Patents
Literature
728 results about "Directory structure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, a directory structure is the way an operating system's file system and its files are displayed to the user. Files are typically displayed in a hierarchical tree structure.
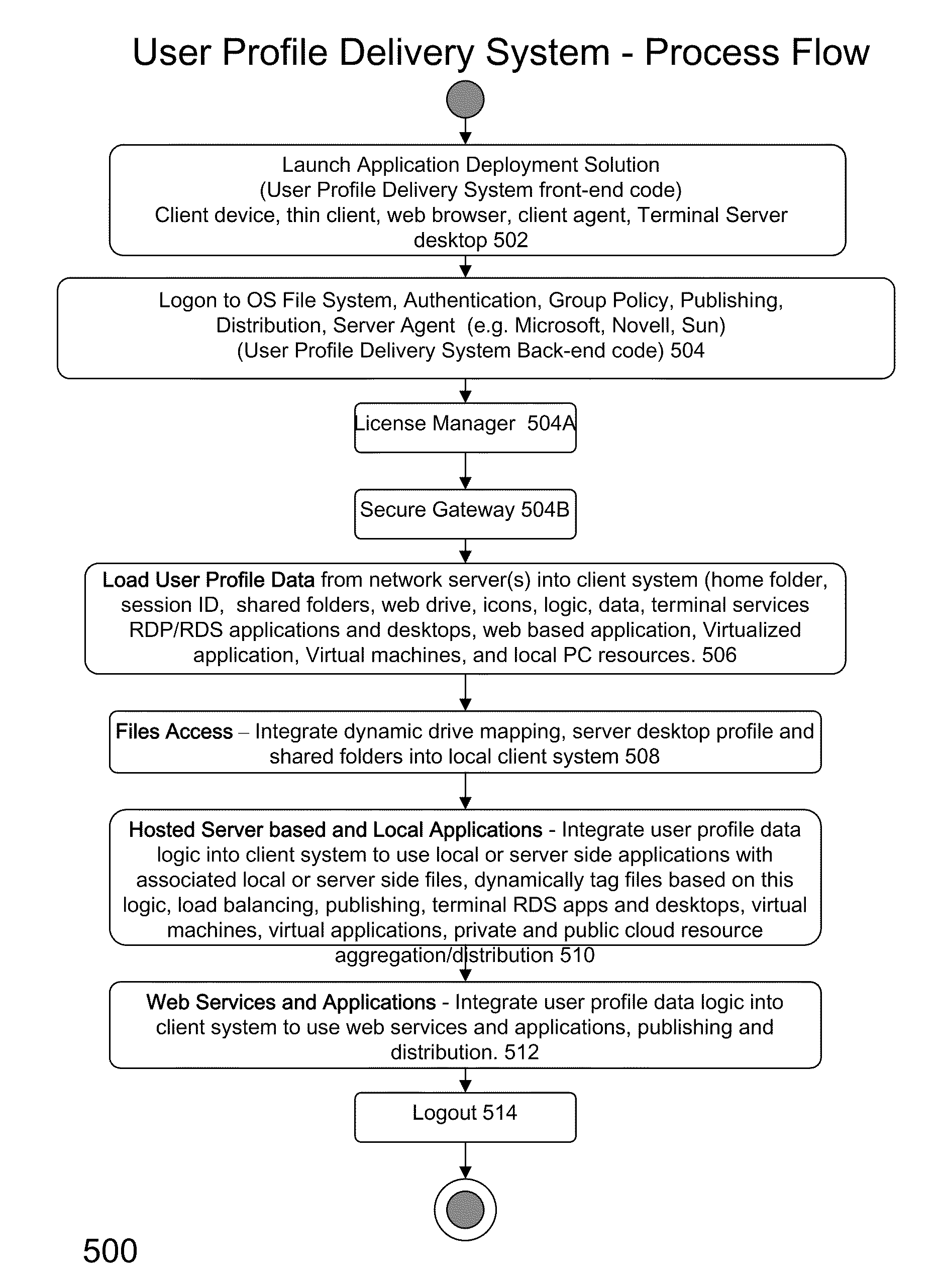
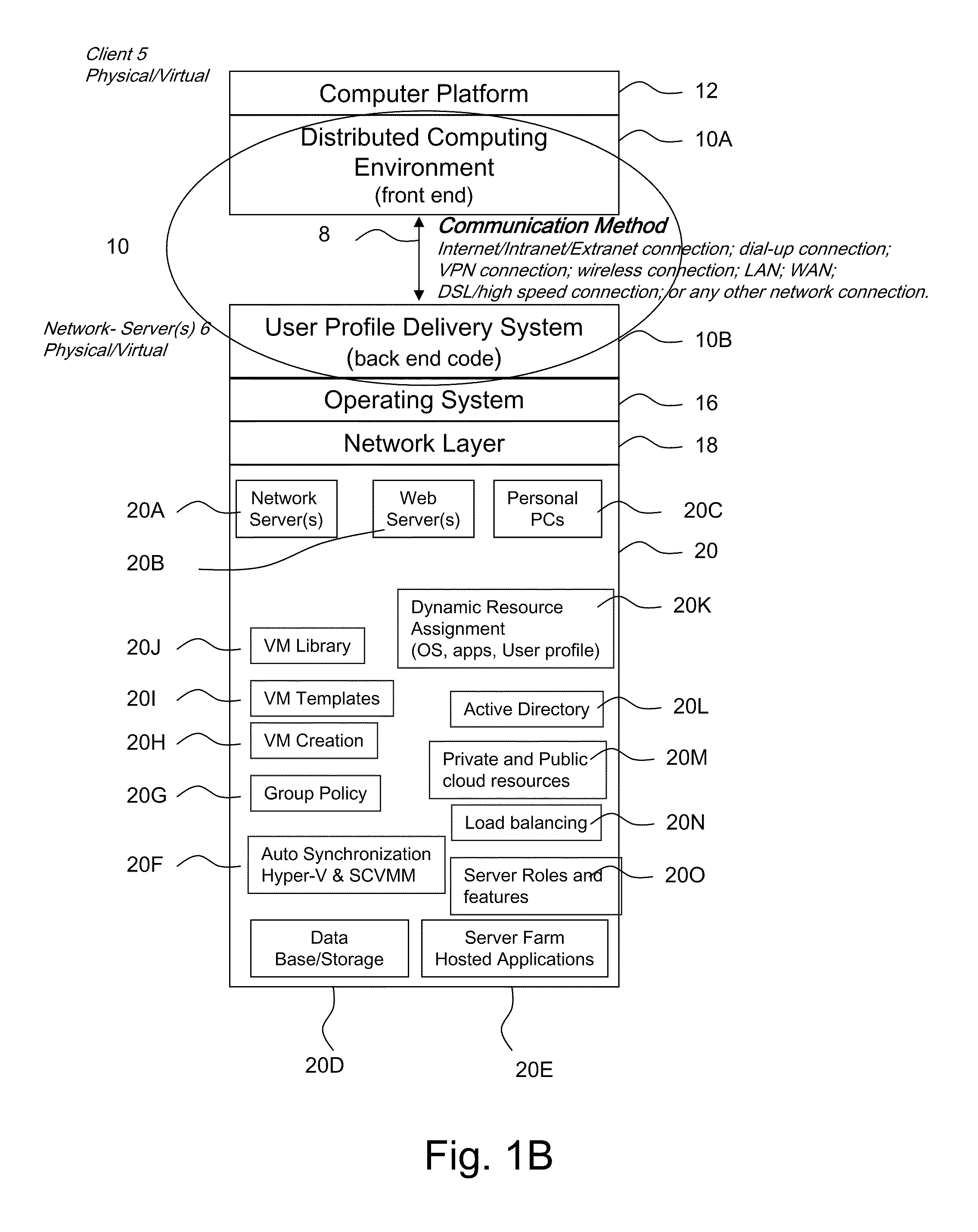
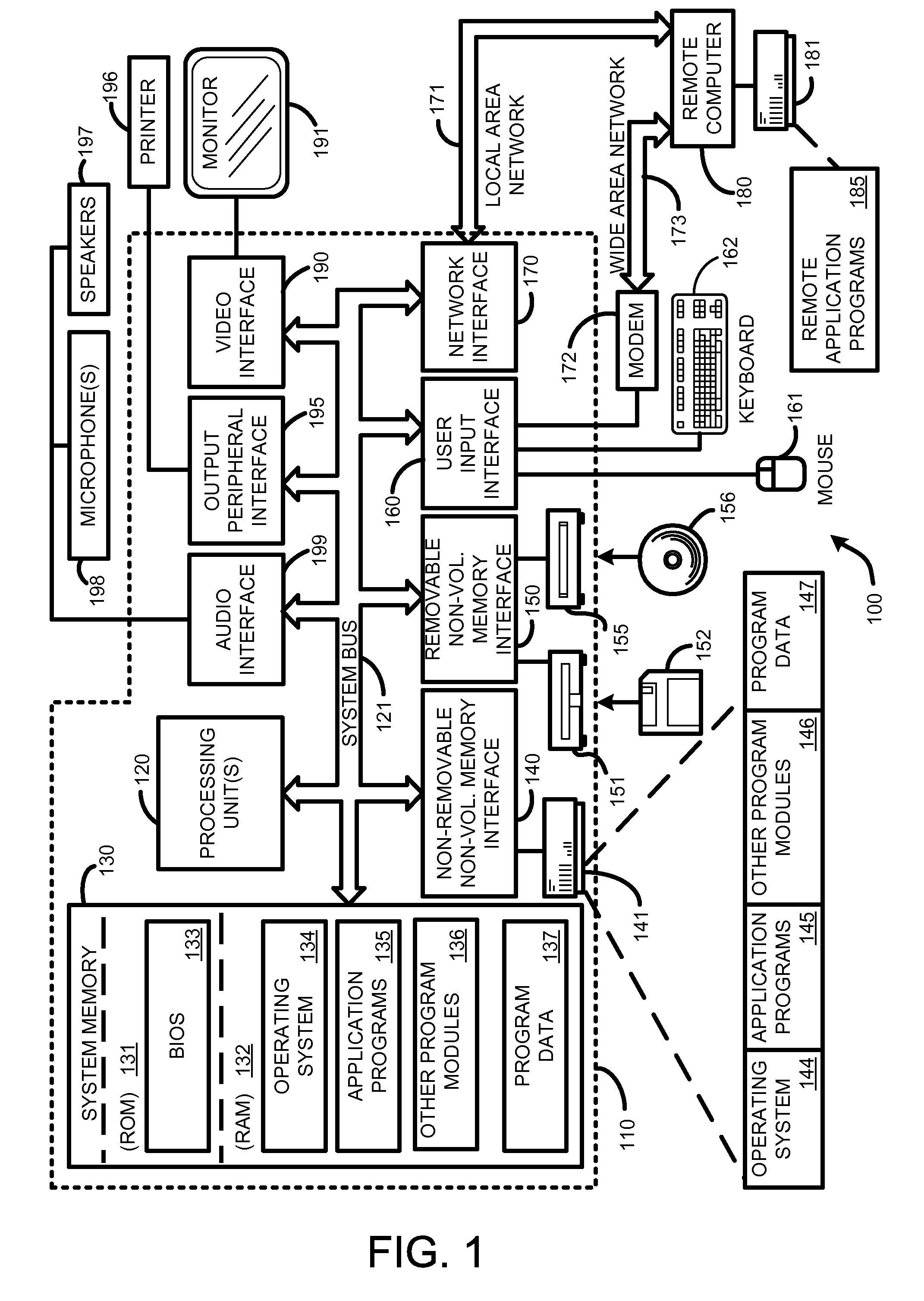
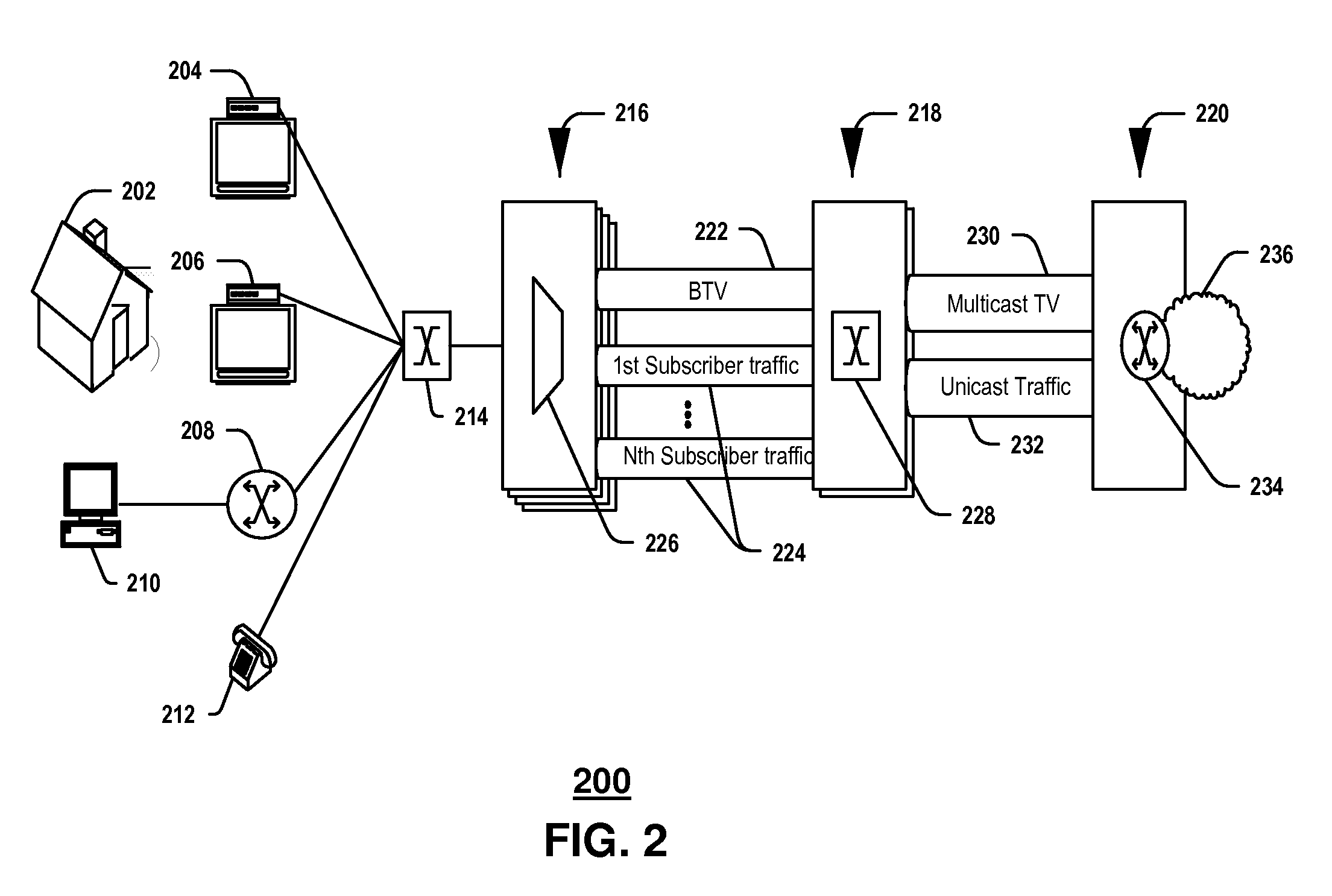
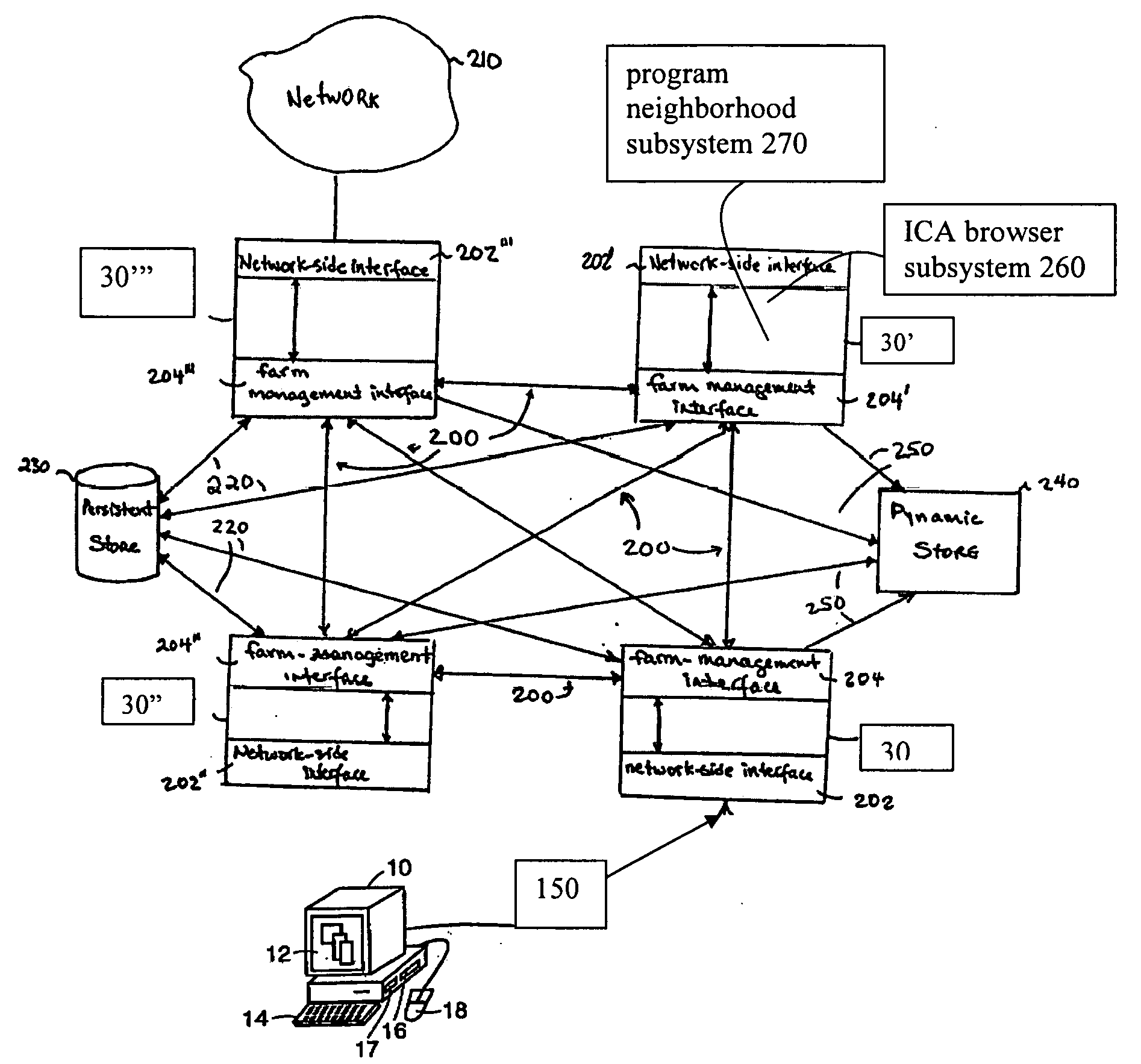
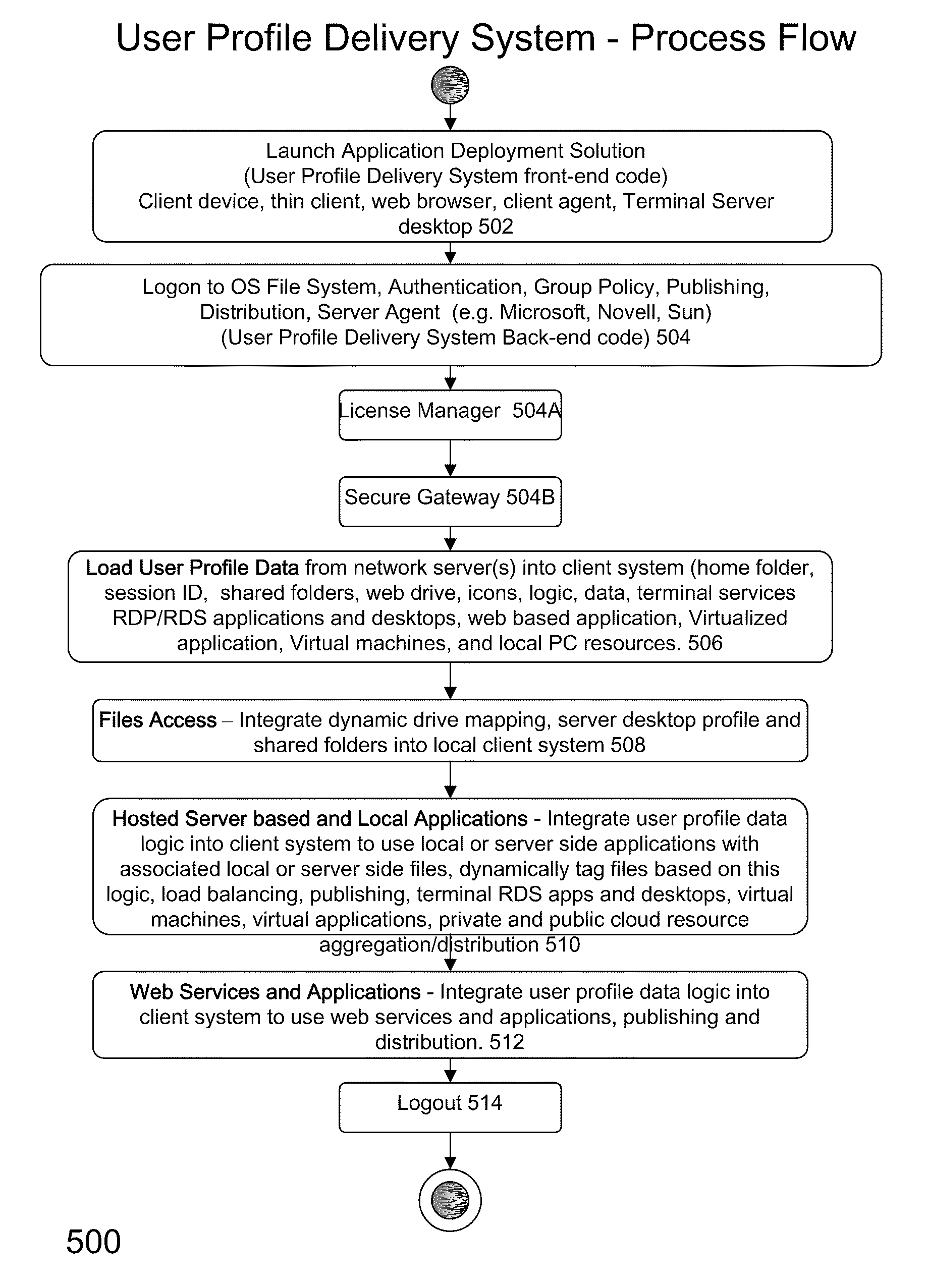
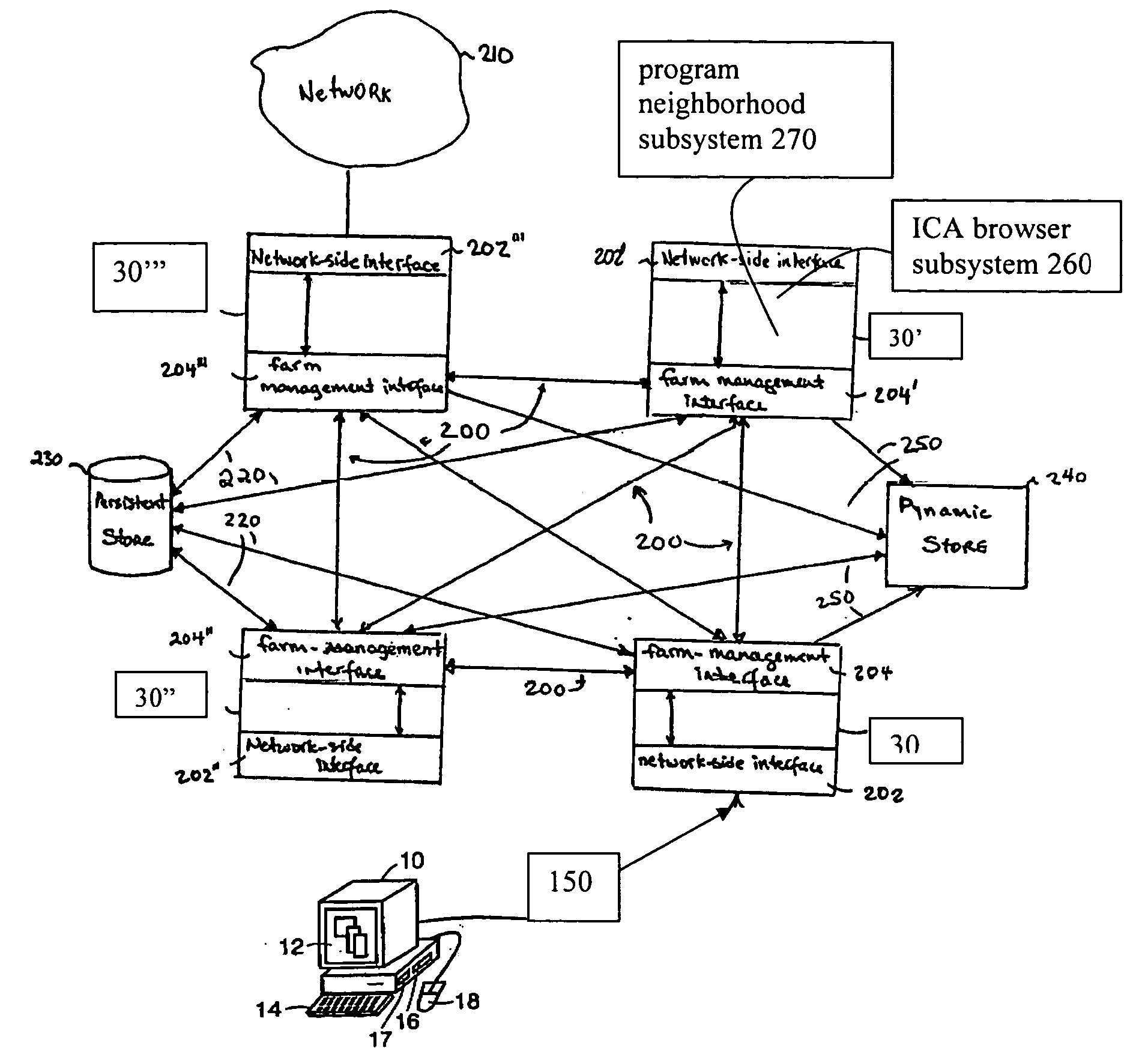
System and method for launching a resource in a network
ActiveUS20110251992A1Provide controlDigital data processing detailsWireless commuication servicesOperational systemDirectory structure
The disclosure provides a system and method for a client connected to a server to a resource in a network. For the system a virtual machine module is provided to access a library and to create virtual machine templates and to create virtual machines from the virtual machine templates. The virtual machine module provides to a host machine in the network access to machines, user profile settings and instances of an application in the network and to multiple operating systems. The client has: access to an instance of the resource; an access module to provide the client with communication to access to the server using load balancing algorithms to access the file using Remote Desktop Protocol (RDP) commands; and an authentication module providing access to a directory structure accessed by the server using Microsoft Group Policy Objects (GPOs) and Active Directory (AD) services to authenticate the client with the server.
