Patents
Literature
327 results about "Key size" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
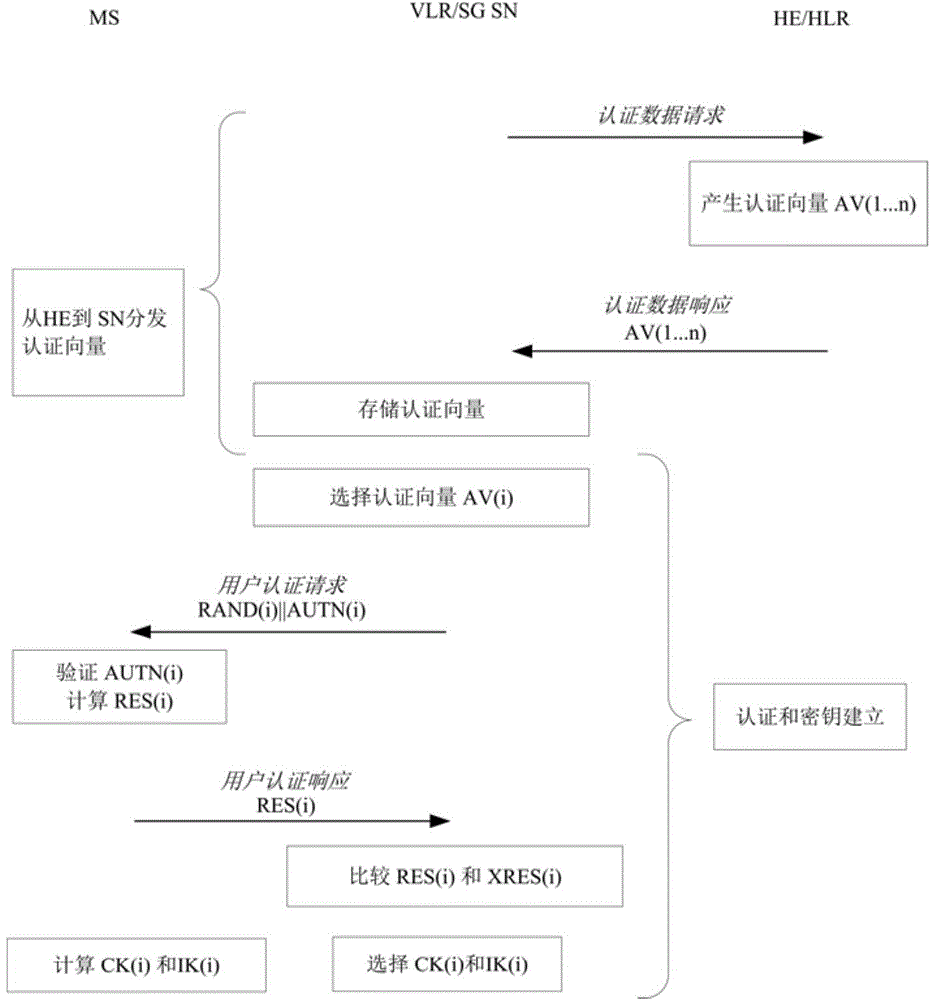
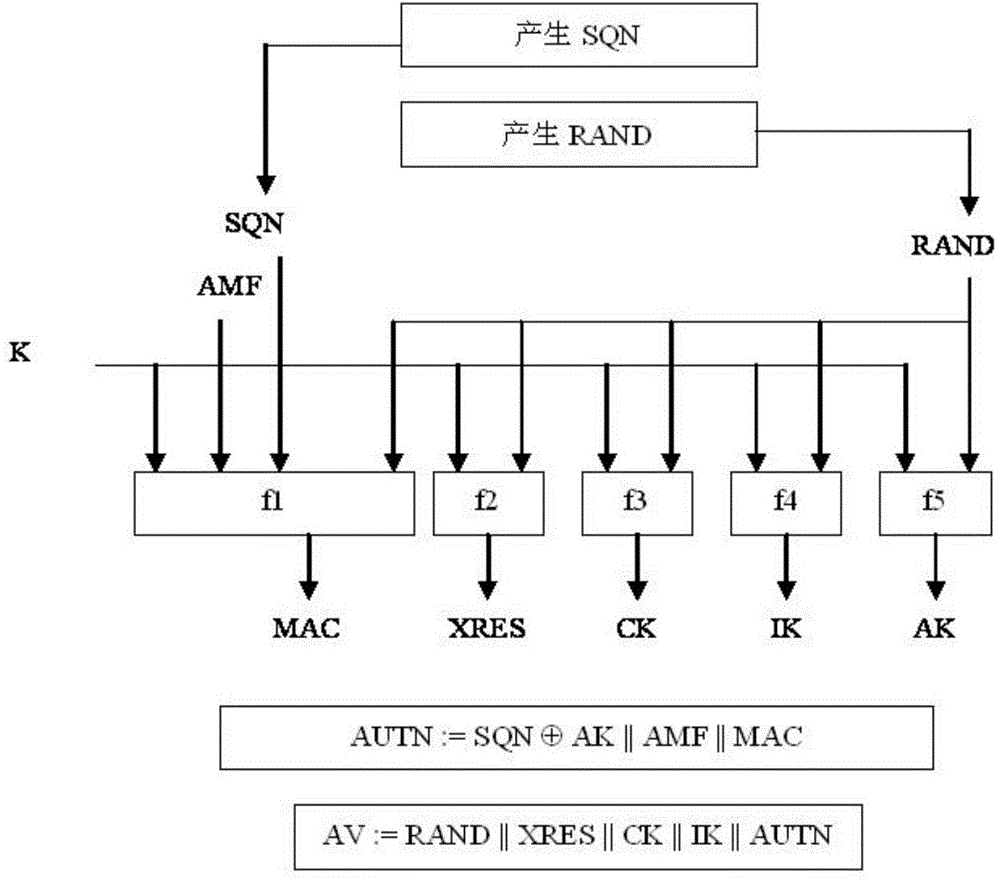
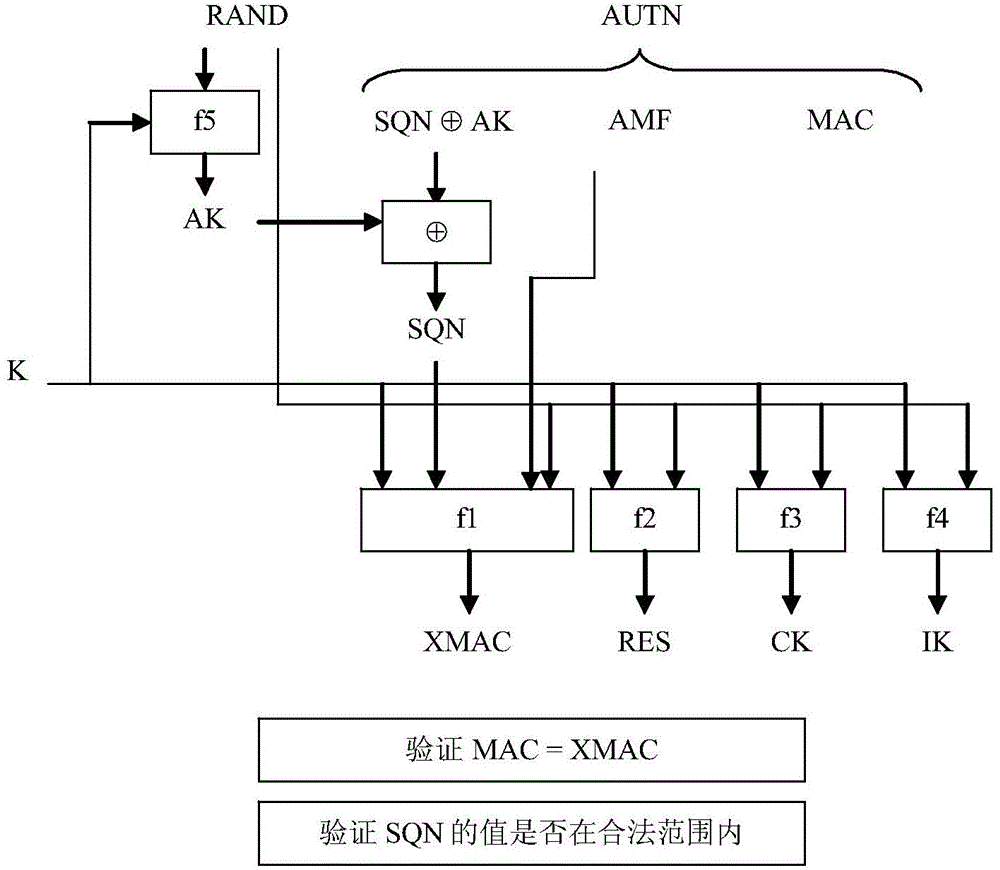
In cryptography, key size or key length is the number of bits in a key used by a cryptographic algorithm (such as a cipher). Key length defines the upper-bound on an algorithm's security (i.e. a logarithmic measure of the fastest known attack against an algorithm, relative to the key length), since the security of all algorithms can be violated by brute-force attacks. Ideally, key length would coincide with the lower-bound on an algorithm's security. Indeed, most symmetric-key algorithms are designed to have security equal to their key length. However, after design, a new attack might be discovered. For instance, Triple DES was designed to have a 168 bit key, but an attack of complexity 2¹¹² is now known (i.e. Triple DES has 112 bits of security). Nevertheless, as long as the relation between key length and security is sufficient for a particular application, then it doesn't matter if key length and security coincide. This is important for asymmetric-key algorithms, because no such algorithm is known to satisfy this property; elliptic curve cryptography comes the closest with an effective security of roughly half its key length.
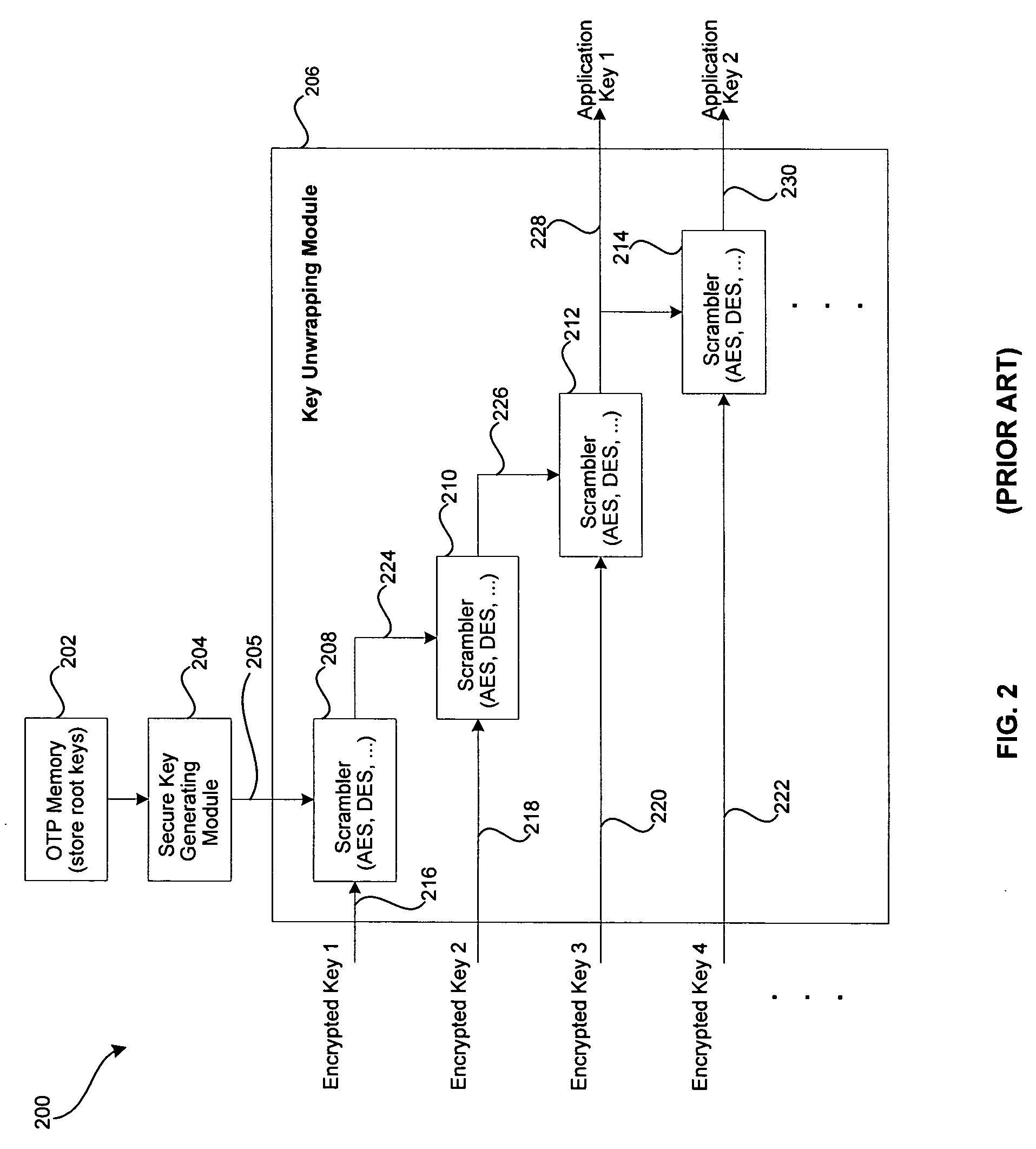
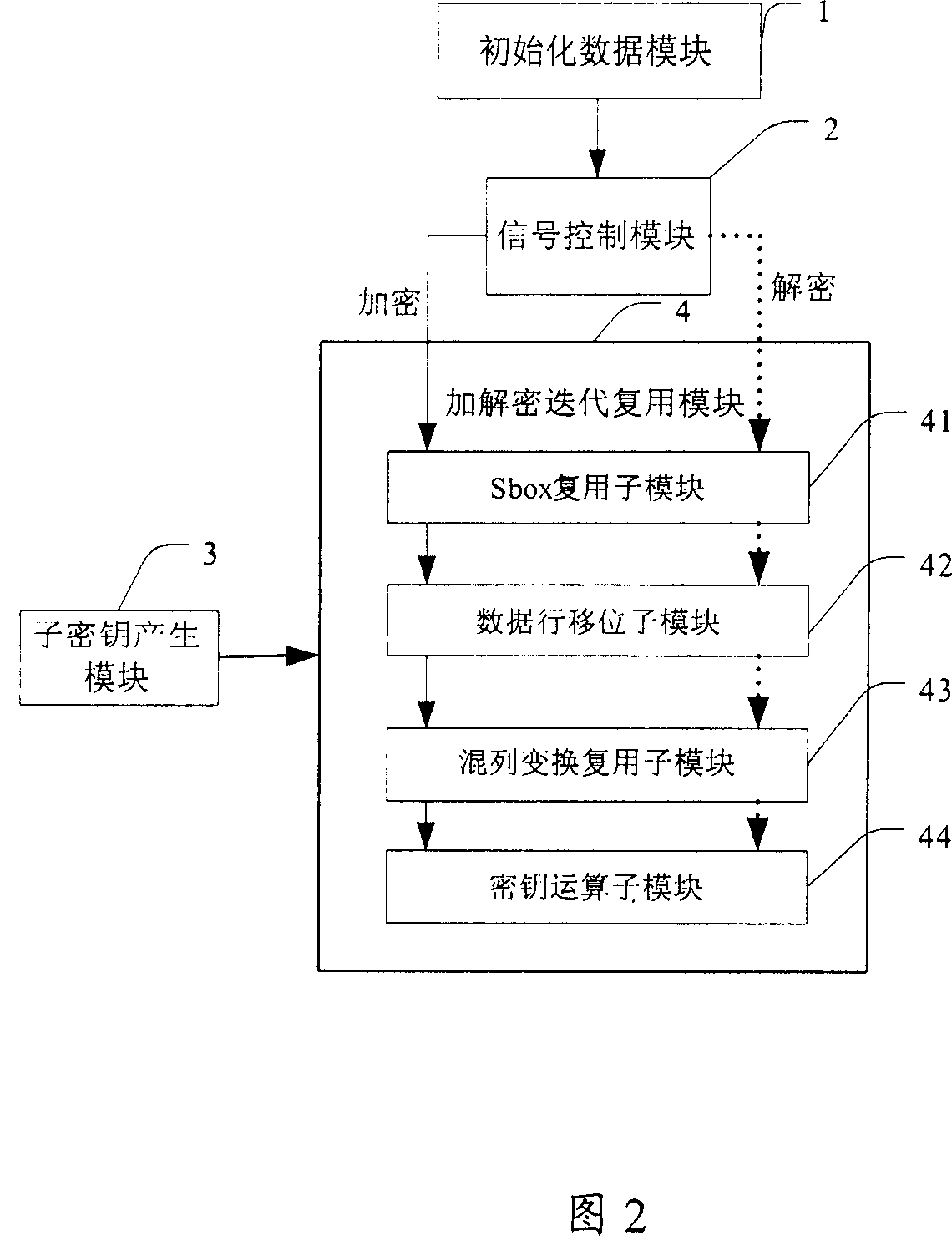
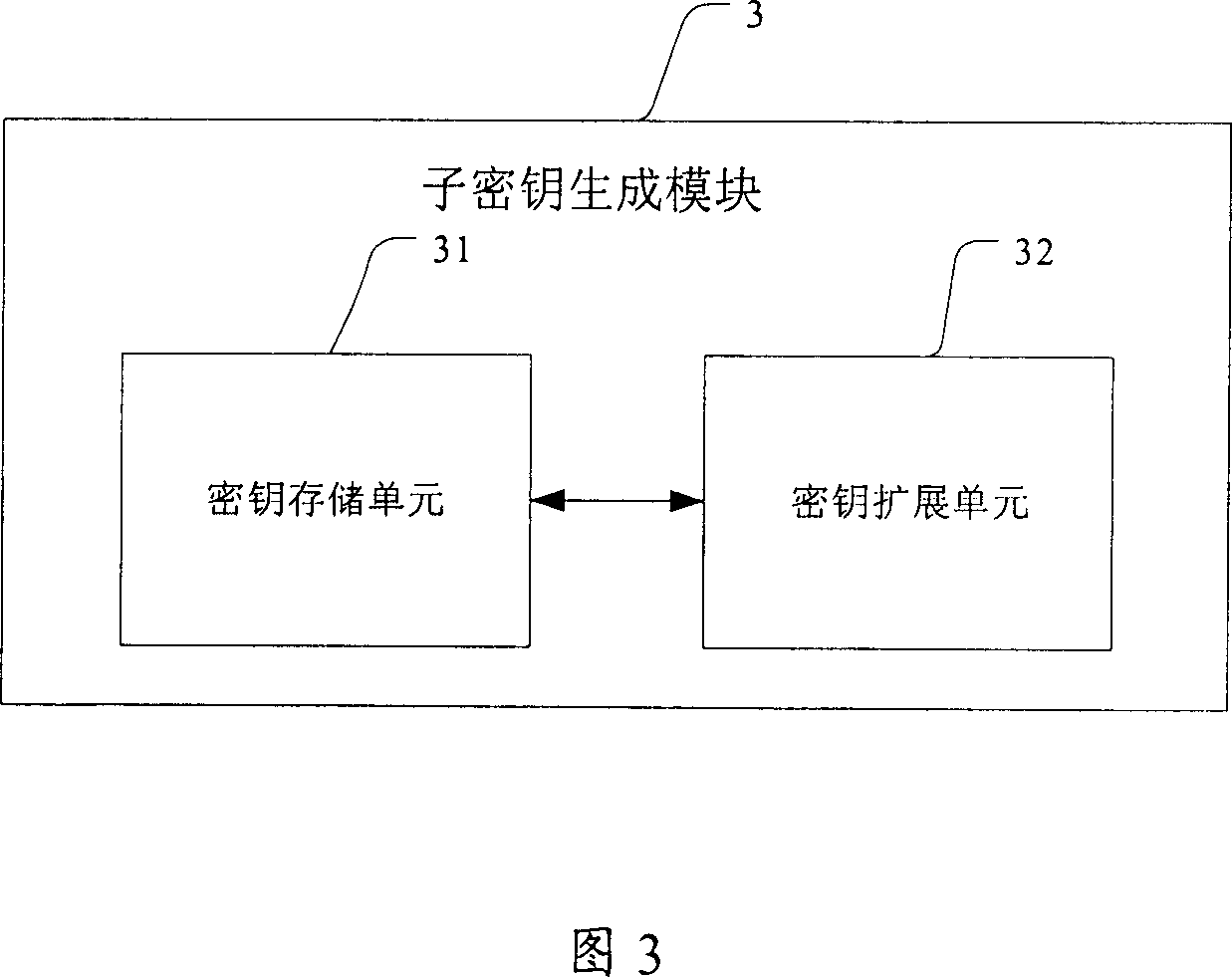
Data encrypting and decrypting apparatus and method
InactiveUS6490353B1Less computationally intensiveEasy data transferKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareKey size
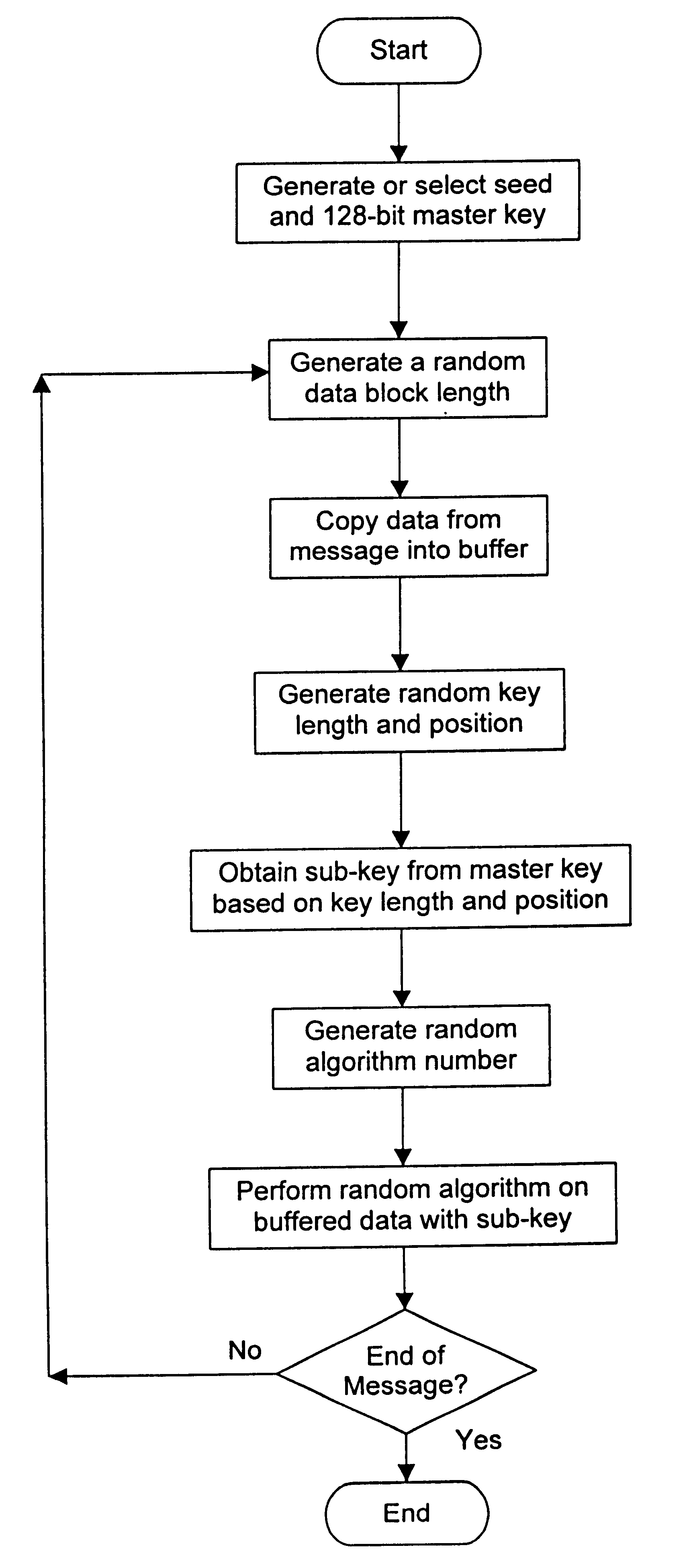
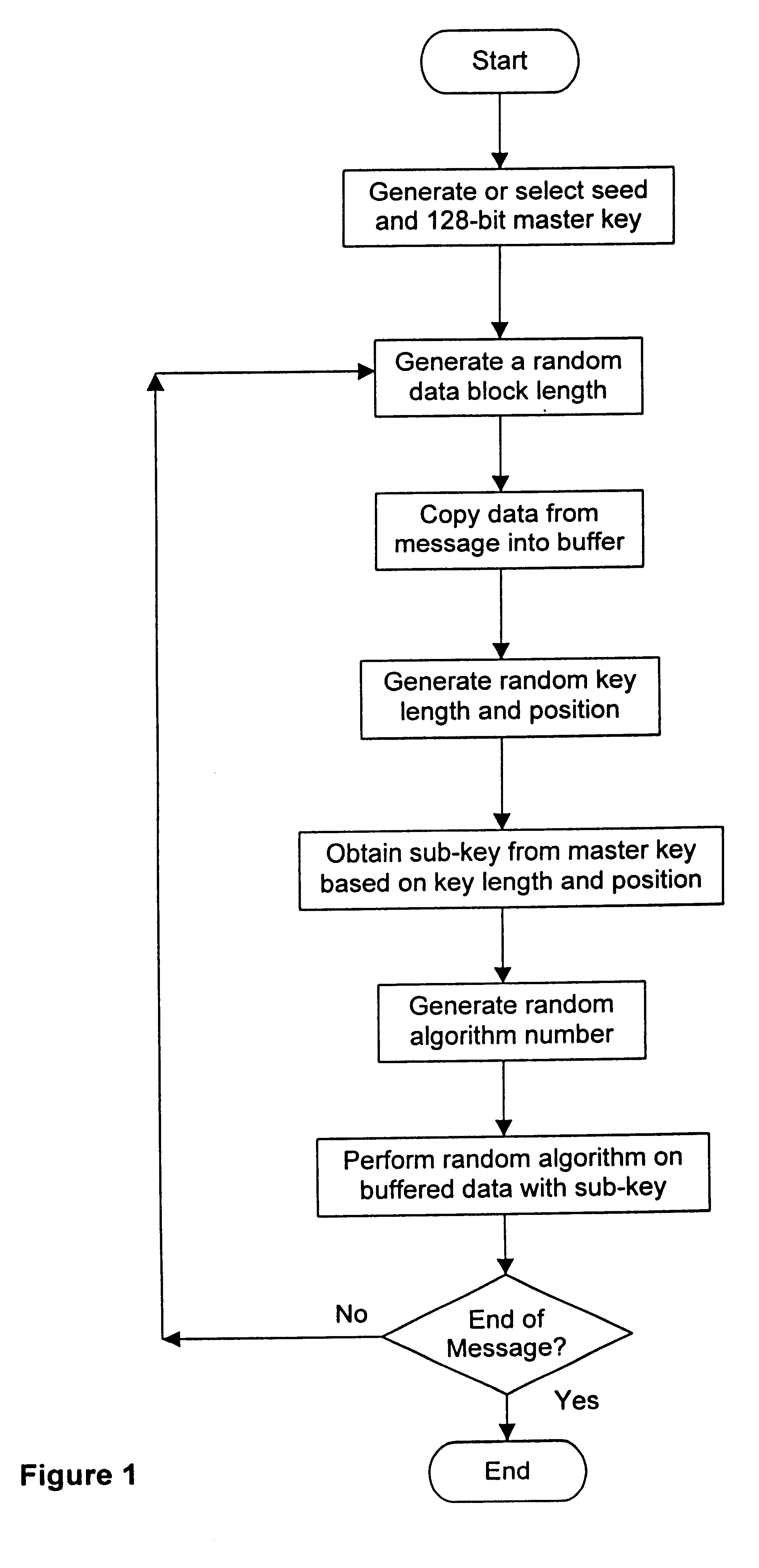
A crytography method of encrypting data is disclosed. The method provides for creating or selecting a master key. Thereafter, the data to be encrypted is segmented into data blocks of equal or variable lengths. For each data block a sub-key of an arbitrary starting position is selected from a pre-defined set of arbitrary positions and of matched or unmatched length from the master key, where the master key length is selected from a pre-defined set of arbitrary lengths. Having acquired the sub-key for each data block, each data block is encrypted using its sub-key and an encryption algorithm.
Owner:TAN DANIEL TIONG HOK
System and method for security key transmission with strong pairing to destination client
ActiveUS20050177741A1Key distribution for secure communicationUser identity/authority verificationKey sizeClient-side
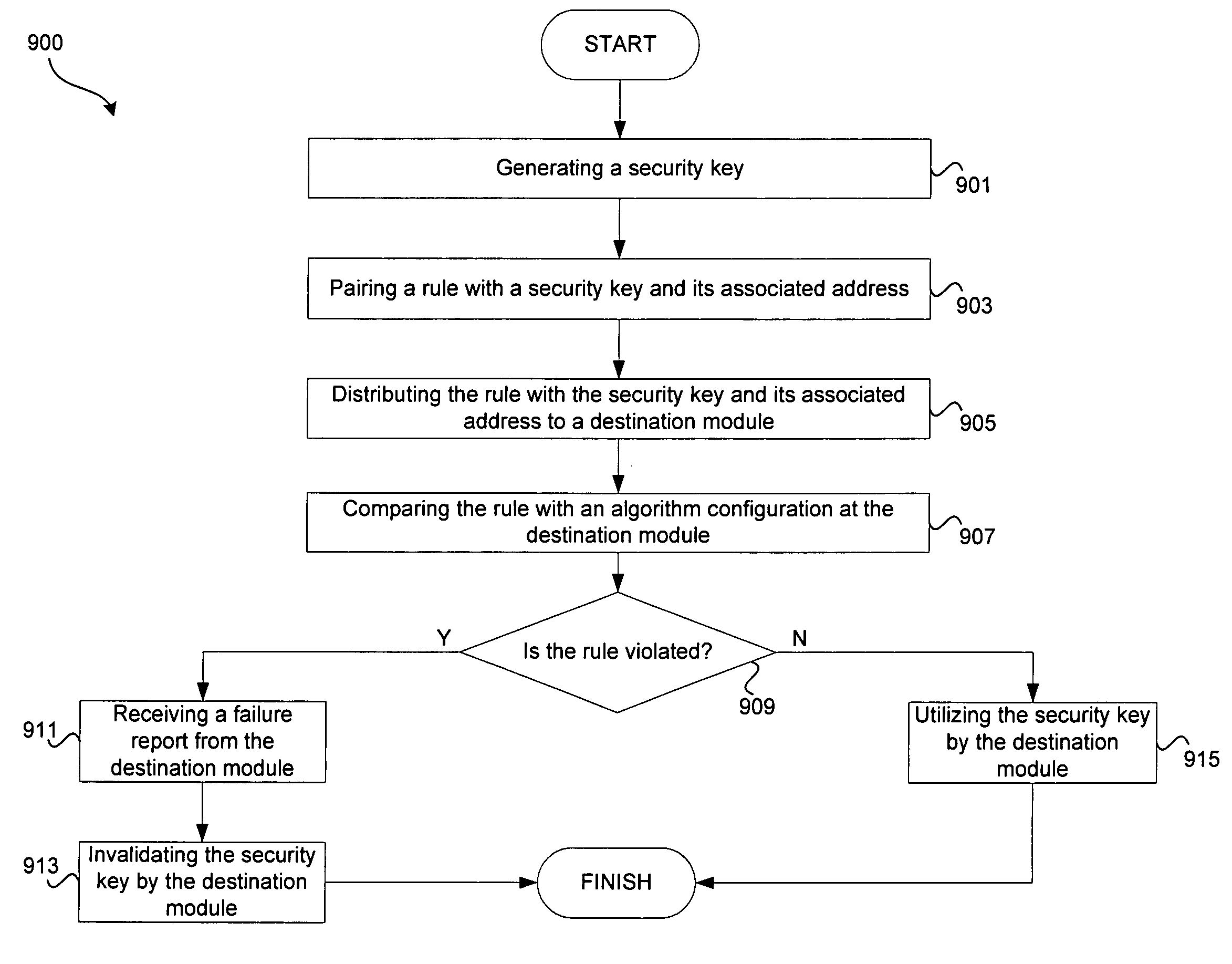
Systems and methods for security key transmission with strong pairing to a destination client are disclosed. A security key may be generated by an on-chip key generator, an off-chip device, and / or software. A rule may then be paired with the security key and an address associated with the security key. The rule may define permissible usage by a destination module, which is defined by the associated address. The rule may comprise a command word, which may be implemented using a data structure associated with a permissible algorithm type, a security key size, and / or a security key source.
