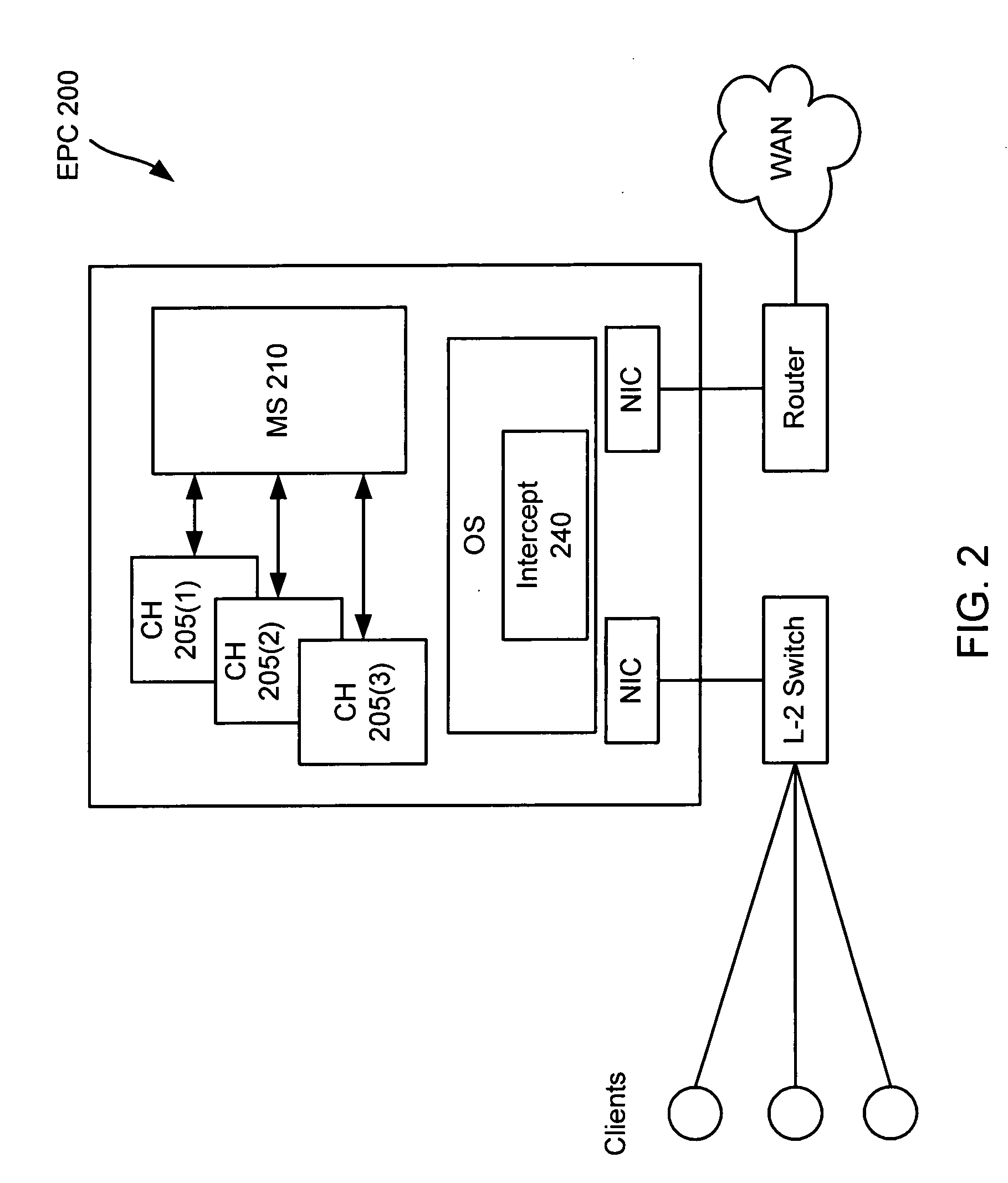
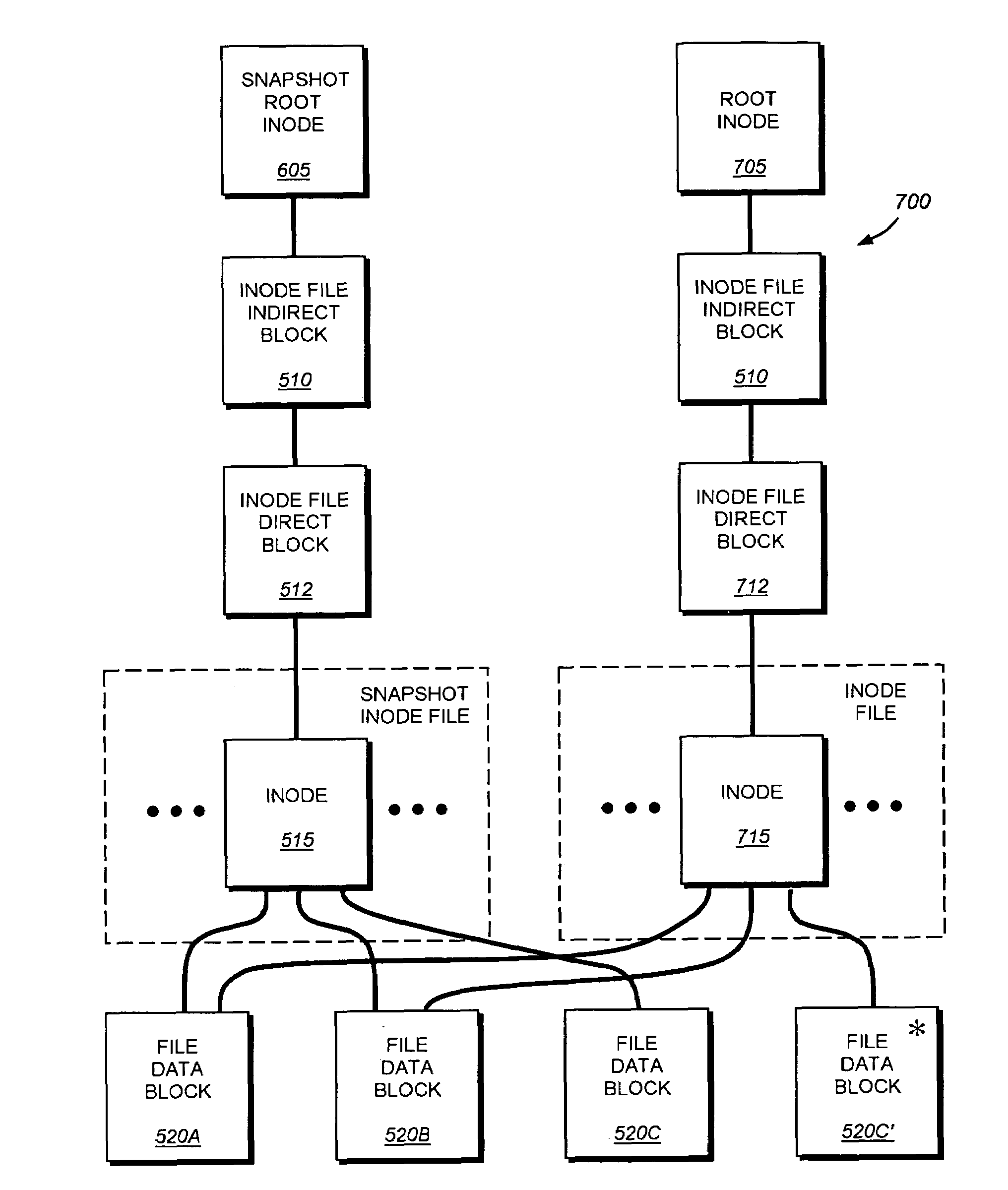
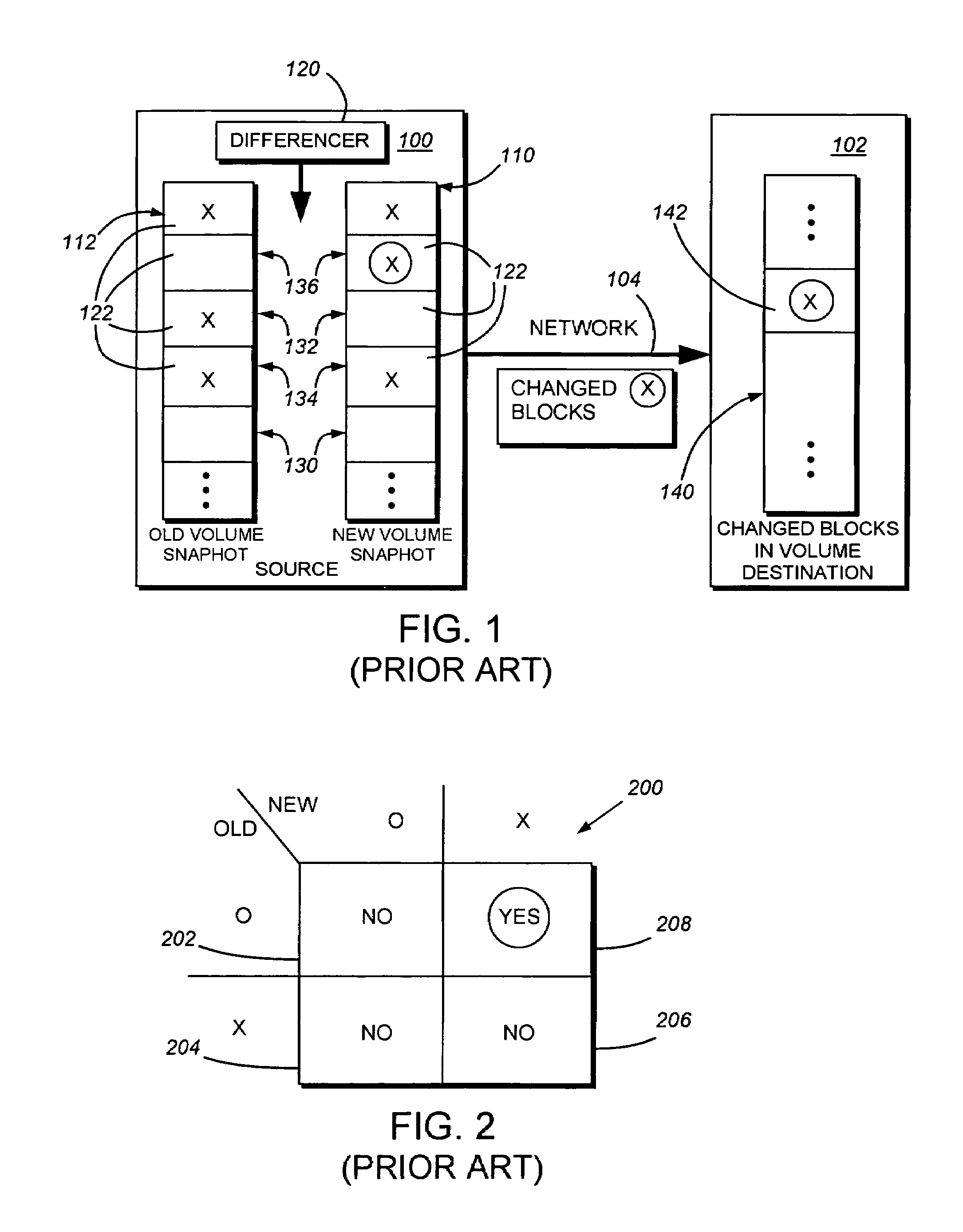
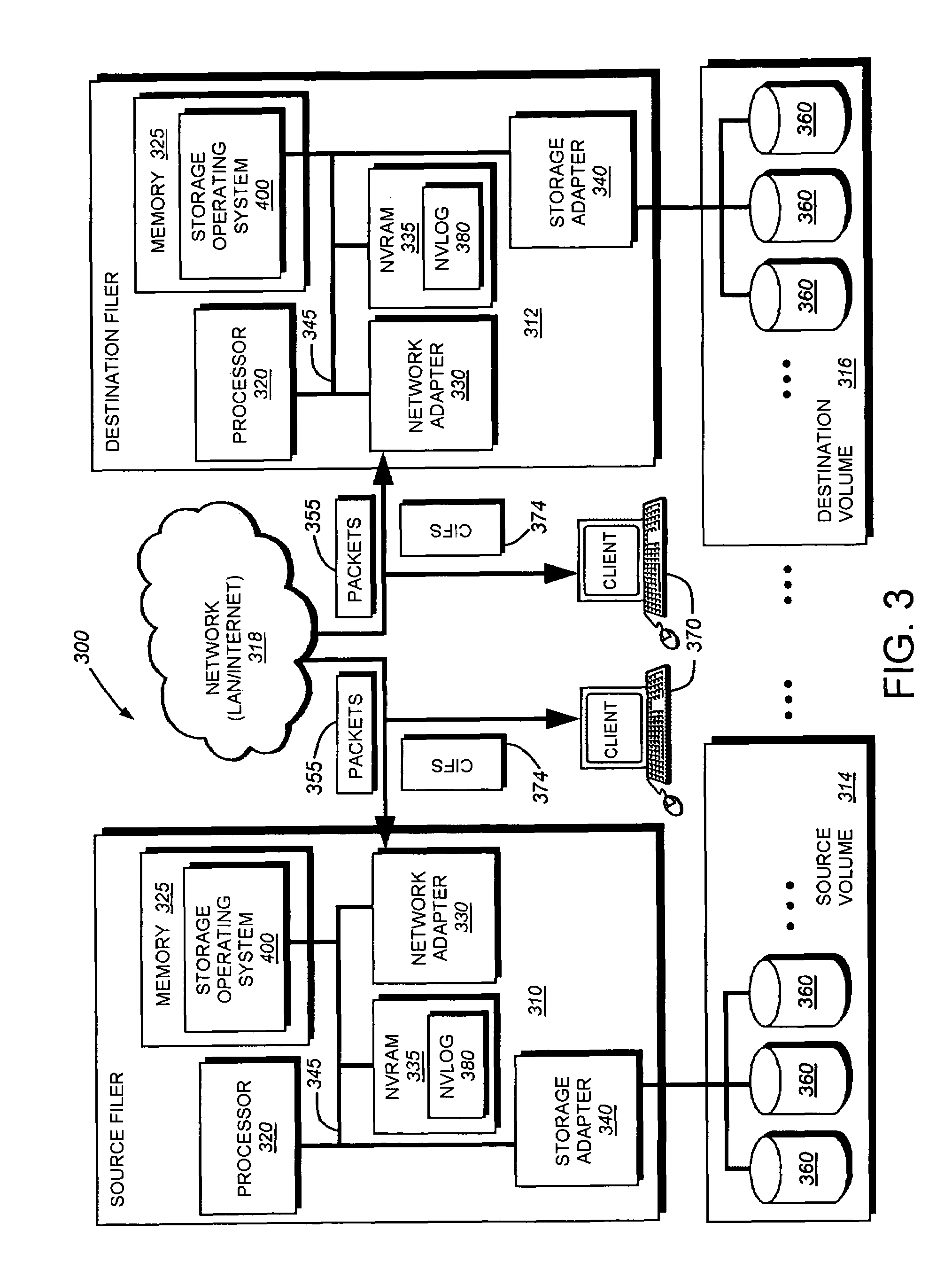
System and method for determining changes in two snapshots and for transmitting changes to destination snapshot
InactiveUS6993539B2Efficient scanningOvercome disadvantagesData processing applicationsSpecial data processing applicationsData streamInode
A system and method for remote asynchronous replication or mirroring of changes in a source file system snapshot in a destination replica file system using a scan (via a scanner) of the blocks that make up two versions of a snapshot of the source file system, which identifies changed blocks in the respective snapshot files based upon differences in volume block numbers identified in a scan of the logical file block index of each snapshot. Trees of blocks associated with the files are traversed, bypassing unchanged pointers between versions and walking down to identify the changes in the hierarchy of the tree. These changes are transmitted to the destination mirror or replicated snapshot. This technique allows regular files, directories, inodes and any other hierarchical structure to be efficiently scanned to determine differences between versions thereof. The changes in the files and directories are transmitted over the network for update of the replicated destination snapshot in an asynchronous (lazy write) manner. The changes are described in an extensible, system-independent data stream format layered under a network transport protocol. At the destination, source changes are used to update the destination snapshot. Any deleted or modified inodes already on the destination are moved to a temporary or “purgatory” directory and, if reused, are relinked to the rebuilt replicated snapshot directory. The source file system snapshots can be representative of a volume sub-organization, such as a qtree.
Owner:NETWORK APPLIANCE INC
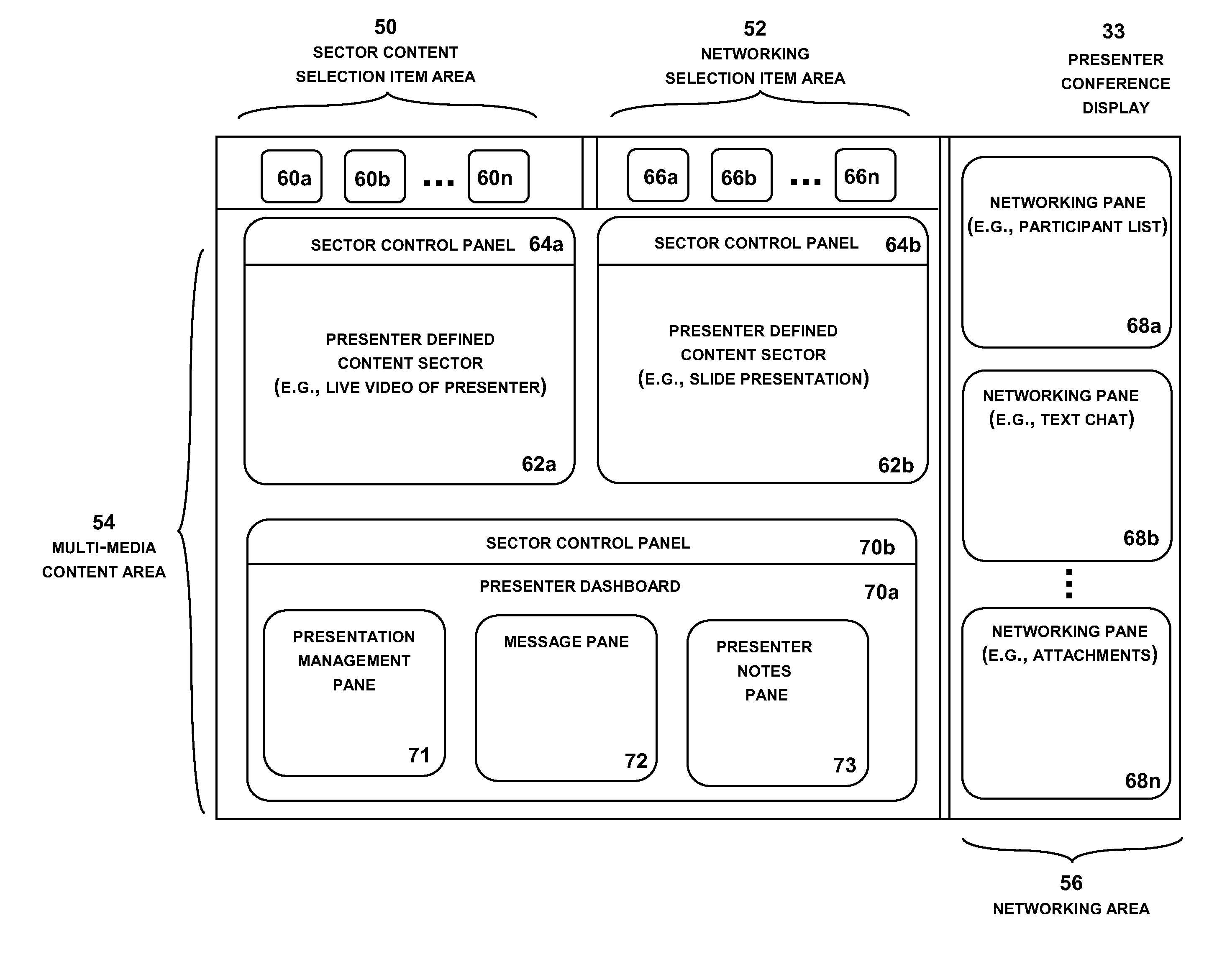
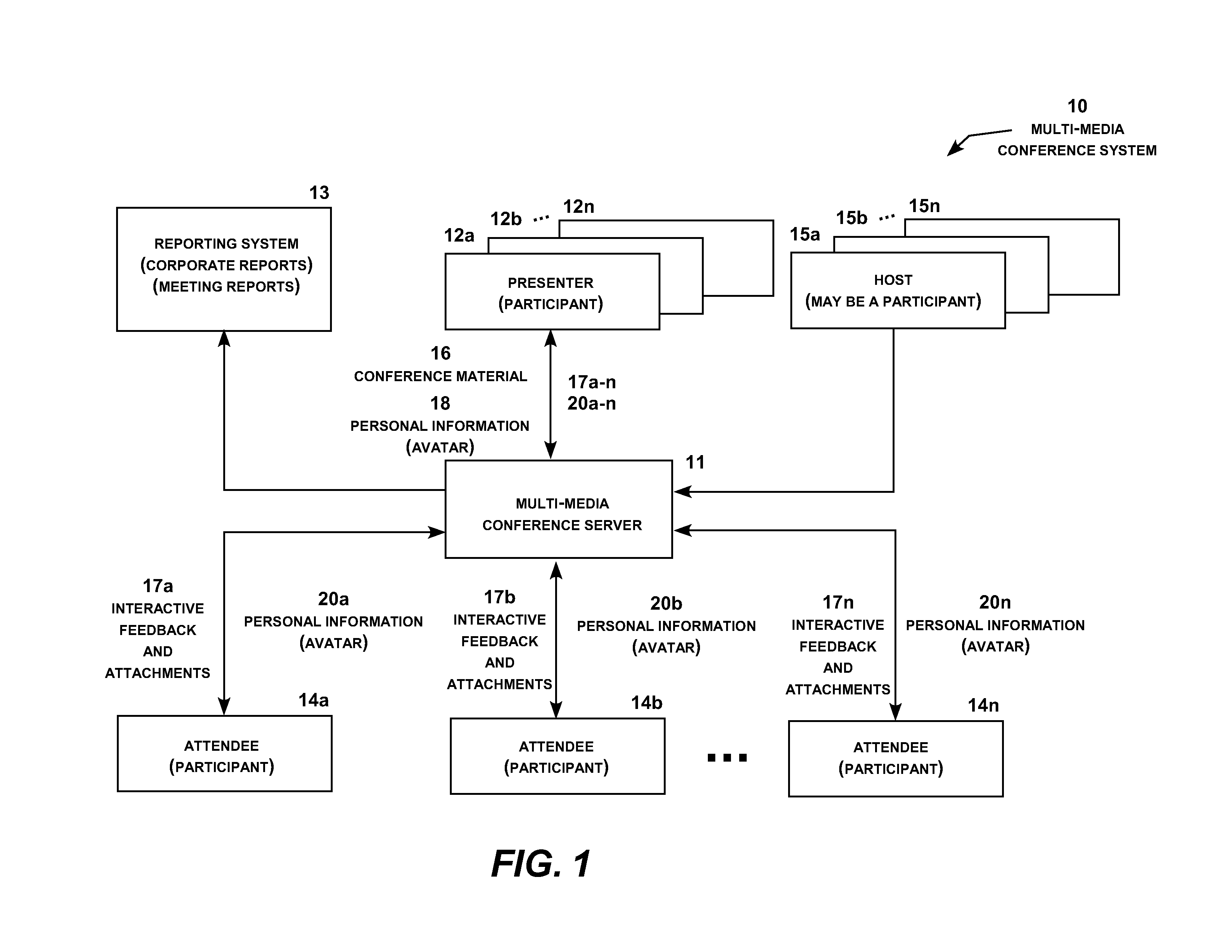
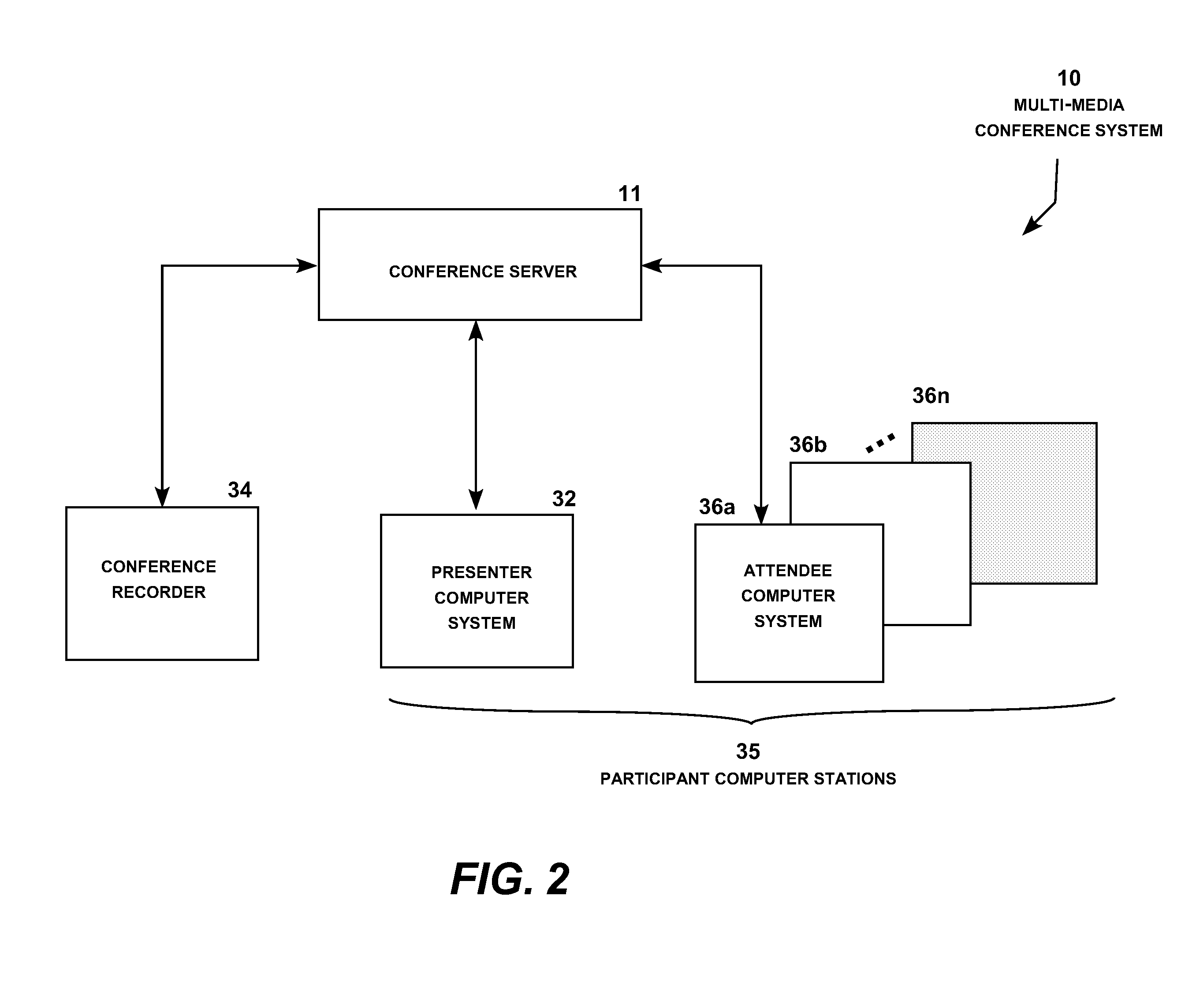
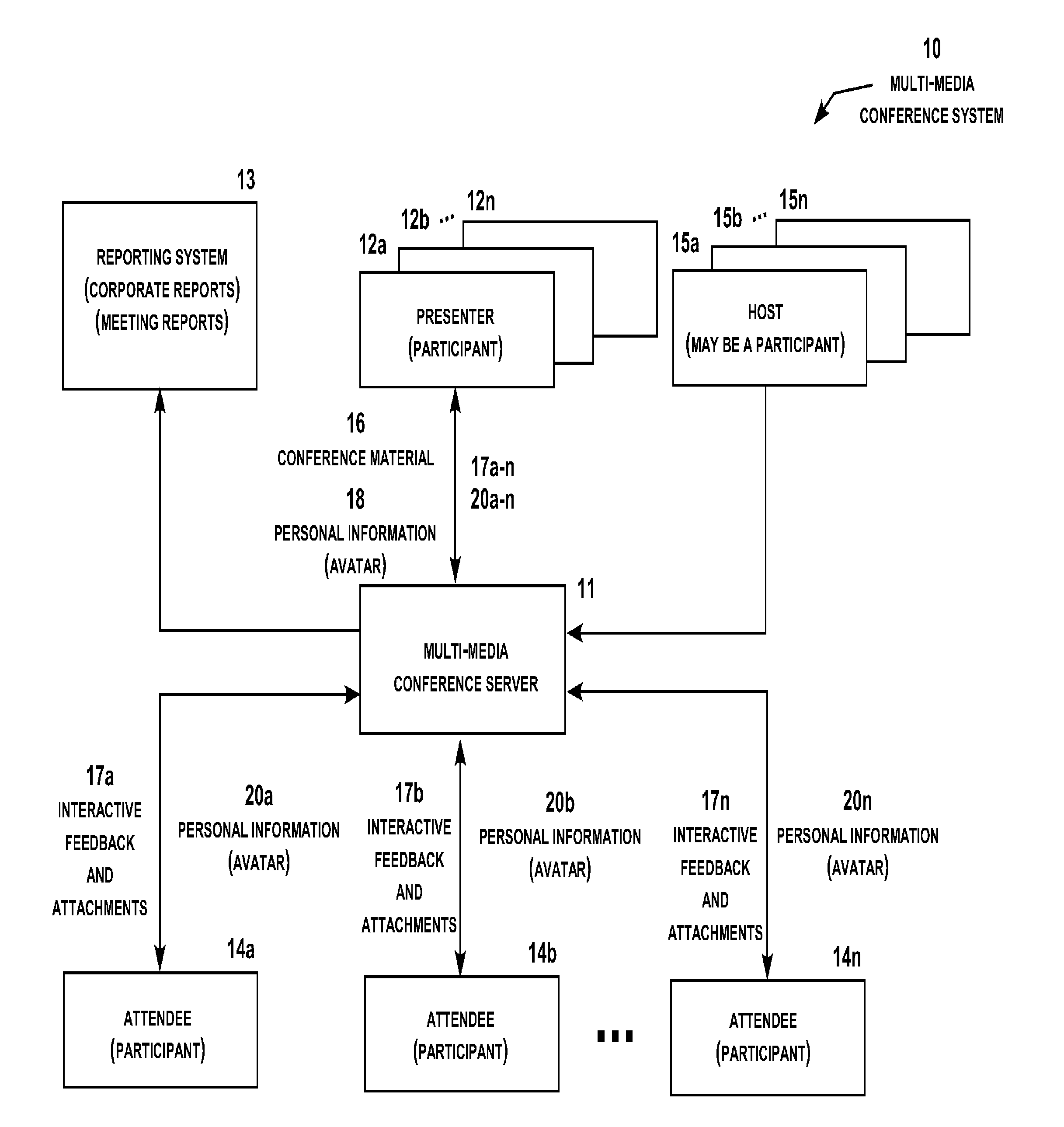
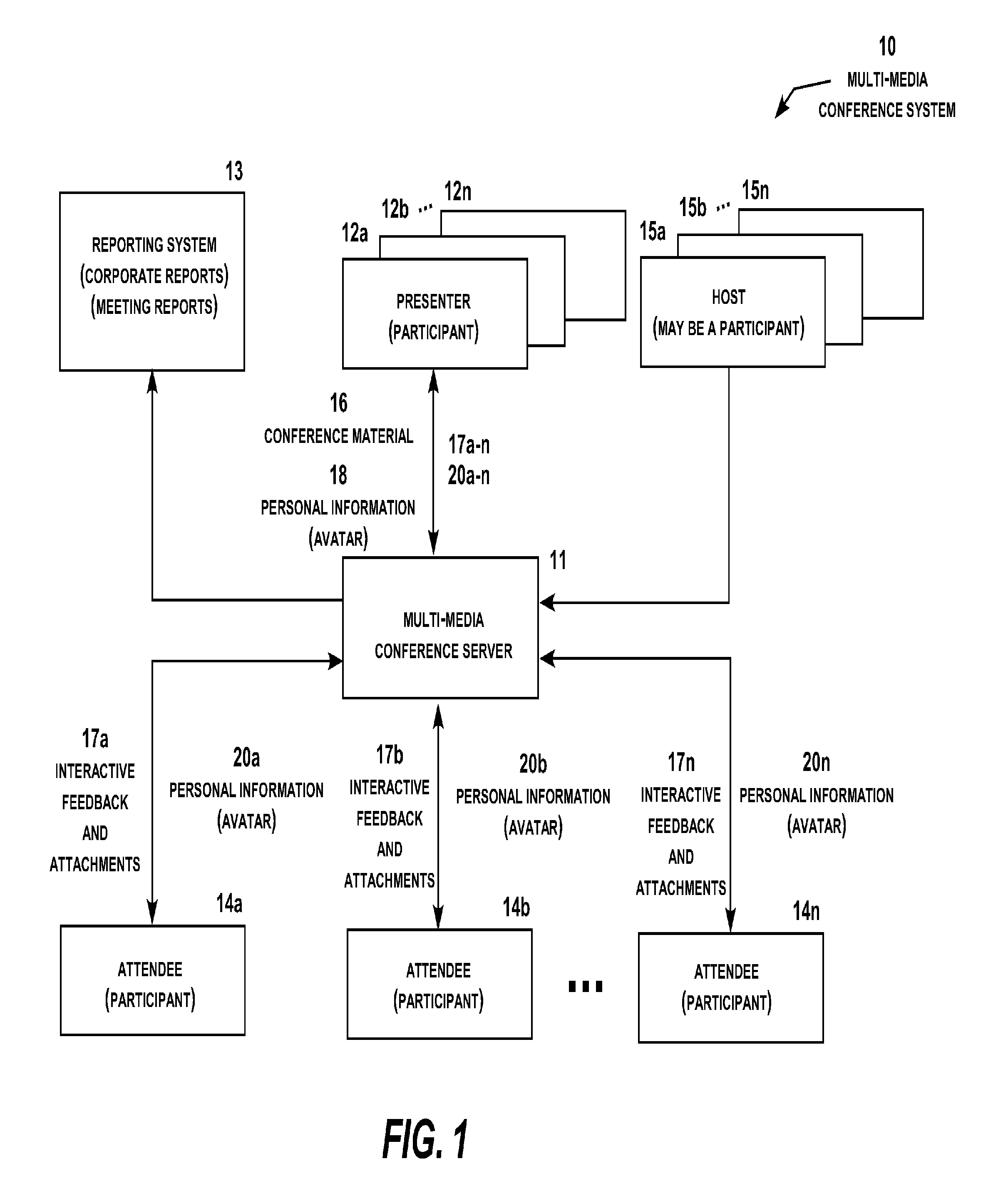
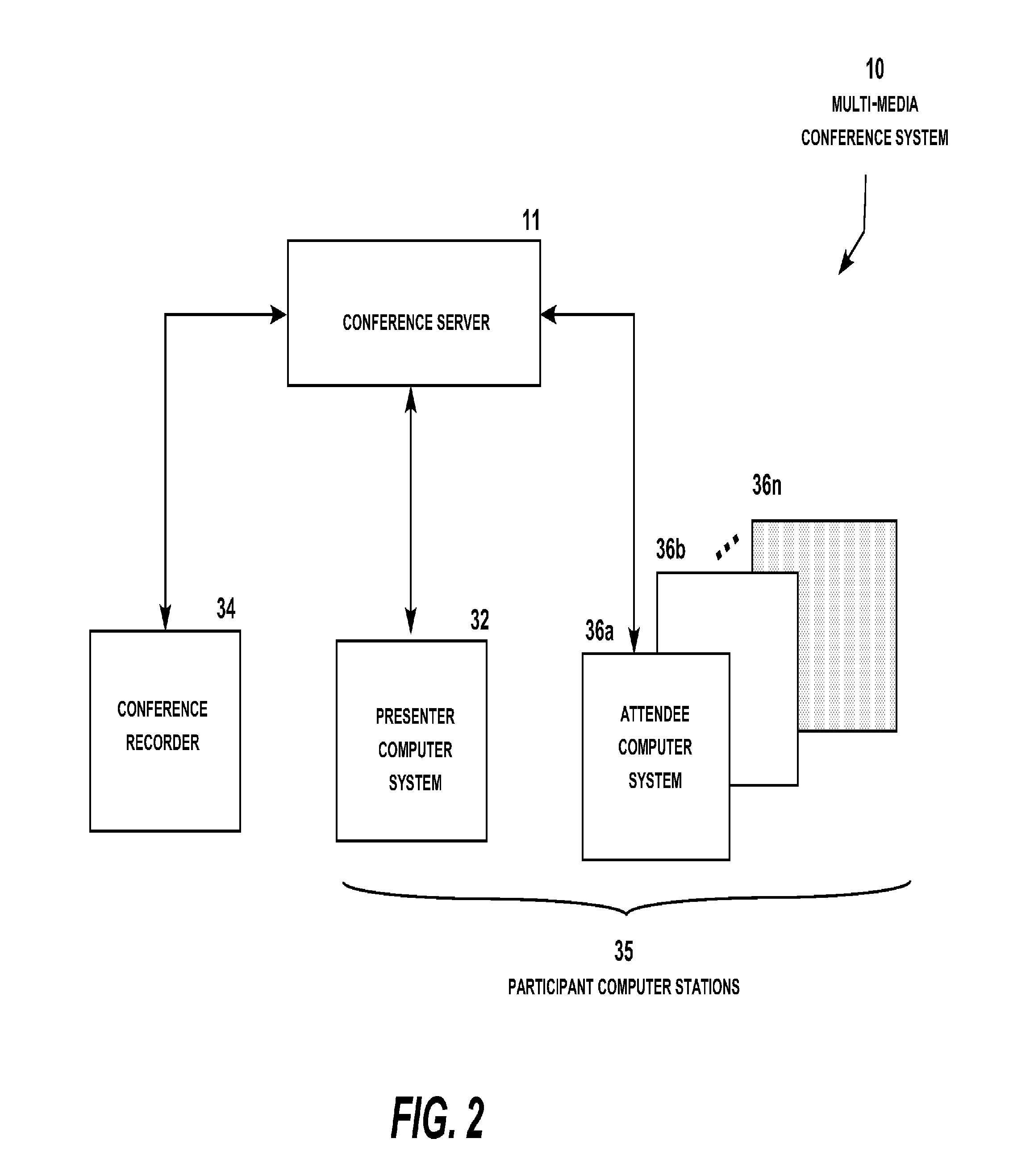
Multi-media conferencing system
InactiveUS20100037151A1Easy to changeInput/output for user-computer interactionOffice automationDashboardDisplay device
A multi-media conferencing system that integrates visual, audio, independent data interaction and modification, collaboration of information, independent video and 3D model viewing and manipulation, and networking among all participants in the meeting. Each participant conference display typically shows two content sectors under the control of the presenter and a selectable number of other content sectors under the control of the participant. The presenter conference display selectively includes a presenter dashboard for managing the presentation. Each content sector on the participant and attendee conference displays may be enlarged to full screen or reduced to a sector display or an icon with a simple command. The system also includes geo-location display functionality, participant monitoring, attendee chat functionality, and a wide range of additional functionality under the control of the conference presenter and attendees.
