Computer safety protective method based on software identity identifying technology
A computer system and software technology, applied in computer security devices, computing, platform integrity maintenance, etc., can solve problems such as inconvenient computer operation, computer security threats, and inapplicability of independent executable files
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
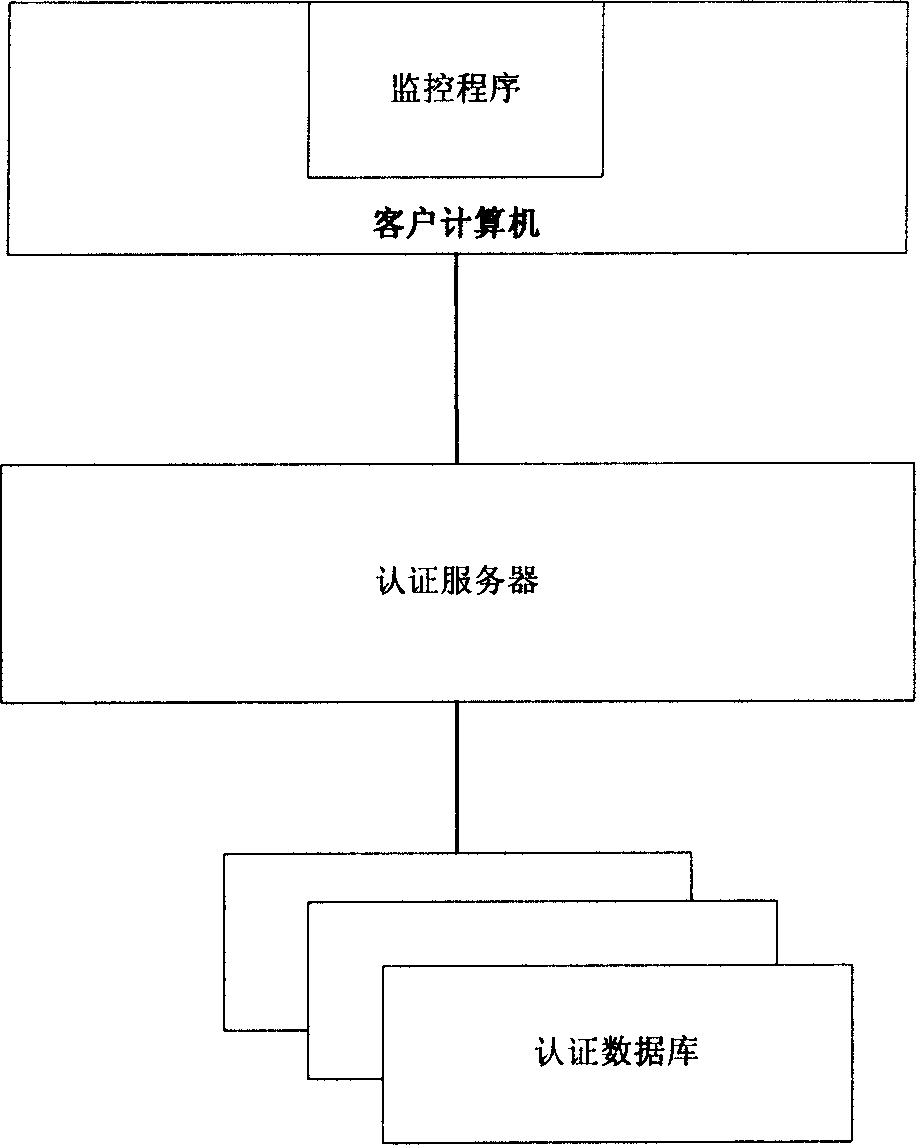
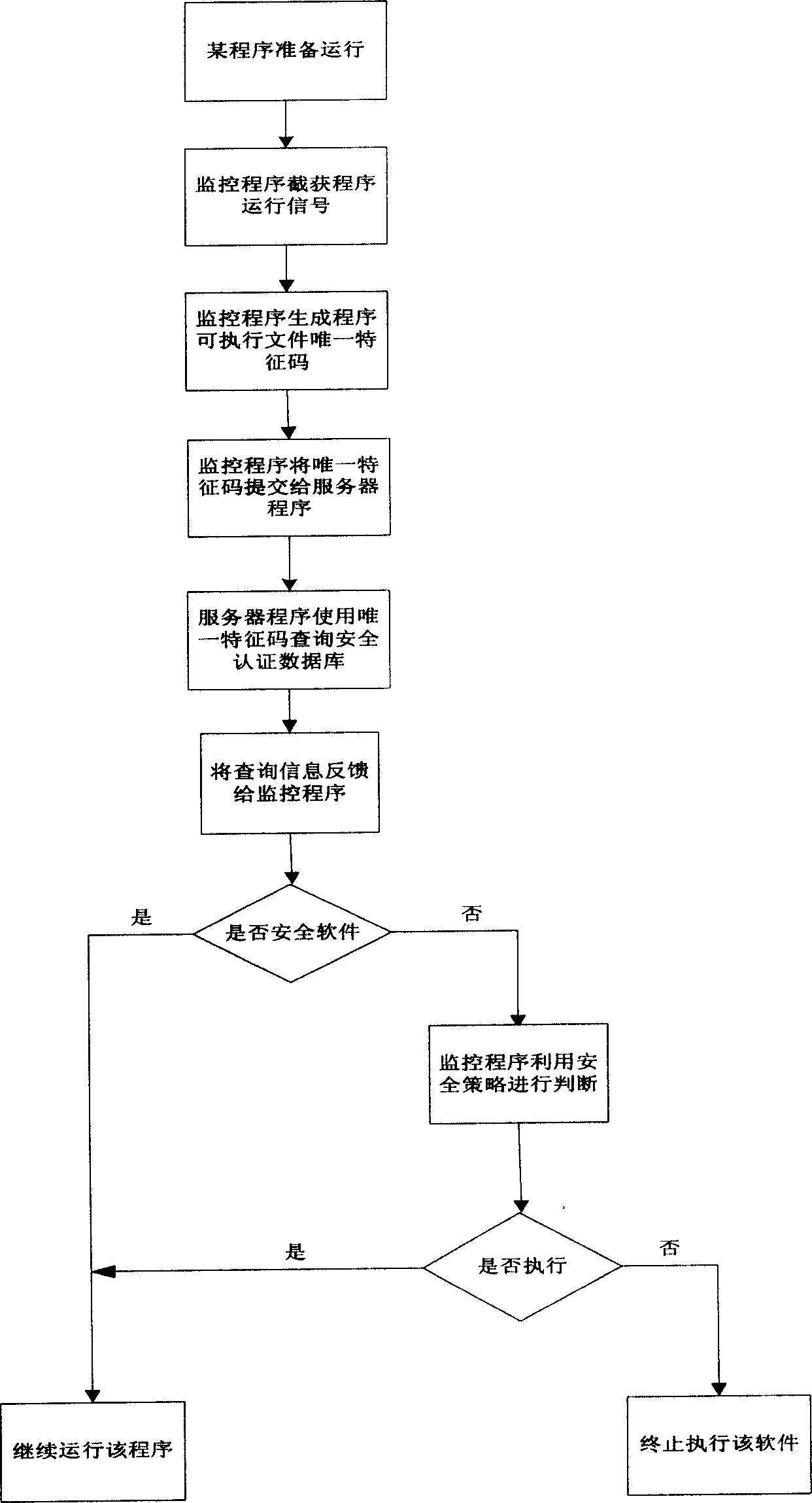
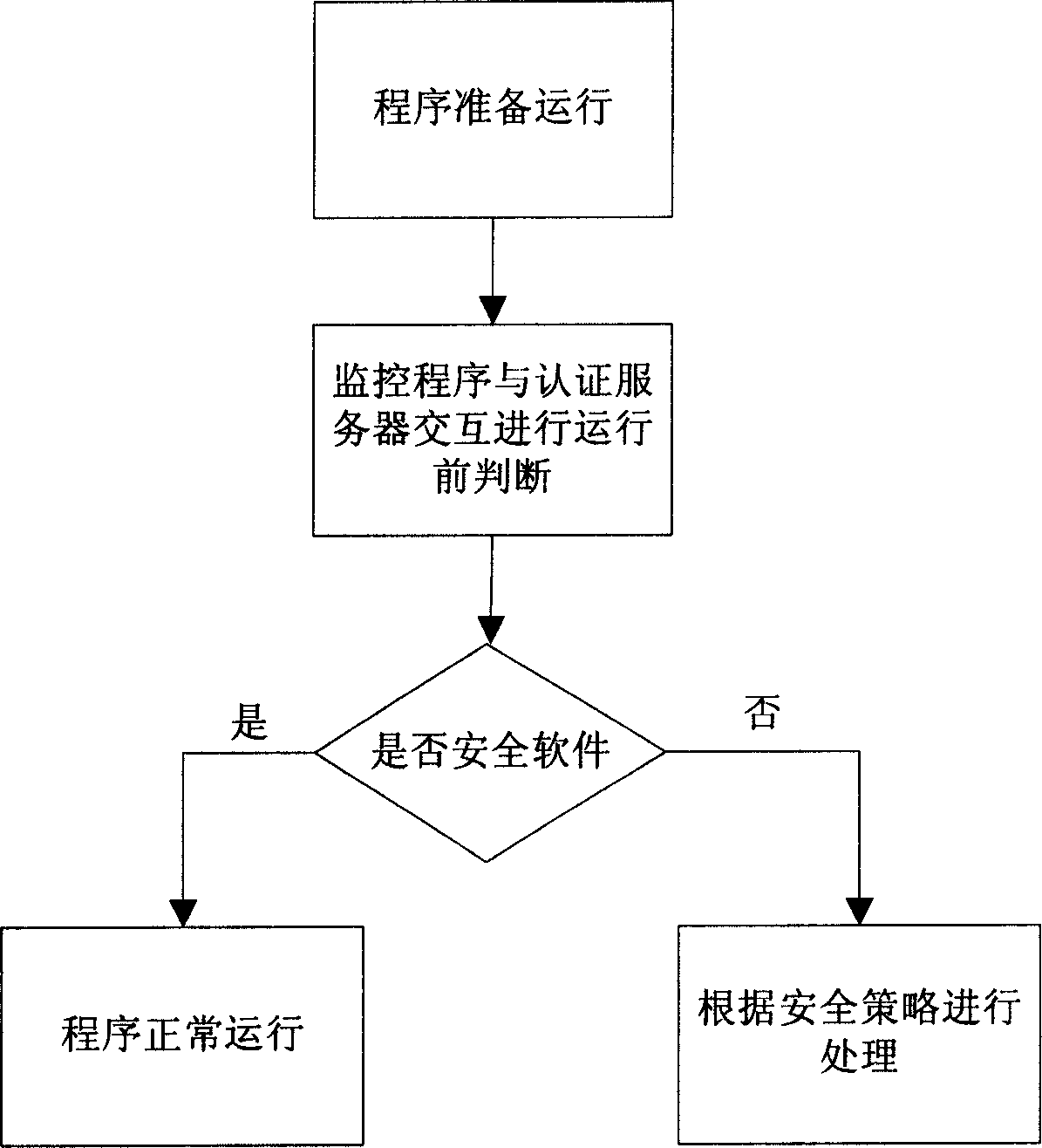
[0017] By implementing the invention, a safe environment can be built in which only known and trusted software can run. The infrastructure necessary to achieve this secure environment includes, for example, figure 1 The following three sections are shown:
[0018] 1. Security authentication database;
[0019] 2. Authentication server program;
[0020] 3. Monitoring program.
[0021] The feature information and security information of various software are stored in the security certification database. The content and scope of software feature information and security information can be adjusted according to actual needs. Generally speaking, feature information includes software name, manufacturer, version, software executable file name, software purpose, etc., while security information includes whether the software is certified as safe, whether it is a virus program, whether it is a Trojan horse program, whether it is vulnerable loopholes etc. These information can be us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com