Owner:AVAGO TECH INT SALES PTE LTD
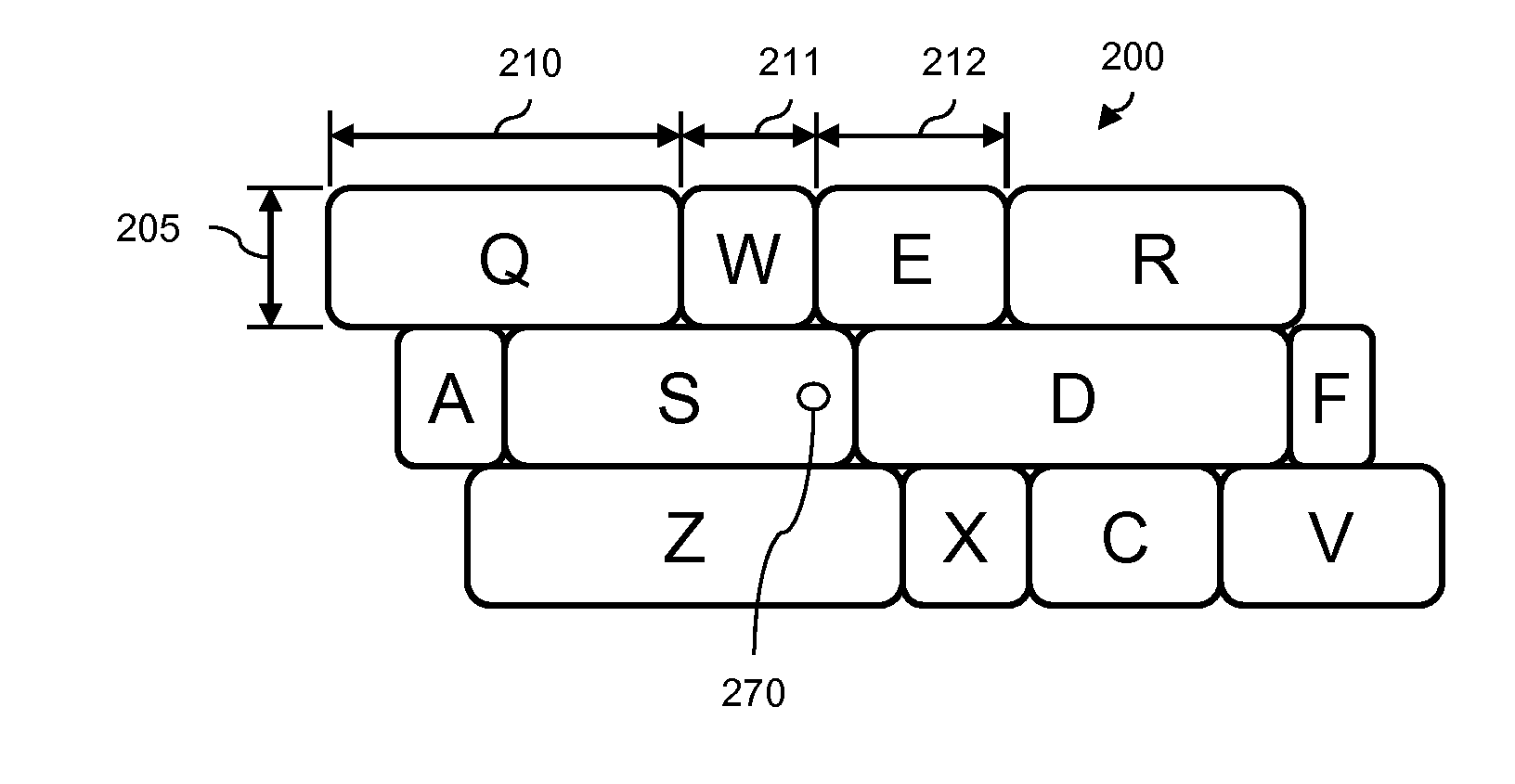
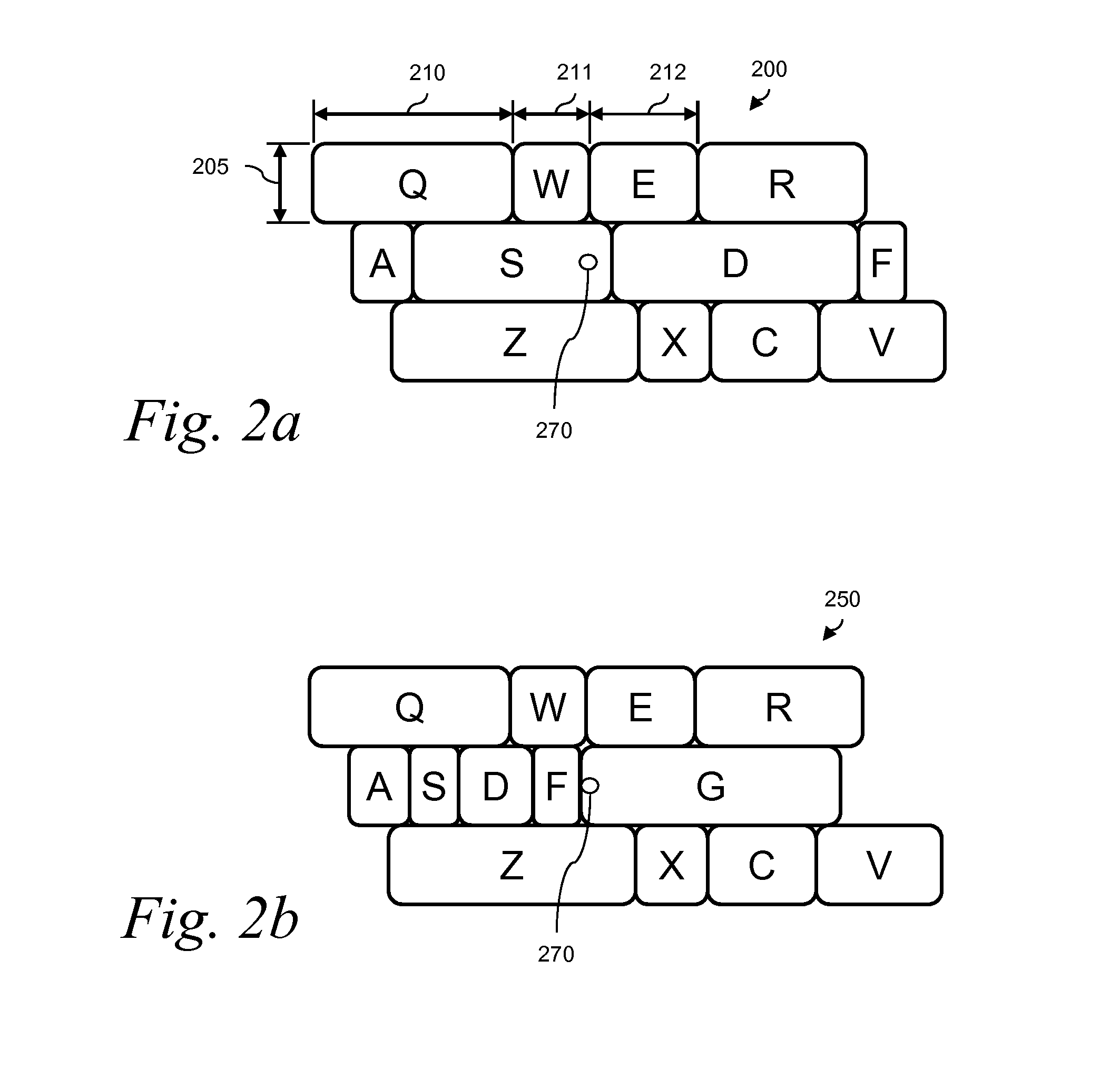
Method for dynamic key size prediction with touch displays and an electronic device using the method
InactiveUS20050071778A1Enlarged keyBetter seeDigital data processing detailsSubstation equipmentComputer hardwareKey size
The invention relates to a method for inputting user commands into an electronic device (1), which uses dynamic I / O input arrangement. After each input command the most potential next input command is emphasized by enlarging the size of a key of the command (23, 24, and 25). The invention also relates to a cellular terminal or PDA utilizing the method and software means to carry out the invention.
Owner:NOKIA CORP
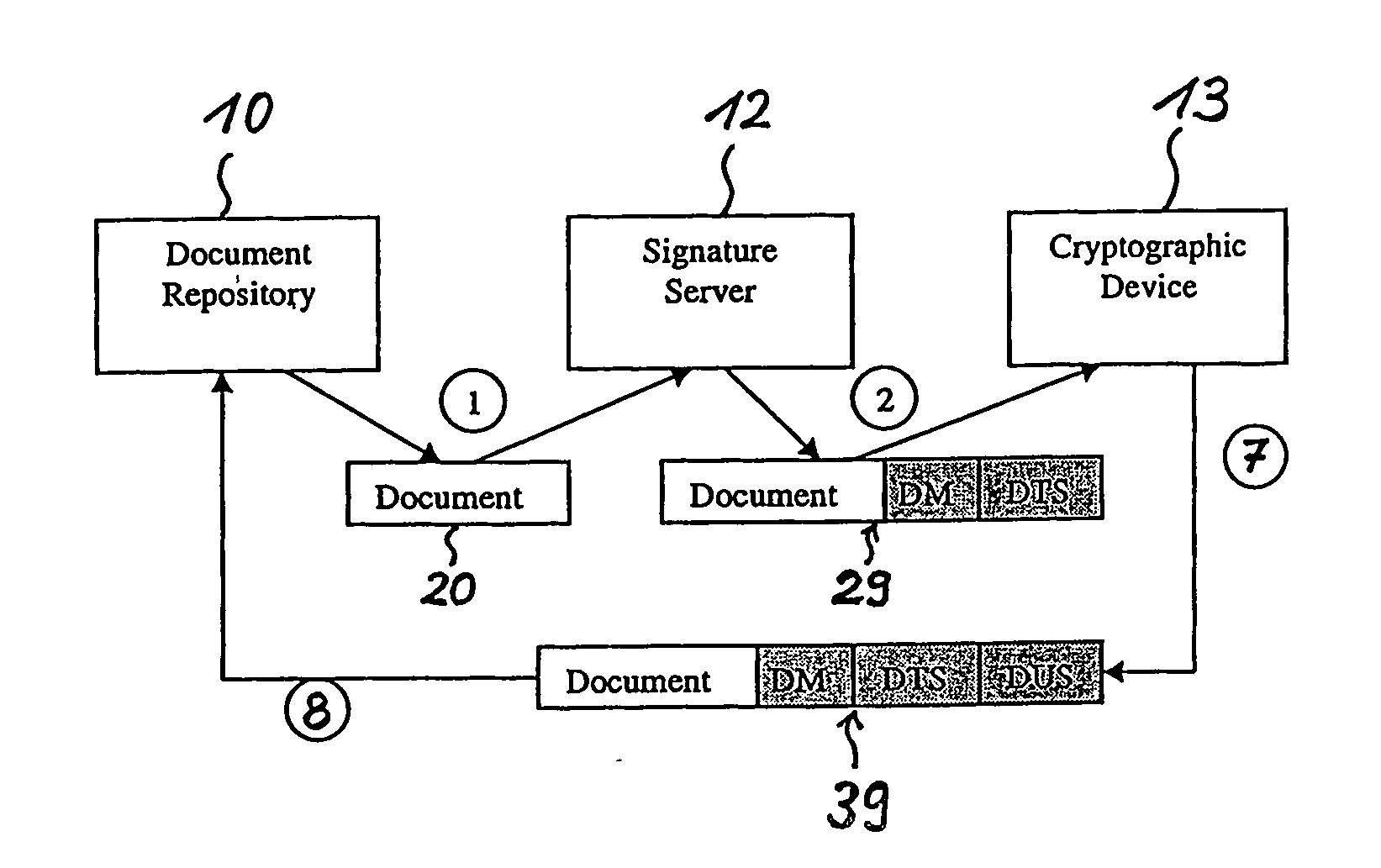
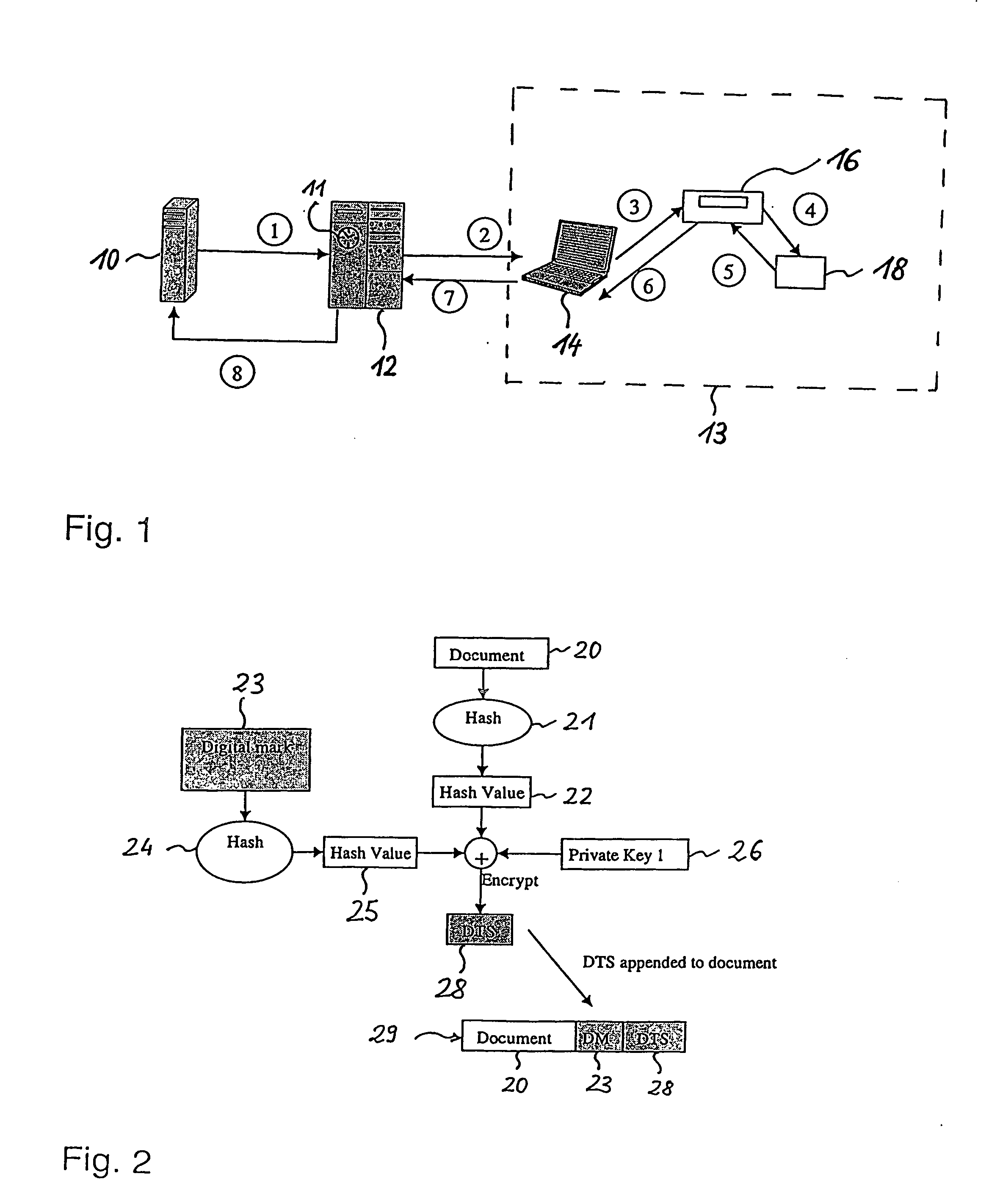
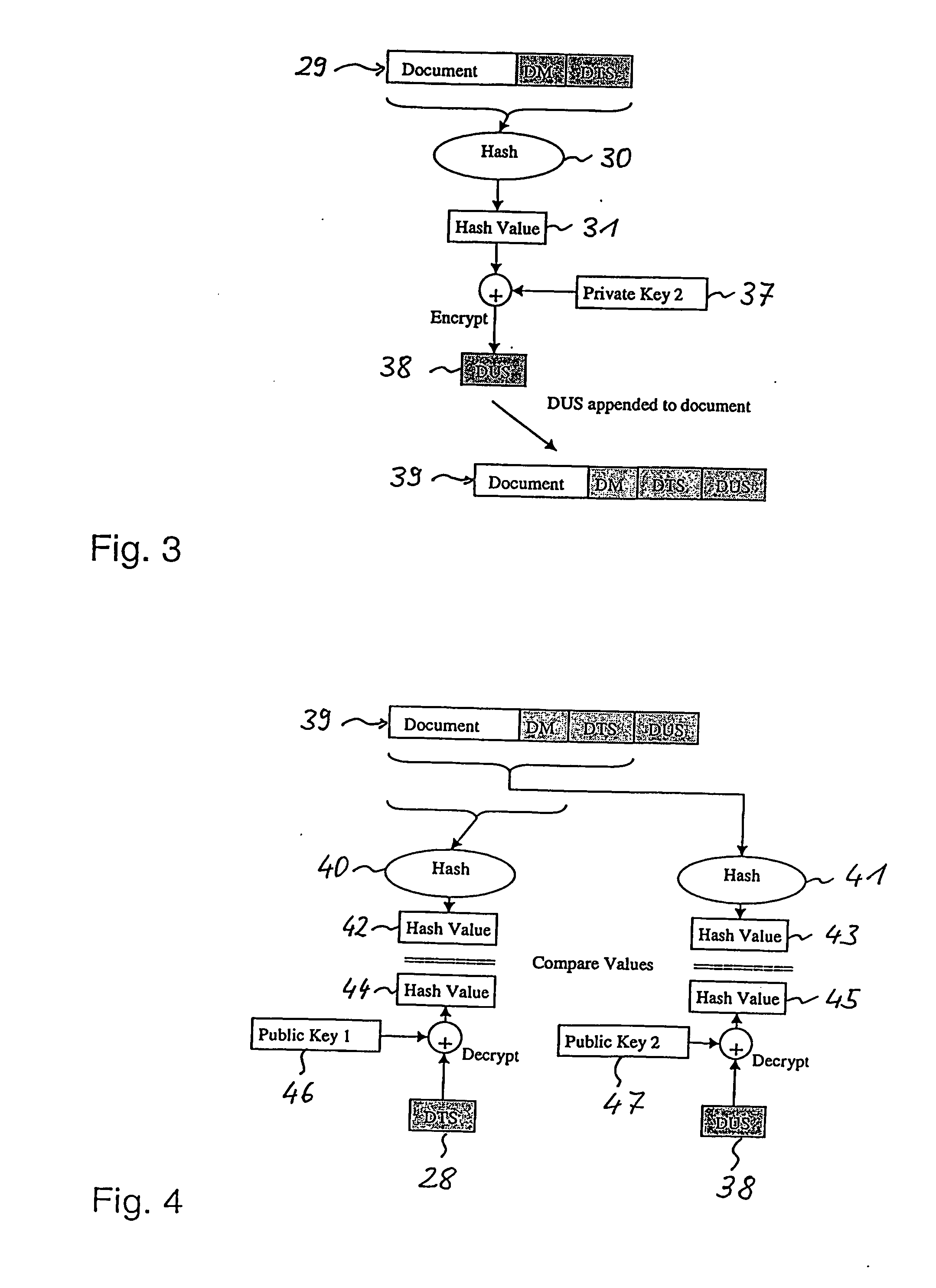
Long-term secure digital signatures
InactiveUS20060288216A1Less generationEasy key revocationUser identity/authority verificationDigital computer detailsElectronic documentKey size
The present invention relates to digitally signing of electronic documents which are to be kept secure for a very long time, thereby taking into account future cryptographic developments which could render current cryptographic key-lengths insufficient. In accordance with the invention a double signature is issued for each document. A first digital signature (DTS) ensures the long time security, whilst a second digital signature (DUS) ensures the involvement of an individual user. Thereby, the second digital signature is less computationally intensive in its generation than the first digital signature.
Owner:IBM CORP
Dual-mode variable key length cryptography system
InactiveUS20090103726A1More robustMore secureSynchronising transmission/receiving encryption devicesKey sizeTime transfer
Owner:LUCENT TECH INC
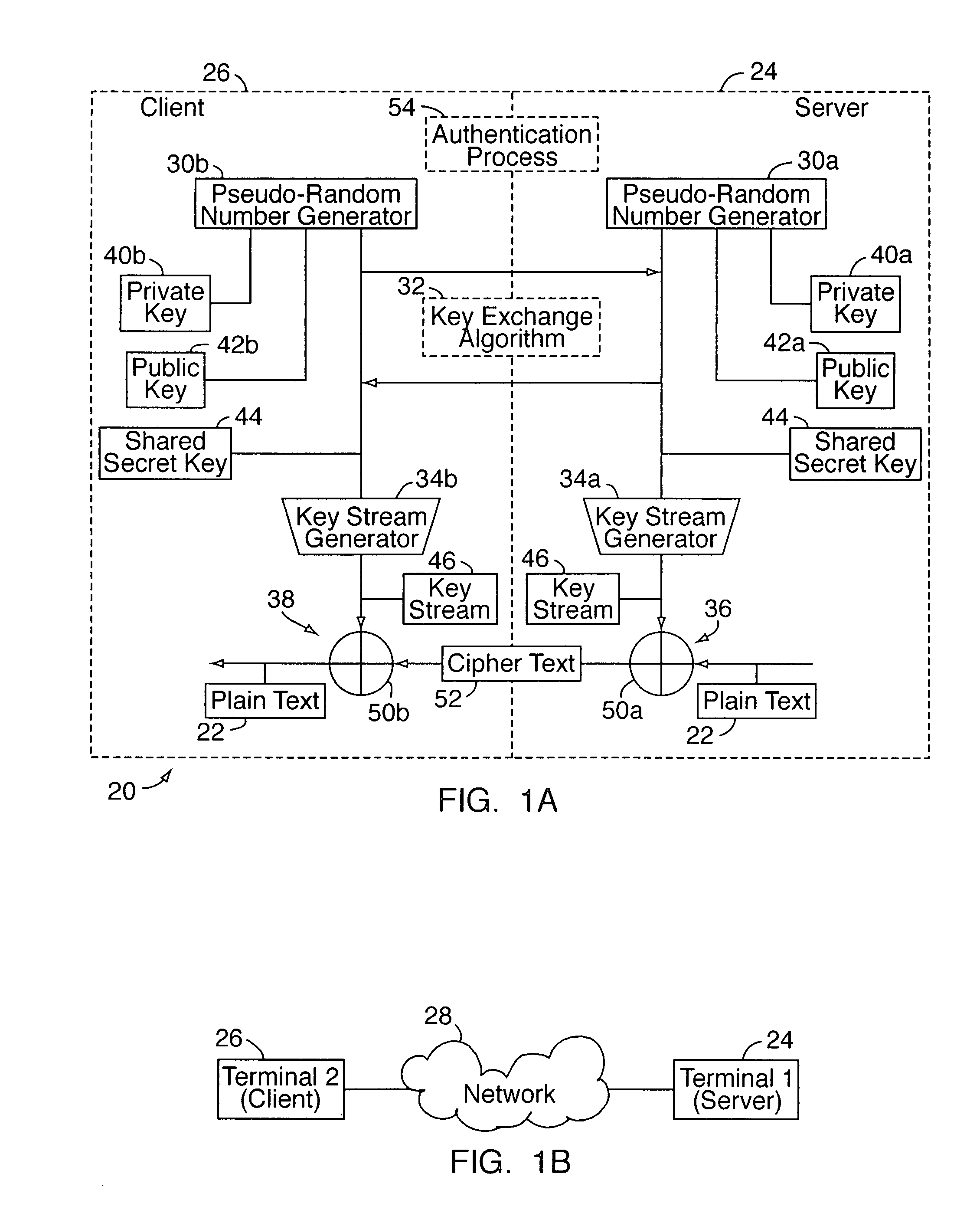
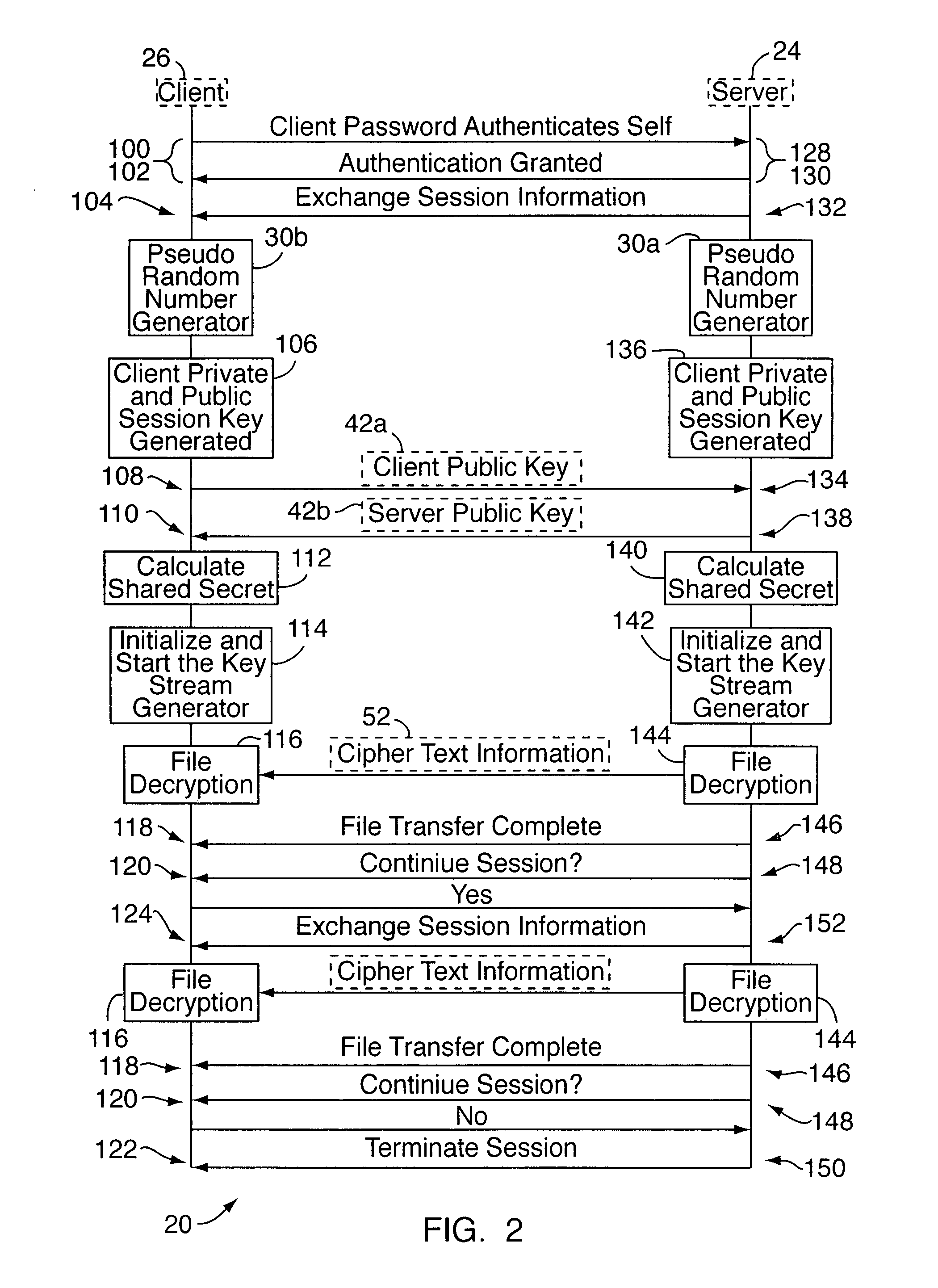
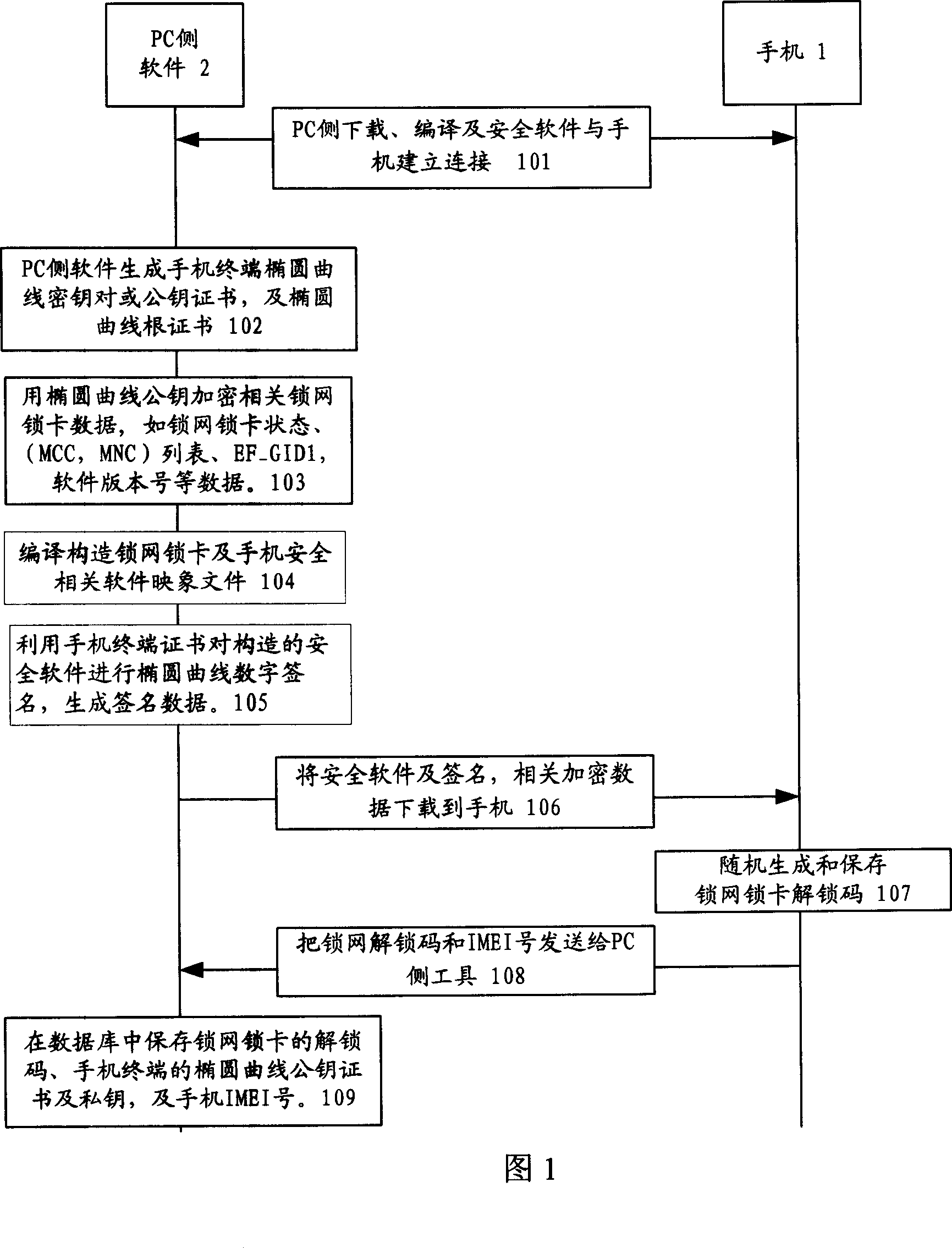
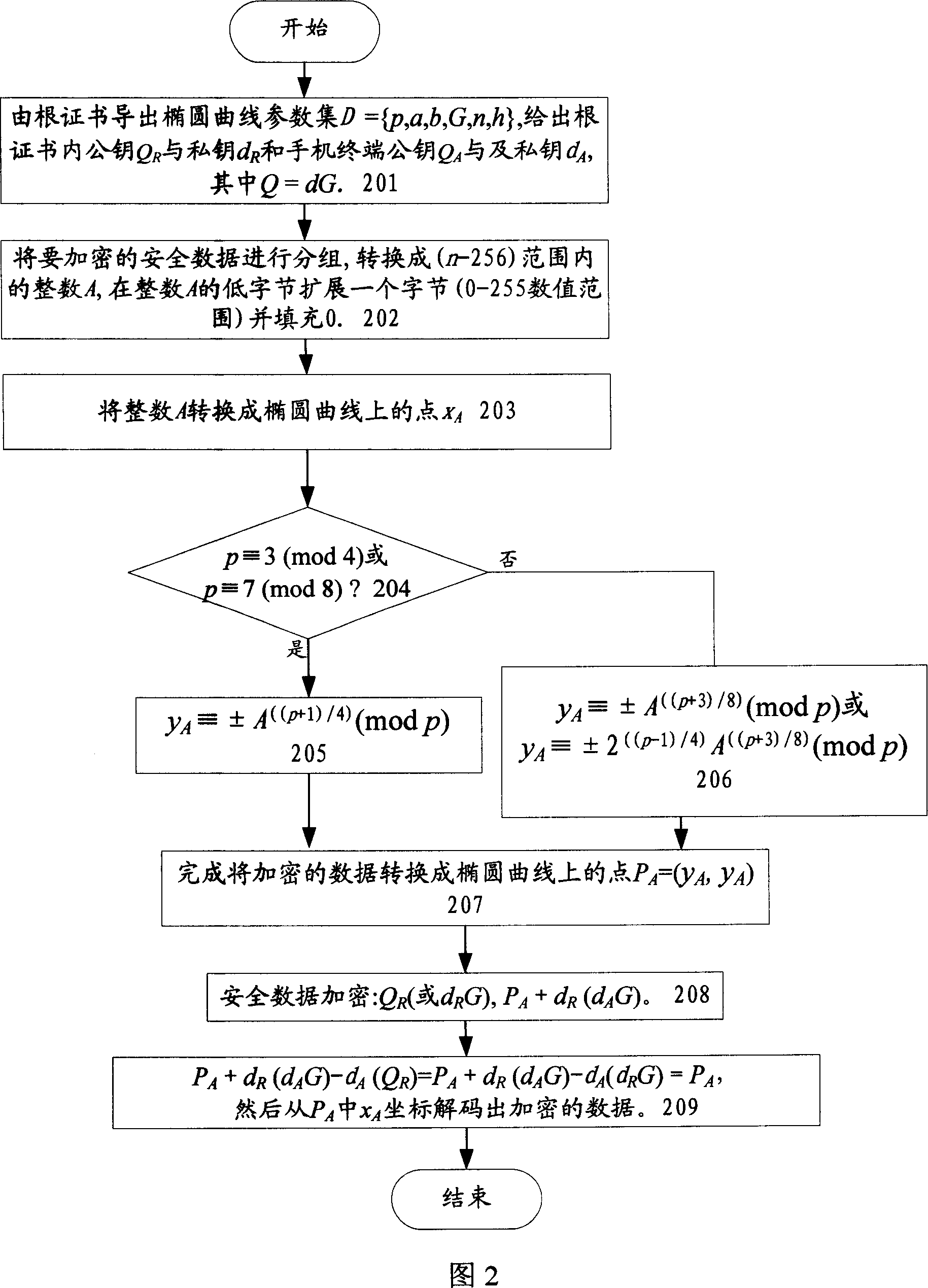
Radio terminal security network and card locking method based on the ellipse curve public key cipher
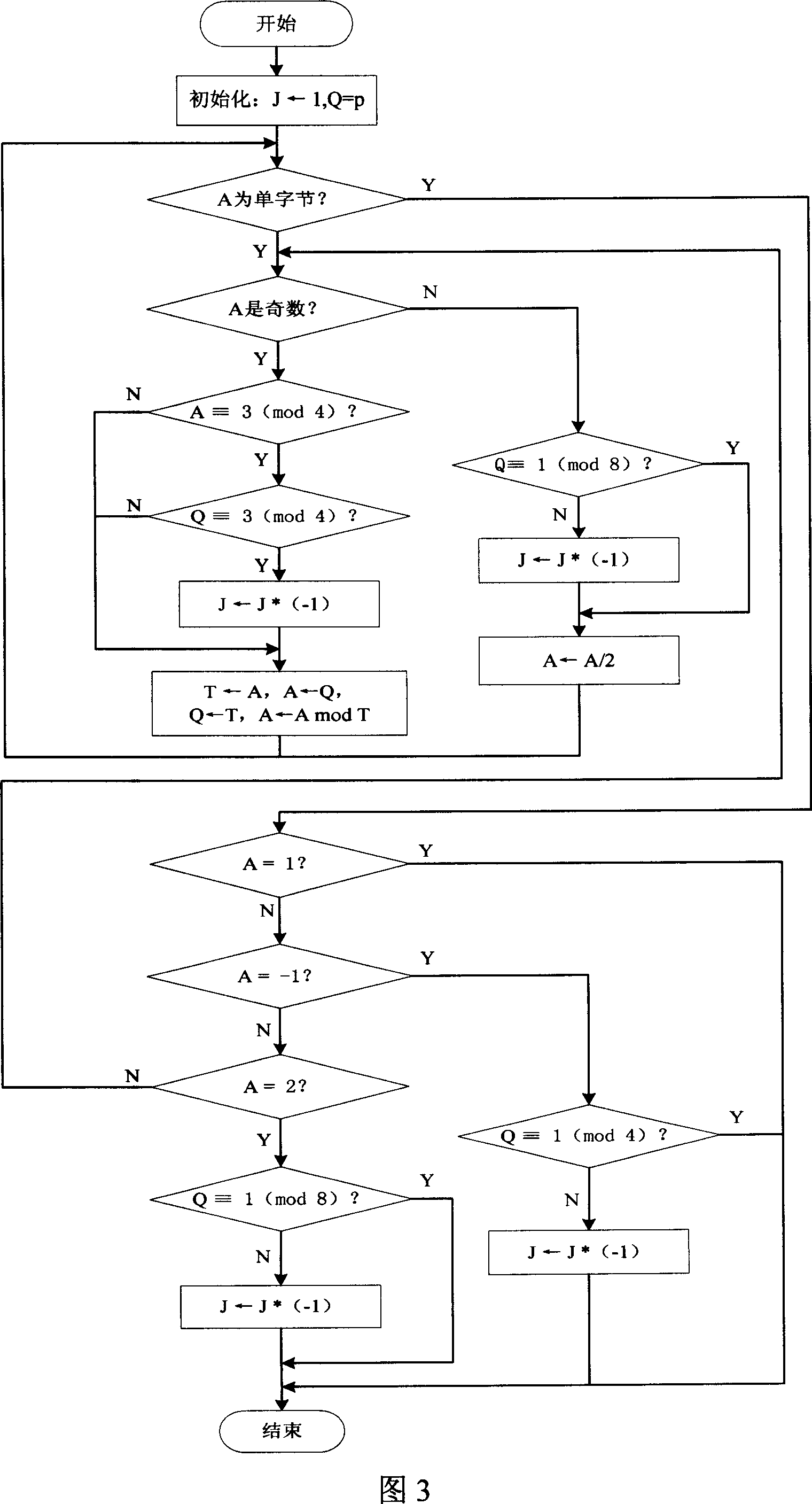
InactiveCN101018125AImprove securityProcessing speedPublic key for secure communicationUser identity/authority verificationKey sizeDigital signature
The related wireless terminal (1) security locking method based on elliptic curve public key cipher comprises: using elliptic curve public key certificate to form digital signature and private key to validate software during startup; deciding by software to provide network service according to current register and pre-set information or reading the IMSI number in user USIM / SIM card to compare with stored one and decide whether provide service. This invention synthesizes lots business, and special fit to terminal with common processing capacity.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
Generating keys having one of a number of key sizes
