Patents
Literature
68 results about "Net-centric" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Net-centric or netcentric refers to participating as a part of a continuously-evolving, complex community of people, devices, information and services interconnected by a communications network to achieve optimal benefit of resources and better synchronization of events and their consequences.
Method and apparatus for a web-based application service model for security management
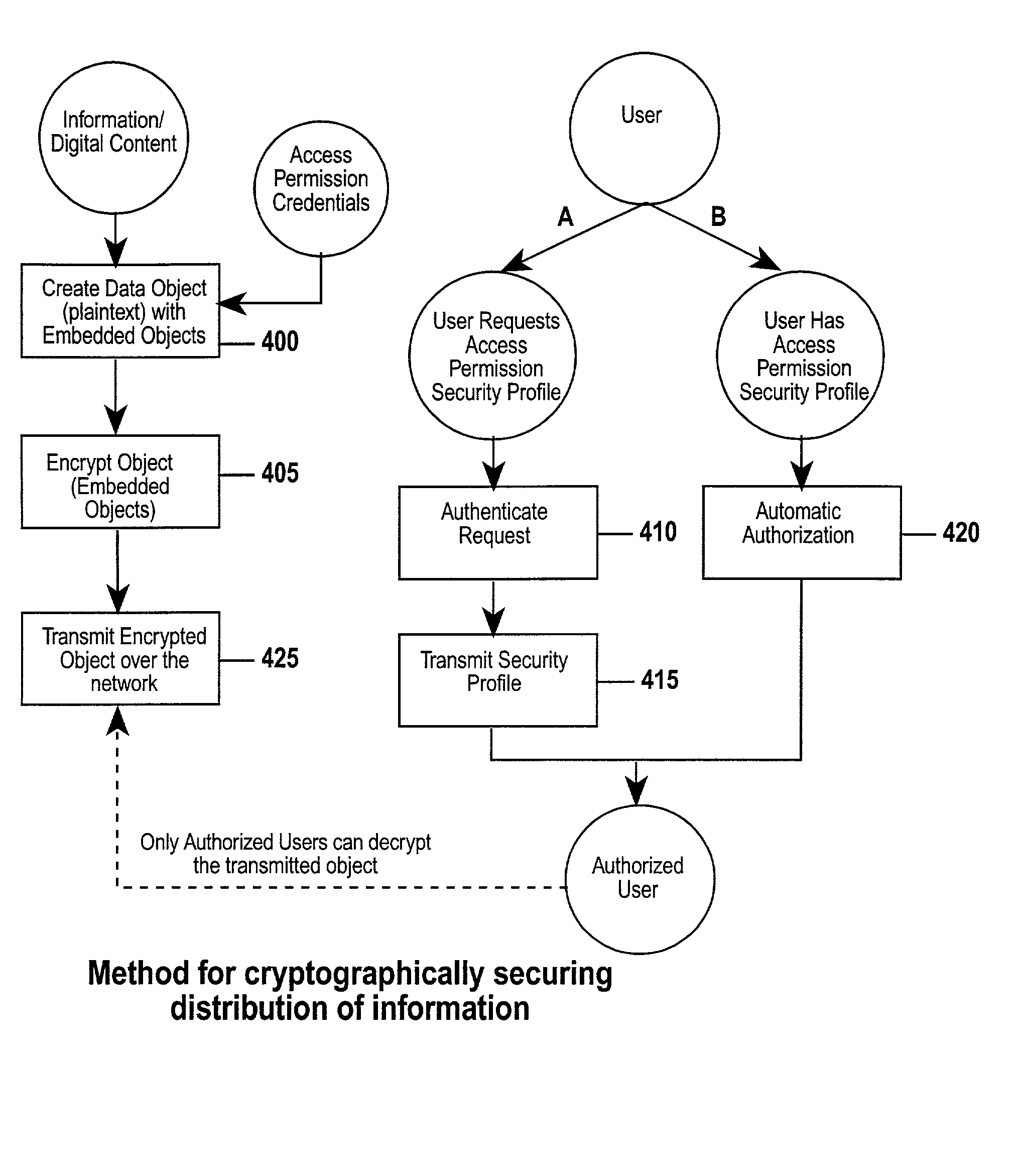
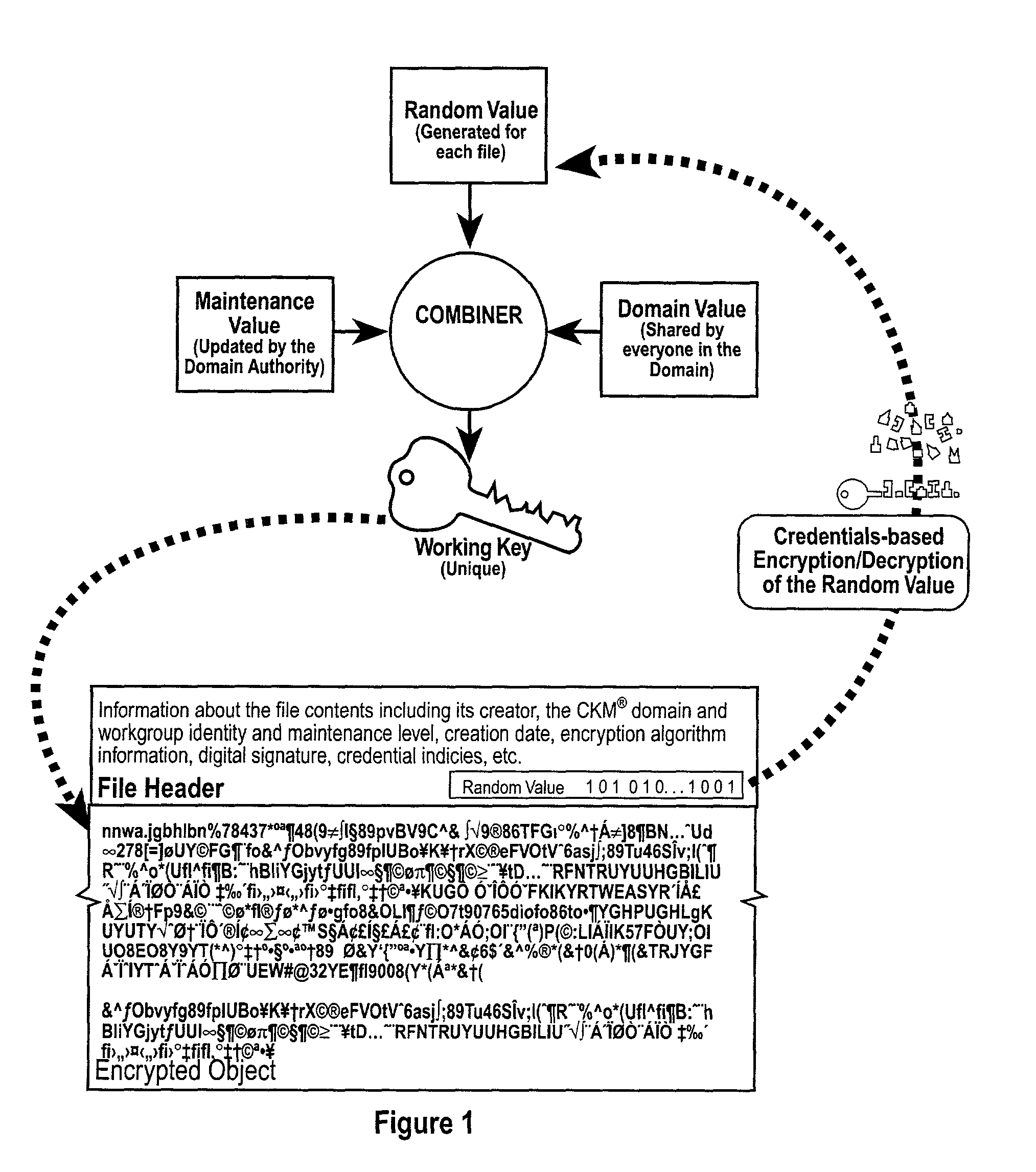
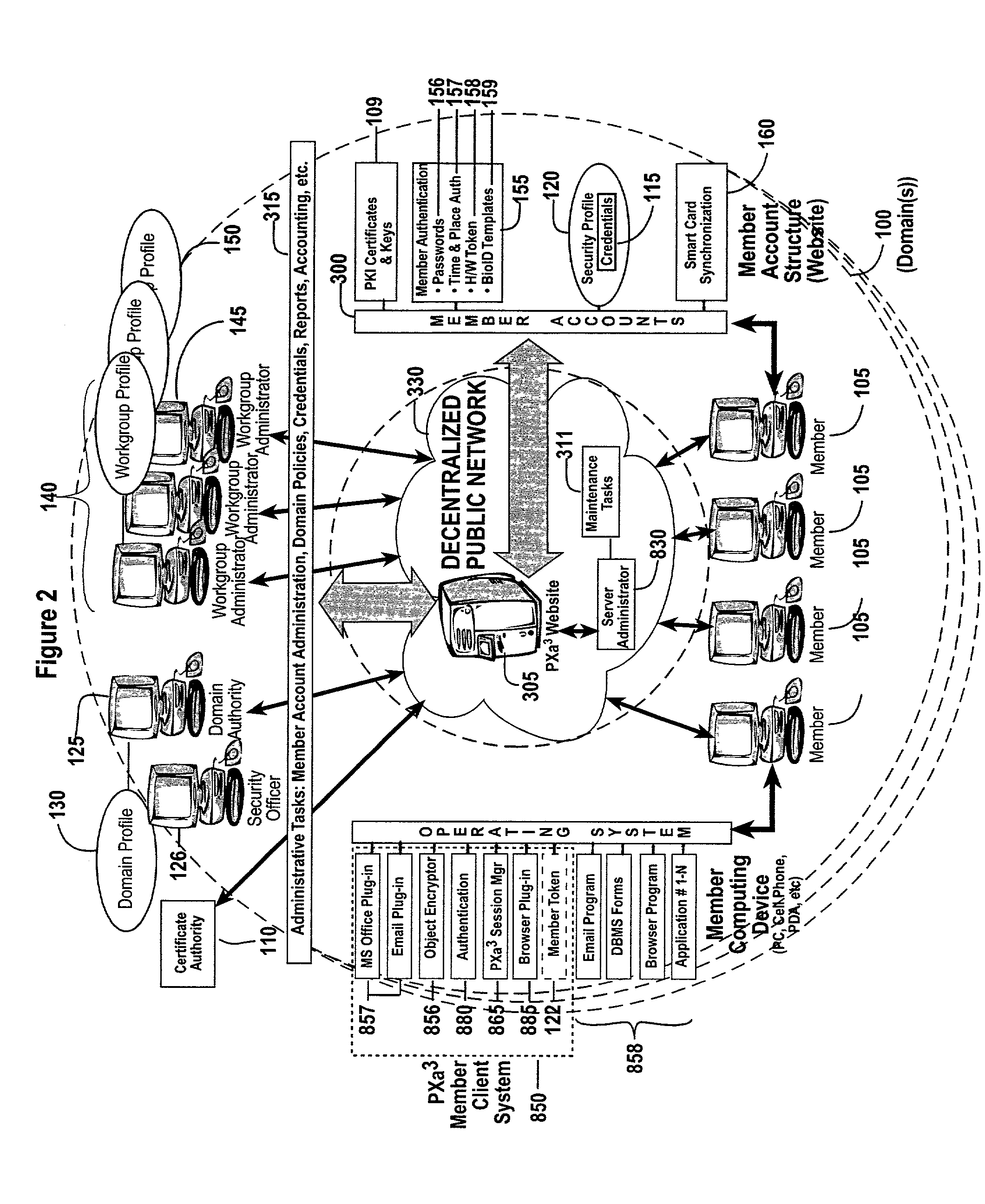
The invention combines cryptographic key management technology with various authentication options and the use of a companion PKI system in a web-centric cryptographic key management security method and apparatus called PXa3(TM) (Precise eXtensible Authentication, Authorization and Administration). The PXa3 model uses a security profile unique to a network user and the member domain(s) he / she belongs to. A PXa3 server holds all private keys and certificates, the user's security profile, including credentials and the optional authentication enrollment data. The server maintains a security profile for each user, and administrators simply transmitted credential updates and other periodic maintenance updates to users via their PXa3 server-based member accounts. Domain and workgroup administrators also perform administrative chores via a connection to the PXa3 web site, rather than on a local workstation. A member's security profile, containing algorithm access permissions, credentials, domain and maintenance values, a file header encrypting key, optional biometric templates, and domain-specific policies is contained in one of two places: either on a removable cryptographic token (e.g., a smart card), or on a central server-based profile maintained for each member and available as a downloadable "soft token" over any Internet connection.
Owner:SIVAULT INC
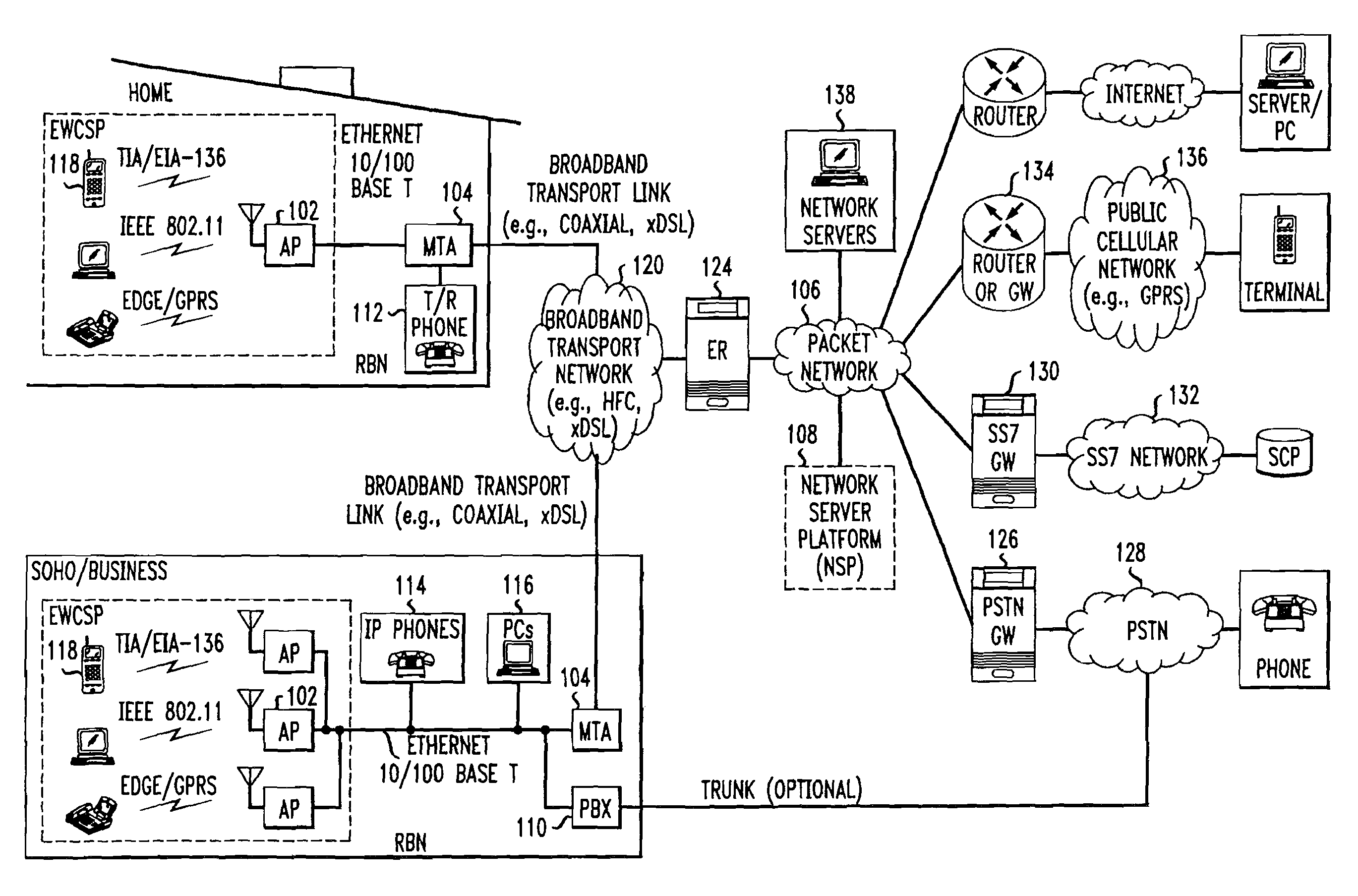
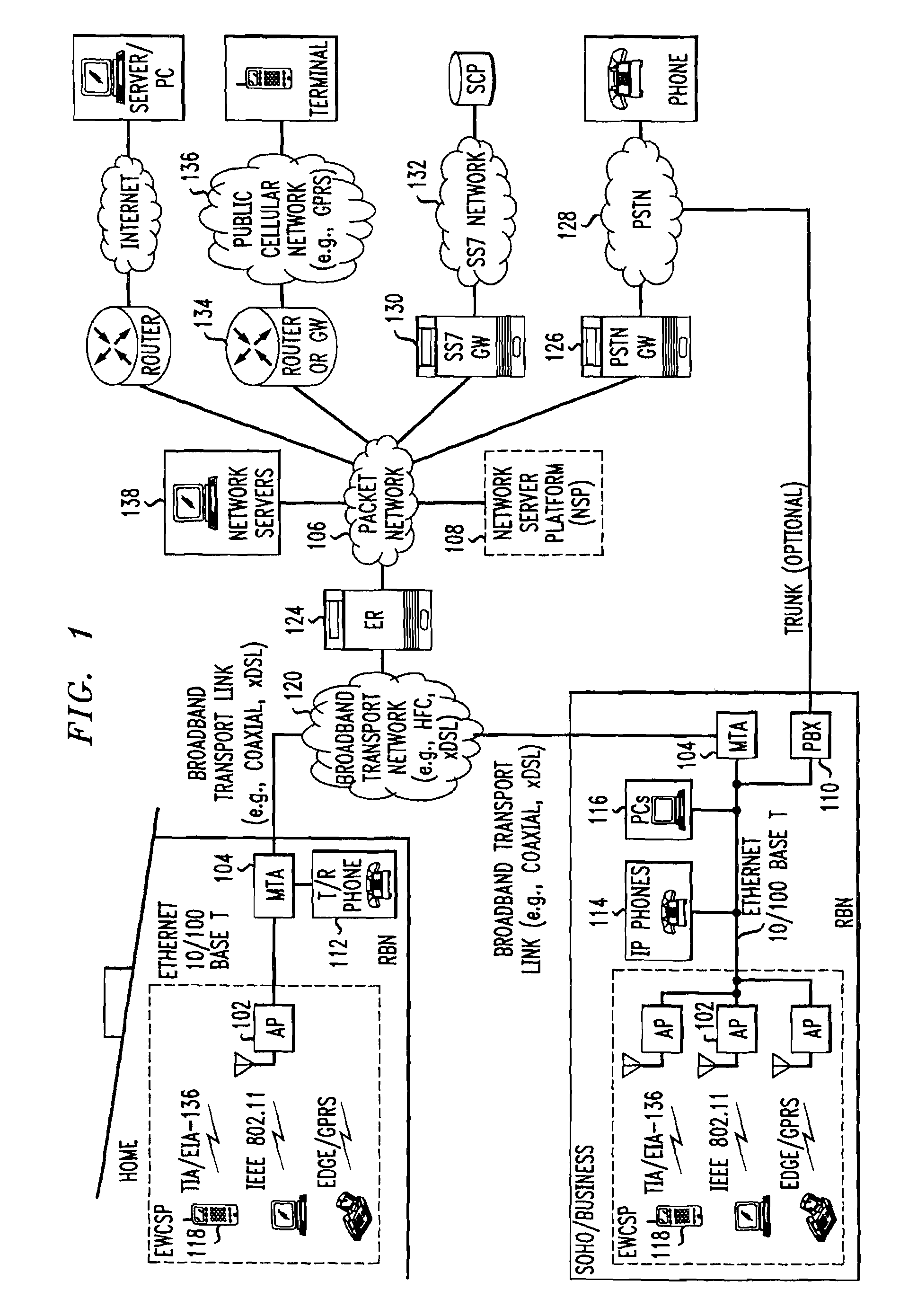
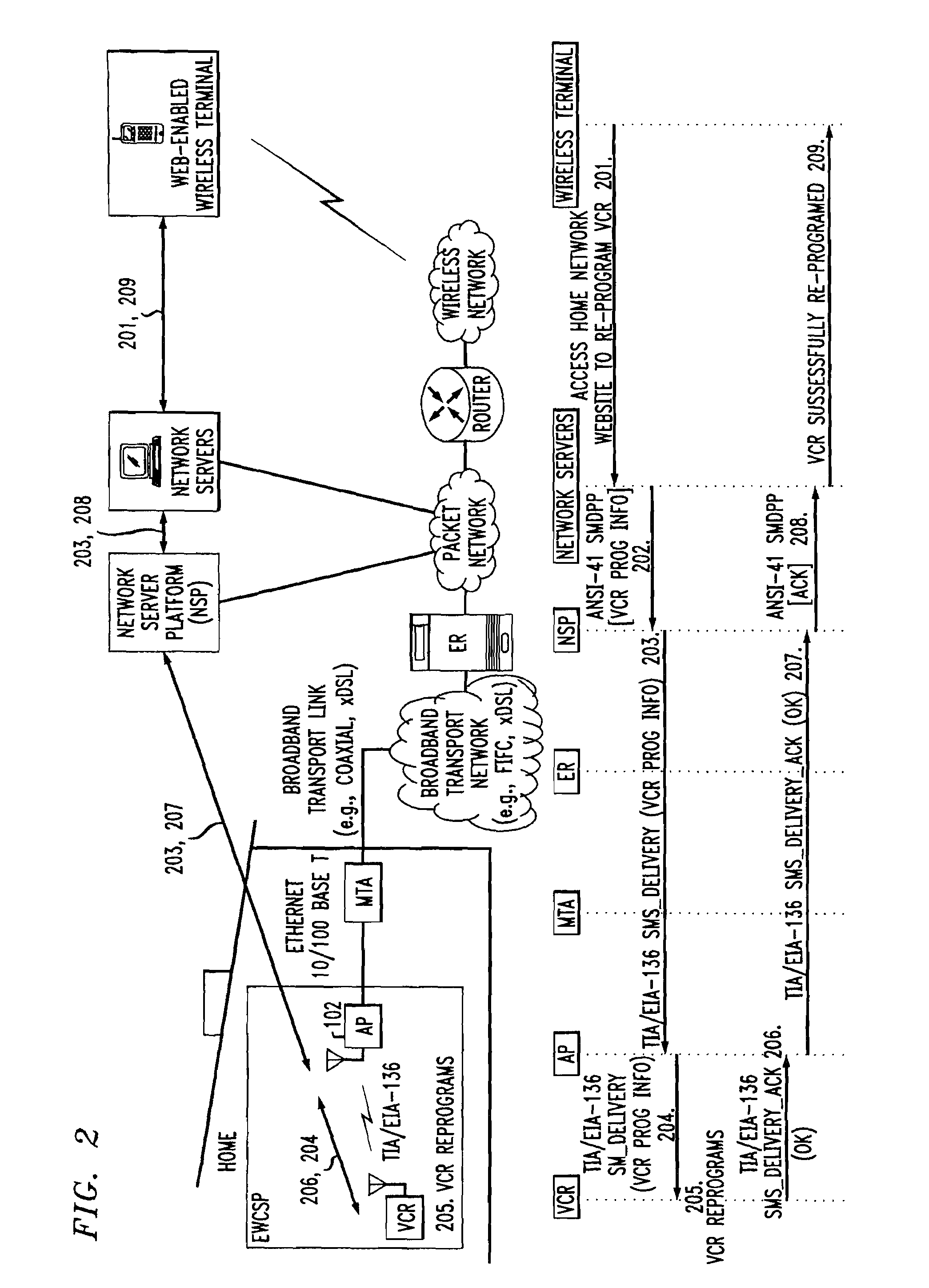
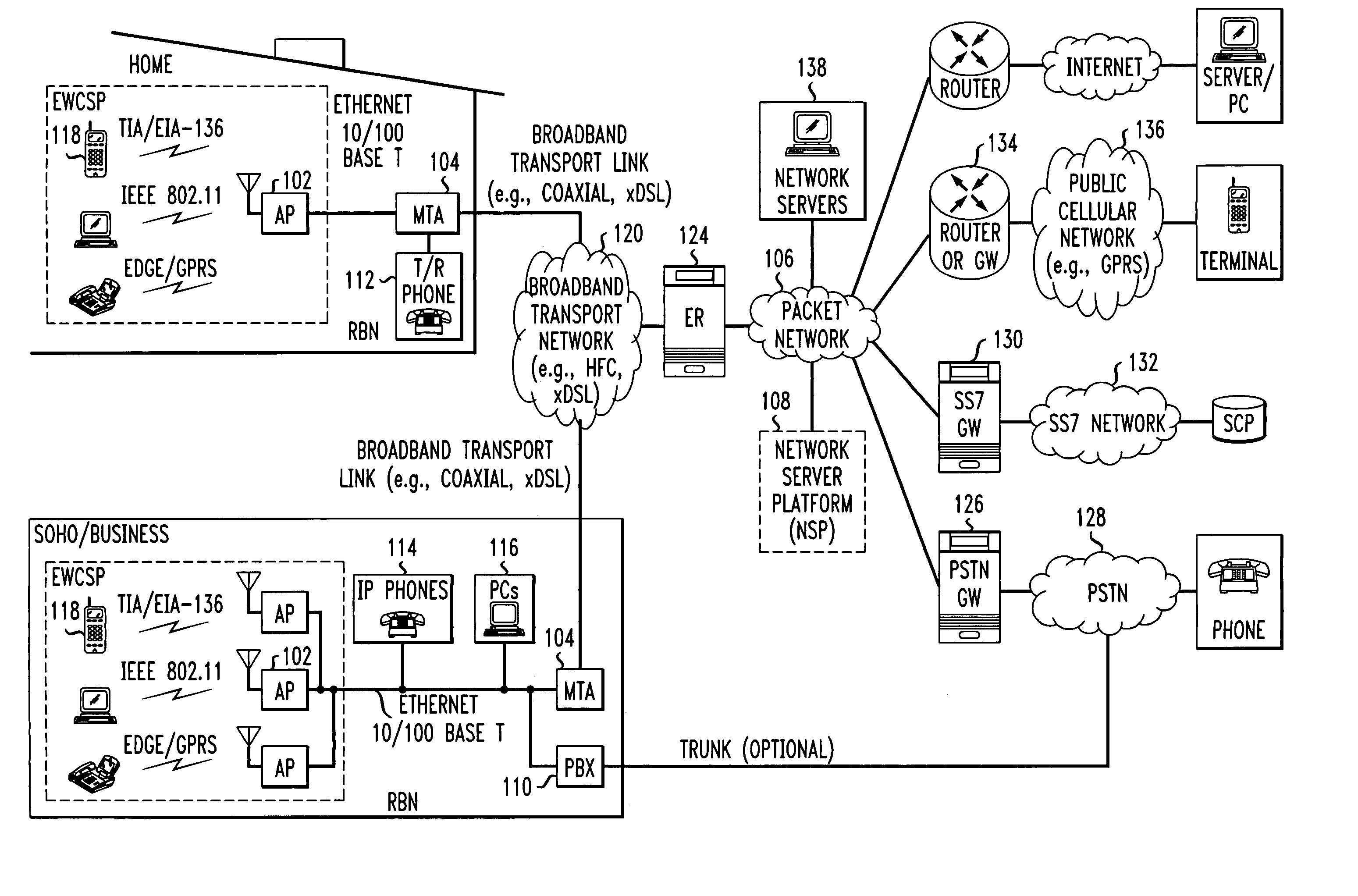
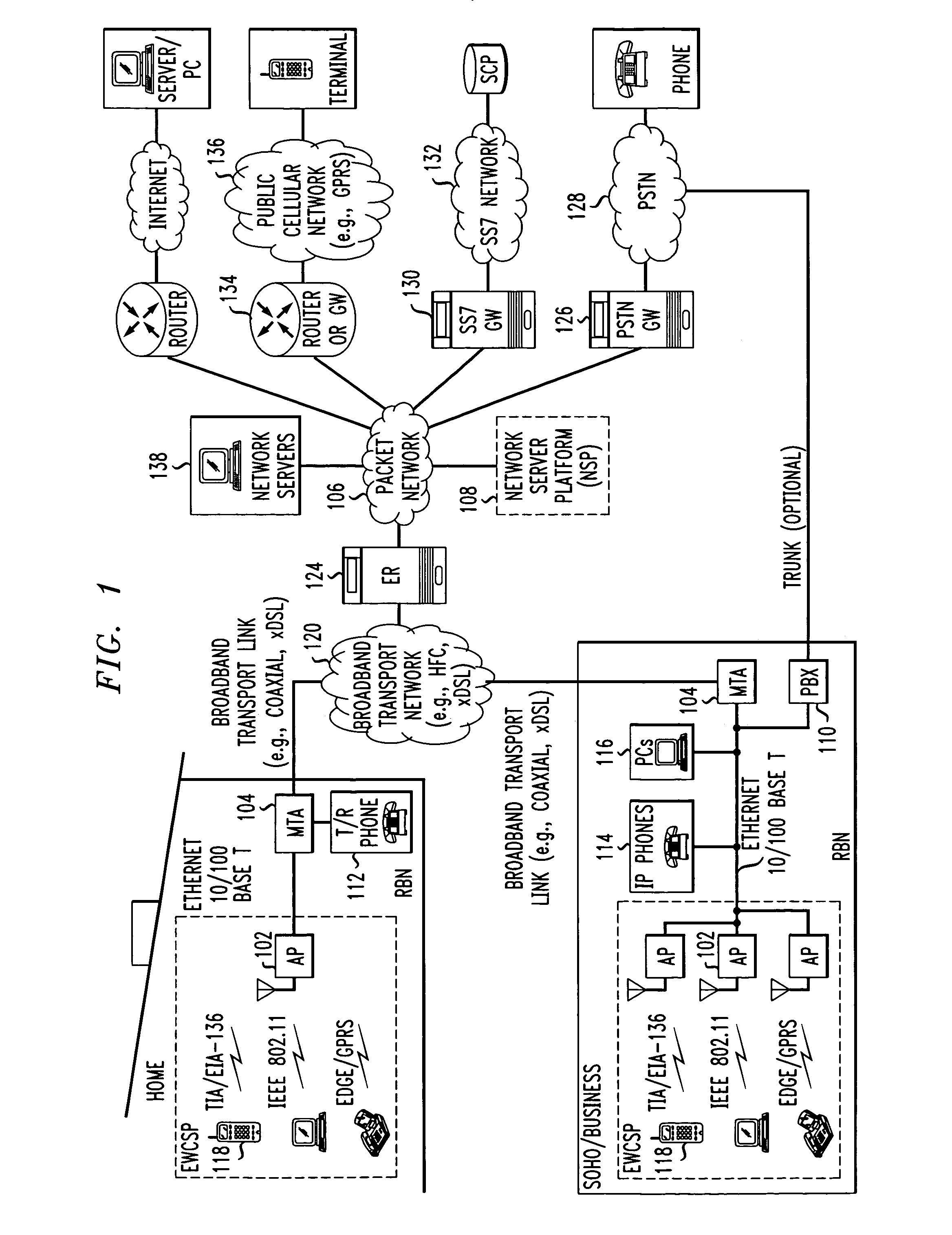
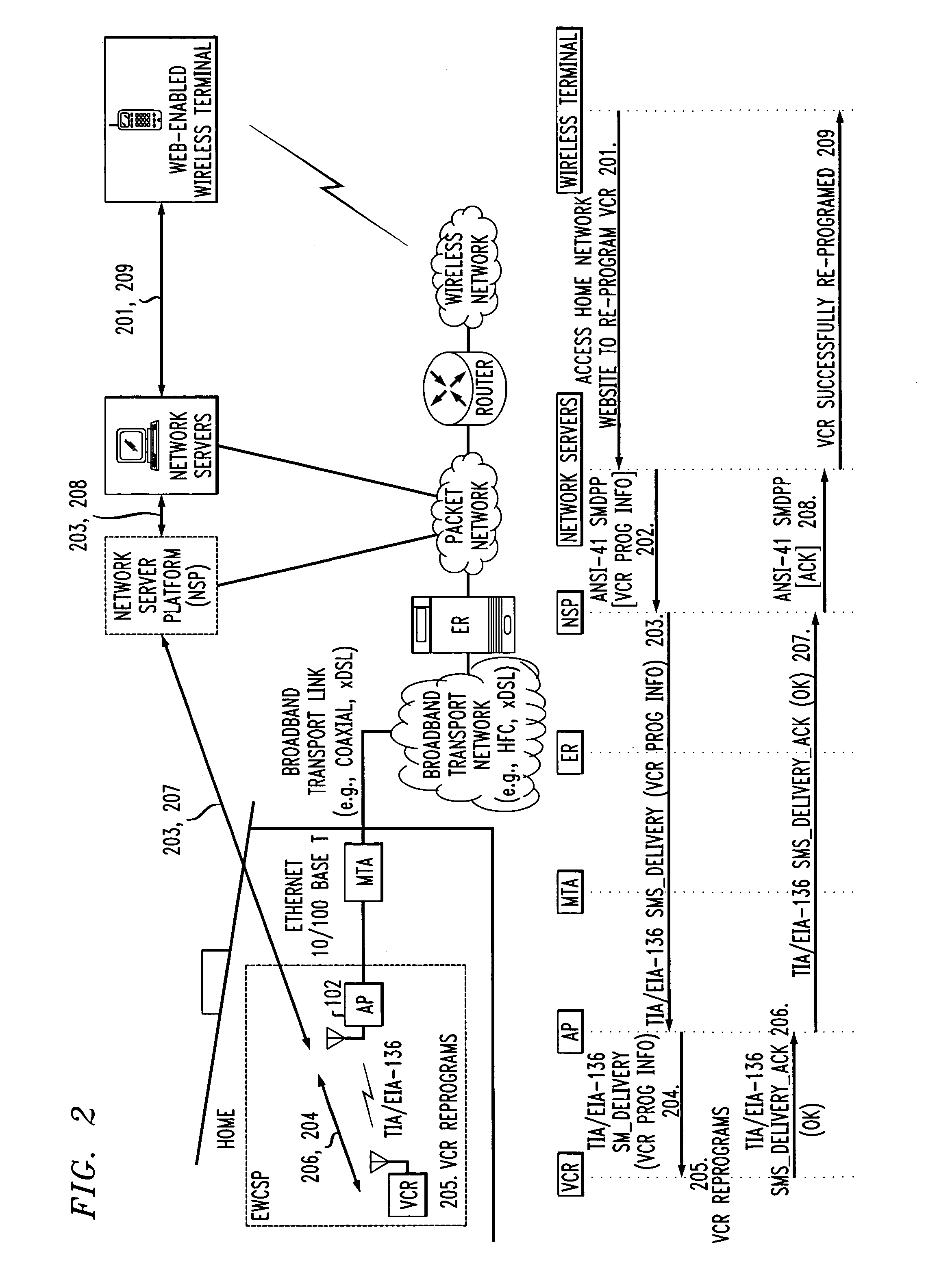
Computer readable medium with embedded instructions for providing communication services between a broadband network and an enterprise wireless communication platform within a residential or business environment
InactiveUS8155155B1Easy maintenanceCost-effectivelyError preventionFrequency-division multiplex detailsModem deviceBroadband transmission
The present invention sets forth computer-readable non-transitory medium having computer-executable instructions for providing network-centric service distribution method that integrates a wireless access system / service with conventional telecommunications services in the residence, SOHO, business or public environment through the use of a local broadband network, such as a Residential-Business Broadband Network (RBN). The RBN communicates with the service provider's broadband transport network and broadband packet network to facilitate end-to-end packet telecommunication services. Signals from a plurality of wireless devices are accepted and forwarded to an IEEE 802.11b interface for a wireless modem and / or to an Ethernet interface for a Voice over Internet Protocol (VOIP) / Ethernet Processor, where the forwarded signals comprise intranet telephony and data.
