Patents
Literature
100results about How to "Stop running" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Computer safety protective method based on software identity identifying technology
InactiveCN1900941AMeet safety requirementsStop runningPlatform integrity maintainanceProtection mechanismAuthentication server
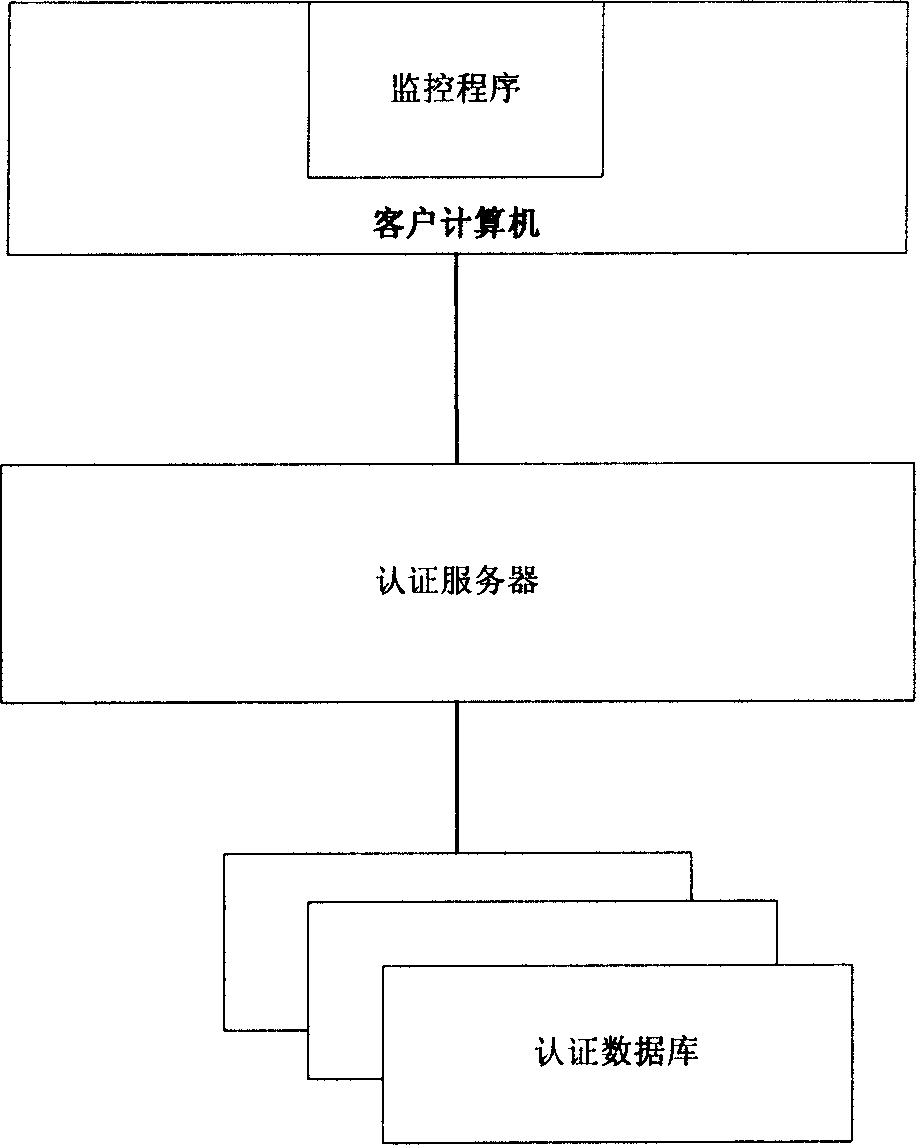
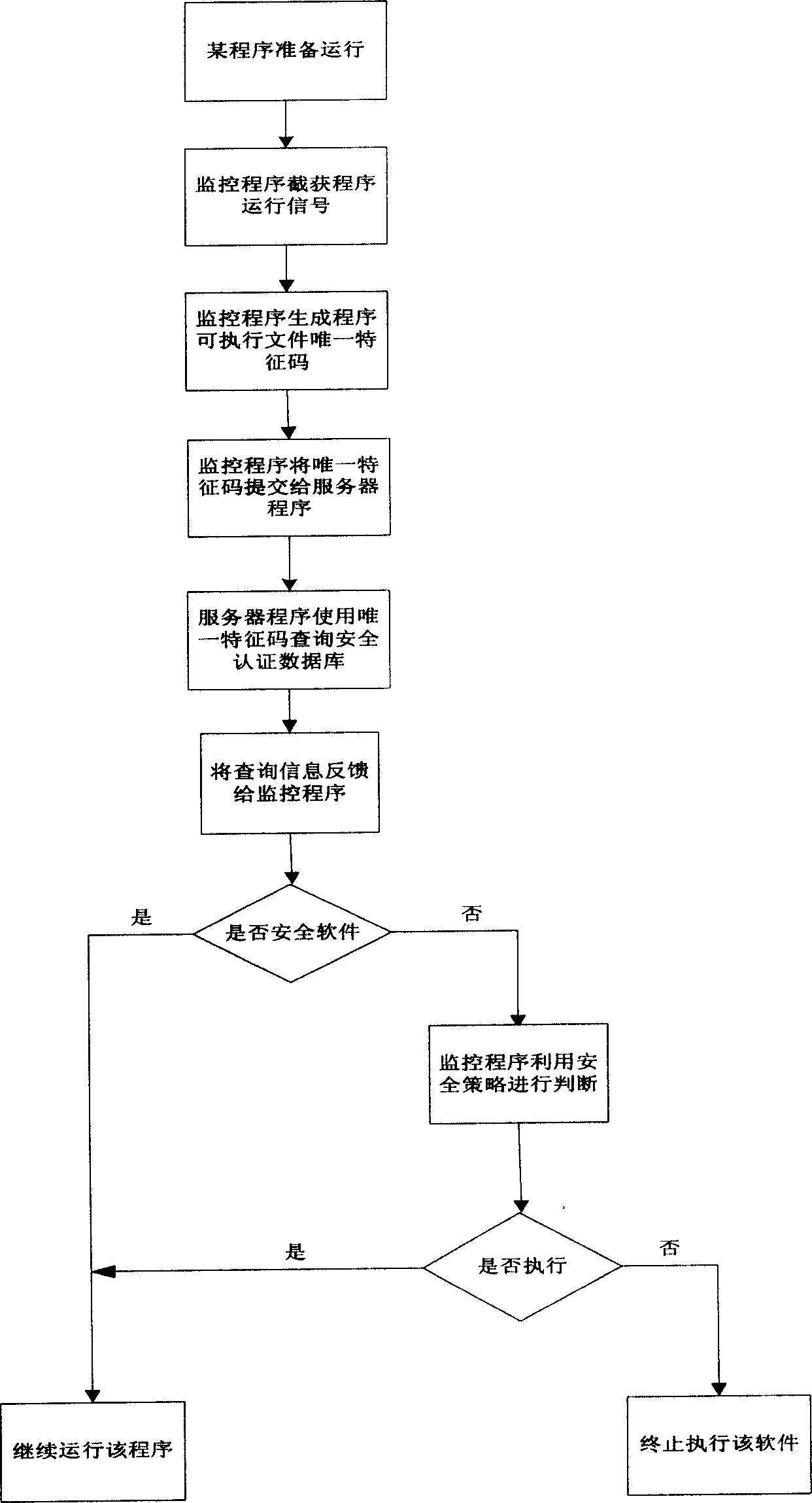
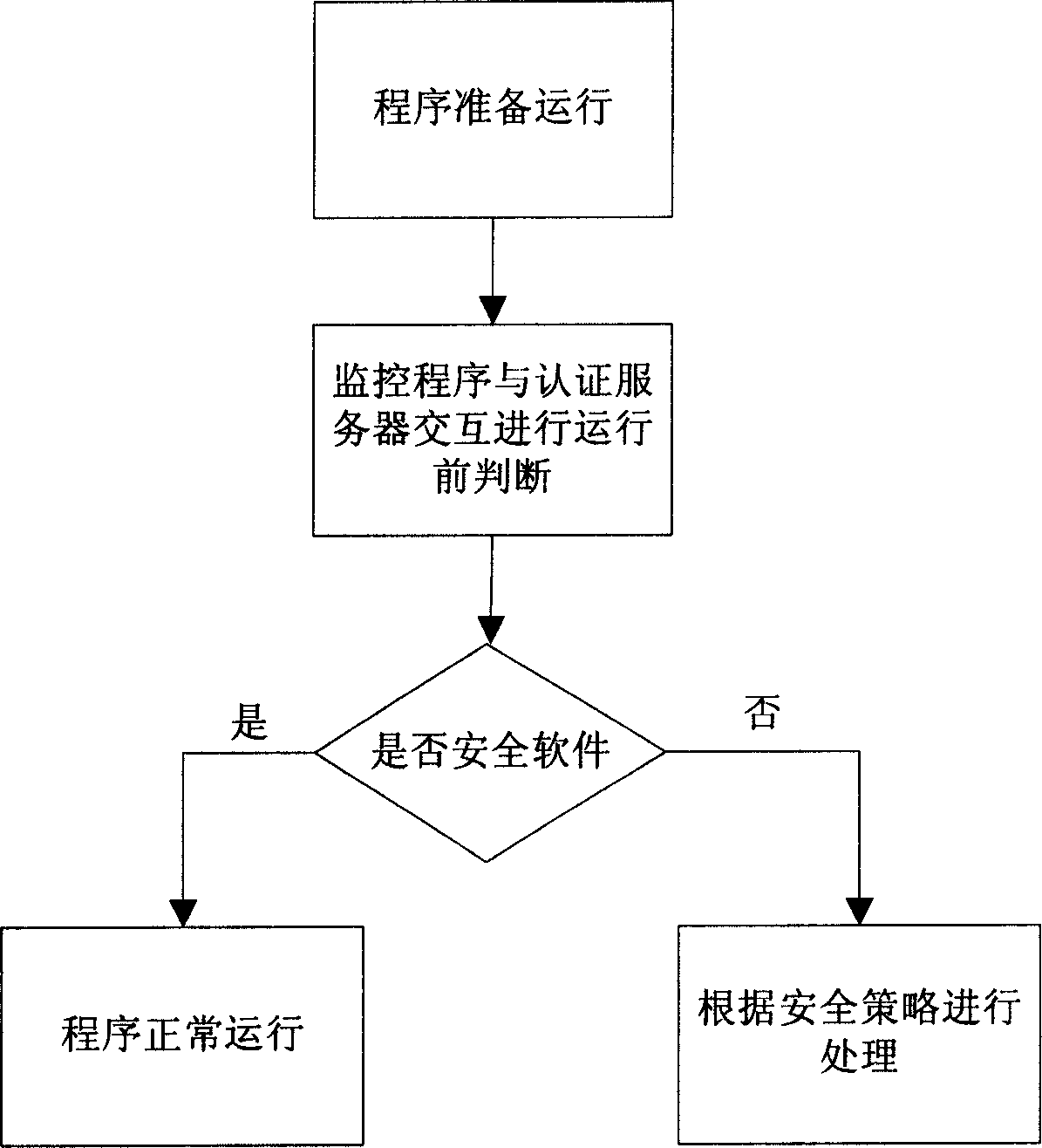
The present invention relates to computer security technology, and is a client end computer security protecting mechanism established around the certificating server based on software identity certification. The present invention includes: 1. establishing security certificating database with the unique flag code as ID; 2. establishing certificating server for providing software security certificating function with the security certificating database as kernel; 3. establishing security policy for limiting the software running in the client end; 4. monitoring the client end computer and extracting the unique ID and submitting it to the certificating server before starting the executable file; 5. inquiring the security certificating database with the certificating server and feeding back the corresponding security information to the client end computer; and 6. the client end computer judging whether to execute the software. Compared with traditional antivirus method, the present invention has more wide protection.
Owner:傅玉生
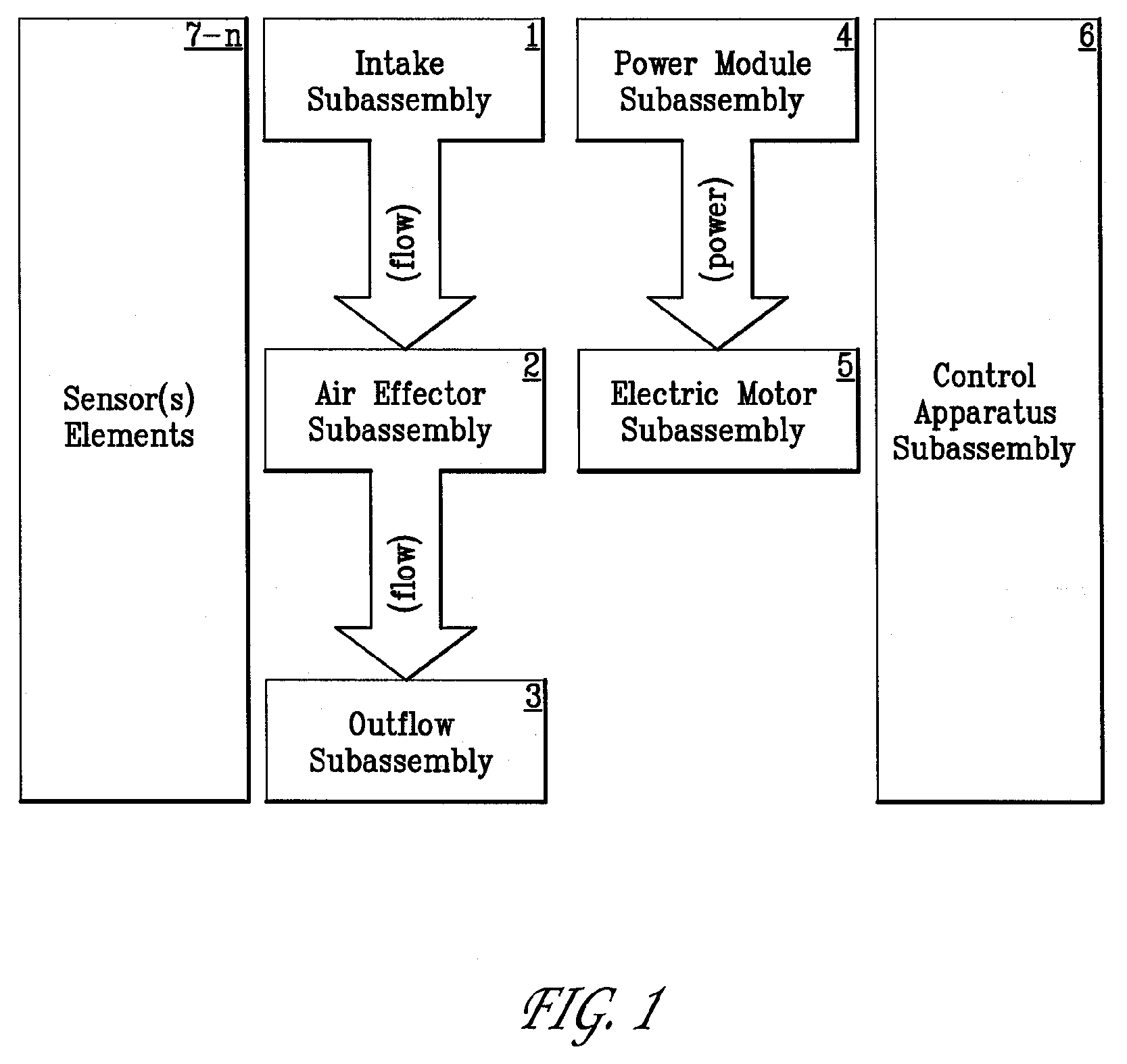
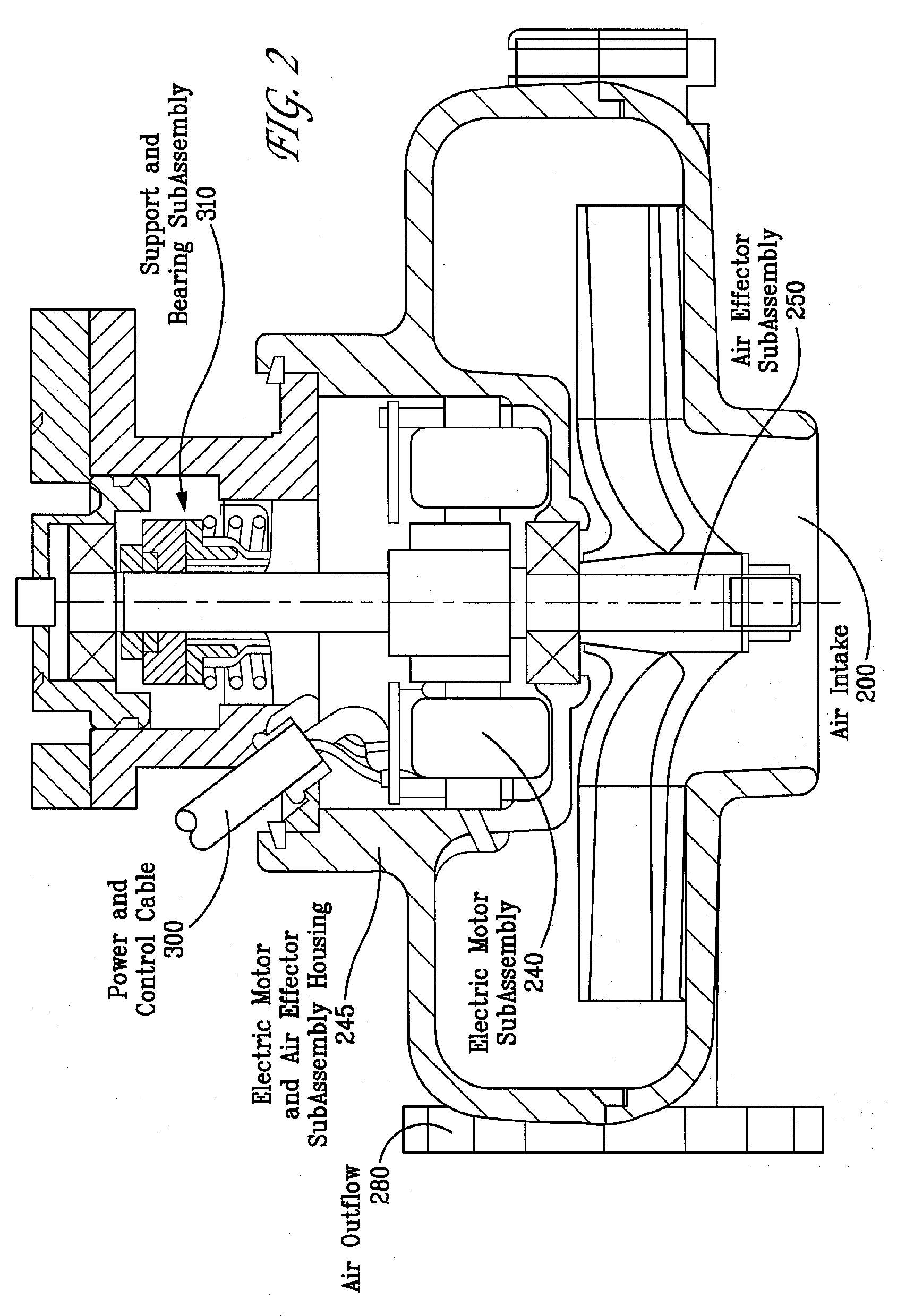
Generation and Management of Mass Air Flow
InactiveUS20080219866A1Increase speedEfficient compatibilityElectrical controlNon-fuel substance addition to fuelEngineeringControl theory
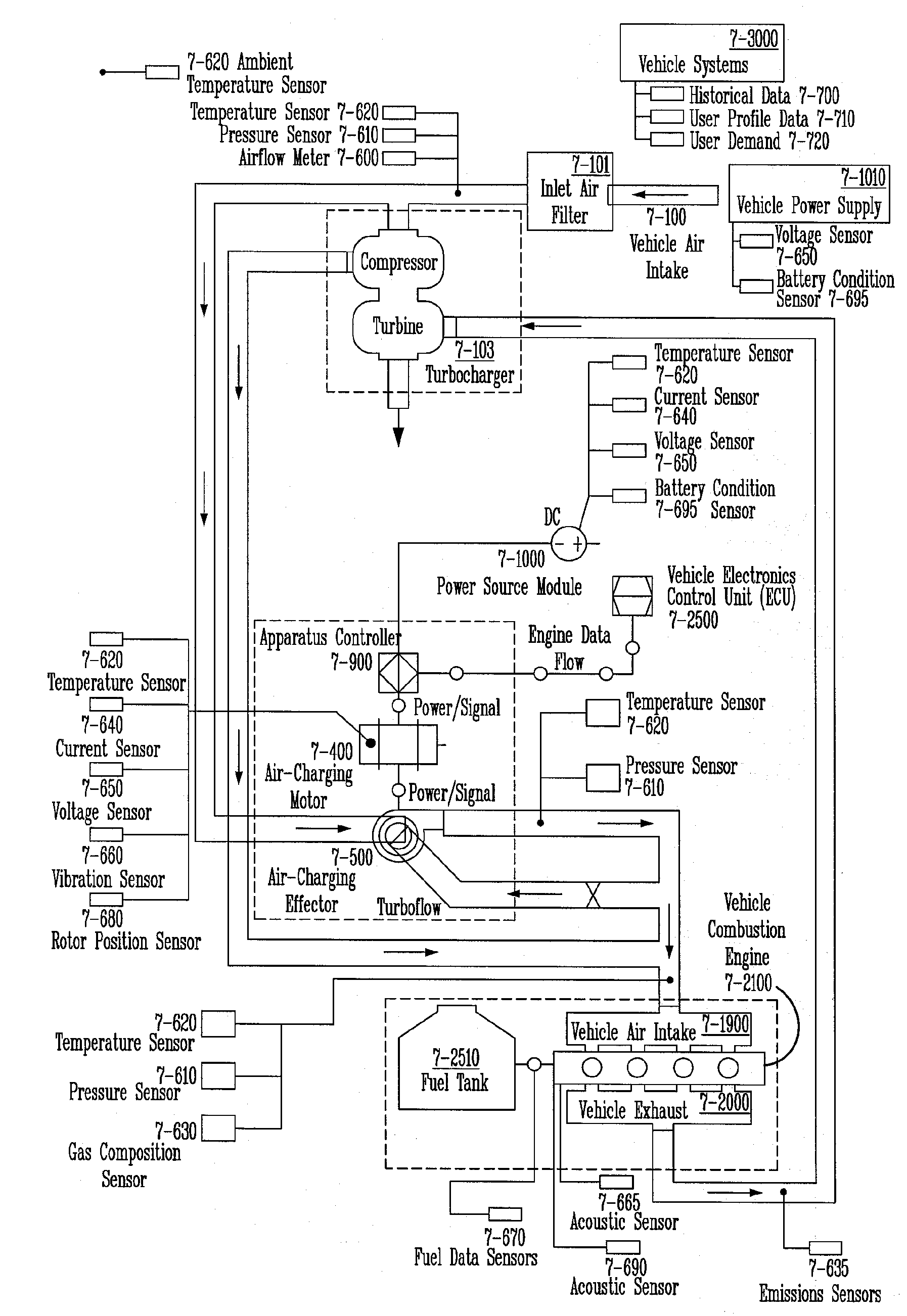
Systems and methods for generating high velocity mass air flows are disclosed. High velocity mass air flow (air charging) devices are needed in a variety of research, industrial, commercial, and consumer applications. The exemplary systems and apparatus described incorporate an electric motor subassembly, an air effector subassembly, a highly intelligent apparatus controller subassembly (and interfaces), and linked sensors, connectors, and wiring. The exemplary method described includes the operational apparatus controller subassembly (e.g., elements, logic, and behavior) that controls the entire apparatus' functions and interactions.
