Patents
Literature
604 results about "Vulnerability scanning" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Vulnerability scanning is an inspection of the potential points of exploit on a computer or network to identify security holes. A vulnerability scan detects and classifies system weaknesses in computers, networks and communications equipment and predicts the effectiveness of countermeasures.
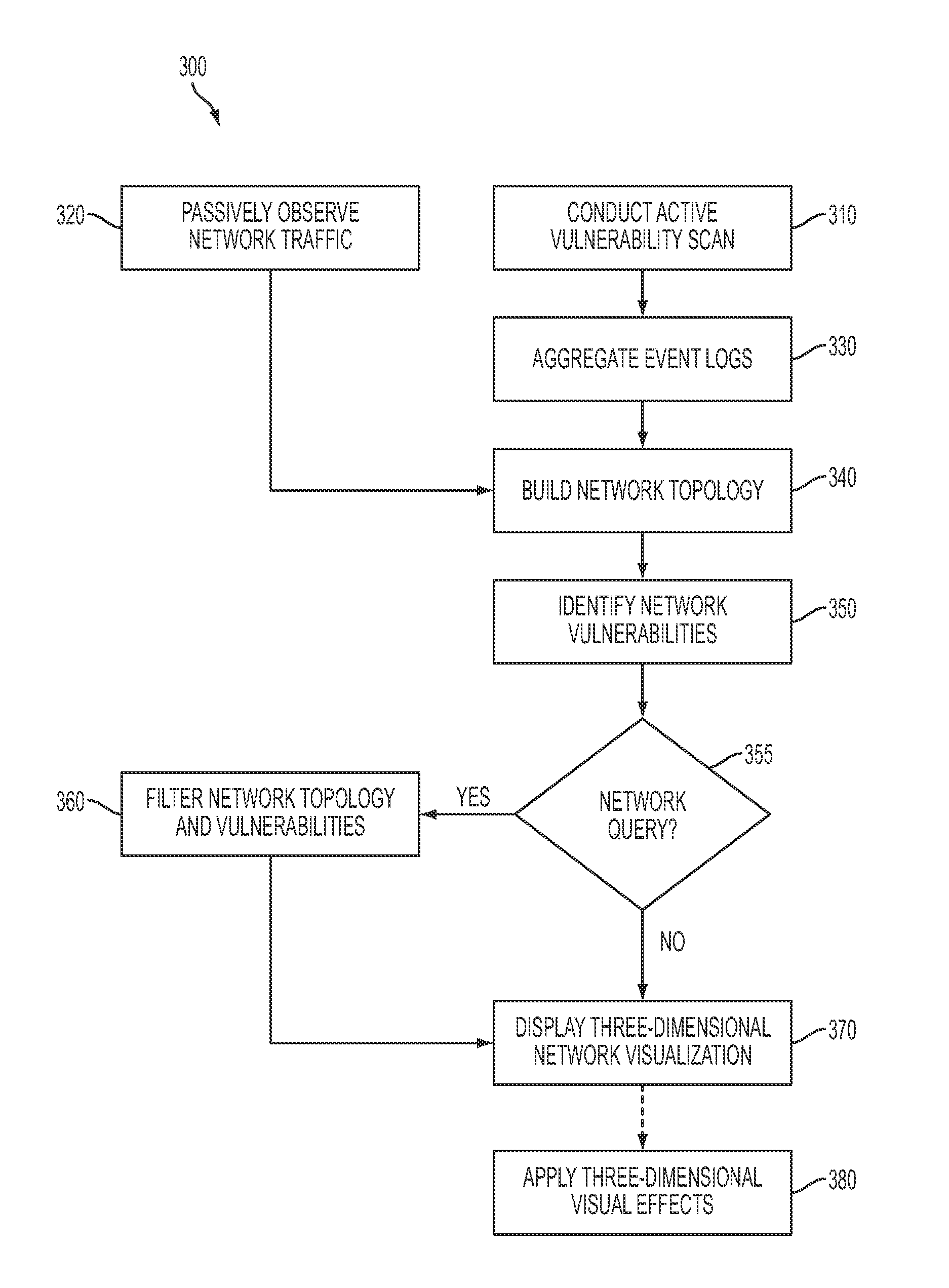
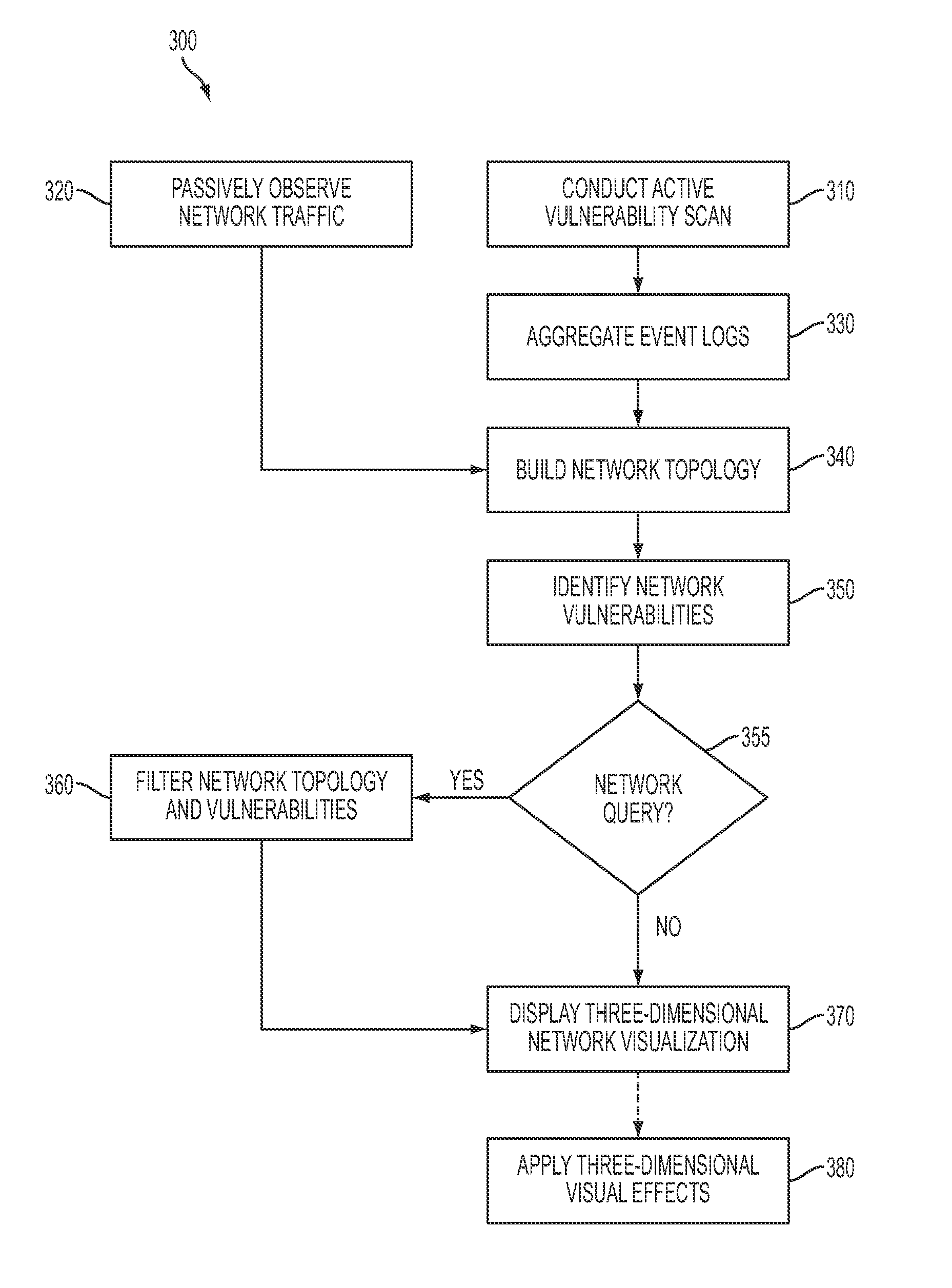
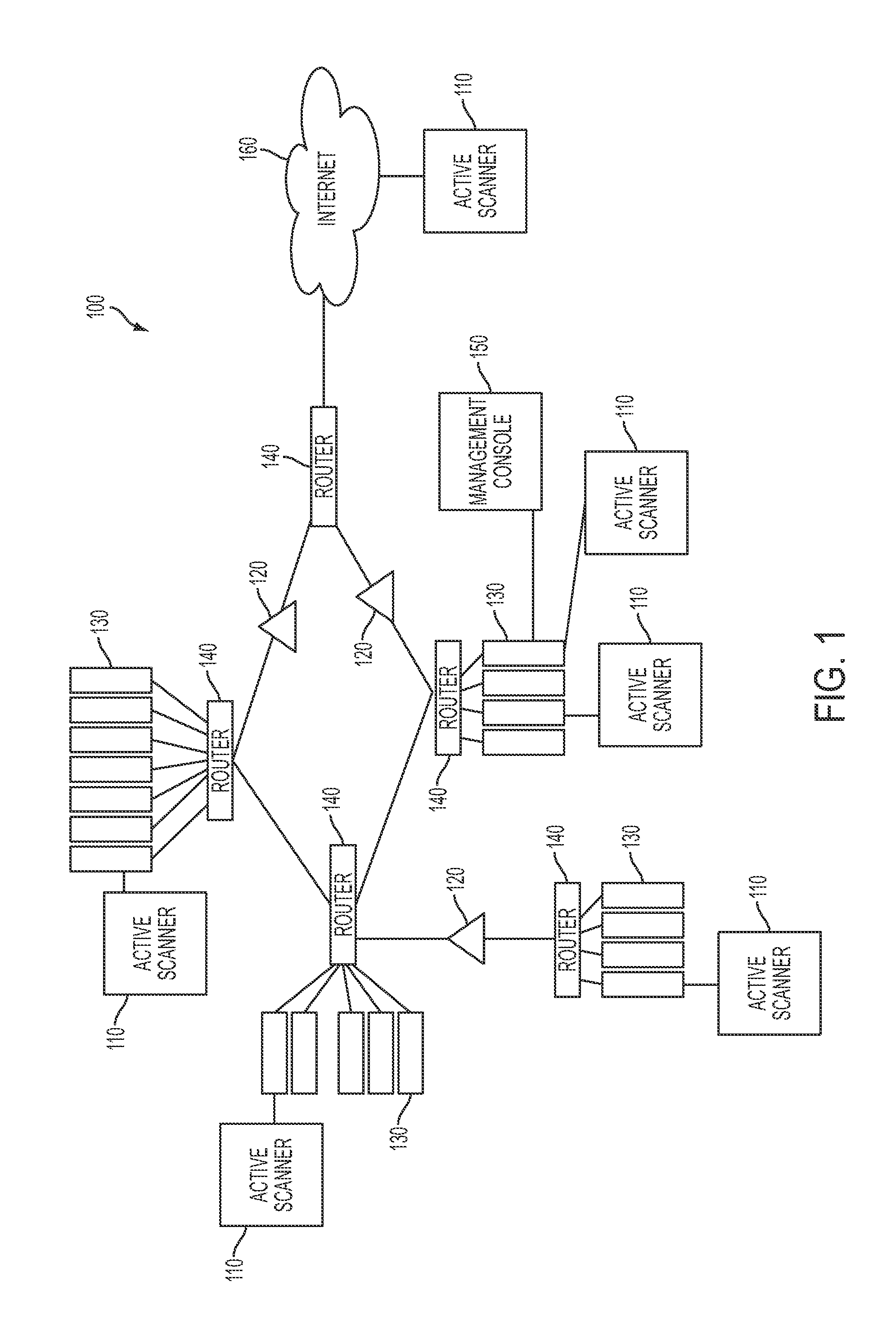
System and method for three-dimensional visualization of vulnerability and asset data
ActiveUS20110277034A1Simplify the management processMemory loss protectionError detection/correctionGraphicsVulnerability scanning
The system and method for three-dimensional visualization of vulnerability and asset data described herein may provide a management console that integrates various active vulnerability scanners, various passive vulnerability scanners, and a log correlation engine distributed in a network. In particular, the management console may include a three-dimensional visualization tool that can be used to generate three-dimensional visualizations that graphically represent vulnerabilities and assets in the network from the integrated information that management console collects the active vulnerability scanners, the passive vulnerability scanners, and the log correlation engine distributed in the network. As such, the three-dimensional visualization tool may generate three-dimensional representations of the vulnerabilities and assets in the network that can be used to substantially simplify management of the network.
Owner:TENABLE INC
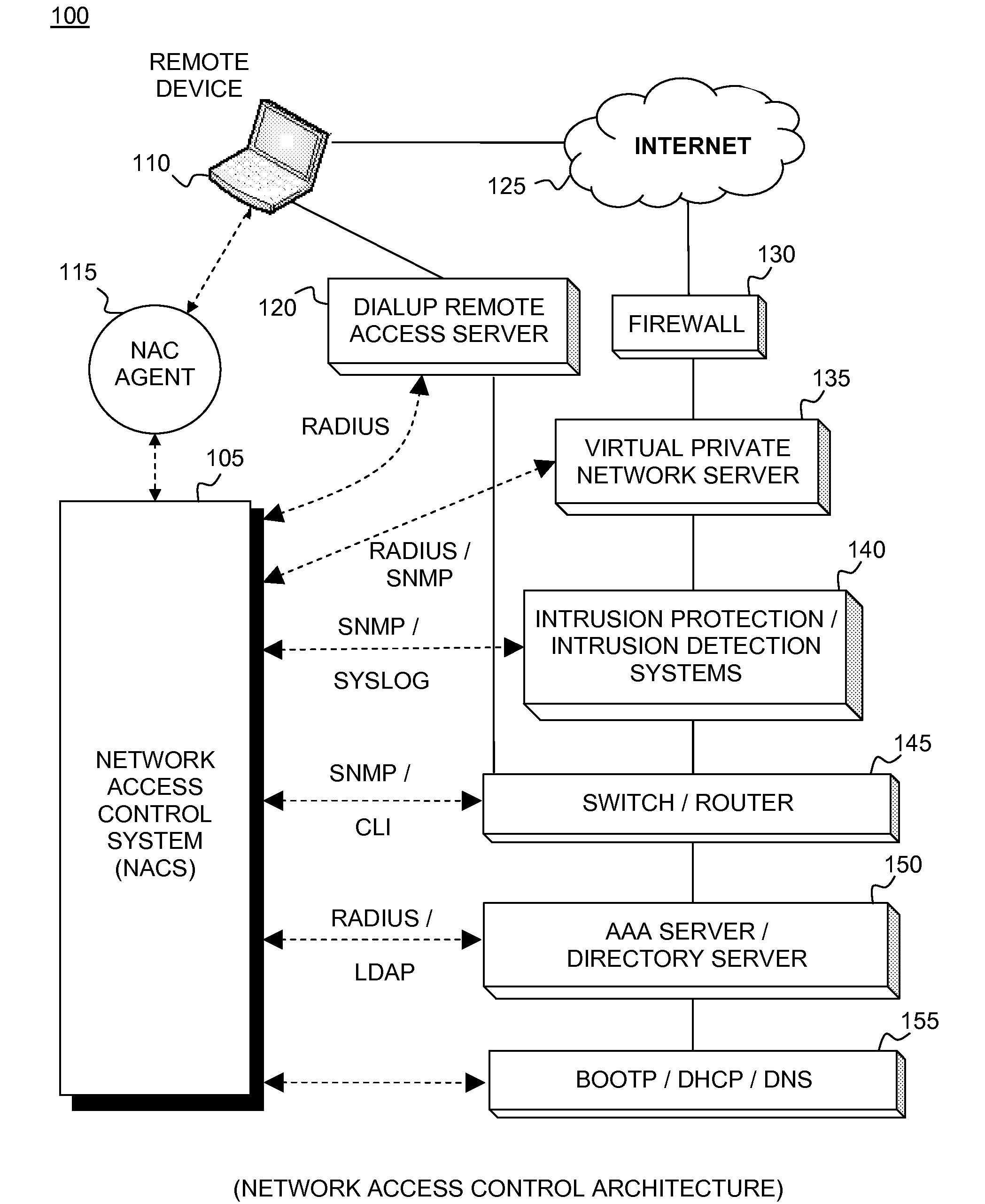
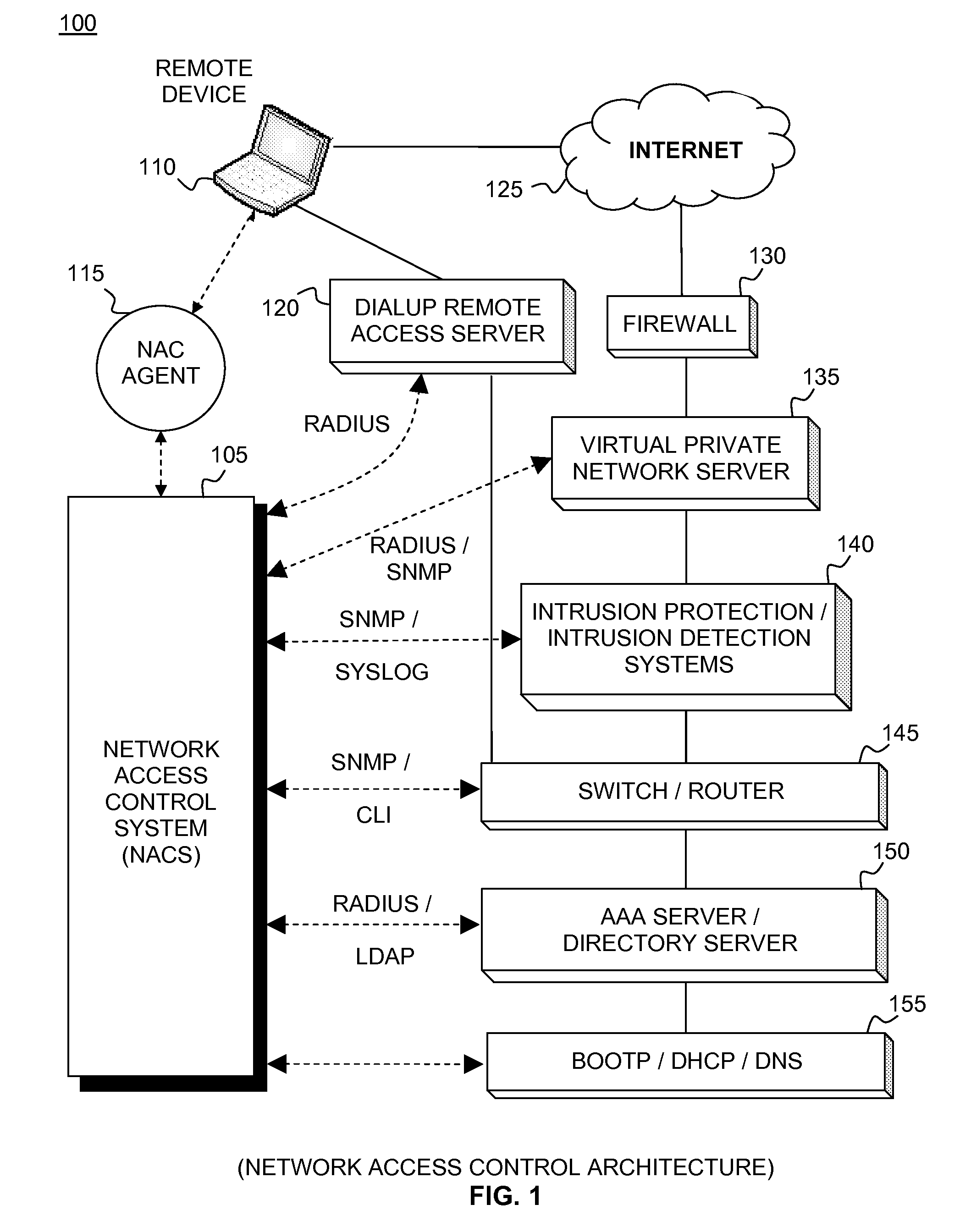
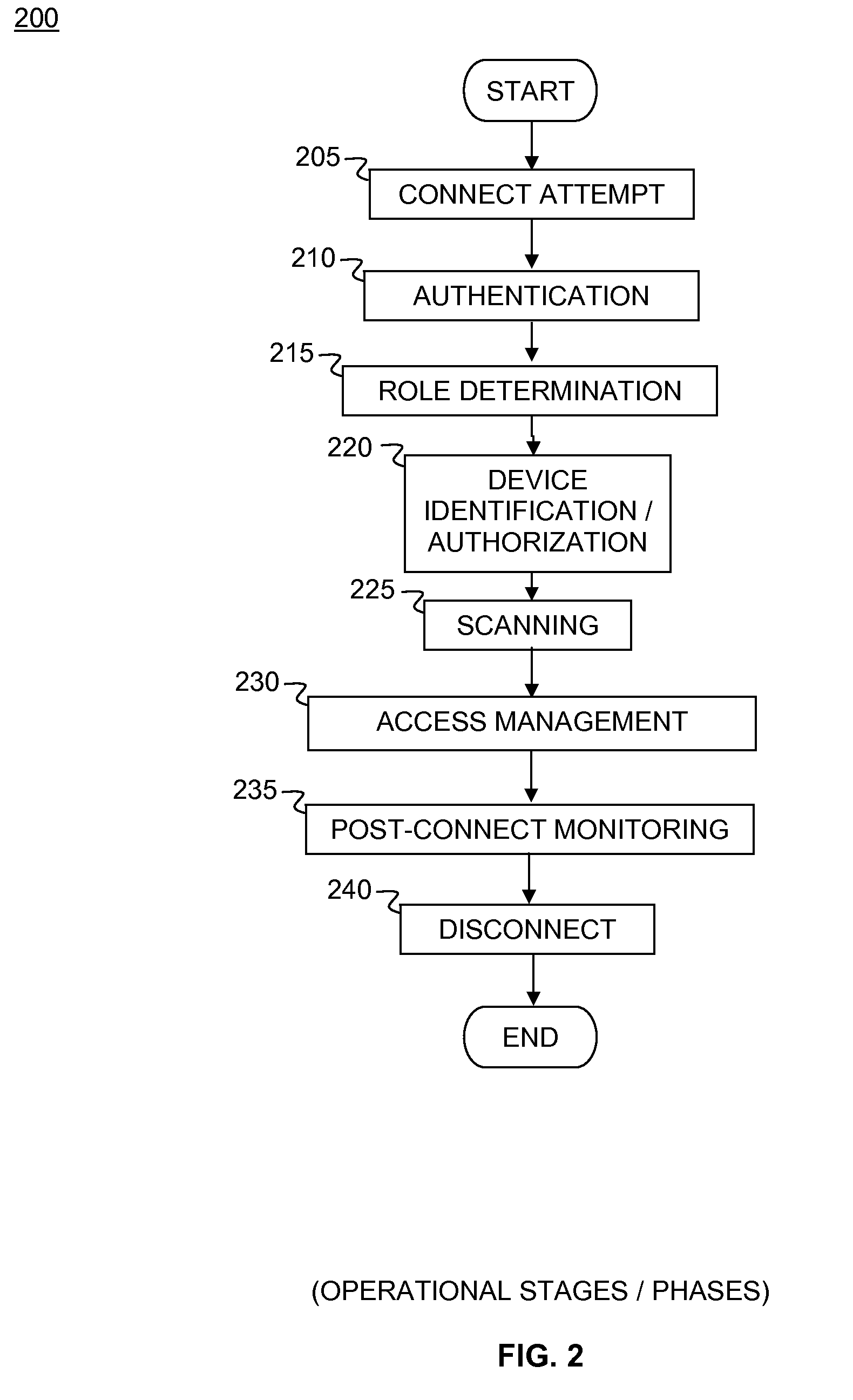
Network access control system and method for devices connecting to network using remote access control methods
ActiveUS20090307753A1Digital data processing detailsMultiple digital computer combinationsControl systemUser authentication
A system and method for network access control (NAC) of remotely connected devices is disclosed. In embodiments, agents support role mapping and policy-based scanning. Embodiments automatically perform authentication, assessment, authorization, provisioning, and remediation. Capabilities include user authentication, role-based authorization, endpoint compliance, alarms and alerts, audit logs, location-based rules, and policy enforcement. Processes collect information about the user as well as the host being used from sources including, but not limited to, LDAP, the remote access device, and the agent. Once this data has been obtained, embodiments construct a comprehensive model of the host. This model is subsequently used to govern the actual host's network access when it connects to the network. Passive monitoring includes vulnerability scanning to control access rights throughout the duration of the connection.
Owner:FORTINET
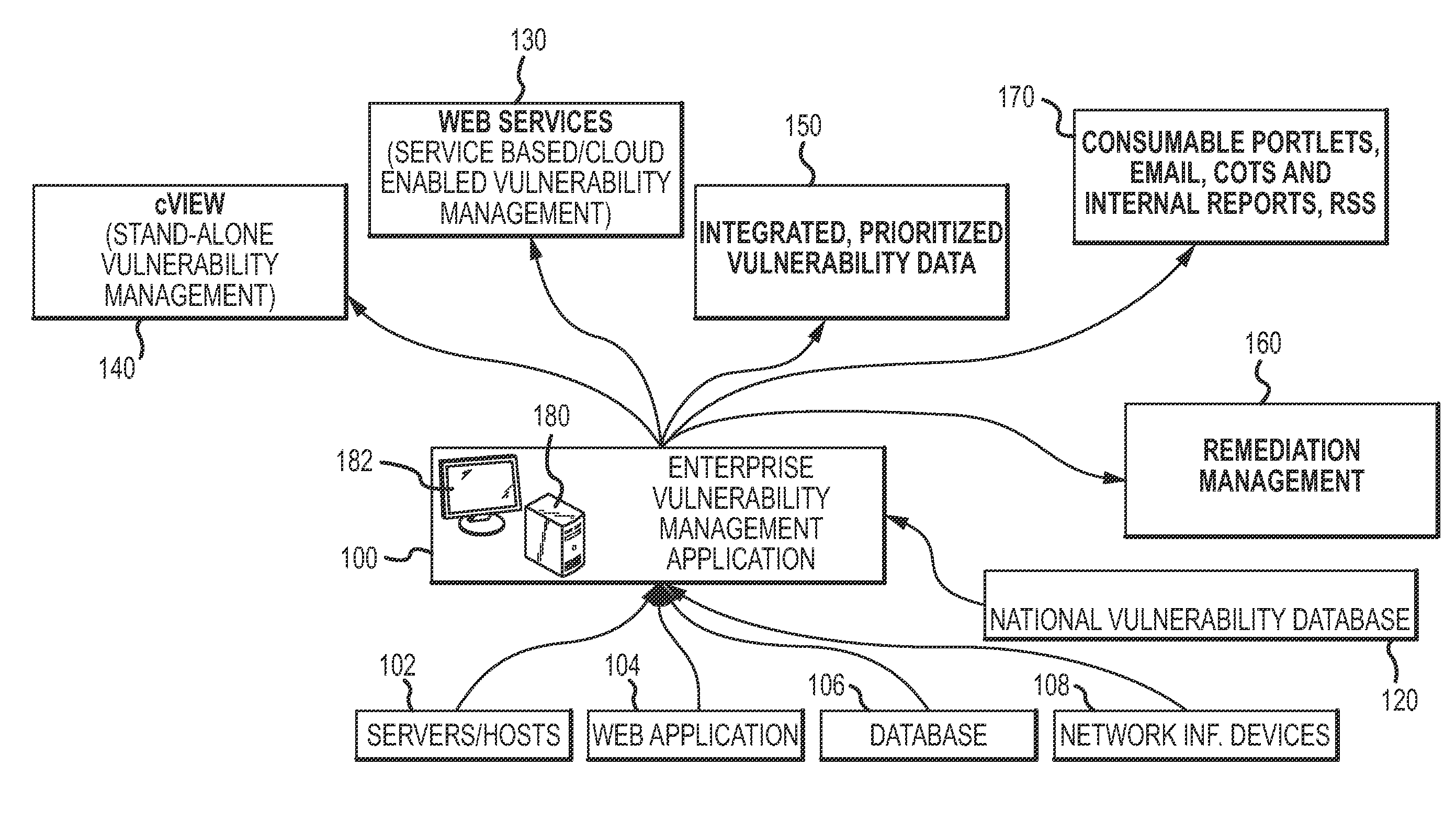
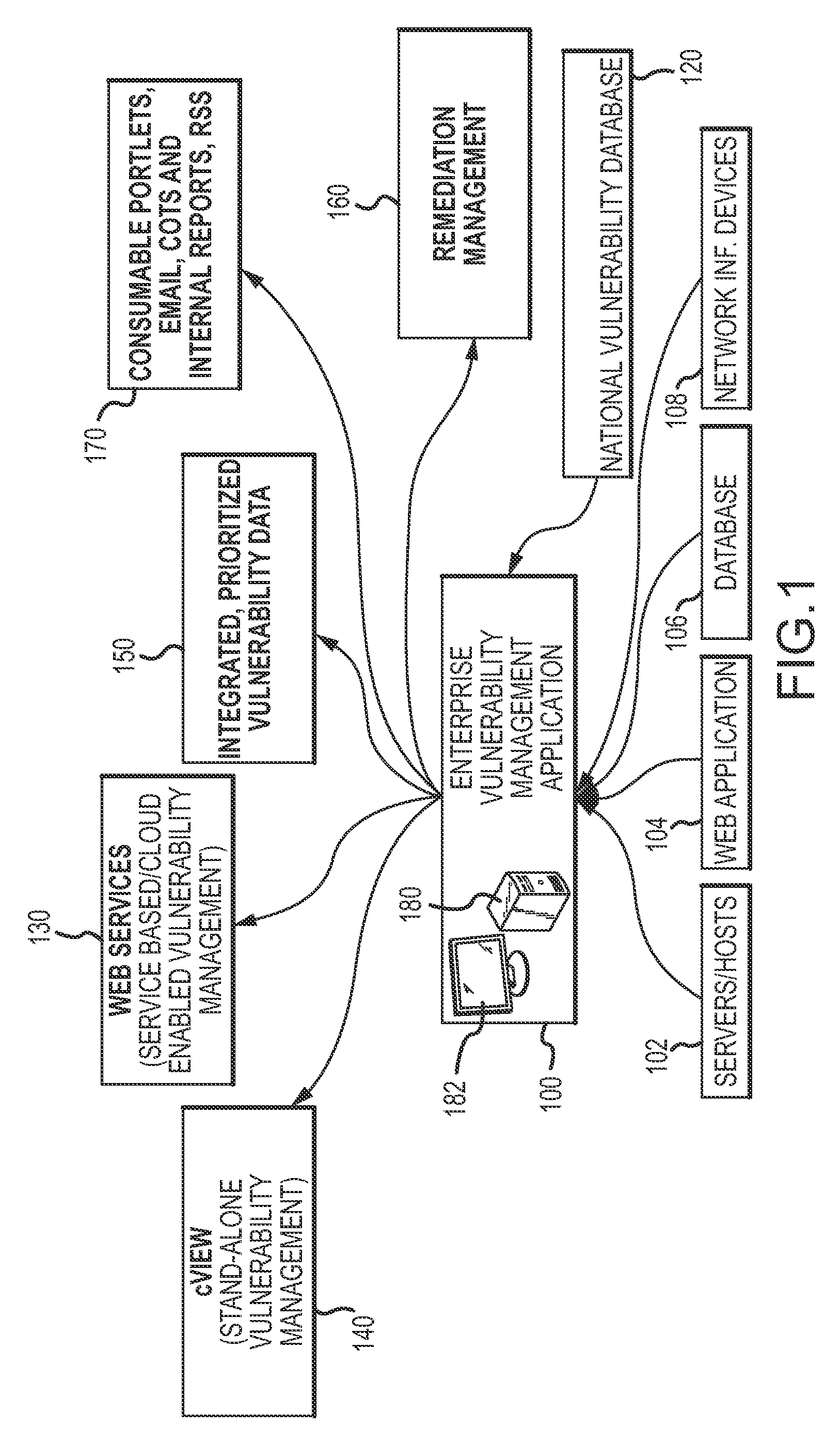
Enterprise vulnerability management
ActiveUS20120304300A1Fast data analysisEasy to addMemory loss protectionError detection/correctionVulnerability managementRemedial action
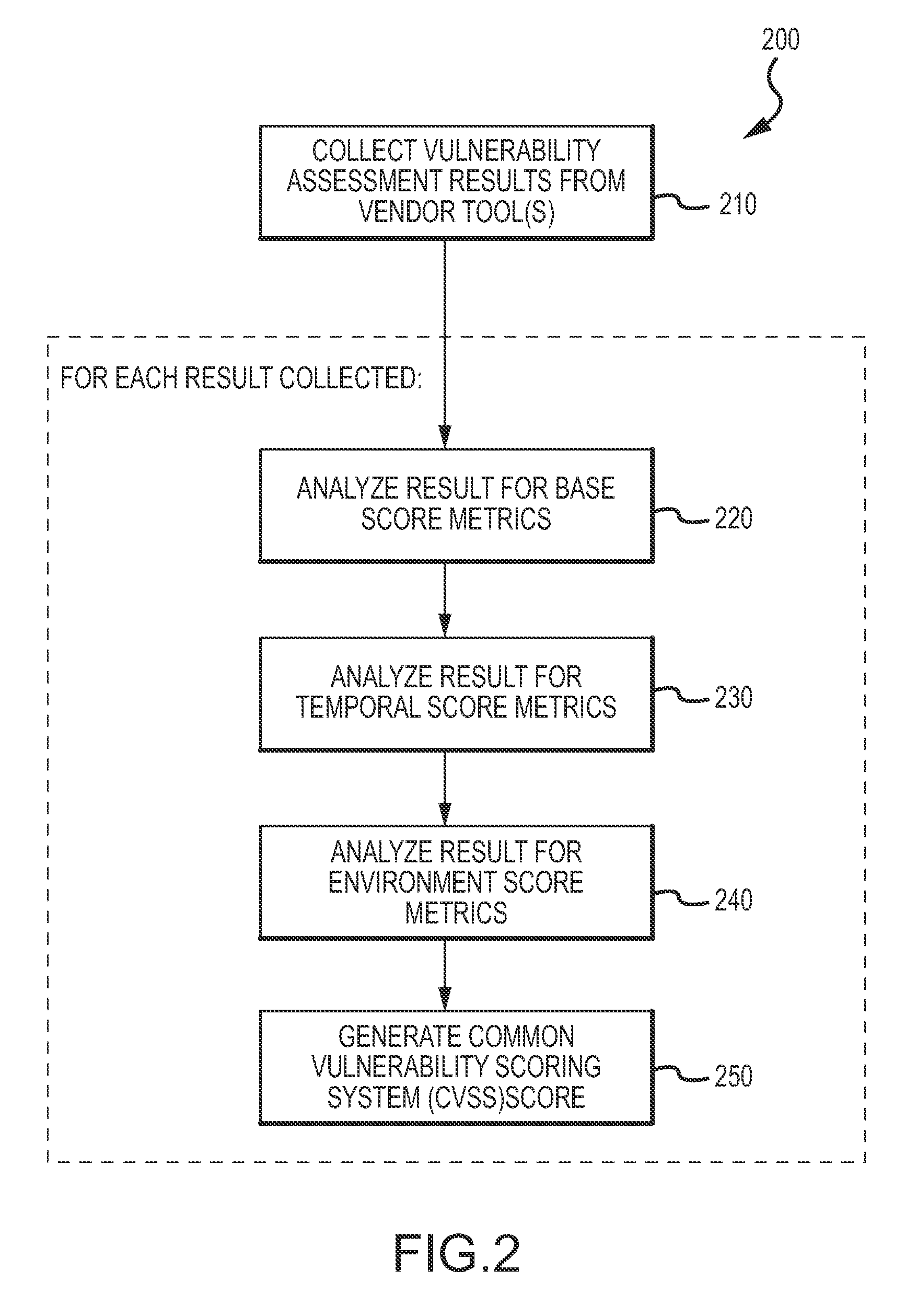
An enterprise vulnerability management application (EVMA), enterprise vulnerability management process (EVMP) and system. In one embodiment, the EVMP may include executing computer software code on at least one computer hardware platform to receive login information from a user, inventory current information technology assets of the enterprise, conduct vulnerability scanning of the inventoried information technology assets, analyze vulnerability correlation and prioritization of the information technology assets, remediate one or more vulnerabilities of the information technology assets, and report to the user about the vulnerabilities and remediation undertaken. As part of the analysis, one or more vulnerability scores such as, for example, Common Vulnerability Scoring System (CVSS) scores, may be generated from base score metrics, temporal score metrics and environment score metrics.
