Patents
Literature
117results about How to "More secure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
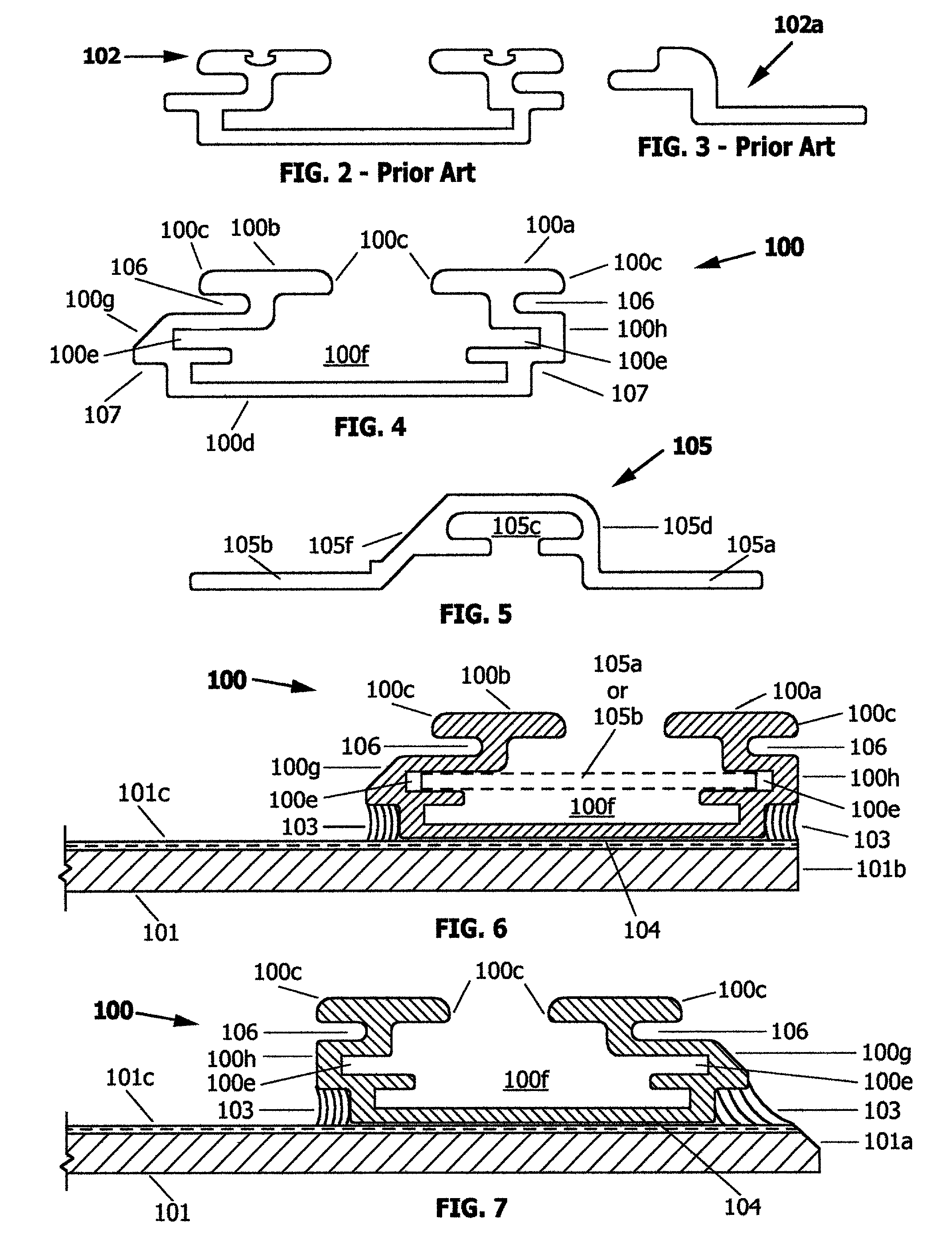
Method and Apparatus for Hardware-Accelerated Encryption/Decryption
ActiveUS20090060197A1Avoid contactMaximize availabilityEncryption apparatus with shift registers/memoriesSecret communicationMultiple encryptionComputer hardware
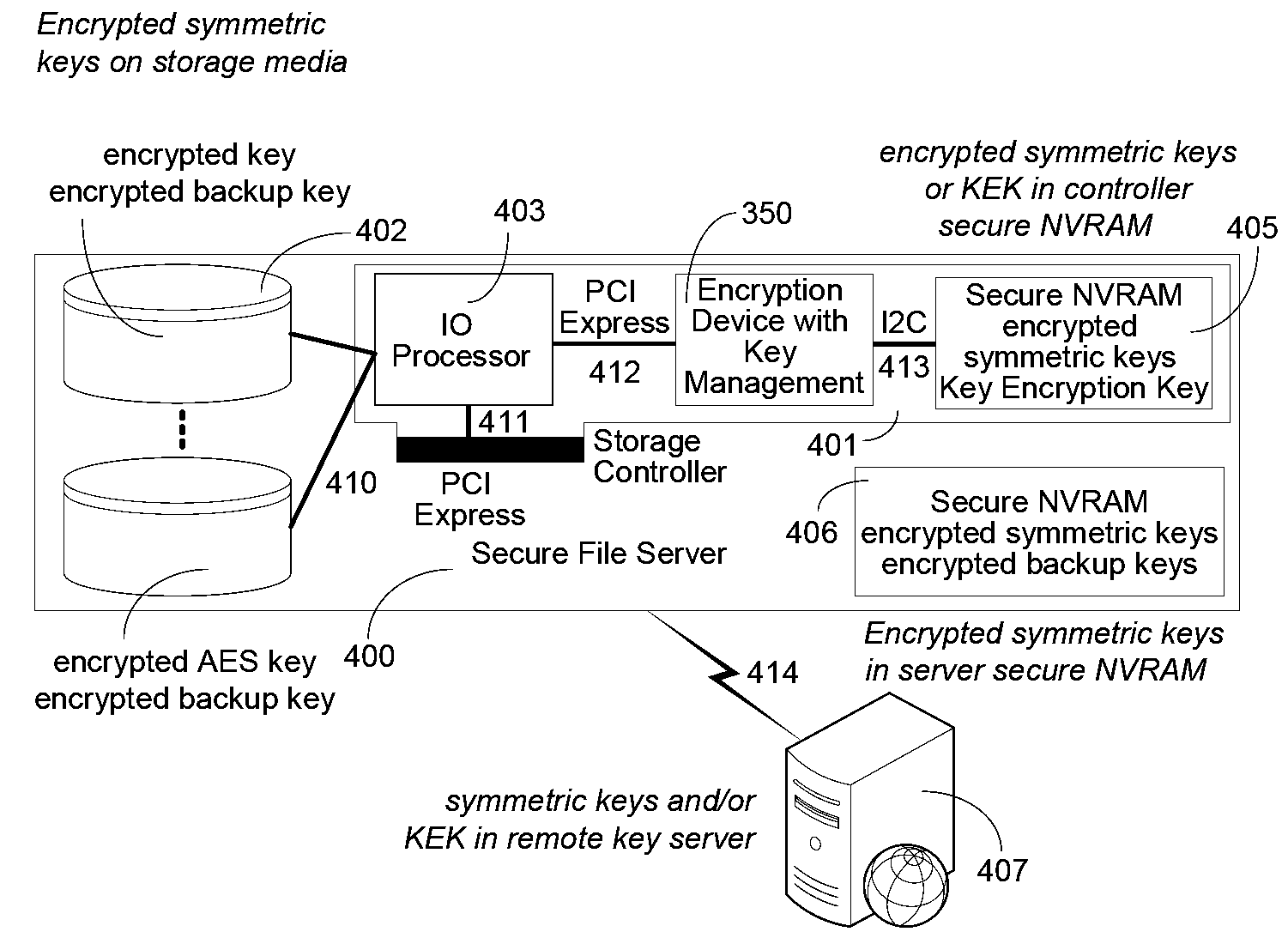
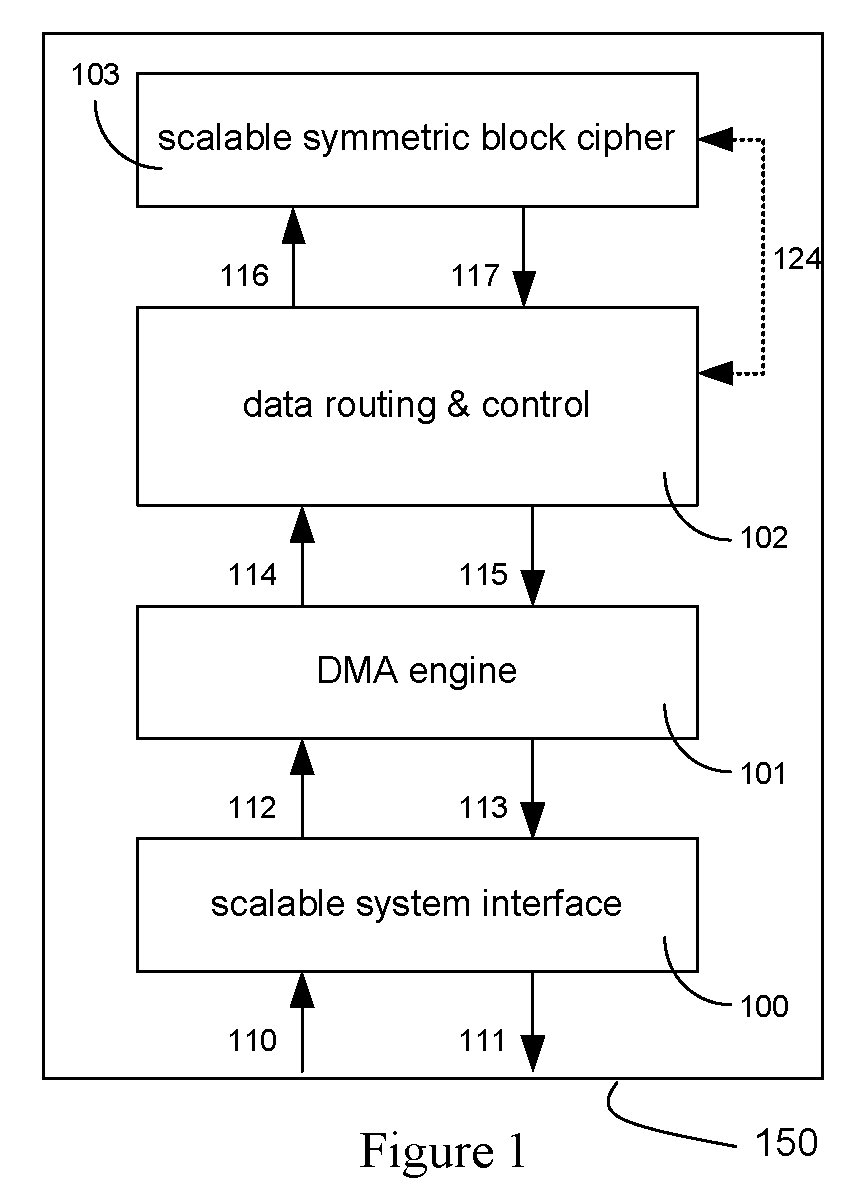
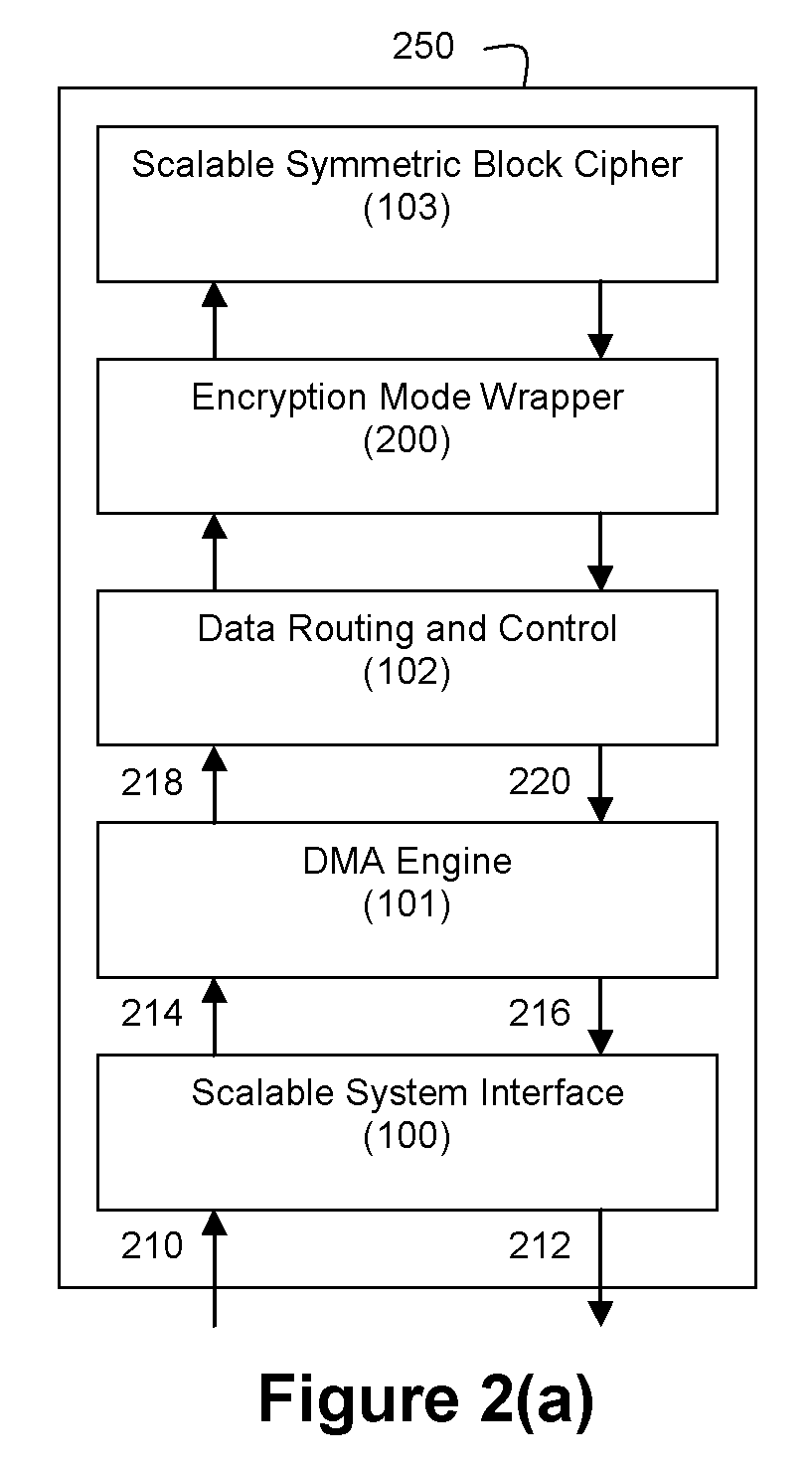
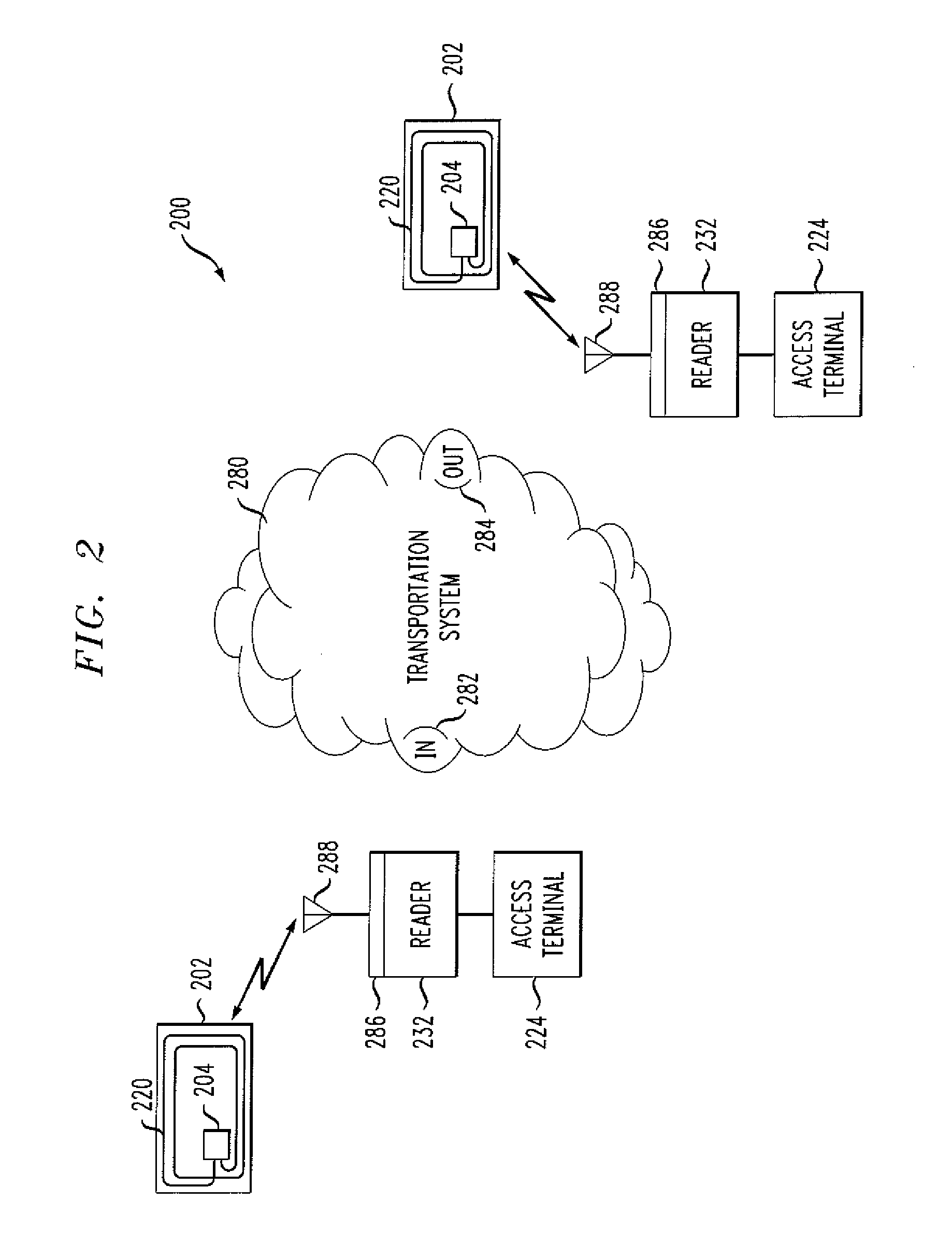
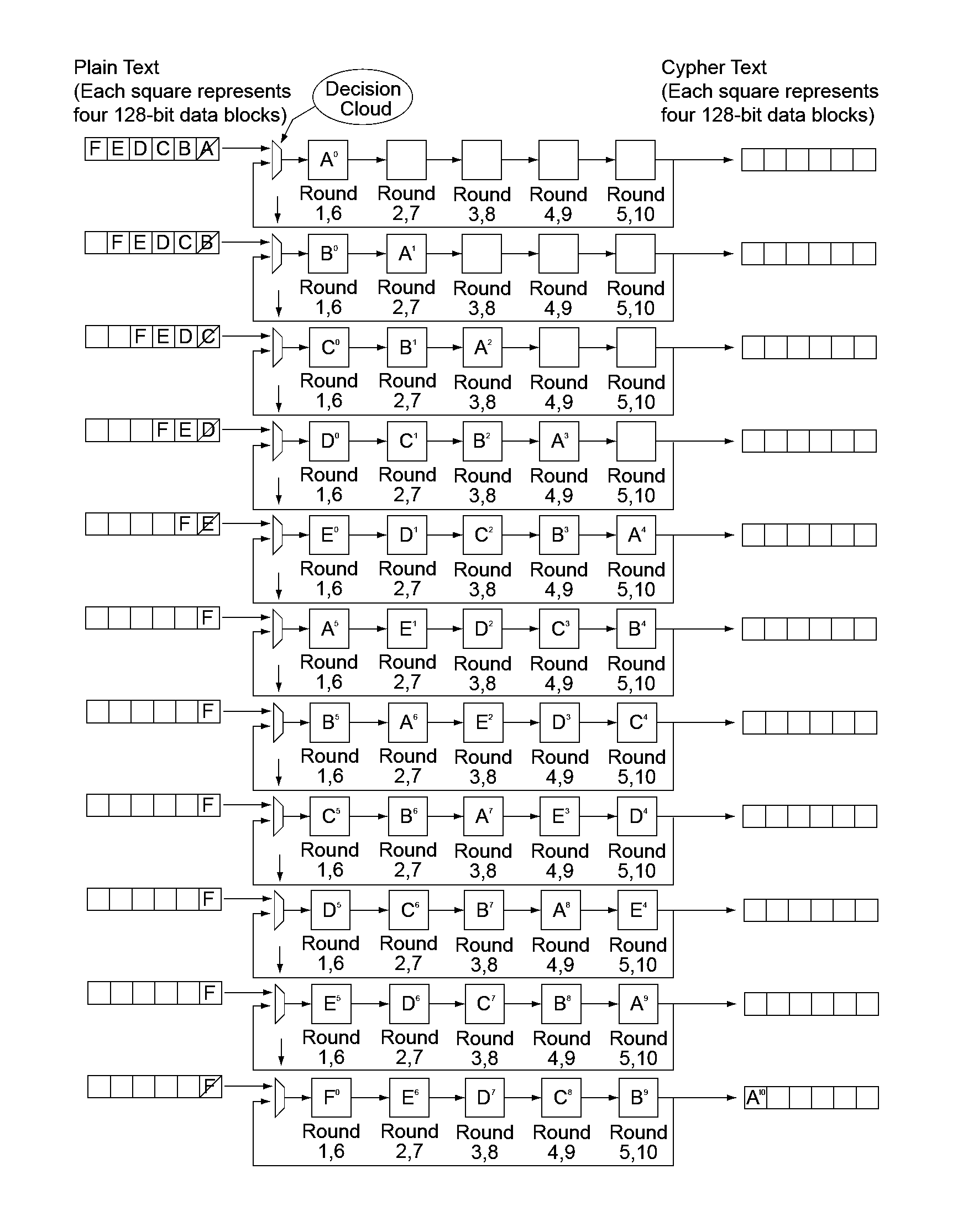
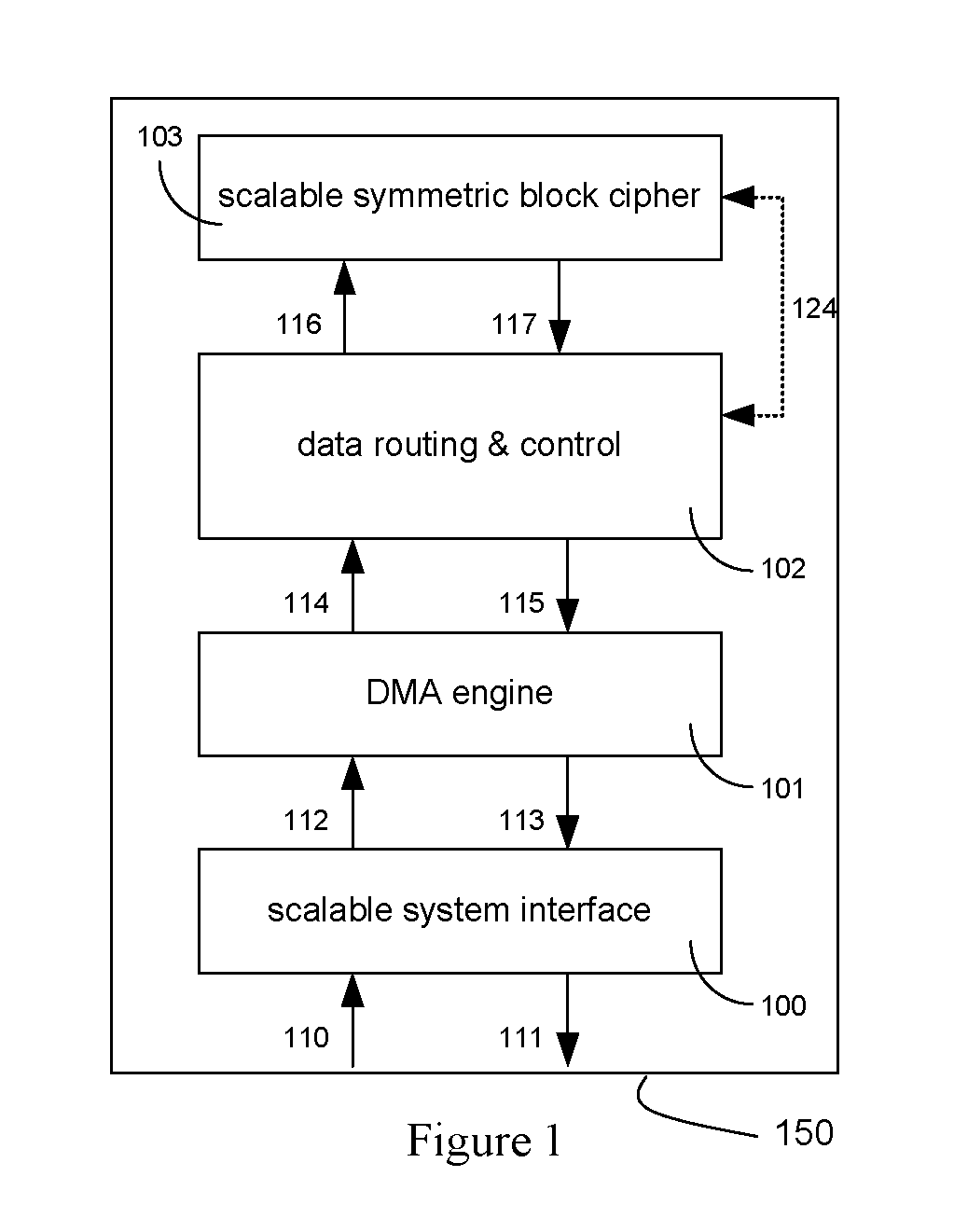
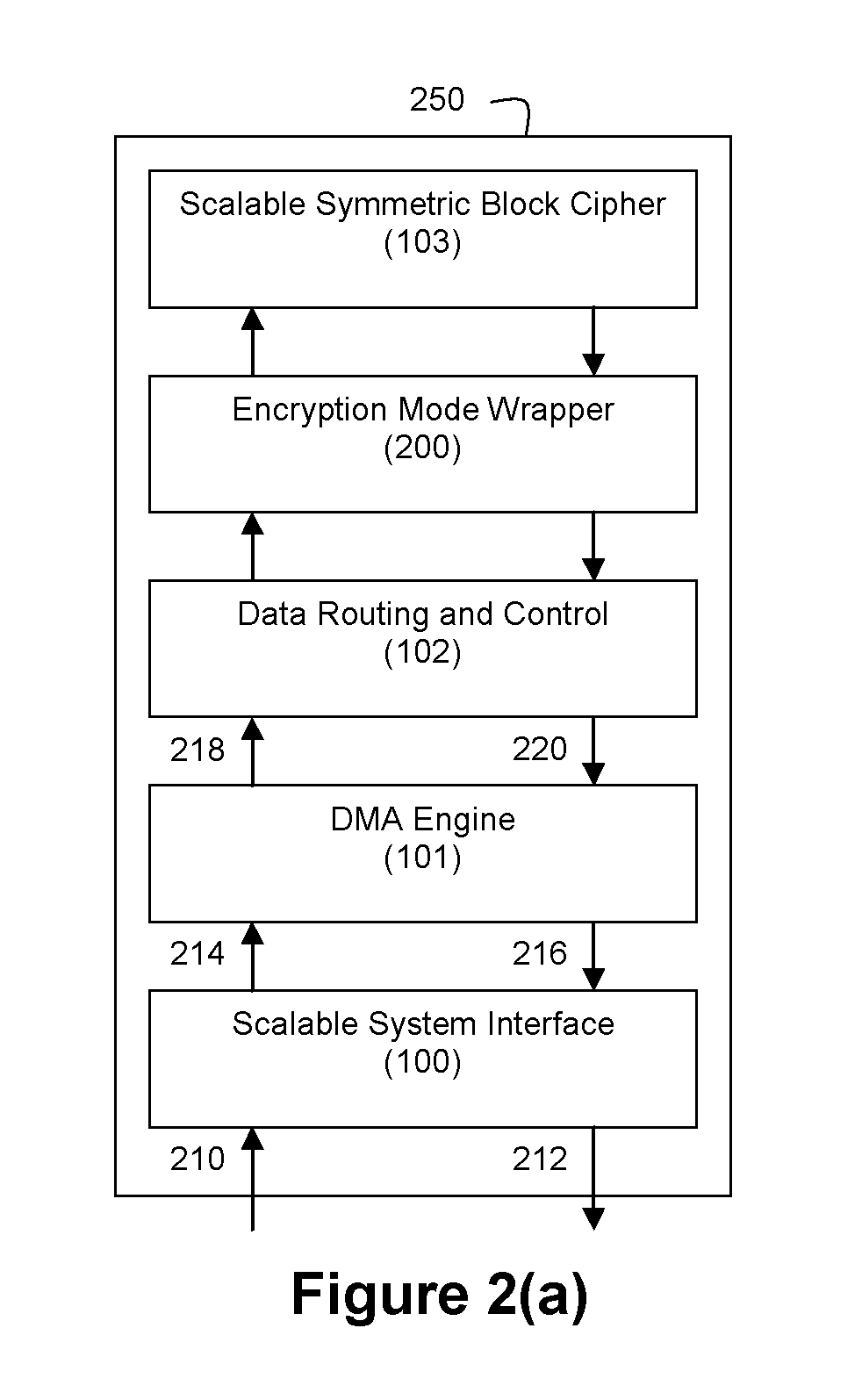
An integrated circuit for data encryption / decryption and secure key management is disclosed. The integrated circuit may be used in conjunction with other integrated circuits, processors, and software to construct a wide variety of secure data processing, storage, and communication systems. A preferred embodiment of the integrated circuit includes a symmetric block cipher that may be scaled to strike a favorable balance among processing throughput and power consumption. The modular architecture also supports multiple encryption modes and key management functions such as one-way cryptographic hash and random number generator functions that leverage the scalable symmetric block cipher. The integrated circuit may also include a key management processor that can be programmed to support a wide variety of asymmetric key cryptography functions for secure key exchange with remote key storage devices and enterprise key management servers. Internal data and key buffers enable the device to re-key encrypted data without exposing data. The key management functions allow the device to function as a cryptographic domain bridge in a federated security architecture.