Owner:TURBODYNE TECH INC
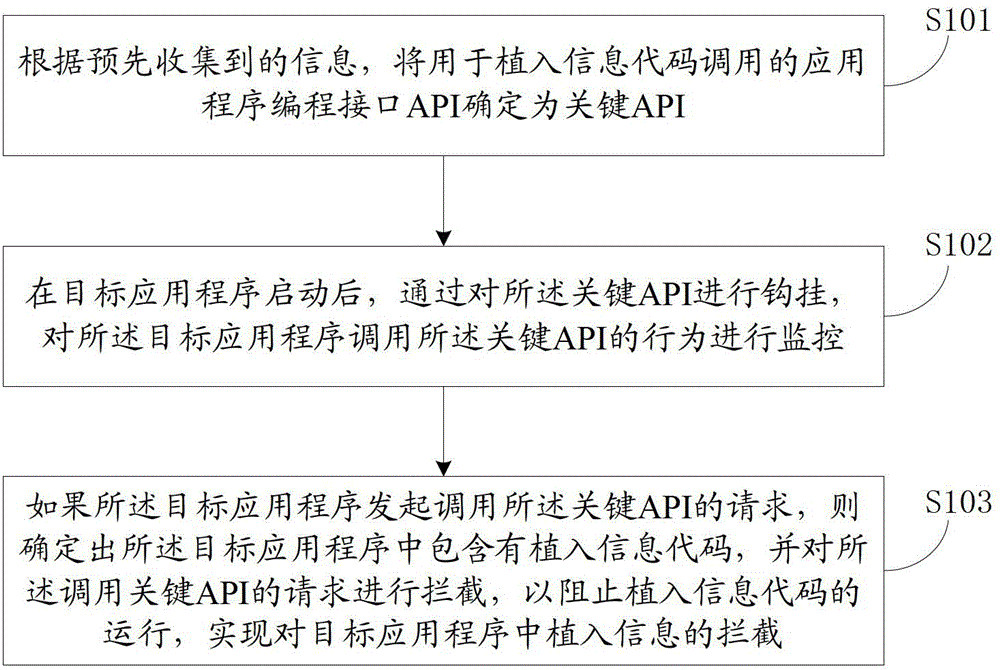
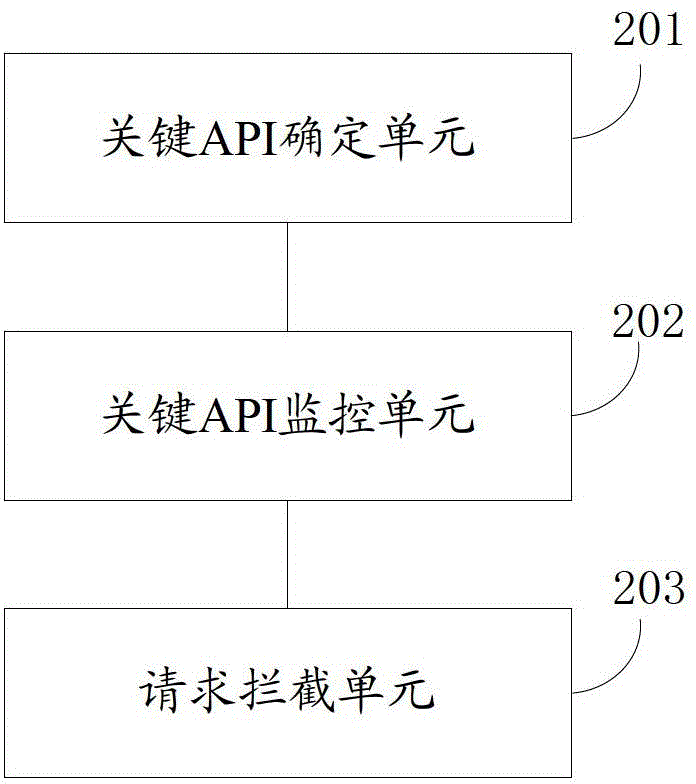
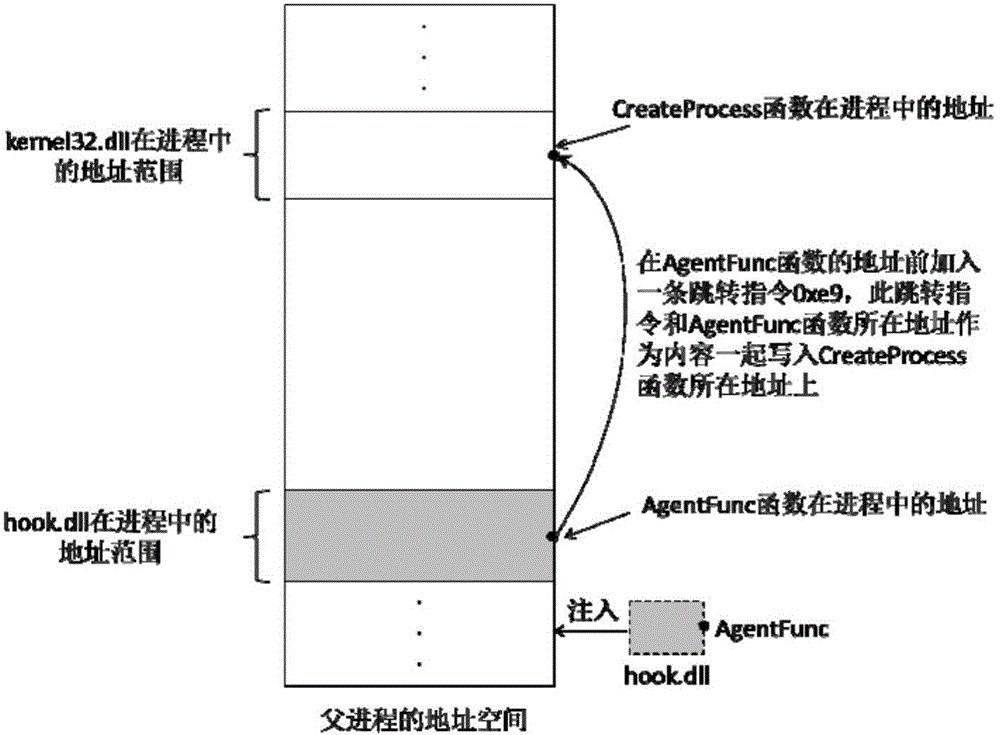
Method and device for intercepting embedded information in application program
ActiveCN103150513AImplement interceptionStop runningInterprogram communicationHardware monitoringOperational systemApplication programming interface
The invention discloses a method and a device for intercepting embedded information in an application program. The method comprises the following steps of determining an application programming interface (API) called by an embedded information code as a key API according to the pre-collected information, wherein the key API is an API provided by an information provider; after a target application program is started up, monitoring the behavior that the target application program calls the key API by hooking the key API; and if the target application program requests to call the key API, determining that the target application program comprises the embedded information code, and intercepting the request of calling the key API to prevent the embedded information code from running, thereby realizing the interception of the embedded information in the target application program. Through the method and the device provided by the invention, the interception of the embedded information in the application program can be effectively realized, and meanwhile, the running of an operating system can not be interfered, and the accuracy of interception is improved.
Owner:BEIJING QIHOO TECH CO LTD
Washing machine door lock detection structure and method
ActiveCN108118498ARun accuratelyStop runningOther washing machinesTextiles and paperUsabilityElectrical and Electronics engineering
The invention discloses a washing machine door lock detection structure and relates to the technical field of washing machines. The structure comprises a control panel base, an upper cover, a door lock and a controller, a spring bolt of the door lock is arranged on the control panel base, and a lock hole of the door lock is formed in the upper cover; the spring bolt stretches out or retracts backunder control of the controller, the structure further comprises a detection switch, and when the upper cover is not closed in place, the spring bolt is not blocked and completely stretches out, and the detection switch sends an upper cover non-locking signal to the controller at this moment; when the upper cover is closed in place, the spring bolt is blocked by the lock hole and partially stretches into the lock hole, and the detection switch sends an upper cover locking signal to the control at this moment. The invention further discloses a washing machine door lock detection method. According to the washing machine door lock detection structure, the stretching state of the spring bolt is detected through the detection switch, whether or not the upper cover is truly closed is accuratelyjudged according to the difference of the stretching length of the spring bolt, the washing machine safety problem caused by inaccurate detection signals in the process of locking the upper cover of an existing door lock is avoided, and the safe usability of the washing machine is improved.
Owner:QINGDAO JIAONAN HAIER WASHING MACHINE +1
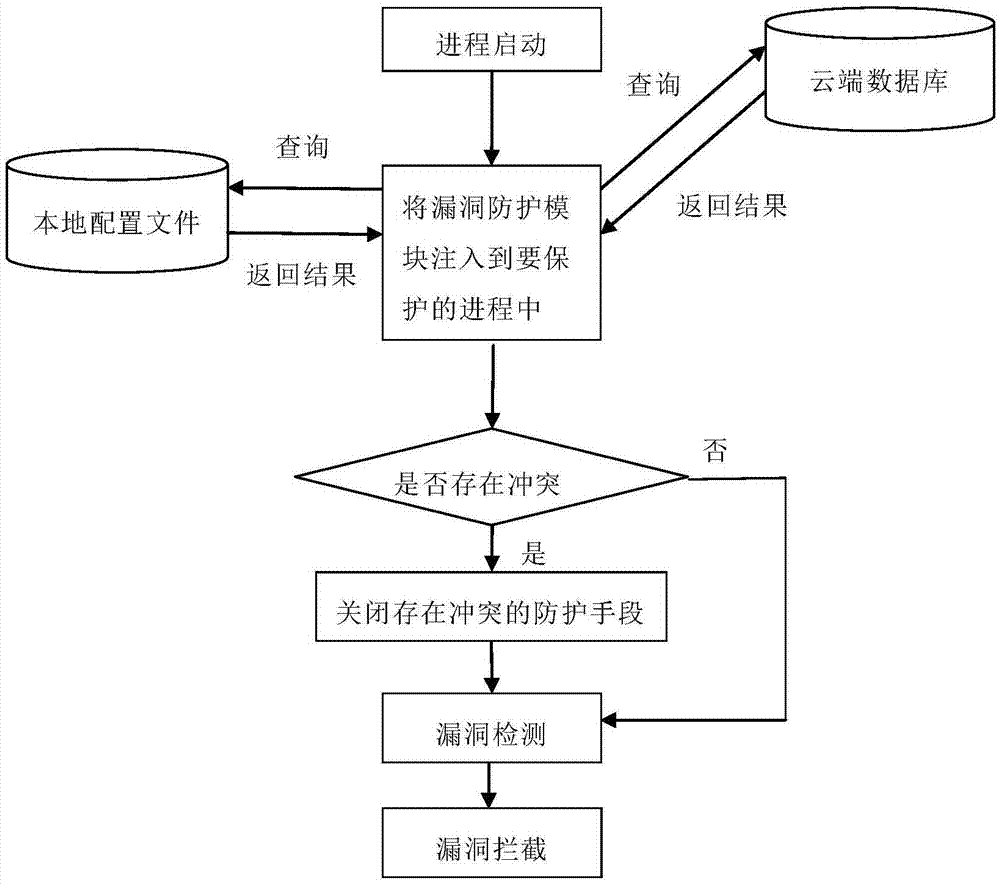
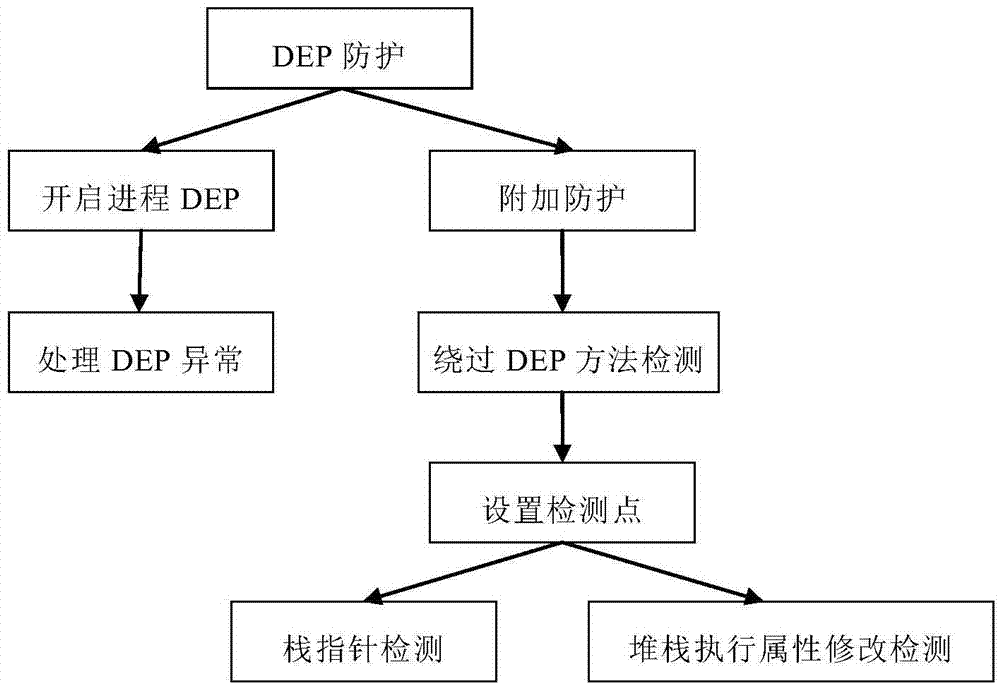
Anti-vulnerability-exploitation method and system
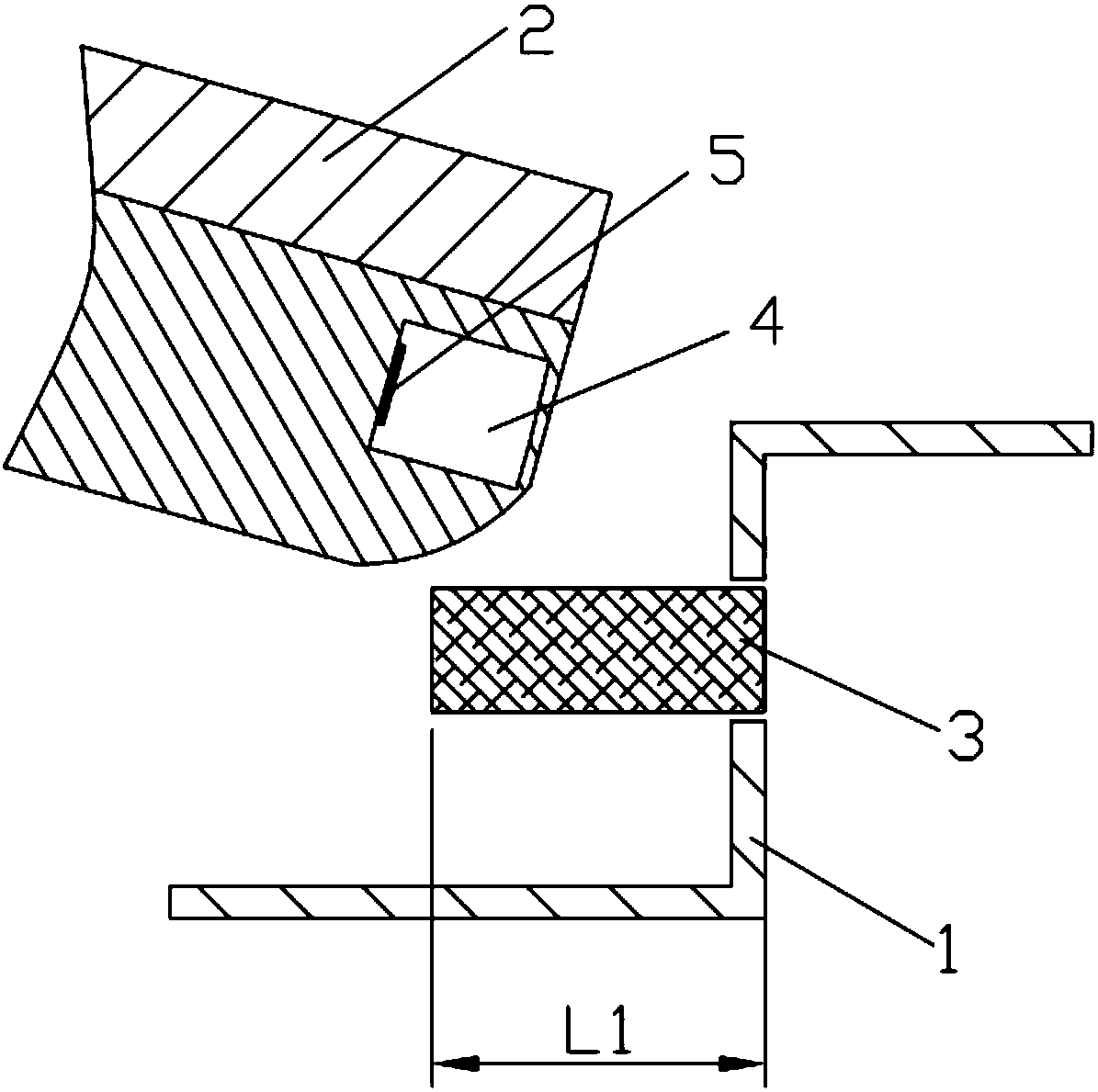
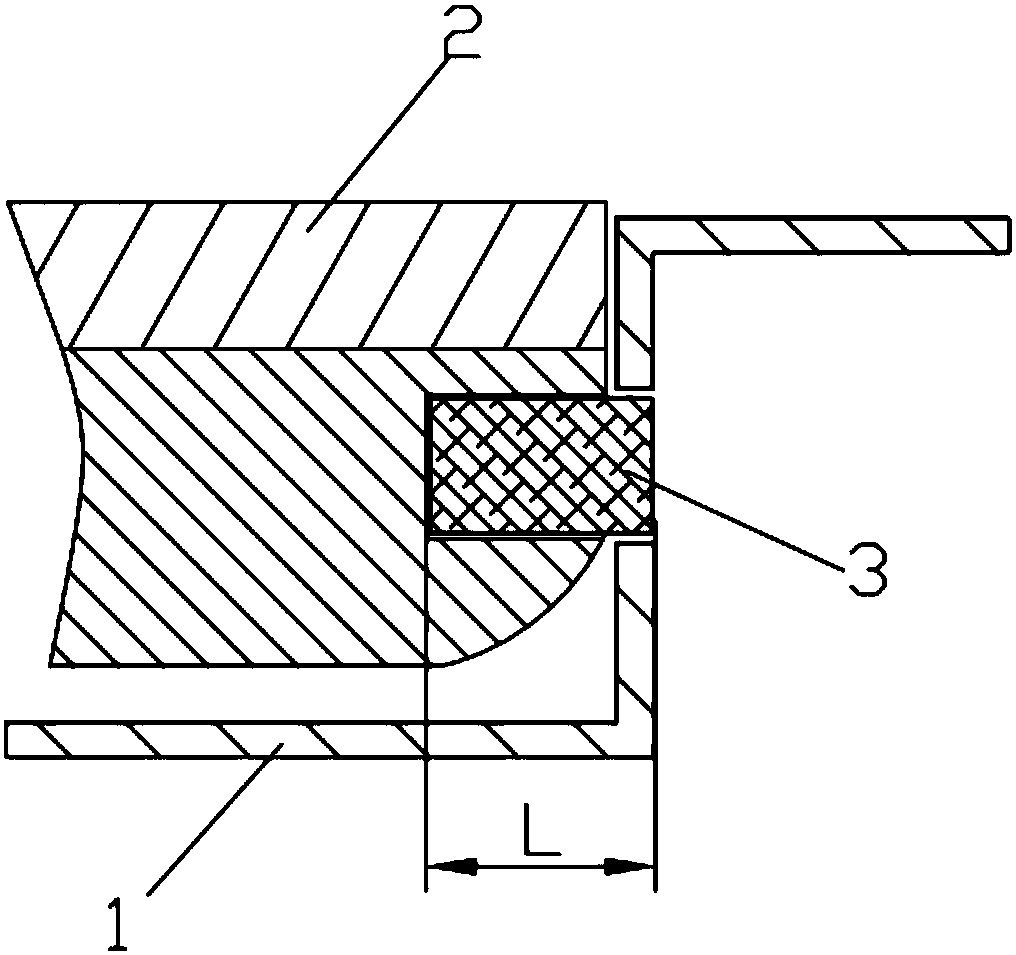
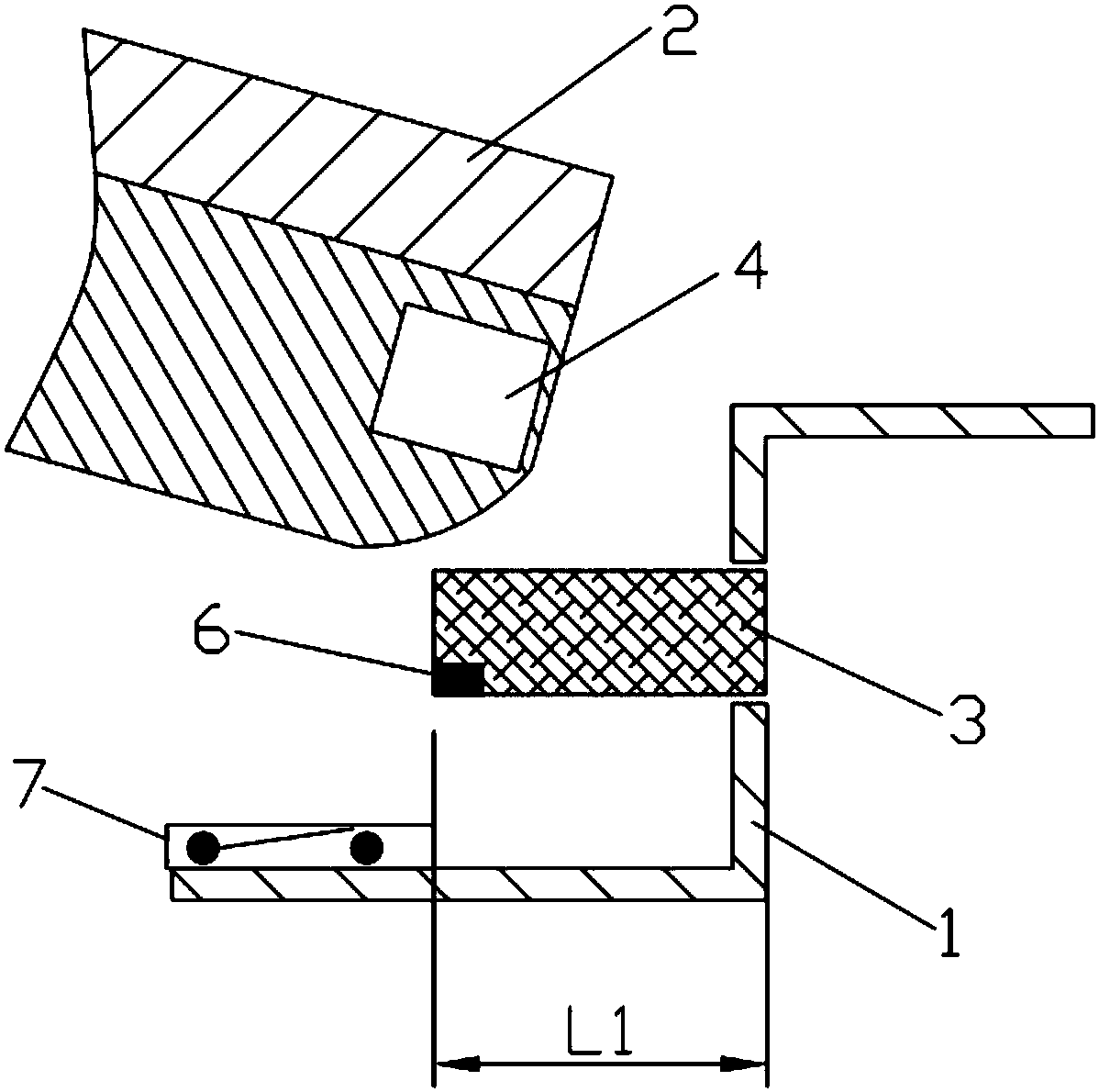
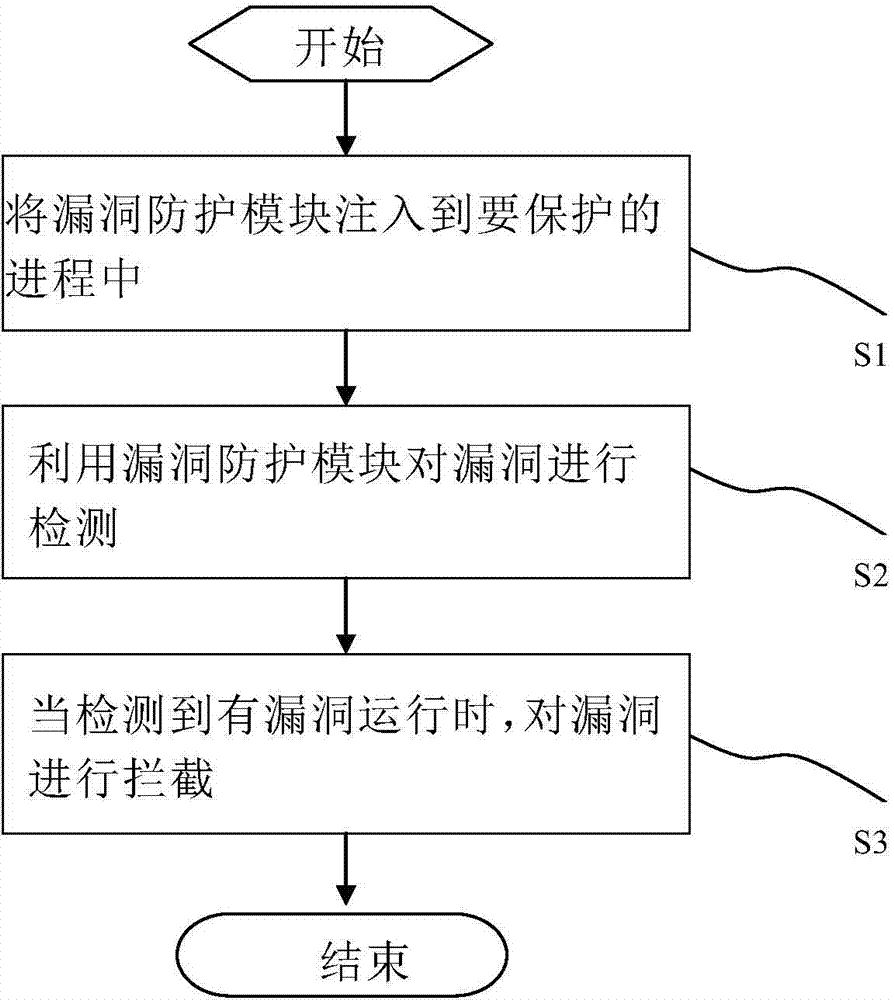
ActiveCN104217157AStop runningImprove quick response abilityPlatform integrity maintainanceVulnerability scanningNetwork security
The invention relates to an anti-vulnerability-exploitation method and system, belongs to the technical field of network security and aims to solve the problems of high maintenance cost and incapability of detecting new overflow vulnerabilities in time in the conventional vulnerability scanning scheme. The method comprises the following steps: injecting a vulnerability protection module into a process to be protected; detecting vulnerabilities by using the vulnerability protection module; intercepting vulnerabilities when running of the vulnerabilities is detected. By adopting the method and the system disclosed by the invention, the vulnerabilities can be detected in time during running of the vulnerabilities, and the vulnerabilities are prevented from running continually.