Owner:LEIDOS INNOVATIONS TECH INC
System and method for resolving vulnerabilities in a computer network
InactiveUS20110138469A1Memory loss protectionError detection/correctionSecurity levelComputer science
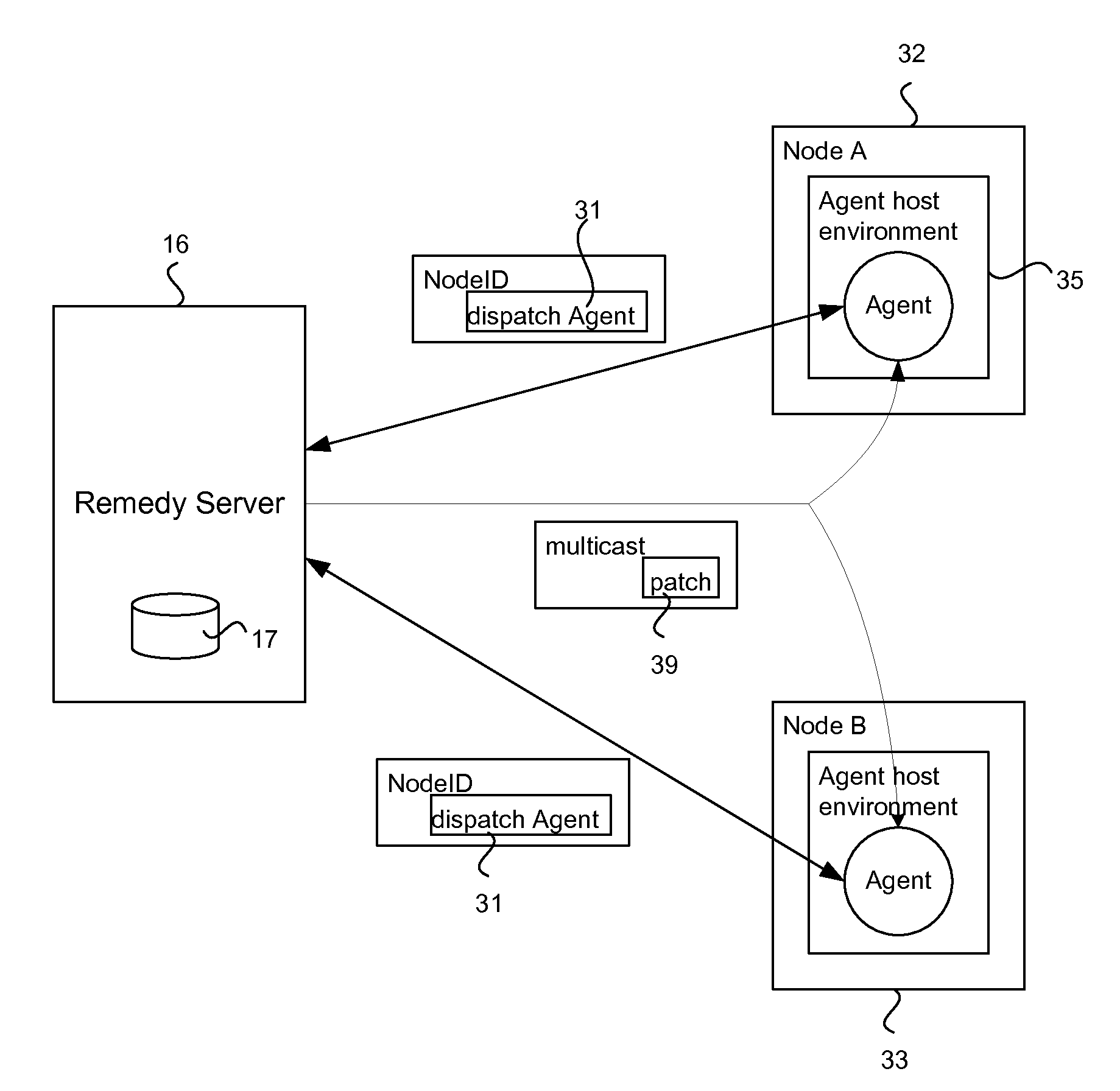
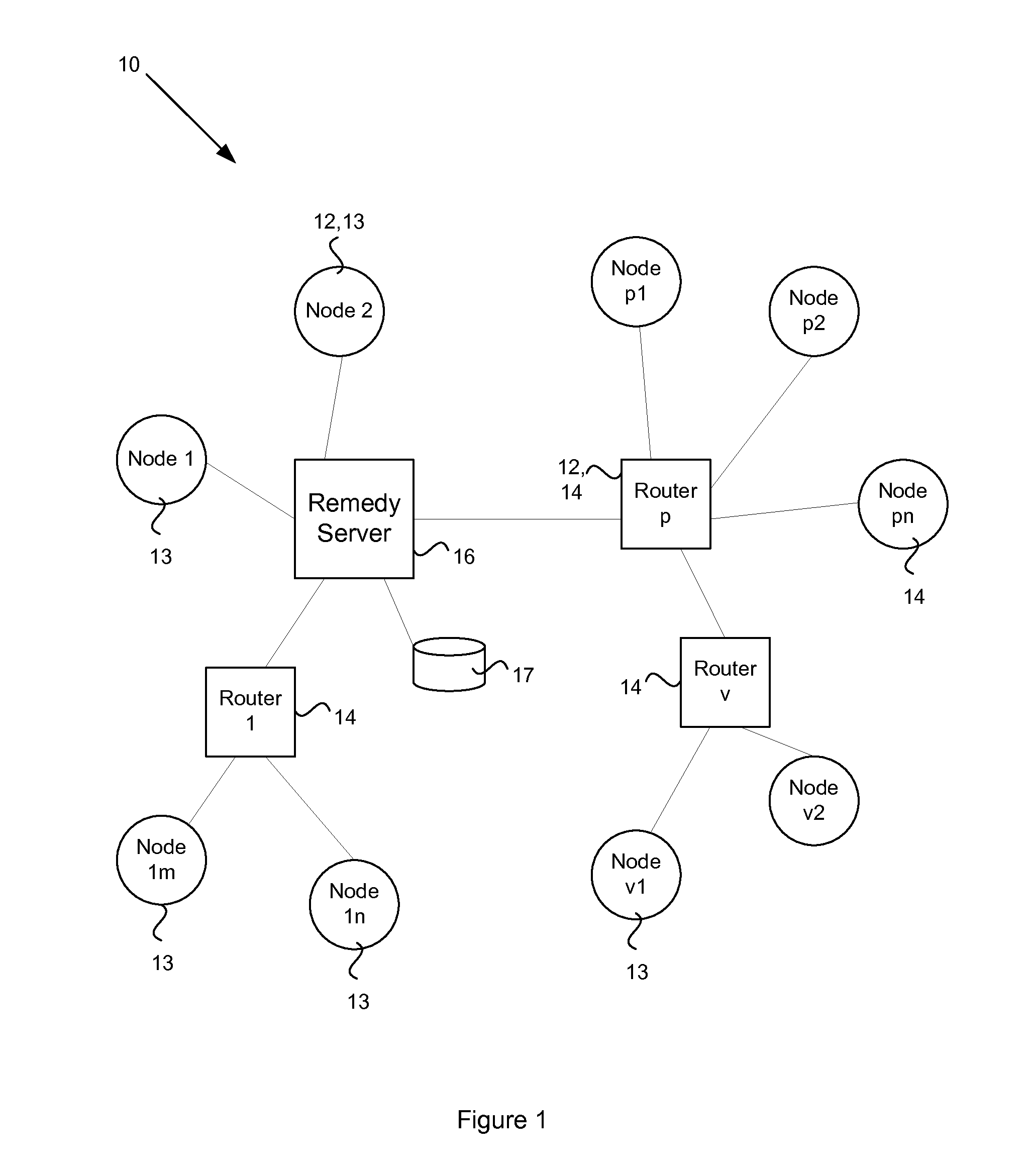
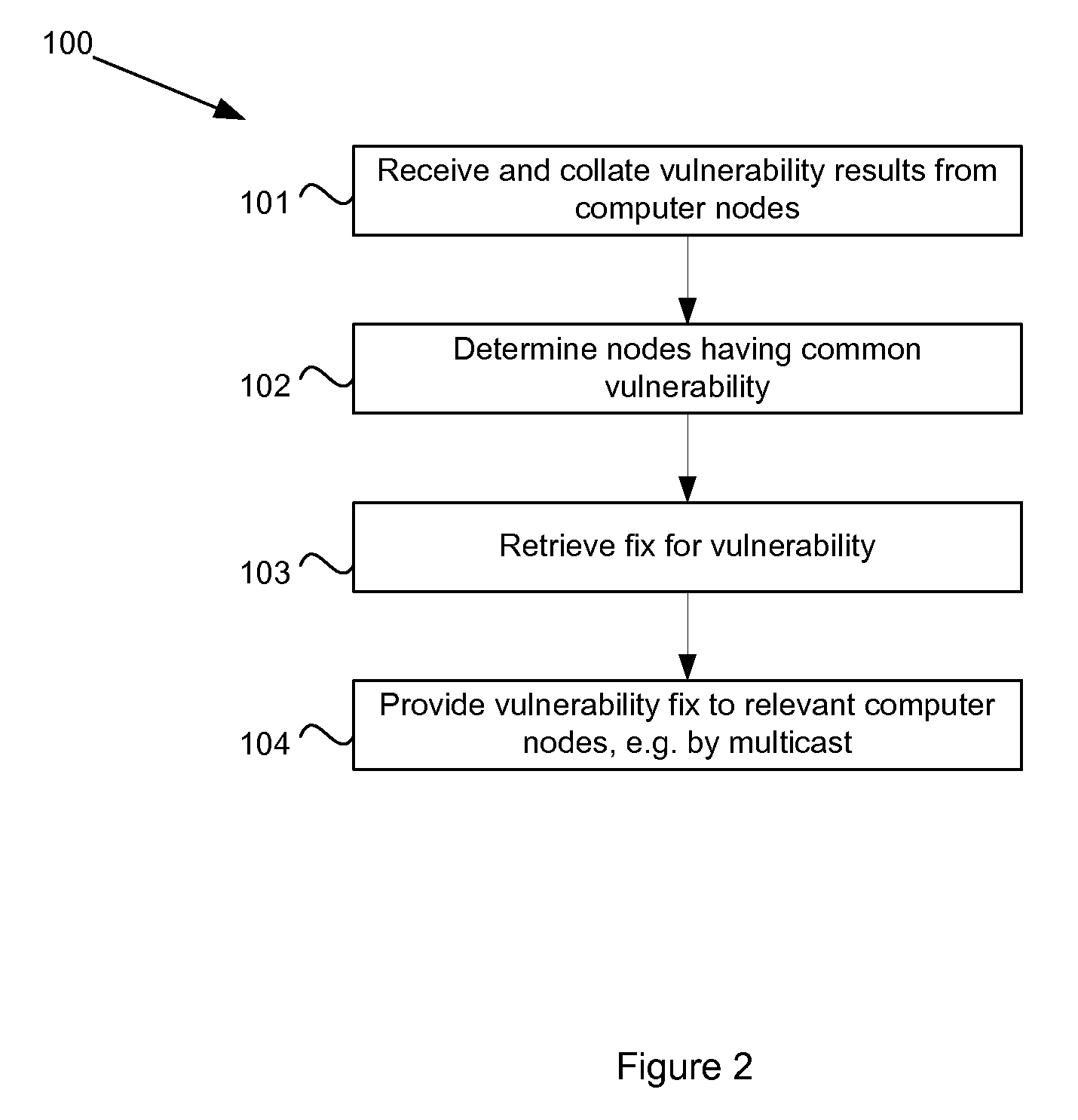
In a computer network, a remedy server may be provided that controls vulnerability scans of the computer nodes. The remedy server determines a security level of a computer node and dispatches an agent to the node with a scan matching the security level. The agent executes the scan and reports the scan results to the remedy server. The remedy server collates scan results from a plurality of the network computers and determines which computers have a common vulnerability. A fix for the vulnerability, such as an executable patch file, is retrieved and multicast to those relevant computers.
Owner:OSOCAD REMOTE LIABILITY
Systems and methods for client-side vulnerability scanning and detection
InactiveUS8752183B1Avoid hard activationImprove accuracyMemory loss protectionError detection/correctionObfuscationWeb browser
Various embodiments presented herein relate to scanning for and detecting web page vulnerabilities, including cross-site scripting (XSS). Some embodiments are configured to scan for and detect vulnerabilities of a target web page using a client-based approach, which may employ a remotely-controlled web browser application capable of generating a document object model (DOM) for the target web page as it is accessed. Some embodiments may scan for and detect web page vulnerabilities by monitoring the DOM associated with a targeted web page as one or more attack vectors are applied to the target web page. Certain embodiments are capable of detecting web page vulnerabilities independent of the complexity or presence of an event model, or obfuscation of the malicious code (e.g., XSS code). Target web pages that are scanned may include those associated with an application coded in a web browser-supported language, such a Rich Internet Application (RIA).
Owner:HOYT TECH
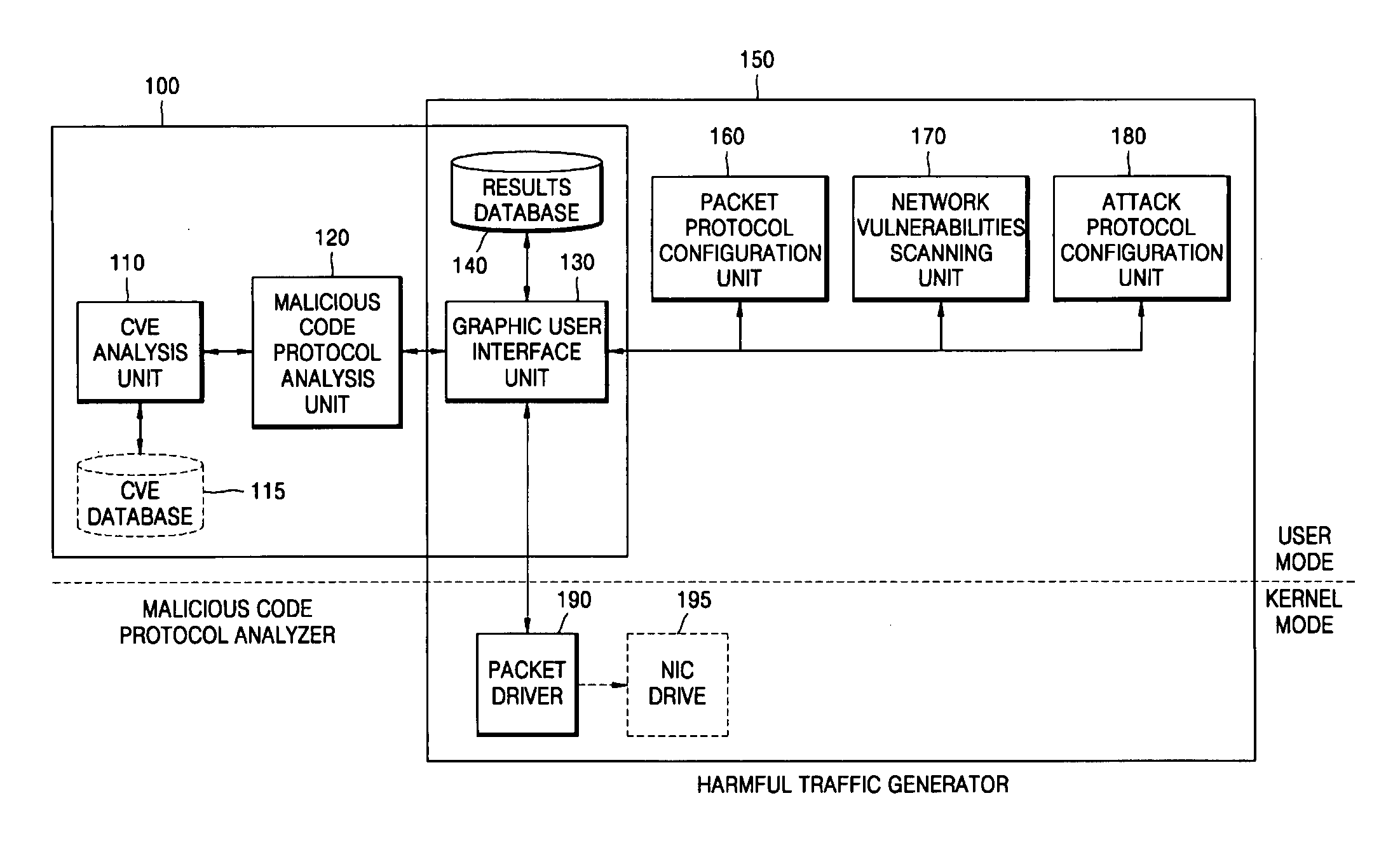
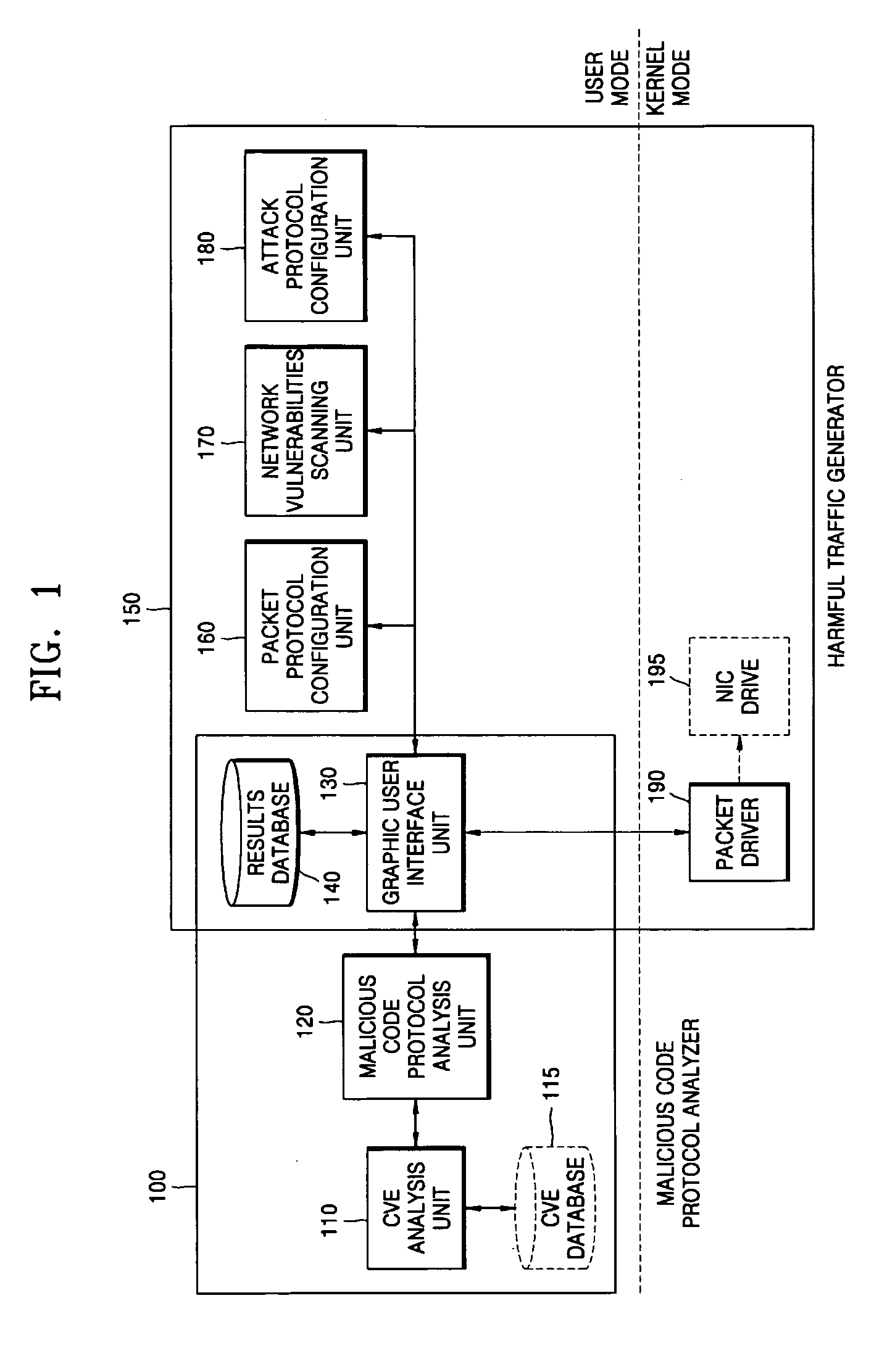
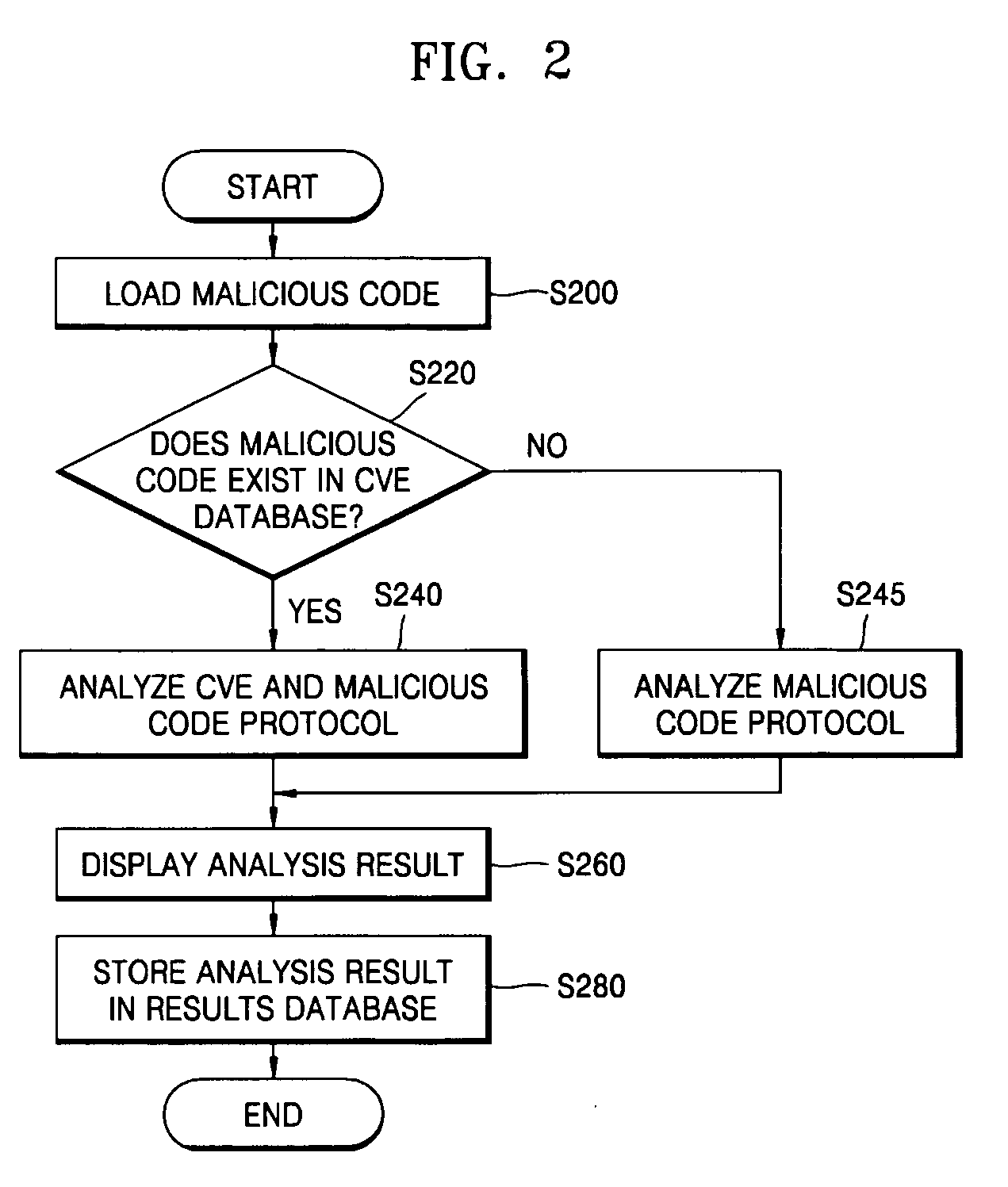
System and method for analyzing malicious code protocol and generating harmful traffic
The provided method and system is a method and system for analyzing the malicious code protocol and generating harmful traffic. The harmful traffic generating method constructs packet protocol information for generating a first attack packet corresponding to the TCP / IP protocol for generating network traffic, and then sets network vulnerability scanning for generating a second attack packet for carrying out network vulnerability scanning. Subsequently, the method constructs attack information for generating a third attack packet in the form of denial of service, and generates harmful traffic using the packet protocol information, network vulnerability scanning and attack information. Accordingly, performance testing of the network security system against malicious code attacks such as the Internet worm can be performed.
