Patents
Literature
11895 results about "File system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
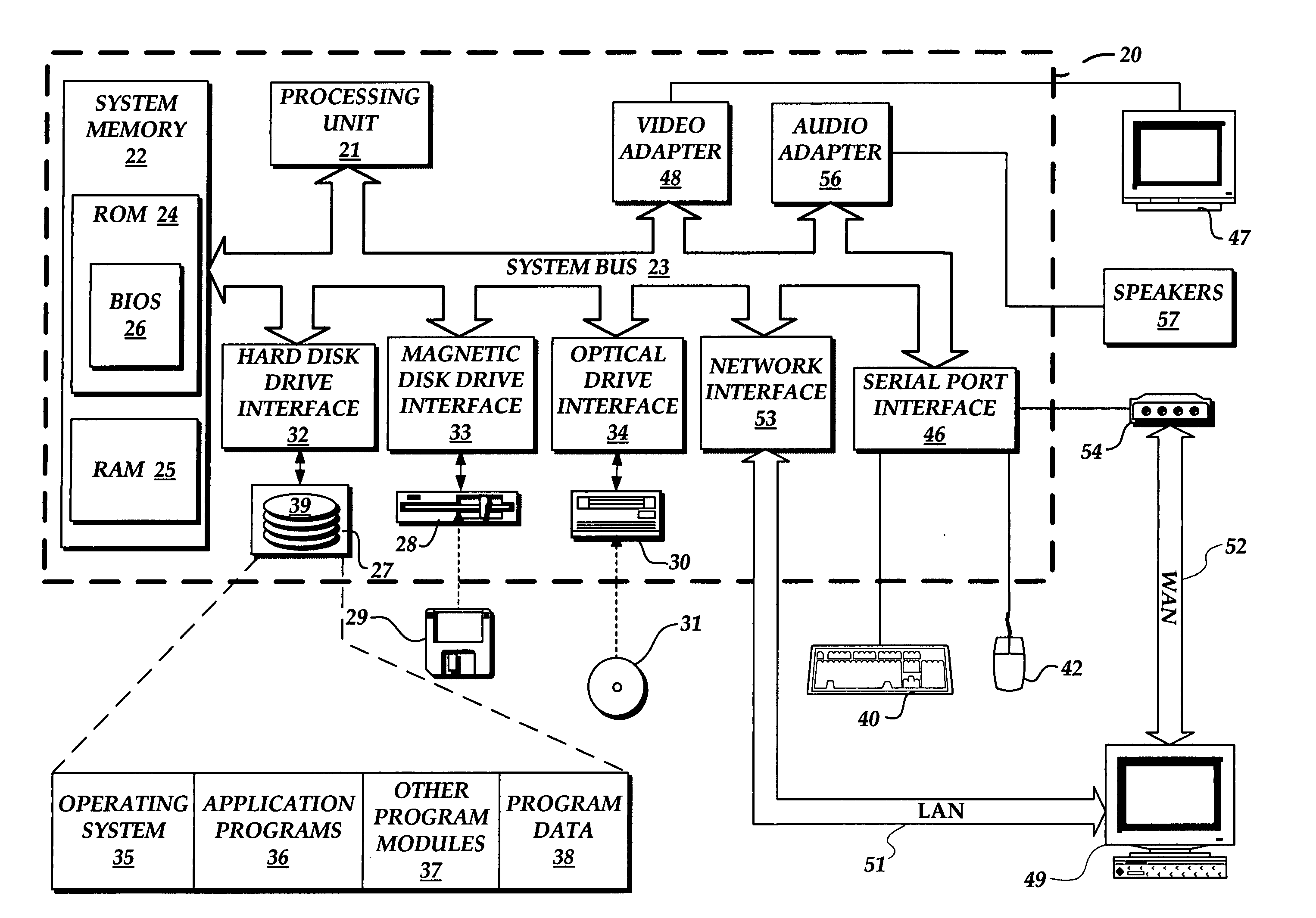
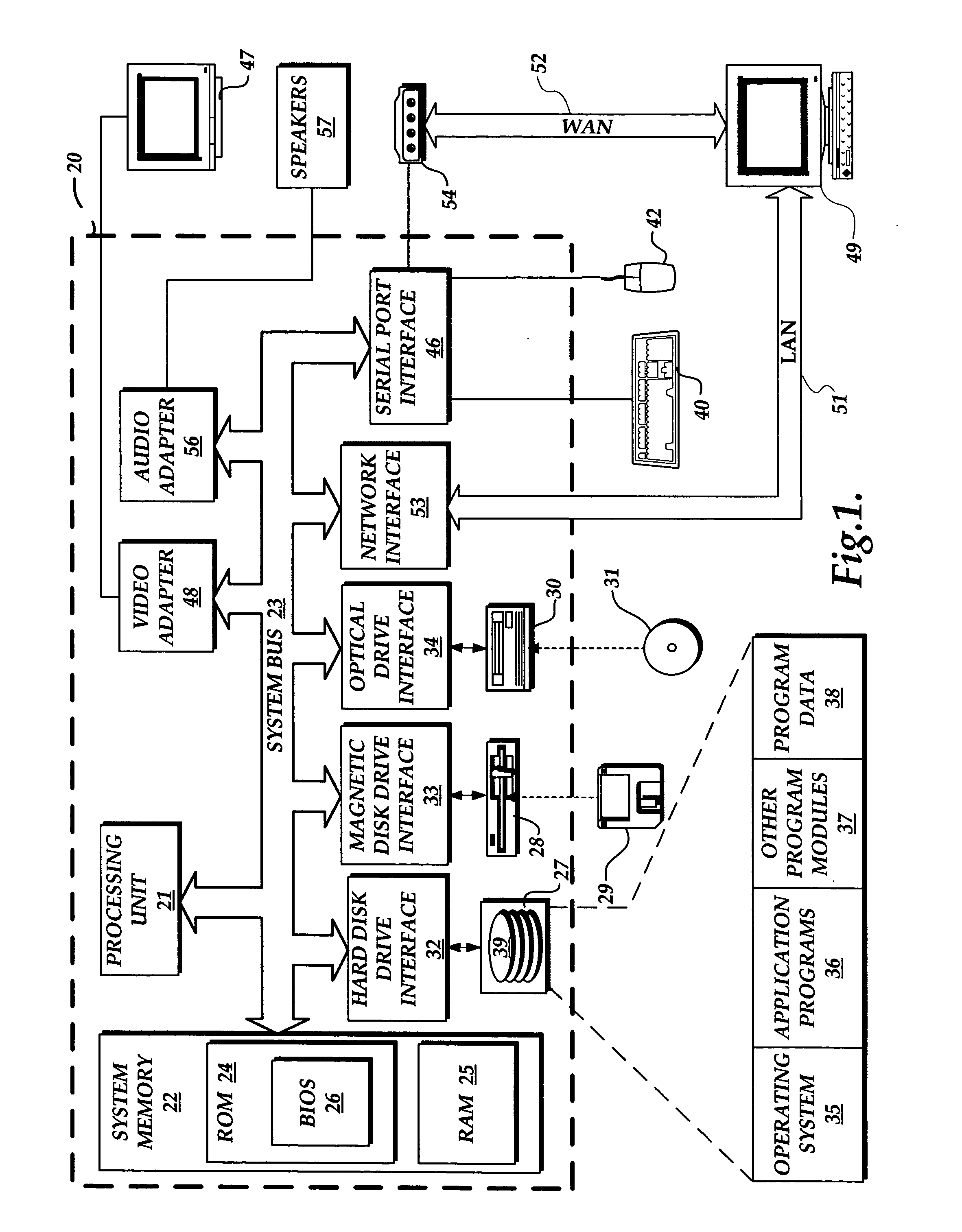
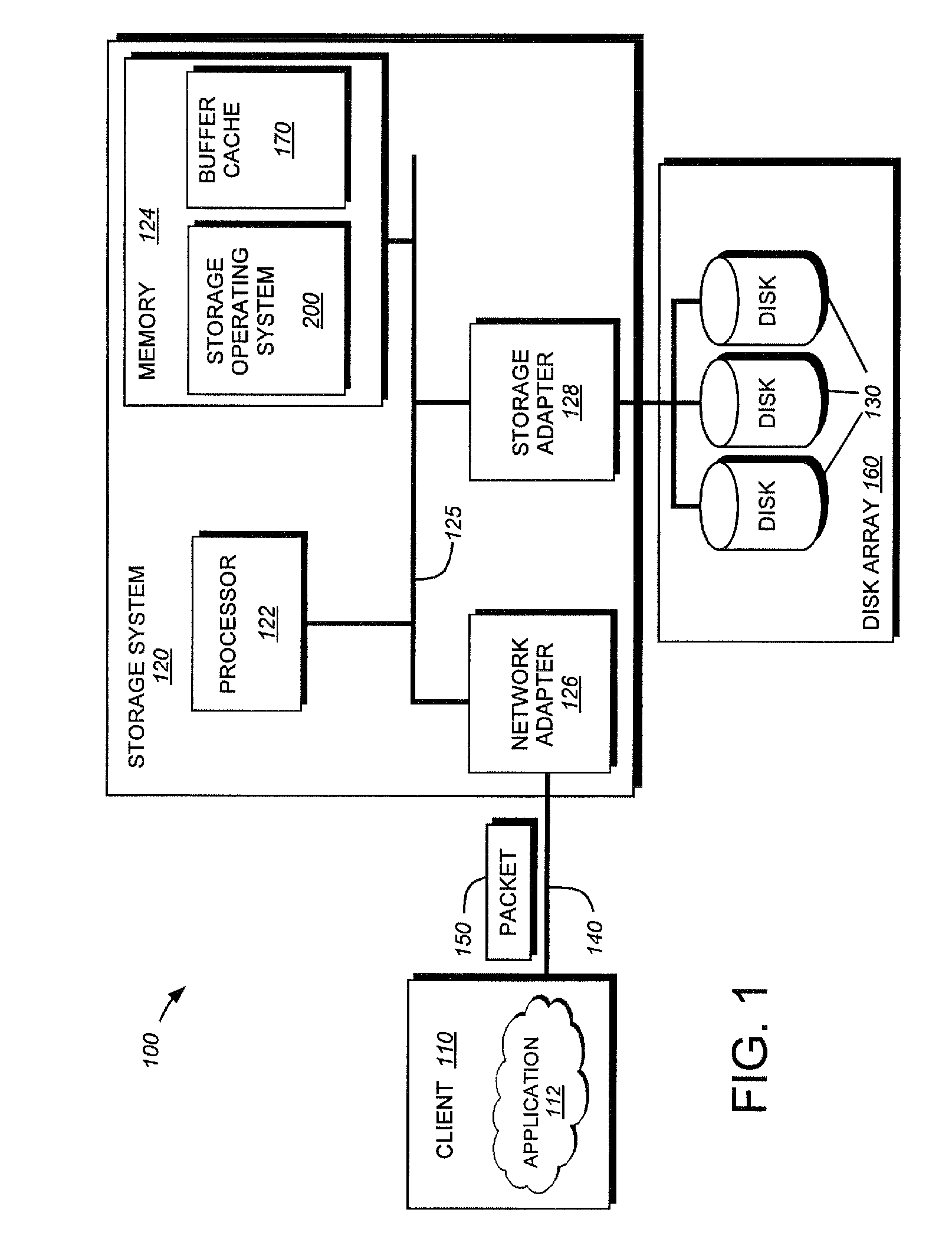
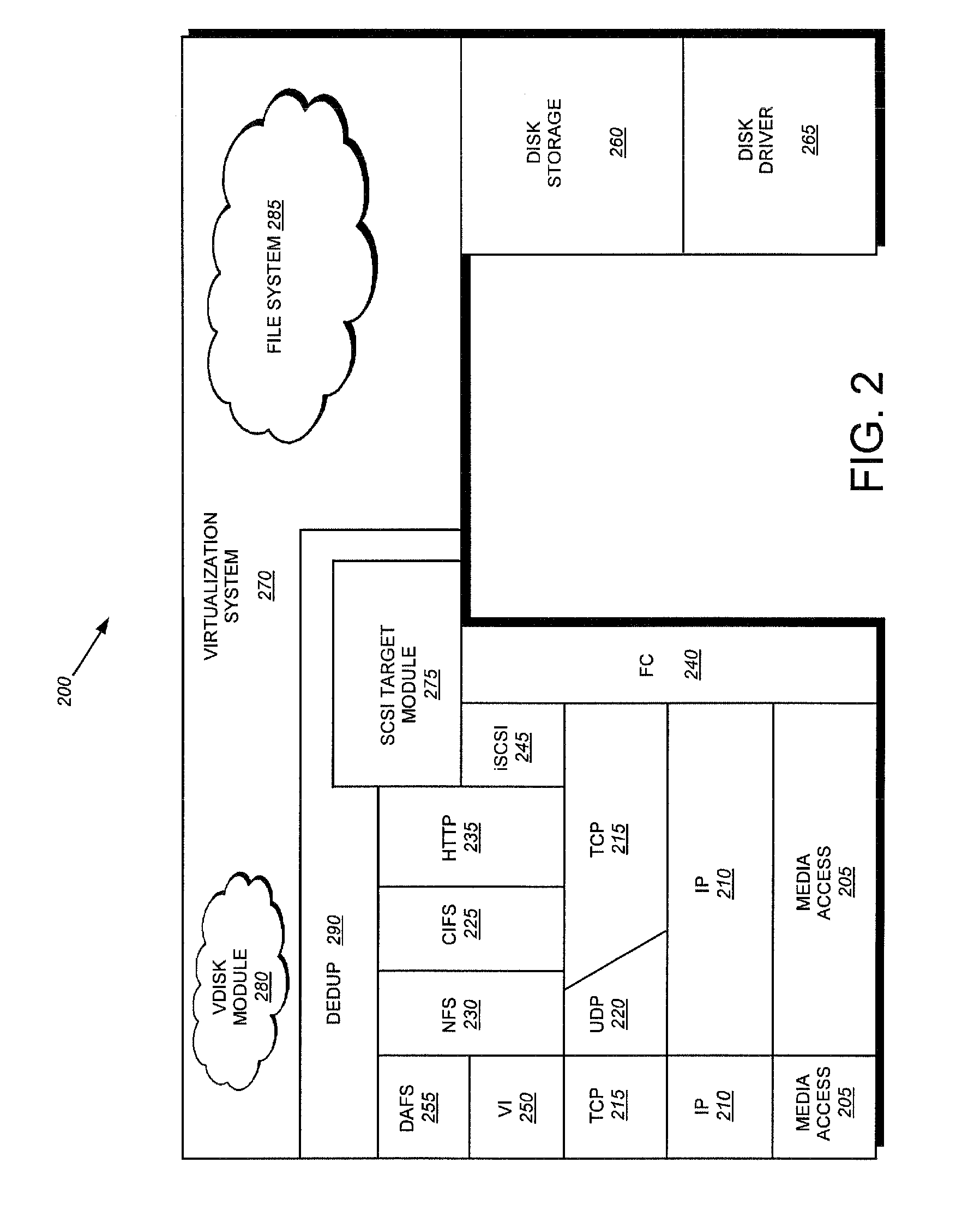
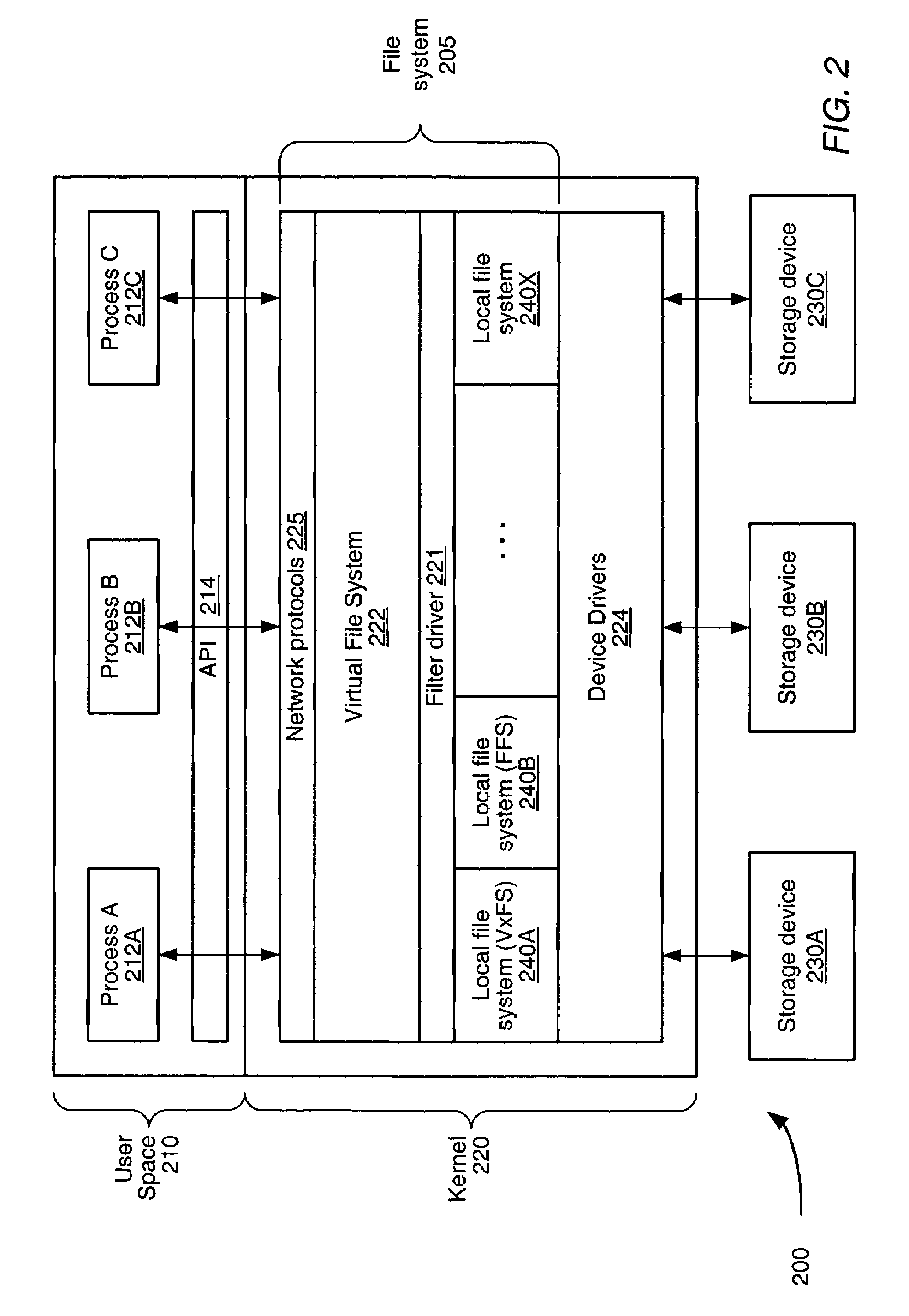
In computing, a file system or filesystem (often abbreviated to fs), controls how data is stored and retrieved. Without a file system, information placed in a storage medium would be one large body of data with no way to tell where one piece of information stops and the next begins. By separating the data into pieces and giving each piece a name, the information is easily isolated and identified. Taking its name from the way paper-based information systems are named, each group of data is called a "file". The structure and logic rules used to manage the groups of information and their names is called a "file system".
Method and system for managing distributed content and related metadata
InactiveUS7272613B2Reduce storage requirementsReduce amountData processing applicationsError detection/correctionControl systemFile system
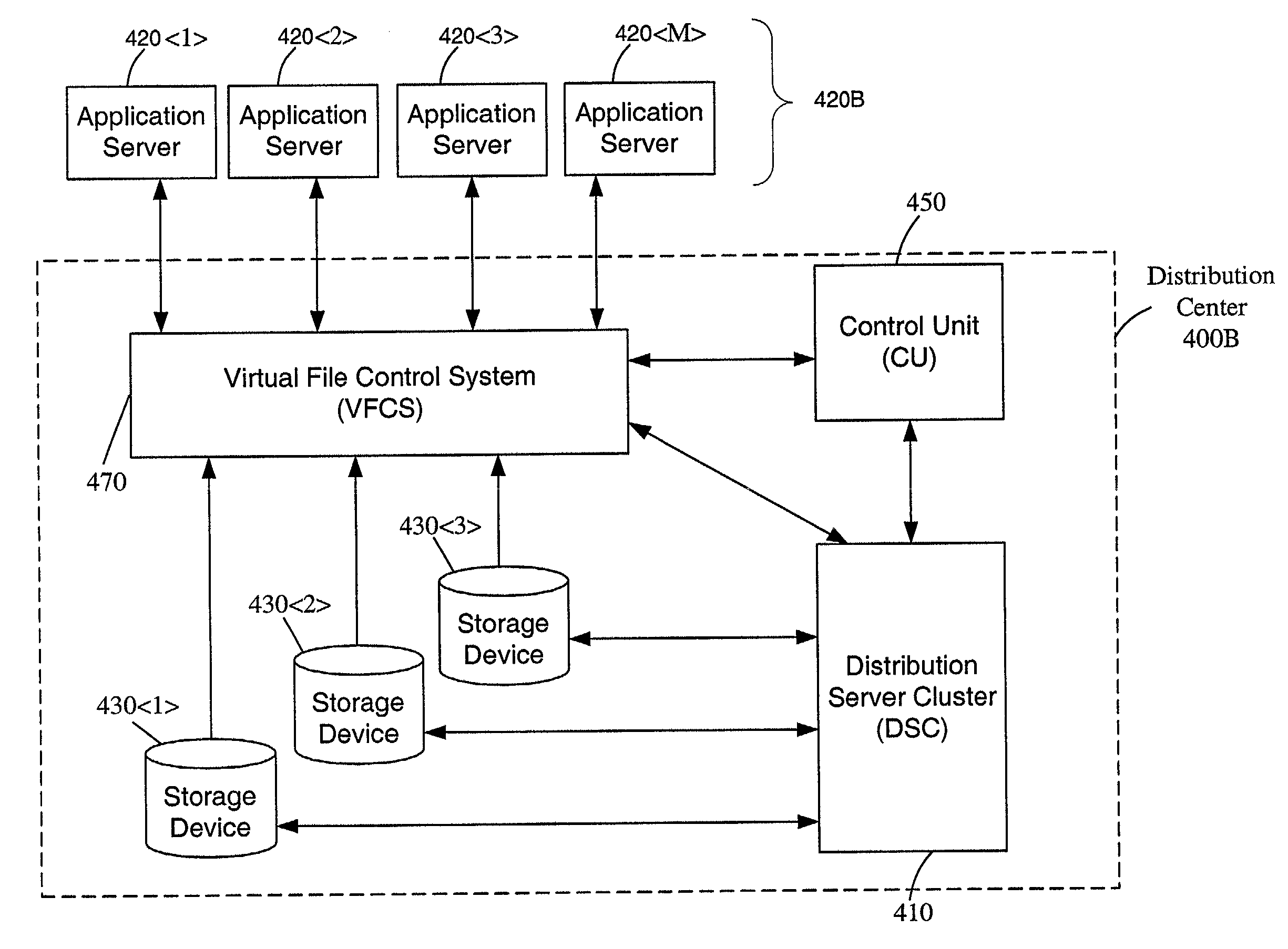
The invention provides a method and system for creating an innovative file system that separates its directory presentation from its data store. The method and system include processing, division, distribution, managing, synchronizing, and reassembling of file system objects that does not delay the presentation of the content to the user, but also uses a reduced amount of storage space. The invention includes the ability to manage and control the integrity of the files distributed across the network, and the ability to serve and reconstruct files in real time using a Virtual File Control System.