Owner:ZHUHAI BAOQU TECH CO LTD
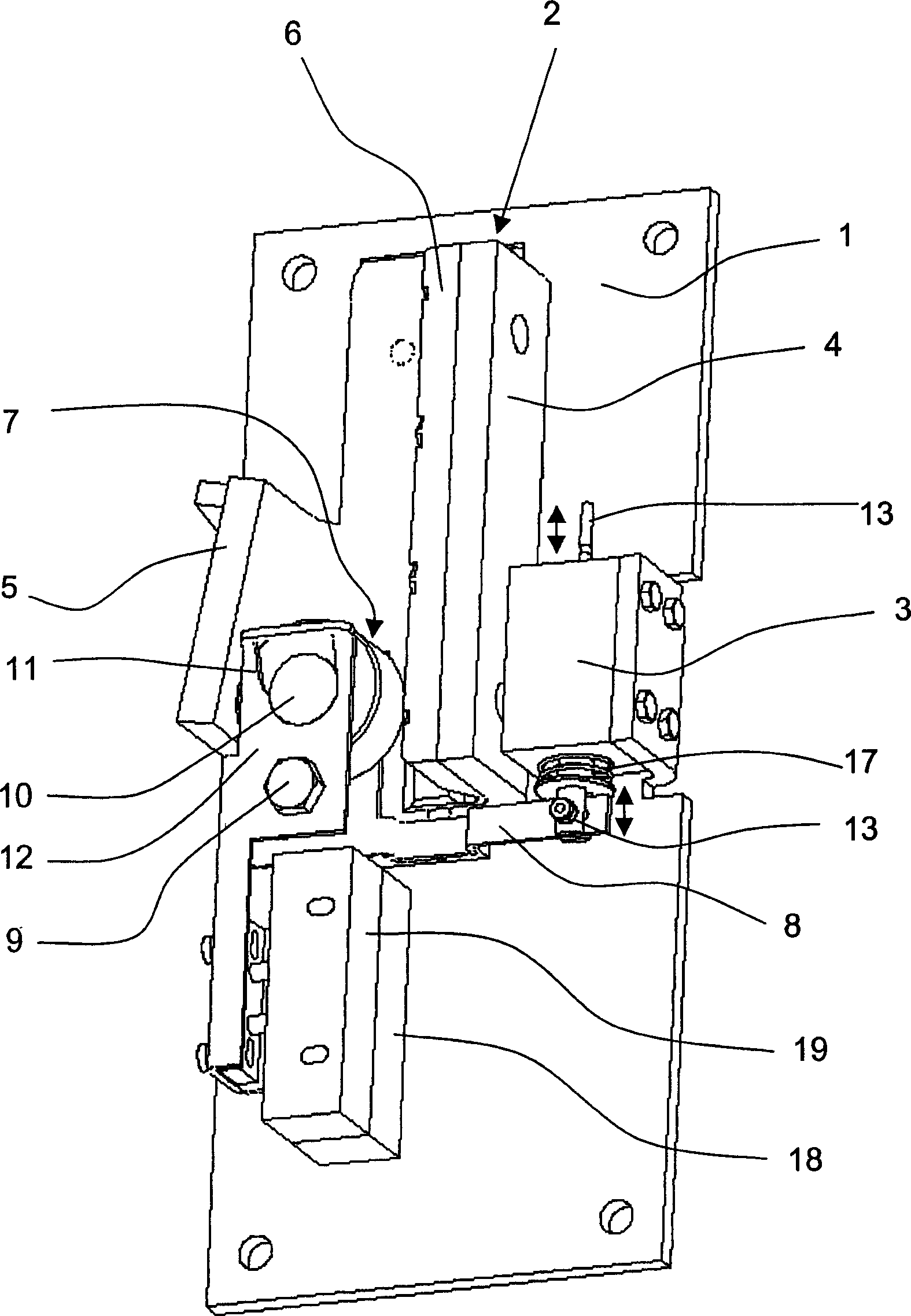
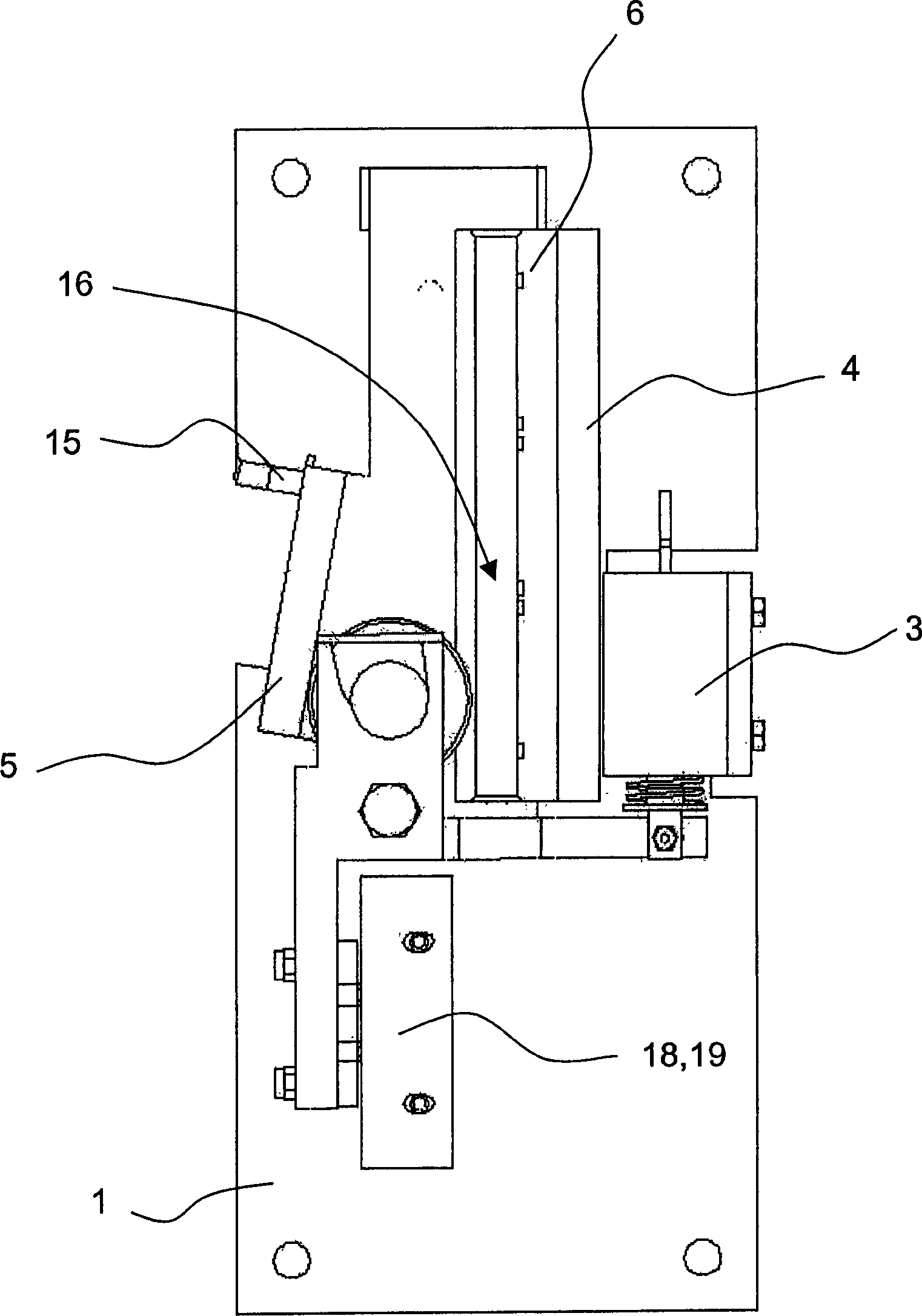
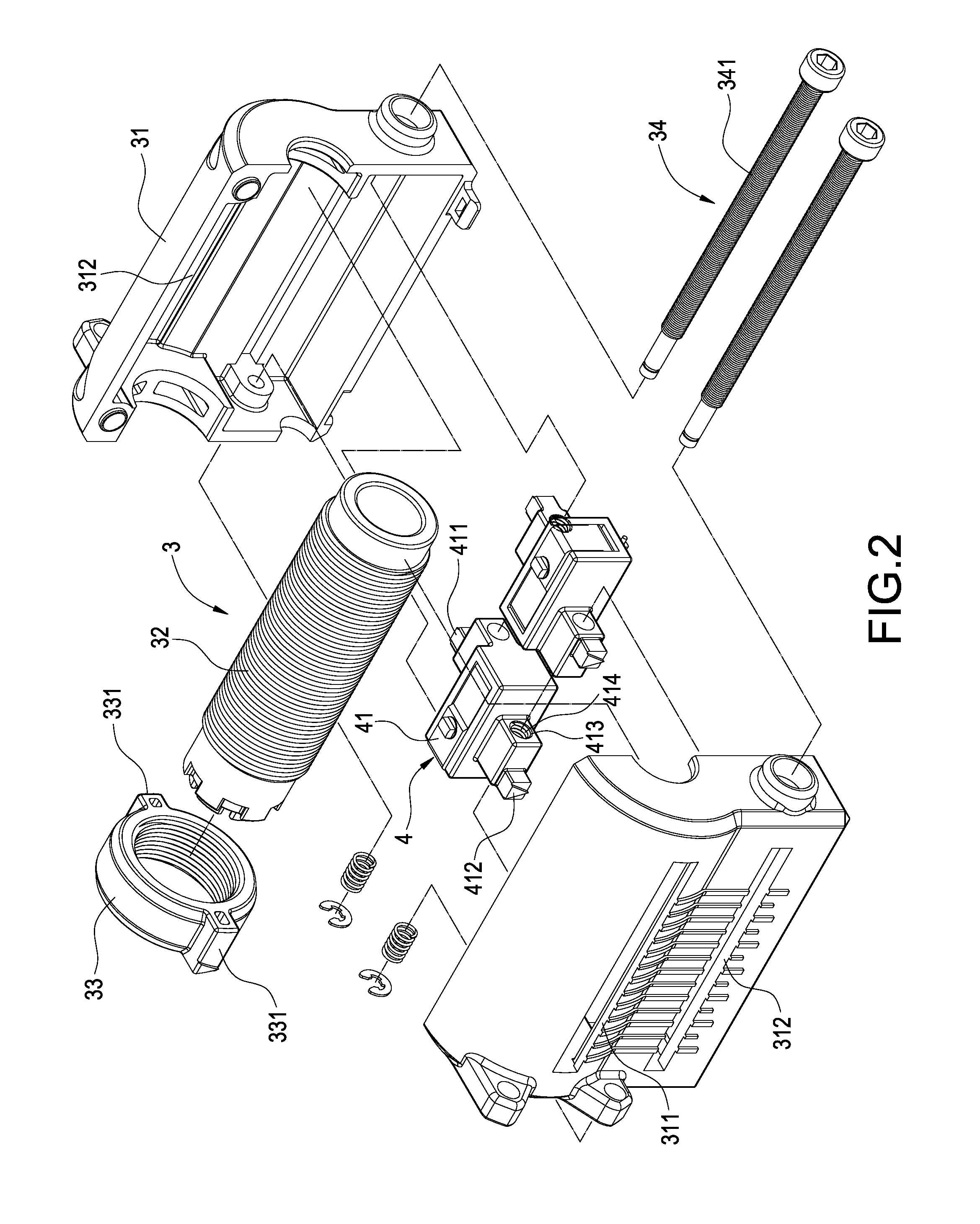
Safety braker of lift
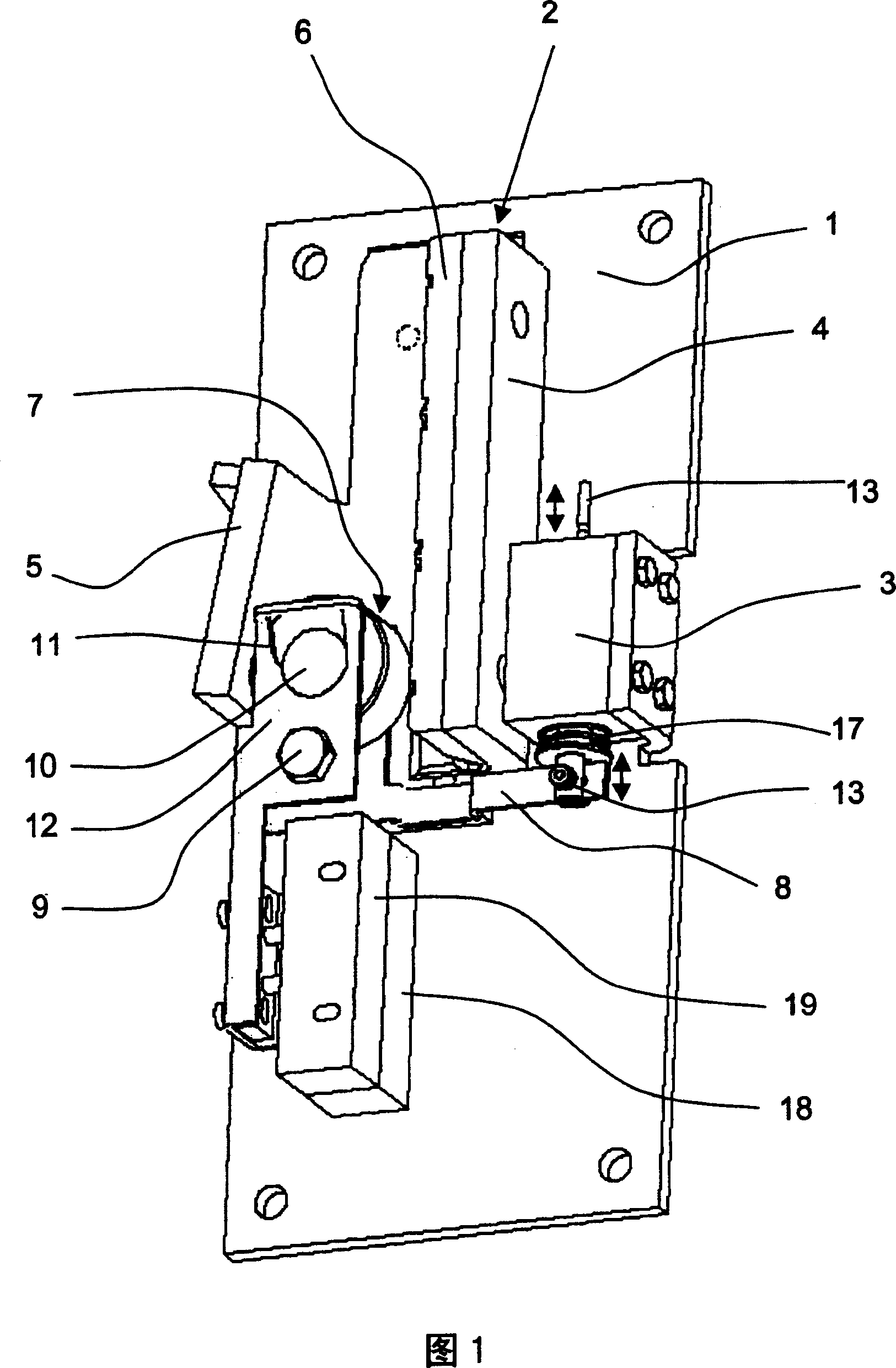
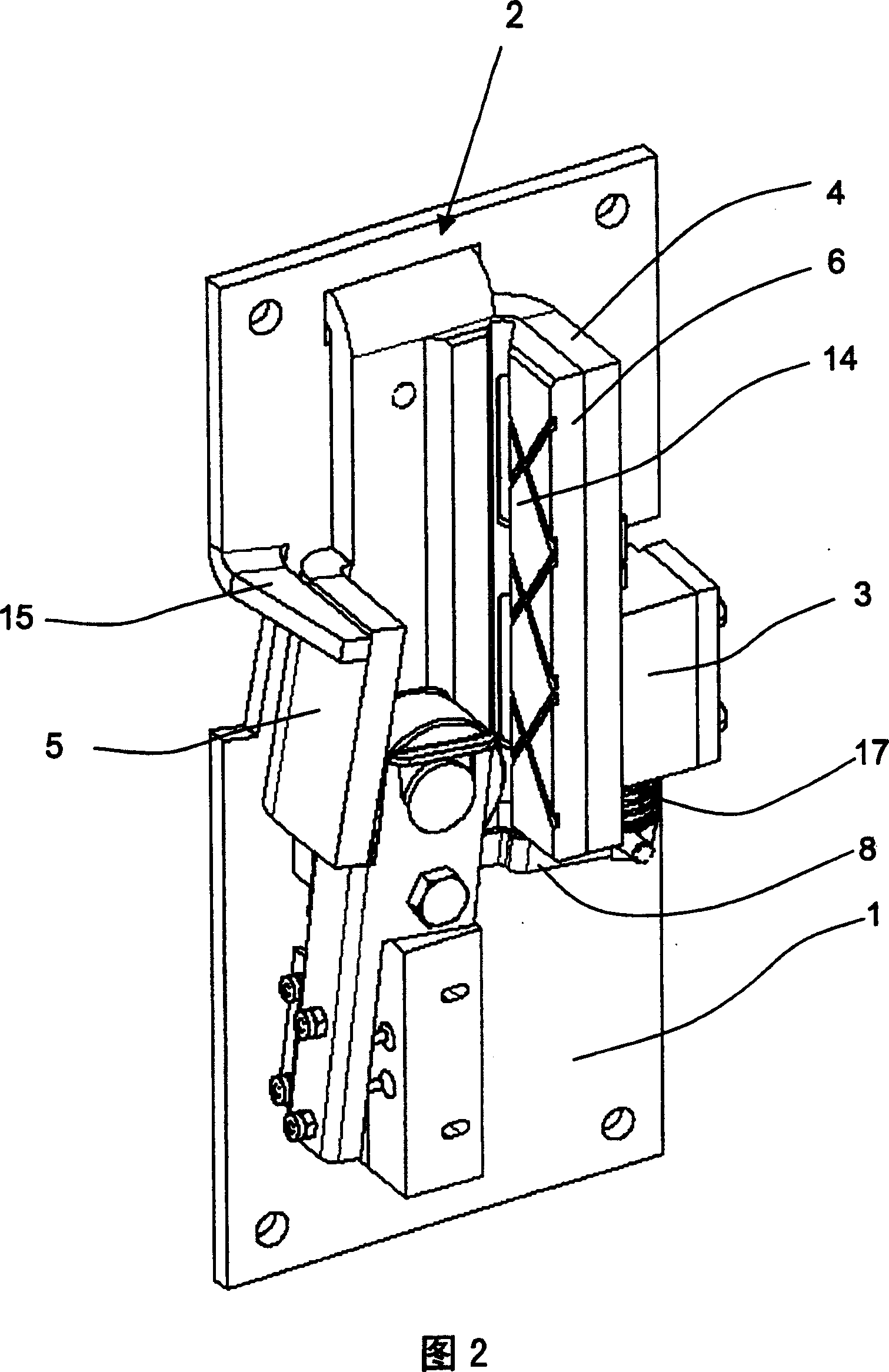
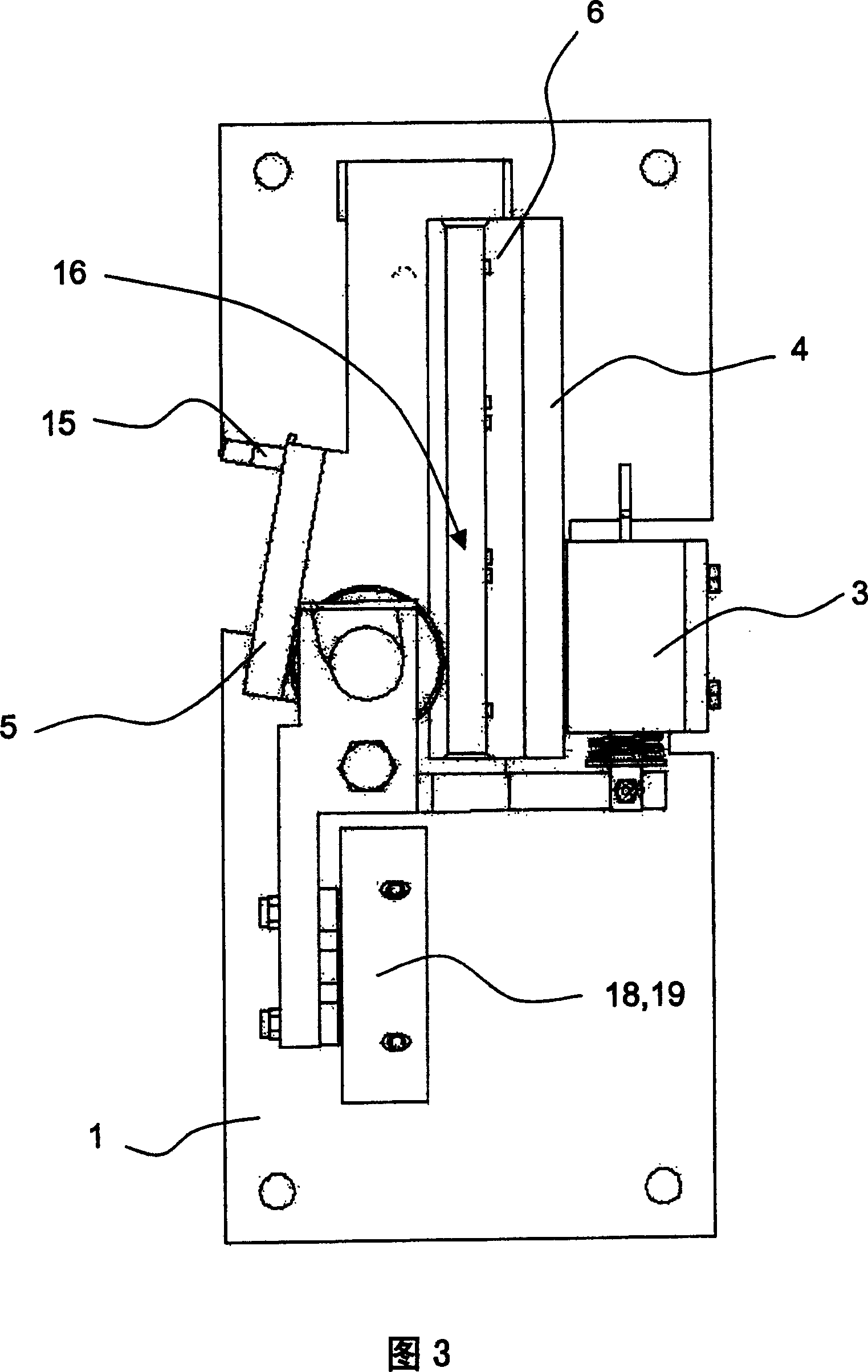
This safety device serves for braking an elevator car in an elevator system provided with a guide rail having a rectangular guide flange. The safety device is provided with a holding device 1, which carries a retaining element 4, 6 and an abutment 5. The safety device is arranged in such a way that the guide flange is positioned between the retaining element 4, 6 and the abutment 5 in operation. A mechanism 8 is available which squeezes a braking member in the form of a blocking roller 7 between the guide flange and the abutment 5 when braking. The mechanism 8, cooperating with an electromagnet 3, exhibits a suspension 12. In such suspension, the braking member 7 is movably placed and can be moved in a controlled way between different positions assigned to different operation conditions of the safety device.
Owner:INVENTIO AG
Method for remotely monitoring safety of application program
The invention discloses a method for remotely monitoring safety of an application program. According to the method, real-time operation is performed on an application program file, a unique binary sequence identity is generated and is compared with a digital fingerprint of the application program in a trusty list, the confidentiality of the digital fingerprint is high, and the digital fingerprint is difficult to crack; a new process needing to be created before the application program is started is monitored, so that starting of the application program can be monitored. The method for remotely monitoring the application program performs remote authorization by customizing the trusty list on a background server, a uniform method for monitoring application programs of a terminal system is provided, the procedure for deploying a monitoring system by a system administrator is simplified, and the work efficiency of an enterprise is improved.