Owner:CHOI BYEONG CHEOL +1
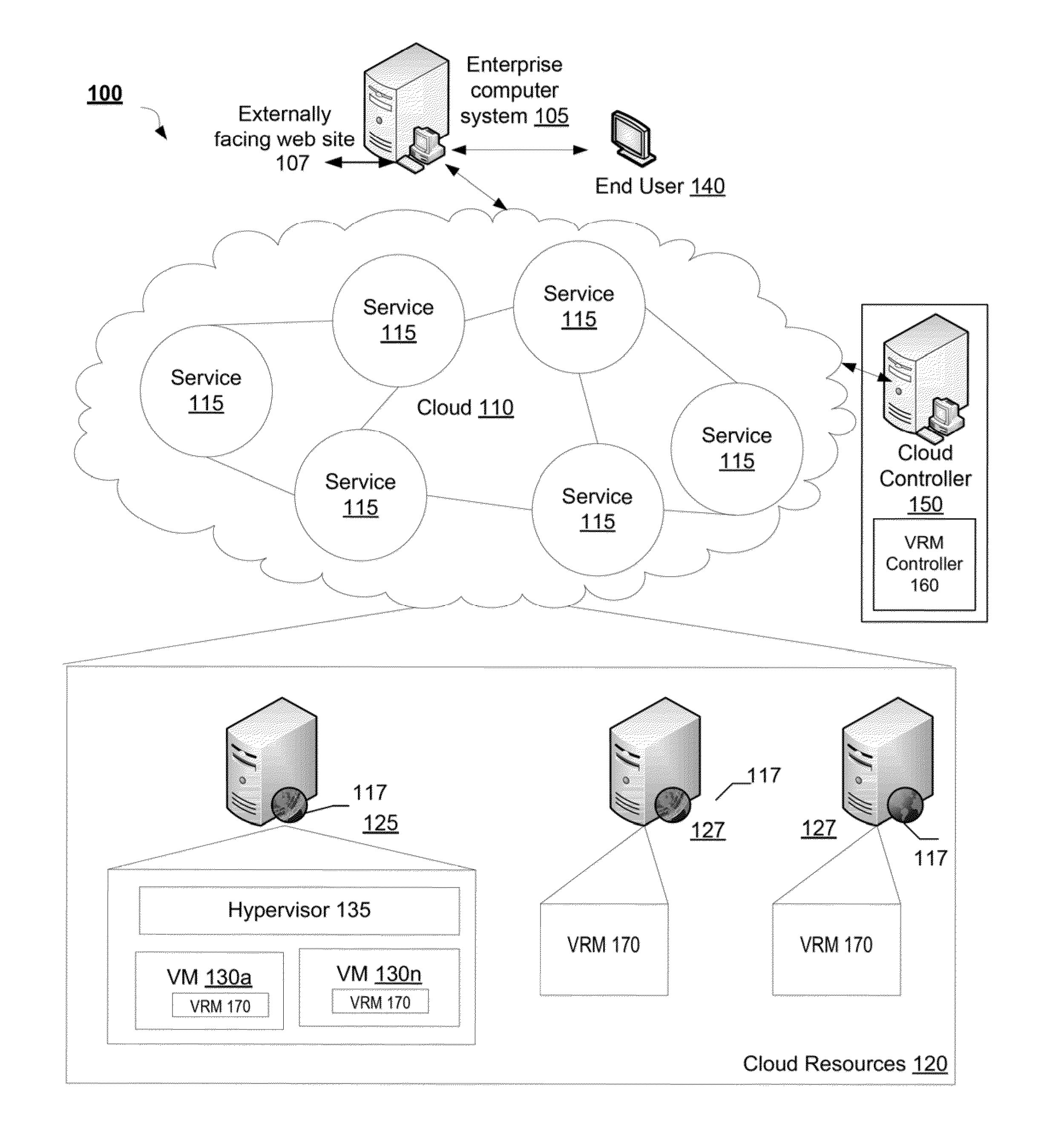
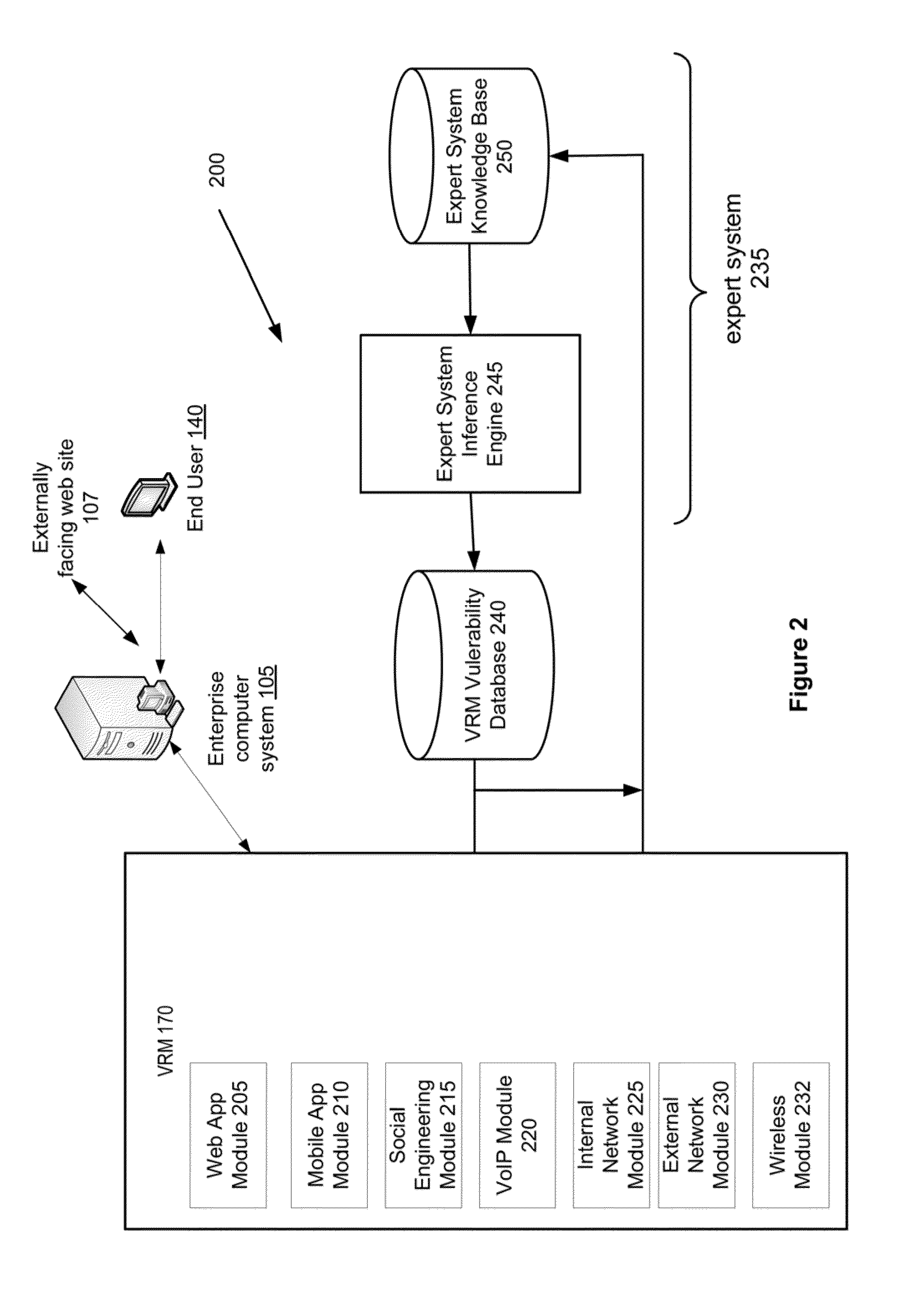
Method and System for Managing Computer System Vulnerabilities
A vulnerability risk management (VRM) module receives an indication of a VRM service to be provided from the end user. The VRM module extracts from the indication either external IP addresses or the web application URL and a list of assets of the enterprise computer system to be tested. The VRM module discovers the assets of the enterprise computer system. The VRM module receives a request for a vulnerability scan using a predefined scan configuration based on preferences of the end user and a specified date and time to conduct the scan. The VRM module reports and stores a preliminary list of potential vulnerabilities in the VRM vulnerability database. The preliminary list is fed to an expert system, which applies specific rule sets using an inference engine and a knowledge base to refine results stored in the VRM vulnerability database by removing extraneous information and false positives.
Owner:NOPSEC
Automatic vulnerability validation method
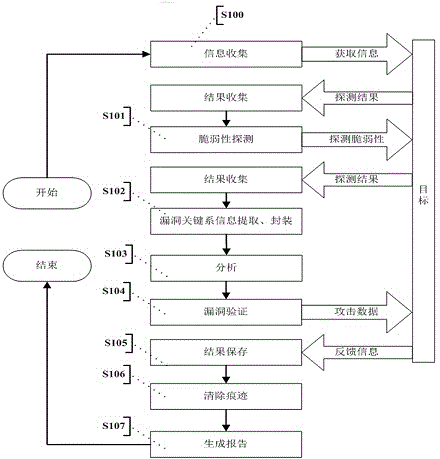
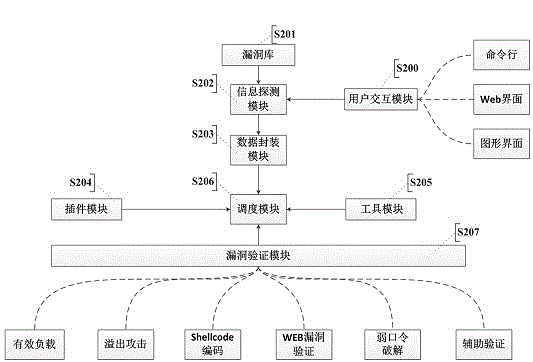
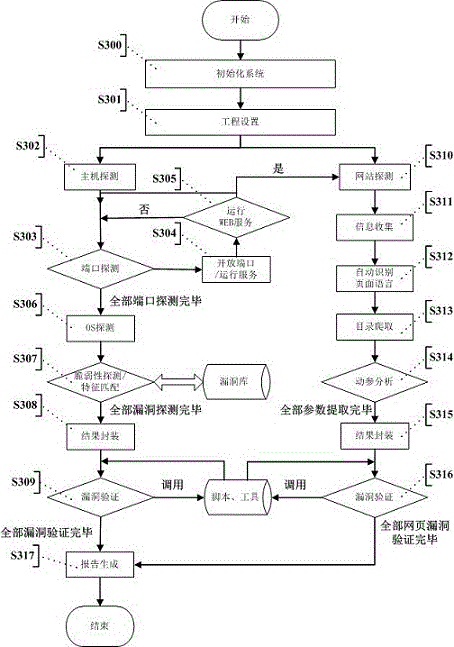
InactiveCN104363236AAutomated verificationUnderstand the dangers of vulnerabilitiesPlatform integrity maintainanceTransmissionValidation methodsModularity
The invention provides an automatic vulnerability validation method. The method comprises the steps that firstly, validation information is collected, wherein an active detection way is adopted for carrying out information detection, topological detection, vulnerability detection and website directory structure detection on a target; secondly, the validation information is packaged, wherein suspicious vulnerability key information in vulnerability detection results is extracted, uniform-interface modularized packaging is carried out on the data; thirdly, a validation strategy is searched for, wherein according to the suspicious vulnerability identity and variety information, an appropriate attack script template and a vulnerability utilizing tool are selected; vulnerability validation is carried out, wherein scripts are called to be loaded into the packaged vulnerability information to carry out validation attack, and an utilization voucher is obtained and stored; fifthly, validation traces are removed, wherein validation attack traces are removed, sessions are recycled; finally, a scanning report is generated. The automatic vulnerability validation method solves the problem that an existing vulnerability scanning system is high in false alarm rate and cannot carry out effective validation, is automatic and procedural, can automatically recognize and validate vulnerabilities, lowers the requirement for the ability of non-professional staff and improves the vulnerability validation efficiency.
Owner:XIAN UNIV OF POSTS & TELECOMM +1
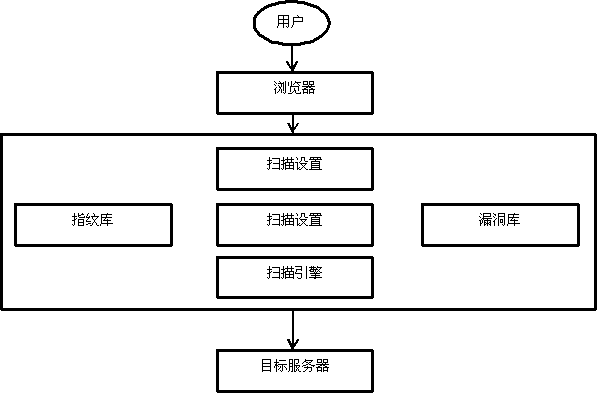
WEB vulnerability scanning method and vulnerability scanner based on fingerprint recognition technology
InactiveCN103065095AImprove accuracyEasy to addPlatform integrity maintainanceTransmissionWeb siteWeb service
The invention provides a WEB vulnerability scanning method and a vulnerability scanner based on fingerprint recognition technology. Since a feature library based security scanning scheme is used to replace a common site security vulnerability scanning scheme based on fully crawling, the scanner is improved in terms of accuracy of vulnerability scanning, flexibility of further processing after detecting vulnerabilities, efficiency of discovering vulnerabilities, and the like, and accordingly a new scheme is provided for the system security scanning and the network vulnerability scanning. The scanner comprises a user side, a browser, a scanning host and a WEB server. According to the abstract appended drawing, the scanning host comprises a control module, a scan parameter setting module, a scan engine module, a WEB fingerprint library module and a WEB vulnerability library module. The user sets scanning parameters in the scan parameter setting module through the control module, the scanning engine is firstly used for fingerprint recognition on the basis of sent parameters, and finally, the vulnerability library is used for testing site vulnerabilities and sending a test report. The scanner is capable of accurately and rapidly helping users to test and analyze vulnerability of the target website, and directly perform corresponding operations on the browser with no need of installation of client side software.
Owner:SICHUAN UNIV
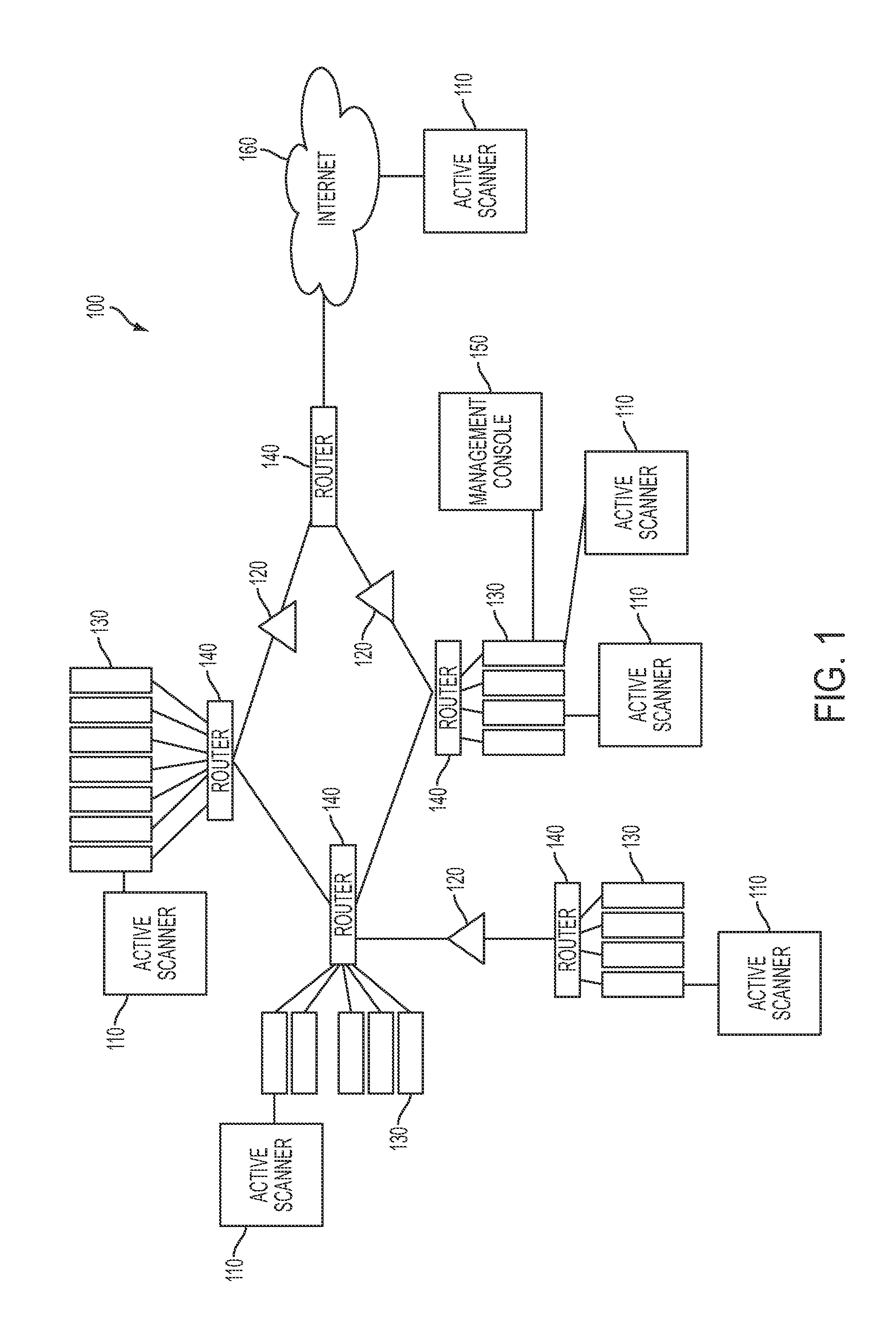
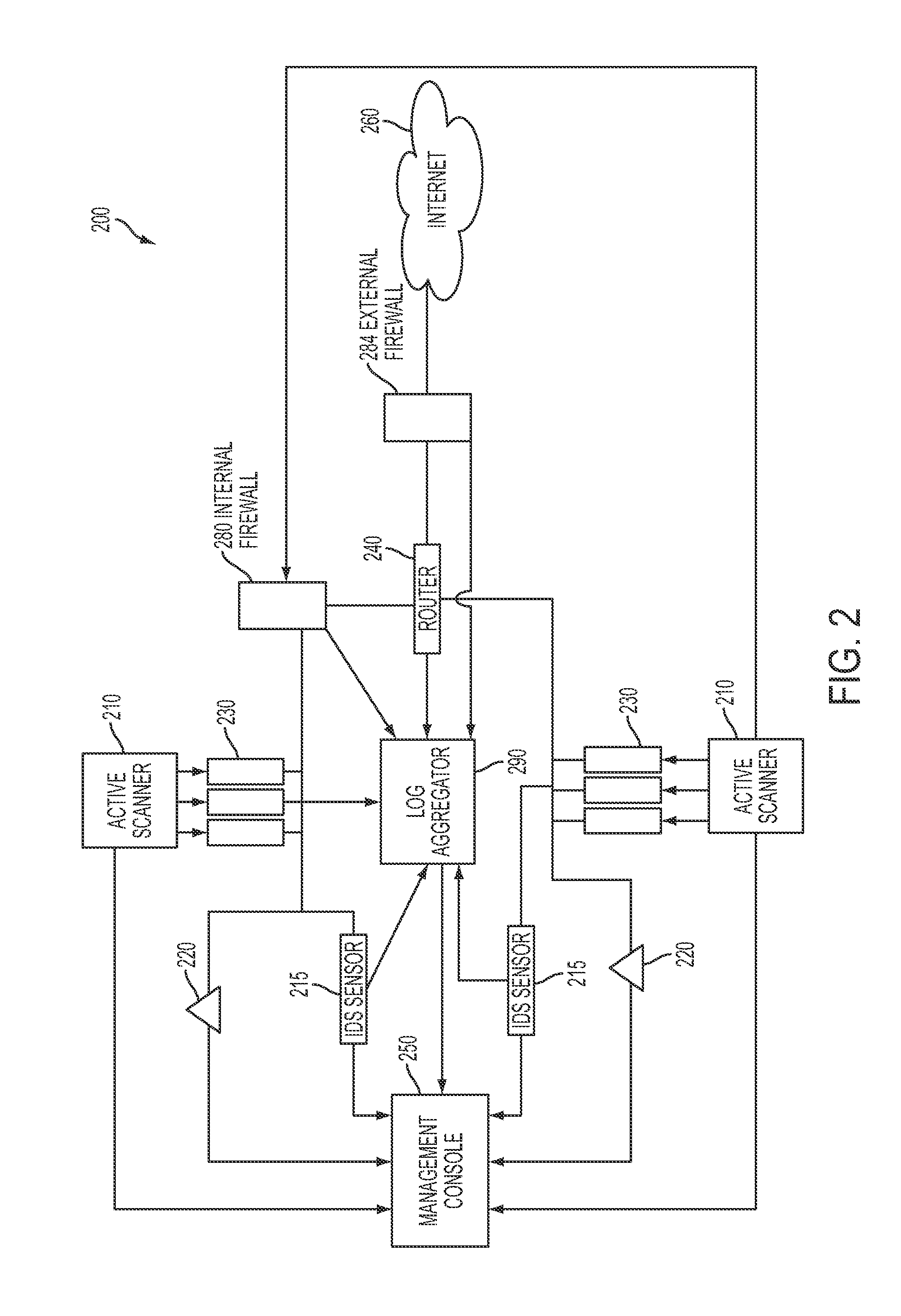
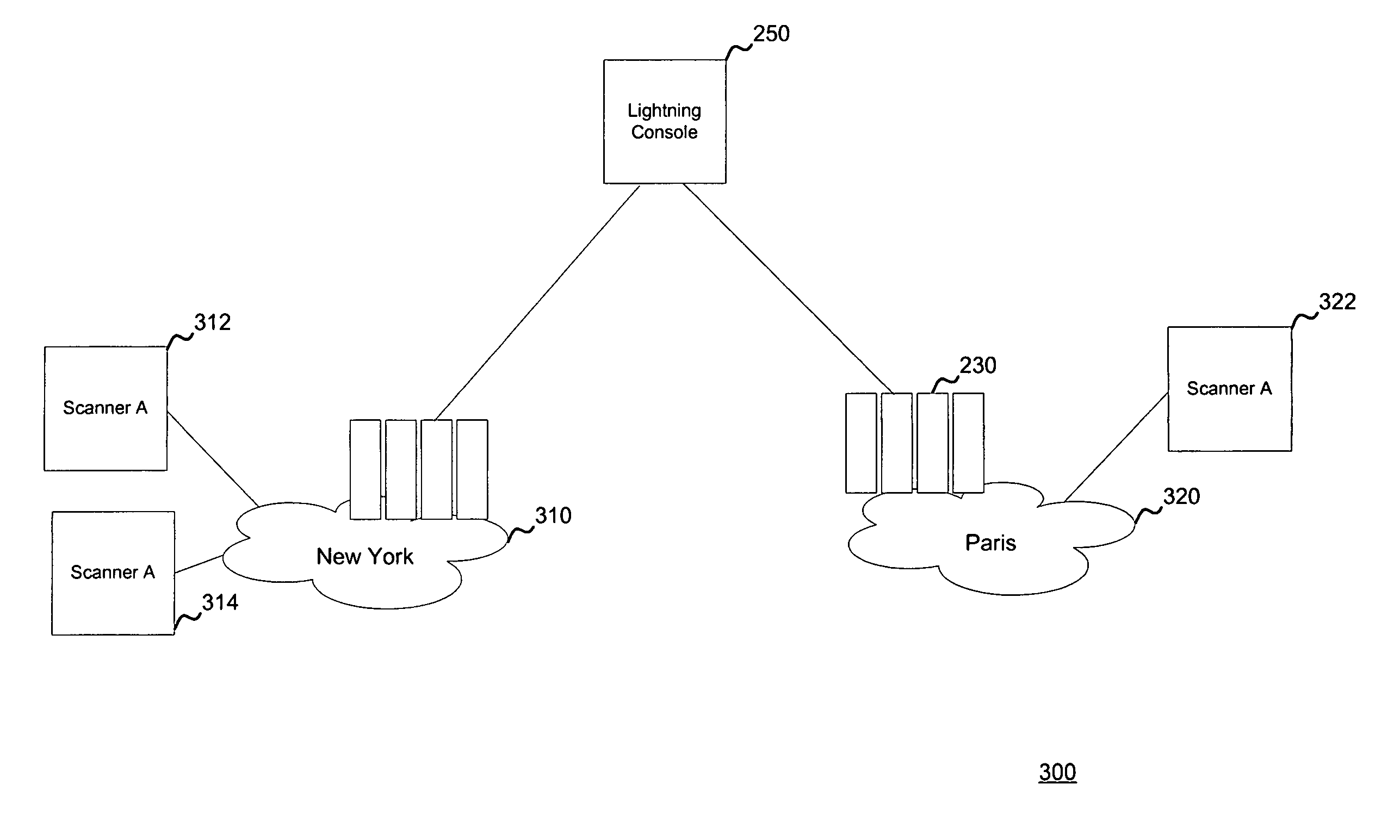
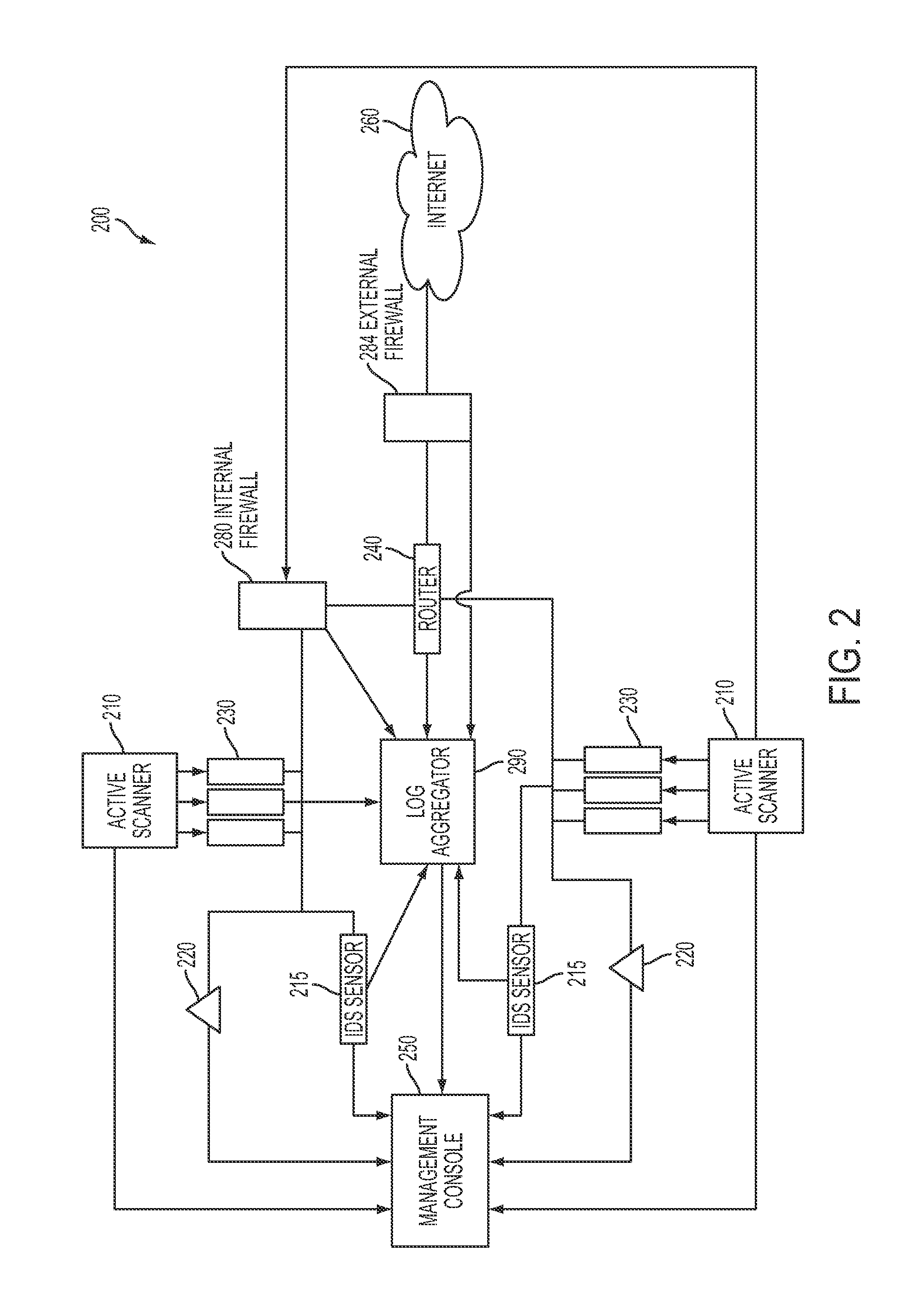
System and method for managing network vulnerability analysis systems
ActiveUS7926113B1Memory loss protectionError detection/correctionSystems managementDistributed security
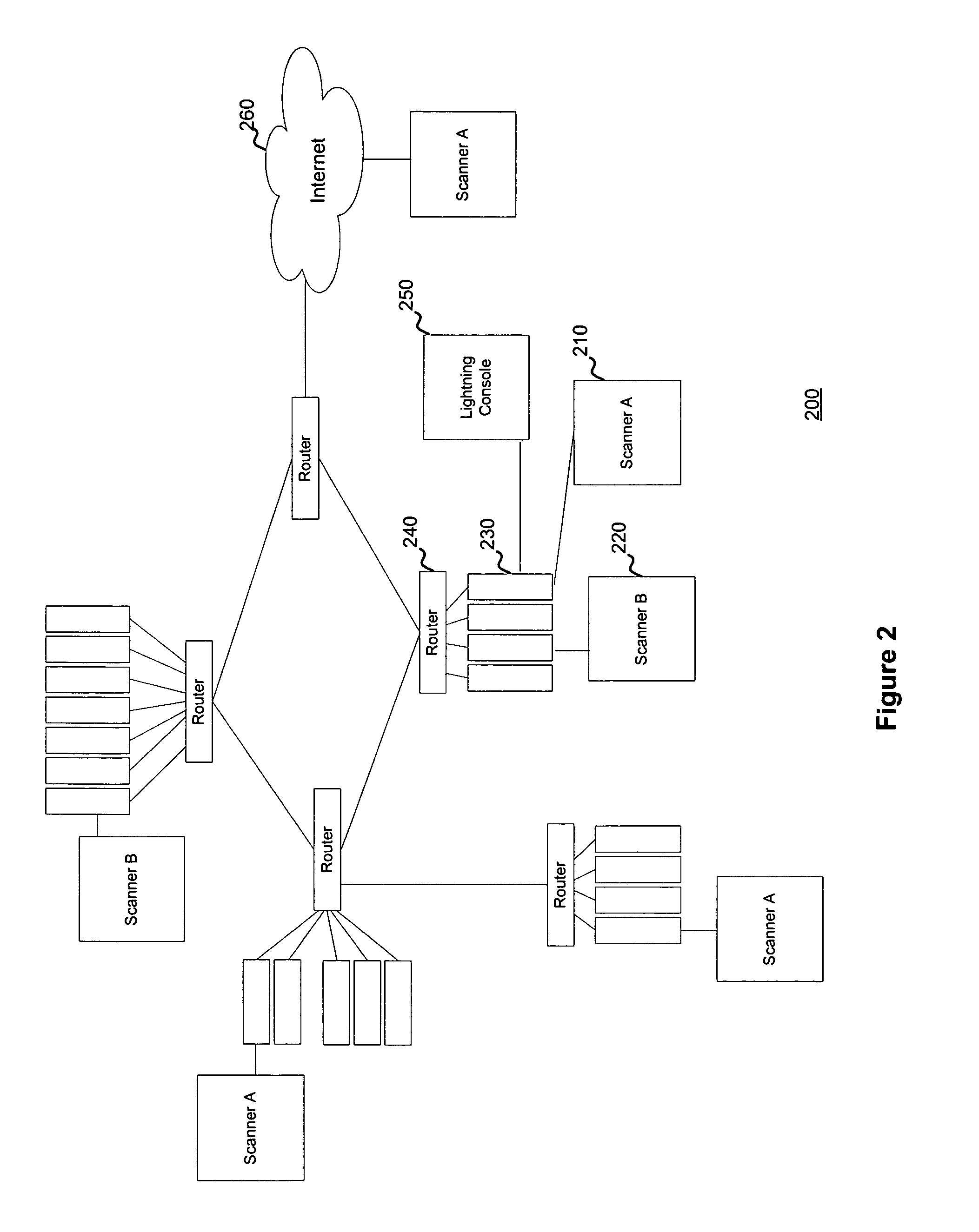
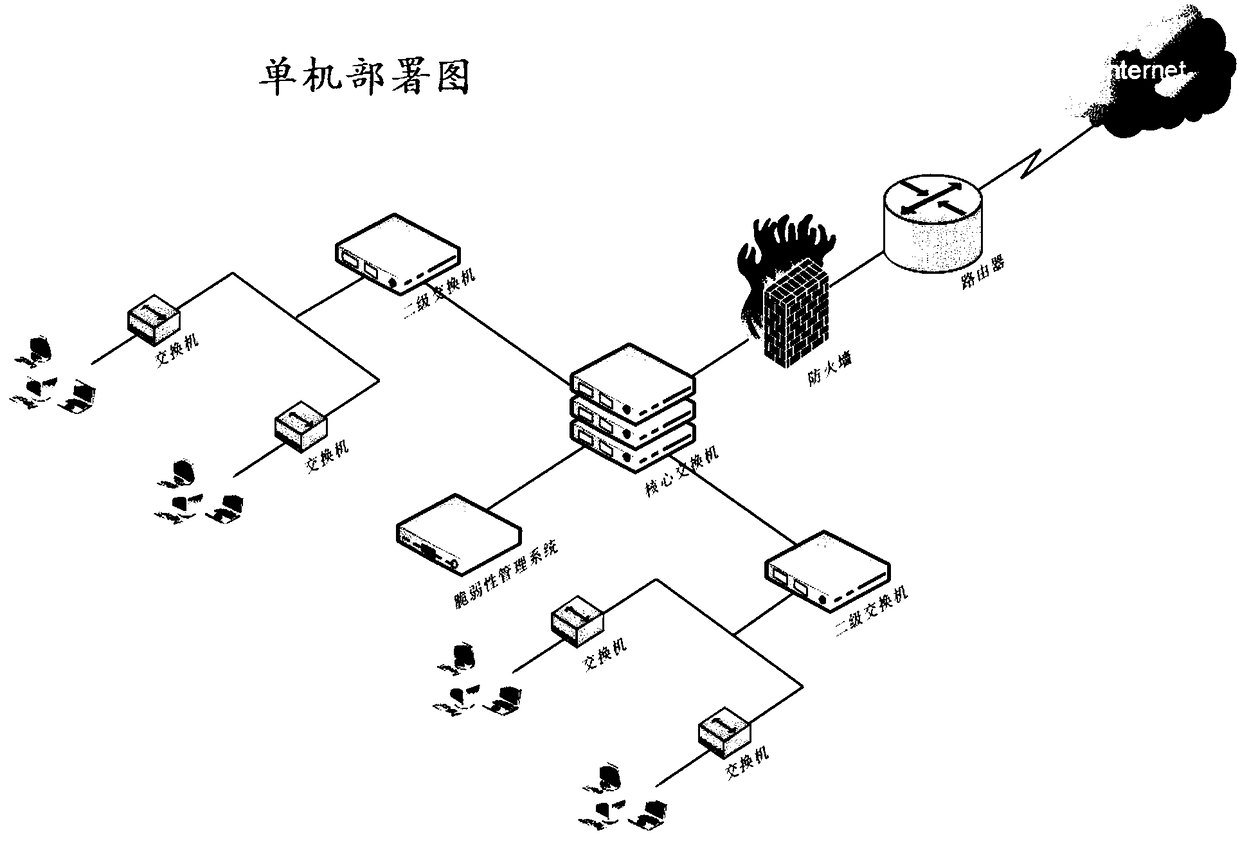
Systems and methods to manage multiple vulnerability scanners distributed across one or more networks using a distributed security management system, herein called a Lightning Console. By distributing multiple scanners across a network, the work load of each scanner may be reduced to significantly reduce the impact on the network routing and switching infrastructure. In addition, scanners may be placed directly behind firewalls for more thorough scanning. Further, scanners may be placed closer to their scanned networks. By placing vulnerability scanners closer, the actual scanning traffic does not cross the core network switch and routing fabric, thereby avoiding potential network outages due to scanning activity. In addition, the closer distance of the scanners to the scanned targets speeds scan times by reducing the distance that the packets must traverse.
