Patents
Literature
510 results about "Enterprise system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
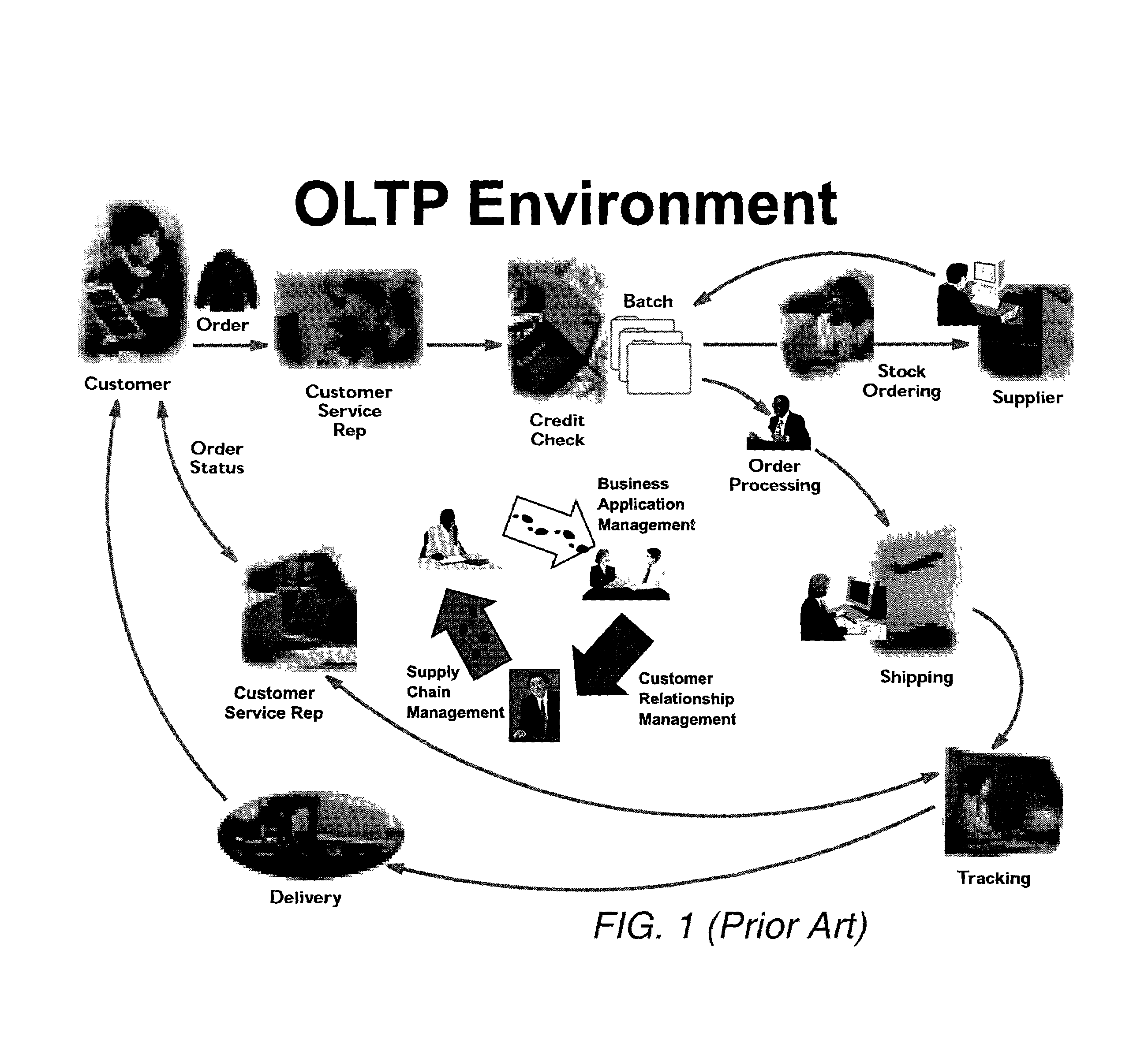
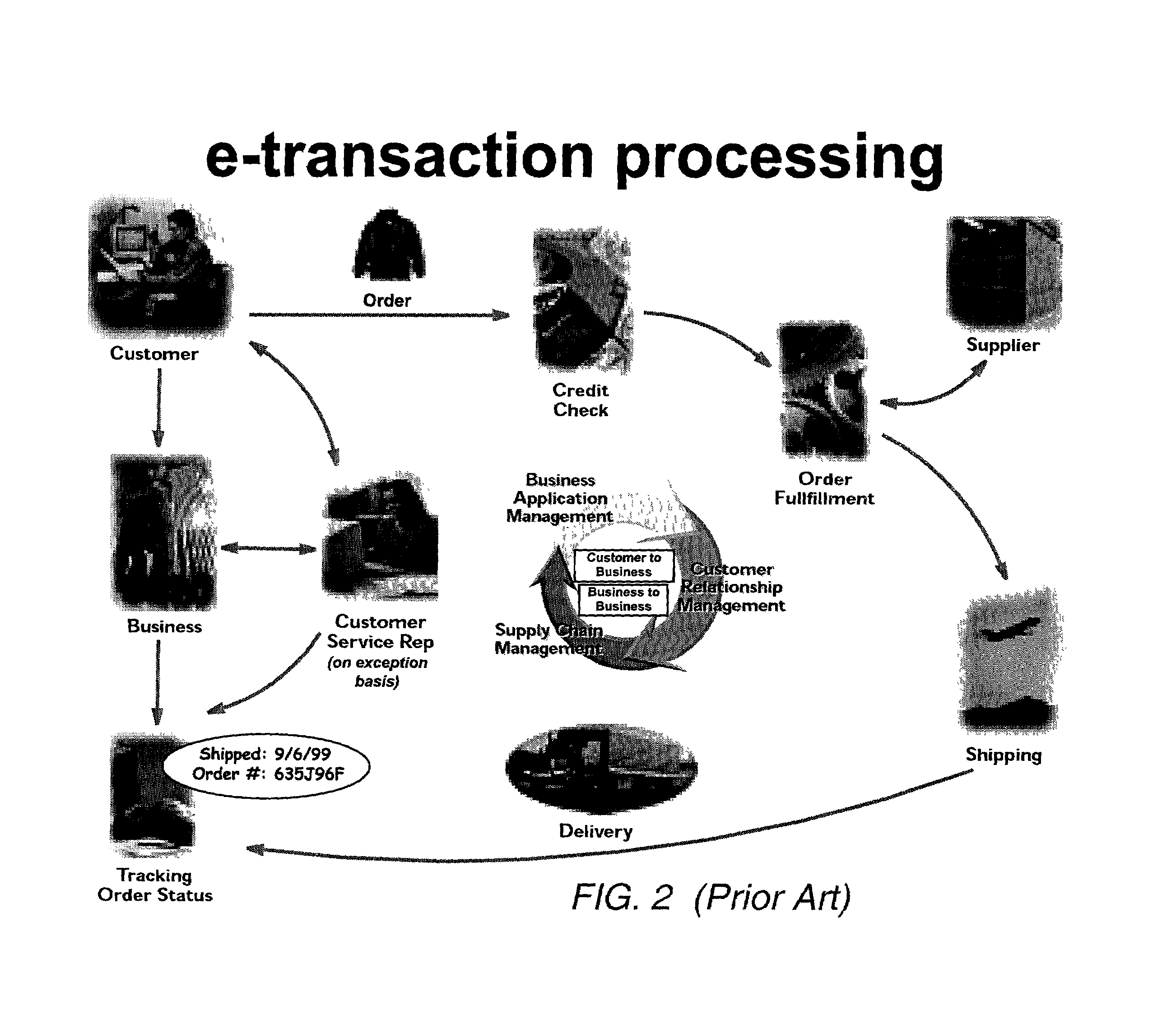
Enterprise systems are large-scale application software packages that support business processes, information flows, reporting, and data analytics in complex organizations. While ES are generally packaged enterprise application software systems they can also be bespoke, custom developed systems created to support a specific organization's needs. Types of enterprise systems include: enterprise resource planning systems, enterprise planning systems, and customer relationship management software. Although data warehousing or business intelligence systems are enterprise-wide packaged application software often sold by ES vendors, since they do not directly support execution of business processes, they are often excluded from the term. Enterprise systems are built on software platforms, such as SAP’s NetWeaver and Oracle's Fusion, and databases. From a hardware perspective, enterprise systems are the servers, storage and associated software that large businesses use as the foundation for their IT infrastructure. These systems are designed to manage large volumes of critical data. These systems are typically designed to provide high levels of transaction performance and data security.
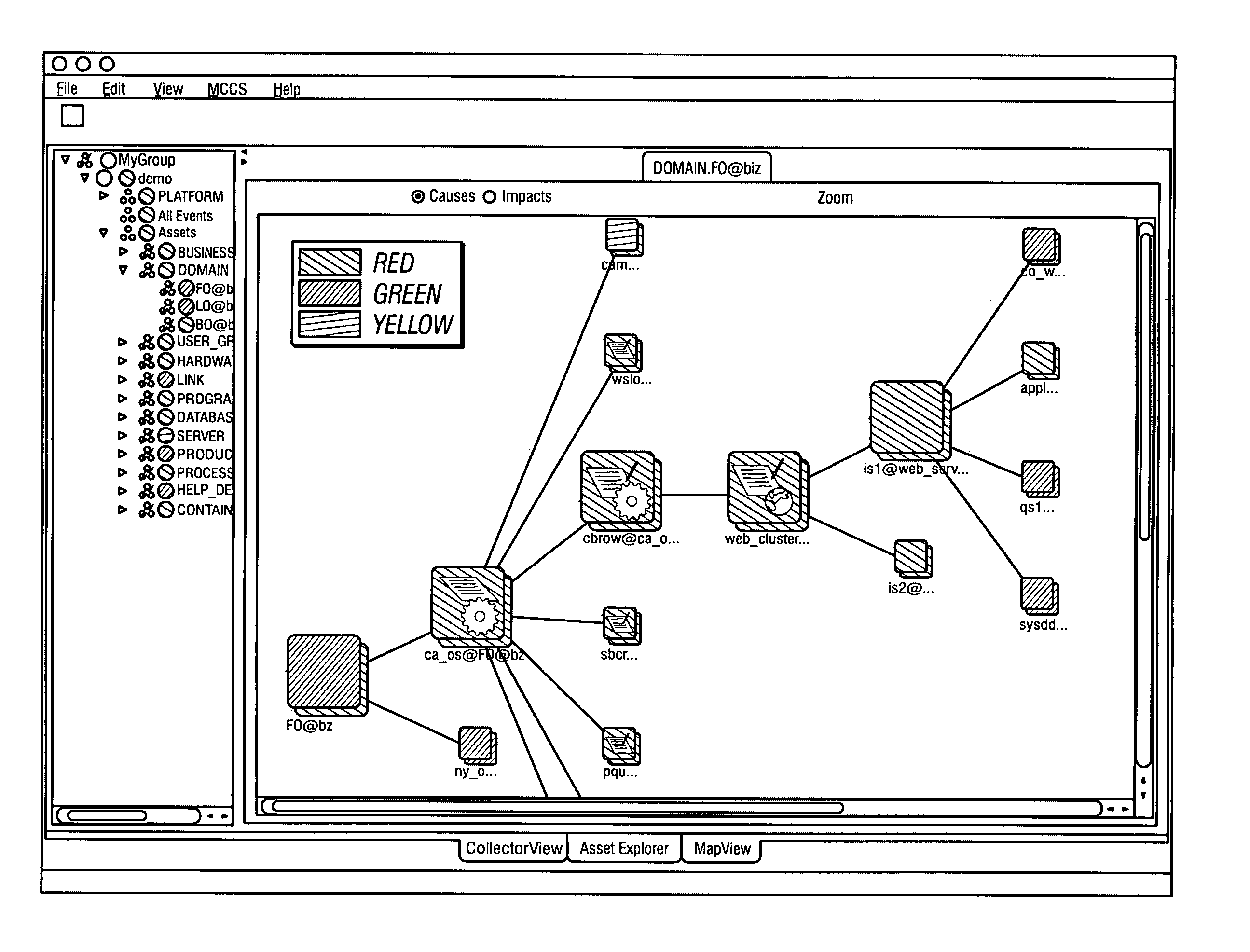
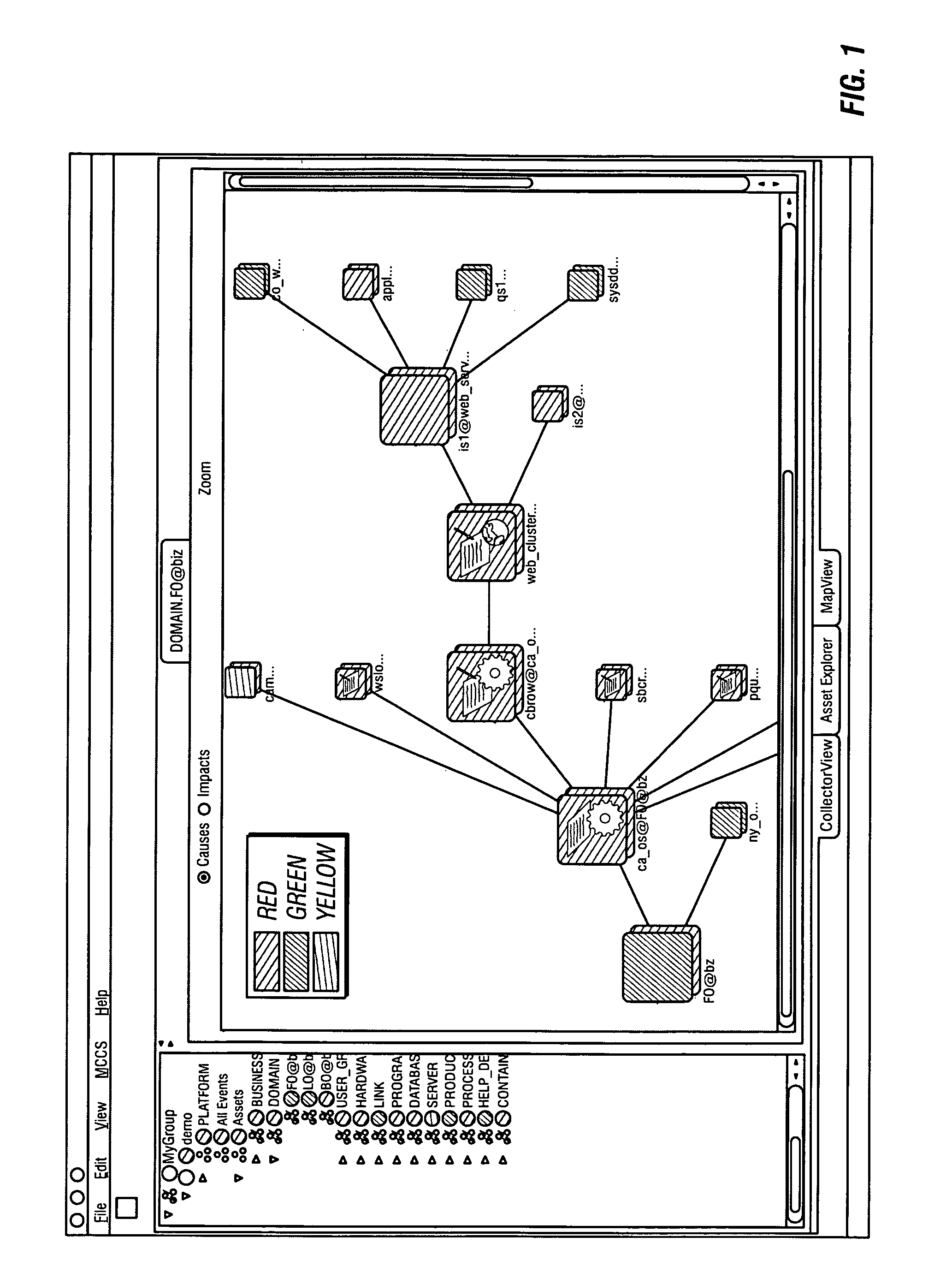
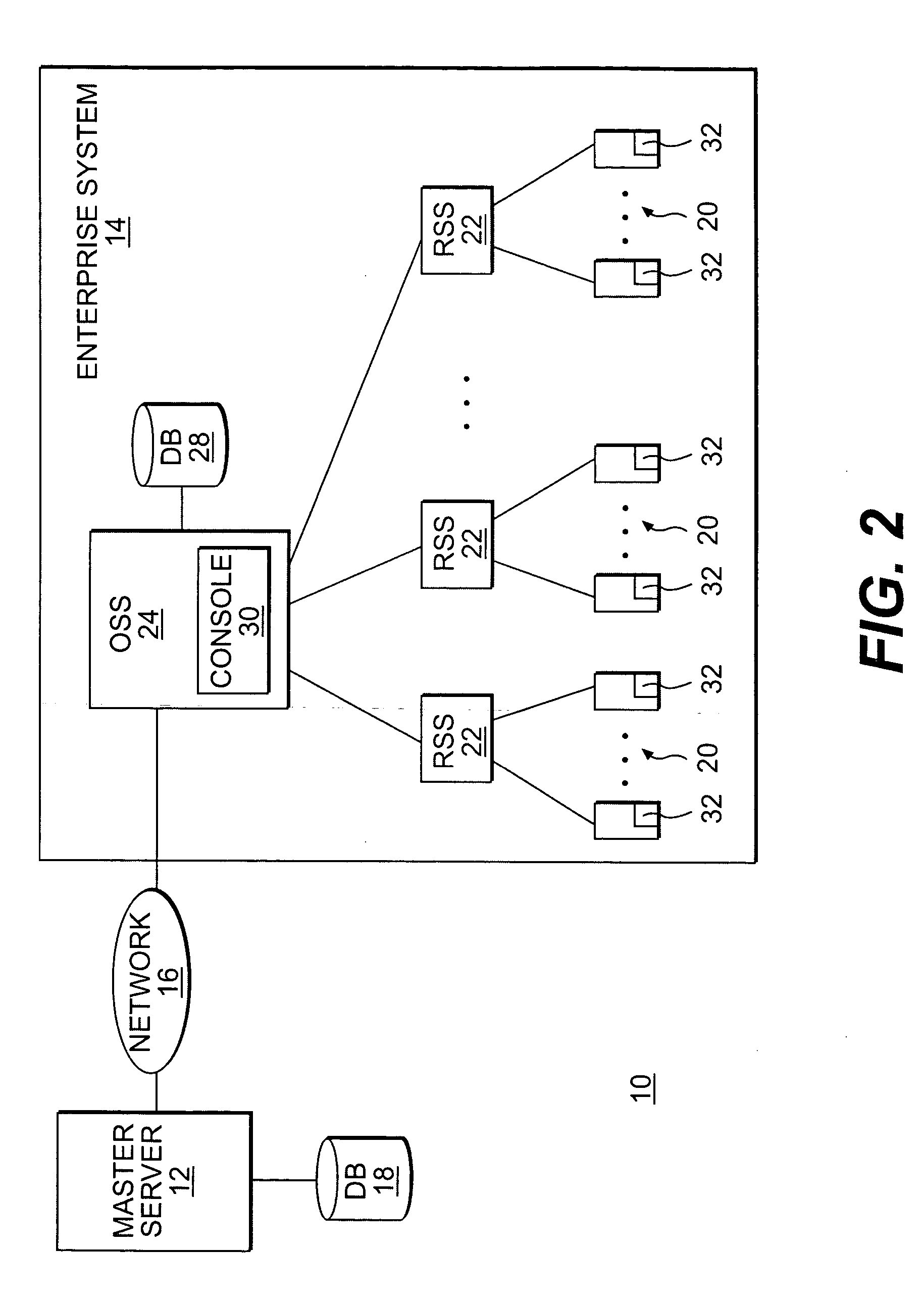
System and method for assessing and indicating the health of components
A system and method for visualization of the components of an enterprise system and the rendering of information about the health or status of the enterprise system, its components, and / or its subcomponents. The invention uses a combination of color codes or other indicators and a combination of algorithms and / or rules-based systems to control the computation of status / severities to associate to components and setup the color codes and indicators.
Owner:BMC SOFTWARE
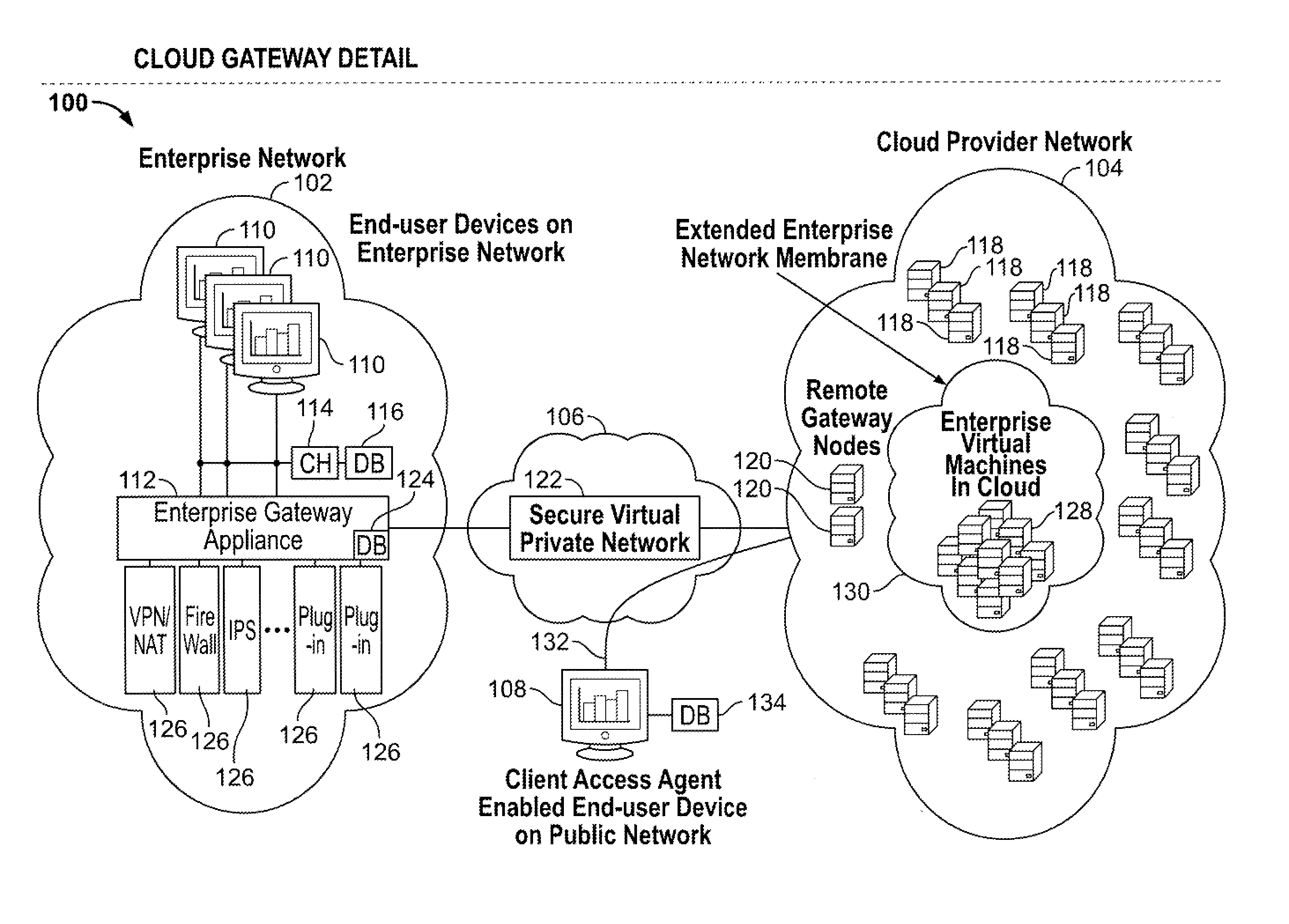
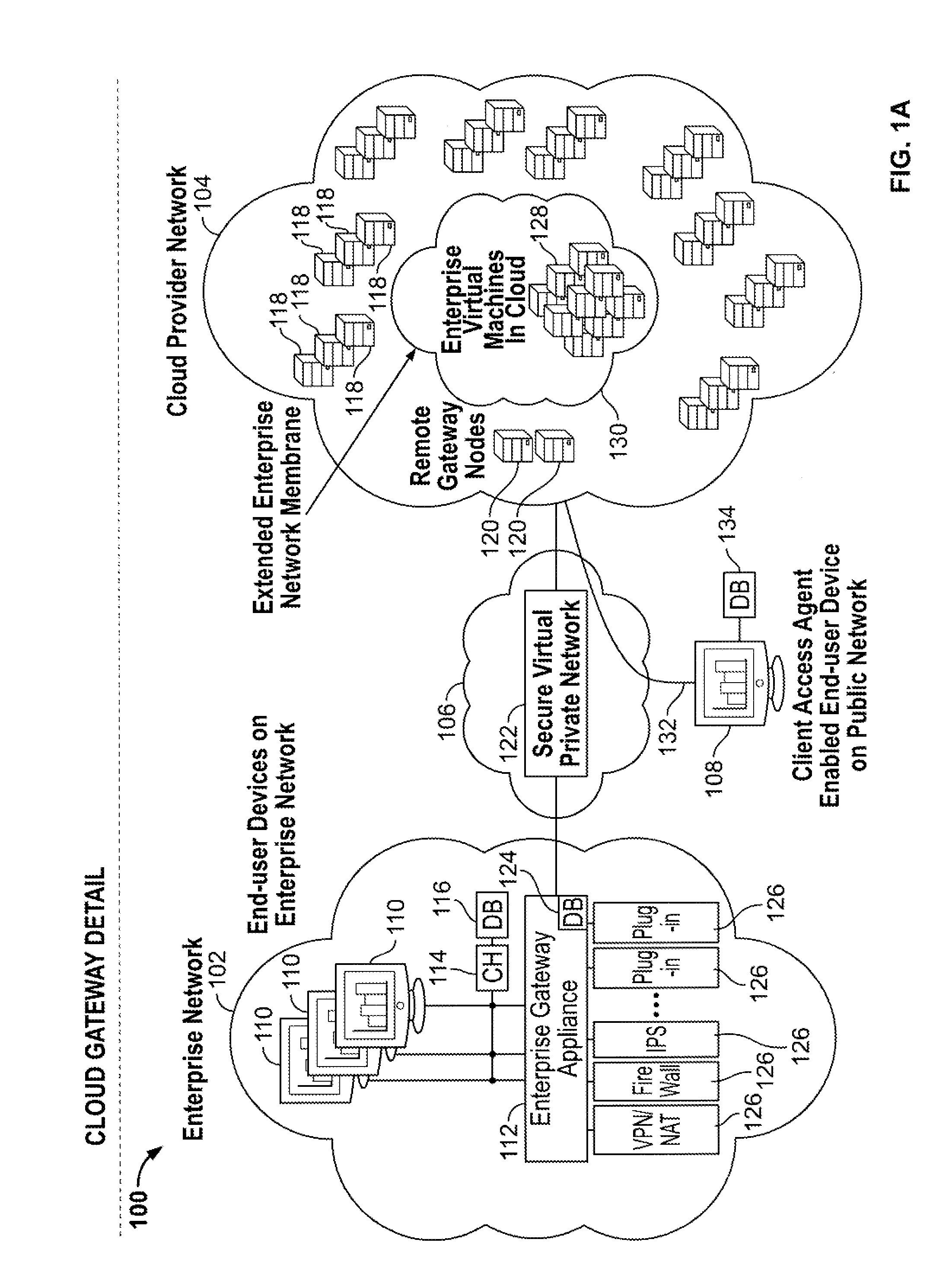
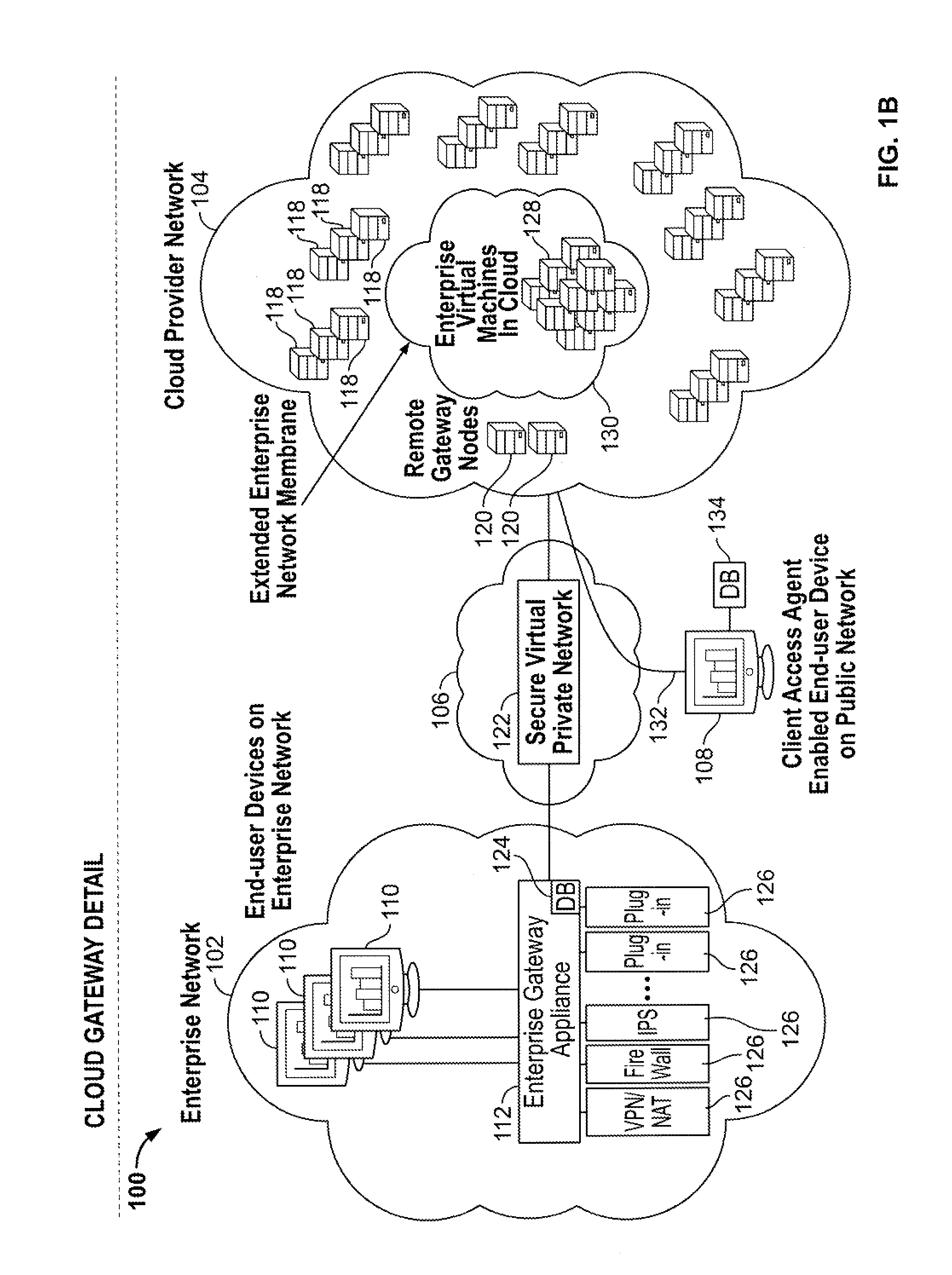
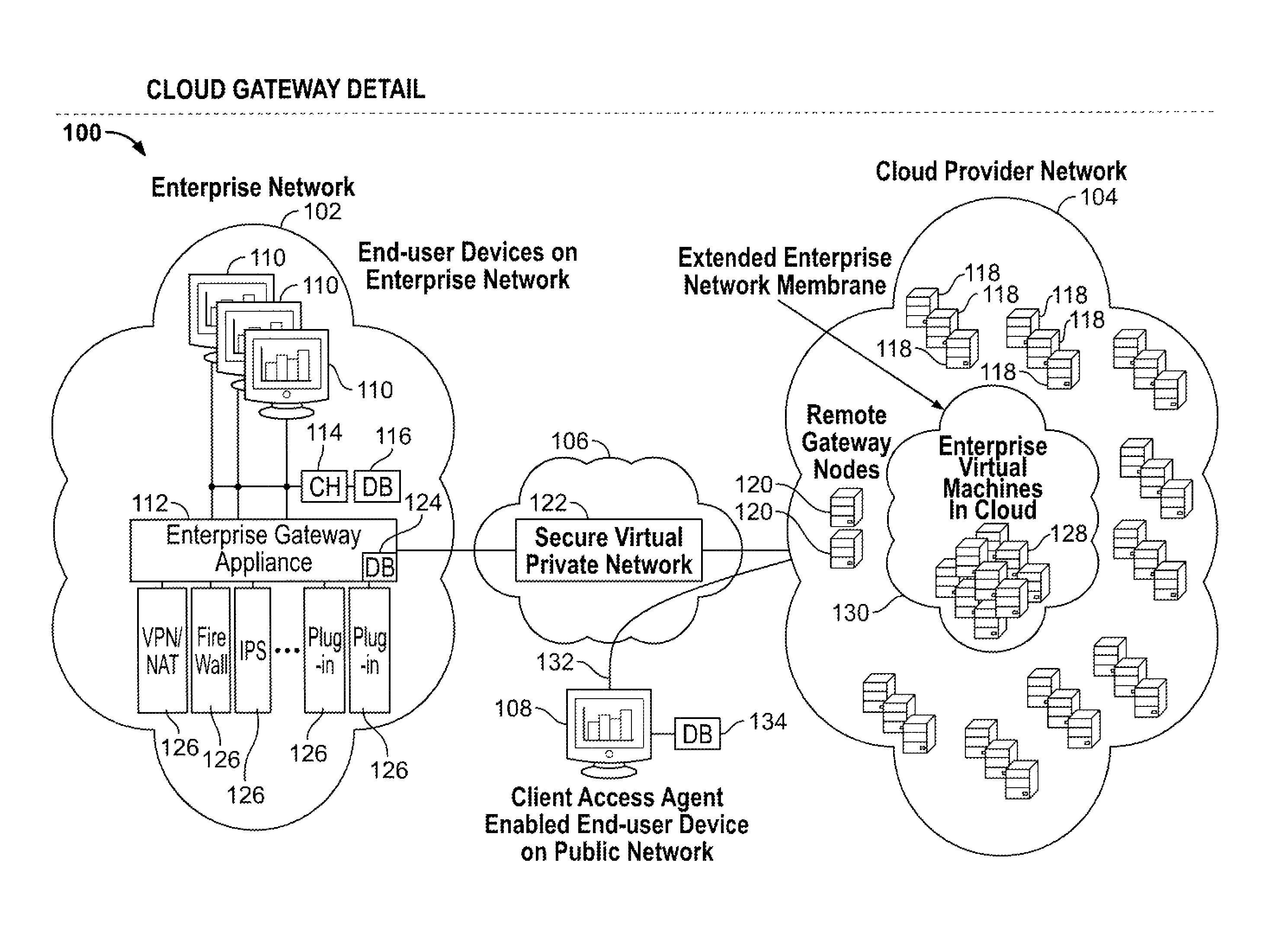
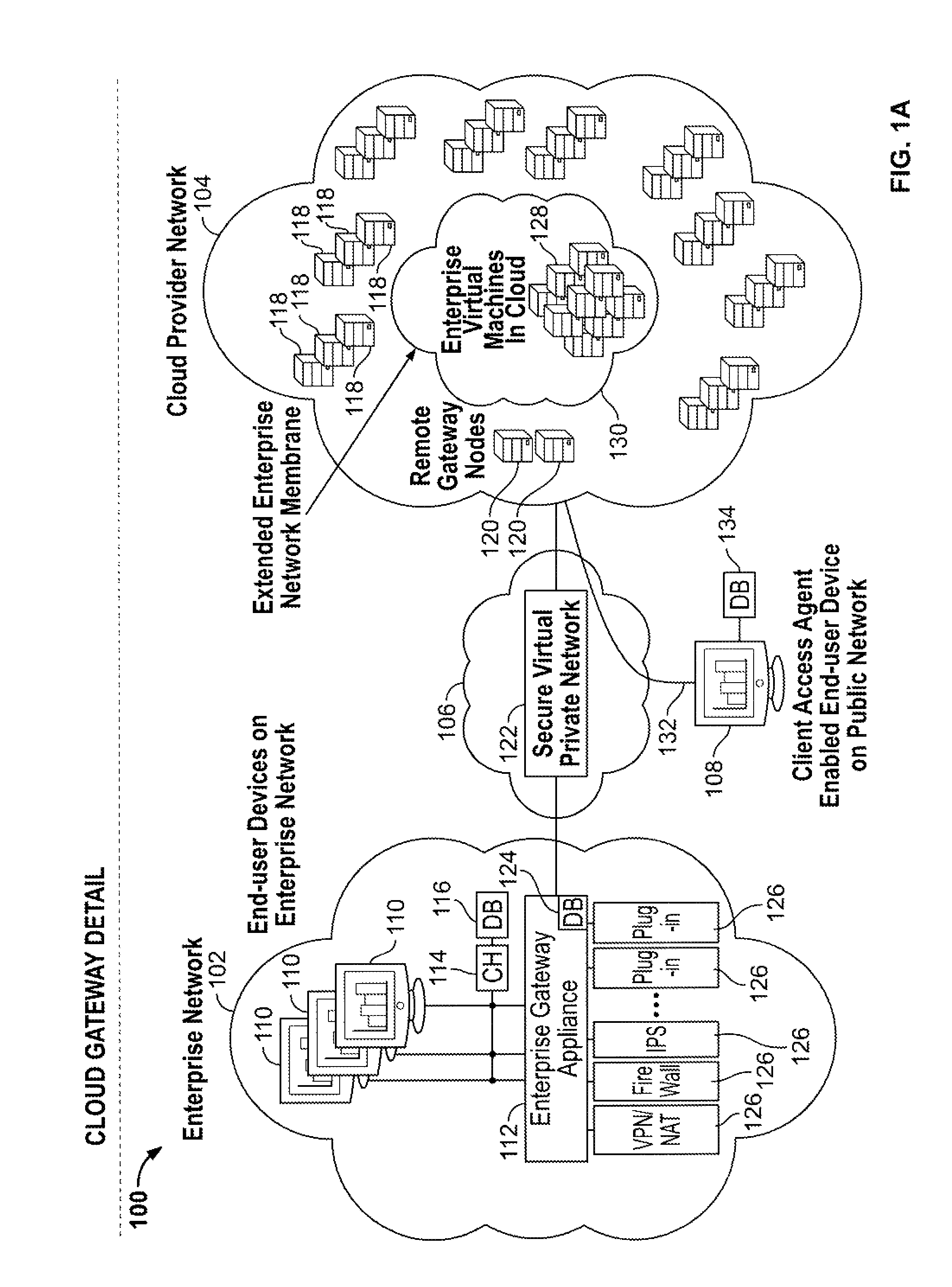
Cloud computing gateway, cloud computing hypervisor, and methods for implementing same
ActiveUS20100027552A1Improve manageabilityQuality improvementData switching by path configurationMultiple digital computer combinationsQuality of serviceManagement tool
Embodiments of the present invention provide a cloud gateway system, a cloud hypervisor system, and methods for implementing same. The cloud gateway system extends the security, manageability, and quality of service membrane of a corporate enterprise network into cloud infrastructure provider networks, enabling cloud infrastructure to be interfaced as if it were on the enterprise network. The cloud hypervisor system provides an interface to cloud infrastructure provider management systems and infrastructure instances that enables existing enterprise systems management tools to manage cloud infrastructure substantially the same as they manage local virtual machines via common server hypervisor APIs.