Owner:IP RESERVOIR
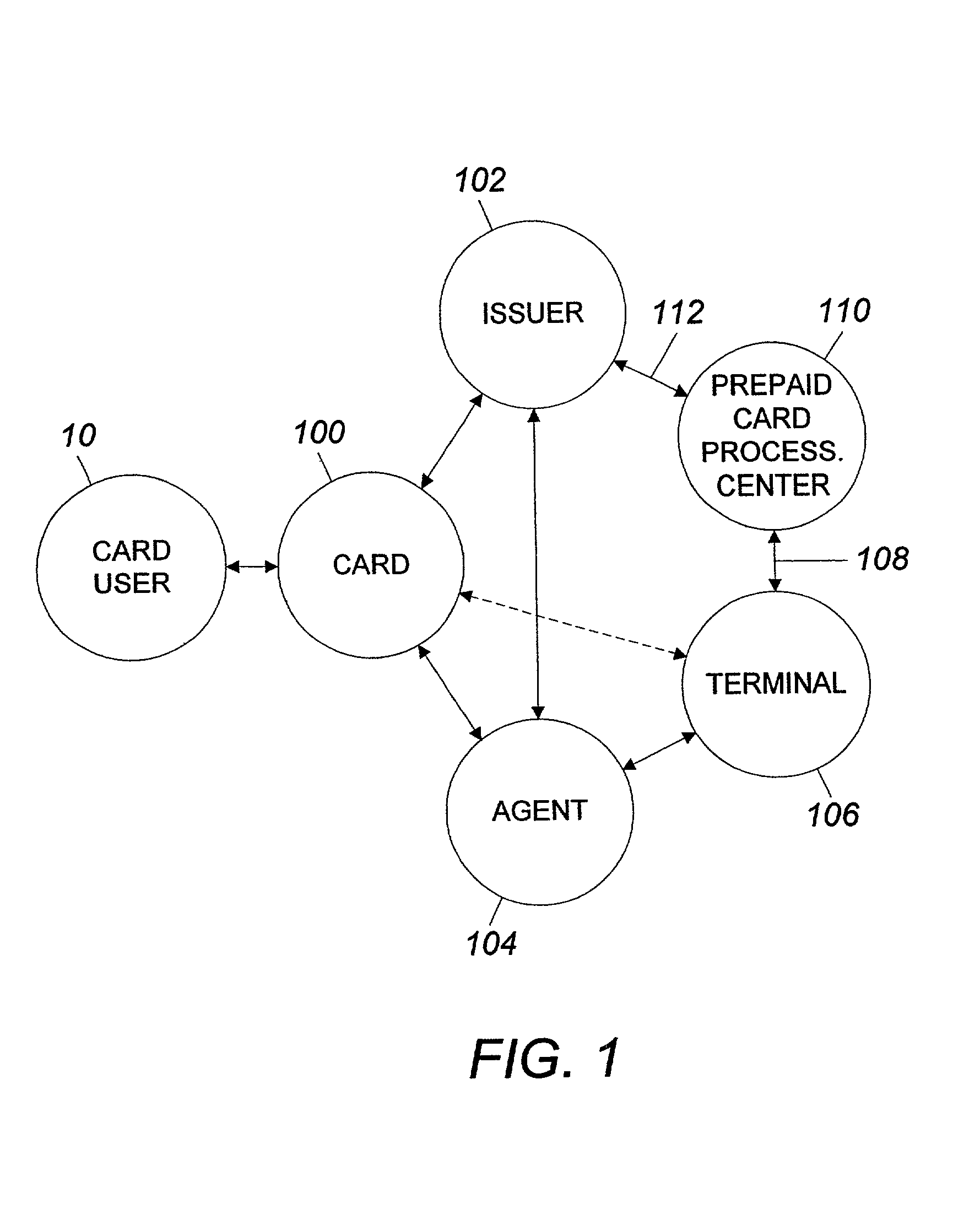
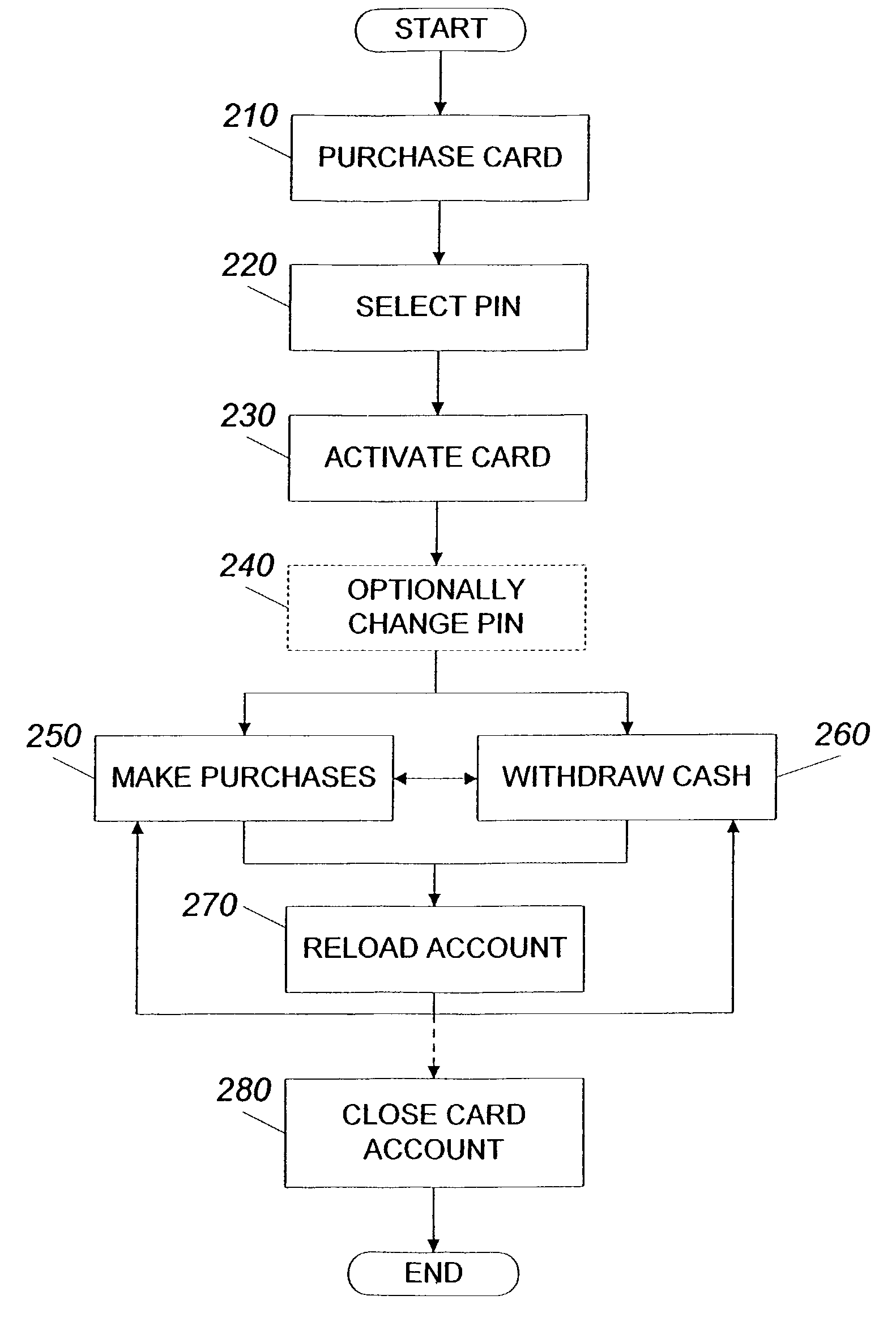
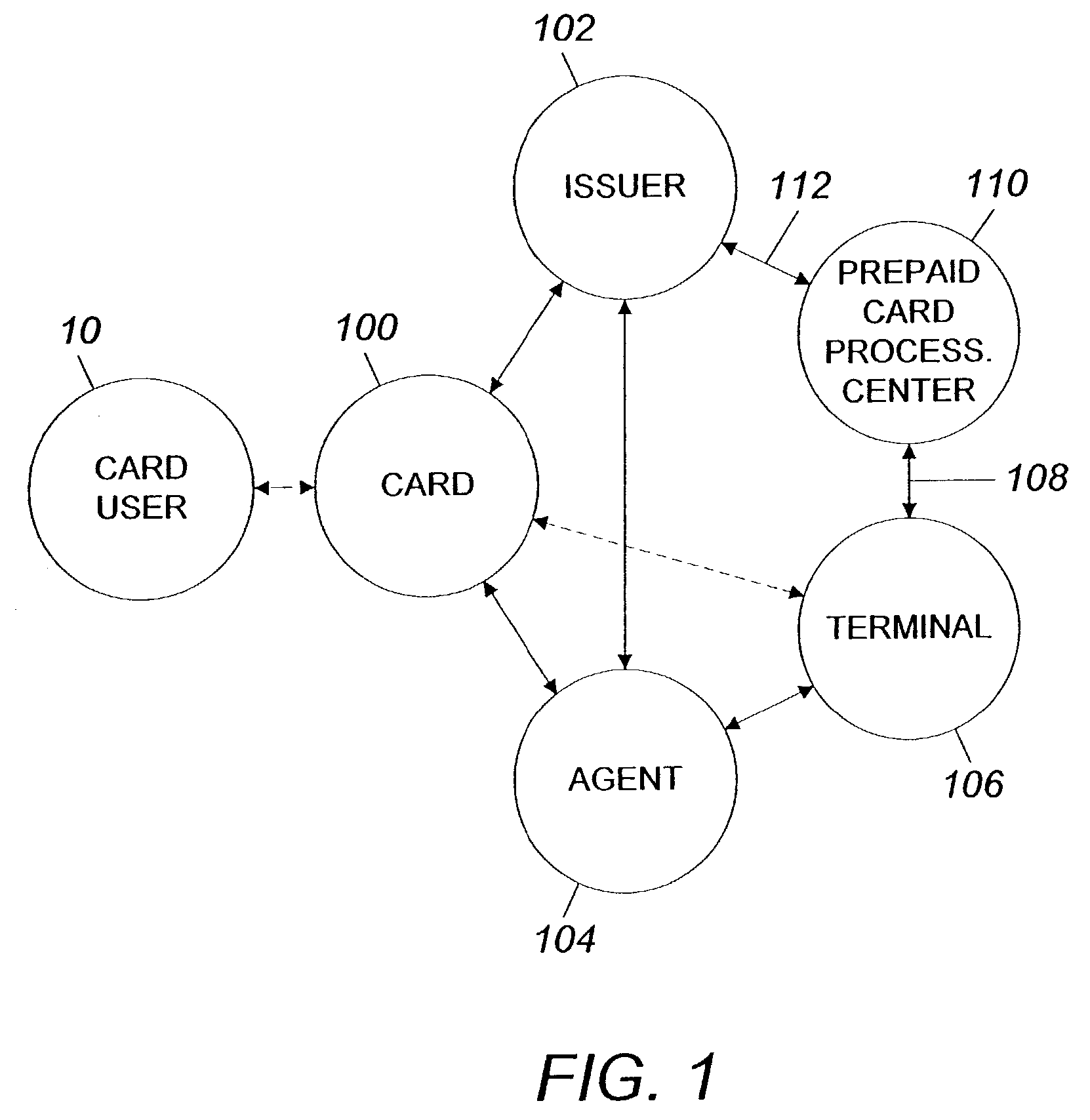
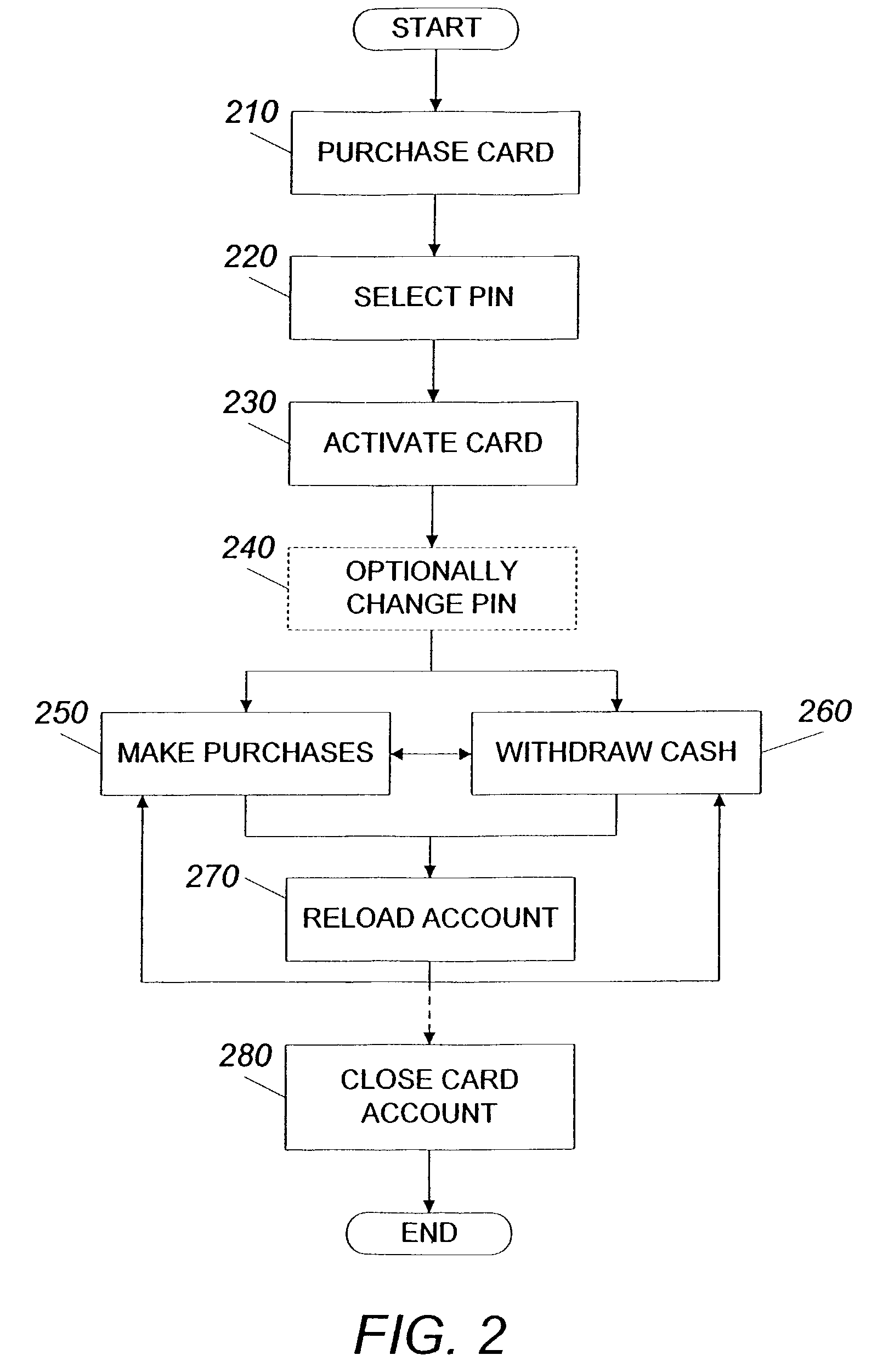
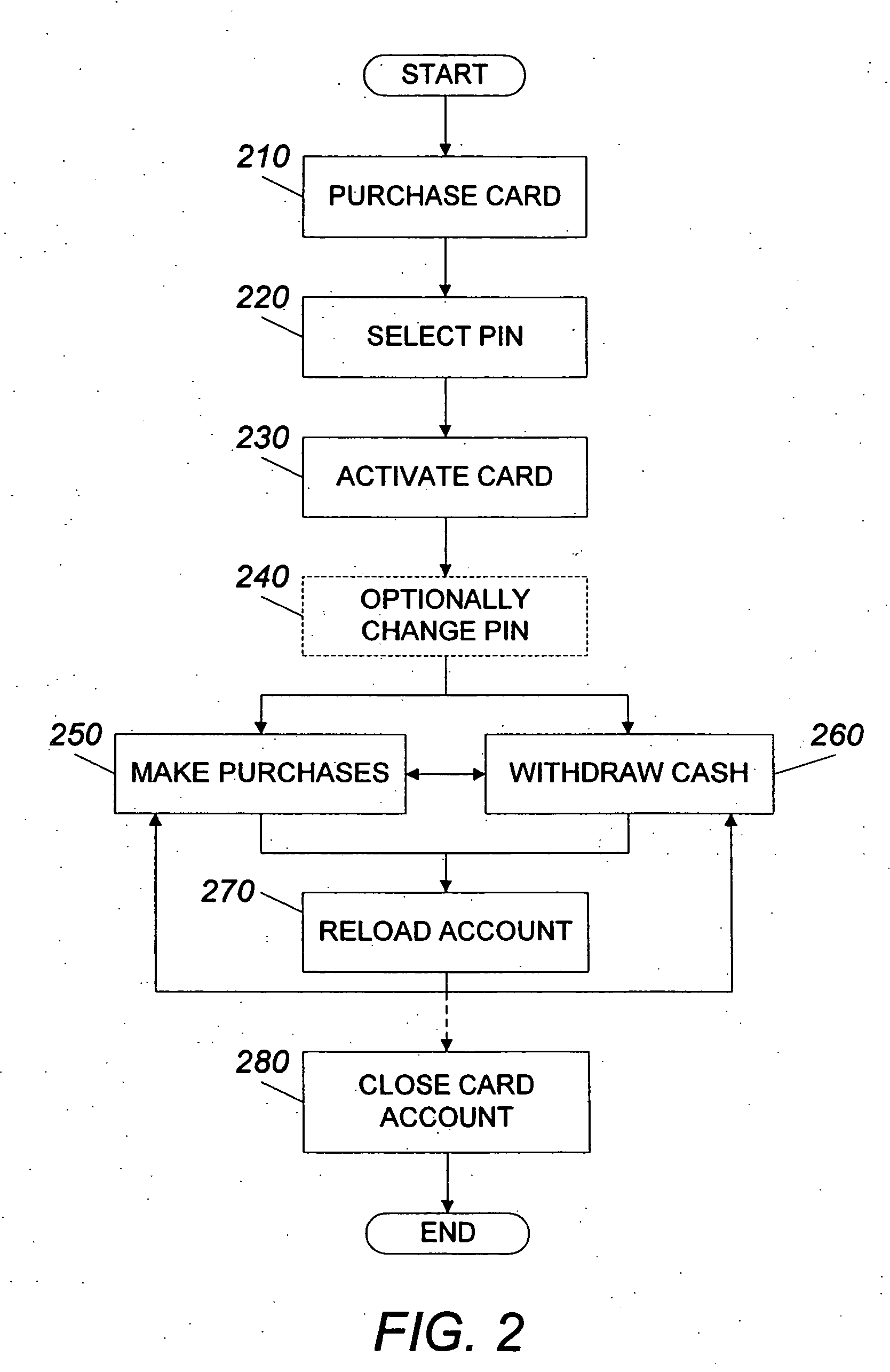
System and method for using a prepaid card
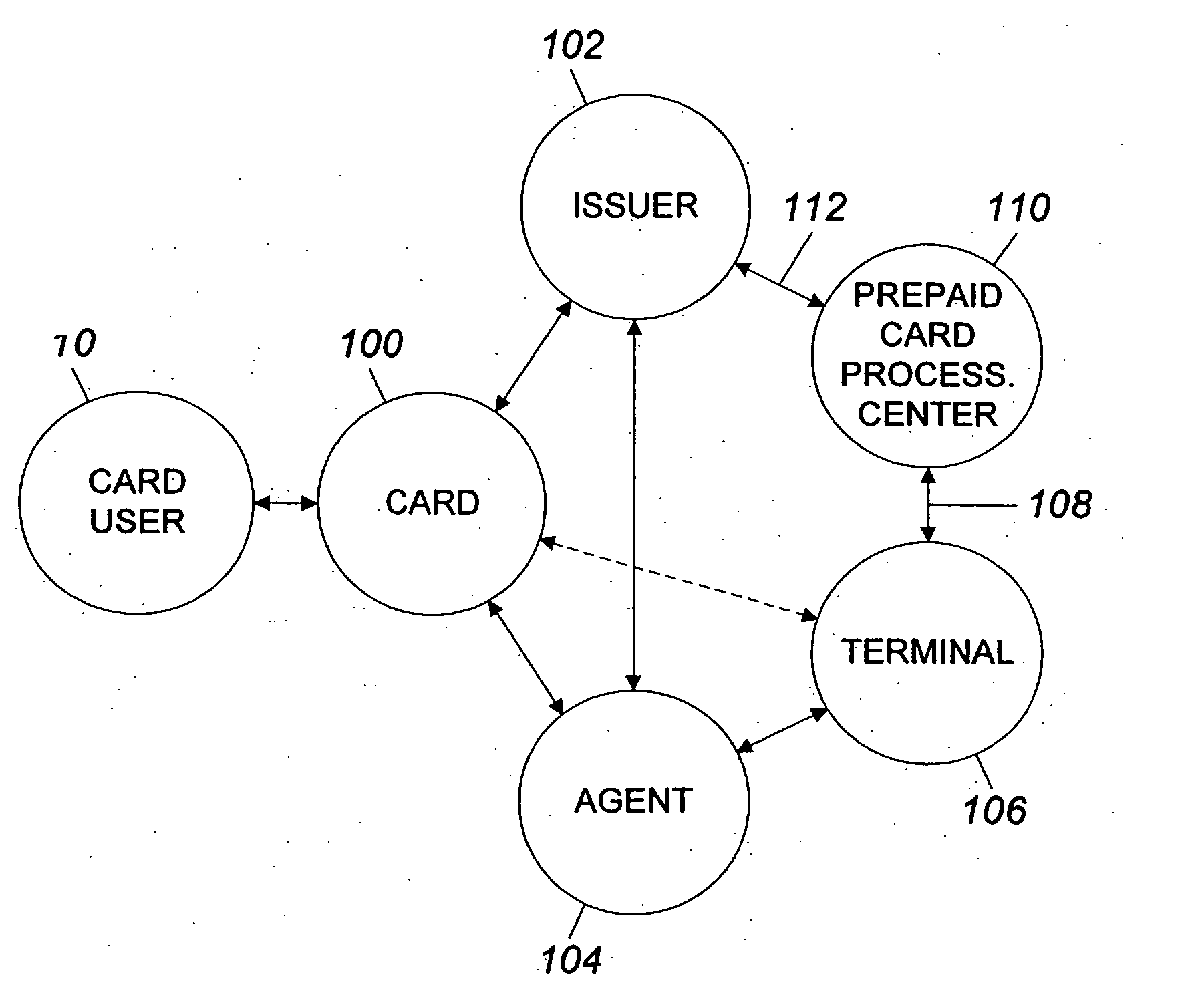
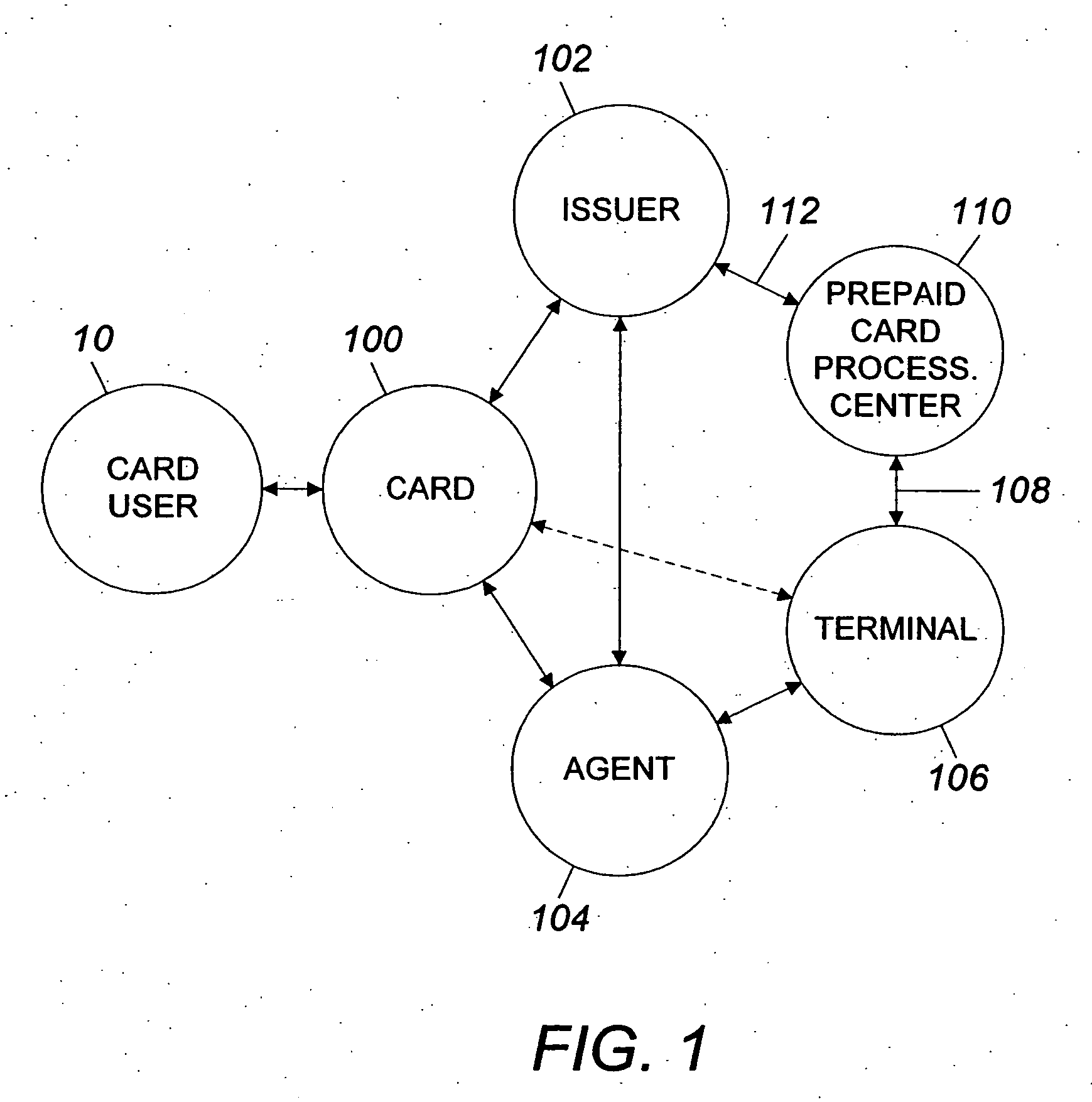
InactiveUS6999569B2Increase valueMeet the need for flexibilityCredit registering devices actuationBilling/invoicingFinancial transactionOperating system
A system and method for transferring money by use of a prepaid card account is disclosed wherein two cards are issued to the user accountholder, one of which is provided to another user, and either user may add value to the prepaid account so that the other user may use the card and that value in a financial transaction.