Owner:CENT SOUTH UNIV
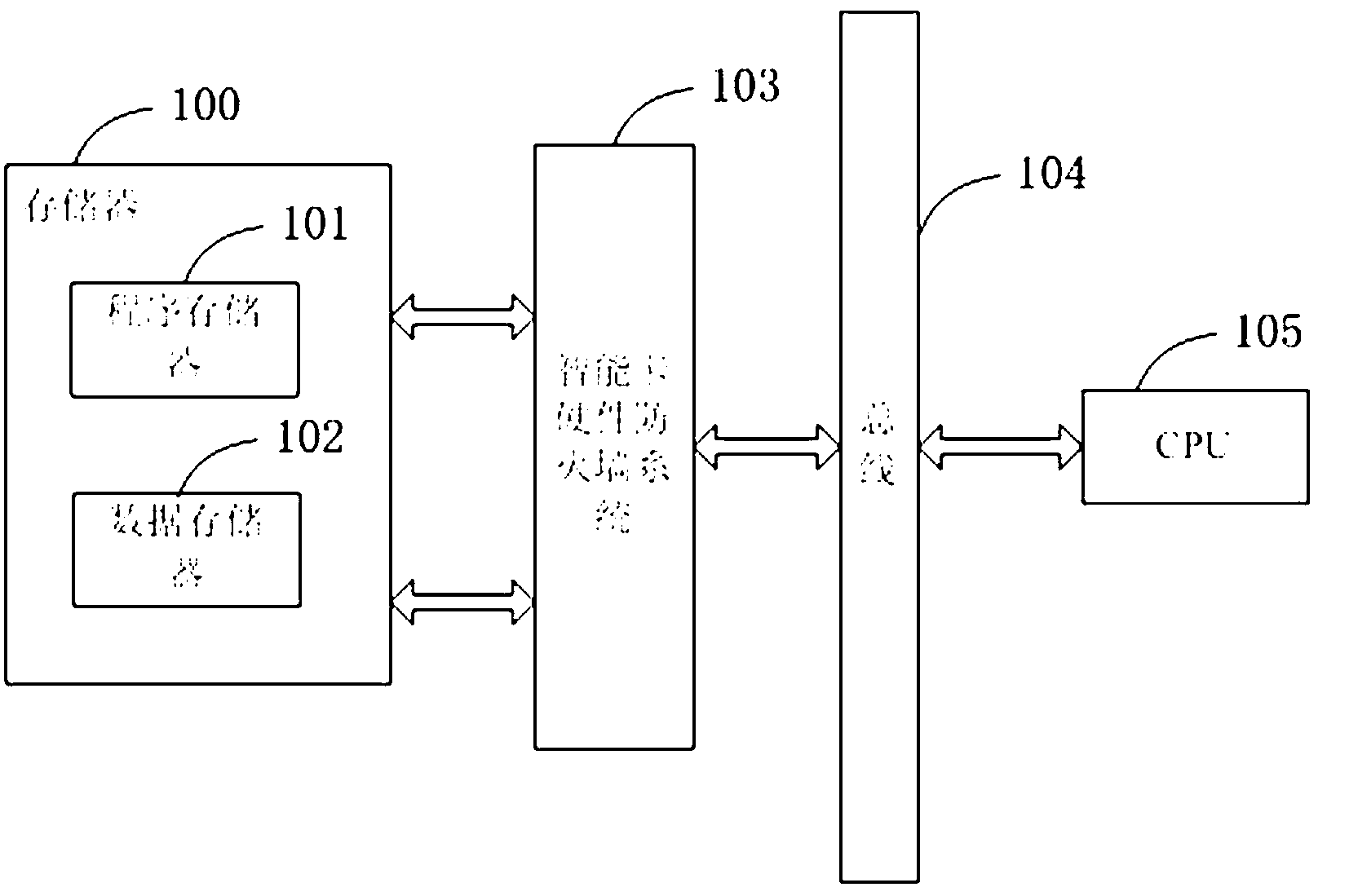
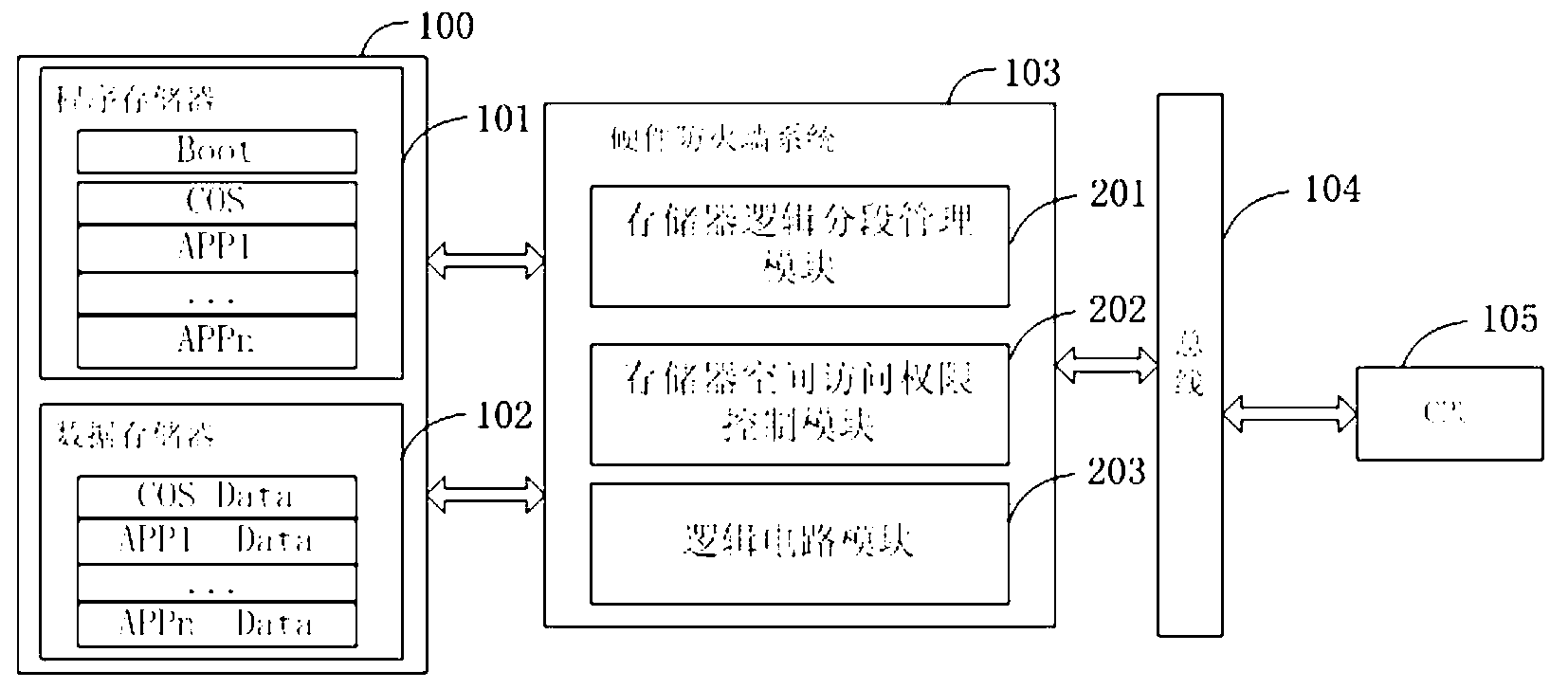
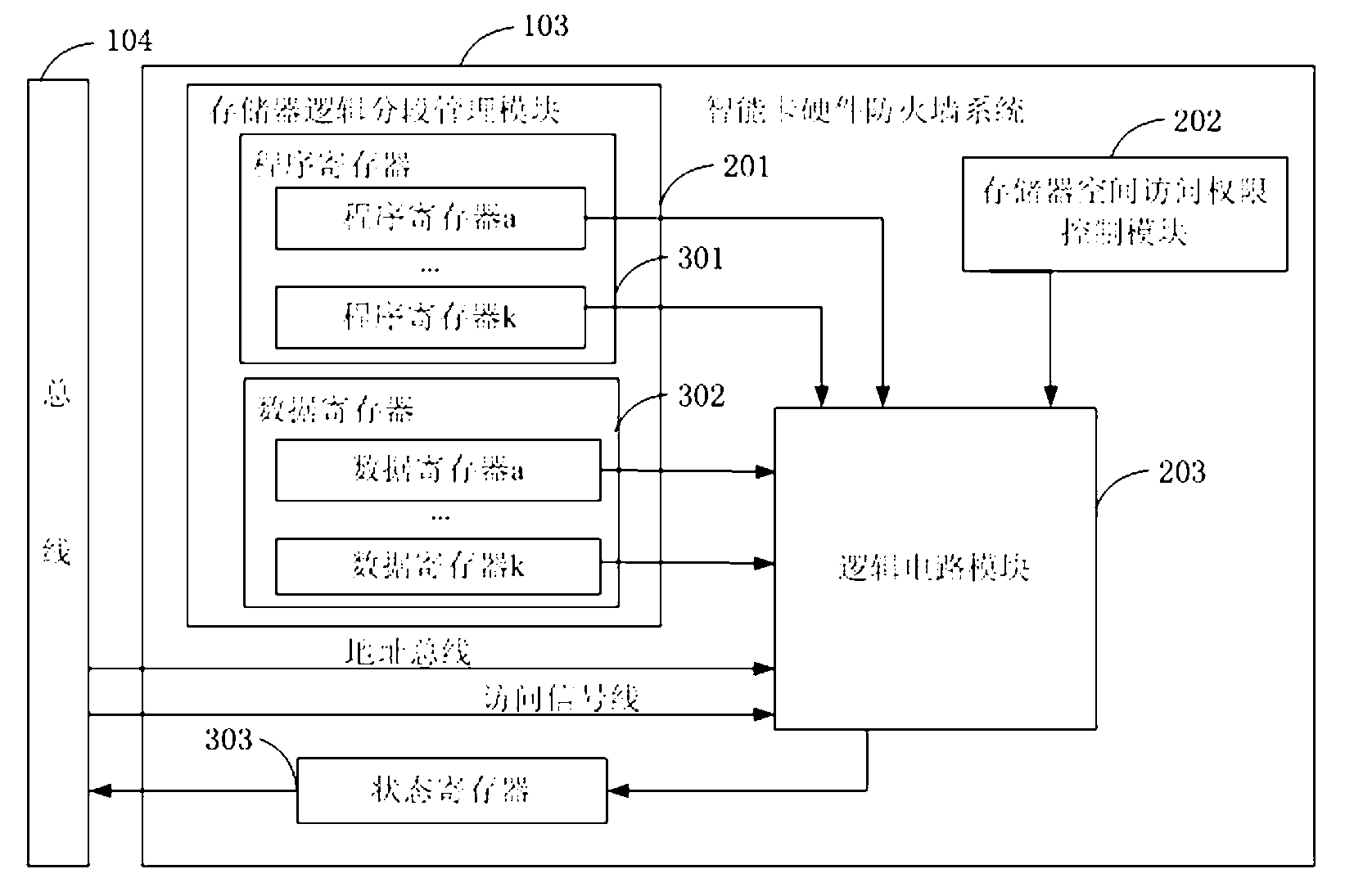
Intelligent card hardware firewall system and realizing method thereof
ActiveCN103136124AImprove safety performanceEnsure safetyUnauthorized memory use protectionData fileAuthorization
The invention relates to an intelligent card hardware firewall system and a realizing method thereof. The system comprises a storage logic subsection management module, a storage space assess authorization control module and a logic circuit module. The storage logic subsection management module is used for dividing a storage into one or a plurality of storage sections which are independent in logic, subsection management is achieved according to storage space, and each storage section stores program codes or data files with independent logical relationship. The storage space assess authorization control module is used for setting access authorization between a program code storage section and a data file storage section. The logic circuit module is used for receiving an address access signal and judging whether the address access signal is valid according to the program code section currently running and the access authorization set by the storage space assess authorization control module. According to the intelligent card hardware firewall system and the realizing method thereof, logic subsection management and space access control are achieved on a storage, so that safe coexisting of a plurality of applications on the same intelligent card is achieved, the hidden danger that an invalid program modifies an access zone and authorization of an application program through an operating system is avoided, and safety of the intelligent card is guaranteed.
Owner:NATIONZ TECH INC
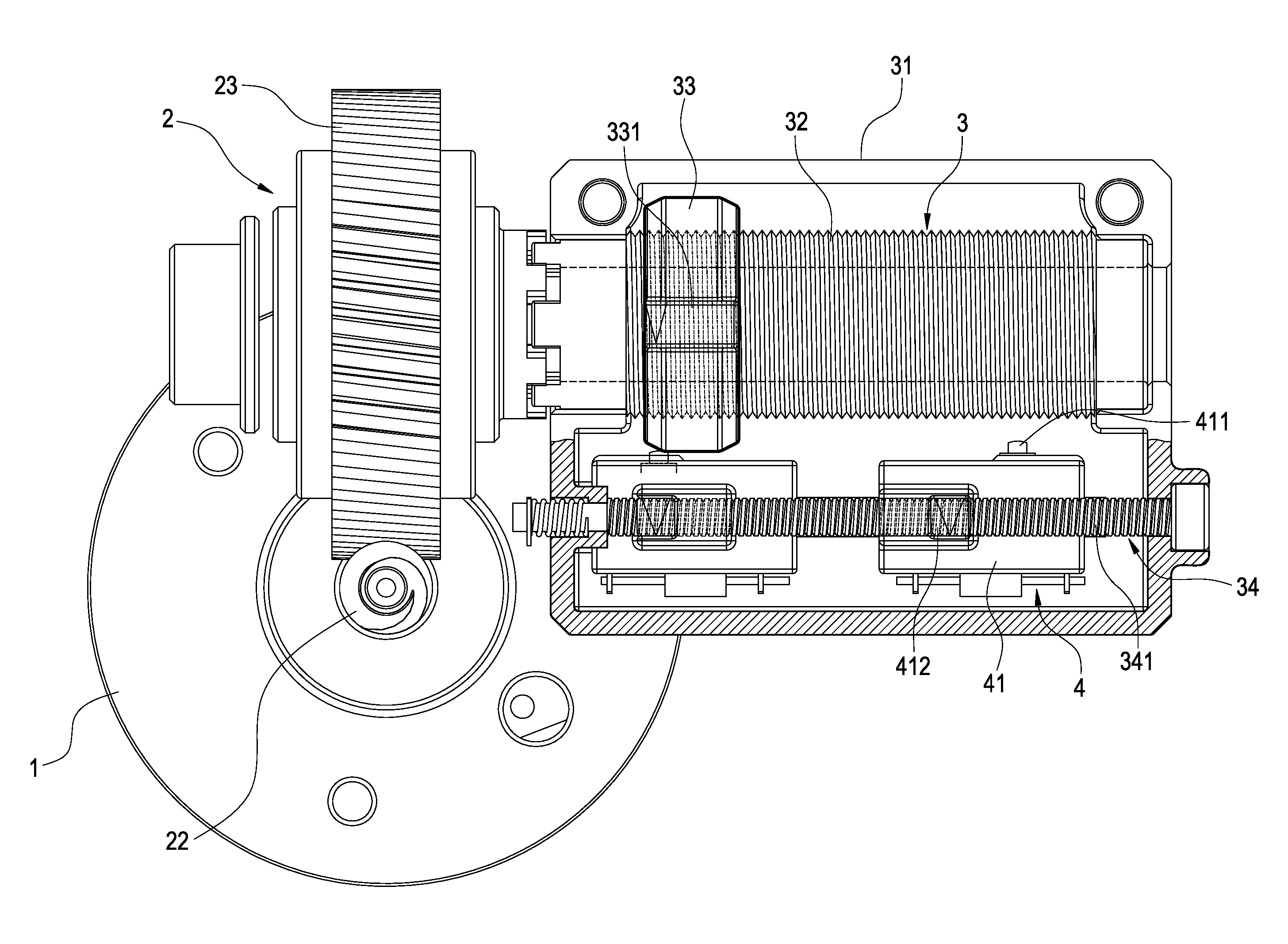
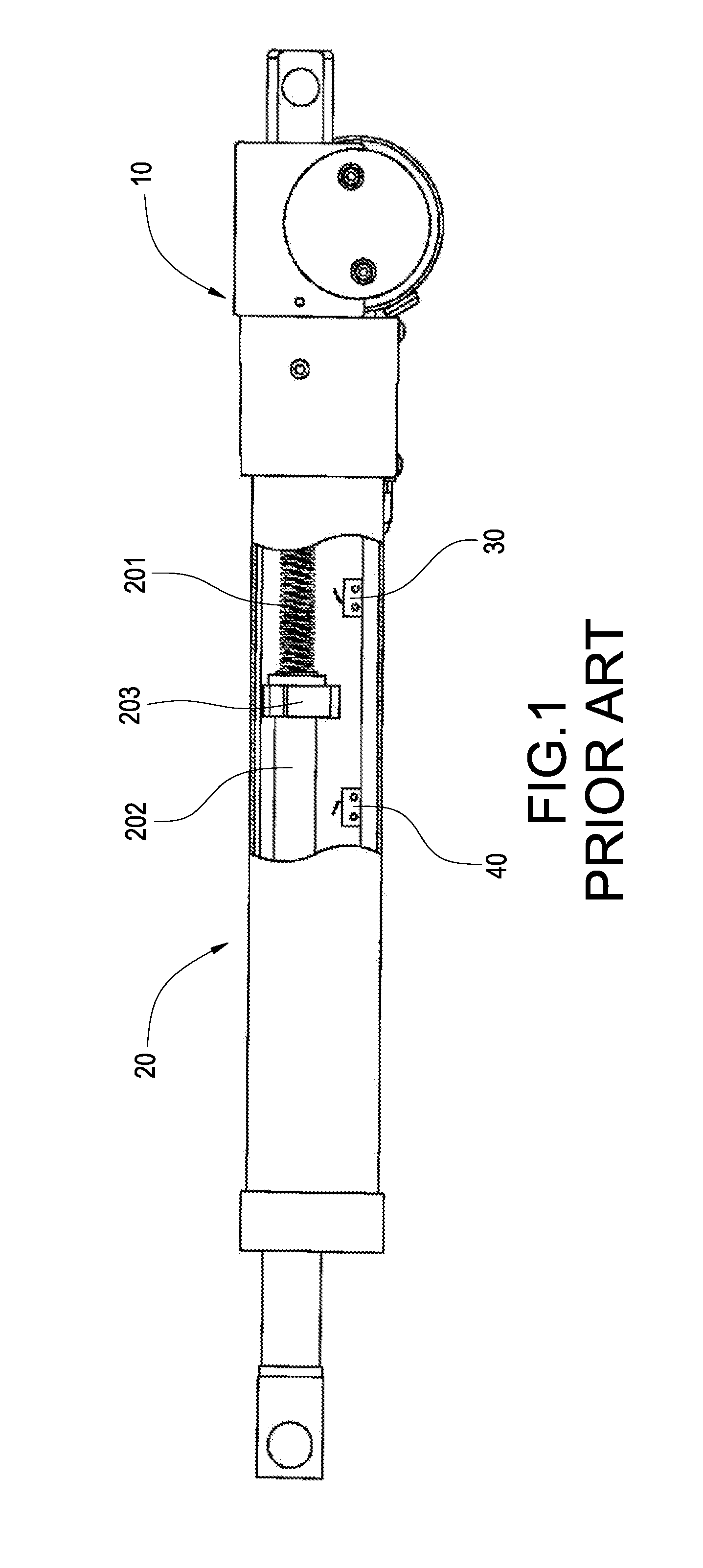
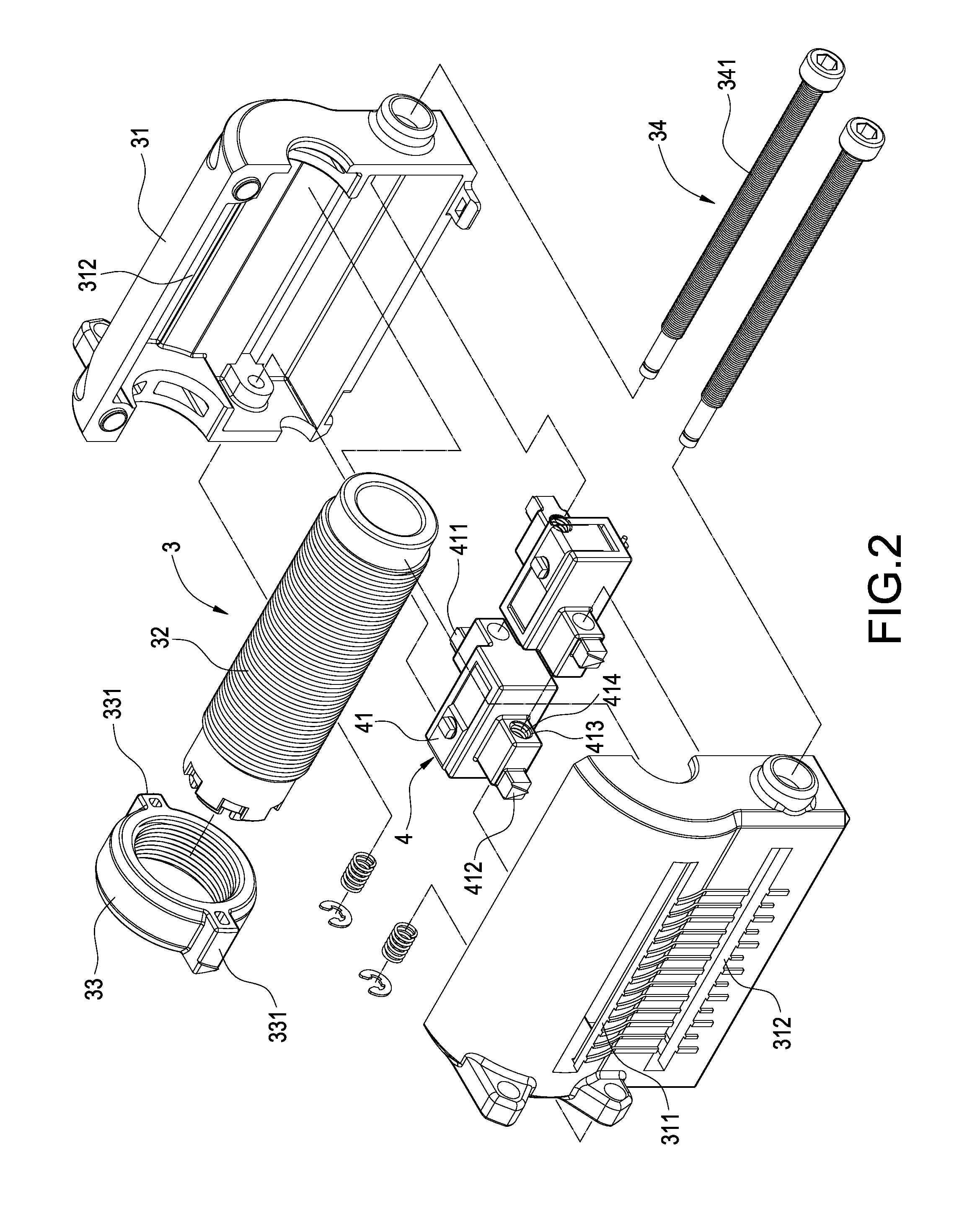
Gear motor having safety mechanism
ActiveUS8794087B2Reduce MechanismsReduce volumeToothed gearingsPortable liftingLeadscrewTouch switch
A gear motor having a safety mechanism includes a motor body, a speed reduction mechanism, a transmission mechanism, and a touch switch. The speed reduction mechanism includes a worm and a worm wheel drivingly engaged with the worm. The transmission mechanism includes a base fixed to the speed reduction mechanism, a lead screw rod pivotally connected to the base and rotatably driven by the worm wheel, and a nut threadedly connected to the lead screw rod. The touch switch is electrically connected to the motor body and provided aside the lead screw rod, thereby stopping the motor body when the nut contacts the touch switch. Thus, the gear motor not only controls the operation of the driven mechanism, but also allows various driven mechanisms to be mounted thereon. The assembled volume of the gear motor and the driven mechanism is reduced.