Owner:TENABLE INC
Deep learning-based network intrusion detection and vulnerability scanning method and devices
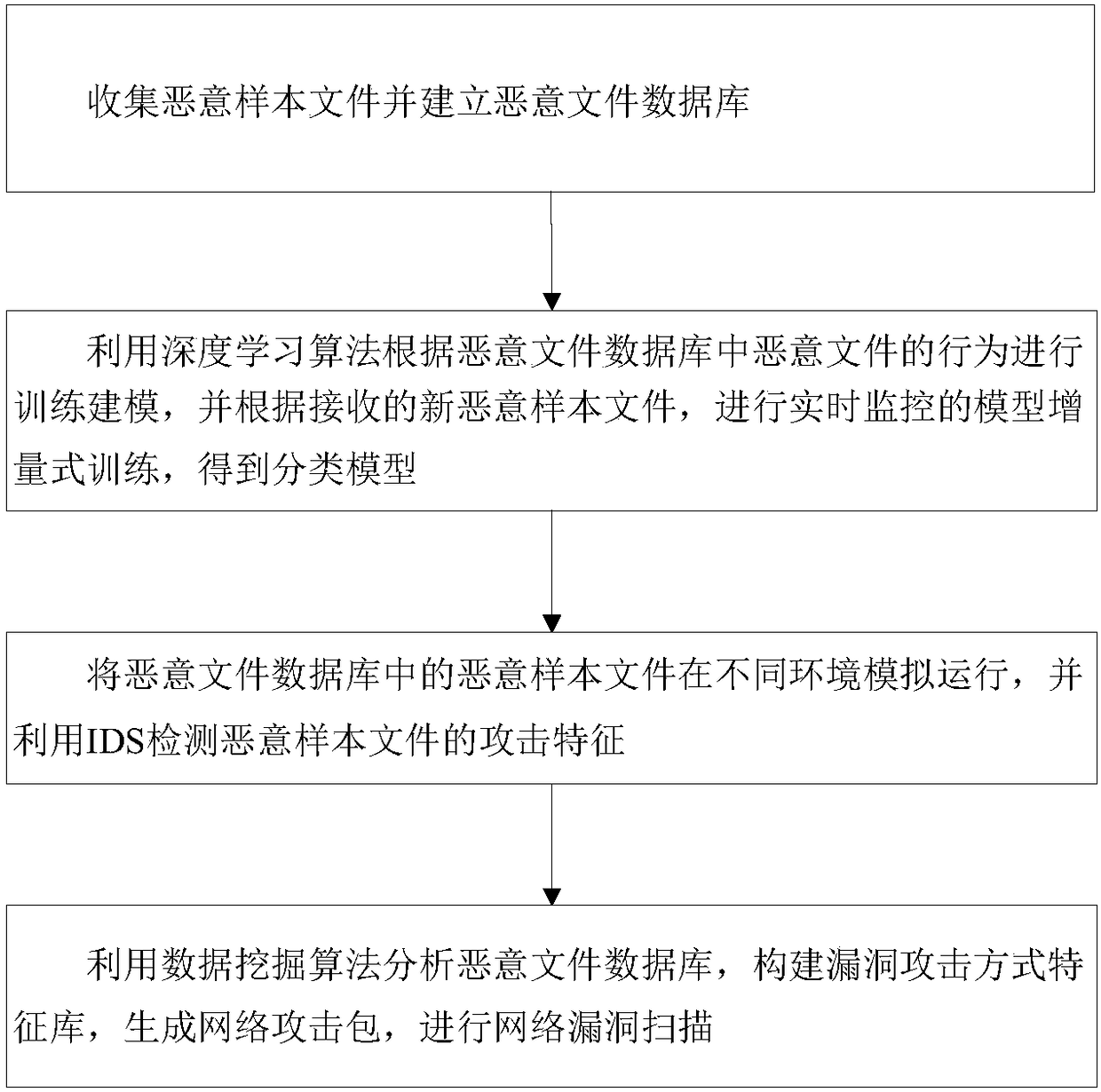
The invention discloses a deep leaning-based network intrusion detection and vulnerability scanning method and devices. The method comprises the steps of collecting malicious sample files and buildinga malicious file database; performing training modeling according to behaviors of malicious files in the malicious file database by using a deep learning algorithm, performing real-time monitored model incremental training according to received new malicious sample files, so as to obtain classified models; simulating and running the malicious sample files in the malicious file database in different environments, and detecting an attack characteristic of the malicious sample files by using IDS; and analyzing the malicious file database by using a data mining algorithm, building a vulnerabilityattack manner characteristic library, generating a network attack package, and scanning network vulnerabilities.
Owner:JINING POWER SUPPLY CO OF STATE GRID SHANDONG ELECTRIC POWER CO +1
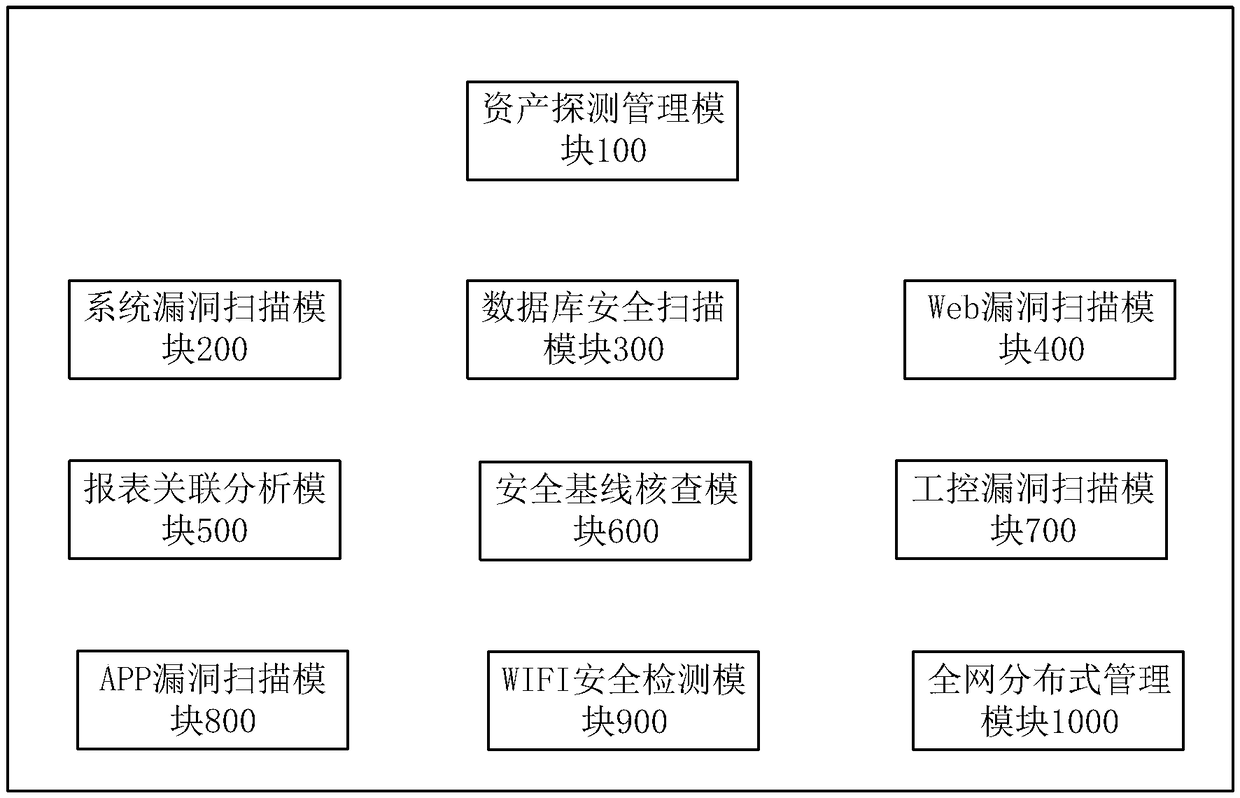
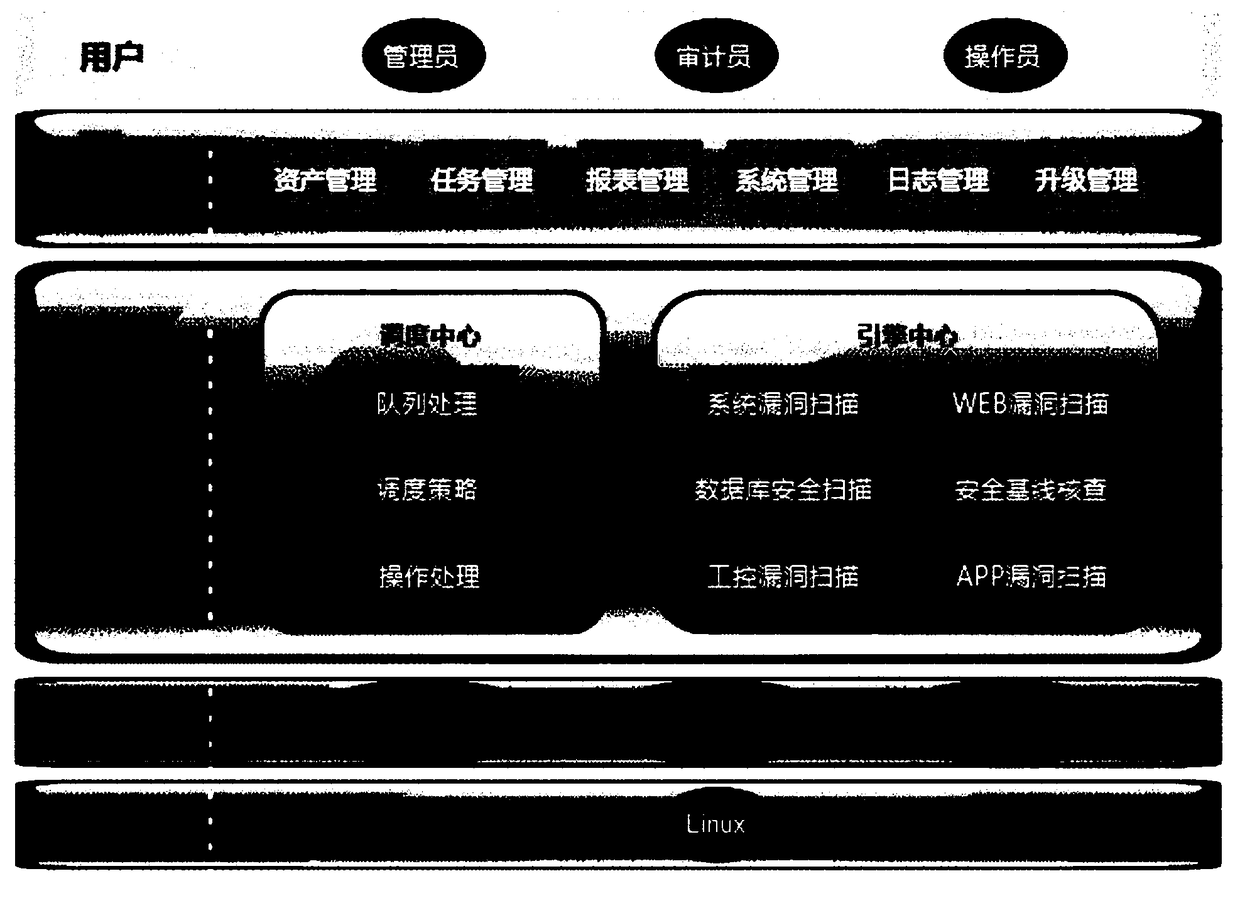
Vulnerability management system based on multi-engine vulnerability scanning association analysis
ActiveCN108737425AMeet safety construction requirementsEfficient and accurate executionTransmissionVulnerability managementOperational system
The invention provides a vulnerability management system based on multi-engine vulnerability scanning association analysis. The vulnerability management system comprises: an asset detection managementmodule used for detecting asset information in a scanning network; a system vulnerability scanning module used for performing vulnerability scanning and analysis on a network device, an operating system, application service and a database according to the asset information, and supporting intelligent service identification; a Web vulnerability scanning module used for automatically parsing data according to the asset information, scanning the data, verifying a discovered WEB vulnerability, and recording a test data packet discovered by vulnerability scanning; a database security scanning module; a security baseline verification module; an industrial control vulnerability scanning module; an APP vulnerability scanning module; a WIFI security detection module; a report association analysismodule; and a whole-network distributed management module. The vulnerability management system provided by the invention can perform association analysis on a detection result and a compliance libraryof information security level protection to generate a level protection evaluation report that meets the specification requirements, and the security requirements of different customers are comprehensively met.
Owner:北京凌云信安科技有限公司
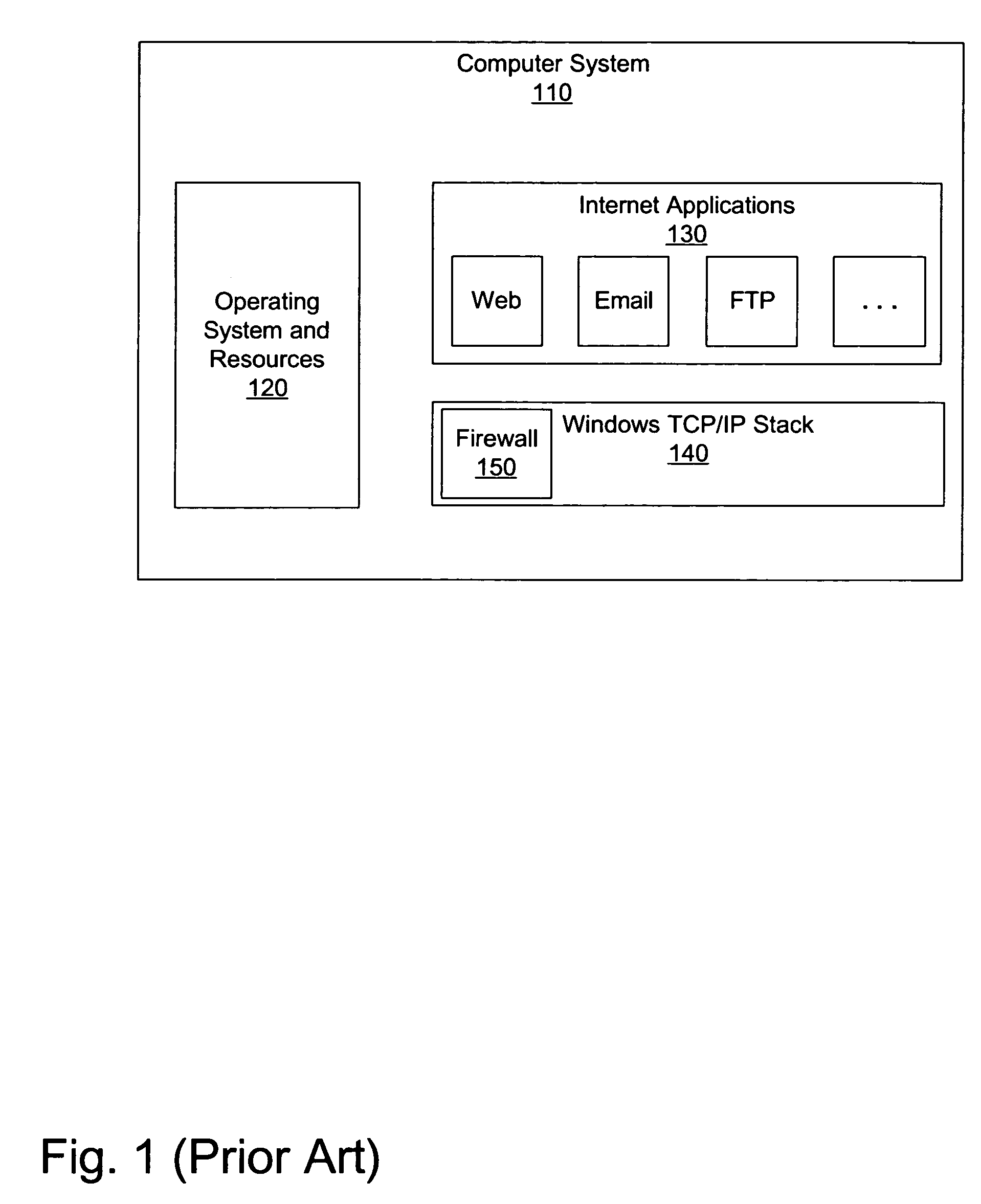
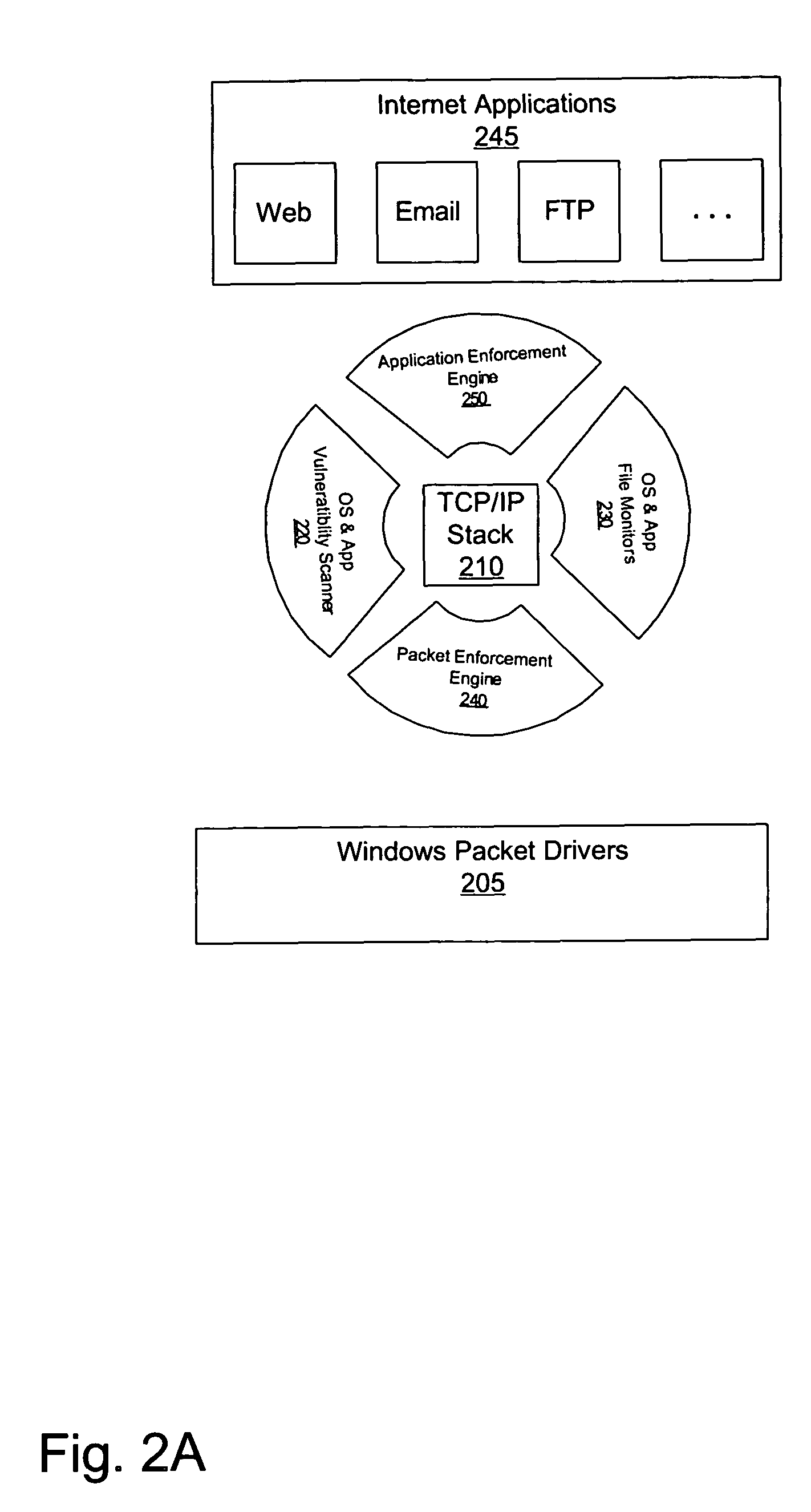
Method and apparatus to secure a computing environment
InactiveUS7797752B1Ensure integrityMemory loss protectionError detection/correctionOperational systemComputerized system
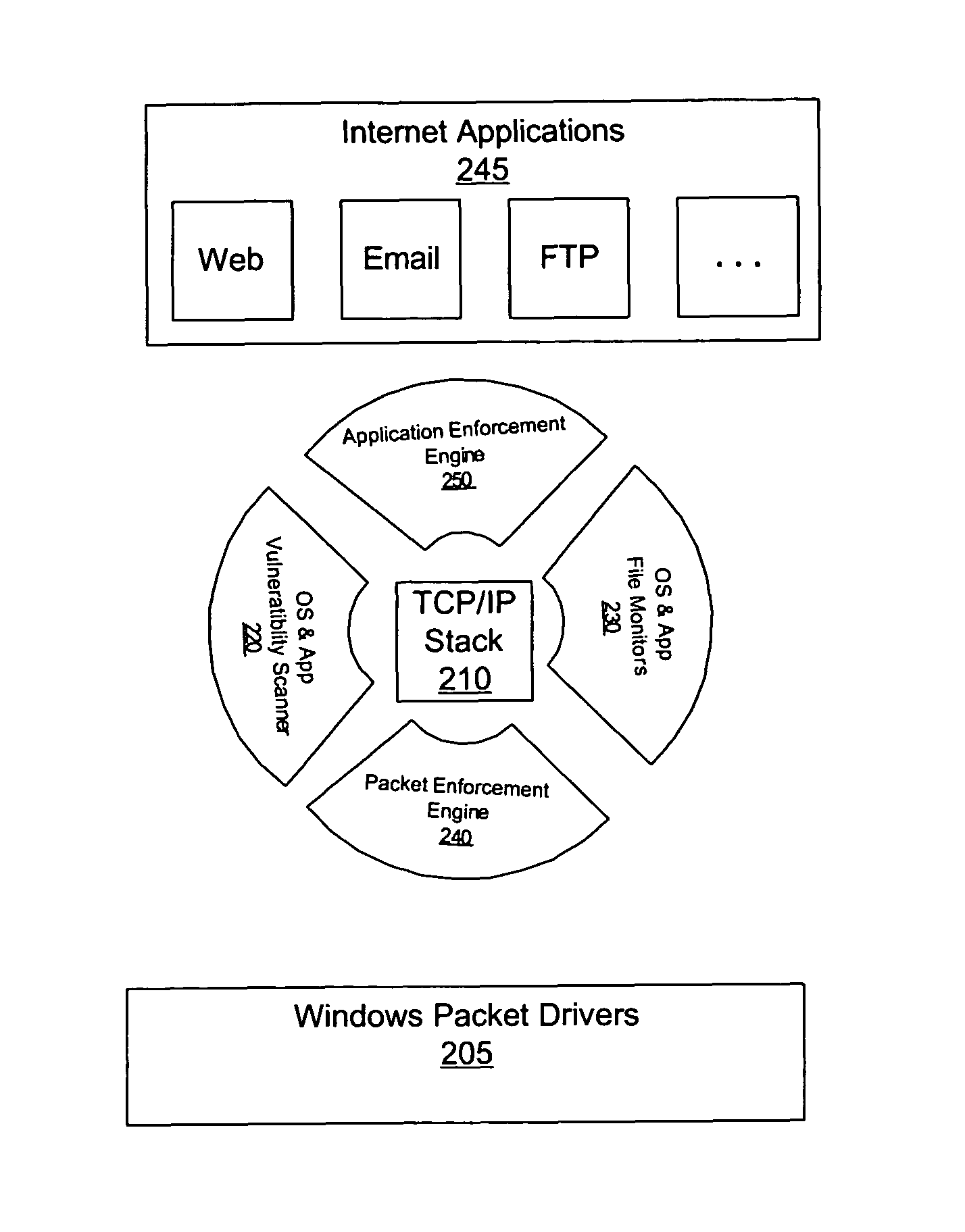
A method and apparatus for a surround security system is provided. The surround security system is embodied on a computer readable medium and includes a packet enforcement engine to screen packets to and from the network and a TCP / IP stack, an application enforcement engine to screen packets to and from the TCP / IP stack and applications on the computer system, a file monitor to verify integrity of files on the computer system and a vulnerability scanner to ensure that the computer system complies with a set level of security. The surround security system provides security which protects accesses through the TCP / IP stack for applications, and an operating system of the computer system.