Owner:CSC AGILITY PLATFORM INC
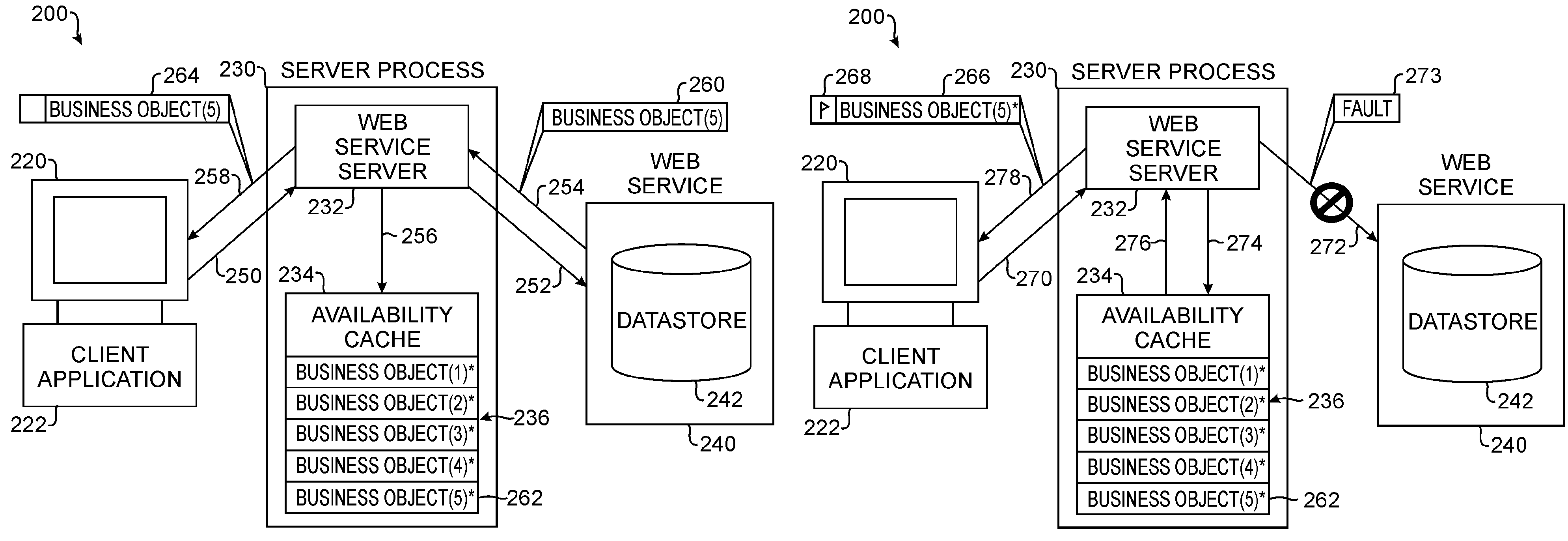
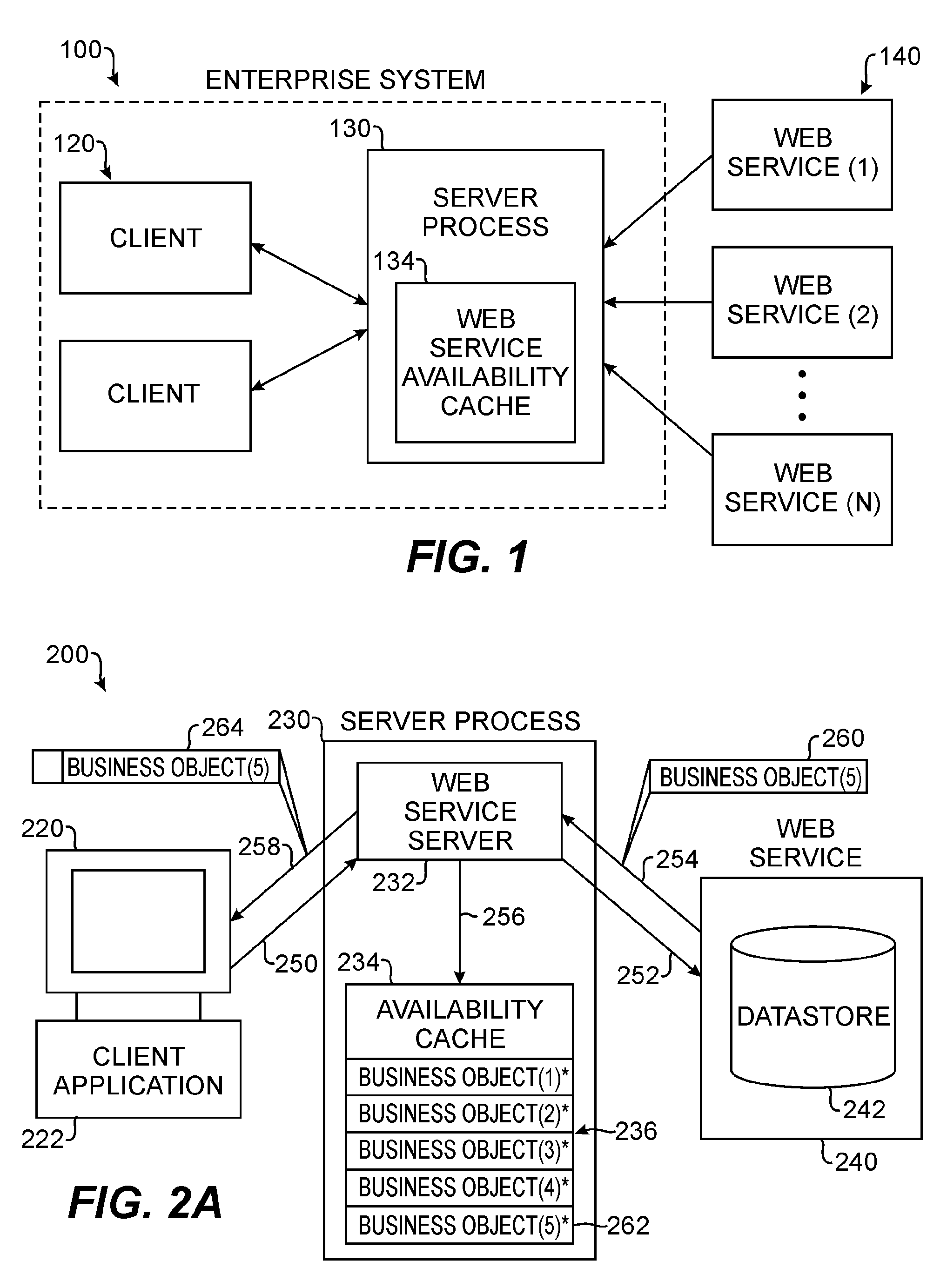
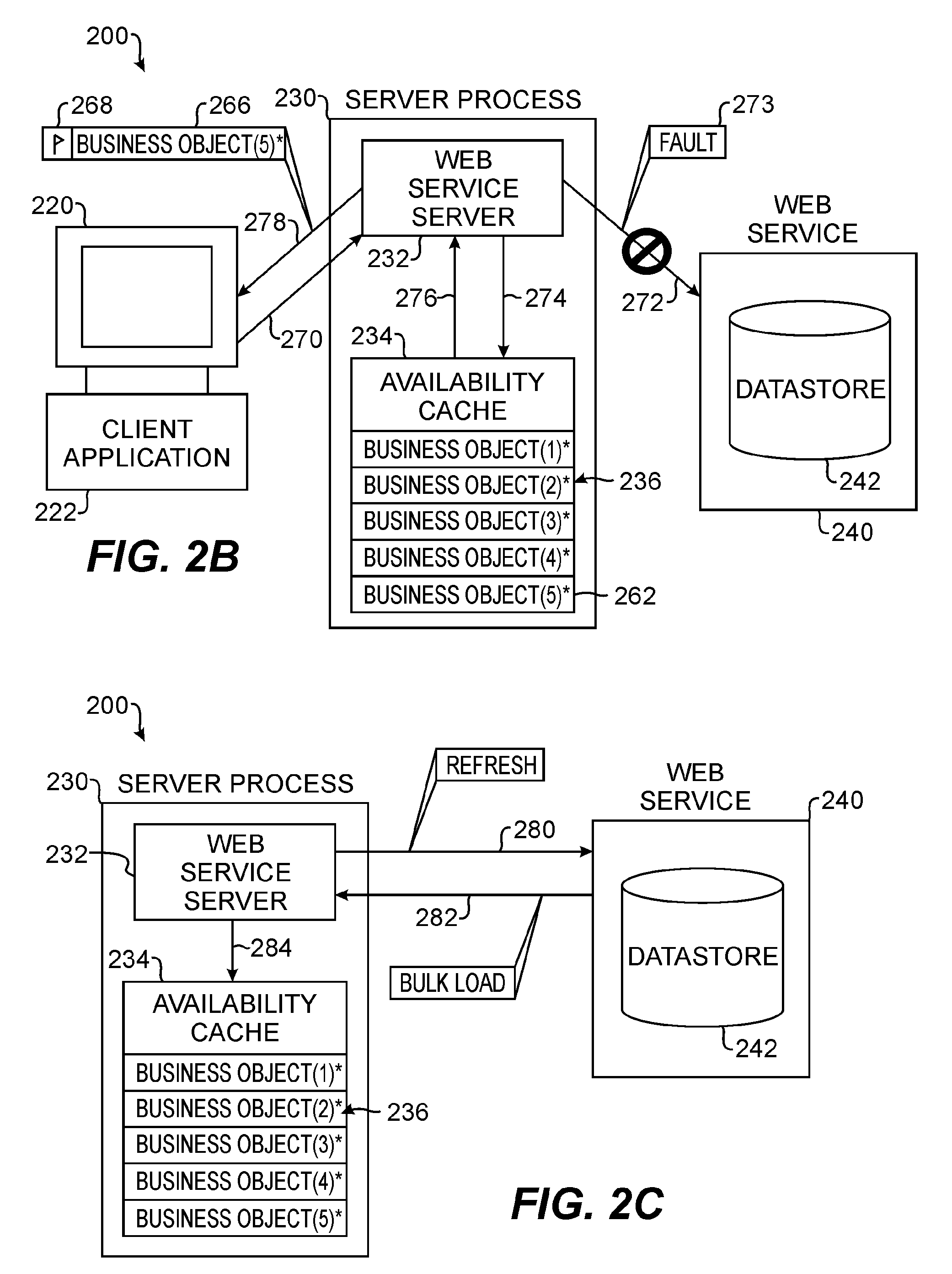
Web services availability cache
ActiveUS7716353B2Multiple digital computer combinationsWebsite content managementNetwork connectionWeb service
A Web Services availability cache is part of a computer system, such as an enterprise system of a business or organization. The availability cache is populated with information from Web Services communicatively connected to the computer system by a network connection. In one embodiment, the availability cache is populated based on each request handled by a server process associated with the availability cache. A server receives a request from a client having an application dependent upon information from the Web Service. The server sends the request to the Web Service and stores returned information in the availability cache. Also, the server sends the returned information to the client, which initiated to request. Once the cache is populated, the server handles subsequent requests for information from the client by using the Web Service if it is available or by using the availability cache if the Web Service is not available.
Owner:BMC SOFTWARE
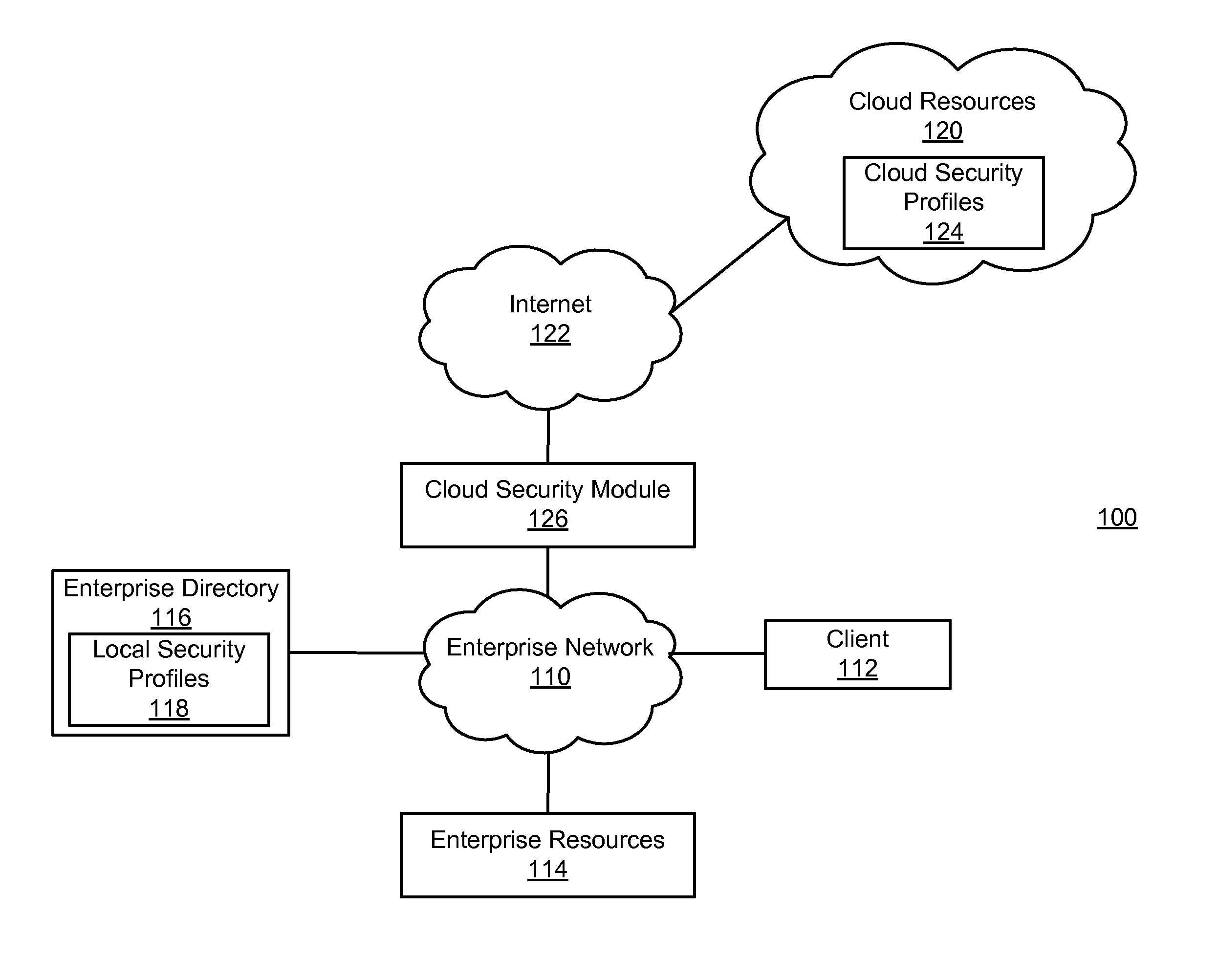
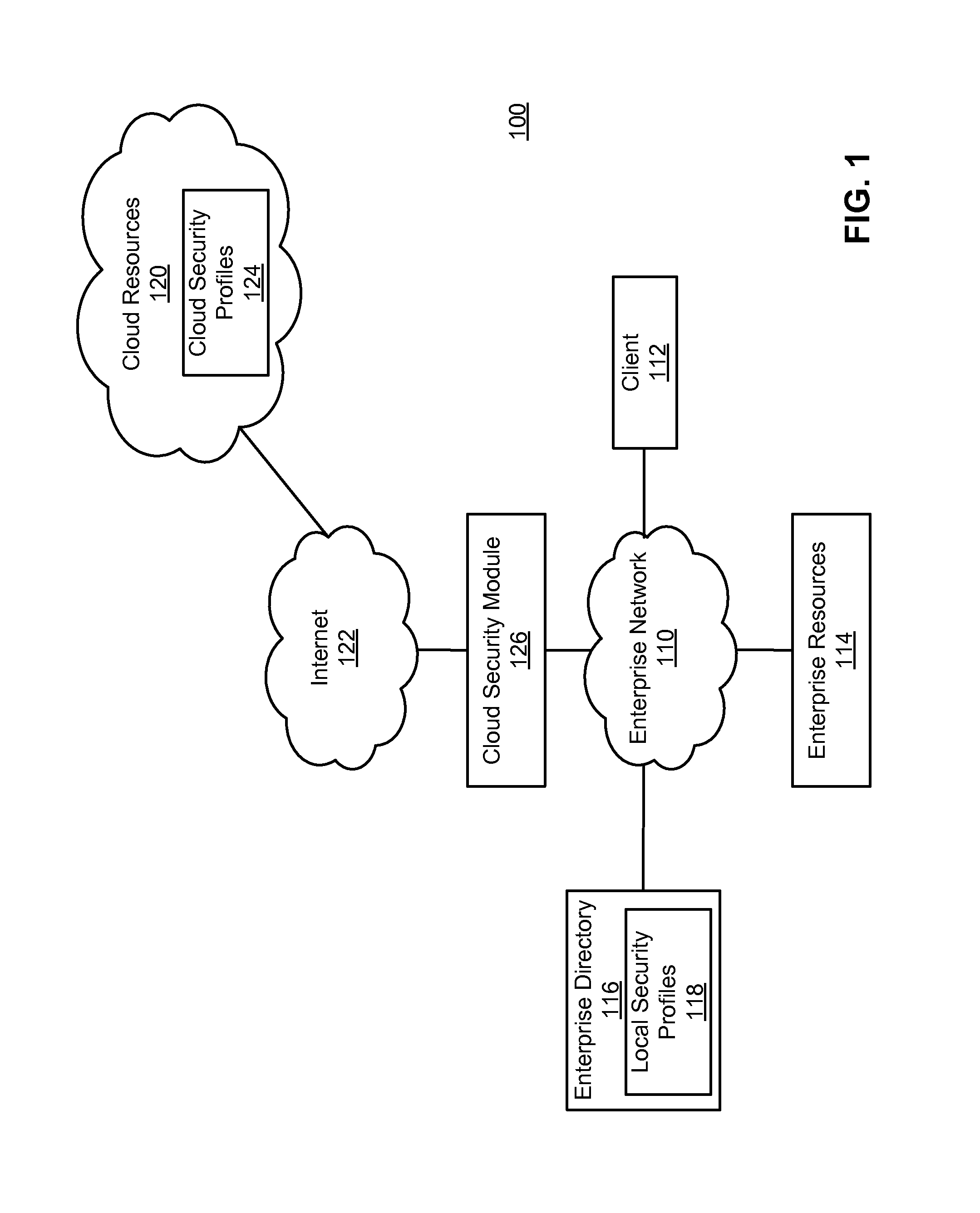
Enforcing consistent enterprise and cloud security profiles
Consistent enterprise and cloud security profiles are enforced. A domain model describing cloud resource objects associated with an enterprise is defined. Further, a relationship map describing relationships between the objects of the domain model and roles of enterprise users described by local security profiles maintained by the enterprise is specified. The domain model and relationship map collectively form an access policy for the cloud resource objects. Network traffic is monitored to detect network traffic attempting to configure a cloud security profile describing permissions of an enterprise user with respect to cloud resource objects in a manner inconsistent with the access policy. Detected network traffic attempting to configure the cloud security profile in the manner inconsistent with access policy is remediated.
