Patents
Literature
210results about How to "Reduce administrative burden" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
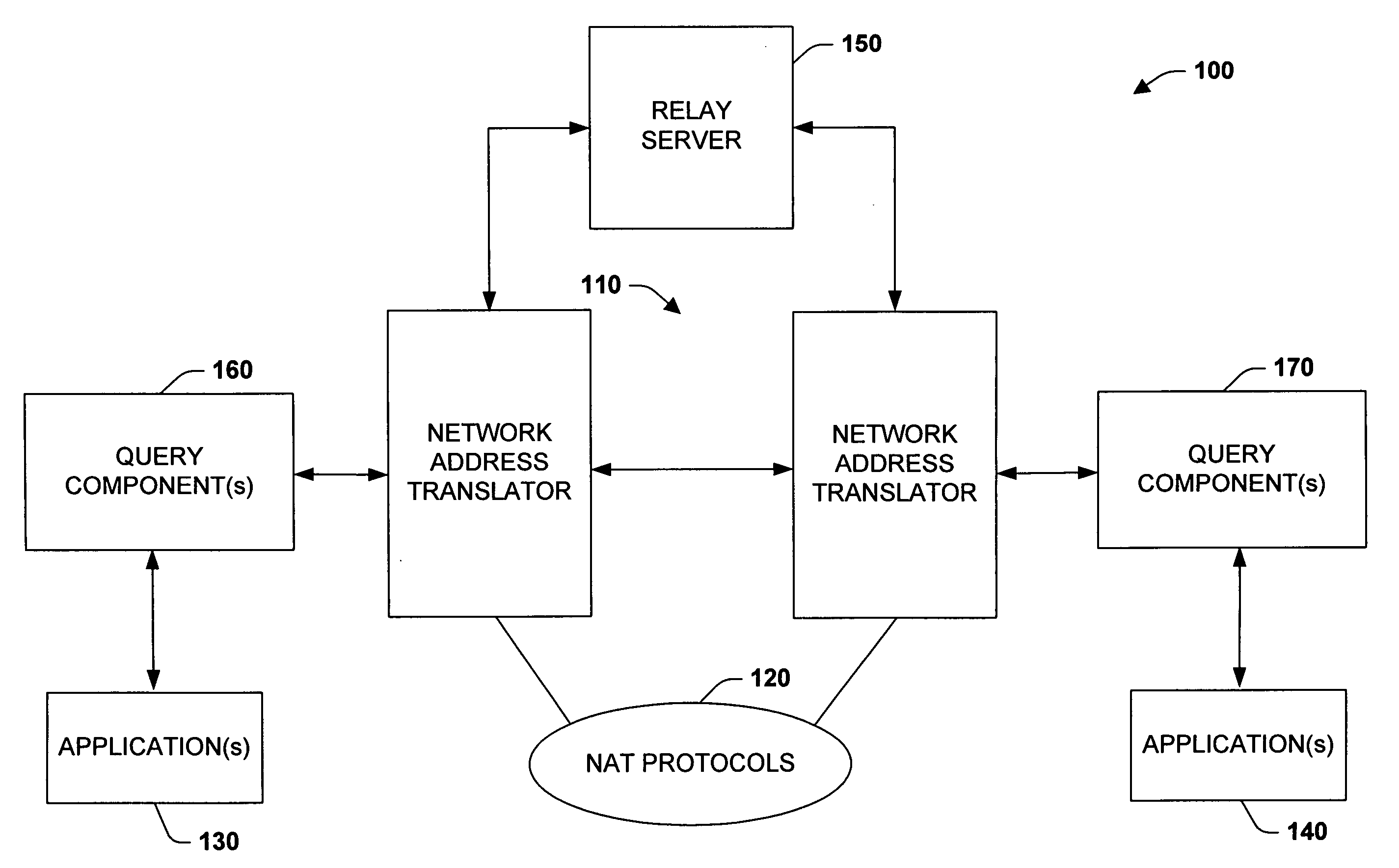
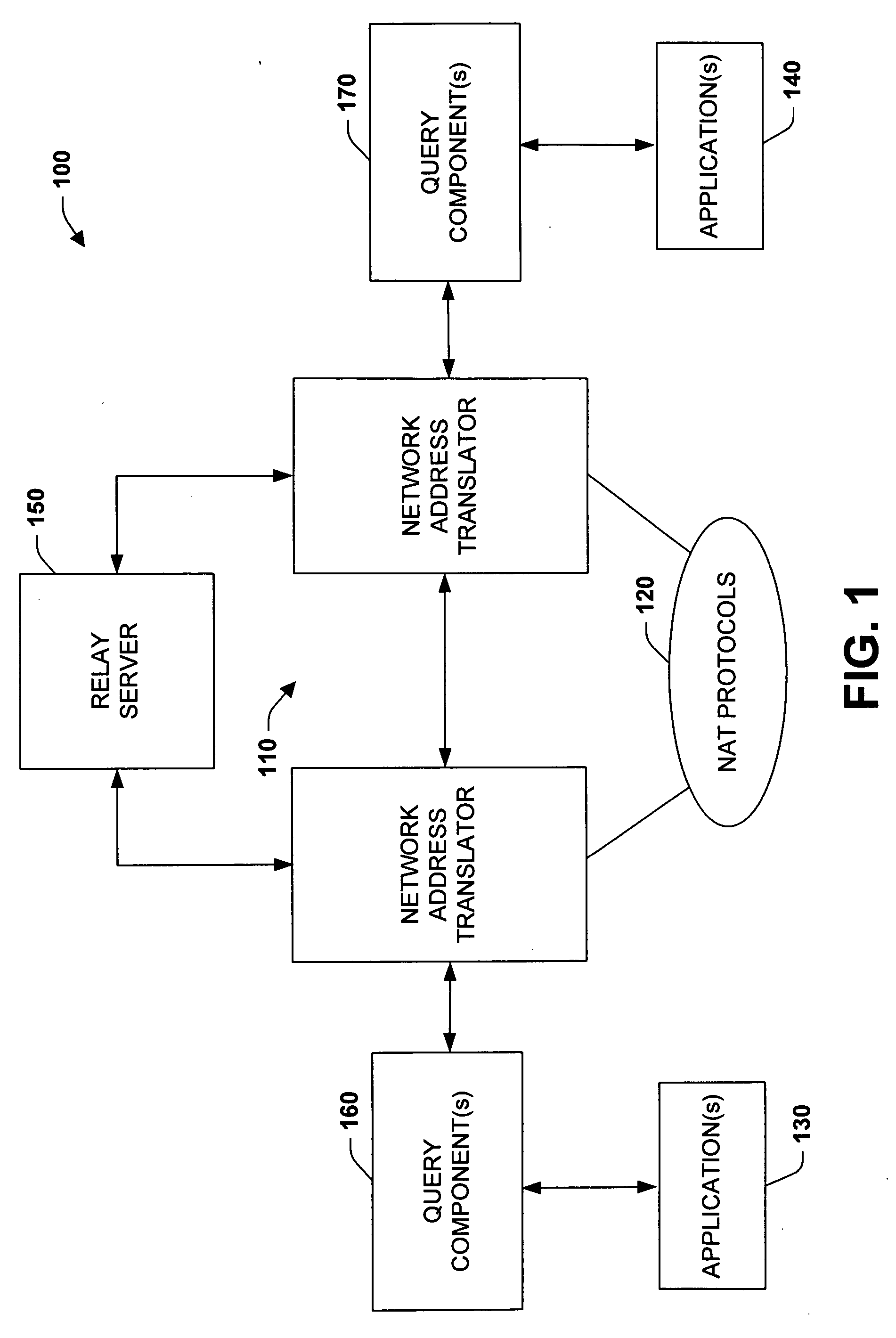
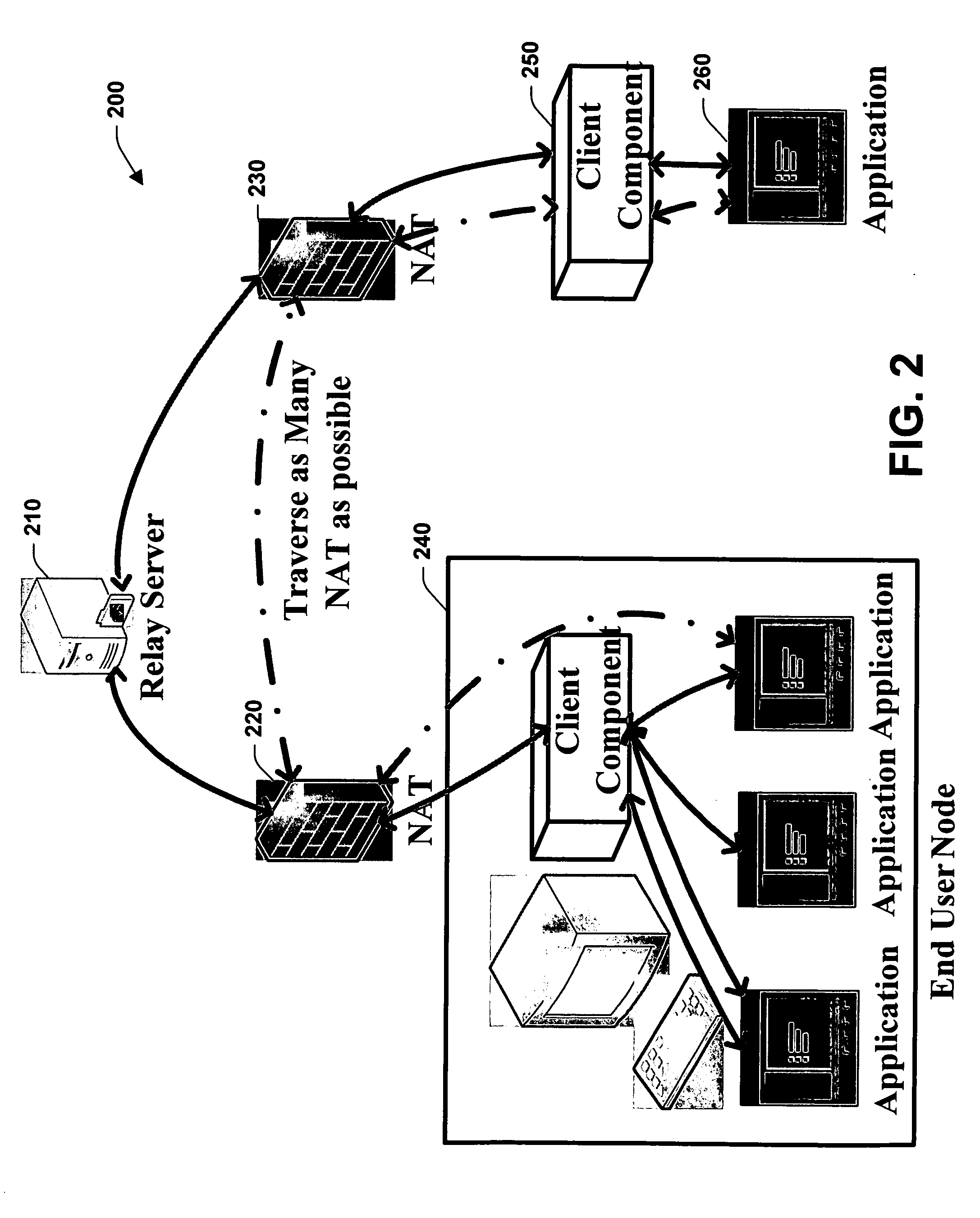
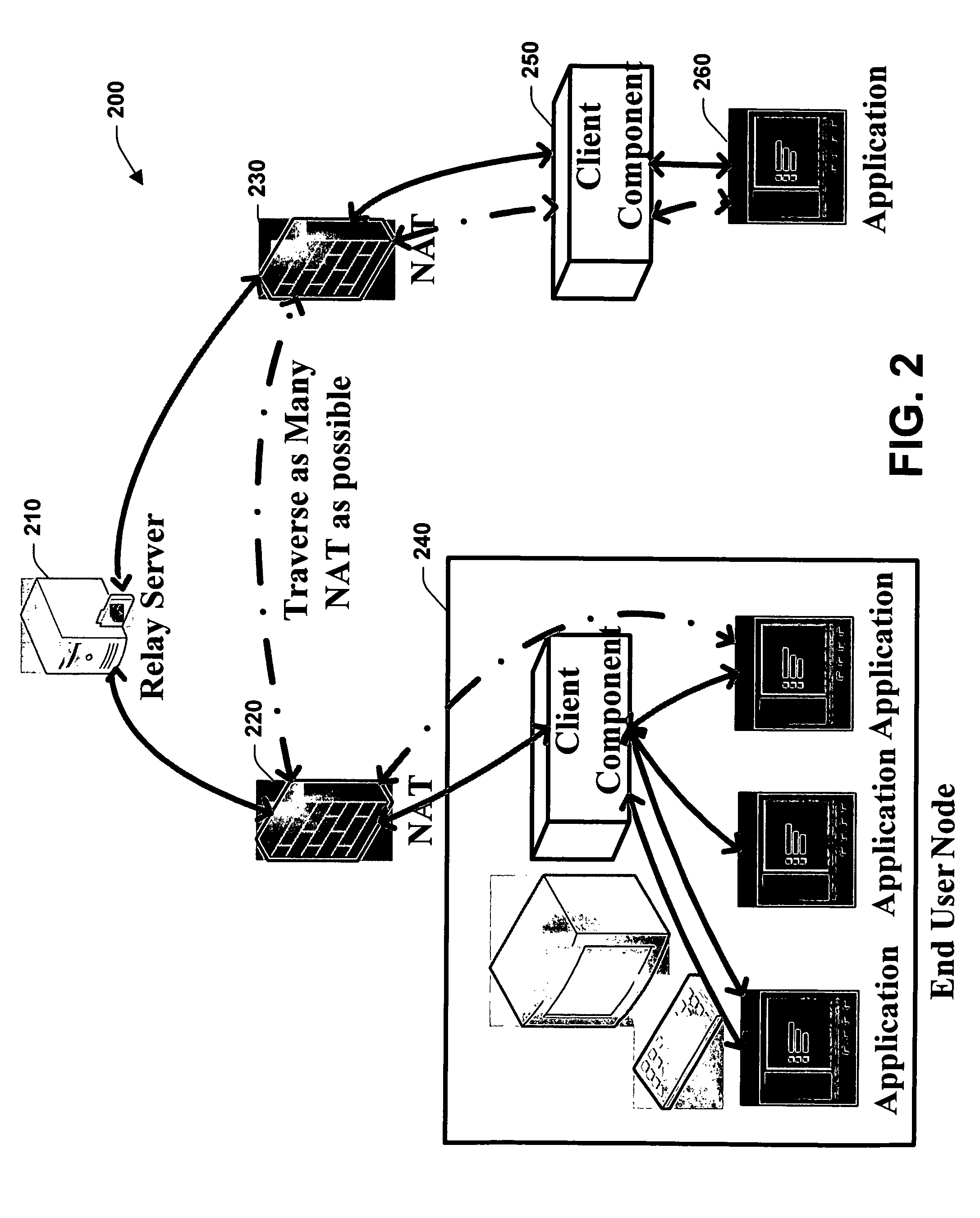
Automated NAT traversal for peer-to-peer networks
InactiveUS20060182100A1Facilitate communicationReduce administrative burdenData switching by path configurationMultiple digital computer combinationsCommunications systemNAT traversal
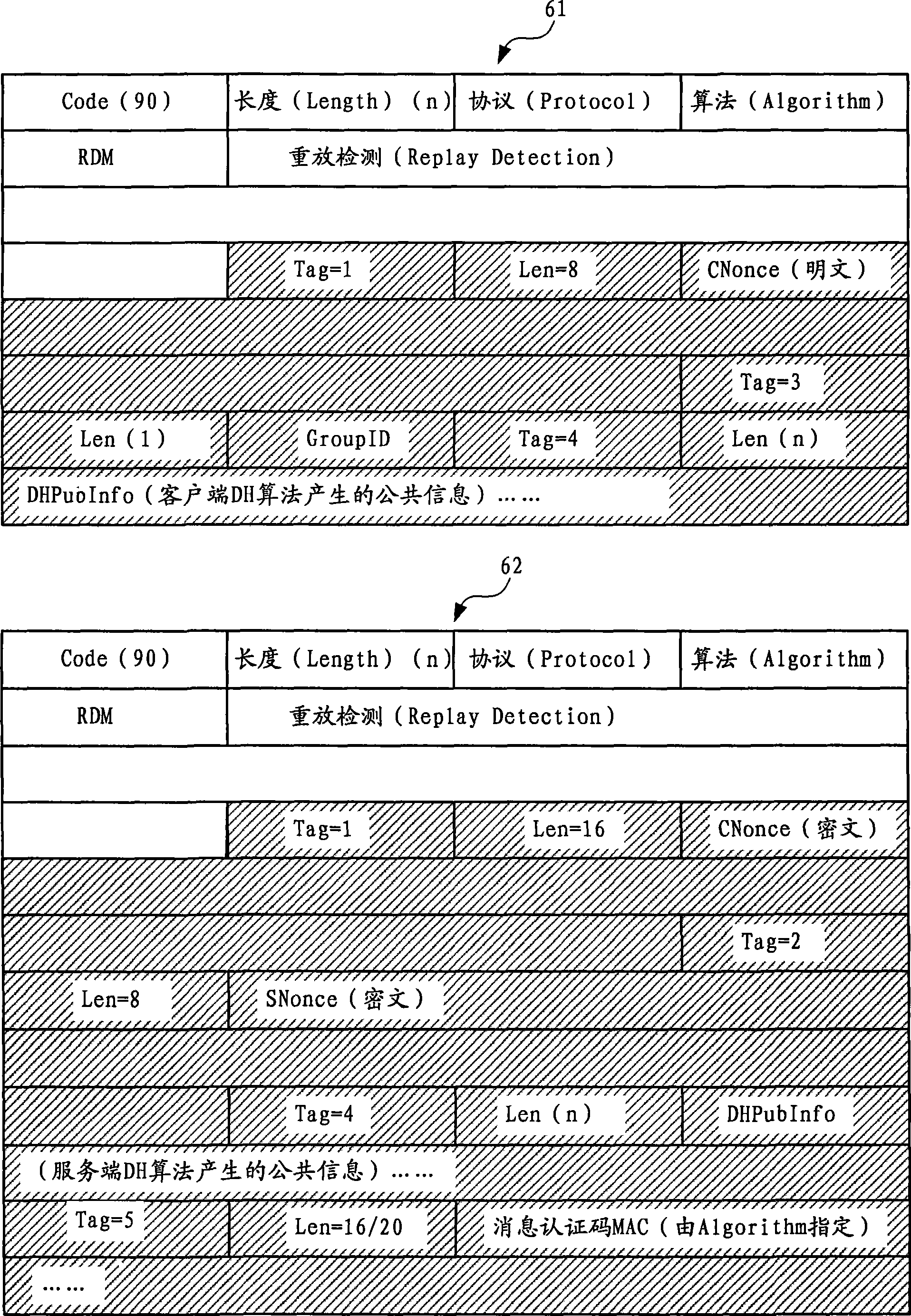
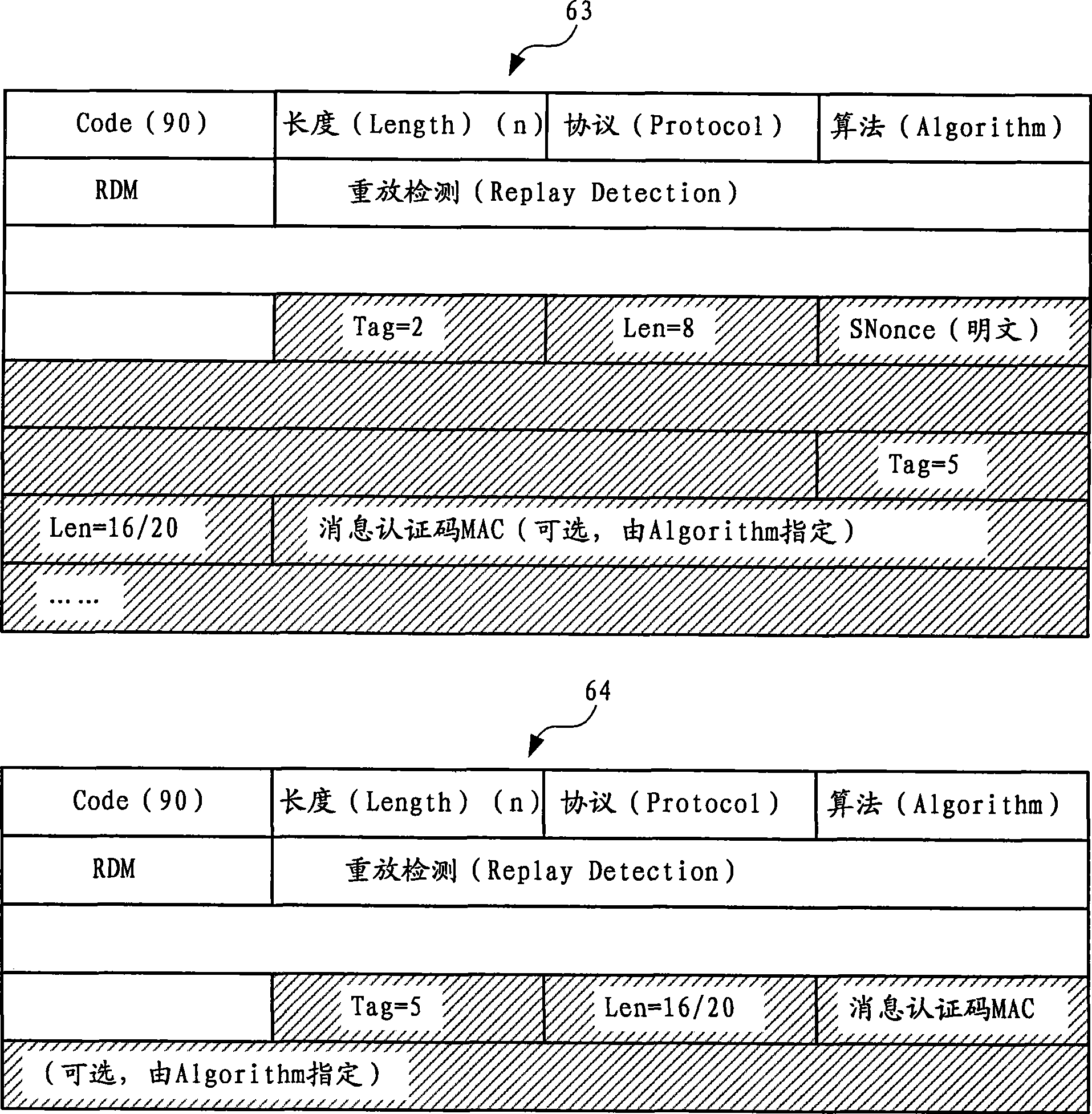
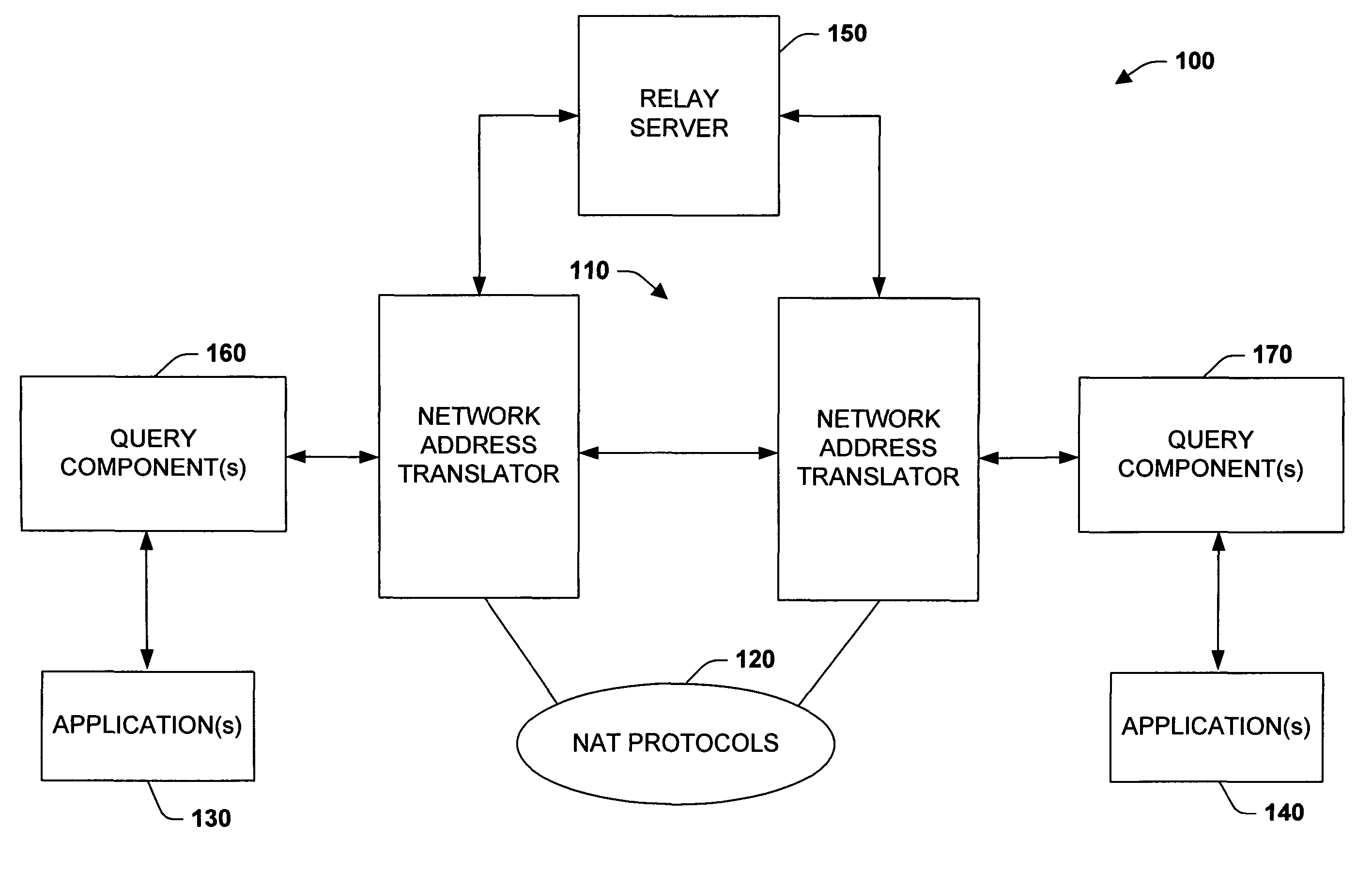
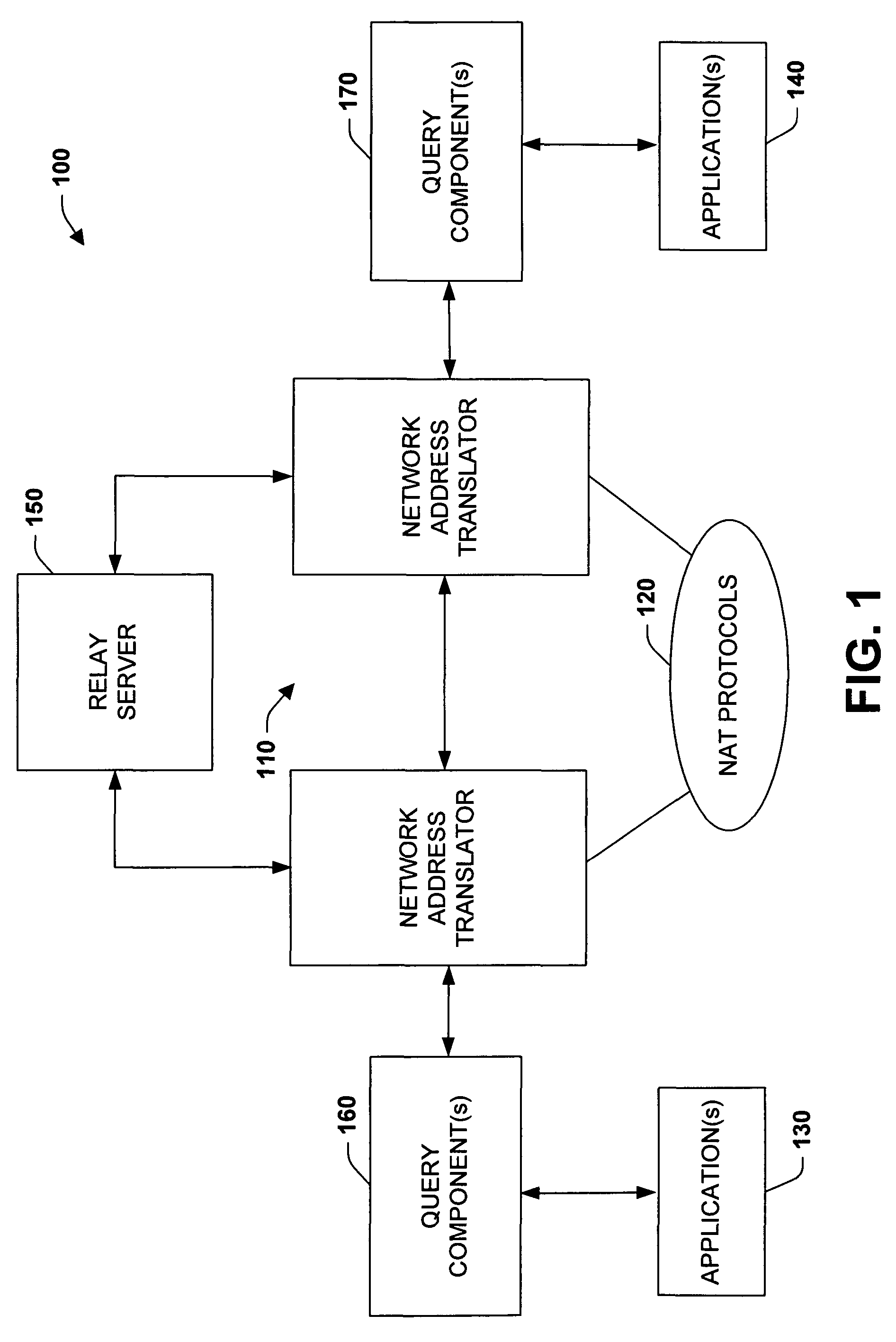
The subject invention relates to systems and methods that facilitate direct network communications between peers that operate behind Network Address Translators. In one aspect, a network communications system is provided. The system includes one or more Network Address Translators (NAT) to communicate data across a network between peers. A protocol selection component that automatically selects among a plurality of protocols according to one or more NAT types in order to determine a subset of the protocols that facilitate communications between the peers.
Owner:MICROSOFT TECH LICENSING LLC
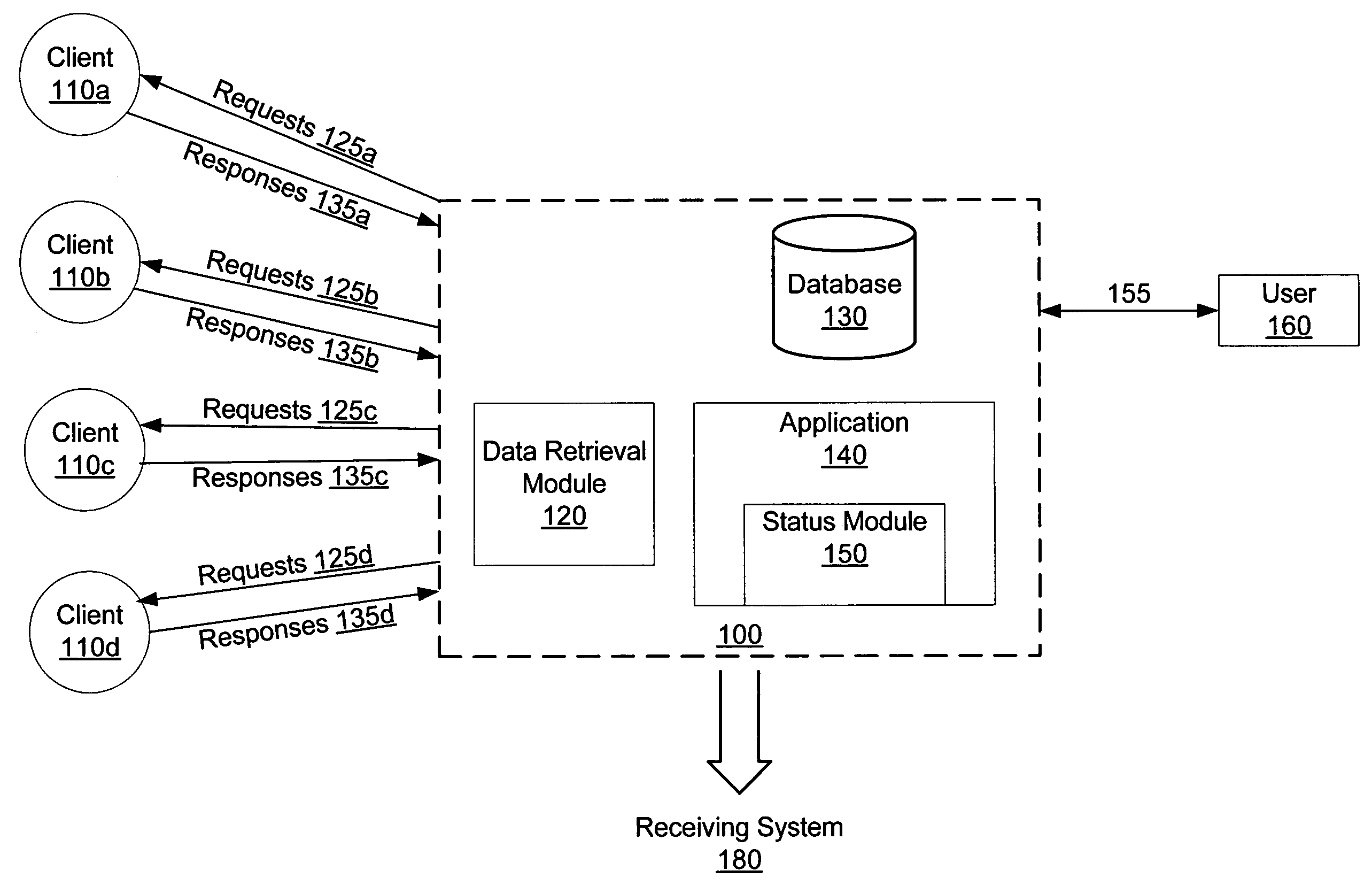
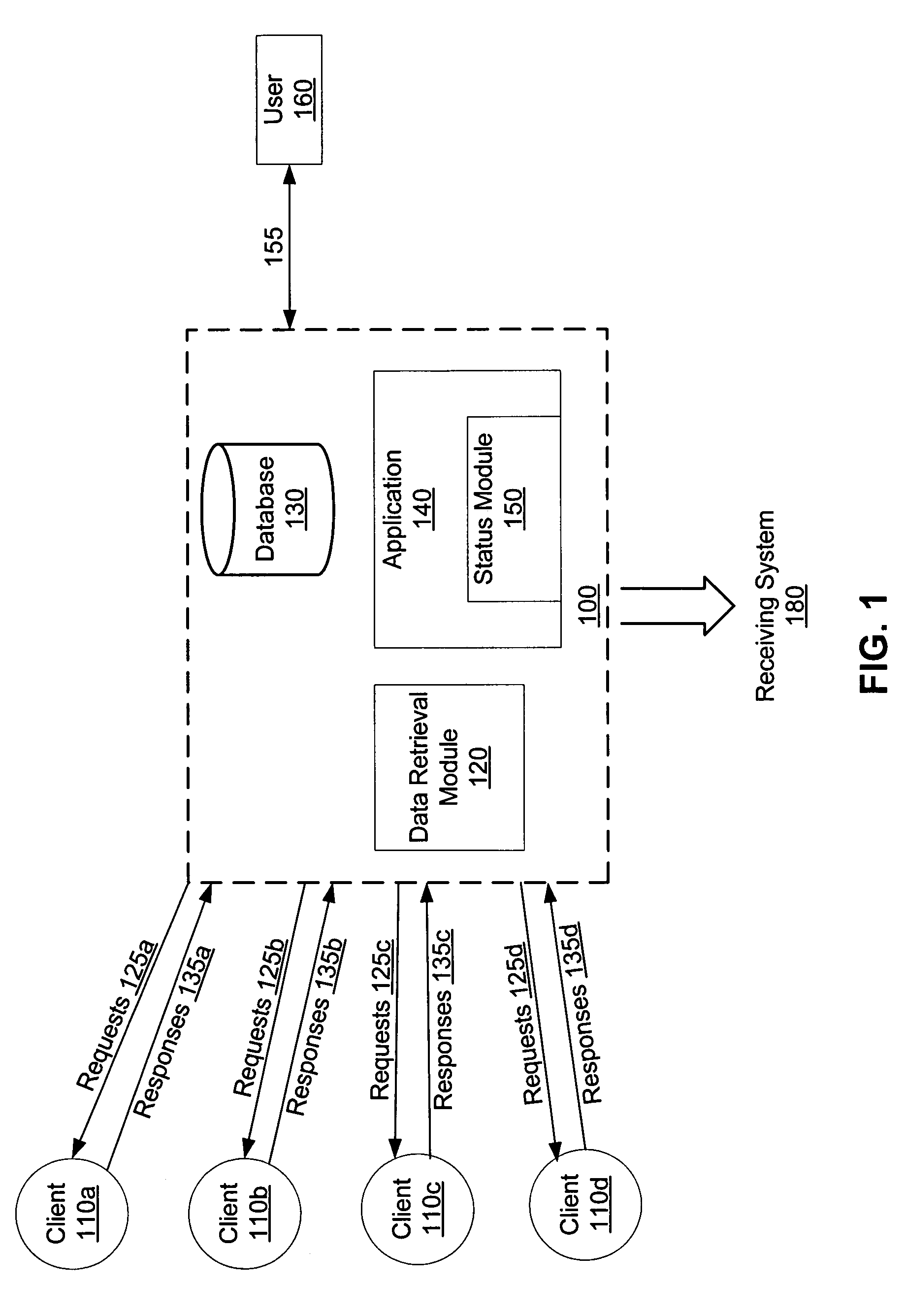
Automated data retrieval
ActiveUS7636742B1Reduce administrative burdenSave troubleData processing applicationsDigital data information retrievalState dependentData retrieval
Information missing from a database record is automatically identified and retrieved. In an embodiment, after the record is initially populated, a status such as complete, incomplete, missing, or verify is assigned to each field in the record. A request for information associated with the status is automatically generated, for instance asking a client to provide missing information or verify existing information. The request is transmitted to the client and solicits the client's response in any of a number of ways, for instance by email, phone, fax, or mail. The information is used to automatically update the record.