Owner:PRISMEDIA NETWORK +1
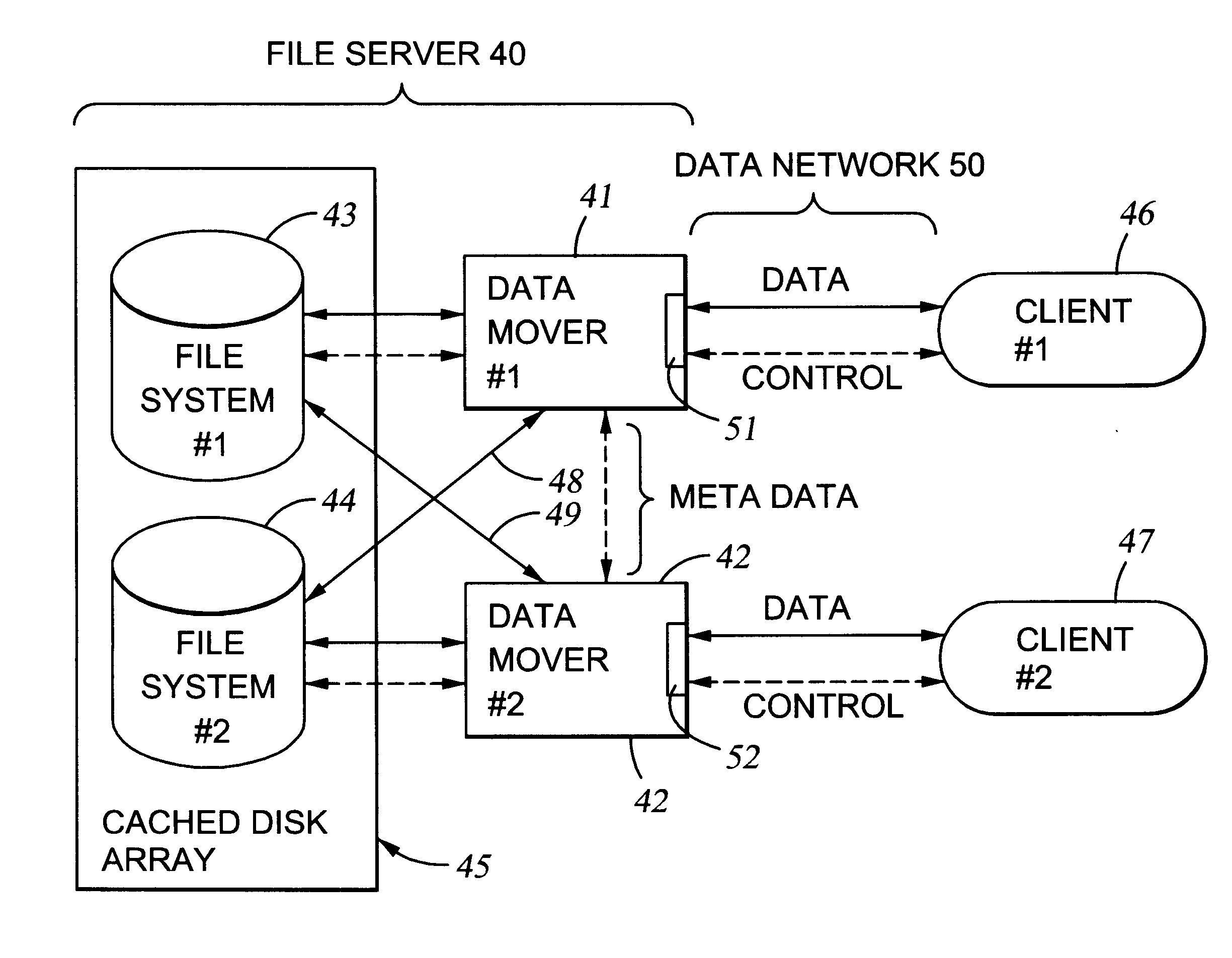
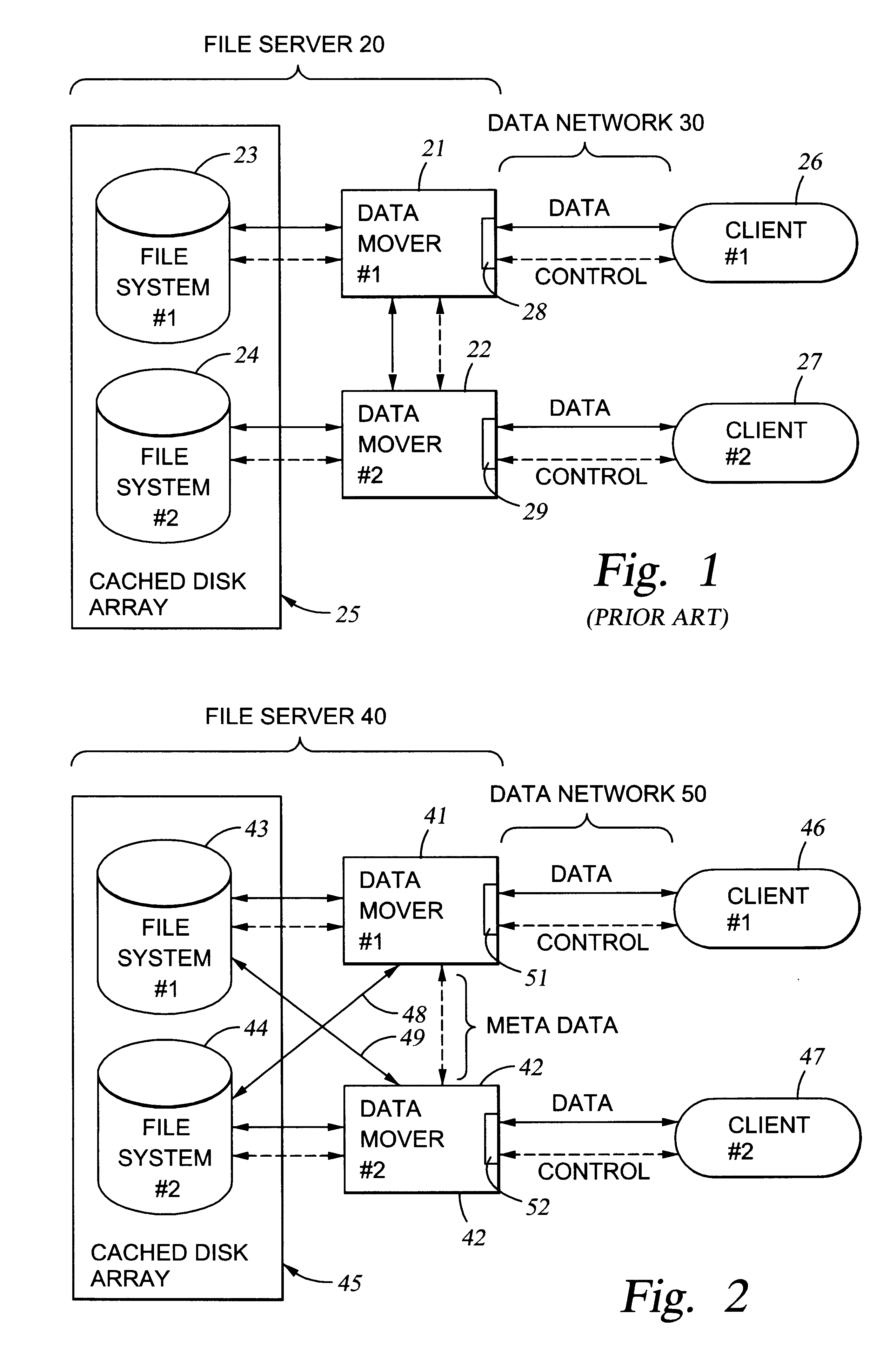
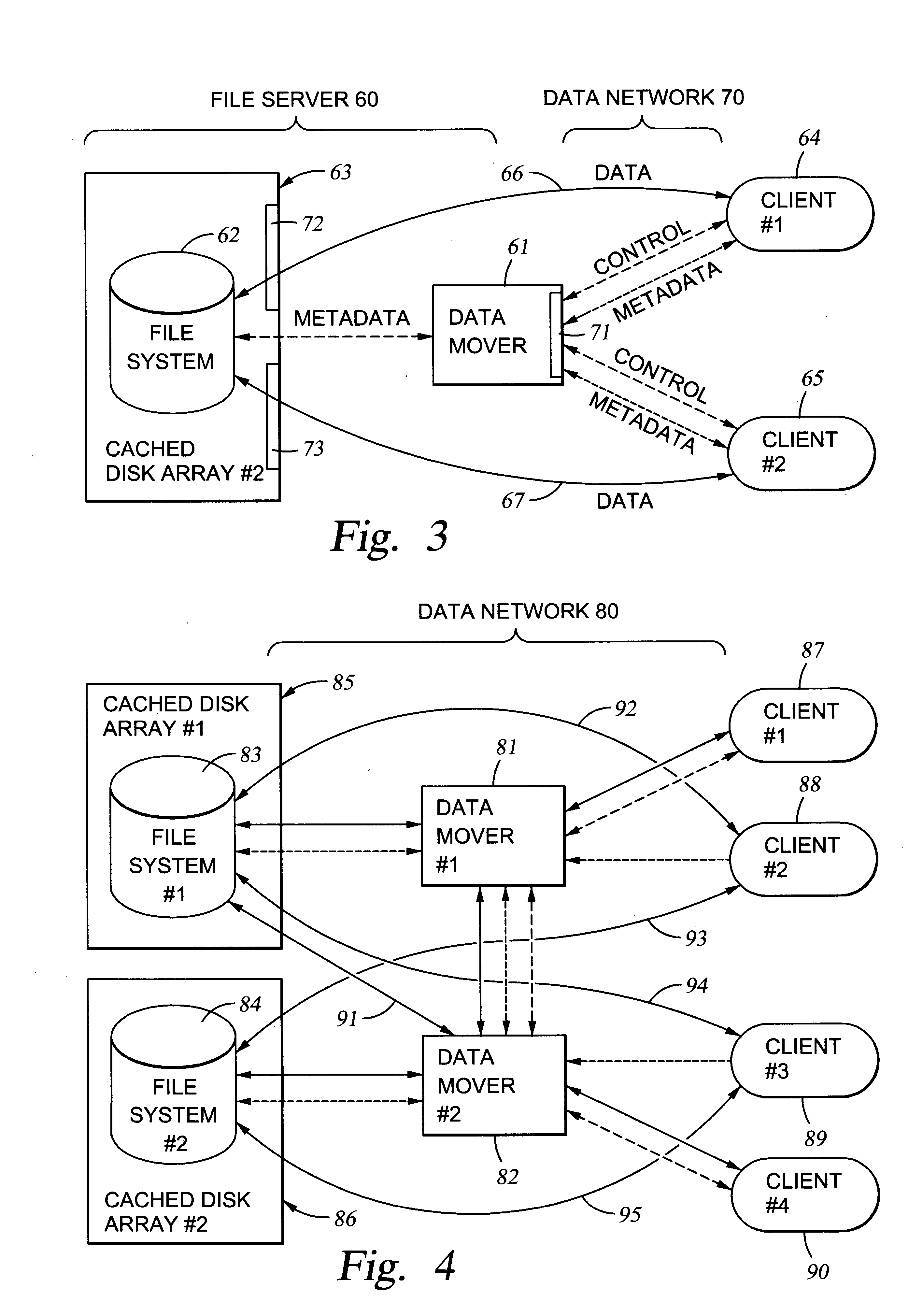
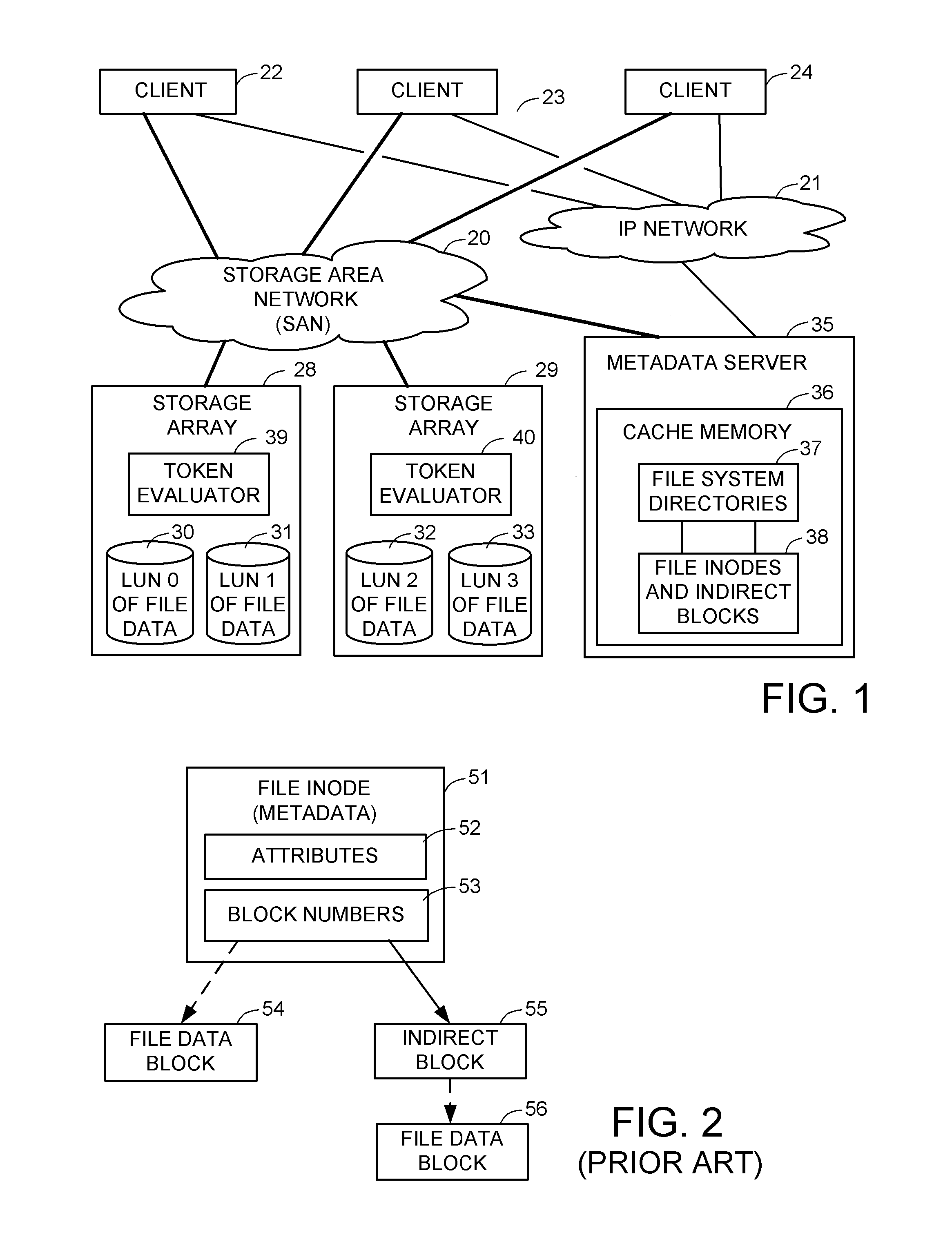
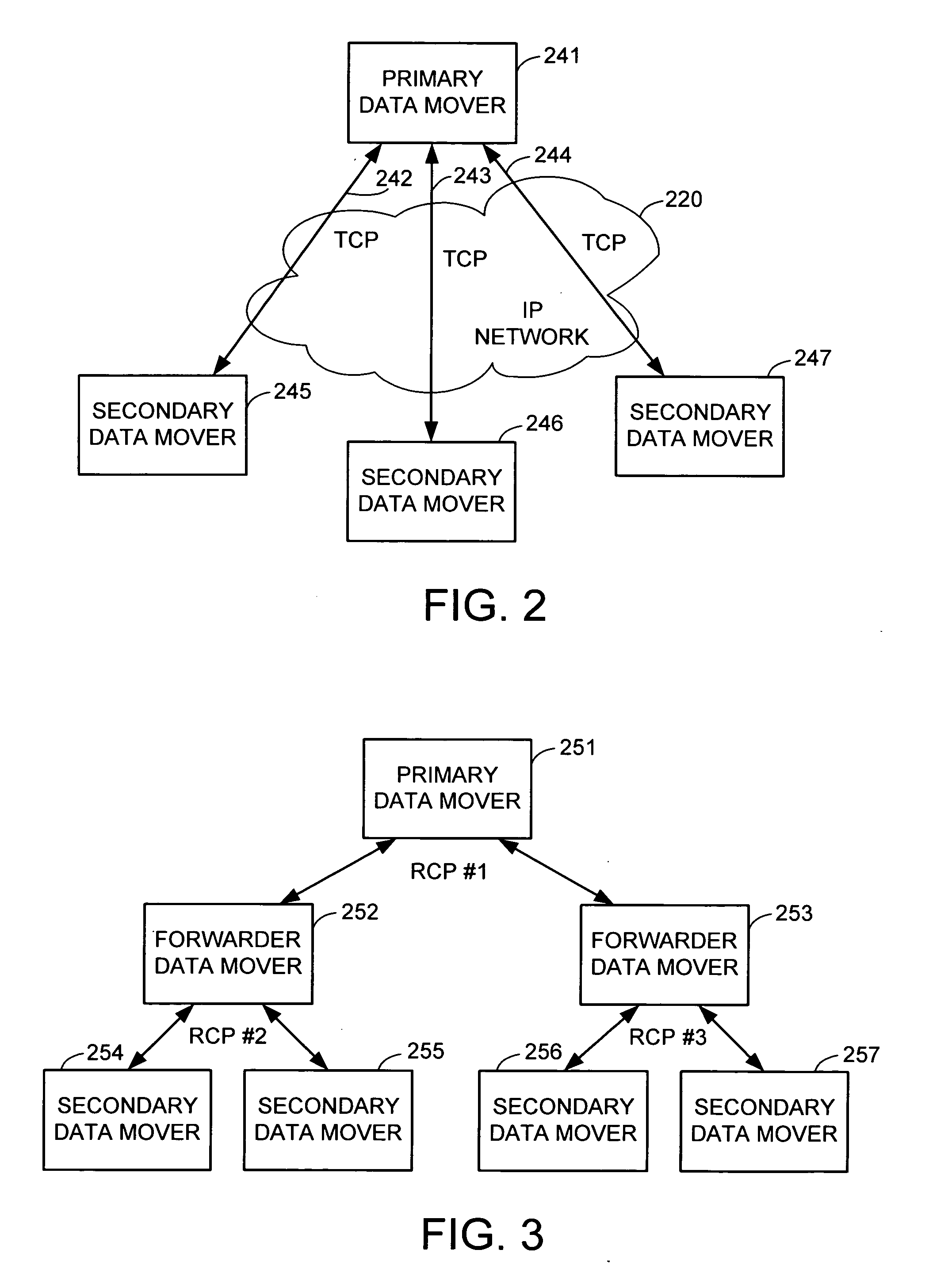
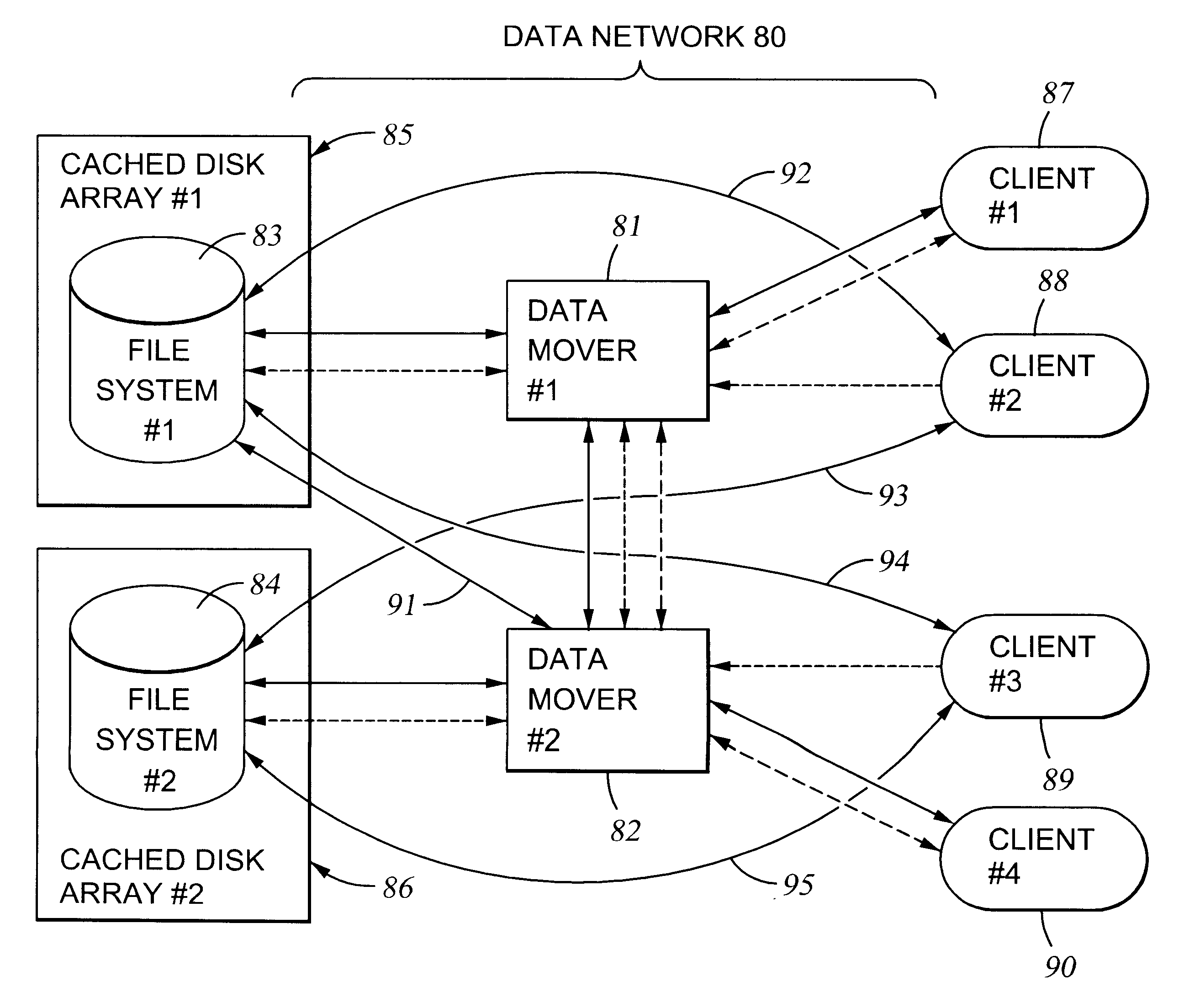
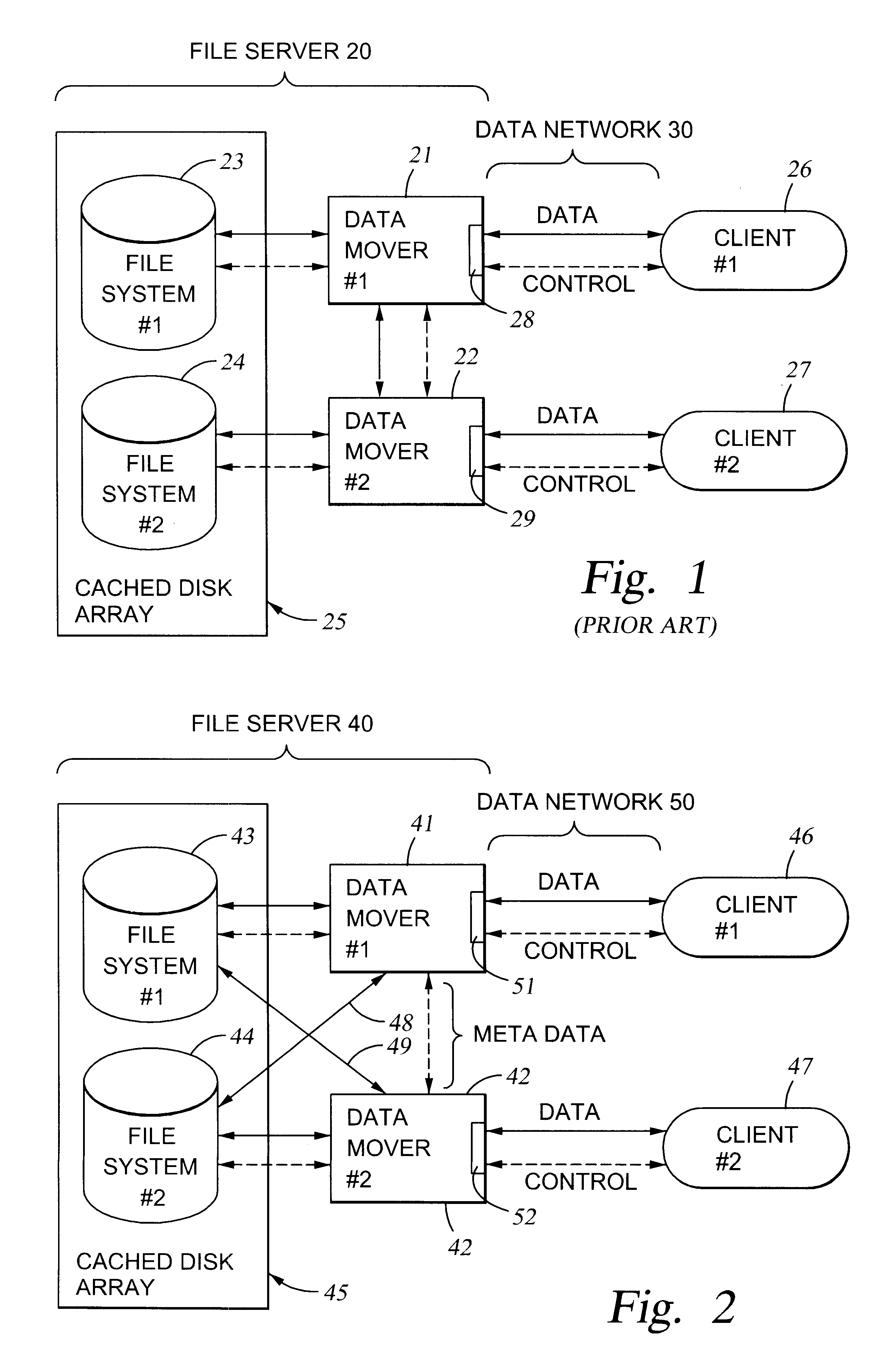
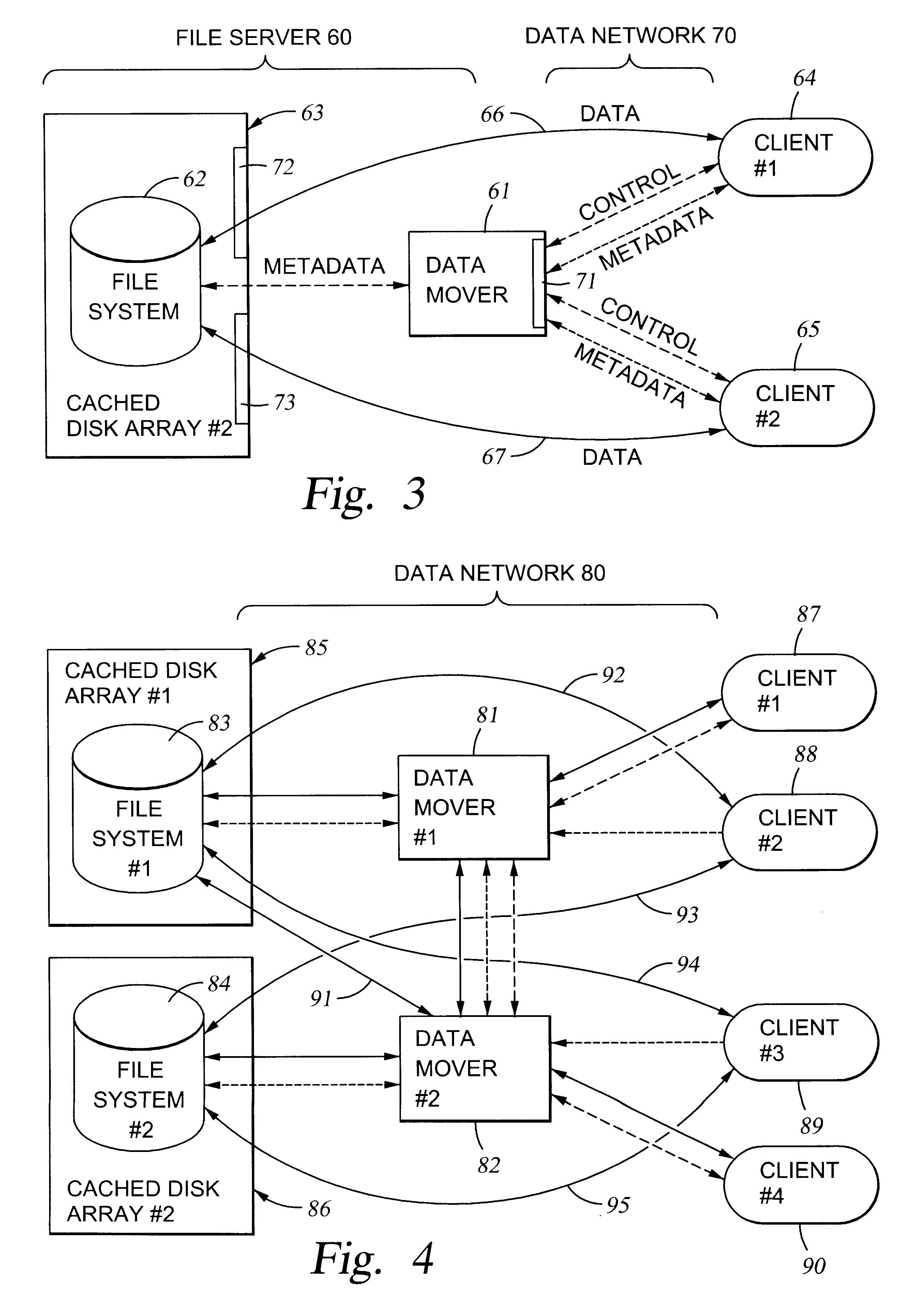
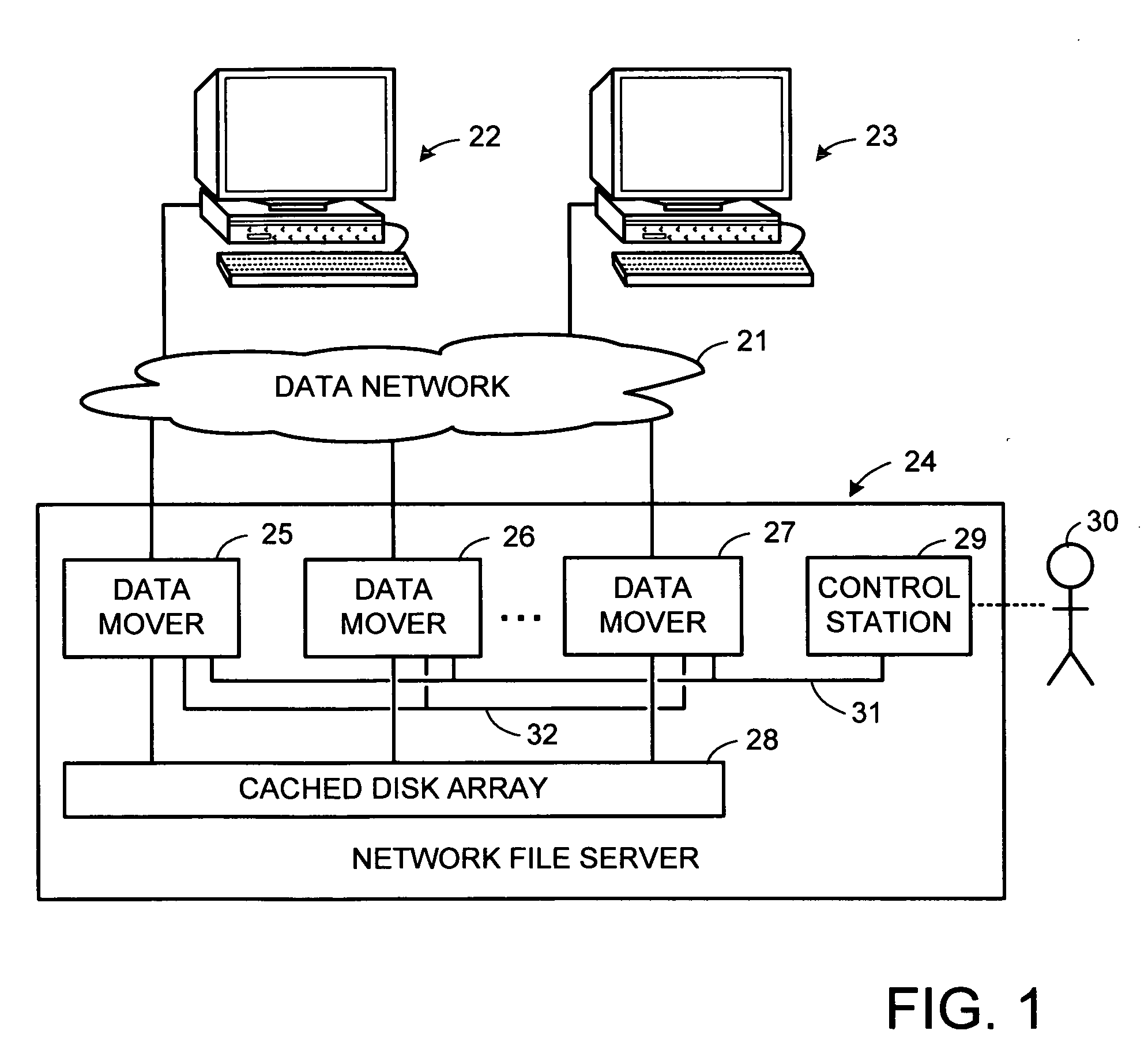
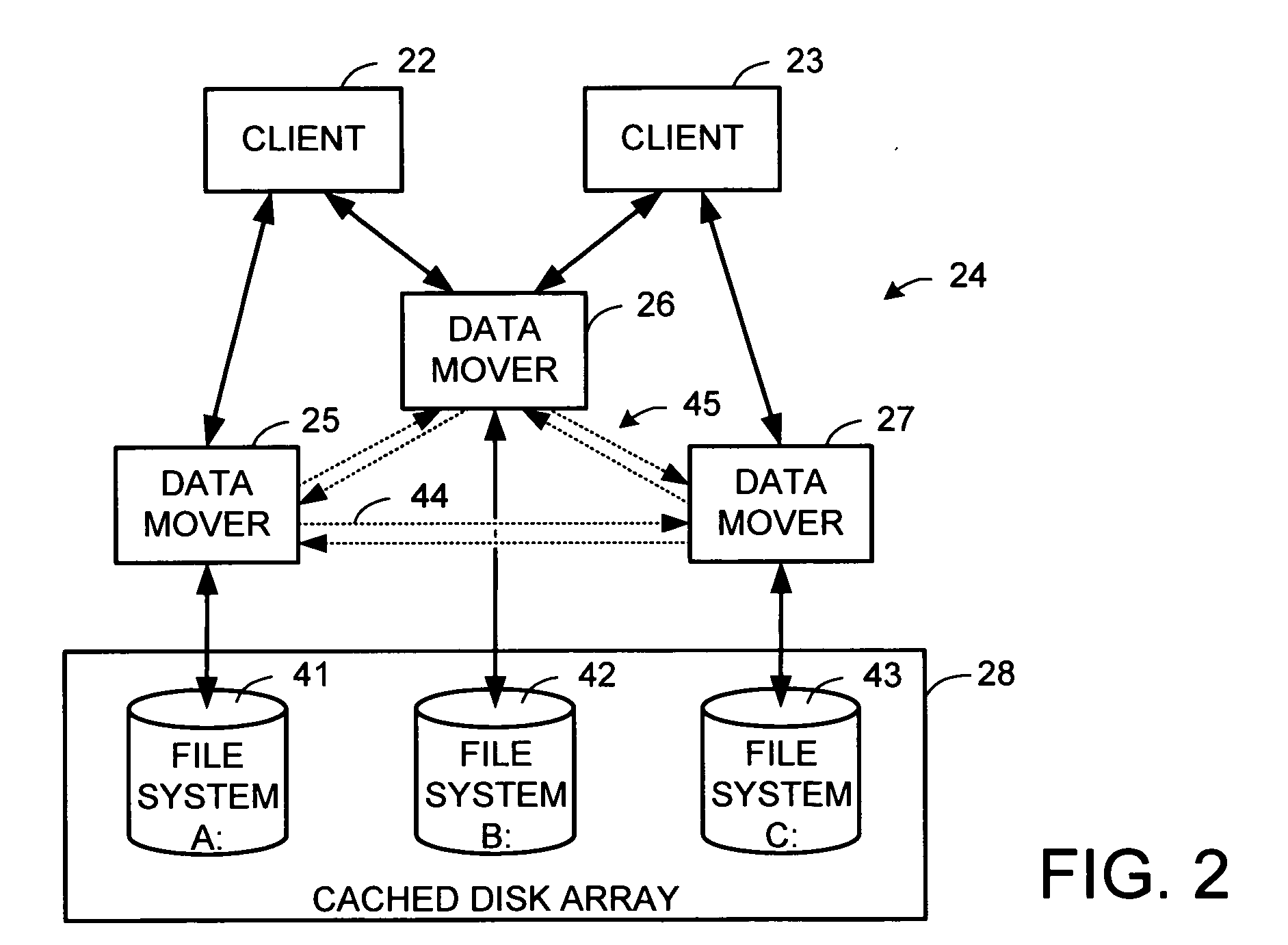
File server system using file system storage, data movers, and an exchange of meta data among data movers for file locking and direct access to shared file systems
InactiveUS6324581B1Digital data information retrievalMultiple digital computer combinationsFile systemData access
A plurality of data mover computers control access to respective file systems in data storage. A network client serviced by any of the data movers can access each of the file systems. If a data mover receives a client request for access to a file in a file system to which access is controlled by another data mover, then the data mover that received the client request sends a metadata request to the data mover that controls access to the file system. The data mover that controls access to the file system responds by placing a lock on the file and returning metadata of the file. The data mover that received the client request uses the metadata to formulate a data access command that is used to access the file data in the file system over a bypass data path that bypasses the data mover computer that controls access to the file system.