Owner:DESKTOPSITES
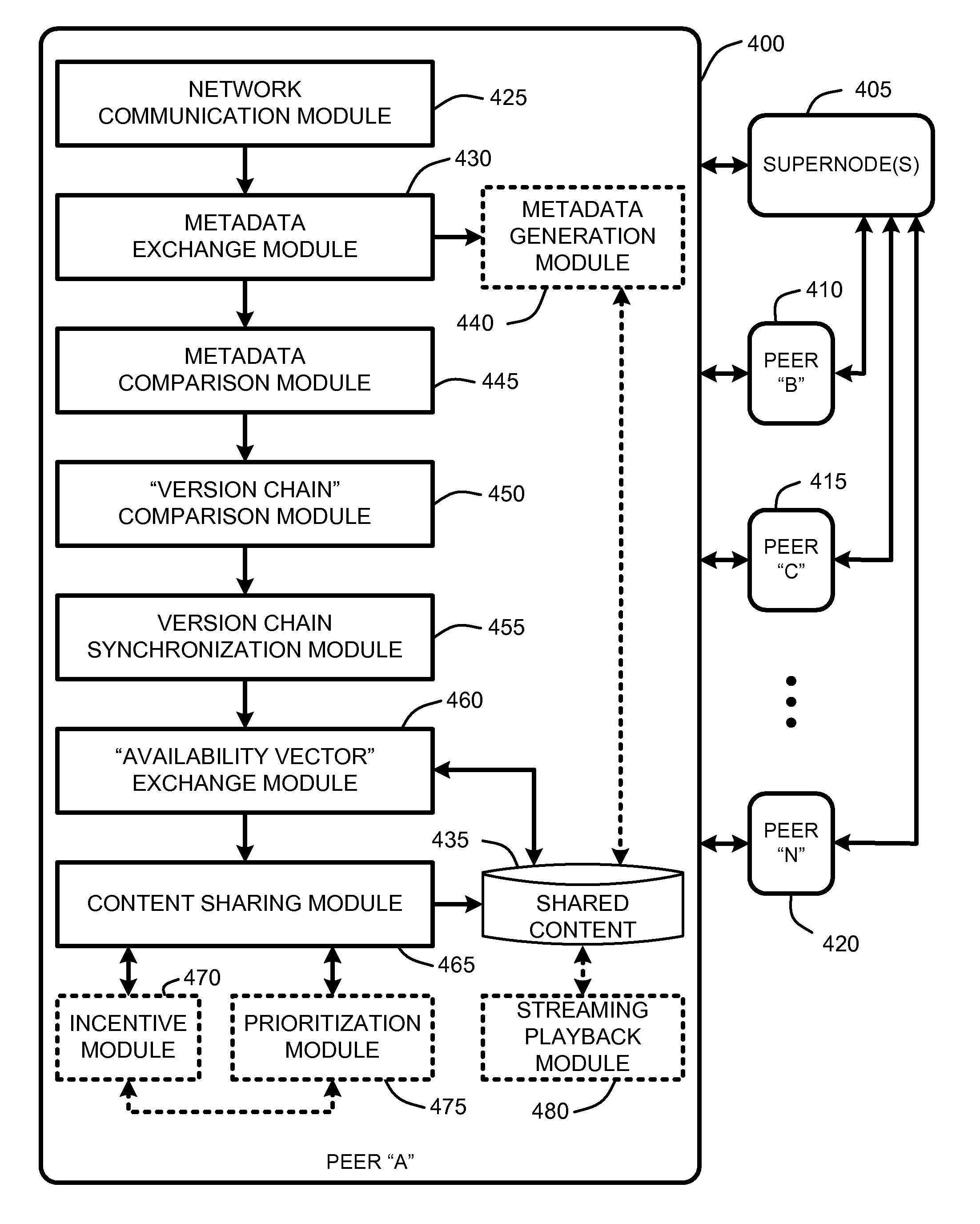
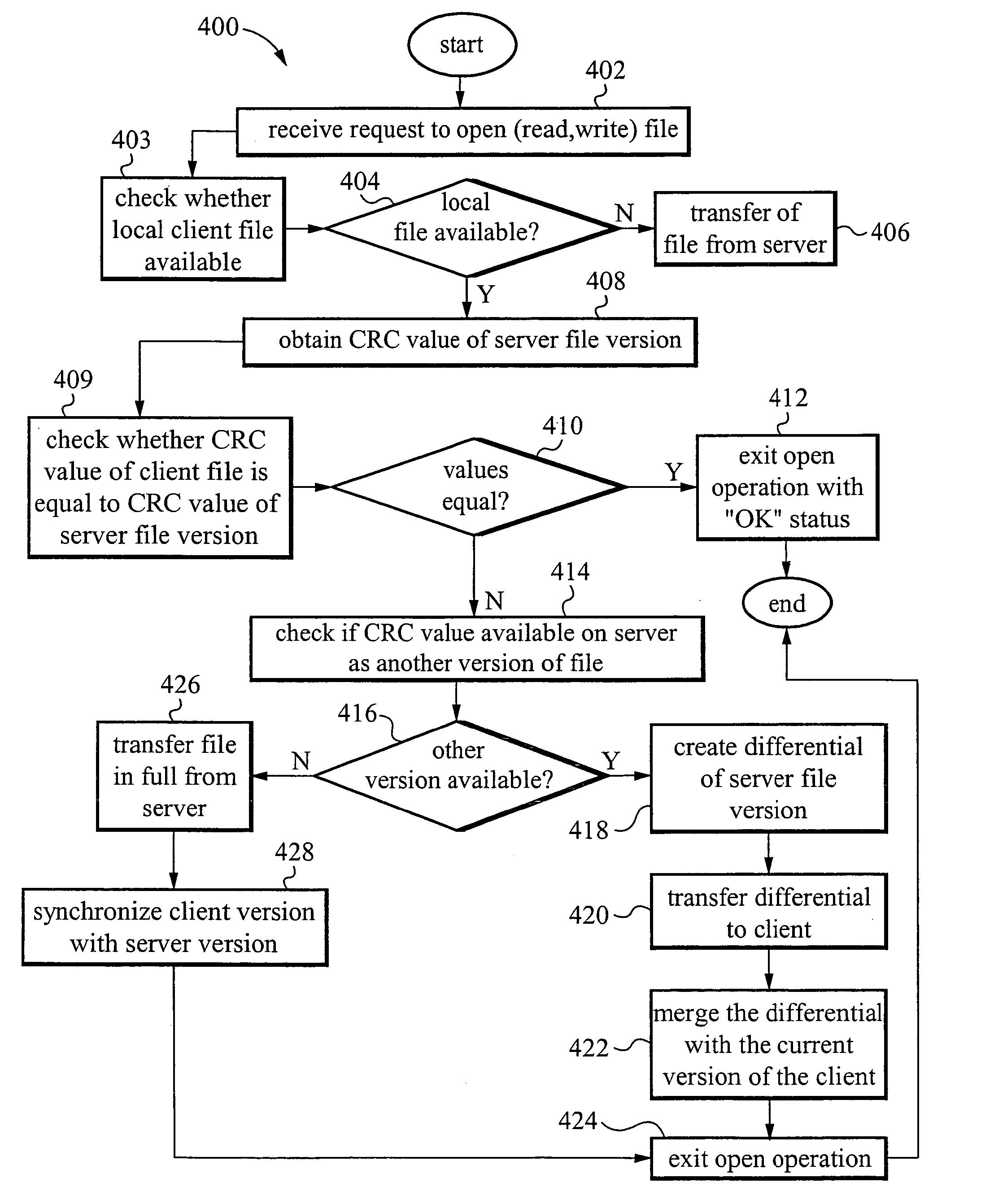
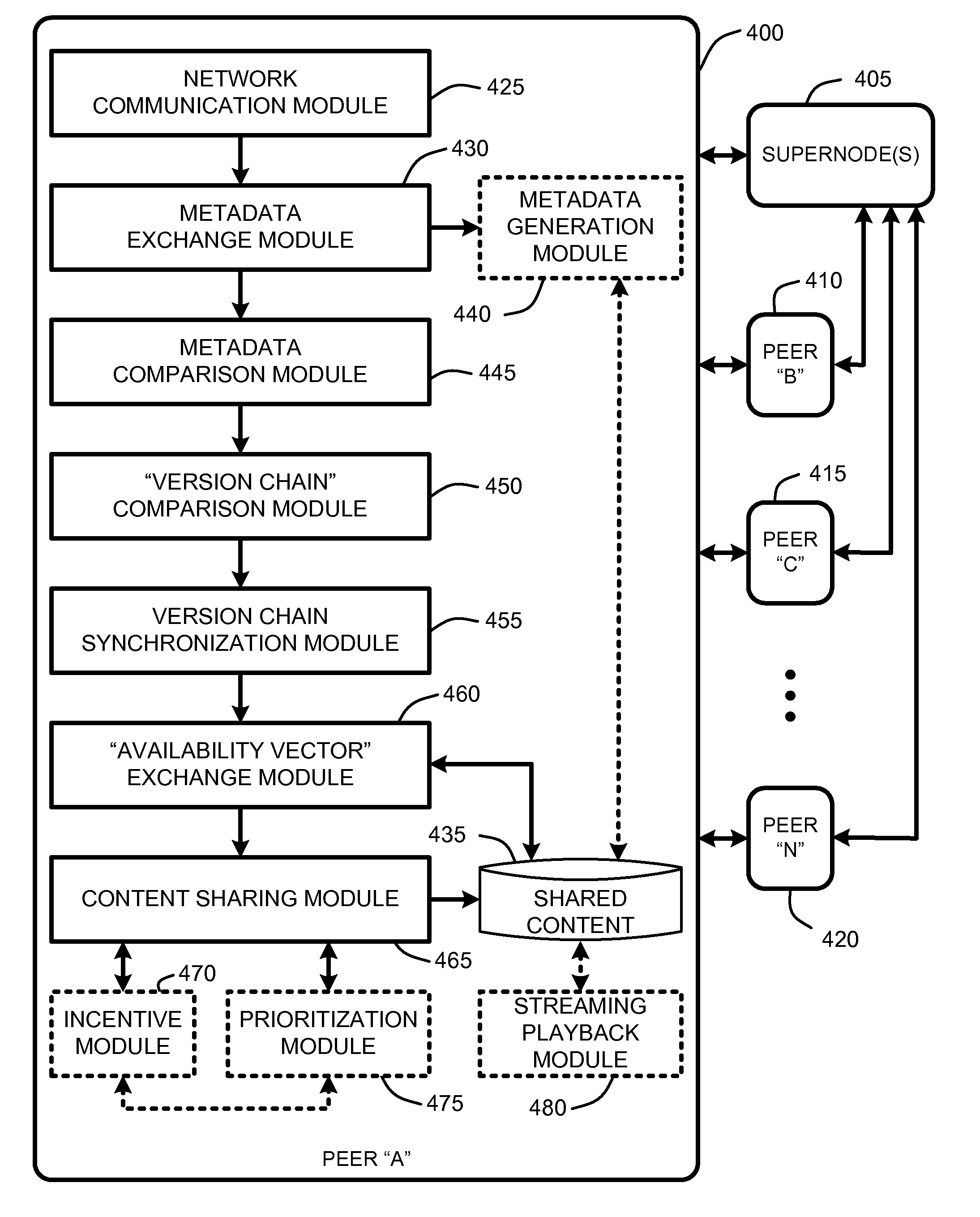
Versioning synchronization for mass p2p file sharing
InactiveUS20080005195A1Digital data information retrievalSpecial data processing applicationsDirectory structureFile sharing
A “Mass File Sharer” (MFS) provides a mass P2P file sharing protocol with optional on-demand file access across a P2P network. Unlike conventional P2P file sharing, the MFS simultaneously asynchronously shares large numbers of files, while providing optional on-demand (synchronous) access to shared files. The MFS uses a unique metadata structure in combination with an inter-peer file / folder version analysis and an inter-peer file / folder availability analysis to share complex directory structures that may include any number of folders, sub-folders, and files. Sharing may be asynchronous and / or synchronous. Specifically, file sharing is generally accomplished as an asynchronous distribution across the network. However, when a particular peer wants direct access particular files, an on-demand access mode is used to enable synchronous delivery of shared files. This combination of asynchronous and synchronous file distribution enables the MFS to support a number of applications, such as on-demand movie viewing, file / folder browsing, etc.
Owner:MICROSOFT TECH LICENSING LLC
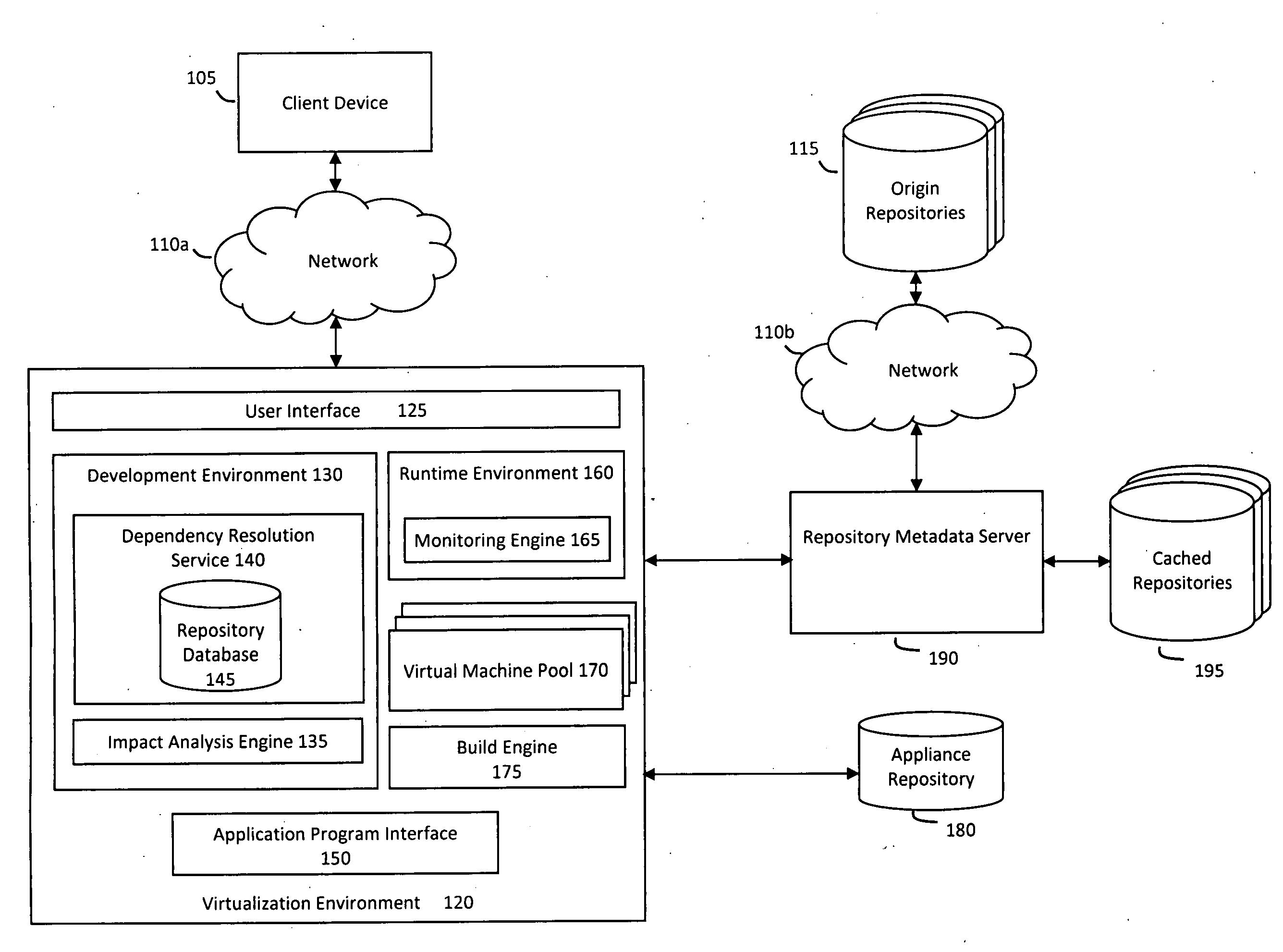
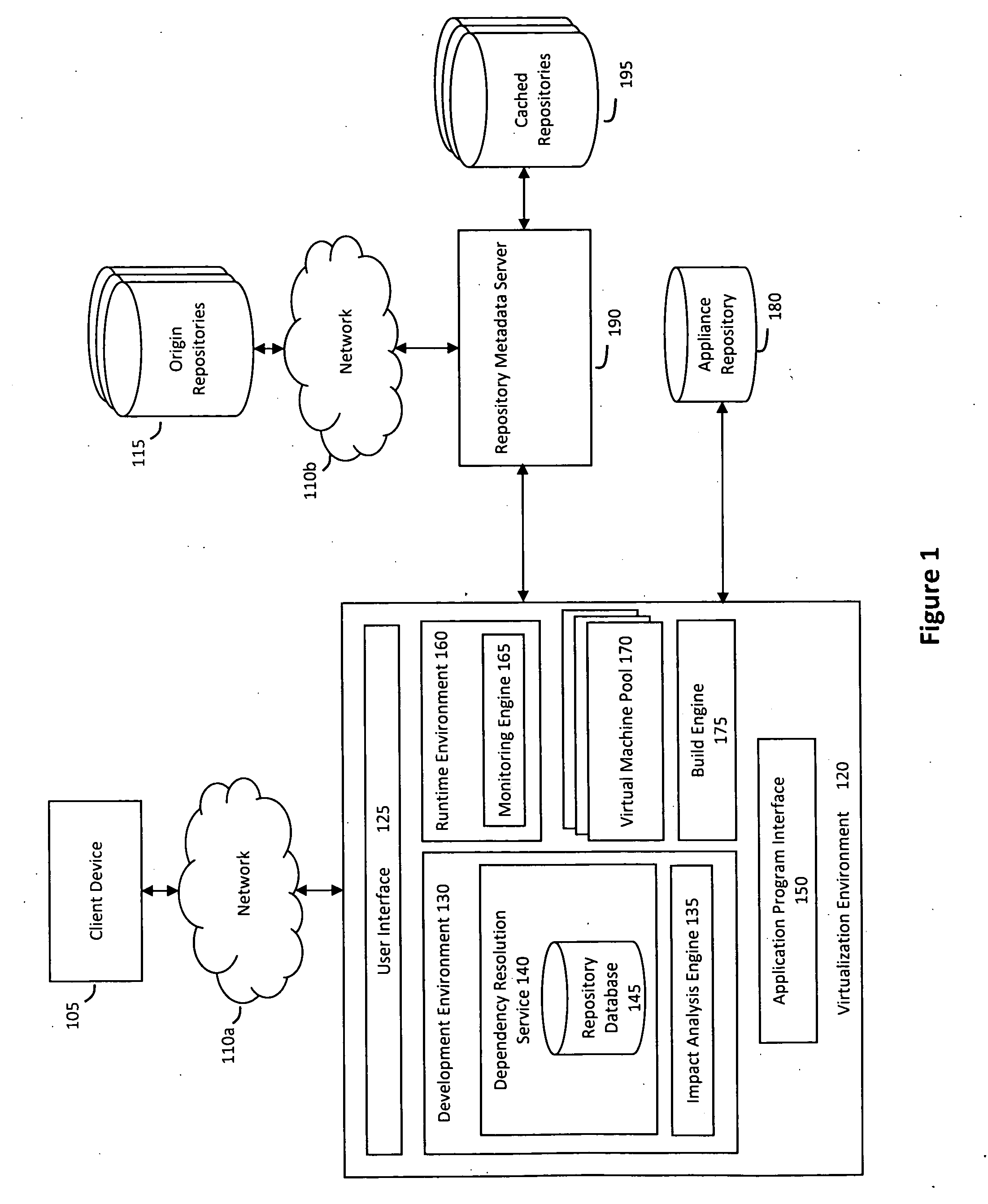
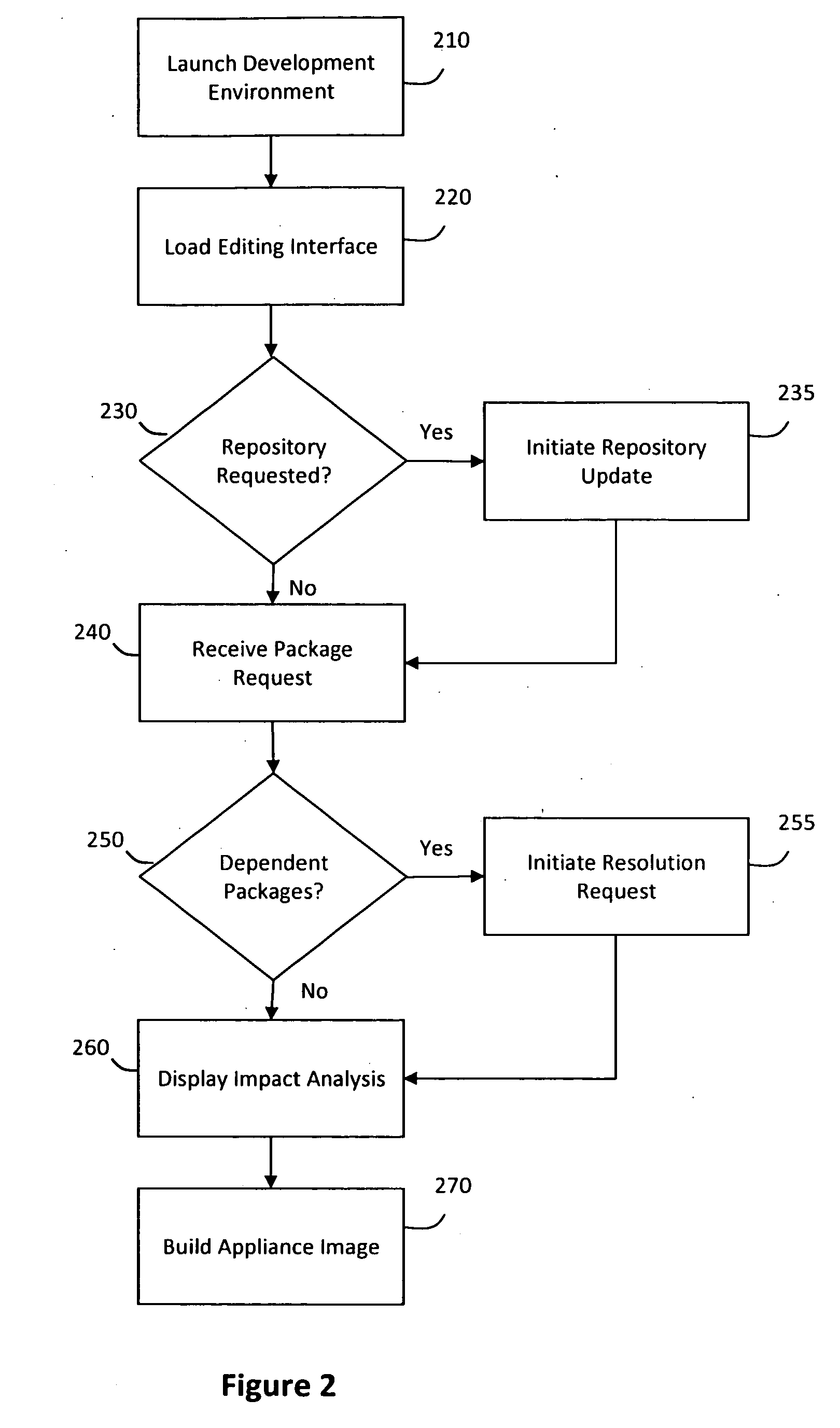
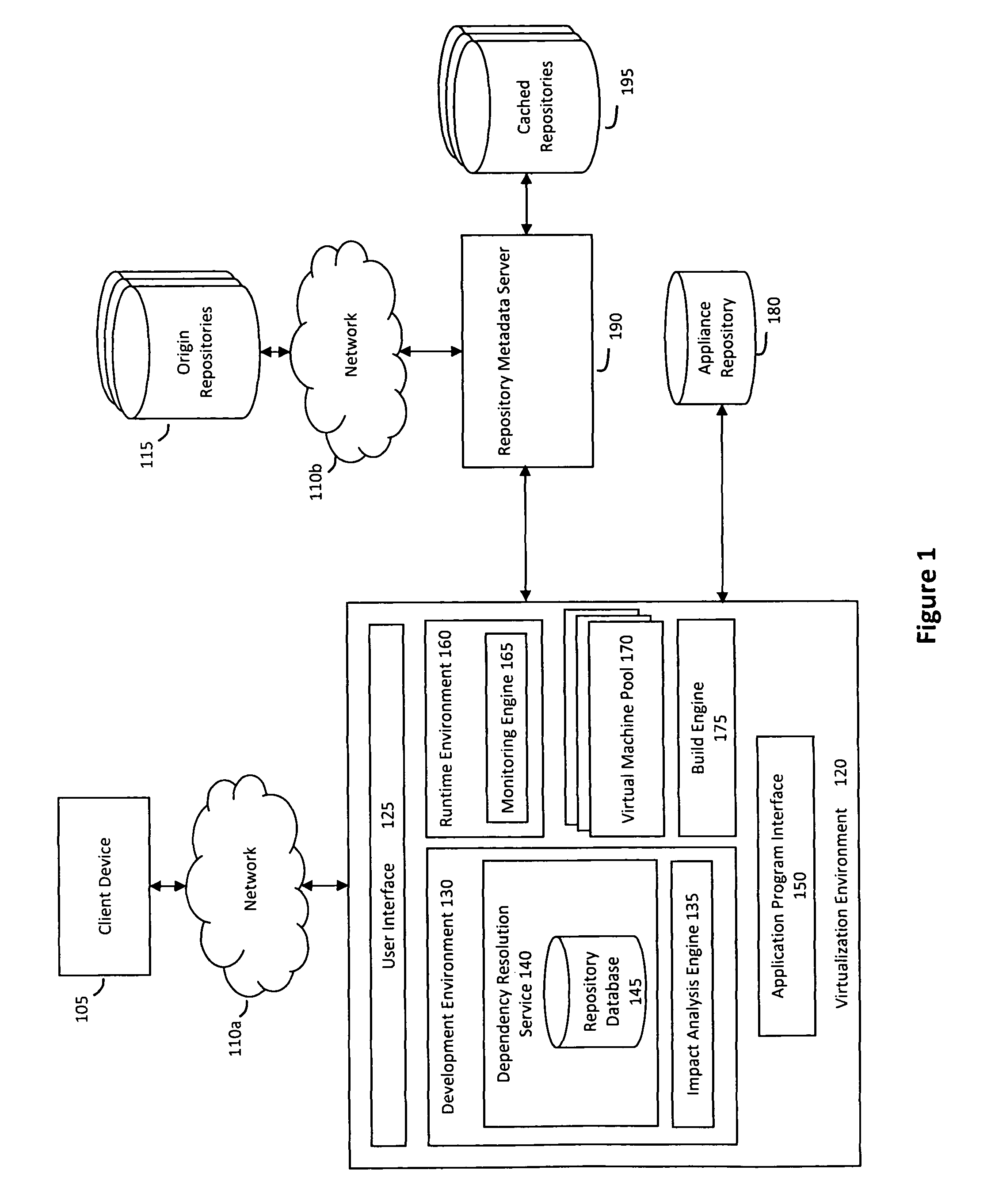
System and method for efficiently building virtual appliances in a hosted environment
ActiveUS20090300057A1Drawback can be addressedMemory loss protectionDigital data processing detailsFile systemHosting environment
