Patents
Literature
218 results about "Biometric templates" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
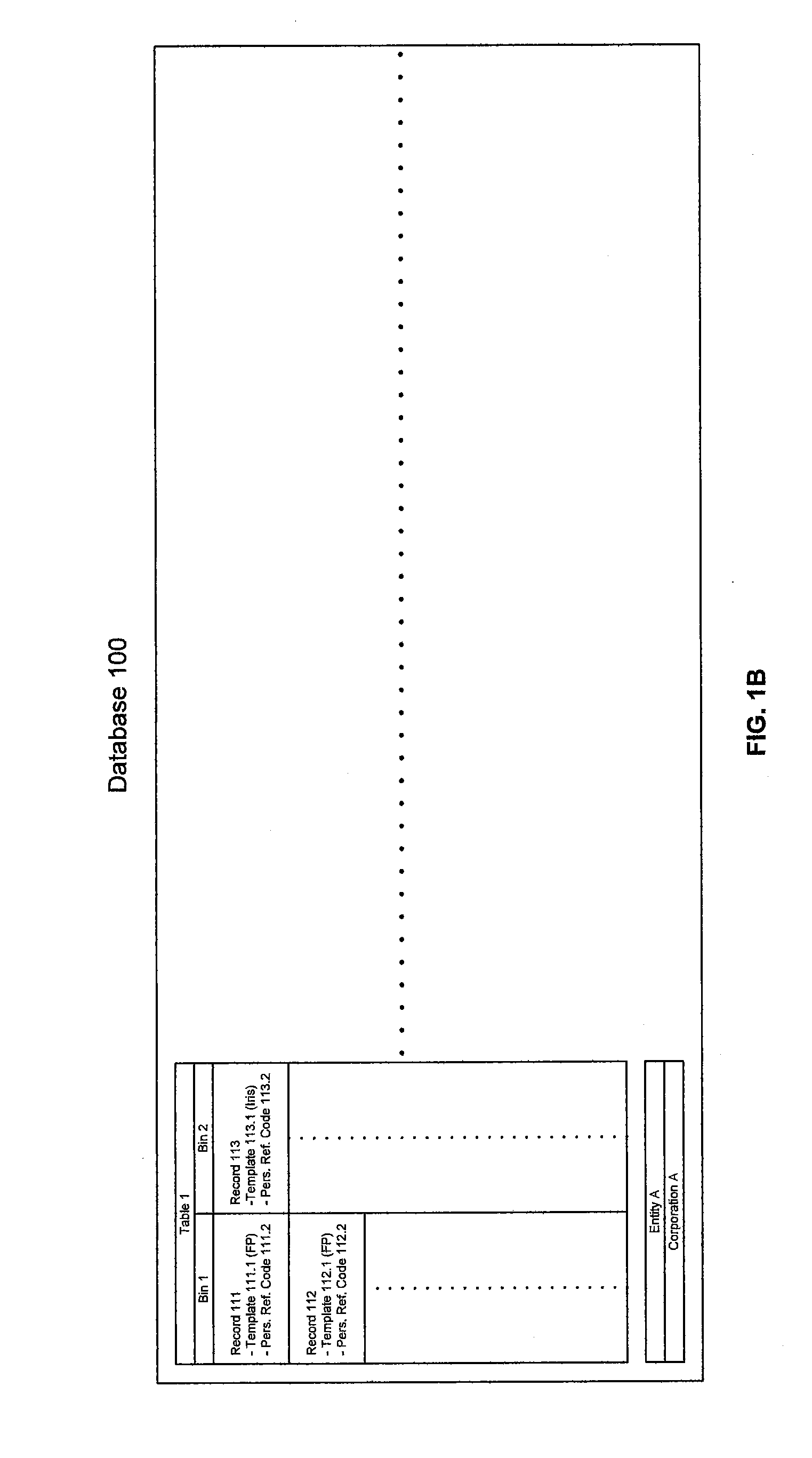
A biometric template (also called template) is a digital reference of distinct characteristics that have been extracted from a biometric sample. Templates are used during the biometric authentication process. Recommended Reading: See Webopedia's How Fingerprint Scanners Work and also learn How Biometrics Security Works.
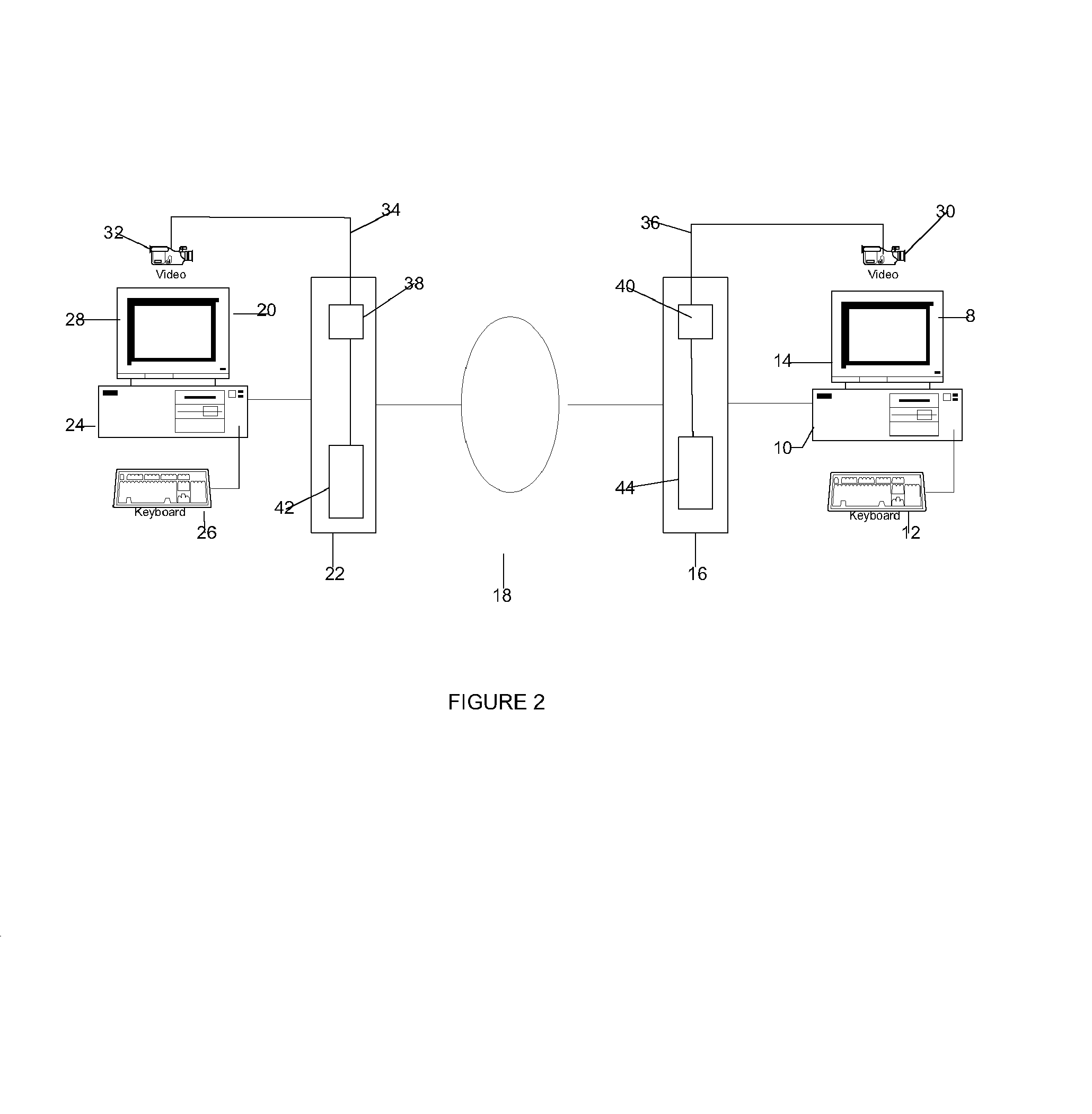
Method and apparatus for a web-based application service model for security management
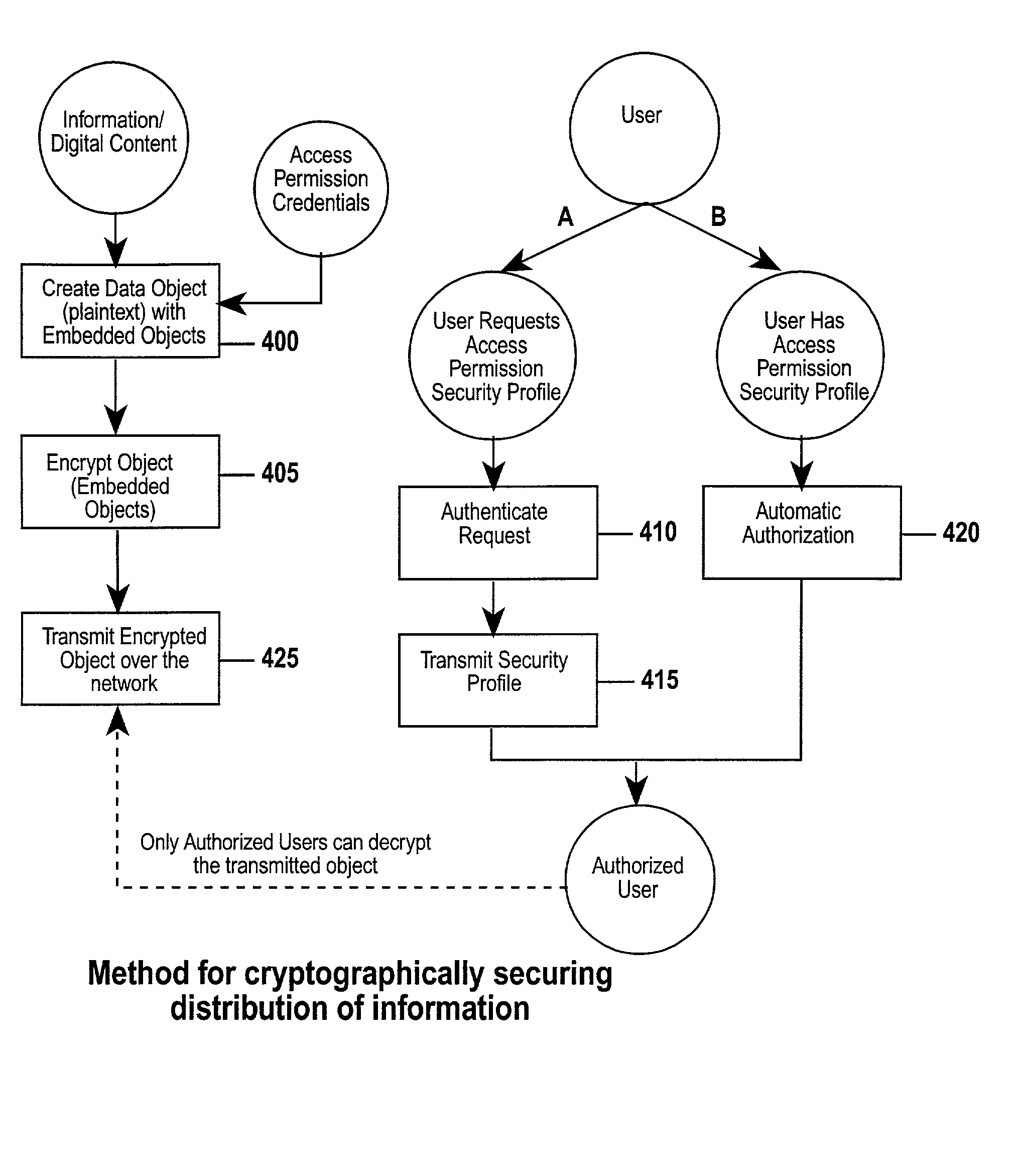
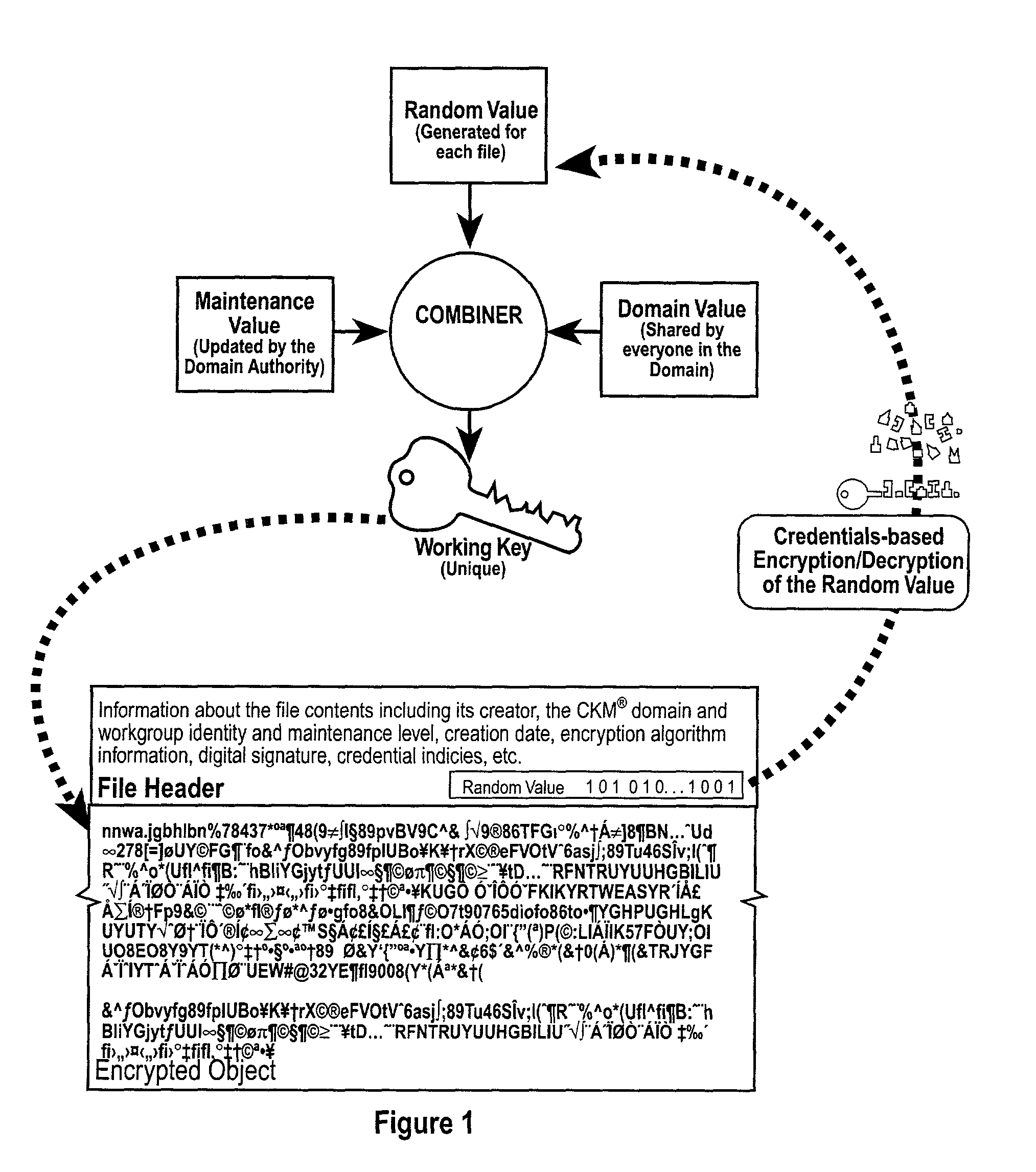
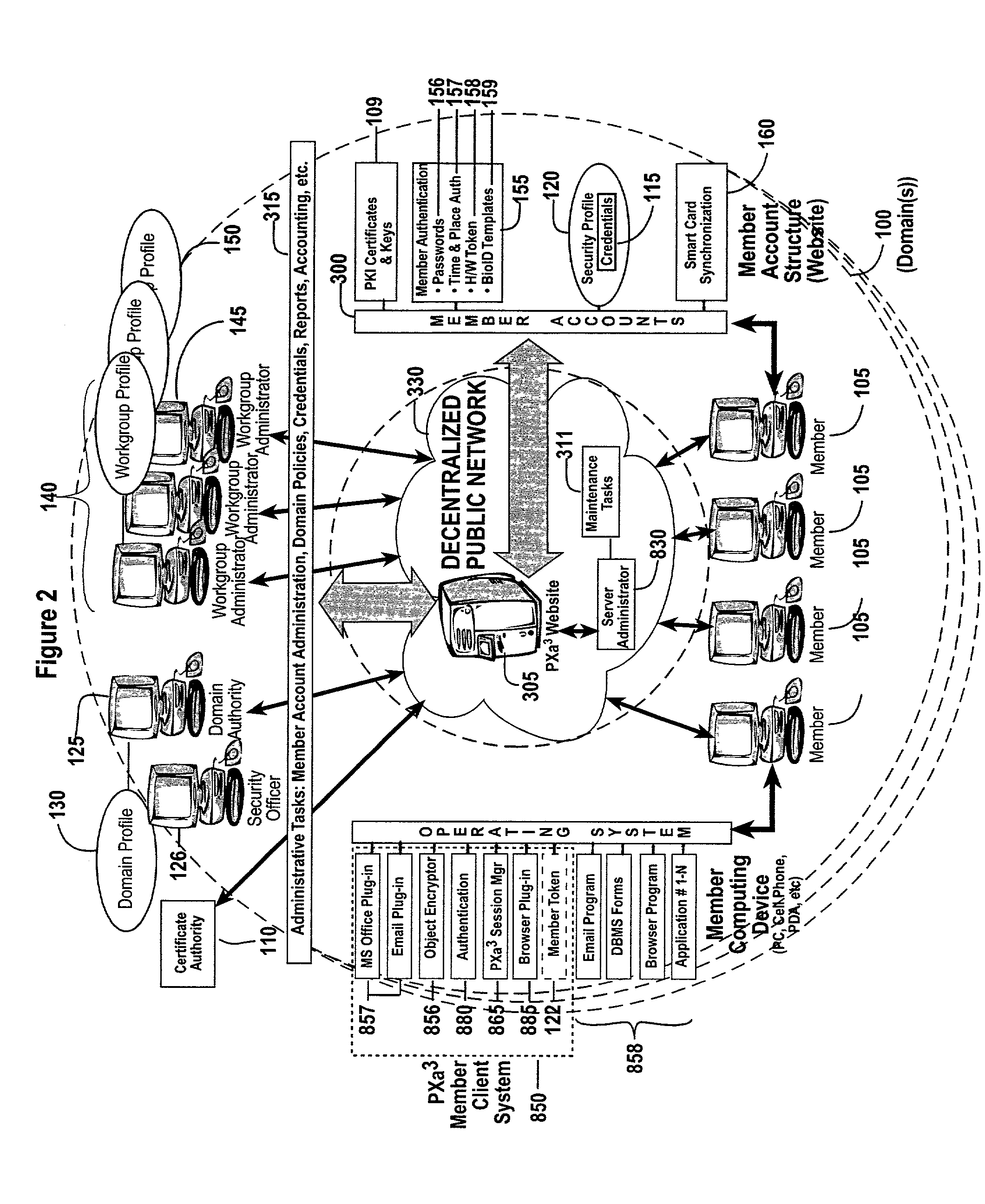
The invention combines cryptographic key management technology with various authentication options and the use of a companion PKI system in a web-centric cryptographic key management security method and apparatus called PXa3(TM) (Precise eXtensible Authentication, Authorization and Administration). The PXa3 model uses a security profile unique to a network user and the member domain(s) he / she belongs to. A PXa3 server holds all private keys and certificates, the user's security profile, including credentials and the optional authentication enrollment data. The server maintains a security profile for each user, and administrators simply transmitted credential updates and other periodic maintenance updates to users via their PXa3 server-based member accounts. Domain and workgroup administrators also perform administrative chores via a connection to the PXa3 web site, rather than on a local workstation. A member's security profile, containing algorithm access permissions, credentials, domain and maintenance values, a file header encrypting key, optional biometric templates, and domain-specific policies is contained in one of two places: either on a removable cryptographic token (e.g., a smart card), or on a central server-based profile maintained for each member and available as a downloadable "soft token" over any Internet connection.
Owner:SIVAULT INC
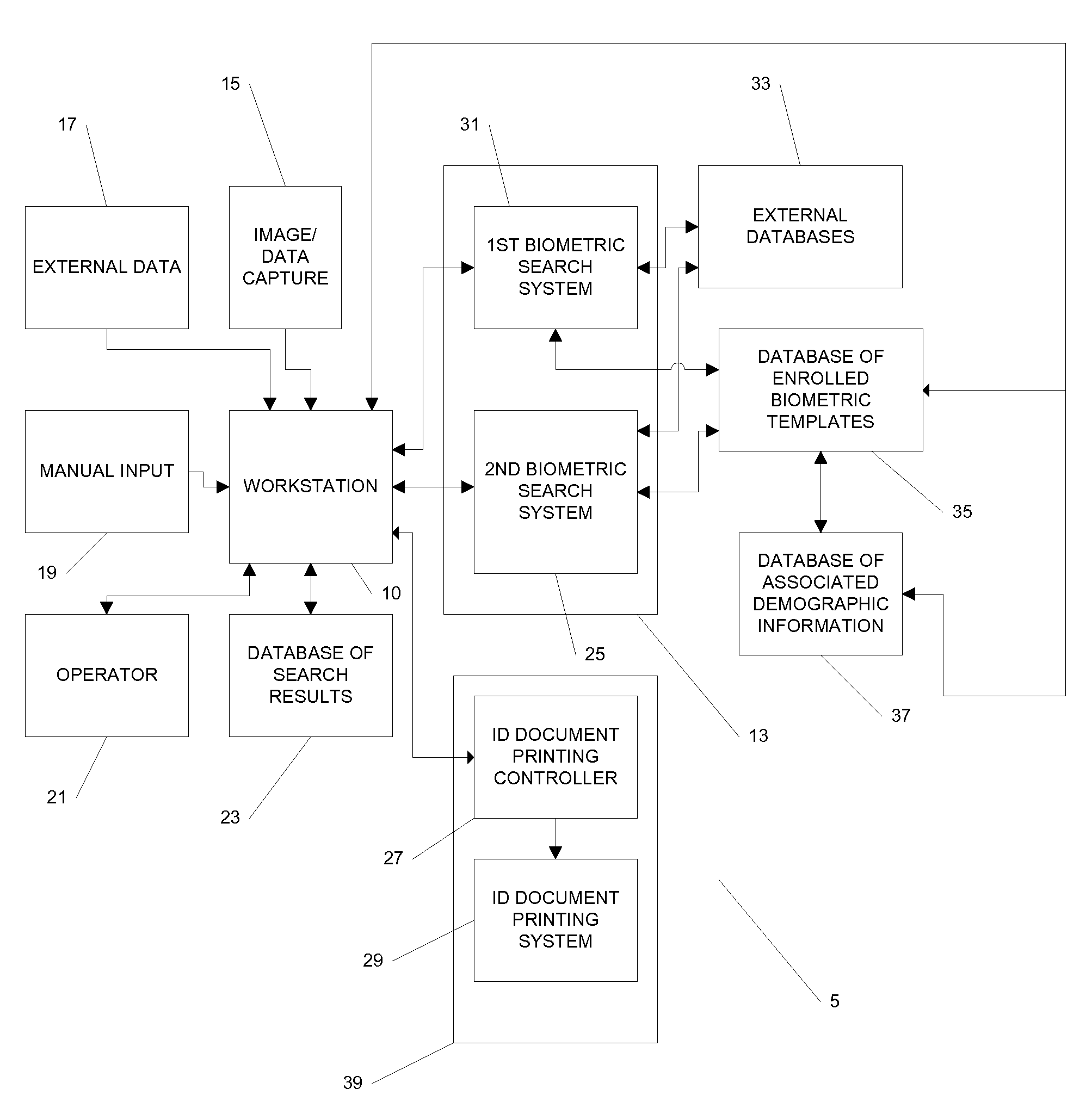
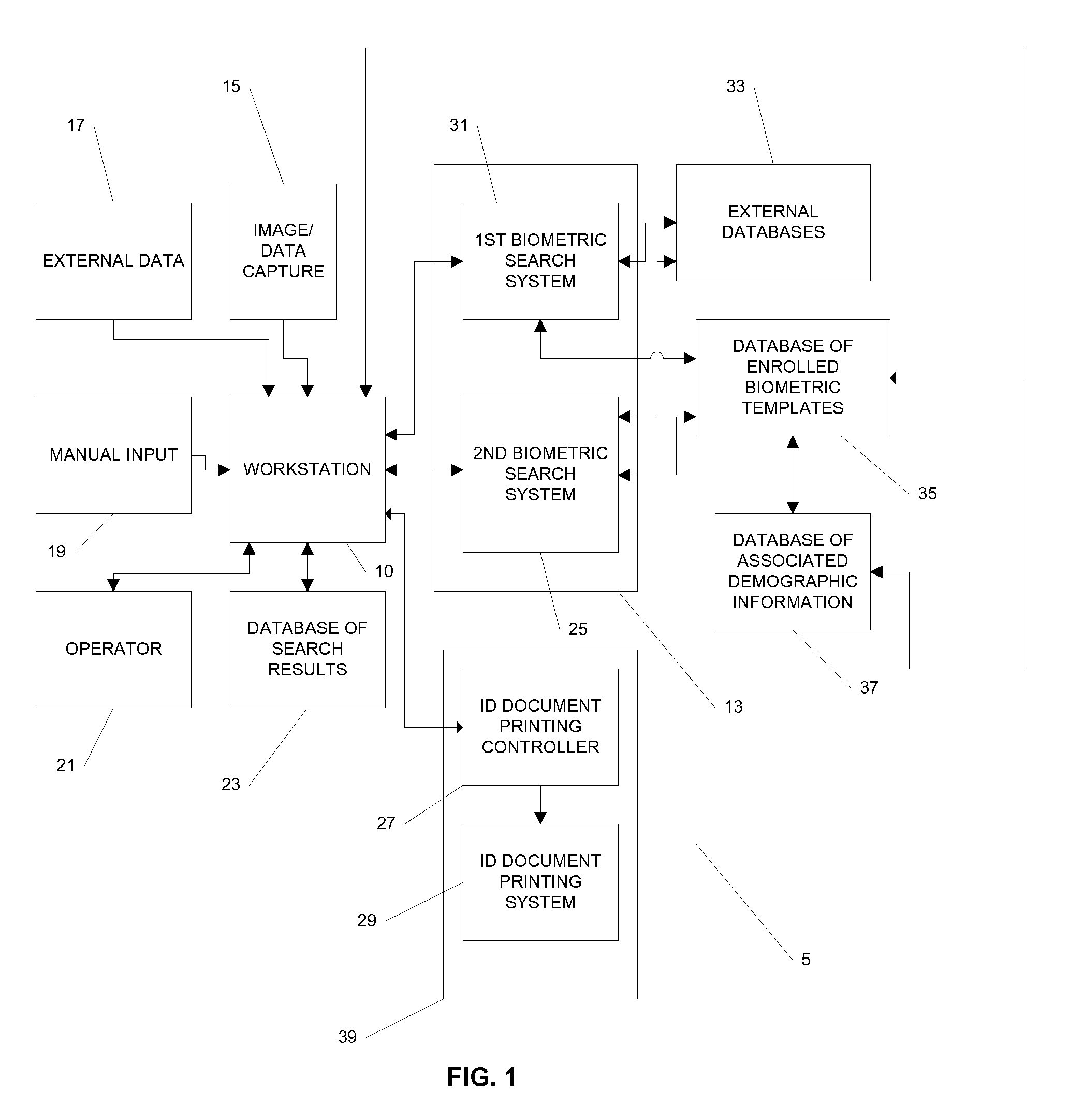
Systems and methods for managing and detecting fraud in image databases used with identification documents
ActiveUS7804982B2Prevent fraudReduce theftCharacter and pattern recognitionIndividual entry/exit registersDocument preparationWorkstation
We provide a system for issuing identification documents to a plurality of individuals, comprising a first database, a first server, and a workstation. The first database stores a plurality of digitized images, each digitized image comprising a biometric image of an individual seeking an identification document. The first server is in operable communication with the first database and is programmed to send, at a predetermined time, one or more digitized images from the first database to a biometric recognition system, the biometric recognition system in operable communication with a second database, the second database containing biometric templates associated with individuals whose images have been previously captured, and to receive from the biometric recognition system, for each digitized image sent, an indicator, based on the biometric searching of the second database, as to whether the second database contains any images of individuals who may at least partially resemble the digitized image that was sent. The a workstation is in operable communication with the first server and is configured to permit a user to review the indicator and to make a determination as to whether the individual is authorized to be issued an identification document or to keep an identification document in the individual's possession.
Owner:L 1 SECURE CREDENTIALING
Systems and methods for recognition of individuals using multiple biometric searches
InactiveUS7277891B2Data processing applicationsDigital data processing detailsPattern recognitionData set
The invention provides a computer-implemented method for determining whether a database contains any images that substantially match at least one image provided of an individual. A probe data set is received, the comprising first and second biometric templates associated with the individual, the first biometric template associated with a different type of biometric than the second type of biometric template. A database of biometric templates is searched using the first biometric template to retrieve a first results set. A first predetermined portion of the first results set is selected. The first predetermined portion of the first results set is searched using the second biometric template to retrieve a second results set. A second predetermined portion of the second results set is selected. The second predetermined portion of the second results is provided for comparison with the image provided of the individual.