Owner:THOMSON LICENSING SA
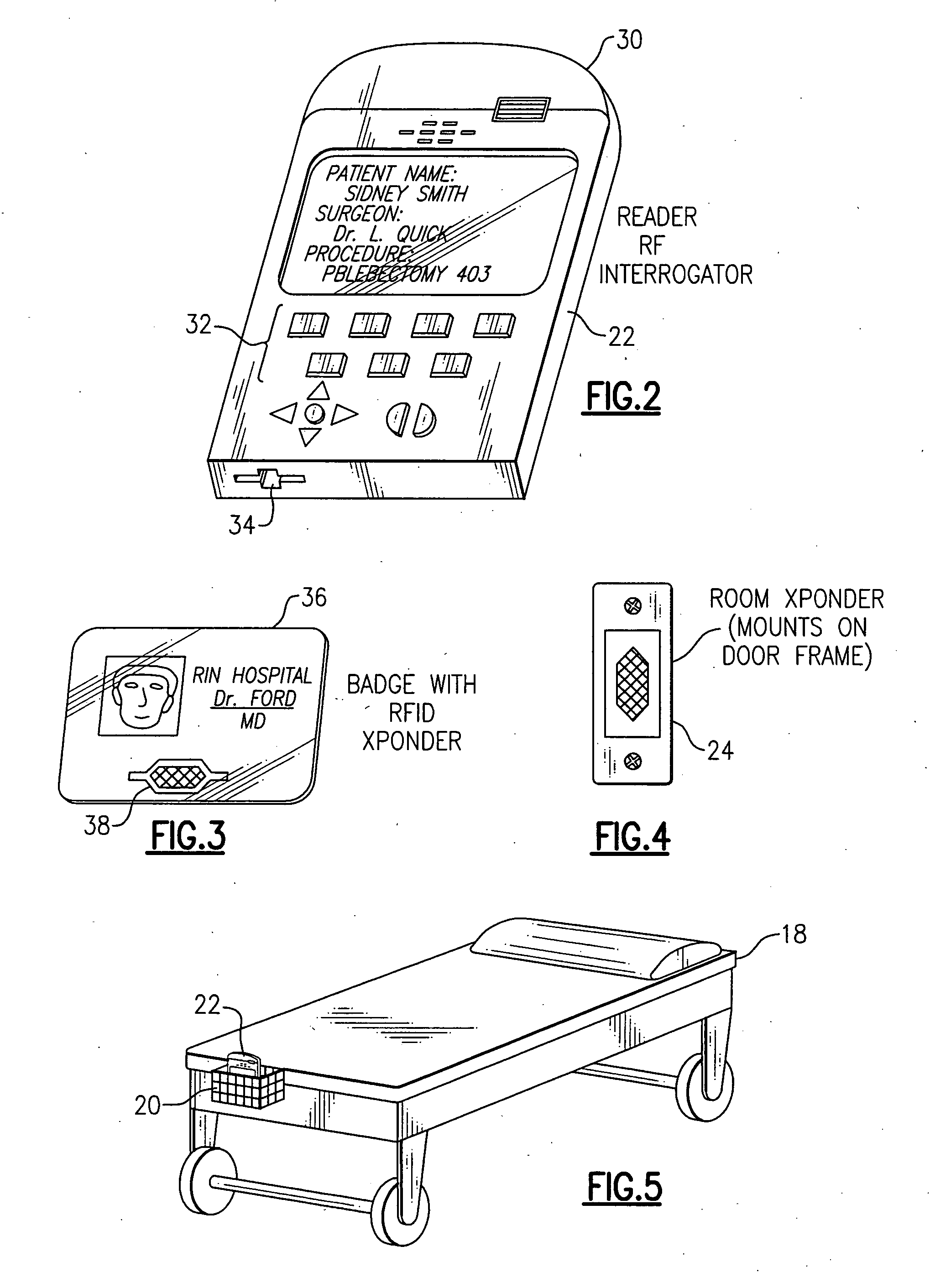
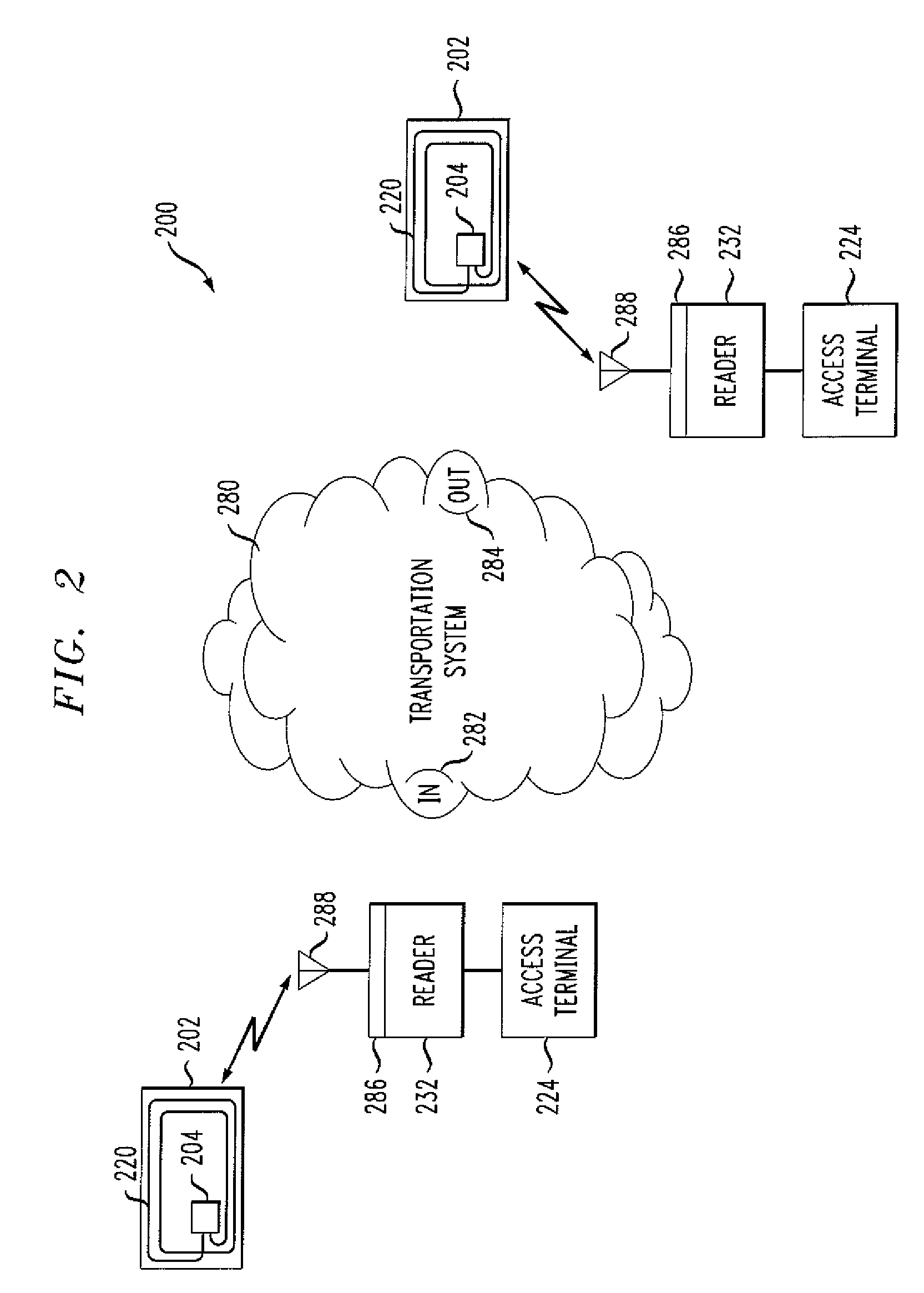
RFID tracking of anesthesiologist and patient time
InactiveUS20050149358A1Simple methodNot easy to copyElectric signal transmission systemsMechanical/radiation/invasive therapiesHand heldOperating theatres
RFID-based system for tracking billable anesthesiology time in a surgical environment employs hand-held RFID reader devices that record and store timed anesthesia events for each surgical patient. Each patient is assigned a reader device, uploaded with patient data. Each anesthesiology professional has an identifying RFID transponder, and room transponders are located on wall or doorway of each room in the surgical suite. A download cradle is used for downloading the patient data collected during surgery to a central computer. The reader devices are synchronized to a high-accuracy clock, eliminating time accounting problems associated with concurrency and discontinuous time.
Owner:SACCO LISA M +1
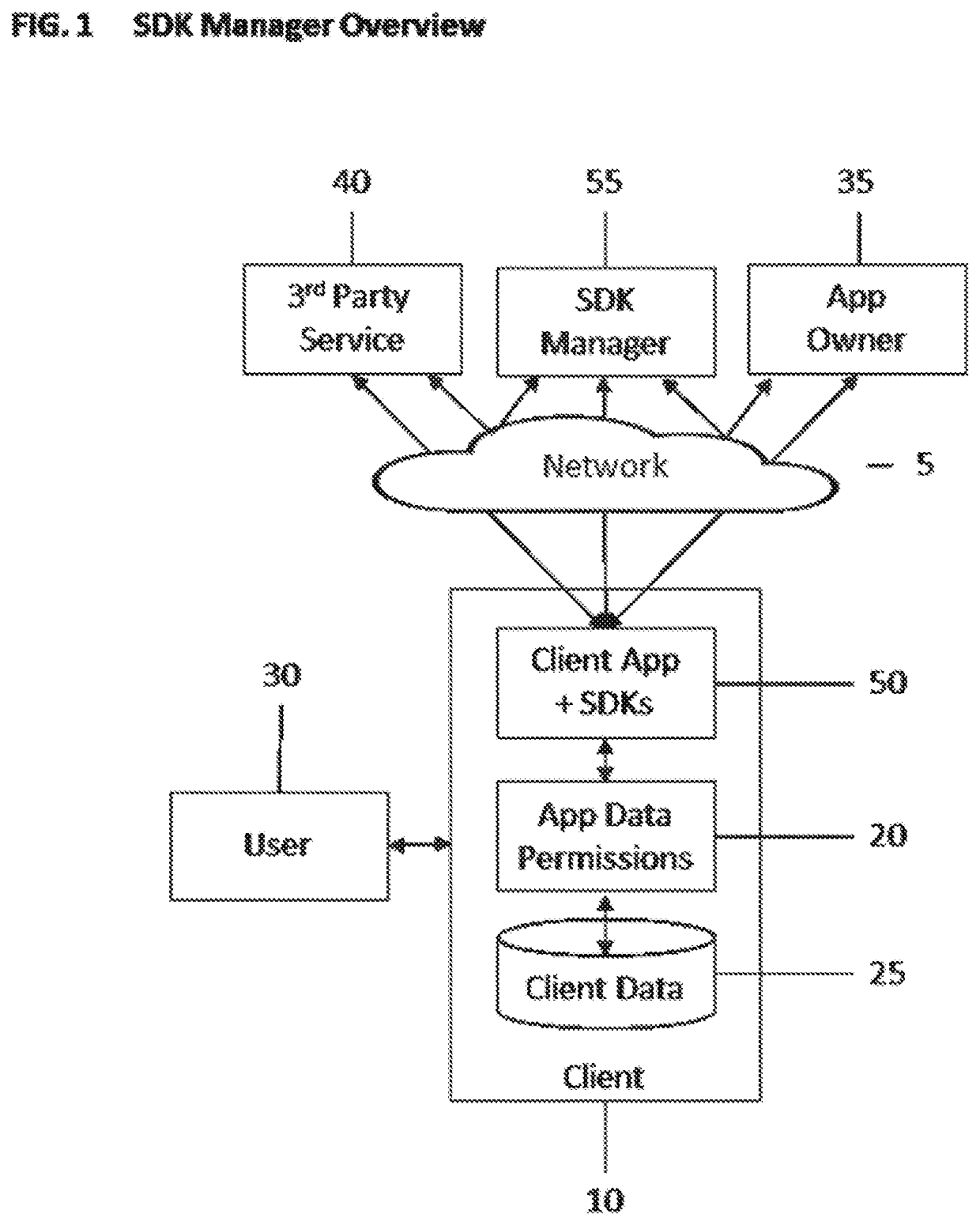
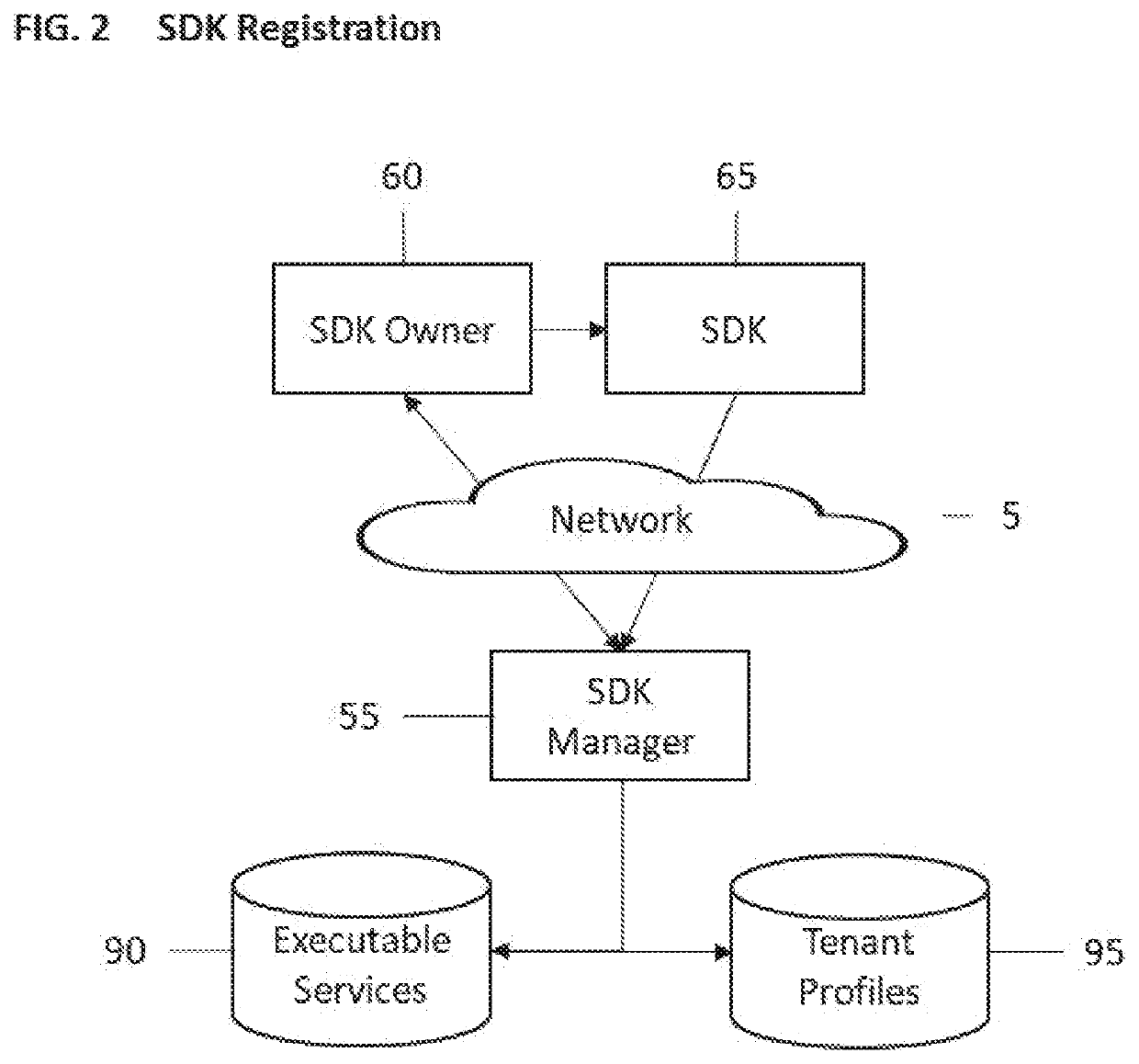
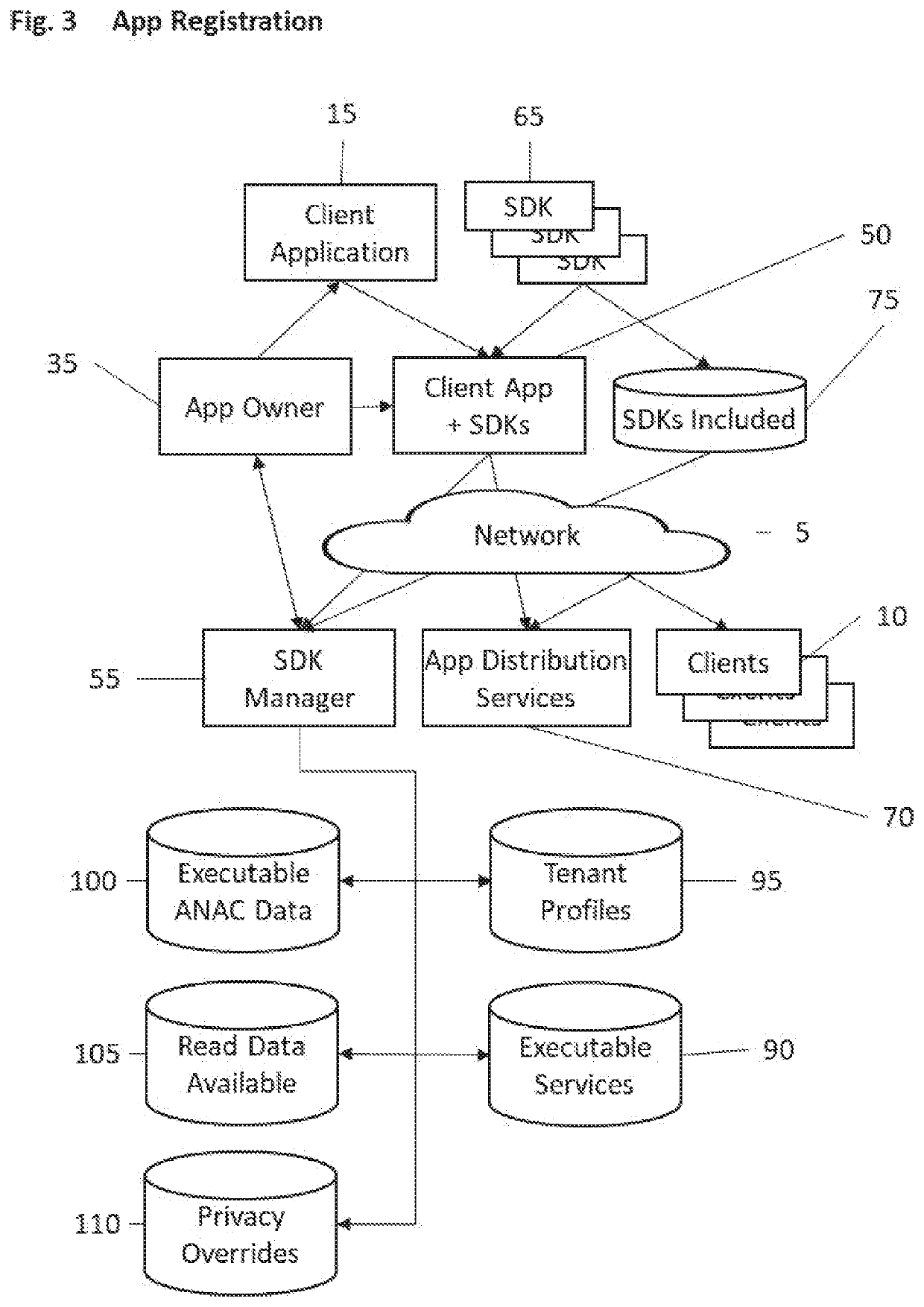
Systems and methods for secured, managed, multi-party interchanges with a software application operating on a client device
ActiveUS20200250342A1Ensure integrityEasy to manageDigital data protectionTransmissionThird partySoftware engineering
A system and methods which manage and secure the interaction between (1) the owner of a client application and third-parties, and (2) between the third-parties and the client application while the client application is operating on a user's client computer. The invention enables interactive primitives such as ensuring the integrity of the client environment, reading data from the client, writing data to the client, collecting data from the user, and ensuring privacy. All functionality is done through the client application and under management and control of the owner of the client application.
Owner:MSIGNIA
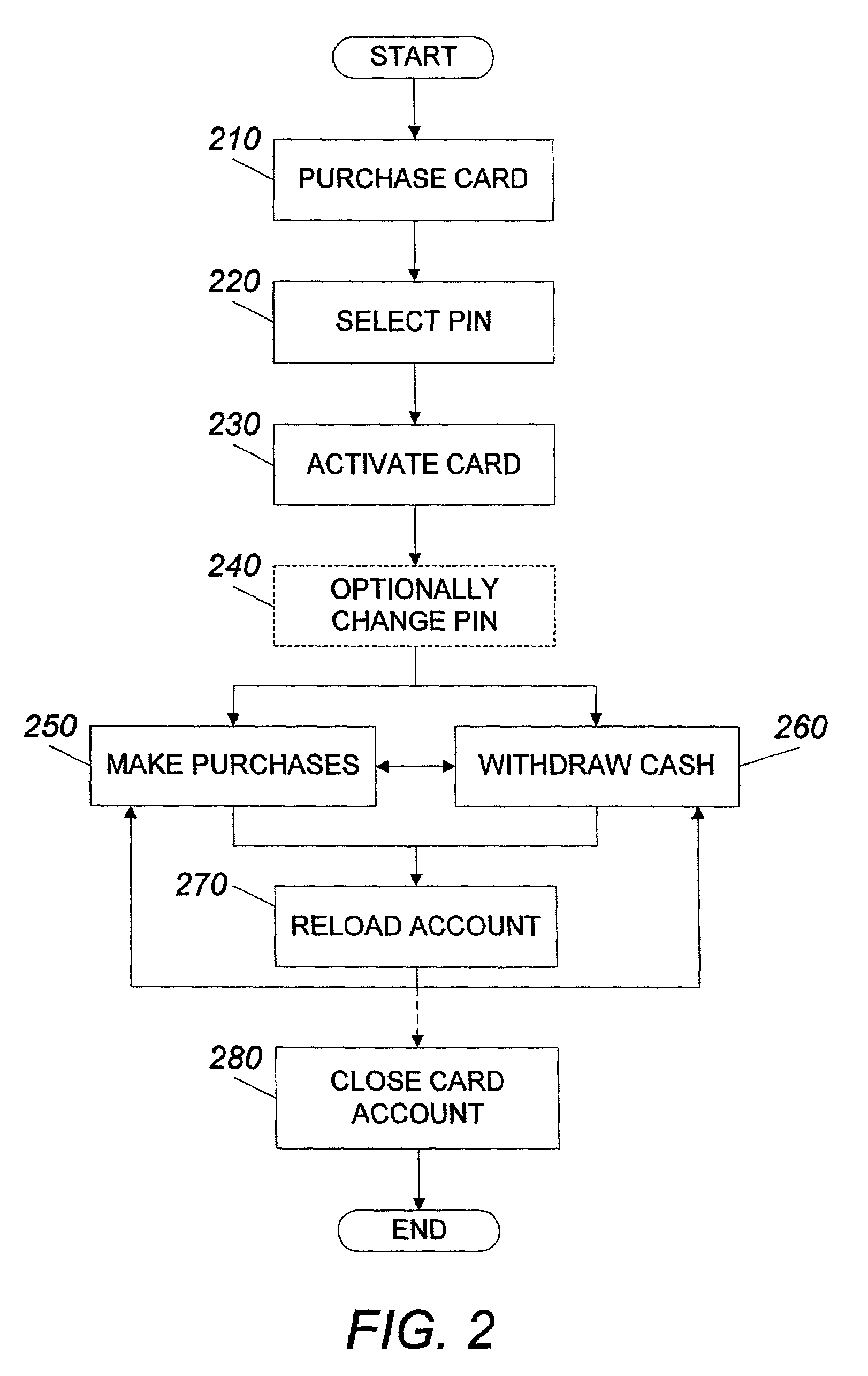
System and method for using a prepaid card
InactiveUS7252226B2Add valueMeet the need for flexibilityCredit registering devices actuationCo-operative working arrangementsSystem usagePoint of sale
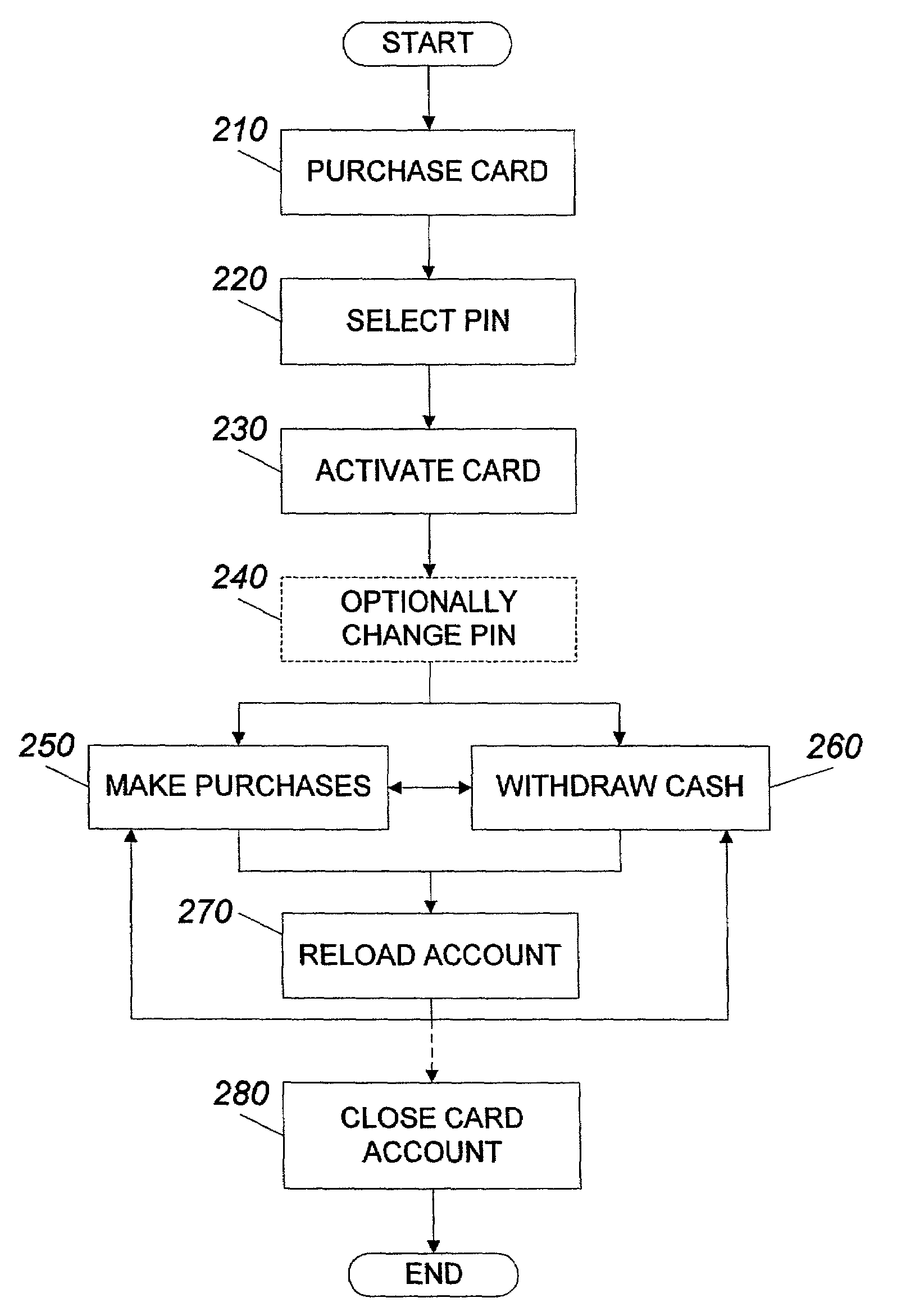
A system for using a prepaid card permits a card user to purchase a card, issued by an issuer such as a bank, through an agent at a retail establishment via a terminal, select a PIN, have the card activated at the point of purchase, use the card to purchase goods and services, and reload the card for future use. The system uses a communications network for issuance, activation, and accounting, and activation is accomplished on a real-time basis, either one account at a time or in a batch mode. The card can be used to purchase a wide range of goods and services including telephone services. The card can also be used to make cash withdrawals at an ATM or a point-of-sale terminal.
Owner:MASTERCARD INT INC
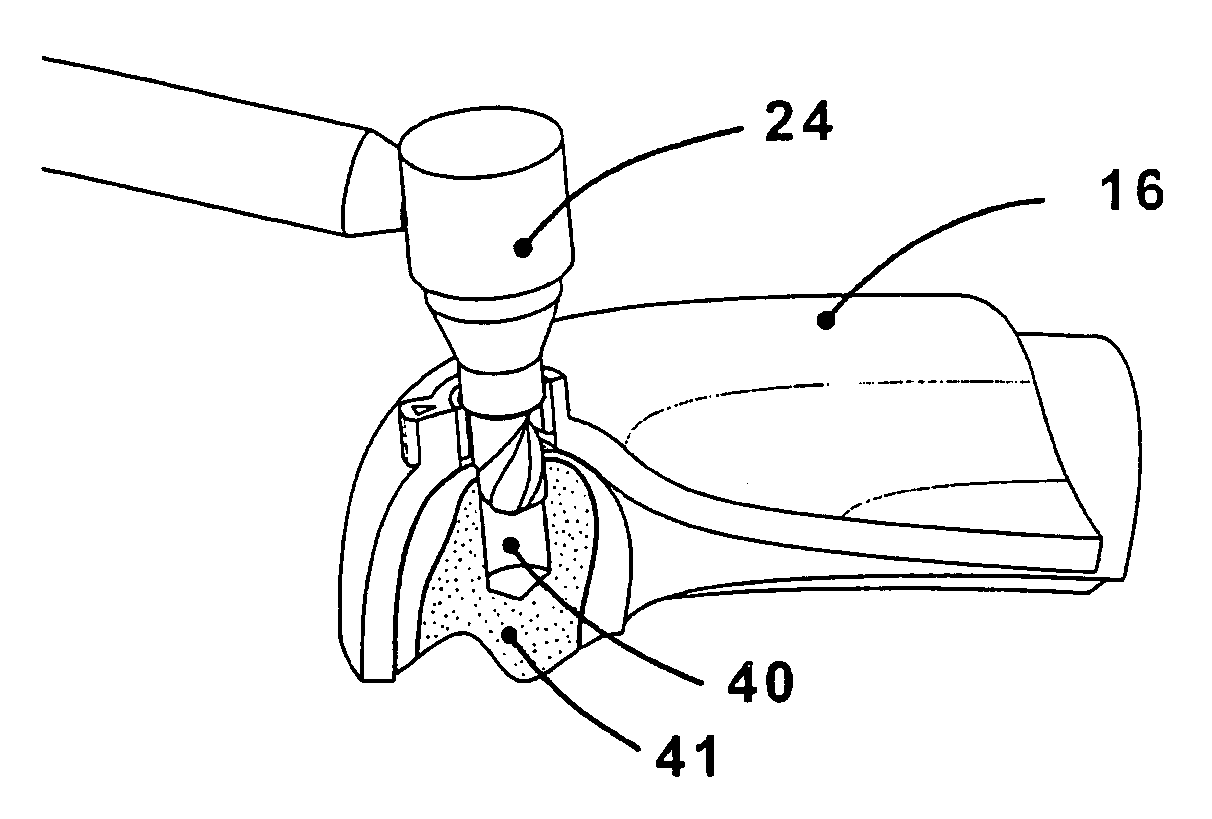
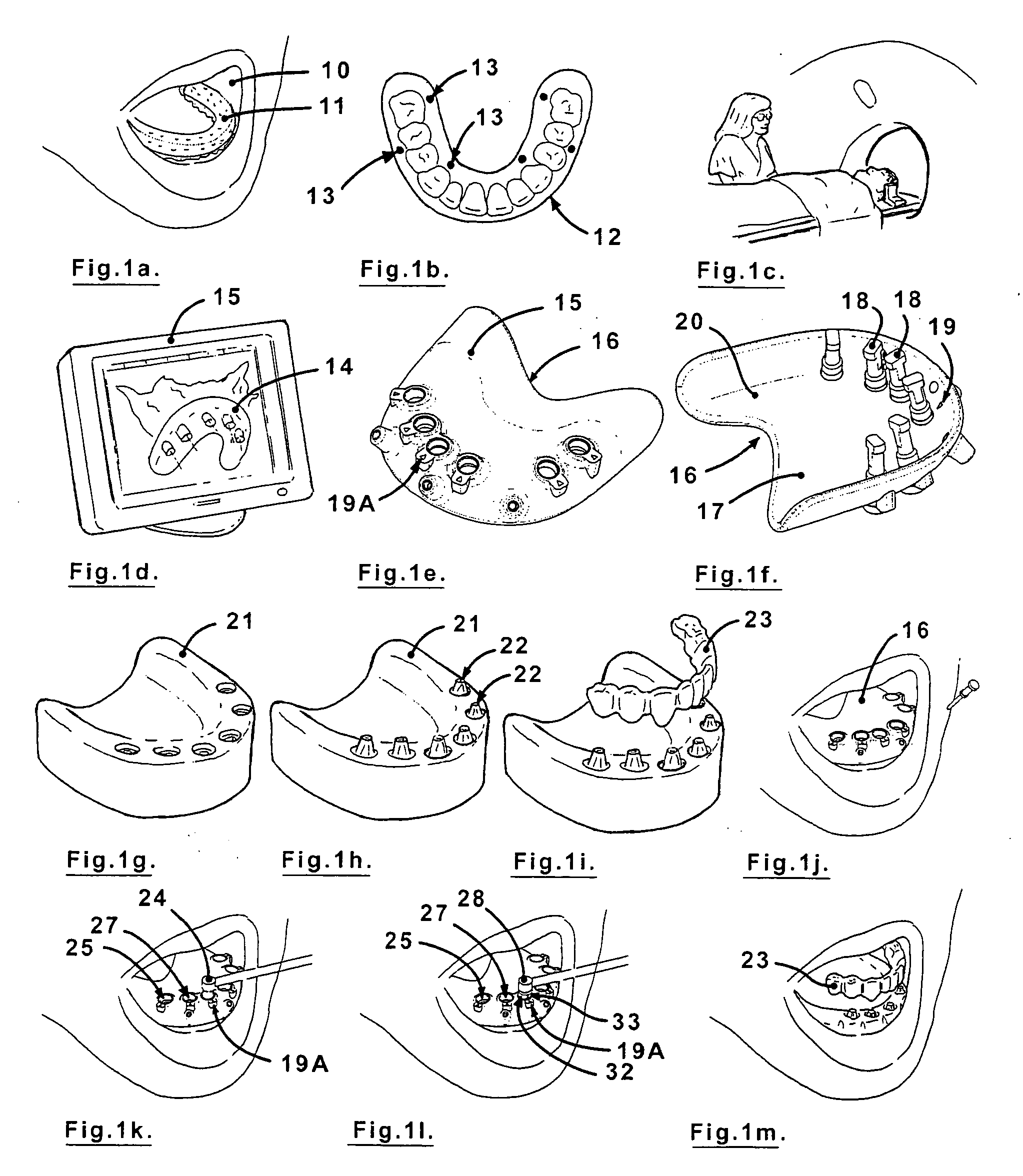
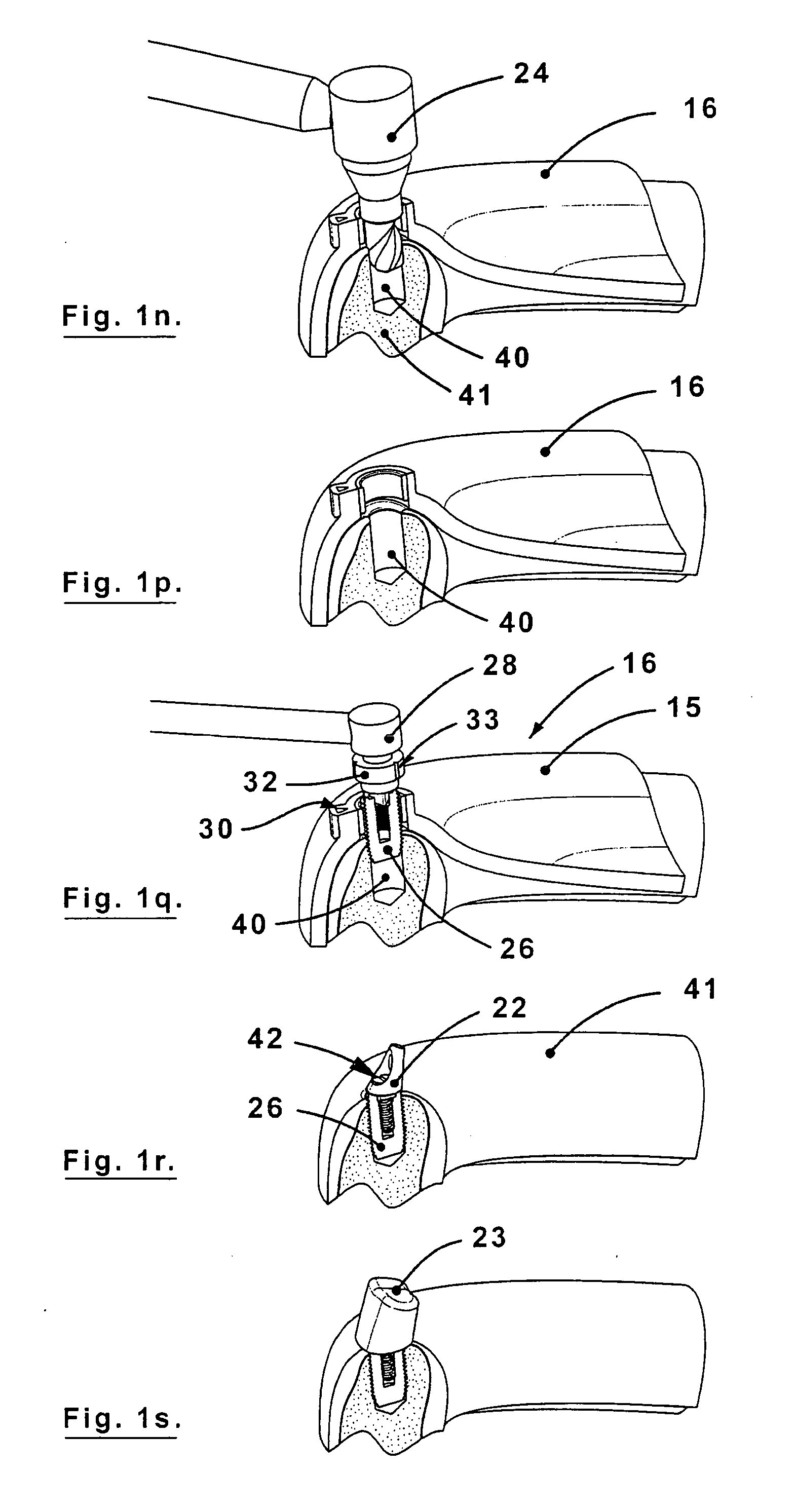
Surgical drill guide and index system
InactiveUS20090011382A1The process is convenient and fastMore accurateTeeth fillingDental toolsSurgical drillAngular orientation
A surgical drill guide for installing dental implants with predetermined angular alignment and rotational orientation for a dental prosthesis, formed of:a. a base part formed to correspond generally to the shape and contour of a patient's upper or lower mouth, the base part having peripheral edges and having opposite tissue and mouth sides and at least one drill guide hole extending through the base part from the tissue side to the mouth side, each of the drill guide holes having a central axis at a predetermined angular orientation relative to the mouth side and having lateral location relative to the peripheral edges, andb. a set of rotational position indicators on the tissue and mouth sides respectively of the base part for each of the drill guide holes, the rotational position indicators of each set being at the same rotational position about the central axis of the drill guide hole.
