Patents
Literature
1110 results about "Cloud resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
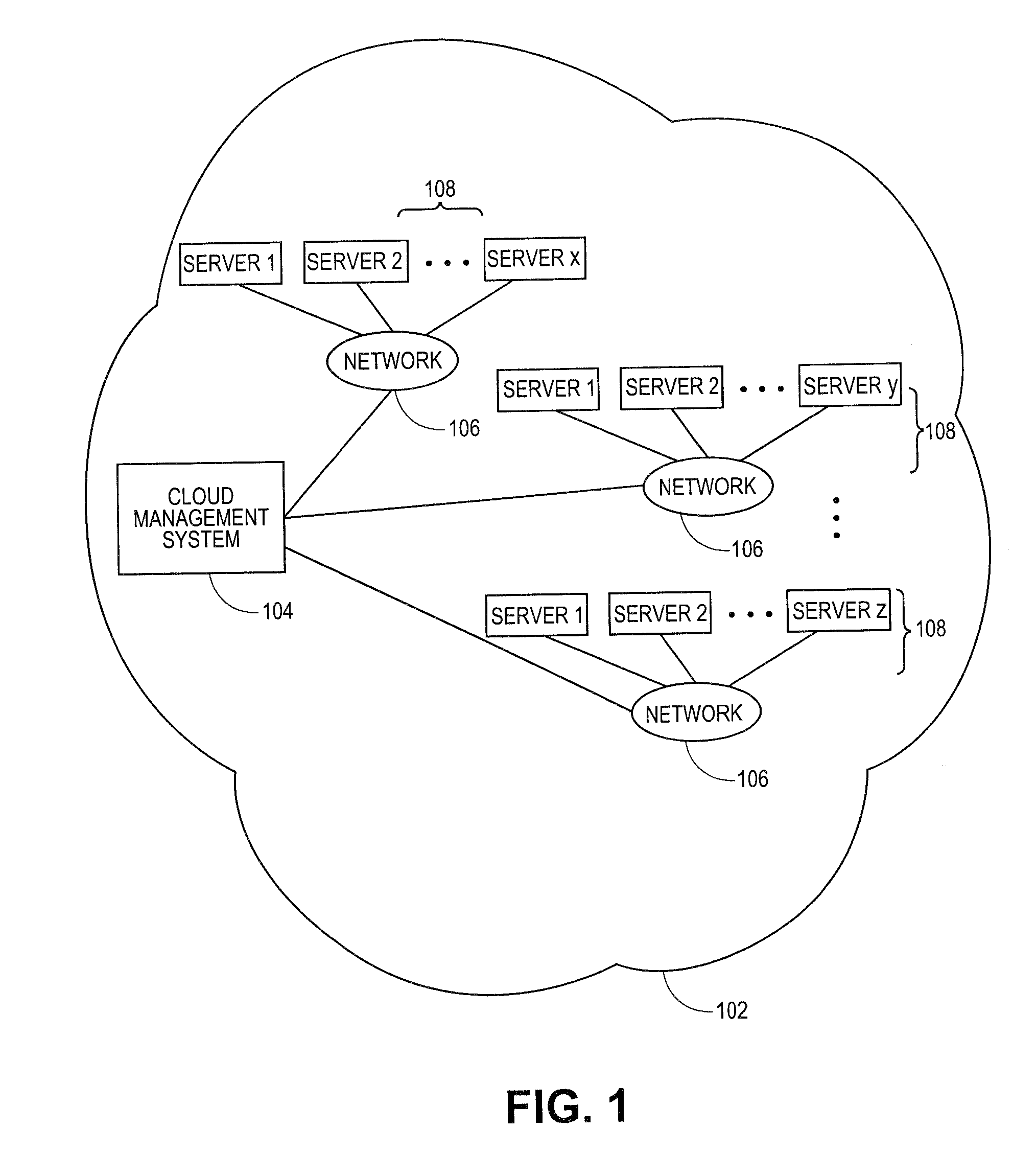
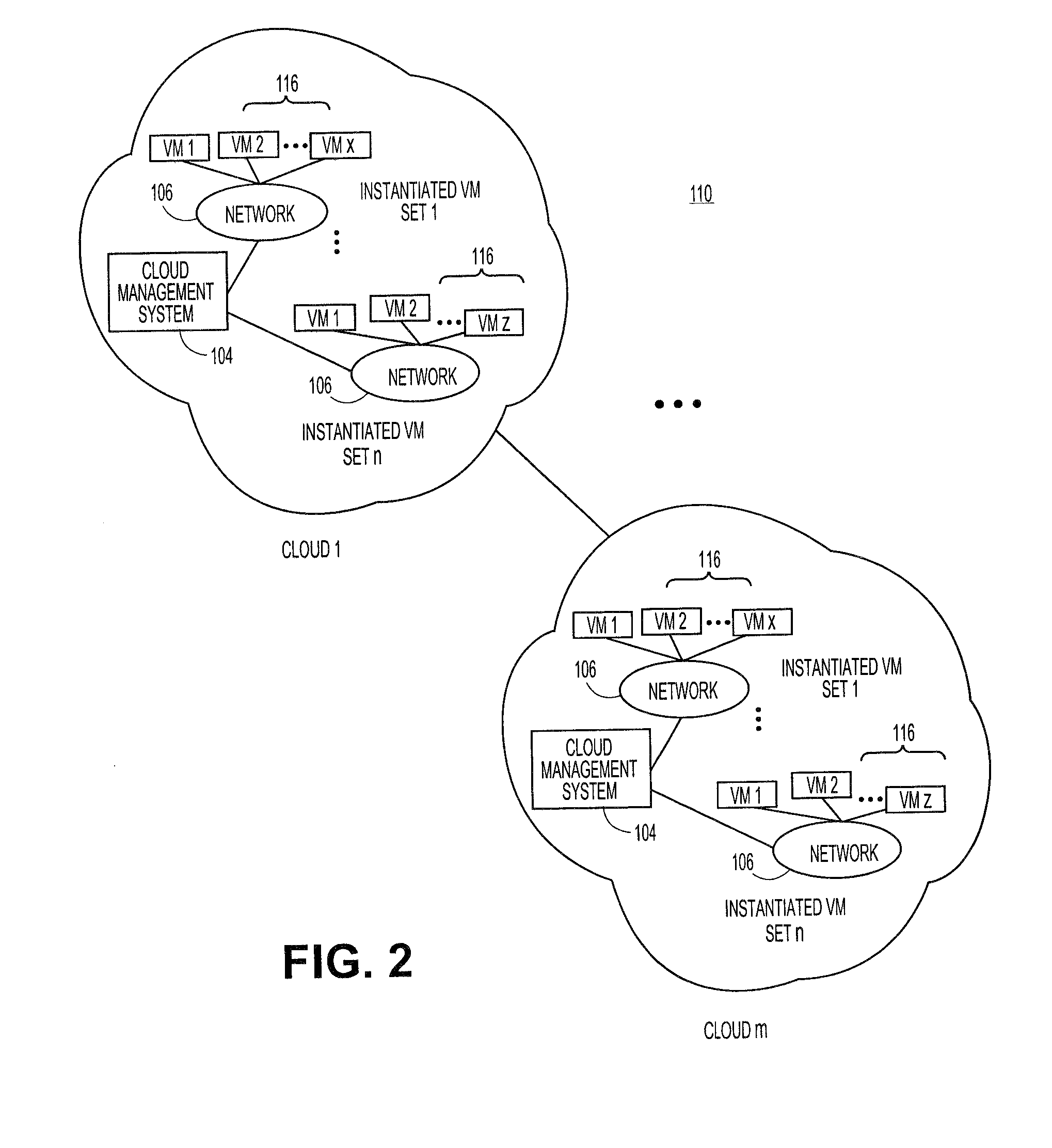
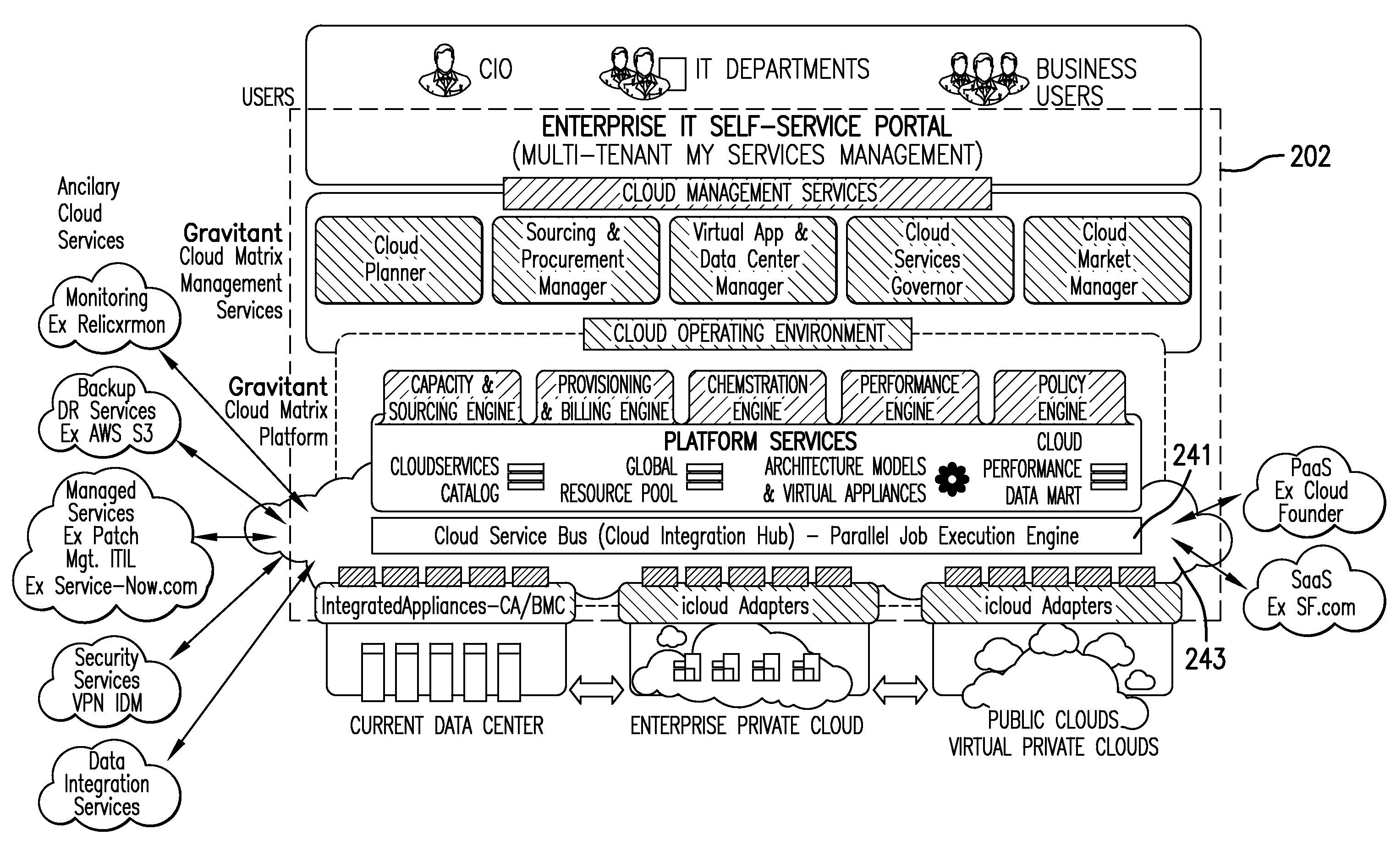
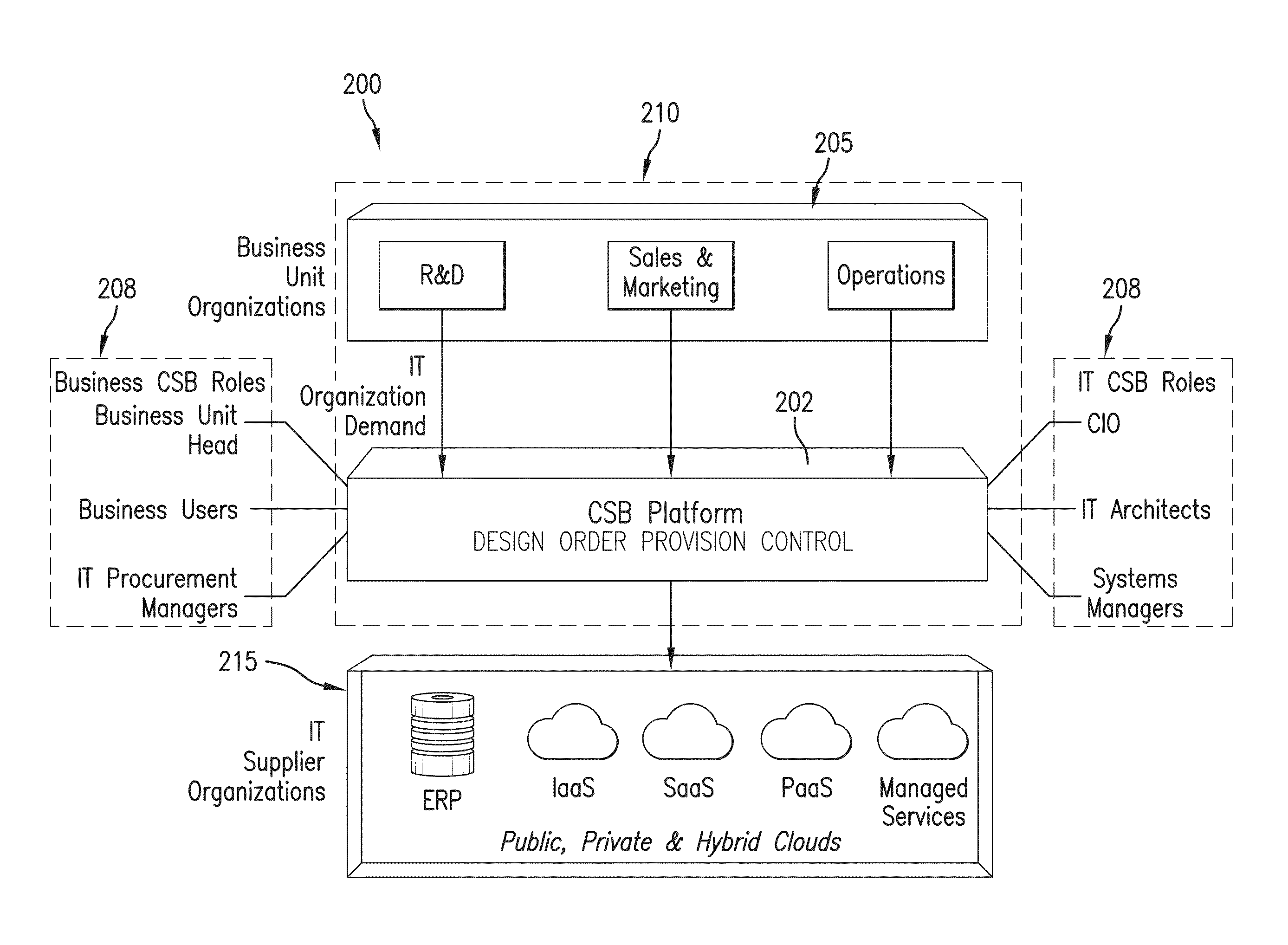
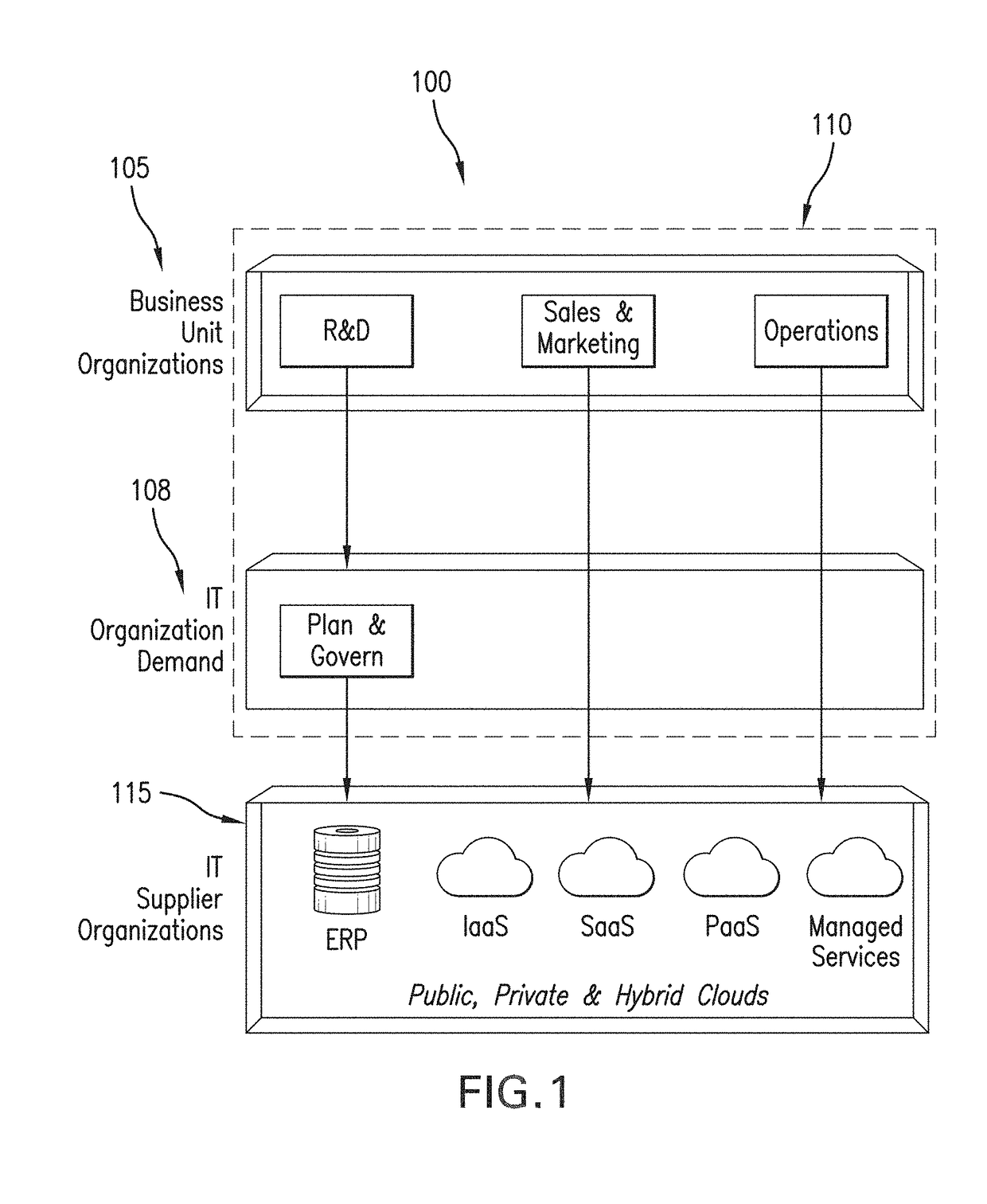
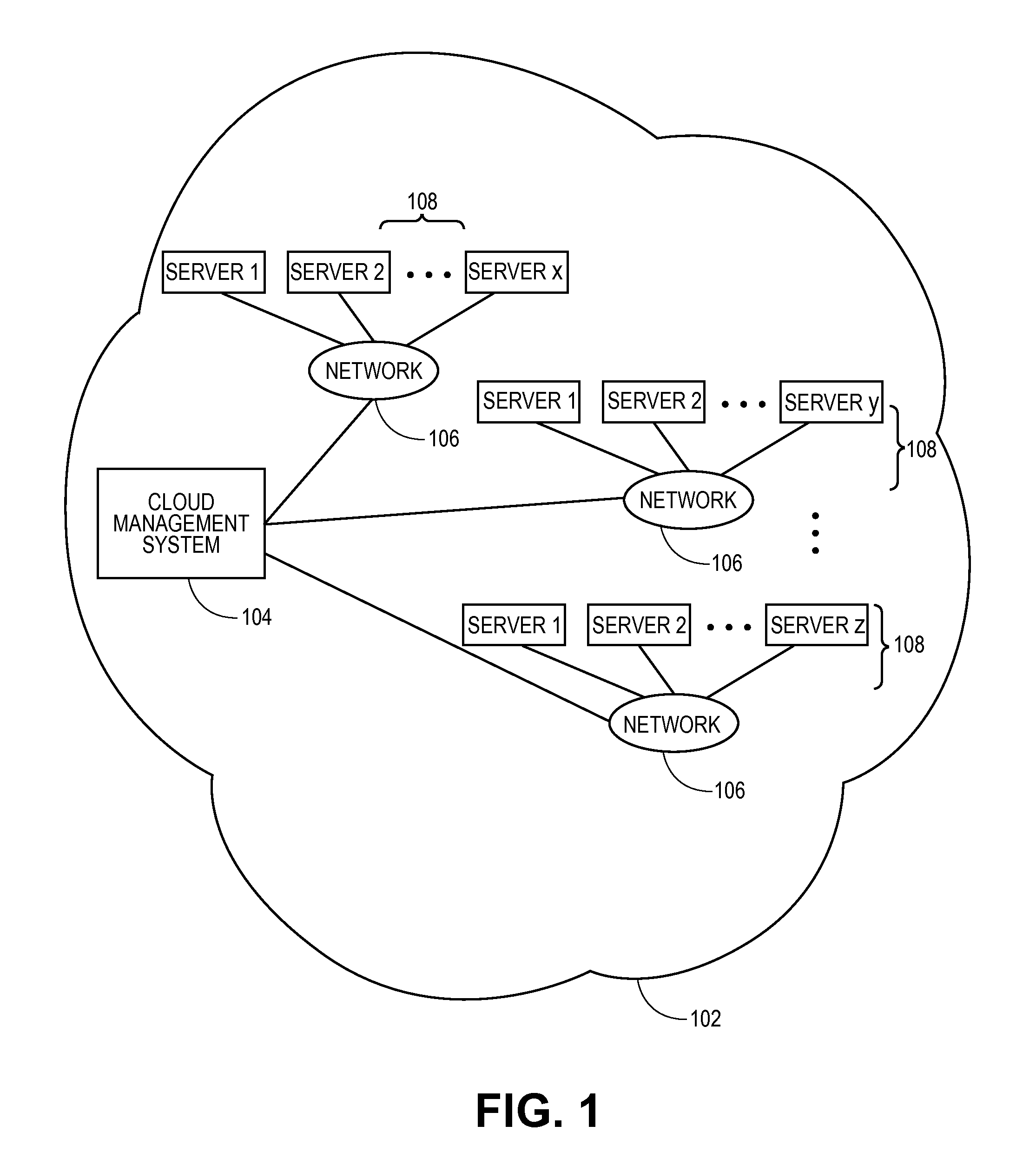
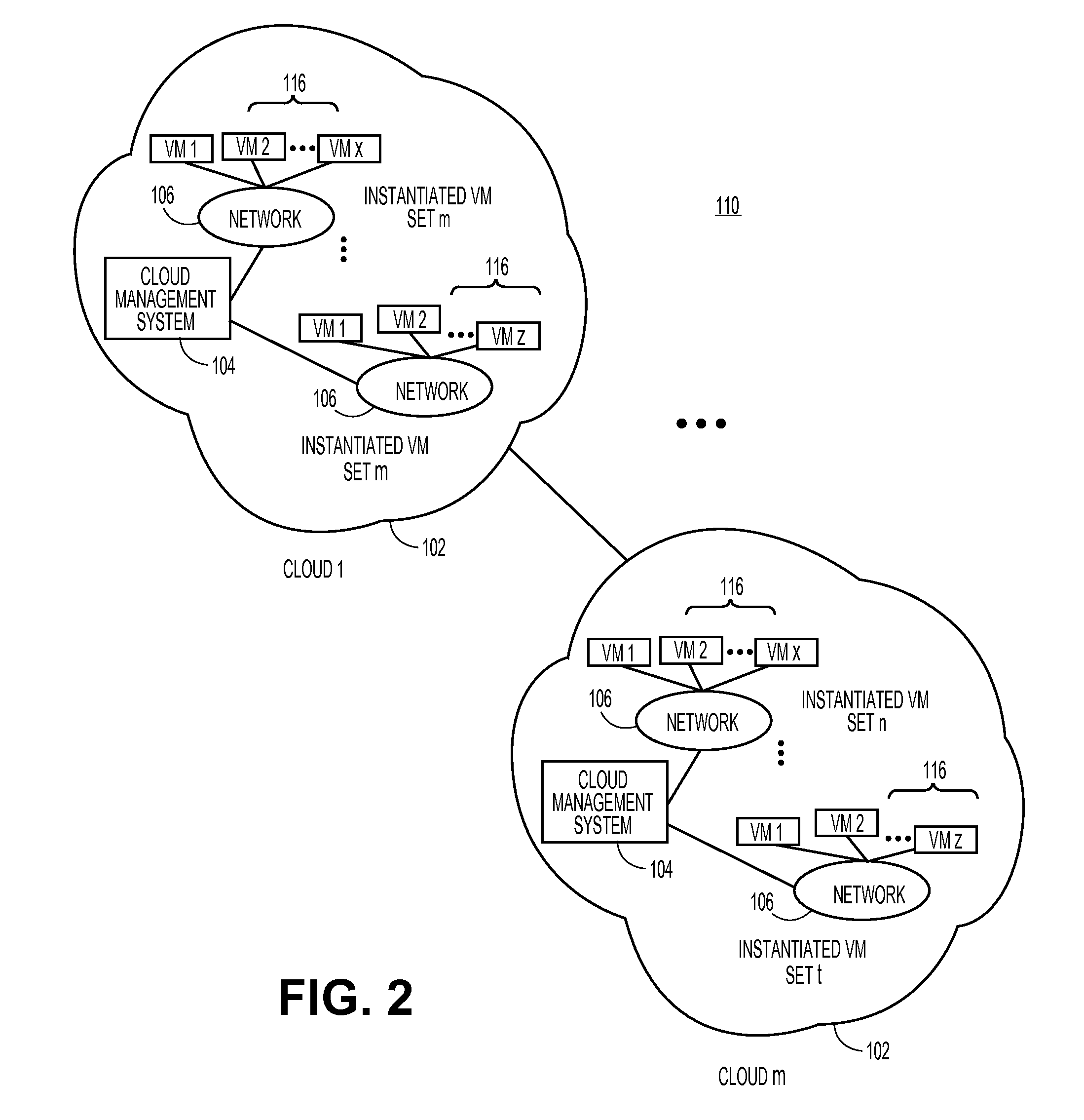
Cloud resources are now organized by common service entities where specific services (for example, Infrastructure as a Service) provide resources extending common service entities where appropriate. The figure below shows the resource model relationships on the common resources and Infrastructure as a service specific resources.