An apparatus is disclosed for generating keys having one of a number of key sizes. Memory sections of a memory element are adapted to store a portion of a key. The memory element has a size at least as large as a largest key size of a number of key sizes, the key having a size of one of the plurality of key sizes. Key generation logic is adapted to generate intermediate key results for the key by operating on values from the memory sections and from the intermediate key results. Key selection logic is adapted to route selected intermediate key results to selected ones of the memory sections. The control logic is adapted to determine the size of the key and, based at least partially on the size of the key, to select the selected intermediate key results and the selected ones of the memory sections. The selected intermediate key results comprise some or all of the key.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
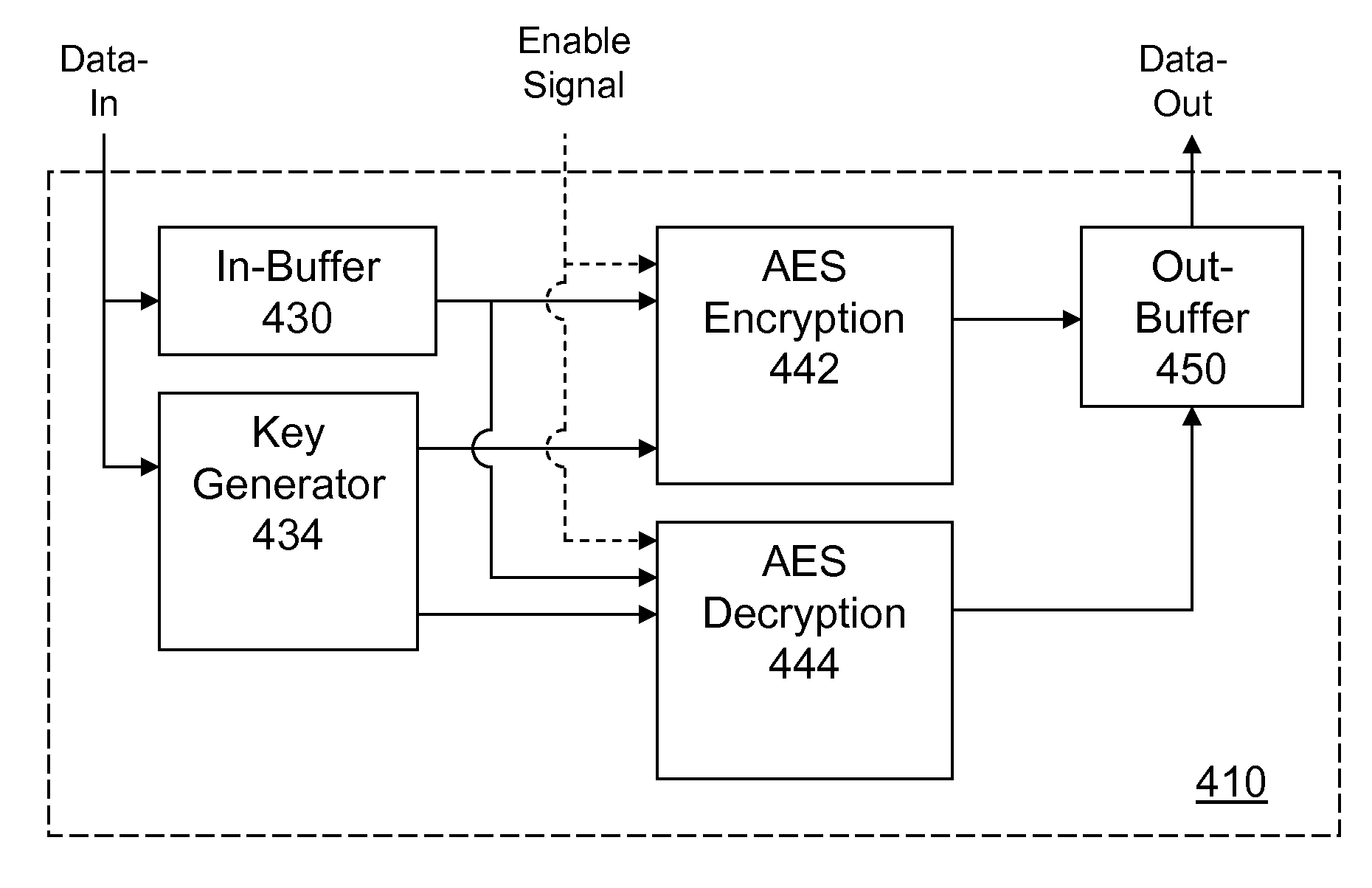
Portable Electronic Storage Devices with Hardware Security Based on Advanced Encryption Standard
InactiveUS20080192928A1Improve securityUnauthorized memory use protectionInternal/peripheral component protectionKey sizeAdvanced Encryption Standard
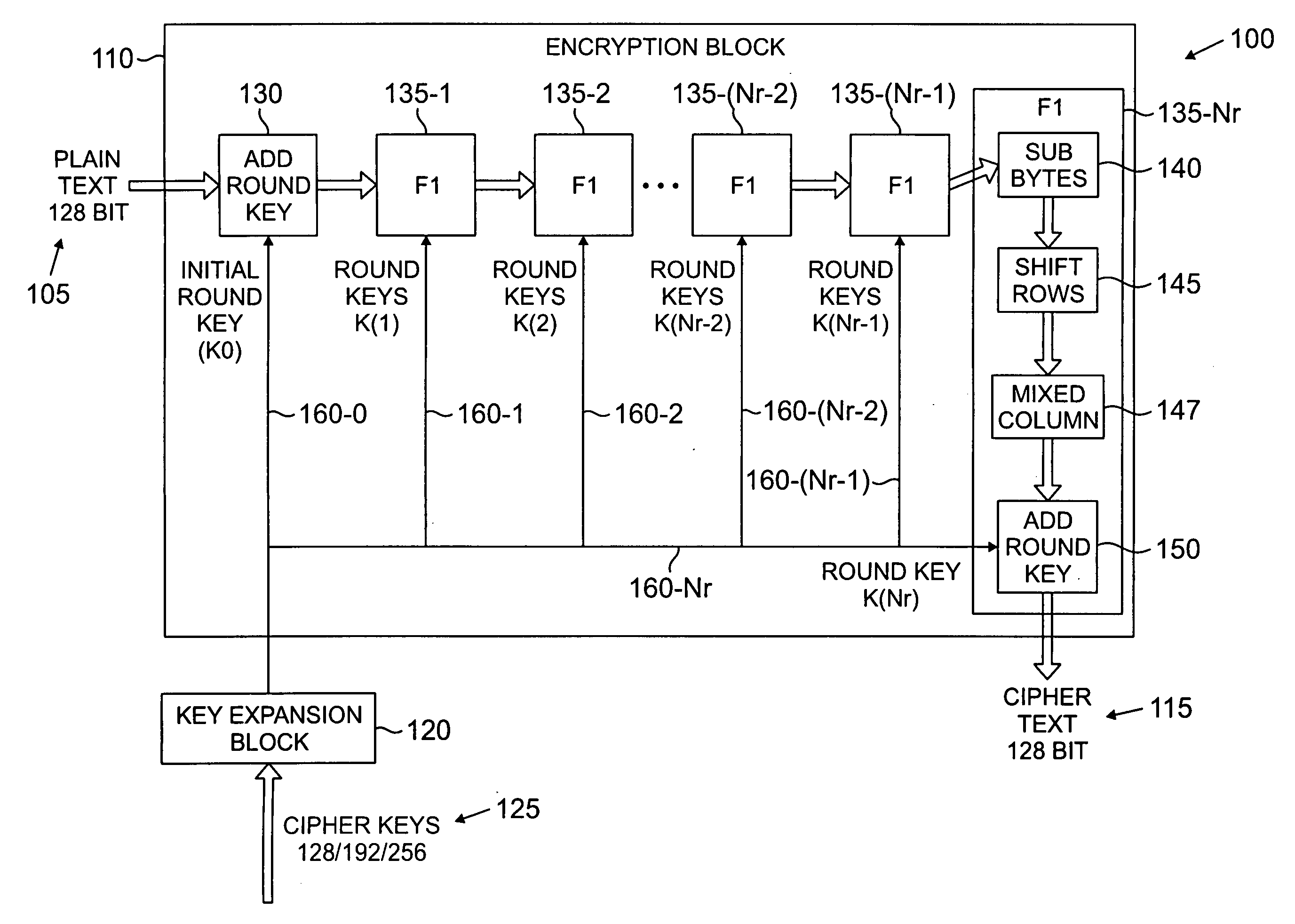
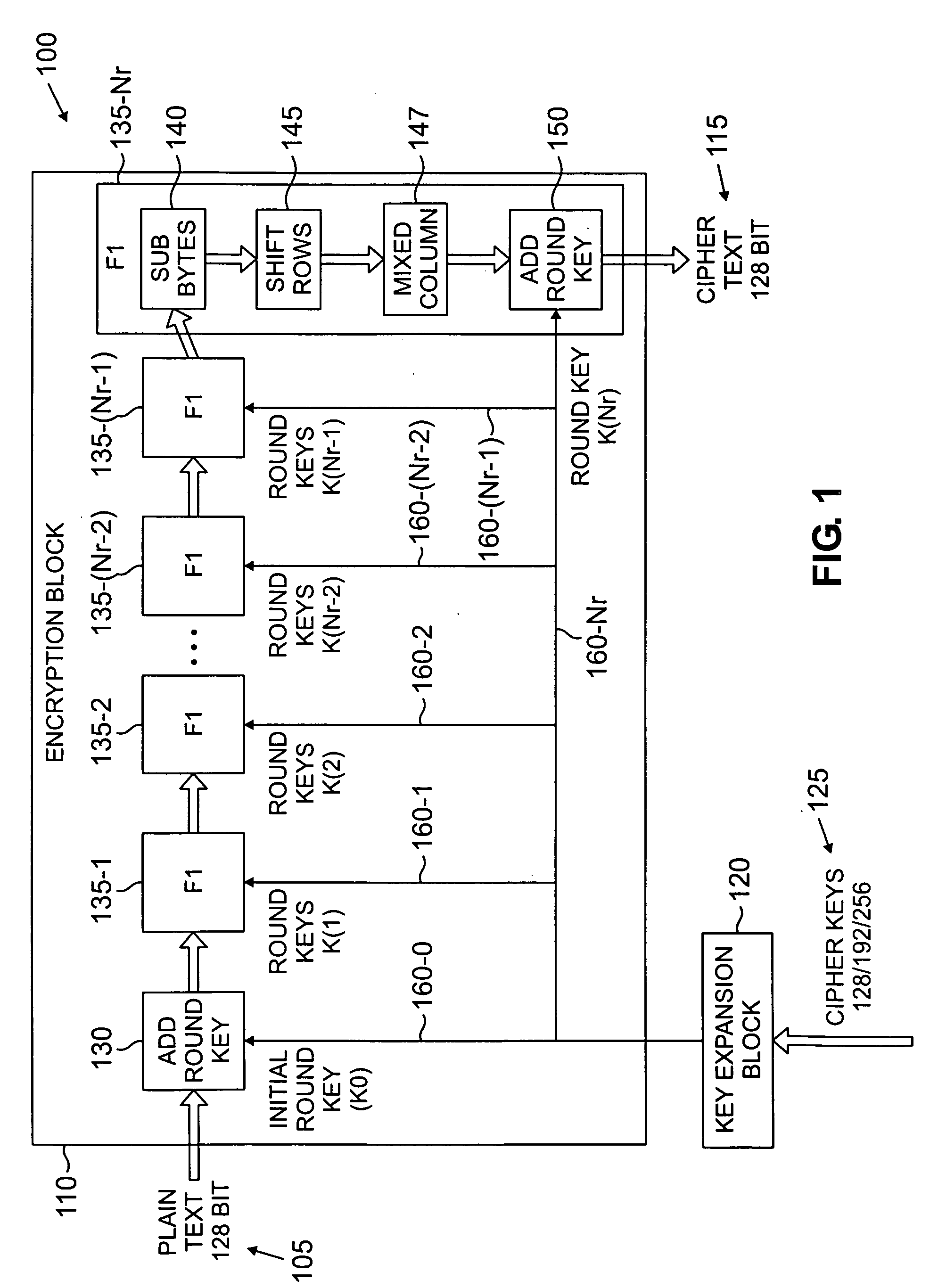
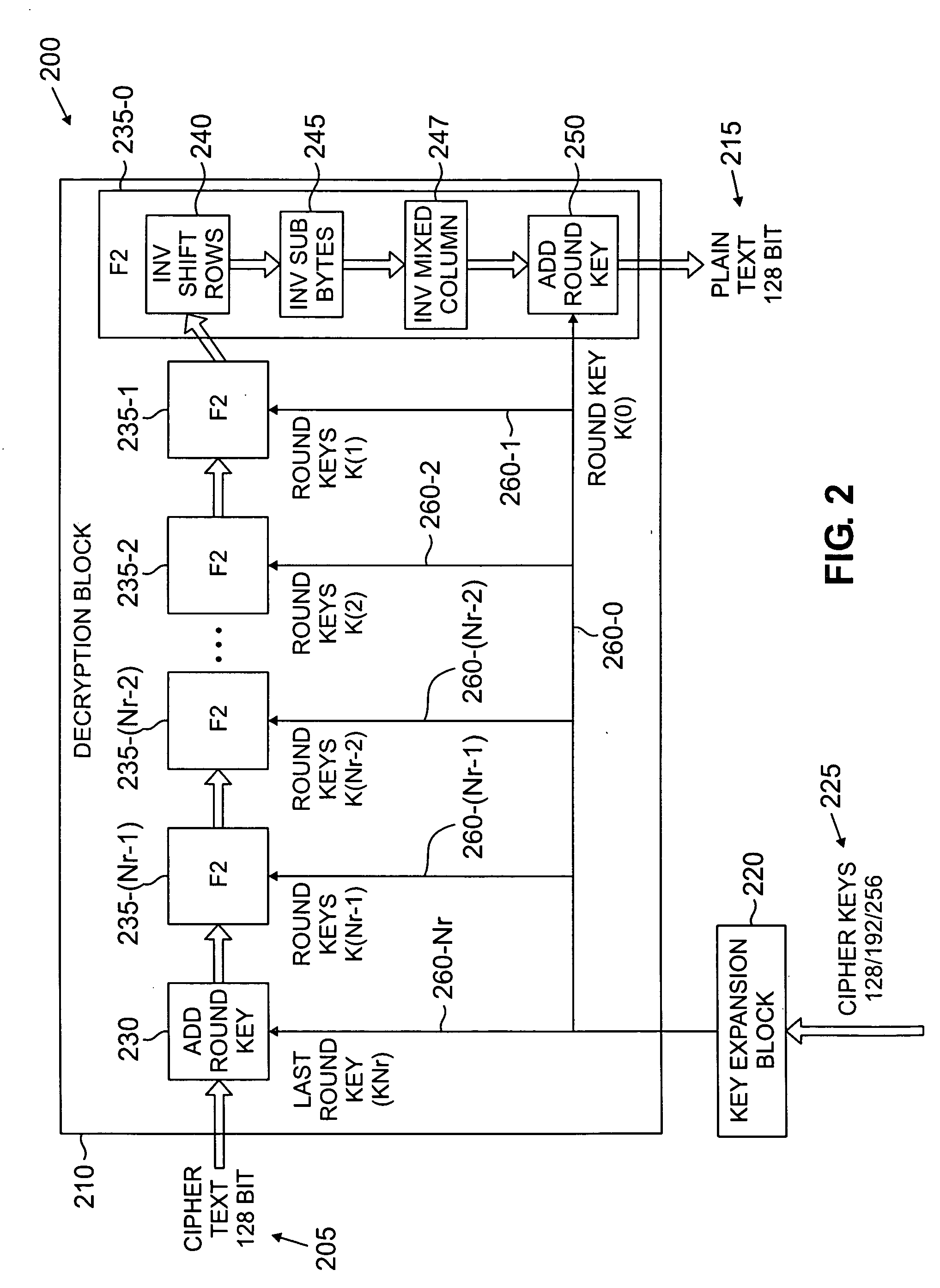
Portable electronic storage devices with hardware based security are described. According to one exemplary embodiment of the present invention, a portable electronic storage device (PESD) comprises a security engine integrated thereon. The security engine is configured to provide data encryption, data decryption, and encryption / decryption key (referred to as a key) generation according to a security standard (e.g., Advance Encryption Standard (AES)). AES is a symmetric encryption algorithm processing data in block of 128 bits. Under the influence of a key, a 128-bit data block is encrypted by transforming the data block in a unique way into a new data block of the same size. AES is symmetric sine the same key is used for encryption and the reverse transformation (i.e., decryption). The only secret necessary to keep for security is the key. AES may use different key-lengths (i.e., 128-bit, 192-bits and 256-bits).
Owner:SUPER TALENT ELECTRONICS
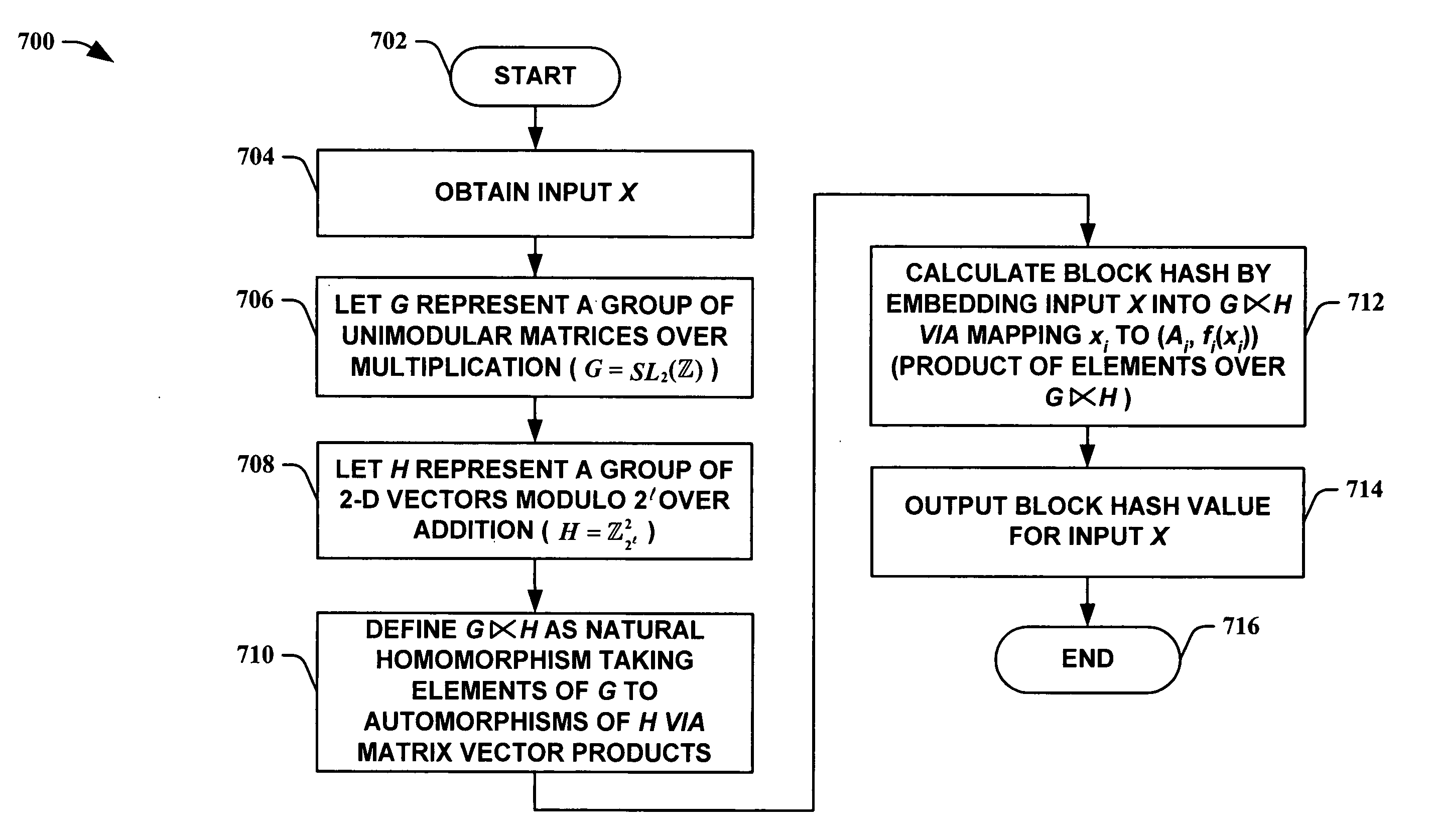
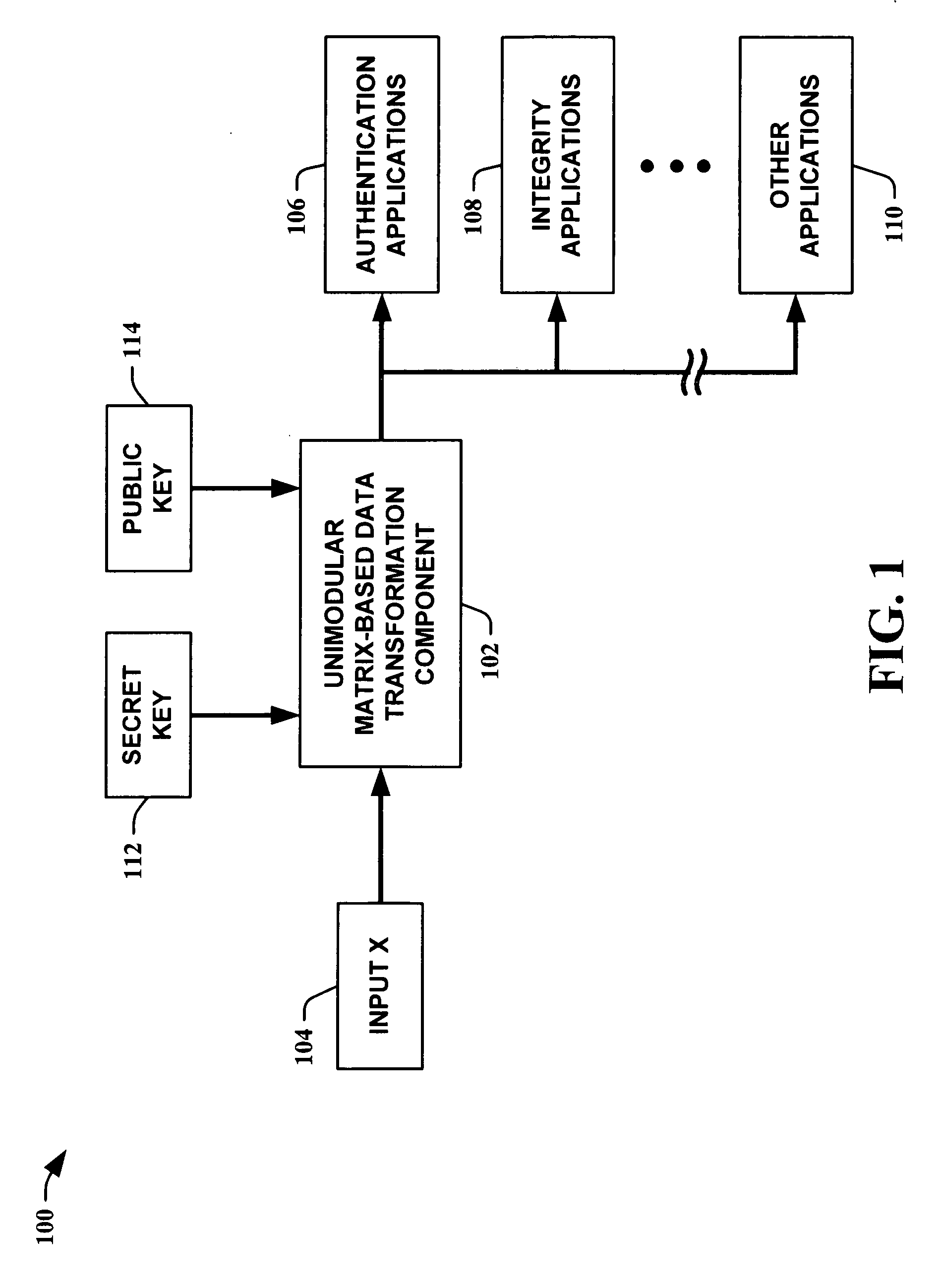
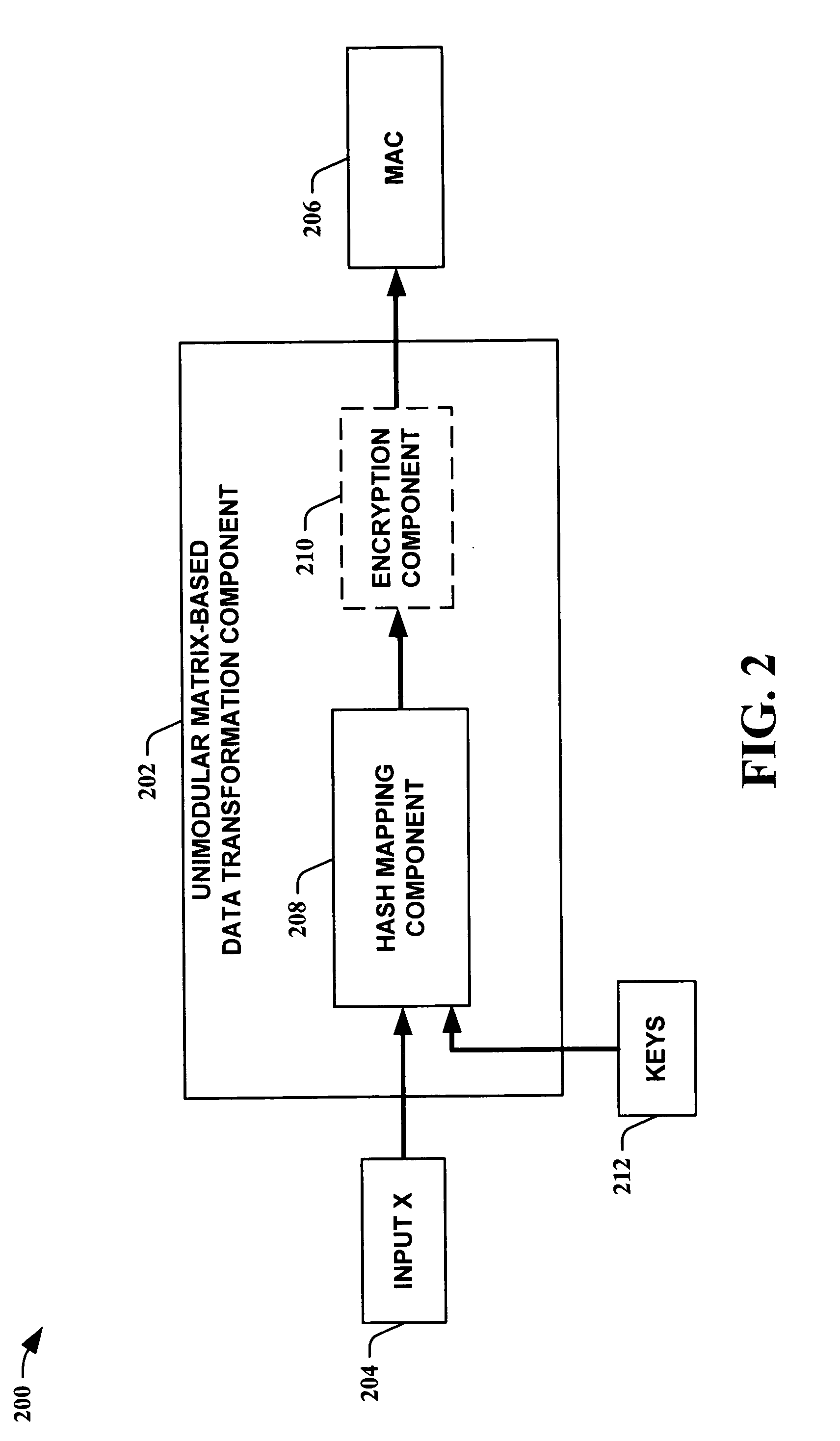
Unimodular matrix-based message authentication codes (MAC)
InactiveUS20050210260A1Improve speed performanceHigh performance hash value generationUser identity/authority verificationMemory systemsKey sizeUniversal hashing
The present invention leverages the invertibility of determinants of unimodular matrices to provide a universal hash function means with reversible properties and high speed performance. This provides, in one instance of the present invention, length controllable hash values comprised of vector pairs that can be processed as one instruction in a SIMD (single instruction, multiple data) equipped computational processor, where the vector pair is treated as a double word. The characteristics of the present invention permit its utilization in streaming cipher applications by providing key data to seed the ciphering process. Additionally, the present invention can utilize smaller key lengths than comparable mechanisms via inter-block chaining, can be utilized to double hash values via performing independent hash processes in parallel, and can be employed in applications, such as data integrity schemes, that require its unique processing characteristics.