Owner:BAVAR TREVOR
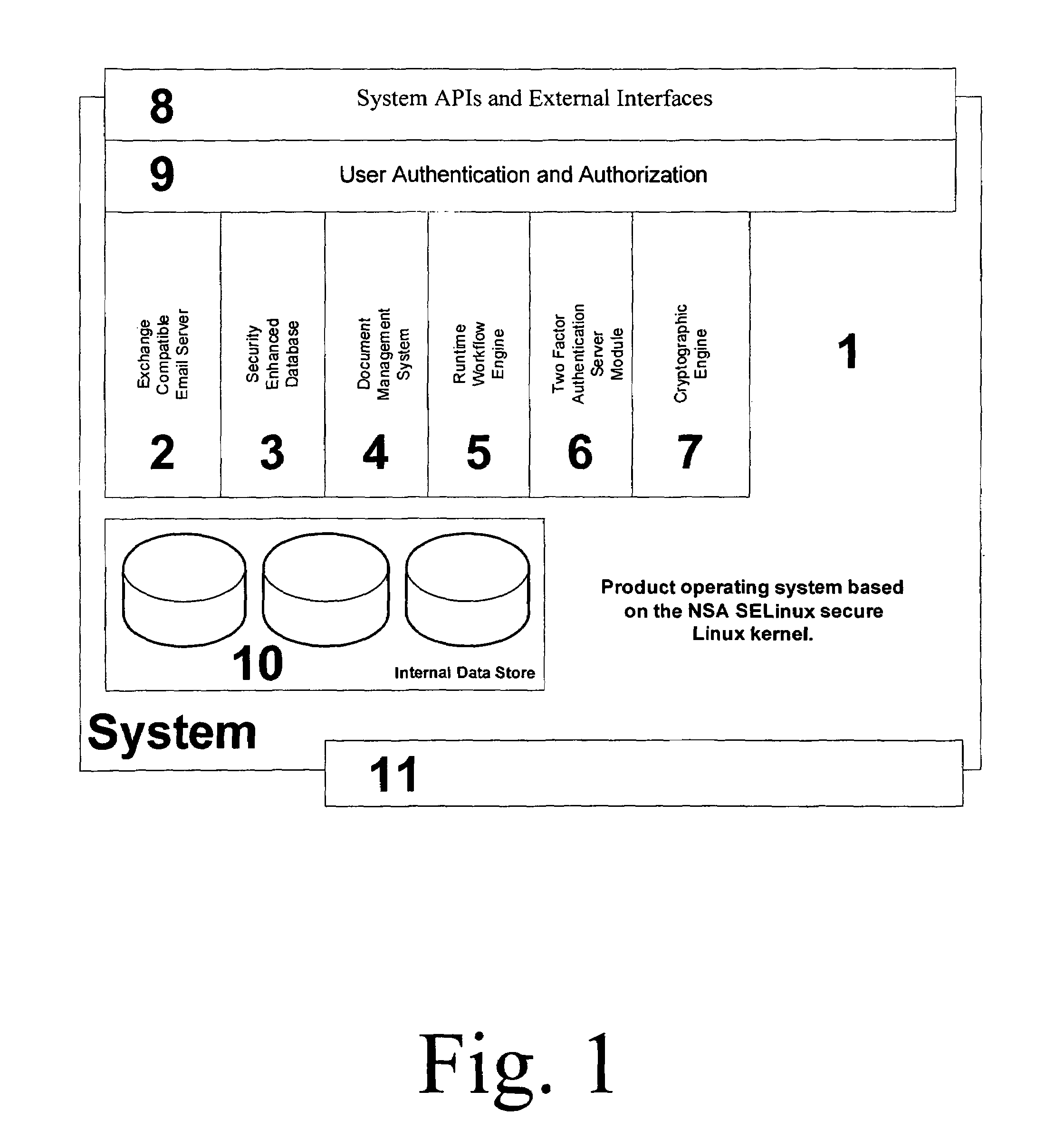
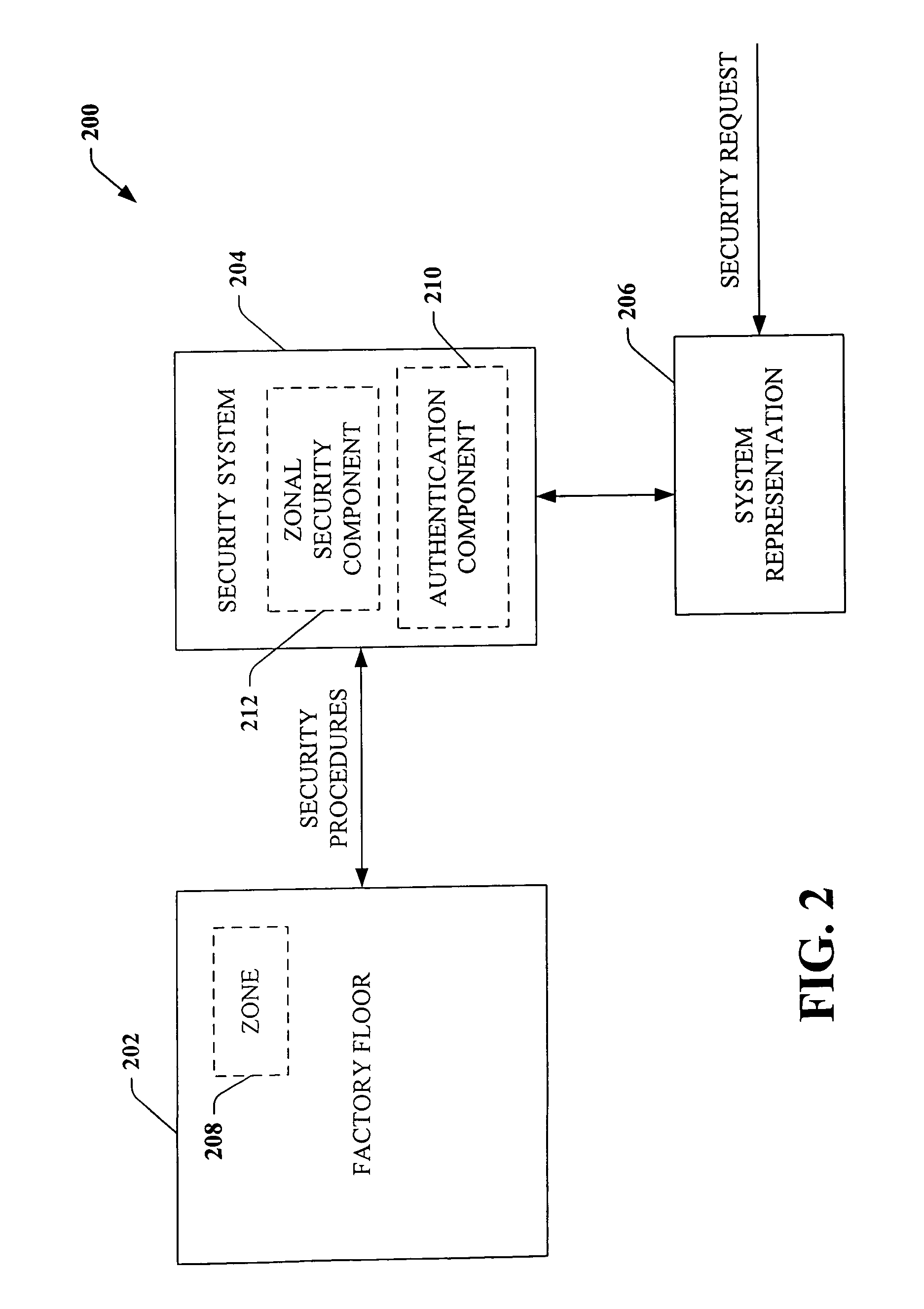
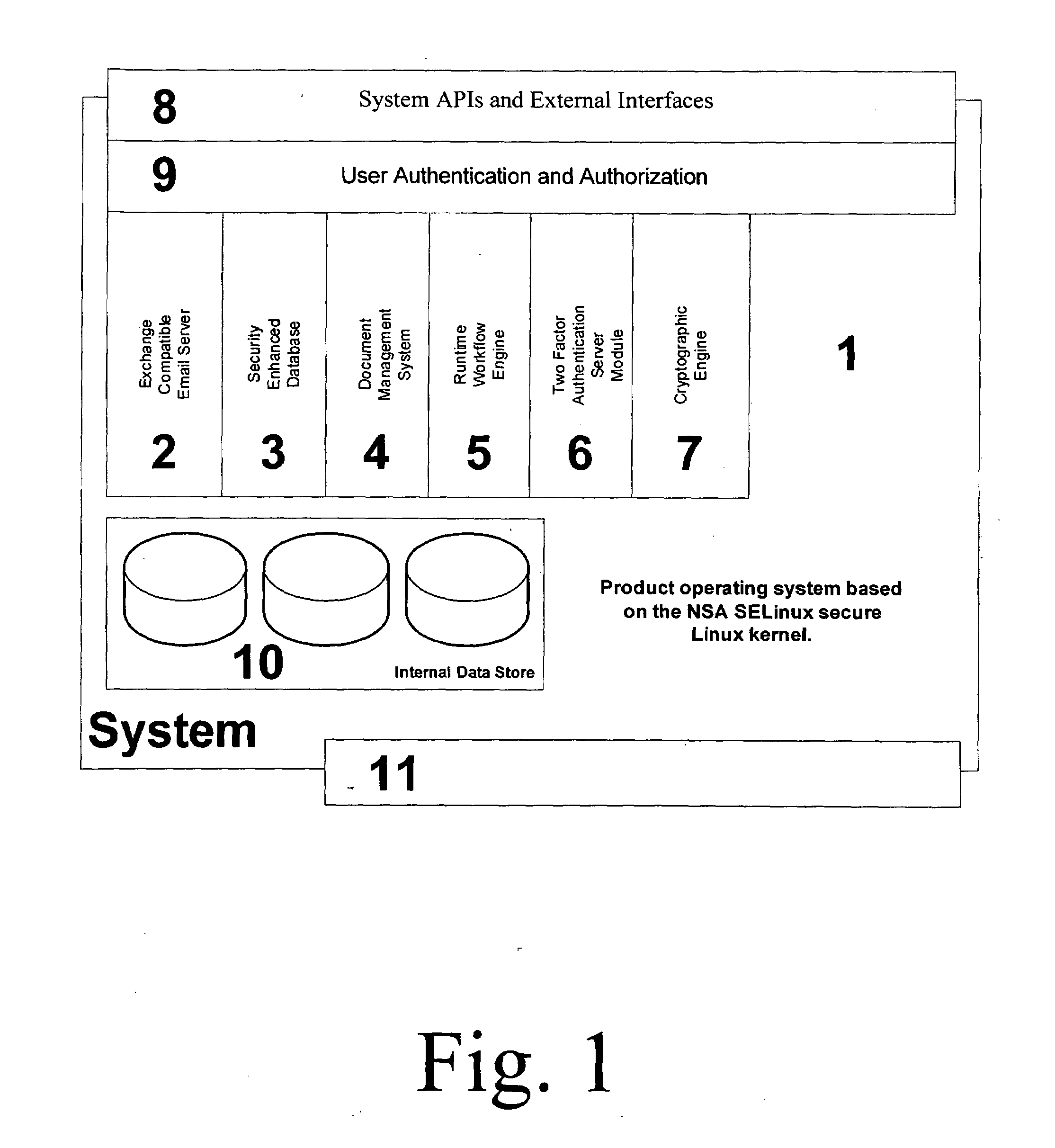
Security Enhanced Data Platform
InactiveUS8161527B2Improve securityConvenient access controlDigital data processing detailsUnauthorized memory use protectionUser PrivilegeInternet privacy
The security enhanced data platform is comprised of two primary subsystems and a host of supporting subsystems. The first primary subsystem is a document management system. A set of client side tools provides the user a way to specify classifications and compartments for selected areas of a document, and a way to save the document in the format required by the system in order to allow the system to enforce the rules and privileges dictated to the system. The second subsystem is a security enhanced database management system. In documents the system allows different user privilege requirements on the document as a whole as well as on pages, paragraphs, sentences, words, and / or letters of a word. A history of document changes is maintained to provide an audit trail after the fact of who did what changes, where those changes were made and when those changes were made.
Owner:CURREN EDWARD
Surgical drill guide and index system
InactiveUS8105081B2The process is convenient and fastMore accurateTeeth fillingDental toolsSurgical drillAngular orientation
Owner:BAVAR TREVOR
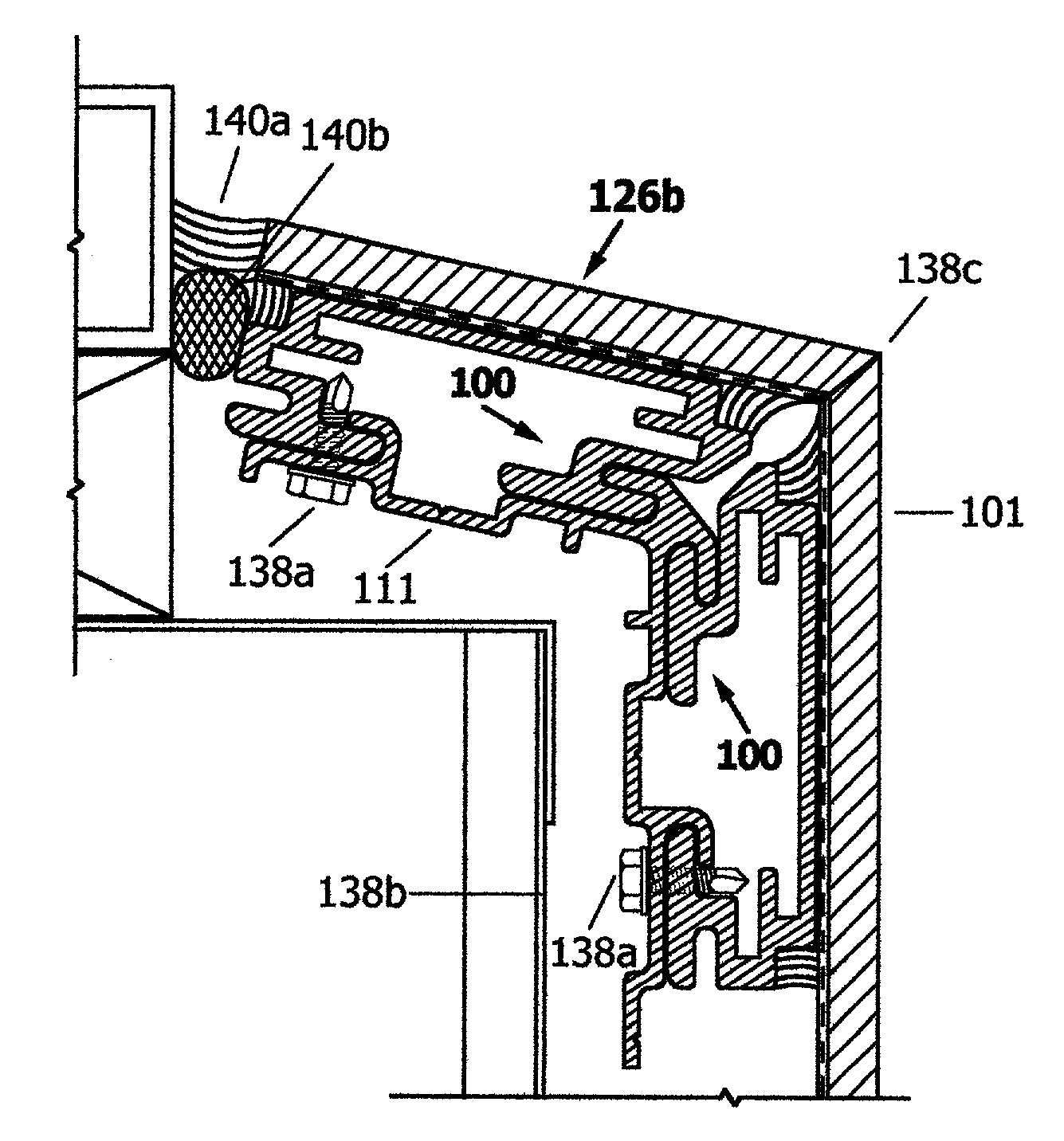
Exterior wall cladding system for panels of thin reinforced natural stone
An installation system designed specifically for thin reinforced natural stone panels used as exterior cladding, re-cladding, or over-cladding of buildings is comprised of a series of extruded aluminum shapes which, when properly applied to the back side of the thin reinforced stone panels, provide structural support for the thin panels and facilitate their installation and will also provide the means for the panels to be pre-assembled in order to obtain desired shapes or profiles and to be easily installed on the building. The series, or family, of extruded aluminum shapes are designed to mate or interlock to perform a variety of tasks such as perimeter frames, structural stiffeners, corner angle supports, interlocking sleeves, runner clips which facilitate attachment to various substrates of a building such as steel stud framing, aluminum curtain wall frames, brick or concrete walls or plywood sheathing.