Owner:AT & T INTPROP II LP
Broadband network with enterprise wireless communication method for residential and business environment
InactiveUS7010002B2Easy to optimizeCost-effective deploymentMultiplex system selection arrangementsTelephone data network interconnectionsModem deviceBroadband transmission
The present invention sets forth a network-centric service distribution architecture and method that integrates a wireless access system / service in the residence, SOHO, business or public environment through the use of a local broadband network, such as a Residential-Business Broadband Network (RBN), to the service provider's broadband transport network and to a service provider's broadband packet network that facilitates end-to-end packet telecommunication services. Access functions for connecting said service provider's broadband packet network to the RBN via said service provider's broadband transport network are provided. Call and service termination functions to a plurality of local RBN devices are also provided. Signals from a plurality of wireless devices are accepted and forwarded to an IEEE 802.11b interface for a wireless modem and / or to an Ethernet interface for a Voice over Internet Protocol (VOIP) / Ethernet Processor, where the forwarded signals comprise intranet telephony and data. Voice signals are also accepted from a plurality of tip / ring interfaces and forwarded to a broadband transport interface for back haul of data and voice packets. A service provider can deploy services in an integrated voice, data and multimedia environment cost-effectively based on one broadband packet network.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
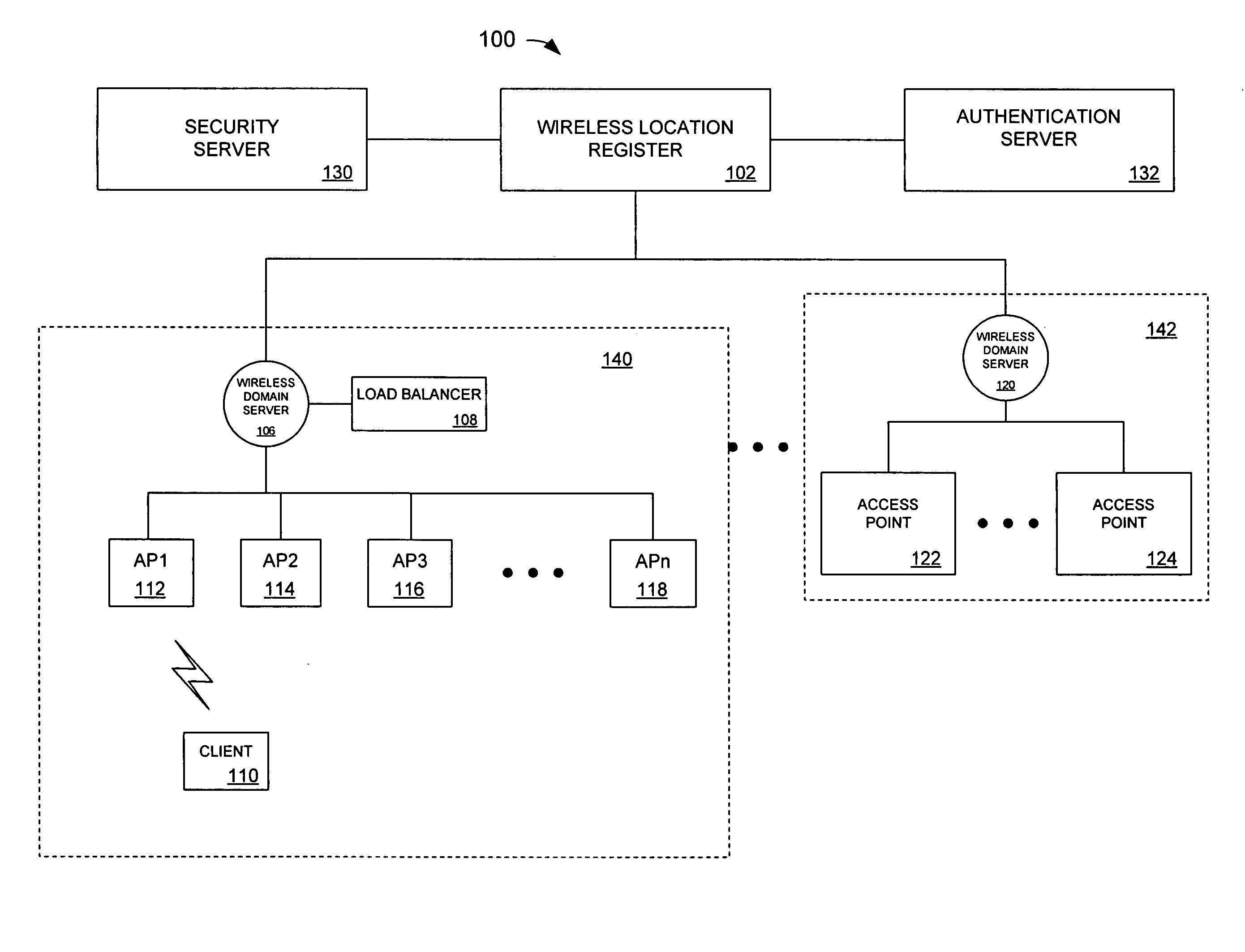
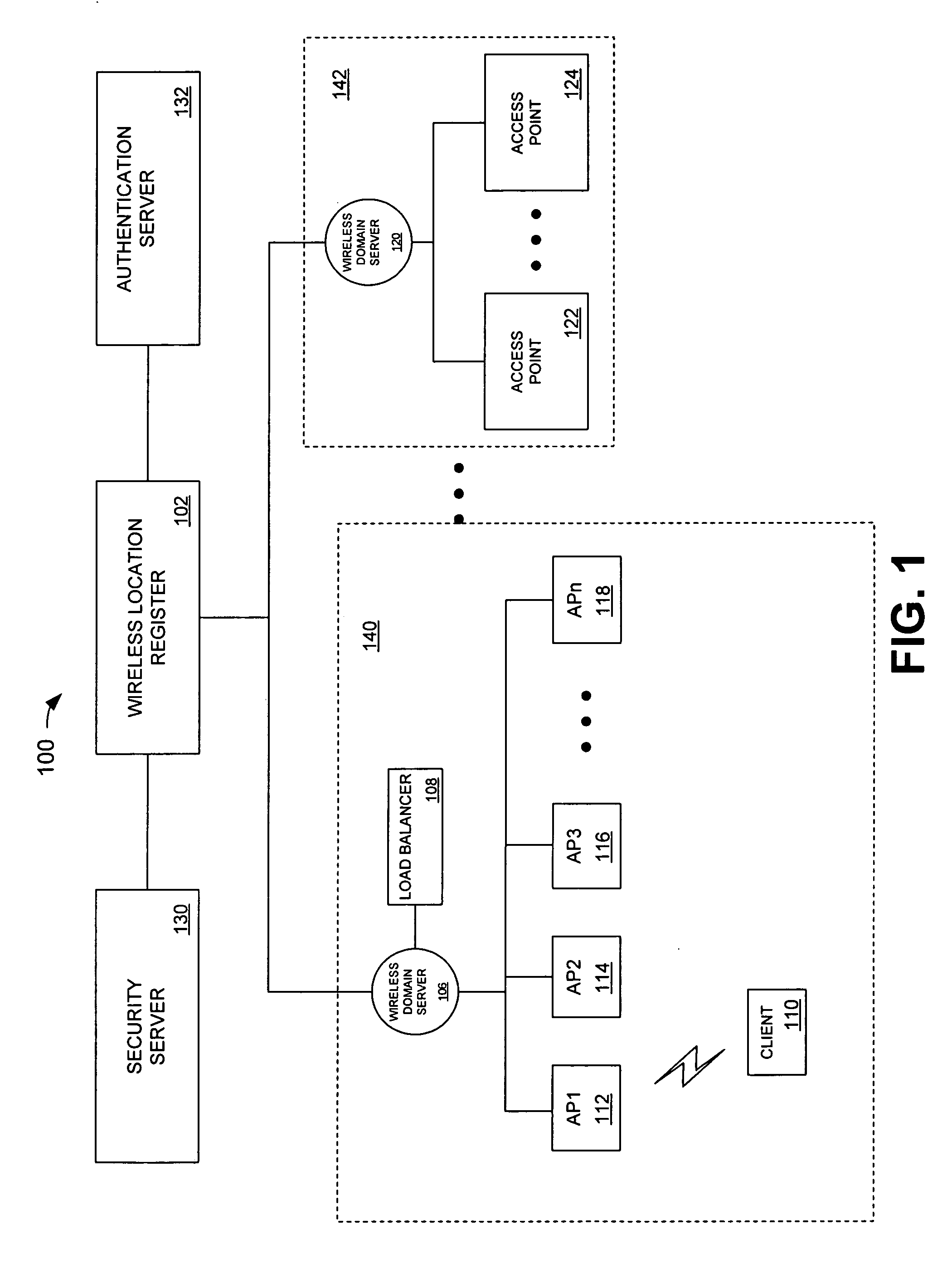
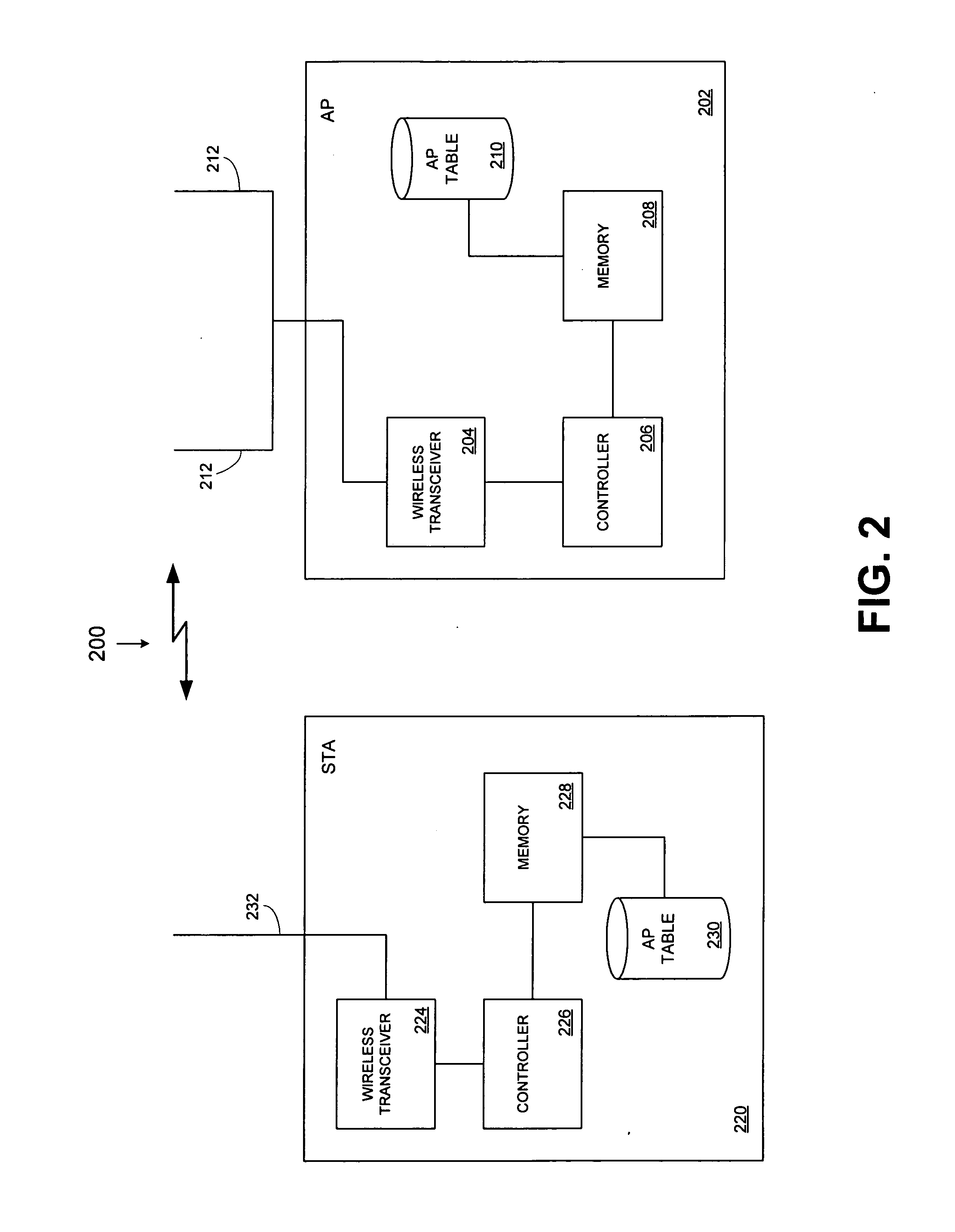
Method and system for filtered pre-authentication and roaming
InactiveUS20070082656A1Easy to manageUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunicationsClient-side
A system and method to manage the pre-authentication service by providing a network-centric, managed list of neighboring / logical access points from which a wireless station should pre-authenticate. An access point is provided with a pre-authentication table. When a wireless station associates with the access point, the access point transmits the pre-authentication table to the client. The client responsive to receiving the table only pre-authenticates with neighboring access points on the table.
Owner:CISCO TECH INC
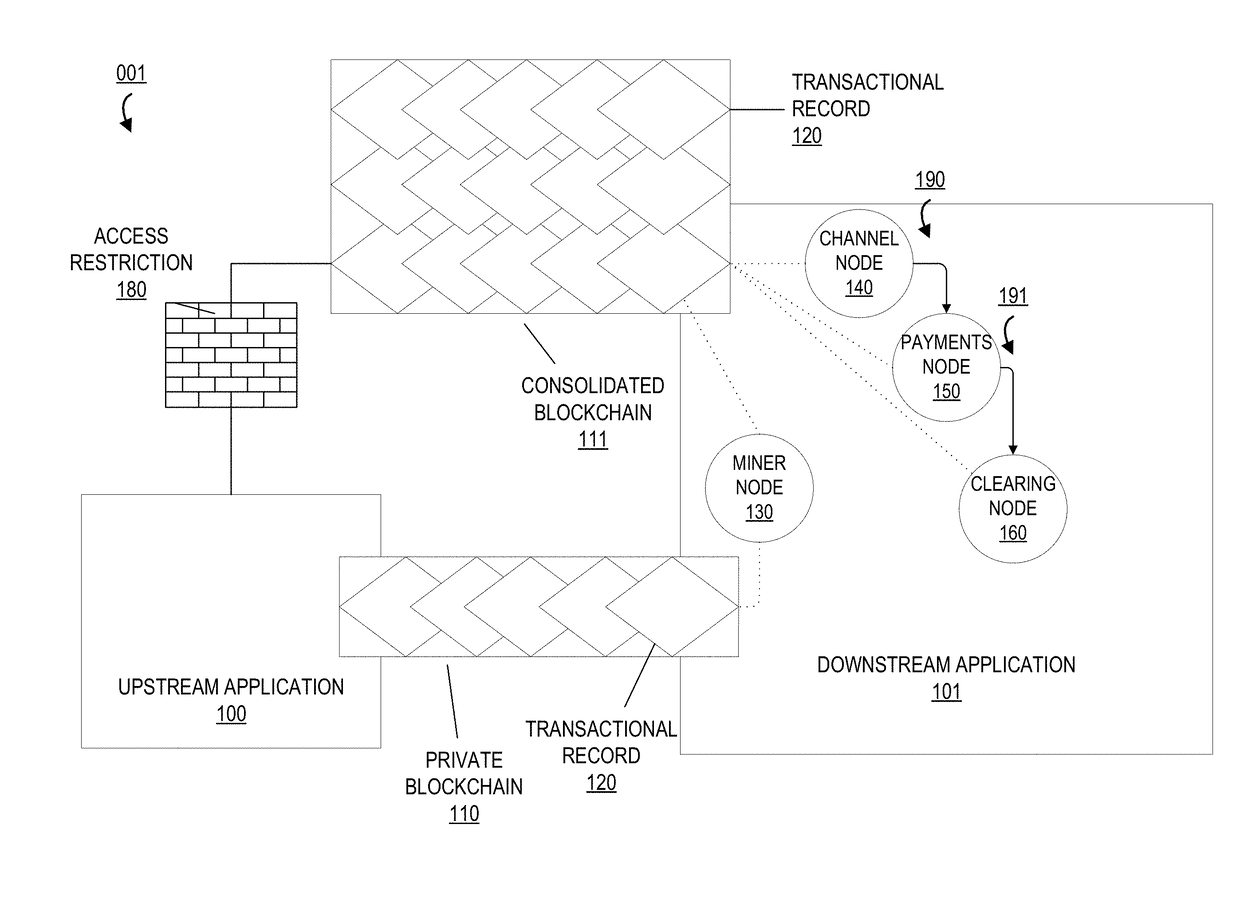
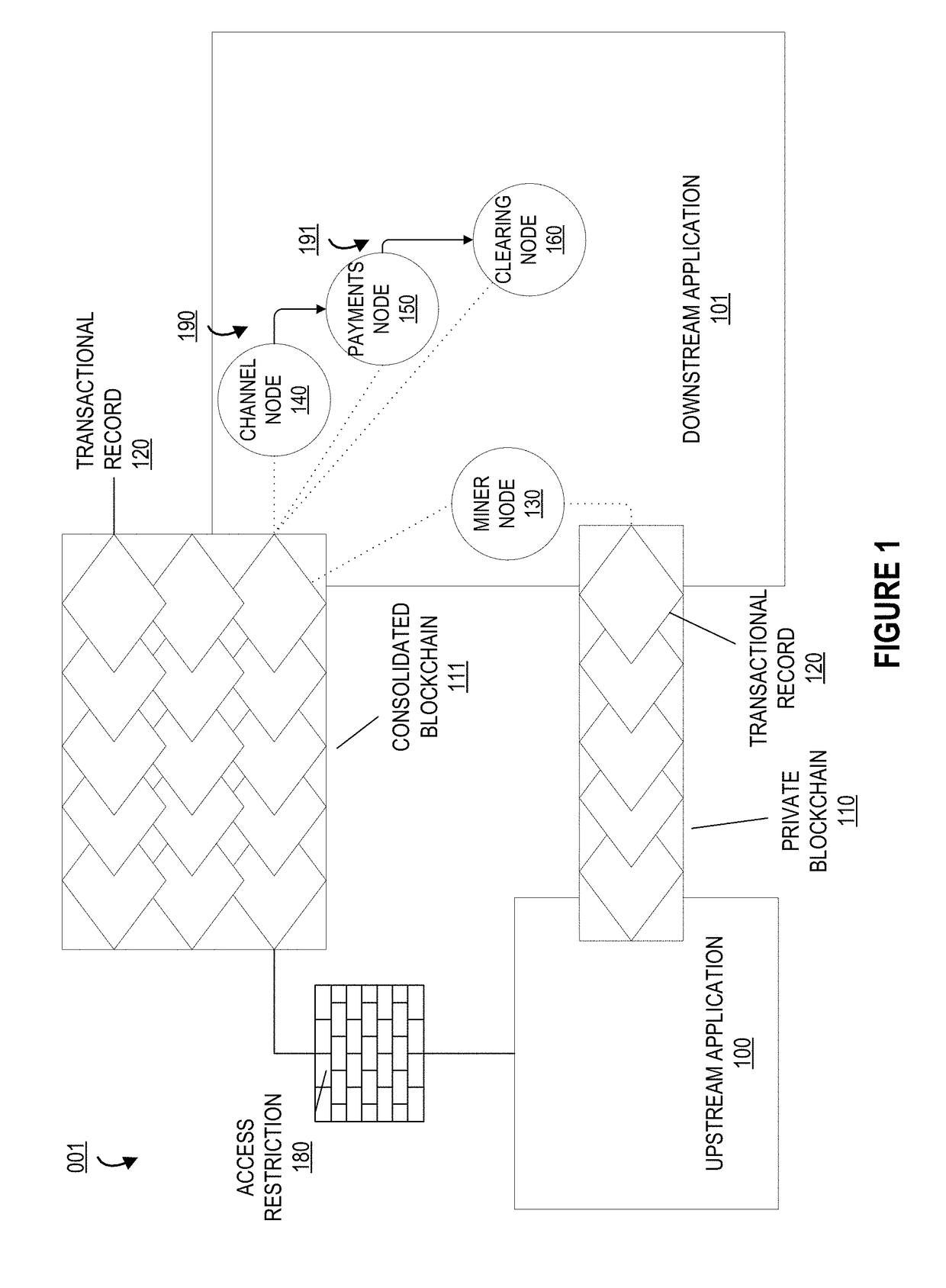
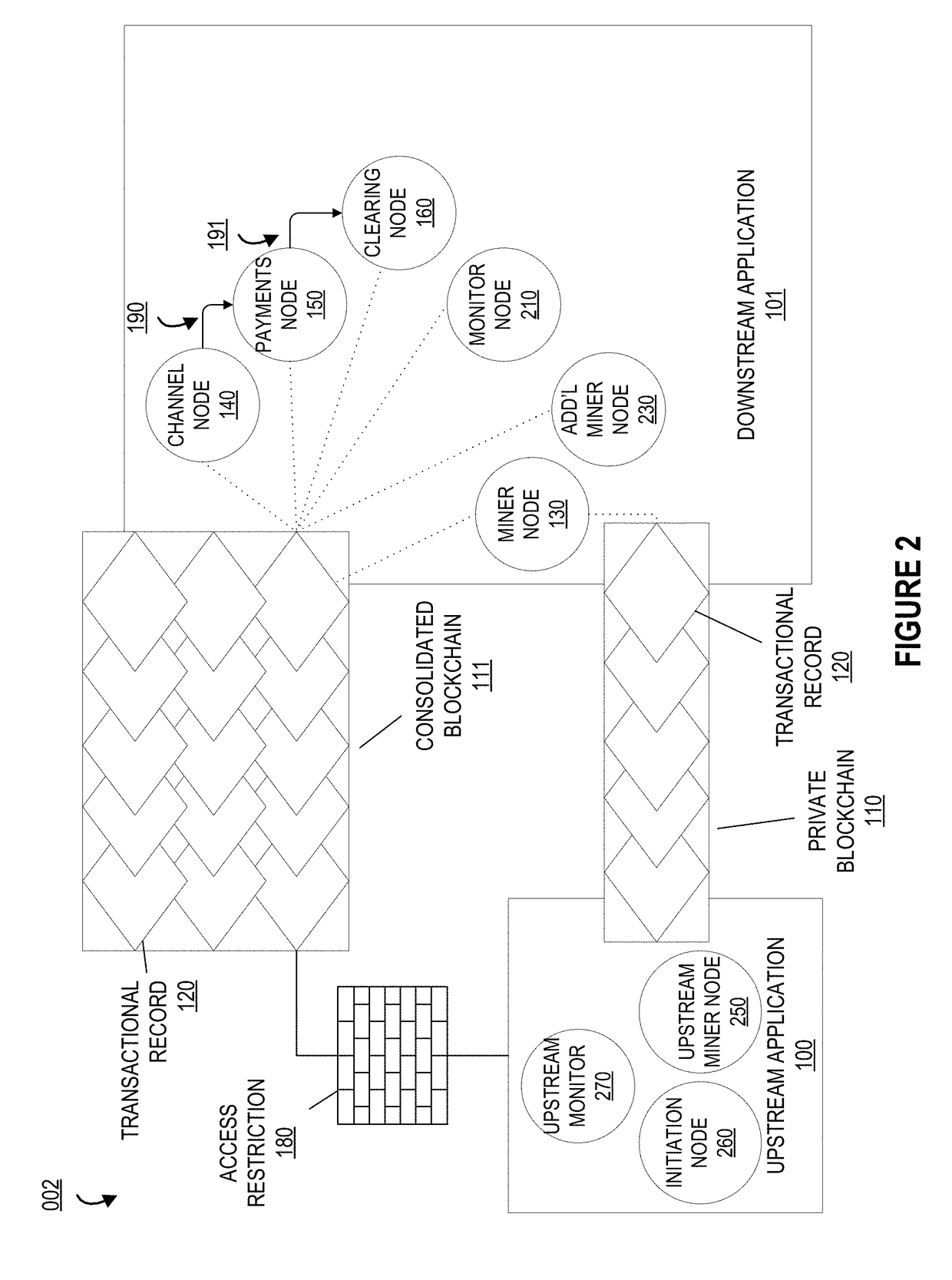
System for managing a virtual private ledger and distributing workflow of authenticated transactions within a blockchain distributed network
ActiveUS20180101848A1Well formedResource allocationCryptography processingAuthorizationOperating system
Embodiments of the present invention provide a system for expediting validation and authorization of transactions between end points. Embodiments of the invention utilize a private blockchain to control transaction workflow amongst compute nodes, provide automatic authorization of transactions in the workflow, and provide efficient record-keeping functions within the virtual ledgers in an upstream and a downstream application. By using a private distributed ledger in this manner, the system addresses the computer networking-centric challenge of processing transactions in a secure and efficient manner; avoiding desynchronization of data as well as preventing the need for authorization and confirmation requests amongst the nodes greatly reduces the amount of computing resources required to process transactions, including, but not limited to, processing power, memory space, storage space, cache space, electric power, networking bandwidth, and I / O calls.
Owner:BANK OF AMERICA CORP
Internet based product data management (PDM) system
InactiveUS6961687B1Defect informationImprove visibilityMultiple digital computer combinationsSound input/outputSystems designApplication software
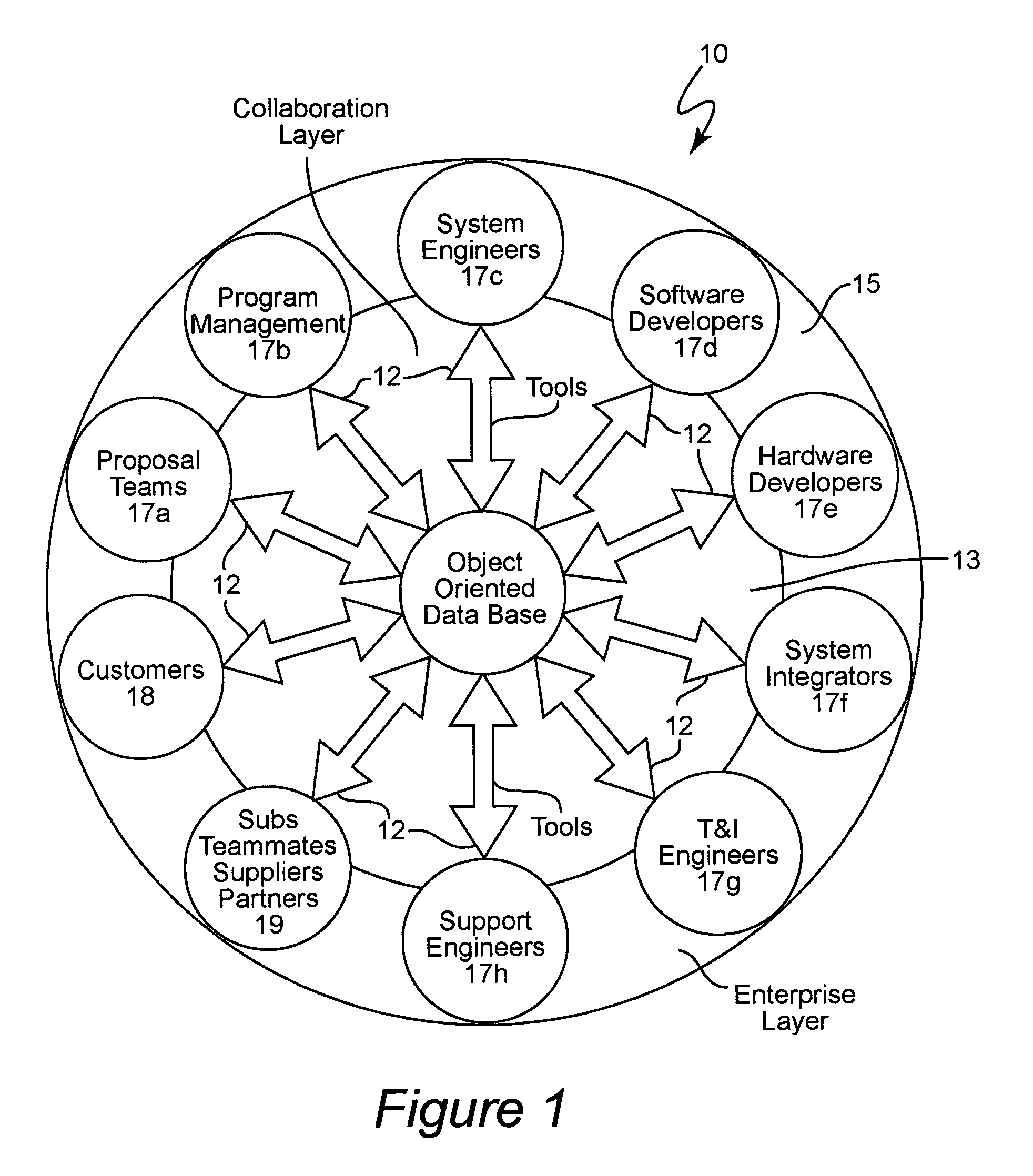
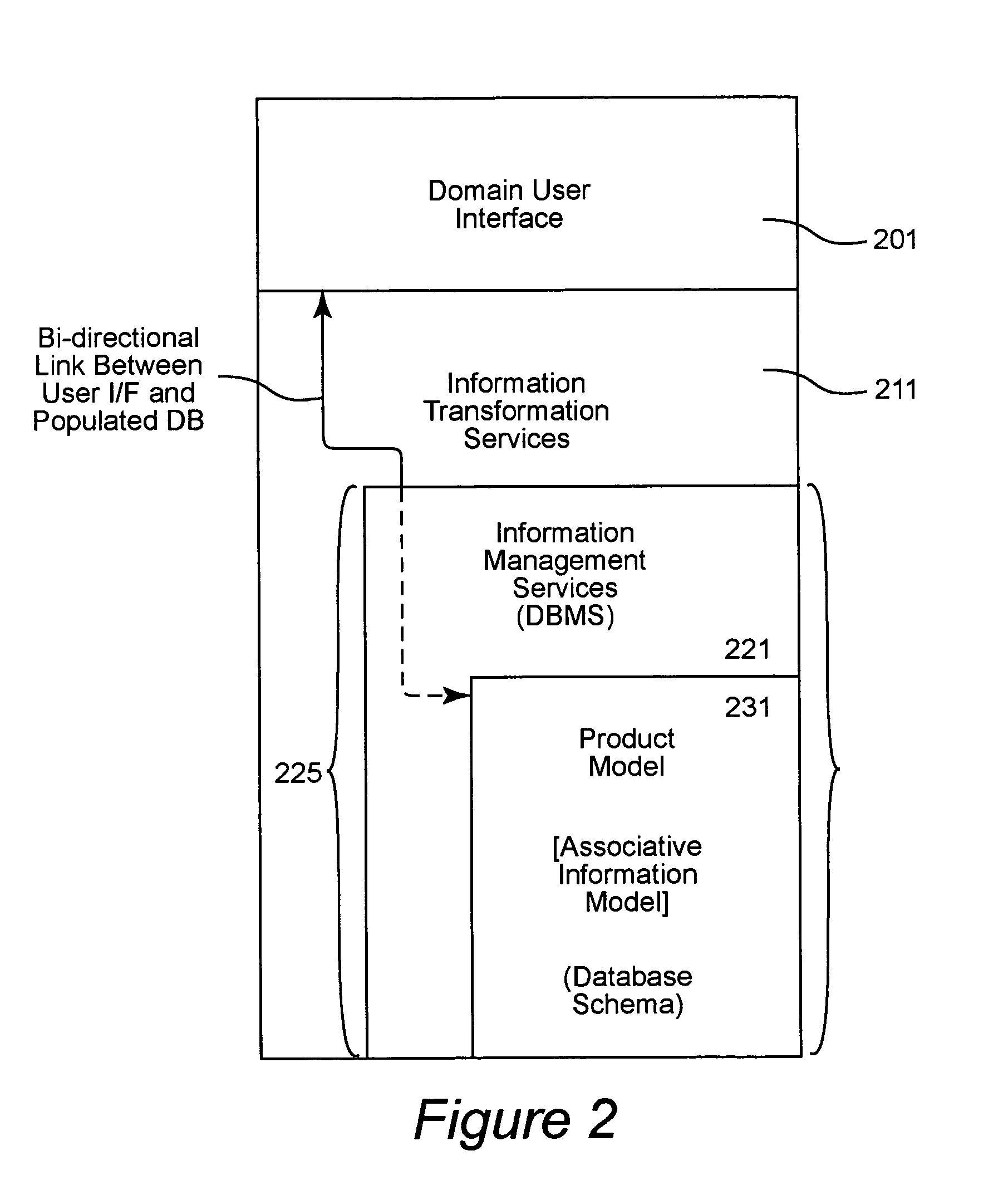
An integrated product data environment for system design and optimization, e.g., a Collaborative Engineering Environment (CEE). The CEE provides a multi-disciplinary engineering team with immediate access to all relevant product information. It is an enterprise system at the program as well as the company levels, managing product information as a program and corporate asset. Product-centric collaborative capabilities for the CEE are provided by extending the functionality of a commercial Product Data Management (PDM) System. Emerging web-centric commercial-off-tho-shelf (COTS) PDM capabilities, object-oriented technologies, associated rapid application development environments, sophisticated engineering toolsets, and COTS computing and communications technologies have been leveraged to establish the CEE for the complex electronic systems integration domain. The CEE offers substantial improvements in productivity, cost savings, cycle time reductions, product integrity and lifetime support of a system.
Owner:LOCKHEED MARTIN CORP
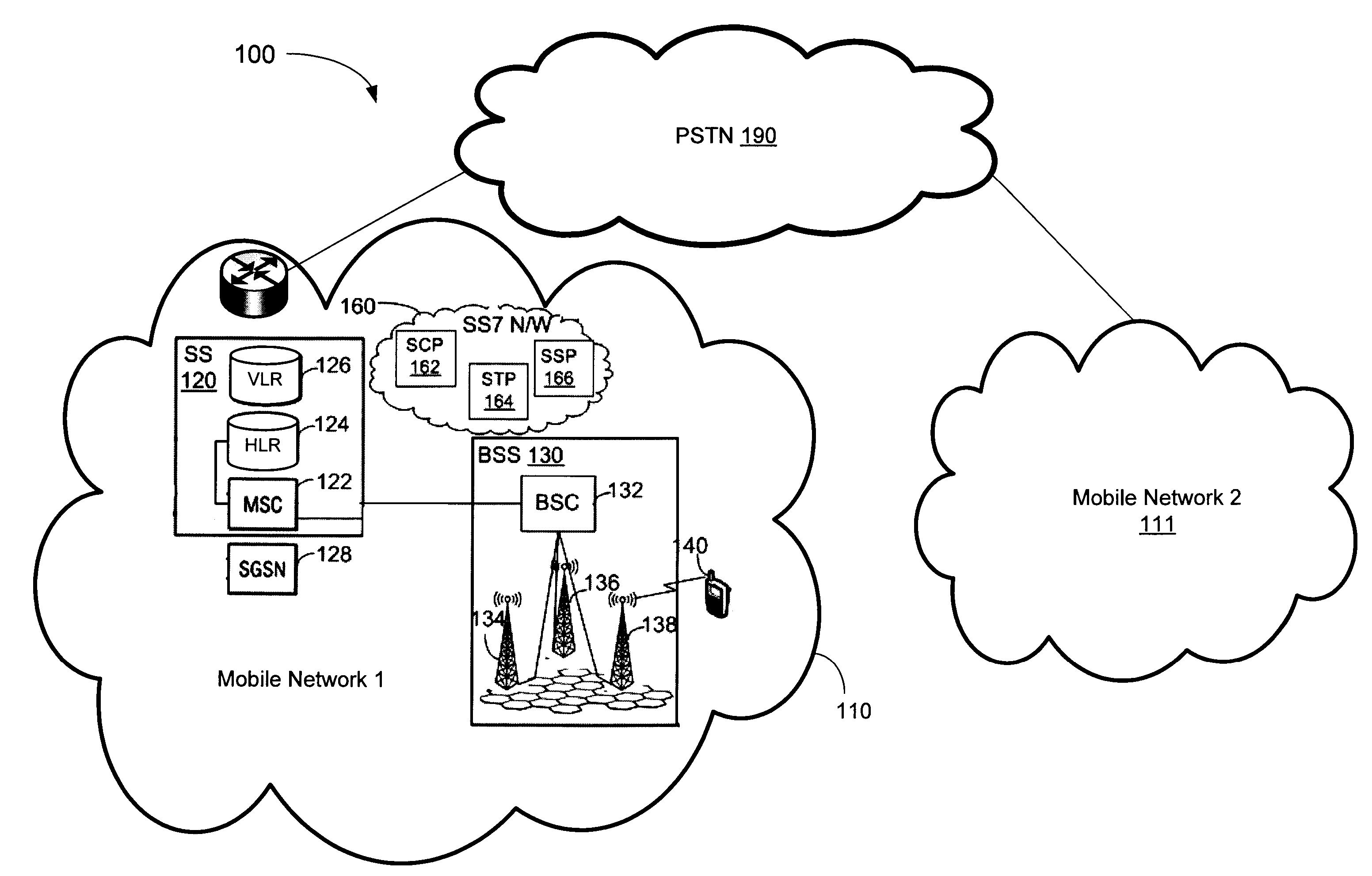
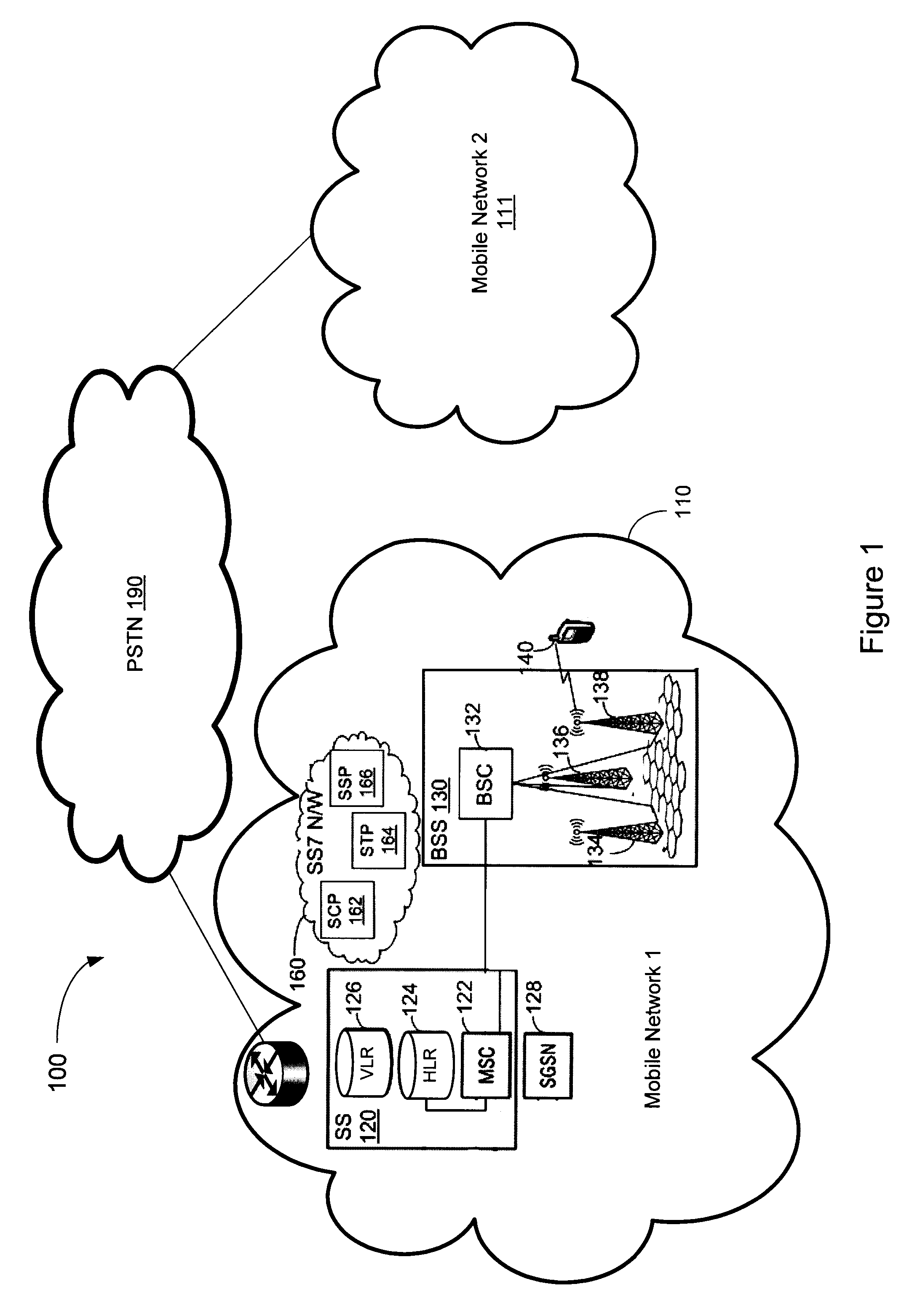
System, Method, and Computer-Readable Medium for Concurrent Termination of Multiple Calls at a Mobile Terminal
A system, method and computer-readable medium for allocating multiple subscriptions to a single mobile terminal thereby allowing concurrent termination of multiple calls at the mobile terminal are provided. A mobile terminal adapted to terminate multiple concurrent calls is described. In one implementation, a network need not have any configuration data regarding the multi-line capabilities of the mobile terminal. In other implementations, network-centric mechanisms are provided for allowing multiple concurrent calls to be terminated by a mobile terminal. Multiple concurrent calls may be terminated at a mobile terminal on separate carrier frequencies or alternatively may be terminated on a common carrier frequency.