A system and method for efficiently building virtual appliances in a hosted environment is provided. In particular, a plurality of image archives may be stored in a build database, with each image archive including a file system having a directory structure and a plurality of files installed within the directory structure. In response to a build request containing an image description, a build engine may create a file system layout defining a directory structure for an image. The build engine may then copy the file system for one of the image archives to the file system layout for the image, wherein the copied file system may provide a subset of the file system for the image. The build engine may then build the image, which may include a file system having various files installed within various directories in accordance with the directory structure defined for the image.
Owner:SUSE LLC
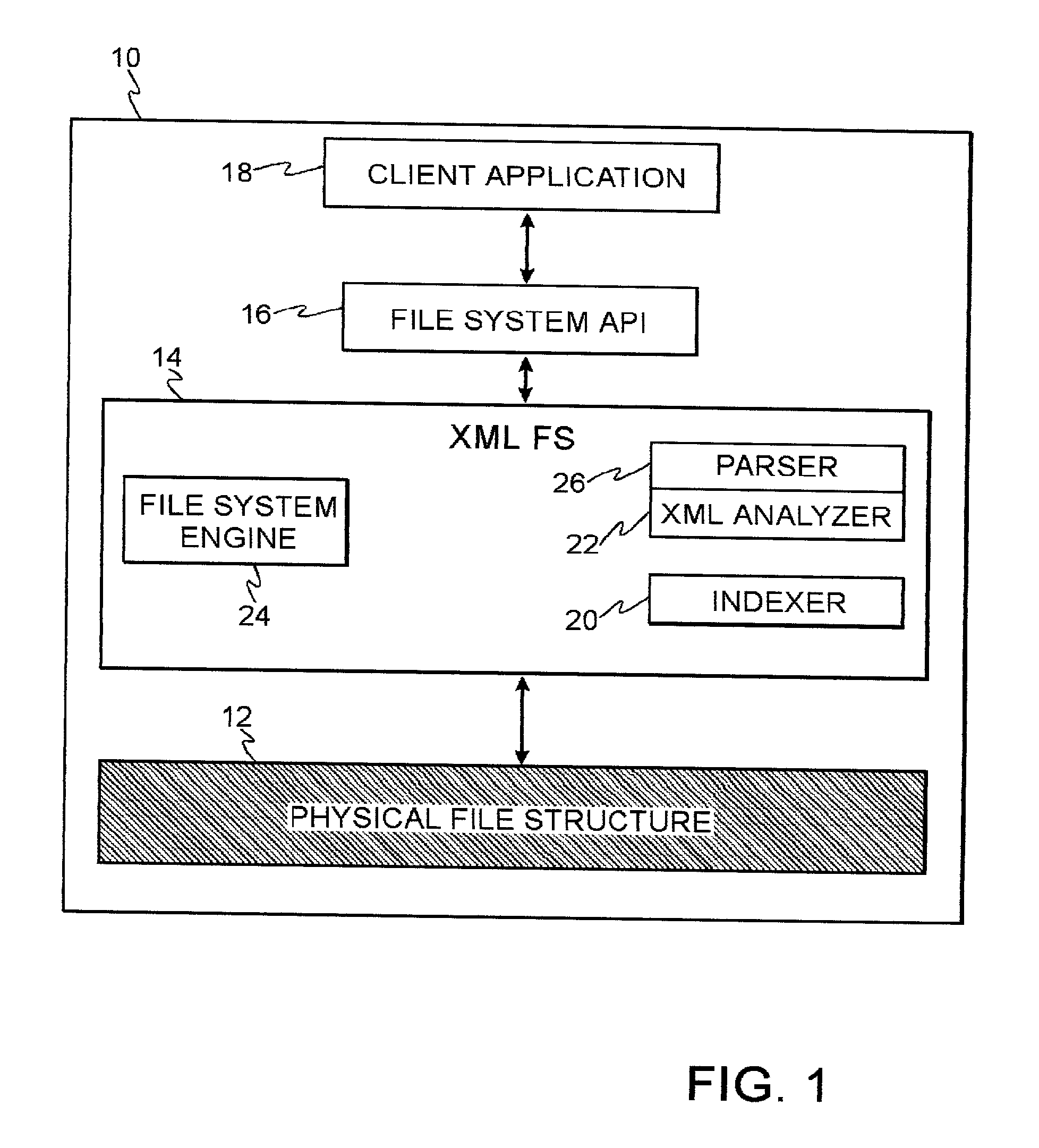
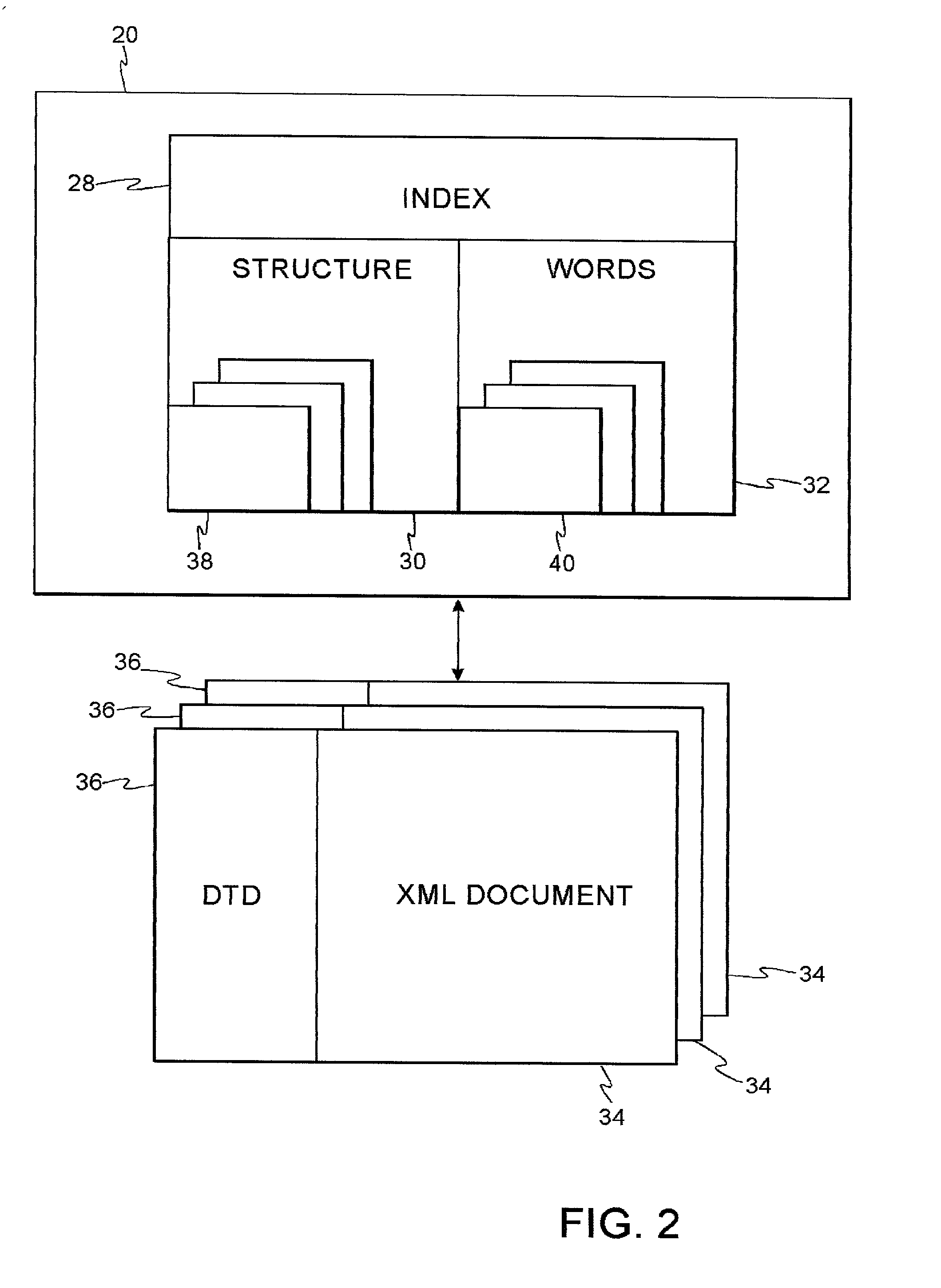
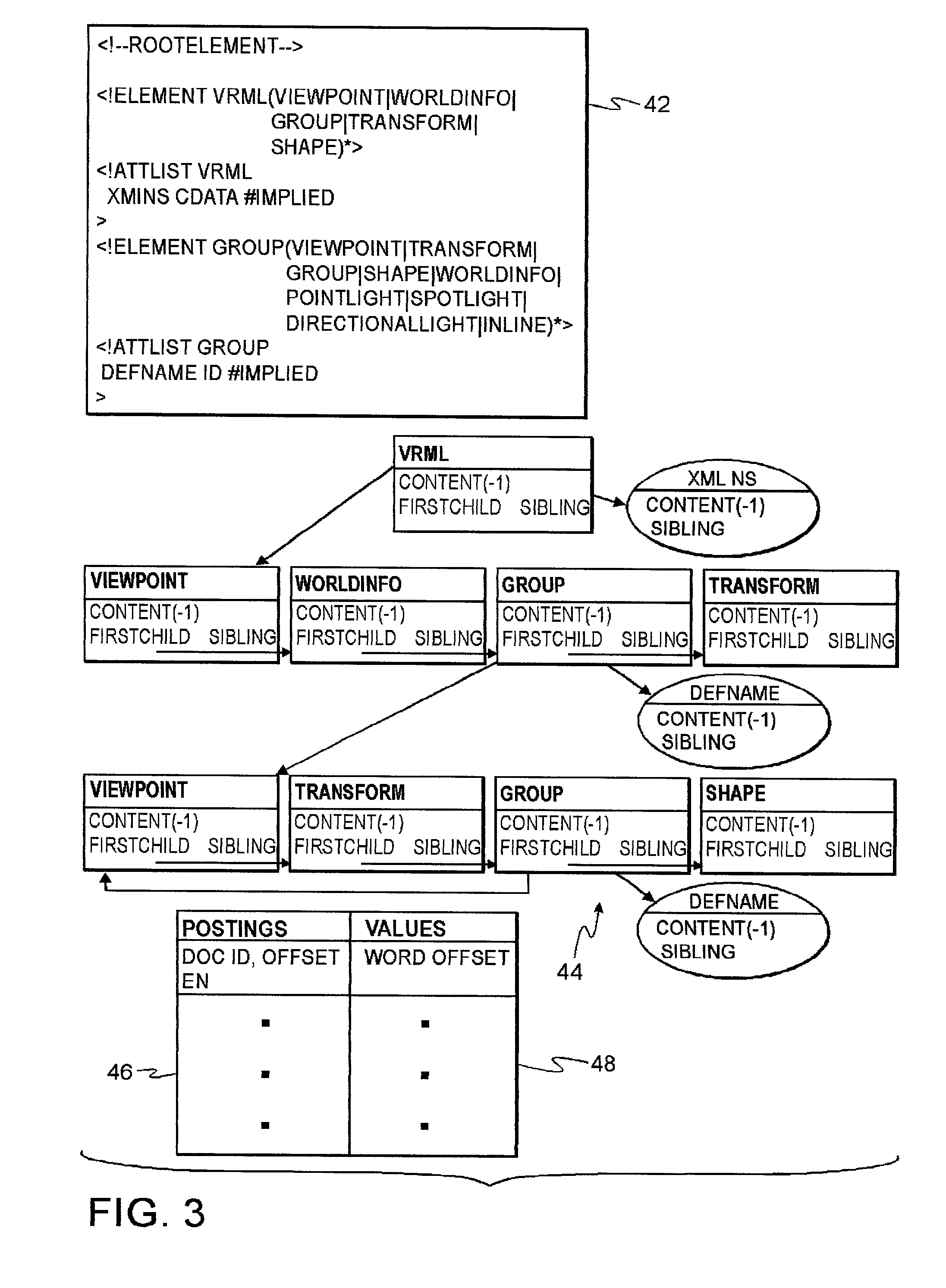
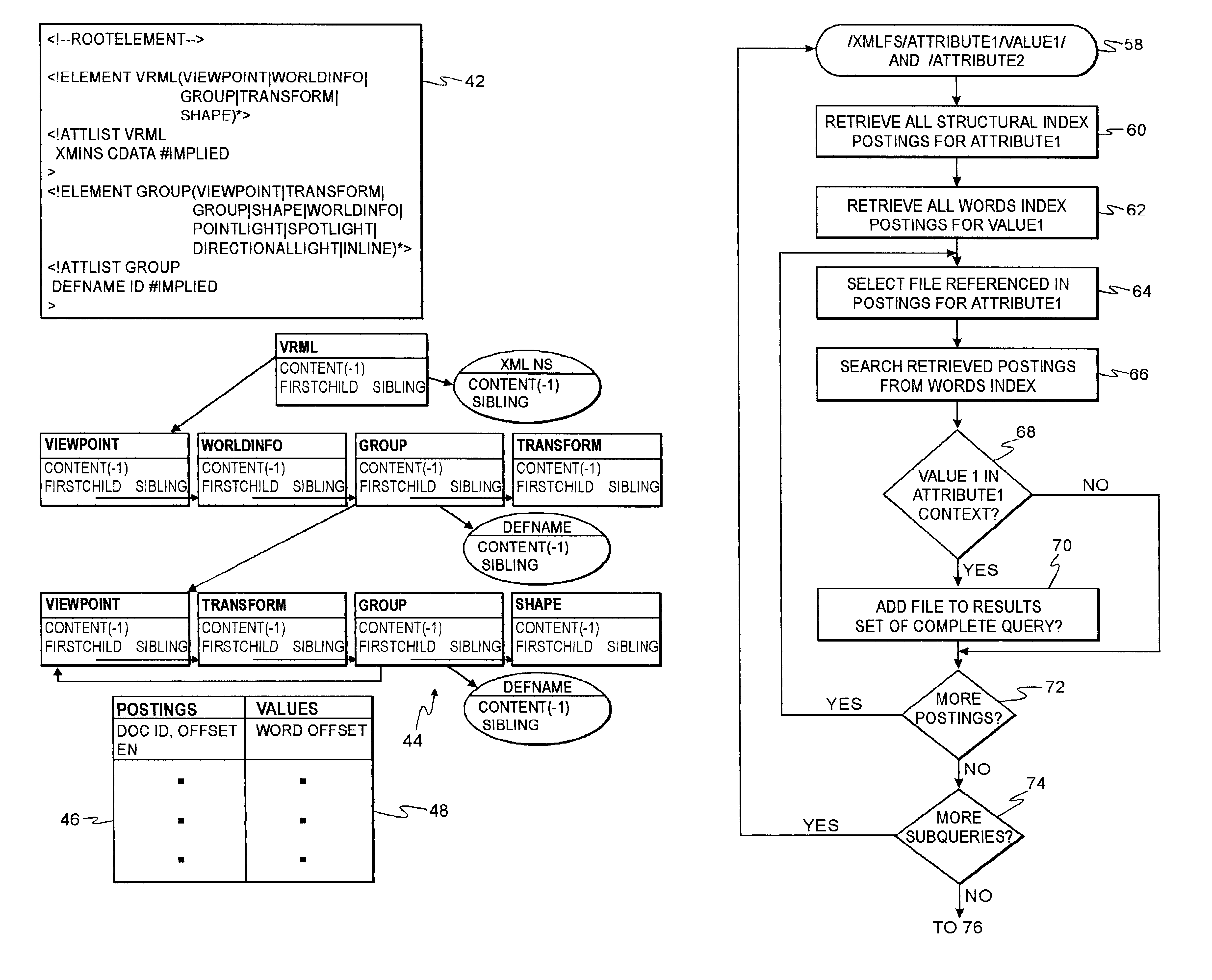
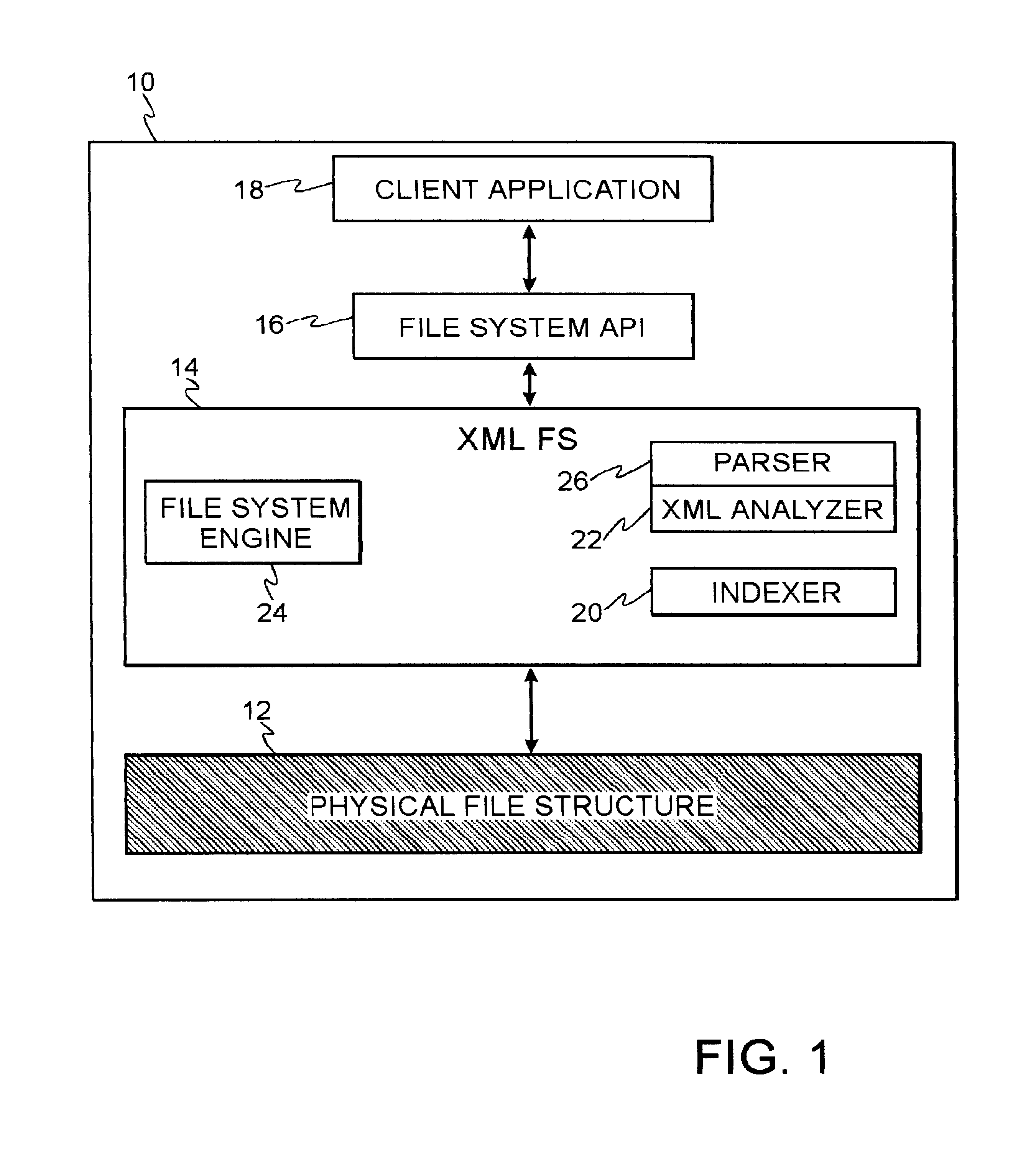
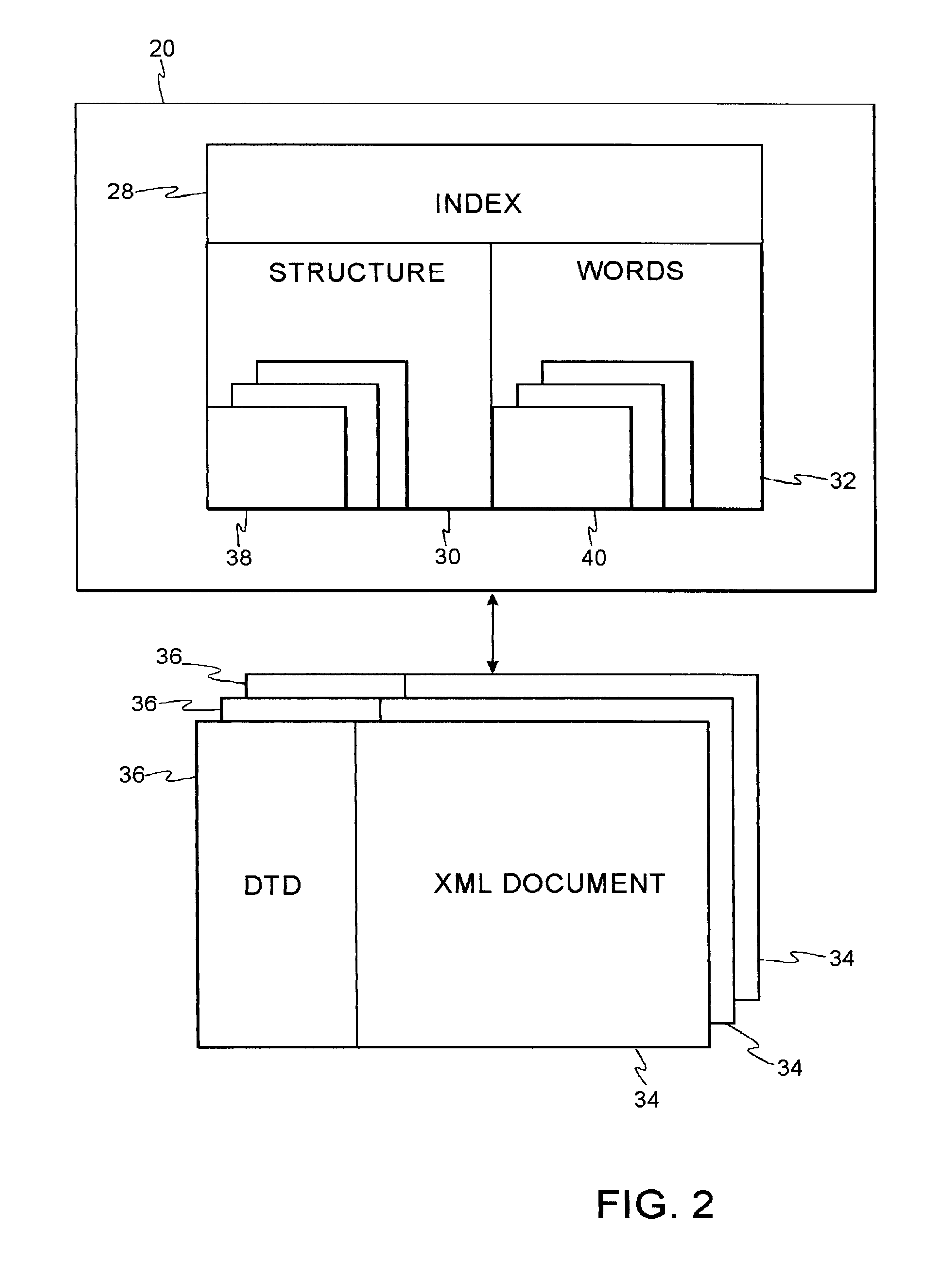
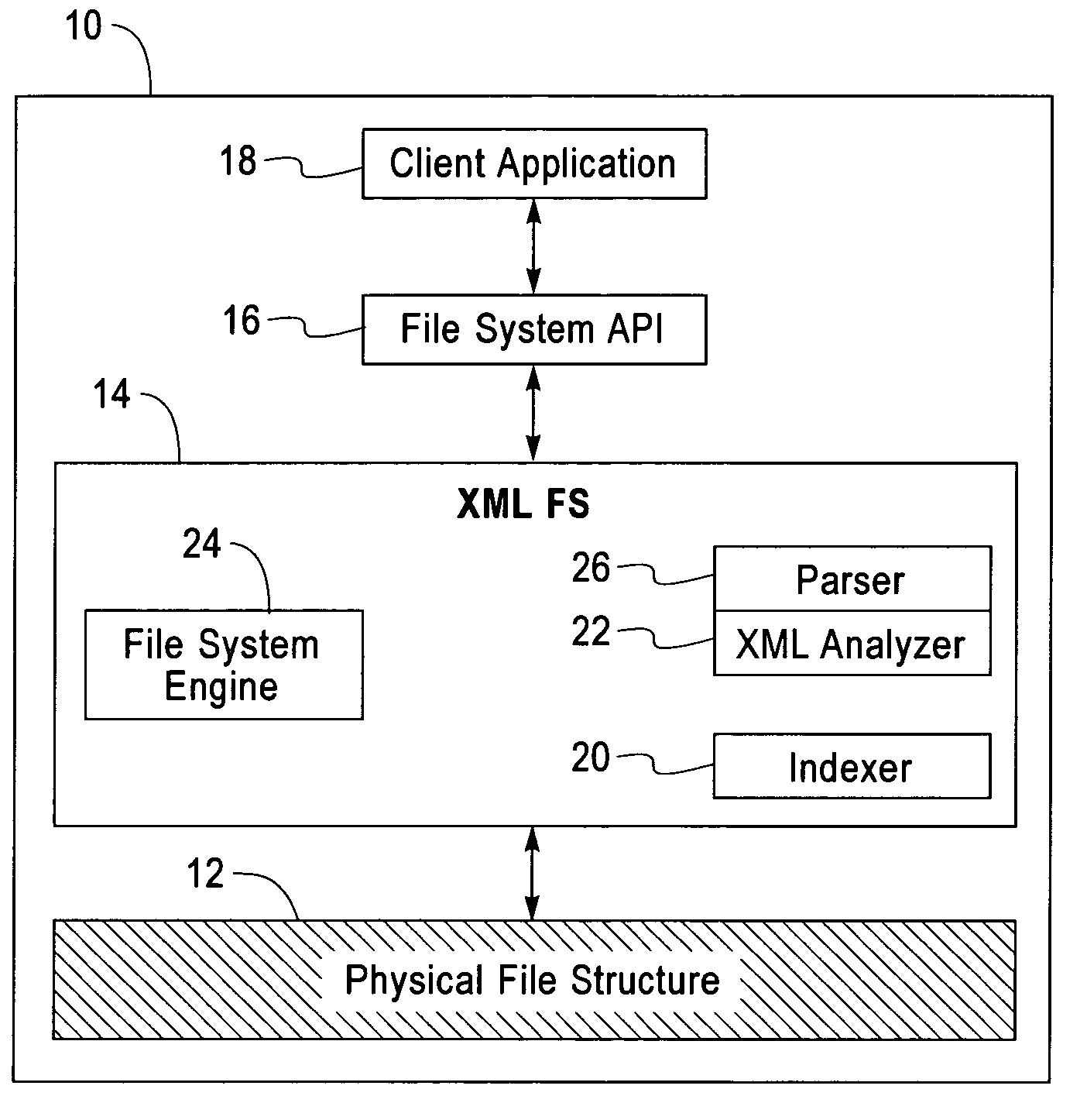
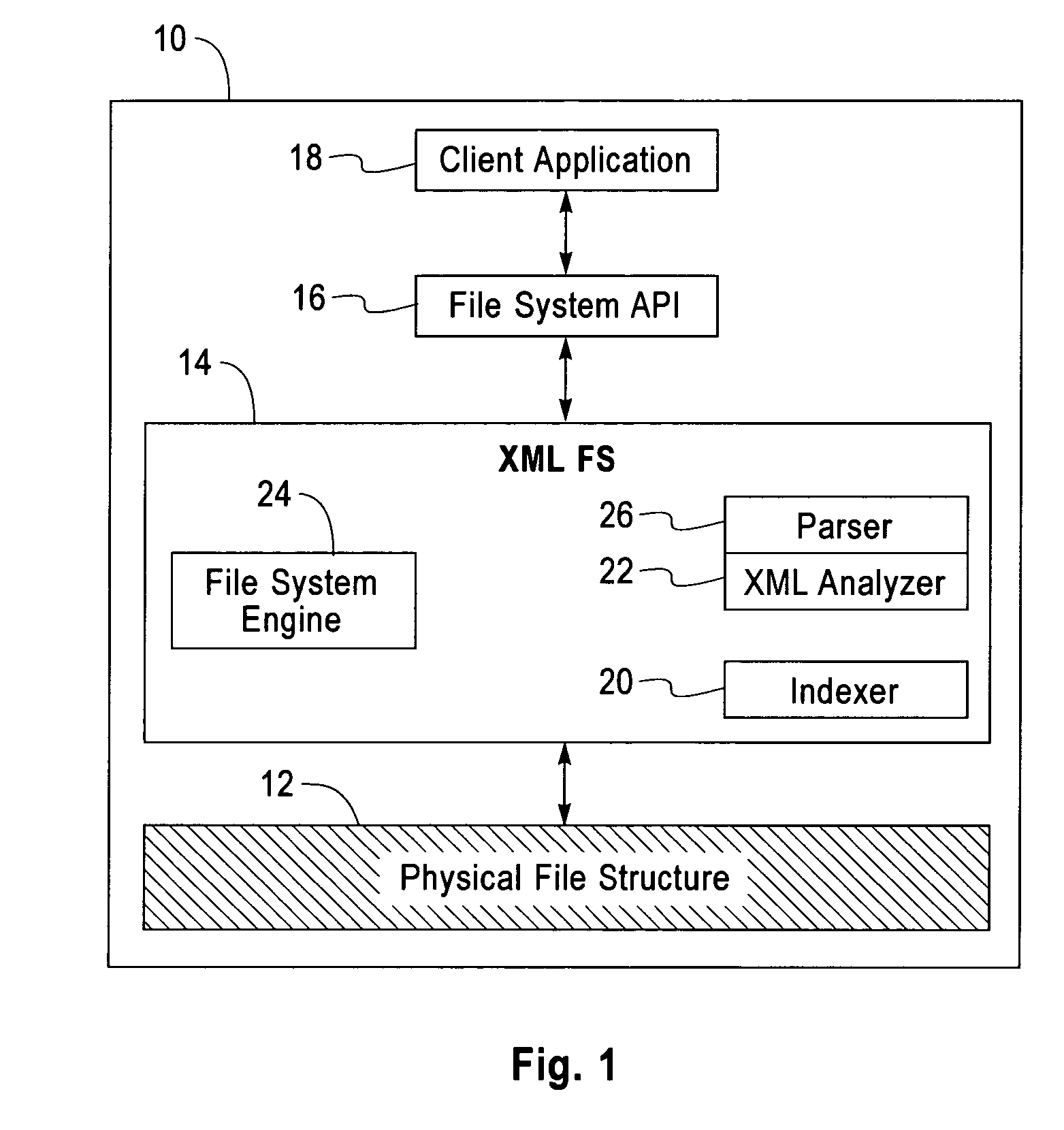
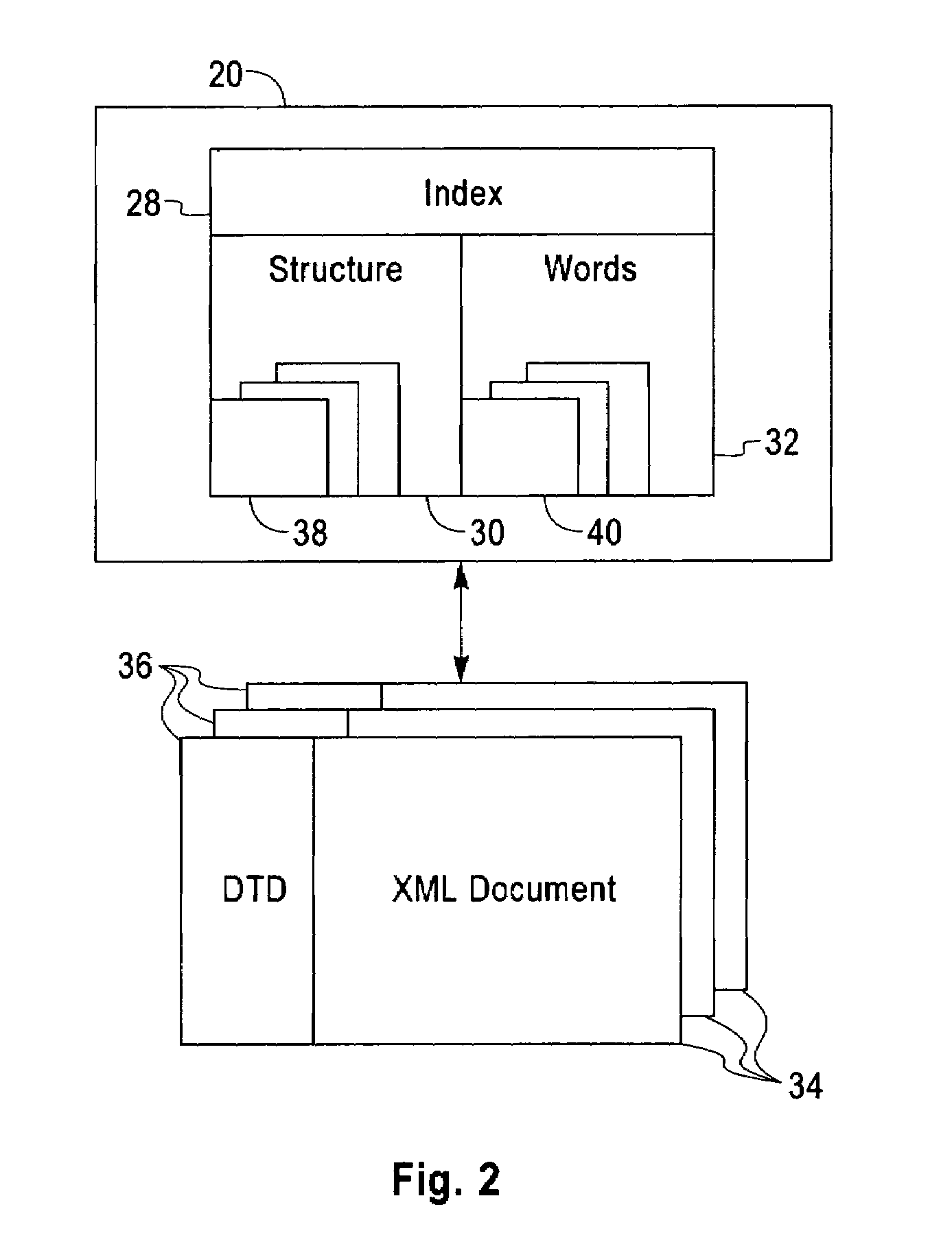
File system with access and retrieval of XML documents
InactiveUS20010049675A1Data processing applicationsWebsite content managementFile systemDirectory structure
An XML-aware file system exploits attributes encoded in an XML document. The file system presents a dynamic directory structure to the user, and breaks the conventional tight linkage between sets of files and the physical directory structure, thus allowing different users to see files organized in a different fashion. The dynamic structure is based upon content, which is extracted using an inverted index according to attributes and values defined by the XML structure.