Owner:THIN STONE SYST
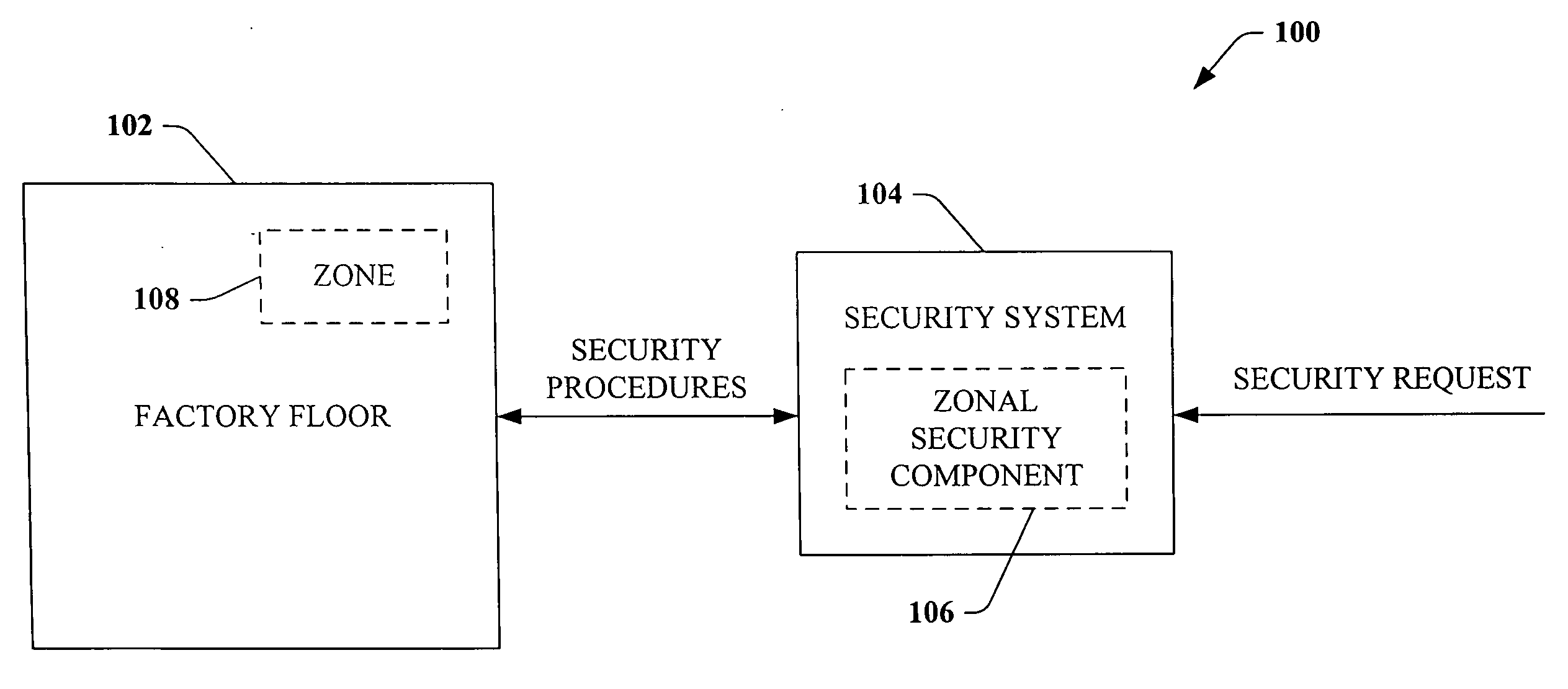
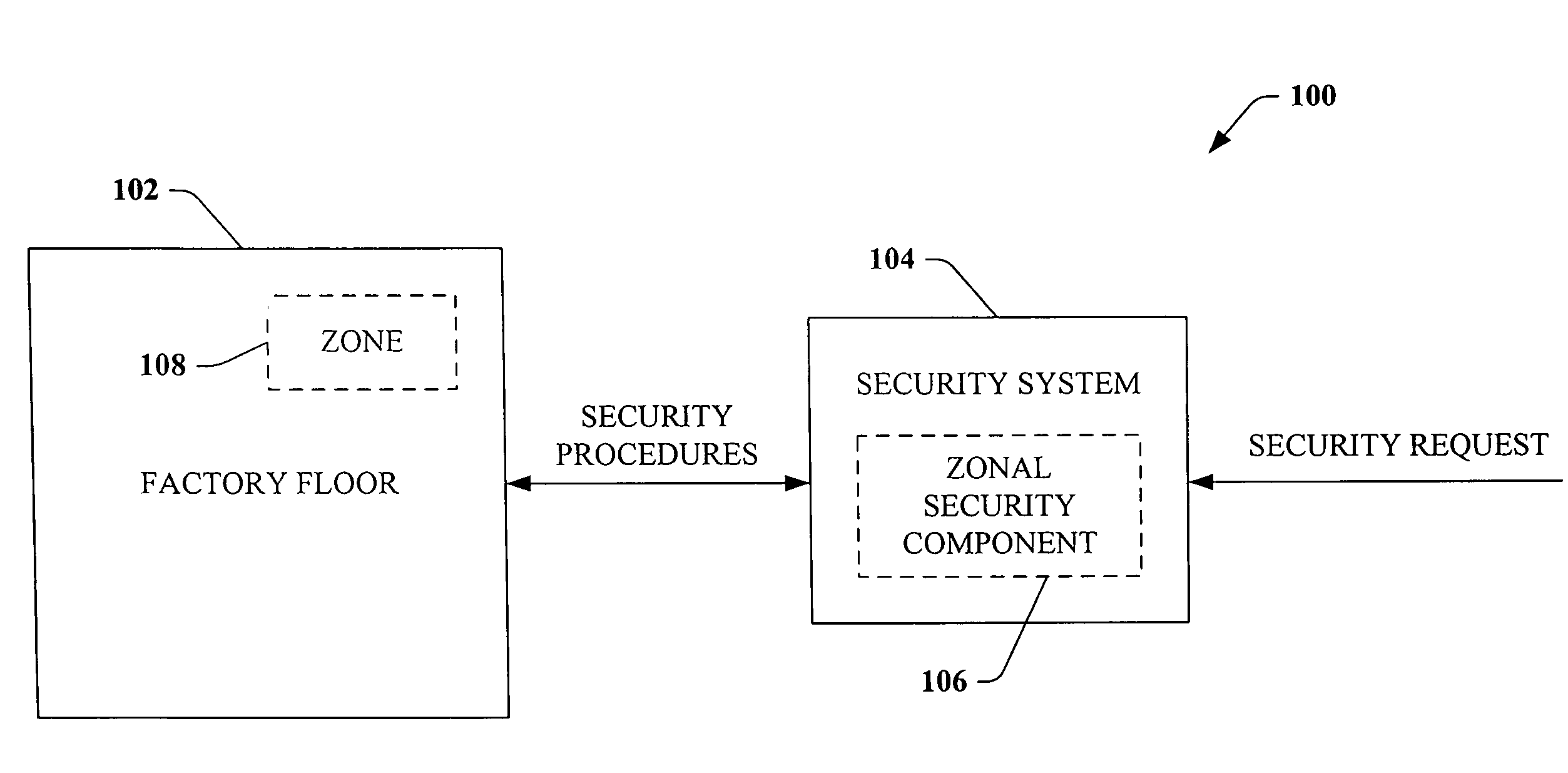
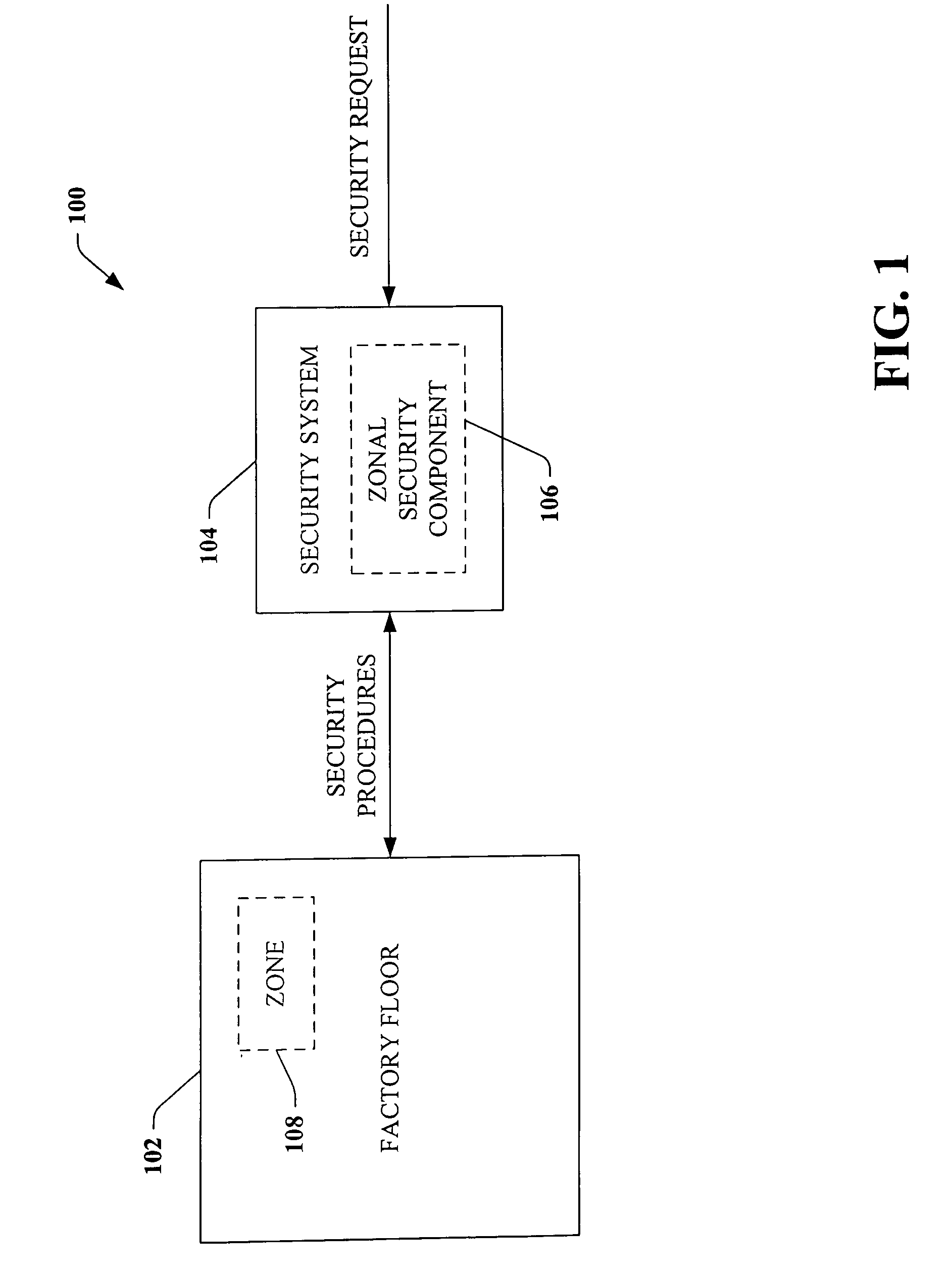
Scalable and flexible information security for industrial automation
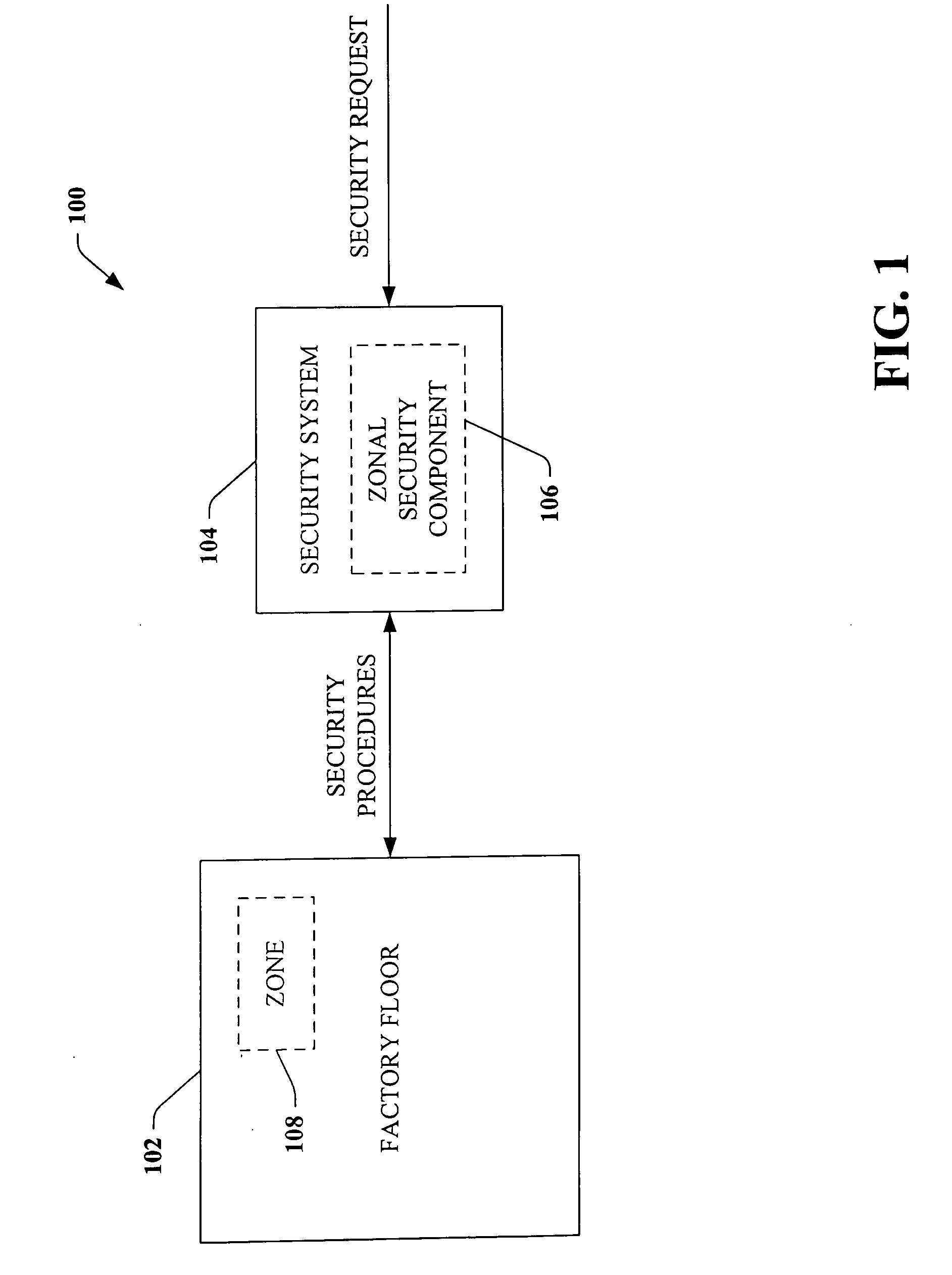
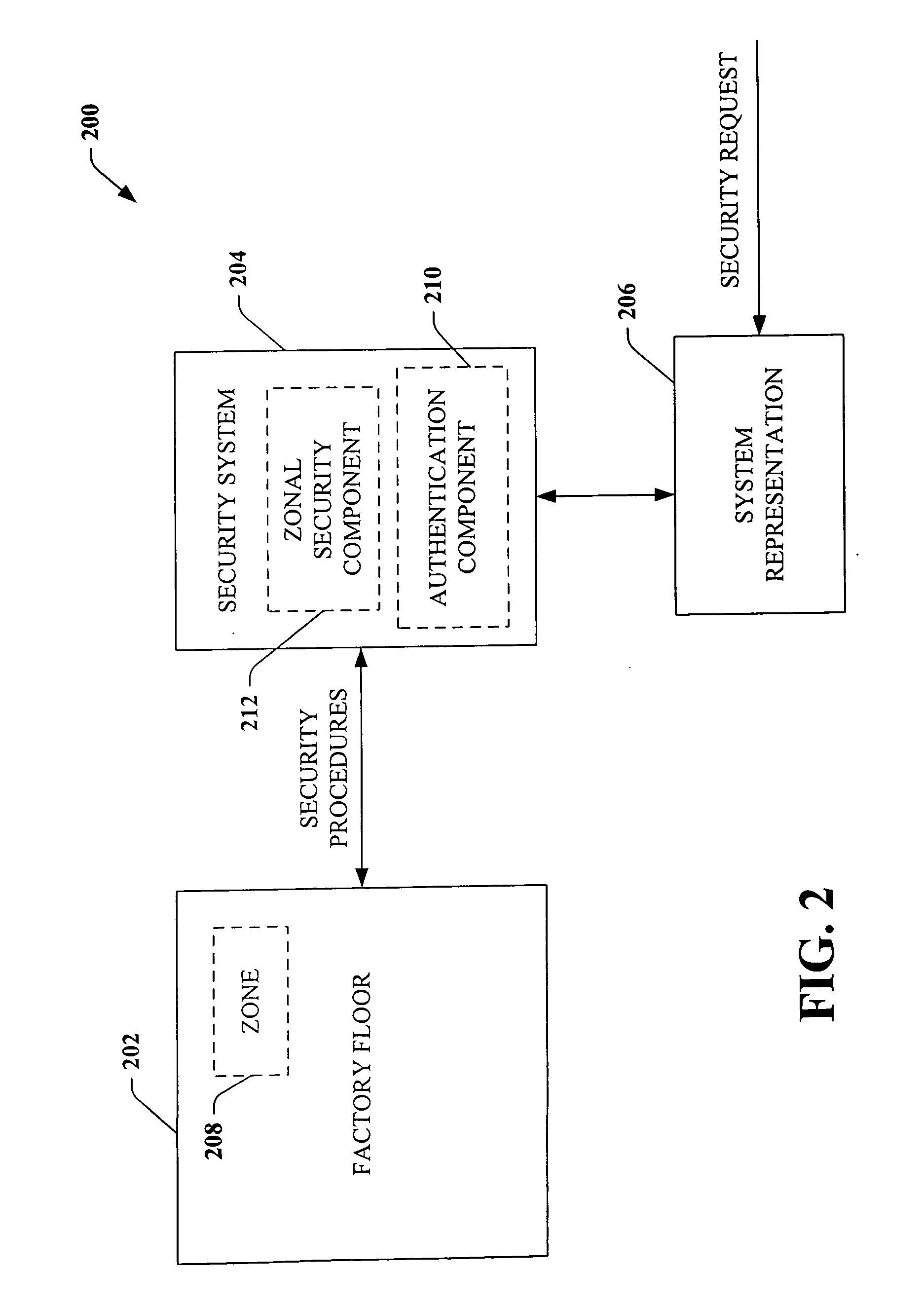
ActiveUS20060074917A1Compromising performance and throughput and securityImprove securityDigital data processing detailsTechnology managementSafe systemSafety procedure
A security system that relates to industrial automation security comprises a component that receives a request to modify security relating to a zone of a factory floor, the zone being less than an entirety of the factory floor. A zonal security component generates security procedures for the zone, the security procedures differ from security procedures implemented on the factory floor outside the zone.
Owner:ROCKWELL AUTOMATION TECH
System and method for using a prepaid card
InactiveUS20060078100A1Meet the need for flexibilityIncrease valueCredit registering devices actuationPre-payment schemesFinancial transactionOperating system
A system and method for transferring money by use of a prepaid card account is disclosed wherein two cards are issued to the user accountholder, one of which is provided to another user, and either user may add value to the prepaid account so that the other user may use the card and that value in a financial transaction.
Owner:MASTERCARD INT INC
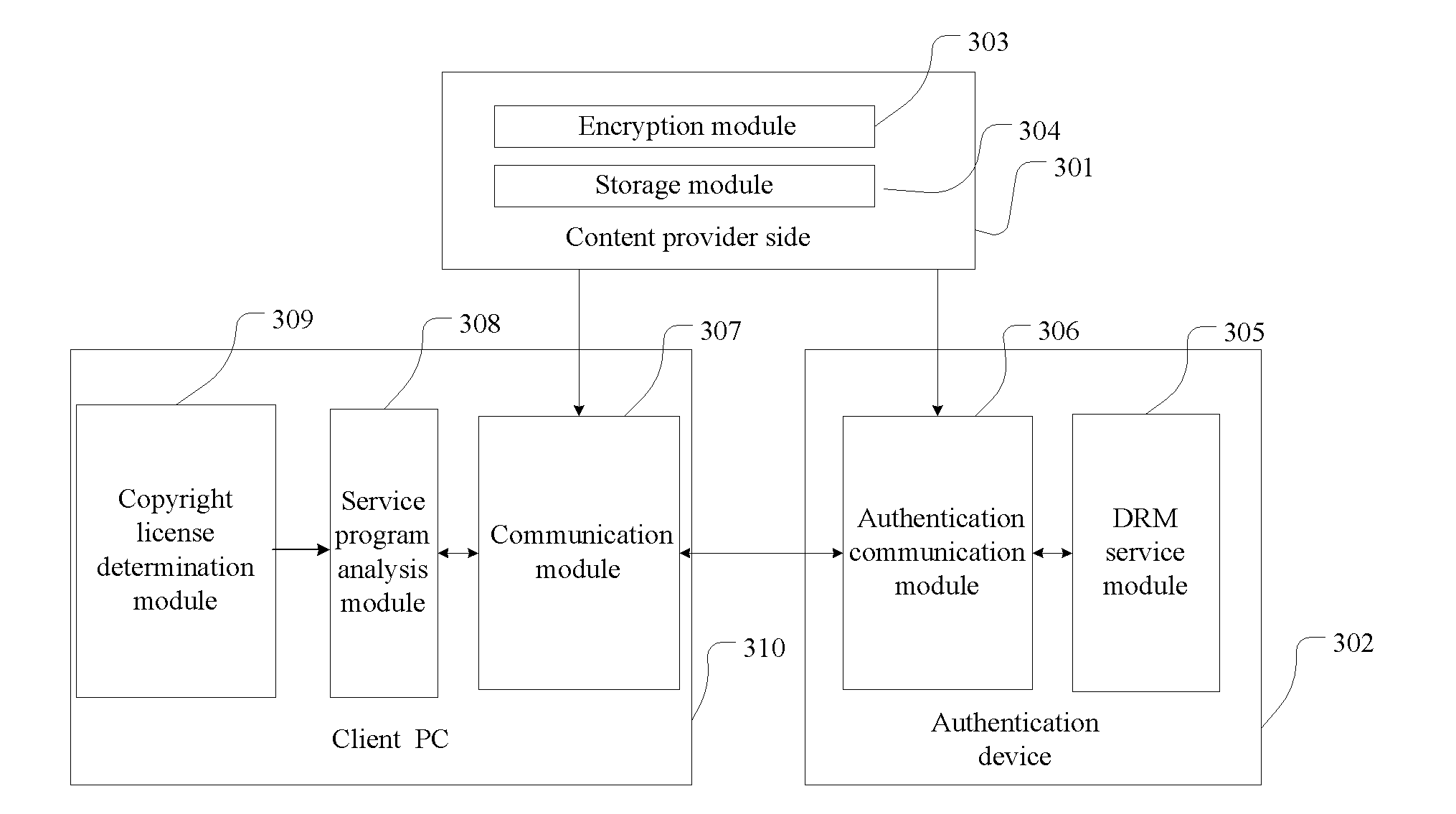
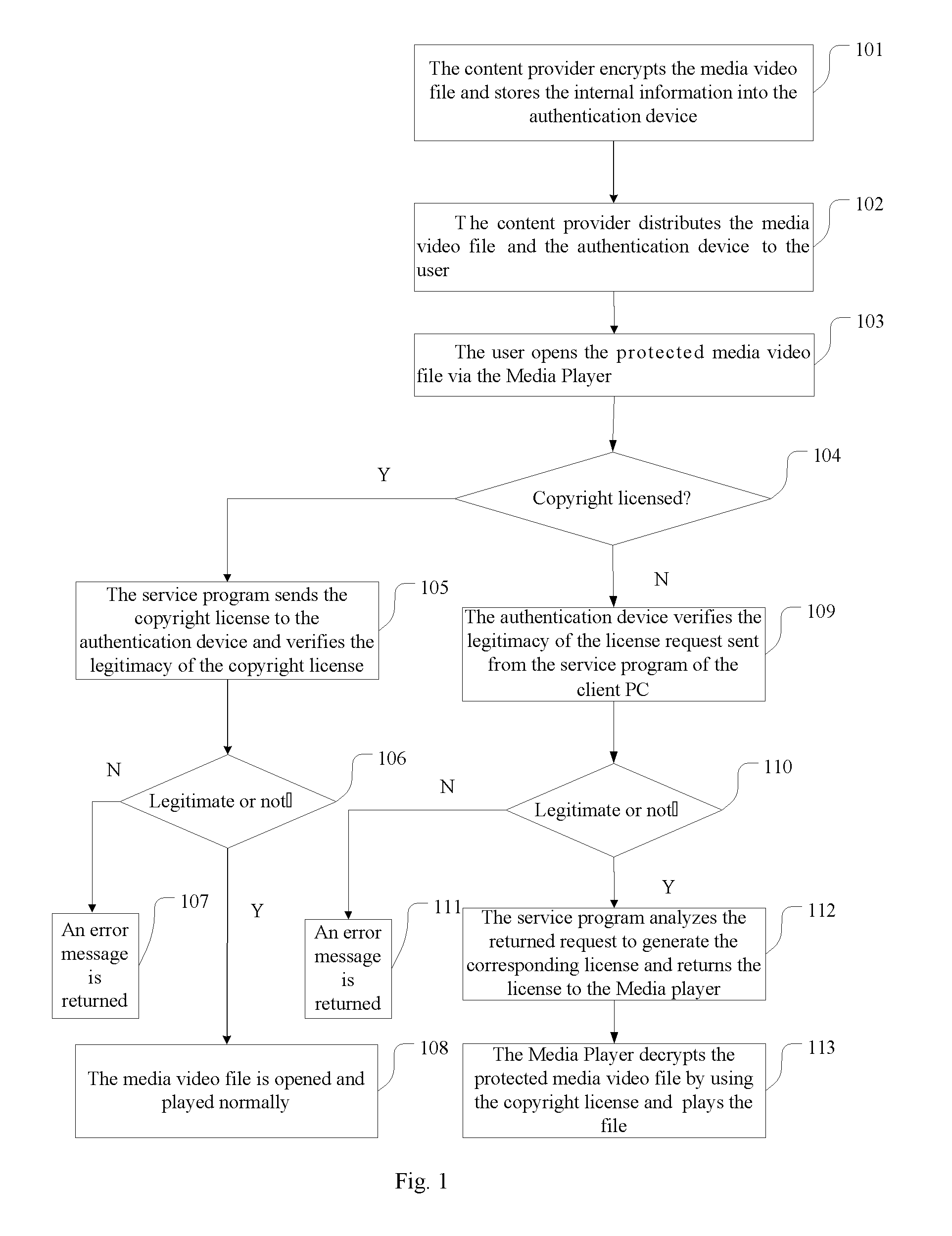
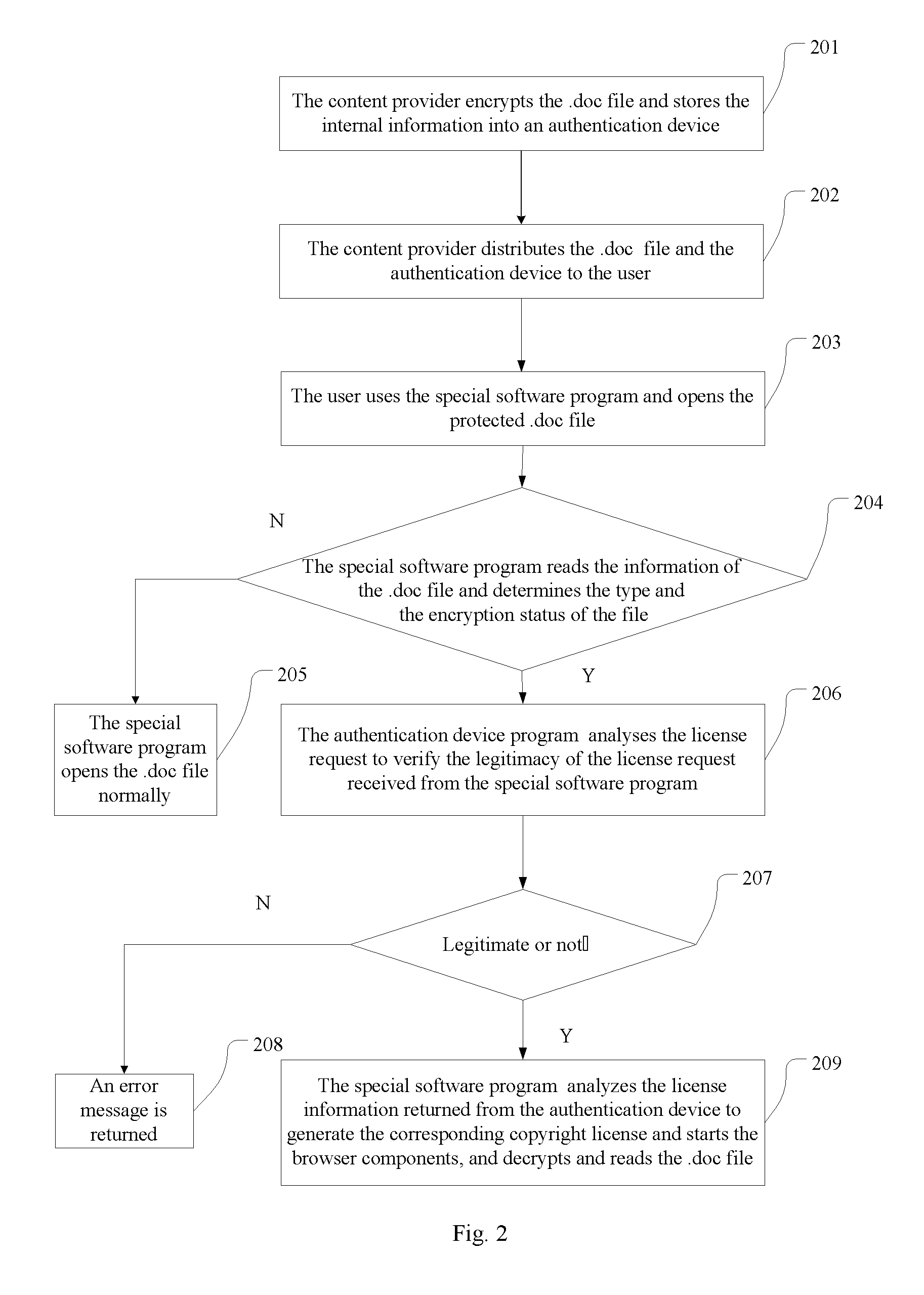
Method for offline drm authentication and a system thereof
ActiveUS20090183001A1Convenient to useCost reductionUser identity/authority verificationProgram/content distribution protectionAuthentication systemClient-side
A method for offline DRM authentication and a system thereof relates to the information security field. In order to solve the problem that a license must be requested from the server in the process of DRM authentication, the invention provides a method for offline DRM authentication, in which, the method comprises: a content provider encrypts the data file with DRM standard and stores the internal information in an authentication device, the authentication device is connected to the local computer, the software program on the local computer opens and reads the data file. A system for offline DRM authentication, in which, the system comprises an authentication device, a client PC and content provider side, the authentication device comprises the DRM service module and authentication communication module. Compared with the prior art, the present invention allows the user to use the DRM protected information without a network connection.
Owner:FEITIAN TECHNOLOGIES
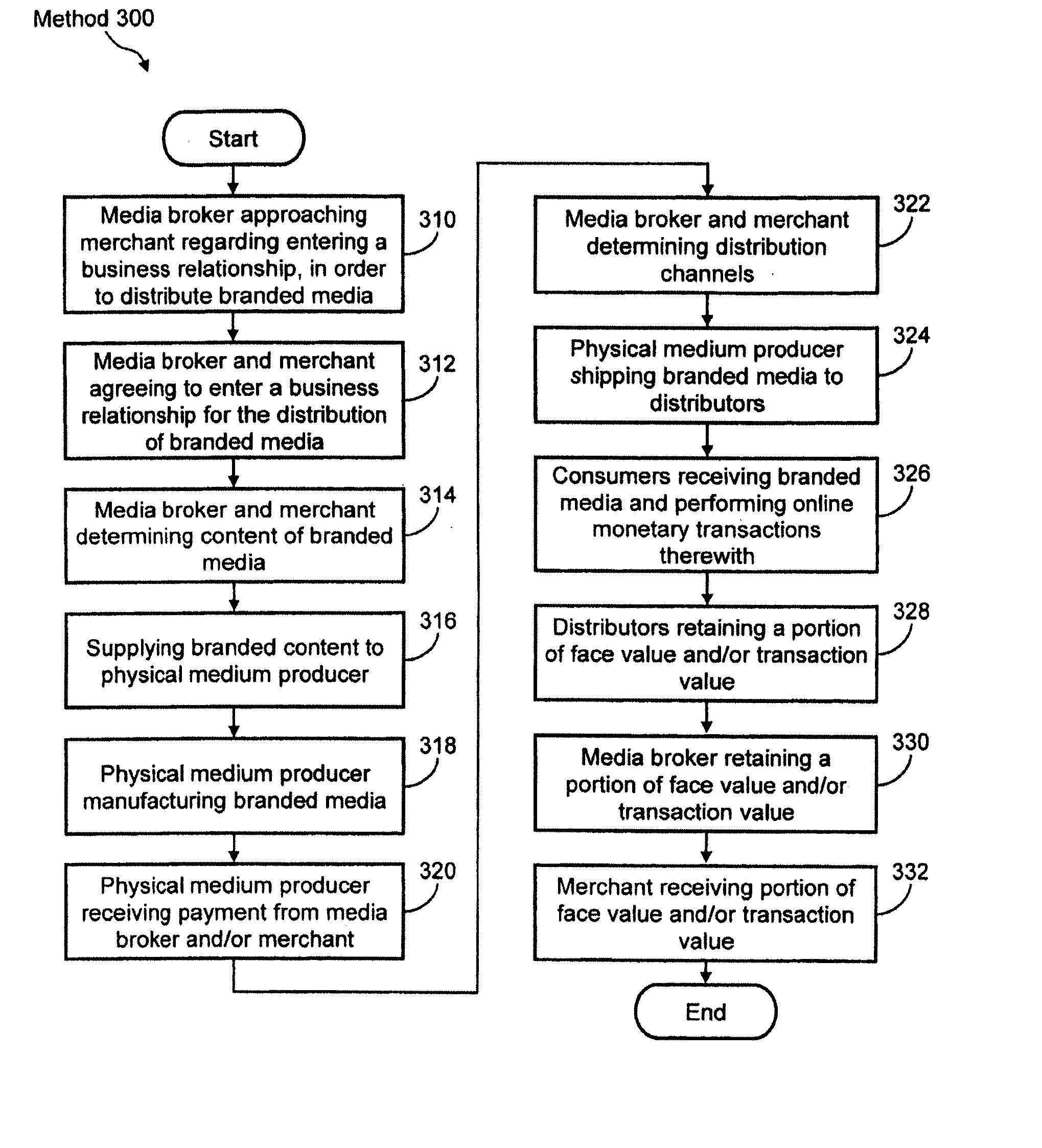
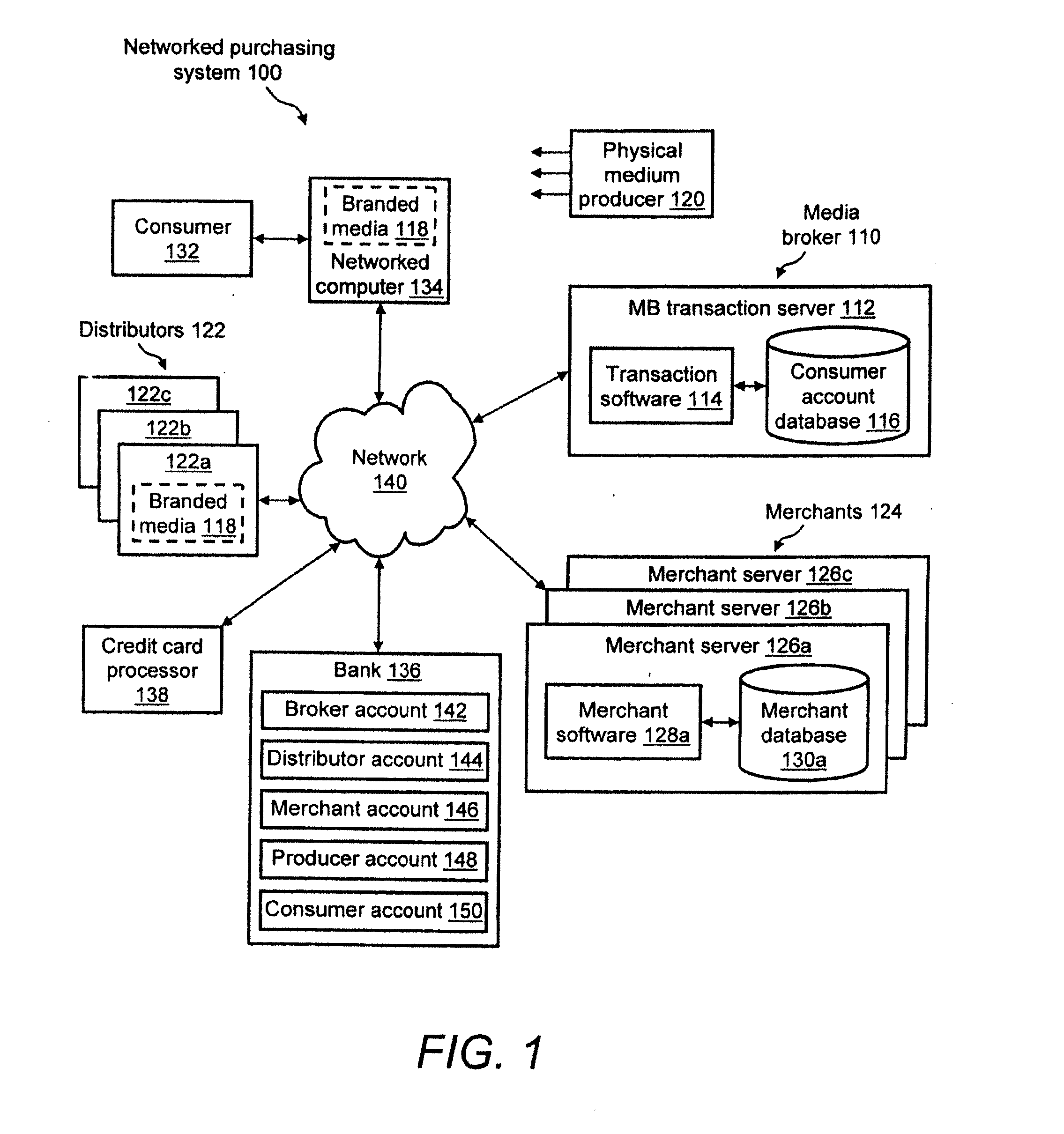
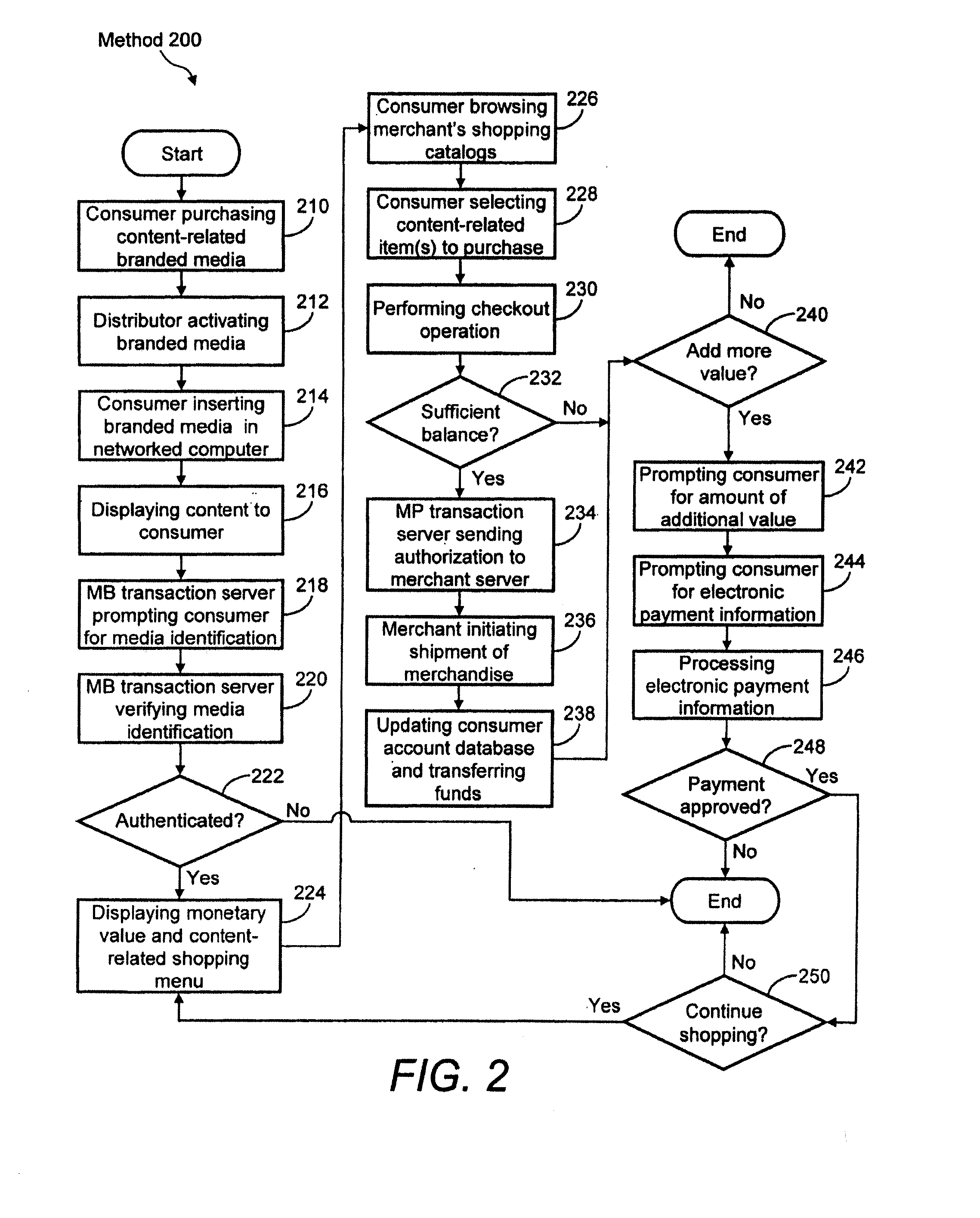
System, method and apparatus for conducting secure online monetary transactions
InactiveUS20070208632A1Convenient transactionSecure and simple and cost-effectiveCredit registering devices actuationPre-payment schemesInternet privacySystems approaches
A system, apparatus, and methods for conducting secure online monetary transactions are disclosed. One implementation of the system is configured to generate an account associated with a distributed branded media element. The account includes an account balance that may be used to purchase goods / services. A system user accesses the distributed branded media element and initiates an authentication / verification process wherein the distributed branded media element is correlated to the created account. The system may also be configured to coordinate transmitting a payment data generation request to a payment facilitation entity. In response to the request, the payment facilitation entity may create a payment id number for use by the system user to make a purchase of goods or services. The request may specify what type of payment id number is requested, for example a credit or debit card number. The request may define additional usage parameters for the payment id number.