Owner:RPX CORP
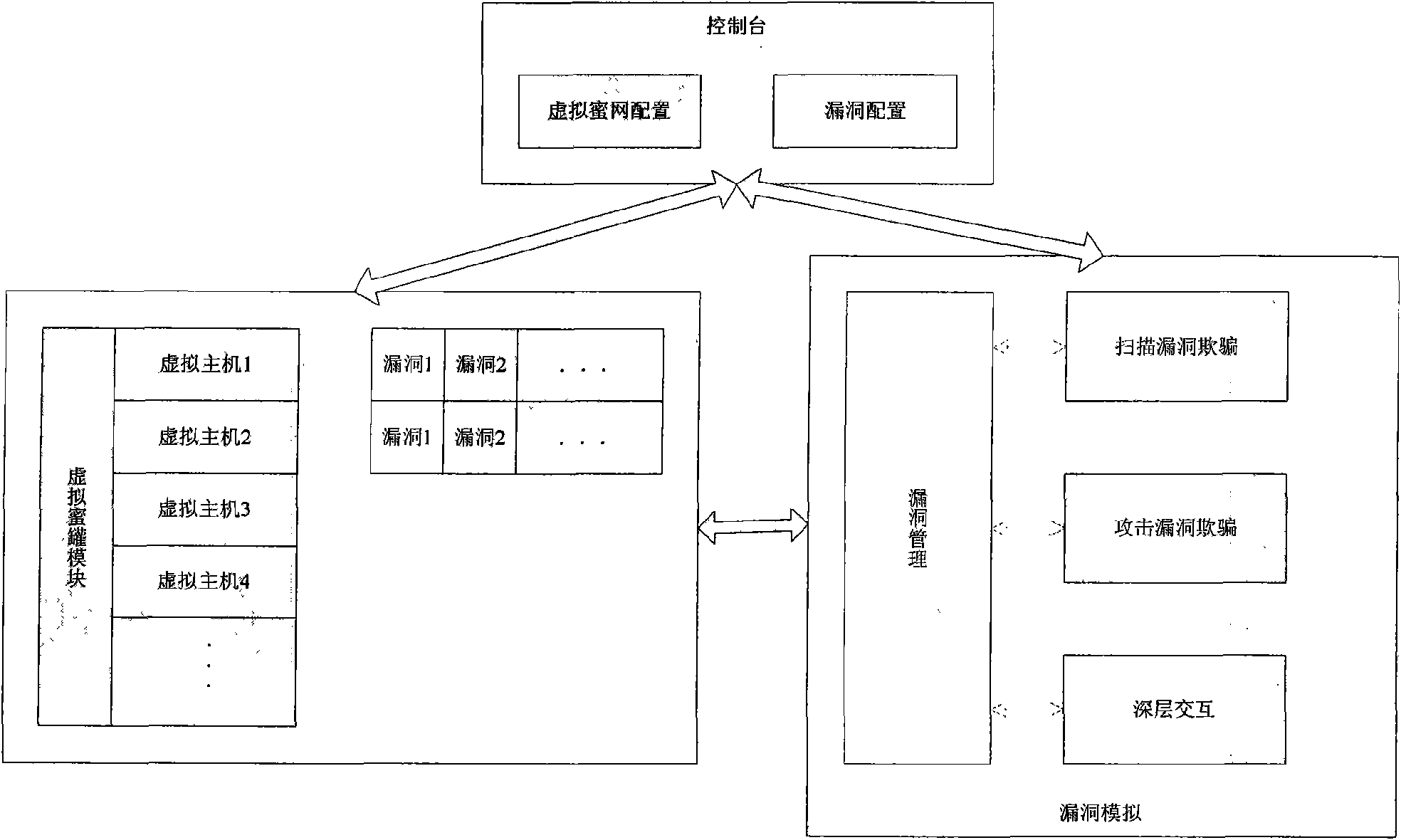
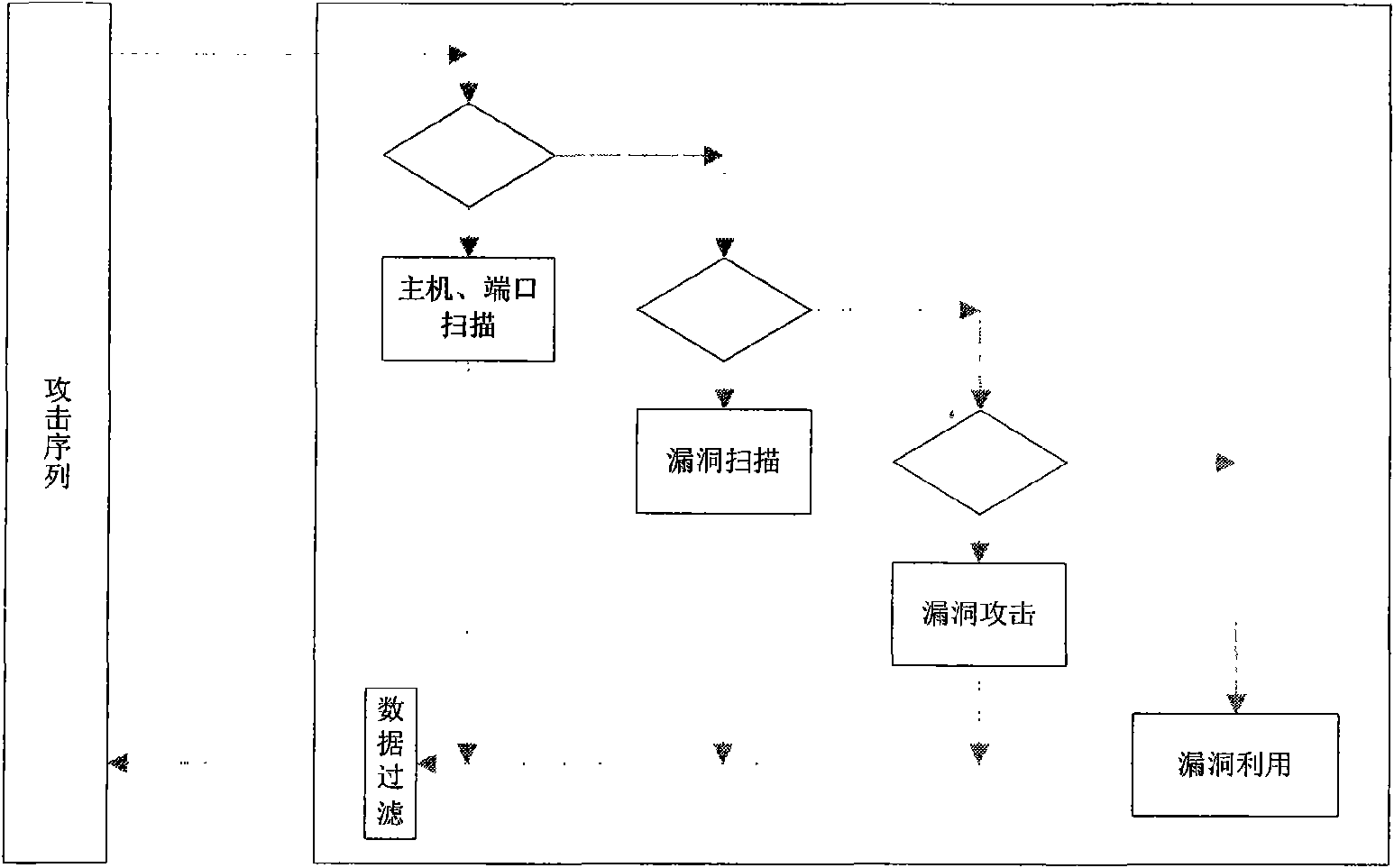
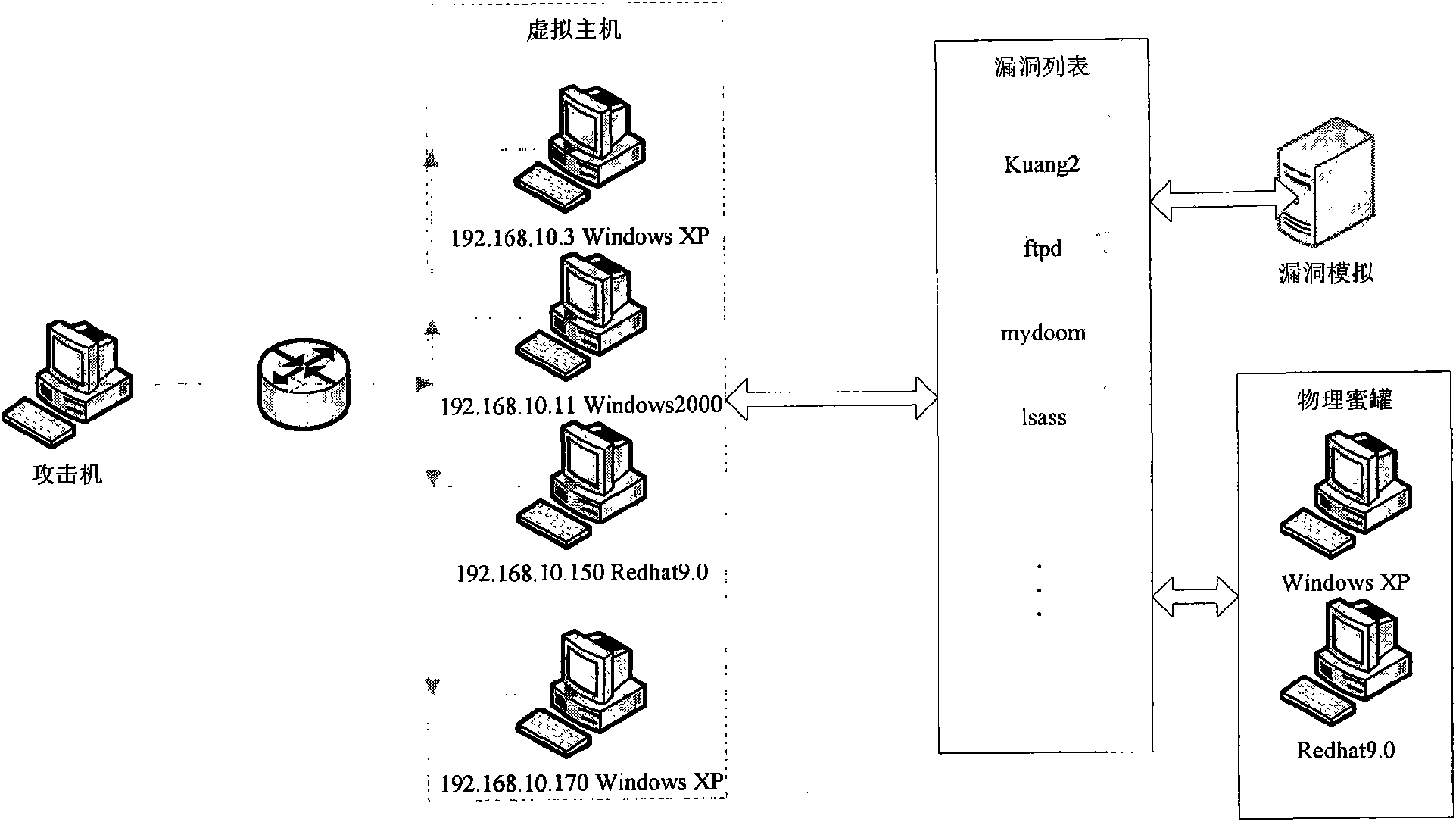
Vulnerability simulation overload honeypot method
InactiveCN101567887AAdd interactive functionComplete Attack DataData switching networksControl powerOperating system
The present invention discloses a vulnerability simulation overload honeypot method which comprises a host computer, a port scanning deception simulating module, a vulnerability scanning deception simulating module, a vulnerability scanning deception simulating module, a vulnerability attach deception simulating module, a data auditing module and a vulnerability utilizing module. When the attach sequence arrives at the simulated honeypot, a simulated honeypot system is used for processing according to the situation. When an attacker executes vulnerability scanning to the virtual host computer, the simulated honeypot responds and processes according to the vulnerability configuration information. Afterwards, these vulnerabilities are used for further attacking. Hereon, the simulated honeypot system transmits the vulnerability attack data flow to a vulnerability honeypot system. The vulnerability utilization attach of the attacker is processed and responded by a vulnerability attack simulating module. Finally, when the attacker successfully obtains the control power through the vulnerability attack, the attack data hereon is transmitted to a physical honeypot module. All attack processes and related data are recorded by a data auditing module for analyzing comprehensively. The method reduces the number of hardware devices in the honeynet and reduces the cost.
Owner:中国人民解放军总参谋部第五十四研究所 +2
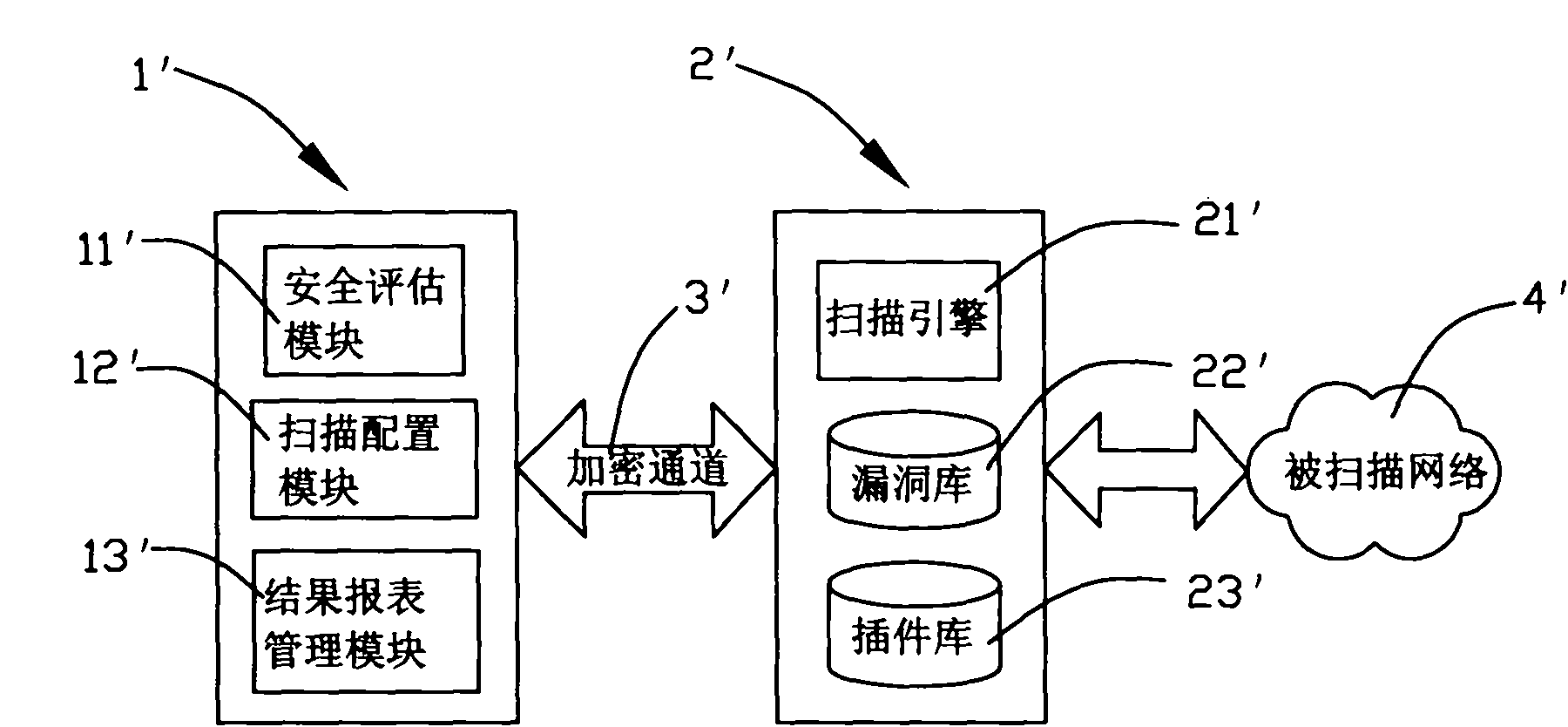
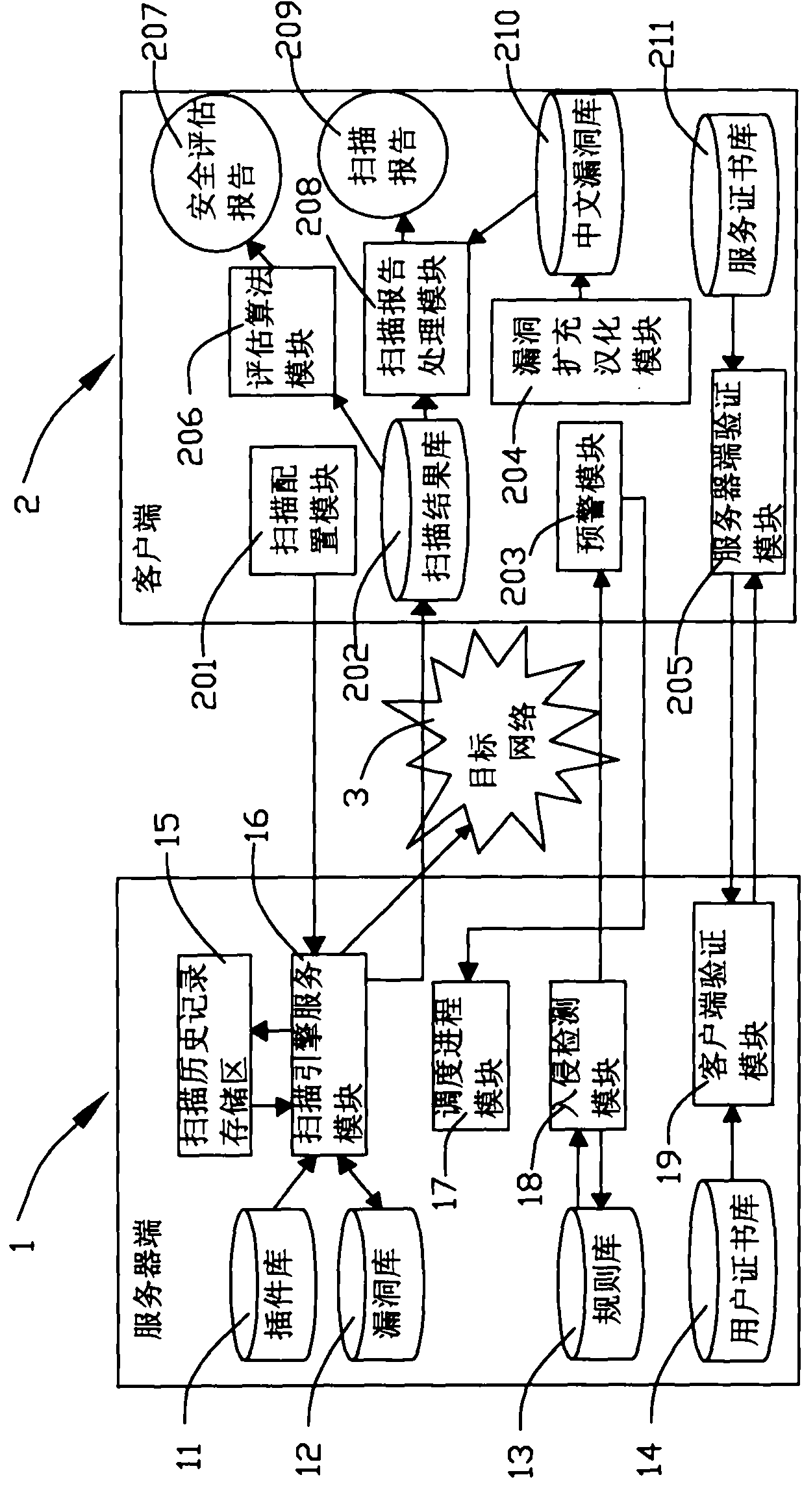
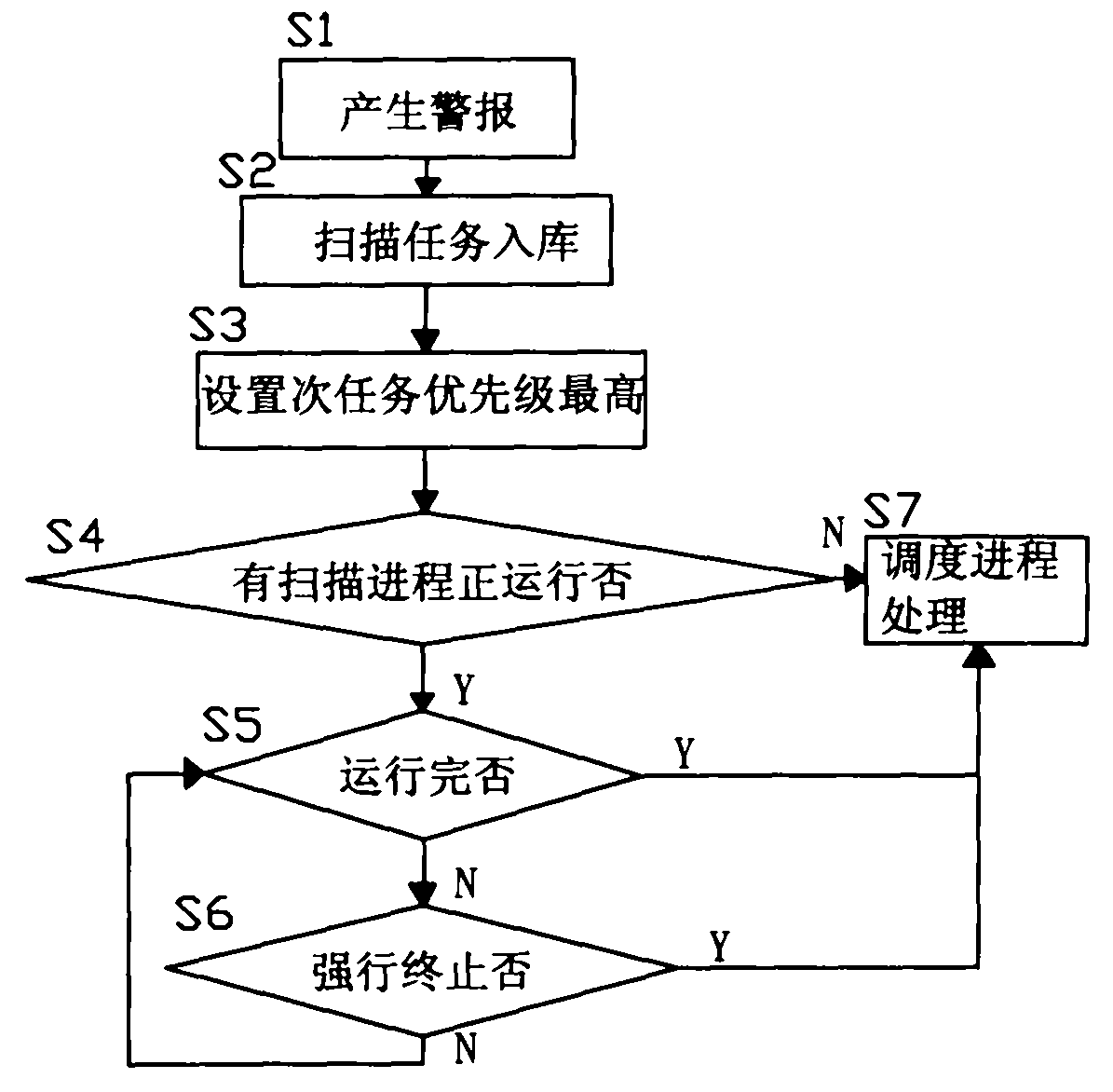
Vulnerability scanning system oriented to safety assessment and processing method thereof
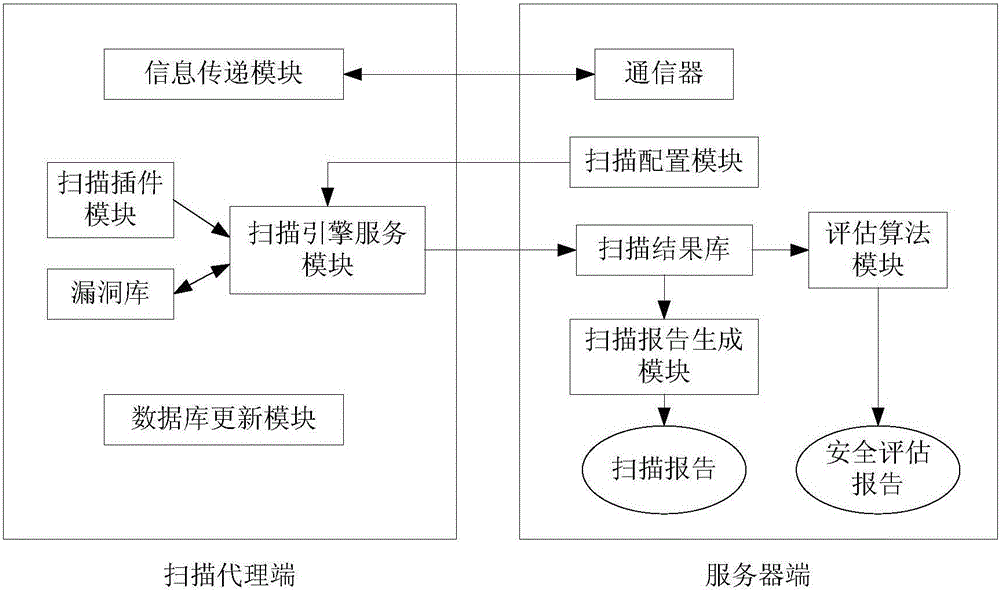
ActiveCN102082659ASafety assessment results are accurate and authoritativeThe scan results are objectiveData switching by path configurationSecuring communicationScheduling functionProcess module
The invention discloses a vulnerability scanning system oriented to safety assessment and a processing method thereof. The system provided by the invention comprises a server side and a client side which are of a C / S (client / server) structure; the server side operates on a Unix or Linux platform, and the client side operates on a Windows platform; the server side comprises a client side verification module, a scanning engine service module, a scheduling process module, an invasion detecting module and the like; the client side comprises a server verification module, a scanning configuration module, a pre-warning module, an evaluation algorithm module, a scanning report processing module, a vulnerability expansion and Chinesization module and the like; and according to the invention, the vulnerability scanning system and the invasion detection system are combined, the pre-warning function and scheduling function are introduced, thus the system can carry out vulnerability scanning and safety assessment selectively and purposively according to the requirements of users, and a relatively objective and accurate vulnerability scanning report forms.