Owner:MICROSOFT TECH LICENSING LLC
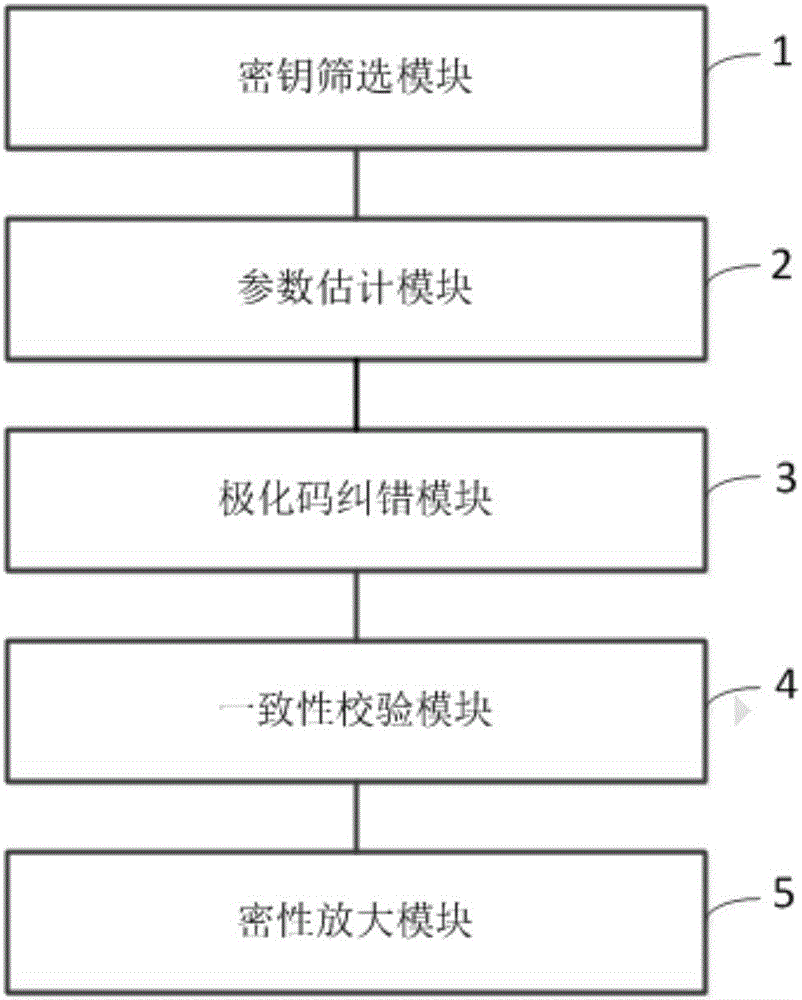
Quantum key distribution after-treatment system and method based on polar code correction
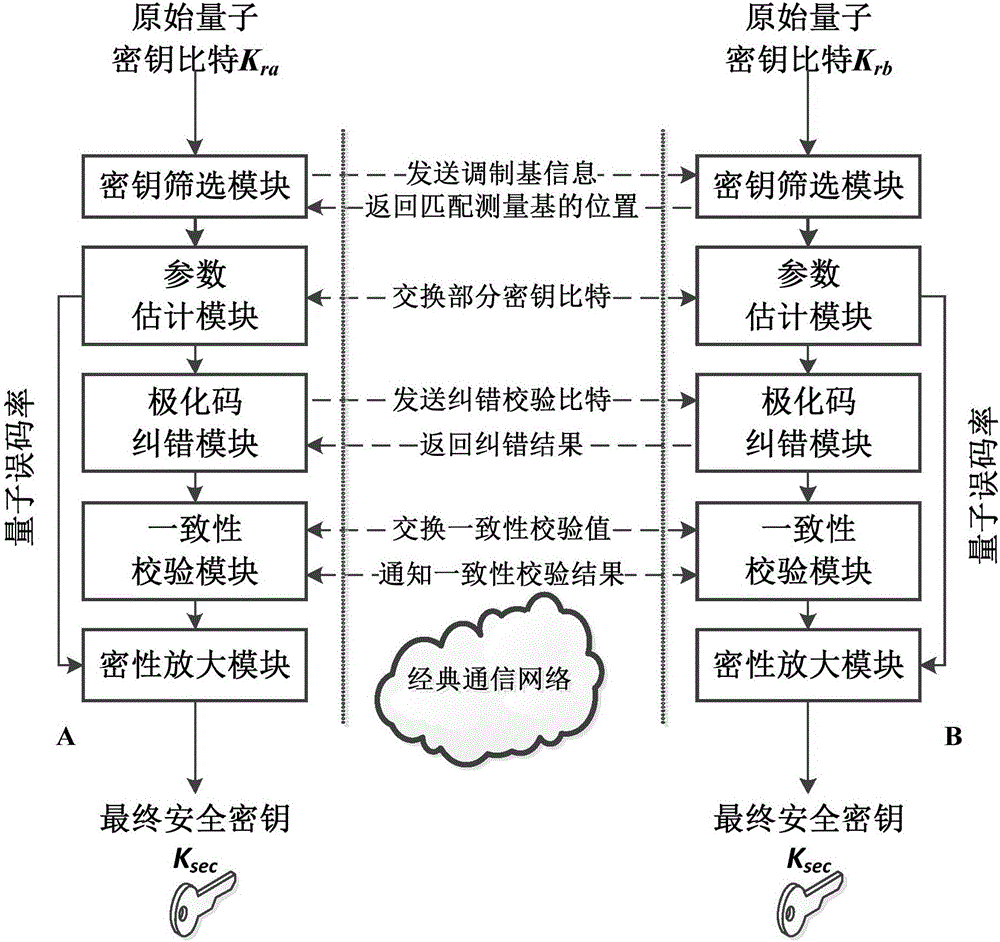
ActiveCN106161012AIncrease spawn rateImprove post-processing speedKey distribution for secure communicationLinear codingTime delays
The invention discloses a quantum key distribution after-treatment system and a quantum key distribution after-treatment method based on polar code correction. The system comprises a key screening module, a parameter estimation module, a polar code correction module, a consistency verification module and a privacy amplification module which are connected in sequence. The method comprises the following steps: only keeping original keys with the same base selection to form screening keys after quantum bite information is transmitted on a quantum channel; commonly selecting partial key bits from the screening keys to perform disclosed comparison; coding and decoding undisclosed key bits by adopting a system polar code algorithm under the condition that the quantum bit error rate is not higher than a safety threshold value; verifying the consistence of the corrected quantum keys by adopting cryptographic algorithm; and calculating safety information entropy and performing information compression to obtain absolutely safe key bits. The quantum key distribution after-treatment system has linear coding / decoding complexity characteristics, so that the after-treatment time delay and key length increase have linear relationship, and the after-treatment speed is improved.
Owner:JINAN UNIVERSITY
Credible data access control method applied to cloud storage of mobile devices
ActiveCN103763315AReduce the amount of data interactionConfidenceTransmissionCryptographic key generationKey size
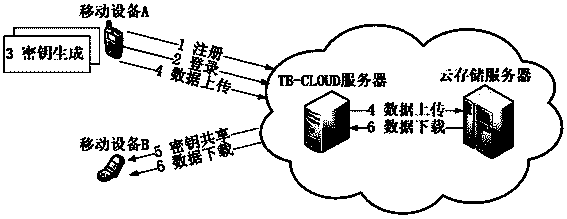
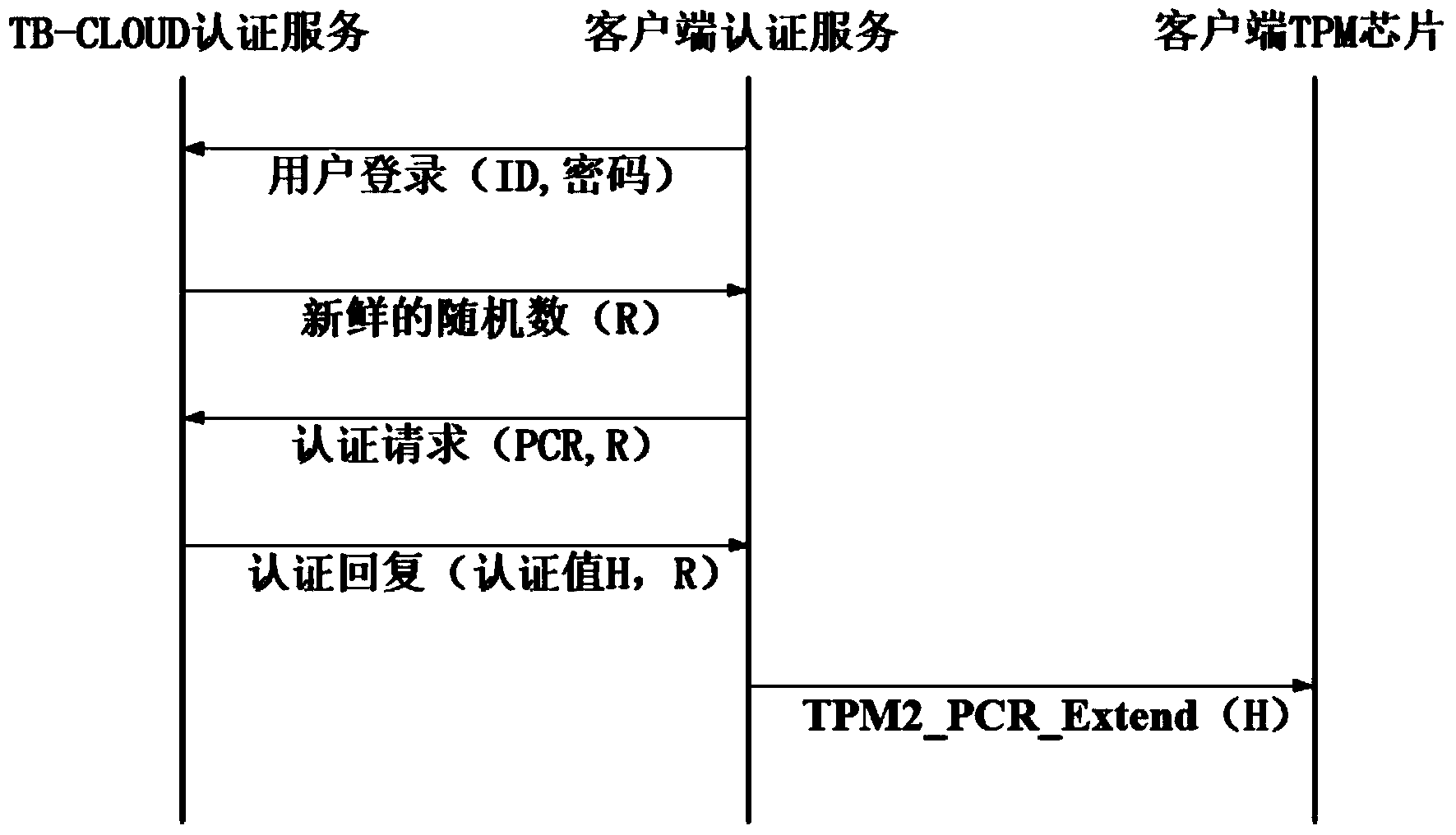
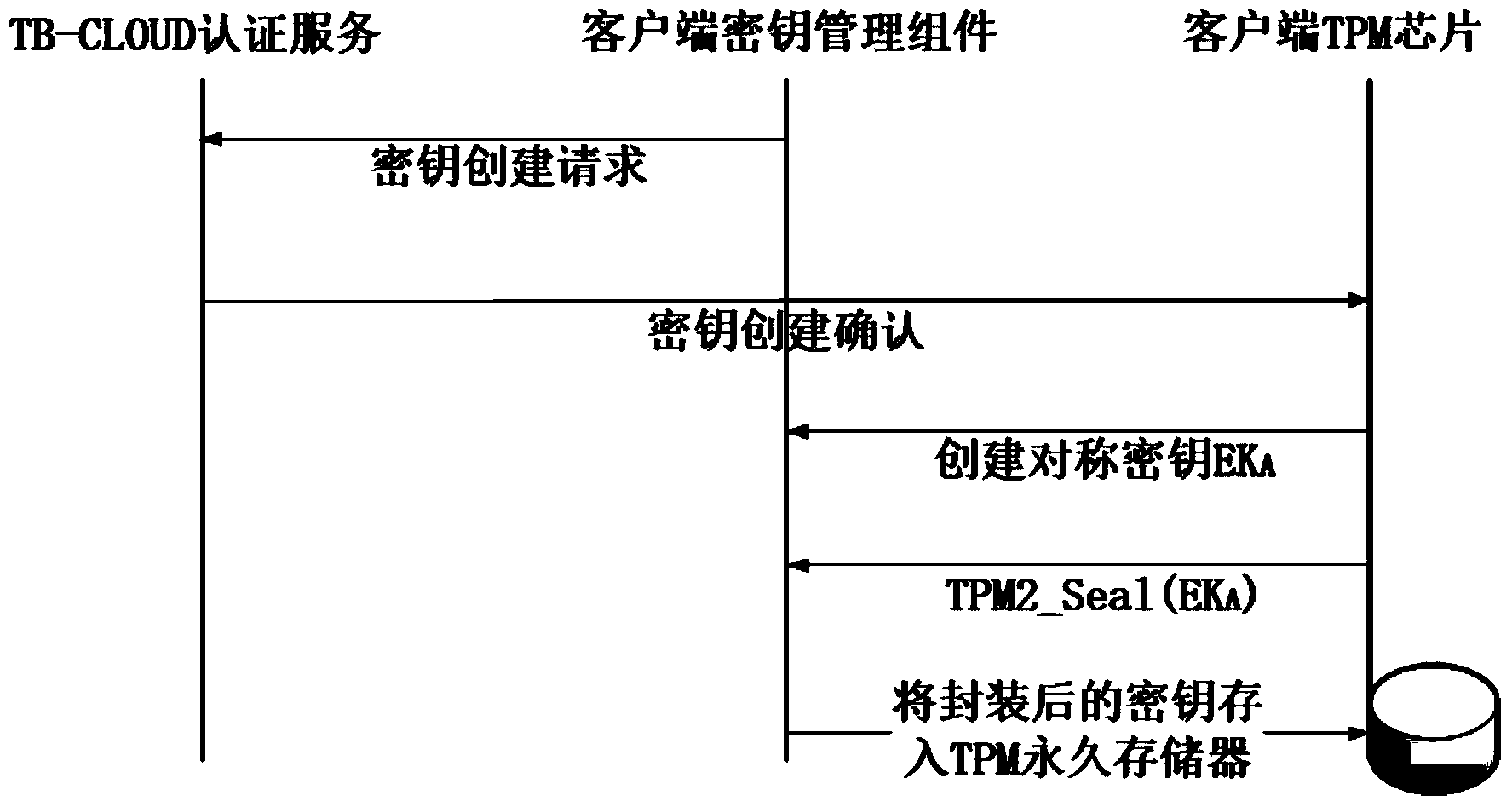
The invention relates to a credible data access control method applied to cloud storage of mobile devices. The credible data access control method includes six steps including user registering, user login, secret key generation, data encryption uploading, data downloading and decryption in three stages. The first step is user registering, the second step is user login with an authentication process, the third step is encryption secret key generation, the fourth step is user data encryption uploading, the fifth step is secret key sharing among the multiple mobile devices, and the sixth step is data downloading and decryption. According to the credible data access control method, transmitting of a credible chain in the secret key exchanging process is guaranteed by a user through a mobile TPM chip, the length of a secret key is reduced through encryption based on a elliptic curve, it is guaranteed that the multiple mobile devices can safely share the secret key, compared with a traditional server terminal or client terminal data encryption method provided by a cloud storage service provider, the credible data access control method is safe, reliable, high in confidence degree and small in interaction data amount, and the good practical value and the wide application prospect are achieved in the technical field of cloud storage safety.
Owner:BEIHANG UNIV
Method for achieving lightweight authentication and key agreement
InactiveCN103560879AReduce data volumeReduce occupancyUser identity/authority verificationKey sizeInternet of Things
The invention relates to a method for achieving lightweight authentication and key agreement. A long-term shared key K is preset between any two network nodes, a counter CTR is stored in each network node, the encryption algorithm E and the PRNG are achieved in the two network nodes, and an authentication and shared key is built between the two network nodes. The method solves the problem that the existing network authentication technology and the existing key agreement technology are not suitable for the resource-constrained communication environment, and can be efficiently and safely suitable for the Internet of Things or the mobile communication network with a large number of resource-constrained nodes. According to the method, the symmetric cryptography algorithm is used only by four times in the authentication and key agreement process, the lightweight grouping symmetric cryptography algorithm can be used, the length of the required key is small, the encryption and decryption speed is high, bi-directional authentication of the authentication process can be completed only through two times of information interaction, the communication data size is small, and occupied network resources are few.
Owner:INST OF INFORMATION ENG CAS
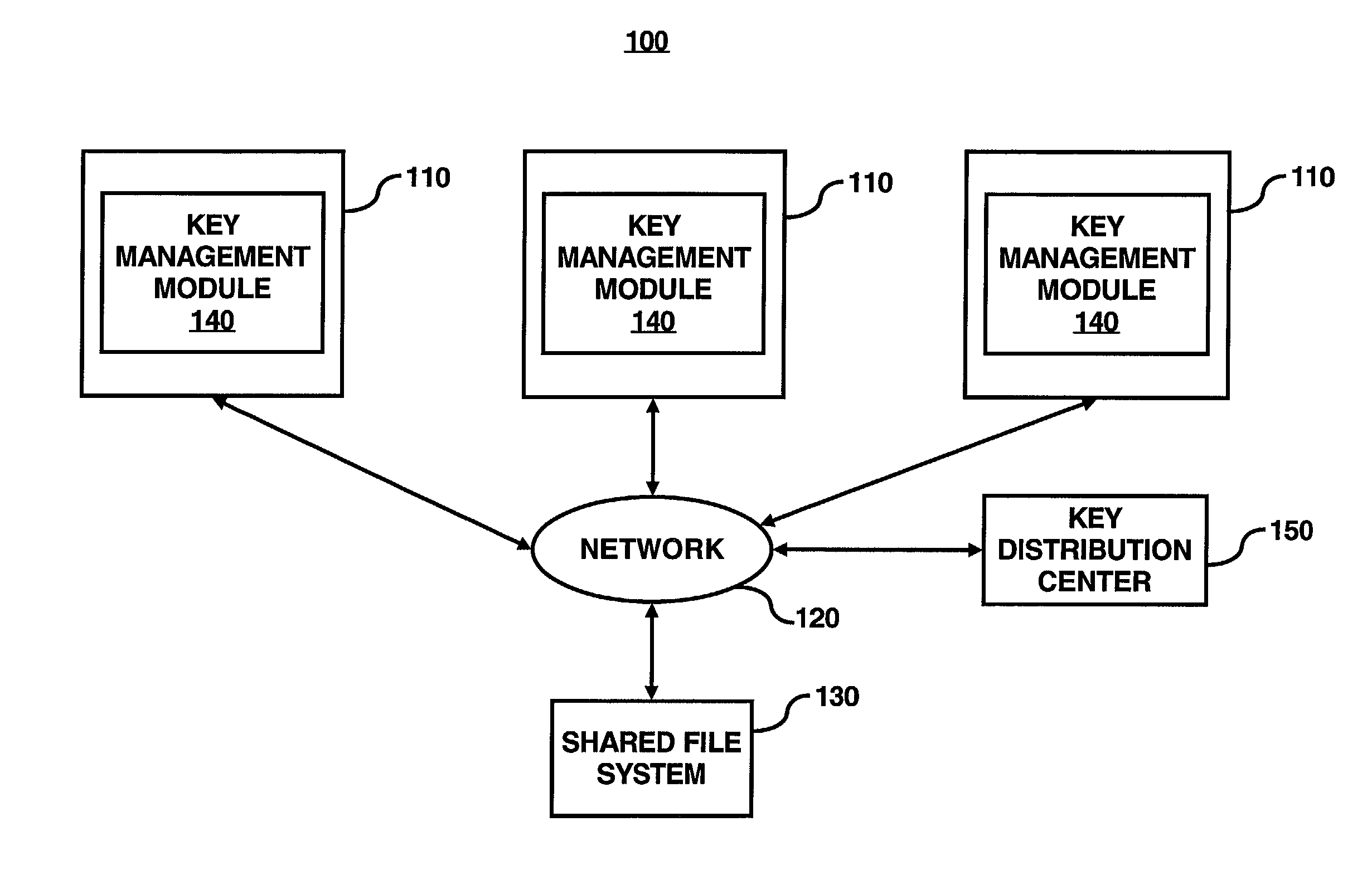
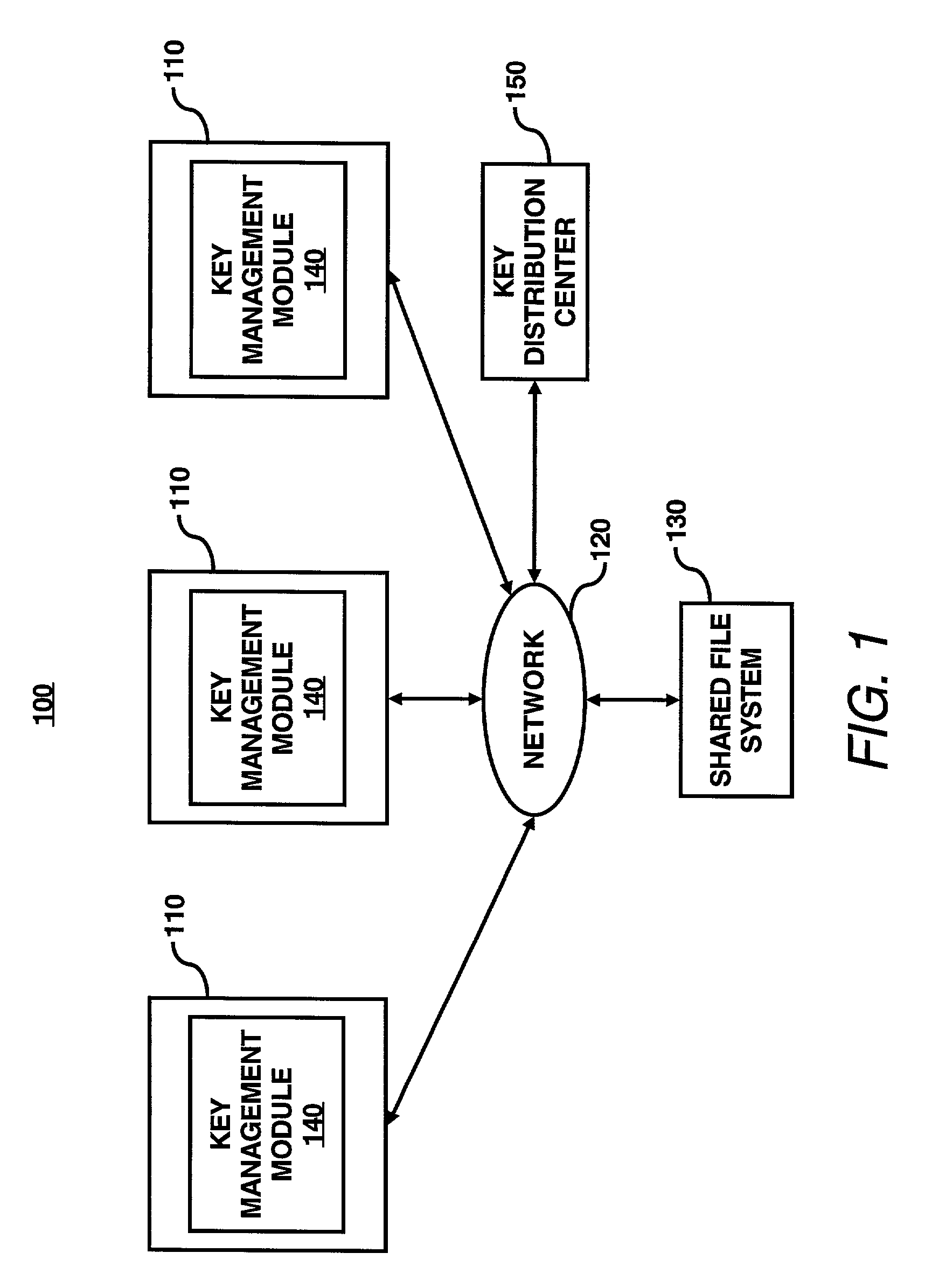
System for encrypted file storage optimization via differentiated key lengths
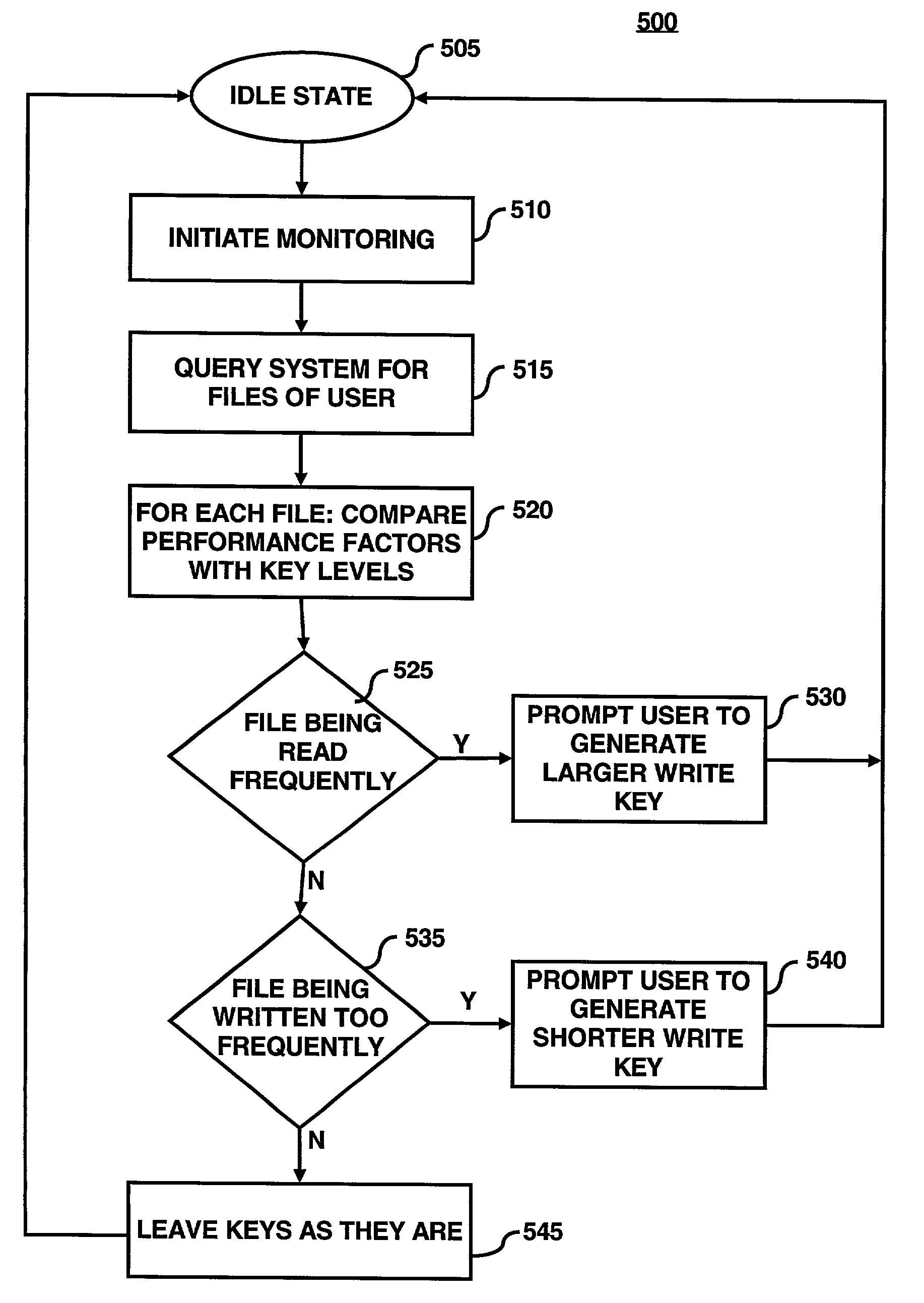
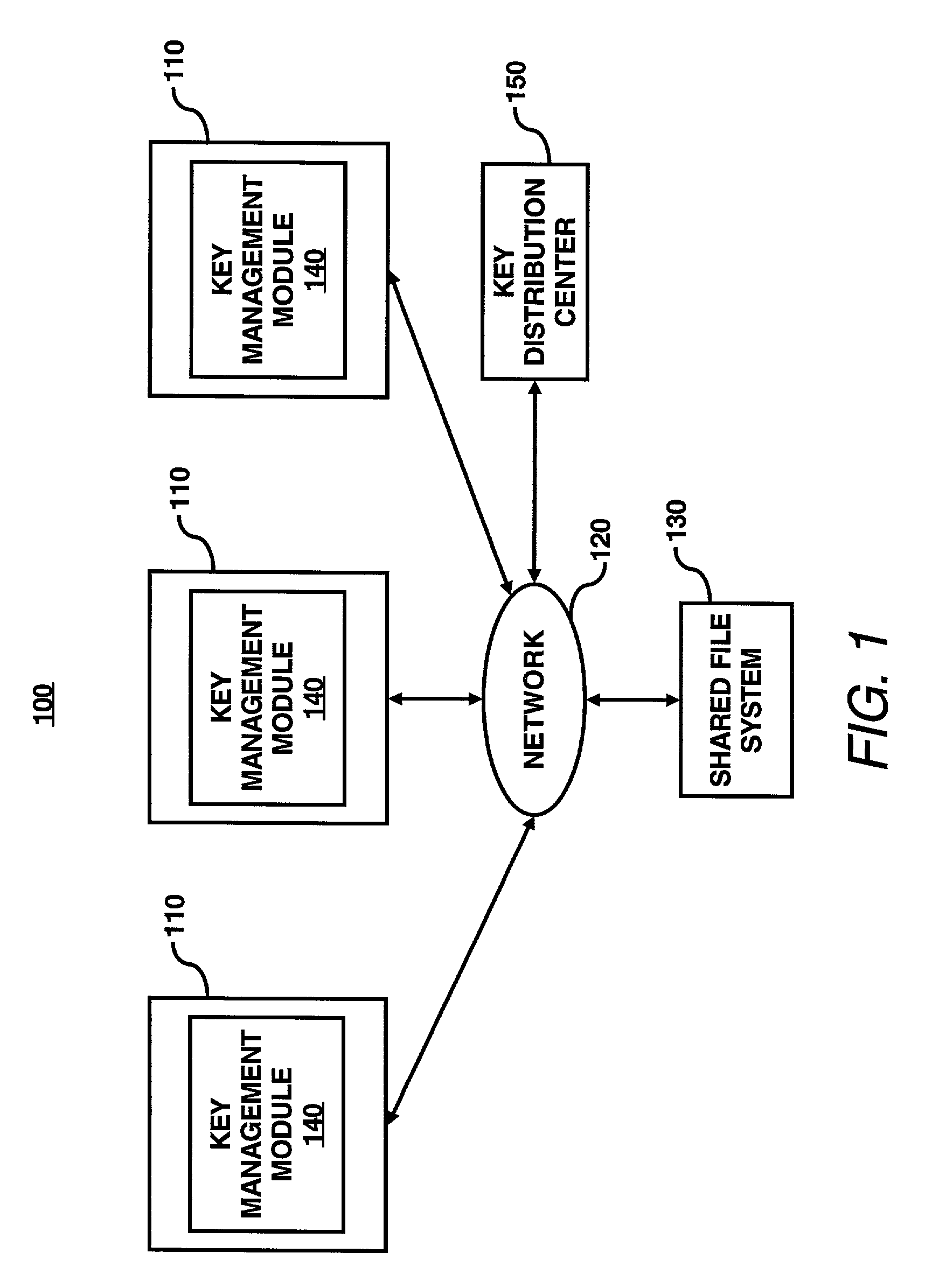
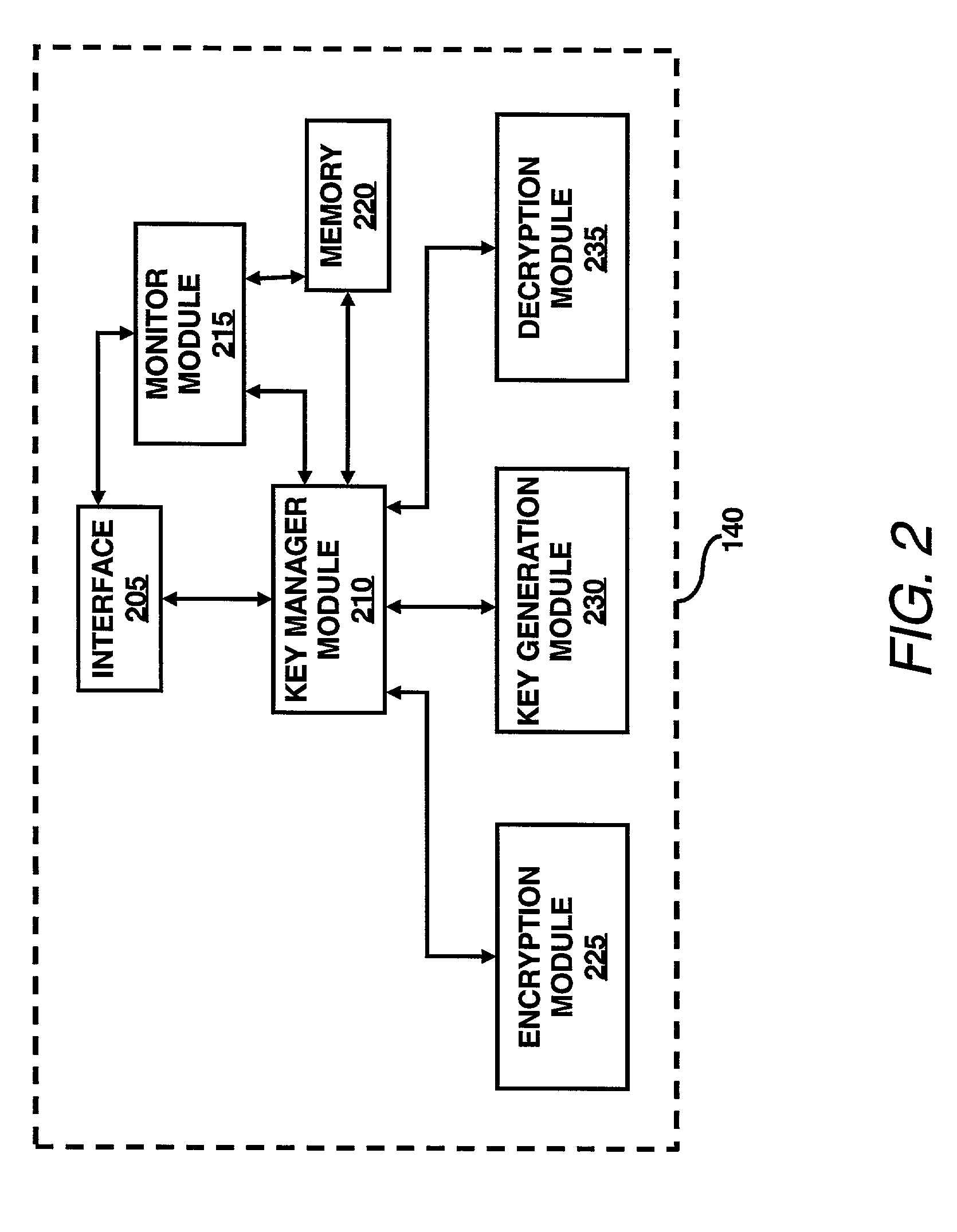
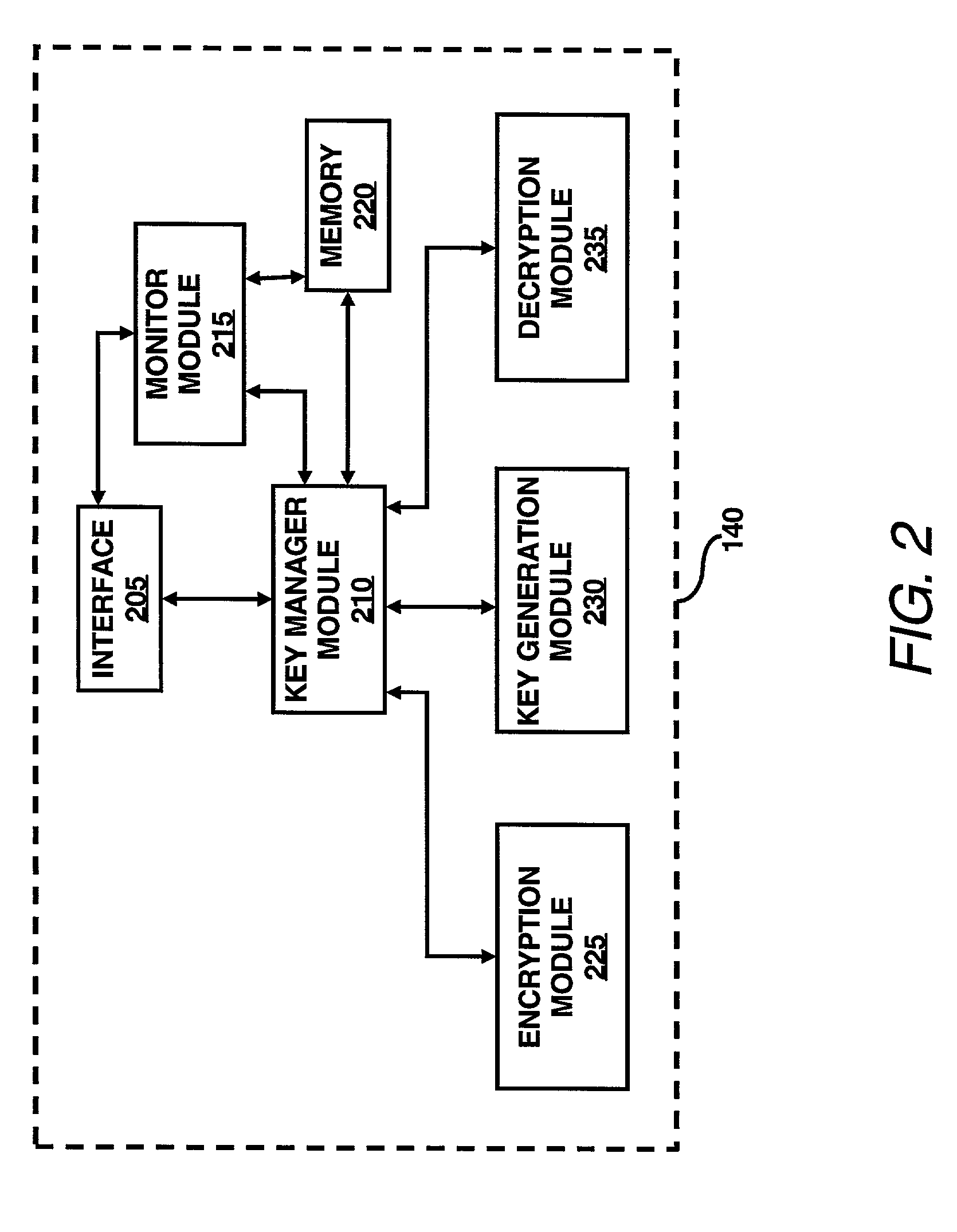
InactiveUS7003116B2Improve system efficiencyImprove efficiencyKey distribution for secure communicationComputer security arrangementsKey sizeAccess frequency
A key management module is utilized to improve efficiency in cryptographic systems. The key management module may monitor file usage and recommend (and / or implement) key pair changes. In particular, the key management module may be configured to periodically examine (or analyze) performance parameters (e.g., number of times written, number of times read, etc.) associated with a user's files. A network monitor module may be configured to gather and maintain records of the associated performance parameters. The key management module may be further configured to compare the performance parameters of a given file with a table of key level ranges. The table of key lengths may be configured to provide a listing of multiple key lengths, each key length corresponding to an activity level of a performance parameter, e.g., relative read / write access frequency. The key management module may recommend changing the relative length of the read and write keys based on the comparison of the performance parameters with the table of key level ranges.