Owner:JIGSAW MEETING
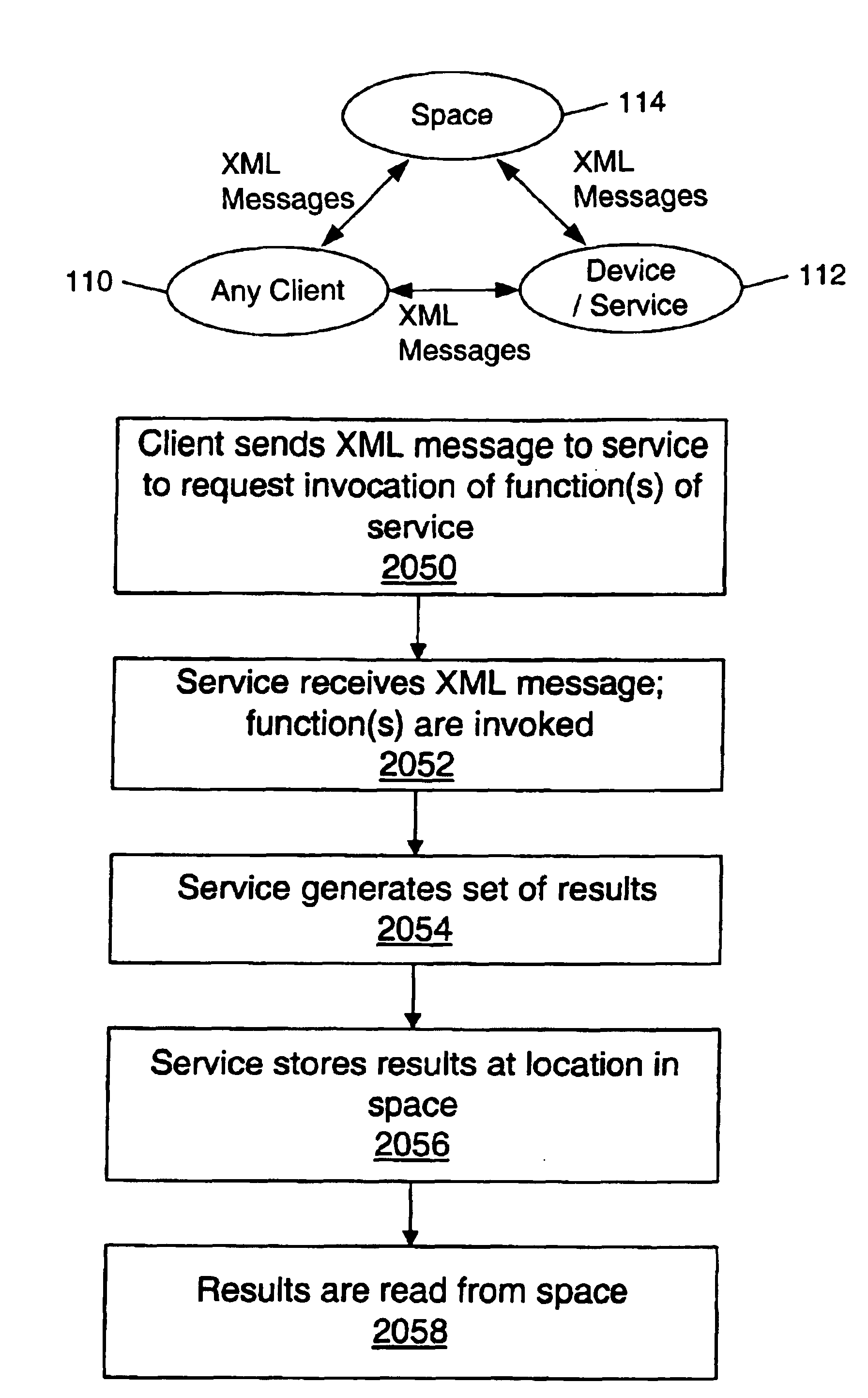
Mechanism and apparatus for returning results of services in a distributed computing environment
InactiveUS6868447B1Easy to storeSimple methodInterprogram communicationDigital computer detailsRepresentation languageDistributed Computing Environment
Systems and methods for returning results of services within a distributed computing environment are provided. After a client invokes one or more functions of a service, results of the function(s) may be returned to the client in a plurality of ways: for example, in a message, in a space (e.g., a network-addressable storage location), in a space wherein the client is notified via an event, using an advertisement returned in a message, using an advertisement returned in a space, and using an advertisement returned in a space wherein the client is notified via an event. The advertisement may include the information necessary to access and read the results in a storage location such as a space. A schema for the service may specify a plurality of messages which are usable to invoke the function(s) of the service. The messages, results, and advertisements may be expressed in a platform-independent and / or programming-language-independent data representation language such as XML. The availability of these plurality of methods may enhance the flexibility and adaptability of the distributed computing environment for a variety of situations, such as for clients having differing capabilities. For additional flexibility, results may also be efficiently passed to another service.
Owner:ORACLE INT CORP
Accelerated RAID with rewind capability
InactiveUS7076606B2Increase exposureImprove read performanceInput/output to record carriersData processing applicationsRAIDData store
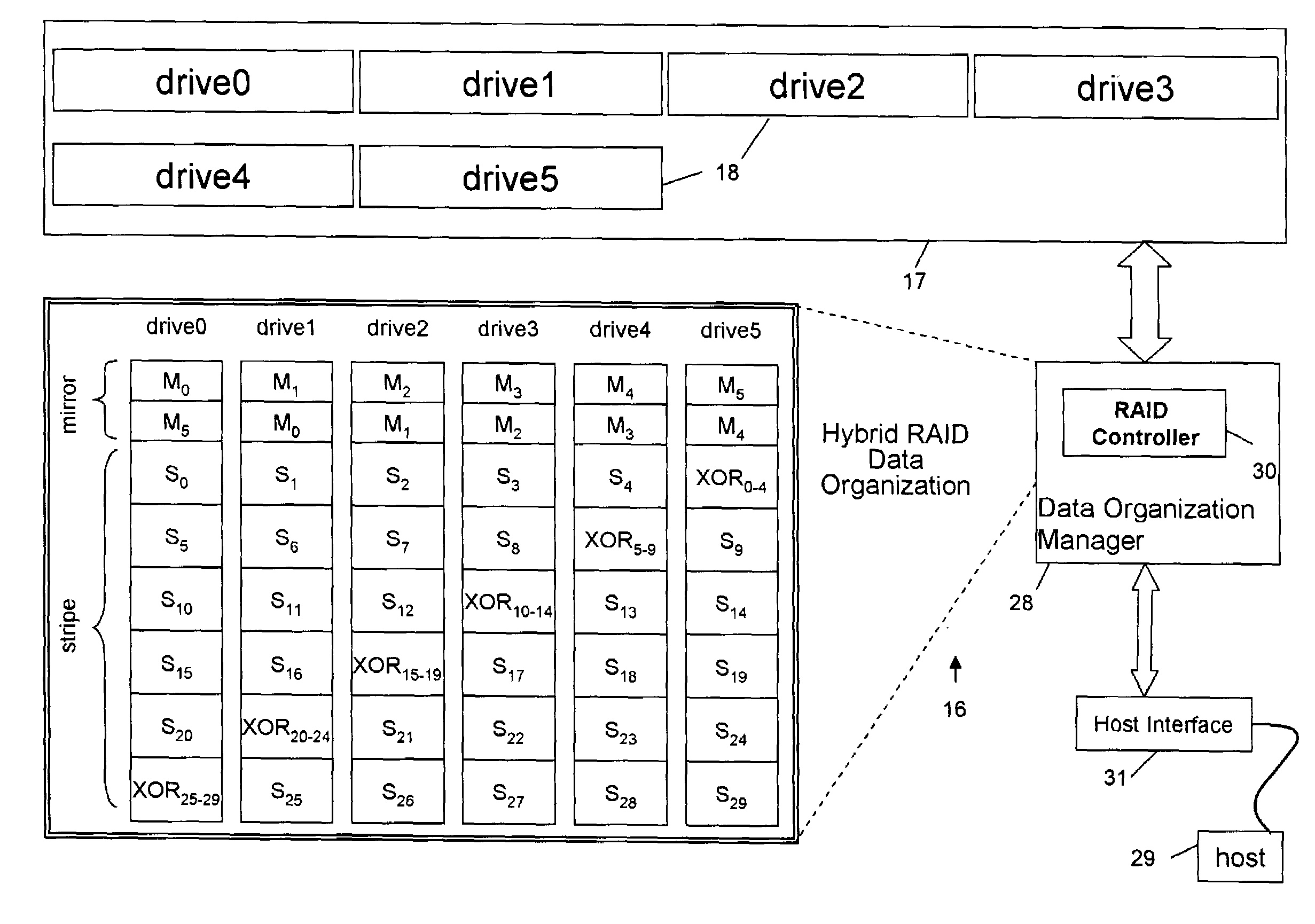
A method for storing data in a fault-tolerant storage subsystem having an array of failure independent data storage units, by dividing the storage area on the storage units into a logical mirror area and a logical stripe area, such that when storing data in the mirror area, duplicating the data by keeping a duplicate copy of the data on a pair of storage units, and when storing data in the stripe area, storing data as stripes of blocks, including data blocks and associated error-correction blocks.
Owner:QUANTUM CORP
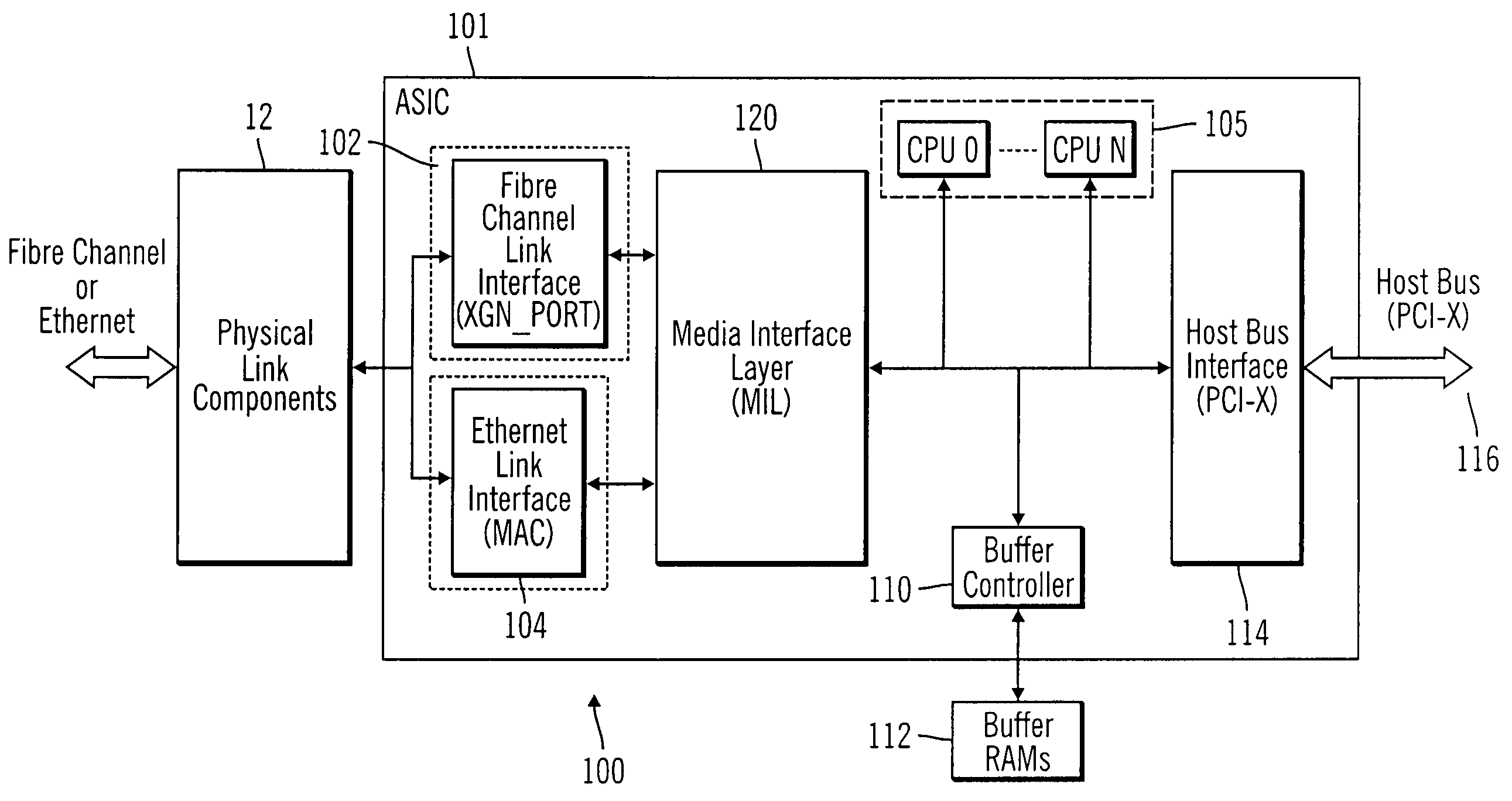
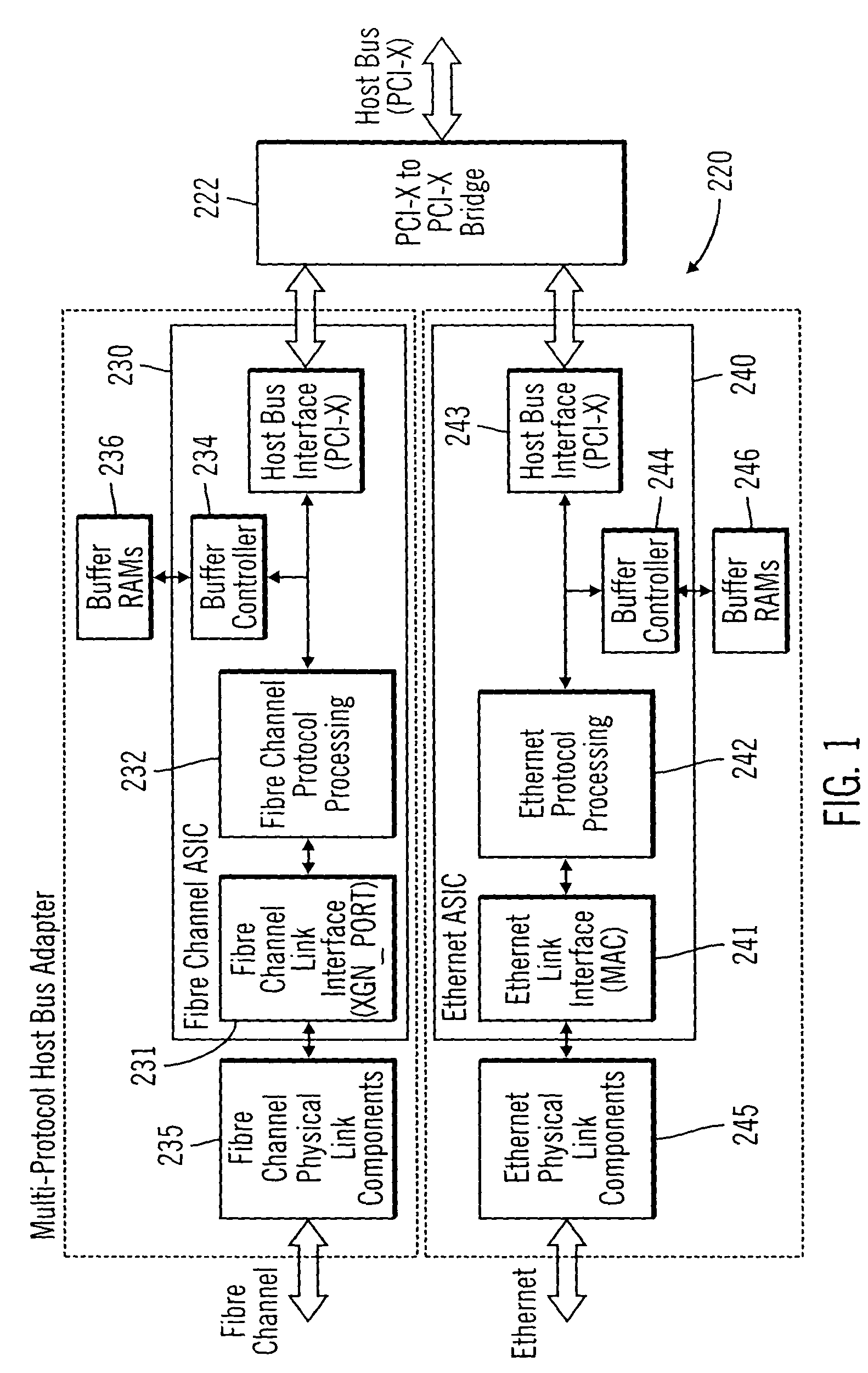
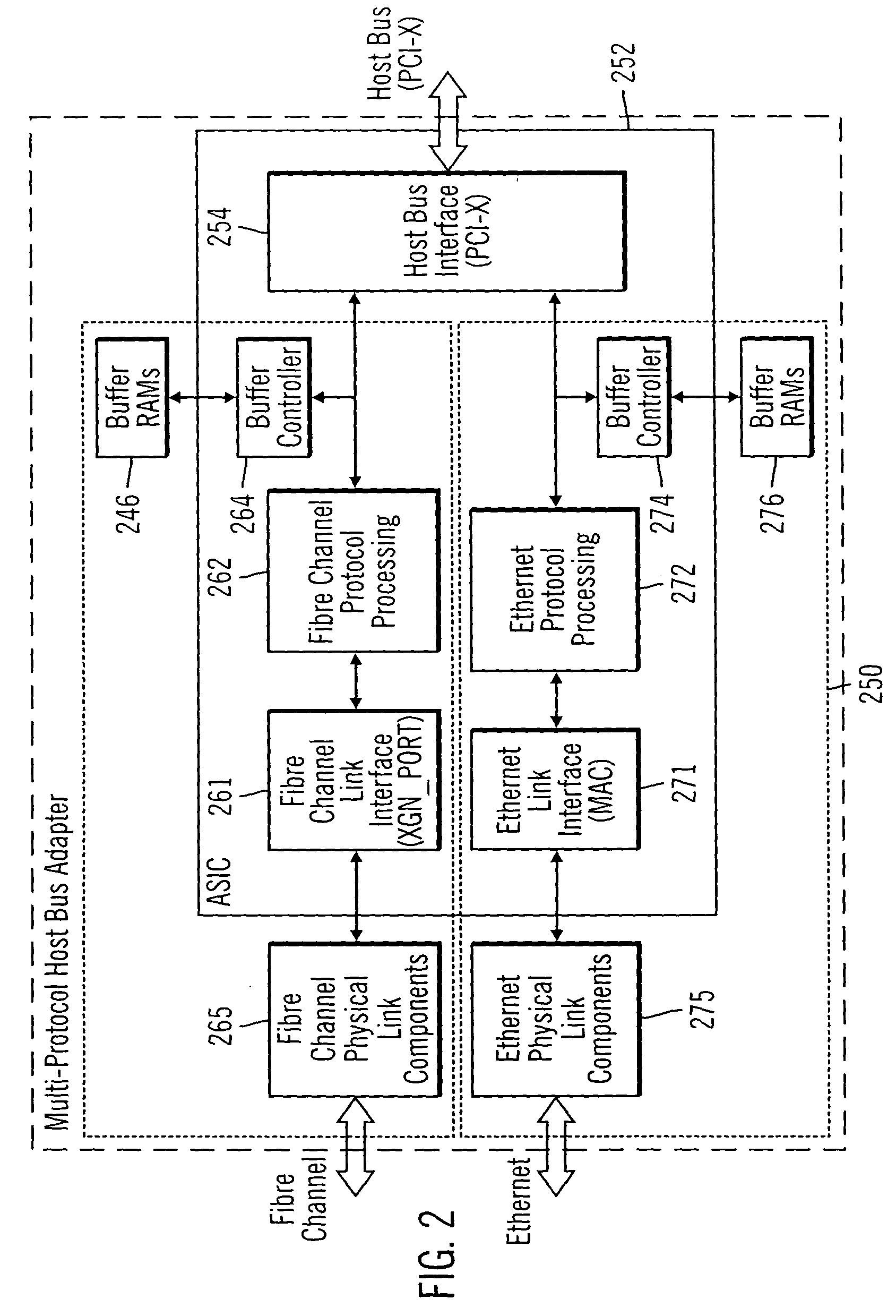
Integrated network interface supporting multiple data transfer protocols
InactiveUS20050066045A1Overcome limitationsTime-division multiplexMultiple digital computer combinationsData streamNetwork interface device
An integrated network interface device that supports data exchange in two or more high-speed network data transfer protocols that are based on different standards of network data transfer architectures, wherein an incoming data stream formatted in accordance with a particular network data transfer standard is processed into data not subject to the network data transfer standard to be output for further processing by a host. In one aspect, a network interface device is provided with a set of shared or common protocol independent physical link components that are used to identify the operating protocol of the incoming data, and a set of dynamically or statically re-configurable, shared or common protocol independent data transfer processing components that support data exchange via the physical link components for all the supported protocols, which may include a protocol specific link interface for each supported protocol.