Owner:CA TECH INC
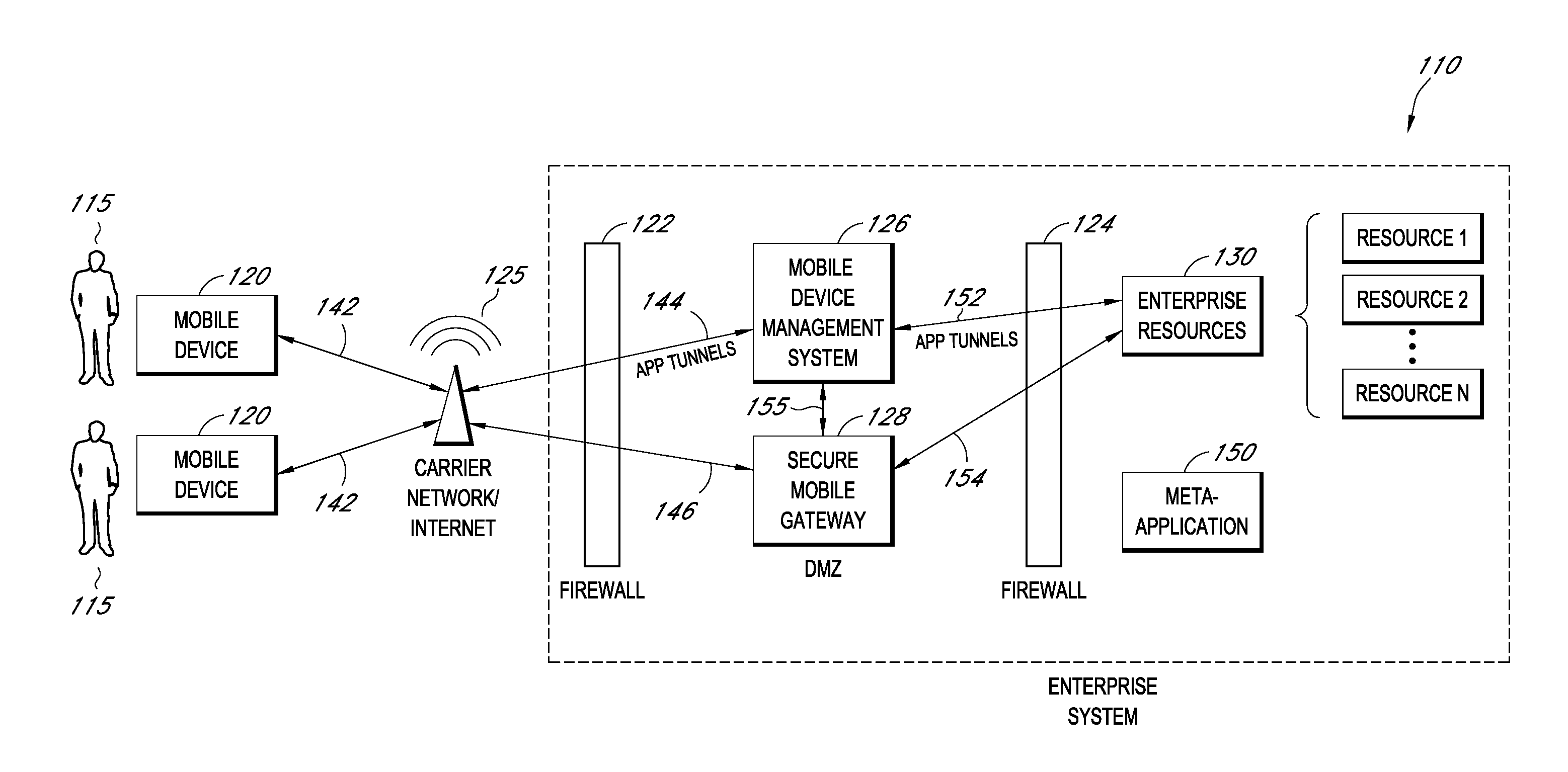
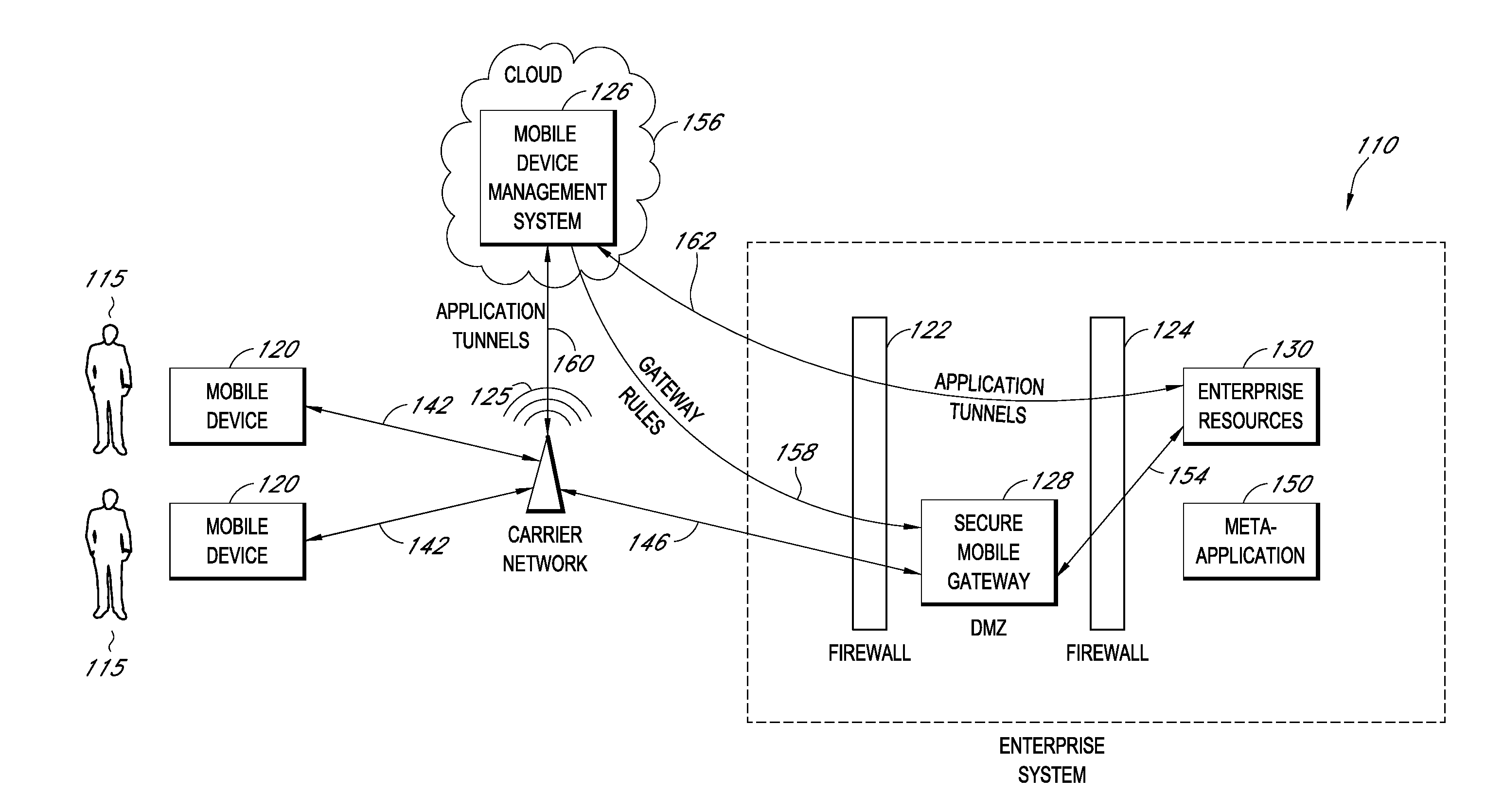
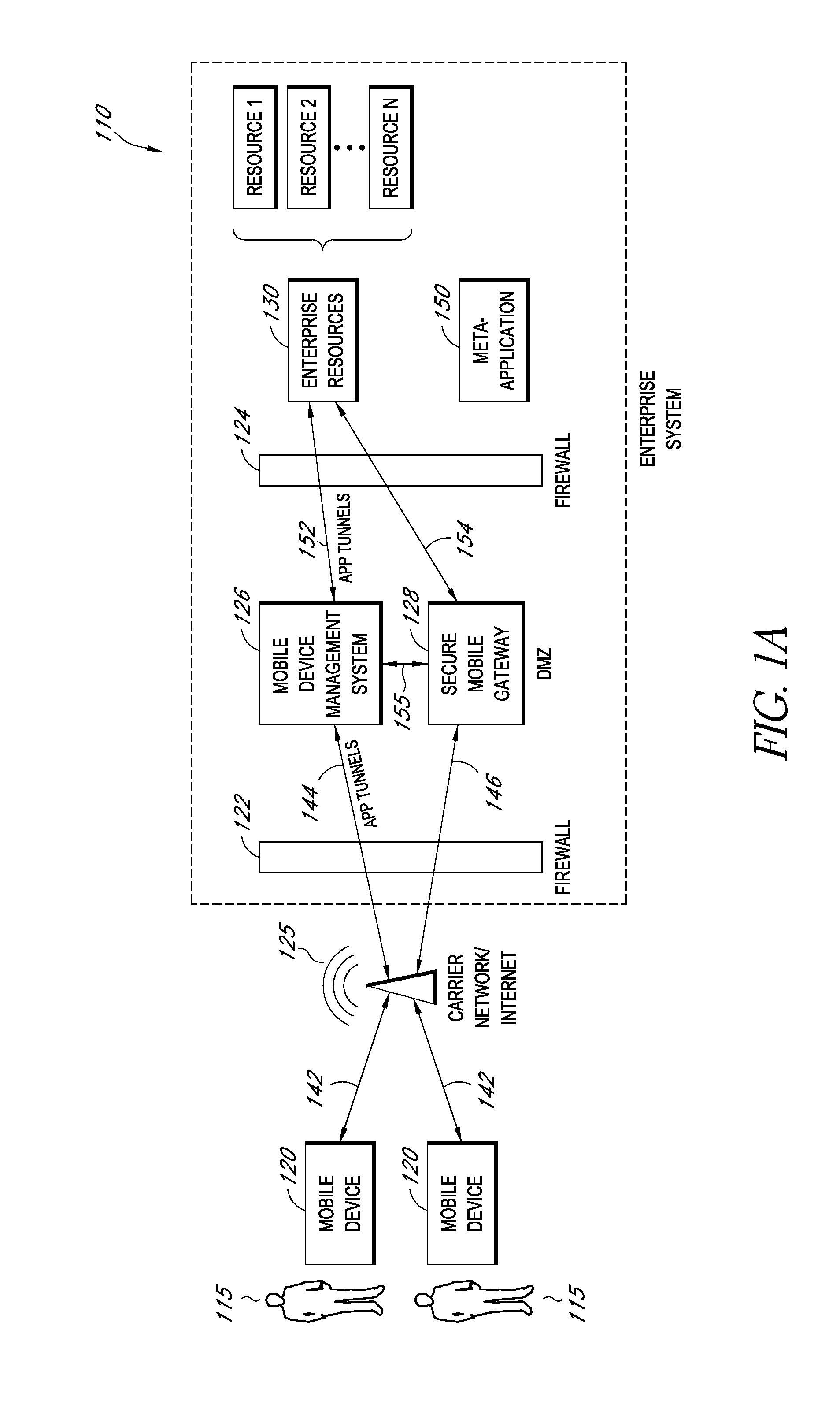
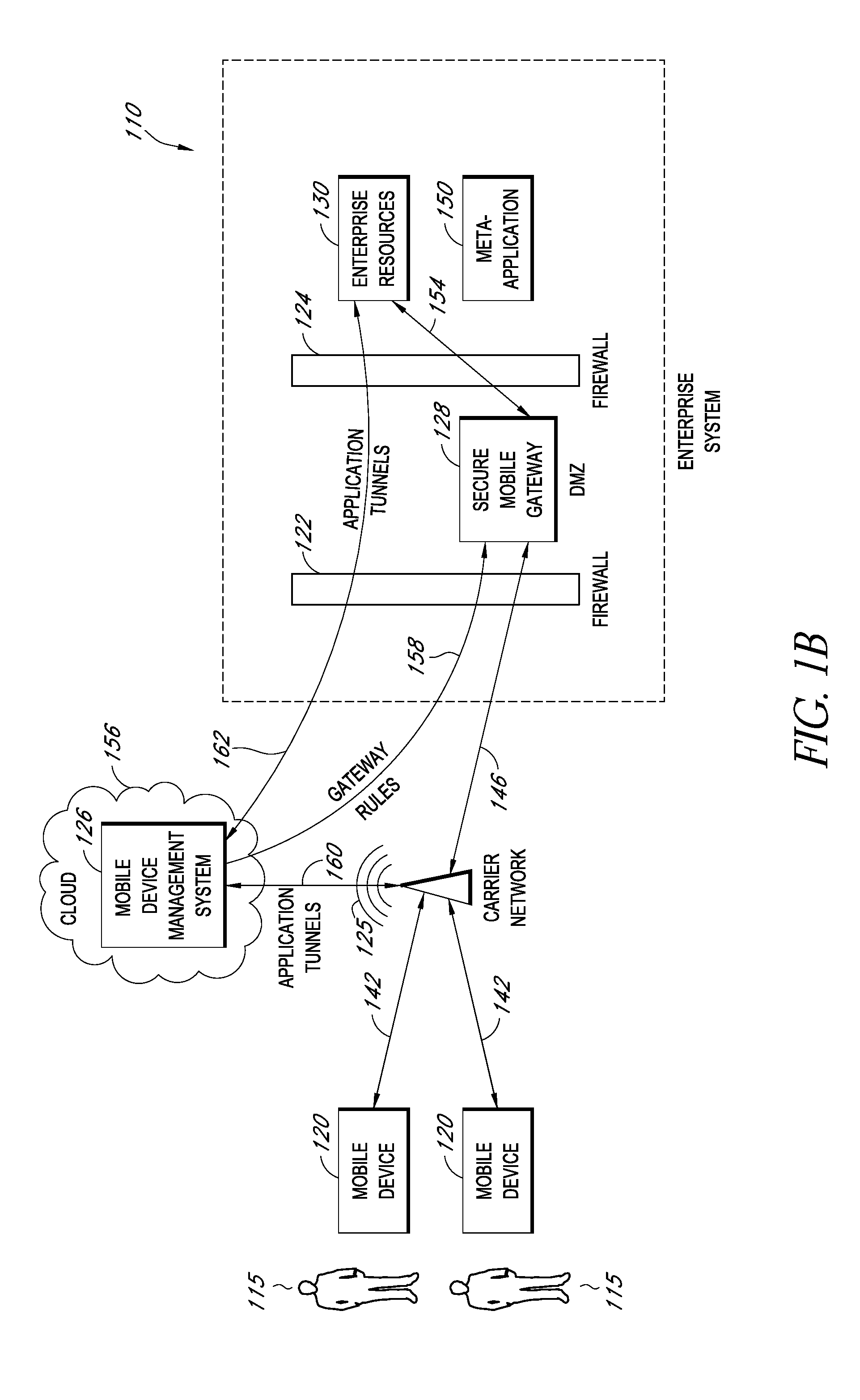
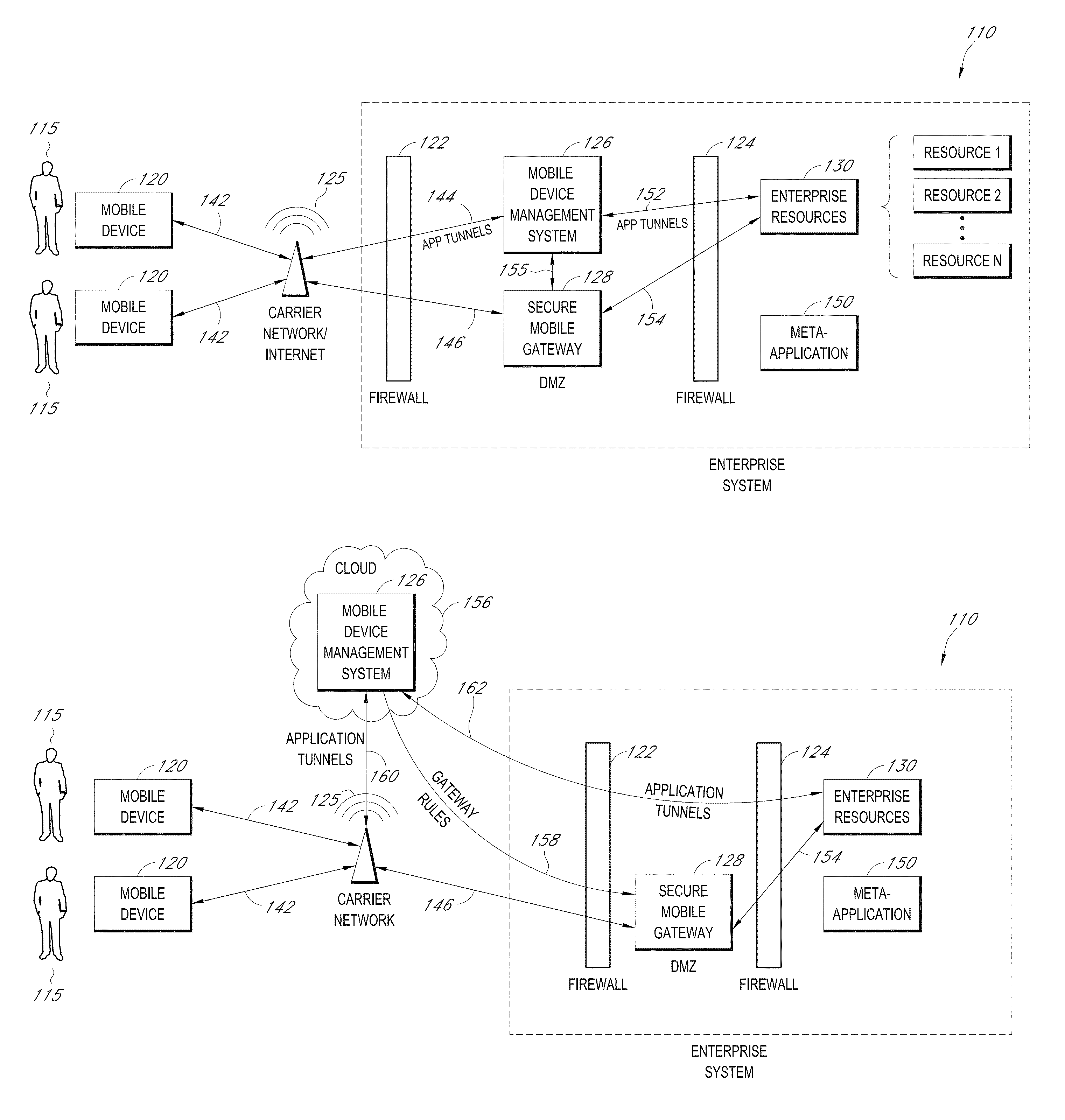
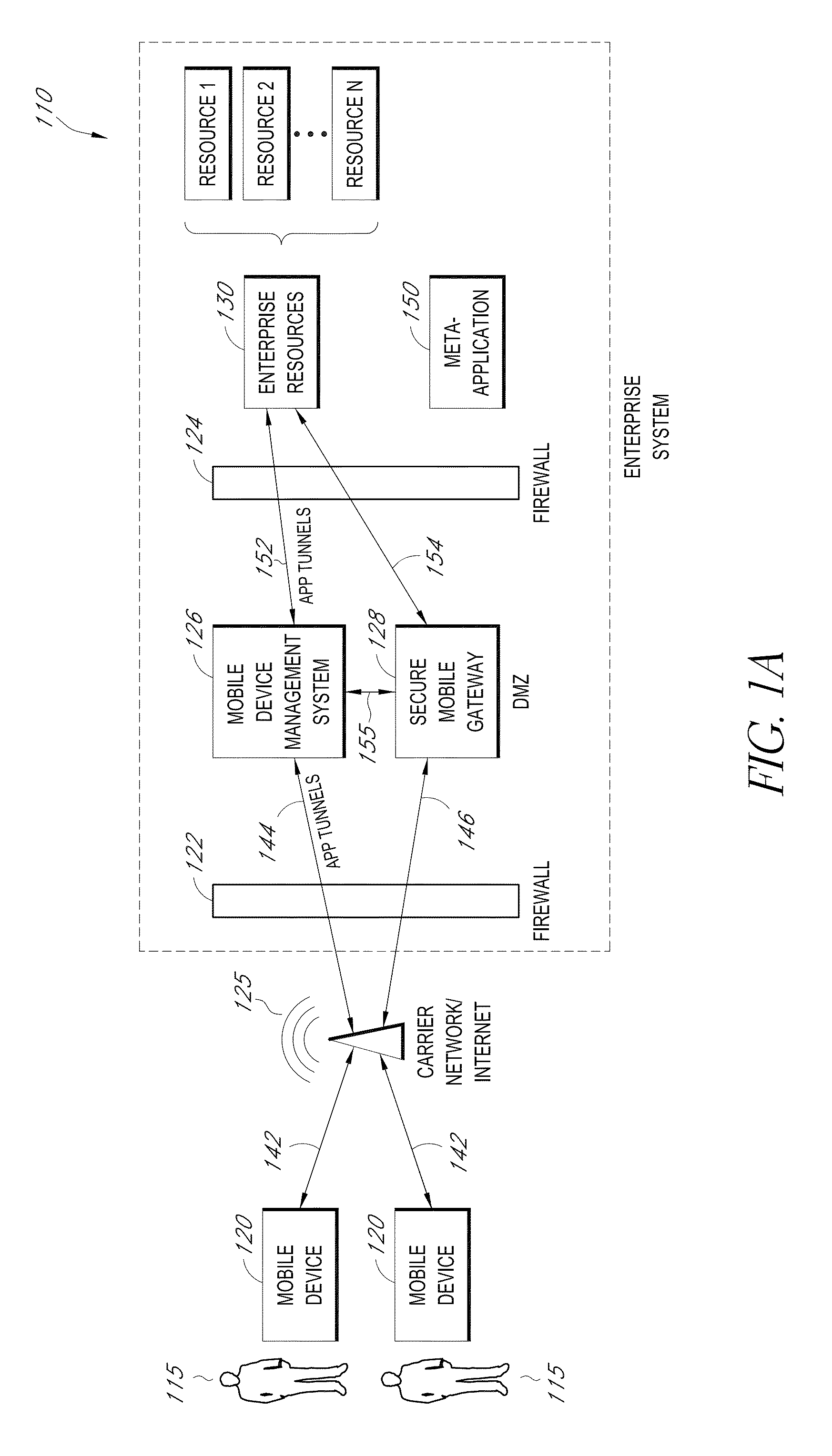
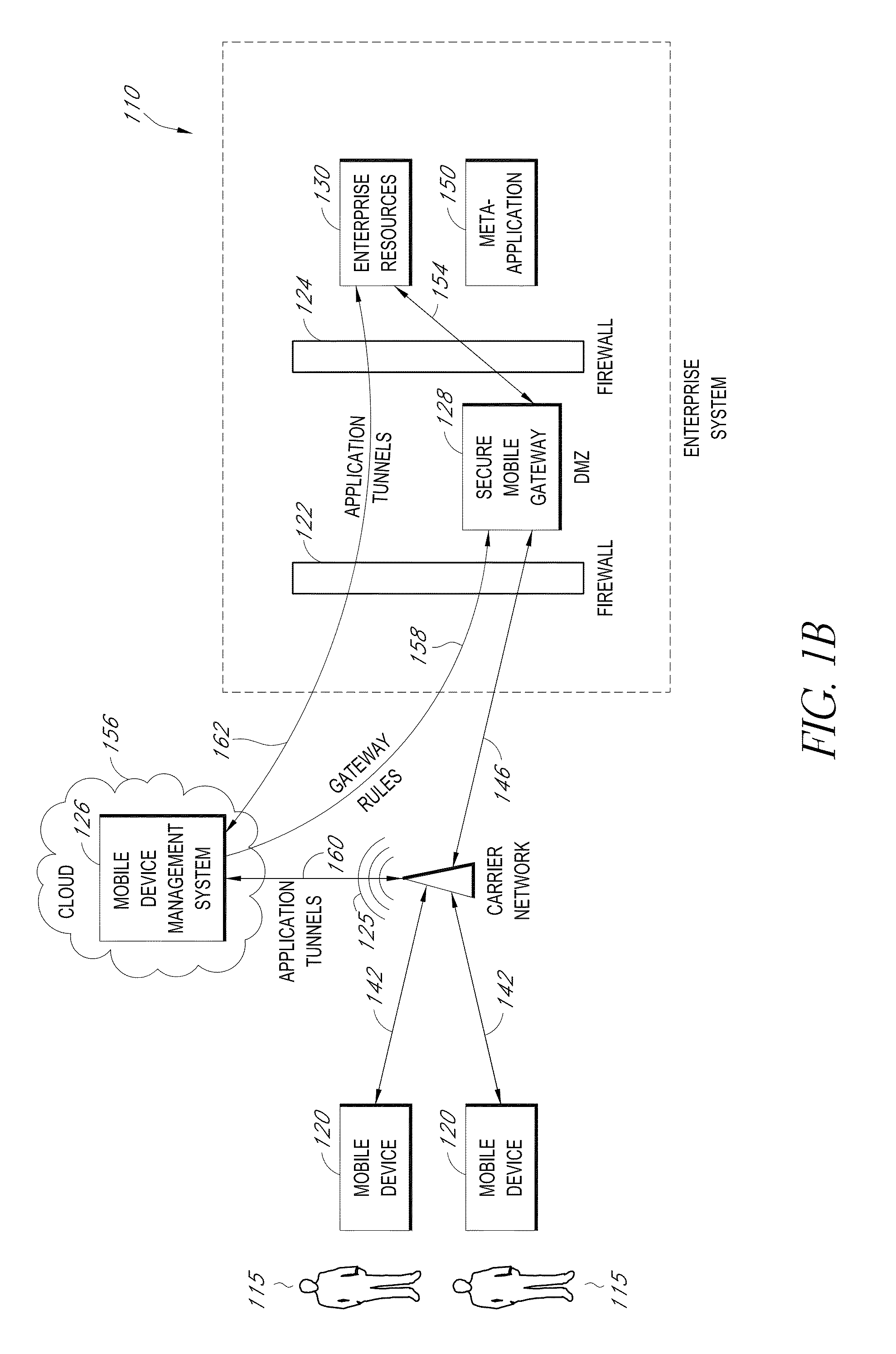
Secure container for protecting enterprise data on a mobile device
ActiveUS20140006347A1Digital data information retrievalDecompilation/disassemblyDocumentation procedureApplication server
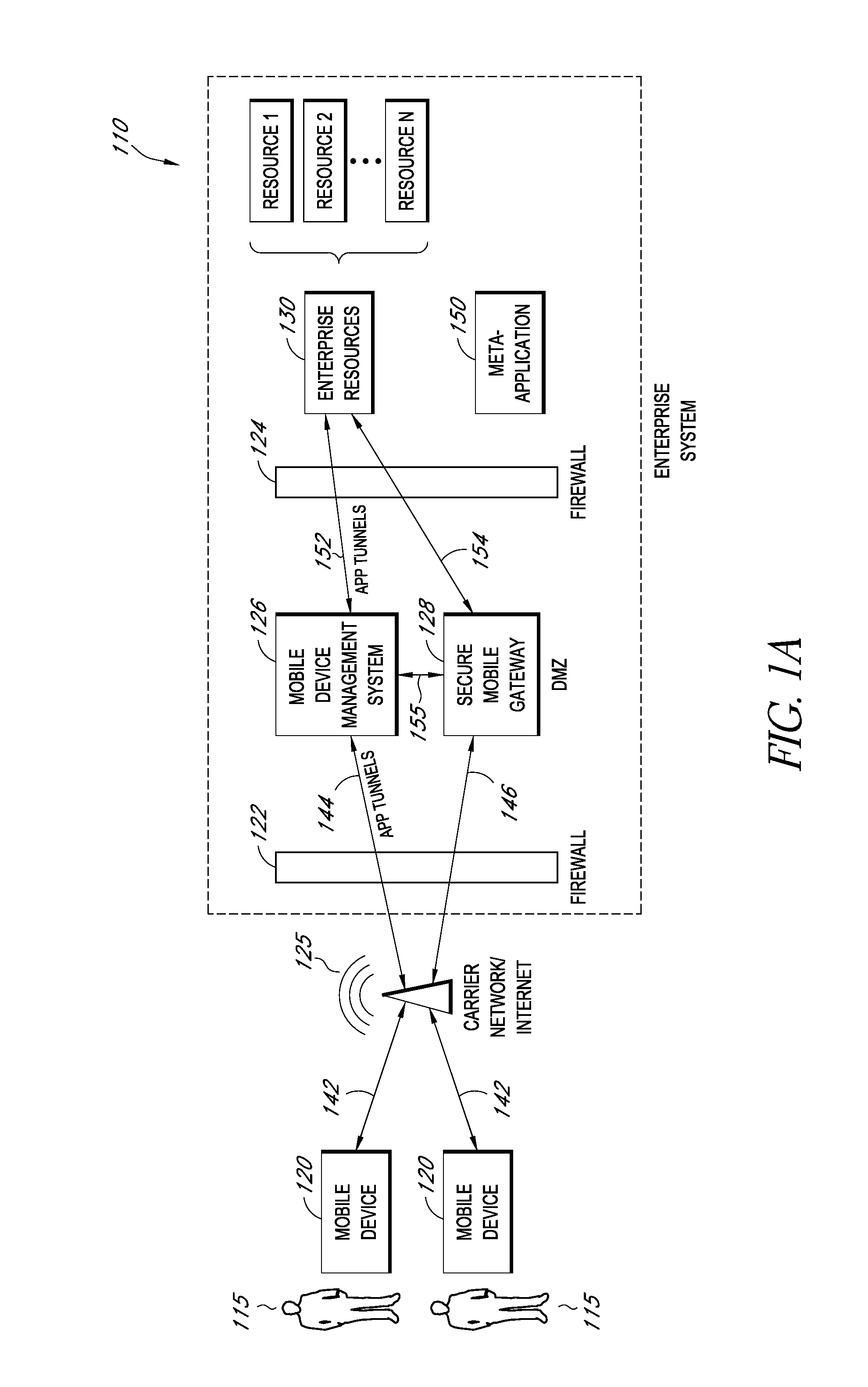
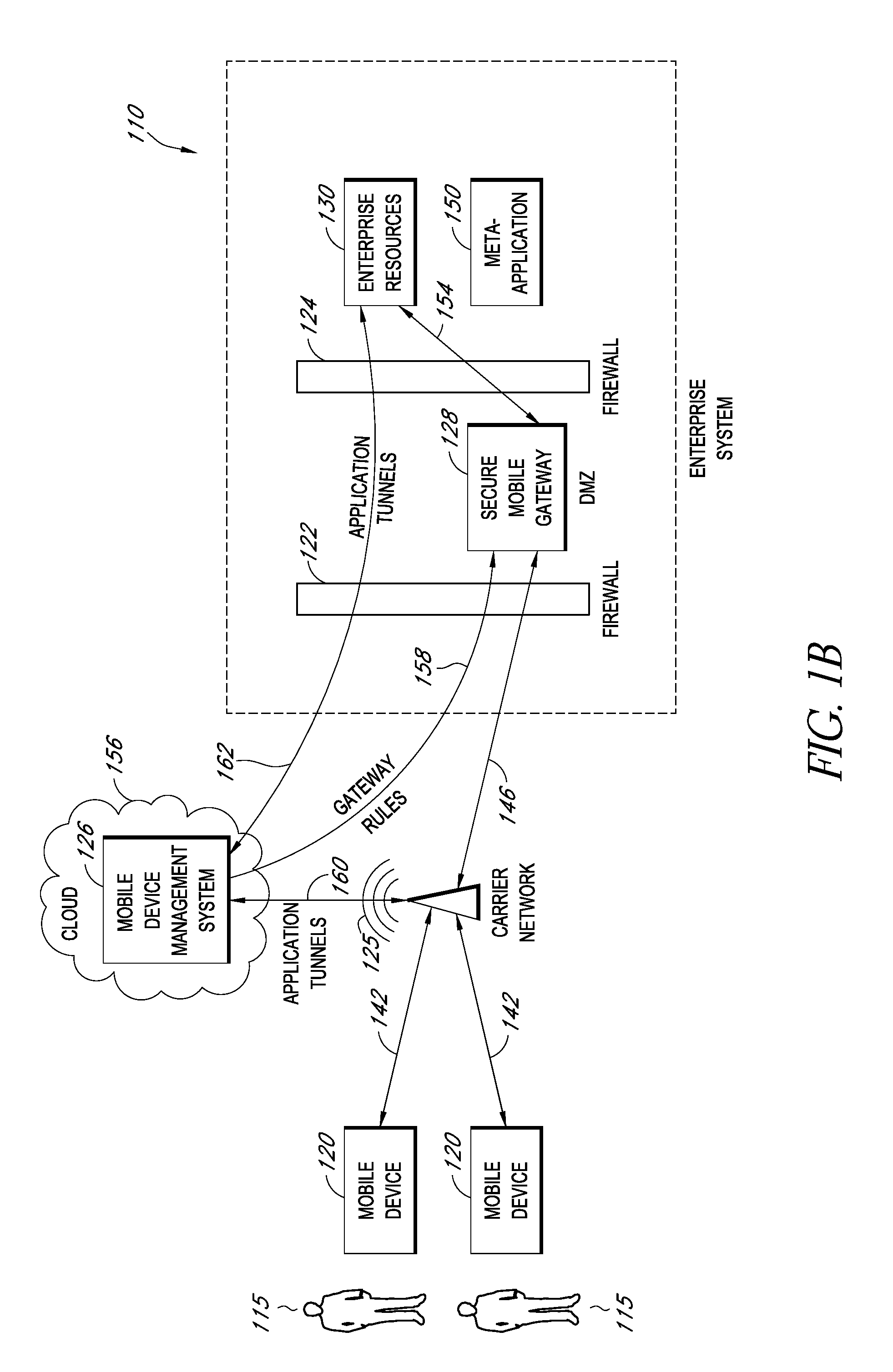
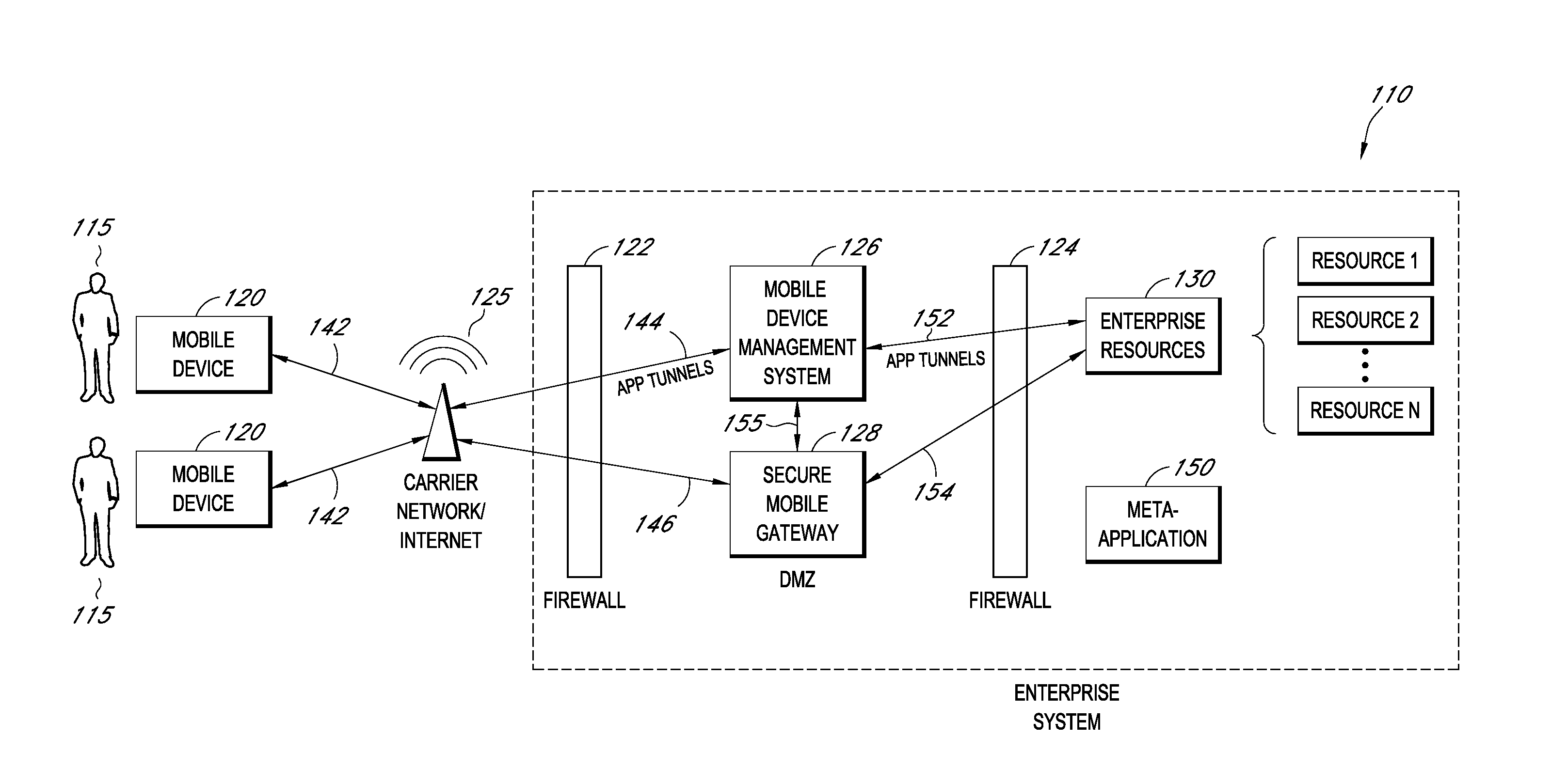
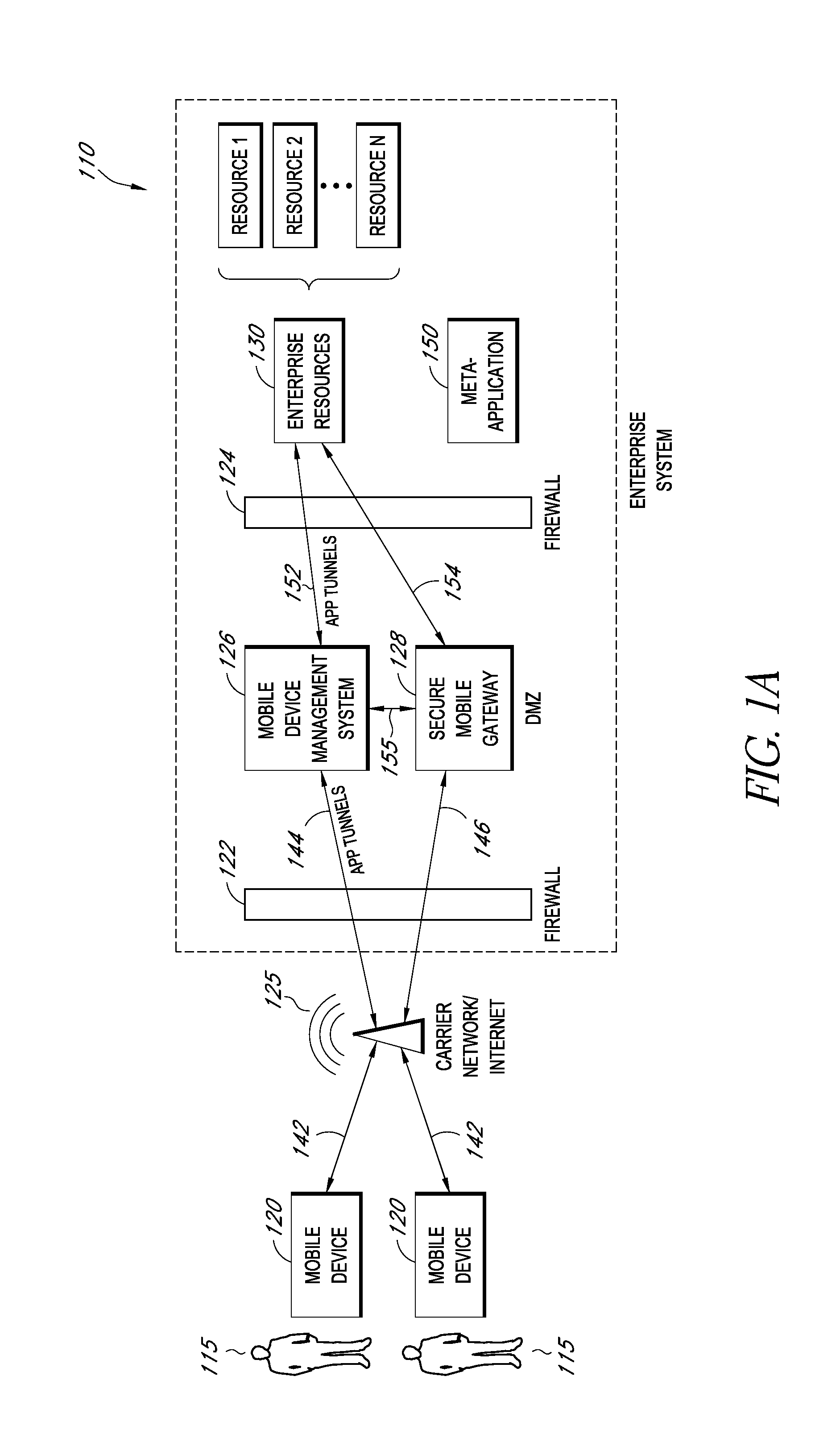
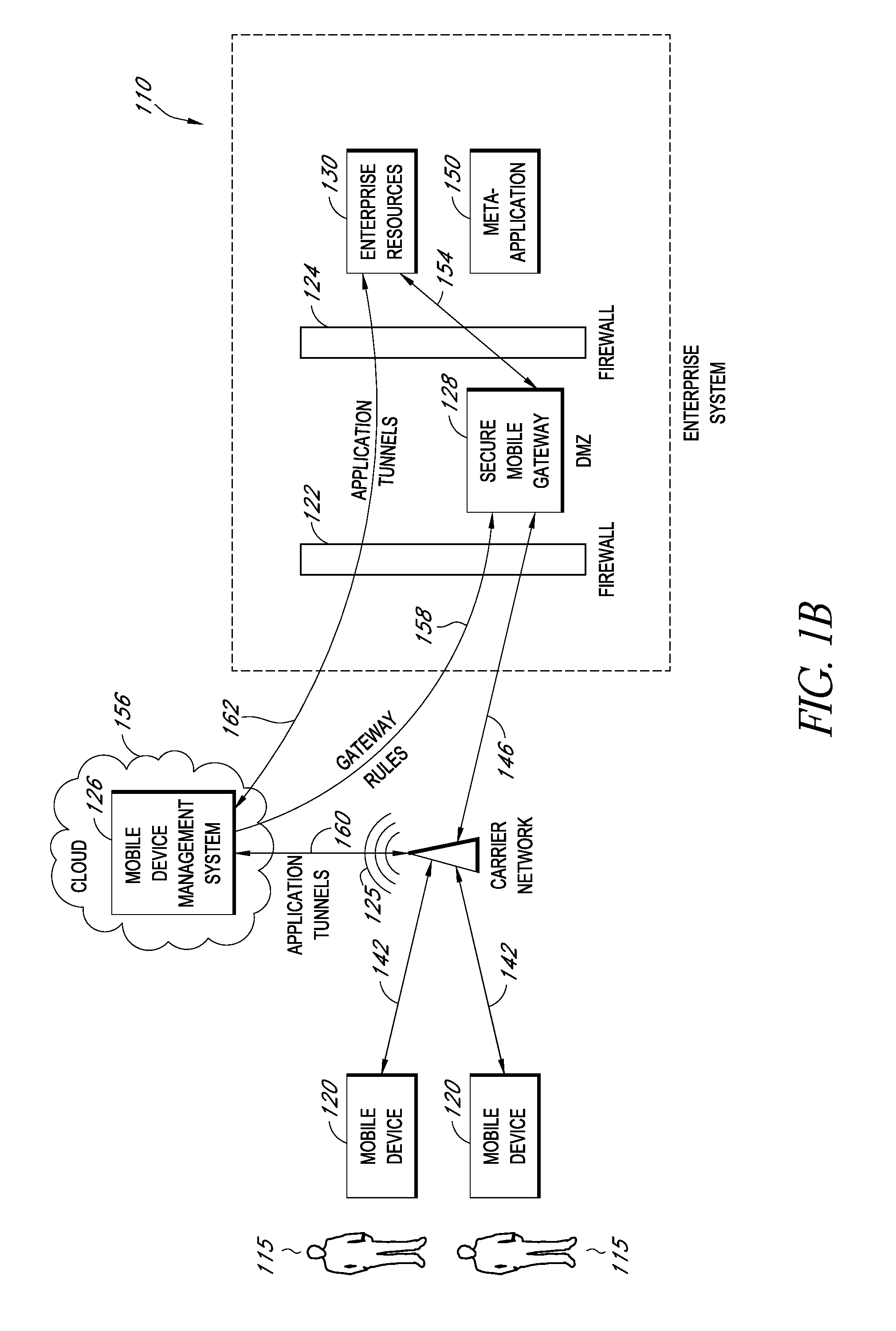
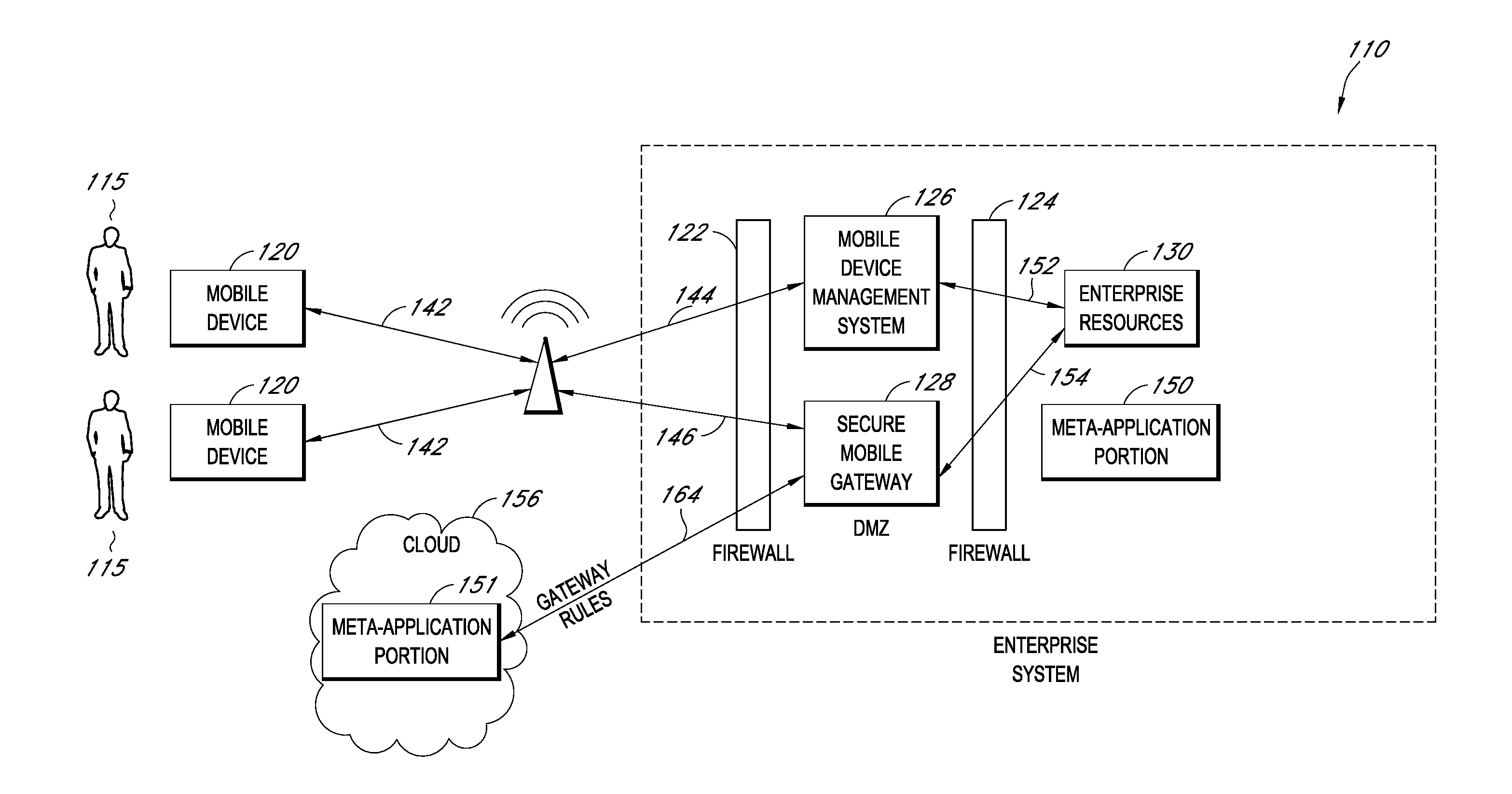
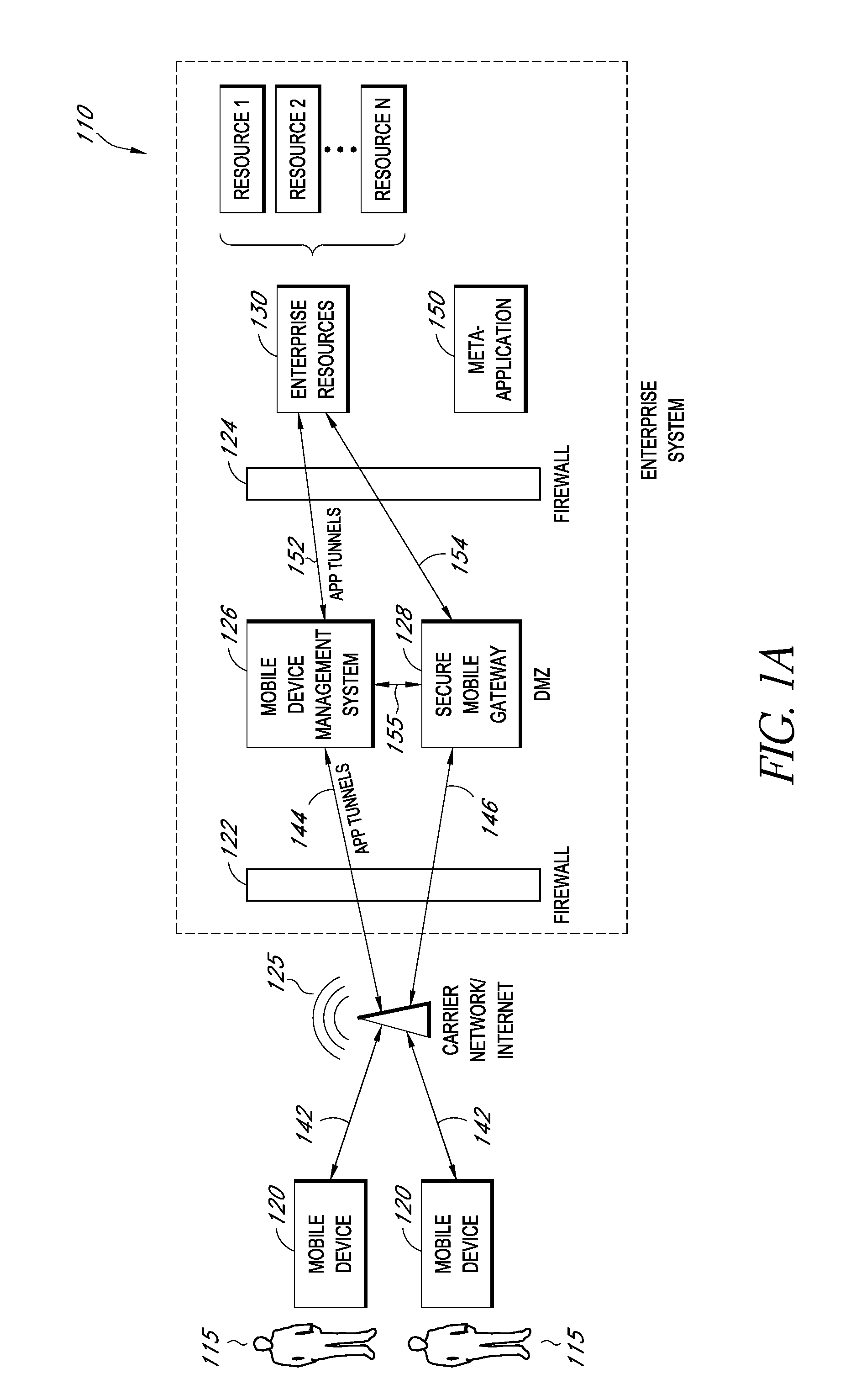
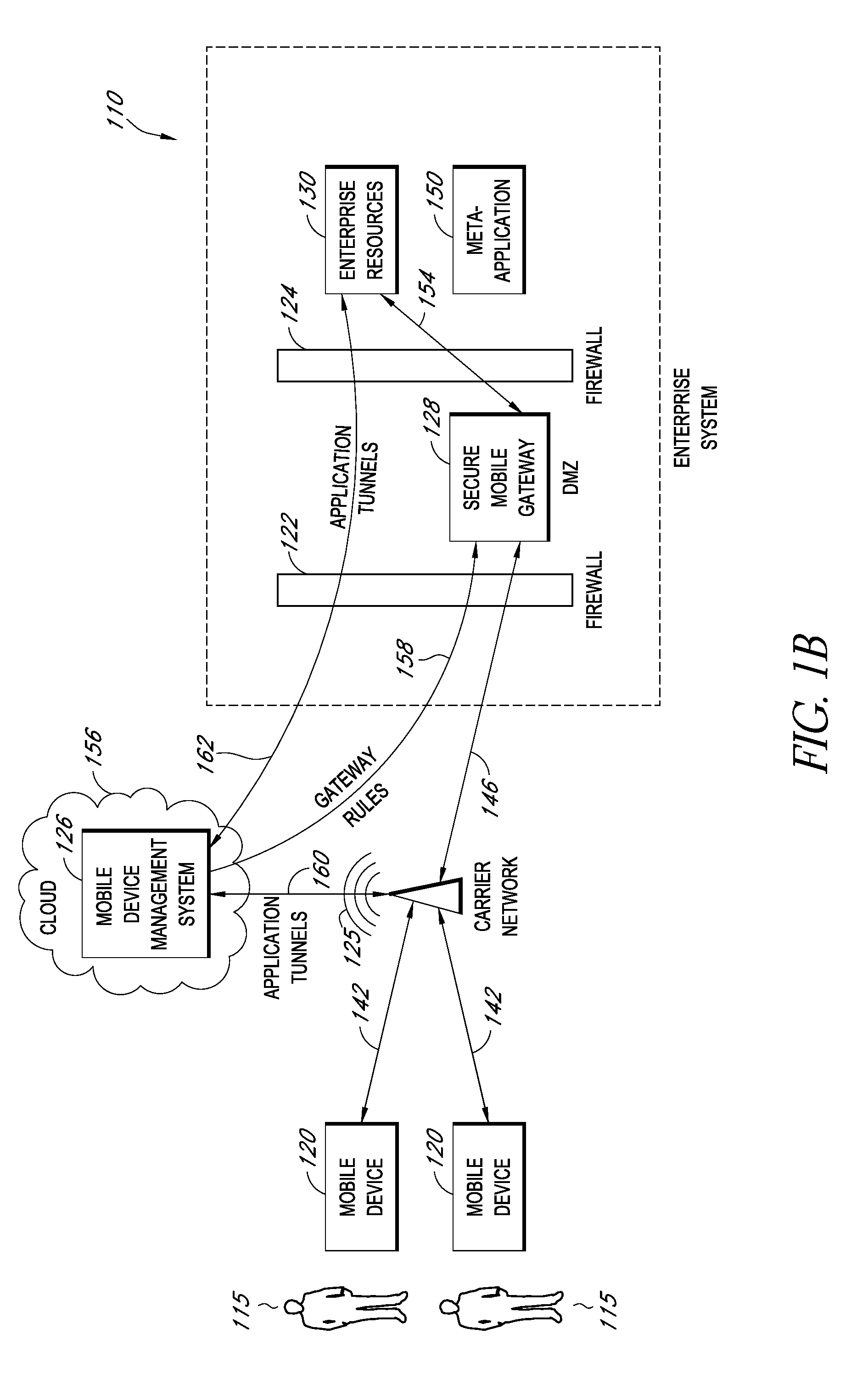
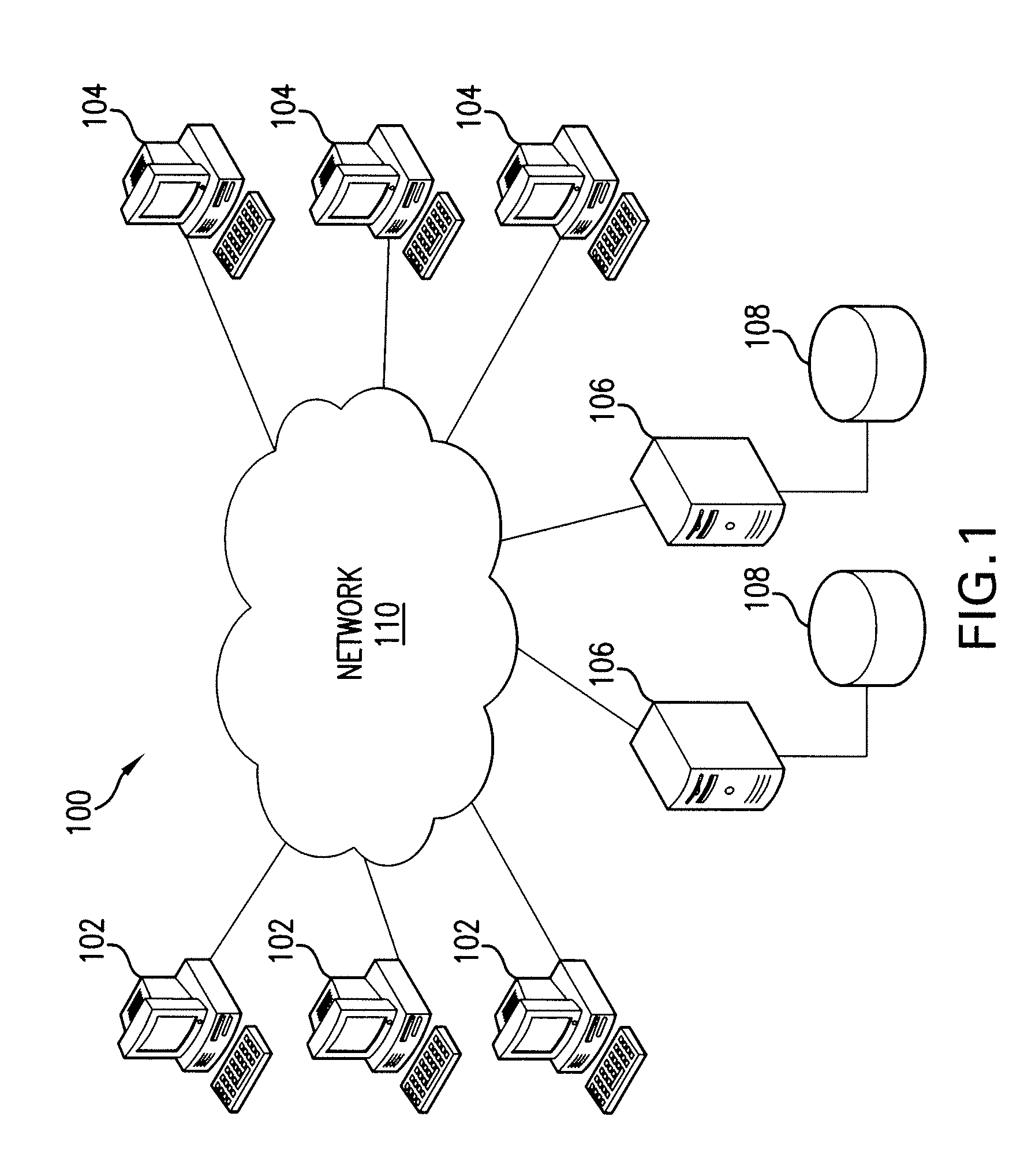
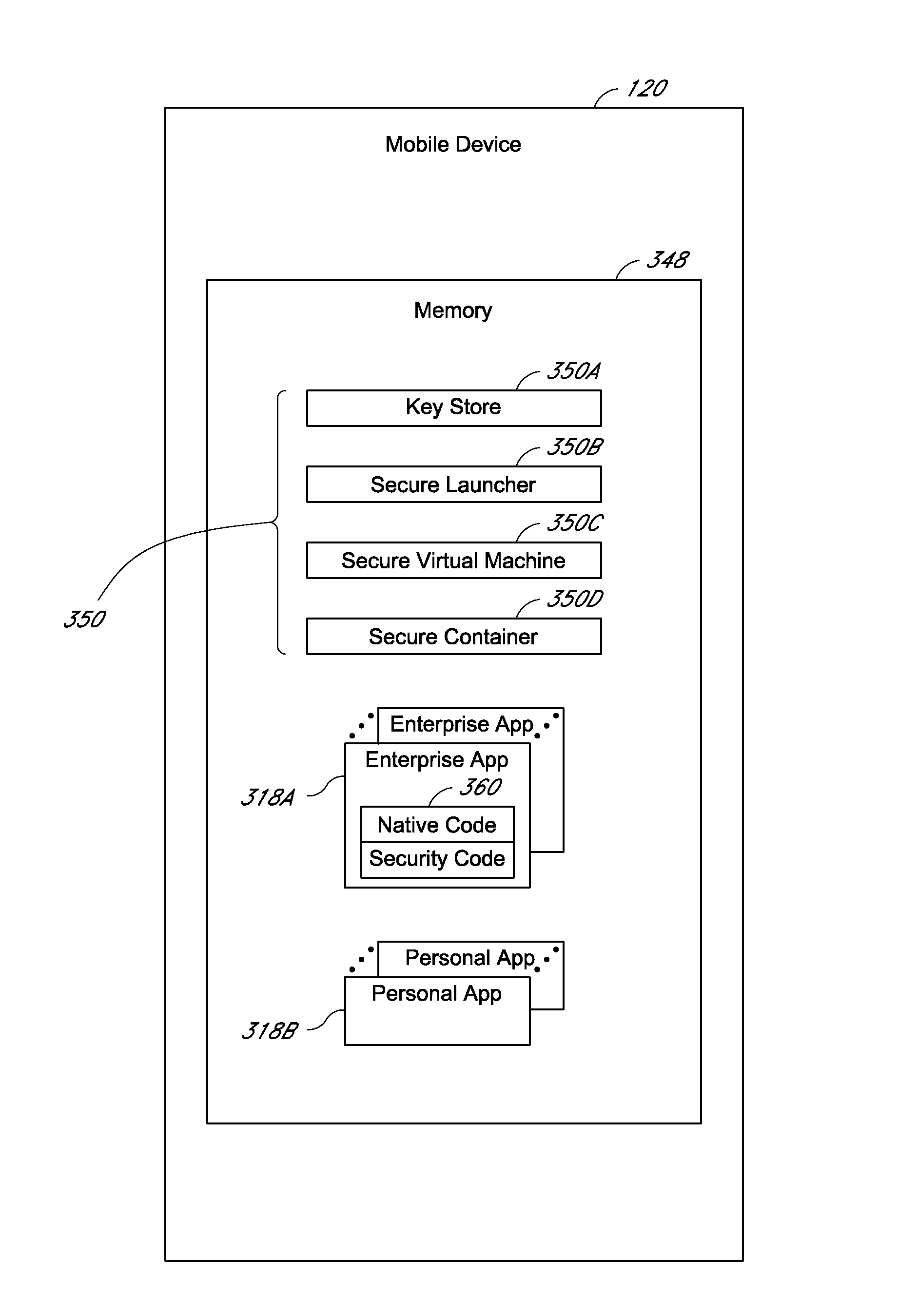
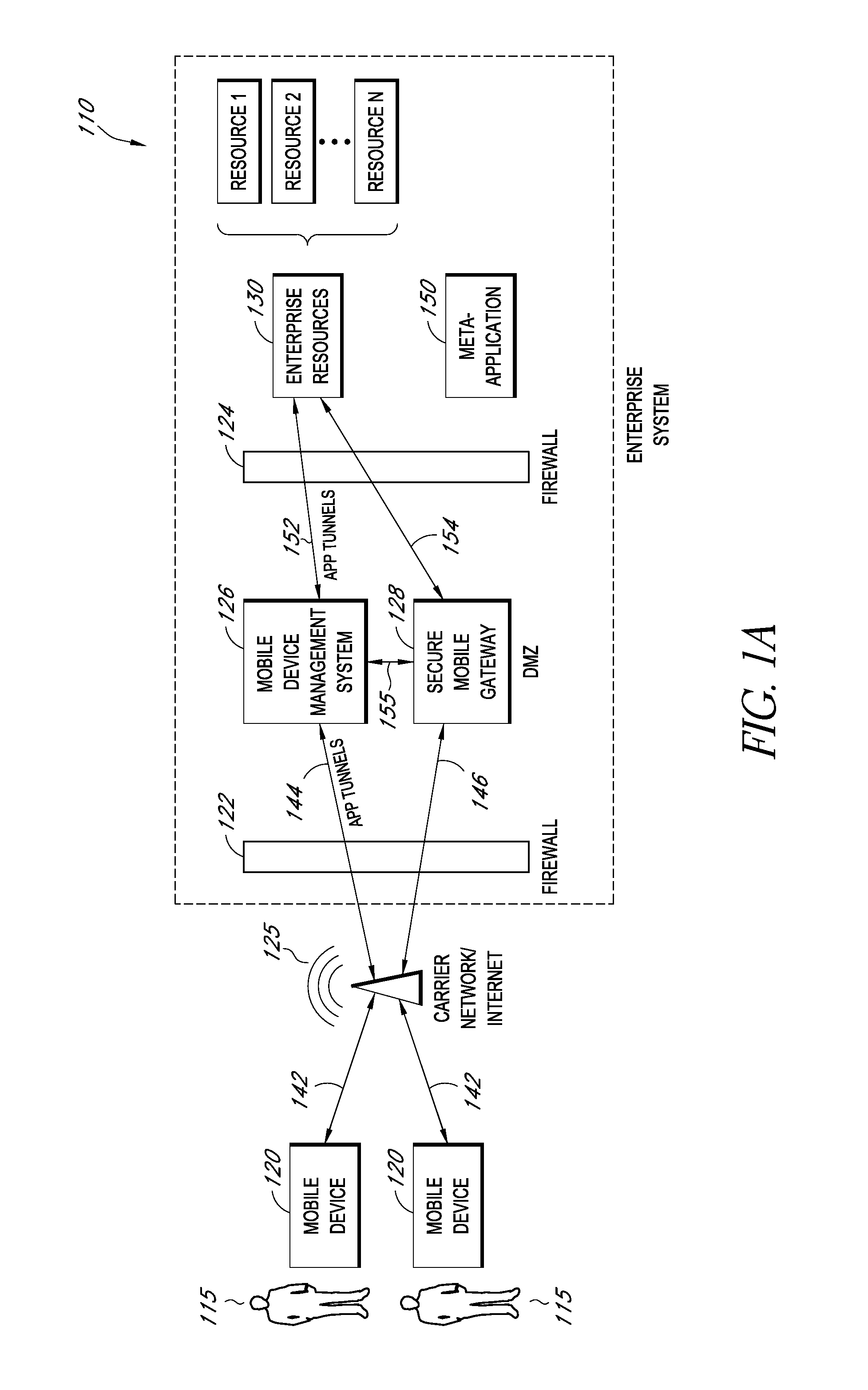
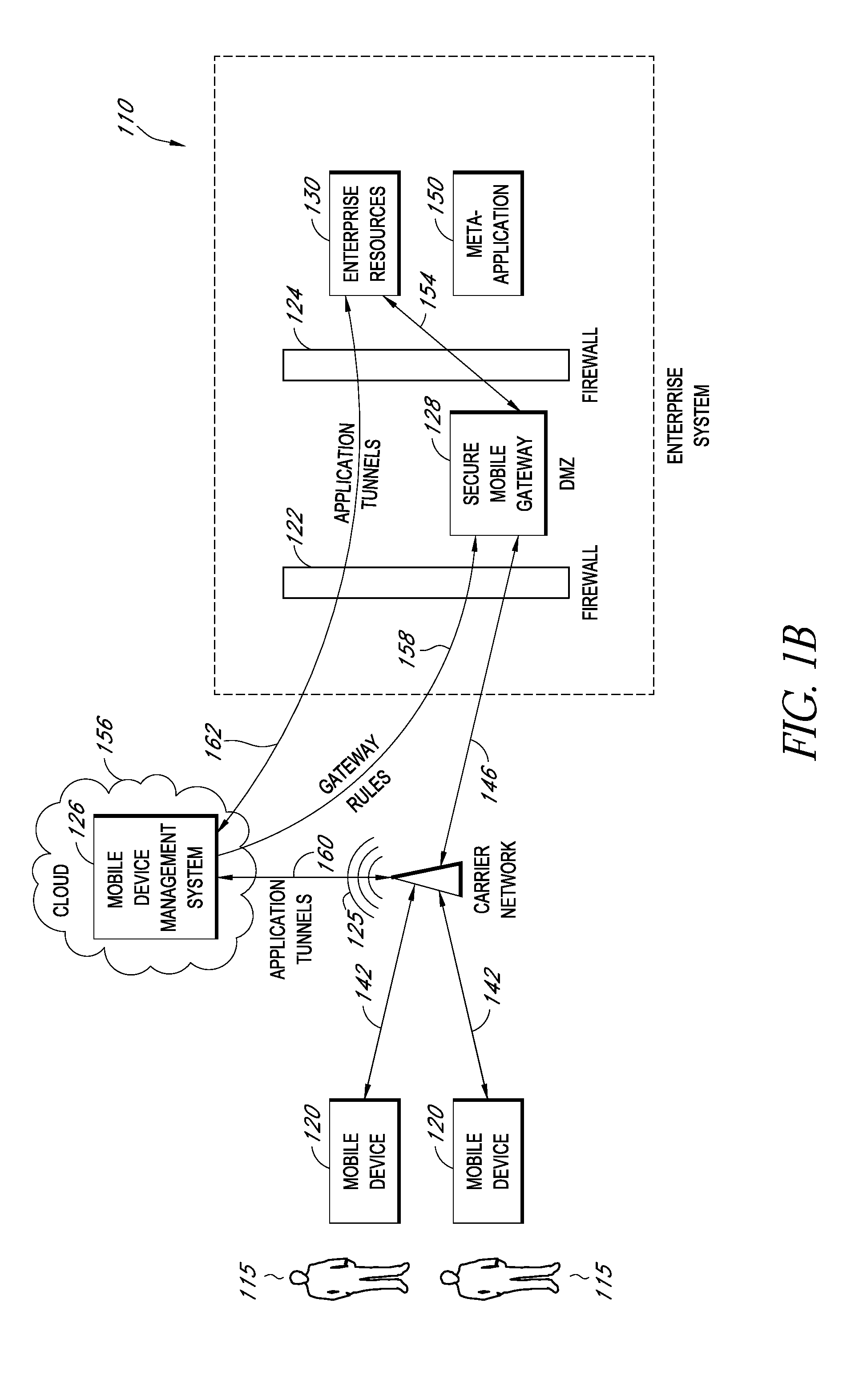
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
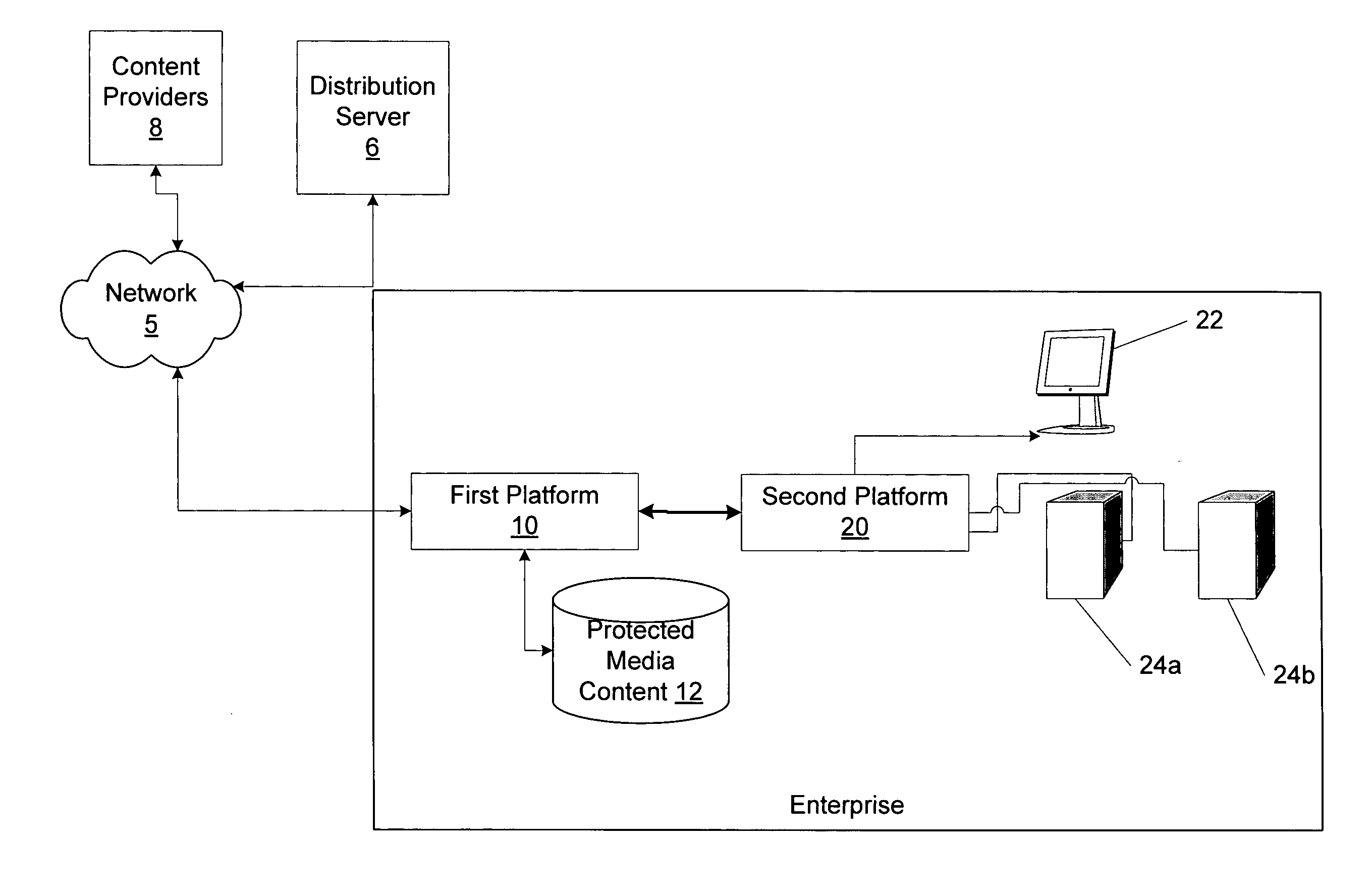
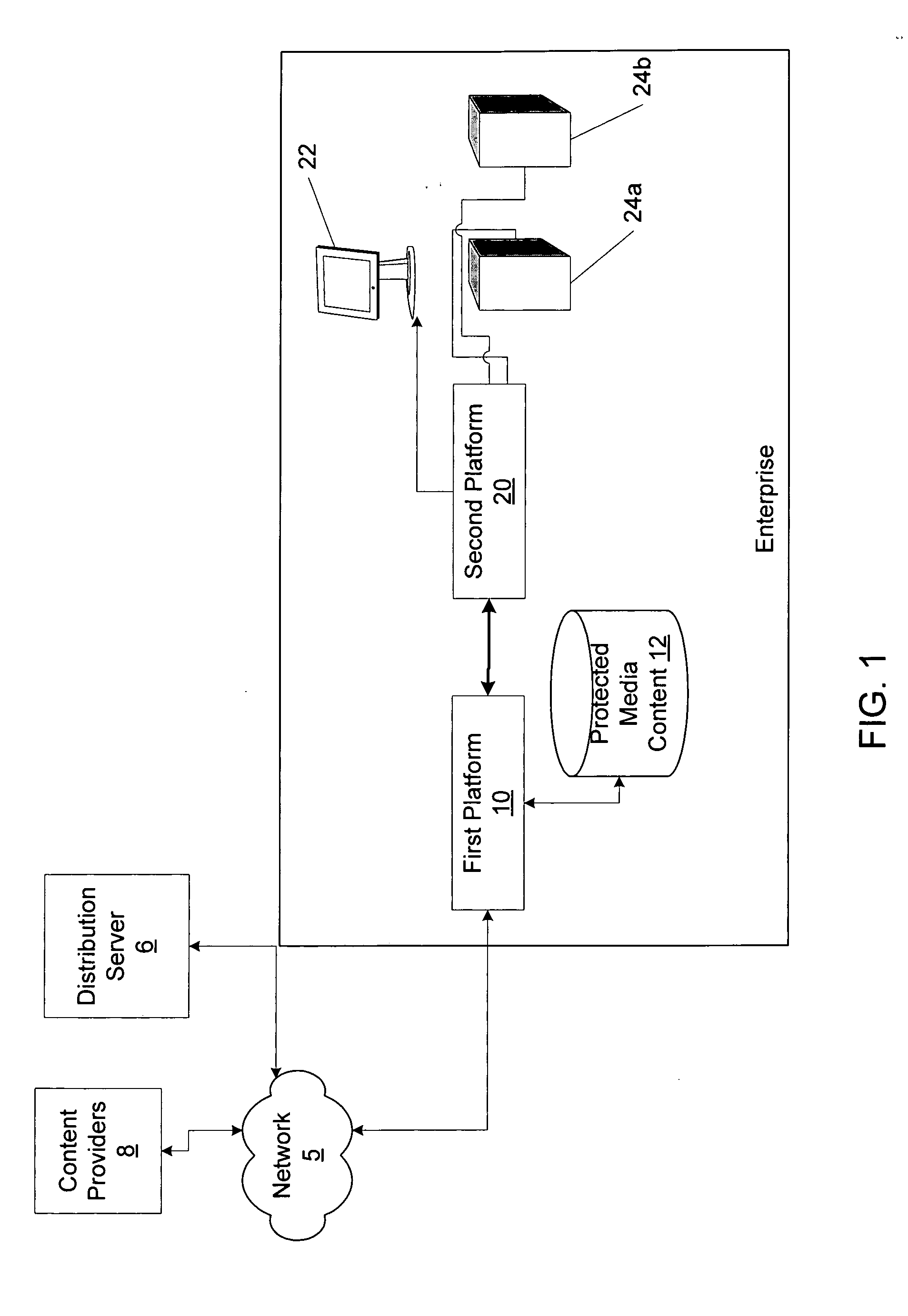
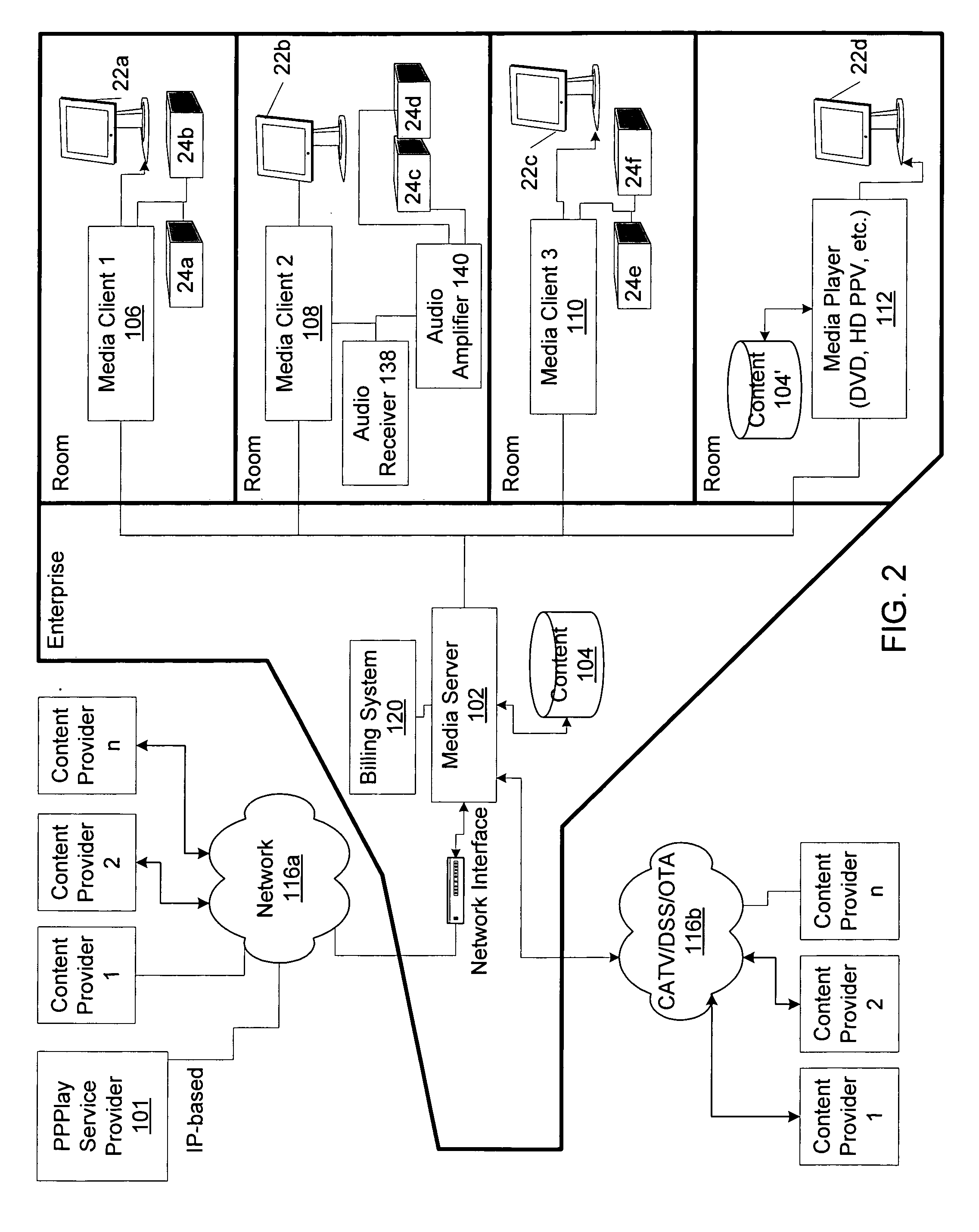
Method and apparatus for distributing media in a pay per play architecture with remote playback within an enterprise
ActiveUS20050283791A1Easy to editAnalogue secracy/subscription systemsTwo-way working systemsEnterprise systemMedia content
Systems and methods for rendering media content are provided. Systems of the invention can comprise a first platform for accessing, storing and distributing media content, wherein the media content comprises an unrenderable state when received by the first platform; a second platform communicatively coupled with the first platform for rendering the stored media content; the first and second platforms cooperatively providing an interface for purchasing a right to render stored