Patents
Literature
483 results about "Public key certificate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
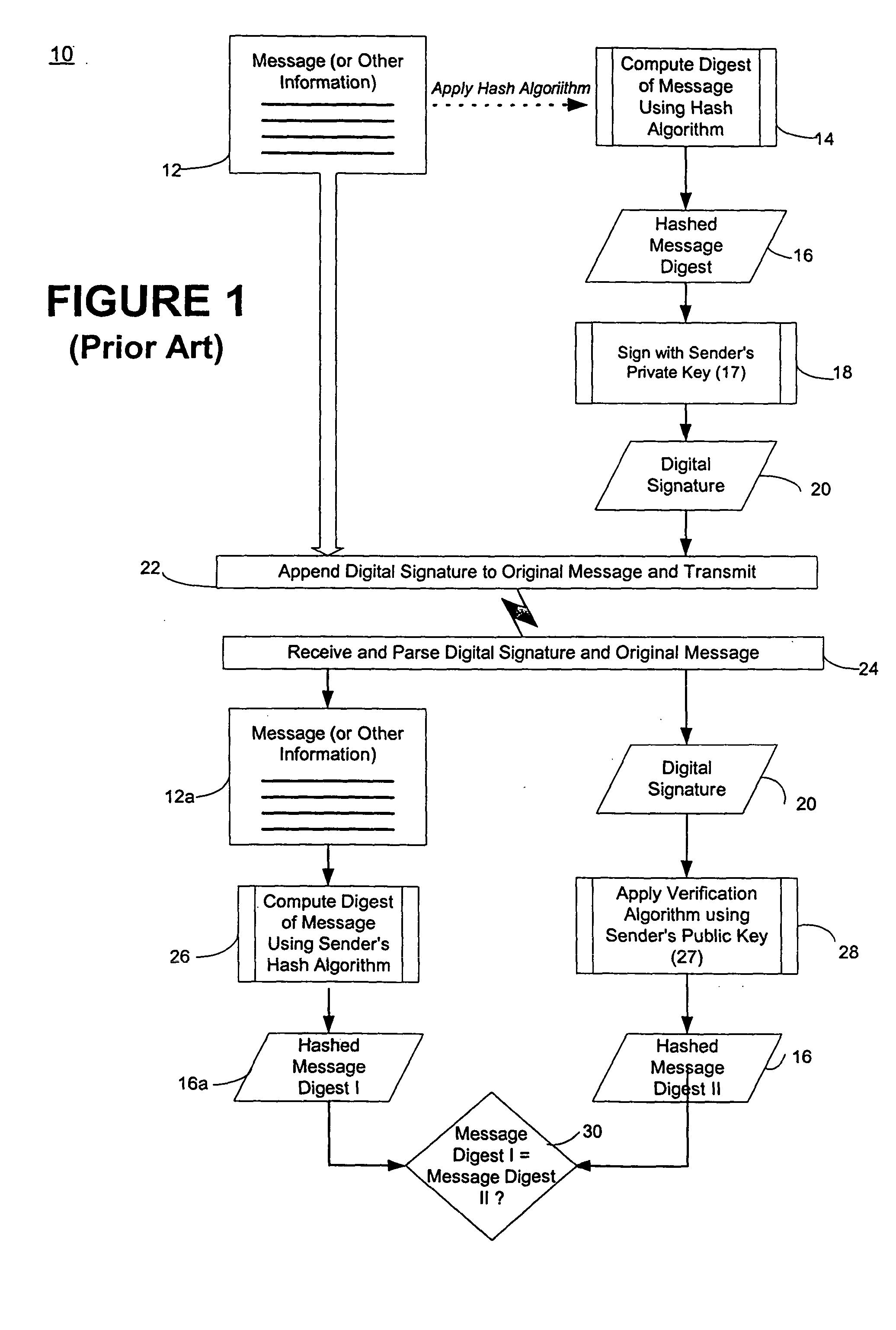
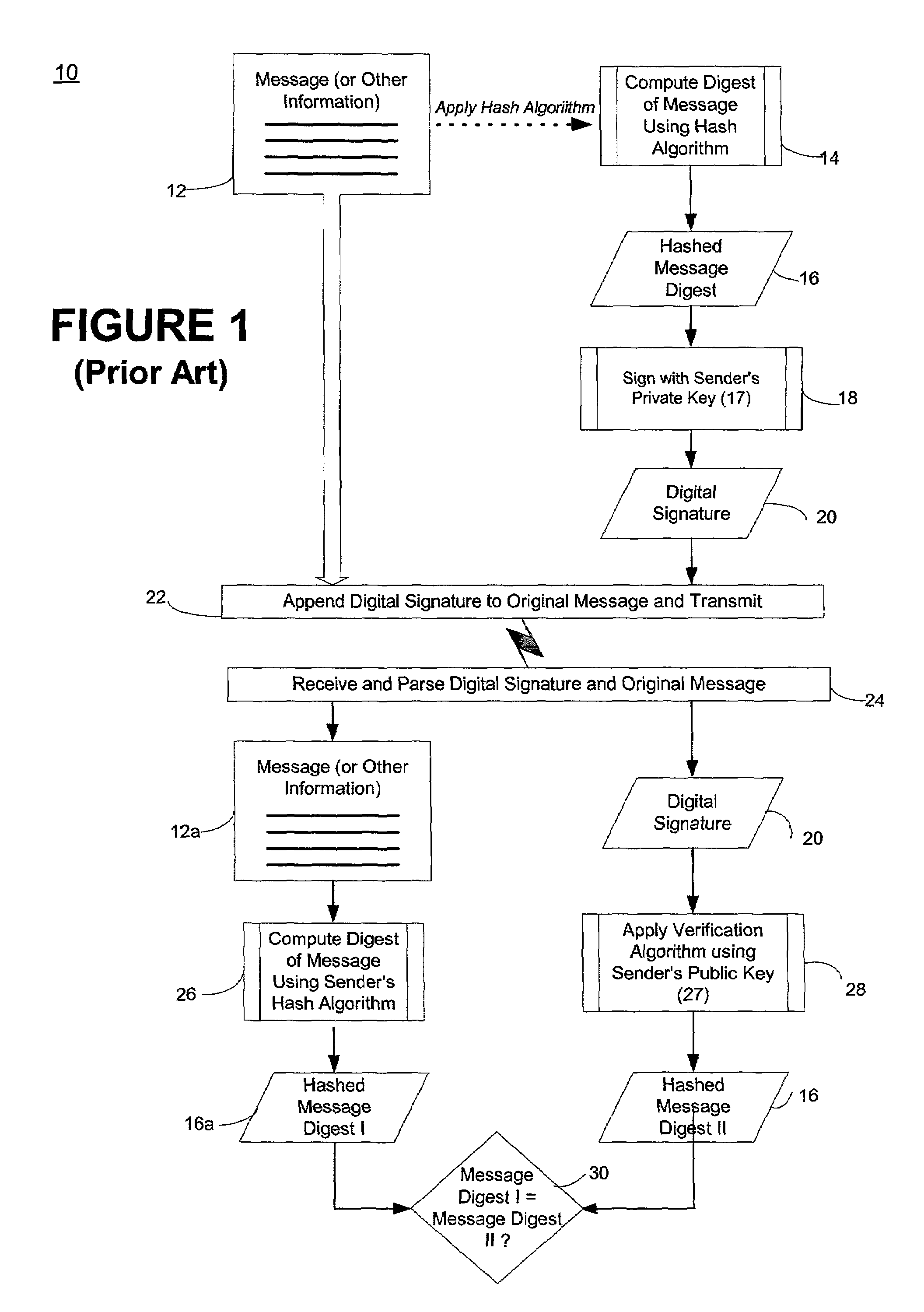
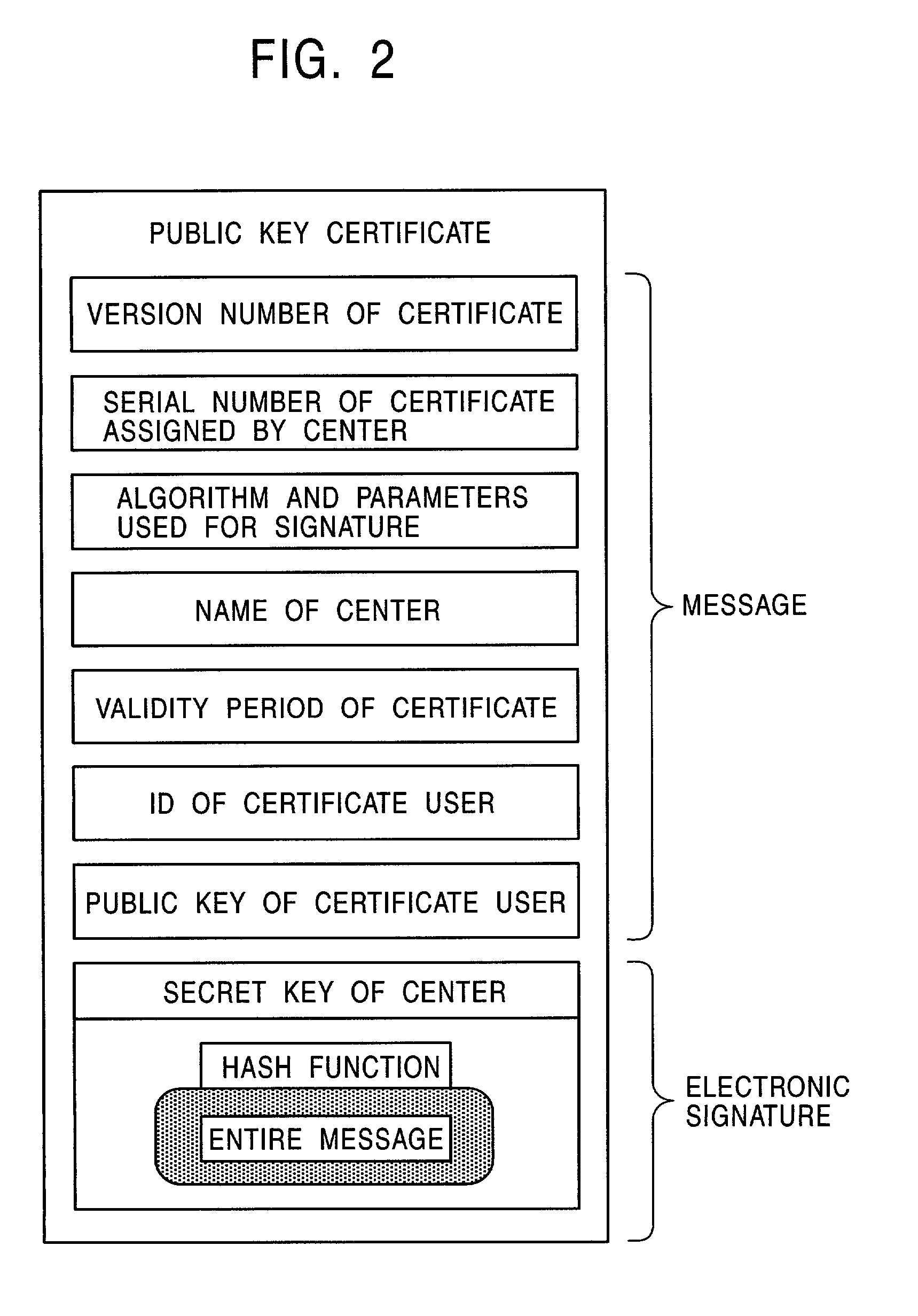
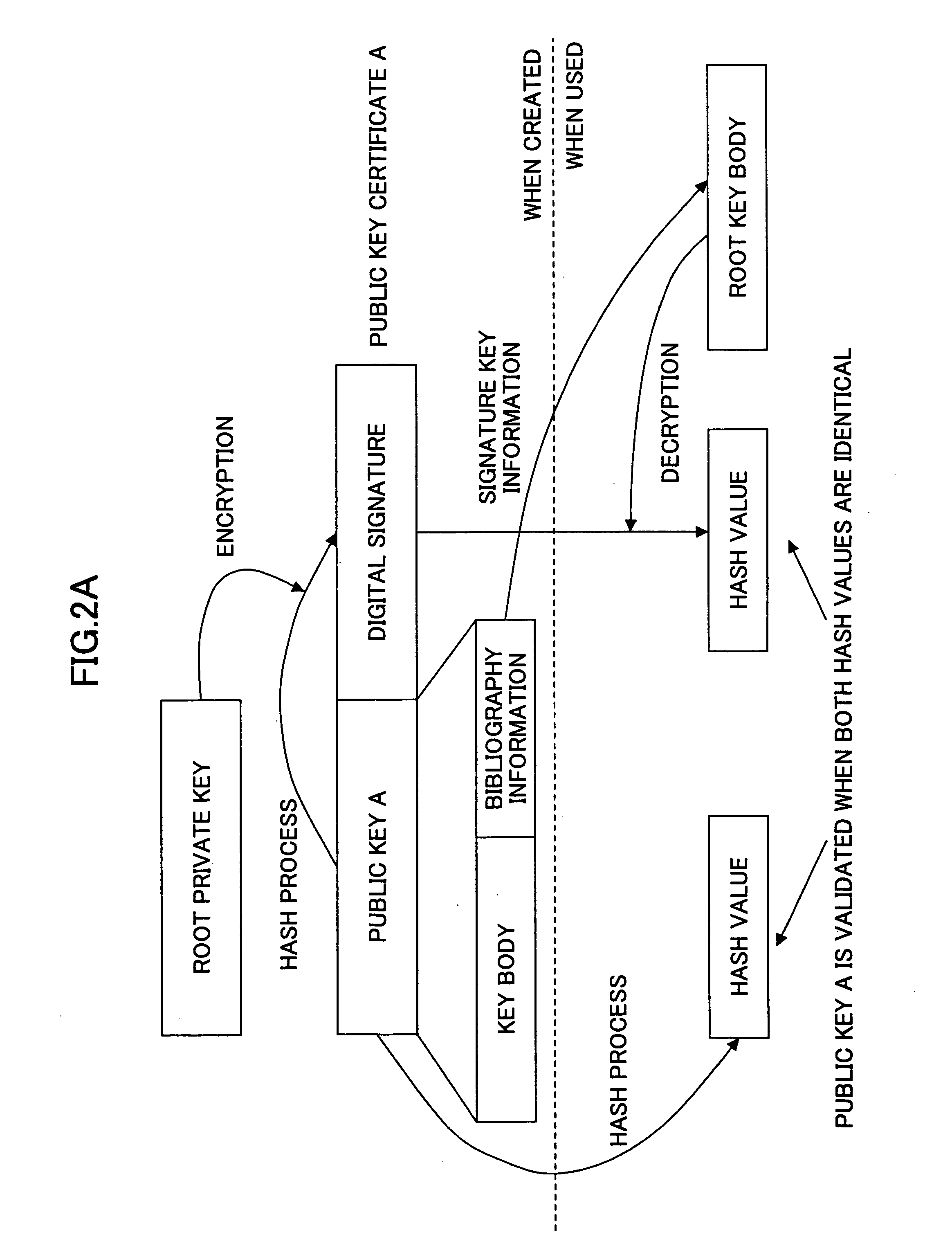
In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the ownership of a public key. The certificate includes information about the key, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate's subject. In email encryption, code signing, and e-signature systems, a certificate's subject is typically a person or organization. However, in Transport Layer Security (TLS) a certificate's subject is typically a computer or other device, though TLS certificates may identify organizations or individuals in addition to their core role in identifying devices. TLS, sometimes called by its older name Secure Sockets Layer (SSL), is notable for being a part of HTTPS, a protocol for securely browsing the web.
Message routing
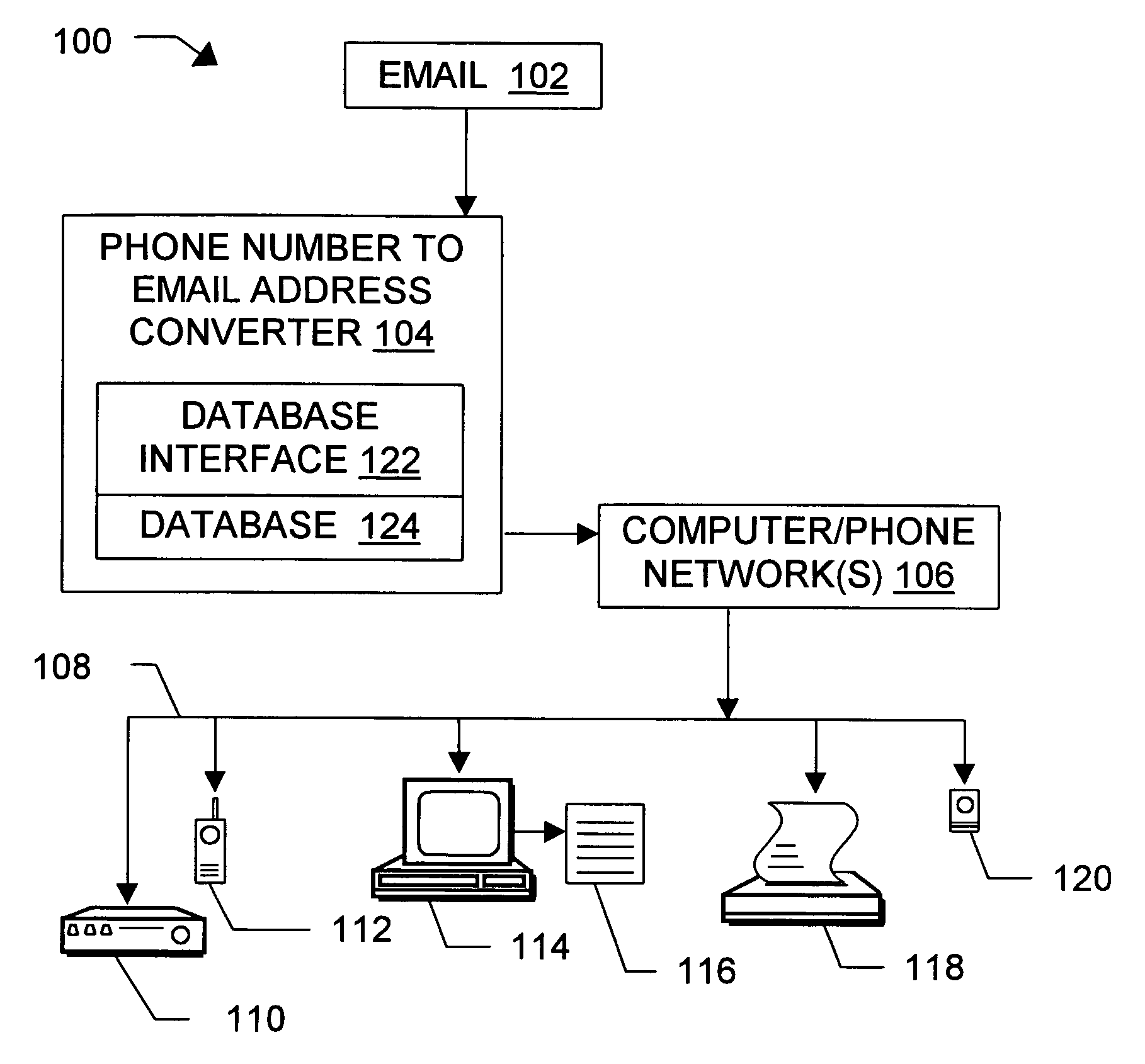
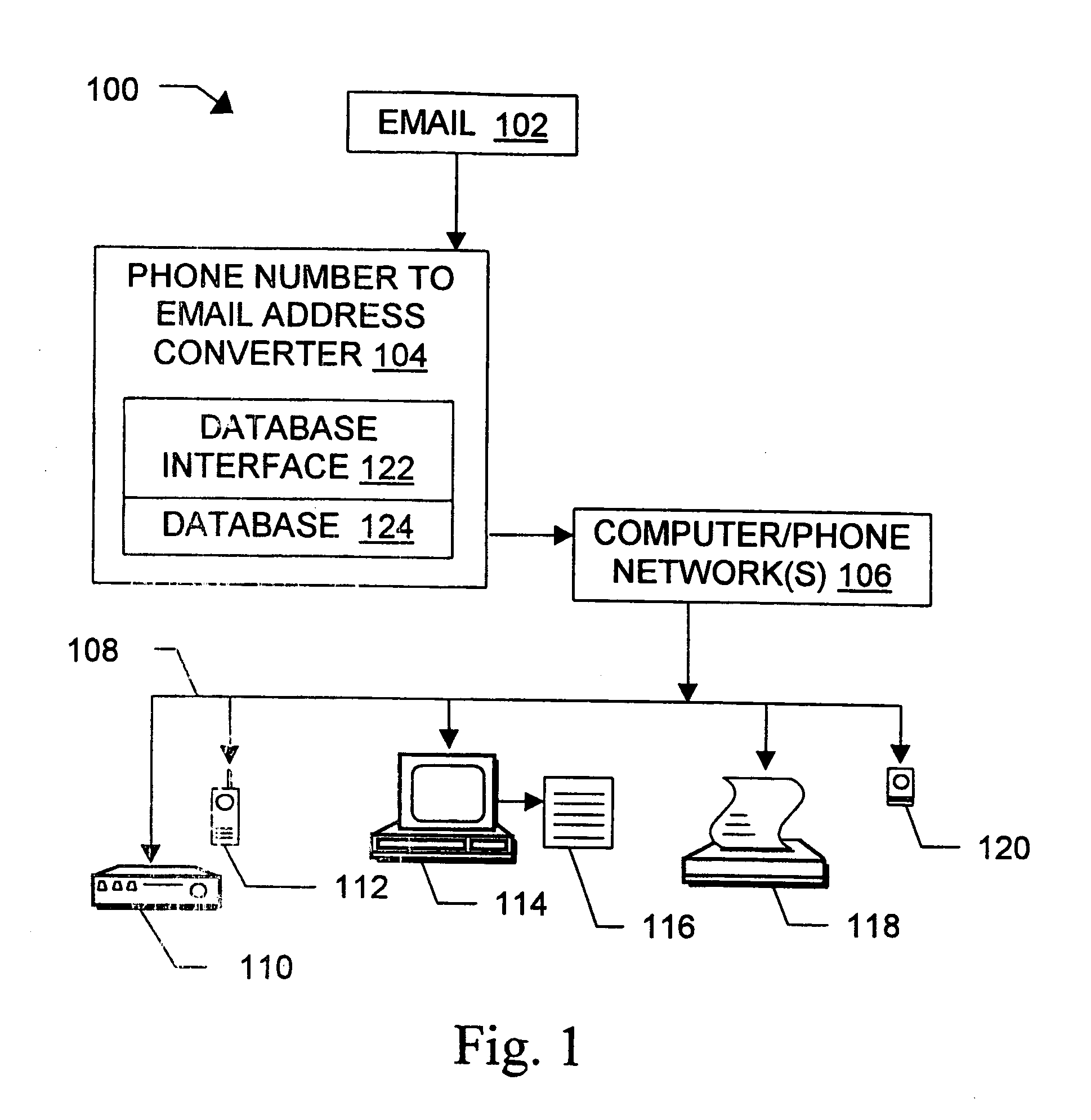
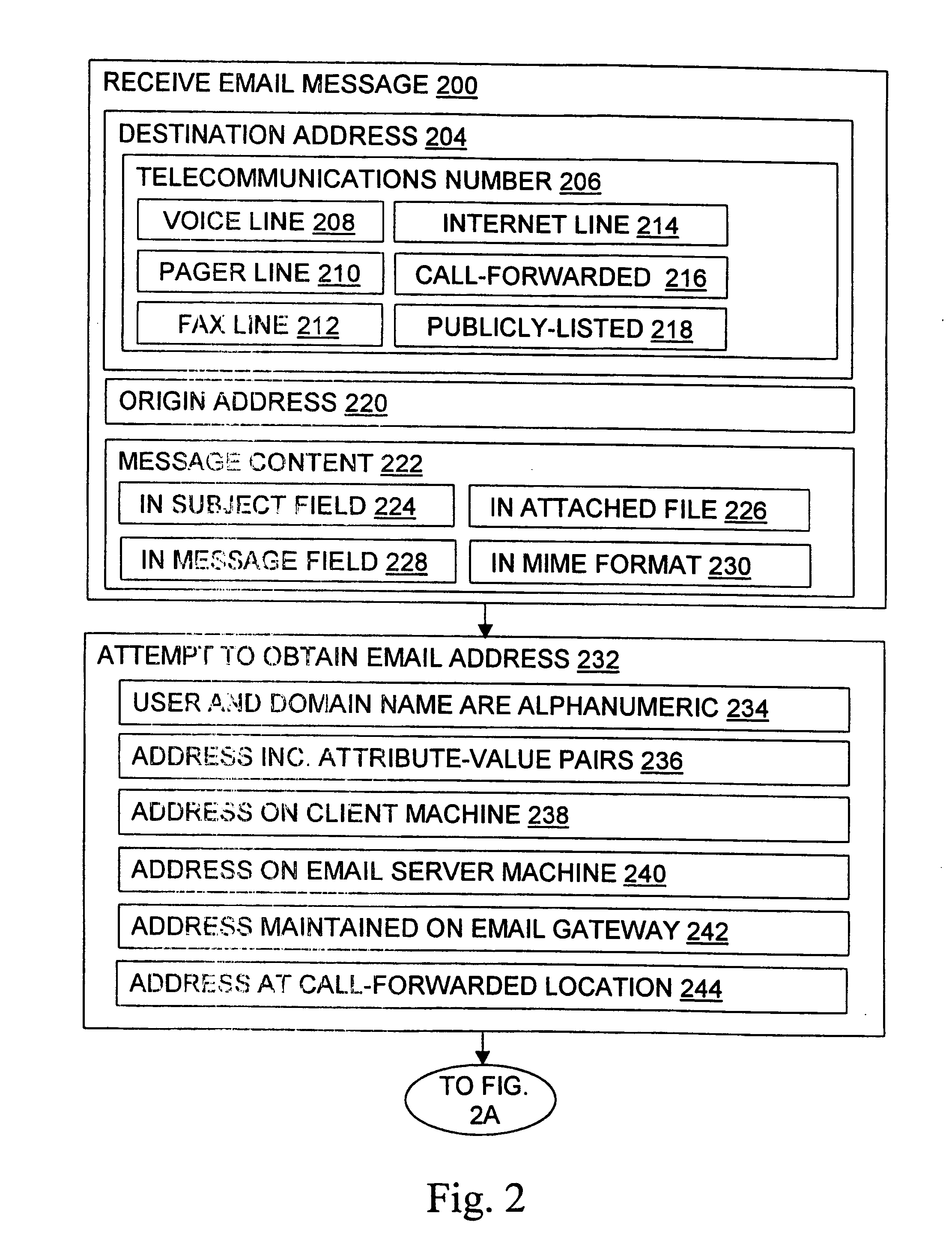
InactiveUS6981023B1Easy to getRemove the burdenInterconnection arrangementsPublic key for secure communicationEmail addressSelective calling
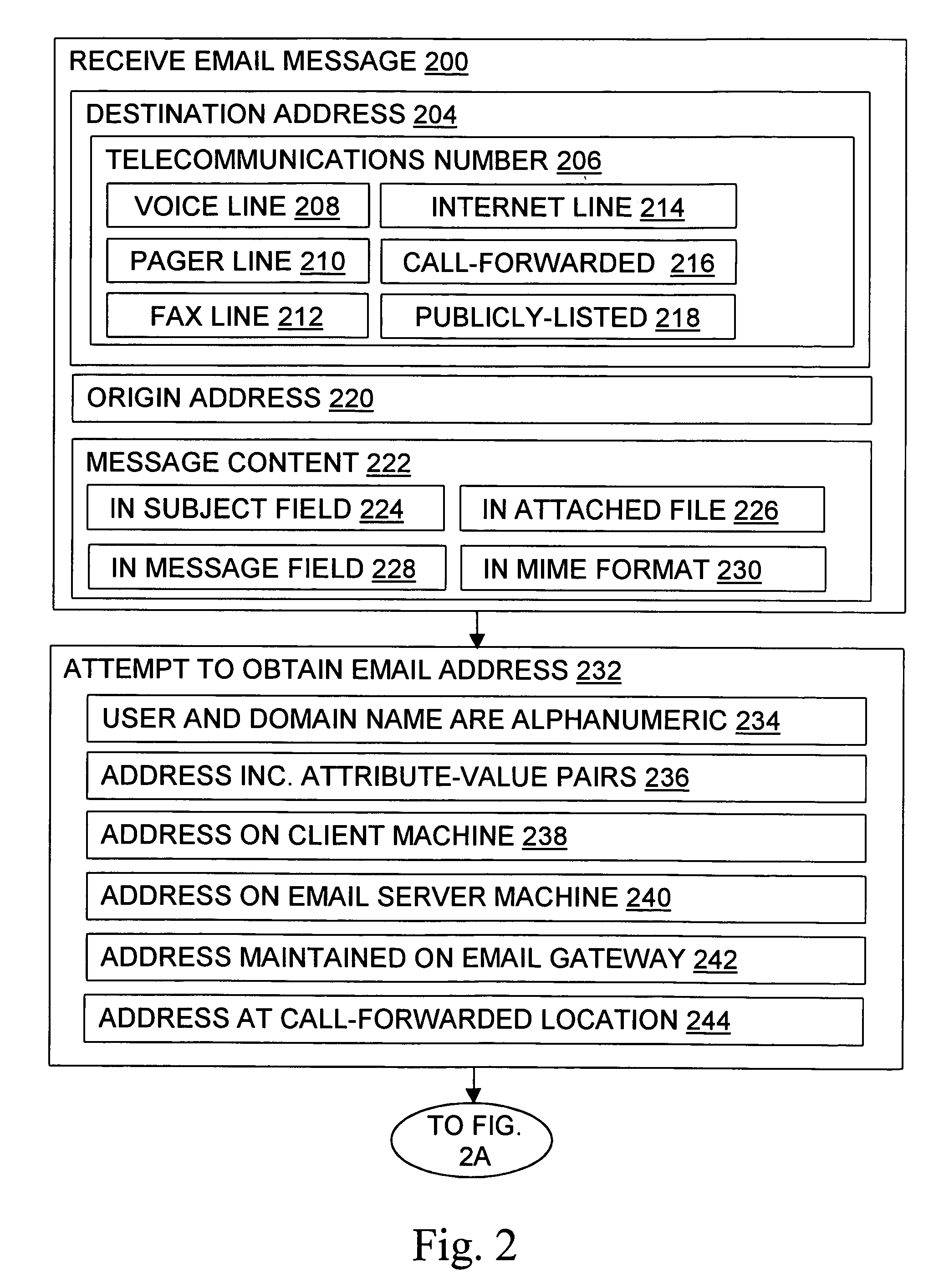
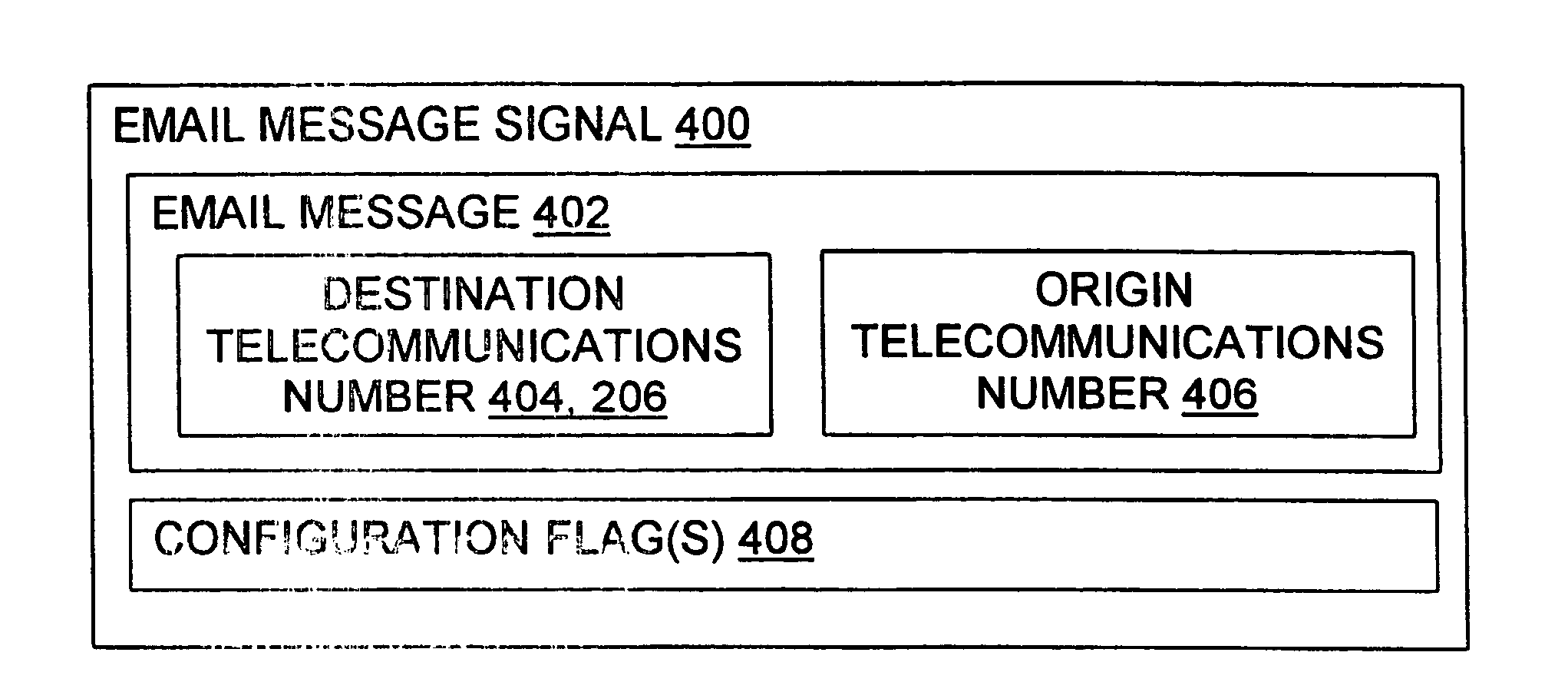
Methods, devices, signals, and systems are provided in a message routing architecture which provides improved capabilities for integrating “digital” communication through email messages with “analog” communication through voice and / or fax or pager messages. Email can be addressed using nothing more than a standard telephone or fax number. If the registered owner of the telephone or fax number has a corresponding email address, then the invention converts the telephone or fax number to the email address for delivery and uses standard email delivery systems to deliver the message. If no conventional delivery email address is known, or if the message sender or recipient specify multiple delivery modes, then the email message content is transformed into voice, pager and / or fax content and delivered to the recipient using the telephone or fax number which was specified as the email address. Familiar telecommunications services such as call forwarding and selective call blocking can also be used with messages that originate as email. The invention also supports use of telecommunications numbers as indexes into databases which contain public key certificates, to make it unnecessary for a proposed message recipient to provide its public key expressly in advance to each particular proposed message originator.