Owner:IBM CORP
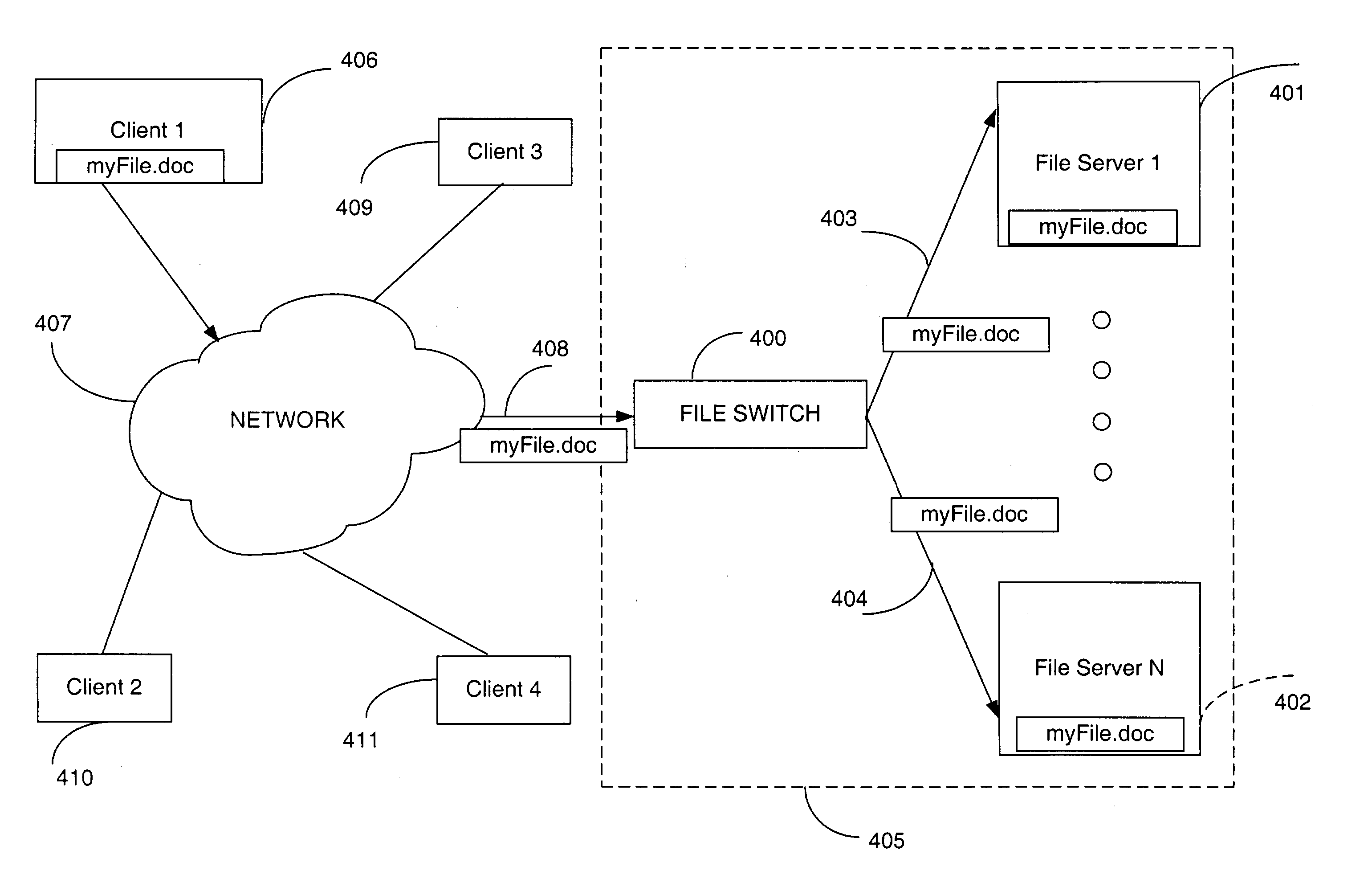
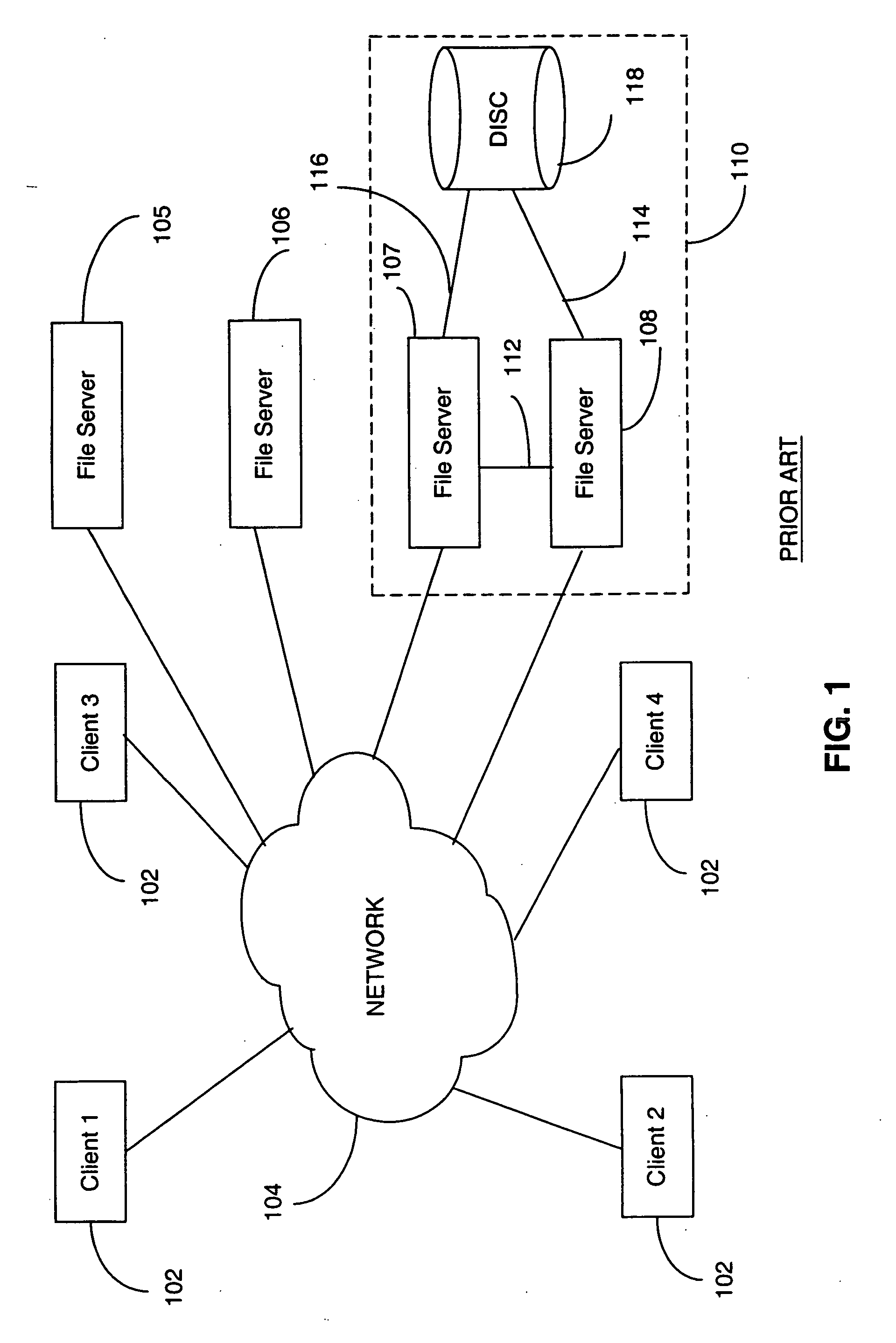
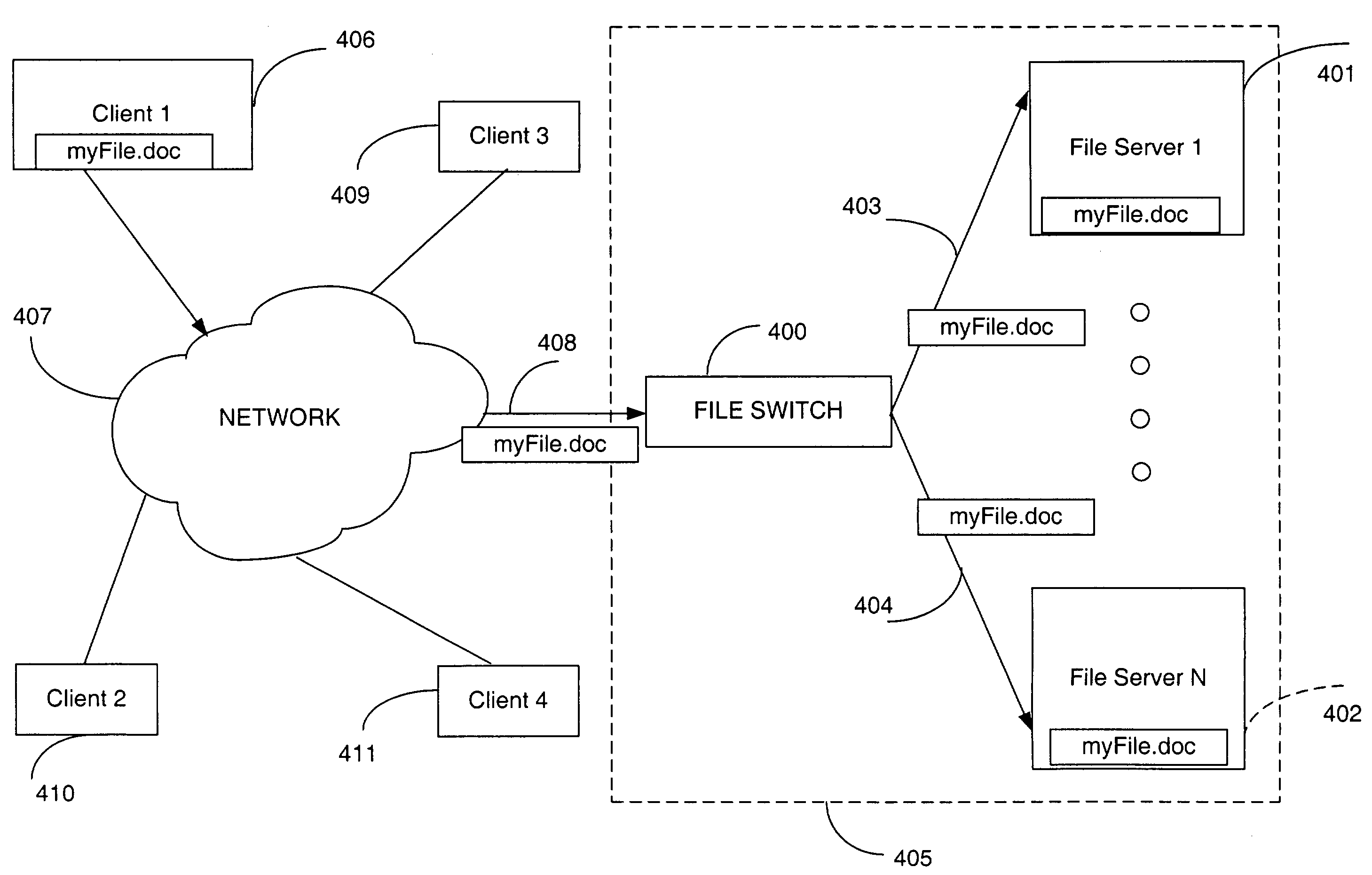
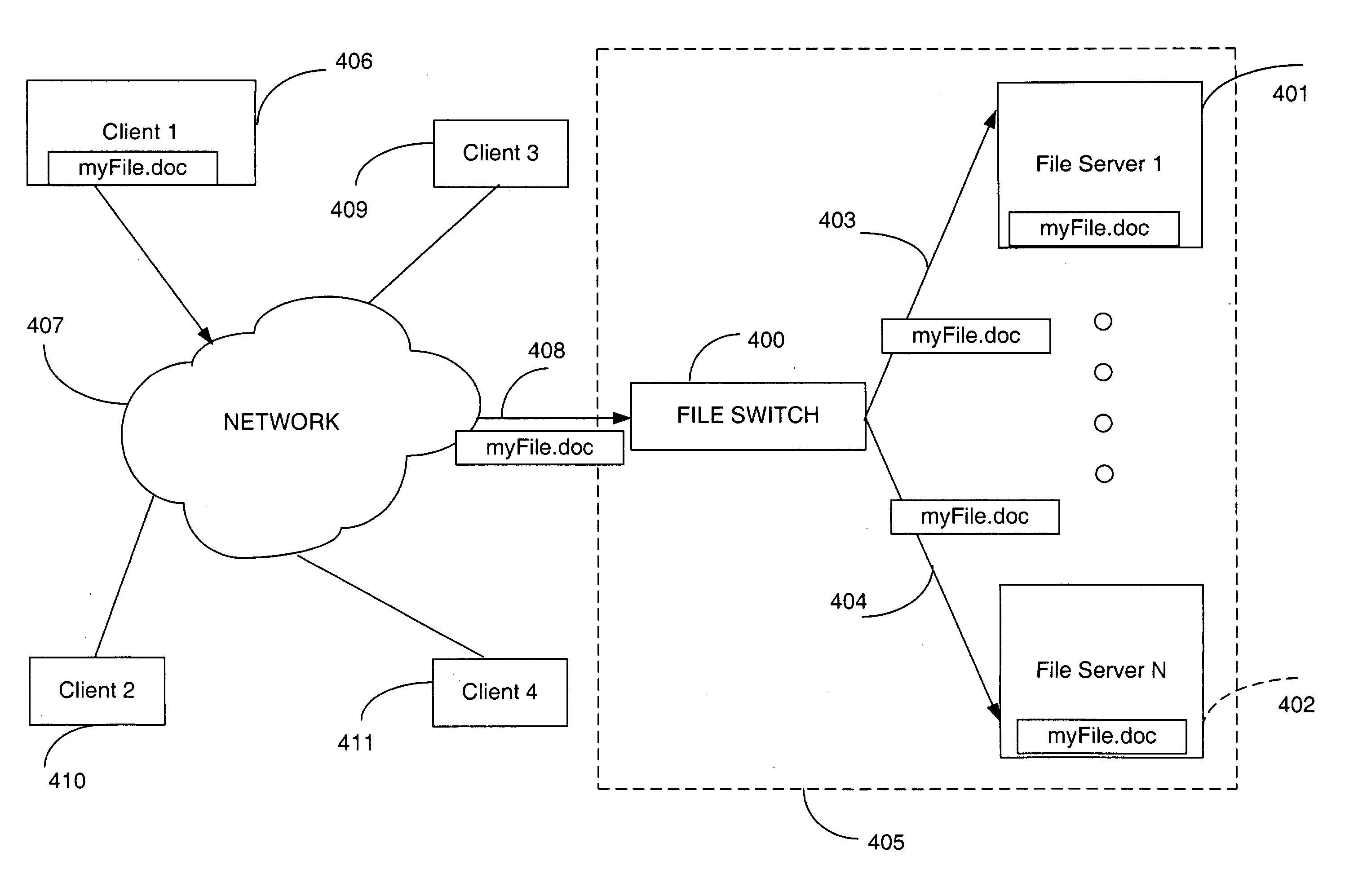
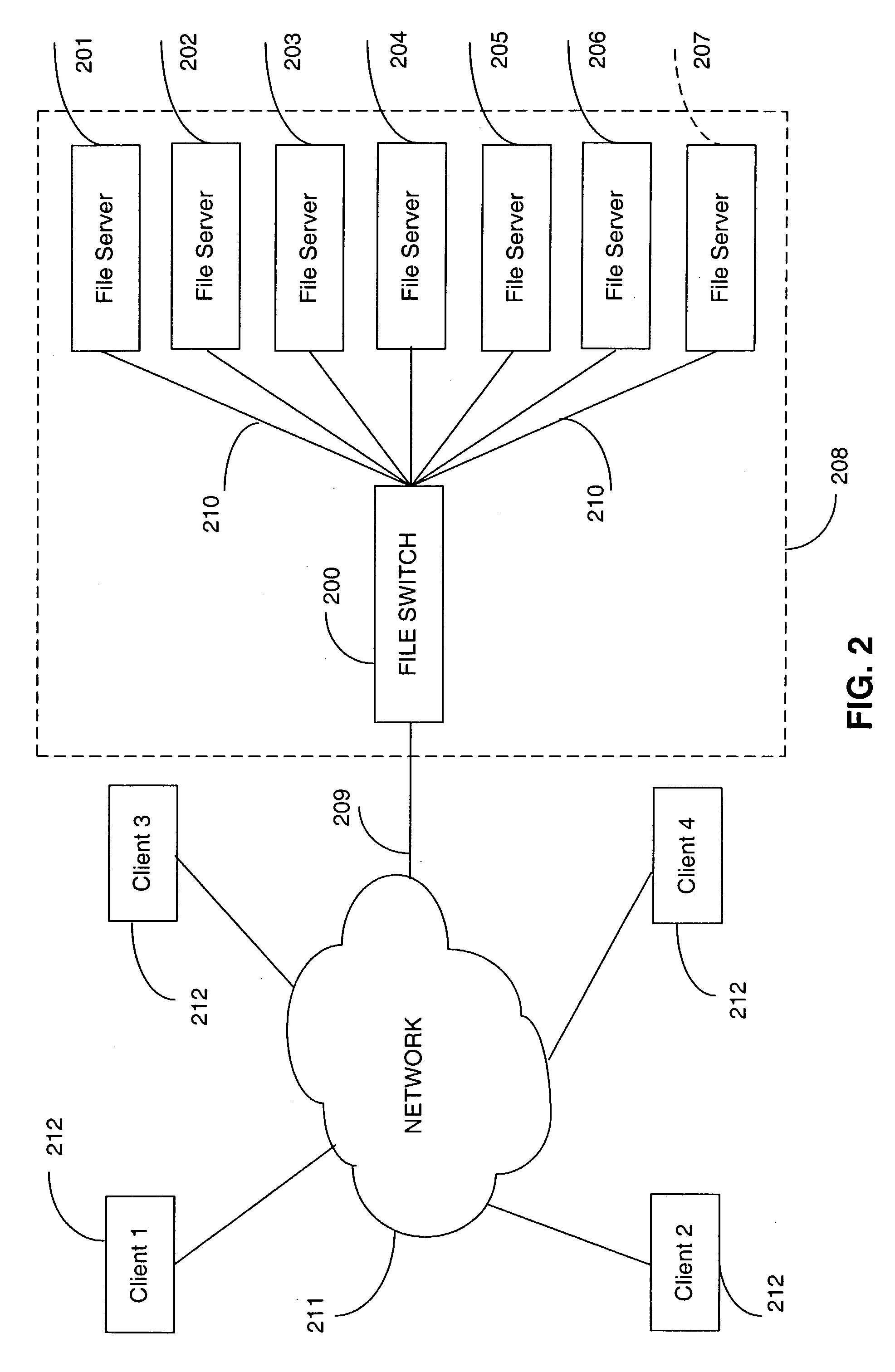
Directory aggregation for files distributed over a plurality of servers in a switched file system
InactiveUS20040133606A1Improve throughputImprove toleranceFile access structuresSpecial data processing applicationsFile systemData file
A file switch, logically positioned between client computers and file servers in a computer network, distributes user files among multiple file servers using an aggregated directory mechanism. A hierarchical directory structure is created on the file servers and used to store metadata files, which store metadata for each user file to indicate where data files, containing portions of the user file, are stored. The file switch automatically spreads the data files and metadata files over a large number of distinct directories on multiple file servers, preventing large number of data files from being stored in a single directory on a single file server. In response to a directory enumeration request from a client computer, one or more directories of metadata files on one or more of the file servers is enumerated, instead of enumerating the data file that store the user file portions.
Owner:RPX CORP
Directory aggregation for files distributed over a plurality of servers in a switched file system
A file switch, logically positioned between client computers and file servers in a computer network, distributes user files among multiple file servers using an aggregated directory mechanism. A hierarchical directory structure is created on the file servers and used to store metadata files, which store metadata for each user file to indicate where data files, containing portions of the user file, are stored. The file switch automatically spreads the data files and metadata files over a large number of distinct directories on multiple file servers, preventing large number of data files from being stored in a single directory on a single file server. In response to a directory enumeration request from a client computer, one or more directories of metadata files on one or more of the file servers are enumerated, instead of enumerating the data file that store the user file portions.
Owner:RPX CORP
System for managing media content
ActiveUS8042054B2Record information storageCarrier indicating arrangementsGraphicsGraphical user interface
Owner:SERVICENOW INC
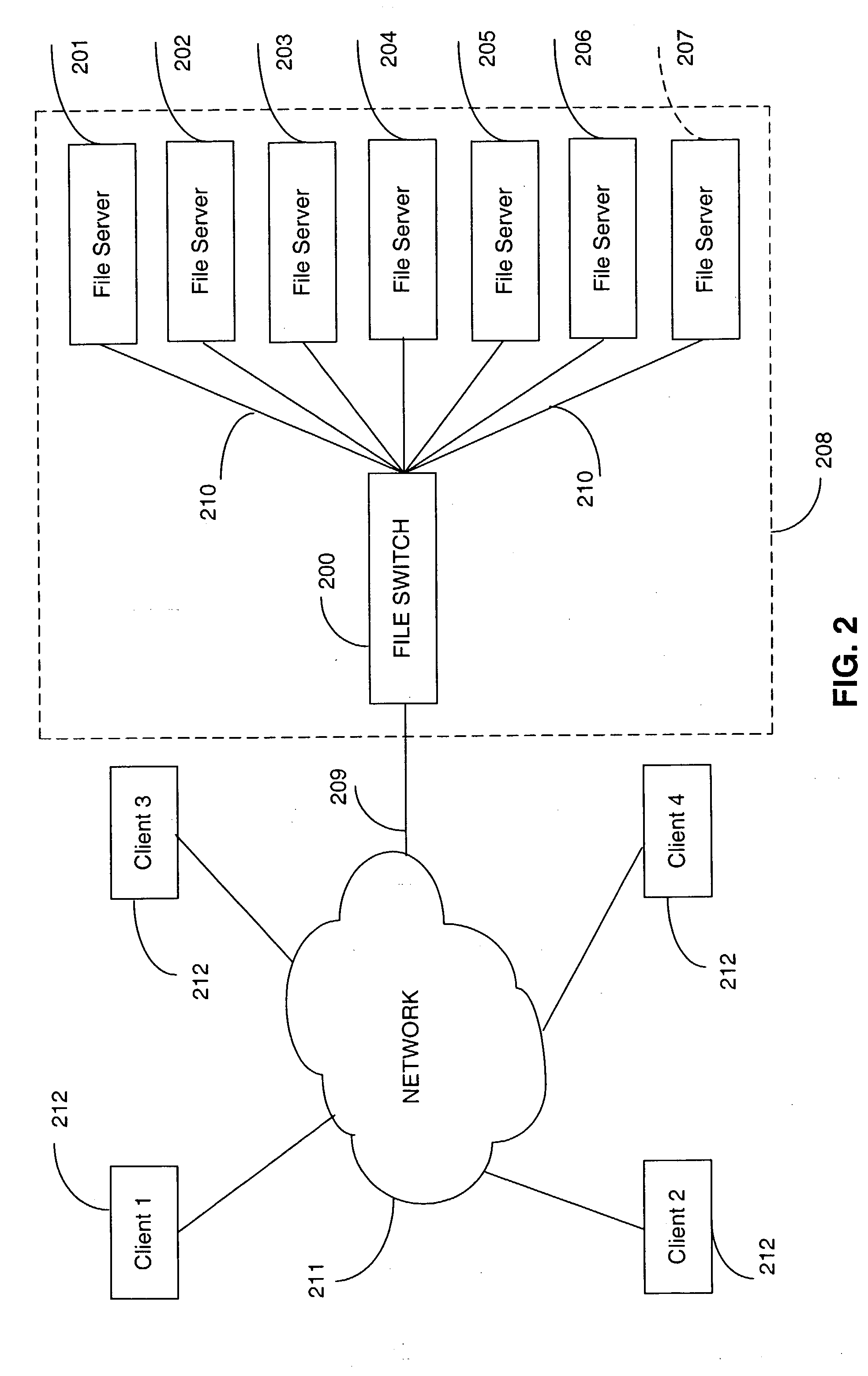
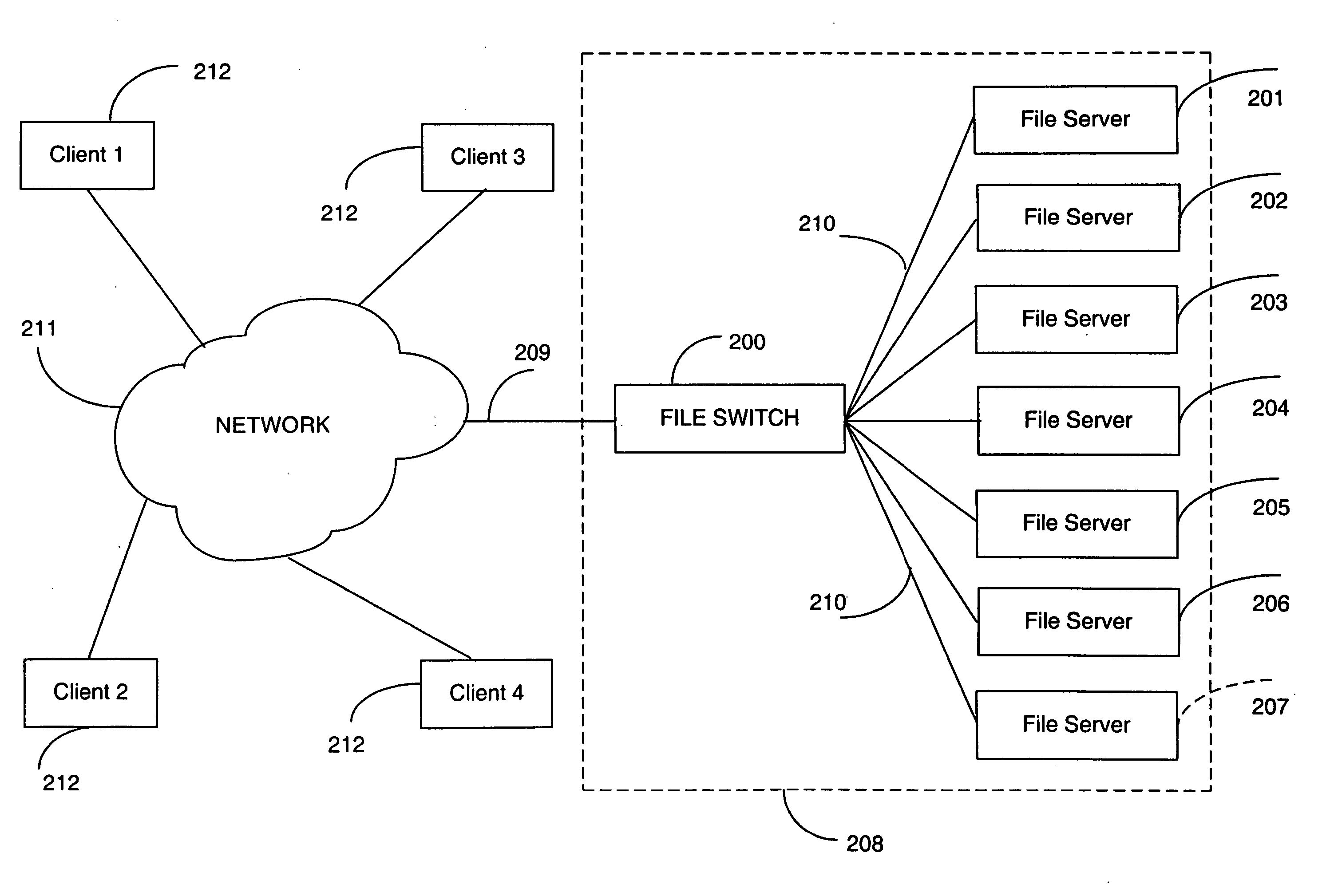
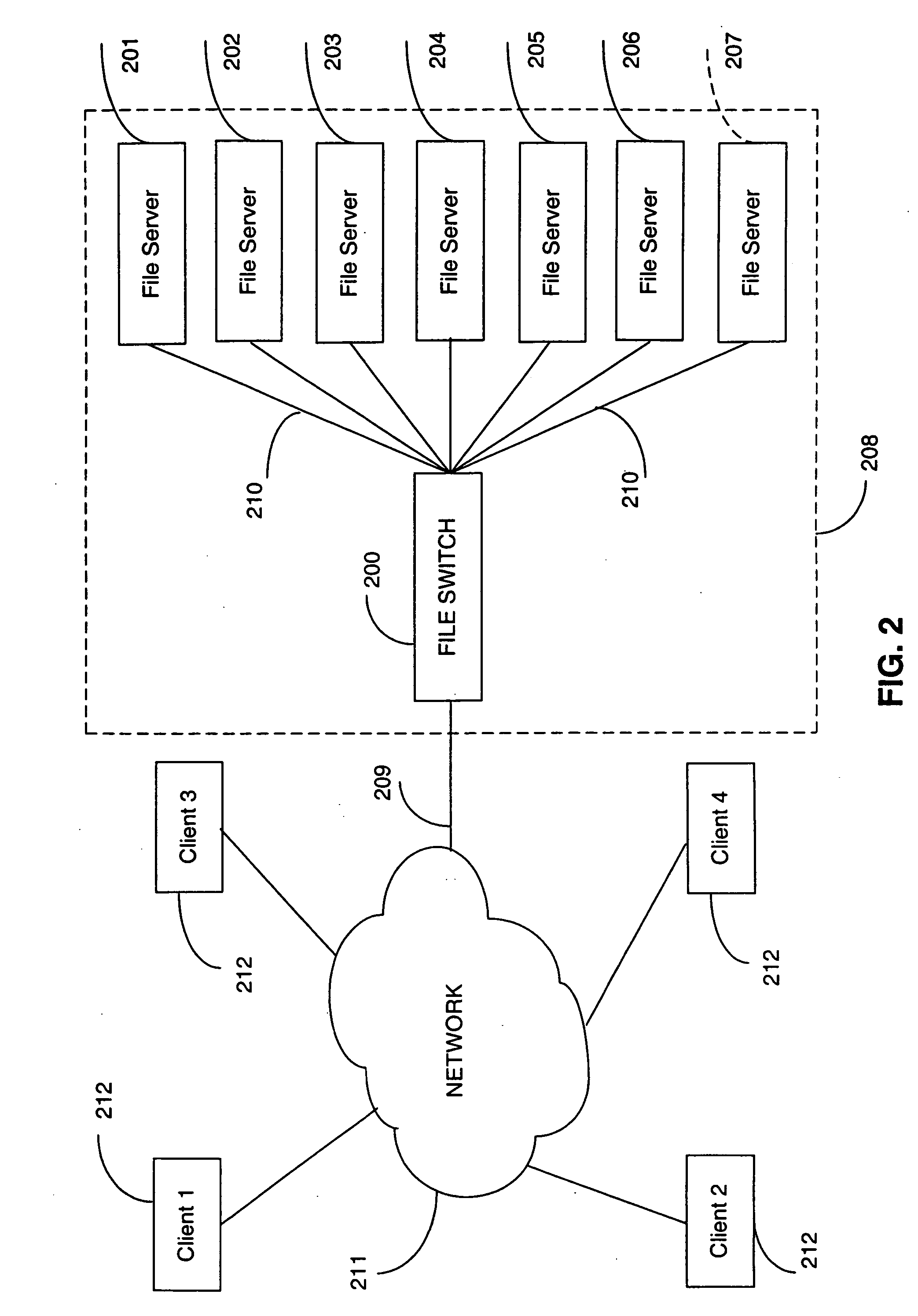
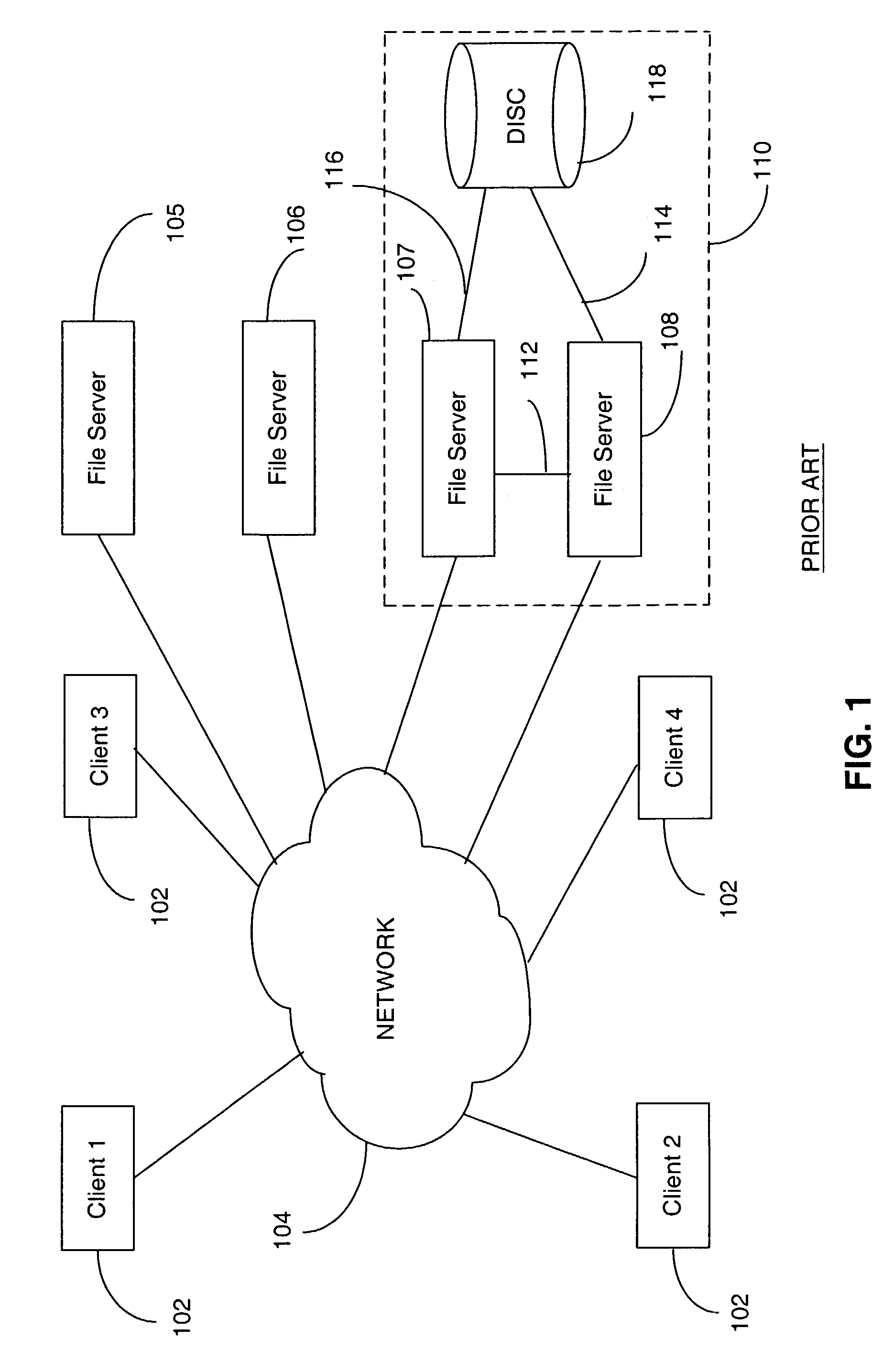
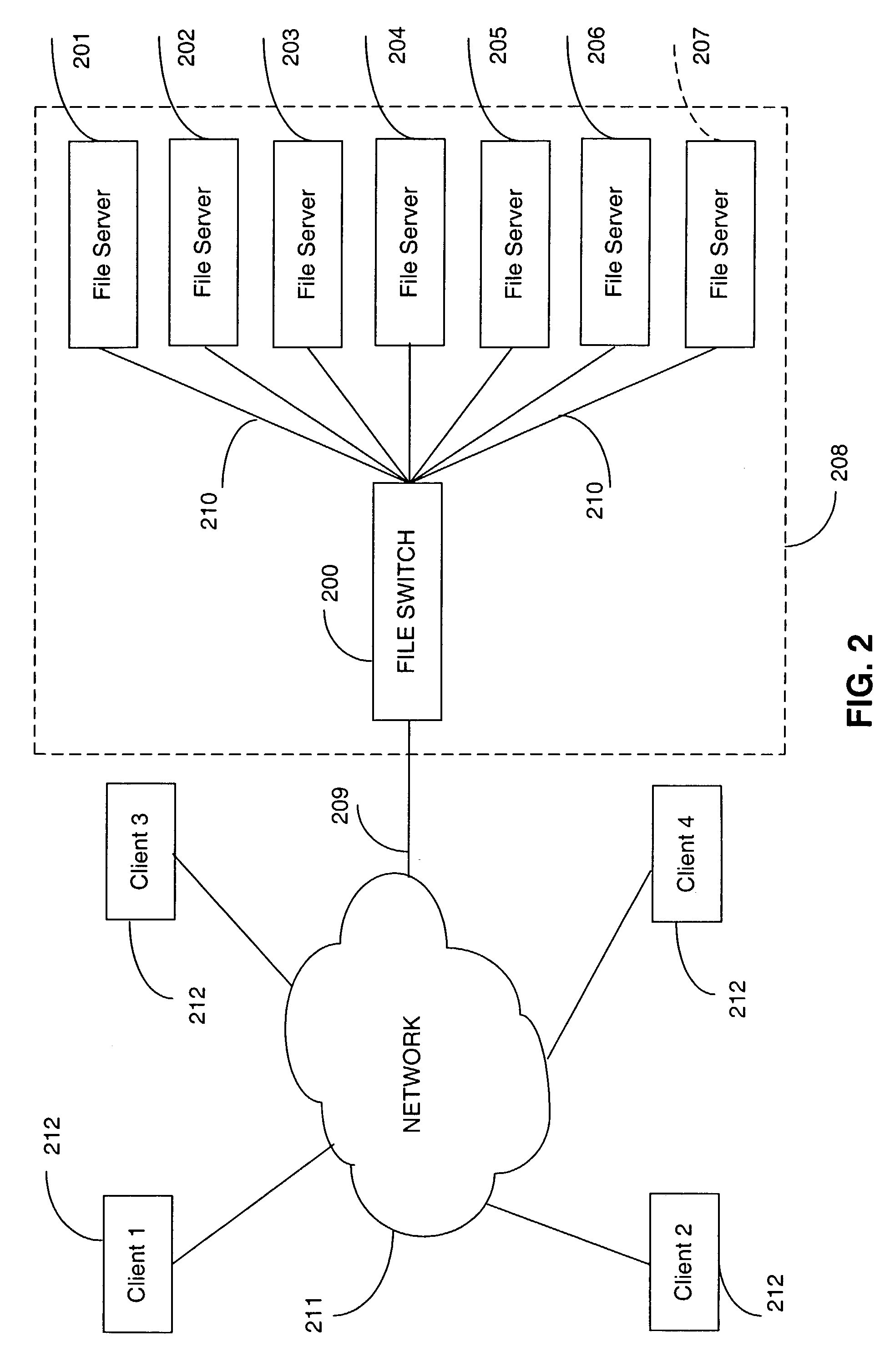
Metadata based file switch and switched file system
InactiveUS7383288B2Lower latencyDigital data information retrievalDigital data processing detailsMirror imageClient machine
An apparatus and method are provided in a computer network to decouple client computers from file servers, by placing a transparent network node, also termed a file switch or file switch computer, between the client computers and the file servers. Usage of such a file switch allows reduced latency in file transfers, as well as scalable mirroring, striping, spillover, and other features. The file switch preferably includes at least one processing unit for executing computer programs, at least one port for exchanging information with the file servers and client computers, and a file aggregation module. The file aggregation module includes computer programs for determining a set of file servers from the group of file servers for storing a specified user file, creating a metadata file storing information identifying the set of file servers for storing the user file; and updating directory structures on the set of file servers to indicate storage of the user file.
Owner:RPX CORP
Method and a system for responding locally to requests for file metadata associated with files stored remotely
ActiveUS20070083522A1Multiple digital computer combinationsSpecial data processing applicationsRemote computerDirectory structure
A method and system for responding locally to requests for file metadata associated with files stored remotely includes a method of responding locally to requests for file metadata without downloading the file from a remote location. A directory structure representing an application program stored by a remote machine and metadata associated with each file comprising the stored application program are received from the remote machine. The directory and the metadata are stored. At least one request to access metadata associated with a specific tile in the directory structure is received. The stored metadata is used to respond to the at least one request.
Owner:CITRIX SYST INC
Metadata based file switch and switched file system
InactiveUS20040133607A1Digital data information retrievalDigital computer detailsFile systemComputer module
An apparatus and method are provided in a computer network to decouple client computers from file servers, by placing a transparent network node, also termed a file switch or file switch computer, between the client computers and the file servers. Usage of such a file switch allows reduced latency in file transfers, as well as scalable mirroring, striping, spillover, and other features. The file switch preferably includes at least one processing unit for executing computer programs, at least one port for exchanging information with the file servers and client computers, and a file aggregation module. The file aggregation module includes computer programs for determining a set of file servers from the group of file servers for storing a specified user file, creating a metadata file storing information identifying the set of file servers for storing the user file; and updating directory structures on the set of file servers to indicate storage of the user file.