Owner:L 1 SECURE CREDENTIALING
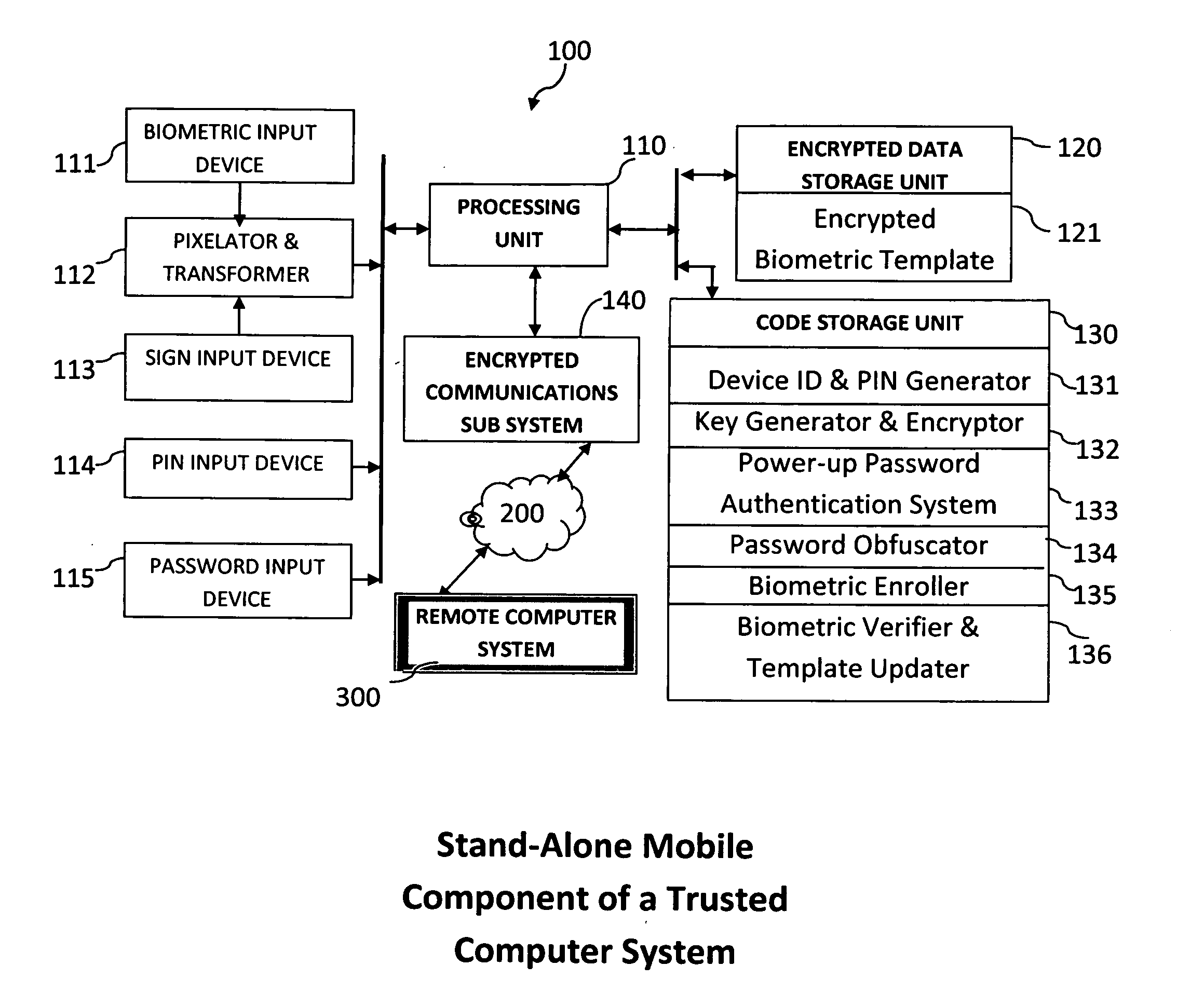
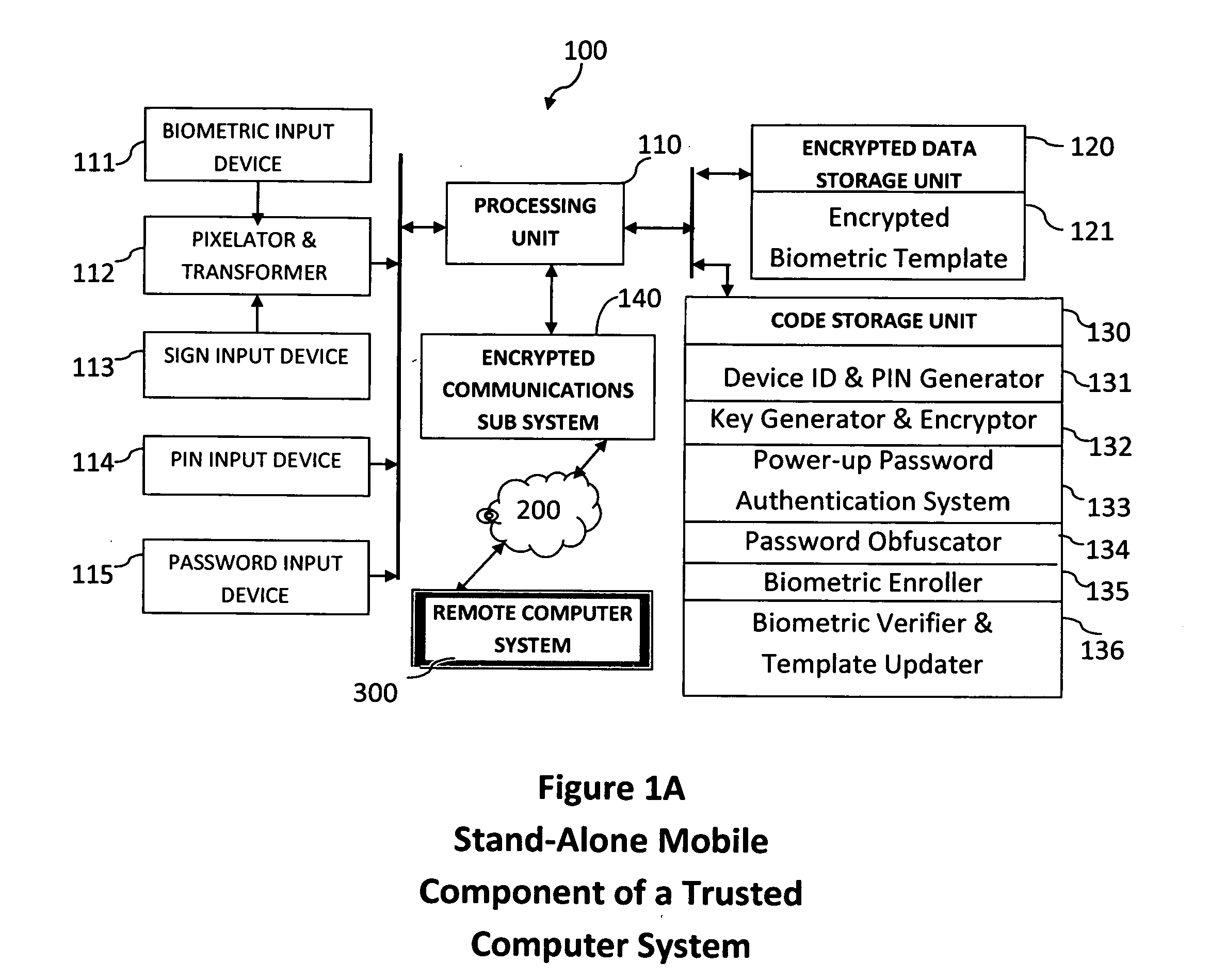
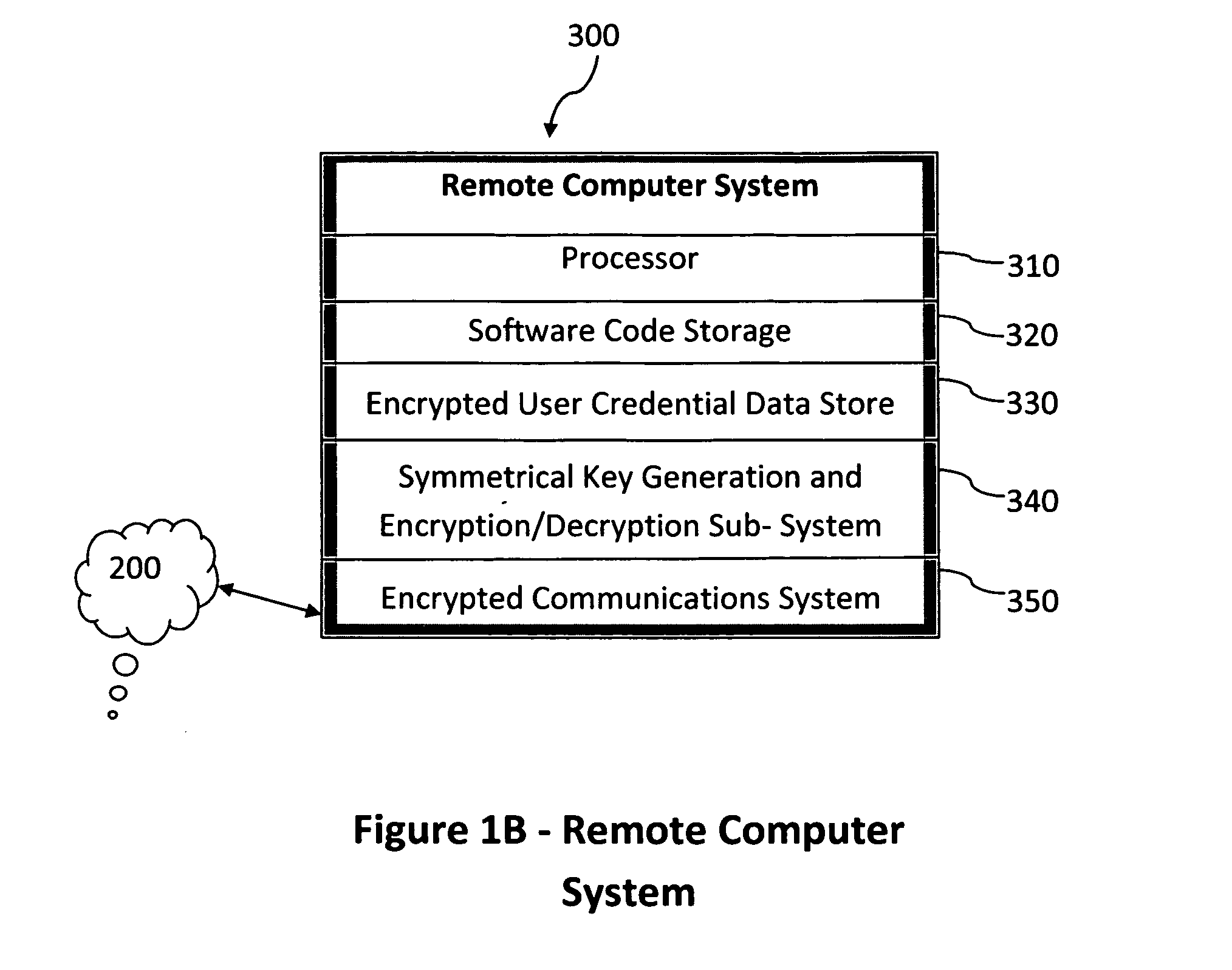
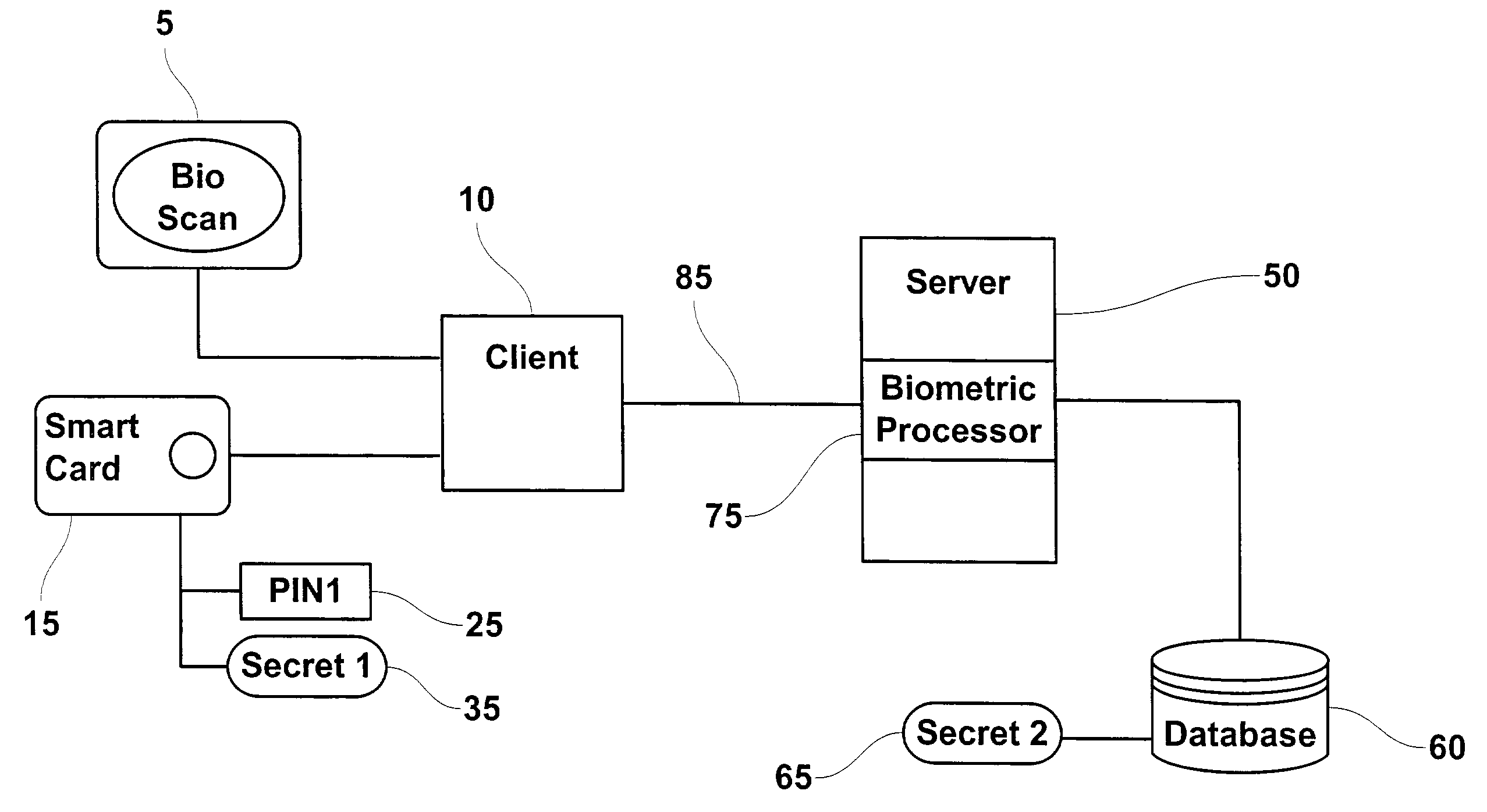
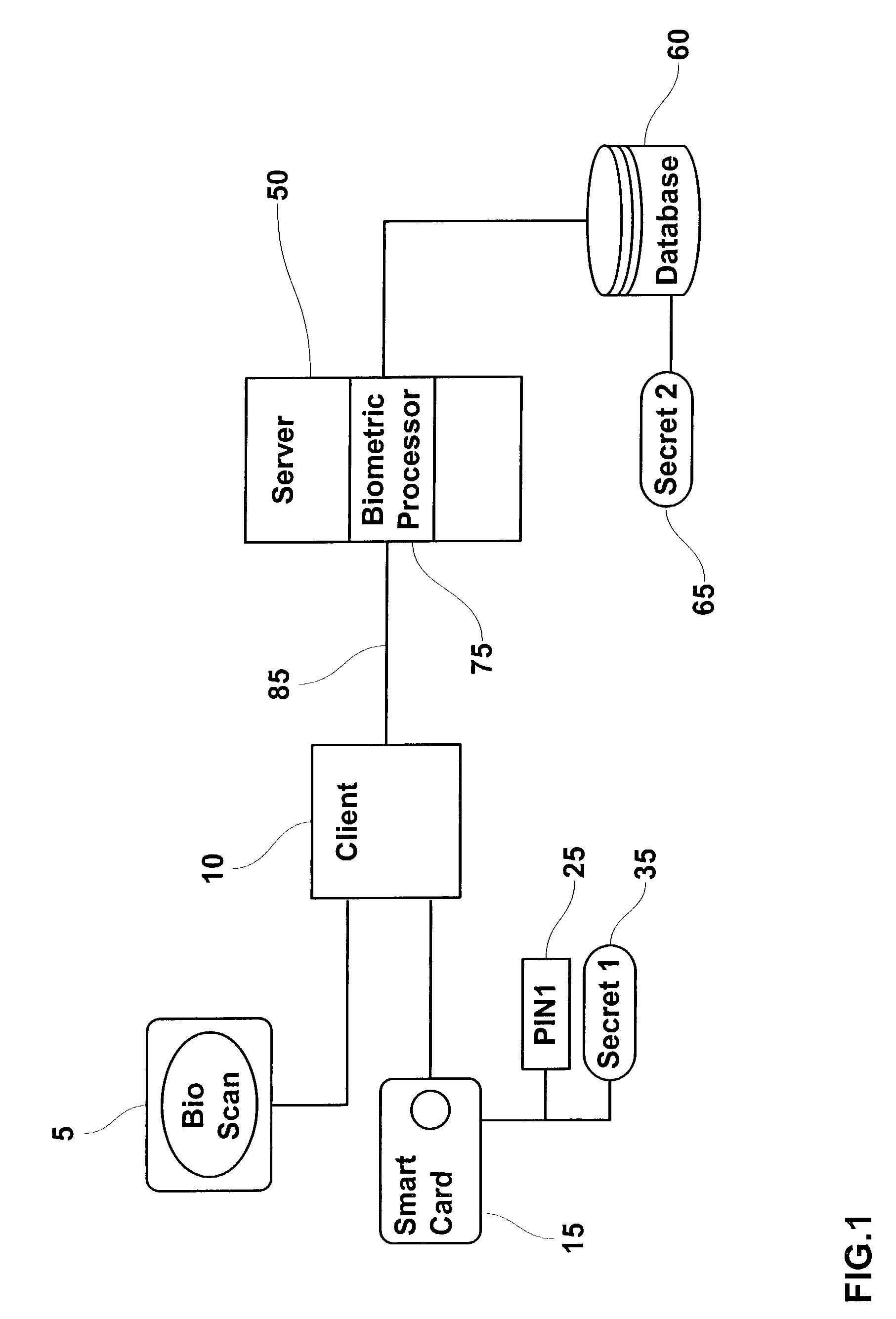
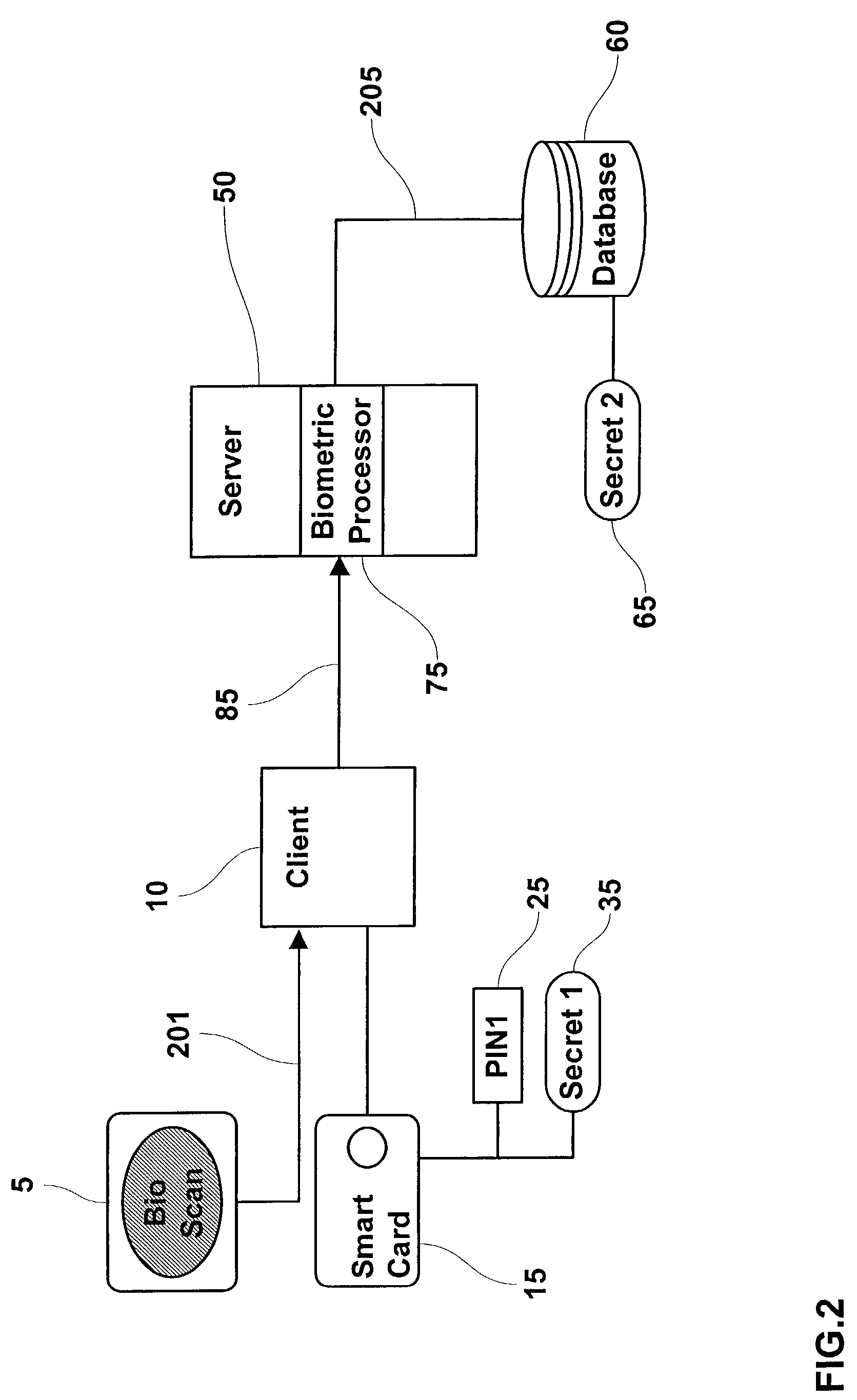
Method and system for combining a PIN and a biometric sample to provide template encryption and a trusted stand-alone computing device
ActiveUS20110126024A1Secure EncryptionEasy to useDigital data processing detailsUser identity/authority verificationBiometric dataTrust relationship
Biometric data, suitably transformed are obtained from a biometric input device contained within a stand-alone computing device and used in conjunction with a PIN to authenticate the user to the device. The biometric template and other data residing on the device are encrypted using hardware elements of the device, the PIN and Password hash. A stored obfuscated password is de-obfuscated and released to the device authentication mechanism in response to a successfully decrypted template and matching biometric sample and PIN. The de-obfuscated password is used to authenticate the user to device, the user to a remote computer, and to encrypt device data at rest on the device and in transit to and from the remote computer. This creates a trusted relationship between the stand-alone device and the remote computer. The system also eliminates the need for the user to remember and enter complex passwords on the device.
Owner:BIOCRYPT ACCESS LLC
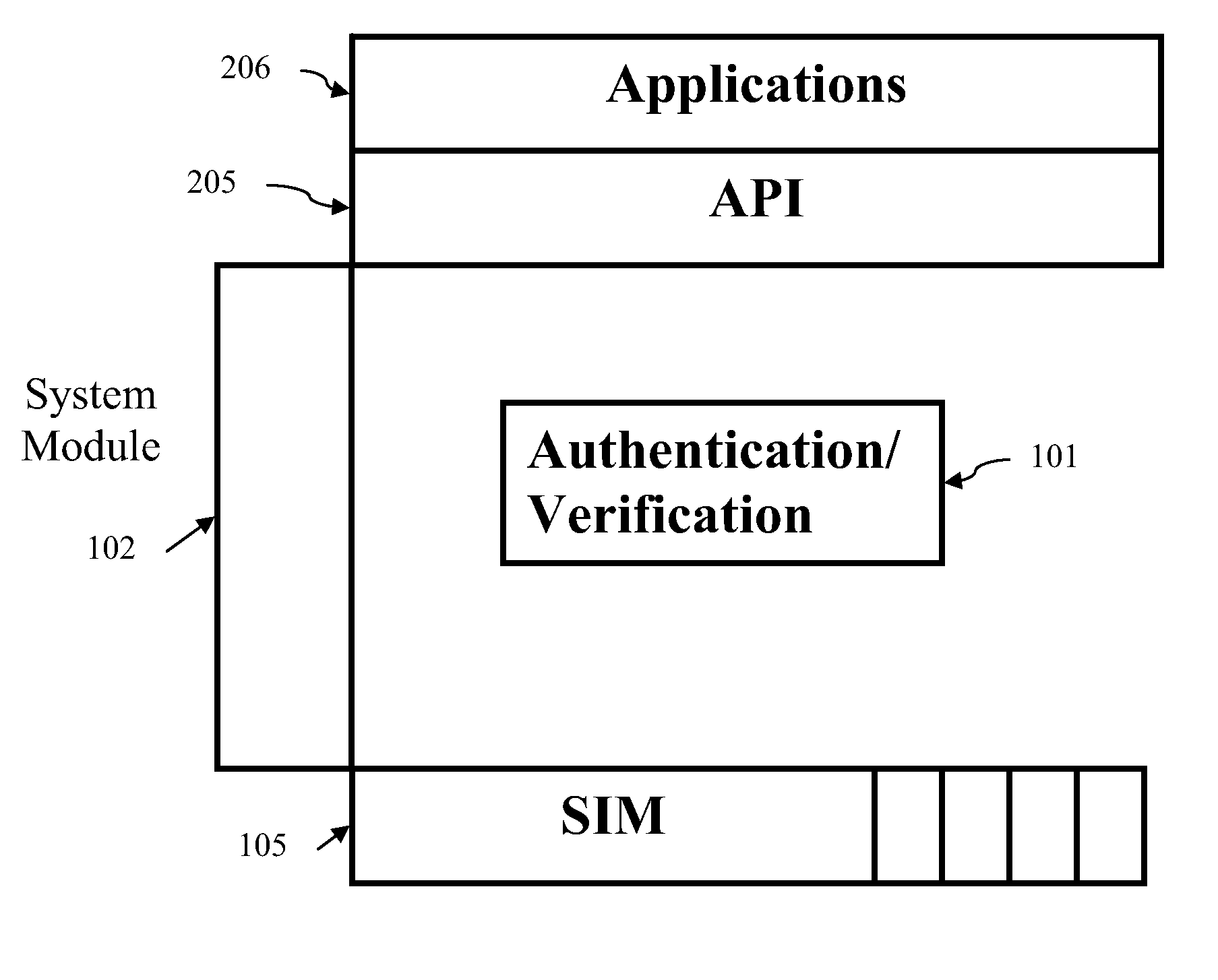
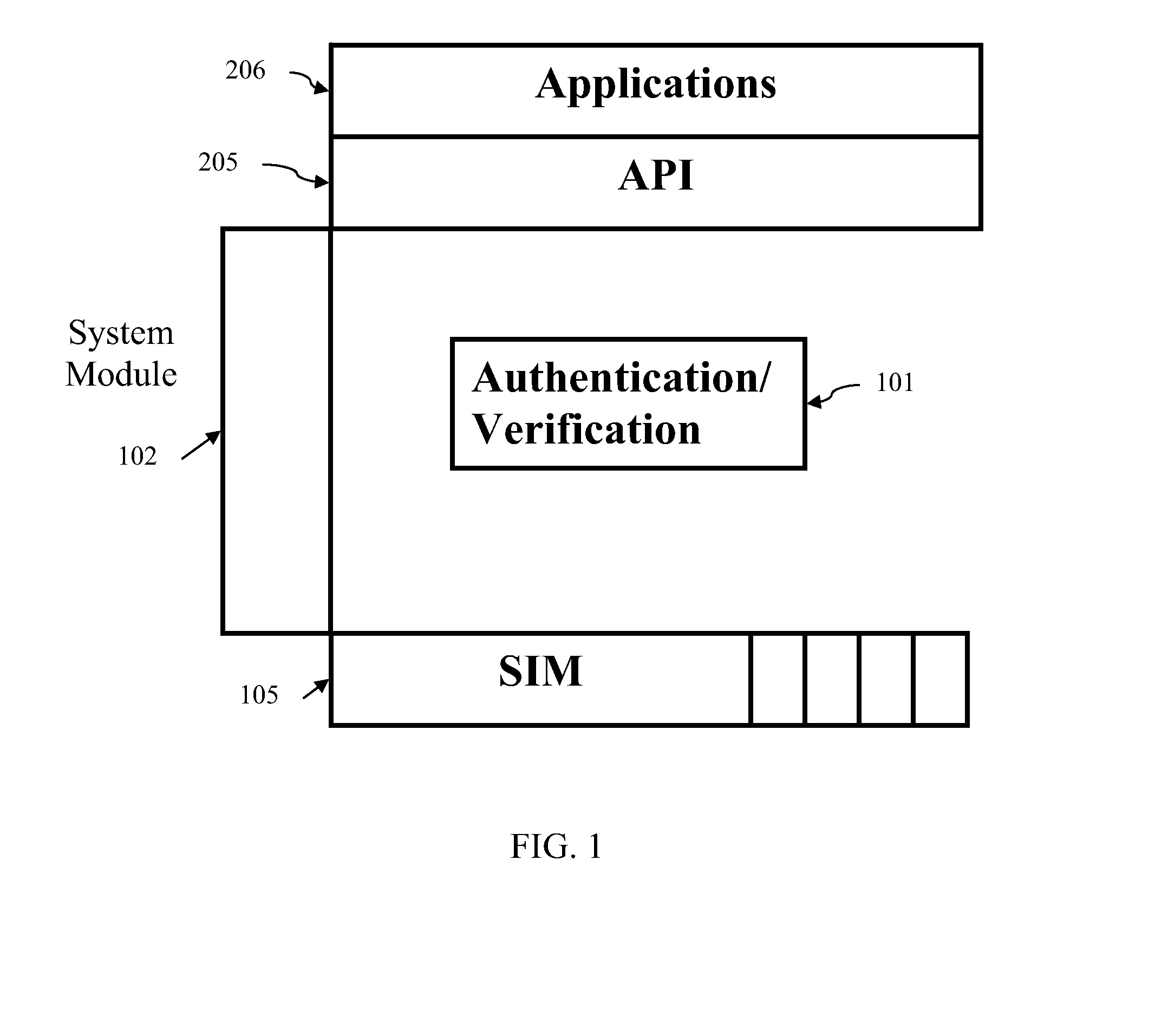
Biometric smart card for mobile devices
InactiveUS20090191846A1Acutation objectsUnauthorised/fraudulent call preventionSmart cardMobile device
A method and apparatus for controlling access to the data stored on a smart card for use in mobile devices. A user initializes the smart card memory by saving an authentication credential in memory. Subsequently, when various applications executed on the mobile device seek to retrieve the data stored in the smart card memory, the user must submit to an authentication process before access to the data stored in the smart card memory is granted. Embodiments utilize biometric traits and biometric templates stored in memory as authentication credentials. Biometric sensors are provided with the smart card so that a candidate biometric trait can be generated and compared with a biometric template stored in memory. If the biometric trait matches the stored biometric template, then access to the data stored in the smart card is granted.