Owner:WAVECREST LAB LLC +1
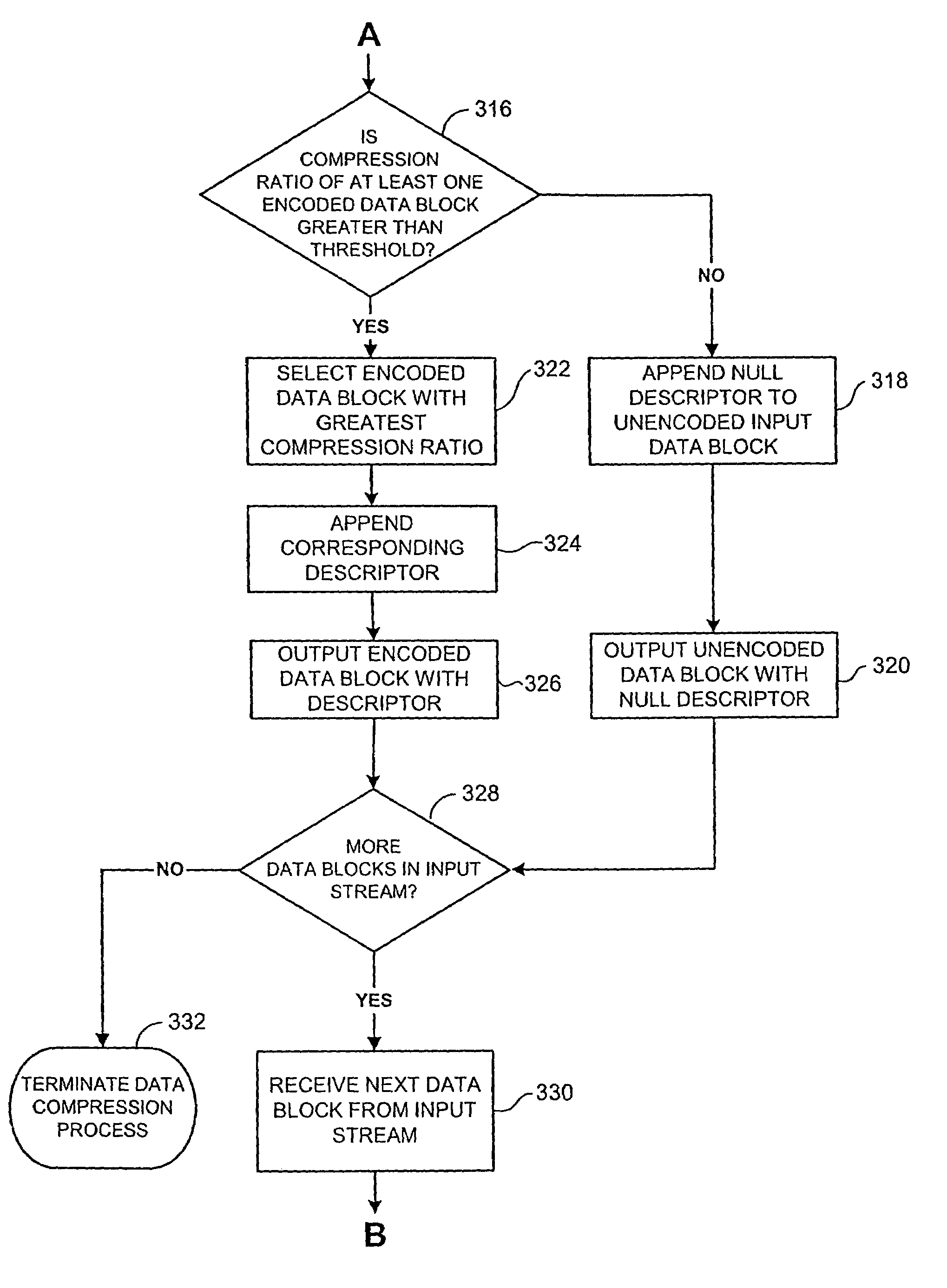
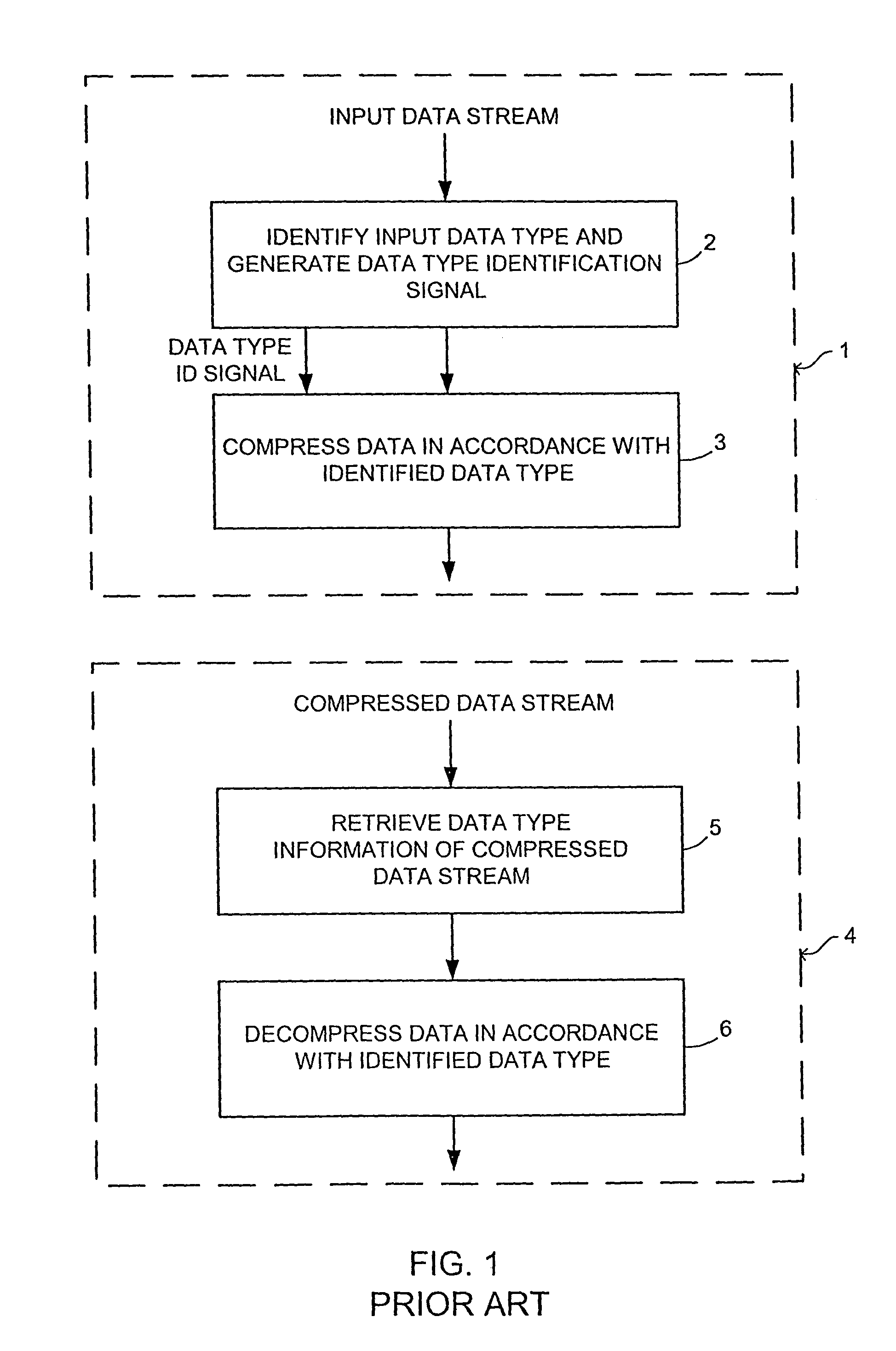
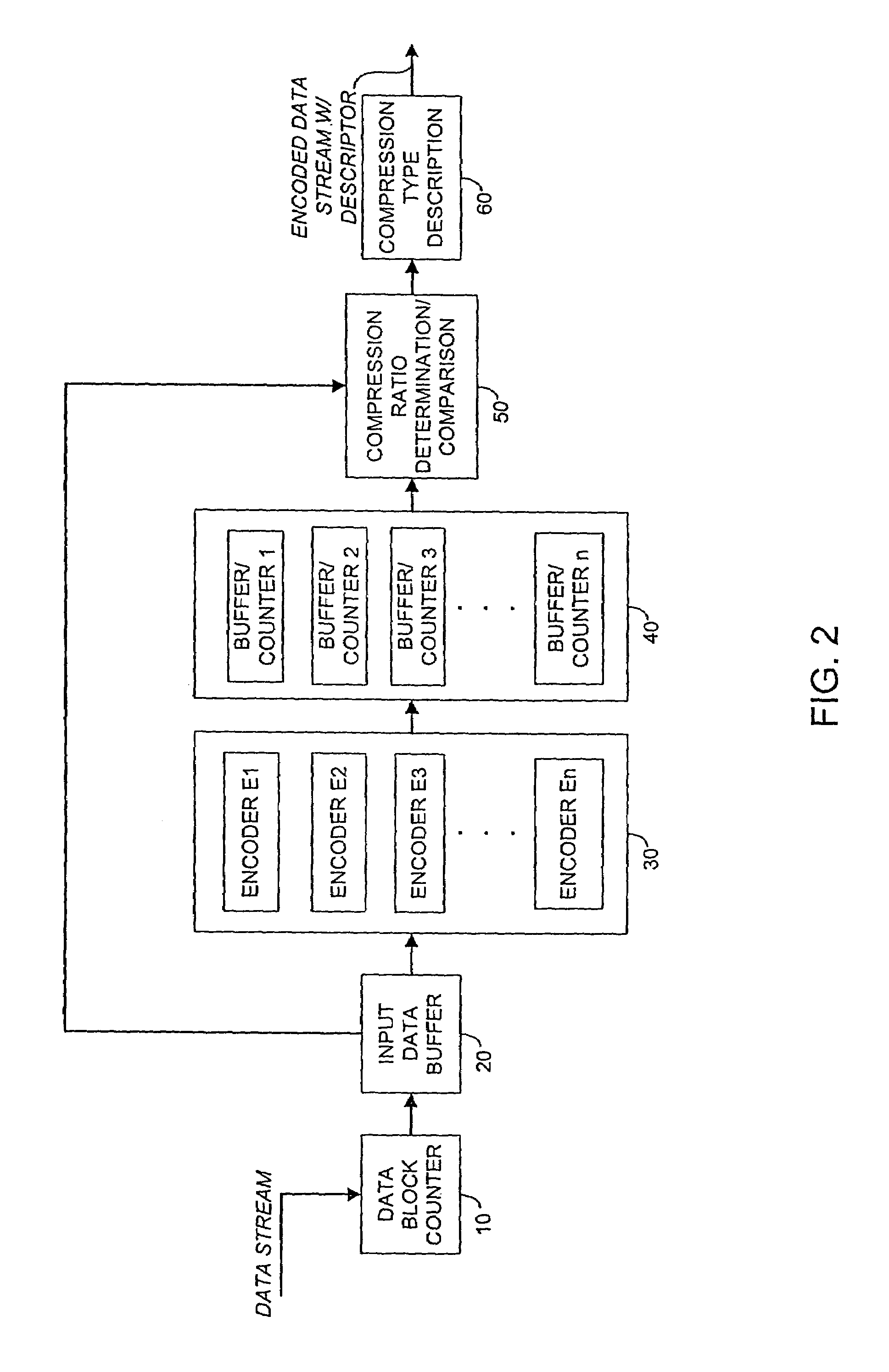
Systems and methods for data compression such as content dependent data compression
Systems and methods for providing fast and efficient data compression using a combination of content independent data compression and content dependent data compression. In one aspect, a method for compressing data comprises the steps of: analyzing a data block of an input data stream to identify a data type of the data block, the input data stream comprising a plurality of disparate data types; performing content dependent data compression on the data block, if the data type of the data block is identified; performing content independent data compression on the data block, if the data type of the data block is not identified.
Owner:REALTIME DATA
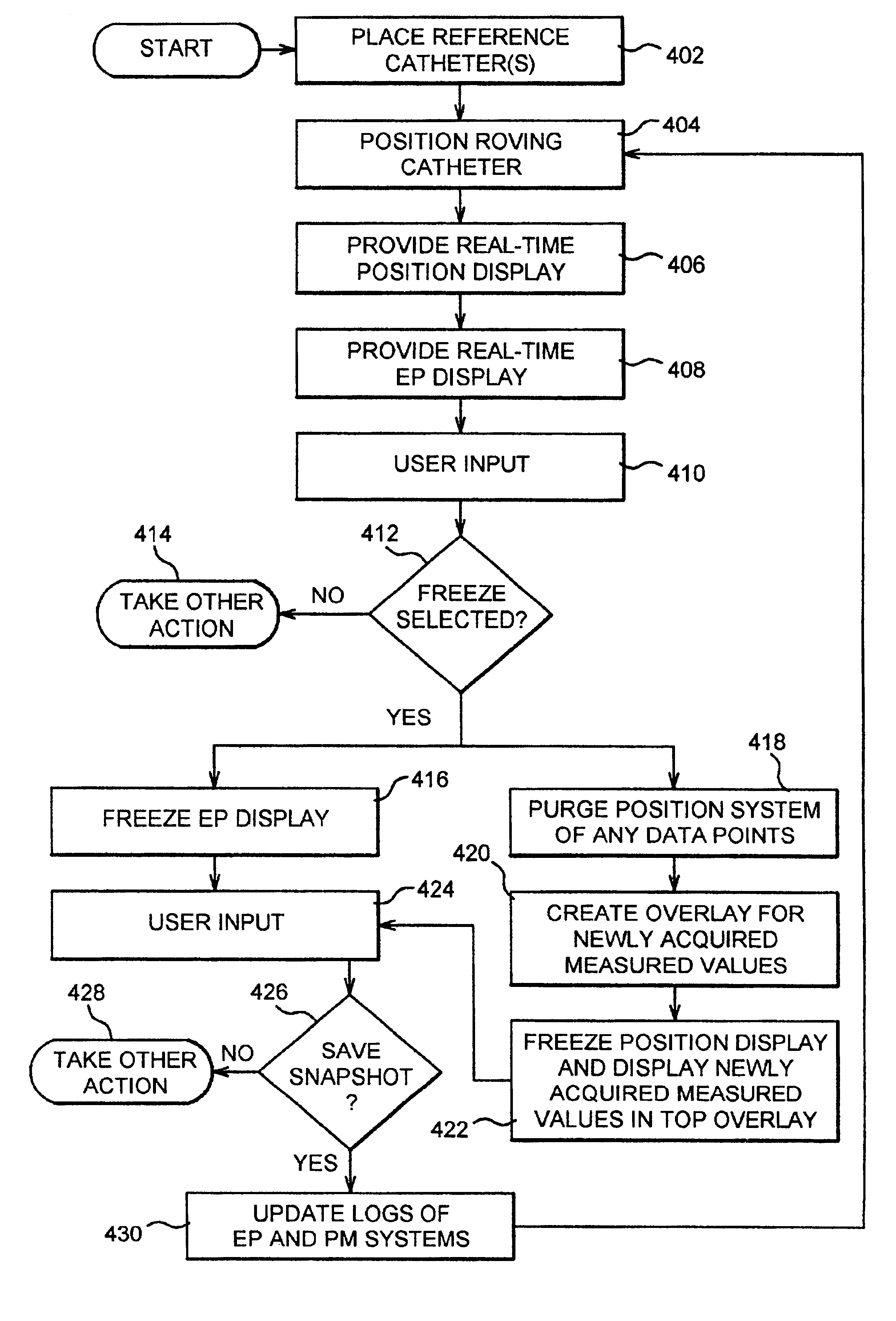
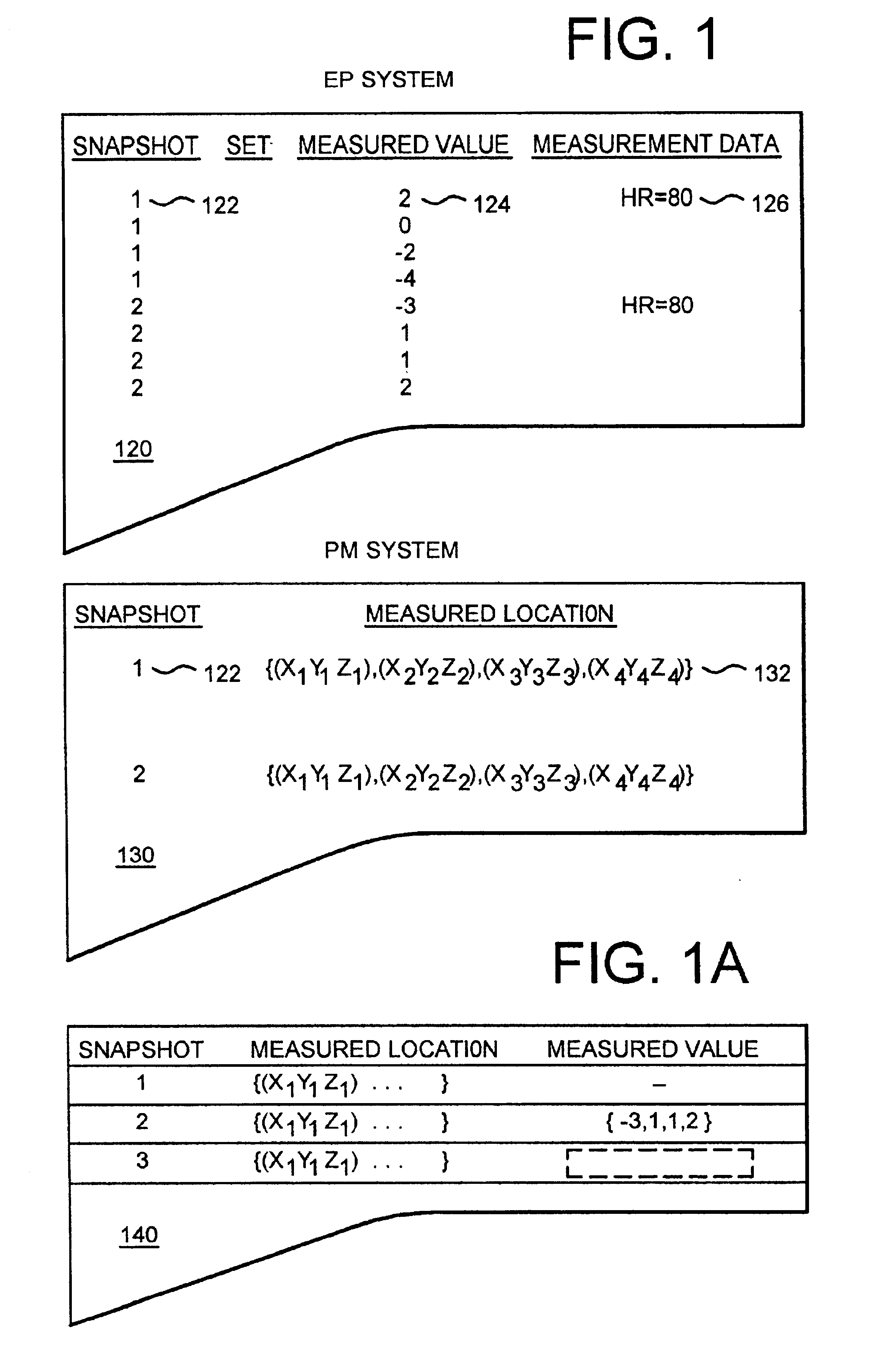
Software controlled electrophysiology data management
Methods for conducting an electrophysiology procedure using a programmed machine are described, including methods for managing discrete data capture requests received throughout the course of an electrophysiology procedure and for discretizing the display of independent data capture events that occur during the course of the electrophysiology procedure. These methods enable an operator to review location maps of sites visited during the course of a procedure and to review data from discrete moments in the procedure and to play back data over a sequence of times throughout the procedure, one moment at a time. The invention further includes software constructs that enable data management.
Owner:BOSTON SCI SCIMED INC
System and methods for permitting open access to data objects and for securing data within the data objects
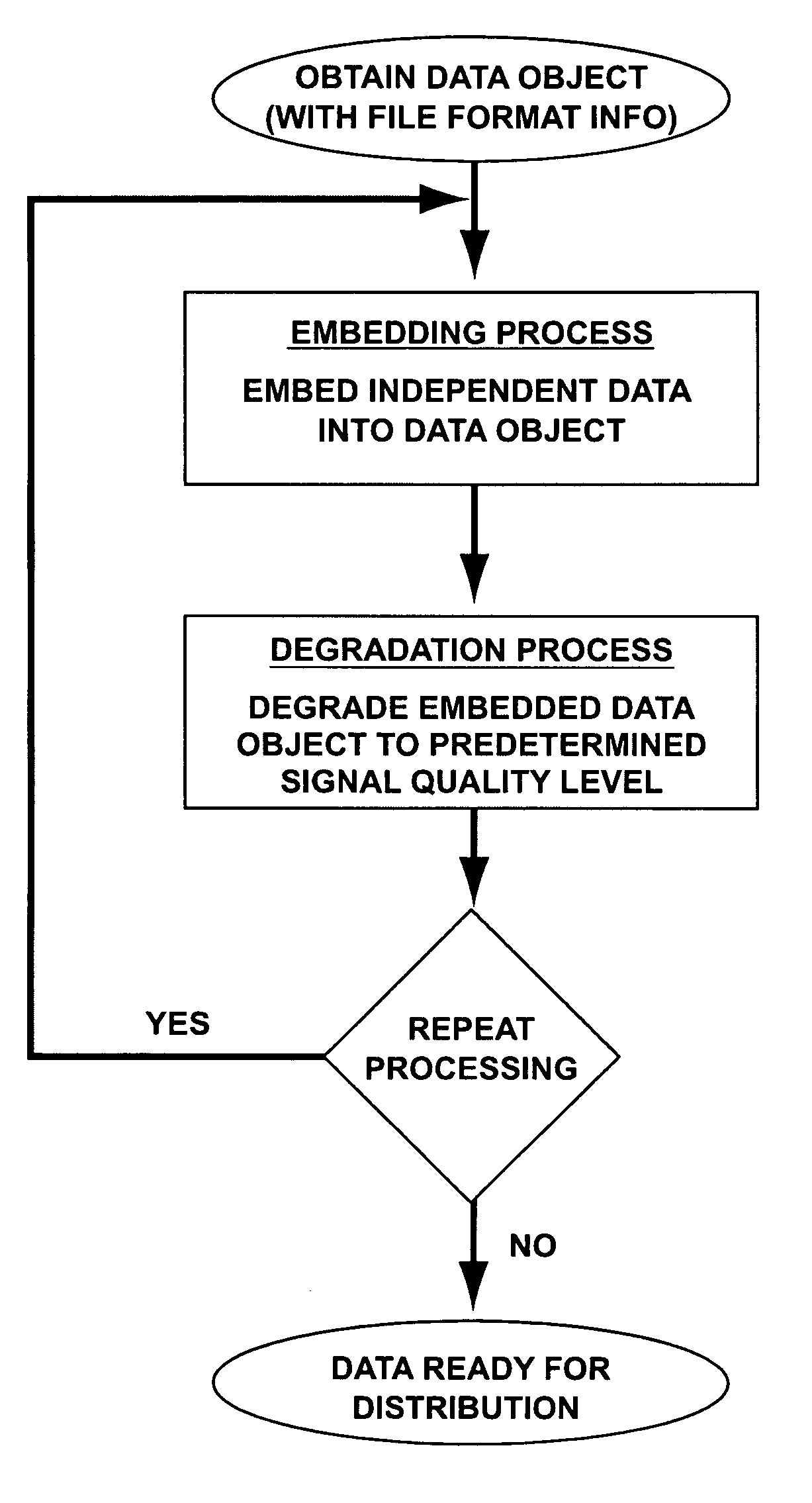
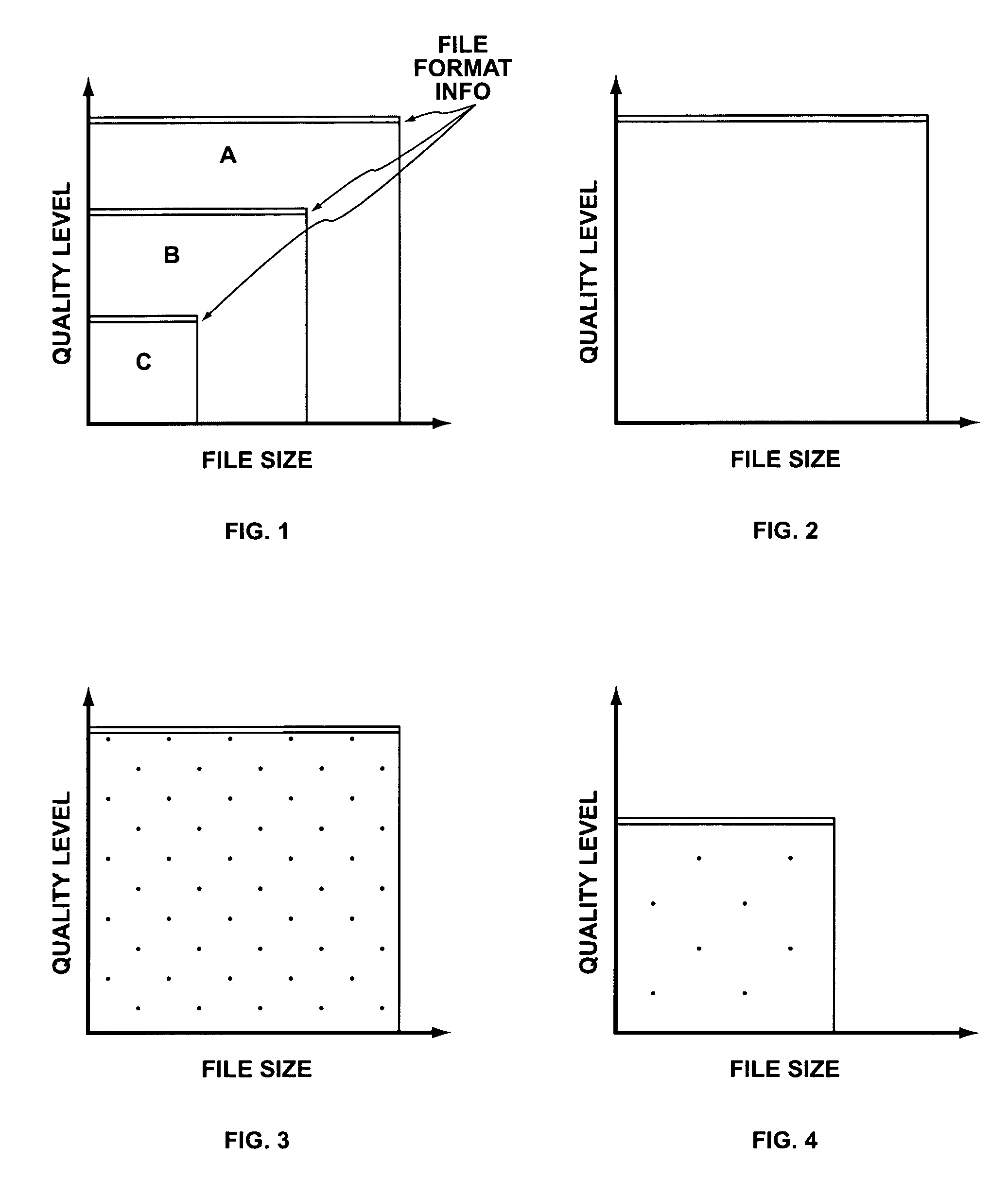
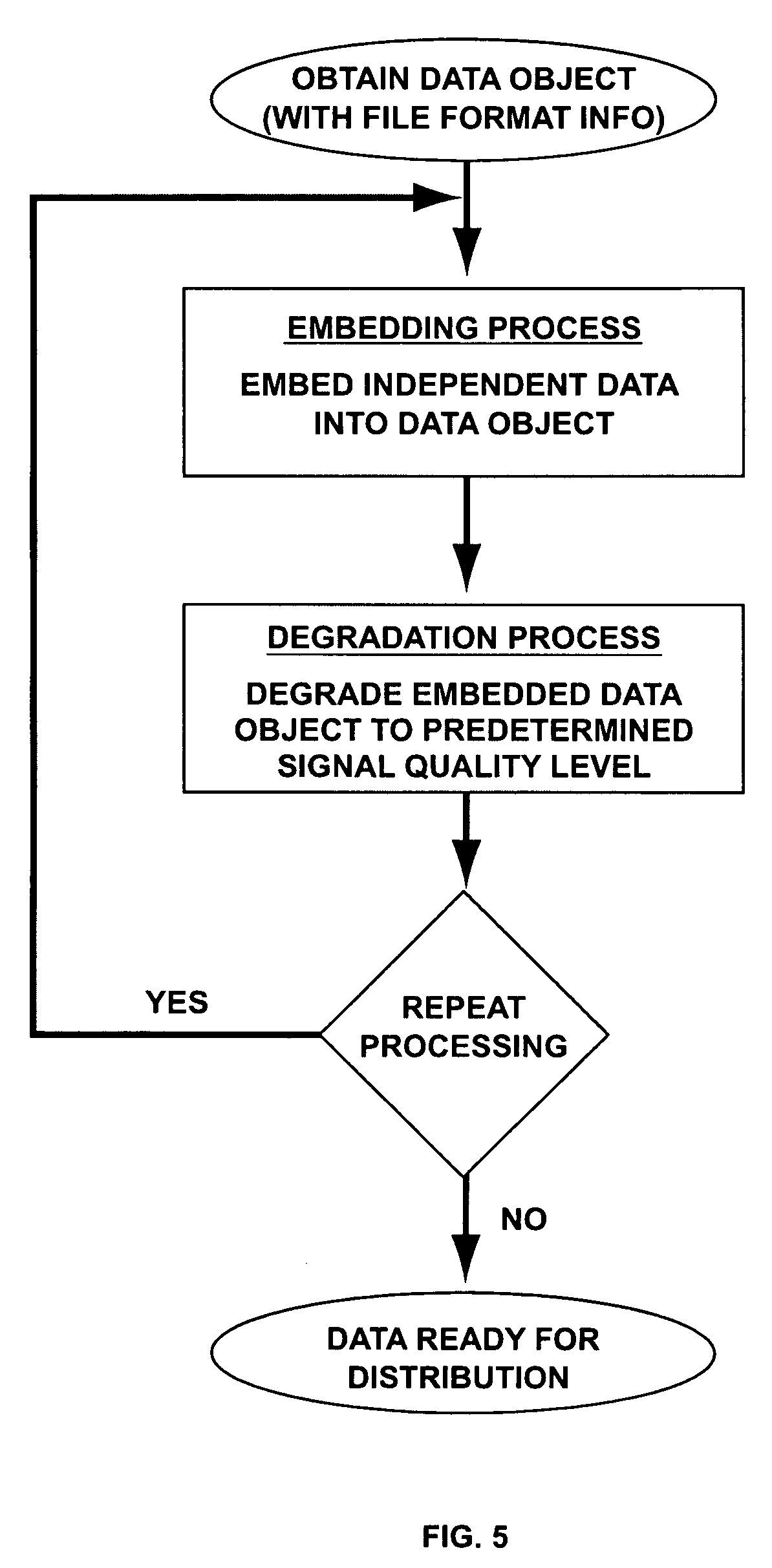
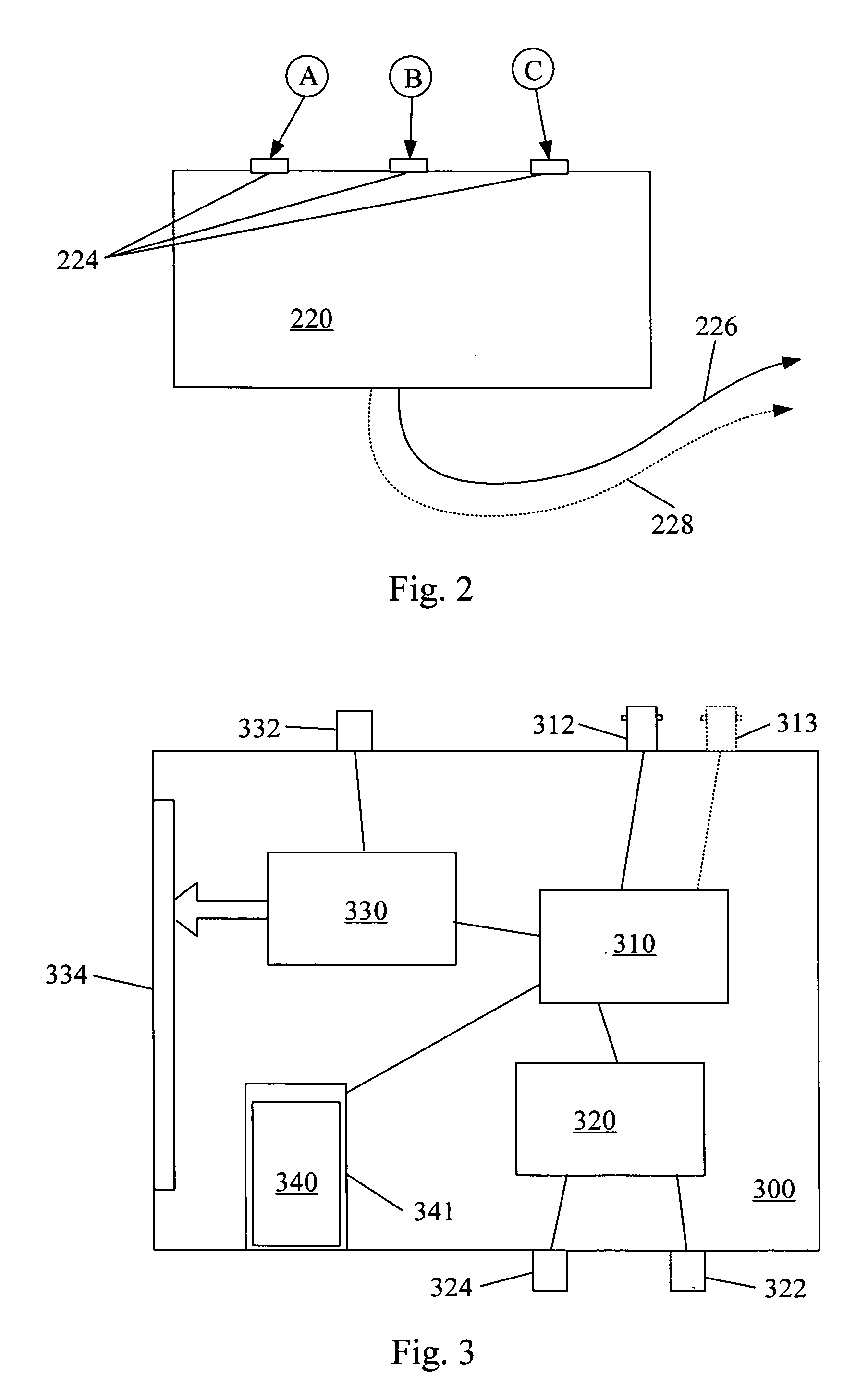
ActiveUS7177429B2Large file sizeQuality improvementRecord information storageSecret communicationDigital dataSignal quality
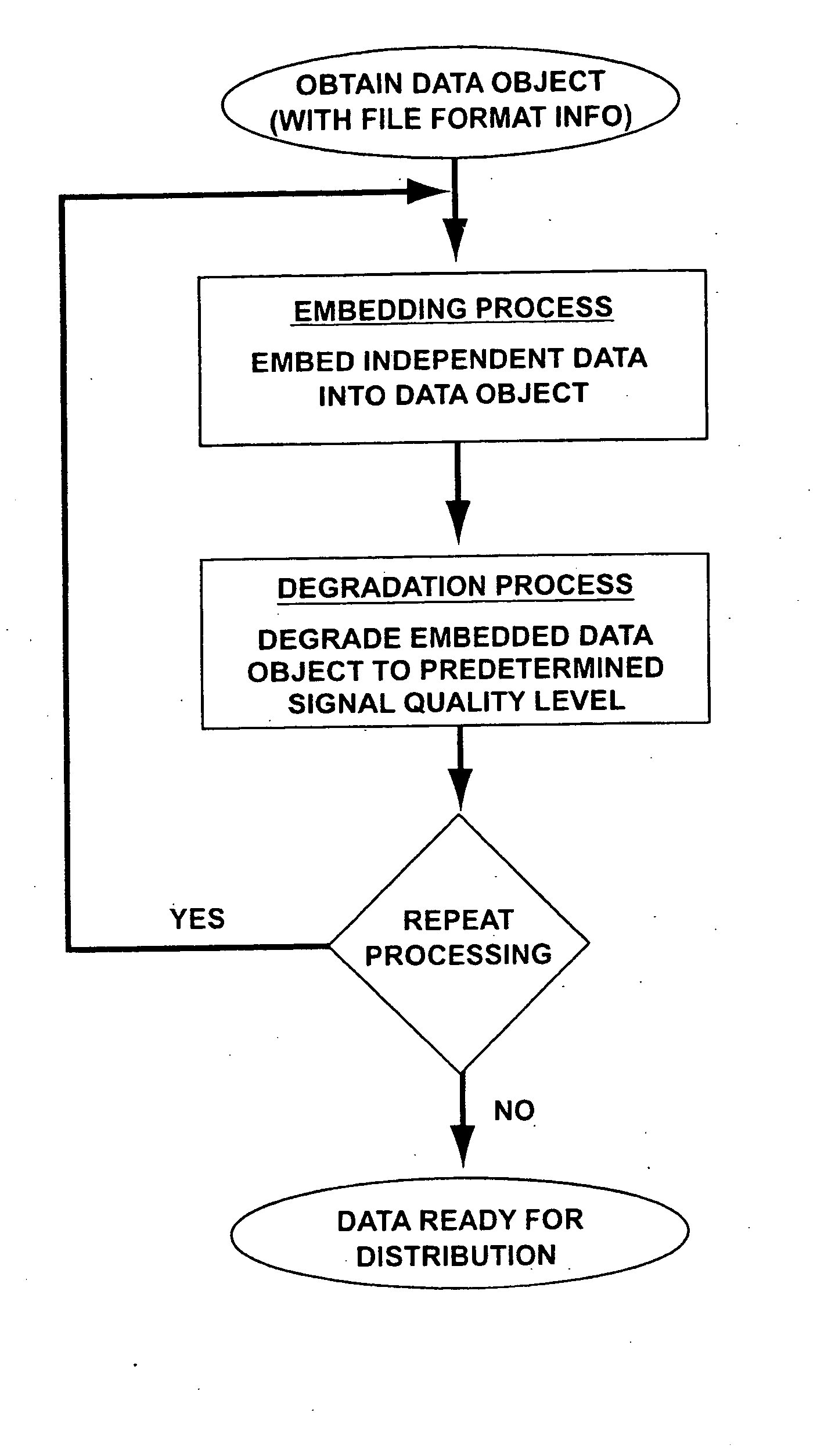
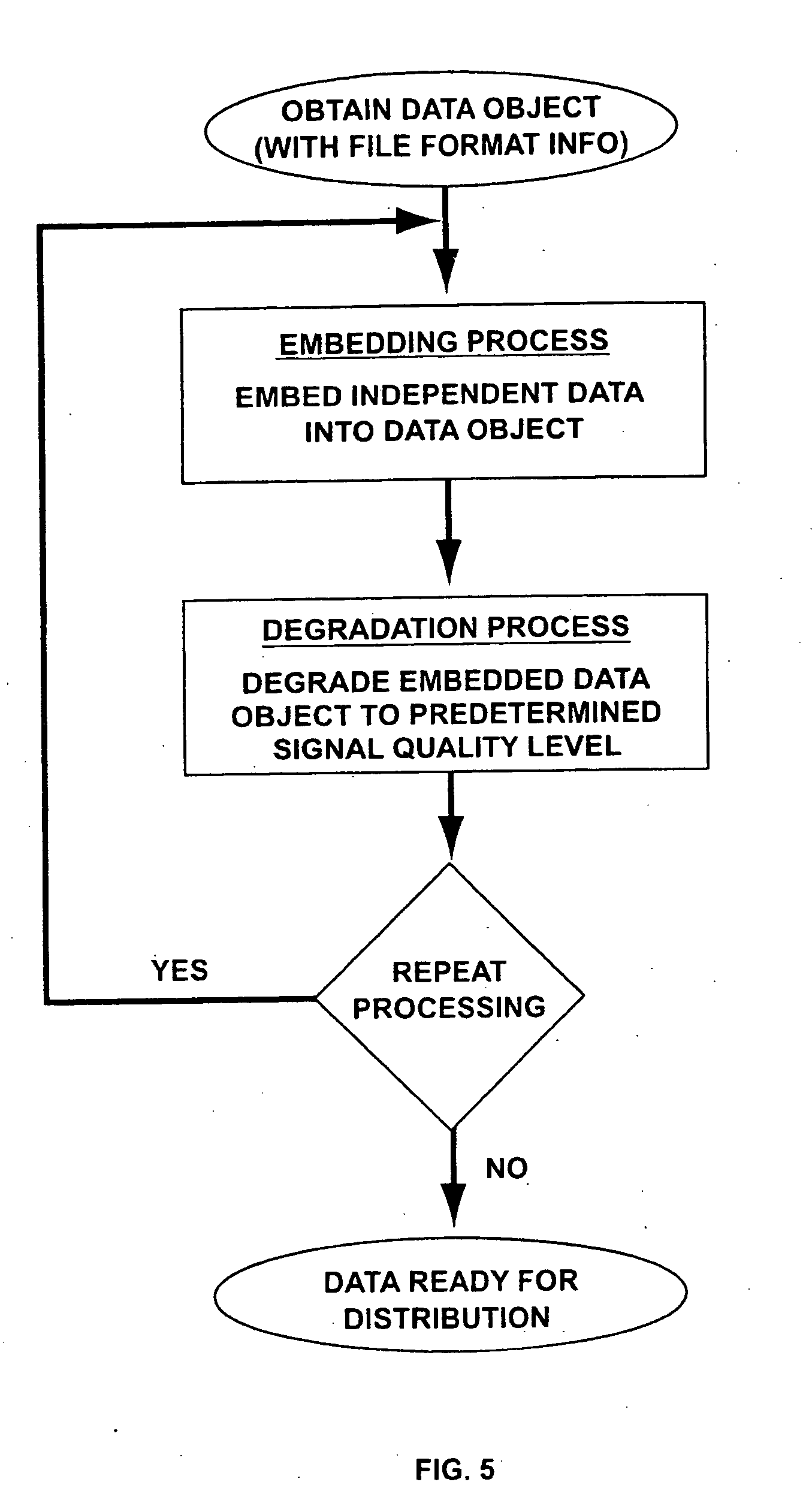
A system and methods for permitting open access to data objects and for securing data within the data objects is disclosed. According to one embodiment of the present invention, a method for securing a data object is disclosed. According to one embodiment of the present invention, a method for securing a data object is disclosed. The method includes the steps of (1) providing a data object comprising digital data and file format information; (2) embedding independent data into a data object; and (3) scrambling the data object to degrade the data object to a predetermined signal quality level. The steps of embedding and scrambling may be performed until a predetermined condition is met. The method may also include the steps of descrambling the data object to upgrade the data object to a predetermined signal quality level, and decoding the embedded independent data. The additional steps of descrambling and decoding may be performed until a predetermined condition is met. The predetermined condition may include, for example, reaching a desired signal quality of the data object.