Owner:EMC IP HLDG CO LLC
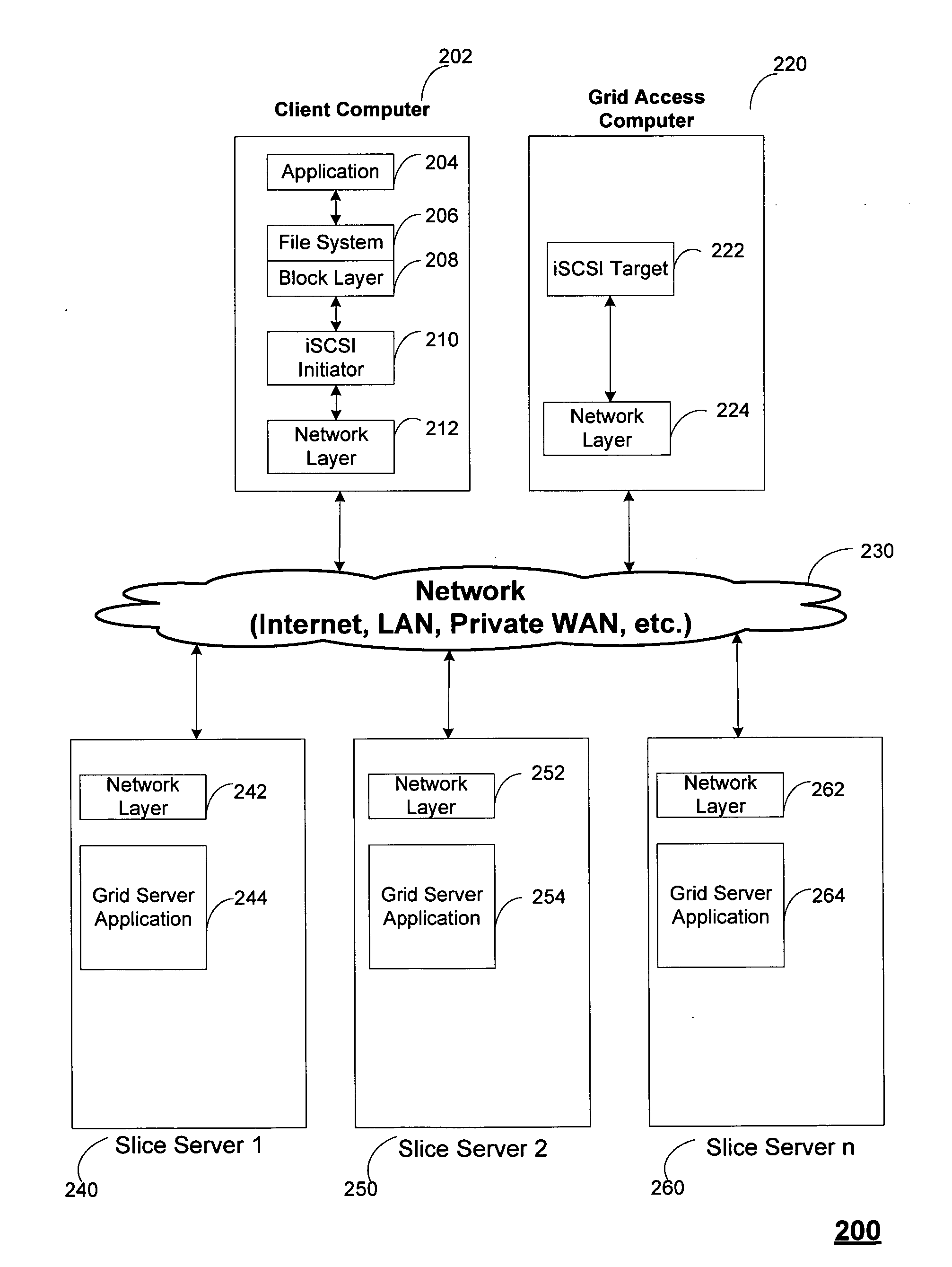
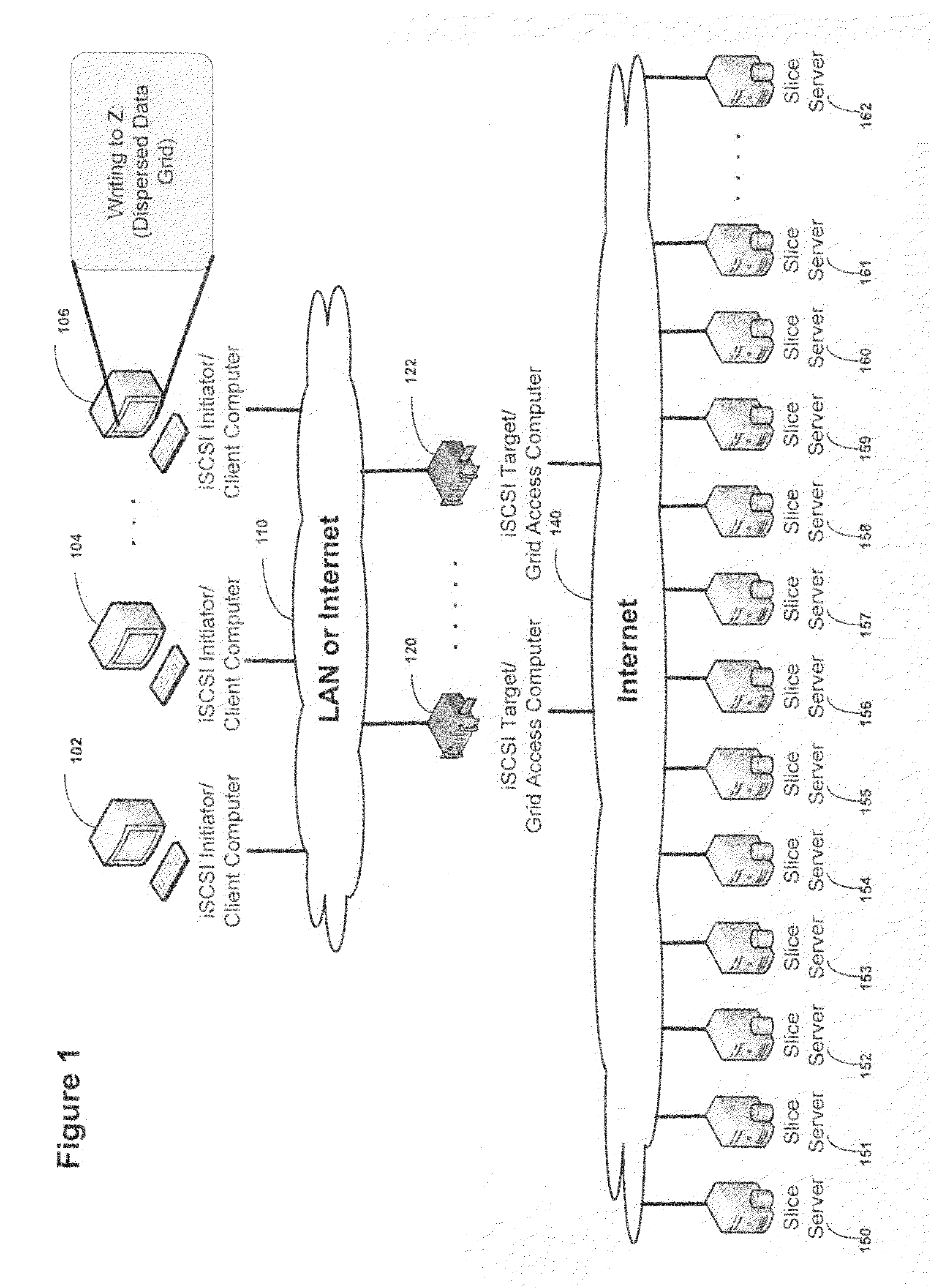
Block based access to a dispersed data storage network
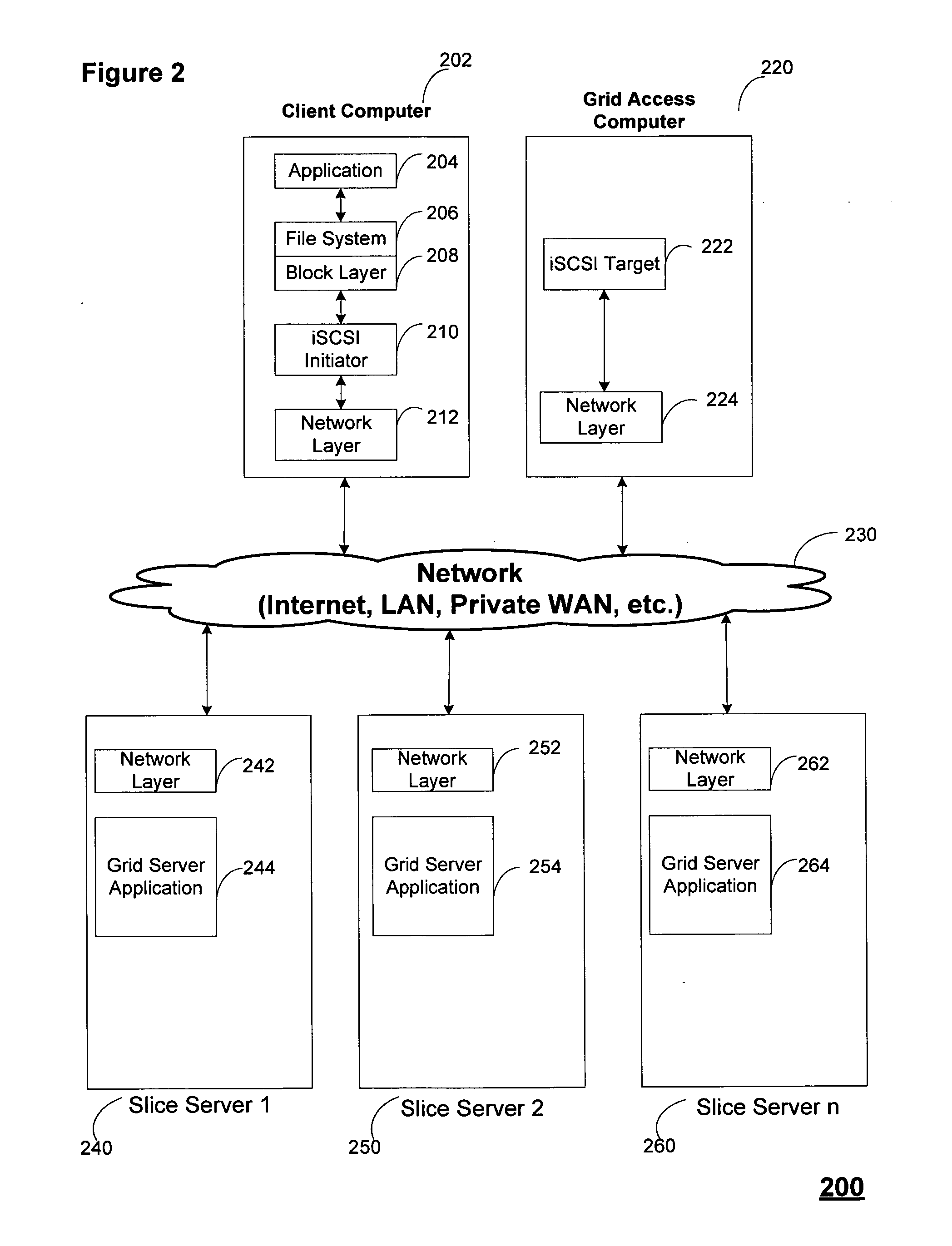
ActiveUS20100023524A1Simple methodDigital data processing detailsError detection/correctionFile systemData store
A block-based interface to a dispersed data storage network is disclosed. The disclosed interface accepts read and write commands from a file system resident on a user's computer and generates network commands that are forwarded to slice servers that form the storage component of the dispersed data storage network. The slice servers then fulfill the read and write commands.
Owner:PURE STORAGE
Peer-to-Peer Redundant File Server System and Methods
InactiveUS20090271412A1Digital data information retrievalMultiple digital computer combinationsHash functionFile system
Peer-to-peer redundant file server system and methods include clients that determine a target storage provider to contact for a particular storage transaction based on a pathname provided by the filesystem and a predetermined scheme such as a hash function applied to a portion of the pathname. Servers use the same scheme to determine where to store relevant file information so that the clients can locate the file information. The target storage provider may store the file itself and / or may store metadata that identifies one or more other storage providers where the file is stored. A file may be replicated in multiple storage providers, and the metadata may include a list of storage providers from which the clients can select (e.g., randomly) in order to access the file.
Owner:OVERLAND STORAGE
File system shell
InactiveUS20060036568A1Adapt quicklyDigital data information retrievalSpecial data processing applicationsView basedProject type
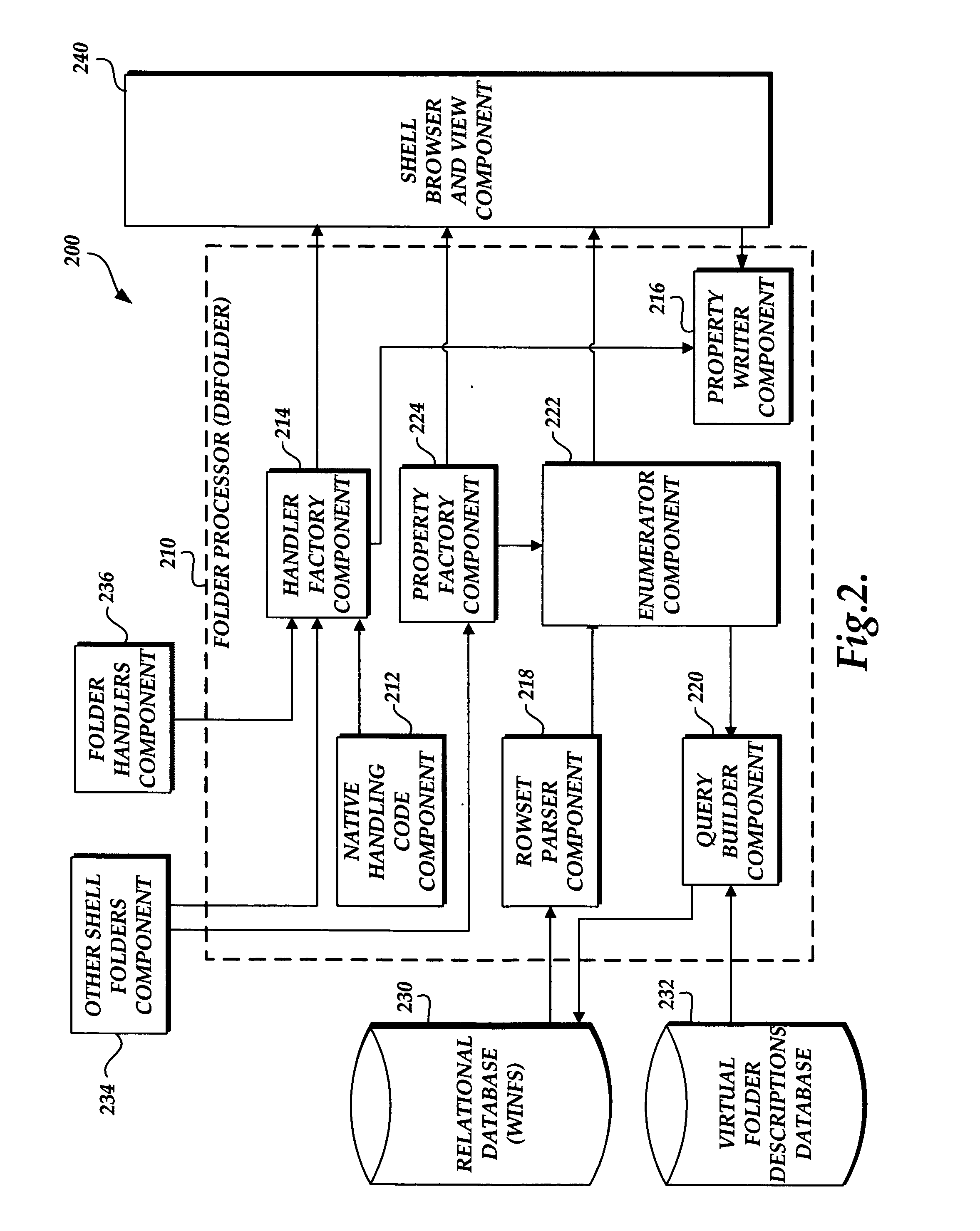
A file system shell is provided. One aspect of the shell provides virtual folders which expose regular files and folders to users in different views based on their metadata instead of the actual physical underlying file system structure on the disk. Users are able to work with the virtual folders through direct manipulation (e.g., clicking and dragging, copying, pasting, etc.). Filters are provided for narrowing down sets of items. Quick links are provided which can be clicked on to generate useful views of the sets of items. Libraries are provided which consist of large groups of usable types of items that can be associated together, along with functions and tools related to the items. A virtual address bar is provided which comprises a plurality of segments, each segment corresponding to a filter for selecting content. A shell browser is provided with which users can readily identify an item based on the metadata associated with that item. An object previewer in a shell browser is provided which is configured to display a plurality of items representing multiple item types.
Owner:MICROSOFT TECH LICENSING LLC
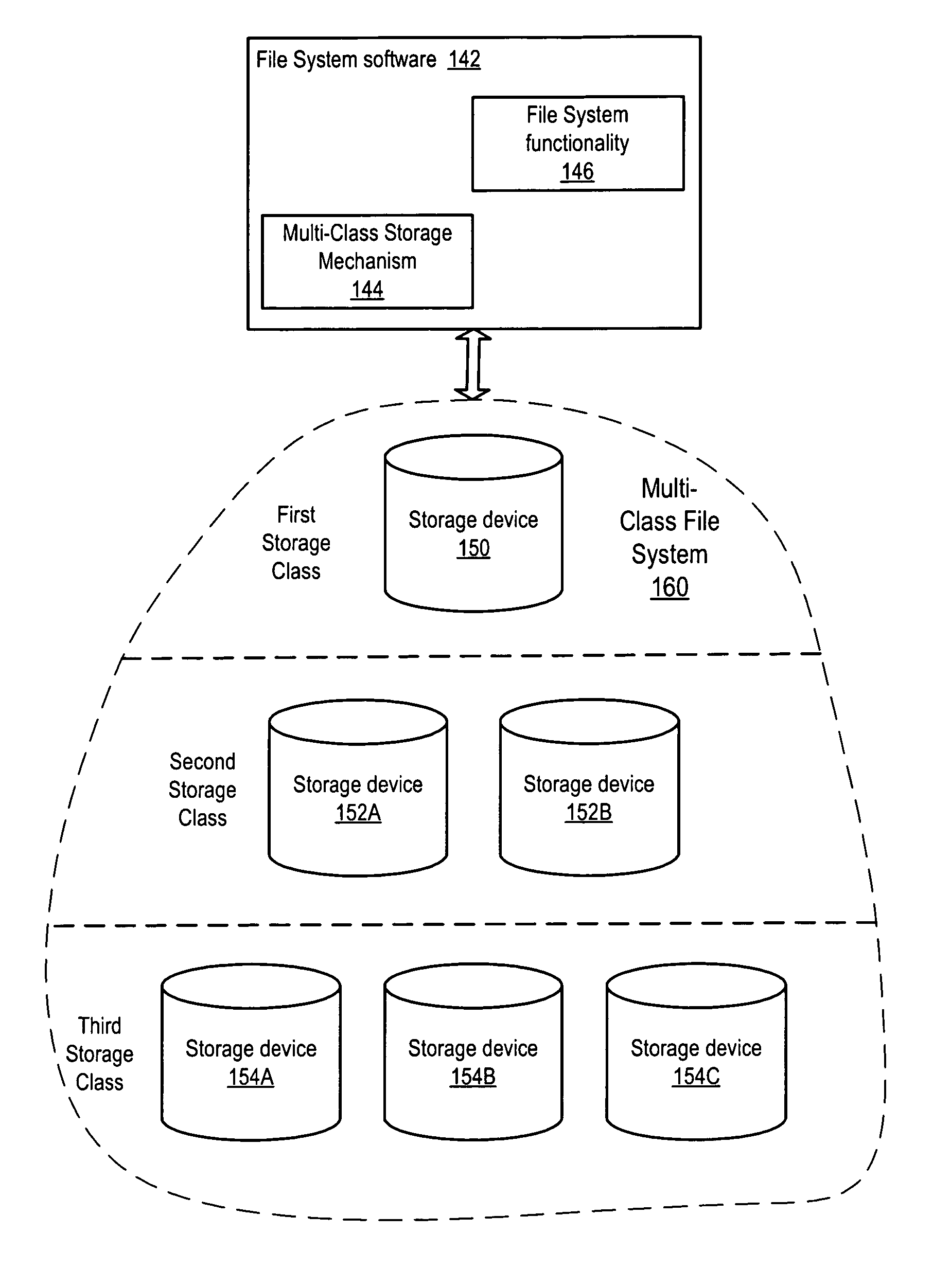
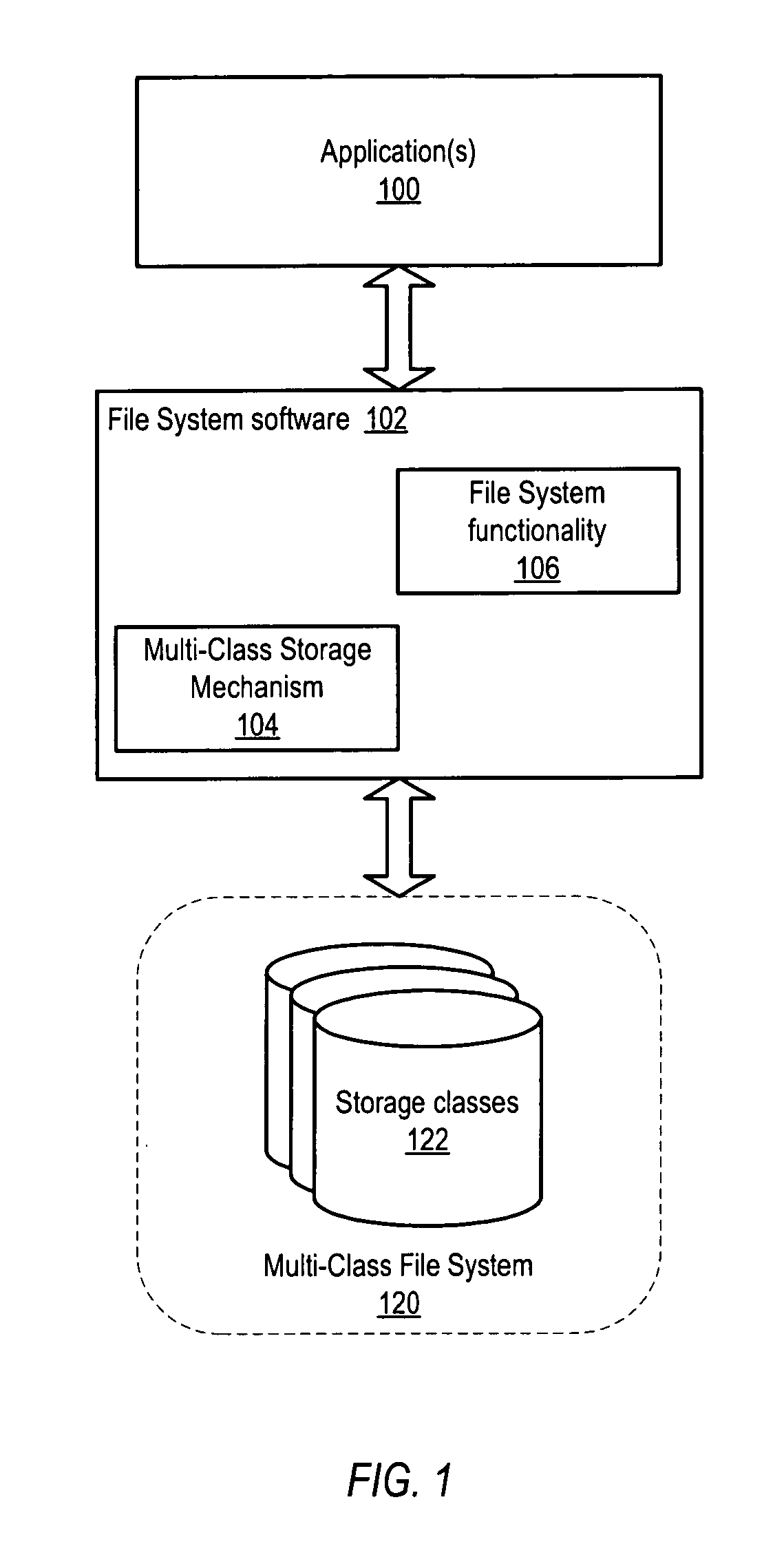
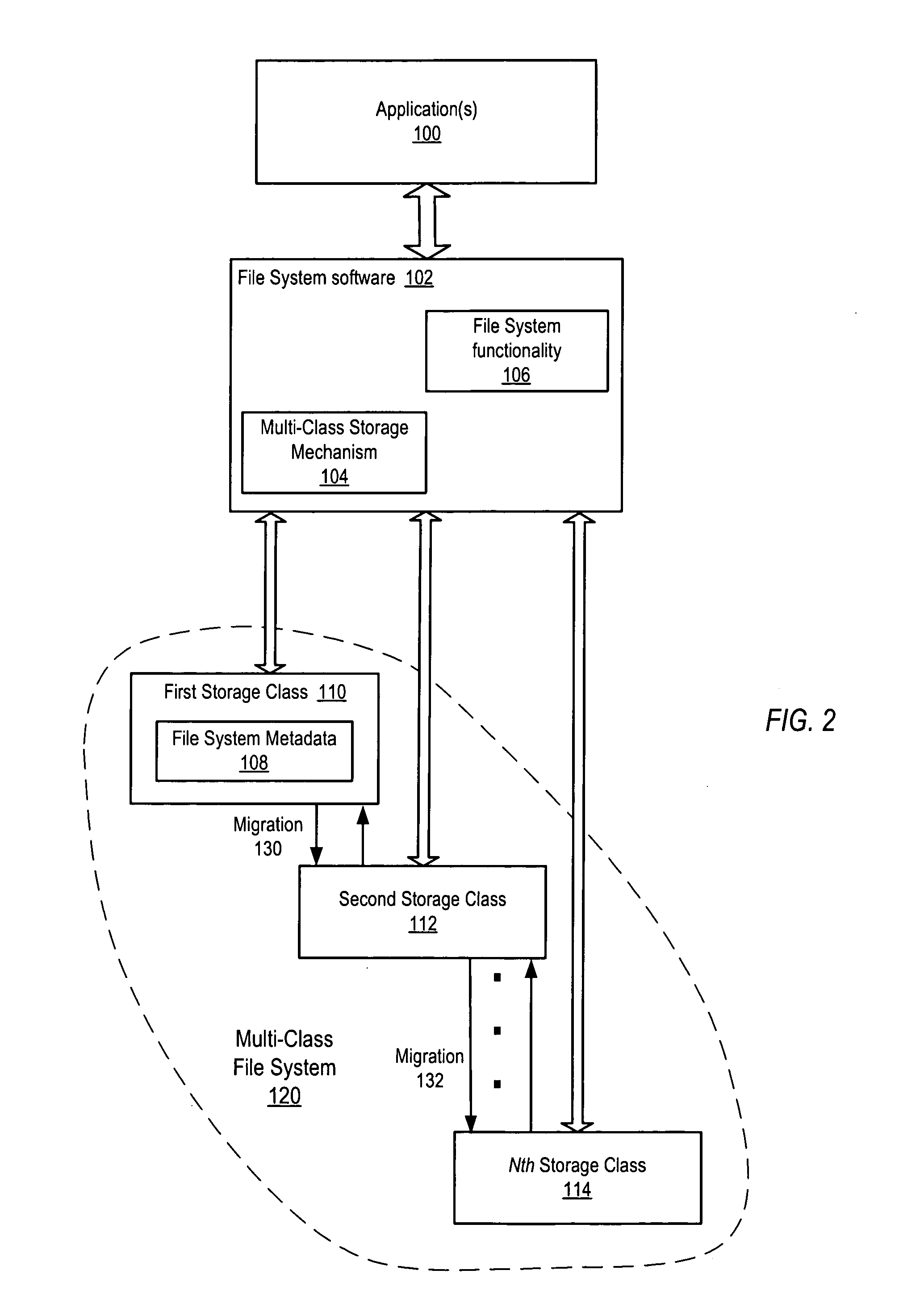
Backup mechanism for a multi-class file system
ActiveUS7103740B1Reduce in quantityData processing applicationsError detection/correctionFile systemComputer science
System and method for performing backups of a multi-class file system are described. In one embodiment, more recently modified data may be assigned and / or migrated to higher storage classes and less recently modified data may be migrated at time intervals to lower storage classes in the multi-class file system. Backups of each of the storage classes may be performed at time intervals. In one embodiment, the backups may be image-based backups of the storage devices in the storage classes. In one embodiment, the lower storage classes may include one or more read-only storage classes including less-recently modified data that are backed up less frequently than higher storage classes including more-recently modified data. In one embodiment, files migrated to lower storage class(es) may be compressed.