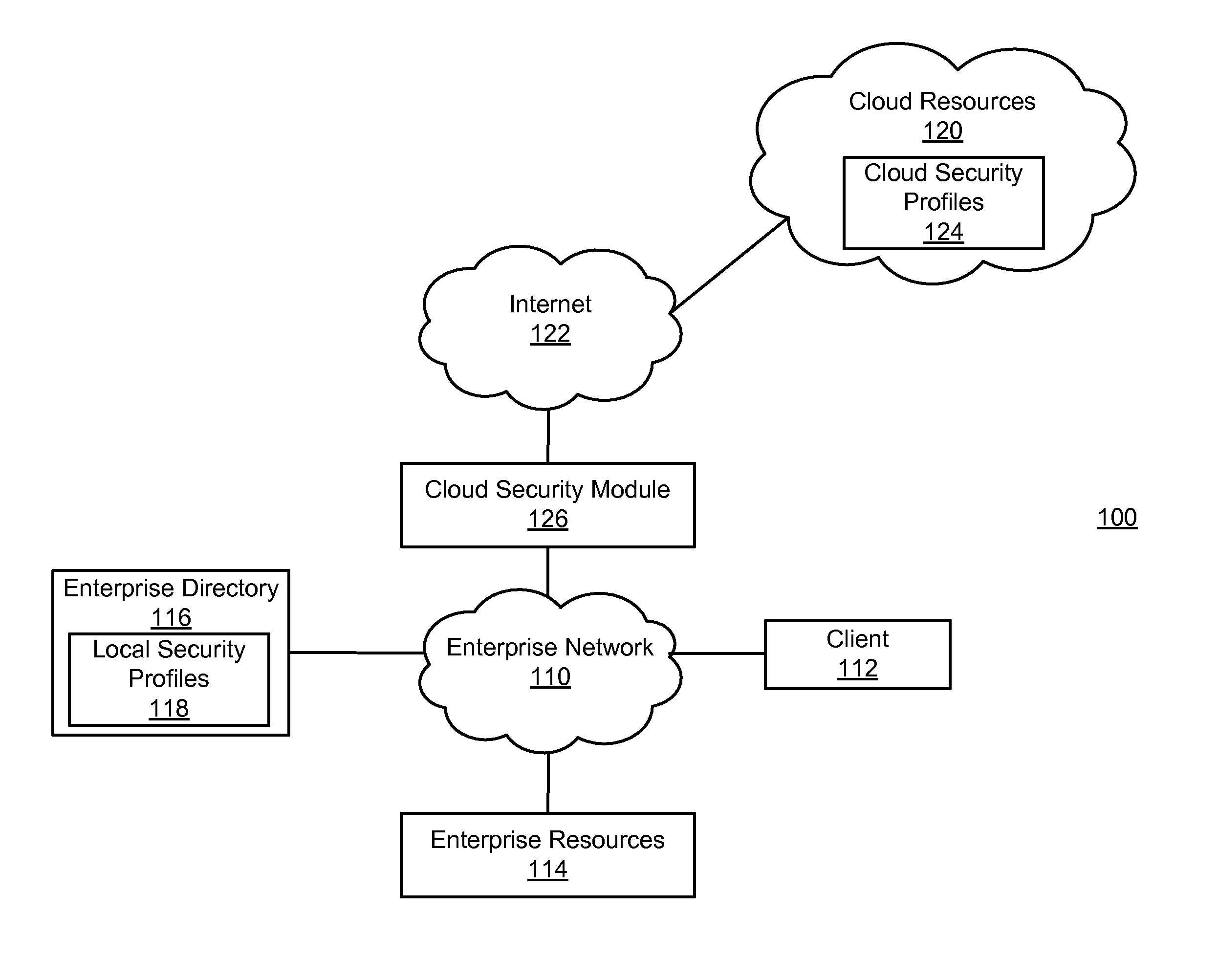
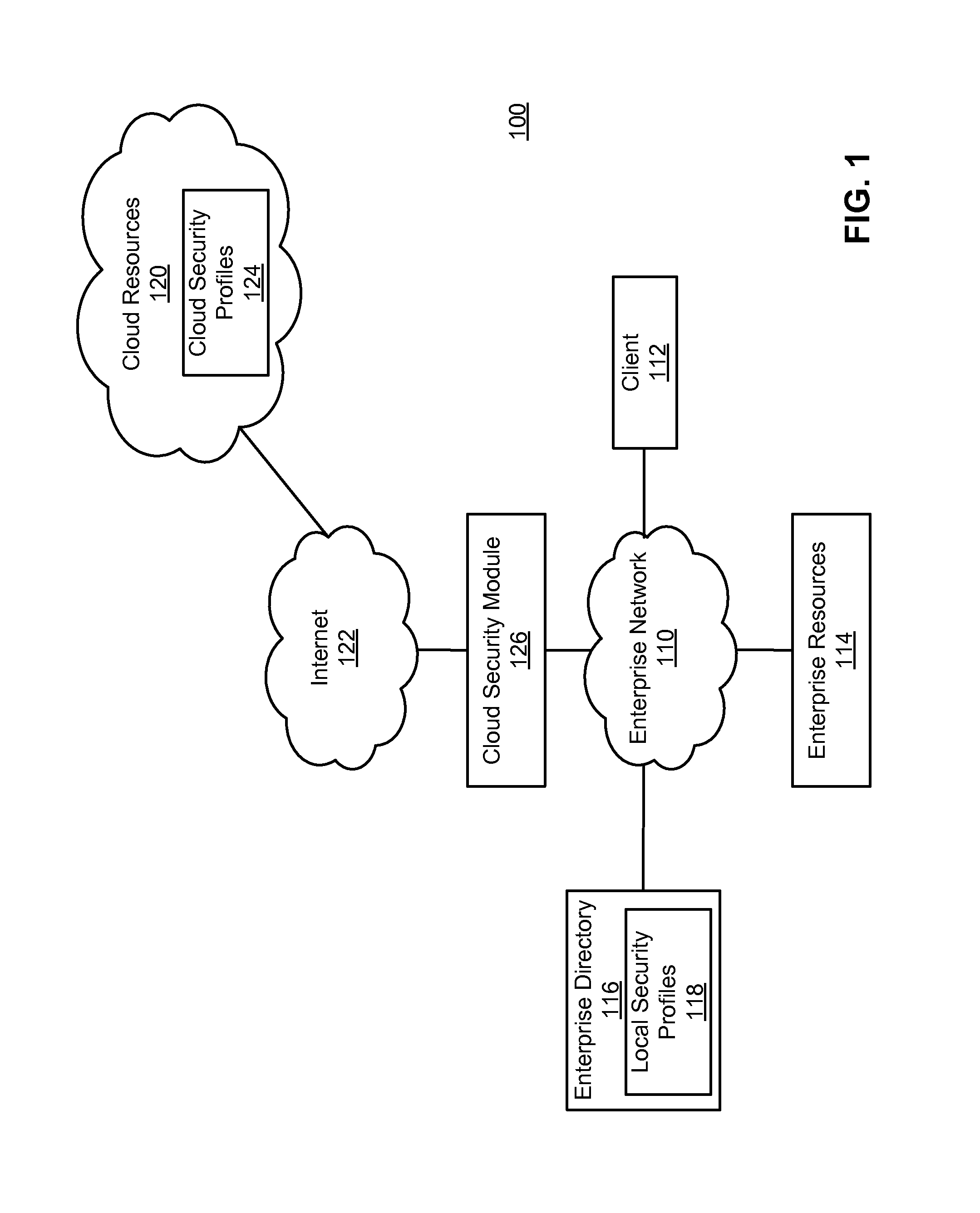
Enforcing consistent enterprise and cloud security profiles
Consistent enterprise and cloud security profiles are enforced. A domain model describing cloud resource objects associated with an enterprise is defined. Further, a relationship map describing relationships between the objects of the domain model and roles of enterprise users described by local security profiles maintained by the enterprise is specified. The domain model and relationship map collectively form an access policy for the cloud resource objects. Network traffic is monitored to detect network traffic attempting to configure a cloud security profile describing permissions of an enterprise user with respect to cloud resource objects in a manner inconsistent with the access policy. Detected network traffic attempting to configure the cloud security profile in the manner inconsistent with access policy is remediated.
Owner:CA TECH INC
Systems and methods for embedding a cloud-based resource request in a specification language wrapper
Embodiments relate to systems and methods for embedding a cloud-based resource request in a specification language wrapper. In embodiments, a set of applications and / or a set of appliances can be registered to be instantiated in a cloud-based network. Each application or appliance can have an associated set of specified resources with which the user wishes to instantiate those objects. For example, a user may specify a maximum latency for input / output of the application or appliance, a geographic location of the supporting cloud resources, a processor throughput, or other resource specification to instantiate the desired object. According to embodiments, the set of requested resources can be embedded in a specification language wrapper, such as an XML object. The specification language wrapper can be transmitted to a marketplace to seek the response of available clouds which can support the application or appliance according to the specifications contained in the specification language wrapper.
Owner:RED HAT
Dynamic provisioning of resources within a cloud computing environment
ActiveUS20110145392A1Efficient and environmentDigital computer detailsProgram controlCost effectivenessCloud base
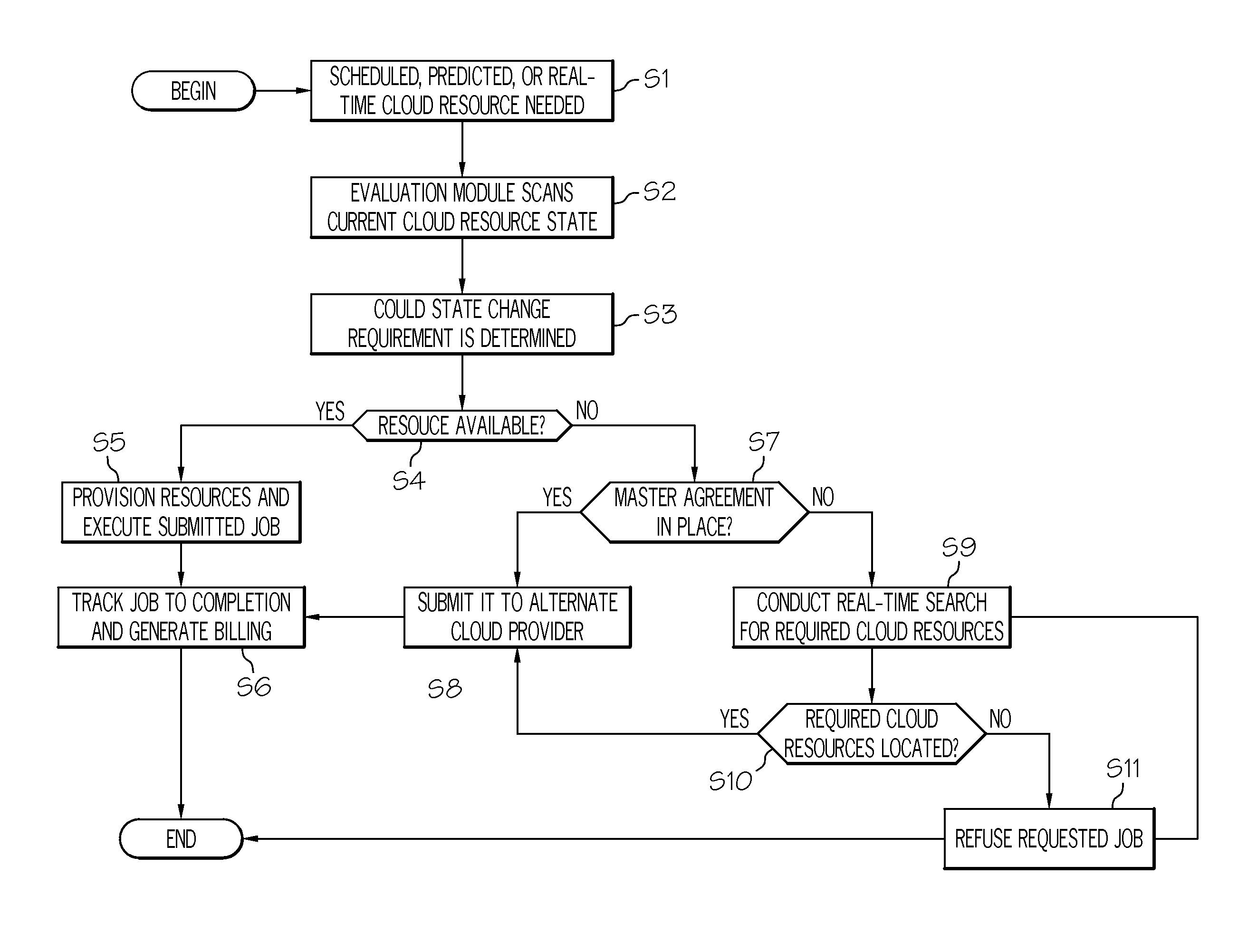
The present invention provides a solution (e.g., rules, techniques, etc.) for enabling the dynamic provisioning (e.g., movement) of Cloud-based jobs and resources. Such provisioning may be within a Cloud infrastructure, from Cloud to Cloud, from non-Cloud to Cloud, and from Cloud to non-Cloud. Each movement scenario is assigned a specific technique based on rules, profiles, SLA and / or other such criteria and agreements. Such dynamic adjustments may be especially advantageous in order to balance real-time workload to avoid over-provisioning, to manage Cloud performance, to attain a more efficient or cost-effective execution environment, to off-load a Cloud or specific Cloud resources for maintenance / service, and the like.
Owner:KYNDRYL INC
Systems and methods for cloud bridging between intranet resources and cloud resources
Embodiments of the present solution provide a cloud bridge to bring network transparency between the otherwise disparate networks of the datacenter and cloud service provider. For example, appliances may be deployed in the datacenter and on the edge of the cloud. These appliances may be configured or designed and constructed to communicate with each other and recognize and understand the local IP and / or public IP network information of the on-premise datacenter of the enterprise and the cloud datacenter. These appliances may manage the flow of network traffic between the on-premise and cloud datacenters in a manner to appear and act seamlessly and transparently as a single network spanning both the on-premise and cloud data centers.