Owner:QUALCOMM INC
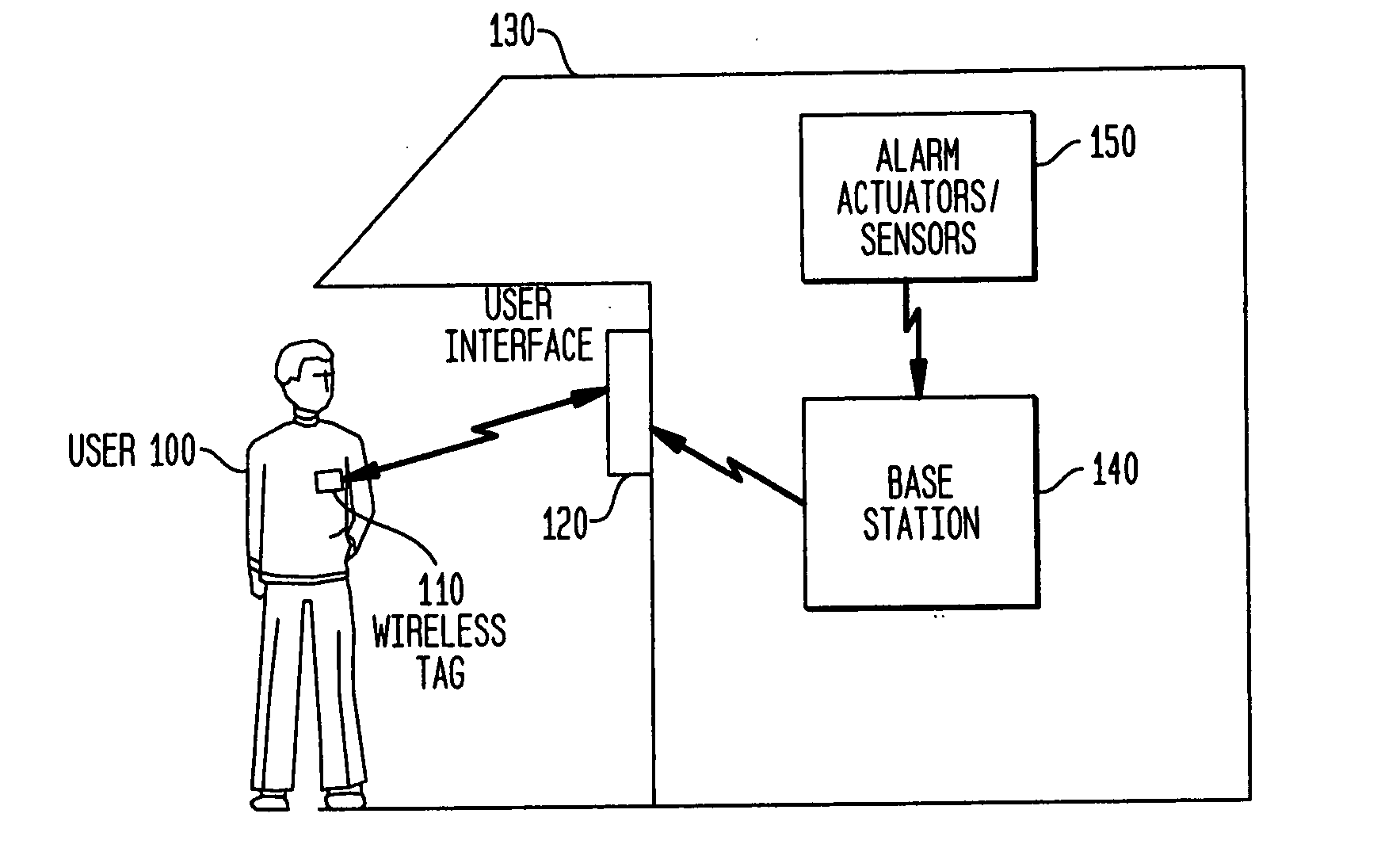
Biometric verification and duress detection system and method
ActiveUS20070198850A1Process safetyElectric signal transmission systemsDigital data processing detailsUser inputIdentification device
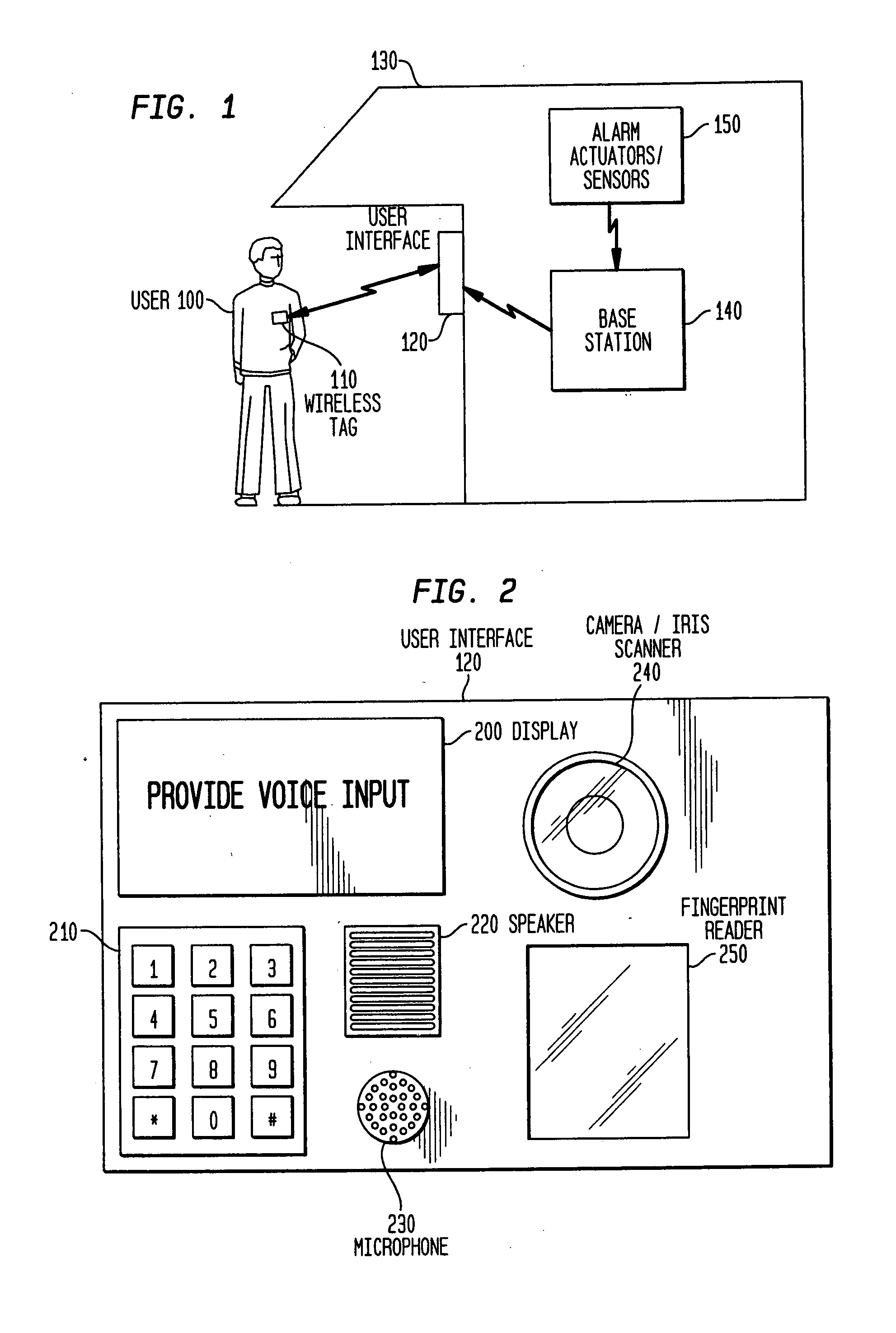
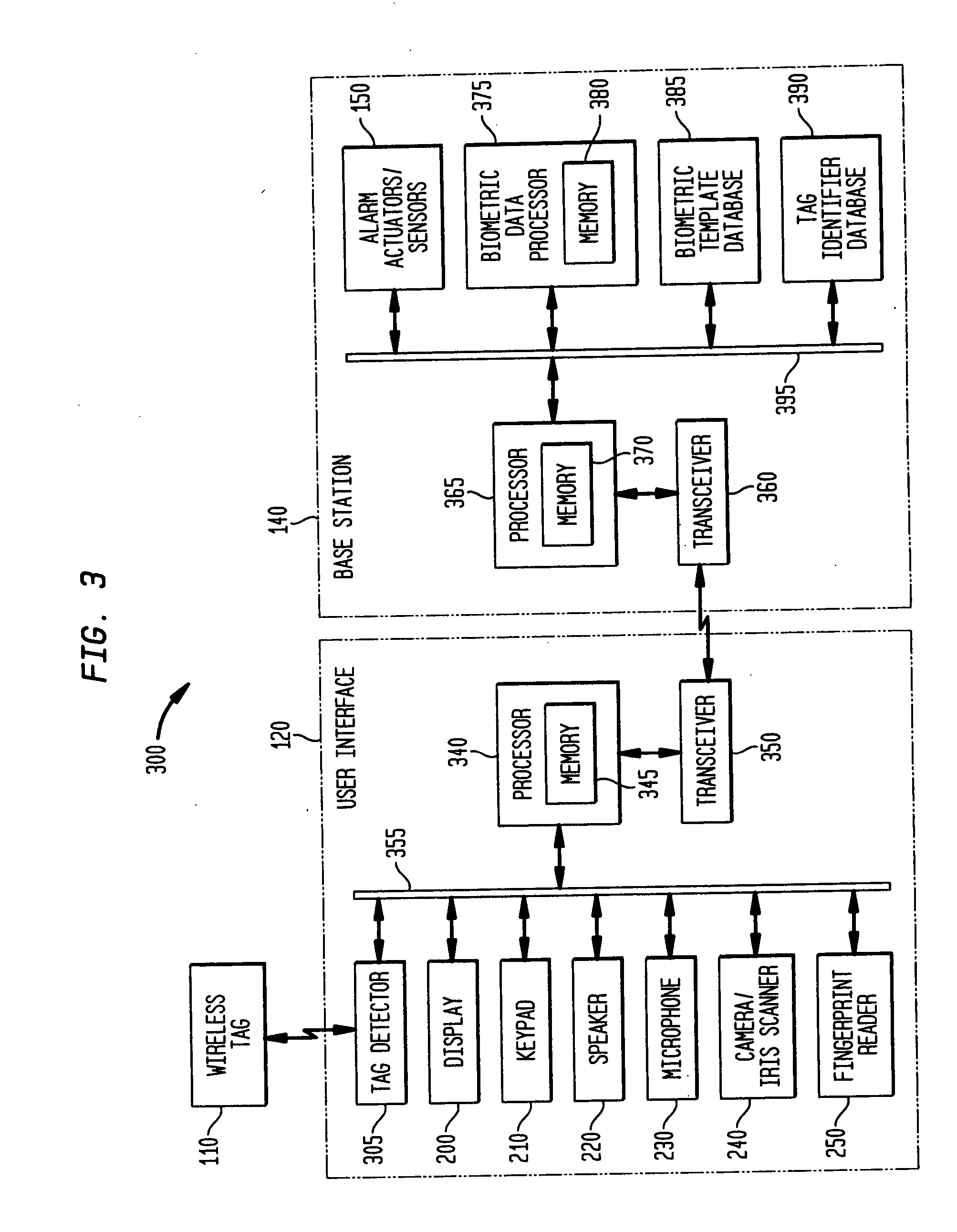
A multi-stage verification system including a first and second identification device to verify the identity of the user and to determine if the user is under duress. When a user approaches an entrance to a building, a first identifier is detected by the first identification device, the identifier is compared to a pre-stored identifier. If there is a match, the user inputs at least one biometric input into the second identification device. The biometric input is compares with pre-stored information in two different databases, a biometric template database and a duress indicator database. If there is a match with the duress indicator database, a silent alarm signal is transmitted to a central monitoring station and the security system is disarmed. If there is a match with the biometric template database, the security system is controlled in the intended manner.
Owner:ADEMCO INC
System for transmitting secure data between a sender and a recipient over a computer network using a virtual envelope and method for using the same
InactiveUS7117370B2Simple methodLimited accessElectric signal transmission systemsImage analysisNetworked Transport of RTCM via Internet ProtocolSecure transmission
A method for secure transmission of data, like e-mail and other secure documents, over a computer network includes the use of biometrics to verify that the sender of the data is confirmed as an individual authorized for secure access transmission of data over the network and by verifying that the recipient of the data is also an individual authorized to receive data by secure access transmission over the network. The methodology comprises creating a database containing the biometric templates of all individuals authorized for secure access transmission of data over the network and connecting the database to a data processor. The transmission of counterfeit messages is prevented by confirming the identity of the sender as an individual authorized for secure access transmission over the network by scanning a predetermined biometric of the sender, and comparing the biometric of the sender with the predetermined biometric of all individuals who are authorized for secure access transmission over the network. The recipient of a secure access message is not permitted to access the message until recipient's identity has been similarly confirmed as an individual authorized to receive messages secure access transmitted over the network. Once the recipient's identity is confirmed the message may be opened. The sender will receive confirmation by return electronic mail that the message has been opened by the authorized recipient.
Owner:KHAN SAL
System and method to facilitate separate cardholder and system access to resources controlled by a smart card
InactiveUS20040034784A1Reduce administrative burdenDigital data processing detailsUser identity/authority verificationPersonal identification numberEngineering
This invention provides a mechanism, which allows a user's personal identification number (PIN) to operate independently from a biometric authentication system. This improvement reduces the administrative burden of having to keep a user's PIN synchronized with the PIN used to access the user's smart card following successful biometric authentication. The first embodiment of the invention incorporates a cryptographic interface, which bypasses the PIN entry and allows the biometric authentication system to directly access card resources. The second embodiment of the invention provides a second system PIN having greater bit strength than the cardholder PIN. Both embodiments of the invention retrieve secrets (either a cryptographic key or system PIN) from a biometric database by comparing a processed biometric sample with known biometric templates. The biometric authentication system incorporates a client-server architecture, which facilitates multiple biometric authentications.
Owner:ASSA ABLOY AB
Biometrically authenticated portable access device
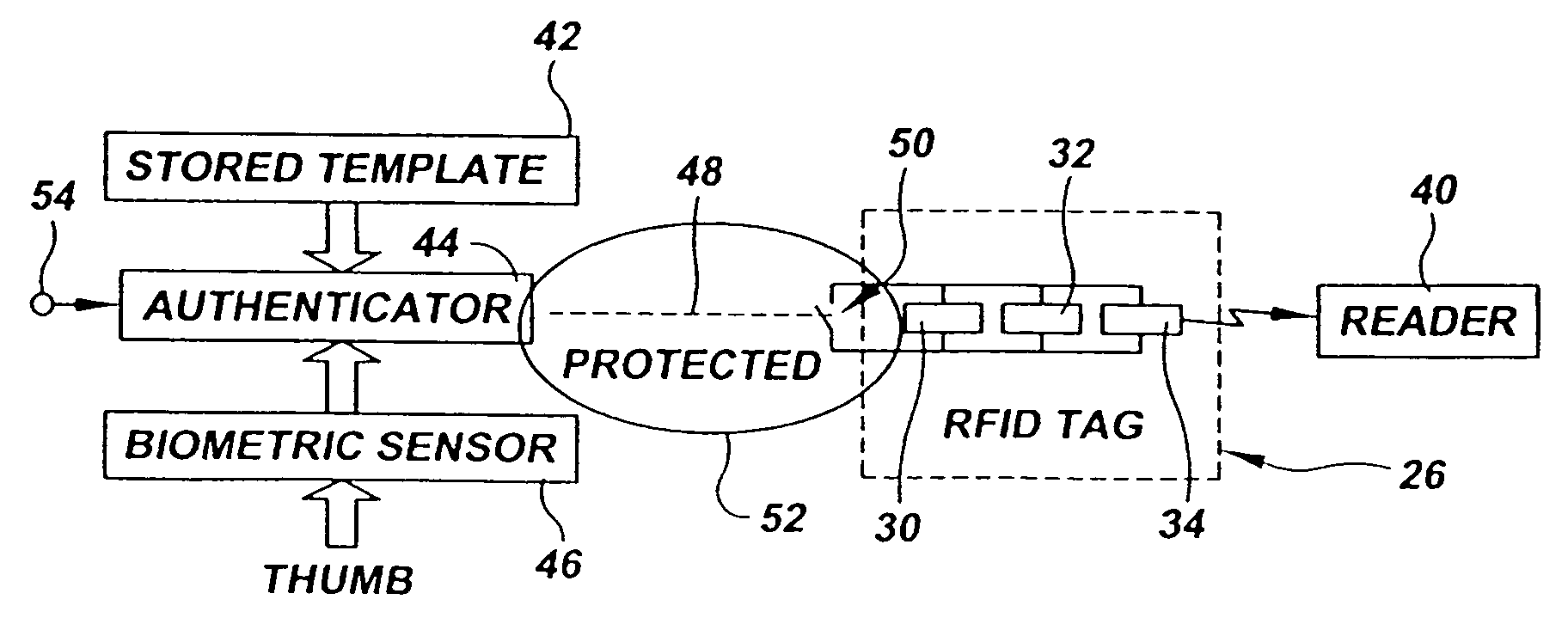
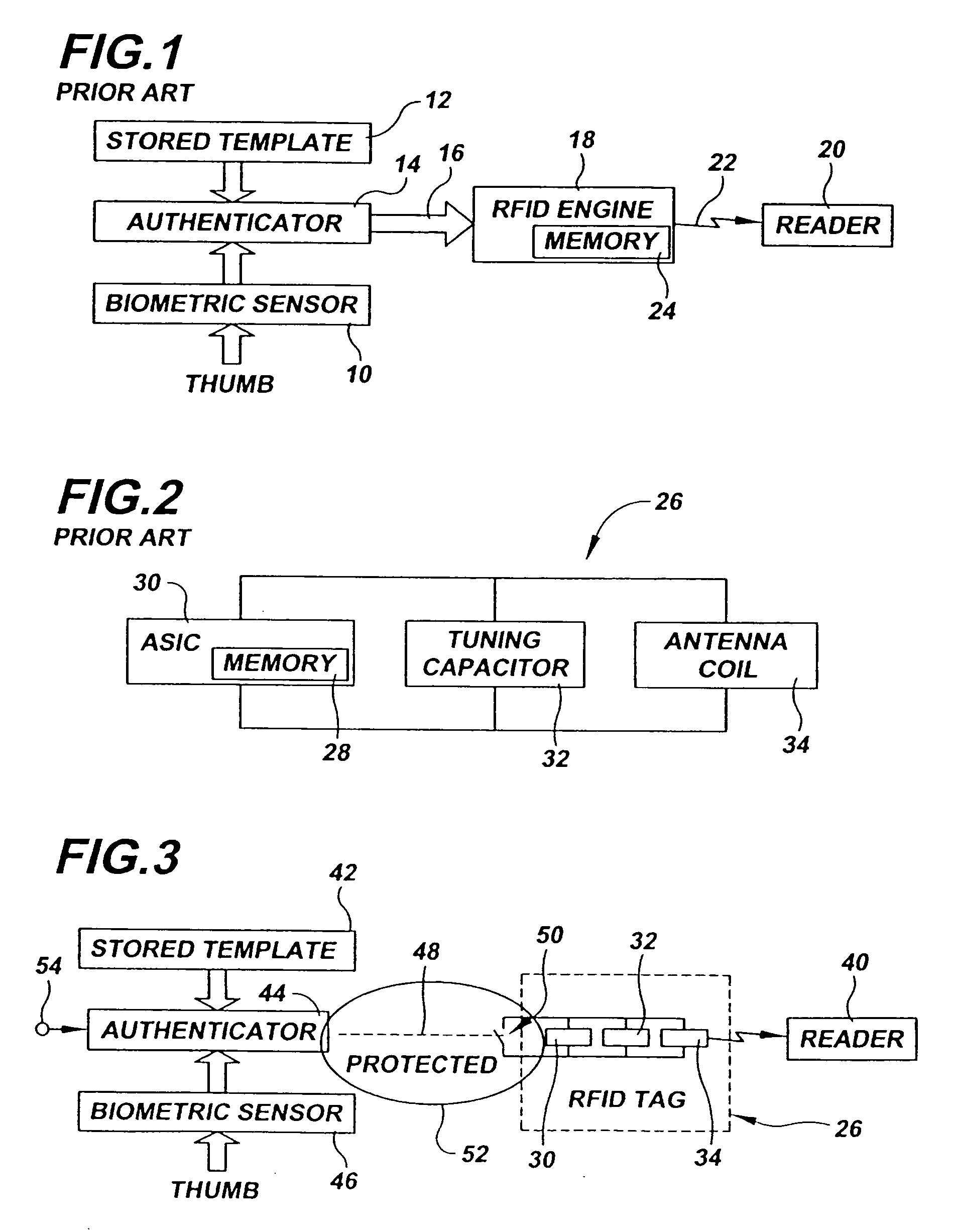
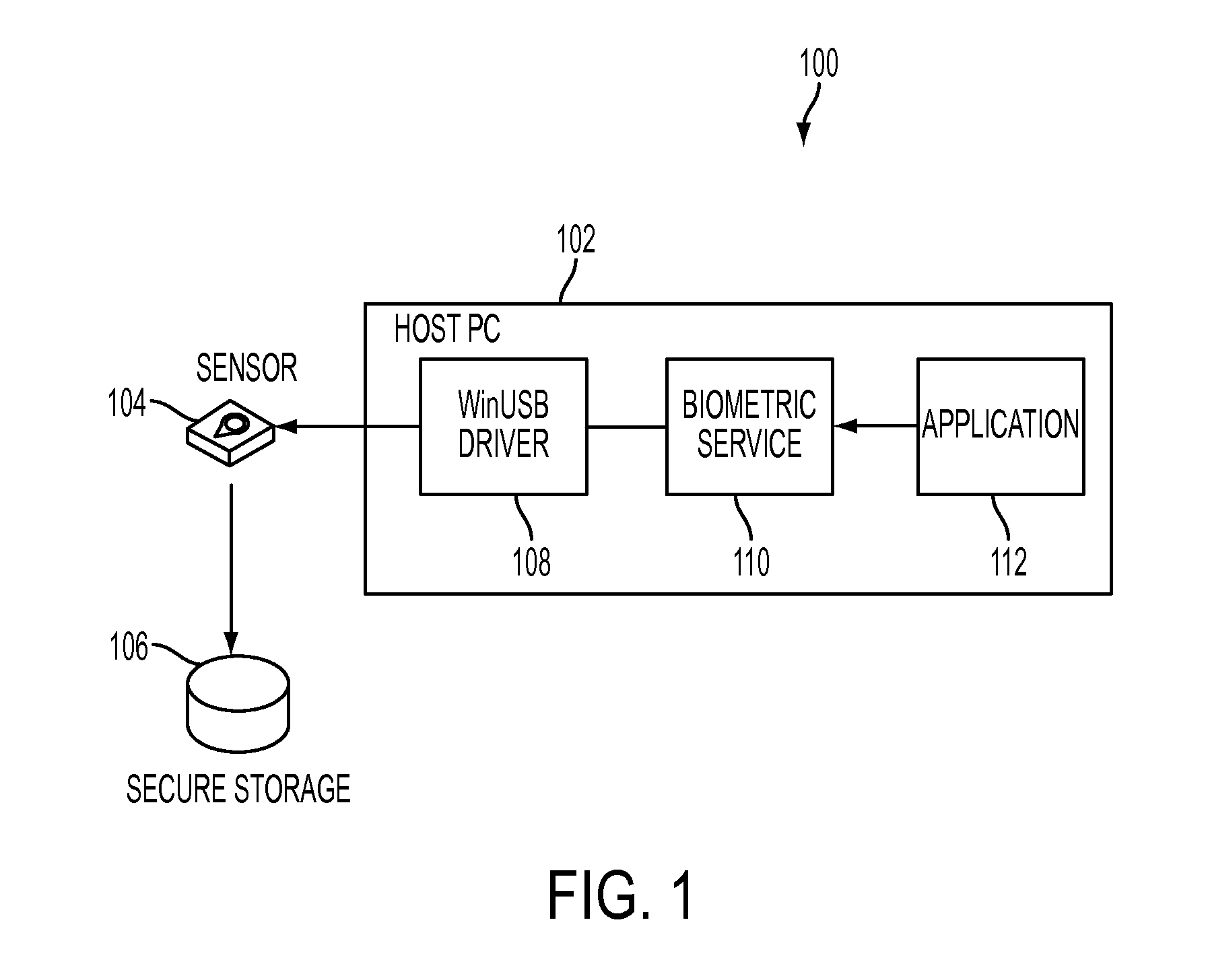
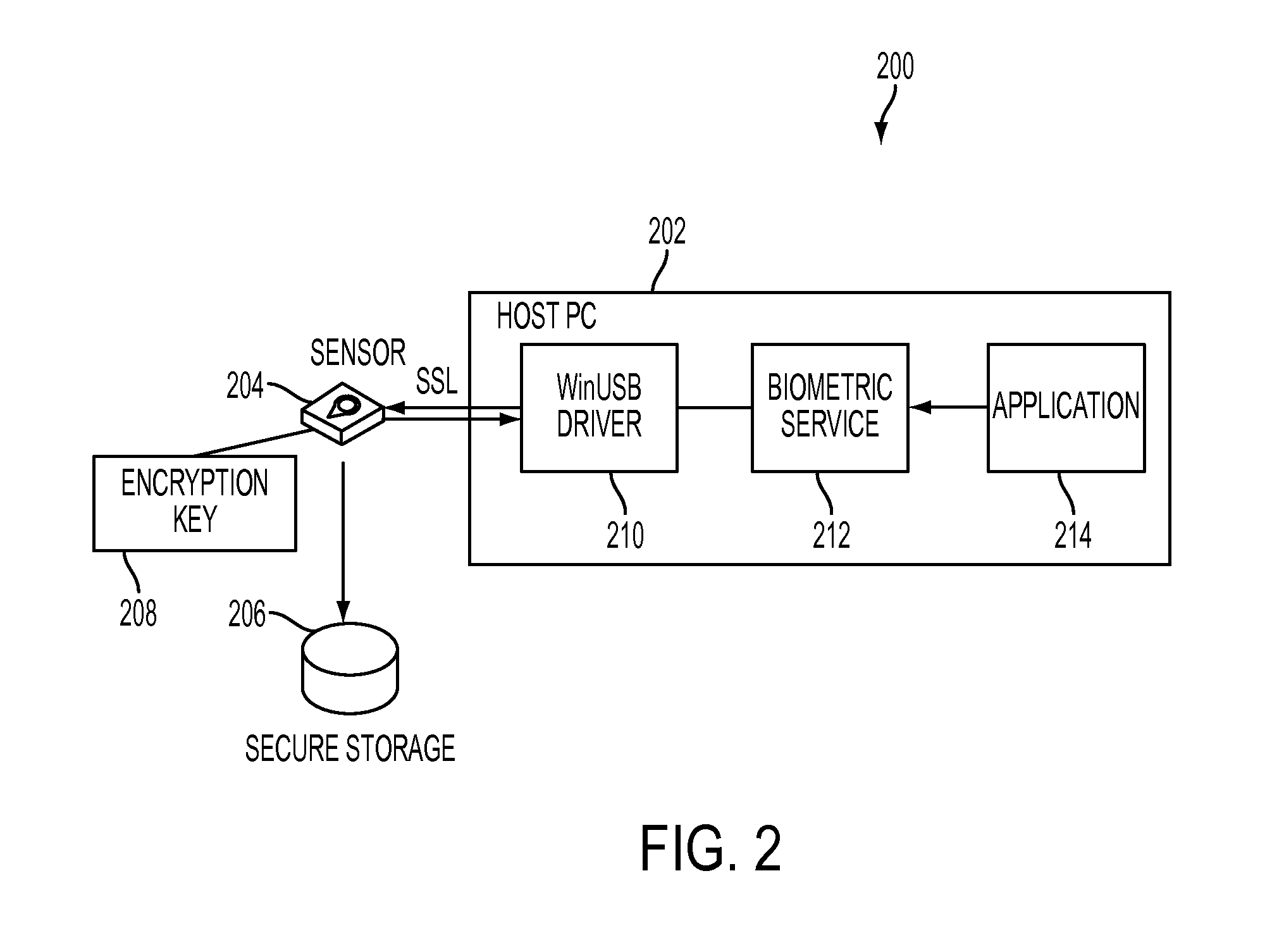
InactiveUS20050253683A1Electric signal transmission systemsImage analysisComputer hardwareBiometric templates
Owner:ASSA ABLOY AB
User authentication for social networks
Systems and methods are provided for social networks that can verify that enrolled users are not misrepresenting facts about themselves such as age and gender. Verification can be performed, for example, by reference to biometric templates stored during the user enrollment process. The biometric templates can also be used to authenticate users logging into the social network to prevent user impersonation. The ability of some users to communicate to other users of the social network can be limited to only certified users, and even to those certified users that match a criterion, such as gender or age.