Owner:TIMOTION TECH CO LTD
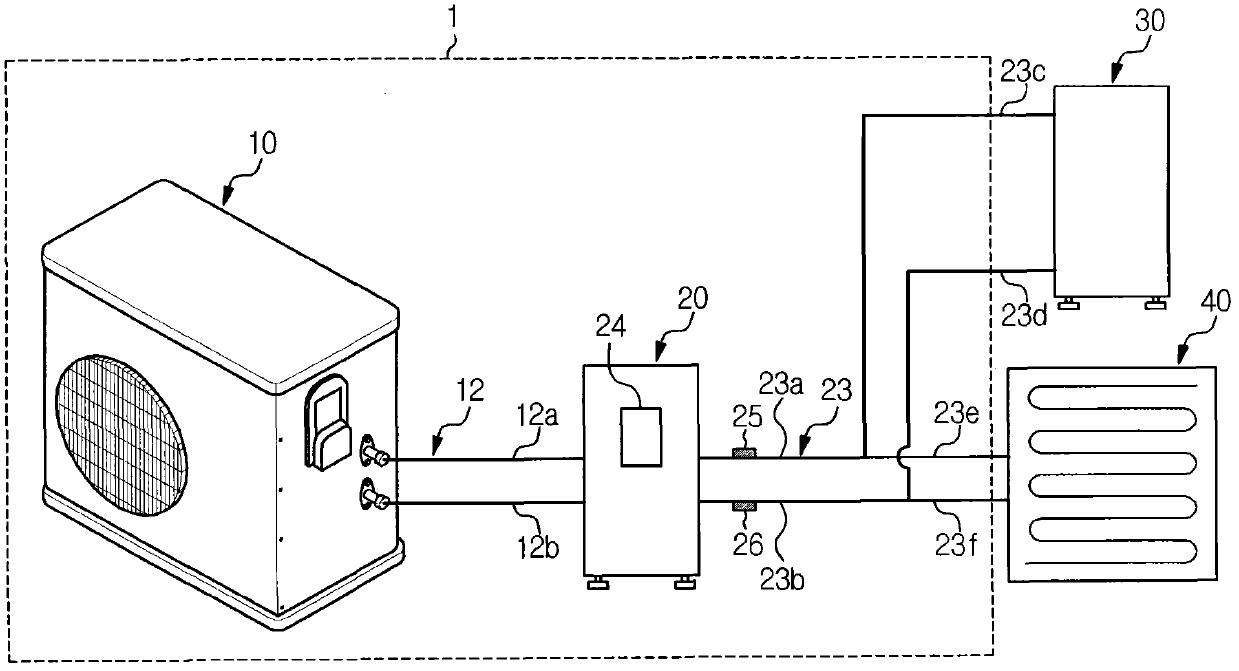
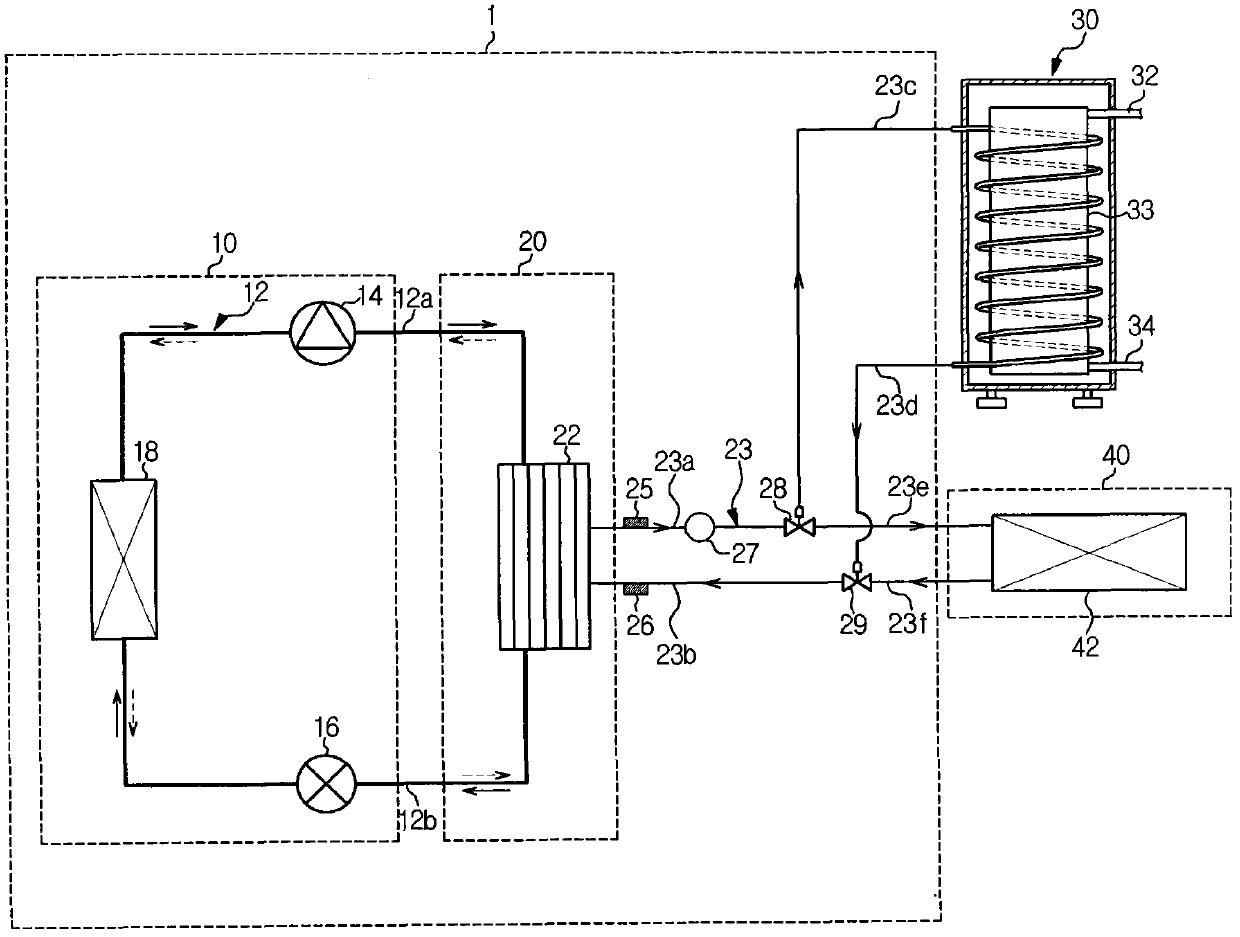
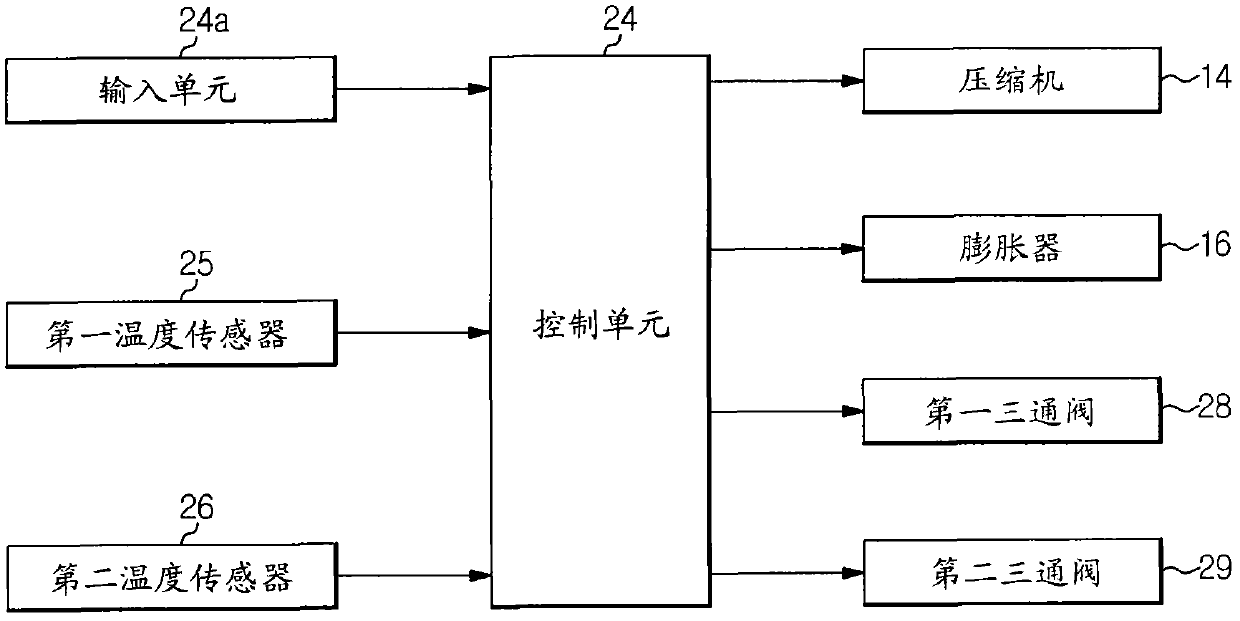
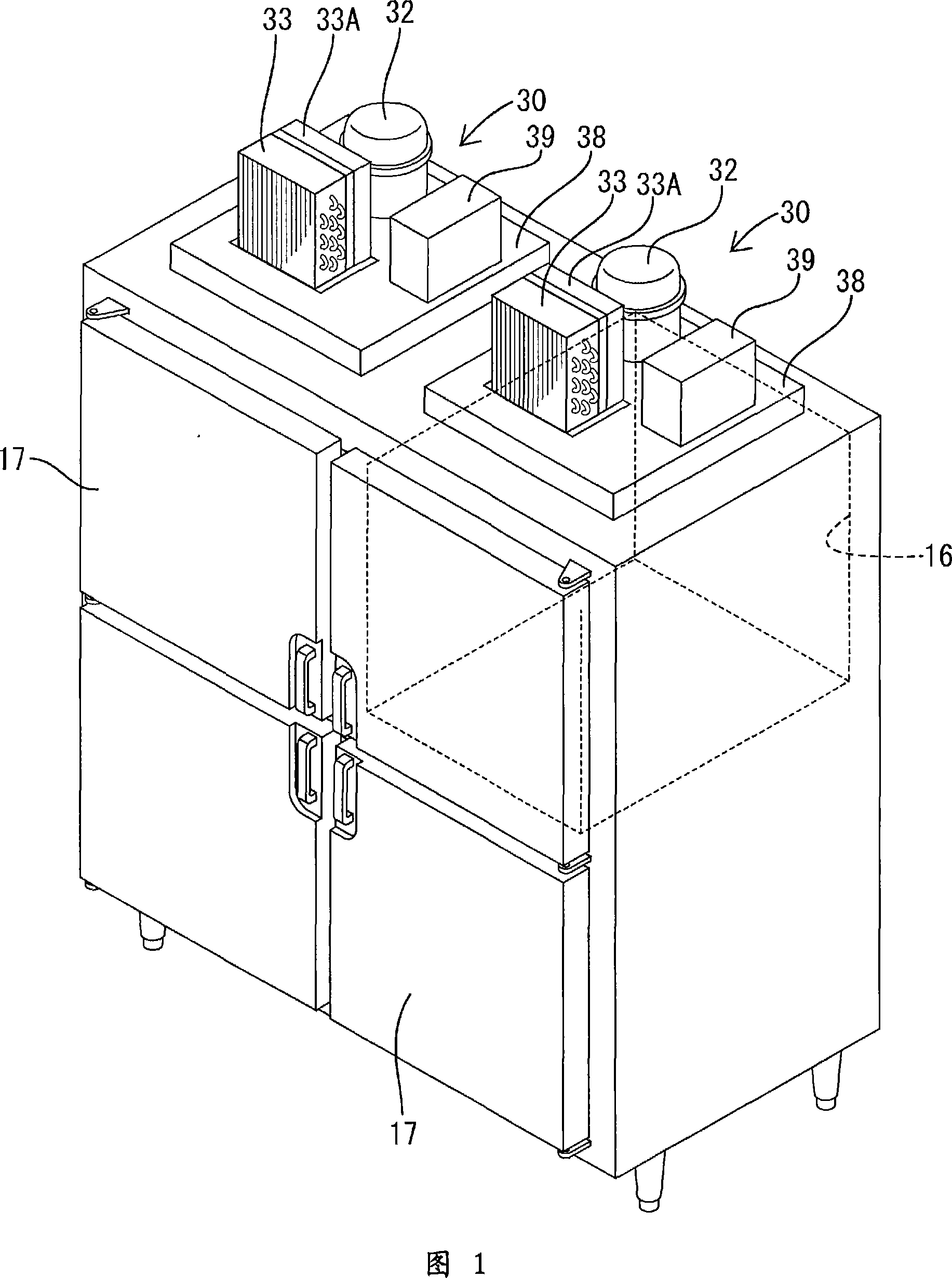
Heat pump system and control method thereof
Owner:SAMSUNG ELECTRONICS CO LTD
Refrigerator
InactiveCN101137875AEasy to operateStop runningDomestic refrigeratorsEfficient regulation technologiesTemperature curveEngineering
During a control cooling operation, data on control cooling operation characteristic is read from a memory and the data is compared to lowering degree of the temperature in the refrigerator actually measured by an in-refrigerator temperature sensor (46). A cooling device is operated so that the in-refrigerator temperature is lowered along a temperature curve stored in advance. If the in-refrigerator temperature is higher than a set temperature by, for example, 7K for 15 minutes, the cooling ability by the cooling device is made higher than the cooling ability based on control of a control operation control device. Even if a door (17) is opened and closed frequently to gradually increase the in-refrigerator temperature, it is rapidly detected so as to suppress the in-refrigerator temperature to the vicinity of the set temperature.
Owner:HOSHIZAKI ELECTRIC CO LTD
Gear motor having safety mechanism
ActiveUS20130327168A1Increase safetyInspect and adjust easilyToothed gearingsTouch switchElectric motor
A gear motor having a safety mechanism includes a motor body, a speed reduction mechanism, a transmission mechanism, and a touch switch. The speed reduction mechanism includes a worm and a worm wheel drivingly engaged with the worm. The transmission mechanism includes a base fixed to the speed reduction mechanism, a lead screw rod pivotally connected to the base and rotatably driven by the worm wheel, and a nut threadedly connected to the lead screw rod. The touch switch is electrically connected to the motor body and provided aside the lead screw rod, thereby stopping the motor body when the nut contacts the touch switch. Thus, the gear motor not only controls the operation of the driven mechanism, but also allows various driven mechanisms to be mounted thereon. The assembled volume of the gear motor and the driven mechanism is reduced.
Owner:TIMOTION TECH CO LTD
Method and device for shutting application program
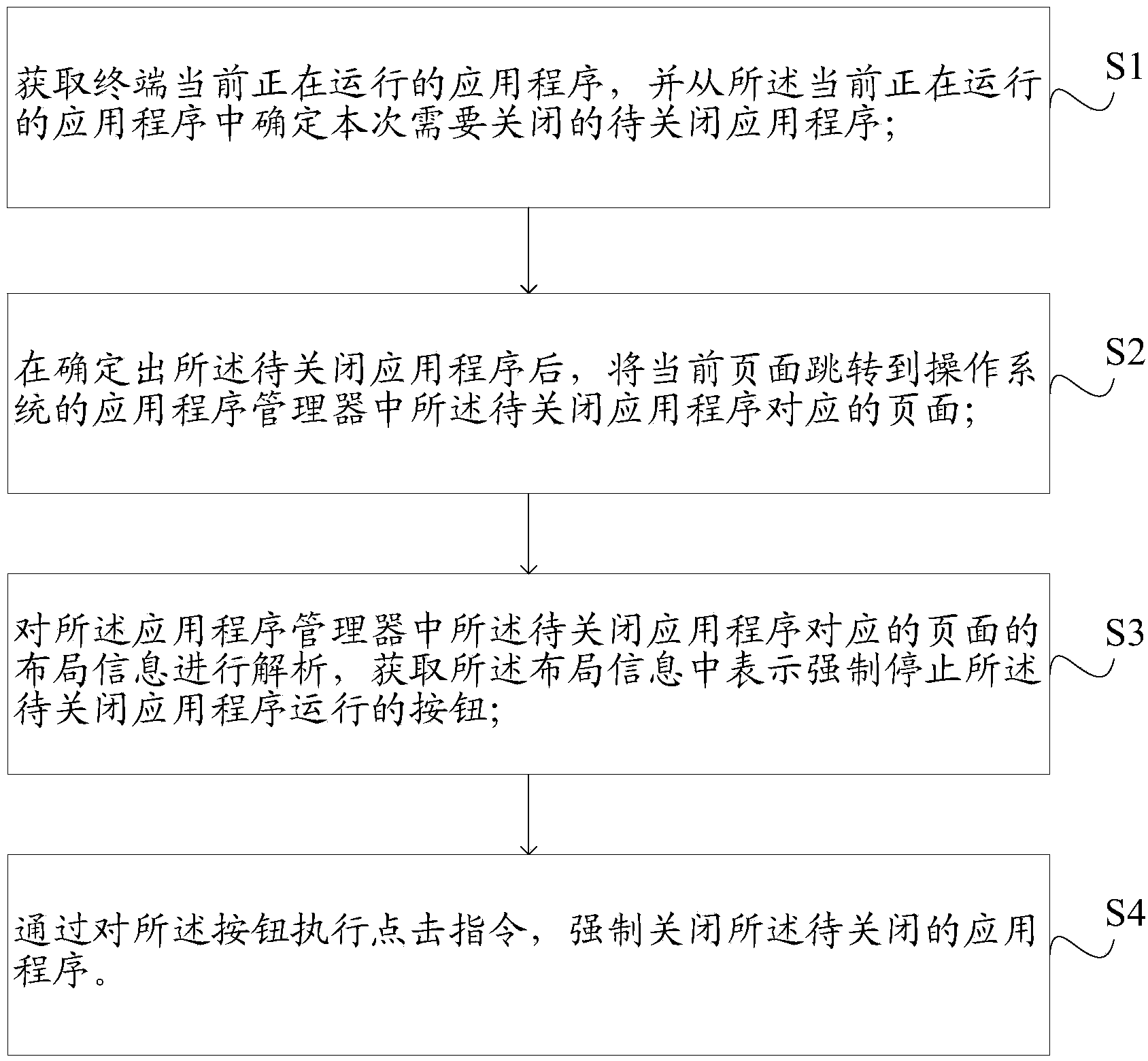
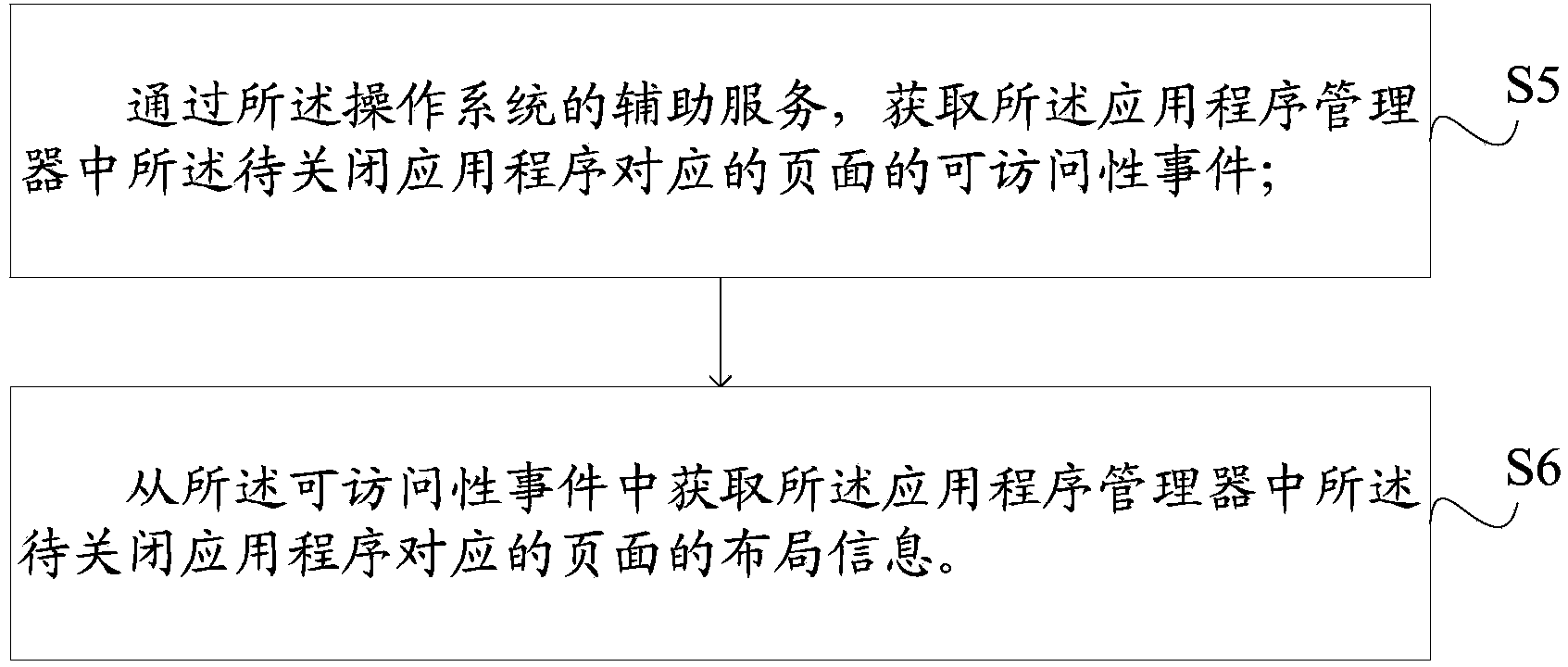
InactiveCN104239131AOff validStop runningMultiprogramming arrangementsComputer terminalProgram manager
The embodiment of the invention discloses a method and a device for shutting an application program and relates to the field of mobile internet technology application programs. The method and the device can be used for effectively shutting operation of the application program. The method for shutting the application program comprises the following steps: acquiring application programs currently operated in a terminal, and determining one to-be-shut application program which needs to be shut each time among the application programs currently operated; after determining the to-be-shut application program, skipping the current page to a page corresponding to the to-be-shut application program in an application program manager of an operating system of the terminal; resolving layout information of the page corresponding to the to-be-shut application program in the application program manager, and acquiring a button for forcibly shutting the operation of the to-be-shut application program in the layout information; executing a click instruction on the button so as to forcibly shut the to-be-shut application program. The method and the device are applicable to an occasion of shutting the operation of the application program.