Owner:INTUIT INC
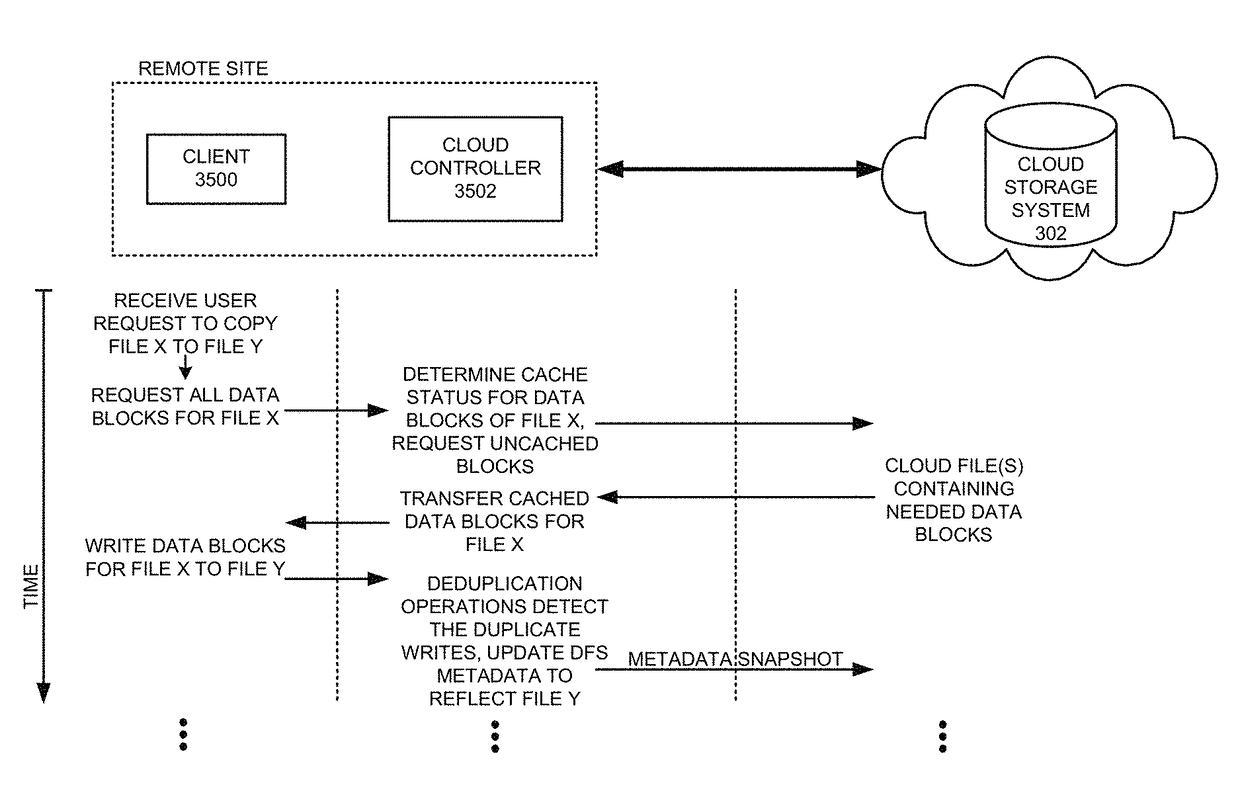
Executing a cloud command for a distributed filesystem
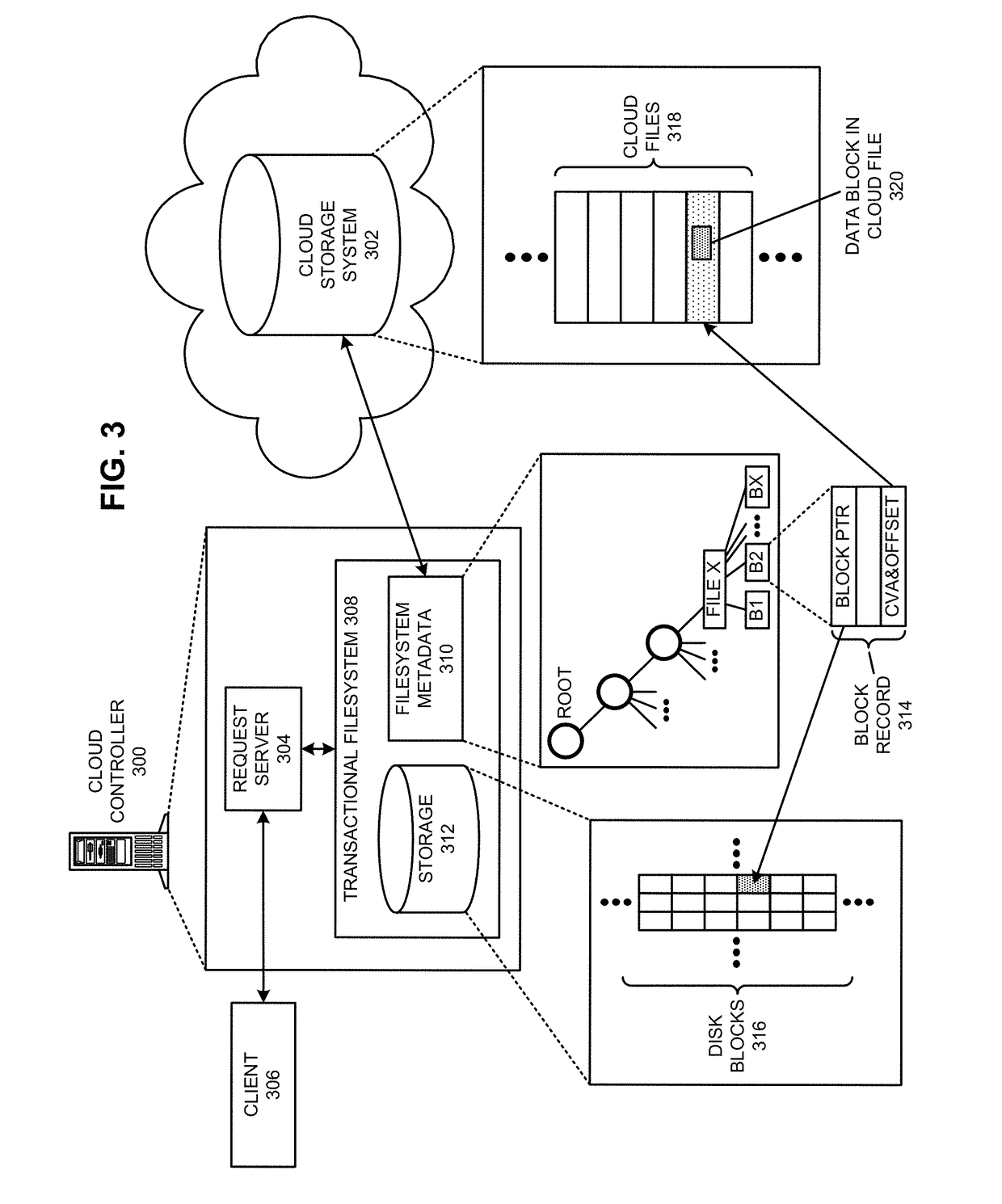
ActiveUS9811532B2Reduce perceived command execution timeReduce administrative burdenInput/output to record carriersDigital data information retrievalFile systemData file
The disclosed embodiments disclose techniques for executing a cloud command for a distributed filesystem. Two or more cloud controllers collectively manage distributed filesystem data that is stored in one or more cloud storage systems; the cloud controllers ensure data consistency for the stored data, and each cloud controller caches portions of the distributed filesystem. During operation, a cloud controller presents a distributed-filesystem-specific capability to a client system as a file in the distributed filesystem (e.g., using a file abstraction). Upon receiving a request from the client system to access and / or operate upon this file, the client controller executes an associated cloud command. More specifically, the cloud controller initiates a specially-defined operation that accesses additional functionality for the distributed filesystem that exceeds the scope of individual reads and writes to a typical data file.
Owner:PANZURA LLC
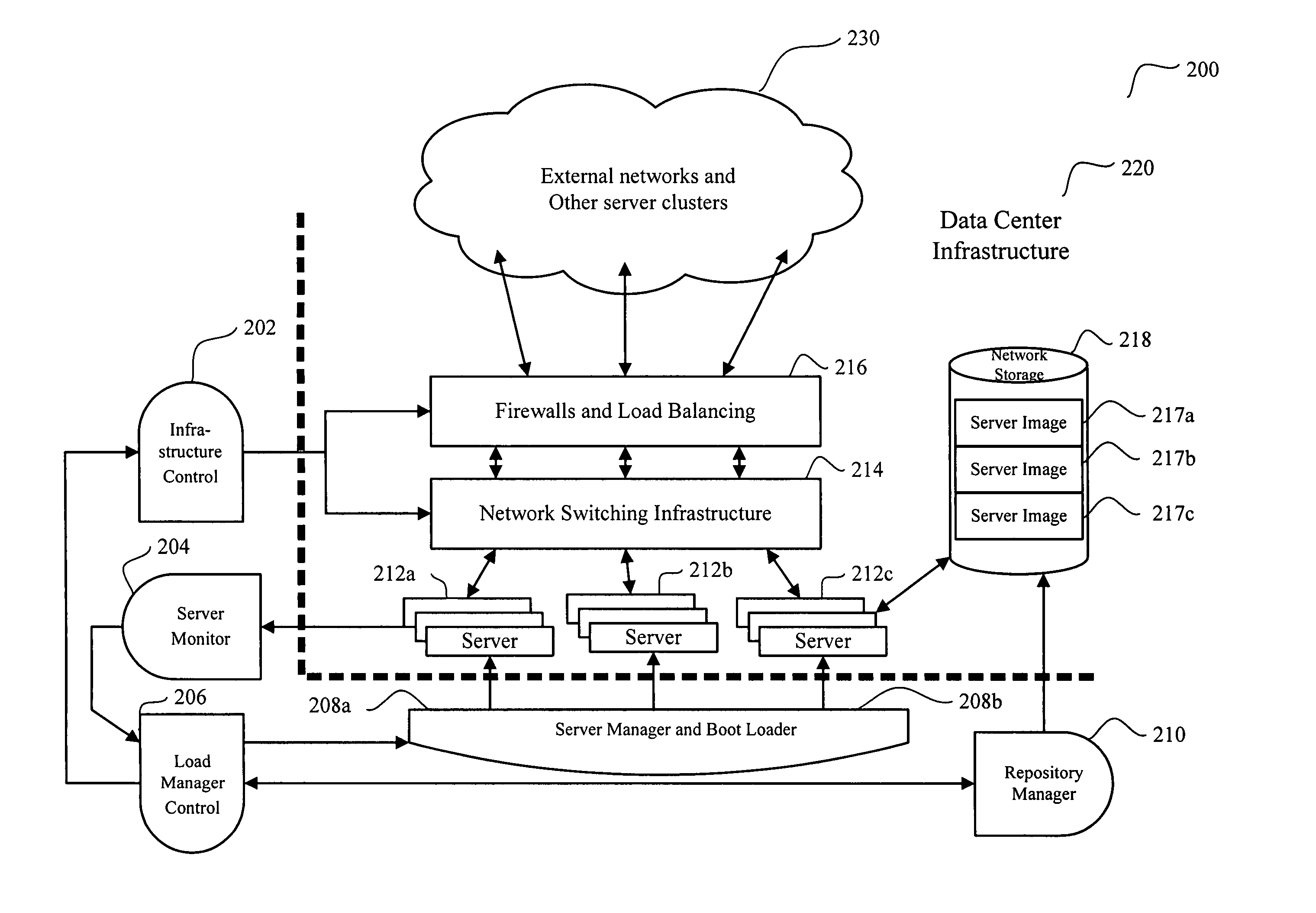
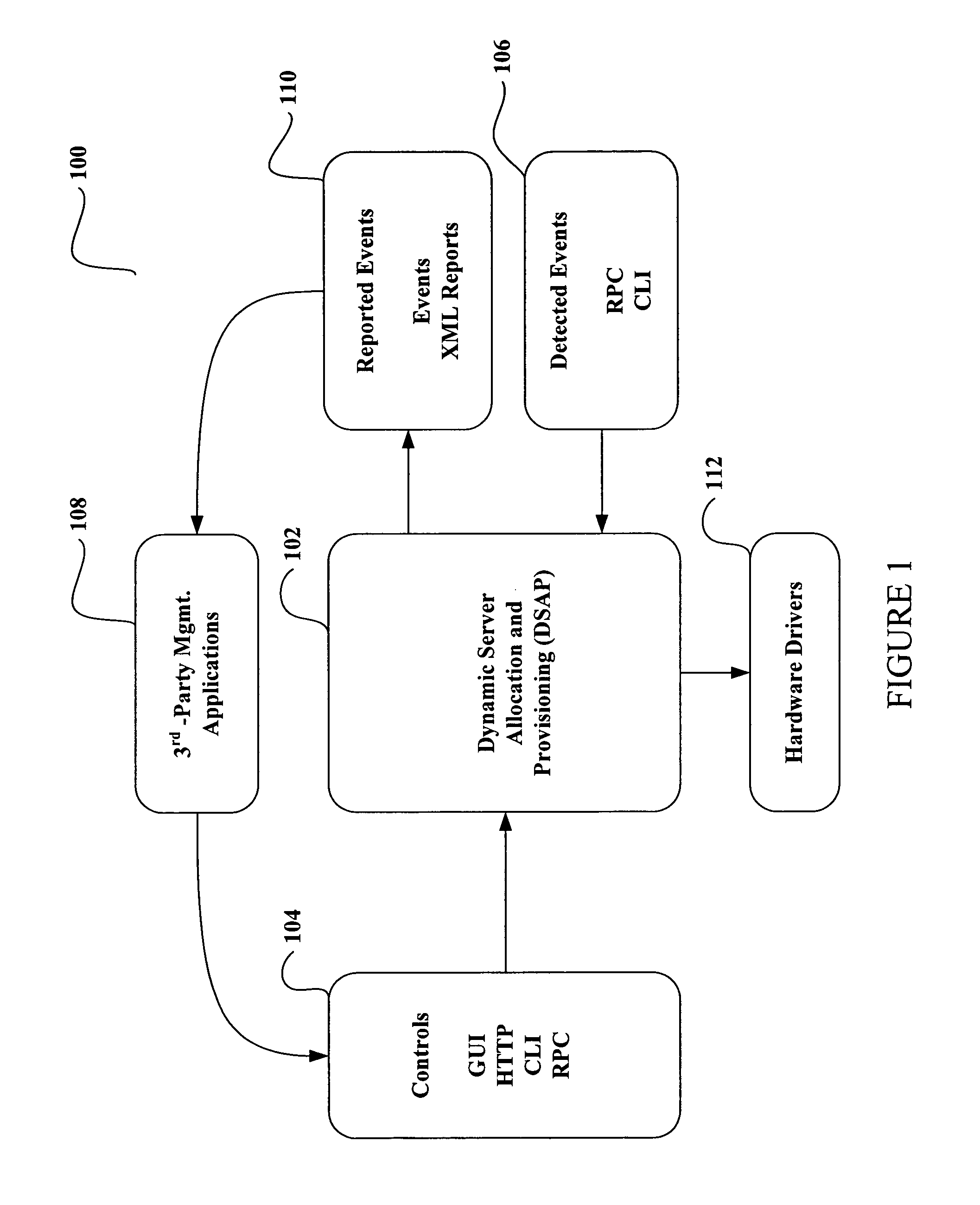
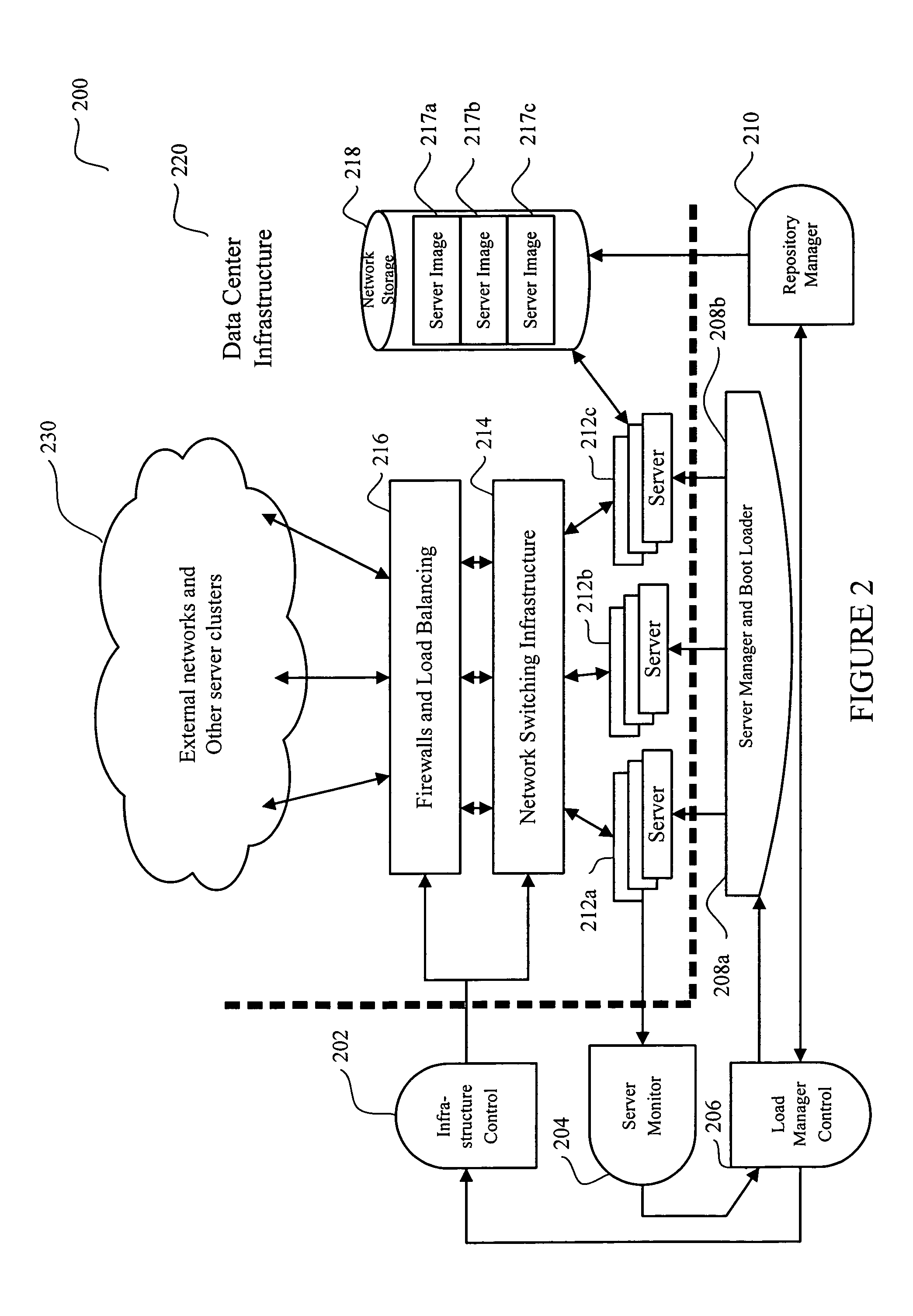
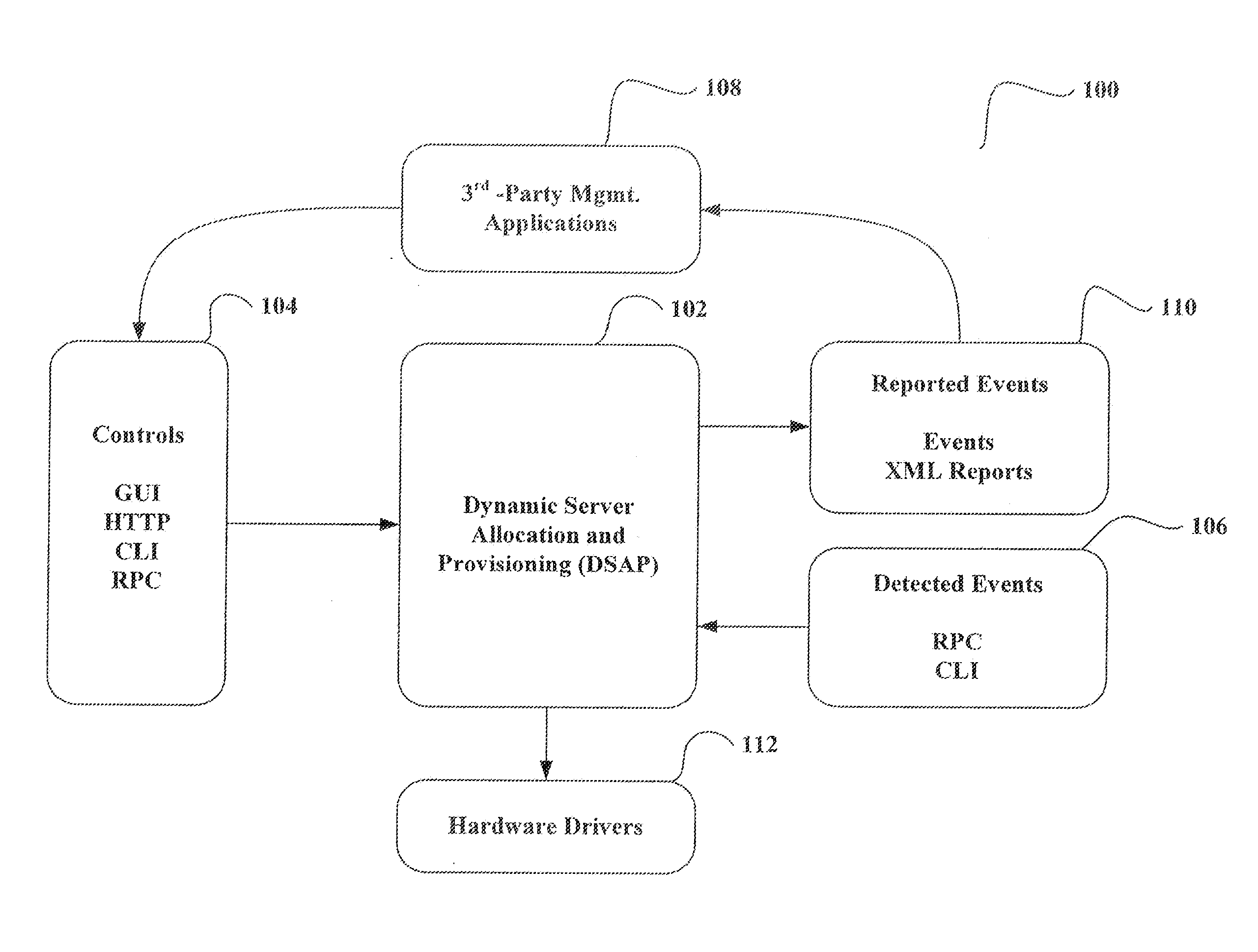
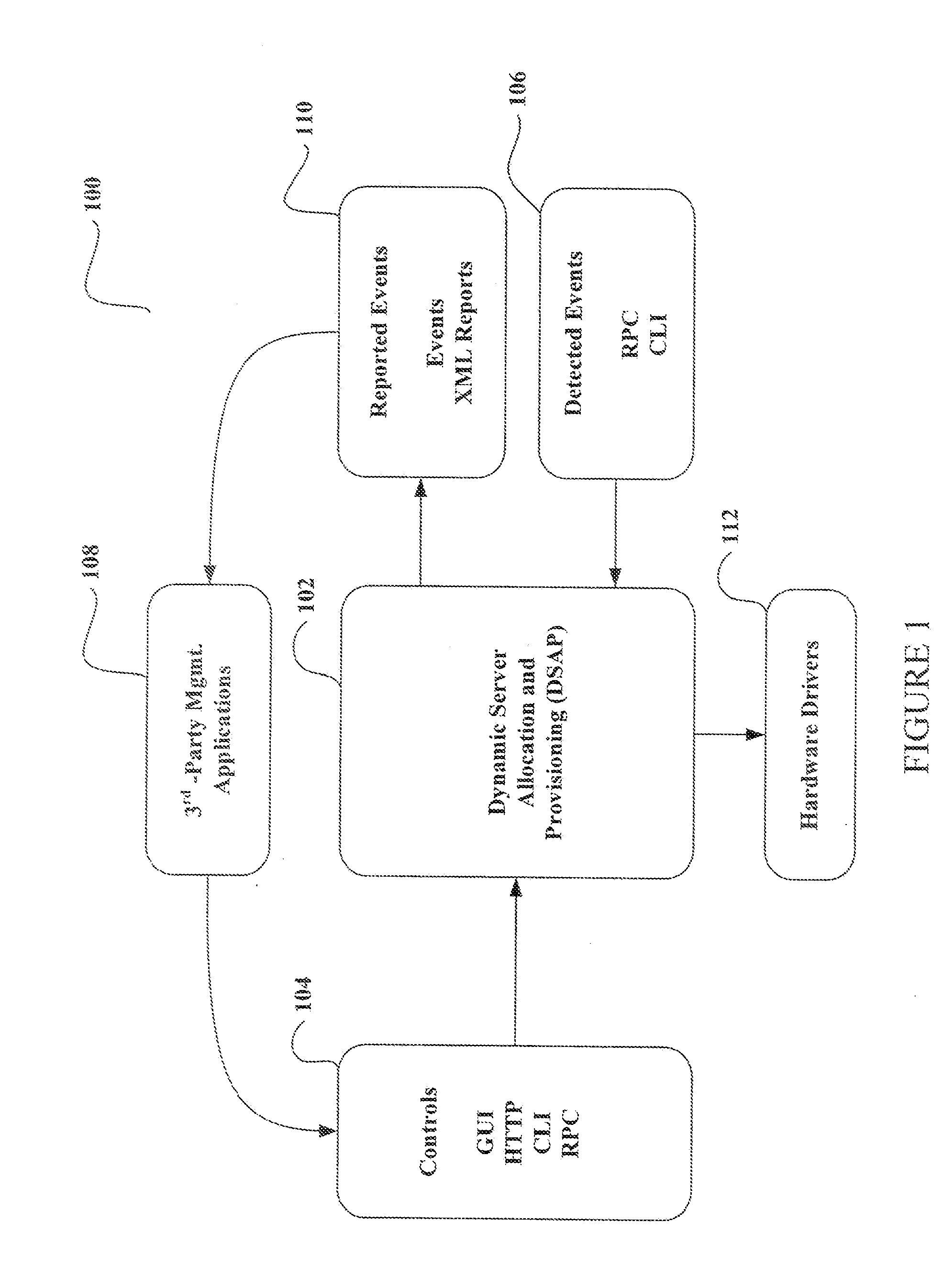
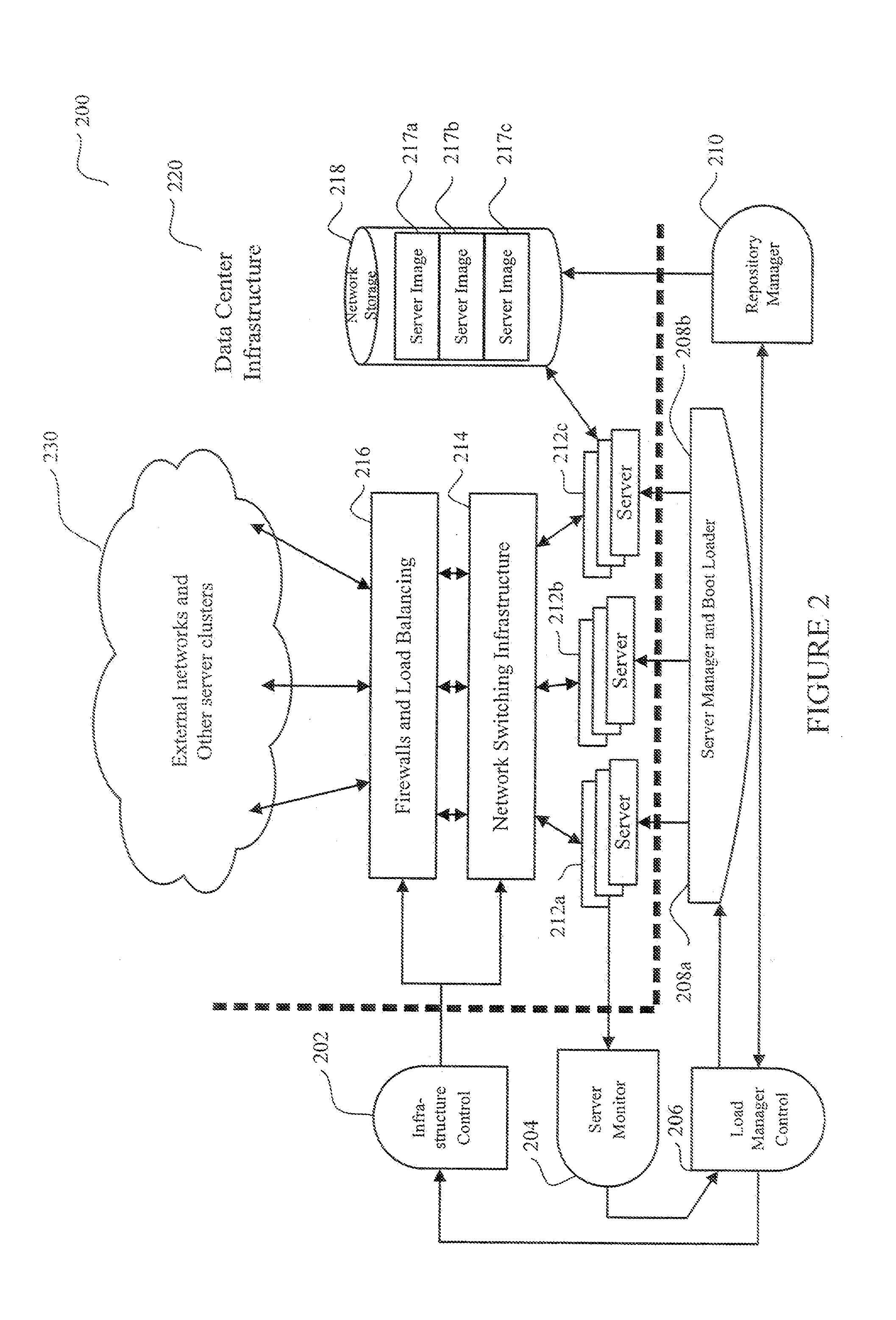
System and method for dynamic server allocation and provisioning
ActiveUS7213065B2Lower cost of capitalQuality improvementResource allocationDigital computer detailsManagement toolVirtual LAN
A management tool that streamlines the server allocation and provisioning processes within a data center is provided. The system, method, and computer program product divide the server provisioning and allocation into two separate tasks. Provisioning a server is accomplished by generating a fully configured, bootable system image, complete with network address assignments, virtual LAN (VLAN) configuration, load balancing configuration, and the like. System images are stored in a storage repository and are accessible to more than one server. Allocation is accomplished using a switching mechanism which matches each server with an appropriate system image based upon current configuration or requirements of the data center. Thus, real-time provisioning and allocation of servers in the form of automated responses to changing conditions within the data center is possible. The ability to instantly re-provision servers, safely and securely switch under-utilized server capacity to more productive tasks, and improve server utilization is also provided.
Owner:RACEMI
System and method for dynamic server allocation and provisioning
InactiveUS20070250608A1Lower cost of capitalQuality improvementResource allocationDigital computer detailsLoad SheddingManagement tool
A management tool that streamlines the server allocation and provisioning processes within a data center is provided. The system, method, and computer program product divide the server provisioning and allocation into two separate tasks. Provisioning a server is accomplished by generating a fully configured, bootable system image, complete with network address assignments, virtual LAN (VLAN) configuration, load balancing configuration, and the like. System images are stored in a storage repository and are accessible to more than one server. Allocation is accomplished using a switching mechanism which matches each server with an appropriate system image based upon current configuration or requirements of the data center. Thus, real-time provisioning and allocation of servers in the form of automated responses to changing conditions within the data center is possible. The ability to instantly re-provision servers, safely and securely switch under-utilized server capacity to more productive tasks, and improve server utilization is also provided.
Owner:RACEMI
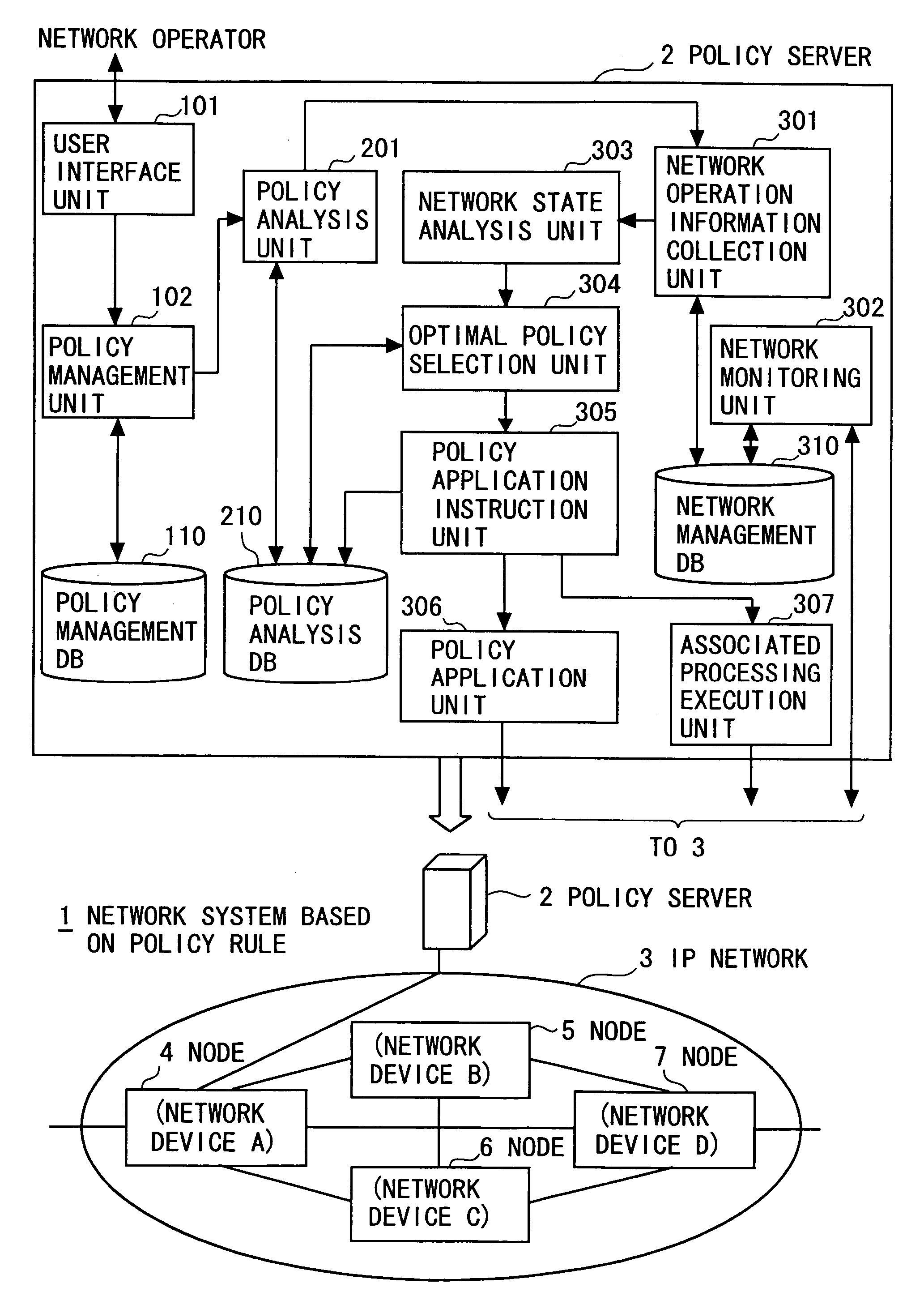
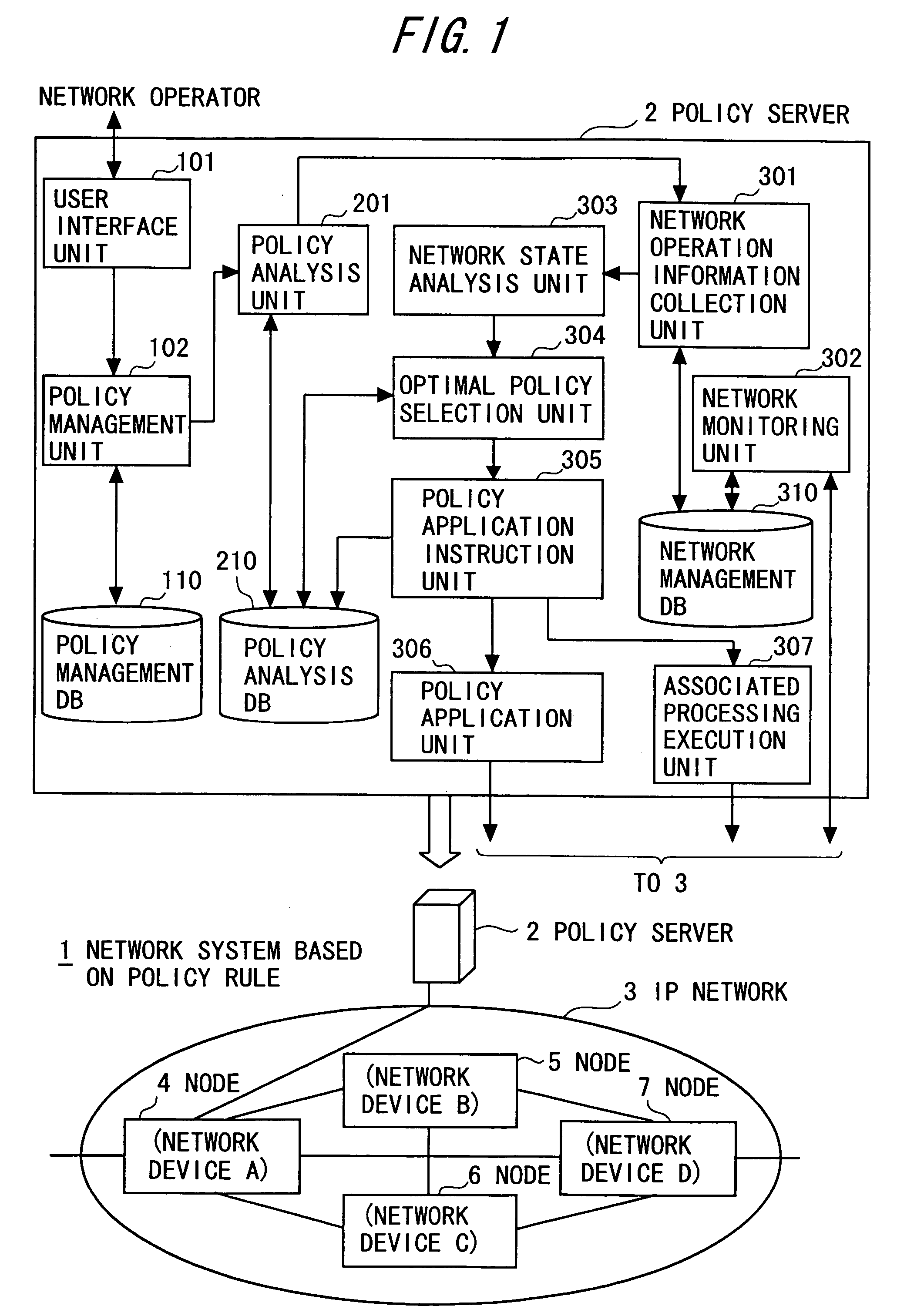
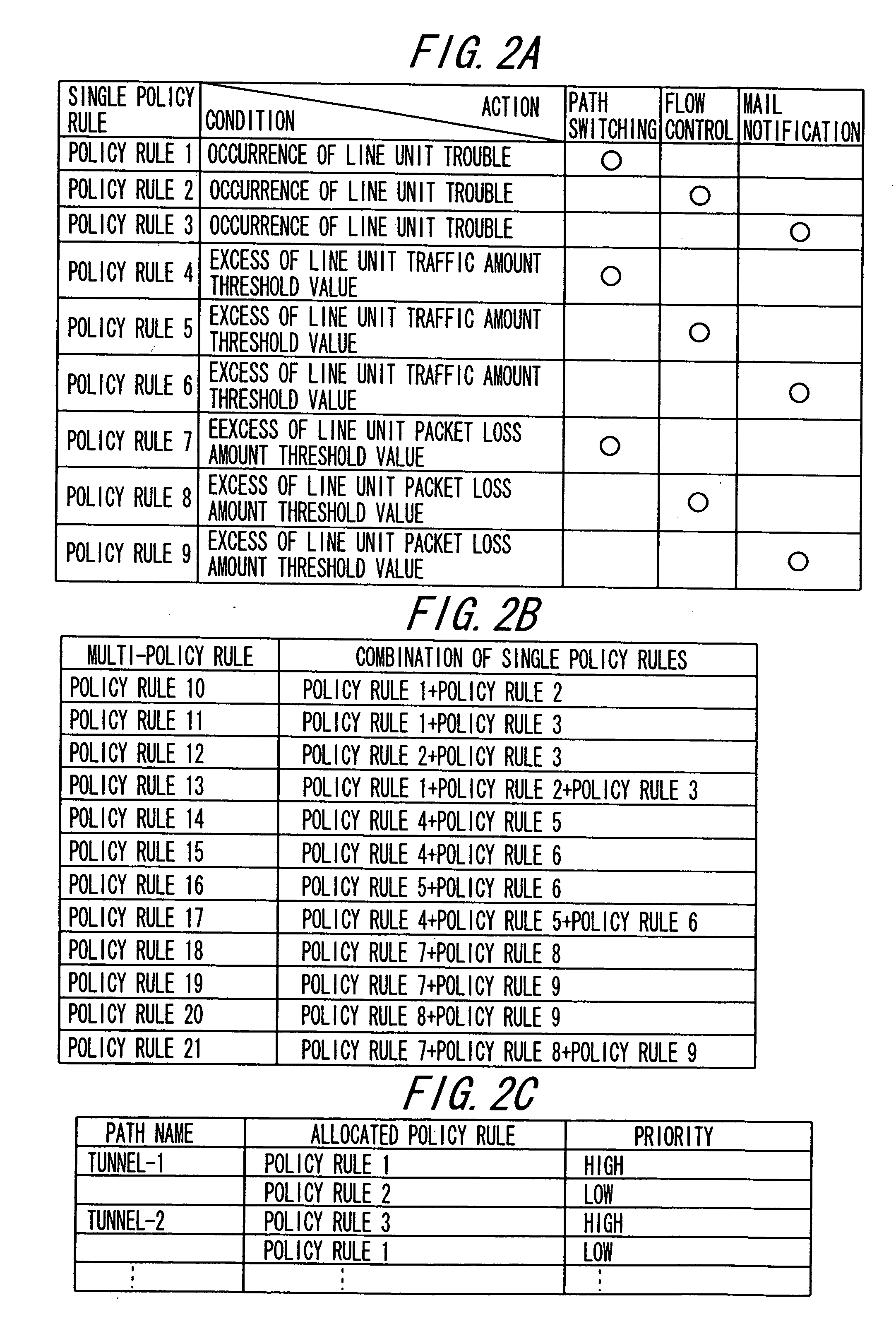
Network system based on policy rule
InactiveUS20060294219A1Suppressing a monotonous increase in single policy rulesReduce loadDigital computer detailsData switching networksControl equipmentStorage cell
A policy control device for reflecting a policy rule defined by a condition and an action corresponding to the condition for operation setting of respective network devices present in a network to be managed, according to a transition of operation states of the network, including a storage unit for storing a plurality of multi-policy rules generated in units of combination of at least two single policy rules having different actions on the same condition, together with particular information of a network device to be applied, in such a manner that the plurality of multi-policy rules and the particular information can be updated; and a control unit for applying one of the plurality of multi-policy rules stored in the storage unit for the operation setting of the network device identified, based on the particular information.