Owner:CITRIX SYST INC
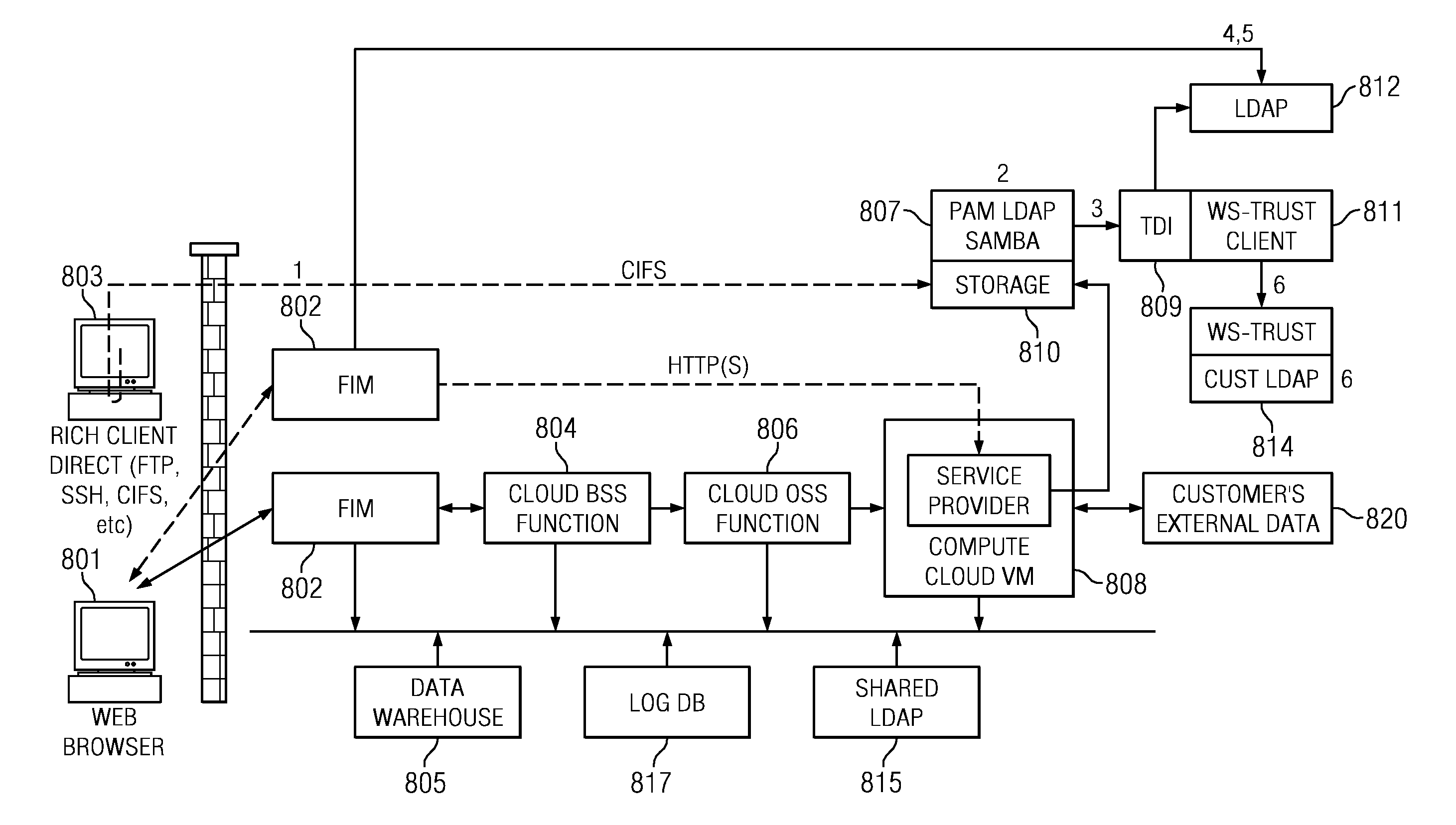
Cross-protocol federated single sign-on (F-SSO) for cloud enablement
ActiveUS20120011578A1Simple on-boarding processRetain controlMultiple keys/algorithms usagePublic key for secure communicationCloud providerCloud resources
A method to enable access to resources hosted in a compute cloud begins upon receiving a registration request to initiate a user's registration to use resources hosted in the compute cloud. During a registration process initiated by receipt of the registration request, a federated single sign-on (F-SSO) request is received. The F-SSO request includes an assertion (e.g., an HTTP-based SAML assertion) having authentication data (e.g., an SSH public key, a CIFS username, etc.) for use to enable direct user access to a resource hosted in the compute cloud. Upon validation of the assertion, the authentication data is deployed within the cloud to enable direct user access to the compute cloud resource using the authentication data. In this manner, the cloud provider provides authentication, single sign-on and lifecycle management for the user, despite the “air gap” between the HTTP protocol used for F-SSO and the non-HTTP protocol used for the user's direct access to the cloud resource.
Owner:SERVICENOW INC
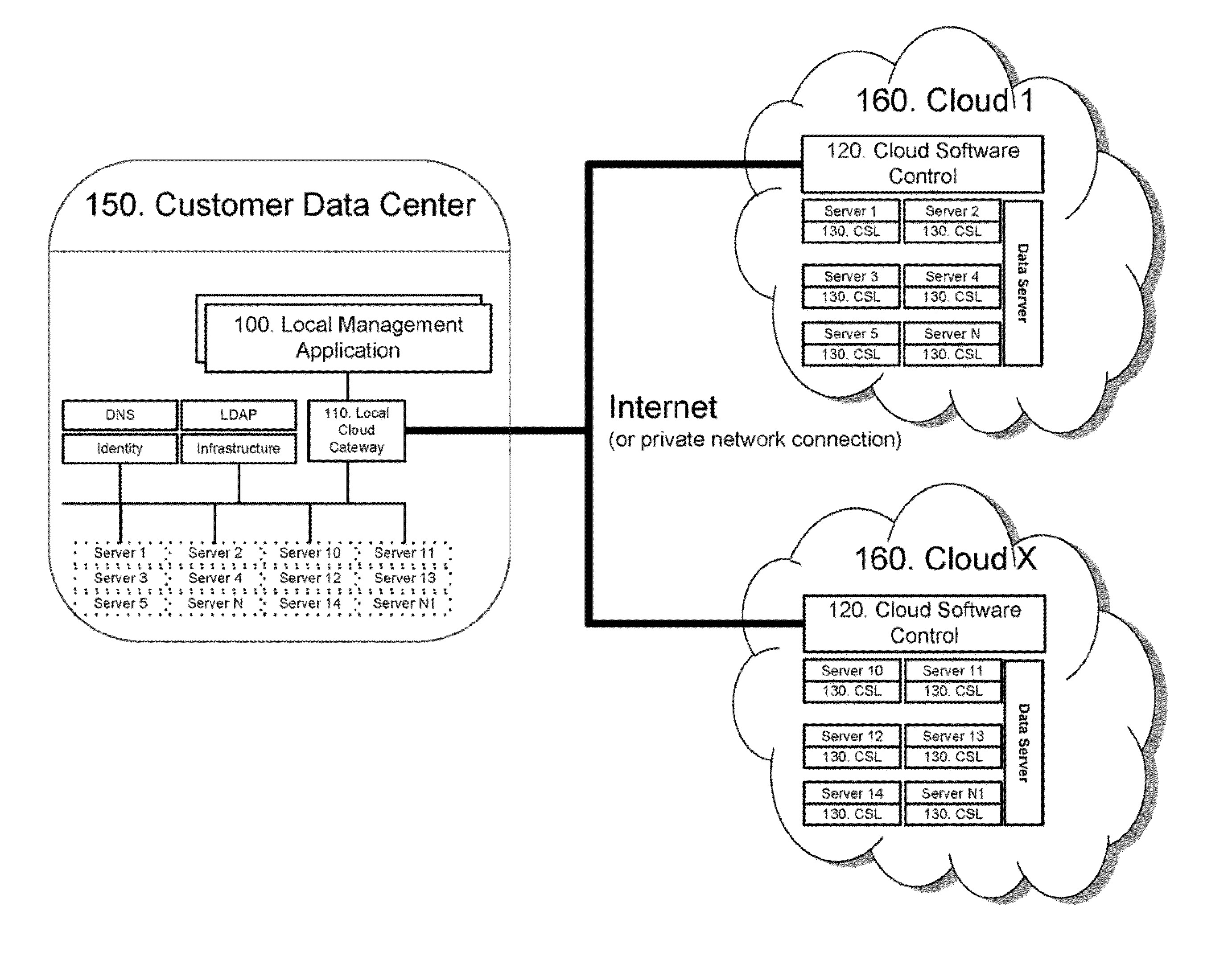
Environment preserving cloud migration and management
ActiveUS8417938B1Maximise its operationProtect environmentProgram controlTransmissionData centerIsolation layer
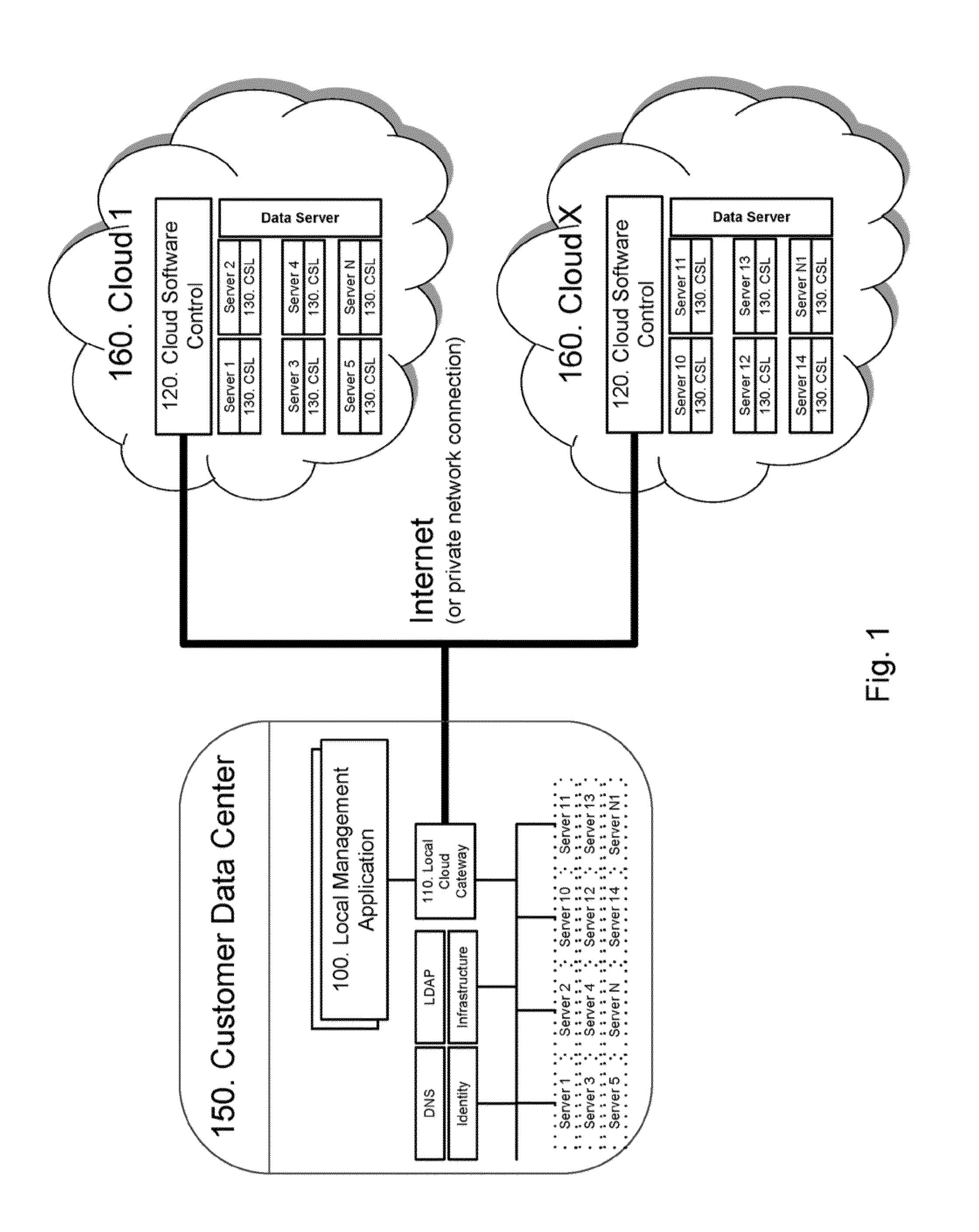
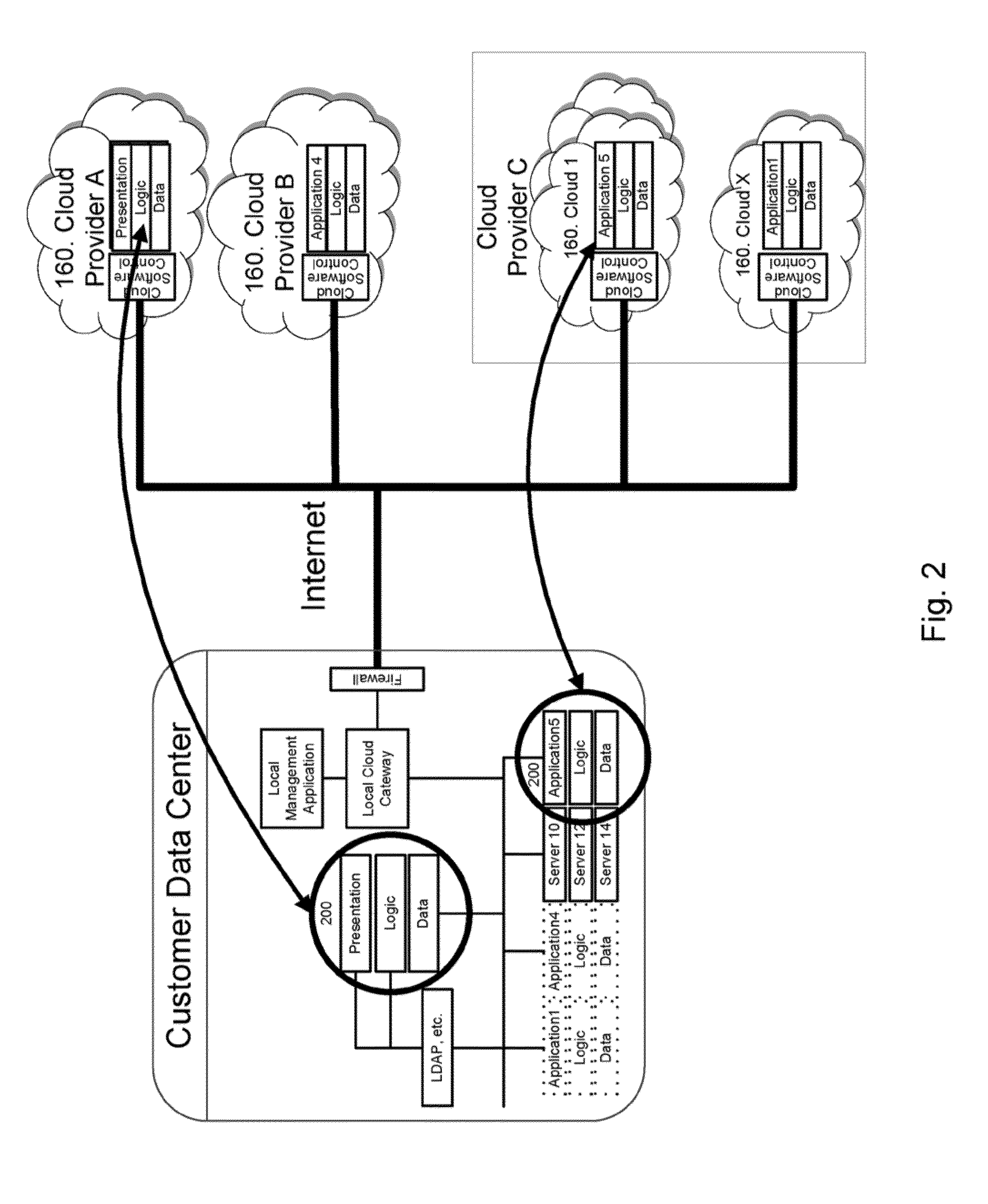
A system and method of operation is disclosed describing migration, management, and operation of applications and servers from customer data centers to cloud computing platforms without modification to existing environments or user access procedures. A cloud isolation layer operates as a virtual layer on the cloud platform, enabling server operation in a virtual environment that appears the same as the prior local environment. A cloud software image and a local cloud gateway act to redirect existing addressing from the local environment to the cloud implementation through secure network and data paths. A local management application provides a control interface and maps and manages the local environment and utilized cloud resources.