Owner:RPX CORP
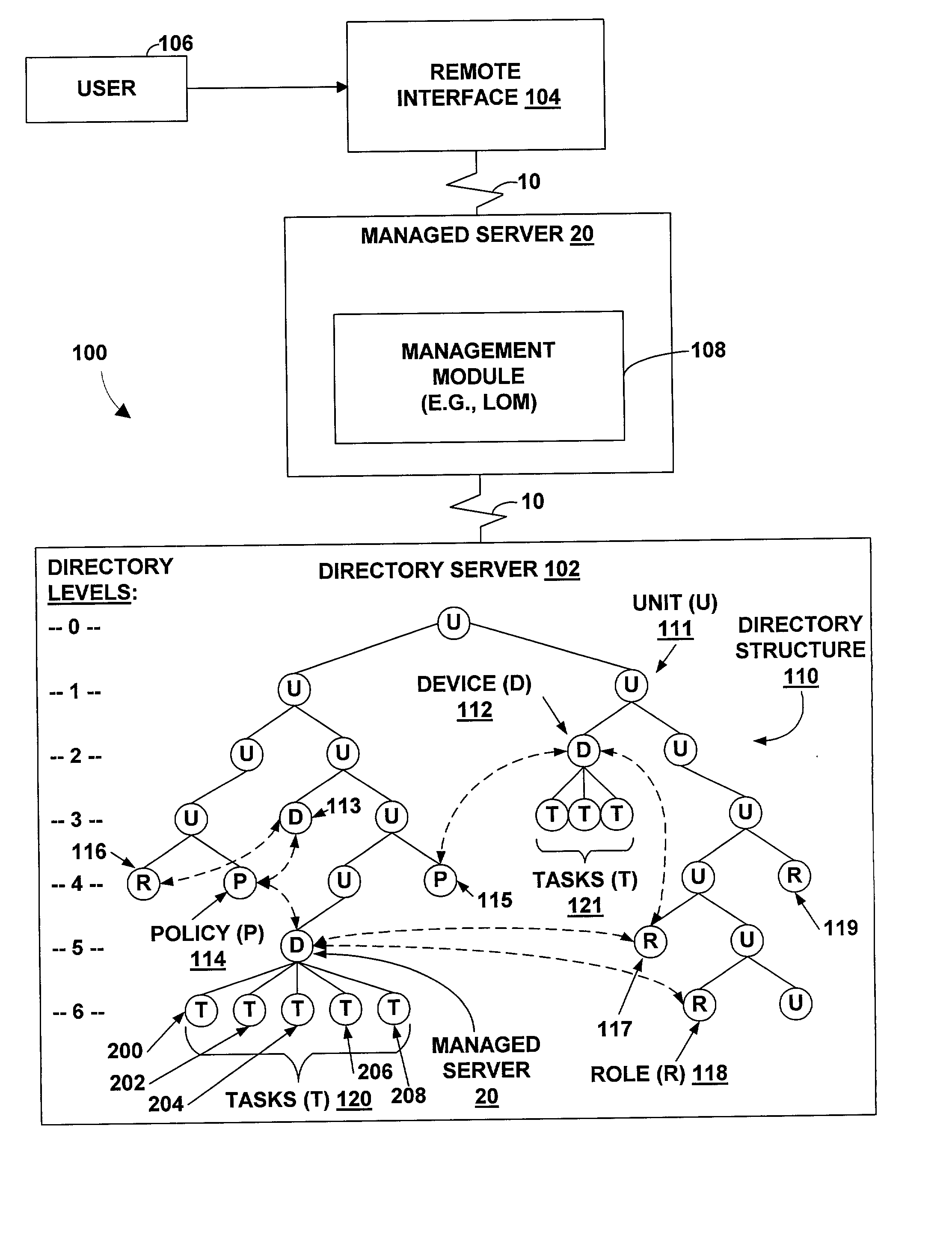
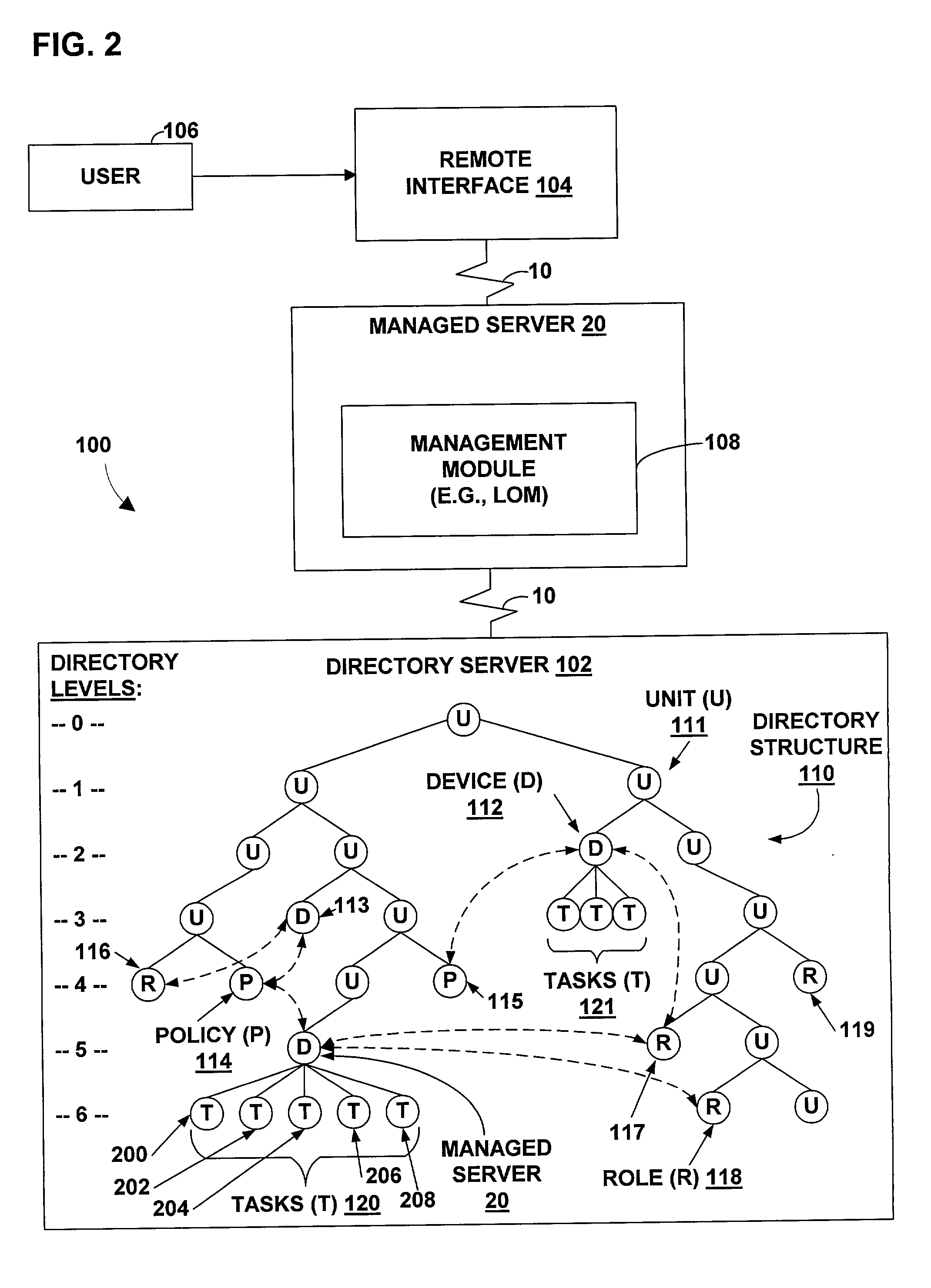
Method and apparatus for increasing the functionality and ease of use of lights out management in a directory enabled environment
InactiveUS20030131113A1Data processing applicationsMultiple digital computer combinationsComputerized systemUsability
A technique is provided for managing network devices and computer systems via a remote directory environment. The remote directory environment organizes various resources, such as servers, in a directory structure and provides access rights and restrictions to the resources based on groups or roles. A user with the proper access rights is then able to access the desired resource, such as a server, and create or modify management operations, device configurations, and other tasks. The subject device may then be notified of the new or modified operation, configuration, or task. The subject device also may routinely or periodically retrieve various management tasks from the remote directory environment.
Owner:HEWLETT PACKARD DEV CO LP
File system with access and retrieval of XML documents
InactiveUS6745206B2Data processing applicationsWebsite content managementFile systemDirectory structure
An XML-aware file system exploits attributes encoded in an XML document. The file system presents a dynamic directory structure to the user, and breaks the conventional tight linkage between sets of files and the physical directory structure, thus allowing different users to see files organized in a different fashion. The dynamic structure is based upon content, which is extracted using an inverted index according to attributes and values defined by the XML structure.
Owner:INT BUSINESS MASCH CORP
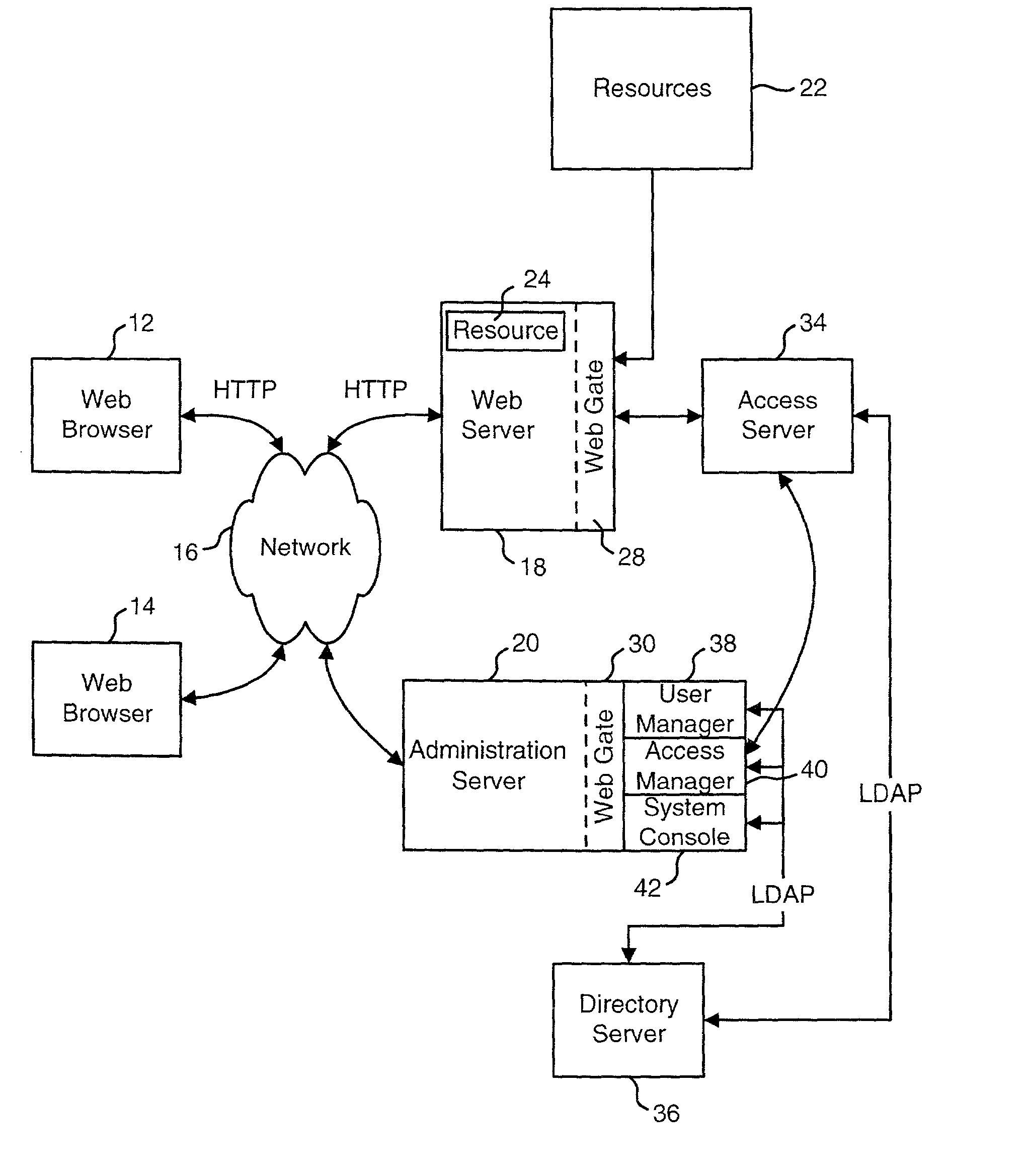
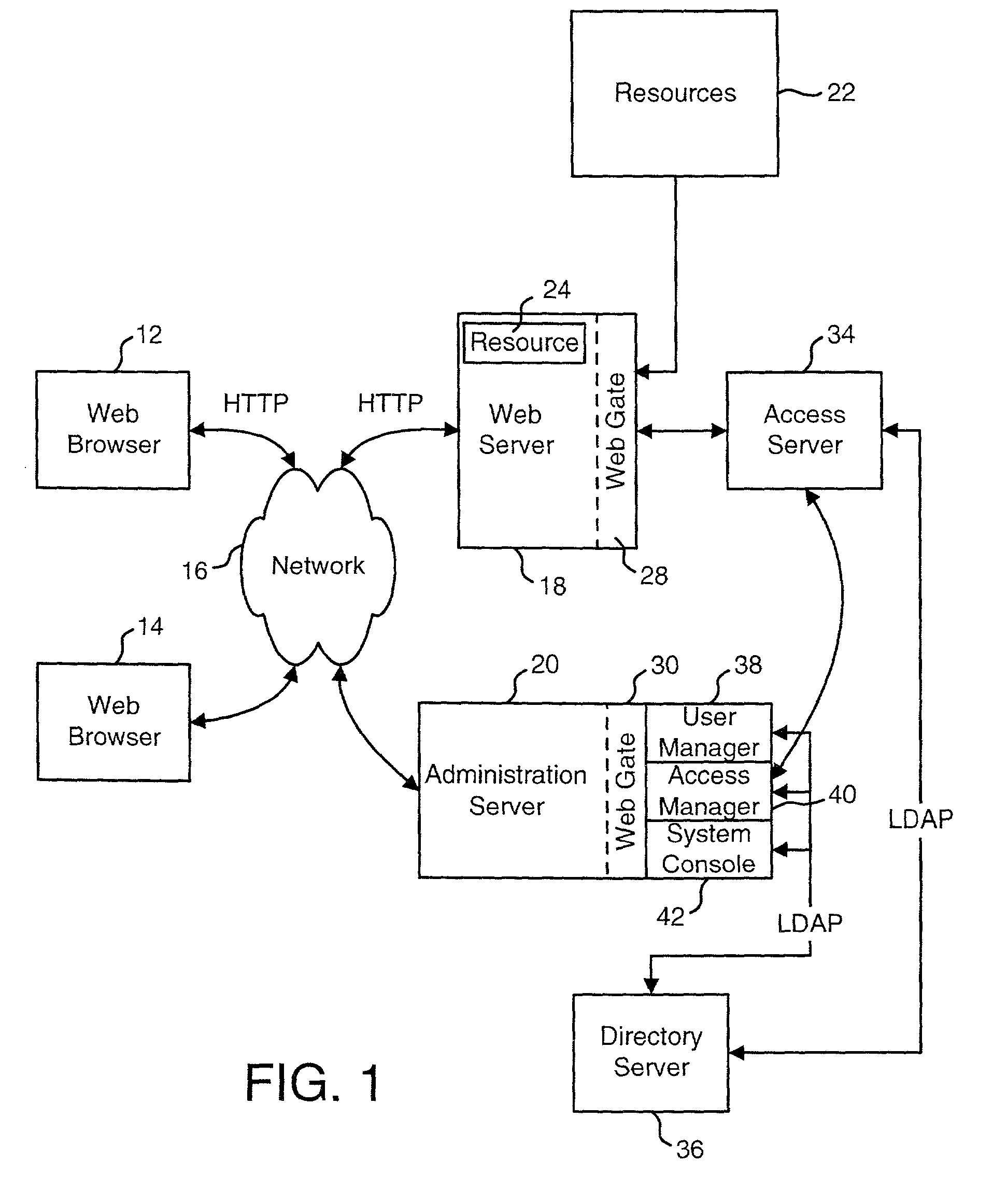
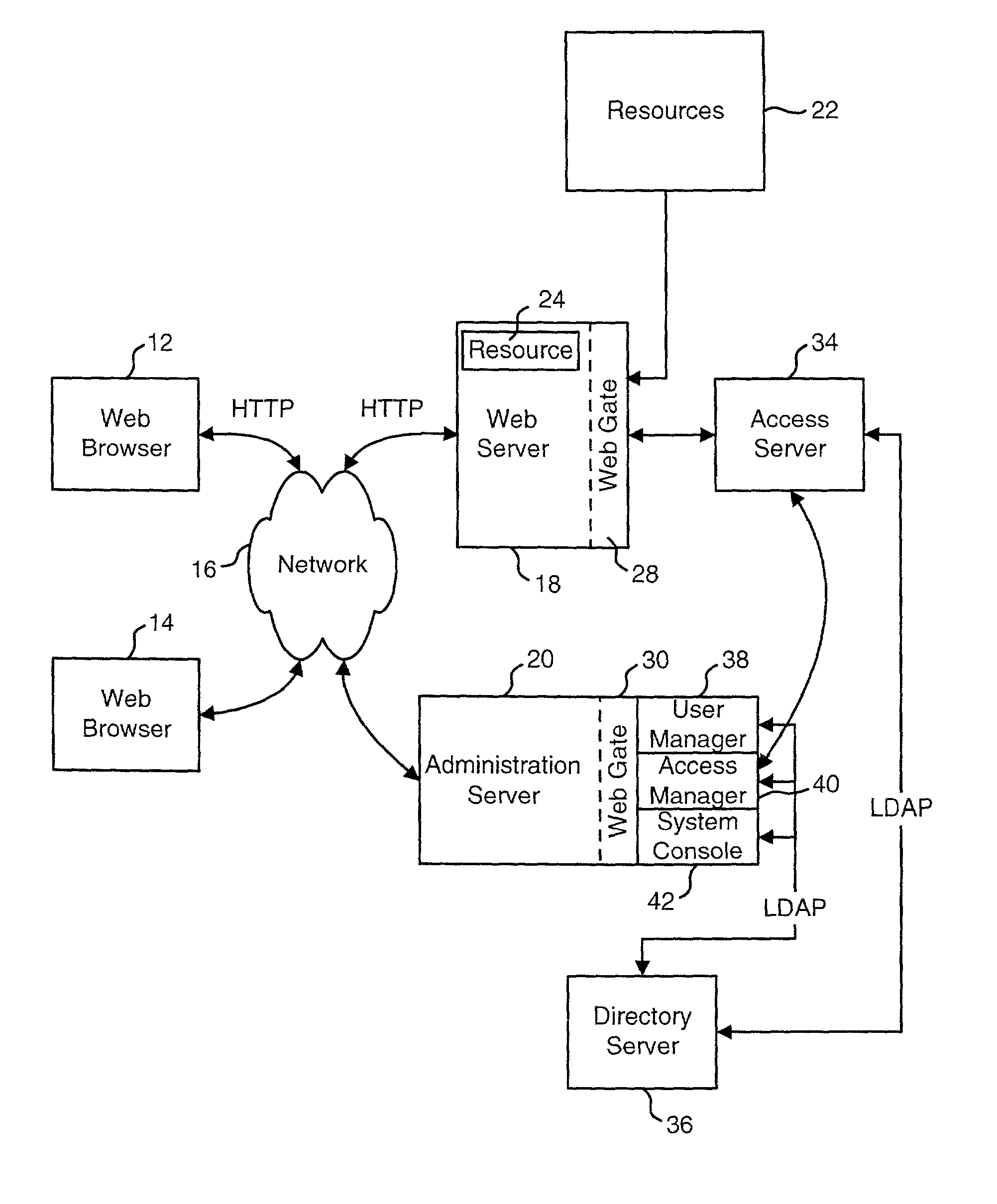
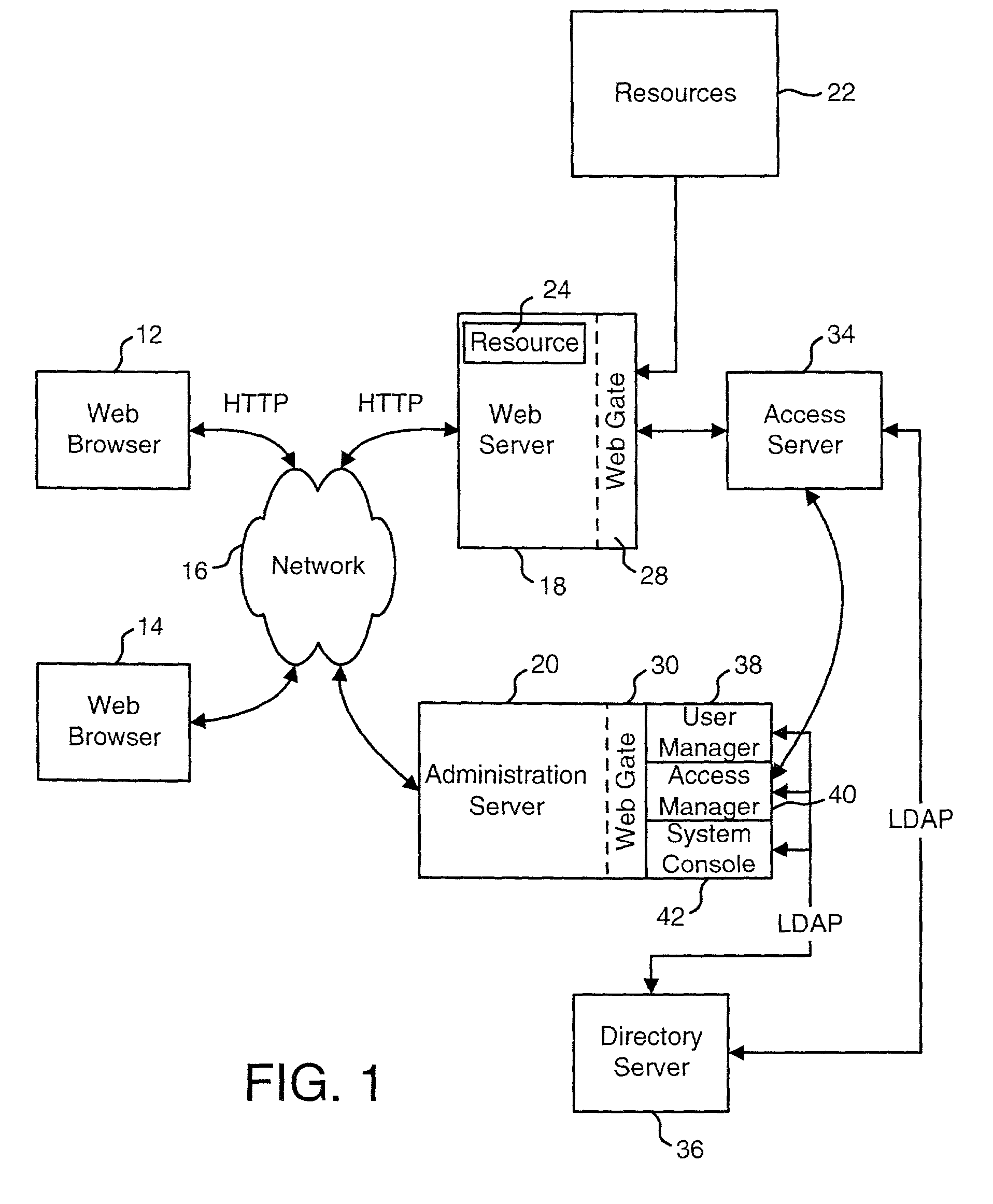
Providing data to applications from an access system
ActiveUS20020091798A1Easy mappingDigital data processing detailsDigital data protectionStructure of Management InformationDirectory structure
An access system is disclosed that can provide data to a downstream application. In one embodiment, the data is provided as header variables associated with an HTTP request. Other embodiments can use other protocols and other means for transmitting the data. The data provided to the downstream applications include information about the user accessing the application. In one embodiment, the data provided to the downstream application includes information from an identity profile stored in an LDAP directory structure.
Owner:ORACLE INT CORP
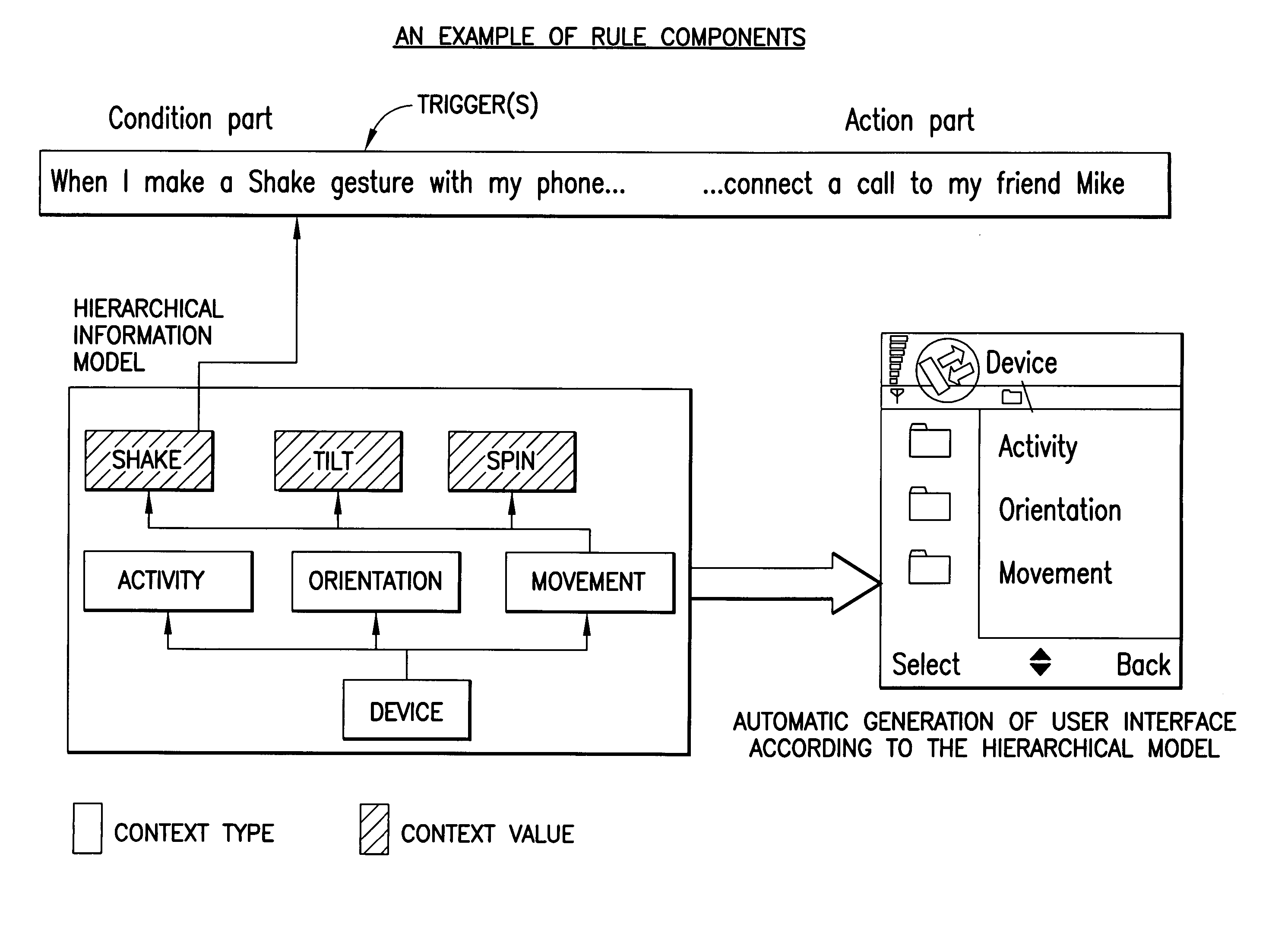
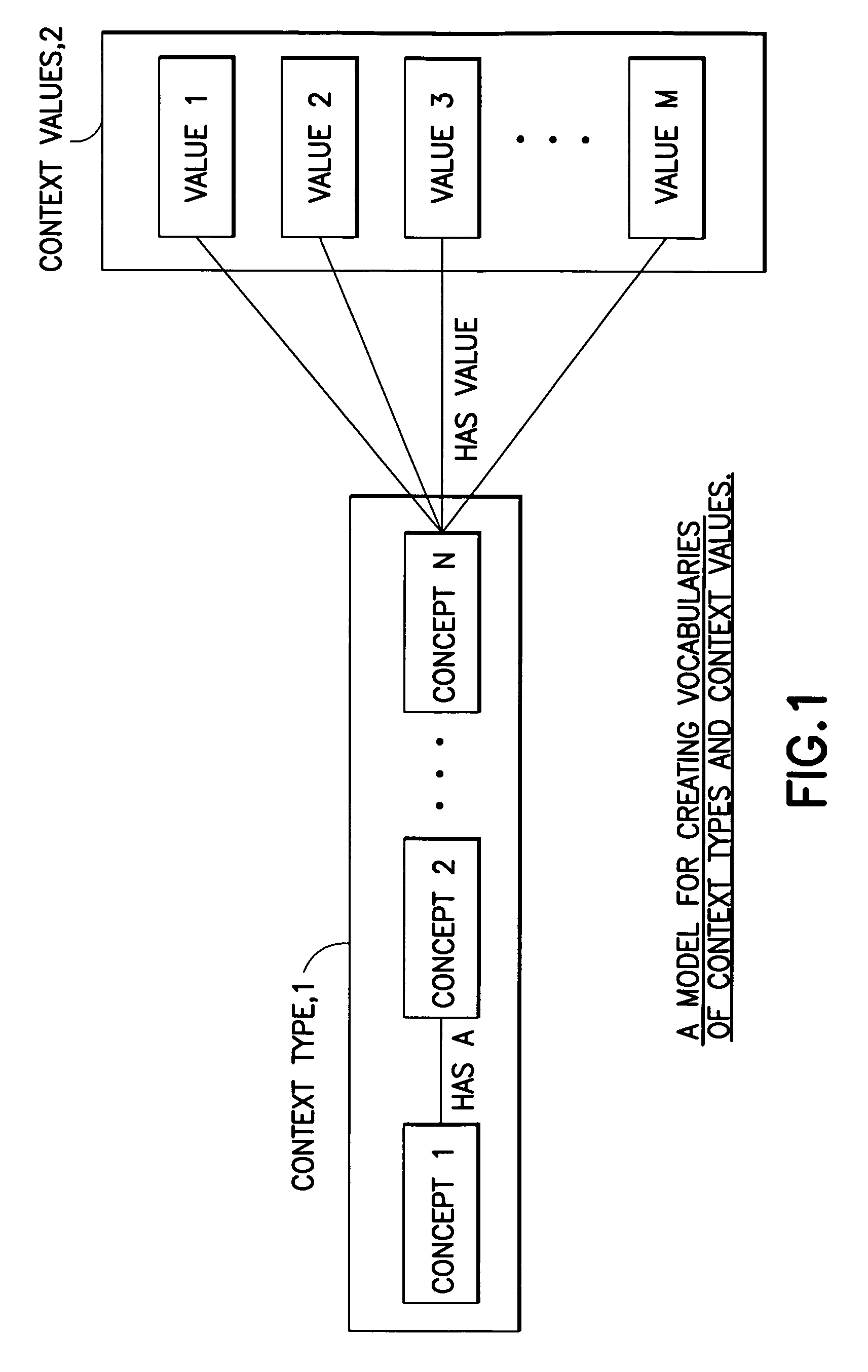
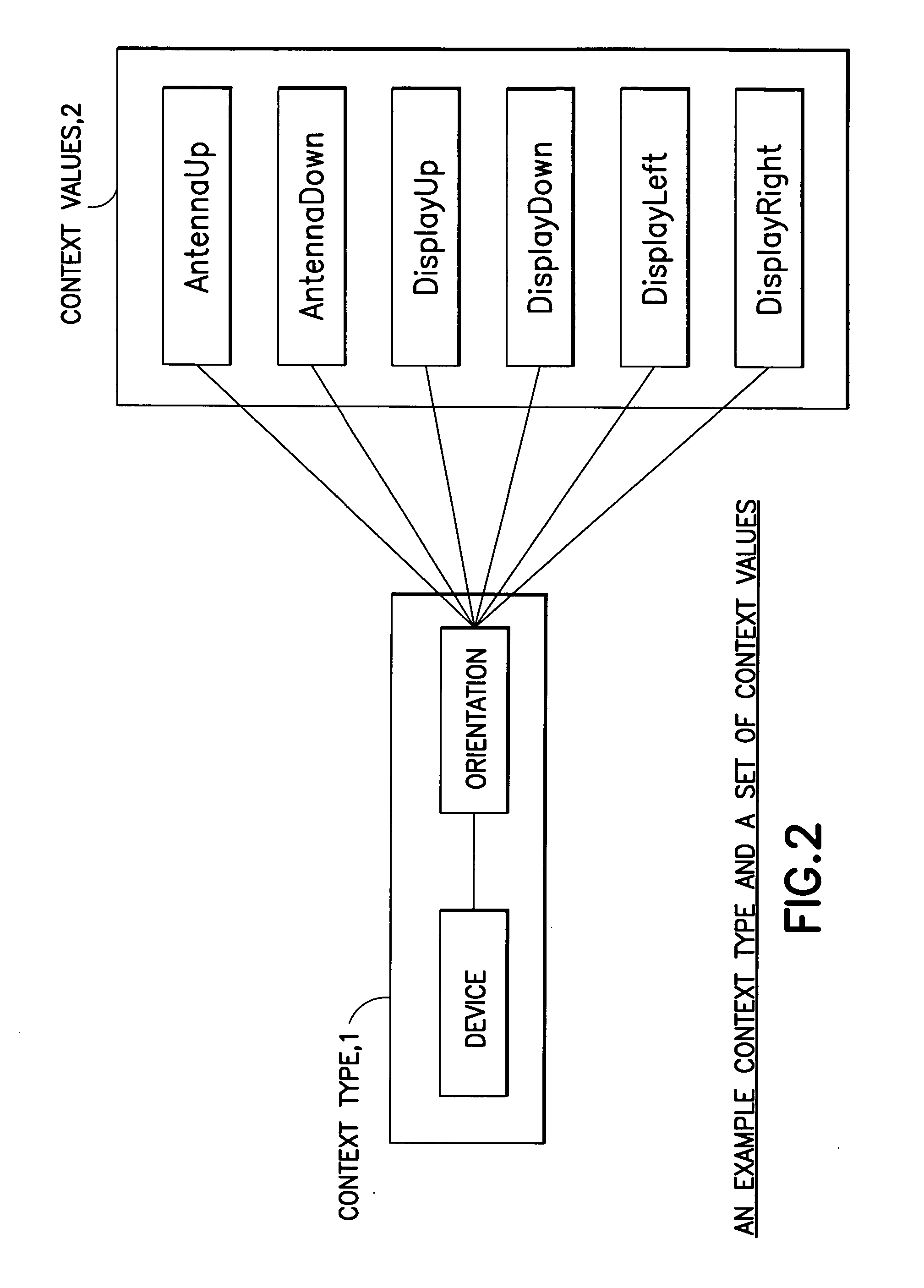
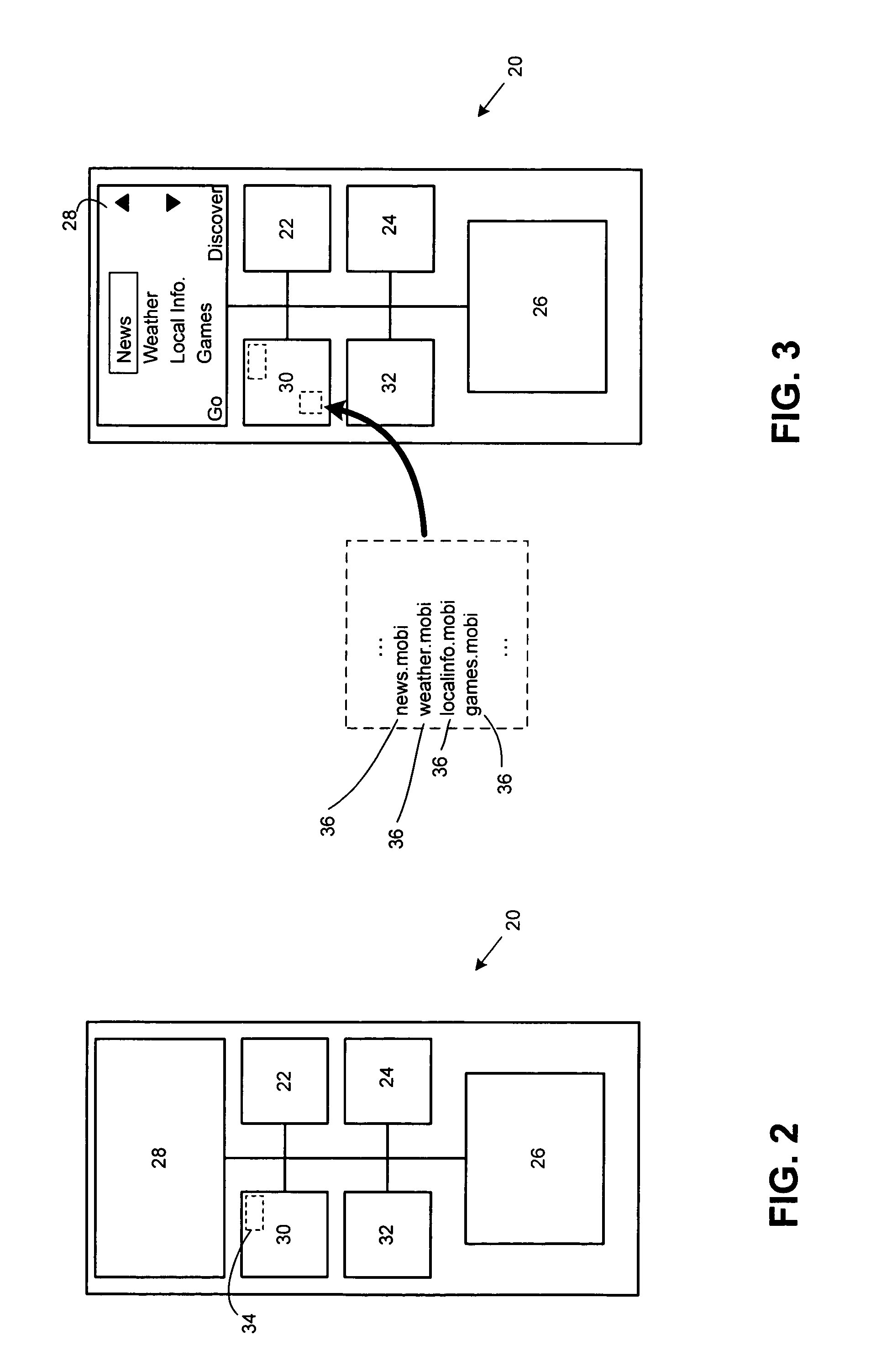
Method, apparatus and computer program product to utilize context ontology in mobile device application personalization
InactiveUS20060005156A1Devices with sensorDetails for portable computersPersonalizationDirectory structure
A mobile terminal includes a user interface specified at least in part by a user. The mobile terminal includes a user interface specification unit that operates in accordance with a programmed data processor to select, in cooperation with the user, at least one trigger and an action, which together form a rule; to automatically generate a directory structure comprising a set of available events in accordance with a hierarchical information model; to select, in cooperation with the user, at least one trigger value from the available set of events and to define an action to be performed by the mobile terminal in responsive to the at least one trigger value being satisfied.