Owner:SYMANTEC OPERATING CORP
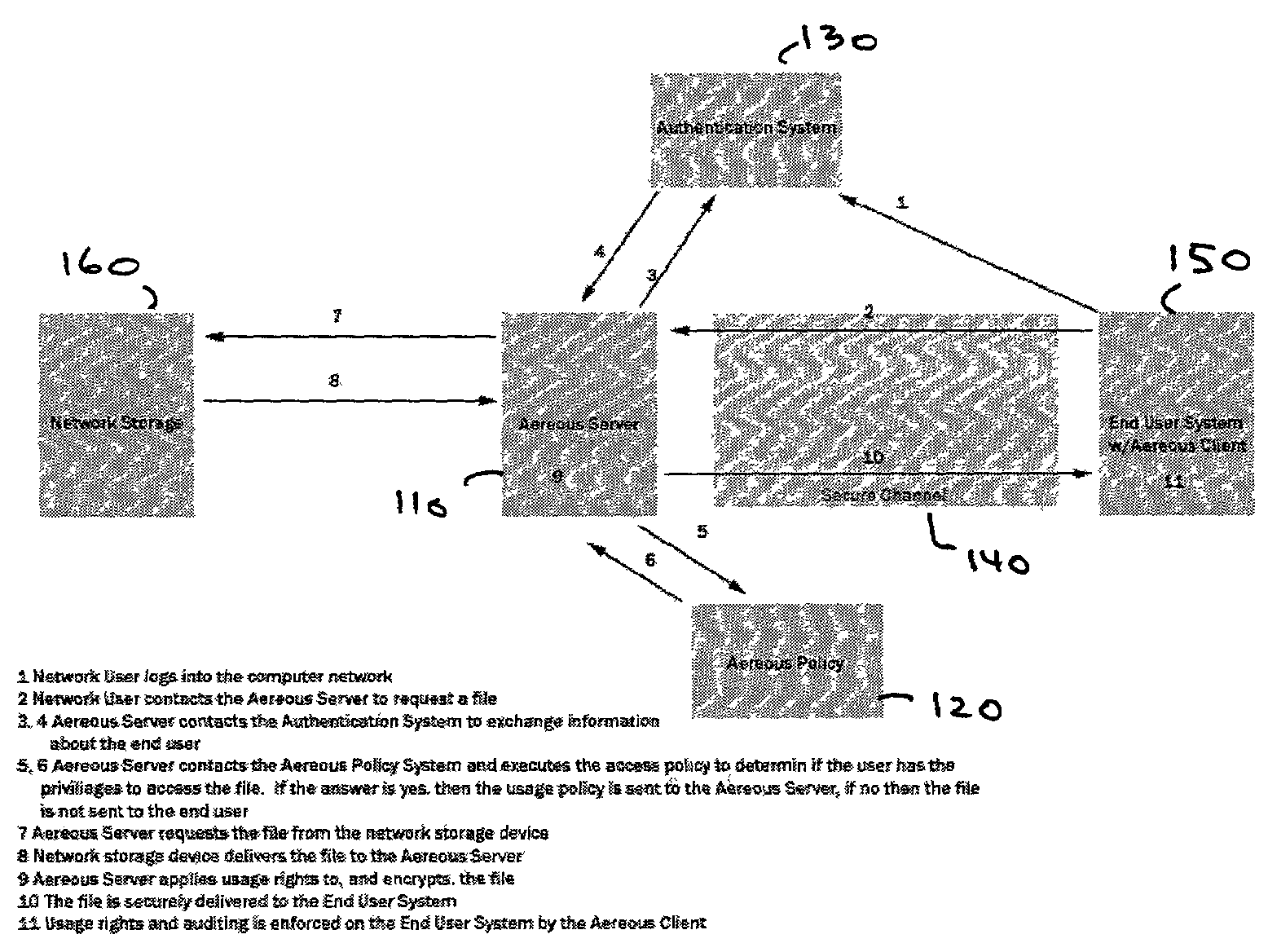
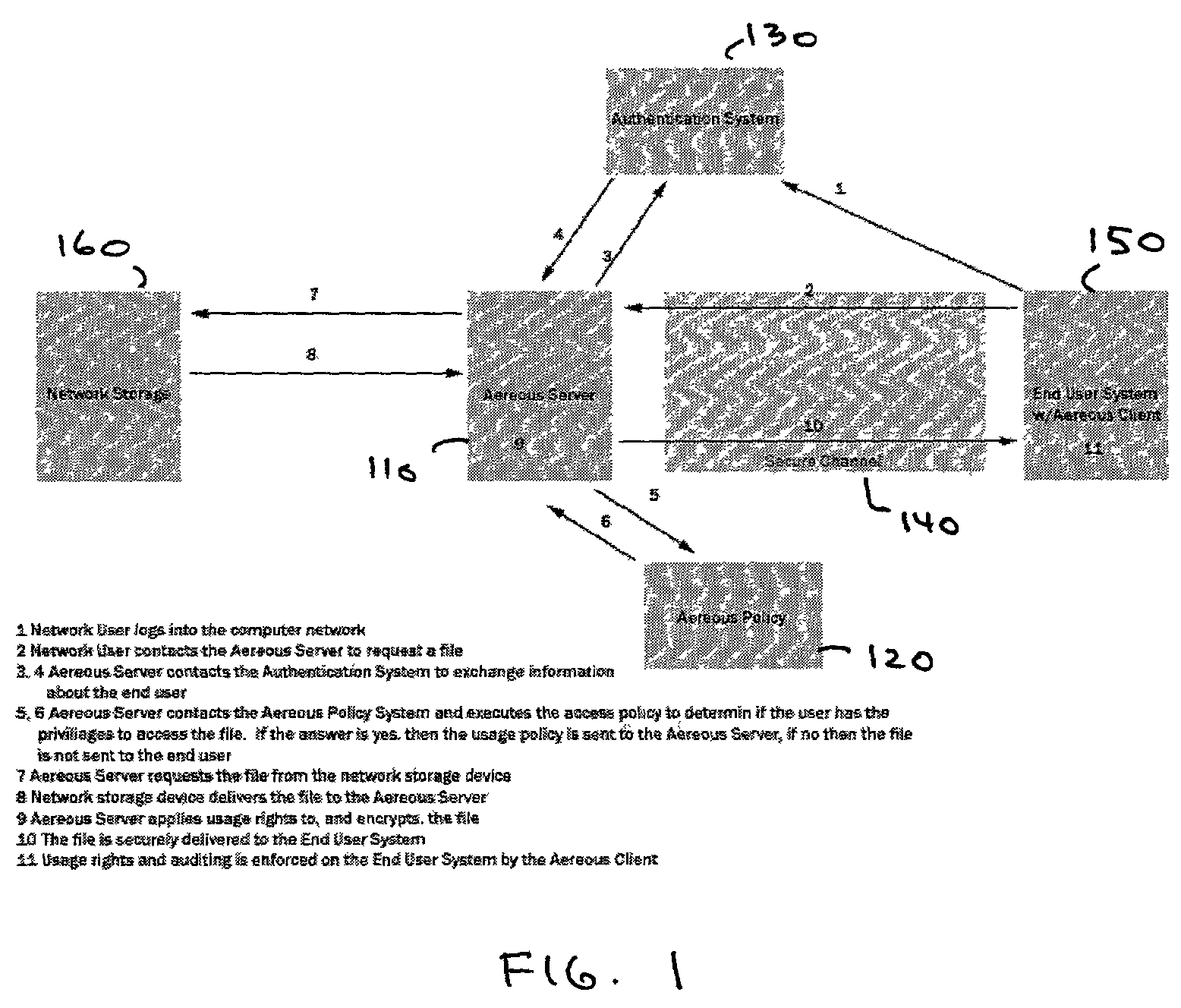
Dynamic file access control and management
InactiveUS7660902B2Improve securitySelectively accessedComputer security arrangementsMultiple digital computer combinationsDistributed File SystemFile system
A dynamic file access control and management system and method in accordance with the present invention may be a proxy file management system that includes one or more file system proxy servers that provide selective access and usage management to files available from one or more file systems or sources. The present invention may embody a secure transport protocol that tunnels distributed file systems, application independent usage controls connected to files on end-user computers, dynamically merging secondary content to a requested file, and applying bandwidth management to any of the foregoing. Embodied in the various implementations of the present invention is enhanced file security. Preferably, the proxy file management system is transparent to an end-user. A dynamic content management system may also be included that selectively adds content to requested files.
Owner:EMC IP HLDG CO LLC
Design pattern for secure store
ActiveUS20150220753A1Improve securityDigital data processing detailsAnalogue secracy/subscription systemsPathPingFile system
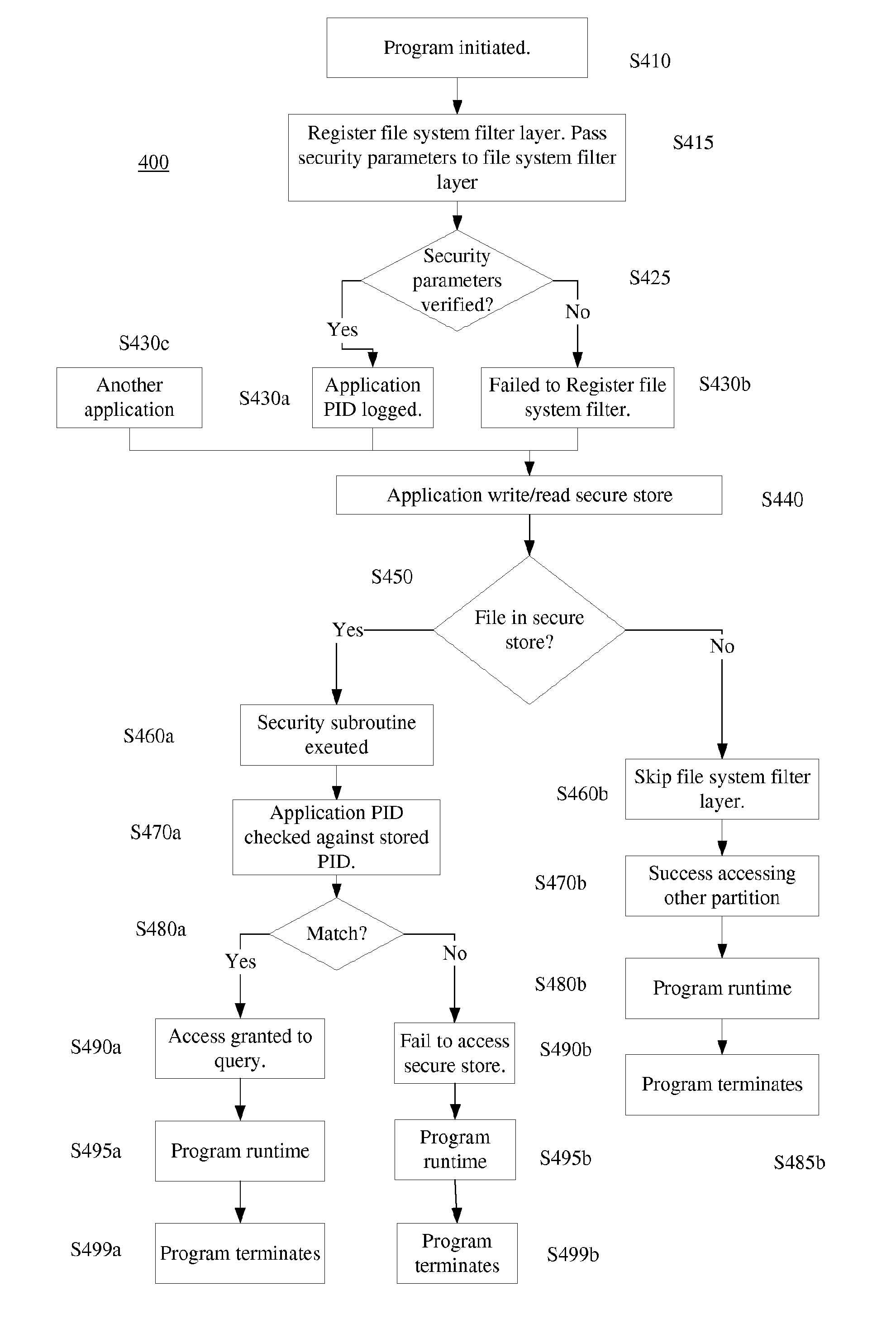
A computer system, computer product, and method for accessing a secure store, which includes receiving a request to access a secure store, checking the file path of the request to make sure it exists in the secure store, verifying security parameters from the process at the file system filter layer, saving the PID of the process by the file system filter layer, comparing the saved PID to the process's PID, and allowing the process to access the path in the secure store specified in the request.
Owner:HONEYWELL INT INC
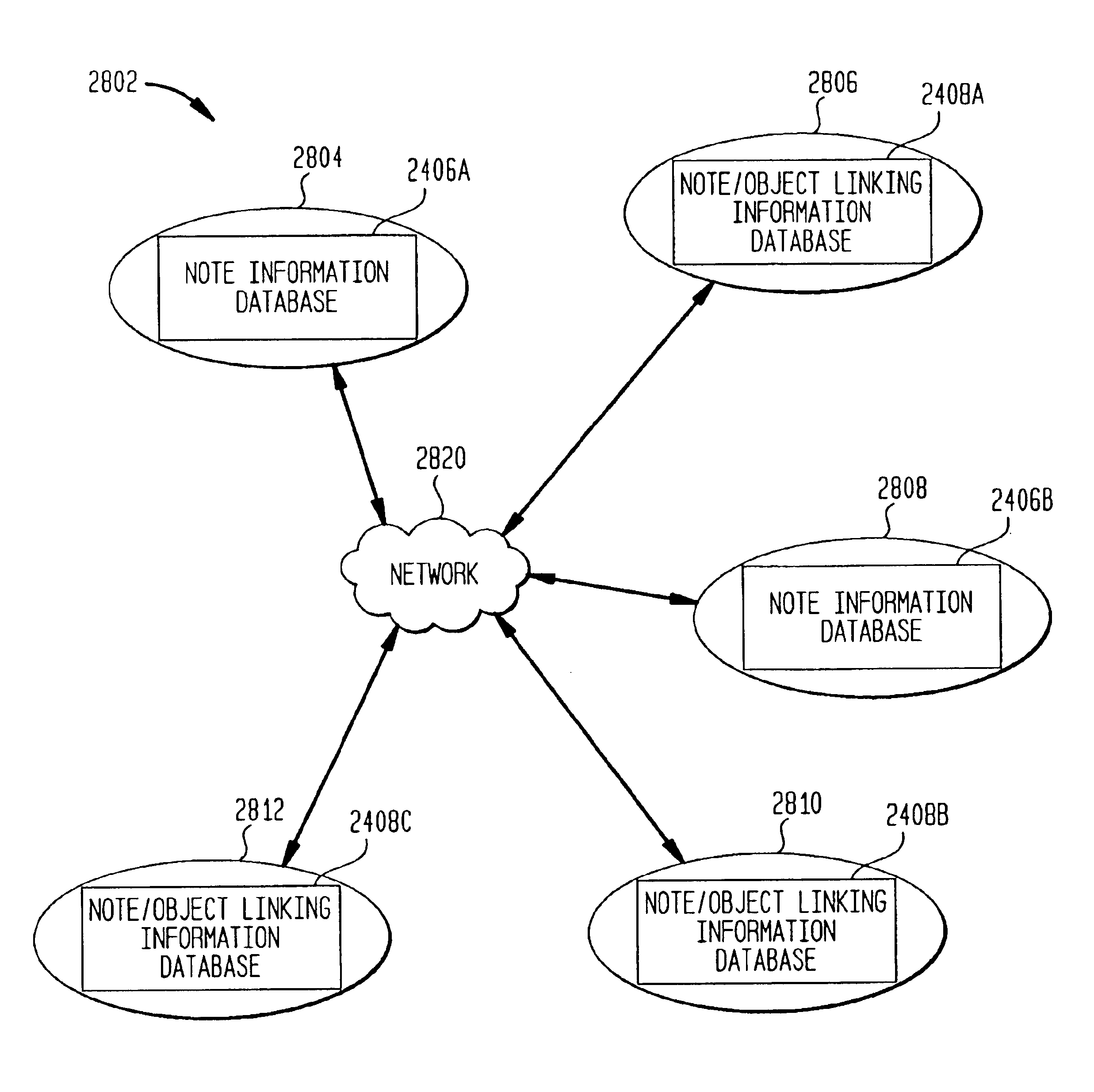
System, method and computer program product for mediating notes and note sub-notes linked or otherwise associated with stored or networked web pages
InactiveUS6877137B1Digital data processing detailsSpecial data processing applicationsWeb siteFile system
A system and method of manipulating notes linked to Web pages, and of manipulating the Web pages. These Web pages (or portions of Web pages) can be stored at a Web site or in a local file system. The method of linking notes to Web pages operates by enabling a user to select a portion of a Web page, creating a annotation, linking the annotation to the selected portion, receiving a request from a user viewing the annotation to display the selected portion linked to the annotation, and invoking an application, if the application is not already invoked, and for causing the application to load the Web page and present the selected portion.
Owner:ROSE BLUSH SOFTWARE +1
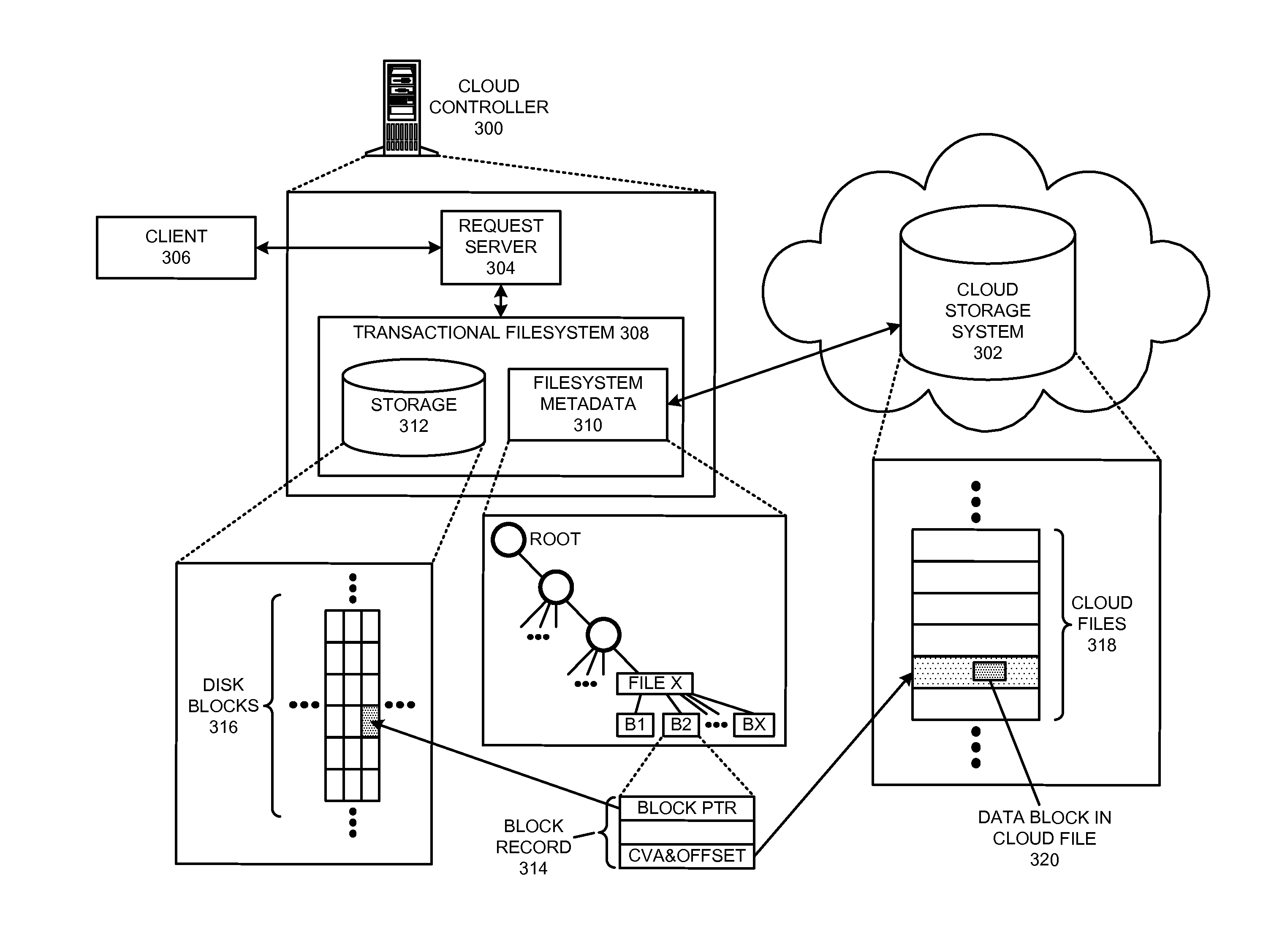
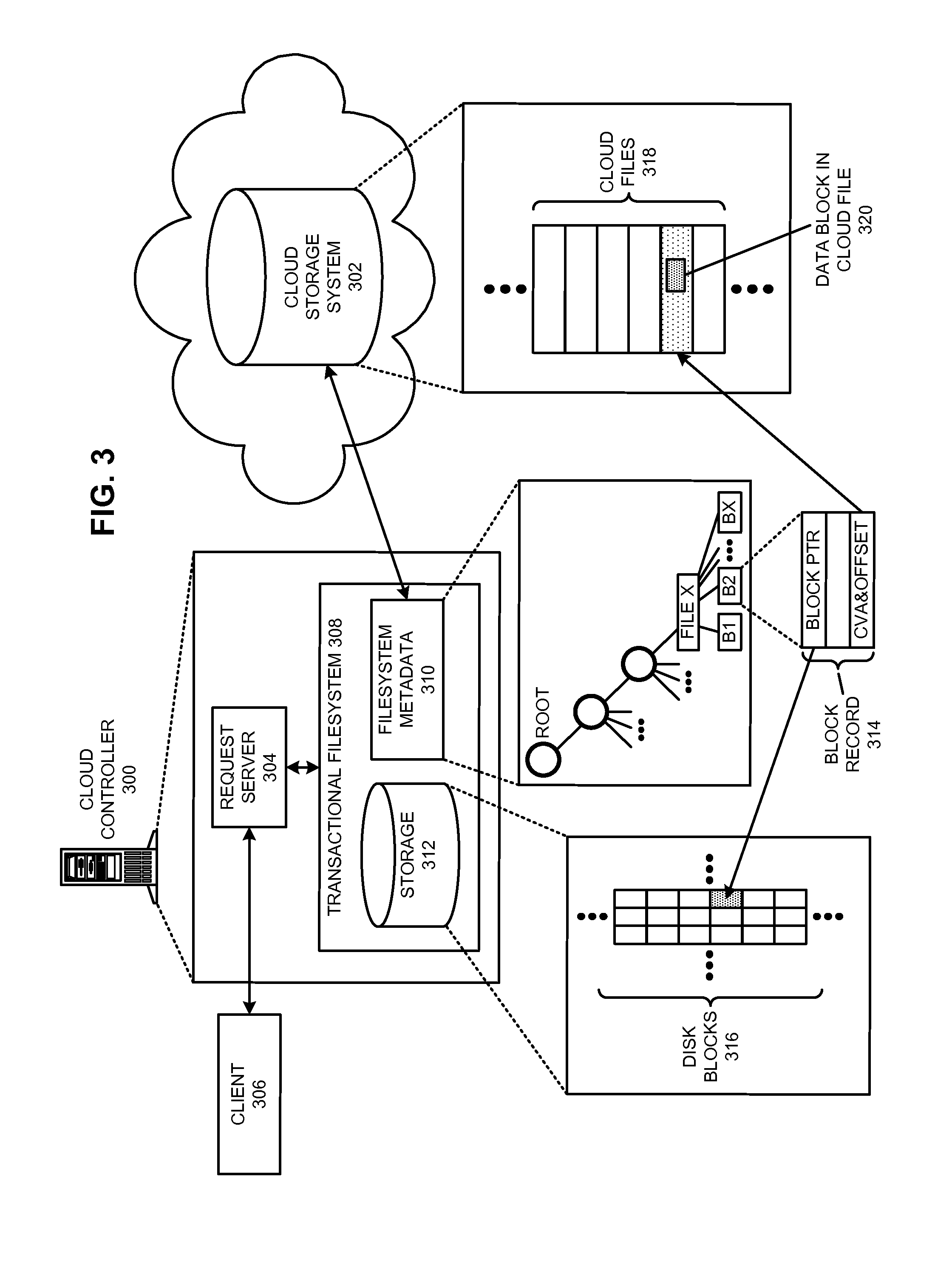
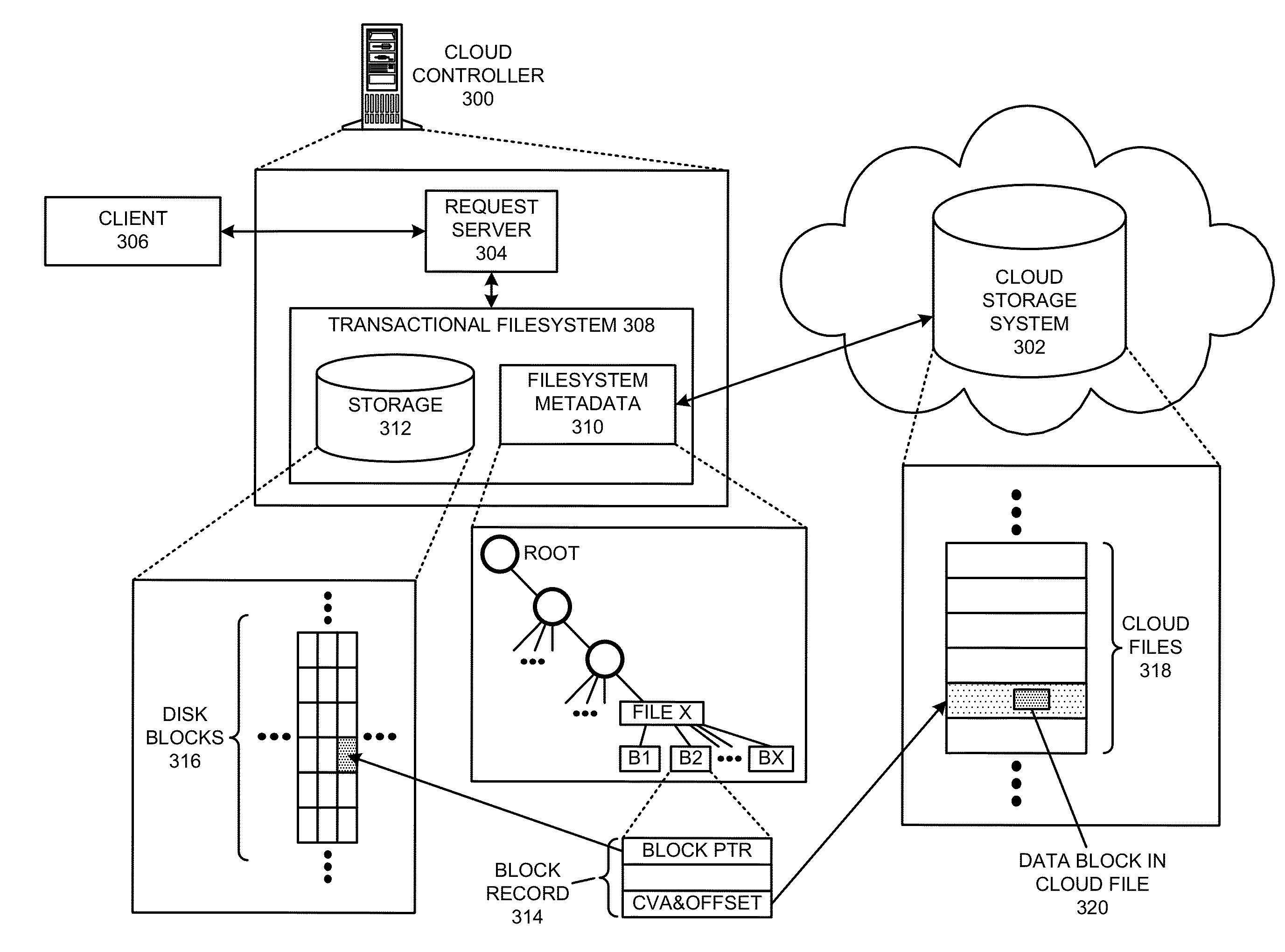
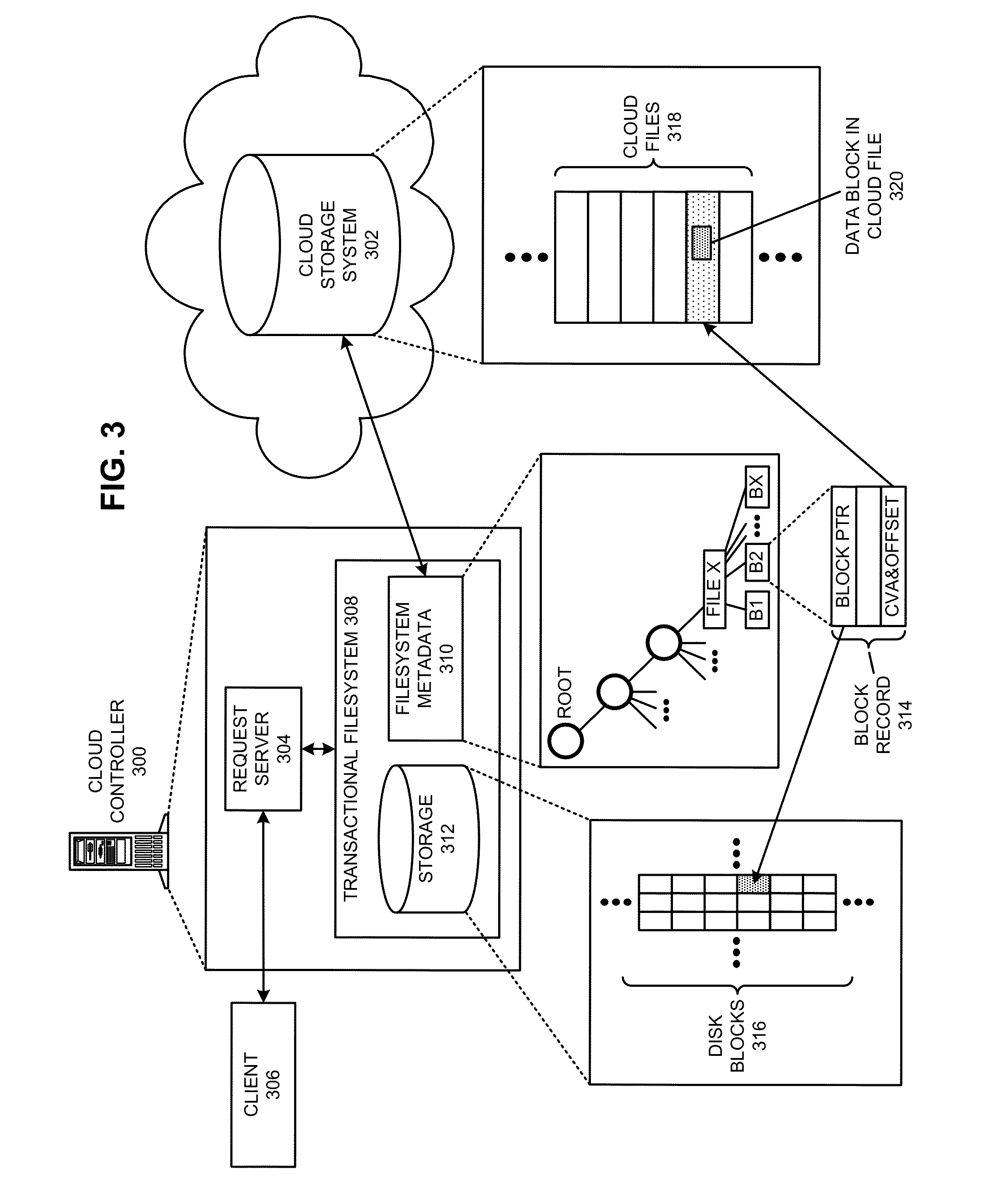
Managing a global namespace for a distributed filesystem
ActiveUS20140006465A1Outweigh additional overheadIncreasing file access performanceDigital data information retrievalSpecial data processing applicationsFile systemCloud storage system
The disclosed embodiments disclose techniques for managing a global namespace for a distributed filesystem. Two or more cloud controllers collectively manage distributed filesystem data that is stored in a cloud storage system; the cloud controllers ensure data consistency for the stored data, and each cloud controller caches portions of the distributed filesystem. Furthermore, a global namespace for the distributed filesystem is also split across these cloud controllers, with each cloud controller “owning” (e.g., managing write accesses for) a distinct portion of the global namespace and maintaining a set of namespace mappings that indicate which portion of the namespace is assigned to each cloud controller. During operation, an initial cloud controller receives a request from a client system to access a target file in the distributed system. This initial cloud controller uses the namespace mappings for the global namespace to determine a preferred cloud controller that will handle the request.