Owner:SAMSUNG ELECTRONICS CO LTD
Authentication system based on biological characteristics and identification authentication method thereof
InactiveCN101330386AAttack is notAttacks are not directlyUser identity/authority verificationCharacter and pattern recognitionInternet privacyComputer terminal
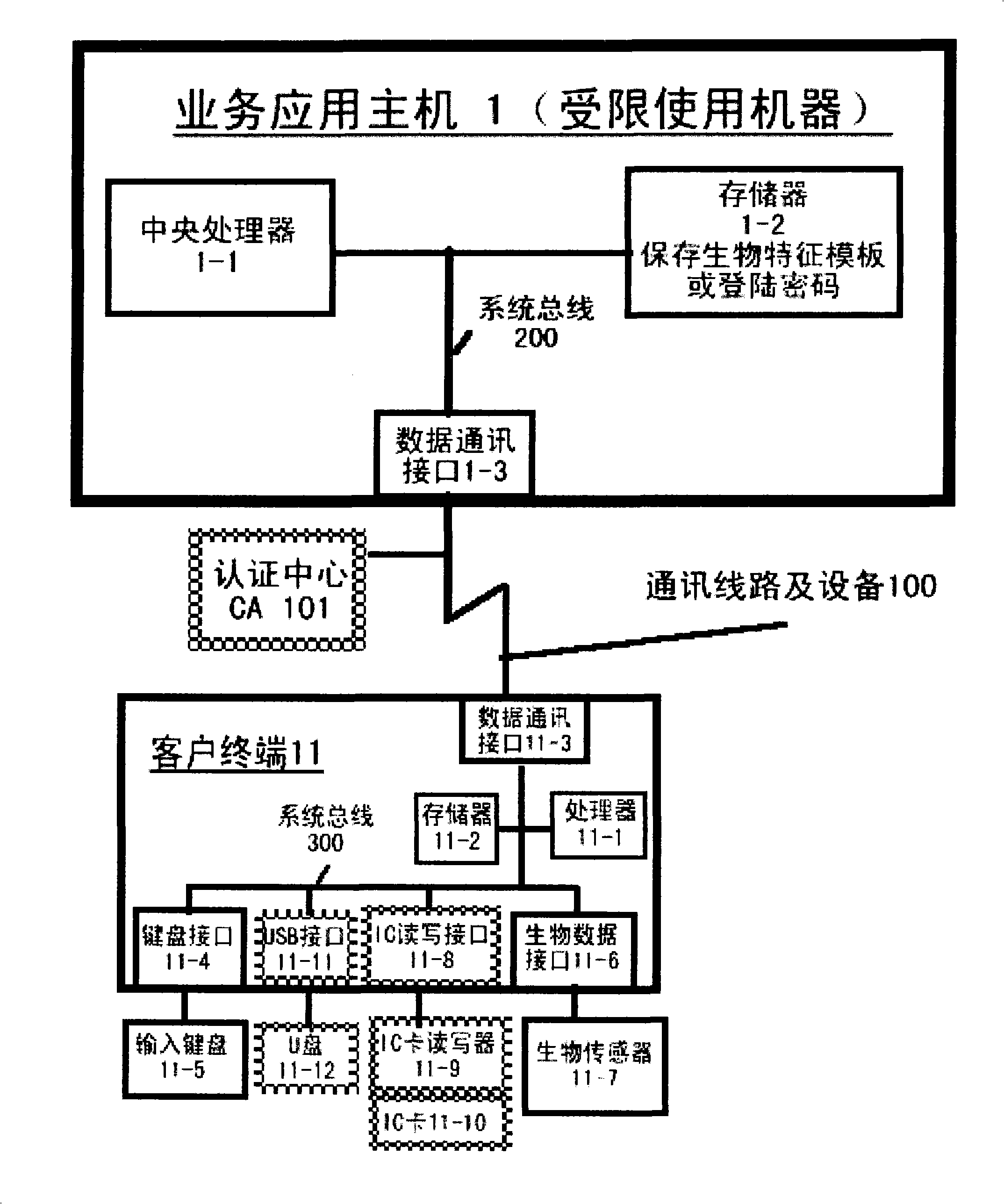
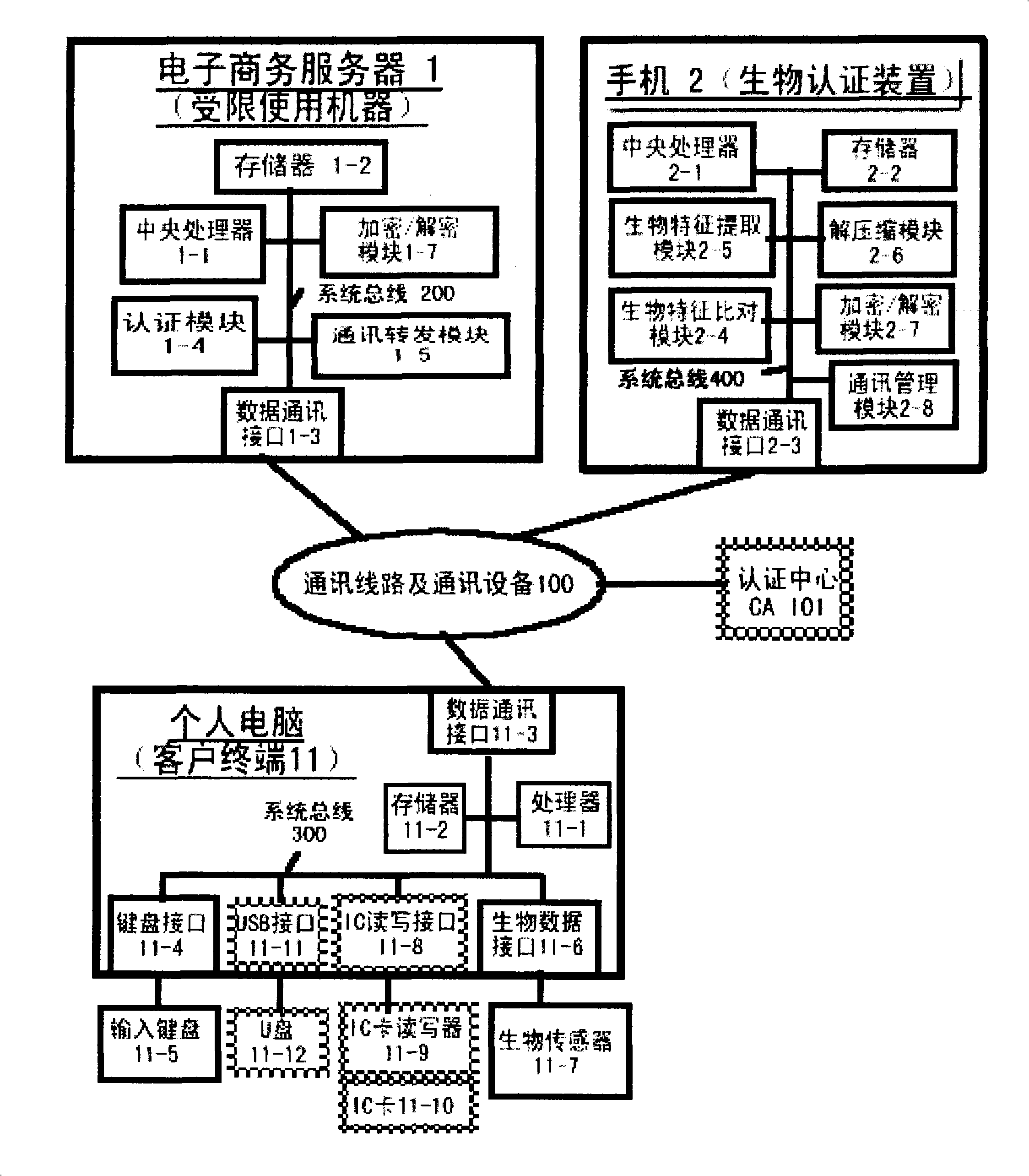
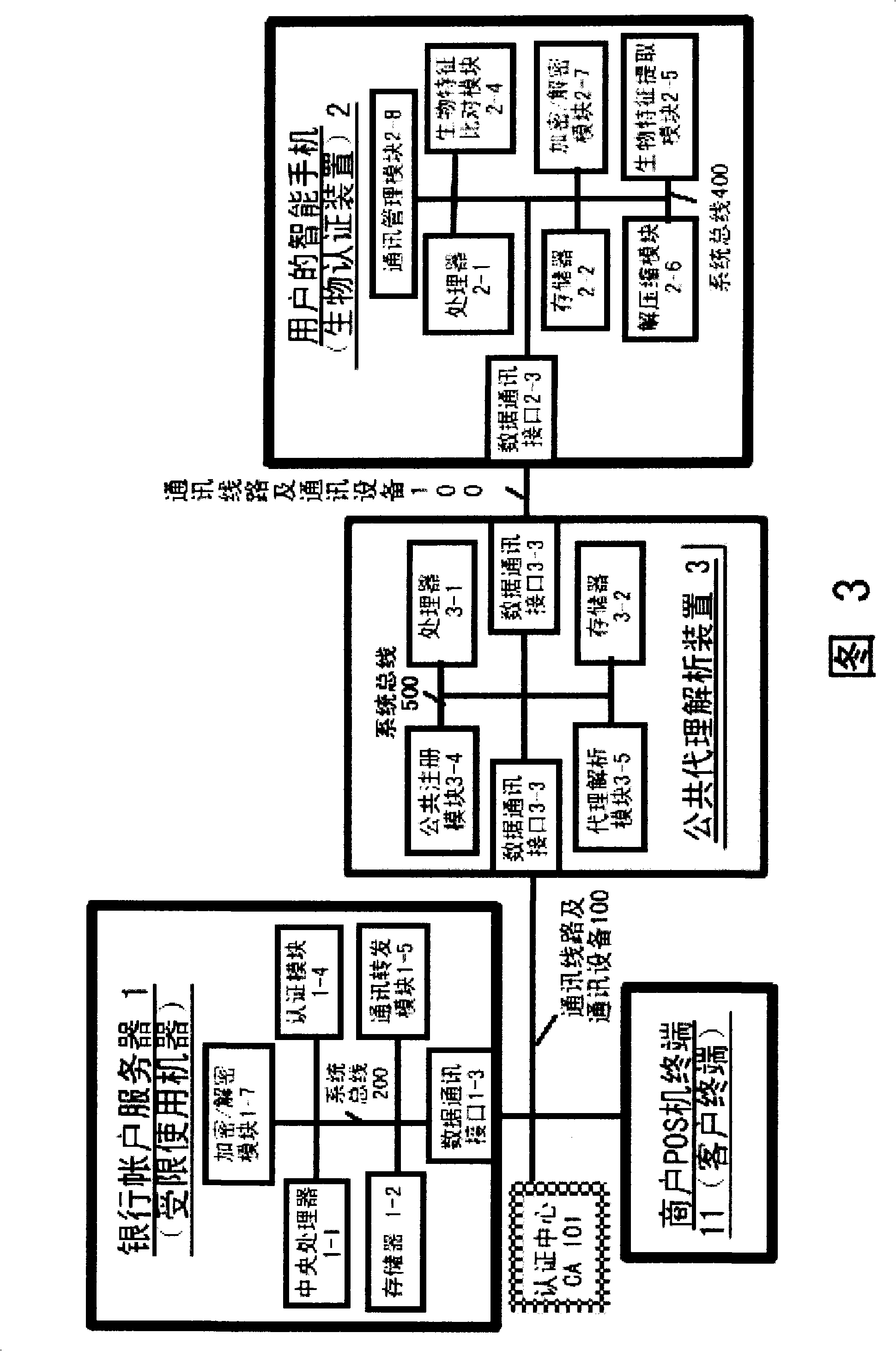
The invention relates to an authentication system and an authentication method based on biological features. The method comprises the steps of conducting centralized storage and biological feature comparison operation for a large quantity of user biological feature templates according to user ID identifiers stored on a memory on a limited use machine and corresponding biding ID identifiers thereof on a biological authentication device of a digital processing terminal; separating the biological feature templates from the authentication function of the limited use machine; allocating to digital processing terminals (including PCs, notebooks or mobile phones, PDAs of users)of users as biological authentication device-storing the biological feature templates with decentralization and operating and processing biological features to be authenticated with decentralization so as to conduct comparison with the biological feature templates pre-stored on the respective digital processing terminals; feeding back comparison and verification results to the limited use machines; authorizing to conduct equal authentication of the biological authentication device ID identifier on the digital processing terminal for the corresponding binding user ID identifiers by the centralized authentication of the limited use machine according to the comparison verification result data.
Owner:刘洪利
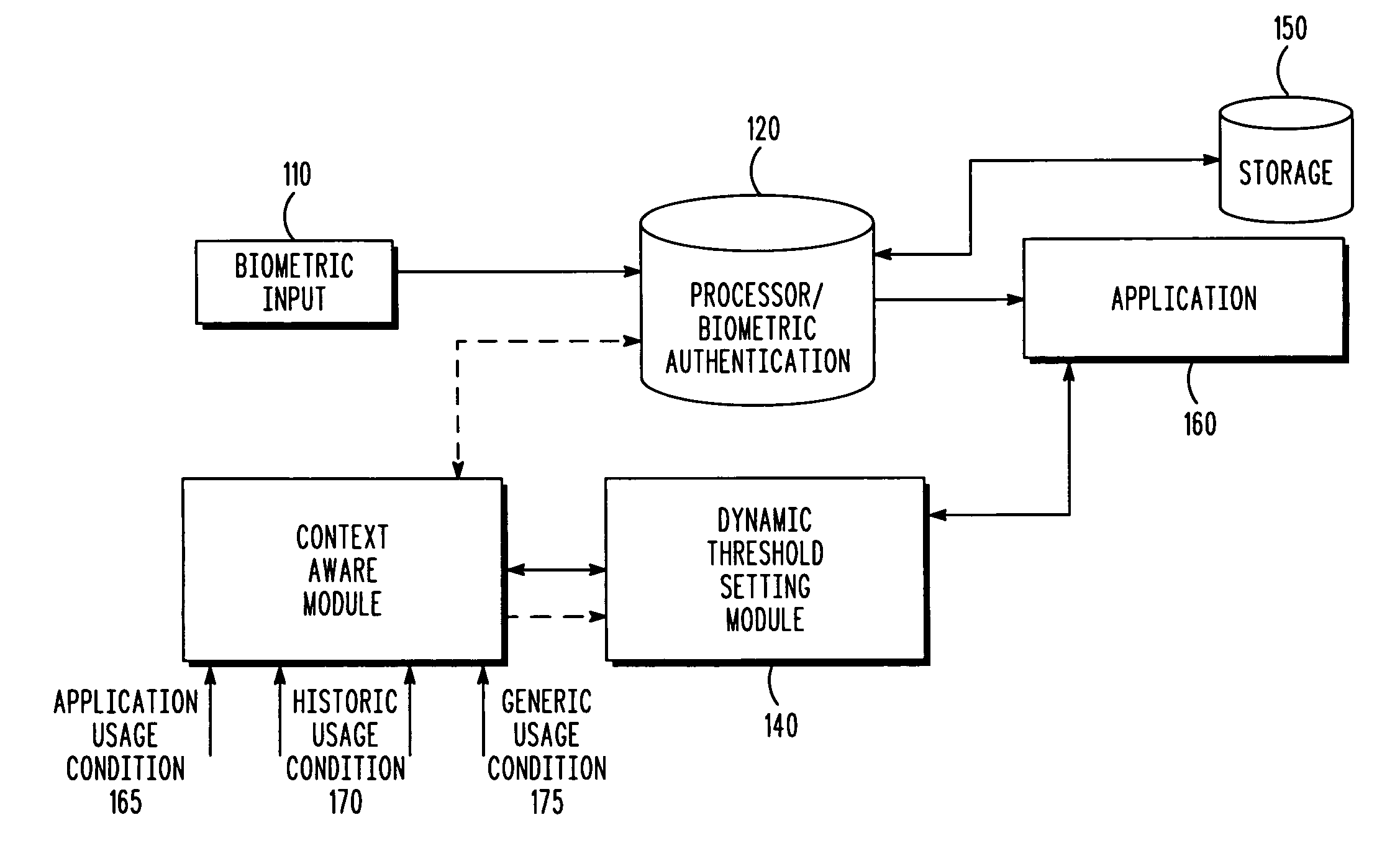
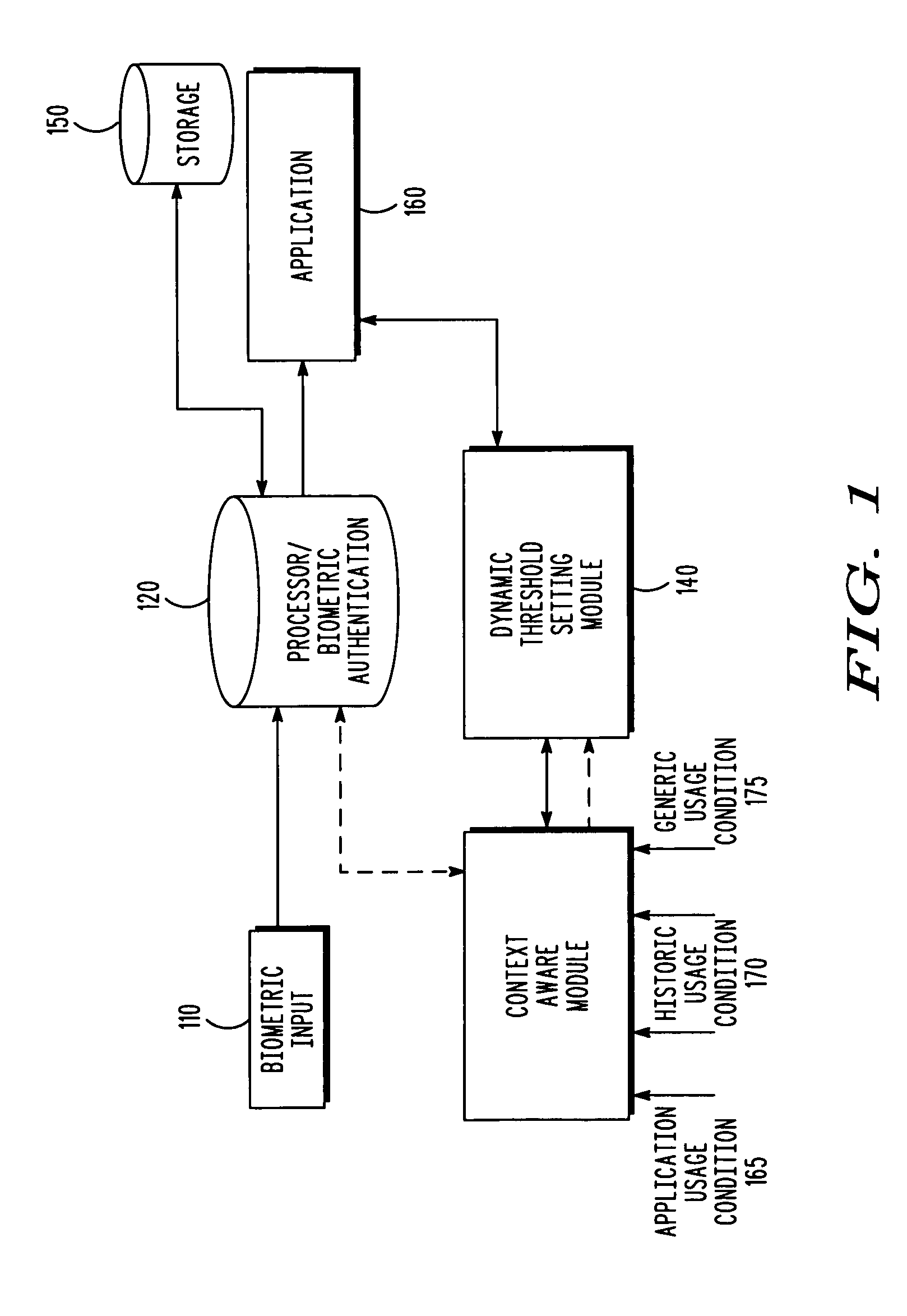
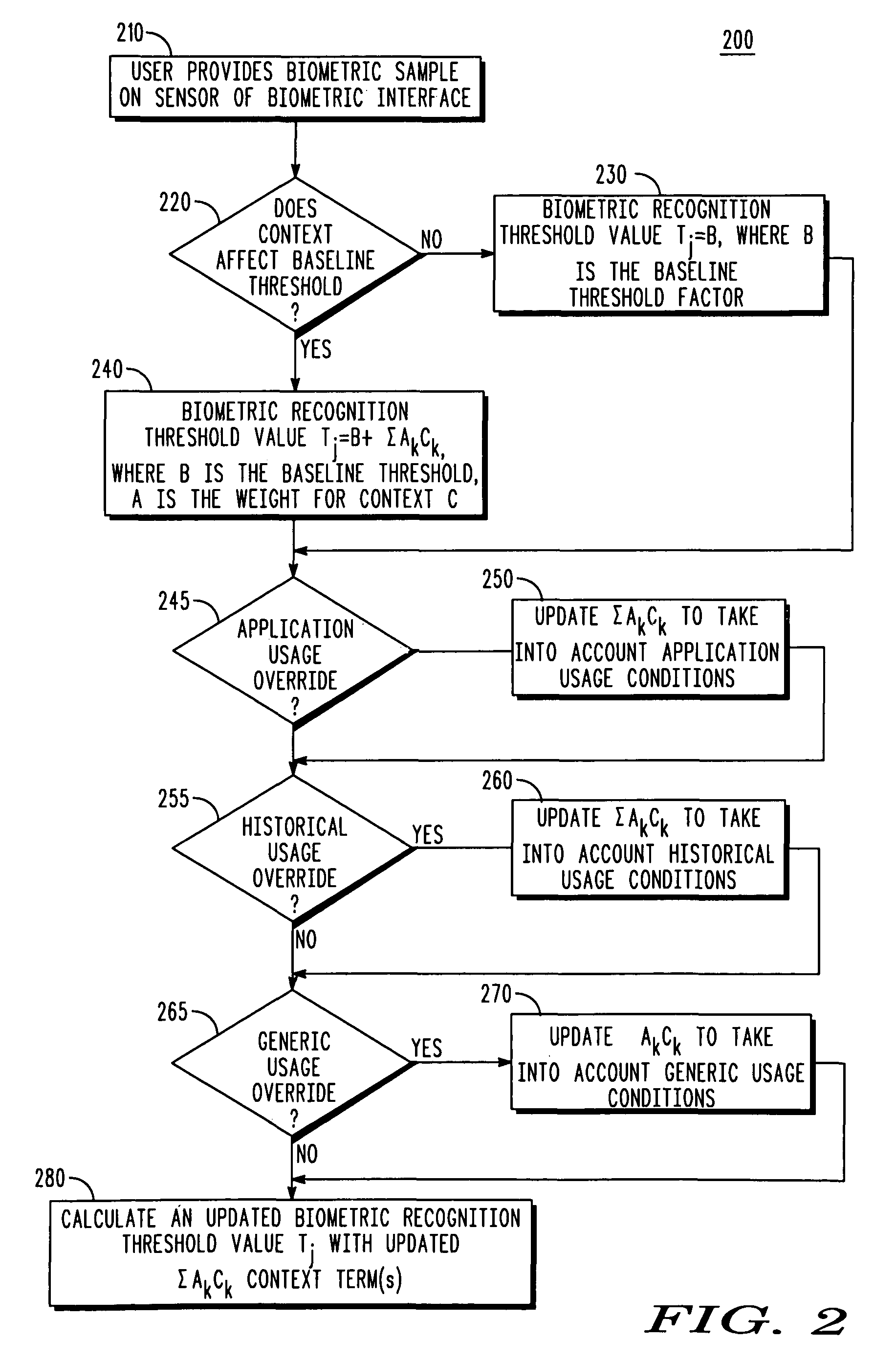
Context aware biometric authentication
ActiveUS8255698B2Digital data processing detailsUnauthorized memory use protectionContext basedSecurity level
A biometric sample of the user is received at a biometric interface of a device as part of a biometric authentication request by the user, with the biometric sample characterized by a match score when the biometric sample matches at least one stored template that uniquely identifies the user. The presence of a context usage override condition of the biometric authentication request causes a context usage factor to be updated based upon the context usage override condition. A biometric recognition threshold required for the user to access the application and indicative of a threshold security level required for biometric authentication is calculated based on the context usage factor. The user is permitted to access the application when the match score of the biometric sample is at least equal to the biometric recognition threshold.
Owner:GOOGLE TECHNOLOGY HOLDINGS LLC
Methods and systems for fingerprint template enrollment and distribution process
A system and method may comprise providing a database comprising a user list and a user device list, the user list comprising a list of user biometric identifiers, each extracted from and unique to a respective template of a user biometric of a verified user, and the user device list comprising a list of user biometric identifiers each extracted from and unique to a respective template of a user biometric of a verified user device associated with the verified user; and determining one of (1) whether a user biometric identifier of a known user biometric received from an unverified user device matches a user biometric identifier on the user device list and (2) whether a user biometric identifier extracted from and unique to a new user biometric template received from a verified user device matches a user biometric identifier in the stored user list.
Owner:SYNAPTICS INC
Method and system for authenticating and validating identities based on multi-modal biometric templates and special codes in a substantially anonymous process
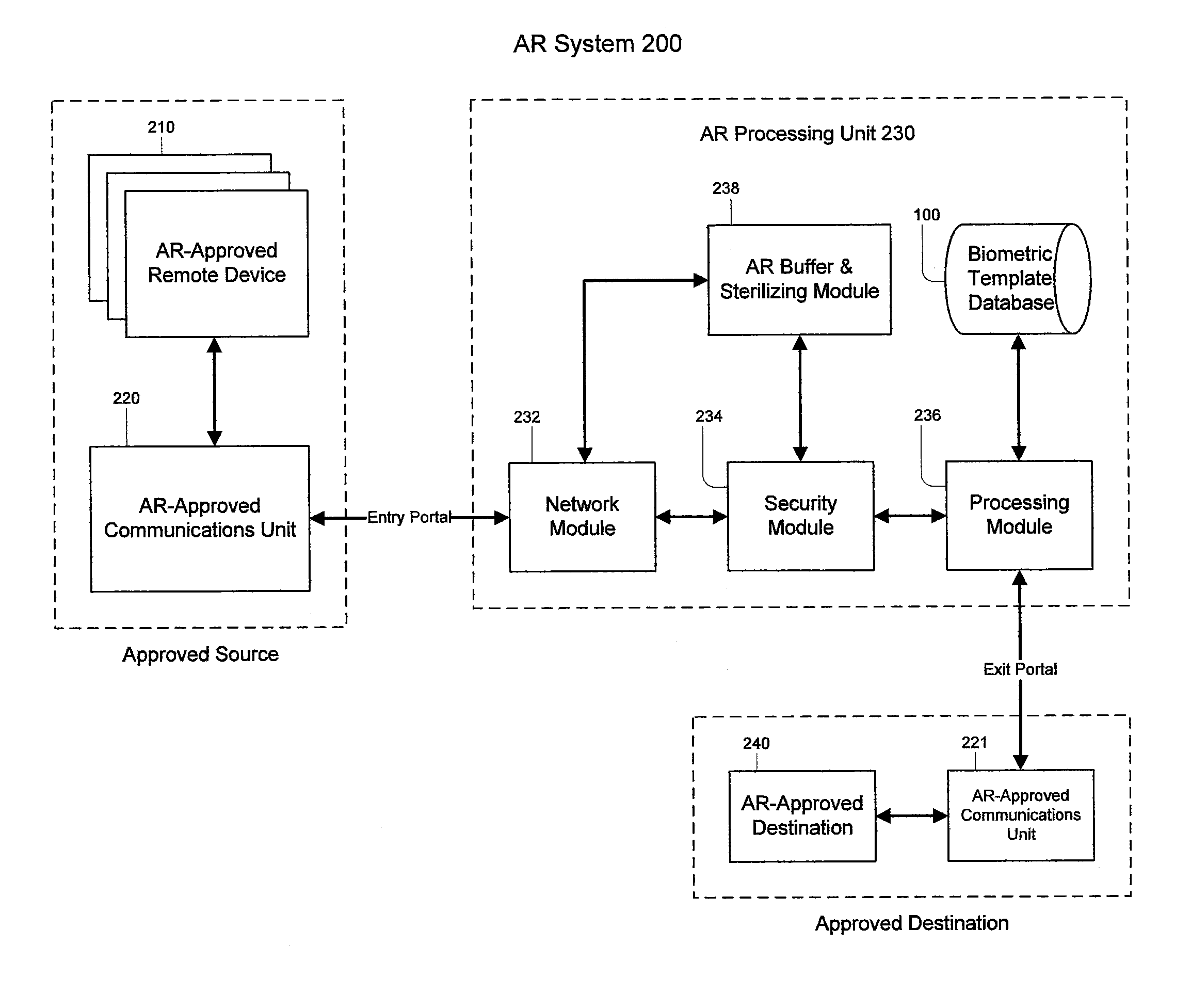
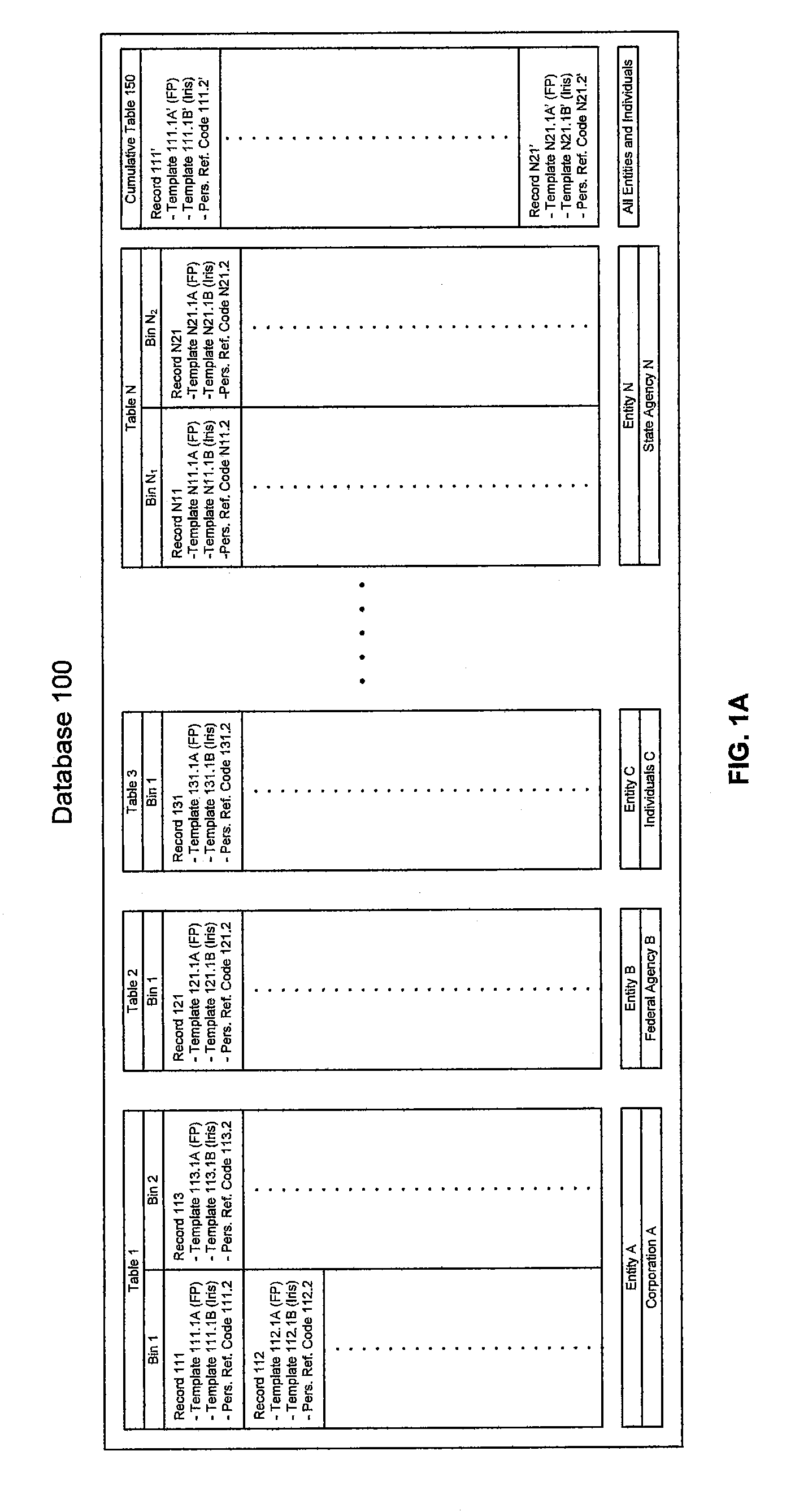
InactiveUS20080052527A1User identity/authority verificationDigital data authenticationInternet privacyBiometric templates
An embodiment of the present invention provides a method for authenticating an identity of an individual received from an approved entity against a centralized multi-modal biometric database in an anonymous process. The method includes receiving an authentication request from the approved entity. The authentication request includes a personal reference code and a biometric template for a biometric feature of the individual but no private or personal data. The method further includes determining if any record in the database exists that includes a personal reference code which matches the reference code of the authentication request. The record in the database further includes one or more stored biometric templates for each individual. Based on the determination of the match, the method compares the biometric template of the authentication request with the stored biometric template and provides an indication to an approved destination of whether the biometric templates match, thus confirming authentic identity.