or accessible media content at least one time; and at least one of the first platform and the second platform being operable to convert the stored or accessible media content to a renderable state upon the purchase of the right to render, wherein the first and second platforms are communicatively coupled to the Internet. Systems are preferably operably connected to the Internet and can provide access to content sources local to and remote from the system of the invention.
Owner:DIRECTV LLC
System and method for application performance management
InactiveUS7350209B2General purpose stored program computerHardware monitoringComputer resourcesUser interface
Owner:BMC SOFTWARE
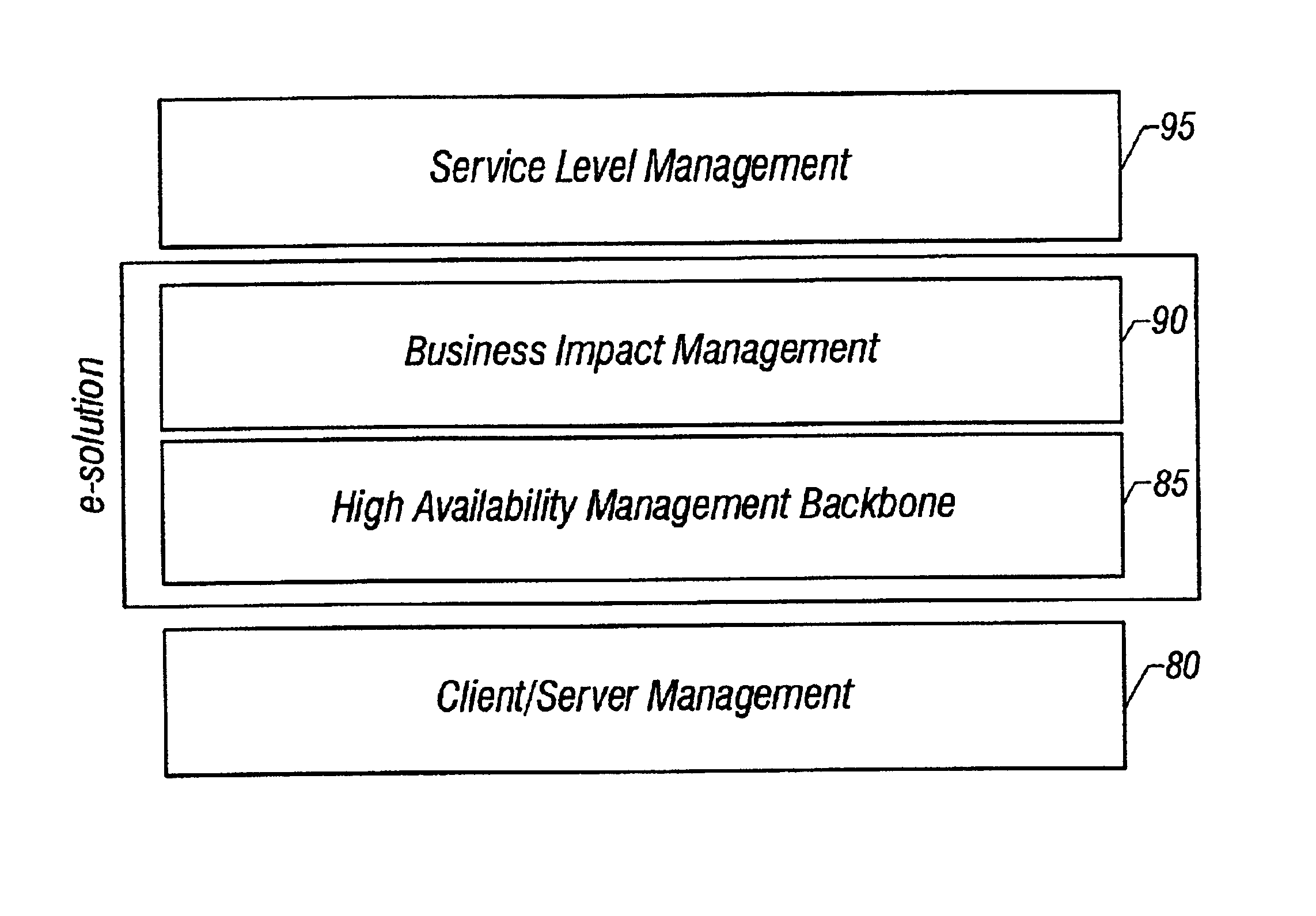
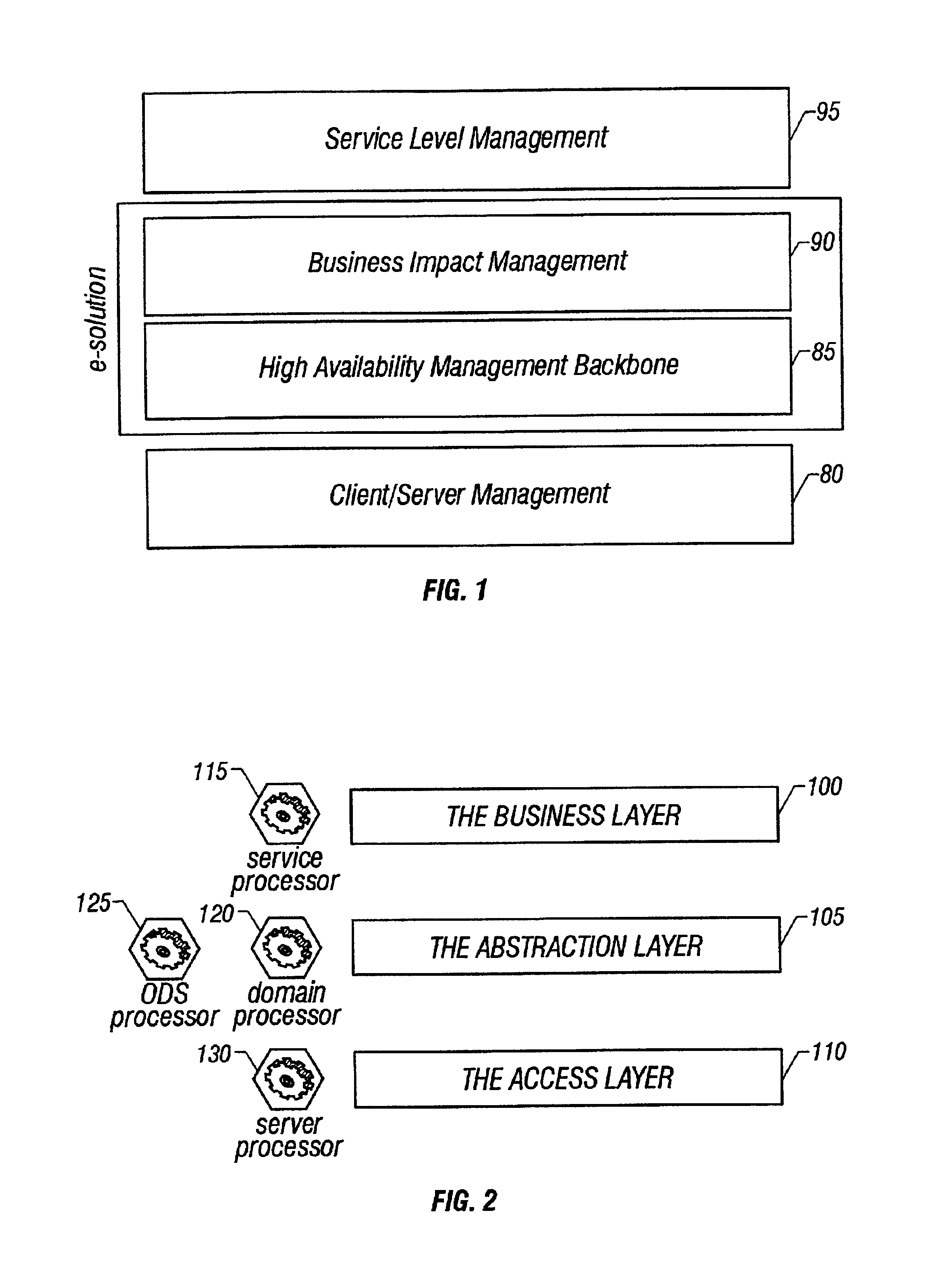
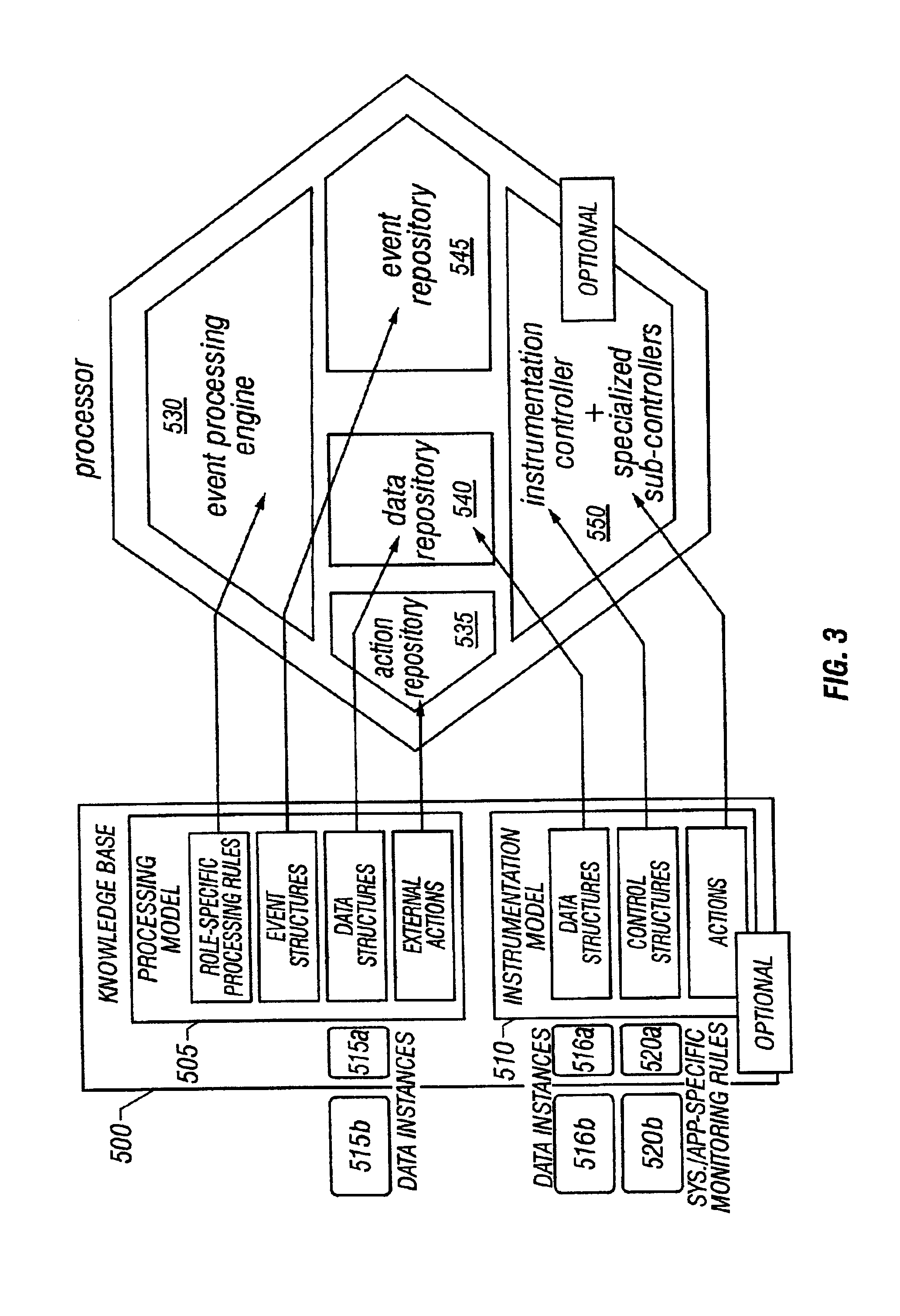
System and method of enterprise systems and business impact management
InactiveUS6983321B2Faster and accurate analysisAvoid lot of costDigital computer detailsPayment architectureBusiness managementPotential impact
A system architecture and a method for management using a cellular architecture to allow multi-tier management of events such as the managing of the actual impact or the potential impact of IT infrastructure situations on business services. A preferred embodiment includes a high availability management backbone to frame monitoring operations using a cross-domain model where IT Component events are abstracted into IT Aggregate events. By combining IT Aggregate events with transaction events, an operational representation of the business services is possible. Another feature is the ability to connect this information to dependent business user groups such as internal end-users or external customers for direct impact measurement. A web of peer-to-peer rule-based cellular event processors preferably using Dynamic Data Association constitutes management backbone crossed by event flows, the execution of rules, and distributed set of dynamic inter-related object data rooted in the top data instances featuring the business services.