Owner:WSOU INVESTMENTS LLC
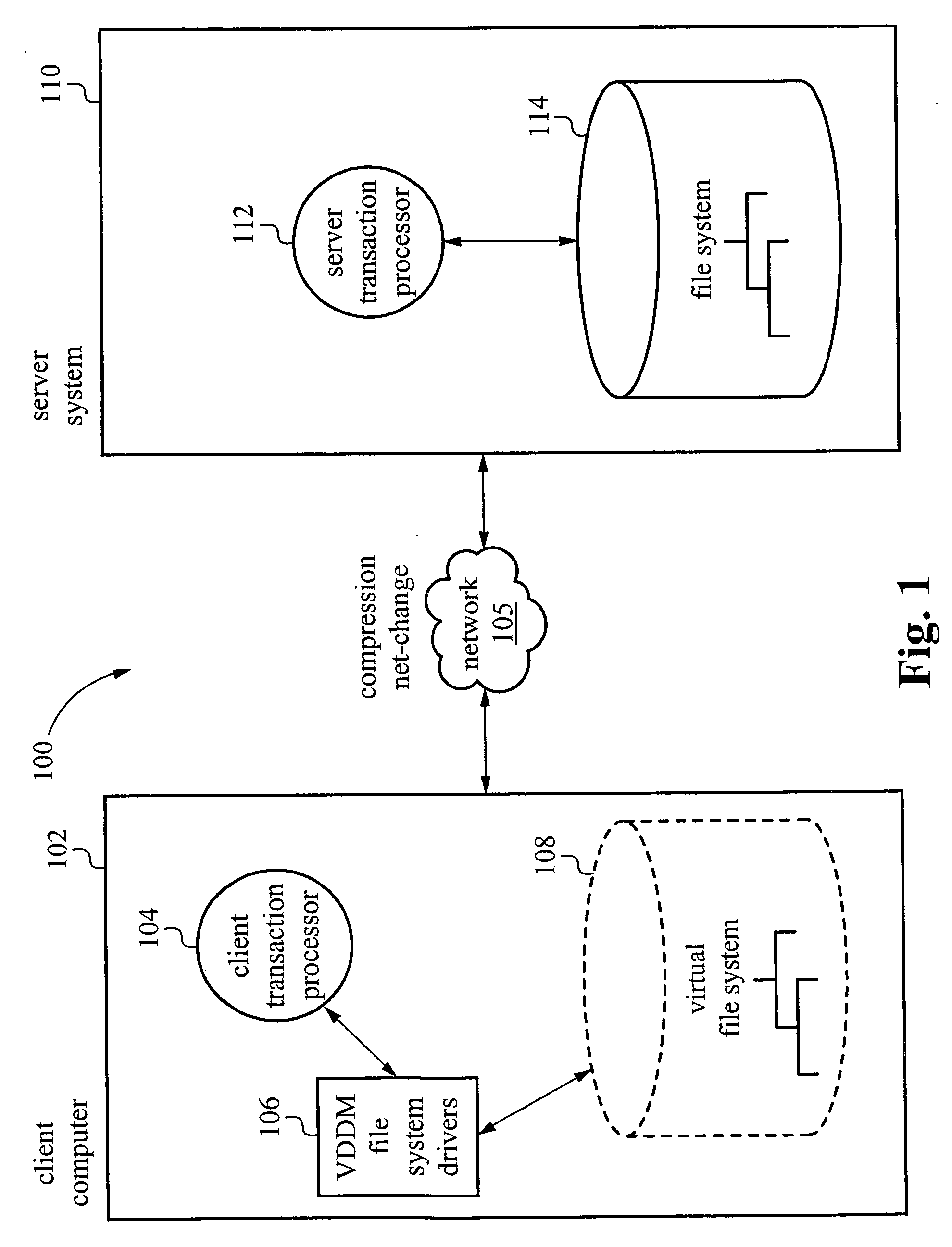
Transaction based virtual file system optimized for high-latency network connections
InactiveUS20060047716A1Problem can be addressedDigital data information retrievalMemory adressing/allocation/relocationVirtual file systemFile system
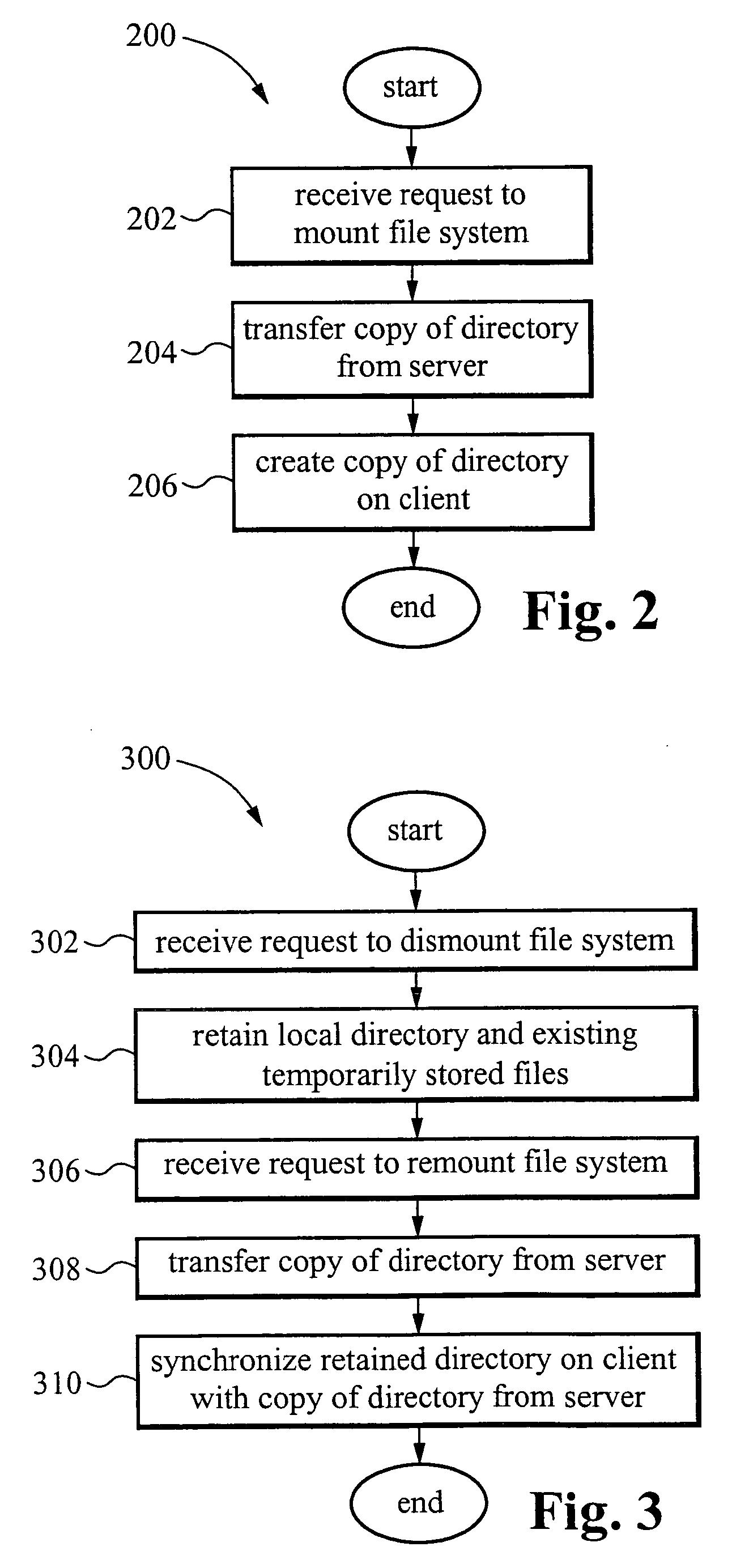
A method and system are provided for a virtual distributed data manager. In one example of the method, the virtual data manager involves receiving a request to mount a file system onto the client computer, wherein the file system is stored on the server system and contains the one or more data files; transferring a copy of a directory structure of the file system stored on the server system to the client computer; and creating on the client computer a virtual file system including the copy of the directory structure. The method is preferably transaction based and provides high performance on high latency network connections.
Owner:GOODRICH JOHN B +1
Using a metadata image of a file system and archive instance to restore data objects in the file system
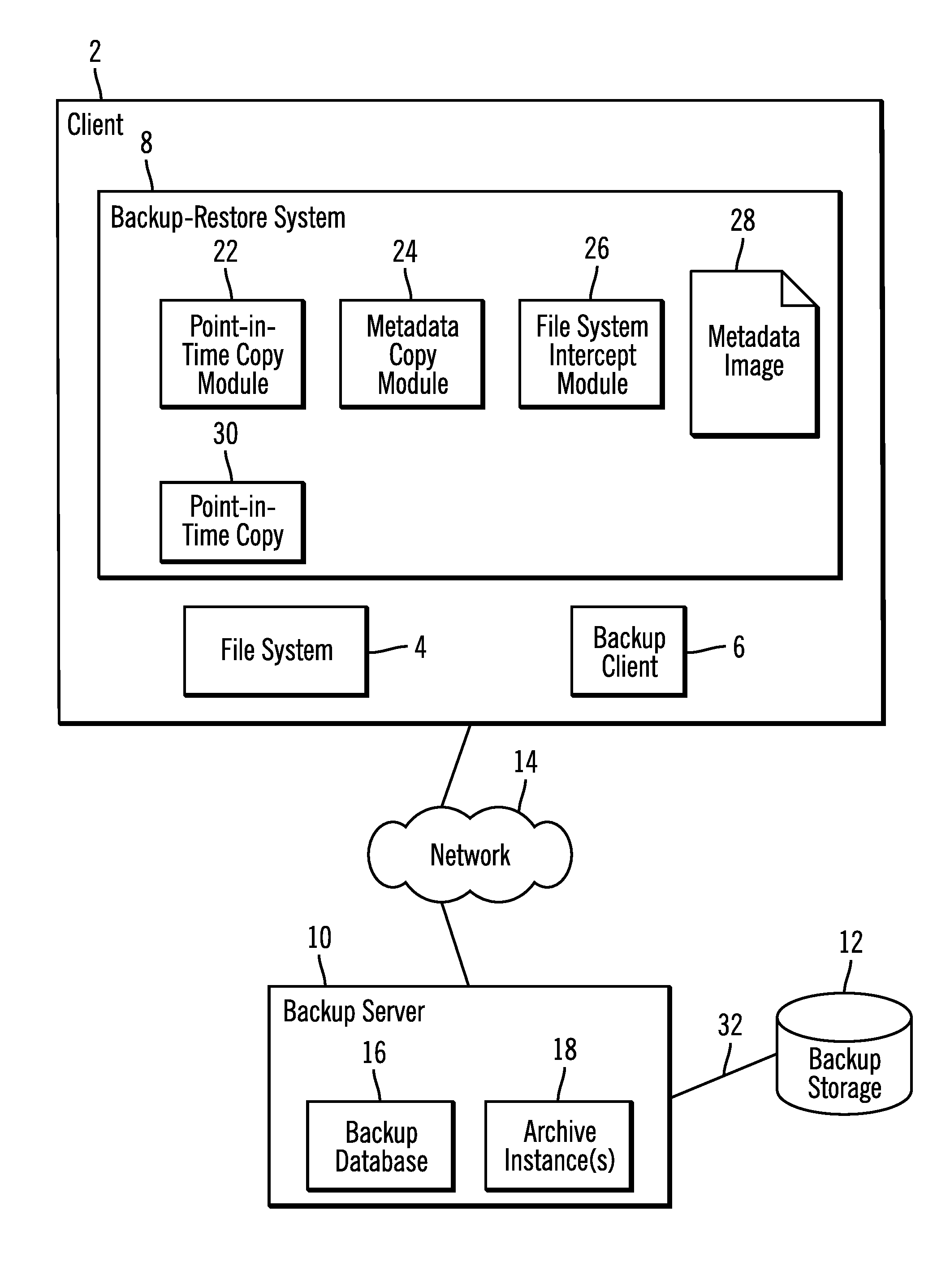
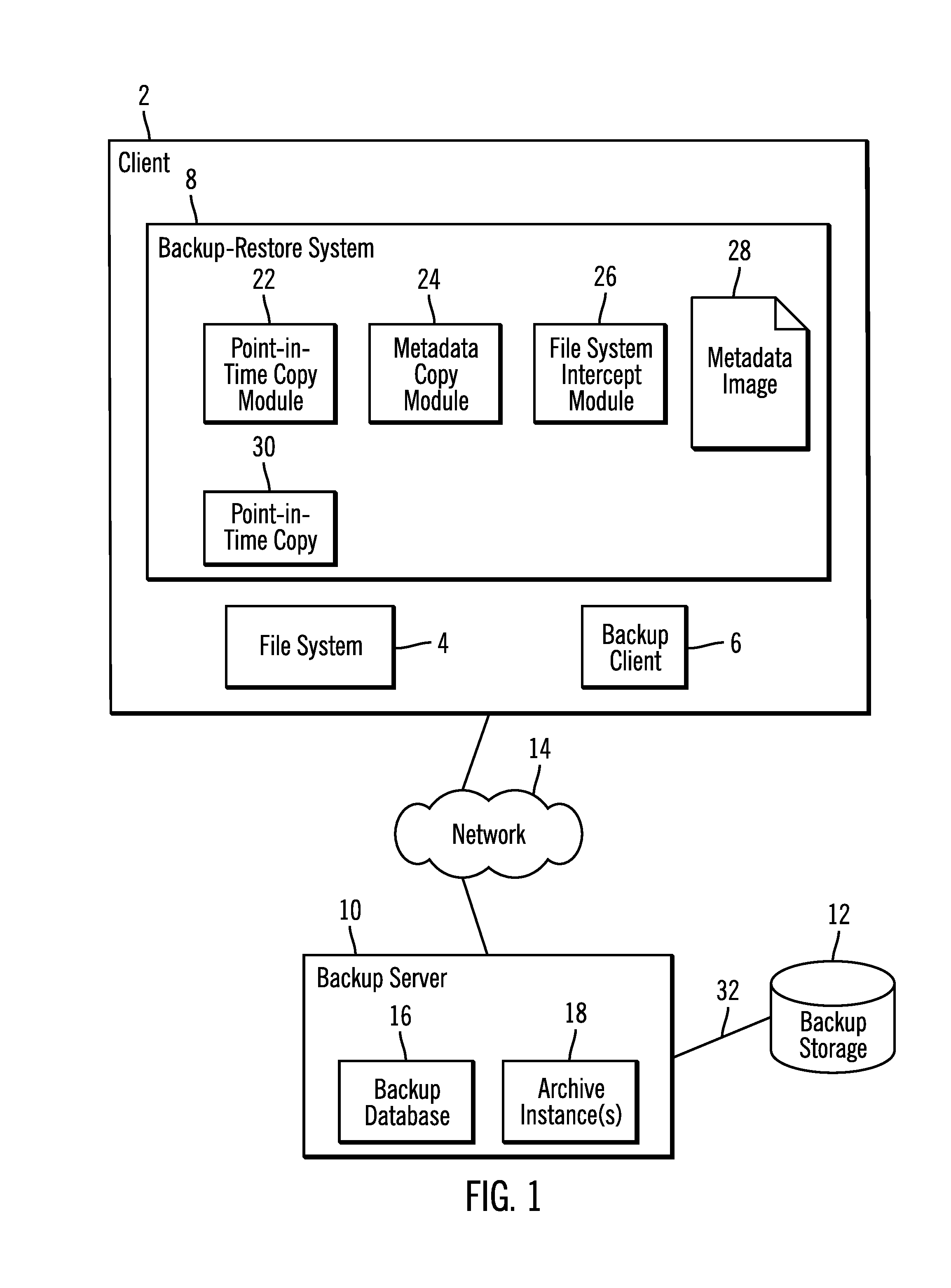
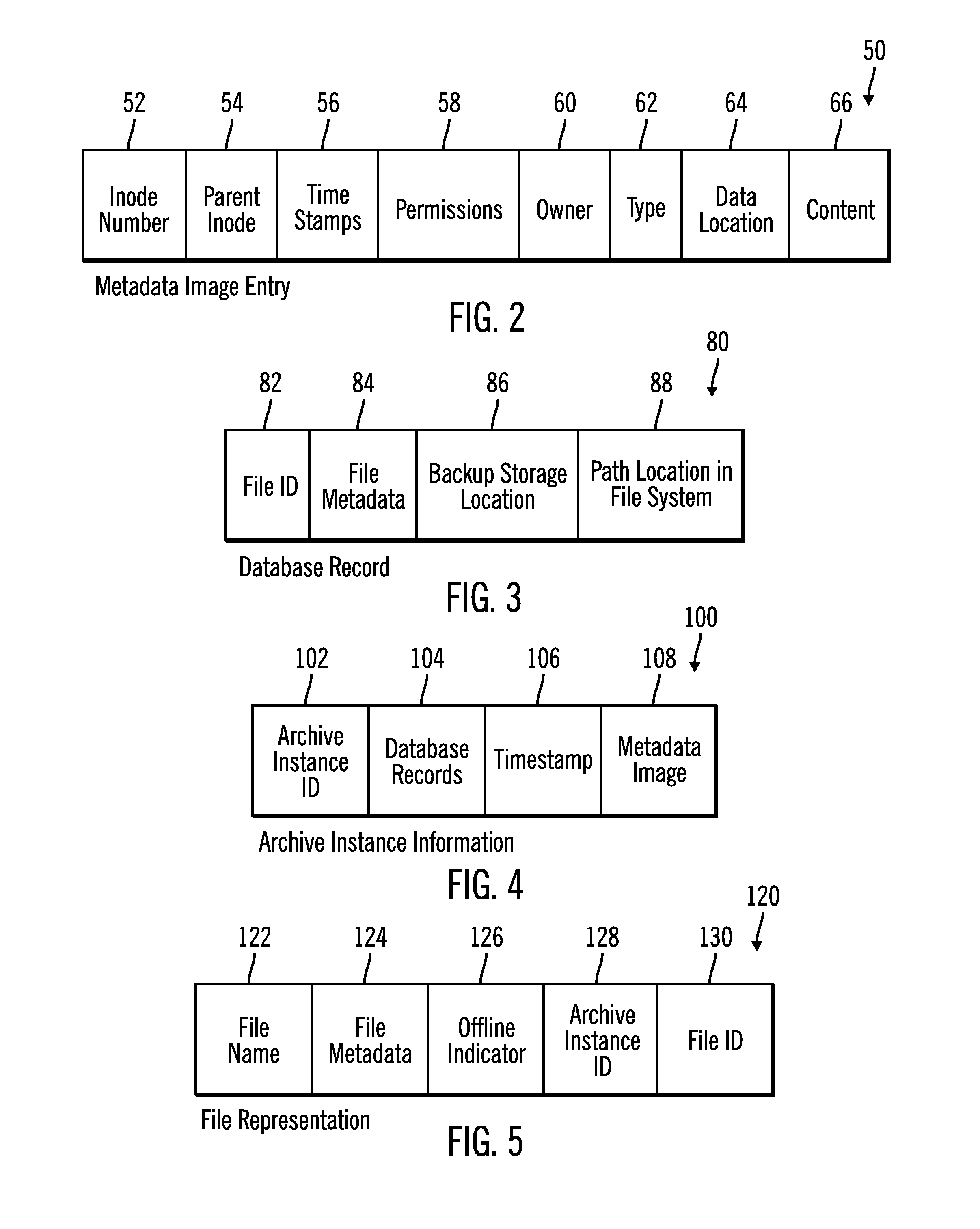
InactiveUS20140074790A1Digital data processing detailsError detection/correctionFile systemDocument representation
Provided are a computer program product, system, and method for using a metadata image of a file system and archive instance to restore files in the file system. A metadata image of the file system for a point-in-time backup as of a point-in-time includes information on files and directories in the file system as of the point-in-time and an archive instance including a copy of database records in the backup database for the files in the point-in-time backup. A restore request is received. A file representation is created of each file to restore in the directory structure of the file system from the metadata image, wherein at least one of the created file representations indicates that the file is stored off-line and has an external identifier used to access information on the file in the database records in the archive instance for the point-in-time backup.
Owner:IBM CORP
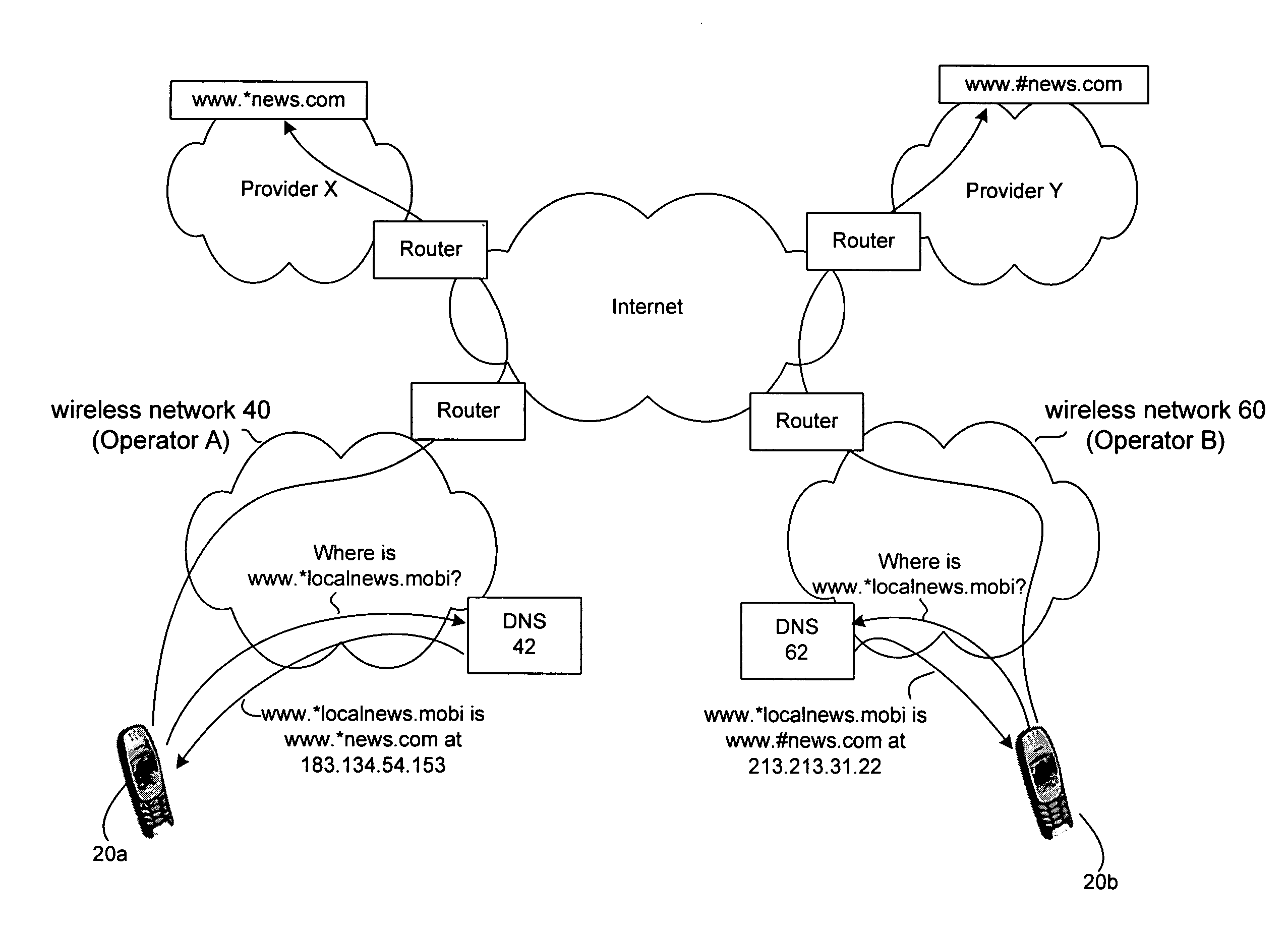
System and method for service naming and related directory structure in a mobile data network
ActiveUS7305252B2Special service for subscribersMultiple digital computer combinationsIp addressInformation resource
In response to a request by a mobile terminal for an information resource associated with a generic service name, one wireless network provides an IP address for a first provider of information. Another wireless network, in response to the same generic service name, provides an IP address for a different information provider. Other wireless networks will provide addresses for still other providers. Upper level generic service names include one or more hierarchically-arranged lower levels of generic service names. This tree of generic service names is used to create, in a consistent manner in different wireless networks, a generic directory of accessible information resources. In certain embodiments, a mobile terminal determines its location and provides location information with (or in connection with) a generic service name.
Owner:RPX CORP
File system with access and retrieval of XML documents
InactiveUS7043472B2Quick fixConvenient to a user seeking to locateData processing applicationsWebsite content managementFile systemDirectory structure
A XML-aware file system exploits attributes encoded in a XML document. The file system presents a dynamic directory structure to the user, and breaks the conventional tight linkage between sets of files and the physical directory structure, thus allowing different users to see files organized in a different fashion. The dynamic structure is based upon content, which is extracted using an inverted index according to attributes and values defined by the XML structure. In one application, a dynamically changing federated repository is searchable using a system of local and merged master indices, wherein query results are presented as virtual directory paths that are semantically organized.