Owner:HAMILTON MICHAEL +1
Methods for authenticating self-authenticating documents
InactiveUS20050038754A1Low costImprove reliabilityUser identity/authority verificationPayment architecturePersonal identification numberDigital signature
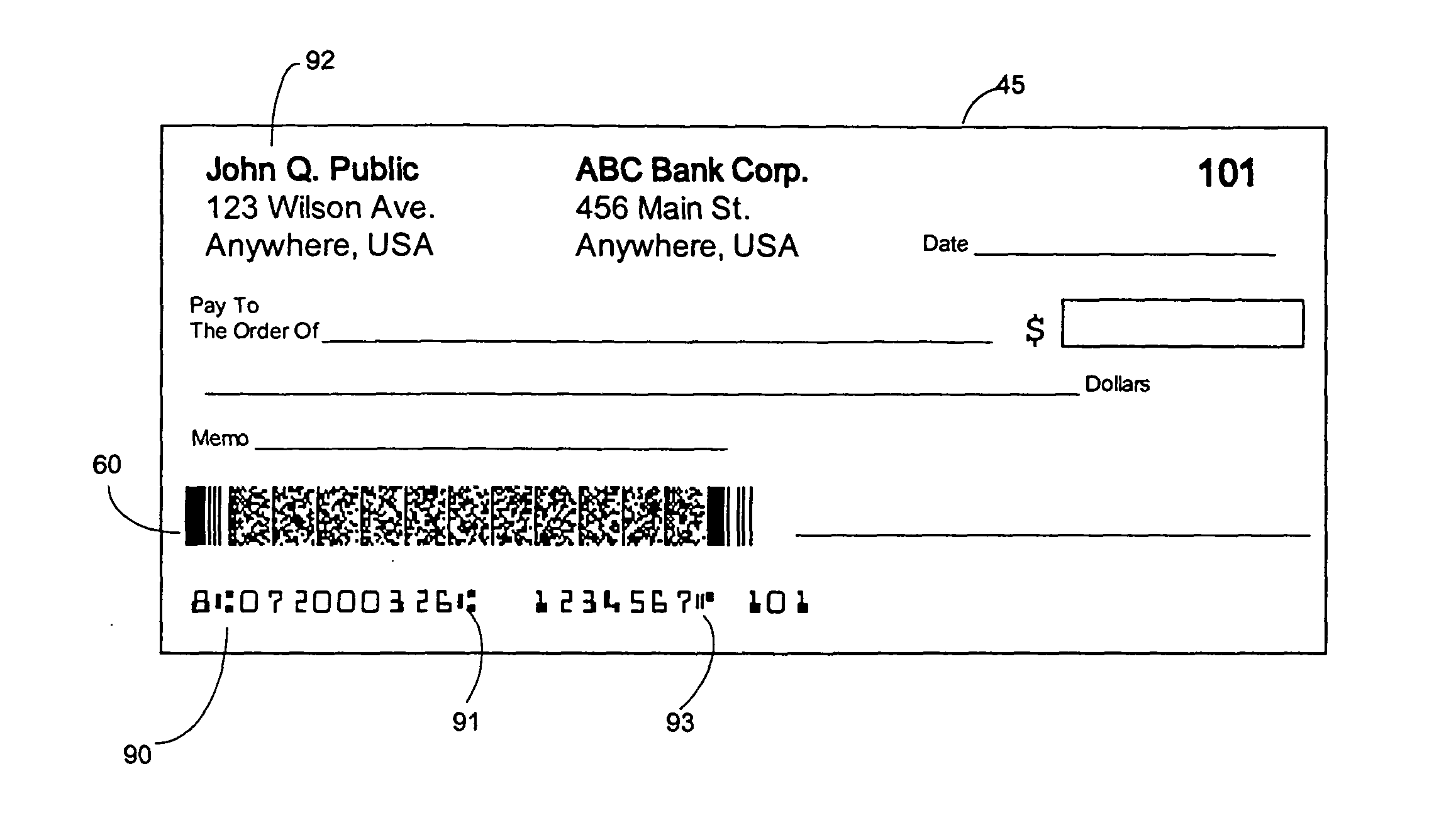
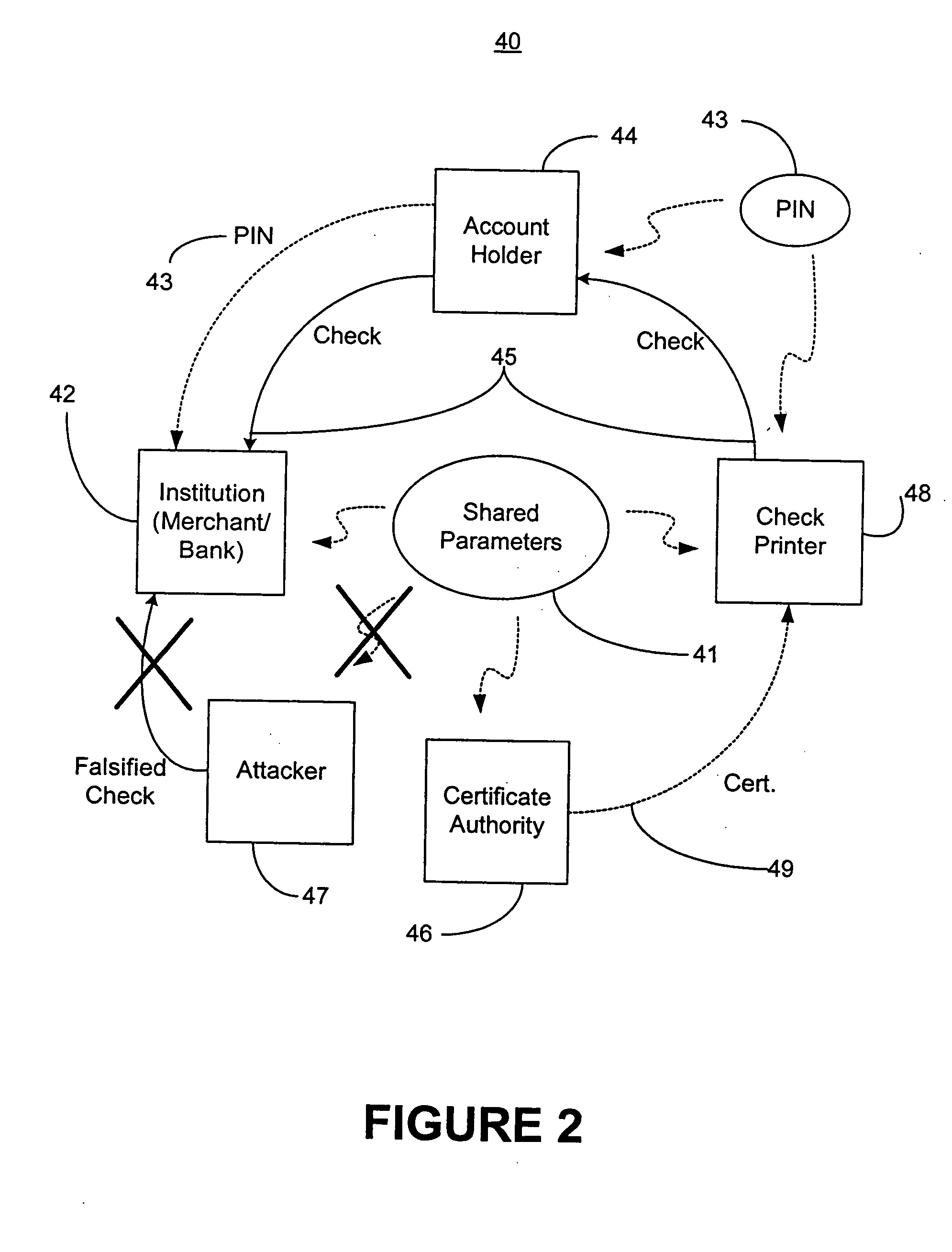
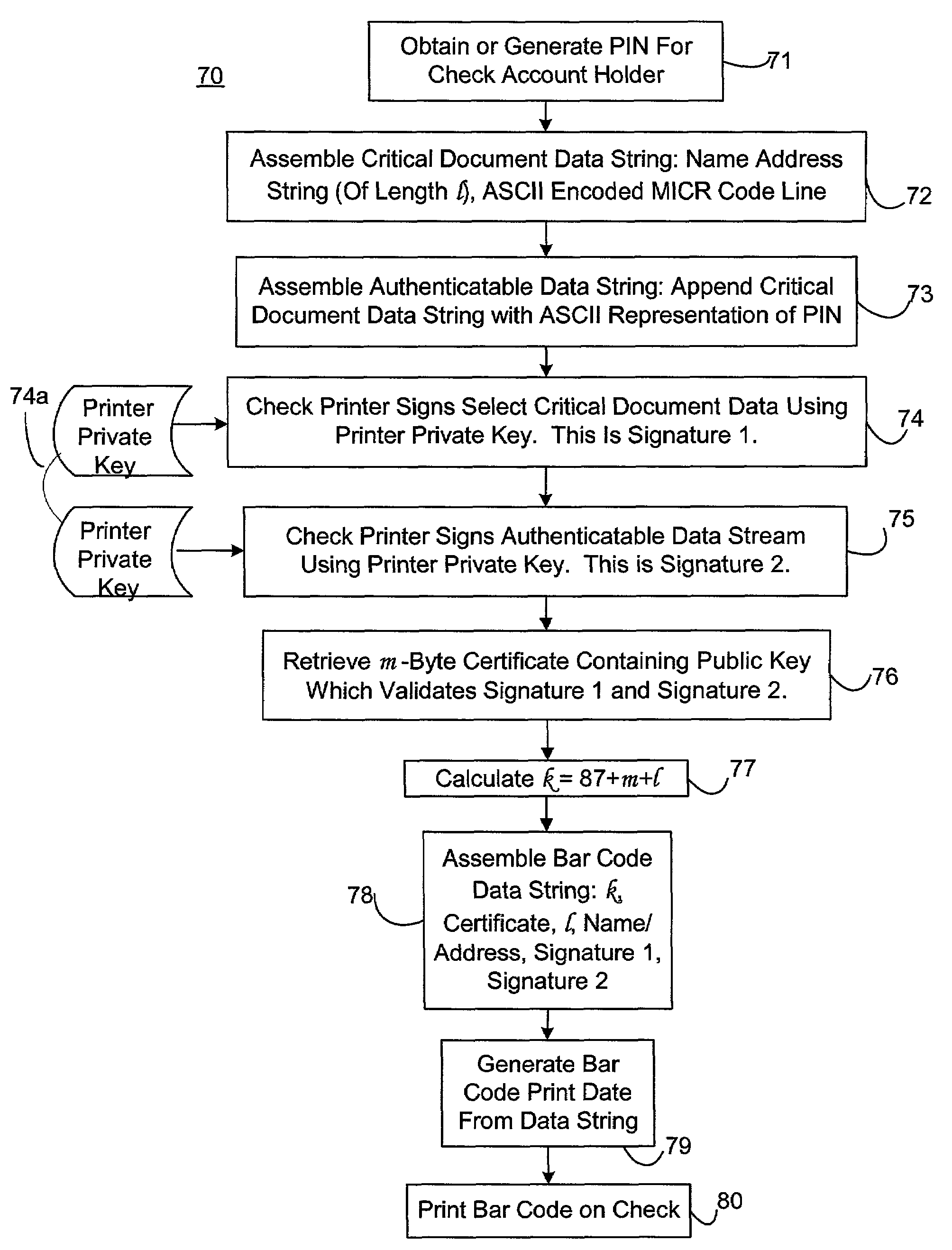
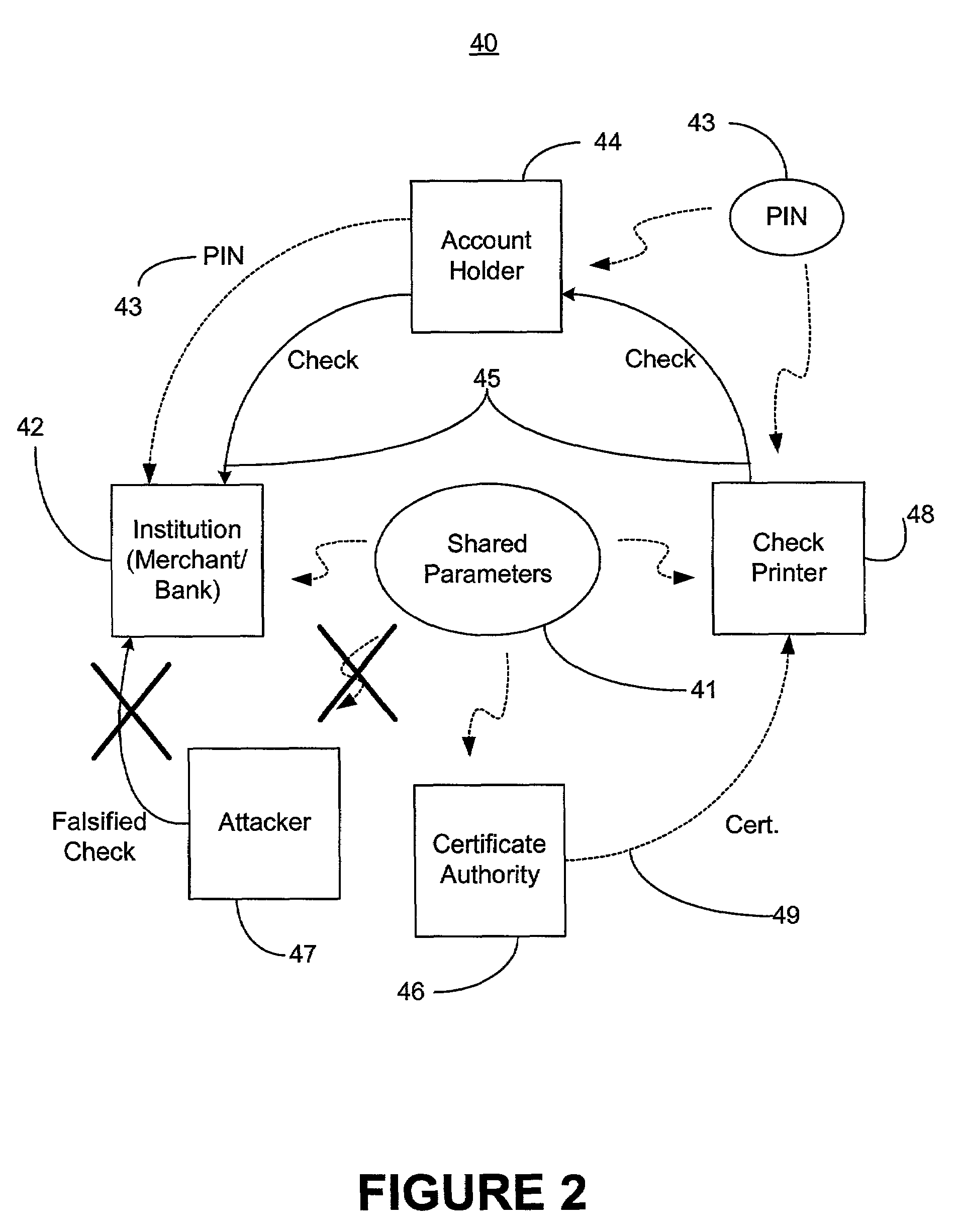
Methods of authenticating self-authenticating documents presented at a point of purchase or financial institution. Data contained on the value document may be signed with a first digital signature and authenticated with a public key certificate. A unique personal identification number (PIN) may be included in the document data that is signed by a second digital signature. The signed data and a public key certificate are stored on the value document. At a point of purchase, a merchant or teller can scan and read the stored data and together with the PIN the customer provides, can authenticate the value document thus presented using the second digital signature. Alternatively, if the customer is not present, the document may be verified using a PIN-generating algorithm. The first digital signature alone may be used to authenticate the document even when the PIN is not available.
Owner:UNISYS CORP
Self-authentication of value documents using digital signatures
ActiveUS7051206B1Low costImprove reliabilityKey distribution for secure communicationPaper-money testing devicesCredit cardPublic key certificate
An encryption-free technique for enabling the self-authentication of value documents (including personal and commercial checks) presented at a point of purchase or financial institution. Certain data contained on the value document may be signed with a first digital signature and authenticated with a public key certificate issued from a trusted certificate authority. The signed data and public key certificate are stored on the value document, preferably in a two-dimensional bar code data format. In the case of certain personal value documents (such as checks, credit cards, passports, birth certificates, Social Security cards, etc.), a unique personal identification number (PIN) also may be included in the document data that is signed by a second digital signature. At a point of purchase, a merchant or teller can scan and read the data stored in the two-dimensional bar code and other magnetically recorded information, and together with the PIN the customer provides, can authenticate the value document thus presented using the second digital signature. Alternatively, if the customer is not present, if the personal value document contains the second digital signature, the document may be verified using a PIN-generating algorithm or other method that generates all permutations of PINs. The first digital signature alone may be used to authenticate selected data within the personal value document even when the PIN is not available. Similarly, in the case of a commercial value documents, authentication of pre-printed data may be based entirely upon only the first digital signature.
Owner:UNISYS CORP
Securely Recovering a Computing Device
ActiveUS20080168275A1Multiple keys/algorithms usagePublic key for secure communicationTelecommunications linkDigital signature
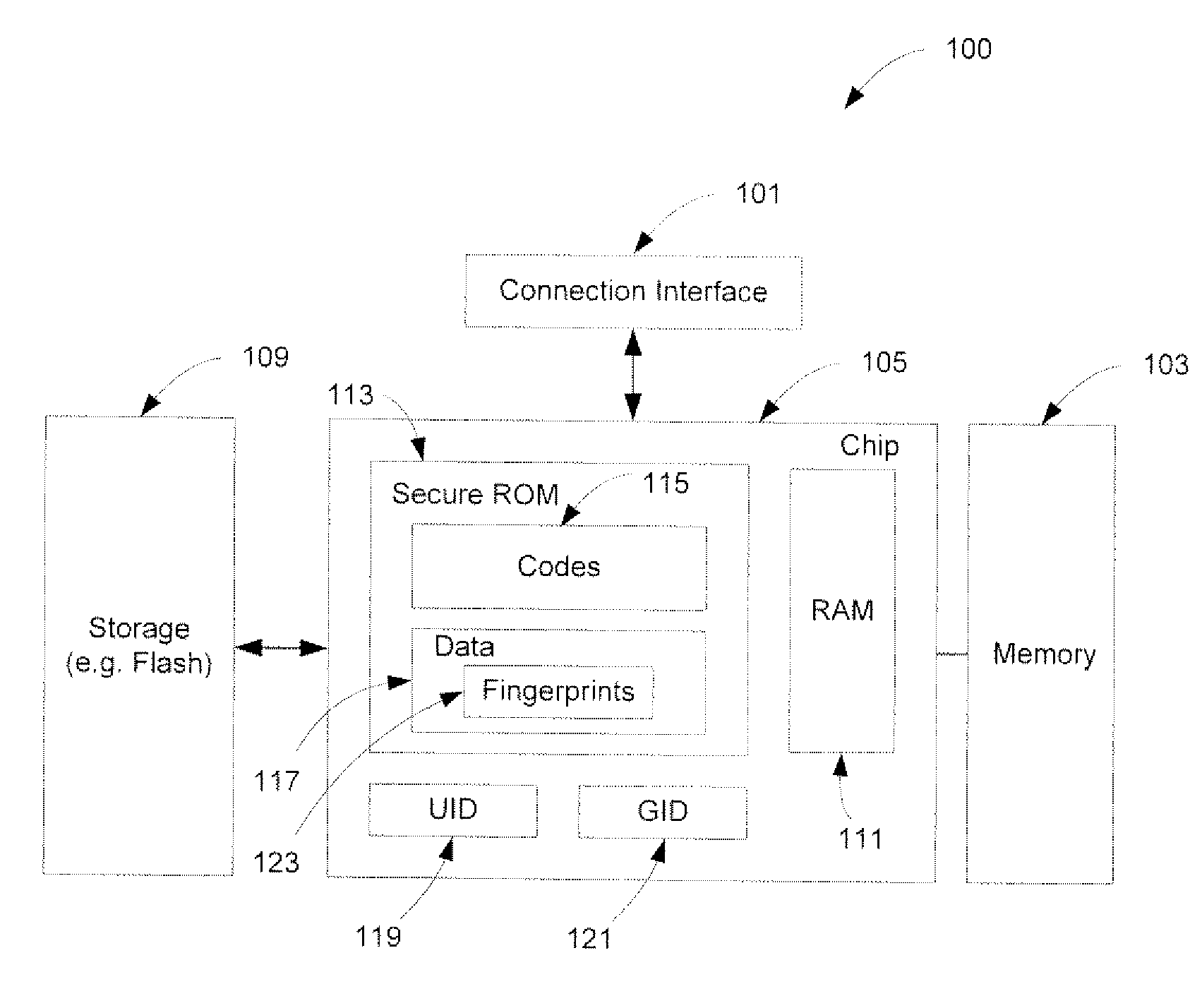
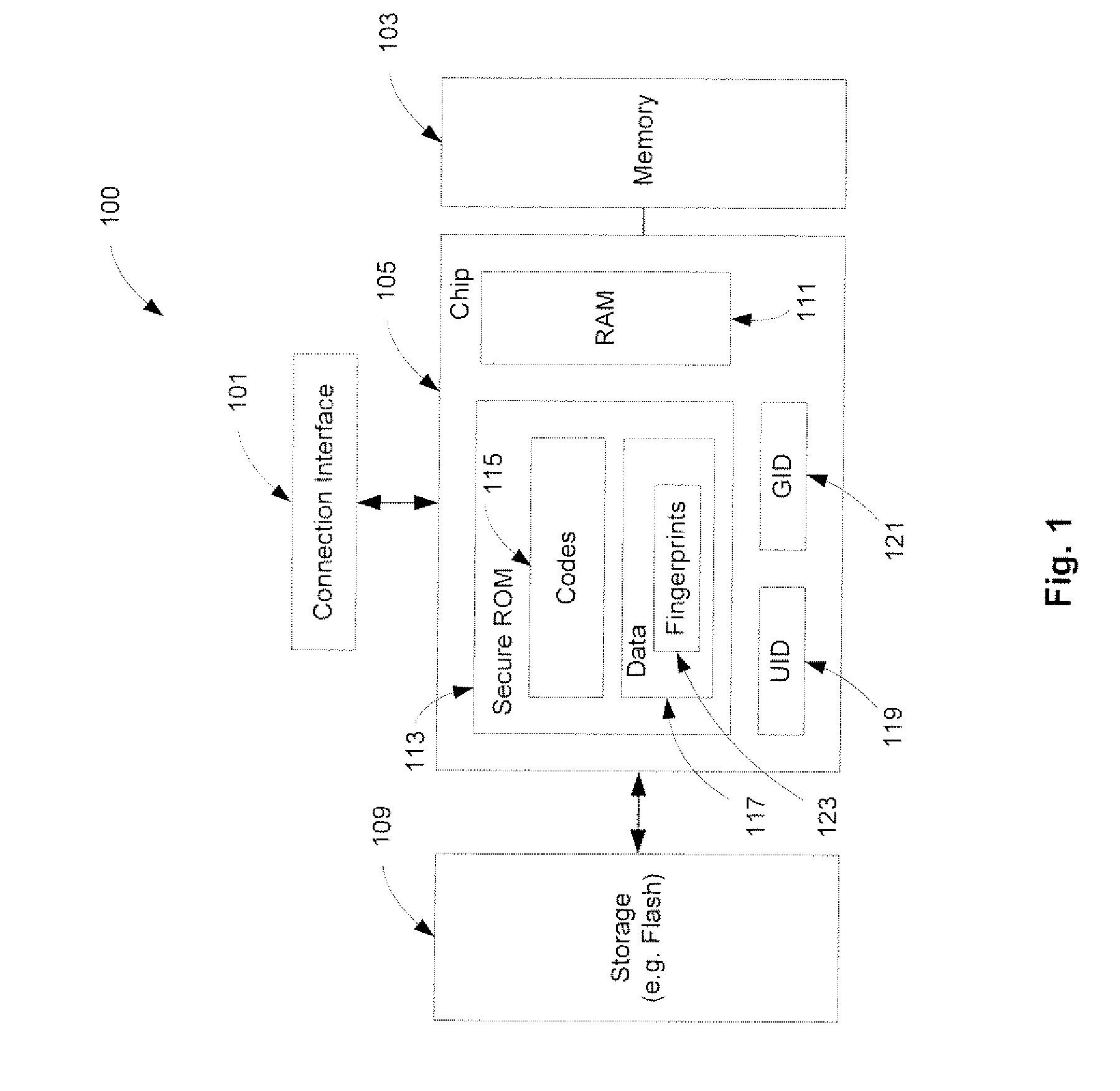
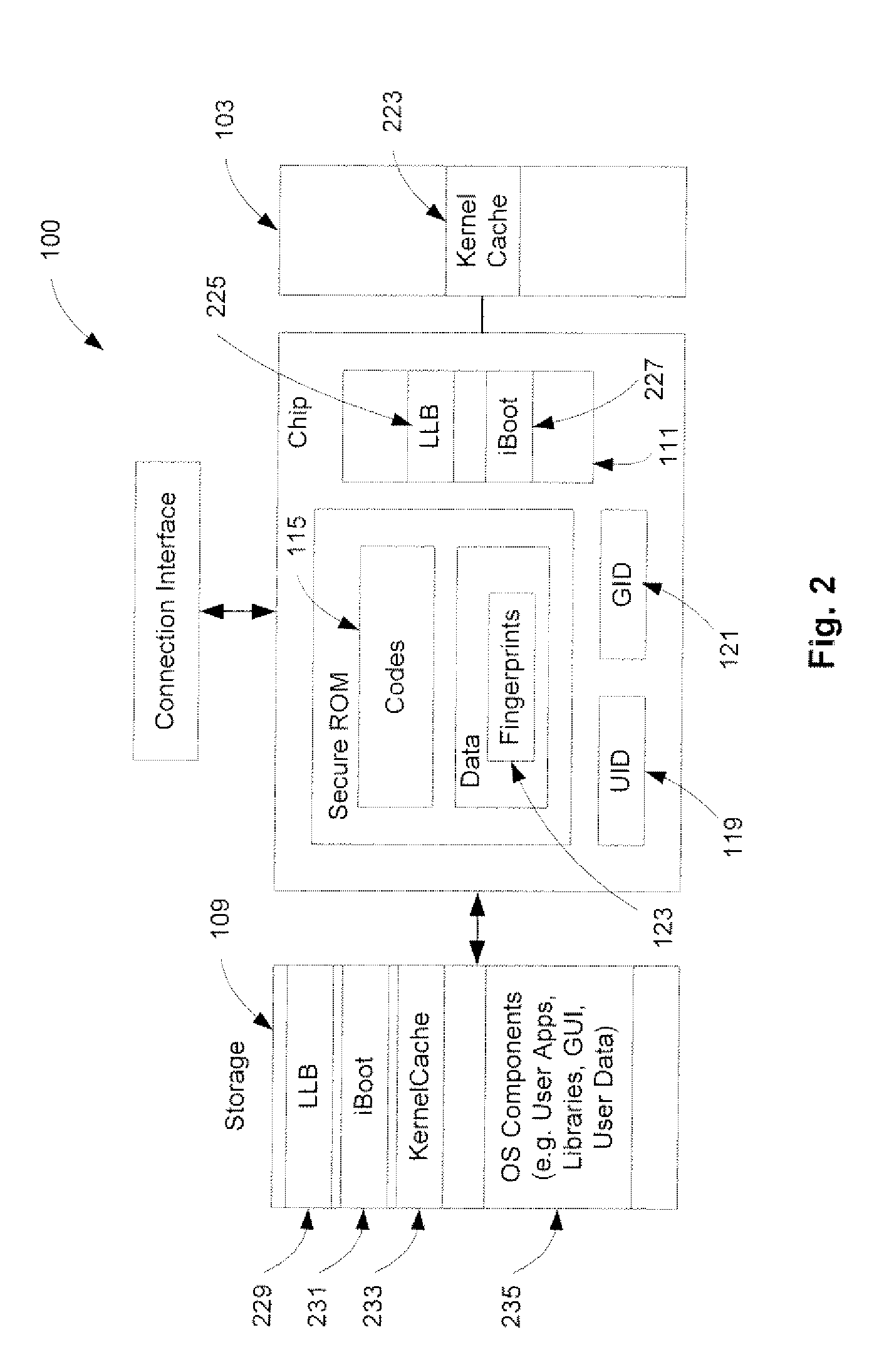
A method and an apparatus for establishing an operating environment by certifying a code image received from a host over a communication link are described. The code image may be digitally signed through a central authority server. Certification of the code image may be determined by a fingerprint embedded within a secure storage area such as a ROM (read only memory) of the portable device based on a public key certification process. A certified code image may be assigned a hash signature to be stored in a storage of the portable device. An operating environment of the portable device may be established after executing the certified code.