Owner:TANGO NETWORKS
Adaptive network-centric online autonomic supply chain management system
InactiveUS20050154653A1Speeding up delivery/retrogradeIncrease supplyDigital data processing detailsResourcesMicrocontrollerOperational costs
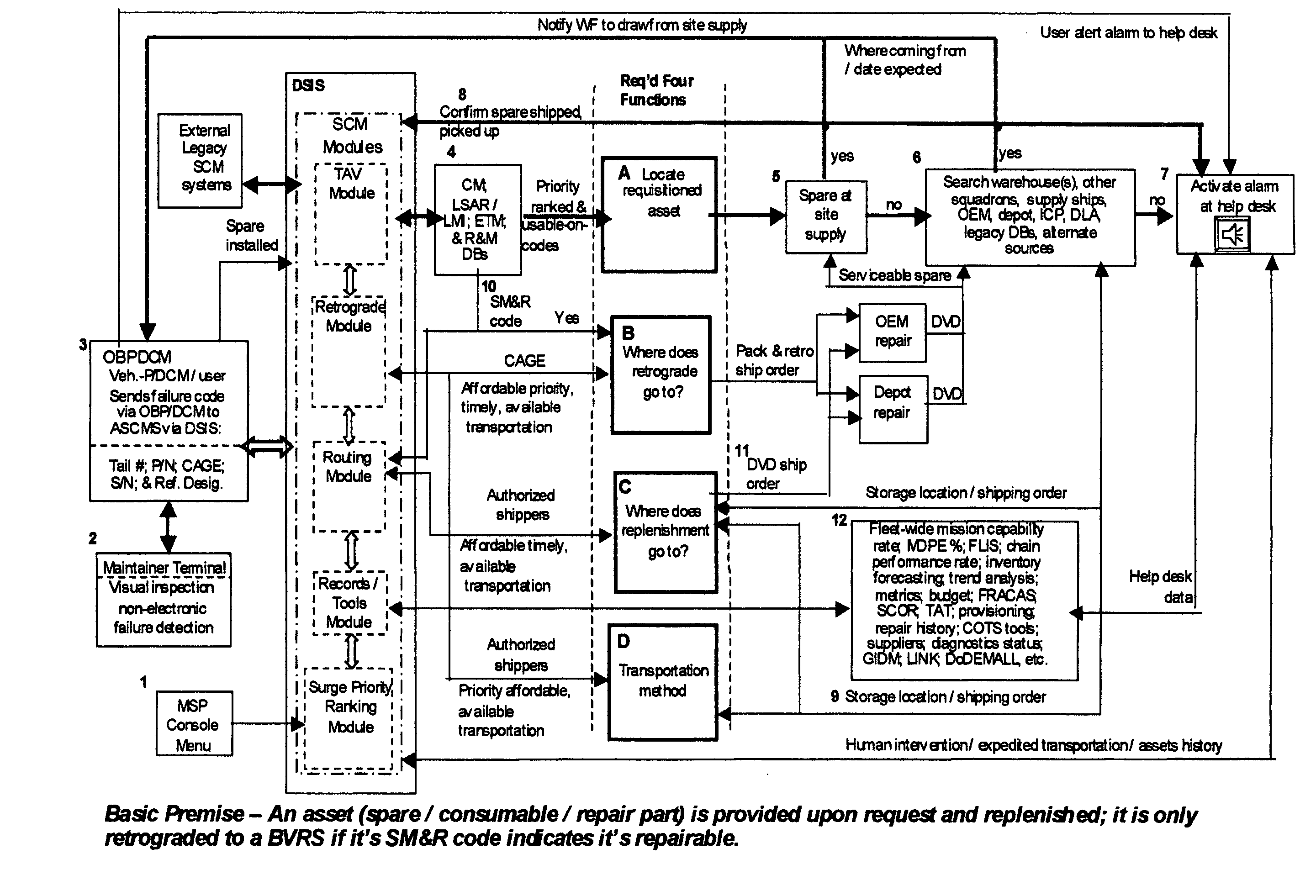
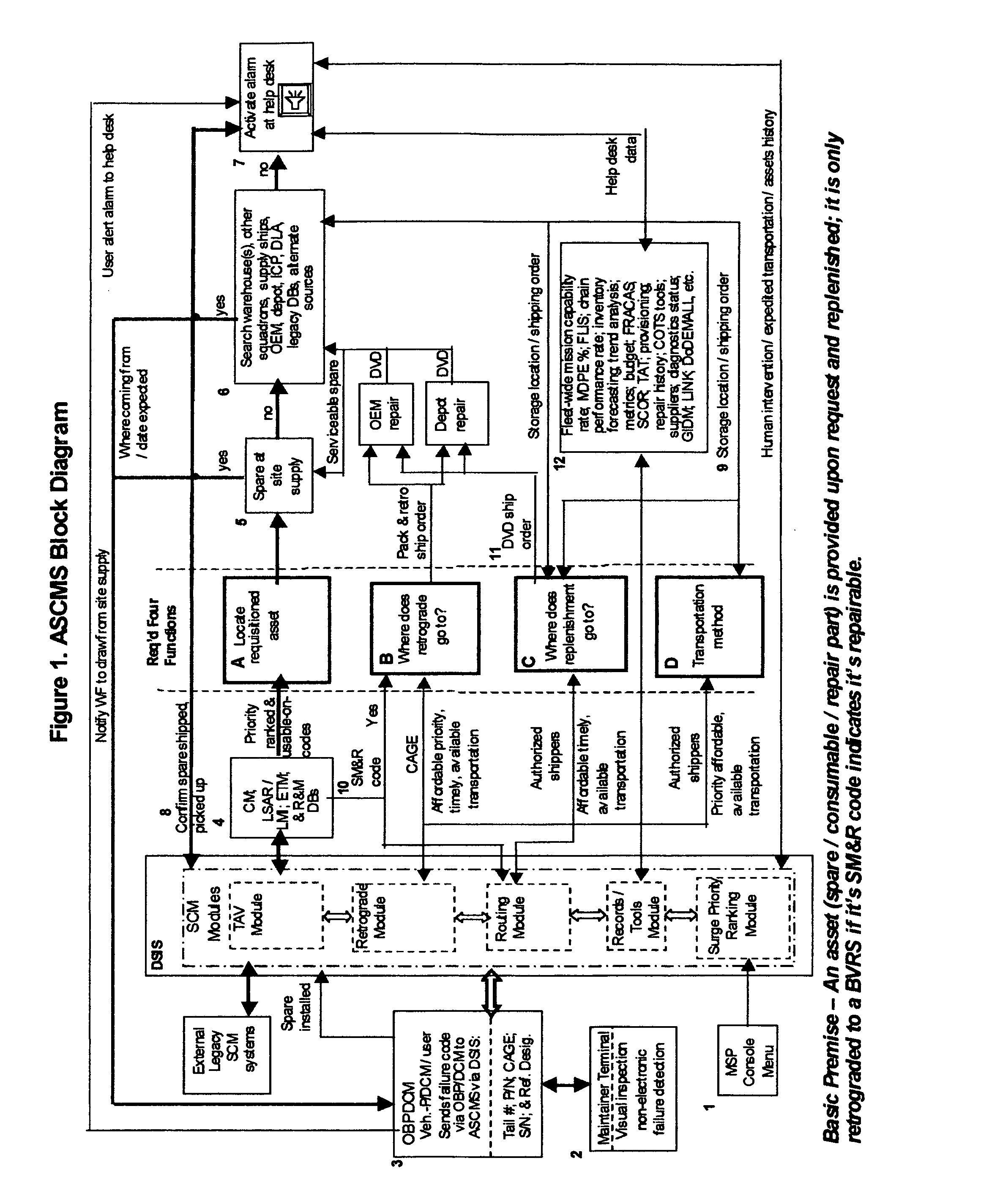
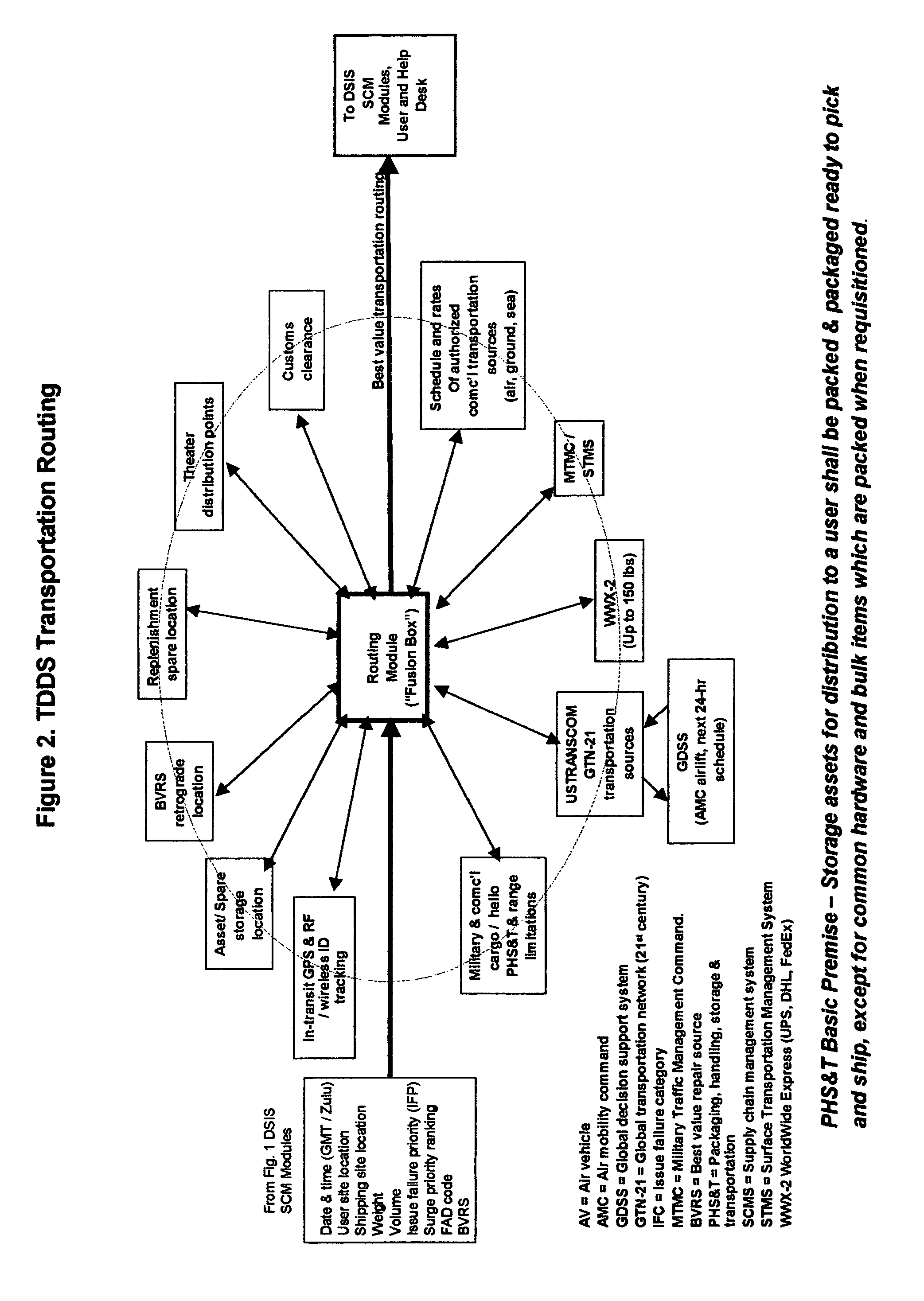
Provided is an agile, adaptive, globally deployable online network-centric autonomic supply chain management system that when triggered by a predictive / diagnostic condition management system, without user-maintainer intervention, autonomously authorizes a complete requisitioning cycle of supply chain assets to warfighters with unprecedented criticality of speed. A requisitioning cycle is comprised of: (1) asset issue authorization to a vehicle / requester (2) retrograde [return] of repairable to depot and (3) replenishment [resupply] of drawn inventory. It also autonomically provides global total asset visibility of the asset(s) of interest and a tempo surge-priority ranking with a calm-down functions. The system operates in either default autonomic mode or a user activated semi-autonomic mode. In either mode of operation a requisition cycle is accomplished autonomically by selection of the most affordable transportation that ensures delivery of an asset to a user in accordance with contractually specified time-definite delivery standards. The system's material delivery performance effectiveness percentage rate is archived for billing purposes and monitoring system performance metrics. The system almost eliminates SCM administration personpower requirements. It accelerates the entire logistics supply pipeline, resulting in:—higher annual inventory turn-rates thus permitting inventory levels to be reduced and smaller wartime pack up kits thereby lowering lifetime total operating costs. Smaller pack up kits reduces the logistics footprint and thus the number of cargo aircraft required to deploy a unit.
Owner:KENNETH JONGEBRLOED
Network centric system and method to enable tracking of consumer behavior and activity
InactiveUS20100312706A1Improve trustMultiple countKey distribution for secure communicationMarket predictionsTraffic capacityThird party
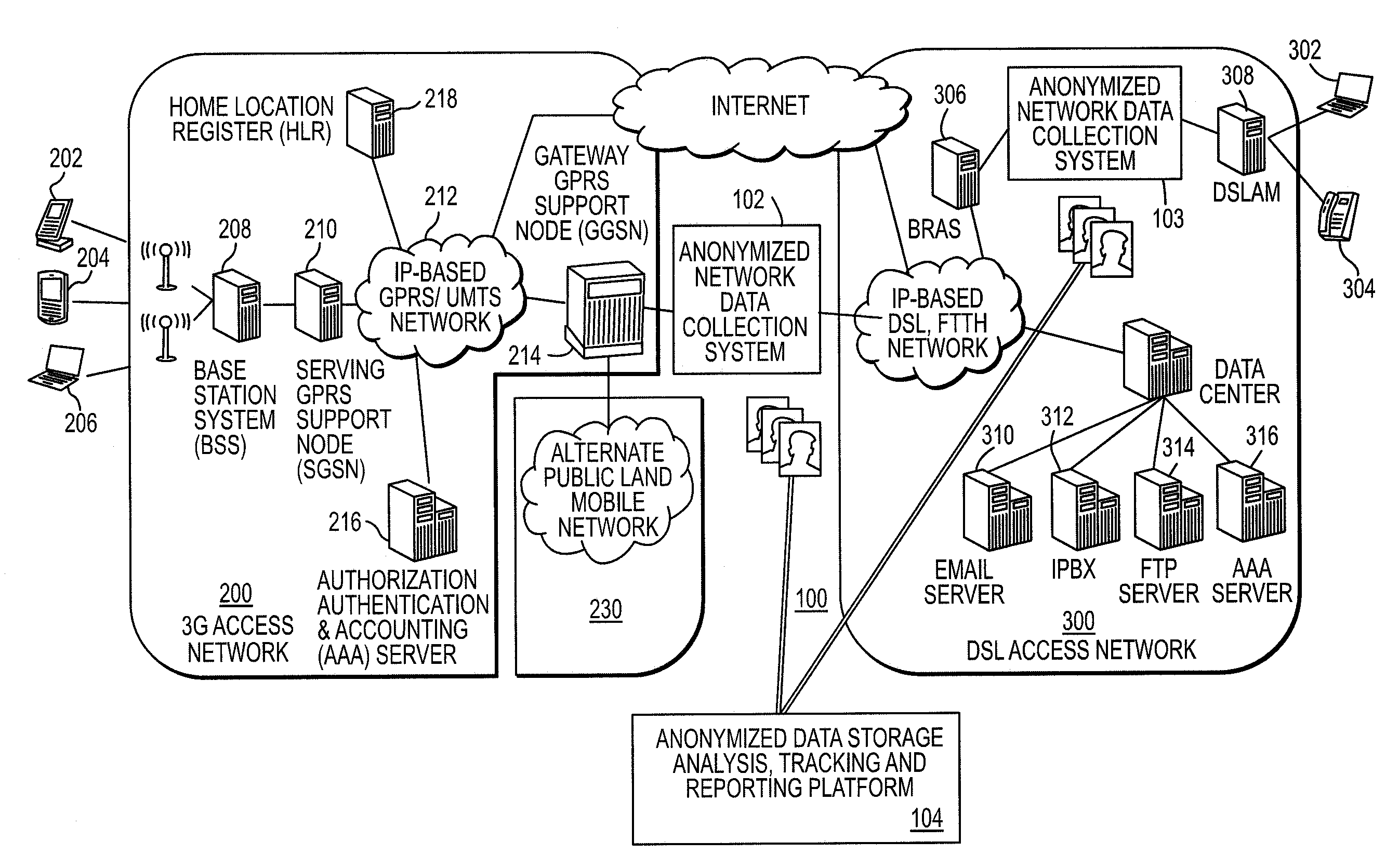
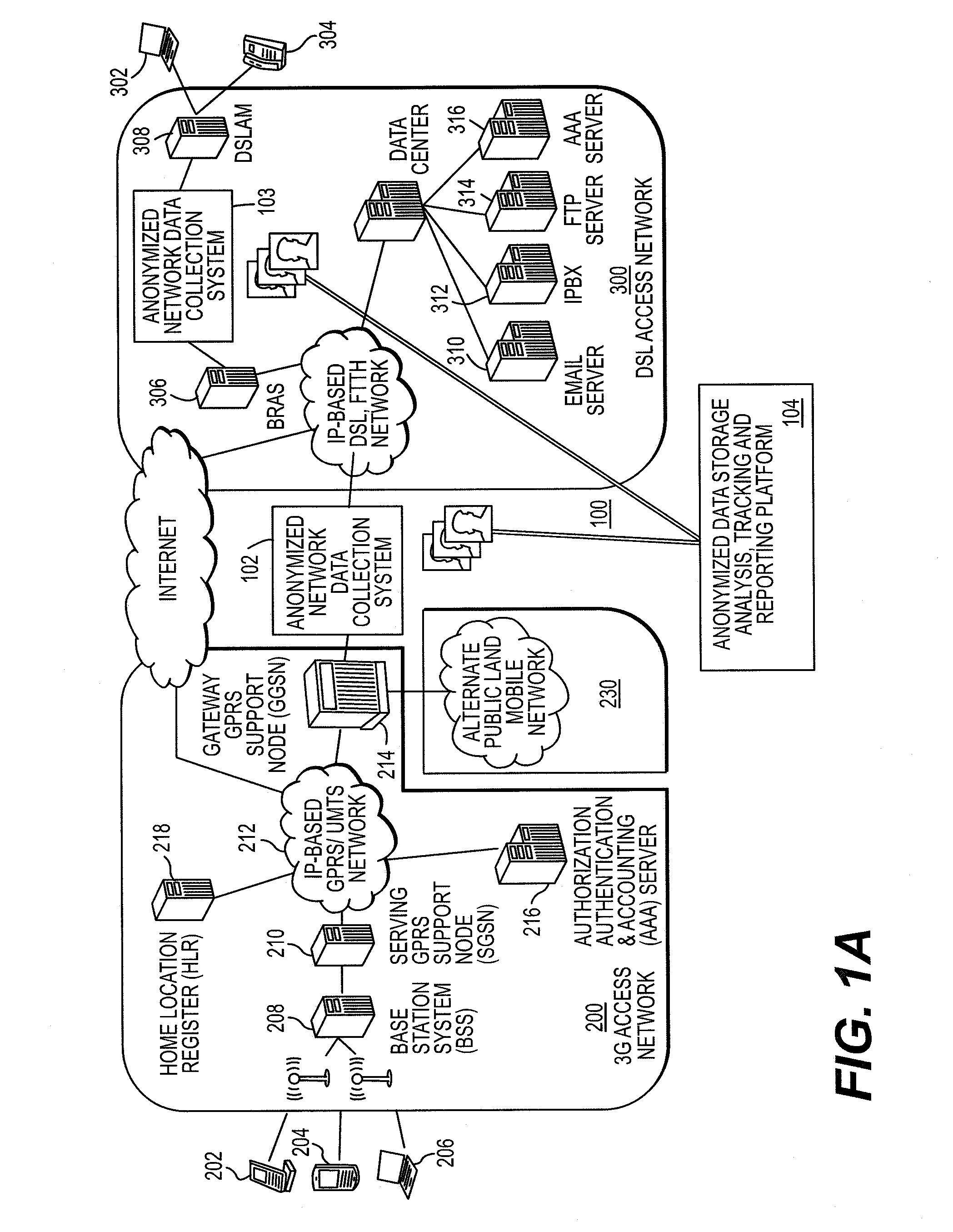
A method for collecting Internet and e-commerce data accessed via messaging devices such as mobile terminals comprises monitoring packet traffic in a communication system providing communication services to the messaging devices and extracting network data from packets associated with respective device users. The portion of extracted network data from which a user's identity might otherwise be determined is encrypted, creating an anonymized, unique identifier correlated to network access data extracted from any packet traffic applicable to that user. Network access data associated with each user is distinguishable from network access data associated with all other users on the basis of the unique identifier. A third party granted access to the anonymized network access data, associated with identifiably unique but anonymous users of the communication system, may retrieve and store the data in a database for analysis. Anonymized network access data associated with those users electing to become voluntary panelists is correlated, solely on the basis of the anonymized unique identifier, to socio-demographic data furnished by such panelists.
Owner:COMBET JACQUES +1
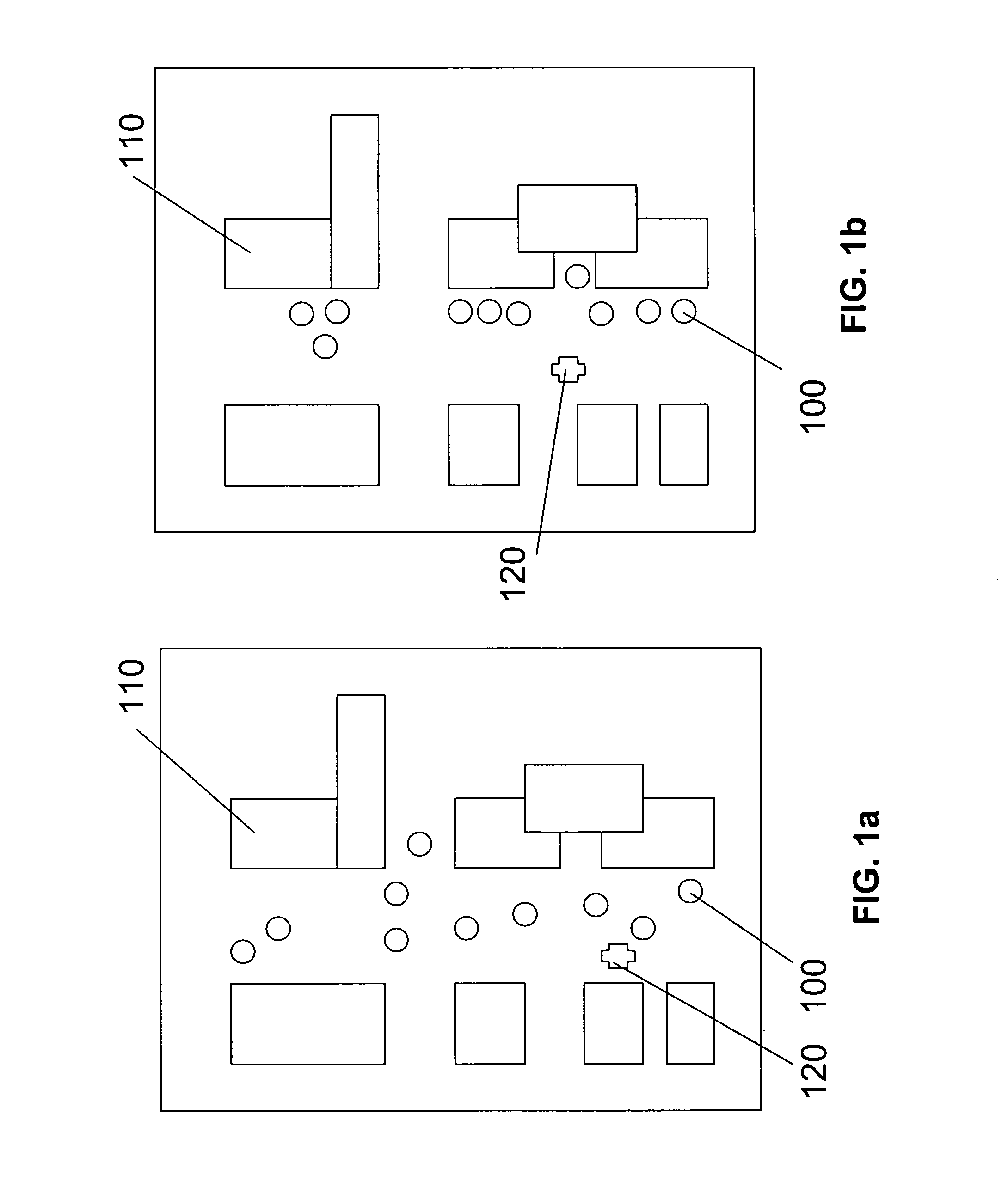
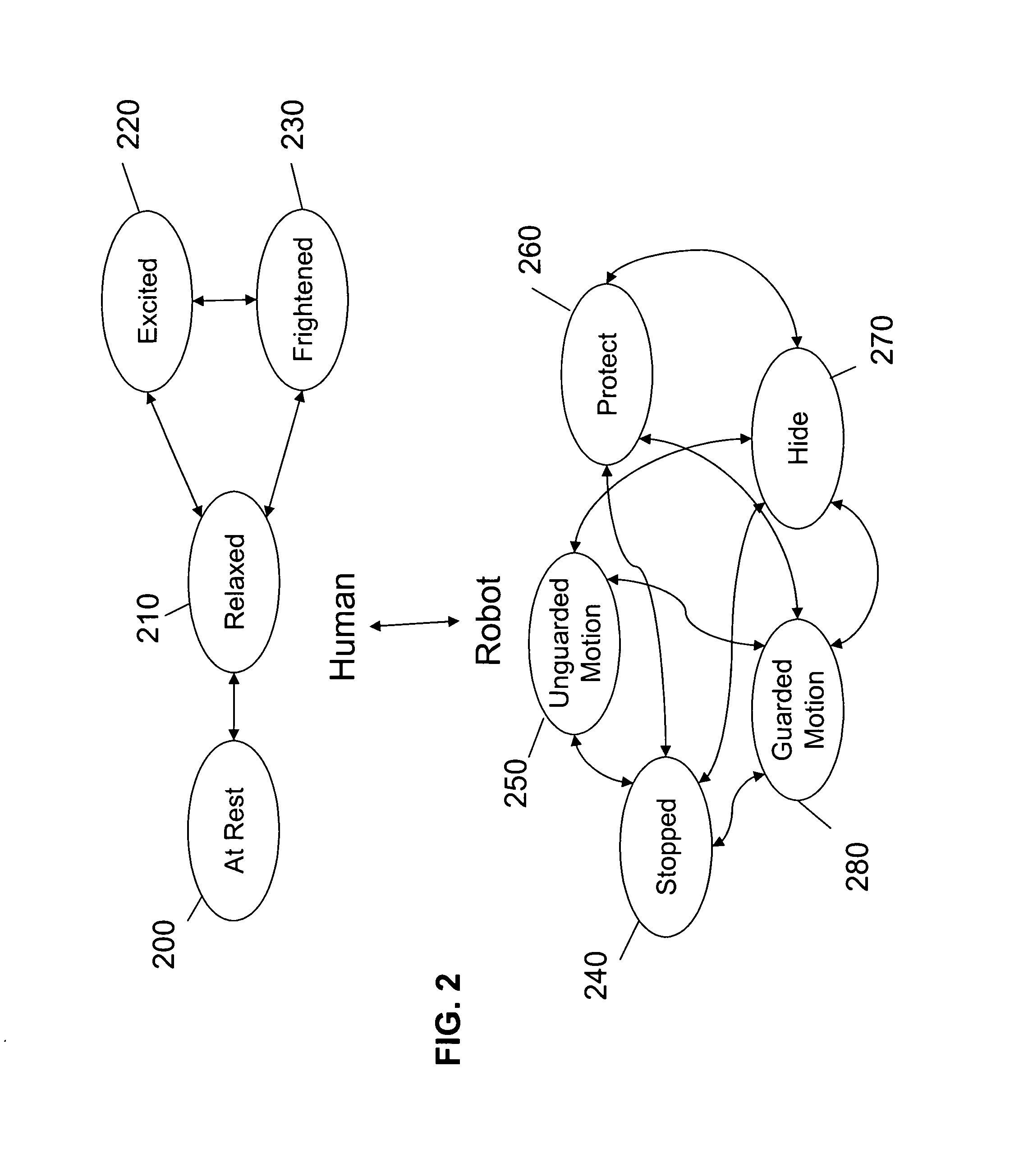
Methods and systems for an autonomous robotic platform
ActiveUS8346391B1Low costDifficult to useProgramme-controlled manipulatorAutonomous decision making processHuman interactionCommand and control
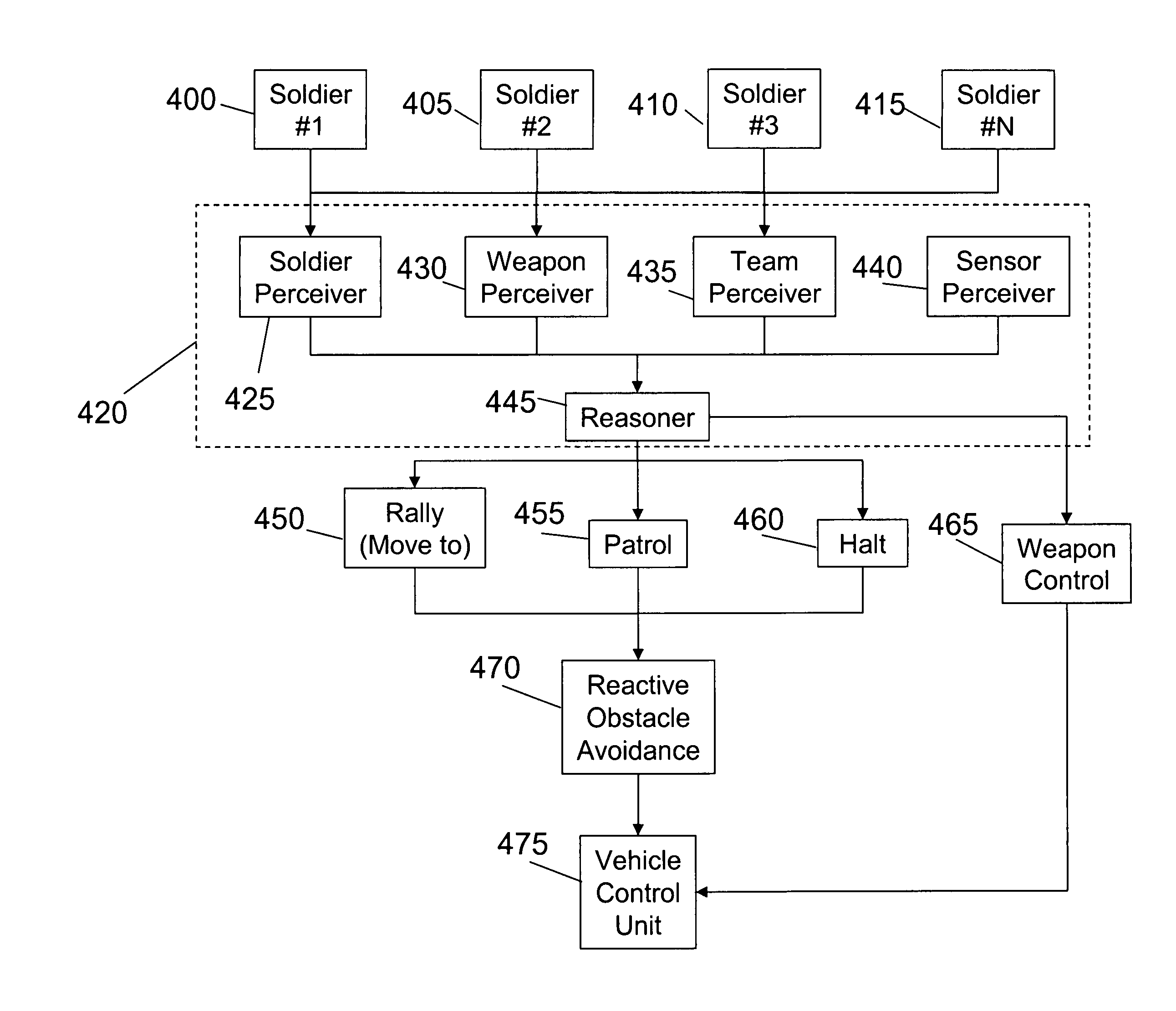
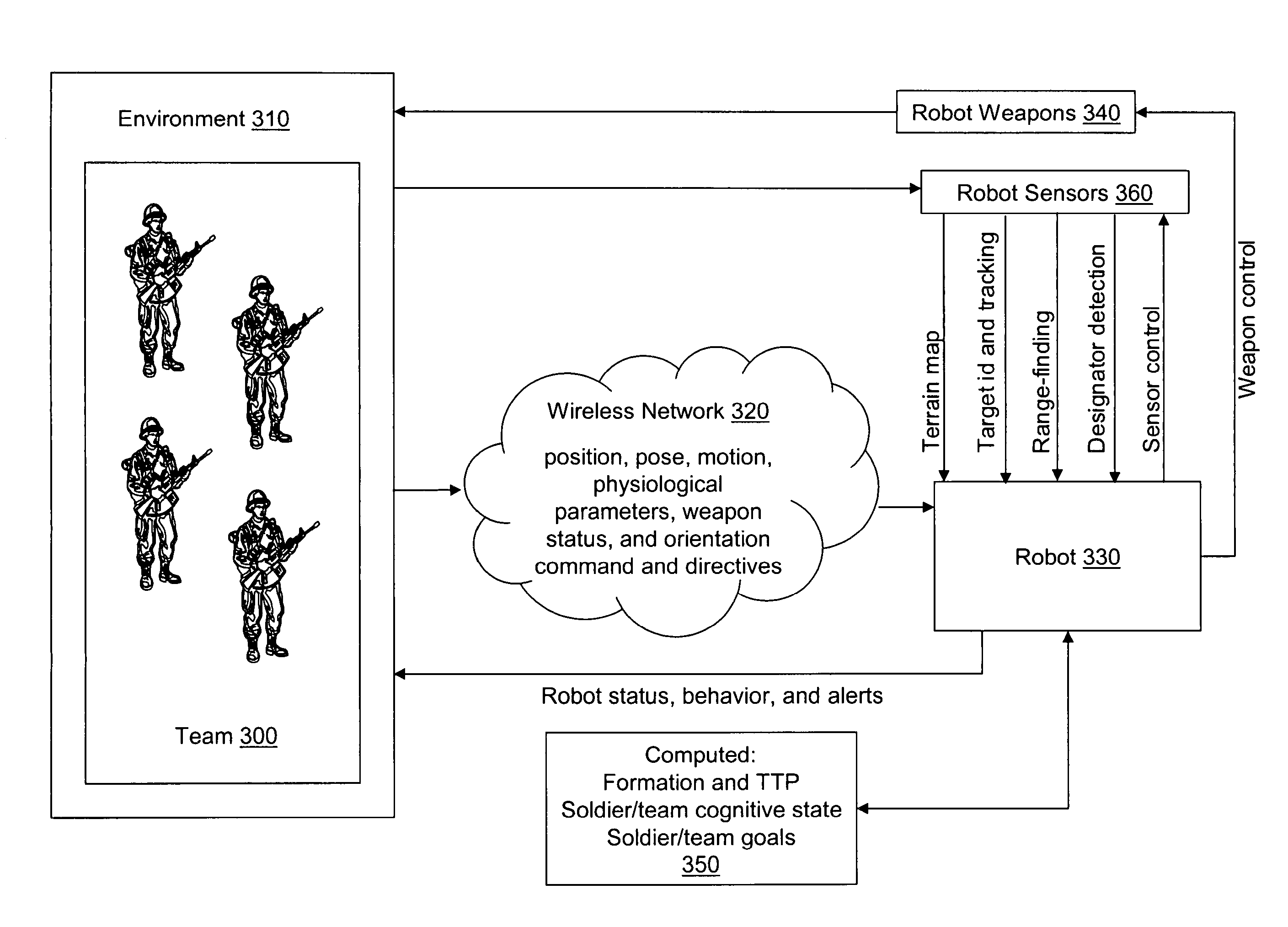
A system and method can provide a command and control paradigm for integrating robotic assets into human teams. By integrating sensor to detect human interaction, movement, physiology, and location, a net-centric system can permit command of a robotic platform without an OCU. By eliminating the OCU and maintaining the advantages of a robotic platform, a robot can be used in the place of a human without fatigue, being immune to physiological effects, capable of non-humanoid tactics, a longer potential of hours per day on-station, capable of rapid and structured information transfer, has a personality-free response, can operate in contaminated areas, and is line-replaceable with identical responses. A system for controlling a robotic platform can comprise at least one perceiver for collecting information from a human or the environment; a reasoner for processing the information from the at least one perceiver and providing a directive; and at least one behavior for executing the directive of the reasoner.
