Patents
Literature
138 results about "Group Policy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
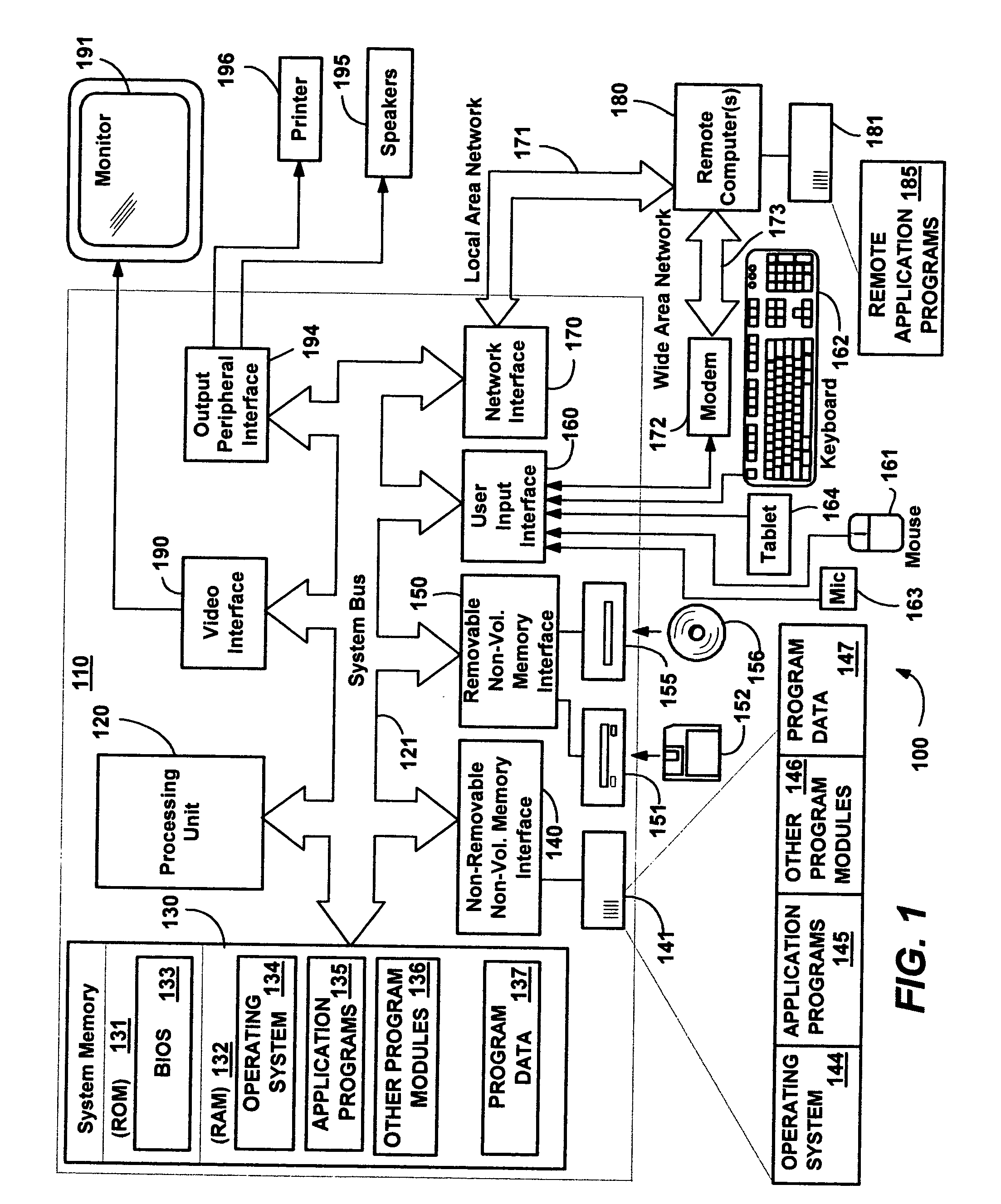
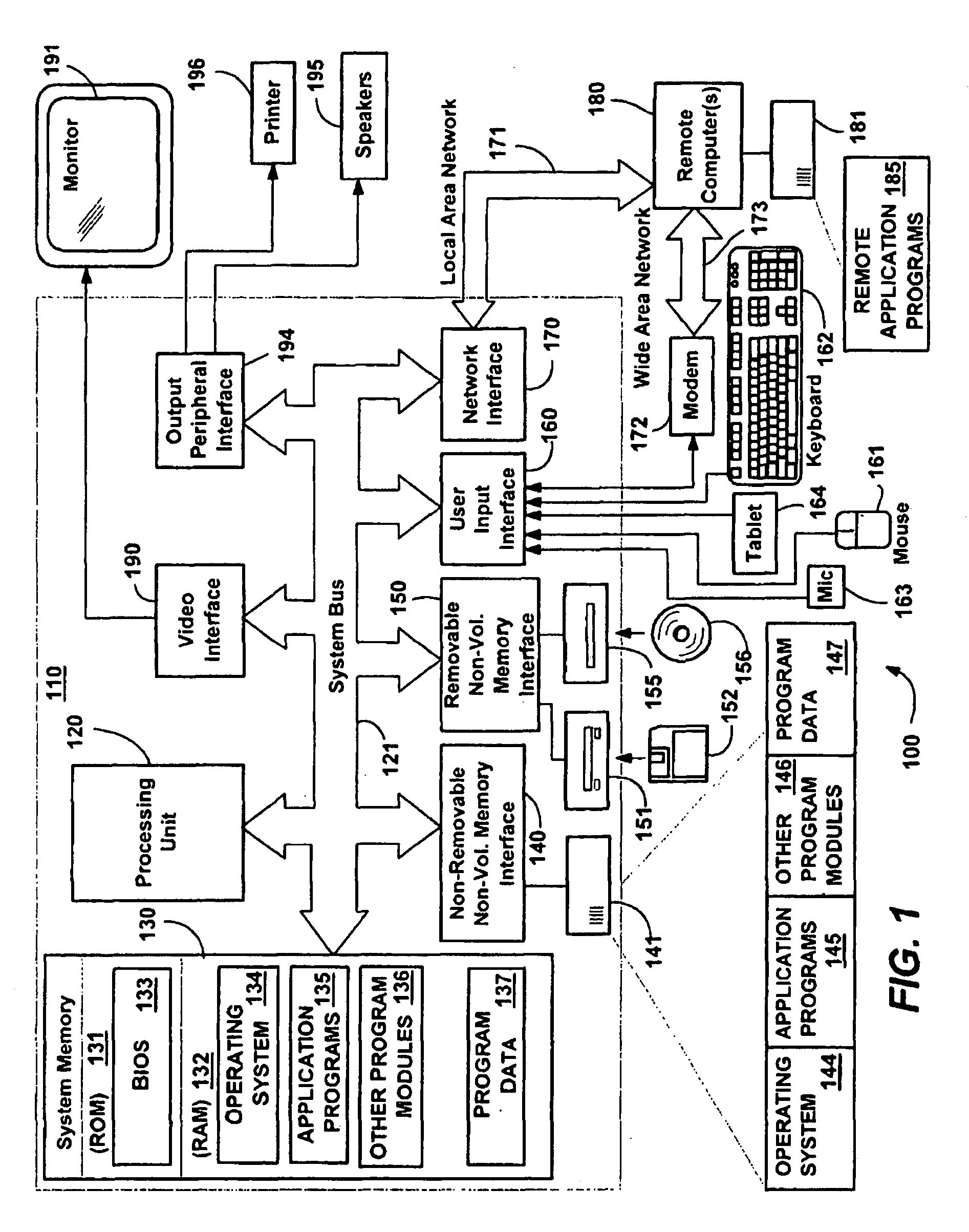
Group Policy is a feature of the Microsoft Windows NT family of operating systems that controls the working environment of user accounts and computer accounts. Group Policy provides centralized management and configuration of operating systems, applications, and users' settings in an Active Directory environment. A set of Group Policy configurations is called a Group Policy Object (GPO). A version of Group Policy called Local Group Policy (LGPO or LocalGPO) allows Group Policy Object management without Active Directory on standalone computers.
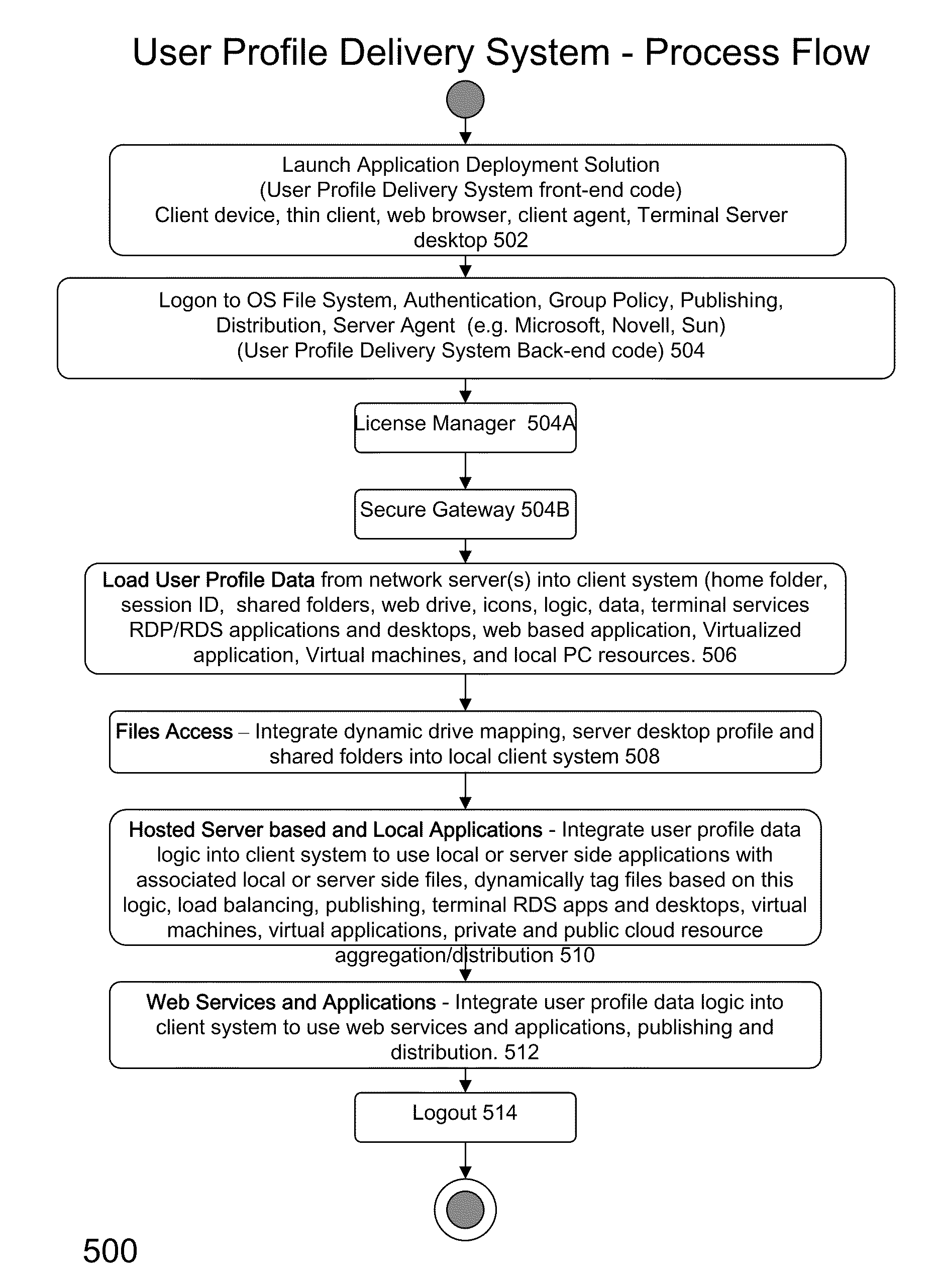
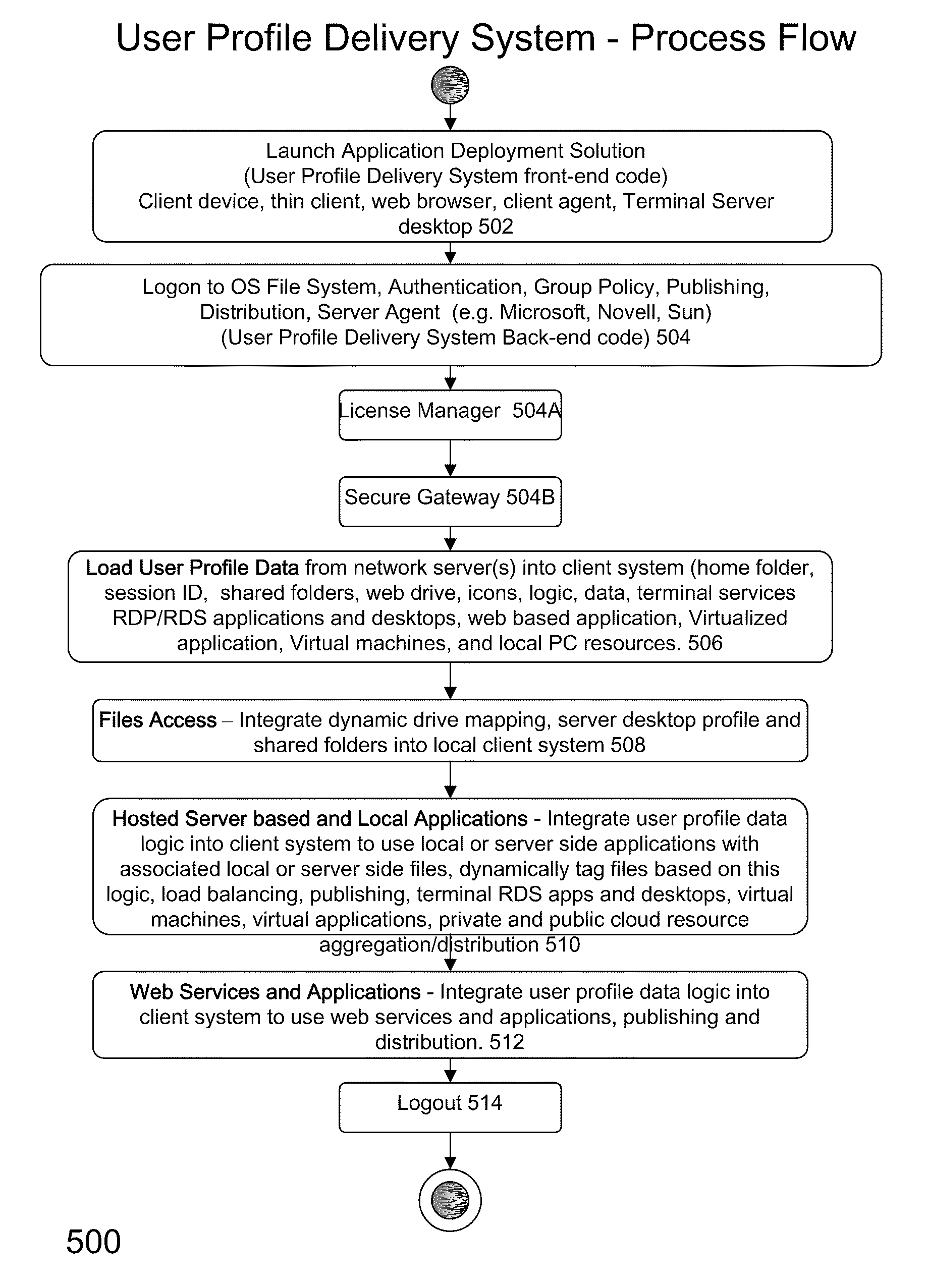
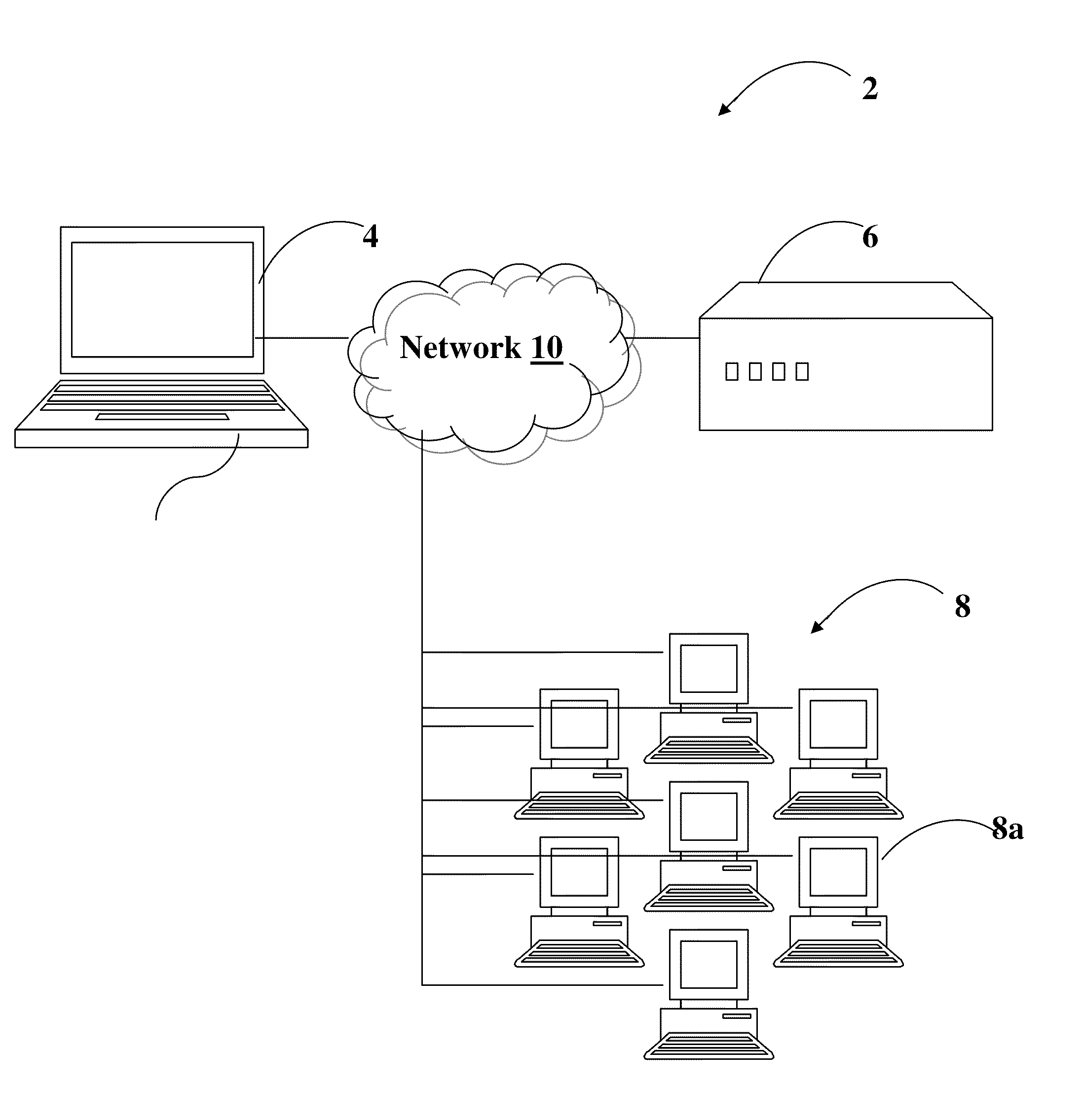
System and method for launching a resource in a network
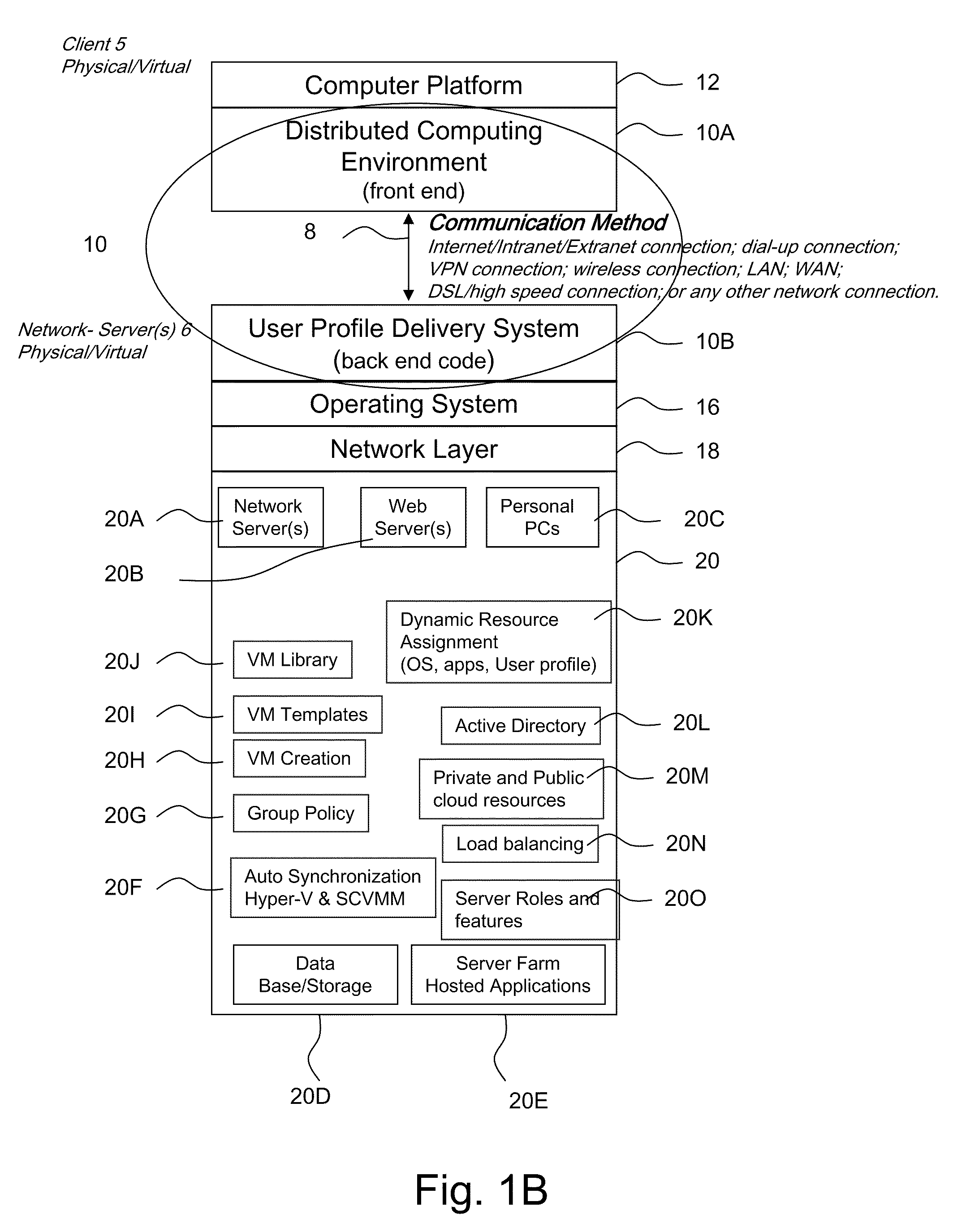
ActiveUS20110251992A1Provide controlDigital data processing detailsWireless commuication servicesOperational systemDirectory structure
The disclosure provides a system and method for a client connected to a server to a resource in a network. For the system a virtual machine module is provided to access a library and to create virtual machine templates and to create virtual machines from the virtual machine templates. The virtual machine module provides to a host machine in the network access to machines, user profile settings and instances of an application in the network and to multiple operating systems. The client has: access to an instance of the resource; an access module to provide the client with communication to access to the server using load balancing algorithms to access the file using Remote Desktop Protocol (RDP) commands; and an authentication module providing access to a directory structure accessed by the server using Microsoft Group Policy Objects (GPOs) and Active Directory (AD) services to authenticate the client with the server.
Owner:DESKTOPSITES
Policies for secure software execution
InactiveUS7350204B2Efficiently constrain (or prevent from running) everything on a machineDigital data processing detailsUnauthorized memory use protectionFile systemDigital signature
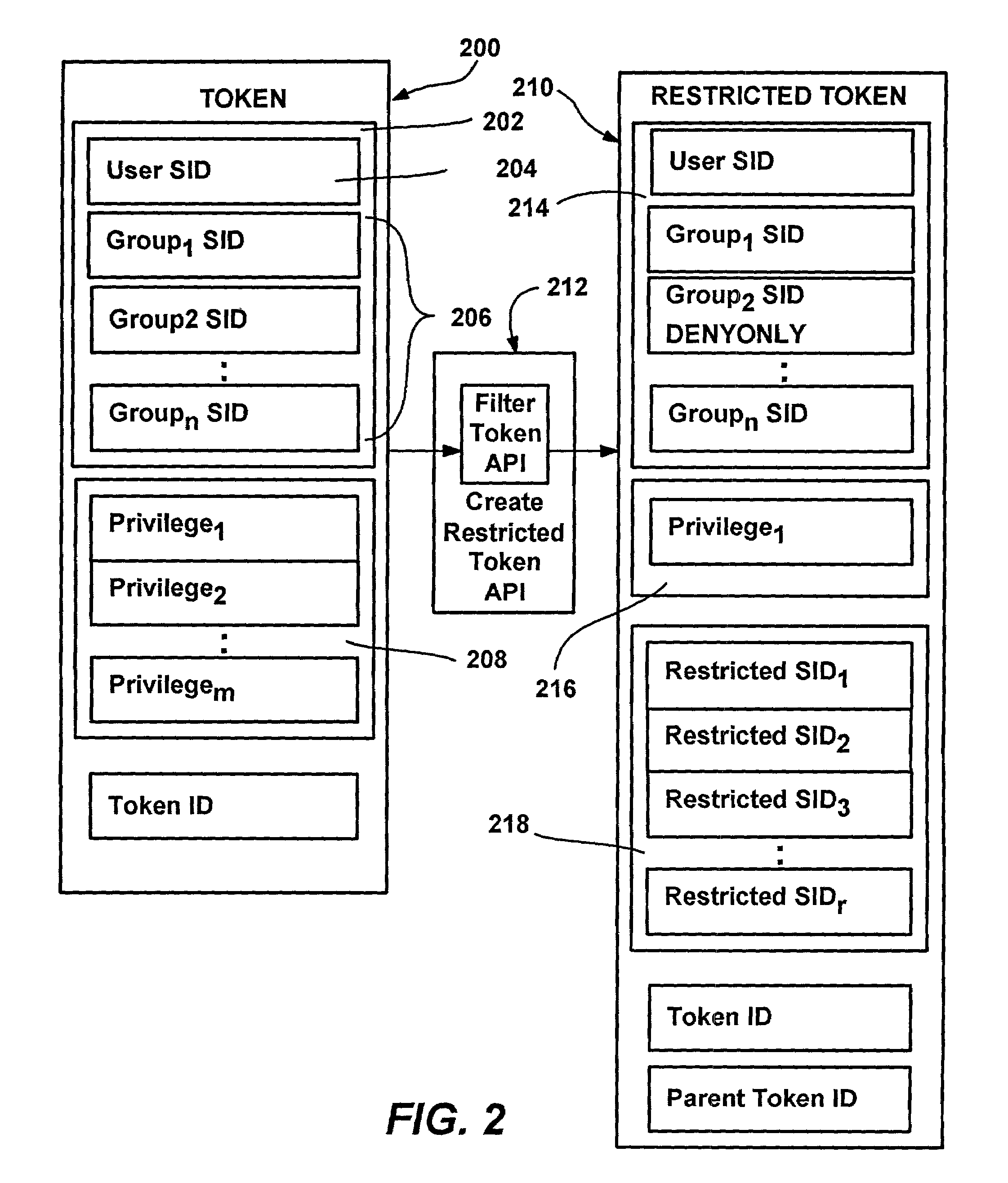
A system and method that automatically, transparently and securely controls software execution by identifying and classifying software, and locating a rule and associated security level for executing executable software. The security level may disallow the software's execution, restrict the execution to some extent, or allow unrestricted execution. To restrict software, a restricted access token may be computed that reduces software's access to resources, and / or removes privileges, relative to a user's normal access token. The rules that control execution for a given machine or user may be maintained in a restriction policy, e.g., locally maintained and / or in a group policy object distributable over a network. Software may be identified / classified by a hash of its content, by a digital signature, by its file system or network path, and / or by its URL zone. For software having multiple classifications, a precedence mechanism is provided to establish the applicable rule / security level.