Owner:APPLE INC
Certificating vehicle public key with vehicle attributes
ActiveUS20150052352A1Public key for secure communicationUser identity/authority verificationImaging processingDigital signature
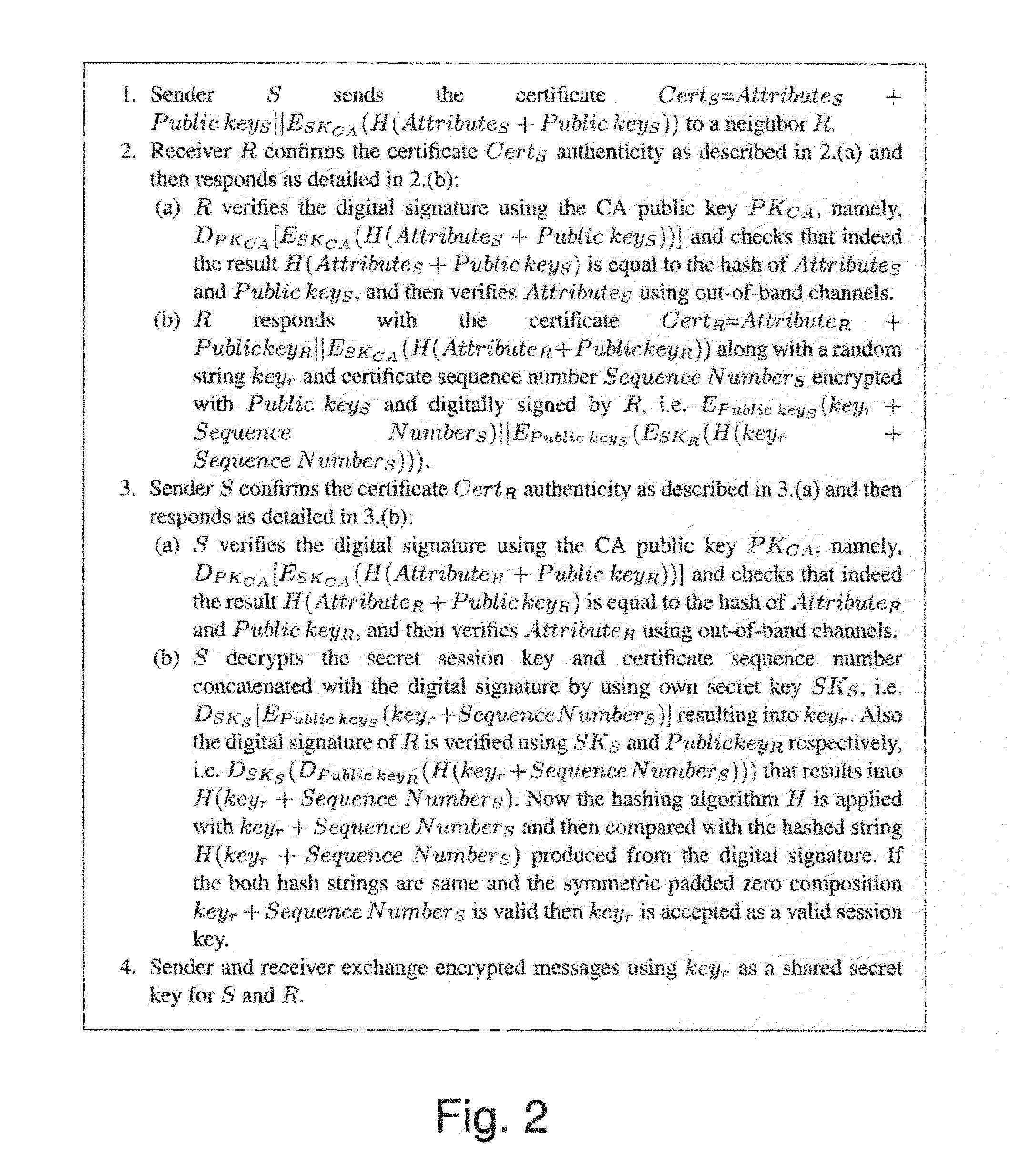
A method for providing secure connection between vehicles over channels of a wireless communication network, according to which, a first unique pair of digitally signed public key and private key is provided to each vehicle, along with additional vehicle-related data including a visually static collection of attributes of the vehicle. A unique certificate number is generated for each vehicle and monolithic data consisting of the public key, the certificate number and the attributes is signed by a trusted certificate generating authority. Prior to wireless communication between a first vehicle and a second vehicle, a verification step is performed during which the first vehicle sends its unique certificate number to a second vehicle over a communication channel; the second vehicle verifies the authenticity of received unique certificate number of the first vehicle and attributes by a camera that captures attributes which are visible, using image processing means. If the attributes are verified successfully, the second vehicle sends its unique certificate number to the first vehicle over a communication channel, along with a secret session key, which is valid for the current session only. Then the first vehicle verifies the authenticity of received unique certificate number of the second vehicle and attributes by a camera that captures attributes of the second vehicle which are visible, using signal processing means and both vehicles are allowed to securely exchange message or data using the secret session key.
Owner:DOLEV SHLOMI +3
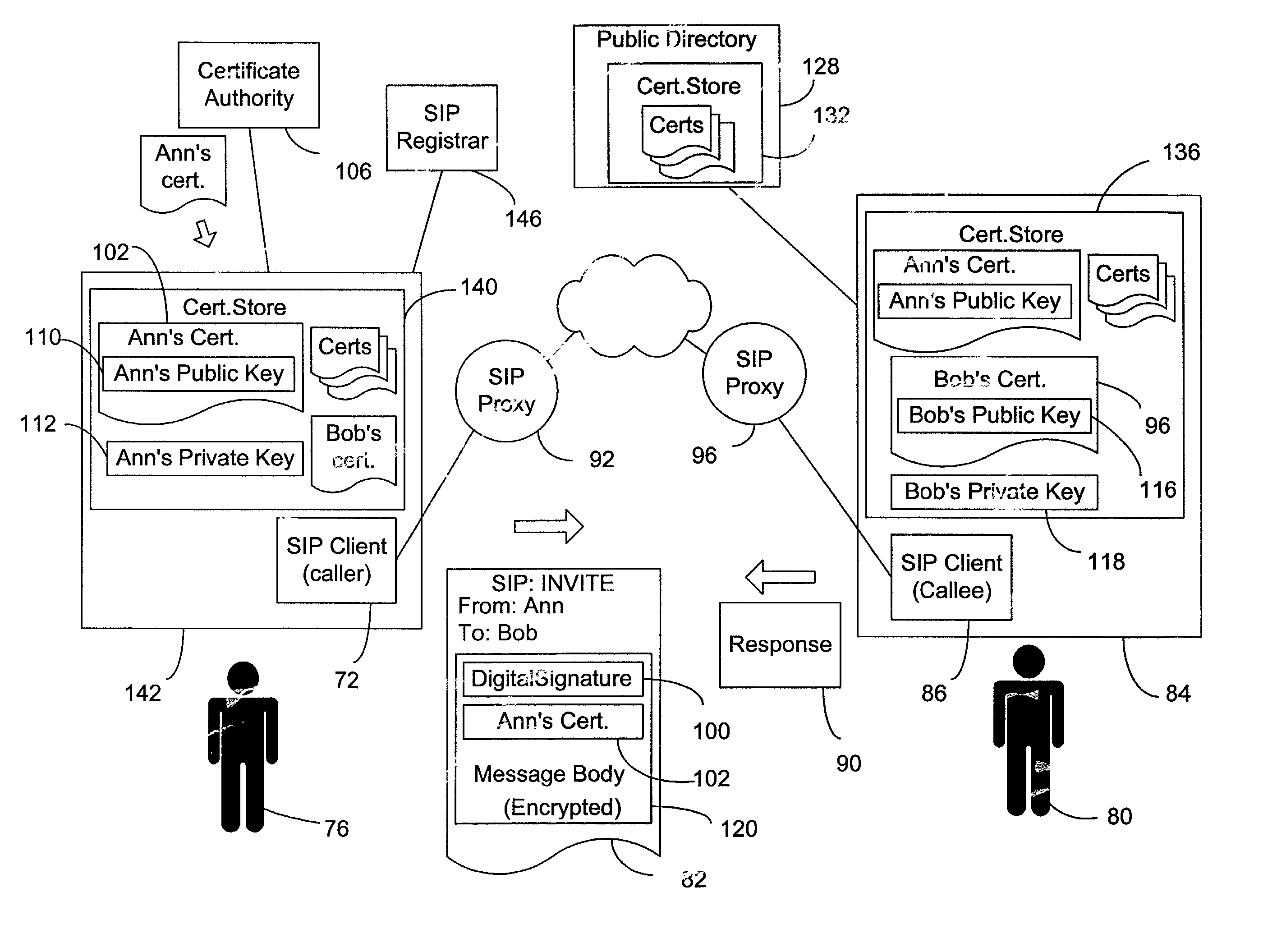
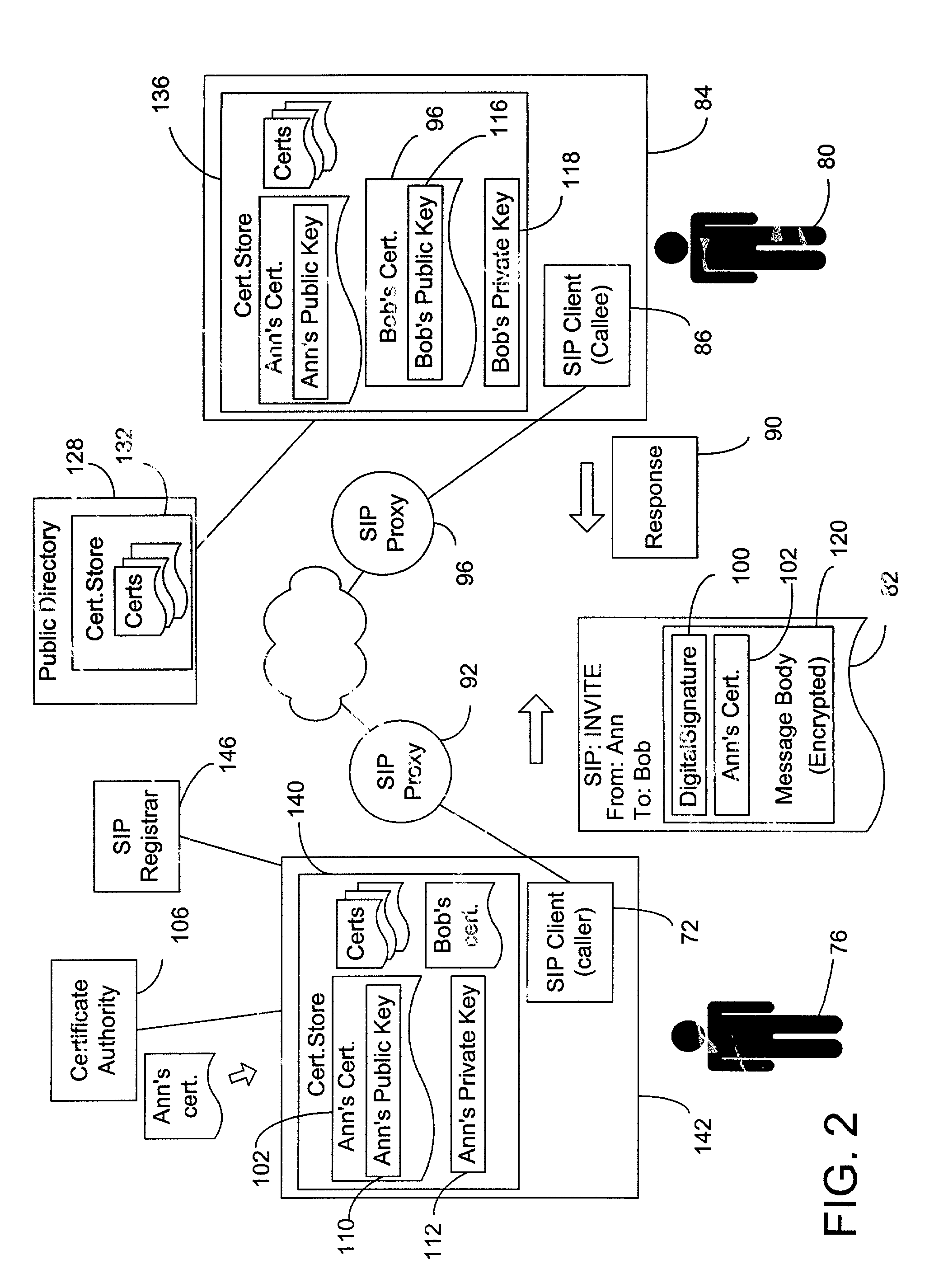
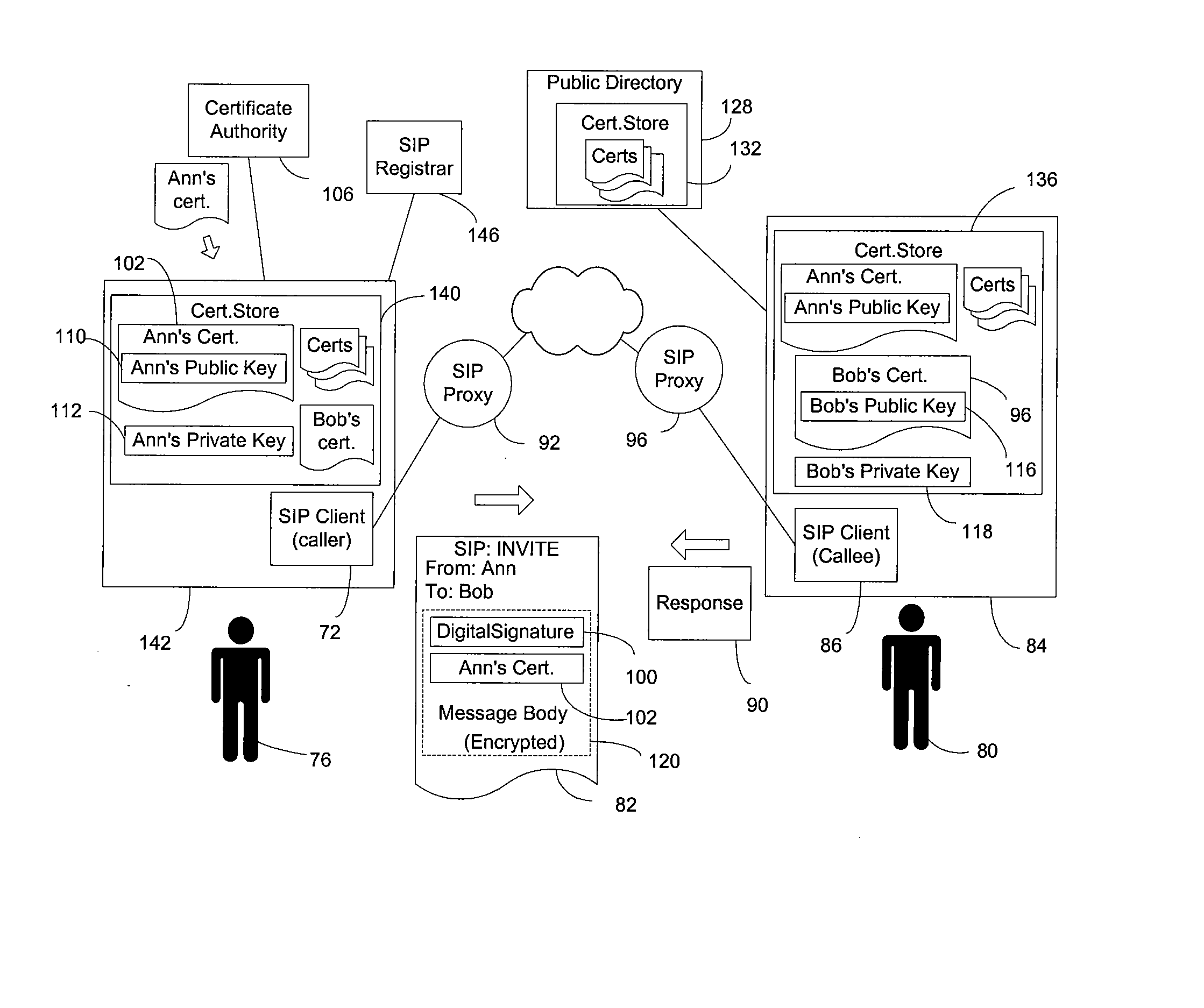
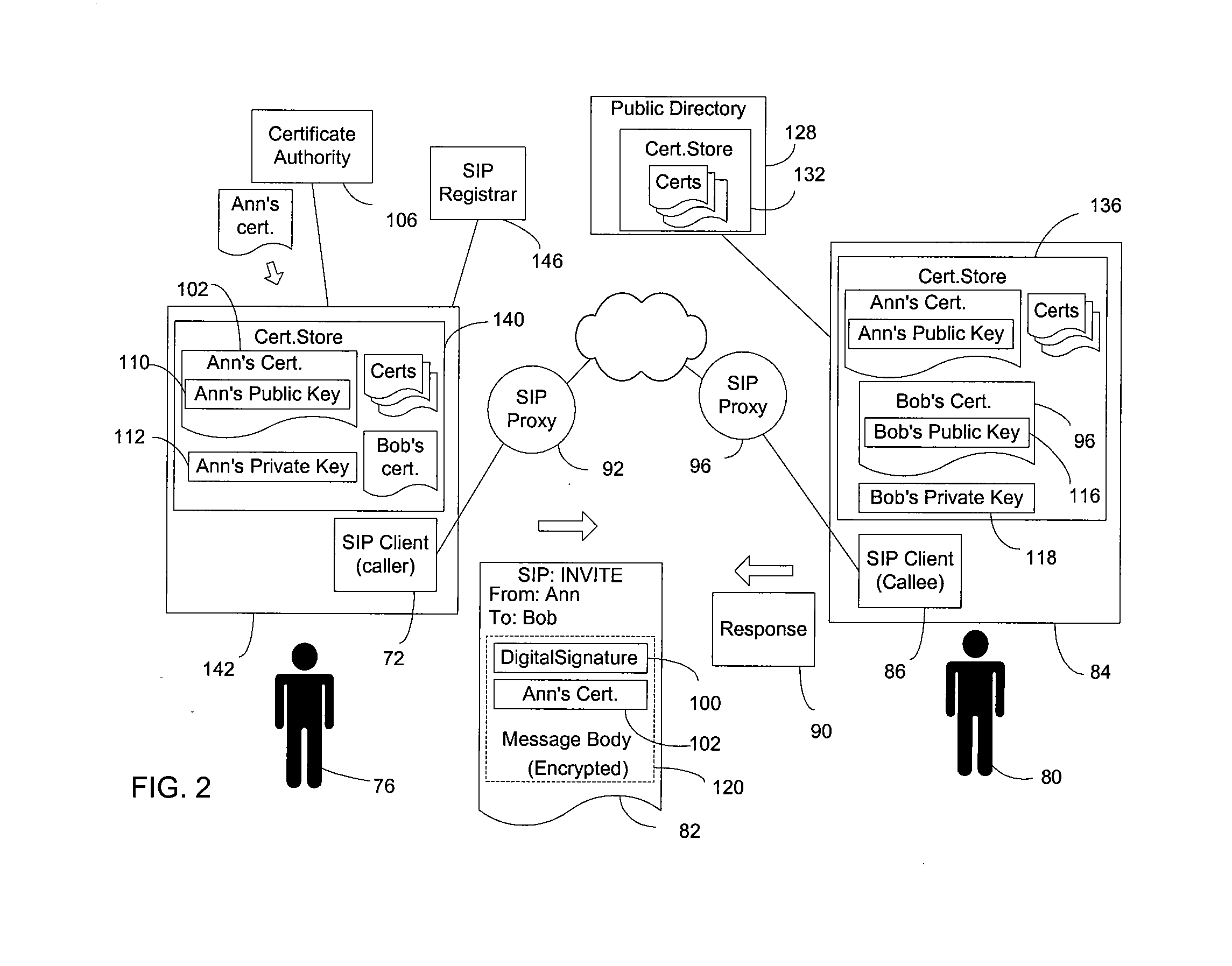
End-to-end authentication of session initiation protocol messages using certificates
InactiveUS7240366B2Multiple digital computer combinationsTelevision systemsSession Initiation ProtocolDigital signature
End-to-end authentication capability based on public-key certificates is combined with the Session Initiation Protocol (SIP) to allow a SIP node that receives a SIP request message to authenticate the sender of request. The SIP request message is sent with a digital signature generated with a private key of the sender and may include a certificate of the sender. The SIP request message may also be encrypted with a public key of the recipient. After receiving the SIP request, the receiving SIP node obtains a certificate of the sender and authenticates the sender based on the digital signature. The digital signature may be included in an Authorization header of the SIP request, or in a multipart message body constructed according to the S / MIME standard.
Owner:MICROSOFT TECH LICENSING LLC
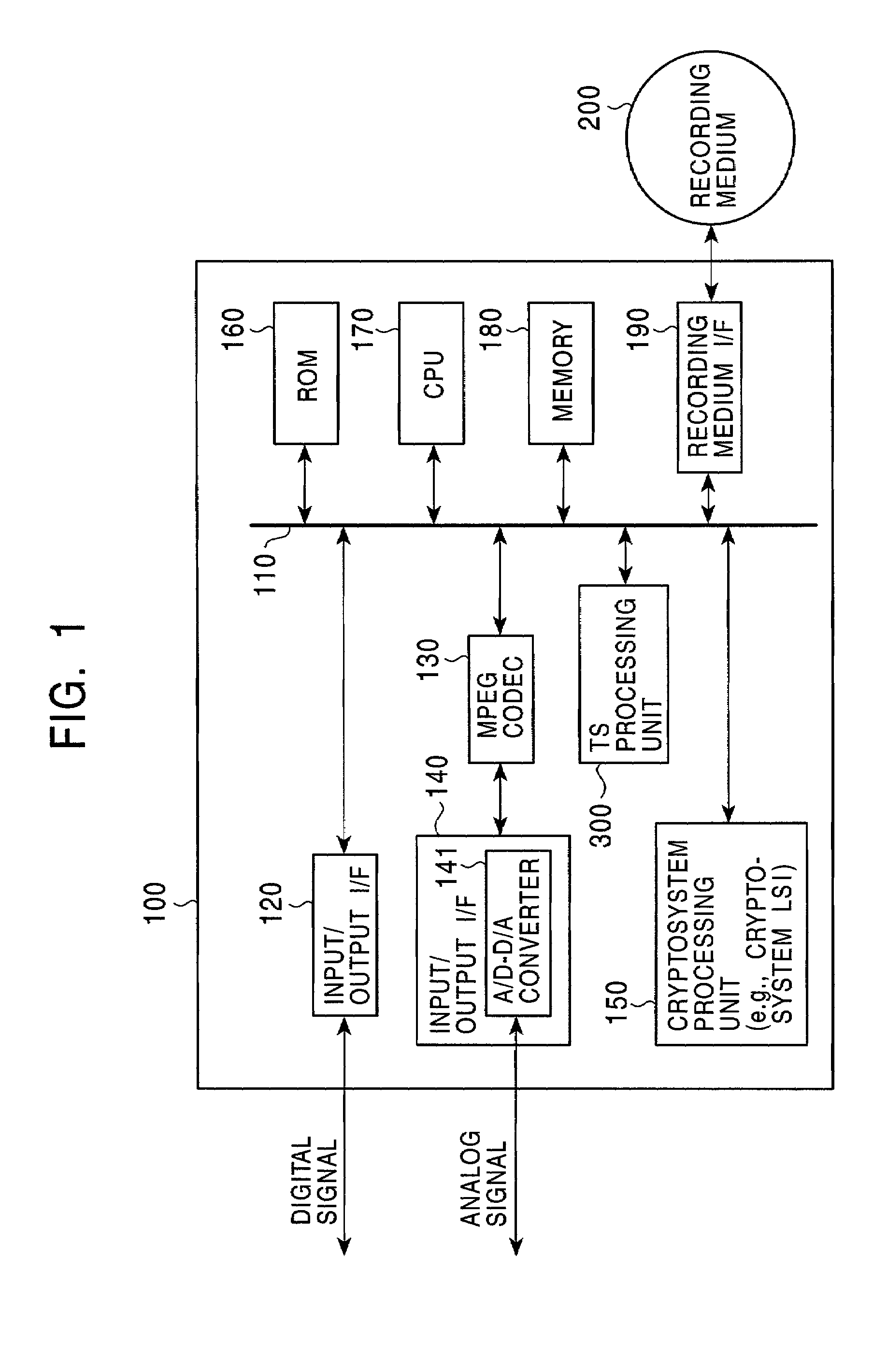
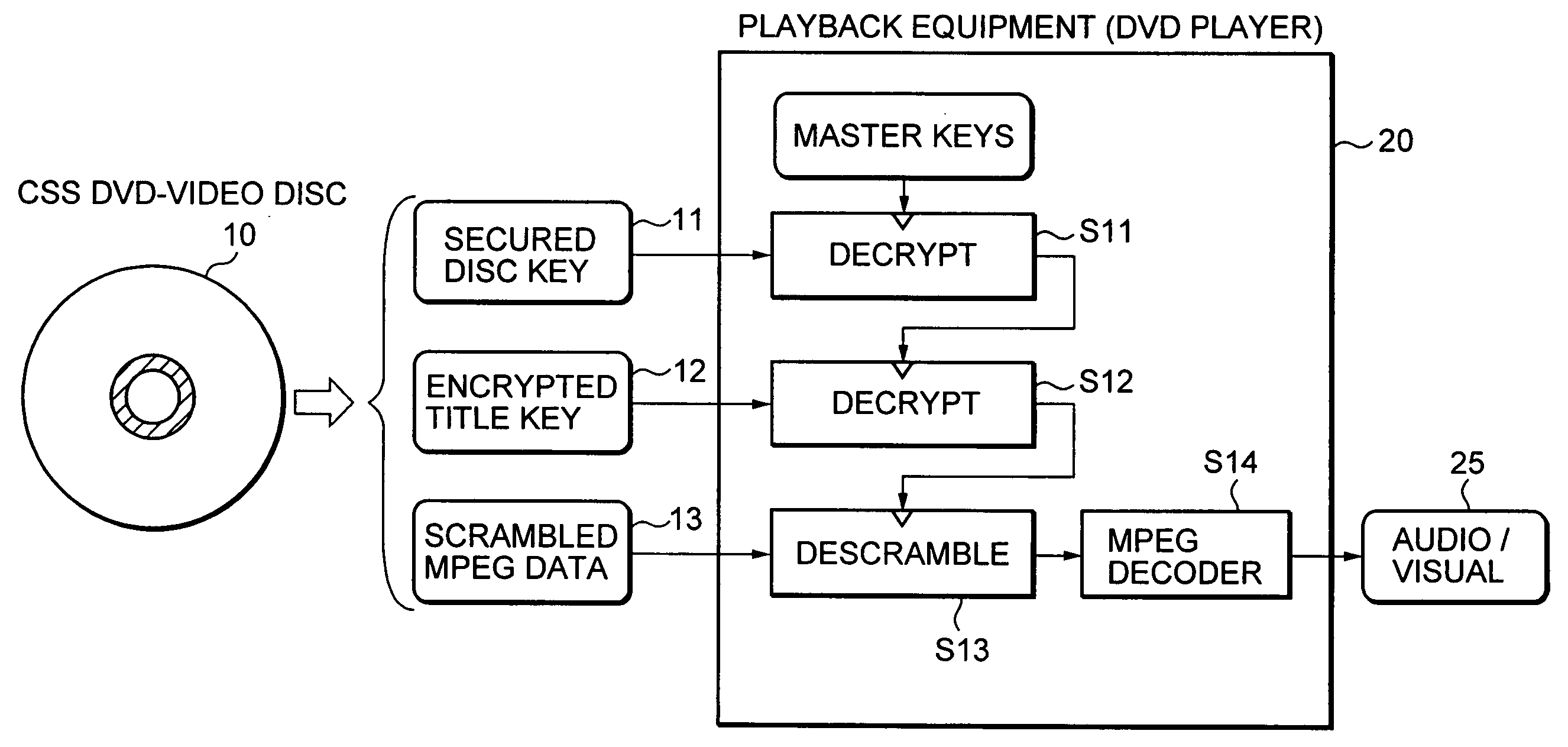
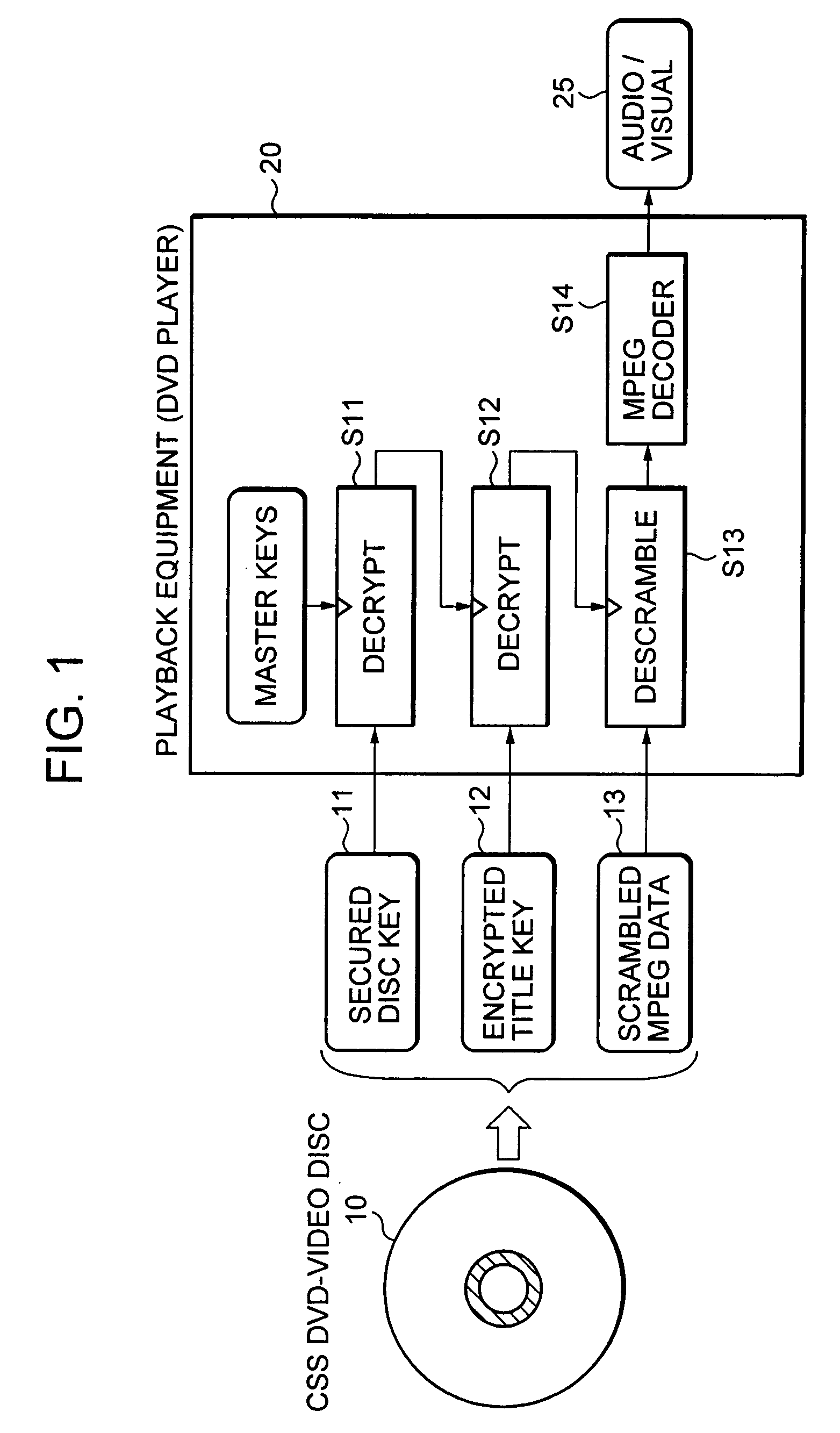
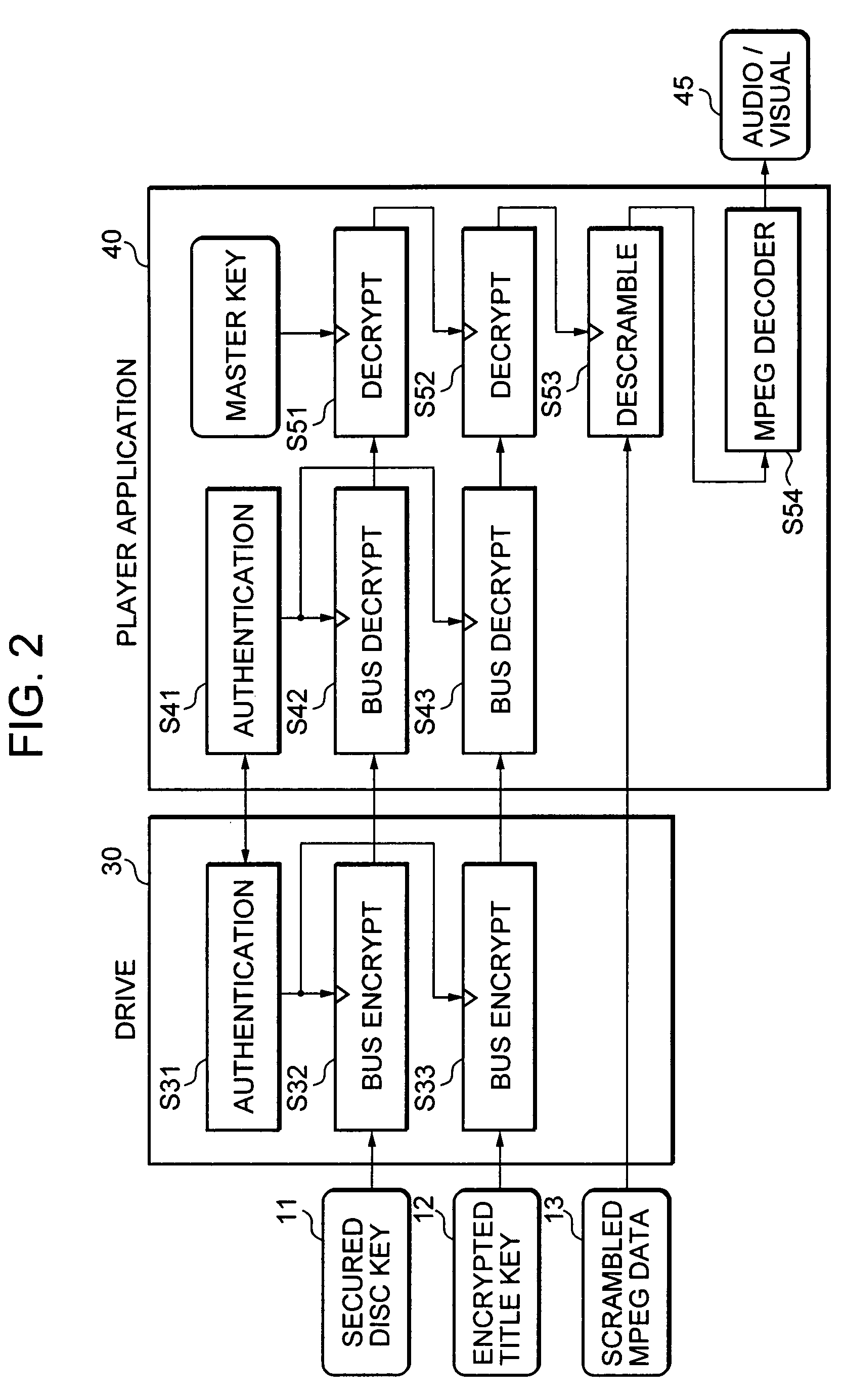
Information playback device, information recording device, information playback method, information recording method, and information recording medium and program storage medium used therewith
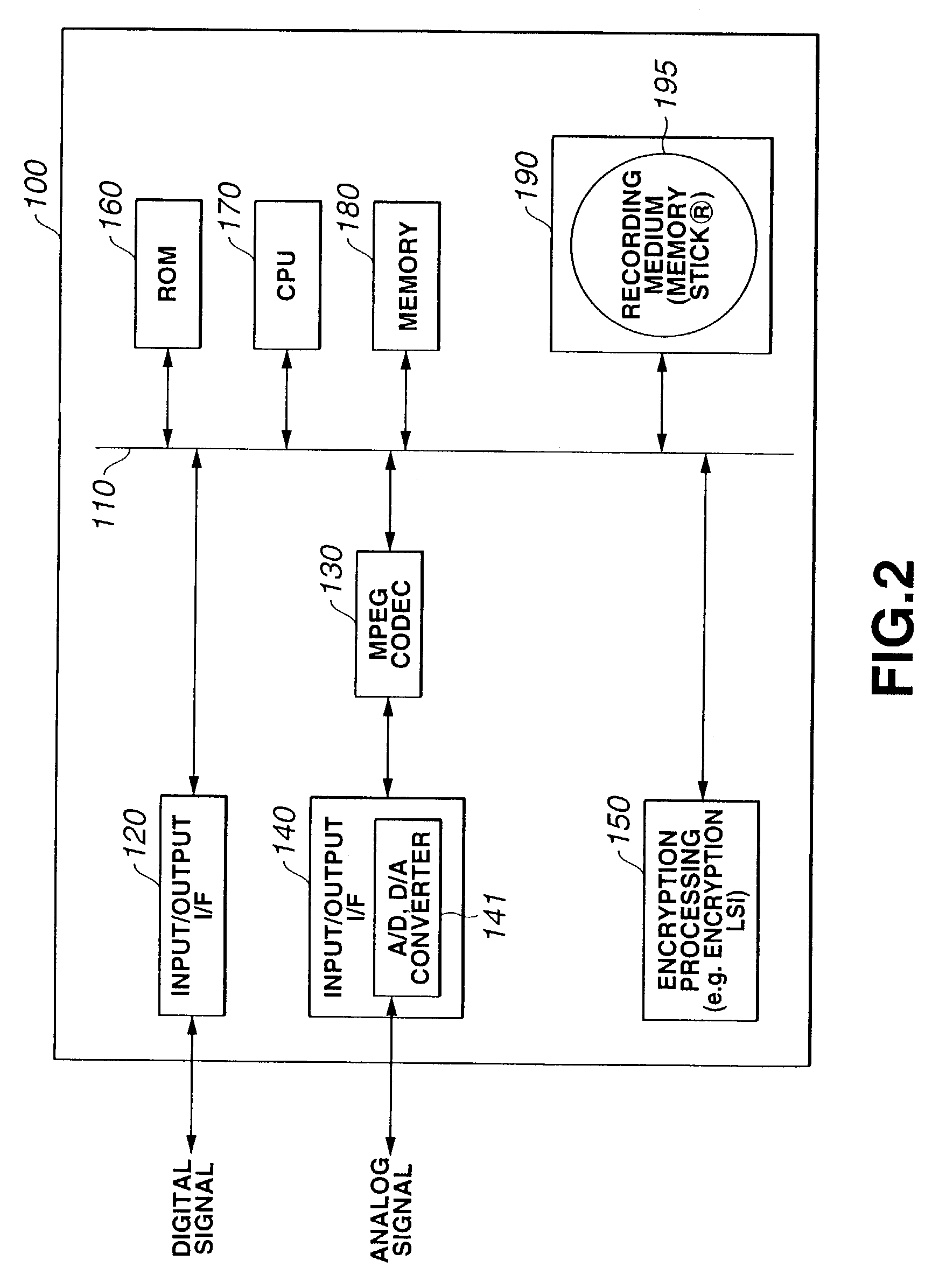
InactiveUS7088822B2Accelerated exclusionEfficient processKey distribution for secure communicationFinanceComputer hardwareDigital signature
By recording a digital signature and a public key certificate when recording data on an information recording medium, a recording device having recorded content can be specified. If recording media including illegally recorded data are distributed, the recording device used for the recording can be specified and can be excluded from the system. An information playback device verifies the validity of the digital signature and public key certificate when reading data, specifies a content recorder, and verifies no falsification in the digital signature and the public key certificate before playing back the data. This structure can efficiently exclude the playback of content recorded by an invalid recording device.