Owner:LEIDOS
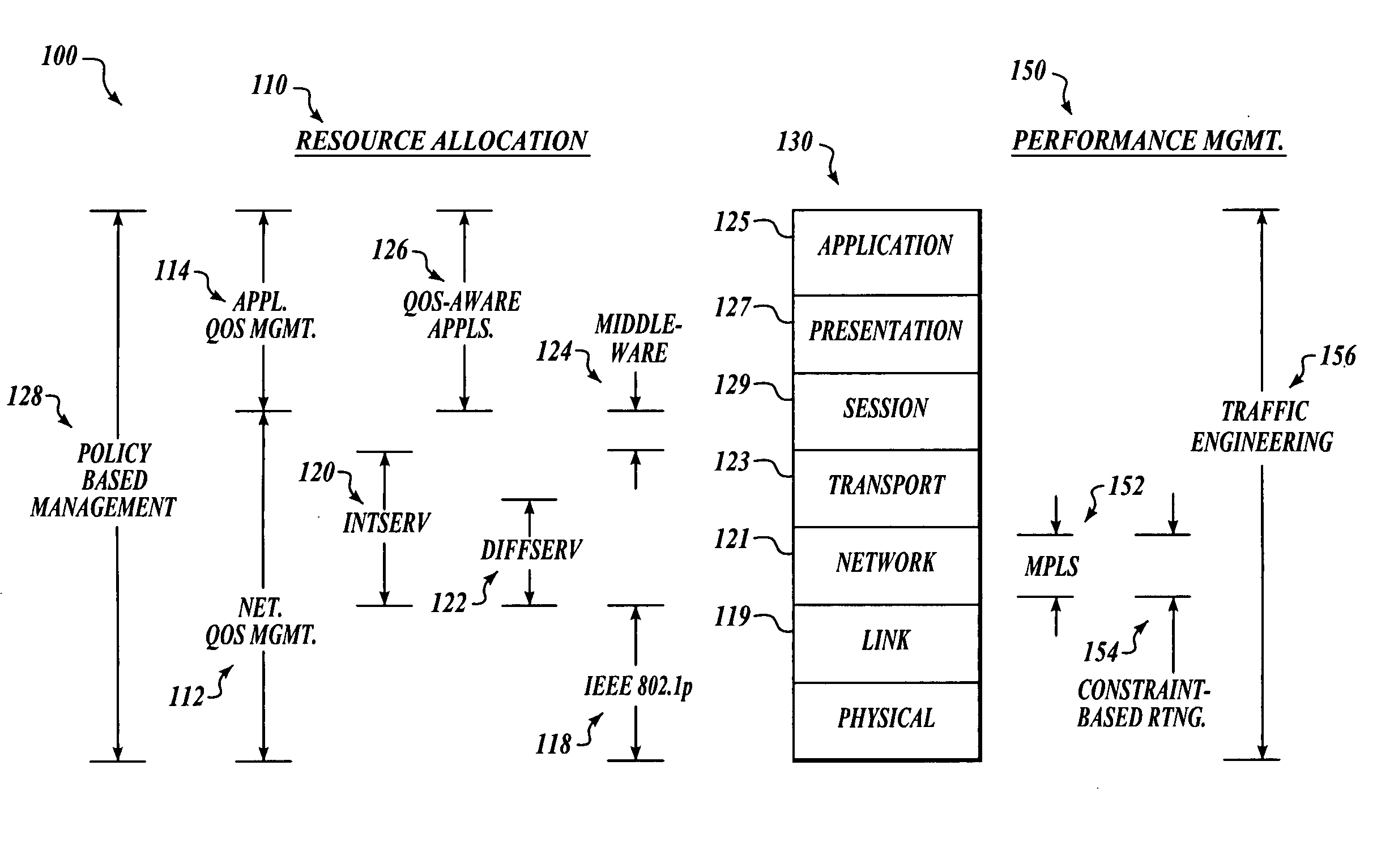
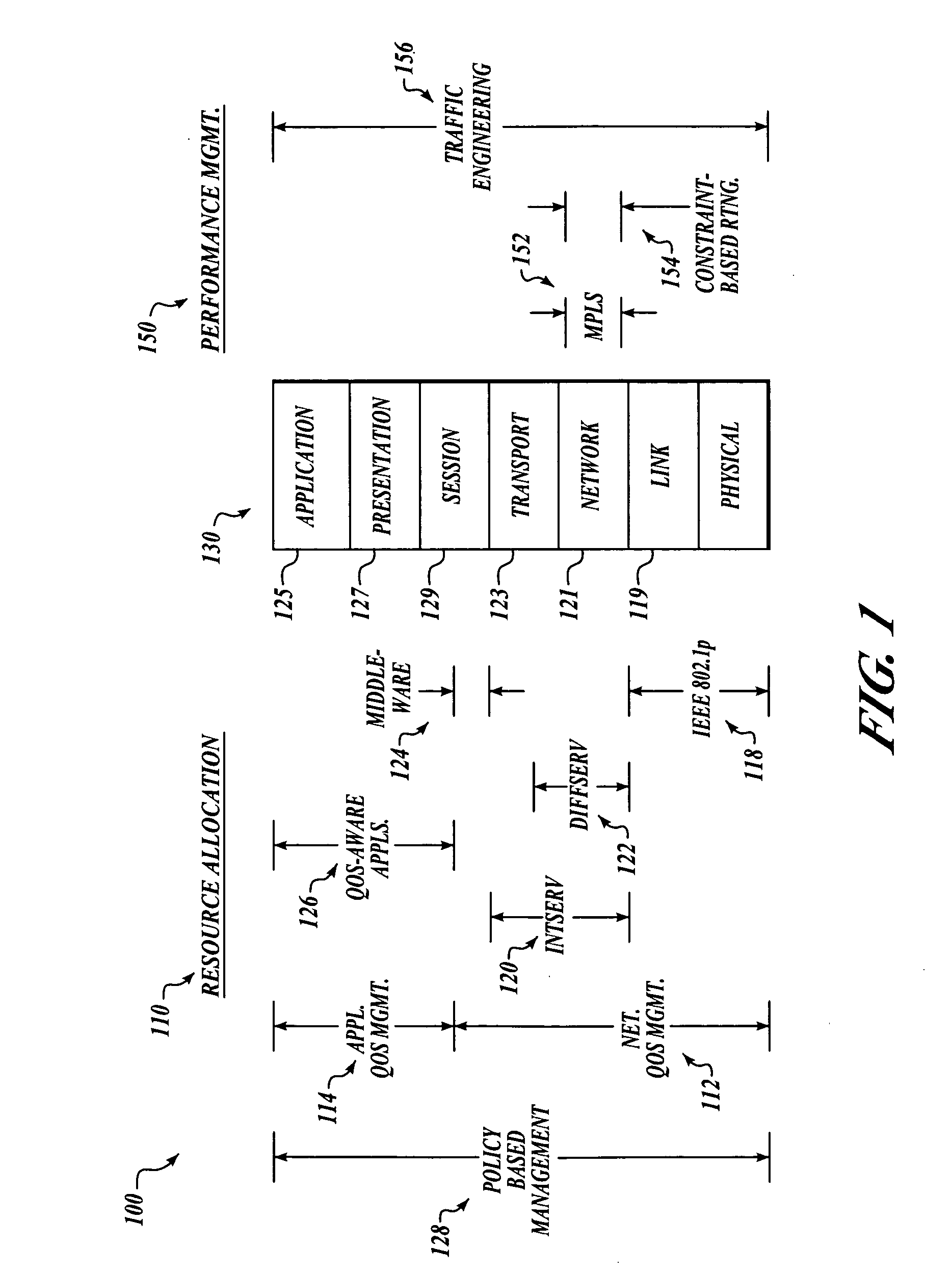
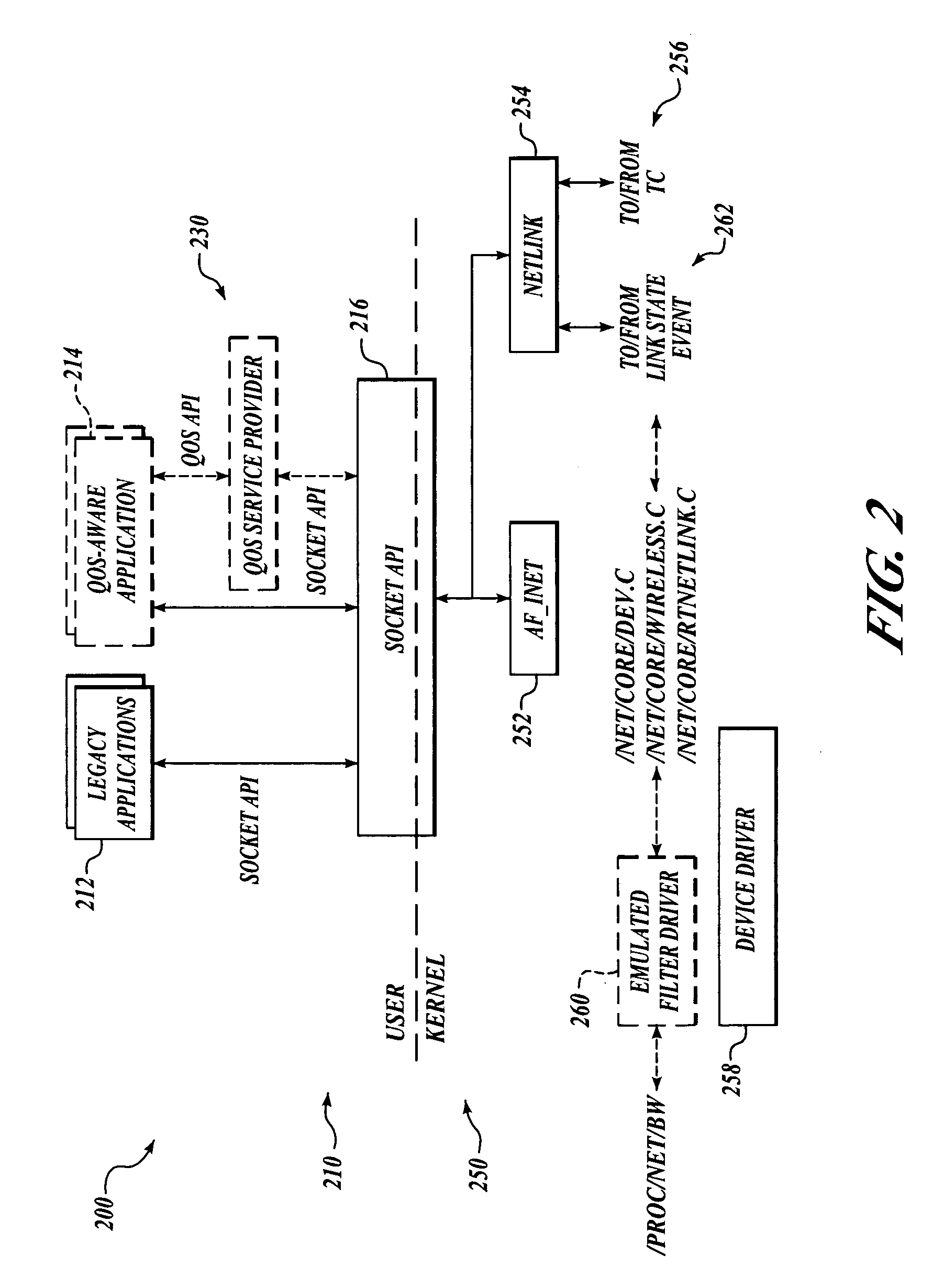
Network centric quality of service using active network technology
InactiveUS20060126504A1Improving network centric qualityError preventionTransmission systemsDifferentiated servicesDifferentiated service
Systems and methods for improving network centric quality of service using active network technology are disclosed. In one embodiment, a method includes controlling how a packet is passed over at least one of the interfaces using a differentiated services portion of a network management architecture, monitoring a request for a Quality of Service (QoS) level from at least one QoS-aware application, and adjusting at least one service rate of packet travel controlled by the differentiated services portion based on at least one of the requested QoS level and an available bandwidth. In an alternate embodiment, the controlling of how a packet is passed over at least one of the interfaces includes using at least one of a queuing discipline, a class, and a filter.
Owner:THE BOEING CO
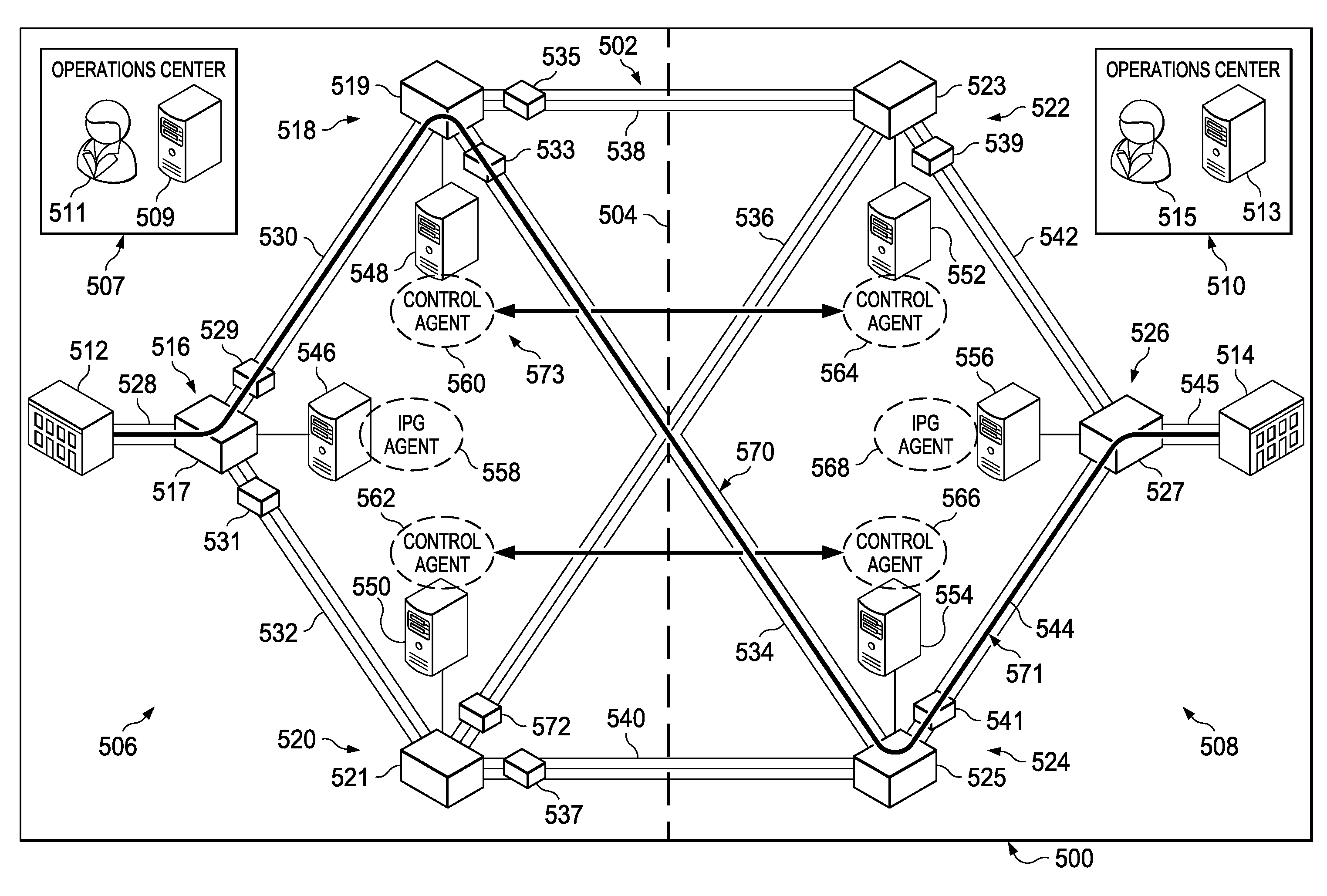
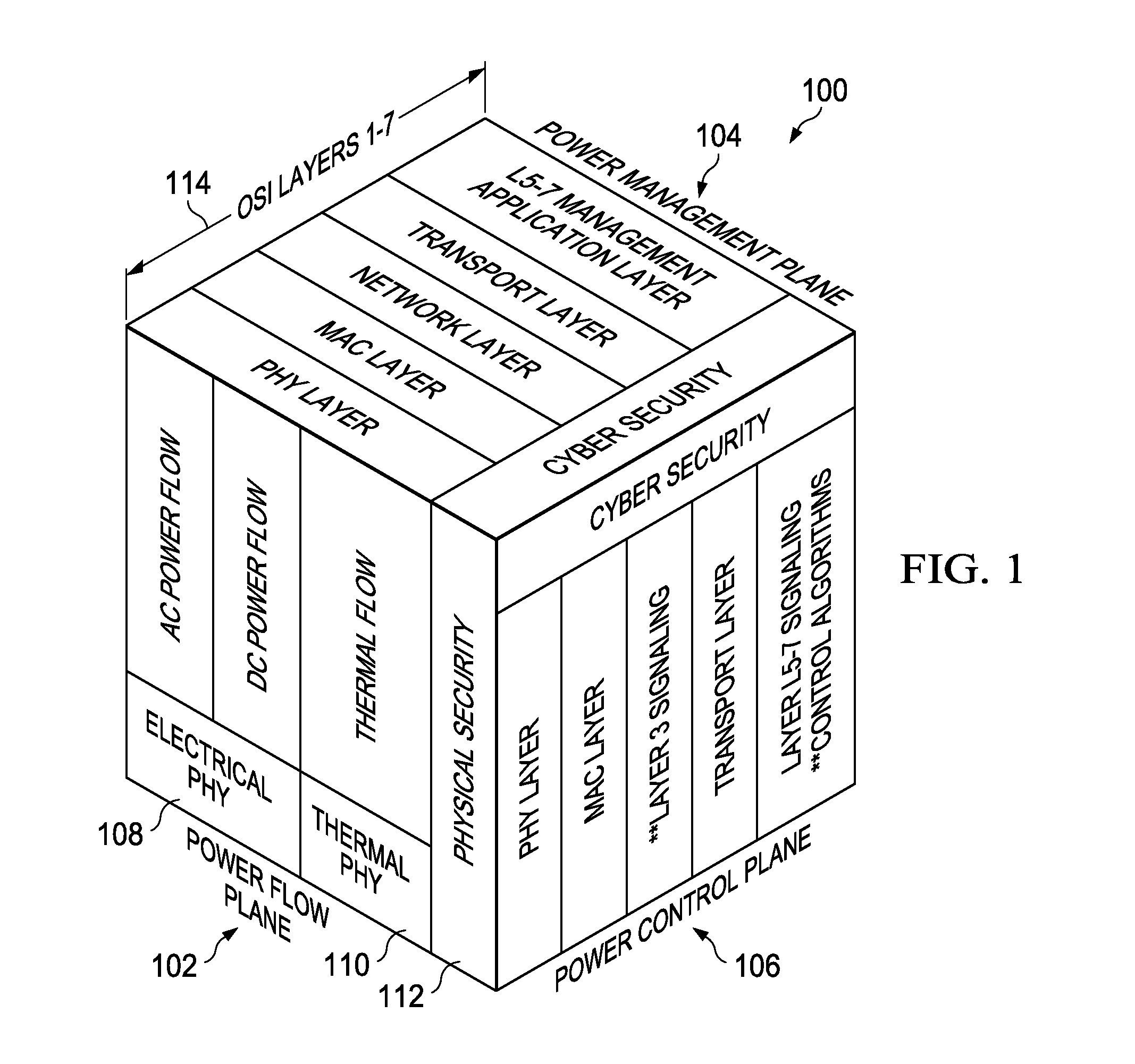
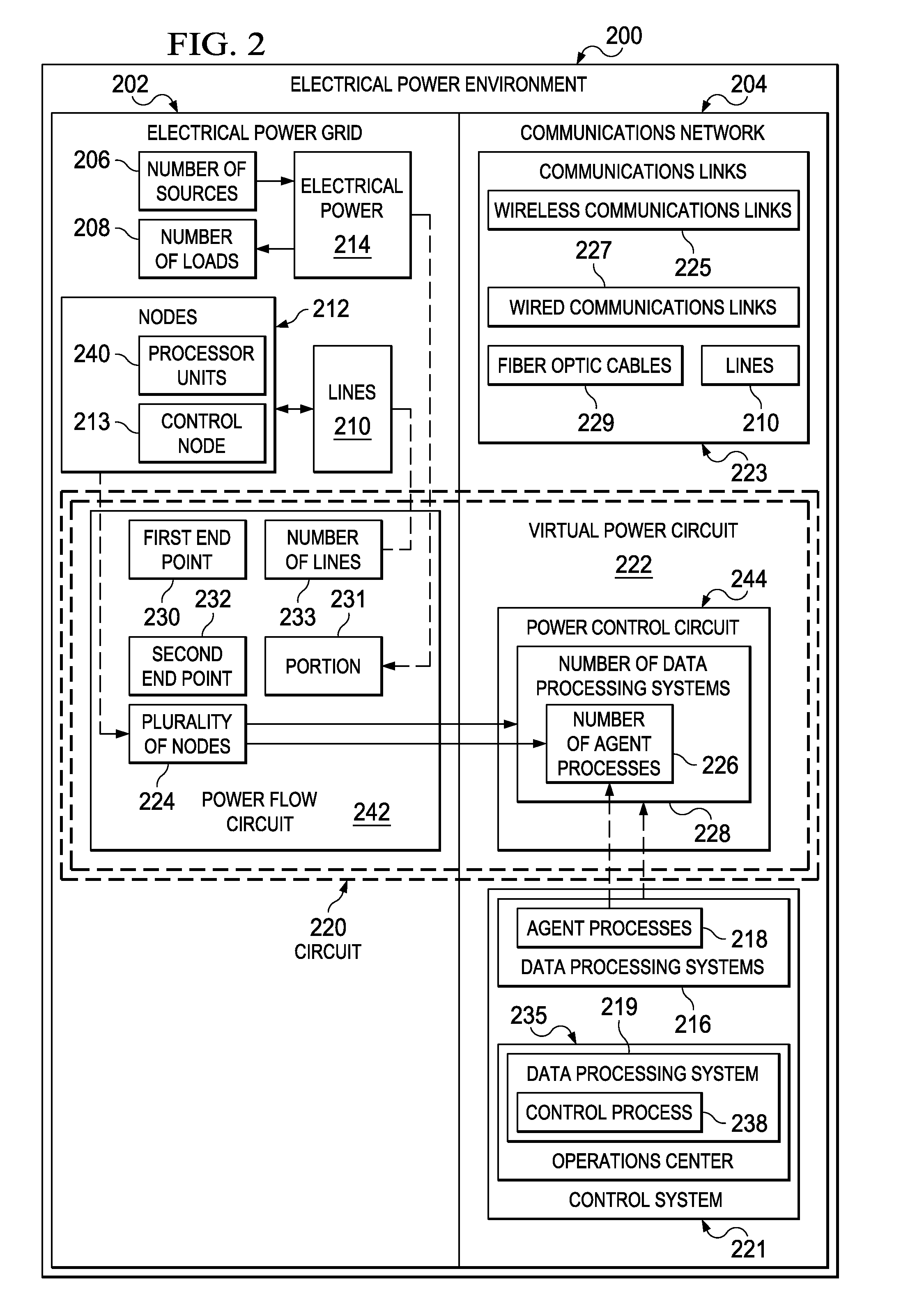
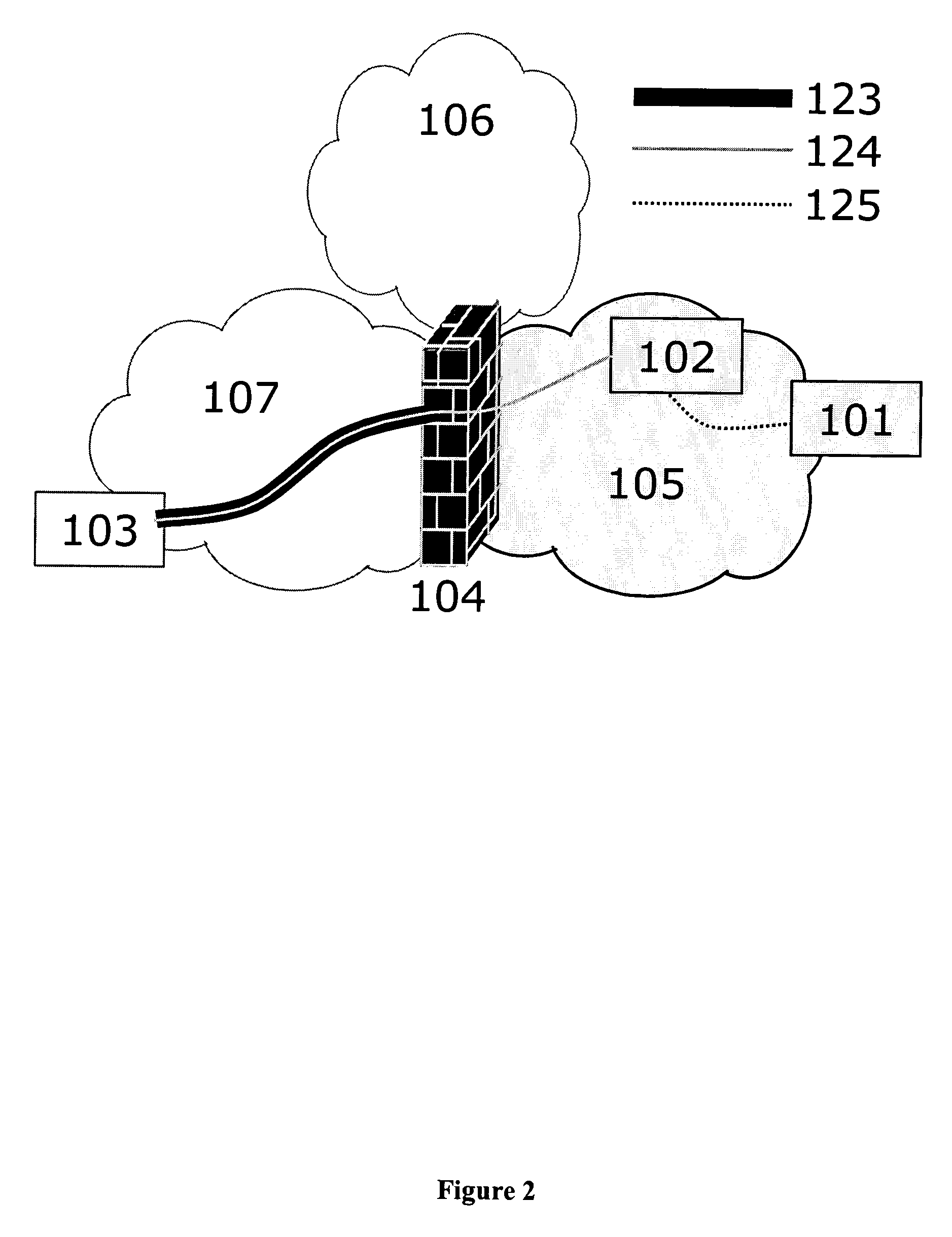
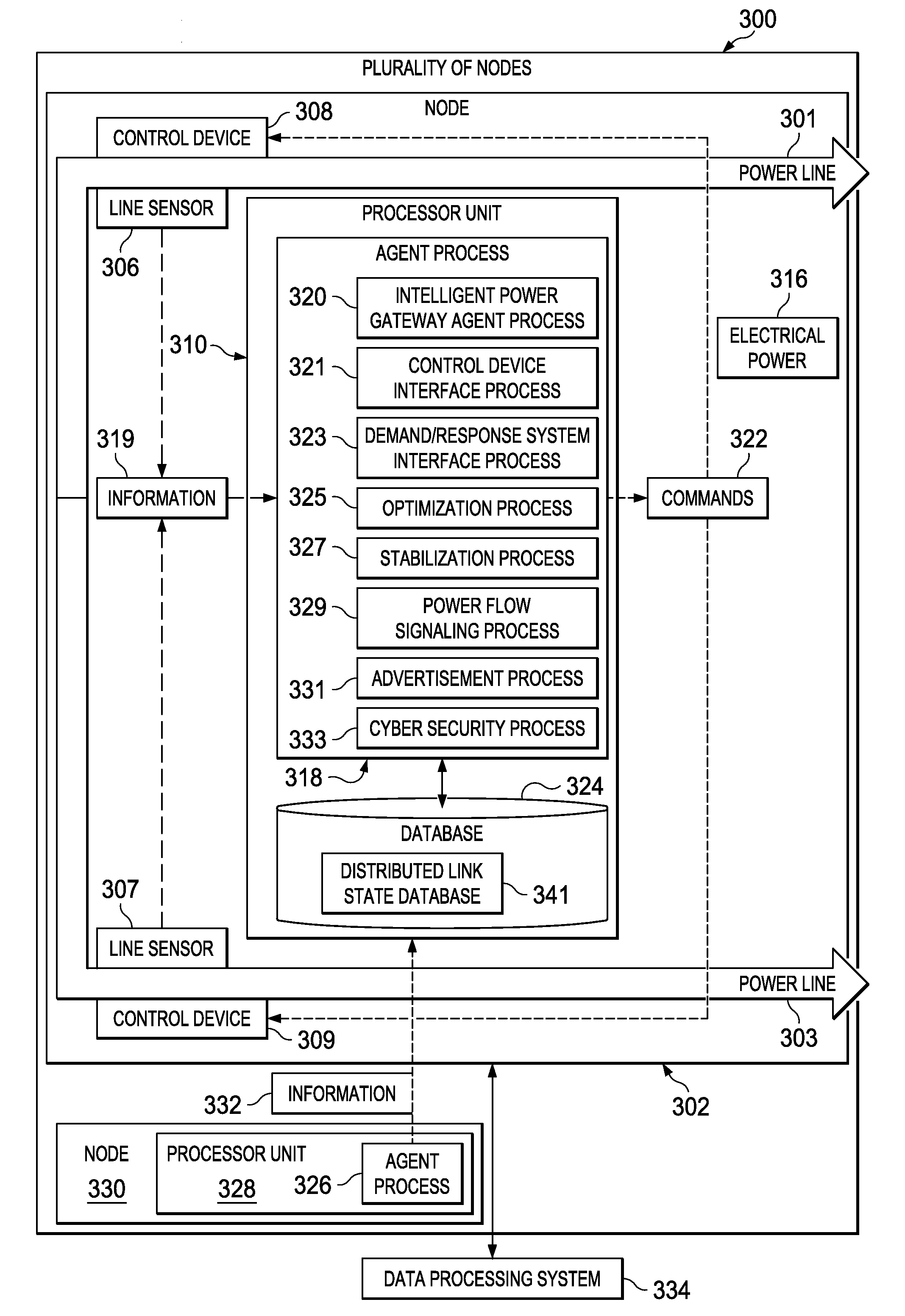
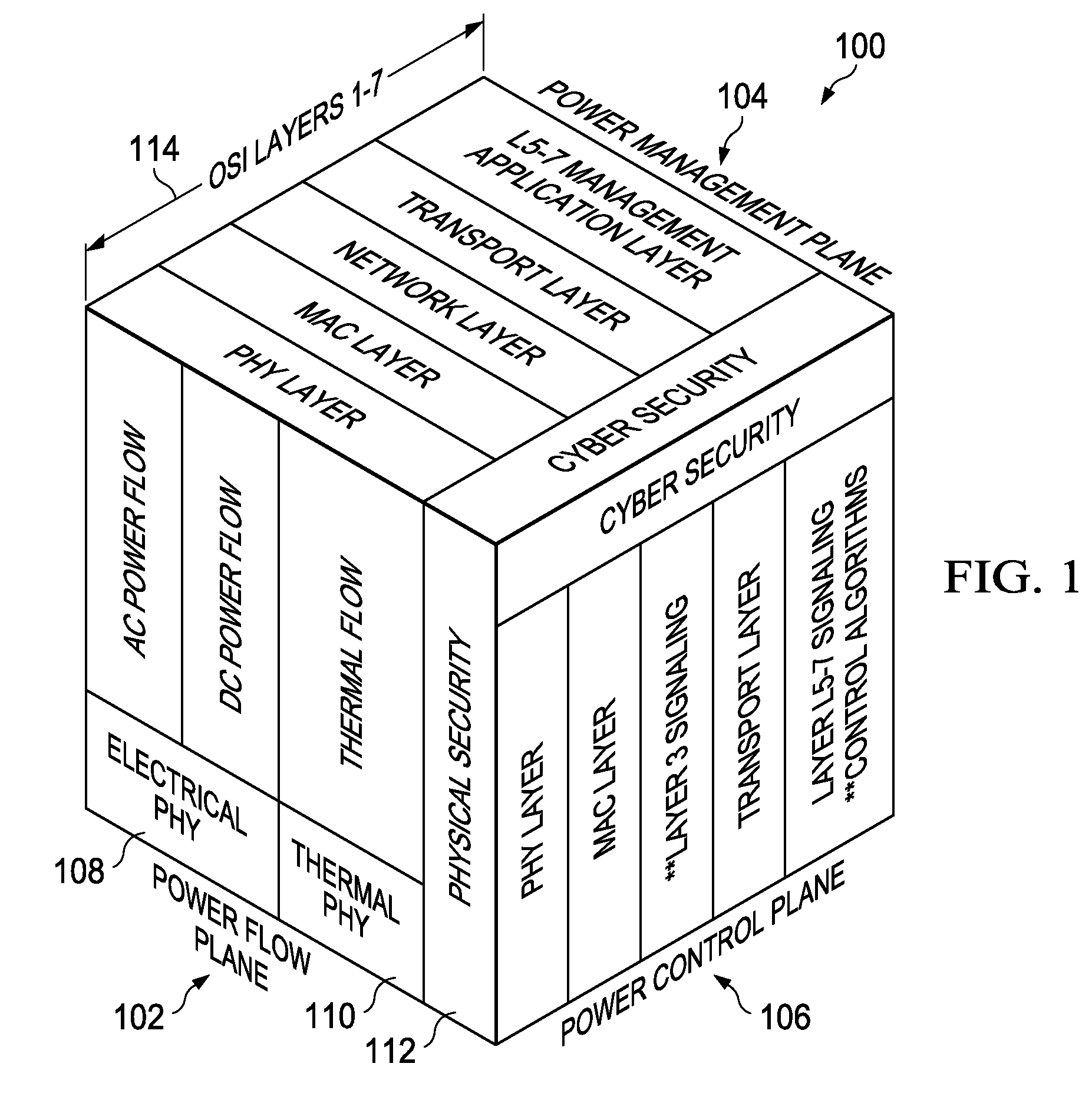
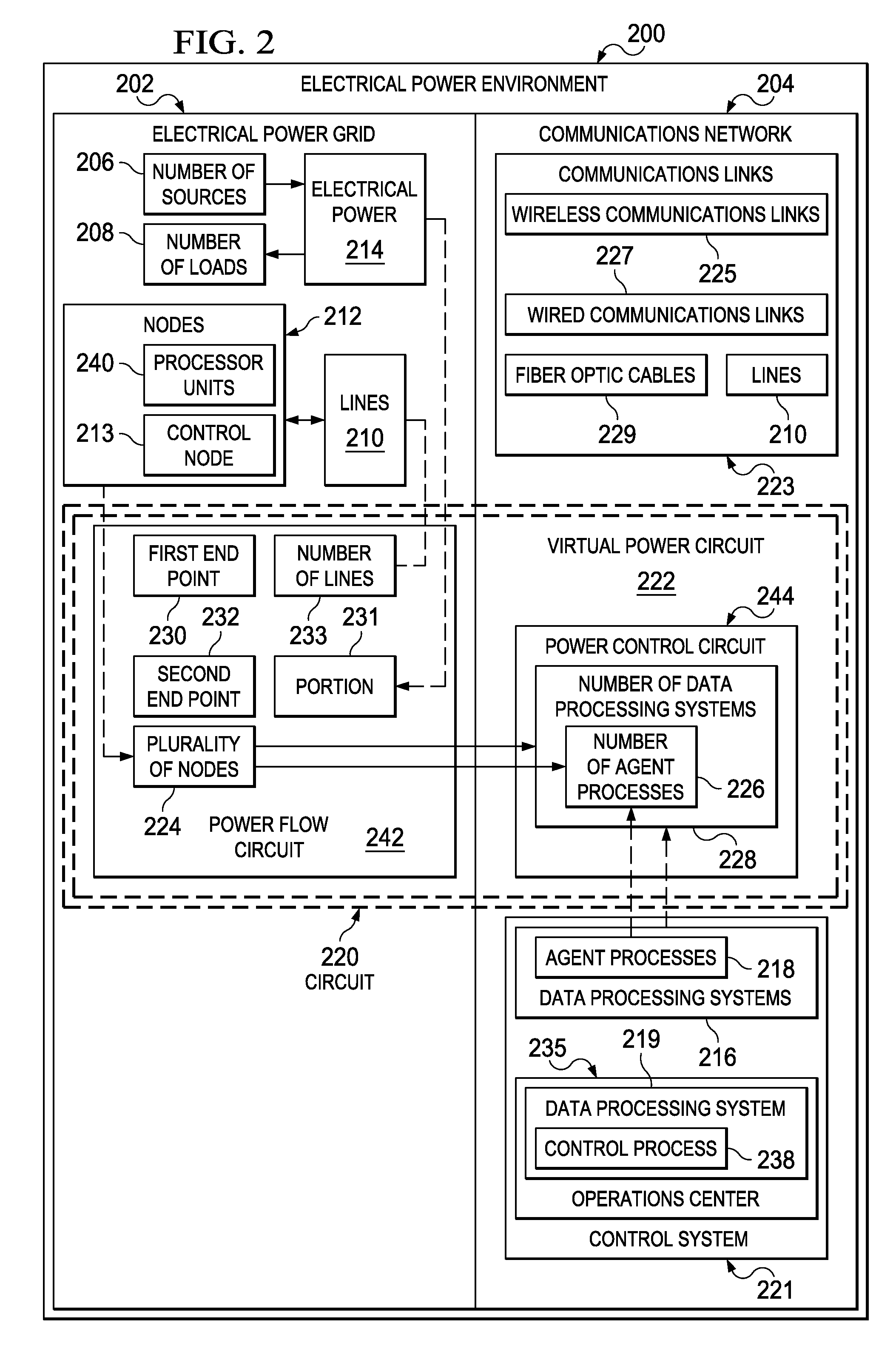
Network Centric Power Flow Control
Owner:THE BOEING CO
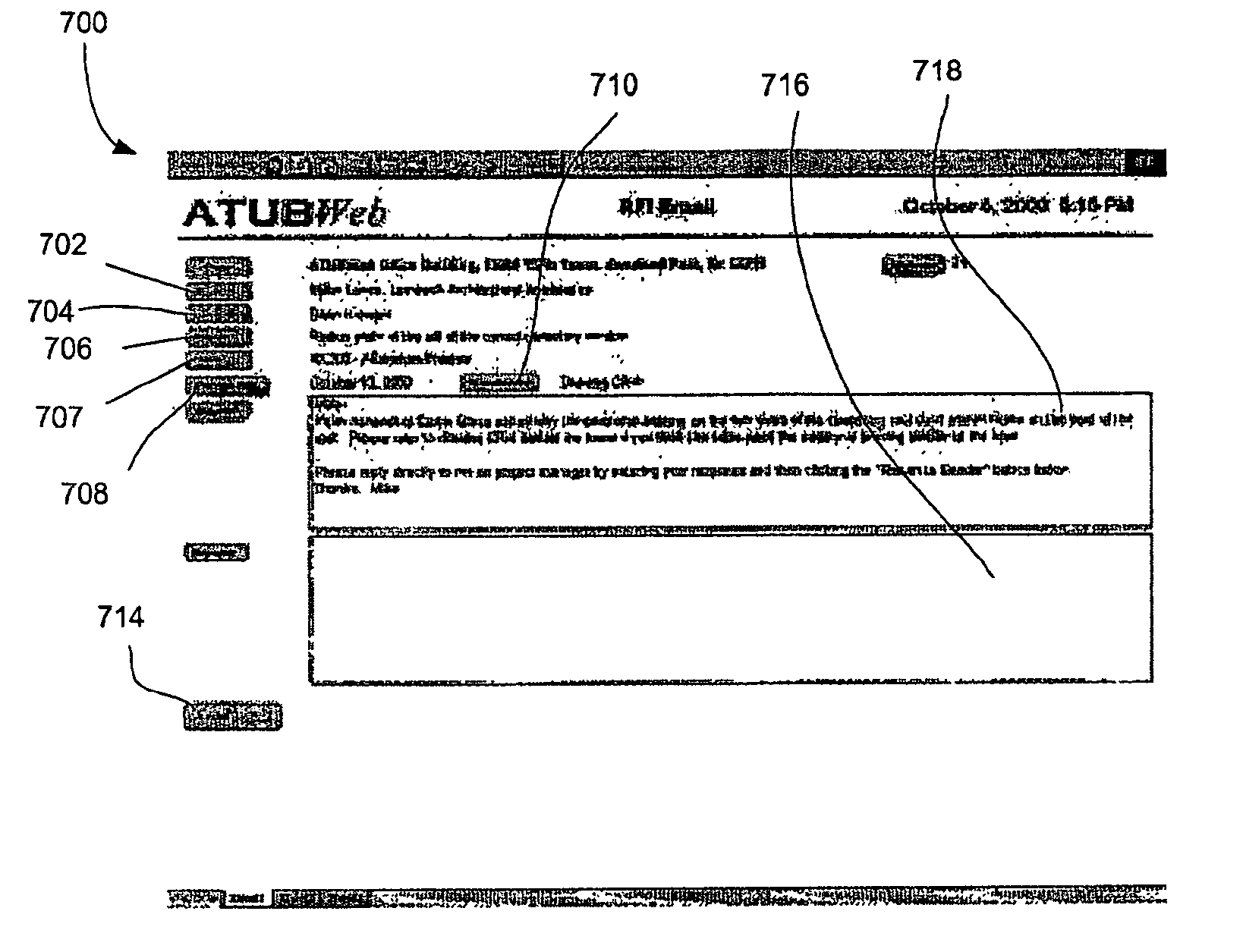
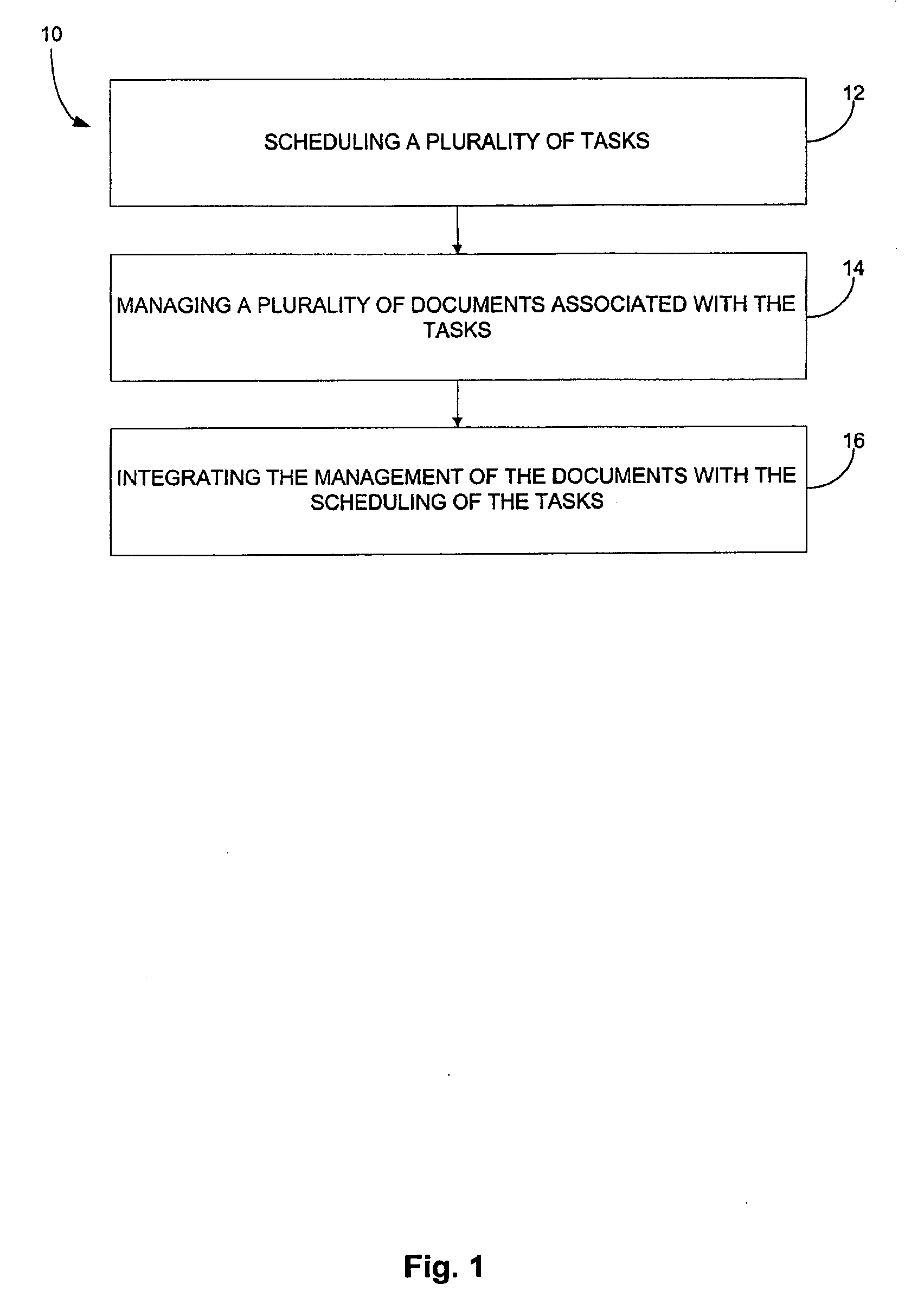
System, method, and article of manufacture for scheduling and document management integration
InactiveUS20070294617A1Digital computer detailsSpecial data processing applicationsTask completionWireless handheld devices
A network-centric project scheduling and management system provides services via a computer network such that users can interact with the system using existing computer hardware and software. The program receives from the user a plurality of project task records, identifies critical project tasks, and creates a critical task schedule based on the task records. The program creates an interface via existing software on a wireless hand-held device by dynamically creating web pages compatible with the device software in response to communication requests from the device. The program further summarizes the value of work performed under various contracts by multiplying a task completion percentage by a task contract price for each task associated with a contract and summing the results.