Owner:HEWLETT PACKARD DEV CO LP
System and method for providing dynamically authorized access to functionality present on an integrated circuit chip
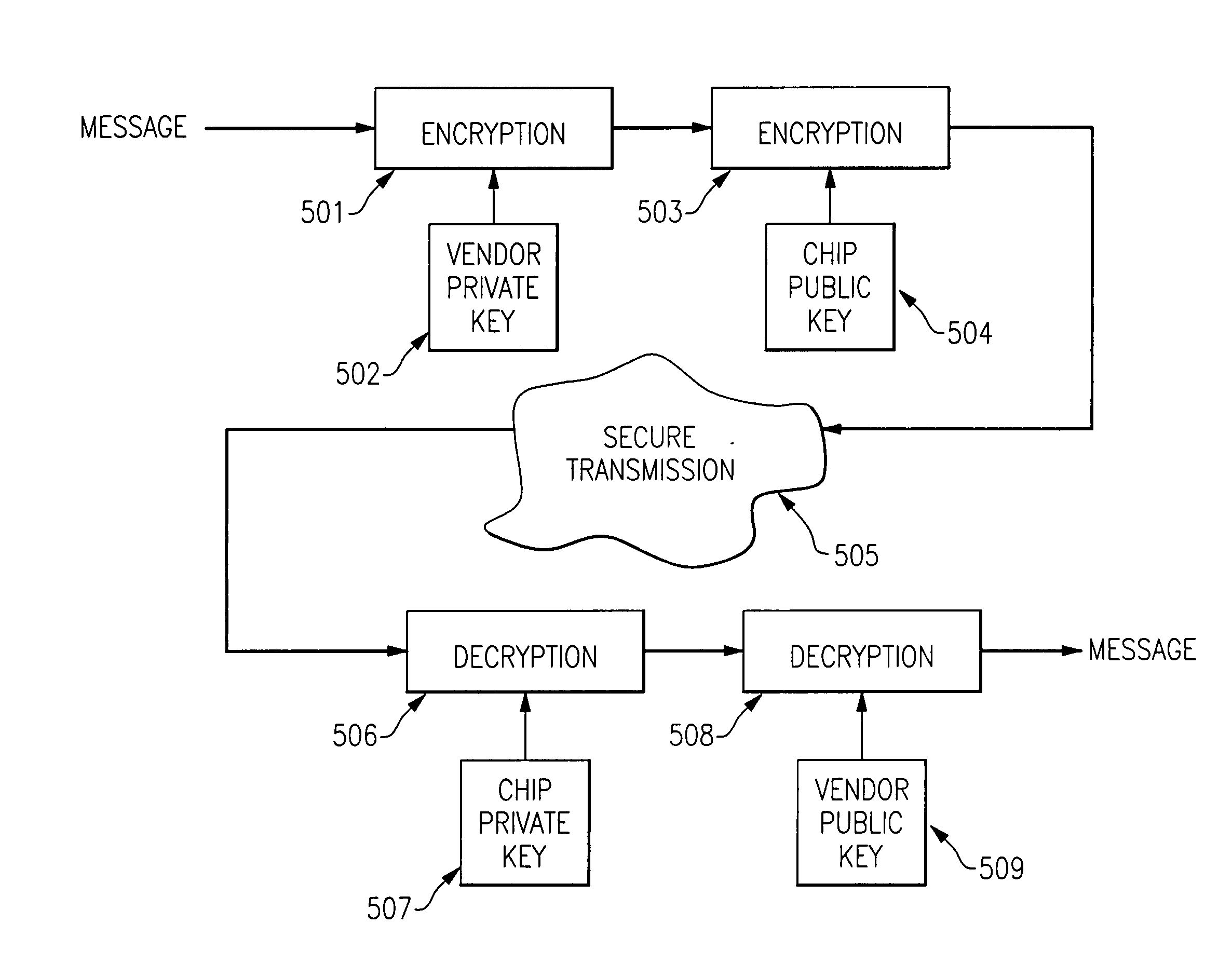
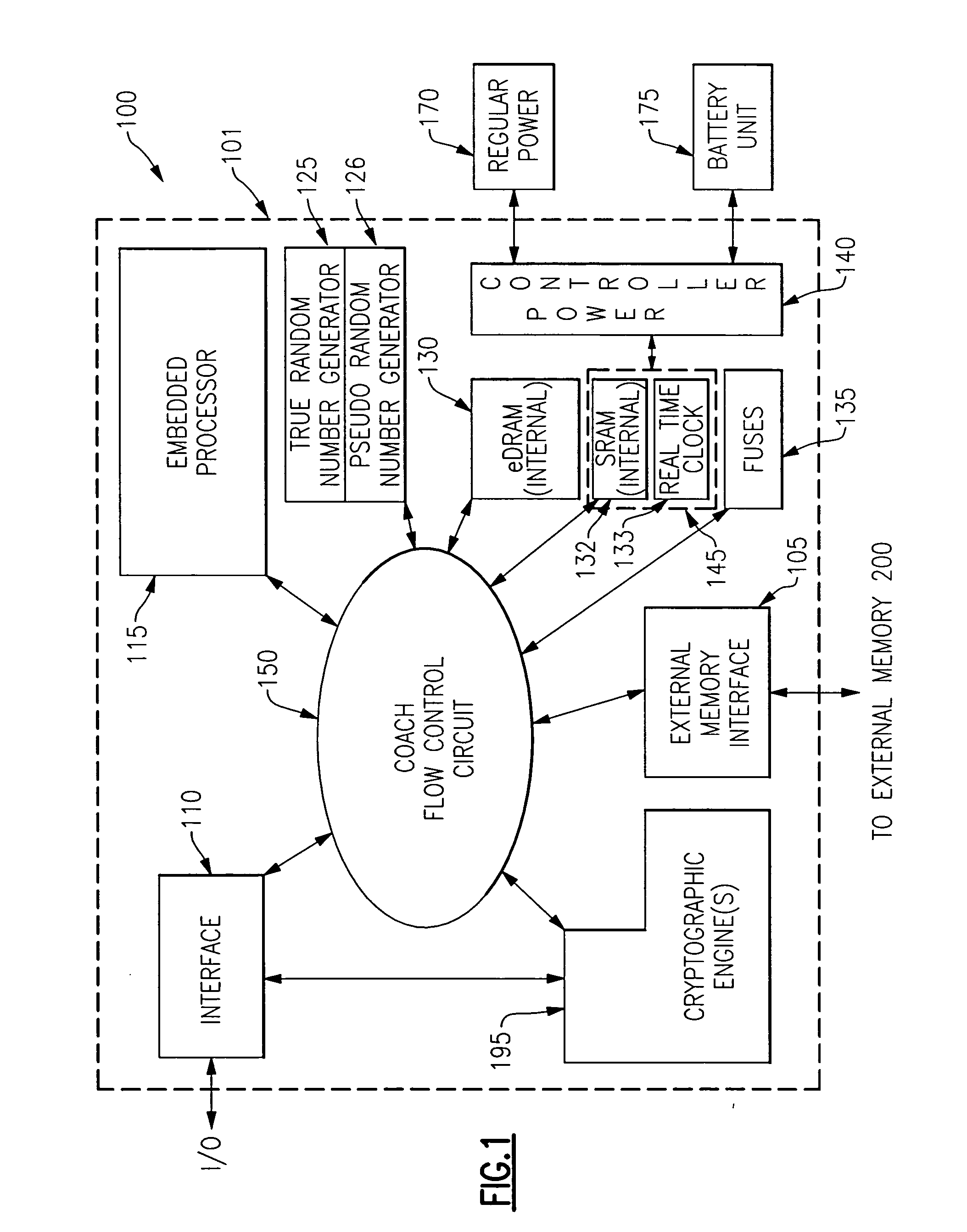
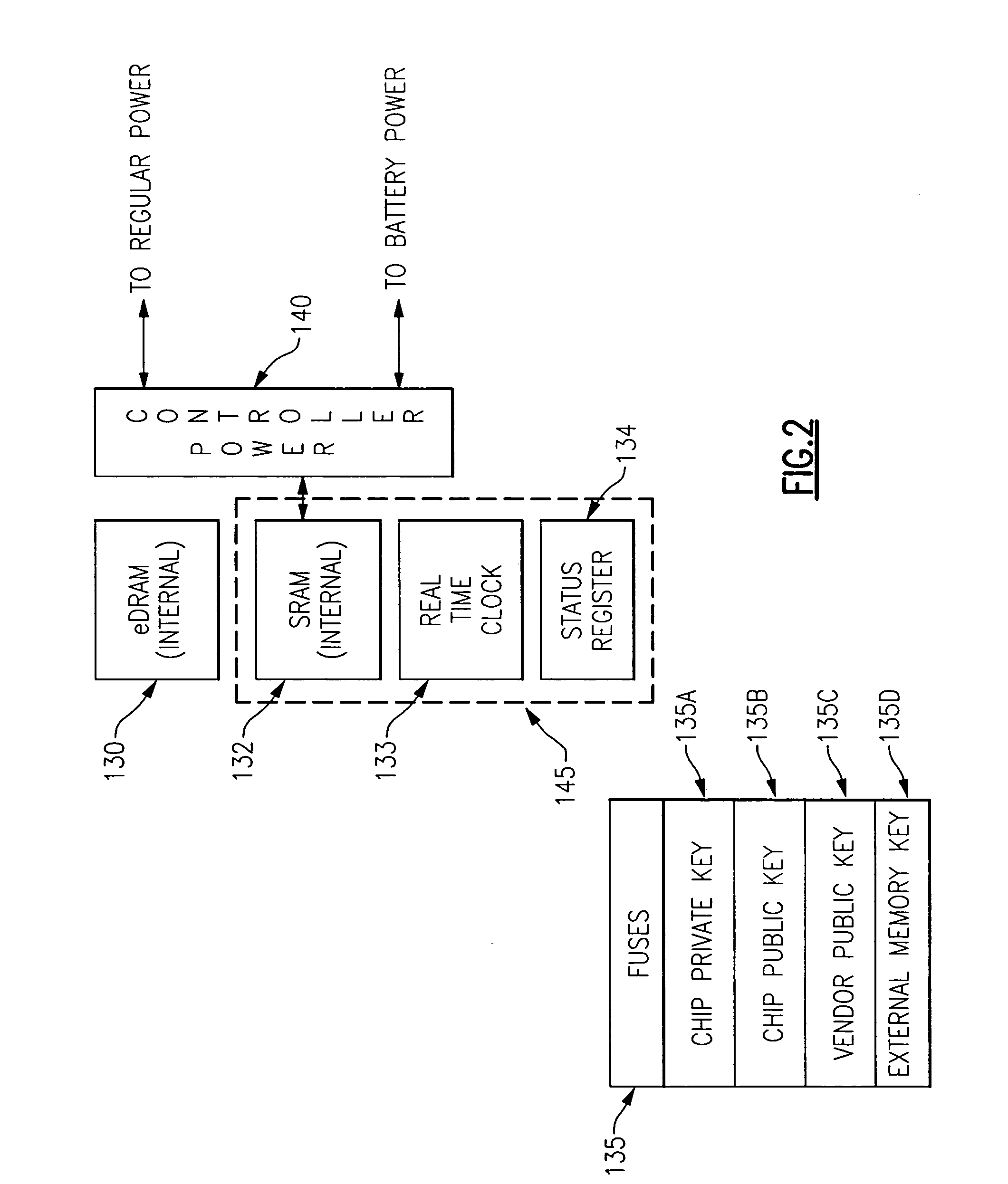
ActiveUS20060059345A1Improve process capabilityInhibit involvementVolume/mass flow measurementUser identity/authority verificationComputer hardwareHard coding
A mechanism is provided in which access to the functionality present on an integrated circuit chip is controllable via an encrypted certificate of authority which includes time information indicating allowable periods of operation or allowable duration of operation. The chip includes at least one cryptographic engine and at least one processor. The chip also contains hard coded cryptographic keys including a chip private key, a chip public key and a third party's public key. The chip is also provided with a battery backed up volatile memory which contains information which is used to verify authority for operation. The certificate of authority is also used to control not only the temporal aspects of operation but is also usable to control access to certain functionality that may be present on the chip, such as access to some or all of the cryptographic features provided in conjunction with the presence of the cryptographic engine, such as key size.
Owner:IBM CORP
Encryption method for network and information security
ActiveCN101764686AHigh speedDiffusion is fastKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareKey size
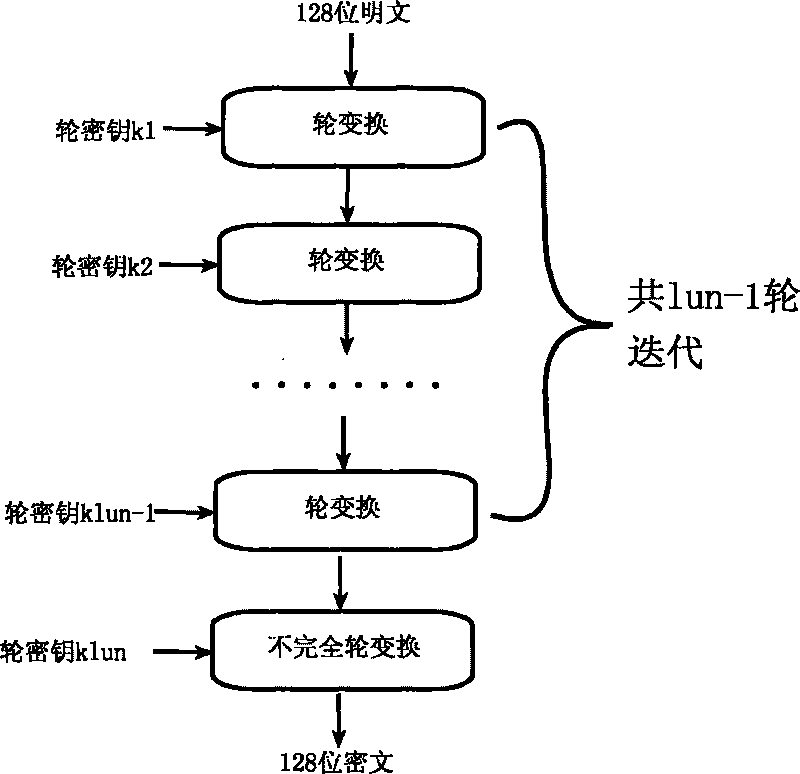
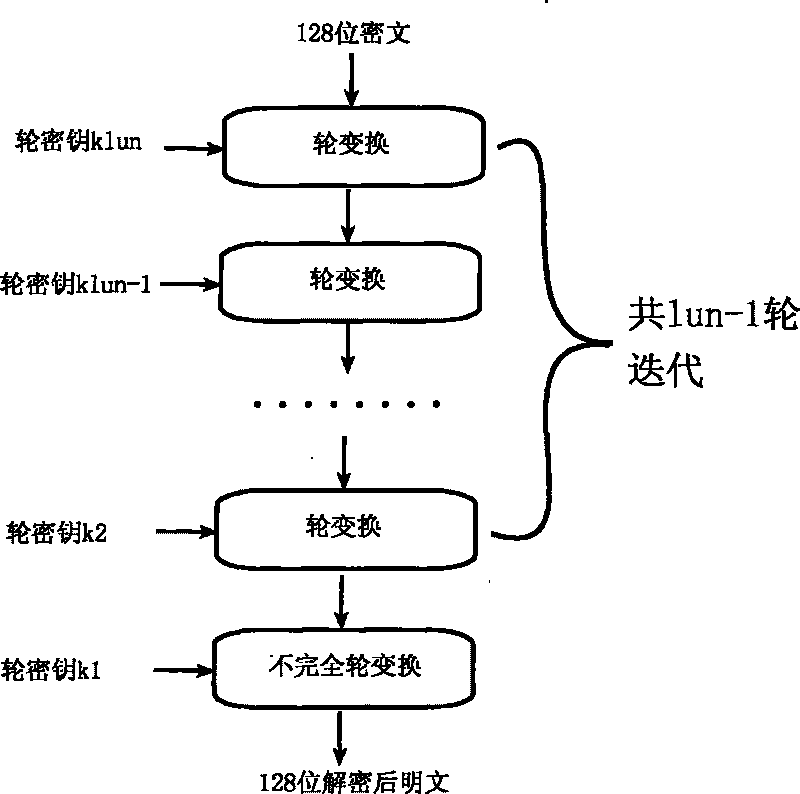
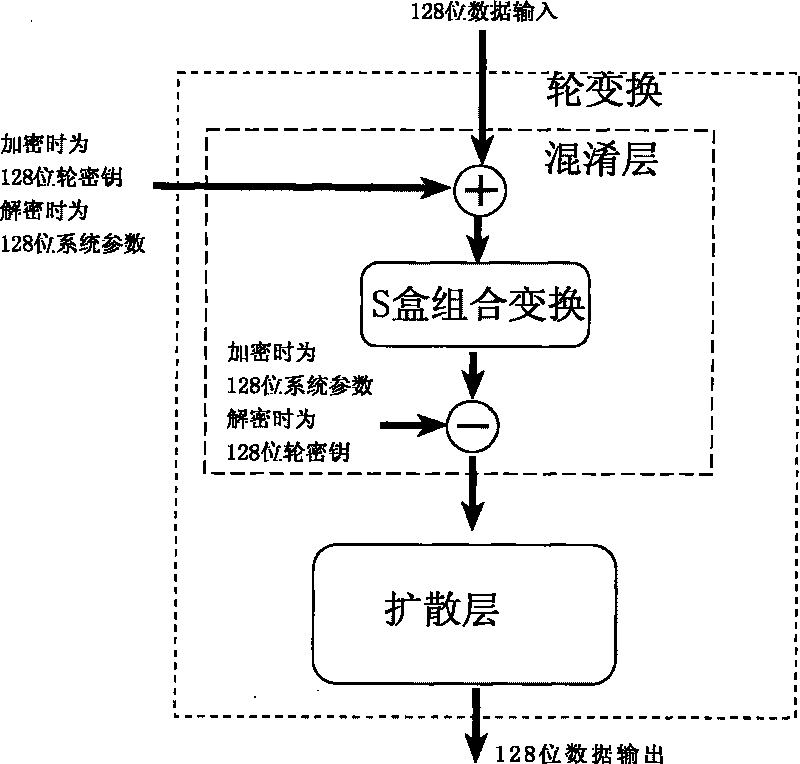
The invention relates to an encryption method for network and information security; the adopted packet length and key length are 128 bits, and a 128-bit system parameter is added; encryption algorithm comprises a plurality of rounds of round transform iteration consisting of mixed layers and diffusion layers, wherein the last round is incomplete round transformation, and the incomplete round transformation consists of the mixed layer; the mixed layer comprises key plus, S box portfolio transform and system parameter minus; the S box portfolio transform comprises 8-input 8-output reversible S box transform and inverse S box transform in the same number which are output by parity exchange; the diffusion layer can construct linear transformation with a reversible re-model polynomial matrix; an encryption round key is generated by an encryption key through encryption round transformation; and decryption algorithm is the inverse transformation of encryption algorithm. The encryption methodfor network and information security has the advantages of high diffusion speed, good security strength, hardware resource saving, and very high speed when being realized by hardware and on a software platform.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
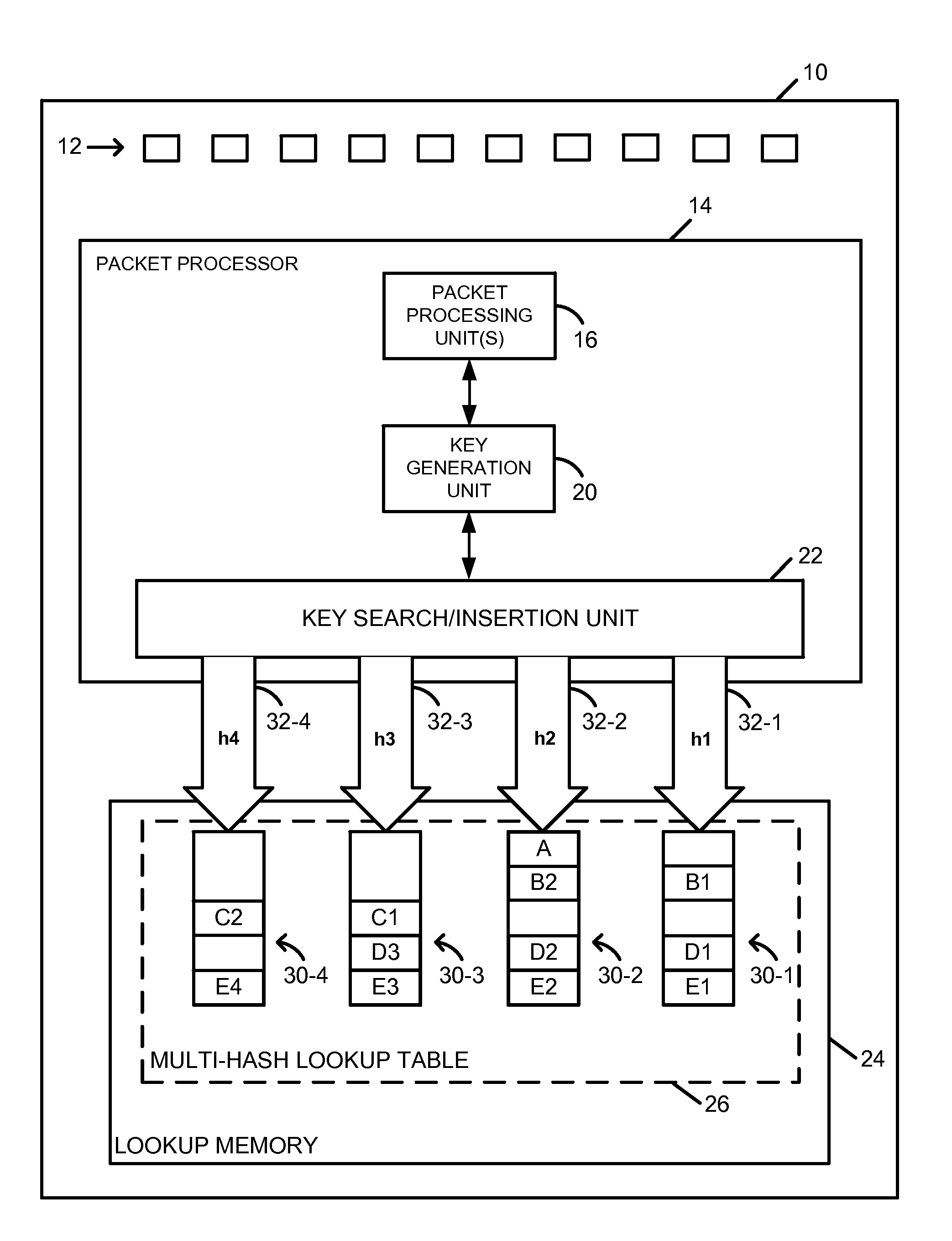
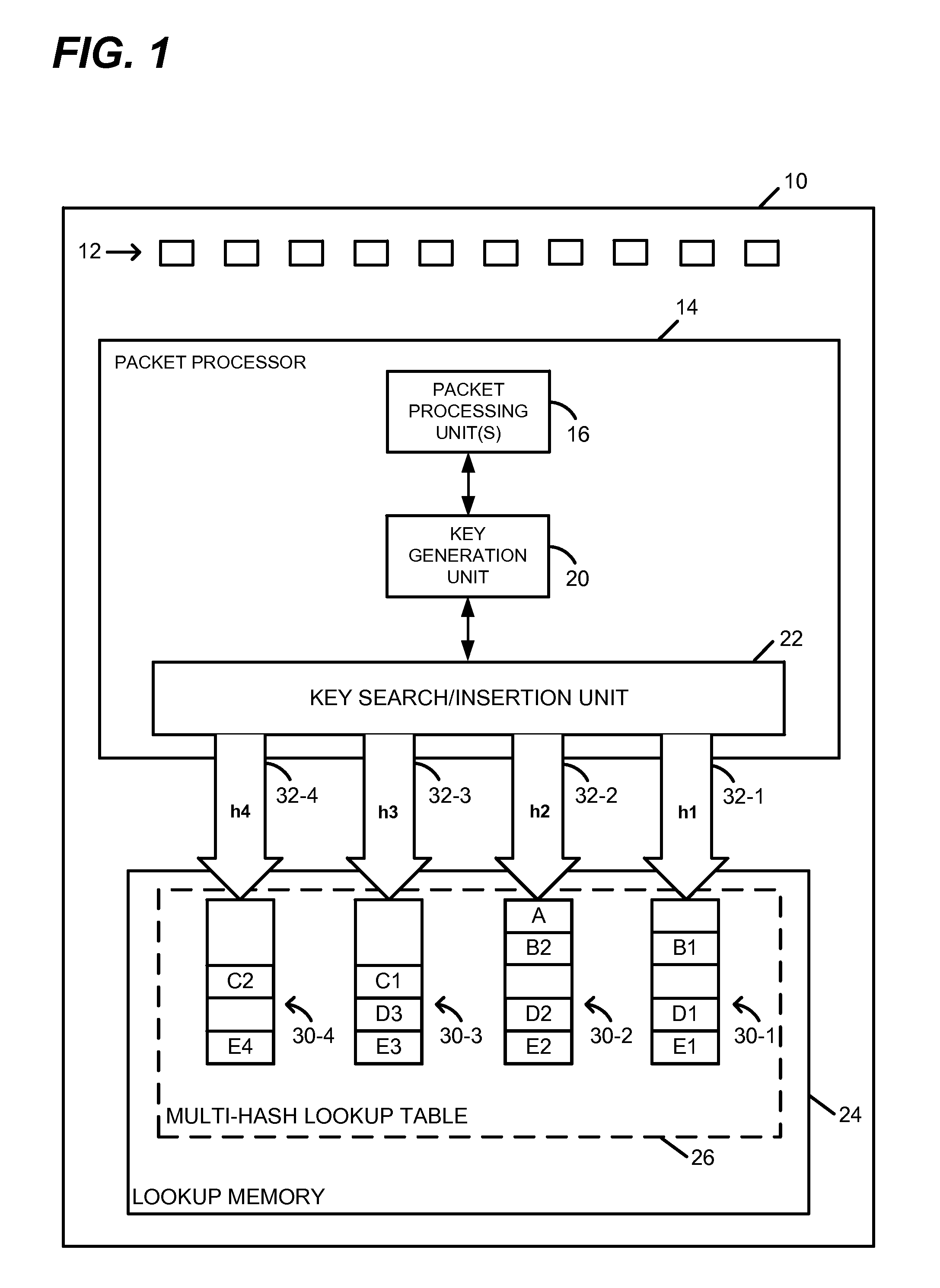
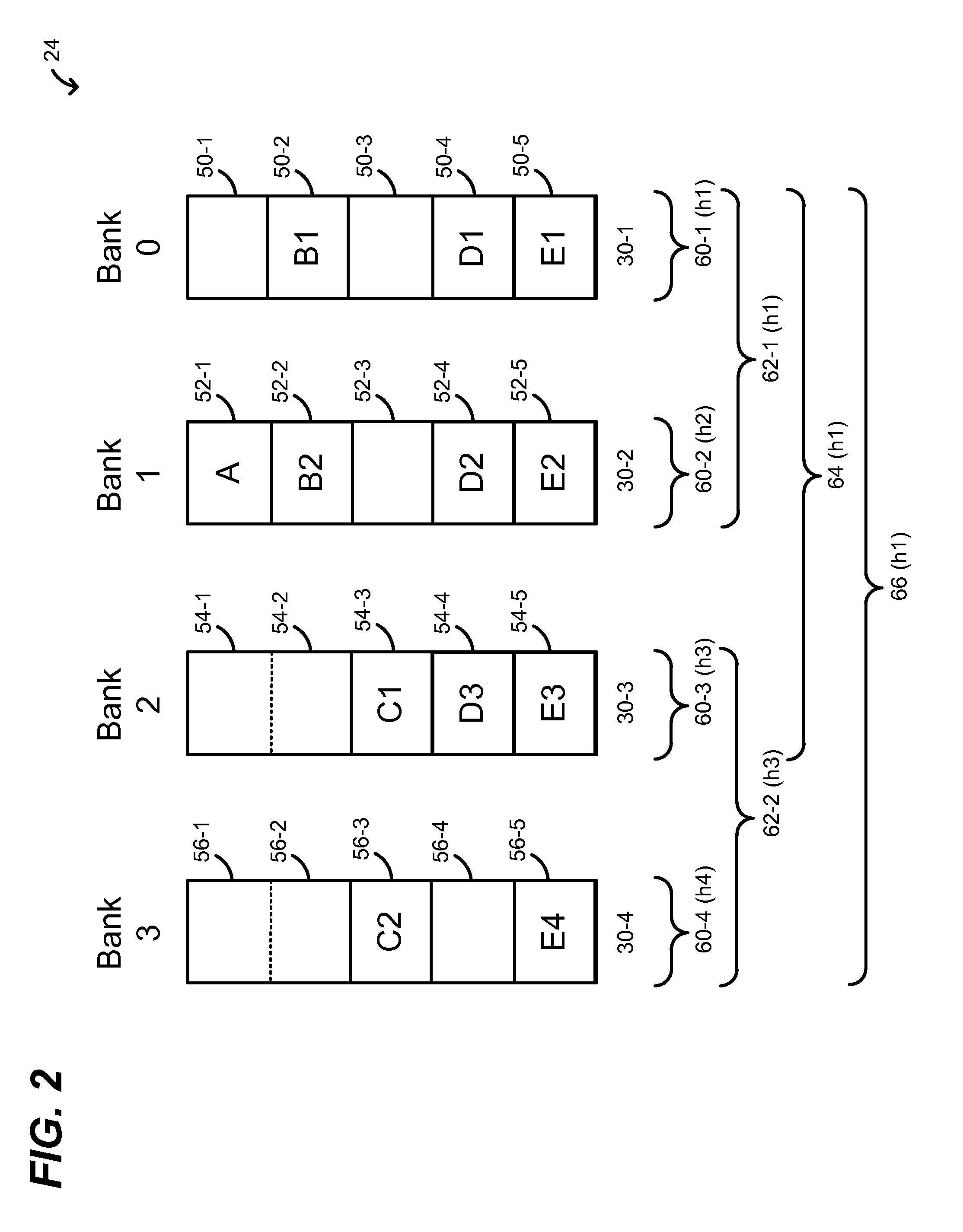
Exact Match Lookup with Variable Key Sizes
ActiveUS20140310307A1Digital data information retrievalDigital data processing detailsKey sizeExact match
In a method for performing an exact match lookup in a network device, a network packet is received at the network device. A lookup key for the network packet is determined at least based on data included in a header of the received network packet. A hash function is selected, from among a plurality of possible hash functions, at least based on a size of the lookup key, and a hash operation is performed on the lookup key using the selected hash function to compute a hashed lookup key segment. A database is queried using the hashed lookup key segment to extract a value exactly corresponding to the lookup key.