Owner:SONY CORP
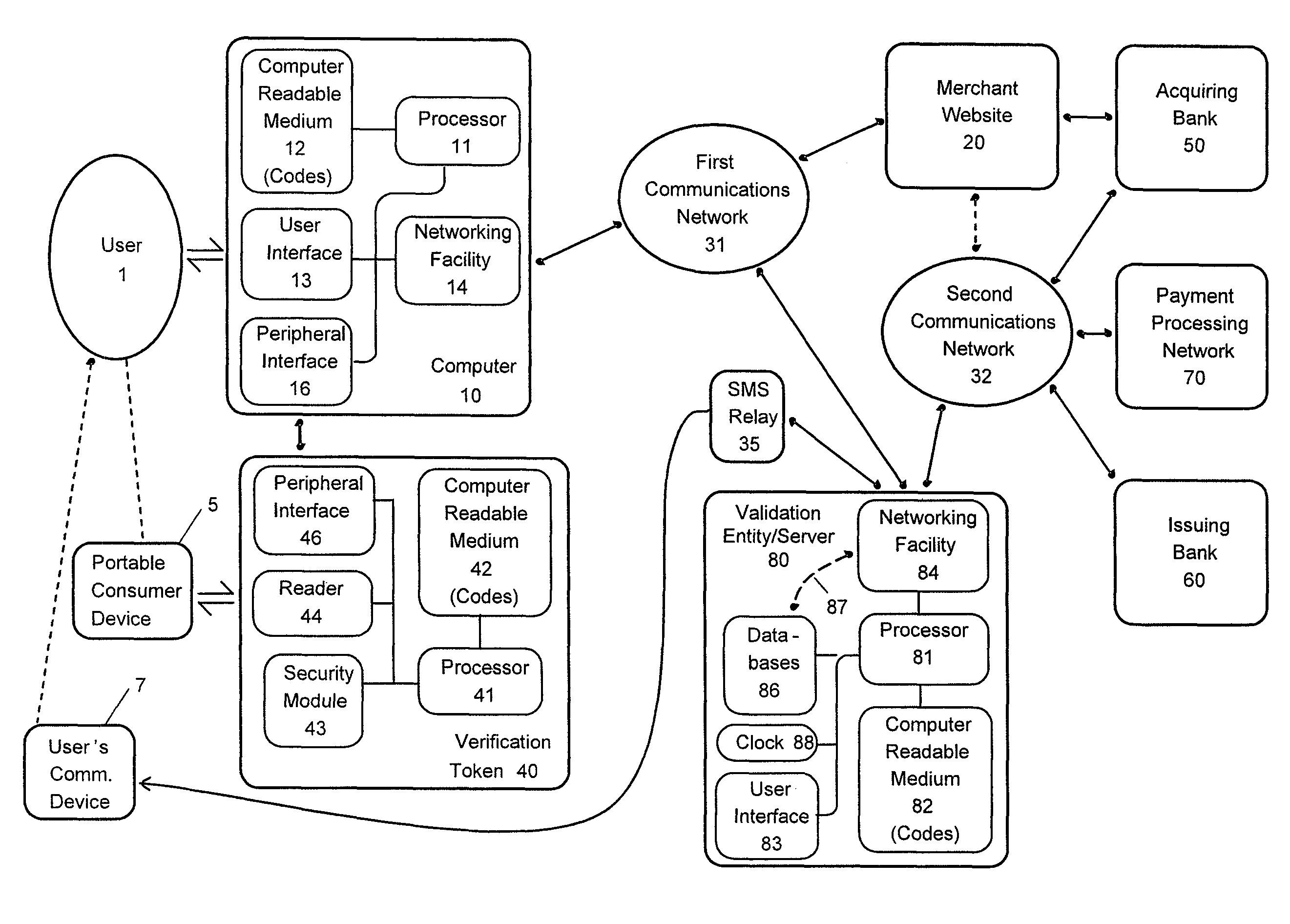
Anytime validation for verification tokens
ActiveUS8528067B2Digital data processing detailsUser identity/authority verificationPublic key certificateMaster key
Systems and method for producing, validating, and registering authentic verification tokens are disclosed. Such systems and methods include generating verification token specific key pairs. The key pairs can be signed by a verification token manufacturer master key or public key certificate for an additional level of authenticity. Related methods and systems for authenticating and registering authorized verification token manufacturers are also disclosed. Once a verification token manufacturer is authenticated, it can be assigned a manufacturer-specific key pair or certificate and in some cases, a predetermined set of serial numbers to assign to the verification tokens it produces. Each serial number can be used to generate a verification token specific key pair specific to the associated verification token. One component of the verification token key pair can be stored to the verification token. Optionally, the component of the verification token key pair stored to the verification token can be signed by the manufacturer specific master key or certificate and stored a verification token public certificate.
Owner:VISA INT SERVICE ASSOC
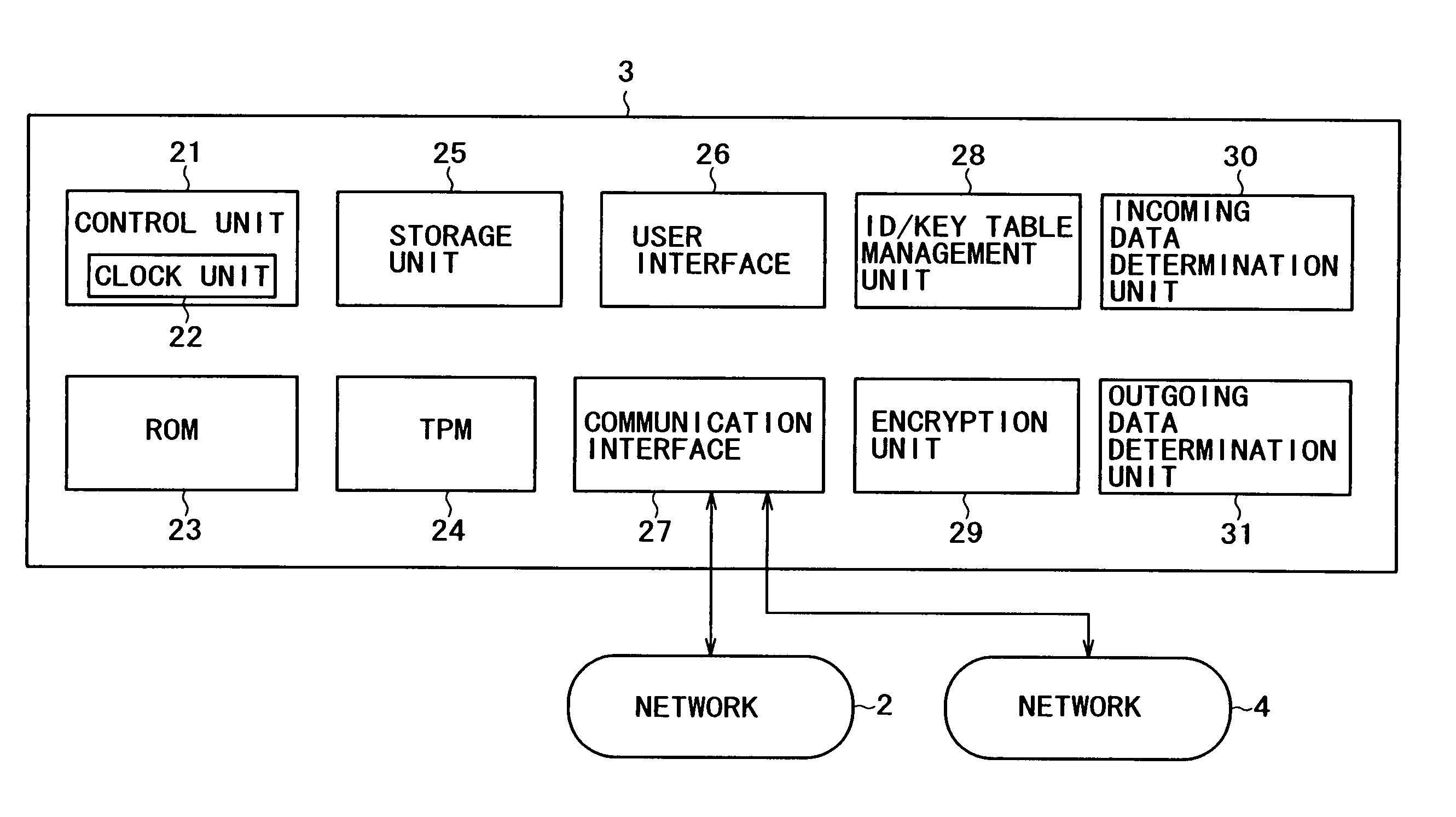
Certificate transmission apparatus, communication system, certificate transmission method, and computer-executable program product and computer-readable recording medium thereof
InactiveUS20060020782A1Reduce the possibilityPossibility of leakageSecuring communicationCommunications systemPublic key certificate
A certificate transmission apparatus includes a receiving part receiving a public key created by a sender device, an examination part examining the sender device of the public key, and a sending part sending a public key certificate including the public key received by the receiving part to the sender device of the public key.
Owner:RICOH KK
Data communicating apparatus, data communicating method, and program
InactiveUS20050187966A1Avoid interceptionUser identity/authority verificationUnauthorized memory use protectionPublic key certificateEncryption
A data communicating method is disclosed for use with a user terminal, the method preventing both members of a given group including the terminal and nonmembers from intercepting, tampering with or falsifying data communicated between the members without recourse to a plurality of encryption keys. In a first step, validity verification data is generated by the terminal. In a second step, the validity verification data and an attestation identity public key certificate are sent from the terminal to a group management device. In a third step, the group management device determines whether the terminal is valid. If the terminal is found valid, then a group name, a member ID and a group-shared key are supplied to the terminal in a fourth step, and a member ID list is further supplied in a fifth step. Thereafter the terminal is allowed to communicate with other members of the same group. The disclosed method can be applied advantageously to video game machines for network-based games.
Owner:SONY CORP
Radio terminal security network and card locking method based on the ellipse curve public key cipher
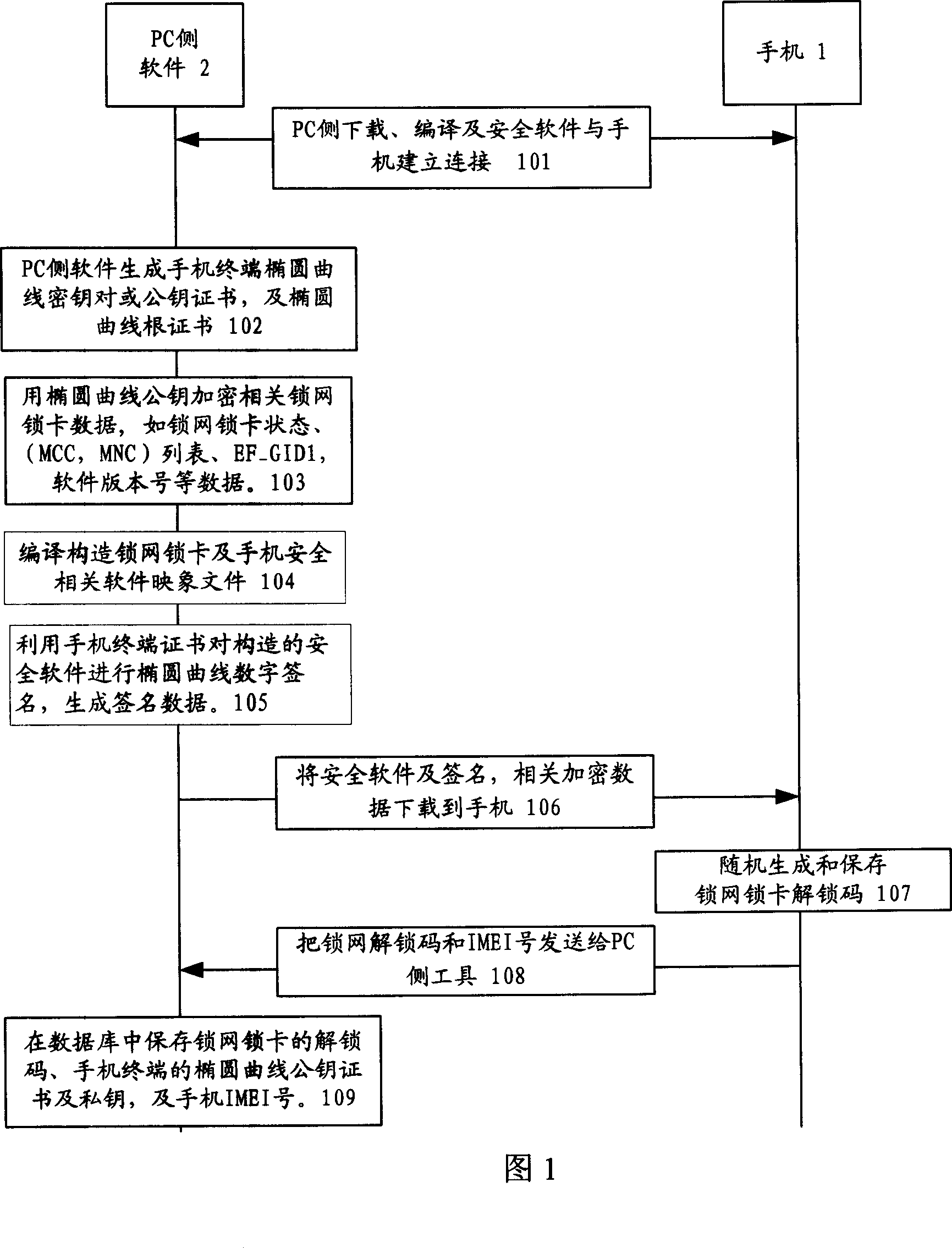
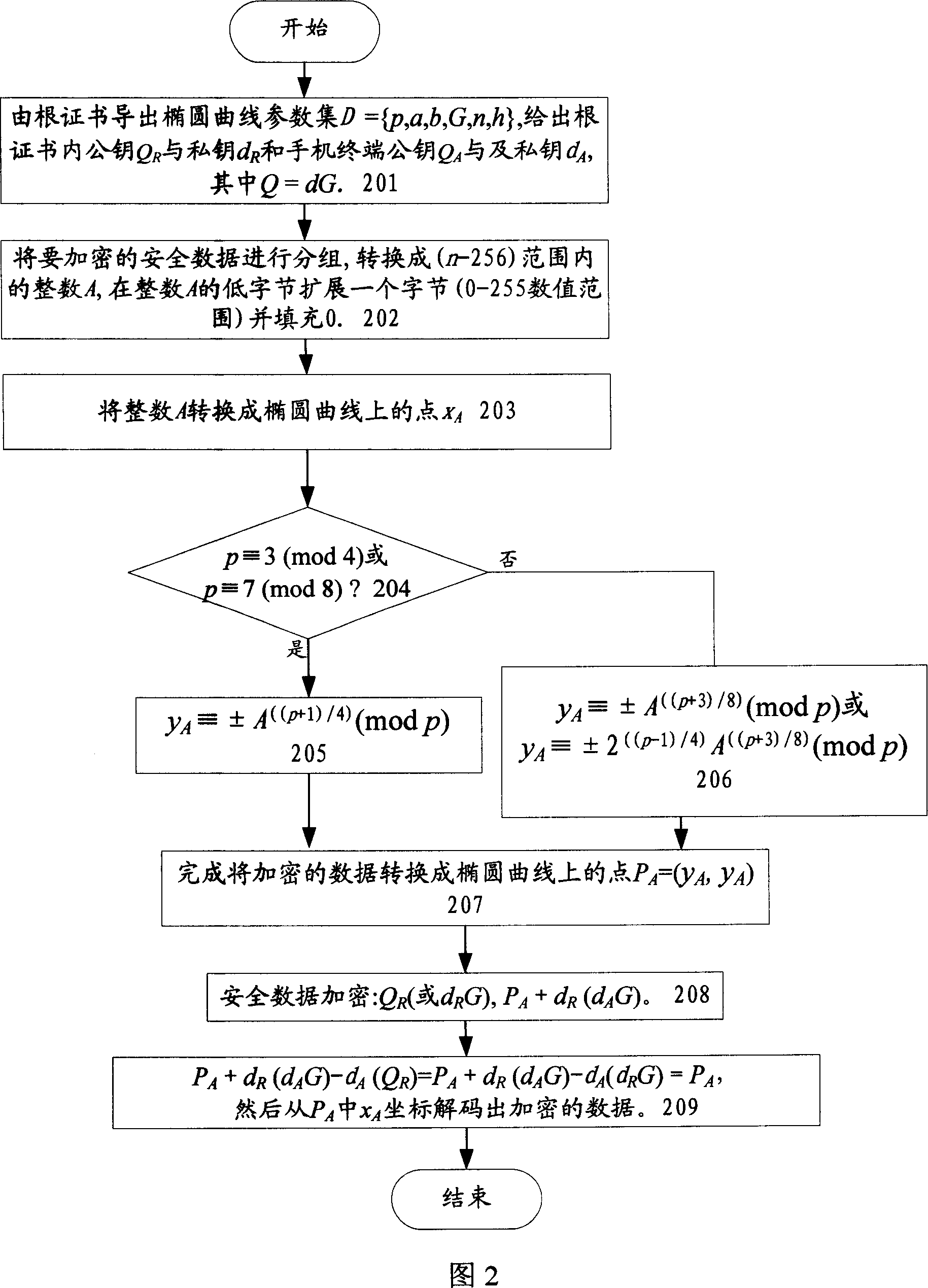
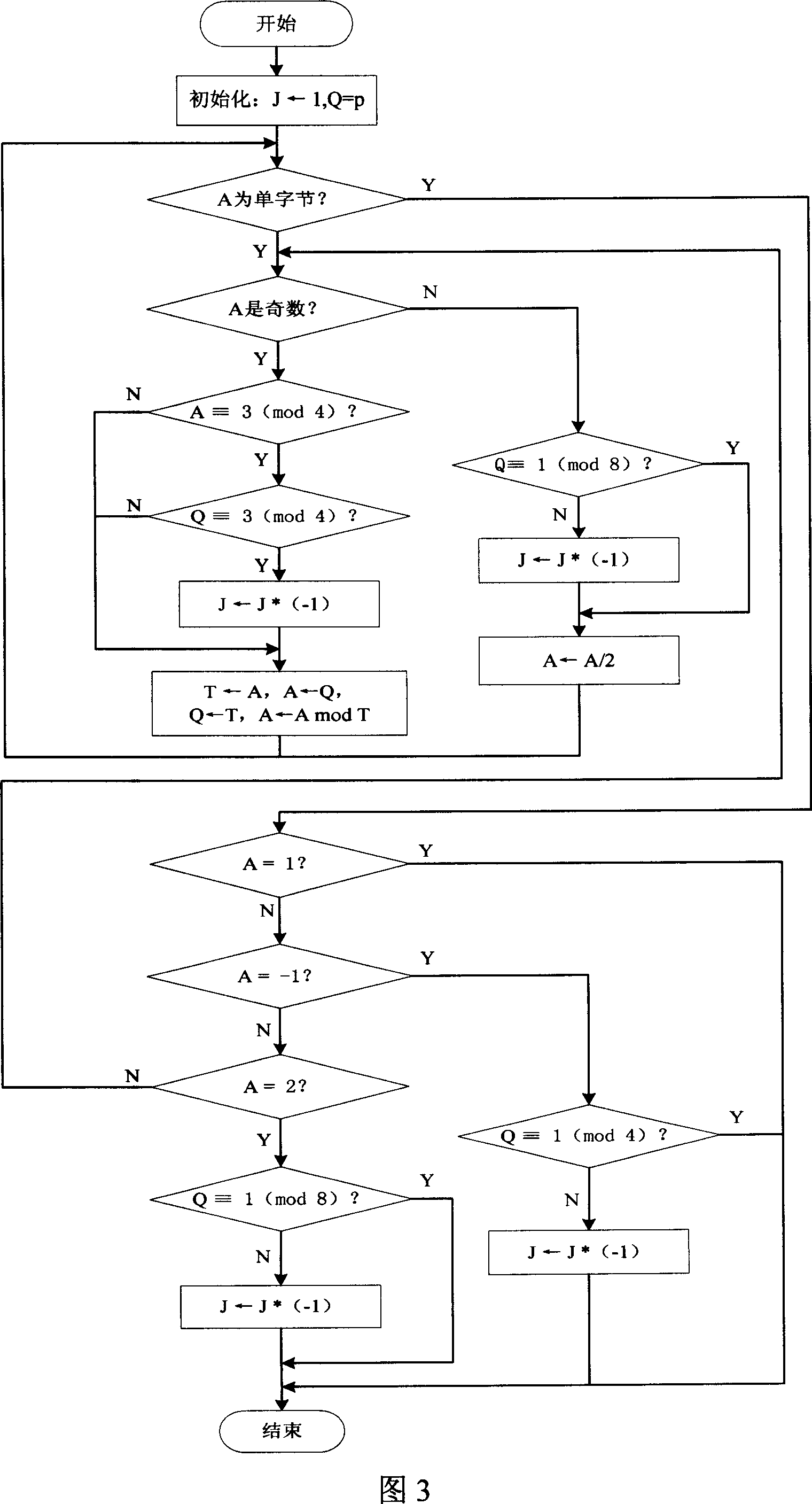
InactiveCN101018125AImprove securityProcessing speedPublic key for secure communicationUser identity/authority verificationKey sizeDigital signature
The related wireless terminal (1) security locking method based on elliptic curve public key cipher comprises: using elliptic curve public key certificate to form digital signature and private key to validate software during startup; deciding by software to provide network service according to current register and pre-set information or reading the IMSI number in user USIM / SIM card to compare with stored one and decide whether provide service. This invention synthesizes lots business, and special fit to terminal with common processing capacity.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
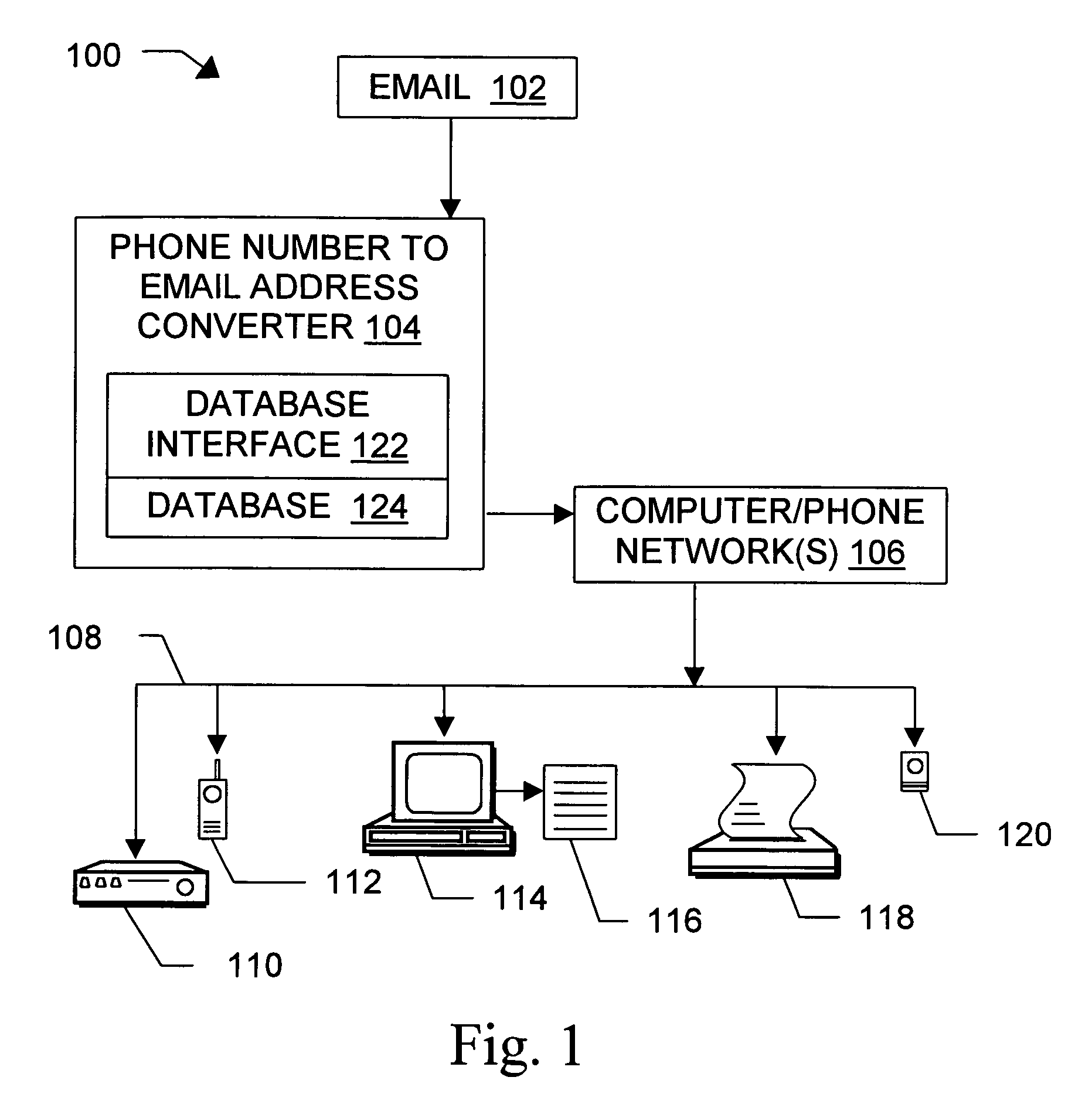
Message routing
InactiveUS20060031364A1Interconnection arrangementsPublic key for secure communicationEmail addressSelective calling
Owner:HAMILTON MICHAEL
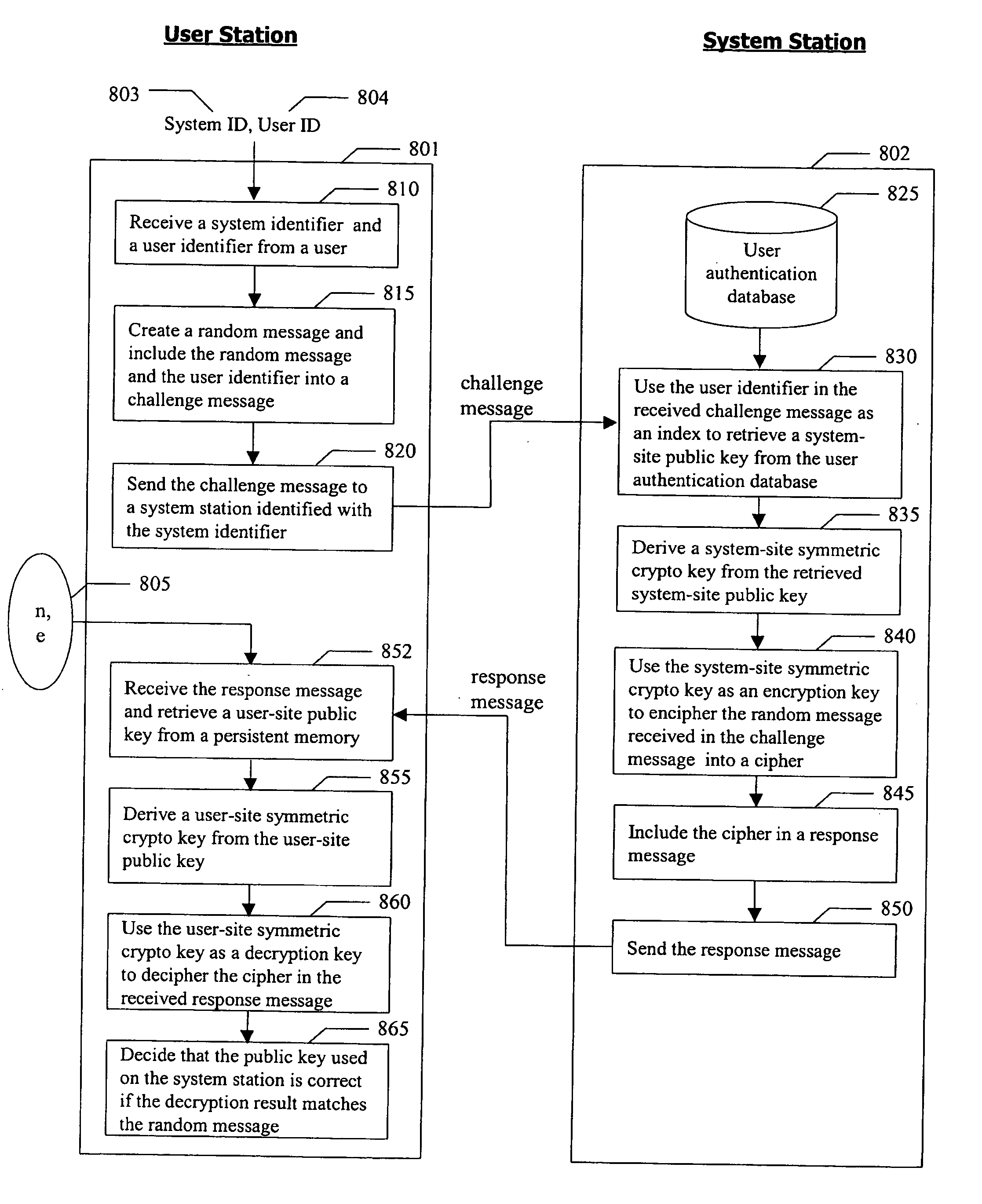
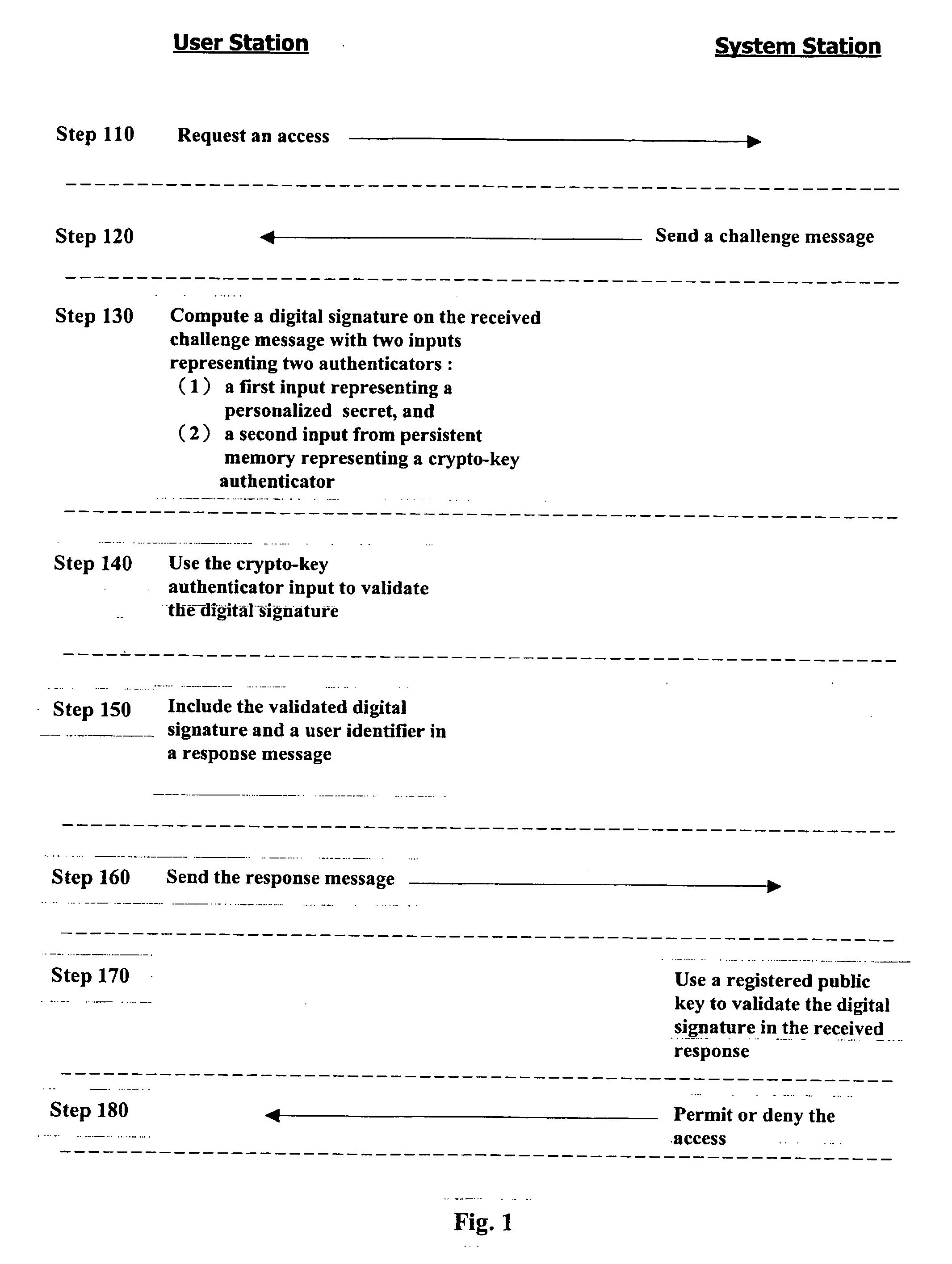
User authentication based on asymmetric cryptography utilizing RSA with personalized secret
InactiveUS20070081667A1Ensure integrityDigital data processing detailsPublic key for secure communicationPersonalizationCryptographic key generation
A method for authenticating a user to a computer system is disclosed, comprising using a first input and a second input in producing a digital signature in response to a challenge. The digital signature is valid when the first input matches a personalized secret and the second input matches a trio comprising a public modulus, a public exponent, and a private-key-dependent exponent. Selection of the personalized secret is discretionary and changeable. A crypto-key generation process uses the personalized secret and two primes as input to produce the trio. The public modulus and public exponent of the trio form a public key used in digital signature validation. Also disclosed is a business method that replaces the conventional public-key certificate with an agreement on the user's public key.