Owner:HEADS UP TECH
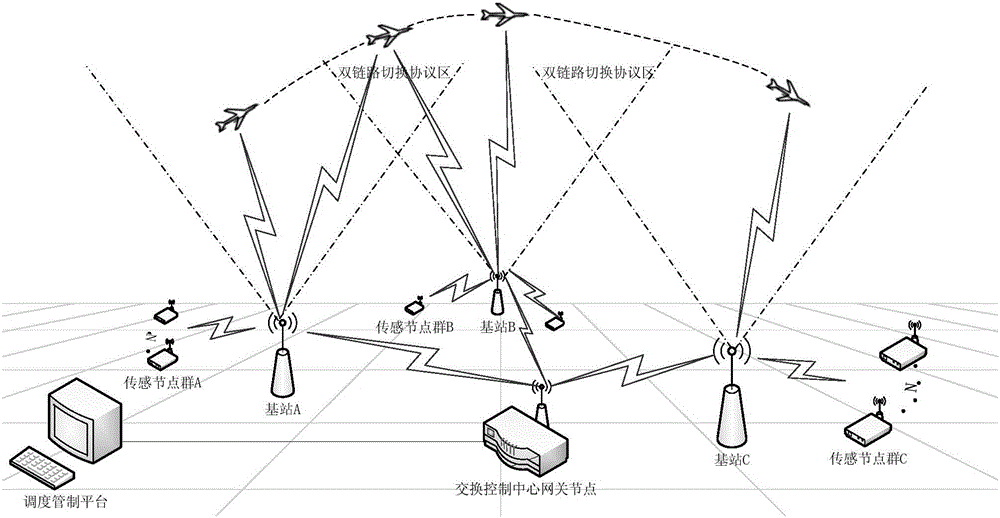
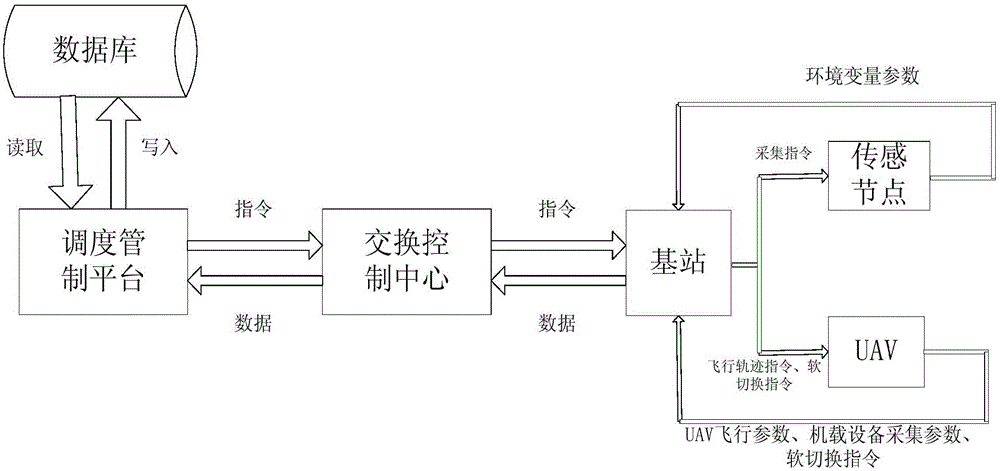
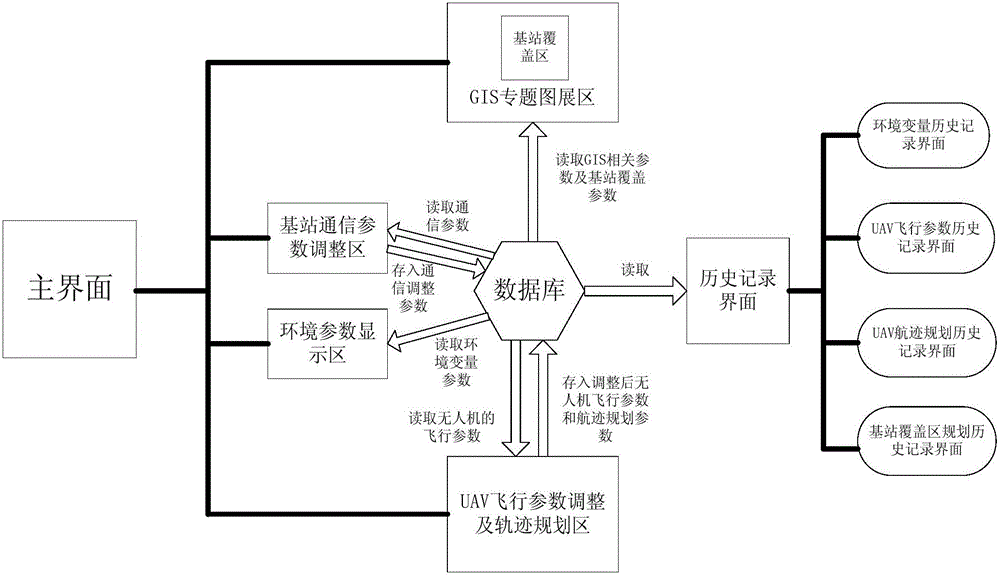
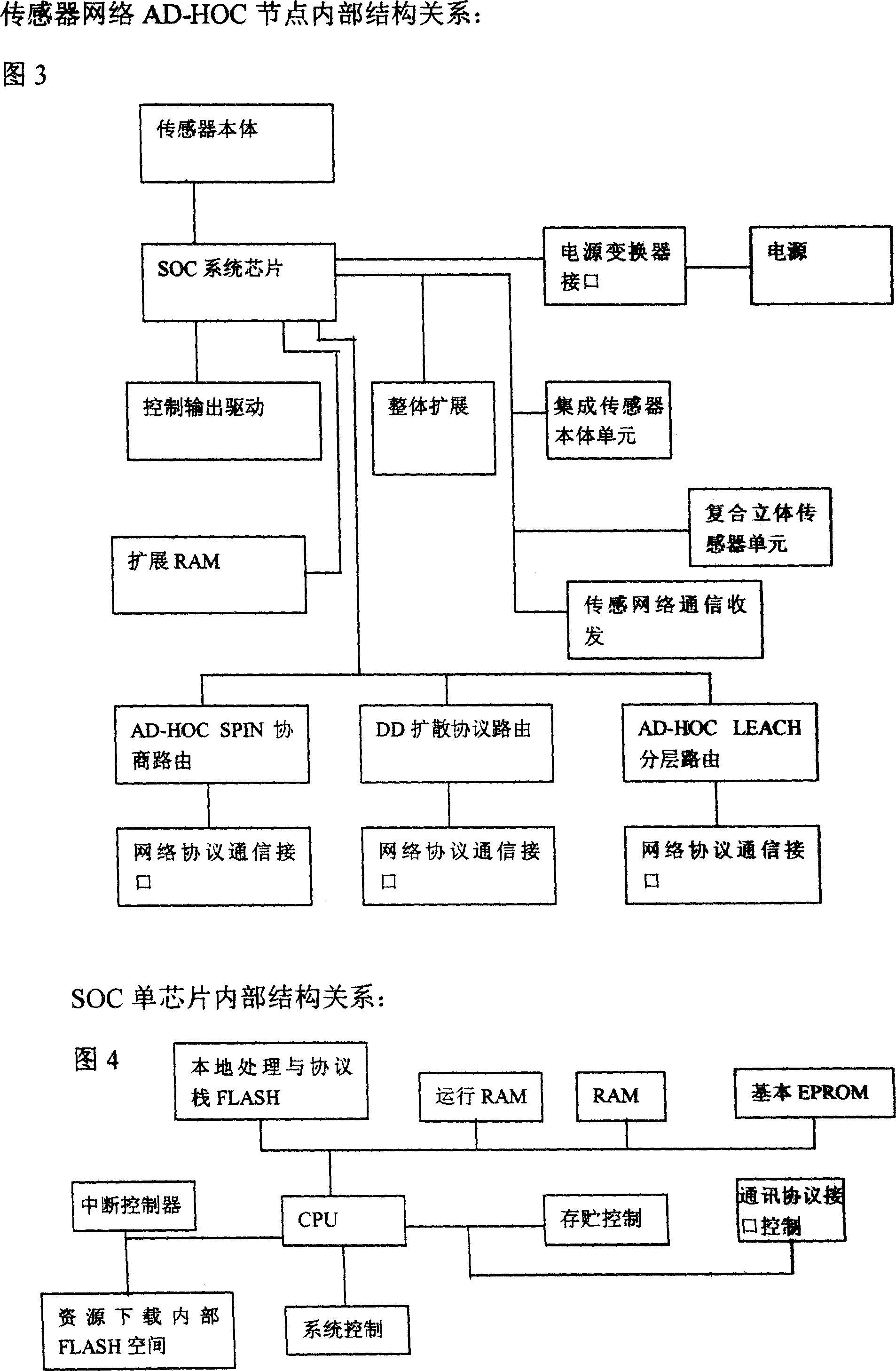
Ground-air wireless sensor network communication device and method compatible with UAV
ActiveCN105828345AExpandable and flexibleEliminate signal blind spotsNetwork topologiesTransmissionGrid networkNetwork communication
The invention discloses a ground-air wireless sensor network communication device compatible with a UAV. The device comprises a sensing monitoring system, a mobile platform system, an integrated Wi-Fi network communication system and a dispatching control platform. The sensing monitoring system indicates that in a sensor network, sensor nodes randomly scattered in a monitored region monitor specific variable objects in a target region in real time. The mobile platform system comprises UAVs for mounting Wi-Fi network communication modules, wherein the controllability of the flying speeds and the paths of the UAVs is realized by using rotor vertical lifting platforms. The integrated Wi-Fi network communication system indicates a structure which takes a Wi-Fi communication mode as the main and refers to a cellular mobile communication network. The dispatching control platform is a set of software platform which is used for controlling flying paths of the unmanned aerial vehicles and collecting wireless network topology control information and environment variable information. According to the device, grid network development demands can be satisfied; and through establishment of the UAV communication network taking the network as the center, sufficient stability and reliability and high interconnection and interoperability can be realized.
Owner:SOUTH CHINA AGRI UNIV
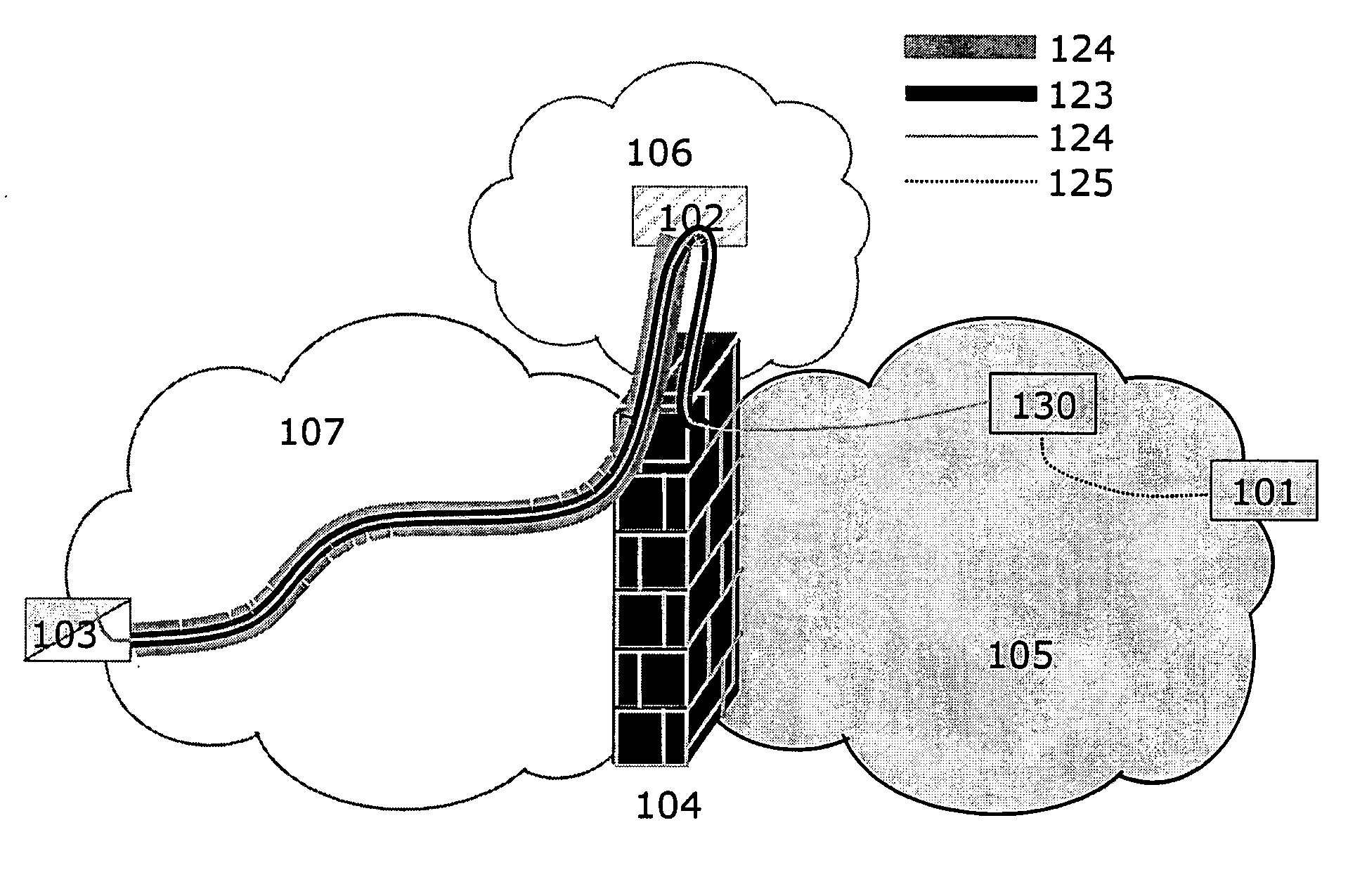
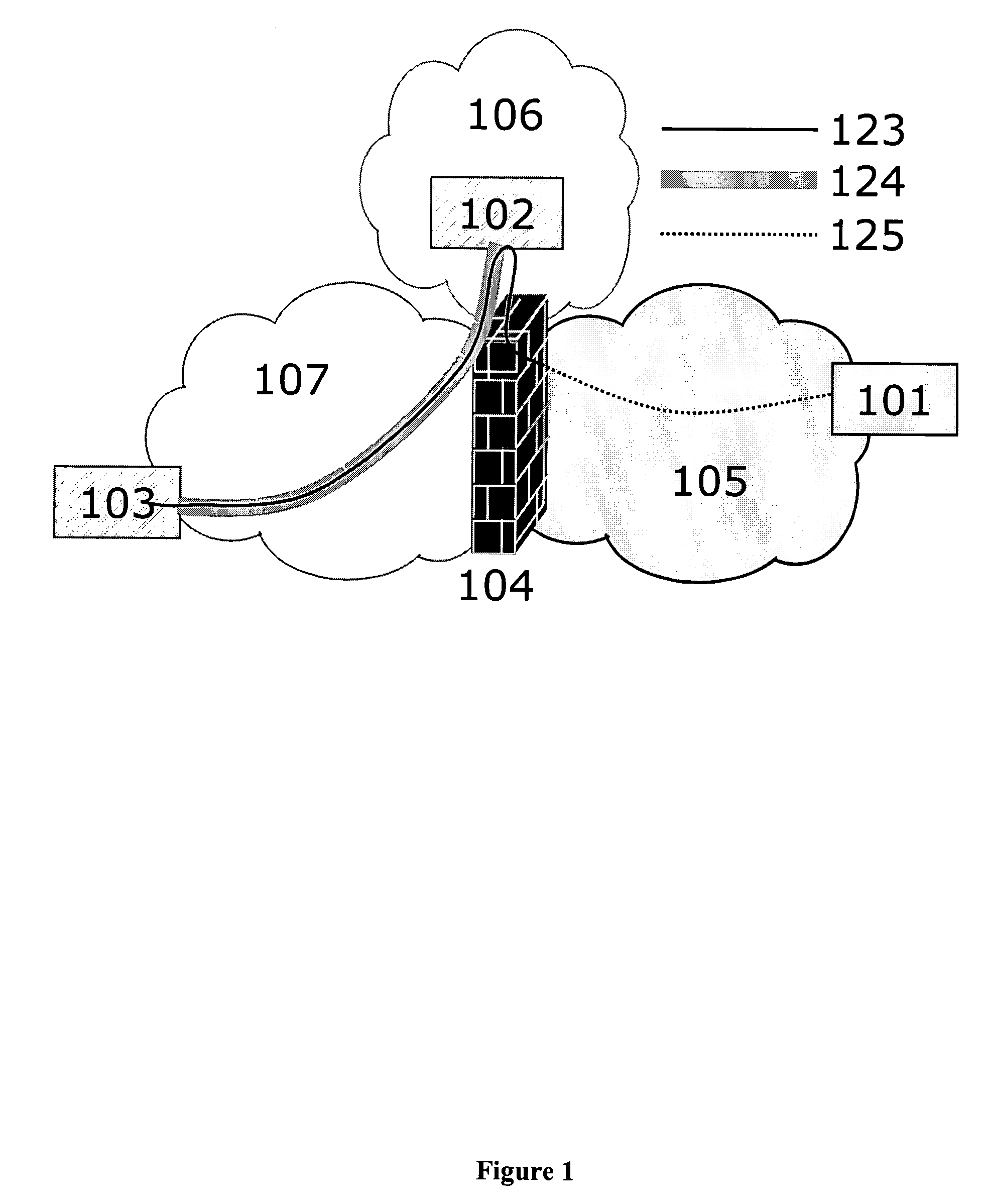
Seamless IP mobility across security boundaries
InactiveUS20040078600A1Digital data processing detailsUnauthorized memory use protectionSecurity solutionUser device
A method, an arrangement and a computer program product, for providing seamless IP mobility across a security boundary between two domains is described. The invention comprises a novel architecture of known network infrastructure components along with enabling client software on the user device. The specific client software as well as the novel architecture represents the invention. Unlike state-of-art today, the method is based on the combined use of independent IP mobility systems in each of the two domains. The key to the invention is client software being able to operate with both mobility systems simultaneously. Moreover, communication takes place in such a way that the ordinary remote access security solution is in control of all access to the secure home domain of the user. The resulting method provides secure and seamless IP mobility in any domain with independent choice of mobility and security technologies. The invention does not require any significant changes (adaptations nor extensions) to any IP mobility or security technology beyond existing or upcoming standards. Nor does it require any significant changes to existing infrastructure components. The mobility client software is the only component that is affected, thus making the method client-centric, as opposed to a network-centric approach that is otherwise the alternative. The invention applies both for the current IPv4 family of standards as well as the forthcoming IPv6 family of standards. The invention applies in particular for the Mobile IP and IPSec VPN standards but is not restricted to these technologies. The invention is applicable for any IP mobility and IP security protocols as long as they are based on the same set of underlying principles.
Owner:BIRDSTEP TECHNOLOGY AS
Network centric power flow control
Owner:THE BOEING CO
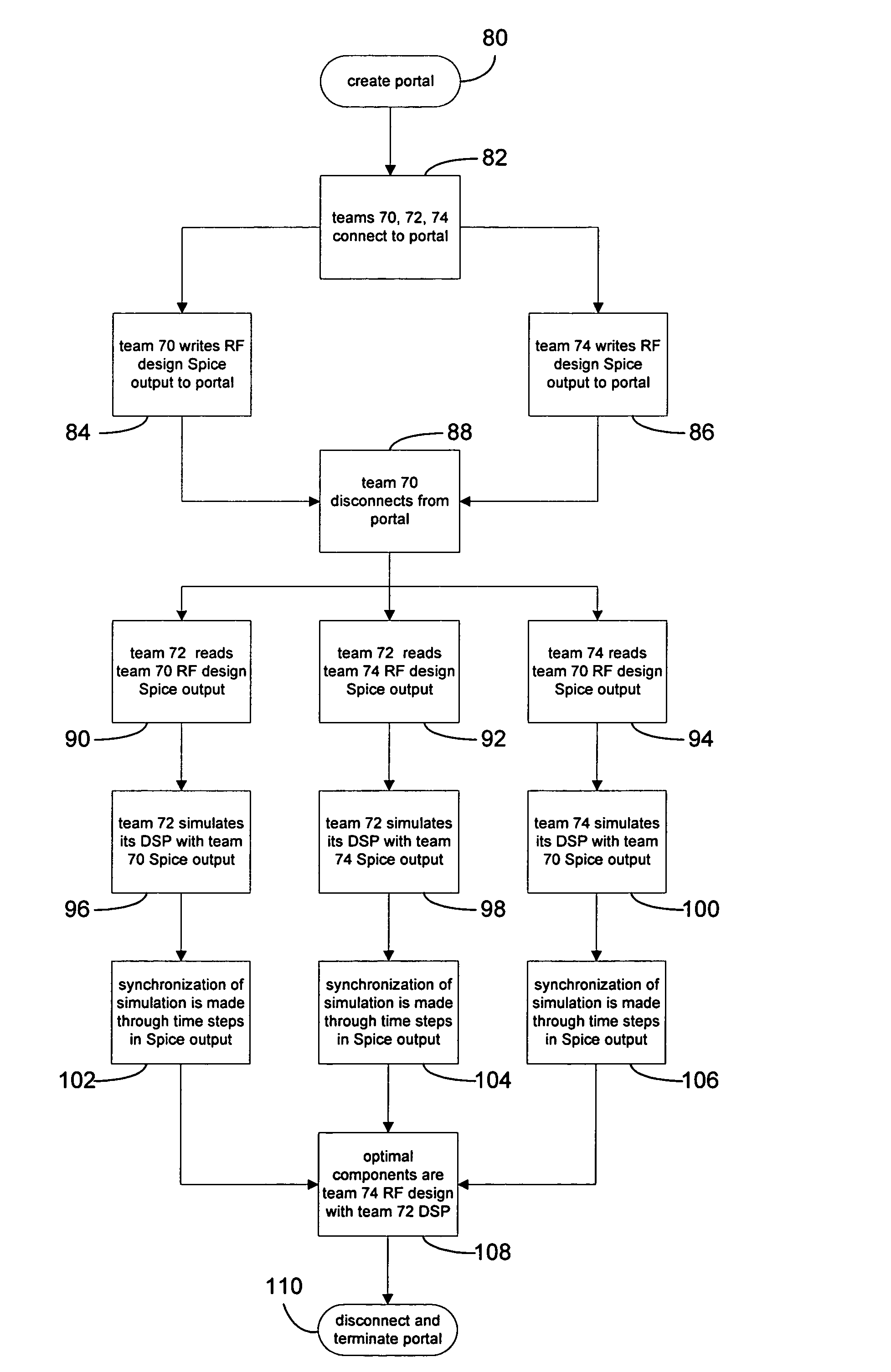
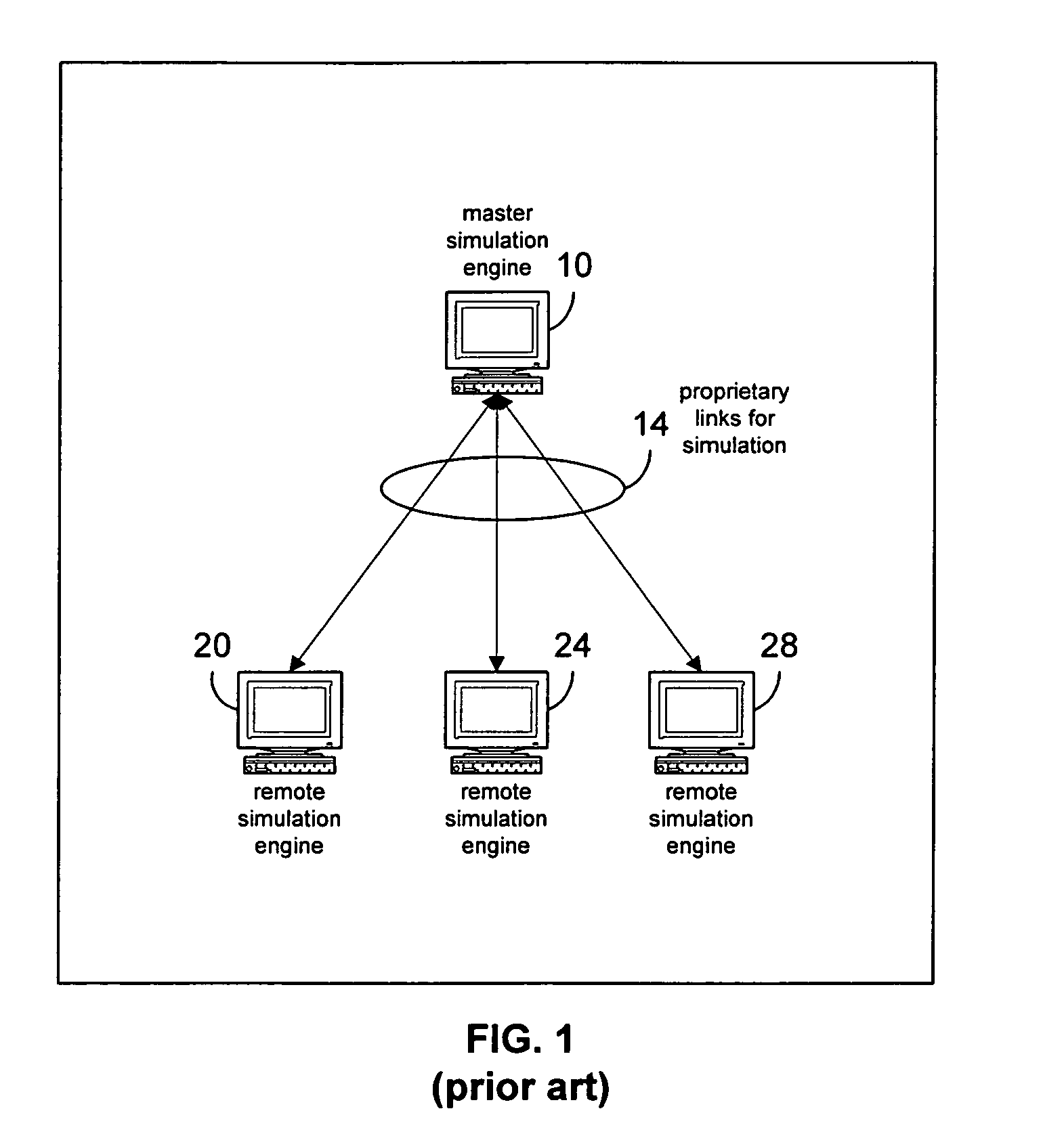
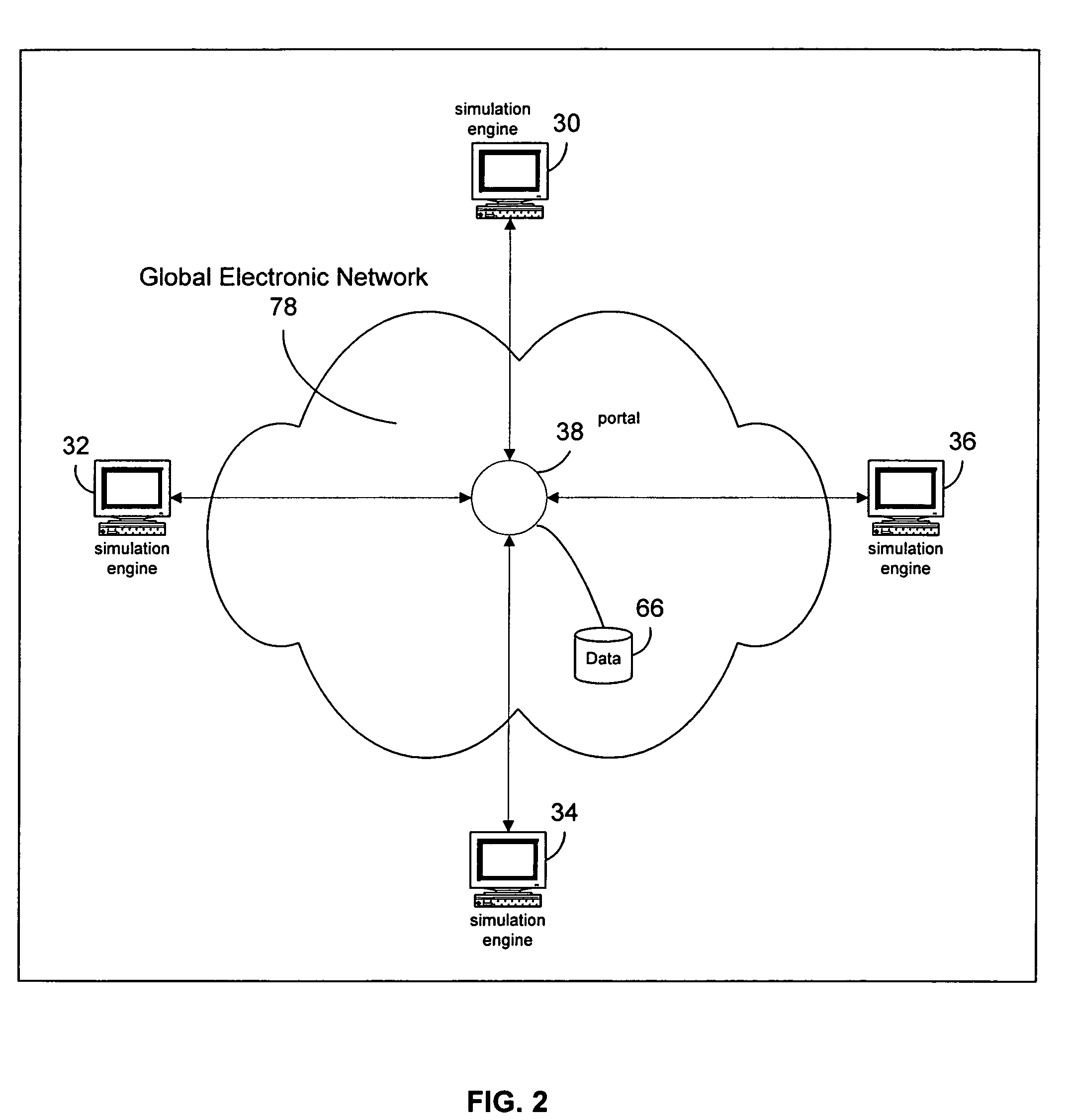
Open system for simulation engines to communicate across multiple sites using a portal methodology
InactiveUS7246055B1Facilitate communicationCooperate wellDetecting faulty computer hardwareMultiple digital computer combinationsElectronic networkData file
An open system for multiple discrete, geographically disperse simulation engines to communicate with each other across a distributed electronic network, such as the Internet, comprises a portal accessible to the simulation engines over the network. Local portions of the simulation may be run separately by each simulation engine, and the output data files are stored on and managed by the portal. A co-simulating engine may request an output data file stored by the portal and use that data as input for its downstream portion of the simulation. In this fashion, multiple geographically disperse simulation engines can test bench their designs in an open, network centric simulation environment.