Owner:MARVELL ISRAEL MISL
Public Key Cryptosystem Based On Partitioning Of Galois Field Elements
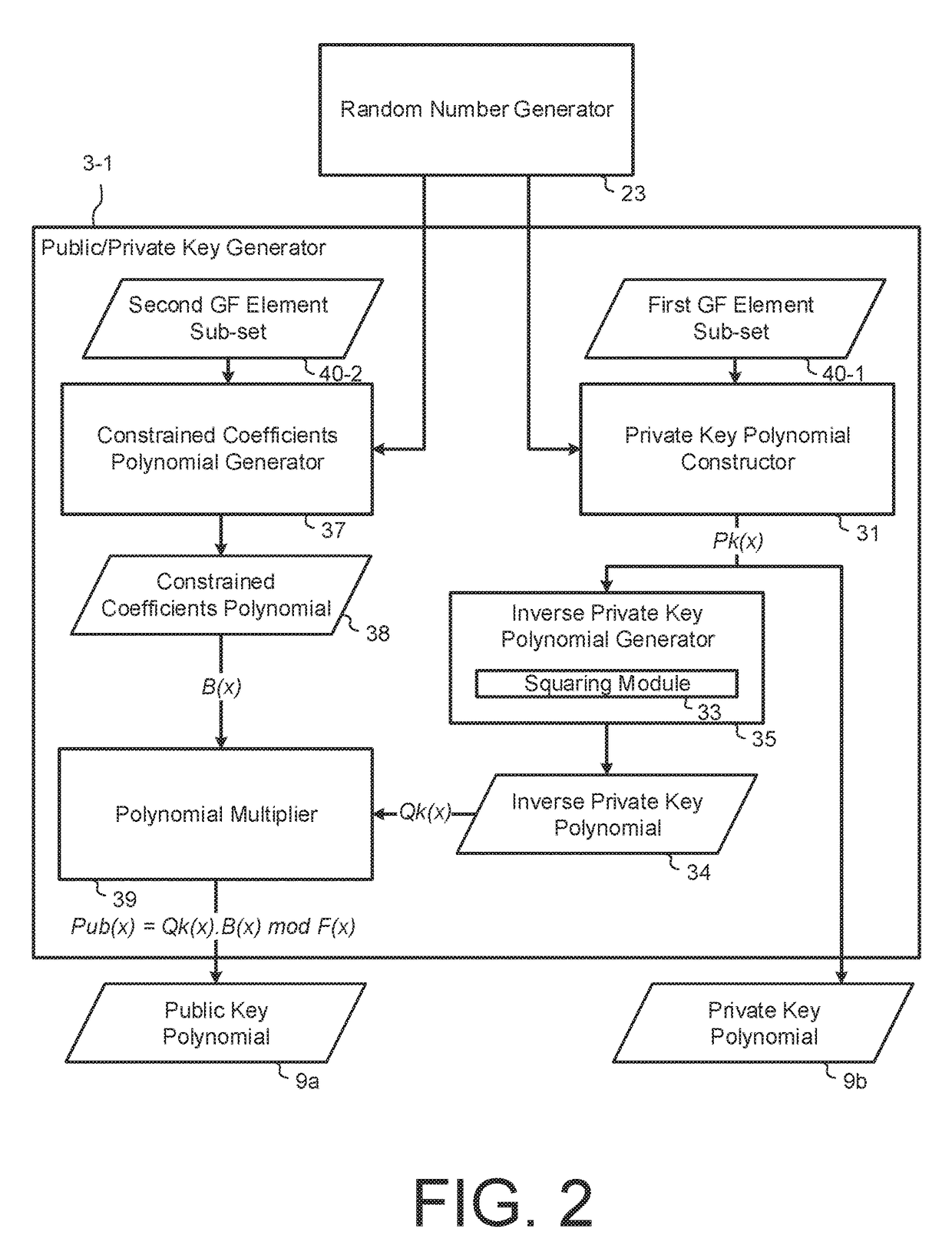
InactiveUS20170324554A1Small public key sizeKey distribution for secure communicationMultiple keys/algorithms usageKey sizeTheoretical computer science
A post-quantum, public key cryptosystem is described which is polynomial based and where the private key polynomial has coefficients from a sub-set of Galois field elements and plain text message polynomials have coefficients from a second sub-set of Galois field elements. The public key polynomial is constructed using the inverse of the private key polynomial and a randomly chosen polynomial having coefficients chosen from a third sub-set of Galois field elements. Cipher texts are constructed using the public key and randomly chosen session key polynomials. Other more complicated embodiments are described. For implementation a small prime base field such as 2, 3 or 5 will usually be used in constructing the prime power Galois field. The system has the advantage of relatively small public key sizes.
Owner:PQ SOLUTIONS LTD
Virtual keyboard text entry method optimized for thumb typing, using partial word completion key entry values
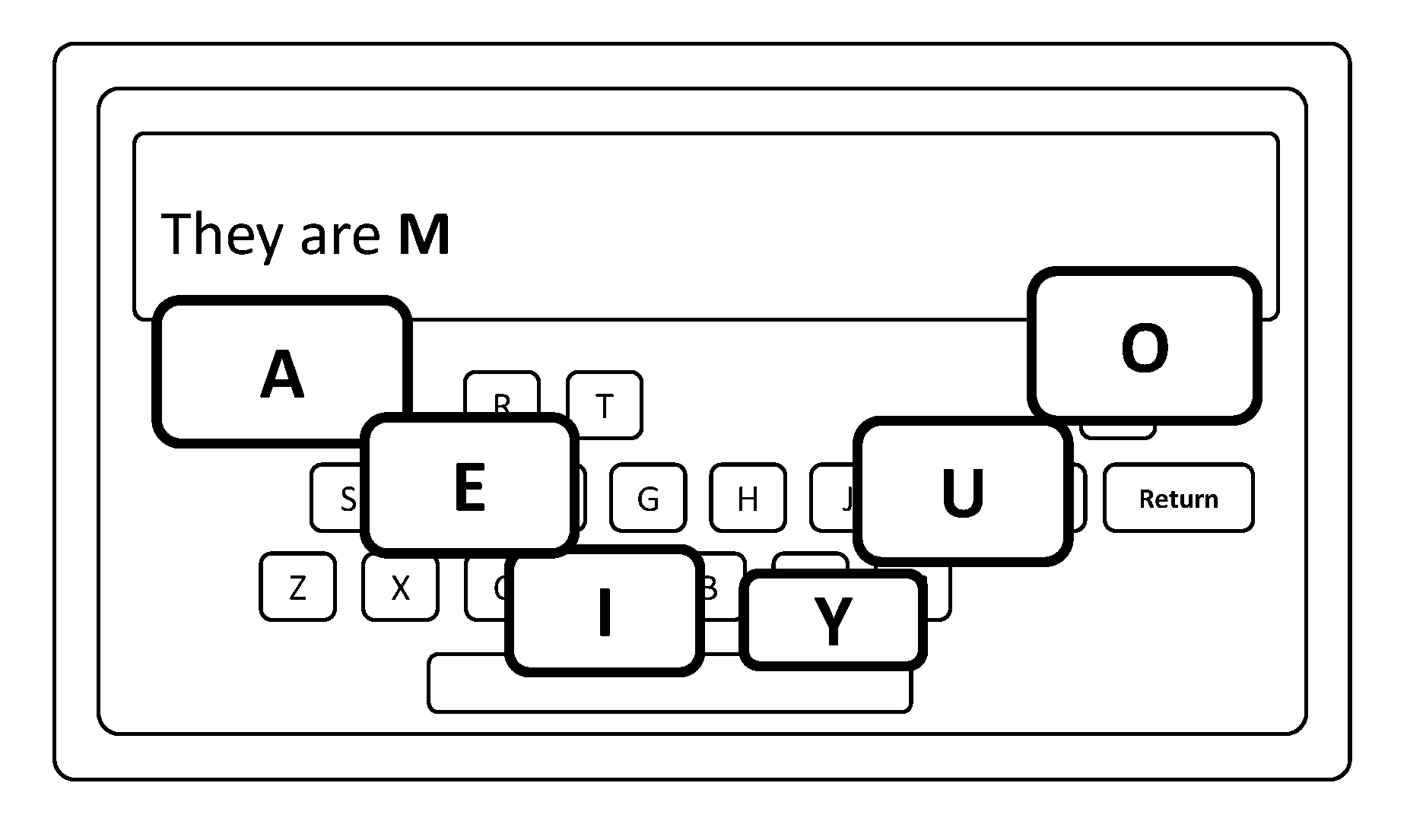
ActiveUS20170052702A1Increase flexibilityLargest possible keysNatural language data processingSpecial data processing applicationsKey sizeTyping
Virtual keyboards become efficient and ergonomic by typing with small, incremental partial word completions, using fewest but largest possible keys, presented in highly condensed layouts, retaining familiar structural patterns of standard keyboards like QWERTY, and utilizing curved thumb typing formats. The keyboard continuously adjusts numbers of keys, key sizes, predictive values and layouts, to minimize keystrokes, reduce errors, and maximize potential words entered, while providing the most ergonomic, minimalist interface possible at any moment, scaling to any size device. Keys display normal default characters concatenated with supplemental predictive characters, forming incremental partial word completions; each represents the longest common building block shortcut of likely intended words derivable from a key's default value. The most relevant keys can generate larger numbers of highly predicted words; the more relevant, the larger the key. Only the most relevant keys are displayed, in stripped down, but familiar layouts, allowing only valid text entry options.
Owner:NORRIS III FORBES HOLTEN
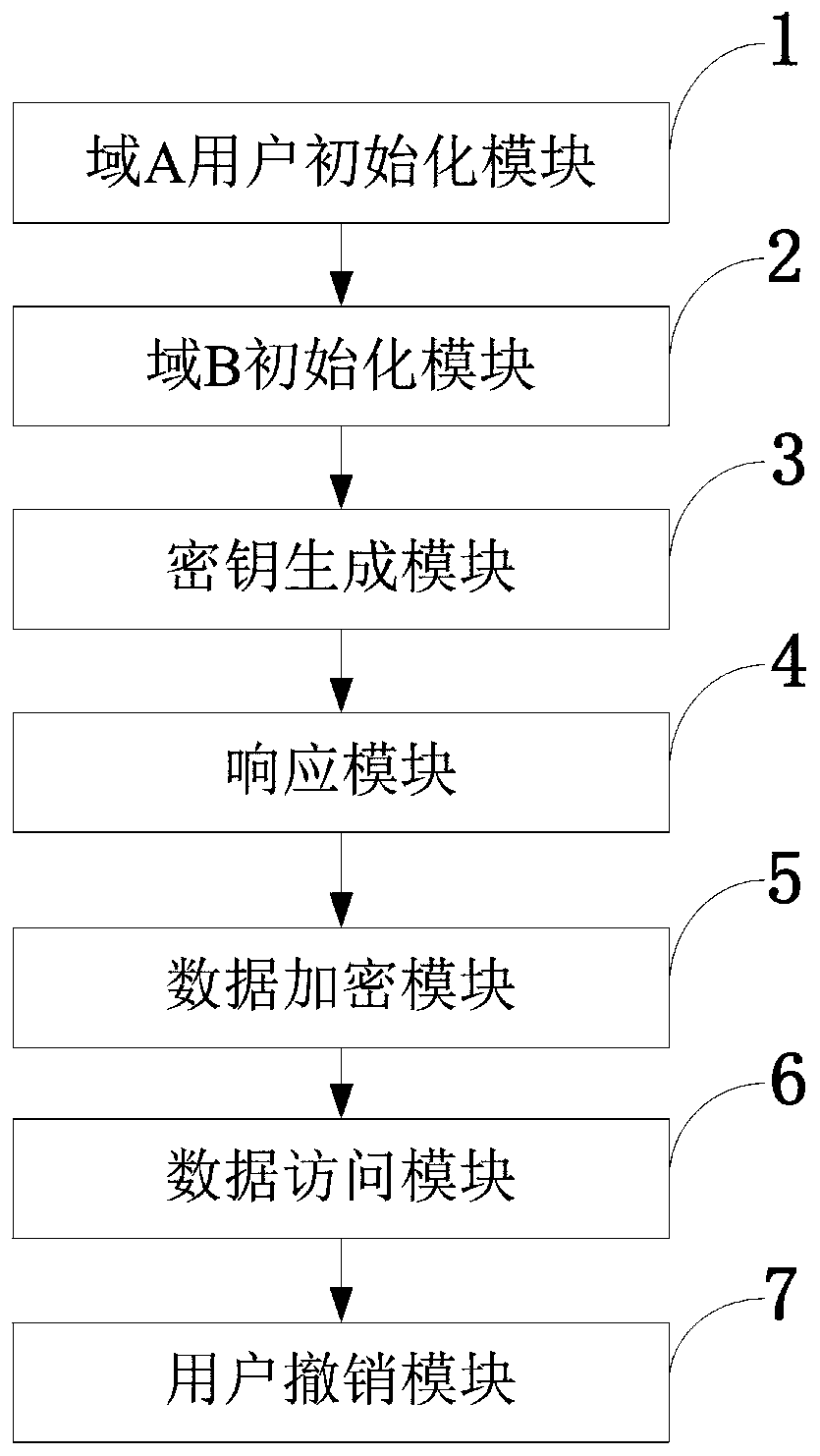
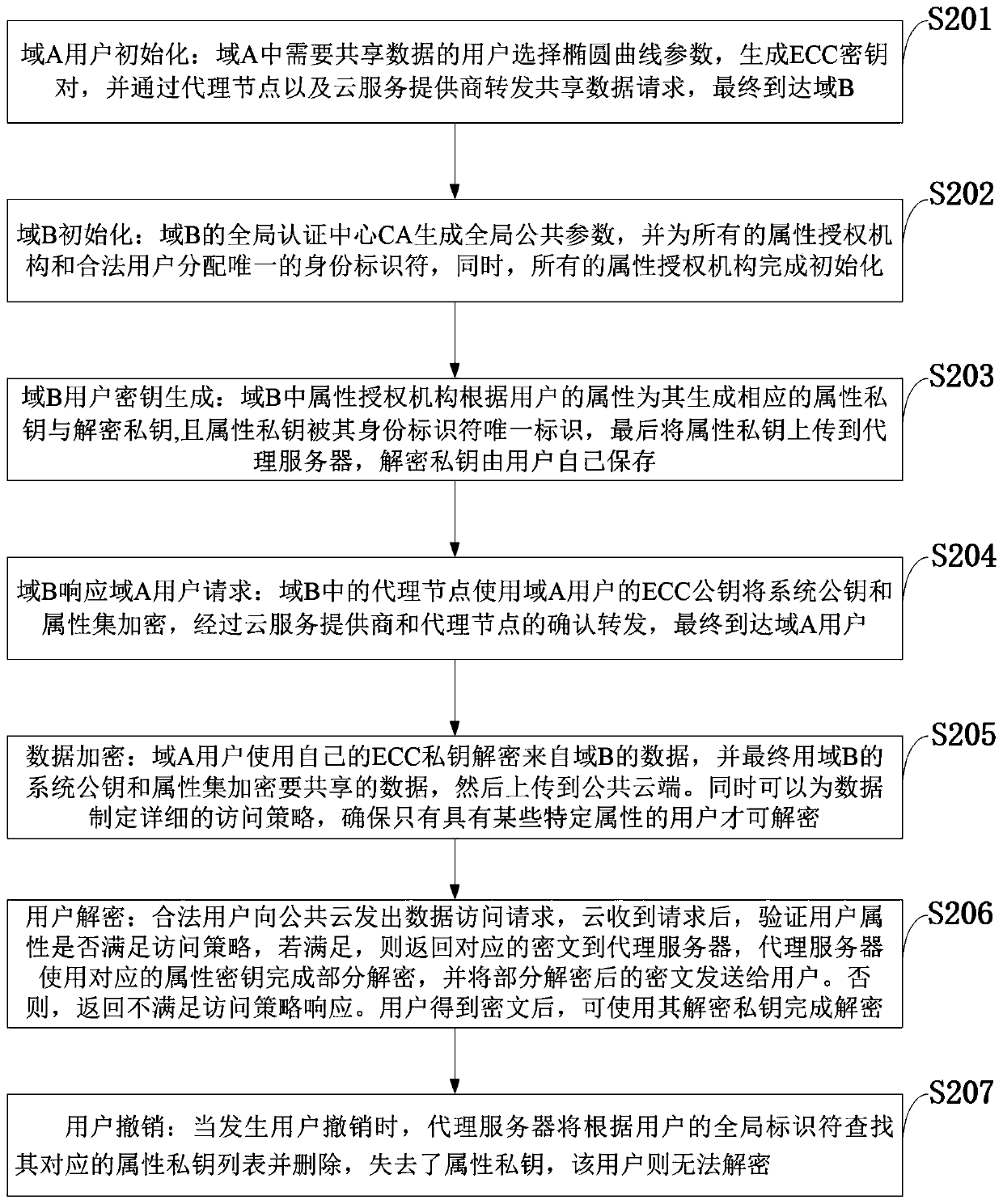
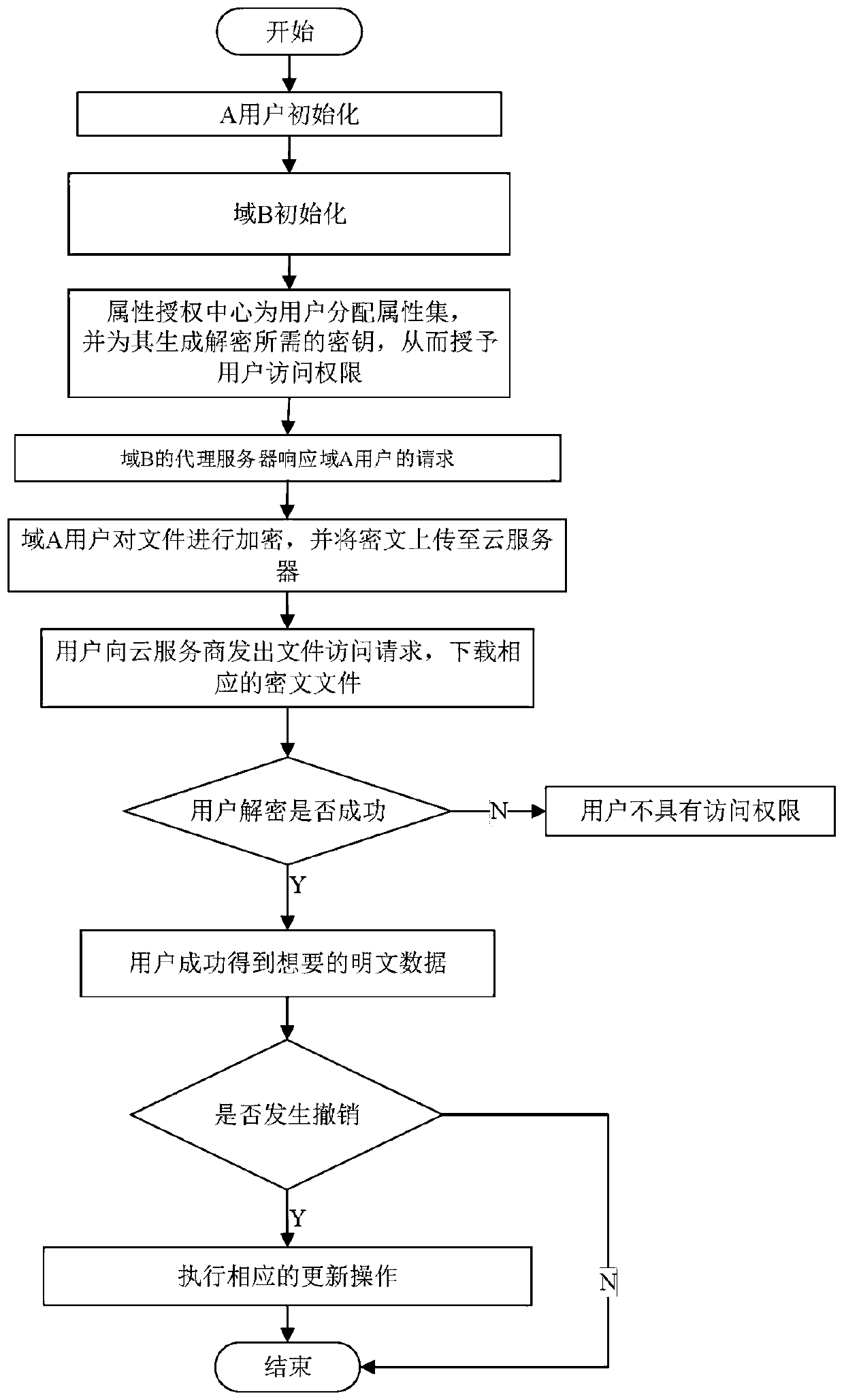
Access control system and method supporting cross-domain data sharing and wireless communication system
ActiveCN110636500AGuaranteed safe transmissionImprove securityPublic key for secure communicationSecurity arrangementKey sizeCommunications system
The invention belongs to the technical field of wireless communication networks, and discloses an access control system and method supporting cross-domain data sharing, and a wireless communication system. Users needing to share data in a domain A select elliptic curve parameters to generate ECC key pairs; a global authentication center CA of the domain B generates a global public parameter; the proxy node in the domain B encrypts the system public key and the attribute set by using the ECC public key of the domain A user; the domain A user decrypts the data from the domain B by using the ECCprivate key of the domain A user and uploads the data to the public cloud; the legal user sends a file access request to the public cloud; and when user revocation occurs, the proxy server searches acorresponding attribute private key list according to the global identifier of the user and deletes the attribute private key list. The method is high in safety under the condition of the same secretkey length. The method gives full play to the characteristic of strong computing power of agent nodes, completes the preprocessing of some data, helps a user to carry out partial decryption, and improves the decryption efficiency of the user.
Owner:XIDIAN UNIV
Countermeasure procedures in an electronic component implementing an elliptical curve type public key encryption algorithm
Elliptical curve based cryptographic algorithms are public key algorithms offering a shorter calculation time and smaller key sizes in comparison with RSA. In a smart card type environment, these algorithms are vulnerable to differential power analysis (DPA) attacks. The disclosed invention provides a countermeasure procedure enabling positive action to be taken against DPA-type attacks. The countermeasure does not reduce performance and is easy to use in a smartcard type component.
Owner:GEMPLU
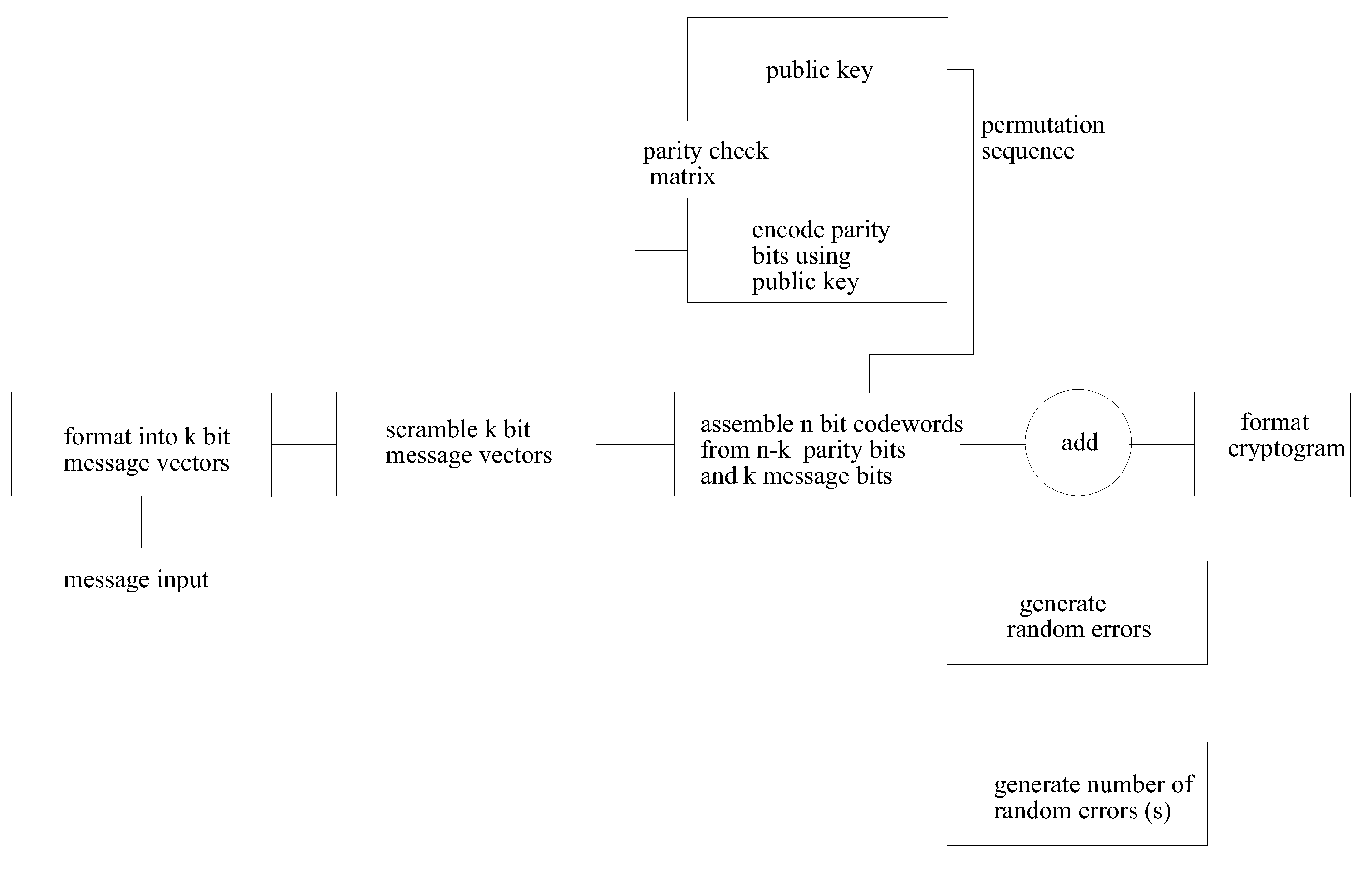
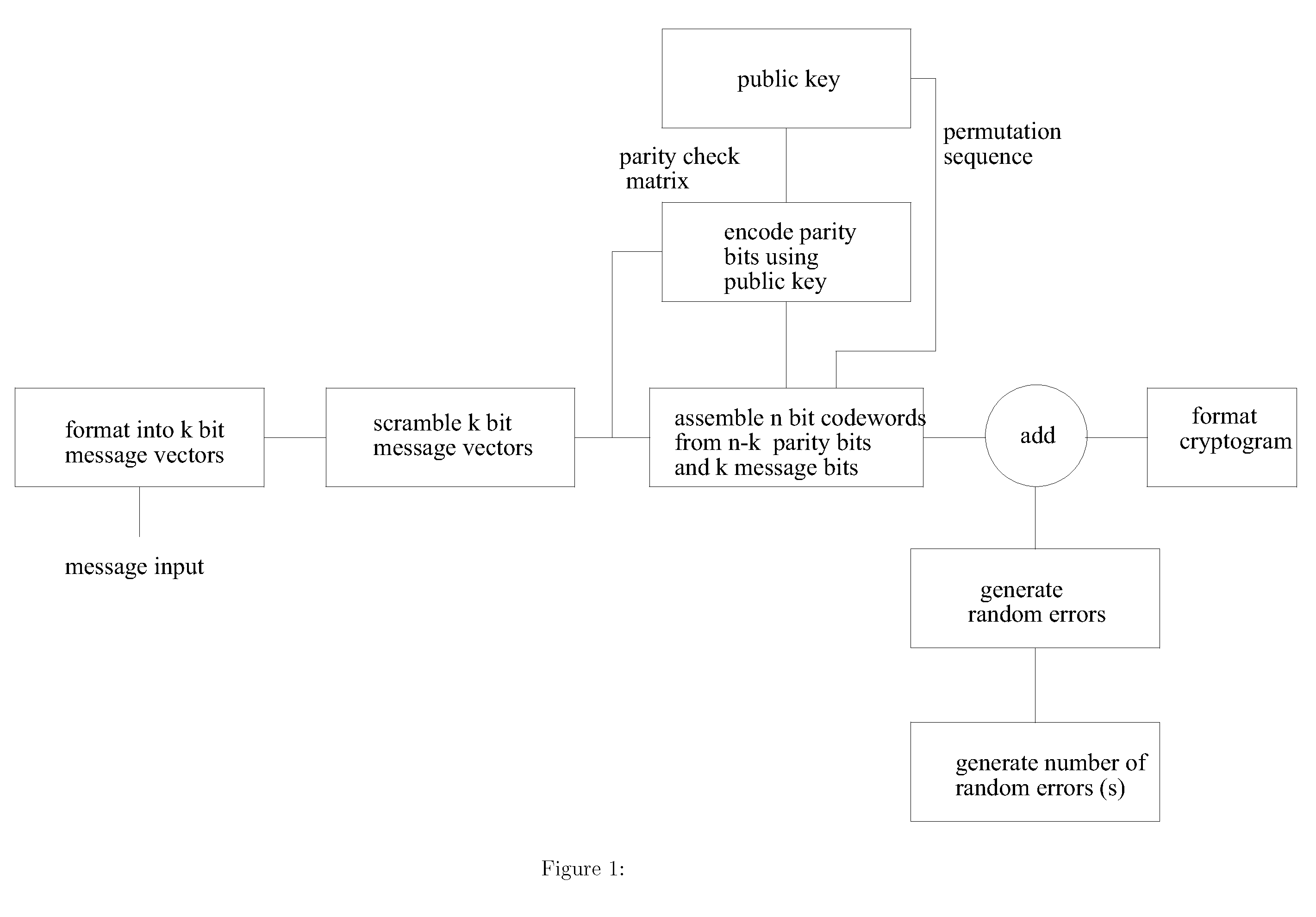
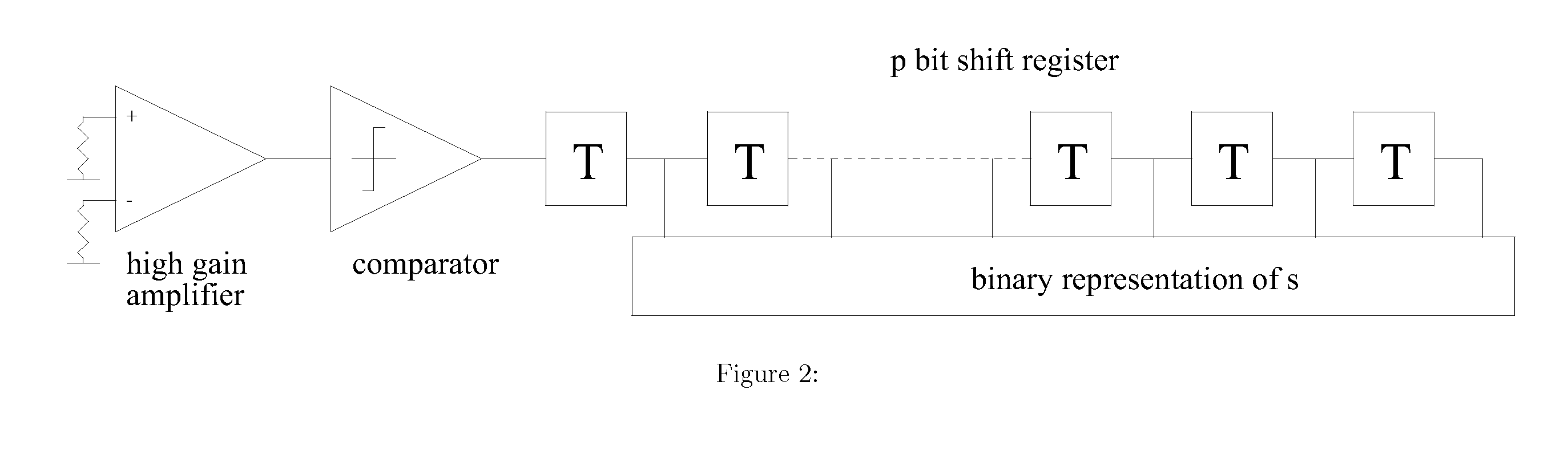
Public key encryption system using error correcting codes
InactiveUS20120121084A1Improving information throughput efficiencyPublic key for secure communicationSecret communicationKey sizeCryptogram
This invention provides improved security and improved throughput of the McEliece public key encryption system and reduces the public key size. Even though the public key is reduced, in some embodiments of the invention the ensemble of cryptograms produced is identical to the ensemble of cryptograms produced by the original system for a given Goppa code, and the same private key. It is possible using this invention that the encrypted message, the cryptogram is a truly random function, not a pseudo random function of the message so that even with the same message and the same public key, a different, unpredictable cryptogram is produced each time. Other embodiments of the invention use a shortened error correcting code allowing the length of the generated cryptogram to match exactly the available transmission or storage media such as is the case of RFID and packet based radio applications.