Owner:WISTARIA TRADING INC
Content locality-based caching in a data storage system
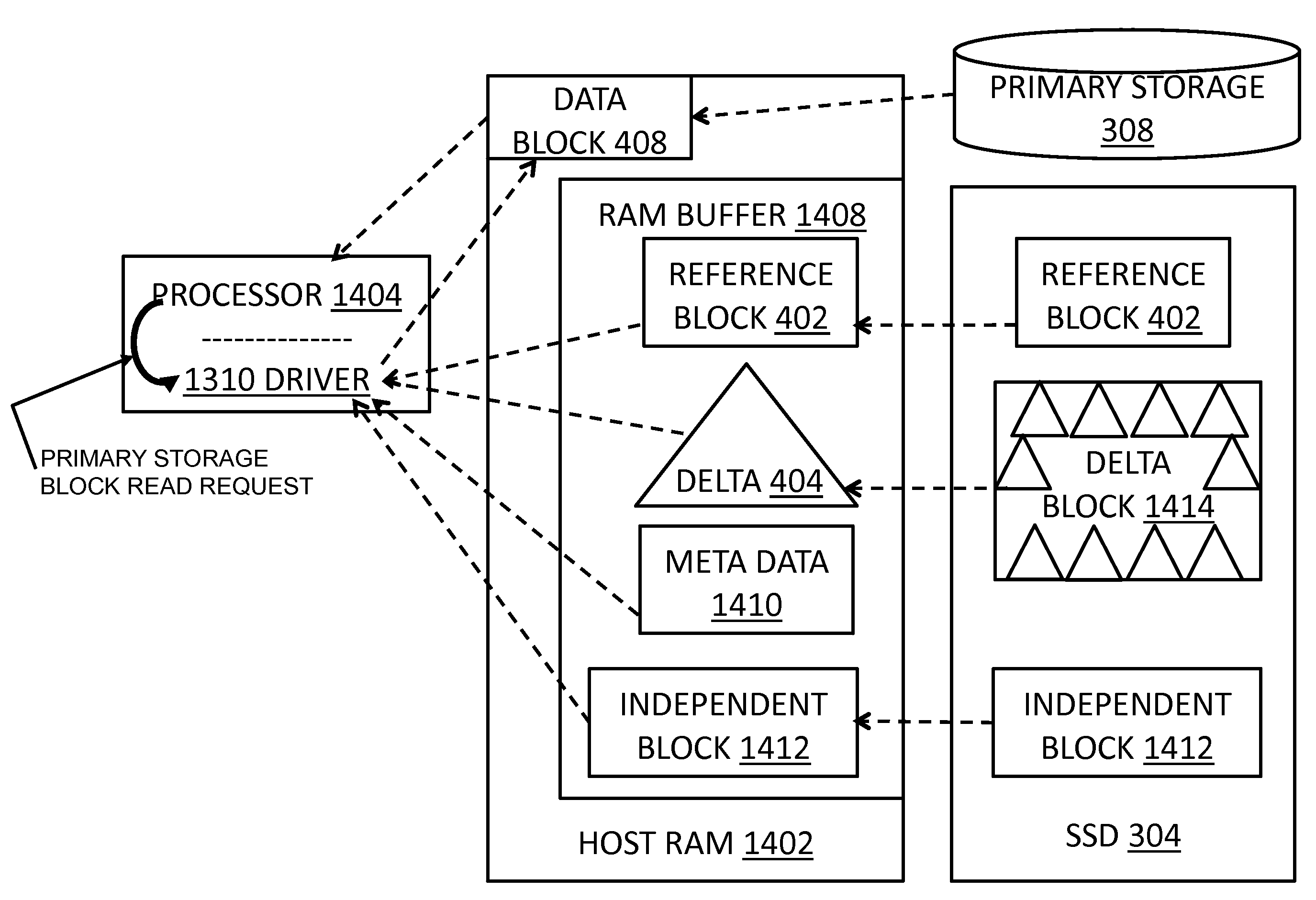
InactiveUS20120137059A1Quick upgradeLow costMemory architecture accessing/allocationEnergy efficient ICTData accessLeast frequently used
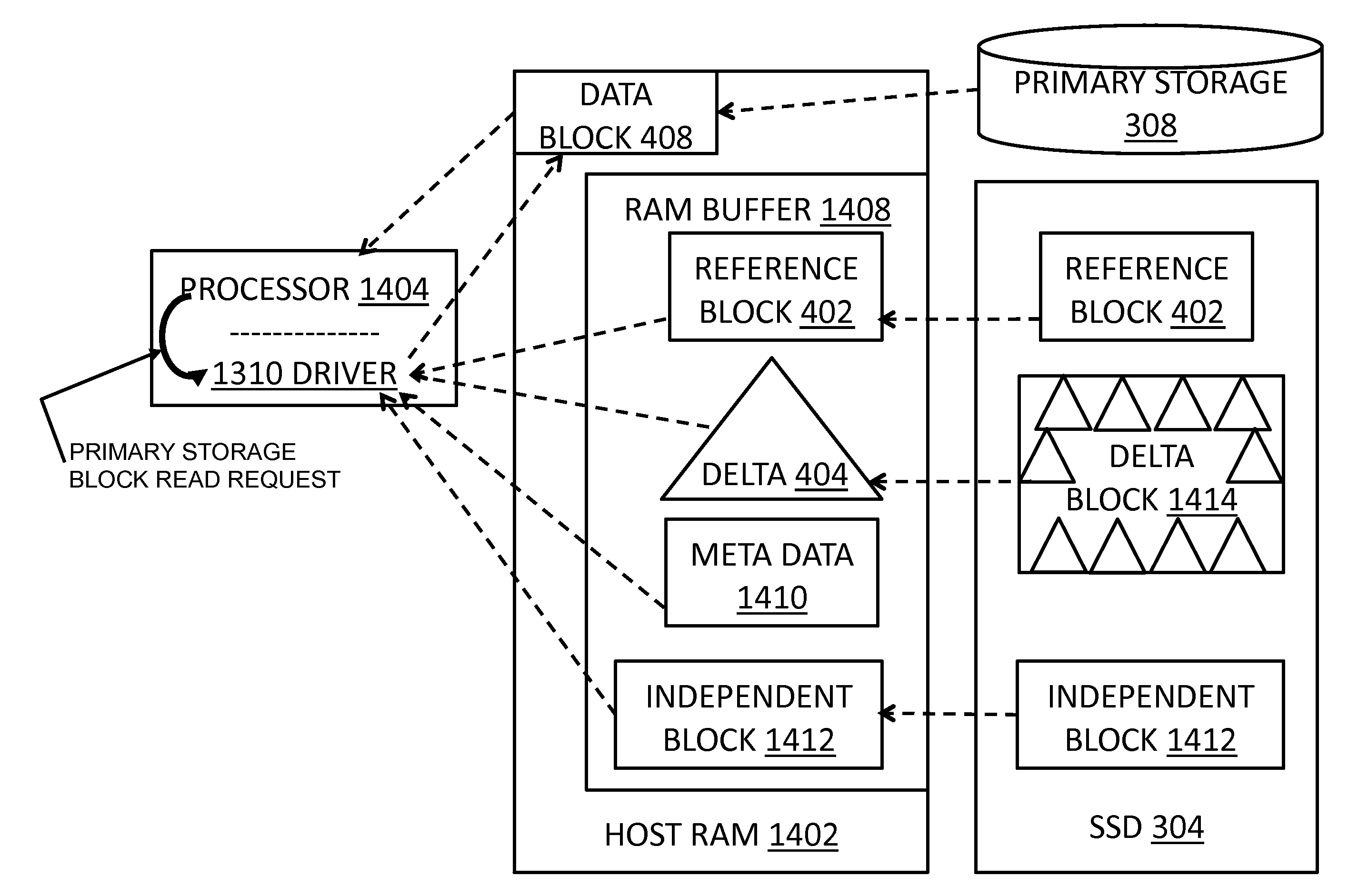
A data storage caching architecture supports using native local memory such as host-based RAM, and if available, Solid State Disk (SSD) memory for storing pre-cache delta-compression based delta, reference, and independent data by exploiting content locality, temporal locality, and spatial locality of data accesses to primary (e.g. disk-based) storage. The architecture makes excellent use of the physical properties of the different types of memory available (fast r / w RAM, low cost fast read SSD, etc) by applying algorithms to determine what types of data to store in each type of memory. Algorithms include similarity detection, delta compression, least popularly used cache management, conservative insertion and promotion cache replacement, and the like.
Owner:VELOBIT
Content delivery for client-server protocols with user affinities using connection end-point proxies
ActiveUS20050125553A1Services signallingMultiple digital computer combinationsBandwidth limitationIndependent data
In a network supporting transactions between clients and servers over a network path having operating characteristics to overcome, data is transported to overcome the operating characteristics using user affinities and dynamic user location information to selectively preload data, or representations, signatures, segments, etc. of data, in order to overcome the one or more operating characteristic. Examples of operating characteristics to overcome include bandwidth limitations, errors and latency. The dynamic location information can be stored in data structures accessible by agents of a data server and the data structures are populated based on user activities with respect to proxies associated with user locations, or the dynamic location information can be obtained implicitly as proxies maintain connections after termination by clients and the use of those maintained connections for preloading of data for the users associated with those clients. The data being preloaded can be protocol-specific data or protocol-independent data.
Owner:RIVERBED TECH LLC
Z-transform implementation of digital watermarks
InactiveUS6853726B1Public key for secure communicationUser identity/authority verificationCarrier signalData encoding
Z-transform calculations may be used to encode (and / or decode) carrier signal independent data (e.g., digital watermarks) to a digital sample stream. Deterministic and non-deterministic components of a digital sample stream signal may be analyzed for the purposes of encoding carrier signal independent data to the digital sample stream. The carrier signal independent data may be encoded in a manner such that it is restricted or concentrated primarily in the non-deterministic signal components of the carrier signal. The signal components can include a discrete series of digital samples and / or a discreet series of carrier frequency sub-bands of the carrier signal. Z-transform calculations may be used to measure a desirability of particular locations and a sample stream in which to encode the carrier signal independent data.
Owner:WISTARIA TRADING INC
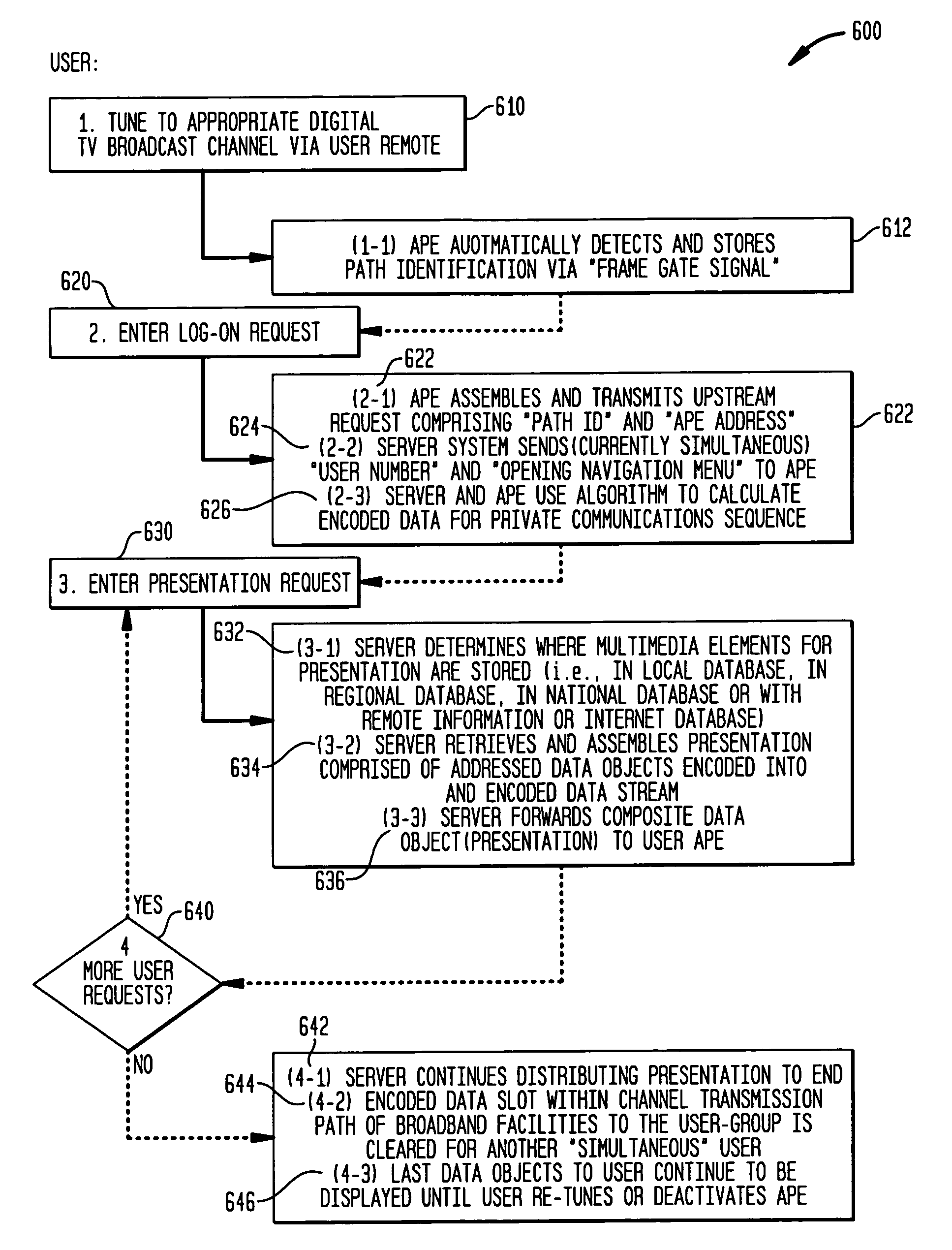
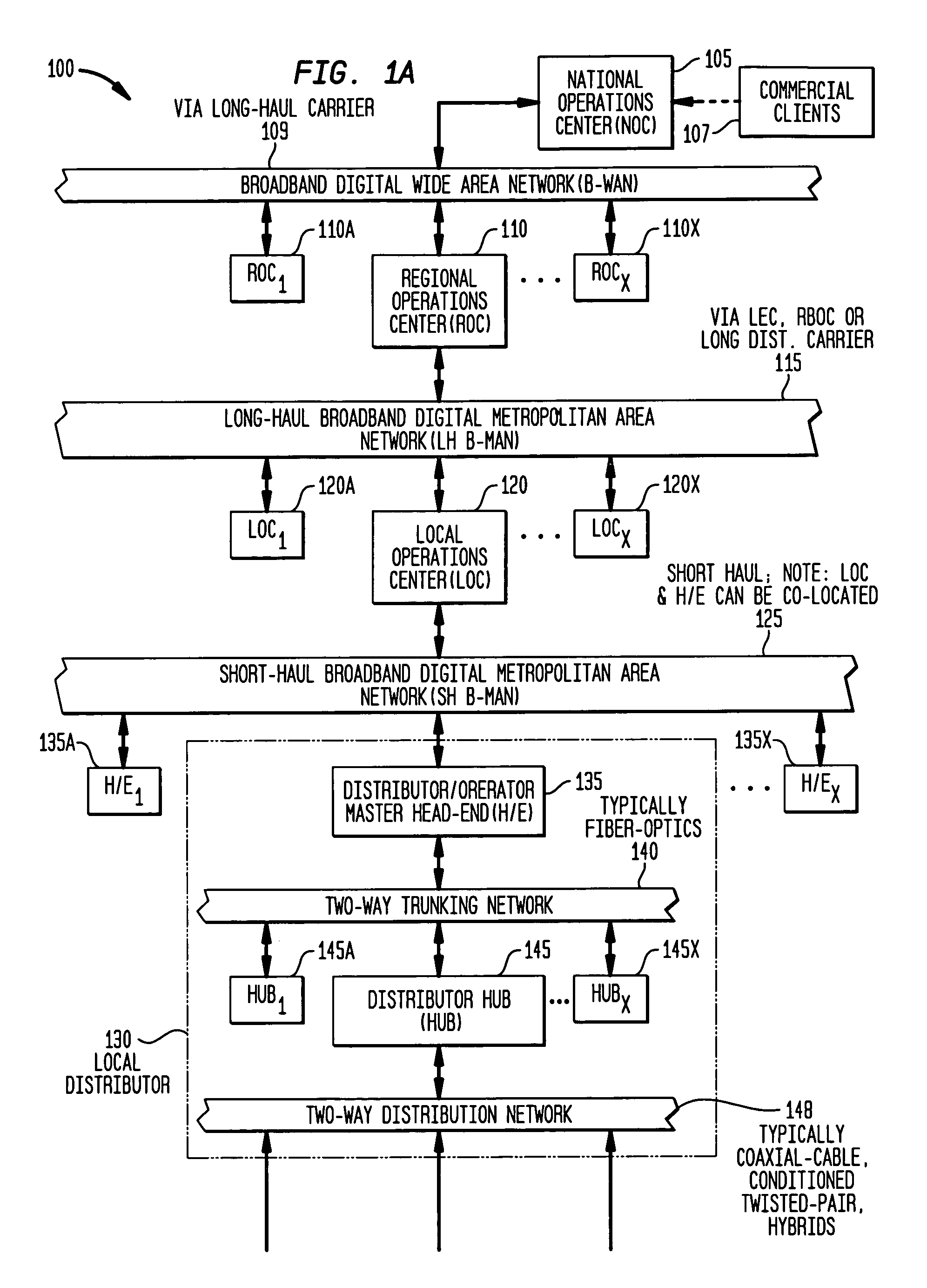
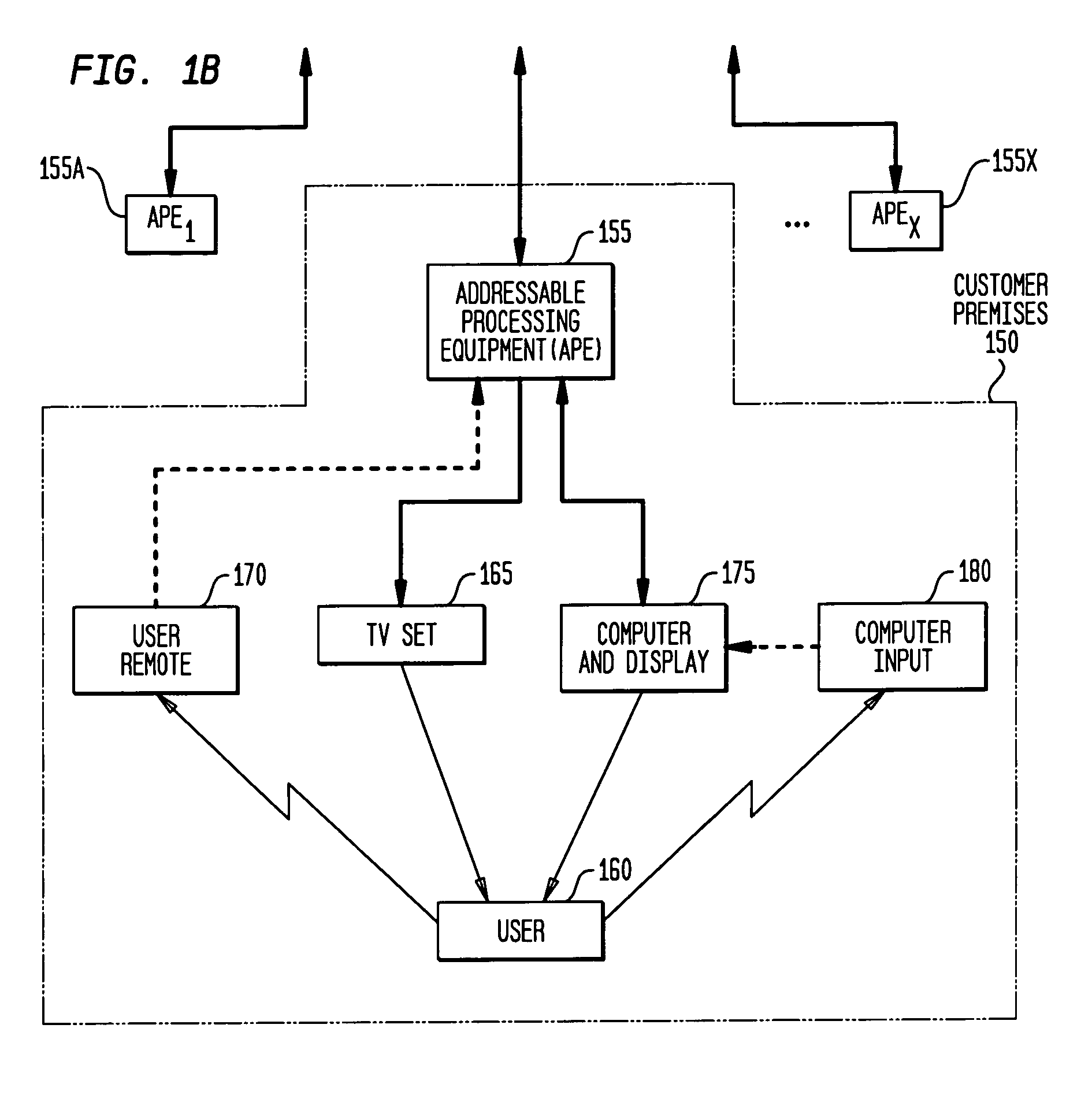
System and method for interactive distribution of selectable presentations
InactiveUS7536705B1Easy to useIncrease profitSpecial service provision for substationTelevision system detailsDigital dataGraphics
A data storage, multiplexing, and distribution method is provided for use in a digital data distribution system. The system provides simultaneous transmission of a plurality of uniquely identified, independent data streams within an assigned channel bandwidth of local, metropolitan and wide area distribution media. The independent data streams can include presentations specifically requested by the receiving user. Upon request from some number of users from their premises, the system assembles a combination of optional image elements such as motion and still frame video, background and descriptive audio, text and graphical overlays into presentation data streams appropriate to the user requests. Individual data streams are multiplexed within a higher bandwidth data stream for simultaneous delivery within the bandwidth assigned for this data transmission. The techniques unique to the system, in regard to storage, timing and synchronization, can be implemented using techniques described within the MPEG profile.