Owner:DOWNES JAMES +1
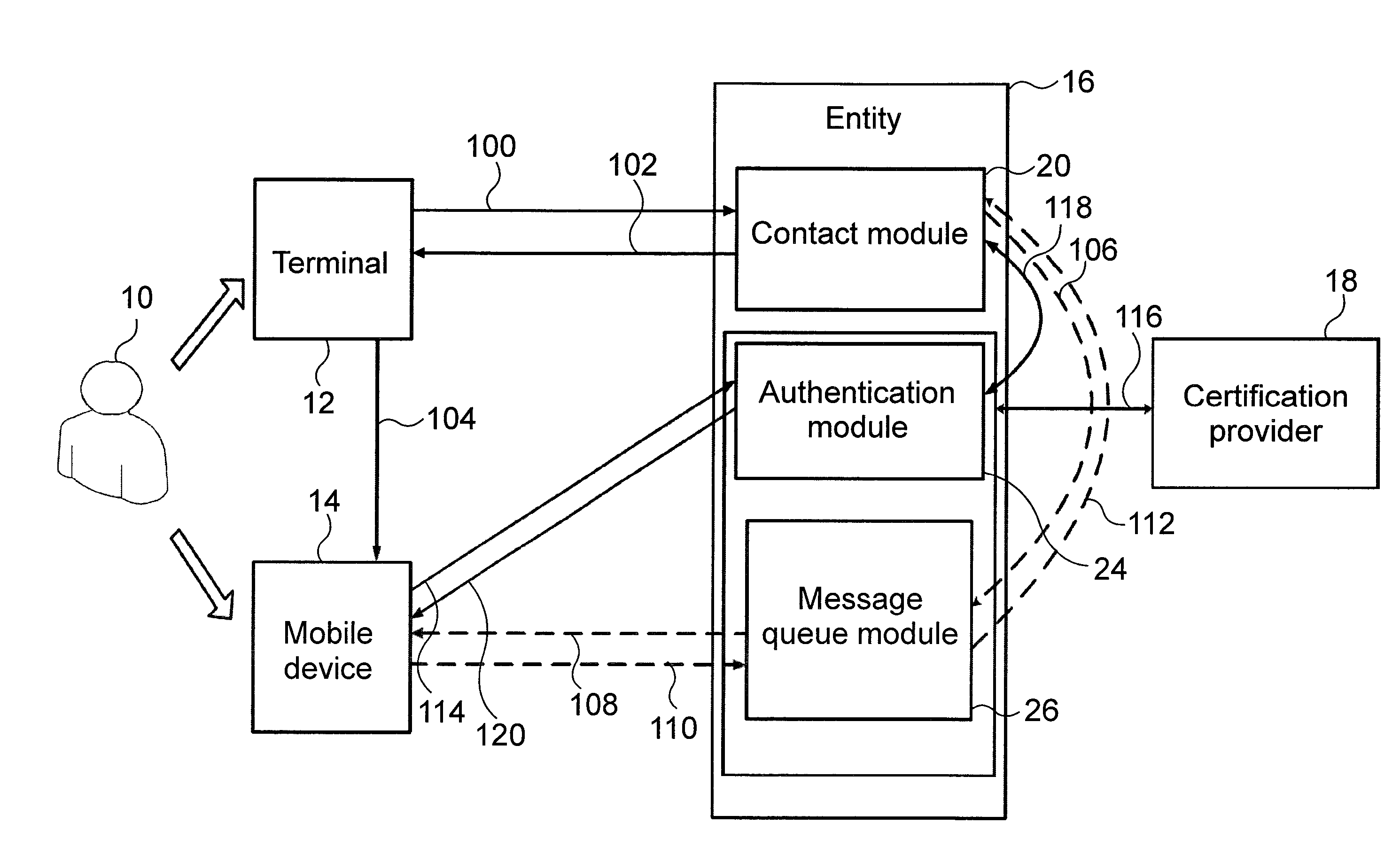
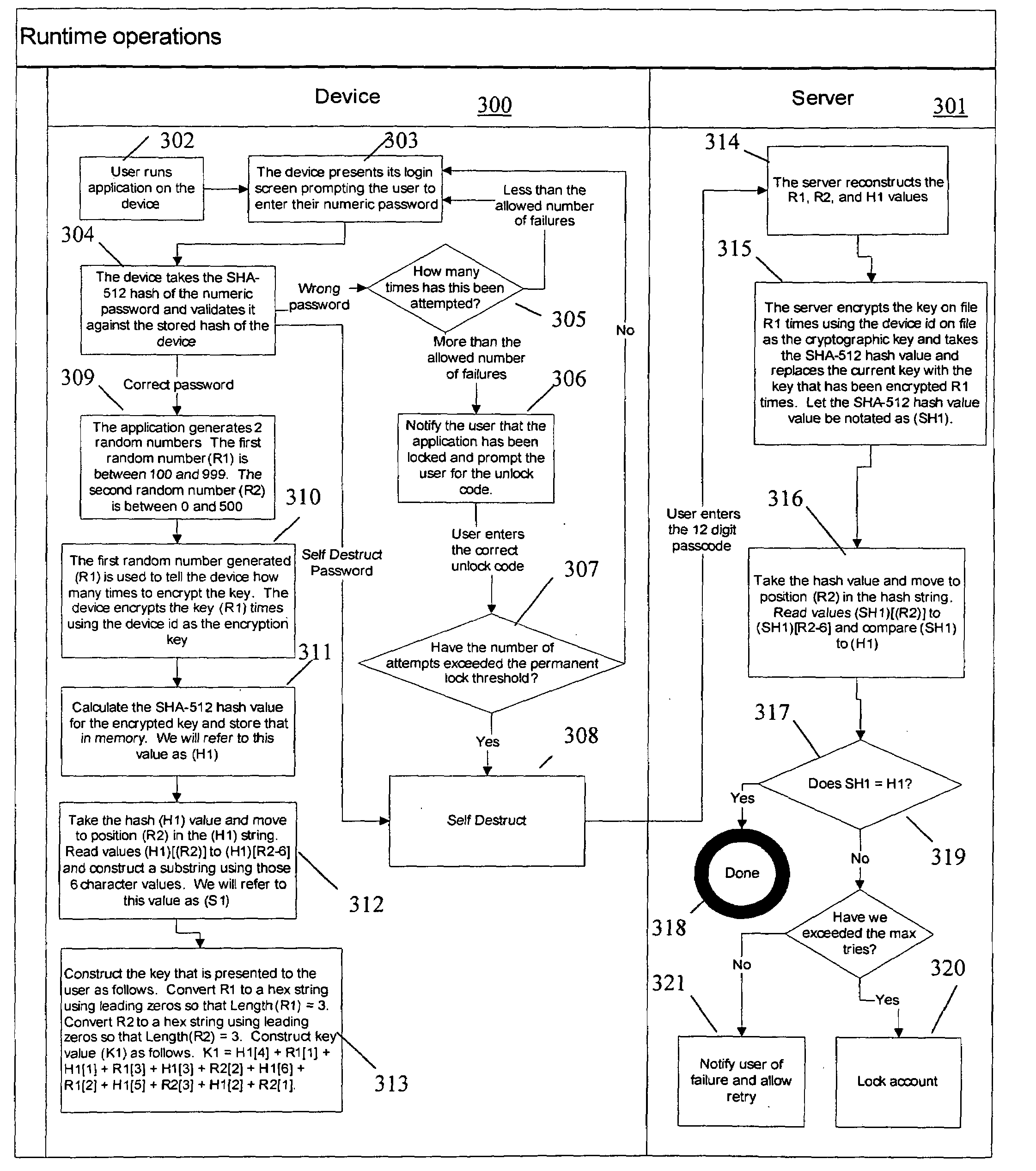
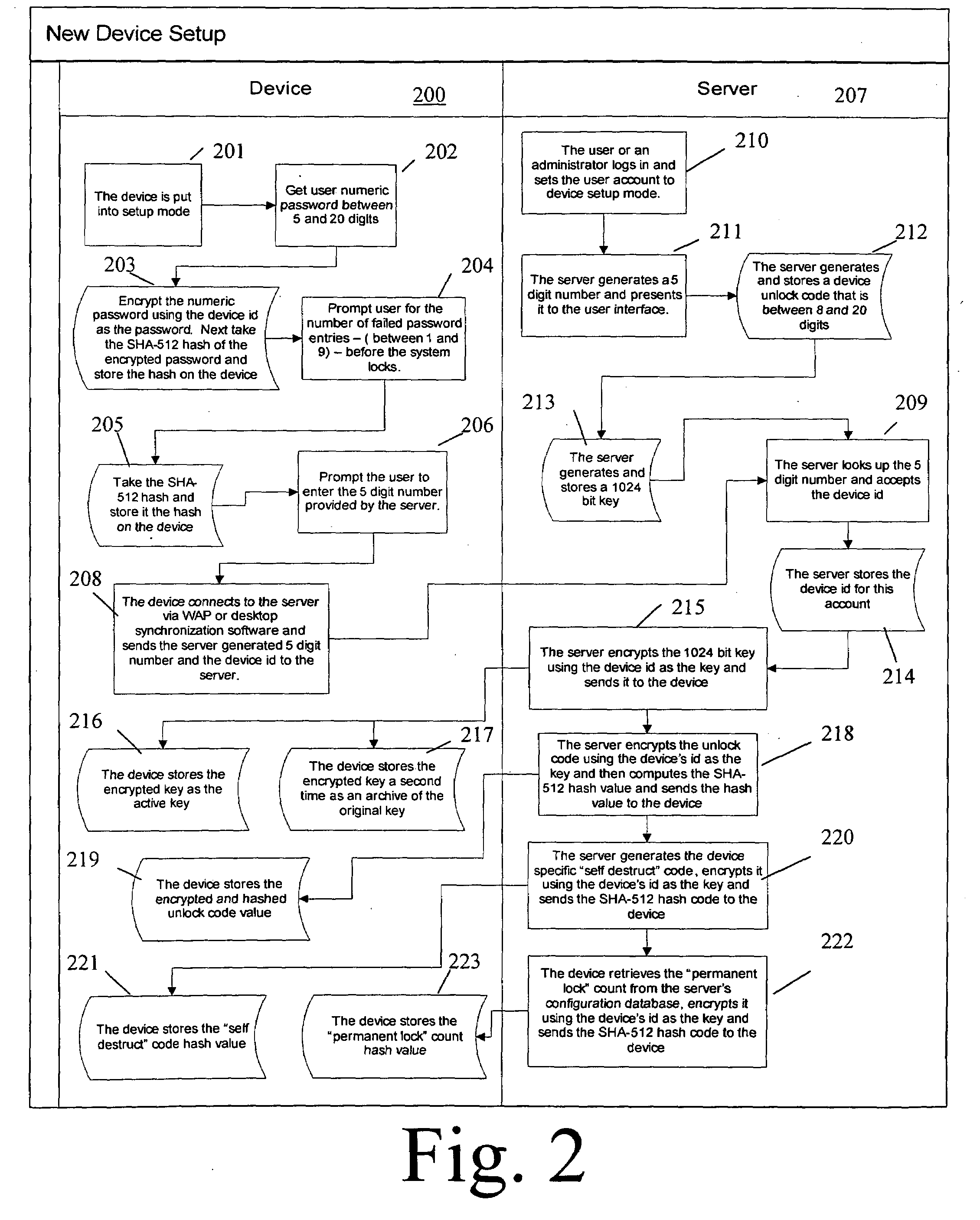
Method And System For Authenticating A User
InactiveUS20160189147A1Protection is in progressMore secureSecurity arrangementSecuring communicationNetwork addressingNetwork address
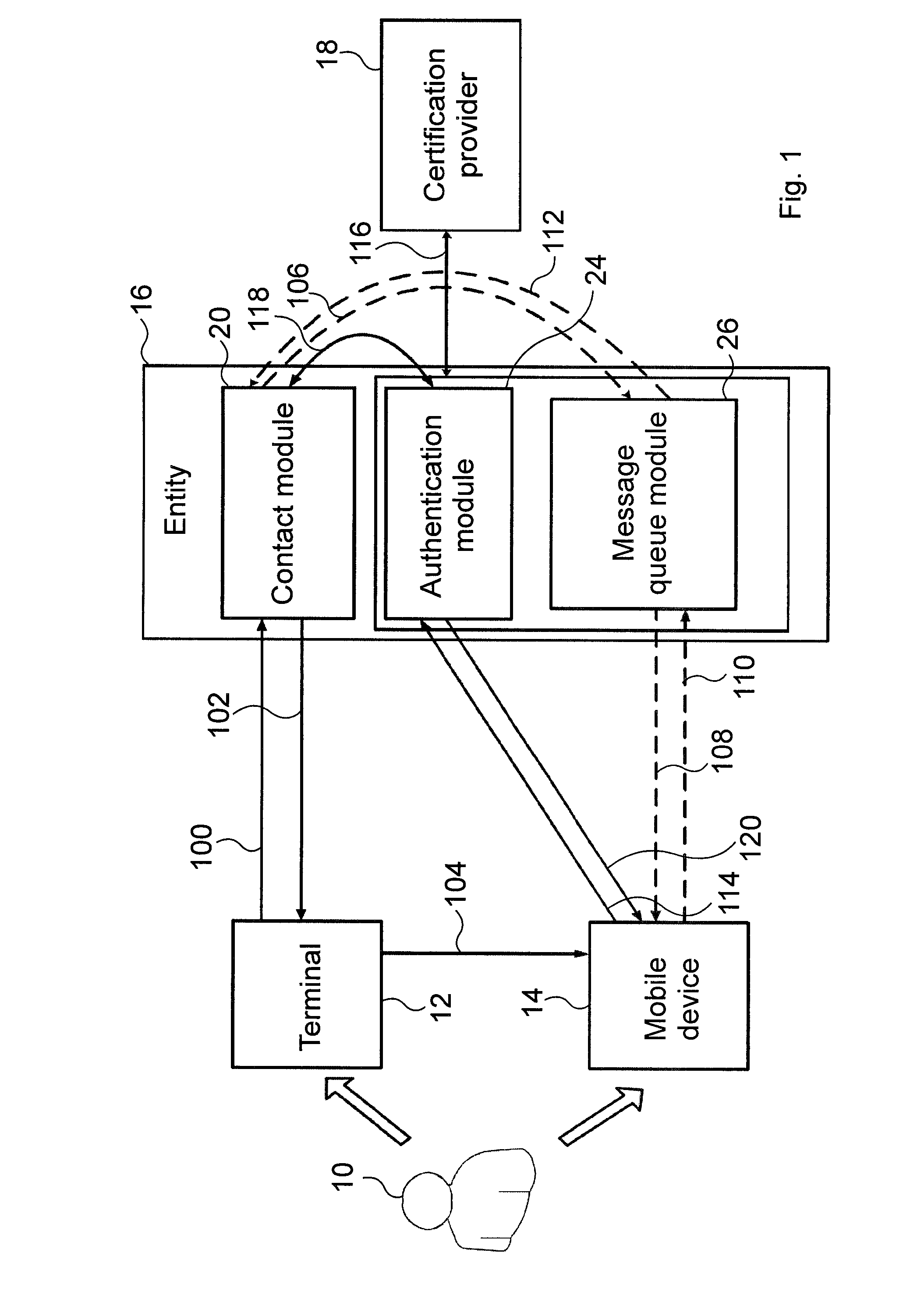
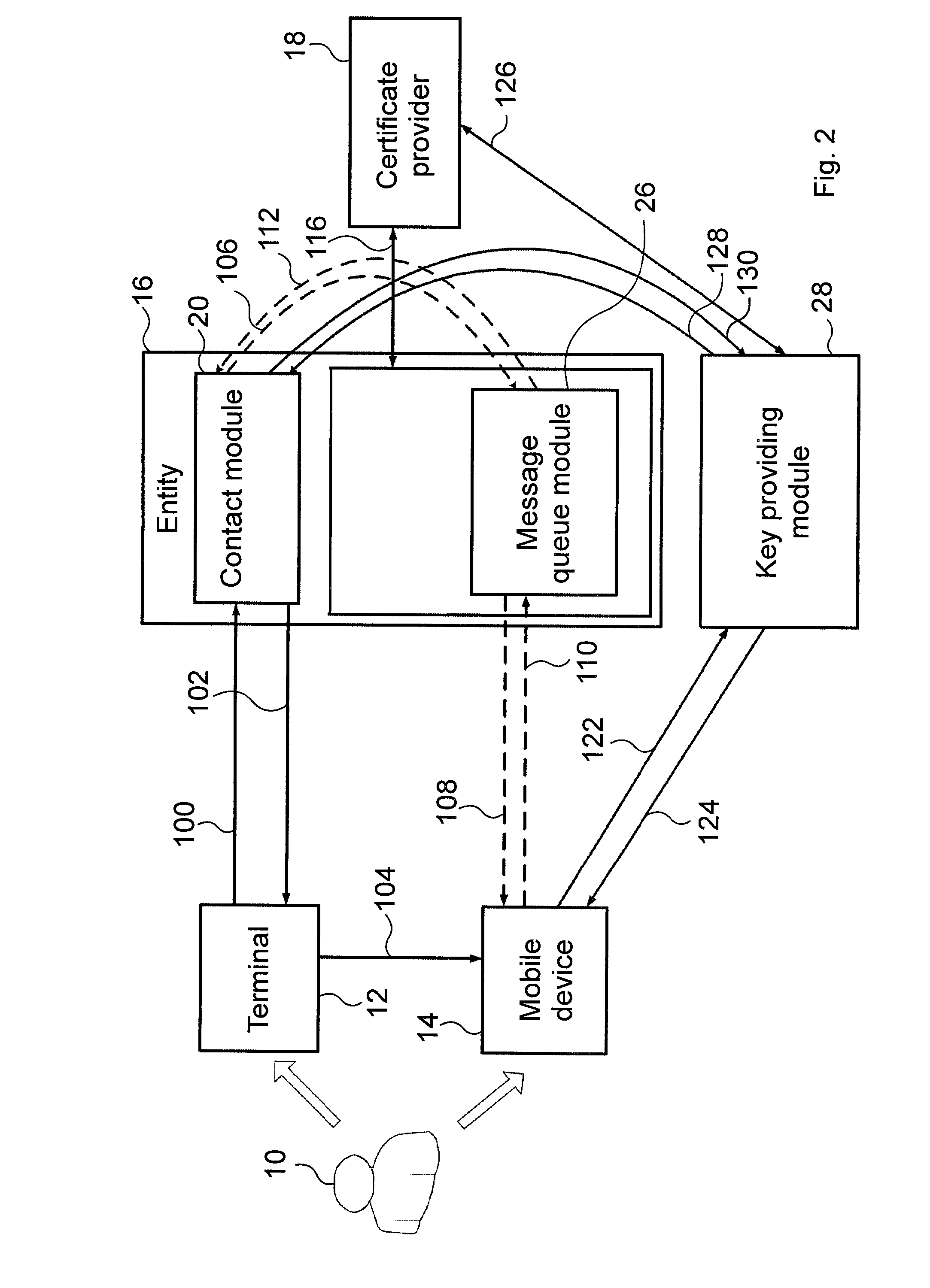
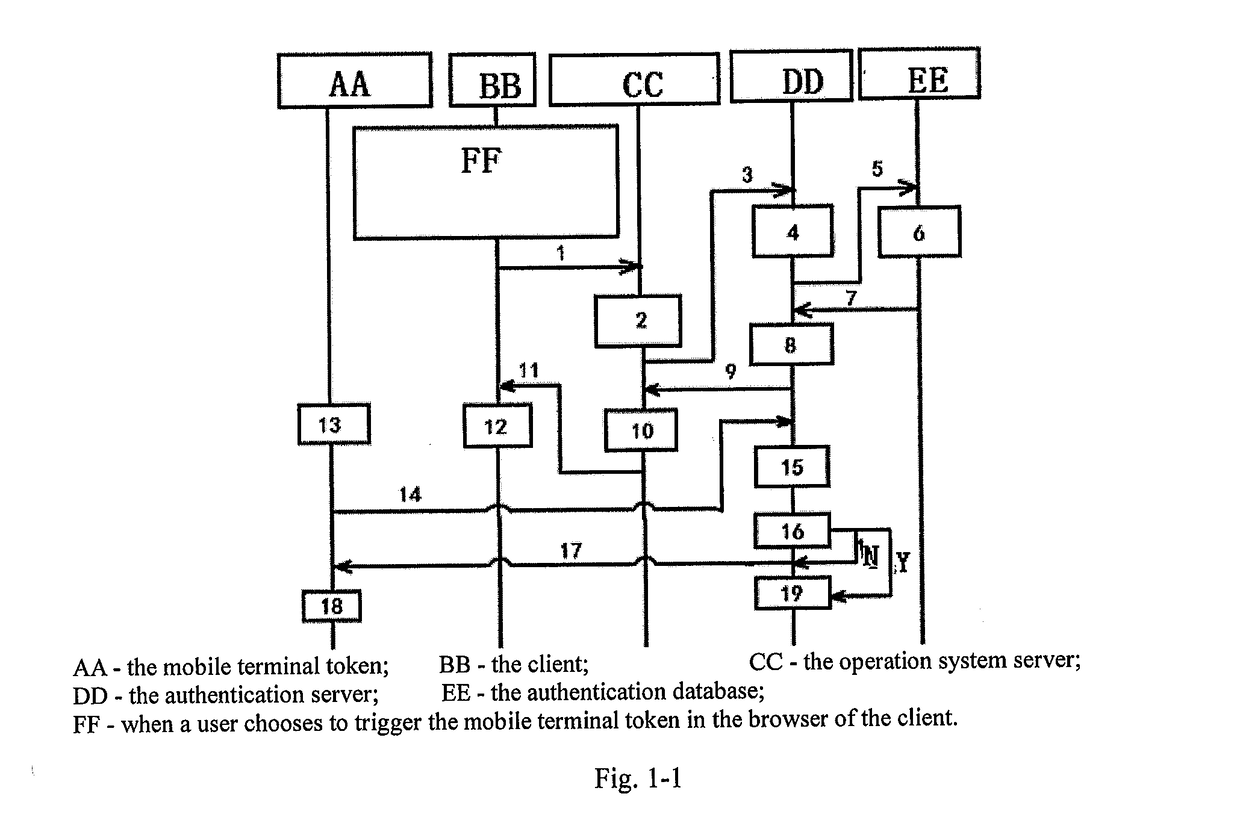
The invention relates to a method for authenticating a user (10) at an entity (16), the method comprising the steps of detecting, by means of a contact module (20) of the entity (16), a contacting of the user (10) made in a browser of a terminal (12), and sending, by means of the contact module (20), a network address of an authentication module (24) of the entity (16) to a mobile device (14) of the user (10) in an authentication message, verifying the acceptability of an entity certificate of the authentication module (24) by means of the mobile device (14) based on the network address, and verifying acceptability of a user certificate of the mobile device (14) by means of the authentication module (24), and in case the entity certificate and the user certificate are acceptable, authenticating the user (10) at the entity (16) by establishing a communication channel (114, 120, 114, 120) between the mobile device (14) and the authentication module (24), whereas in case the entity certificate or the user certificate is not acceptable, rejecting the user (10) at the entity 16. The invention also relates to a system for authenticating a user (10) at an entity (16).
Owner:MICROSEC SZAMITASTECHN FEJLESZTO ZRT
Techniques for co-existence of multiple stored value applications on a single payment device managing a shared balance
ActiveUS20070131761A1No longer accessibleKeep for a long timeAcutation objectsFinancePaymentApplication software
A method of managing a first stored value application having a first application balance and a second stored value application having a second application balance, can include the steps of facilitating conducting of a first transaction by the first stored value application, and synchronizing the second stored value application with the first stored value application. The synchronization can be substantially contemporaneous with the transaction. The applications can reside on the same portable payment device.
Owner:MASTERCARD INT INC
Method and apparatus for hardware-accelerated encryption/decryption
ActiveUS8879727B2Maximize availabilityLimited operating lifeKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMultiple encryptionKey exchange
An integrated circuit for data encryption / decryption and secure key management is disclosed. The integrated circuit may be used in conjunction with other integrated circuits, processors, and software to construct a wide variety of secure data processing, storage, and communication systems. A preferred embodiment of the integrated circuit includes a symmetric block cipher that may be scaled to strike a favorable balance among processing throughput and power consumption. The modular architecture also supports multiple encryption modes and key management functions such as one-way cryptographic hash and random number generator functions that leverage the scalable symmetric block cipher. The integrated circuit may also include a key management processor that can be programmed to support a wide variety of asymmetric key cryptography functions for secure key exchange with remote key storage devices and enterprise key management servers. Internal data and key buffers enable the device to re-key encrypted data without exposing data. The key management functions allow the device to function as a cryptographic domain bridge in a federated security architecture.
Owner:IP RESERVOIR
Scalable and flexible information security for industrial automation
ActiveUS8132225B2Compromising performance and throughput and securityImprove securityDigital data processing detailsTechnology managementFactory floorInformation security
A security system that relates to industrial automation security comprises a component that receives a request to modify security relating to a zone of a factory floor, the zone being less than an entirety of the factory floor. A zonal security component generates security procedures for the zone, the security procedures differ from security procedures implemented on the factory floor outside the zone.
Owner:ROCKWELL AUTOMATION TECH
Security Enhanced Data Platform
InactiveUS20100189251A1Improve securityConvenient access controlDigital data processing detailsUser identity/authority verificationUser PrivilegeDocumentation procedure
The security enhanced data platform is comprised of two primary subsystems and a host of supporting subsystems. The first primary subsystem is a document management system. A set of client side tools provides the user a way to specify classifications and compartments for selected areas of a document, and a way to save the document in the format required by the system in order to allow the system to enforce the rules and privileges dictated to the system. The second subsystem is a security enhanced database management system. In documents the system allows different user privilege requirements on the document as a whole as well as on pages, paragraphs, sentences, words, and / or letters of a word. A history of document changes is maintained to provide an audit trail after the fact of who did what changes, where those changes were made and when those changes were made.