Owner:KENIU NETWORK TECH BEIJING
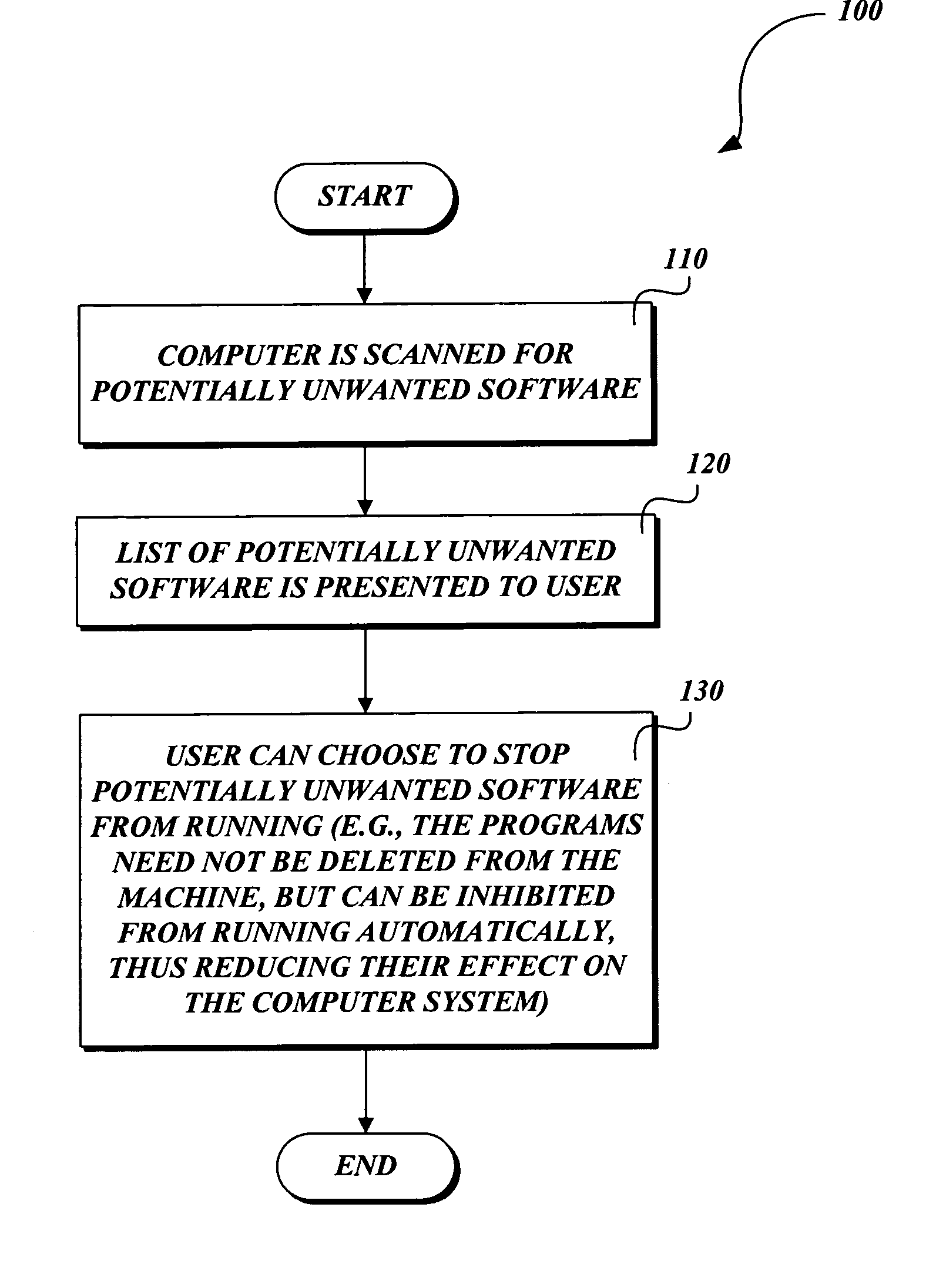
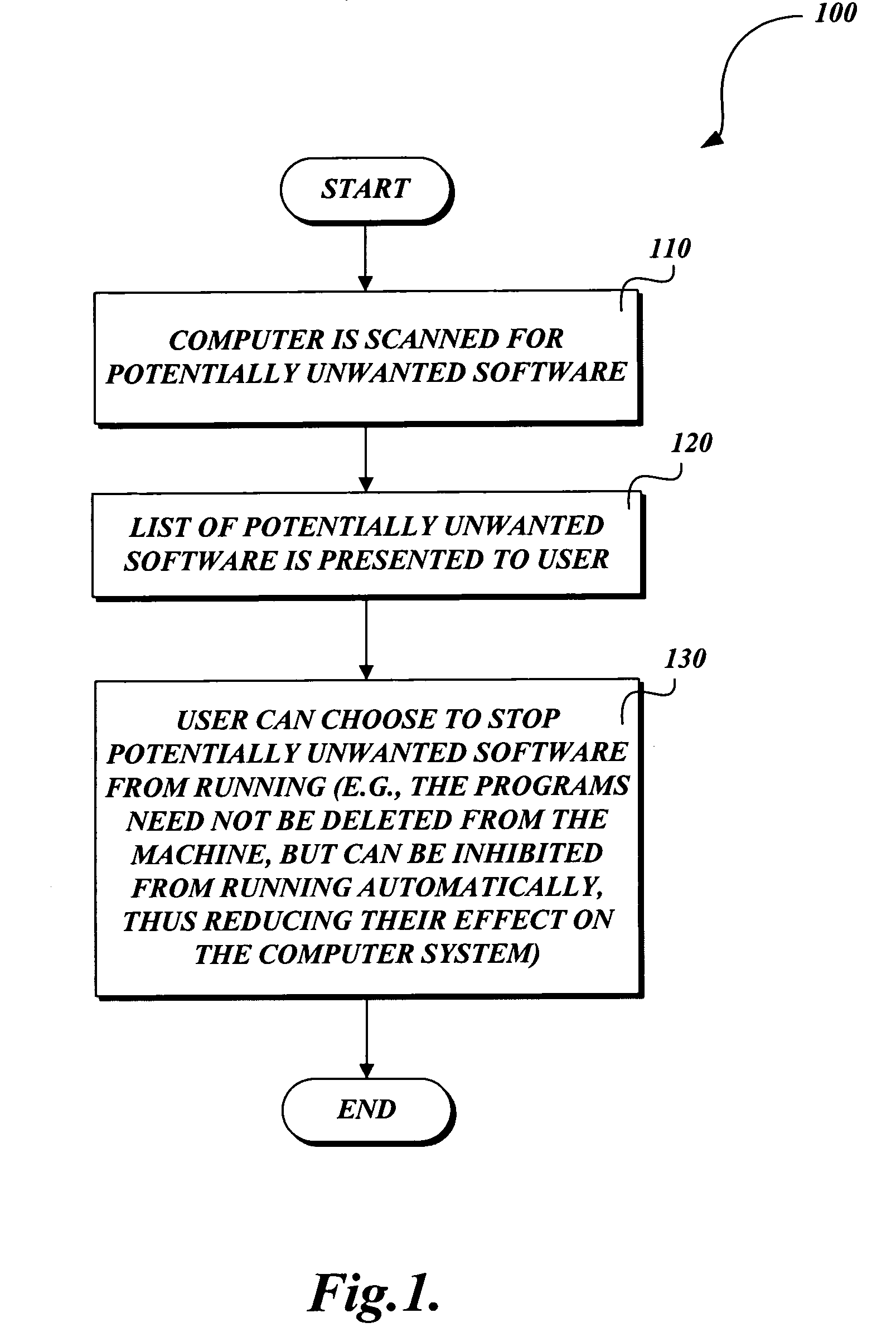
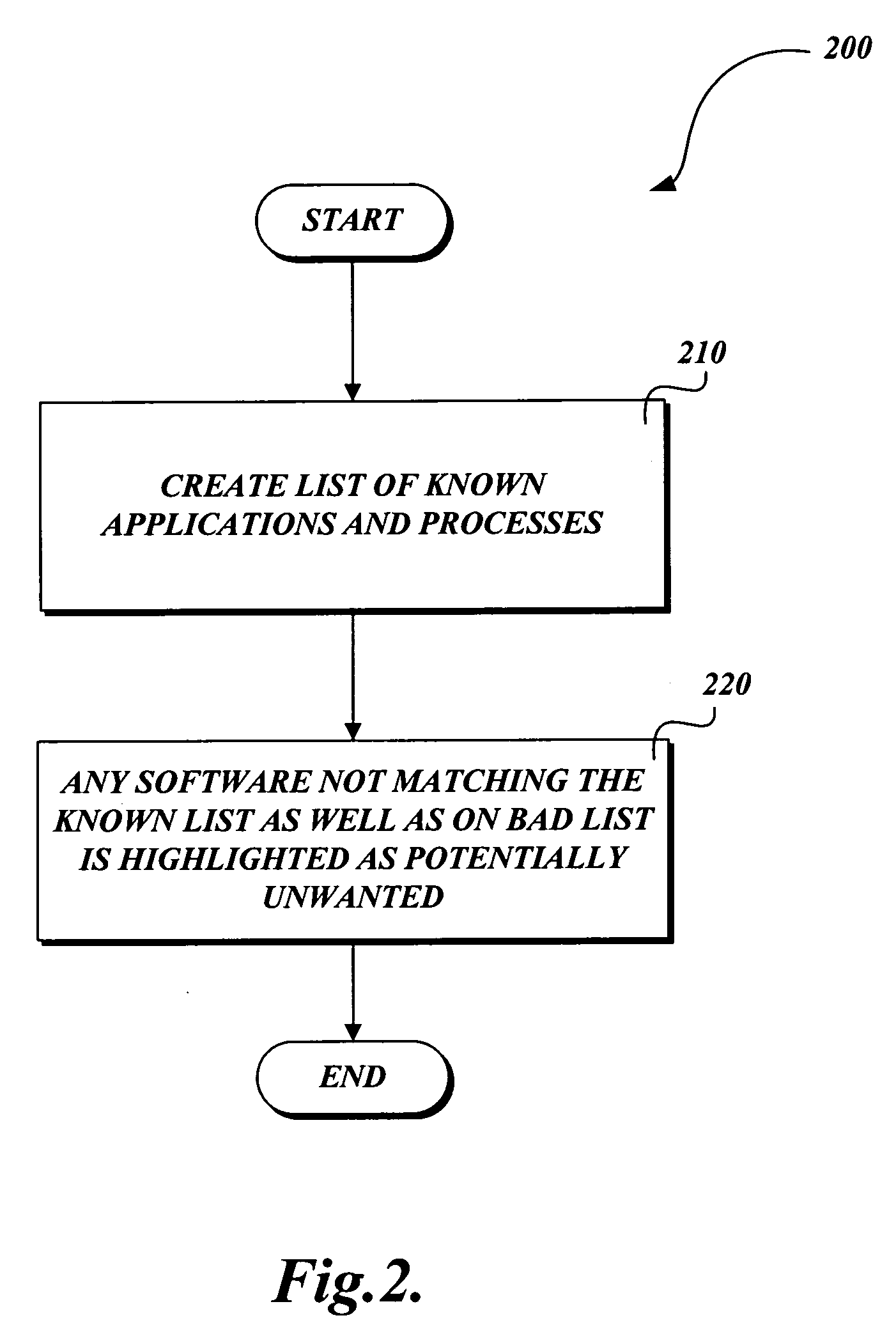
System and method for identifying and removing potentially unwanted software
ActiveUS20060218145A1Safely disabledSafe removalMemory loss protectionDigital computer detailsSoftware engineeringSoftware
A system and method for identifying and removing potentially unwanted software. A mechanism is provided that identifies suspect programs to a user and allows the user to prevent the suspect programs from running without actually deleting them. In one embodiment, scanner data identifying potentially unwanted software is displayed in a GUI that allows the user to inhibit its continued execution. For example, any software not on a list of known, benign applications / processes may be identified as potentially unwanted. Similarly, software that displays one or more suspect behaviors may be so identified, allowing the user to distinguish between normal and suspect software without irreversibly altering the user's system.
Owner:MICROSOFT TECH LICENSING LLC
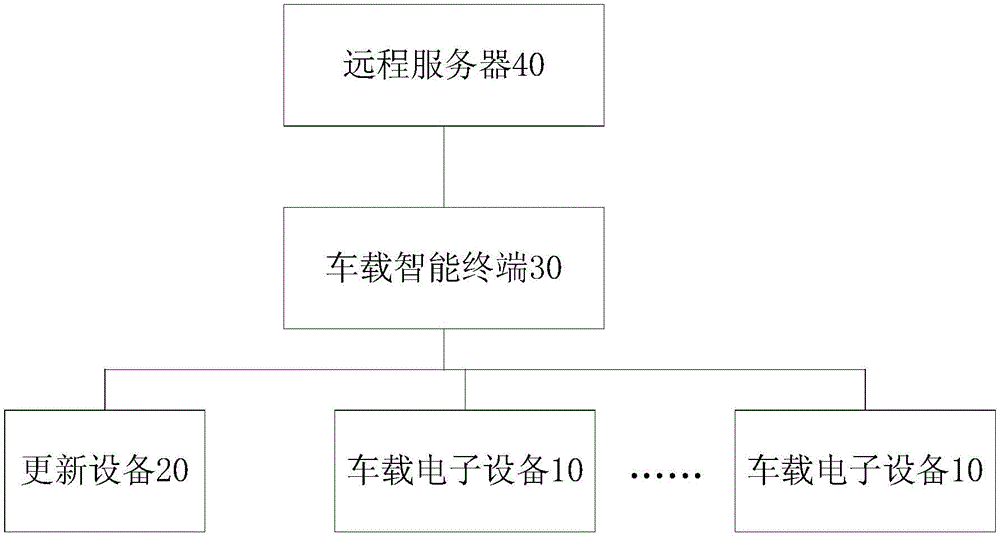
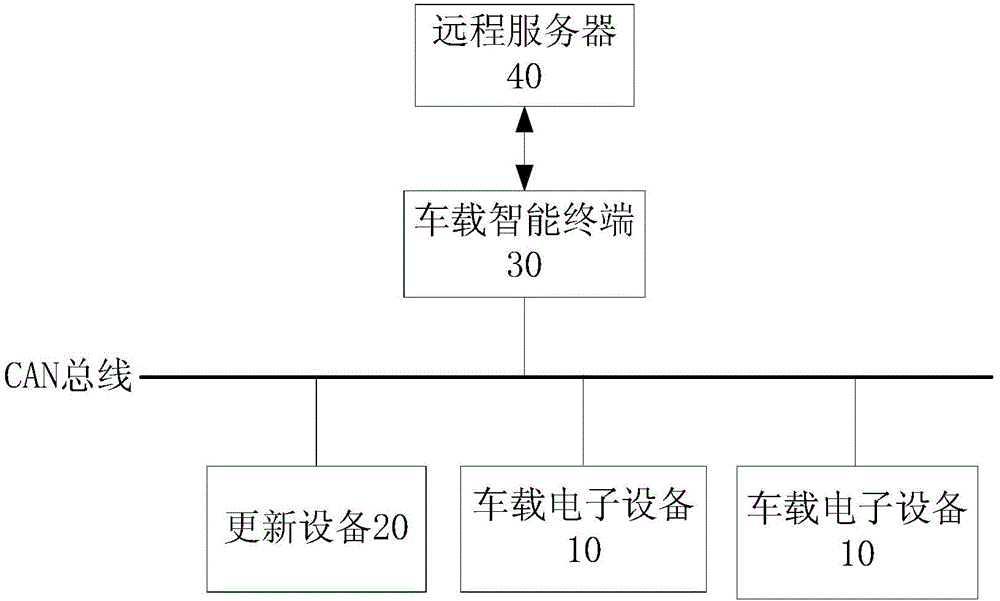
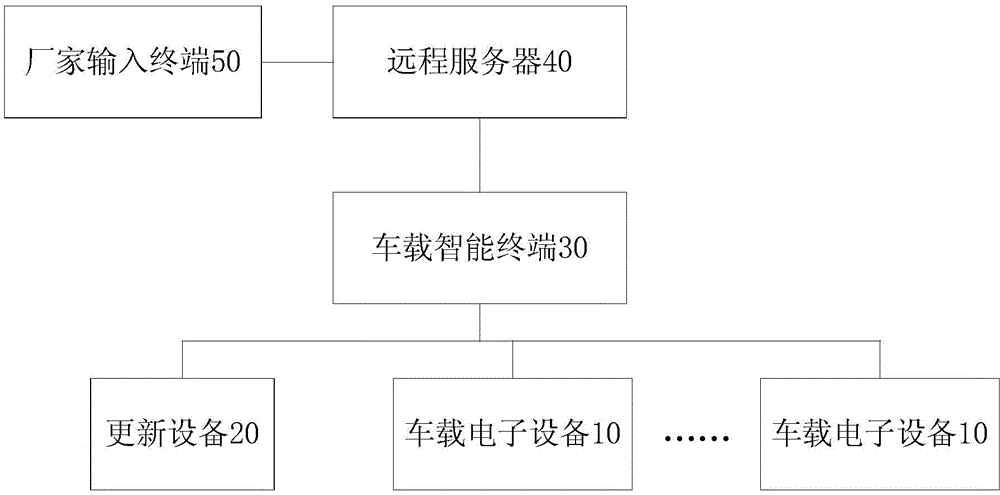
Software updating system and method for vehicle-mounted electronic device
ActiveCN105468385AReduce usageEnsure driving safetyProgram loading/initiatingSpecial data processing applicationsStopped workSoftware update
The invention discloses a software updating system and method for a vehicle-mounted electronic device. The system comprises a vehicle-mounted intelligent terminal, a remote server and an updating device. The vehicle-mounted intelligent terminal is used for obtaining an identifier code of the updating device when the updating device is connected to a vehicle diagnosis interface, sending the identifier code of the updating device to the remote server, receiving a judgment result sent by the remote server, generating and sending a first control instruction to the updating device when a judgment result is legal, and generating and sending a second control instruction to the updating device when the judgment result is illegal; the remote server is used for judging whether the identifier code of the updating device is legal or not and sending a judgment result to the vehicle-mounted intelligent terminal; and the updating device is used for updating software of at least one vehicle-mounted electronic device according to the first control instruction or stopping working according to the second control instruction. According to the system provided by an embodiment of the invention, a user can be prevented from using the illegal updating device privately, thereby ensuring travel safety.
Owner:BYD CO LTD
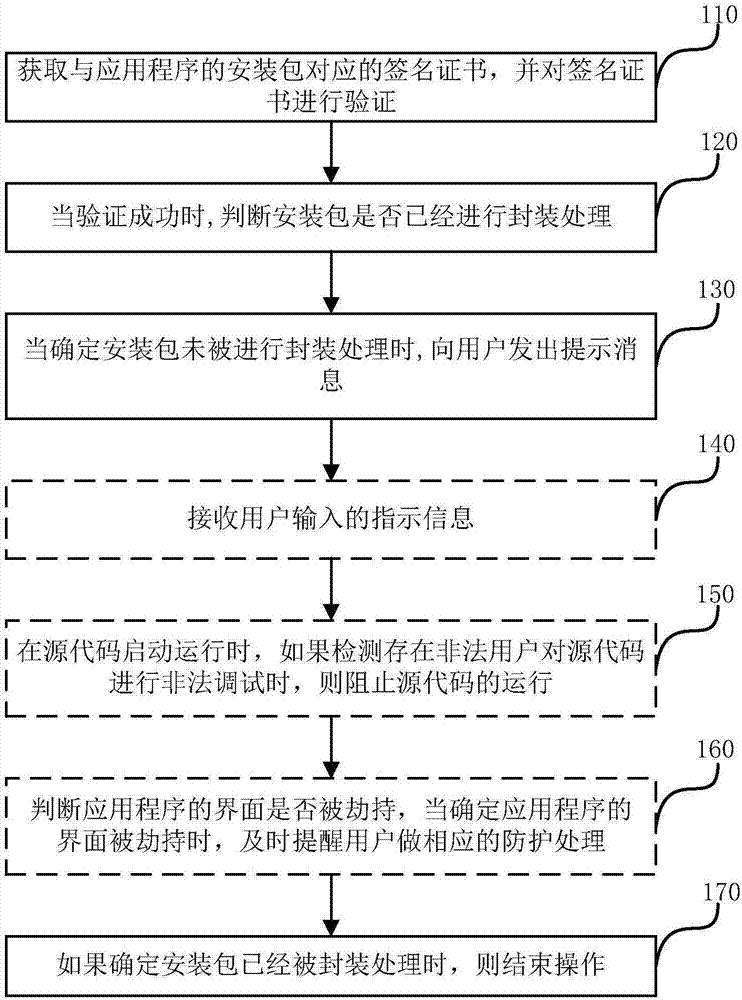
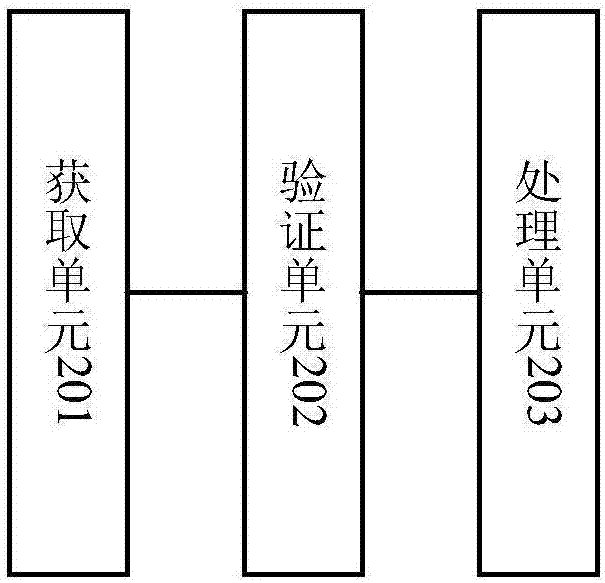
Security detection method and apparatus for application program
InactiveCN107145781AEnsure safetyIntegrity guaranteedDigital data authenticationPlatform integrity maintainanceApplication softwareSoftware engineering
The invention relates to a security detection method and apparatus for an application program. The security detection method comprises the steps of obtaining a signature certificate corresponding to an installation package of the application program; performing verification on the signature certificate; when the verification is successful, judging whether the installation package is subjected to packaging treatment or not; when it is determined that the installation package is not subjected to packaging treatment, sending prompting information to a user, wherein the prompting information is used for indicating that the installation package has security risk, so that the user can perform packaging treatment conveniently; or when it is determined that the installation package is already subjected to packaging treatment, completing operation. Whether the application program is safe or not is detected from different angles; when it is detected that the application program has dangerous factors, corresponding measures can be taken in time; and by reinforcing the application program, security, completeness and effectiveness of data can be realized indirectly.
Owner:北京思特奇信息技术股份有限公司
Safety monitor
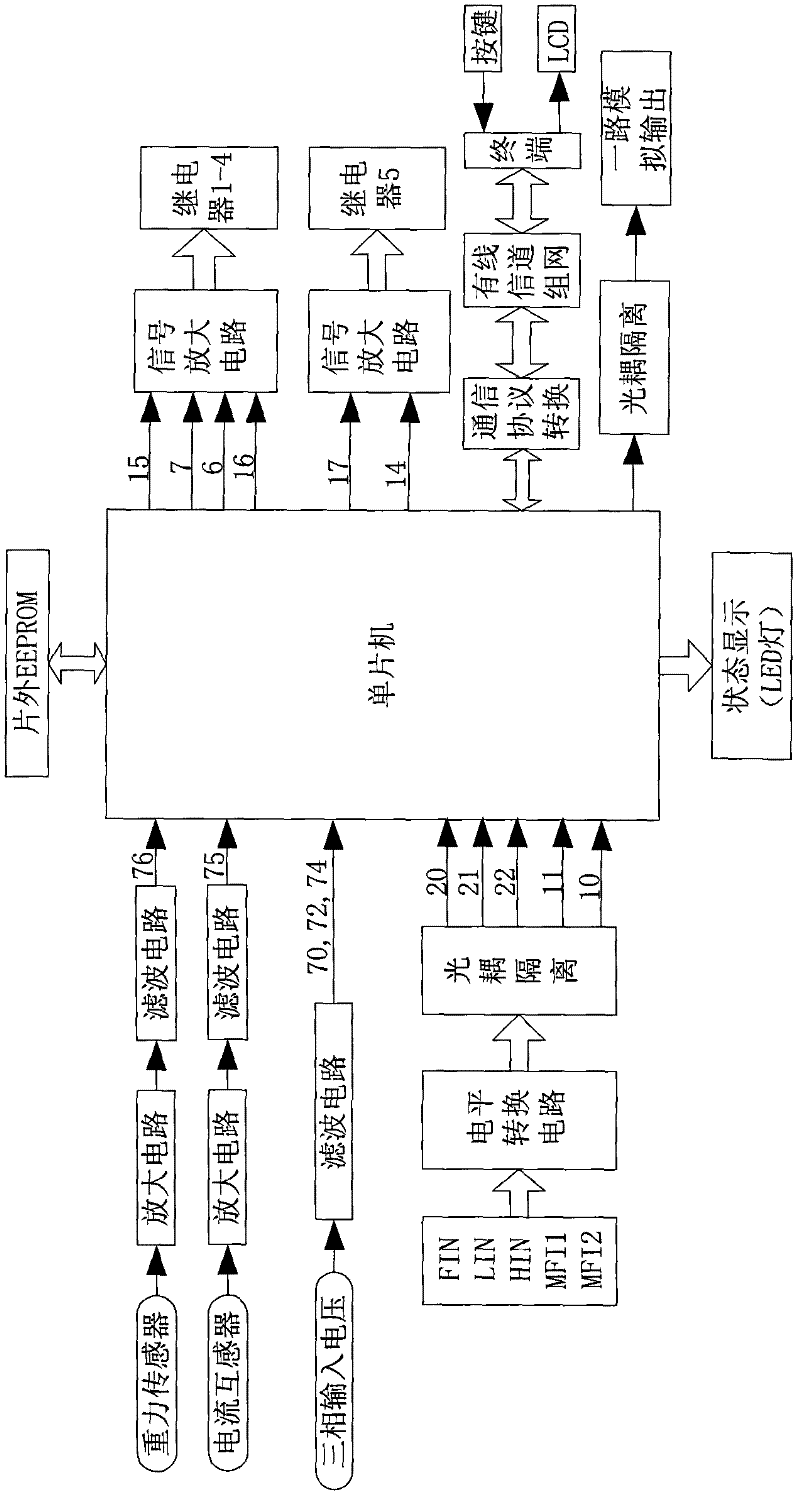
The invention discloses a safety monitor comprising a single chip microcomputer, a gravity sensor, three-phase input voltage and a relay, wherein the three-phase input voltage is accessed into the single chip microcomputer through a filter circuit; the gravity sensor is accessed into the single chip microcomputer through an amplification circuit and the filter circuit; and the single chip microcomputer controls the action of the relay. The single chip microcomputer is used for detecting whether the three-phase input voltage is lack of phase; and the safety monitor displays a failure cause when the three-phase input voltage is lack of phase. The safety monitor is used for managing and protecting a crane, adjusting the use of the crane and preventing the crane from operating when a potential hazard condition is probably caused. The safety monitor can realize overload protection on the crane, monitor the operation of the crane, failures, phase sequence of a main power supply, phase lacking of the main power supply as well as control the voltage, achieve low-speed starting and low-speed stopping functions, record operation time, and implement relay output and tonnage display.