Owner:PANZURA LLC
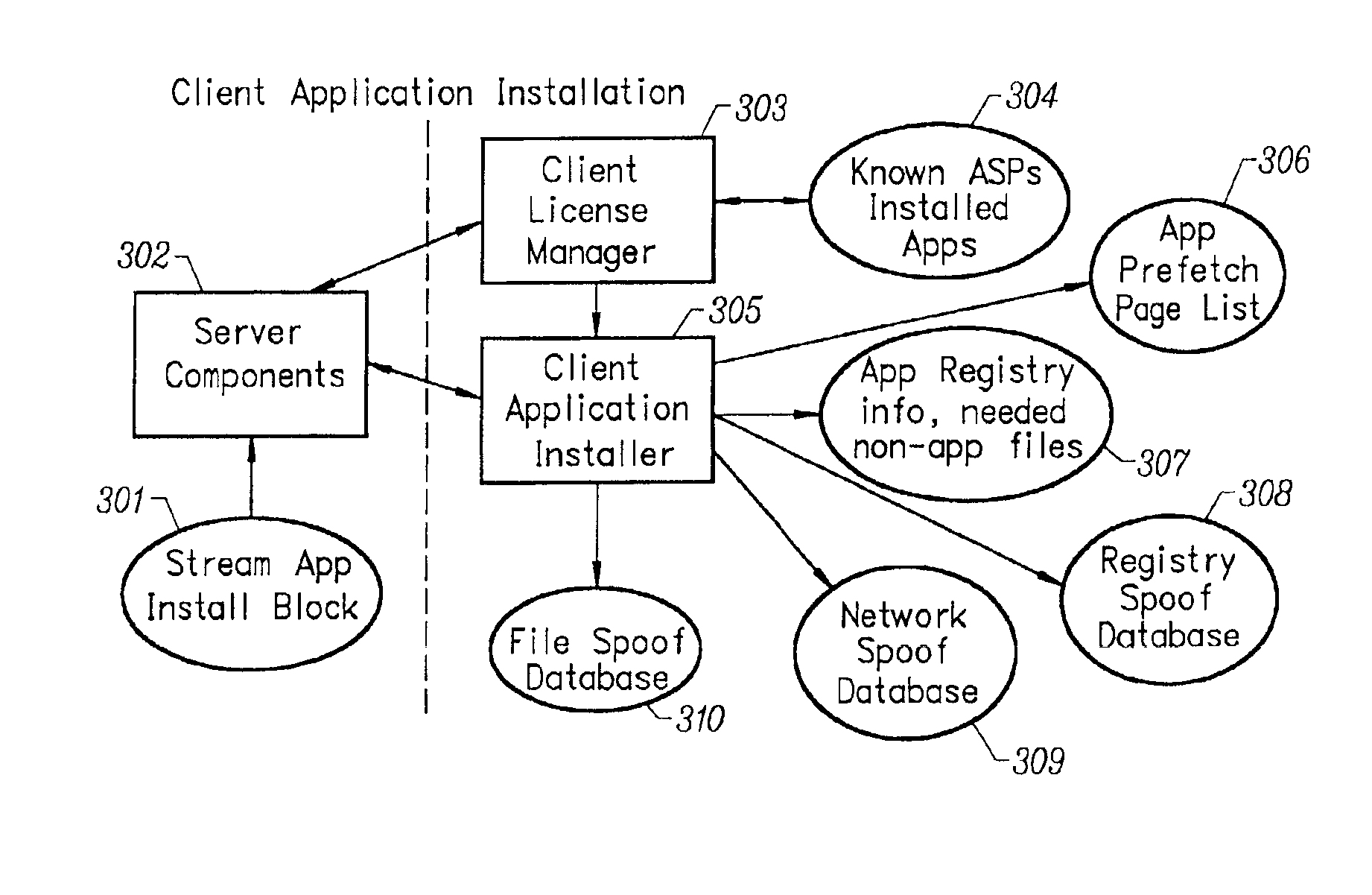
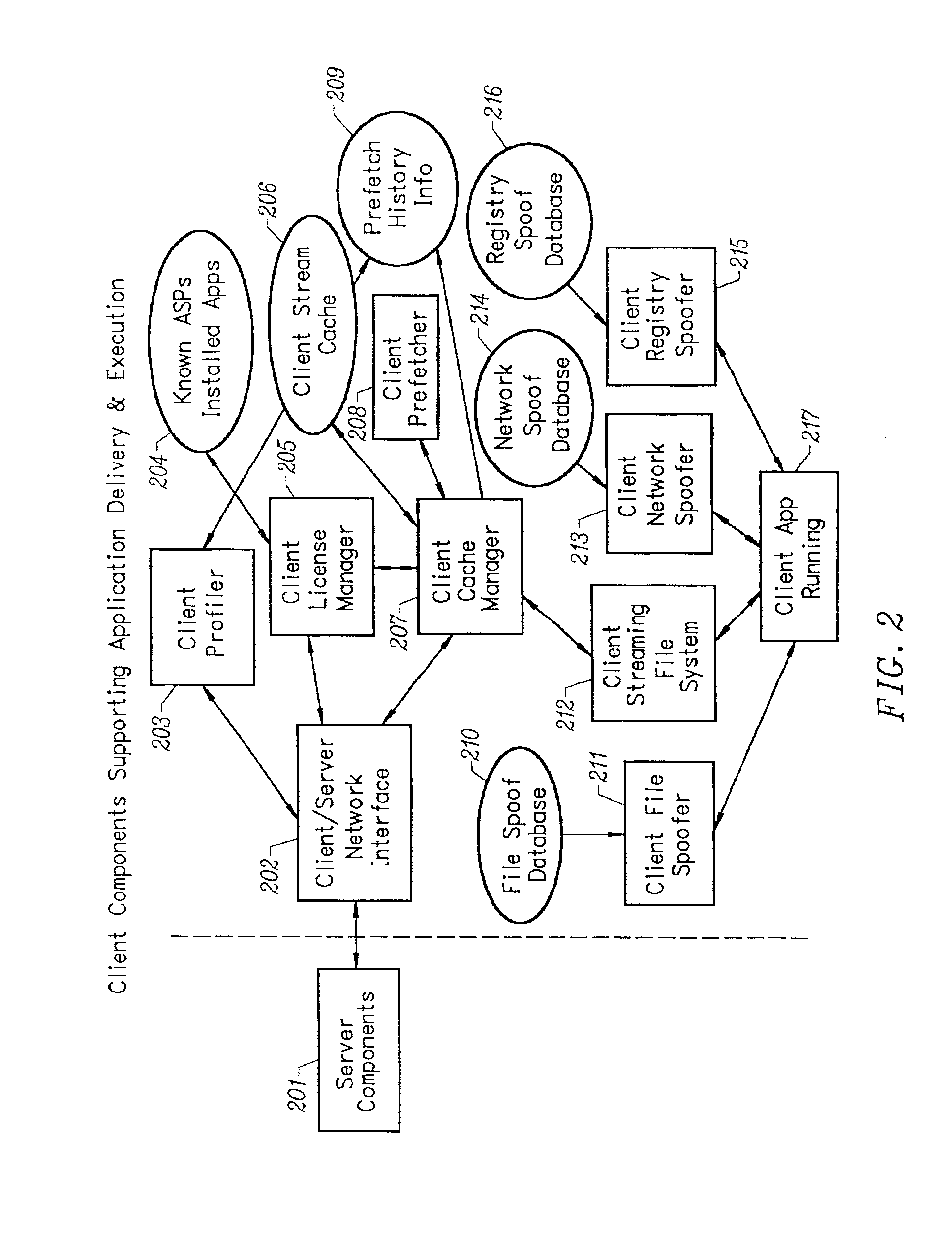
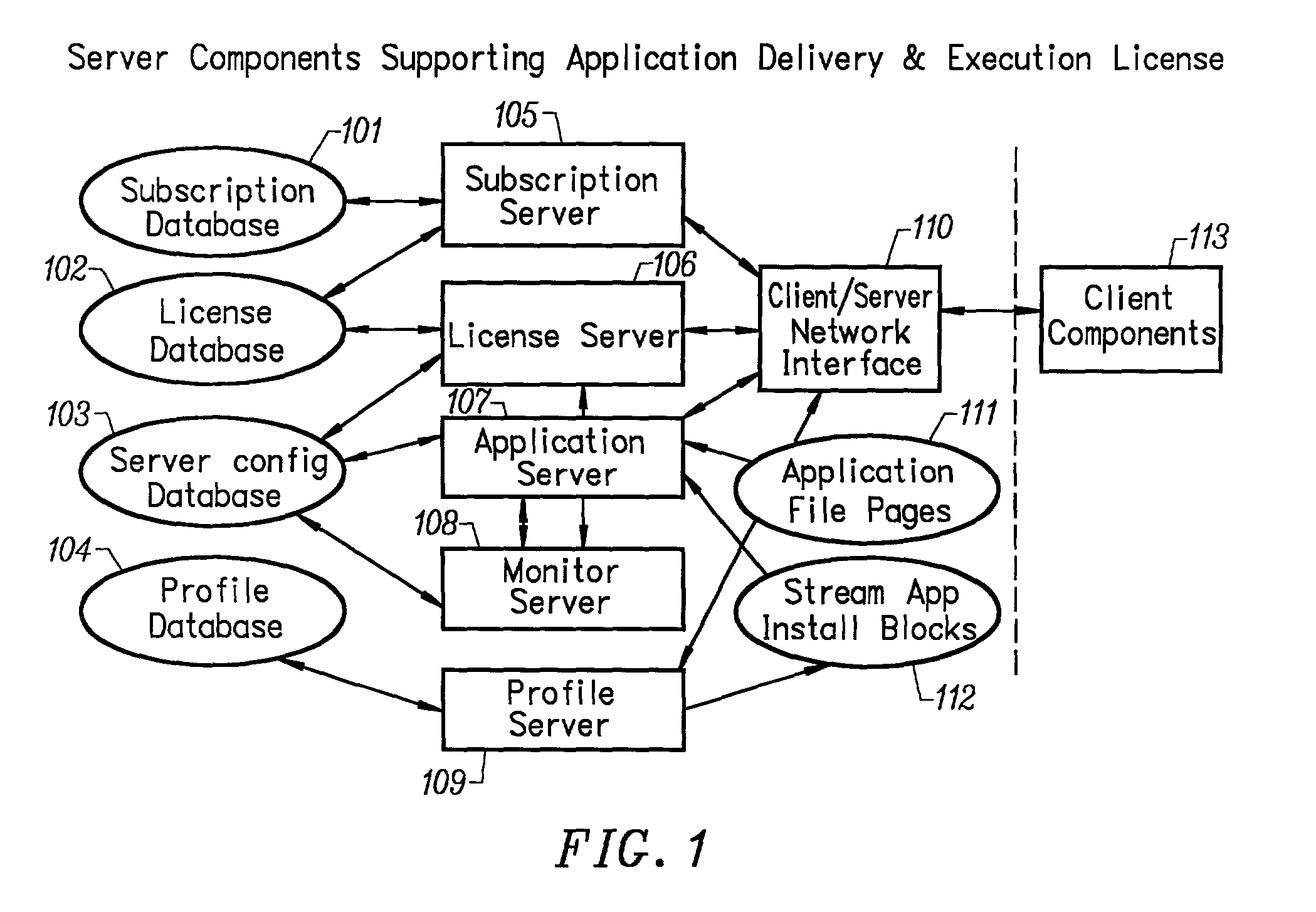
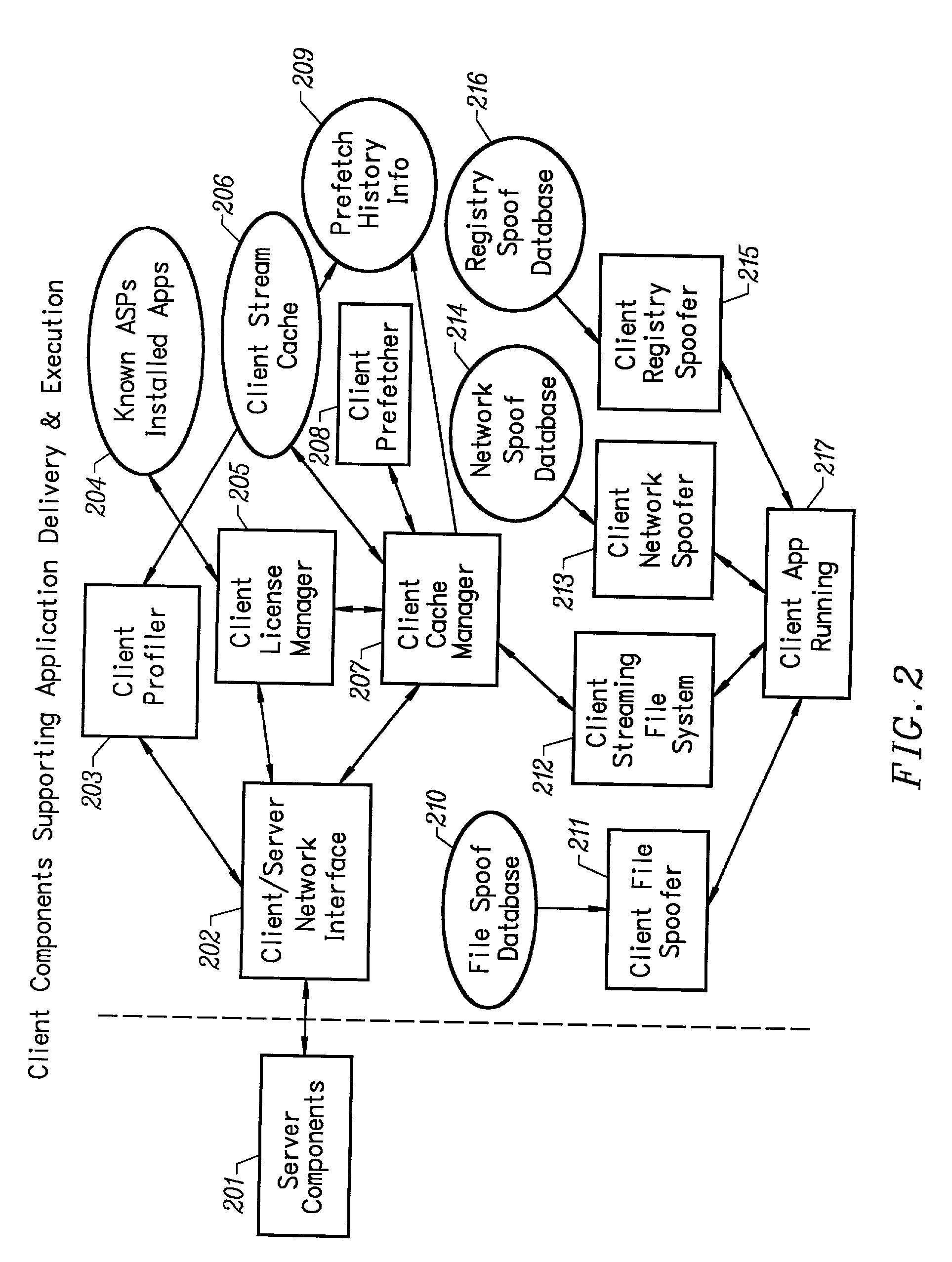
Client installation and execution system for streamed applications
InactiveUS6918113B2Multiple digital computer combinationsProgram loading/initiatingRegistry dataFile system
Owner:NUMECENT HLDG +1
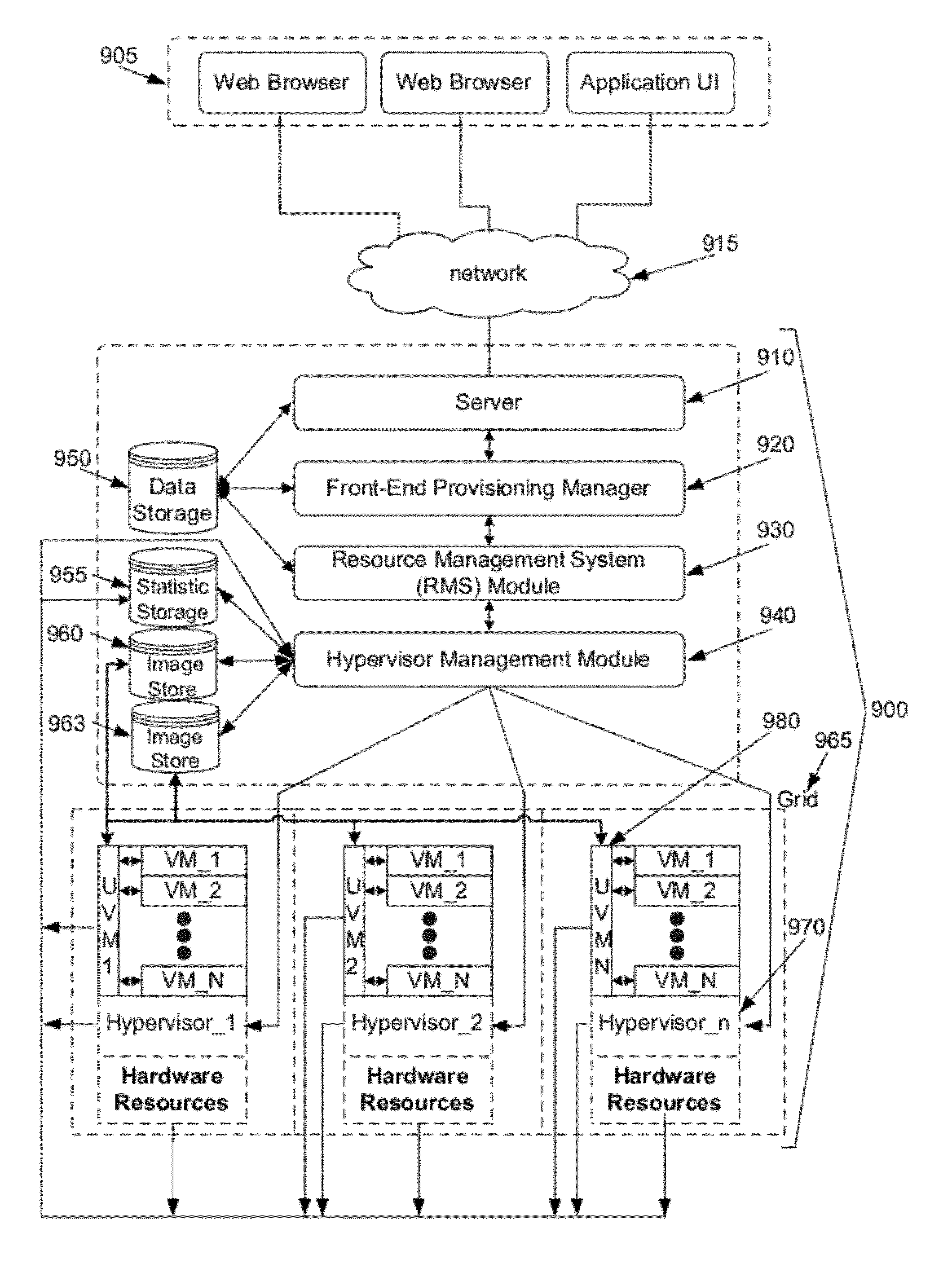
System and method for automated configuration of hosting resources
ActiveUS8352608B1Facilitate efficient deploymentMaximize useDigital computer detailsProgram controlAuto-configurationFile system
Some embodiments provide a method for automated configuration of a set of resources for hosting a virtual machine at a particular node in a hosting system. The hosting system includes several nodes for hosting several virtual machines. The method, at a first virtual machine operating using a first set of resources of the particular node, receives a configuration for a second virtual machine to be hosted on a second set of resources of the particular node. The method, from the first virtual machine, accesses the second set of resources to partition a file system for storing the second virtual machine. The method modifies the file system to configure the second virtual machine as specified by the configuration.
Owner:GOOGLE LLC
Clustered file management for network resources
InactiveUS6101508AData processing applicationsProgram synchronisationFile systemClustered file system
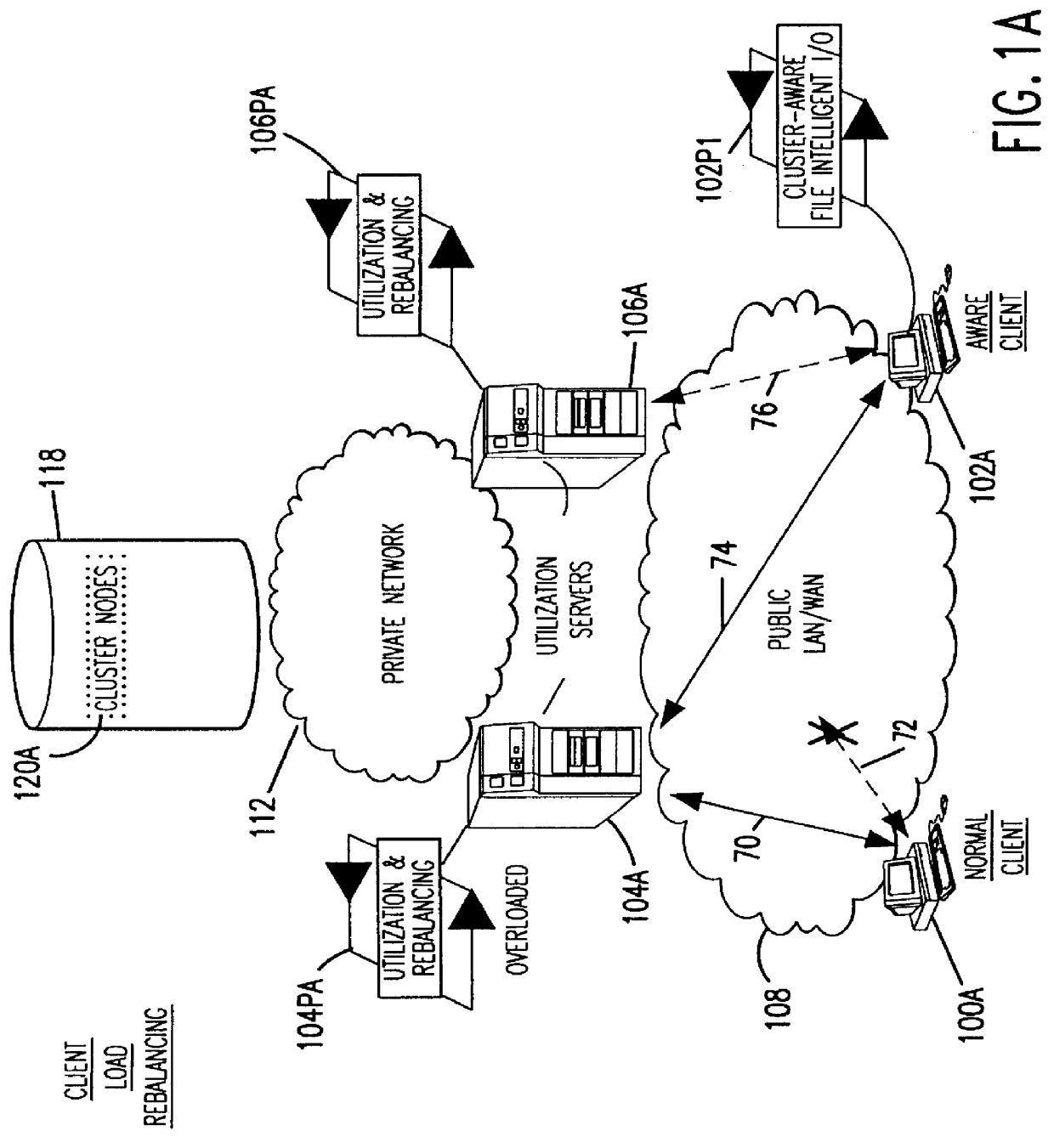
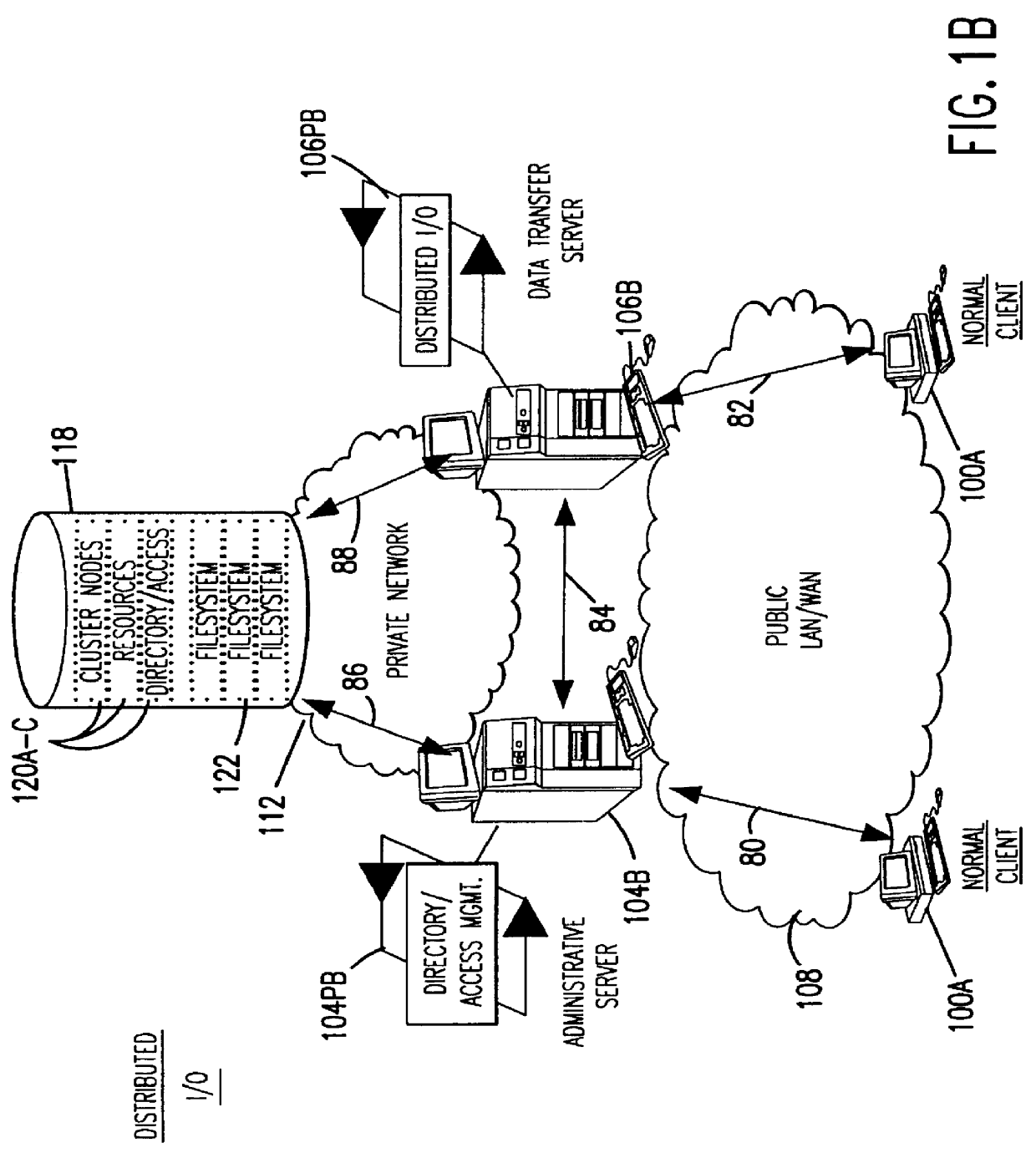
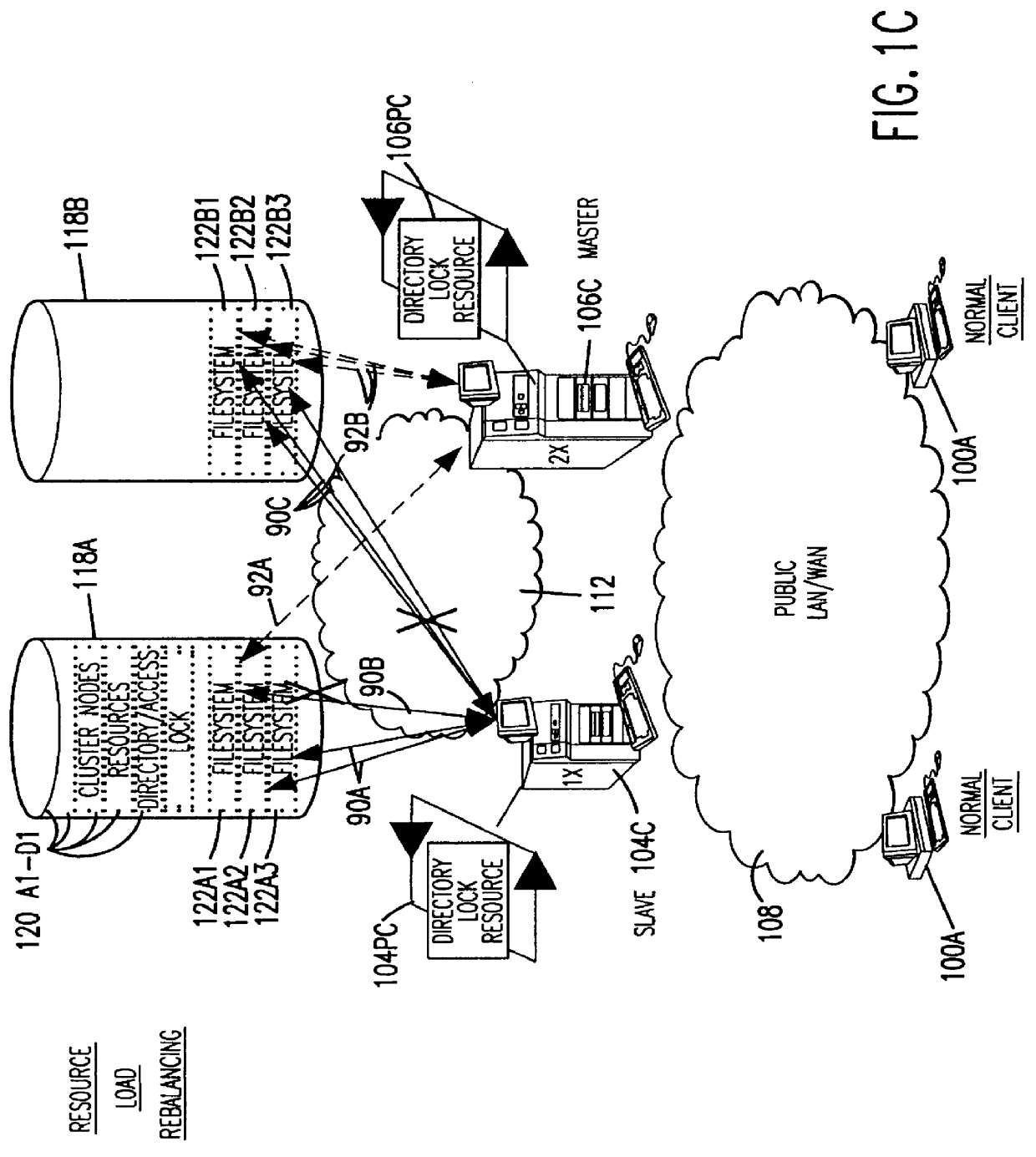
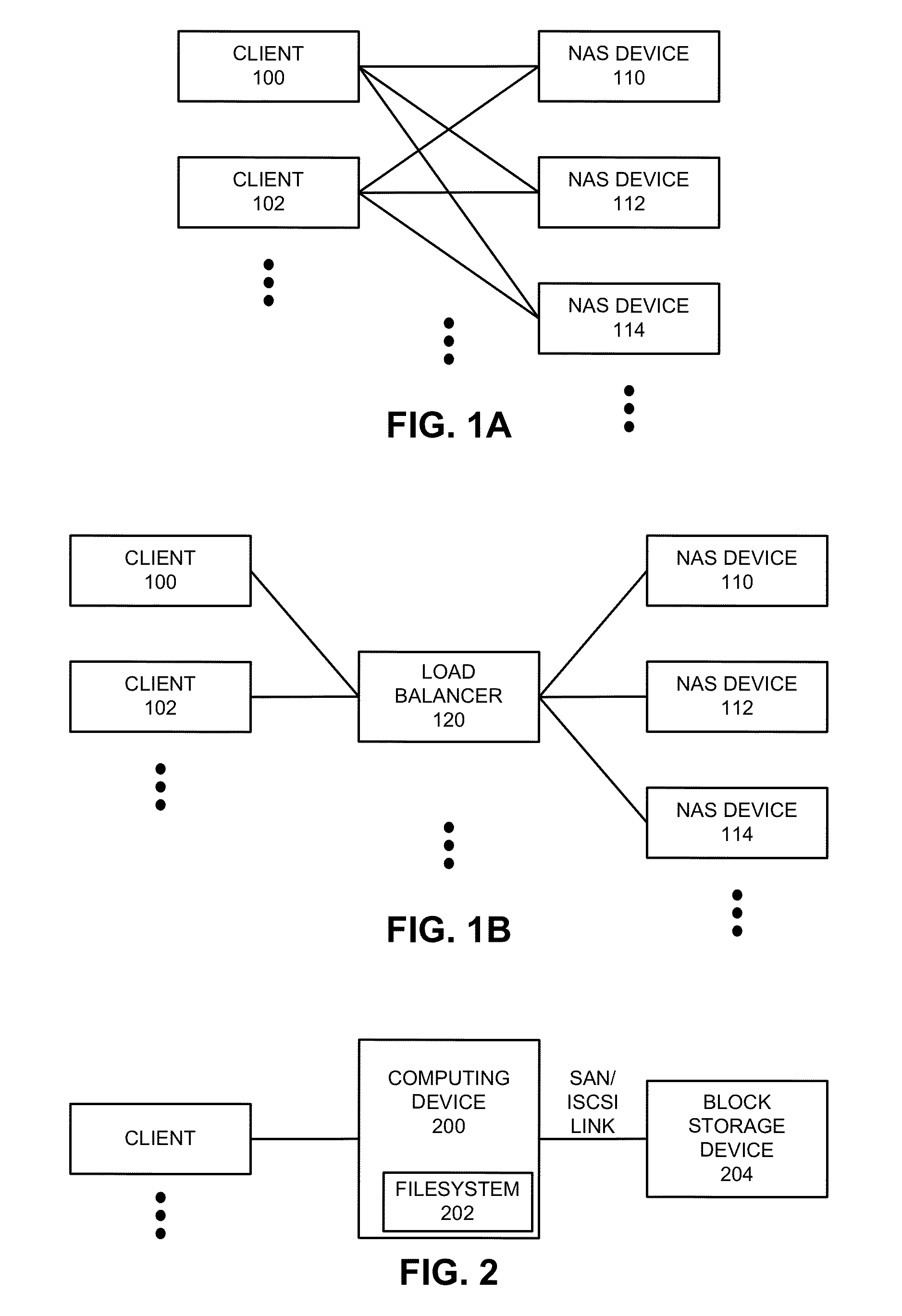
Methods for operating a network as a clustered file system is disclosed. The methods involve client load rebalancing, distributed Input and Output (I / O) and resource load rebalancing. Client load rebalancing refers to the ability of a client enabled with processes in accordance with the current invention to remap a path through a plurality of nodes to a resource. Distributed I / O refers to the methods on the network which provide concurrent input / output through a plurality of nodes to resources. Resource rebalancing includes remapping of pathways between nodes, e.g. servers, and resources, e.g. volumes / file systems. The network includes client nodes, server nodes and resources. Each of the resources couples to at least two of the server nodes. The method for operating comprising the acts of: redirecting an I / O request for a resource from a first server node coupled to the resource to a second server node coupled to the resource; and splitting the I / O request at the second server node into an access portion and a data transfer portion and passing the access portion to a corresponding administrative server node for the resource, and completing at the second server nodes subsequent to receipt of an access grant from the corresponding administrative server node a data transfer for the resource. In an alternate embodiment of the invention the methods may additionally include the acts of: detecting a change in an availability of the server nodes; and rebalancing the network by applying a load balancing function to the network to re-assign each of the available resources to a corresponding available administrative server node responsive to the detecting act.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Access control to block storage devices for a shared disk based file system