Owner:CHANG GUNG UNIVERSITY
Anytime validation for verification tokens
ActiveUS20110173684A1Digital data processing detailsUser identity/authority verificationPublic key certificateMaster key
Systems and method for producing, validating, and registering authentic verification tokens are disclosed. Such systems and methods include generating verification token specific key pairs. The key pairs can be signed by a verification token manufacturer master key or public key certificate for an additional level of authenticity. Related methods and systems for authenticating and registering authorized verification token manufacturers are also disclosed. Once a verification token manufacturer is authenticated, it can be assigned a manufacturer-specific key pair or certificate and in some cases, a predetermined set of serial numbers to assign to the verification tokens it produces. Each serial number can be used to generate a verification token specific key pair specific to the associated verification token. One component of the verification token key pair can be stored to the verification token. Optionally, the component of the verification token key pair stored to the verification token can be signed by the manufacturer specific master key or certificate and stored a verification token public certificate.
Owner:VISA INT SERVICE ASSOC
End-to-end authentication of session initiation protocol messages using certificates
InactiveUS20080046745A1User identity/authority verificationMultiple digital computer combinationsSession Initiation ProtocolDigital signature
End-to-end authentication capability based on public-key certificates is combined with the Session Initiation Protocol (SIP) to allow a SIP node that receives a SIP request message to authenticate the sender of request. The SIP request message is sent with a digital signature generated with a private key of the sender and may include a certificate of the sender. The SIP request message my also be encrypted with a public key of the recipient. After receiving the SIP request, the receiving SIP node obtains a certificate of the sender and authenticates the sender based on the digital signature. The digital signature may be included in an Authorization header of the SIP request, or in a multipart message body constructed according to the S / MIME standard.
Owner:MICROSOFT TECH LICENSING LLC
Metro ticket buying and checking method based on two-dimension code recognition
ActiveCN104134142AImprove comfortReduced comfortTicket-issuing apparatusUser identity/authority verificationKey issuesPublic key certificate
The invention discloses a metro ticket buying system and an entrance and exit ticket checking system based on the two-dimension code recognition technology. Smartphone terminals, smartphone application programs, a metro ticket selling and checking system background recharging server, automatic metro entrance and exit ticket checking systems and a CA center are included. The metro ticket selling and checking system background recharging server, each smartphone application program and each automatic metro entrance and exit ticket checking system respectively have a unified center public key issued by the CA center, a public key and a private key which are independent of each other and issued by the CA center and a public key certificate issued by the CA center. A user buys a ticket and has the ticket checked through the mobile phone program and two-dimension codes. The ticket buying efficiency is improved, the ticket buying time is saved, ticket card cost is reduced, paper is saved, timeliness and uniqueness of ticket cards are guaranteed, and metro tickets can be bought and checked fast, efficiently and safely.
Owner:SOUTHEAST UNIV
Information processing device, information processing method, and program storage medium
InactiveUS7224804B2Data augmentationKey distribution for secure communicationUser identity/authority verificationInformation processingTheoretical computer science
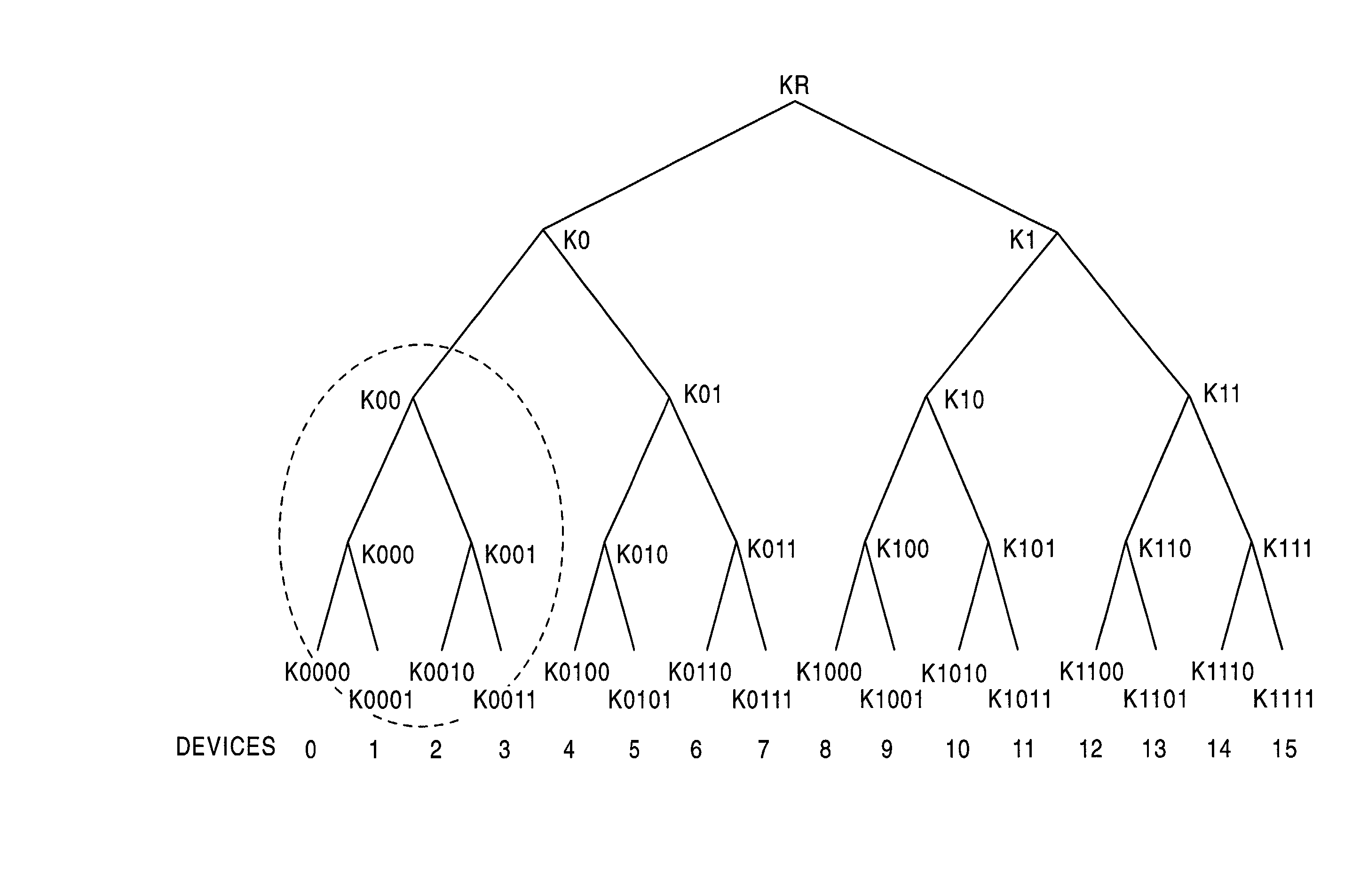
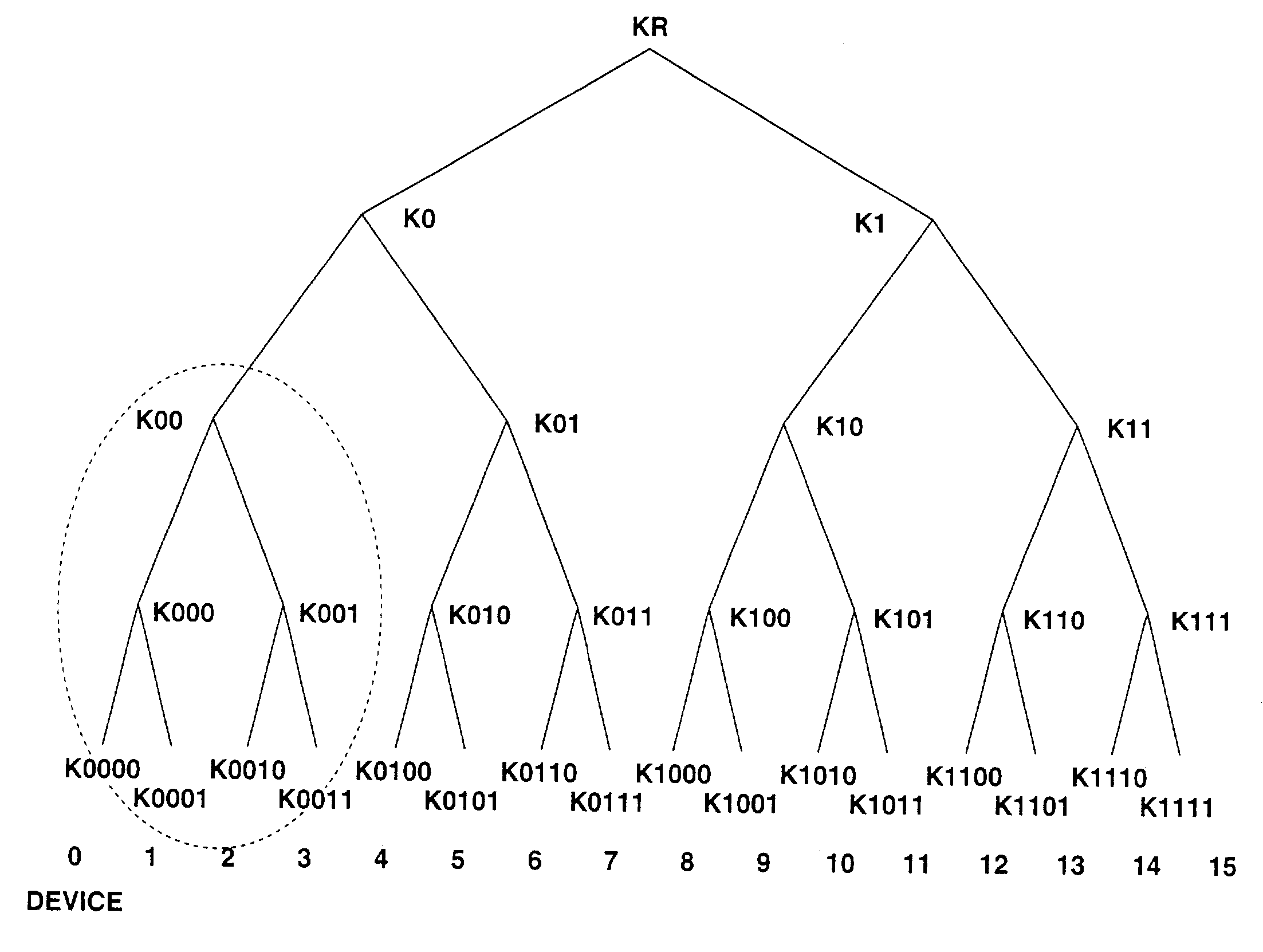
In an information processing system and method which enables detection processing of a revoked entity using an enabling key block (EKB), a device or a service provider as a revoked entity is determined on the basis of the enabling key block (EKB) used for key distribution in a tree structure. ID which enables position identification in the hierarchical key distribution tree is stored in a public key certificate and tracing processing using a tag of the enabling key block (EKB) is executed on the basis of the ID acquired from the public key certificate, thus determining whether or not the ID is of a position where EKB processing (decryption) is possible and determining the presence / absence of revocation of an entity corresponding to the ID.
Owner:SONY CORP
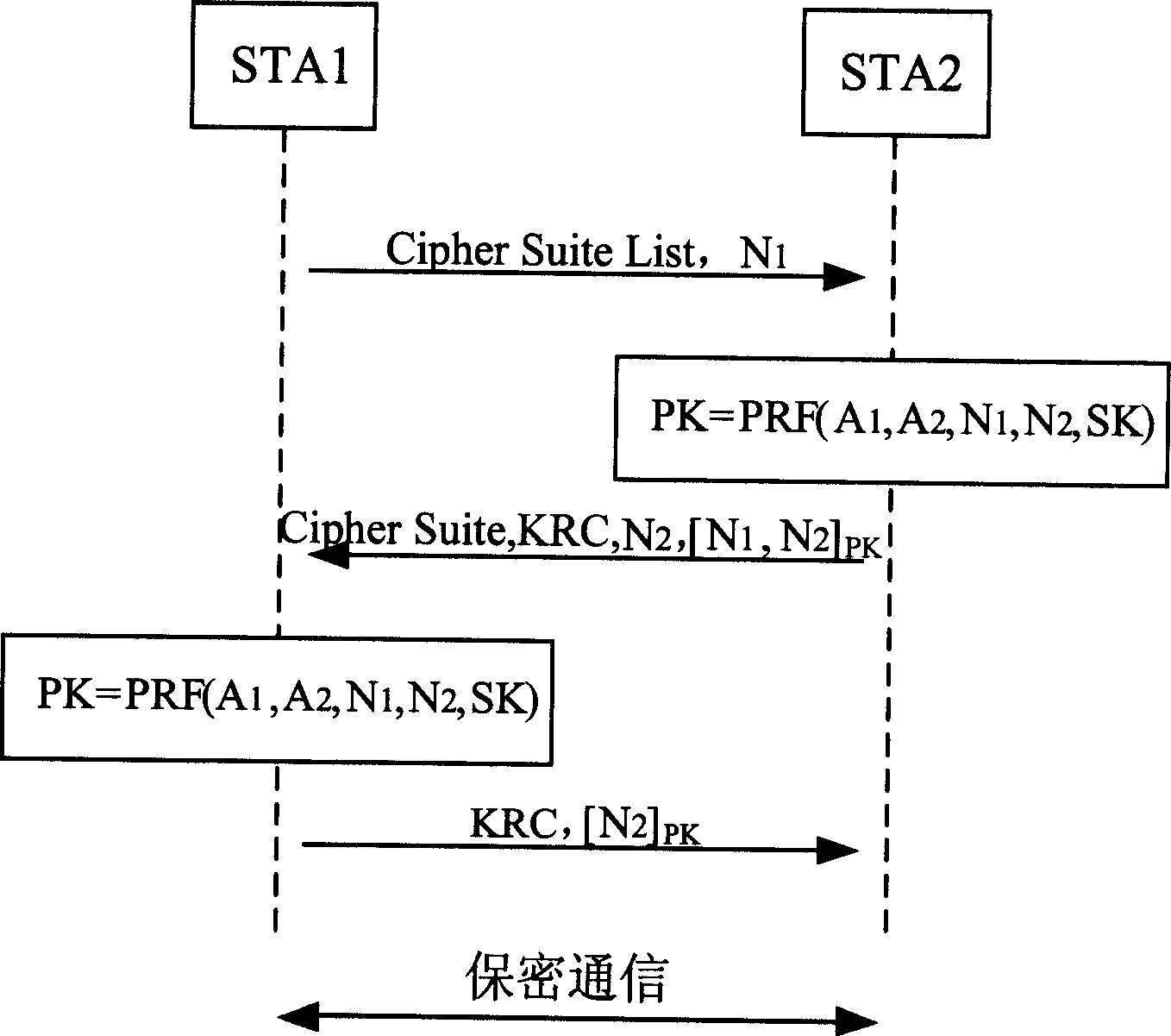
Self arranged net mode shared key authentication and conversation key consulant method of radio LAN
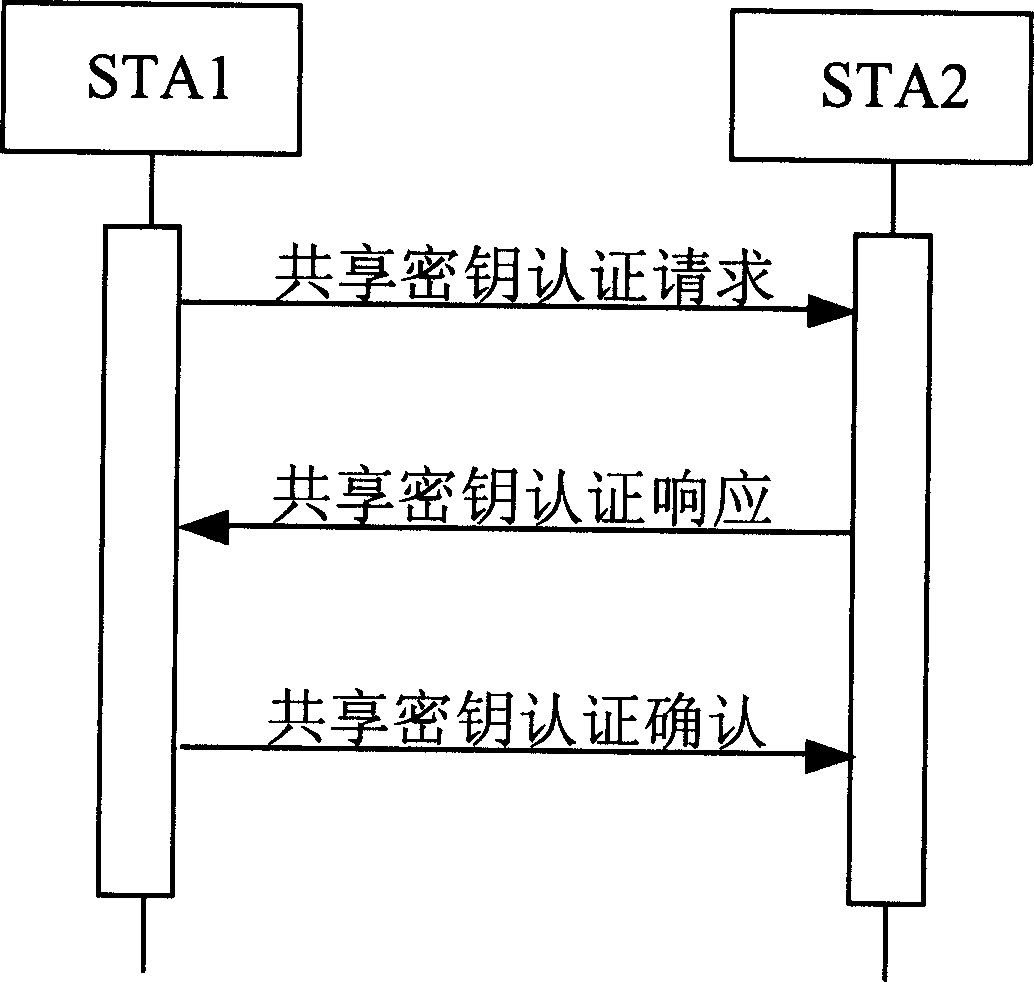
ActiveCN1564514AGuaranteed confidentialityImprove securitySynchronising transmission/receiving encryption devicesPublic key for secure communicationPublic key certificateKey authentication
The method includes processing steps: request of shared cryptographic key authentication; response of shared cryptographic key authentication; acknowledgement of shared cryptographic key authentication. Through configured shared cryptographic key in advance, intercheck authentication and negotiation of session key is able to carry out between wireless terminals in self built network, thus, complicated public key certificate application and installation procedure is not needed any more. Features are: high security, small amount of calculation, and high efficiency.
Owner:ZTE CORP
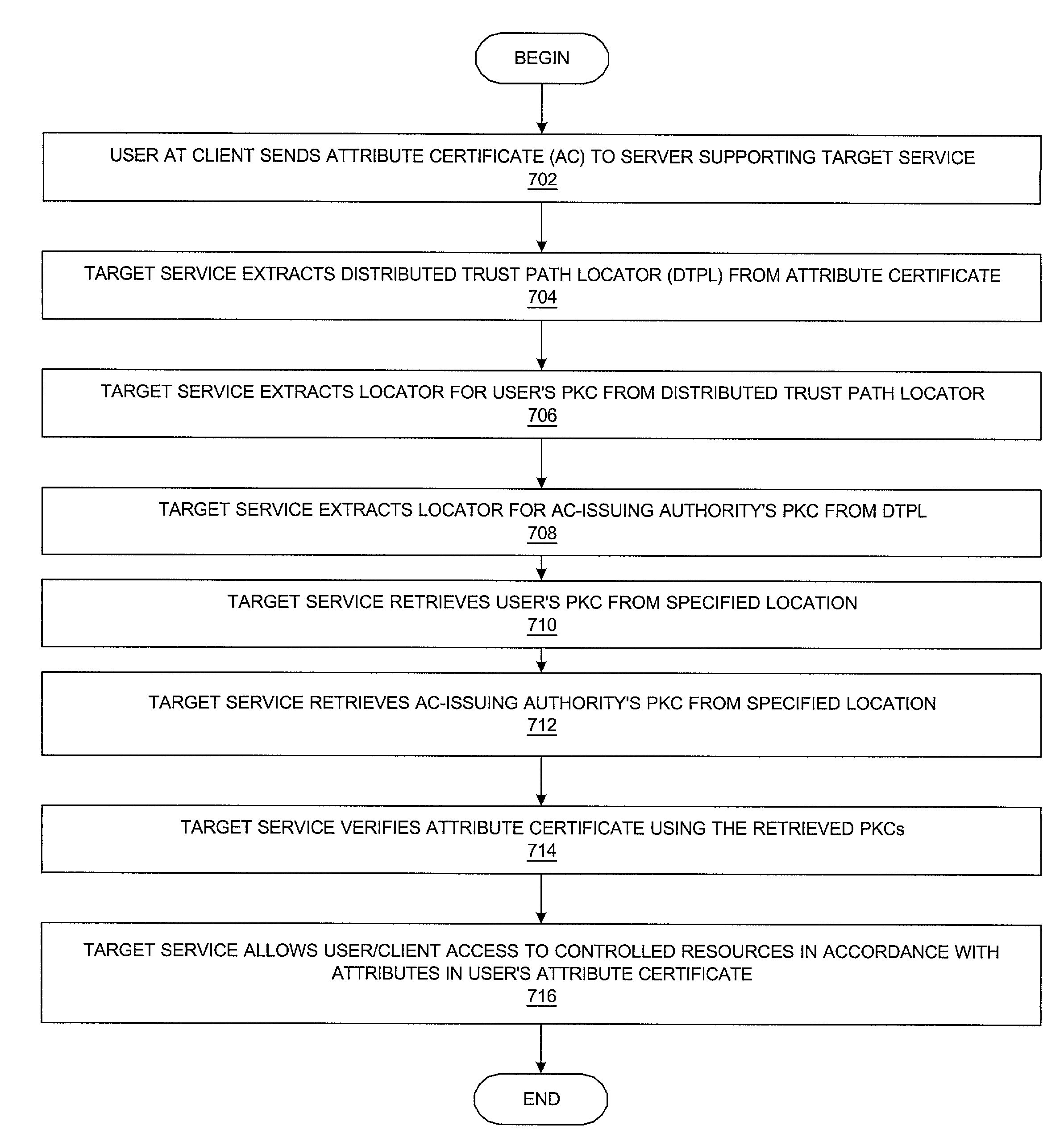
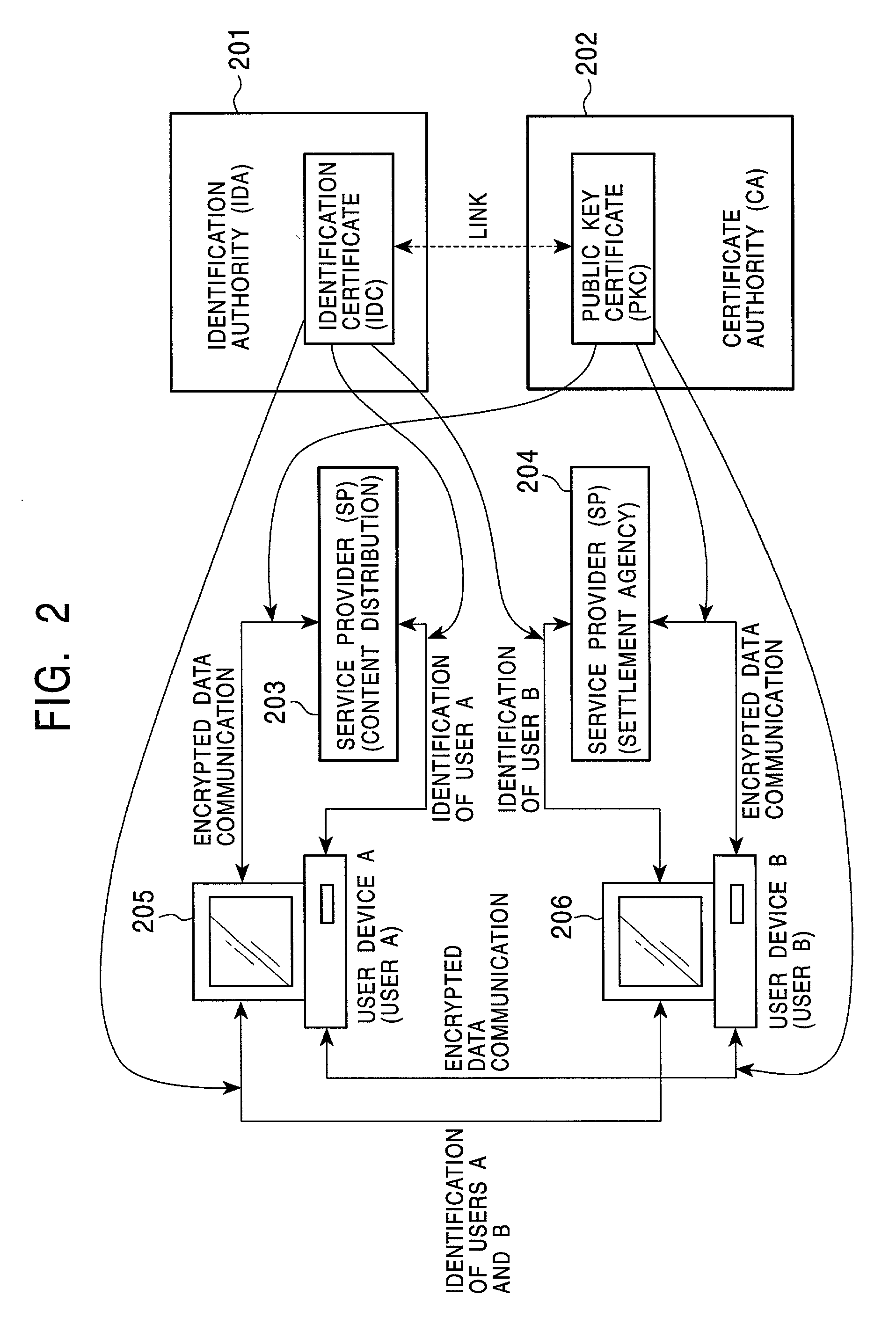
Method and system for managing a distributed trust path locator for public key certificates relating to the trust path of an X.509 attribute certificate
InactiveUS7356690B2Data processing applicationsDigital data processing detailsPublic key certificatePKCS
A method and a system is presented for managing attribute certificates. An extension within an attribute certificate, called a distributed trust path locator, allows an attribute certificate to be physically disassociated from its supporting public key certificates while remaining logically associated with its supporting public key certificates. The user's attribute certificate and its supporting PKCs allows any server using an attribute certificate to locate and retrieve the PKC of the user and of the AC-issuing authority. The user is not required to communicate his / her PKC to a target service. In addition, configuring the target service to accept attribute certificates does not require the deployment of a PKC for every AC-issuing authority.