Owner:MICROSOFT TECH LICENSING LLC
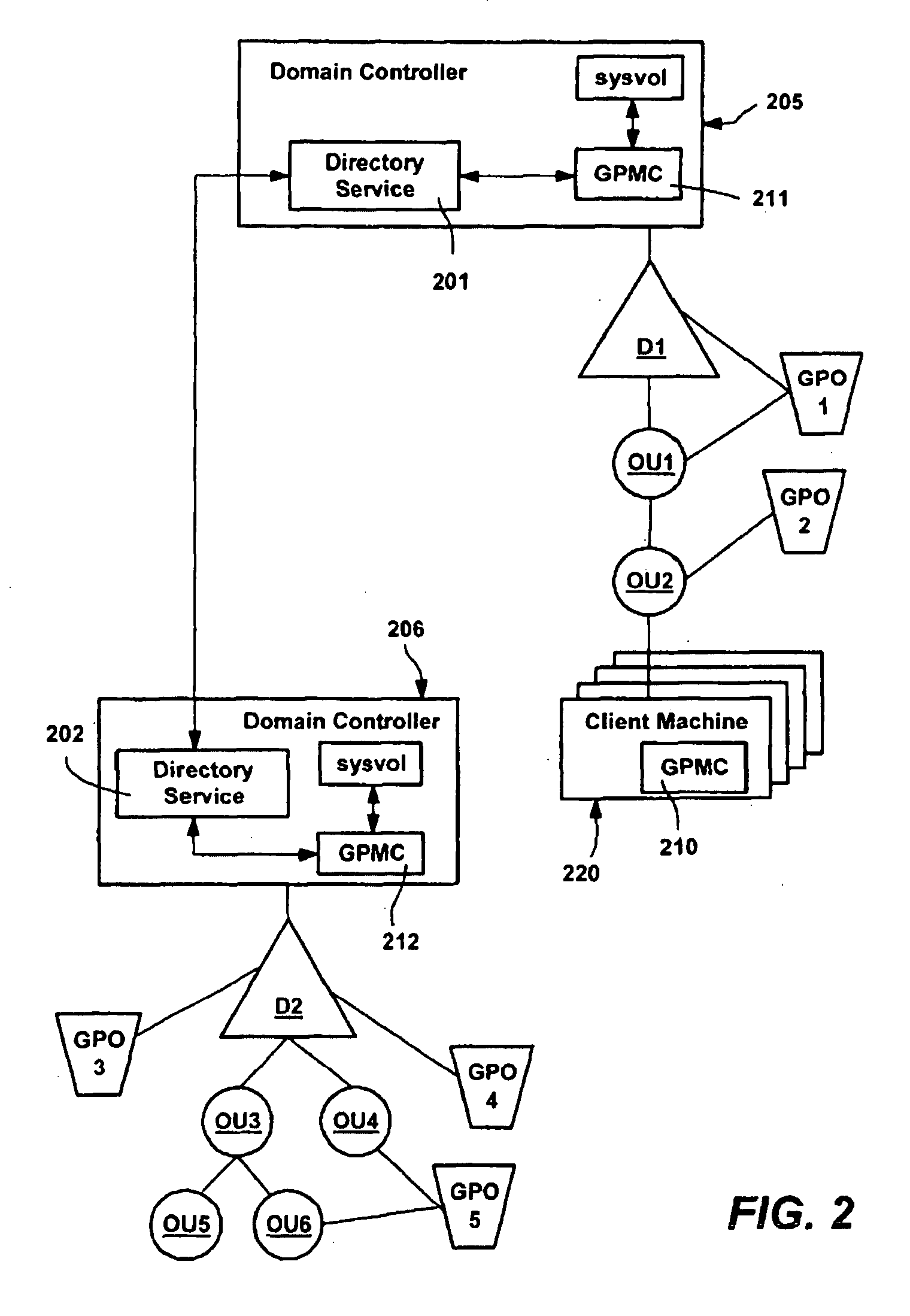
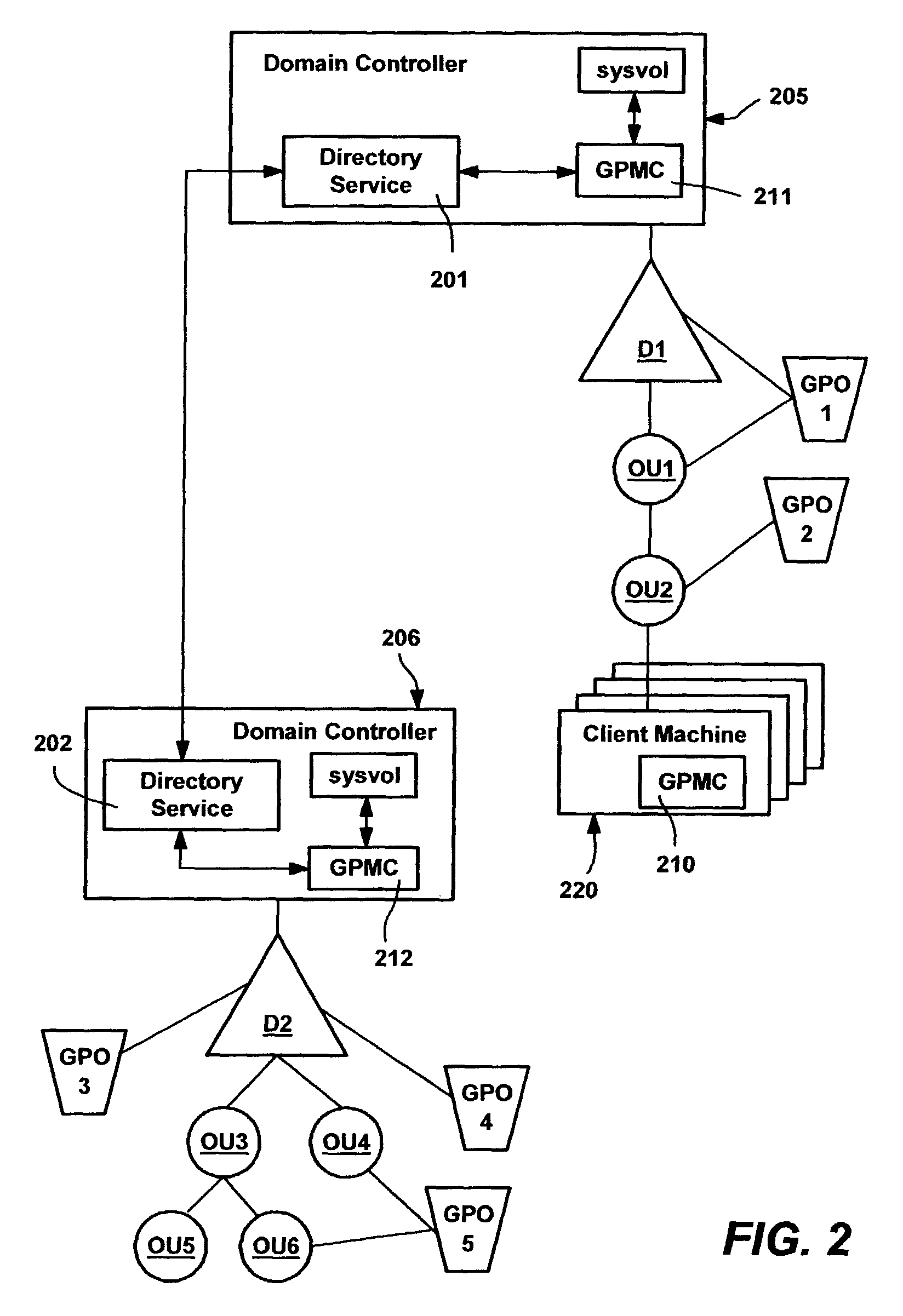
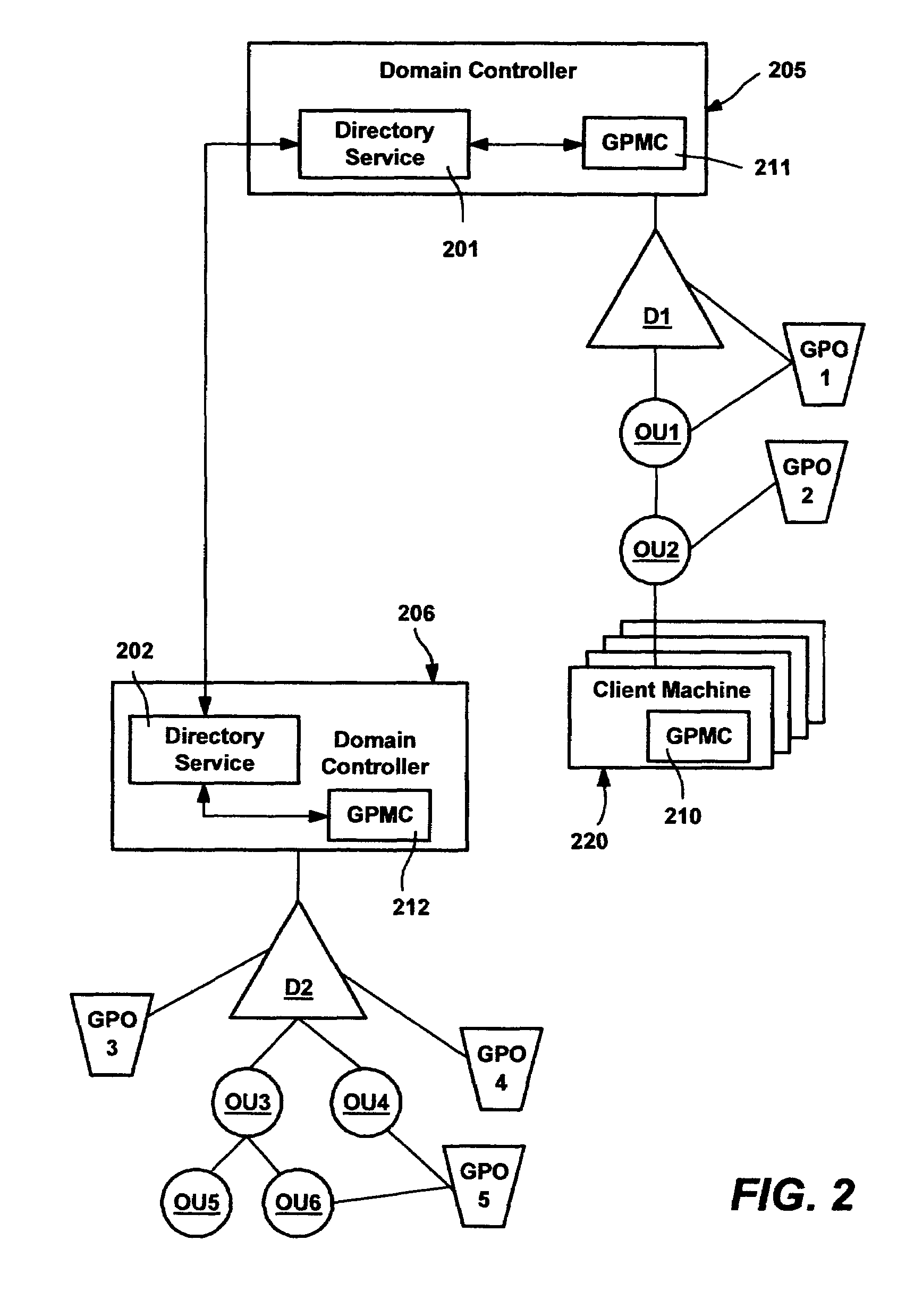
System and method for implementing group policy
InactiveUS6950818B2Digital data protectionMultiple digital computer combinationsIt policyGroup Policy
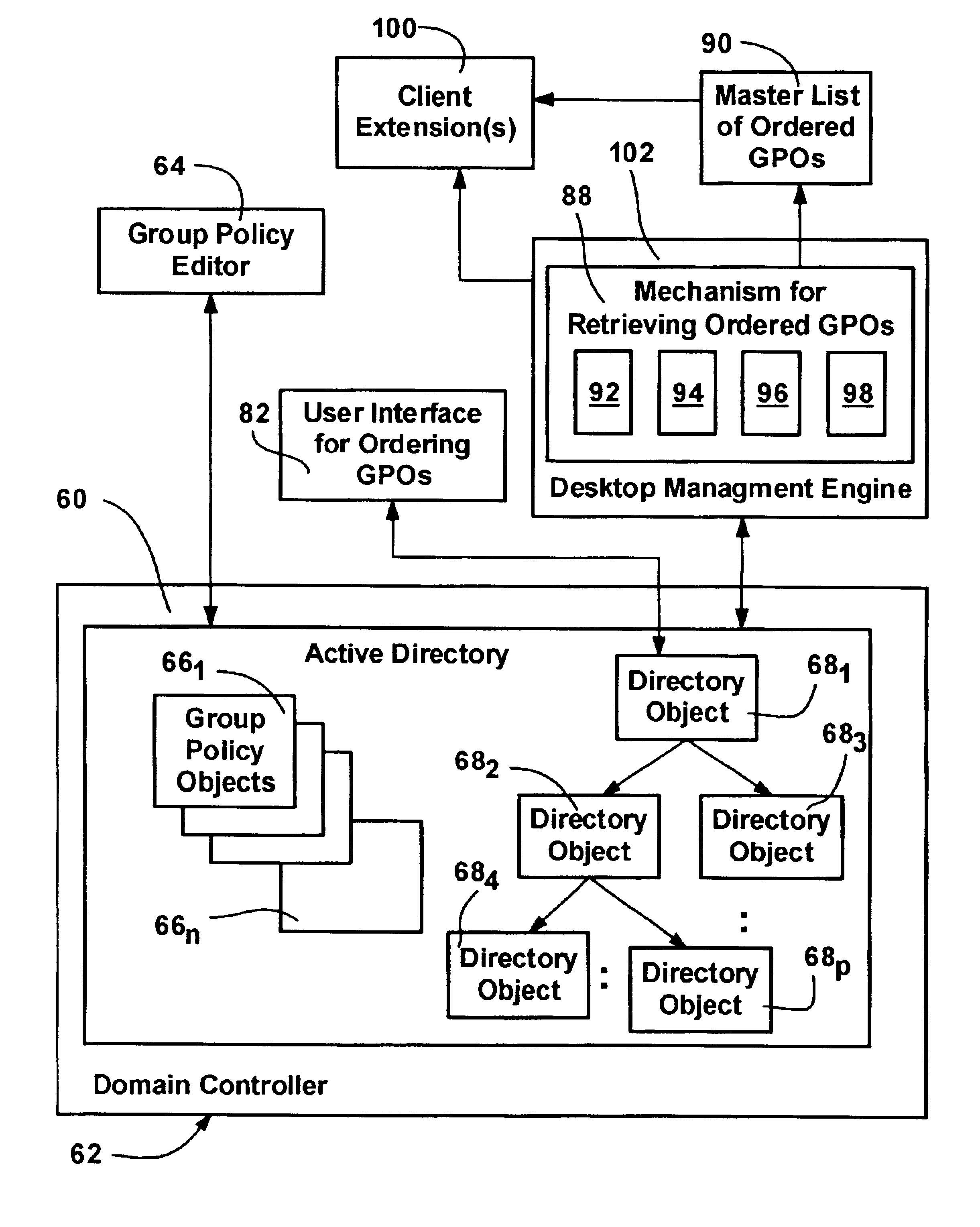
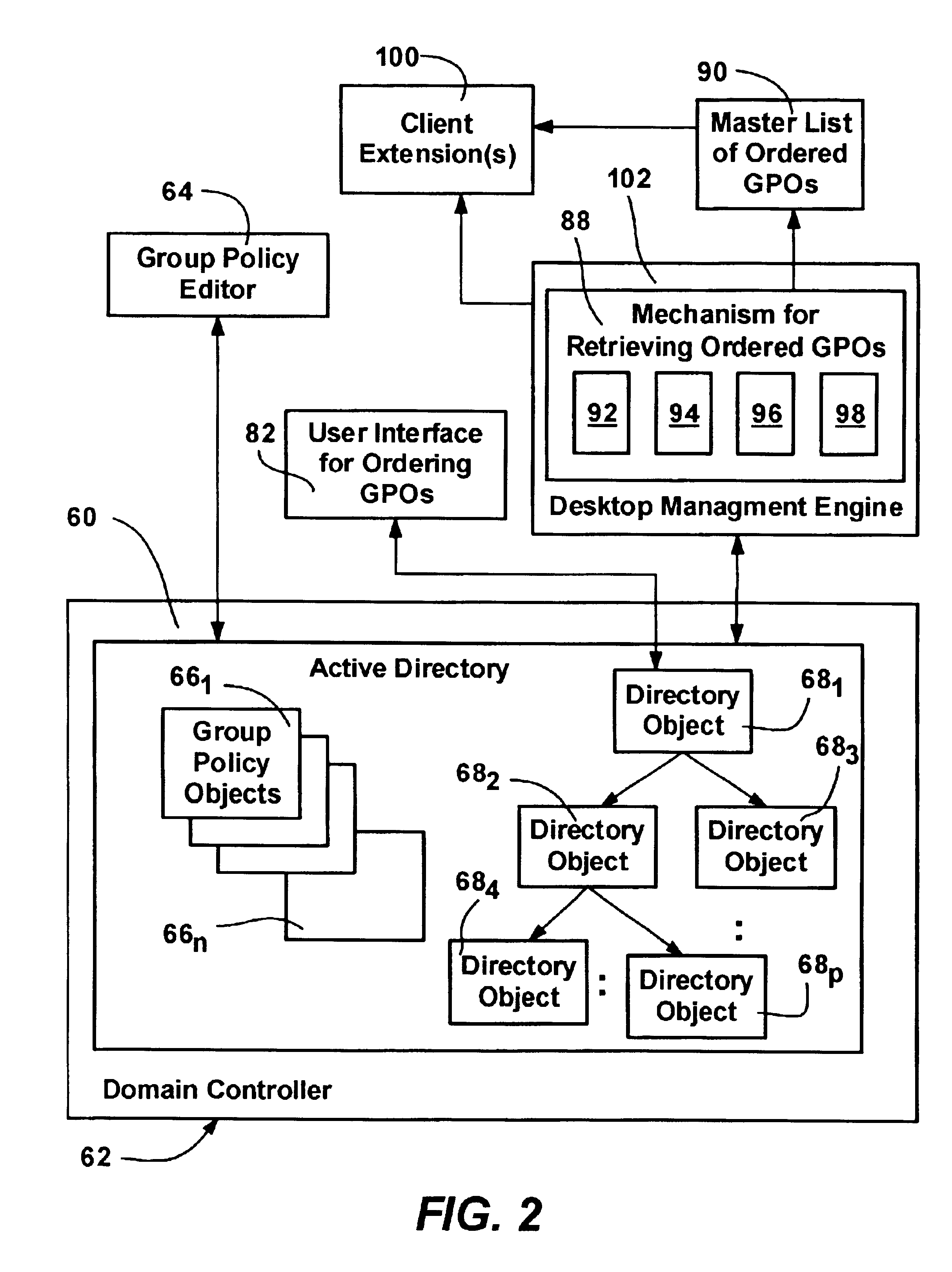
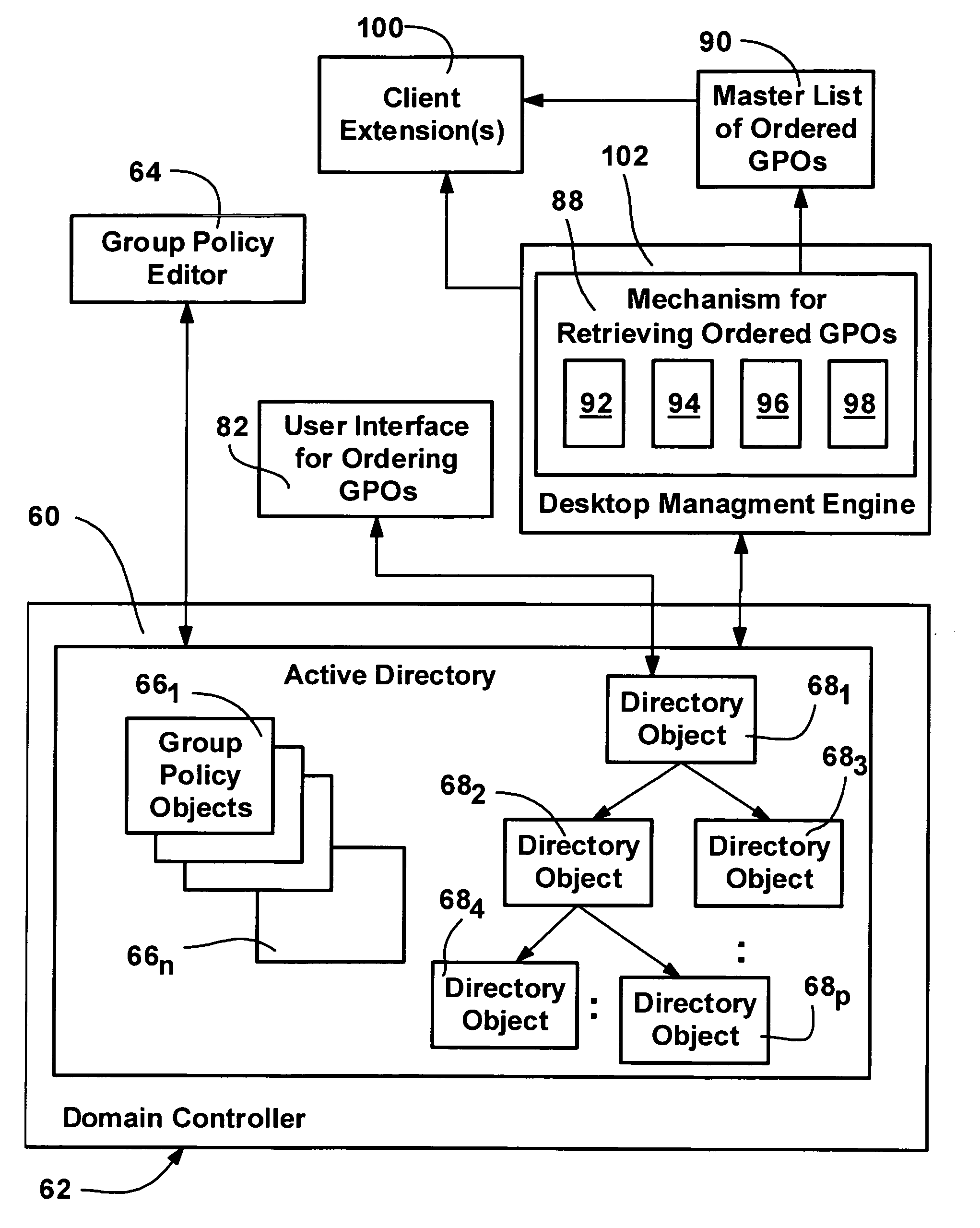
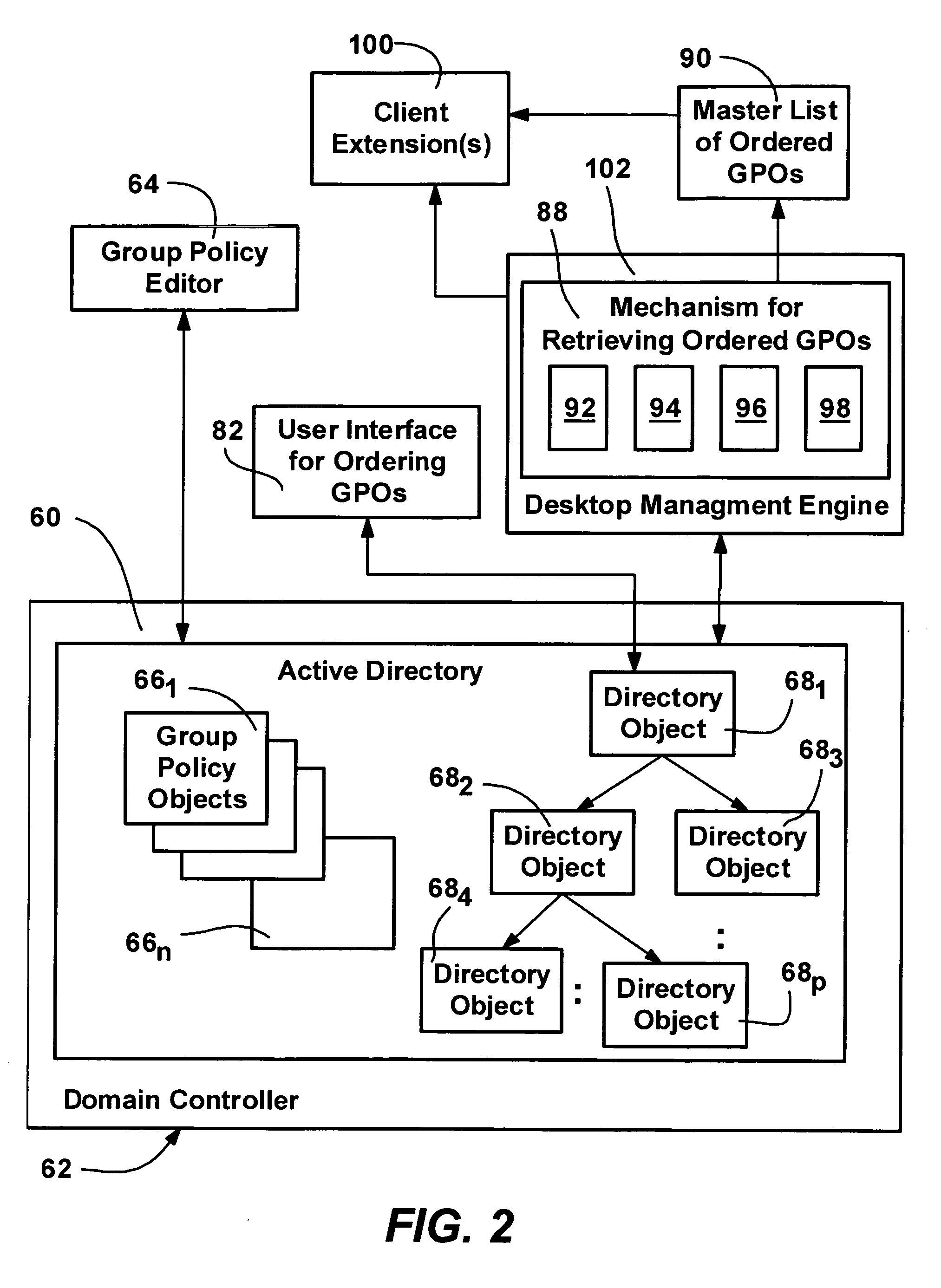
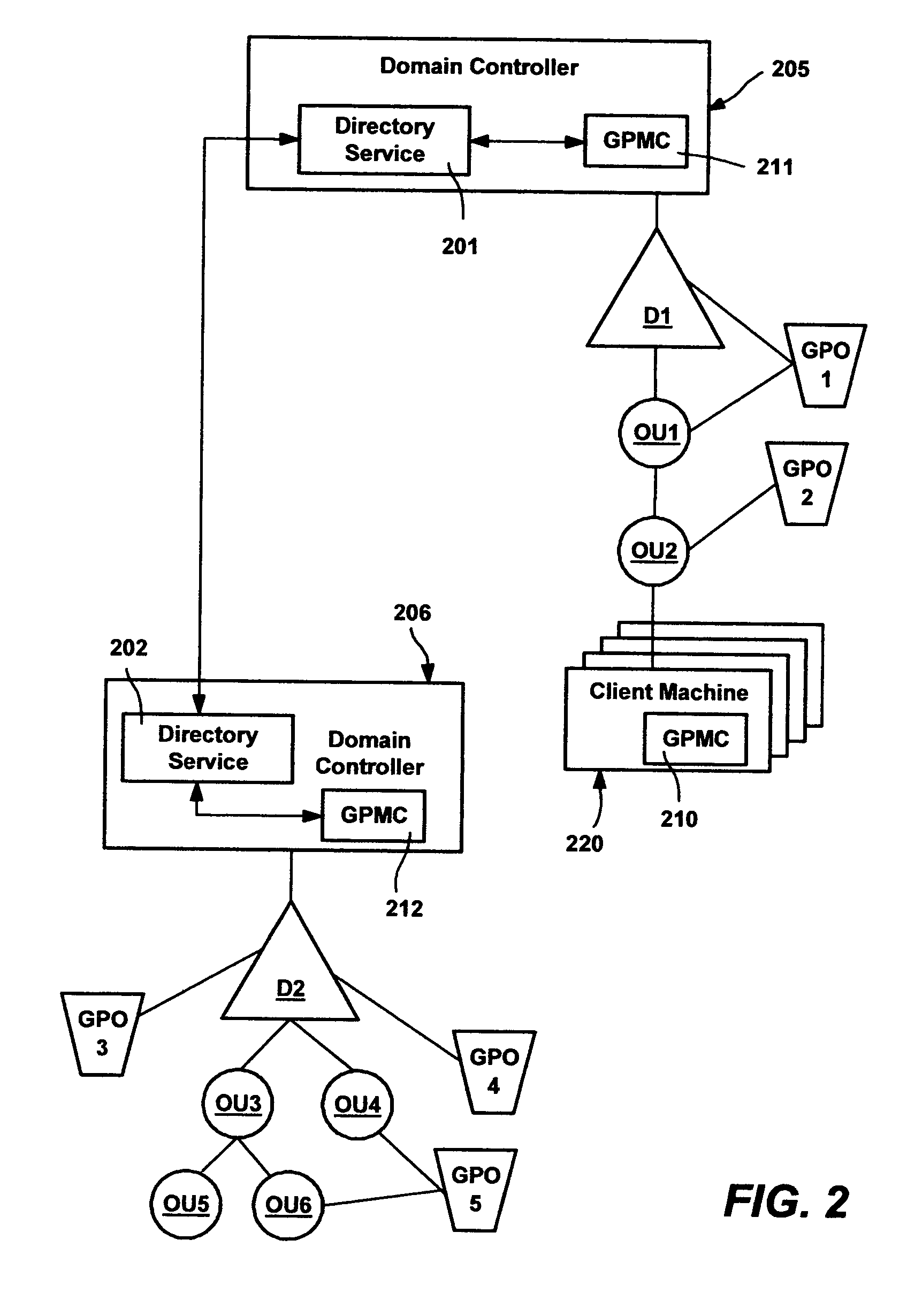
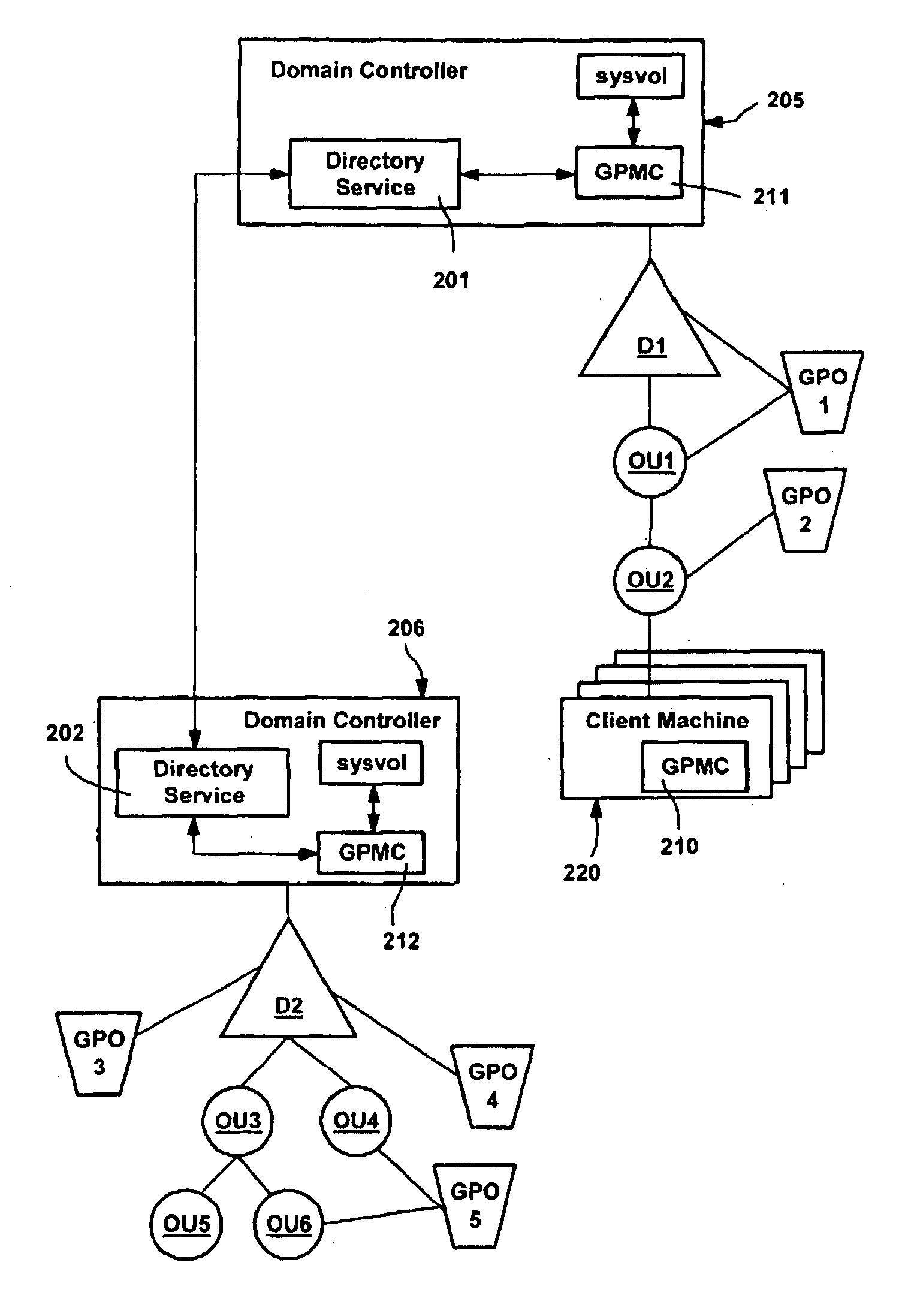
A method and system for implementing policy by accumulating policies for a policy recipient from policy objects associated with a hierarchically organized structure of containers, such as directory containers (sites, domains and organizational units) that includes the policy recipient. Based on administrator input, policy settings for the policy recipient may be accumulated into a specific order by inheriting policy from higher containers, which may enforce their policy settings over those of lower containers. Policy that is not enforced may be blocked at a container. The result is an accumulated set of group policy objects that are ordered by relative strength to resolve any policy conflicts. Policy may be applied to a policy recipient by calling extensions, such as an extension that layers the policy settings into the registry or an extension that uses policy information from the objects according to the ordering thereof.