Owner:CURREN EDWARD
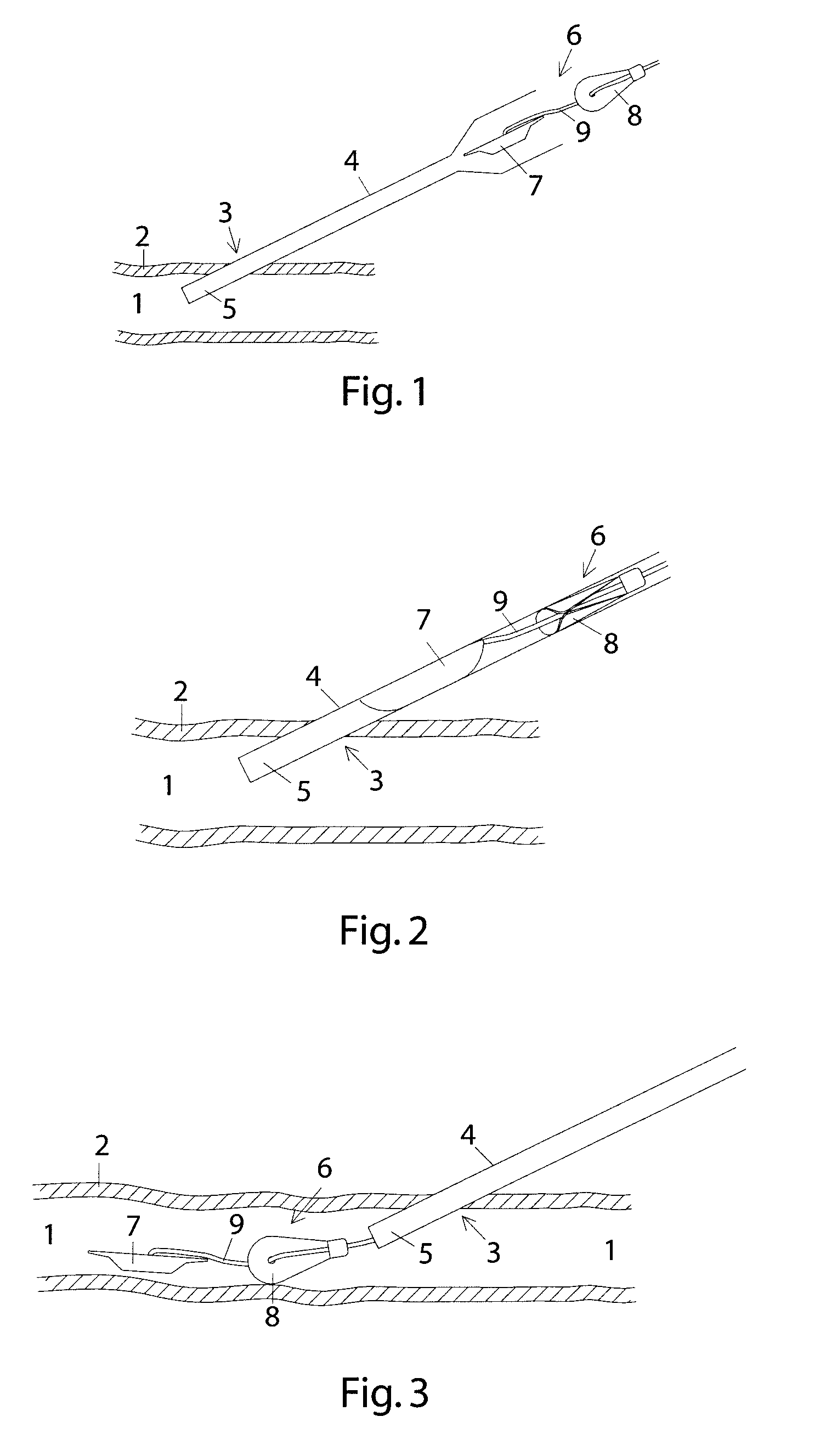
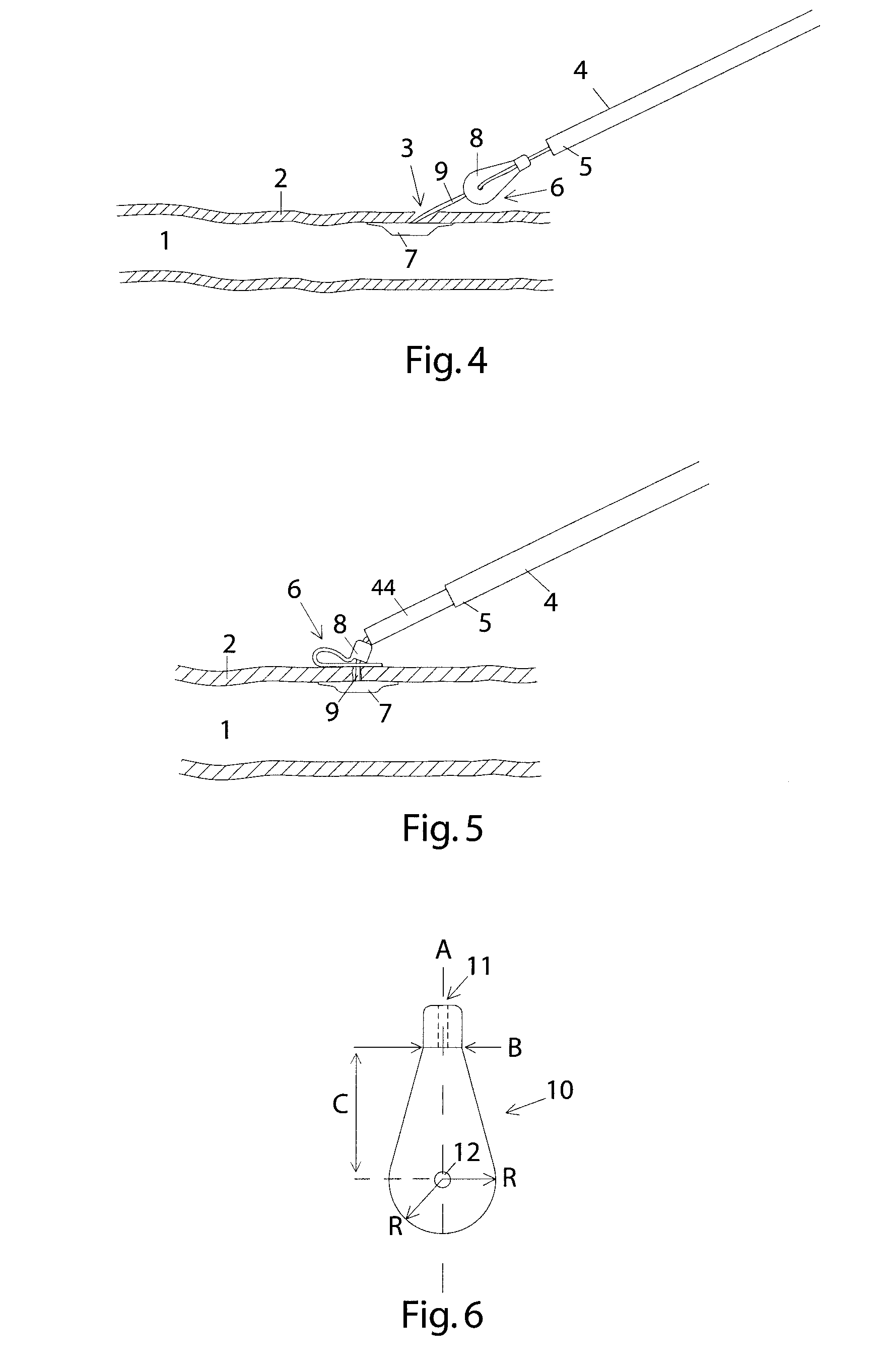
Method and device for sealing a puncture hole in a bodily organ
InactiveUS20090112257A1Precise deploymentMore secureSuture equipmentsSurgical veterinaryAbutmentSurgery
A method for sealing a hole in a bodily organ includes introducing a first member and a second member into the bodily organ, the first and second members being connected by an elongated member. The first and second members are retracted proximally until the first member abuts an inner surface of the bodily organ and the second member is retracted out of the hole in the bodily organ. Then, the second member is pushed distally into abutment with an outer surface of the bodily organ. A sealing device for sealing a puncture in tissue is also described.
Owner:ST JUDE MEDICAL COORDINATION CENT
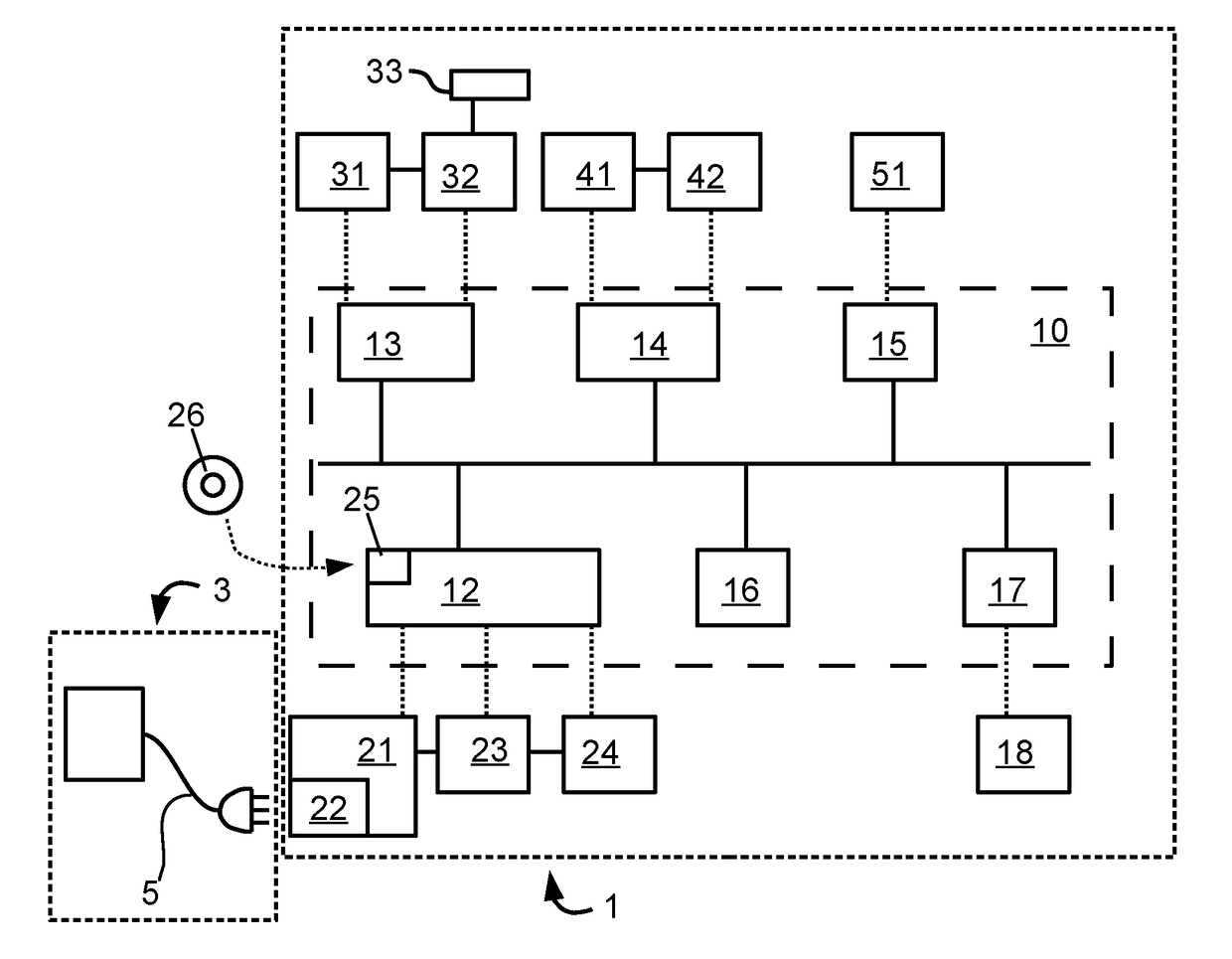
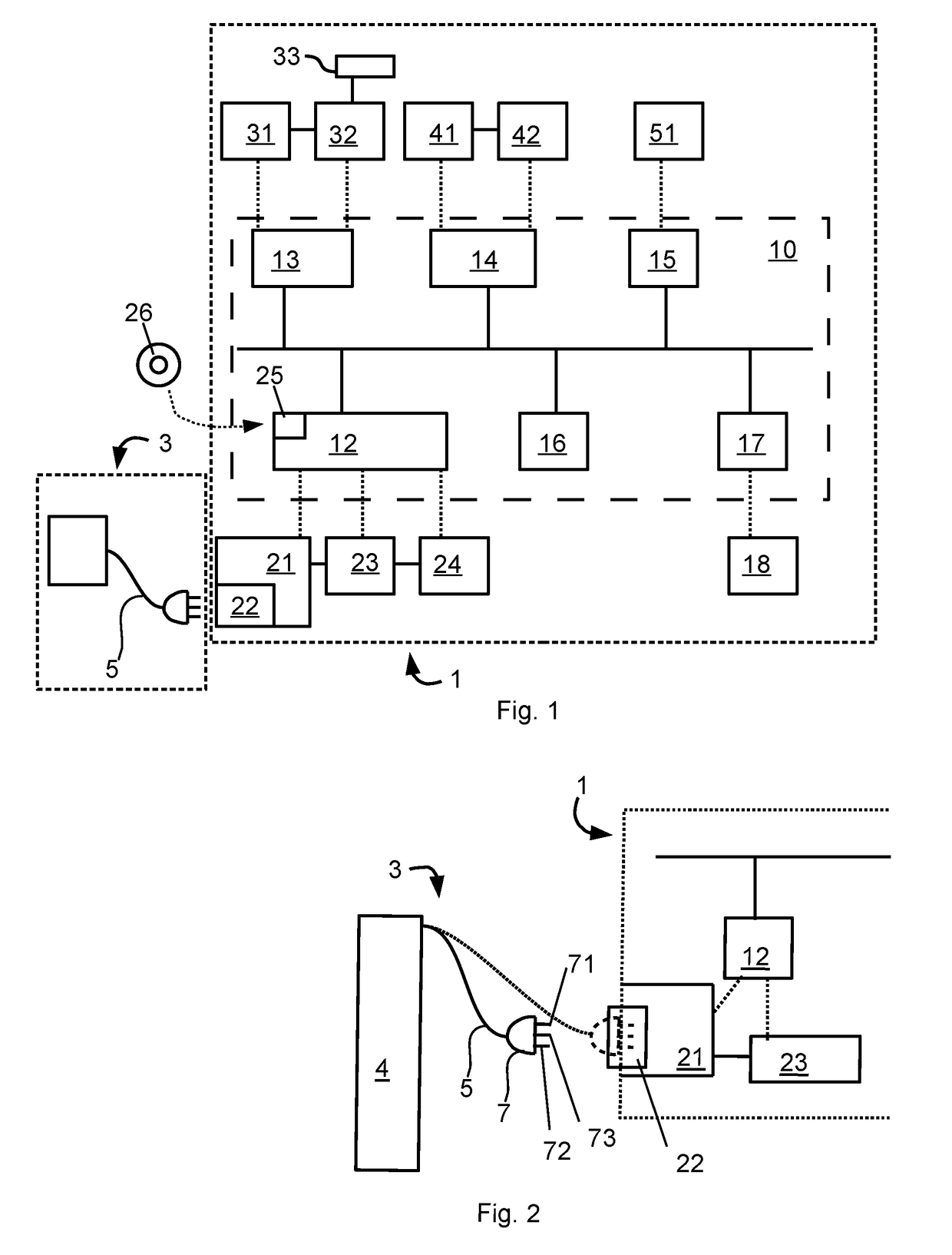
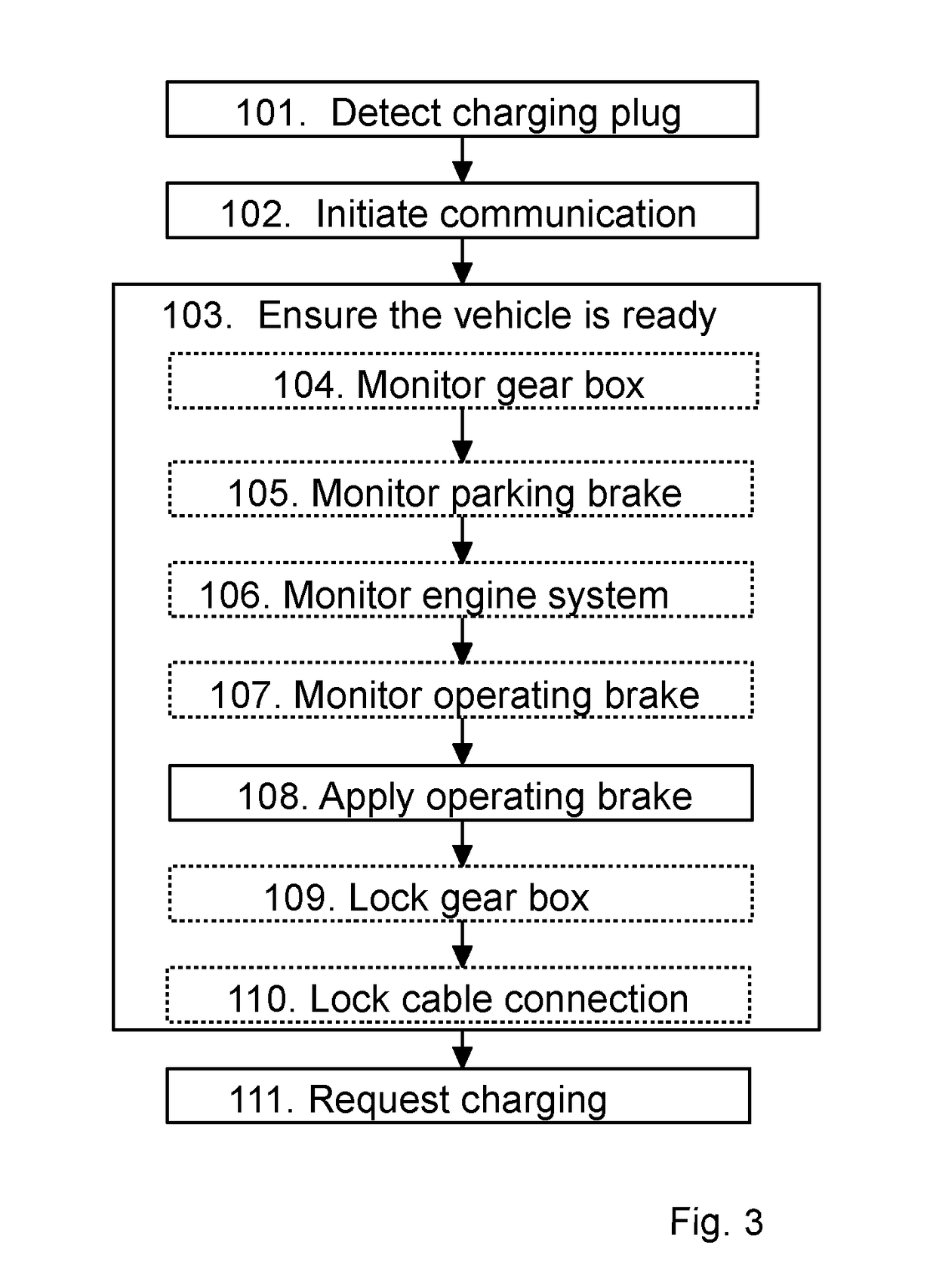
Method and control system for charging a vehicle
InactiveUS20180029488A1More reliableMore secureHybrid vehiclesVehicular energy storageControl systemHybrid electrical vehicle
A method for controlling charging of a hybrid vehicle, a control system for charging of a hybrid vehicle and a hybrid vehicle comprising the control system is described. The hybrid vehicle comprises a fuel engine, a parking brake, an electronically controllable operating brake, and a hybrid system comprising a charging unit, an energy storage, and an electric motor system. The control system is connectable to the hybrid system, the fuel engine, the operating brake, and the parking brake. The control system is configured to control the charging of the energy storage in accordance with the charging method. The charging method comprises: detecting connection of a charging cable of an external charging station, ensuring that the hybrid vehicle is ready for charging, and requesting charging from the charging station. Ensuring that the vehicle is ready for charging includes applying the operating brake, also called service brake, of the hybrid vehicle.
Owner:SCANIA CV AB
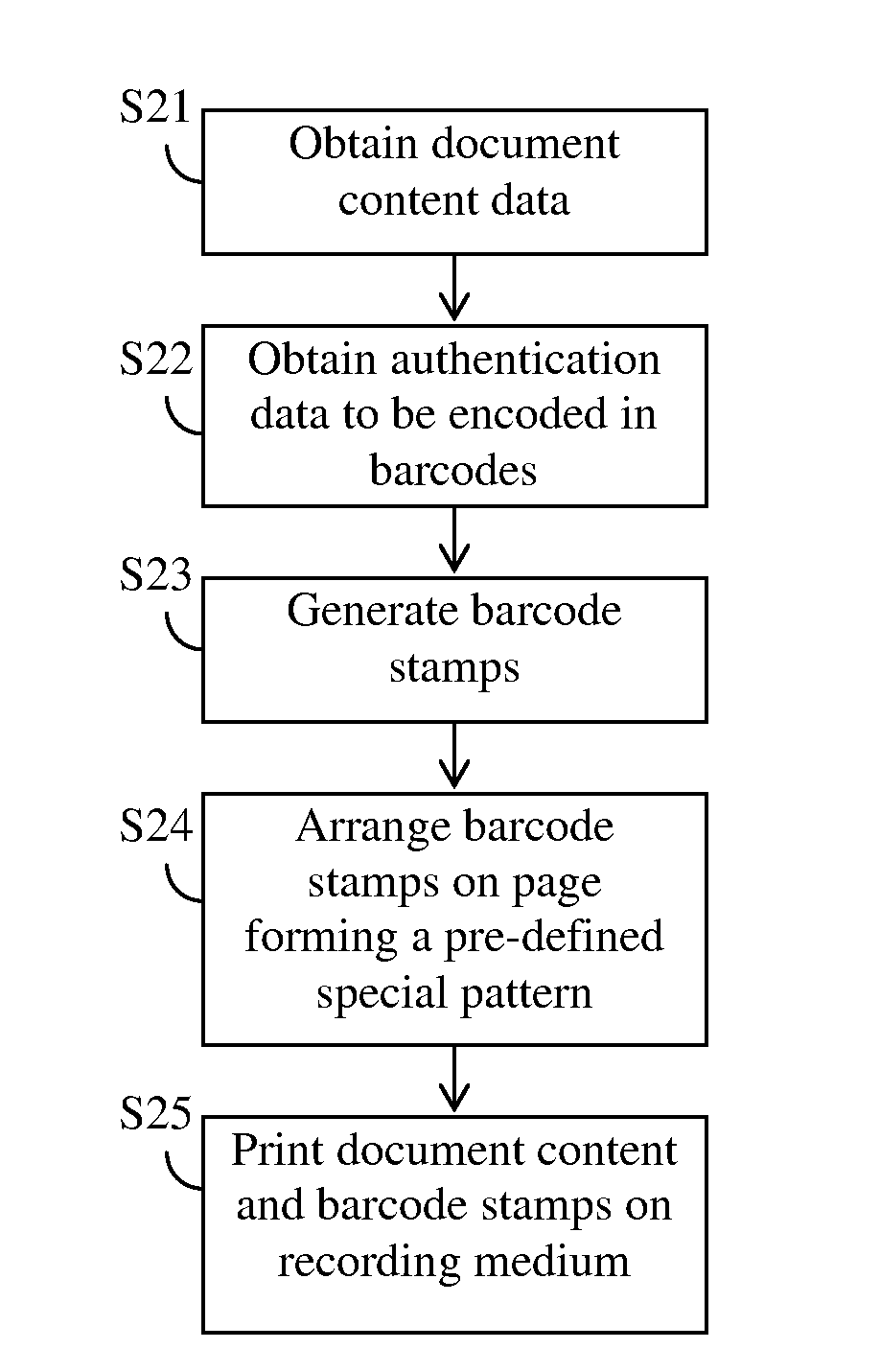
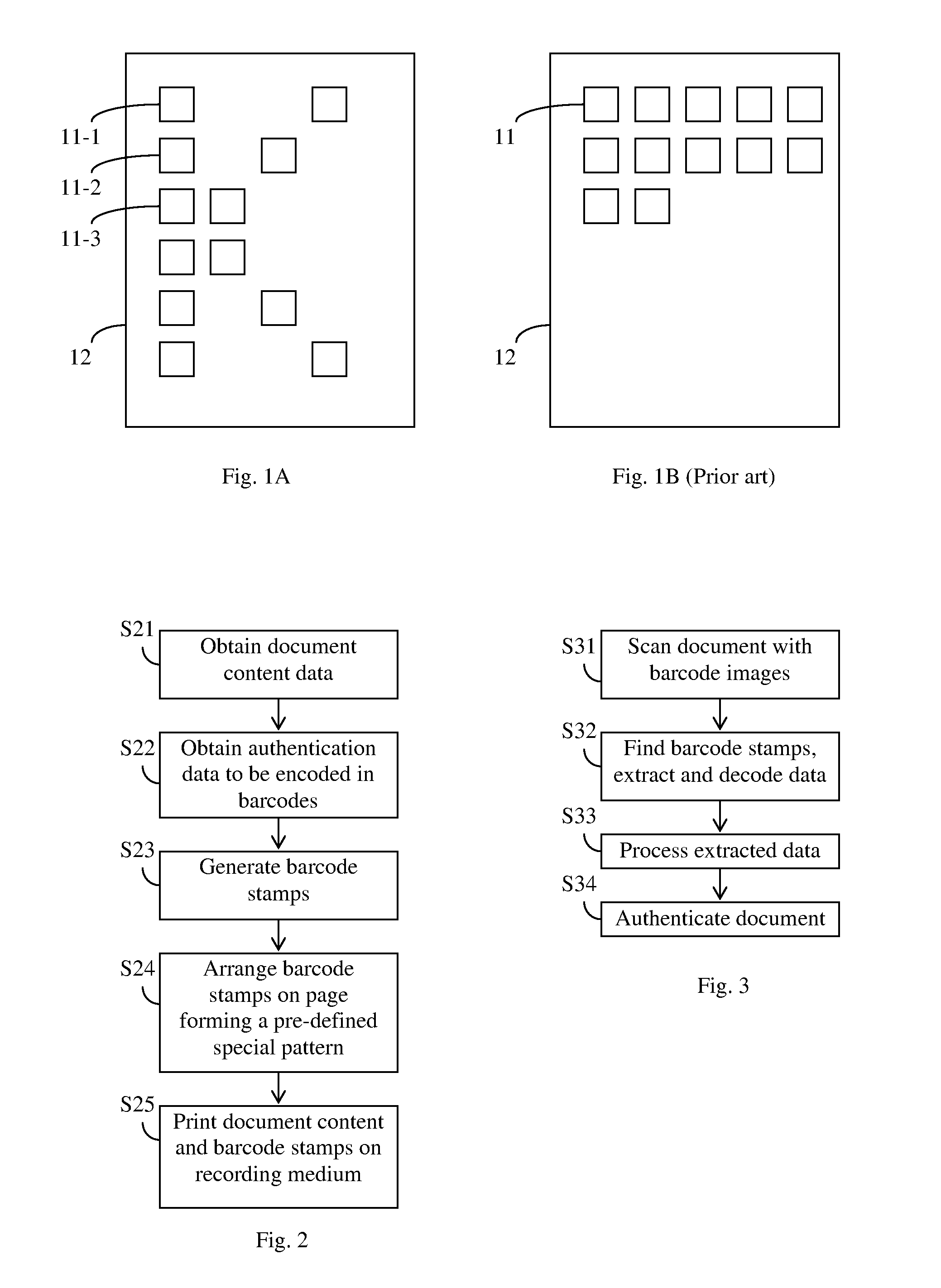
Creation and placement of two-dimensional barcode stamps on printed documents for storing authentication information
ActiveUS20100157318A1Appealing appearanceMore secureDigitally marking record carriersPaper-money testing devicesBarcodeDocumentation
A document authenticating method is disclosed by which a plurality of two-dimensional barcode stamps are generated and printed on a back side of the document forming a pre-defined special pattern. The barcode stamps collectively encode the content of the document to be used for document authentication. Each barcode stamp encodes linking information indicating the position of the next barcode stamp. An index barcode may be printed on the front side of the document which encodes the position information for all of the barcode stamps on the back side.
Owner:KONICA MINOLTA LAB U S A INC
Techniques for co-existence of multiple stored value applications on a single payment device managing a shared balance
ActiveUS7657486B2No longer accessibleKeep for a long timeAcutation objectsFinancePaymentApplication software
A method of managing a first stored value application having a first application balance and a second stored value application having a second application balance, can include the steps of facilitating conducting of a first transaction by the first stored value application, and synchronizing the second stored value application with the first stored value application. The synchronization can be substantially contemporaneous with the transaction. The applications can reside on the same portable payment device.