Owner:IBM CORP
Biological feature based safety certification method and device
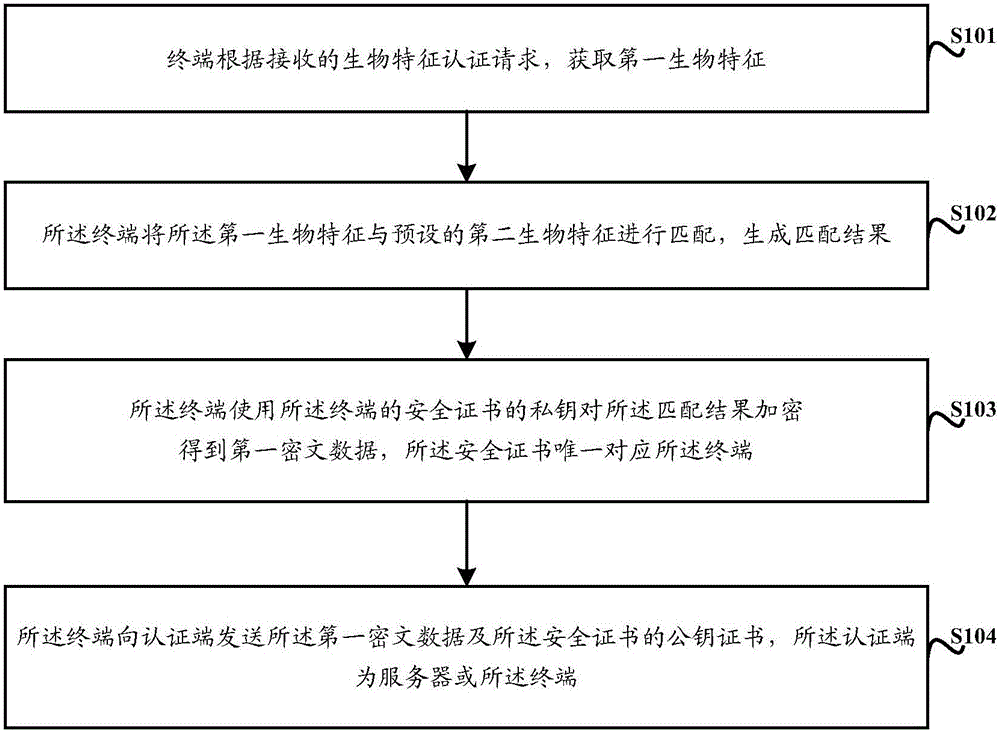
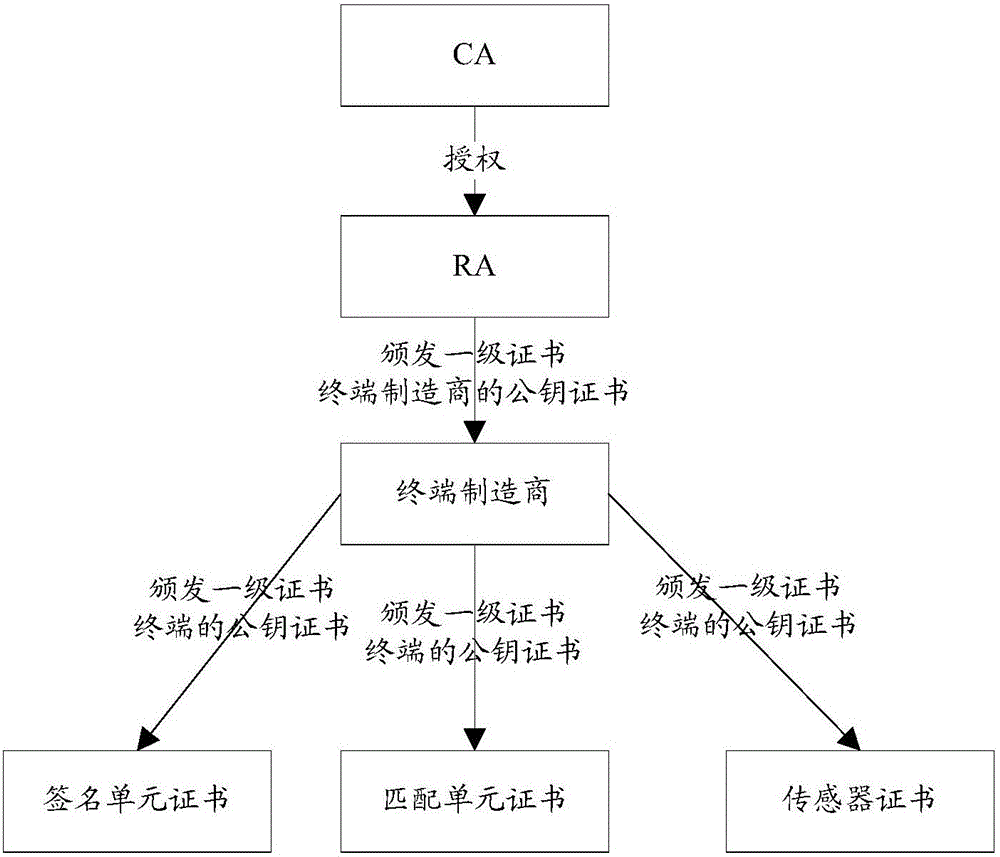
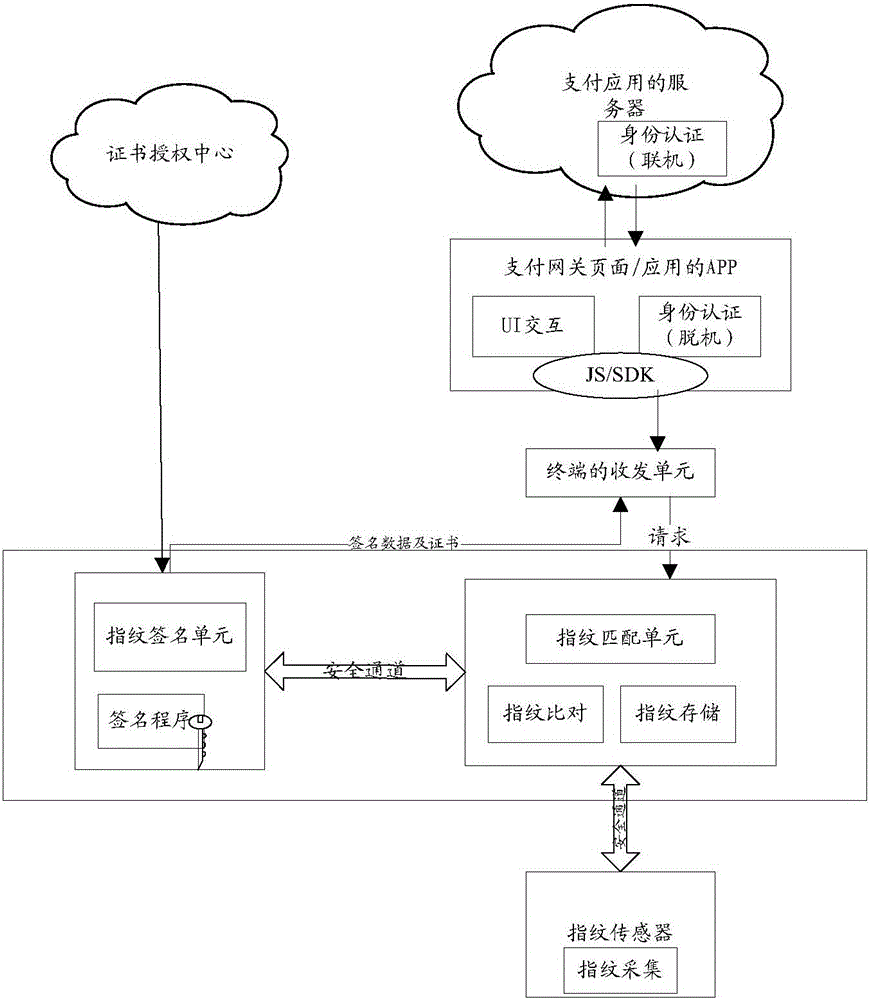
InactiveCN105959287AExact matchUser identity/authority verificationProtocol authorisationCiphertextPublic key certificate
The invention discloses a biological feature based safety certification method and device. The method comprises that a terminal obtains a first biological feature according to a received biological feature certification request; the terminal matches the first biological feature and a preset second biological feature to generate a matching result; the terminal uses a secrete key of a safety certificate, which corresponds to the terminal uniquely, of the terminal to encrypt the matching result to obtain first cryptograph data; and the terminal sends the first cryptograph data and a public key certificate of the safety certificate to a certification end which is a server or the terminal. The method and device of the invention can solve the problem that present identity certification has hidden safety troubles.
Owner:CHINA UNIONPAY
Information processing apparatus, information processing method, and program providing medium
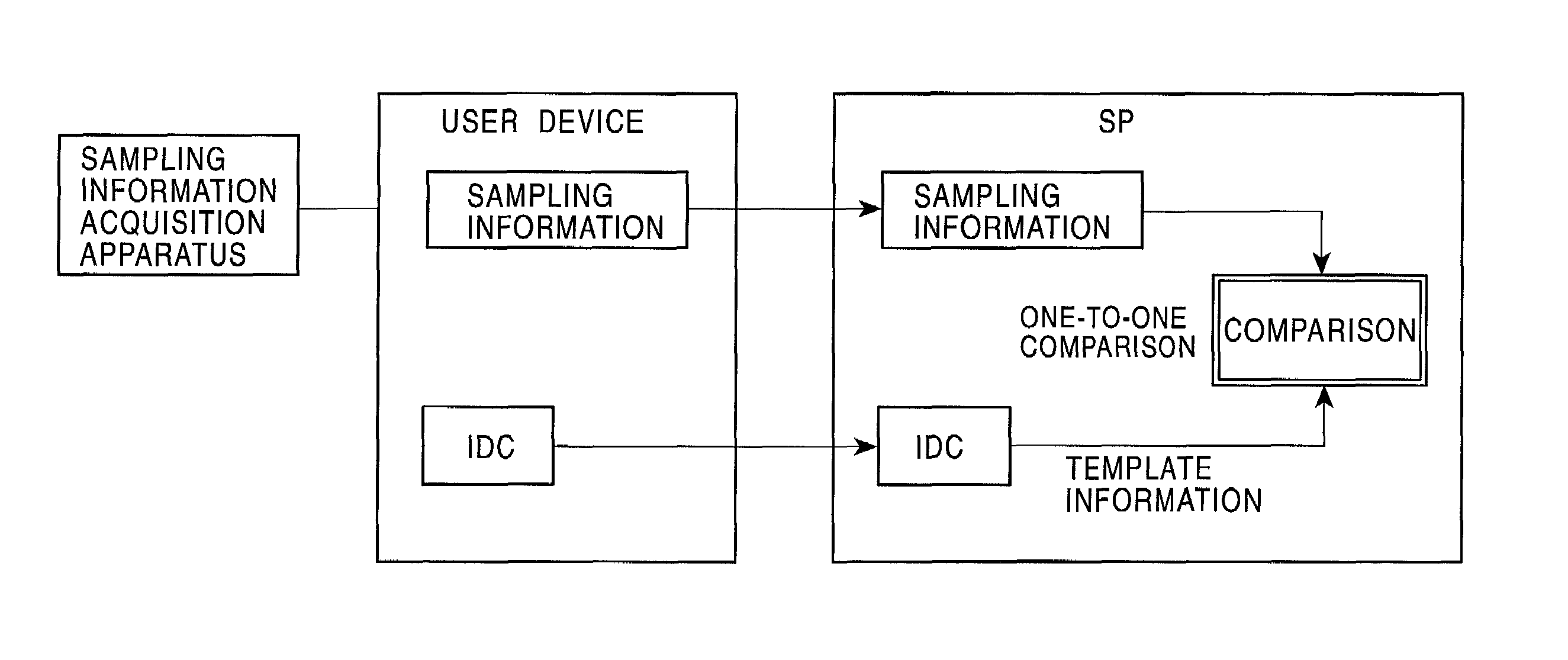
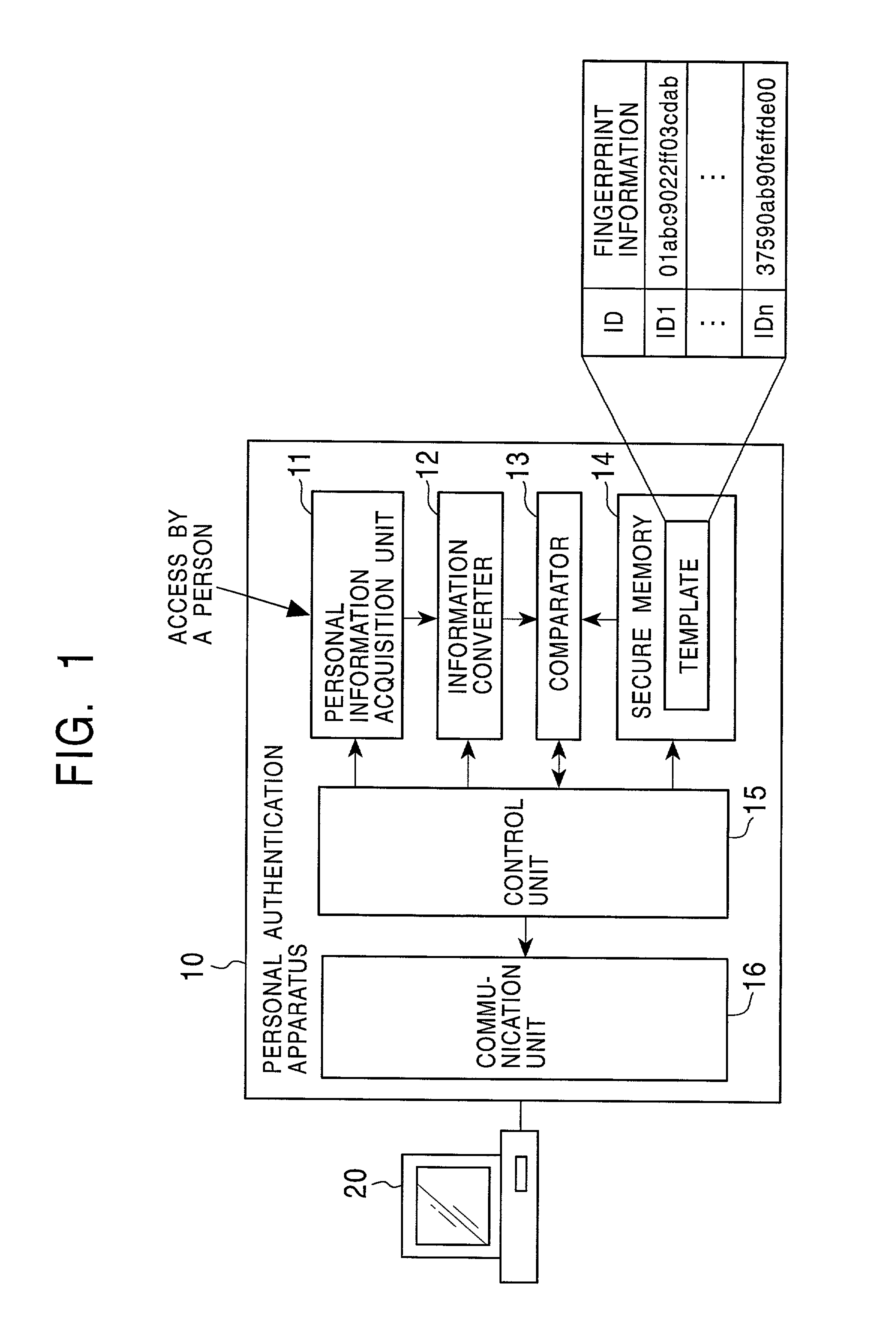
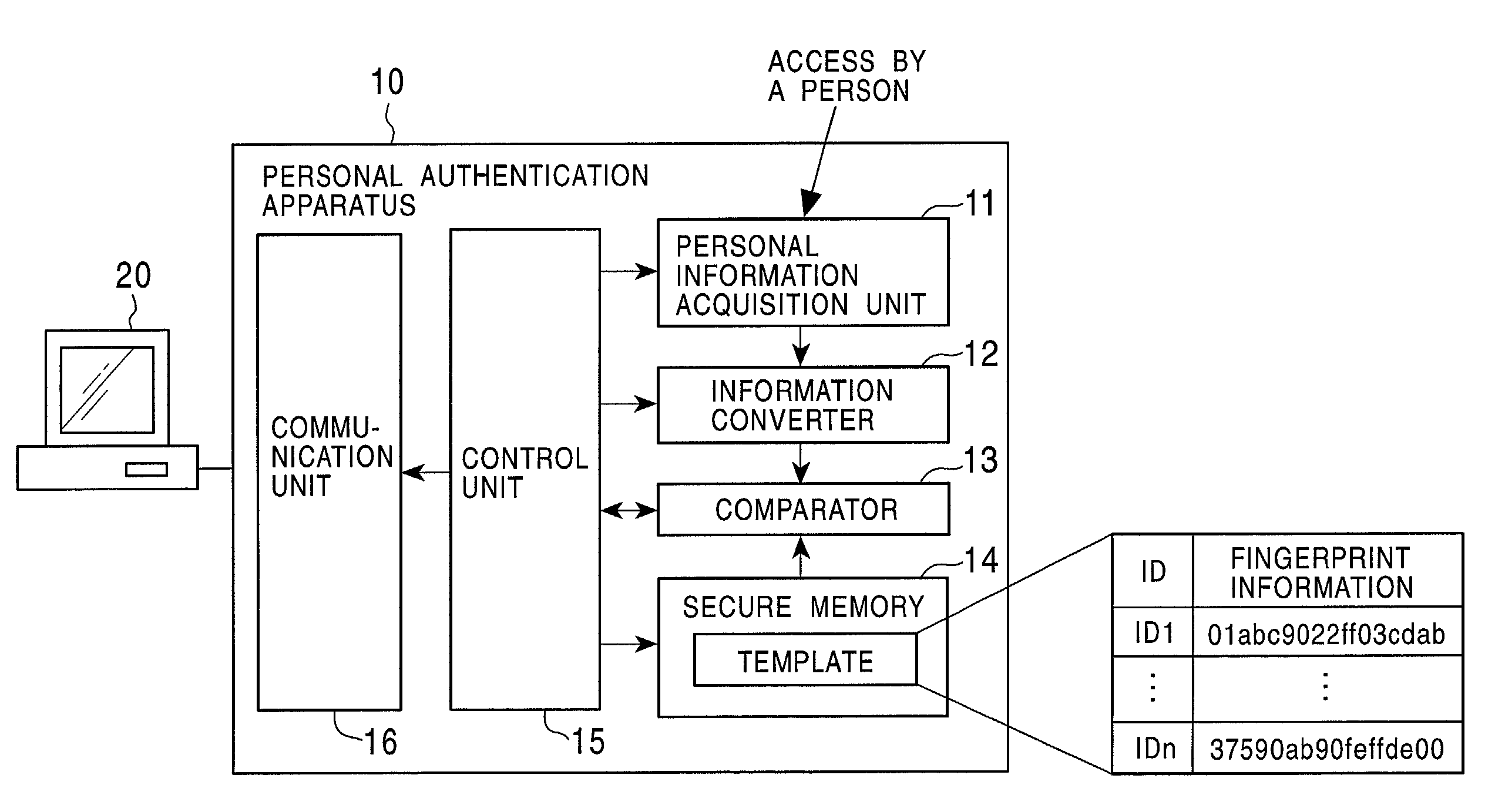
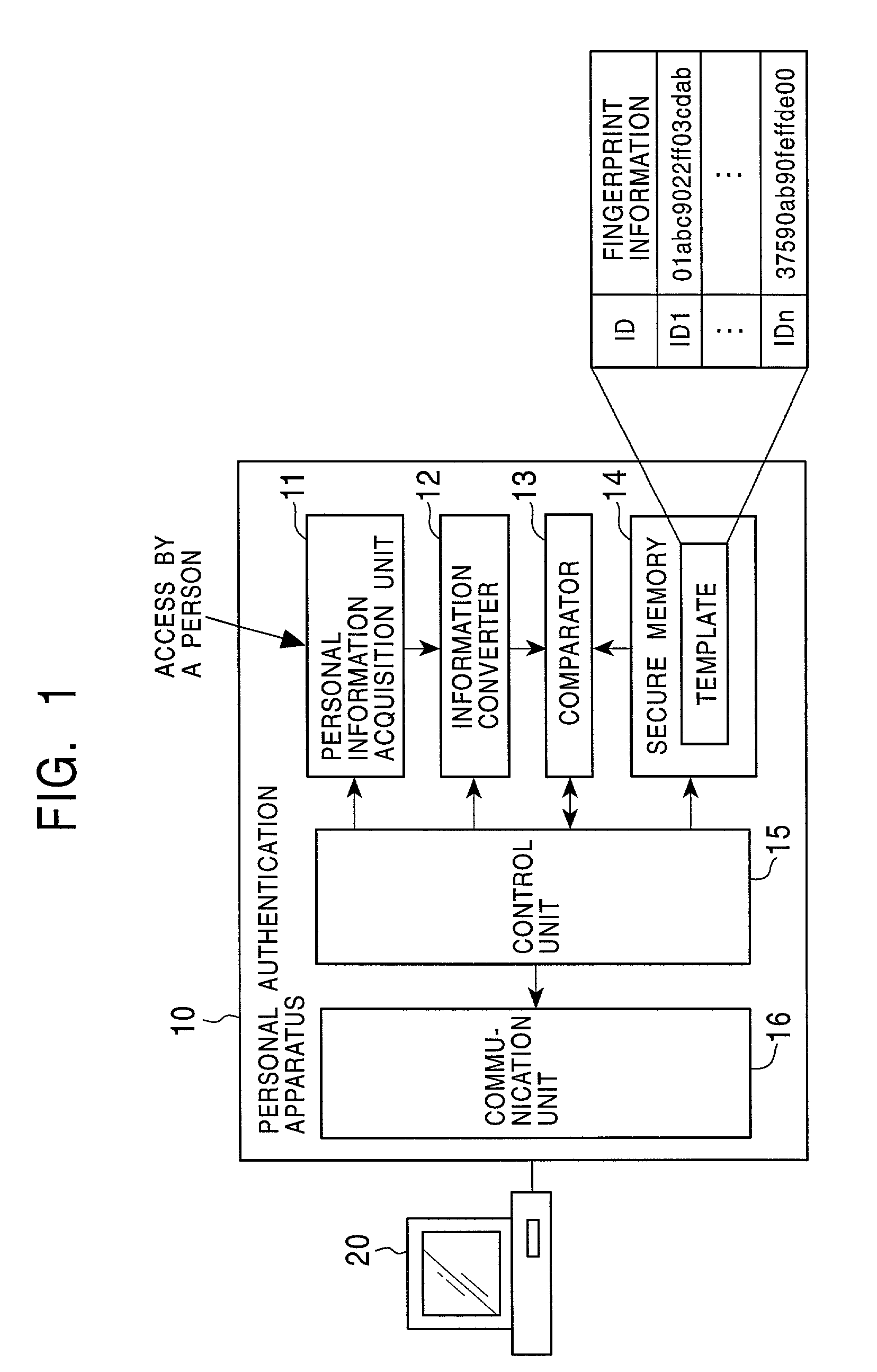
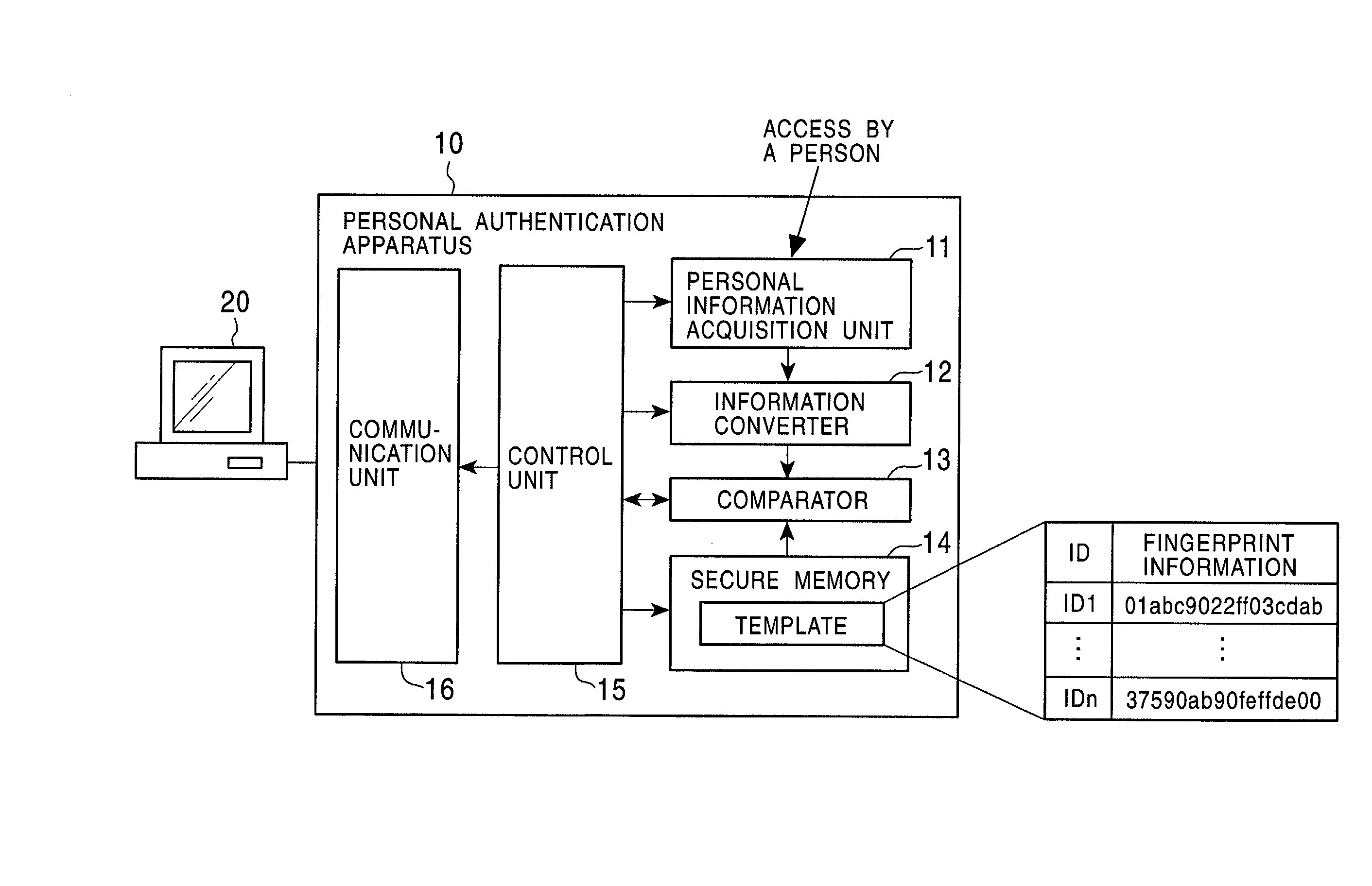
InactiveUS7103778B2Improve reliabilitySafe storageUser identity/authority verificationDigital data authenticationInformation processingComputer hardware
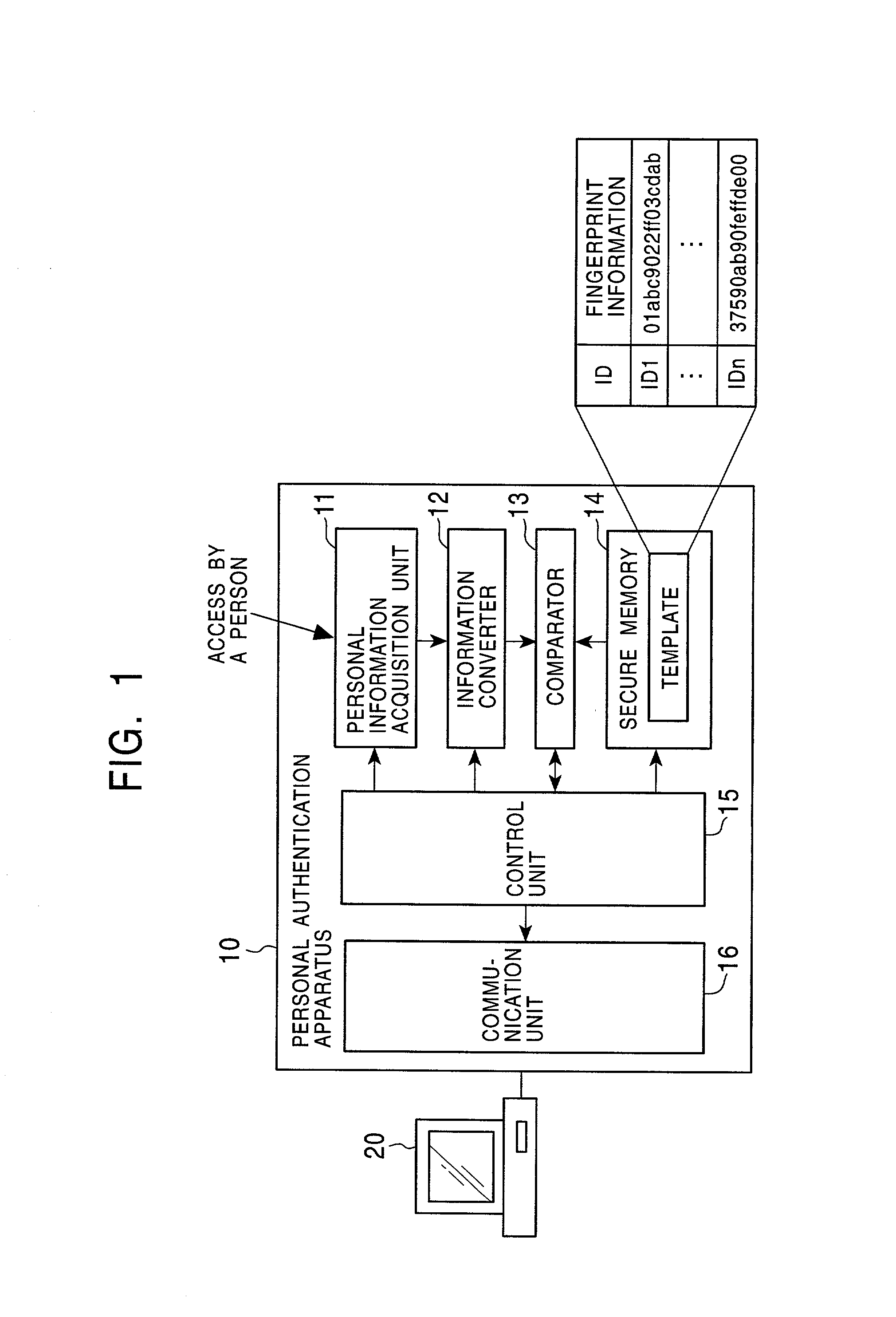
Disclosed are an information processing apparatus and an information processing method which execute person authentication and allows various services such as receiving of contents to be received, provided that the authentication is successfully passed. In the information processing apparatus for executing, by a connection to an external server providing various services such as contents transmission, a process such as receiving of contents, person authentication is executed by comparing a template acquired from a person identification certificate storing a template which is person identification data of a user using the information processing apparatus with sampling information input by the user, and a connection to the external server is executed provided that the authentication is successfully passed. In addition, the person identification certificate and the public key certificate are stored in a memory together with link information in which the person identification certificate and the public key certificate applied during a process of establishing a connection to the server are related to each other.