Owner:MICROSOFT TECH LICENSING LLC
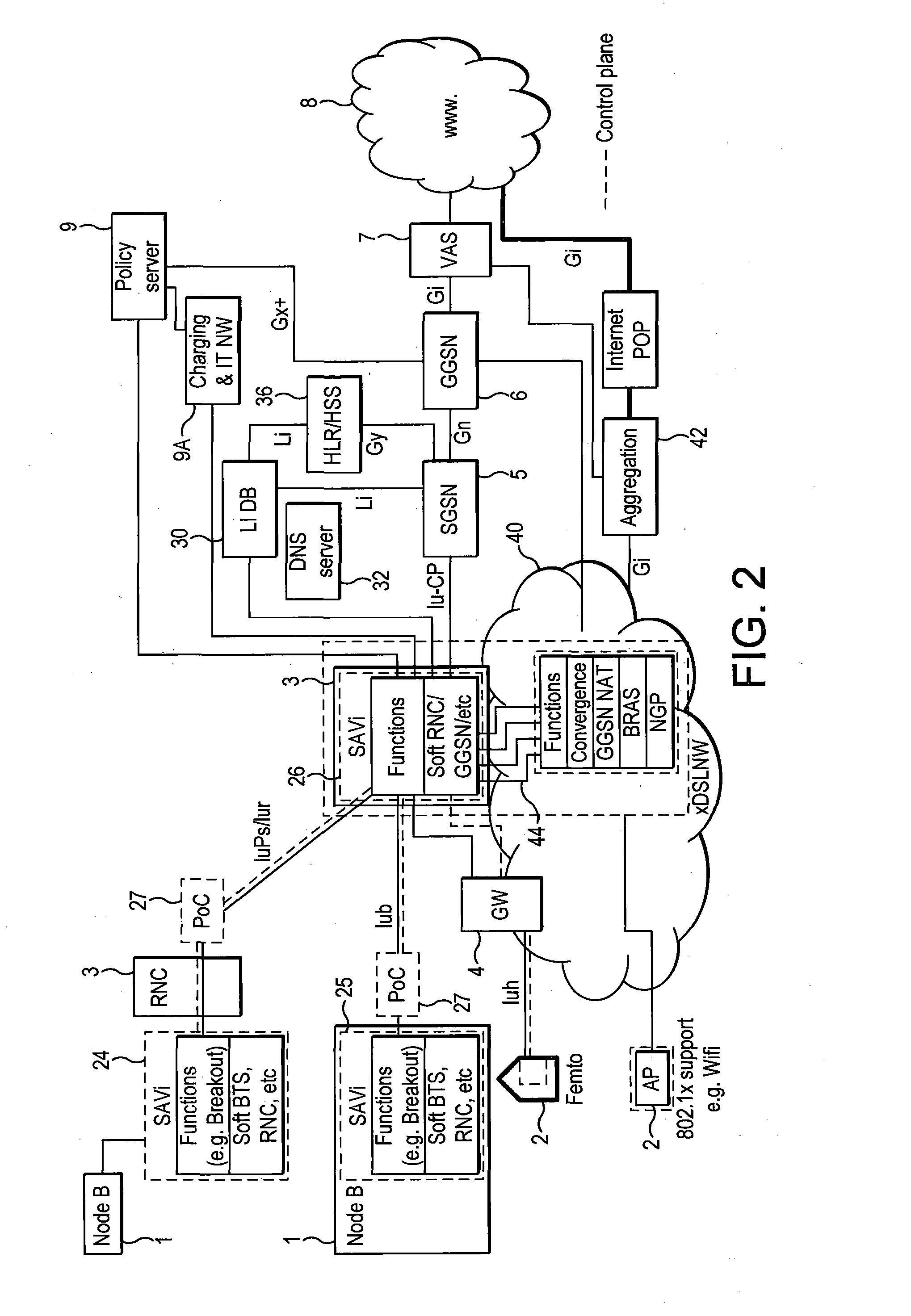
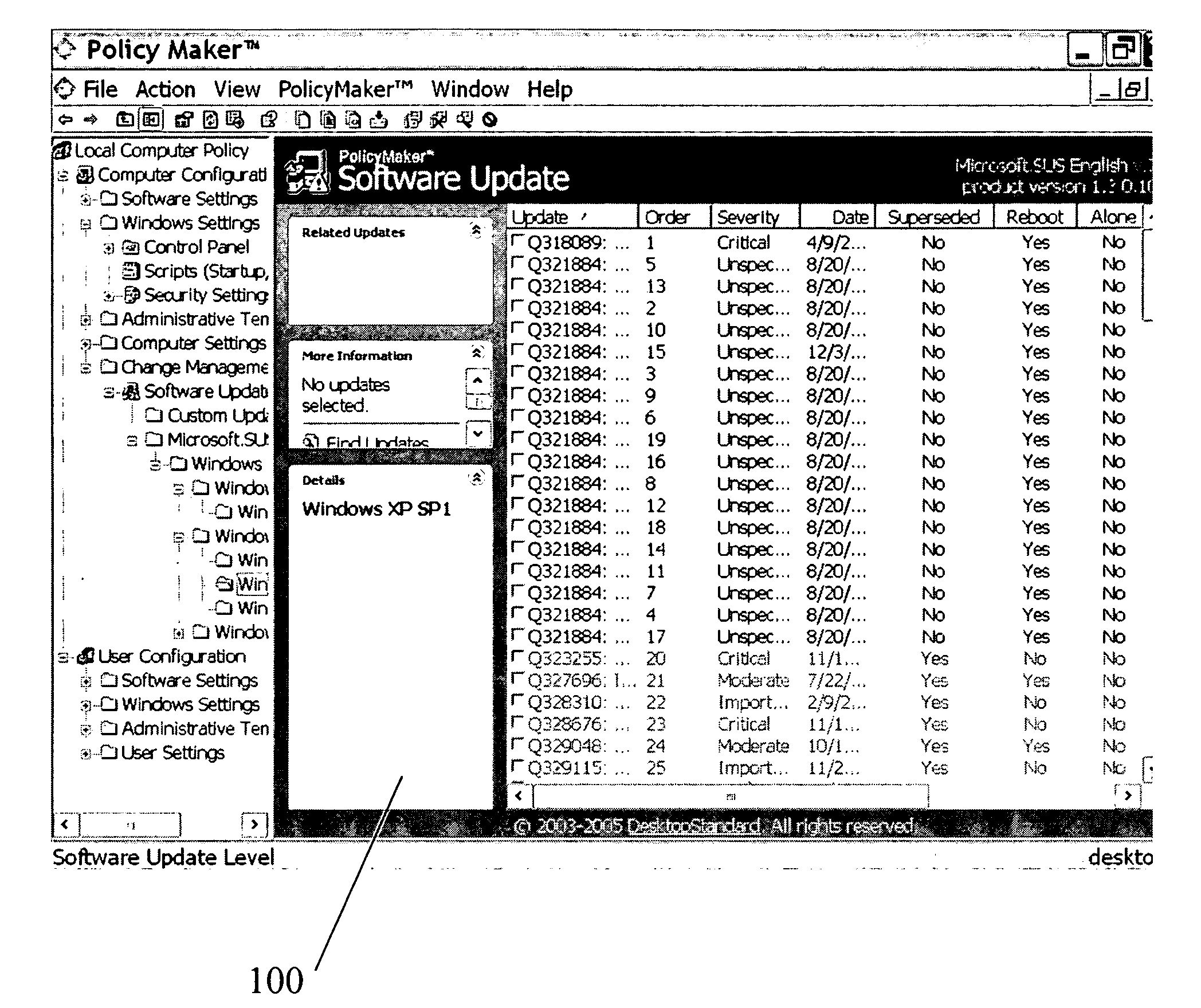
System for policy-based management of software updates
ActiveUS20050262076A1Program loading/initiatingSpecial data processing applicationsSoftware updateSystem maintenance
A computer system configured for policy-based management of software updates is disclosed. The system maintains group-policy objects, with which groups of computers are associated. The system obtains identities of software updates from a source of software updates. The system also obtains filter criteria for each update, for determining whether the update should be applied to a particular computer or not. The system assigns newly available updates to respective selected group-policy objects and adds the obtained filter criteria to each such group-policy object. The system performs necessary installations of updates by, for each group-policy object, determining whether, for each combination of a computer belonging to a group associated with that policy object and an update assigned to that policy object, the computer satisfies the filter criteria for the update, and if so, applying the update to that computer, but if not, refraining from applying the update.
Owner:MICROSOFT TECH LICENSING LLC
System and method for implementing group policy
A method and system for implementing policy by accumulating policies for a policy recipient from policy objects associated with a hierarchically organized structure of containers, such as directory containers (sites, domains and organizational units) that includes the policy recipient. Based on administrator input, policy settings for the policy recipient may be accumulated into a specific order by inheriting policy from higher containers, which may enforce their policy settings over those of lower containers. Policy that is not enforced may be blocked at a container. The result is an accumulated set of group policy objects that are ordered by relative strength to resolve any policy conflicts. Policy may be applied to a policy recipient by calling extensions, such as an extension that layers the policy settings into the registry or an extension that uses policy information from the objects according to the ordering thereof. Linking of group policy objects to one or more containers (e.g., sites, domains and organizational units) is provided, as is exception management. The effects of group policy may be filtered based on users' or computers' membership in security groups.
Owner:MICROSOFT TECH LICENSING LLC
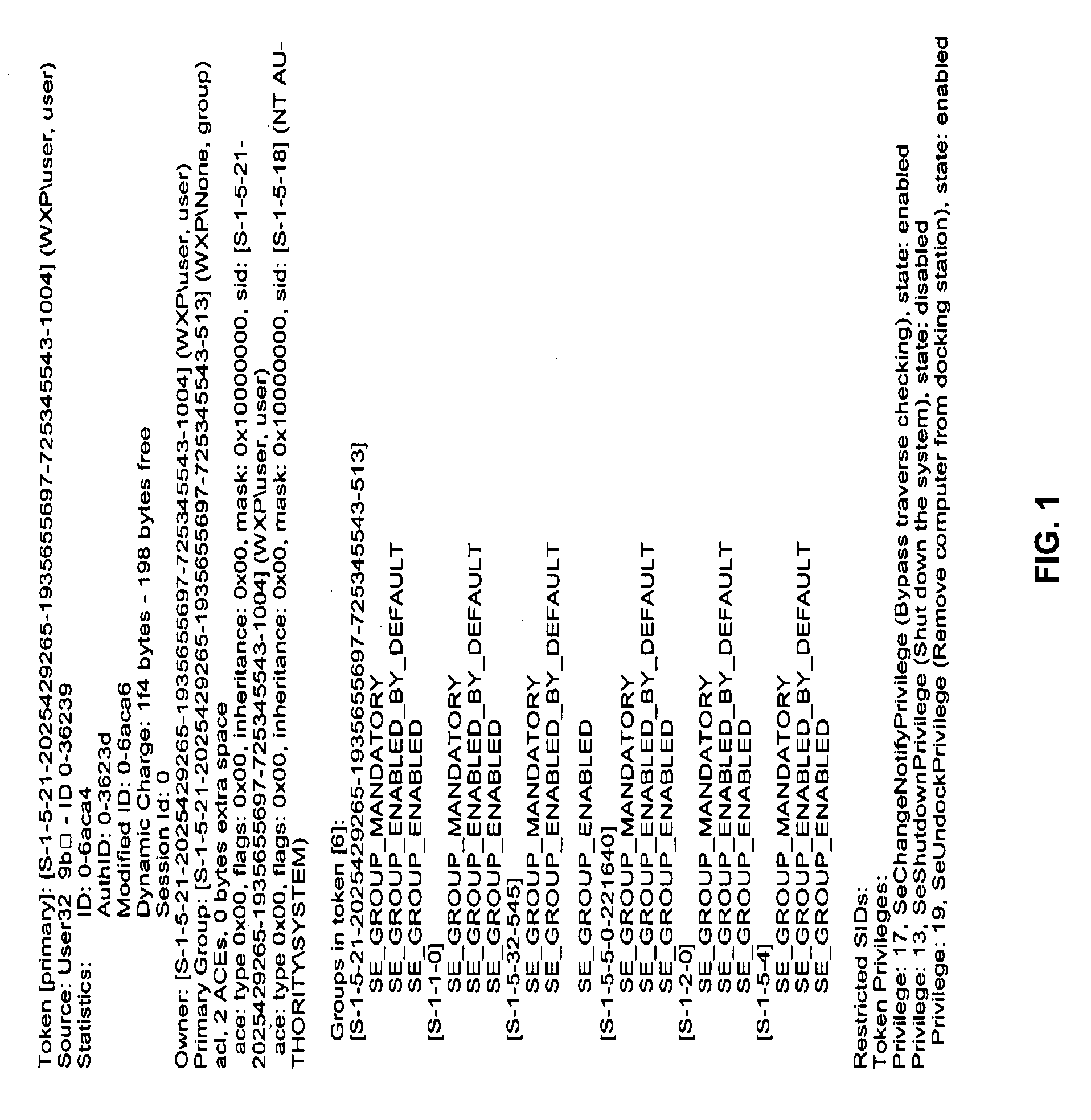
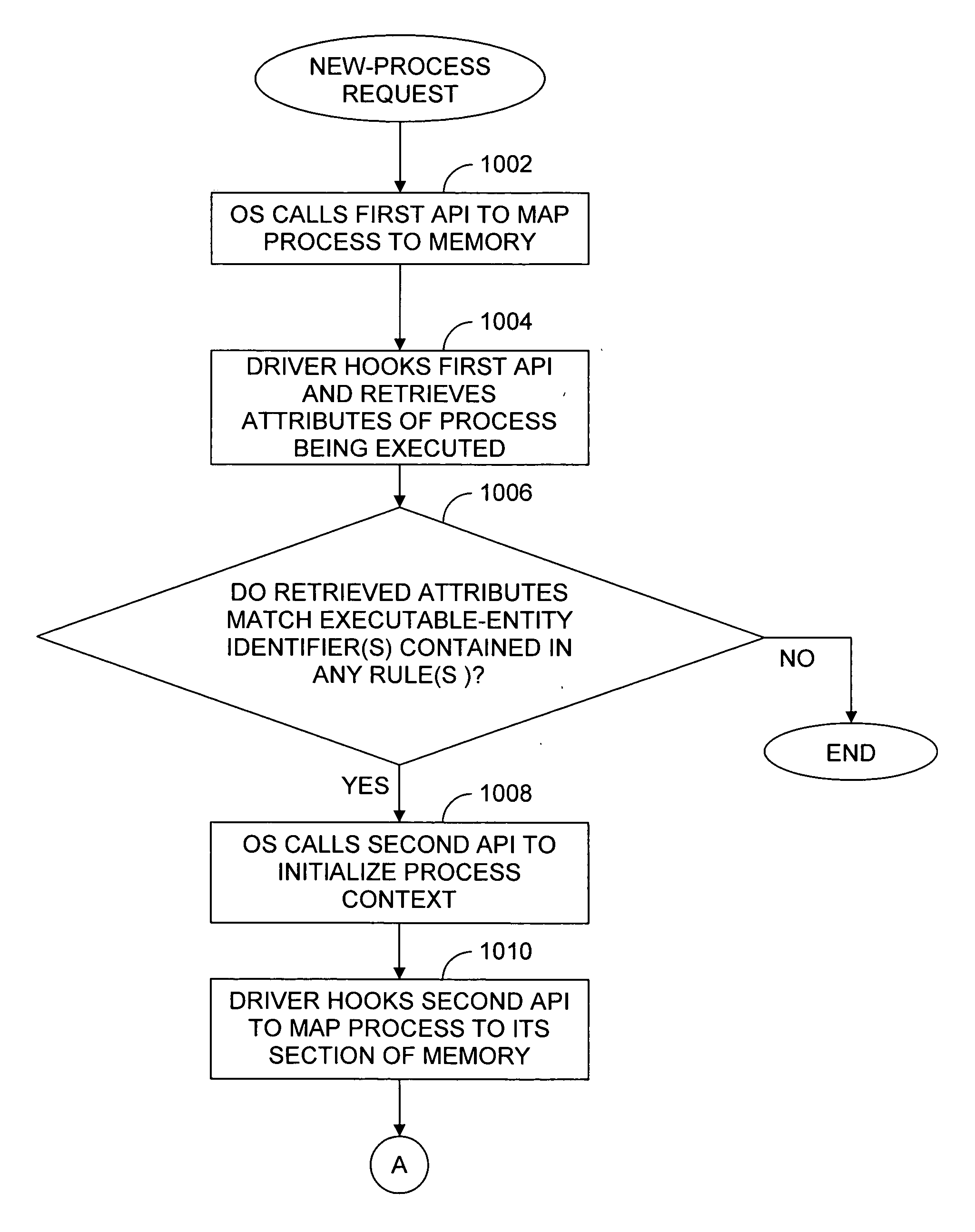
Methods and Systems for Controlling Access to Resources and Privileges Per Process
ActiveUS20110030045A1Specific access rightsDigital data processing detailsGroup PolicyWorld Wide Web
To control privileges and access to resources on a per-process basis, an administrator creates a rule that may be applied to modify a token of a process. The rule may include an application-criterion set and changes to be made to the groups and / or privileges of the token. The rule may be set as a policy within a group policy object (GPO), where a GPO is associated with one or more groups of computers or users. When a GPO containing a rule is applied to a computer, a driver installed on the computer may access the rule(s) anytime a logged-on user executes a process. If the executed process satisfies the criterion set of a rule, the changes contained within the rule are made to the process token, and the user has expanded and / or contracted access and / or privileges for only that process.
Owner:BEYONDTRUST SOFTWARE INC
System and method for launching a resource in a network
ActiveUS8732182B2Digital data processing detailsWireless commuication servicesOperational systemDirectory structure
Owner:DESKTOPSITES
Methods and systems for network-based management of application security
ActiveUS20070043943A1Digital data processing detailsUnauthorized memory use protectionComputer accessApplication security
To control privileges and access to resources on a per-process basis, an administrator creates a rule that may be applied to modify a process's token. The rule includes an application-criterion set and changes to be made to the groups and / or privileges of a token. The rule is set as a policy within a group policy object (GPO), where a GPO is associated with one or more groups of computers. When a GPO containing a rule is applied to a computer, a driver installed on the computer accesses the rule(s) anytime a logged-on user executes a process. If the executed process satisfies the criterion set of a rule the changes contained within the rule are made to the process token, and the user has expanded and / or contracted access and / or privileges for only that process.
Owner:BEYONDTRUST SOFTWARE
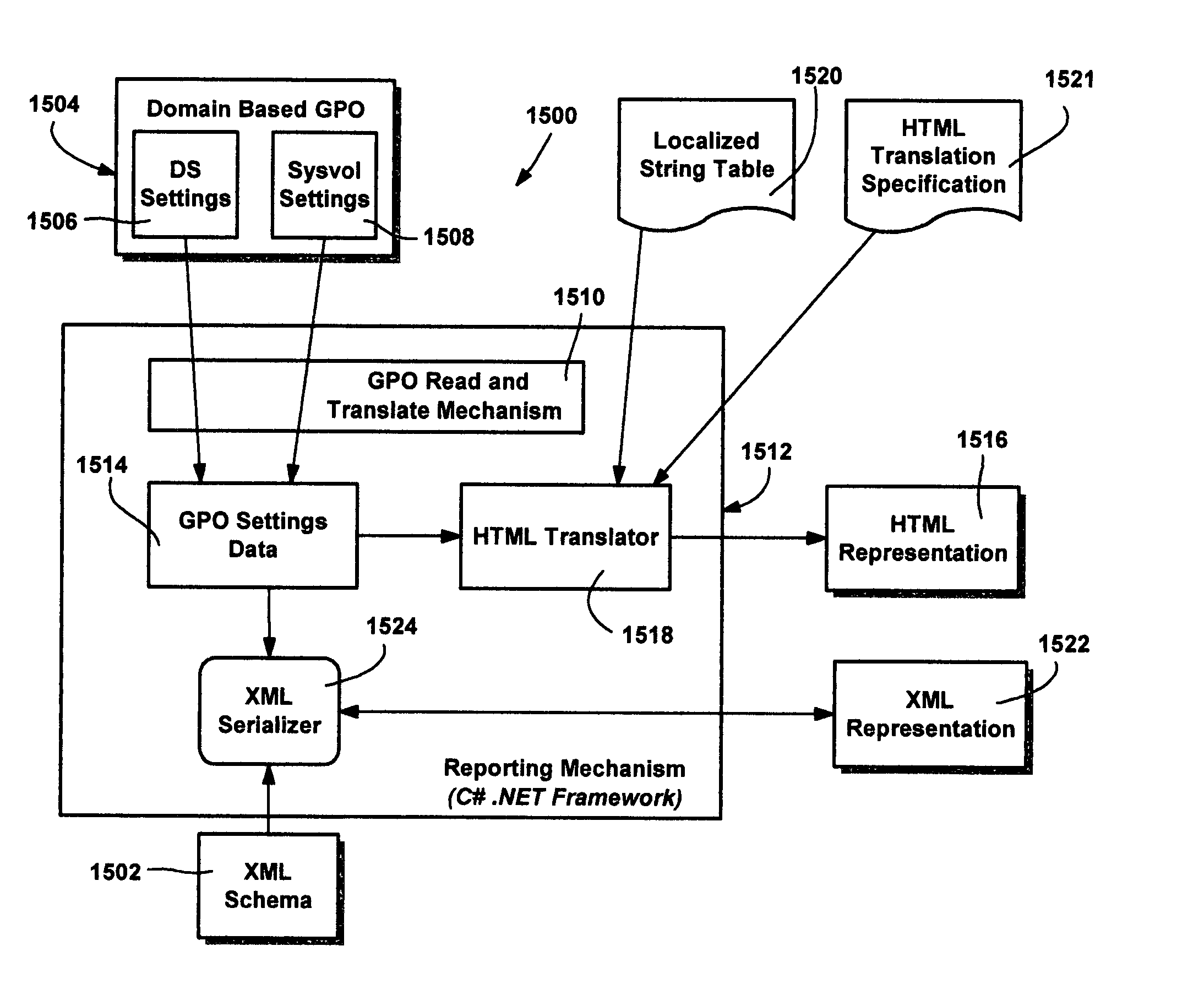
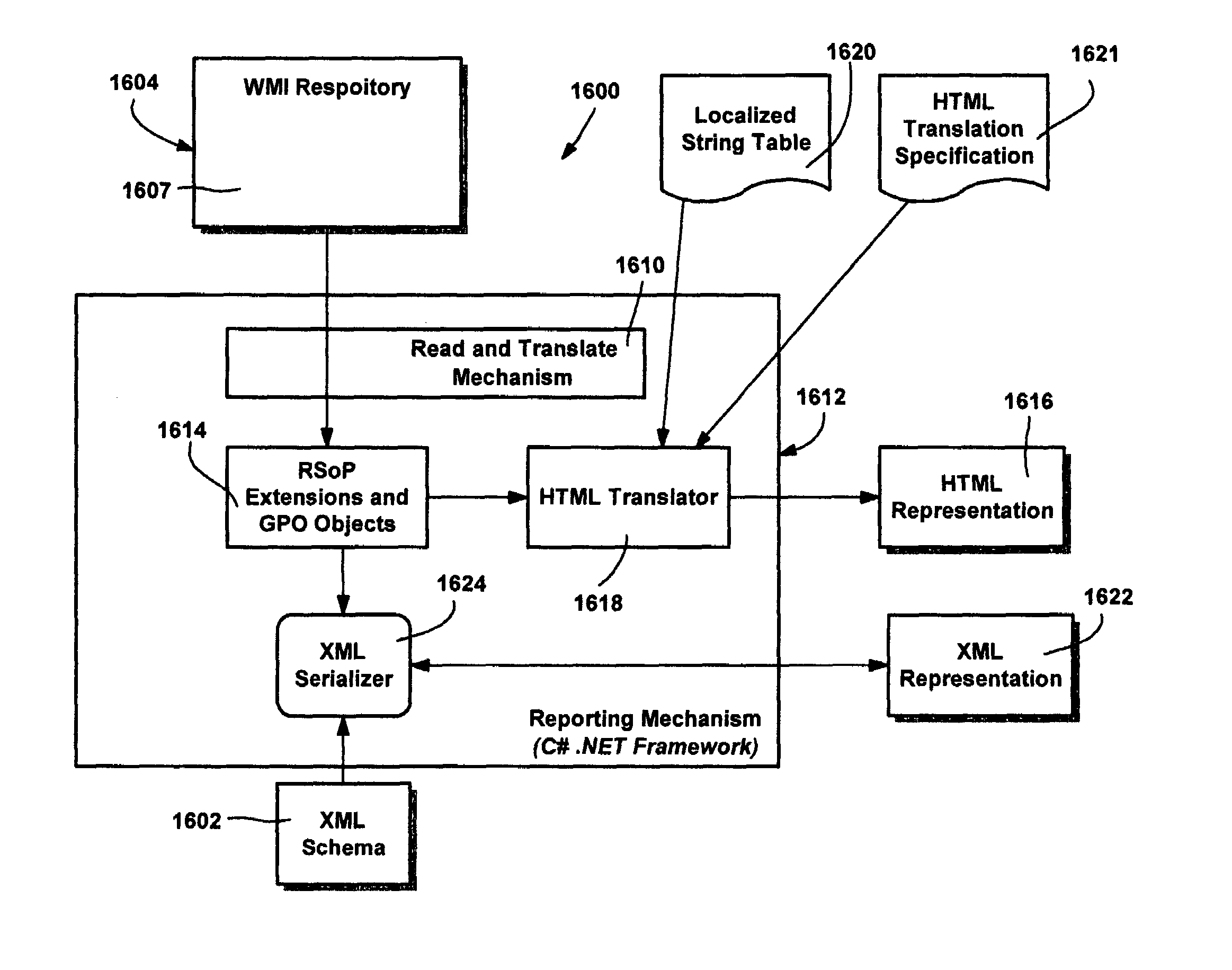
System and method for reporting hierarchically arranged data in markup language formats
InactiveUS20050005233A1Easy to operateDigital computer detailsSemi-structured data mapping/conversionXML schemaPaper document
A system and method comprising a reporting mechanism for outputting an HMTL and XML document from a collection of hierarchically maintained settings such as group policy object settings or resultant set of policy data. The reporting mechanism provides a substantially complete view of which settings are configured (enabled) in a given group policy object, or a view for a resultant set of policy (that is applied to a given SOM), along with the values of the settings. The markup language format enables viewing a flat representation of the settings, and printing, saving and / or transporting of the settings. XML schemas describe a valid representation of group policy settings, and a valid representation of resultant set of policy.
Owner:MICROSOFT TECH LICENSING LLC
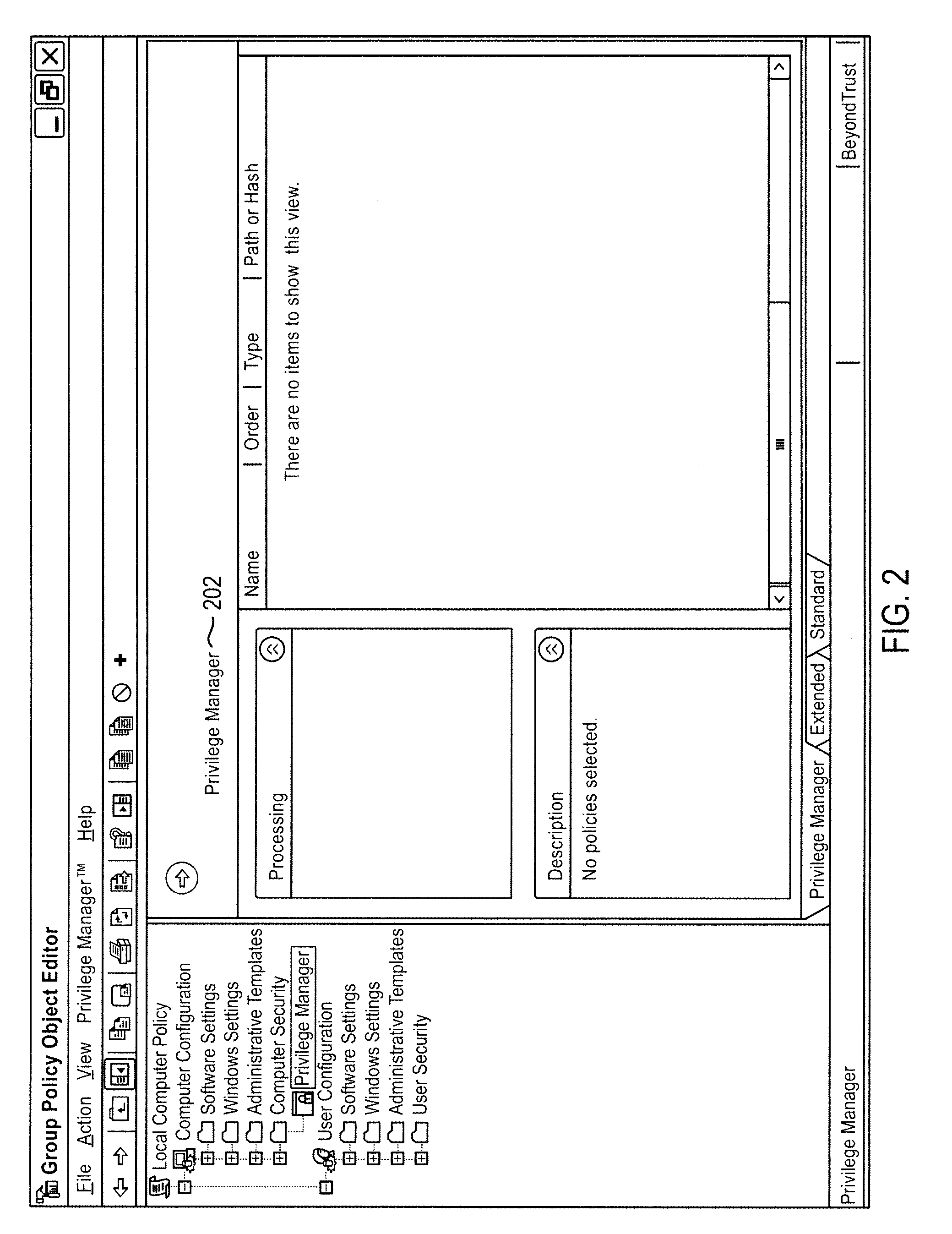
Interfaces and methods for group policy management
InactiveUS20090222884A1Easy to manageCreate accuratelyDigital data processing detailsData switching networksManagement objectGroup Policy
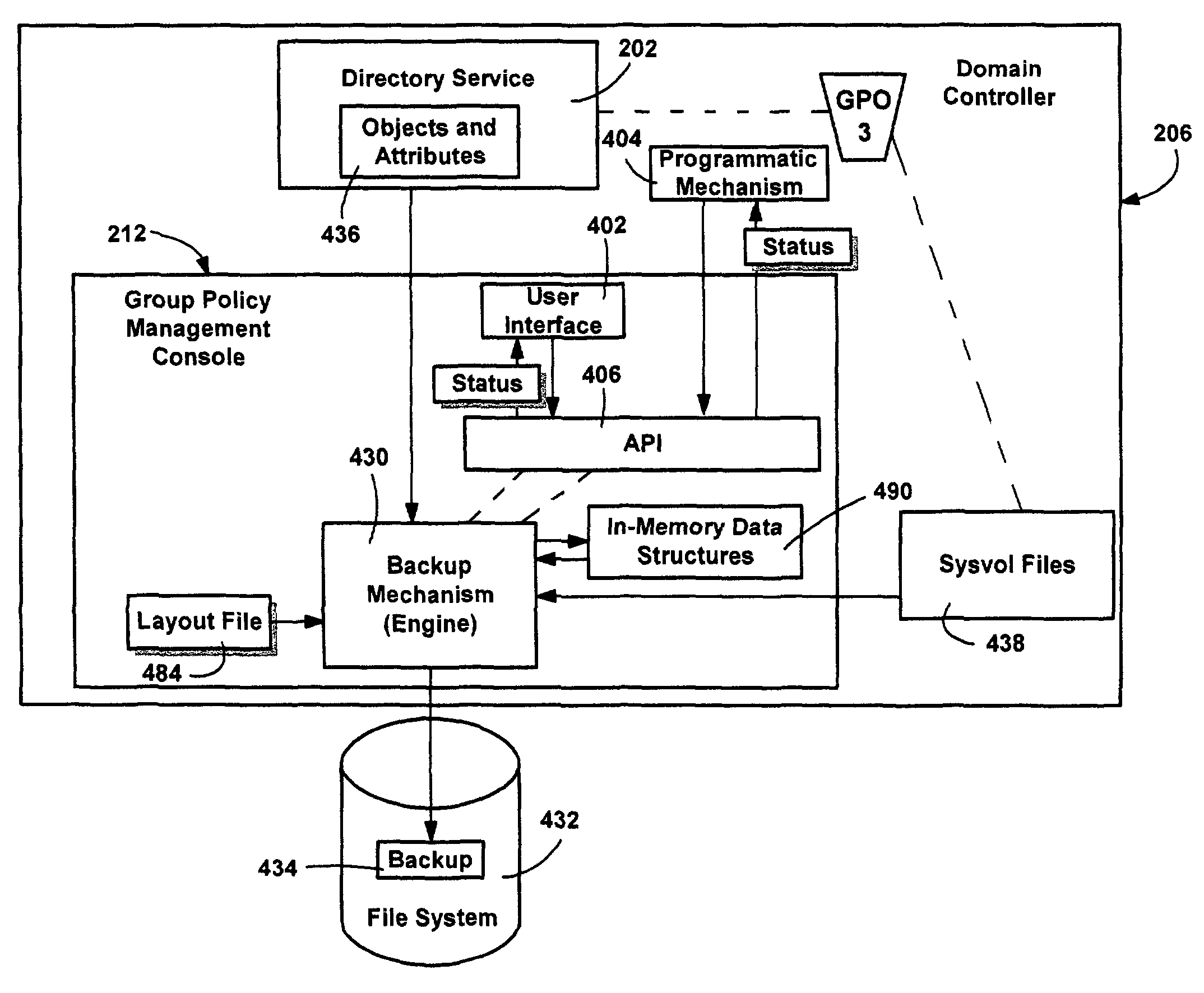
A system and method for managing group policy objects in a network, including interfaces that allow access by programs or a user interface component to functions of a group policy management console that performs management tasks on group policy objects and other related objects. The interfaces abstract the underlying data storage and retrieval, thereby facilitating searching for objects, and providing the ability to delegate, view, change and permissions on those objects, and check and save those permissions. Modeling and other test simulations are facilitated by other interfaces. Other interfaces provide dynamic and interactive features, such as to convey progress and rich status messages, and allow canceling of an ongoing operation. Still other interfaces provide methods for operating on group policy related data, including group policy object backup, restore, import, copy and create methods, and methods for linking group policy objects to scope of management objects.