Owner:FUJITSU LTD
Wireless microphone for use with an in-car video system
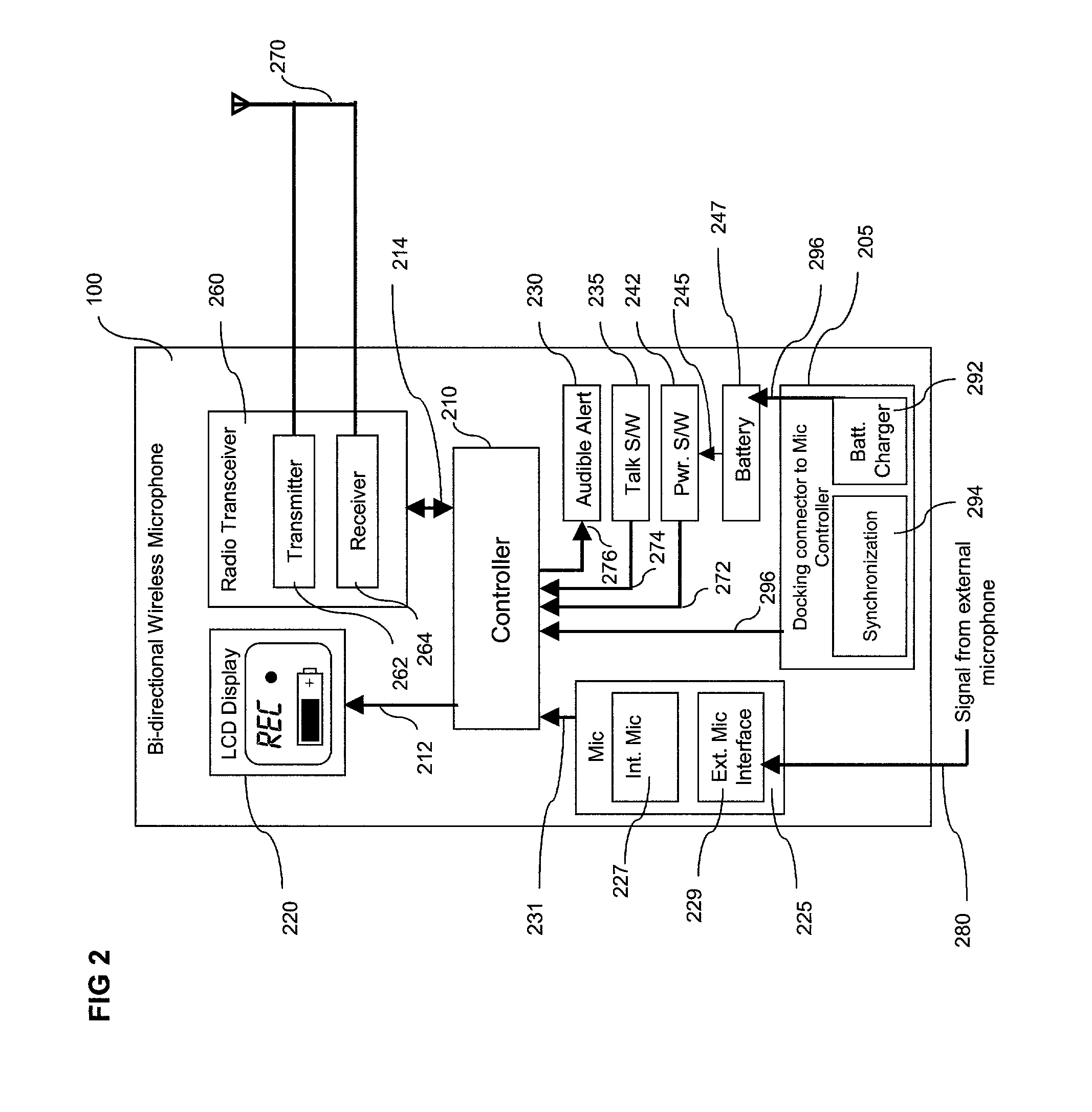
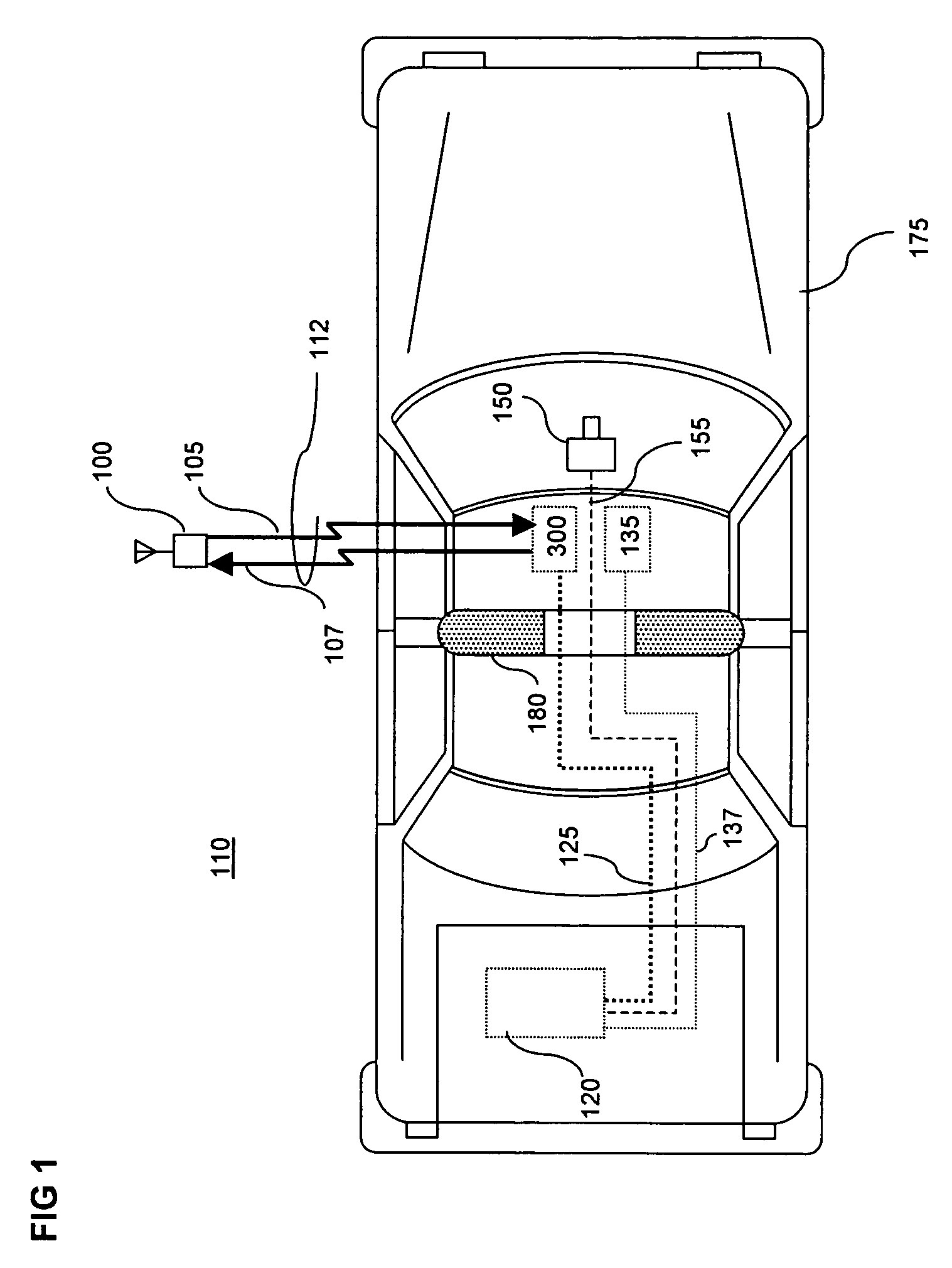
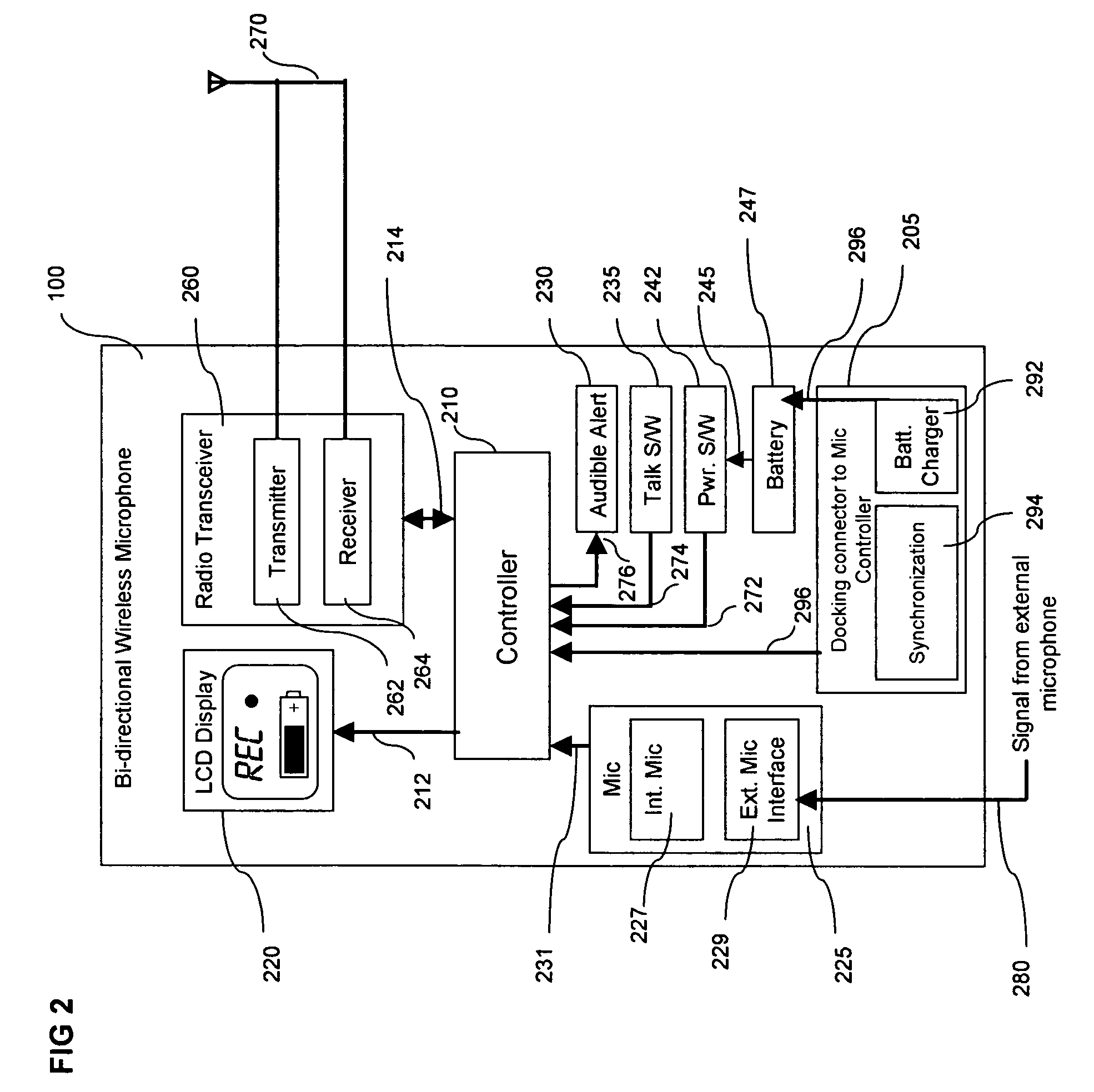
InactiveUS7119832B2Highly stressfulReduce administrative burdenColor television detailsClosed circuit television systemsWireless microphoneVocal tract
An in-car video system and method is provided where a wireless microphone is configured with bi-directional communications capability. In response to a received RF activation signal, the wireless microphone is automatically switched on to capture (and transmit back to the in-car video system) an audio soundtrack that accompanies the images captured by the car-mounted video camera. A wireless microphone controller mounted in the car transmits the RF activation signal to the wireless microphone. The wireless microphone controller is arranged to transmit the RF activation signal when the video recording device starts recording. In an illustrative embodiment of the invention, the wireless microphone receives information, including a confirmation that the video recording device is recording, from an RF information signal received from the wireless microphone controller mounted in the car. The wireless microphone displays the information to the officer on a display screen. The wireless microphone sounds an audible alert when it receives the RF activation or information signals.
Owner:L 3 COMM MOBILE VISION
System and method to facilitate separate cardholder and system access to resources controlled by a smart card
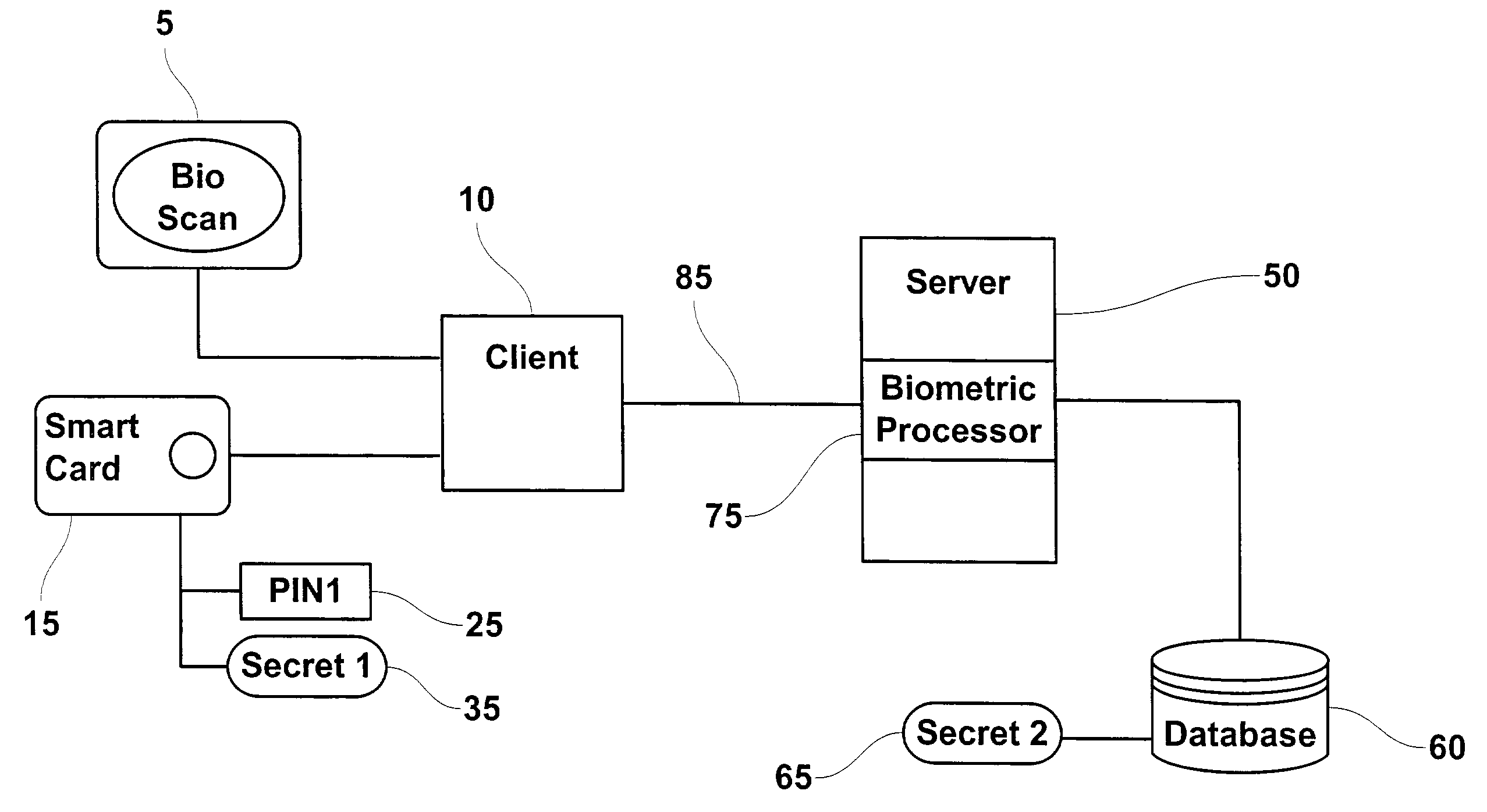
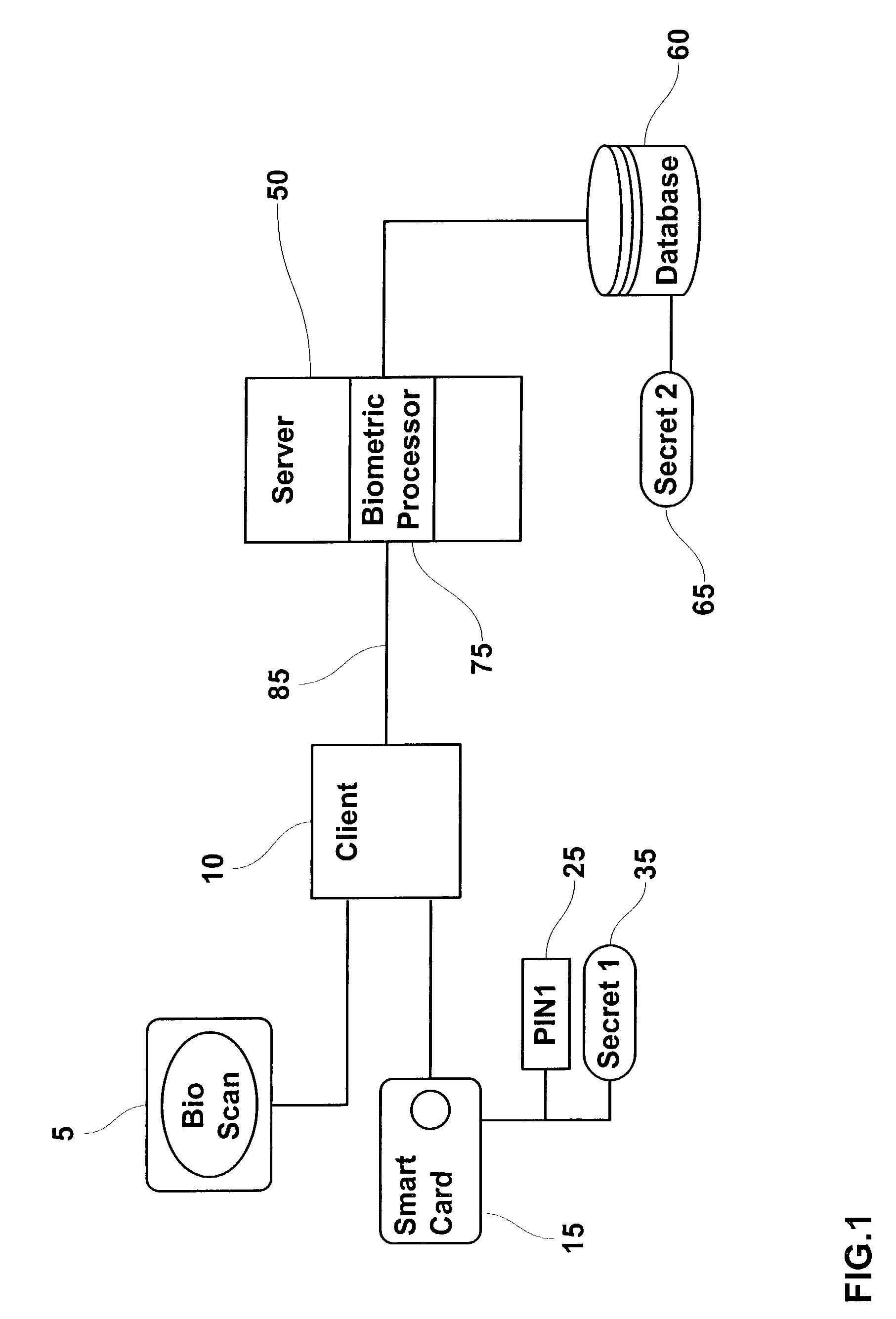
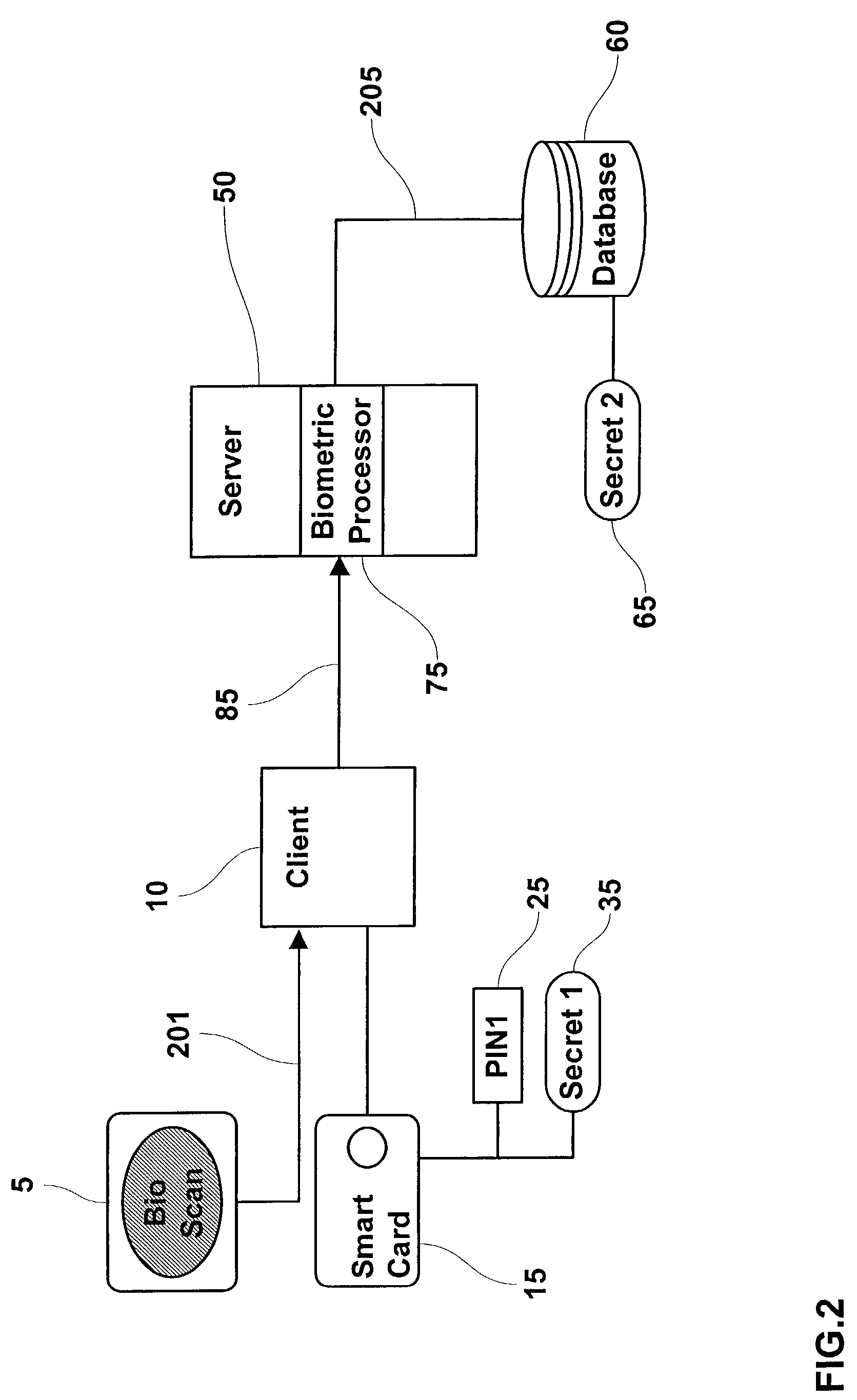
InactiveUS20040034784A1Reduce administrative burdenDigital data processing detailsUser identity/authority verificationPersonal identification numberEngineering
This invention provides a mechanism, which allows a user's personal identification number (PIN) to operate independently from a biometric authentication system. This improvement reduces the administrative burden of having to keep a user's PIN synchronized with the PIN used to access the user's smart card following successful biometric authentication. The first embodiment of the invention incorporates a cryptographic interface, which bypasses the PIN entry and allows the biometric authentication system to directly access card resources. The second embodiment of the invention provides a second system PIN having greater bit strength than the cardholder PIN. Both embodiments of the invention retrieve secrets (either a cryptographic key or system PIN) from a biometric database by comparing a processed biometric sample with known biometric templates. The biometric authentication system incorporates a client-server architecture, which facilitates multiple biometric authentications.
Owner:ASSA ABLOY AB
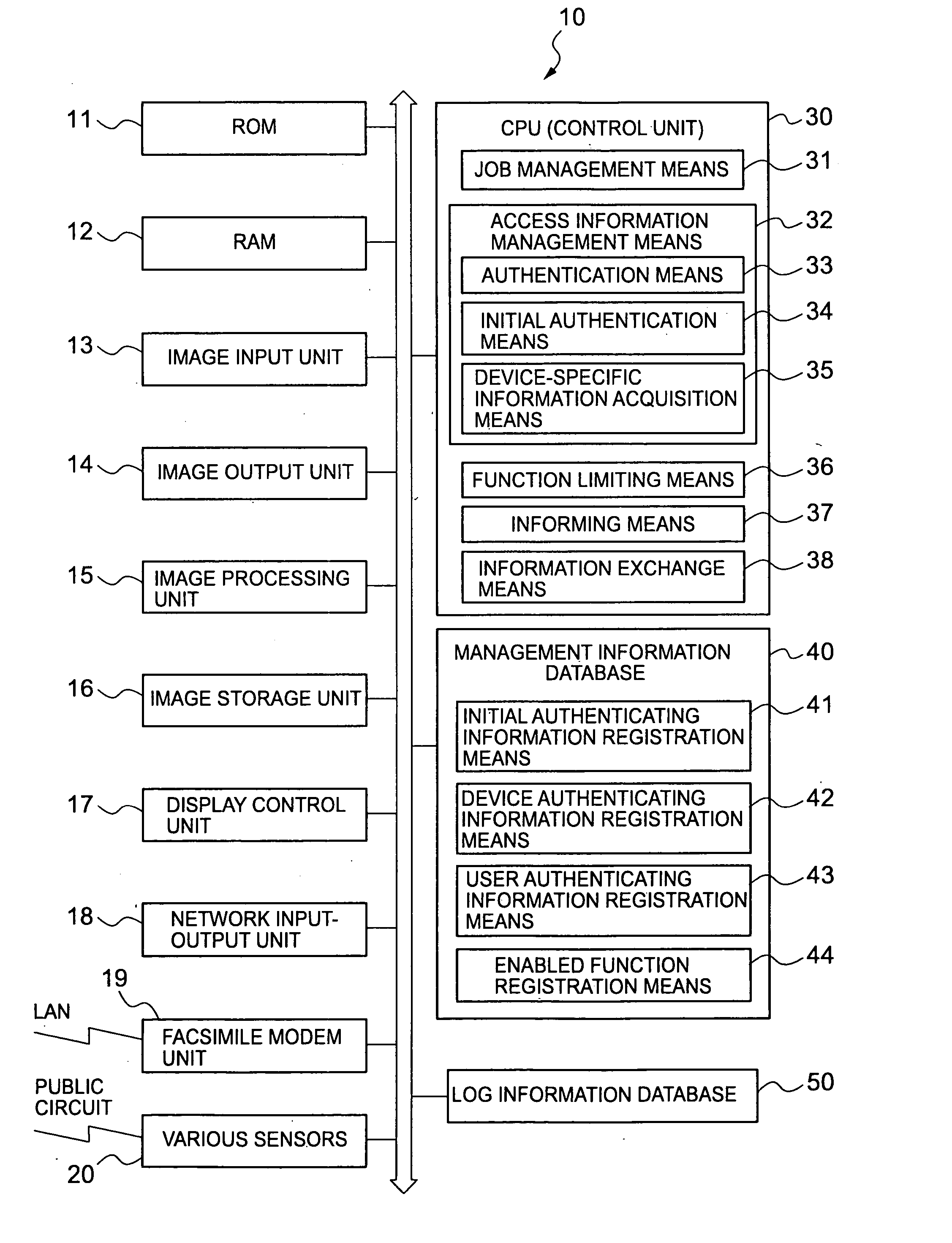
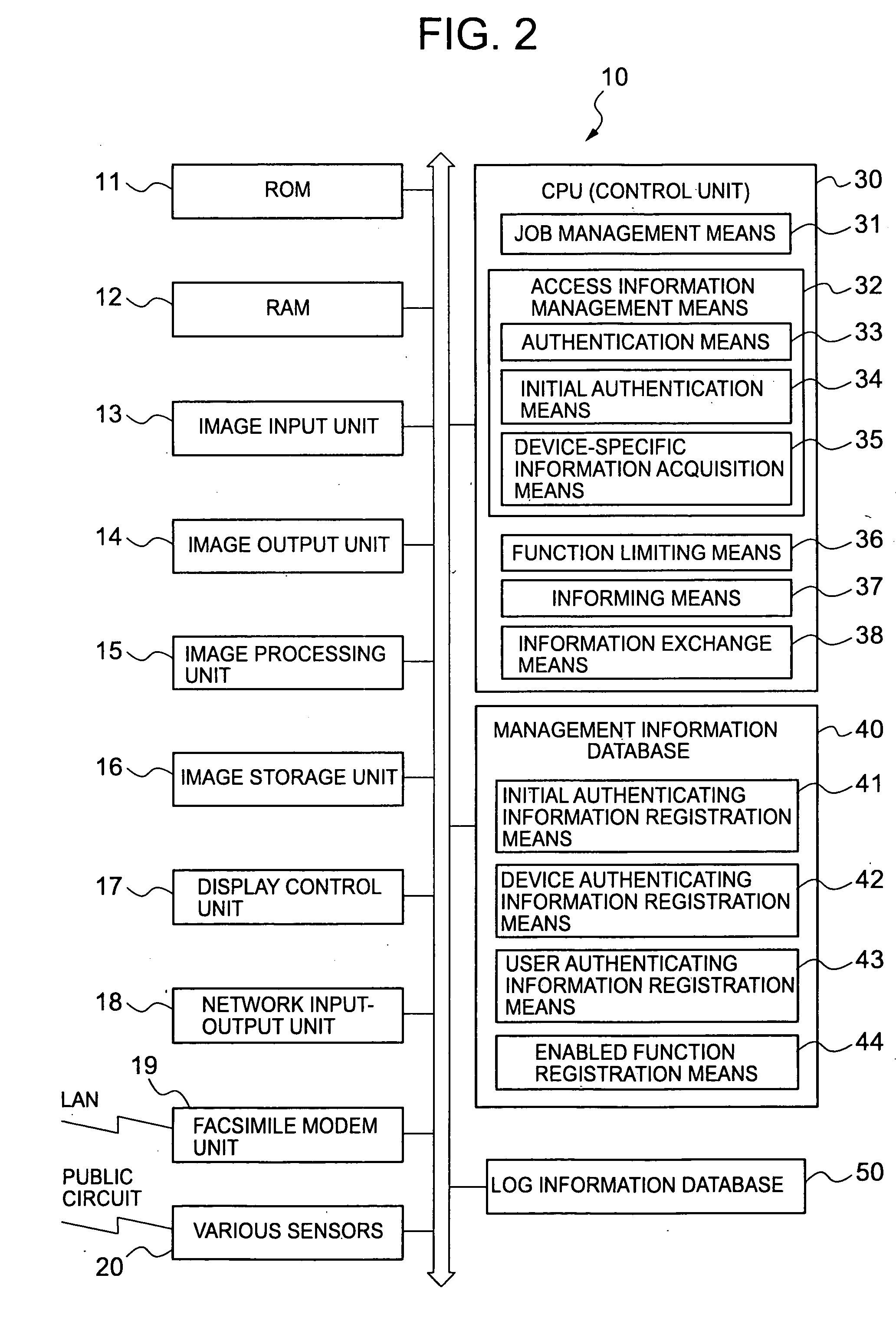
Remote processor
InactiveUS20050055547A1Reduce burdenIncreased operational burdenDigital data processing detailsHardware monitoringClient-sideInternet privacy
A remote processor for executing processing requested from a client via a network, wherein an access right is authenticated using authenticating information generated by combining user-configurable user setting information such as a user name and a password with device-specific information specific to the client such as a MAC address to improve security for remote accesses. An initial access is authenticated using user setting information specified by an administrator. If the authentication is successful, the device-specific information of the client is automatically acquired and registered. Subsequent accesses are authenticated by using the user setting information and the device-specific information as conditions logically ANDed together for the access right authentication.