Owner:XIAMEN MEIYA PICO INFORMATION
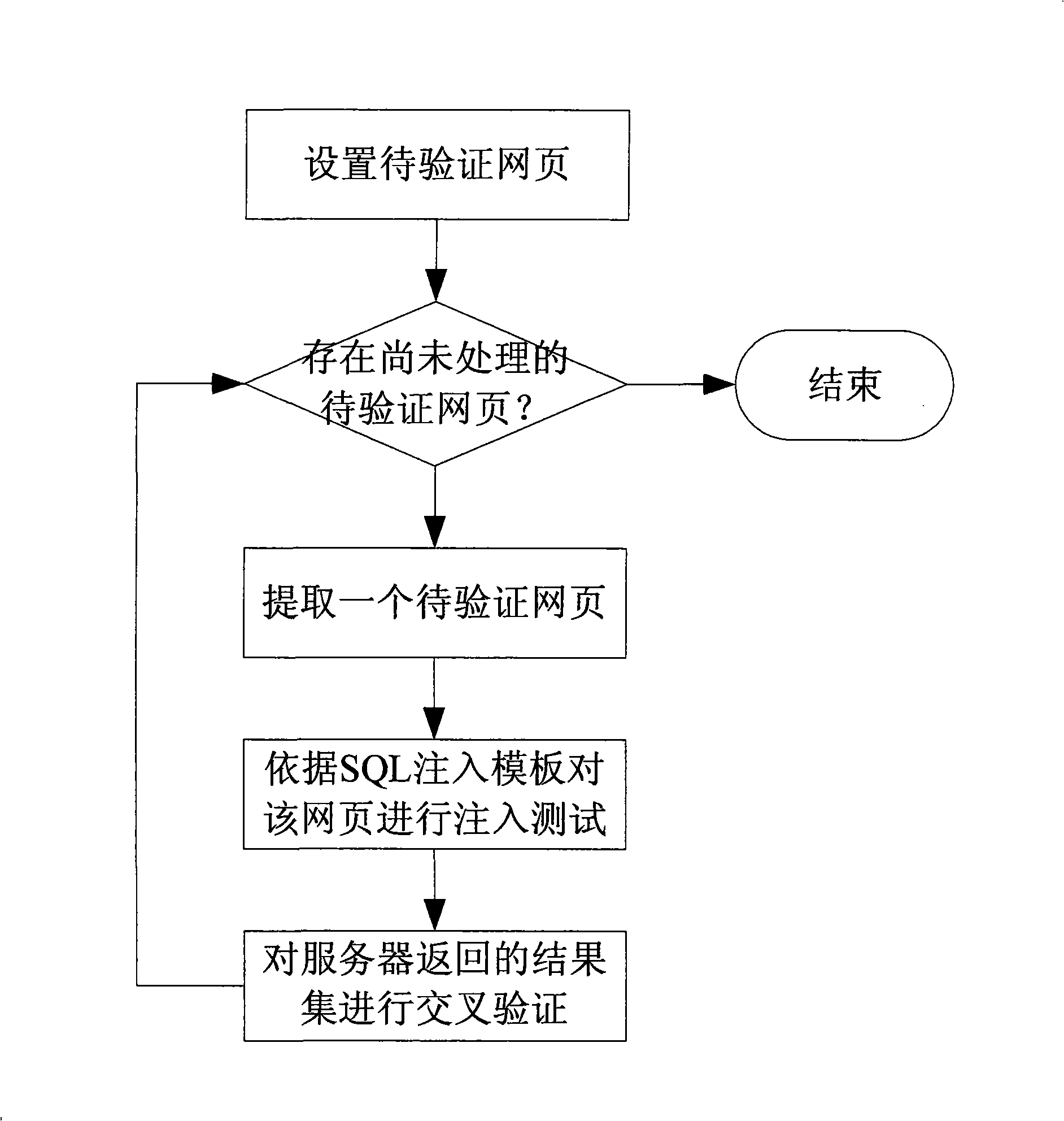
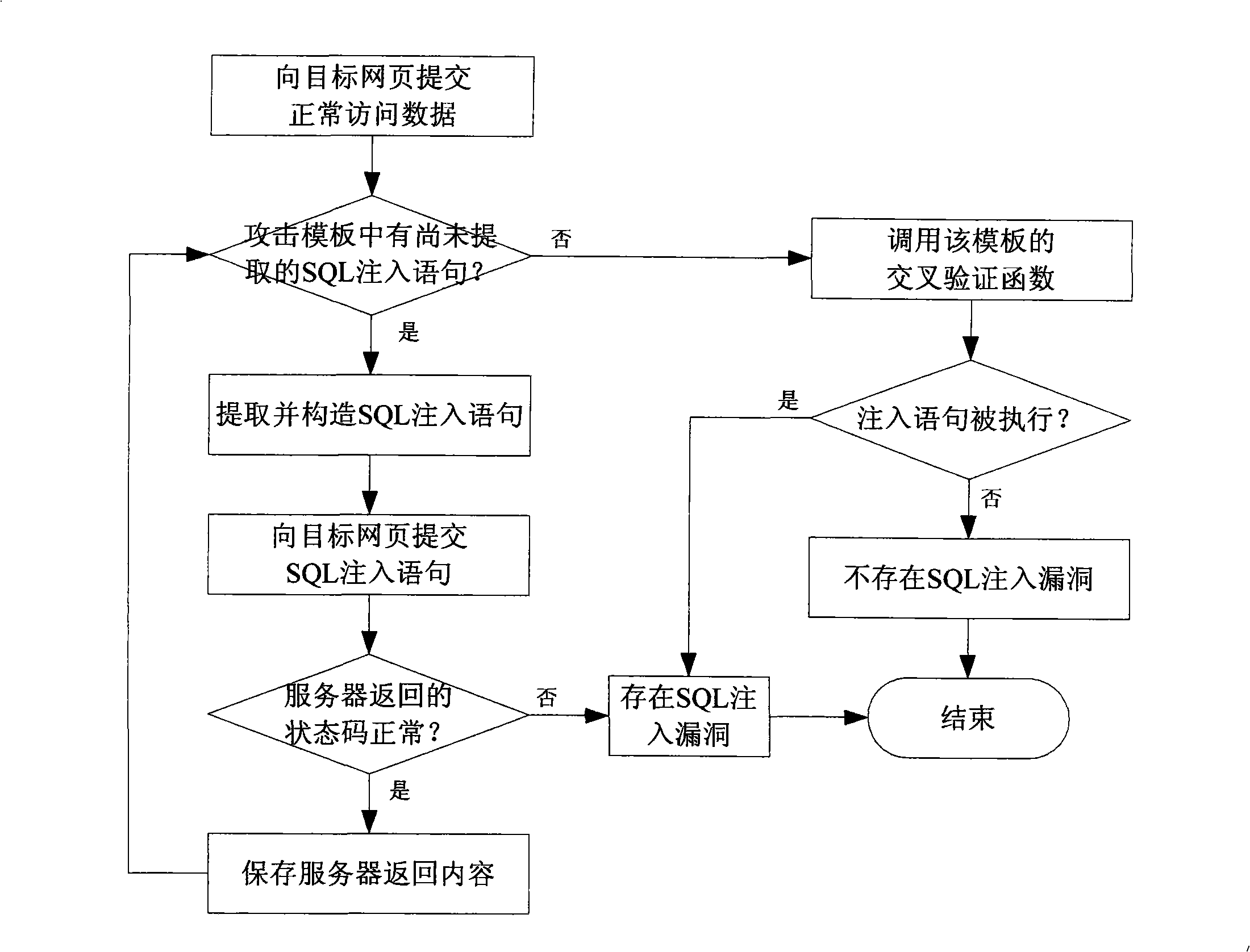
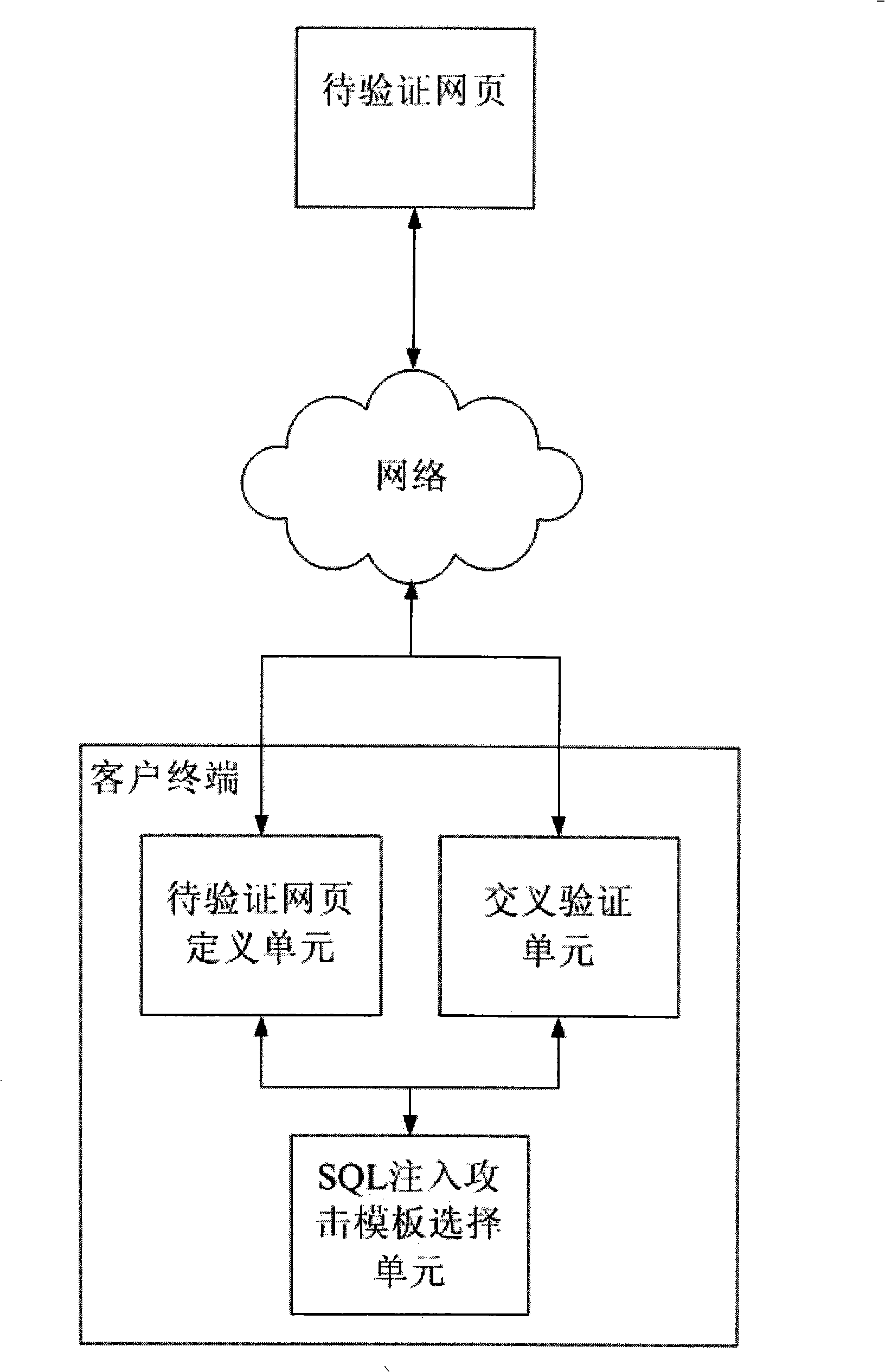
Detection method and system for SQL injection loophole
The invention discloses a key technique-SQL injection vulnerability detection technique of a host vulnerability scanning system as one important product for network security. The SQL injection vulnerability detection technique is characterized by submitting normal access request data and different types of SQL injection data to a server, receiving results returned by the server, then cross-comparing the returned results of different requests, and further determining exists of SQL injection vulnerabilities from the processing of submitted data by the server according to the compared results. To-be-certified website addresses are defined by means of website crawler, browser plug-in and manual input. One or a plurality of attacking templates of four different types of attacking templates can be selected to detect exists of SQL injection vulnerabilities on the to-be-certified websites. And the exists of SQL injection vulnerabilities during processing the user-submitted data by the server can be judged through cross-comparing the returned results of the normal access requests and SQL injection statements, under the condition that the server shields error information.
Owner:BEIJING VENUS INFORMATION TECH
System and method for three-dimensional visualization of vulnerability and asset data
ActiveUS8549650B2Simplify the management processMemory loss protectionError detection/correctionGraphicsVulnerability scanning
The system and method for three-dimensional visualization of vulnerability and asset data described herein may provide a management console that integrates various active vulnerability scanners, various passive vulnerability scanners, and a log correlation engine distributed in a network. In particular, the management console may include a three-dimensional visualization tool that can be used to generate three-dimensional visualizations that graphically represent vulnerabilities and assets in the network from the integrated information that management console collects the active vulnerability scanners, the passive vulnerability scanners, and the log correlation engine distributed in the network. As such, the three-dimensional visualization tool may generate three-dimensional representations of the vulnerabilities and assets in the network that can be used to substantially simplify management of the network.
Owner:TENABLE INC
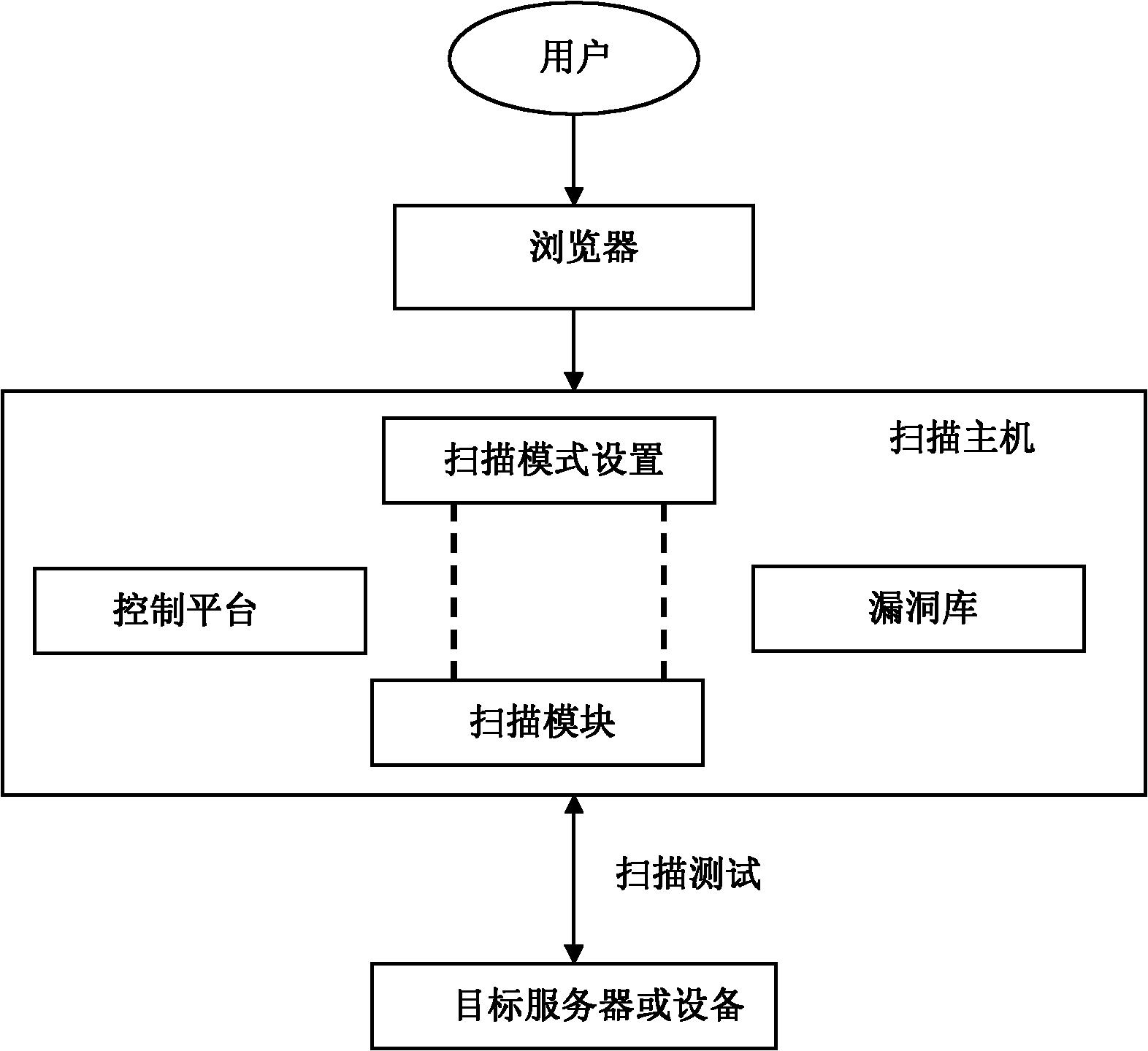
Web vulnerability scanning method and device based on infiltration technology
The invention provides a web vulnerability scanning method and device based on an infiltration technology. The scanning device comprises a client, a Web browser, a scanning host and a Web server which are sequentially connected and is characterized in that the scanning host comprises a control platform, a scanning mode setting module, a scanning module and a vulnerability library, a scanning modeis set in the scanning mode setting module by a user through the control platform, a scanning depth is extended from a first-class scanning to a second-class scanning or even a deeper scanning in thescanning module, and finally, a target website is scanned by using the vulnerability library and a test report is given. By virtue of the complete crawling-based website security vulnerability scanning method, improvements on a further treatment (strengthening the depth of detection) after vulnerabilities are detected and the flexibility of a detection mode are realized, and a comprehensive and effective solution is provided for system / network vulnerability scanning and processing.
Owner:WUXI TONGWEI TECH
Electric power information network vulnerability threat evaluation model establishment method faced to electric power CPS risk evaluation and evaluation system based on the model
ActiveCN105763562AImprove accuracyImprove timelinessPlatform integrity maintainanceTransmissionDistributed structureStructure of Management Information
The invention discloses an electric power information network vulnerability threat evaluation model establishment method faced to electric power CPS risk evaluation and an evaluation system based on the model, the model selects three groups of security vulnerability evaluation factors including vulnerability distribution threat degree, access approach and utilization complexity; an analytic hierarchy process is adopted to establish a vulnerability threat degree evaluation model, and a parameter construction method is provided; on the basis of quantitative evaluation, the evaluation result defines a vulnerability threat level, and the objectivity of quantitative evaluation and visibility of qualitative evaluation are considered; and the system related to the invention comprises a vulnerability detection part and a server part which adopt distributed structure. According to the invention, a vulnerability scanning system and a security area of the electric power information network are combined, an electric power information network vulnerability threat evaluation algorithm based on CVSS and analytic hierarchy process is adopted to perform vulnerability threat evaluation, so that the system can be safer and more accurate for performing vulnerability scanning and safety evaluation on the electric power information network.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
Script-based website vulnerability scanning method and system
The invention relates to the field of network application security, and provides a script-based website vulnerability scanning method and system. The script-based website vulnerability scanning method comprises the steps of setting a website URL to be scanned, selecting security vulnerability types needing to be detected by a website, starting a scanning engine module, constructing and sending an HTTP request to the URL needing to be detected, receiving an HTTP response, storing all data into the scanning engine module, and respectively executing corresponding vulnerability detection script modules according to the security vulnerability types selected by a user. The website vulnerability scanning system comprises the scanning engine module and the vulnerability detection script modules. According to the script-based website vulnerability scanning method and system, vulnerability detection logic is separated from a scanning engine, the coupling degree of the vulnerability detection logic and the scanning engine is reduced, the vulnerability detection logic is achieved through a vulnerability detection script, and the scanning engine has the general basic function not special for vulnerabilities of a certain kind.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Method and device for assigning large-scale vulnerability scanning task
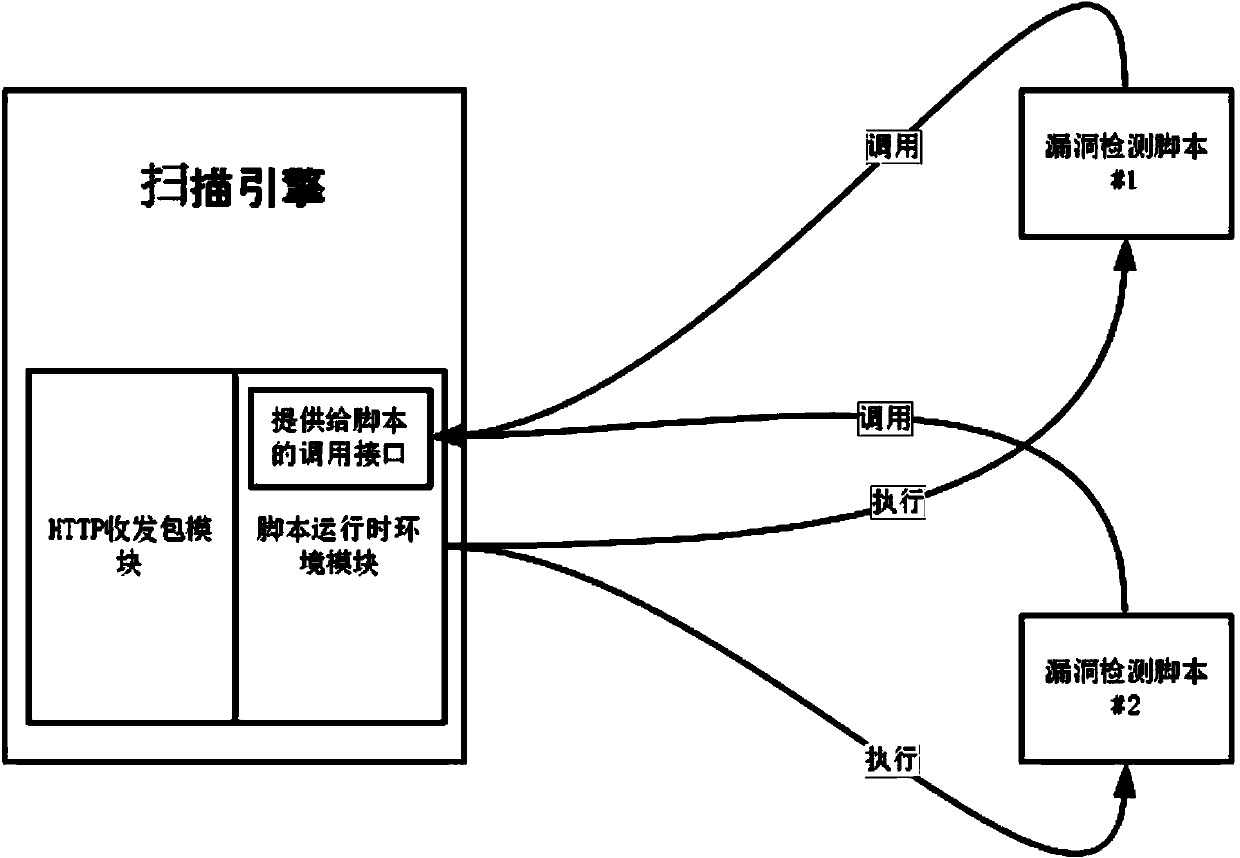
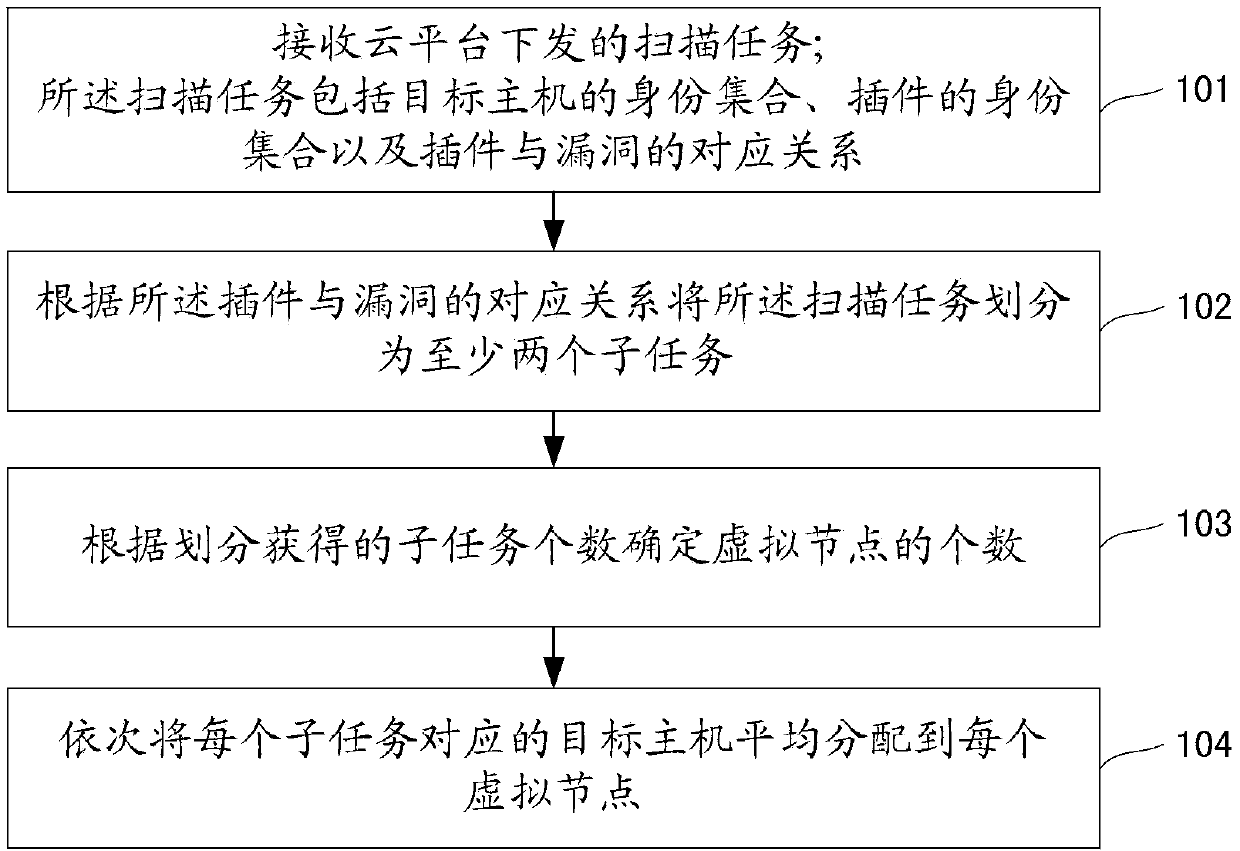
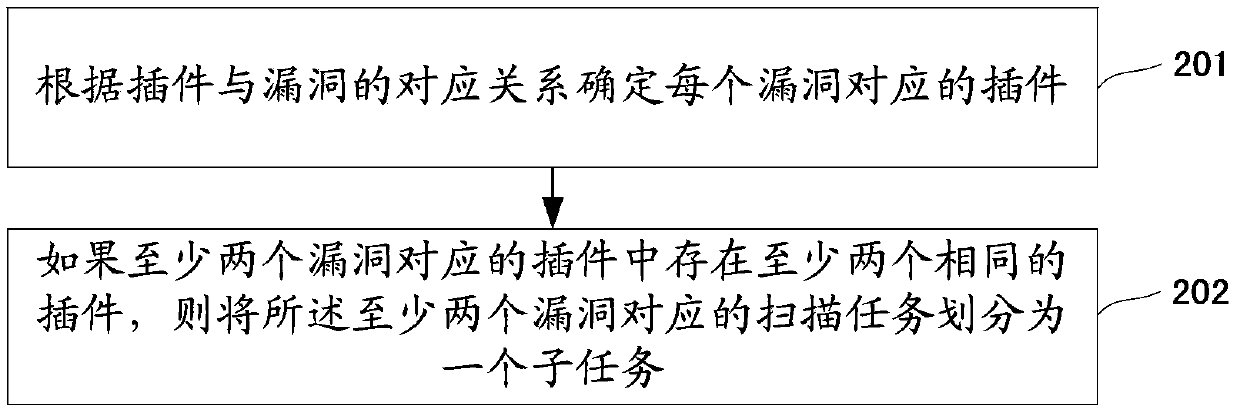
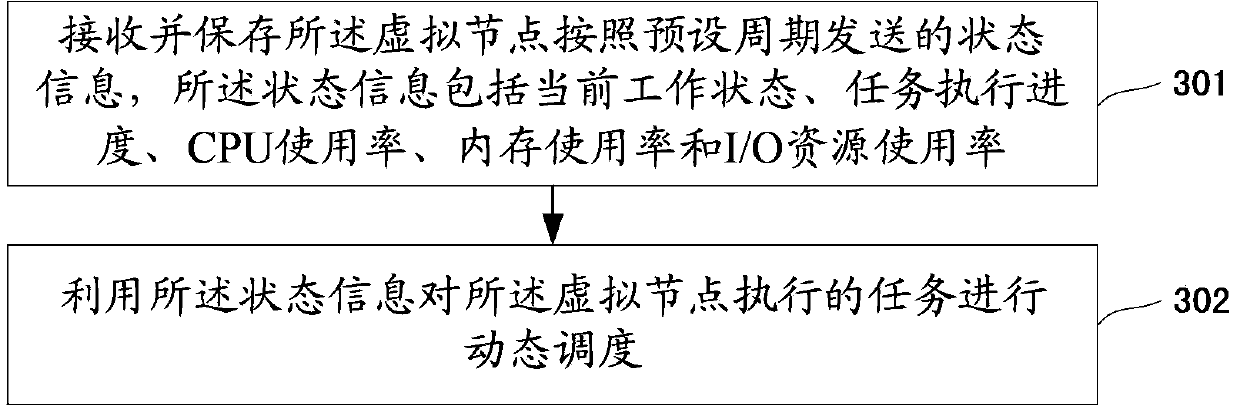
ActiveCN103870334AImprove scanning efficiencyImprove rationalityResource allocationTransmissionNODALOperating system
The invention discloses a method and a device for assigning a large-scale vulnerability scanning task. The method comprises the following steps: receiving a scanning task issued by a cloud platform, wherein the scanning task comprises the identity set of target hosts, the identity set of a plug-in and a corresponding relation of the plug-in and vulnerability; partitioning the scanning task into at least two sub-tasks according to the corresponding relation of the plug-in and vulnerability; determining the number of virtual nodes according to the number of partitioned sub-tasks; assigning target hosts corresponding to each sub-task to each virtual node on average in sequence. By adopting the technical scheme of the invention, the scanning task assigning rationality and the vulnerability scanning efficiency are increased.