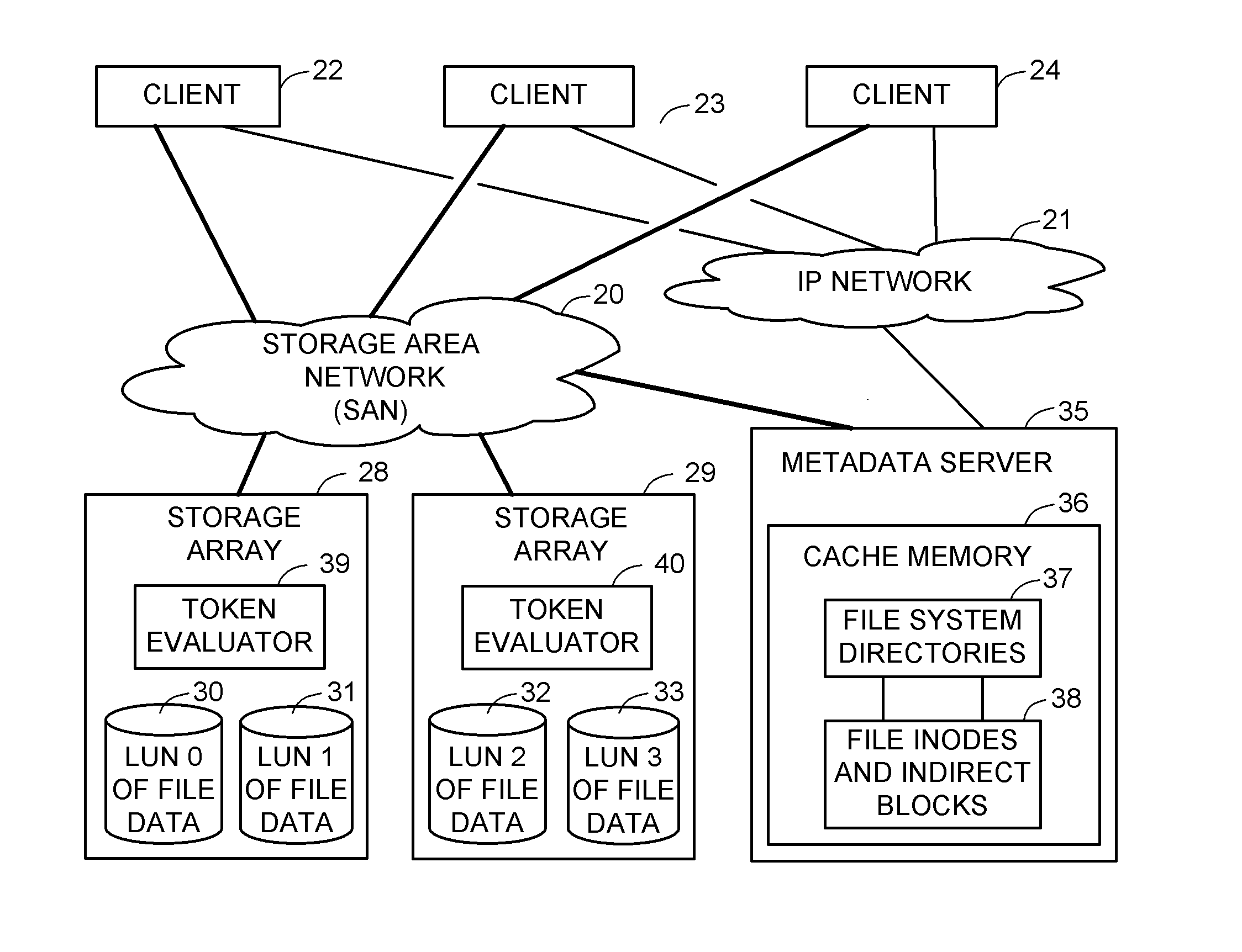
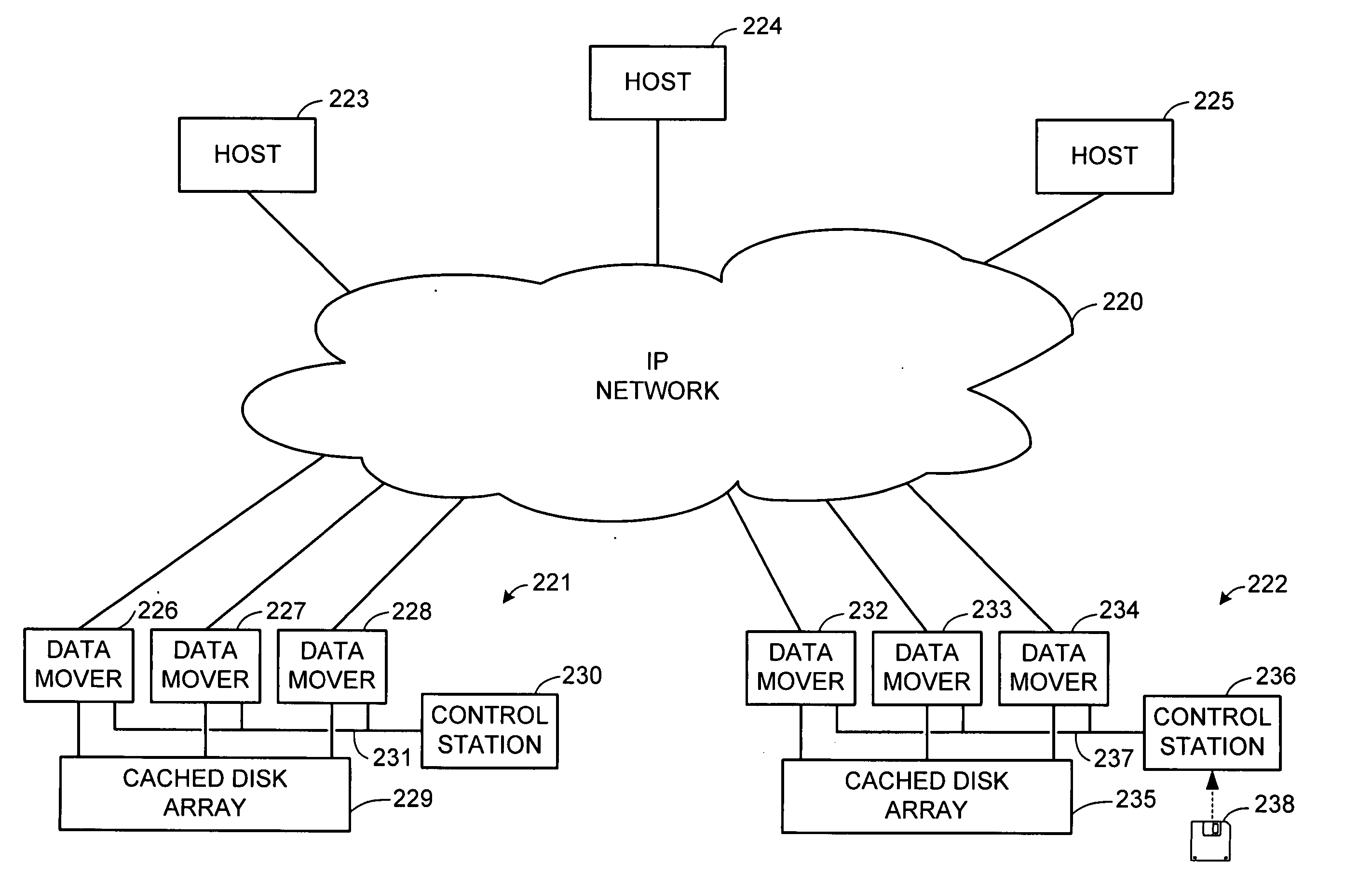
ActiveUS8086585B1Improve securityChangeDigital data information retrievalDigital data processing detailsSCSILogical block addressing
For enhanced access control, a client includes a token in each read or write command sent to a block storage device. The block storage device evaluates the token to determine whether or not read or write access is permitted at a specified logical block address. For example, the token is included in the logical block address field of a SCSI read or write command. The client may compute the token as a function of the logical block address of a data block to be accessed, or a metadata server may include the token in each block address of each extent reported to the client in response to a metadata request. For enhanced security, the token also is a function of a client identifier, a logical unit number, and access rights of the client to a particular extent of file system data blocks.
Owner:EMC IP HLDG CO LLC
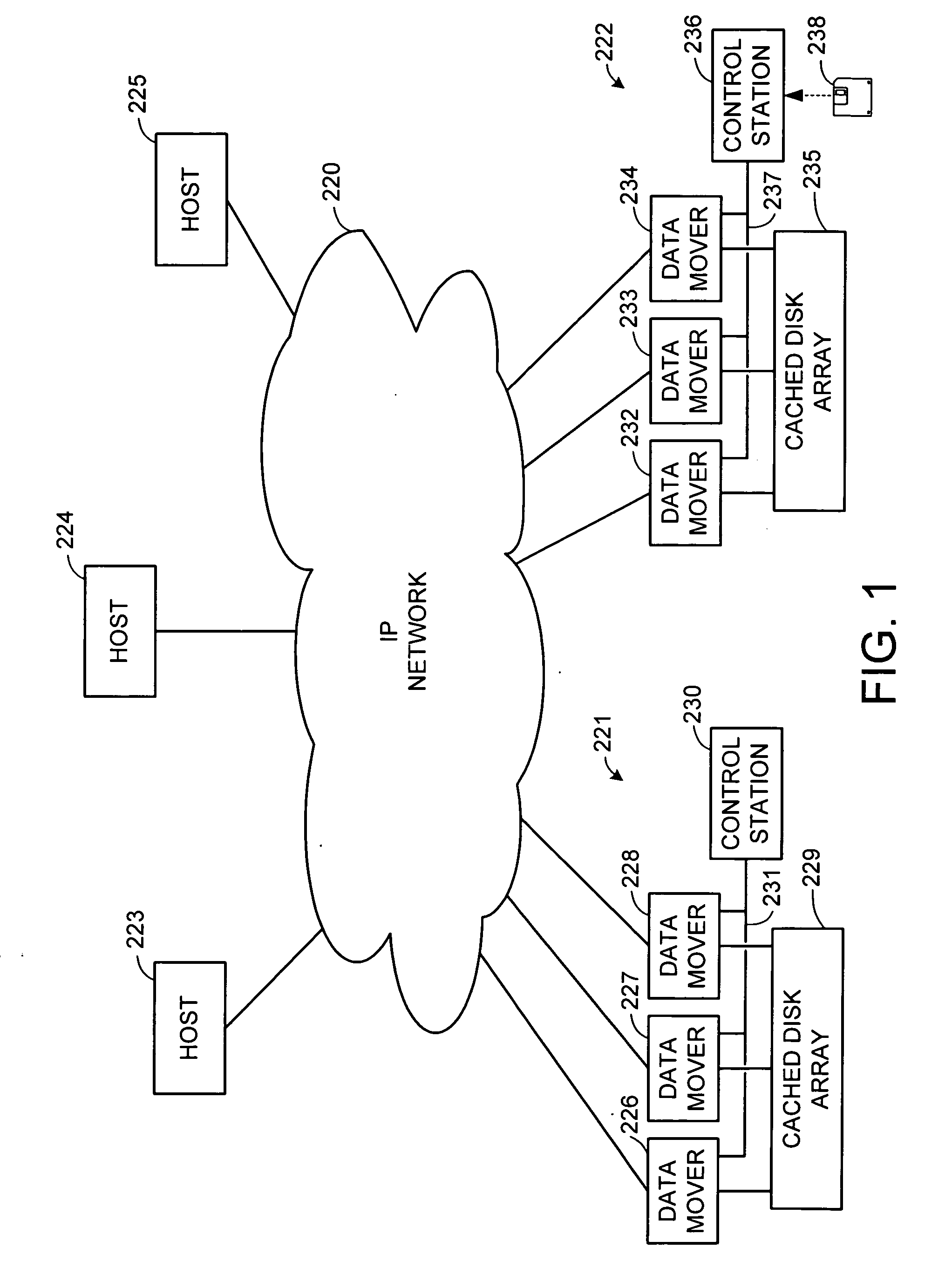
Internet protocol based disaster recovery of a server
For disaster recovery of a file server at an active site, the files that define the user environment of the file server are replicated to a virtual server at a disaster recovery site. To switch over user access from the active site to the disaster recovery site, the disaster recovery system determines whether there are sufficient network interfaces and file system mounts at the disaster recovery site. If so, the required resources are reserved, and user access is switched over. If not, an operator is given a list of missing resources or discrepancies, and a choice of termination or forced failover. Interruptions during the failover can be avoided by maintaining a copy of user mappings and a copy of session information at the disaster recovery site, and keeping alive client-server connections and re-directing client requests from the active site to the disaster recovery site.
Owner:EMC IP HLDG CO LLC
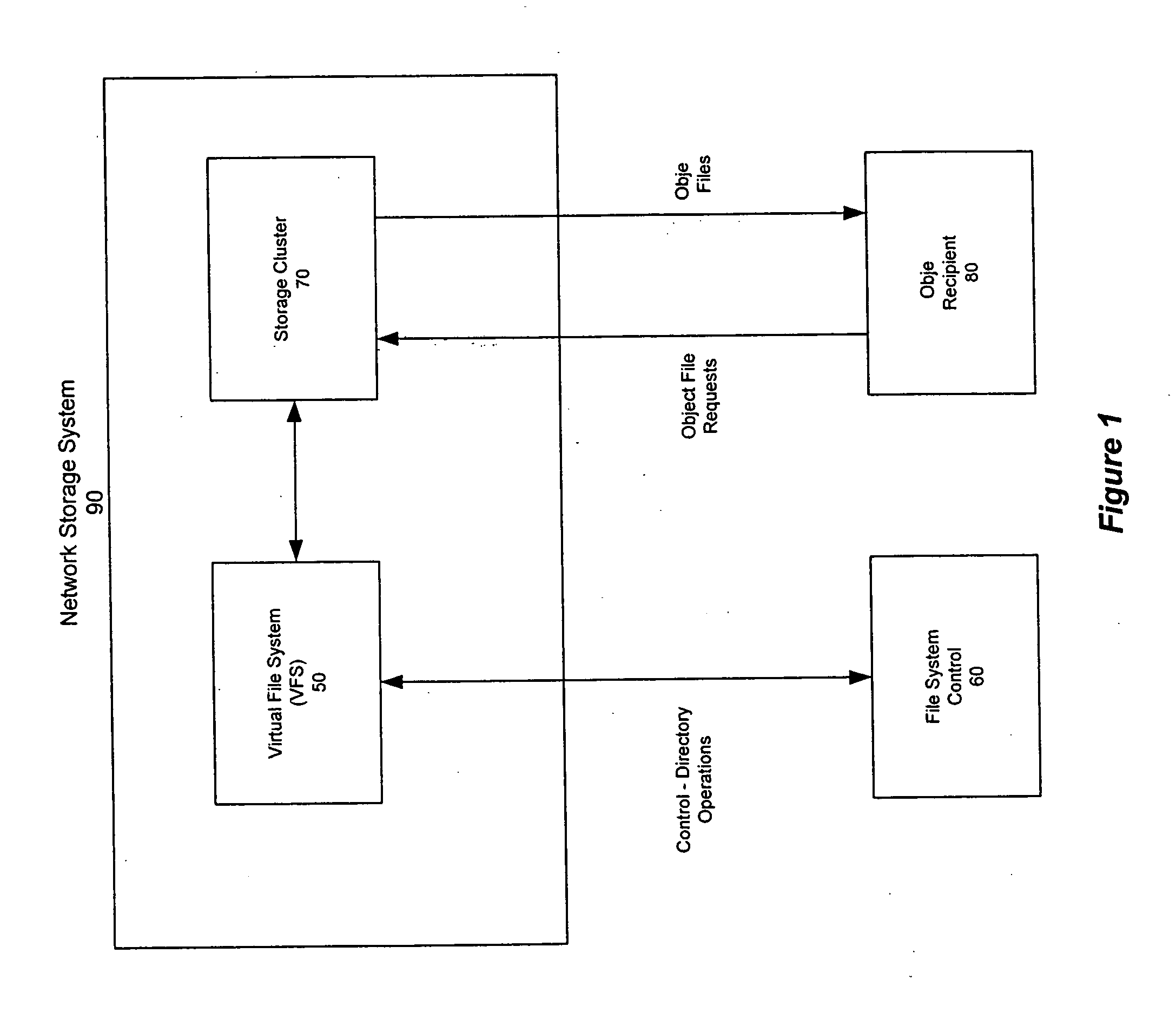
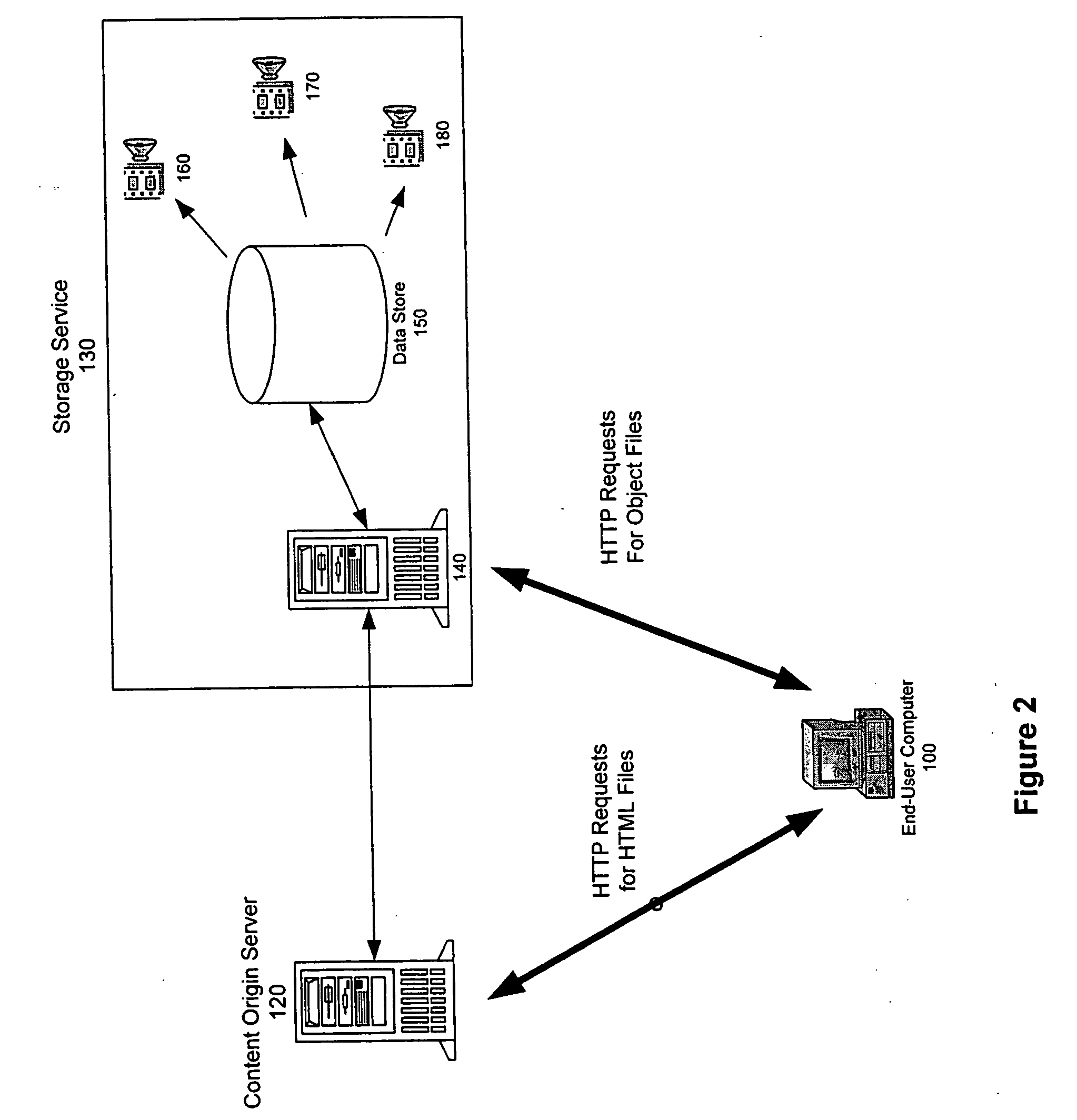
Distributed storage cluster architecture
InactiveUS20050246393A1Input/output to record carriersDigital data information retrievalVirtual file systemDistributed object
A network storage system includes a virtual file system (“VFS”) that manages the files of the network storage system, and a storage center that stores the files. The VFS and the storage center are separated, such that a client accesses the VFS to conduct file system operations and the client accesses the storage center to upload / download files. The client accesses the network storage system through one or more storage ports. The storage center includes a plurality of distributed object storage managers (DOSMs) and a storage cluster that includes a plurality of intelligent storage nodes. The network storage system includes additional storage centers at geographically disparate locations. The network storage system uses a multi-cast protocol to maintain file information at the DOSMs regarding files stored in the intelligent storage nodes, including files stored in disparate storage centers.