Owner:KONICA MINOLTA BUSINESS TECH INC
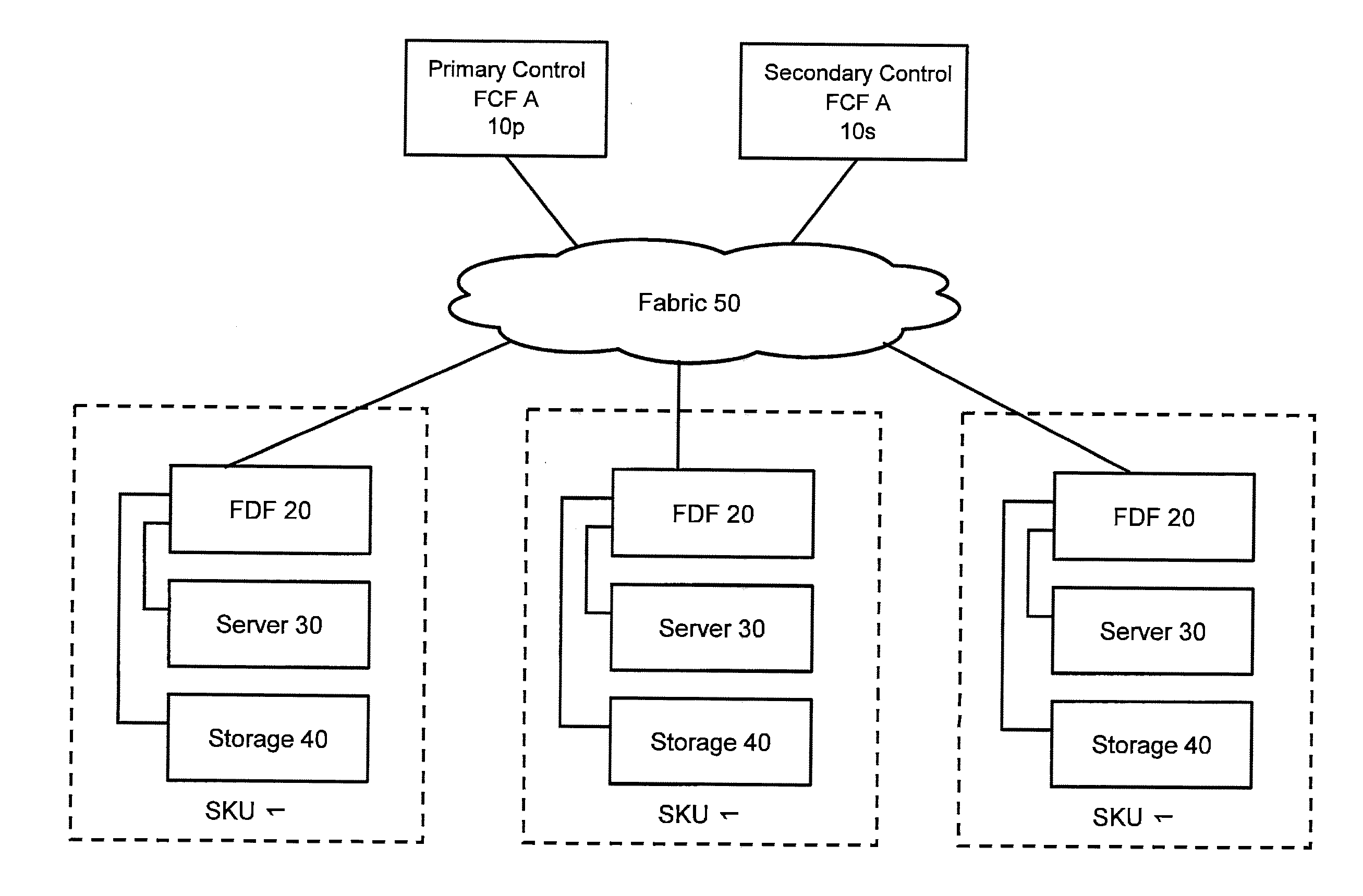
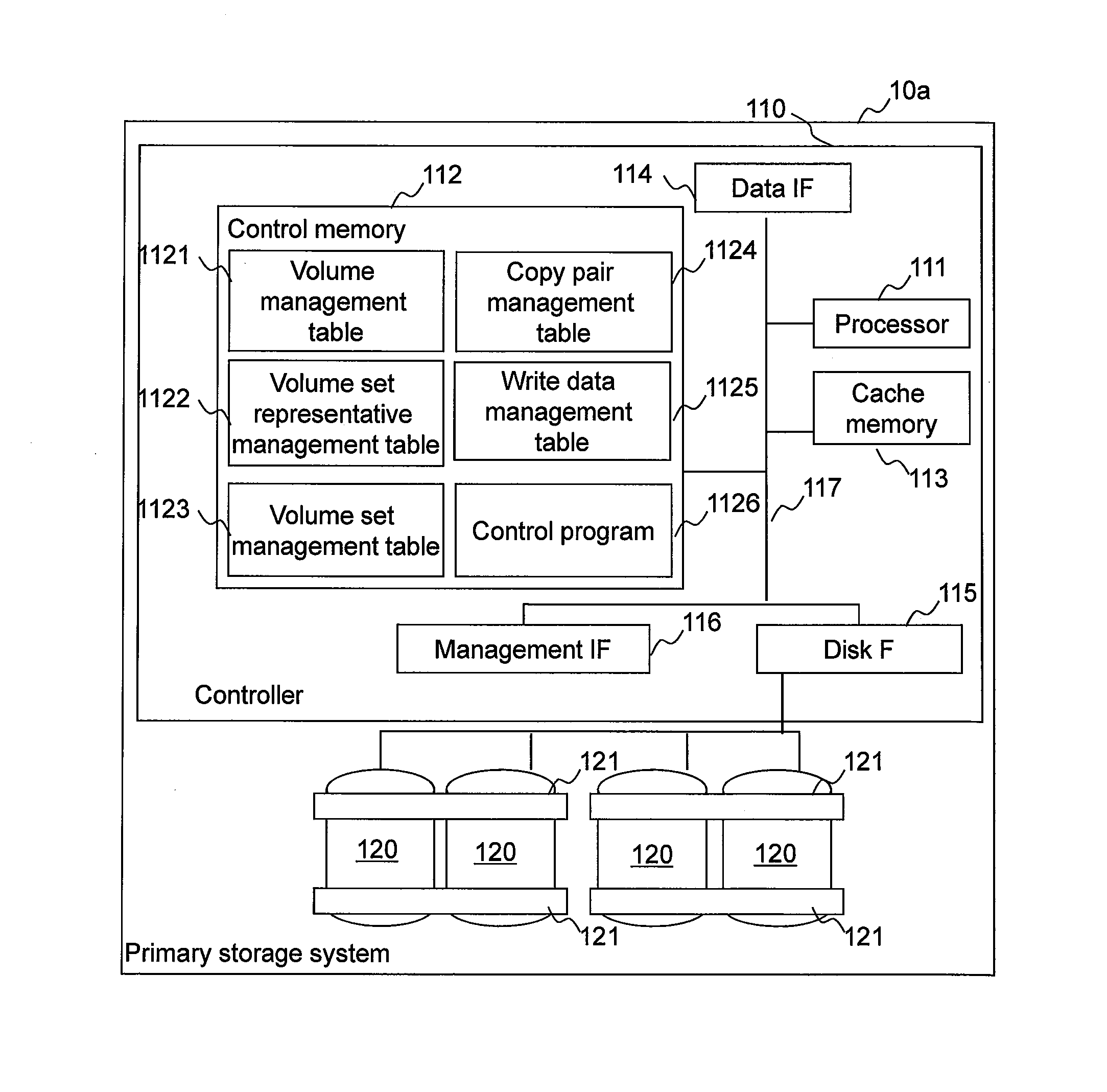
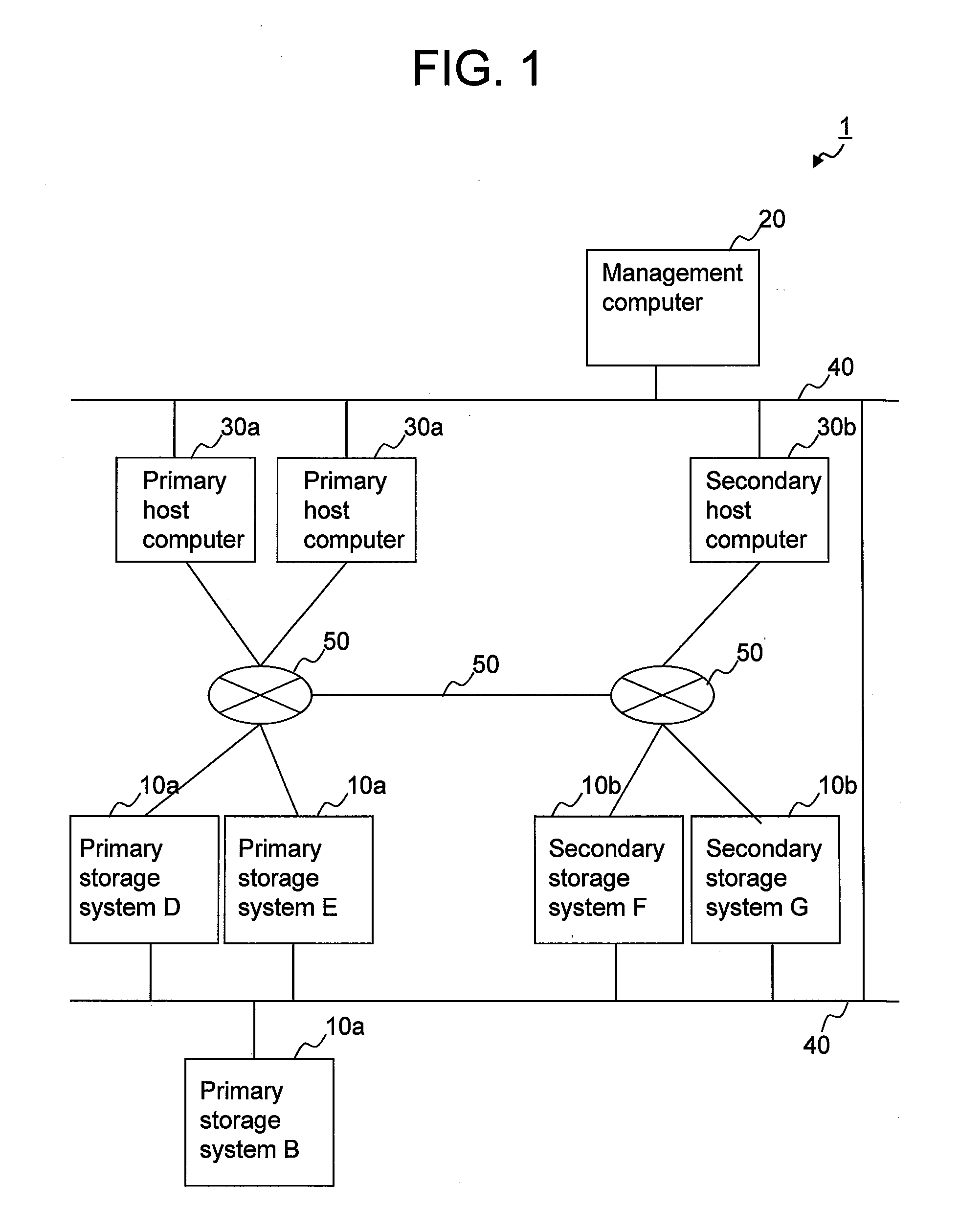
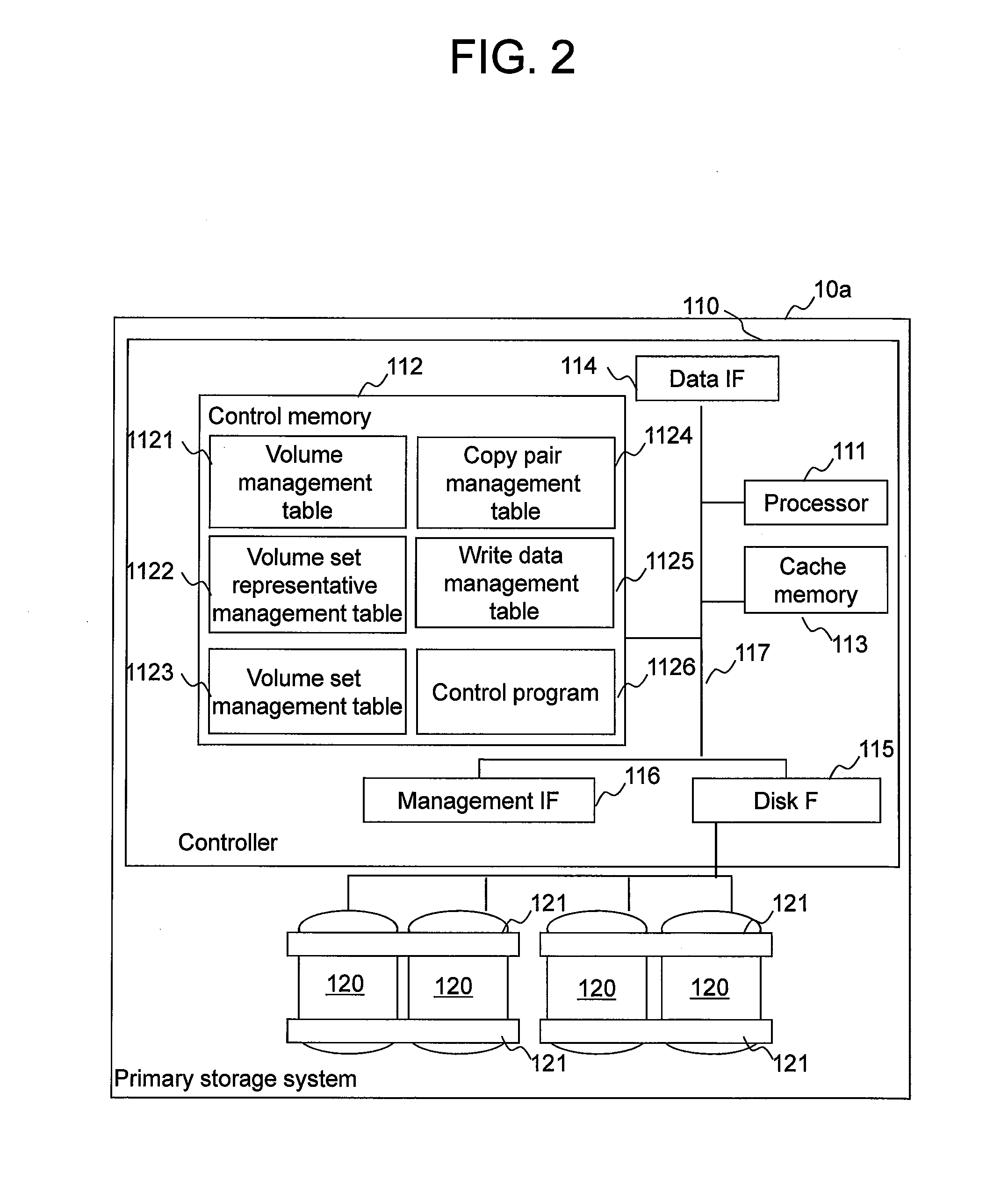
Computer system and computer system management method
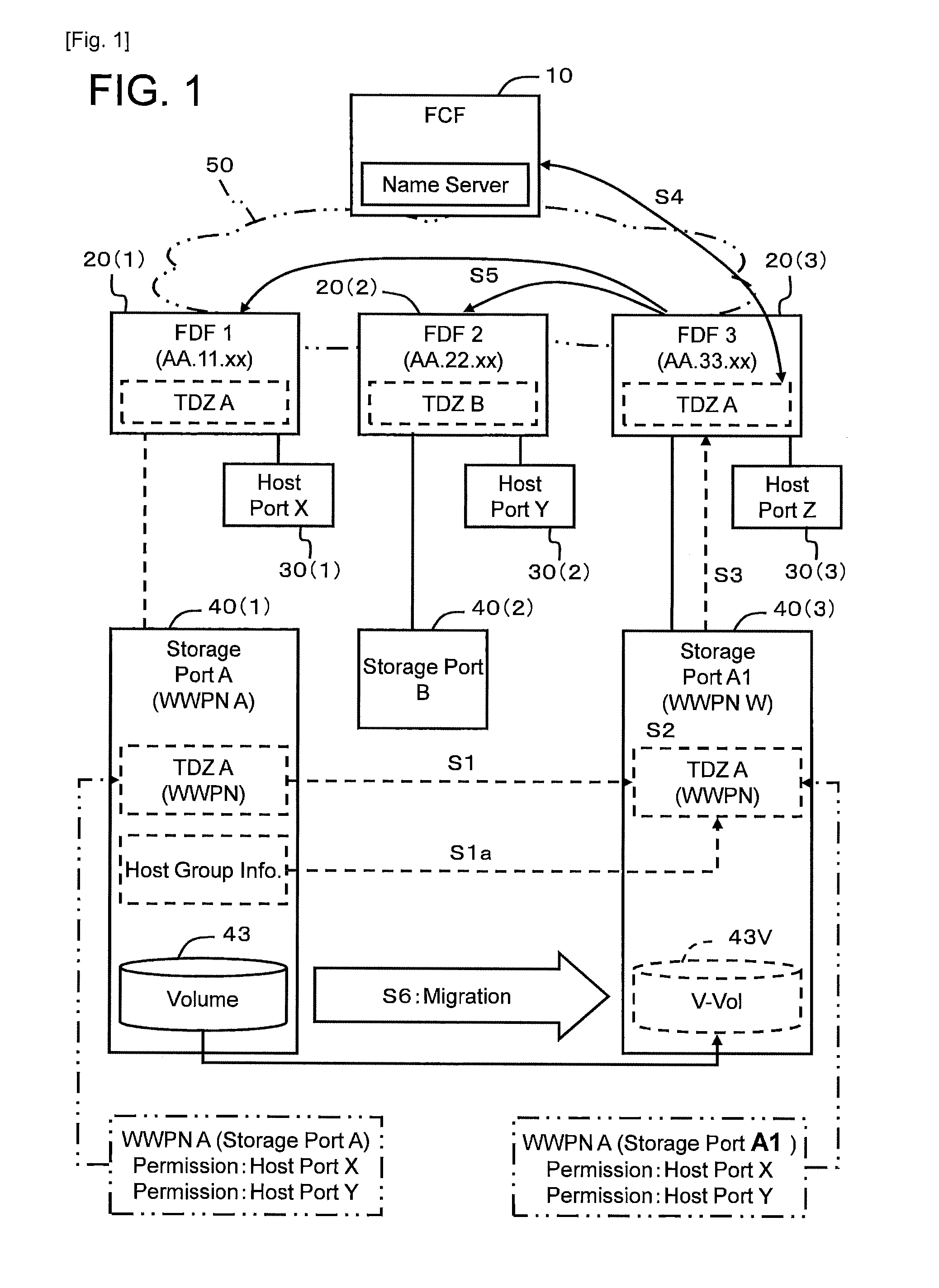
ActiveUS20120254554A1Reduce administrative burdenReduced usabilityTransmissionMemory systemsSystems managementFibre Channel
A computer system in which one or more host computers 30 having a FC (Fibre Channel) node port and one or more storage apparatuses 40 having a FC node port are coupled via a FC fabric. The storage apparatus acquires first information related to access control for controlling access to a relevant storage apparatus by the host computer. The storage apparatus, based on the first information, creates second information for defining the host computer that is able to access the relevant storage apparatus, and registers this second information in the fabric.
Owner:HITACHI LTD
Mail distribution system, mail distribution method, and mail distribution program
ActiveUS7558827B2Reduce administrative burdenIncrease speedData processing applicationsMultiple digital computer combinationsMail DistributionsComputer terminal
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
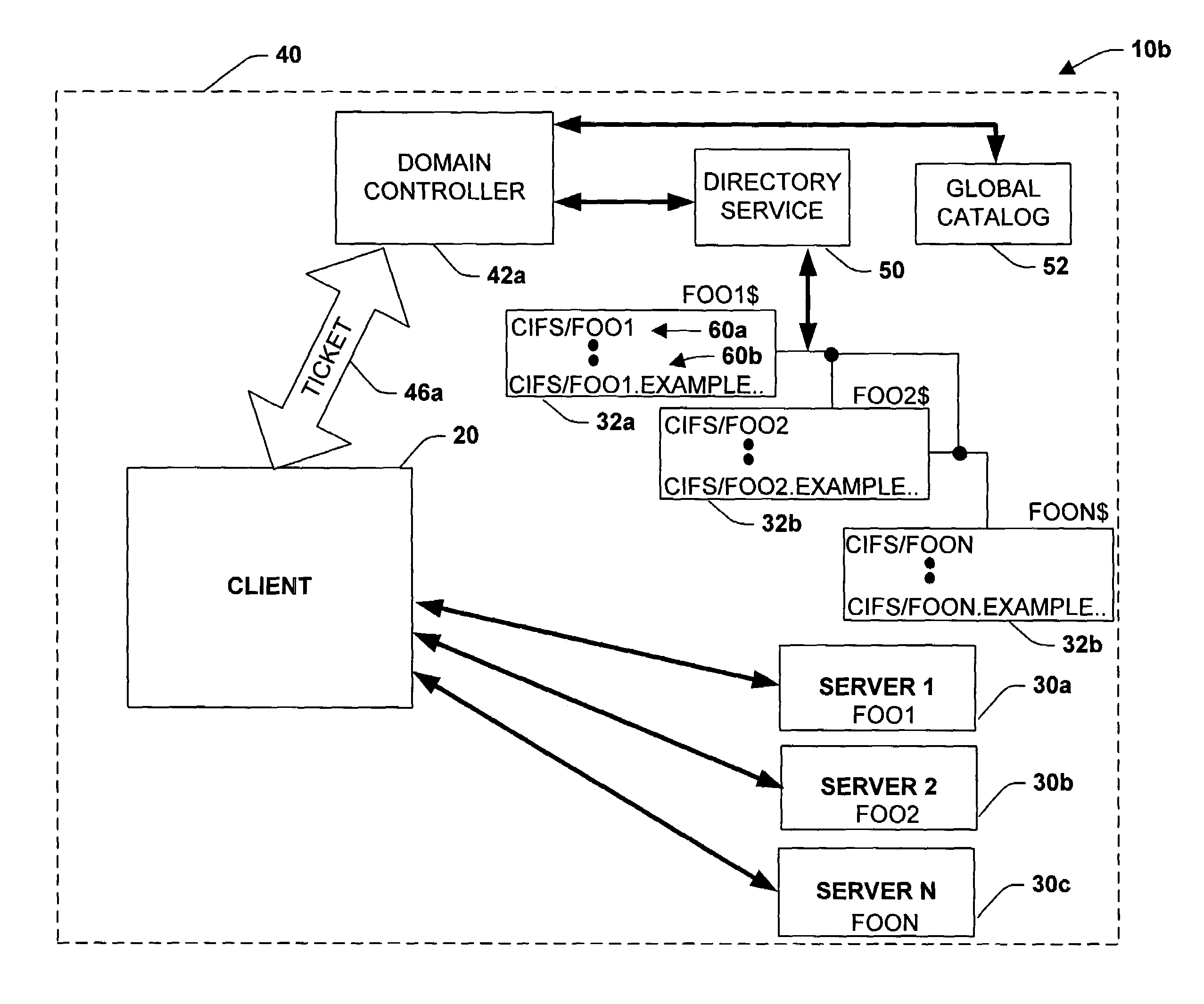
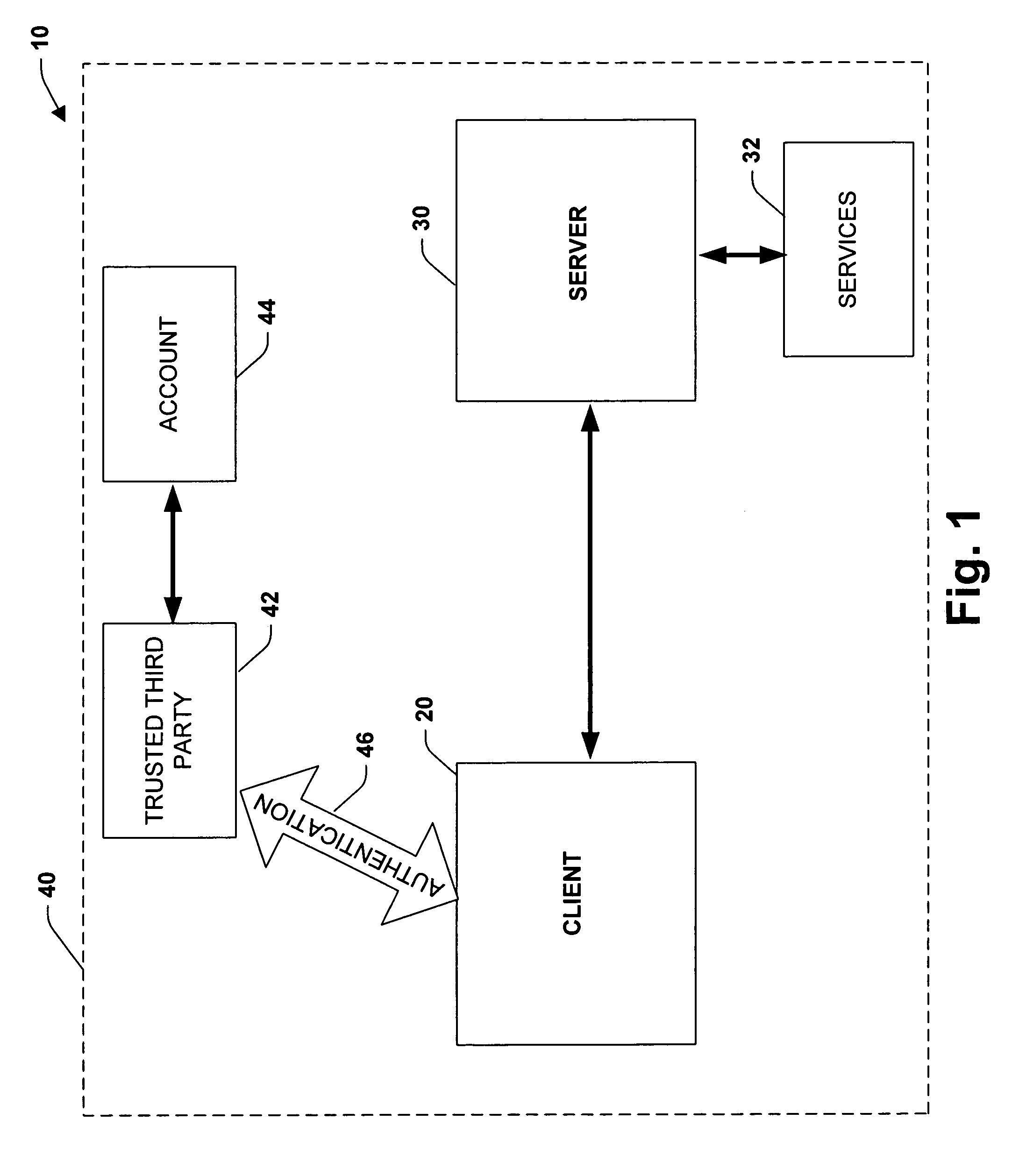
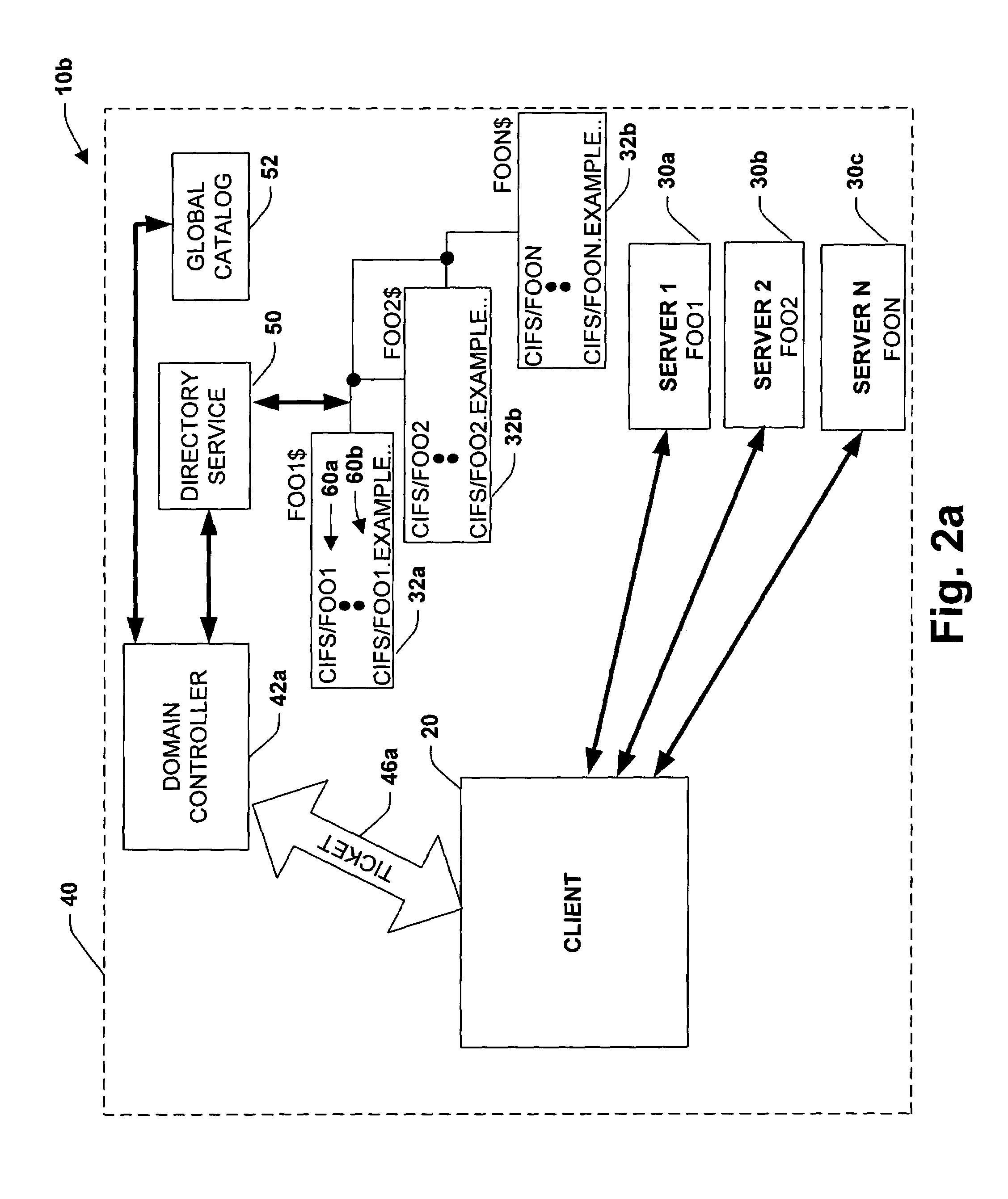
System and method for managing and authenticating services via service principal names
InactiveUS7308709B1Reduce administrative burdenConvenient registrationDigital data processing detailsMultiple digital computer combinationsAuthenticationComputer science
A methododology is provided for facilitating authentication of a service. The methodology includes making a request to a first party for authentication of a service, the request including a first alias. A list of aliases associated with the service is then searched enabling a second party making the request to access the service if a match is found between the first alias and at least one alias of the list of aliases.
Owner:MICROSOFT TECH LICENSING LLC
Predicting database system performance
ActiveUS8010337B2Reduce administrative burdenError detection/correctionDigital data processing detailsPrediction systemTransaction Type
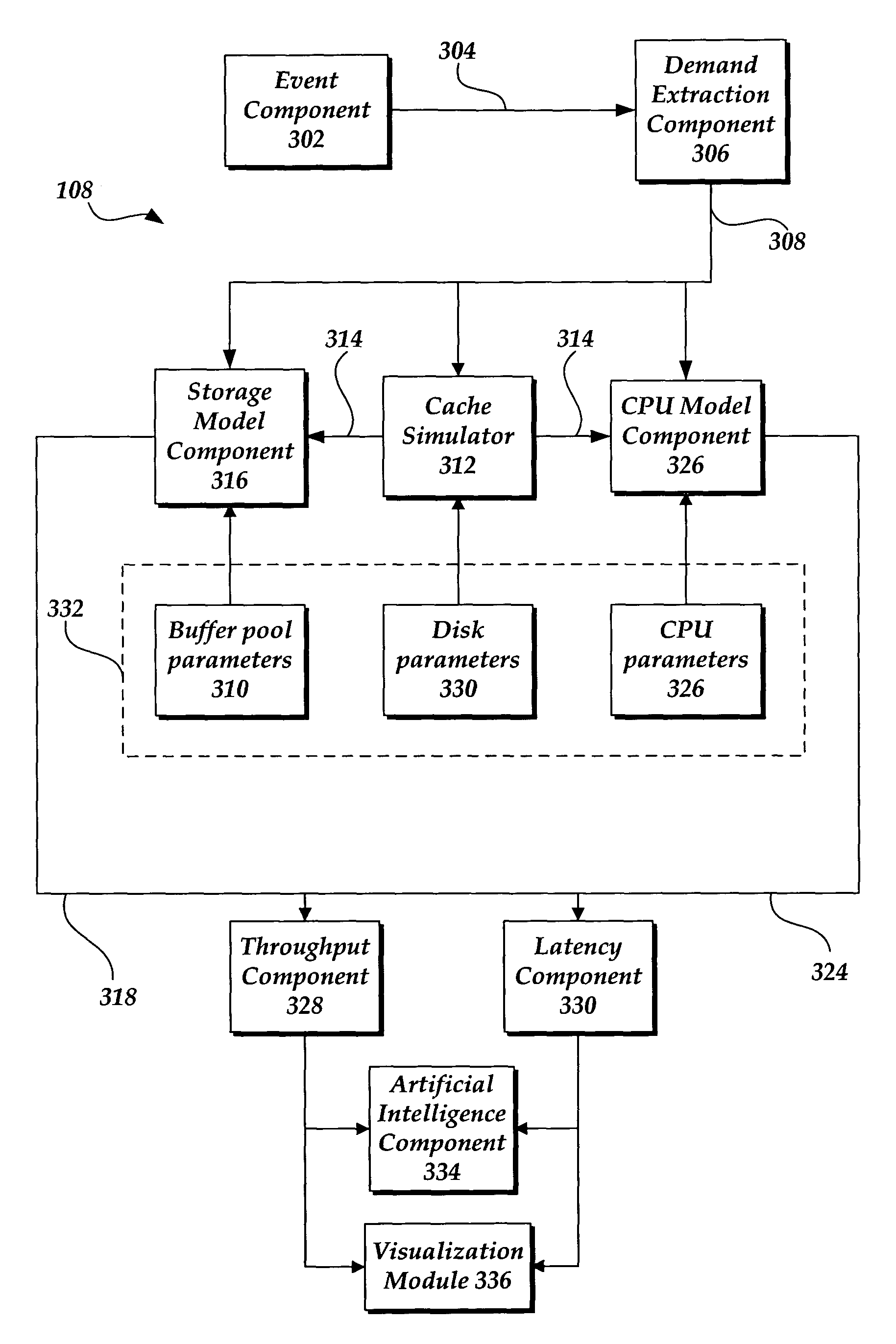
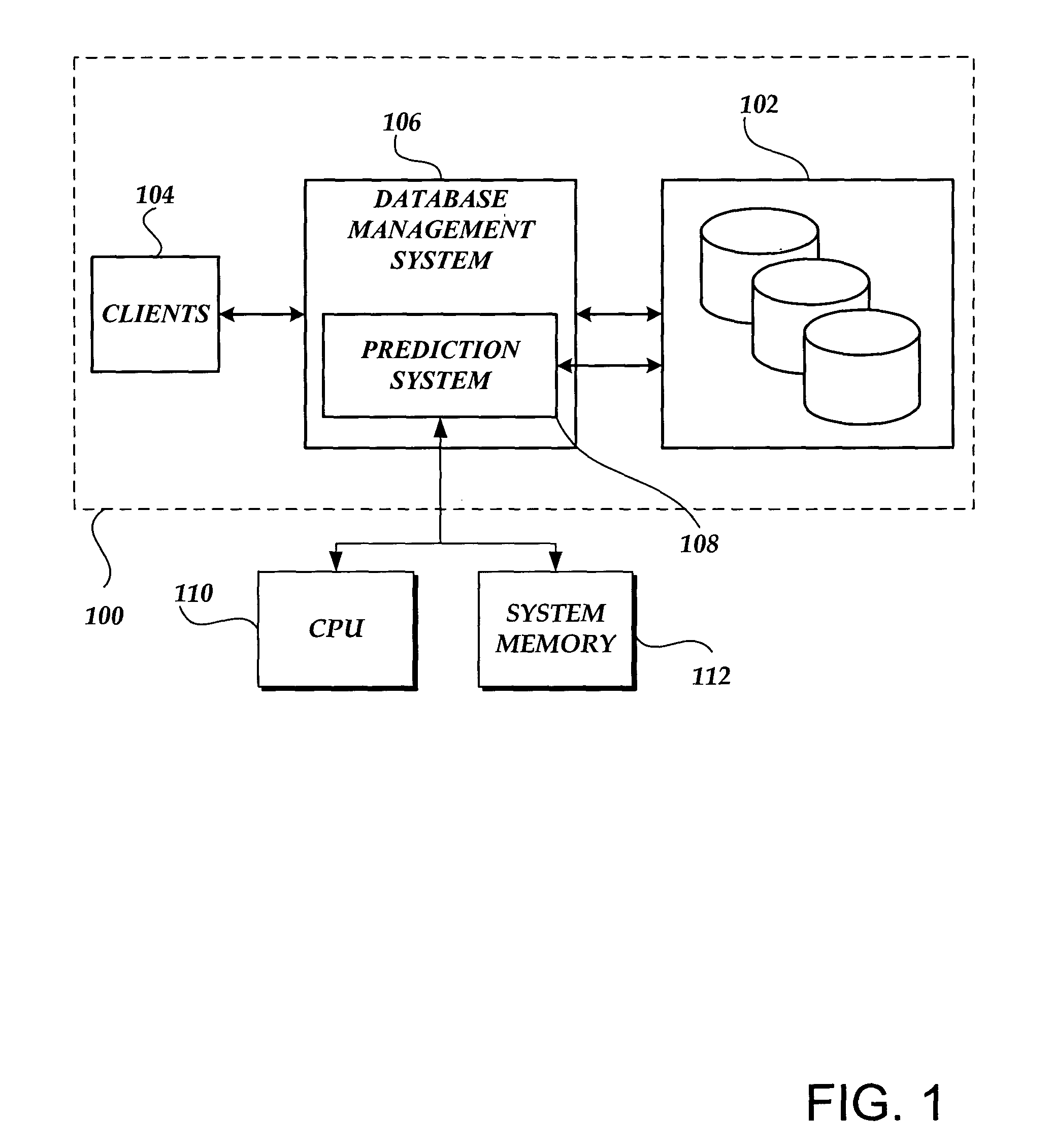
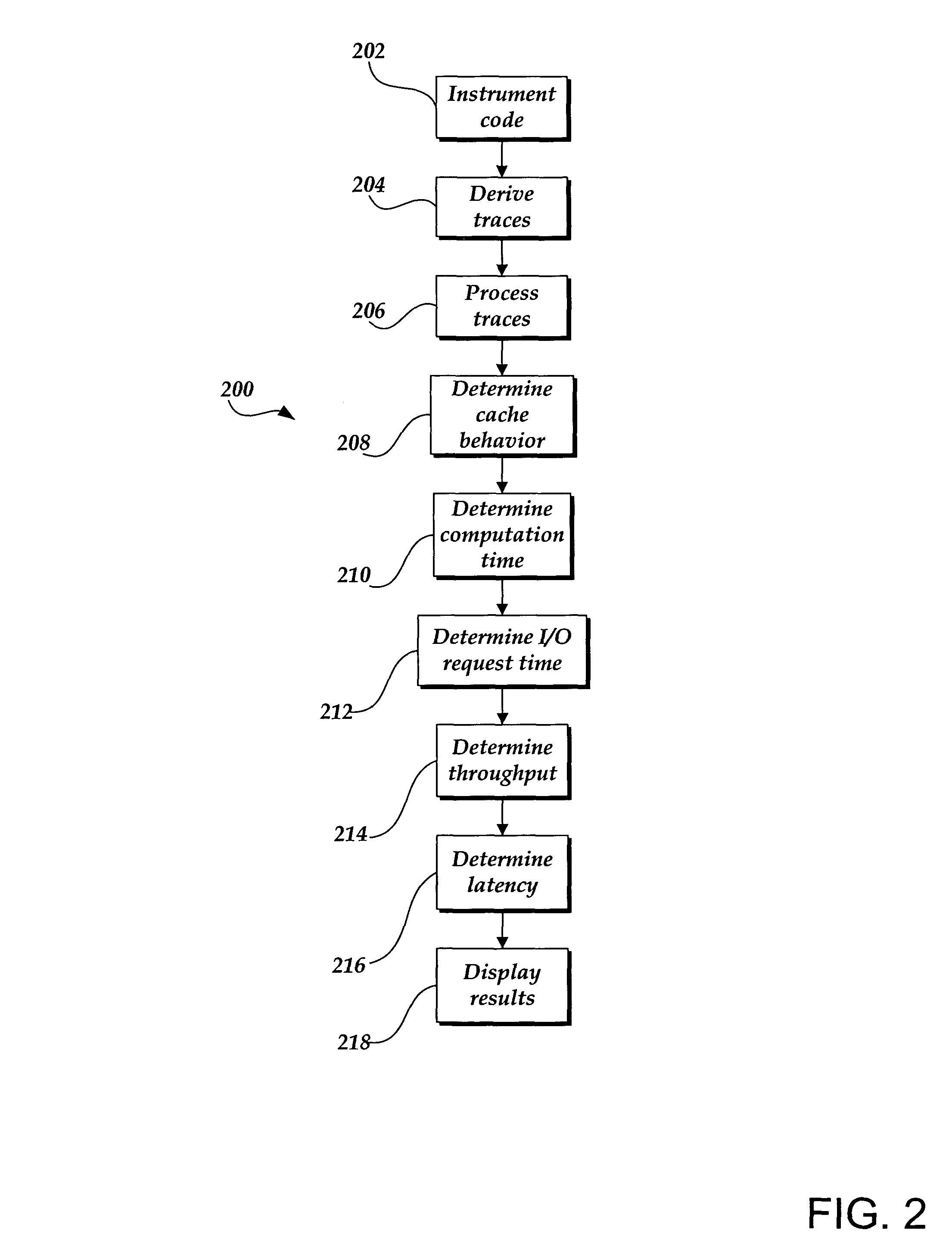
A prediction system may perform capacity planning for one or more resources of a database systems, such as by understanding how different workloads are using the system resources and / or predicting how the performance of the workloads will change when the hardware configuration of the resource is changed and / or when the workload changes. The prediction system may use a detailed, low-level tracing of a live database system running an application workload to monitor the performance of the current database system. In this manner, the current monitoring traces and analysis may be combined with a simulation to predict the workload's performance on a different hardware configuration. More specifically, performance may be indicated as throughput and / or latency, which may be for all transactions, for a particular transaction type, and / or for an individual transaction. Database system performance prediction may include instrumentation and tracing, demand trace extraction, cache simulation, disk scaling, CPU scaling, background activity prediction, throughput analysis, latency analysis, visualization, optimization, and the like.