Owner:NAT BIOMETRIC SECURITY PROJECT
Systems and Methods for Recognition of Individuals Using Multiple Biometric Searches
ActiveUS20090174526A1Electric signal transmission systemsDigital data processing detailsPattern recognitionDrill down
Owner:L 1 SECURE CREDENTIALING
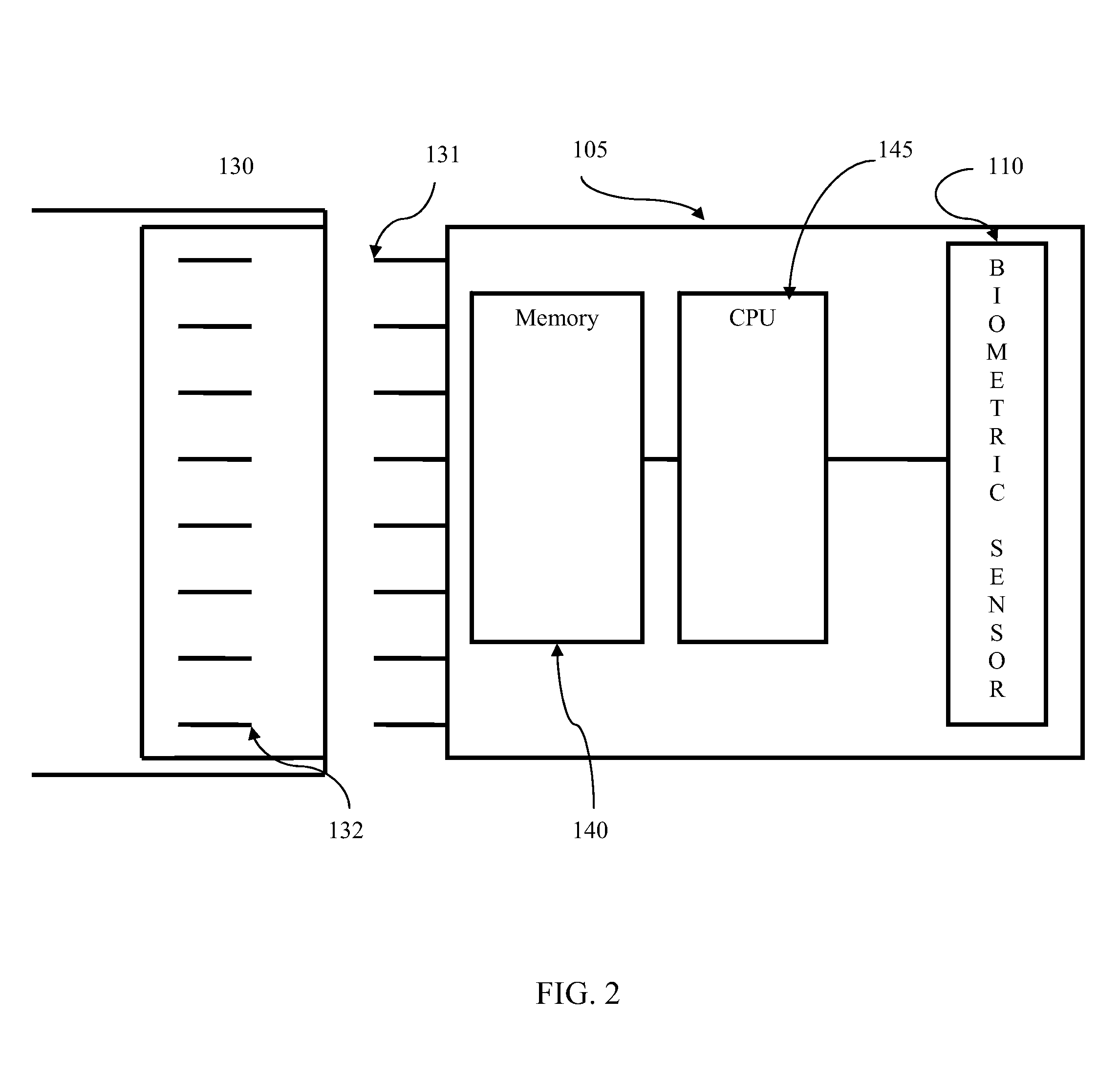
Method and apparatus for access control using dual biometric authentication
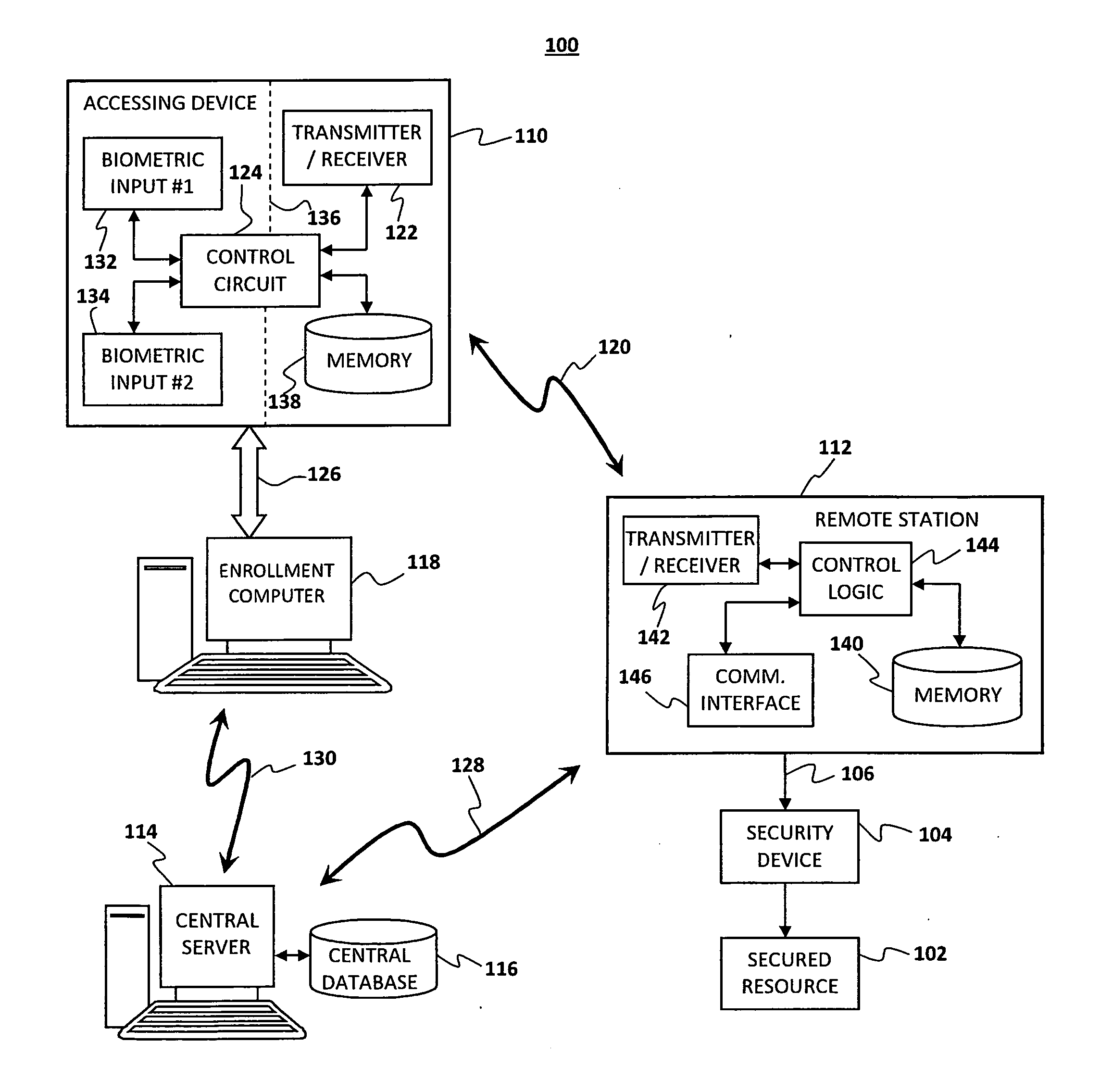
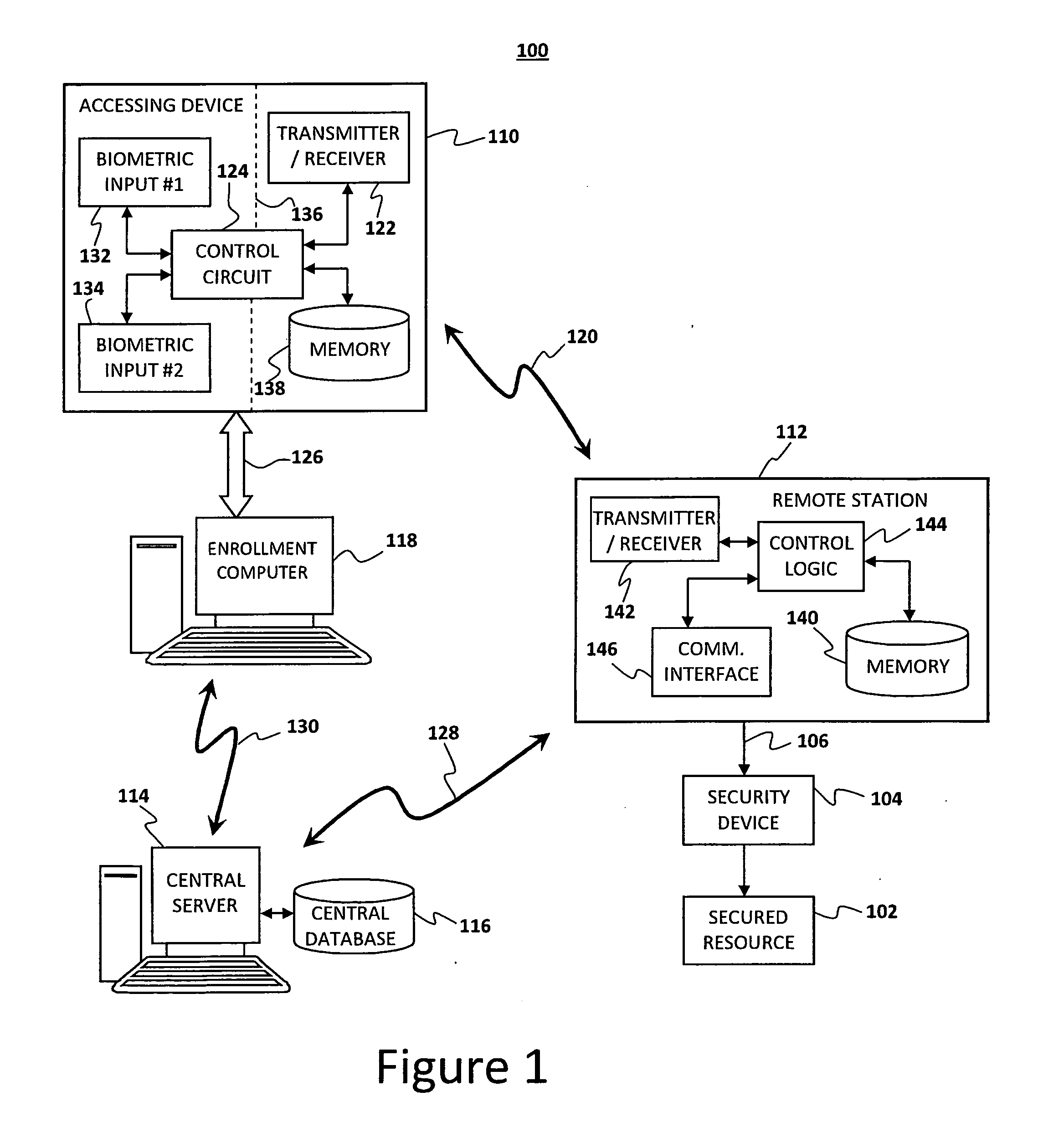
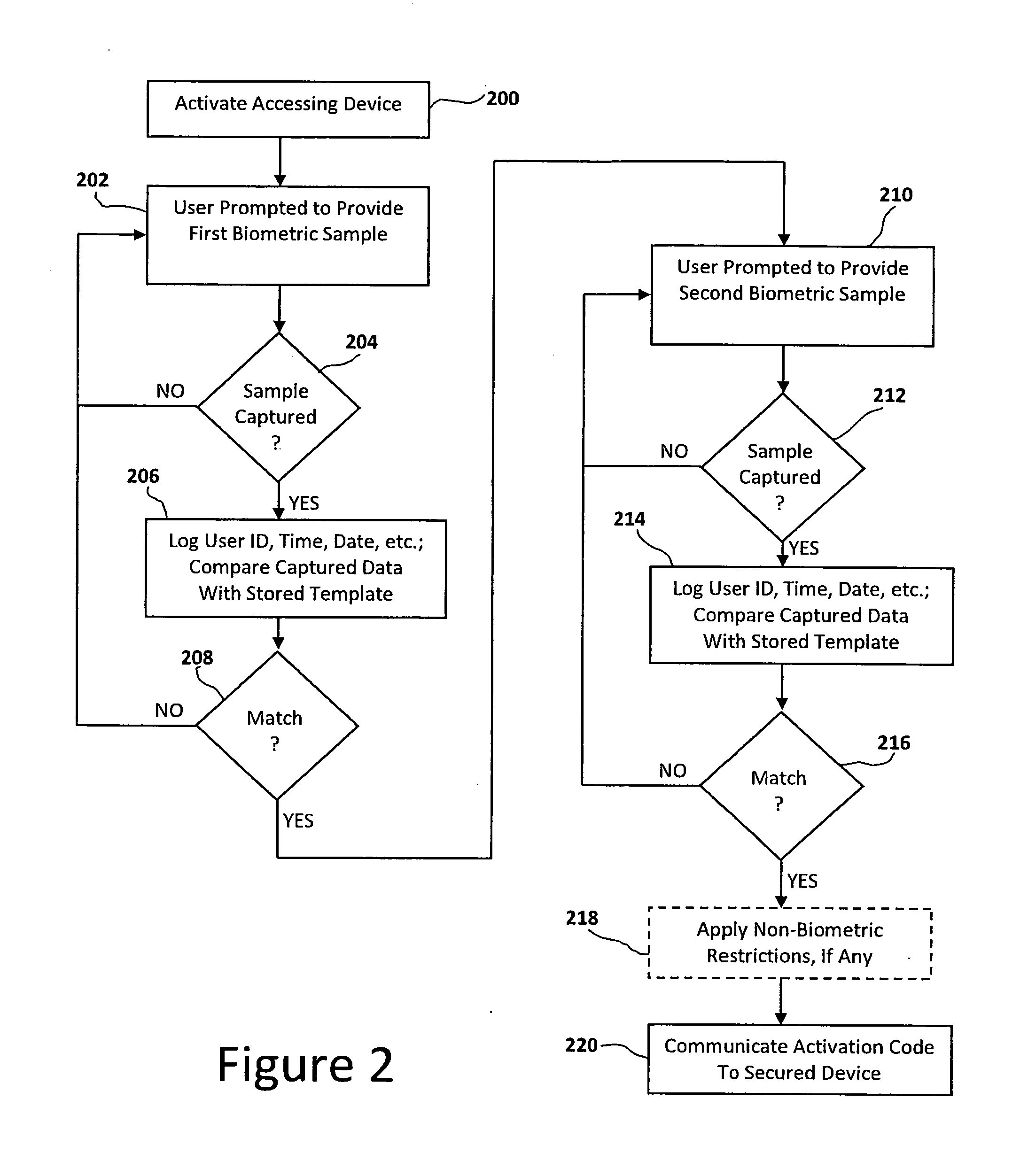
ActiveUS20110205016A1Programme controlElectric signal transmission systemsComputer hardwareBiometric data
A biometrically authenticated access control in which a wireless authentication signal is provided from a primary instrumentality of access, only after a dual-stage biometric verification of the user's identity is performed. In one embodiment, an accessing device includes memory for storing a device identification code and an authentication code, along with first and second biometric templates corresponding to biometric samples from a user. In another embodiment, an accessing device includes memory for storing a device identification code and more than one authentication code, for separate users, along with first and second biometric templates corresponding to biometric samples from multiple users. In order to gain access to a secured resource, a user undergoes first and second biometric sampling to generate biometric data to be compared with the first and second biometric templates. Upon authentication of the user by positive matches with said first and second biometric samples, the accessing device communicates the accessing device identification code and authentication code to a remote station controlling access to the secured resource. A central server maintains a central database of records each establishing a correlation between an enrolled accessing device's identification code and an authentication code assigned to that accessing device.
Owner:DOMAIN STANDARD INC THE
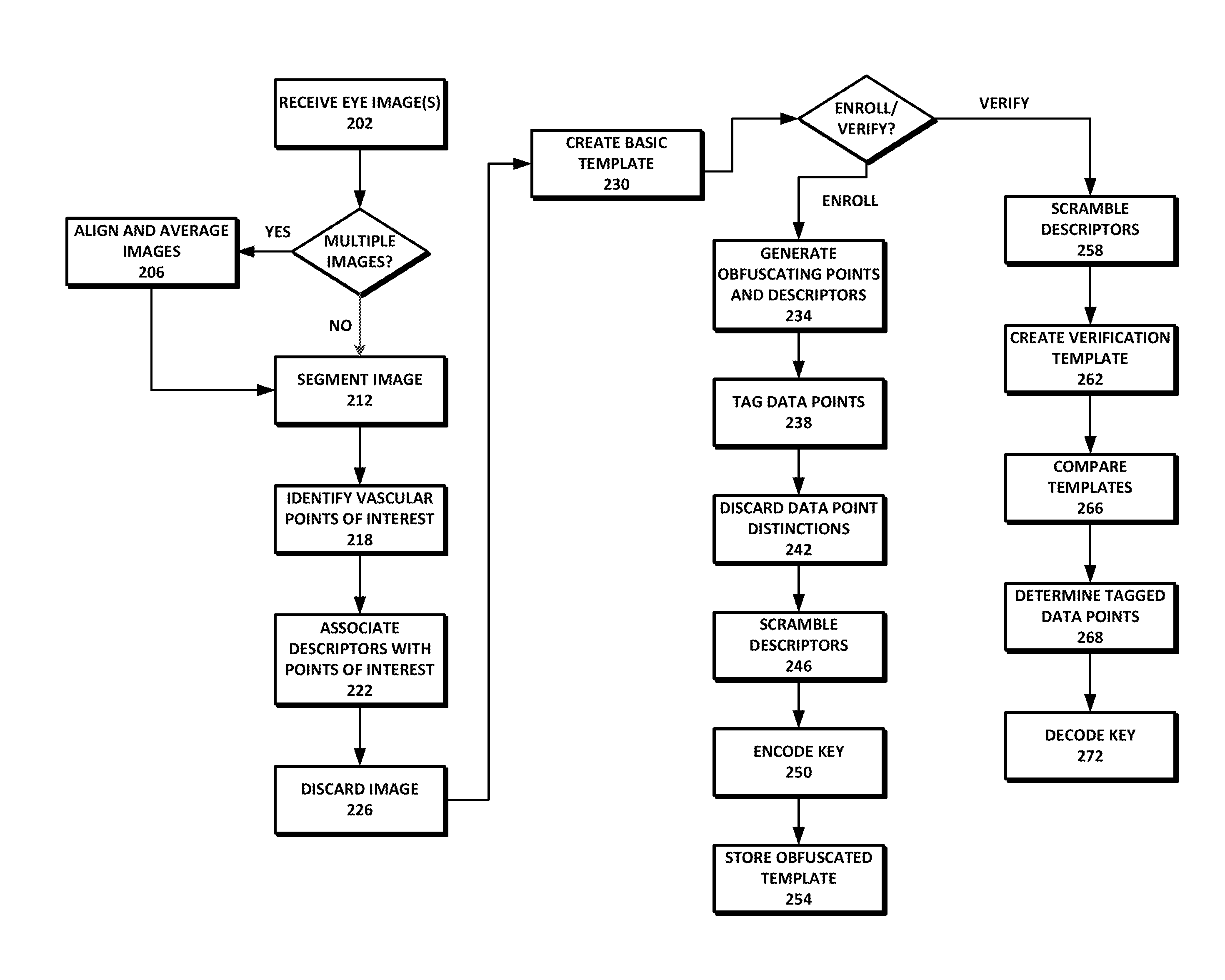
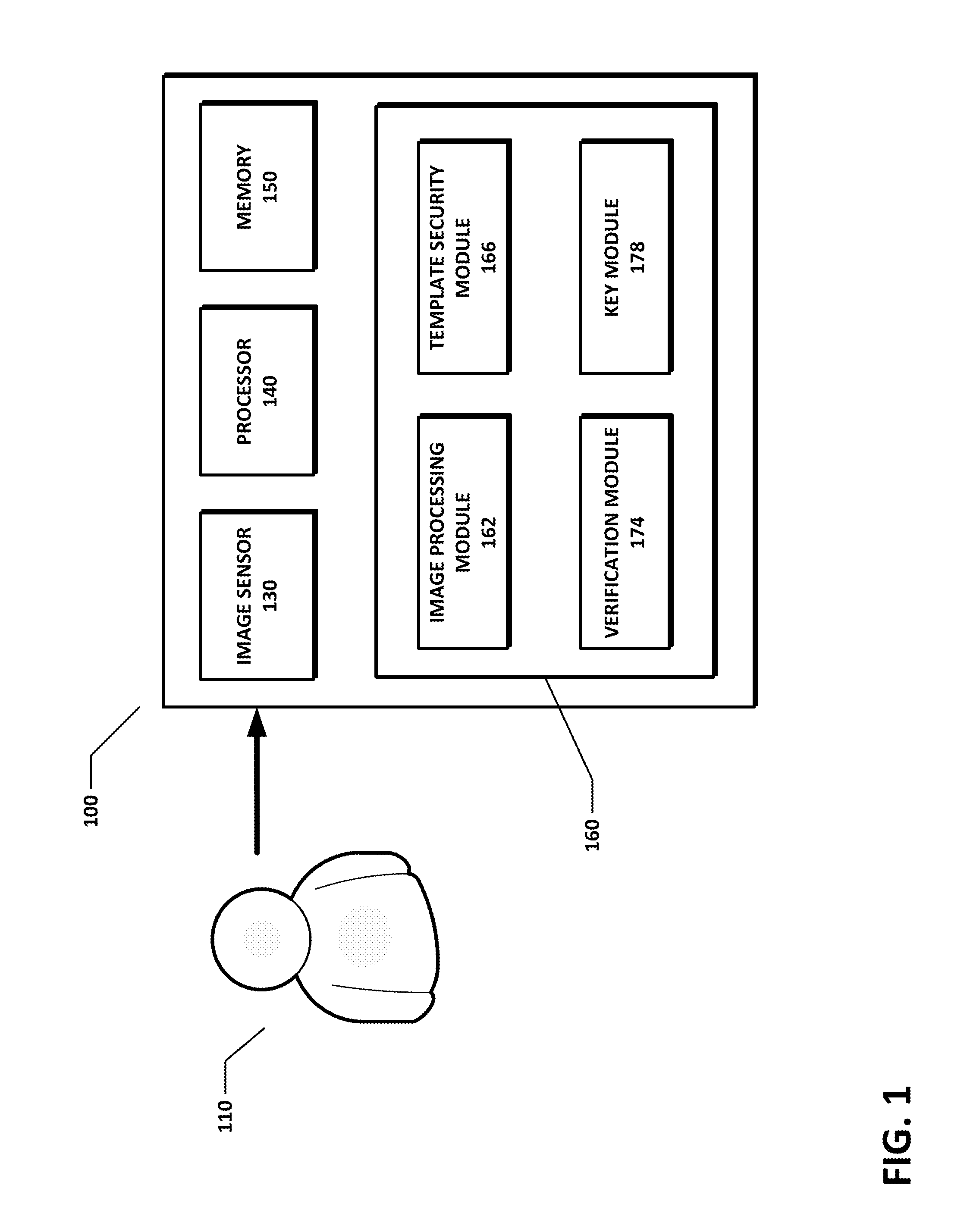
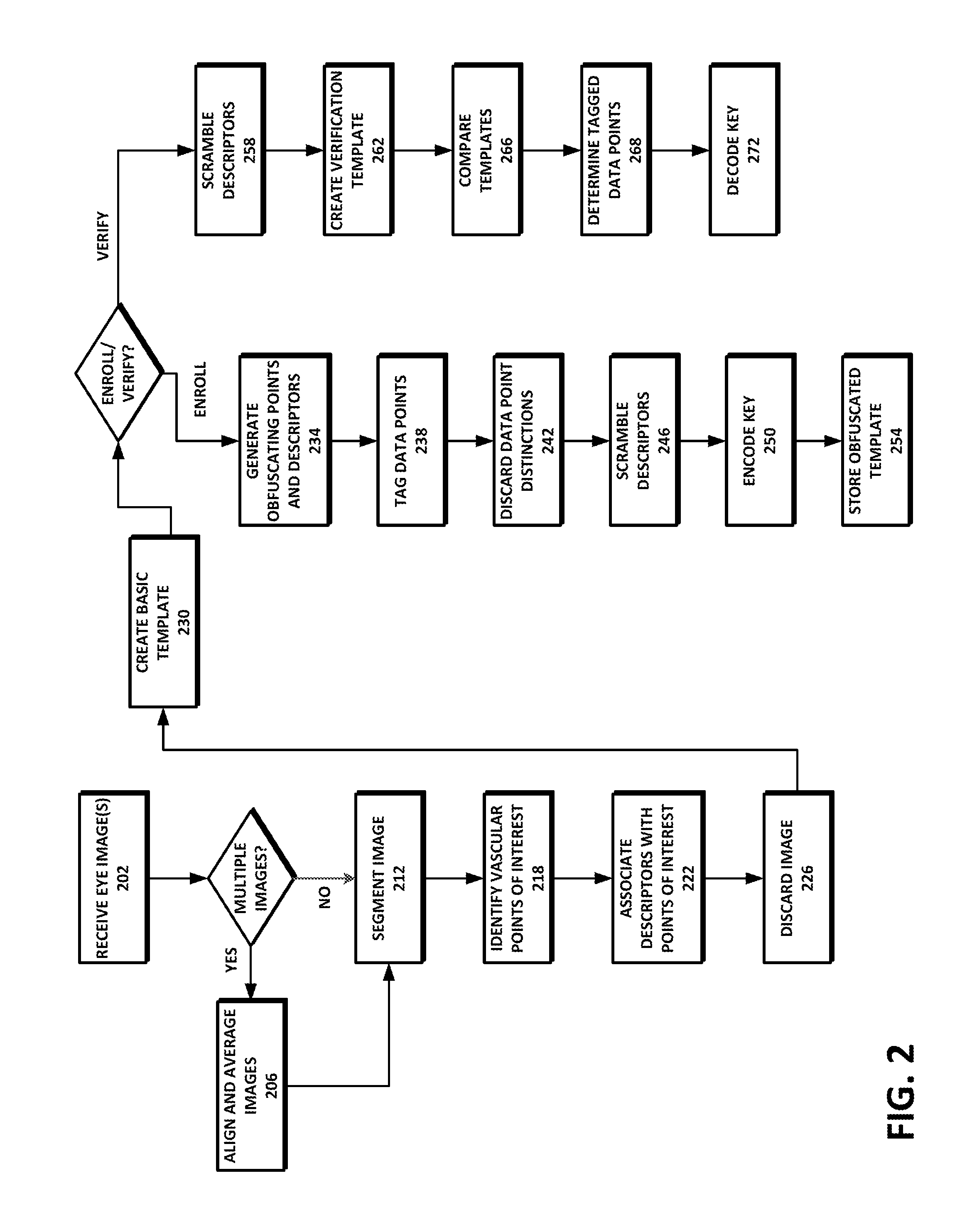
Biometric template security and key generation
ActiveUS8965066B1Reduce dimensionalityMultiple keys/algorithms usageAcquiring/recognising eyesPattern recognitionTemplate security
Methods and systems for securing biometric templates and generating secret keys are provided. One or more images are received. Interest points are identified based on the received images, and a plurality of obfuscating data points are generated based on the interest points. An obfuscated template based on the interest points and the obfuscating data points is created and stored. A secret key can be encoded using a subset of at least one of the obfuscating data points and the interest points in the template.
Owner:JUMIO CORP
Method and system of accounting for positional variability of biometric features
ActiveUS20110188709A1Character and pattern recognitionDigital data authenticationPattern recognitionBiometric data
A method of text-based authentication that accounts for positional variability of biometric features between captured biometric data samples includes capturing biometric data for a desired biometric type from an individual, and processing the captured biometric data to generate a biometric image and a biometric feature template. A selected conversion algorithm is executed by superimposing a positional relationship medium on the biometric image. The positional relationship medium includes a plurality of cells textually describable with words derivable from the positional relationship medium. The positions of biometric features are permitted to vary in overlapping border regions within the positional relationship medium. The method also includes identifying the position of at least one biometric feature within the overlapping border regions and generating a plurality of words for the at least one biometric feature.
Owner:DAON TECH
Biometric verification and duress detection system and method
ActiveUS7856558B2Programme controlElectric signal transmission systemsUser inputIdentification device
A multi-stage verification system including a first and second identification device to verify the identity of the user and to determine if the user is under duress. When a user approaches an entrance to a building, a first identifier is detected by the first identification device, the identifier is compared to a pre-stored identifier. If there is a match, the user inputs at least one biometric input into the second identification device. The biometric input is compares with pre-stored information in two different databases, a biometric template database and a duress indicator database. If there is a match with the duress indicator database, a silent alarm signal is transmitted to a central monitoring station and the security system is disarmed. If there is a match with the biometric template database, the security system is controlled in the intended manner.
