Deep learning-based network intrusion detection and vulnerability scanning method and devices
A technology of network intrusion detection and deep learning, applied to electrical components, transmission systems, etc., to achieve the effects of enhanced defense capabilities, improved test efficiency, and high detection rates
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0065] The purpose of Embodiment 1 is to provide a network intrusion detection and vulnerability scanning method based on deep learning.
[0066] In order to achieve the above object, the present invention adopts the following technical scheme:
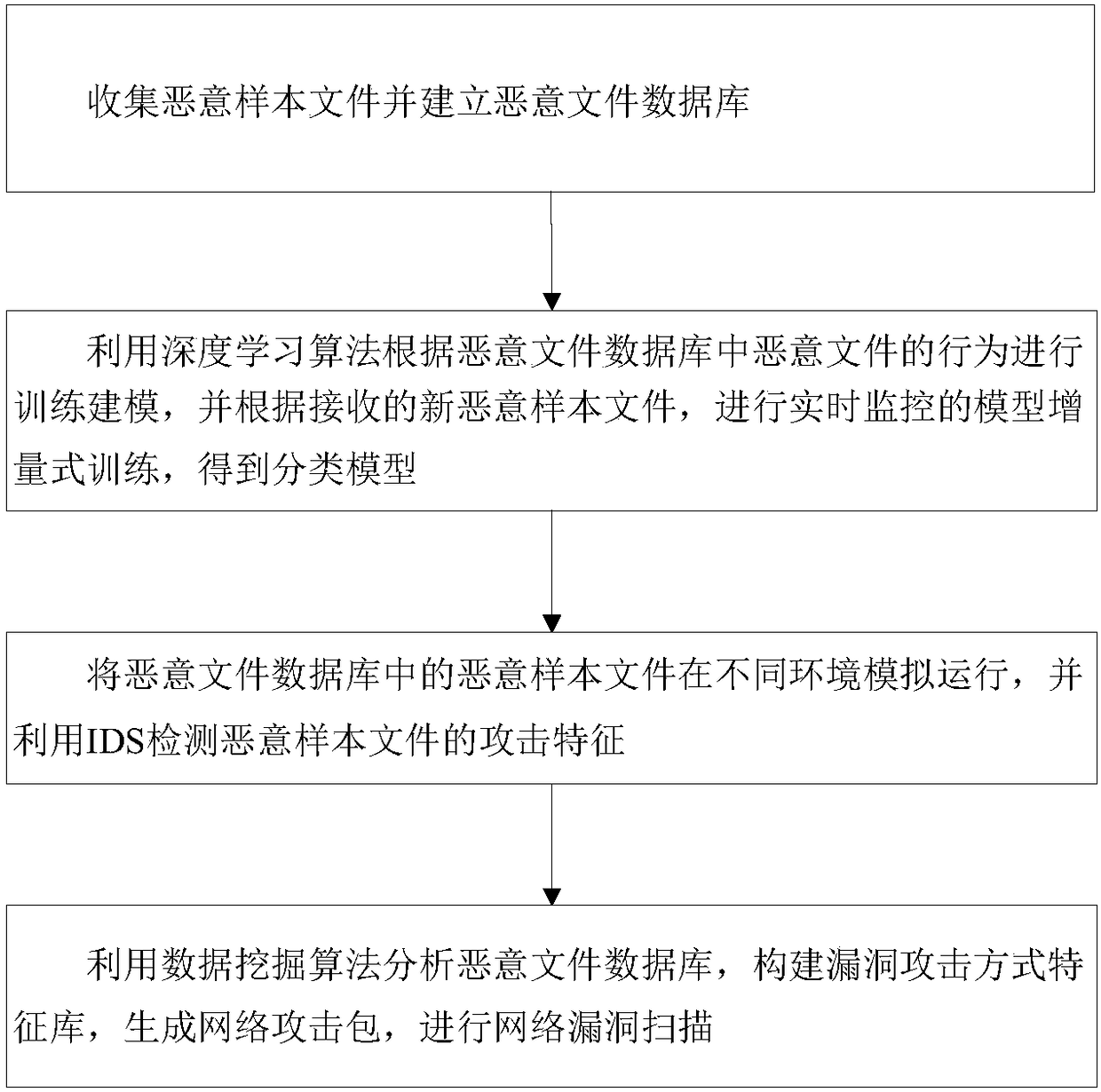
[0067] Such as figure 1 as shown,
[0068] A network intrusion detection and vulnerability scanning method based on deep learning, the method comprising:
[0069] Step (1): collecting malicious sample files and establishing a malicious file database;
[0070] Step (2): Use the deep learning algorithm to carry out training modeling according to the behavior of malicious files in the malicious file database, and carry out real-time monitoring model incremental training according to the received new malicious sample files to obtain the classification model;
[0071] Step (3): simulate the malicious sample files in the malicious file database in different environments, and use IDS to detect the attack characteristics of the malicious s...
Embodiment 2
[0114] The purpose of Embodiment 2 is to provide a computer-readable storage medium.
[0115] In order to achieve the above object, the present invention adopts the following technical scheme:
[0116] A computer-readable storage medium, in which a plurality of instructions are stored, and the instructions are adapted to be loaded by a processor of a terminal device and perform the following processing:
[0117] Step (1): collecting malicious sample files and establishing a malicious file database;
[0118] Step (2): Use the deep learning algorithm to carry out training modeling according to the behavior of malicious files in the malicious file database, and carry out real-time monitoring model incremental training according to the received new malicious sample files to obtain the classification model;
[0119] Step (3): simulate the malicious sample files in the malicious file database in different environments, and use IDS to detect the attack characteristics of the malicio...
Embodiment 3
[0122] The purpose of Embodiment 3 is to provide a terminal device.
[0123] In order to achieve the above object, the present invention adopts the following technical scheme:
[0124] A terminal device, including a processor and a computer-readable storage medium, the processor is used to implement instructions; the computer-readable storage medium is used to store multiple instructions, and the instructions are suitable for being loaded by the processor and performing the following processing:
[0125] Step (1): collecting malicious sample files and establishing a malicious file database;
[0126] Step (2): Use the deep learning algorithm to carry out training modeling according to the behavior of malicious files in the malicious file database, and carry out real-time monitoring model incremental training according to the received new malicious sample files to obtain the classification model;
[0127] Step (3): simulate the malicious sample files in the malicious file datab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com