Owner:RAKUTEN GRP INC
Cloud-Based Test System and Method and Computer-Readable Storage Medium with Computer Program to Execute the Method
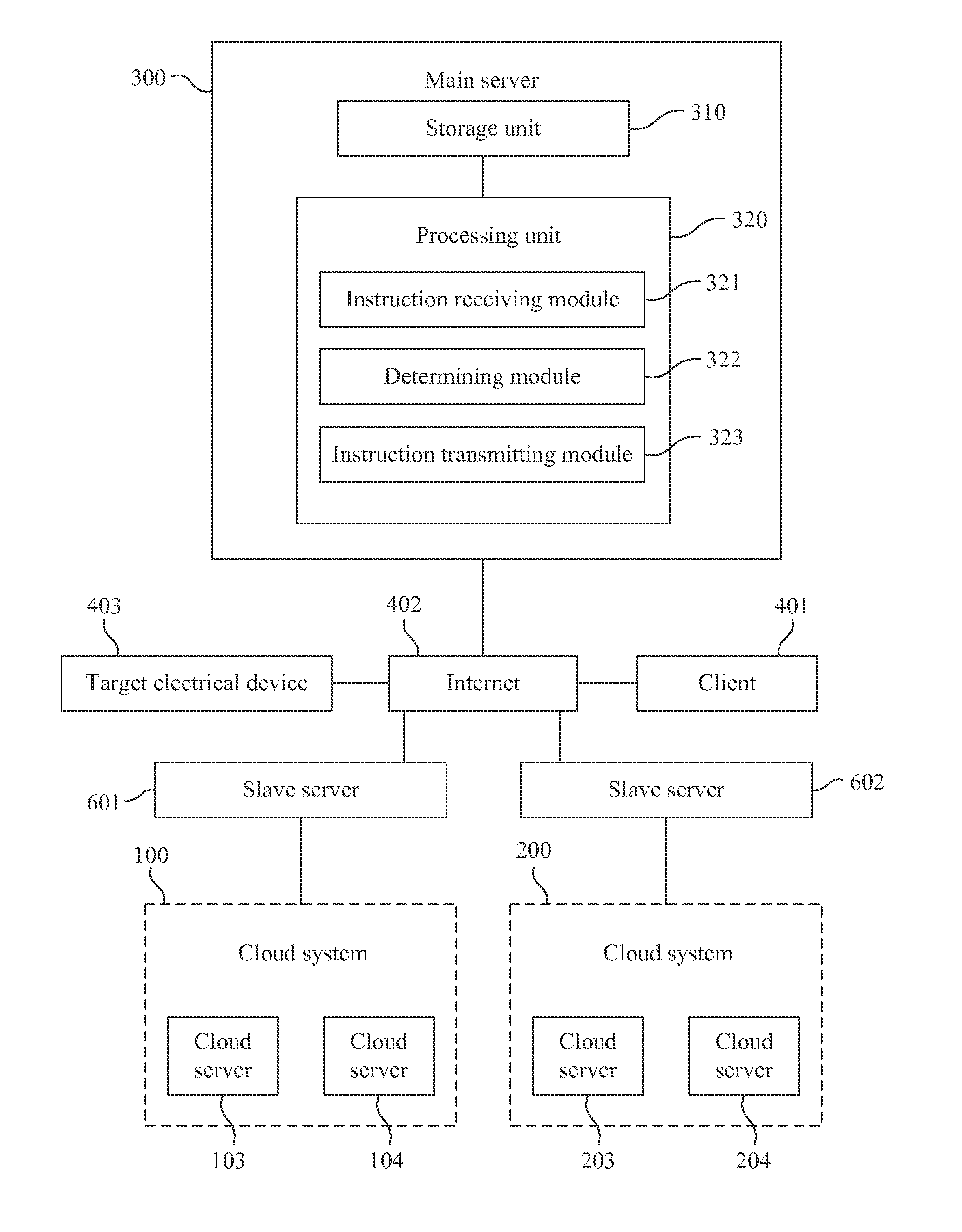
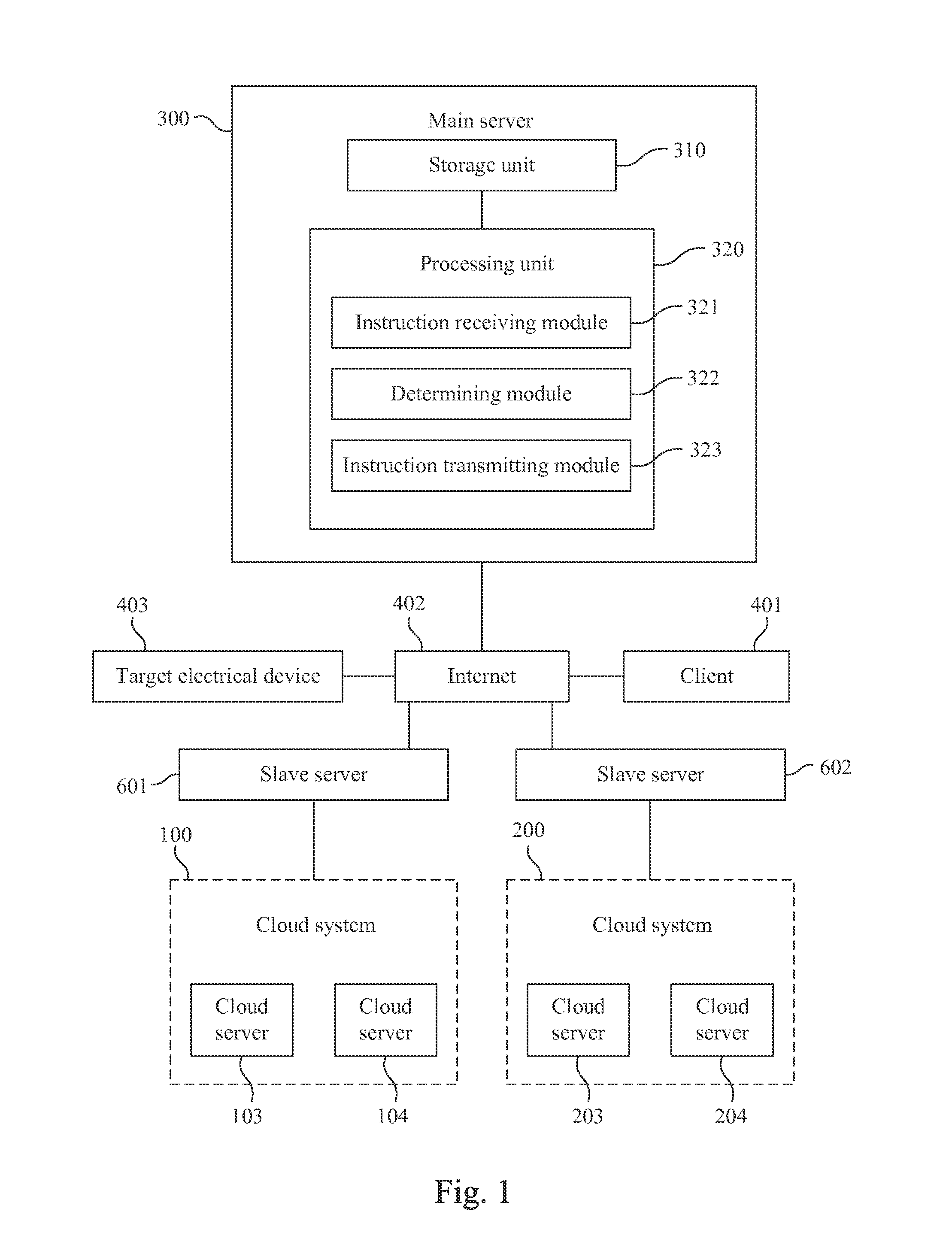
ActiveUS20130019242A1Efficient executionImprove performanceMultiple digital computer combinationsTransmissionCloud systemsCloud resources
A cloud-based test system is disclosed. The cloud-based test system utilizes several cloud systems for testing. Each cloud system includes several cloud servers for providing a cloud resource to simulate several virtual test machines. The cloud-based test system includes several slave servers and a main server. Each slave server corresponds to one of the cloud systems for controlling the corresponding virtual test machines. The main server receives a test instruction, which is utilized to execute a target test item for a target electrical device, from a client, and generates a test environment condition corresponding to the test instruction. The main server determines the virtual test machines for executing the target test item and the at least one server to control the virtual test machines. The main server transmits the test instruction and the corresponding test environment condition to the server slave servers for testing.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
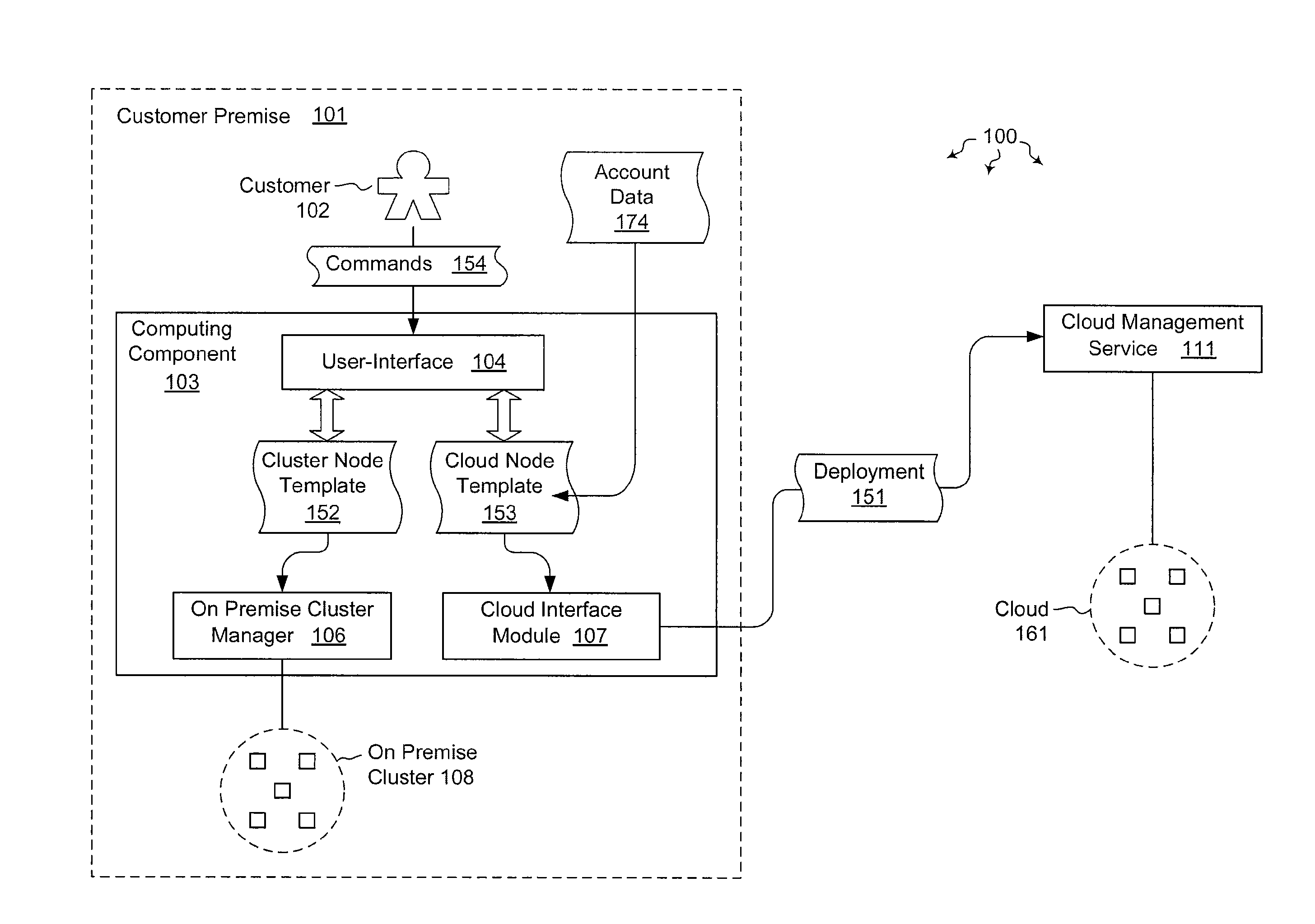
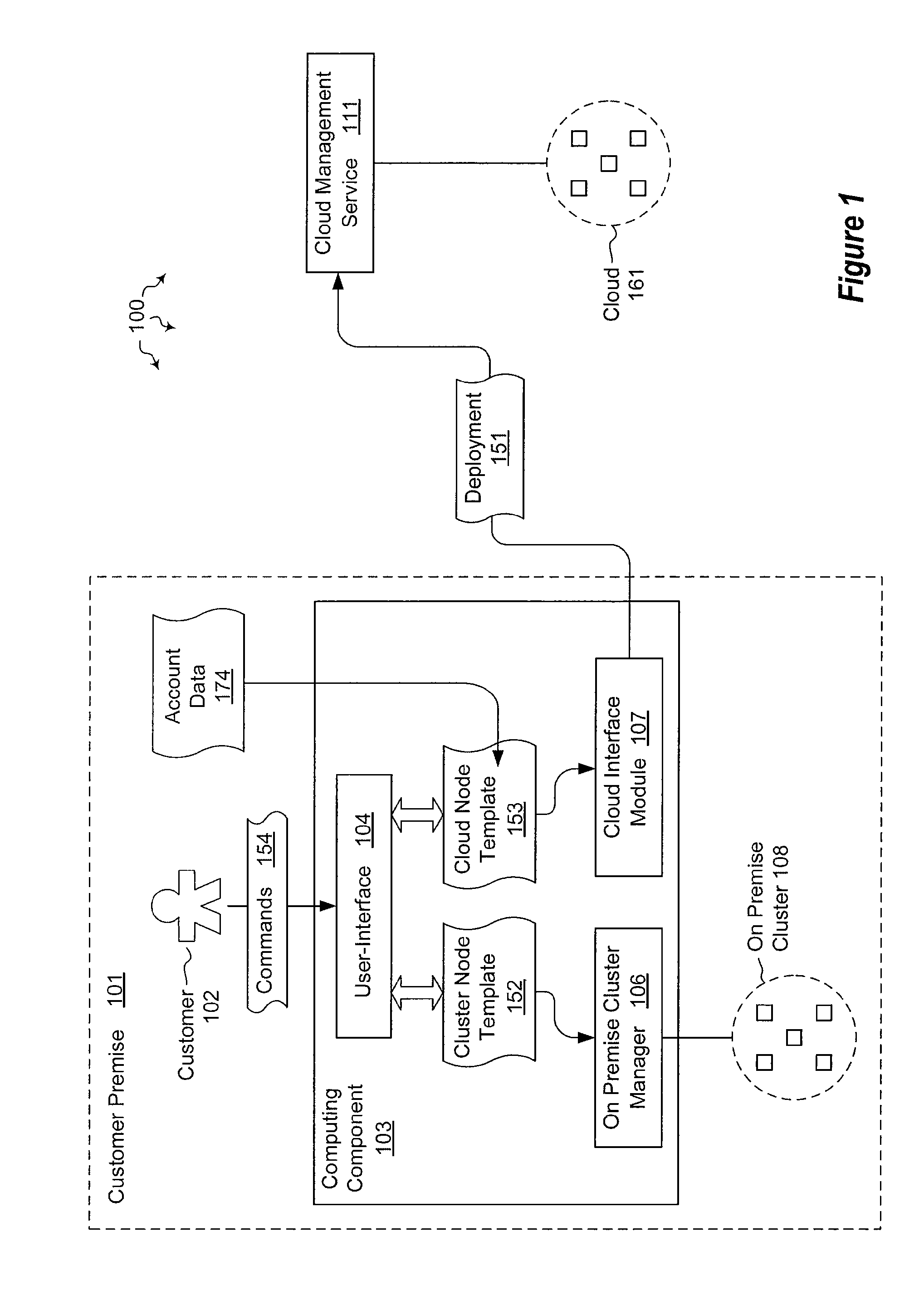
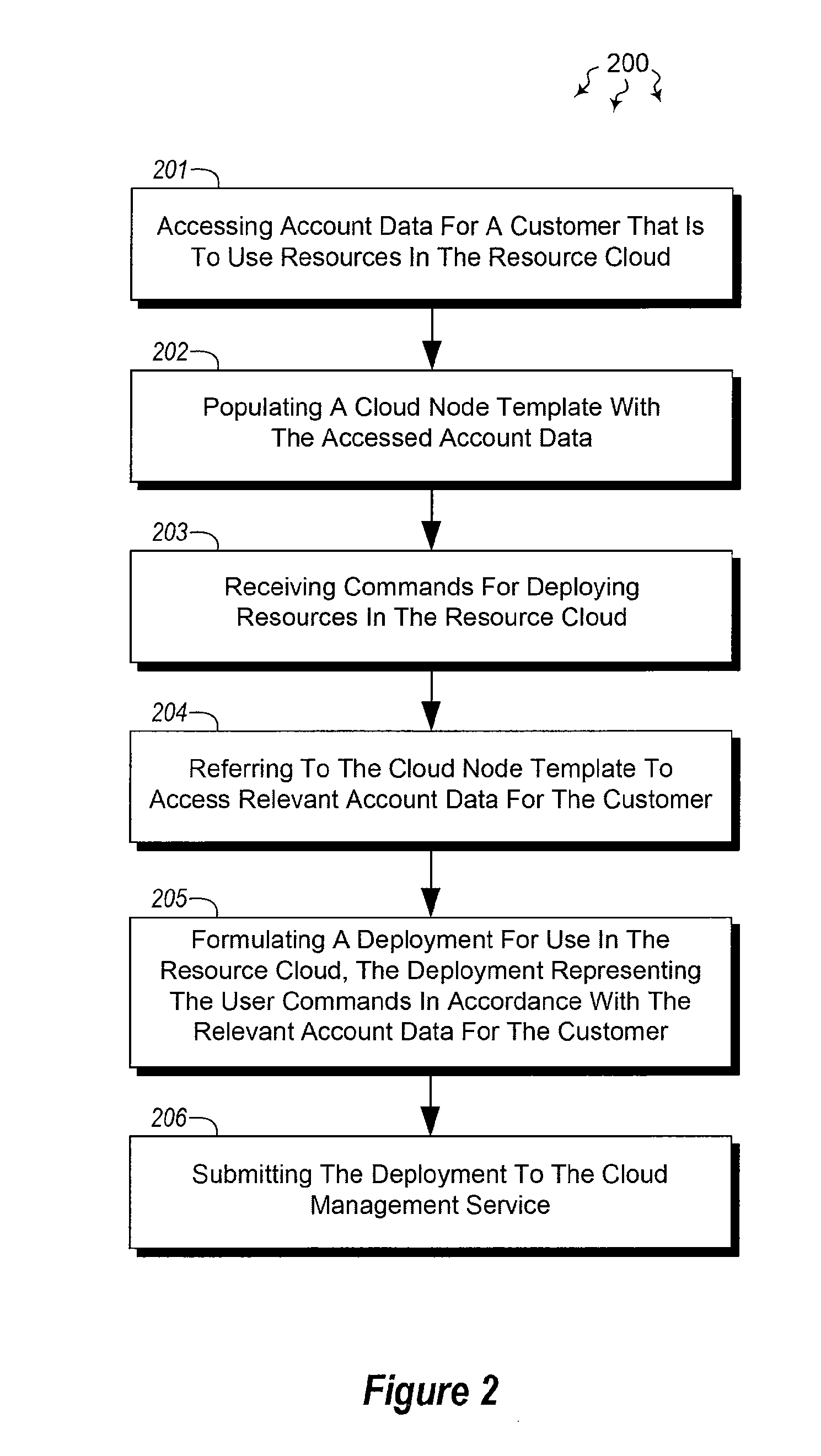
Using templates to configure cloud resources
ActiveUS20120072597A1Well formedDigital computer detailsProgram controlTheoretical computer scienceCloud resources
The present invention extends to methods, systems, and computer program products for using templates to configure cloud resources. Embodiments of the invention include encapsulating cloud configuration information in an importable / exportable node template. Node templates can also be used to bind groups of nodes to different cloud subscriptions and cloud service accounts. Accordingly, managing the configuration of cloud based resources can be facilitated through an interface at a (e.g., high performance) computing component. Templates can also specify a schedule for starting / stopping instance running within a resource cloud.
Owner:MICROSOFT TECH LICENSING LLC
Configuring cloud resources
InactiveUS20140365662A1Enhancing cloud serviceEfficient and effectiveDigital computer detailsResourcesCloud resourcesVirtual machine
A non-transitory computer-readable storage medium has tangibly embodied thereon and accessible therefrom instructions interpretable by at least one data processing device. The instructions are configured for causing the at least one data processing device to perform a method comprising creating a resource group for providing cloud services, receiving a request to increase a quantity of the virtual machines of the resource group; and instantiating one or more additional virtual machines within the resource group in response to receiving the request. The resource group includes one or more virtual machines that all have virtual machine specifications of a particular configuration. Instantiating the one or more additional virtual machines includes providing each one of the one or more additional virtual machines with virtual machine specifications of the particular configuration.
Owner:HCL TECH LTD
Inter-cloud resource sharing within a cloud computing environment
InactiveUS20110137805A1Amount of timeDigital computer detailsPayment architectureFinancial transactionCloud provider
The present invention provides a system and method for establishing inter-Cloud resource sharing agreements and policies such that dynamic expansion / contraction of Cloud resource requests can be seamlessly addressed without requiring physical build-out of the primary Cloud infrastructure and advertising the need for additional resources or the offer to provide additional resources can be brokered through an established marketplace. The financial transaction will support a symbiotic bi-lateral fair-share method that better aligns with an alternating supplier / consumer business model. Using this system and method will decrease the amount of time needed to respond to a given Cloud service request while advantaging a resource sharing model amongst established Cloud providers.
Owner:KYNDRYL INC
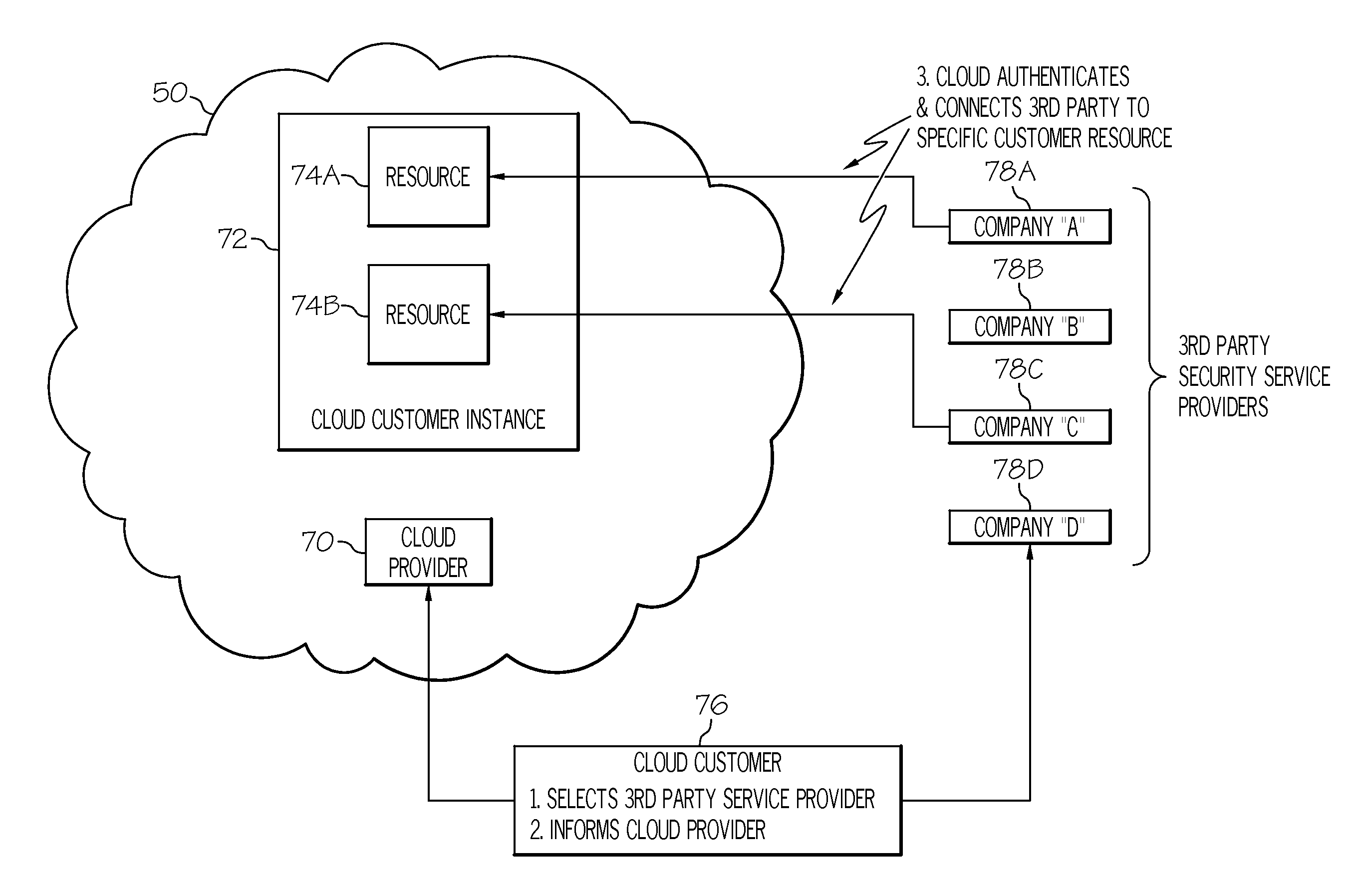
Providing security services within a cloud computing environment
InactiveUS20110219434A1Digital data processing detailsUser identity/authority verificationThird partySecurity properties
Embodiments of the present invention allow for the provisioning of security services within a Cloud computing environment by third parties. Specifically, under the present invention, a Cloud provider will publish a set of potential security attributes (e.g., a list), which can be monitored, to the Cloud customer. The Cloud customer will designate / select one or more of those attributes that the Cloud customer wishes to have monitored for one or more Cloud resources that it is using. The Cloud provider will then provide to the Cloud customer a set of third party security service providers capable of monitoring the attributes the Cloud customer designated. The Cloud customer will then select one or more third party providers from the provided set, and the Cloud provider will associate the given Cloud resources with the respective third party providers. Once third party providers have been associated with Cloud resources, a secure relationship between the third party provider(s) and the Cloud providers will be established.