Owner:CADENCE DESIGN SYST INC
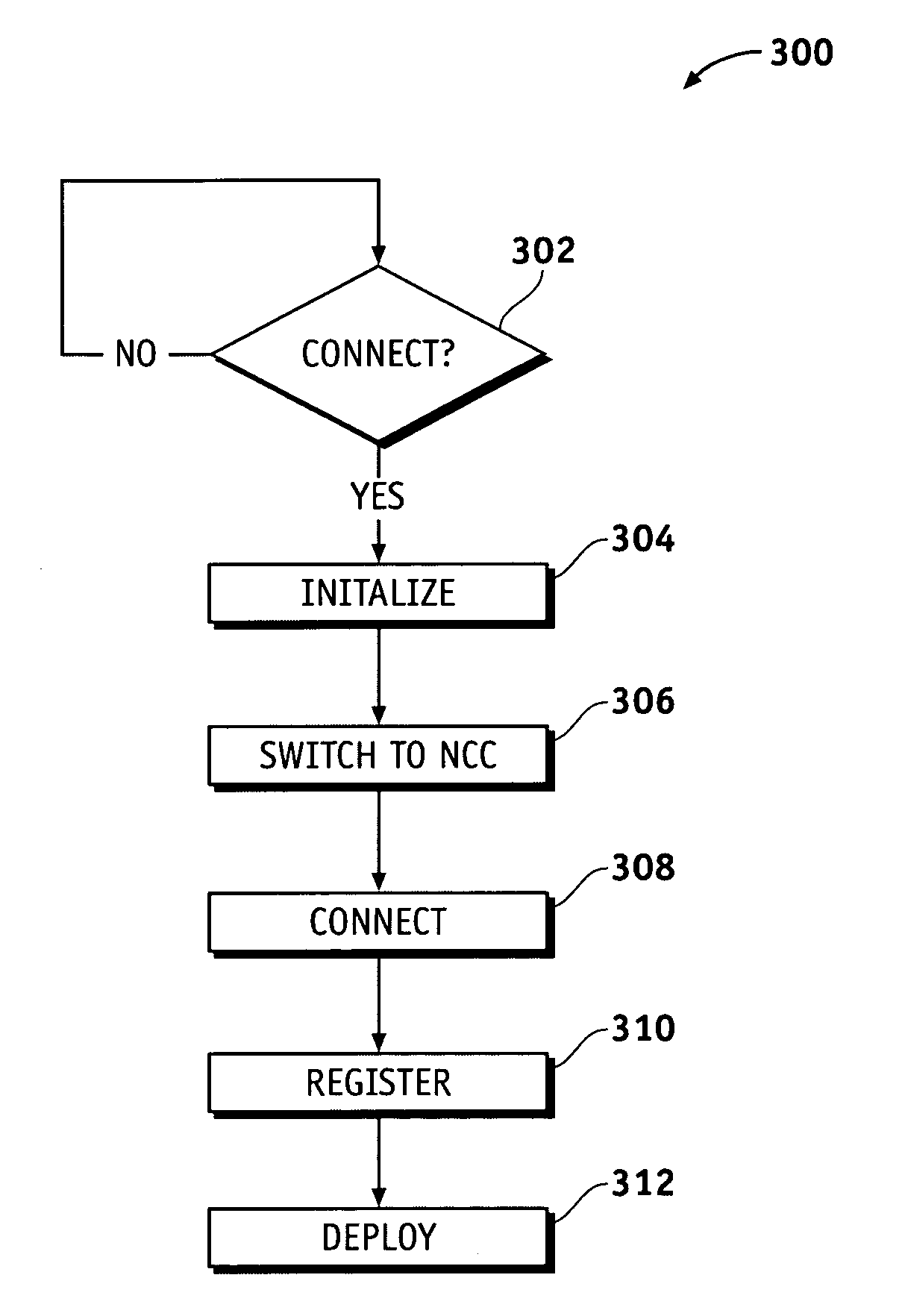
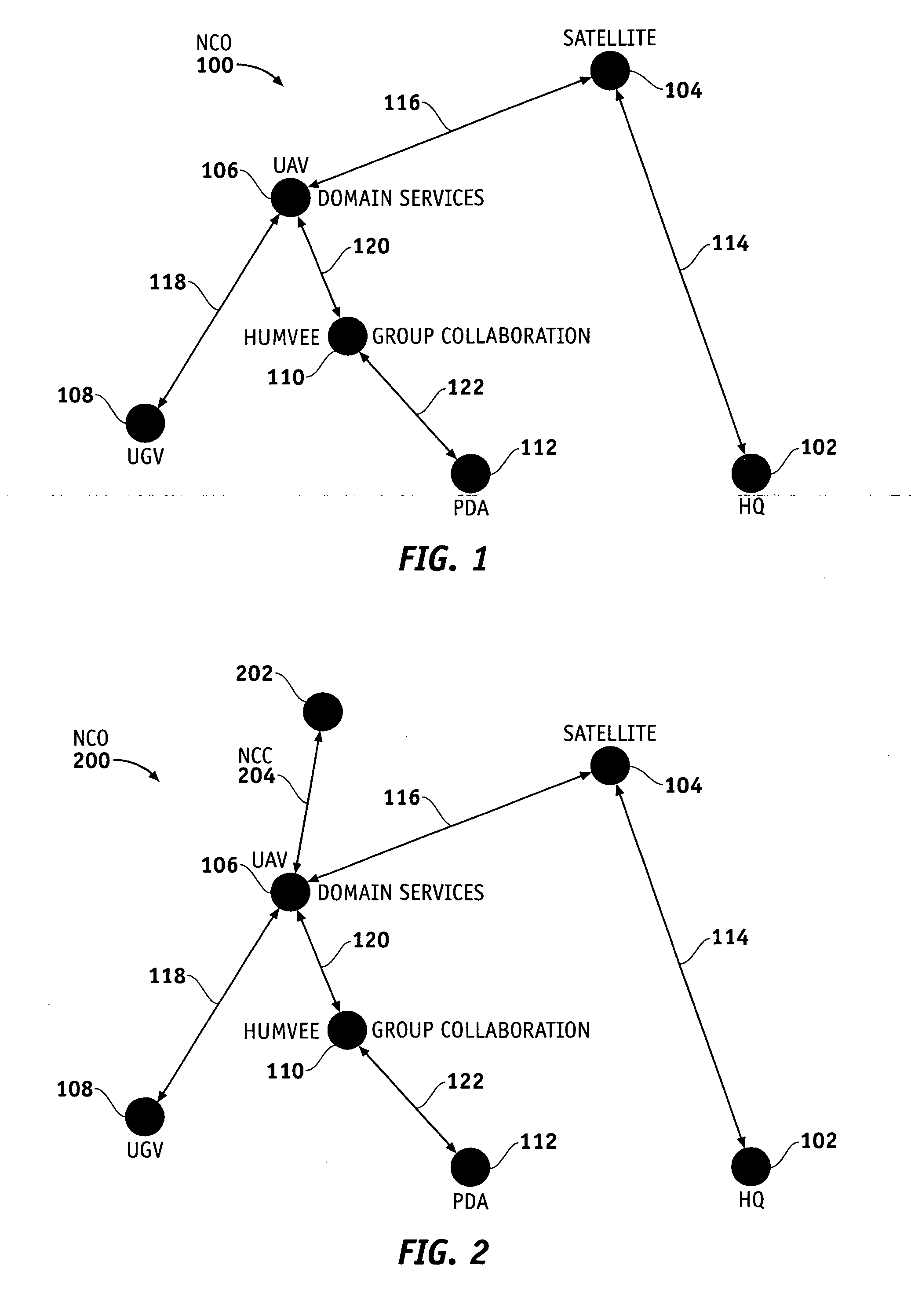
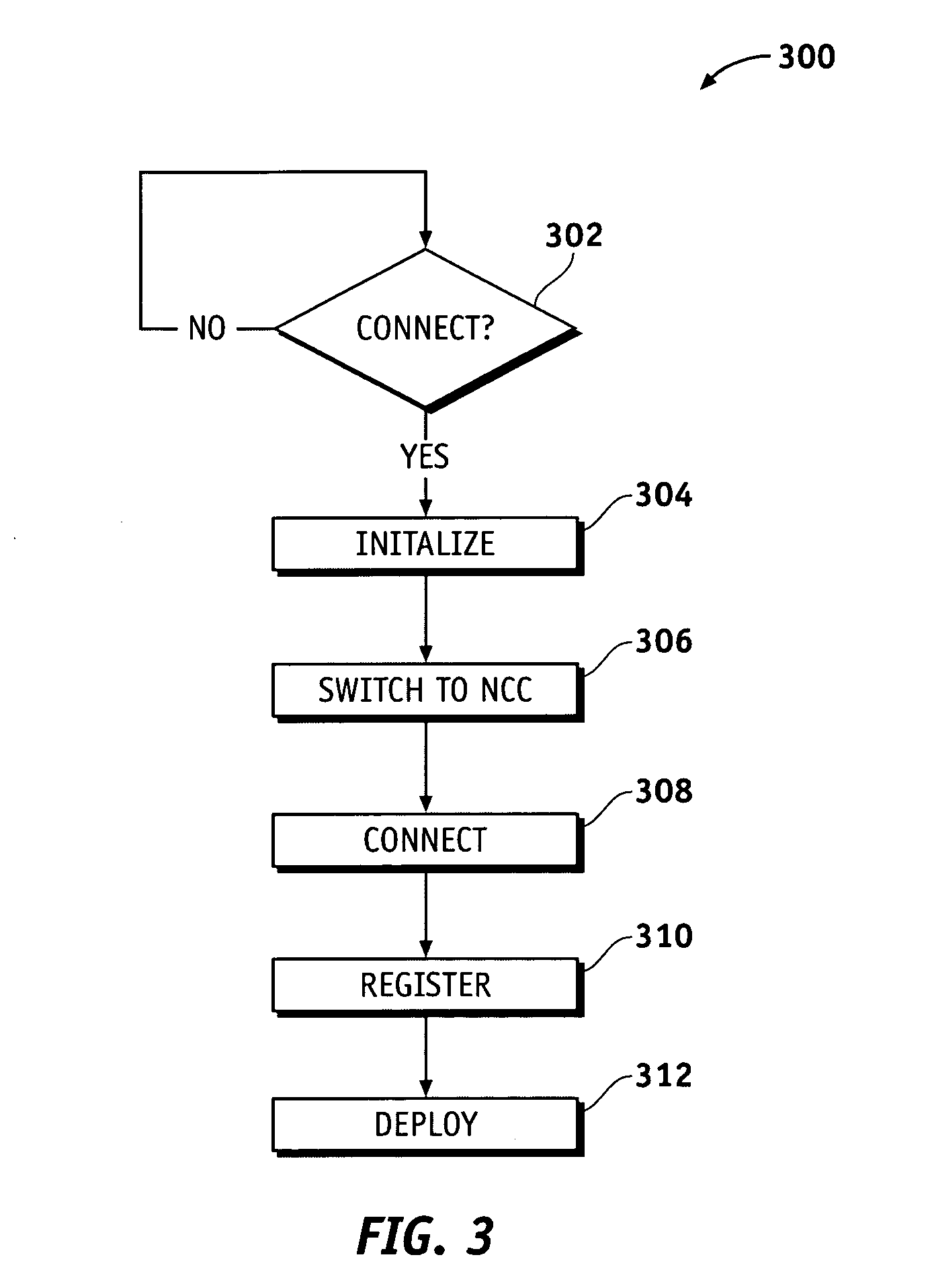
Net-centric coordination channel (NCC)
ActiveUS20060229080A1Firmly connectedFacilitate discoveryError preventionTransmission systemsTelecommunications linkFrequency spectrum
Methods and apparatus are provided for registering an unanticipated node into an ad-hoc network. A communication channel is dedicated as the link between a registry within the network and unanticipated nodes. The dedicated communication link typically comprises primary and secondary frequencies in the RF spectrum. An unanticipated node can be registered “on-the-fly” via the dedicated communication link by identification, authentication, and non-repudiation. The unanticipated node can then interoperate with the network via a standard communication protocol.
Owner:THE BOEING CO
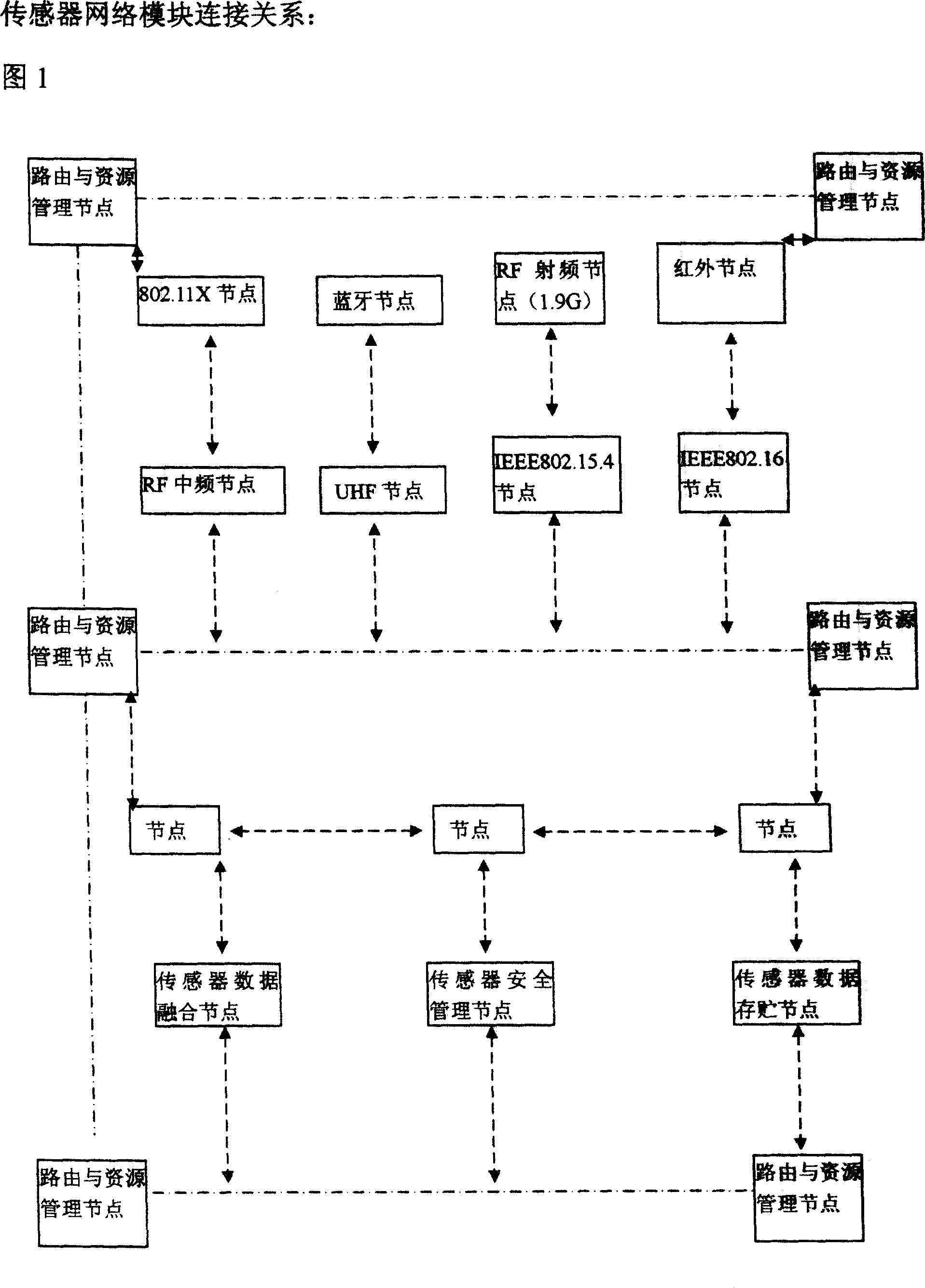
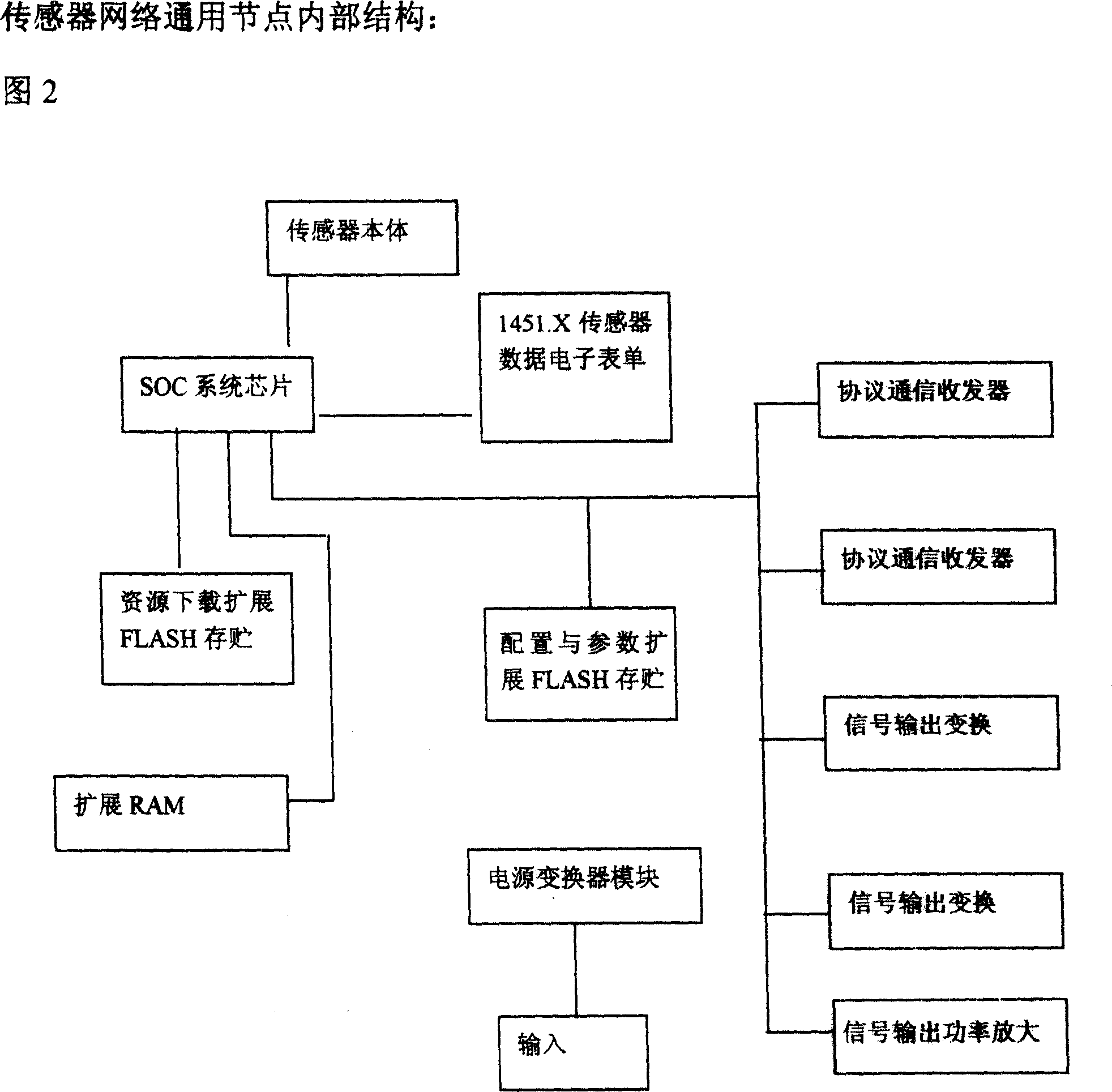
Self-adapted sensor network of the network control platform based on the multi-protocol module structure
InactiveCN101018236AHigh cost performanceLower base costTransmission systemsTransmissionSelf maintenanceMicro structure
The related adaptive sensor network control system based on multiprotocol communication embedded module structure is self diagnosis, self maintenance and self management. The architecture merges the advanced network and micro-structure software technology, forms the 'micro-structure sensing and controlling integration' mode, belongs to new running mode, new networking mode, and new theory application, and enables the sensor network replace computer network in many fields hopefully.
Owner:刘恒春
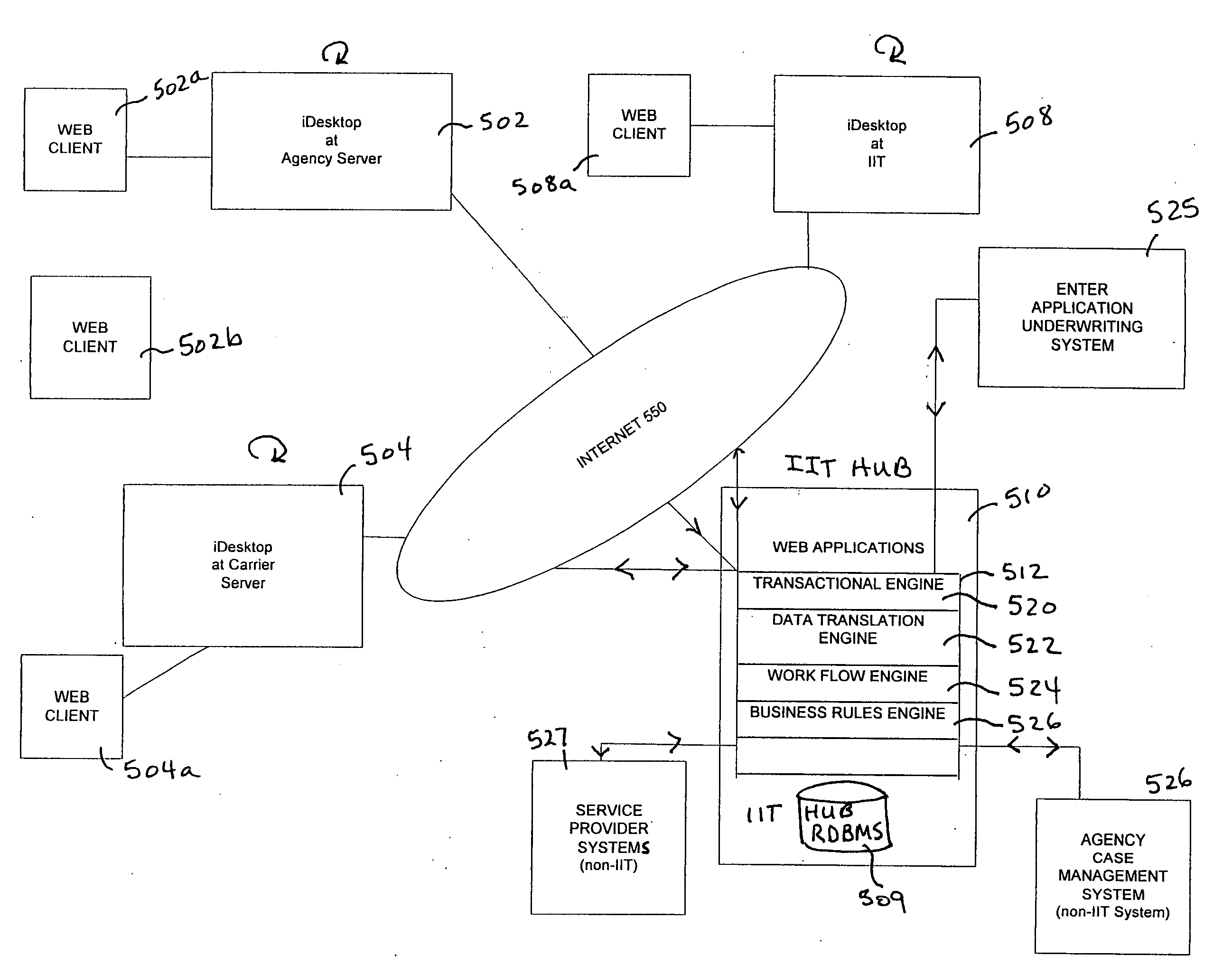
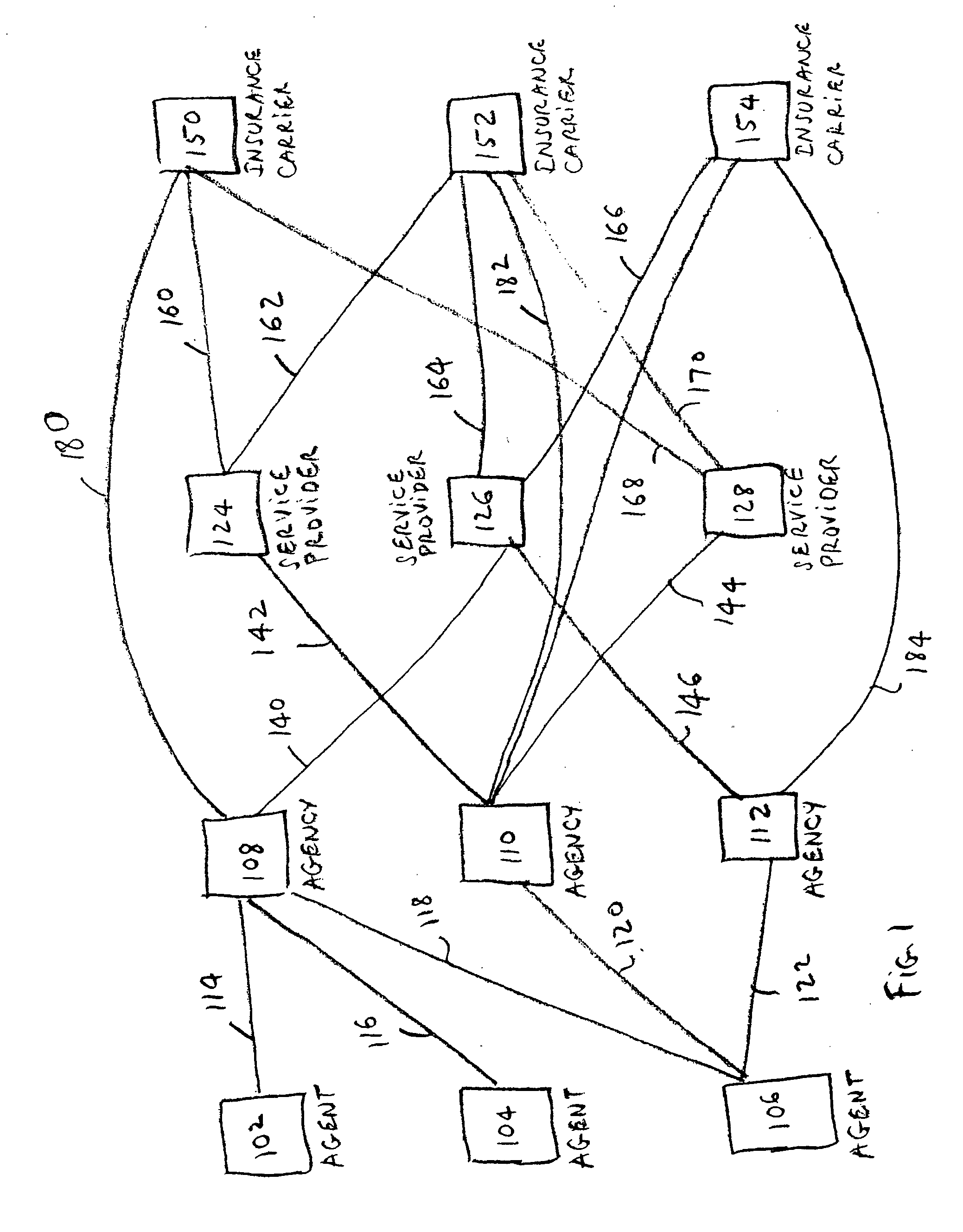
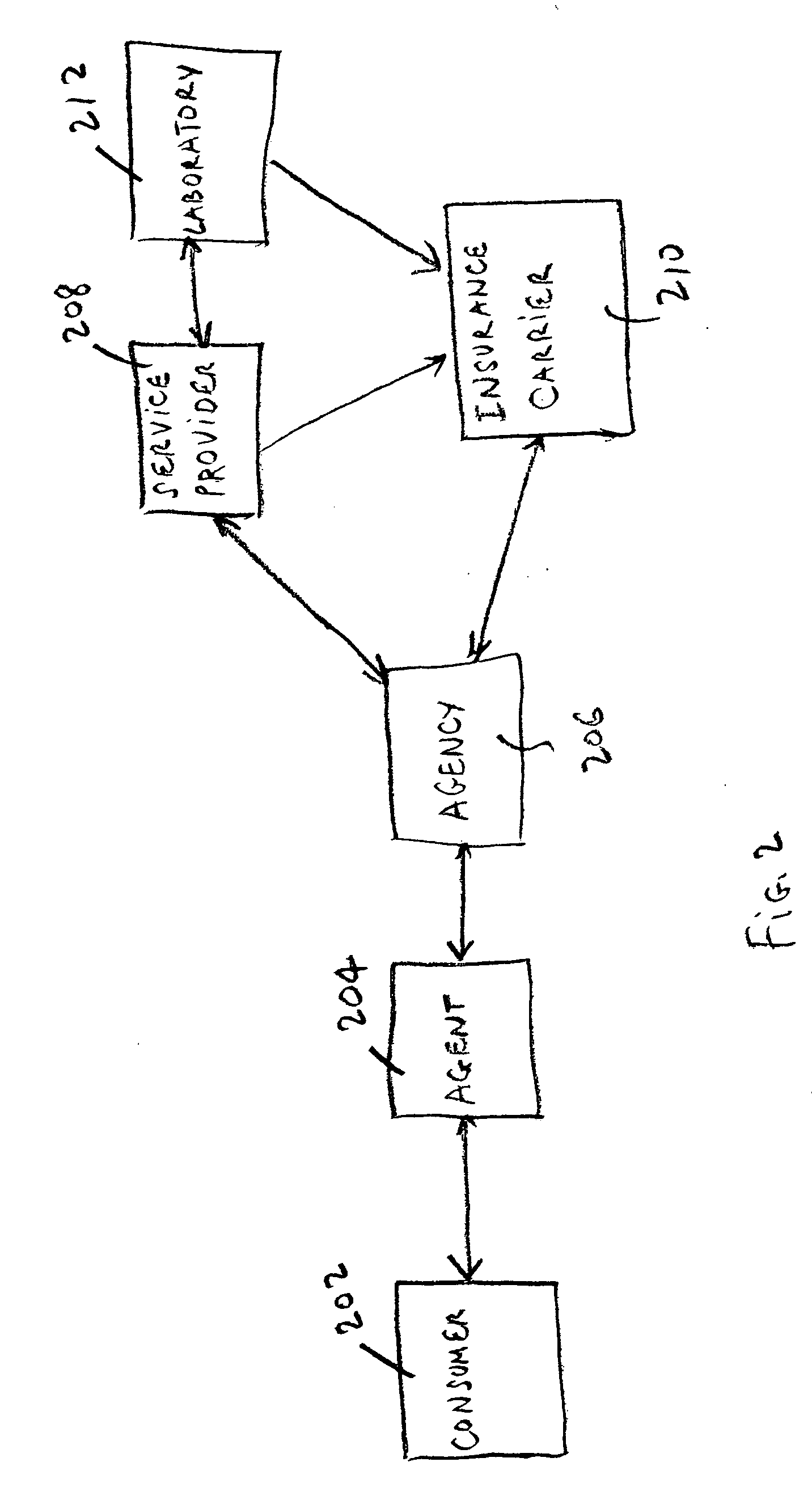
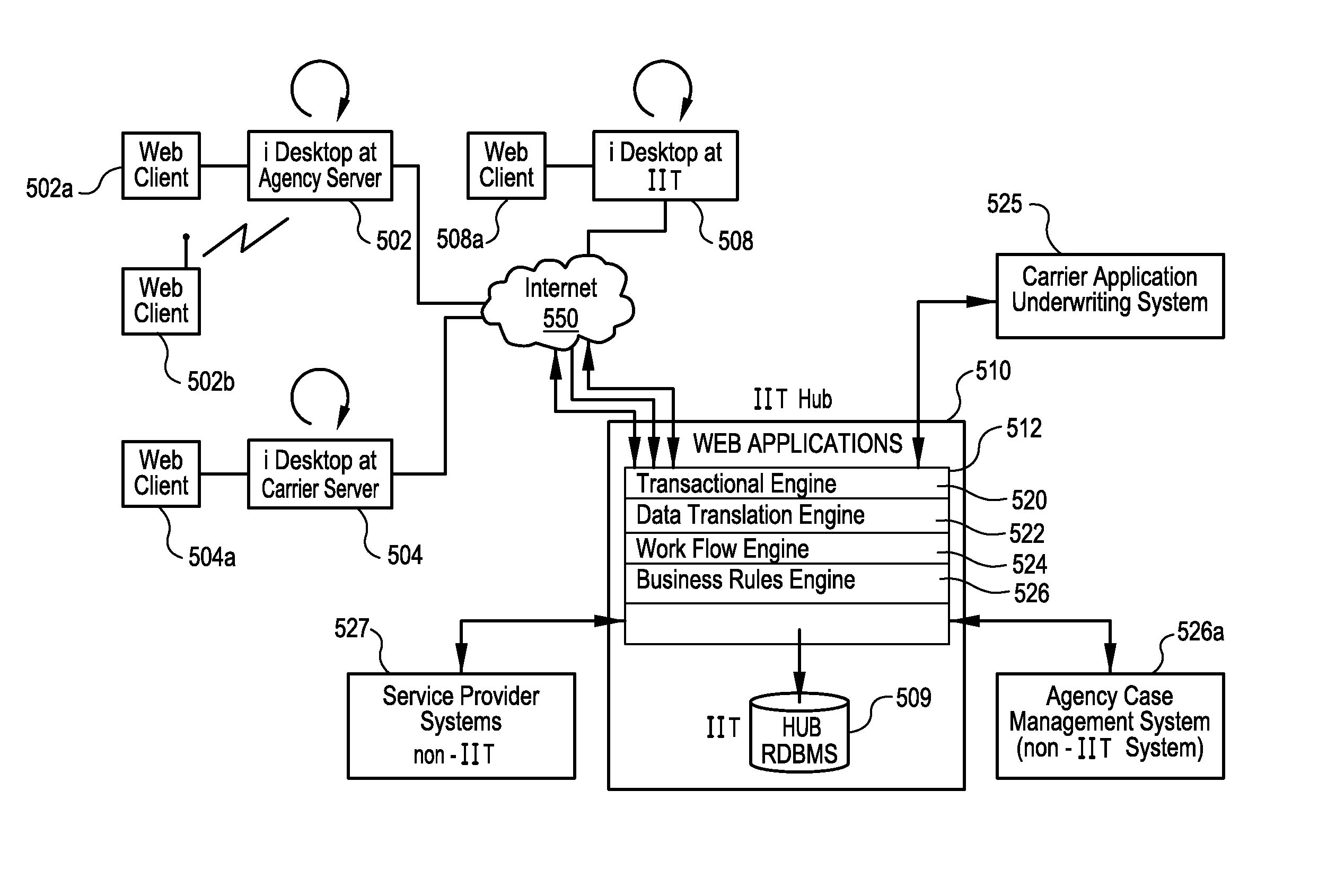
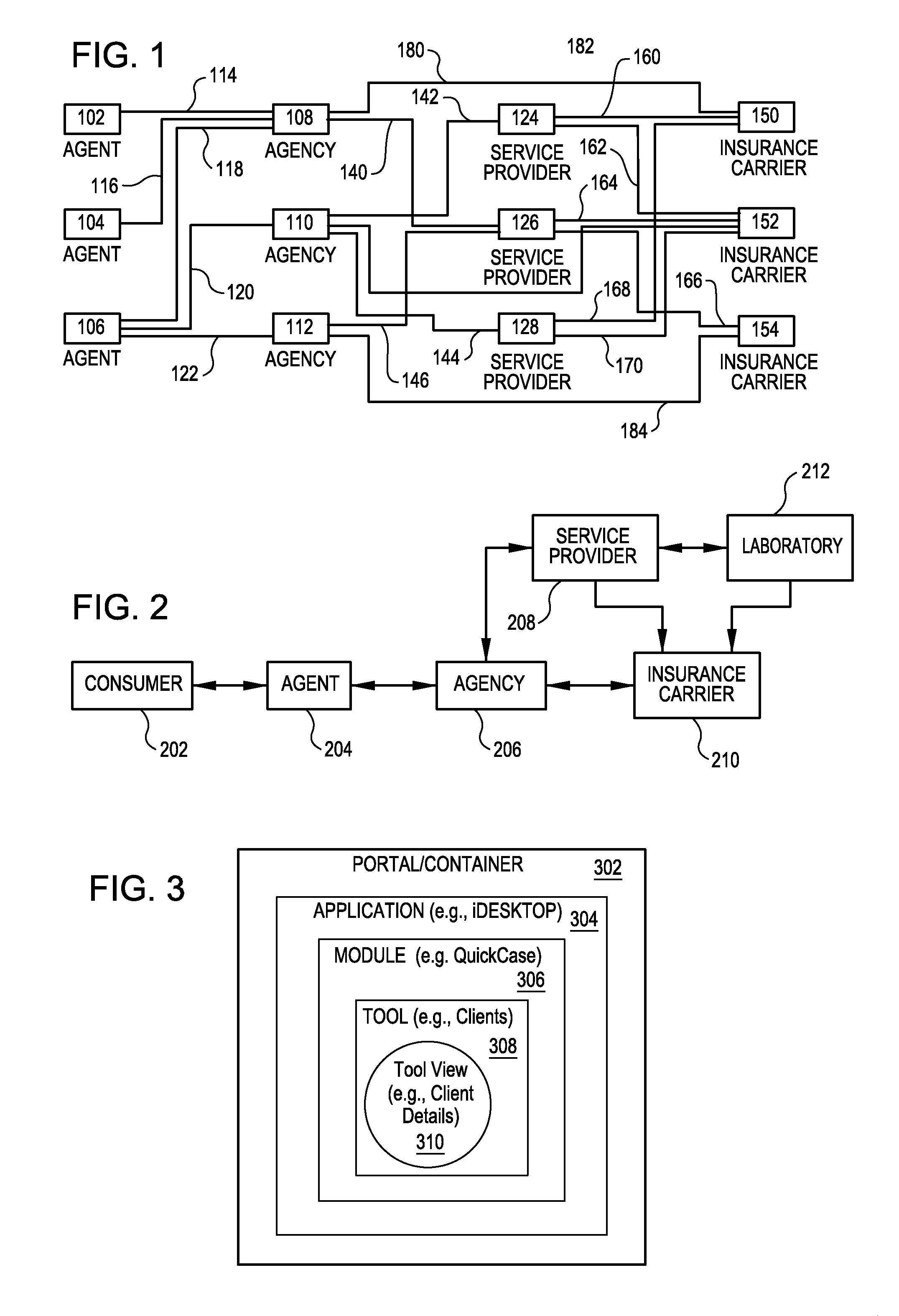
Techniques for underwriting insurance policies using web-centric insurance management system
InactiveUS20090089101A1Efficient and secureFacilitate creation of newFinanceDigital data processing detailsService provisionComputer module
A scalable, adaptable, modular, and web-centric Insurance Back-Office System (IBOS) for serving the needs of carriers, agencies, agents, and service providers in the insurance industry is disclosed. The IBOS provides a framework for allowing web-centric collaboration among agents, agencies, carriers, and service providers, using applications that manage applicants, cases, and policies in an efficient and secure manner. The IBOS infrastructure is designed to facilitate the creation of a new application, module, tool, or view in a simplified manner. The web-centric application includes a first module for creating a case and a second module for tracking the case after the case has been submitted to the carrier for consideration.