Owner:MICROSOFT TECH LICENSING LLC
Apparatus and method for tracking and managing physical assets
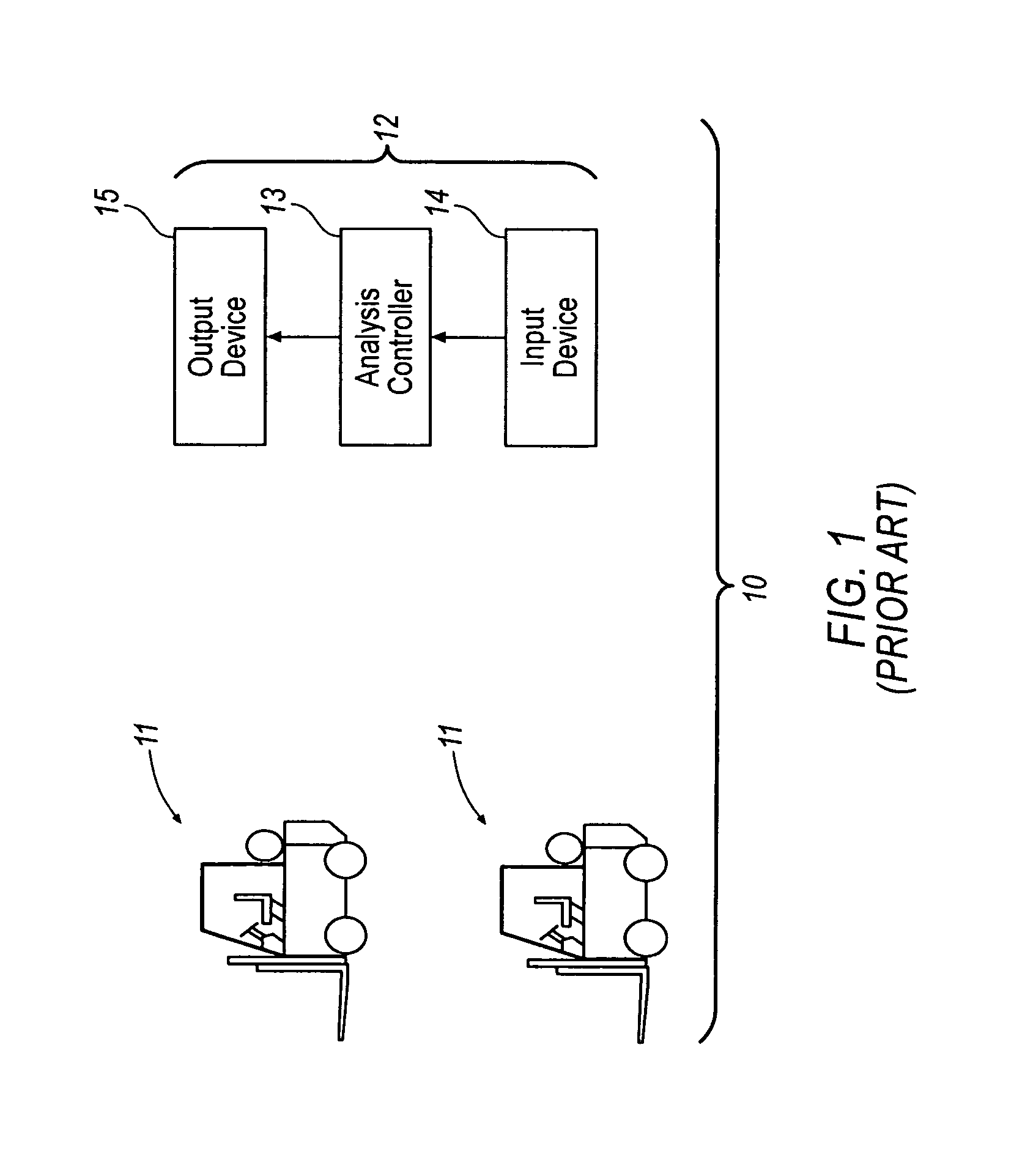
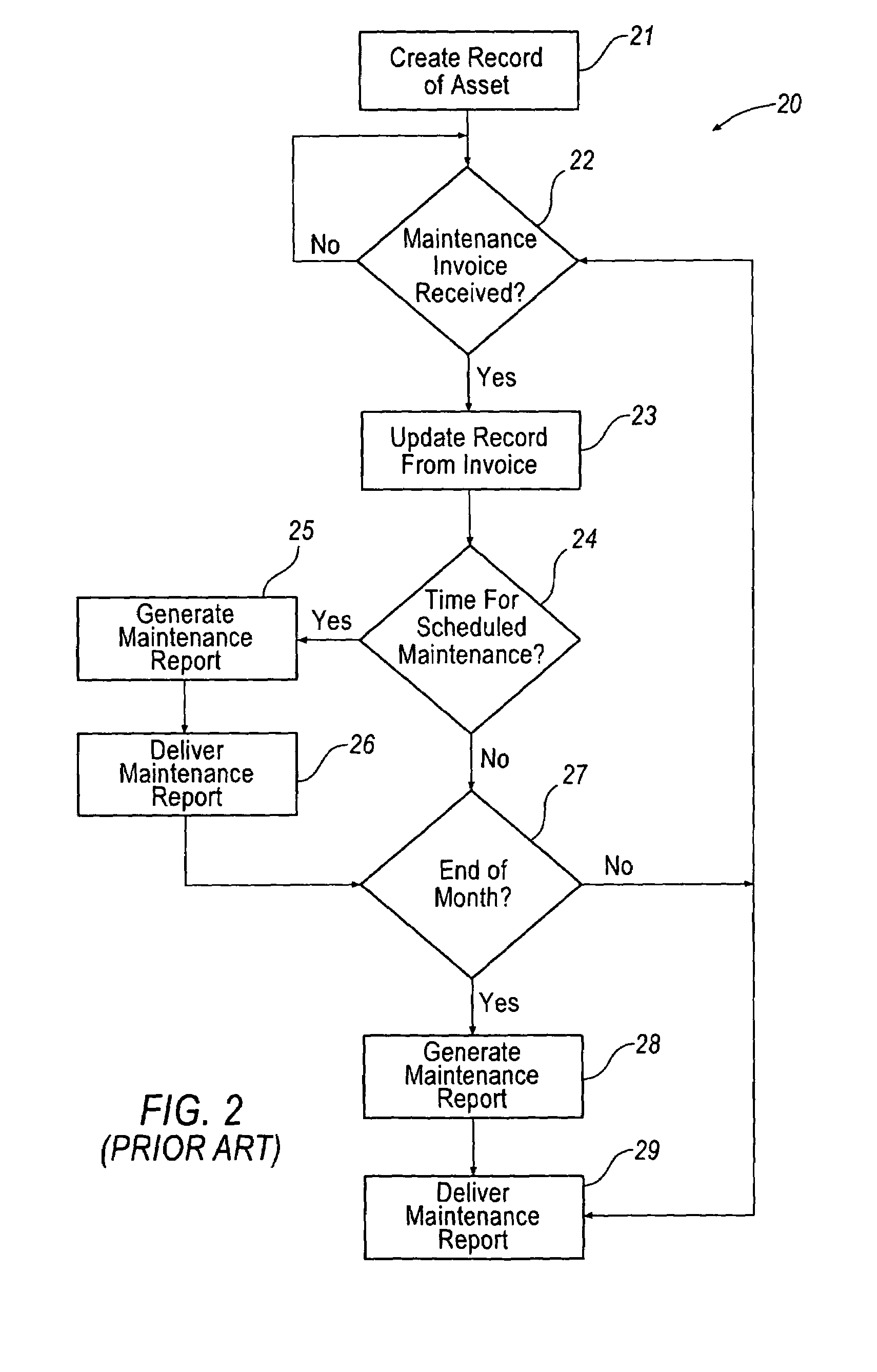
InactiveUS7062446B1Maximize productivityReduce operating costsTechnology managementCommerceProduction rateData acquisition
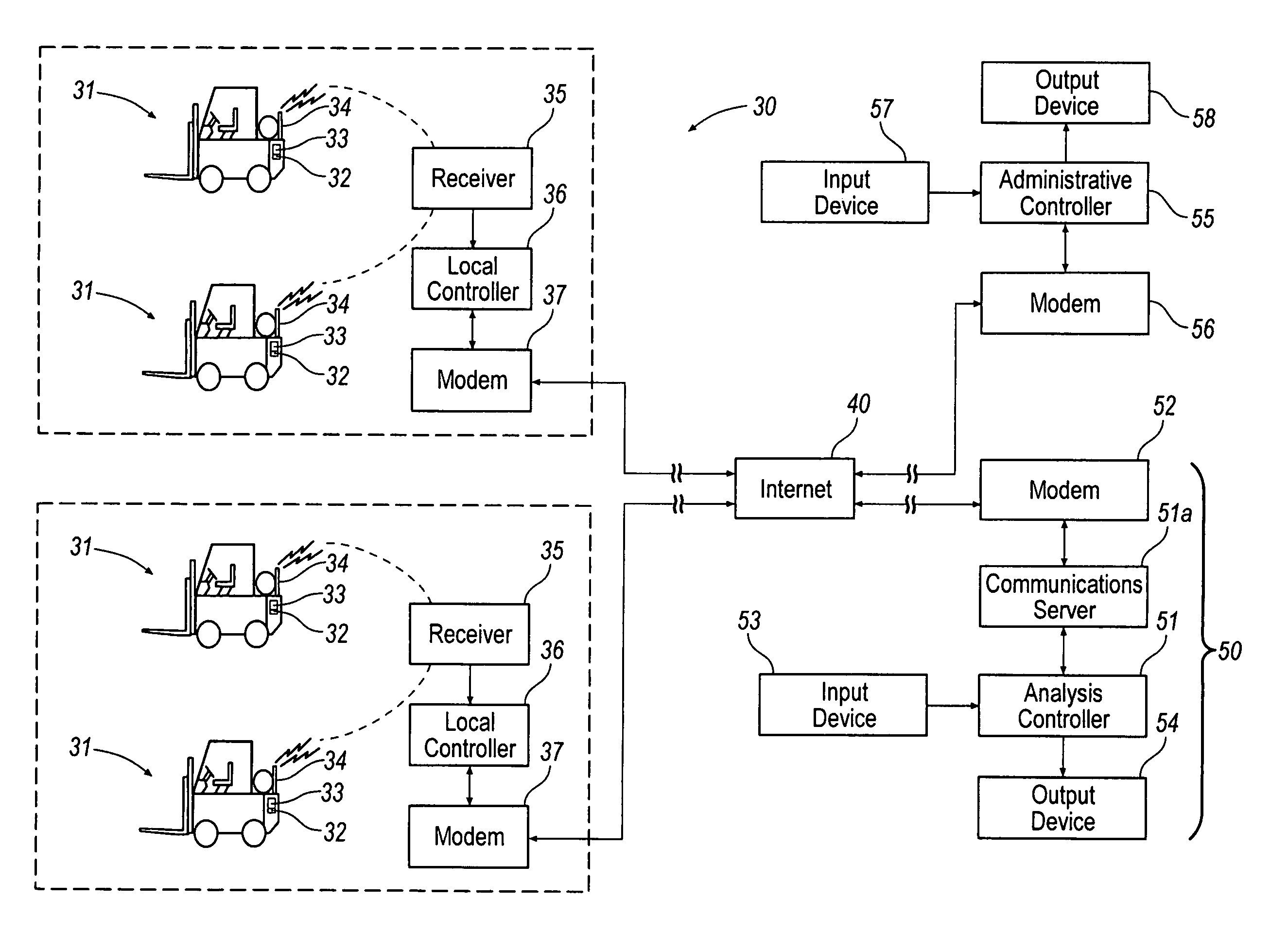
A computer based system automatically gathers, analyzes, and delivers information relating to the procurement and utilization of a plurality of such assets, such as a fleet of industrial equipment, so as to maximize productivity and to reduce operating costs and administrative burdens. Each of the assets is preferably provided with a data acquisition device for sensing and storing one or more operating characteristics associated therewith. That information can be transmitted through space to a receiver connected to a local controller for storing such information and for transmitting such information over the internet to a remote analysis system. The remote analysis system automatically updates individual records associated with each of the assets with the information received from the internet. In response to such information, the remote analysis system automatically analyzes the newly provided information and generates reports regarding scheduled maintenance, warranty coverage, and other management information. These reports can be transmitted back over the internet to an administrative controller for review by one or more persons responsible for managerial review. Additionally or alternatively, the remote analysis system can automatically post such reports on a website and, thus, be made available to one or more of such persons upon request.
Owner:DANA AUTOMOTIVE SYST GRP LLC
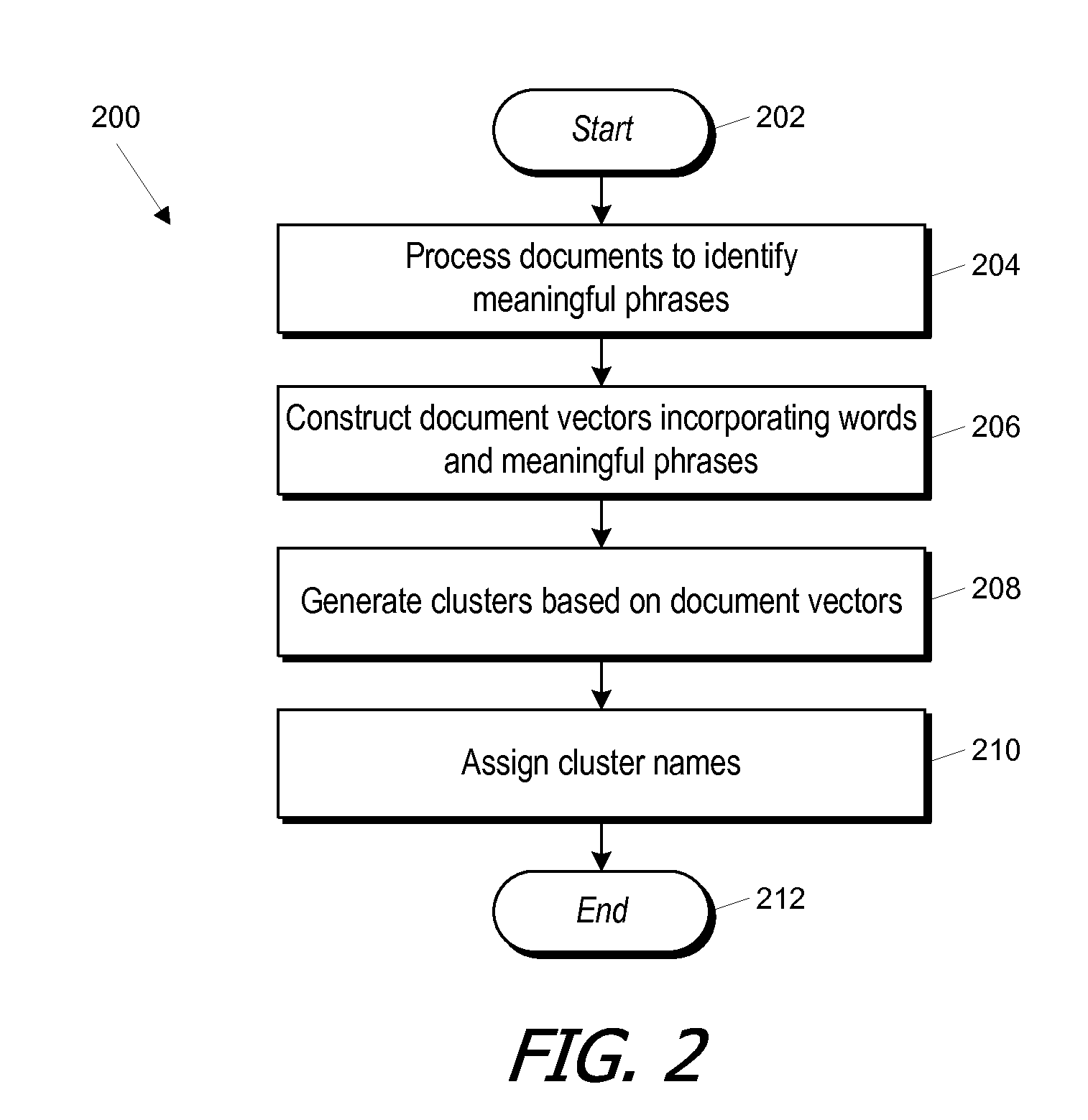
Phrase-based document clustering with automatic phrase extraction
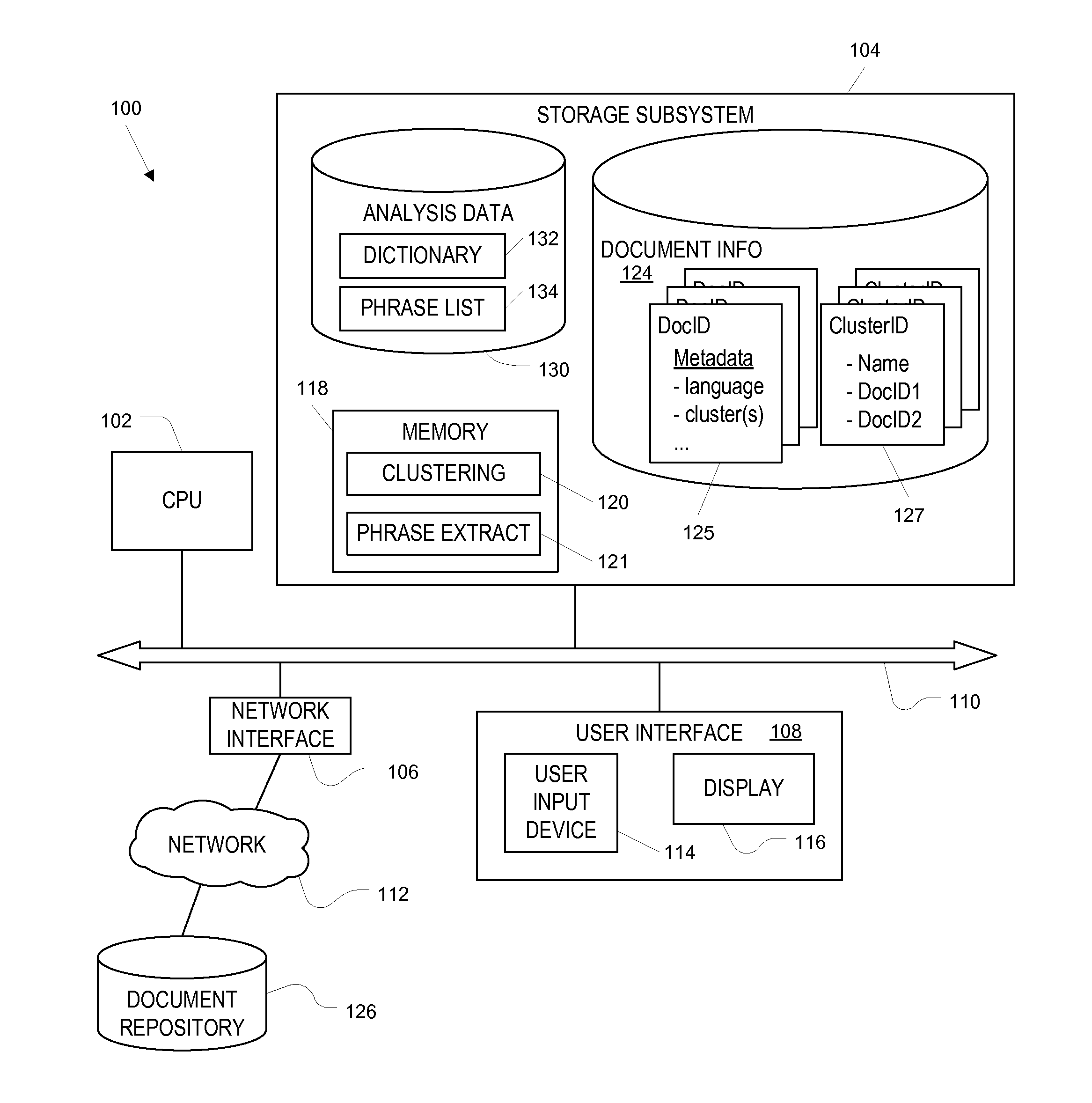
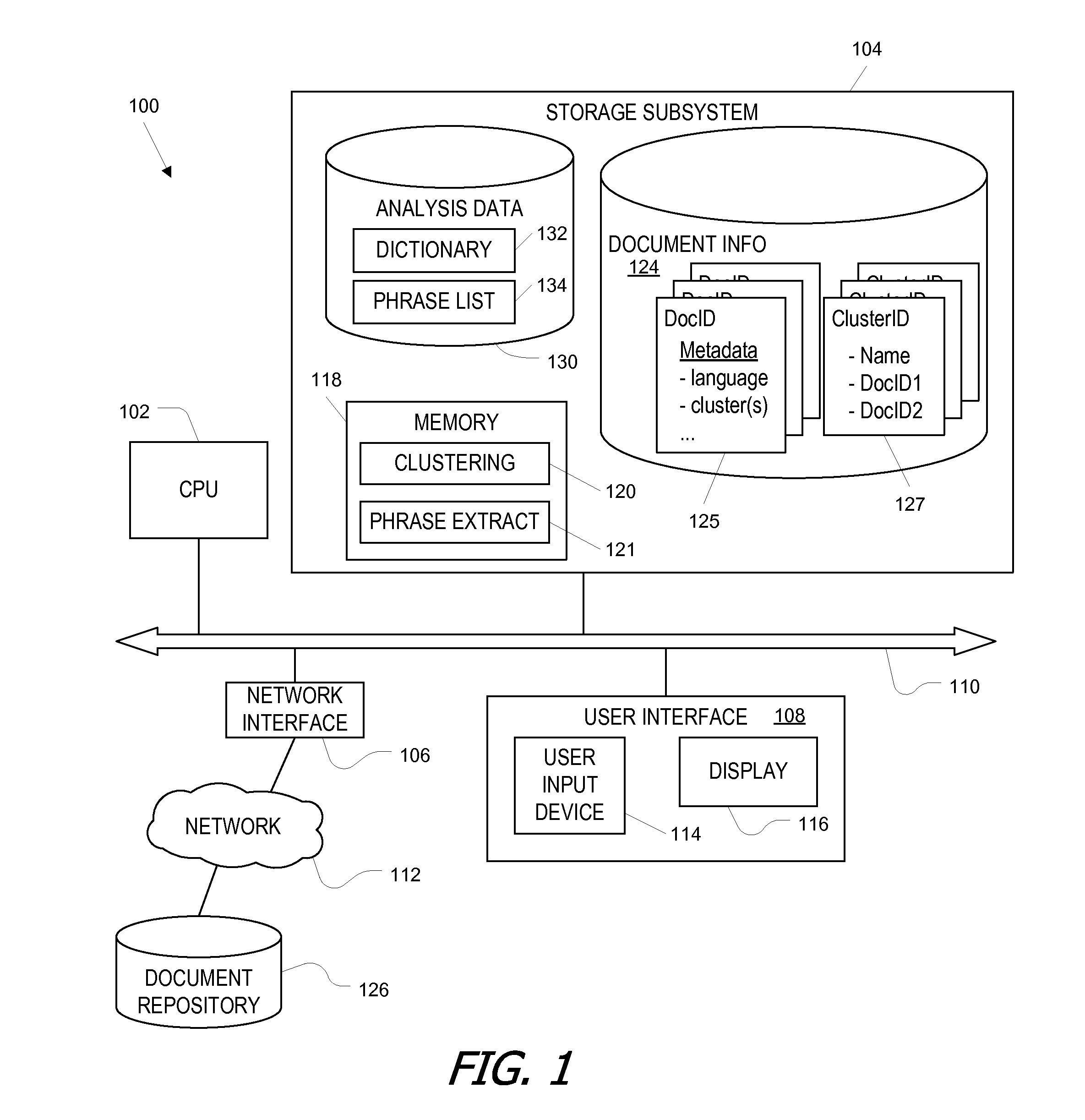
InactiveUS20110191098A1Reduce data management burdenReduce administrative burdenNatural language data processingSpecial data processing applicationsRecognition algorithmMutual information
Meaningful phrases are distinguished from chance word sequences statistically, by analyzing a large number of documents and using a statistical metric such as a mutual information metric to distinguish meaningful phrases from groups of words that co-occur by chance. In some embodiments, multiple lists of candidate phrases are maintained to optimize the storage requirement of the phrase-identification algorithm. After phrase identification, a combination of words and meaningful phrases can be used to construct clusters of documents.
Owner:MICRO FOCUS LLC
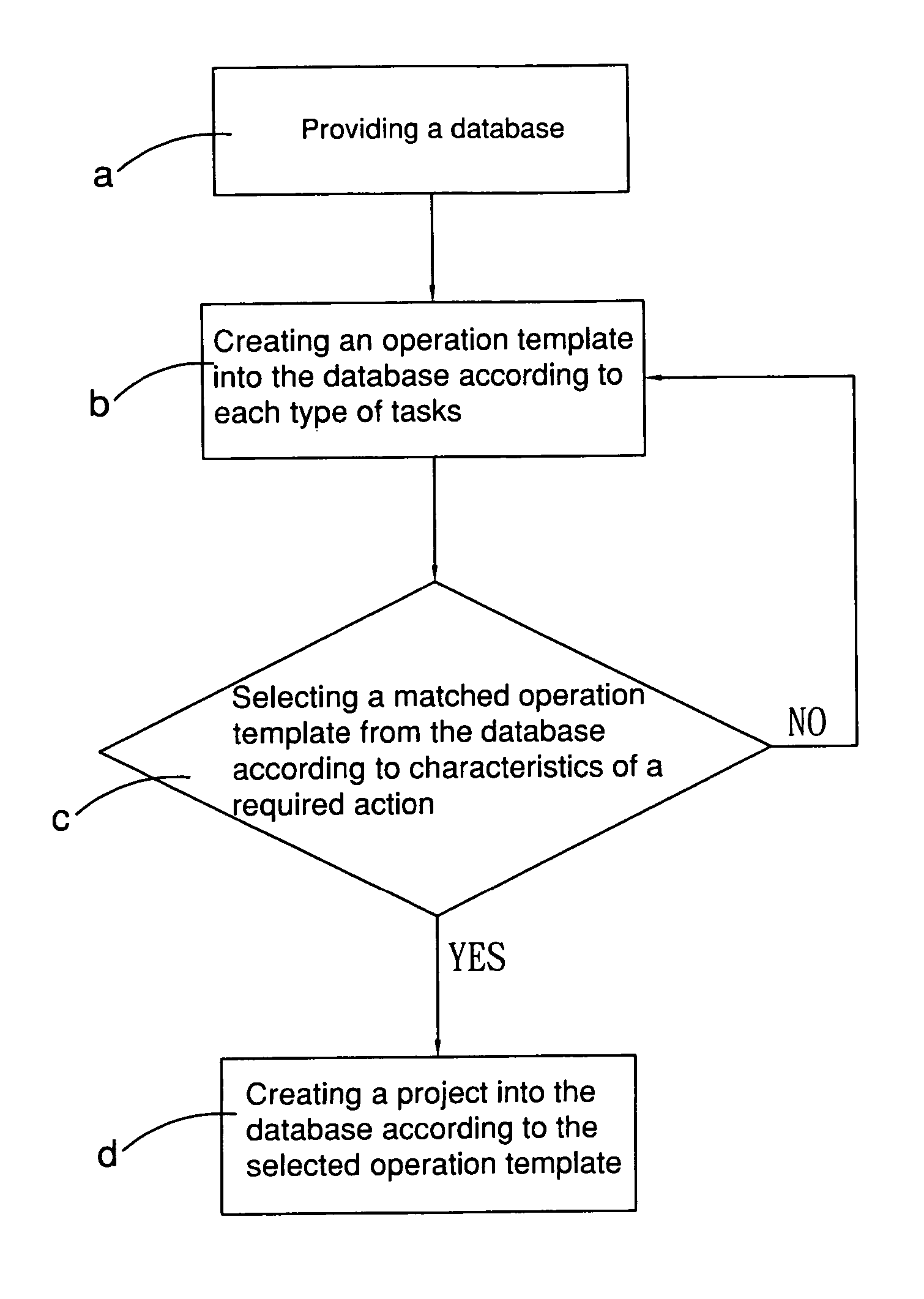
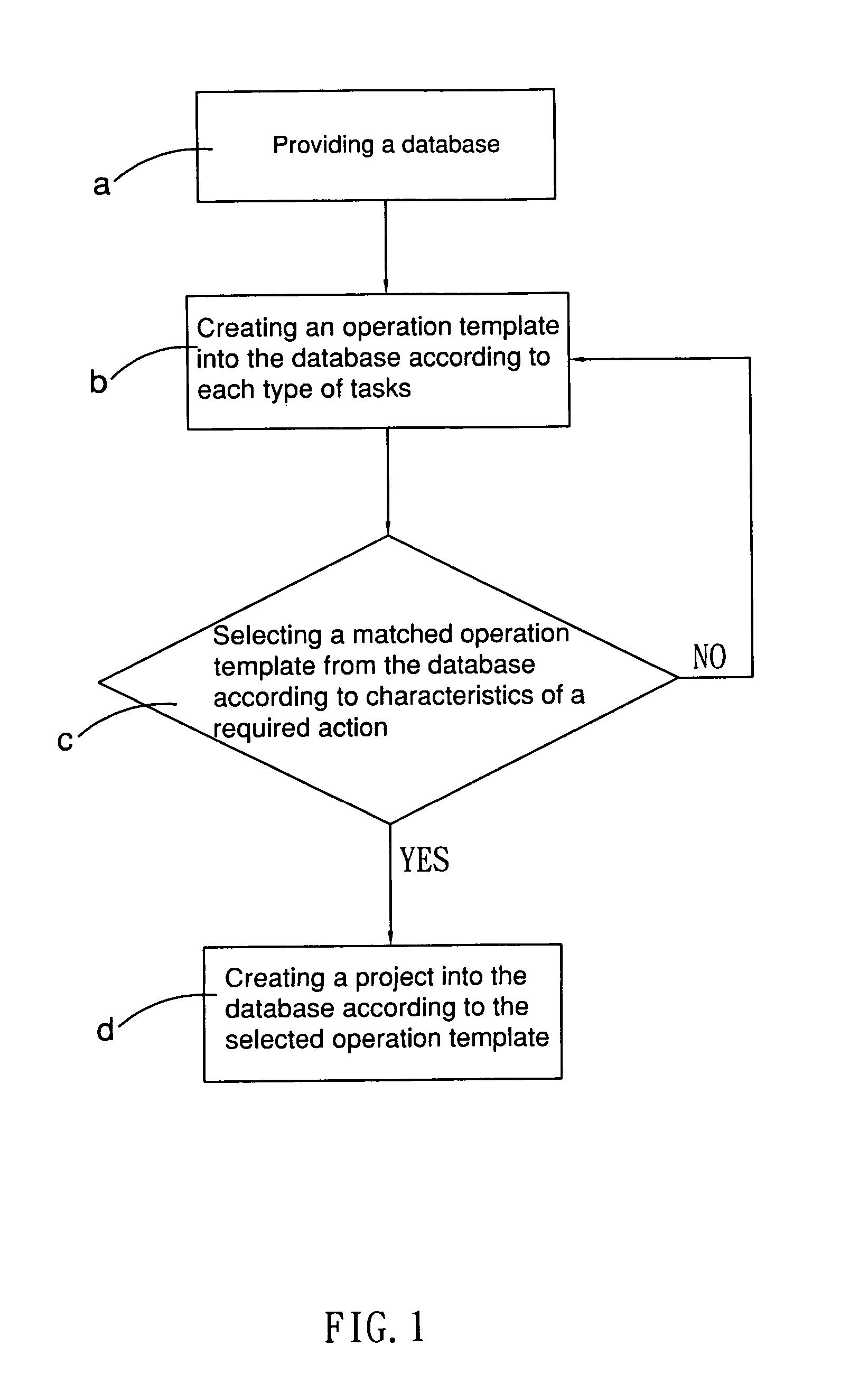
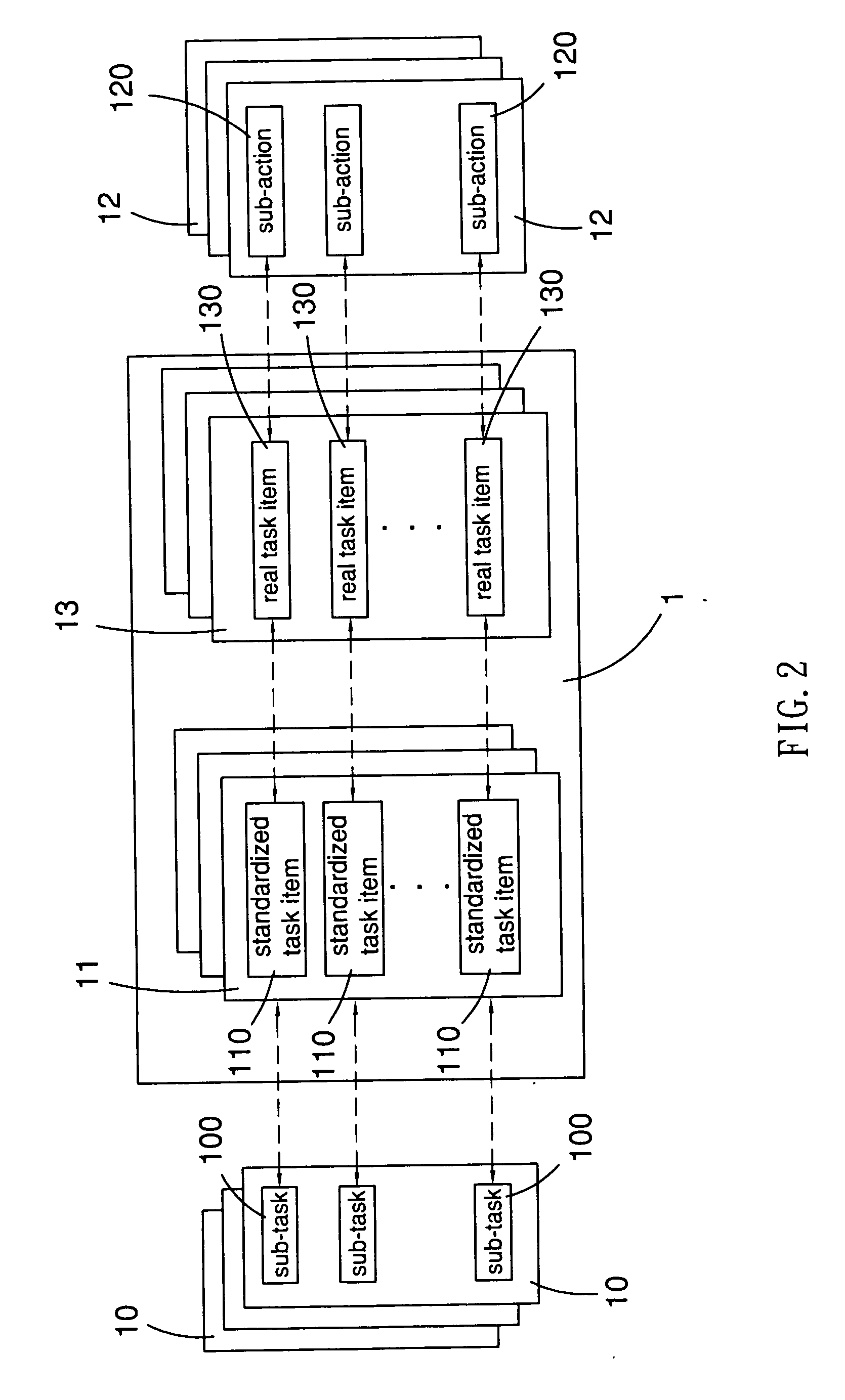
Method and system of intelligent work management
InactiveUS20070198558A1Labor savingShorten the timeDigital data processing detailsResourcesComputer scienceJob management
An intelligent work management method comprises steps of providing a plurality of operation templates, and creating a project according to a selected one of the operation templates. The project has a plurality of real task items, each having an executive. The method further comprises a step of saving as a corresponding real task item with the executable status into a task pool so as to allow each of the executives to control his / her own real task items. The method can be carried out via a system. The system has a database, a task pool, a daily executable task pool, and a work management program. The work management program is provided for creating operation templates and projects into the database; and correspondingly creating an executable task item into the task pool according to the corresponding real task item with the executable status among the database; and correspondingly creating a daily task item into the daily executable task pool according to a respective one of the executable task items among the task pool.