Owner:BMC SOFTWARE
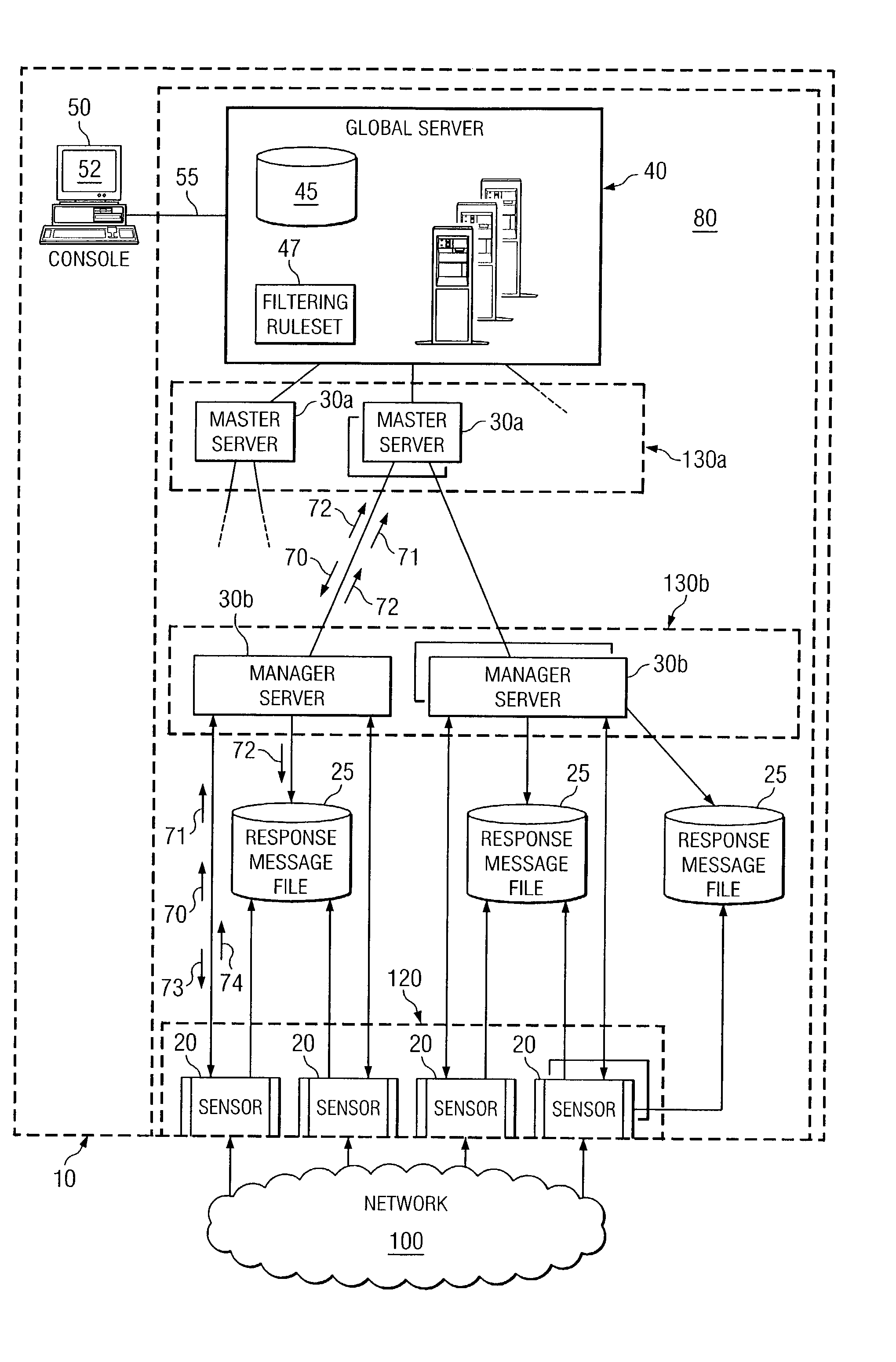
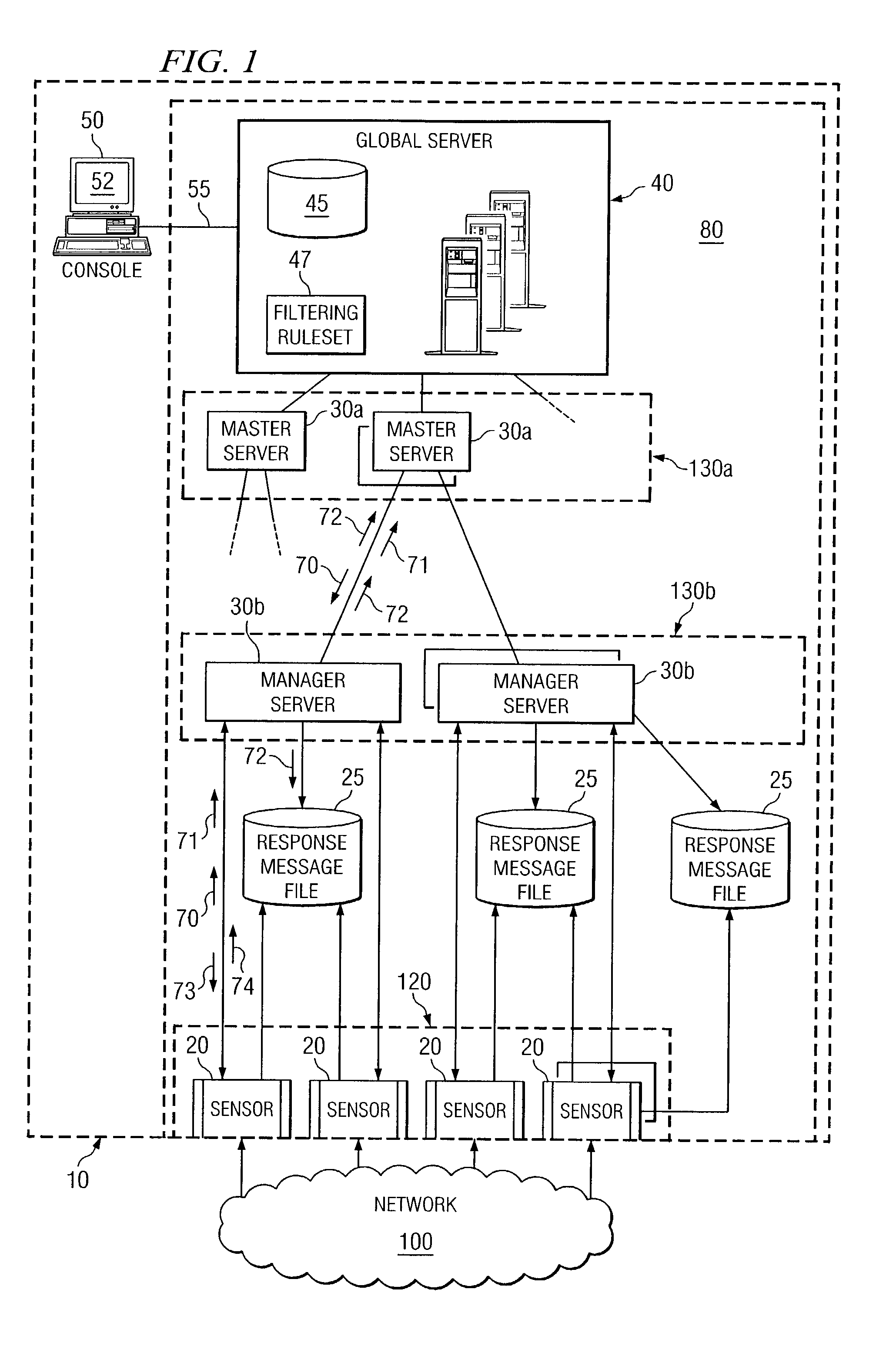
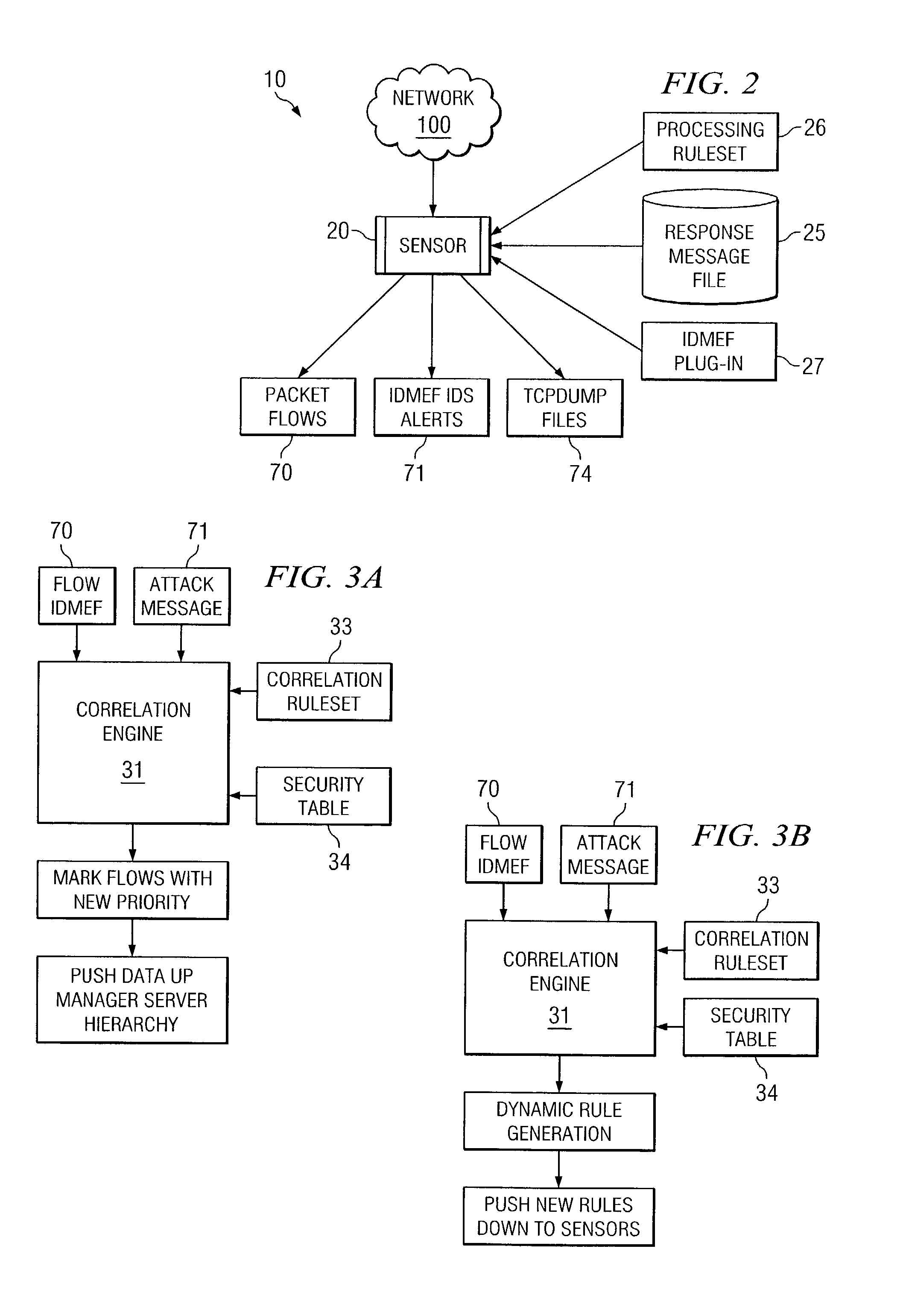
Dynamic rule generation for an enterprise intrusion detection system
ActiveUS7895649B1Lower the volumeReadily apparentMemory loss protectionDigital data processing detailsPacket lossEnterprise system
A method for dynamically generating rules for an enterprise intrusion detection system comprises receiving a packet flow from a sensor. The packet flow is dynamically processed to detect if the packet flow represents an attack on the enterprise system. A response message is automatically generated in response to the attack, the response message comprising a signature to identify the attack. The response message is automatically communicated to a response message file, the response message file comprising at least one response message.
Owner:FORCEPOINT FEDERAL
Method, system and article of manufacture for data preservation and automated electronic software distribution across an enterprise system
InactiveUS20050055357A1Digital data processing detailsMultiple digital computer combinationsSoftware distributionWorkstation
A method, system and article of manufacture for data preservation. A method for preserving data during system migration includes determining which files on a computer should not be preserved, preserving all files from the computer not identified by the determining step, performing a system migration on the computer, and downloading the preserved files to the computer. The determining step may determines which files should not be preserved by applying rules that specify which files should not be preserved. A system for preserving data during system migration includes a plurality of workstation computers and a remote site server connected to the plurality of workstation computers. Each workstation computer includes a plurality of files. The remote site server includes a processor that executes instructions on a memory, the memory including instructions for preserving data during system migration.
Owner:SECUREINFO CORP
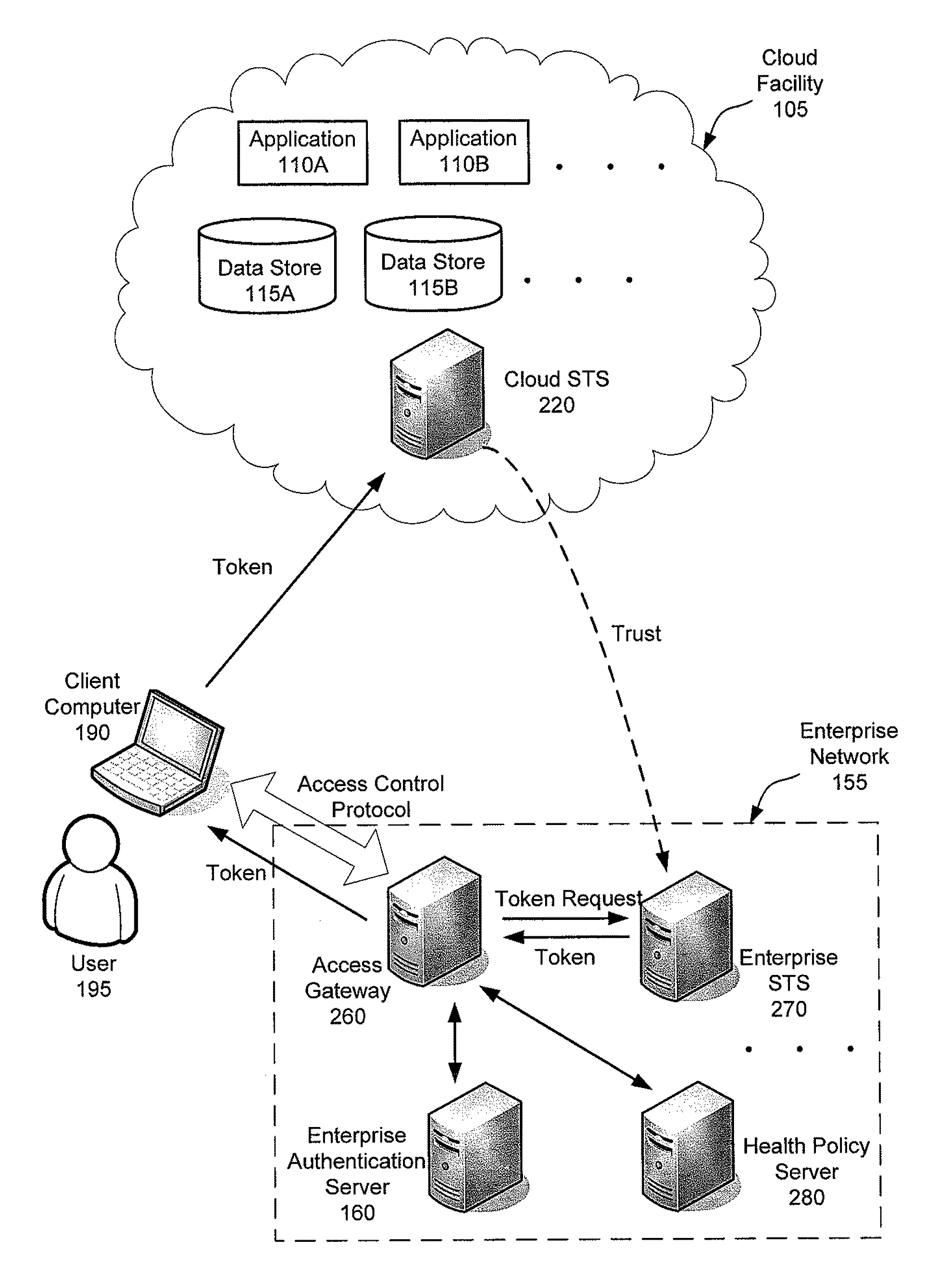
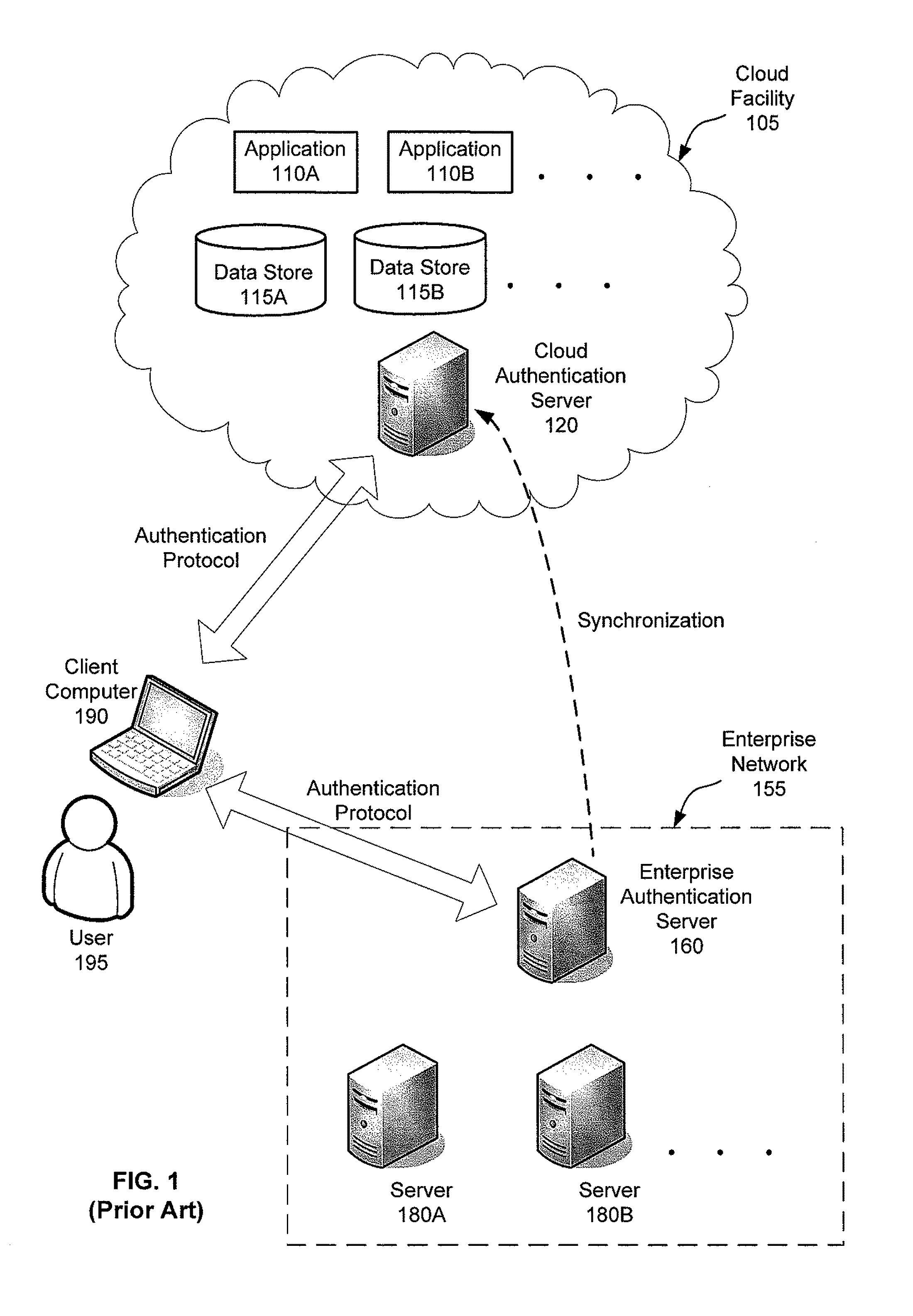
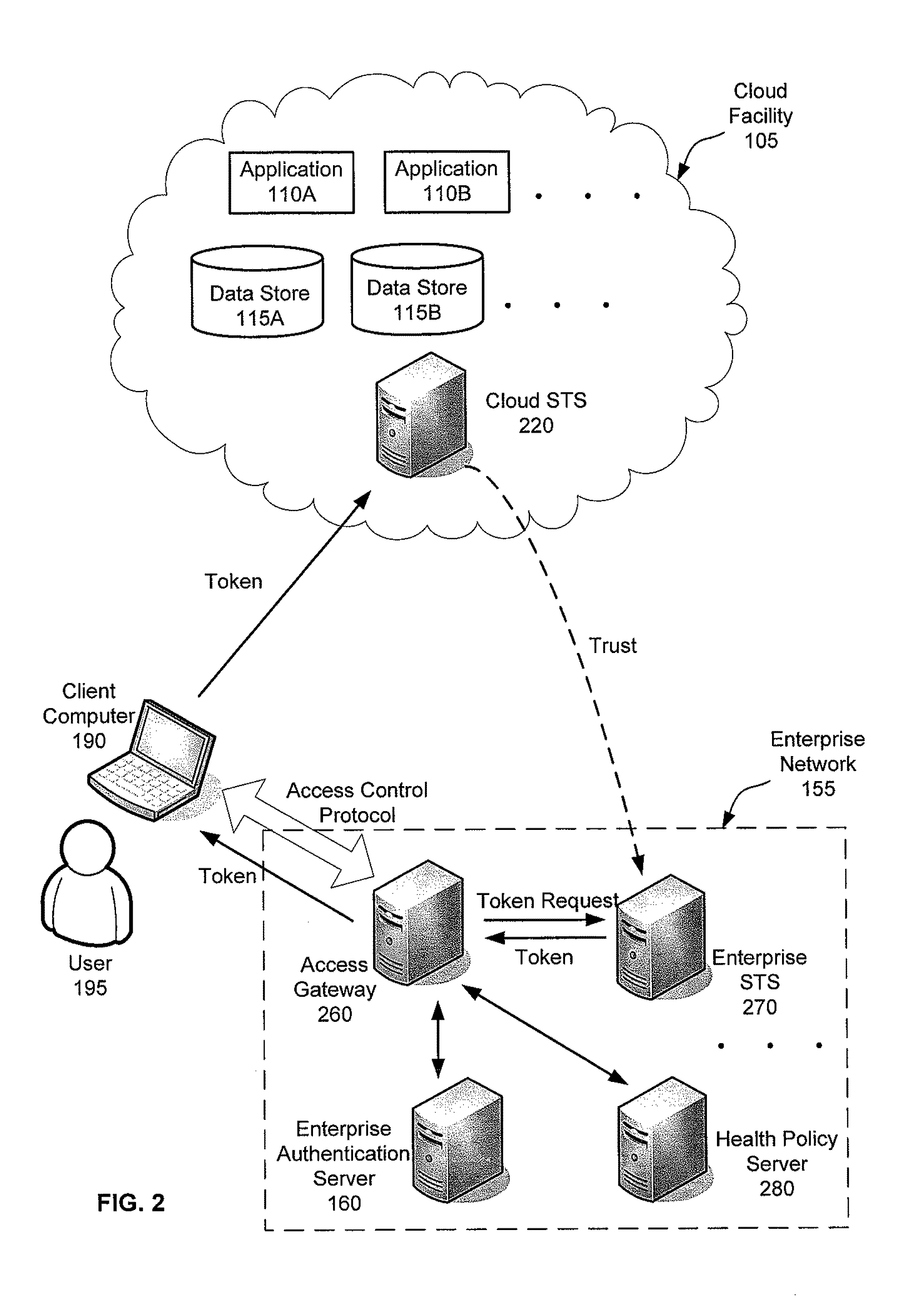
Flexible end-point compliance and strong authentication for distributed hybrid enterprises
ActiveUS20110307947A1Digital data processing detailsMultiple digital computer combinationsUser authenticationClient-side
Systems, methods and apparatus for accessing at least one resource hosted by at least one server of a cloud service provider. In some embodiments, a client computer sends authentication information associated with a user of the client computer and a statement of health regarding the client computer to an access control gateway deployed in an enterprise's managed network. The access control gateway authenticates the user and determines whether the user is authorized to access the at least one resource hosted in the cloud. If the user authentication and authorization succeeds, the access control gateway requests a security token from a security token service trusted by an access control component in the cloud and forwards the security token to the client computer. The client computer sends the security token to the access component in the cloud to access the at least one resource from the at least one server.