Owner:MICROSOFT TECH LICENSING LLC
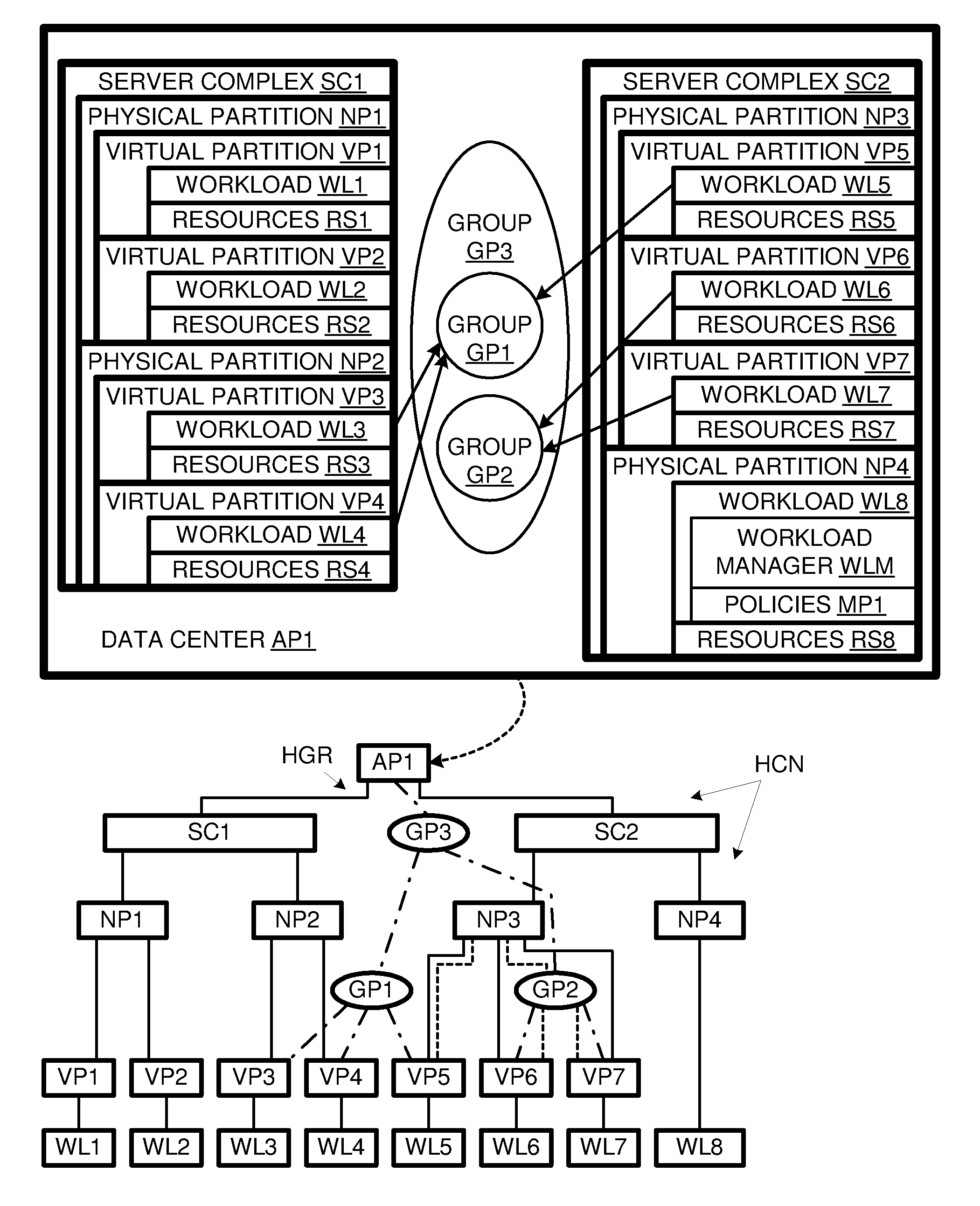
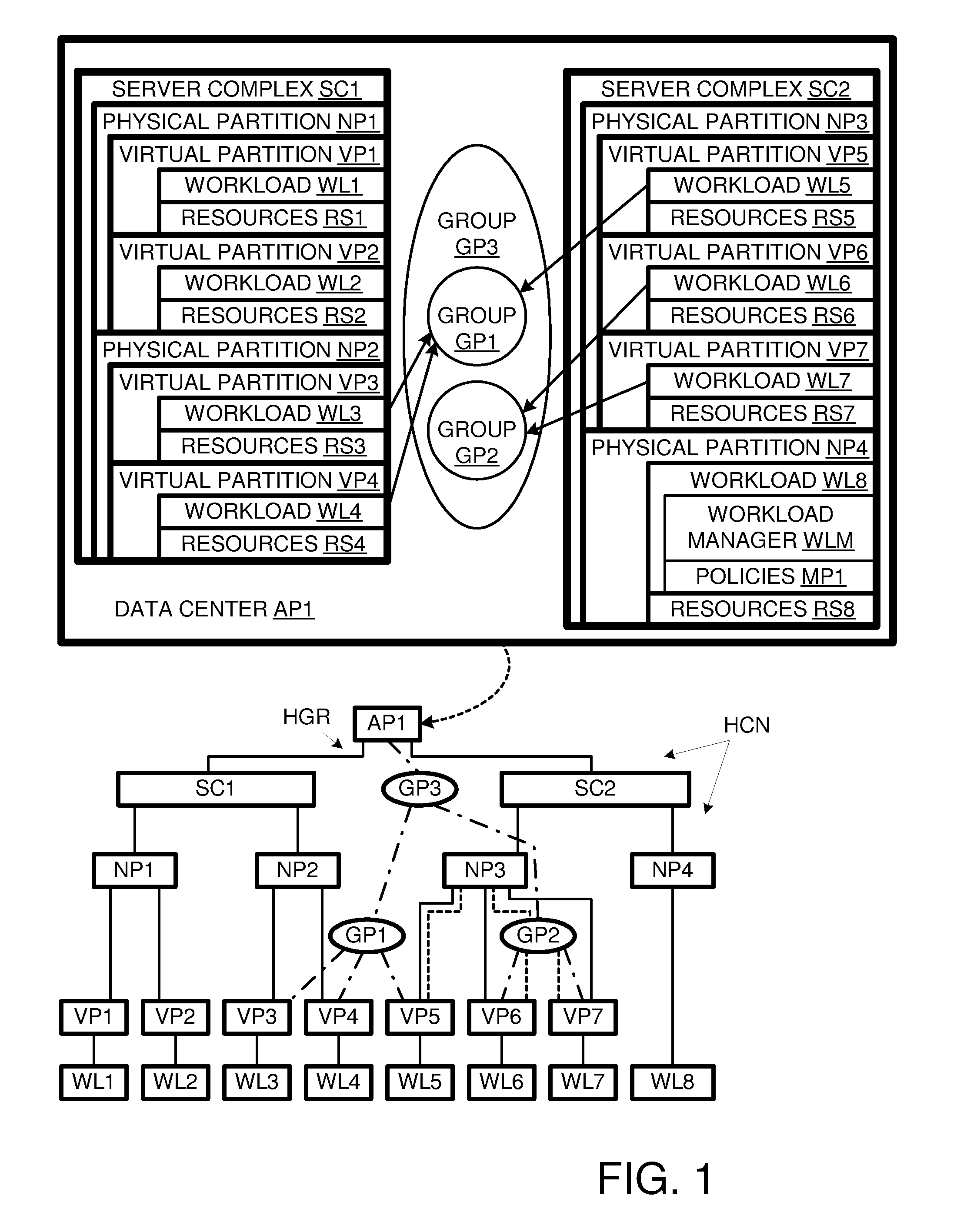
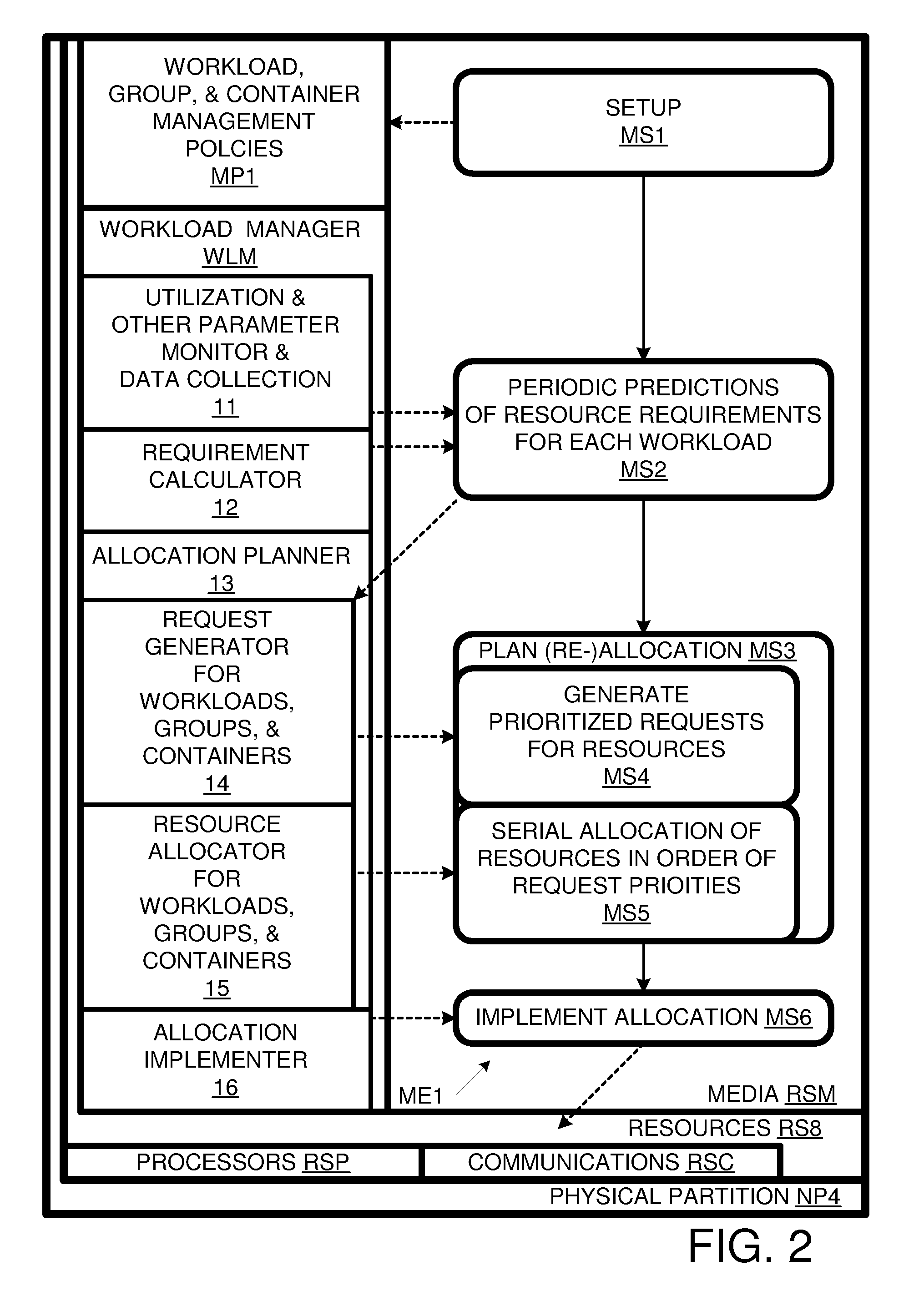
Workload management for computer system with container hierarchy and workload-group policies
A computer system characterized by a container hierarchy uses a workload manager to allocate computing resources to workloads. The workload manager can allocate resources as a function of aggregate characteristics of a group of workloads, even where the group does not conform to the container hierarchy.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
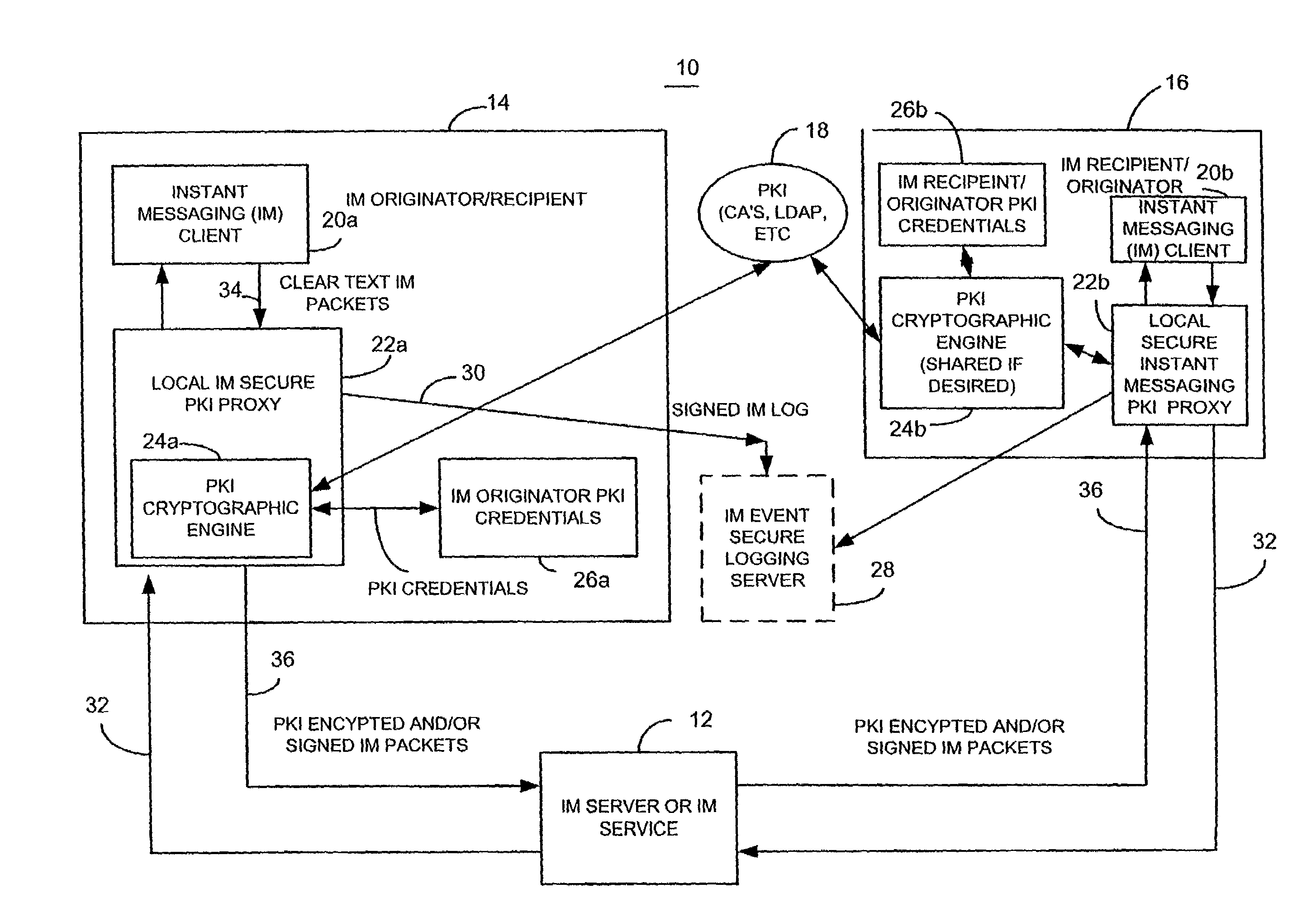
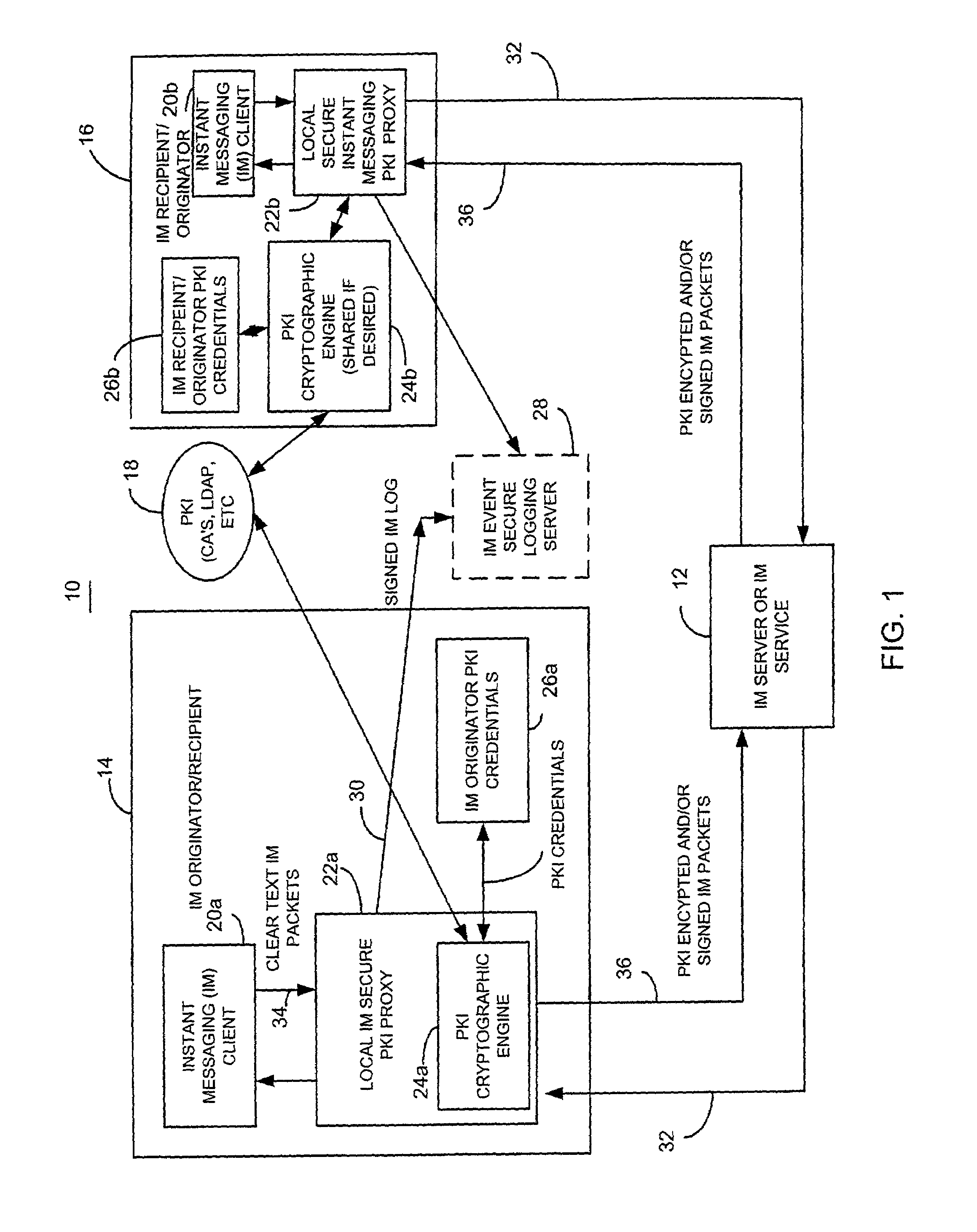
Secure instant messaging system using instant messaging group policy certificates
A method and apparatus for facilitating instant messaging utilizes a secure instant message group policy certificate issued by an instant messaging public key infrastructure policy certificate issuing unit. The secure instant messaging group policy certificate is received, such as through a local instant messaging secure public key infrastructure proxy, and contains data defining the group members, references to other groups, security controls and relevant data such as allowed algorithms. The secure instant messaging group policy certificate defines a plurality of different instant messaging groups, each identified by an instant messaging group identifier. Each instant messaging group identifier is associated with a plurality of instant message group number identifiers.
Owner:CYGNACOM SOLUTION INC +1
Resource allocation system and resource allocation method in private cloud environment
InactiveCN101986274AImprove resource utilizationImprove maintenance efficiencyResource allocationResource allocation systemsCloud resources
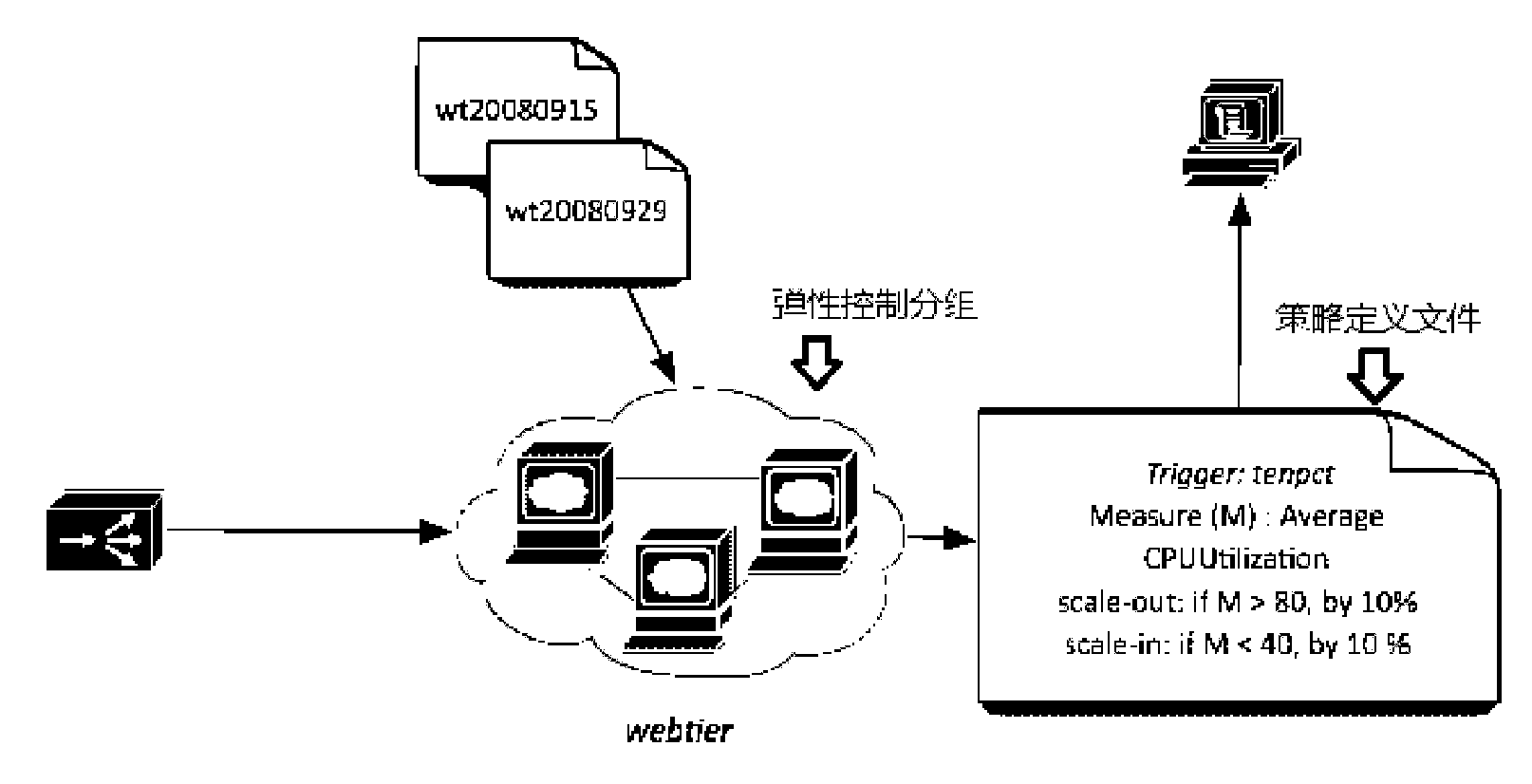
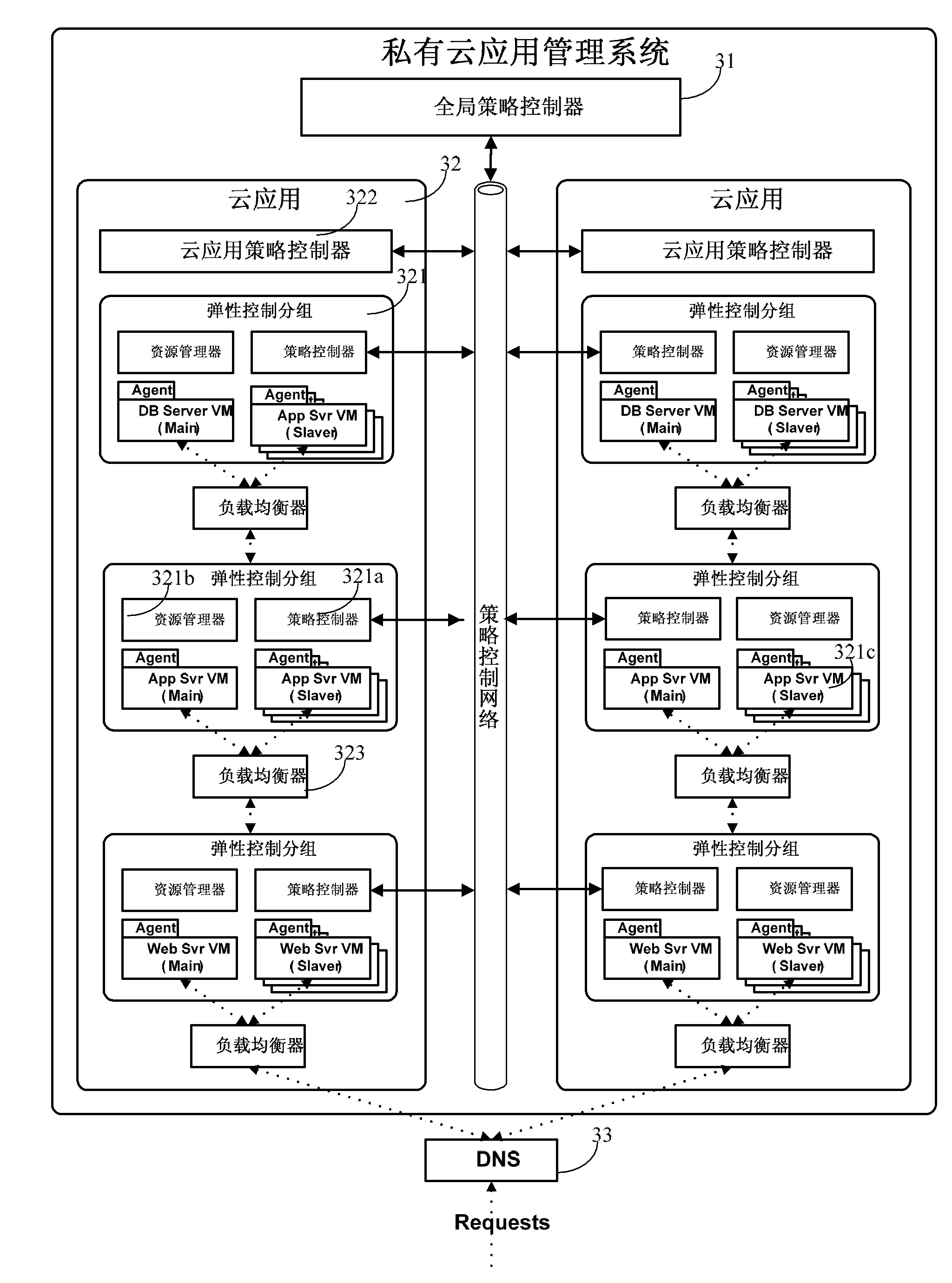
The invention relates to a resource allocation system in a private cloud environment. The system comprises a global policy controller, cloud application policy controllers and group policy controllers, wherein a resource manager interacts with a resource exploring proxy, receives index data, judges whether an alarm is generated for the index data or not according to alarm conditions, and if so, submits the alarm to a policy control network; the group policy controller first processes the alarm, generates a resource adjusting plan if the alarm can be processed, and reports the alarm to the cloud application policy controller if the alarm cannot be processed; the cloud application policy controller processes the received alarm, generates the resource adjusting plan if the alarm can be processed, and reports the alarm to the global policy controller if the alarm cannot be processed; the global policy controller processes the received alarm and generates the resource adjusting plan; the policy control network returns the resource adjusting plan to the resource manager; and the resource manager executes the resource adjusting plan. By constructing graded control policies and assisting coordination mechanisms among the control policies in different grades, the invention effectively improves the utilization rate of private cloud resource.