Owner:PQ SOLUTIONS LTD
Method and system for monitoring etch process
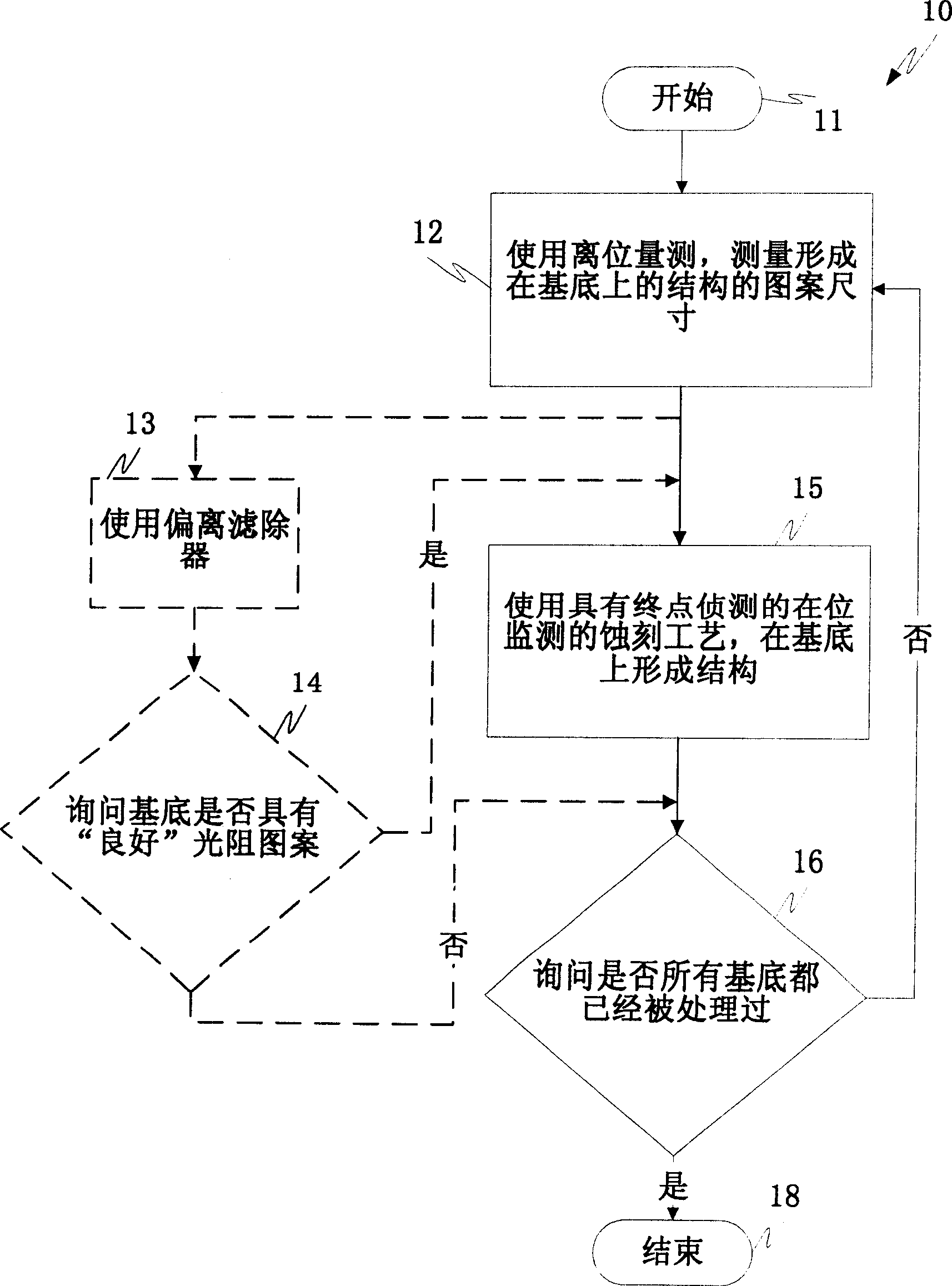
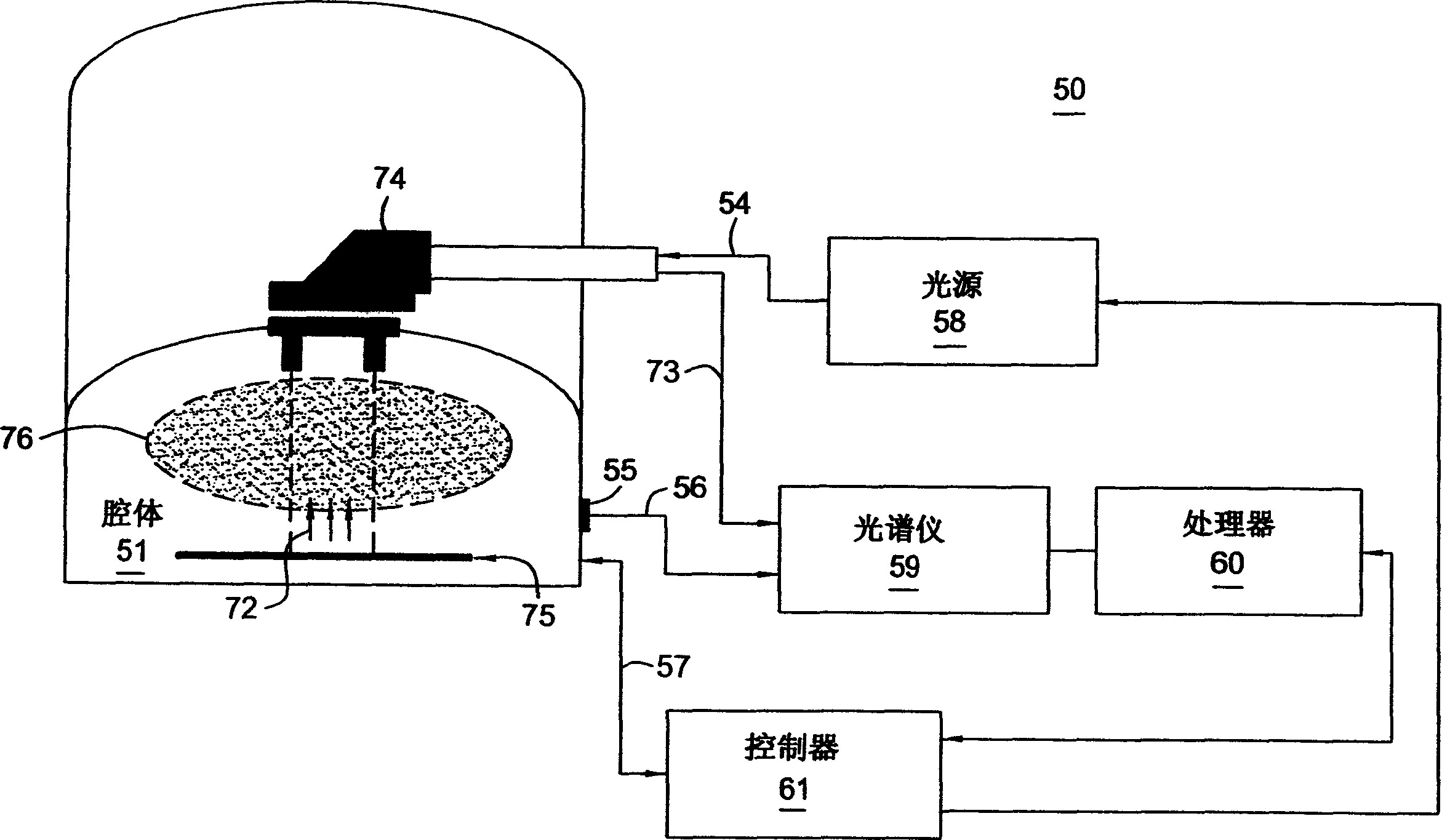
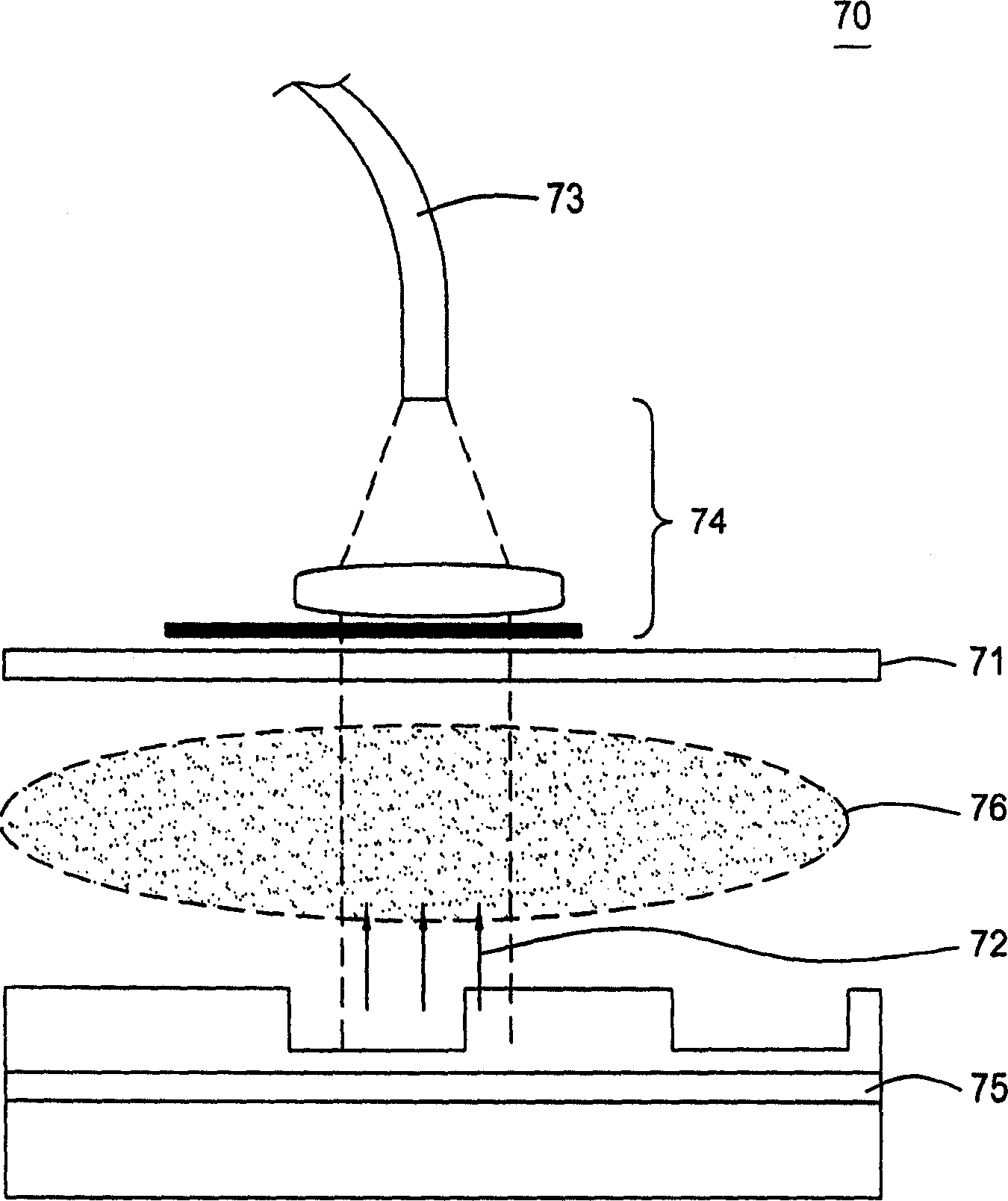
InactiveCN1619788ASemiconductor/solid-state device testing/measurementElectric discharge tubesKey sizeProcess error
A method and system for monitoring an etching process. The etch process can be monitored using metrology information, such as critical dimensions or layer thicknesses, etc. The metrology information is provided by ex-situ and in-situ monitoring of the etch process performed during the etch process, such as spectroscopic analysis, interferometry, scatterometry, and reflectometry. Off-site measurement information and on-site monitoring can be used to monitor, for example, an end point of an etch process, a feature of the etch depth profile formed on a substrate, and error detection of an integrated circuit process.
Owner:APPLIED MATERIALS INC
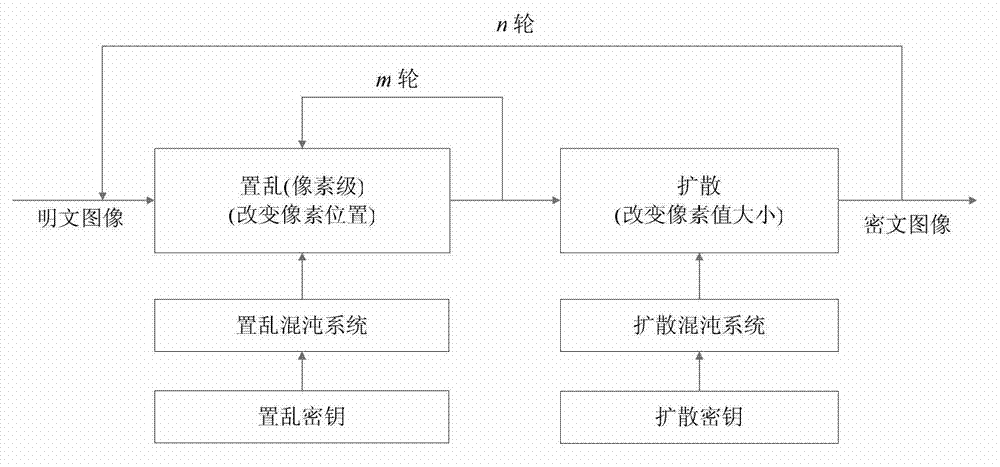
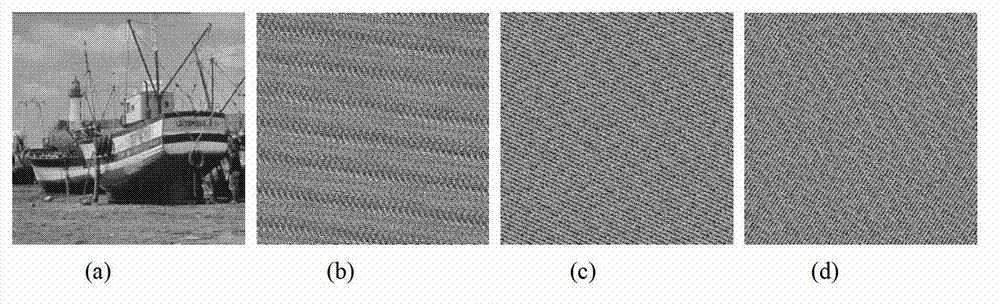
Digital image encryption method based on Cat mapping and hyper-chaos Lorenz system
InactiveCN103167213ASimple structureHigh speedSecuring communicationPictoral communicationKey sizeChosen-plaintext attack
The invention discloses a digital image encryption method based on a Cat mapping and hyper-chaos Lorenz system, and belongs to the field of image encryption. According to the digital image encryption method, a key length of an image encryption system is 247 digits and is higher than classical cryptography algorithms of the data encryption standard (DES, 56 digits), the advanced encryption standard (AES, the basic standard is 128 digits) and the international data encryption algorithm (IDEA, 128 digits). By introducing a secret key stream generative mechanism related to plaintexts, secret key streams are enabled to be related to both secret keys and the plaintexts, and even when the same diffusion secret keys are used to encrypt different plaintext images, the generated secret key streams are different. Therefore, the known-resistant / plaintext-selective attack capacity of the encryption system is obviously improved.
Owner:NORTHEASTERN UNIV
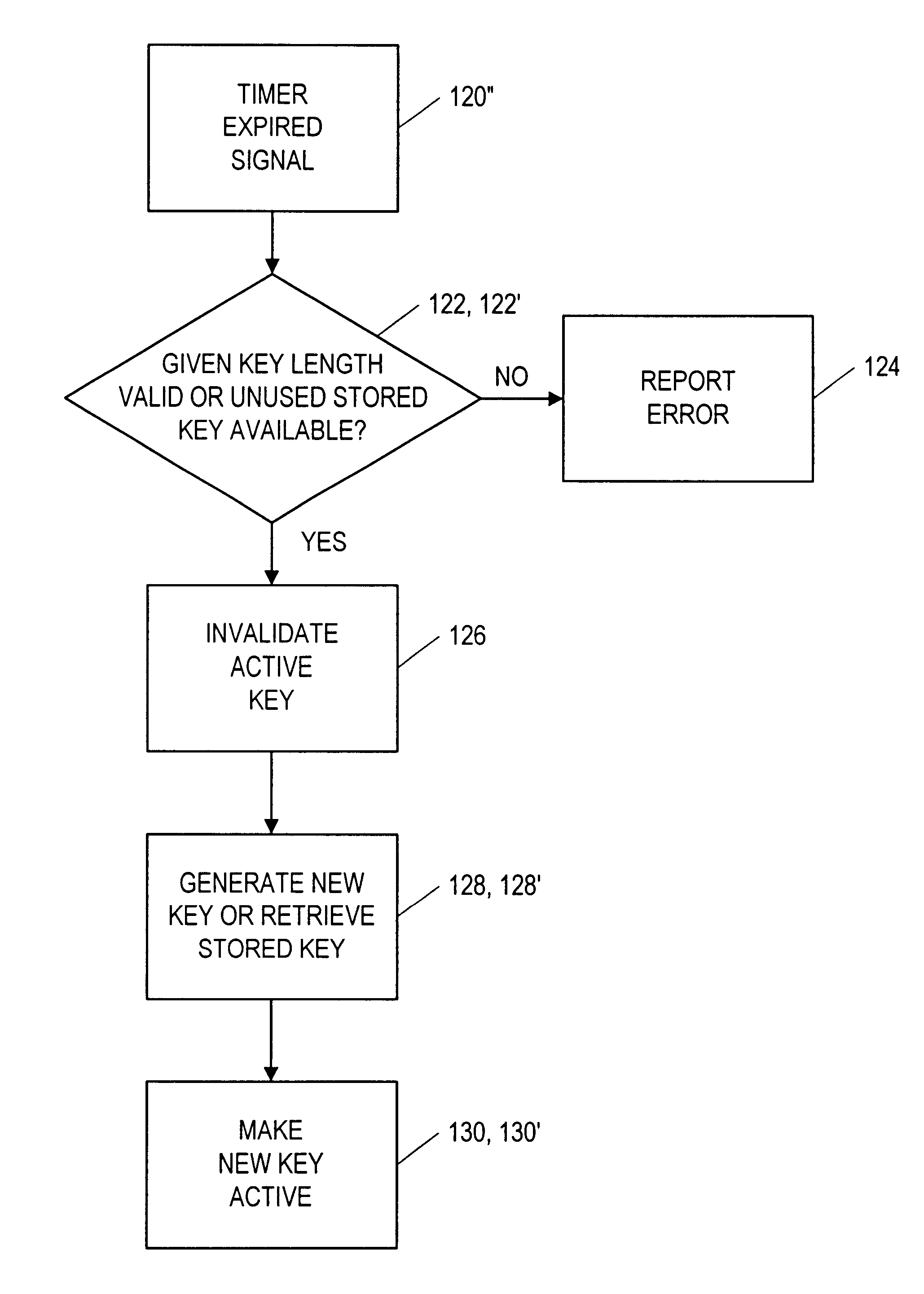
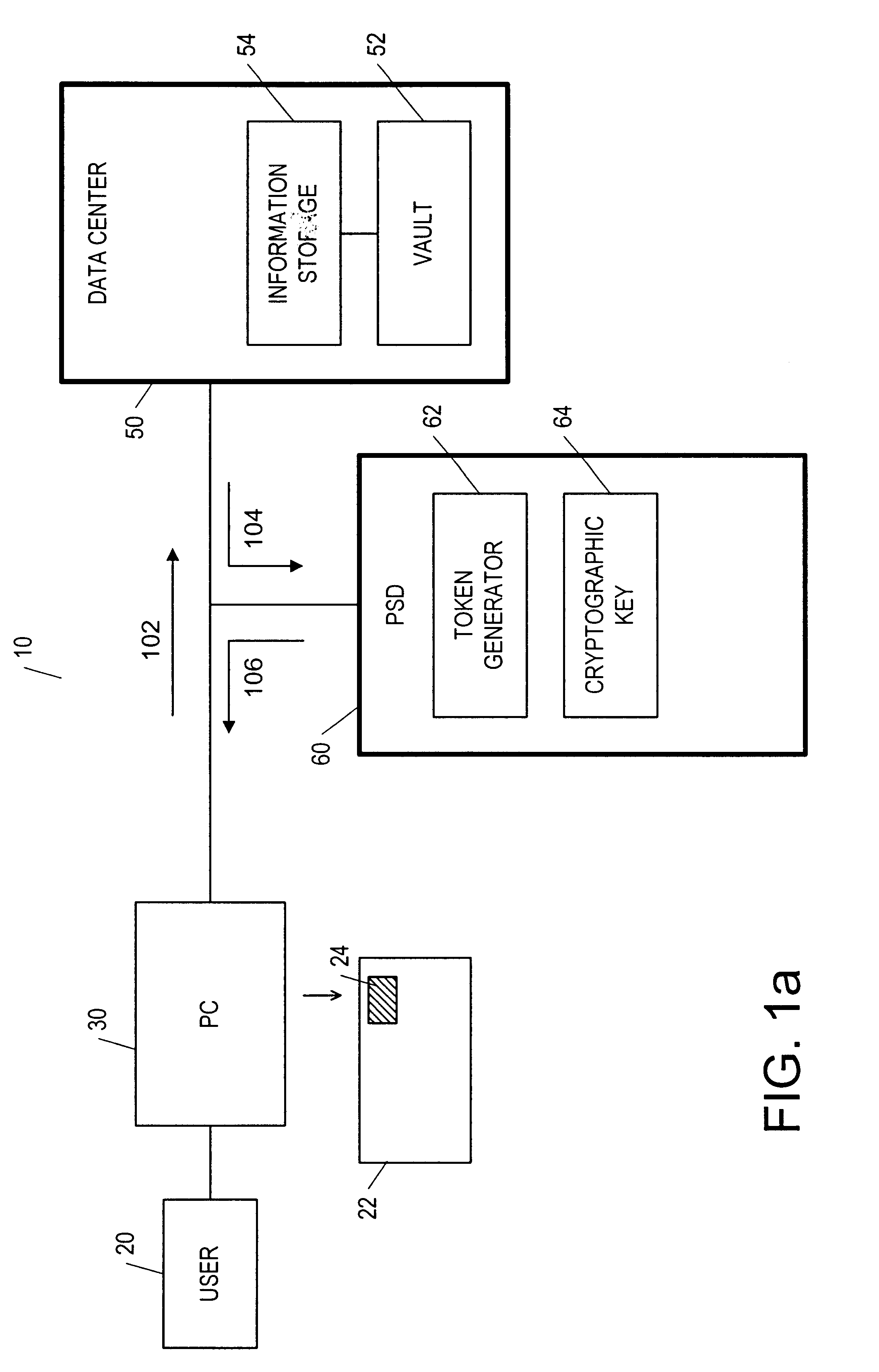
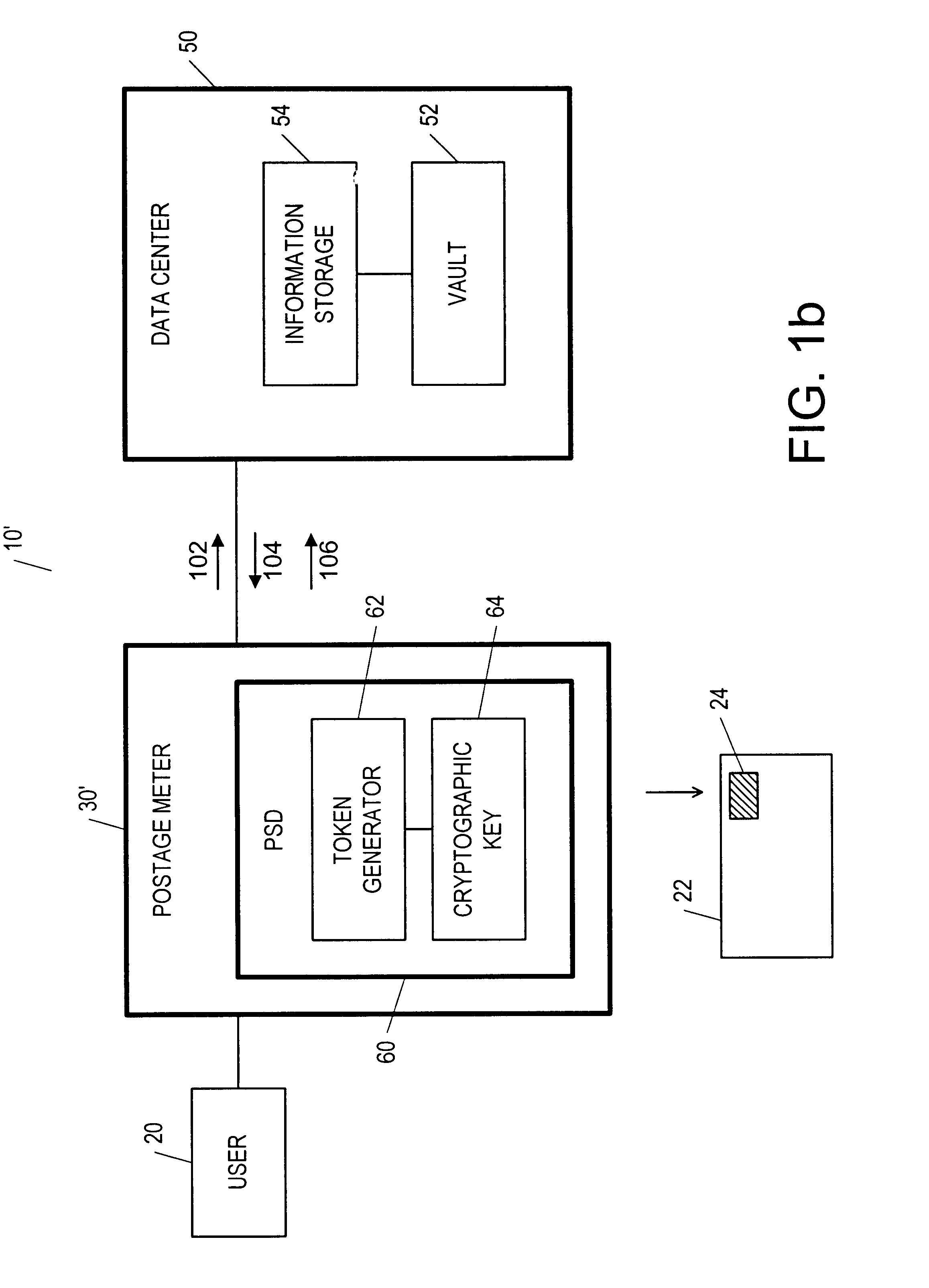
Postage security device having cryptographic keys with a variable key length
InactiveUS6868407B1Improve security levelComputer security arrangementsPayment architectureKey sizeCryptographic key generation
Owner:PITNEY BOWES INC
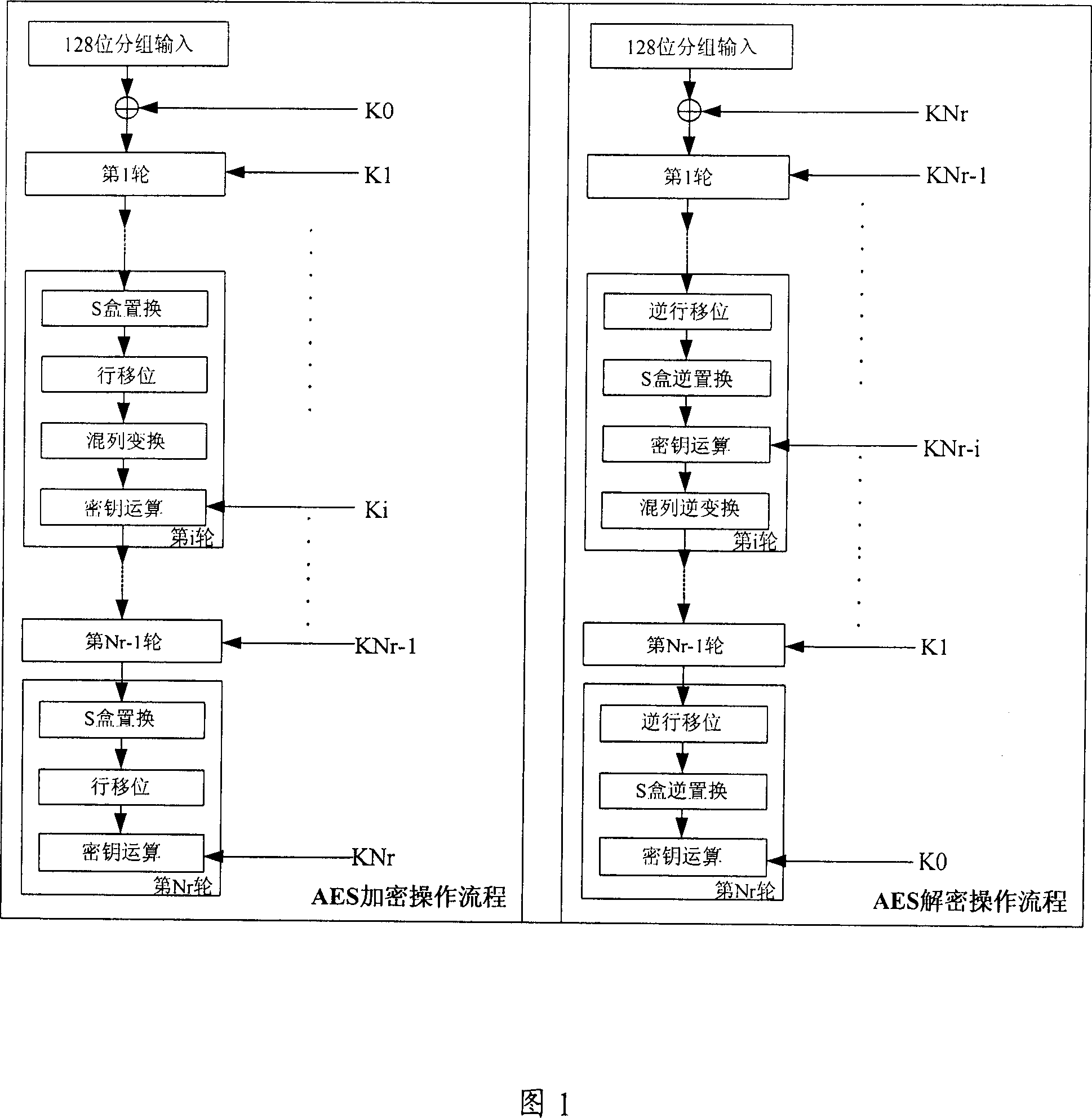
Encrypting-decrypting method based on AES algorithm and encrypting-decrypting device
The invention relates to a method for coding and decoding, based on AES algorism. Wherein, it comprises that a, based on the key length, fixing the literate time Nr; b, initializing the data, before first literating the input data, treating it with key operation on it with sub key; c, loading coding or decoding control signal; d, under the control of coding control signal, the decoding / coding literate complex module processes Nr literate operation for Nr times, and under the control of decoding control signal, said module processes decoding literate for Nr times. The invention also provides a relative decoder or coder, which comprises a decoding / coding literate complex module. The invention has a circuit which can simplify the AES algorism, with low power consumption and cost.
Owner:HUAWEI TECH CO LTD
System for encrypted file storage optimization via differentiated key lengths
InactiveUS20030086570A1Key distribution for secure communicationComputer security arrangementsKey sizeAccess frequency
A key management module is utilized to improve efficiency in cryptographic systems. The key management module may monitor file usage and recommend (and / or implement) key pair changes. In particular, the key management module may be configured to periodically examine (or analyze) performance parameters (e.g., number of times written, number of times read, etc.) associated with a user's files. A network monitor module may be configured to gather and maintain records of the associated performance parameters. The key management module may be further configured to compare the performance parameters of a given file with a table of key level ranges. The table of key lengths may be configured to provide a listing of multiple key lengths, each key length corresponding to an activity level of a performance parameter, e.g., relative read / write access frequency. The key management module may recommend changing the relative length of the read and write keys based on the comparison of the performance parameters with the table of key level ranges.