Owner:KYNDRYL INC
Method, system and computer readable medium for provisioning cloud resources
InactiveUS20140282536A1Enhancing cloud serviceEfficient and effectiveFinanceTransmissionData centerCloud resources
A non-transitory computer-readable storage medium has tangibly embodied thereon and accessible therefrom instructions interpretable by at least one data processing device. The instructions are configured for causing the at least one data processing device to perform a method for provisioning cloud resources. The method comprises creating an instantiation of a cloud service resource; associating the cloud service resource with each one of a virtual data center, a cloud resource application, a cloud resource application environment, and a cloud resource architectural layer; and provisioning the cloud service resource with at least one instance of a virtual machine.
Owner:HCL TECH LTD
Cloud servicing brokering
InactiveUS20110145094A1Digital data processing detailsBuying/selling/leasing transactionsProgram planningResource based
The present invention provides a solution to perform pricing and brokering of Cloud services. Illustrative pricing / charging plans include “pay as you go (subscription)” and “pay for what you use (dynamic)”. The present invention also provides a way to display a price next to service. In general, a broker agent (hereinafter referred to as “agent”) executes within the environment and queries available and acceptable Cloud resources from a plurality of providers. Based on resources, published rates, and rate projections, the broker schedules, reschedules, moves, and otherwise manages Cloud jobs based on job criteria and optimized execution cost.
Owner:IBM CORP
Method and System for Utilizing Spare Cloud Resources
ActiveUS20130247034A1Software simulation/interpretation/emulationMemory systemsCloud resourcesComputing systems
A cloud computing system including a computing device configured to run virtual machine instances is disclosed. The computing device includes a hypervisor program for managing the virtual machine instances. A customer virtual machine instance is run by the hypervisor program on the computing device, and a grid virtual machine instance is run by the hypervisor program on the computing device. The grid virtual machine instance is configured to run only when a resource of the computing device is not being utilized by the customer virtual machine instance.
Owner:RACKSPACE US
Metering resource usage in a cloud computing environment
InactiveUS20110138034A1Accurate trackingPrecise managementError detection/correctionDigital computer detailsCloud resourcesResource use
An approach that provides assigning and tracking inter-Cloud operational transactions within a Cloud computing environment in order to meter Cloud resource usage when processing a Cloud service request. In one embodiment, there is a Cloud usage and accounting tool, including a route management component configured to define and manage the physical implementation of delineation points between Clouds. The Cloud usage and accounting tool further includes a workflow control component configured to track inter-Cloud operational transactions as they pass through the delineation points.
Owner:IBM CORP
Cross provider security management functionality within a cloud service brokerage platform
ActiveUS20150188927A1Good serviceEfficient and effectiveDigital data processing detailsMultiple digital computer combinationsSystems managementHardware security module
Implementation of cross provider security in accordance with the disclosures made herein enables users of a system (e.g., a cloud services brokerage platform) in a cloud environment provides for system-managed provisioning and management of keys to cloud resources thereby allowing the user to manage data security and enable secured access to their cloud resources. To this end, cross provider security management functionality in accordance with the disclosures made herein can include provisioning system-generated keys across different regions in a provider, provisioning cloud brokerage system-generated keys across different providers; and associating (i.e., managing) the keys from the system to a hardware security module. The keys can be managed by / though a variety of different resources (e.g., brokering system, VDC, user group concepts, etc).
Owner:HCL TECH LTD
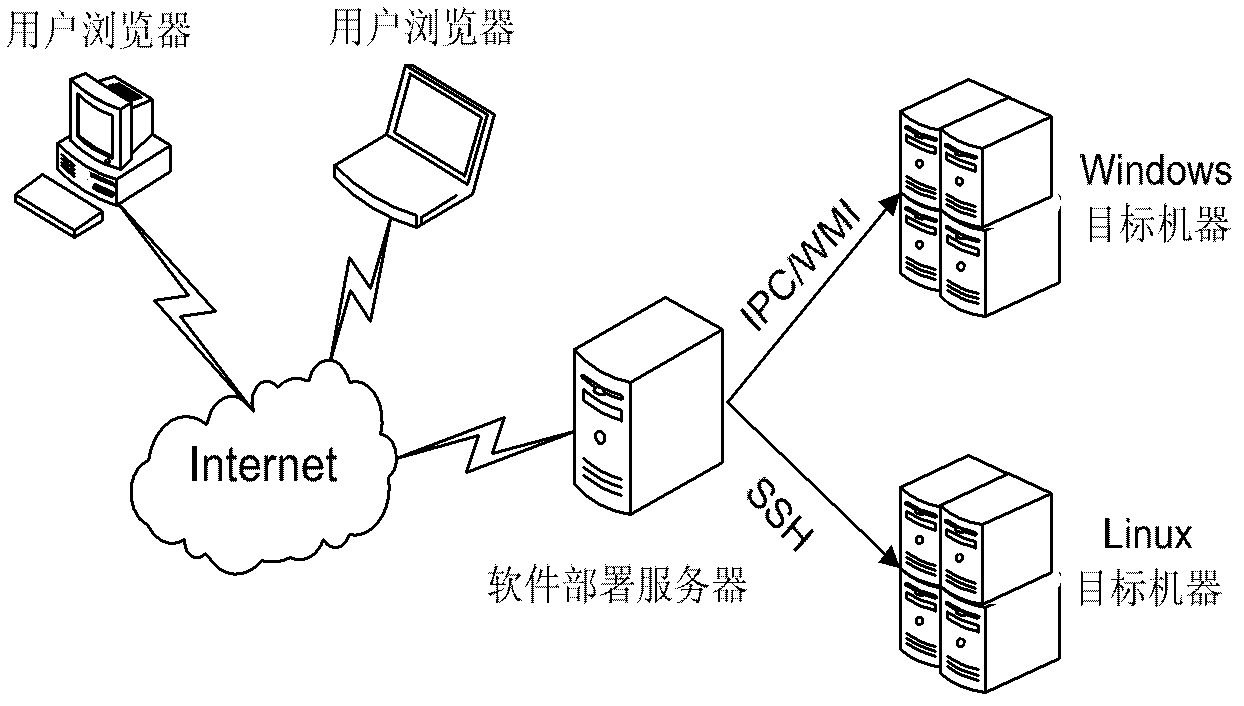
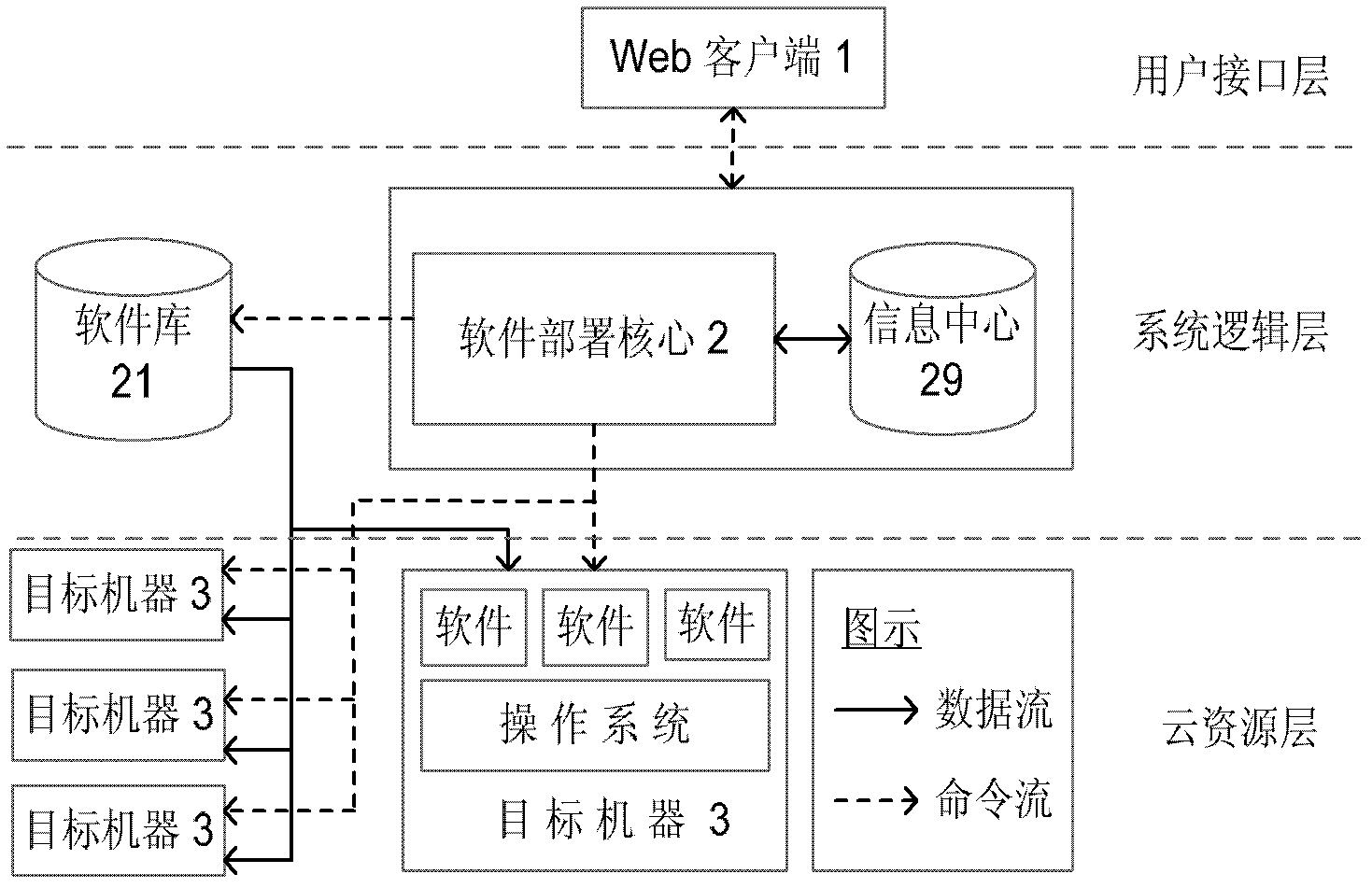
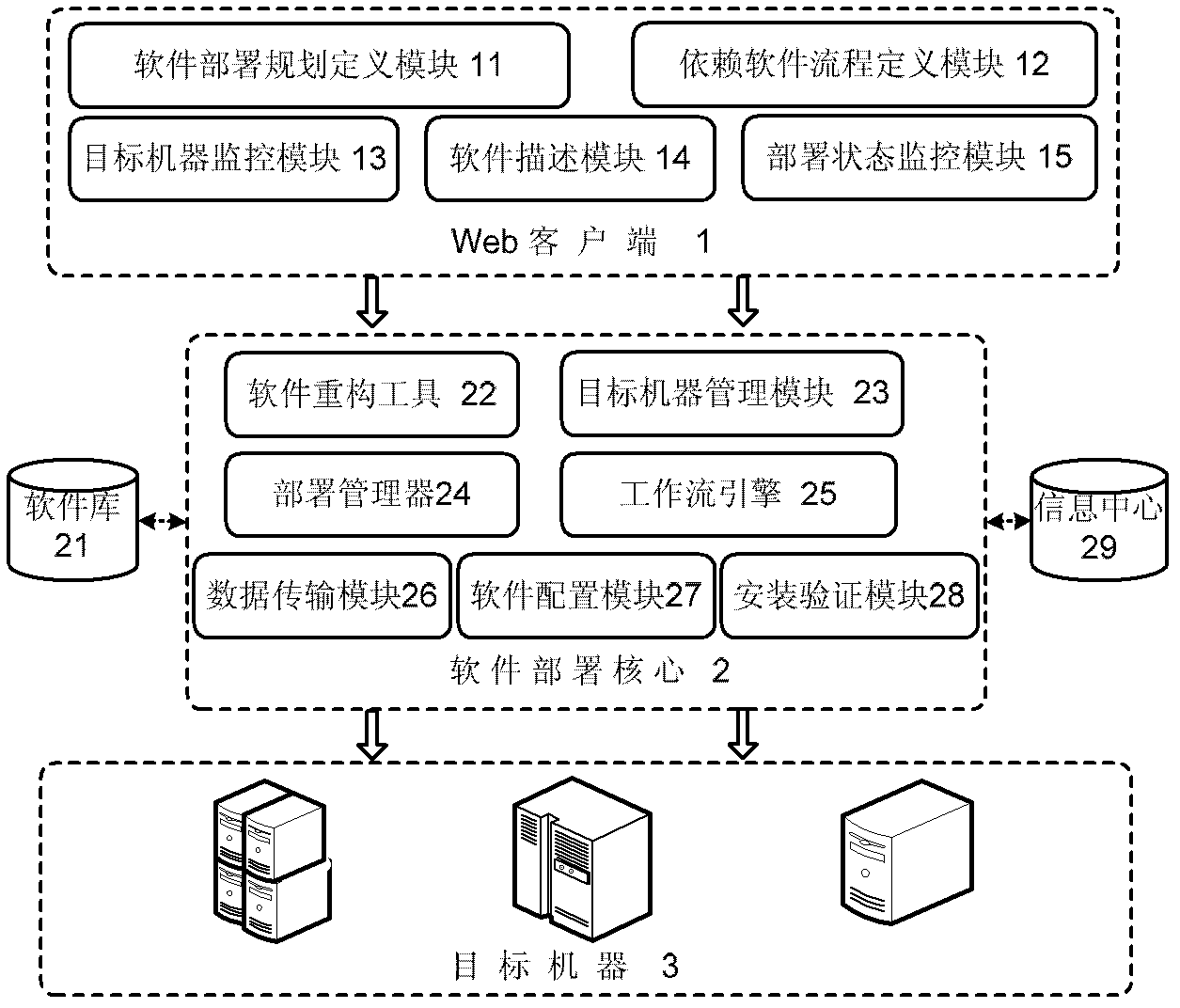
Software deployment system and deployment method based on workflow in cloud computing environment
InactiveCN102404381ASupport automatic deploymentImprove deployment efficiencyMultiprogramming arrangementsTransmissionMulti machineOperational system
The invention provides a software deployment system and a software deployment method based on workflow in a cloud computing environment. The software deployment system comprises a user interface layer, a system logic layer and a cloud resource layer, wherein the user interface layer is used for a user to describe a software deployment plan, define a dependence relation between software, inquiry the node state of a target machine, describe software attribute and monitor a software deployment process; the system logic layer is used for analyzing a soft deployment plan file submitted by the user and deploying a software packet on a remote cloud resource node according to the deployment plan of the user; and the cloud resource layer is used for deploying software. The system and the method have the advantages that automatic software deployment under a Windows operating system and a Linux operating system is supported; comprehensive and accurate verification of the software deployment is provided; on the basis of a workflow technology, automatic deployment dependent on the software is supported; multi-machine concurrent transmission and software packet deployment are supported; the deployment efficiency is improved; and automatic software inverse deployment is supported.
Owner:XI AN JIAOTONG UNIV
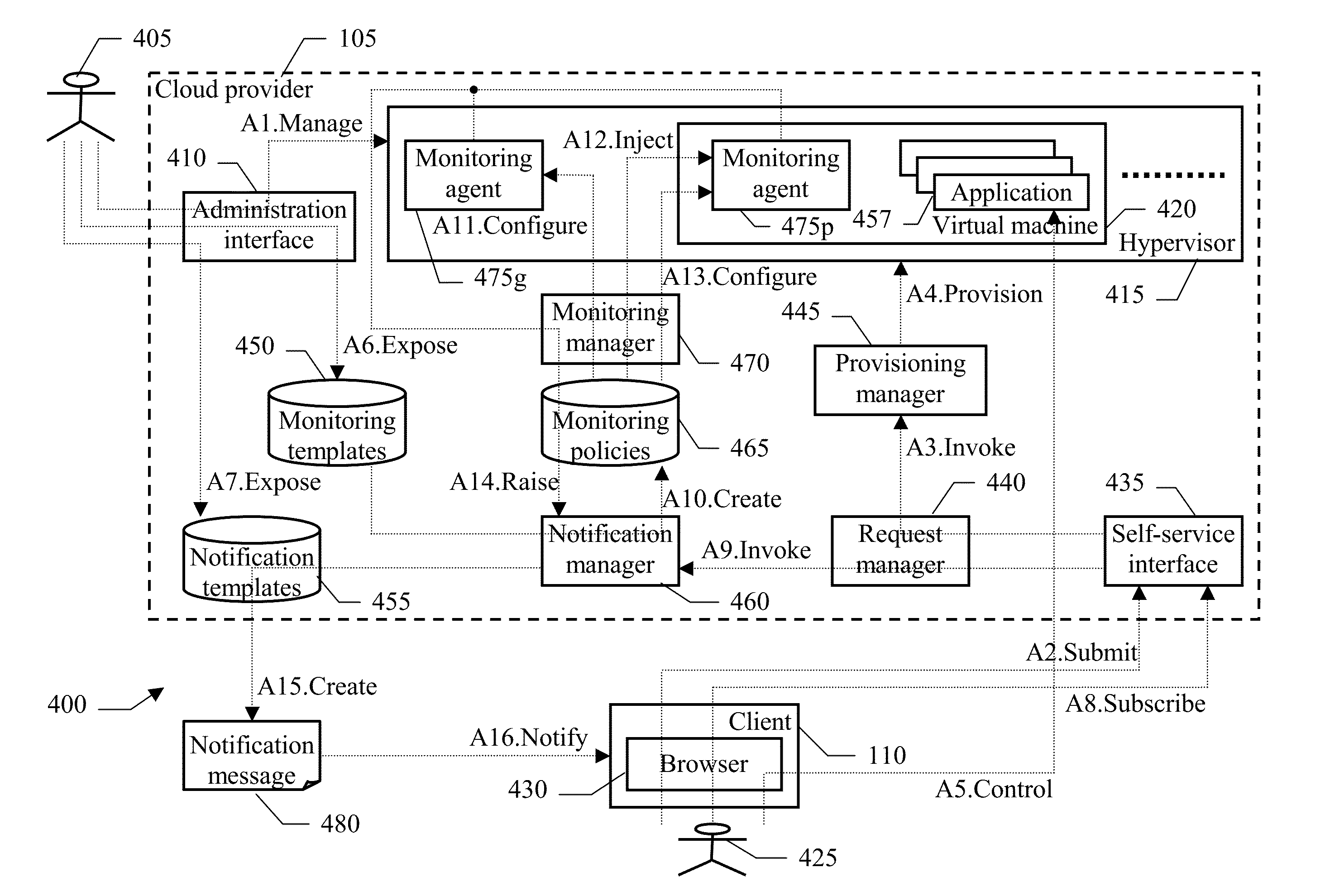
Monitoring resources in a cloud-computing environment
InactiveUS20130007265A1Error detection/correctionDigital computer detailsCloud resourcesComputer program
Provided are a computer program product, system, and method for monitoring resources in a cloud computing environment. A set of cloud resources is provisioned to a user of the cloud-computing environment. A set of private resources is provided for the user, each private resource being provisioned within the set of cloud resources of the user. Monitoring templates are exposed, each one for a corresponding type of a private resource to the user. A user subscription is received to at least one of the monitoring templates, wherein each of the subscribed monitoring templates is for one of the user private resources. A private monitoring agent is provided within the cloud resources of the user housing the private resource of the user to monitor the private resource according to the corresponding selected monitoring template.