Owner:NEUSOFT CORP
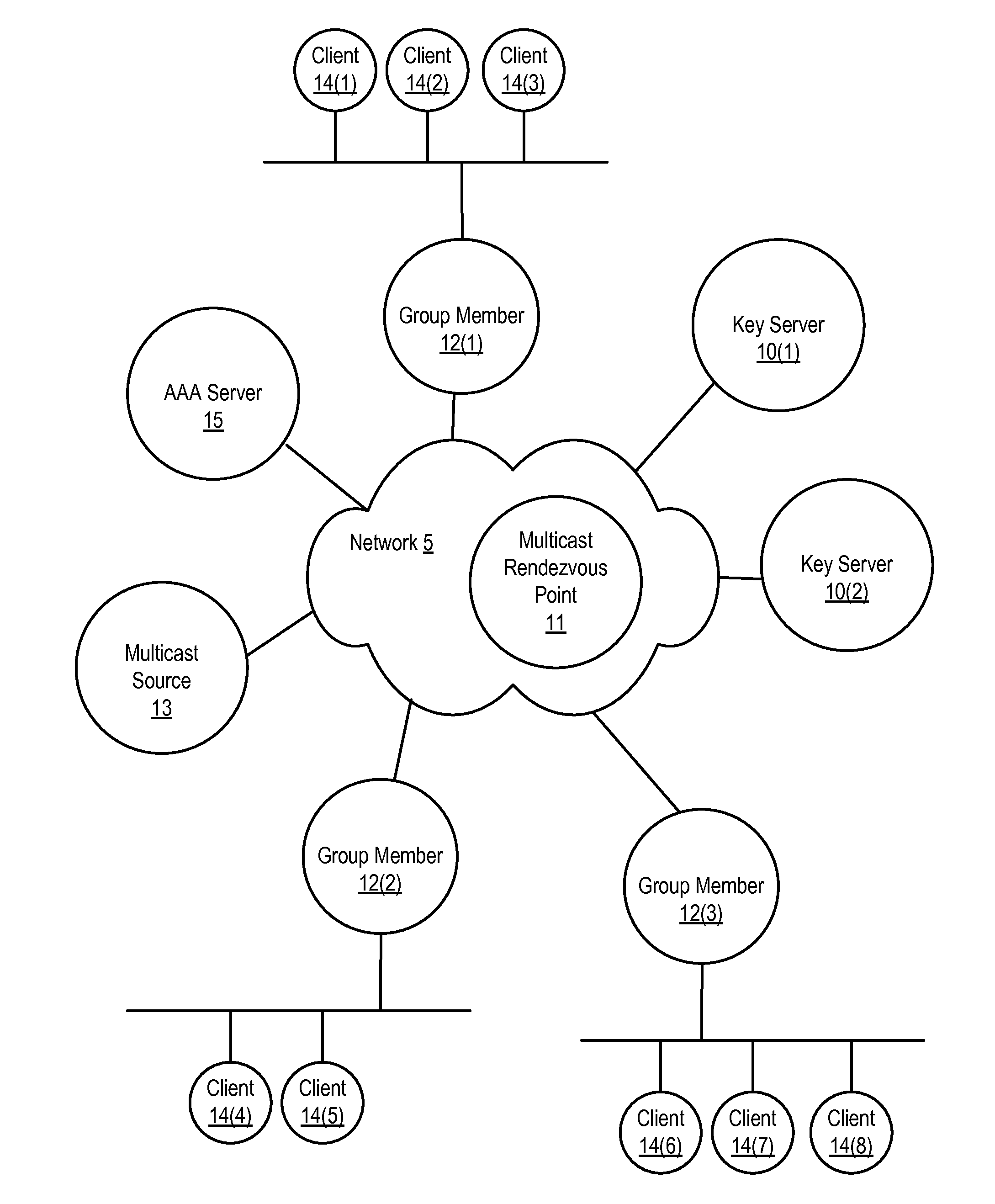
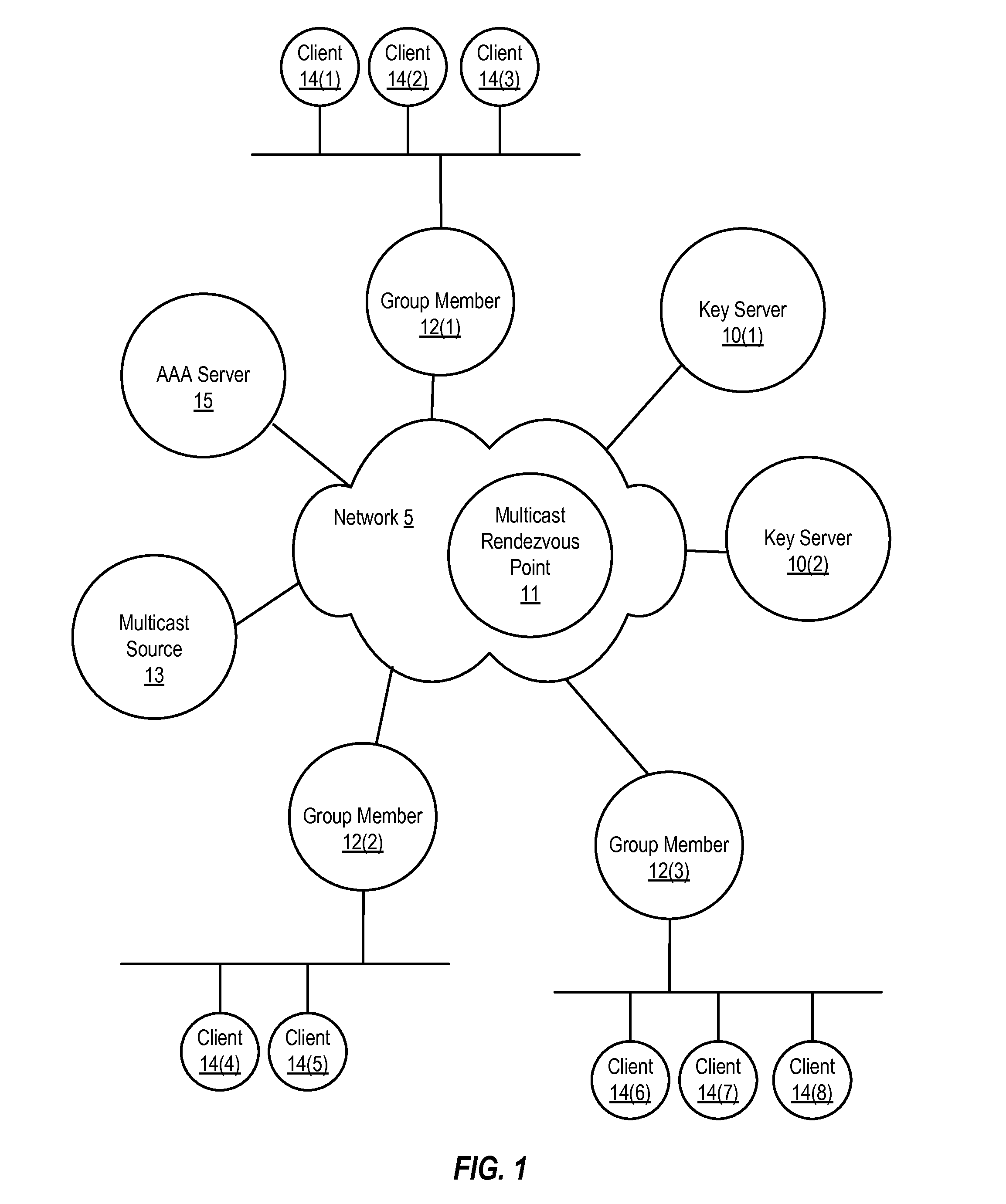
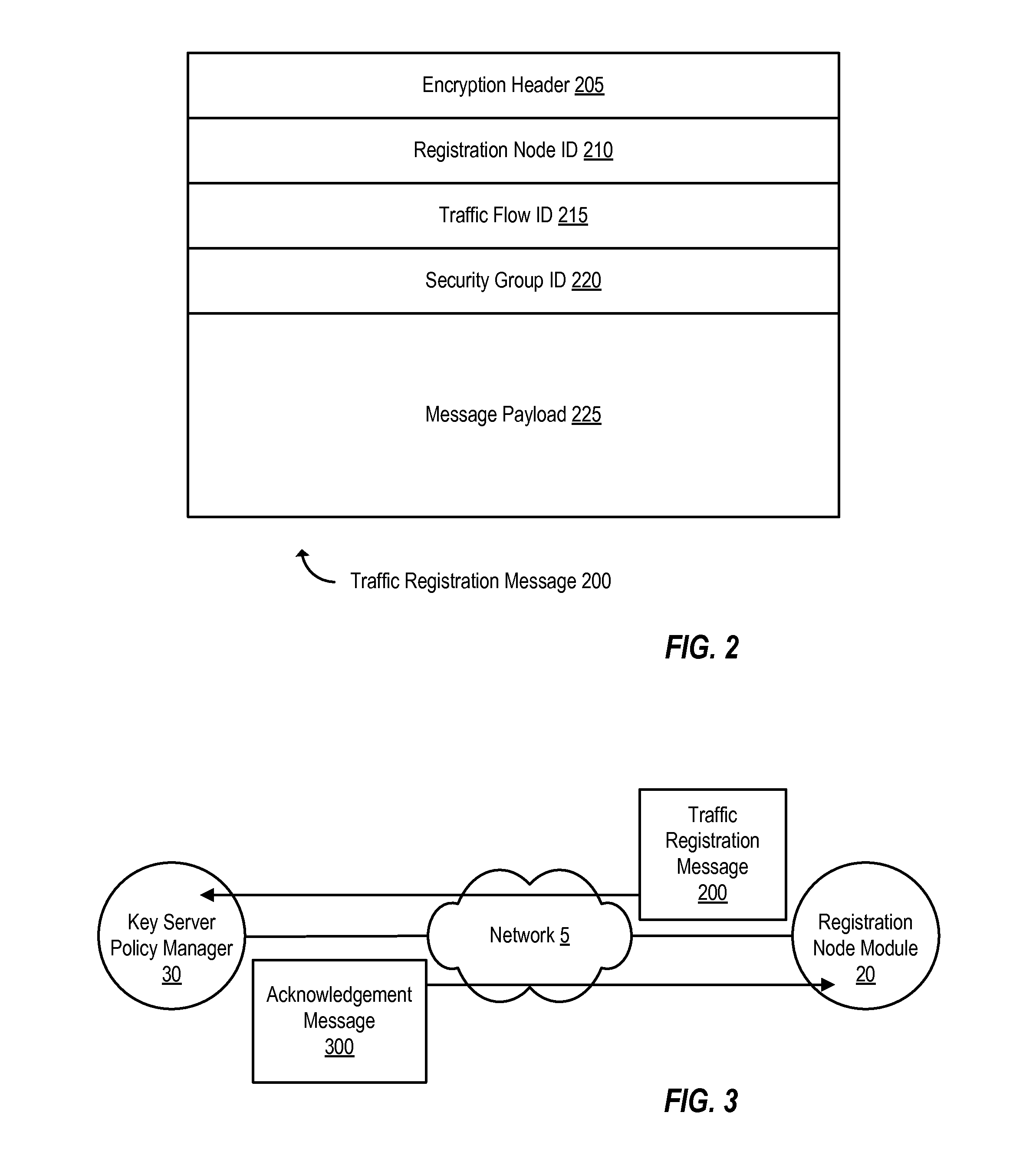
Dynamic group creation and traffic flow registration under a group in a group key infrastructure
ActiveUS20130219035A1Digital computer detailsElectric digital data processingTraffic capacityGroup Policy
Upon detection of a new traffic flow, a registration node can dynamically register the new traffic flow with a key server policy manager by sending a registration request on behalf of the new traffic flow. A registration request indicates the new traffic flow should be protected by a security group. A registration request may also include a request to dynamically generate a new security group to protect the traffic flow. The registration request is received by a key server policy manager, which performs authentication and authorization checks of the requesting registration node, and determines whether to accept or reject the registration request. If accepted, the key server policy manager registers the new traffic flow by including a description of the traffic flow in a group policy of an existing security group or a newly created security group, depending on the registration request.
Owner:CISCO TECH INC
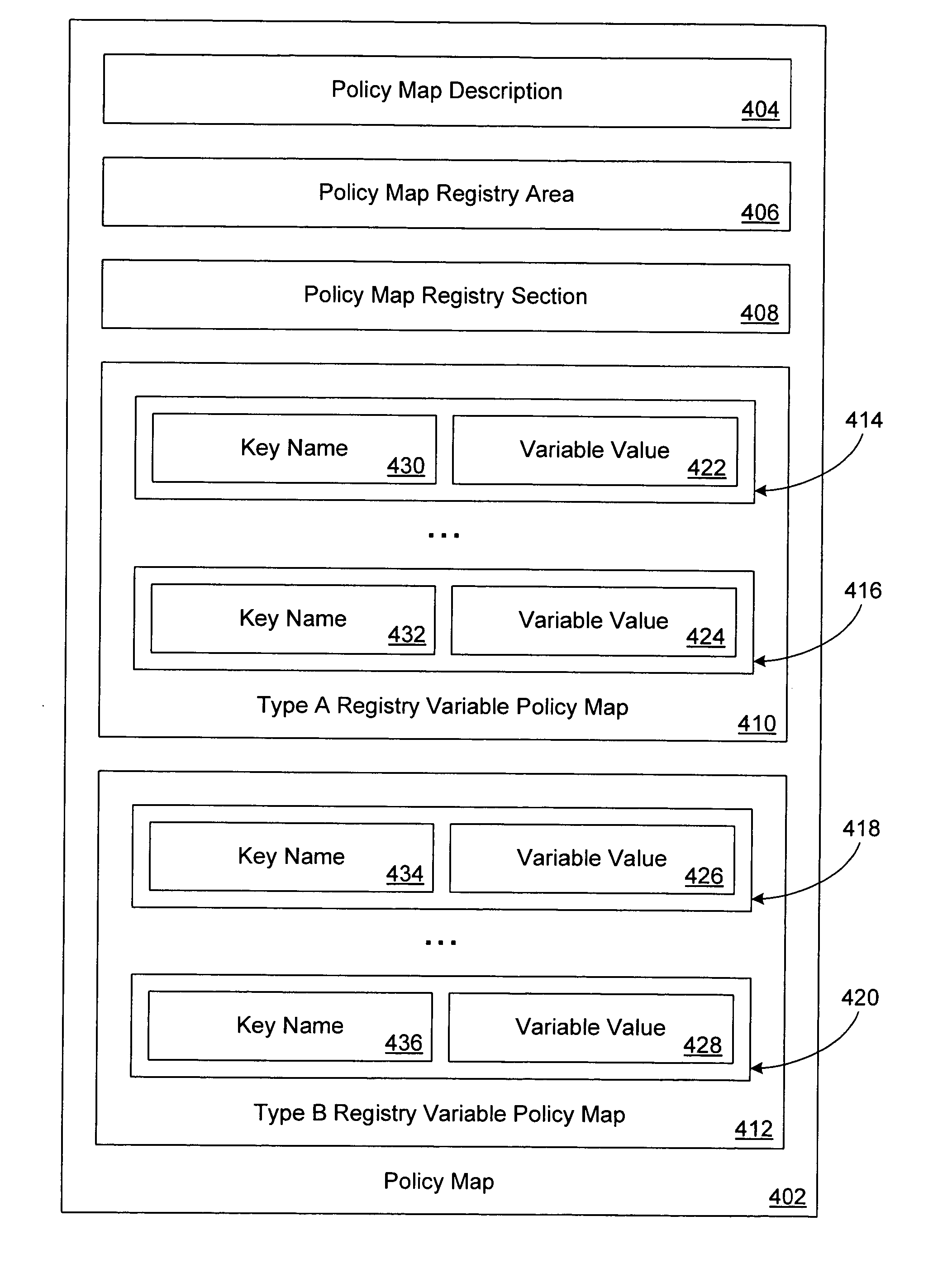
System and method for efficient configuration of group policies
InactiveUS20060174320A1Well formedPlatform integrity maintainanceSpecial data processing applicationsConfigfsGroup Policy
A registry of system information may have several sections. Group policies may be represented by entries in particular sections of the registry. A policy map may map group policies to the sections and entries of the registry. A policy map registry section field of the policy map may specify one or more sections of the registry to which group policies are mapped. The policy map may include one or more registry variable policy map fields, each of which may specify mappings for different types of registry variables. A configuration file repository may include sets and versions of policy configuration files that include policy maps. A group policy configuration tool may retrieve and parse policy maps, and update group policies corresponding to the policy maps.
Owner:MICROSOFT TECH LICENSING LLC
Automatic provisioning of resources to software offerings
ActiveUS8589557B1Easy to deploySimple to executeDigital computer detailsMultiprogramming arrangementsSystem usageWork breakdown structure
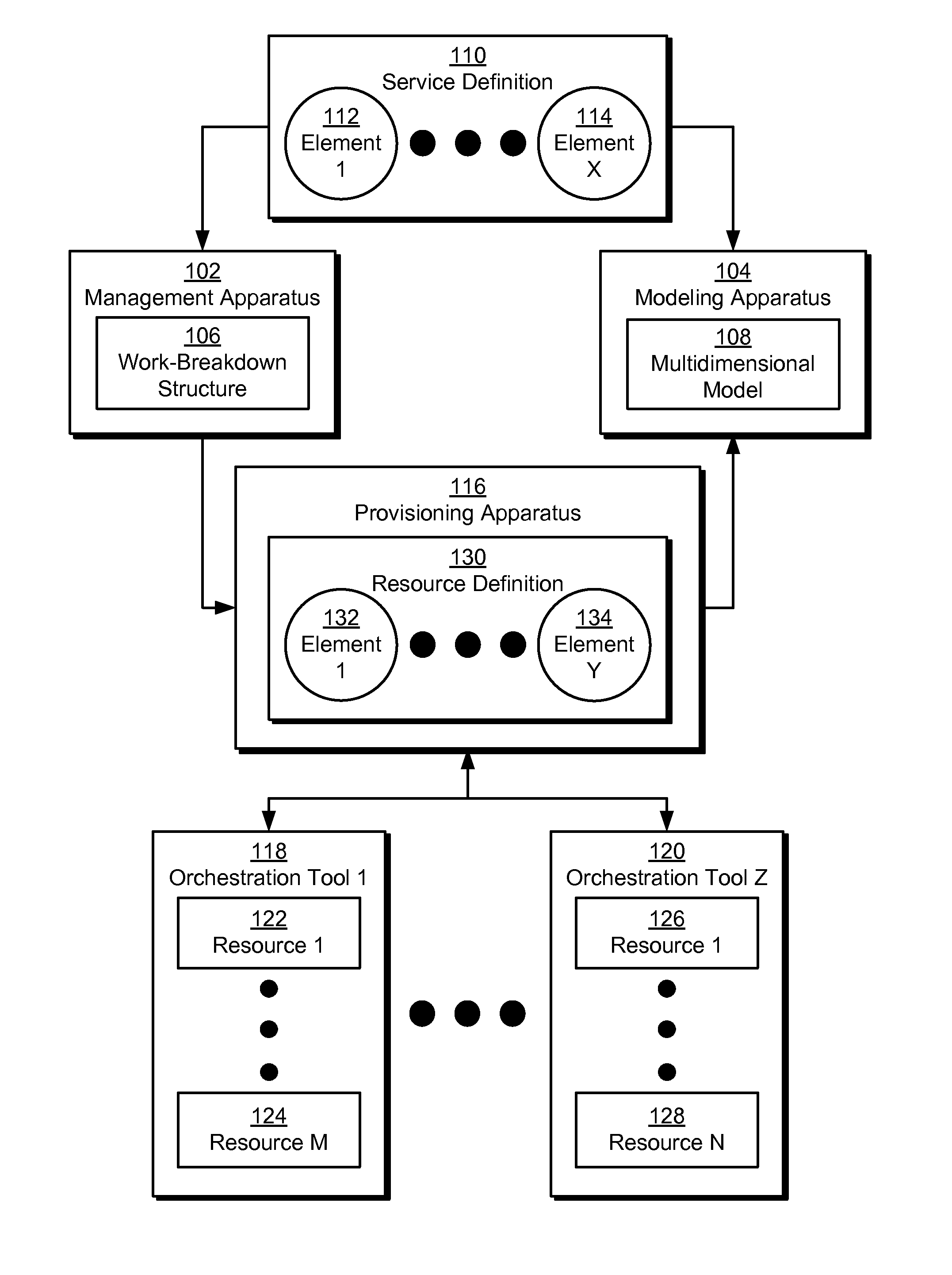
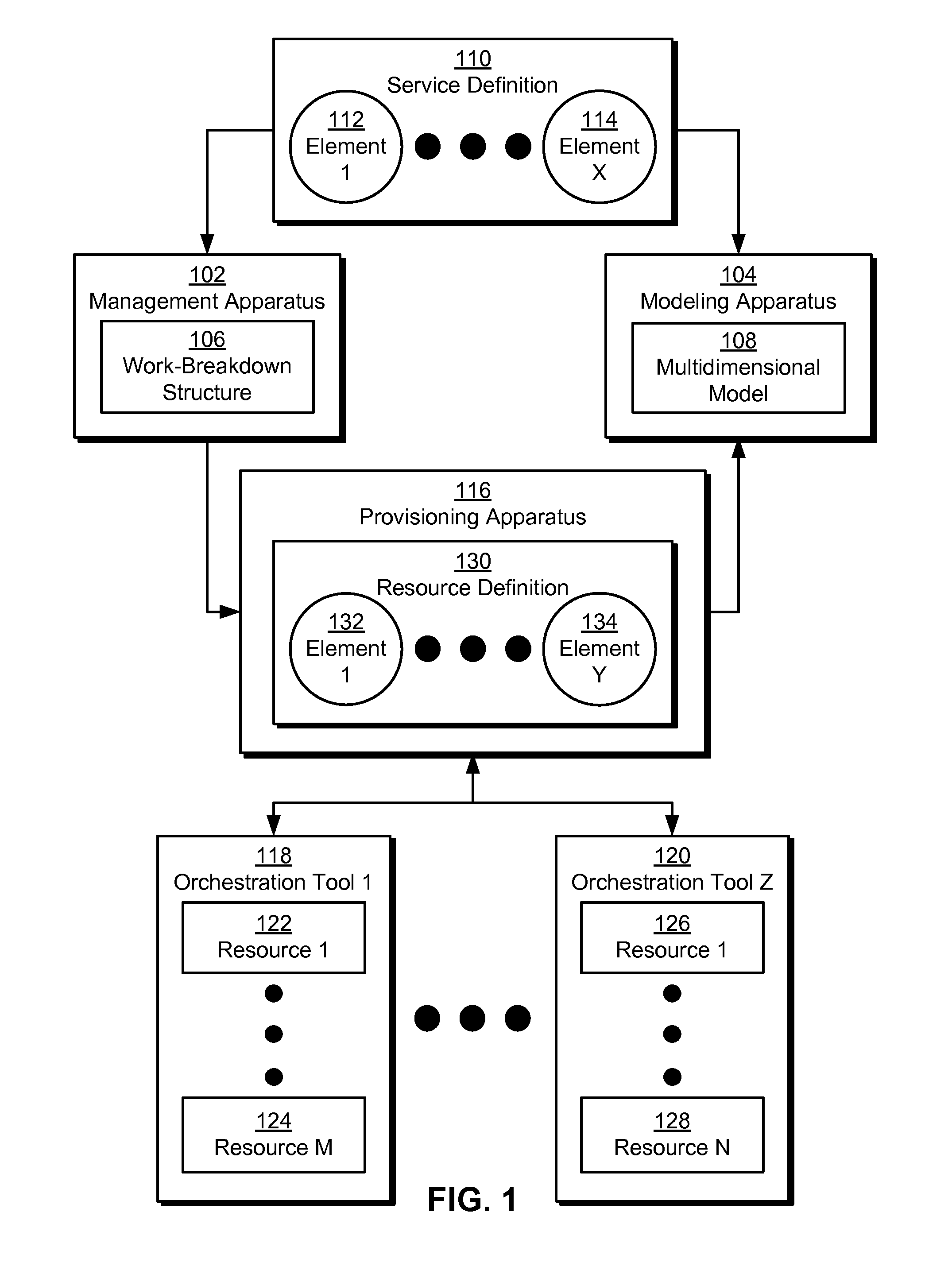
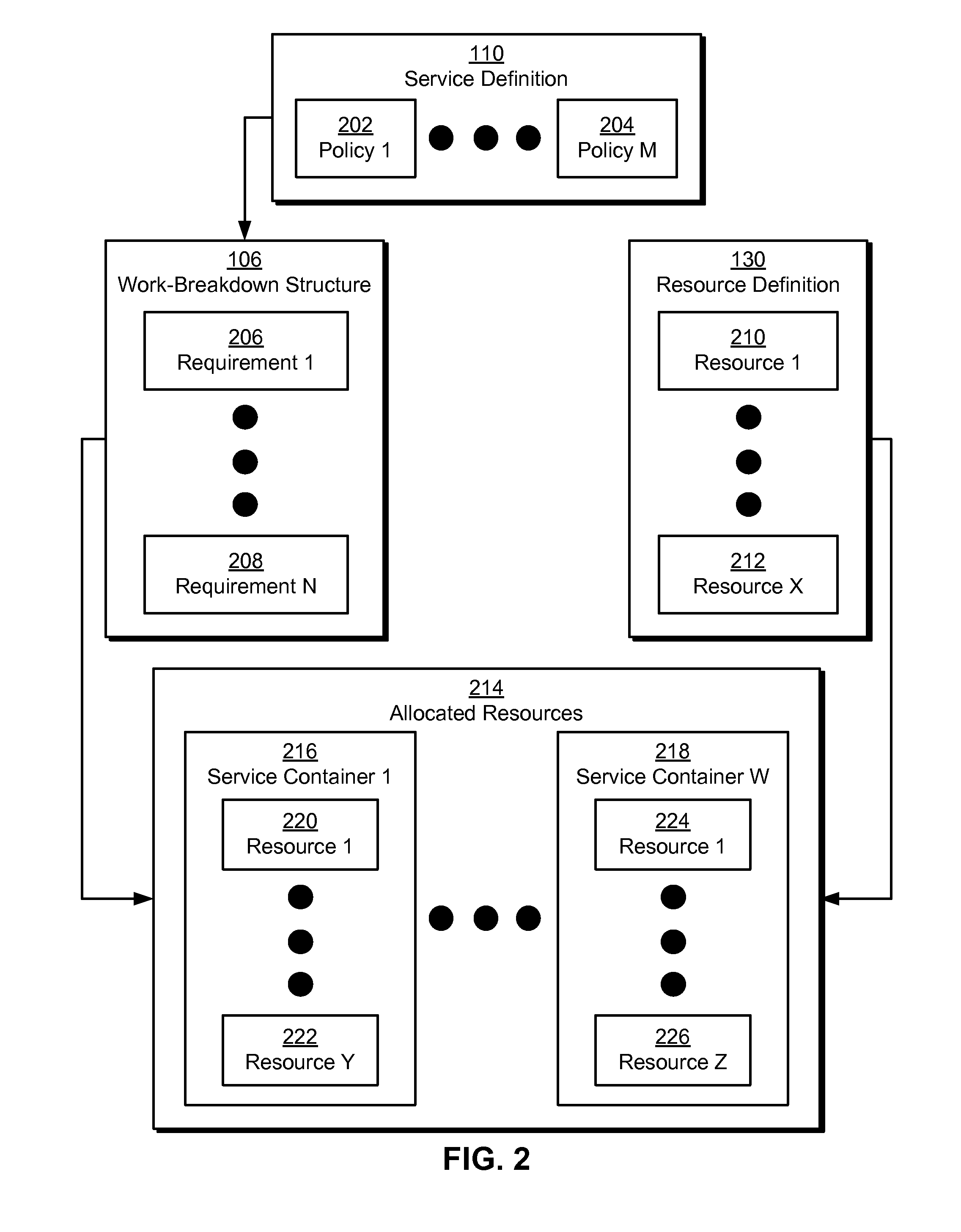
The disclosed embodiments provide a system that facilitates the deployment and execution of a software offering. During operation, the system obtains a service definition of the software offering. Next, the system creates a work-breakdown structure based on a set of policies from the service definition. Finally, the system uses the work-breakdown structure to automatically provision a set of resources for use by the software offering without requiring manual configuration of the resources by a user.
Owner:INTUIT INC
Inheritance based network management
ActiveUS20060212924A1Special data processing applicationsSecuring communicationComputer hardwareControl system
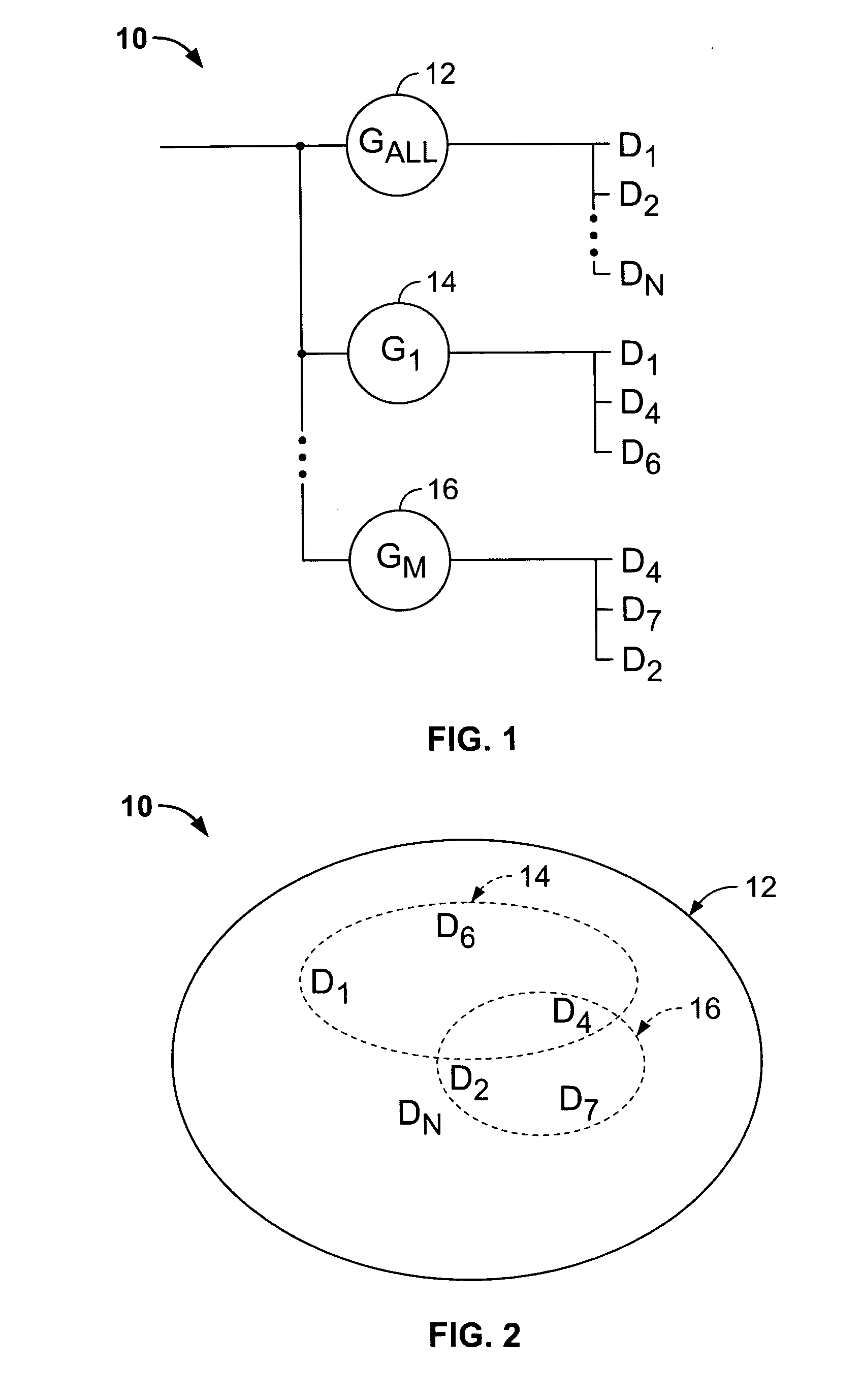
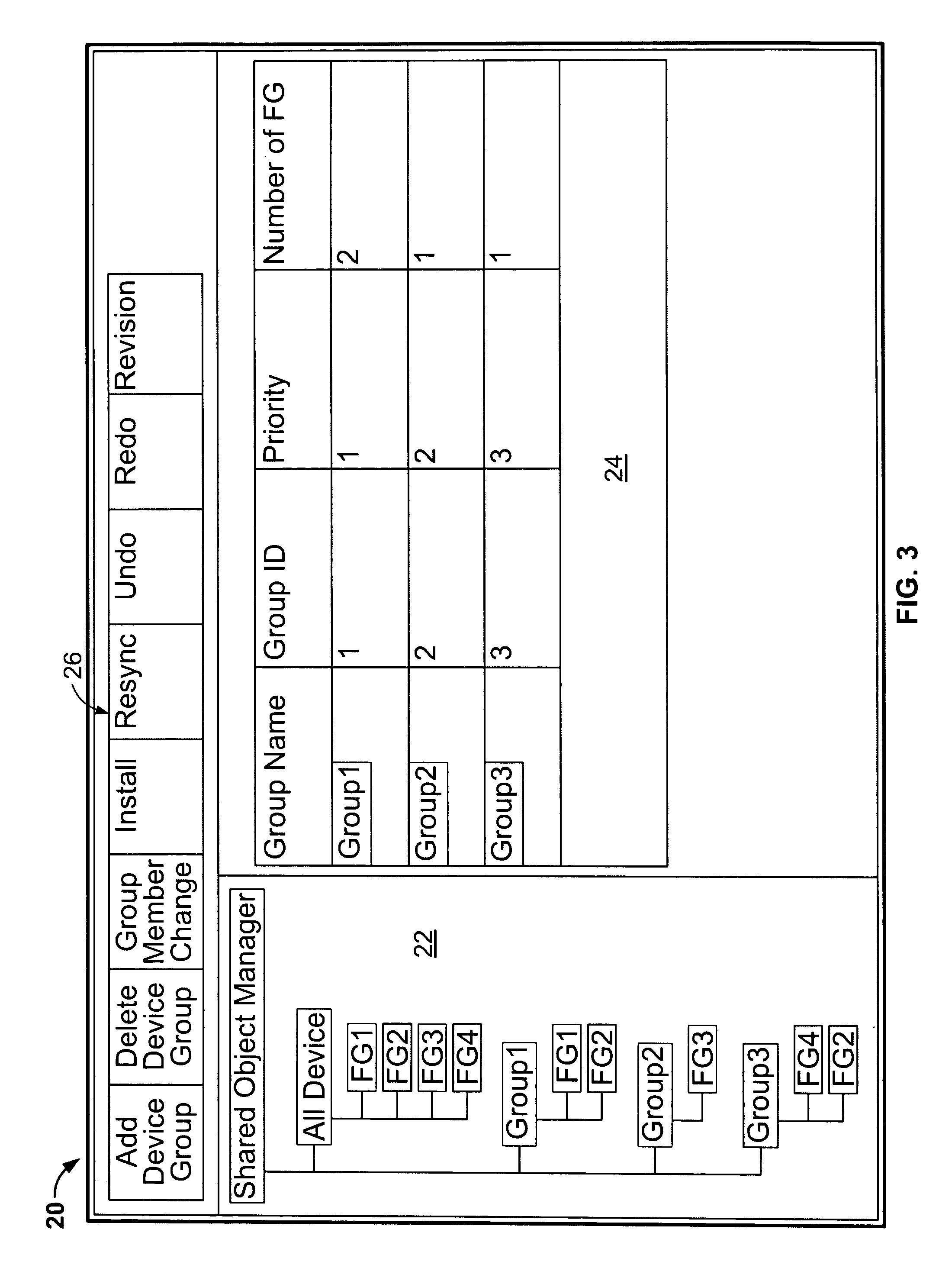
The present invention teaches a methodology for provisioning and managing a network having many network devices. In certain embodiments, groups of member devices are created each having a group policy configuration inherited by member devices. A variety of rules regarding prioritization, versioning, system snapshot, redo and undo are also taught. This embodiment is useful when the network devices can be partitioned into groups of similar type devices for similar applications. Similar physical attributes can also be mappend into identical virtual attributes, enabling policy configurations to be applied to varying devices and physical attribute configurations can be resolved upon device installation.