Owner:CHEN WEN HSIEN
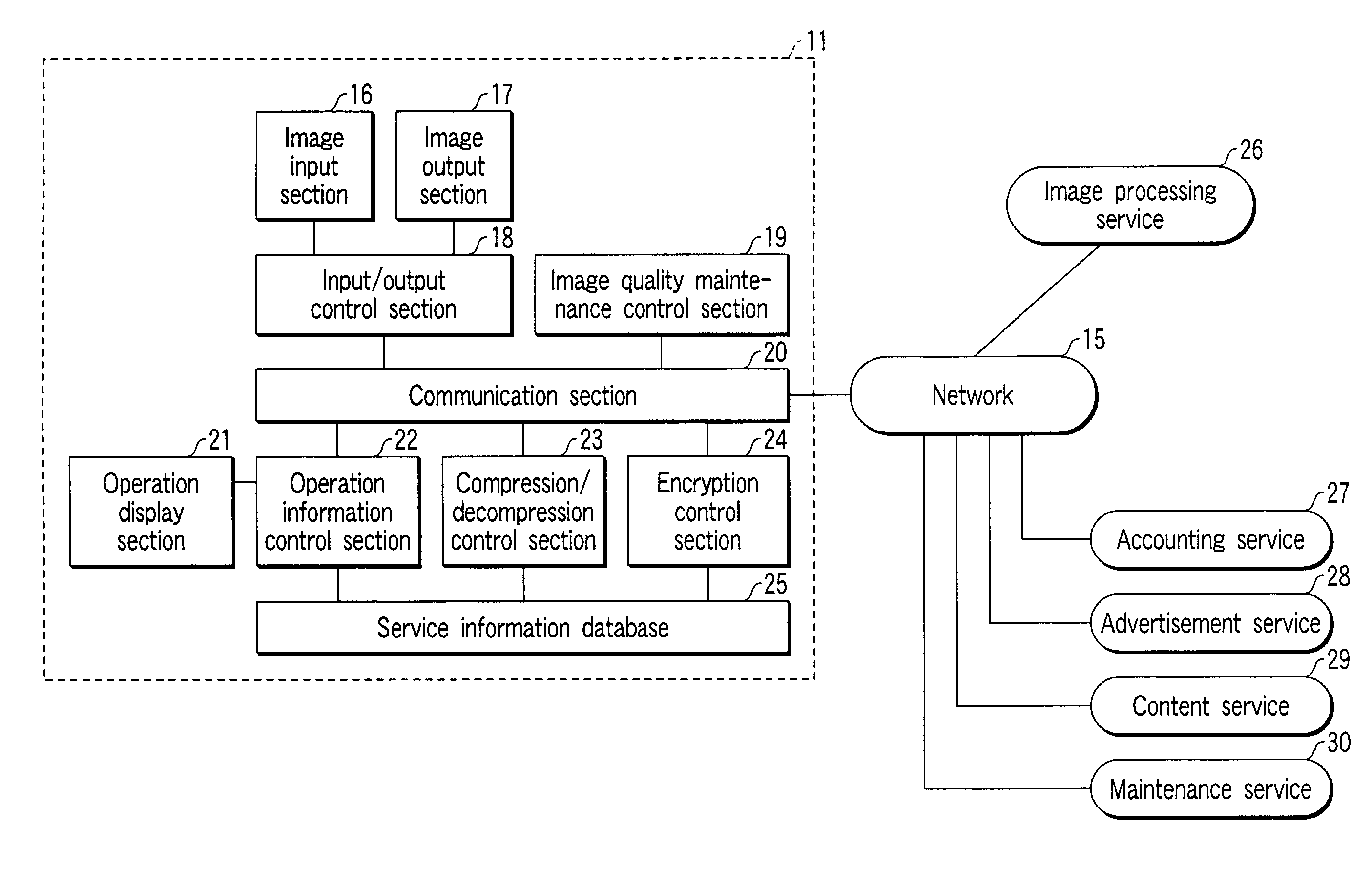
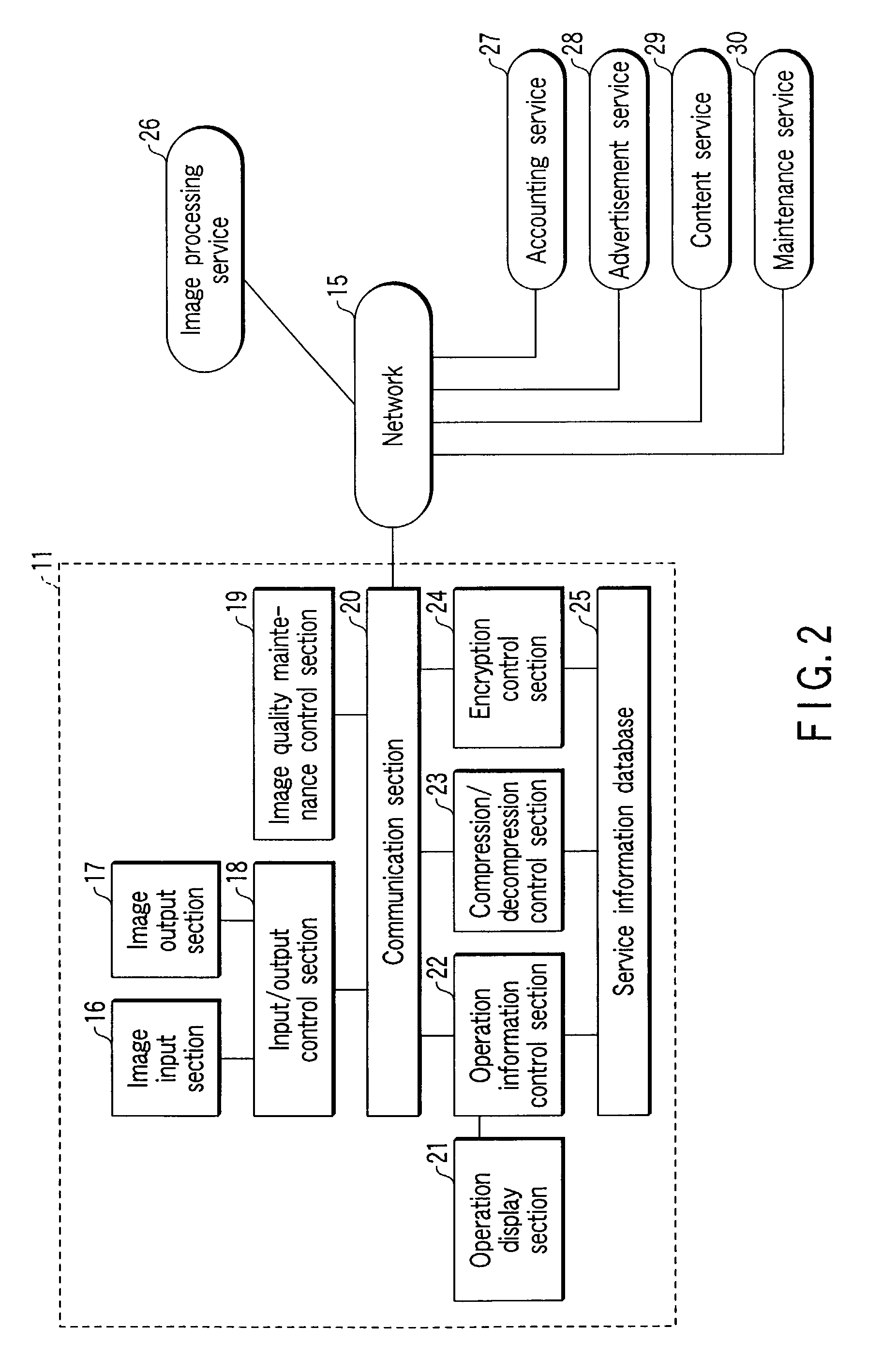
Image processing service system
ActiveUS7102777B2High priceHeavy functioningDigitally marking record carriersDigital computer detailsImaging processingComputer science
The present invention provides a predetermined image processing service via a network to an image processing apparatus having an image information input / output function. In this case, the image processing service is provided by a dedicated server connected to a network or by a local or remote image processing apparatus.
Owner:KK TOSHIBA +1
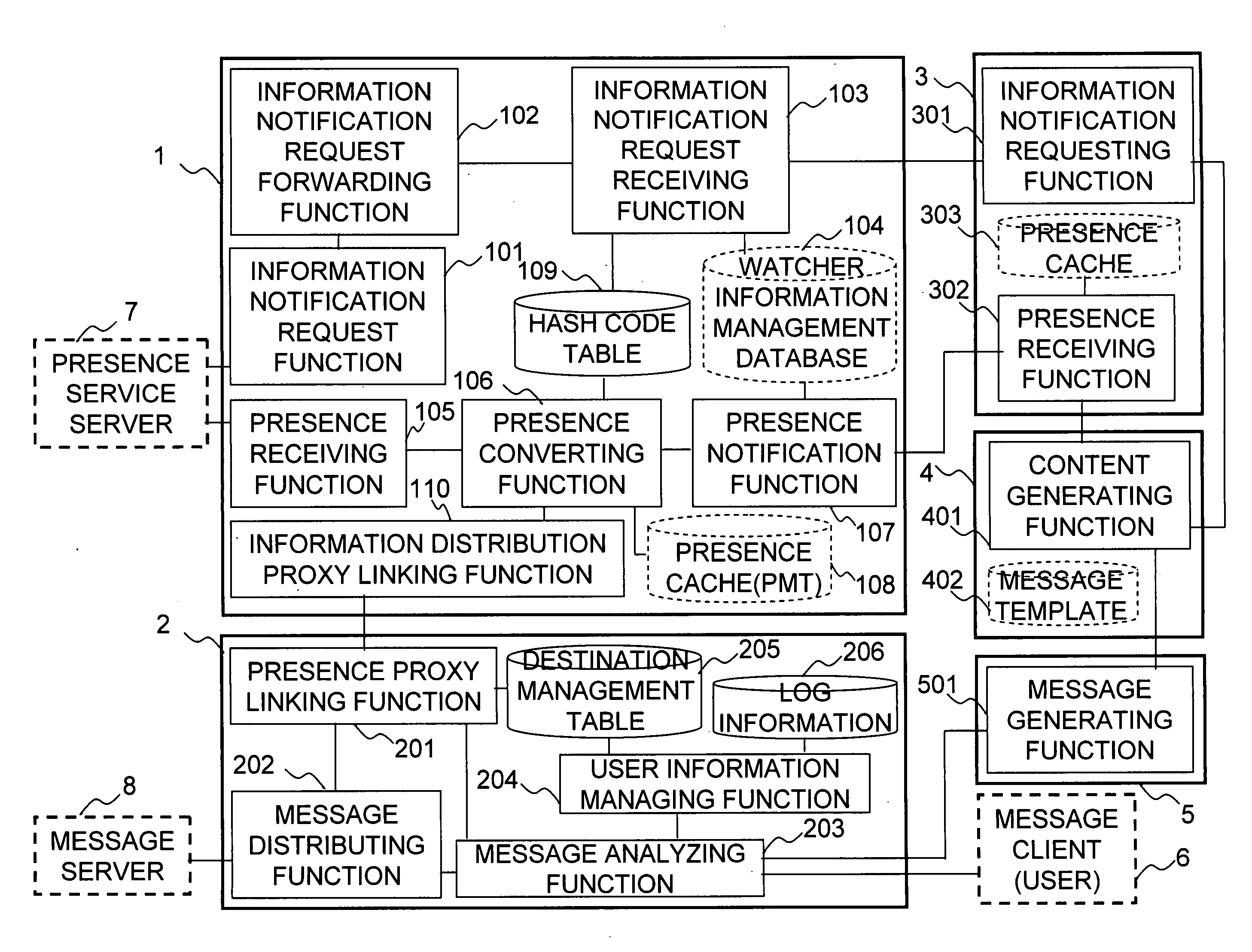
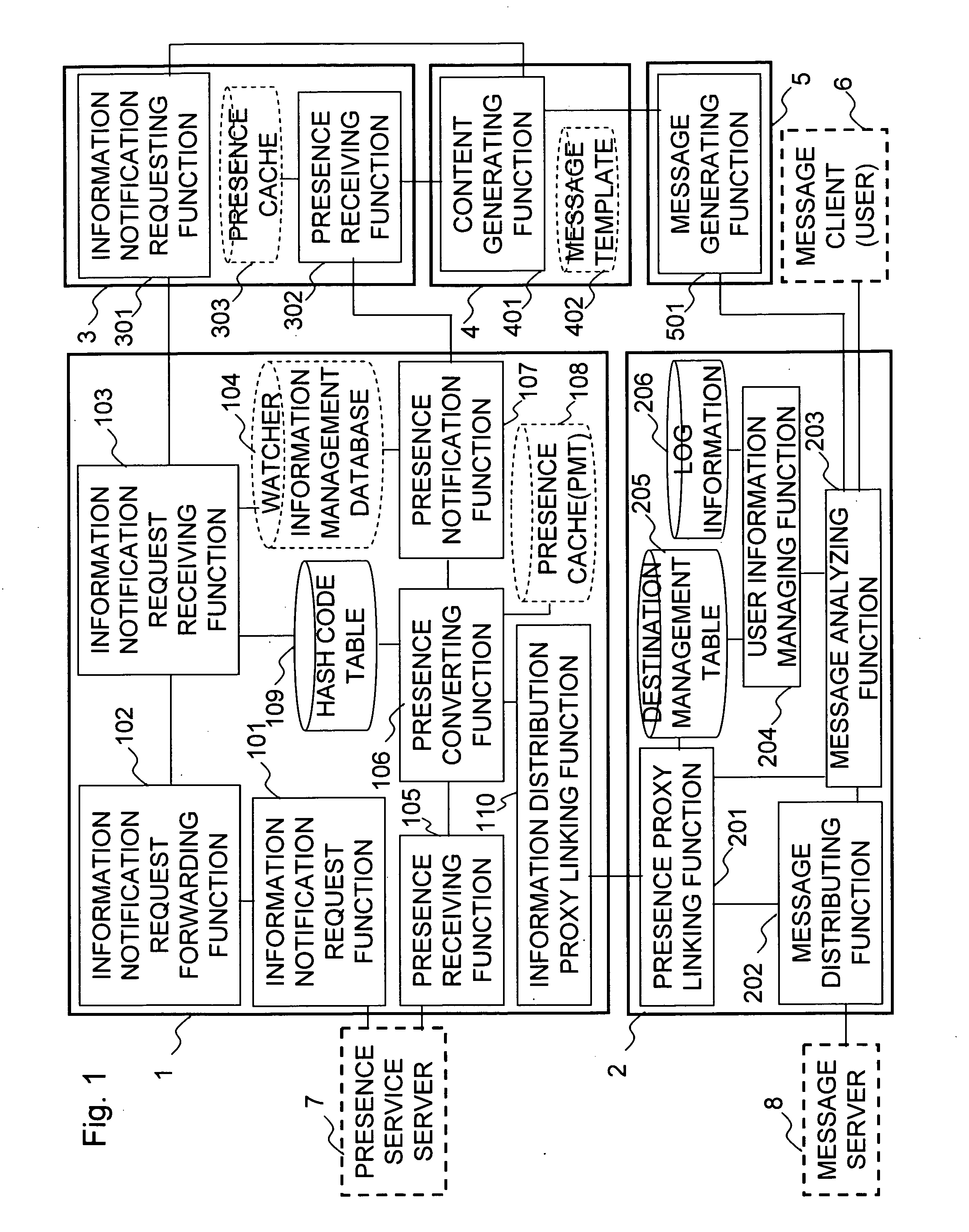
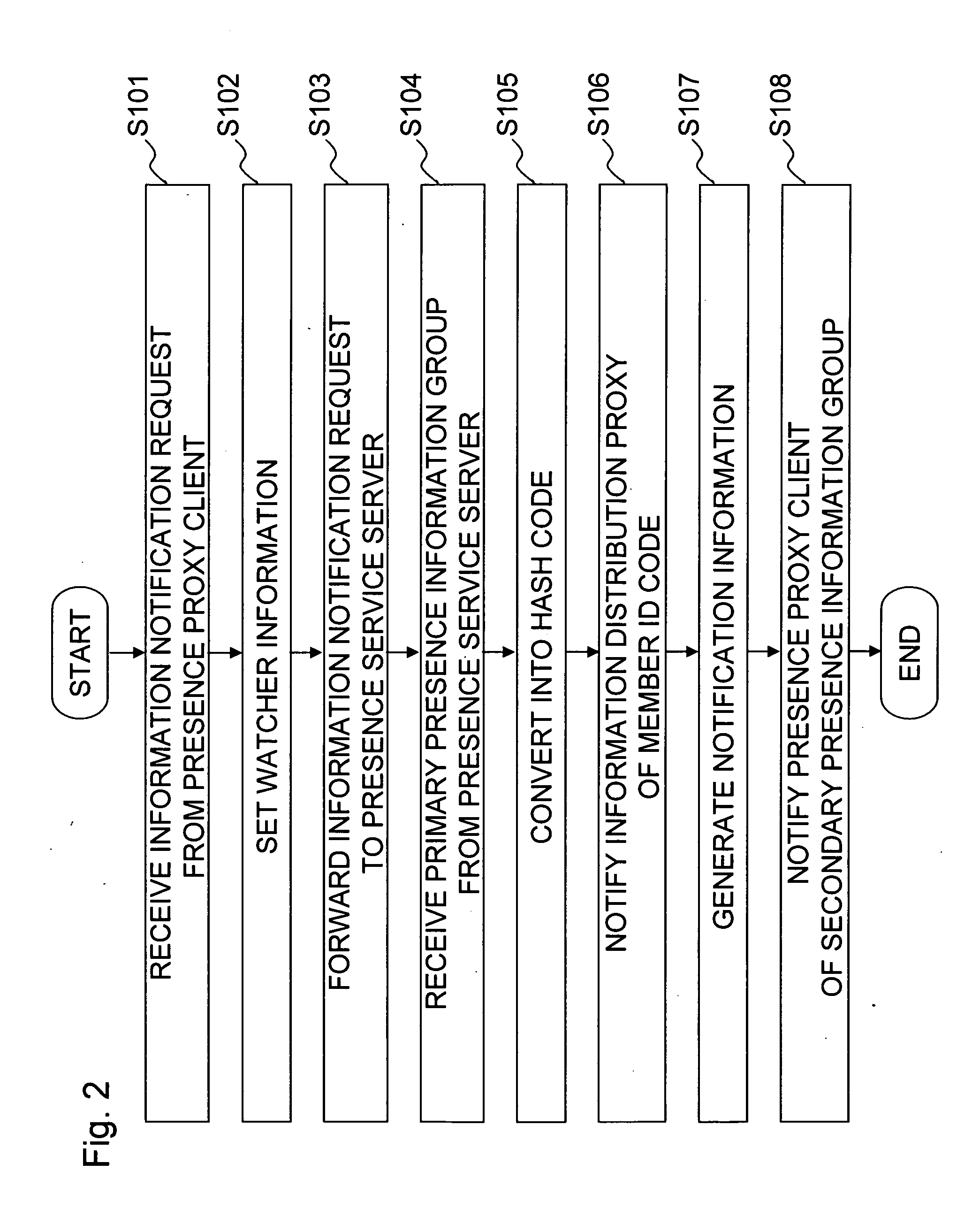
System for providing anonymous presence information, method thereof and program storage medium storing program thereof
InactiveUS20070274489A1Distribute a large amount of presence information efficientlyEffective distributionSpecial service for subscribersApplication serverClient-side
An application server receives presence information with anonymous identification information of a presentity client. The application server transmits a message to an information distribution proxy. The message is addressed not to the identification information of the presentity client, but to the anonymous identification information of the presentity client. The information distribution proxy converts the anonymous identification information into real identification information, and forwards the message to the presentity client. Therefore, the application server does not know the real identification information of the presentity client. That is, there is no need for the application server to directly treat personal information, thereby producing the effect of eliminating the need for strict management of presence information.
Owner:FUJITSU LTD
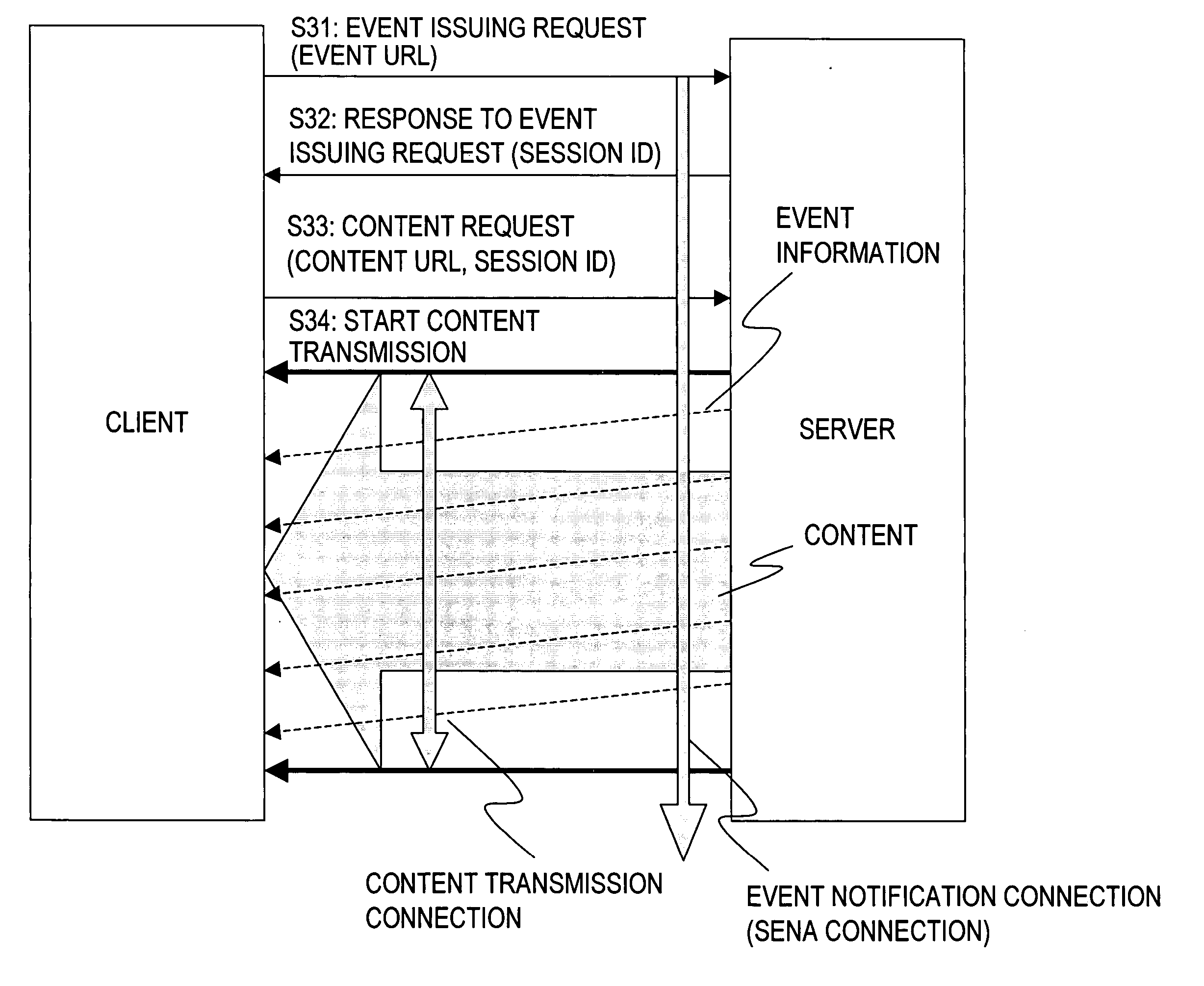
Information processing apparatus and content information processing method
ActiveUS20060195545A1Efficiently and accurately executingExecuted accurately and efficientlyData processing applicationsMultiple digital computer combinationsInformation processingClient-side
The present invention provides an apparatus and method capable of efficiently sending an event corresponding to content to be transmitted from a server to each client. A content providing server assigns a session ID to each client on condition that the server receives an event notification request, which specifies an event URL, from the client and then manages an event notification process on the basis of the event URL and the session ID. When respectively transmitting pieces of content to a plurality of clients, the server determines event information to be transmitted on the basis of each event URL regarding the corresponding piece of content and controls event notification timing for each client on the basis of the corresponding session ID. According to the present configuration, the load of managing data in the event notification process on the server can be reduced and a correct event synchronized with transmission content can be sent to each client.
Owner:SONY CORP
Mail distribution system, mail distribution method, and mail distribution program
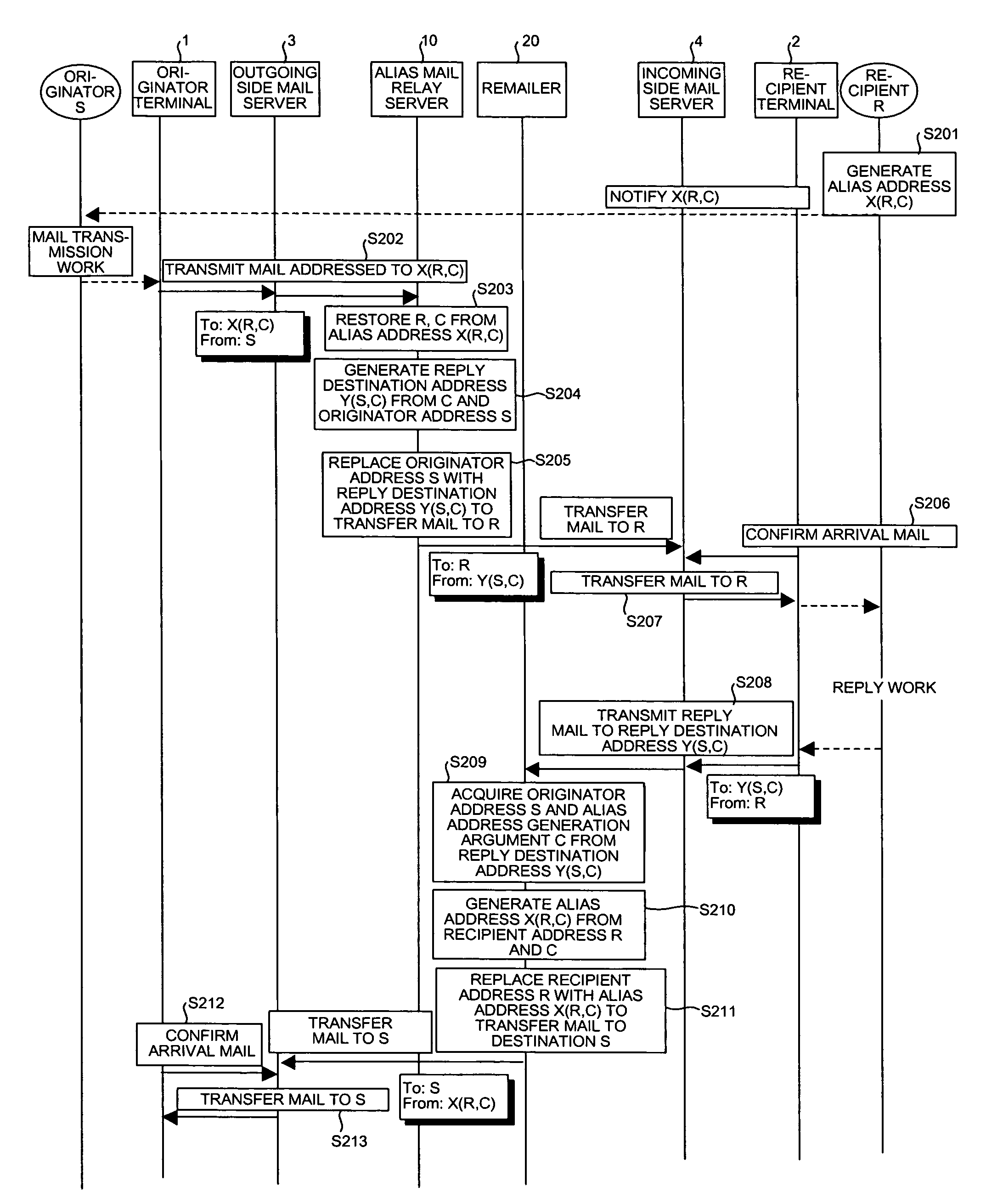
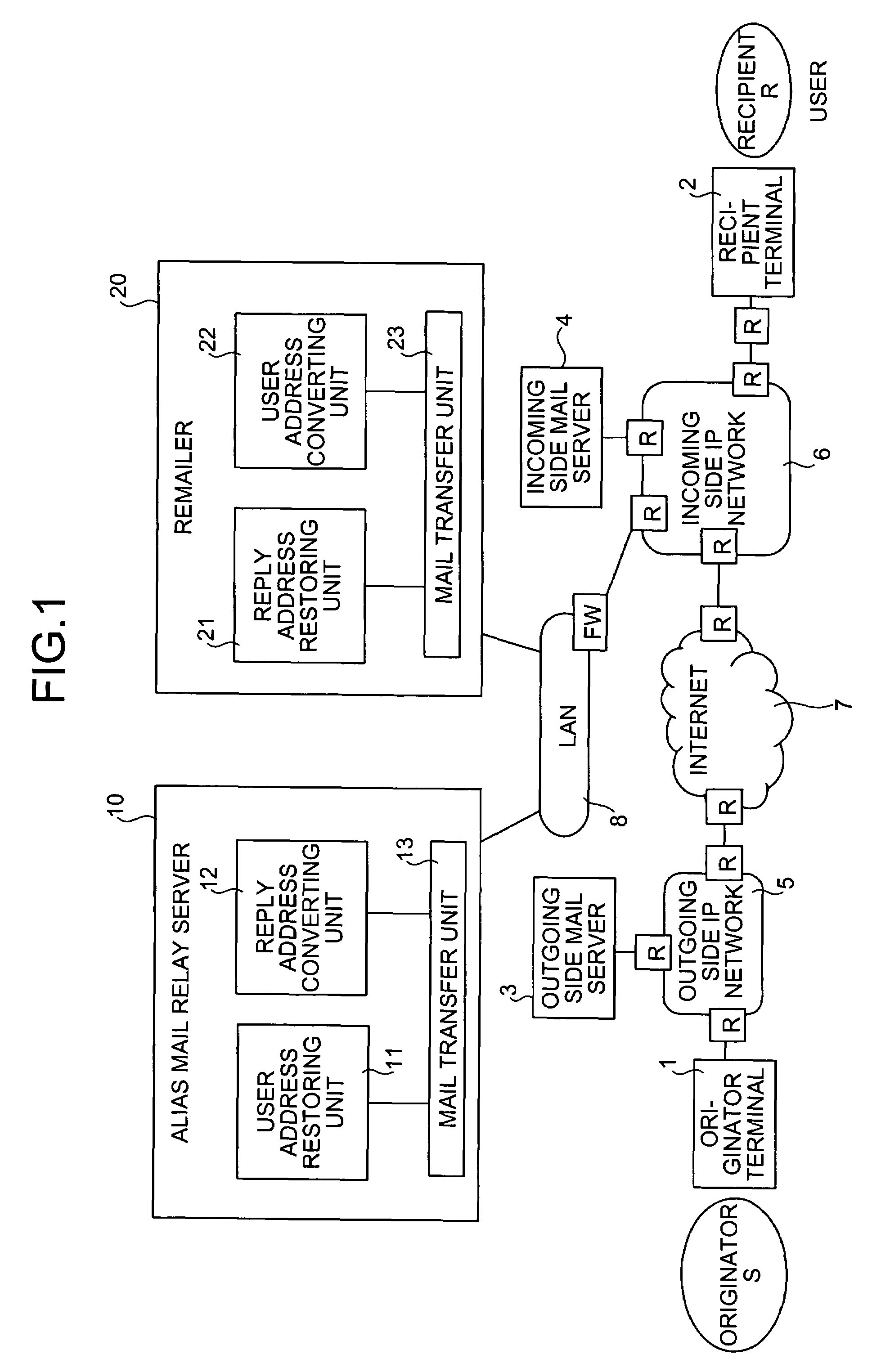
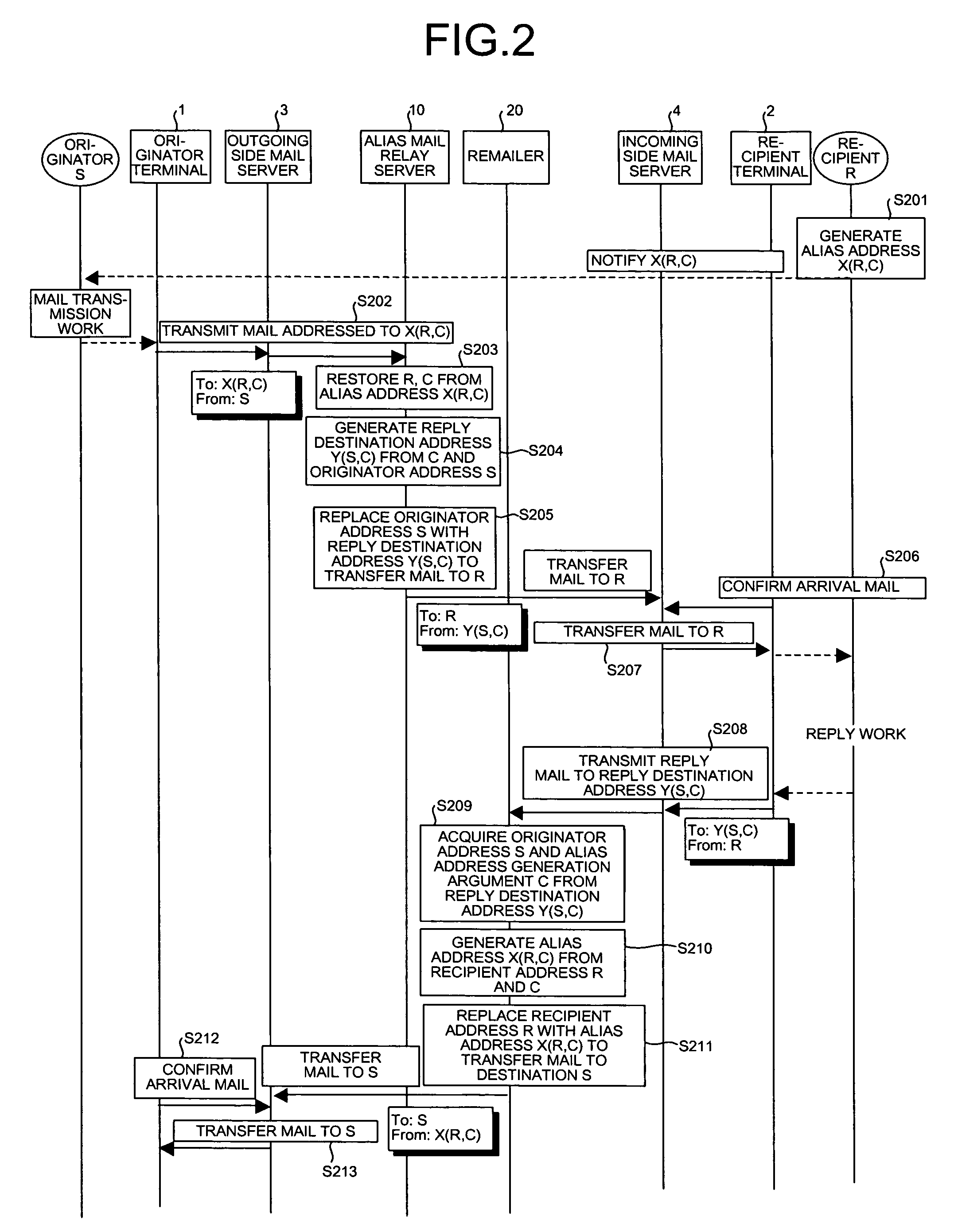
ActiveUS20070011245A1Reduce administrative burdenIncrease speedData processing applicationsMultiple digital computer combinationsMail DistributionsRecipient side
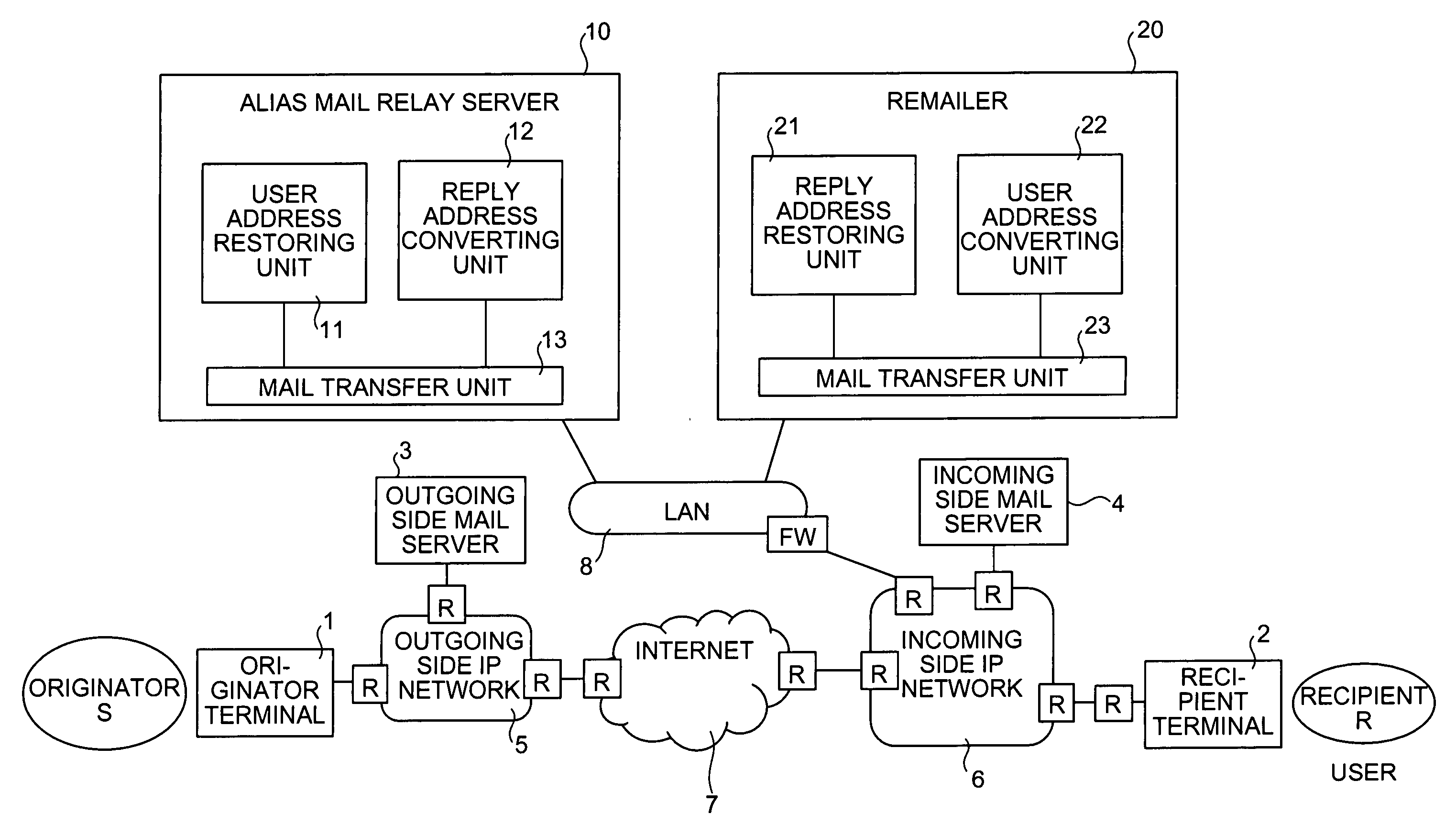
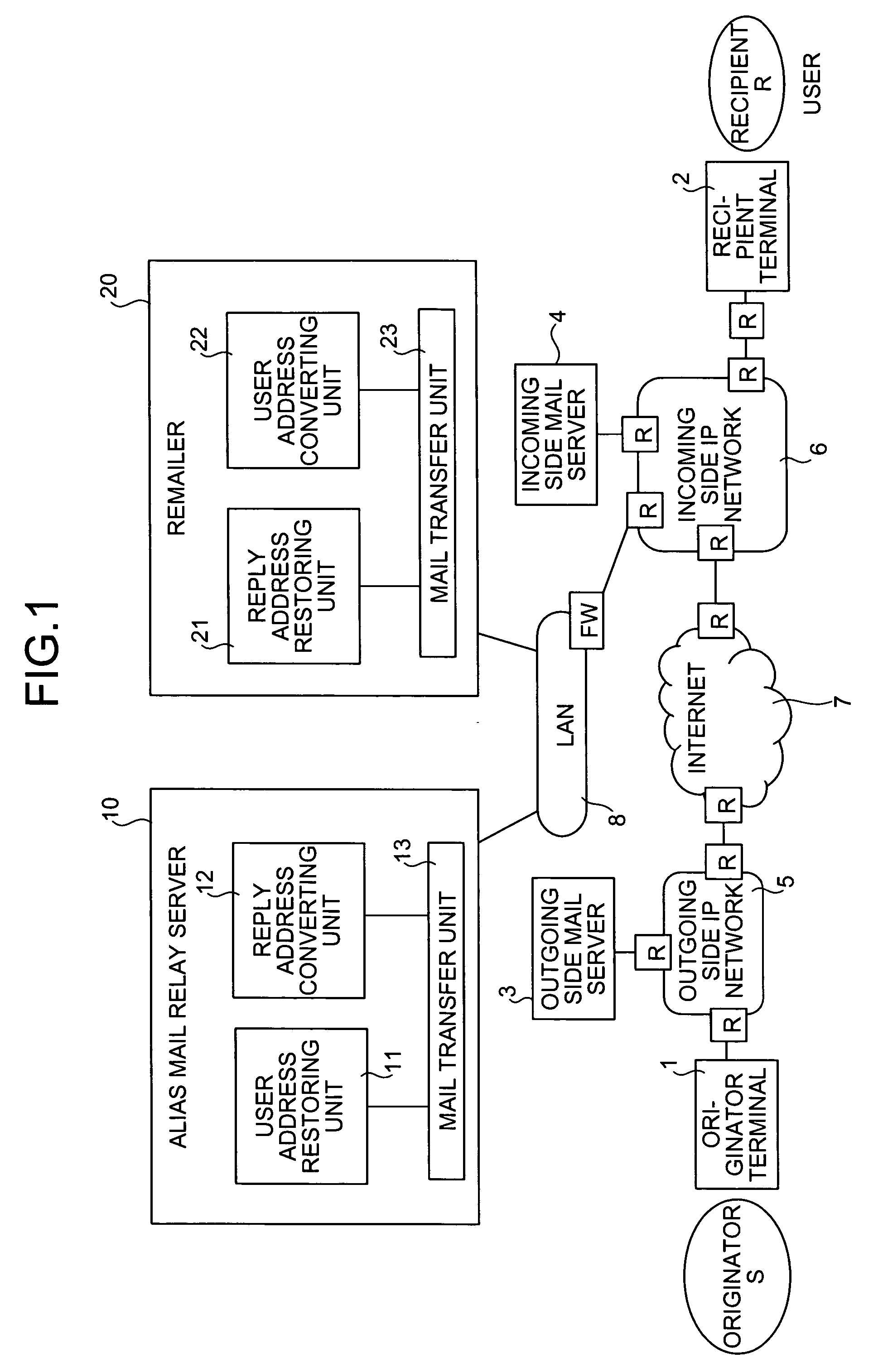
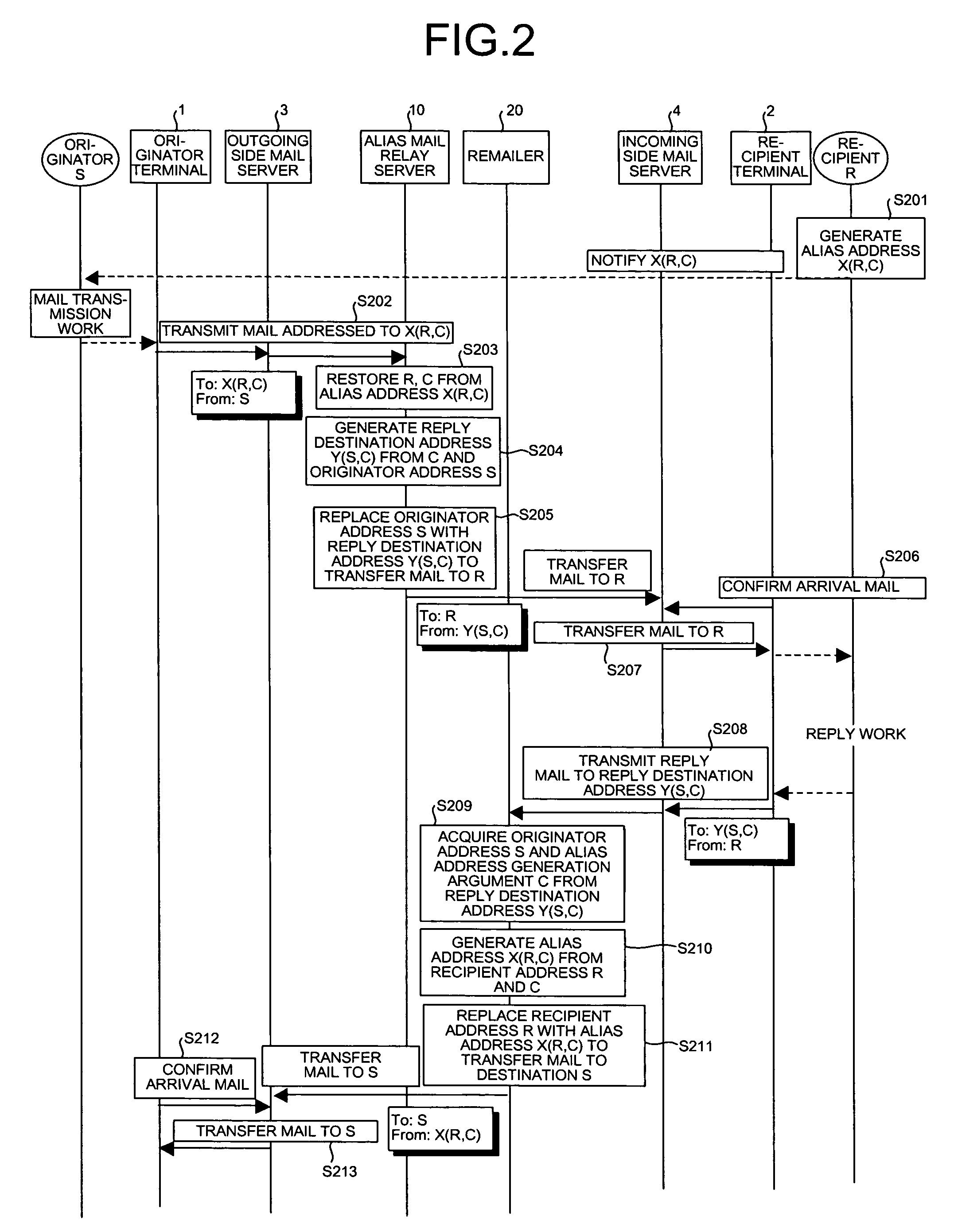
When an alias mail having an alias address X as a destination is received from an originator terminal, an alias mail relay server restores a recipient address R and an alias address generation argument C, generates a reply destination address Y including the generation argument C restores and an originator address S, and replaces the destination and a transmission source with the recipient address R and Y to transfer the alias mail to a recipient terminal. On the other hand, when a reply mail is received from the recipient terminal, a remailer restored the originator address S and the generation argument C from Y, regenerates X from the generation argument C restored and the recipient address R, and replaces a destination and a transmission source with the originator address S and X to transfer the reply mail to the originator terminal.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
System and method for encrypted communication