Owner:ADEMCO INC
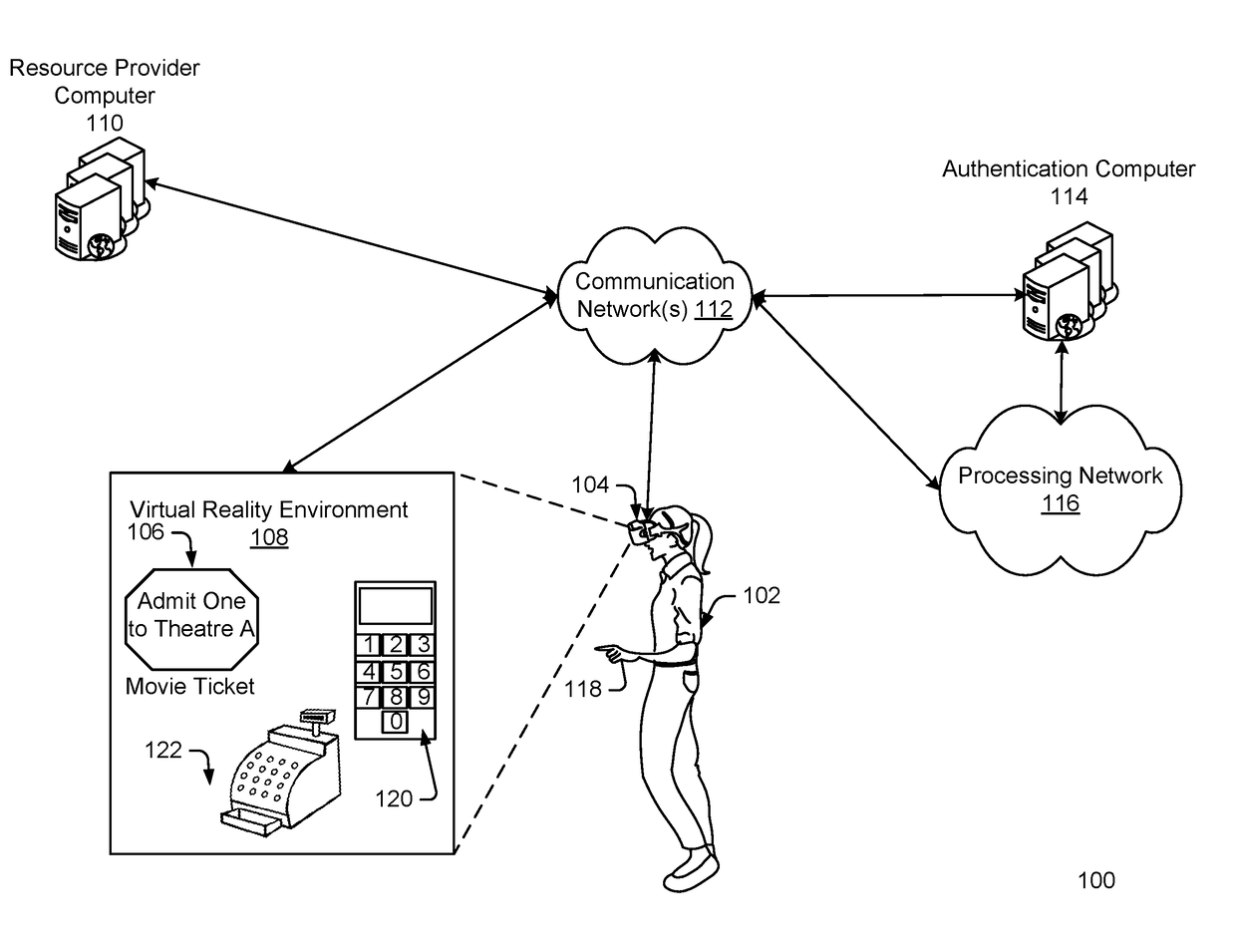
Security approaches for virtual reality transactions
One embodiment of the invention is directed to a computer-implemented method comprising, receiving an indication that an avatar of a user has initiated a transaction in a virtual reality environment. The method further comprises obtaining a first biometric sample from the user interacting with the virtual reality hardware. The method further comprises generating a partial biometric template based at least in part on the first biometric sample. The method further comprises providing the partial biometric template and personal authentication information for the avatar to an authentication computer where the personal authentication information and the partial biometric template are used to authenticate the avatar.
Owner:VISA INT SERVICE ASSOC
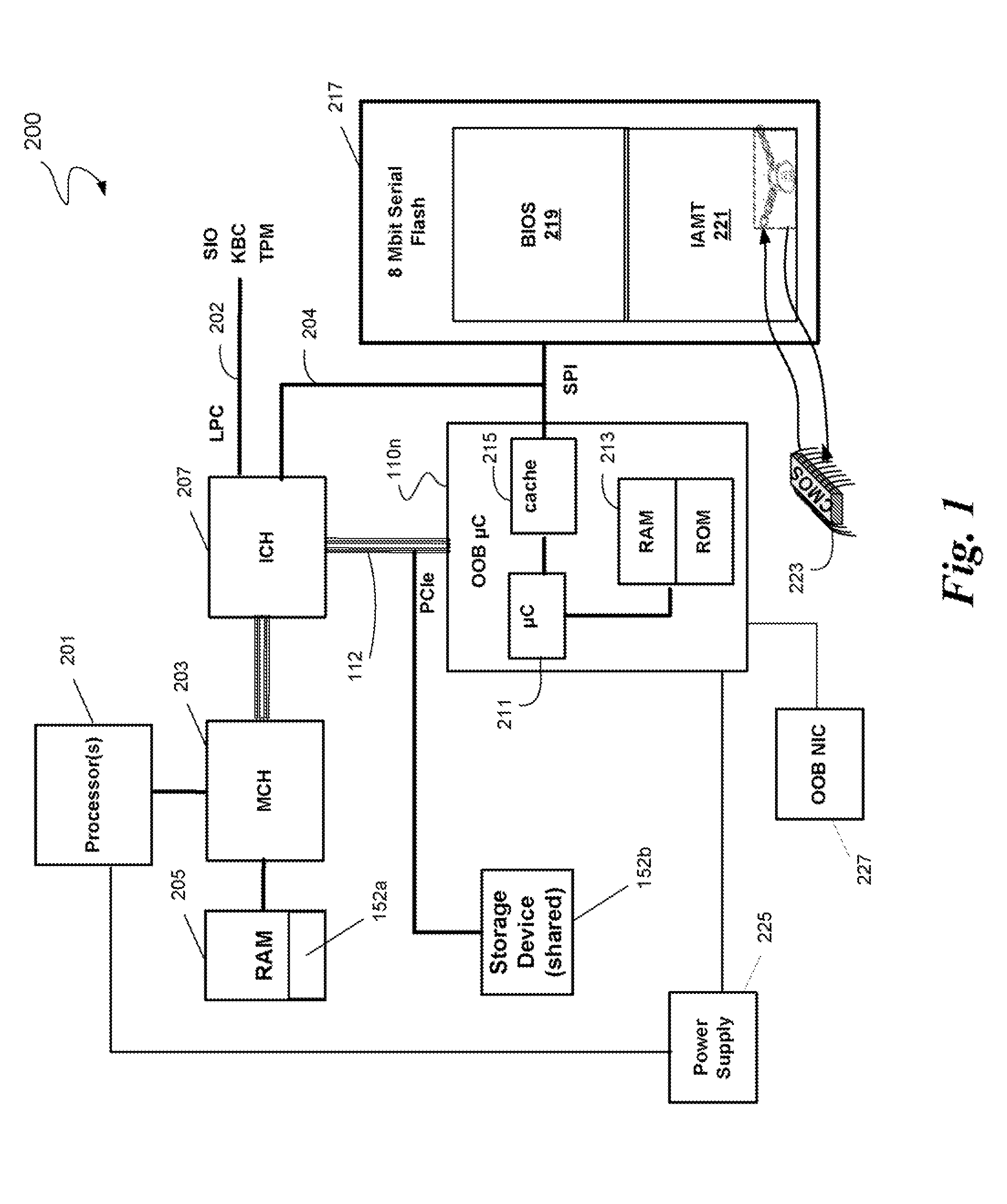
System and method for out-of-band assisted biometric secure boot
ActiveUS20090006859A1Computer security arrangementsSecret communicationBiometric dataBiometric templates
In some embodiments, the invention involves using a dedicated service processor with out-of-band capabilities to enable a secure boot using biometric data to authenticate the user. In some embodiments, at least a secondary token is used enhance the secure boot. An off-line database may be accessed by the service processor during boot to store or retrieve biometric templates to compare with scanned, live, biometric data. Other embodiments are described and claimed.
Owner:INTEL CORP
Method and system for secure transmission of biometric data
InactiveUS20060112280A1Improve quality scoreSecure transmissionDigital data authenticationSecret communicationBiometric dataSecure transmission
Embodiments of the invention provide methods and systems for securely transmitting a biometric identifier template across a network using a transport unit formed by appending a trusted time-stamp to the biometric template, and for authenticating such templates based on the time stamp. The method is applicable to fingerprint and other biometric identifier based identification and authentication systems.
Owner:TRIAD BIOMETRICS LLC
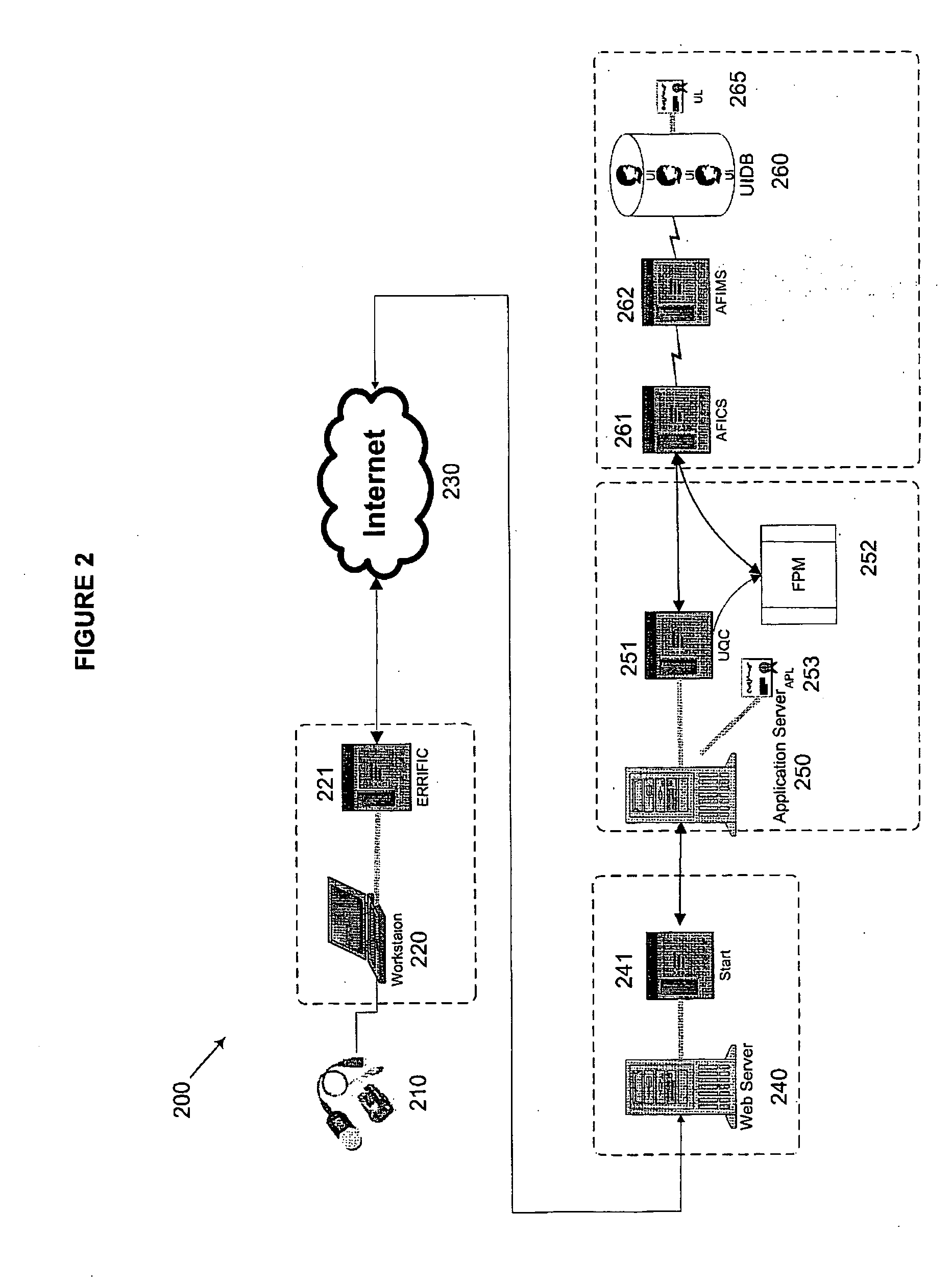
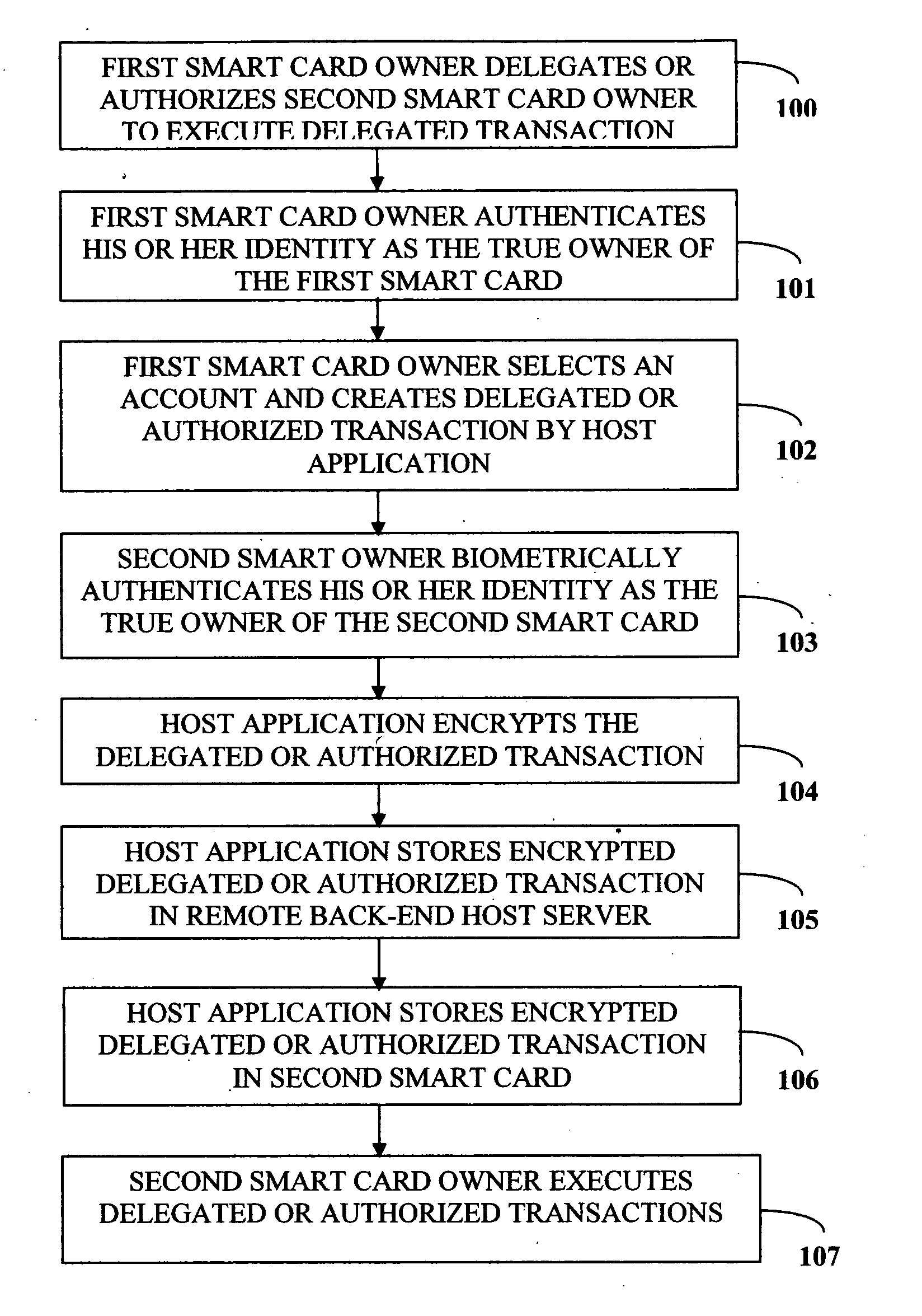
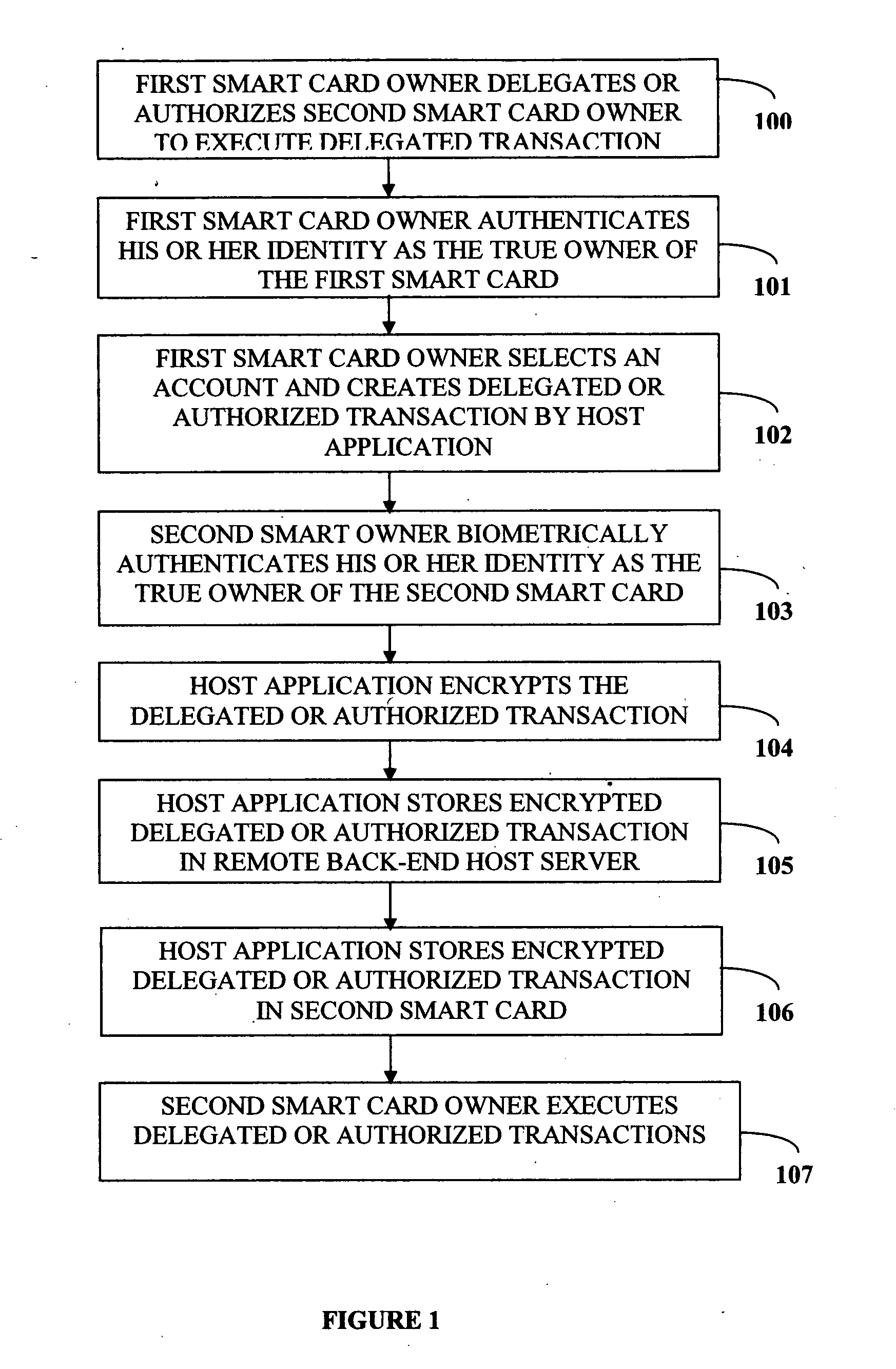
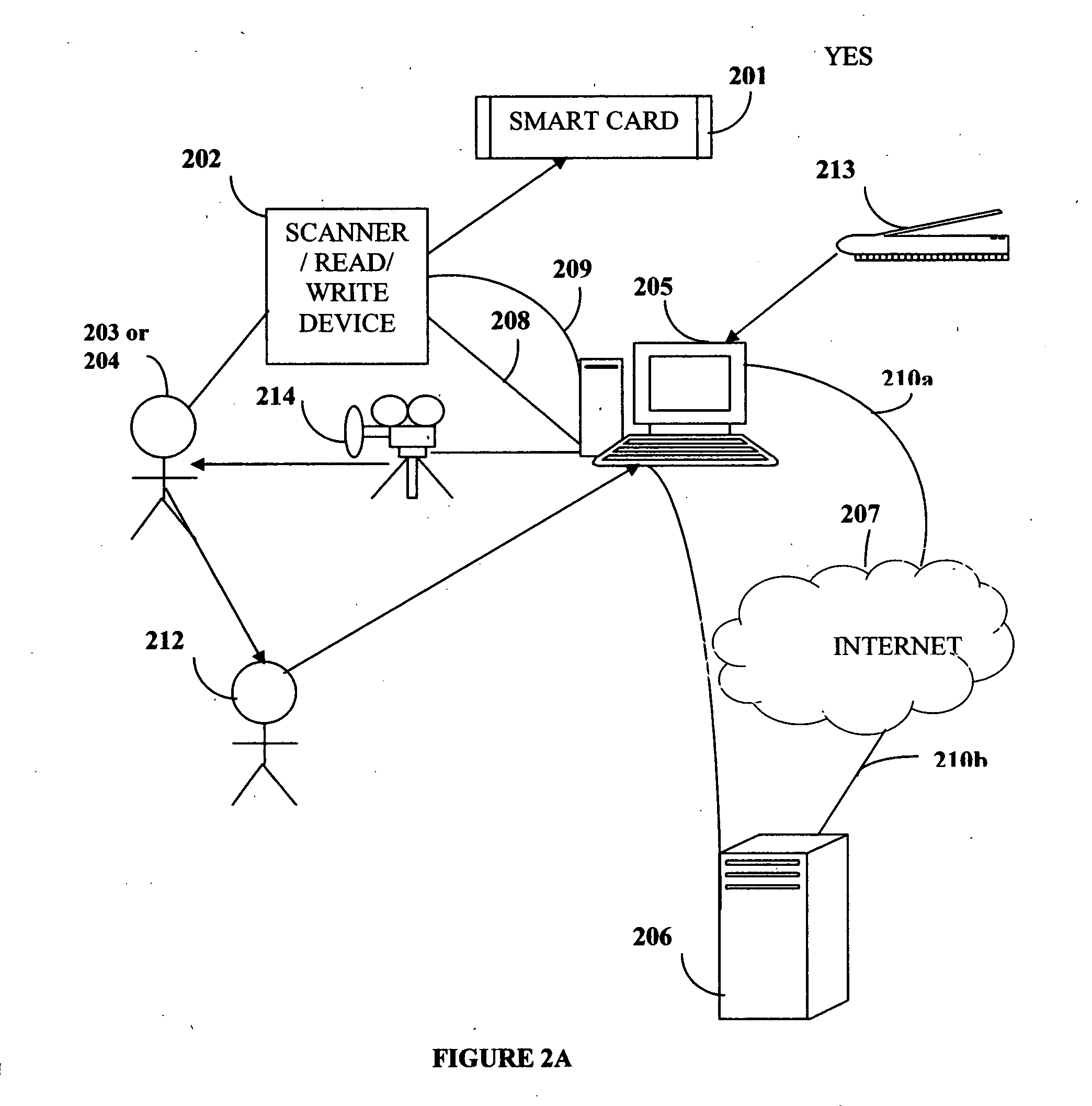
Biometric delegation and authentication of financial transactions
A method and system that enables a customer to delegate or authorize another individual to perform a financial transaction is provided. This system uses a smart card and a biometric scanner or reader writer, or a biometric device without a smart card. The smart card holds personal and financial accounts information about the customer including a set of biometric templates of the customer. The second smart card owner is identified as the true owner of a smart card after the second smart card passes a biometric authentication using a read write device. The first smart card owner specifies the desired transaction that is to be performed by the second smart card. The delegated or authorized transaction created by the first smart card is encrypted and stored in the second smart card and / or to a remote back-end host server.
Owner:ENENIA BIOMETRICS
Identification with RFID asset locator for entry authorization
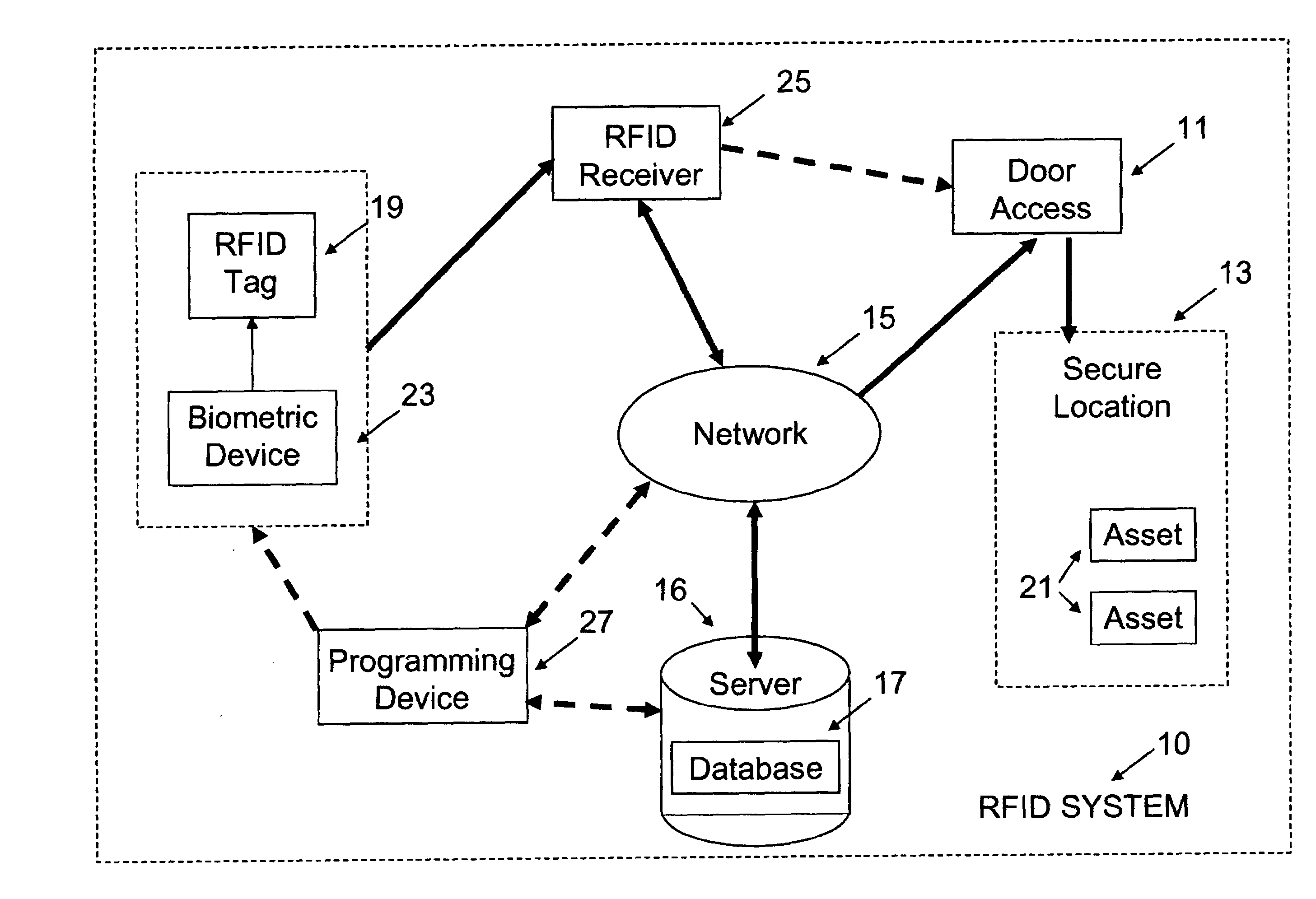
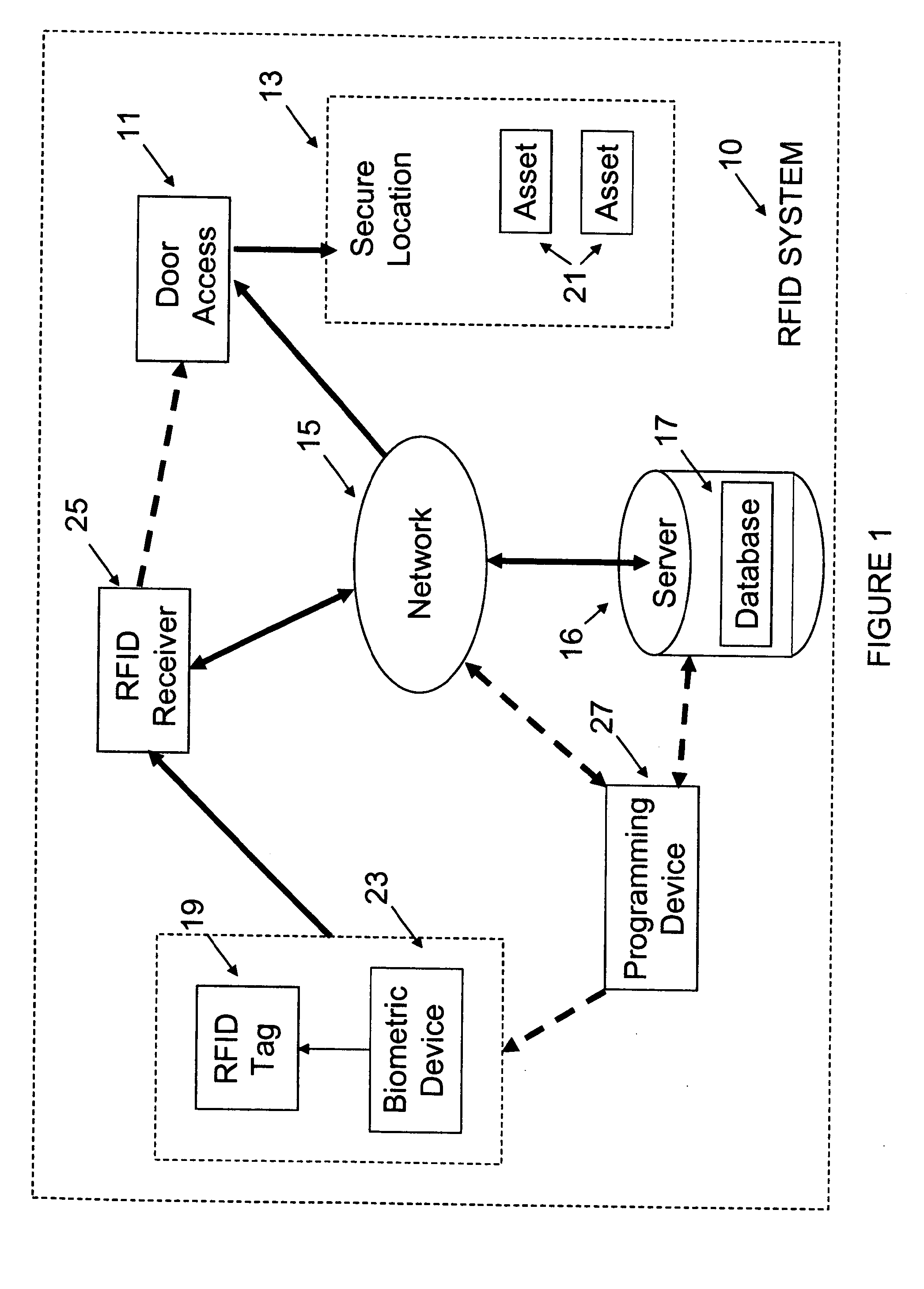
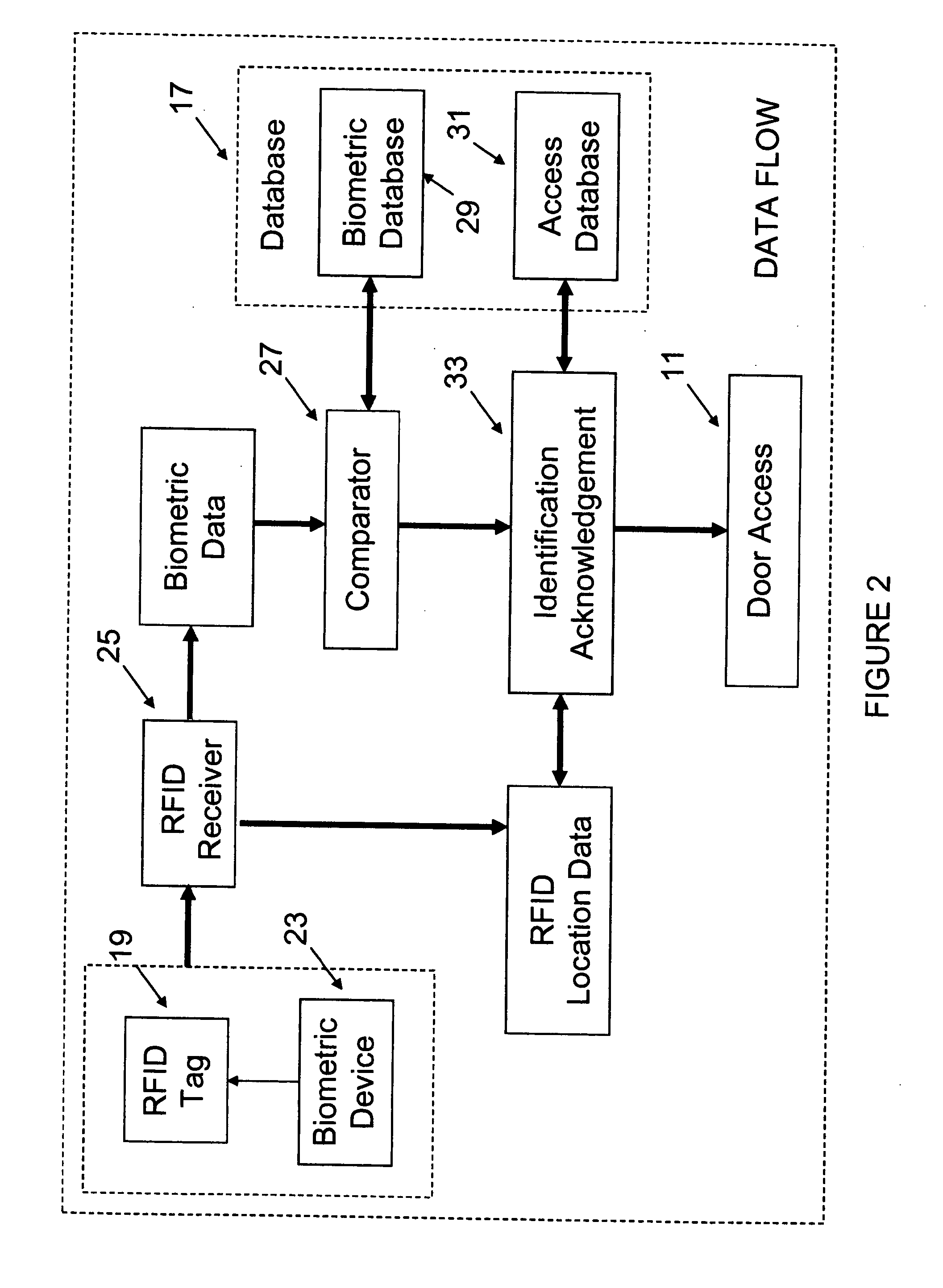
InactiveUS20090237203A1Electric signal transmission systemsMultiple keys/algorithms usageIdentification deviceData store
A system for controlling access at secure facilities to locations and assets contained in those locations, comprising a biometric identification device, an RFID tag and receiver, and a database for processing information from them to allow or deny access to the locations and assets. The system ties into an existing network in the facility and also includes a programming device for evaluation of the biometric template and acknowledgement of the identification, if made. The system also controls the permissible locations of assets such as laptops, desktop computers, photographic equipment, weapons such as rifles, data storage devices and the like, such that while a person may have access to a location, use of an asset or removal of the asset may not be part of that person's authorized conduct.