Owner:SOURCESUITE LLC & SOURCESUITE CANADA INC +1
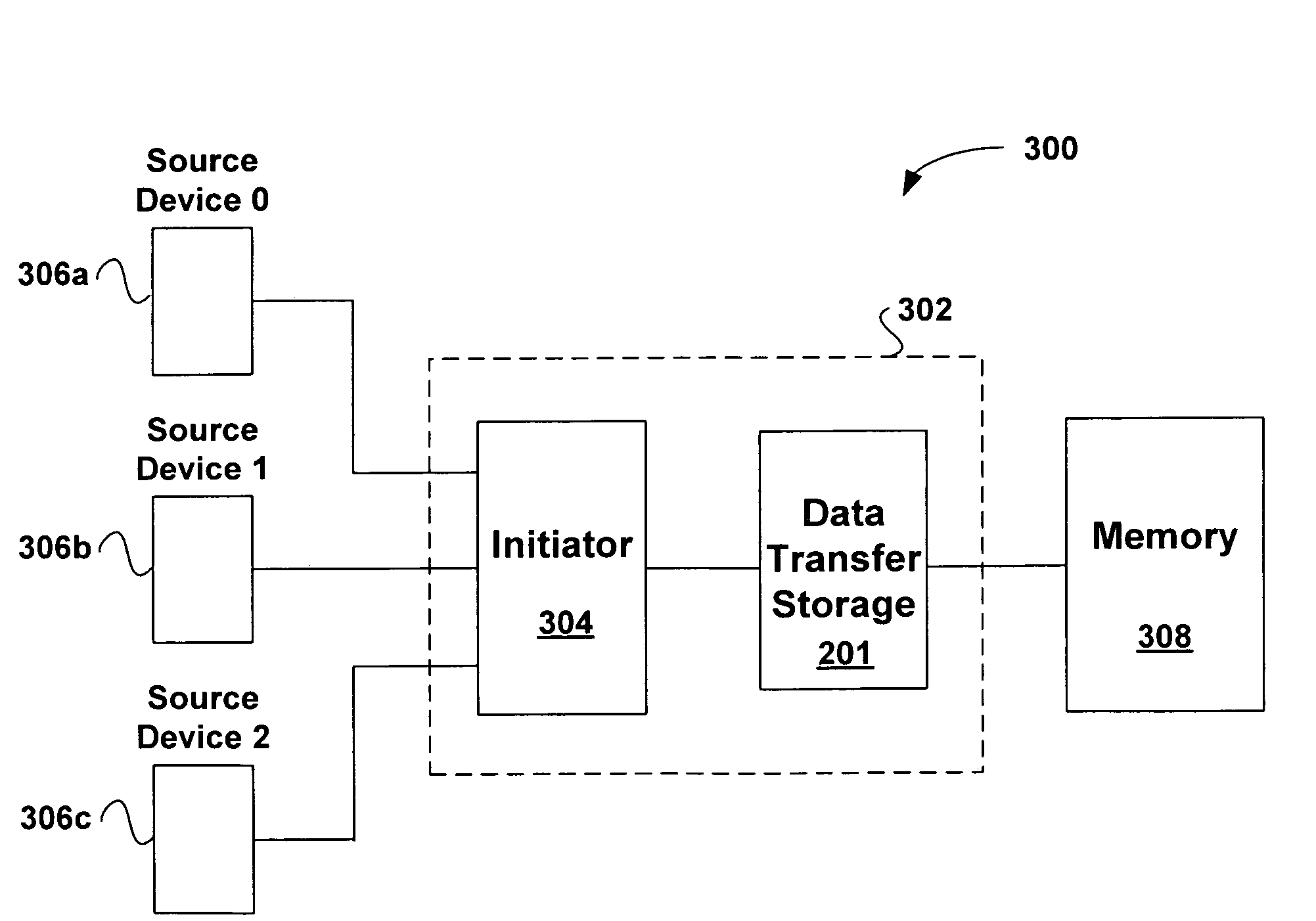
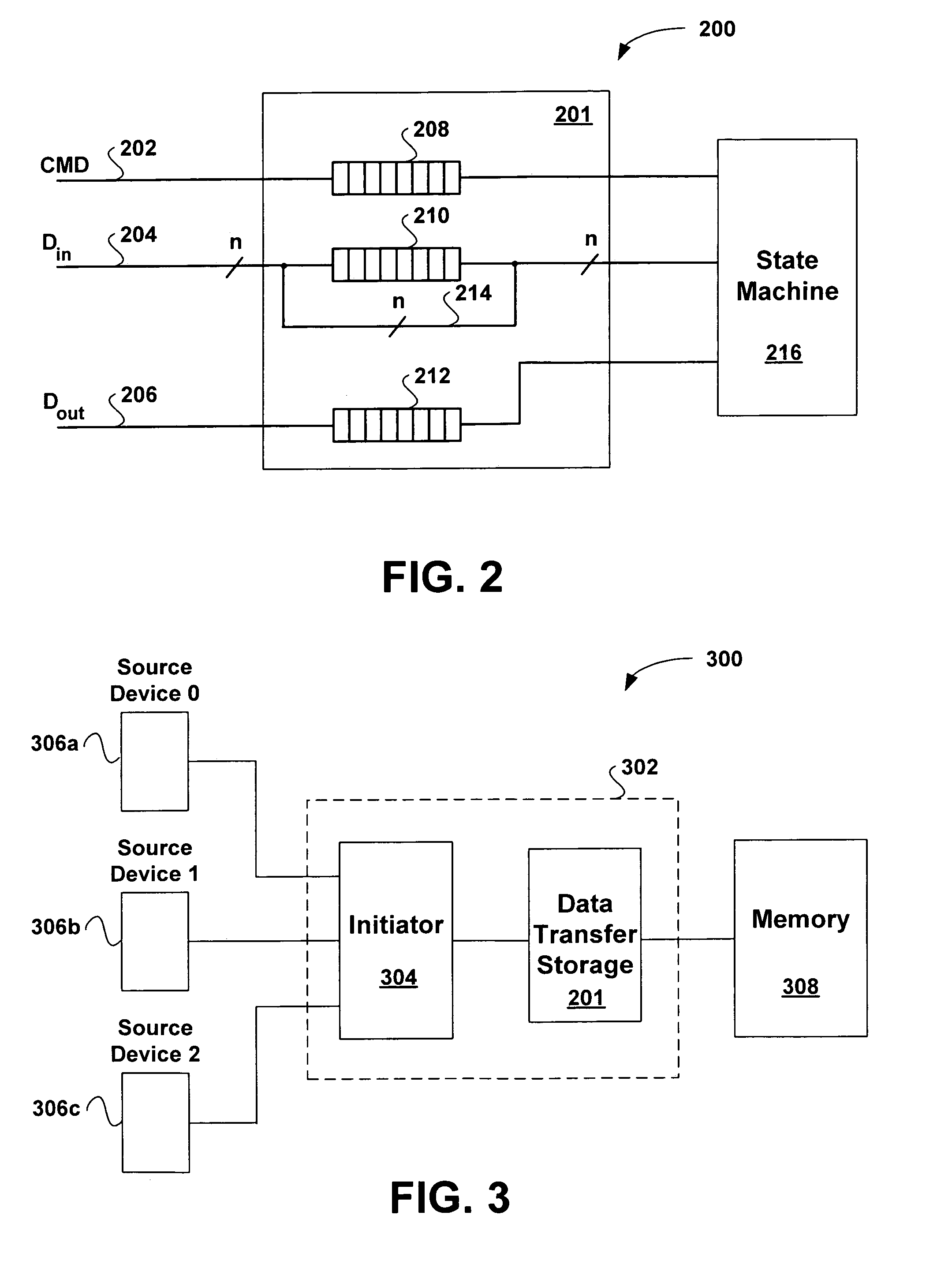
Port independent data transaction interface for multi-port devices
A port independent data transaction interface for multi-port devices is provided. The port independent data transaction interface includes a command channel that receives command data and a source id. The source id indicates a source device that transmitted the command data. In addition, a data-in channel is included that receives write data and a write source id. Similar to the source id, the write source id indicates a source device that transmitted the write data. The port independent data transaction interface further includes a data-out channel that provides read data and a read id. The read id indicates a source device that transmitted a read command corresponding to the read data. The port independent data transaction interface utilizes the source id to associate command data with corresponding write data and read data.
Owner:CADENCE DESIGN SYST INC
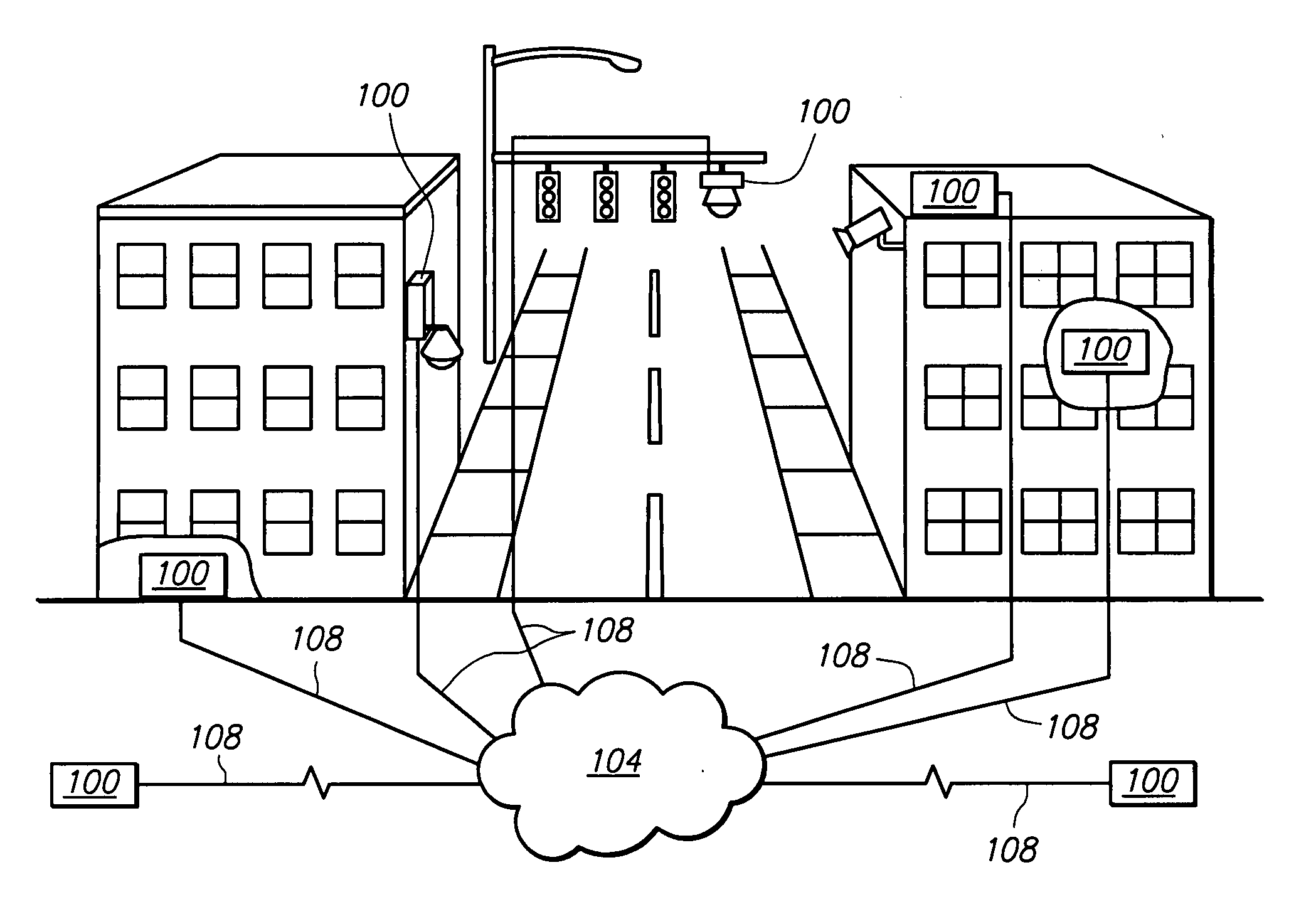
Peer to peer surveillance architecture
ActiveUS20090289788A1Color television detailsClosed circuit television systemsIndependent dataSingle point of failure
A peer to peer surveillance architecture comprising a plurality of independent nodes for capturing, analyzing, storing, and viewing surveillance information is disclosed. The surveillance architecture has no central controller or single point of failure because of the peer to peer or independent relationship between its nodes. Generally, surveillance information of various types is captured by one or more capture nodes and transmitted to or one or more viewing, content storage, or server nodes for display, analysis, storage, or a combination thereof. Server nodes may provide authentication services to validate user or device credentials prior to granting access to surveillance information. In one or more embodiments, specialized video compression hardware is provided to allow high quality video surveillance information to be transmitted across low bandwidth connections. Compression may also be performed on other types of surveillance information.
Owner:LEVERAGE INFORMATION SYST INC
Method and apparatus for using multiple data-stream pathways
InactiveUS20060056372A1Broadcast transmission systemsRadio/inductive link selection arrangementsData streamDatapath
A method for using multiple independent data pathways to accomplish a task is disclosed. The method includes determining availability of multiple independent data pathways, where at least one of the data pathways utilizes transmission and receipt of data through an over-the-air antenna, selecting at least two of the data pathways, based on certain criteria and sending and receiving data along the selected at least two data pathways to accomplish a task.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
System and methods for permitting open access to data objects and for securing data within the data objects
A system and methods for permitting open access to data objects and for securing data within the data objects is disclosed. According to one embodiment of the present invention, a method for securing a data object is disclosed. According to one embodiment of the present invention, a method for securing a data object is disclosed. The method includes the steps of (1) providing a data object comprising digital data and file format information; (2) embedding independent data into a data object; and (3) scrambling the data object to degrade the data object to a predetermined signal quality level. The steps of embedding and scrambling may be performed until a predetermined condition is met. The method may also include the steps of descrambling the data object to upgrade the data object to a predetermined signal quality level, and decoding the embedded independent data. The additional steps of descrambling and decoding may be performed until a predetermined condition is met. The predetermined condition may include, for example, reaching a desired signal quality of the data object.
Owner:WISTARIA TRADING INC
Pre-cache similarity-based delta compression for use in a data storage system
ActiveUS20120137061A1Quick upgradeHigh-speed random readMemory architecture accessing/allocationEnergy efficient ICTIndex compressionLeast frequently used
A data storage caching architecture supports using native local memory such as host-based RAM, and if available, Solid State Disk (SSD) memory for storing pre-cache delta-compression based delta, reference, and independent data by exploiting content locality, temporal locality, and spatial locality of data accesses to primary (e.g. disk-based) storage. The architecture makes excellent use of the physical properties of the different types of memory available (fast r / w RAM, low cost fast read SSD, etc) by applying algorithms to determine what types of data to store in each type of memory. Algorithms include similarity detection, delta compression, least popularly used cache management, conservative insertion and promotion cache replacement, and the like.
Owner:WESTERN DIGITAL TECH INC
Independent data input system for casino play
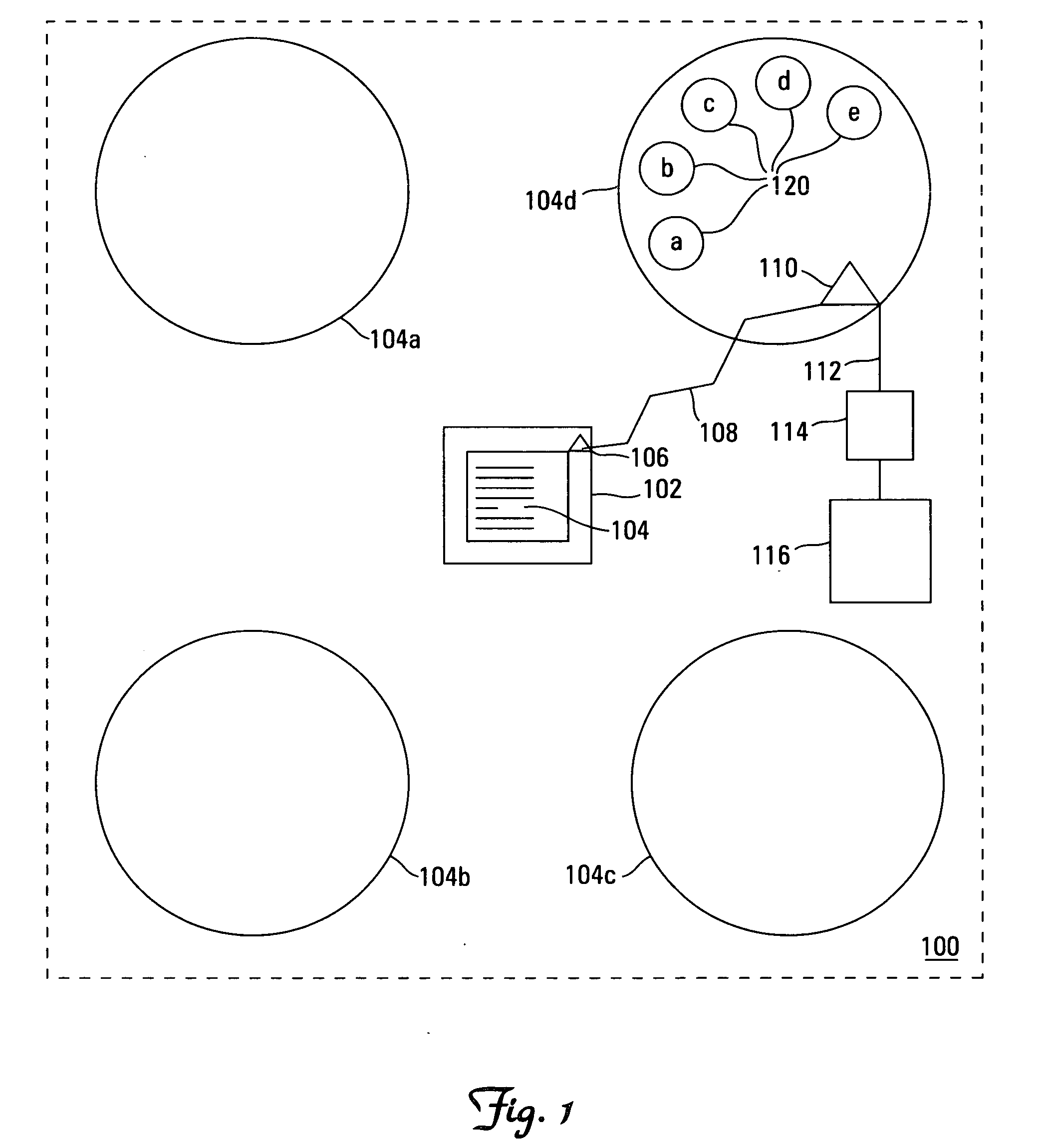
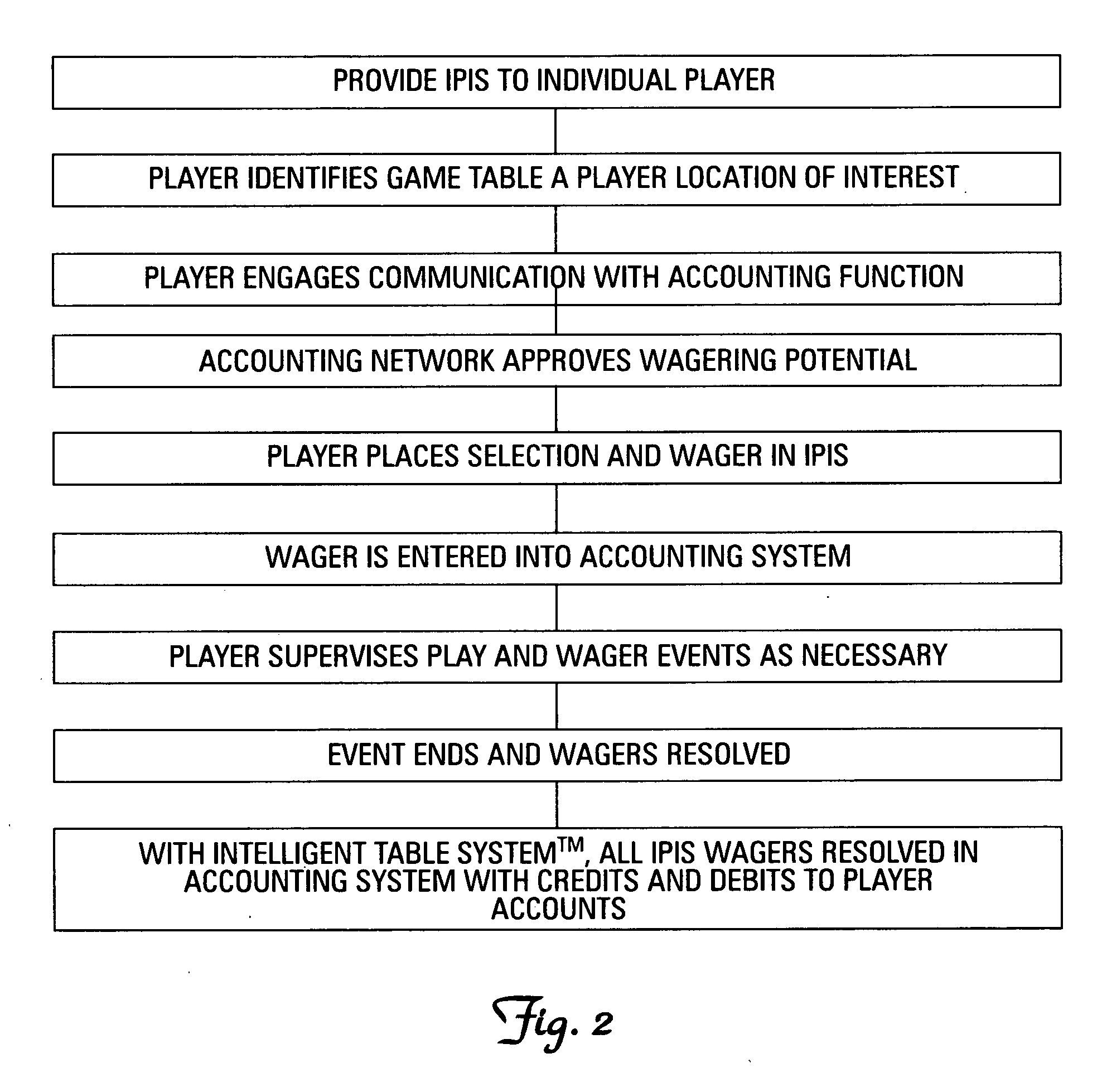
InactiveUS20070111775A1Board gamesApparatus for meter-controlled dispensingComputer hardwareGame play
A casino table card system and method is played on a casino card table having a playing surface. Multiple player positions on the casino card table have at least a first player position and second player position. A processor receives electronic game information comprising wager information relating to casino card games played on the casino card table. At least one player input capability from a passive player has wager input capability for placing wagers on the active player position. The wager information on the active player is electronically transmitted to the processor, which accepts input from the passive player position on an outcome at the active player position. The system resolves wagers from the passive player on events at an active player position.
Owner:SHUFFLE MASTER
System and method for determining changes in two snapshots and for transmitting changes to a destination snapshot
InactiveUS7603391B1Efficient scanningOvercome disadvantagesData processing applicationsRedundant operation error correctionData streamInode
A system and method for remote asynchronous replication or mirroring of changes in a source file system snapshot in a destination replica file system using a scan (via a scanner) of the blocks that make up two versions of a snapshot of the source file system, which identifies changed blocks in the respective snapshot files based upon differences in volume block numbers identified in a scan of the logical file block index of each snapshot. Trees of blocks associated with the files are traversed, bypassing unchanged pointers between versions and walking down to identify the changes in the hierarchy of the tree. These changes are transmitted to the destination mirror or replicated snapshot. This technique allows regular files, directories, inodes and any other hierarchical structure to be efficiently scanned to determine differences between versions thereof. The changes in the files and directories are transmitted over the network for update of the replicated destination snapshot in an asynchronous (lazy write) manner. The changes are described in an extensible, system-independent data stream format layered under a network transport protocol. At the destination, source changes are used to update the destination snapshot. Any deleted or modified inodes already on the destination are moved to a temporary or “purgatory” directory and, if reused, are relinked to the rebuilt replicated snapshot directory. The source file system snapshots can be representative of a volume sub-organization, such as a qtree.