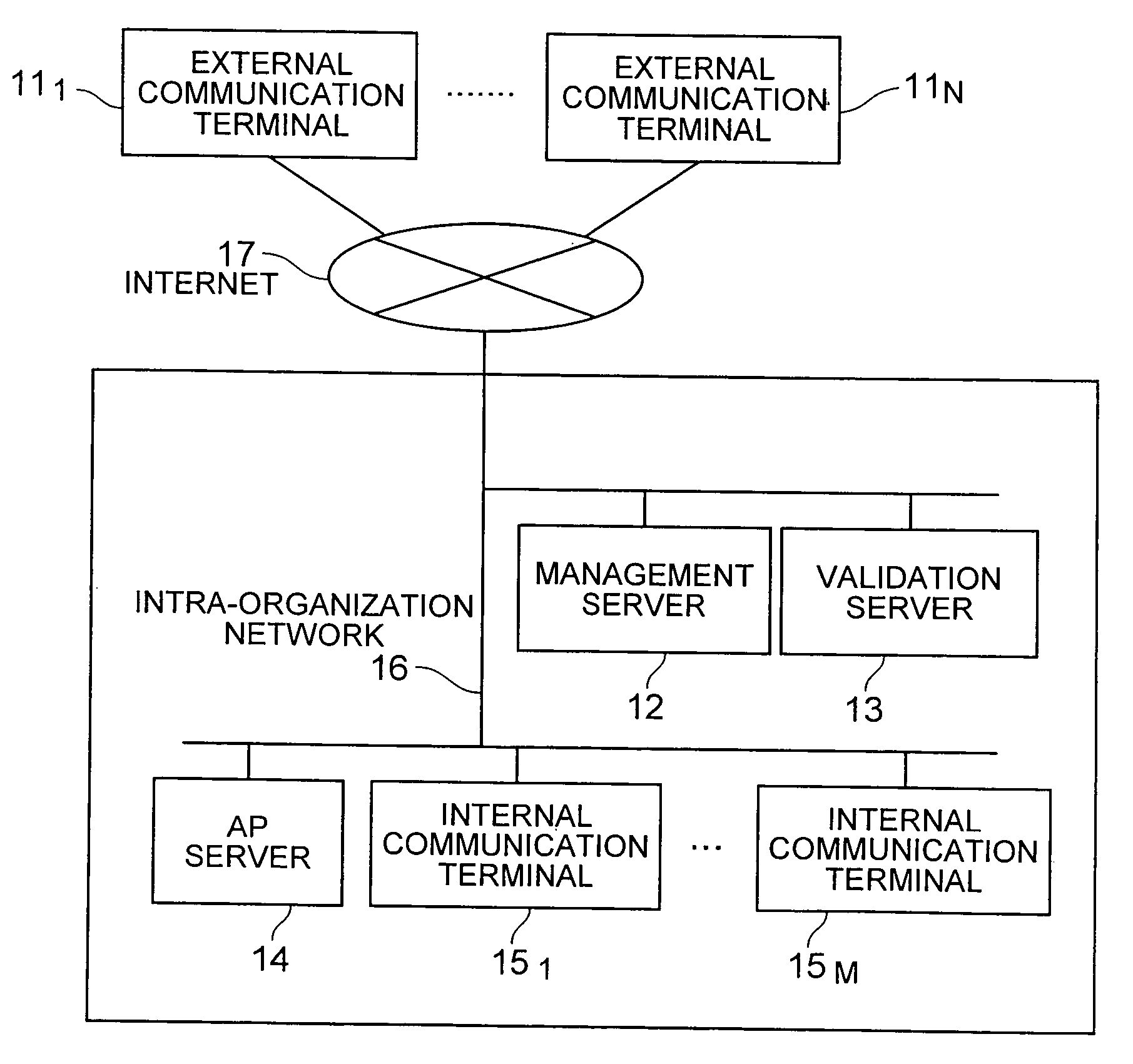
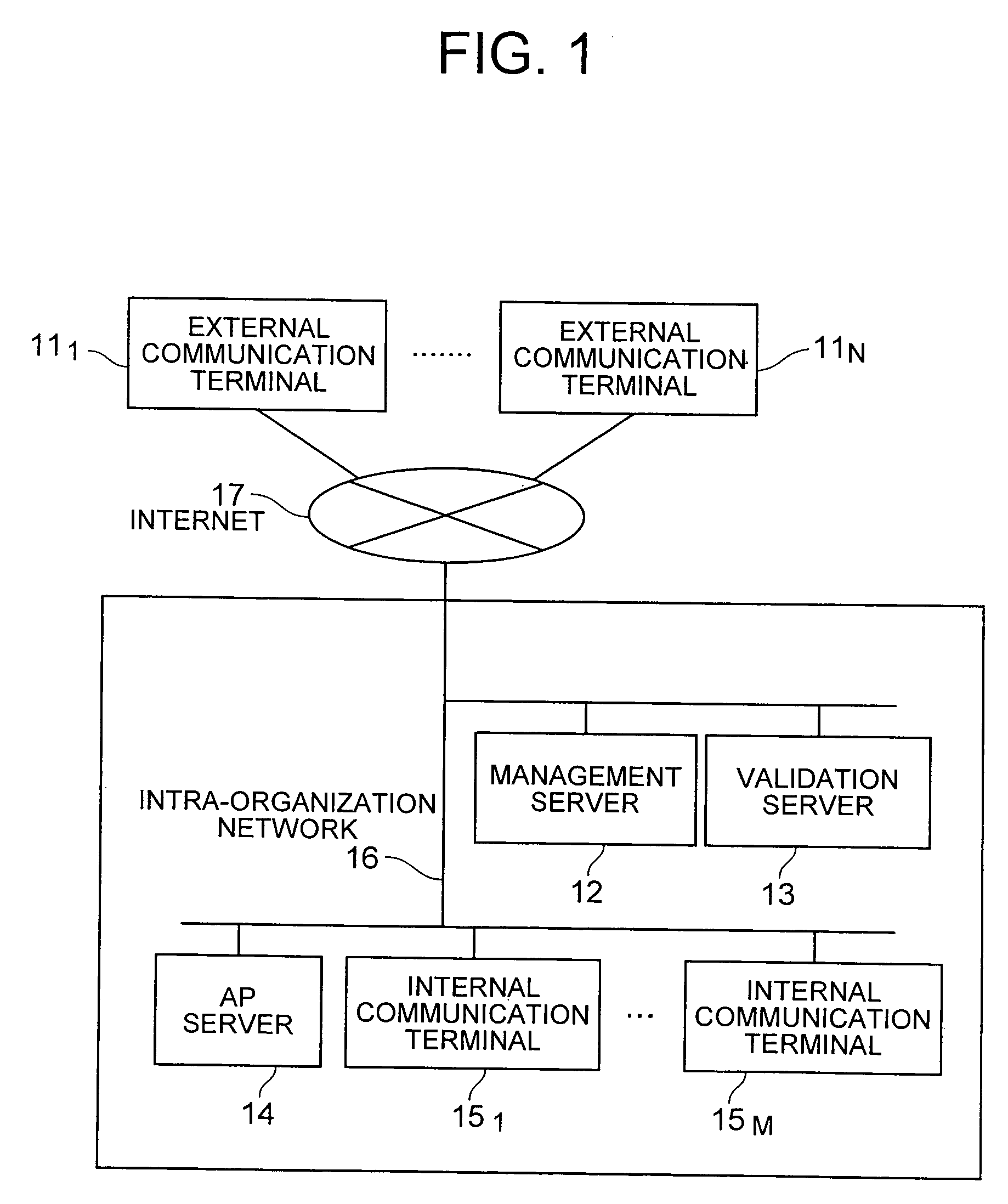
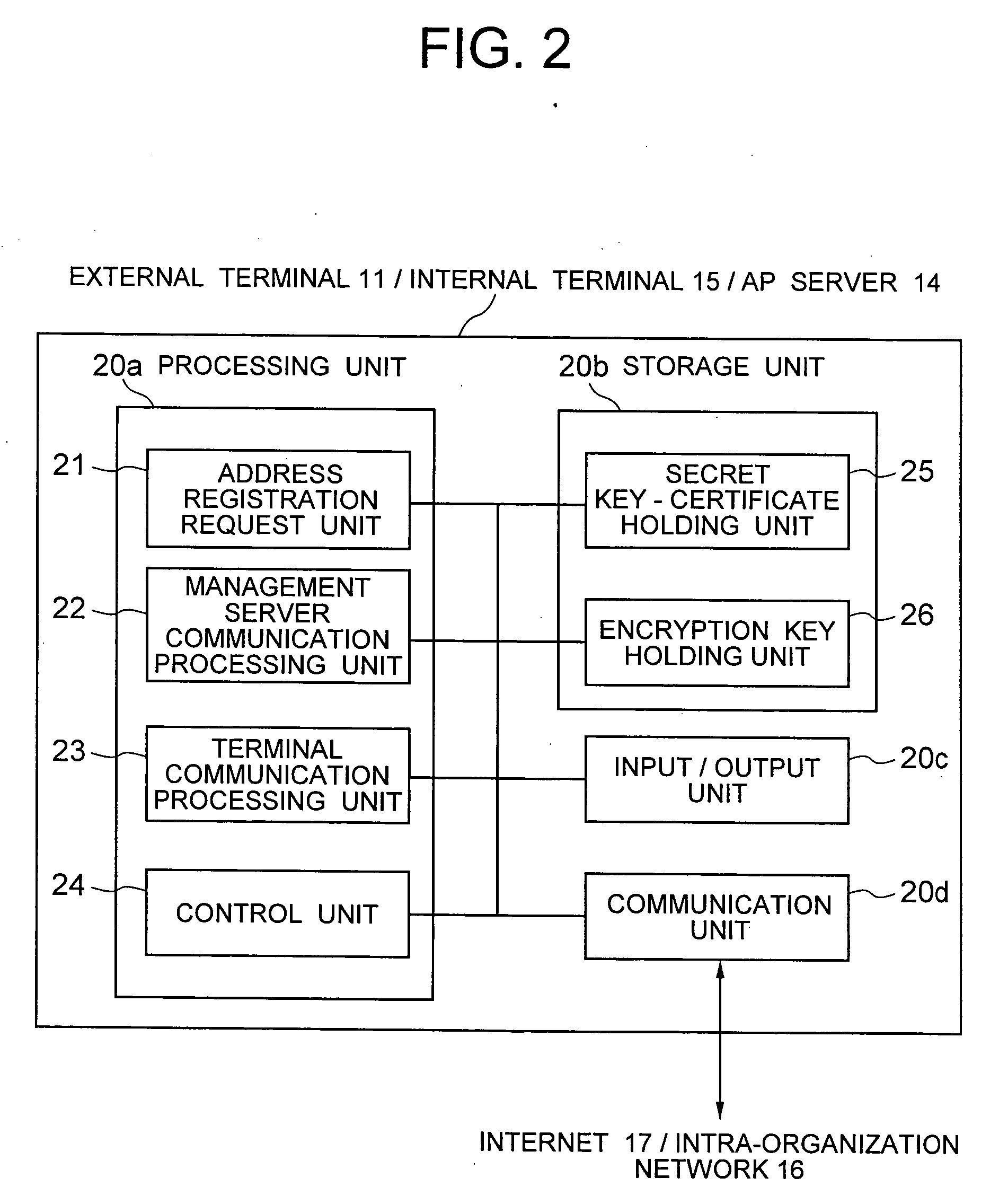
InactiveUS20060277406A1Reduce loadAuthentication is simpleDigital data processing detailsUser identity/authority verificationApplication serverEncryption
In an encryption communication using VPN technologies, a load on a VPN system becomes large if the number of communication terminals increases. When an external terminal accesses via an internal terminal an application server, processes become complicated because it is necessary to perform authentication at VPN and authentication at the application server. A management server is provided for managing external terminals, internal terminals and application servers. The management server authenticates each communication terminal and operates to establish an encryption communication path between communication terminals. Authentication of each terminal by the management server relies upon a validation server. When the external terminal performs encryption communication with the application server via the internal terminal, two encryption communication paths are established and used between the external terminal and internal terminal and between the internal terminal and application server.
Owner:HITACHI LTD
Method, server and customer apparatus for acquiring dynamic host configuration protocol cipher
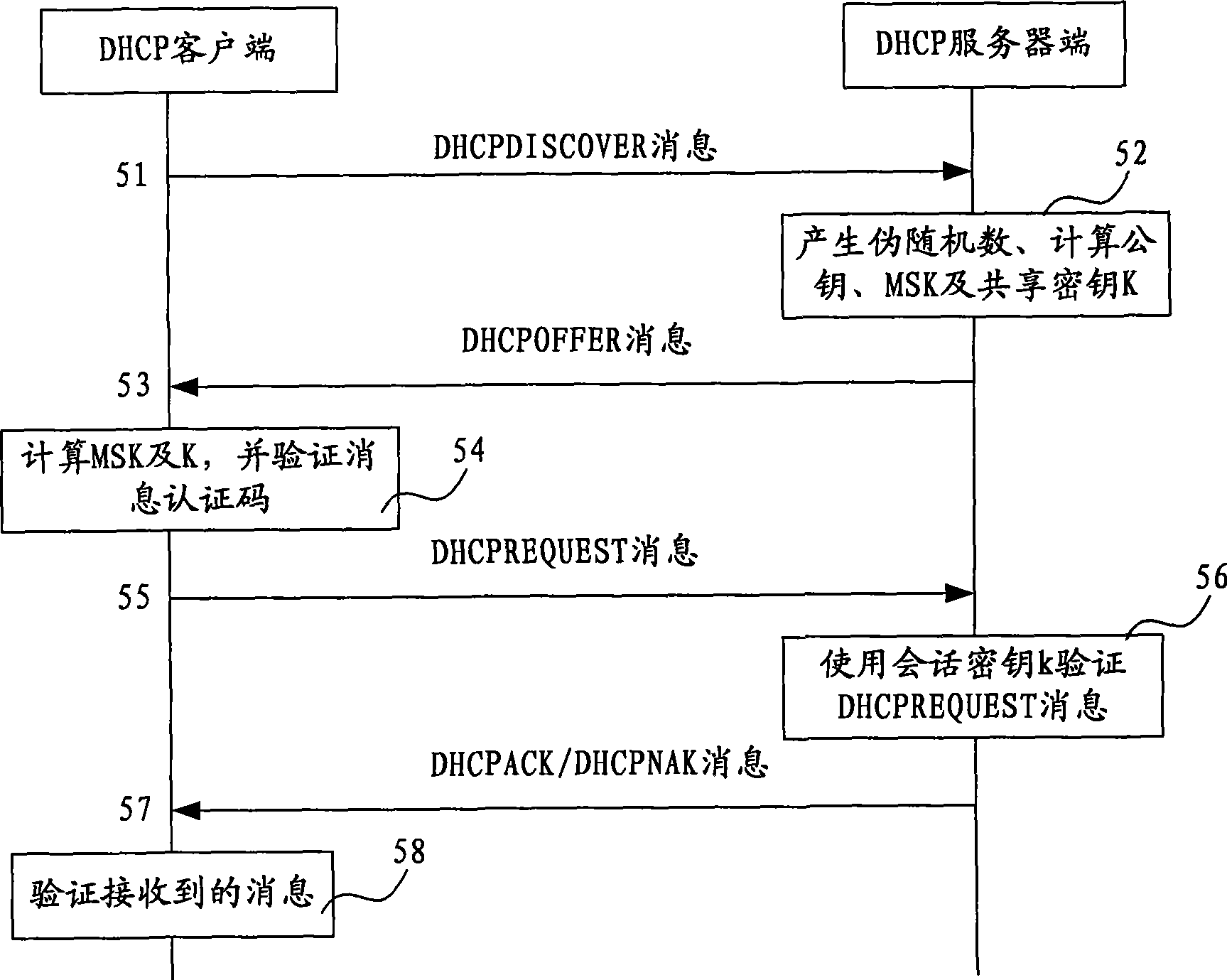
ActiveCN101388770AImprove securityReduce administrative burdenPublic key for secure communicationUser identity/authority verificationClient-sideKey generation
The invention relates to a method for obtaining a key of a dynamics host machine allocating protocol, a server and a user end device, wherein the method comprises the following steps: receiving a user end public key which is sent by a DHCP user end, using the Diffie-Hellman algorithm to calculate a private key of the server end, carrying out the Diffie-Hellman algorithm to the private key of the server end and the public key of the user end and obtaining a master key, the server comprises a receiving unit, a key generating unit and a master key generating unit, and the user end device comprises the key generating unit, the receiving unit and the master key generating unit. The invention further relates to a DHCP system which comprises the server and the user end device, wherein the DHCP user end and the server end negotiate the master key through DH, thereby different conversation keys are used in each conversation, thereby the safety of DHCP conversation is increased. And the DHCP user end and the server end do not need to store the master key for a long-period and share the key, and thereby the management burdens due to sharing the key are reduced.
Owner:HUAWEI TECH CO LTD
Automated NAT traversal for peer-to-peer networks
InactiveUS7912046B2Facilitate communicationReduce administrative burdenData switching by path configurationMultiple digital computer combinationsNAT traversalCommunications system
The subject invention relates to systems and methods that facilitate direct network communications between peers that operate behind Network Address Translators. In one aspect, a network communications system is provided. The system includes one or more Network Address Translators (NAT) to communicate data across a network between peers. A protocol selection component that automatically selects among a plurality of protocols according to one or more NAT types in order to determine a subset of the protocols that facilitate communications between the peers.
Owner:MICROSOFT TECH LICENSING LLC
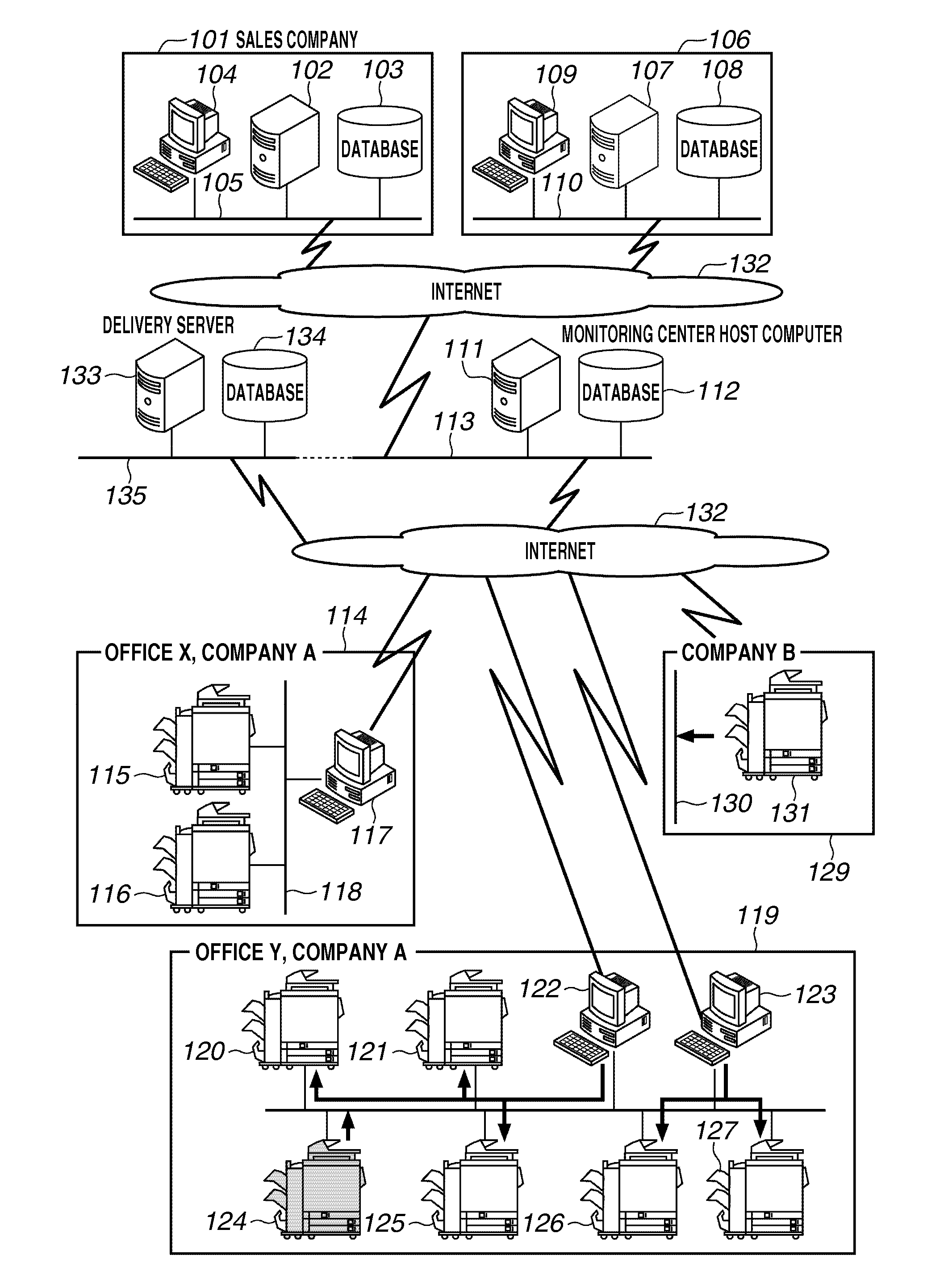
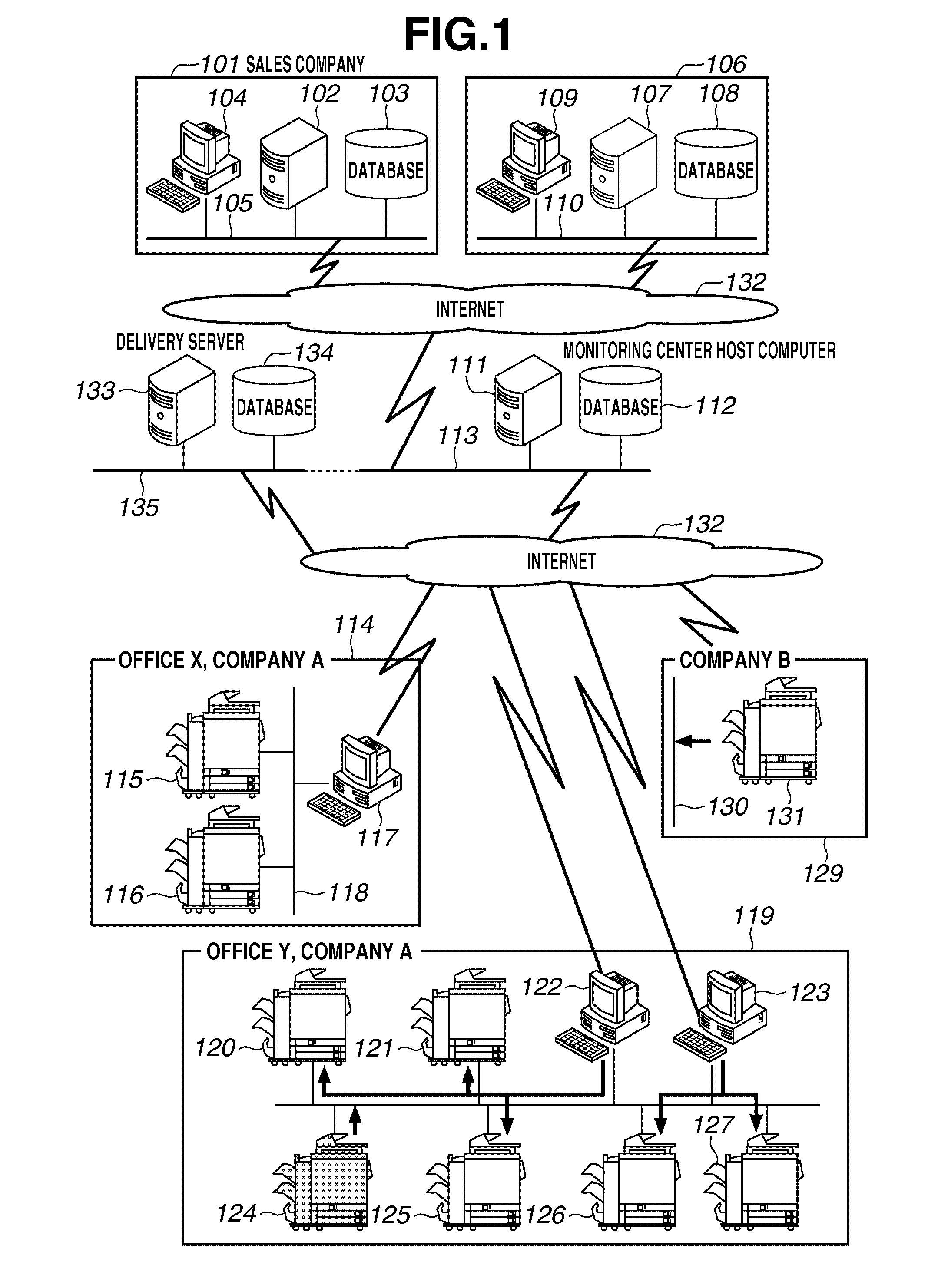
Image forming apparatus, firmware updating method, and program
ActiveUS20120062948A1Reduce loadEasy to operateSoftware engineeringPictoral communicationApplication timeControl unit
A confirmation time at which confirmation processing for confirming whether firmware applicable to an image forming apparatus is managed by a delivery server and an application time at which the firmware is applied to the image forming apparatus are set in advance by an operation unit of the image forming apparatus, and an update control unit performs the confirmation processing at an actual confirmation time which is acquired by shifting the confirmation time, and if firmware applicable to the image forming apparatus is managed by the delivery server, the firmware is downloaded from the delivery server, and the firmware is stored in a storage device, and the update control unit applies the stored firmware to the image forming apparatus at the application time.