Owner:HONEYWELL INT INC
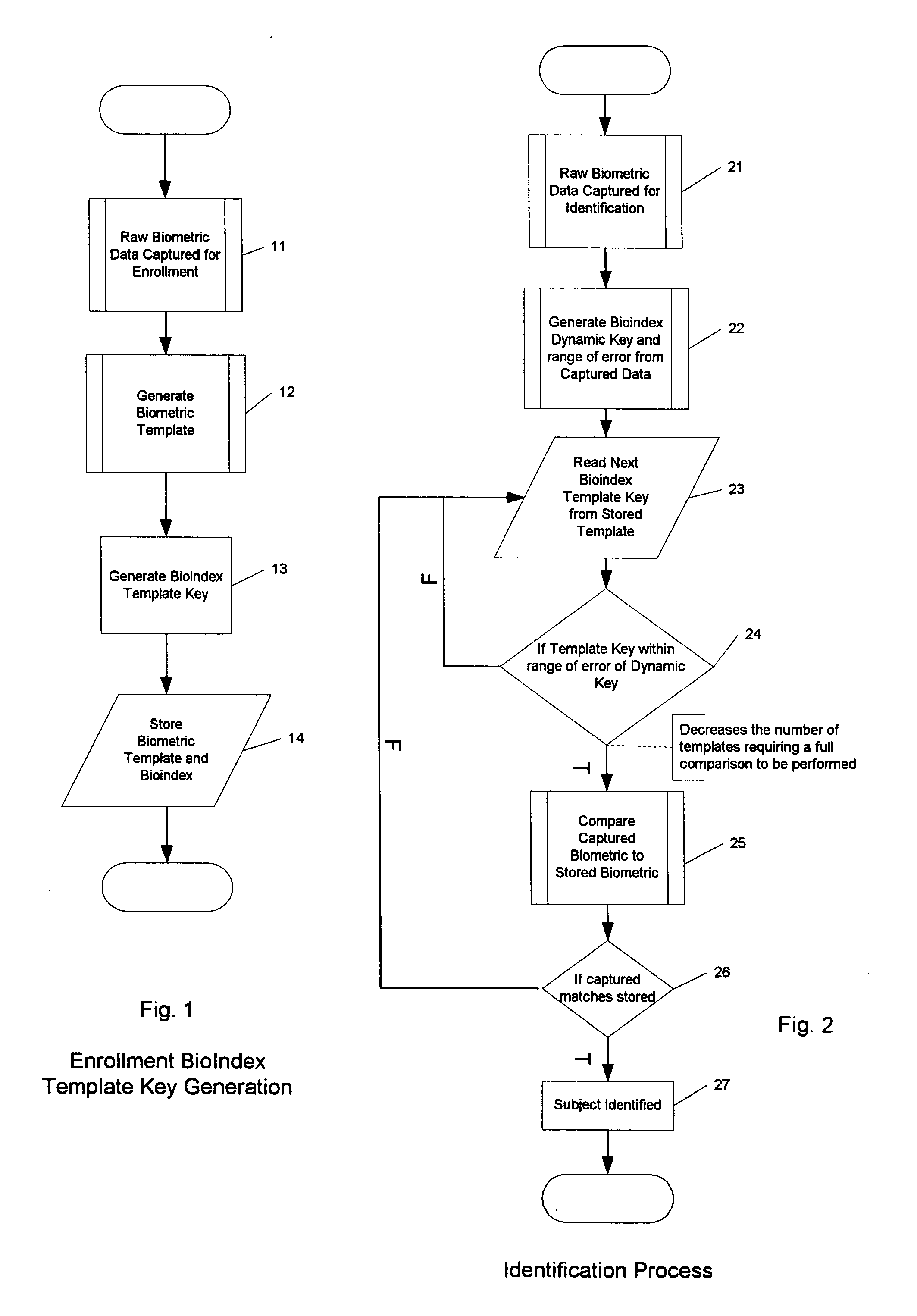
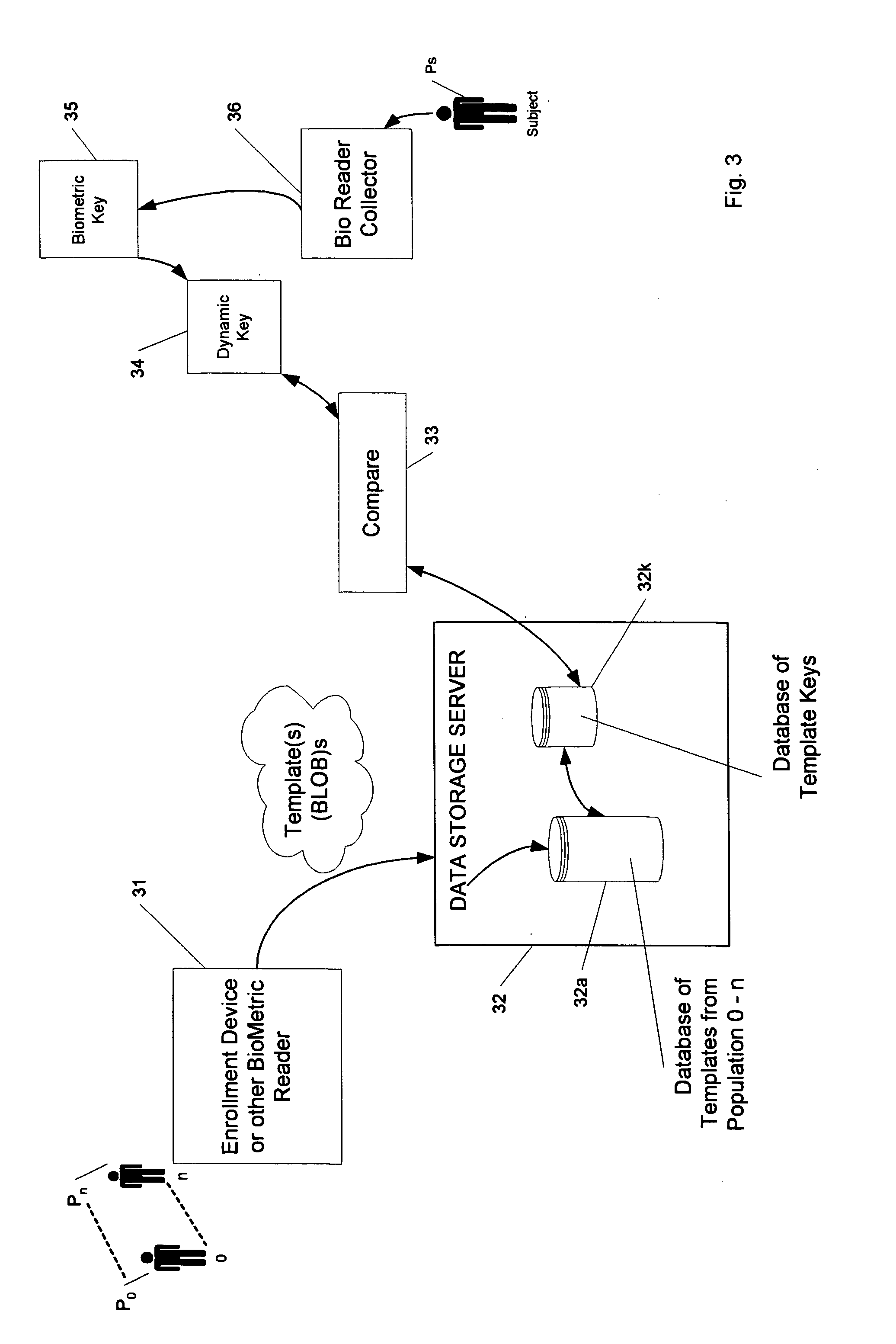
Bioindex mechanism for increasing the relative speed of biometric indentification against large population samples
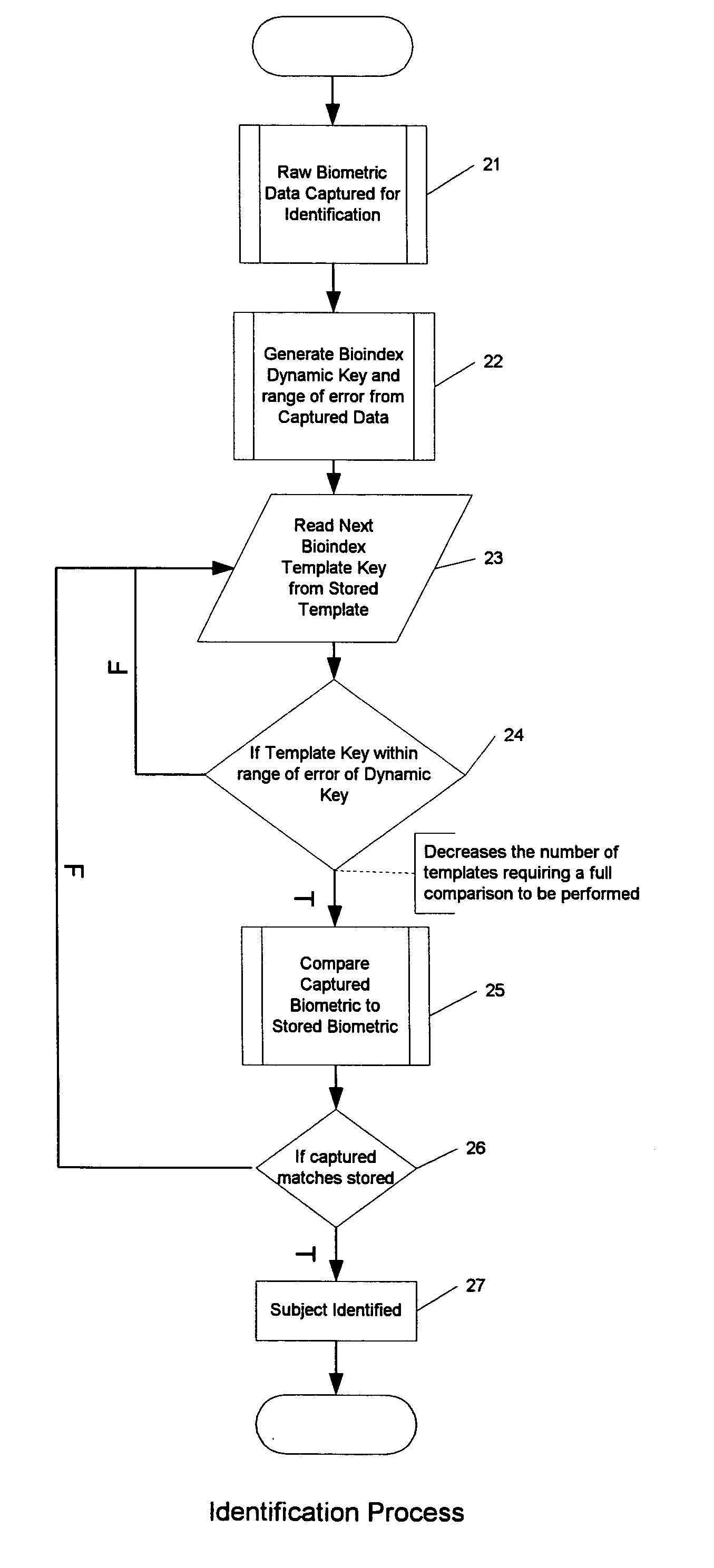
ActiveUS20090016573A1Reduce the populationIncrease rangeDigital data processing detailsUnauthorized memory use protectionSmall sampleAlgorithm
Owner:UNISYS CORP
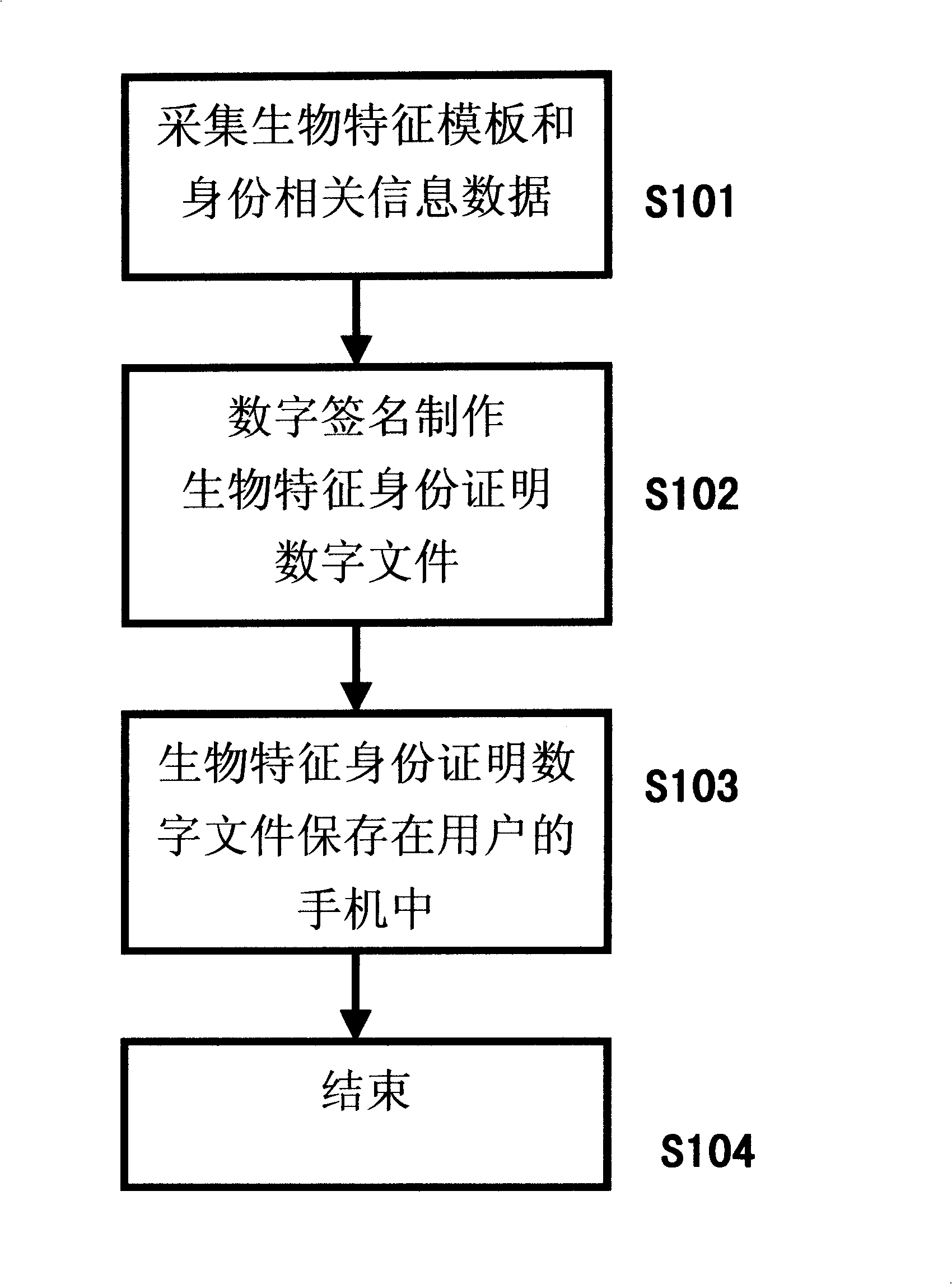
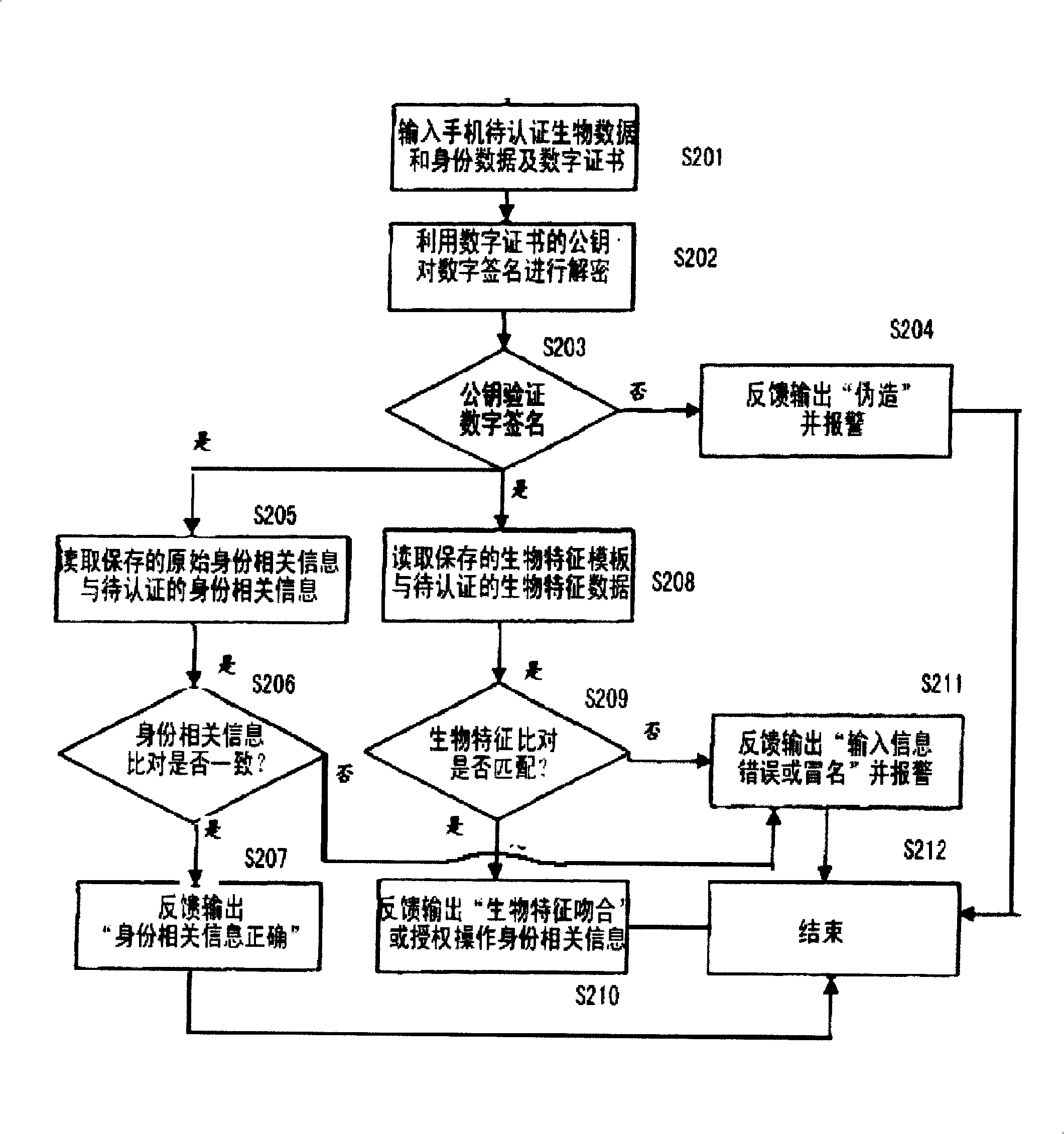
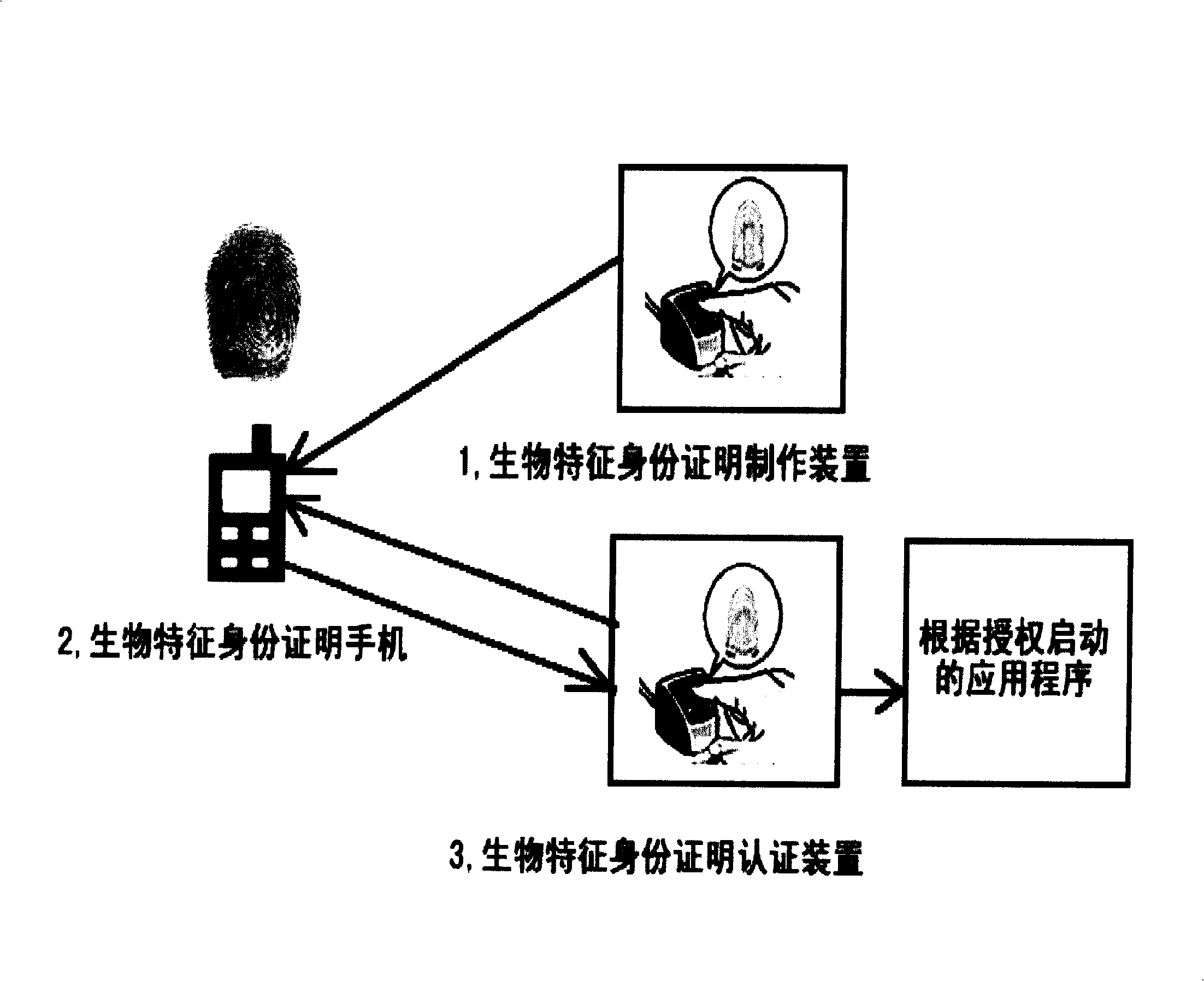
Mobile phone biological identity certification production and authentication method, and its authentication system
InactiveCN101321069AOvercoming technical biasPrivacy protectionUser identity/authority verificationRadio/inductive link selection arrangementsBiometric dataDigital signature
A biologic character template of a user and the related information of the user's identity constitute a whole data block, comprising: selecting an asymmetric key algorithm, using the private key to perform the digital signature or the digital seal, manufacturing the biologic character ID digital file of the digital signature, which is stored in the mobile phone of the user. The biologic character data of the user to be validated is collected on the site, and the digital certiuficate including the public key is sent to the user; mobile phone for storing the biologic character ID digital file in advance for verification; the mobile phone of the user uses the public key in the digital certificate to validate the digital signature of the biologic character ID digital file; the biologic character data to be certificated are inputted, to compare with the corresponding biologic character template in the biologic character ID digital file; the mobile phone of the user outputs the result data of the comparing and the validate, to display the result or output the authorization data of the further operation.