Owner:IBM CORP
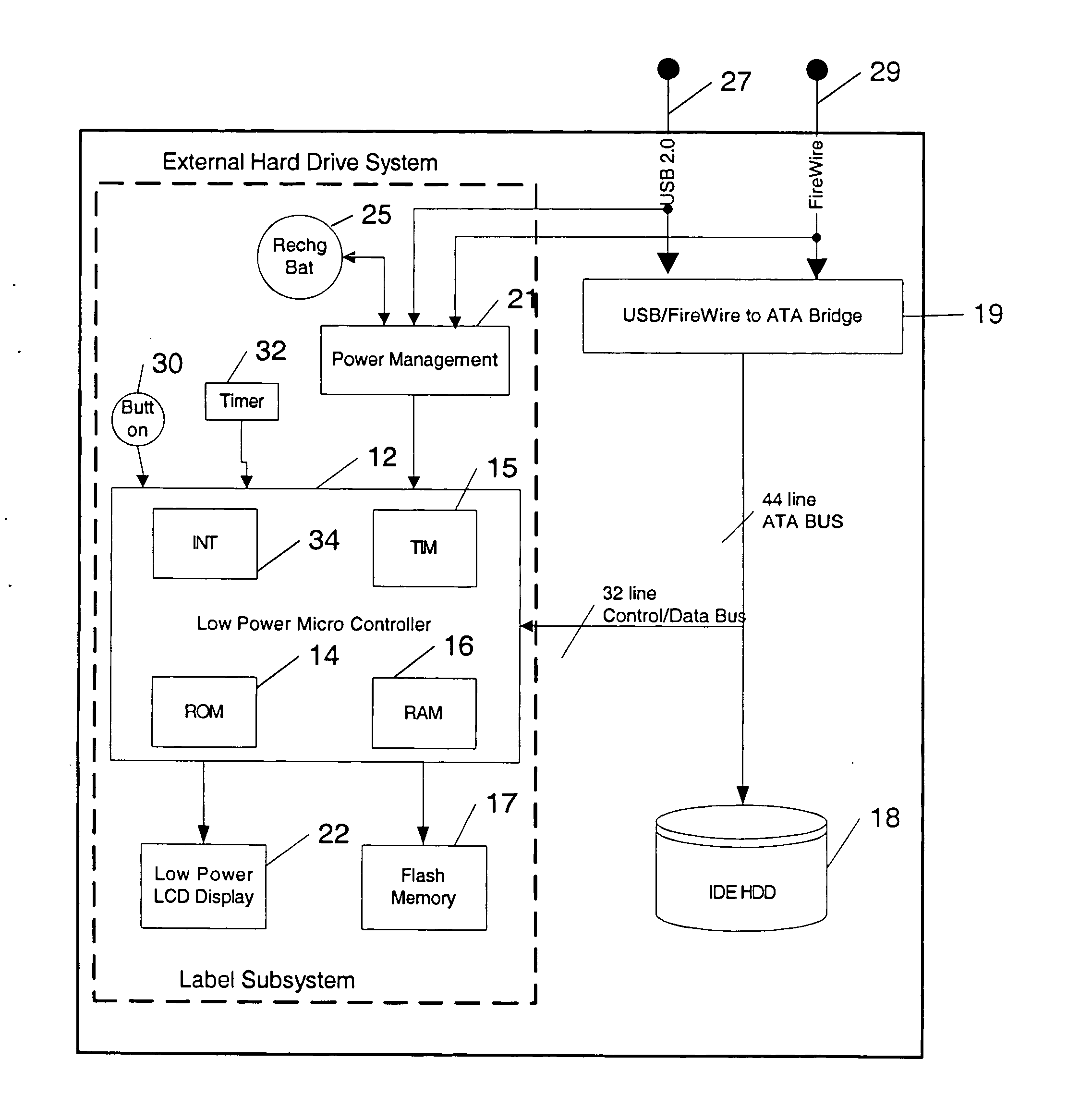
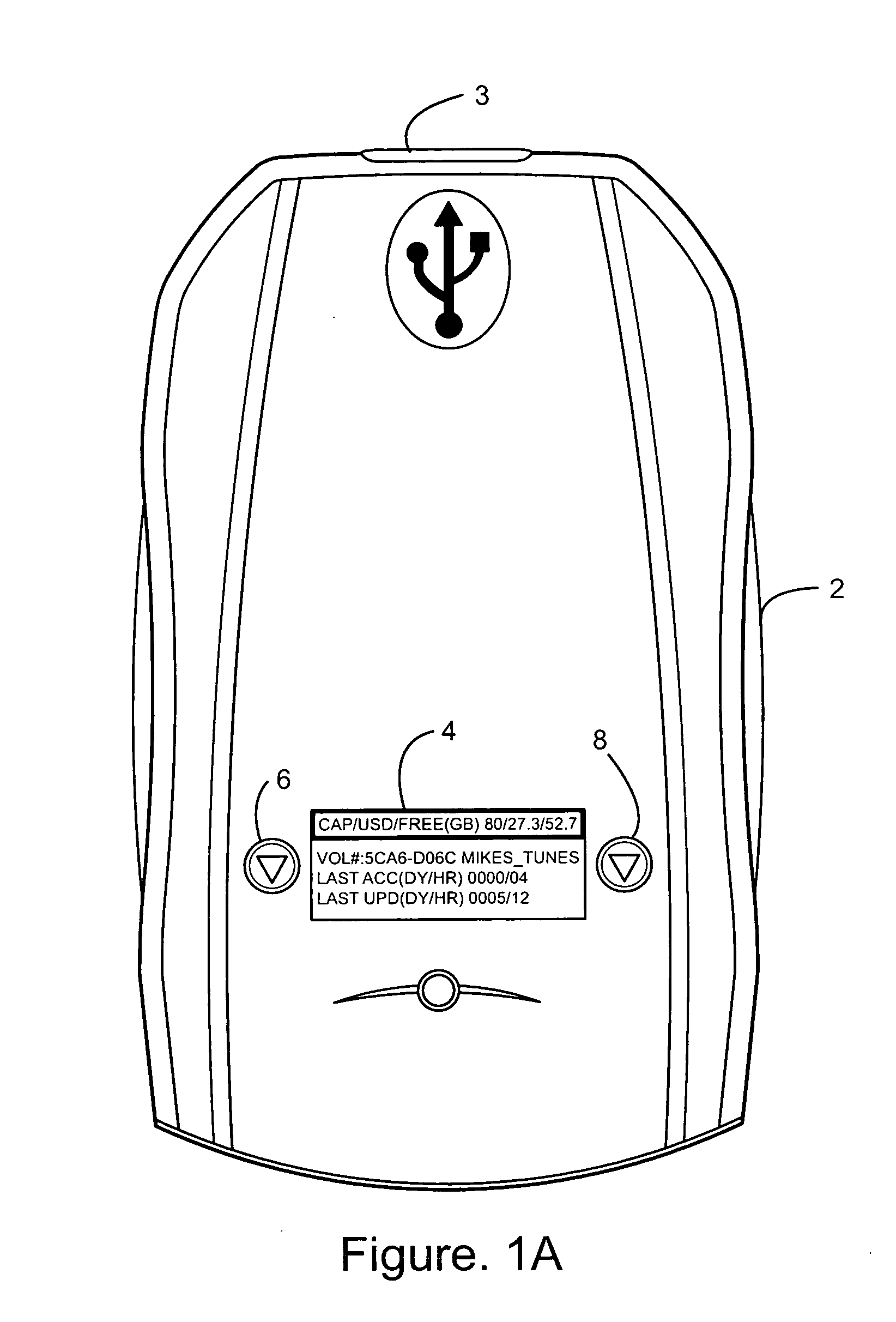
Self-labeling digital storage unit
InactiveUS20060095647A1Good adhesionEasy detachmentCarrier indicating/warning arrangementsCarrier casesDigital storageDirectory structure
Portable storage units are equipped with human readable electronic displays that contain information pertaining to the content and state of the storage units. The information displayed changes as the contents of the storage unit change. Such electronic labels can contain a variety of useful information. Some information would be static, such as owner identification, while other information will be dynamic such as the amount of free space. Still other information will be browseable such as the directory structure, file contents, storage unit total capacity, storage unit available space, storage unit directory structure, storage unit file names. storage unit file contents and device reliability statistics.
Owner:CMC MAGNETICS CORPORATION
Small file optimization storage method based on HDFS
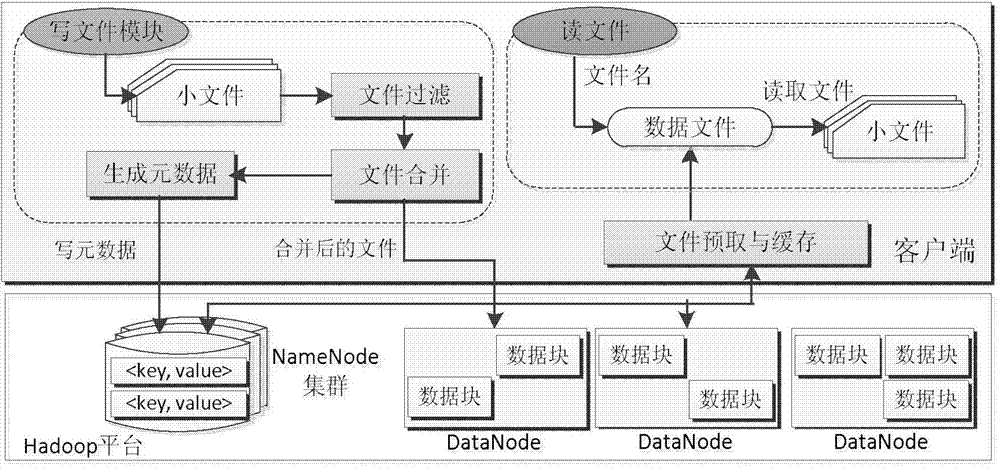
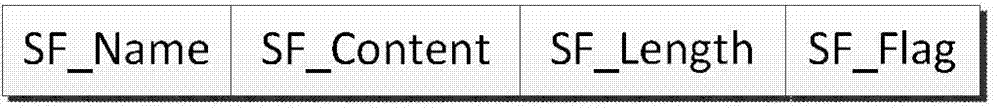
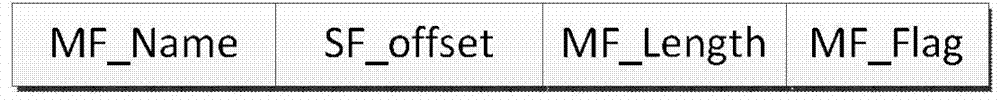
ActiveCN103577123AImprove reading efficiencyImprove performanceInput/output to record carriersSpecial data processing applicationsDirectory structureSmall files
The invention discloses a small file optimization storage method based on a HDFS, wherein the efficiency for the HDFS to read small files is improved, and the overall performance of the system is improved. The method includes the steps that first, the small files are combined and undergo storage preprocessing, wherein the storage preprocessing on the small files is achieved through filtering of the filers, combination of the small files, generation of metadata and generation of object IDs; second, after the files are stored into the HDFS in a combined mode, the mapping relations between the small files and combined files in the HDFS are stored into the metadata of the small files in a mode of file metadata, a directory structure of the files is stored in a file name, and the metadata are stored in a mode of distributed clusters on the basis of a Chord protocol; third, the directory structure of the files is optimized, and generated key values of the metadata are decomposed into Directory IDs and Small File IDs. The Directory IDs serve as key values for the metadata to skip into nodes in a metadata cluster, and therefore the files under the same directory are stored into the same node. The Small File IDs are generated in metadata nodes, and therefore each of the metadata corresponds to unique ID identification in the whole system.
Owner:HOHAI UNIV
Personal electronic storage device container and labeling
InactiveUS6140936AQuick collectionEasy to trackElectric signal transmission systemsDigital data processing detailsDirectory structureMemory cards
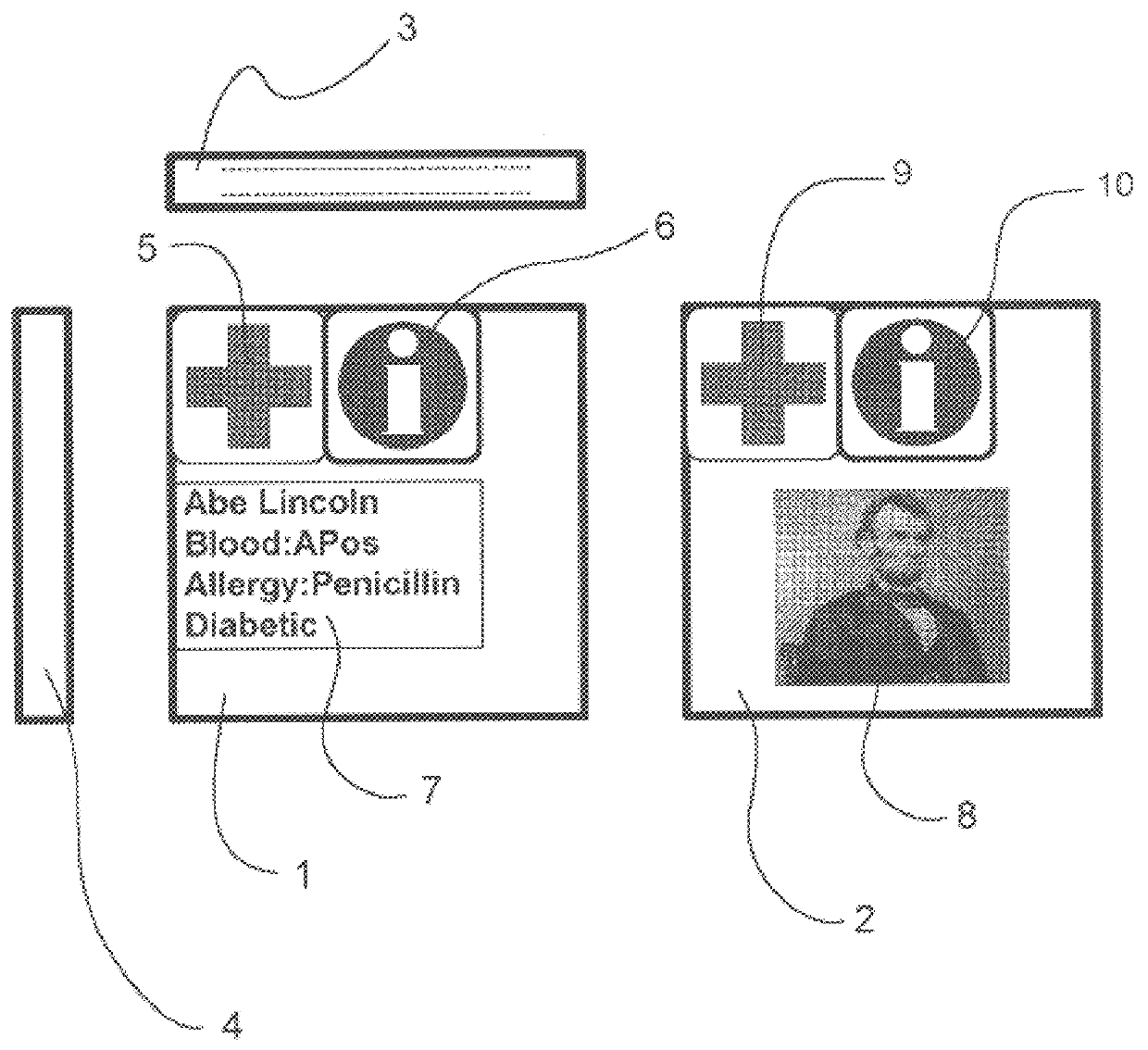
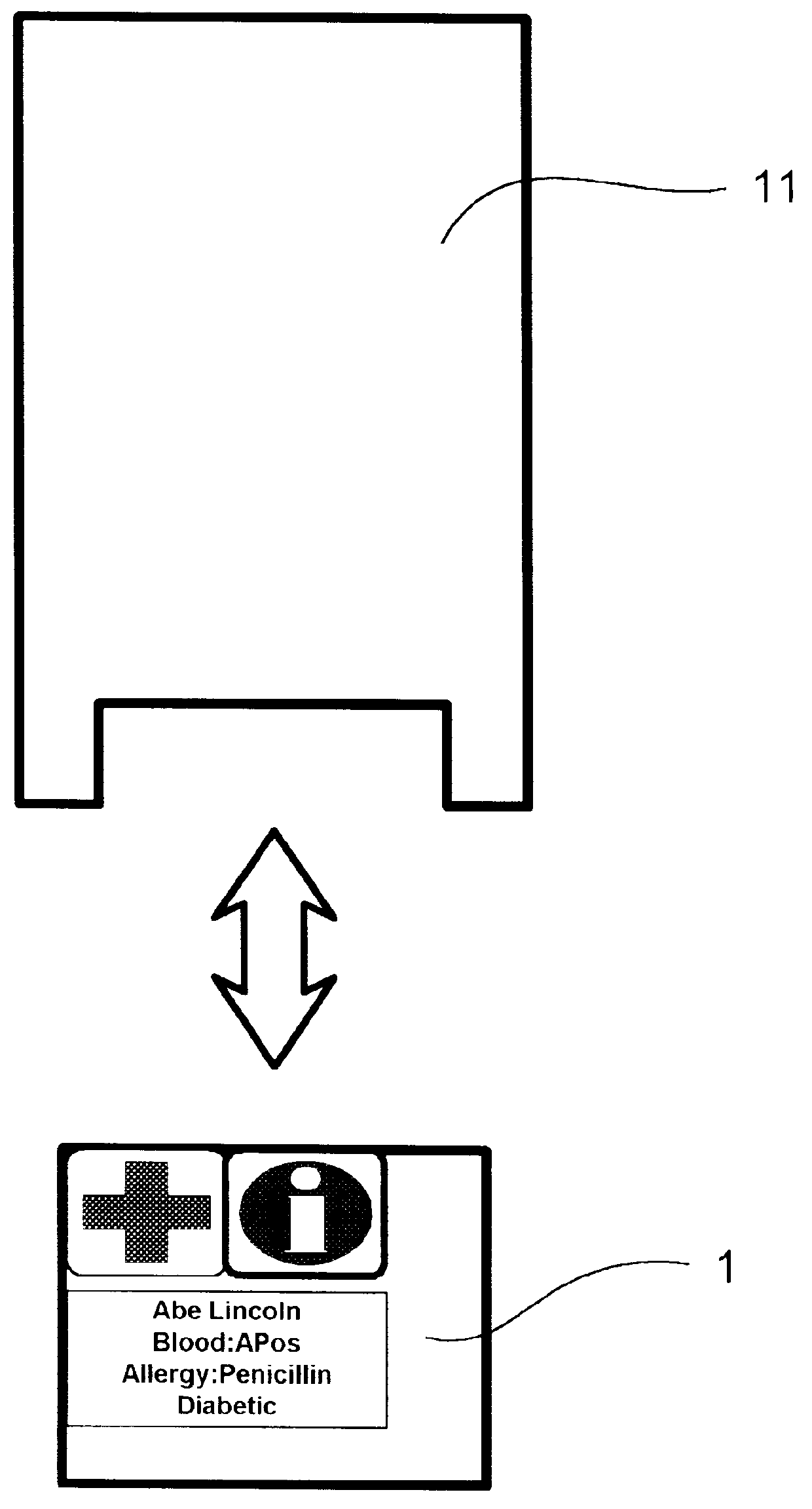
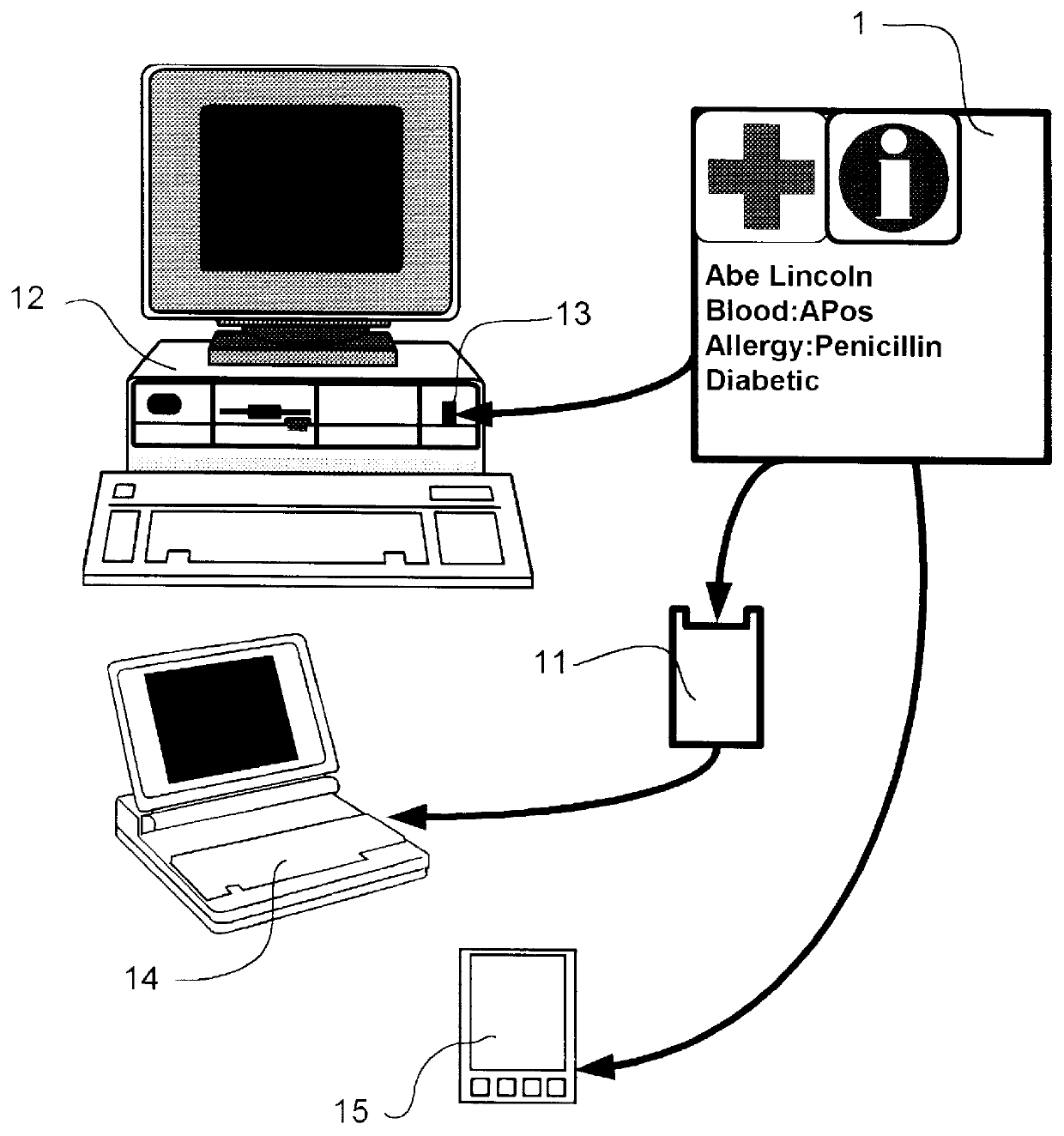
A reusable electronic storage device comprised of a memory card and a protective container with attachment points for jewelry. The memory card contains medical or veterinary information about the bearer. The information is stored in electronic files in a standard directory structure. Labels show critical treatment data and indicate that the memory card contains information related to medical or veterinary treatment for the bearer. The container and / or medical card may be worn as a jewelry item.
Owner:ARMSTRONG JAY ALAN
System and method for data management
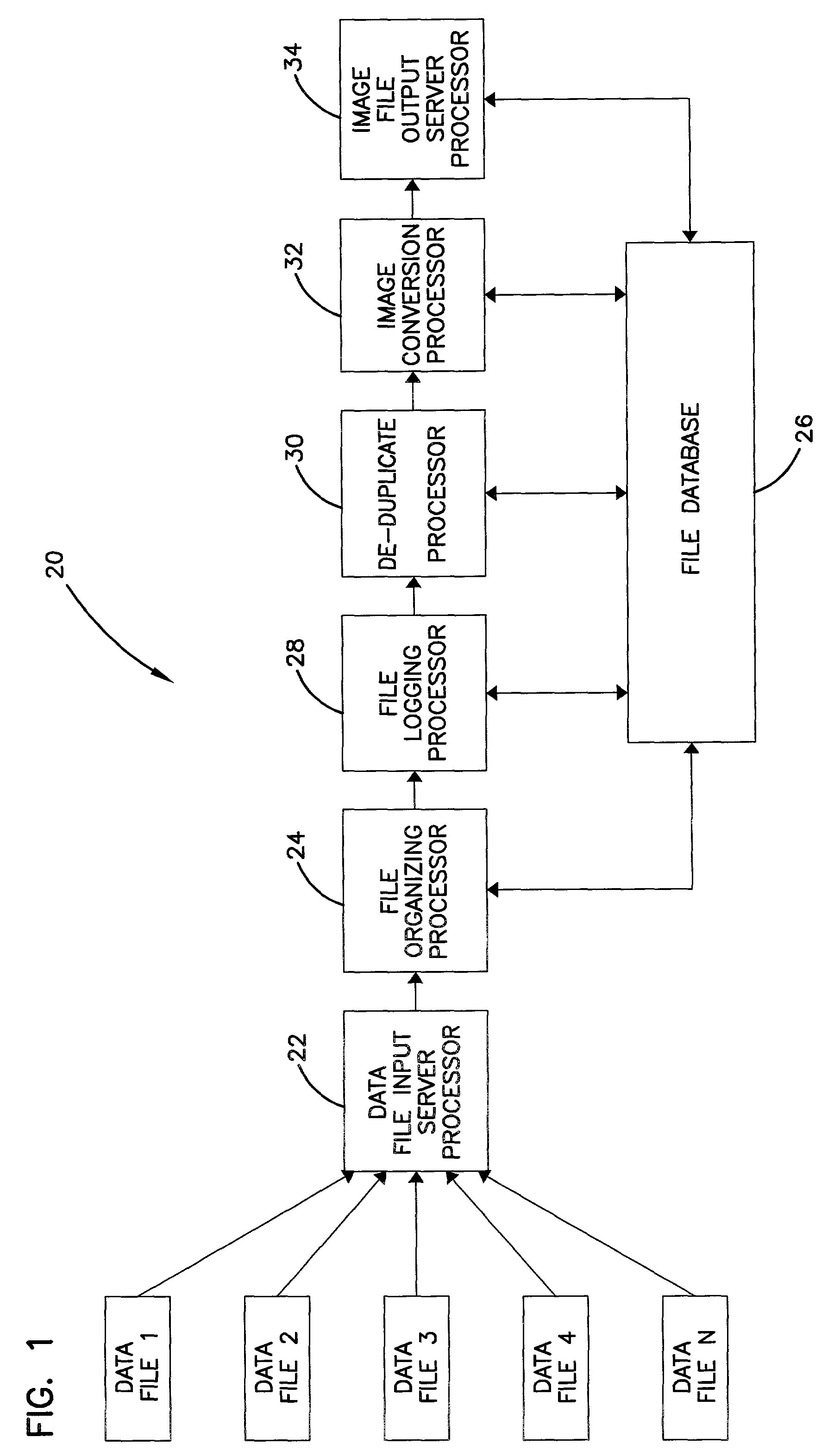
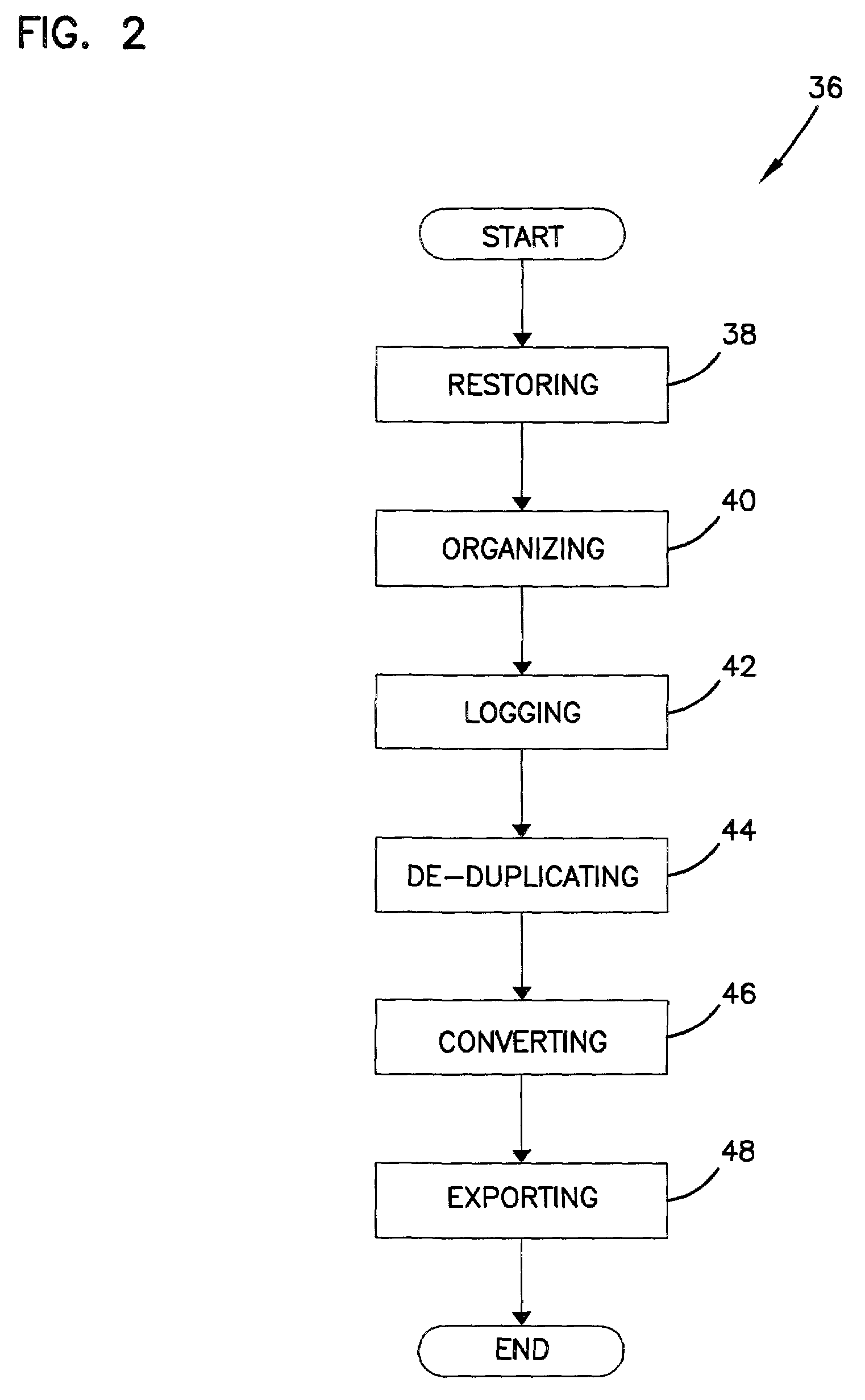
InactiveUS7103602B2Exclude dataSmall sizeData processing applicationsSpecial data processing applicationsOperational systemData file
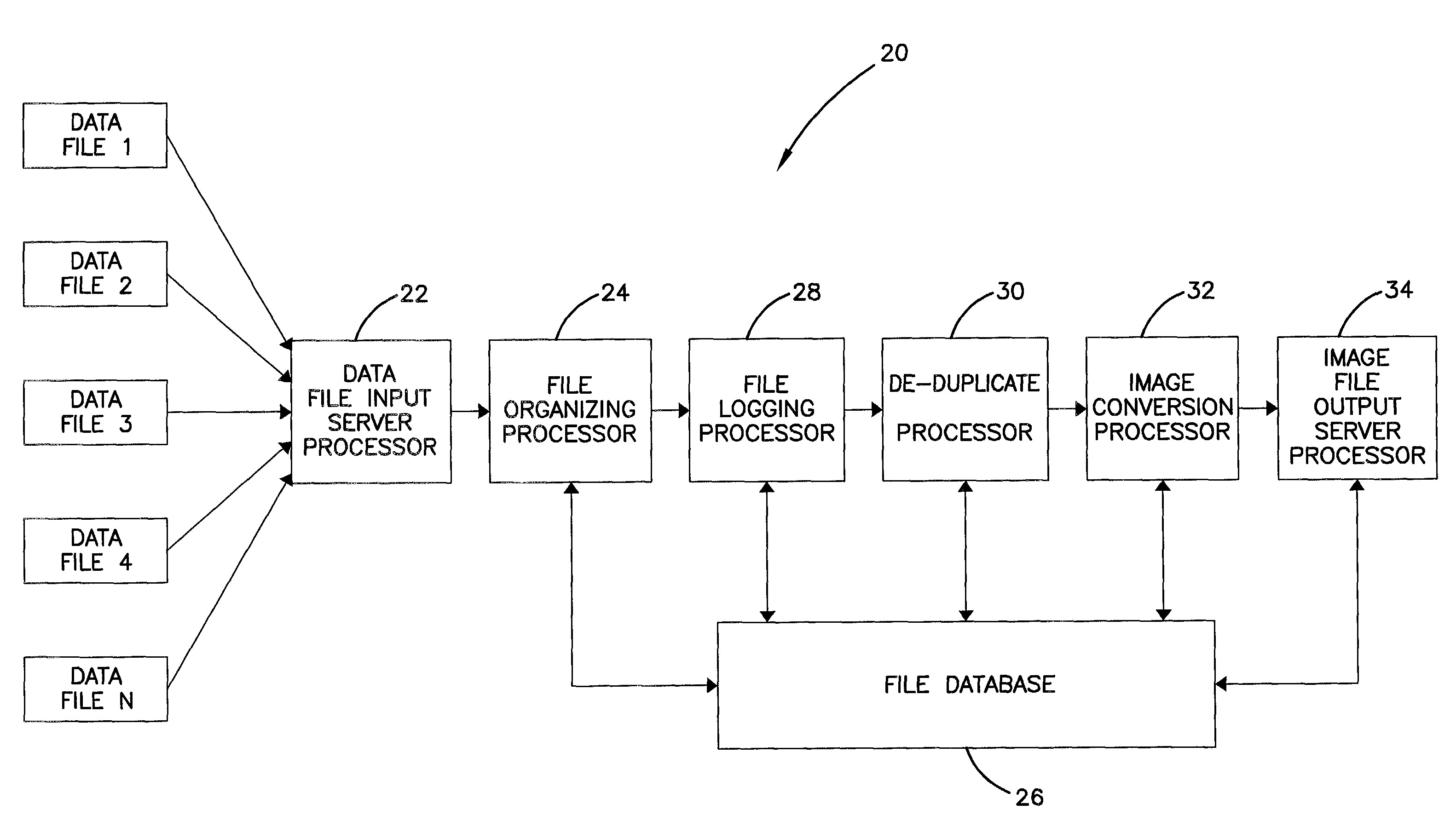
An automated data management system and method for logging, processing, and reporting a large volume of data having different file types, stored on different media, and / or run by different operating systems, includes a first server processor for restoring a plurality of received data files, the data files being capable of being different file types; a file organizing / categorizing processor for organizing the received data files, based on a predetermined user list, into a source directory structure and a destination directory structure; a file logging processor for logging the received data files into a database formed by the source and destination directory structures and identifying a file type of the received data files; a de-duplicate processor for calculating a SHA value of the received data files to determine whether the received data files have duplicates and flagging duplicated data files in the database; an image conversion processor for converting the remaining data files into image files, respectively; and a second server processor for exporting the image files.