Owner:MICROSOFT TECH LICENSING LLC
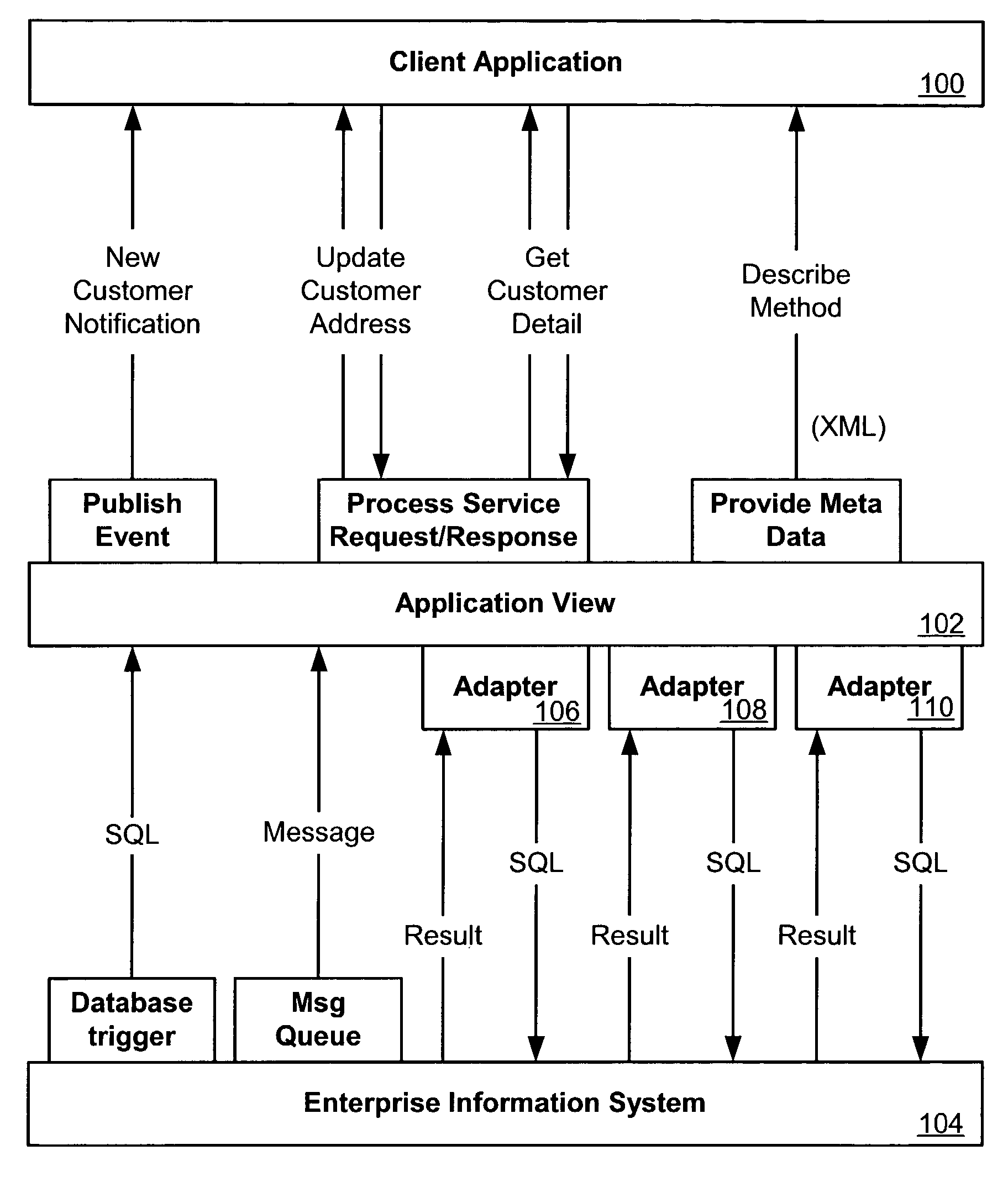
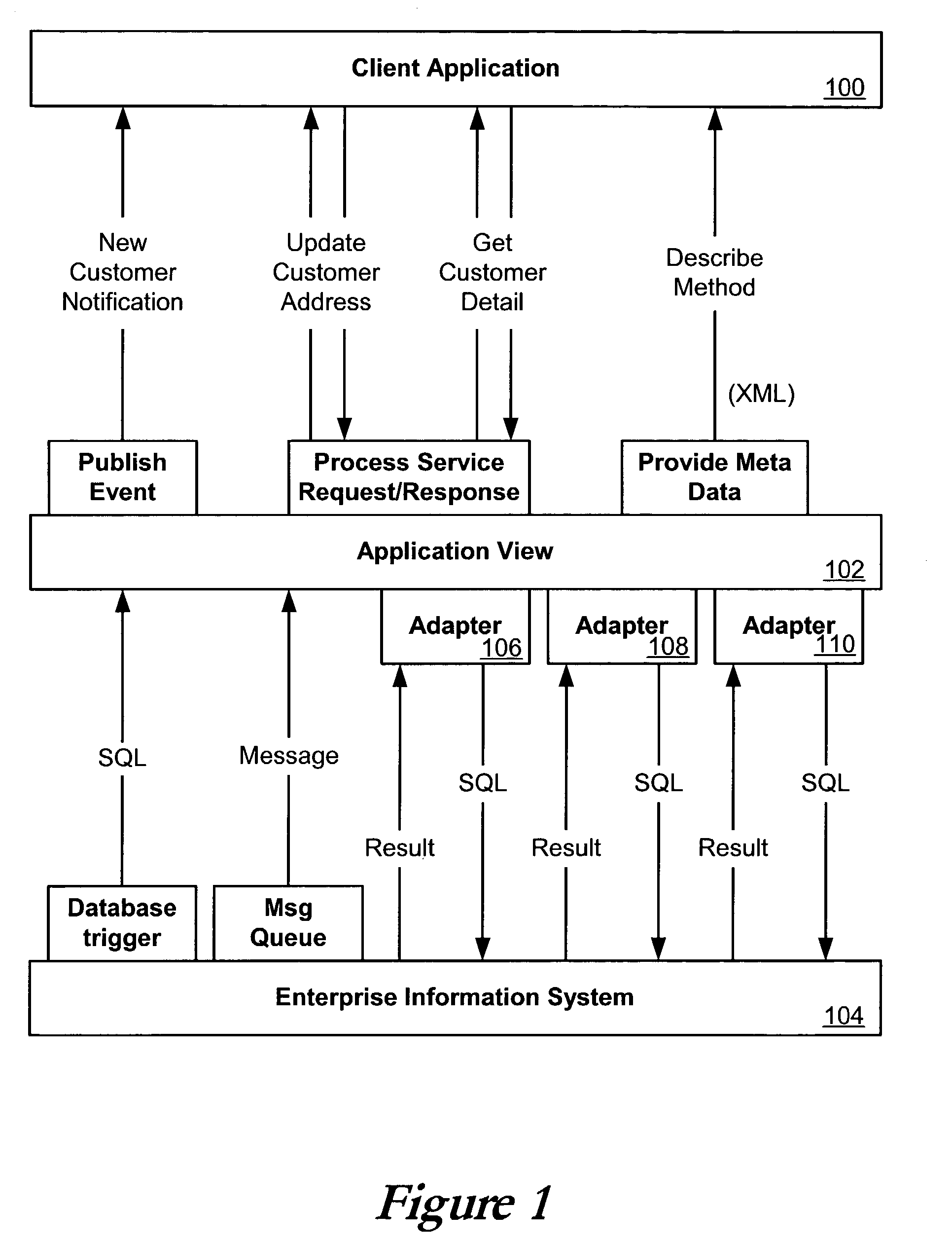
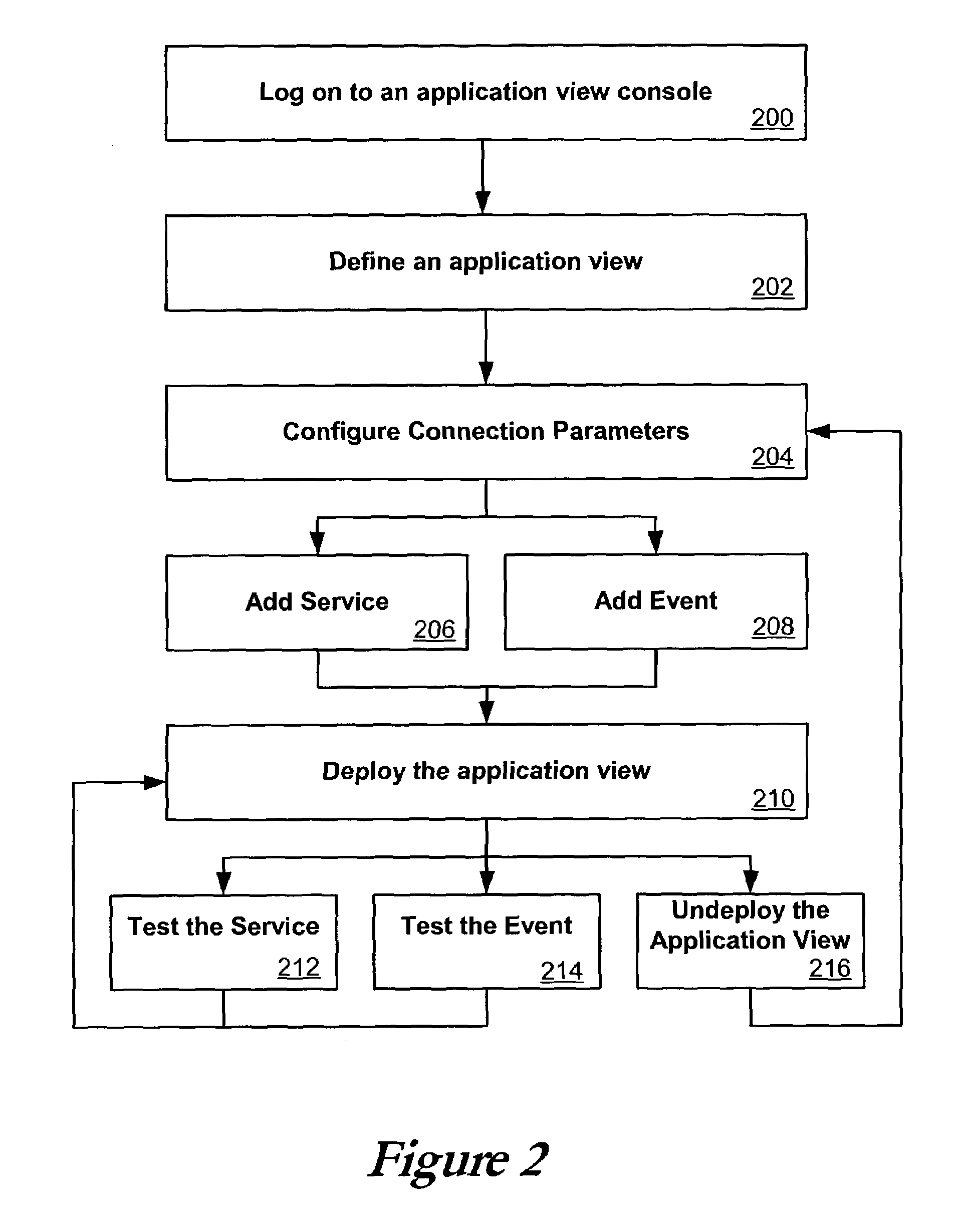
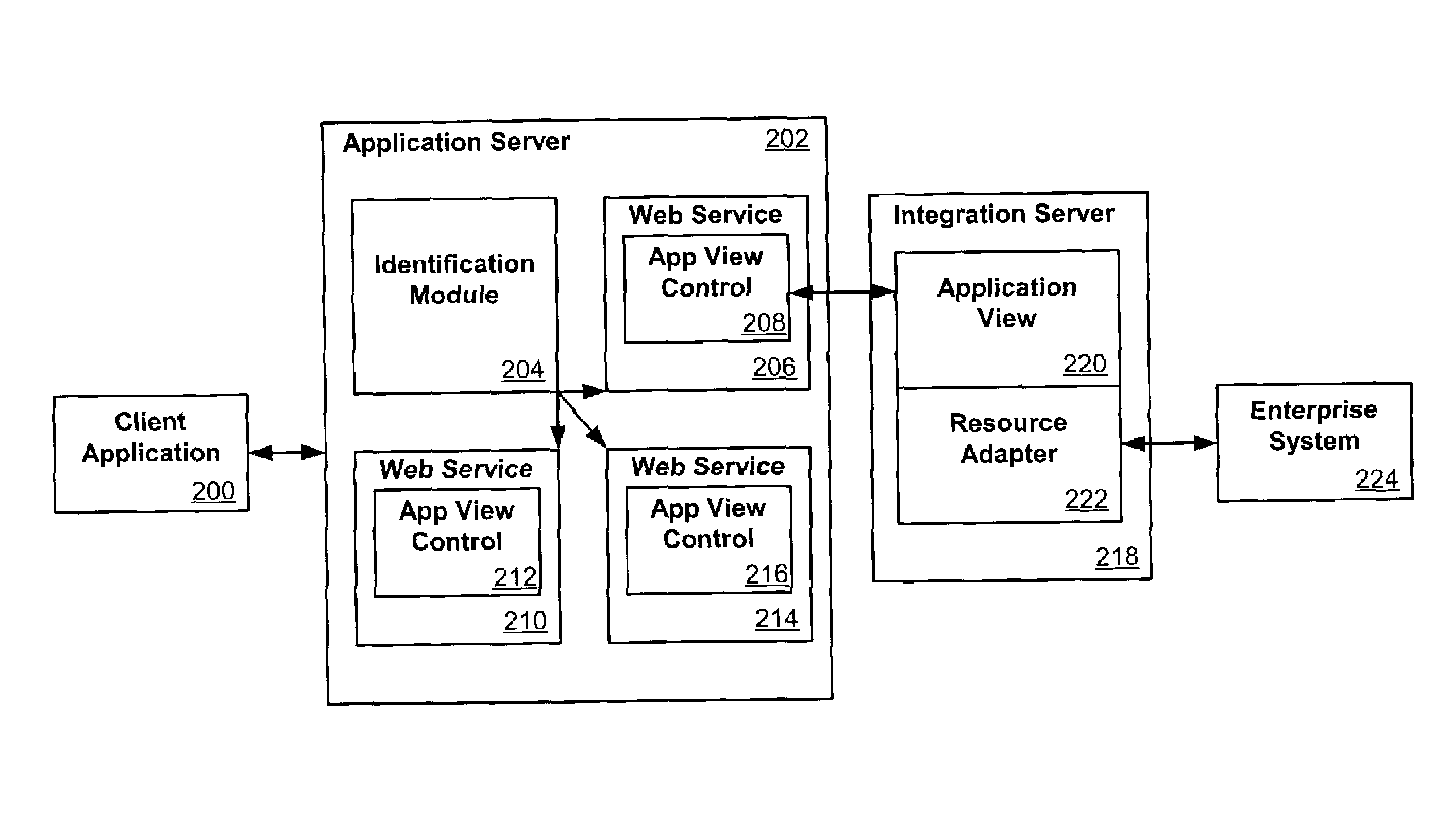
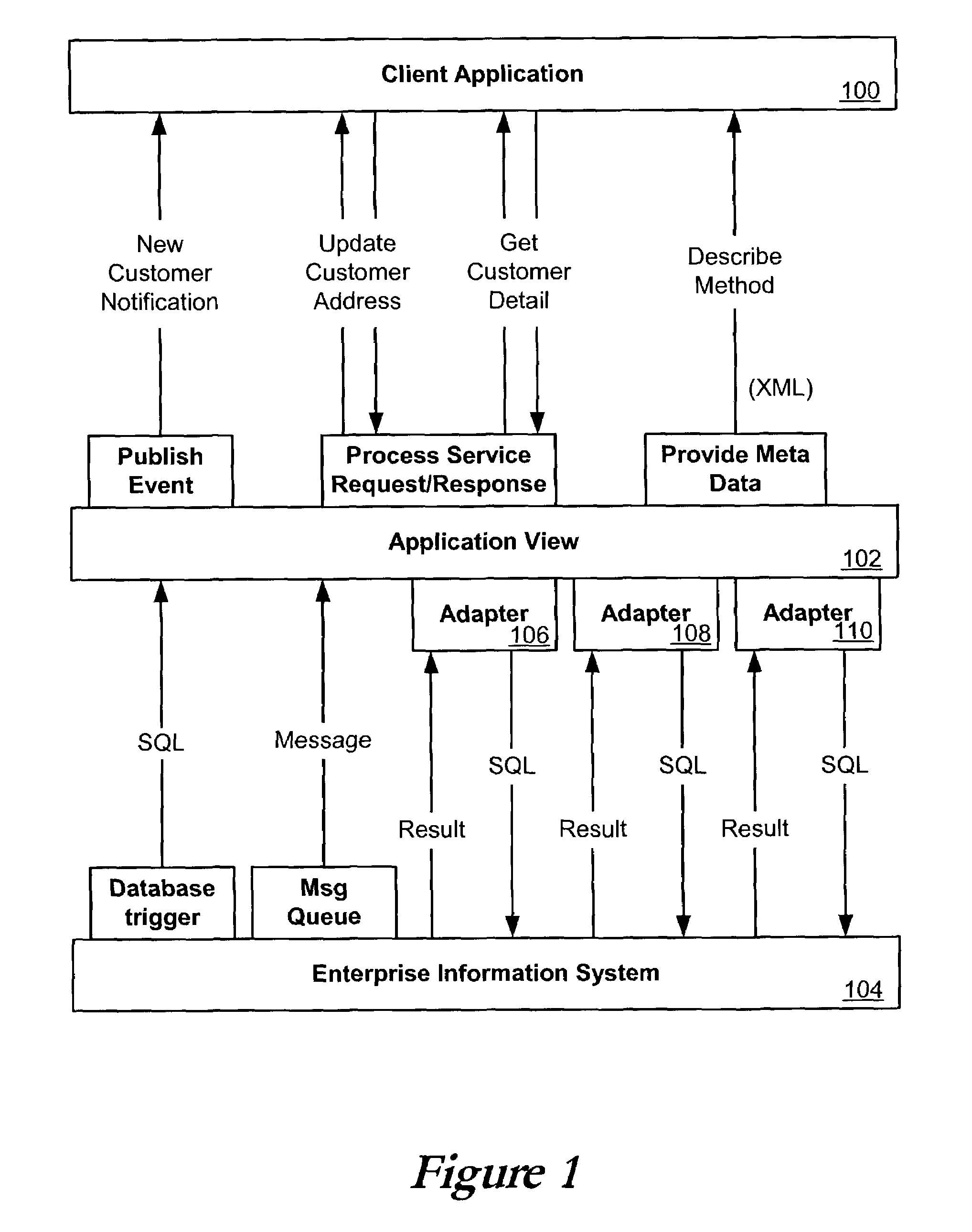
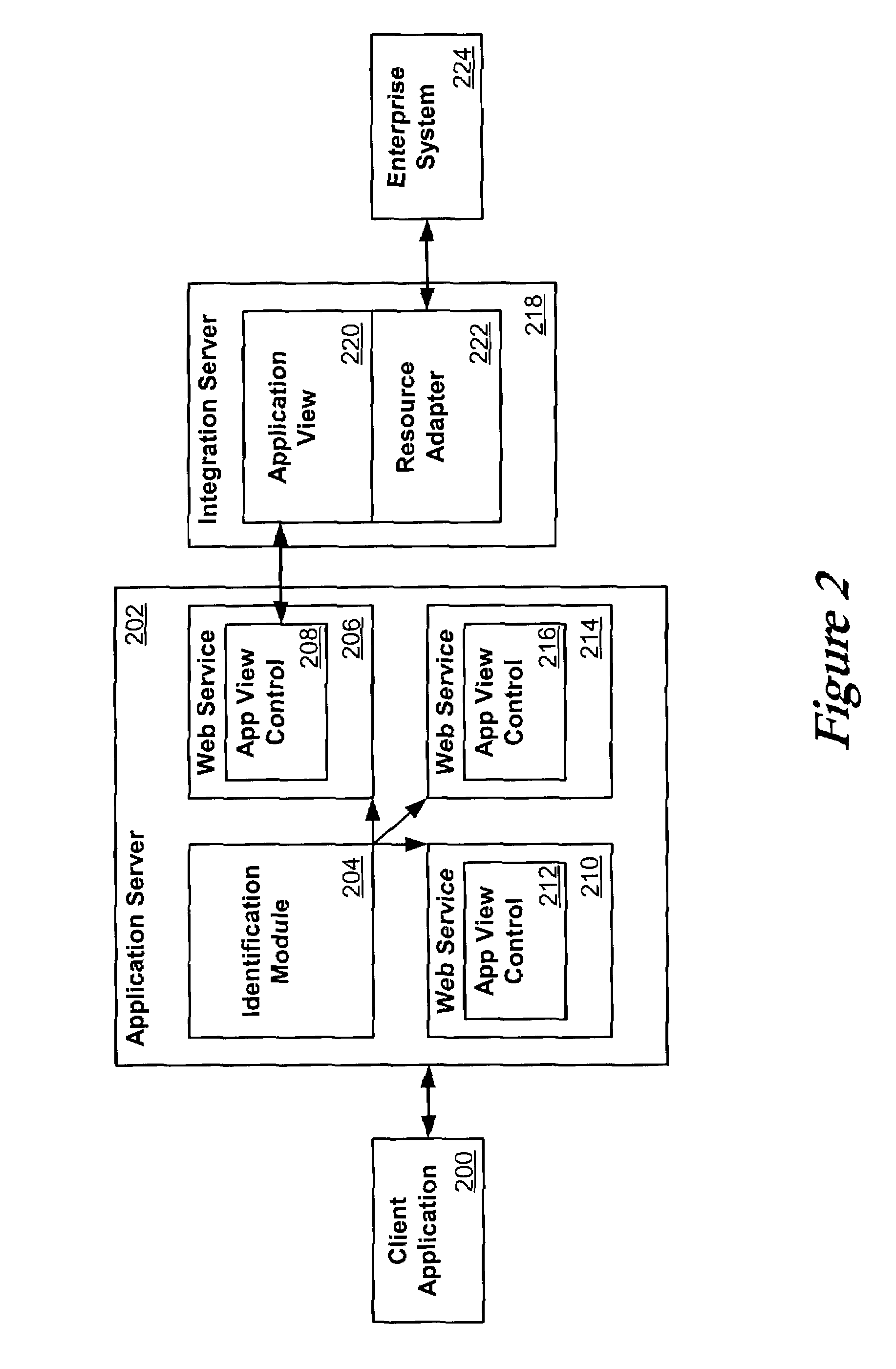
Application view component for system integration
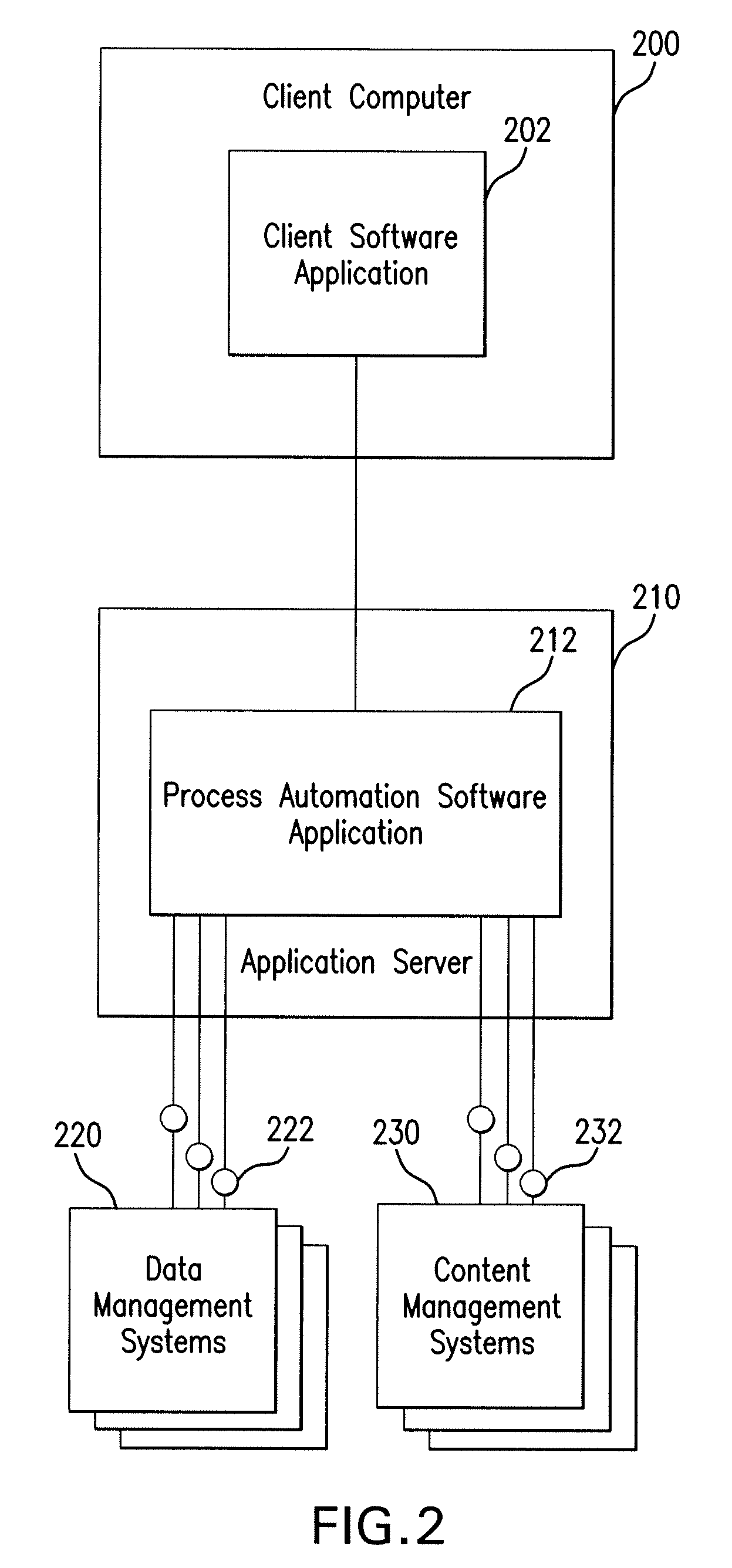
ActiveUS7080092B2Data processing applicationsDigital data processing detailsSystem integrationApplication software
An application view, or application view component, can represent a self-describing interface to functionality in a resource such as an application or enterprise system. An application view can abstract away much of the complexity in dealing with the application, such that non-programmers can maintain the services and events exposed by an adapter for that application. Application views can also simplify the way in which adapters are accessed, and can allow the functionality exposed by the adapter to be invoked as a business service. An application view can be specific to a single adapter, and can define a set of functions on the corresponding application.This description is not intended to be a complete description of, or limit the scope of, the invention. Other features, aspects, and objects of the invention can be obtained from a review of the specification, the figures, and the claims.
Owner:ORACLE INT CORP
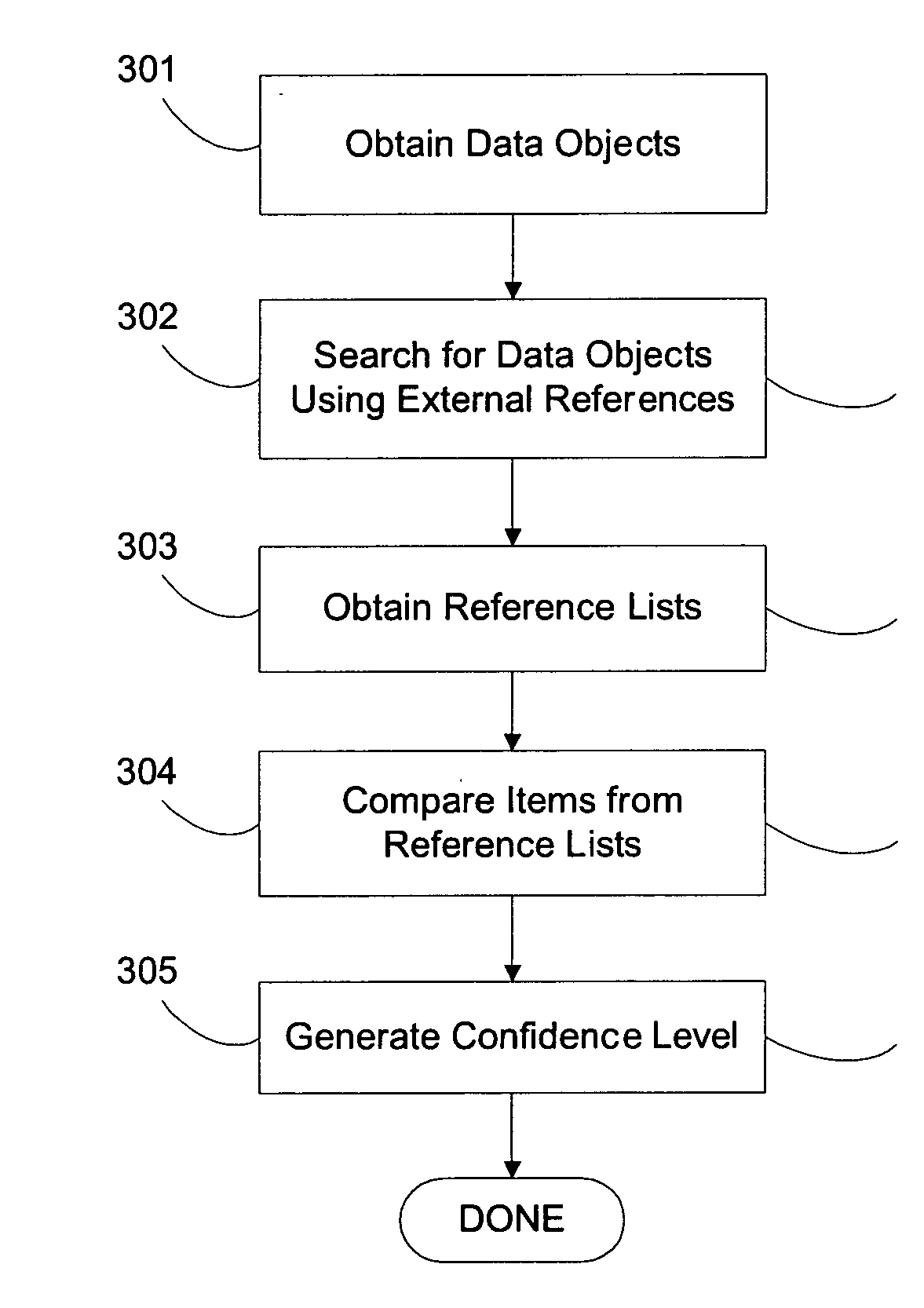
System and method for using external references to validate a data object's classification / consolidation
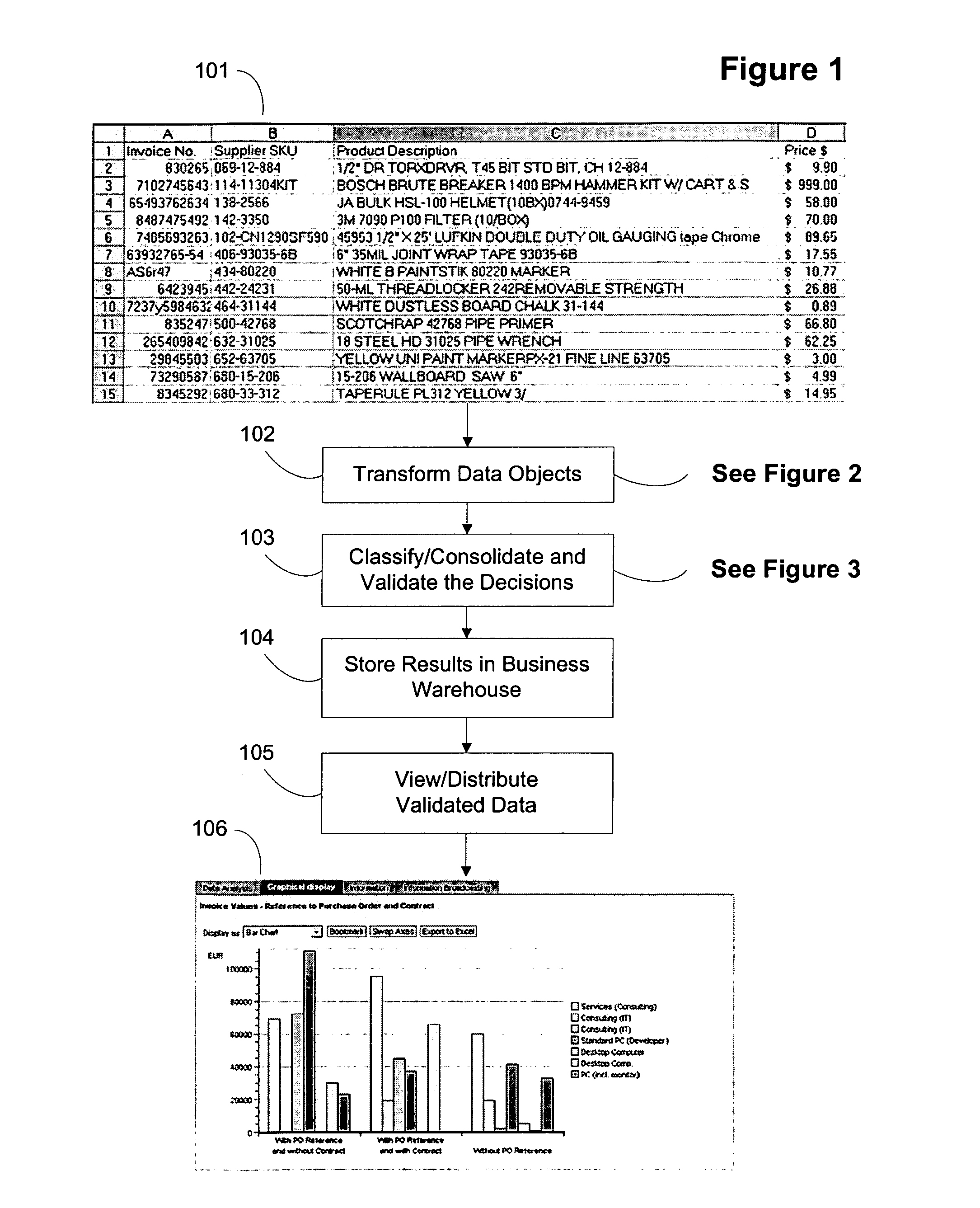
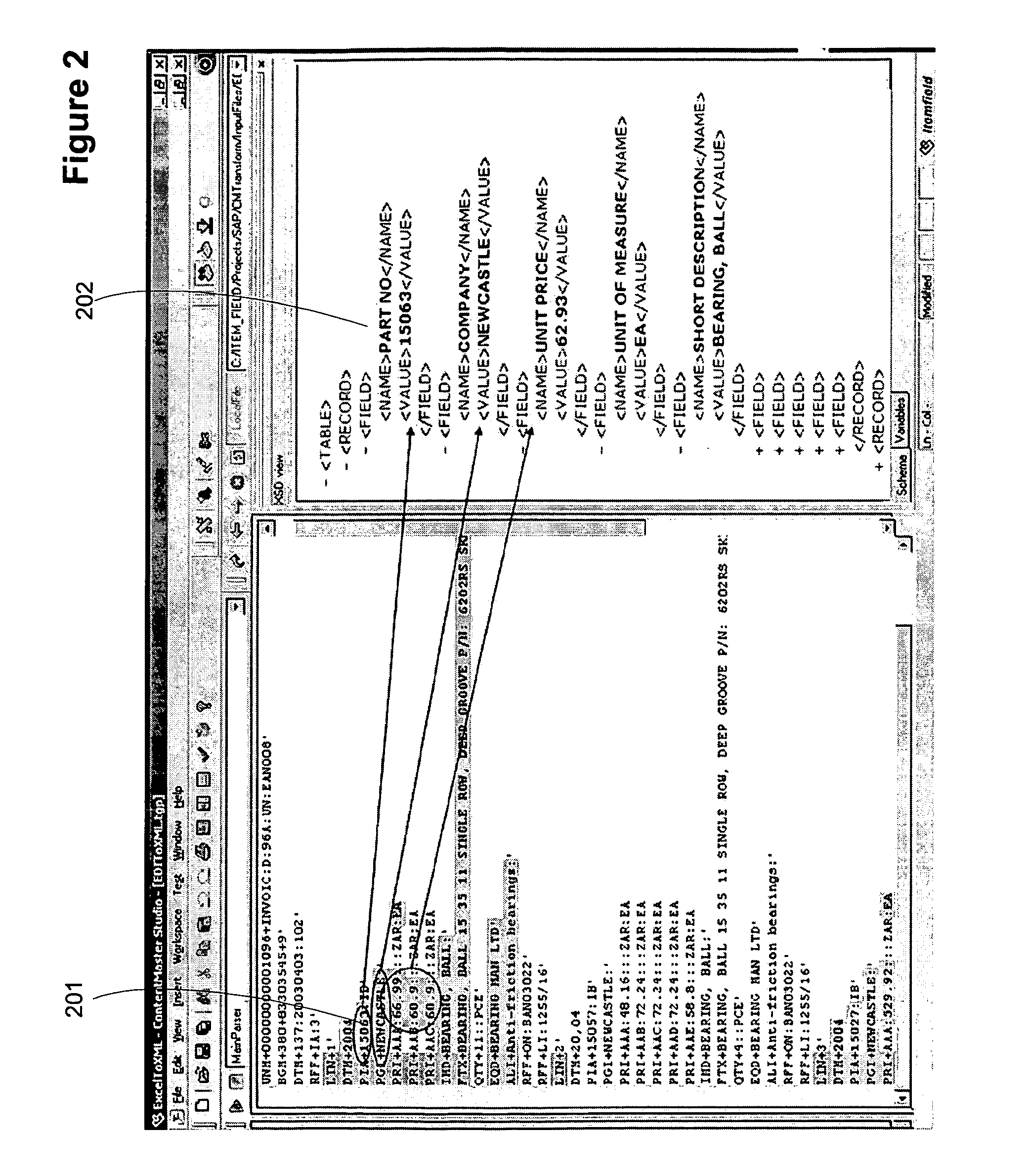
ActiveUS20070162414A1Improve trustTake substantial amountDigital data information retrievalDigital data processing detailsOriginal dataExternal reference
A computer system and method for validating data object classification and consolidation using external references. The external references may be web pages, product catalogs, external databases, URLs, search results provided by a search engine or subsets or combinations of any of these to validate a classification or consolidation of records. Embodiments validate a data object classification or consolidation decision by searching external data sources, such as databases, the Internet etc. for references to the transactional data object and determining a confidence level based on the original data object and the unstructured information reference, URL, or search result for example. Decisions may be verified or denied based on the comparison of the external references related to each data object. Embodiments of the invention save substantial labor in validating business data objects and make data more reliable across enterprise systems.
Owner:SAP AG
Controlling mobile device access to enterprise resources
ActiveUS20140007183A1Decompilation/disassemblyDigital data protectionApplication serverEnterprise resource planning
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Cloud computing gateway, cloud computing hypervisor, and methods for implementing same
ActiveUS8514868B2Improve manageabilityQuality improvementData switching by path configurationMultiple digital computer combinationsQuality of serviceManagement tool
Embodiments of the present invention provide a cloud gateway system, a cloud hypervisor system, and methods for implementing same. The cloud gateway system extends the security, manageability, and quality of service membrane of a corporate enterprise network into cloud infrastructure provider networks, enabling cloud infrastructure to be interfaced as if it were on the enterprise network. The cloud hypervisor system provides an interface to cloud infrastructure provider management systems and infrastructure instances that enables existing enterprise systems management tools to manage cloud infrastructure substantially the same as they manage local virtual machines via common server hypervisor APIs.
Owner:CSC AGILITY PLATFORM INC
Gateway for controlling mobile device access to enterprise resources
ActiveUS20140007214A1Decompilation/disassemblyDigital data processing detailsApplication serverResource based
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
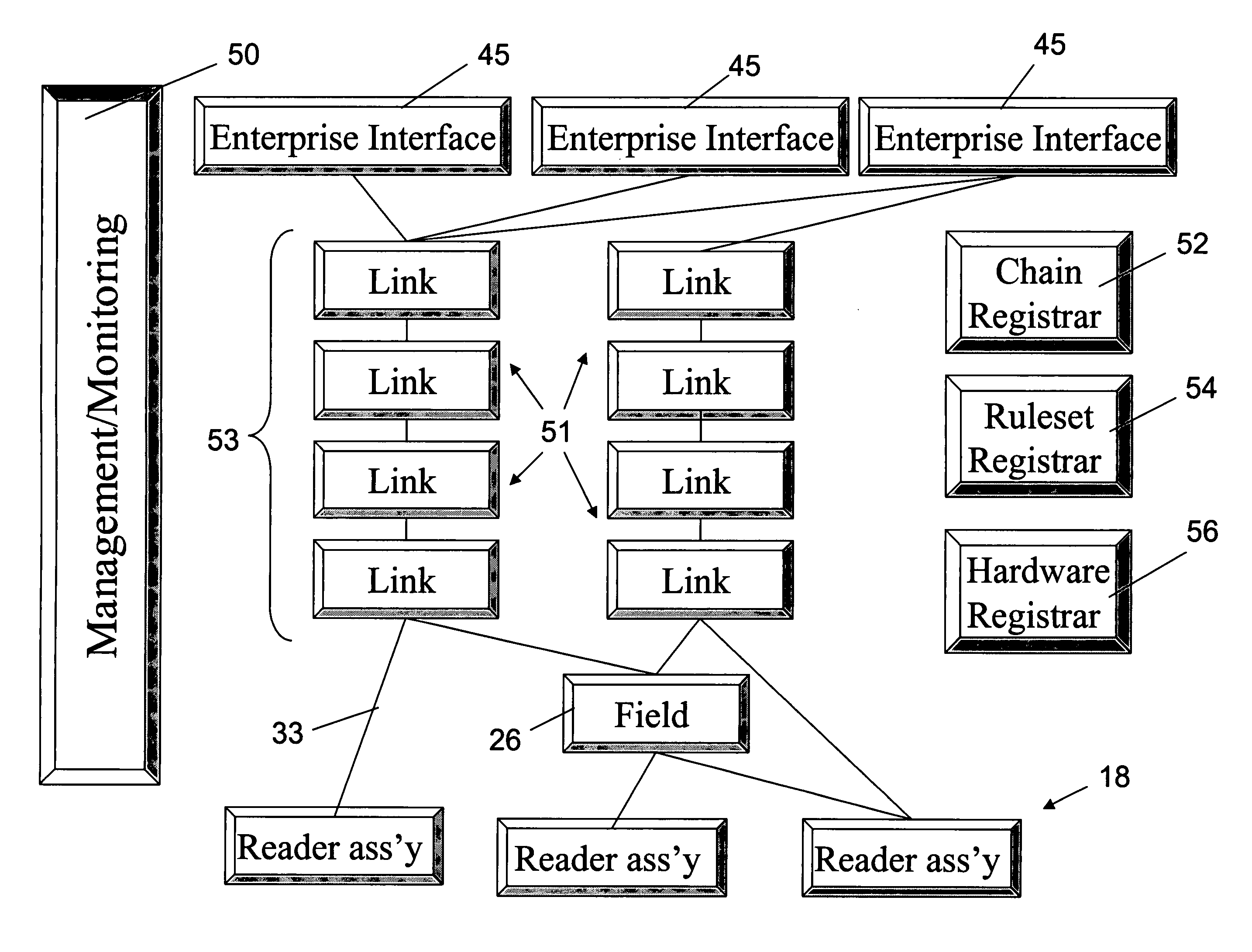
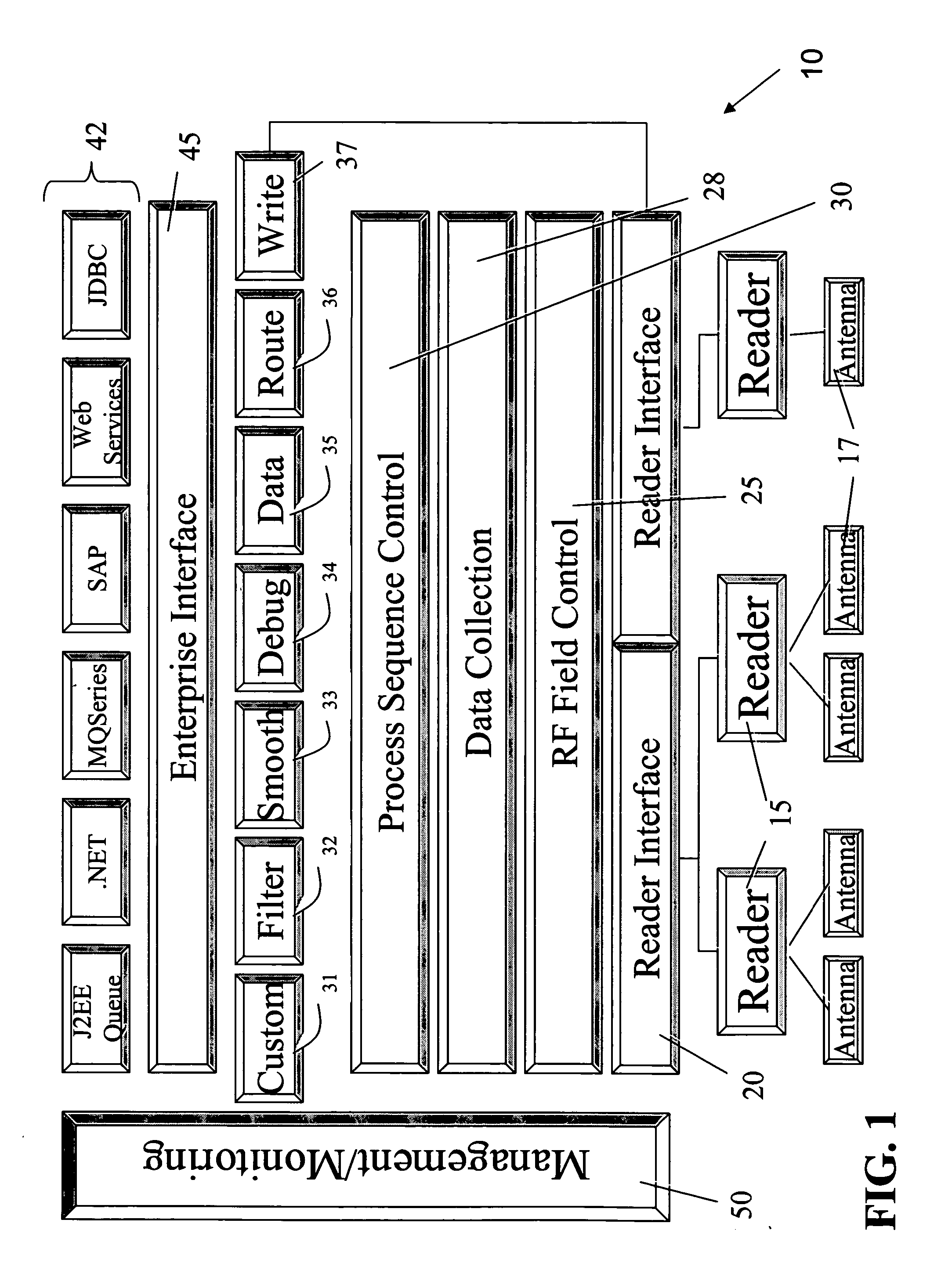
System and method for RFID system integration
ActiveUS20050092825A1Low specificityNot adequateElectric signal transmission systemsDigital data processing detailsSystem integrationEnterprise system
A robust system, method and environment for the programming, collection, manipulation, and propagation of RFID data enhances the integration of RFID elements into new and existing enterprise systems.