Owner:SONY CORP
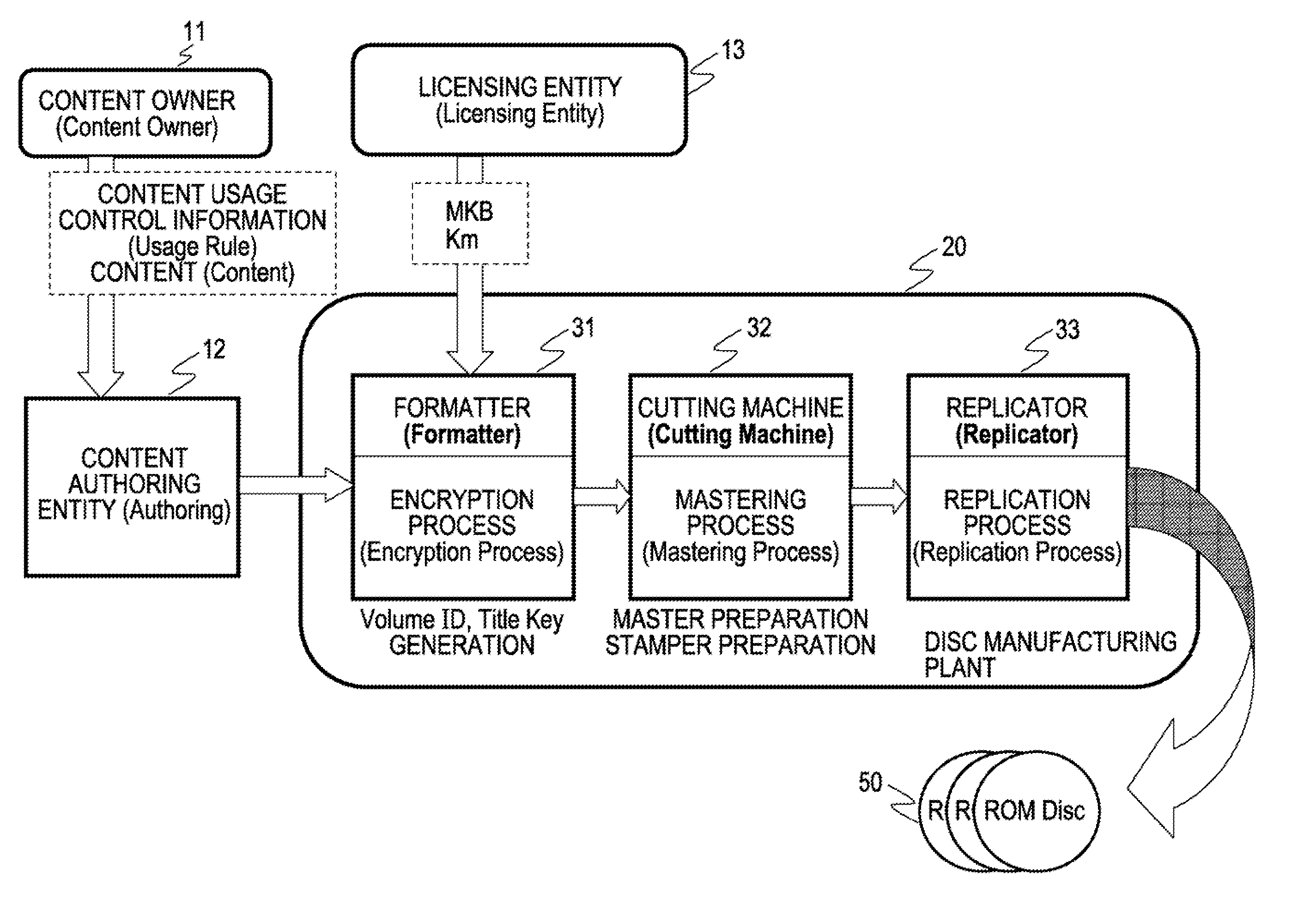
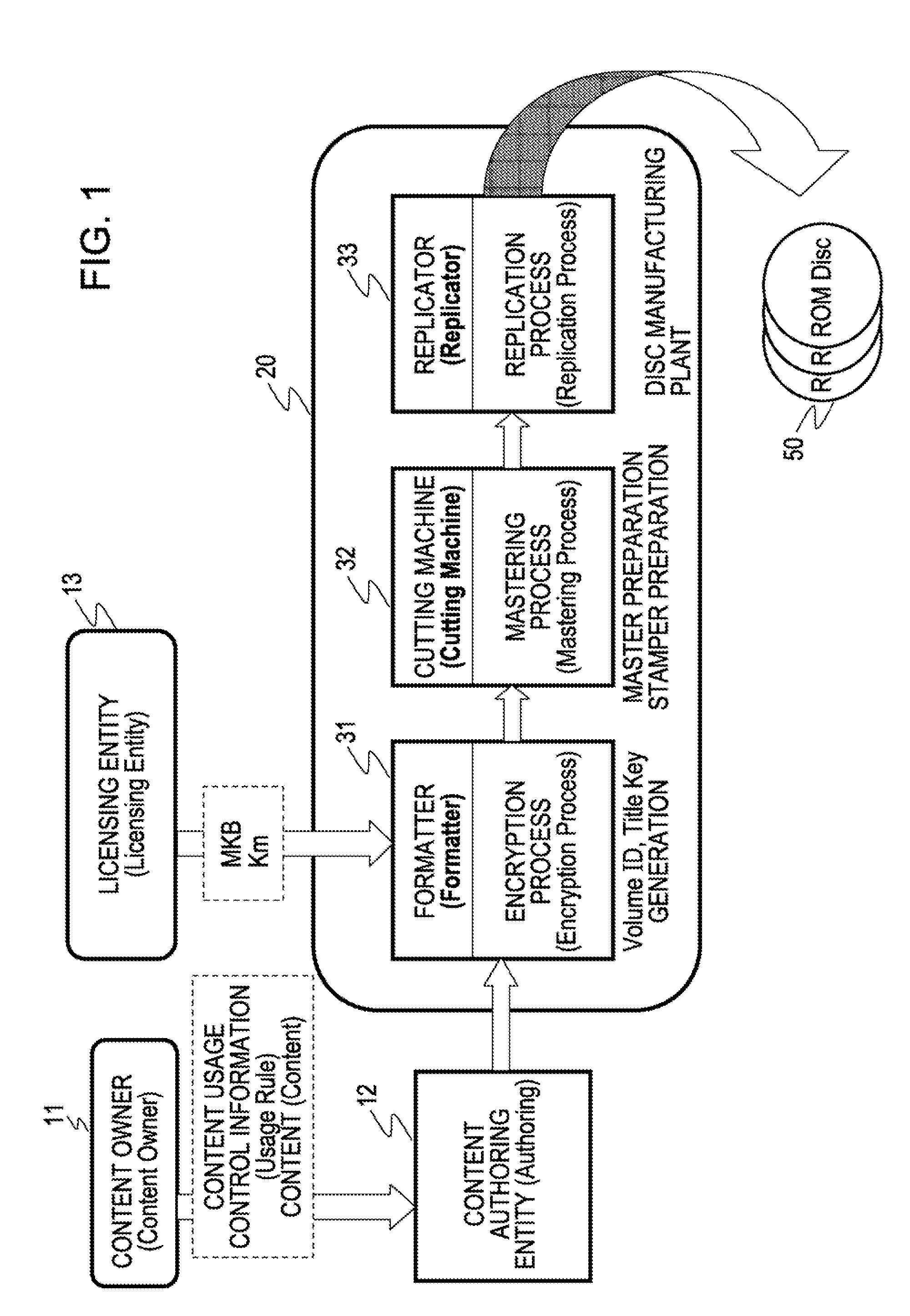
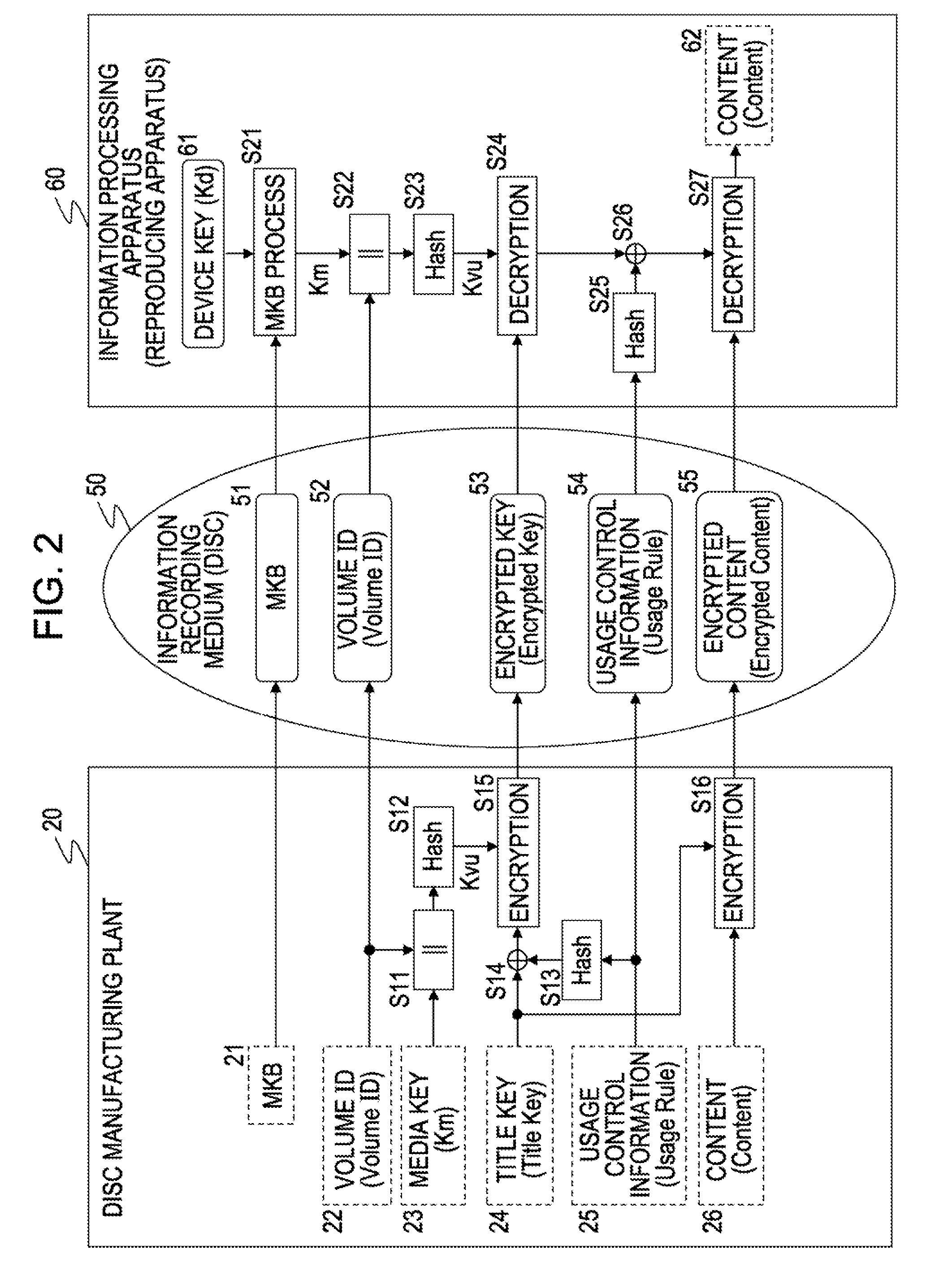
Disc manufacturing method, data recording apparatus, information recording medium, information processing apparatus and method, and computer program
InactiveUS20090238362A1Prevent illegal usePrevent unauthorized reproduction and useDigital data processing detailsRecord information storageInformation processingPublic key certificate
A product mark including a public key certificate issued with respect to an information-recording-medium manufacturing entity or information-recording-medium manufacturing equipment, and an encrypted volume ID calculated by computation based on a product-mark-associated value such as a hash value generated on the basis of the product mark, and a volume ID as an identifier set with respect to a given set of discs to be manufactured, are generated. The product mark and the encrypted volume ID are set as information for generating a key used for decryption of encrypted content, and recorded onto a disc by a reflective-film-removal recording method. Due to this configuration, the product mark and the encrypted volume ID as key generating information cannot be read from a pirated disc produced by physically copying a pit pattern on the basis of a legitimate commercial disc, thereby making it possible to prevent unauthorized reproduction or use of content.
Owner:SONY CORP
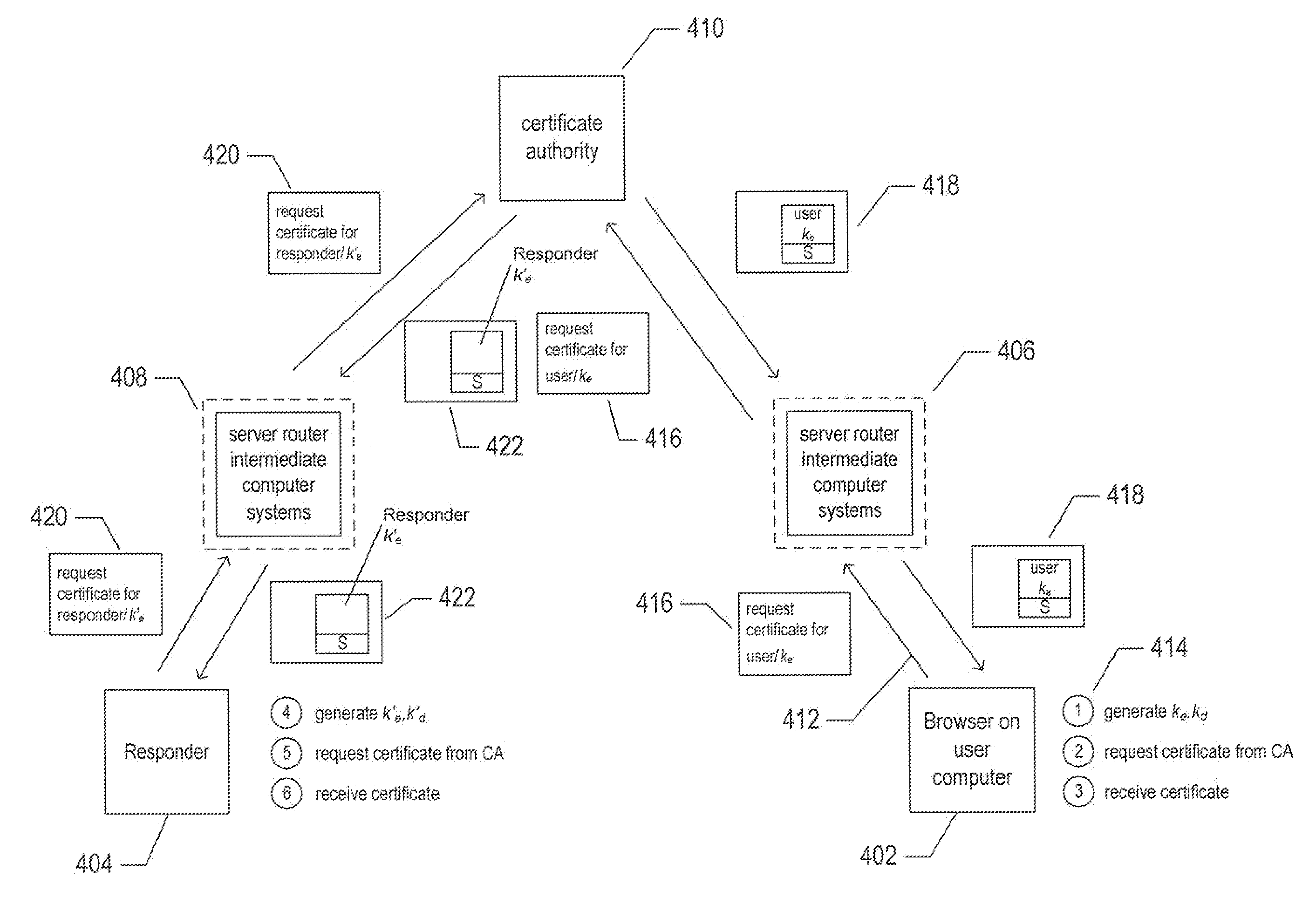
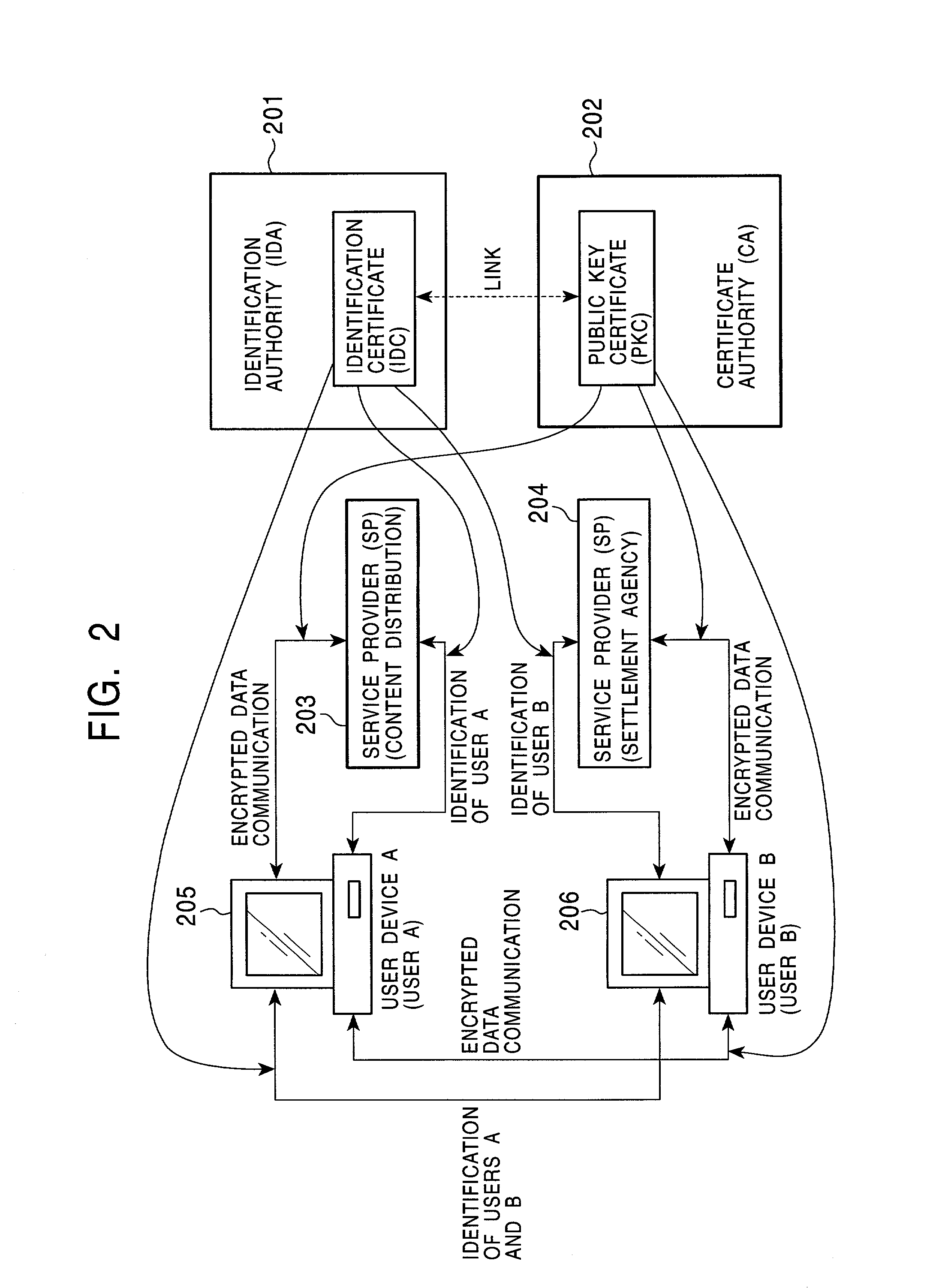
Secure publishing of public-key certificates
The current application is directed to methods and systems for secure distribution of public-key certificates using the domain name system with security extensions (“DNSSEC”), a publisher component, and additional client-side functionality. These methods and systems, when combined with public / private-key-based cryptography used for encrypting digitally encoded information, provides a computationally efficient and well-understood method and system for secure communications and digitally-encoded-information verification without current difficulties and inefficiencies attendant with distributing and managing the public keys used for encrypting digitally encoded information.
Owner:SECURE64 SOFTWARE
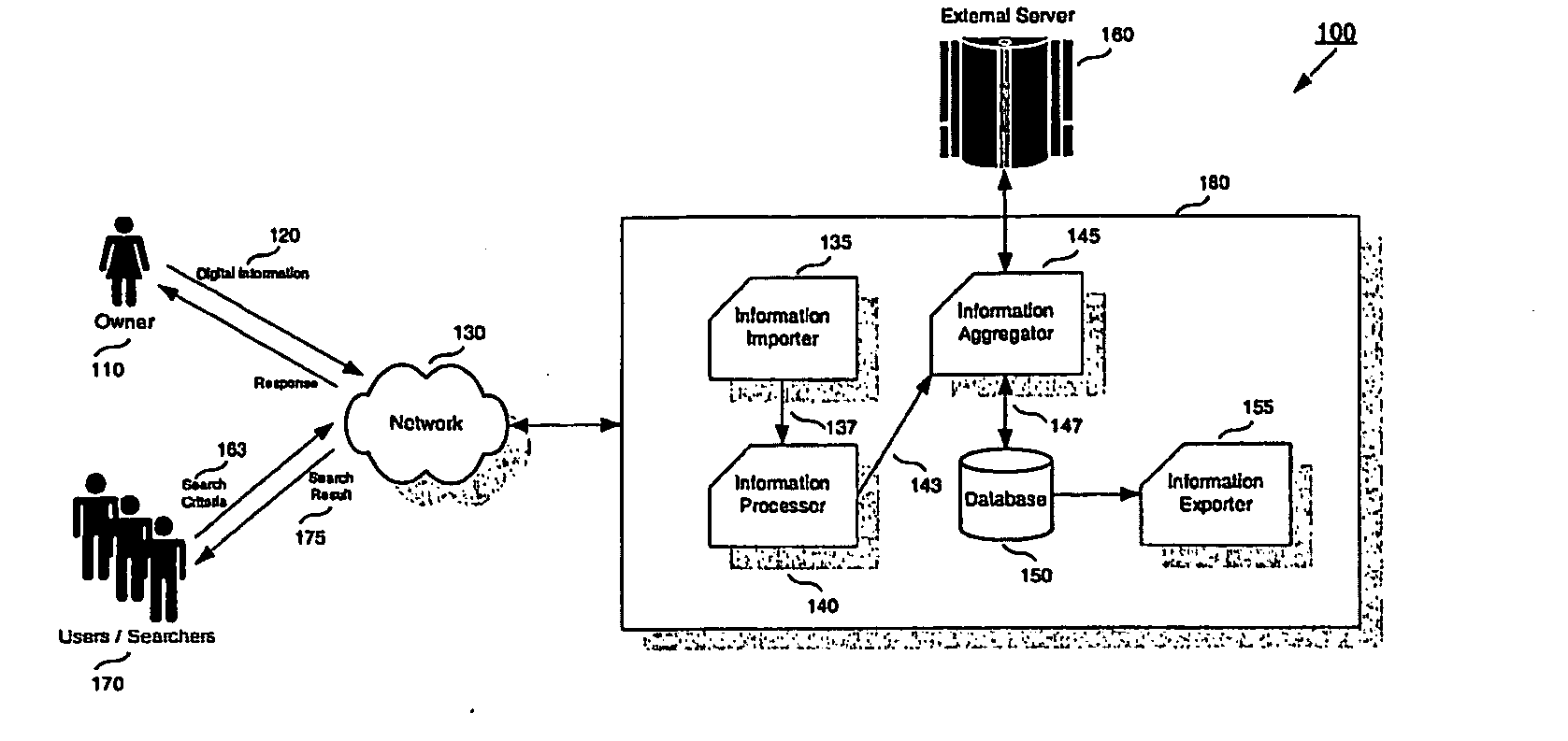
Electronic document management system
InactiveUS20050044369A1Easy to manageUser identity/authority verificationDigital data protectionElectronic documentDigital signature
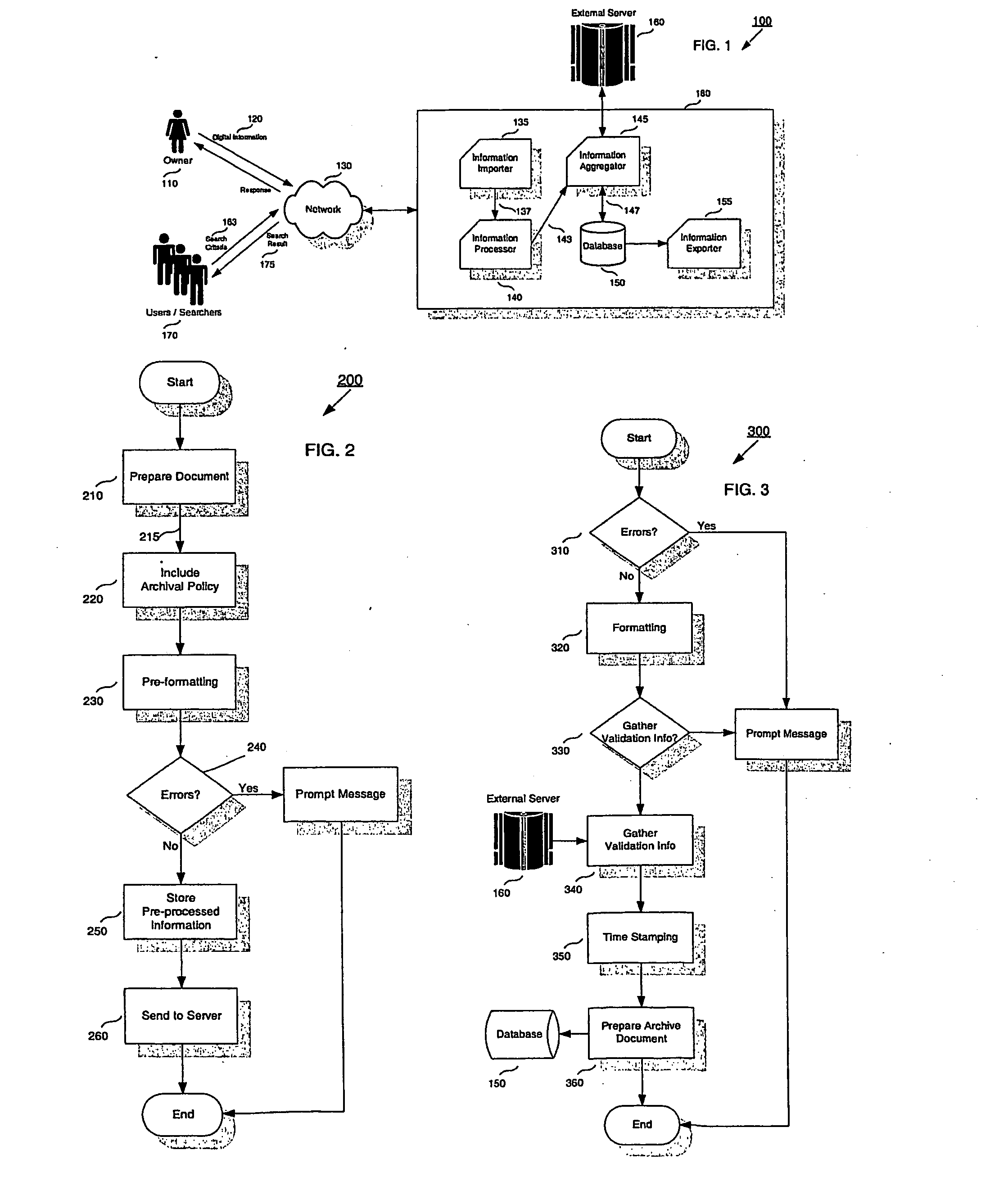
An apparatus, method and computer program for the management of digital information bearing digital signatures is disclosed. The invention includes an apparatus for the management of digital information in a database. This apparatus further includes the means for importing the digital information; means for processing the digital information, wherein the digital information may include at least one digital document, at least one digital signature, at least one public key certificate, at least one archival policy; means for obtaining data from an external server and means for exporting output information from the apparatus, whereby a user when importing the digital information to the apparatus, causes the digital information to be processed thereby generating the output information that is stored in the database.