Owner:CHINA MOBILE COMM GRP CO LTD
Field operation terminal security access protection and detection system
ActiveCN110691064AAchieving the goal of comprehensive protectionImprove security levelTransmissionCollection systemInformation security
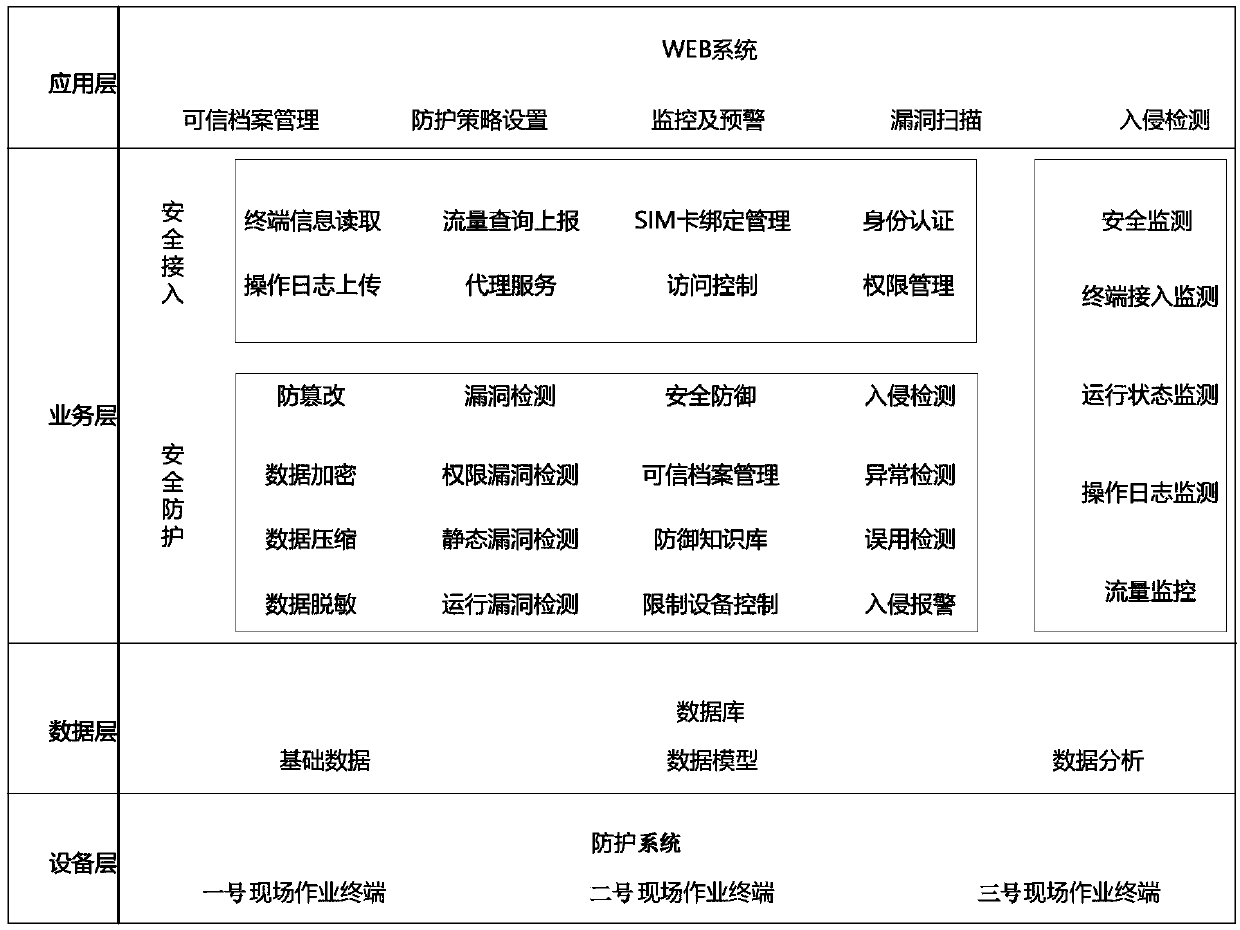
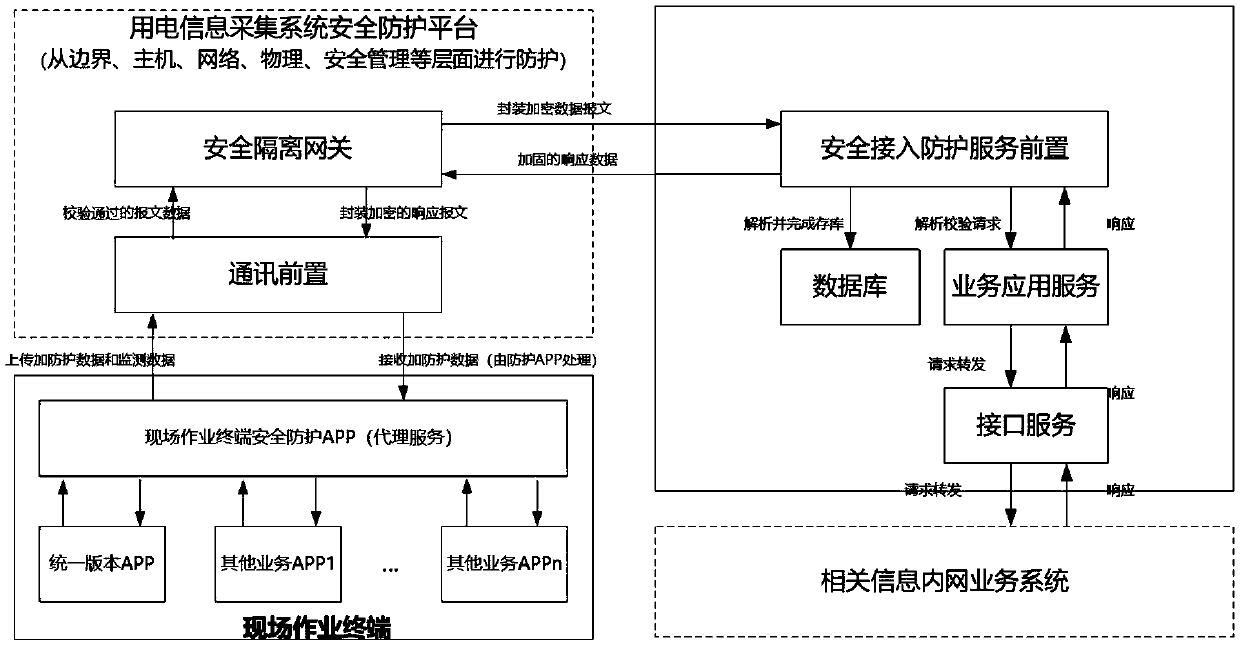
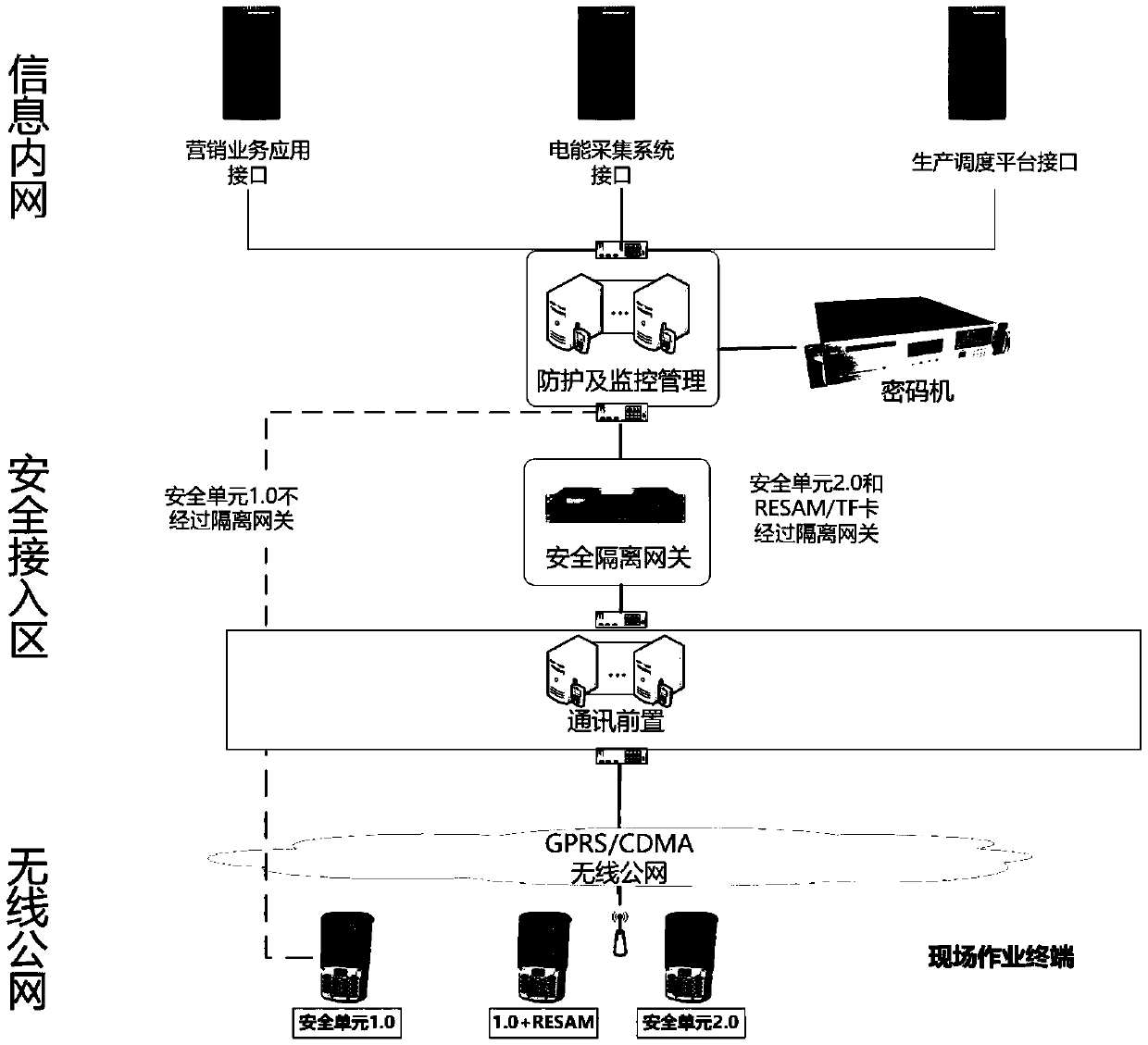
The invention discloses a field operation terminal security access protection and detection system, which comprises an equipment layer, a data layer, a service layer and an application layer; the access layer is used for the field operation terminal to access the protection system; the data layer is used for storing basic data, constructing a data model and analyzing real-time data; the service layer is composed of a security access part, a security protection part and a security monitoring part; the application layer is composed of a unified management platform of a WEB terminal with trustedarchive management, protection strategy setting, monitoring and early warning, vulnerability scanning and intrusion detection service functions; safety protection is carried out from the aspects of field operation terminals, terminal applications, data and the like, and the comprehensive protection target of information safety of the collection system is achieved; through omnibearing safety management of equipment access, access protection, access monitoring and early warning, multi-dimensional analysis and processing are carried out on a protection main body, a protection strategy, a monitoring mechanism and the like, and the information safety level of the acquisition system is improved.
Owner:STATE GRID CORP OF CHINA +3
Cloud data center real-time risk assessment method based on mainframe log analysis
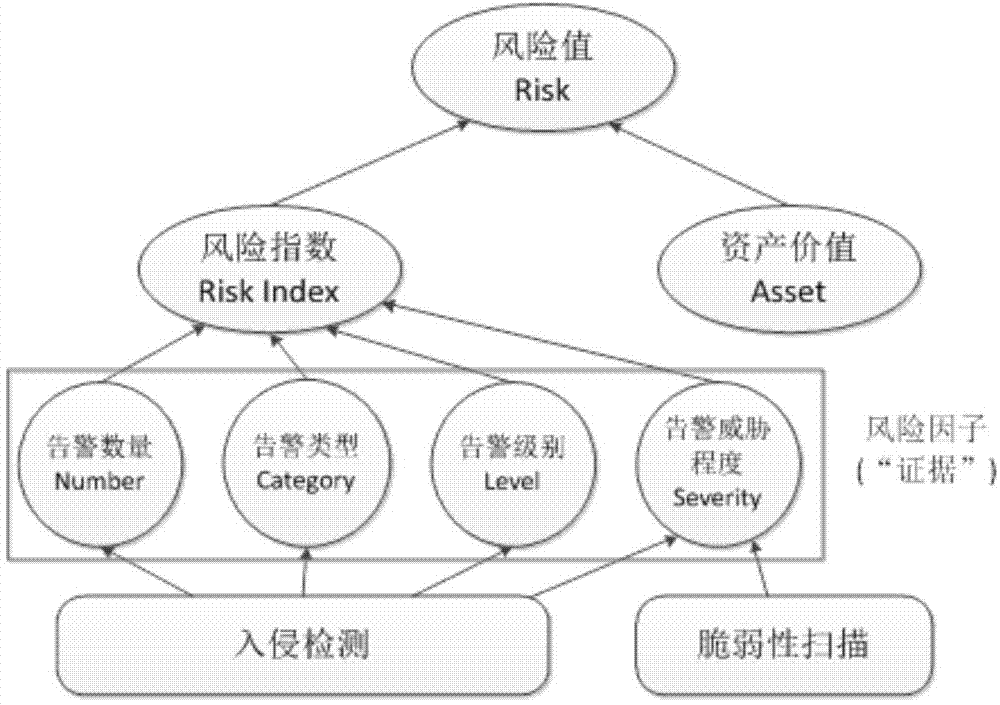
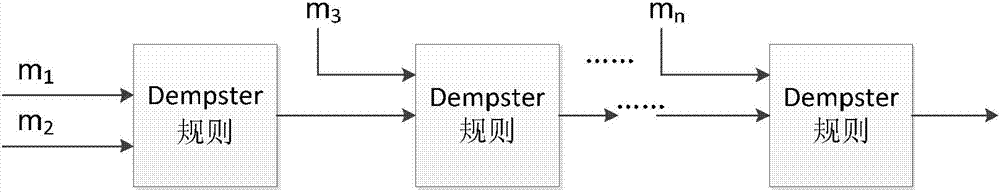
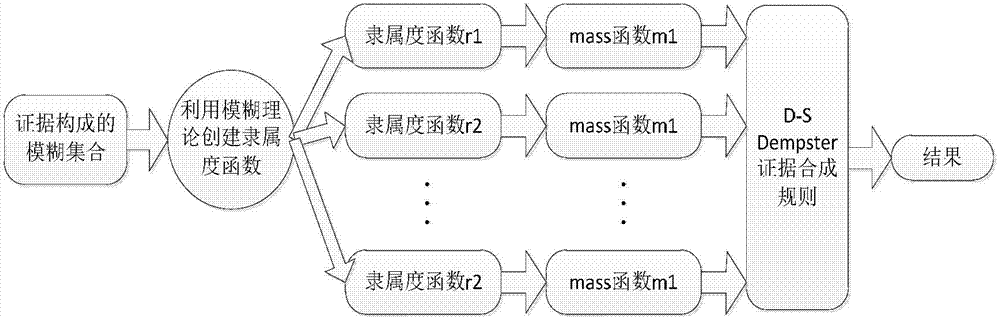
The invention belongs to the technical field of cloud computing and network safety, and in particular relates to a cloud data center real-time risk assessment method based on mainframe log analysis. The method comprises: providing four risk factors, namely alarm quantity, alarm type, alarm type and alarm threat level, influencing an asset risk index based on an intrusion detection system and a vulnerability scanning tool OSSEC of a mainframe log, and using the four risk factors as evidences for assessing the risk situation of asset, combining evidence theory (D-S theory) with thought of fuzzy mathematics, designing DSFM (D-S Fuzzy Mathematic) algorithm, and combining the evidences to obtain the asset risk index RI; combination of the risk index and asset value is the risk value R of the asset; combination of all asset risk values of one data center is the risk value of the data center. Simulated strike experiment shows that the method can be used for assessing the risk of whole cloud data center system in real time, and the obtained assessing result is high in accuracy.
Owner:FUDAN UNIV
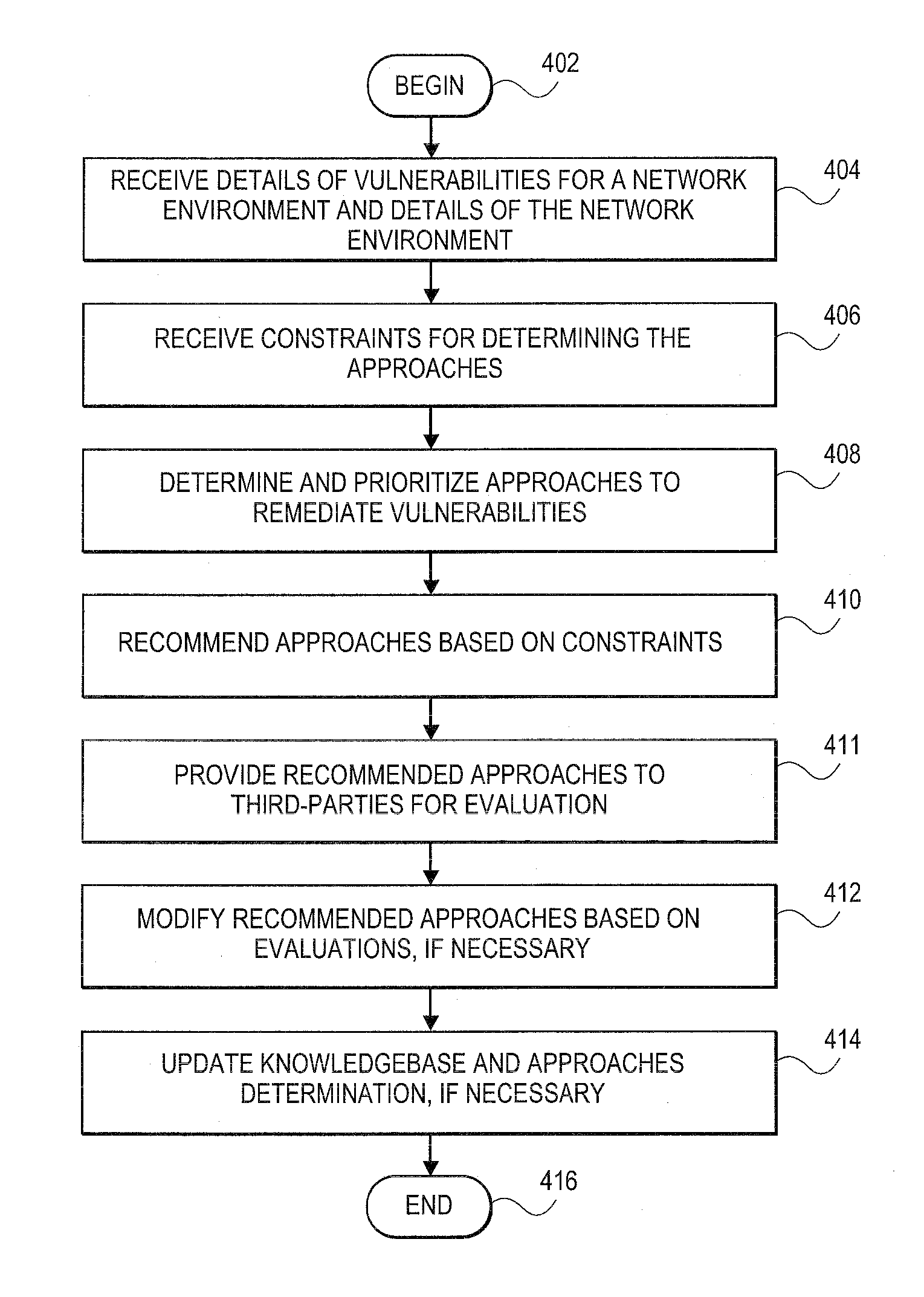
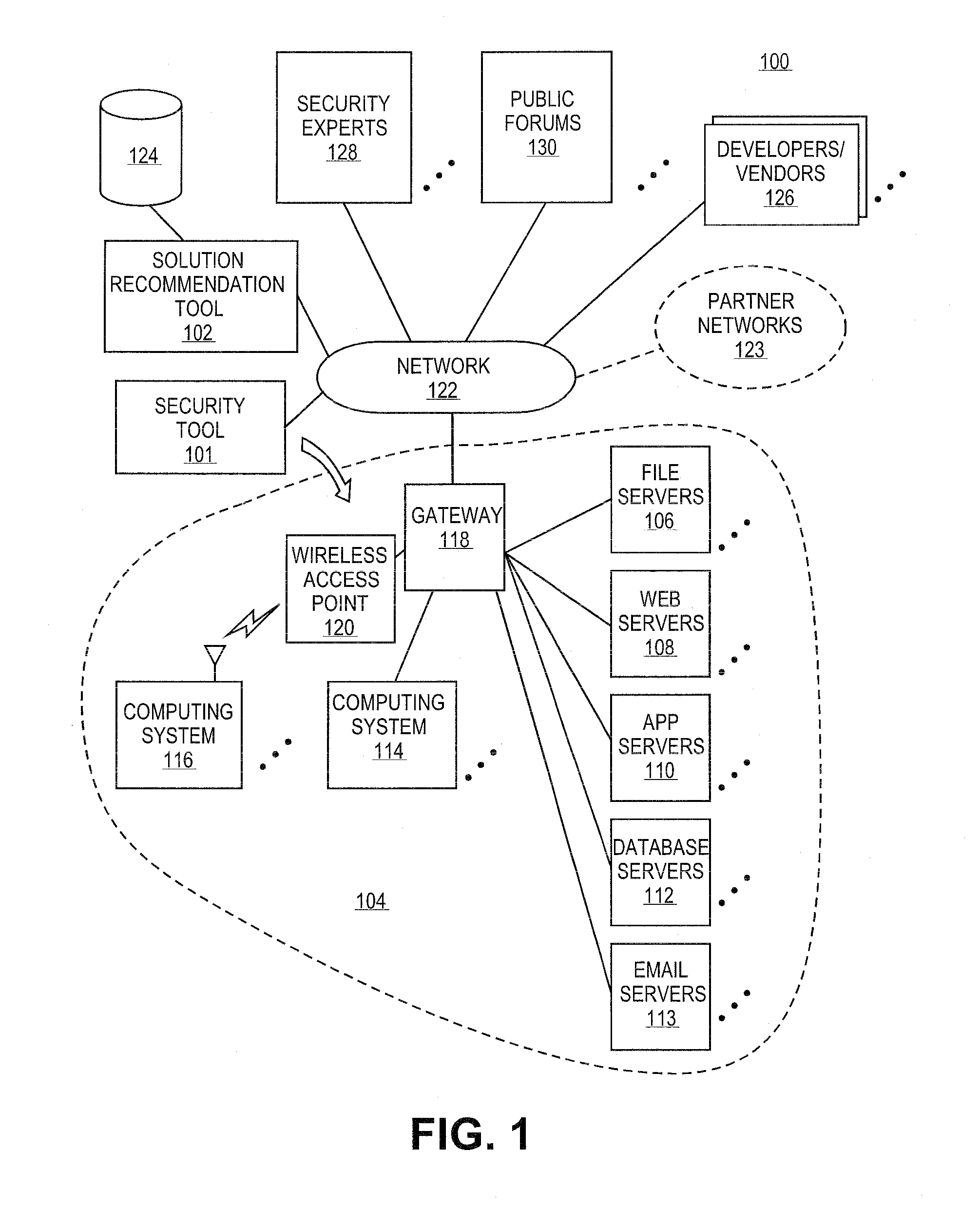
Methods and systems for providing recommendations to address security vulnerabilities in a network of computing systems
A solution recommendation (SR) tool can receive vulnerabilities identified by a vulnerability scanner and / or penetration testing tool. The SR tool can determine various approaches for remediating or mitigating the identified vulnerabilities, and can prioritize the various approaches based on the efficiency of the various approaches in remediating or mitigating the identified vulnerabilities. The SR tool can recommend one or more of the prioritized approaches based on constraints such as cost, effectiveness, complexity, and the like. Once the one or more of the prioritized approaches are selected, the SR tool can recommend the one or more prioritized approaches to third-party experts for evaluation.
Owner:RAPID7
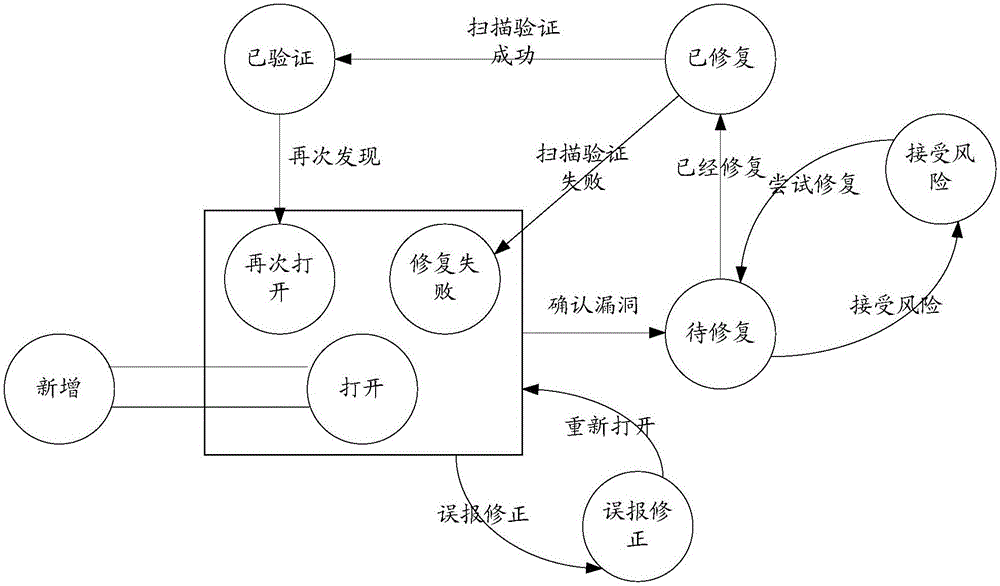
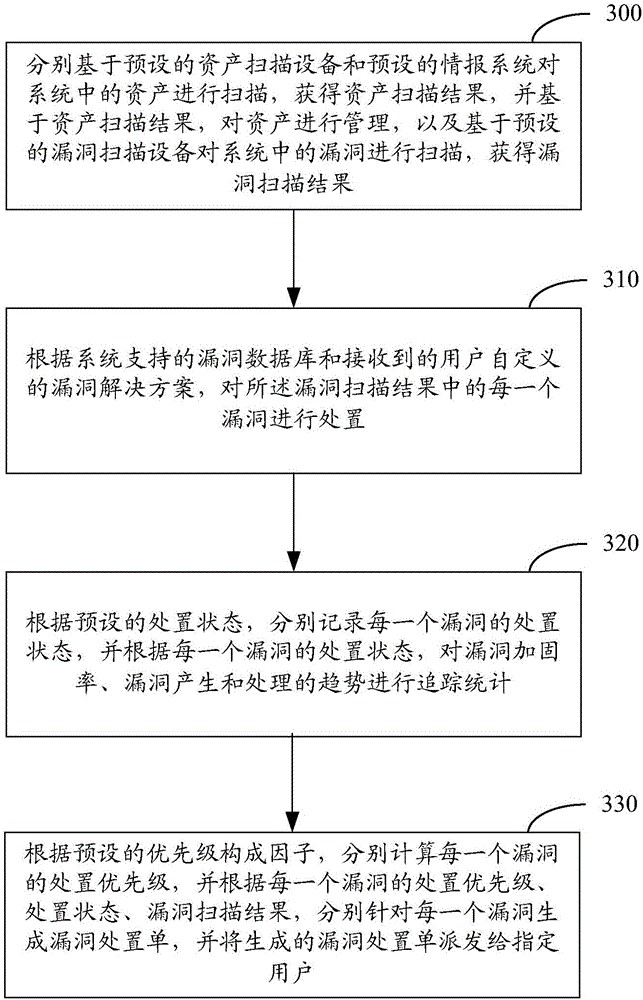
Vulnerability management system and vulnerability management method
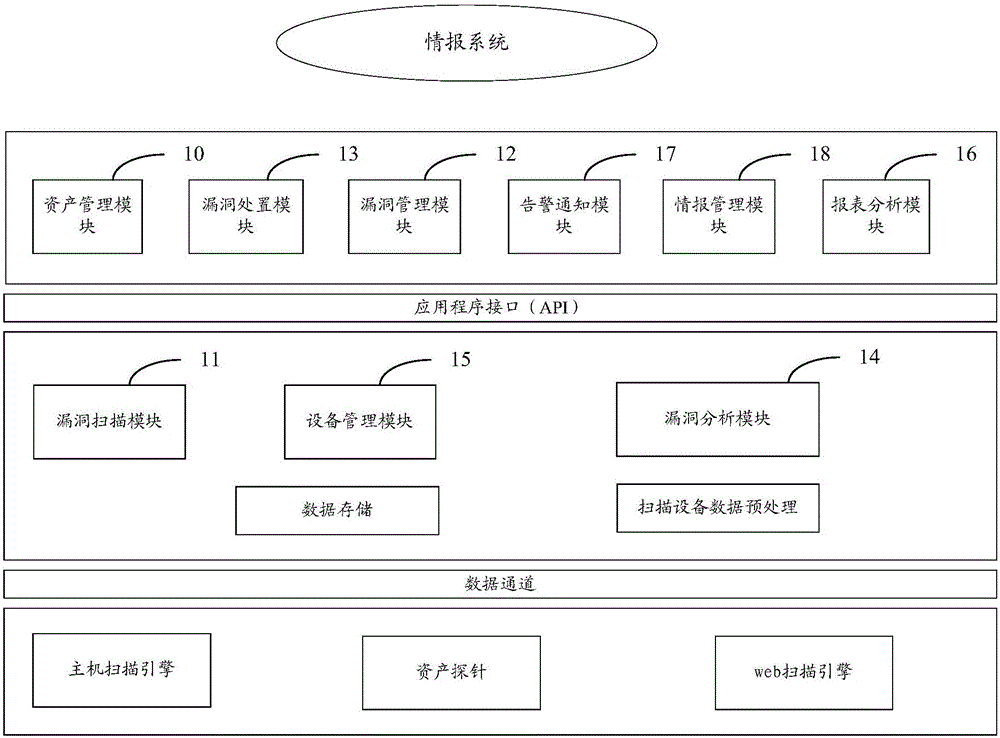
ActiveCN106790190ADiscover comprehensiveSolve the problem that Internet assets cannot be accurately discoveredTransmissionVulnerability managementManagement efficiency
The invention relates to the field of information security, and in particular to a vulnerability management system and a vulnerability management method. The vulnerability management system comprises an asset management module, a vulnerability scanning module, a vulnerability management module, a vulnerability processing module and a vulnerability analyzing module; all assets including public network assets and vulnerability can be comprehensively found by the asset management module and the vulnerability scanning module; analysis, trace and management of the vulnerability are realized by the vulnerability analyzing module, the vulnerability processing module and the vulnerability management module, so that the vulnerability management system has the effects that detailed record and trace can be carried out on the assets and the vulnerability, security conditions of the assets and the vulnerability in the system also can be evaluated and the management efficiency of the assets and the vulnerability in the system is improved.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
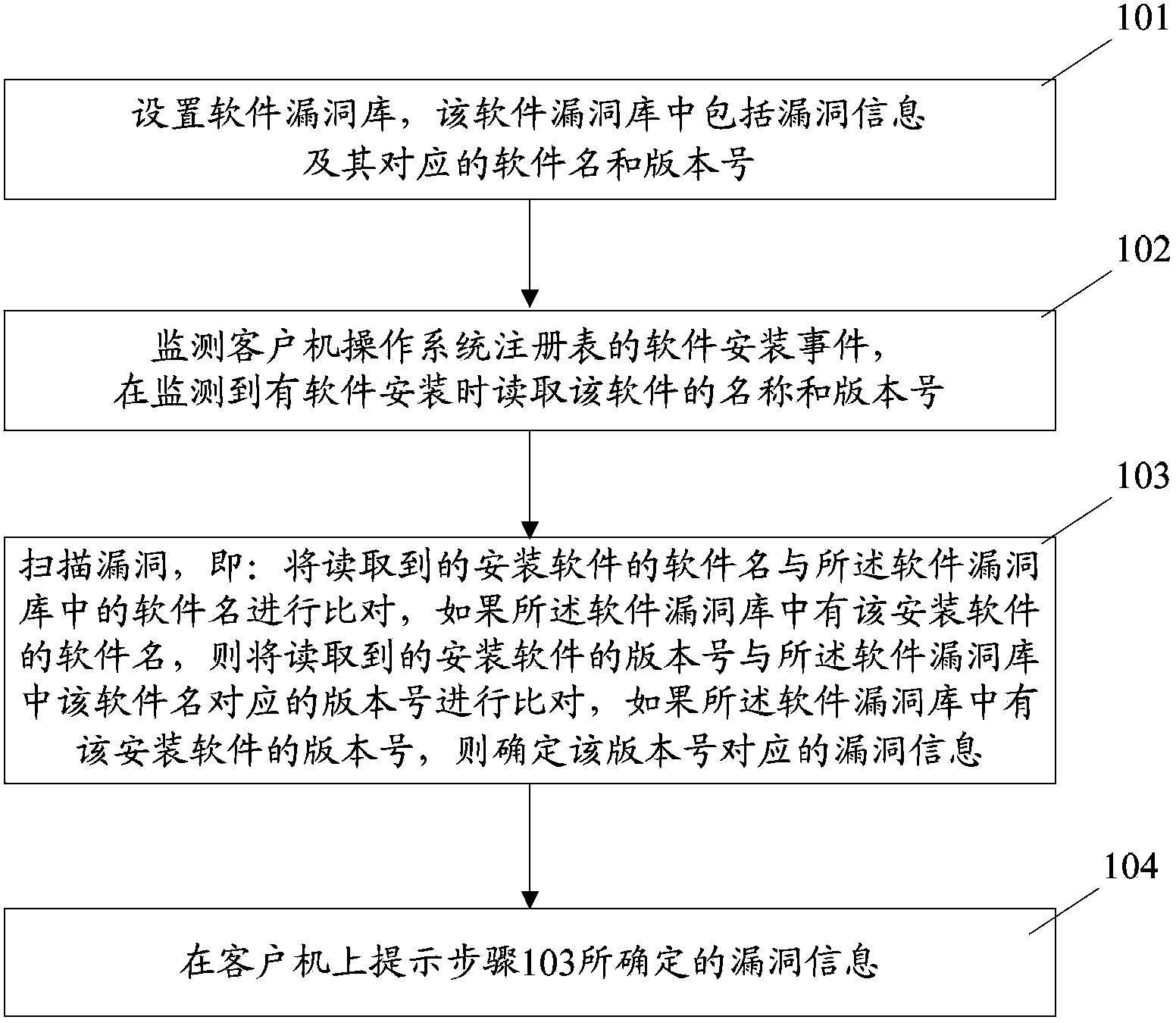
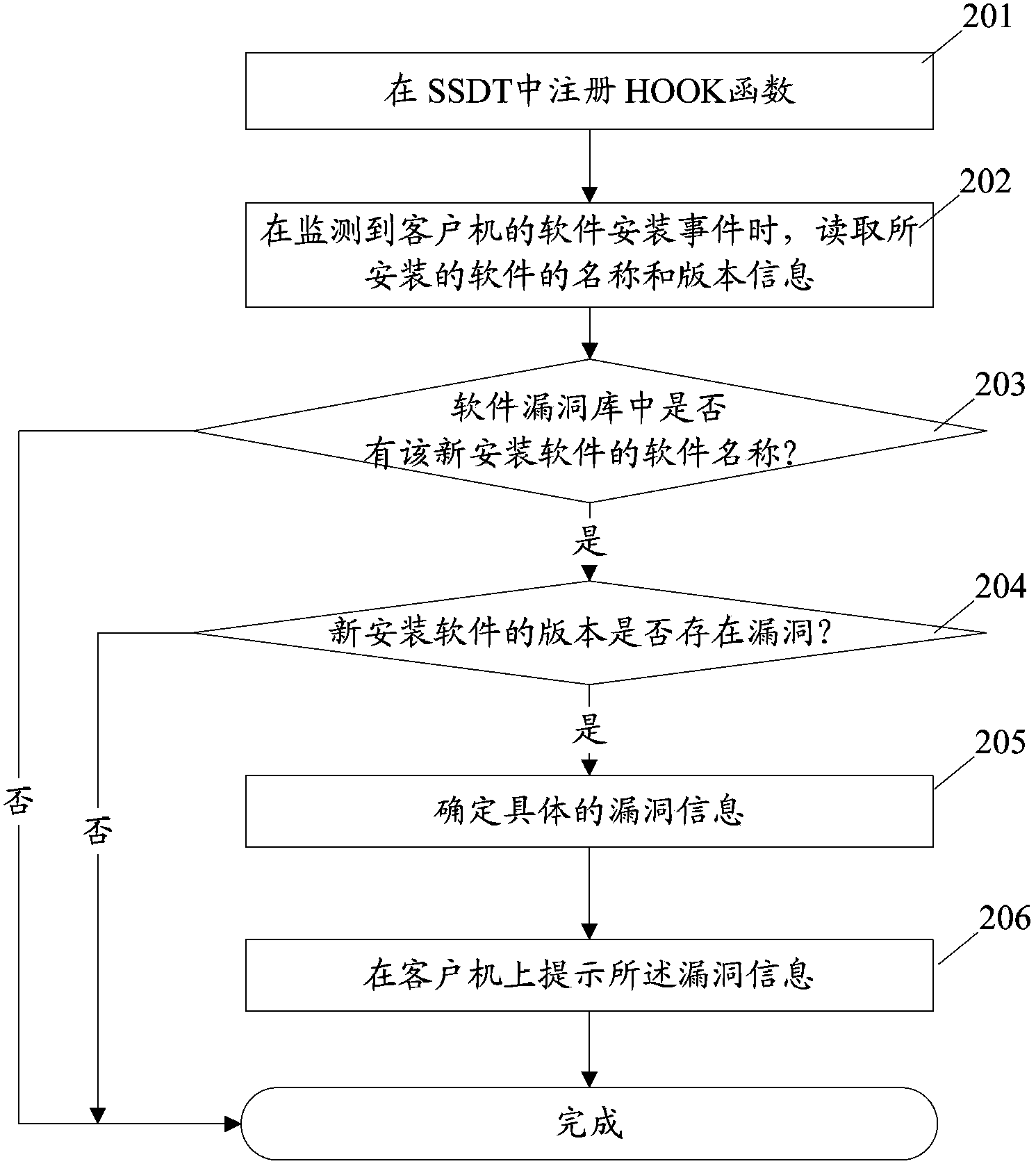
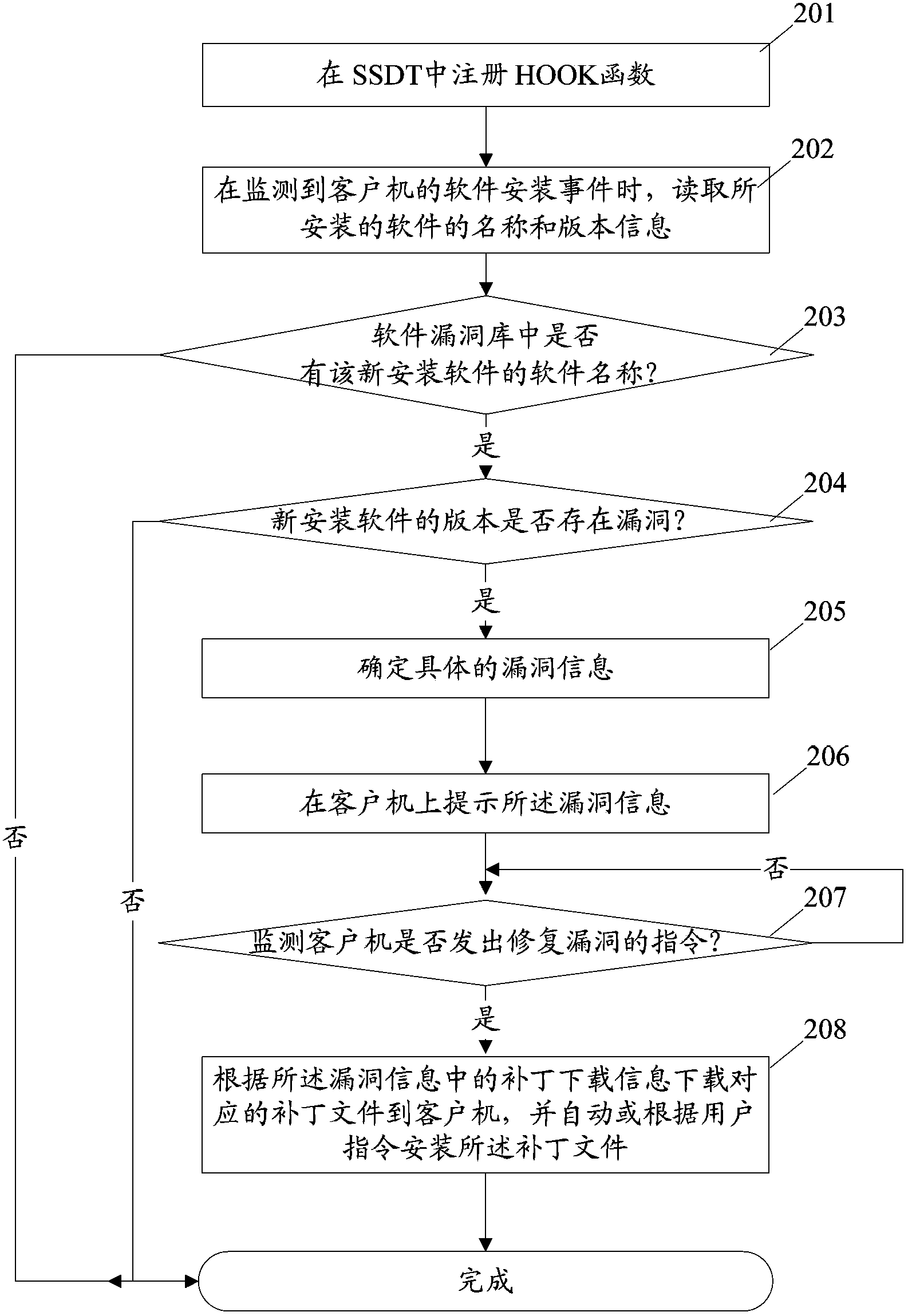
Scanning prompt method and device for software vulnerabilities
ActiveCN103473505AImprove securityEnsure safetyPlatform integrity maintainanceVulnerability scanningSoftware