Owner:FORTINET
Servers and Methods for Controlling Group Management
InactiveUS20070220005A1Enhanced advantageSpecial service provision for substationNetwork topologiesCommunications systemUser privacy
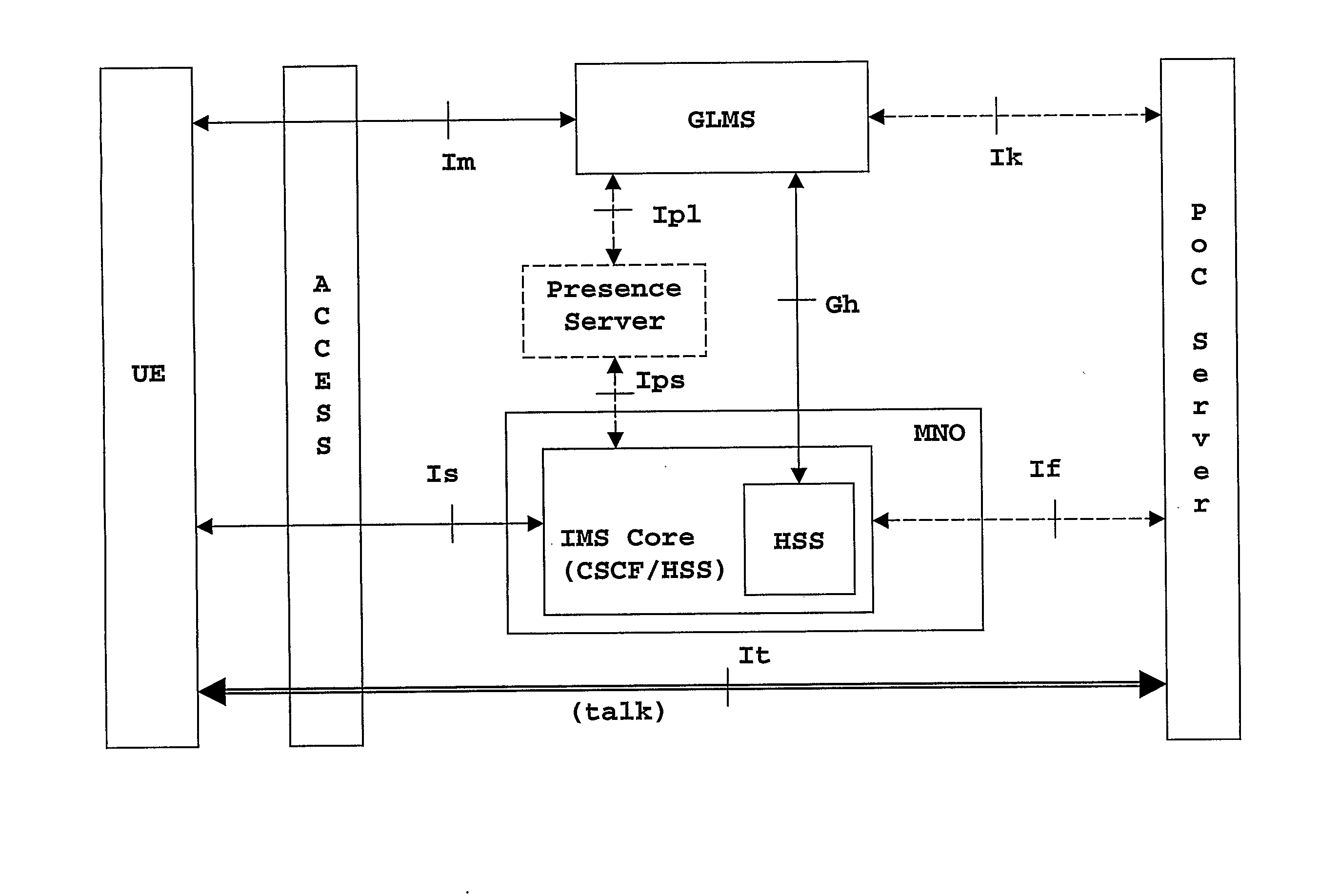
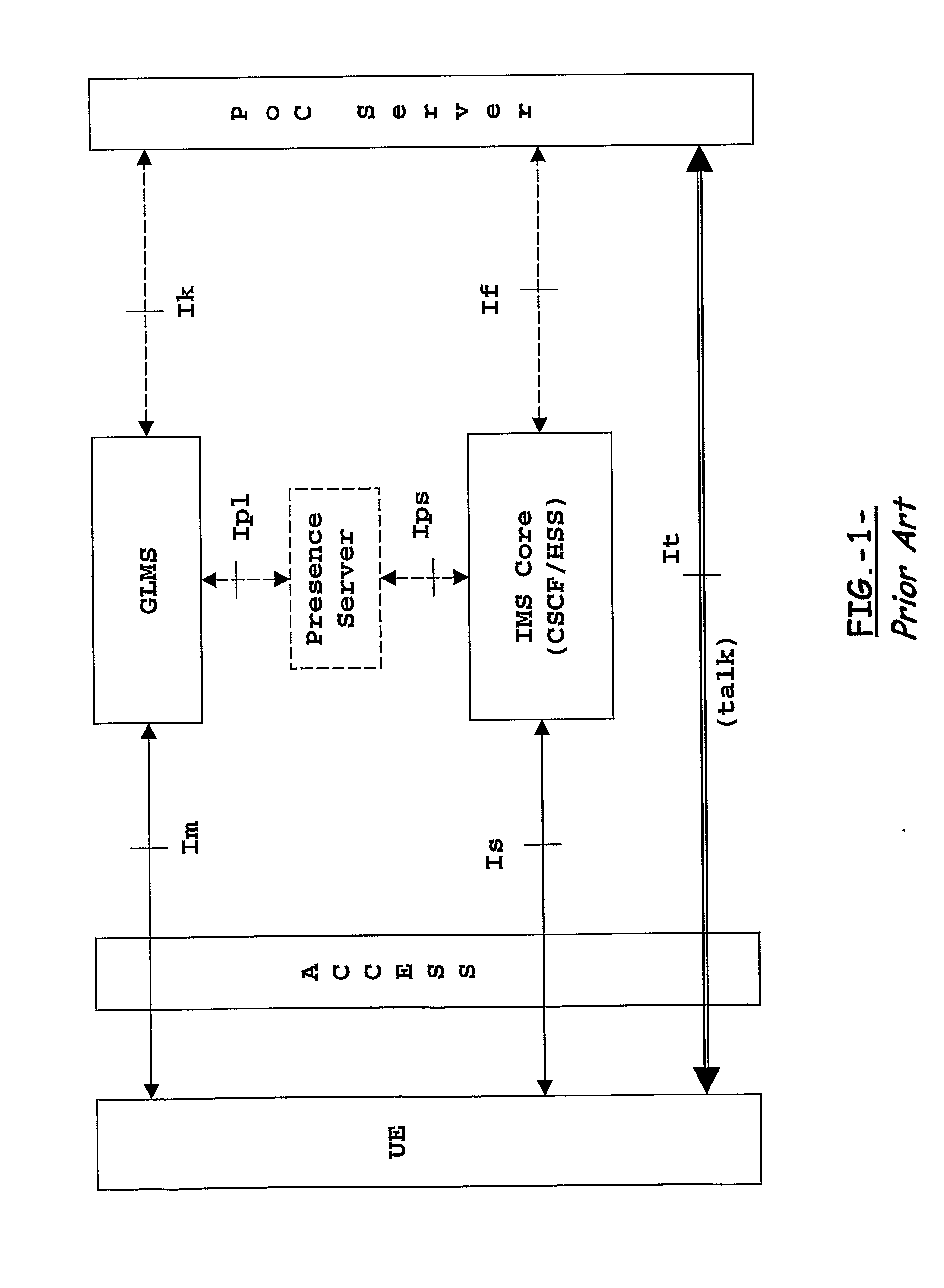
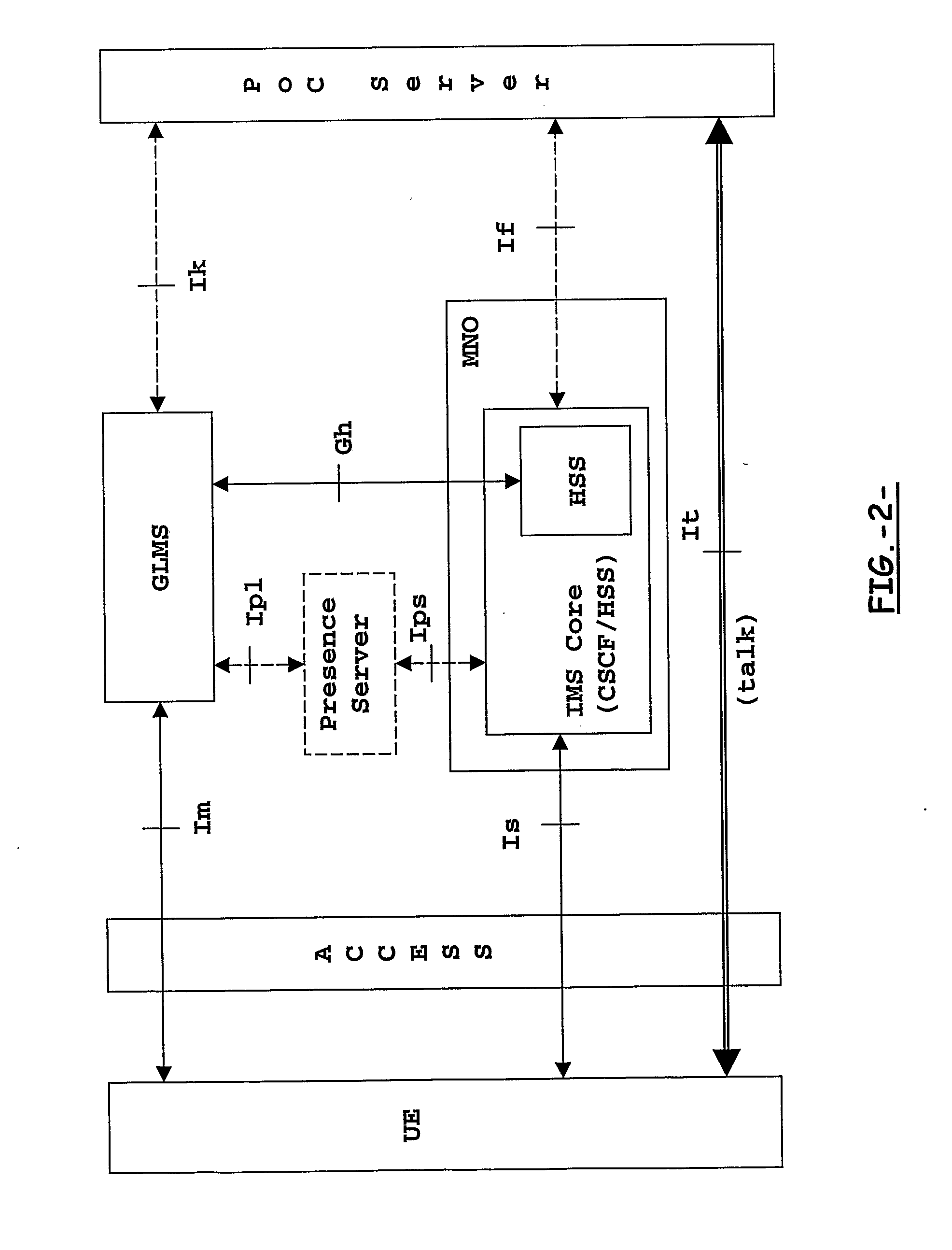
The present invention addresses the management of user groups, user contact lists, and user access lists in a telecom-communication system whereby a user access to a group and list management server for creating, deleting or modifying a group, contact list and access list in terms of group policies and members. User groups, user contact lists, and user access lists are operated without any validation other than being syntactically correct, and without taking into consideration the users access capabilities, the users privacy, and even the user existence. In particular, the telecommunication system may comprise a number of networks operated by different network operators where the users hold subscriptions. The present invention offers a new interface between a group management server and a subscriber server of a network operator where the users hold their subscriptions, so that user policies in the subscriber server govern operations on groups, contact lists and access lists.
Owner:TELEFON AB LM ERICSSON (PUBL)
Terminal equipment remote software version distribution method and system
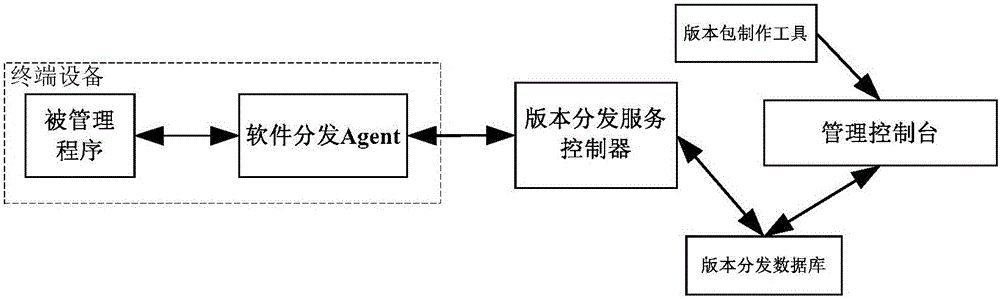
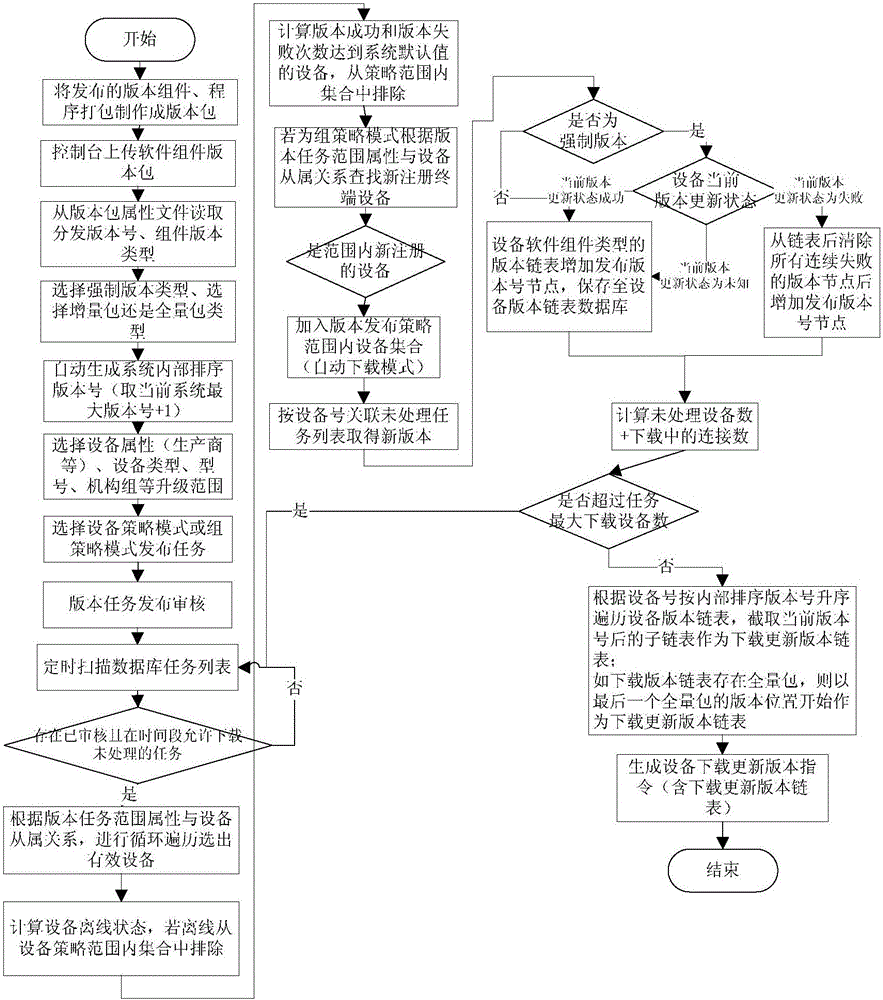
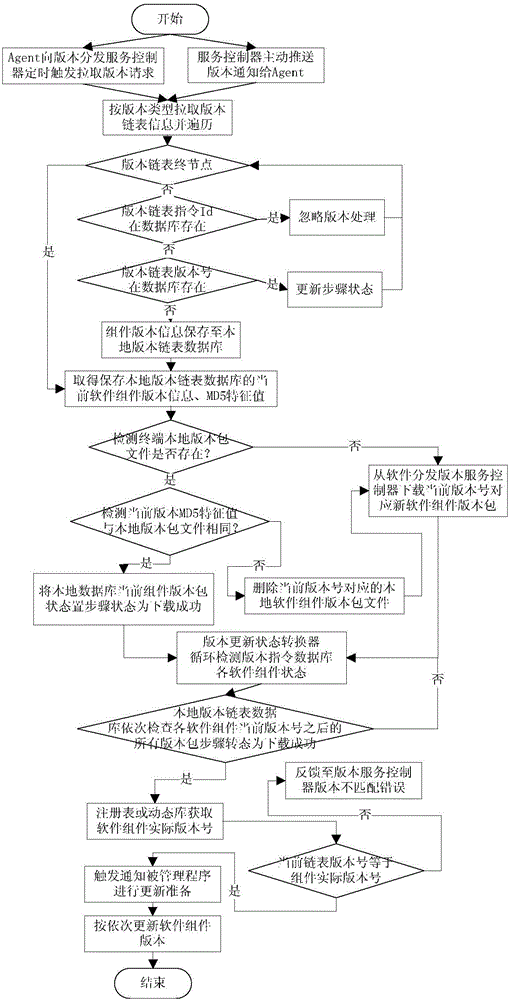
ActiveCN105763369AControllable version informationEasy to manageVersion controlData switching networksSoftware distributionSystems management
The invention provides a terminal equipment remote software version distribution method and system. A version link list is maintained for each set of terminal equipment managed by the system, the terminal equipment programs are supported to be split according to any number of software component types easy to manage, the version link list is established for each type of software component, different software component types have separately independent upgrading lines, and upgrading of all types of software components is not mutually dependent; a group policy mode is utilized, and automatic upgrading after registration of new equipment within group range can be supported; and a software distribution agent side acquires the real version number of the software components through the agreed program interface or system storage data to be matched with the version number recorded in a server side so that authenticity and uniqueness of the version link list can be guaranteed. Fine control and management of terminal equipment remote software distribution and unified version management can be efficiently, safely and conveniently performed.
Owner:HUNAN GREATWALL INFORMATION FINANCIAL EQUIP
Method and system for implementing group policy operations
ActiveUS8244841B2Facilitates their access and their ability can be foundDigital data processing detailsDigital computer detailsFile systemApplication software
A system and method for performing various operations on group policy objects, by manipulating group policy objects as a single entity to perform backup, restore, import and copy operations. The backup operation transfers the various subparts of a selected group policy object to a file system. A restore operation restores a backed-up group policy object to its domain, in the same state as when the backup was performed. An import operation transfers the settings within a backed-up source group policy object to a destination group policy object, erasing its previous settings. A copy operation transfers the settings from a source group policy object to a new group policy object. Copy and import operations can be cross-domain, and a migration table can be used to convert security group and UNC pathnames as appropriate for the destination domain. Backup management, rollback of incomplete operations, and support for application deployment are also provided.
Owner:MICROSOFT TECH LICENSING LLC
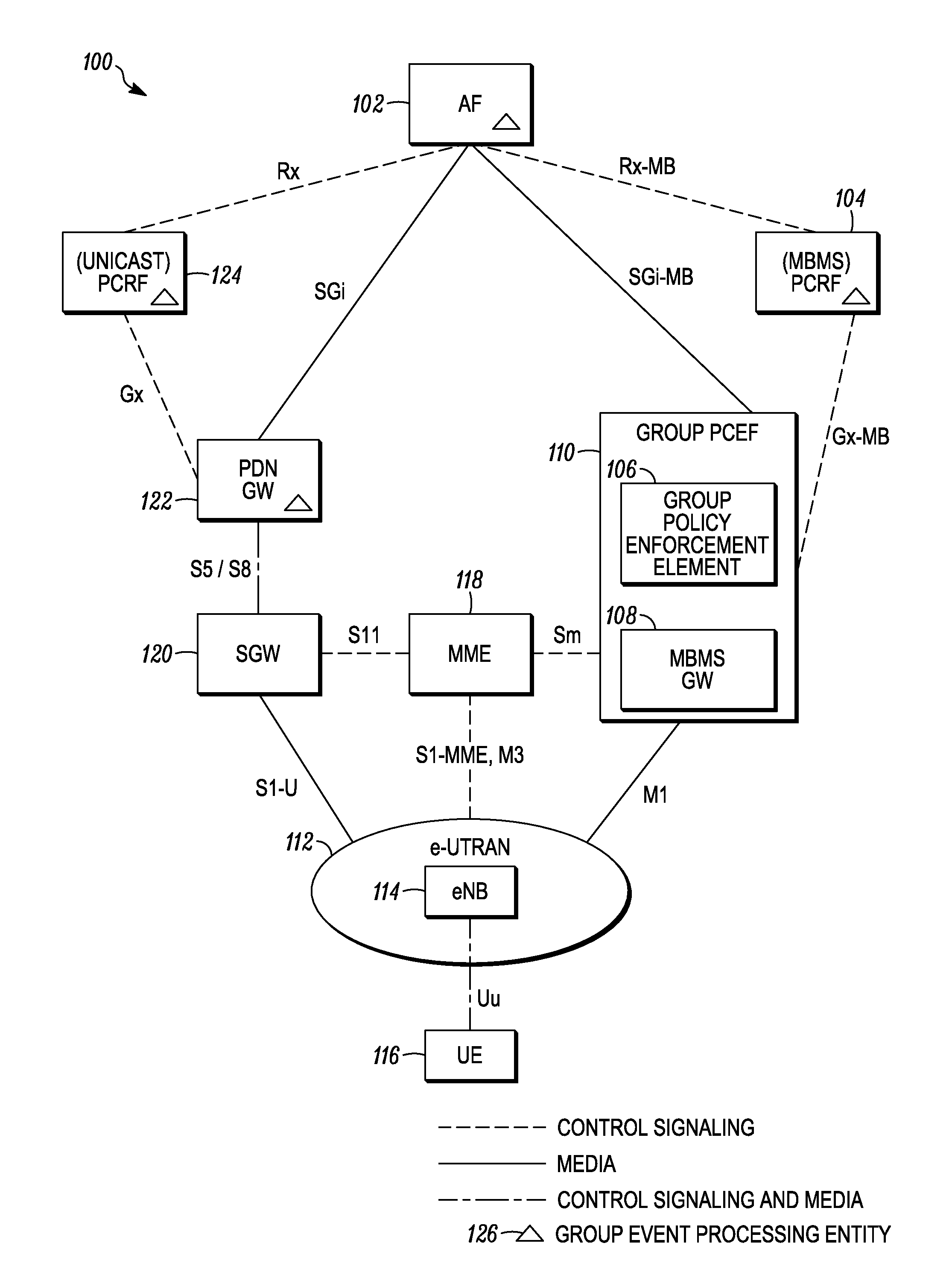
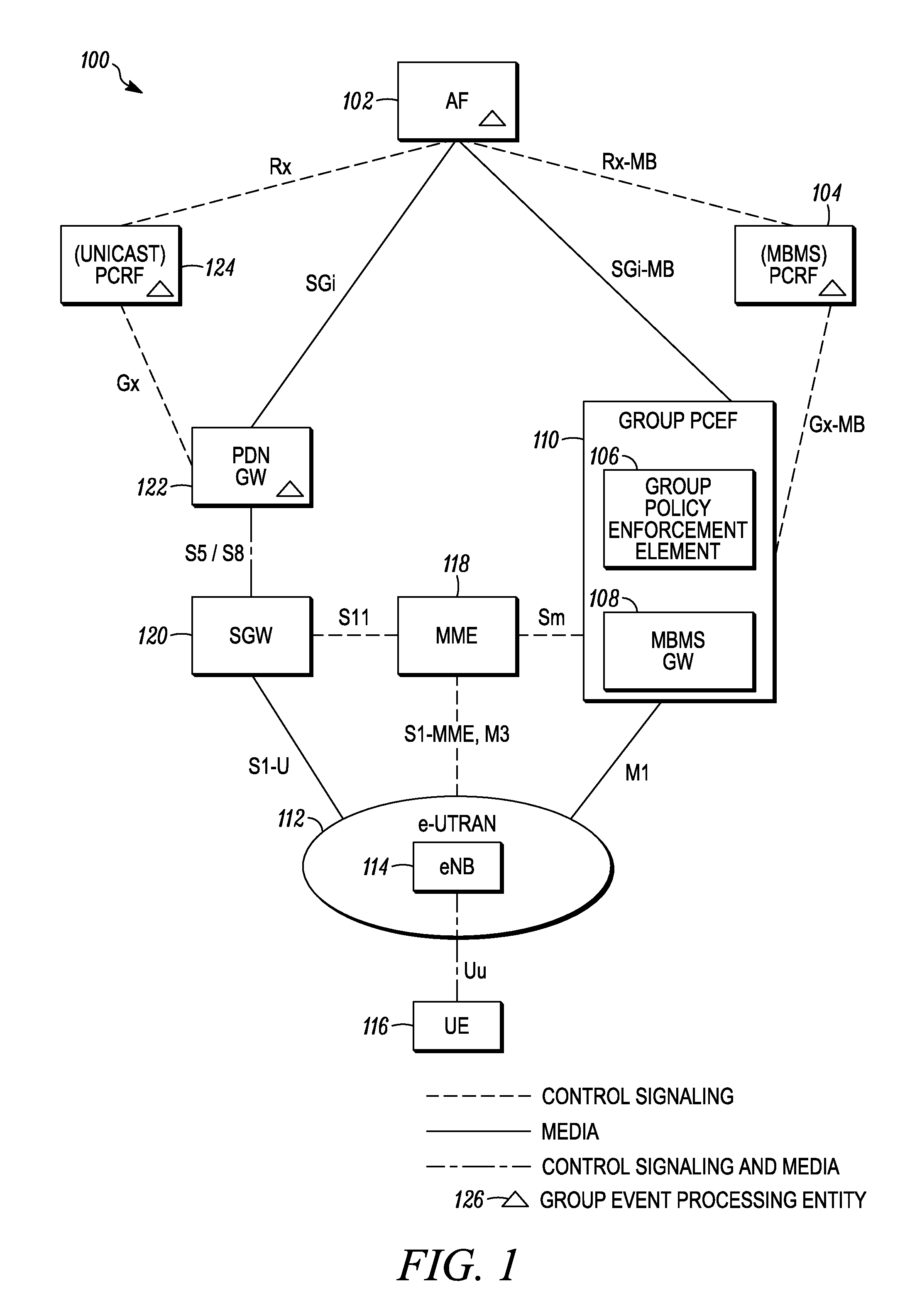
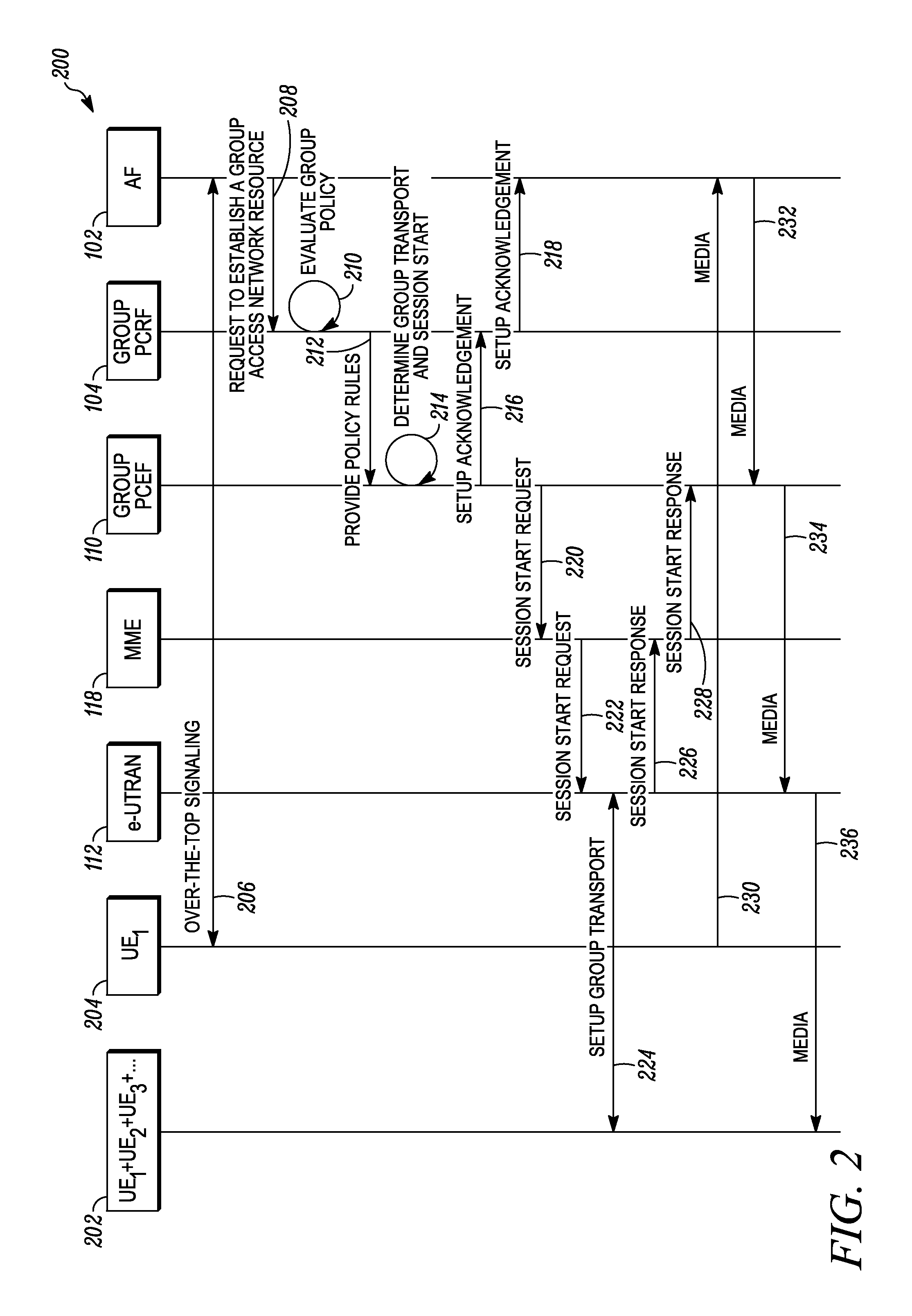
Method and apparatus for processing group event notifications and providing group policy in a communication system
ActiveUS20130159521A1Digital computer detailsConnection managementAccess networkCommunications system
A group event processing entity receives and processes a group event notification wherein a set of policy rules is determined that controls the performance of an action as relates to at least one of a member user equipment of a group session or an access network resource for the group session. Additionally, a group policy decision entity receives a request to establish a group access network resource for a group of user equipment and determines a set of applicable policy rules for establishing the group access network resource, wherein the set includes a policy rule that controls performance of an action when a base station in a wireless access network is unable to provide resources to support the requested group access network resource. The group policy decision entity provides the set of applicable policy rules to a group policy enforcement entity.