Owner:NETWORK APPLIANCE INC
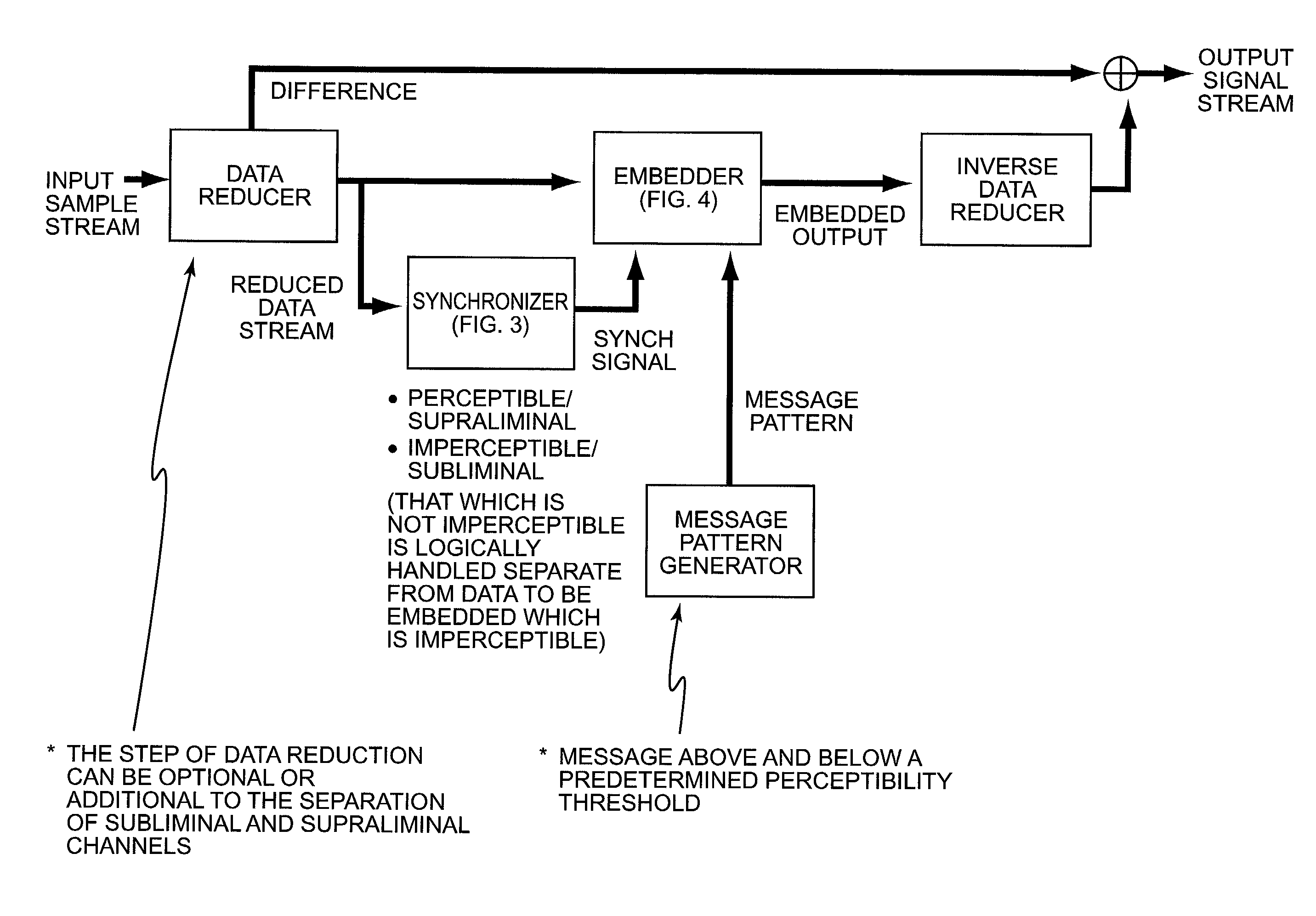
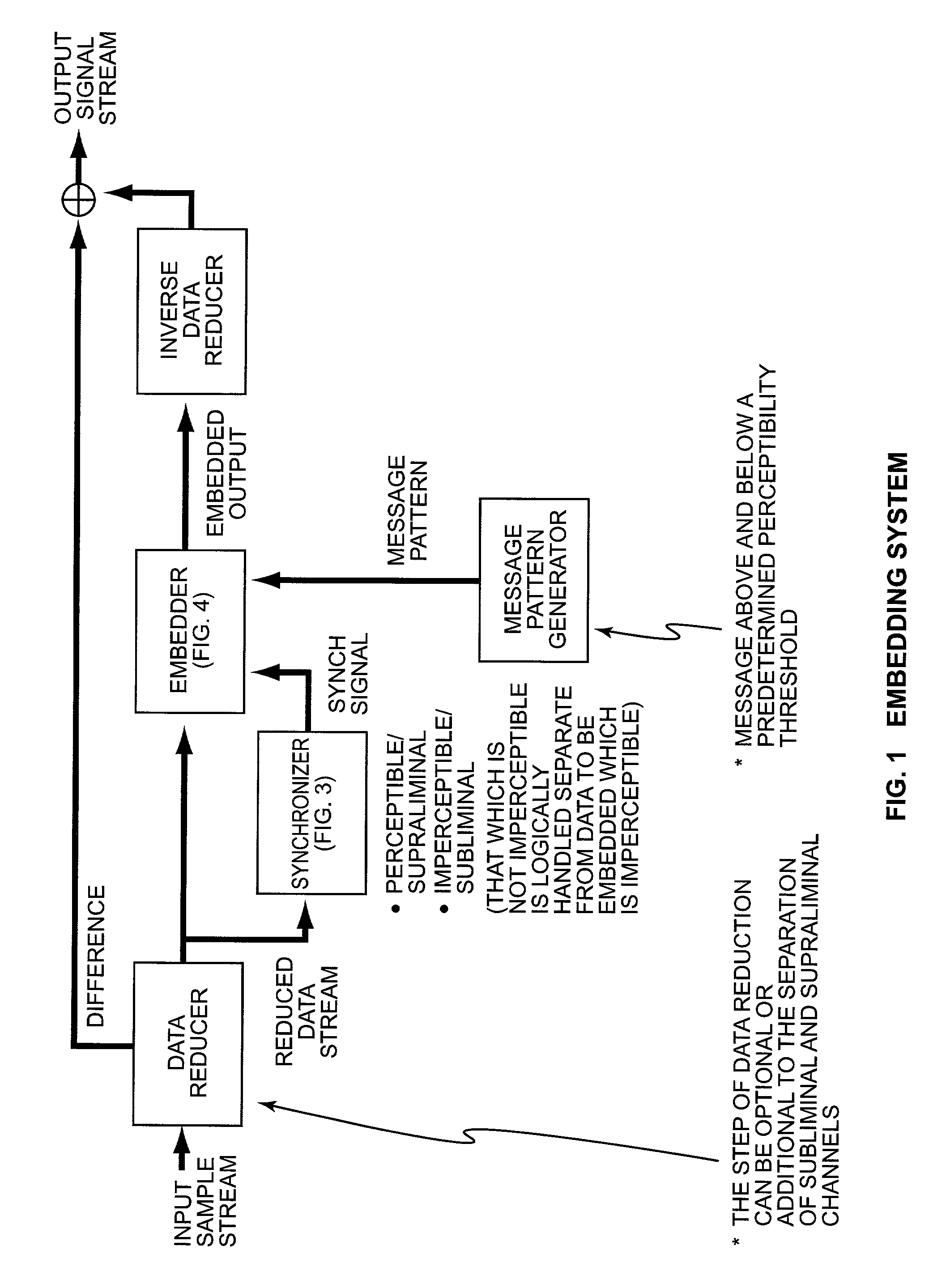
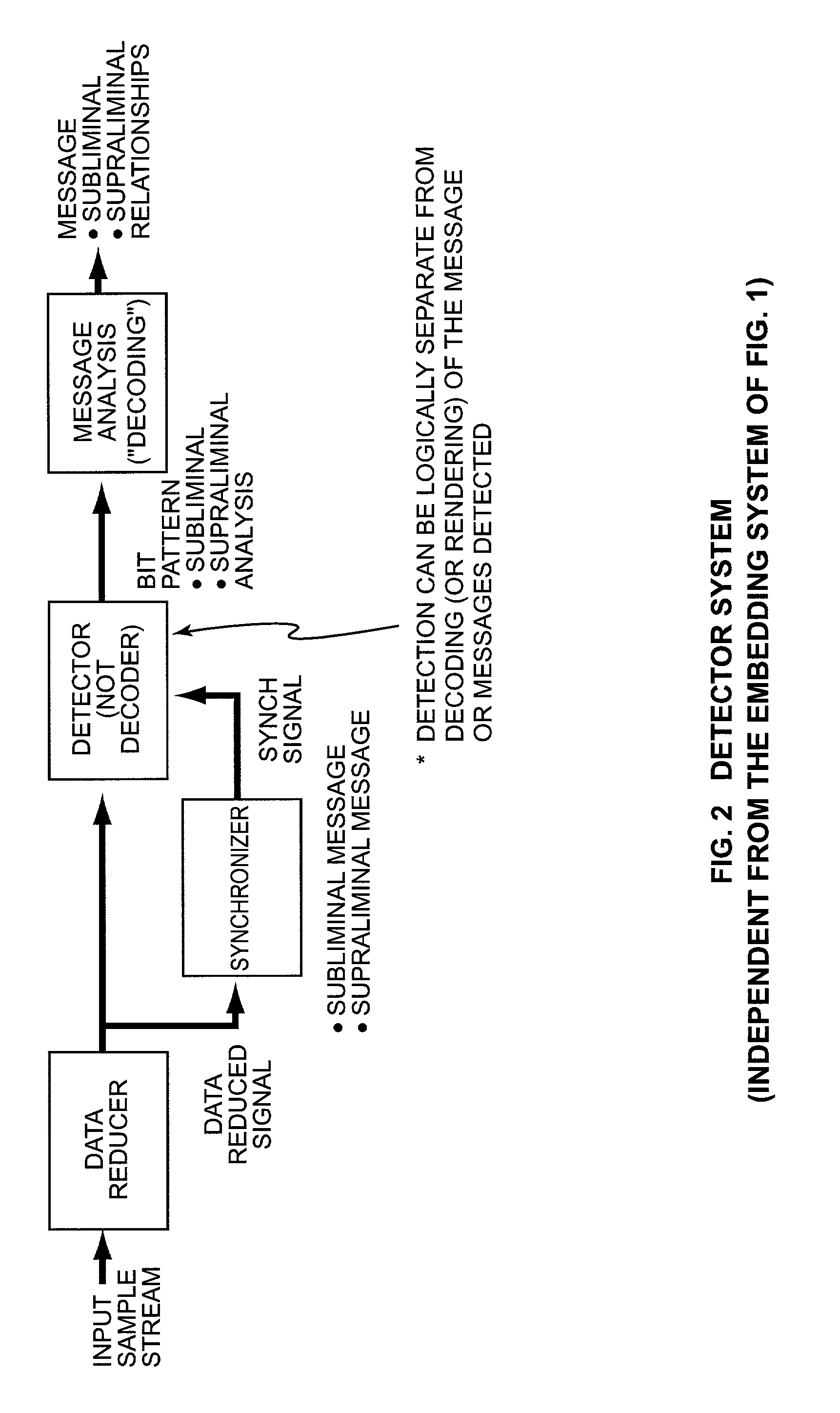
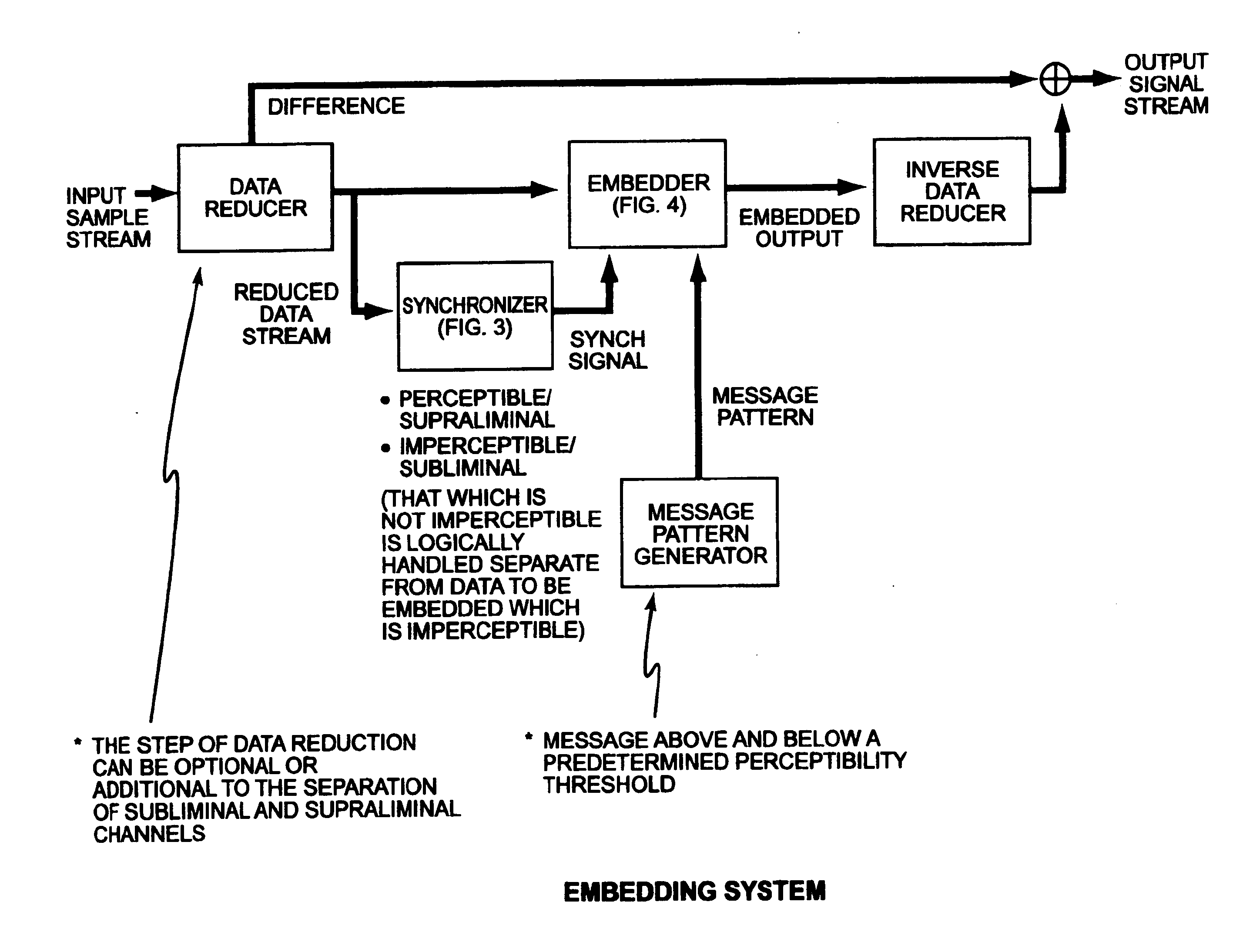
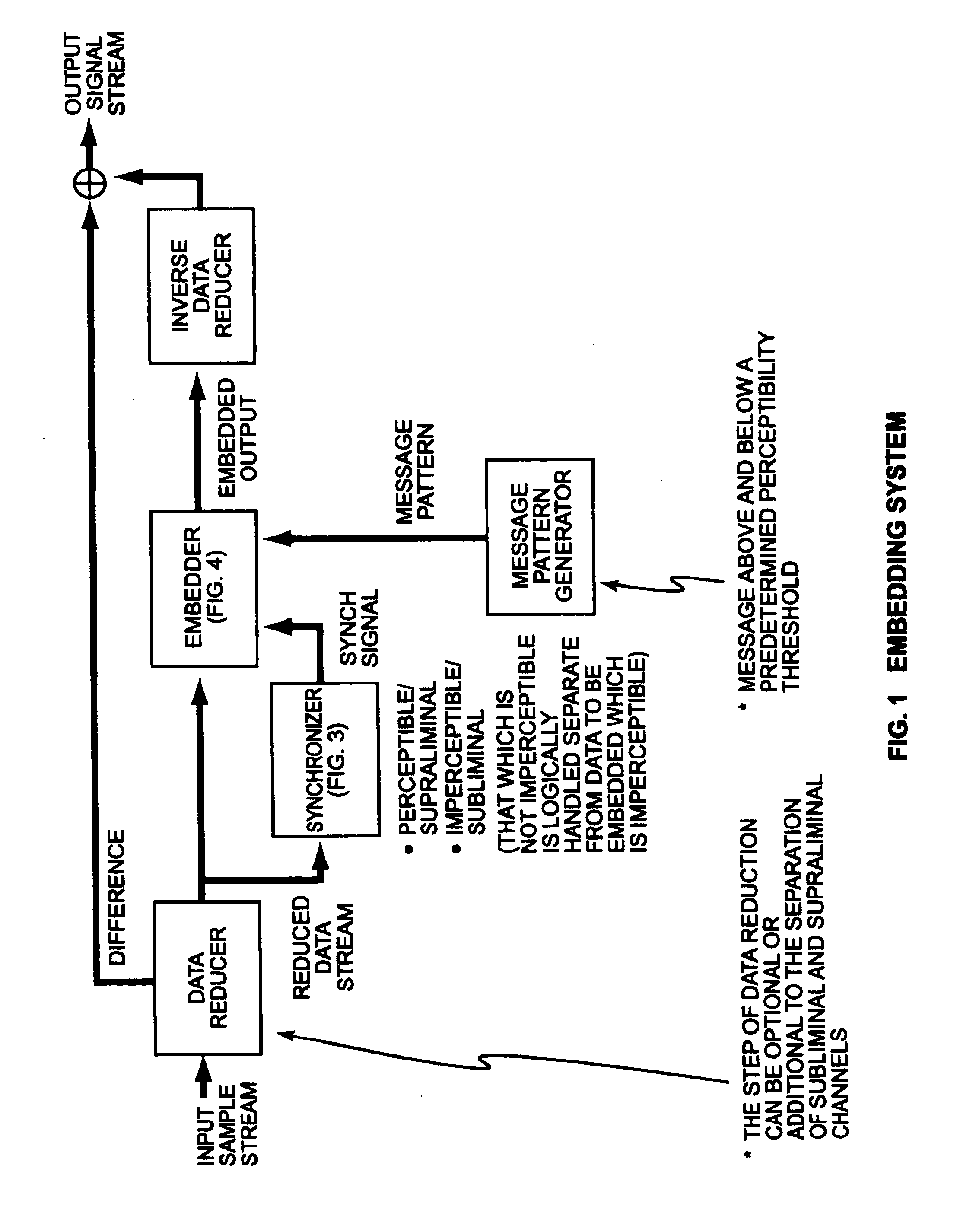
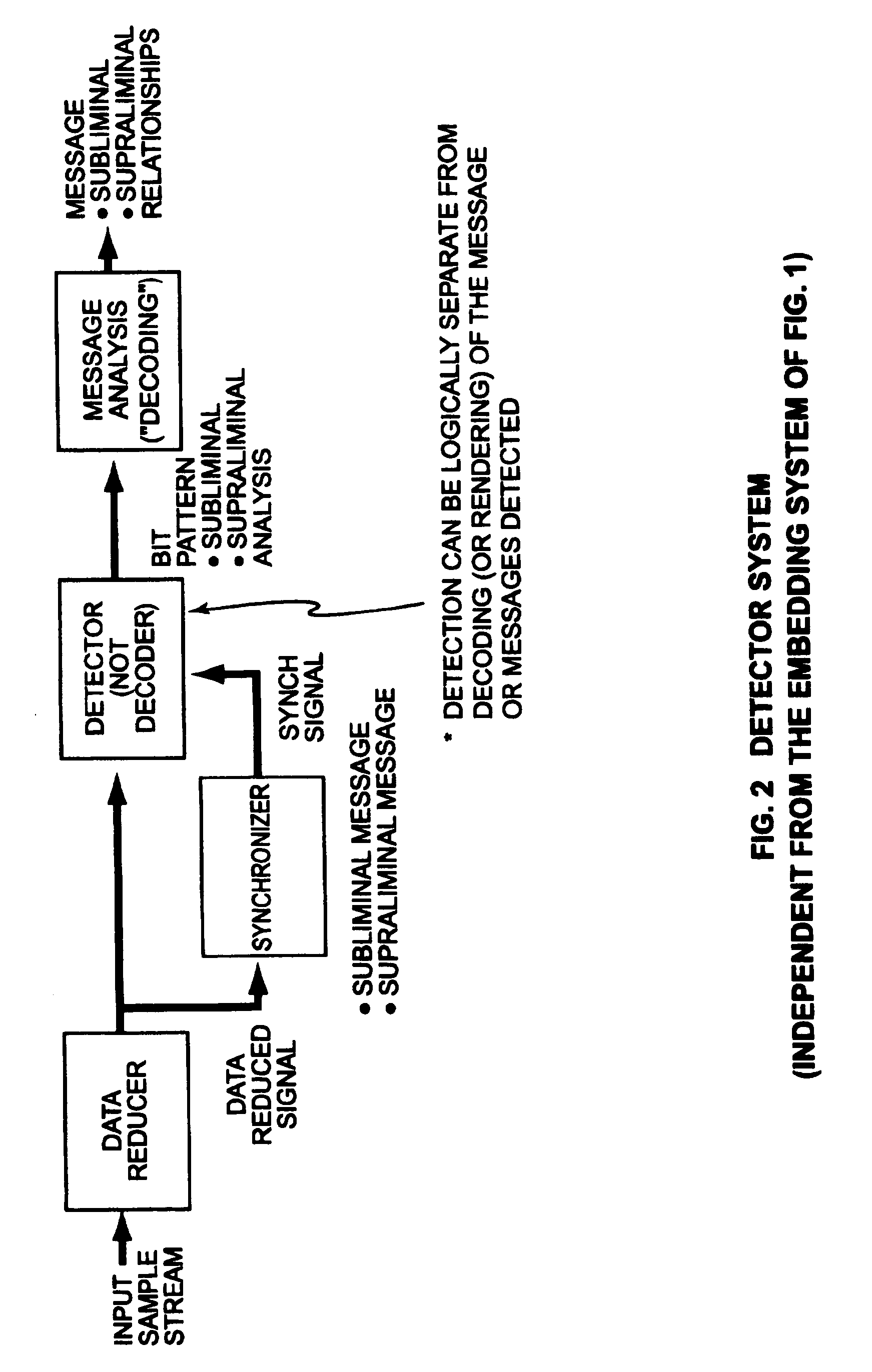
Security based on subliminal and supraliminal channels for data objects
ActiveUS7127615B2Digital data processing detailsUser identity/authority verificationData signalDigitization
This invention relates to security for data objects; more particularly, the present invention relates to improved security based on subliminal and supraliminal channels for data objects.In one embodiment, a method for protecting a data signal comprises: providing a data signal to be encoded; using a first predetermined key to encode a first set of independent data into the data signal imperceptibly; and using a second predetermined key to encode a second set of independent data into the data signal perceptibly.In another embodiment, a method of protecting a data object comprises: steganographically encoding a subset of candidate bits in a digitized sample stream; perceptibly manipulating data in the digitized sample stream; and combining the imperceptible and perceptible data changes to create a secure / unique digital sample stream.In yet another embodiment, a method for securing a data signal comprises: preanalyzing said data signal for candidate watermark / signature bits; steganographically encoding independent data into the data signal into a subset of the candidate watermark bits, at least one time; and encoding the data signal subsequently with a perceptible technique.In yet another embodiment, a method of protecting a data signal comprises: imperceptibly embedding data using a watermarking technique; perceptibly signing the data using the receiver's public key; encrypting the data signal using the receiver's public key and the private key used to watermark the signal; and enabling a receiver to authenticate / verify (separate steps) the data signal while connected to a communications channel.
Owner:WISTARIA TRADING INC
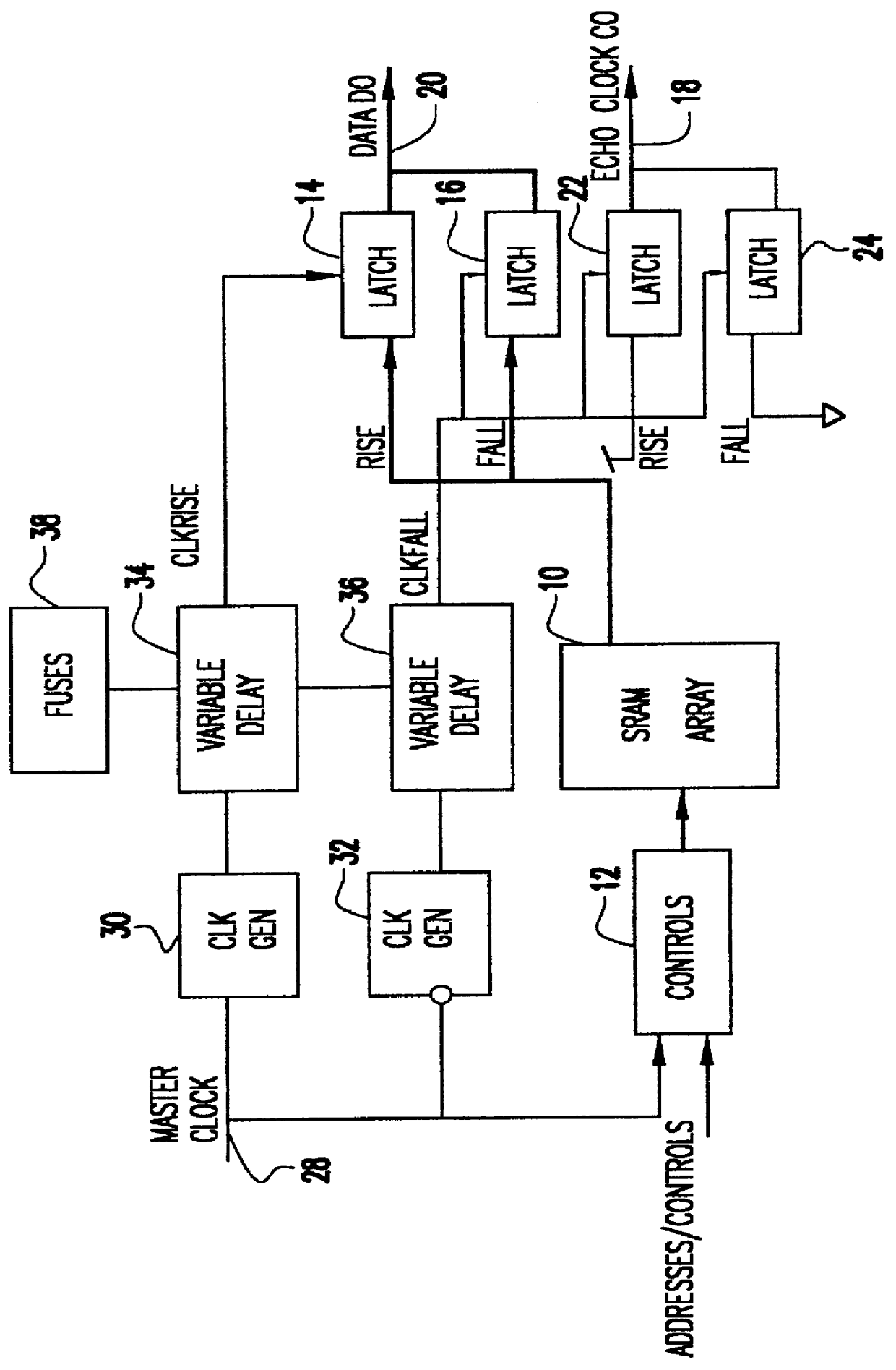
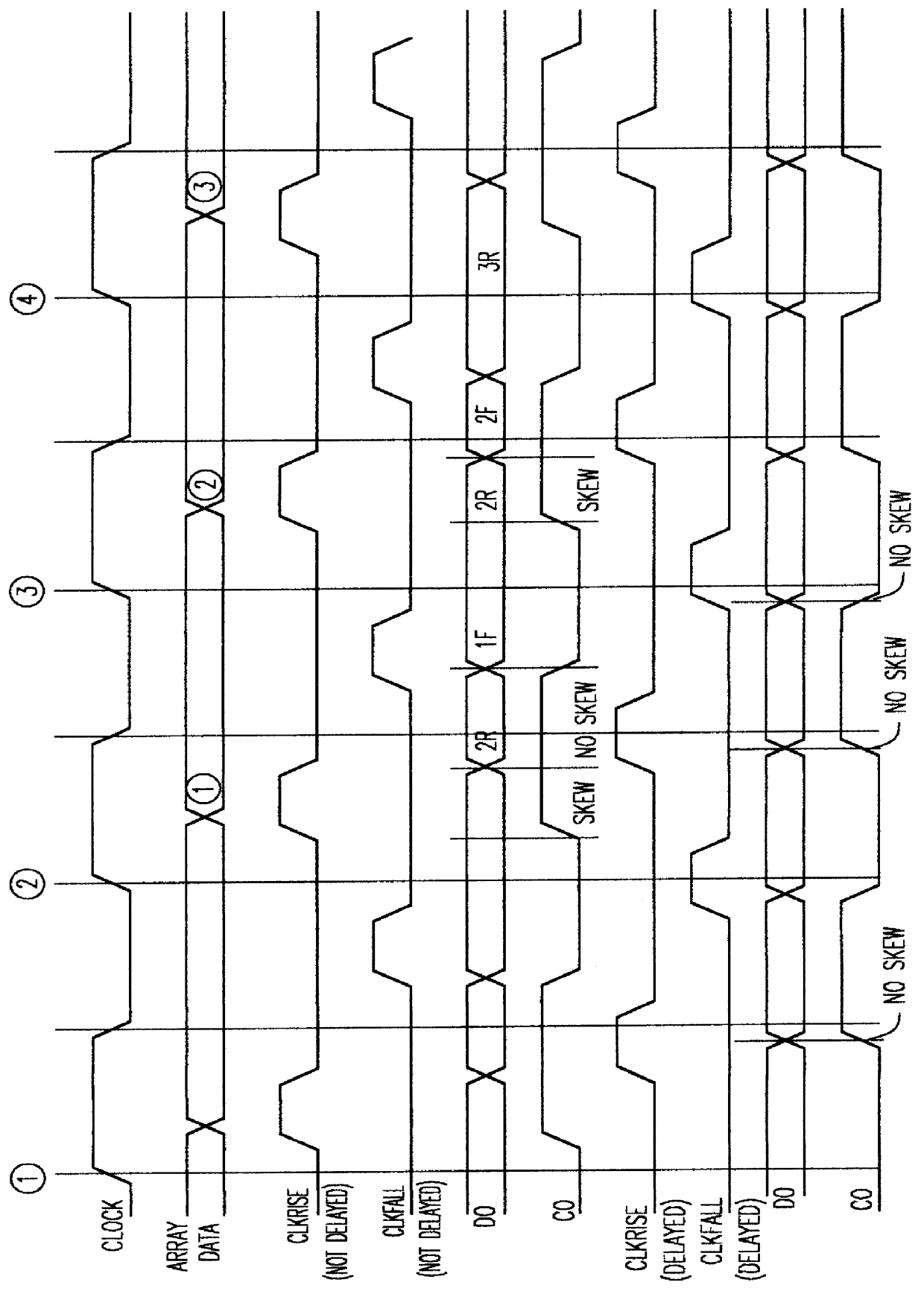
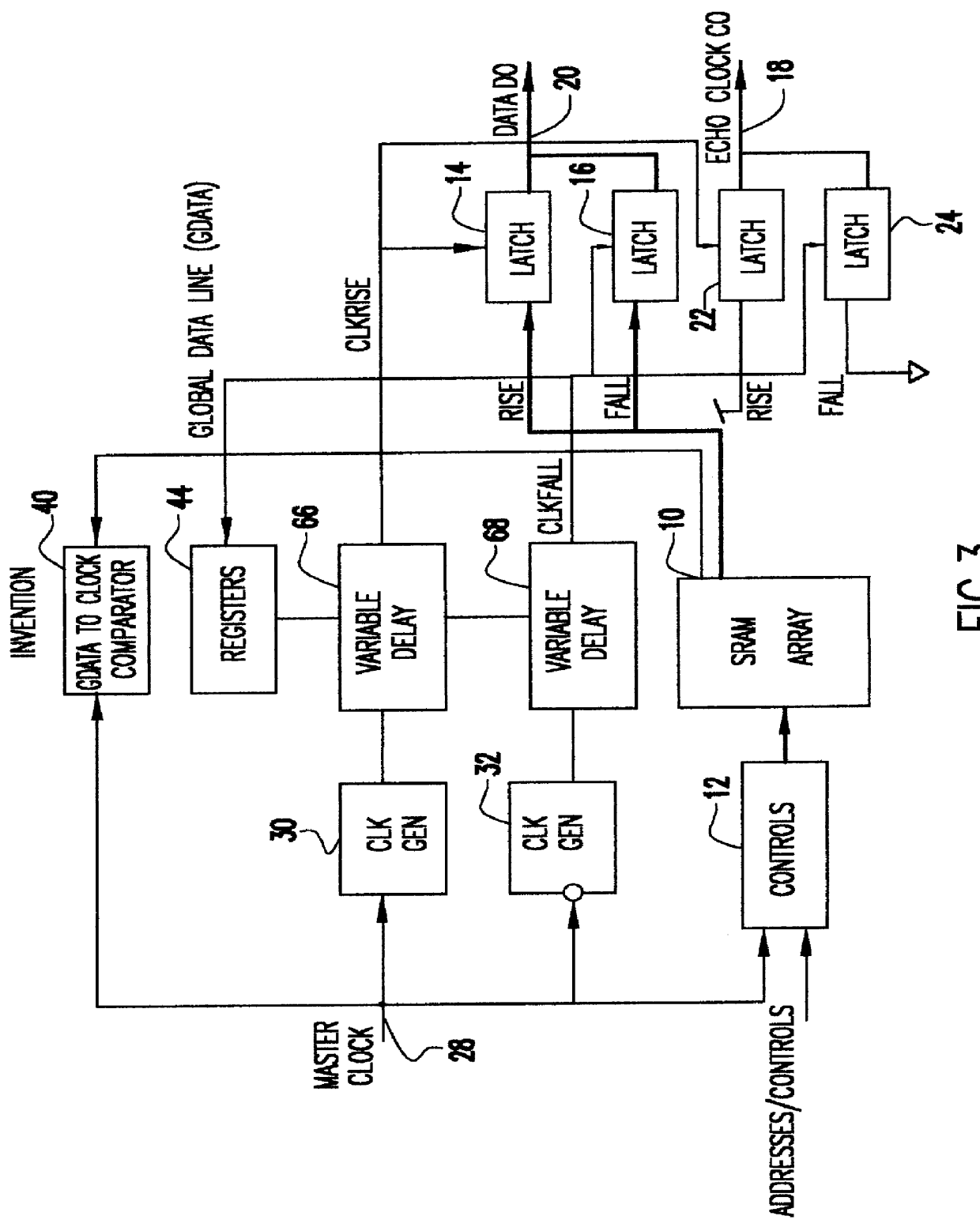
Cycle independent data to echo clock tracking circuit
InactiveUS6134182AAvoid dataDigital storageGenerating/distributing signalsDouble data rateData signal
A comparator and variable delay circuit are provided to maintain the tracking between data and echo clocks in a double data rate (DDR)RAM device. This is accomplished by providing a global data signal (dummy data signal) that tracks with the actual memory array data. This global data signal is compared to the timing of the RAM clock (CLOCK) to determine a delay time between the two by which the pipeline clocks (CLKRISE / CLKFALL) must be delayed. As a result, the pipeline clocks are pushed out as needed so that they always transition after the array data arrives at the output latch. Therefore, as cycle time decreases, both echo clocks and data are pushed out identically and maintain their required tracking.
Owner:IBM CORP
Authenticity verification methods, products and apparatuses
InactiveUS7853792B2Enhanced advantagePaper-money testing devicesUser identity/authority verificationCardboardMaterial type
Owner:INGENIA HLDG LTD
Security based on subliminal and supraliminal channels for data objects
InactiveUS20080028222A1User identity/authority verificationPayment protocolsData signalComputer science
This invention relates to security for data objects; more particularly, the present invention relates to improved security based on subliminal and supraliminal channels for data objects. In another embodiment, a method of protecting a data object comprises: steganographically encoding a subset of candidate bits in a digitized sample stream; perceptibly manipulating data in the digitized sample stream; and combining the imperceptible and perceptible data changes to create a secure / unique digital sample stream. In yet another embodiment, a method for securing a data signal comprises: preanalyzing said data signal for candidate watermark / signature bits; steganographically encoding independent data into the data signal into a subset of the candidate watermark bits, at least one time; and encoding the data signal subsequently with a perceptible technique.