Owner:奥力通起重机(北京)有限公司
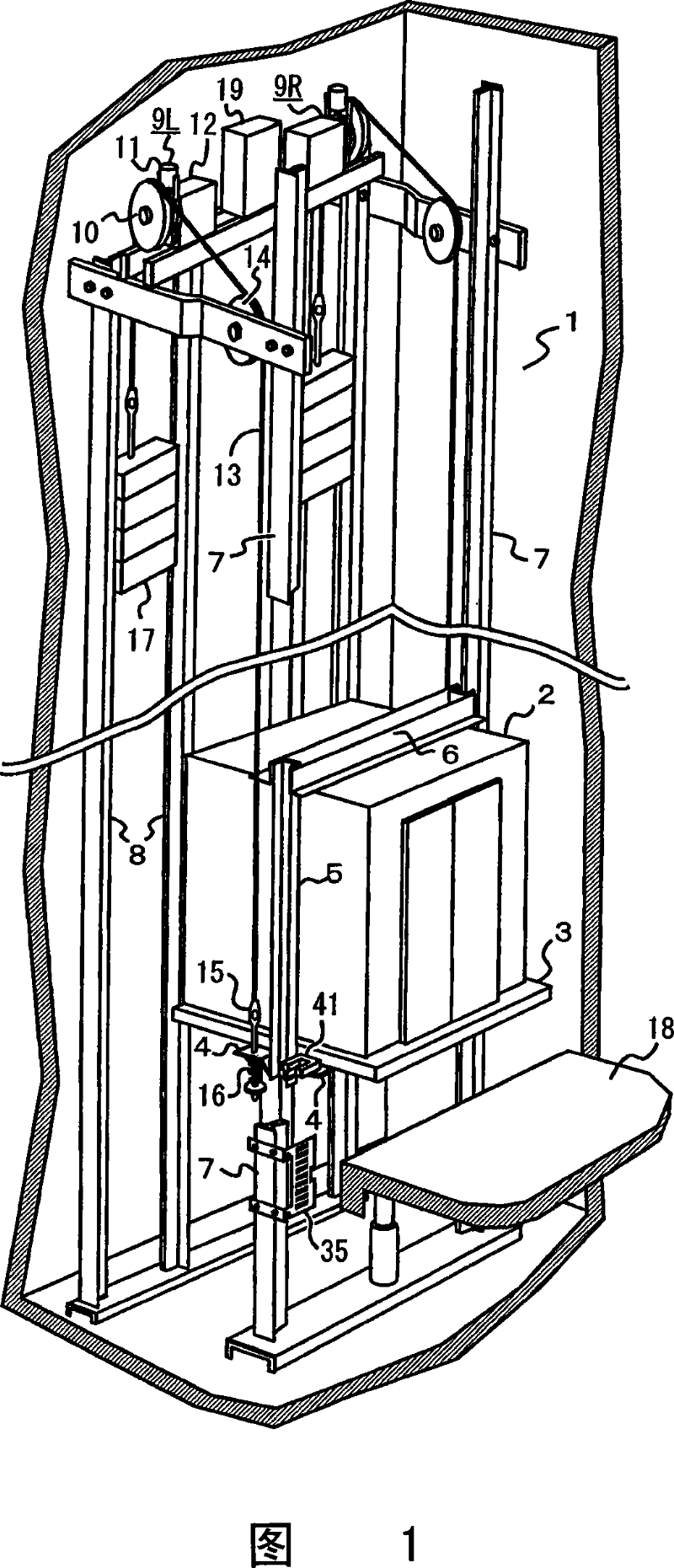
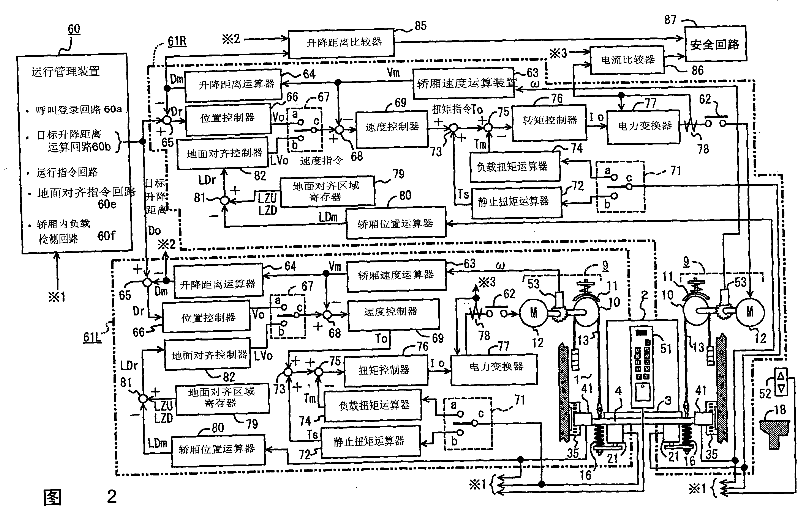
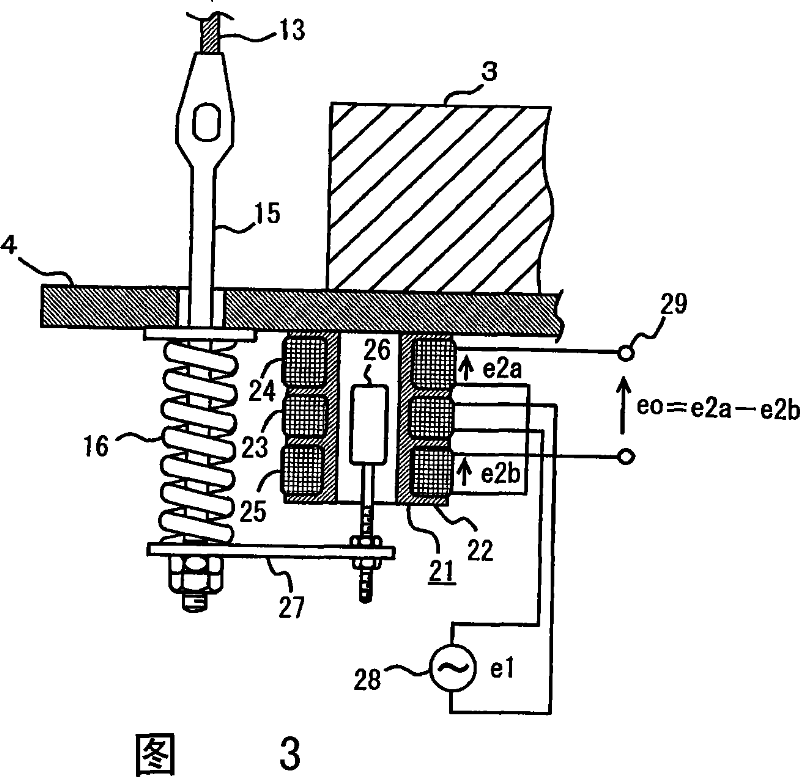
Elevator control device
An elevator control device, which can fasten a main cable at multiple portions of the compartment lifting in the lifting well, and wind the main cable on multiple windlasses upward arranged correspondingly to drive the compartment to lift, characterized in that with respect to the main cable fixing portions, the control device can detect the difference between the storey floor and the compartment floor when the compartment arrives at the destination storey, when the detection value exceeds the specified value, the corresponding windlasses will be used to drive the main fixing portions to move upward and downward respectively, thus to align the floor and reduce the difference. Therefore, even though the windlasses make the main cable move relatively and make the compartment floor incline, the inclination can be corrected by aligning the floors, so that the relative movement of the main cable will not accumulate.
Owner:MITSUBISHI ELECTRIC CORP
Device and method for operating a hand-held working apparatus
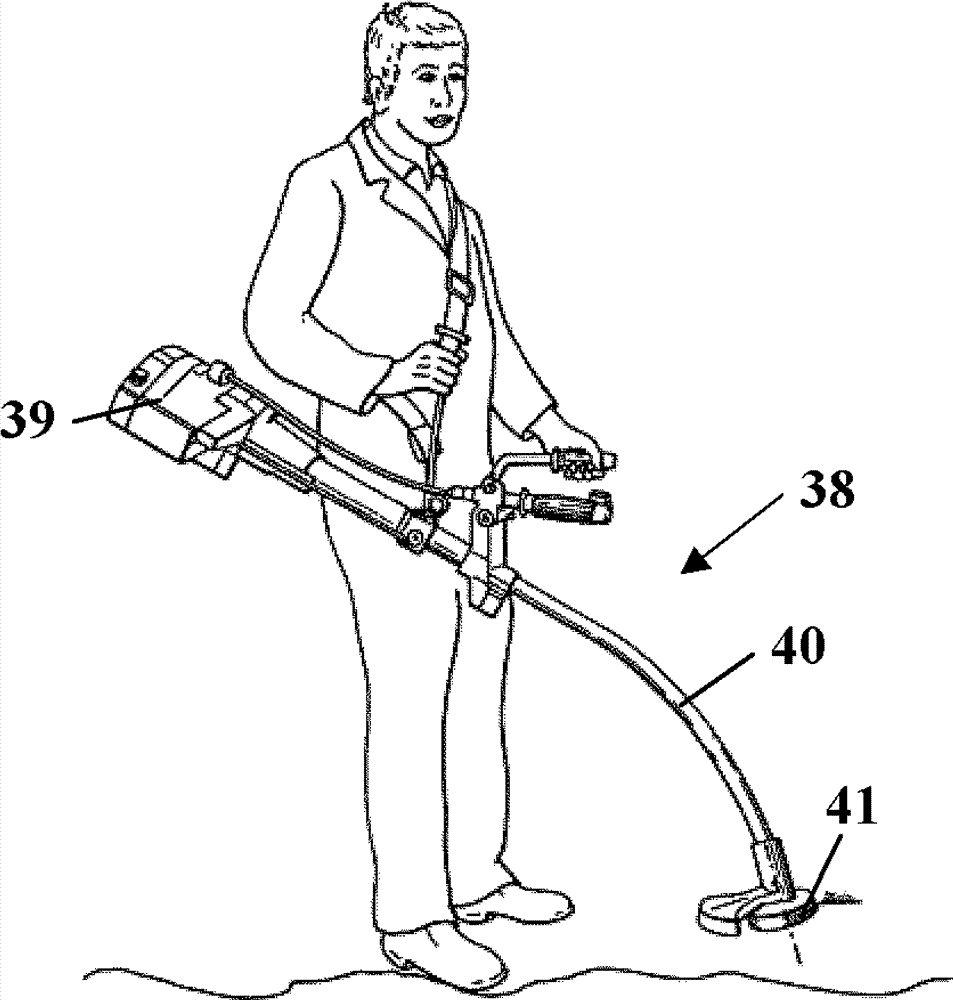
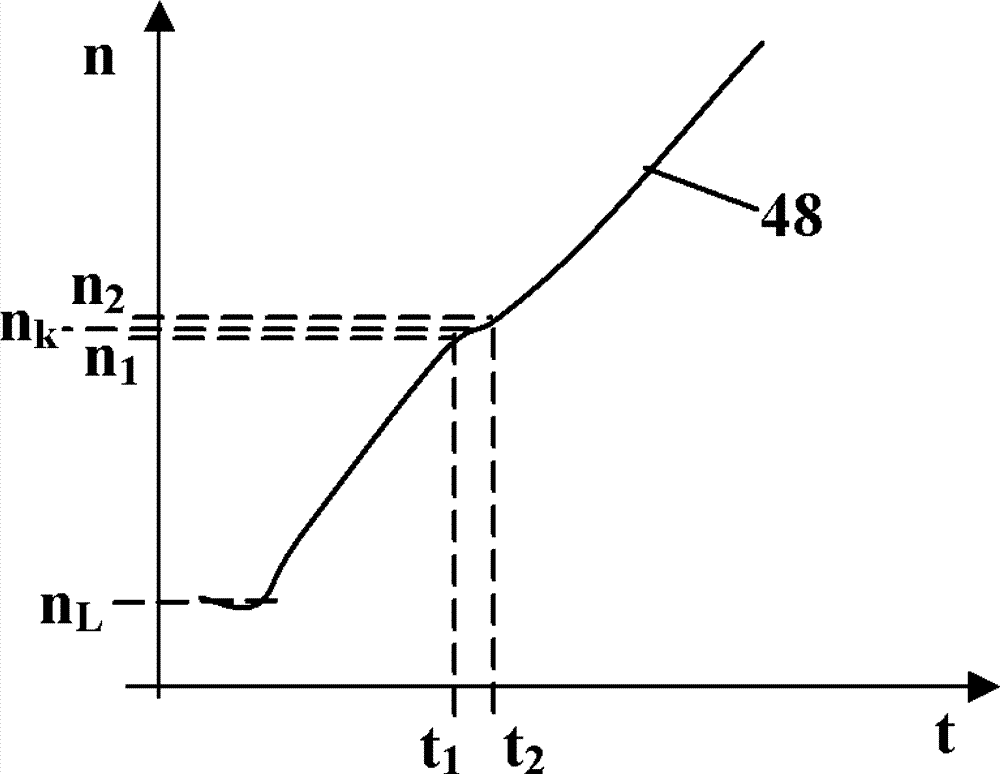
ActiveCN103161591AImprove functionalityAccelerates well and powerfullyElectrical controlInternal combustion piston enginesInternal combustion engineCentrifugal clutch
The invention relates to a method for operating a hand-held working apparatus. A hand-held working apparatus has an internal combustion engine having a crankshaft which is driven in rotation. The crankshaft drives at least one tool of the working apparatus via a centrifugal clutch. The working apparatus has a device for determining the speed of the internal combustion engine and a control device which controls the internal combustion engine. It is provided that the profile of the speed of the internal combustion engine is evaluated by the control device, and that the engagement speed of the centrifugal clutch is determined from the profile of the speed of the internal combustion engine.
Owner:ANDREAS STIHL AG & CO KG
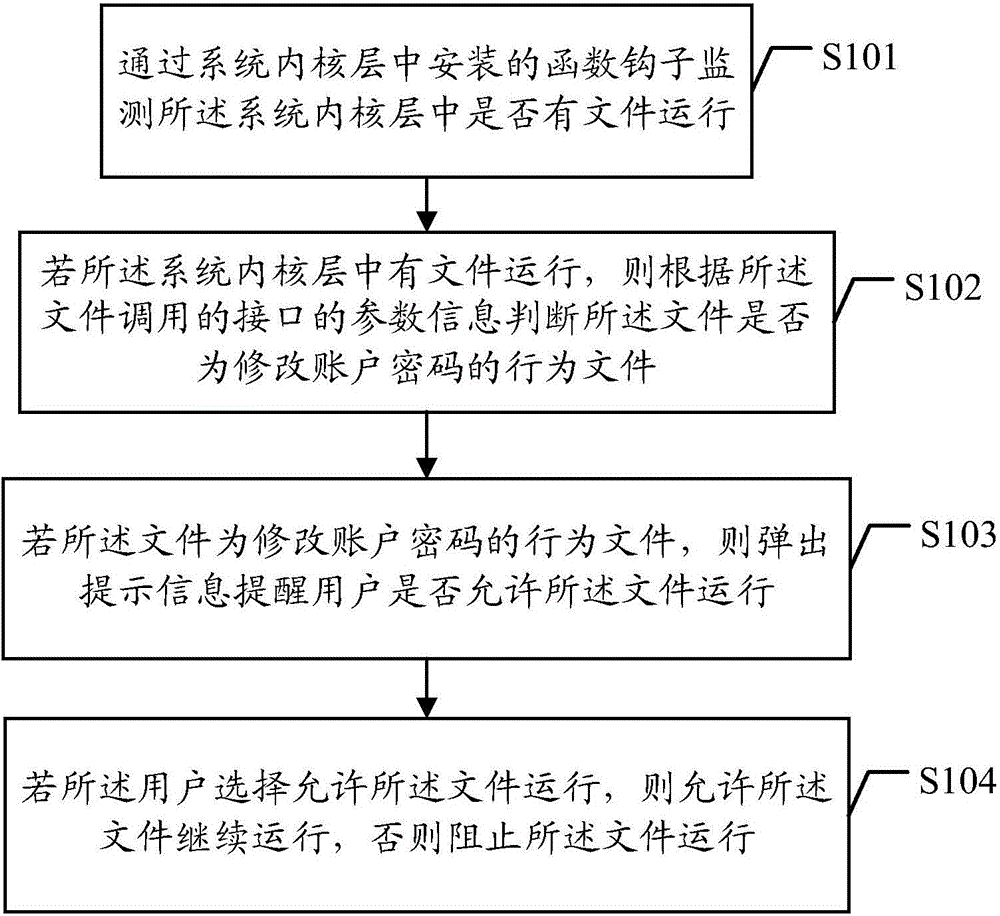
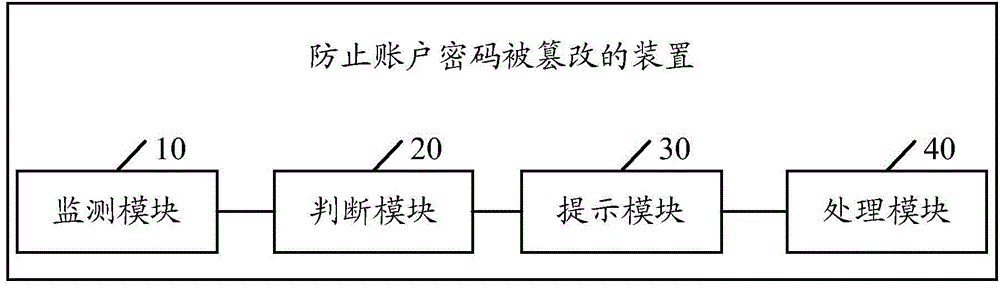
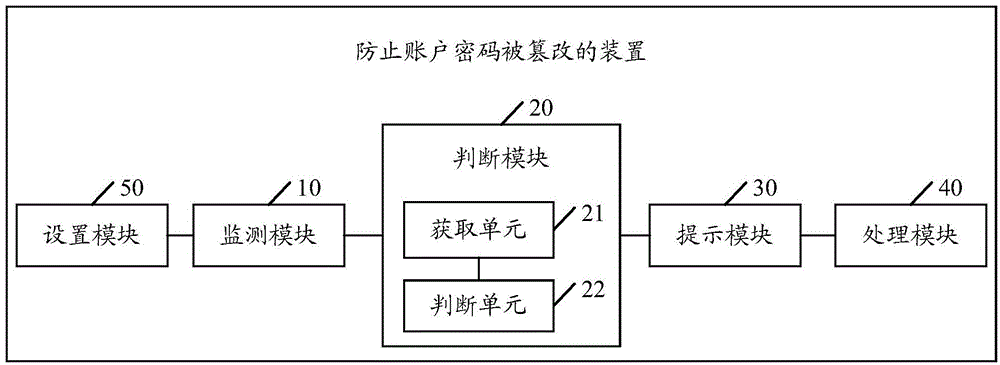
Device and method for preventing account passwords from being tampered
InactiveCN104156661AImprove securityImprove recognition efficiencyPlatform integrity maintainanceSpecial data processing applicationsPasswordCipher
An embodiment of the invention discloses a method for preventing account passwords from being tampered. The method includes: monitoring whether files in a system kernel layer are in operation or not by the aid of a function hook mounted in the system kernel layer; if files in the system kernel layer are in operation, judging whether the files are behavior files altering the account passwords according to parameter information of file calling interfaces; if the files are behavior files altering the account passwords, popping up a prompt message to prompt a user whether to allow the files to operate or not; if the user chooses to allow the files to operate, allowing the files to continue operating, and otherwise, stopping the files from operating. The embodiment of the invention further discloses a device for preventing the account passwords from being tampered. The method and the device for preventing the account passwords from being tampered have the advantages of simplicity in operation, high applicability, improvement of file recognition efficiency and reinforcement in safety of system account passwords.
Owner:ZHUHAI JUNTIAN ELECTRONICS TECH
Percussion tool
ActiveUS20110005786A1Reduce risk of damageStop runningConstructionsReciprocating drilling machinesReciprocating motionEngineering
A pneumatic percussion tool (1) for demolition and / or breaking work in for example concrete and connectable to an insert tool (2). The percussion tool has a percussion cylinder (4), a piston (5), arranged to travel in the bore of the cylinder (4), a buffer (8), and a valve unit (6), designed to act on the piston (5) during operation and produce a repetitive reciprocating travel in the bore of the cylinder (4) by alternately applying pressure to the upper or lower end of the cylinder (4) while the insert tool (2) is subject to influence by the stroke of the piston (5) when this is at its dead centre at the lower end of the cylinder (4). The percussion tool comprises a means (11) of preventing the piston's reciprocating motion when the buffer (8) reaches a predetermined degree of wear and the tool is not pressed against any object being worked.
Owner:ATLAS COPCO AIRPOWER NV
Non-curing asphalt rubber waterproof coating film and processing technology thereof
InactiveCN103756565AIncrease the cured contentExcellent extension performanceBituminous coatingsPollutantButadiene-styrene rubber
The invention discloses a non-curing asphalt rubber waterproof coating film and a processing technology thereof; the waterproof coating film is prepared by 40% of 100# asphalt, 13% of SBS (Styrene Butadiene Styrene), 7% of SEBS, 8% of terpene resin, 11% of softening oil, 10% of talcum powder and 11% of plasticizer DOS; the processing technology comprises the steps of burdening, stirring, even grinding, finished product inspecting, testing, packaging and warehousing; as the technical scheme is adopted, macromolecules and asphalt combined in this manner can exert respective performances to the greatest degree under the most stable state so as to improve the condensate content, stability and product performance of paint; moreover, the processing technology is simple and feasible, and is unlikely to generate pollutants.
Owner:王勇
Oil field test and separation system
ActiveUS9216367B1Accurate measurementLow costLiquid separation auxillary apparatusLiquid degasification regulation/controlParticulatesSurge tank
An improved fluid separator and tester having a vessel, an adjustably buoyant float member, an external surge tank, and a gas vent connected to the fluid separator having a float and gas valve assembly, the improvement comprising a set of risers set to equal height, at least one valve to redirect fluid flow to test flow meters, and a spill preventer having a connection to a vertical gas valve, a housing, at least one internal freely movable float, upper float seat adapted to receive a float to seal and prevent the escape of particulates while allowing the venting of gas, a float support means, and discharge means for expelling the contents, whereby the improvements provide increased accuracy in determining a volume of each type of input fluid during operations, allow for the assessment of proper operation of the meters, and prevent environmental contamination in the event of system malfunction.
Owner:CALDWELL DENNIS P
Method and device for preventing viruses in mobile memory from infecting computer
InactiveCN102110214AAvoid spreadingReduce privilegesInternal/peripheral component protectionPlatform integrity maintainanceRemovable mediaVirus
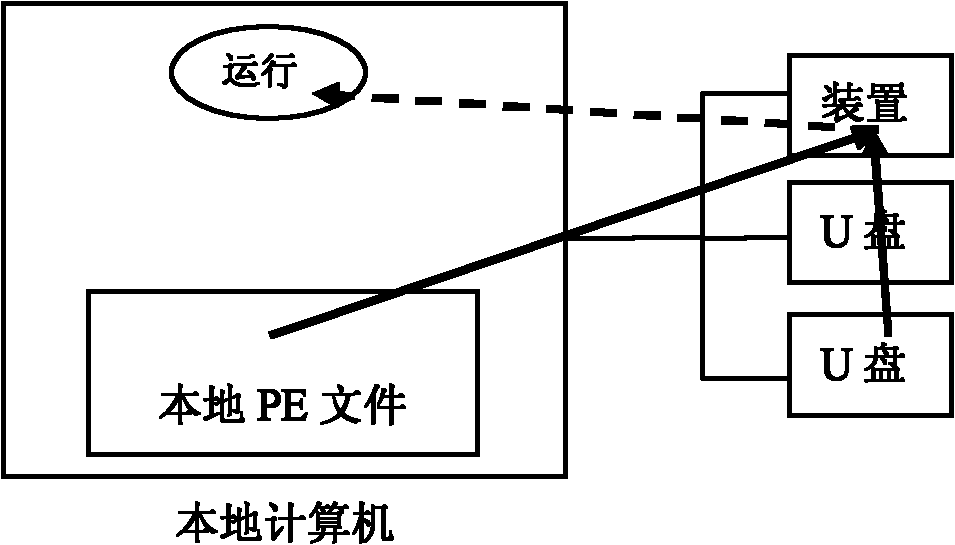
The invention discloses a method and a device for preventing viruses in a mobile memory from infecting a computer. A running main program, an injection program and an event processing program are set; and after the mobile memory is connected to the computer, the running main program automatically runs, and the injection program intercepts portable executable (PE) file program running modes of a computer system and guides all running PE files to run through the event processing program so as to control the running modes of all the PE files. The method and the device are used for preventing thepossible virus files in the mobile memory from infecting the computer and preventing the viruses from being diffused and propagated together with the mobile memory; a single machine runs in the method and the device, networking update is not needed, and full-automatic virus protection is realized for the mobile memory; and at least one mobile memory and the device are connected together with the computer, so the viruses in the mobile memory cannot infect / be propagated to the local computer or destroy the program of the invention no matter the viruses automatically run or are manually activated / opened / operated.
Owner:姚志浩
Sheet processing apparatus and sheet processing method
InactiveUS8070151B2Improve stabilityImproves quality and efficiencyFunction indicatorsArticle feedersControl signalFront edge
A sheet processing apparatus includes a sheet-table unit, a sheet-separating unit disposed at a downstream end of the sheet-table unit along a convey direction of the sheets, a convey unit arranged at a downstream end of sheet-separating unit, a discharge unit located at a downstream end of the convey unit, an sheet processing unit placed between the convey unit and the discharge unit, a speed sensor arranged at an upstream end of the sheet-separating unit for detecting a movement of each sheet for forming a sheet interval between two adjacent sheets, and an edge sensor located between the sheet-separating unit and the sheet processing unit. The edge sensor detects a front edge and a rear edge of each sheet passing therethrough, and sends corresponding control signals to a system controller which delays a predetermined time according to the control signals to control the sheet processing unit to start and stop processing.
Owner:FOXLINK IMAGE TECH
Bitmap format software serial number as well as manufacturing method and application method thereof
ActiveCN103778354AReduce the chance of decipheringIncrease the difficultyDigital data authenticationProgram/content distribution protectionStart timeLaunch Time
The invention relates to a bitmap format software serial number. The bitmap format software serial number is a 128*128 pixel color picture, three components of bitmap pixels discretely and randomly record authorization information subjected to algorithm encryption; the authorization information includes hardware checking code character strings and time information character strings, wherein the hardware checking code character strings include hard disc serial numbers and central processing unit serial numbers, and the time information character strings include test duration, serial number generation time, registration time, starting use time, last starting time and last finishing time. The invention also relates to a manufacturing method and a use method of the bitmap format software serial number. The software serial number is shown in an encrypted non-plaintext form, and the the probability that the software serial number is decoded is reduced to a great degree.