Owner:KLDISCOVERY ONTRACK LLC
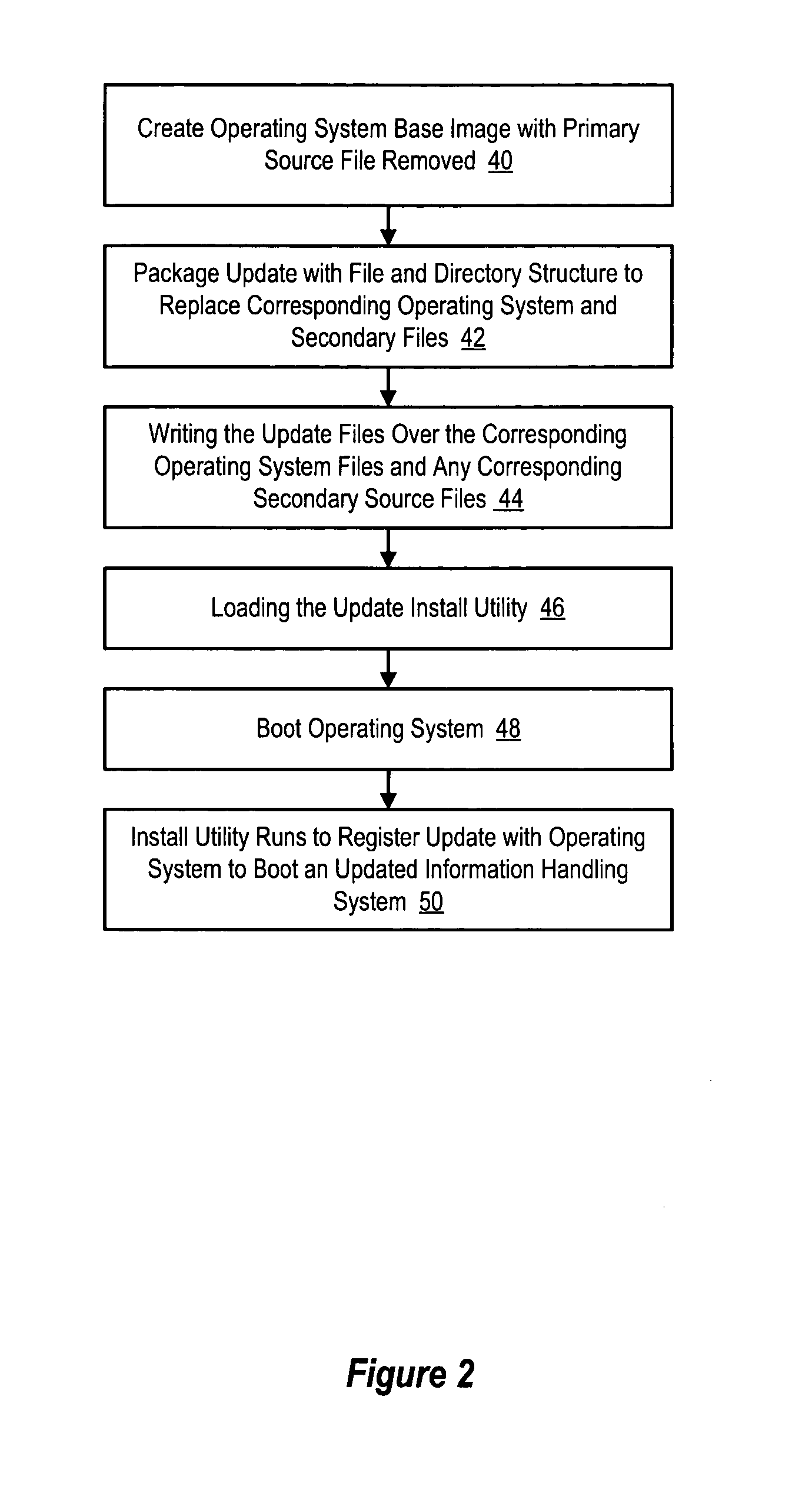
System and method for preintegration of updates to an operating system
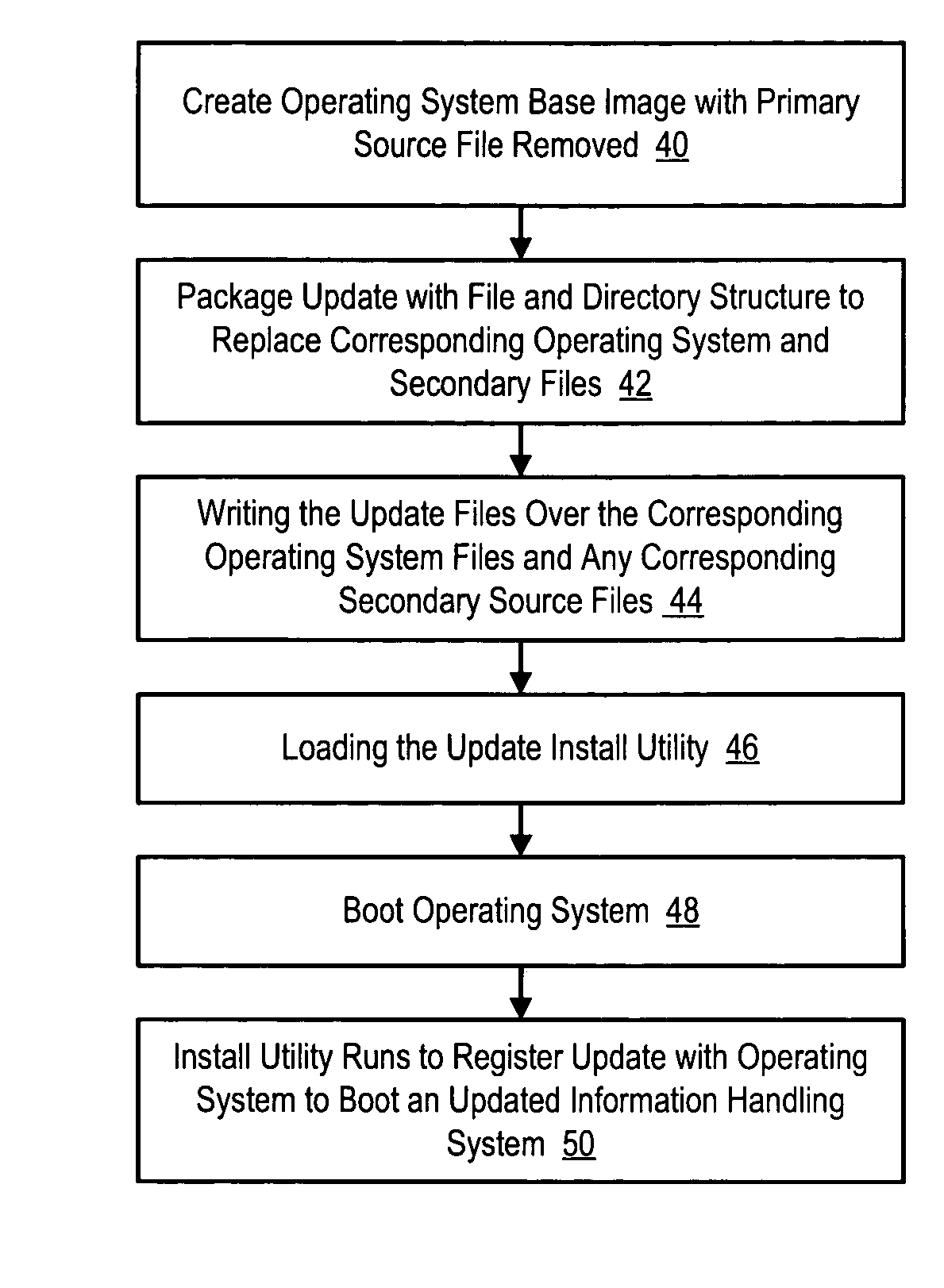
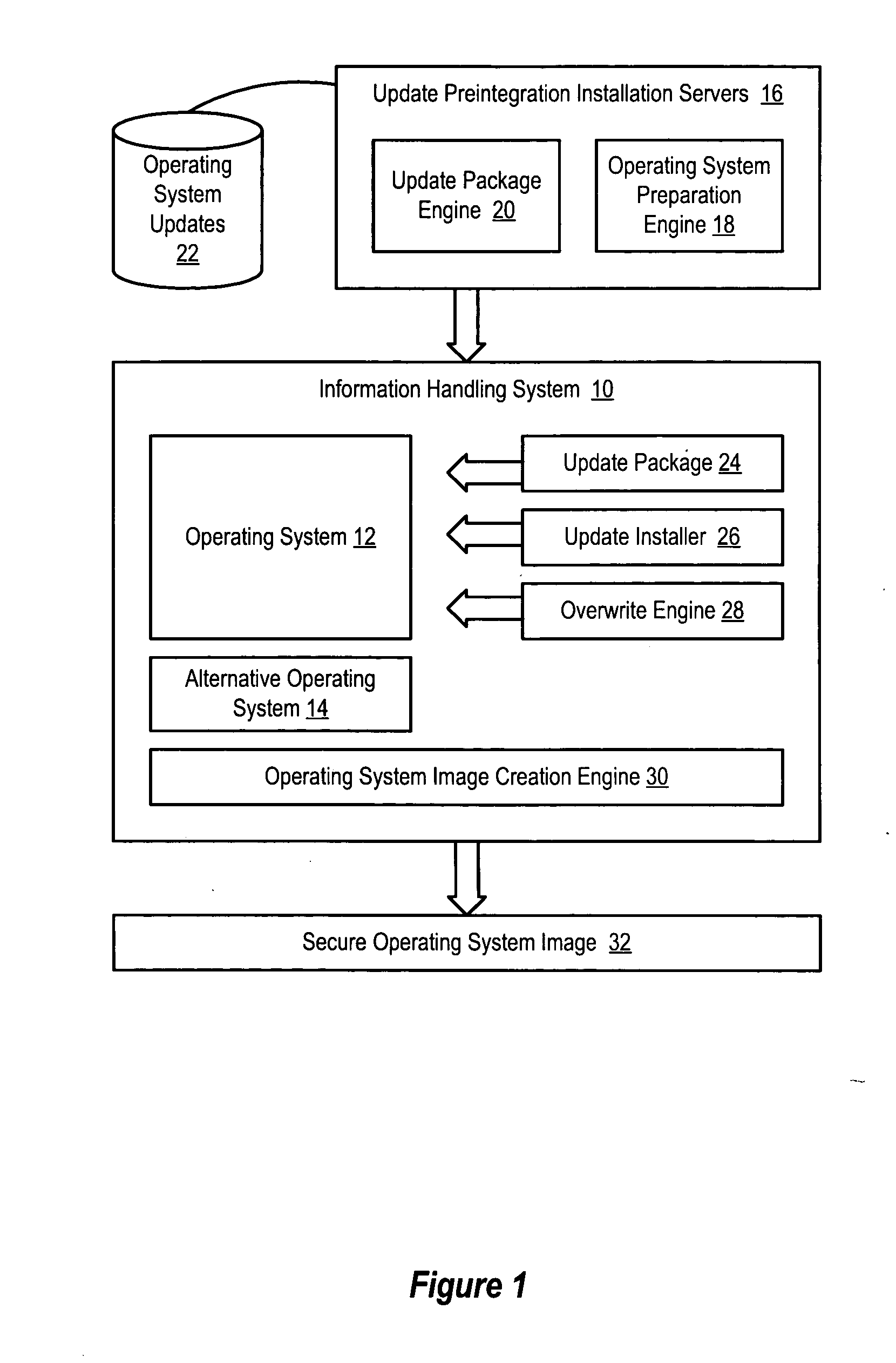
InactiveUS20050172280A1Reduce risk of disruptionReduce disadvantagesPlatform integrity maintainanceProgram loading/initiatingOperational systemOperating system security
An operating system has security updates preintegrated to reduce vulnerability of the operating system to malicious programs, such as worms. Preintegration writes update files over corresponding operating system files before boot of the operating system so that malicious programs are not provided an opportunity to attack the operating system during a post-boot security update. An update package extracts update files, such as QFE files, and prepares the update files within a file and directory structure corresponding to the operating system. An overwrite engine running on an alternative operating system writes the update files to the operating system so that the operating system boots secure from attack by worms that the updates are intended to prevent.
Owner:DELL PROD LP
Automatic vulnerability validation method
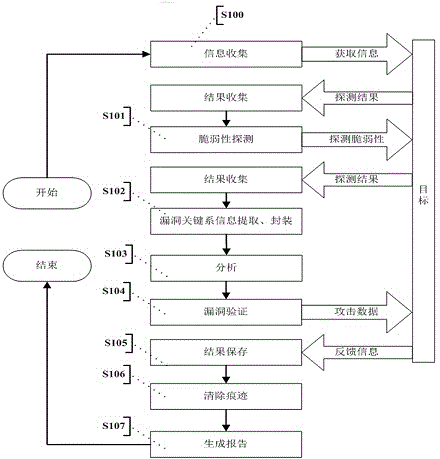
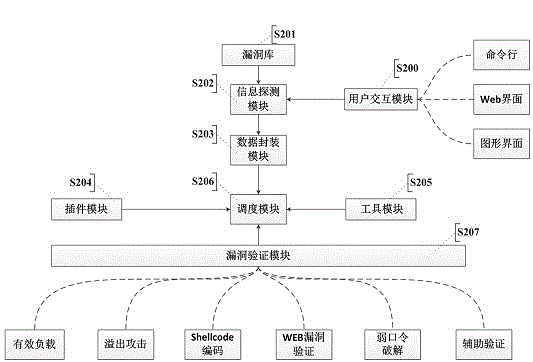
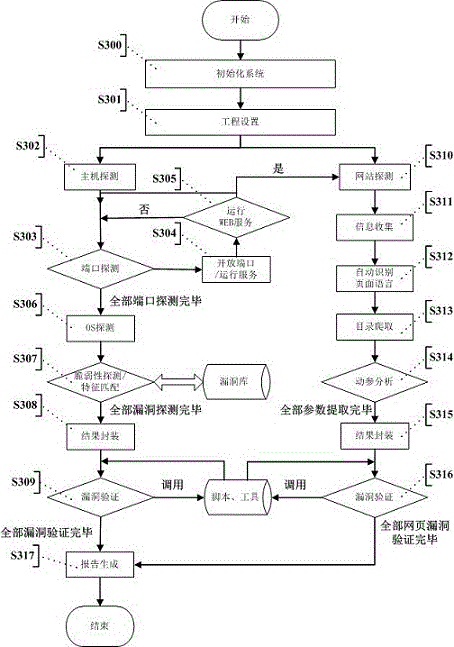
InactiveCN104363236AAutomated verificationUnderstand the dangers of vulnerabilitiesPlatform integrity maintainanceTransmissionValidation methodsModularity
The invention provides an automatic vulnerability validation method. The method comprises the steps that firstly, validation information is collected, wherein an active detection way is adopted for carrying out information detection, topological detection, vulnerability detection and website directory structure detection on a target; secondly, the validation information is packaged, wherein suspicious vulnerability key information in vulnerability detection results is extracted, uniform-interface modularized packaging is carried out on the data; thirdly, a validation strategy is searched for, wherein according to the suspicious vulnerability identity and variety information, an appropriate attack script template and a vulnerability utilizing tool are selected; vulnerability validation is carried out, wherein scripts are called to be loaded into the packaged vulnerability information to carry out validation attack, and an utilization voucher is obtained and stored; fifthly, validation traces are removed, wherein validation attack traces are removed, sessions are recycled; finally, a scanning report is generated. The automatic vulnerability validation method solves the problem that an existing vulnerability scanning system is high in false alarm rate and cannot carry out effective validation, is automatic and procedural, can automatically recognize and validate vulnerabilities, lowers the requirement for the ability of non-professional staff and improves the vulnerability validation efficiency.
Owner:XIAN UNIV OF POSTS & TELECOMM +1
System and method for launching a resource in a network
ActiveUS8732182B2Digital data processing detailsWireless commuication servicesOperational systemDirectory structure
Owner:DESKTOPSITES
Providing data to applications from an access system
InactiveUS7134137B2Digital data processing detailsUser identity/authority verificationStructure of Management InformationDirectory structure
An access system is disclosed that can provide data to a downstream application. In one embodiment, the data is provided as header variables associated with an HTTP request. Other embodiments can use other protocols and other means for transmitting the data. The data provided to the downstream applications include information about the user accessing the application. In one embodiment, the data provided to the downstream application includes information from an identity profile stored in an LDAP directory structure.
Owner:ORACLE INT CORP
On-demand file transfers for mass p2p file sharing
InactiveUS20080005114A1Digital data information retrievalMultiple digital computer combinationsFile transmissionDirectory structure
A “Mass File Sharer” (MFS) provides a mass P2P file sharing protocol with optional on-demand file access across a P2P network. Unlike conventional P2P file sharing, the MFS simultaneously asynchronously shares large numbers of files, while providing optional on-demand (synchronous) access to shared files. The MFS uses a unique metadata structure in combination with an inter-peer file / folder version analysis and an inter-peer file / folder availability analysis to share complex directory structures that may include any number of folders, sub-folders, and files. Sharing may be asynchronous and / or synchronous. Specifically, file sharing is generally accomplished as an asynchronous distribution across the network. However, when a particular peer wants direct access particular files, an on-demand access mode is used to enable synchronous delivery of shared files. This combination of asynchronous and synchronous file distribution enables the MFS to support a number of applications, such as on-demand movie viewing, file / folder browsing, etc.
Owner:MICROSOFT TECH LICENSING LLC
Conversion of data in particular for playing of audio and/or video information
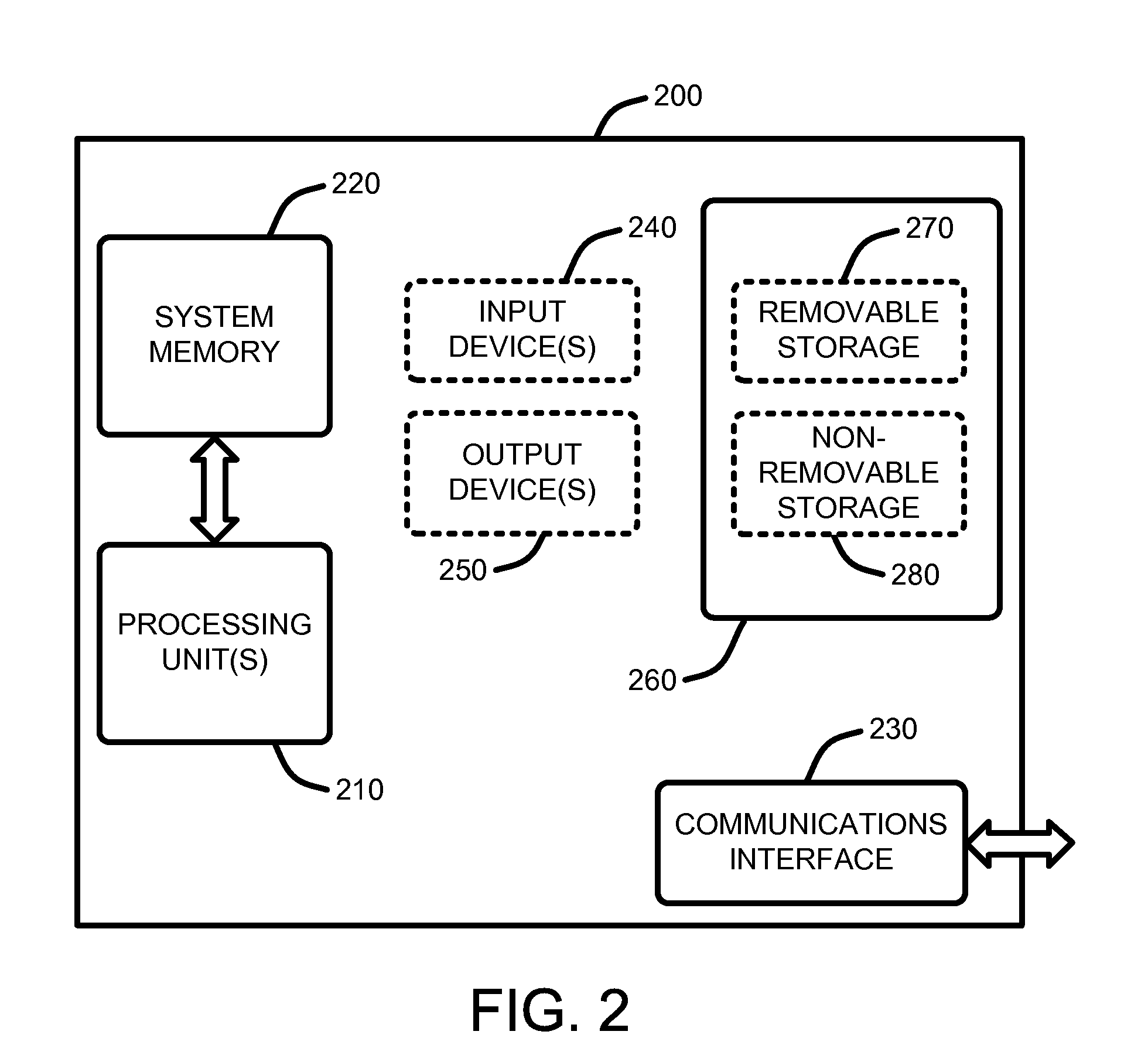
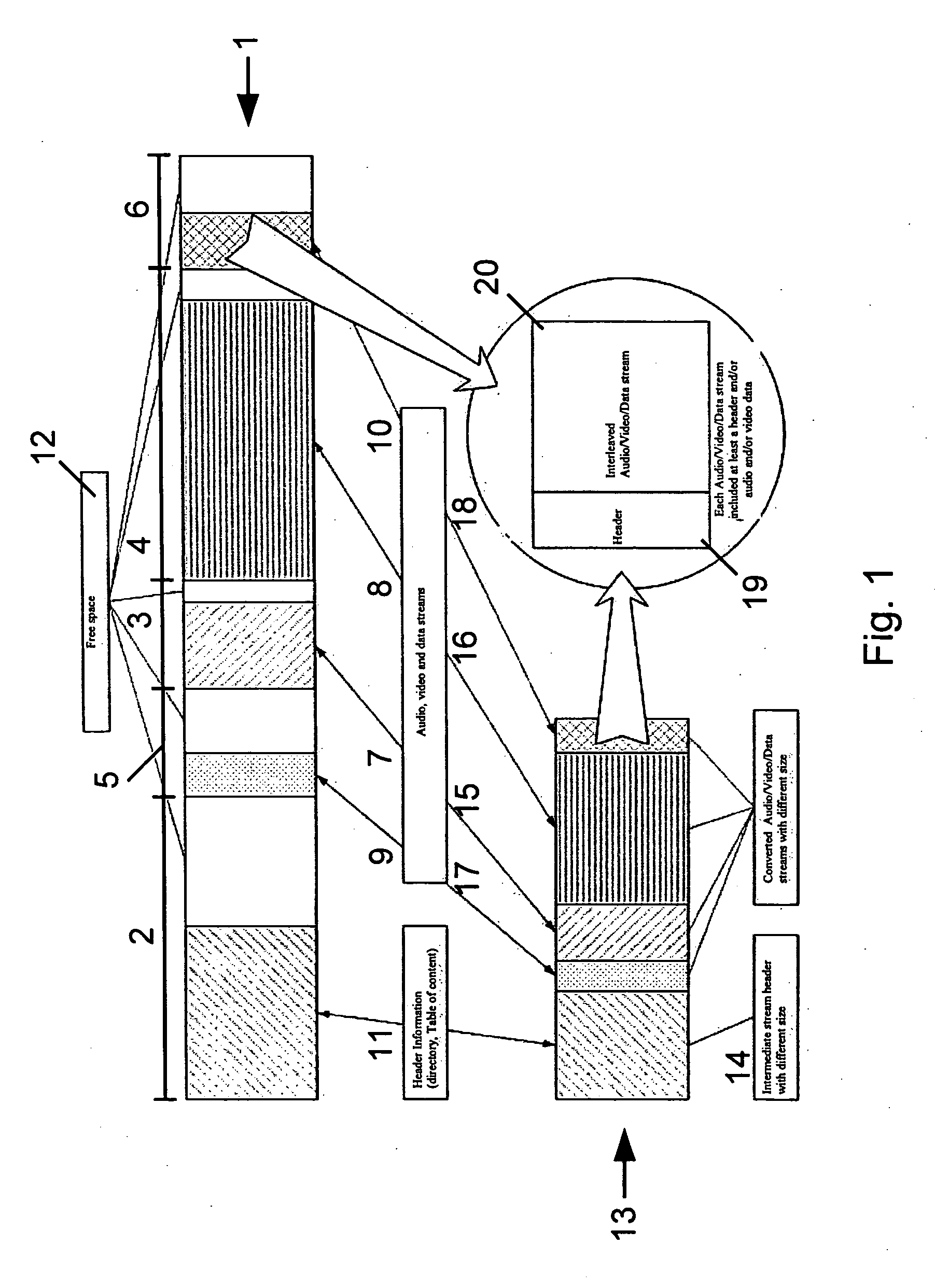
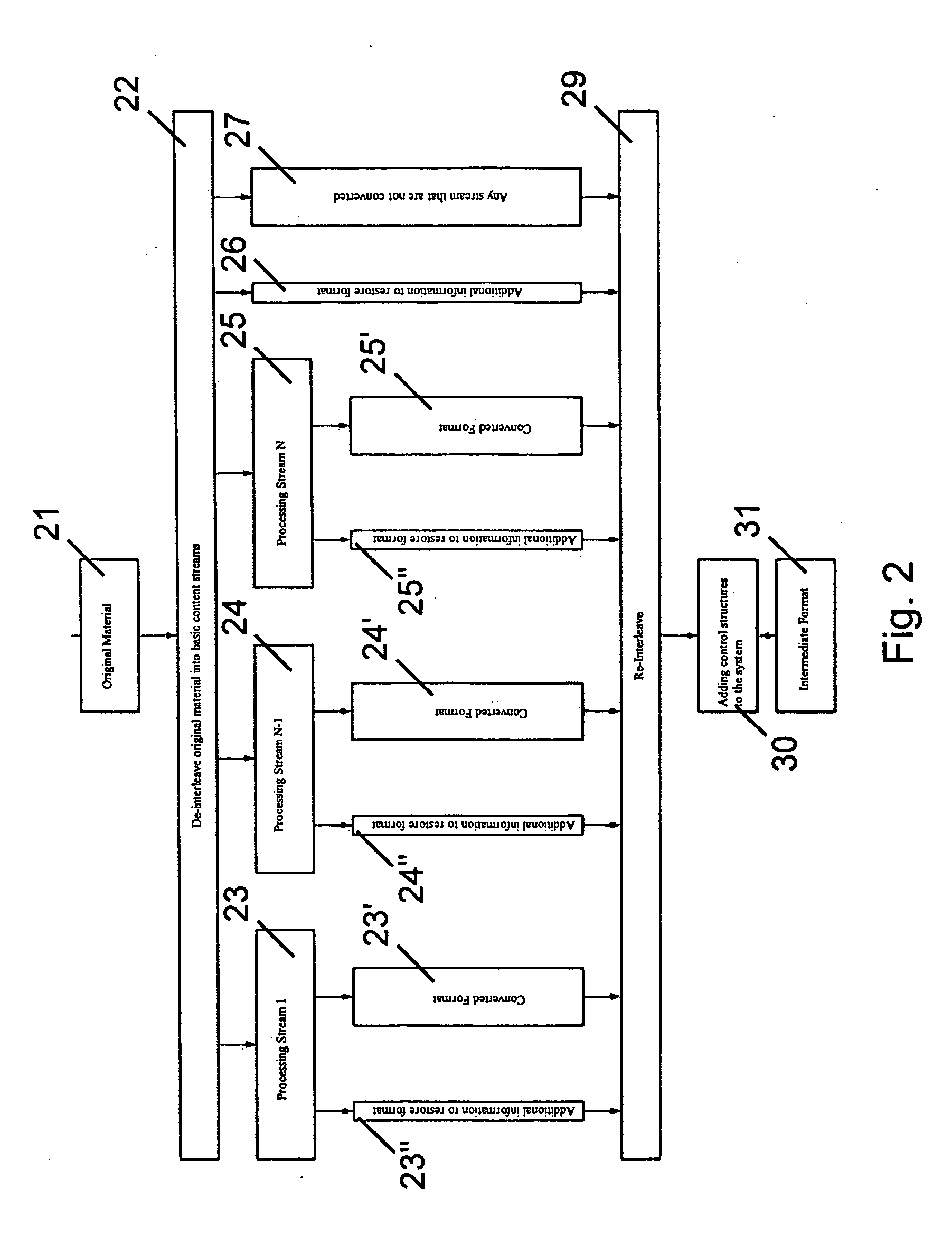
InactiveUS20060173887A1Less storage capacityReduced space requirementsDigital data processing detailsUsing non-detectable carrier informationDirectory structureDatabase Specification
A method for converting databases, structurally summarized in directories of data of an initial format meeting predetermined database specifications. The directory structure of the initial format is recorded. A directory structure of an intermediate format, having at least one database of data, is composed based on the directory structure of the initial format by at least one selection. The directory of the intermediate format is produced according to the selection. The contents of the database of data of the initial format are coded and correspond with the at least one database of data of the intermediate format in accordance with the directory of the intermediate format. The at least one database of data of the intermediate format is produced in accordance with the coding. Also, a method for reconstructive conversion of databases and a method for generating an initial format for feedback of audio and / or video information.
Owner:AVT AUDIO VISION TECH
Method and system for accessing a remote file in a directory structure associated with an application program executing locally
ActiveUS20070083501A1Digital data processing detailsSpecial data processing applicationsDirectory structureFile server
A method and system for accessing a file in a directory structure associated with an application includes a method of accessing a file in a directory structure associated with an application. A request by an application for access to a file is intercepted. The request is redirected to a first isolation environment. A determination is made that the requested file does not exist in the first isolation environment. The request is redirected to a second isolation environment responsive to a determination that the file is identified in an enumeration of a directory structure including a plurality of application files residing on a remote machine. The requested file is retrieved from a file server, responsive to a determination that the second isolation environment does not contain the file and that the file is identified in the enumeration.
Owner:CITRIX SYST INC
System and method for efficiently building virtual appliances in a hosted environment
ActiveUS8176094B2Drawback can be addressedError detection/correctionDigital data processing detailsFile systemImage description
A system and method for efficiently building virtual appliances in a hosted environment is provided. In particular, a plurality of image archives may be stored in a build database, with each image archive including a file system having a directory structure and a plurality of files installed within the directory structure. In response to a build request containing an image description, a build engine may create a file system layout defining a directory structure for an image. The build engine may then copy the file system for one of the image archives to the file system layout for the image, wherein the copied file system may provide a subset of the file system for the image. The build engine may then build the image, which may include a file system having various files installed within various directories in accordance with the directory structure defined for the image.
Owner:SUSE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com