Owner:CAPTECH VENTURES
Secure mobile browser for protecting enterprise data
ActiveUS8869235B2Decompilation/disassemblyDigital data information retrievalDocumentation procedureApplication server
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
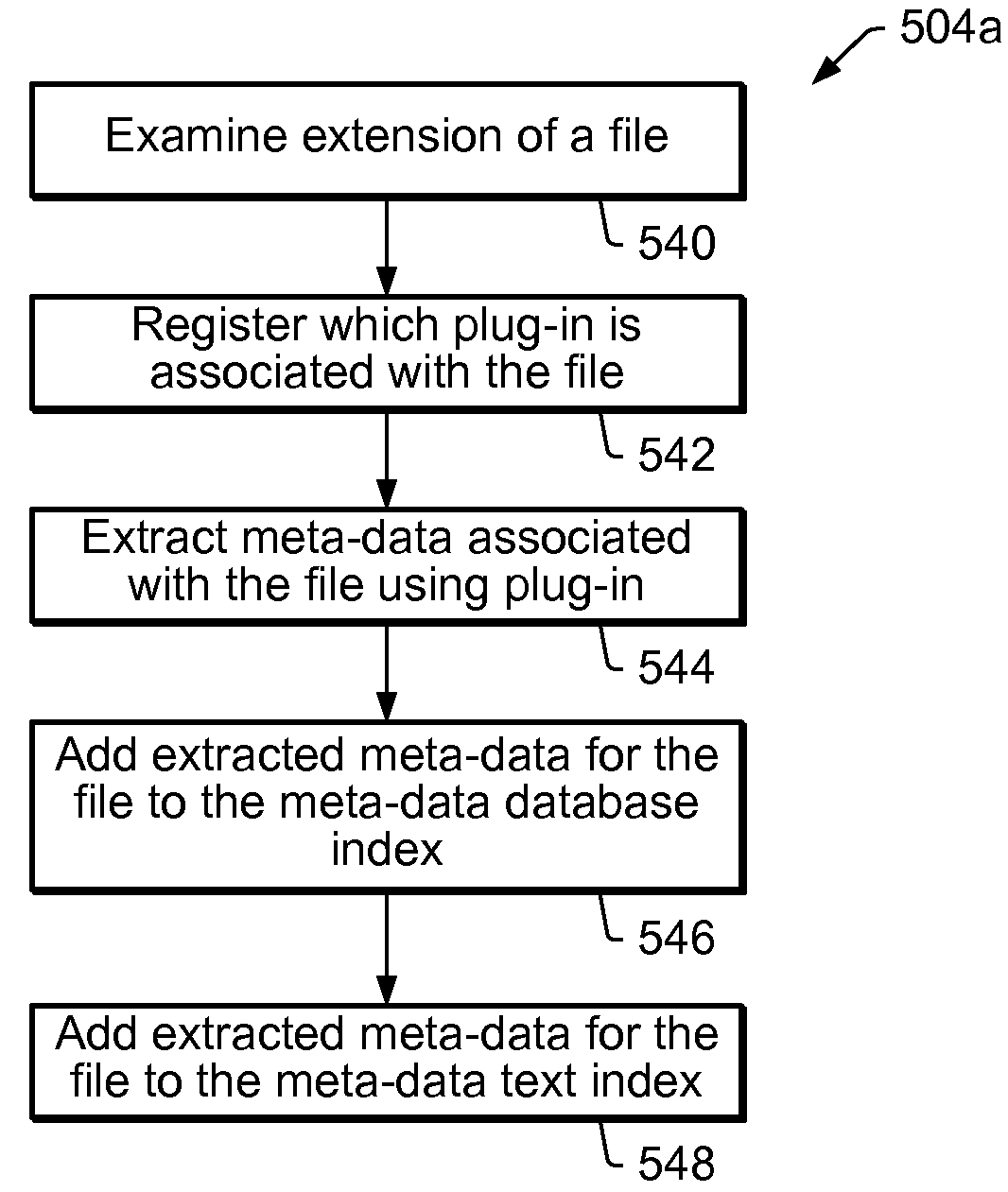
Intelligent storing and retrieving in an enterprise data system
ActiveUS8099400B2Digital data processing detailsSpecial data processing applicationsData fileData system
A method and system is presented which provides a TDM framework for managing self-describing measurement data. The TDM framework provides applications with a central platform for accessing measurement data across an entire enterprise system. By means of individual plug-ins, which may be specific to a given data file format, meta-data for each data store in the enterprise may be indexed in a unified manner. The unified indexing, in turn, provides the ability to browse and query the indexed measurement data without requiring the opening or reading from a source data file.
Owner:NATIONAL INSTRUMENTS
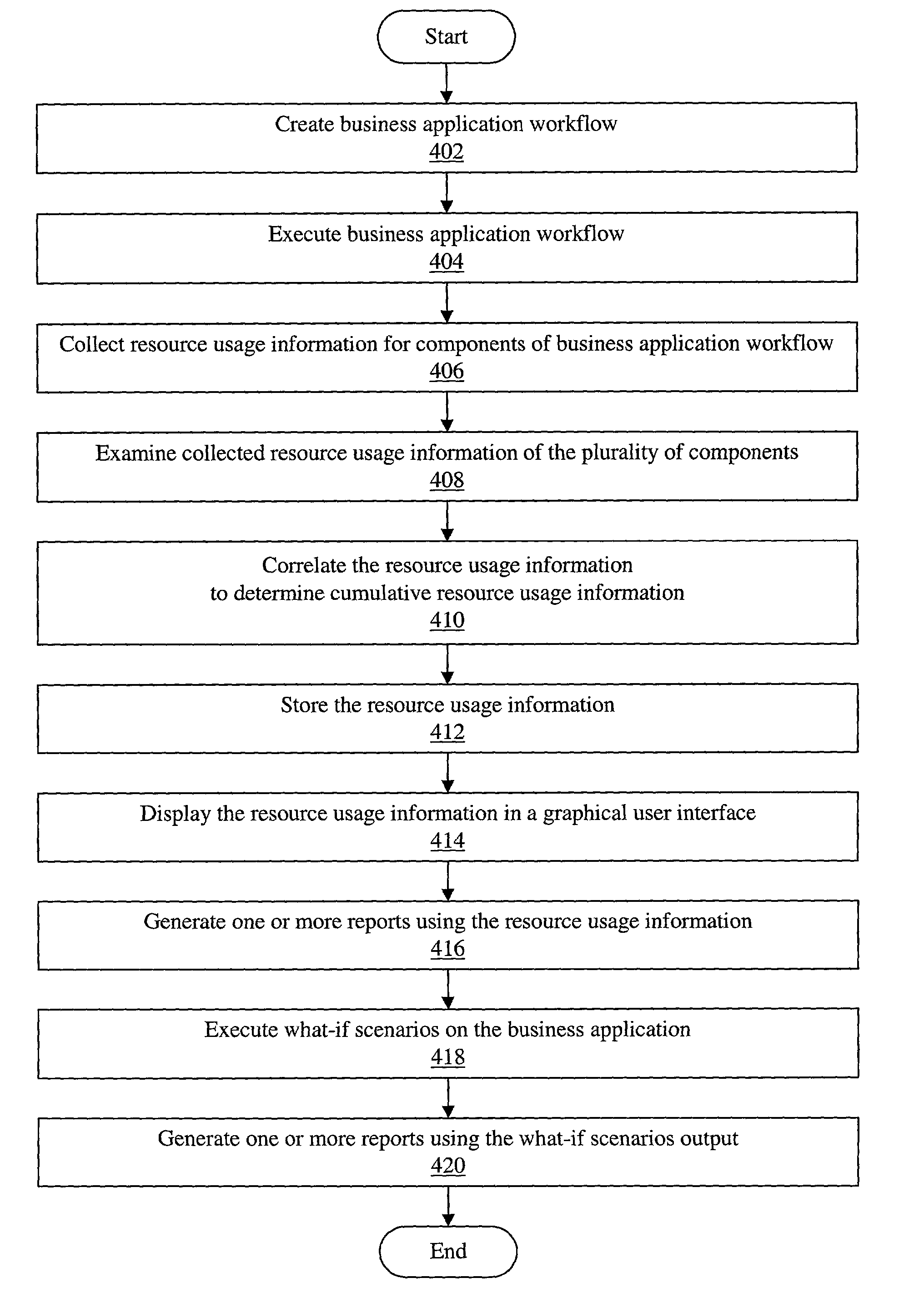
System and method for application performance management
ActiveUS20030009507A1General purpose stored program computerHardware monitoringComputer resourcesApplication software
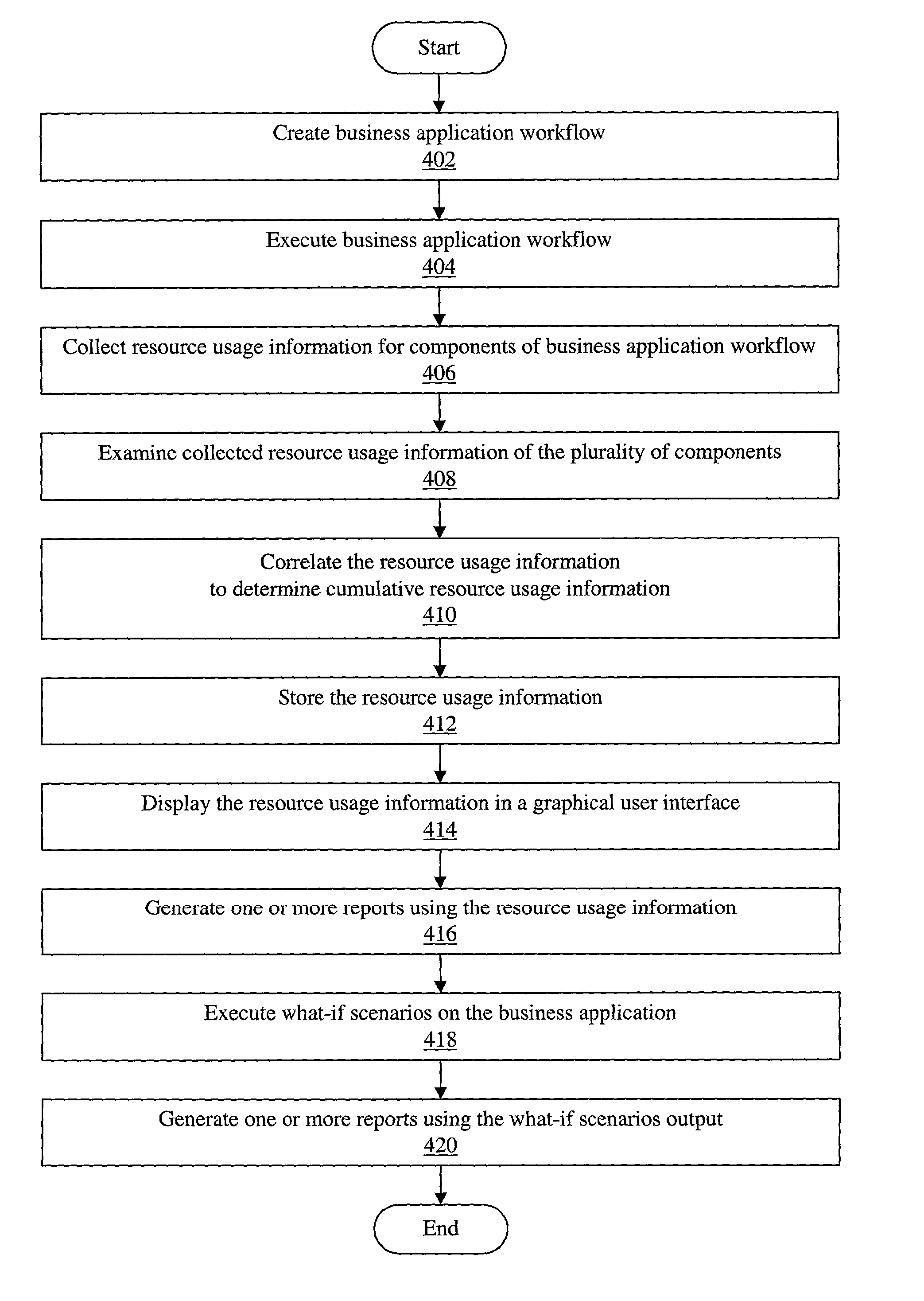
An improved method and system for complex and integrated application performance management which tracks end-to-end computer resource consumption of a first business application workflow in an enterprise system. The first business application workflow may include a plurality of components. The plurality of components may further include one or more component types. A second or subsequent business application workflow may be embedded or linked as a component of the first business application workflow. Resource usage information of the plurality of components (including resource usage information of underlying units of work of the plurality of components) may be correlated to determine cumulative resource usage information for the first business application workflow. The resource usage information may be displayed in a graphical user interface. User input may be received indicating one or more of the following for the first business application workflow: an application name, a natural business unit, and a mission-critical ranking.
Owner:BMC SOFTWARE
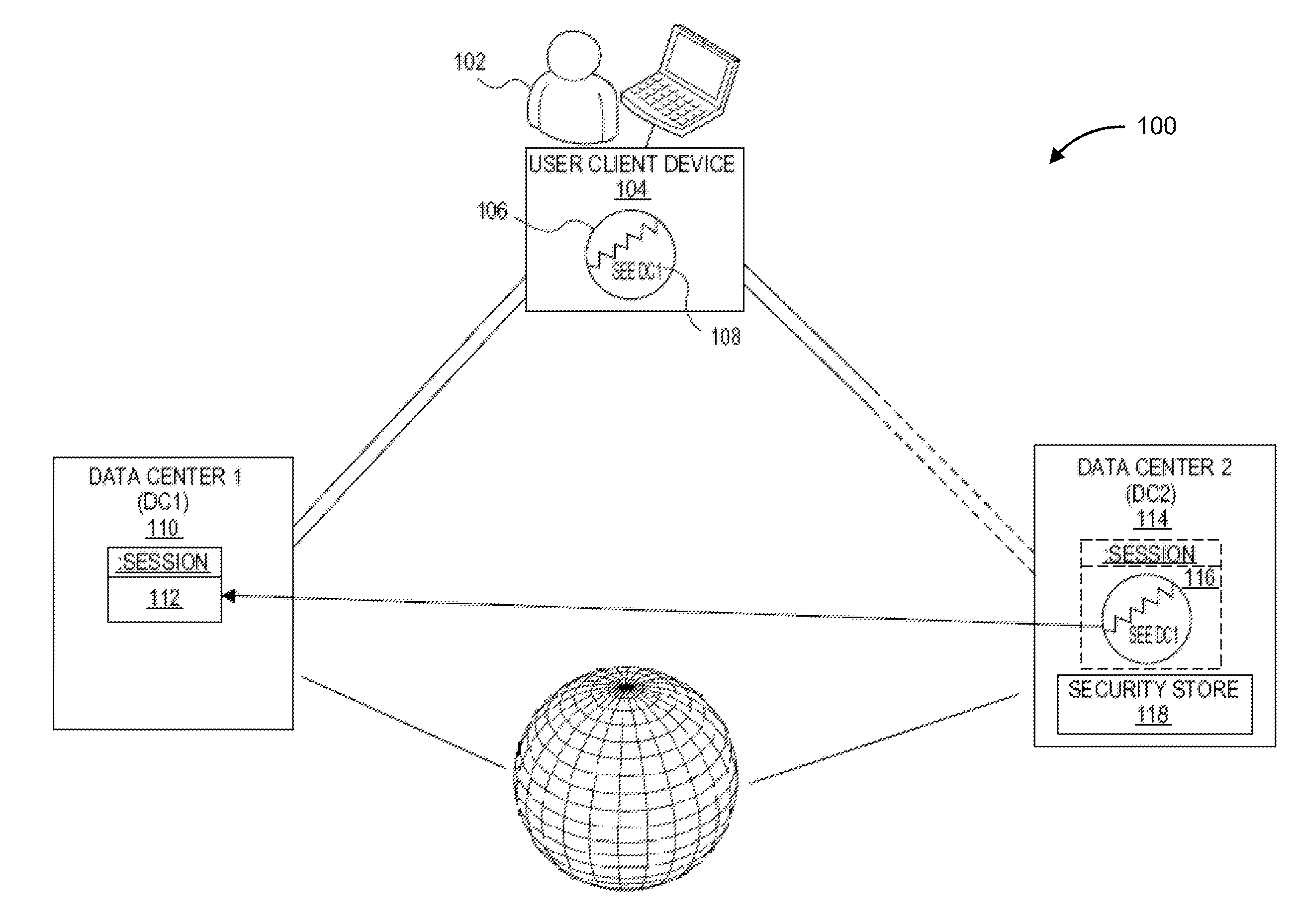
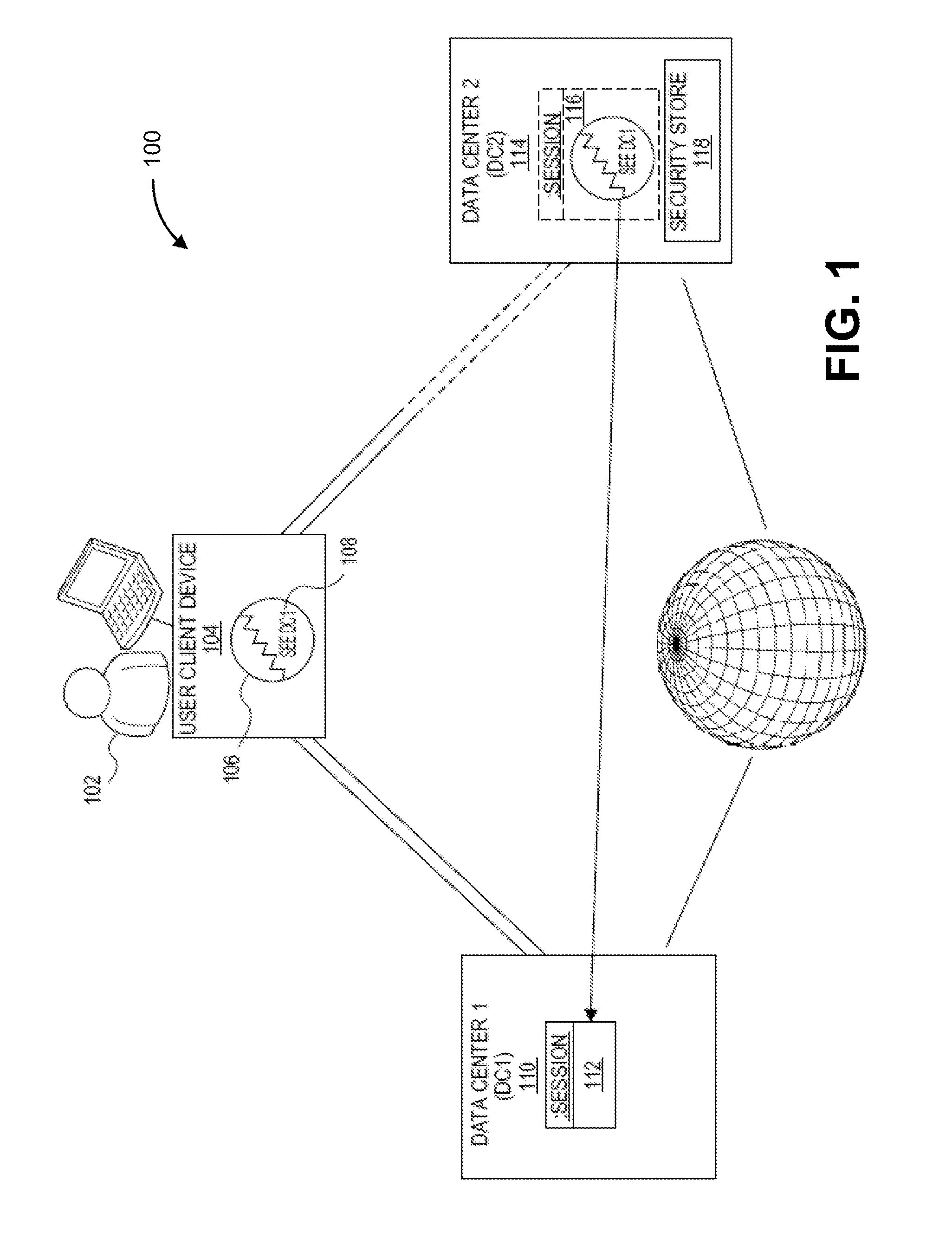
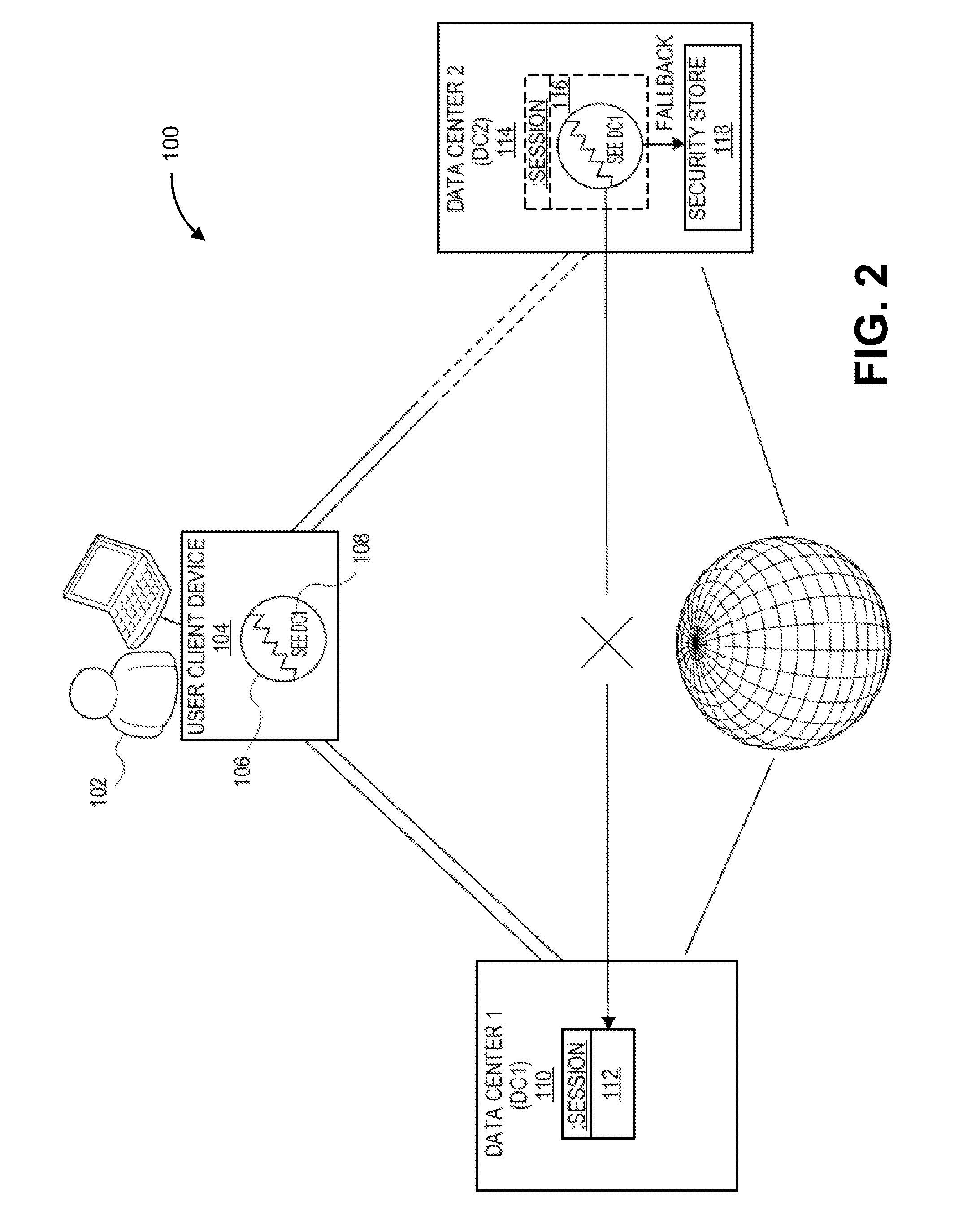
Single sign-on between multiple data centers
ActiveUS20150089614A1Digital data processing detailsMultiple digital computer combinationsData centerClient-side
Systems and methods are disclosed for a single sign-on (SSO) enterprise system with multiple data centers that use a lightweight cookie on a user's client device. The lightweight cookie includes a reference to a data center in which the user is already authenticated, and a new data center contacts the old data center for creating a session for the user on the new data center. If the old data center is unavailable, then the new data center may fall back to accessing a local security store, a backup of keys, security tokens, and / or other security data, in order to create a local session for the user on the new data center.
Owner:ORACLE INT CORP
Secure mobile browser for protecting enterprise data
ActiveUS20140007182A1Decompilation/disassemblyDigital data protectionDocumentation procedureApplication server
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
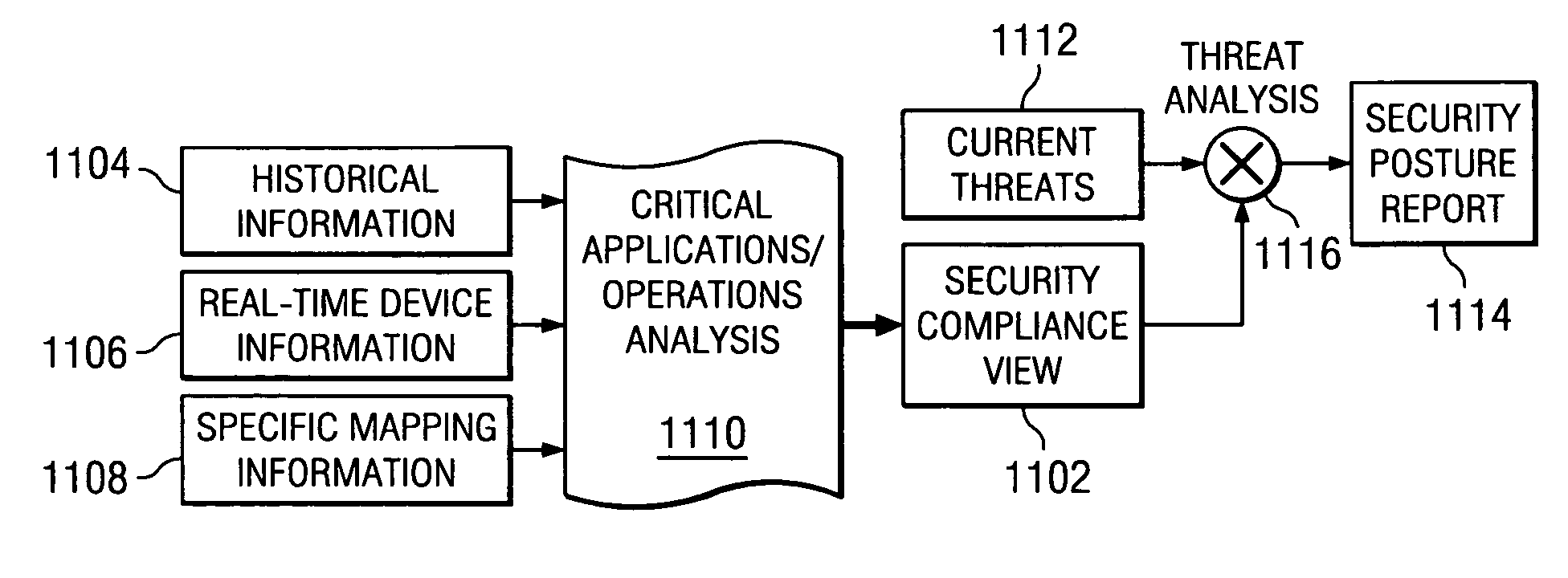
Method of assuring enterprise security standards compliance
ActiveUS20060156408A1Random number generatorsUser identity/authority verificationRisk impactSecurity compliance
A method, apparatus, and computer instructions for providing a current and complete security compliance view of an enterprise system. The present invention provides the ability to gain a real-time security posture and security compliance view of an enterprise and to assess the risk impact of known threats and attacks to continued business operations at various levels is provided. Responsive to a change to an enterprise environment, a request, or an external threat, an administrator loads or updates at least one of a Critical Application Operations database, a Historical database, an Access Control database, a Connectivity database, and a Threat database. Based on a comparison of information in the databases against similar security data elements from company or external policies, the administrator may generate a Security Compliance view of the enterprise. A Security Posture view may also be generated by comparing the Security Compliance view against data in the Threat database.
Owner:TWITTER INC
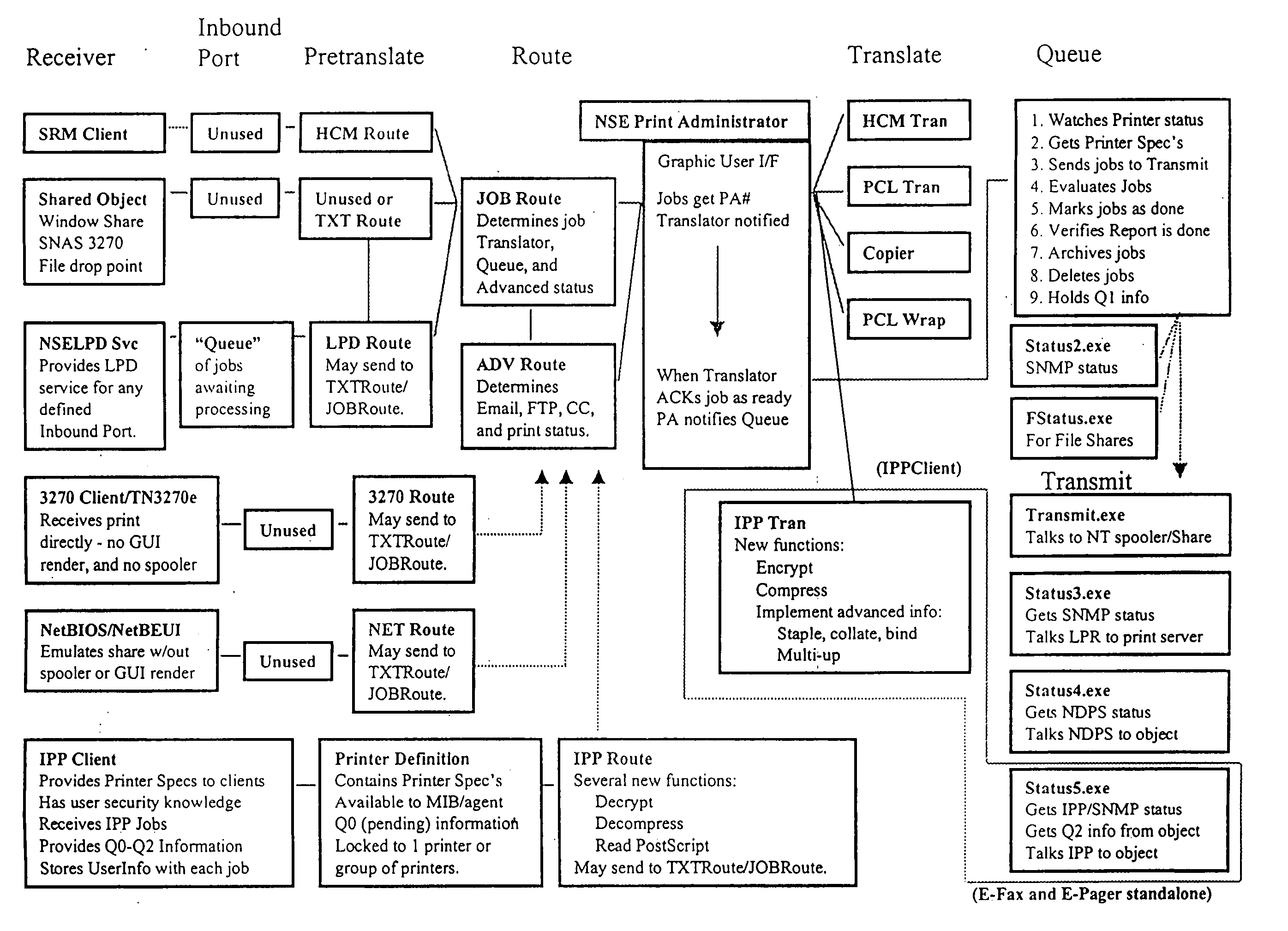
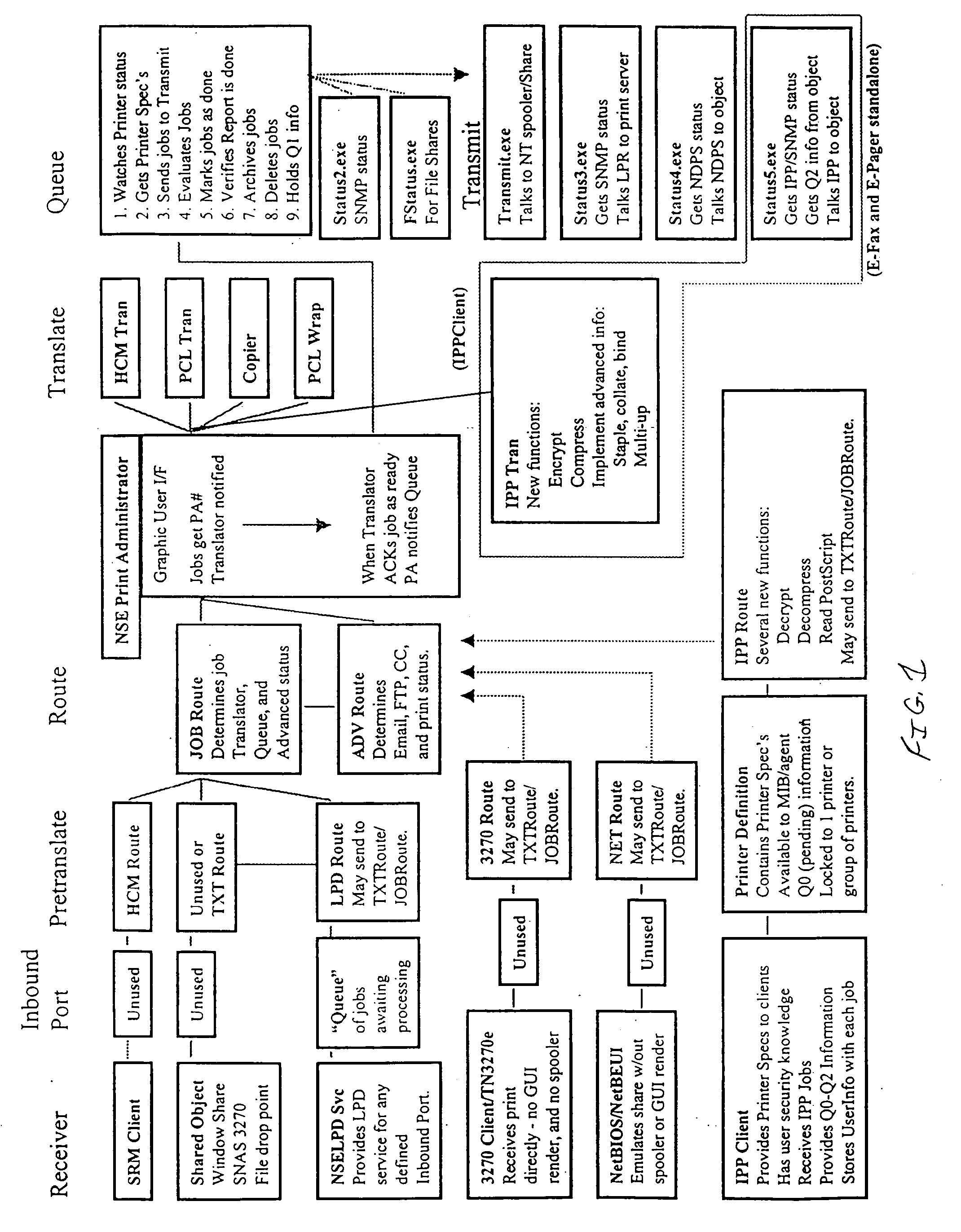
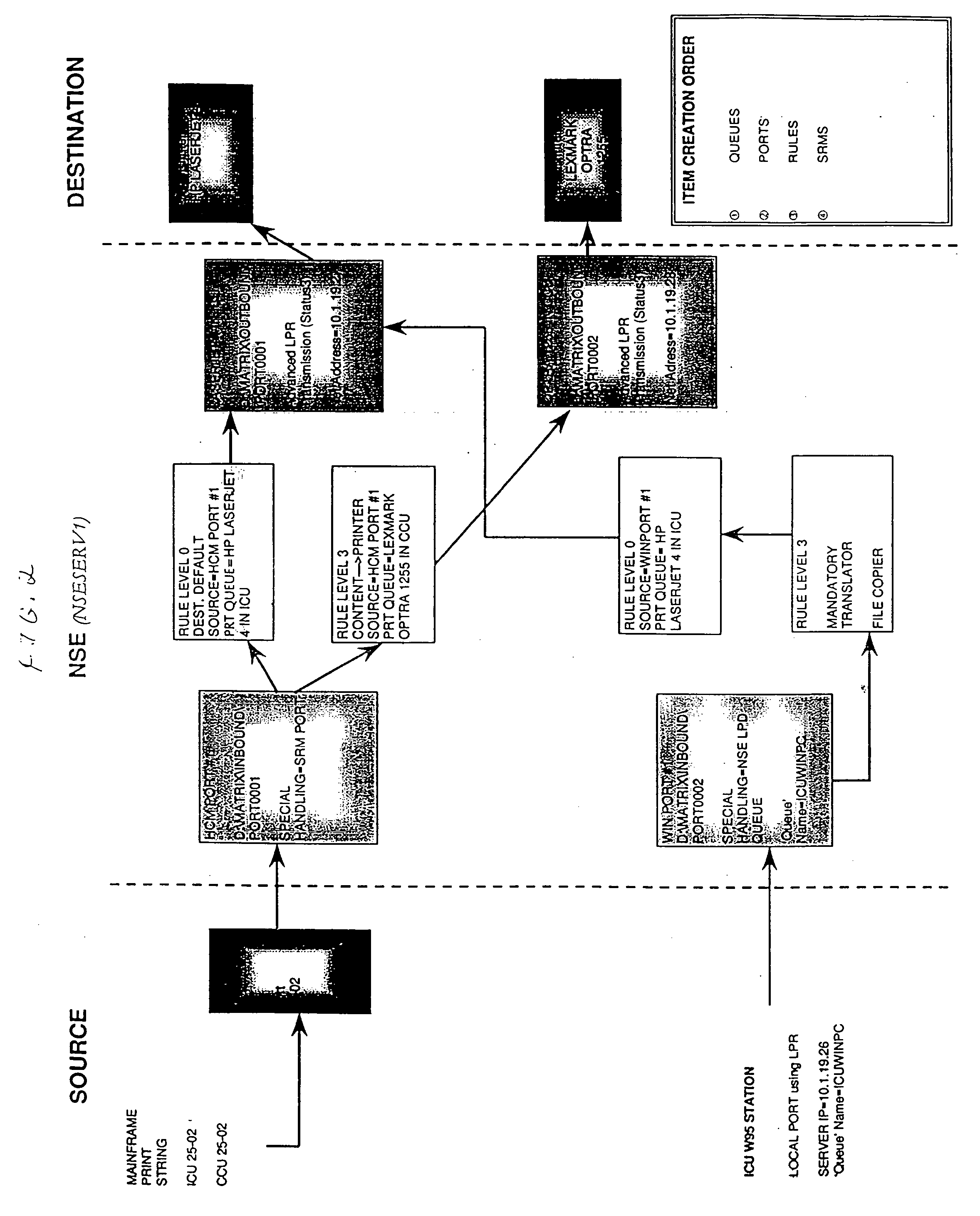
Printer control and document management system
InactiveUS20040105122A1Digital data processing detailsVisual presentation using printersComputer printingElectronic form
A printer control and information management system is provided employing numerous individual satellite modules, and providing an enterprise-wide output system capable of receiving all types of input and redirecting of all types of output. Data can be inputted from any location in an enterprise system and coordinated into a coherent format for reporting and forms processing. Forms can be automatically generated based on the data inputted, which forms can be directed to the appropriate personnel. The system provides for notifications to the appropriate personnel in order to resolve problems which may arise from the operation of the various equipment utilized in the enterprise network system. Information can be redirected to anyone within the system, the user identifying the manner and format of the information to be presented. Thus, inbound reports can be received from different systems and outputs delivered in the format that is preferred by the user. Report recognition is provided for any application, with the ability to merge textual information with electronic forms. Additionally, the forms can be completed with bar code information to prevent inadvertent disclosure of sensitive information. Large and contiguous host generated reports can be electronically distributed to users, as well as the ability to automatically fax any type of report directly to any recipient. The system can be accessed via the Internet for ease of inputting and reviewing information at any location.