Owner:AIRBNB
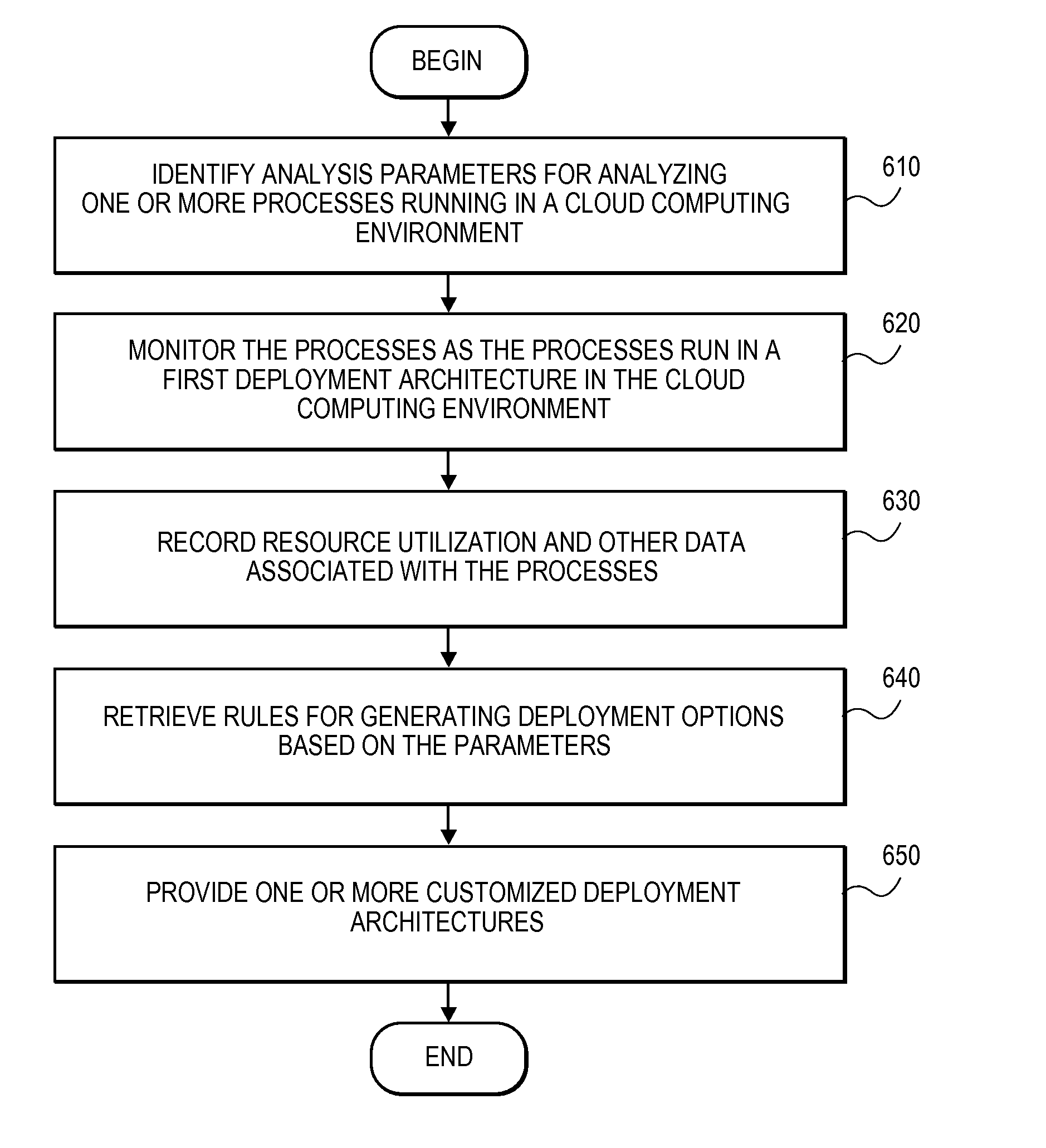
Methods and Systems for Providing Deployment Architectures in Cloud Computing Environments
ActiveUS20110213875A1Error detection/correctionDigital computer detailsDecision systemComputation process
A decision system for providing customized deployment architectures to users of a cloud computing environment. The decision system can identify one or more parameters for analyzing applications and processes running in a cloud, monitor the applications and processes executed in the cloud, and collect information such as usage of cloud resources, number and type of computing processes instantiated, software programs utilized by the computing processes. The decision system can then generate customized deployment architectures based on the collected information.
Owner:RED HAT
Method, apparatus and system pertaining to cloud computing
The present disclosure outlines a system, method, and apparatus for the design of network services, including the automatic sourcing an aggregating of data on the available resources. In a further aspect, the present disclosure outlines a system, method, and apparatus for the allocation of cloud resources. In yet a further aspect, the present disclosure outlines a system, method, and apparatus for redirecting traffic through an alternative gateway.
Owner:ANUTA NETWORKS
Methods and systems for monitoring cloud computing environments
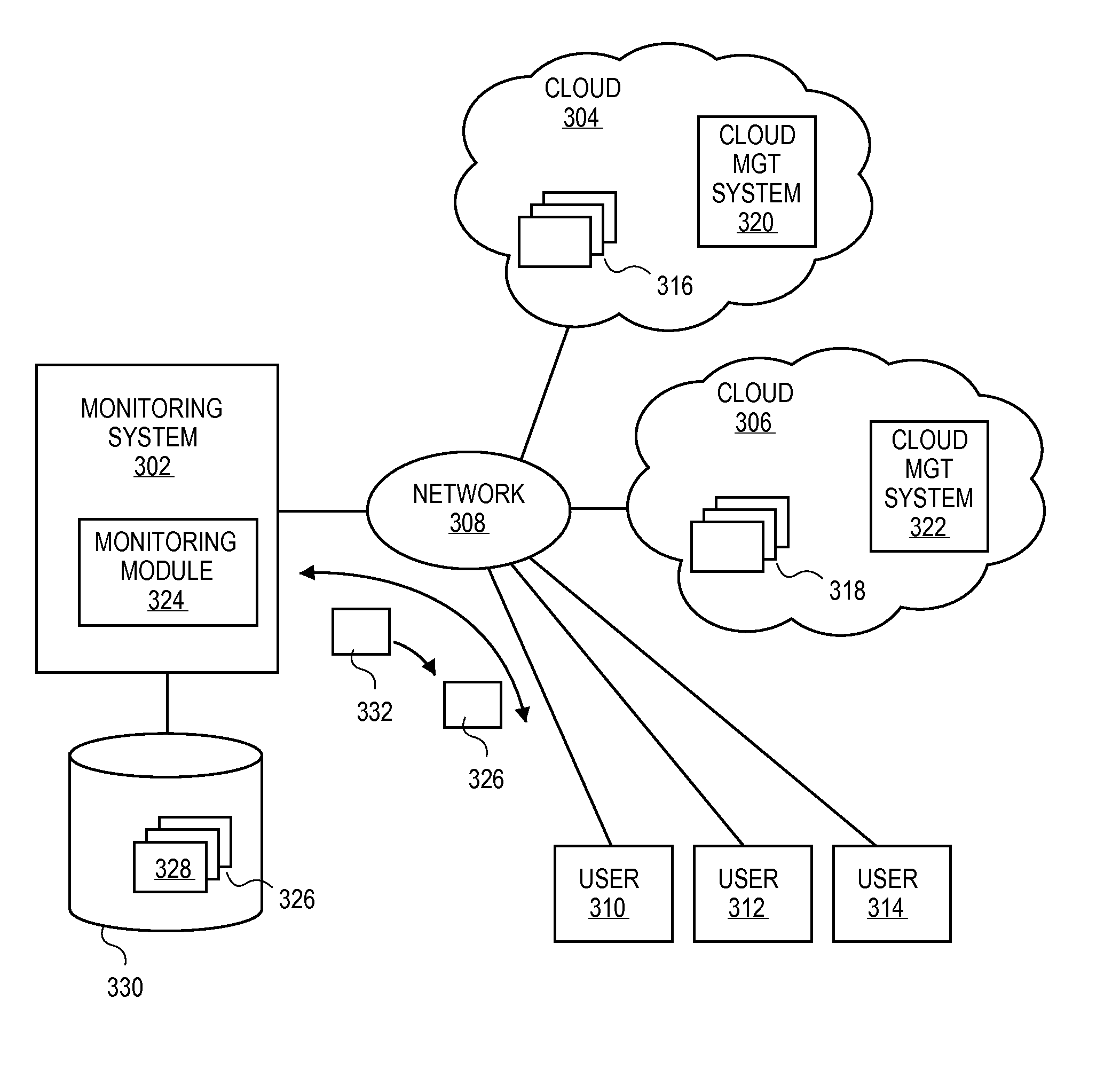
ActiveUS20110131499A1Input/output for user-computer interactionError detection/correctionMonitoring systemCloud resources
A monitoring system can provide monitoring services to users of cloud computing environment. The monitoring system can receive access information from users subscribing to the monitoring services. Once received, the monitoring system can access clouds utilizing the access information and monitor the computing processes instantiated in the clouds and associated with the user. The monitoring system can monitor the computing processes and collect information such as usage of cloud resources, number and type of computing processes instantiated, software programs utilized by the computing processes.
Owner:RED HAT
Virtualized infrastructure platform for cloud data centers
ActiveCN103281306AEnsure safetyFunction extension of scheduling controlTransmissionSoftware simulation/interpretation/emulationInteraction systemsPython language
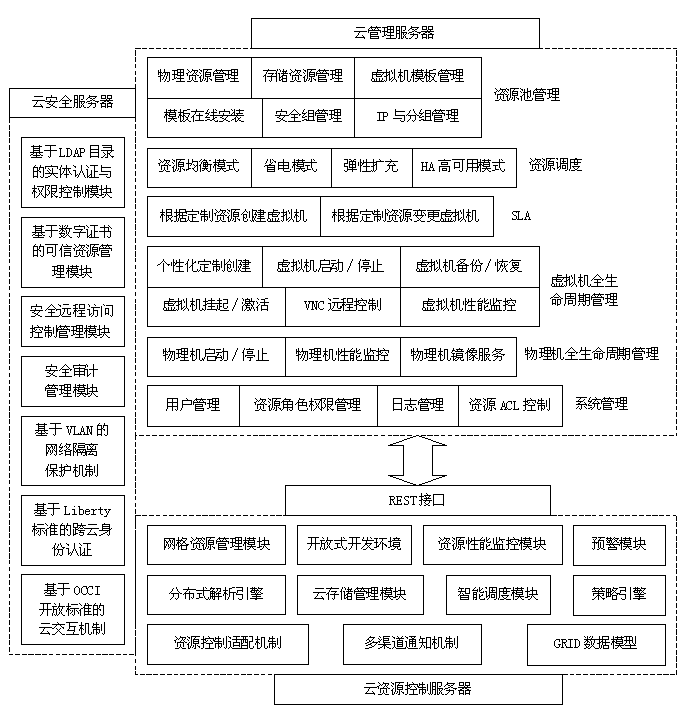
The invention discloses a virtualized infrastructure platform for cloud data centers, which comprises a cloud management server, a cloud resource control server and a cloud security server, the whole life cycles of various computational resources of a cloud platform are monitored and managed by the cloud management server, the various resources of the physical layer of the cloud platform are scheduled, controlled and managed by the cloud resource control server, and the cloud security server is used for establishing a cloud computation security control system in a private cloud and a secure interaction system for the private cloud and a public cloud; the cloud management server is integrated with the cloud resource control server through REST interfaces, and the cloud security server is respectively connected with the cloud management server and the cloud resource control server. The virtualized infrastructure platform for cloud data centers can realize security gateway-based unified remote virtual machine control and management, providing administrators with a unified access entrance for the management of virtual resources, and moreover, by means of directory service, the virtualized infrastructure platform for cloud data centers checks the validity of user identities; and a user can use the Python language to extend the resource scheduling control function.
Owner:INFORMATION & TELECOMM COMPANY SICHUAN ELECTRIC POWER
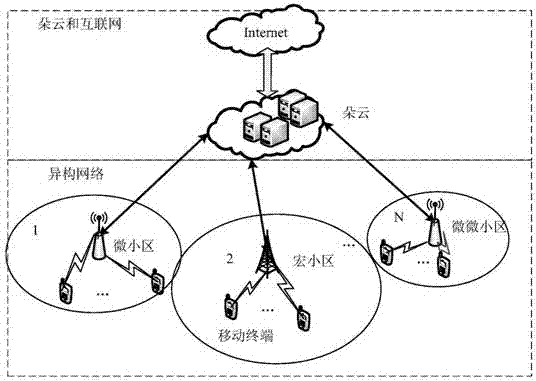
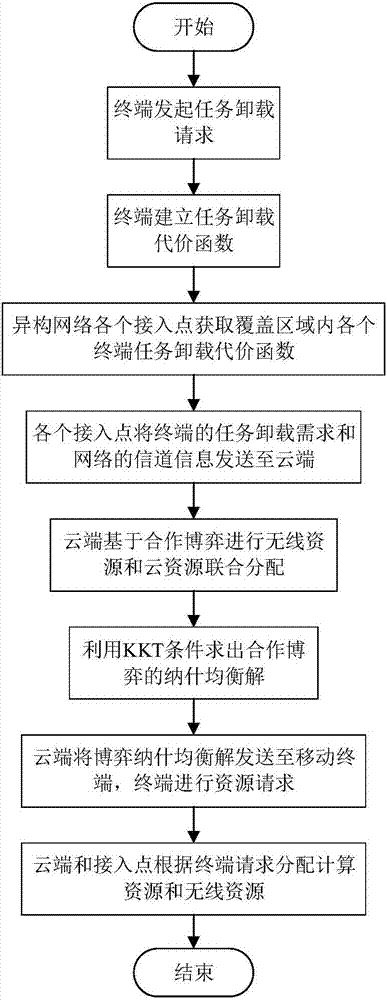
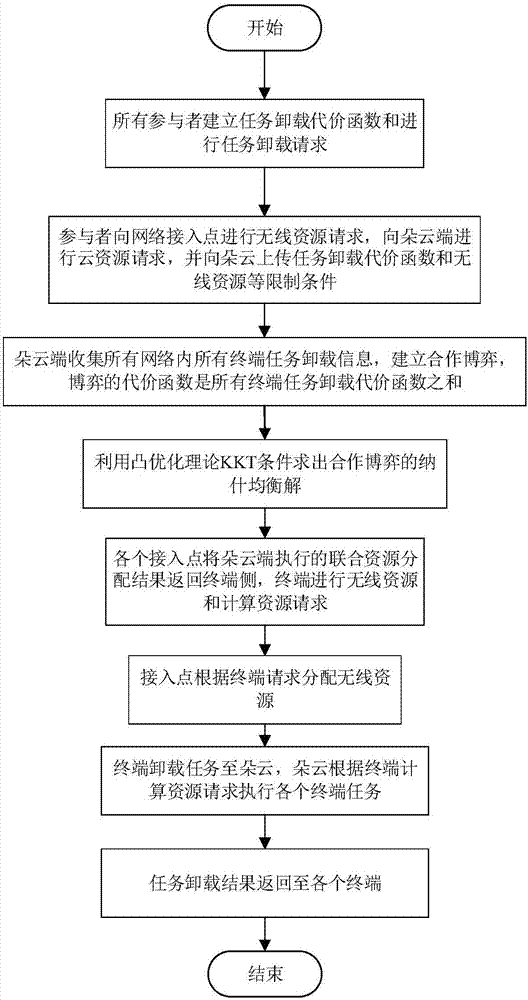
Wireless resource and cloud resource combined distribution method in MEC
ActiveCN107249218AGuaranteed real-timeSatisfy task offloading requirementsPower managementData switching networksDistribution methodHeterogeneous network
The invention discloses a wireless resource and cloud resource combined distribution method in an MEC. The method comprises that (1) a terminal in the MEC initiates a task uninstalling request, and a task uninstalling cost function of the terminal is established; (2) different access points in the heterogeneous network obtains the task uninstalling cost functions of different terminals in a coverage area, and sends the task uninstalling requests of the terminals and channel information of the network to cloudlets; (3) the cloudlets distribute wireless and cloud resources in a combined manner on the basis of a cooperative game, obtains a Nash equilibrium solution via KKT conditions, and sends the Nash equilibrium solution to the terminals; (4) each terminal requests the cloudlets and the access points for computing and wireless resources according to the Nash equilibrium solution; and (5) the cloudlets and the access points distribute the computing and wireless resources according to the request of the terminal. On the basis of the cooperative game, limited computing resources in the cloudlets are utilized fully, the instantaneity of the tasks of the terminals is ensured while minimizing task uninstalling cost of all the terminals is taken as the objective, and the task uninstalling requirements of the different mobile terminals are met.
Owner:SOUTHEAST UNIV
Cross provider security management functionality within a cloud service brokerage platform
ActiveUS9832205B2Good serviceEfficient and effectiveFinanceProgram loading/initiatingSystems managementHardware security module
Implementation of cross provider security in accordance with the disclosures made herein enables users of a system (e.g., a cloud services brokerage platform) in a cloud environment provides for system-managed provisioning and management of keys to cloud resources thereby allowing the user to manage data security and enable secured access to their cloud resources. To this end, cross provider security management functionality in accordance with the disclosures made herein can include provisioning system-generated keys across different regions in a provider, provisioning cloud brokerage system-generated keys across different providers; and associating (i.e., managing) the keys from the system to a hardware security module. The keys can be managed by / though a variety of different resources (e.g., brokering system, VDC, user group concepts, etc).
Owner:HCL TECH LTD
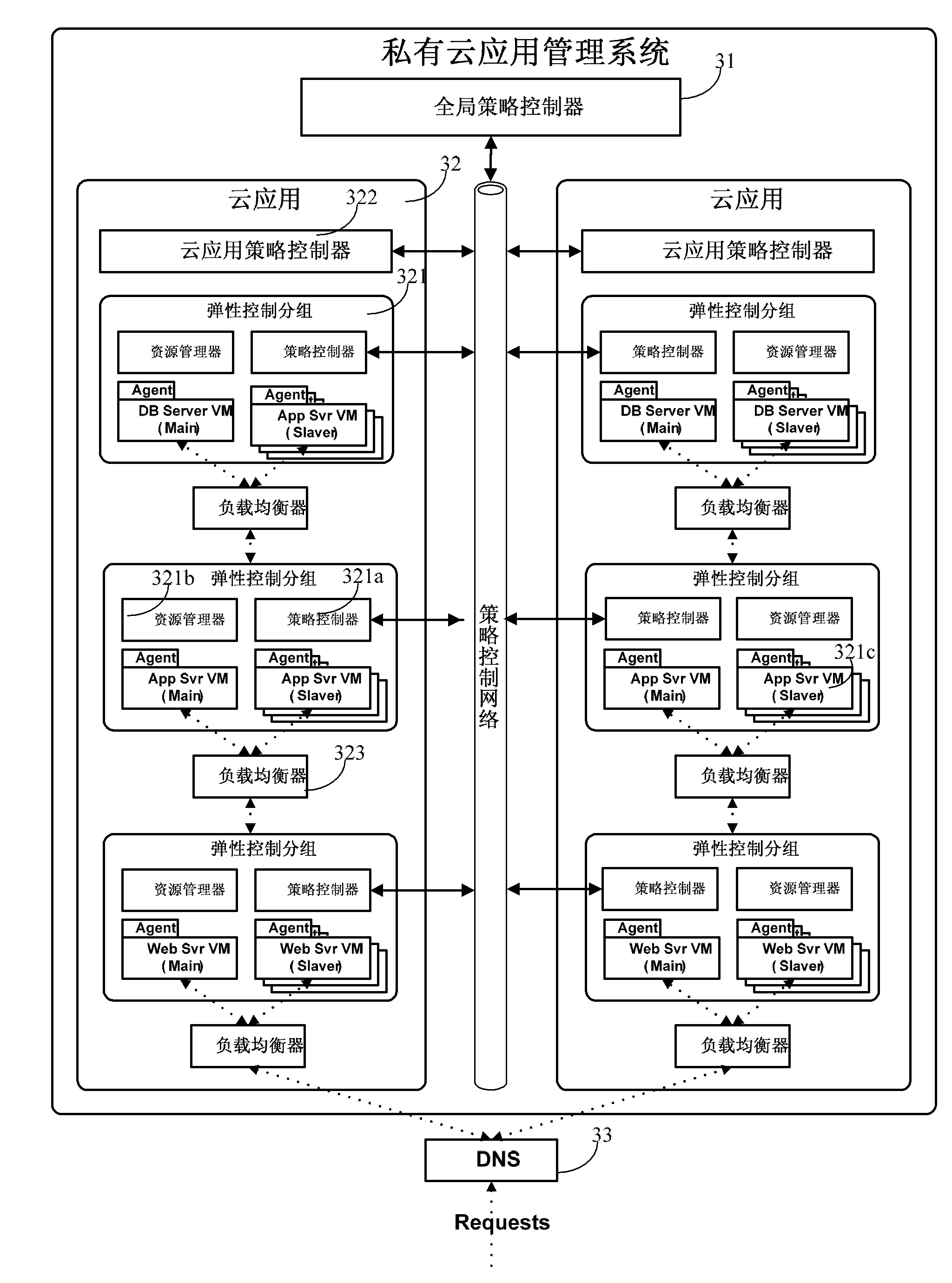
Resource allocation system and resource allocation method in private cloud environment
InactiveCN101986274AImprove resource utilizationImprove maintenance efficiencyResource allocationResource allocation systemsCloud resources
The invention relates to a resource allocation system in a private cloud environment. The system comprises a global policy controller, cloud application policy controllers and group policy controllers, wherein a resource manager interacts with a resource exploring proxy, receives index data, judges whether an alarm is generated for the index data or not according to alarm conditions, and if so, submits the alarm to a policy control network; the group policy controller first processes the alarm, generates a resource adjusting plan if the alarm can be processed, and reports the alarm to the cloud application policy controller if the alarm cannot be processed; the cloud application policy controller processes the received alarm, generates the resource adjusting plan if the alarm can be processed, and reports the alarm to the global policy controller if the alarm cannot be processed; the global policy controller processes the received alarm and generates the resource adjusting plan; the policy control network returns the resource adjusting plan to the resource manager; and the resource manager executes the resource adjusting plan. By constructing graded control policies and assisting coordination mechanisms among the control policies in different grades, the invention effectively improves the utilization rate of private cloud resource.