Owner:WISTARIA TRADING INC
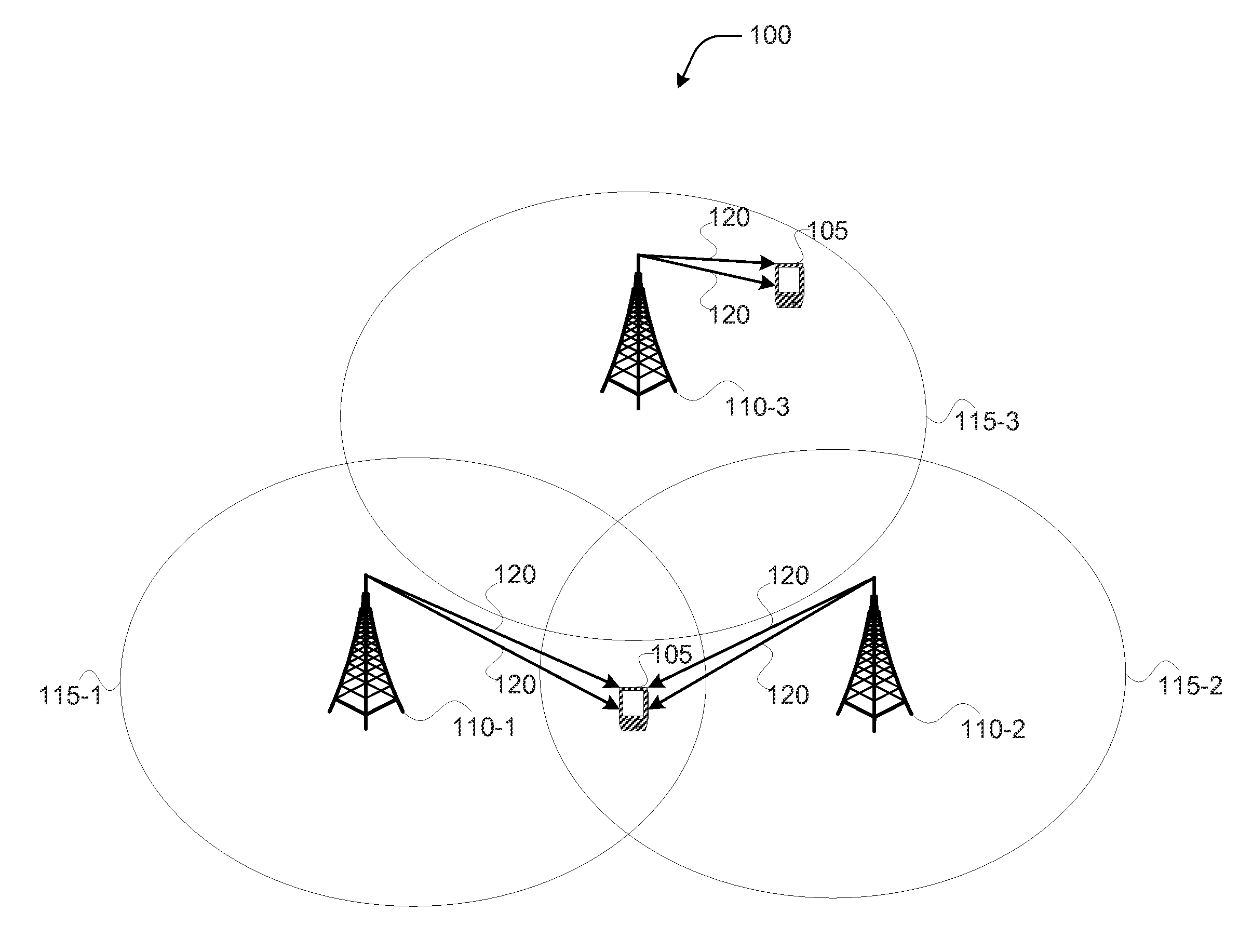
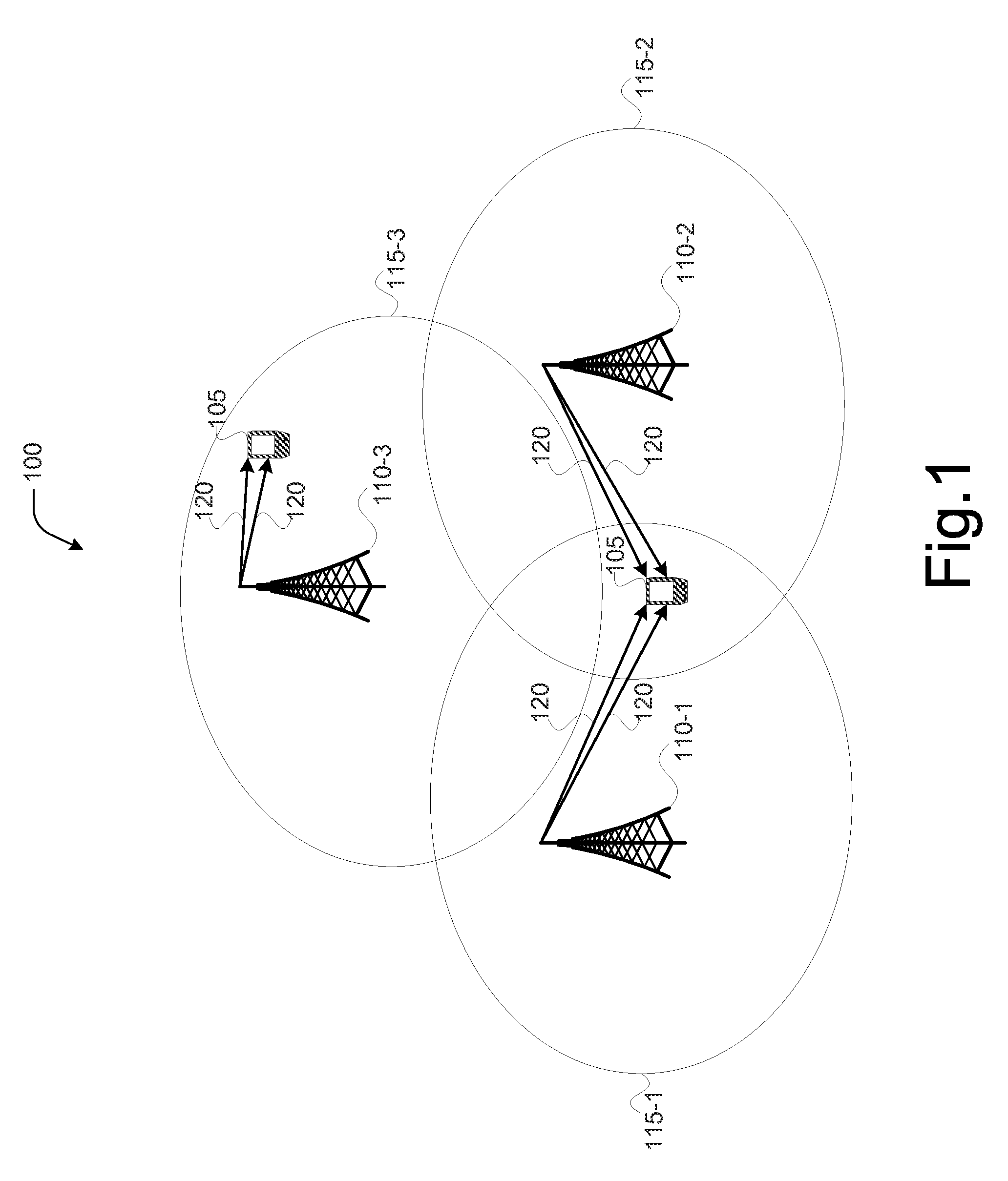
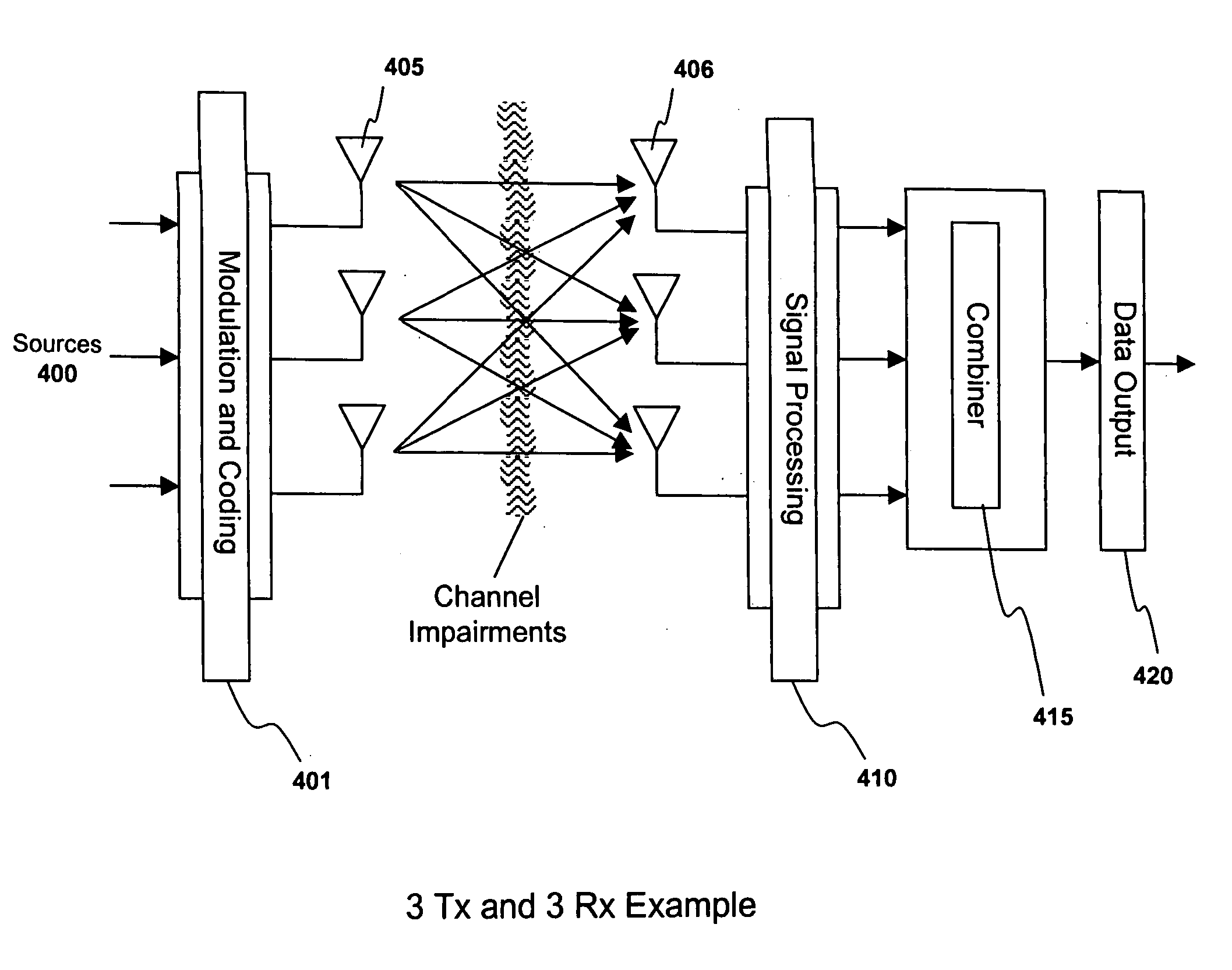
Methods, apparatuses, and systems for multi-point, multi-cell single-user based multiple input and multiple output transmissions
Methods, systems, and storage media for providing multi-cell, multi-point single user (SU) multiple input and multiple output (MIMO) operations are described. In embodiments, an apparatus may receive and process a first set of one or more independent data streams received in a downlink channel from a first transmission point. The apparatus may receive and process a second set of one or more independent data streams received in a downlink channel from a second transmission point. The apparatus may process control information received from the first transmission point or the second transmission point. The control information may include an indication of a quasi co-location assumption to be used for estimating channel characteristics for reception of the first set of one or more independent data streams or the second set of one or more independent data streams. Other embodiments may be described and / or claimed.
Owner:APPLE INC
System and method for updating database statistics according to query feedback
ActiveUS20080133454A1Fast executionSmall sizeData processing applicationsDigital data information retrievalLearning basedQuery optimization
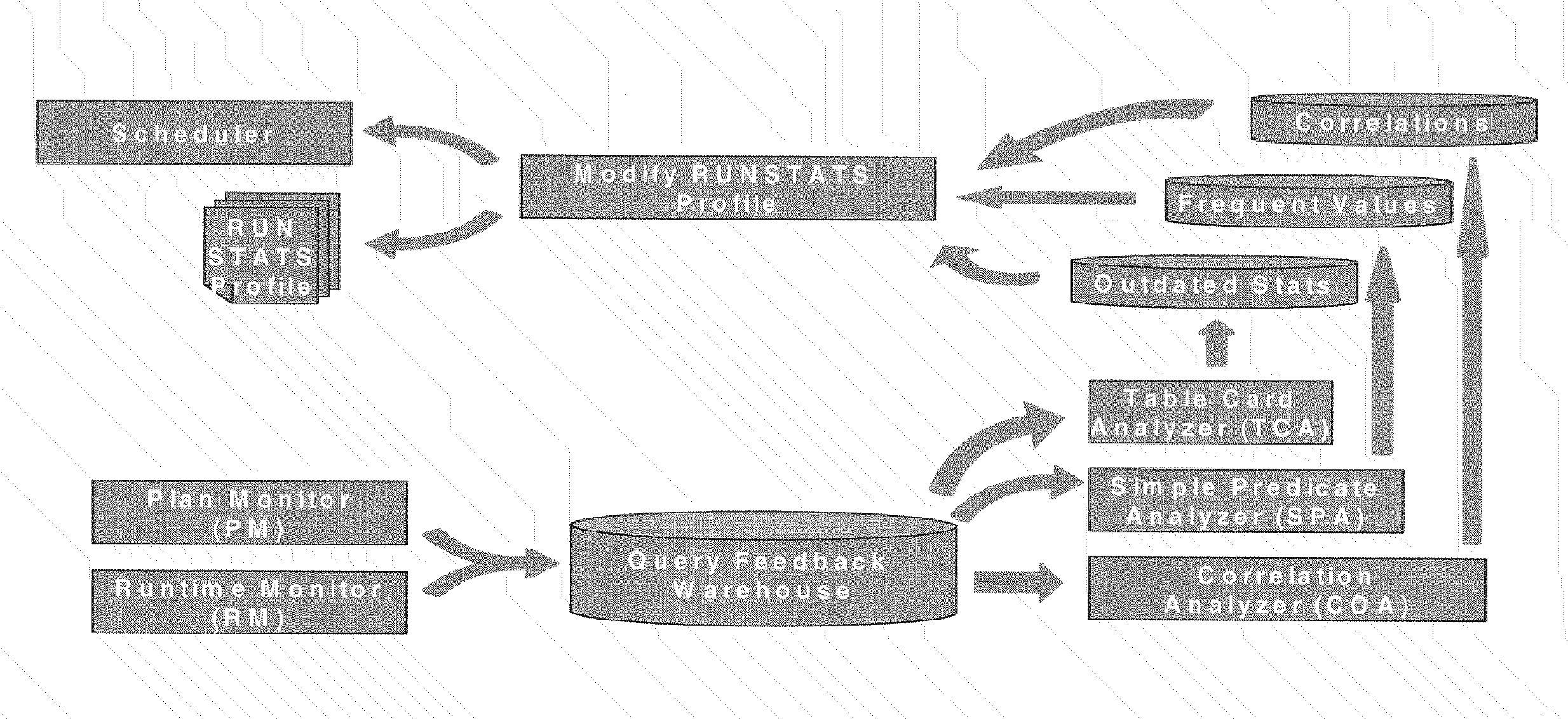
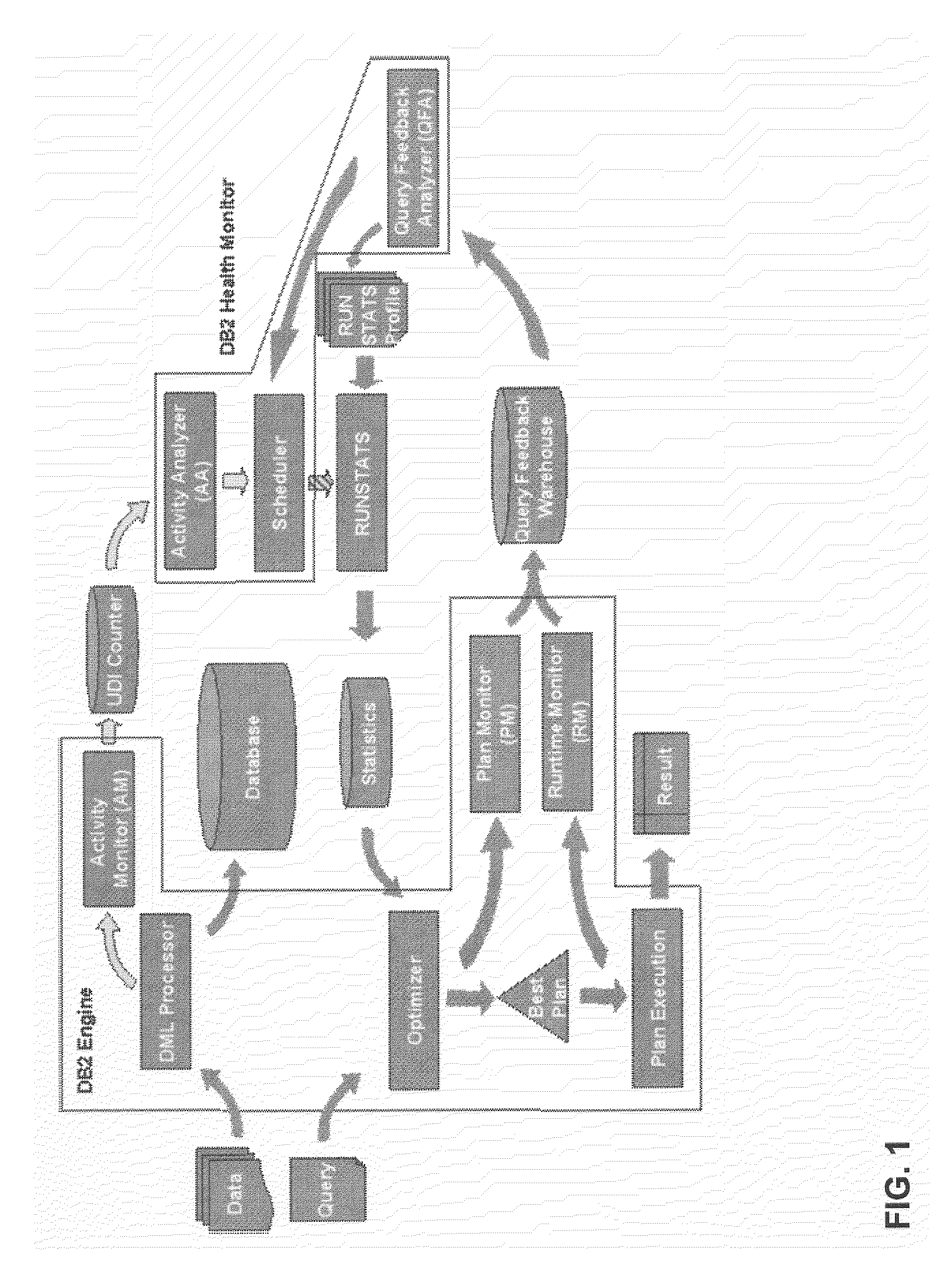
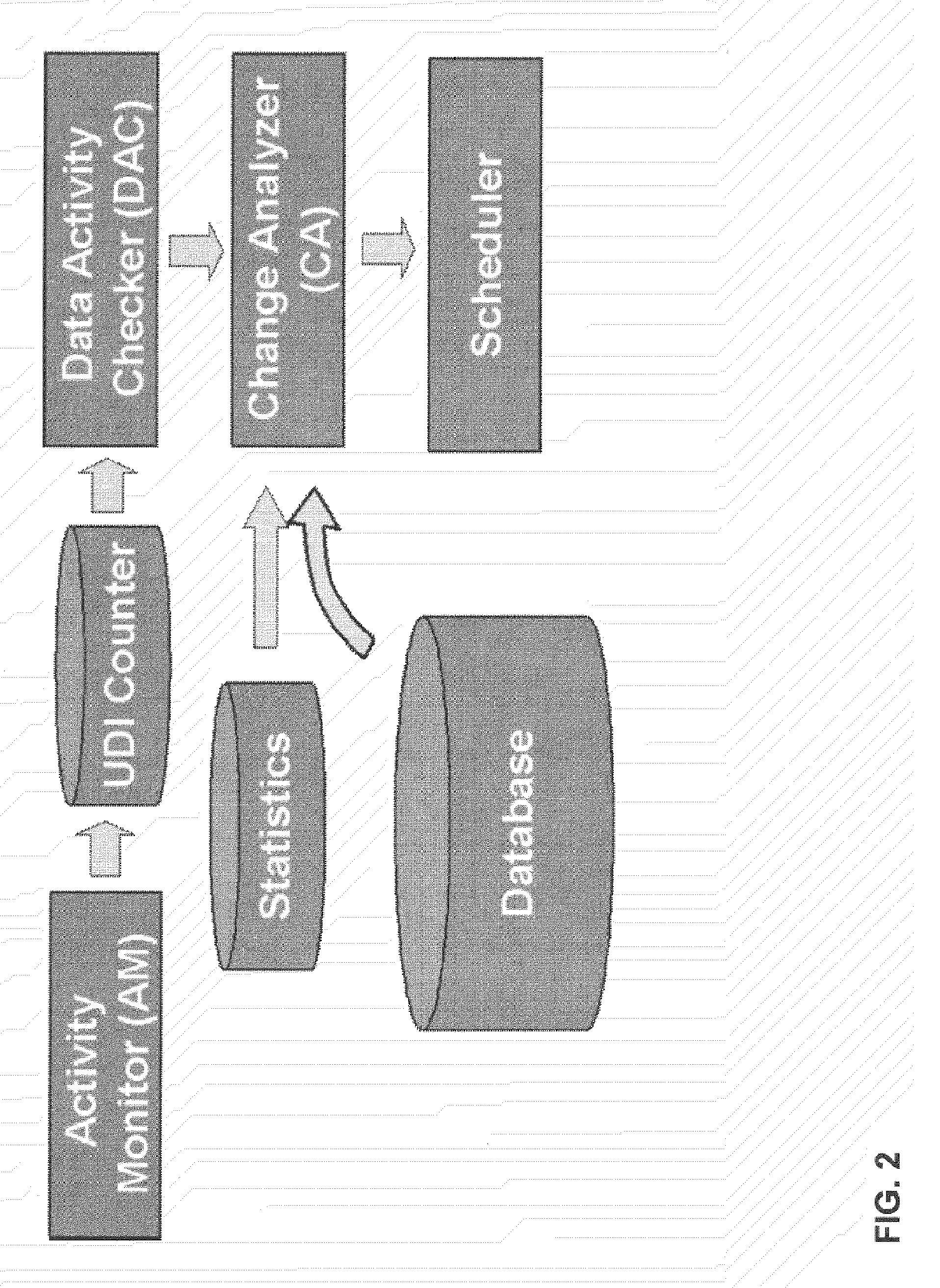
An autonomic tool that supervises the collection and maintenance of database statistics for query optimization by transparently deciding what statistics to gather, when and in what detail to gather them. Feedback from data-driven statistics collection is simultaneously combined with feedback from query-driven learning-based statistics collection, to better process both rapidly changing data and data that is queried frequently. The invention monitors table activity and decides if the data in a table has changed sufficiently to require a refresh of invalid statistics. The invention determines if the invalidity is due to correlation between purportedly independent data, outdated statistics, or statistics that have too few frequent values. Tables and column groups are ranked in order of statistical invalidity, and a limited computational budget is prioritized by ranking subsequent gathering of improved statistics. Multiple tables can have their statistics refreshed over time, and the maintenance effort is concentrated on the most important tables.
Owner:WORKDAY INC
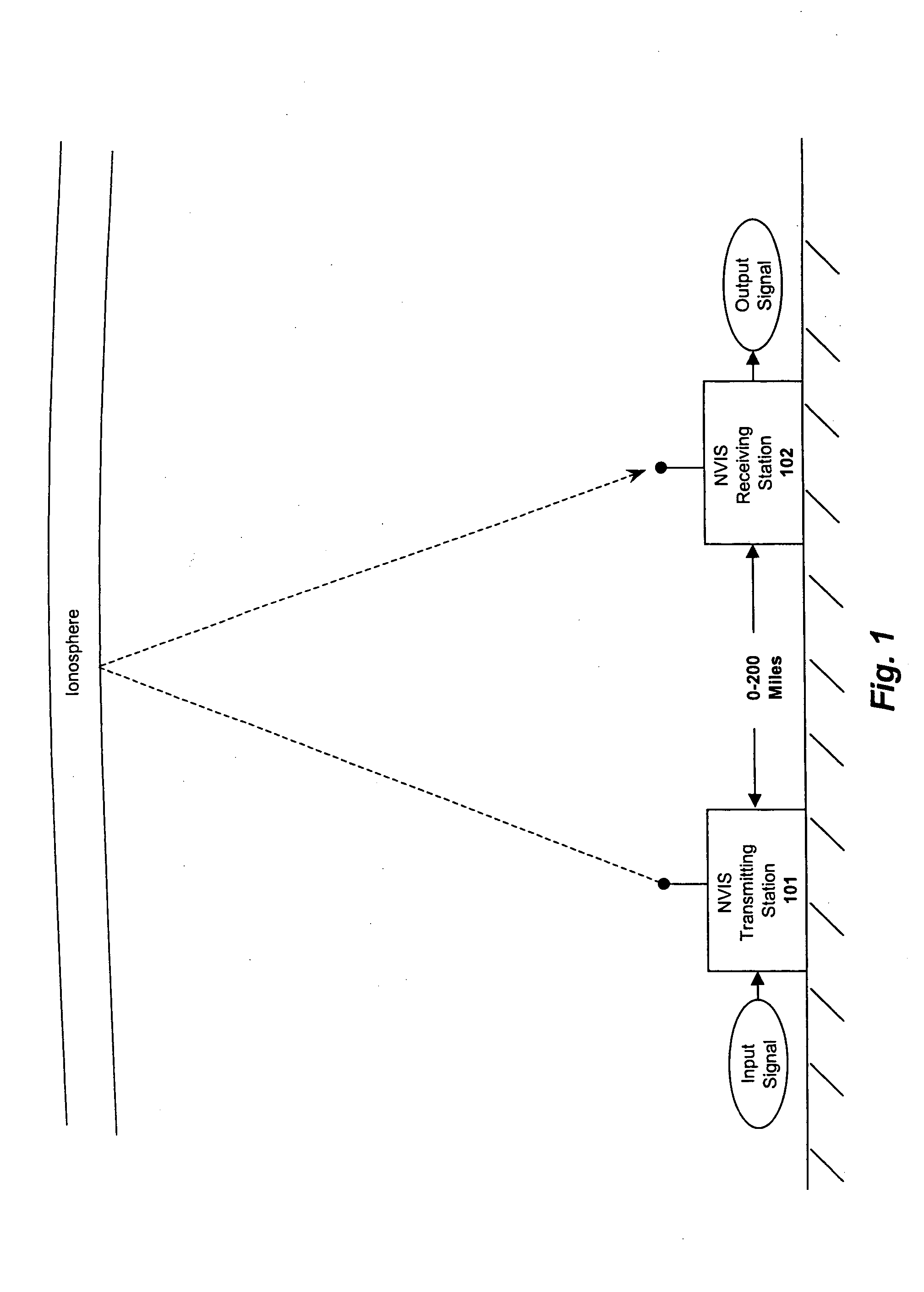
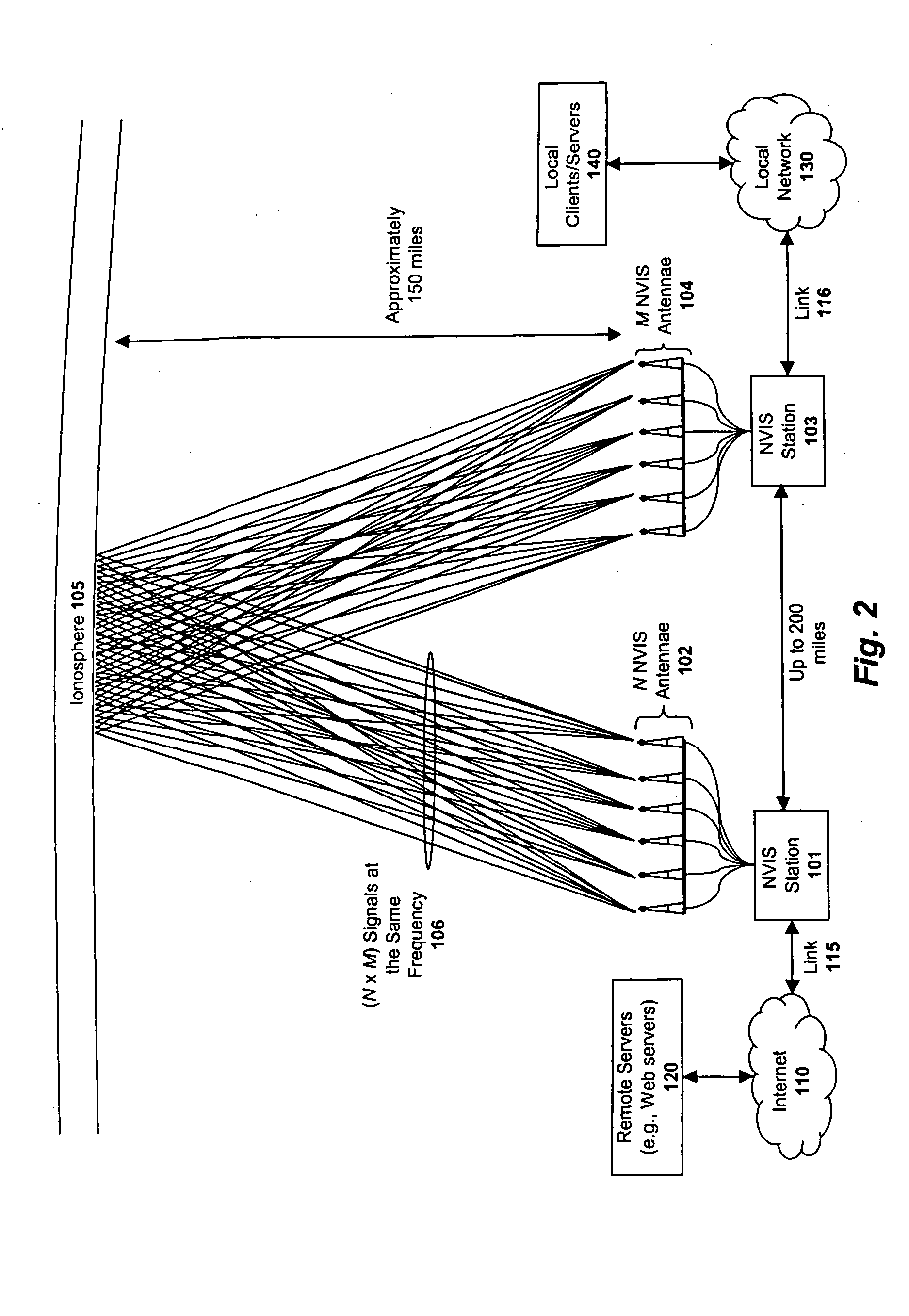
System and method for enhancing near vertical incidence skywave ("NVIS") communication using space-time coding
ActiveUS20050220207A1Polarisation/directional diversityMultiplex communicationCommunications systemData stream
A system and method are described in which space-time coding techniques are used to transmit and receive multiple data streams within a near vertical incidence skywave (“NVIS”) communication system. Within the NVIS communication system, multiple independent data streams may be transmitted from a transmitting station at a high radiation angle, approaching or reaching 90 degrees. The data streams are reflected off of the ionosphere of the earth and received by one or more receiving stations. In one embodiment, the space-time coding techniques are multiple-input multiple-output (“MIMO”) signal communication techniques.