Owner:INTEL CORP
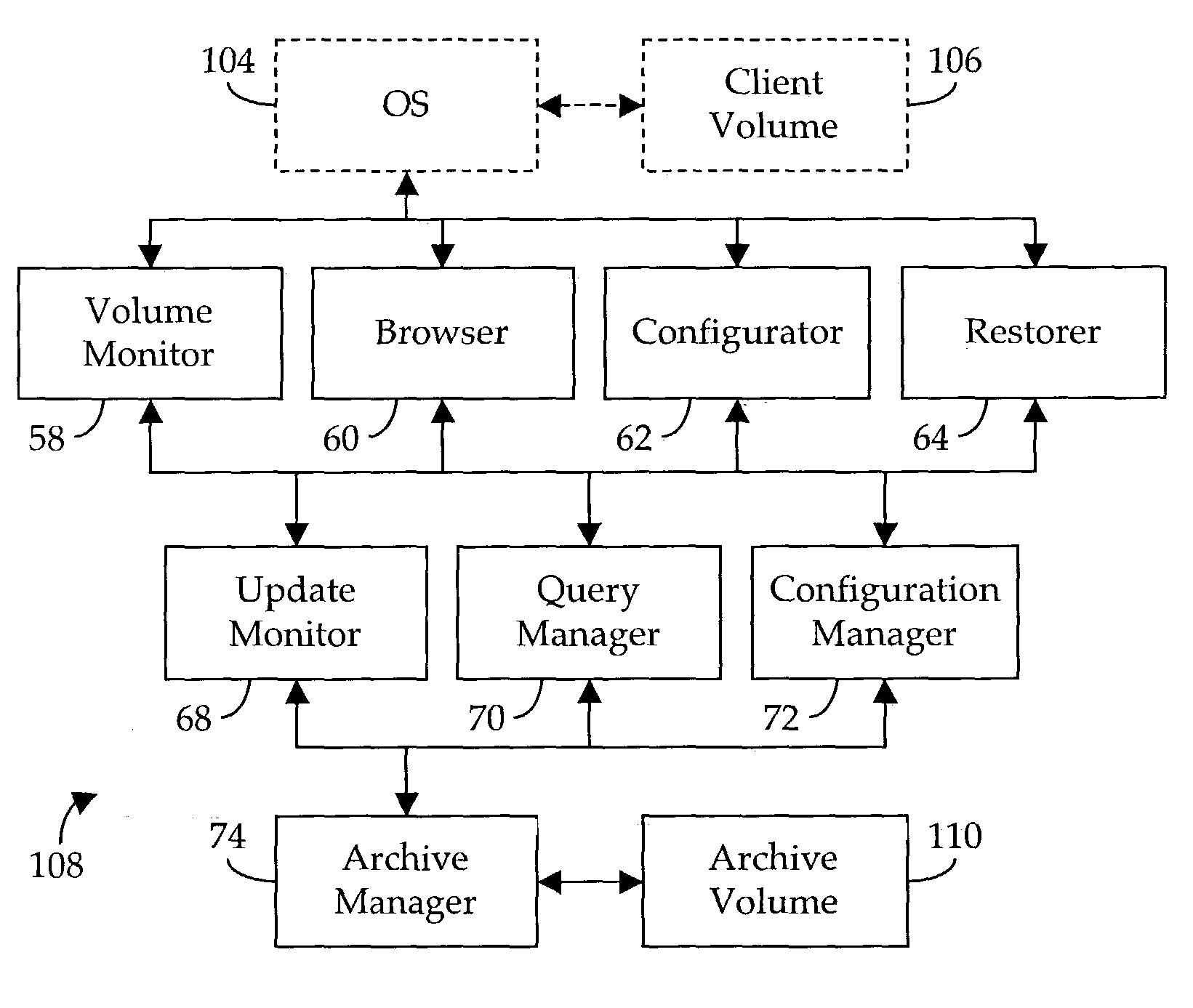
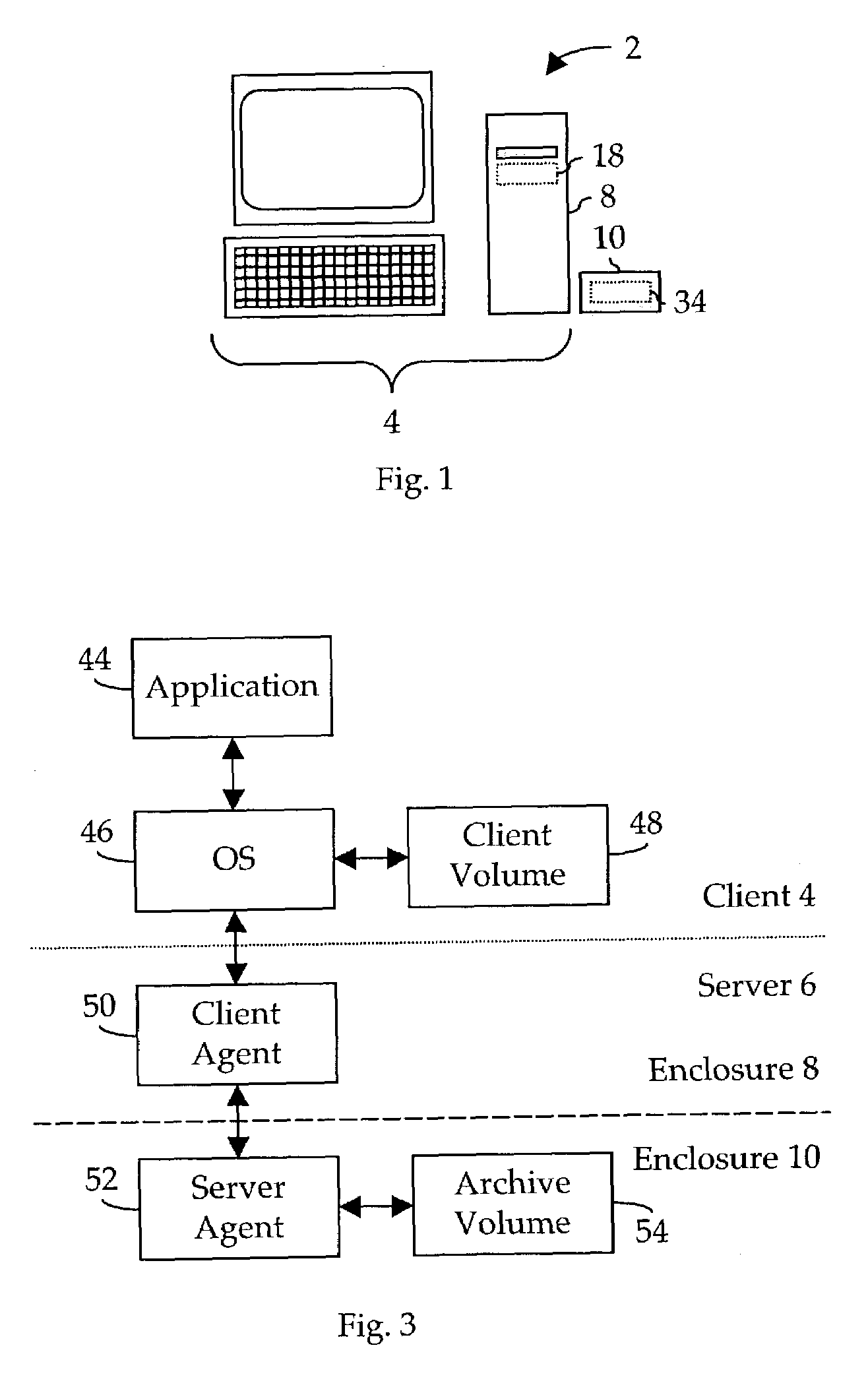
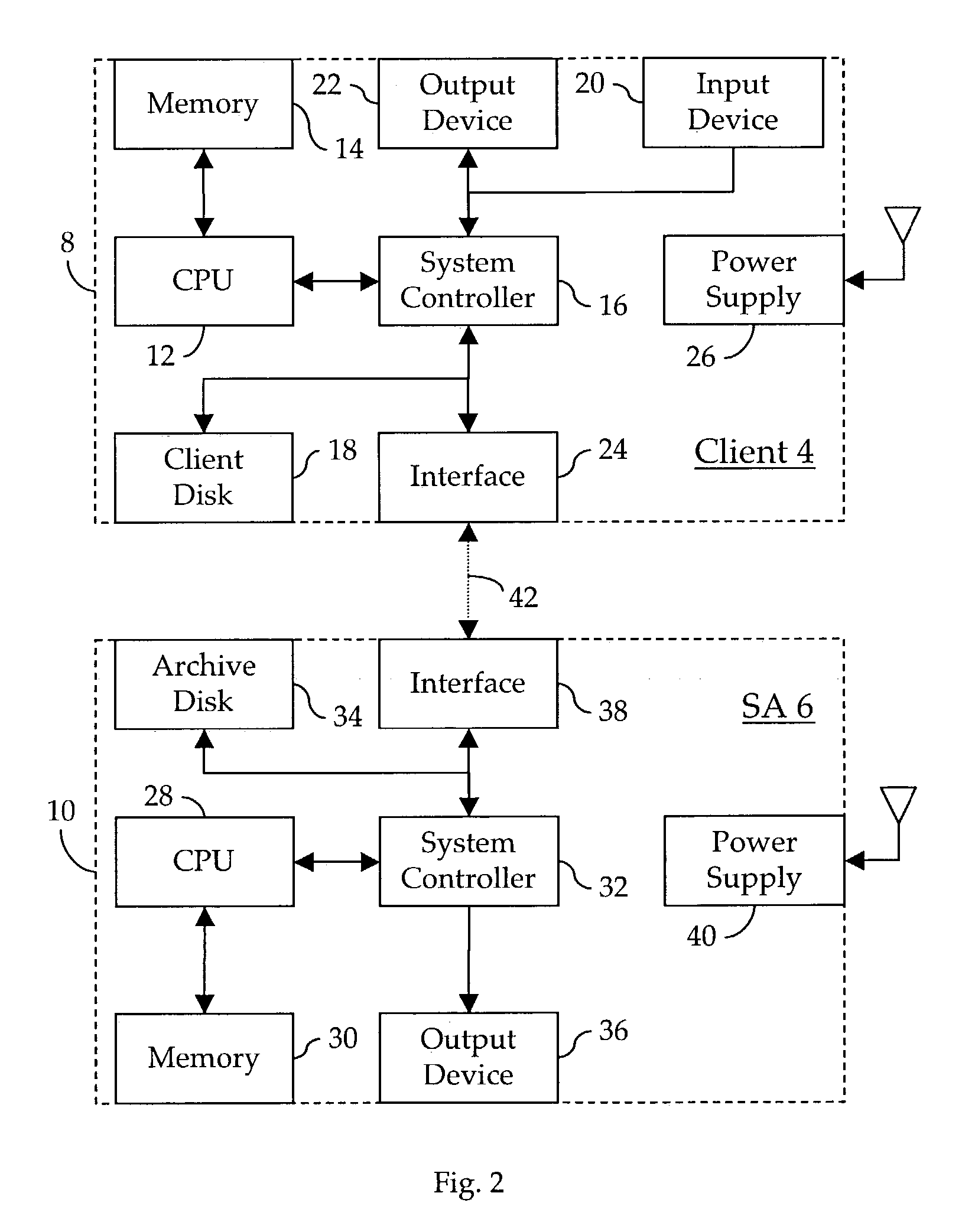
Method and apparatus for automatically archiving a file system
In a digital data processing system having an on-line file system component, a method and apparatus for archiving the contents of a selected client volume stored on the file system. The archiving is performed automatically, beginning with an initial duplication of the existing contents of the client volume into an archive volume, then continuing as changes, including additions, deletions and modifications, are made to the files comprising the client volume. Older, previously-archived versions of modified files are gracefully discarded so as to moderate the rate of growth of the archive volume. The archive volume may be used to restore the client volume, either selectively or in whole, in the event of inadvertent damage to, or loss of, files in the client volume.
Owner:DIGITAL CACHE LLC
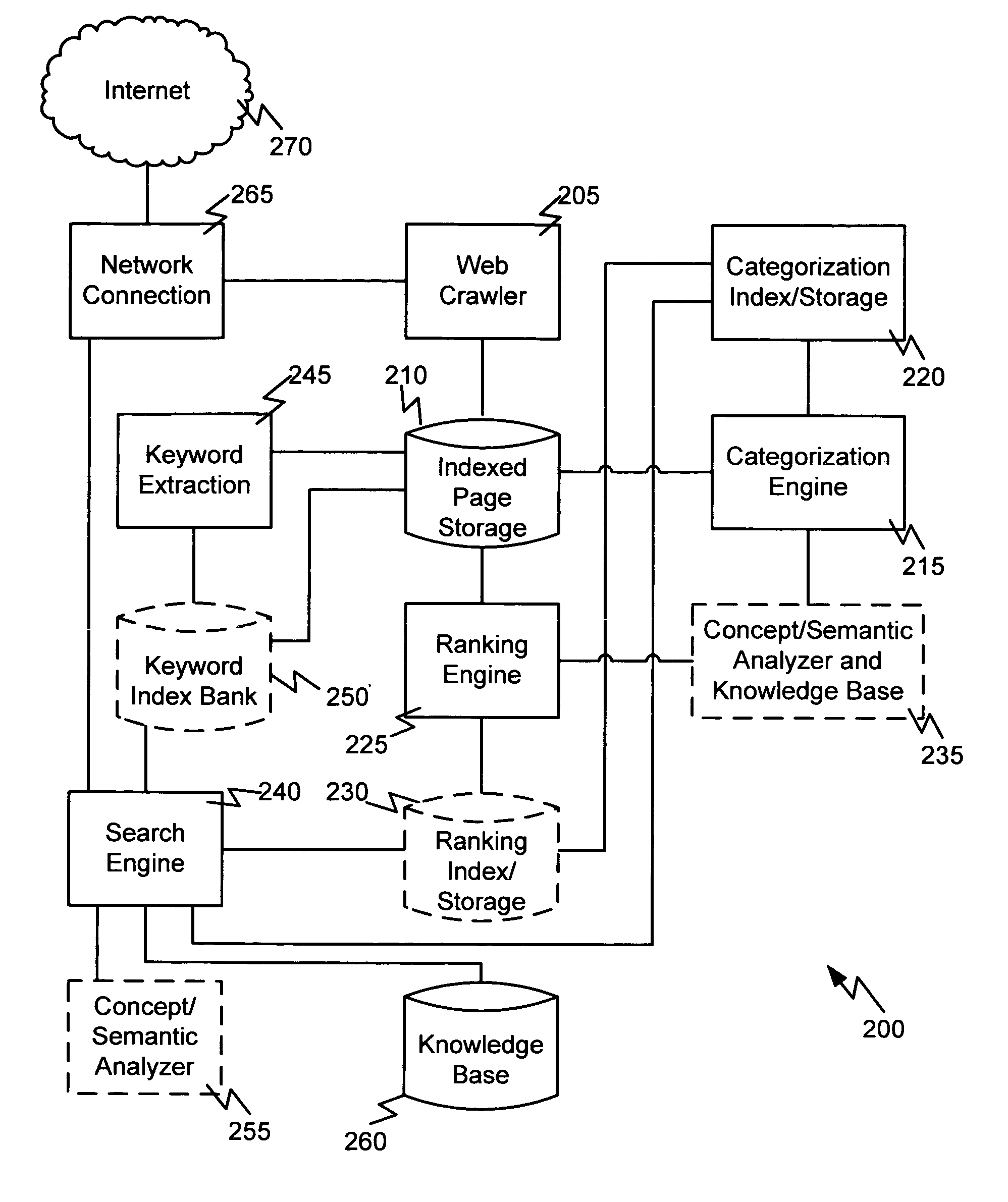
Advanced search, file system, and intelligent assistant agent
The present invention presents embodiments of methods, systems, and computer-readable media for advanced computer file organization, computer file and web search and information retrieval, and intelligent assistant agent to assist a user's creative activities. The embodiments presented herein categorize search results based on the keywords used in the search, provide user selectable ranking, use user's search objectives and advices to refine search, conduct search within an application program and using a file based, provide always-on search that monitors changes over a period of time, provide a high level file system that organizes files into categories, according to relations among files, and in ranking orders along multiple categorization and ranking dimensions and multiple levels of conceptual relationships, conduct searches for associations between keywords, concepts, and propositions, and provide validations of such associations to assist a user's creative activity.
Owner:LIANG PING
Mechanisms for moving data in a hybrid aggregate
ActiveUS20100281230A1Improved performance characteristicsMemory architecture accessing/allocationMemory adressing/allocation/relocationPolicy decisionFile system
At least certain embodiments disclose a method, system and apparatus for relocating data between tiers of storage media in a hybrid storage aggregate encompassing multiple tiers of heterogeneous physical storage media including a file system to automatically relocate the data between tiers. The hybrid storage aggregate includes one or more volumes, each volume including a volume block number space spanning at least a first-tier of storage media and a second tier of storage media of the multiple tiers of heterogeneous physical storage media and the hybrid storage aggregate further includes a control module to cooperatively manage the tiers of the multiple tiers of heterogeneous physical storage media and a file system coupled with the control module, the file system including a policy module configured to make policy decisions based on a set of one or more policies and configured to automatically relocate data between different tiers of the multiple tiers of heterogeneous physical storage media based on the set of policies.
Owner:NETWORK APPLIANCE INC
Device, System and Method for Storage and Access of Computer Files
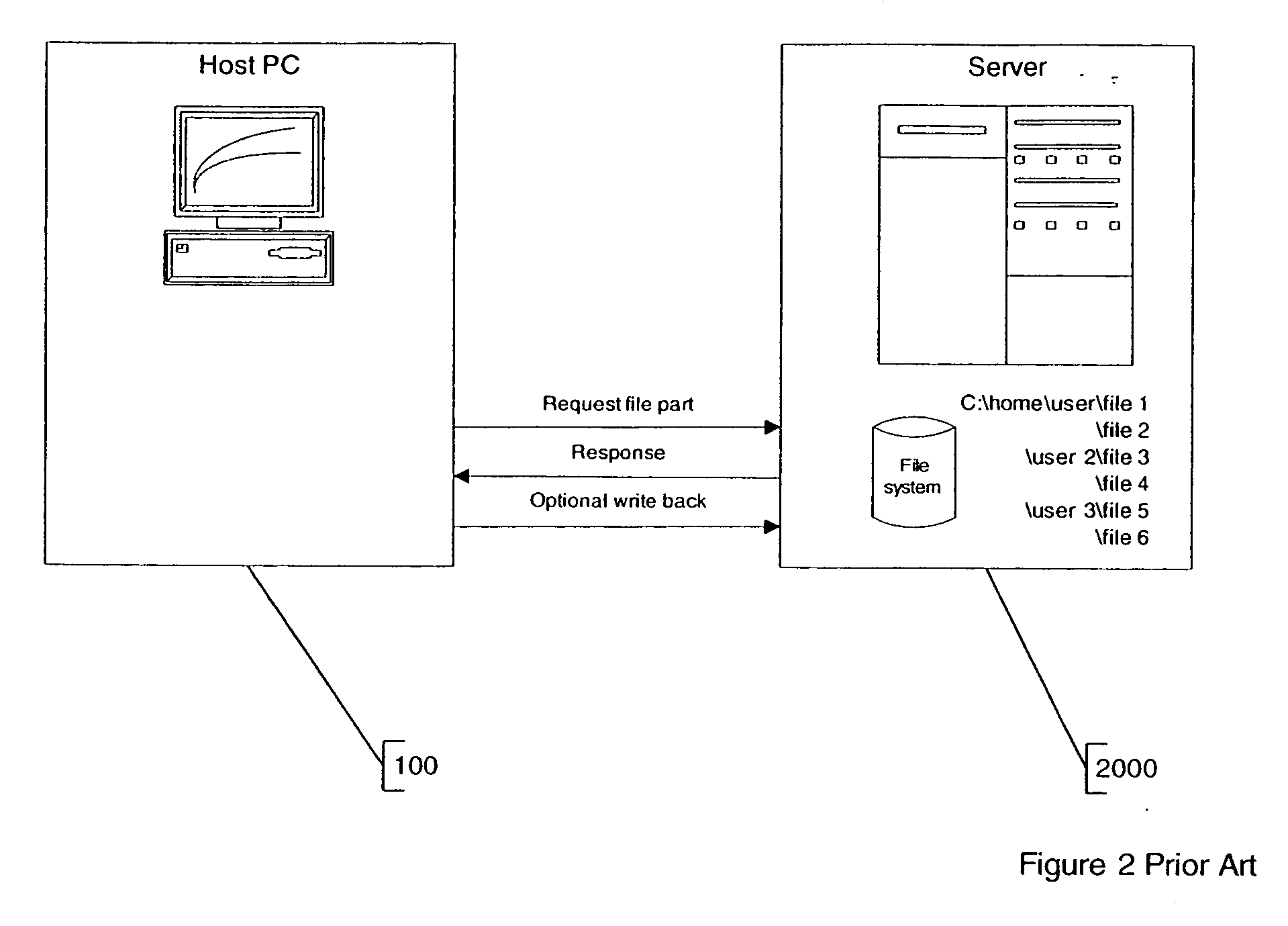
InactiveUS20070226320A1Digital data information retrievalMultiple digital computer combinationsFile systemClient server systems
Briefly, some embodiments of the invention provide, for example, devices, systems and methods for storage and access of computer files. A method in accordance with an embodiment of the invention may include, for example, receiving from a remote site a request to access a first file having a plurality of blocks, said request having a pre-defined format encapsulating an original request of a client of a synchronous client-server system and in accordance with a pre-defined file system; determining, for each of at least some of said plurality of blocks, a differential portion representing a difference between each said block and a corresponding block of a second file; and sending said differential portion to said remote site.
Owner:DISKSITES RES & DEV
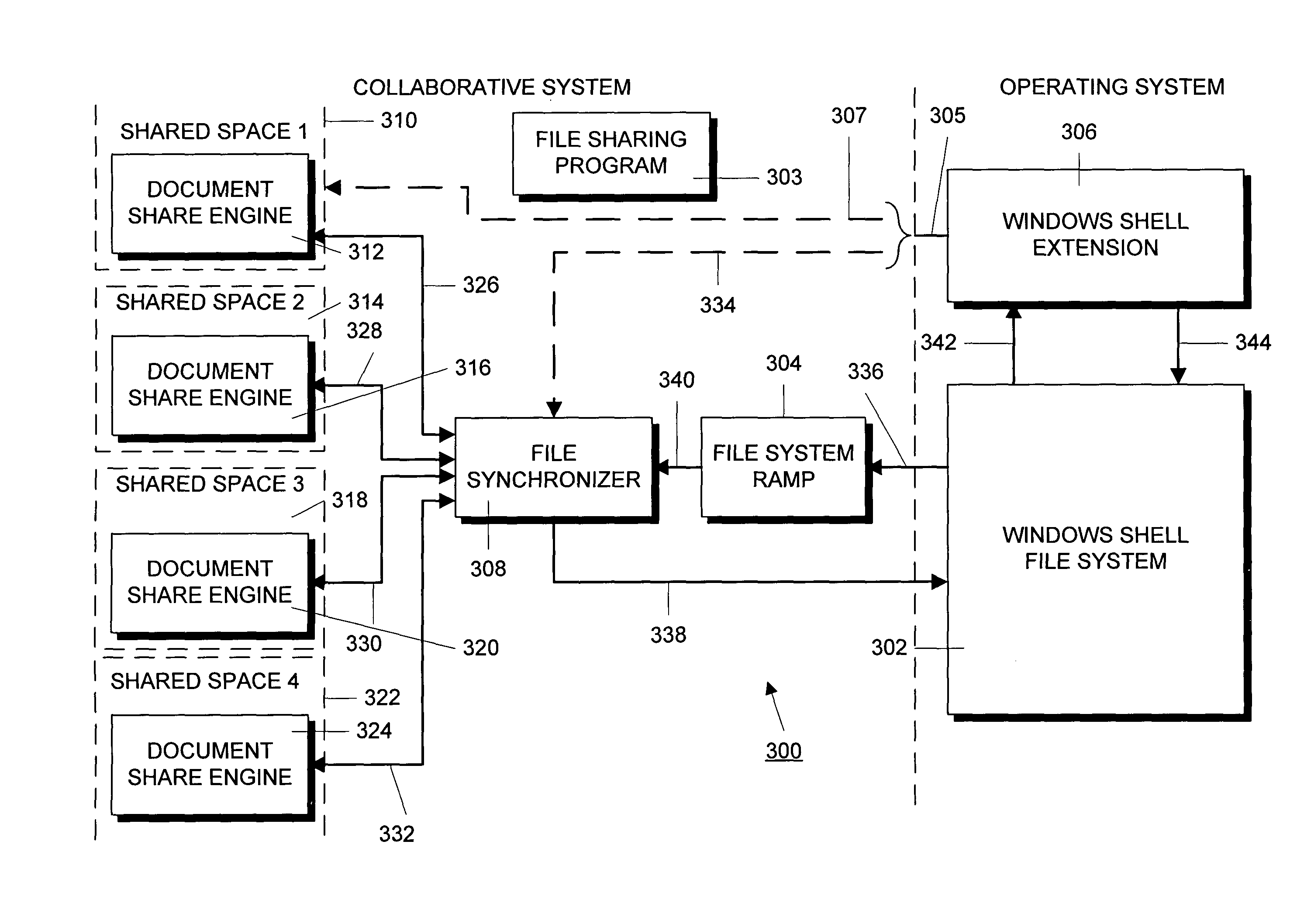
Method and apparatus for providing attributes of a collaboration system in an operating system folder-based file system
ActiveUS20090138808A1Multiple digital computer combinationsOffice automationOperational systemFile system
A conventional operating system folder or directory based file system is implemented with, or enhanced to provide, attributes of shared collaborative workspaces. In particular, the conventional file system is connected to either a server based or a distributed collaboration system and the user interface of the operating system file system is augmented to allow it to control aspects of the collaboration system. Each folder or directory can be synchronized and treated as a “workspace” that can be viewed and shared with other users or groups of users. Folder can also be provided with “awareness” information that indicates collaborators that are present and those that are sharing the workspace.
Owner:MICROSOFT TECH LICENSING LLC
System and method for on-the-fly elimination of redundant data
ActiveUS20080294696A1Digital data information retrievalDigital data processing detailsOperational systemFile system
Owner:NETWORK APPLIANCE INC
File server system using connection-oriented protocol and sharing data sets among data movers
InactiveUS6453354B1Digital data information retrievalMultiple digital computer combinationsMultiplexingData set
A first data mover computer services data access requests from a network client, and a second data mover computer is coupled to the first data mover computer for servicing data access requests from the first data mover computer. The first data mover computer uses a connection-oriented protocol to obtain client context information and to respond to a session setup request from the client by authenticating the client. Then the first data mover computer responds to a file system connection request from the client by forwarding the client context information and the file system connection request to the second data mover computer. Then the first data mover computer maintains a connection between the first data mover computer and the second data mover computer when the client accesses the file system and the first data mover computer passes file access requests from the client to the second data mover computer and returns responses to the file access requests from the second data mover computer to the client. In a preferred embodiment, the connection-oriented protocol is the Common Internet File System (CIFS) Protocol, and multiple clients share a Transmission Control Protocol (TCP) connection between the first data mover computer and the second data mover computer by allocation of virtual channels within the shared TCP connection and multiplexing of data packets of the virtual channels over the shared TCP connection.
Owner:EMC IP HLDG CO LLC
Executing a cloud command for a distributed filesystem
ActiveUS20140006354A1Reduce administrative burdenReduce overheadDigital data information retrievalDigital data processing detailsDistributed File SystemFile system
The disclosed embodiments disclose techniques for executing a cloud command for a distributed filesystem. Two or more cloud controllers collectively manage distributed filesystem data that is stored in one or more cloud storage systems; the cloud controllers ensure data consistency for the stored data, and each cloud controller caches portions of the distributed filesystem. During operation, a cloud controller presents a distributed-filesystem-specific capability to a client system as a file in the distributed filesystem (e.g., using a file abstraction). Upon receiving a request from the client system to access and / or operate upon this file, the client controller executes an associated cloud command. More specifically, the cloud controller initiates a specially-defined operation that accesses additional functionality for the distributed filesystem that exceeds the scope of individual reads and writes to a typical data file.
Owner:PANZURA LLC
Preparation of metadata for splicing of encoded MPEG video and audio
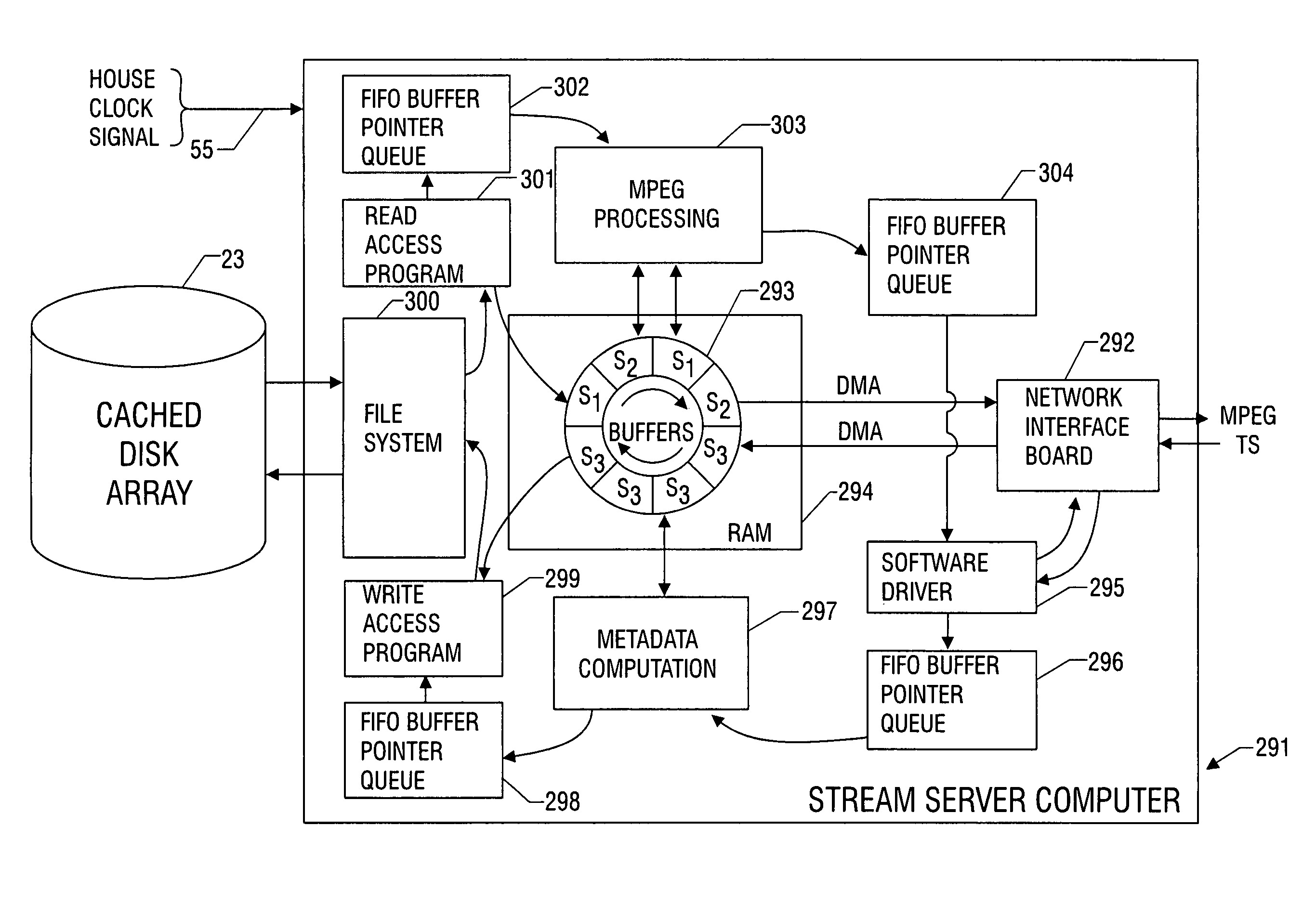
InactiveUS7096481B1Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningMPEG transport streamData stream
Metadata for splicing of an encoded digital motion video stream (such as an MPEG Transport Stream) is prepared in real time while recording at the encoding bit rate and faster than encoded bit rate for off line encoding independent of the bit rate and mechanisms for ingestion of the data stream into data storage. Preprocessing is performed during a metered file transfer protocol (FTP) and includes pseudo real-time encoding. The preprocessing includes Group of Pictures (GOP) level pre-processing of splicing In Points and results in an intimate linkage between metadata and the file system in which the video data is stored. The preferred file system enables access to metadata in parallel to writing the data on disk. The pre-processing is performed simultaneous to writing the data to the disk using a carousel type buffer mechanism.
Owner:EMC IP HLDG CO LLC +1
Metadata offload for a file server cluster
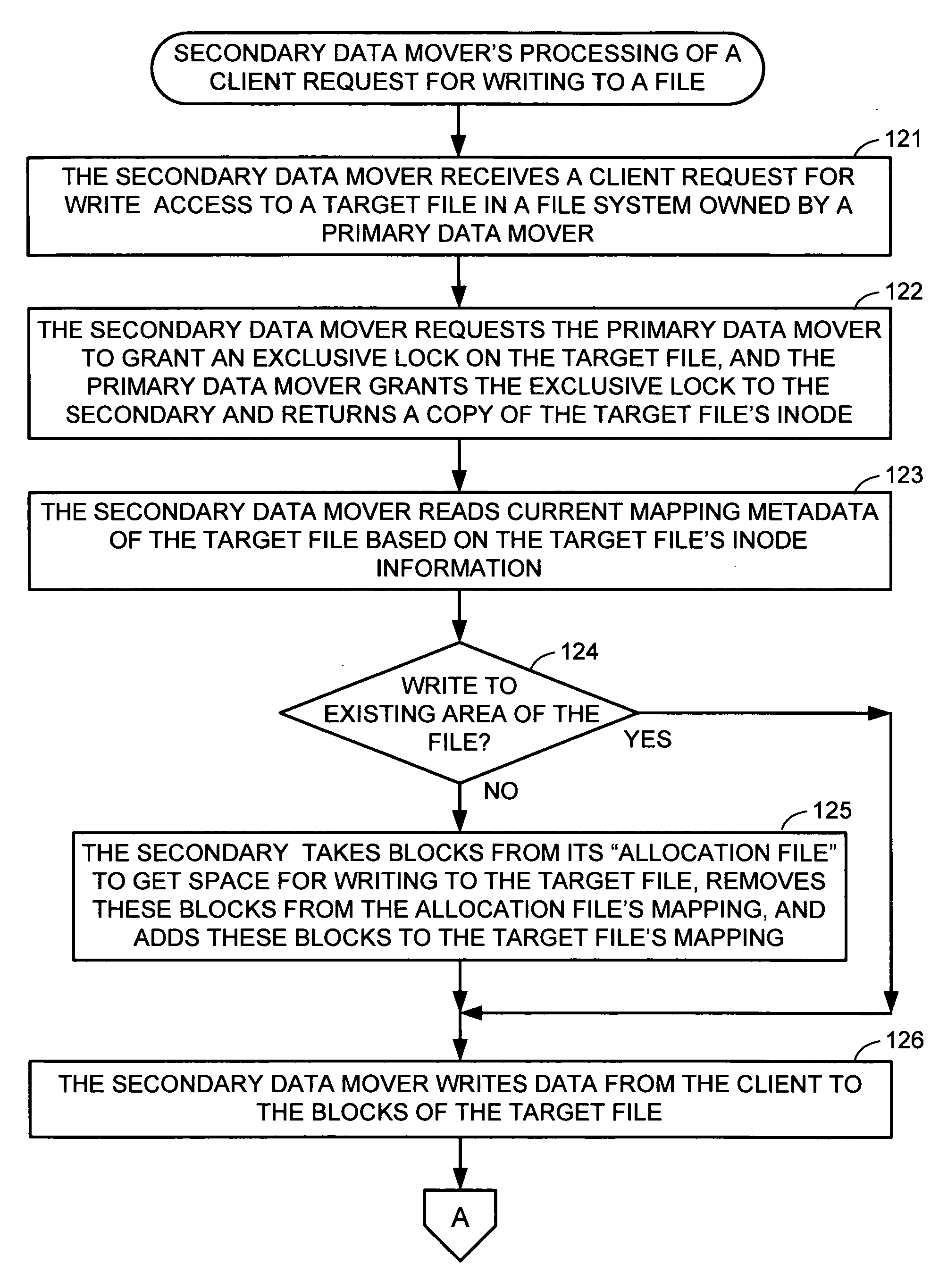
ActiveUS20070055702A1Promote recoveryReduce processDigital data information retrievalSpecial data processing applicationsFile systemData treatment
A file server system has a cluster of server computers that share access to a file system in shared storage. One of the server computers has primary responsibility for management of access to the file system. In order to reduce the possibility of primary server overload when a large number of the clients happen to concurrently access the same file system, most metadata processing operations are offloaded to secondary server computers. This also facilitates recovery from failure of a primary server computer since only a fraction of the ongoing metadata operations of a primary server computer is interrupted by a failure of the primary server computer. For example, a secondary data mover may truncate, delete, create, or rename a file in response to a client request.