Owner:MOTOROLA SOLUTIONS INC
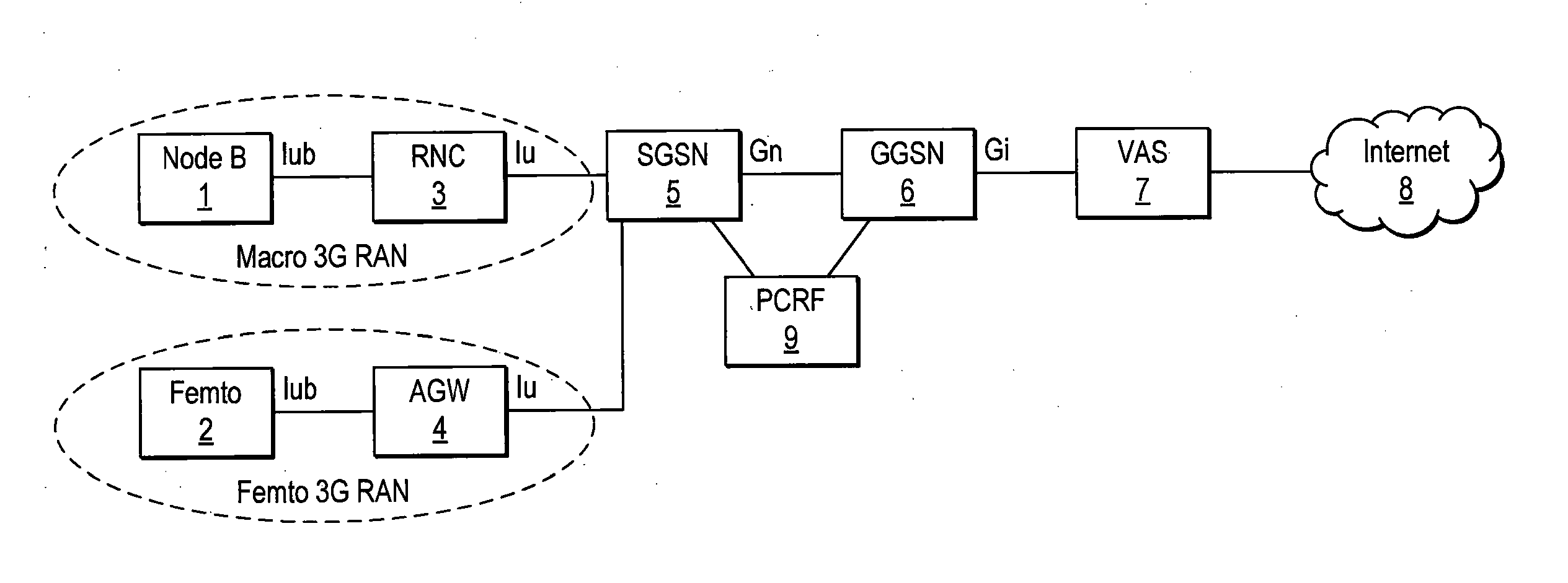
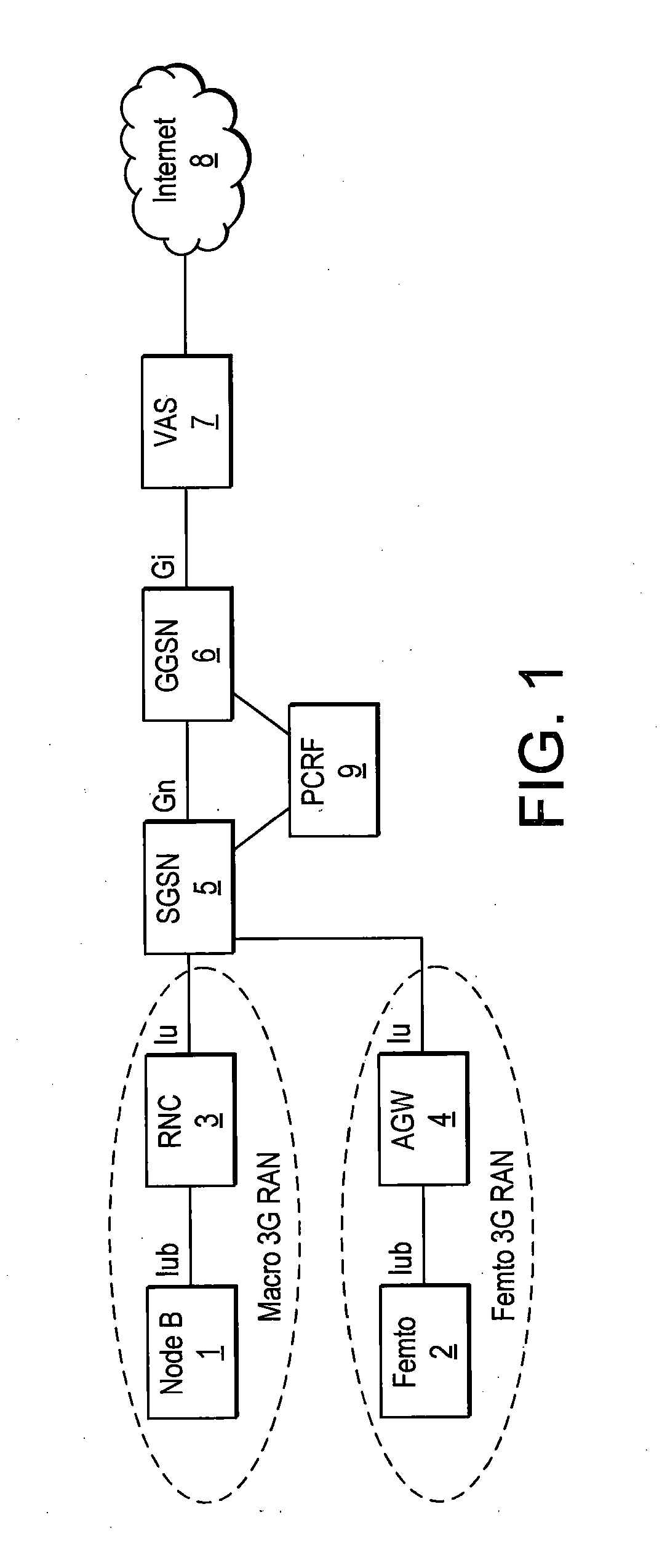
Telecommunications networks
ActiveUS20160330748A1Reduce the amount requiredTelephonic communicationBroadcast service distributionAccess networkTelecommunications network
A mobile telecommunications network includes: a radio access network having radio means (2000) for wireless communication with a plurality of terminals (10) registered with the telecommunications network and control means (700) operable to control interaction of the terminals with the radio access network; and a core (2030) including a store of policy information comprising group policy data (2210) applicable to a group of the terminals and individual policy data applicable to respective ones of the terminals (10), and distribution means operable to provide to the control means associated with each of the terminals an indicator of the group policy data applicable to each of the terminals and the individual policy data applicable to each of the terminals.
Owner:VODAFONE IP LICENSING
System for policy-based management of software updates
ActiveUS7496910B2Program loading/initiatingSpecial data processing applicationsSoftware updateComputerized system
A computer system configured for policy-based management of software updates is disclosed. The system maintains group-policy objects, with which groups of computers are associated. The system obtains identities of software updates from a source of software updates. The system also obtains filter criteria for each update, for determining whether the update should be applied to a particular computer or not. The system assigns newly available updates to respective selected group-policy objects and adds the obtained filter criteria to each such group-policy object. The system performs necessary installations of updates by, for each group-policy object, determining whether, for each combination of a computer belonging to a group associated with that policy object and an update assigned to that policy object, the computer satisfies the filter criteria for the update, and if so, applying the update to that computer, but if not, refraining from applying the update.
Owner:MICROSOFT TECH LICENSING LLC
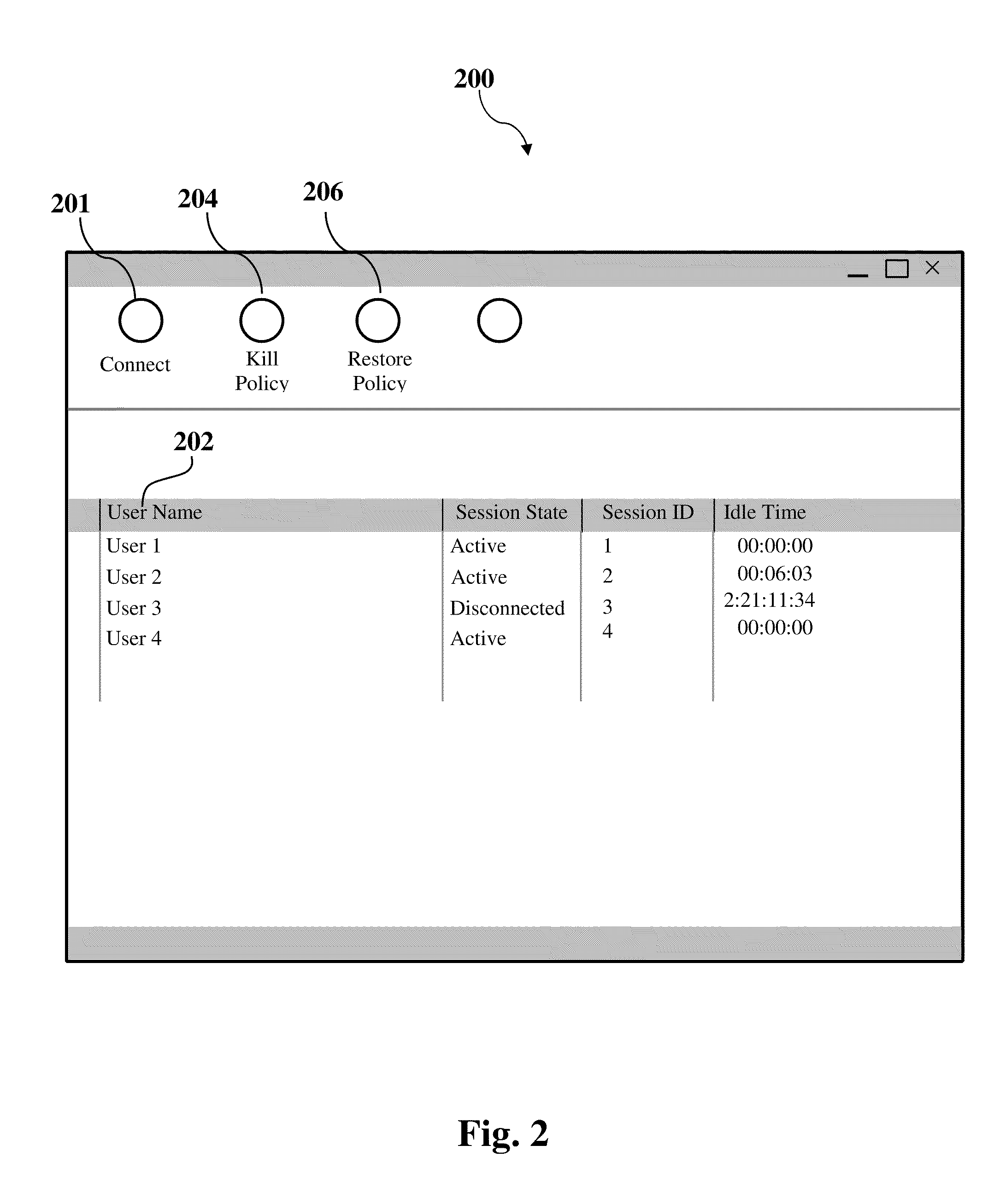
Method and system for temporarily removing group policy restrictions remotely
A device, system and method is provided for remotely changing a policy setting on a first computer. A second computer may remotely connect to the first computer. The first computer may have an initial policy setting. The second computer may change one or more key values stored in the registry of the first computer. The key values may define the policy setting of the first computer. The second computer may start an application in the first computer that automatically retrieves the key values stored in the registry of the first computer to apply a corresponding new policy setting to the first computer. The second computer may be operated by an administrator investigating a problem and providing maintenance to the first computer in a system network by temporarily removing a restrictive policy setting on the first computer.
Owner:SMART X SOFTWARE SOLUTIONS
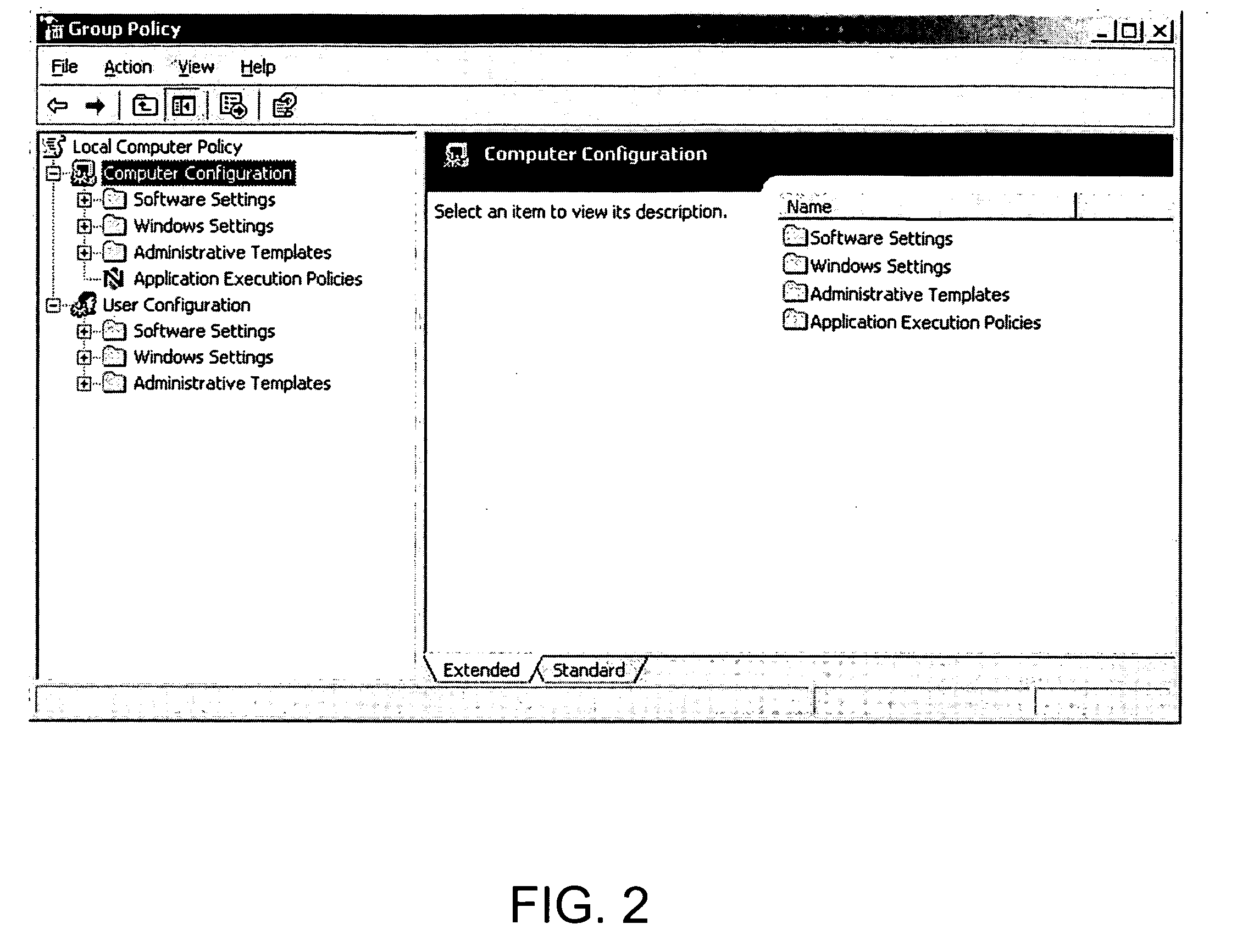
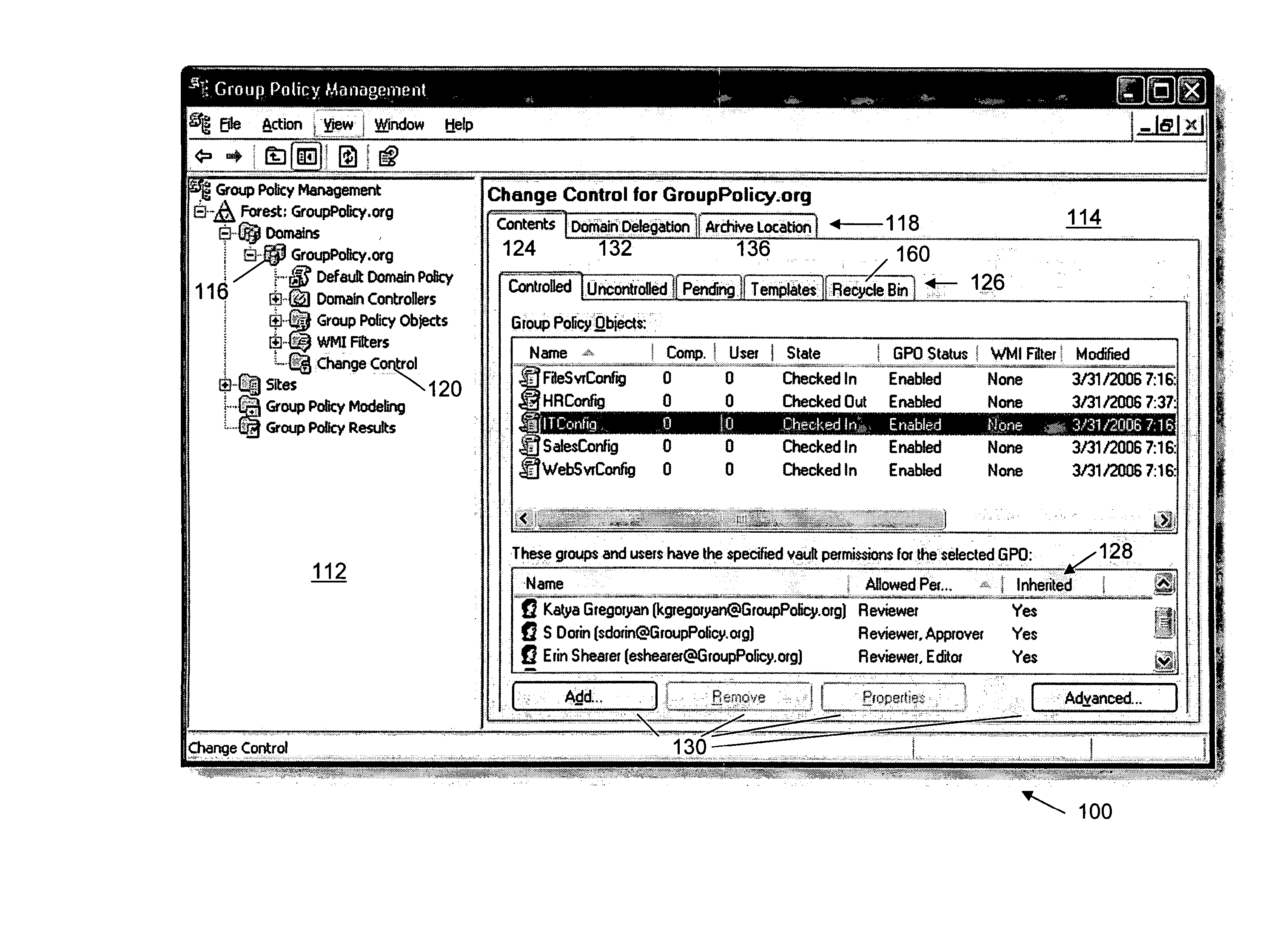
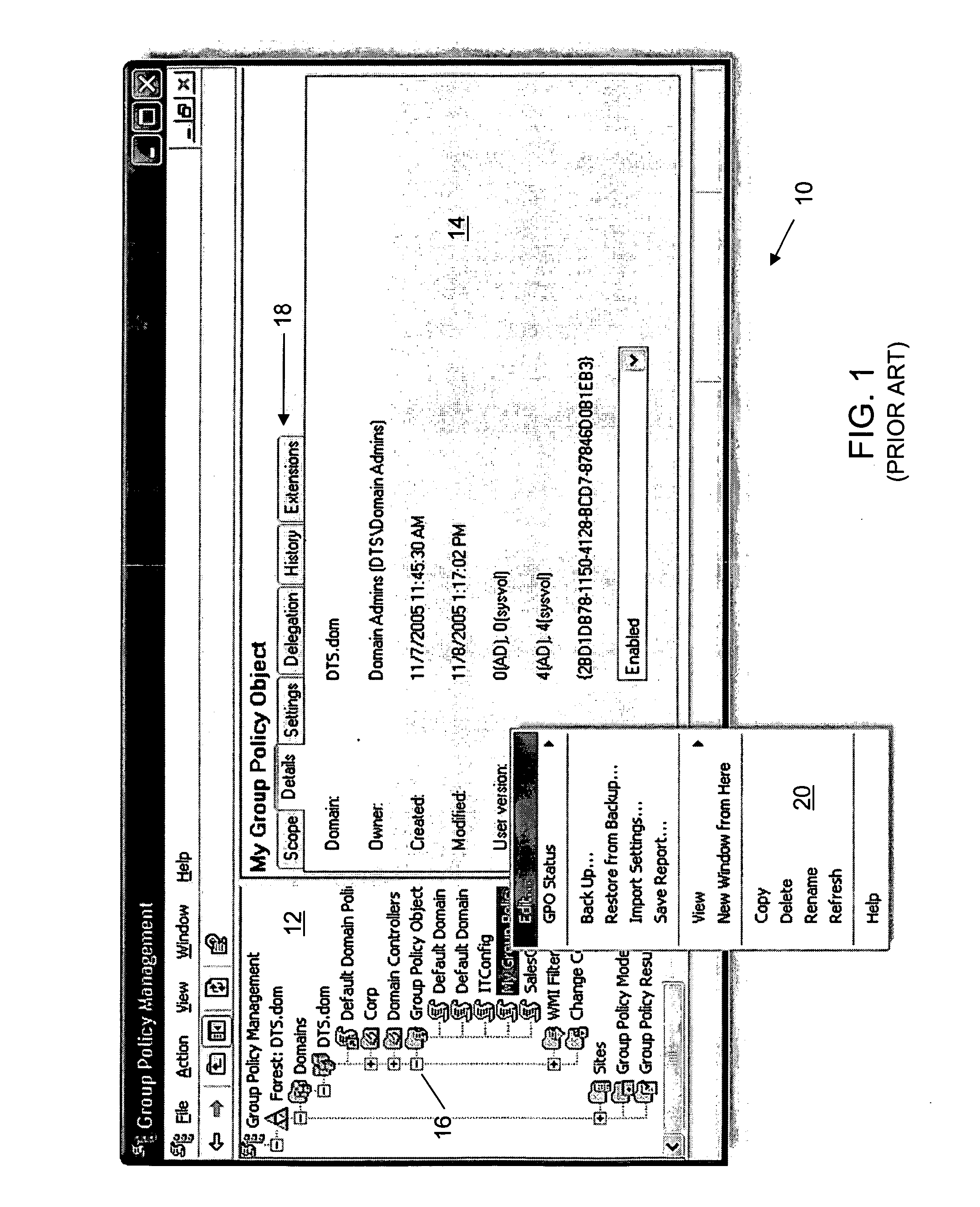
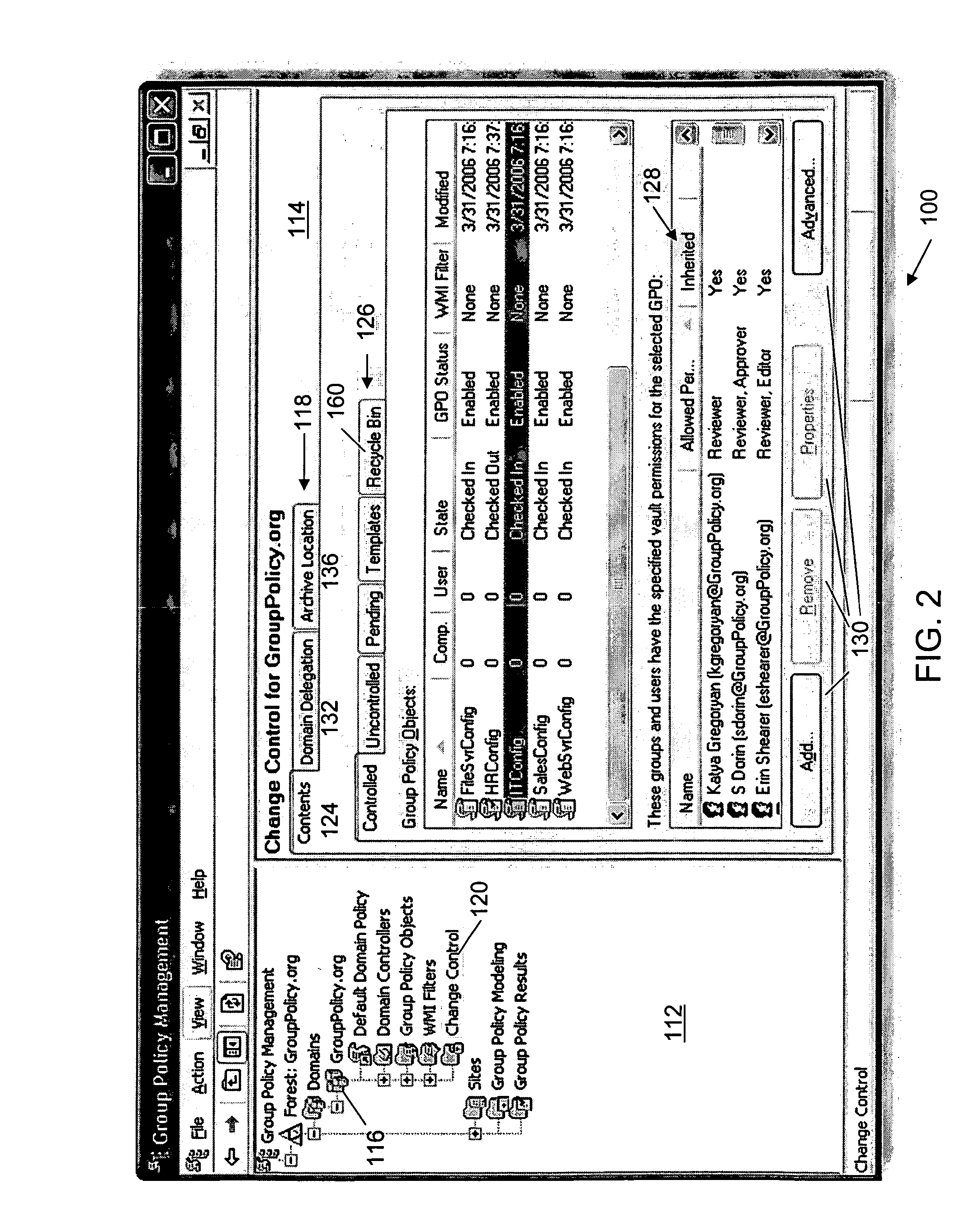
Methods and systems for change management for a group policy environment
InactiveUS20070244897A1Easy to manageReducing infrastructure requirementDigital data information retrievalSpecial data processing applicationsChange managementChange control
Comprehensive change control and enhanced management of GPOs in a client-server environment is described. A Group Policy Management Console (GPMC) extension provides seamless integration with GPMC. The application or extension provides a secure archive for controlling changes to GPOs. To change a GPO, an administrator “checks out” the GPO from the archive or vault. When changes are complete, the GPO is “checked in” to the vault. Differences between archived versions and / or live versions are reviewed using GPMC-style reports. When a GPO is ready for deployment, it can be transferred to the live environment. At any time, one or more live GPOs can be “rolled back” to an archived version. GPO data in the secure archive is maintained in XML files, greatly reducing infrastructure requirements.