Owner:POWERCHINA HEBEI ELECTRIC POWER SURVEY & DESIGN INST CO LTD
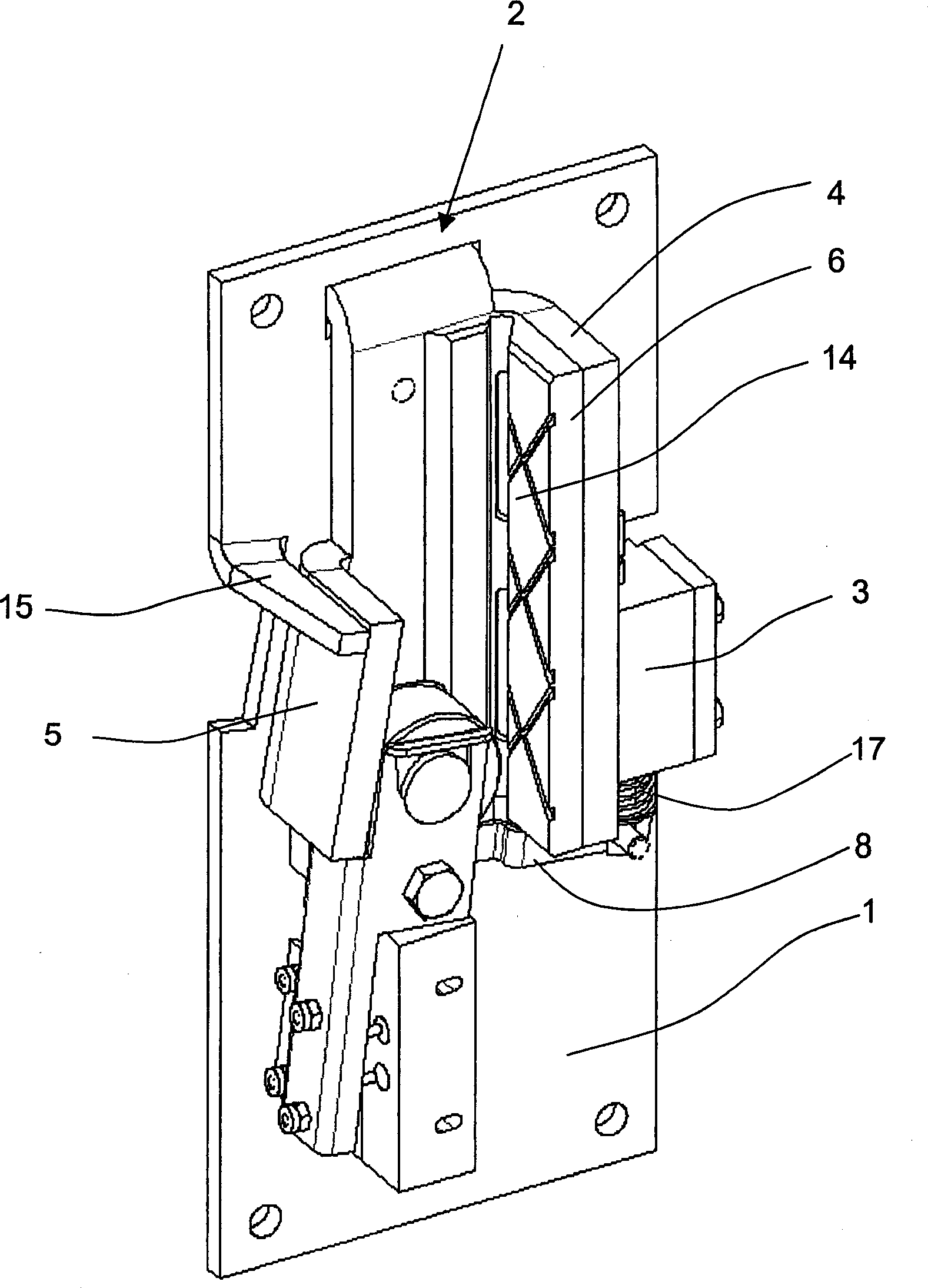
Safety braker of lift
This safety device serves for braking an elevator car in an elevator system provided with a guide rail having a rectangular guide flange. The safety device is provided with a holding device 1, which carries a retaining element 4, 6 and an abutment 5. The safety device is arranged in such a way that the guide flange is positioned between the retaining element 4, 6 and the abutment 5 in operation. A mechanism 8 is available which squeezes a braking member in the form of a blocking roller 7 between the guide flange and the abutment 5 when braking. The mechanism 8, cooperating with an electromagnet 3, exhibits a suspension 12. In such suspension, the braking member 7 is movably placed and can be moved in a controlled way between different positions assigned to different operation conditions of the safety device.
Owner:INVENTIO AG
Vacuum pump
InactiveCN102007299AStop runningGuaranteed originalityPump componentsTransmission systemsVacuum pumpStator
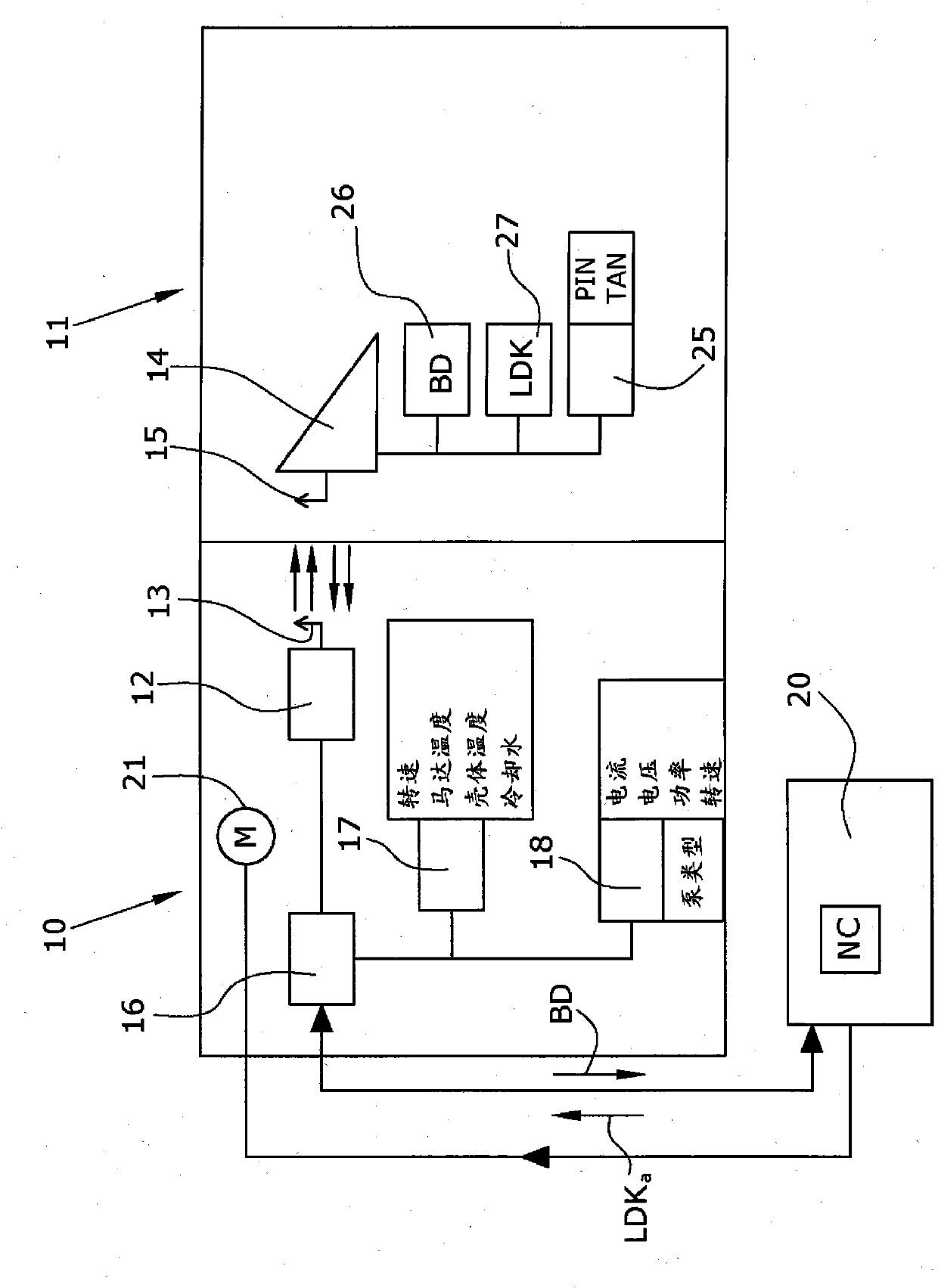
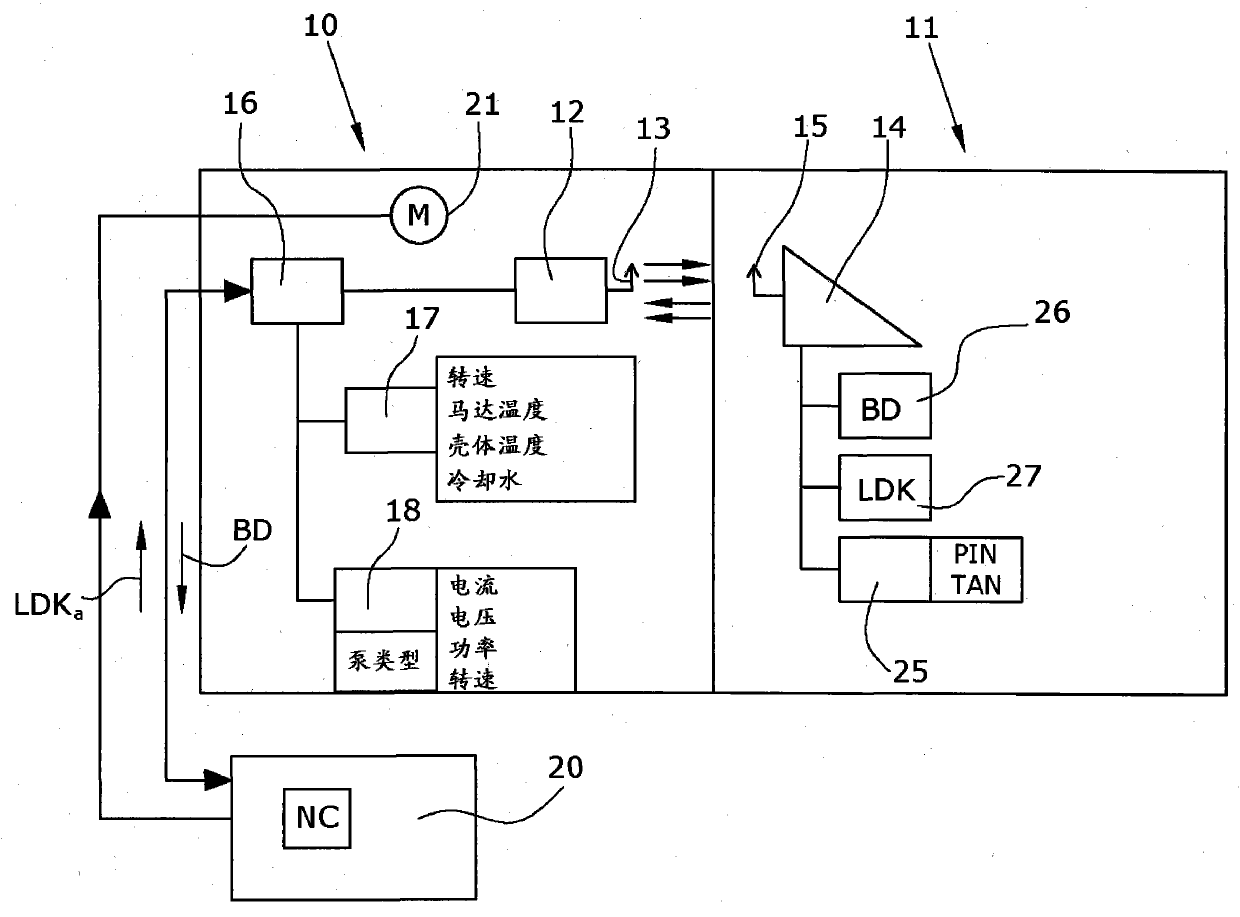
The invention relates to a vacuum pump with a pump stator (10) and a pump rotor (11). The pump rotor (11) contains a transponder (14) that can be read out by a reader of the pump stator. The pump rotor (11) also contains sensors (26) for determining operating data (BD), and a memory (27). The memory (27) stores either the history of the measured operating data (BD) or a service life characteristic (LDK). In this way, the rate of wear of the respective rotor is determined and stored in the rotor, and the rotor therefore contains all of the information relating to maintenance. The rotor-related information remains in the rotor even if the rotor is used in another vacuum pump.
Owner:OERLIKON LEYBOLD VACUUM
Loop circuit self-test and self-healing method and device
InactiveCN106789626AStop runningAvoid paralysisData switching networksSelf-healingBroadcast radiation
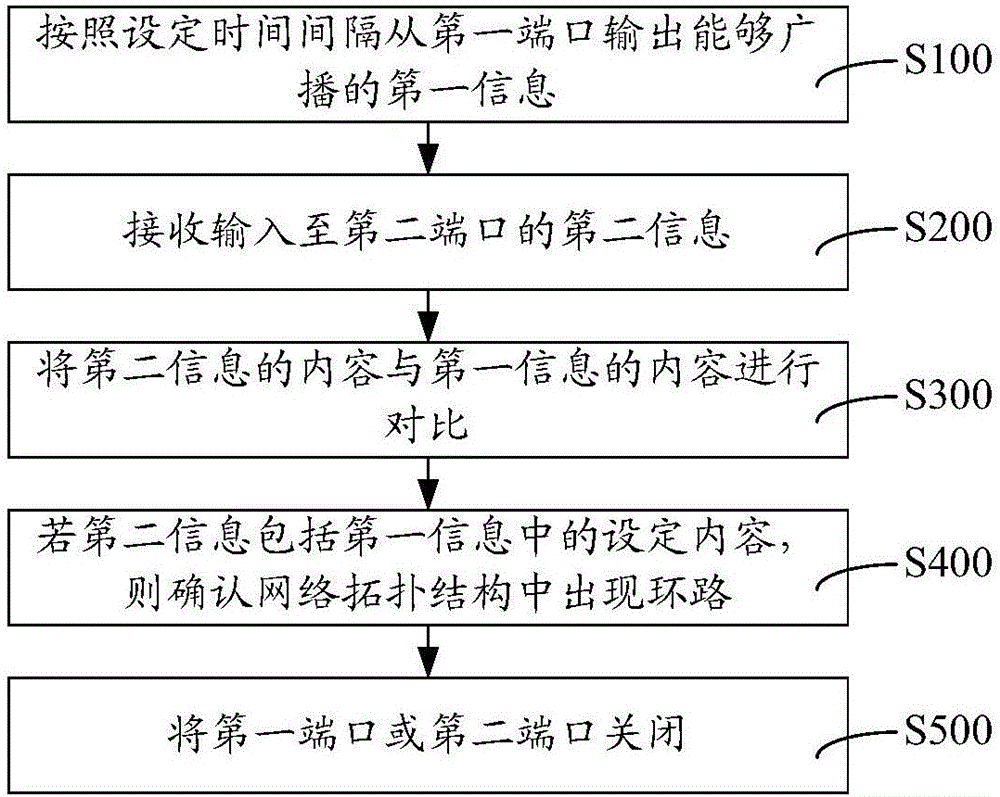
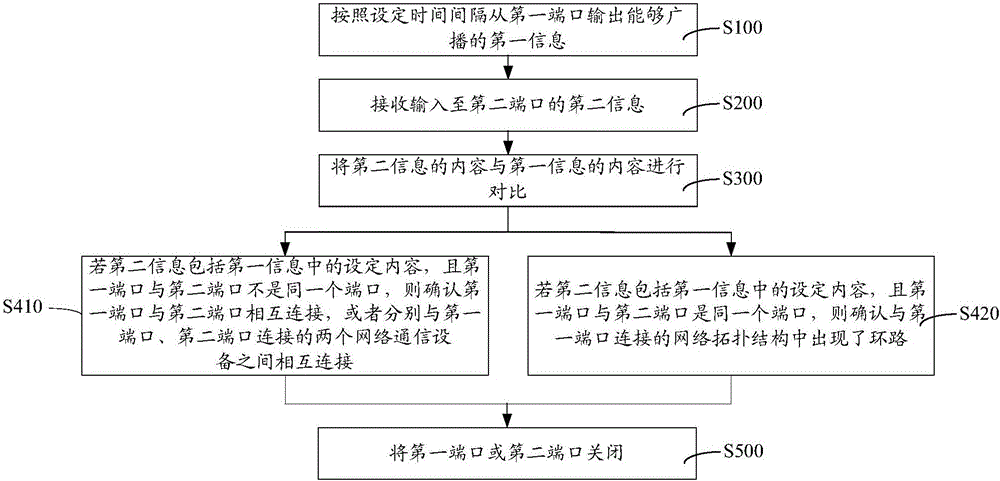
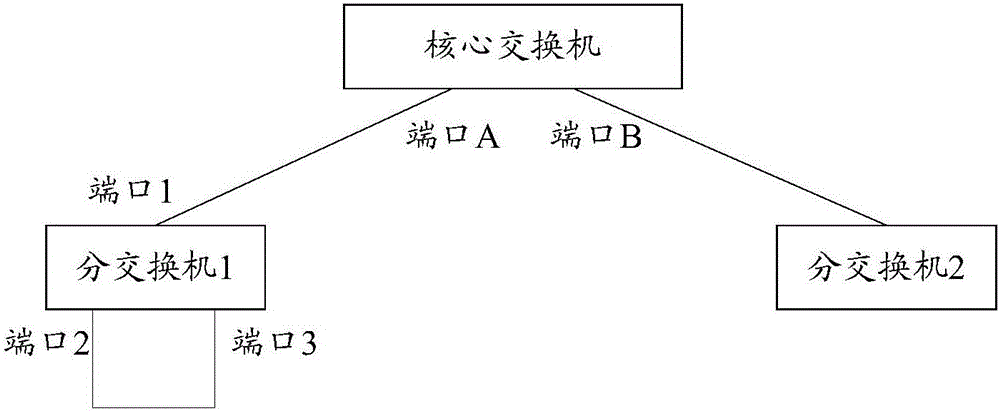
This invention relates to a loop circuit self-test and self-healing method and device, and is applied in the execution of the network communications equipment of a network topology structure. The loop circuit self-test and self-healing method comprises the steps that the first information which can be broadcasted is outputted from a first port according to the set time interval; the second information inputted in a second port is received; the content of the second information and the content of the first information are compared; if the second information includes the set content in the first information, the loop circuit is confirmed to appear in the network topology structure; and the first port or the second port is closed. According to the loop circuit self-test and self-healing method and device, loop circuits can be detected in time, and the loop circuits are promptly destroyed, so that the loop circuits are prevented from continuing running, in order to avoid paralysis in the broadcast storm, or even in an entire network; the negative impact of loop circuits in a network topology can be avoided through using the above loop circuit self-test and self-healing method and device.
Owner:SHENZHEN TG NET BOTONE TECH
Method for protecting copyright by combining IP (Internet Protocol) address
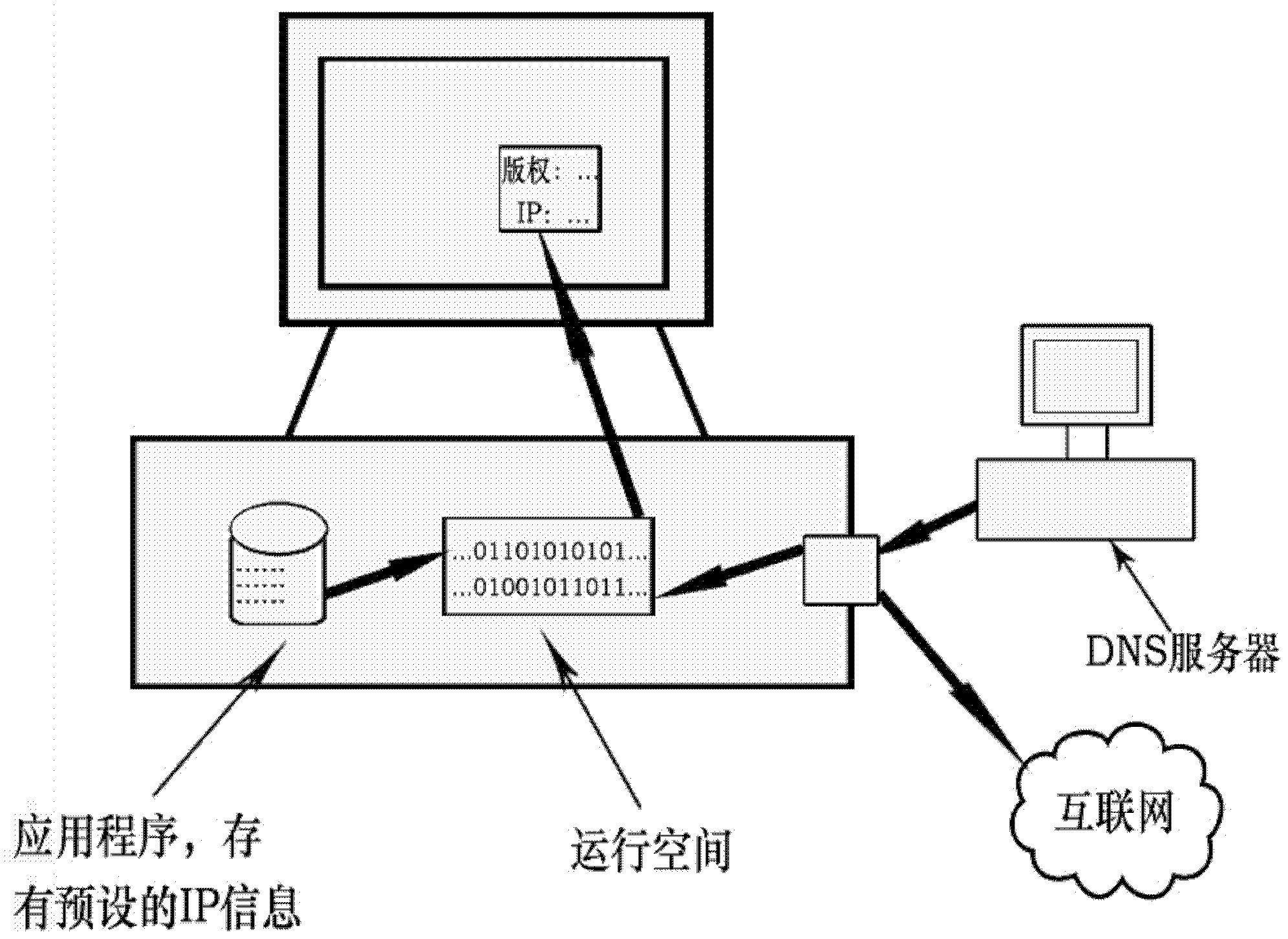
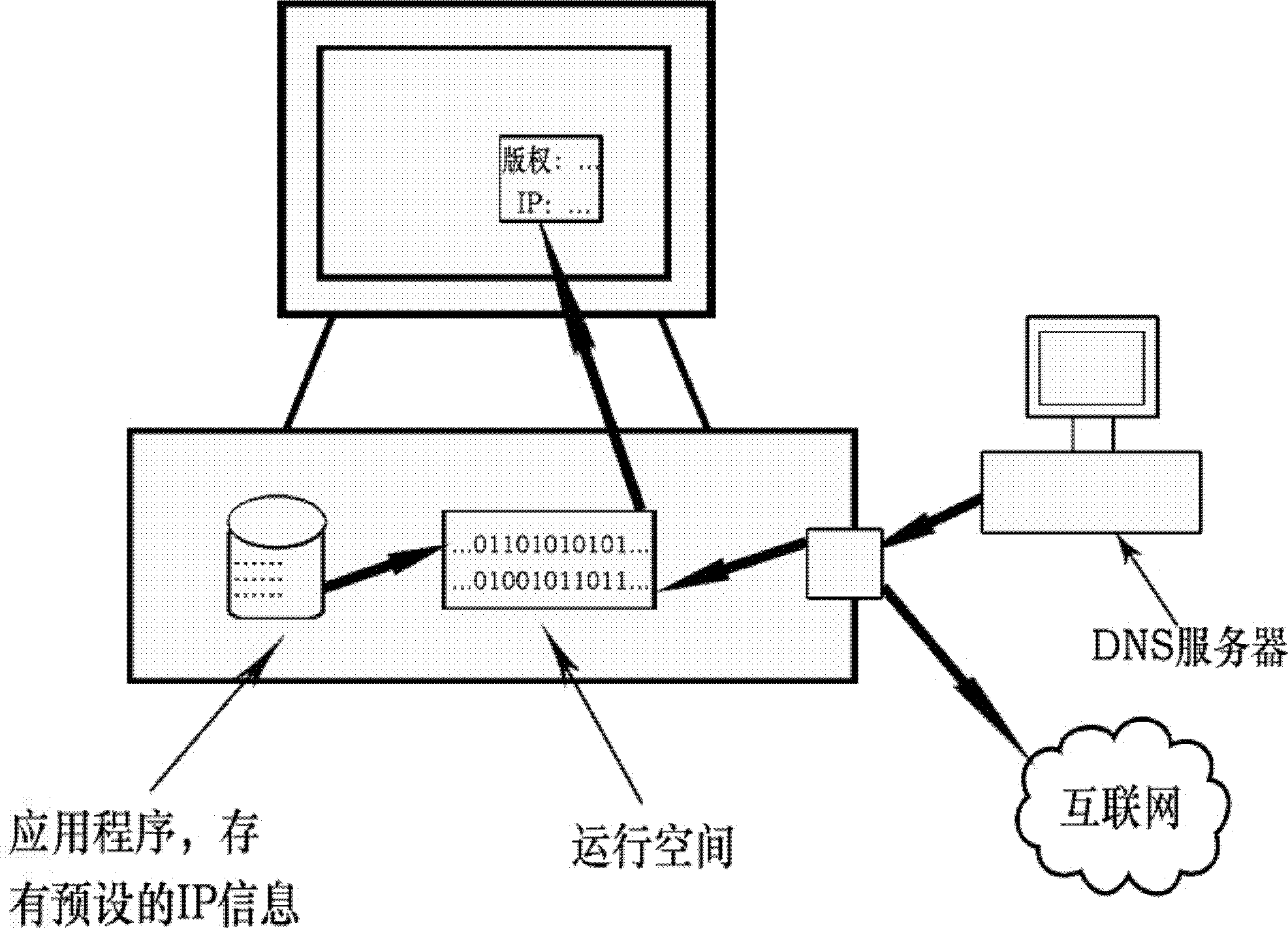
InactiveCN102354358AEasy accessStop runningTransmissionProgram/content distribution protectionIp addressApplication software
The invention provides a method for protecting a copyright by combining an IP (Internet Protocol) address. The method comprises the steps: aiming at the IP address or IP address sector of a computer to be provided with a software copy, a compiling file is generated, the IP address of the computer is read later when the software copy is operated, and when the IP address is not matched or not in the IP address sector, software cannot be used. A copyright page of the software copy not only displays a developer, but also displays the IP address of the computer onto which the software is installed, which is used as copyright information. The method has the advantages that the IP address is generally unique for each fixed computer, and customized software can be fundamentally prevented from operating on other machines through binding application software and IP. In addition, the method is practical and feasible and is convenient for acquiring the IP when a program is started up and operated every time.
Owner:WUXI NUOBAO TECH DEV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com