Owner:NEUSOFT CORP
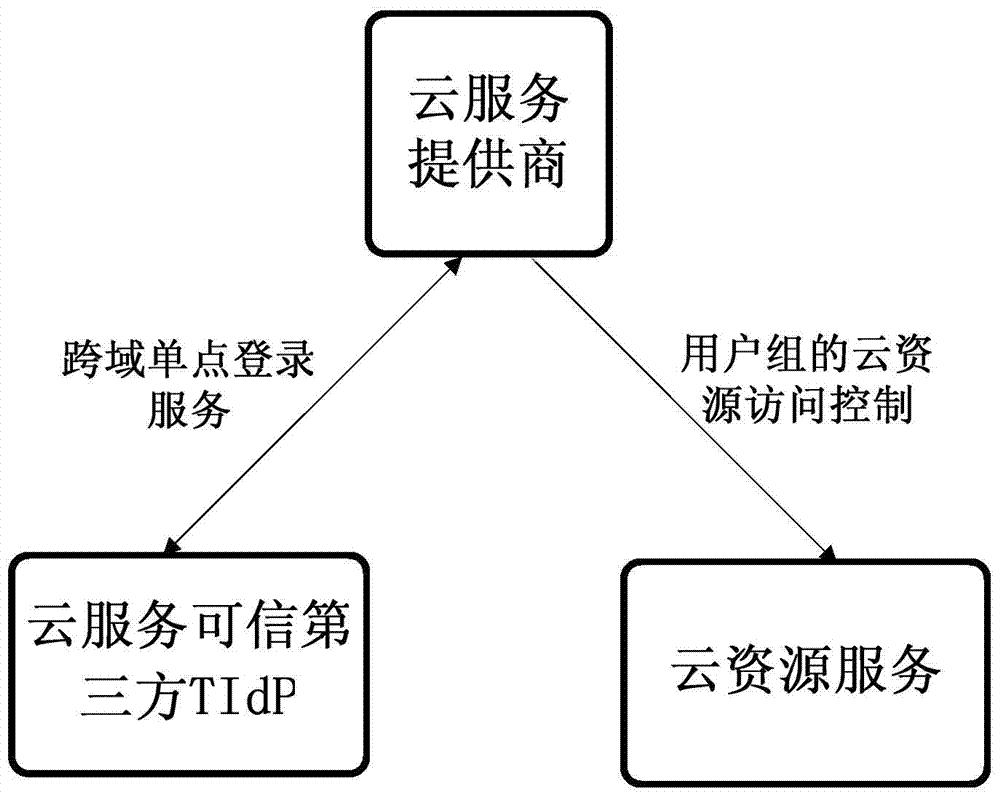
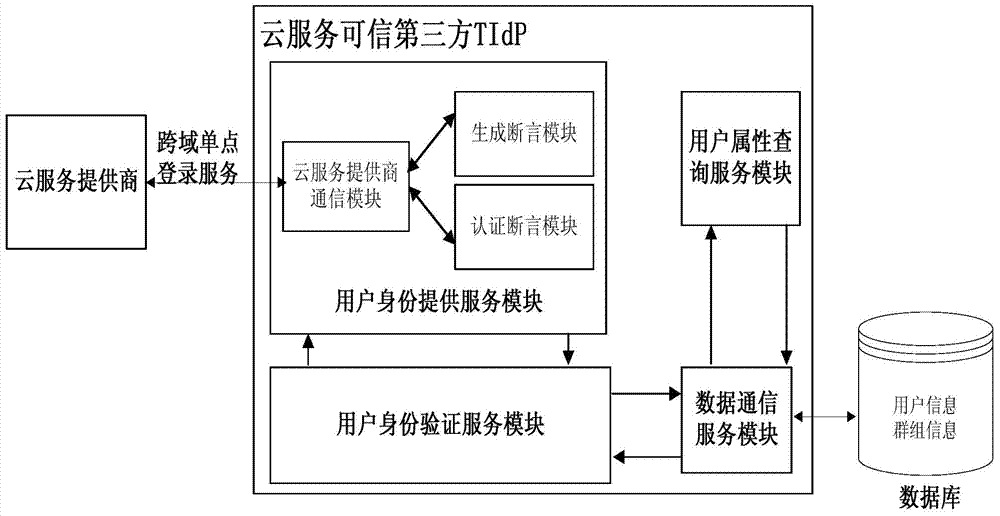
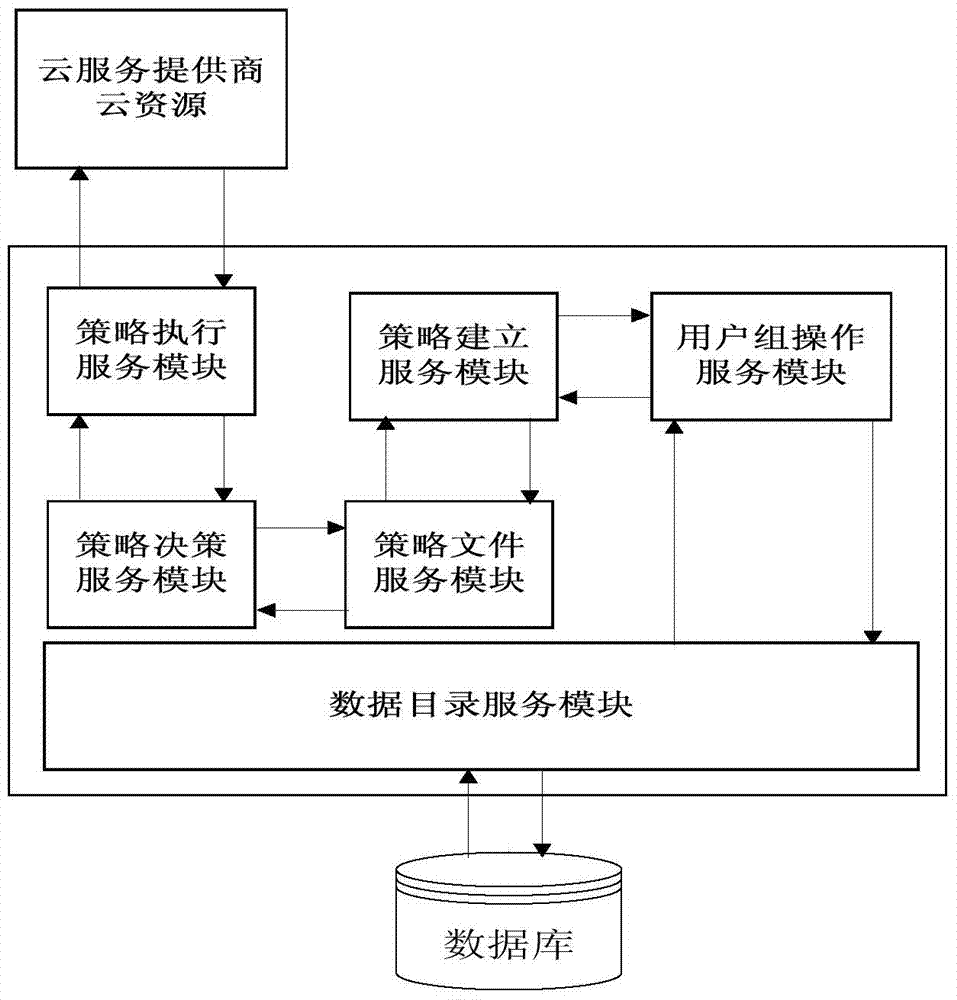
Identity escrow and authentication cloud resource access control system and method for multiple tenants
InactiveCN103532981AImprove qualityReduce management costsUser identity/authority verificationThird partyControl system
The invention provides an identity escrow and authentication cloud resource access control system and an identity escrow and authentication cloud resource access control method for multiple tenants. The system is characterized in that the cloud service business of a cloud service provider is divided into two parts of an identity authentication permission part and a cloud resource access control part, wherein the business of the identity authentication permission part is hosted by a credible third party TIdP of the cloud service, and the TIdP is in charge of governing hosted user information and group information of the tenant, completes the user identity authentication work of a hosting user and generates cross-domain security credential service containing identity recognition information; the cloud resource access control part is responsible for assigning corresponding permission for a group where the user is located, and analyzes the access request of the user and implements an access control decision according to the existing resource access control strategy when the user accesses to the cloud resource, so as to achieve safety access control over the cloud resource.
Owner:INST OF INFORMATION ENG CAS
Methods and systems for providing deployment architectures in cloud computing environments
ActiveUS8255529B2Error detection/correctionMultiple digital computer combinationsDecision systemCloud resources
A decision system for providing customized deployment architectures to users of a cloud computing environment. The decision system can identify one or more parameters for analyzing applications and processes running in a cloud, monitor the applications and processes executed in the cloud, and collect information such as usage of cloud resources, number and type of computing processes instantiated, software programs utilized by the computing processes. The decision system can then generate customized deployment architectures based on the collected information.
Owner:RED HAT
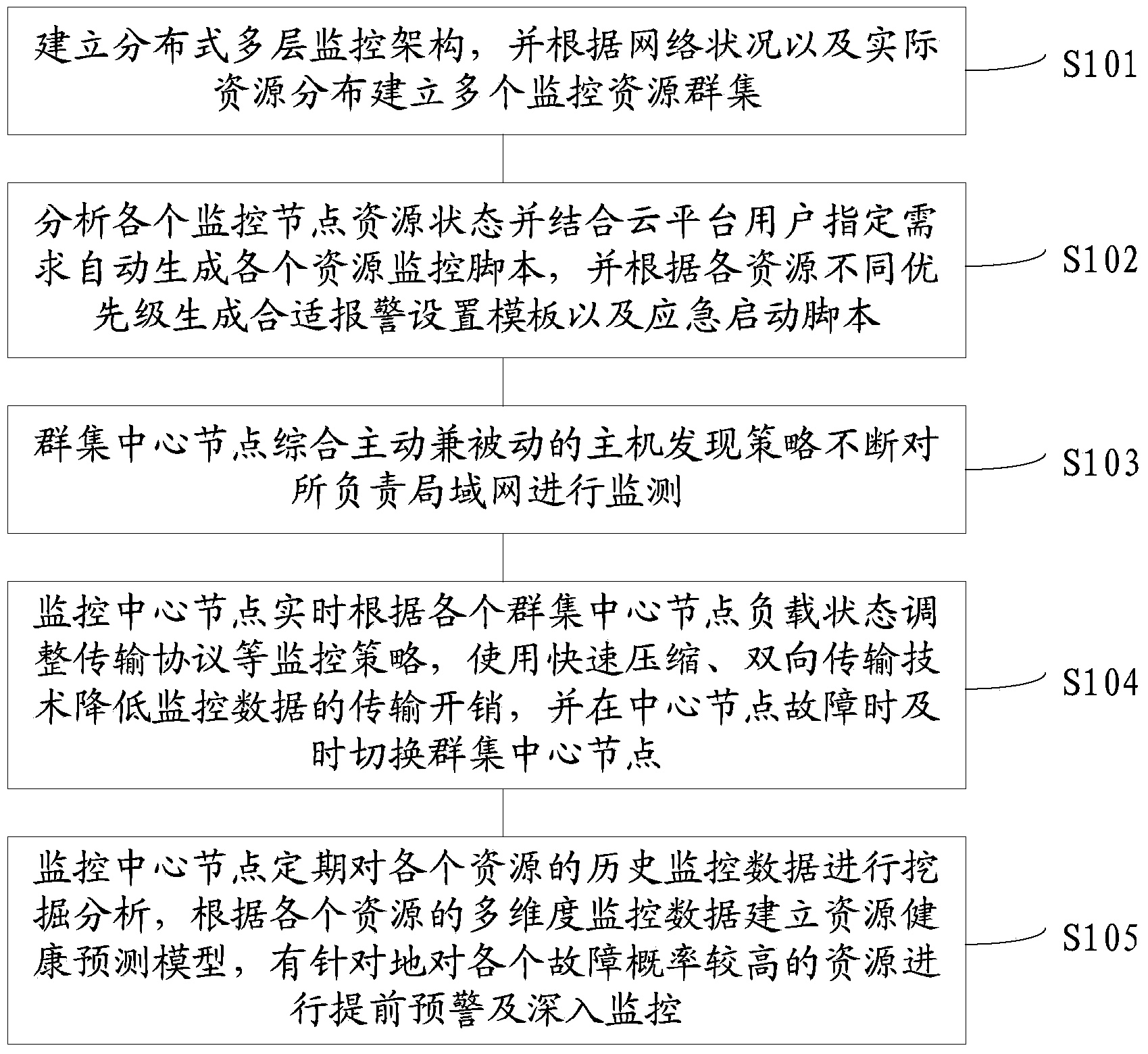
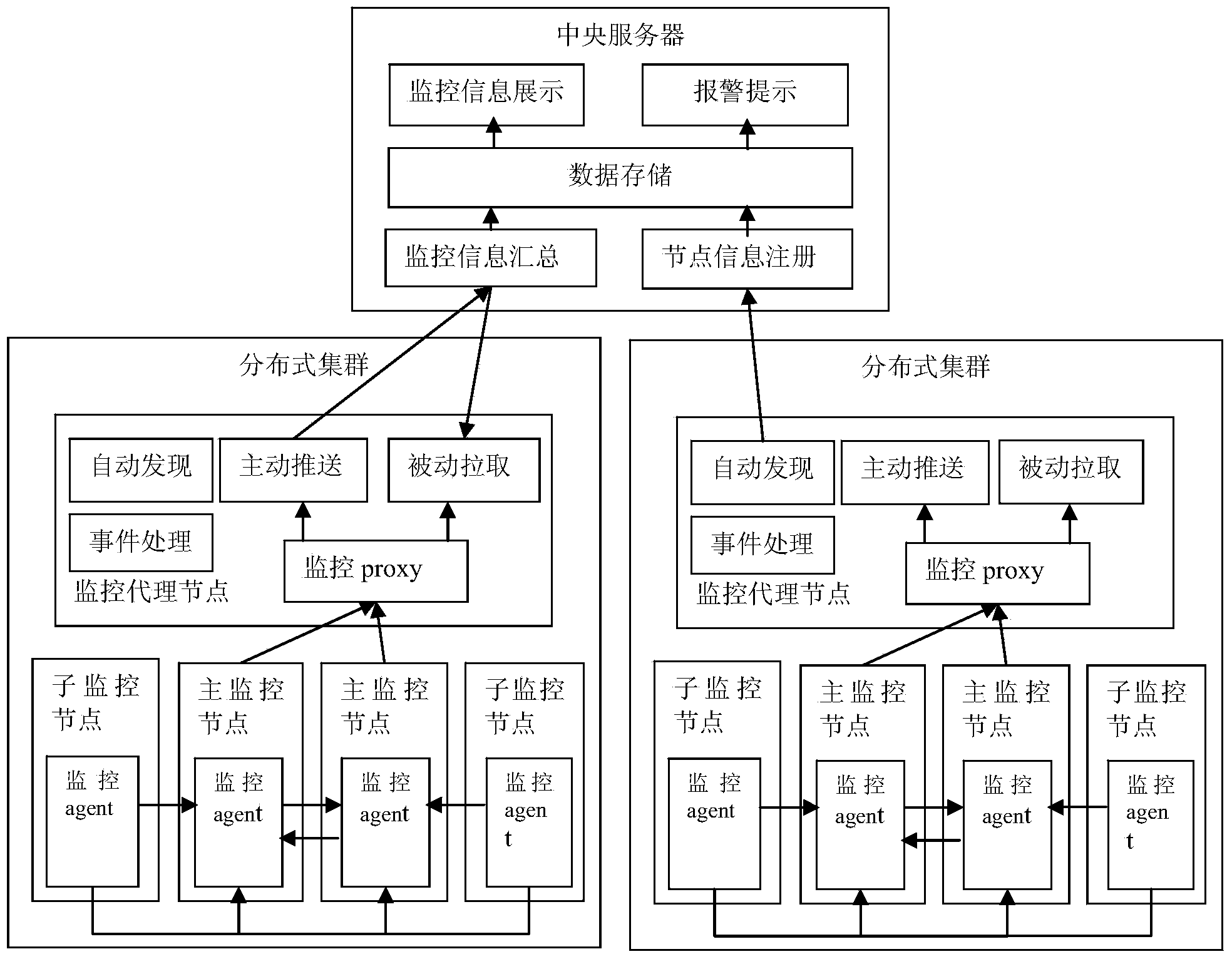
Multi-hierarchy load balancing cloud resource monitoring method
ActiveCN104184819ANo interruptionQuick restartTransmissionTransmission protocolBidirectional transmission
The invention discloses a multi-hierarchy load balancing cloud resource monitoring method. The multi-hierarchy load balancing cloud resource monitoring method includes the steps that a distributed type multi-layer monitoring framework is set up; the resource states of all monitoring nodes are analyzed, and all resource monitoring scripts are automatically generated according to cloud platform user designated requirements; cluster center nodes integrate active and passive mainframe discovery strategies to continuously monitor local area networks which the cluster center nodes are responsible for; a monitoring center node adjusts monitoring strategies such as transmission protocols according to the load states of all the cluster center nodes, the transmission expenditure of monitoring data is reduced through a fast-compression and bidirectional-transmission technology, and the cluster center nodes are switched in time when the monitoring center node breaks down; the monitoring center node conducts mining and analyzing on historical monitoring data of all resources regularly and conducts warning and deep monitoring in advance. According to the multi-hierarchy load balancing cloud resource monitoring method, new cluster nodes are automatically found according to the features of the large-scale distributed type cloud environment, a load balancing technology is used, a powerful fault-tolerant mechanism and a powerful event engine are adopted, and therefore the high reliability and safety of the cloud environment are ensured.