Owner:ORACLE INT CORP
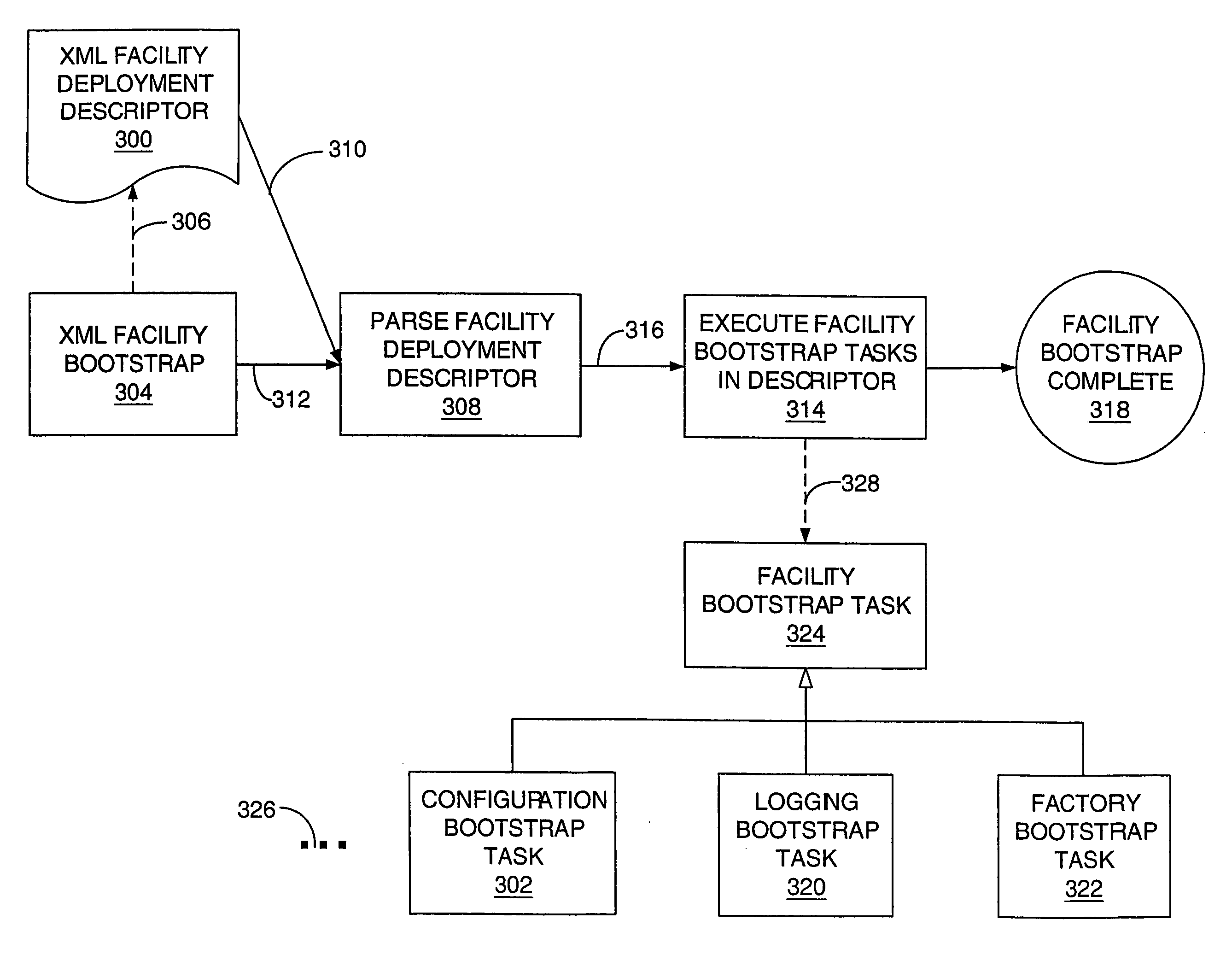
Application framework for use with net-centric application program architectures
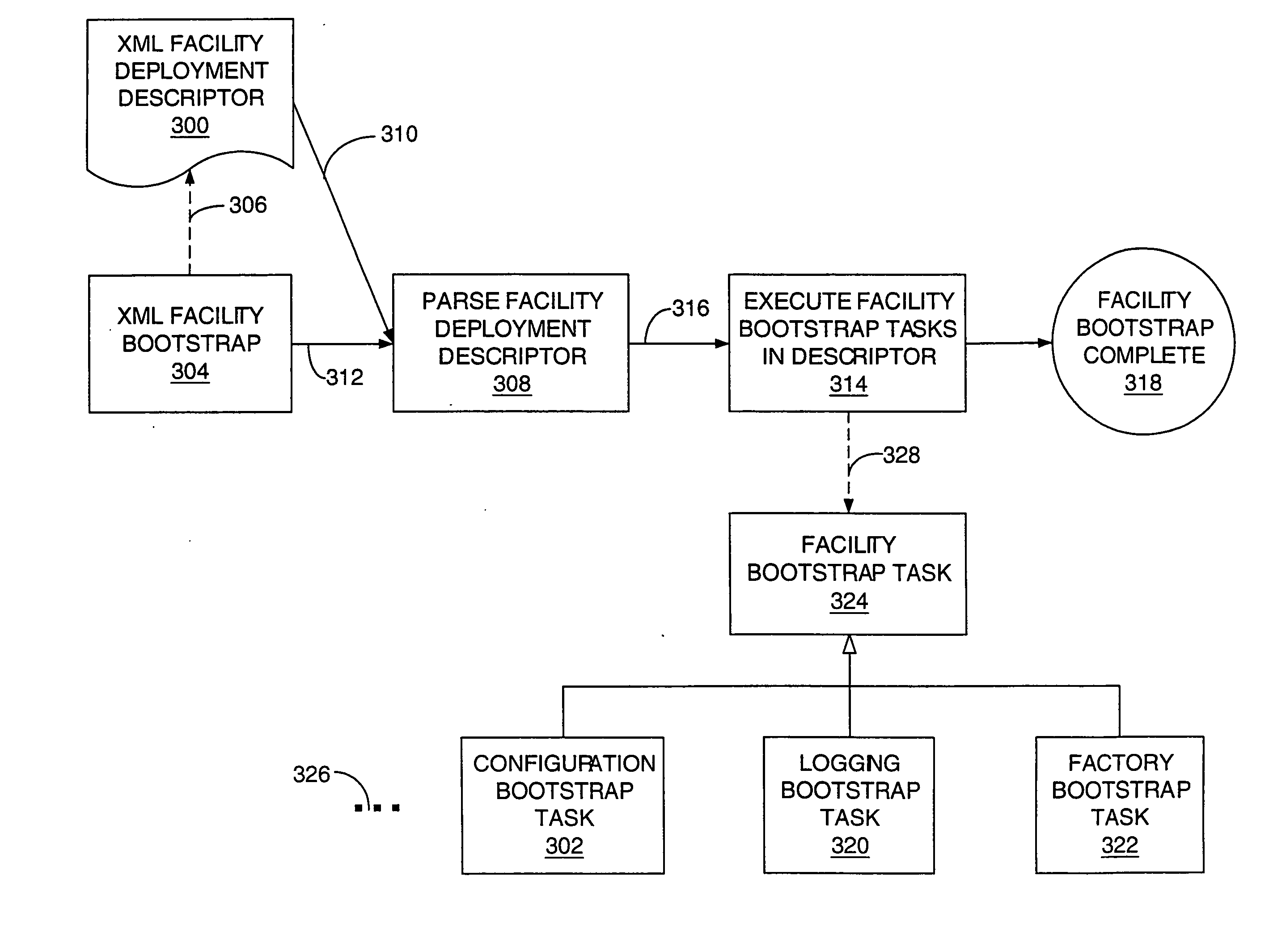
InactiveUS20060064574A1Speed up the processFacilitate modification and maintenanceProgram initiation/switchingDigital computer detailsTechnical standardApplication software
A robust toolkit provides facilities that can be assembled in a modular manner to specify the fundamental architecture of a net-centric application. A bootstrapping process assembles various facilities within the architecture. A configuration facility defines an API for getting properties that can be defined in any number of different types of sources. A factory de-couples how a resource is produced from where the resource is used. A selector framework applies standard query language to contexts other than querying a database. A pipeline architecture defines a model view controller-like framework for a processing pipeline. Selectors are used to specify when certain portions of a Web conversation should be made available to a user. An authorization facility associates permissions with a user to specify which portions of an application a user is authorized to use.
Owner:ACCENTURE GLOBAL SERVICES LTD
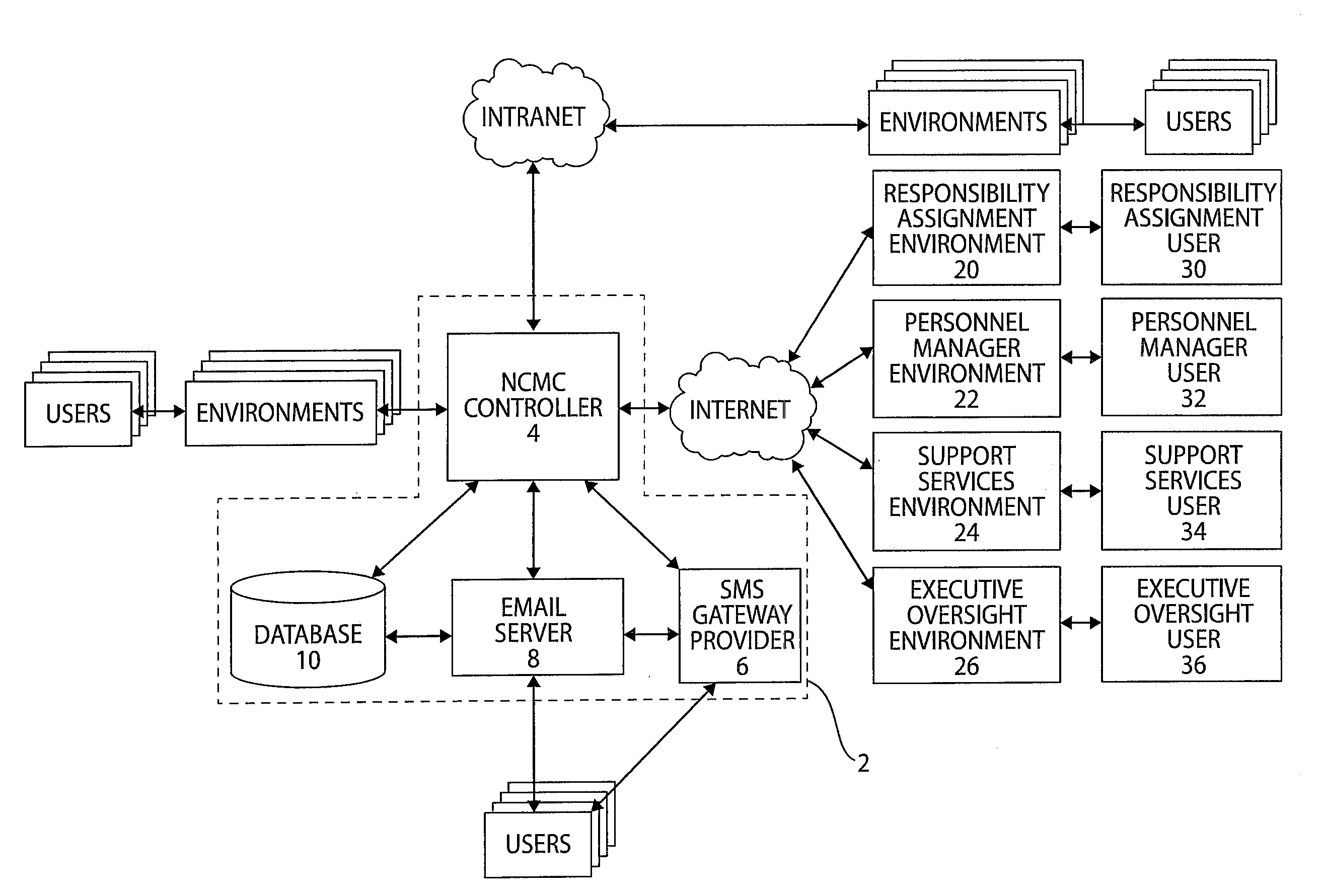
Network Centric Structured Communications Network
InactiveUS20120036255A1Prevent wrong actionDigital computer detailsElectric digital data processingTelecommunications linkCommunications system
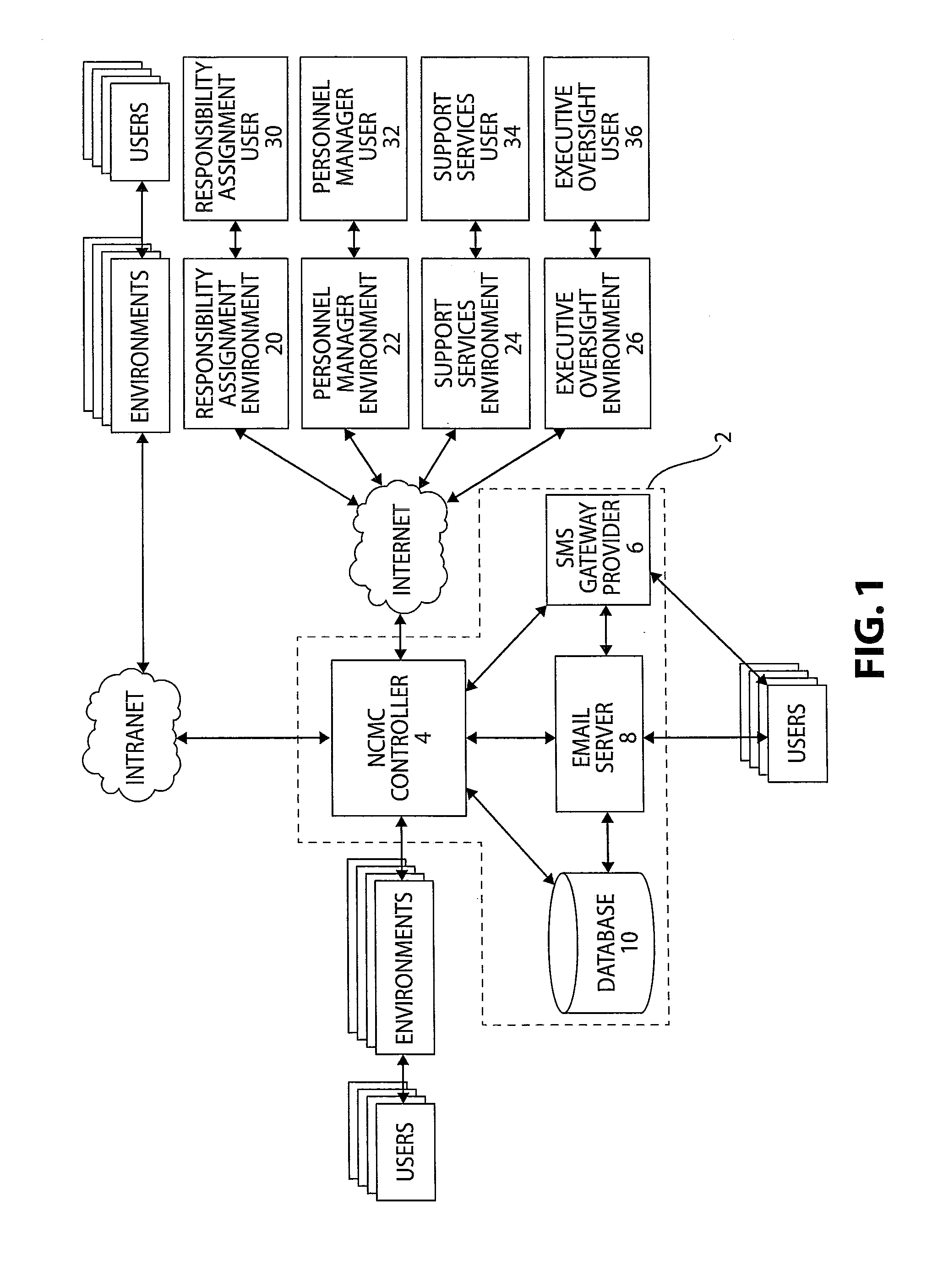
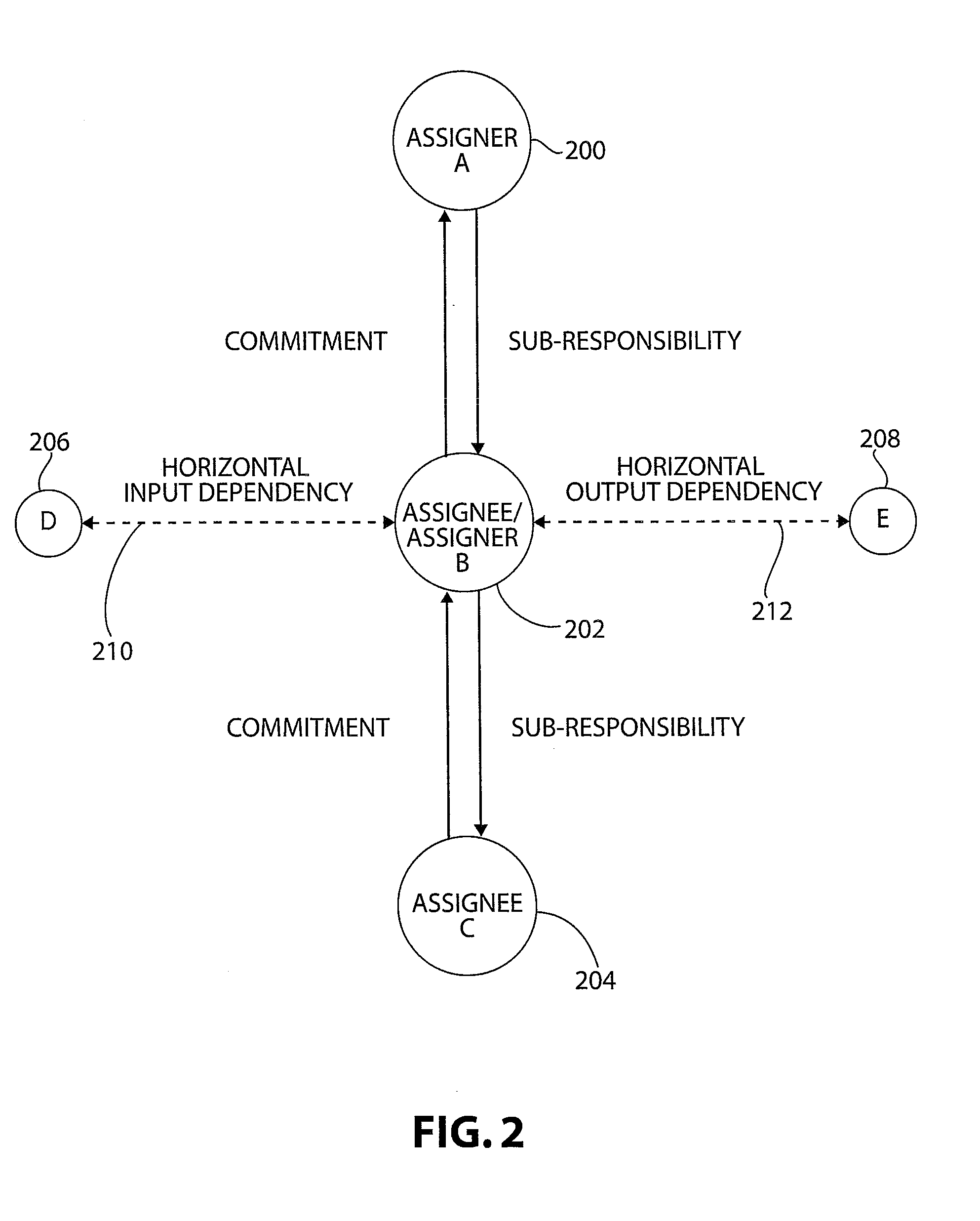
The present invention is a network centric management and communications system and method enabling users with commitments to communicate, manage, notify, assign, link, and / or collaborate with other users. The system includes a database storing one or more user accounts corresponding to nodes on a network, user accounts connected by interdependencies forming social connections between individual users having responsibilities and structuring communications via dependency links between interdependent users. The system includes a data server, receiving responsibility data comprising requirements data for creating interdependencies, transmitting assigned commitments, and updating responsibility data. The system further includes a communications link to provide status updates and / or notifications of responsibilities to affected users regarding their status that appropriate corrective action may be taken before one or more commitments to requirements are broken, wherein one or more commitments of a responsibility are modified and / or updated. The system can host multiple projects simultaneously in the data server.
Owner:EPMOD
Dynamic networking method and equipment for network access points
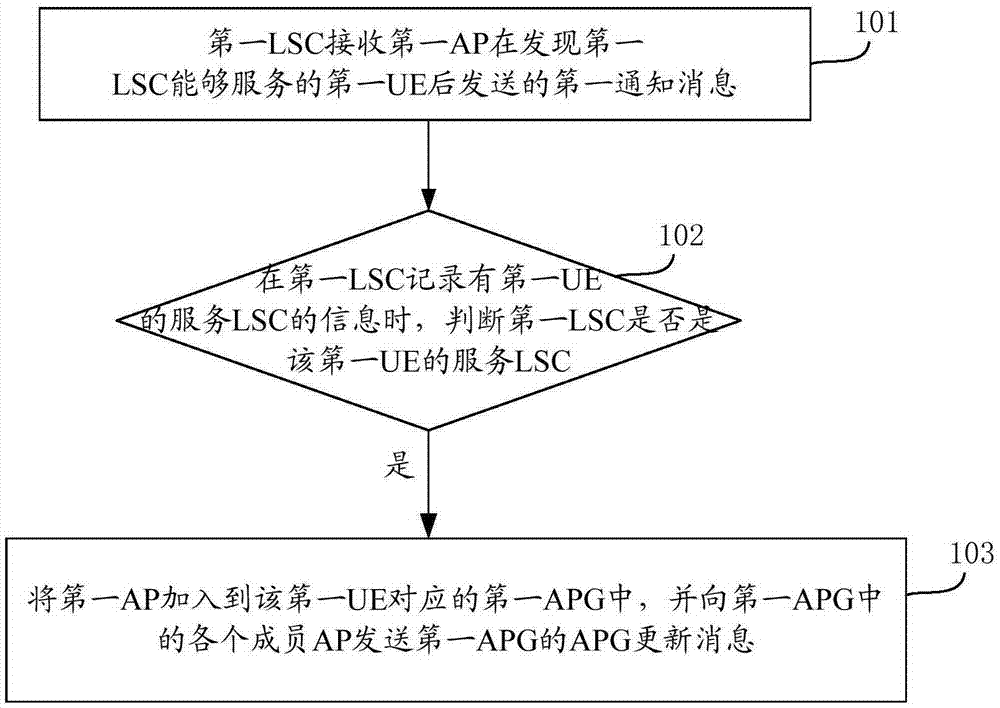
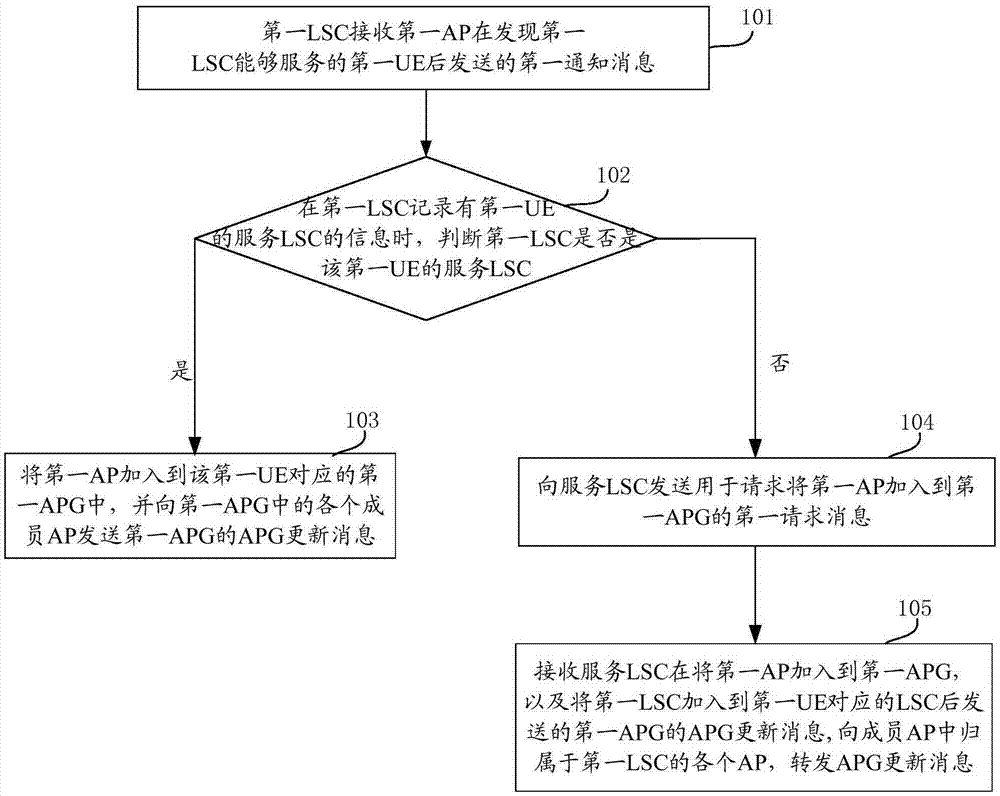
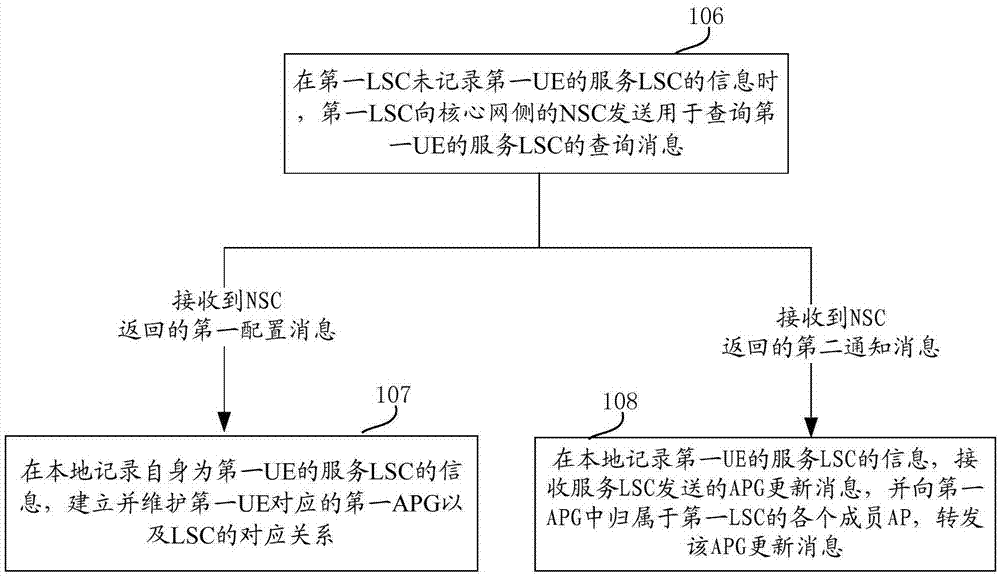
ActiveCN105451250AReduce switching timesAvoid frequent perceptionNetwork traffic/resource managementNetwork data managementNetwork Access ProtectionStatic mode
The invention provides a dynamic networking method and equipment for network access points. According to the embodiment of the invention, the traditional network-centered idea is changed into the user-centered idea and services are provided for users, thereby preventing the user from sensing the network environment frequently and providing a data transmission service of the user in a low-speed or static mode by an APG. Moreover, during the movement process of the user, the user service transmission can be realized based on dynamic APG updating and AP cooperation in the APG. Therefore, the number of times for user switching can be reduced and user switching in the APG does not need to use the core network, thereby reducing the signaling load of the core network.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Pipeline architecture for use with net-centric application program architectures
ActiveUS20060064573A1Speed up the processFacilitate modification and maintenanceProgram initiation/switchingDigital computer detailsTechnical standardModularity
A robust toolkit provides facilities that can be assembled in a modular manner to specify the fundamental architecture of a net-centric application. A bootstrapping process assembles various facilities within the architecture. A configuration facility defines an API for getting properties that can be defined in any number of different types of sources. A factory de-couples how a resource is produced from where the resource is used. A selector framework applies standard query language to contexts other than querying a database. A pipeline architecture defines a model view controller-like framework for a processing pipeline. Selectors are used to specify when certain portions of a Web conversation should be made available to a user. An authorization facility associates permissions with a user to specify which portions of an application a user is authorized to use.
Owner:ACCENTURE GLOBAL SERVICES LTD
Methods and Systems for An Autonomous Robotic Platform
ActiveUS20130103195A1Low costDifficult to useProgramme-controlled manipulatorAutonomous decision making processHuman interactionCommand and control
A system and method can provide a command and control paradigm for integrating robotic assets into human teams. By integrating sensor to detect human interaction, movement, physiology, and location, a net-centric system can permit command of a robotic platform without an OCU. By eliminating the OCU and maintaining the advantages of a robotic platform, a robot can be used in the place of a human without fatigue, being immune to physiological effects, capable of non-humanoid tactics, a longer potential of hours per day on-station, capable of rapid and structured information transfer, has a personality-free response, can operate in contaminated areas, and is line-replaceable with identical responses. A system for controlling a robotic platform can comprise at least one perceiver for collecting information from a human or the environment; a reasoner for processing the information from the at least one perceiver and providing a directive; and at least one behavior for executing the directive of the reasoner.