The invention discloses a scanning prompt method and device for software vulnerabilities. The method comprises the steps of setting vulnerability information and a software name and a version number corresponding to the vulnerability information in a software vulnerability database; monitoring a software installing event of a client operation system registry by a monitoring module, and reading the software name and version number when the monitoring module monitors the installation of the software; comparing the software name of the installed software obtained by read with the software name in the software vulnerability database by a vulnerability scanning module; if the software name of the installed software is in the software vulnerability database, comparing the version number of the installed software obtained by read with the version number corresponding to the software in the software vulnerability database; if the version number of the installed software is in the software vulnerability database, determining the corresponding vulnerability information of the version number; and prompting the vulnerability information determined by the vulnerability scanning module on the client by a prompt module. By using the method and device disclosed by the invention, the security of the newly installed software can be improved, and the calculated amount of vulnerability scanning is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
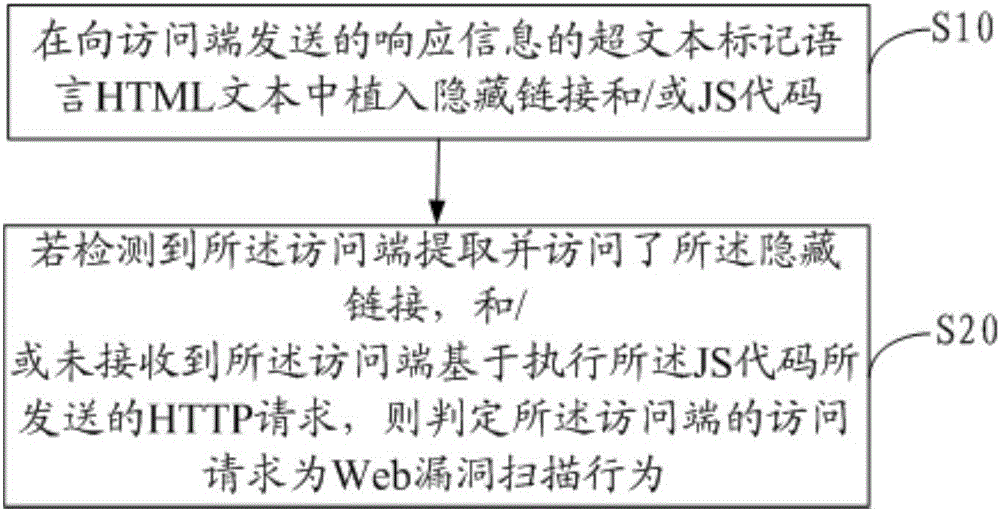
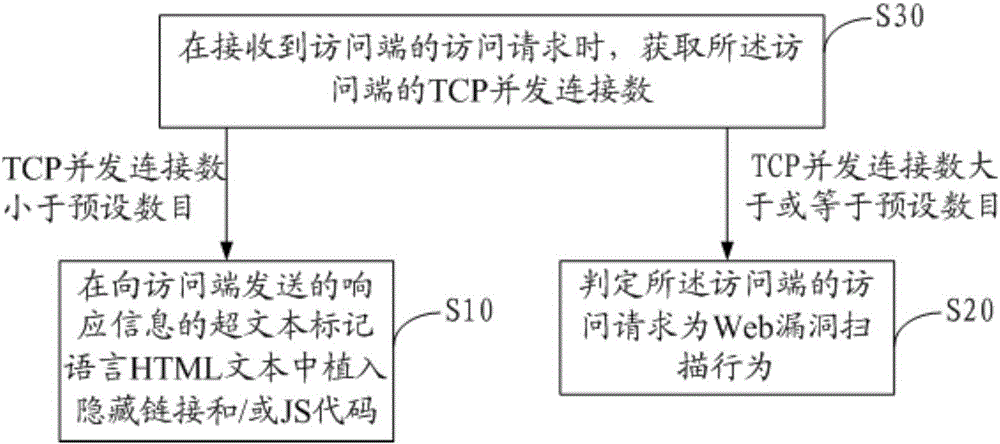
Method and device for detecting Web vulnerability scanning behavior
The invention discloses a method for detecting a Web vulnerability scanning behavior. The method comprises the following steps: embedding a hidden link and / or a JS (Javascript) code into an HTML (Hyper Text Markup Language) text of response information sent to an access side; and if detecting the access side extracts and accesses the hidden link, and / or does not receive an HTTP request which is sent by the access side on the basis of executing the JS code, judging an access request of the access side as the Web vulnerability scanning behavior. The invention further discloses a device for detecting the Web vulnerability scanning behavior. According to the method and the device disclosed by the invention, the accuracy of judging the vulnerability scanning behavior is improved, and the misreporting and the underreporting when the Web vulnerability scanning behavior is detected are reduced.
Owner:SANGFOR TECH INC
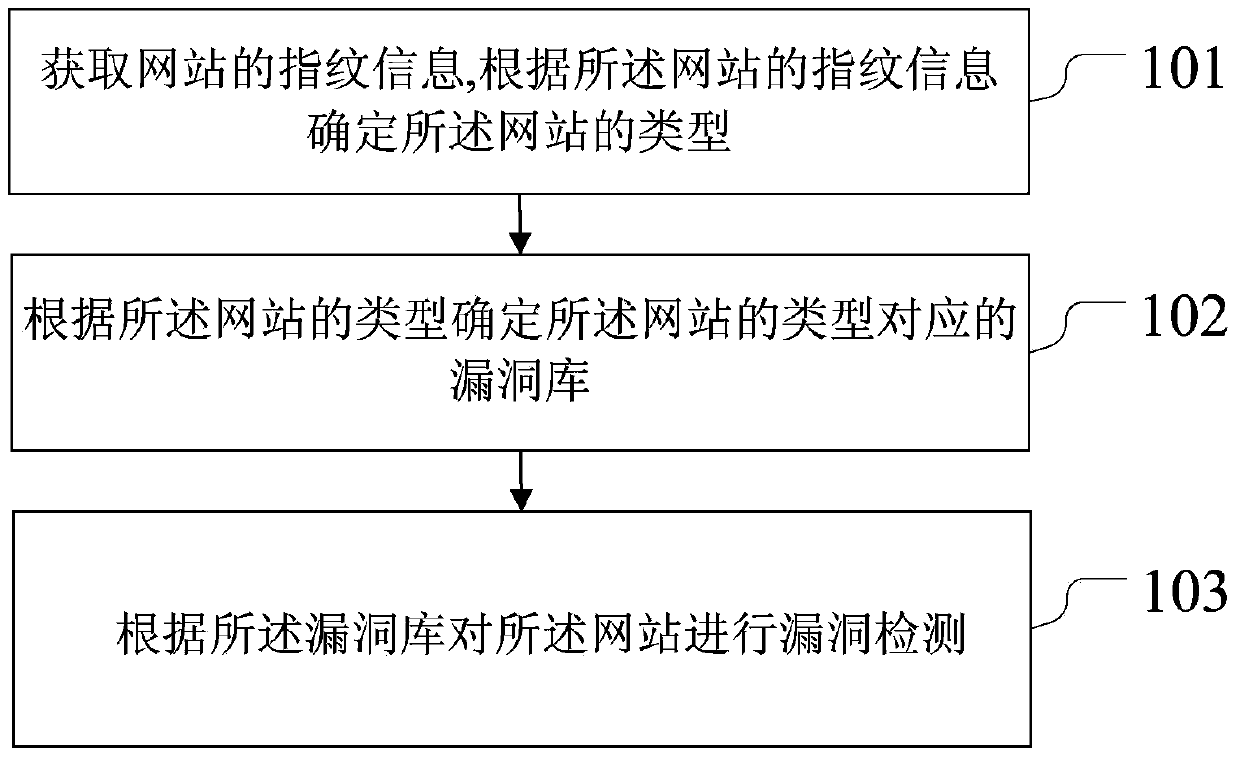
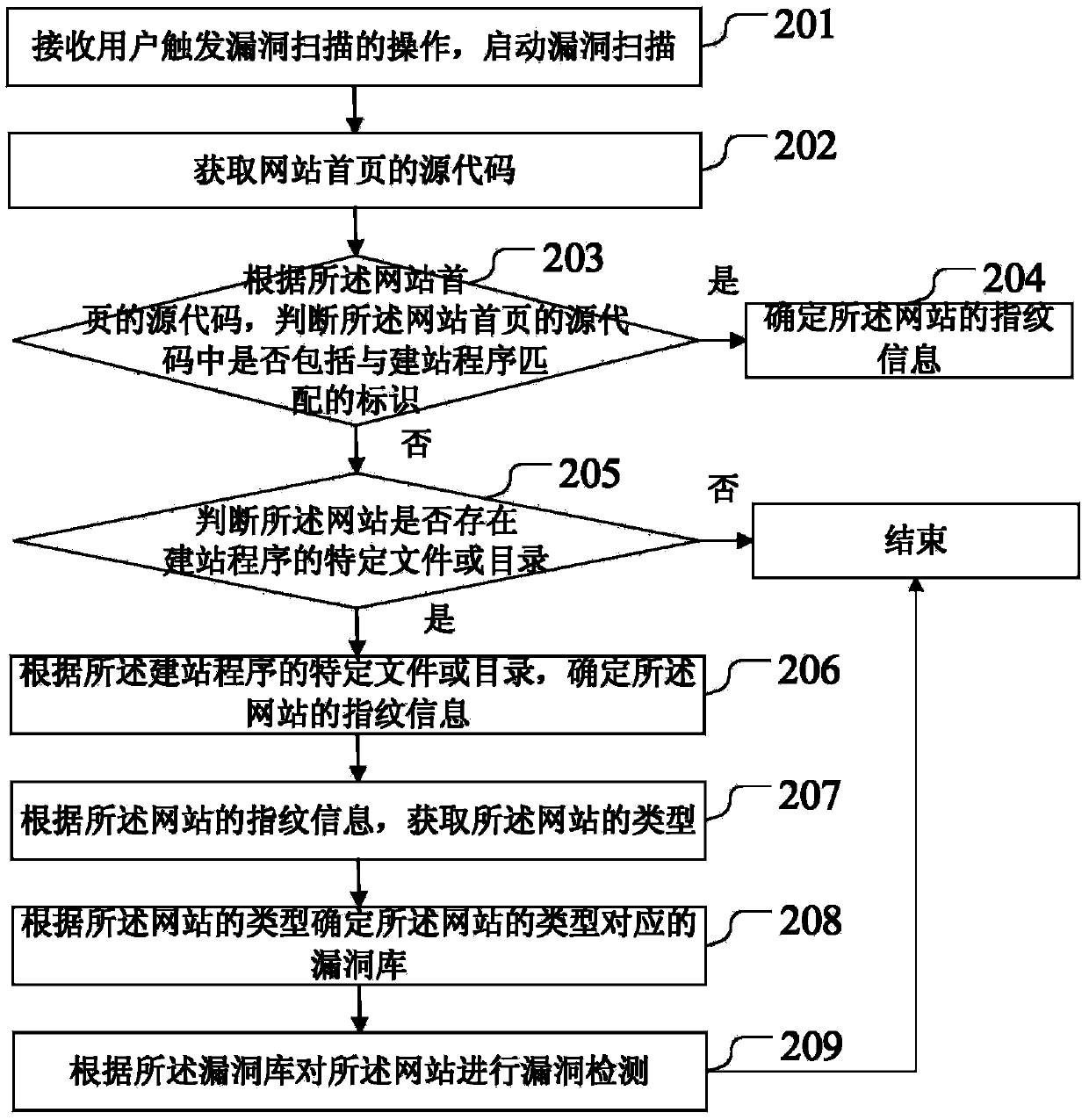
Method and device for detecting website bugs
ActiveCN103632100ALow efficiencyImprove accuracyPlatform integrity maintainanceSpecial data processing applicationsWeb siteEngineering
The invention discloses a method and device for detecting website bugs, and relates to the technical field of network security. The method includes the steps of obtaining fingerprint information of a website, determining the type of the website according to the fingerprint information of the website, determining a bug library corresponding to the type of the website according to the type of the website, and carrying out bug detection on the website according to the bug library. Time for bug scanning can be shortened, the efficiency for bug scanning can be improved, and the accuracy rate of bug scanning is high. The method and device are suitable for bug scanning.
Owner:BEIJING QIANXIN TECH
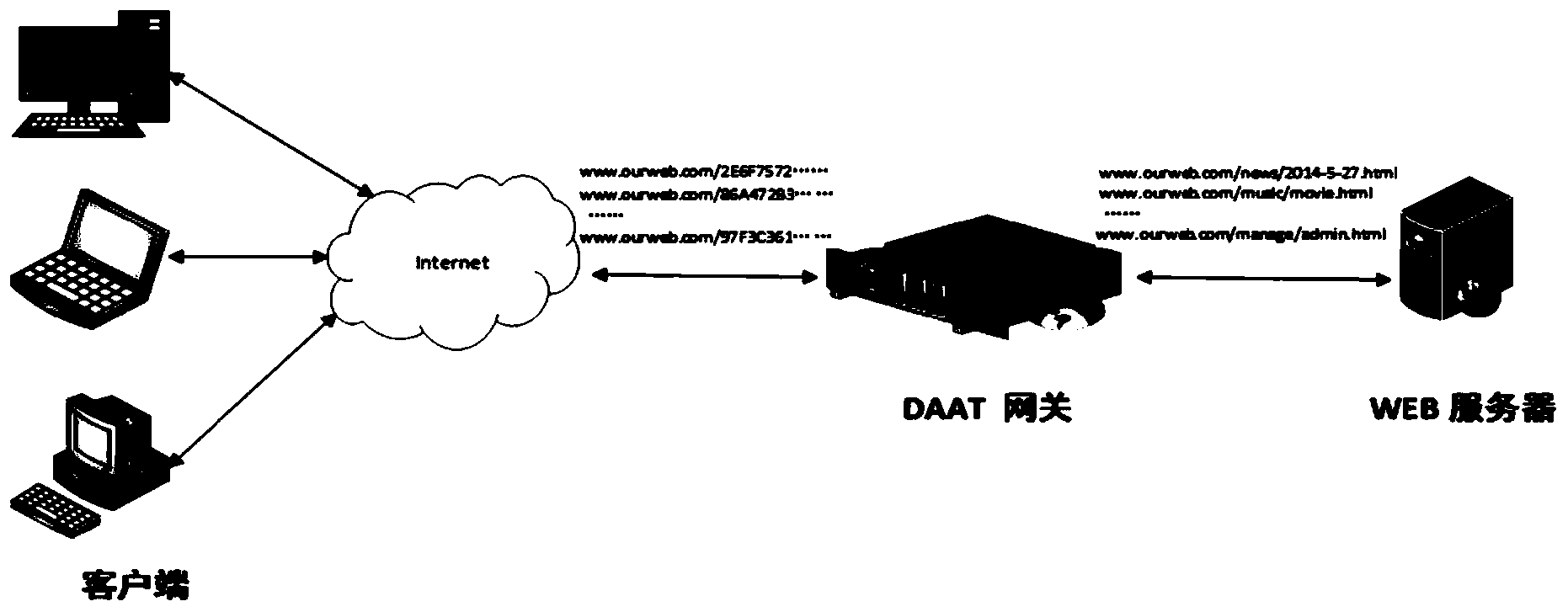
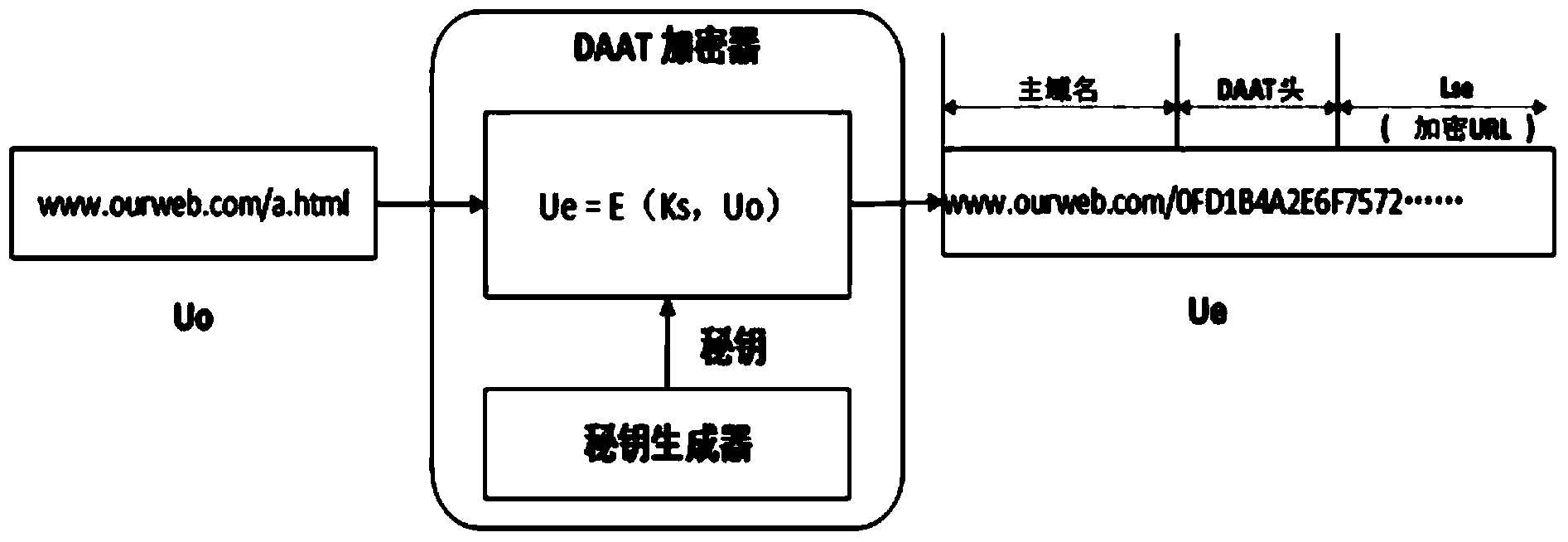
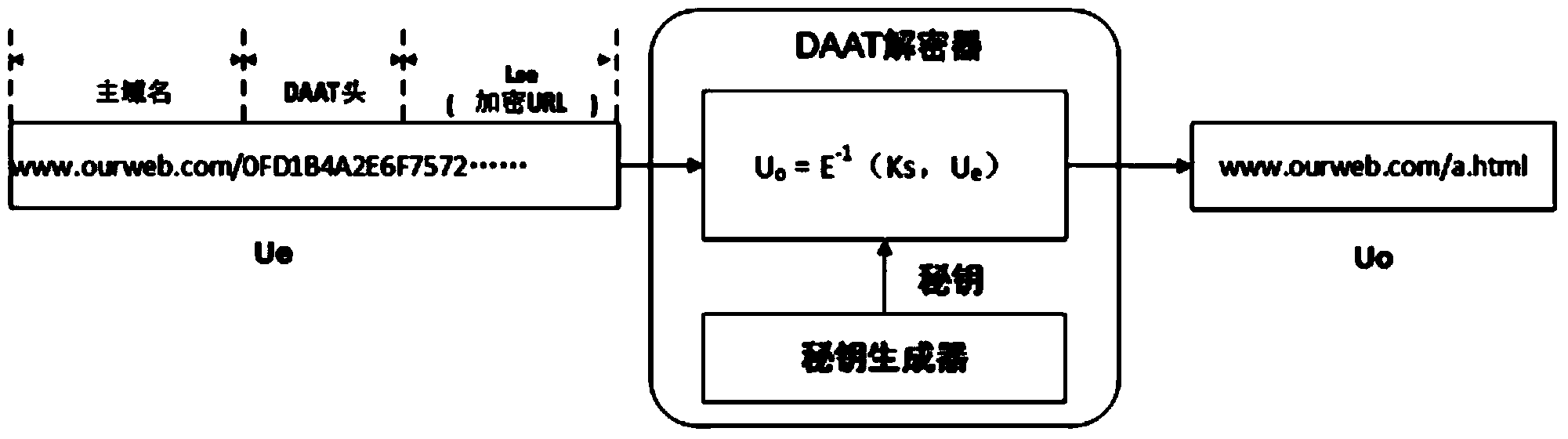
Dynamic application address conversion method and gateway system
ActiveCN104378363AIncrease attack difficultyHide vulnerabilityKey distribution for secure communicationGateway systemVulnerability scanning
The invention relates to a dynamic application address conversion method and gateway system. A novel Web application attack defense method is achieved. URL addresses are dynamically converted, attack faces of an application system are converted, vulnerability of Web applications is hidden, the attack difficulty of an attacker is increased, and the difficulty in which the attacker conducts vulnerability scanning and attack injection on Websites through URLs is greatly increased. By the adoption of a DAAT method, the security threats of the attacker to the Web applications can be dynamically and effectively reduced, and security of the Web application system is improved.
Owner:INST OF INFORMATION ENG CAS
Software continuous delivery acceptance method based on continuous integration and automated testing
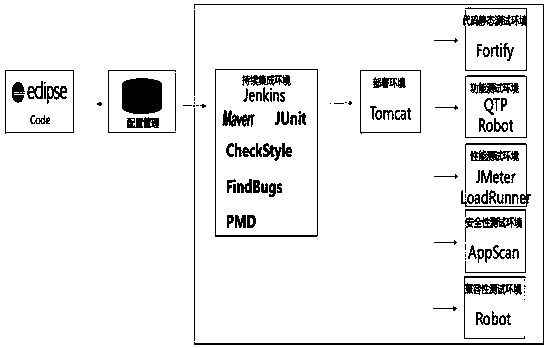
InactiveCN108334437AComprehensive test resultsImprove test efficiencyHardware monitoringSoftware testing/debuggingTest scriptContinuous integration
The invention discloses a software continuous delivery acceptance method based on continuous integration and automated testing. From source code submission, a code is downloaded from a source code configuration tool to carry out automated construction, and FindBugs code vulnerability scanning is integrated through a construction tool; after construction is finished, Docker is used for creating deployment environment or integrating with existing environment; then, function test script management, performance test script management, compatibility test script management and code vulnerability scanning configuration management are realized; the integrated environment of integrated function testing, performance testing, compatibility testing and source code auditing is provided; and various tests are executed, and results are uniformly managed. Through the method, test personnel do not need to build the complex continuous integration and testing environment, the test of each dimension of one item can be quickly realized, the comprehensive test result of the whole item is provided, and test efficiency is greatly improved.
Owner:JIANGSU ELECTRIC POWER INFORMATION TECH +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com