Owner:EMC IP HLDG CO LLC
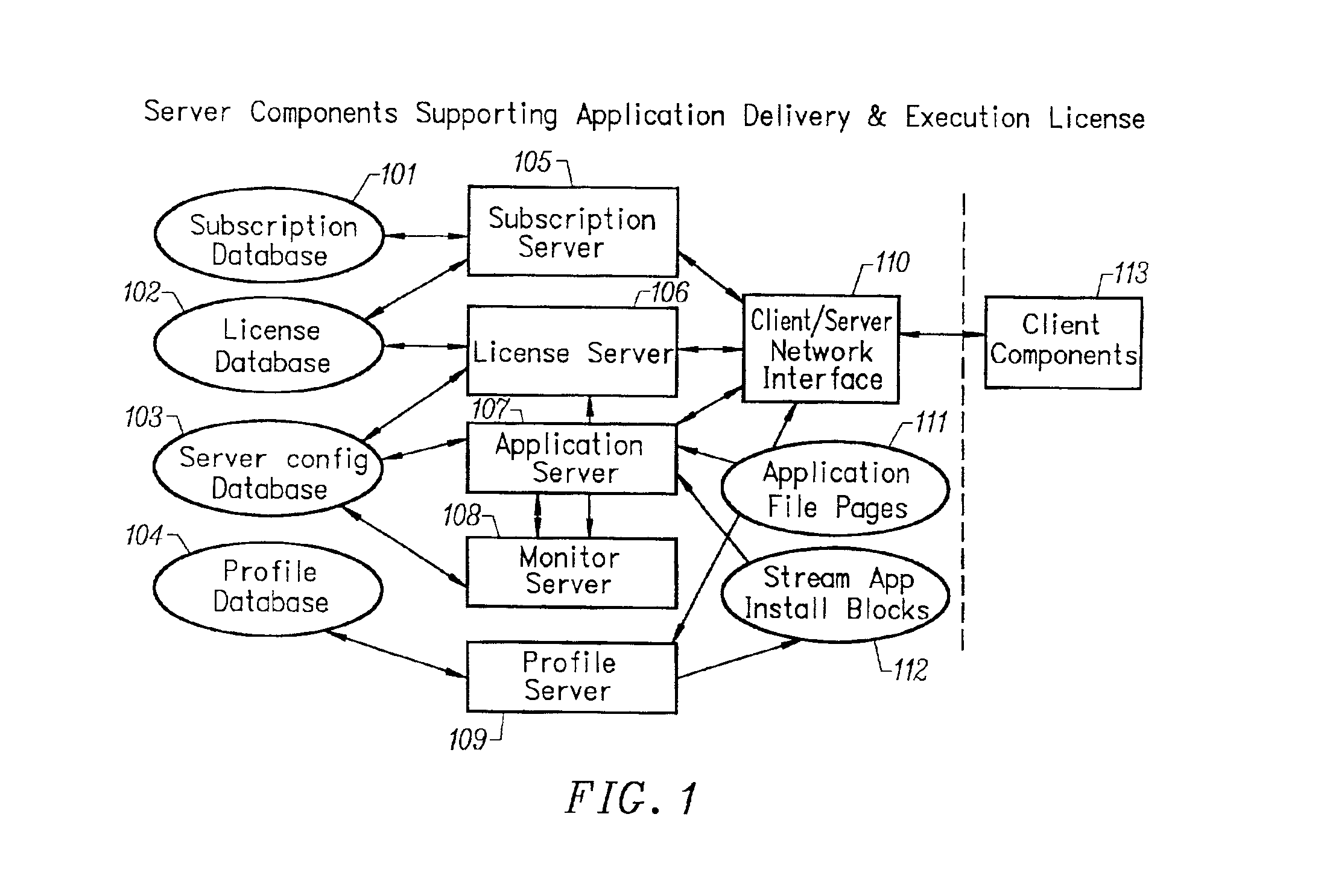
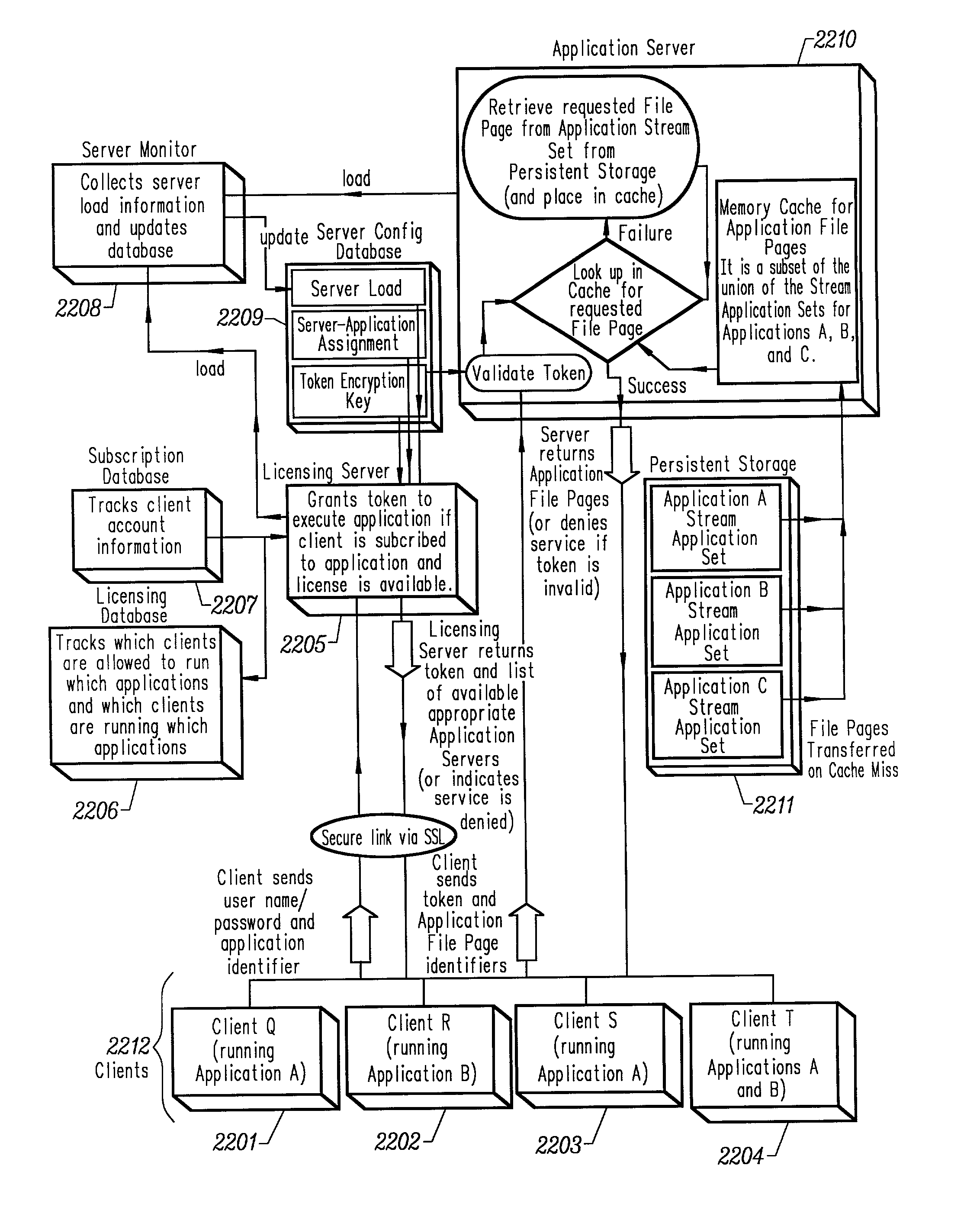
Intelligent network streaming and execution system for conventionally coded applications
InactiveUS7062567B2Multiple digital computer combinationsDigital data authenticationIntelligent NetworkApplication server
An intelligent network streaming and execution system for conventionally coded applications provides a system that partitions an application program into page segments by observing the manner in which the application program is conventionally installed. A minimal portion of the application program is installed on a client system and the user launches the application in the same ways that applications on other client file systems are started. An application program server streams the page segments to the client as the application program executes on the client and the client stores the page segments in a cache. Page segments are requested by the client from the application server whenever a page fault occurs from the cache for the application program. The client prefetches page segments from the application server or the application server pushes additional page segments to the client based on the pattern of page segment requests for that particular application. The user subscribes and unsubscribes to application programs, whenever the user accesses an application program a securely encrypted access token is obtained from a license server if the user has a valid subscription to the application program. The application server begins streaming the requested page segments to the client when it receives a valid access token from the client. The client performs server load balancing across a plurality of application servers. If the client observes a non-response or slow response condition from an application server or license server, it switches to another application or license server.
Owner:NUMECENT HLDG
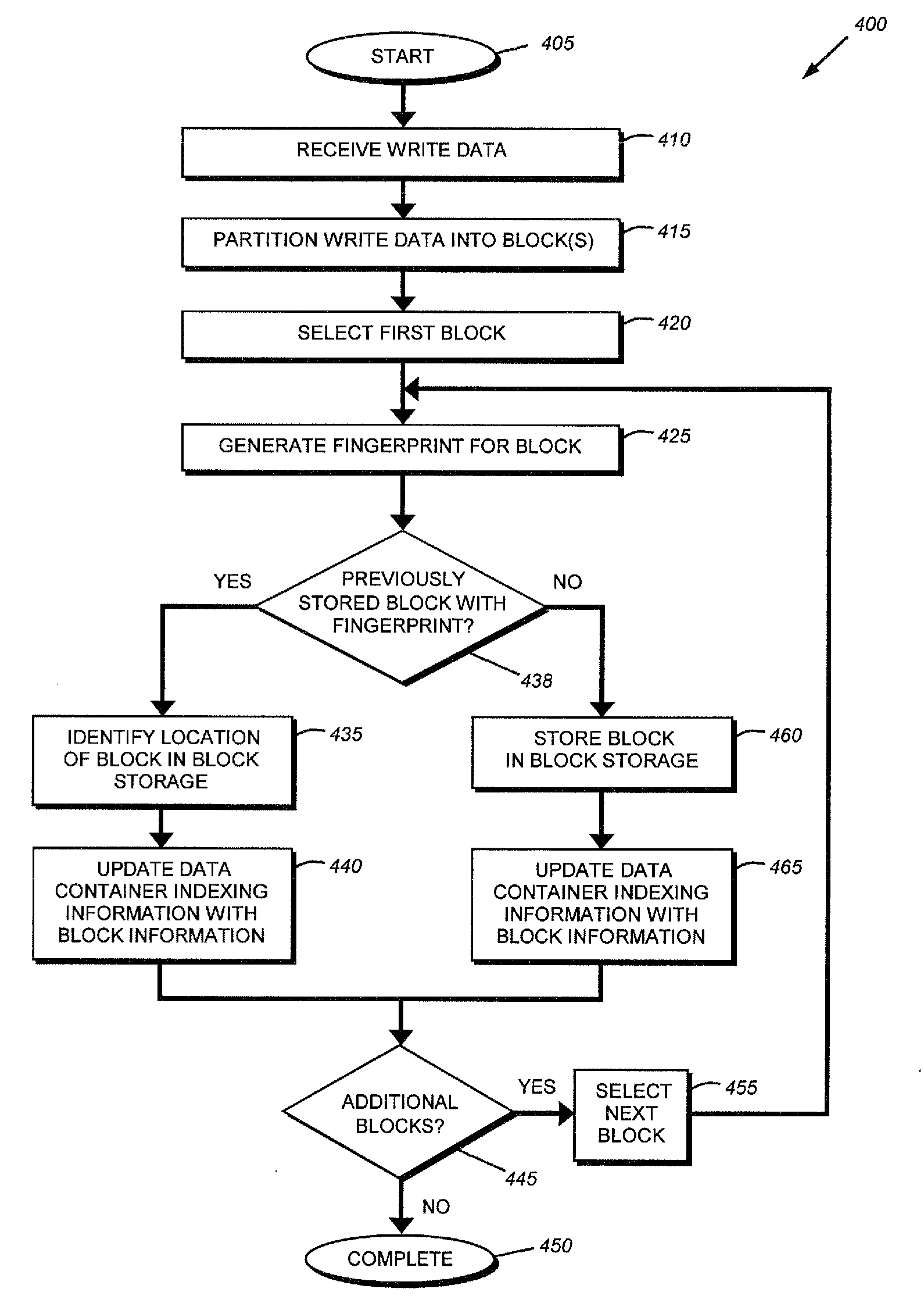
System and method for detecting and storing file content access information within a file system
In one embodiment, a system may include a storage device configured to provide a storage space for data storage and a file system configured to map files to the storage space for storage and to manage application accesses to the storage device. The file system may be configured to determine a signature of a first file stored on the storage device dependent upon at least a portion of the first file, detect an operation to access content of the first file, where the operation is generated by an application distinct from the file system, and, subsequent to detecting the operation, store a record of the operation associated with the first file, where the record includes a signature corresponding to the first file, information indicating the operation type and information identifying the application.
Owner:SYMANTEC OPERATING CORP
Policy based composite file system and method
InactiveUS20060259949A1Digital data information retrievalSpecial data processing applicationsFile systemConfigfs
A policy configurable file system includes a computer system upon which the policy configurable file system operates, a policy source for providing the configuration policies, and one or more file servers. The computer system includes software for enforcing one or more configuration policies. The policy source is typically either a policy server such that the policy is derived from the policy server, or a policy configurable file system, such that the policy is embedded in the policy configurable file system. The one or more file servers each uses a protocol, wherein the protocols of the one or more file servers are not all the same. In one case, the one or more of the configurable policies are separable from the policy configurable file system. In another case, the one or more configurable policies are downloadable to the computer system.
Owner:MICROSOFT TECH LICENSING LLC
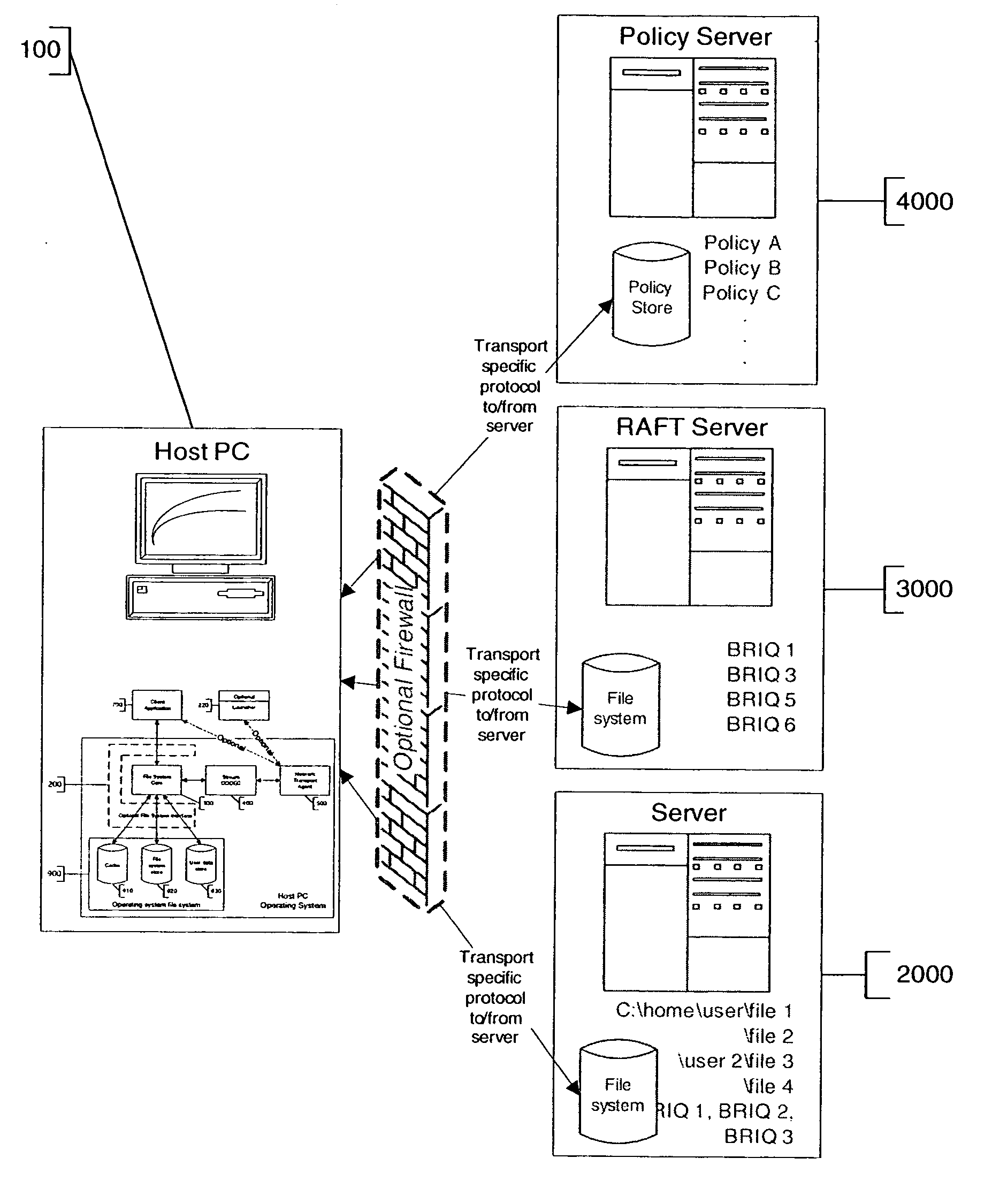
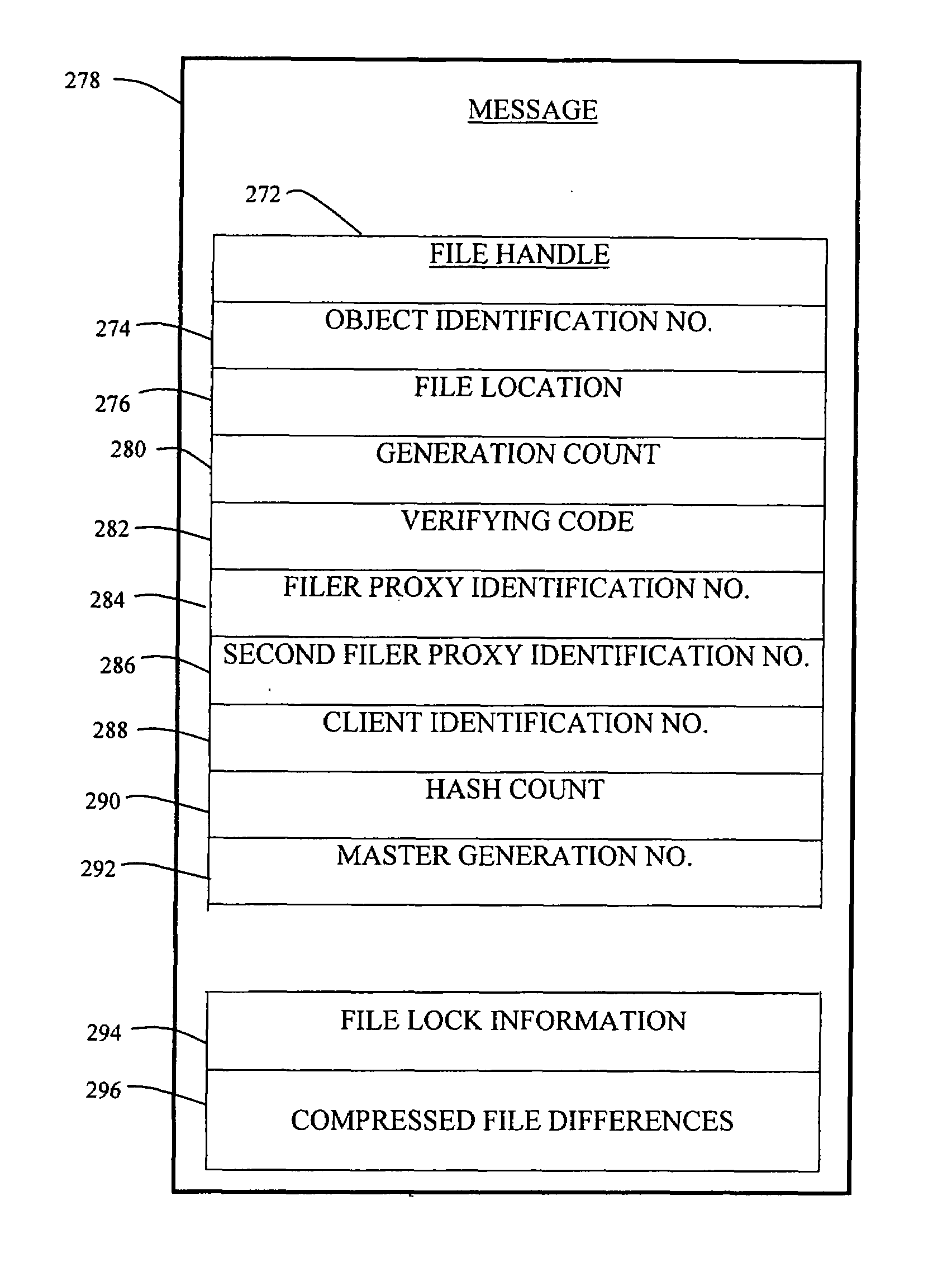
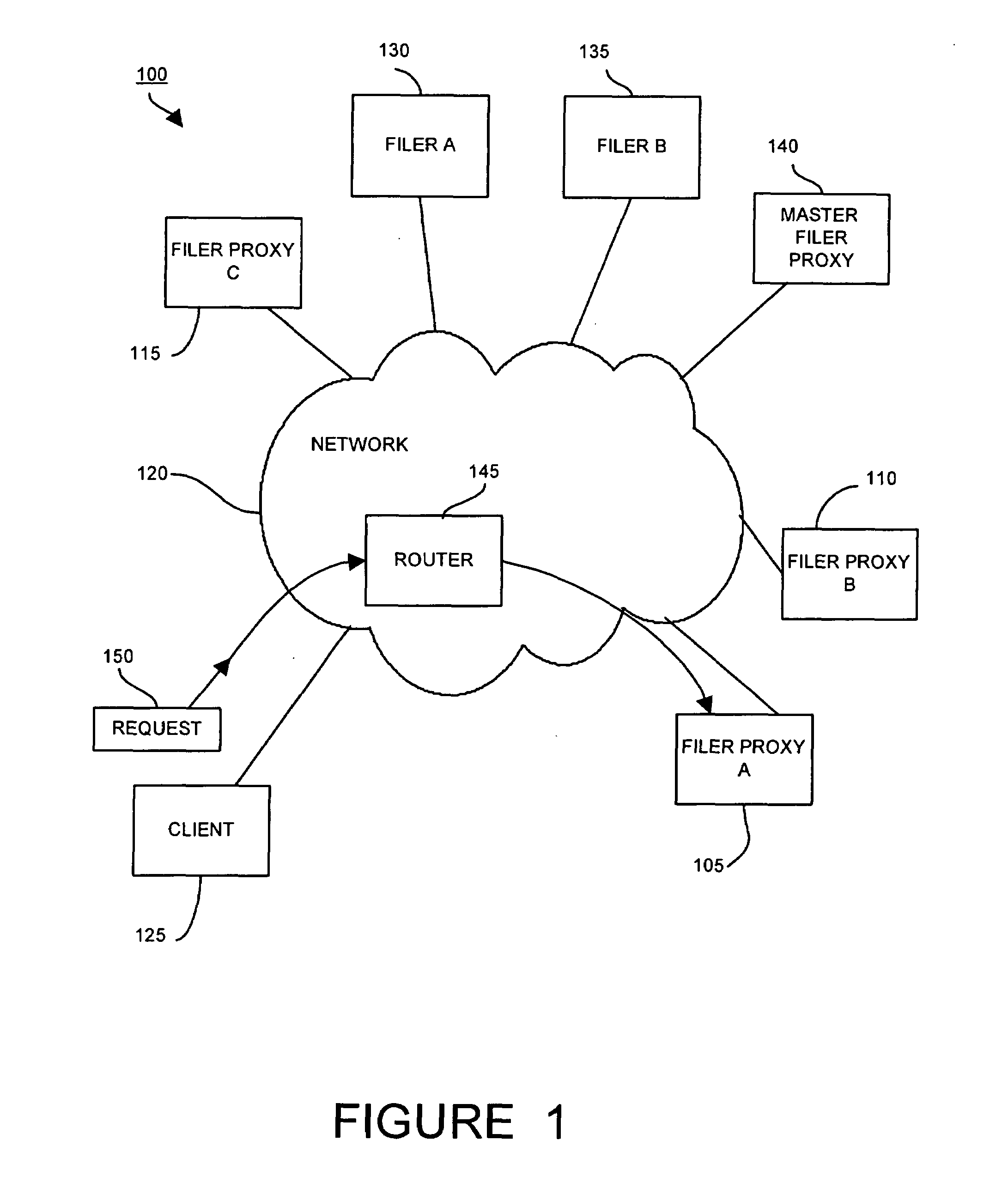
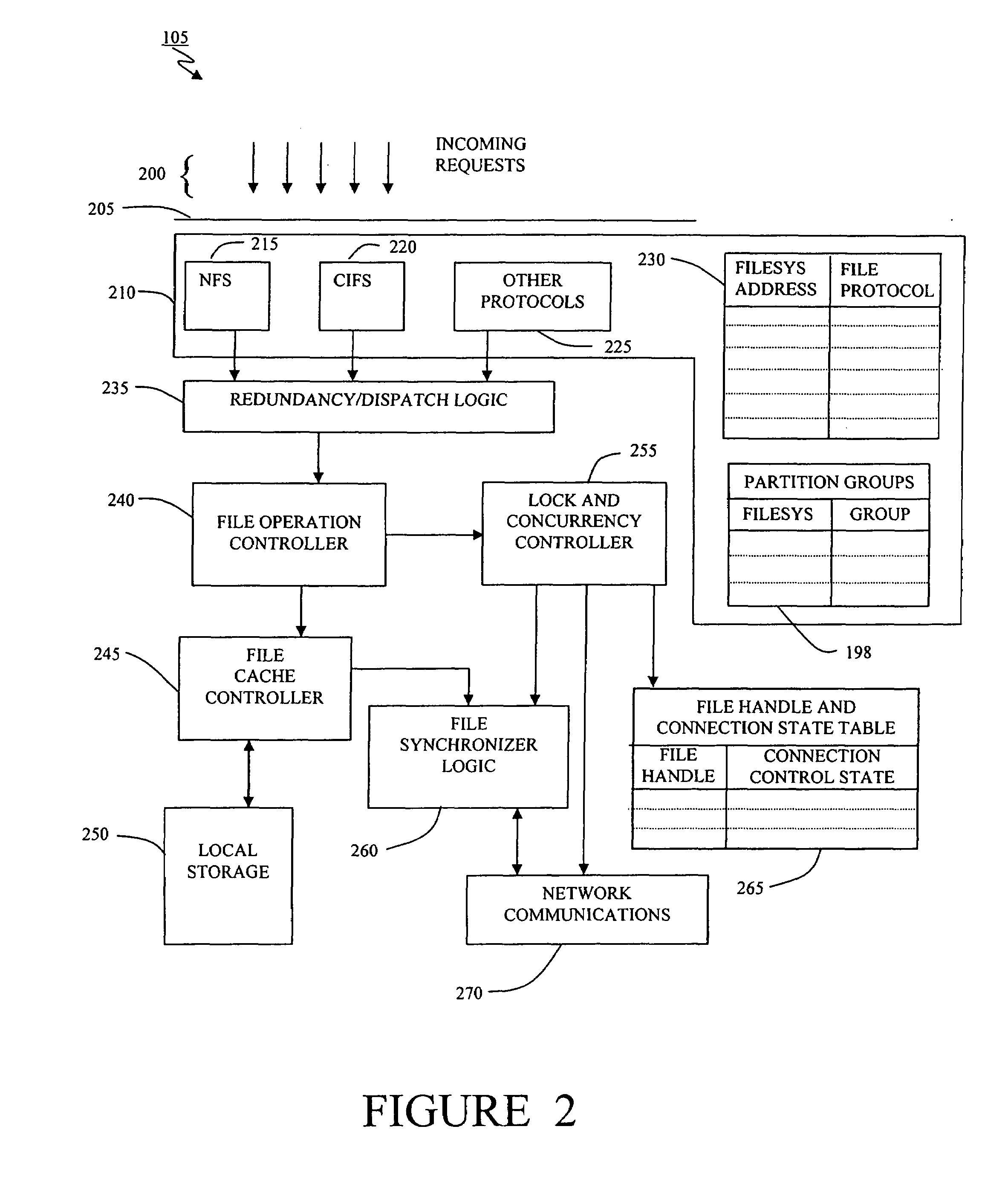
Method and apparatus for transparent distributed network-attached storage with web cache communication protocol/anycast and file handle redundancy
ActiveUS7254636B1Data processing applicationsDigital data processing detailsContent distributionNetwork connection
A distributed network-attached storage network provides content distribution using conventional file transfer protocols such as NFS and CIFS. A filer proxy accepts a client request and translates the client request to a file transfer protocol accepted at the file system having the file requested in the client request. The filer proxy generates a file handle for the file containing redundant filer proxy information to be used for failover to a backup filer proxy in the event of a network error or failure of an original filer proxy. The file handle also contains information for network security purposes such as detection of forged file handles.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com