Owner:LEIDOS
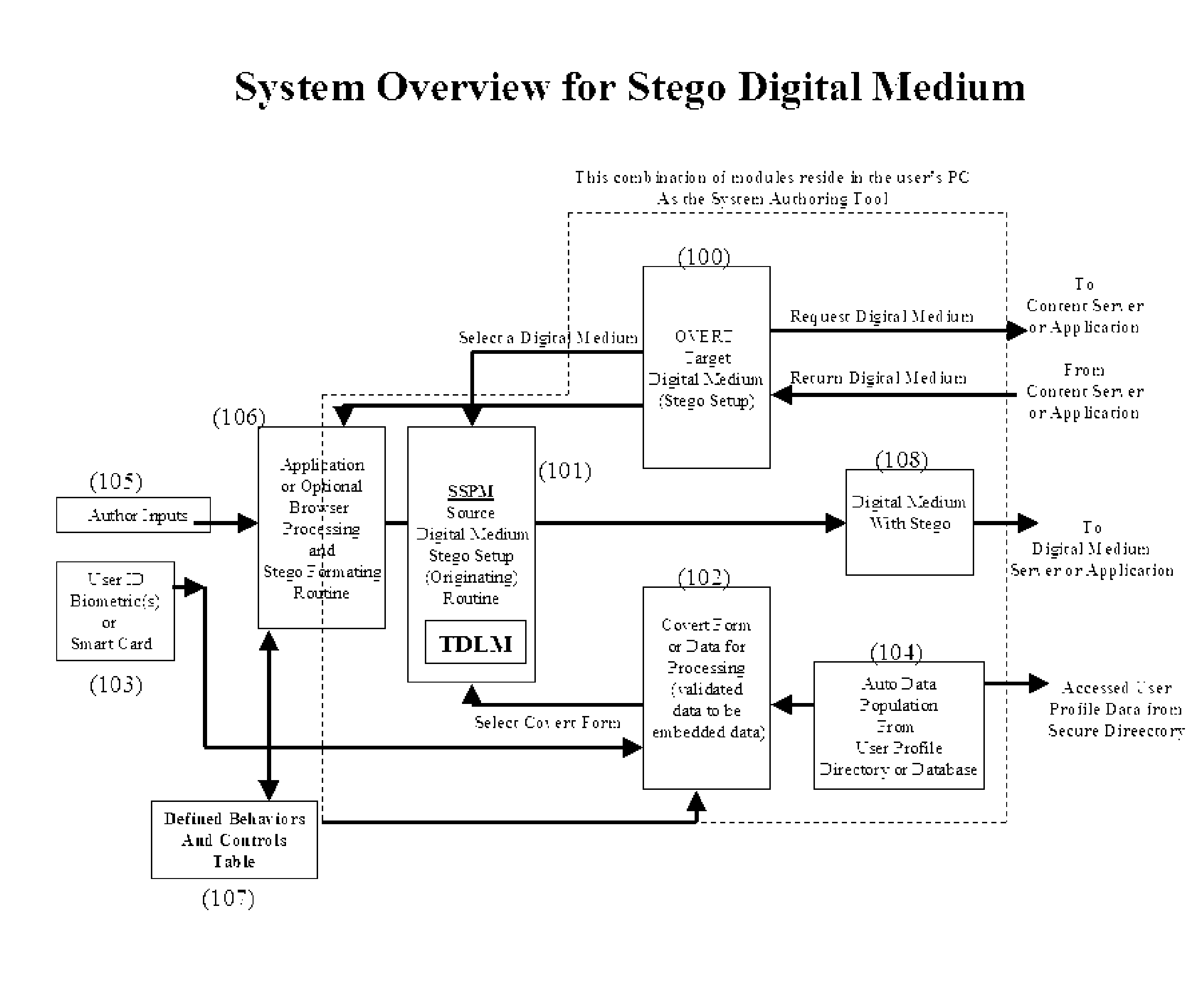
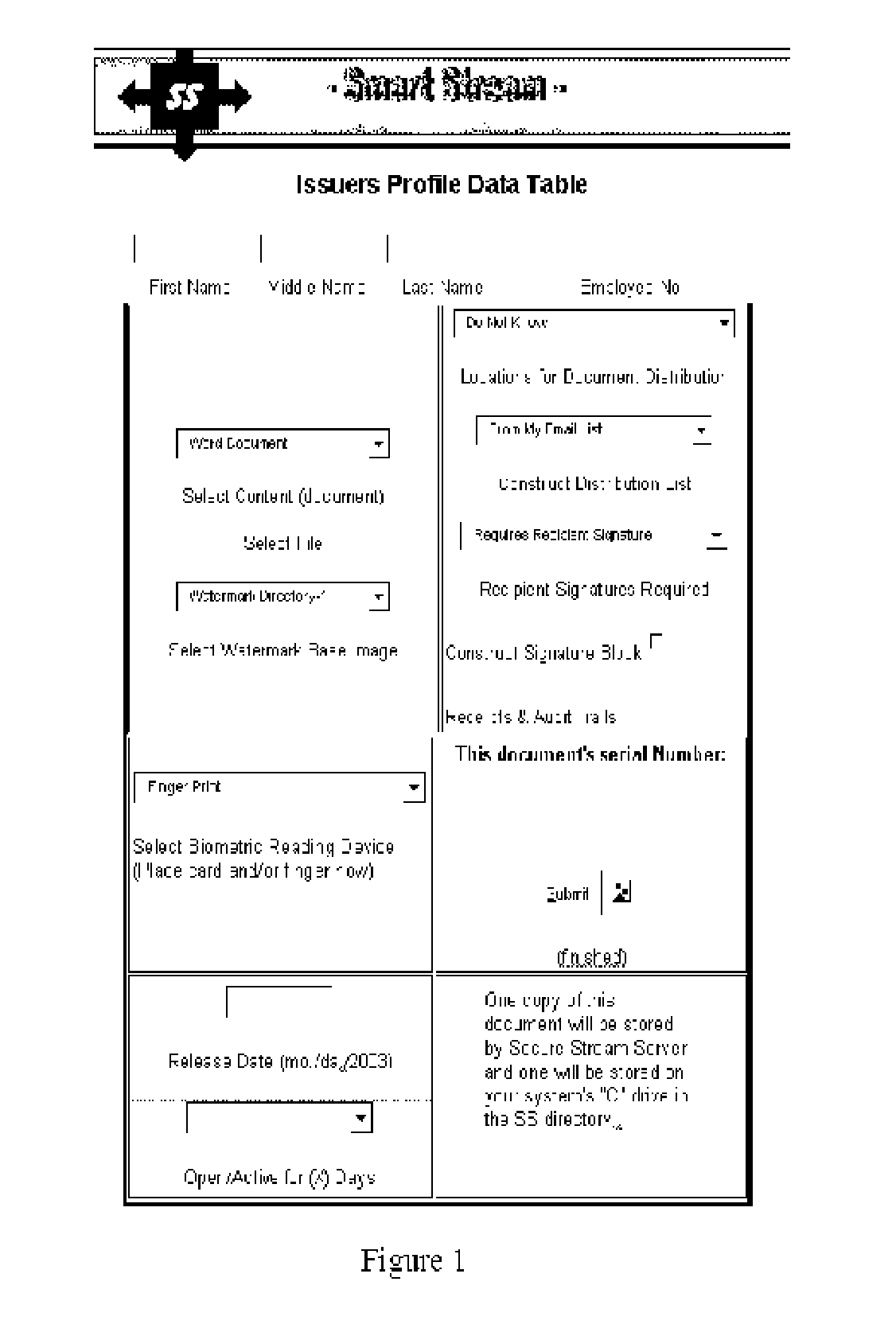
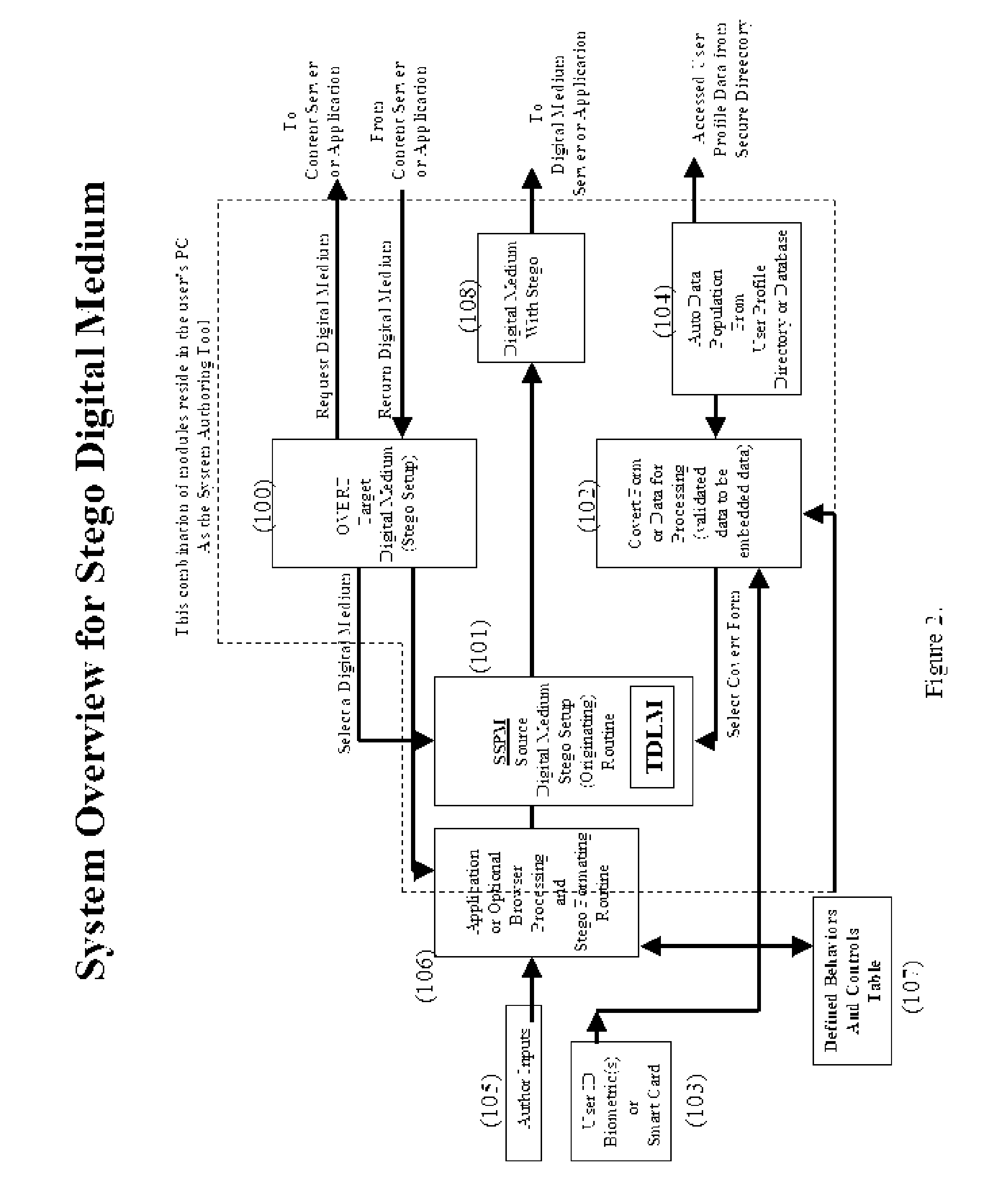
A system for embedding, extracting, and executing self-governing behavior and use controls within digital medium content
InactiveUS20060177094A1Improve securityCharacter and pattern recognitionOffice automationEmbedded securityBehavior control
Steganography is the art of hiding information within information. The hidden information is called “covert” and the carrier information is called “overt.” In the digital world, steganography as a security technique differs considerably from encryption, watermarking, or placing data within digital envelopes. This invention uses steganographic techniques to embedded hidden behaviors, controls, and security within content creating self-governance of the content itself. The hidden behaviors include who, what, when, where, and how content is to be used. The hidden controls govern what can be done with the content such as copied, stored, deleted, and archived. The hidden embedded security includes authentication of author, source, and user of the content. In effect, the content becomes “smart content” and does not require network-centric security controls allowing ubiquitous exchanges across enterprises. This invention renders content counterfeit resistant, one-of-a-kind and includes self-editing schema for multimedia applications.
Owner:SMITH MR ROBERT E +1
Techniques for ensuring data security among participants in a web-centric insurance management system
A scalable, adaptable, modular, and web-centric Insurance Back-Office System (IBOS) for serving the needs of carriers, agencies, agents, and service providers in the insurance industry is disclosed. The IBOS provides a framework for allowing web-centric collaboration among agents, agencies, carriers, and service providers, using applications that manage applicants, cases, and policies in an efficient and secure manner. The IBOS infrastructure is designed to facilitate the creation of a new application, module, tool, or view in a simplified manner.
Owner:ORACLE INT CORP
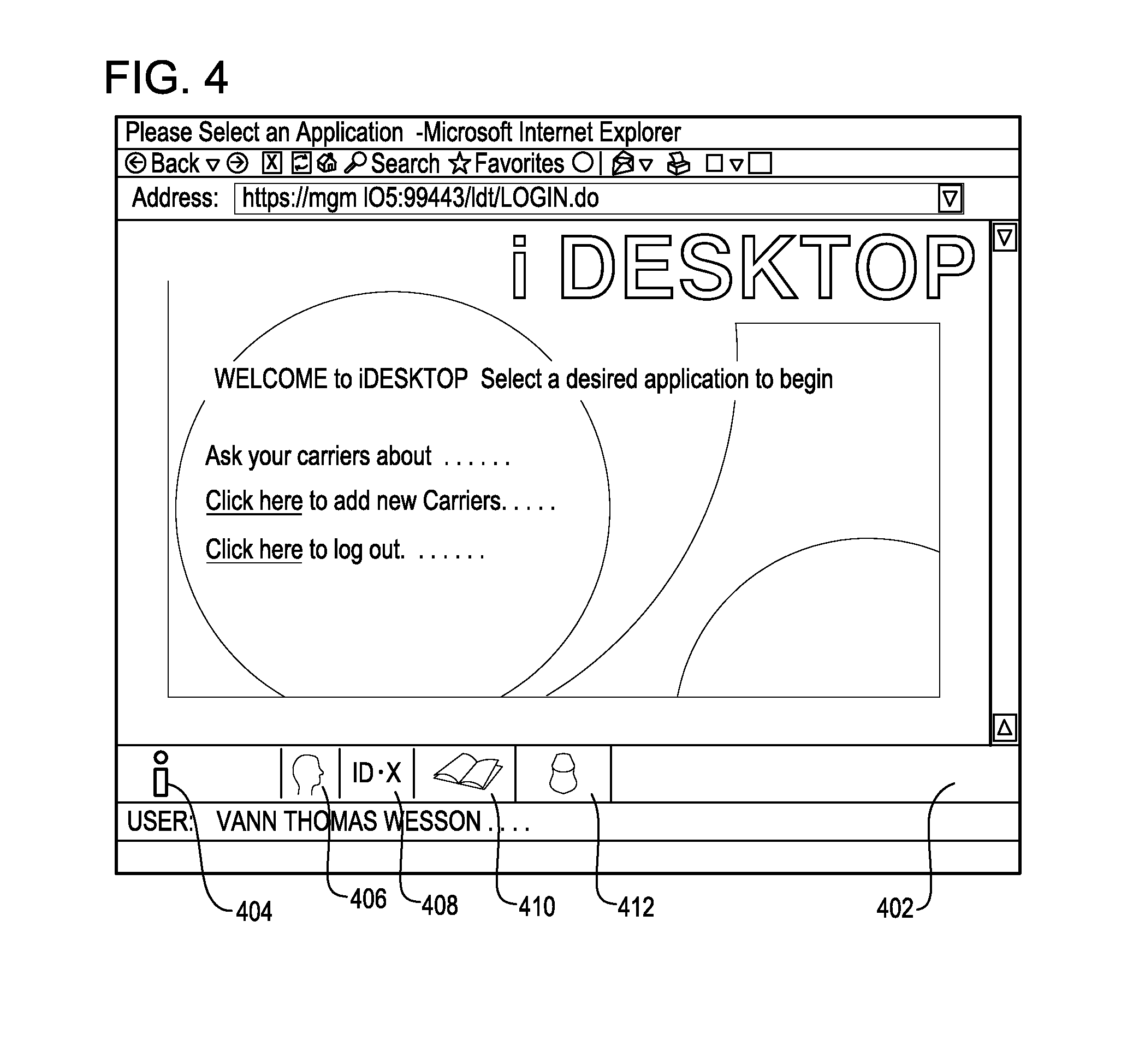
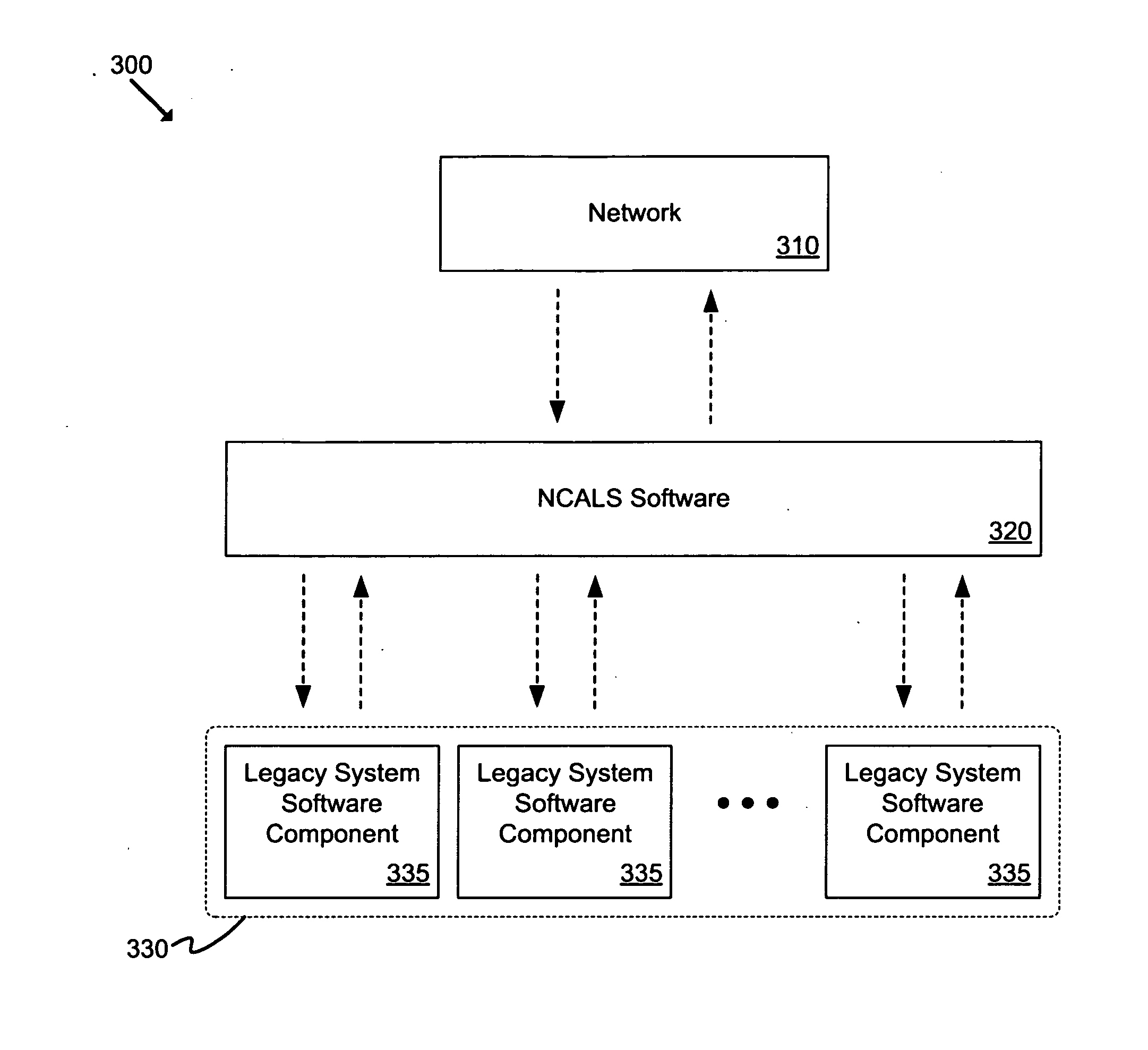
Net-centric adapter for interfacing enterprises systems to legacy systems
InactiveUS20140201418A1Facilitate communicationCreate quicklyTransmissionElectric digital data processingLegacy systemComputer module
A configurable system for translating, exchanging and integrating data and services among disparate software applications is provided. The system includes a first connection that interfaces with an enterprise system, a second connection that interfaces with a legacy system, and an adapter module coupled to the first and second connections. The adapter module is configured to receive data from the first connection and pass data to the second connection. The system may also include a transform module configured to manipulate data received at the second connection. The adapter module may be single-channel or multi-channel. A multi-channel adapter module is able to interface with multiple legacy systems and / or multiple enterprise systems.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
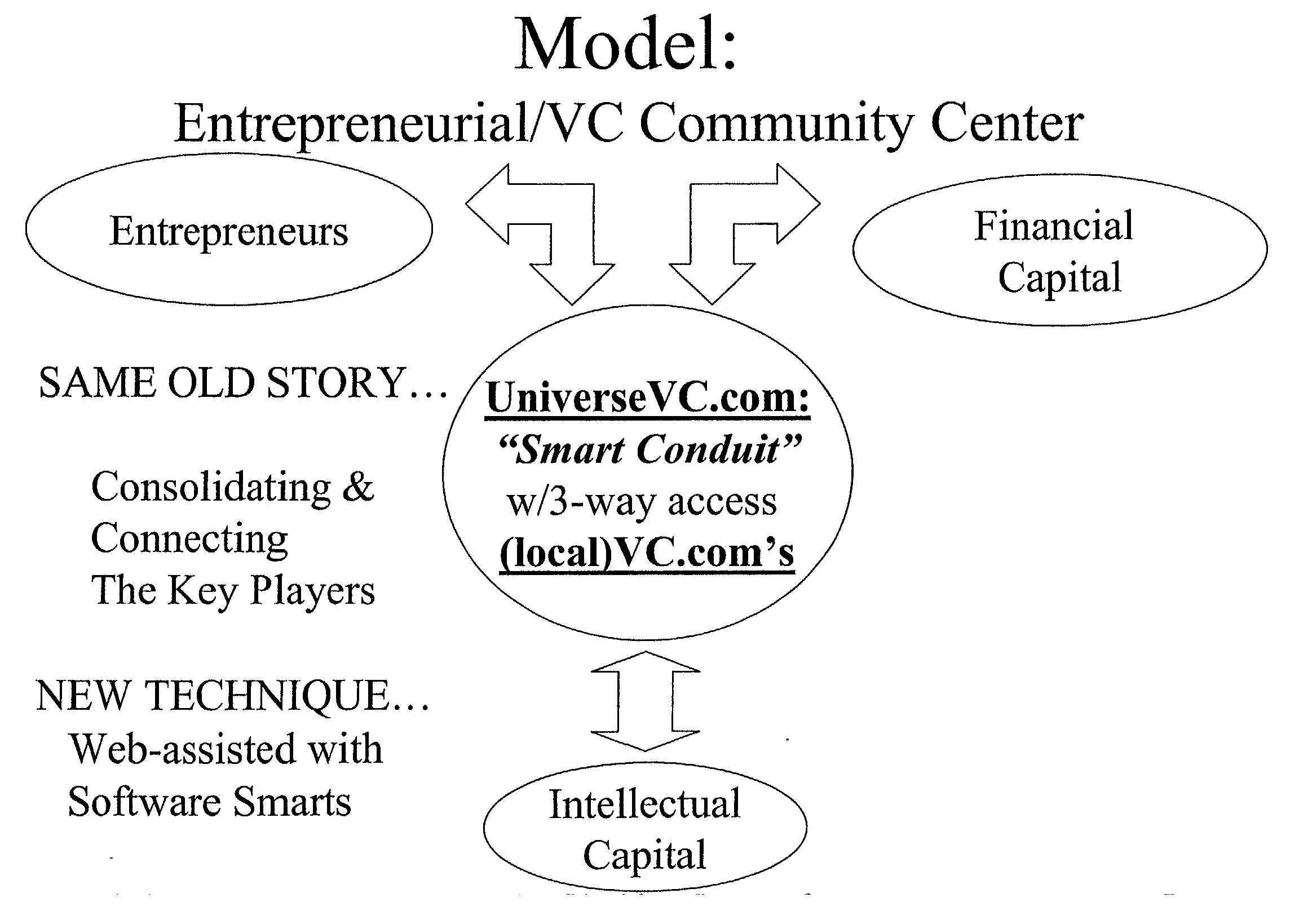
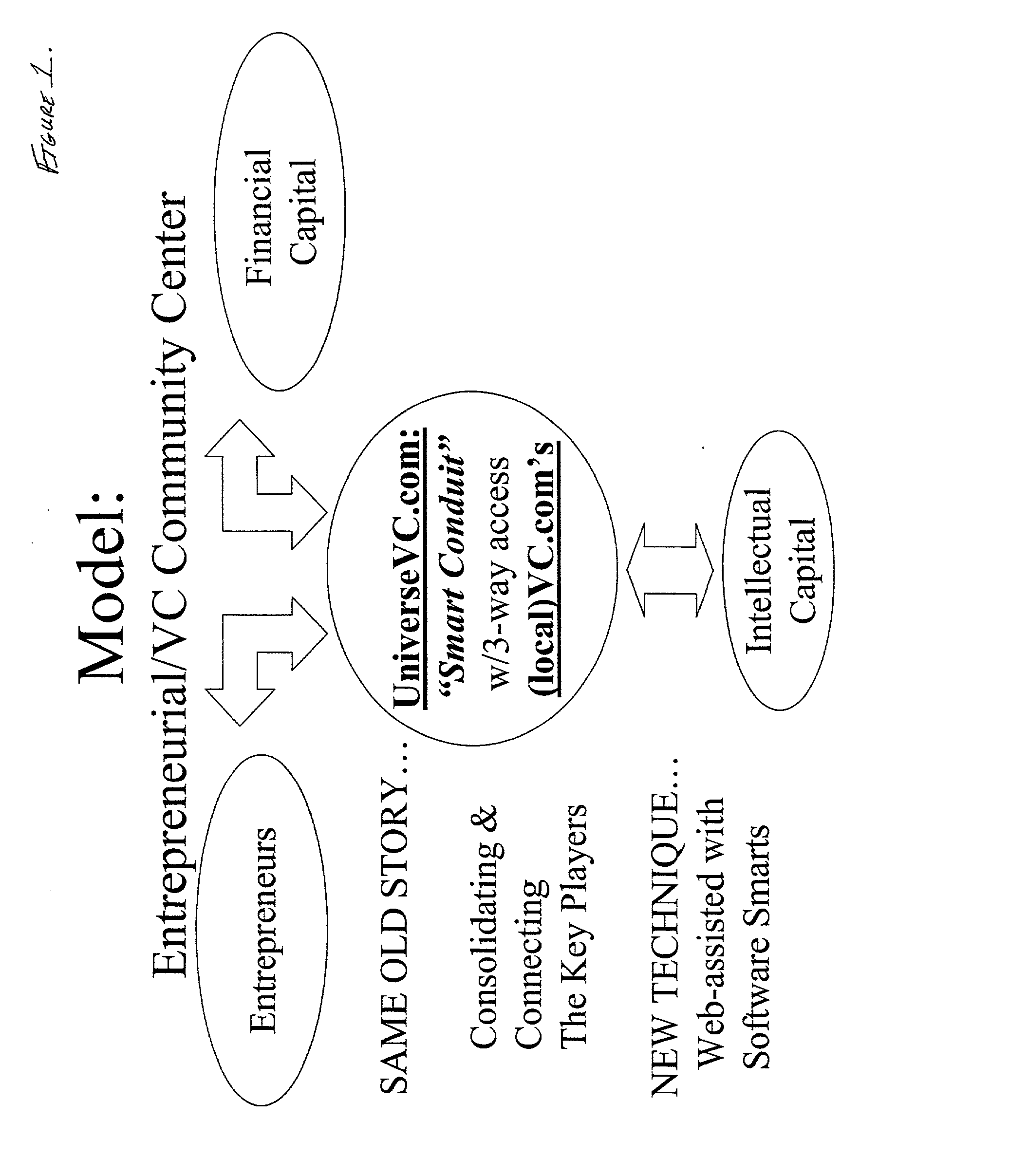
System and method for venture acceleration
A web-centric application which acts as a beacon for an entrepreneurial and venture capital community or series of communities that offers a plurality of interactive products that primarily profile, map and match needs to capabilities for new and improved methods for venture incubation and acceleration. A set of interactive business planning and management tools, and, access to capital, investments, strategic alliances, and mergers and acquisitions that offer electronic access and downloadable hard copy within a private self-contained profiling system that maximizes business efficiencies. A method for the formulation of a virtual local community through one or a series of nodes that are capable of being connected through a central point or associated links in order to enhance and expand knowledge-bases, services, networks and business opportunities. A method for collaboration and networking amongst the members within the local community(s).
Owner:CHANDLER W JEFFREY +2
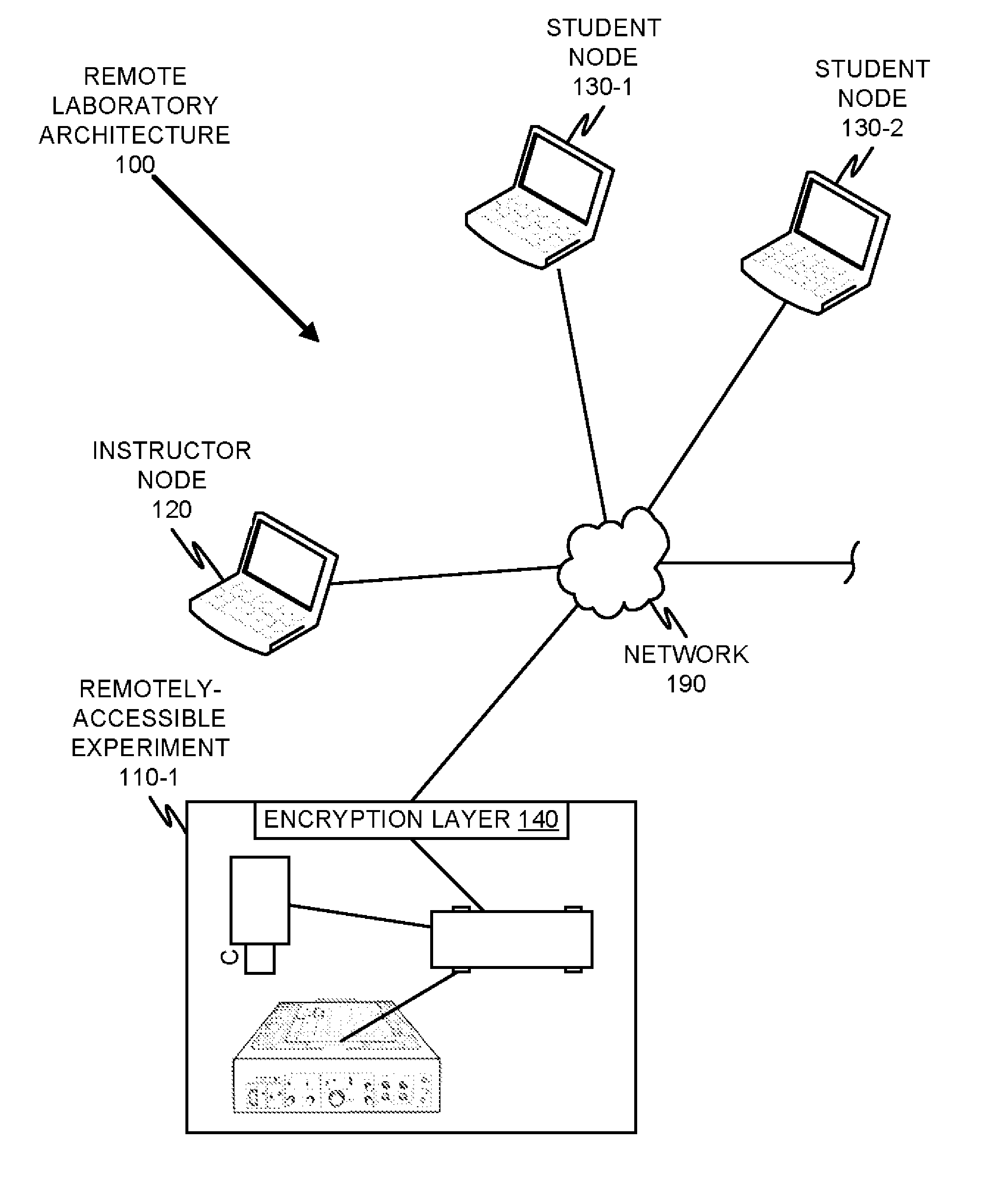
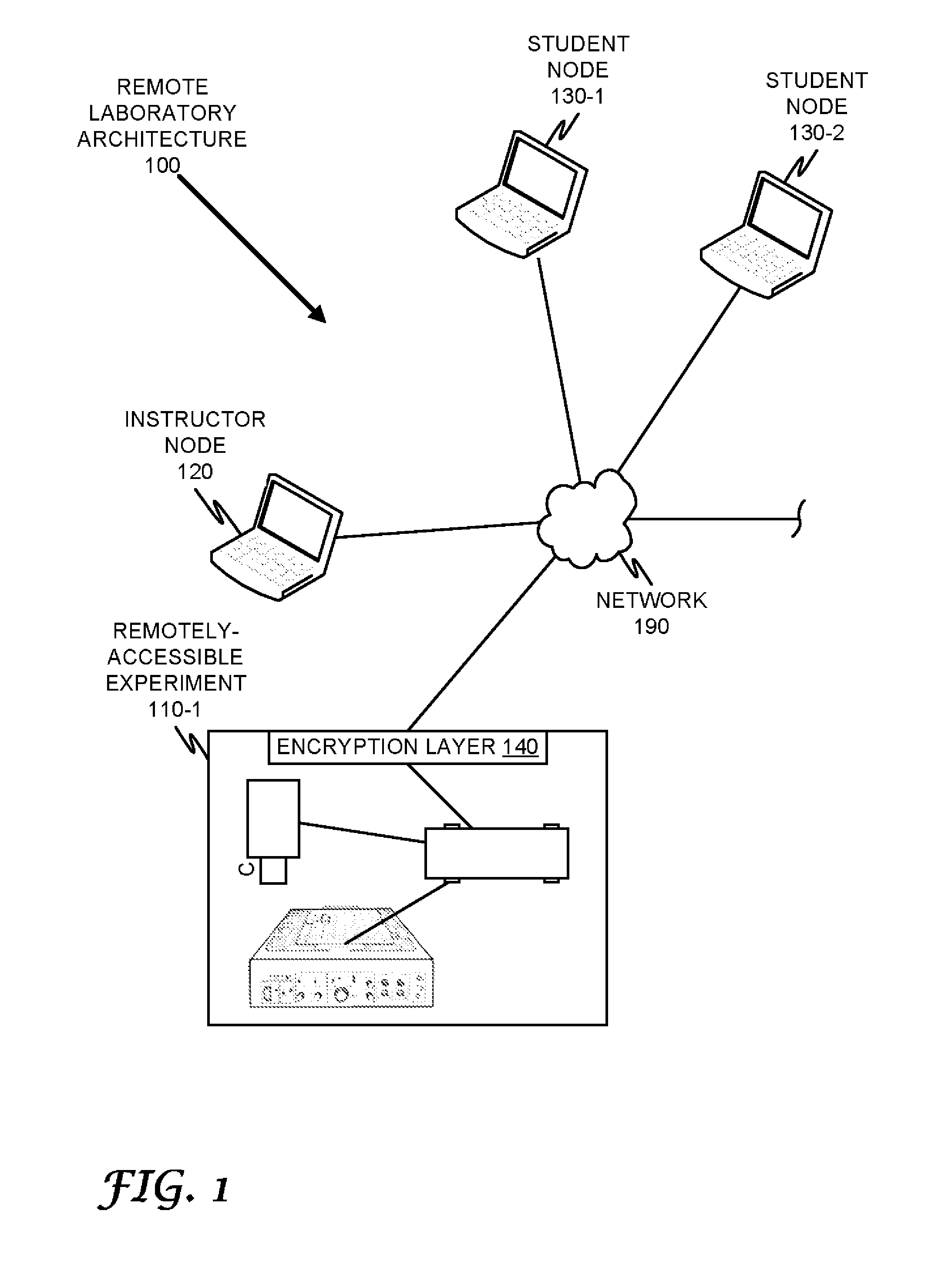
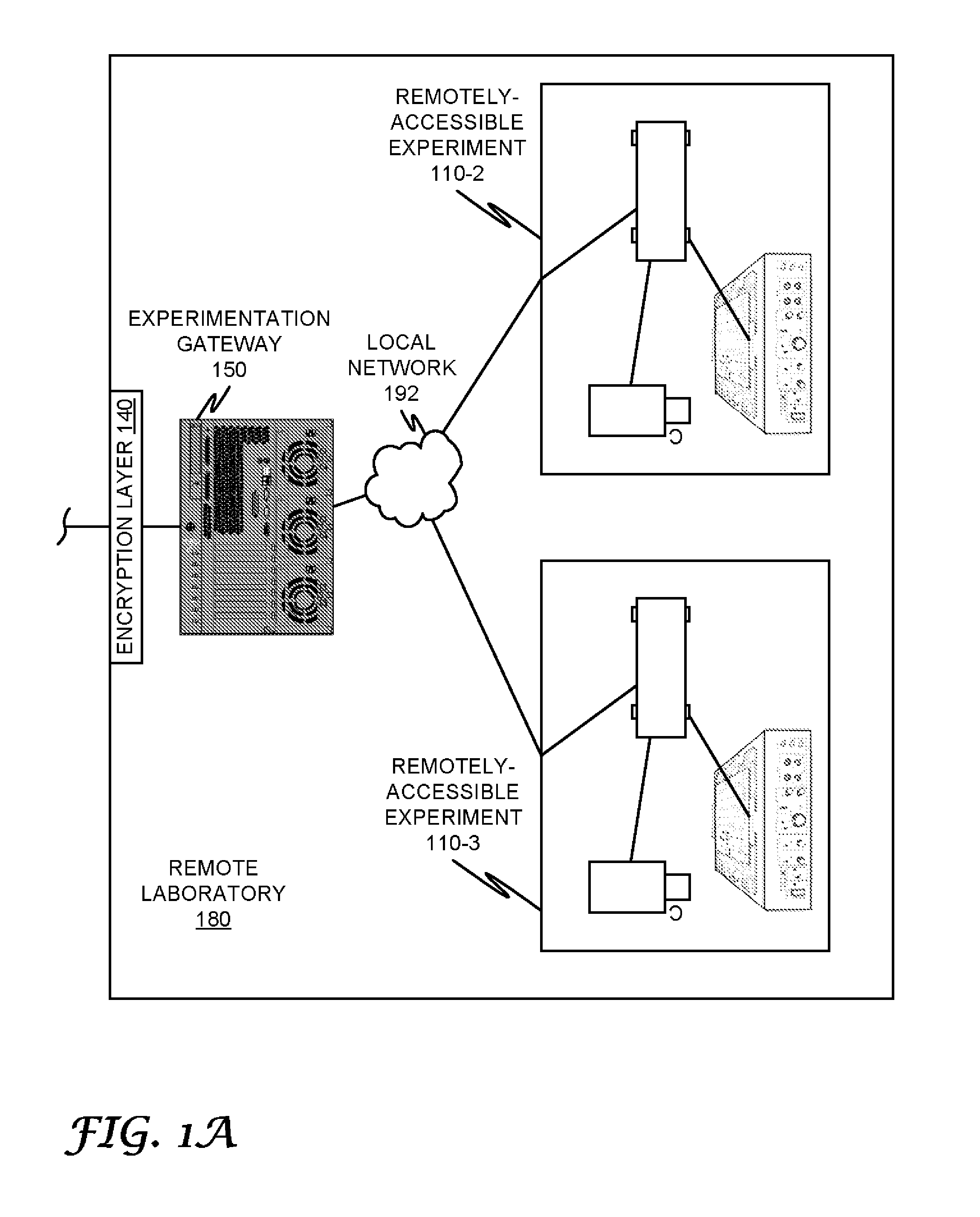
Remote Laboratory Gateway
ActiveUS20130117019A1Easy accessData processing applicationsStatic indicating devicesGraphicsGraphical user interface
A remote laboratory gateway enables a plurality of students to access and control a laboratory experiment remotely. Access is provided by an experimentation gateway, which is configured to provide secure access to the experiment via a network-centric, web-enabled interface graphical user interface. Experimental hardware is directly controlled by an experiment controller, which is communicatively coupled to the experimentation gateway and which may be a software application, a standalone computing device, or a virtual machine hosted on the experimentation gateway. The remote laboratory of the present specification may be configured for a software-as-a-service business model.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com