Owner:CANON KK
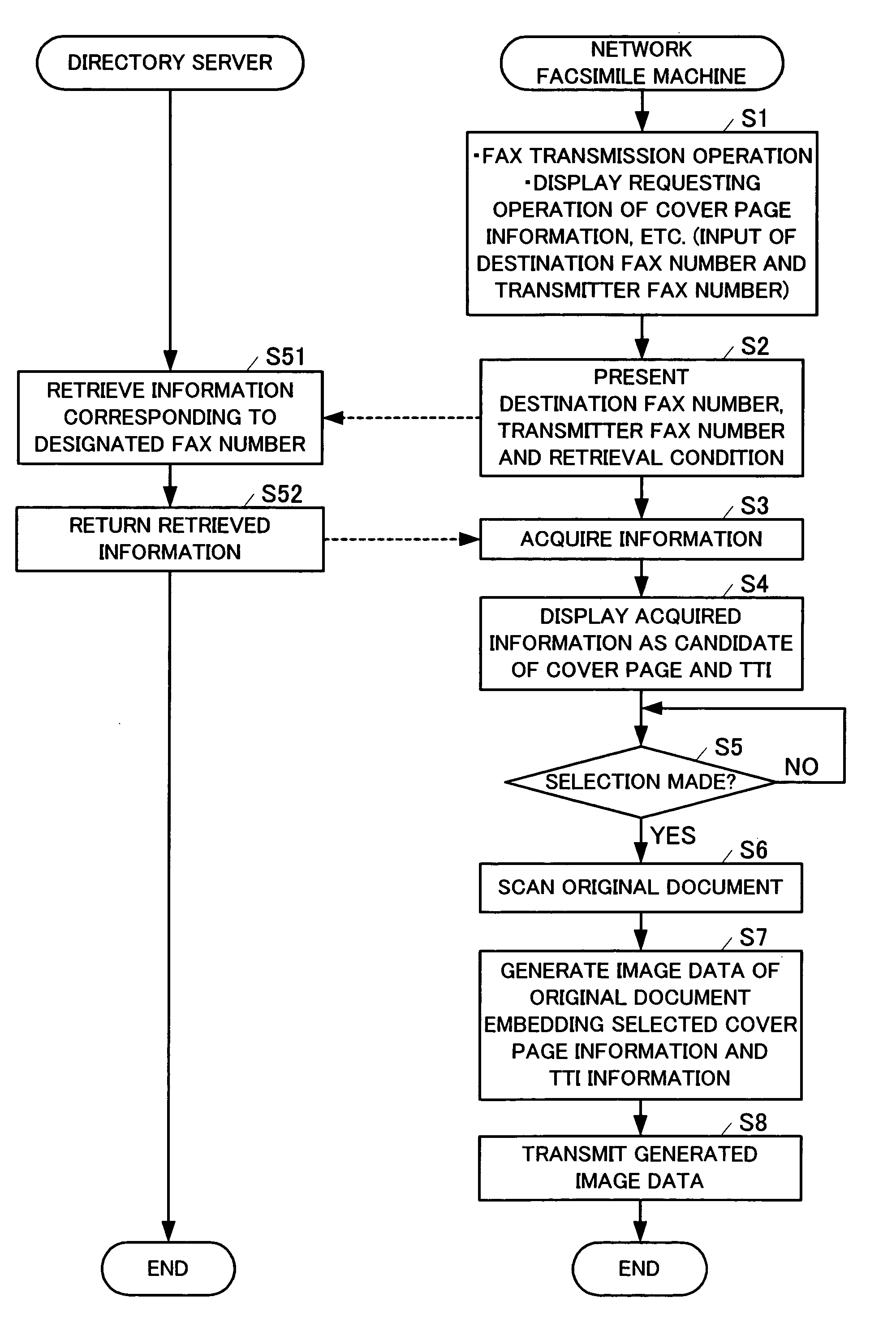
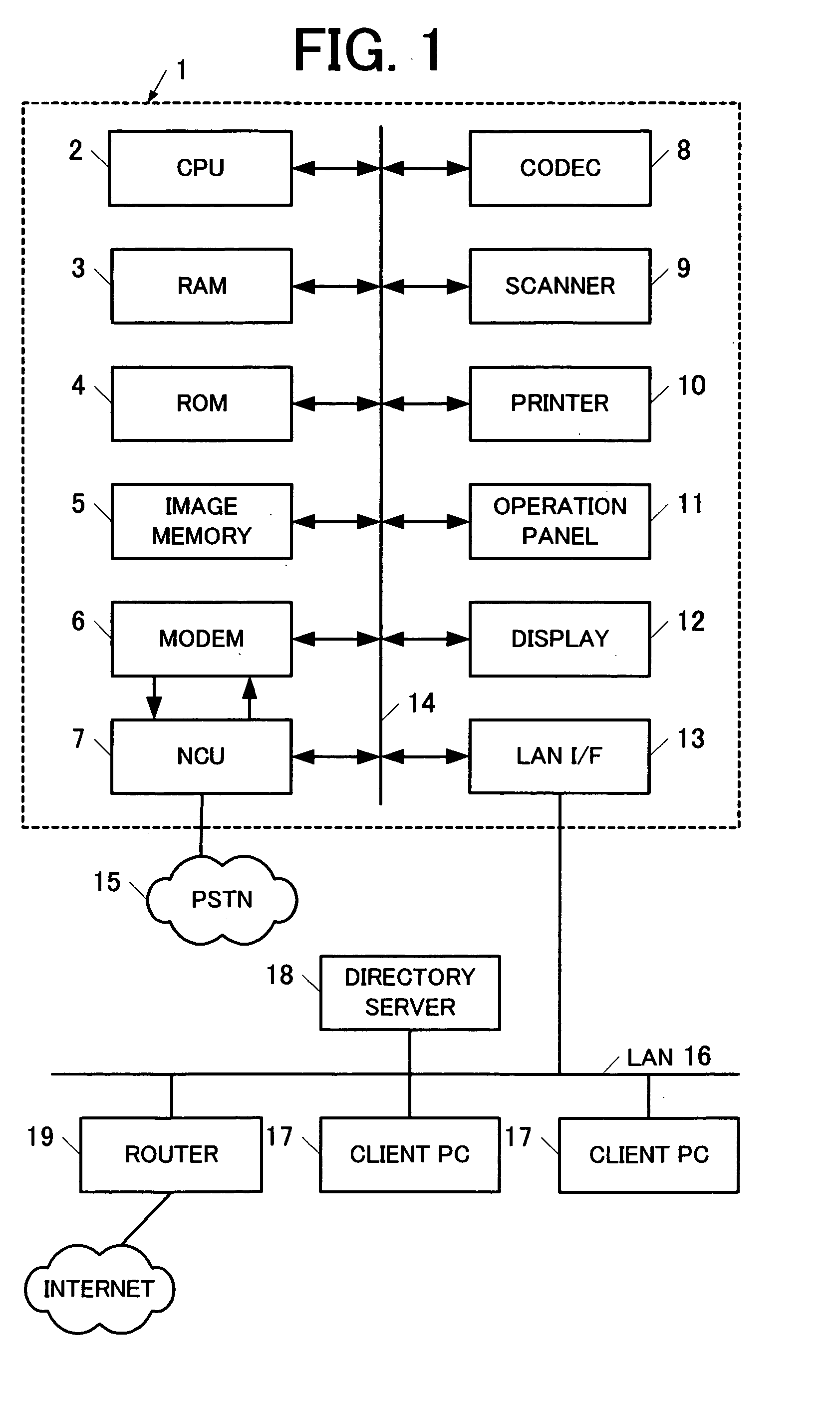
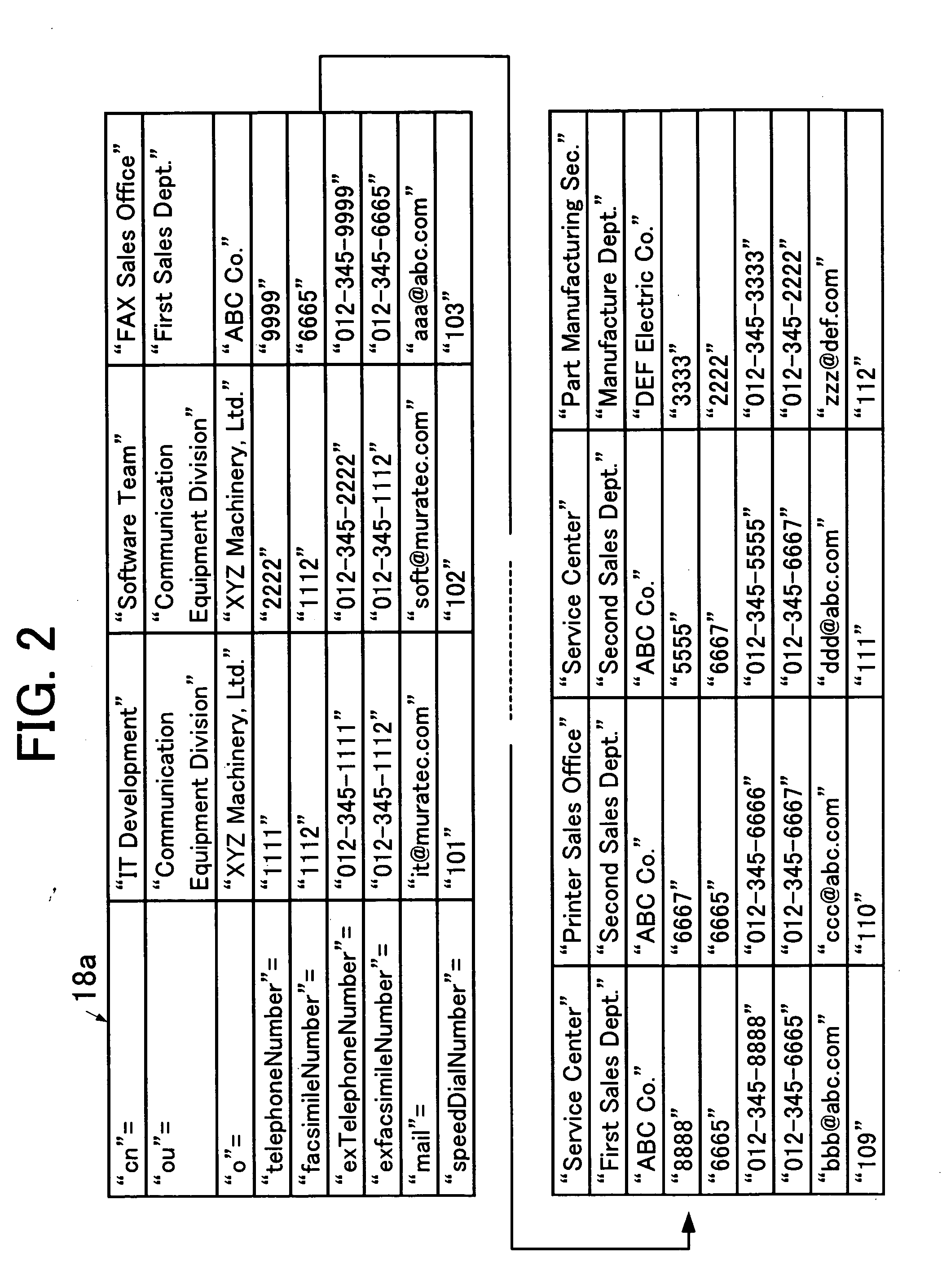
Network facsimile machine and network facsimile communication method
InactiveUS20050168774A1Reduce administrative burdenEasy to operateDigital computer detailsData switching networksData transmissionPaper document
A network facsimile machine accepts designation information for designating information to be embedded in image data of a transmission original document, presents the accepted designation information to a remote device, acquires information as a response and generates image data in which the acquired information is embedded in the transmission original document.
Owner:MURATA MASCH LTD
Wireless microphone for use with an in-car video system
InactiveUS20070030351A1Highly stressfulReduce administrative burdenColor television detailsClosed circuit television systemsWireless microphoneAudio frequency
An in-car video system and method is provided where a wireless microphone is configured with bi-directional communications capability. In response to a received RF activation signal, the wireless microphone is automatically switched on to capture (and transmit back to the in-car video system) an audio soundtrack that accompanies the images captured by the car-mounted video camera. A wireless microphone controller mounted in the car transmits the RF activation signal to the wireless microphone. The wireless microphone controller is arranged to transmit the RF activation signal when the VCR starts recording. In an illustrative embodiment of the invention, the wireless microphone receives information, including a confirmation that the VCR is recording, from an RF information signal received from the wireless microphone controller mounted in the car. The wireless microphone displays the information to the officer on a display screen. The wireless microphone sounds an audible alert when it receives the RF activation or information signals.
Owner:L 3 COMM MOBILE VISION +1
Storage system group including scale-out storage system and management method therefor
InactiveUS20120030440A1Reduce administrative burdenMemory loss protectionError detection/correctionStorage managementManagement system
A management system is coupled to a storage system group including a scale-out storage system (a virtual storage system). The management system has storage management information, which includes information denoting, for each storage system, whether or not a storage system is a component of a virtual storage system. The management system, based on the storage management information, determines whether or not a first storage system is a component of a virtual storage system, and in a case where the result of this determination is affirmative, identifies, based on the storage management information, a second storage system, which is a storage system other than the virtual storage system that includes the first storage system, and allows a user to perform a specific operation only with respect to this second storage system.
Owner:HITACHI LTD
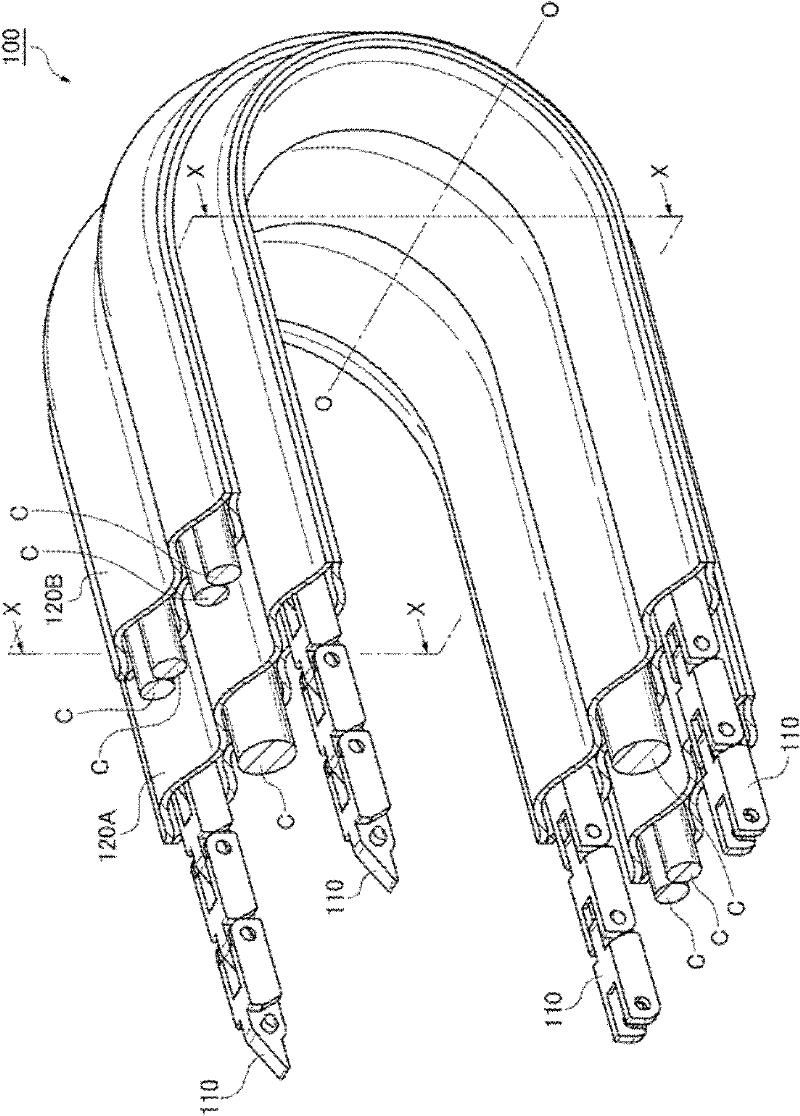
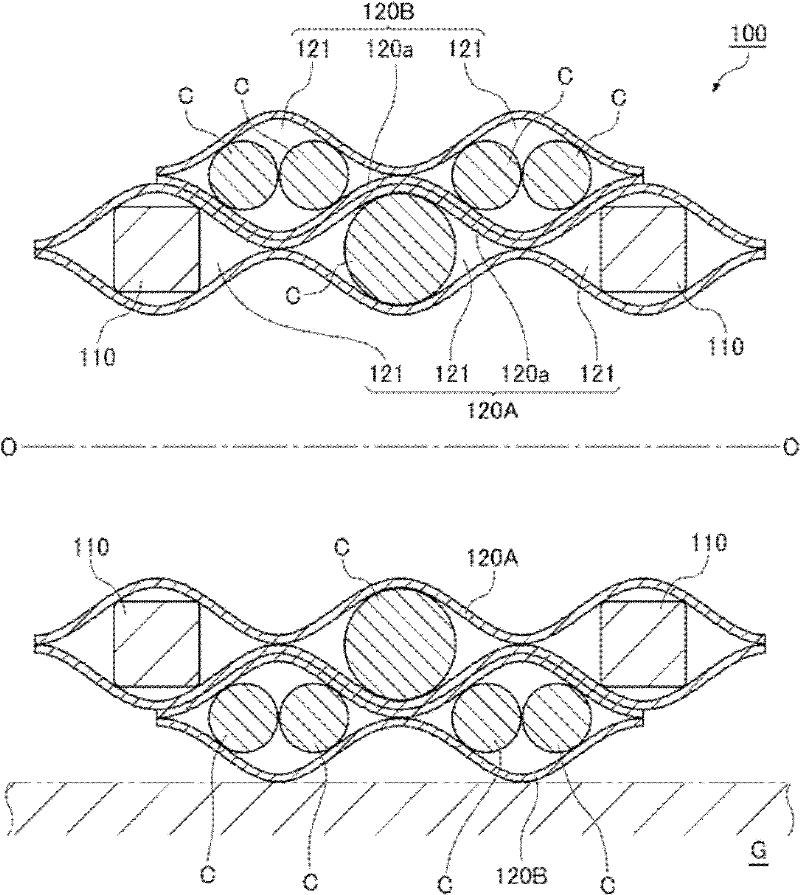
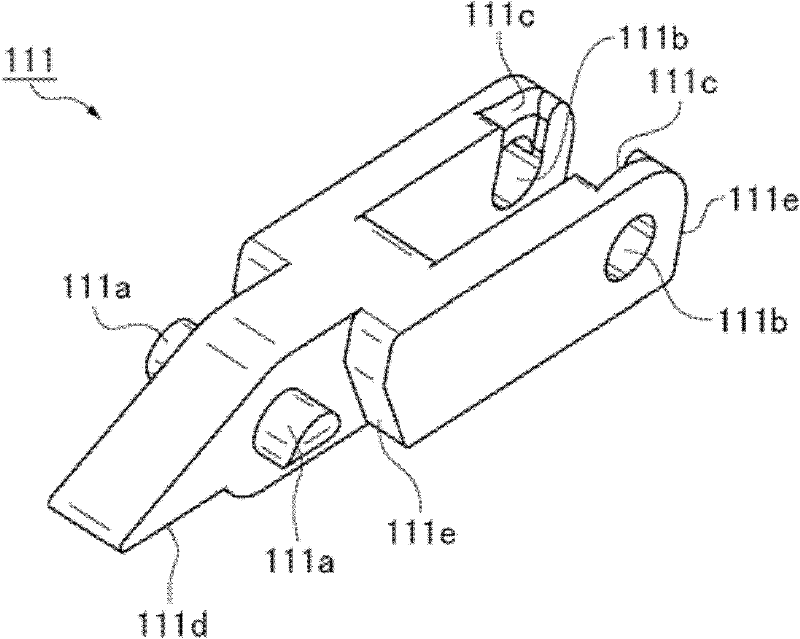
Articulated cable protection and guide device
ActiveCN102611045AReduce in quantityReduce administrative burdenPipe supportsArrangements using extensible carrierSynthetic resinMechanical engineering
There is provided an articulated cable protection and guide apparatus that can securely and stably guide a large number of cables and can assure durability of articulated supporting members operating between straight and bending postures for a long period of time. The articulated supporting members can be easily cut and connected. The articulated cable protection and guide apparatus 100 comprises a plurality of articulated supporting members 110 including a large number of synthetic resin block bodies linked with each other, and A plurality of flexible belt members 120A,120B including tubular storing portions 121 formed in parallel in a belt width direction.The flexible belt members are overlapped vertically along the length direction, and the articulated supporting members are inserted and stored in the tubular storing portions arranged on the right side and the left side of at least one of the flexible belt members.
Owner:TSUBAKIMOTO CHAIN CO
Therapeutic agent for autoimmune diseases comprising PD-1 agonist
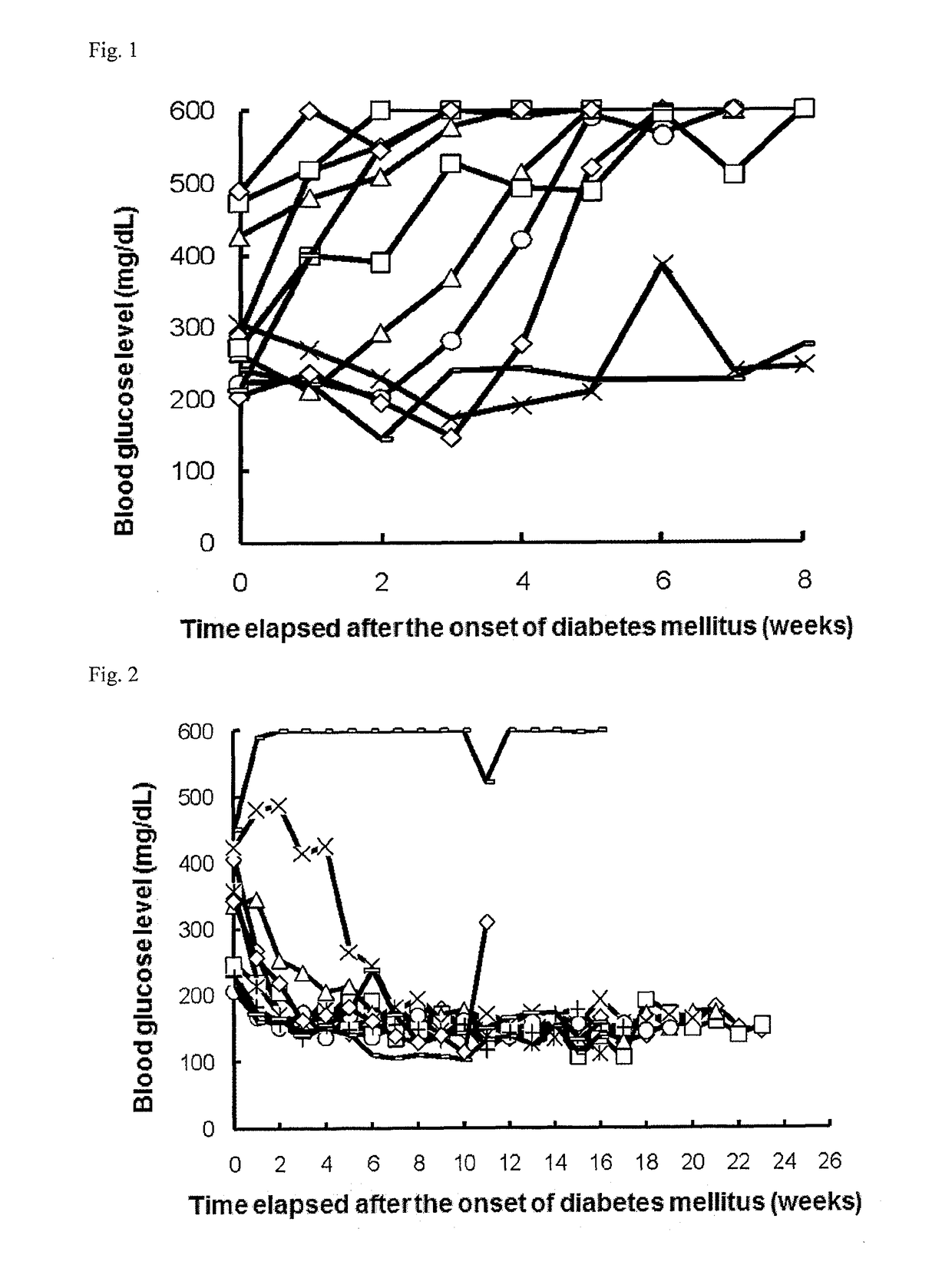
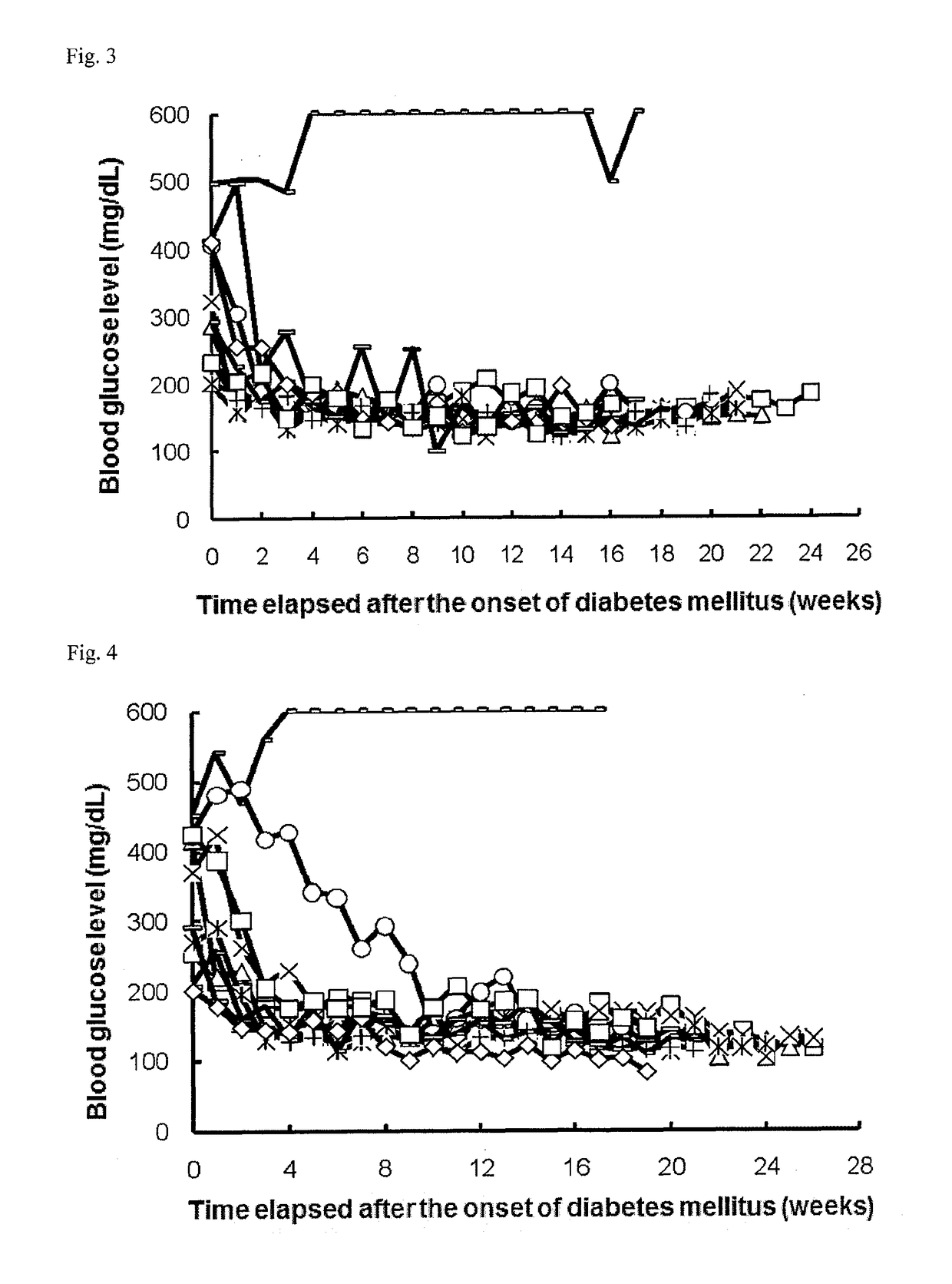
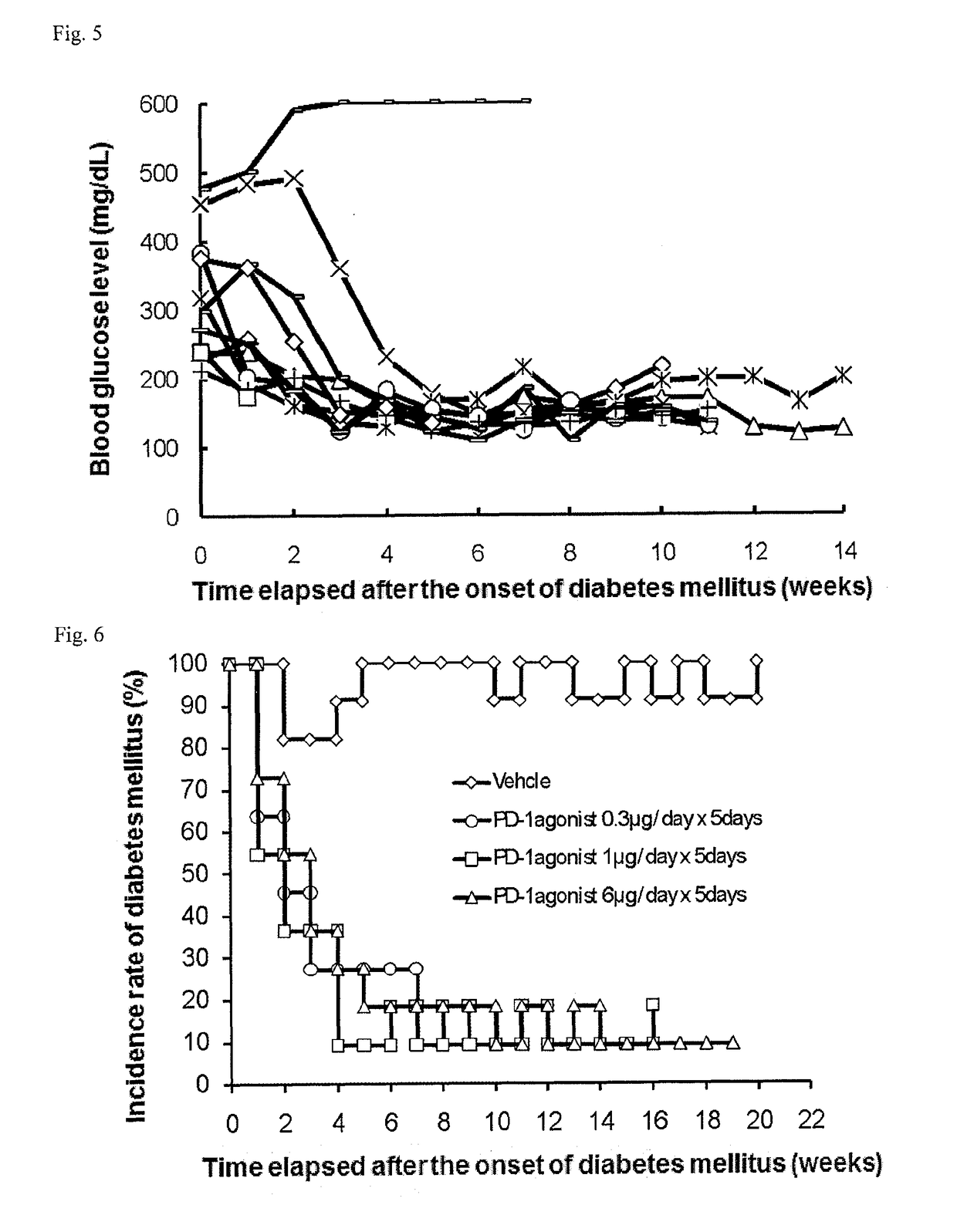
ActiveUS9701749B2Reduce the risk of infectionReduce administrative burdenNervous disorderAntipyreticDiseaseAutoimmune responses
Owner:ONO PHARMA CO LTD
Device management system
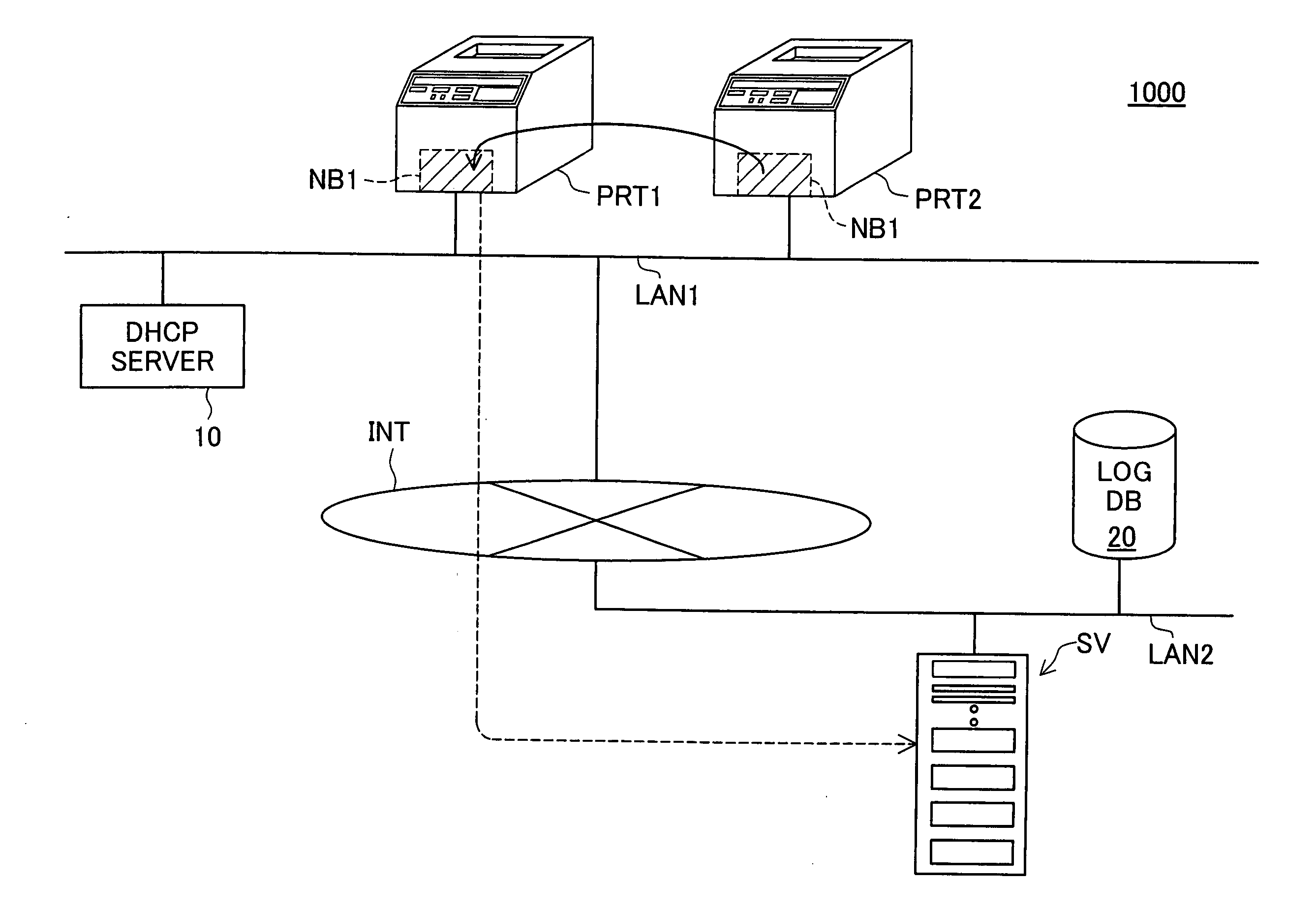
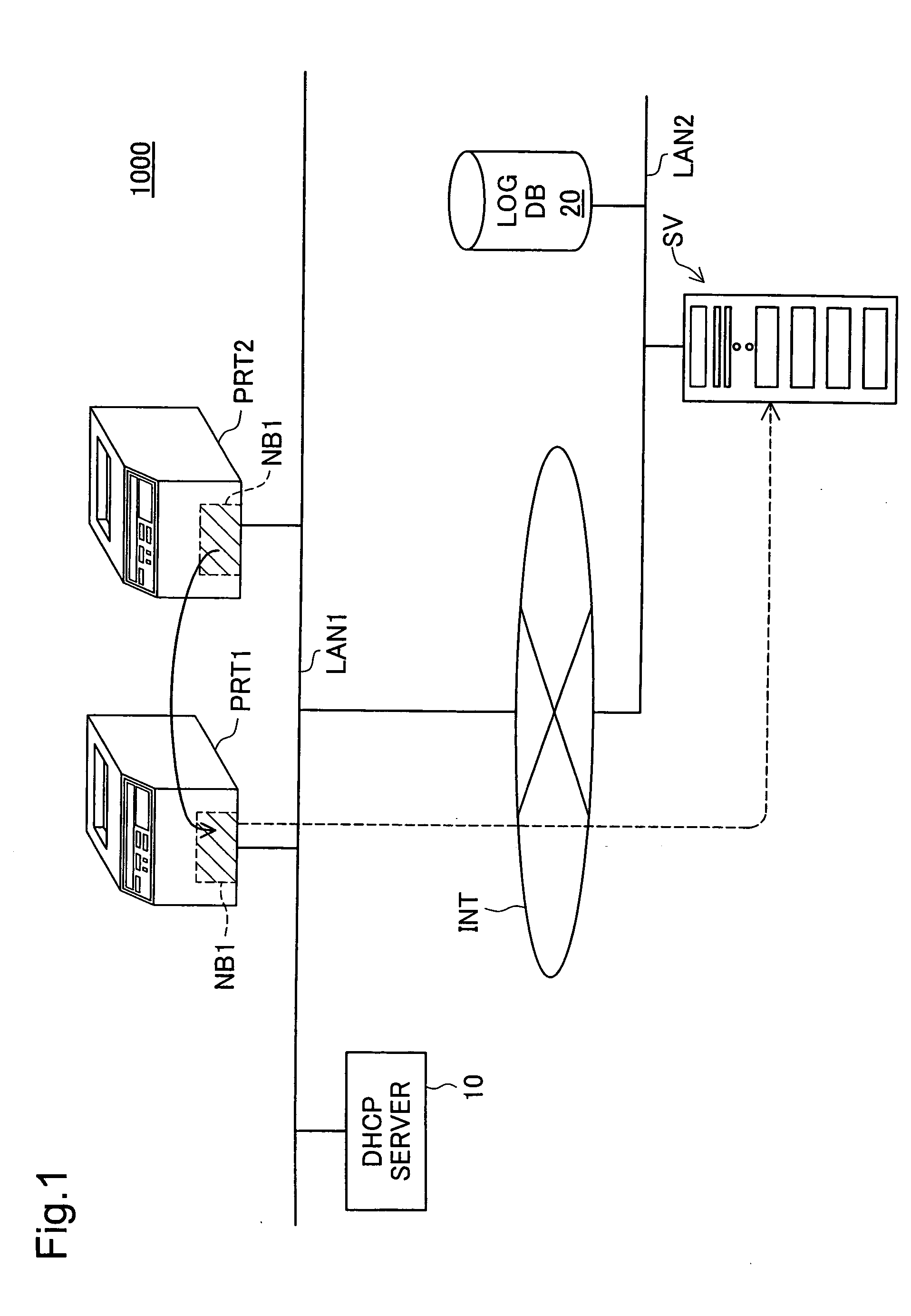
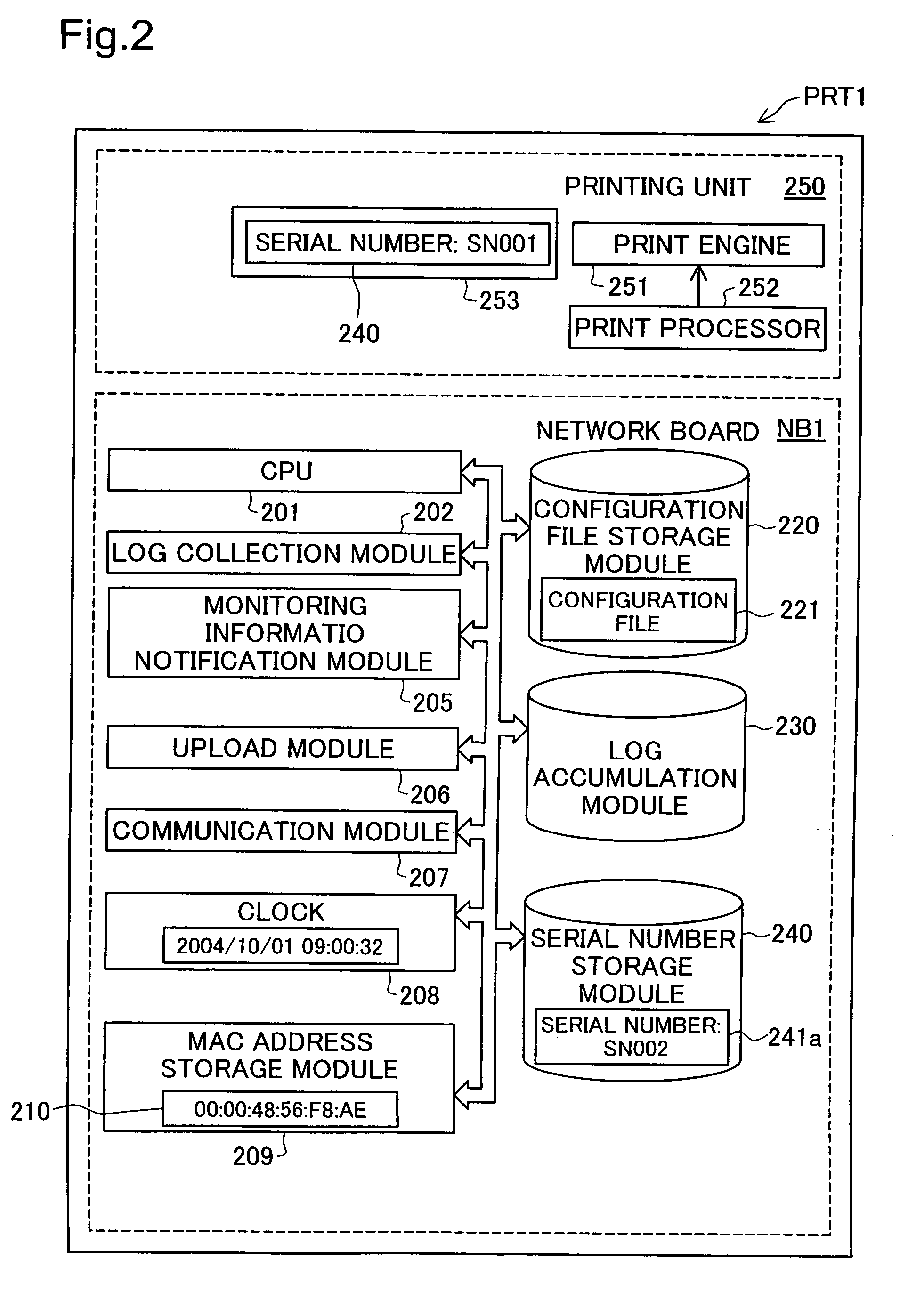
InactiveUS20060050304A1Reduce administrative burdenMaintain consistencyDigital output to print unitsAcquisition timeManagement system
A management server has printer monitoring information that associates the time at which a network board begins printer monitoring and the printer being monitored. The management server receives from the network board the printer's serial number, the network board's MAC address and the time at which the network board was replaced, and registers these items of information in the printer monitoring information. The network board monitors the printer and collects log information. For each log file uploaded from the network board, the management server specifies and associates which printer the log file belongs to based on the time at which the log file was collected and printer monitoring information and stores the log file in the log database while maintaining such association.
Owner:SEIKO EPSON CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com