Owner:刘洪利
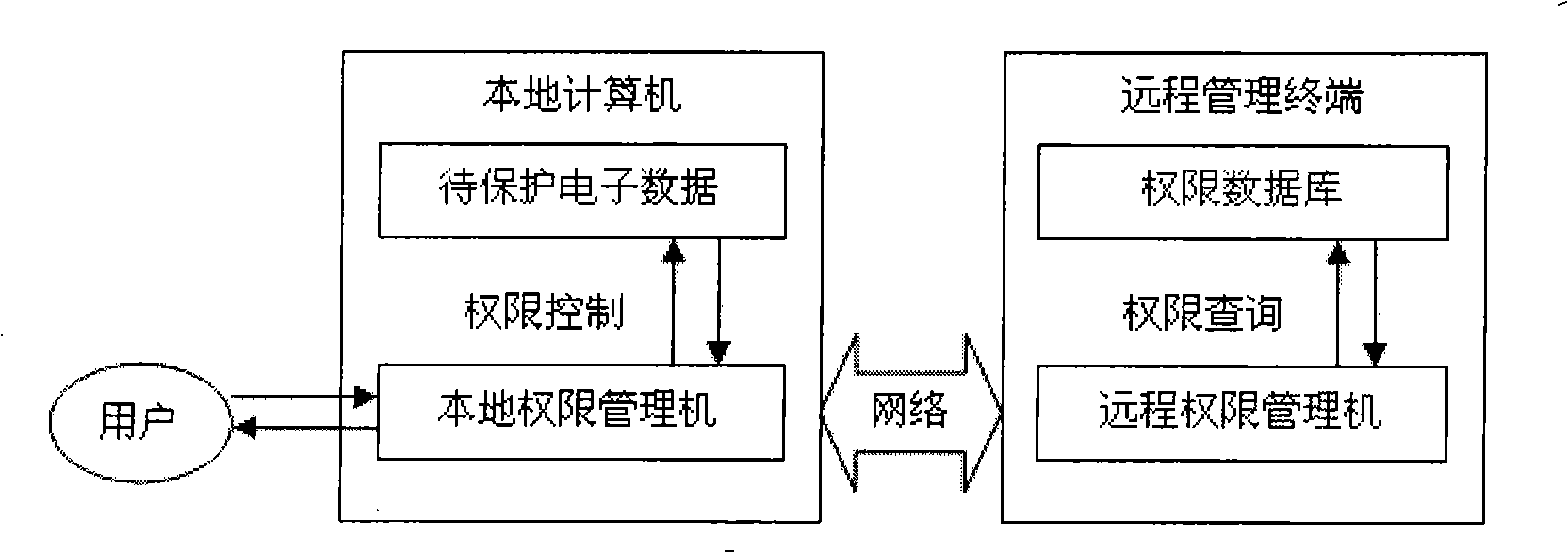
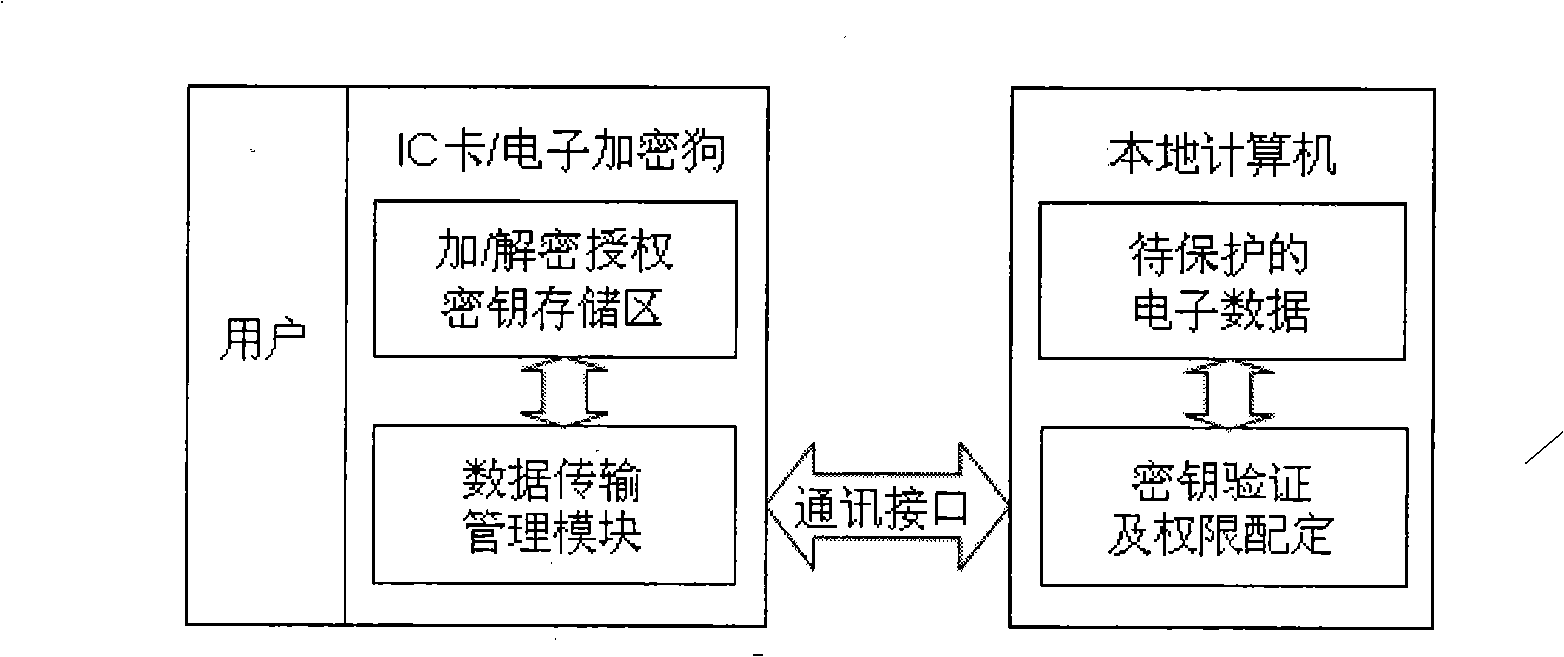
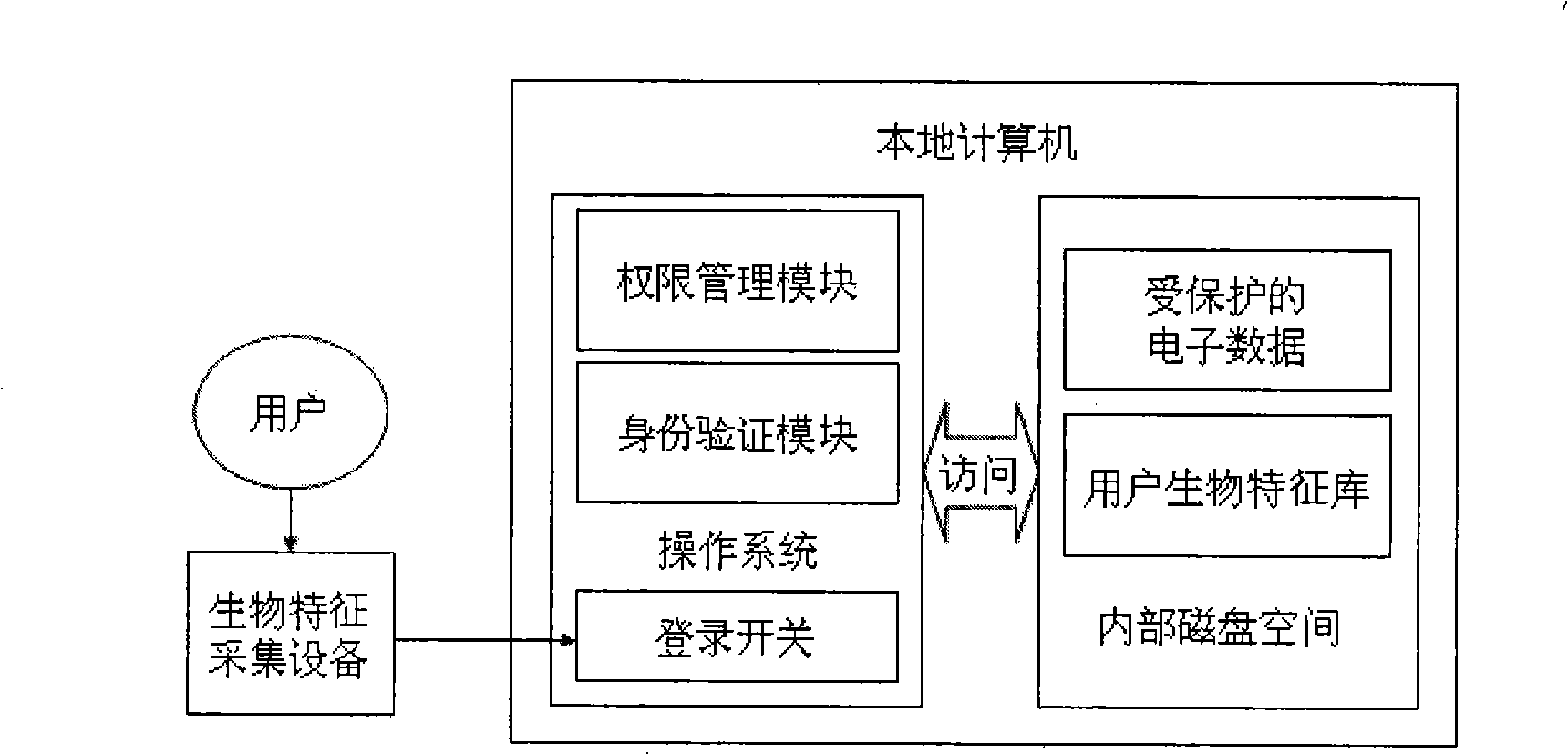
Electronic data protection method and device based on biological characteristic and mobile cryptographic key
InactiveCN101345619AImprove securityReduce riskPublic key for secure communicationCharacter and pattern recognitionPlaintextCiphertext
A electronic data protection method based on biological characteristic and mobile key comprises that user accesses mobile key device to local computer for register, storing mixedly of biological characteristic template ciphertext and secondary key in the device; enciphering or deciphering the access file, accessing the device for detecting communication pipeline safety; analyzing the ciphertext and secondary key, deciphering biological characteristic template using secondary cipher and returning to local computer; inputting user biological characteristic, checking validity of key ownership; if checking is passing, enciphering or deciphering the file using the biological characteristic template cleartext, or operation is forbidden. In the invention, the biological characteristic and secondary key are transferred to mobile device, correlation is introduced to key and owner, key safety is promoted. The local computer has not key and has only ciphered data, even if deciphering guard system obtains enciphered data, it can not decipher the enciphered data for lack of key.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
Optimized Biometric Authentication Method and System
ActiveUS20090193151A1Digital data processing detailsUser identity/authority verificationComputer scienceBiometric templates
An efficient exchange of messages in a system for authenticating access to a base device is facilitated through the selection of a particular biometric template from among a plurality of biometric templates. Rather than transmitting the template to a peripheral device, an indication of a location of the particular biometric template within the plurality of biometric templates is transmitted to the peripheral device. At the peripheral device, once the indication of the location and a biometric candidate are received, the particular biometric template may be located and compared to the biometric candidate. Finally, an indication of a result of the comparing may be transmitted to the base device.
Owner:MALIKIE INNOVATIONS LTD
Page back intrusion detection device
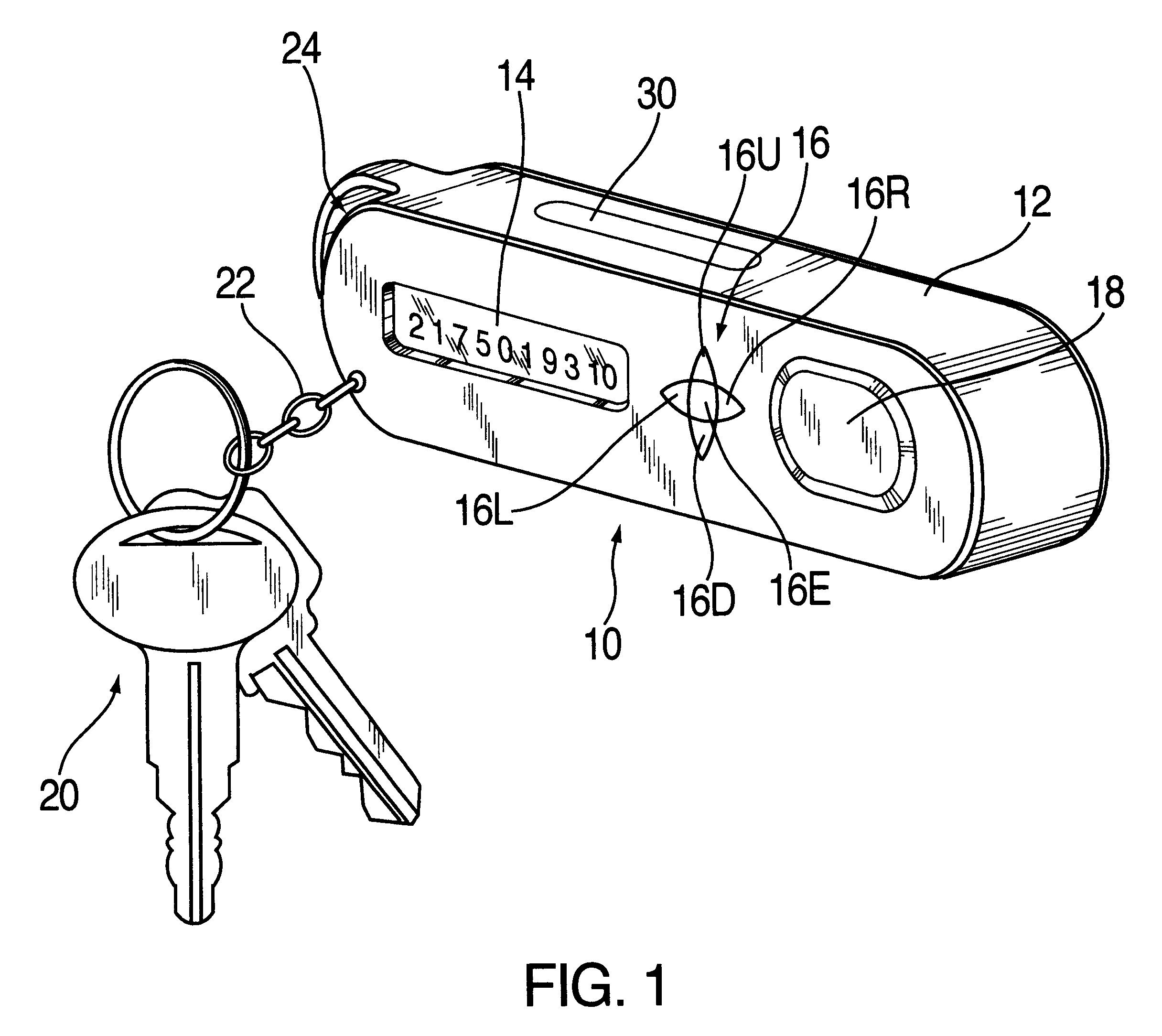
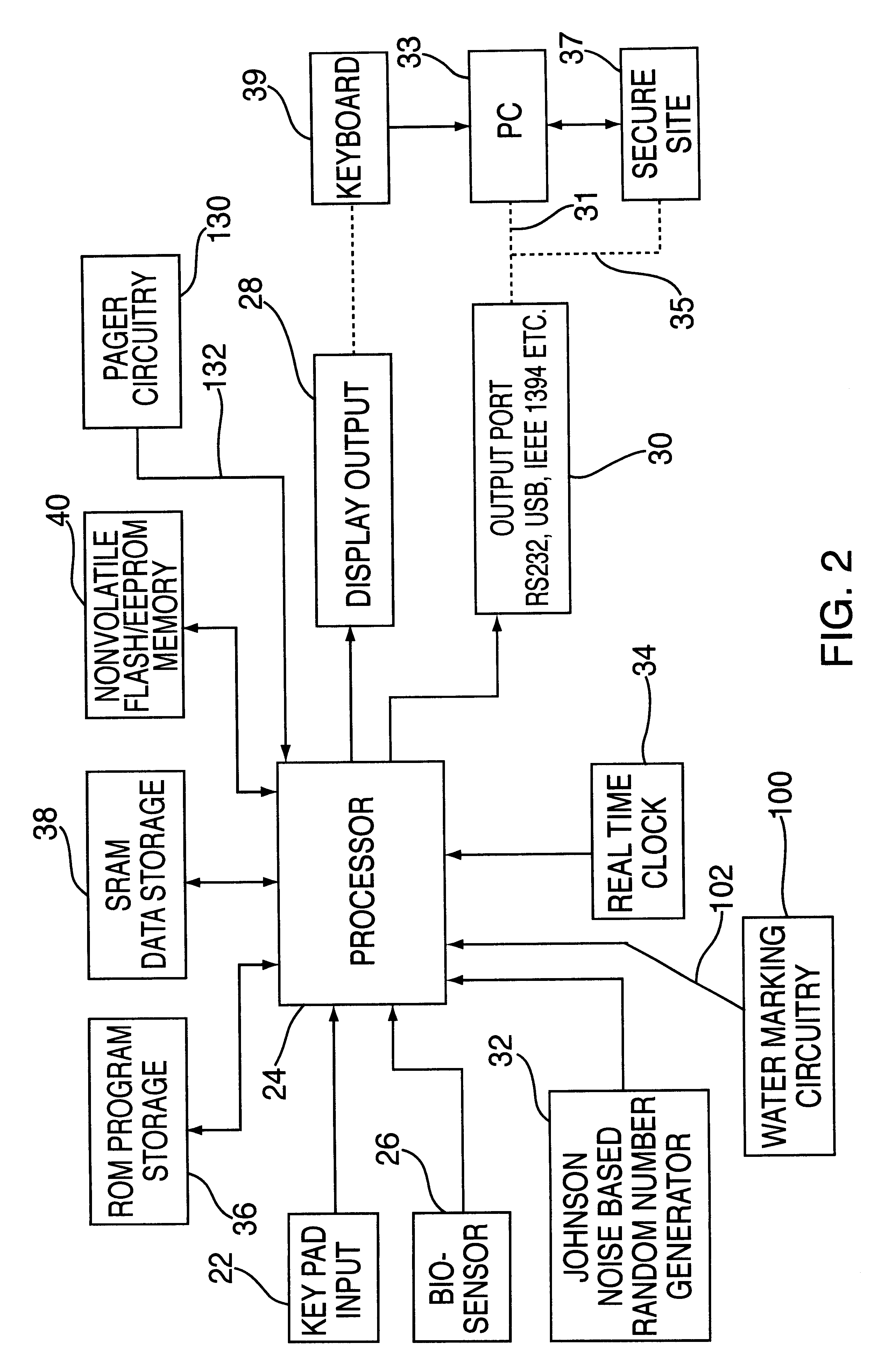
InactiveUS6580815B1Electric signal transmission systemsImage analysisPagerIntrusion detection system
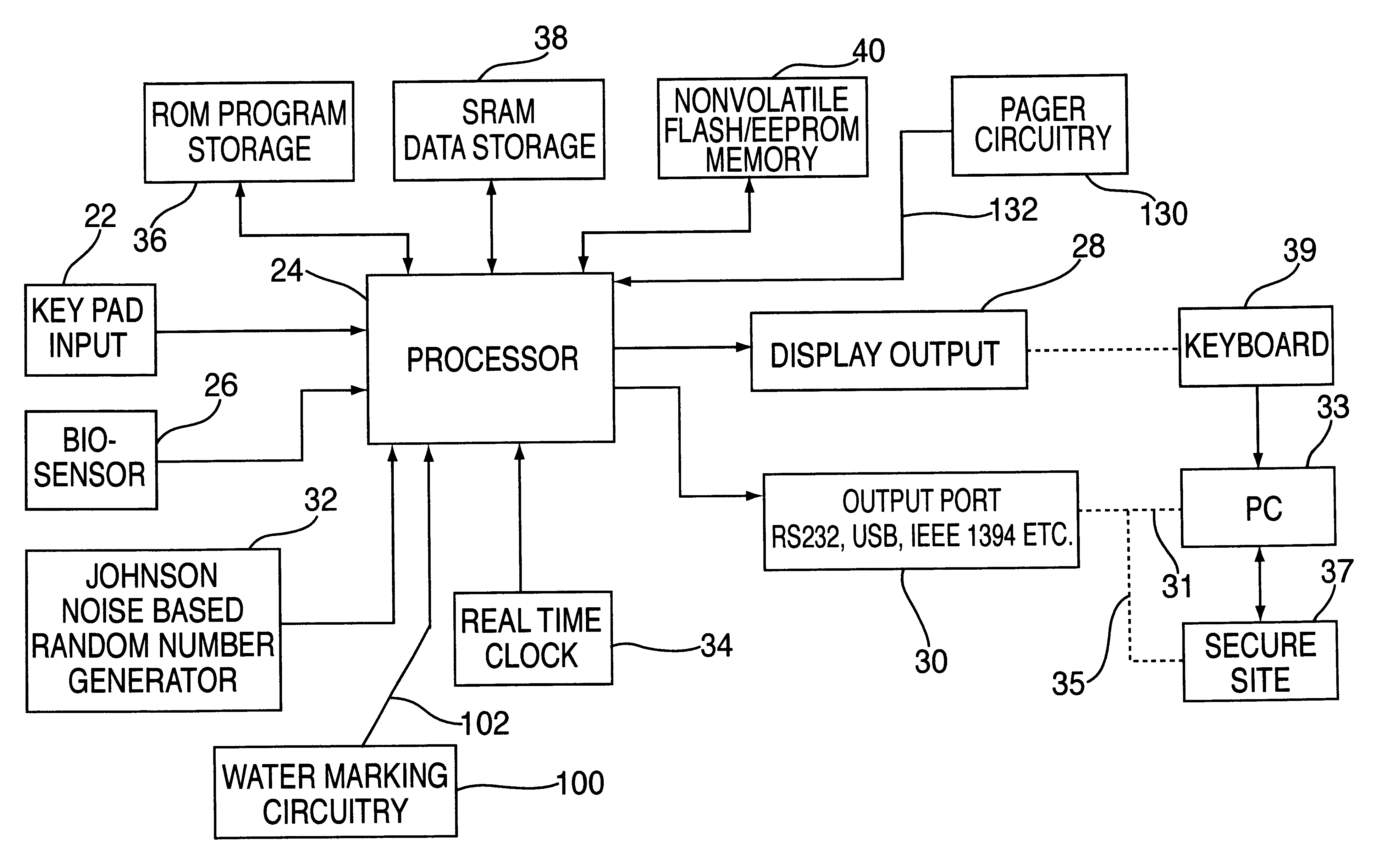
A device for use by an authorized person having an unique biometric parameter to obtain information for use in accessing a secured site. The device comprises a biometric interface unit engaged with a portable body member. The device further comprises biometric circuitry adapted to generate and store an initialized biometric template upon presentment of the person's unique biometric parameter to the biometric interface unit. The biometric circuitry is further adapted to generate a second biometric template upon subsequent presentment of the person's unique biometric parameter to the biometric interface unit. The device further comprises compare circuitry adapted to generate an first signal indicative that the second biometric template is substantially identical to the initialized biometric template. The device further comprises a storage device for storing a plurality of passwords. The device further comprises password circuitry adapted to generate a password in response to the first signal from the compare circuitry. The password circuitry being adapted to store the password in the storage device. The device further comprises water marking circuitry adapted to generate and embed a watermark within the password. The water marking circuitry may further comprise a plurality of memory registers and a data base having a plurality of public domain watermarks randomly assigned to each memory register. The device further comprises pager circuitry adapted to receive a signal from the secure site indicative that access has been attempted using said password and to generate an audible tone.
Owner:MANDYLION RES LABS
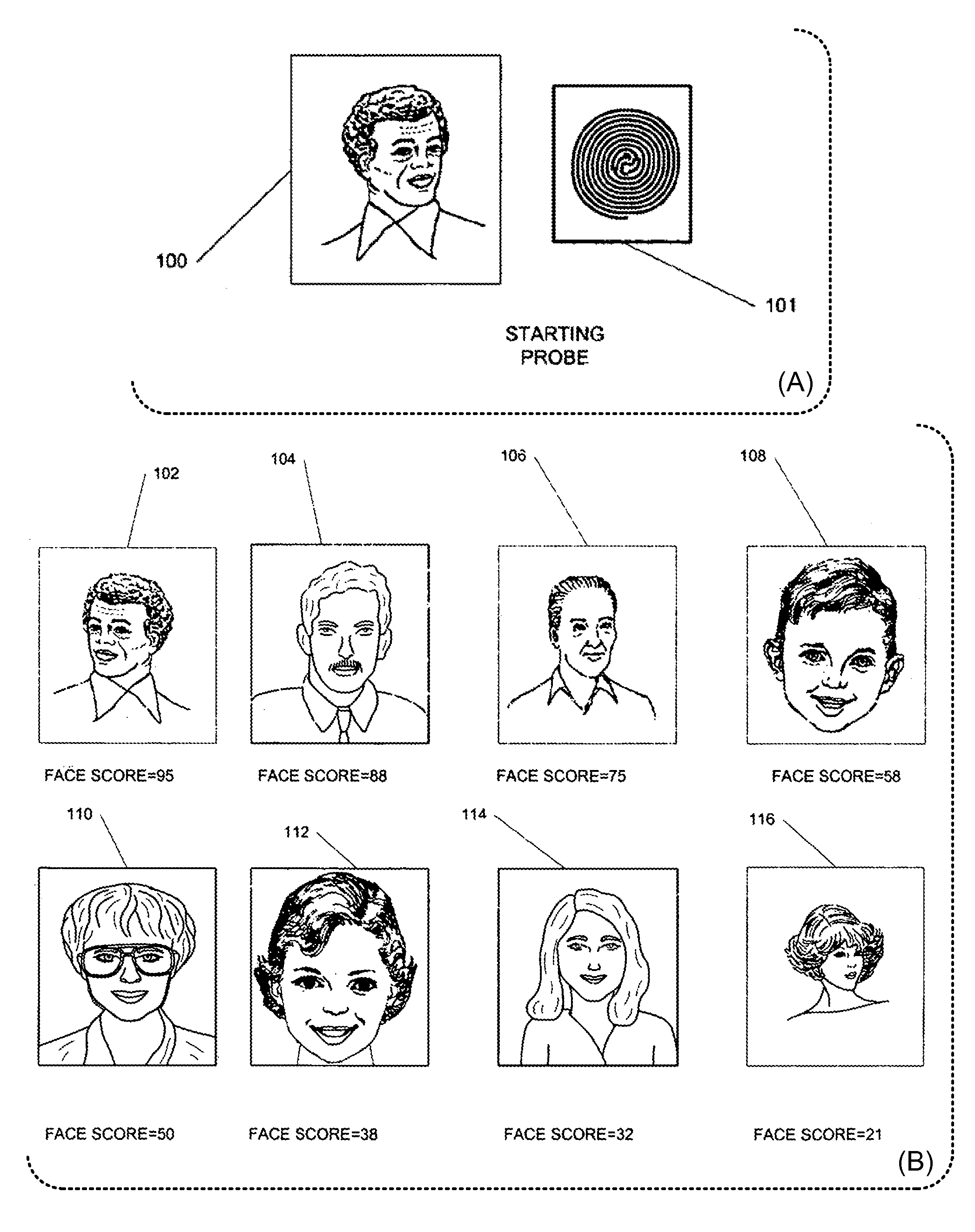
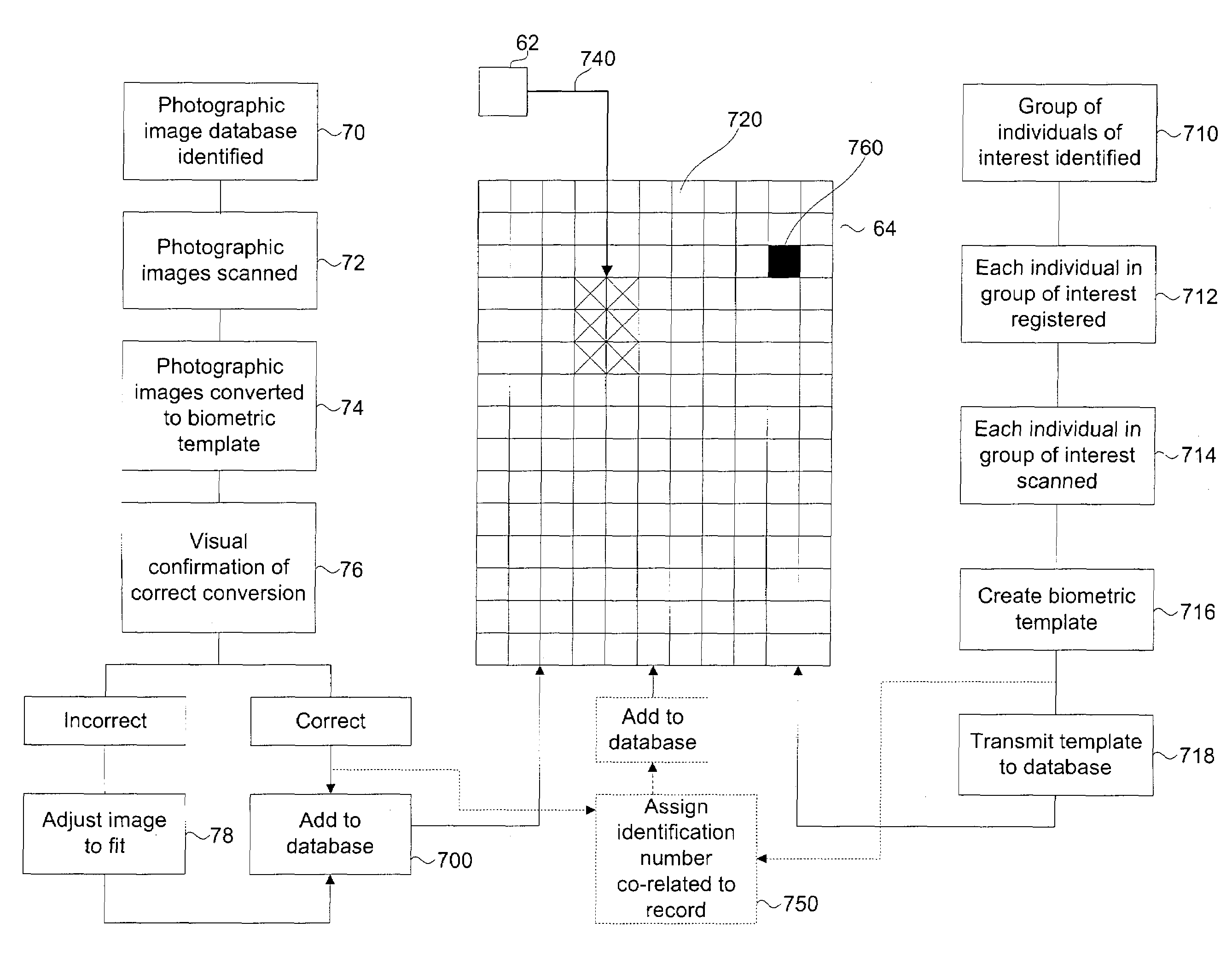
Secure system for the identification of persons using remote searching of facial, iris and voice biometric templates
InactiveUS7225338B2Cost-effective informationTime cost-effectiveDigital data information retrievalDigital data processing detailsConfidence intervalThe Internet
A system and method that permits a plurality of clients to remotely search and share biometric information contained in single or a plurality of databases over a local area network, wide area network or public network such as the Internet. The system comprises one ore more remote workstations each having a camera and means for converting facial images of persons of interest to biometric templates. A biometric search query may be placed from the remote workstation to one or more searchable databases containing a plurality of biometric templates. The databases are connected to the workstation by communication means through a server that manages data traffic between the remote workstation and the database. A search engine compares the biometric template of the person of interest to those stored on the database(s) and indicates a match according to a predetermined confidence interval. A predetermined number of matches are prioritized in order of similarity to the person of interest and returned to the workstation for review.
Owner:KHAN SAL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com