Owner:DESKTOPSTANDARD CORP +1
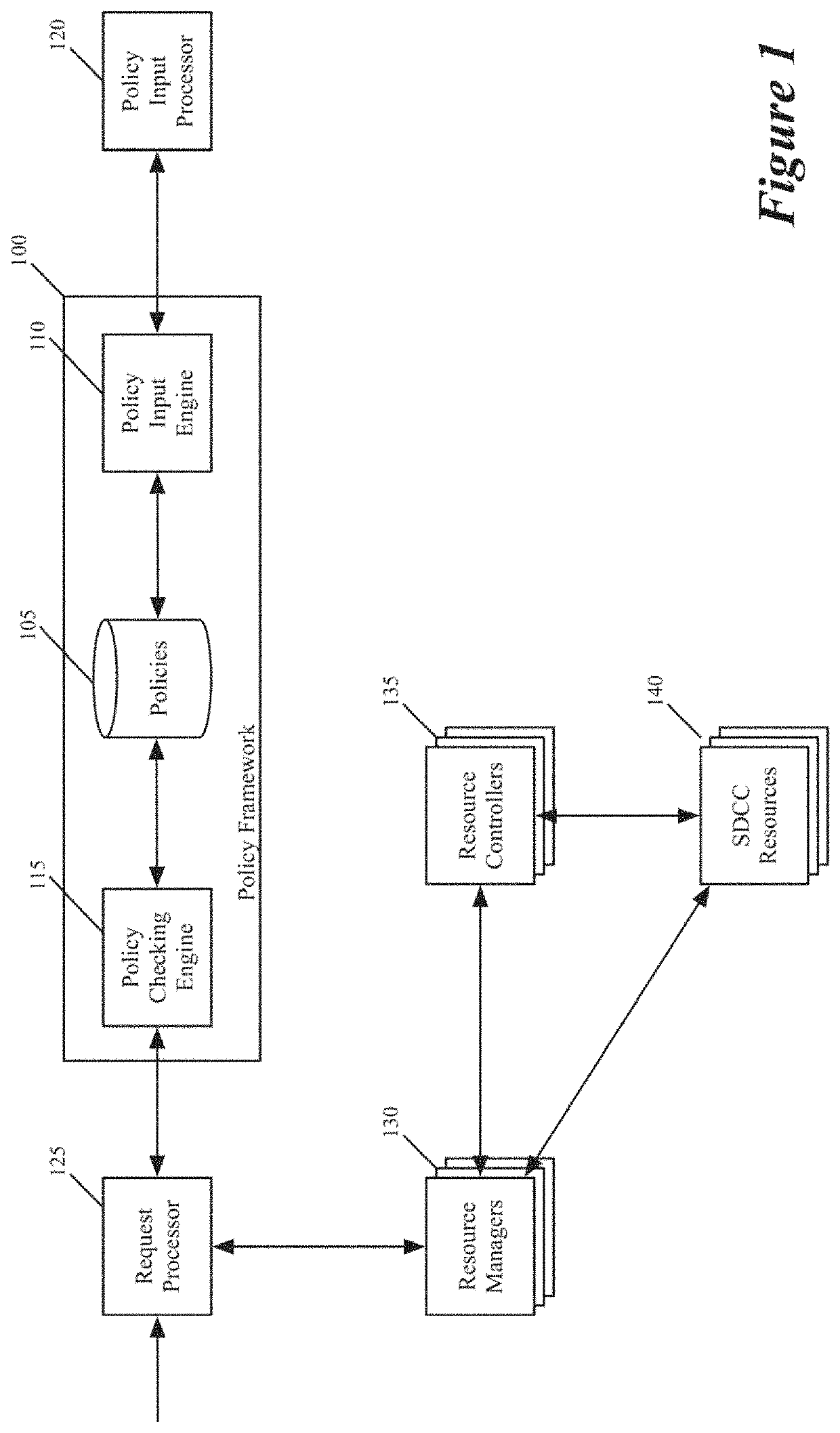
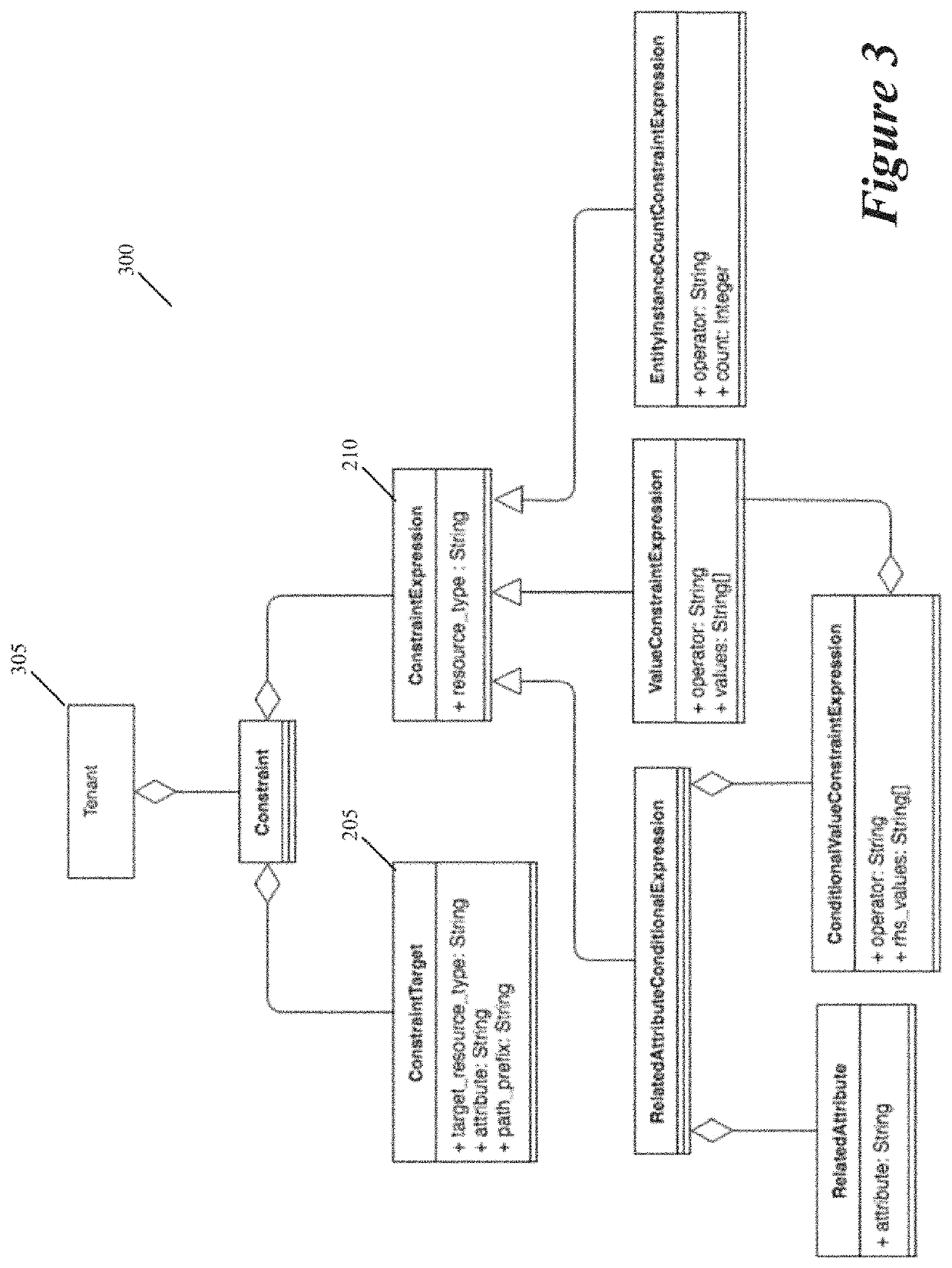
Policy constraint framework for an sddc
Some embodiments of the invention provide a method for processing requests for performing operations on resources in a software defined datacenter (SDDC). The resources are software-defined (SD) resources in some embodiments. The method initially receives a request to perform an operation with respect to a first resource in the SDDC. The method identifies a policy that matches (i.e., is applicable to) the received request for the first resource by comparing a set of attributes of the request with sets of attributes of a set of policies that place constraints on operations specified for resources. In some embodiments, several sets of attributes for several policies can be expressed for resources at different hierarchal resource levels of the SDDC. The method rejects the received request when the identified policy specifies that the requested operation violates a constraint on operations specified for the first resource.
Owner:VMWARE INC
Method and device for achieving function of security group
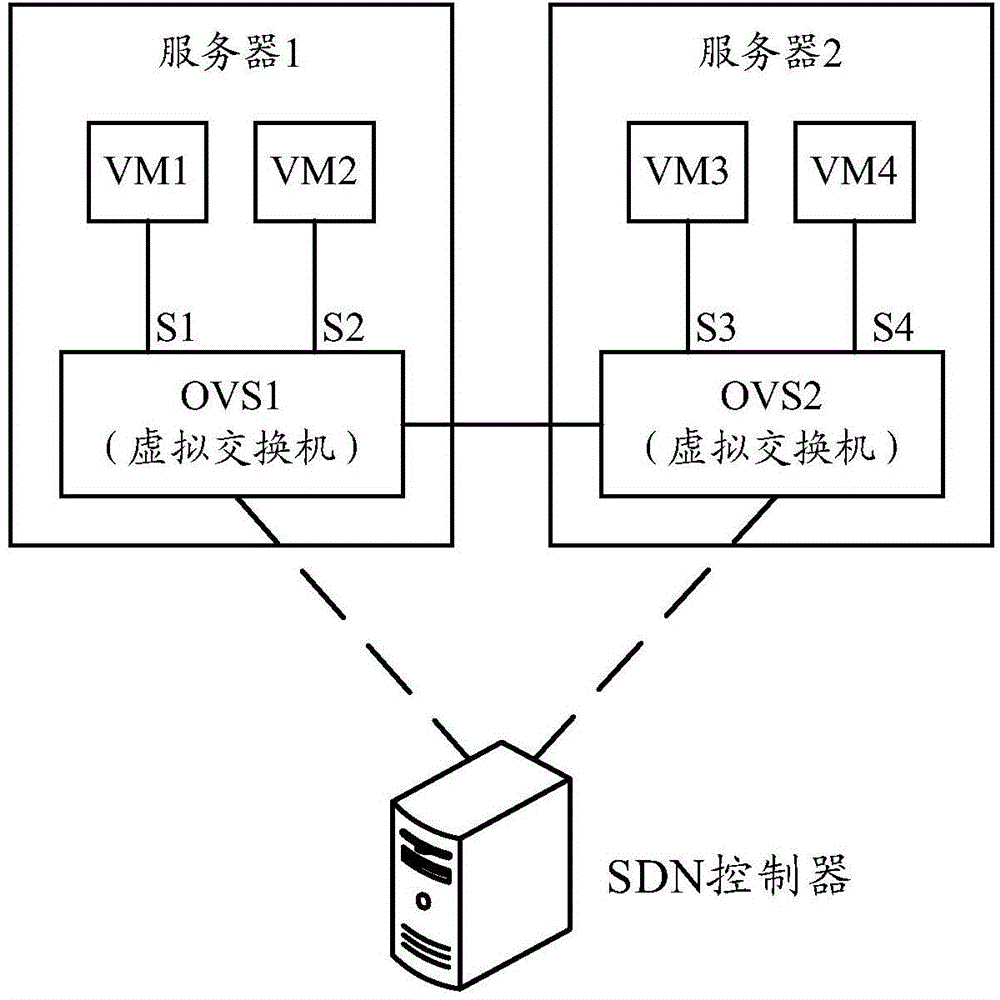
InactiveCN104394080AAvoid wastingImprove work efficiencyData switching networksVirtual switchGroup Policy
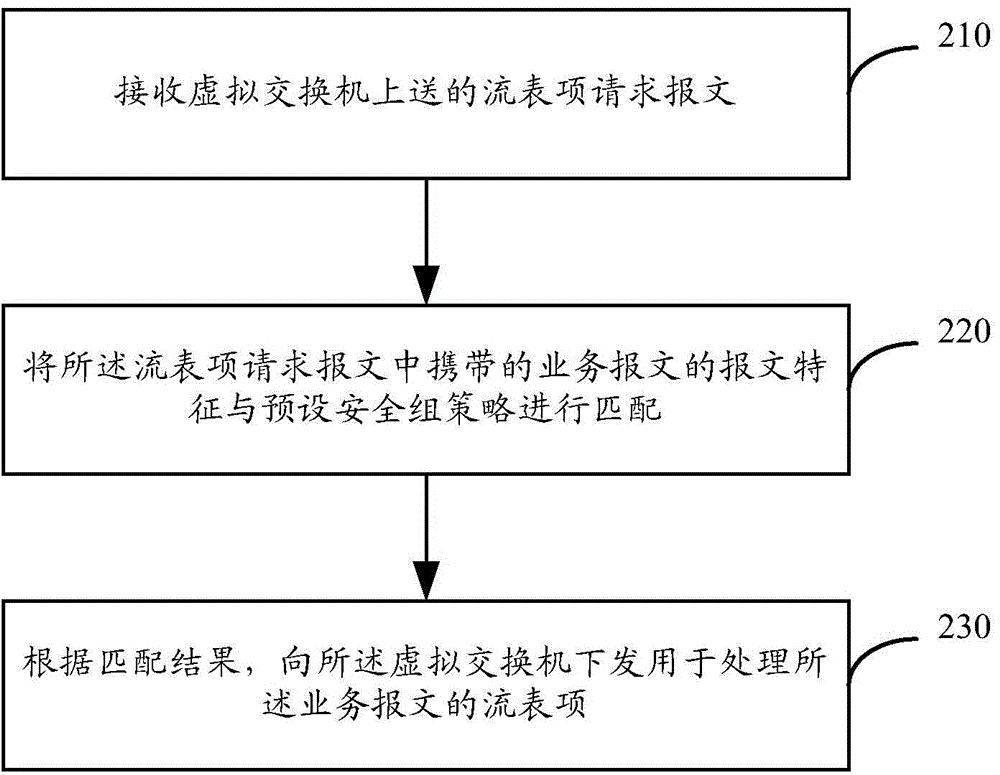
The application provides a method and device for achieving function of security group; the method and device for achieving function of security group are applied for software definition network SDN controller. The method comprises the following steps: receiving a flow table entry request message uploaded by a virtual switch; matching a message characteristic of a service message carried in the flow table entry request message with a preset security group policy; issuing a flow table entry for processing the service message to the virtual switch based on the match result. By carrying out the security group check in the controller, the method and device for achieving function of security group avoids wasting the system resources, and increases the work efficiency of the system.
Owner:NEW H3C TECH CO LTD
Policy application method for machine type communication, and policy and charging enforcement function
InactiveUS20130044646A1Shorten application timeSave network resourcesSpecial service provision for substationMultiplex system selection arrangementsAccess networkProtocol for Carrying Authentication for Network Access
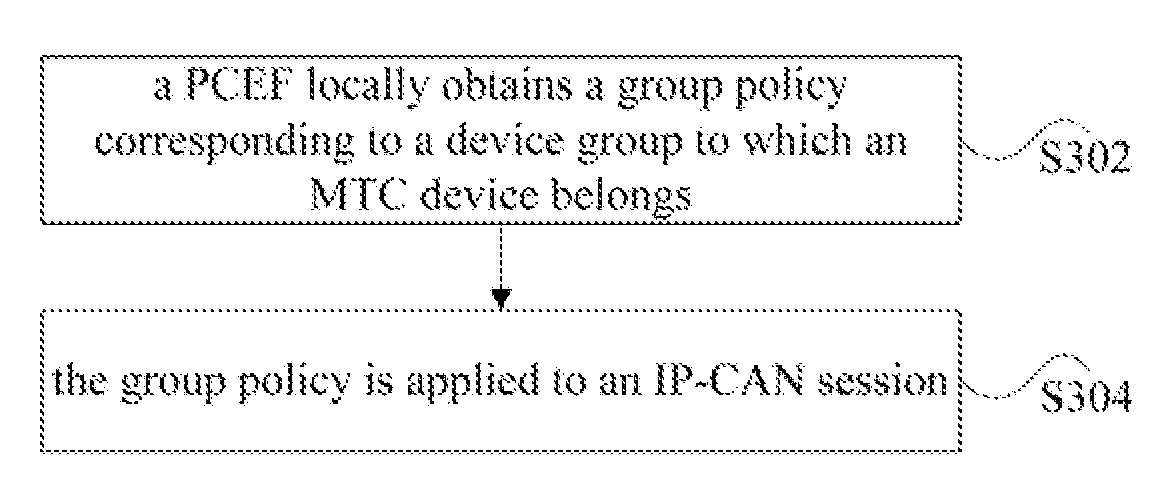
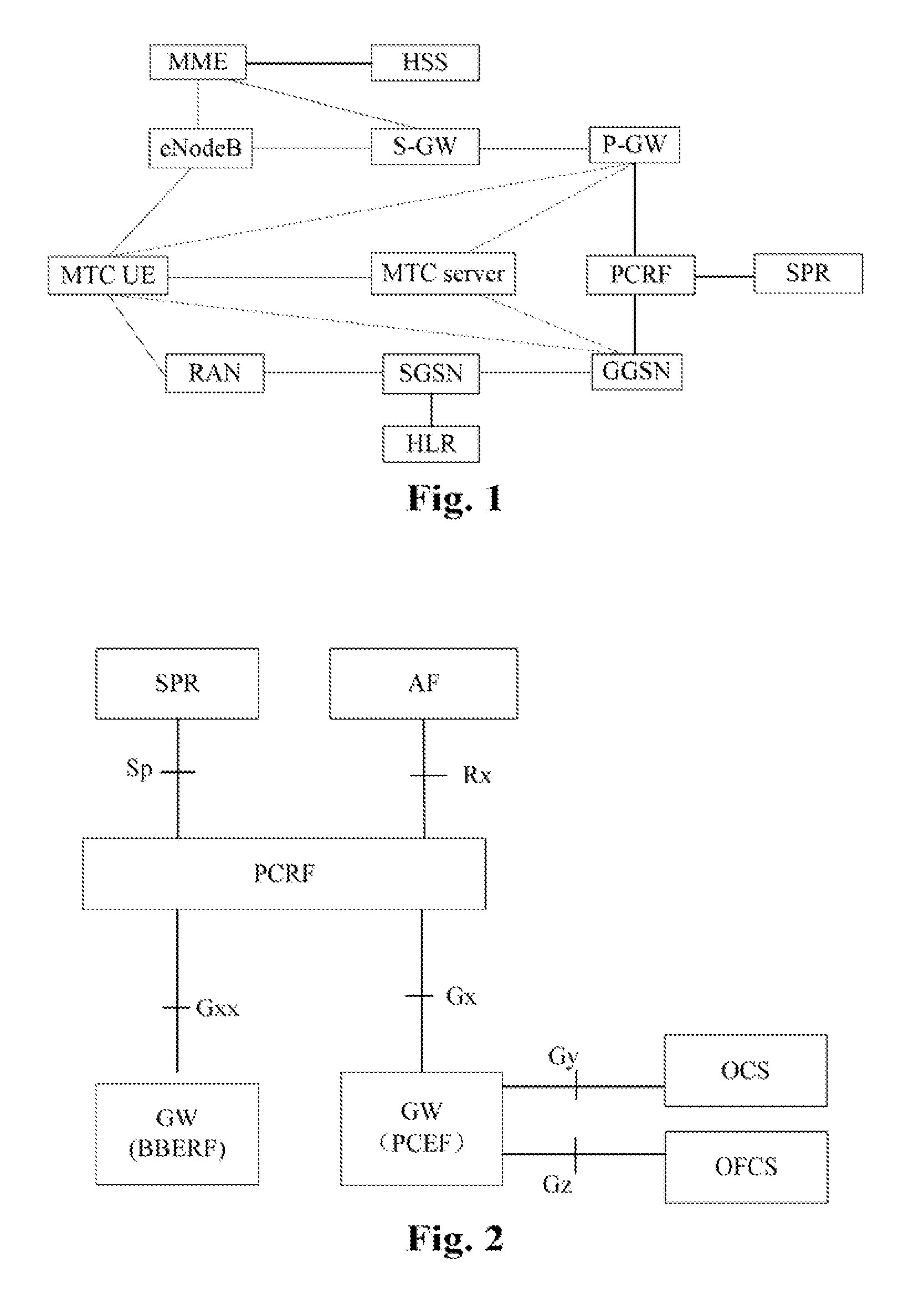
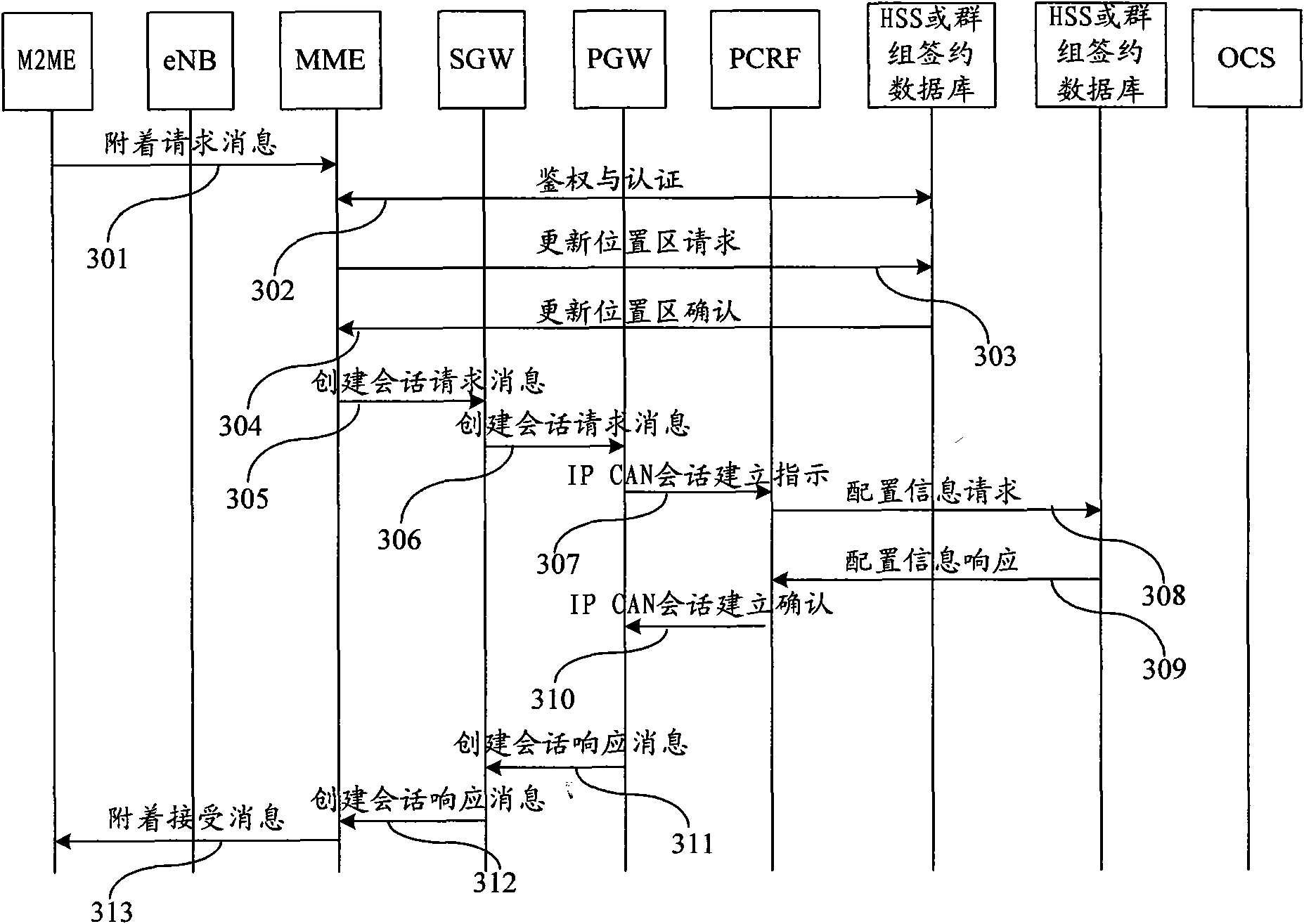
A policy application method for Machine Type Communication (MTC) and a Policy and Charging Enforcement Function (PCEF) are provided by the disclosure. The method comprises that in a course in which an MTC device attached to a PCEF establishes an Internet Protocol-Connectivity Access Network (IP-CAN) session, the PCEF locally obtains a group policy corresponding to a device group to which the MTC device belongs (S302); the group policy is applied in the IP-CAN session (S304). The technical solution of the disclosure reduces the time required by applying the MTC policy by the PCEF, saves network resources, and increases utilization of the network resources.
Owner:ZTE CORP
Group policy and charging rule treatment method and device, and communication system
InactiveCN102014343AImprove policy control efficiencyReduce complexityMetering/charging/biilling arrangementsAccounting/billing servicesCommunications systemGroup Policy
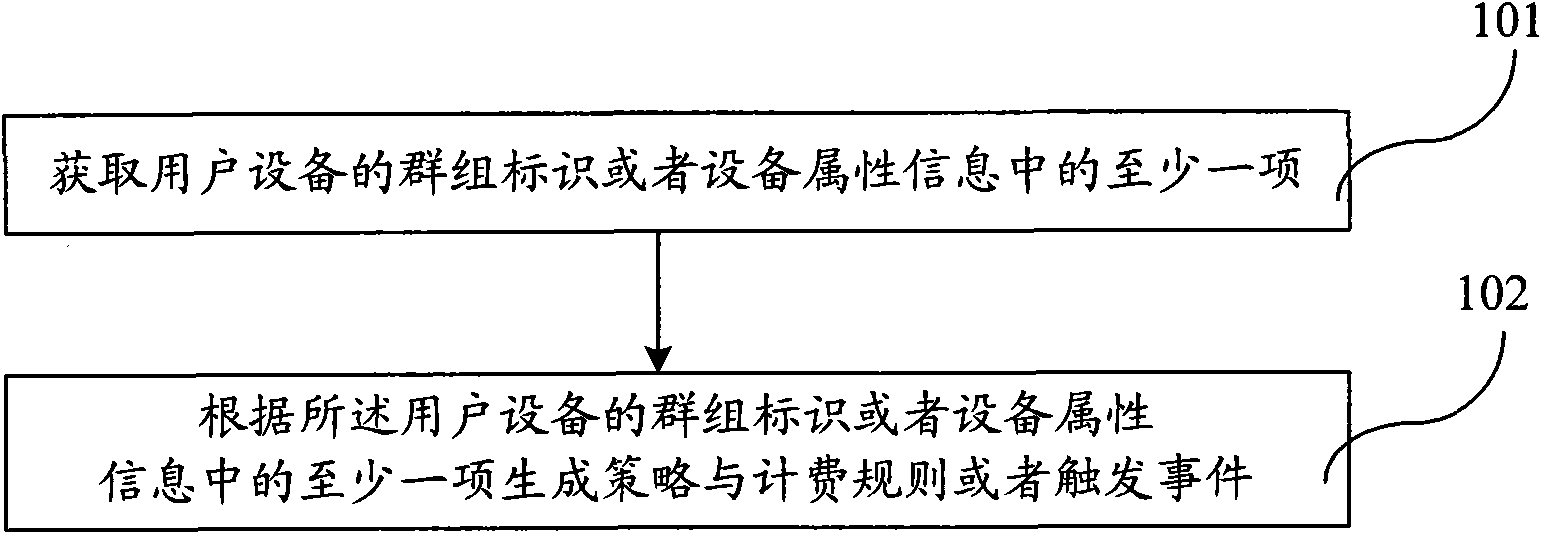
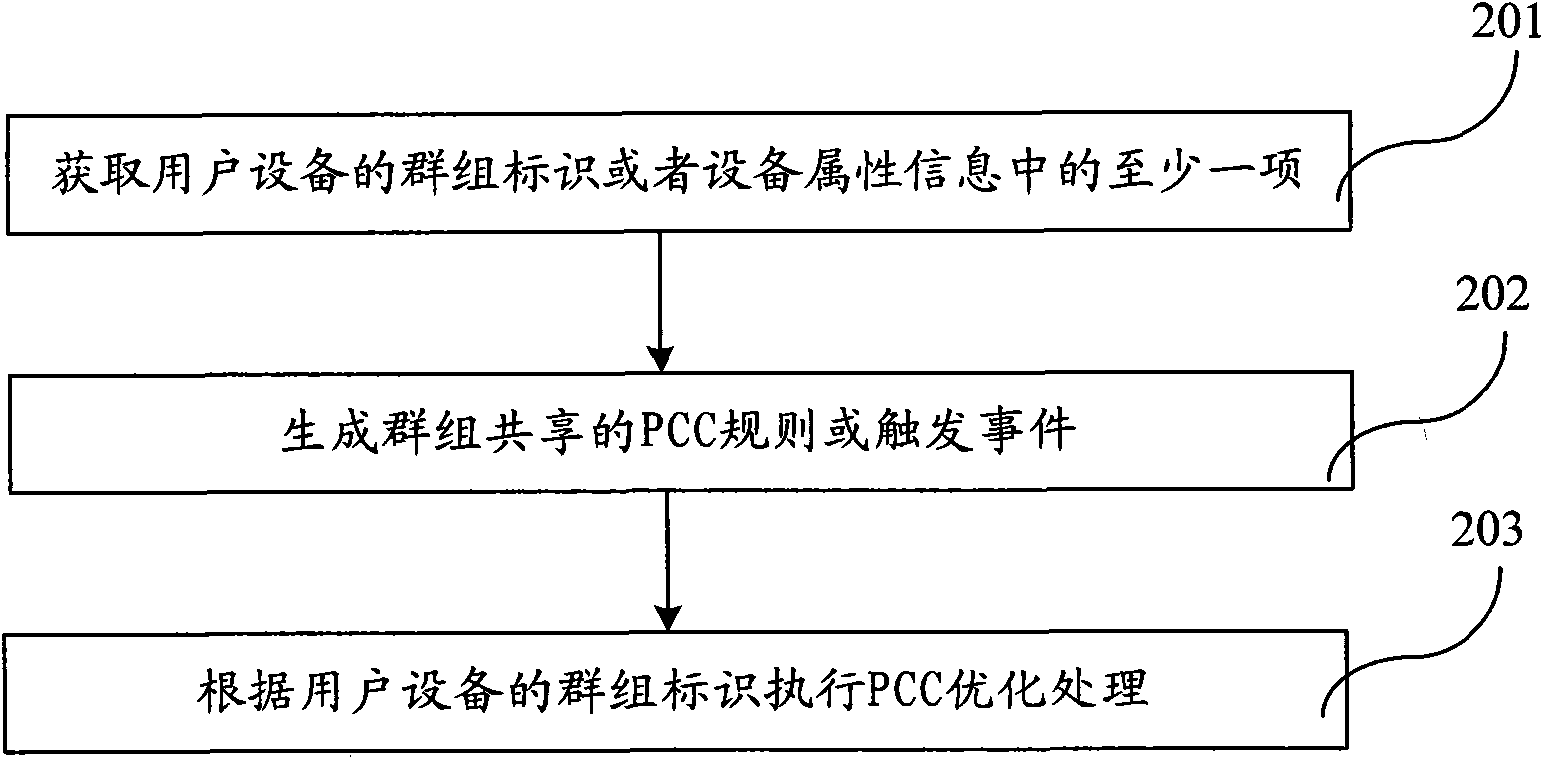
The embodiment of the invention provide a group policy and charging rule treatment method and device, and a communication system, wherein the group policy and charging rule treatment method comprises the steps of: obtaining at least one item of group identifiers or attribute information of user equipment; and generating a policy and charging rule or triggering an event according to the at least one item of group identifiers or attribute information of the user equipment. The device comprises an obtaining module used for obtaining the at least one item of group identifiers or attribute information of the user equipment, and a rule generating module used for generating the policy and charging rule or triggering the event according to the at least one item of group identifiers or attribute information of the user equipment. The embodiment of the invention also provides a communication system comprising the device. The method, device and system provided in the embodiment of the invention can improve the policy control efficiency and reduce the complexity of the policy maintenance and management.
Owner:HUAWEI TECH CO LTD
System and method for reporting hierarchically arranged data in markup language formats
InactiveUS7299410B2Easy to operateDigital computer detailsSemi-structured data mapping/conversionXML schemaData set
A system and method comprising a reporting mechanism for outputting an HMTL and XML document from a collection of hierarchically maintained settings such as group policy object settings or resultant set of policy data. The reporting mechanism provides a substantially complete view of which settings are configured (enabled) in a given group policy object, or a view for a resultant set of policy (that is applied to a given SOM), along with the values of the settings. The markup language format enables viewing a flat representation of the settings, and printing, saving and / or transporting of the settings. XML schemas describe a valid representation of group policy settings, and a valid representation of resultant set of policy.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com