Owner:KENT RIDGE DIGITAL LABS
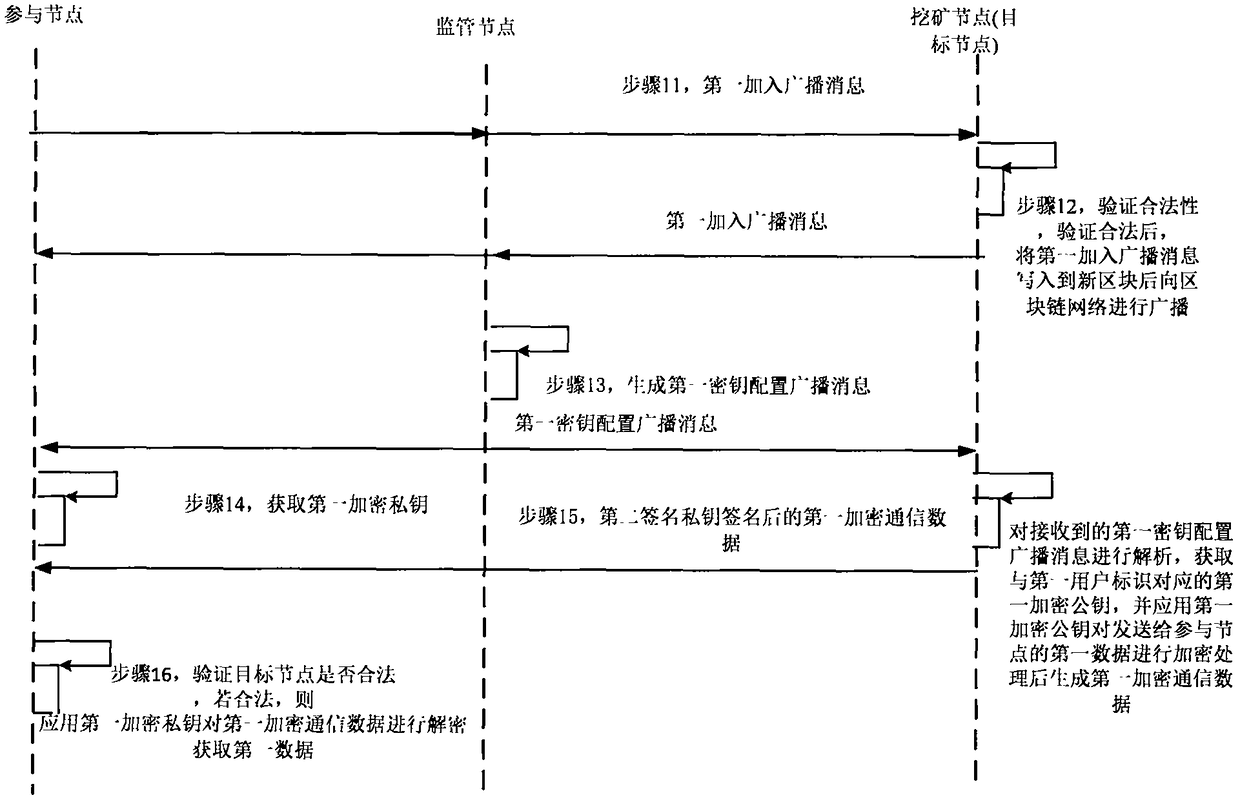
Encrypted communication method and system of block chain node
InactiveCN108737430AEnsure communication securityAvoid accessSpecial service provision for substationKey distribution for secure communicationSecure communicationCommunications security
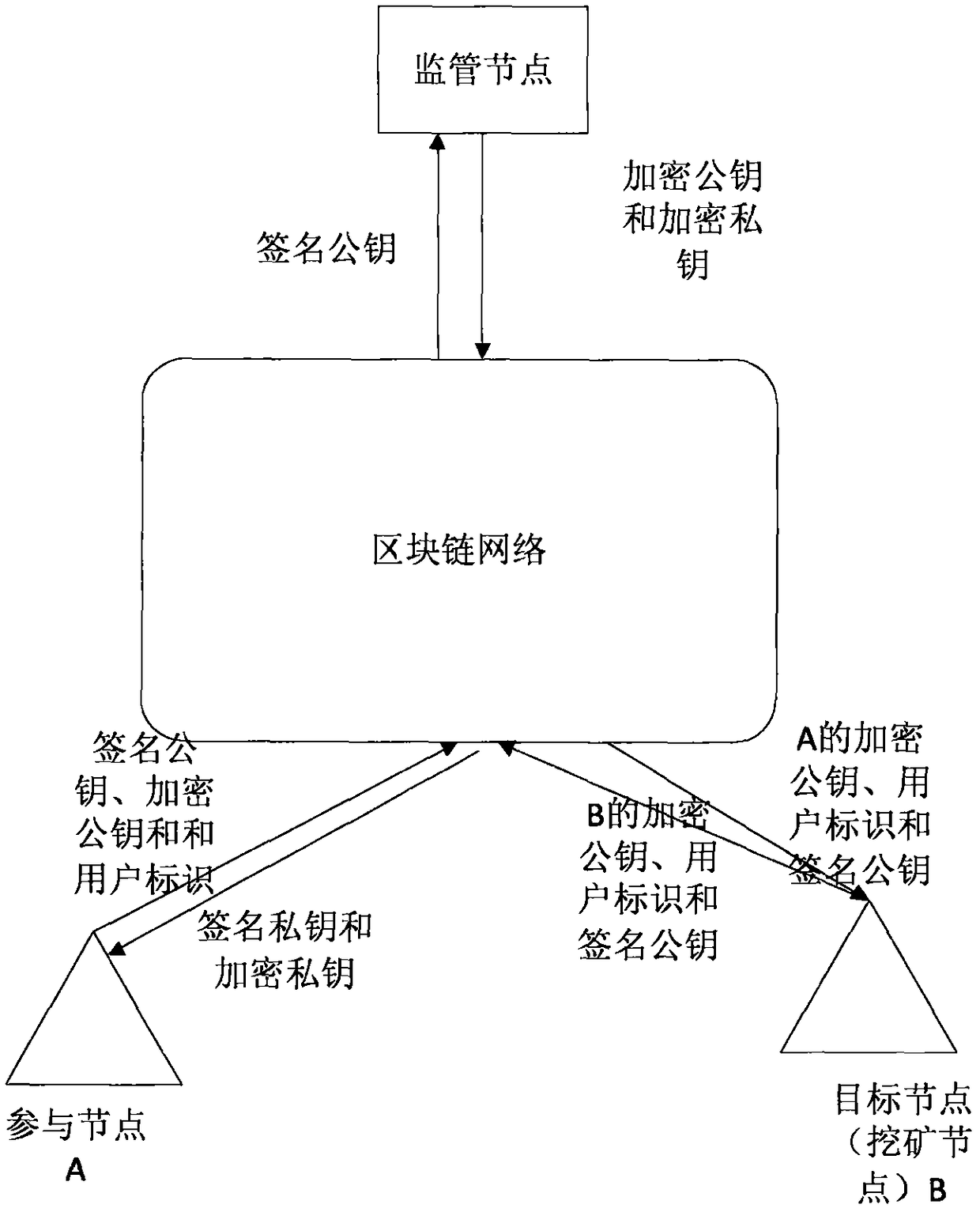
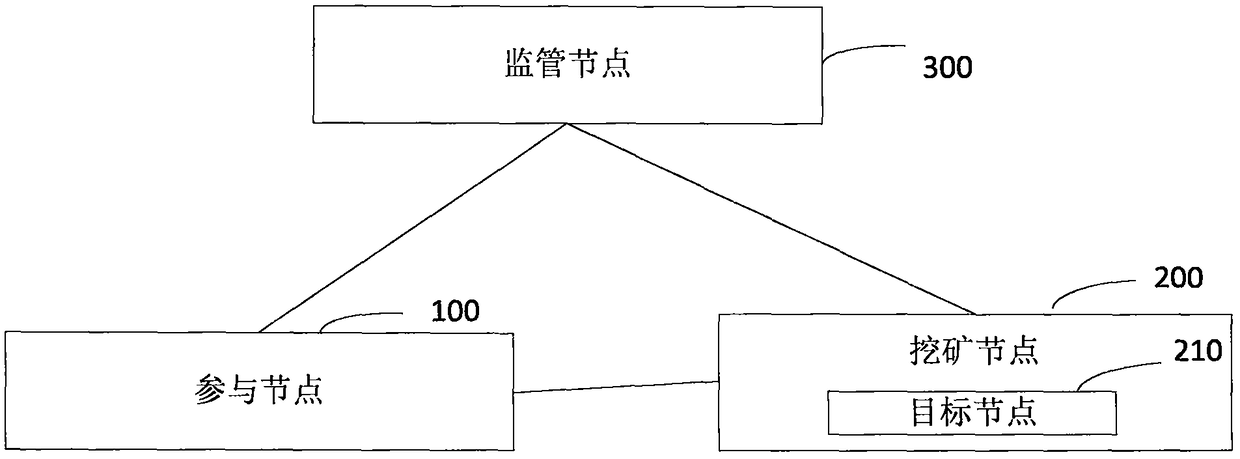
The invention provides an encrypted communication method and system of a block chain node. The method comprises the following steps: for a participating node firstly added in a block chain network, afirst user identifier and a first signature private key of the participating node are signed by using a first signature private key of the participating node, and a first adding broadcast message is sent by the block chain network after the timestamp is stamped thereon through a timestamp server; a mining node analyzes the first adding broadcast message to acquire the first user identifier and thefirst signature public key, and performs the legality verification on the participating node according to the first signature public key; a supervision node generates and distributes the first encryption public key and the first encryption private key corresponding to the first user identifier according to the first signature public key; the participating node perform safety communication with the target node based on the first encryption public key and the first encryption private key. Therefore, the public key certificate scheme is combined with the block chain network to guarantee the communication security of the block chain network.
Owner:全链通有限公司
Information processing apparatus, authentication processing method, and computer program
InactiveUS20050198529A1Eliminate illegal acquisitionElimination contentTelevision system detailsMemory loss protectionInformation processingPublic key certificate
An information processing apparatus, an authentication processing method, and computer program provided. The present invention includes an interface for carrying out data transfer processing, and a data processor for executing data processing. The data processor executes authentication processing with a target of data transfer as a condition of executing data processing accompanying data transfer via the interface. In the authentication processing, the data processor verifies channel type applied in data transfer based on data stored in a public key certificate held by an authentication counterpart, and determines whether or not it is possible to establish authentication based on the channel type.
Owner:SONY CORP
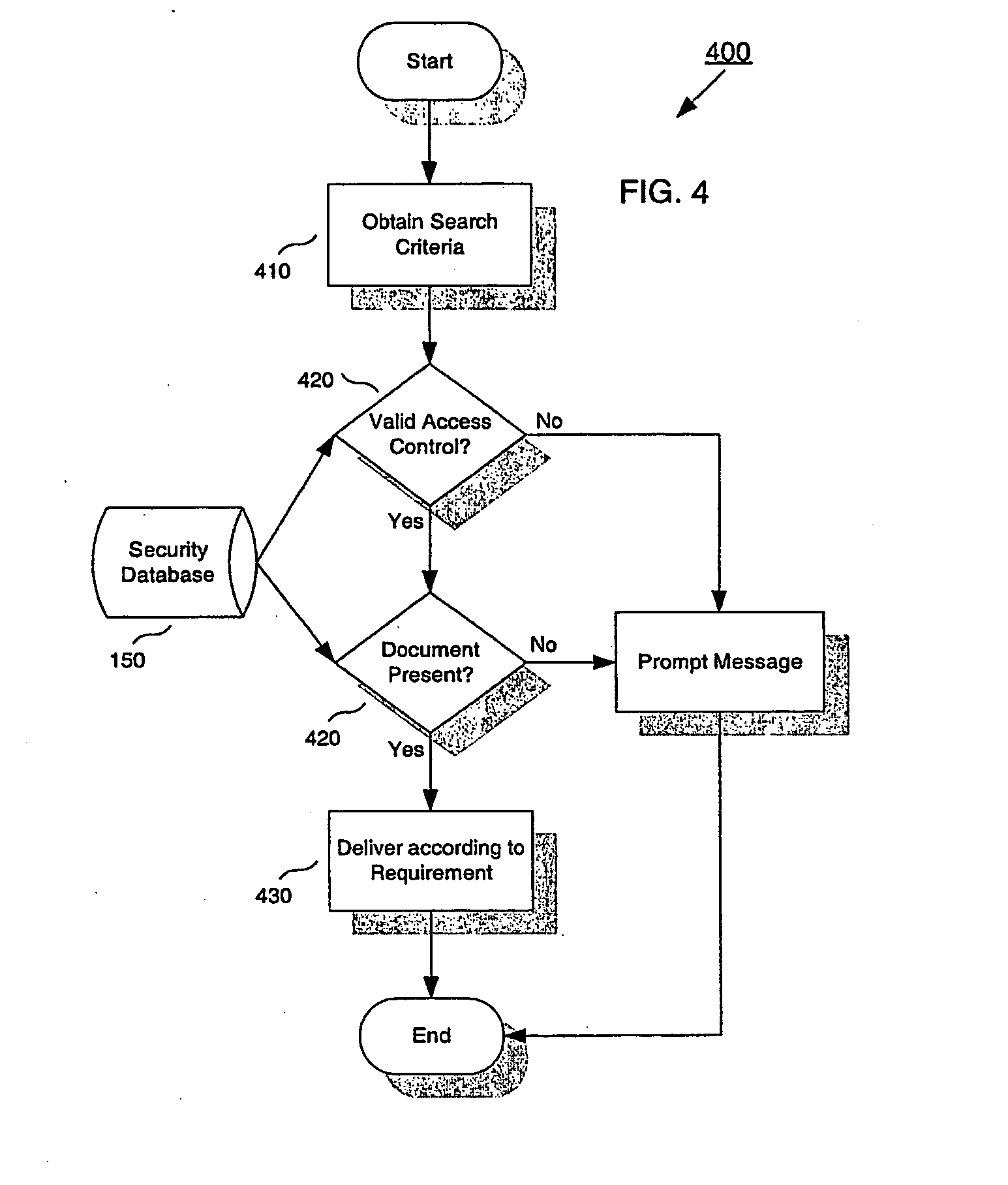
Public key certificate using system, public key certificate using method, information processing apparatus, and program providing medium
InactiveUS7100044B2Improve reliabilityEasy to useKey distribution for secure communicationDigital data processing detailsInformation processingPublic key certificate
In a public key certificate using system, a template which serves as person identification data of a person requesting a public key certificate is obtained from a person identification certificate of the person, a person authentication is executed by comparing sampling information of the person against the template, and a public key certificate for the person is issued by a certificate authority on condition that the person authentication is established, thus reducing the load on the certificate authority for person authentication. The public key certificate issued to the user is deleted upon completion of a processing session involving use of the public key certificate, restricting the use of the public key certificate to the particular processing session.
Owner:SONY CORP
Person identification certificate link system, information processing apparatus, information processing method, and program providing medium
InactiveUS7096363B2Warranty periodEasy to implementFinanceUser identity/authority verificationInformation processingService provision
A person identification certificate link system forms a link between a person identification certificate which stores a template serving as person identification data and which is generated by a person identification certificate authority and a public key certificate which stores a public key, thereby specifying one certificate based on the other certificate. With this arrangement, a cryptographic key to the template stored in the person identification certificate can be specified. It is also possible to quickly obtain a combination of the person identification certificate and the public key certificate which are both utilized in transaction with a service provider, thereby improving the processing efficiency.
Owner:SONY CORP
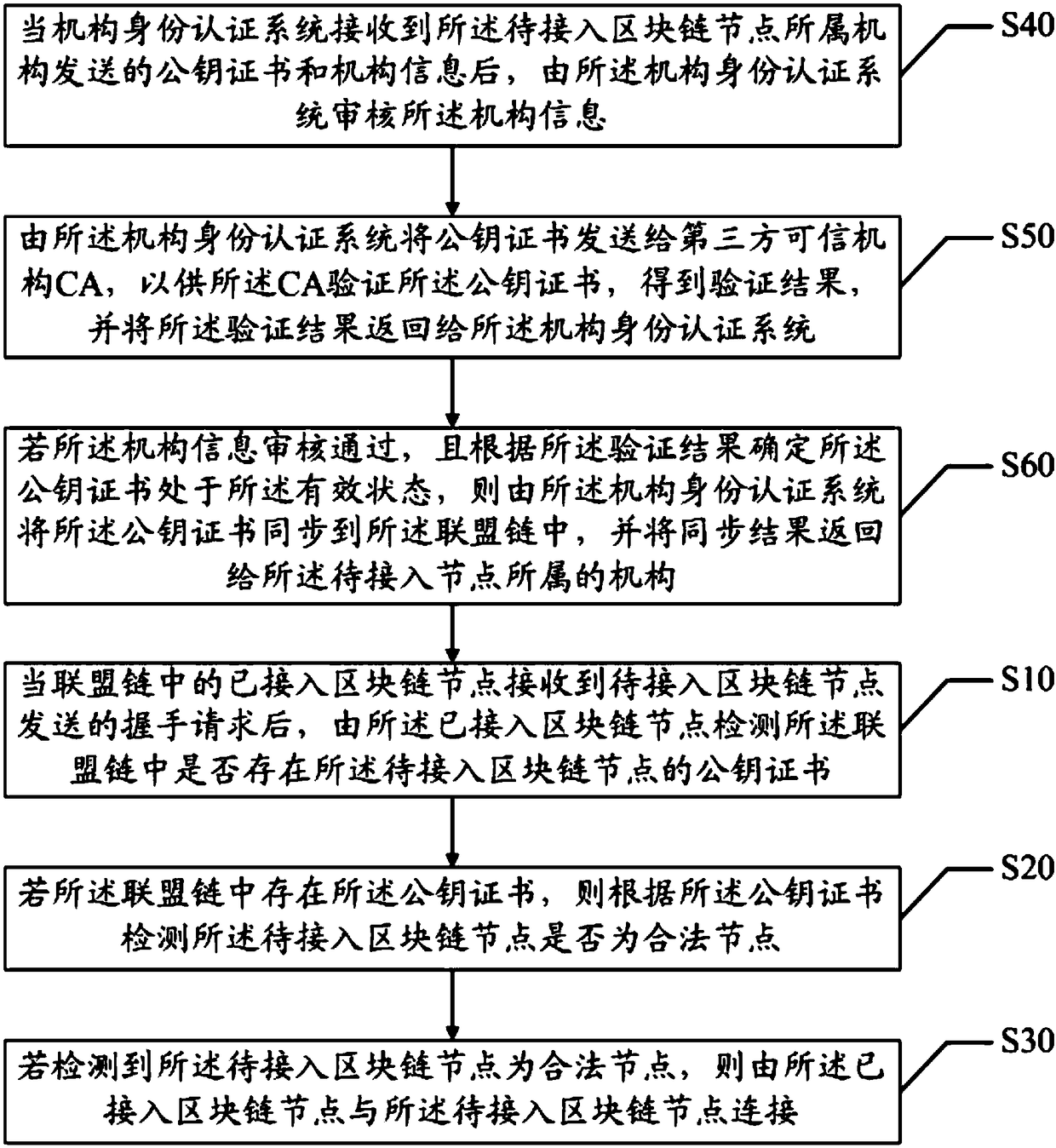
Block chain node connection method and system and computer readable storage medium
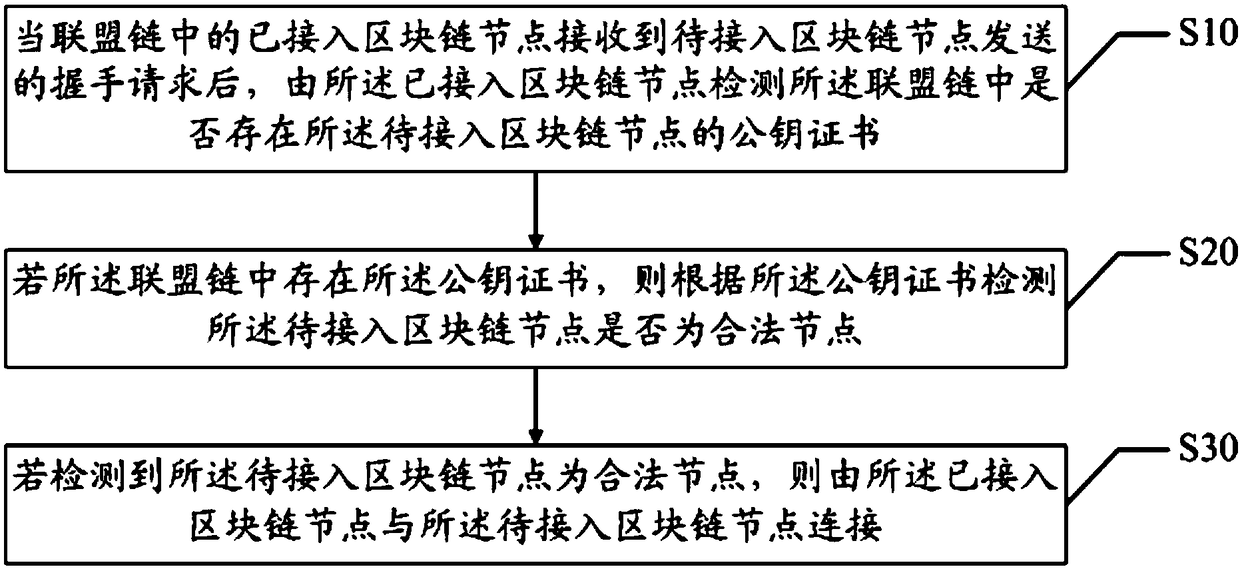
InactiveCN108416589APrevent Malicious ConnectionsImprove securityPayment protocolsPublic key certificateBlockchain
The invention discloses a block chain node connection method and system and a computer readable storage medium. The method comprises the steps that when the connected block chain node of the league chain receives the handshake request transmitted by the block chain node to be connected, the connected block chain node detects existence of the public key certificate of the block chain node to be connected in the league chain; if the public key certificate exists in the league chain, whether the block chain node to be connected is the valid node is detected according to the public key certificate; and if the detection result indicates that the block chain node to be connected is the valid node, the connected block chain node is connected with the block chain node to be connected. The situation that the invalid block chain node maliciously connects the block chain node in the league chain can be avoided so that the security of the block chain node in the league chain can be enhanced.
Owner:WEBANK (CHINA)
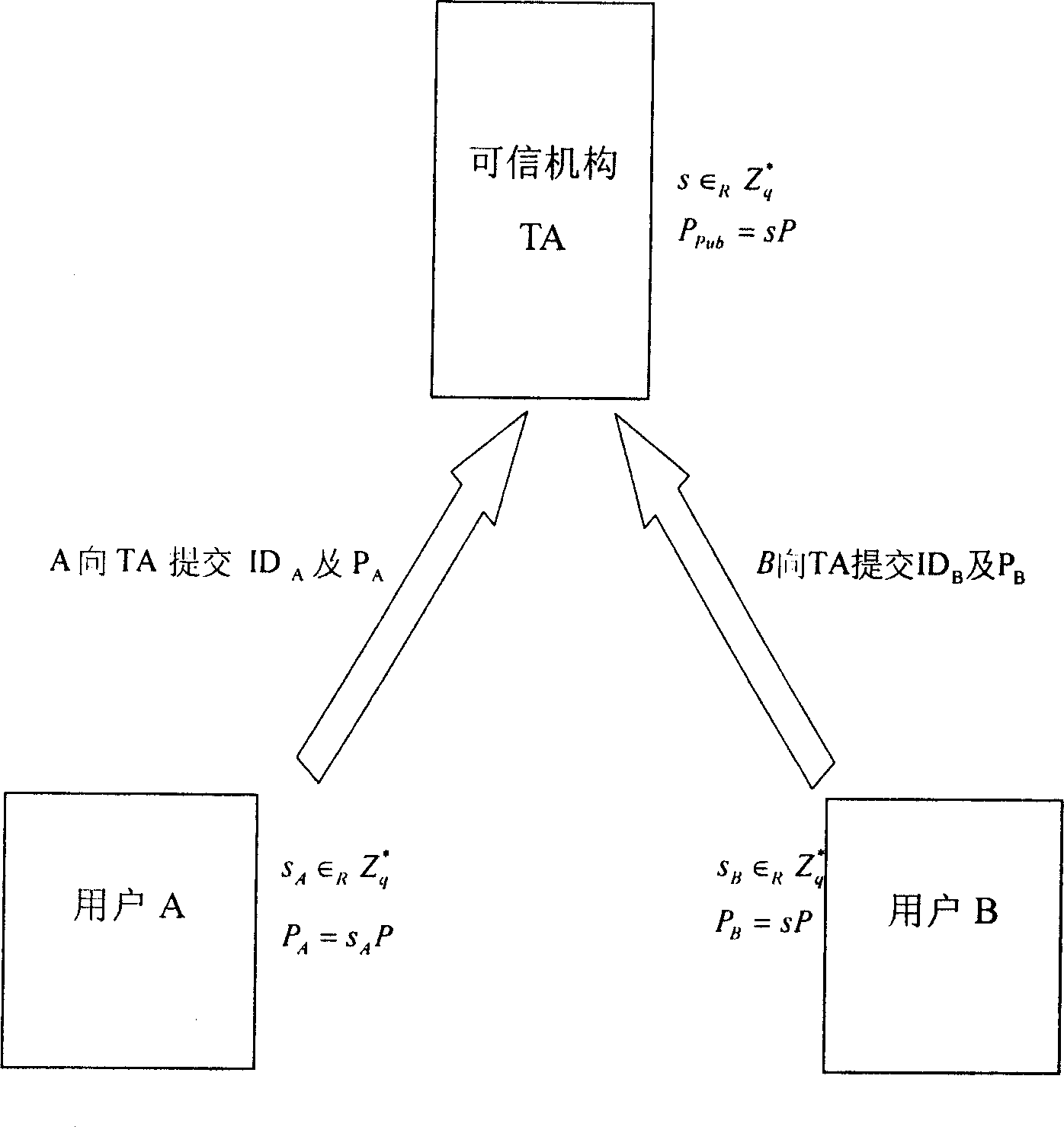
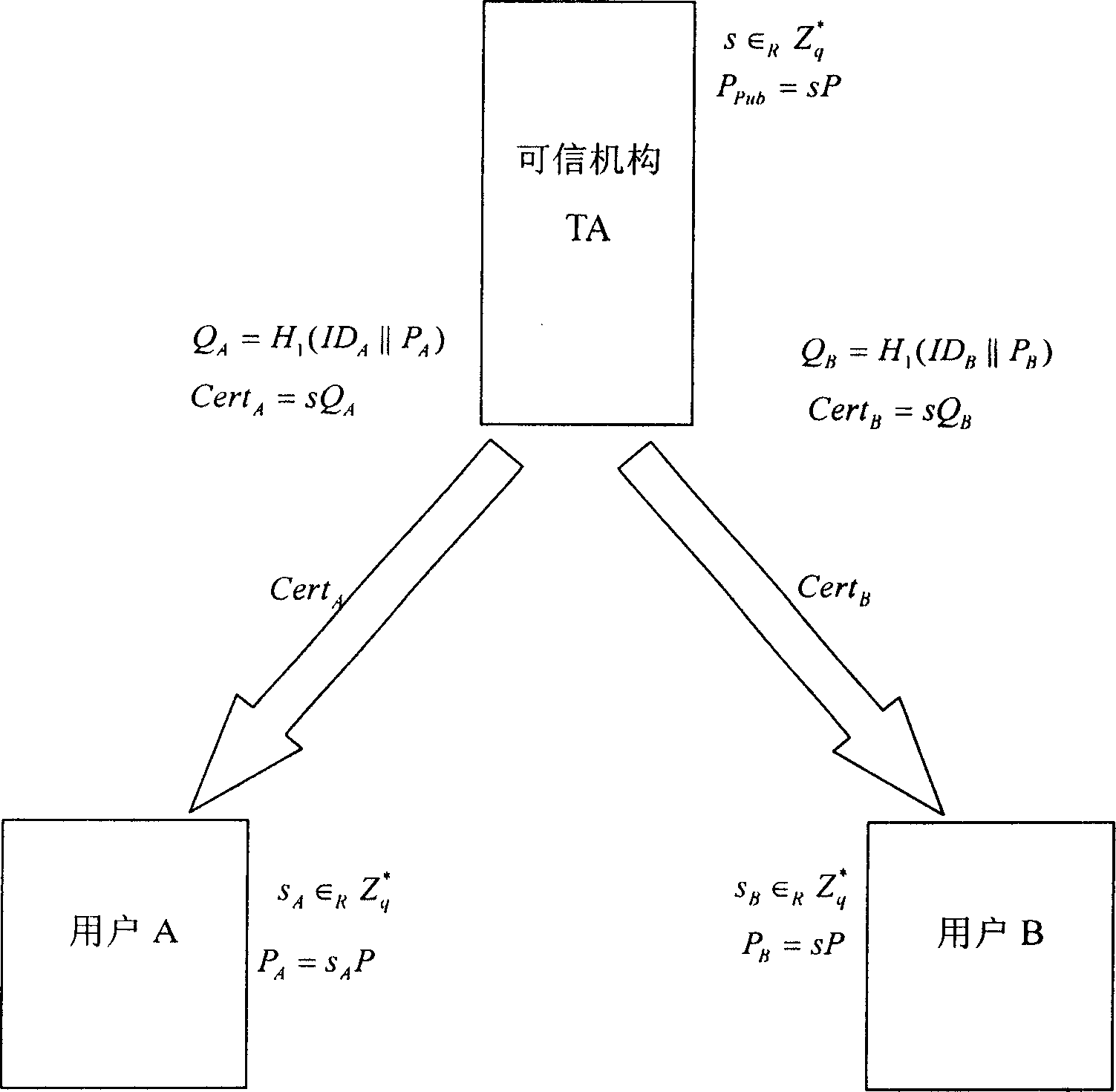
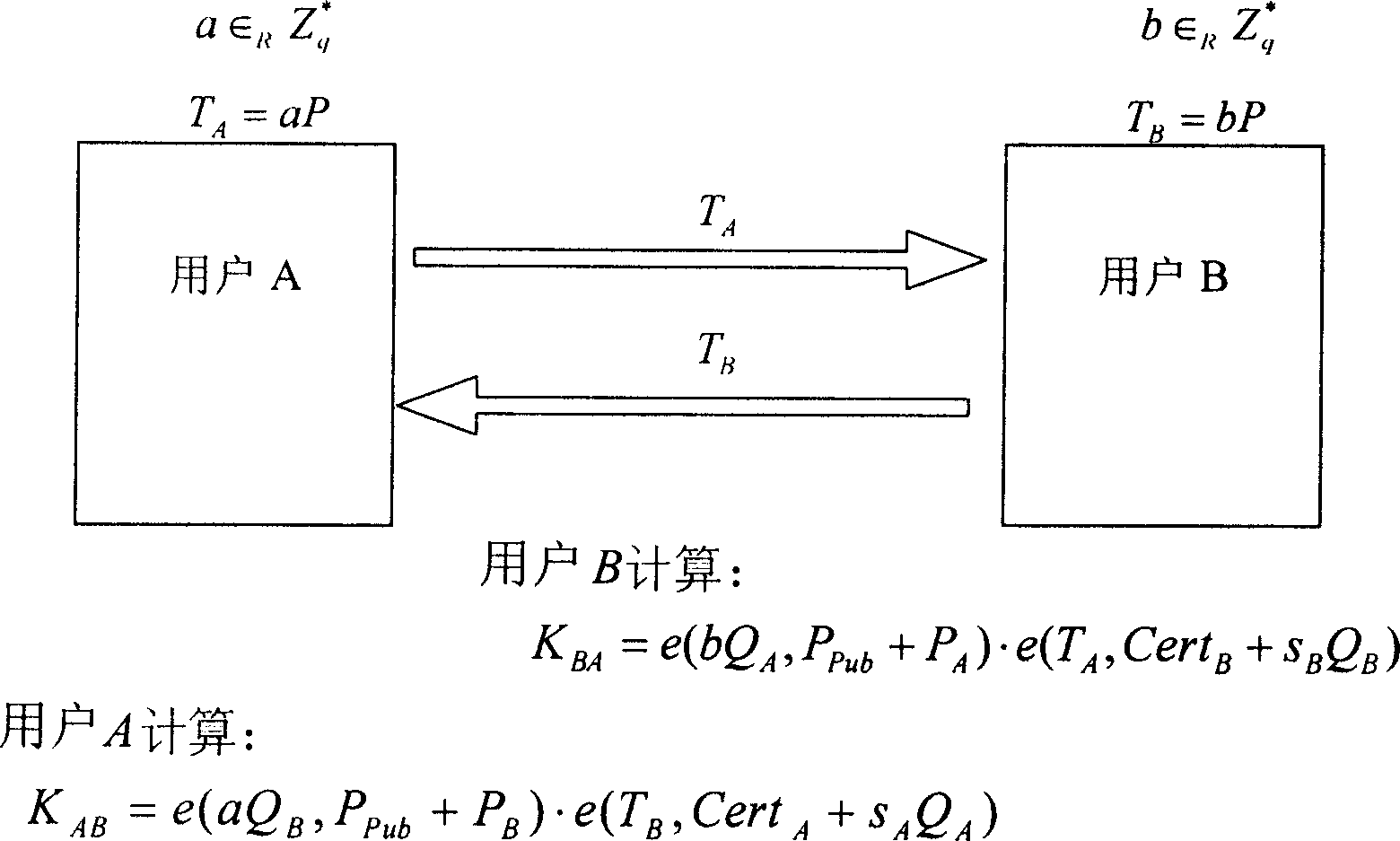
Mutual identifying key consultation method and system based on hidden common key certificate
InactiveCN1889433AComputationally efficientEfficient calculation loadSynchronising transmission/receiving encryption devicesPublic key for secure communicationThree stageKey escrow
This invention relates to a negotiation method and a system for both party certificated cryptographic keys based on hidden public key certificates, which applies three stages of system initialization, user end registration, generation of hidden public key certificates and distribution and certificated cryptographic key negotiations to utilize the traditional cipher plan of PKI and identity base to eliminate unnecessary trusteeship of the cryptographic keys on one hand and keep the advantages of part of identity base ciphers on the other, besides, this invention also discloses a system for realizing negotiation method of both party certified keys based on hidden public key certificates.
Owner:SHANGHAI JIAO TONG UNIV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com