Owner:HEWLETT PACKARD DEV CO LP
Method and system for a symmetric block cipher using a plurality of symmetric algorithms
InactiveUS20110069834A1Increase the difficultyImprovement effortsMultiple keys/algorithms usageSecret communicationKey sizeComputer hardware
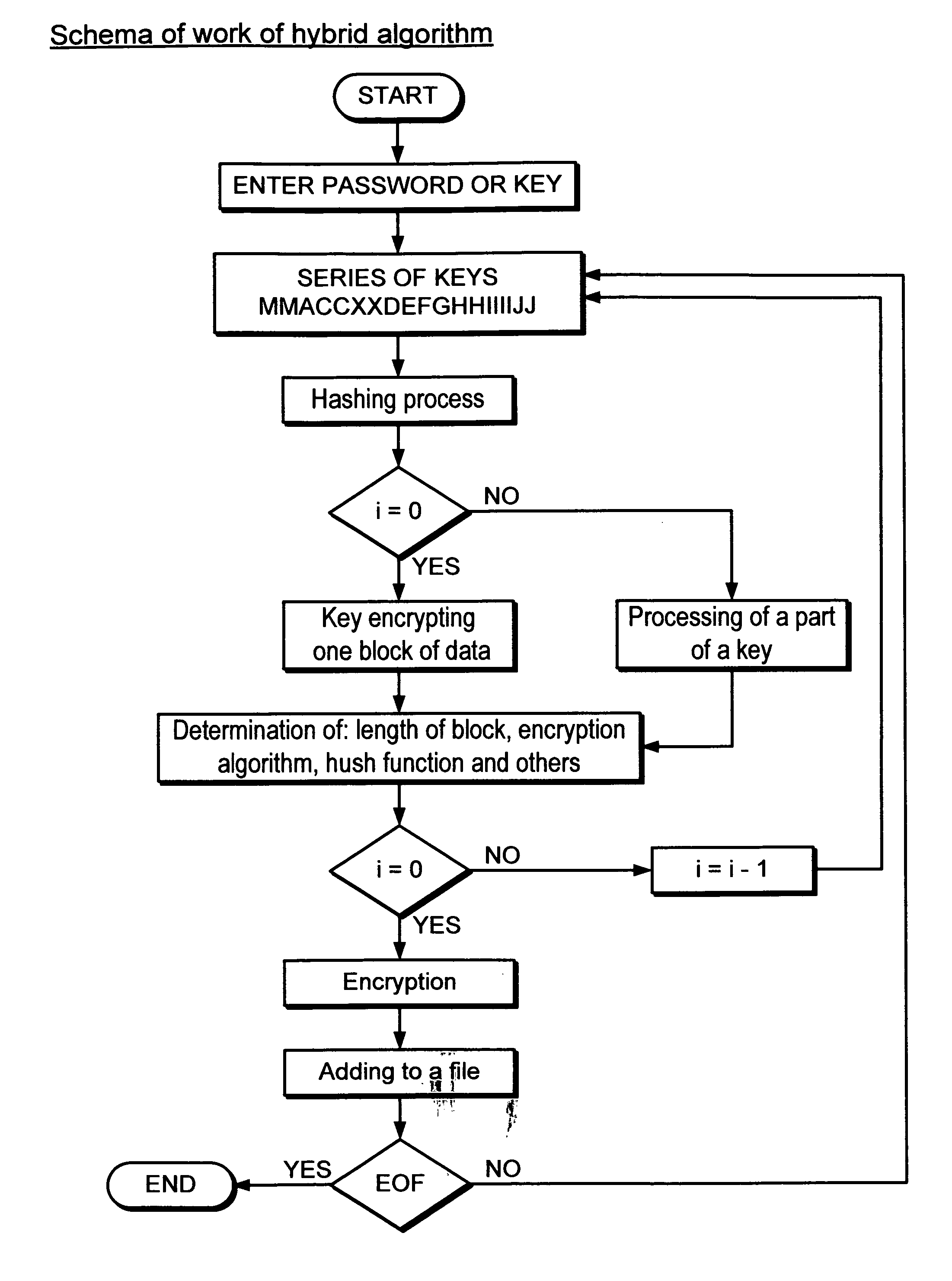
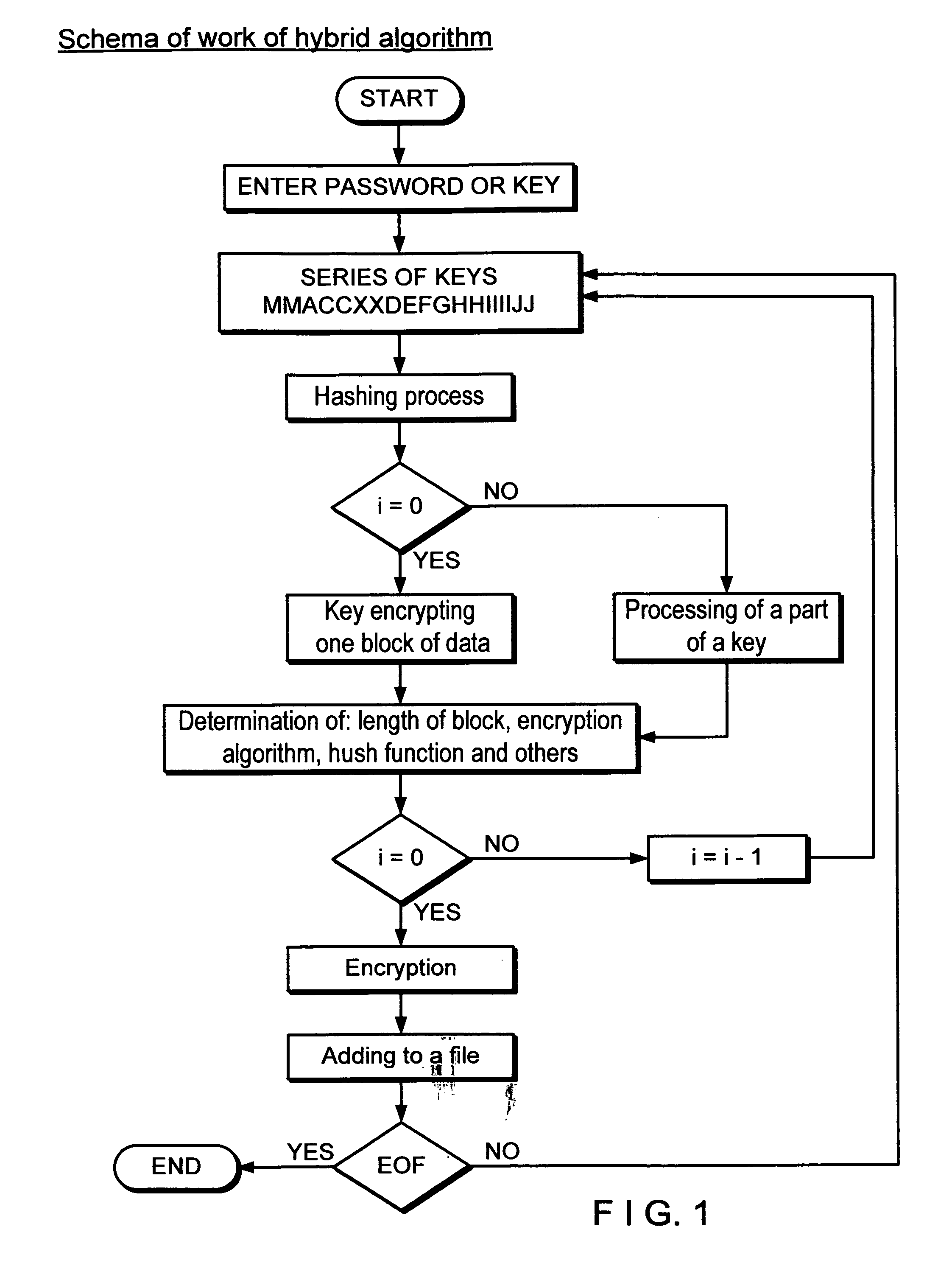
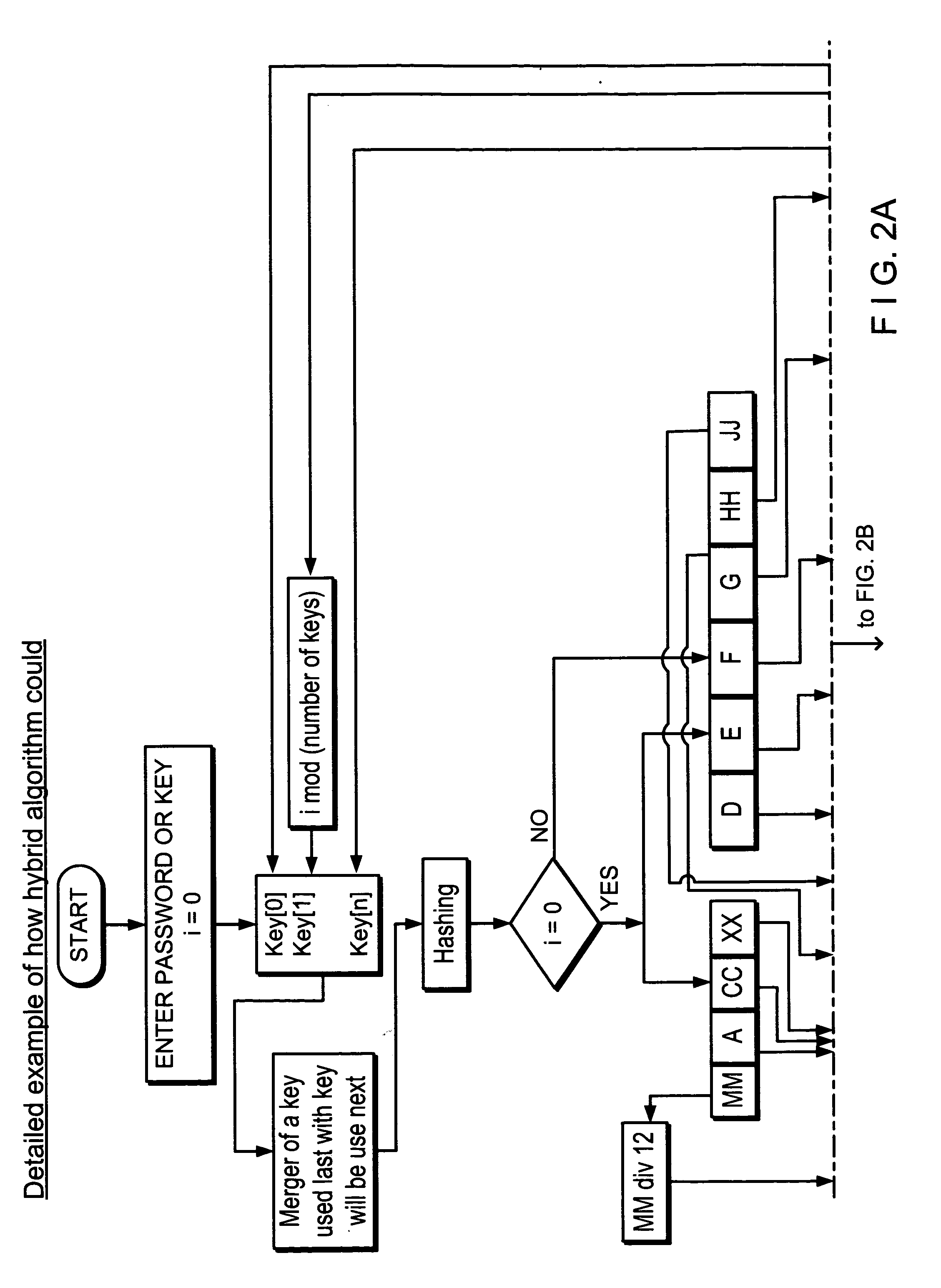
A method and system for hybrid encryption wherein all of the round function variables including the encryption algorithm change for each round. This permits the generation of block sizes and key sizes of any length and use standard block sizes and key sizes for the respective symmetric algorithm for each round function.
Owner:URBANIK JERZY HENRYK +1
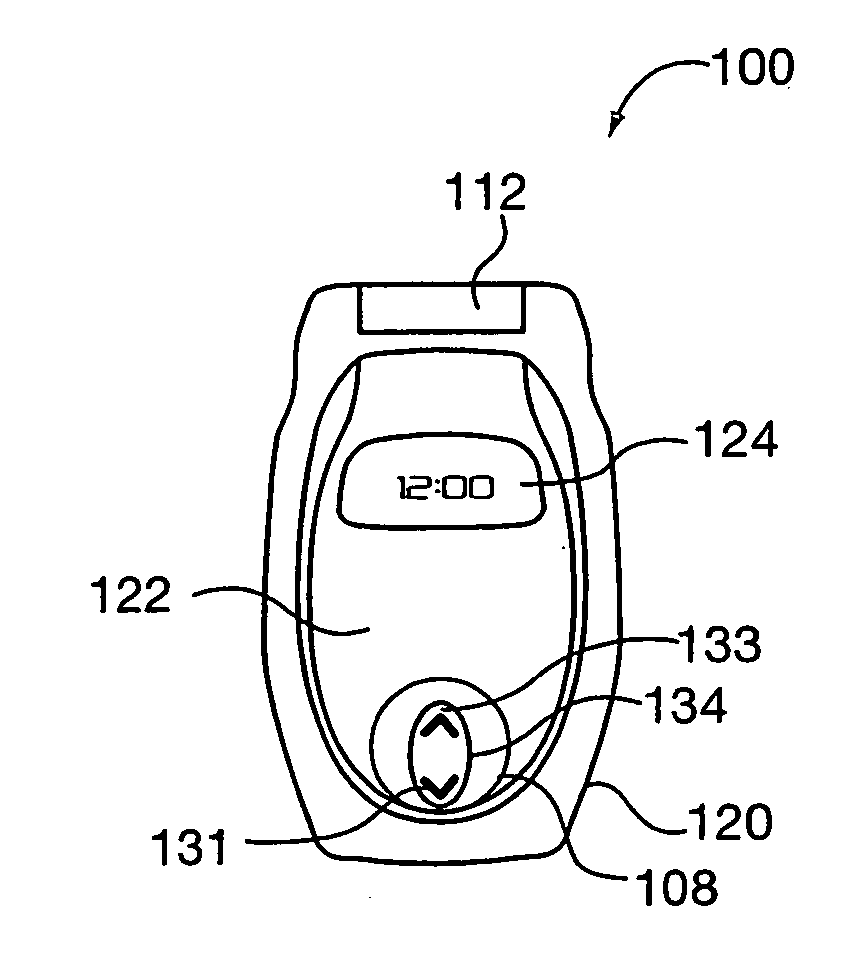
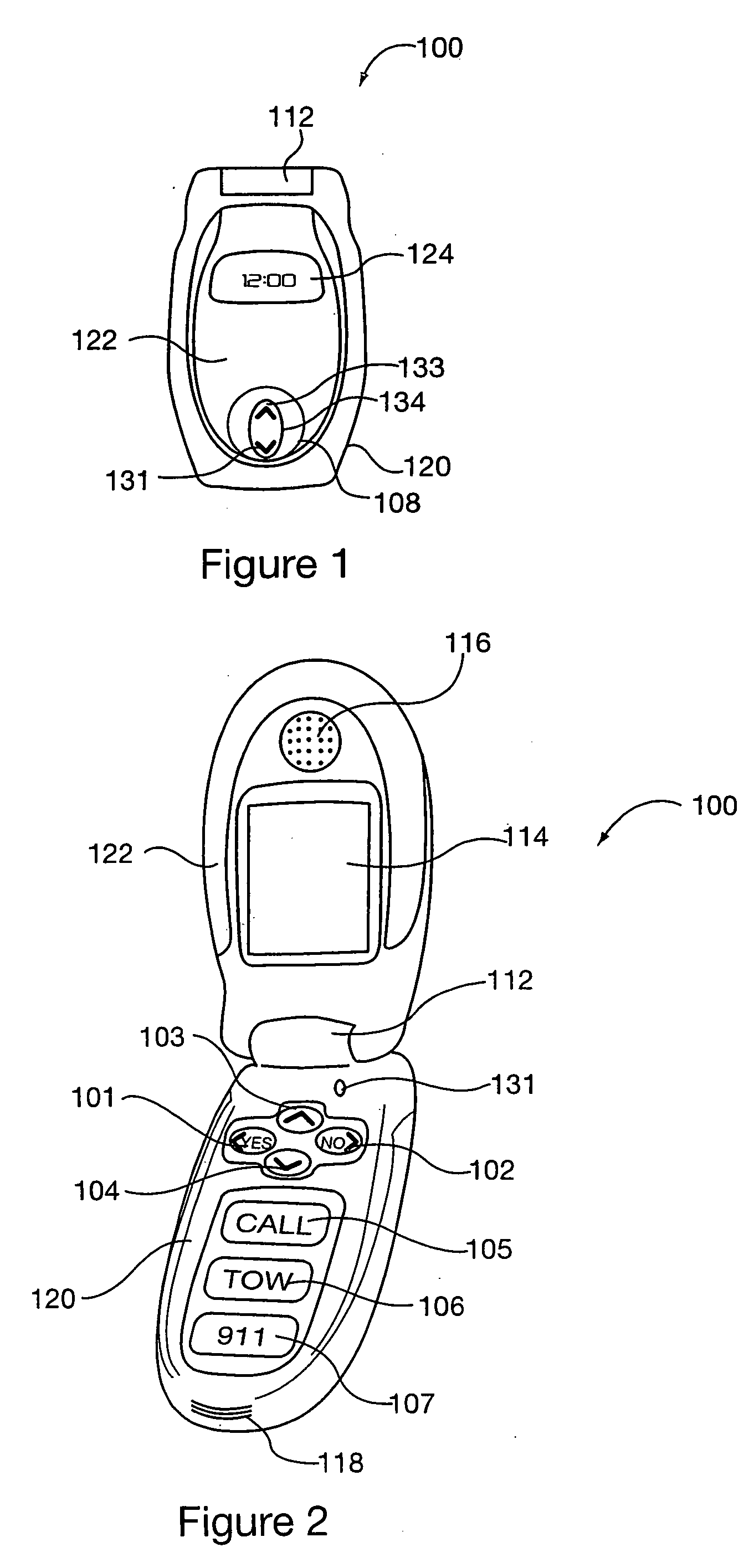
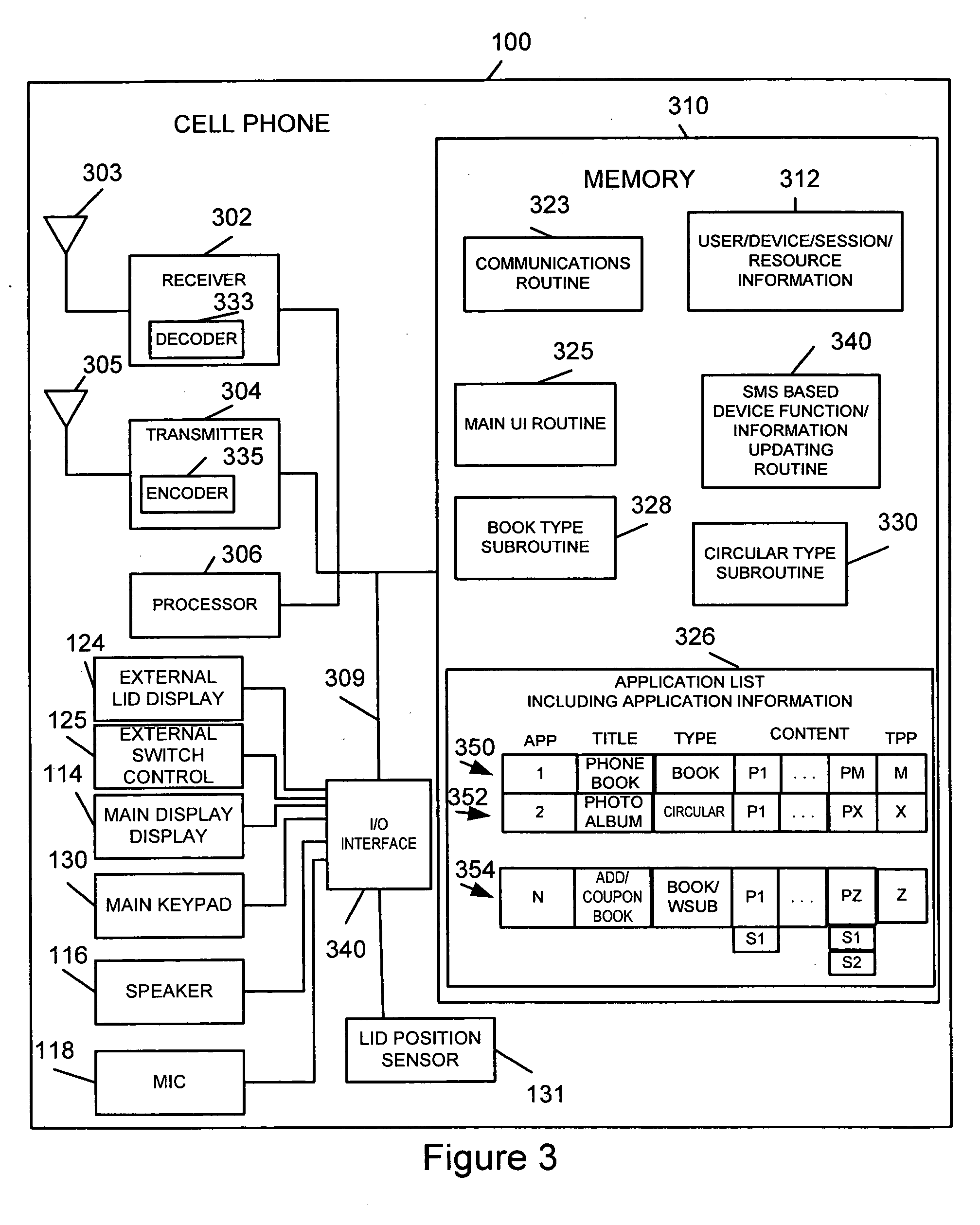
Simplified intuitive cell phone user interface
InactiveUS20070087775A1Reduce complexityQuantity minimizationSubstation equipmentAutomatic exchangesKey sizeUser interface
A portable communications device, e.g., a cell phone with a simplified user interface and easy to use keys is described. The user interface supports book type and circular type applications. Book interface type applications are applications in which a user is stopped from moving beyond the last page when a next page operation is selected. In circular applications a user is allowed to move from the last page of an application to the first page of the application by selecting a next page option. Regardless of the application type, in response to a displayed page a user, in some embodiments, is presented with at most 4 options. This allows navigation between applications, pages and selection of actions corresponding to pages to be supported using relatively few keys, e.g., 4 keys, thereby allowing the number of keys on the phone to be kept small and the key size large.
Owner:DYNA
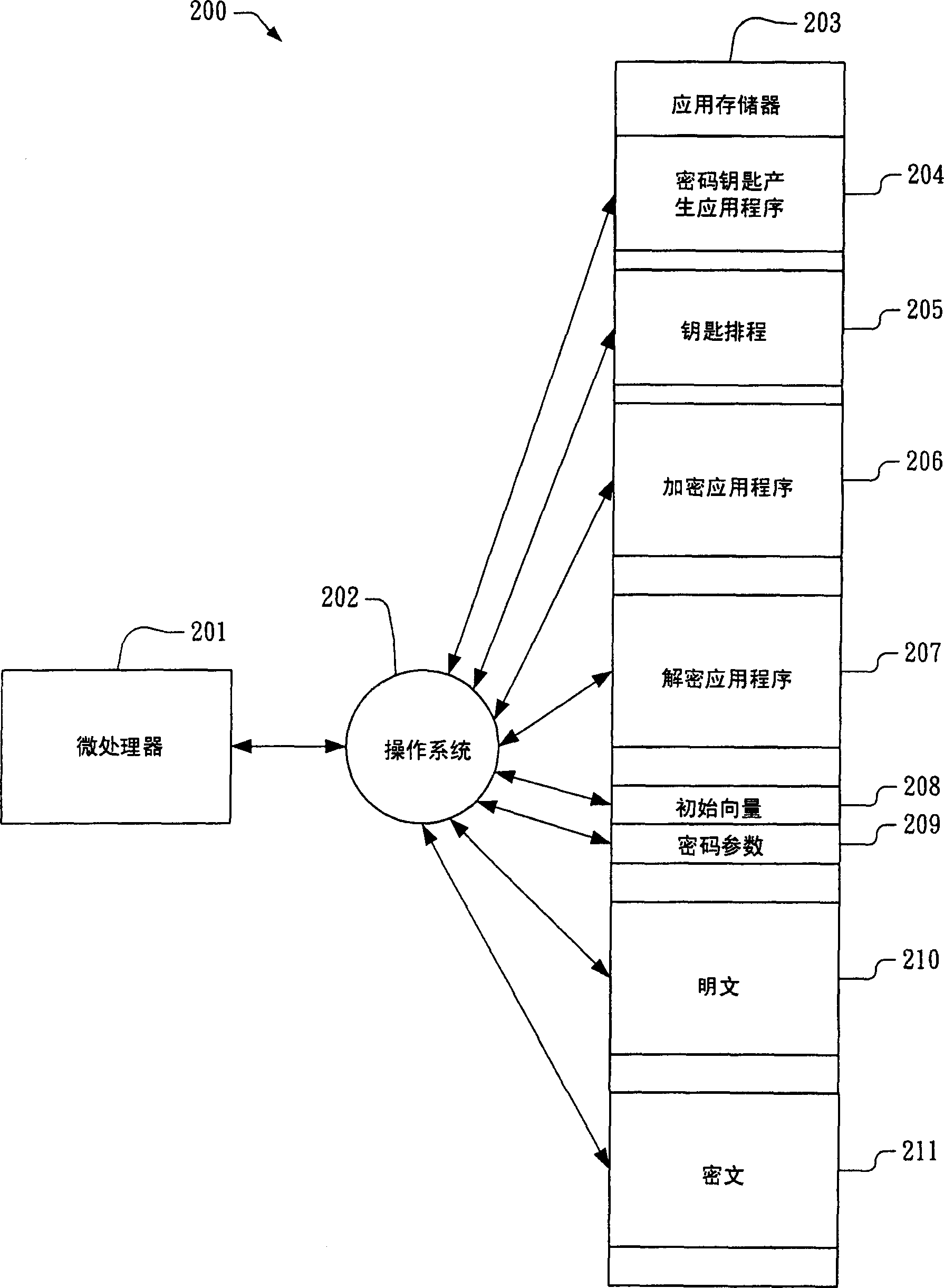
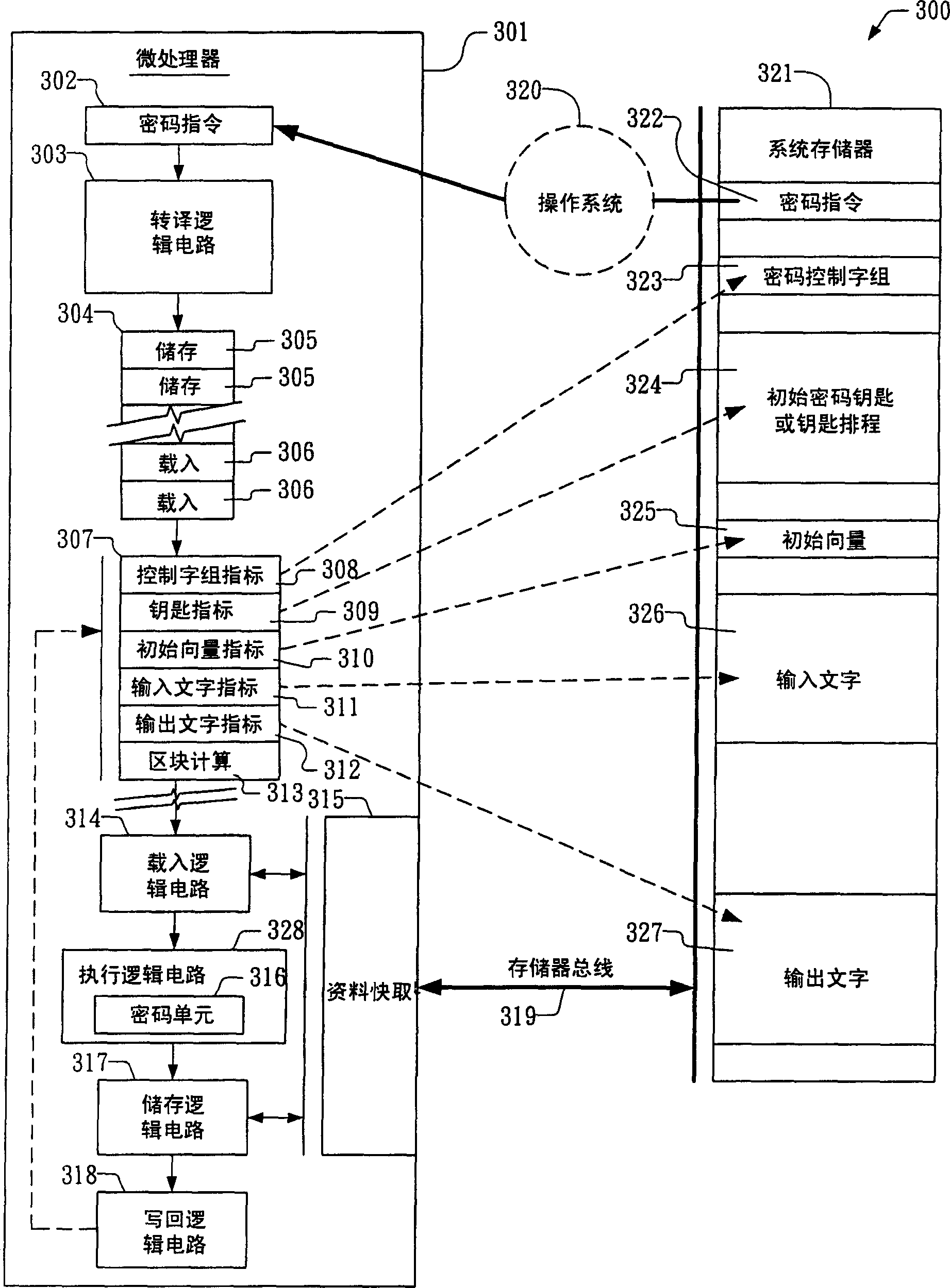
Apparatus and method for providing configurable cryptographic key size
ActiveCN1655496AKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer hardwareKey size
The present invention provides an apparatus and method for performing cryptographic operations. In one embodiment, an apparatus is provided for performing cryptographic operations. The apparatus includes a cryptographic instruction, keygen logic, and execution logic. The cryptographic instruction is received by a computing device as part of an instruction flow executing on the computing device. The cryptographic instruction prescribes one of the cryptographic operations, and also prescribes that a provided cryptographic key be expanded into a corresponding key schedule for employment during execution of the one of the cryptographic operations. The keygen logic is operatively coupled to the cryptographic instruction. The keygen logic directs the computing device to expand the provided cryptographic key into the corresponding key schedule. The execution logic is coupled to the keygen logic. The execution logic expands the provided cryptographic key into the corresponding key schedule.
Owner:VIA TECH INC
Method and Apparatus for Securing Input of Information via Software Keyboards
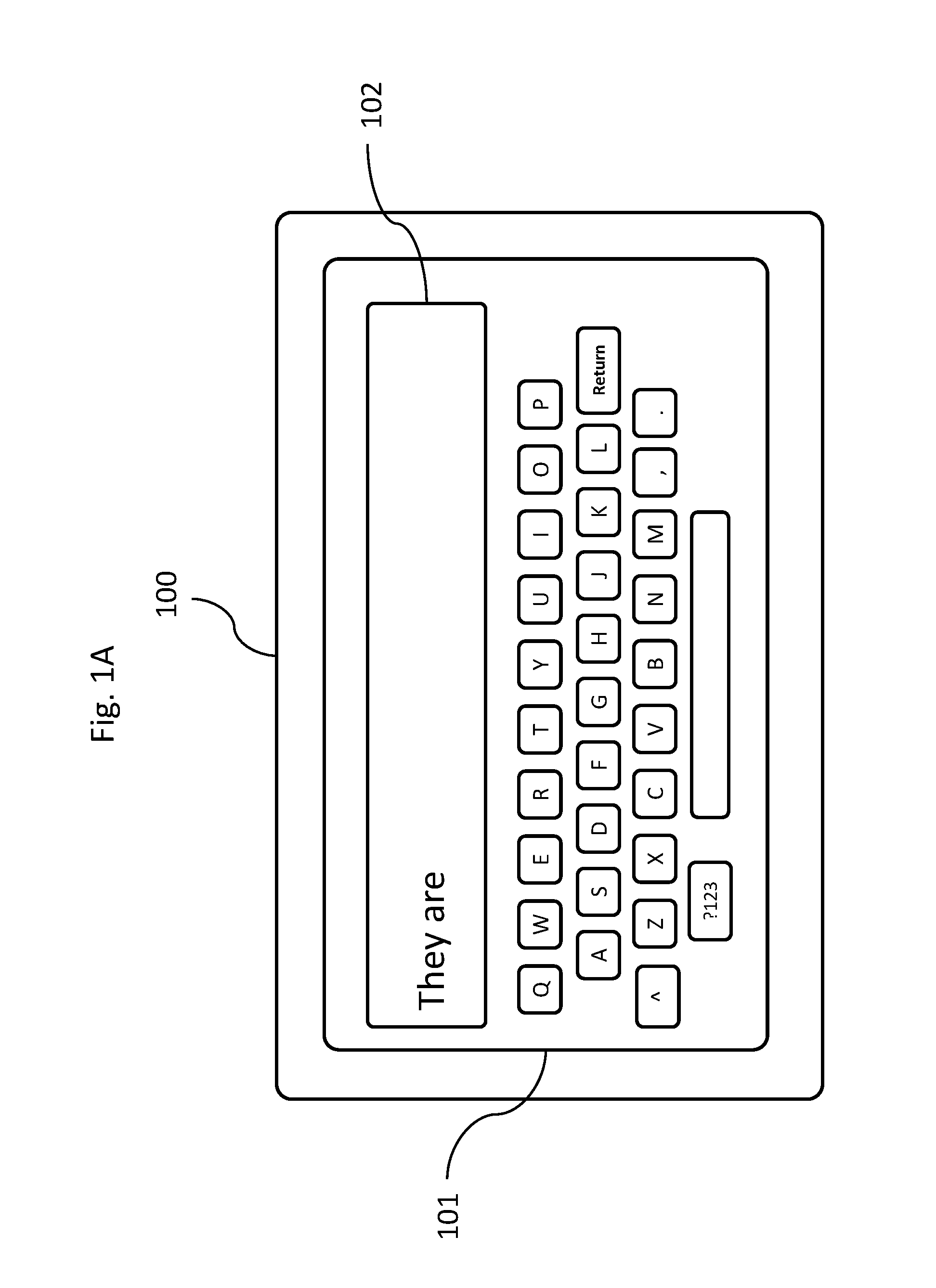
InactiveUS20140098141A1Cathode-ray tube indicatorsPlatform integrity maintainanceComputer hardwareKey size
Data entry using a software keyboard such as a touchscreen keyboard is secured by varying key sizes in the keyboard from key to key and from software keyboard configuration to software keyboard configuration, decoupling display locations from keys. Multiple software keyboard configurations are generated, each having different sets of key sizes. The keyboard configuration may be changed with each keystroke, or may be changed for each prompted entry including multiple keystrokes.
Owner:AT&T INTPROP I L P
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com