Owner:REARDEN
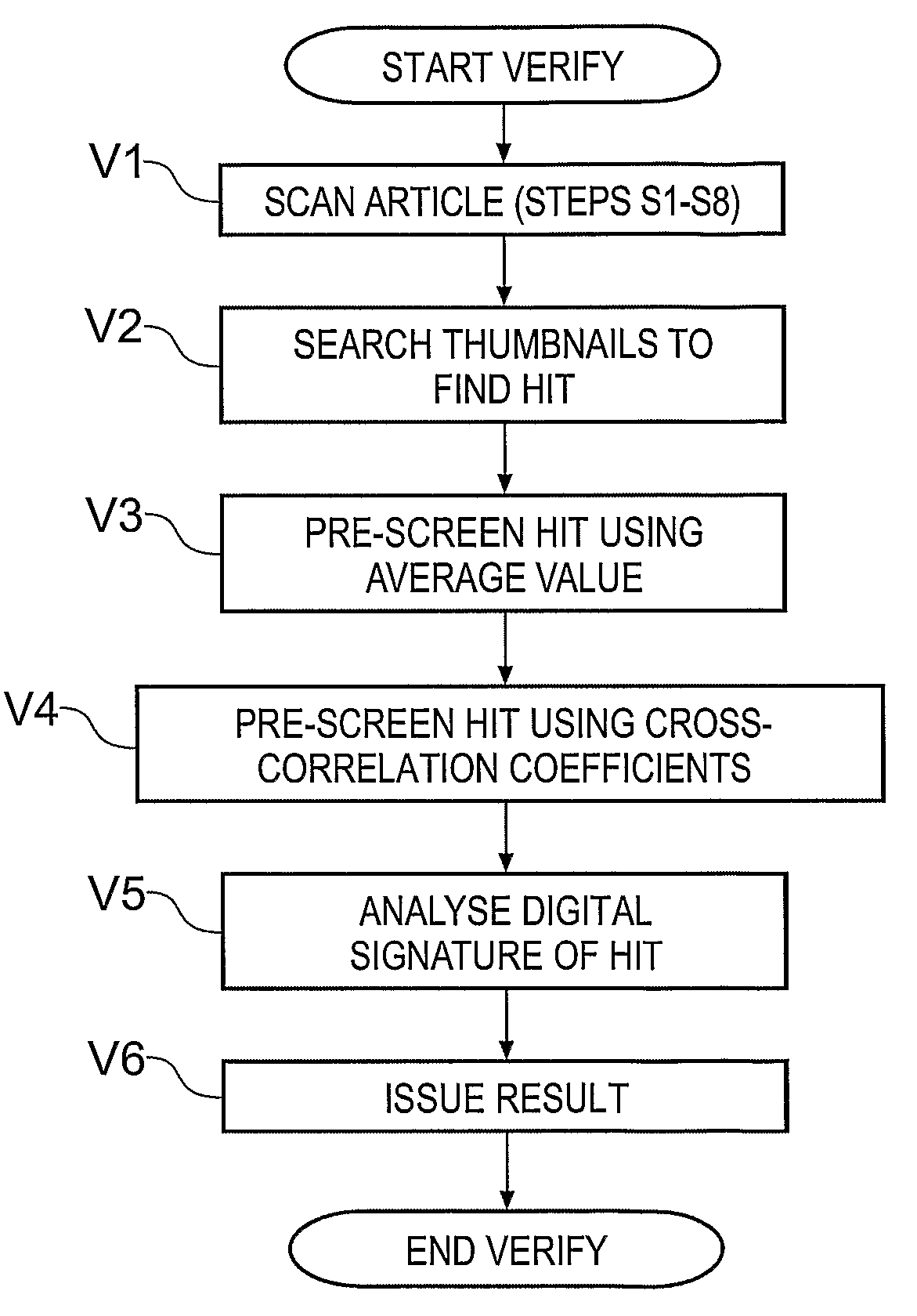
Methods and Apparatuses for Creating Authenticatable Printed Articles and Subsequently Verifying Them
InactiveUS20080002243A1Improve security levelImprove security systemInking apparatusPaper-money testing devicesCardboardMaterial type
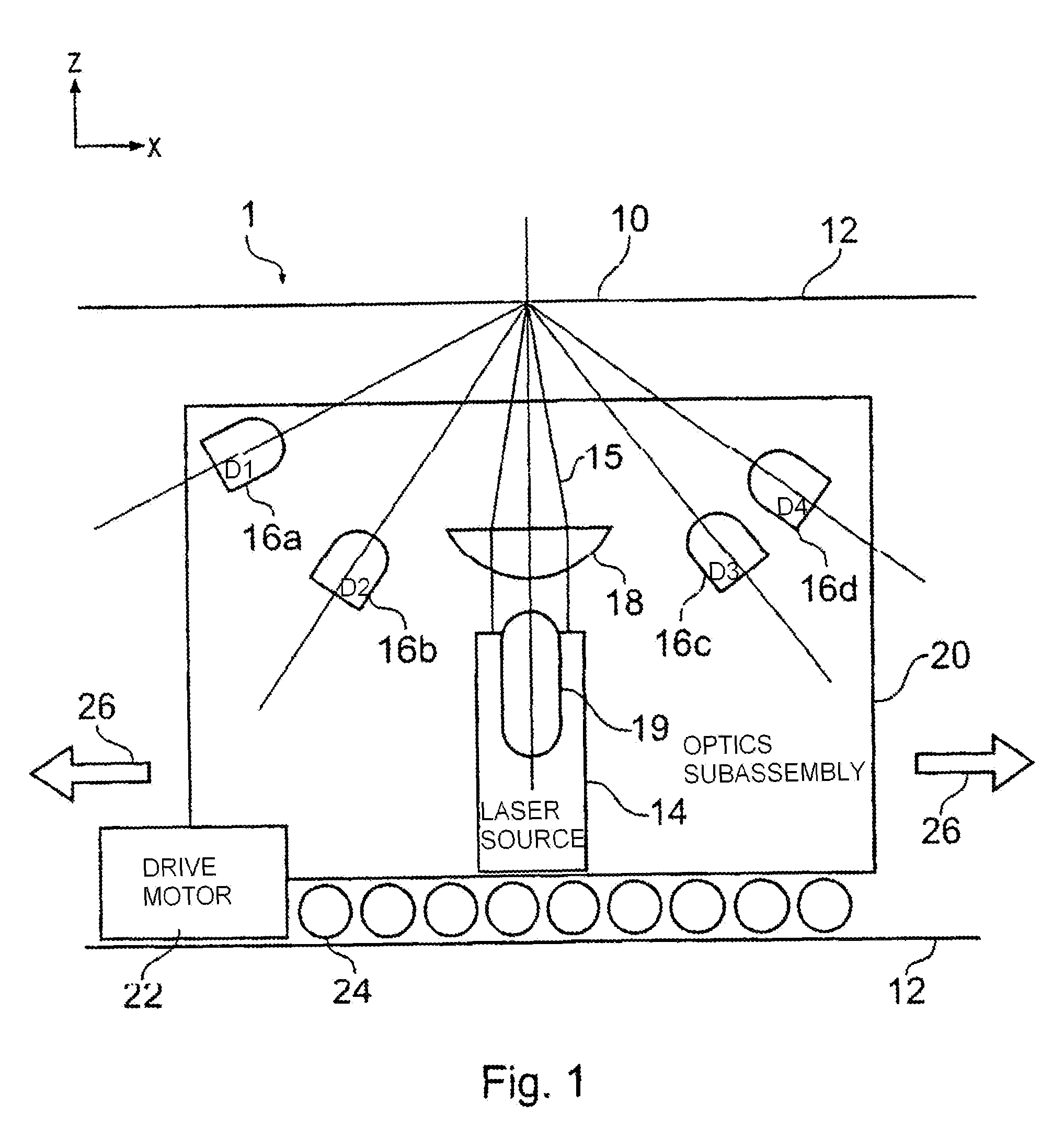
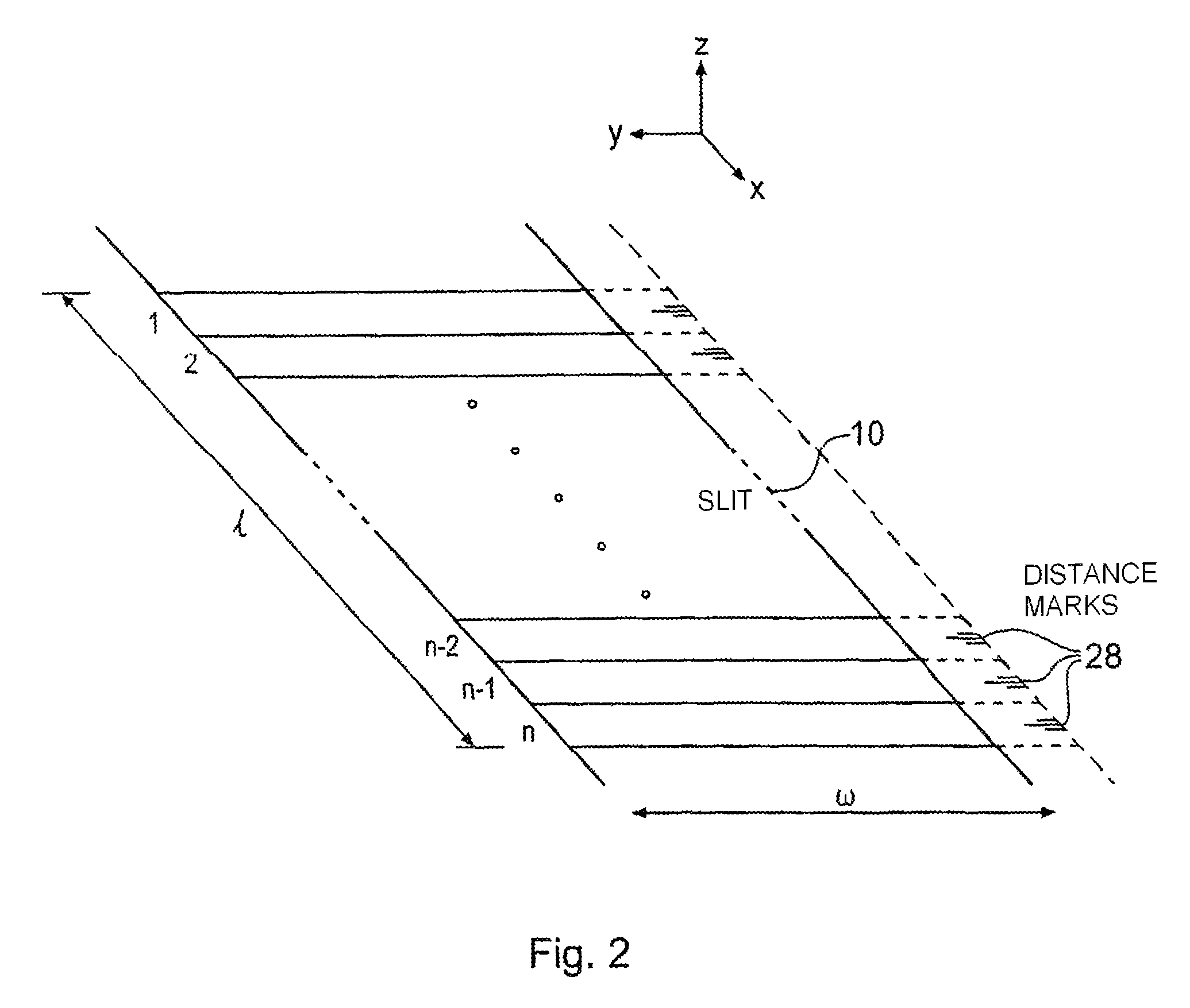
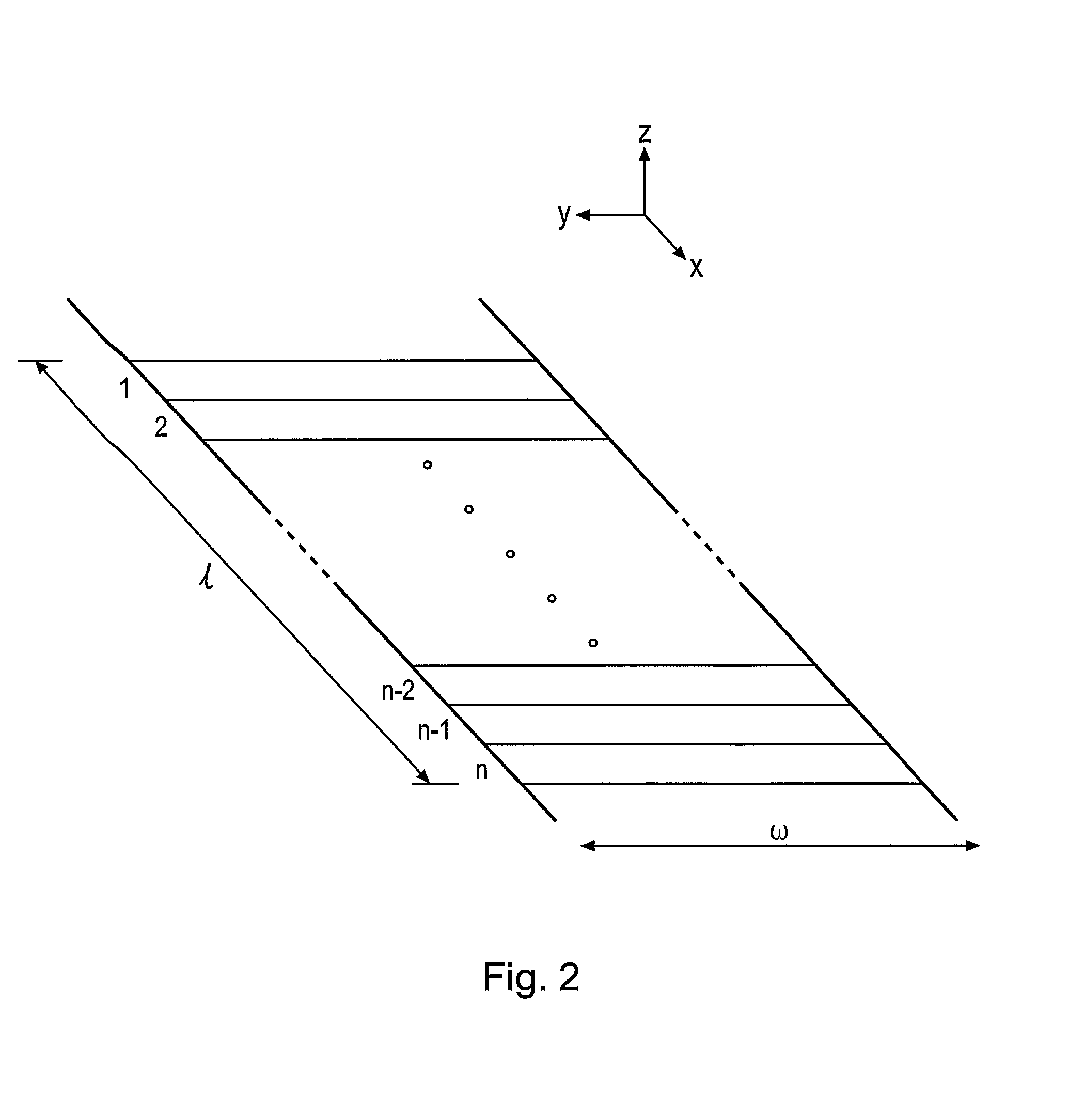
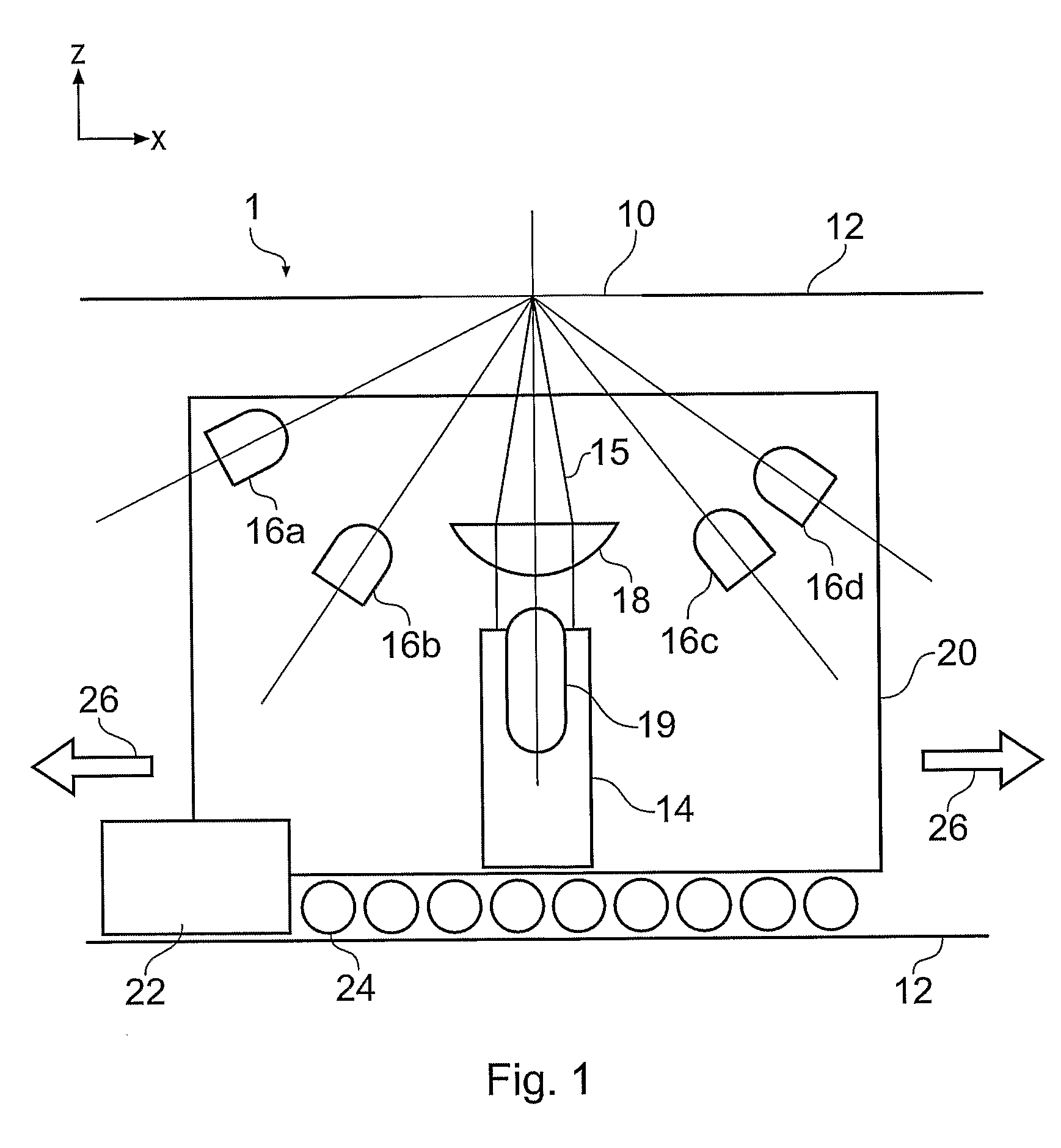
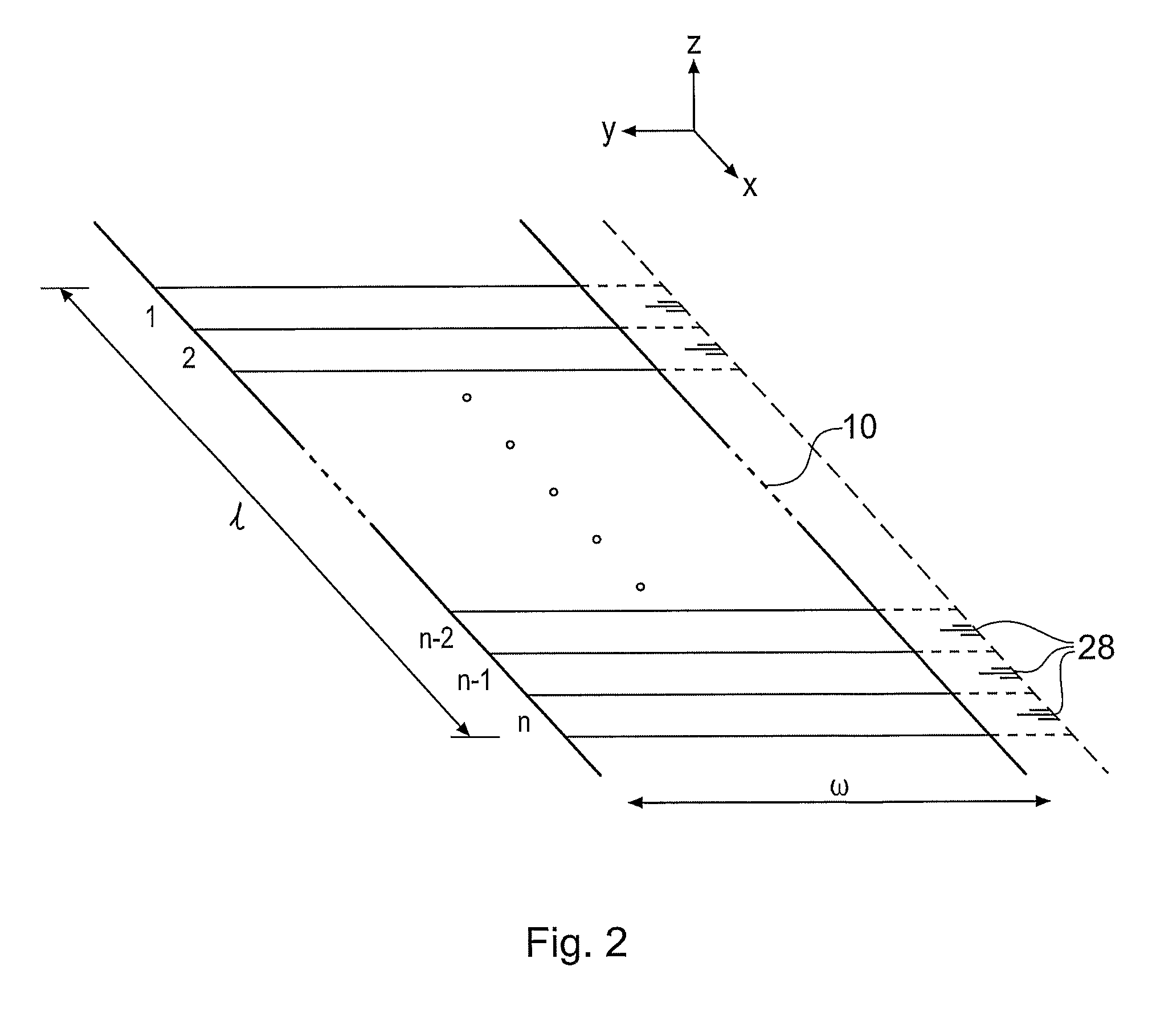
A method and apparatus for determining a digital signature from an article made of paper, cardboard, plastic or many other material types. A coherent source directs a beam to illuminate the article and a detector arrangement collects data points from light scattered from many different parts of the article to collect a large number of independent data points, typically 500 or more. By collecting a large number of independent signal contributions specific to many different parts of the article, a digital signature can be computed that is unique to the area of the article that has been scanned. This measurement can be repeated whenever required to test authenticity of the article. Using this method, it has been discovered that it is essentially pointless to go to the effort and expense of making specially prepared tokens, since unique characteristics are measurable in a straightforward manner from a wide variety of every day articles.
Owner:INGENIA HLDG LTD
Authenticity verification methods, products and apparatuses
InactiveUS20070192850A1Enhanced advantageDigital data processing detailsUser identity/authority verificationCardboardMaterial type
A method and apparatus for determining a digital signature from an article made of paper, cardboard, plastic or many other material types. A coherent light source directs a beam to illuminate the article and a detector arrangement collects data points from light scattered from many different parts of the article to collect a large number of independent data points, typically 500 or more. By collecting a large number of independent signal contributions specific to many different parts of the article, a digital signature can be computed that is unique to the area of the article that has been scanned. This measurement can be repeated whenever required to test authenticity of the article. Using this method, it has been discovered that it is essentially pointless to go to the effort and expense of making specially prepared tokens, since unique characteristics are measurable a in a straightforward manner from a wide variety of every day articles.
Owner:INGENIA HLDG LTD
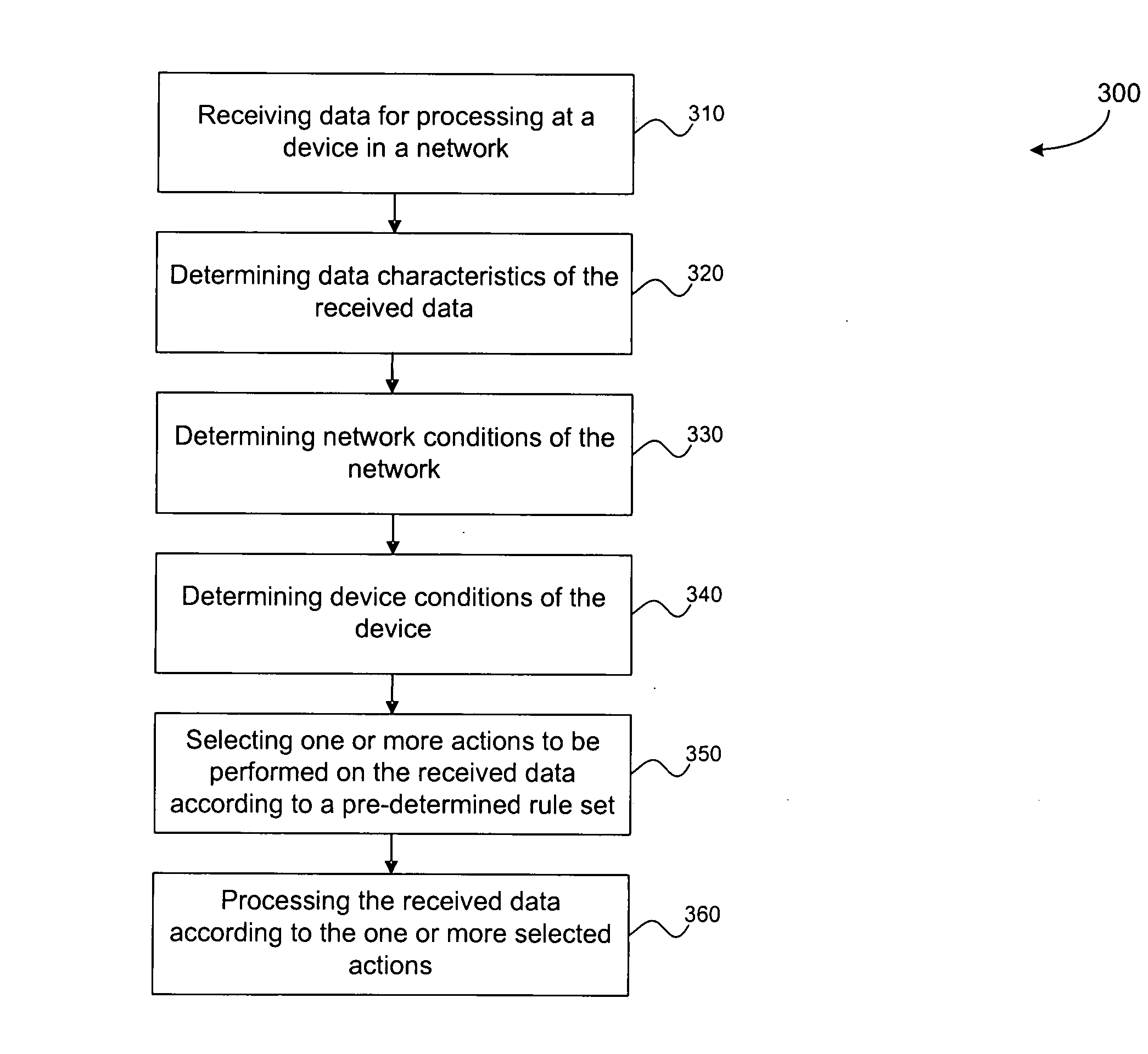
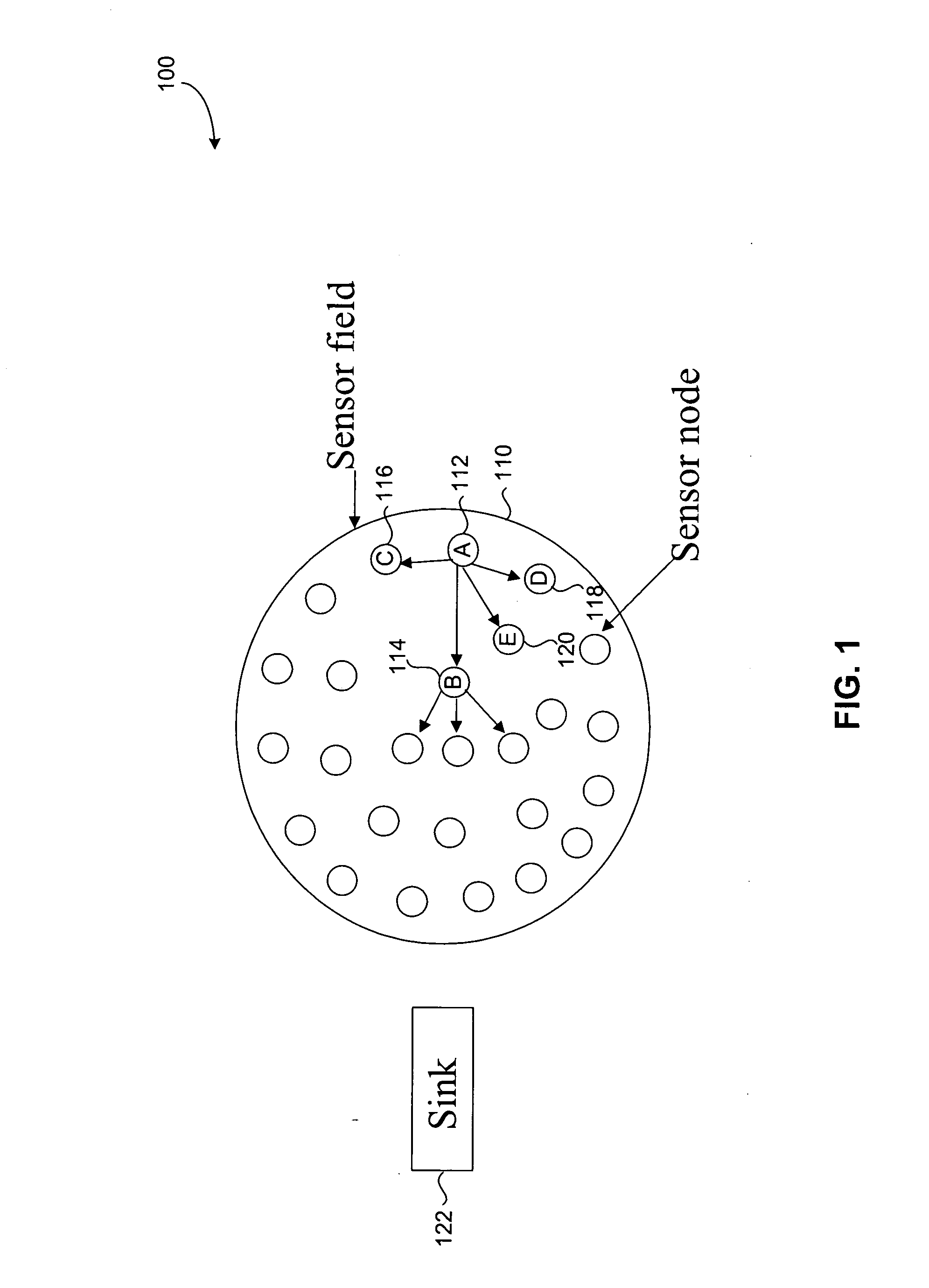
Smart data dissemination
ActiveUS20070239862A1Easily configurableEasily modifiableNetwork topologiesMultiple digital computer combinationsQuality of serviceWireless mesh network
Methods and systems for smart data processing and dissemination in wireless sensor networks are provided herein. In one aspect, the present invention provides dynamic and independent data processing and dissemination at individual sensor nodes in a wireless sensor network. In another aspect, the present invention provides data processing and / or dissemination methods at a sensor node that are responsive to, among other parameters, network traffic conditions, network connectivity conditions, conditions at the sensor node, and the data characteristics and QOS (Quality of Service) requirements of the data being processed and / or disseminated. In yet another aspect, data processing and / or dissemination rules according to the present invention are easily configurable and modifiable depending on the specific sensor networking application.
Owner:MITRE SPORTS INT LTD
Multi-Media Conferencing System
ActiveUS20140362165A1Resource is changedEasy to changeTelevision conference systemsOffice automationGeographic siteGeolocation
A multi-media conferencing system that integrates visual, audio, independent data interaction and modification, collaboration of information, independent video and 3D model viewing and manipulation, and networking among all participants in the meeting. Each participant conference display typically shows two content sectors under the control of the presenter and a selectable number of other content sectors under the control of the participant. The presenter conference display selectively includes a presenter dashboard for managing the presentation. Each content sector on the participant and attendee conference displays may be enlarged to full screen or reduced to a sector display or an icon with a simple command. The system also includes geo-location display functionality, participant monitoring, attendee chat functionality, and a wide range of additional functionality under the control of the conference presenter and attendees.
Owner:JIGSAW SOFTWARE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com