Owner:CITY CLOUD TECH HANGZHOU CO LTD
Method and system for secure resource management utilizing blockchain and smart contracts
ActiveUS20190319861A1Lower capability requirementsEasy to controlEncryption apparatus with shift registers/memoriesPayment circuitsComputer networkEdge server
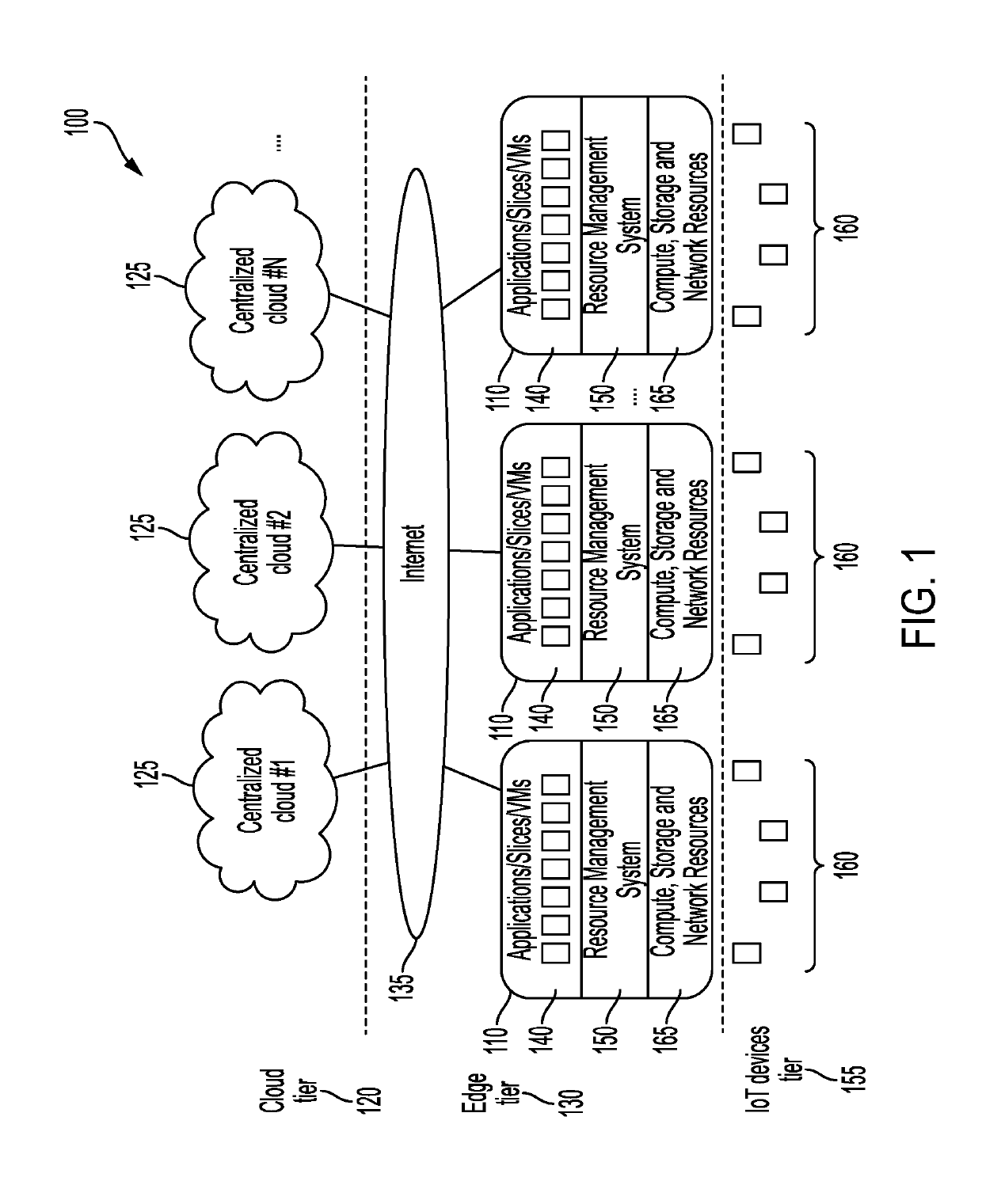
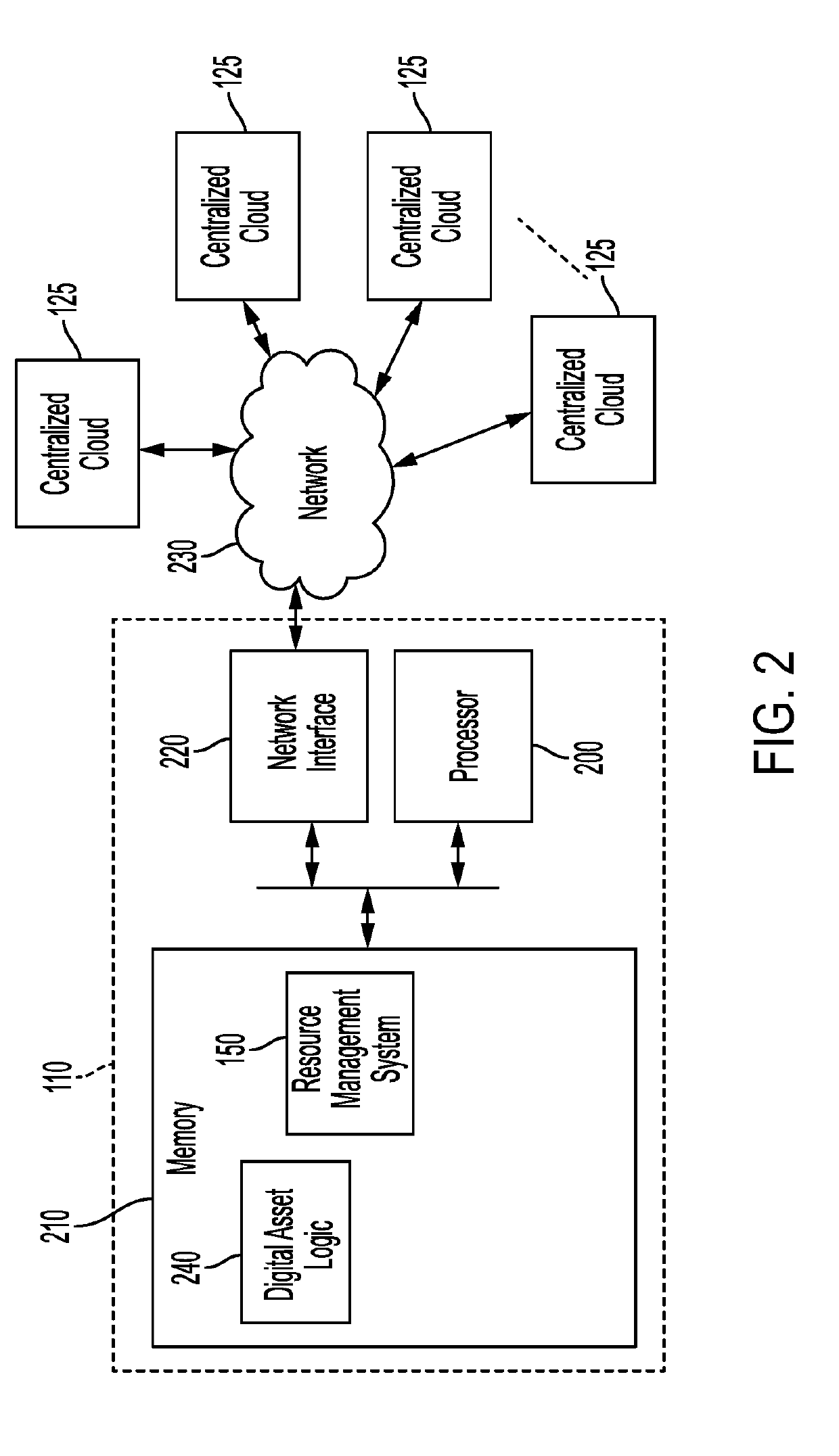
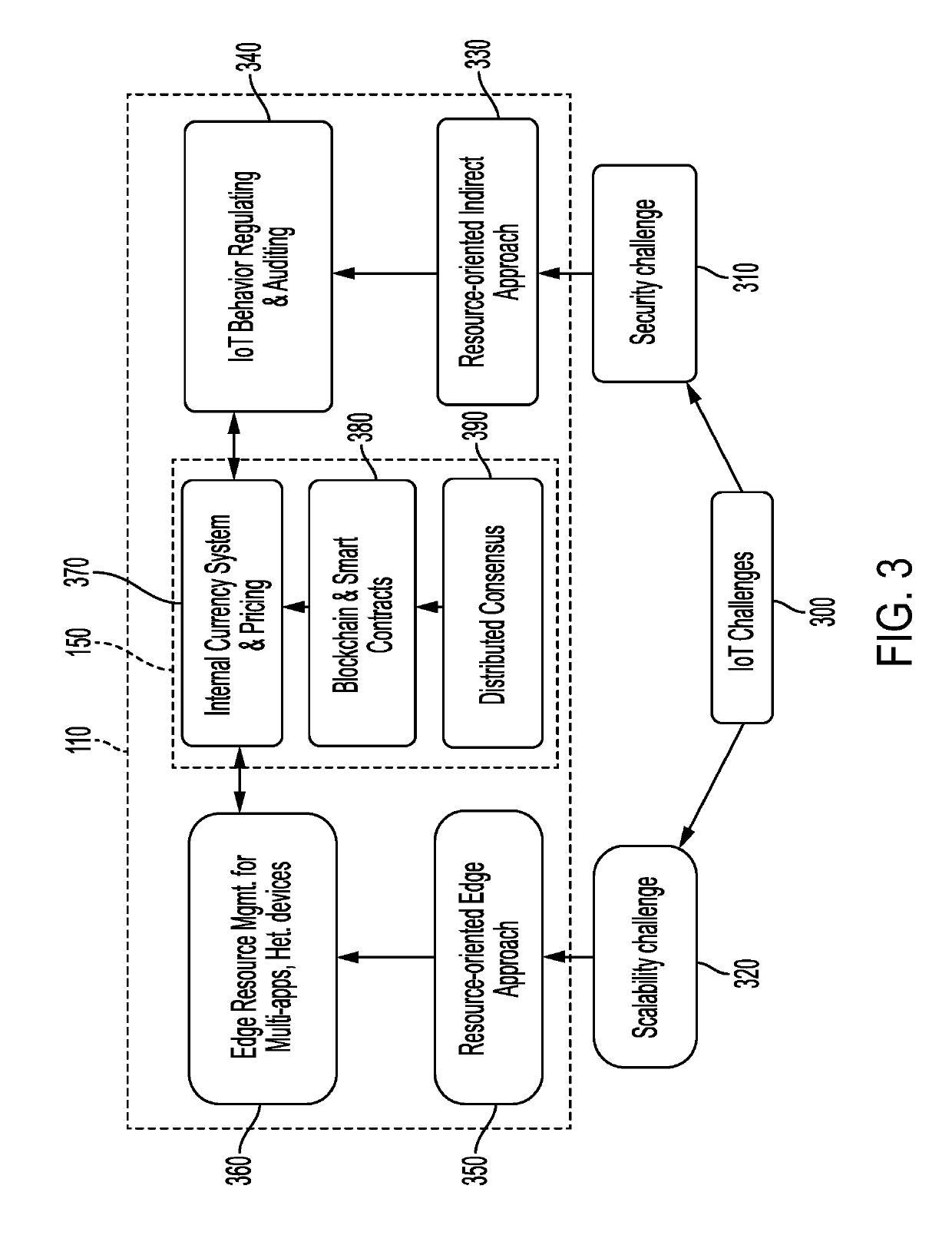
This disclosure relates to a resource management system of a computing network. The design of the resource management system is an edge-Internet of Things (IoT) framework based on blockchain and smart contracts. The resource management system integrates a permissioned blockchain to link the edge cloud resources with each account for an IoT device, resource usage, and behavior of the IoT device. The resource management system uses credit-based resource management to control the resource of the IoT device that can be obtained from the edge server. Smart contracts are used to regulate behavior of the IoT device and enforce policies.
Owner:UNIVERSITY OF MISSOURI
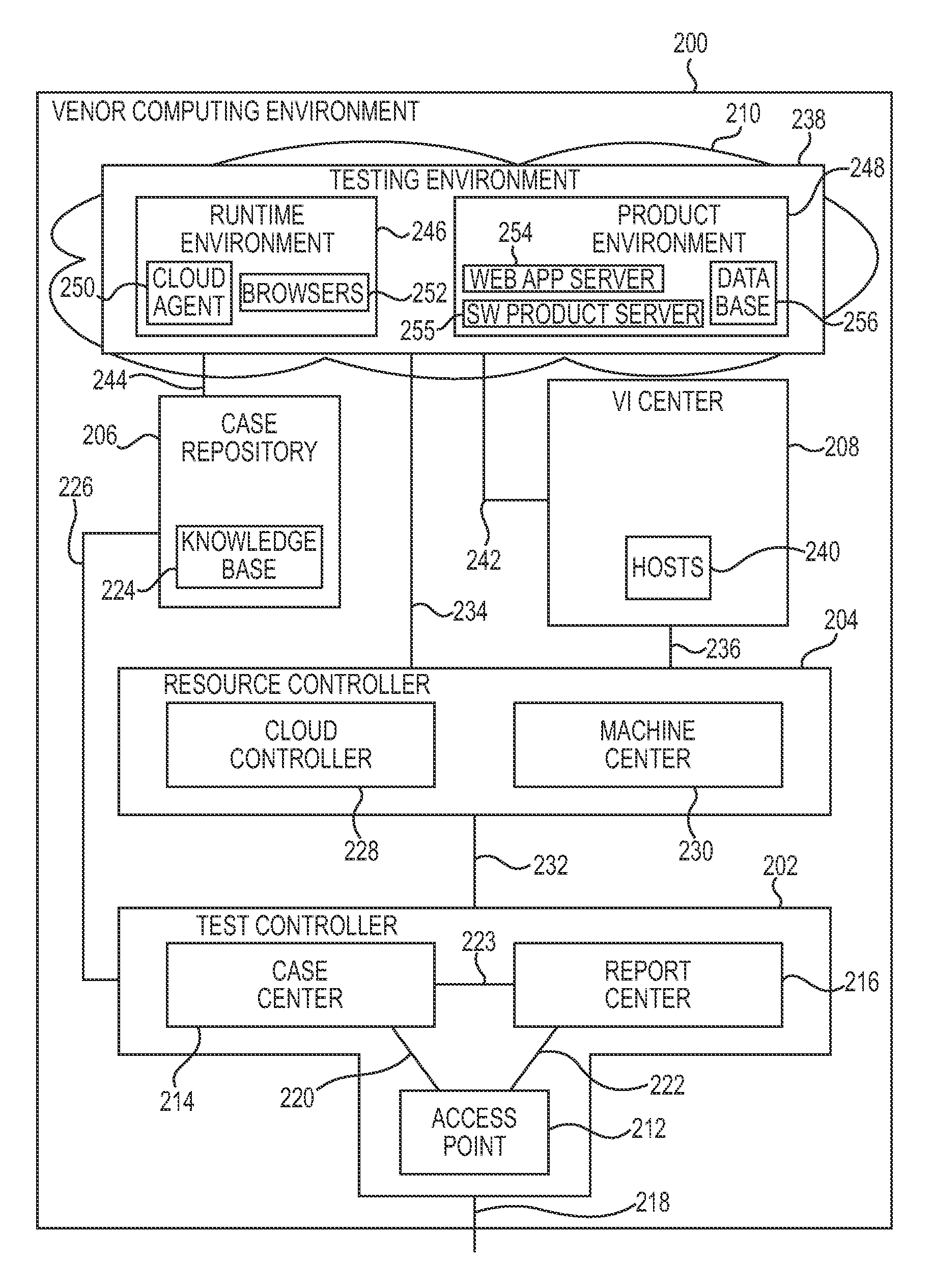
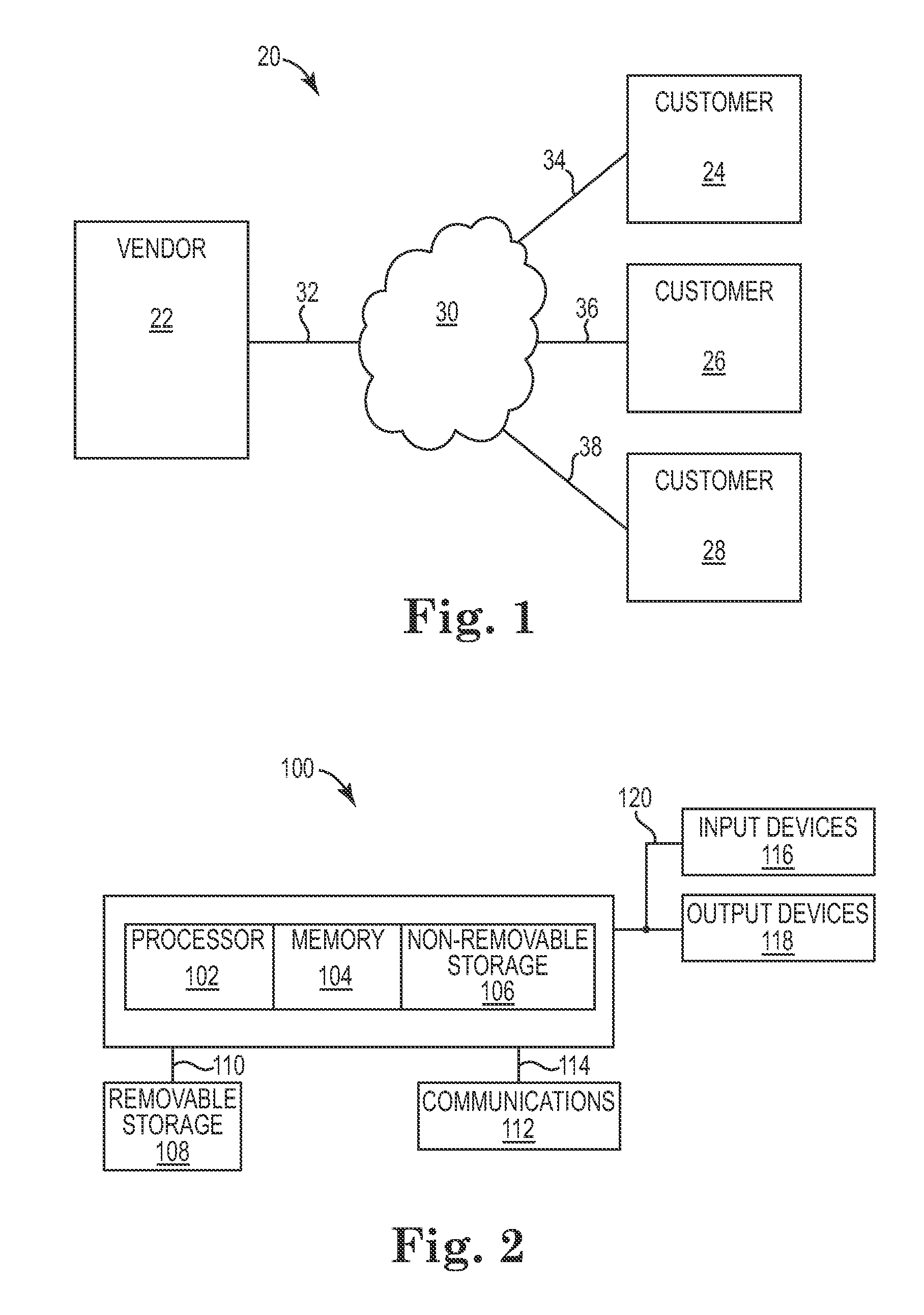
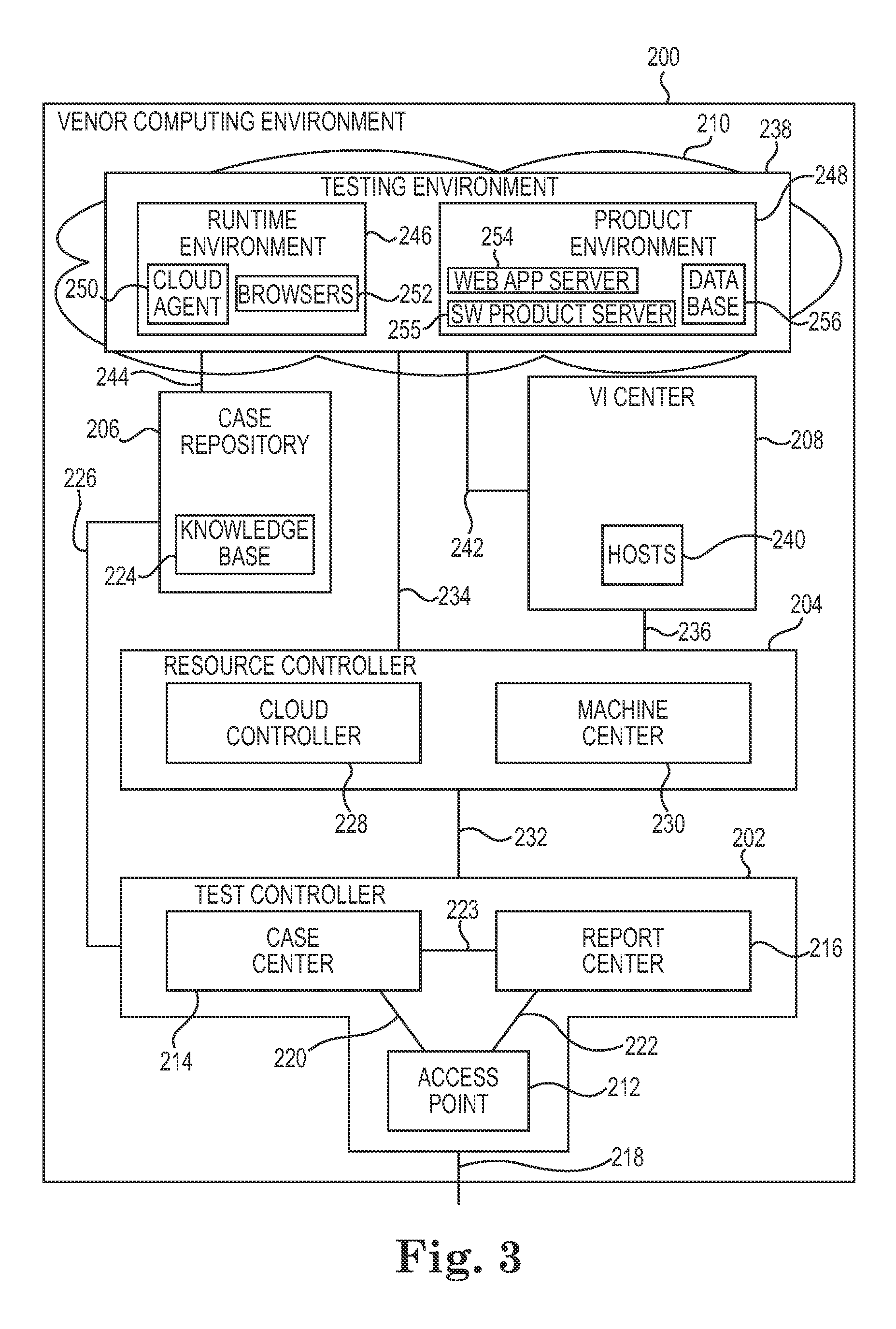
System including a vendor computer system for testing software products in a cloud network
A system including a vendor computer system. The vendor computer includes a test controller and a resource controller. The test controller is configured to provide a central access point to the vendor computer system and to manage test cases. The resource controller is configured to control testing of software products. The resource controller allocates cloud resources in a cloud network to test the software products via the test case.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com