Owner:ST CLAIR MANAGEMENT RESOURCES
Method and system for managing enterprise content
InactiveUS20090249446A1Consistent flowDigital data processing detailsComputer security arrangementsUser inputData content
A method and system for providing a consistent flow documents and data content across different organizational units of a company or agency where the documents and data come from different enterprise systems and data stores but are related to linked processes that share models for organizing the content in the business context and in a format that enables a user to relate the content to the process step or steps they are performing. The system includes a network service that enables a configuration utility to automatically discover the objects and metadata and provides for a mapping of selected fields of the metadata to regions displayed in the user interface view with provision for filtering the data by mapping selected fields to a user input form. Thereby, a business analyst can create solutions without writing and maintaining complex program logic for each combination of presentation environment, enterprise system and data store.
Owner:OPEN TEXT CORPORATION
Modifying pre-existing mobile applications to implement enterprise security policies
ActiveUS20140007048A1Decompilation/disassemblyDigital data protectionApplication serverCorporate security
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
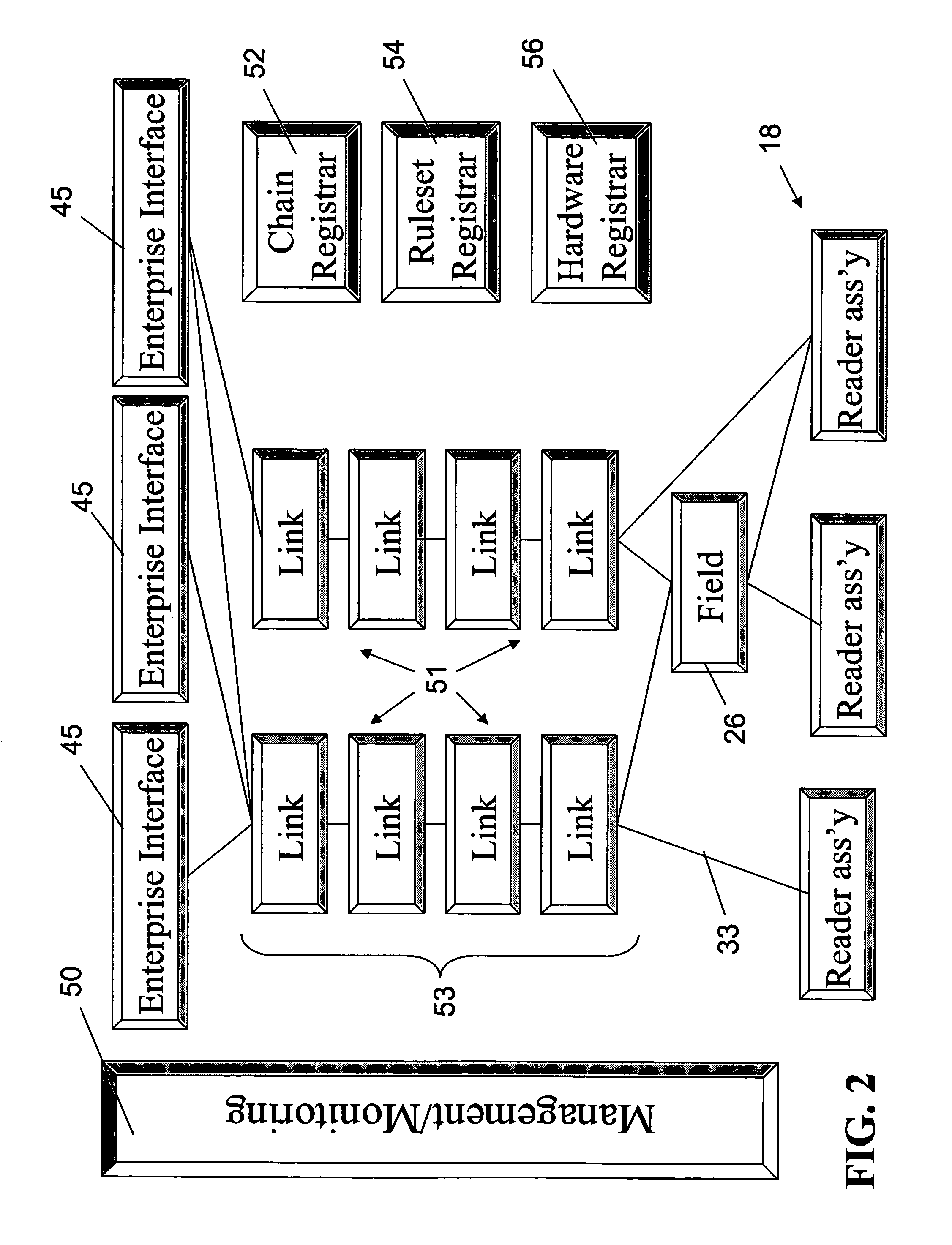
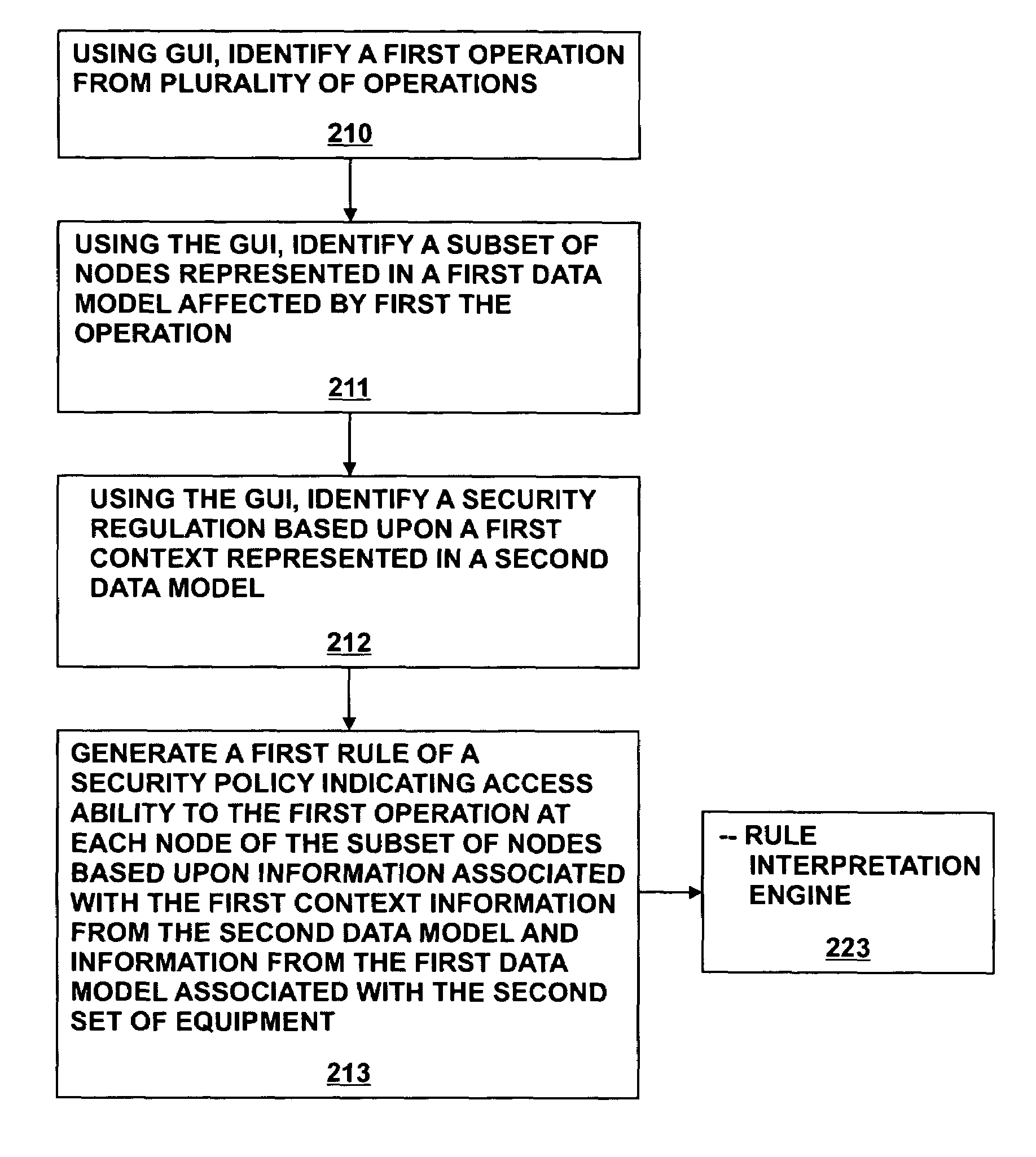
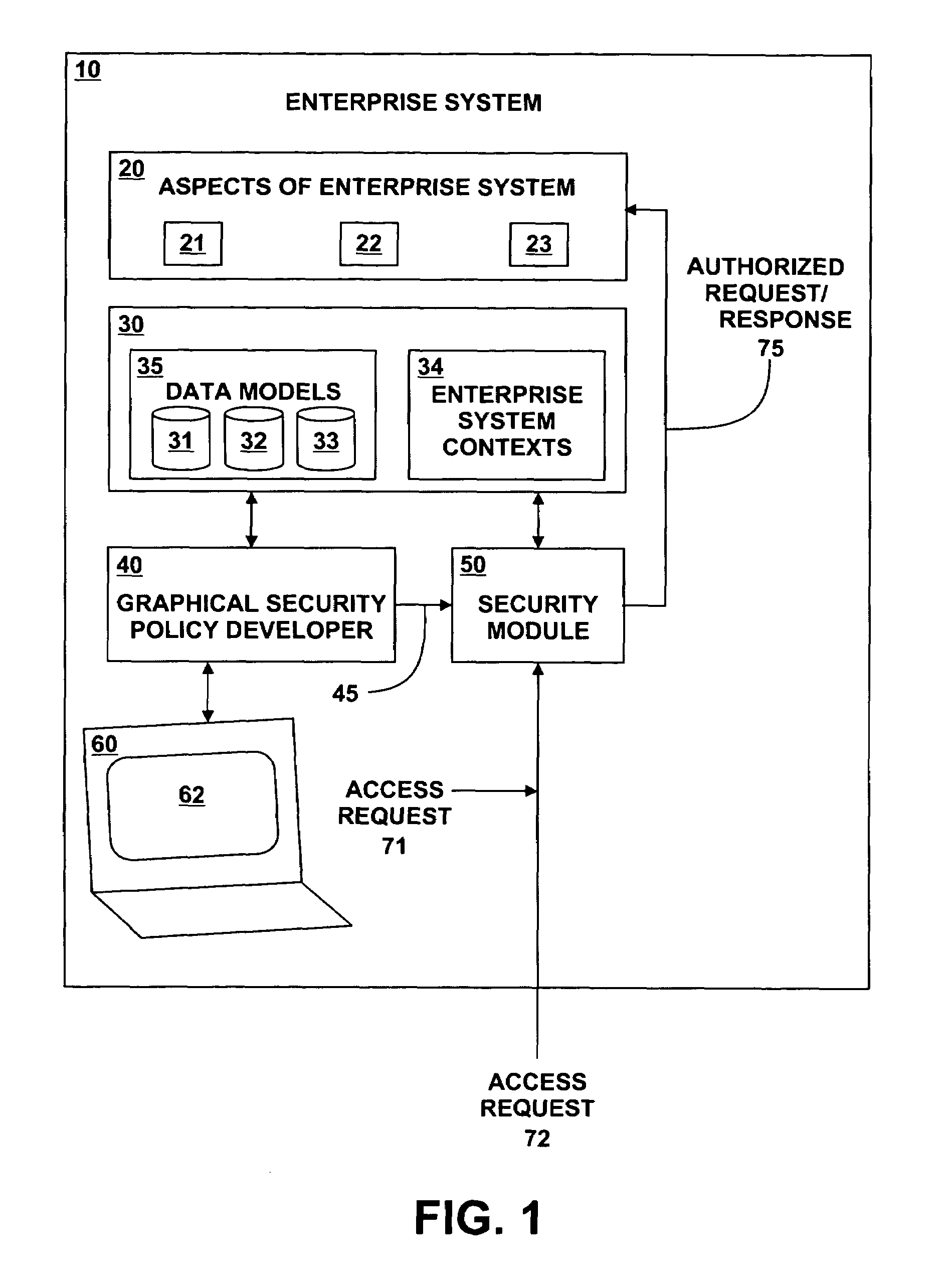
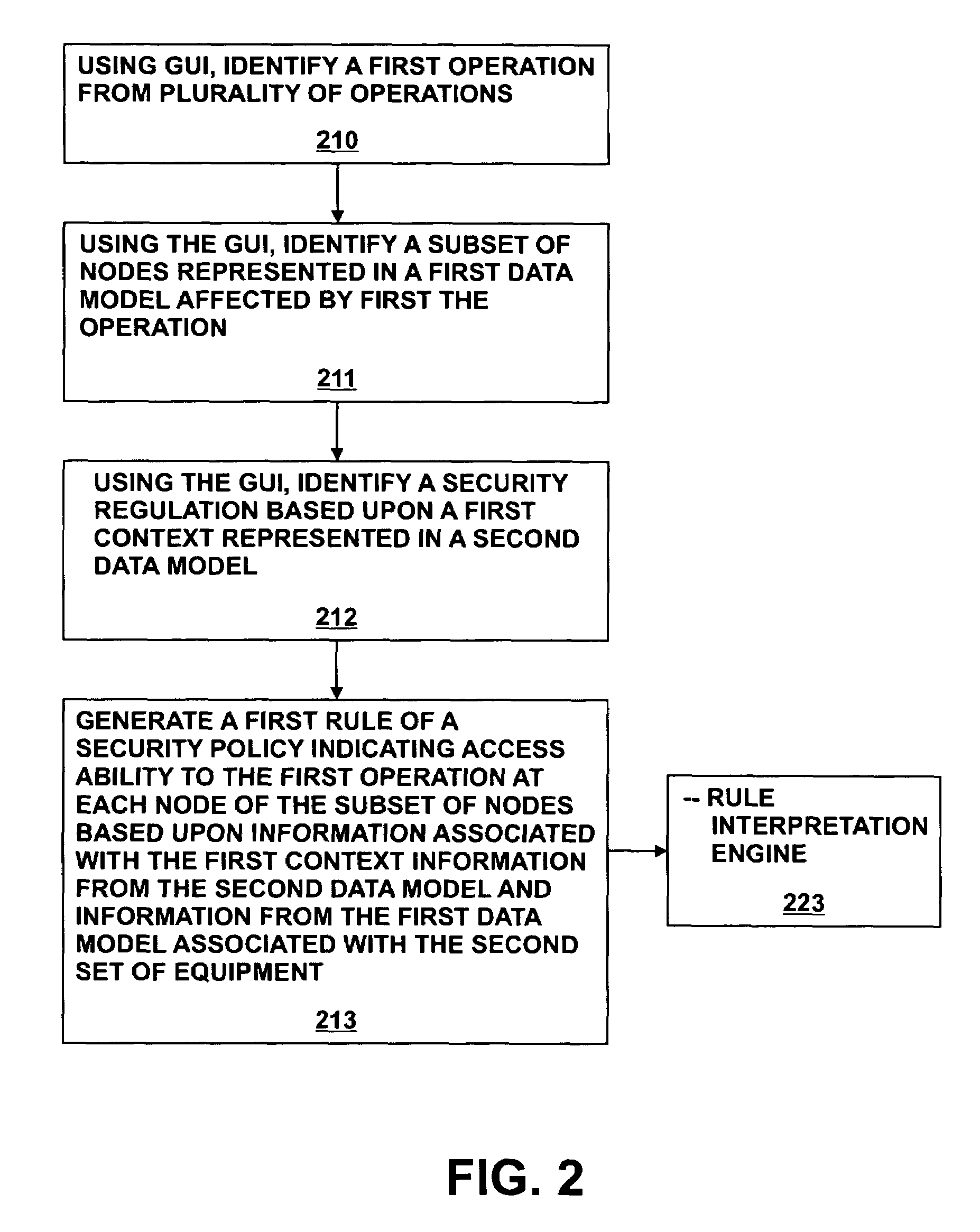
Method and system for generating access policies
A method and system for generating security rules for implementation by a rule interpretation engine to define accessibility to one or more aspects of an Enterprise System is described. The method and system allow a security officer to graphically indicate an operation to be affected by the security rule being defined; a specific aspect of the system affected by the rule; a security regulation to be implemented by the rule; and an access type to be permitted by the rule.
Owner:ADVANCED MICRO DEVICES INC +2
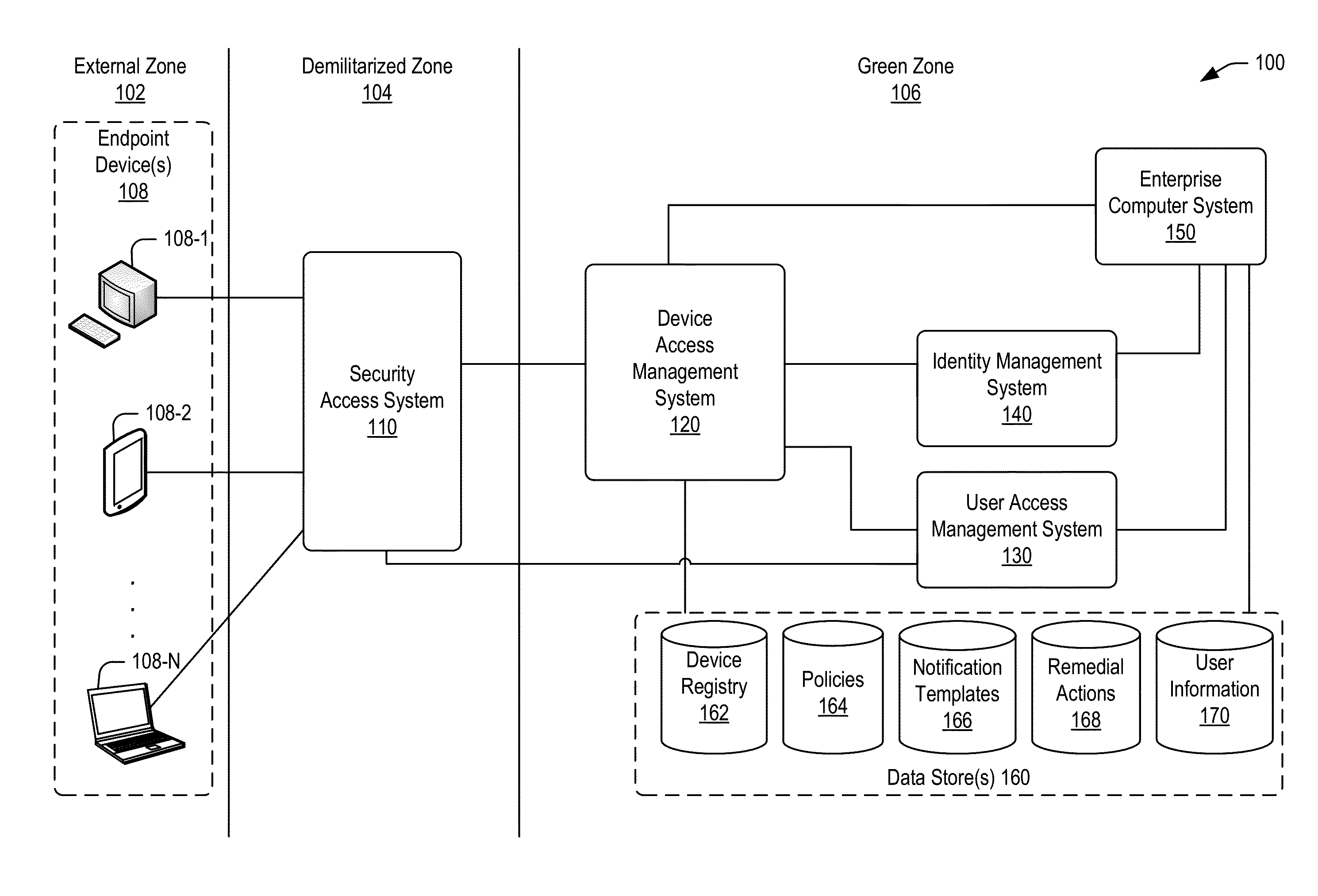
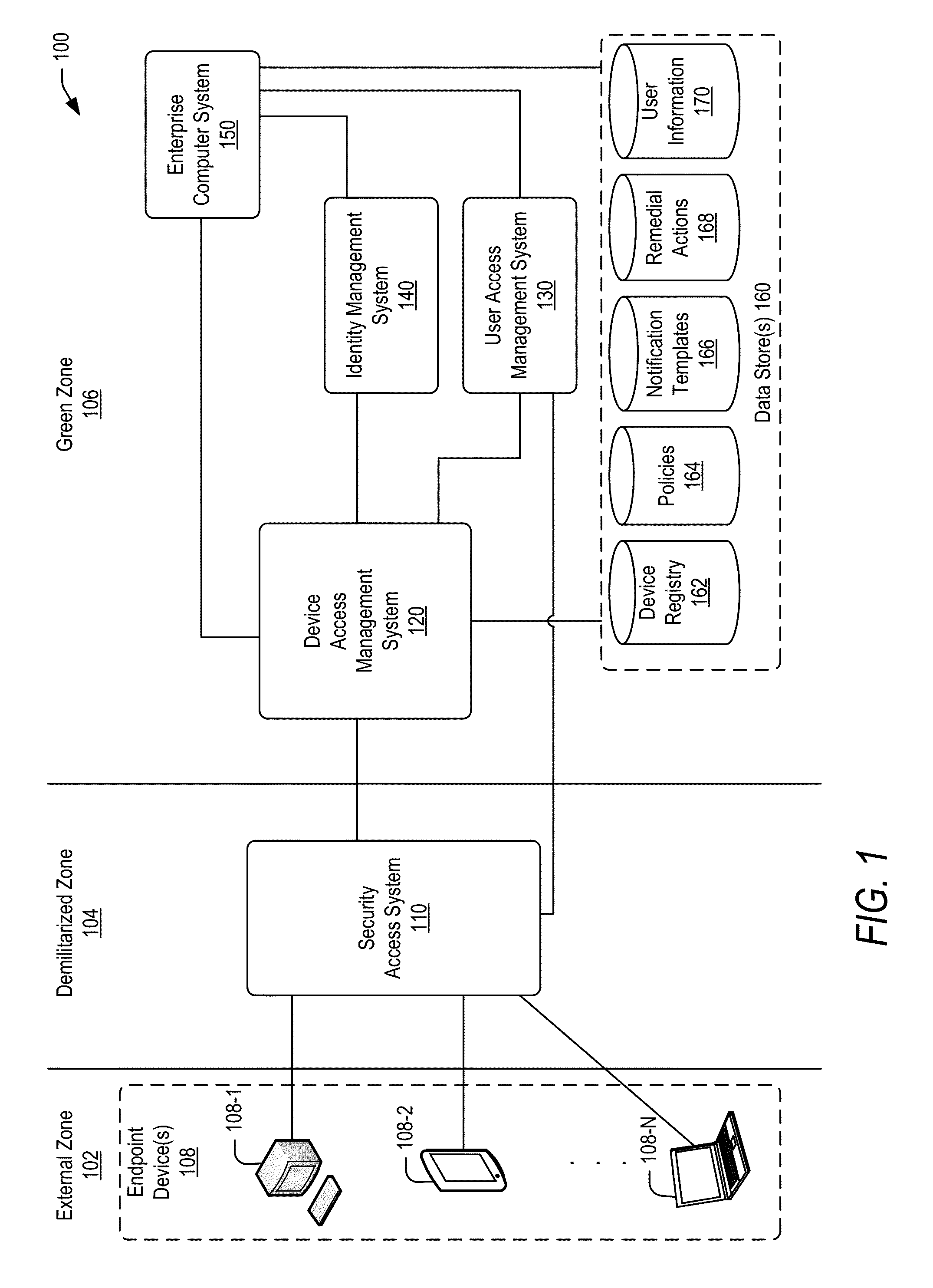
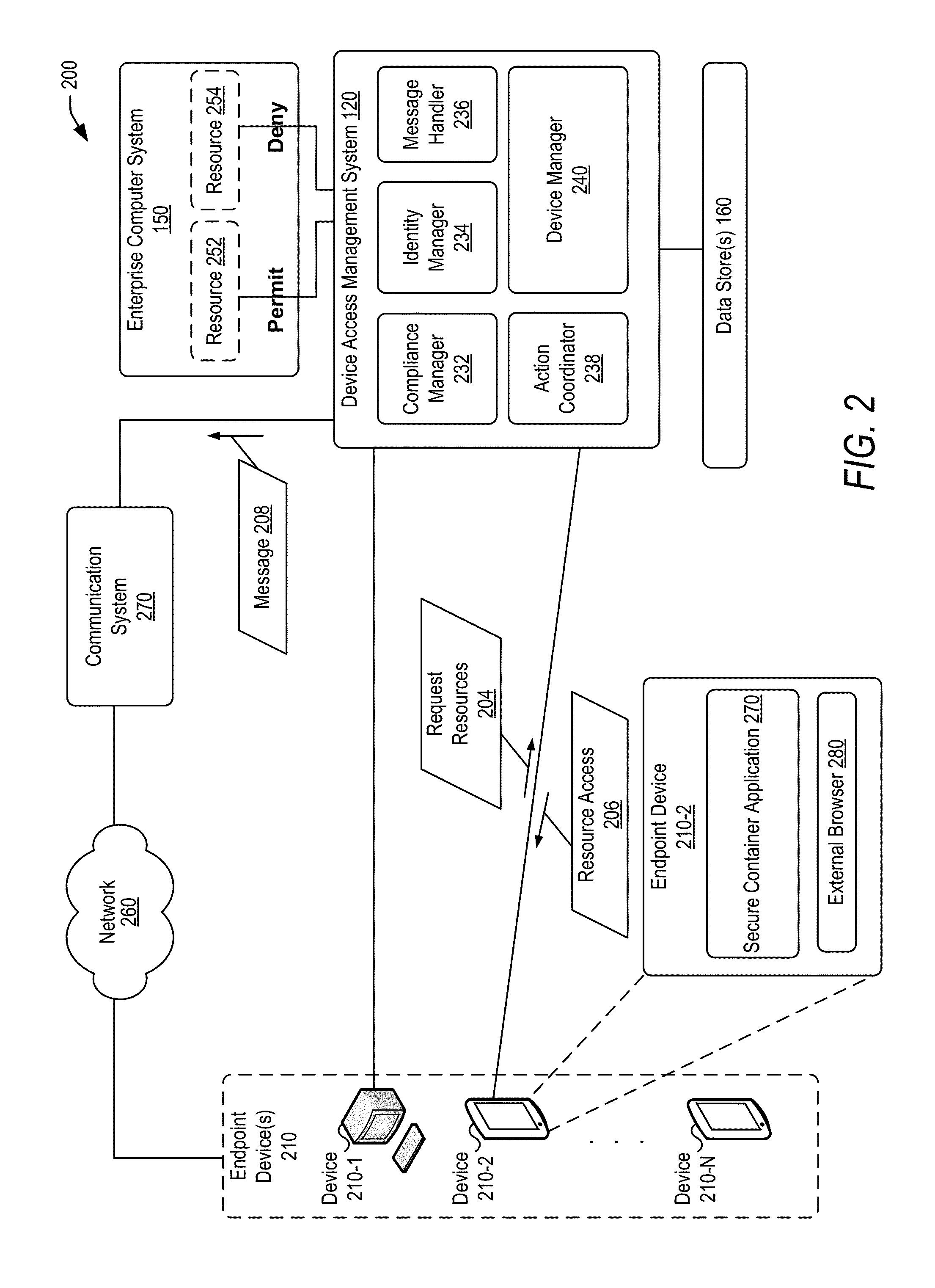
Policy-based compliance management and remediation of devices in an enterprise system
ActiveUS20160088021A1Reduce the burden onAvoid accessService provisioningVersion controlNon complianceEnterprise system
The present disclosure relates generally to managing compliance of remote devices that access an enterprise system. More particularly, techniques are disclosed for using a compliance policy to manage remediation of non-compliances of remote devices that access an enterprise system. A device access management system may be implemented to automate remediation of non-compliances of remote devices accessing an enterprise system. Remediation may be controlled based on different levels of non-compliance, each defined by one or more different non-compliances. In some embodiments, a level of non-compliance may be conditionally defined by one or more user roles for which non-compliance is assessed. Access to computing resources of an enterprise system may be controlled for a remote device based on compliance of the remote device. Access may be inhibited for those resources not permitted during a time period of a non-compliance.
Owner:ORACLE INT CORP
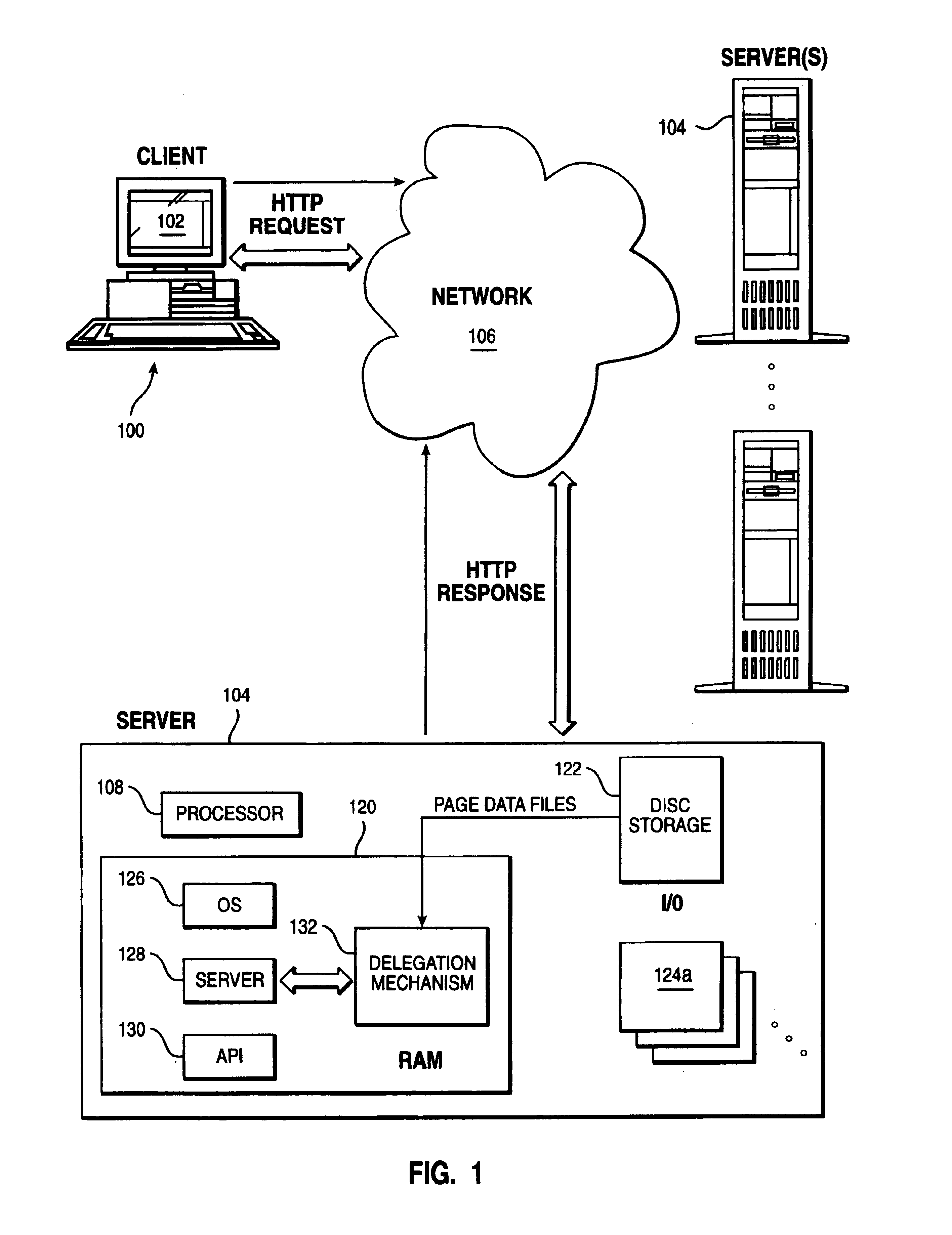
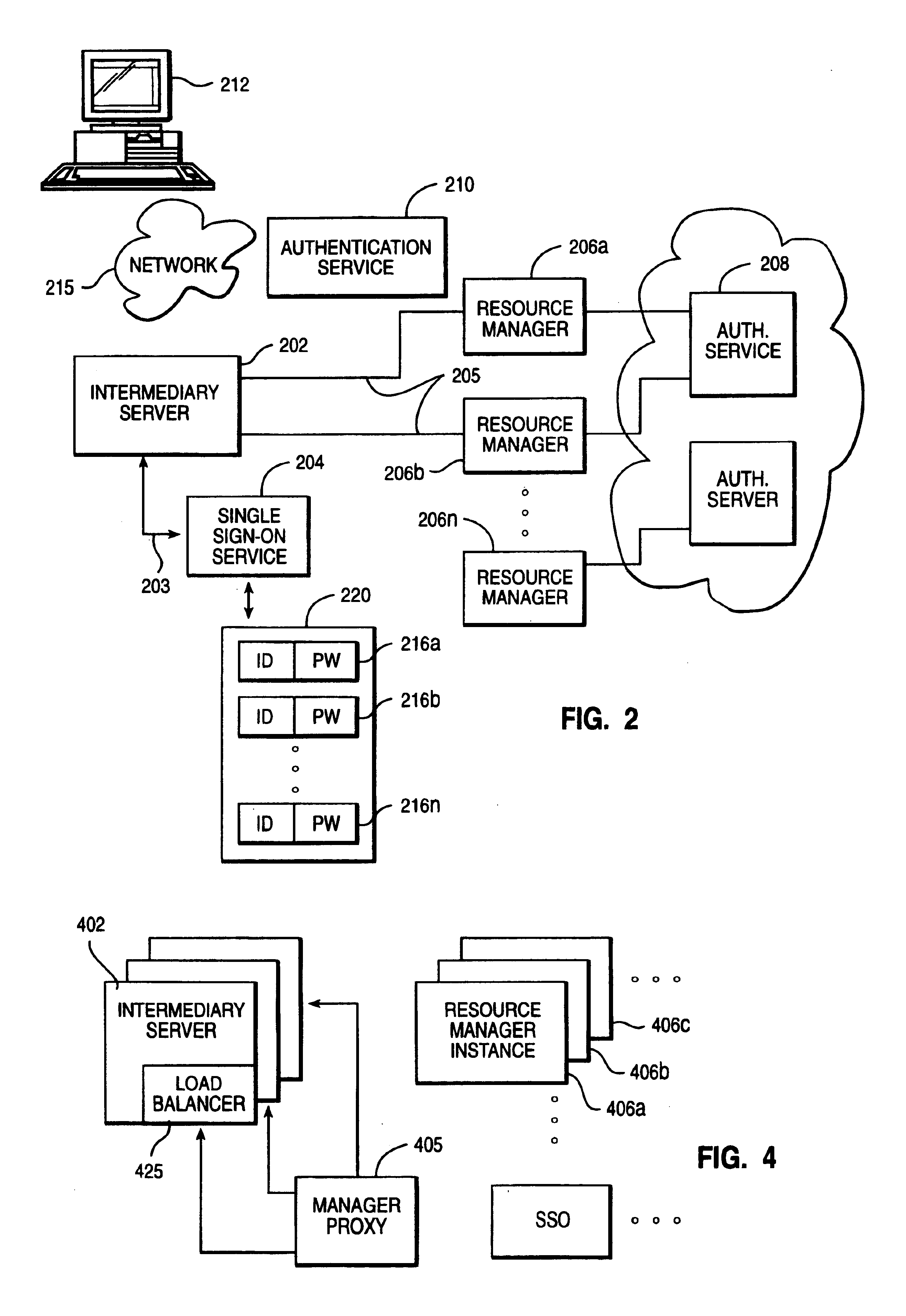
Method of enabling an intermediary server to impersonate a client user's identity to a plurality of authentication domains
InactiveUS7039714B1Multiple digital computer combinationsTransmissionEnterprise computingResource management
An enterprise computing environment such as a corporate web portal includes an intermediary server, a sign on service, and one or more backend enterprise systems managed by resource managers. Before or after user primary logon, which establishes a user primary account identity, the intermediary server uses its own identity to authenticate to the sign on service its right to retrieve user secondary account identities with respect to the backend enterprise systems. Retrieved secondary account identities are then used by the intermediary server to perform user secondary logons to respective resource managers in the environment. The intermediary server also manages the passing of resource requests and associated replies between the user and the resource managers.
Owner:IBM CORP
System and method for using web services with an enterprise system
InactiveUS7340714B2Data processing applicationsDigital data processing detailsWeb serviceClient-side
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com