Owner:MASTERCARD INT INC
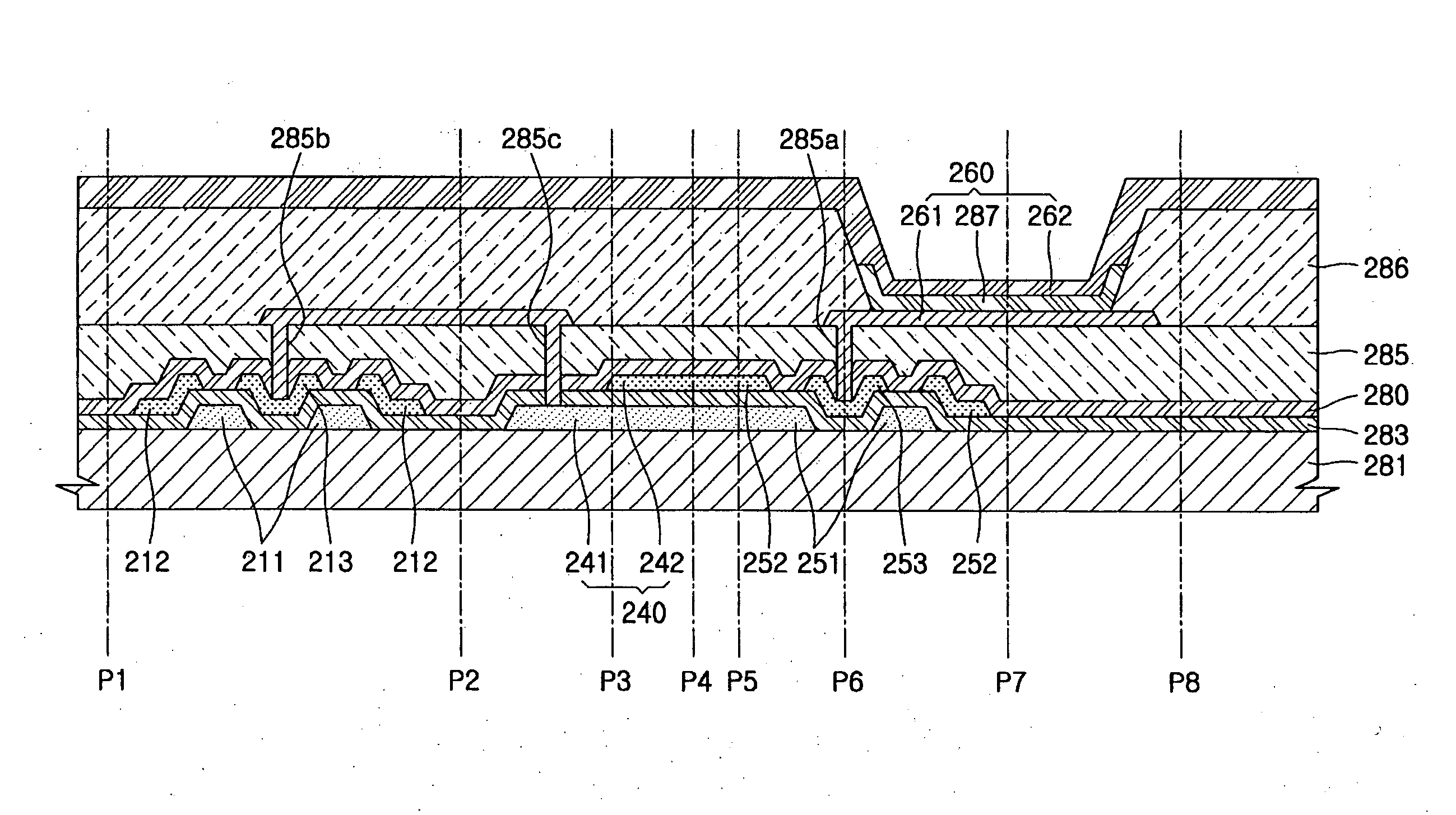
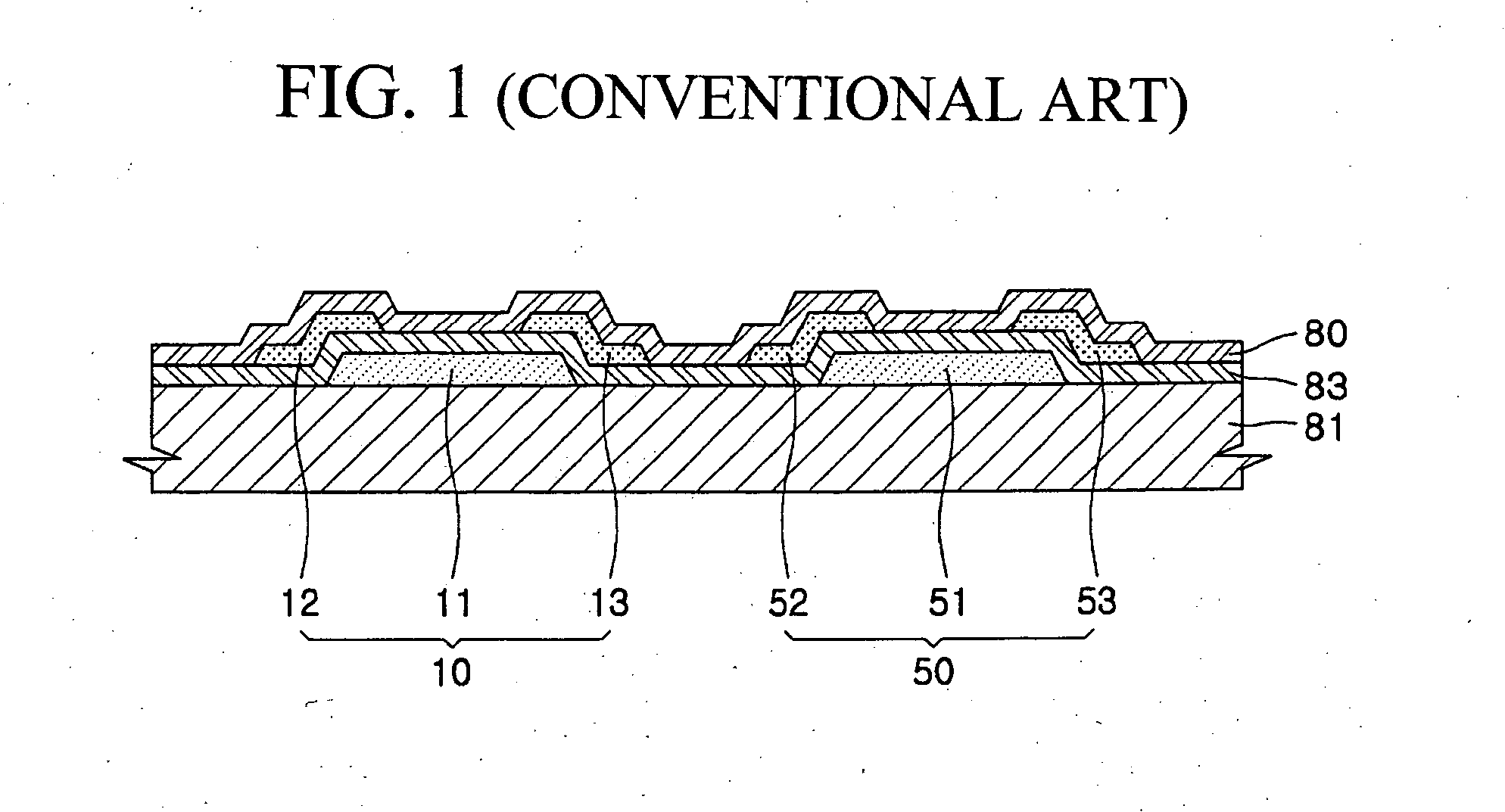
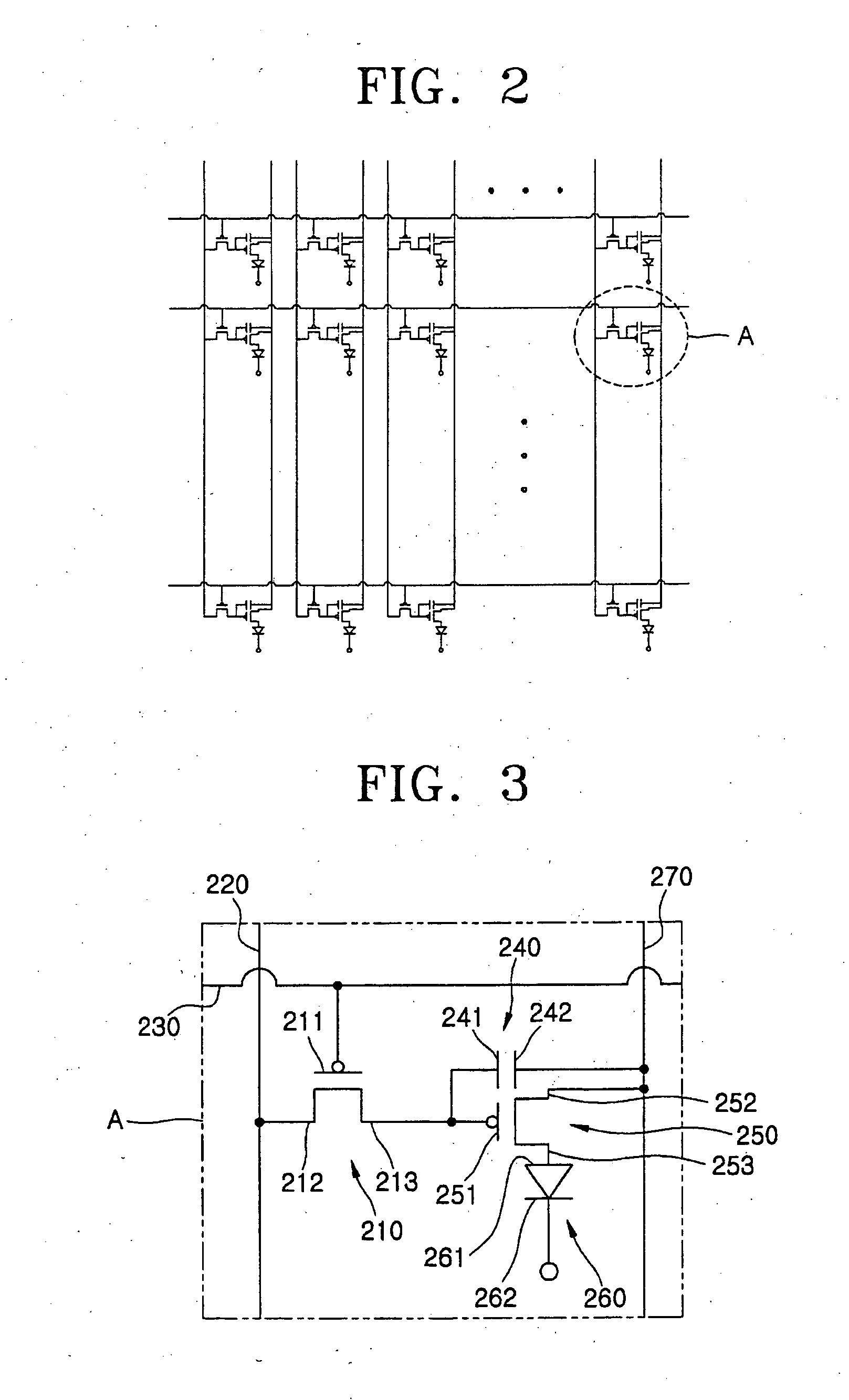
Flat panel display device
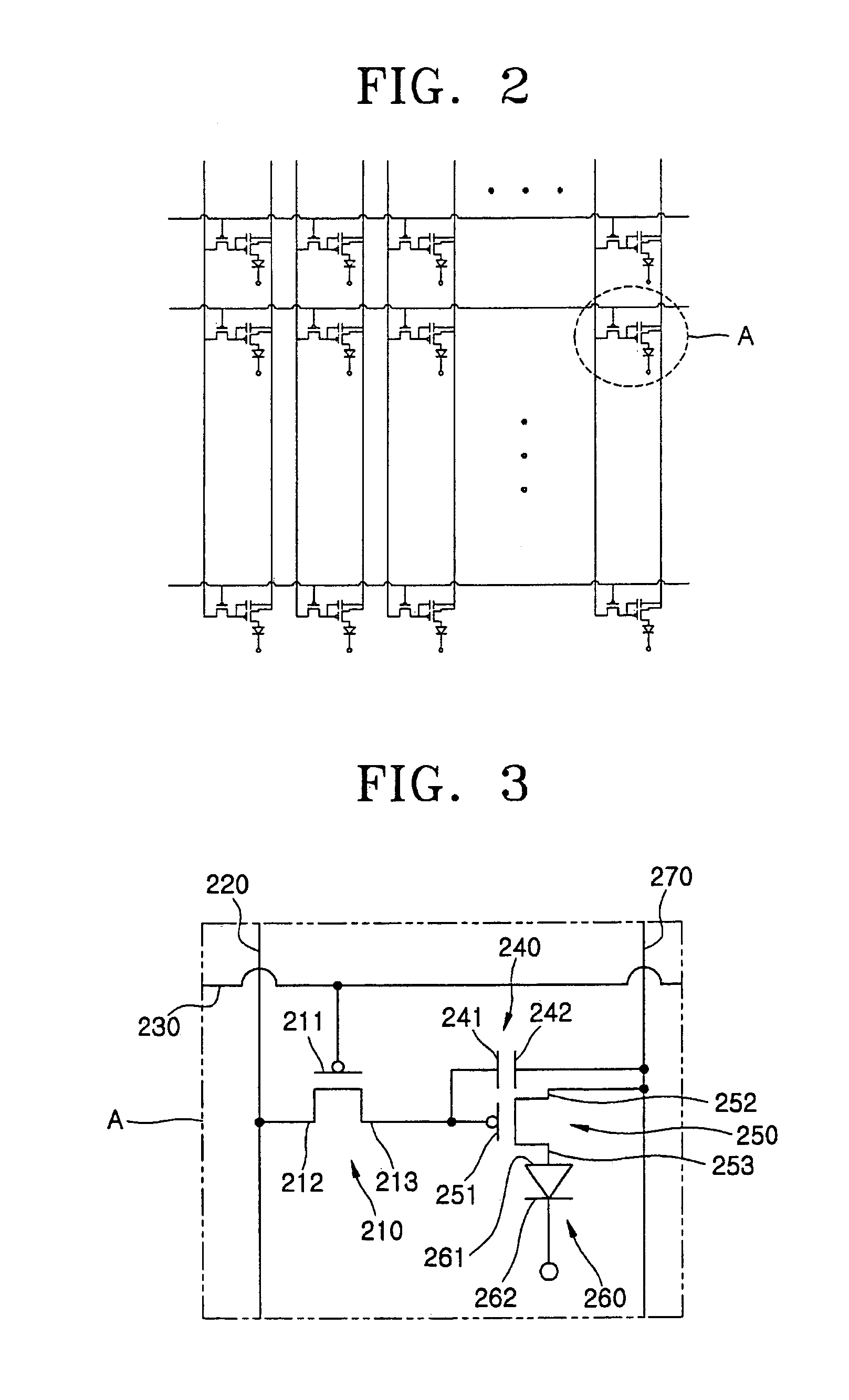
ActiveUS20060108916A1Minimize cross-talkCross-talk is minimizedDischarge tube luminescnet screensLamp detailsEngineeringCrosstalk minimization
A flat panel display device has a transistor in which cross-talk is minimized. The flat panel display device includes a substrate, a first gate electrode formed on the substrate, a first electrode insulated from the first gate electrode, a second electrode insulated from the first gate electrode and surrounding the first electrode in the same plane, a semiconductor layer insulated from the first gate electrode and contacting the first electrode and the second electrode, and a display element including a pixel electrode electrically connected to one of the first electrode and the second electrode.
Owner:SAMSUNG DISPLAY CO LTD
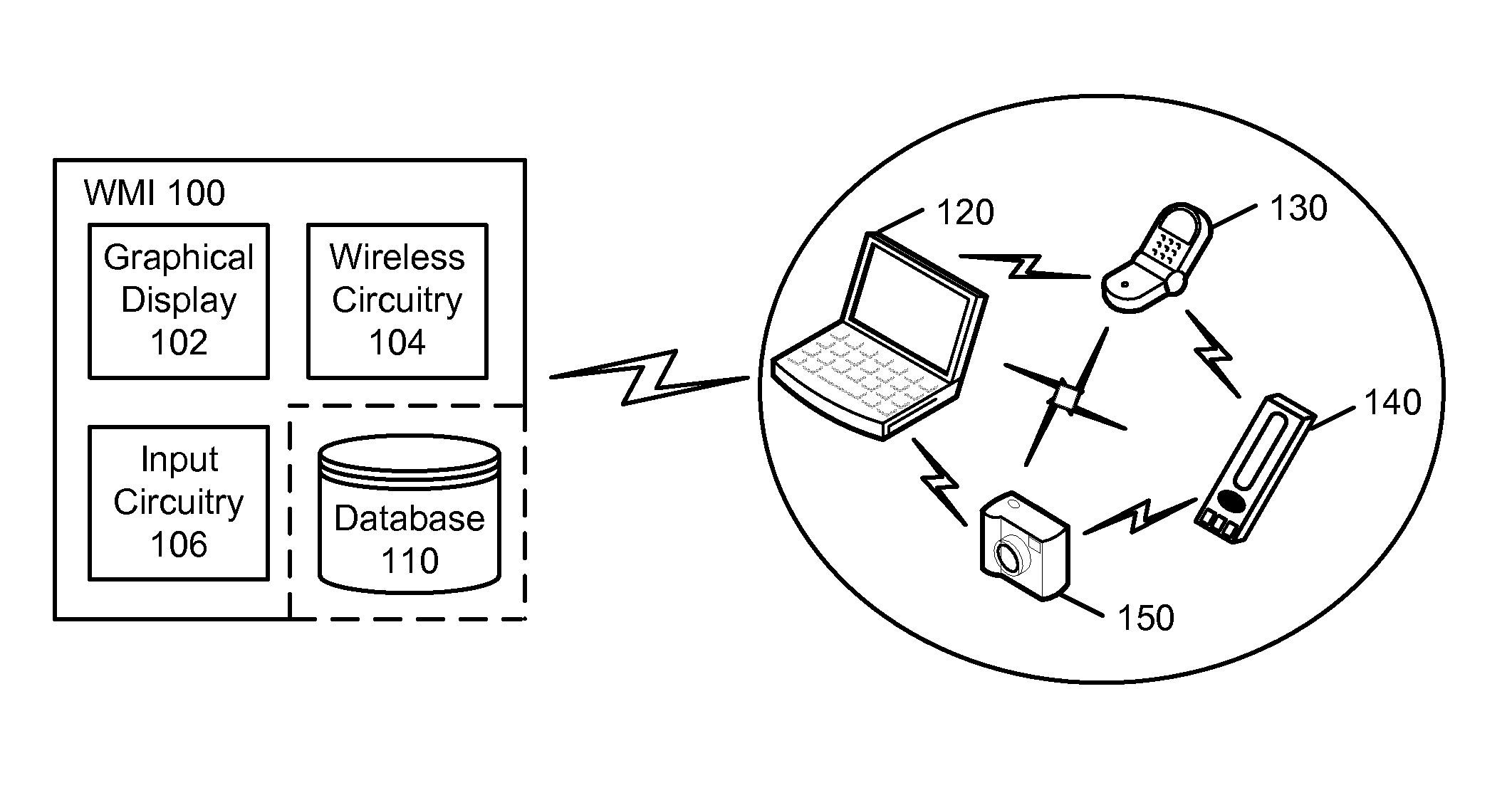
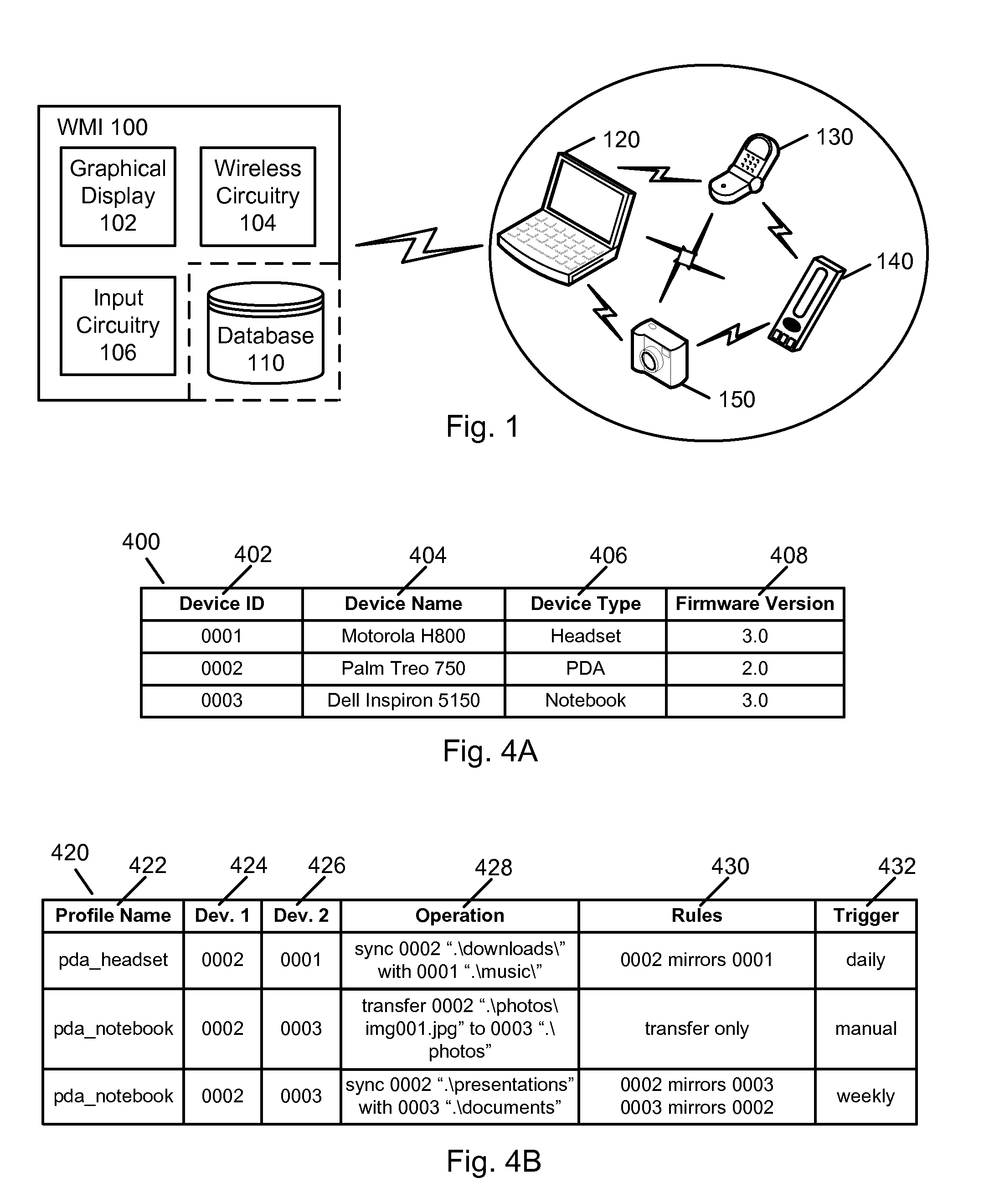
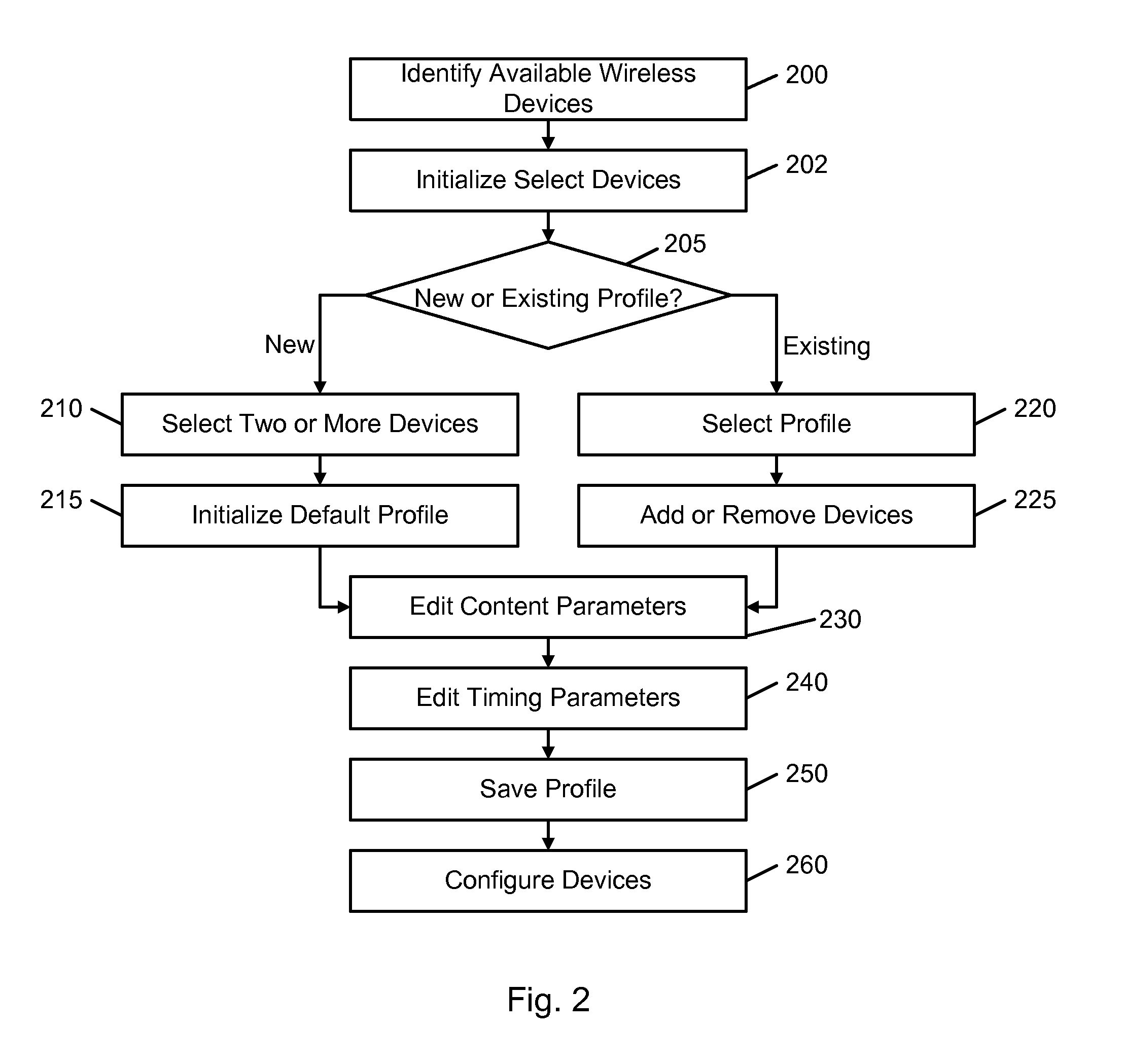
Wireless Management Interface
InactiveUS20090031251A1Improve interoperabilityReduce complexityDatabase distribution/replicationTransmissionGraphicsComputer hardware
It is an object of the present invention to overcome the limitations of the prior art through the use of a wireless management interface (WMI). The WMI enables a user to securely manage the wireless transfer and synchronization of data between two or more wireless-equipped devices. The WMI is preferably implemented in a combination of hardware and software and operates by enabling a user, via a graphical display and user input capabilities, to establish a communication profile for any two or more devices. The communication profile includes one or more content parameters and one or more timing parameters. In response to receiving configuration instructions from the WMI, the devices then operate to transfer or synchronize designated content at a designated time according to the communication profile. Synchronization is further facilitated by a database that is accessible to the WMI and maintains the communication profiles and other device-specific configuration information.
Owner:GOFERTECH
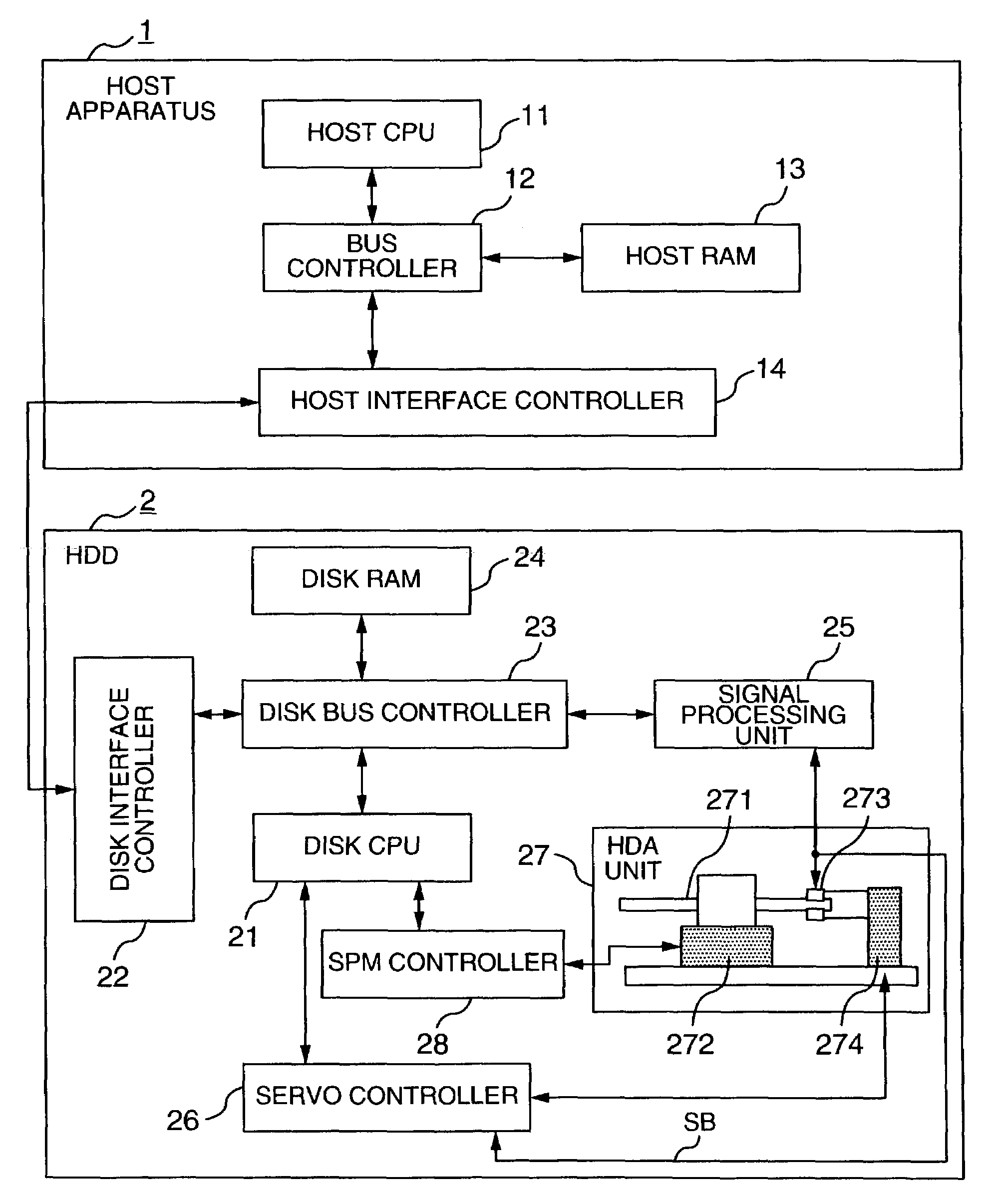
Magnetic disk drive which accesses host RAM
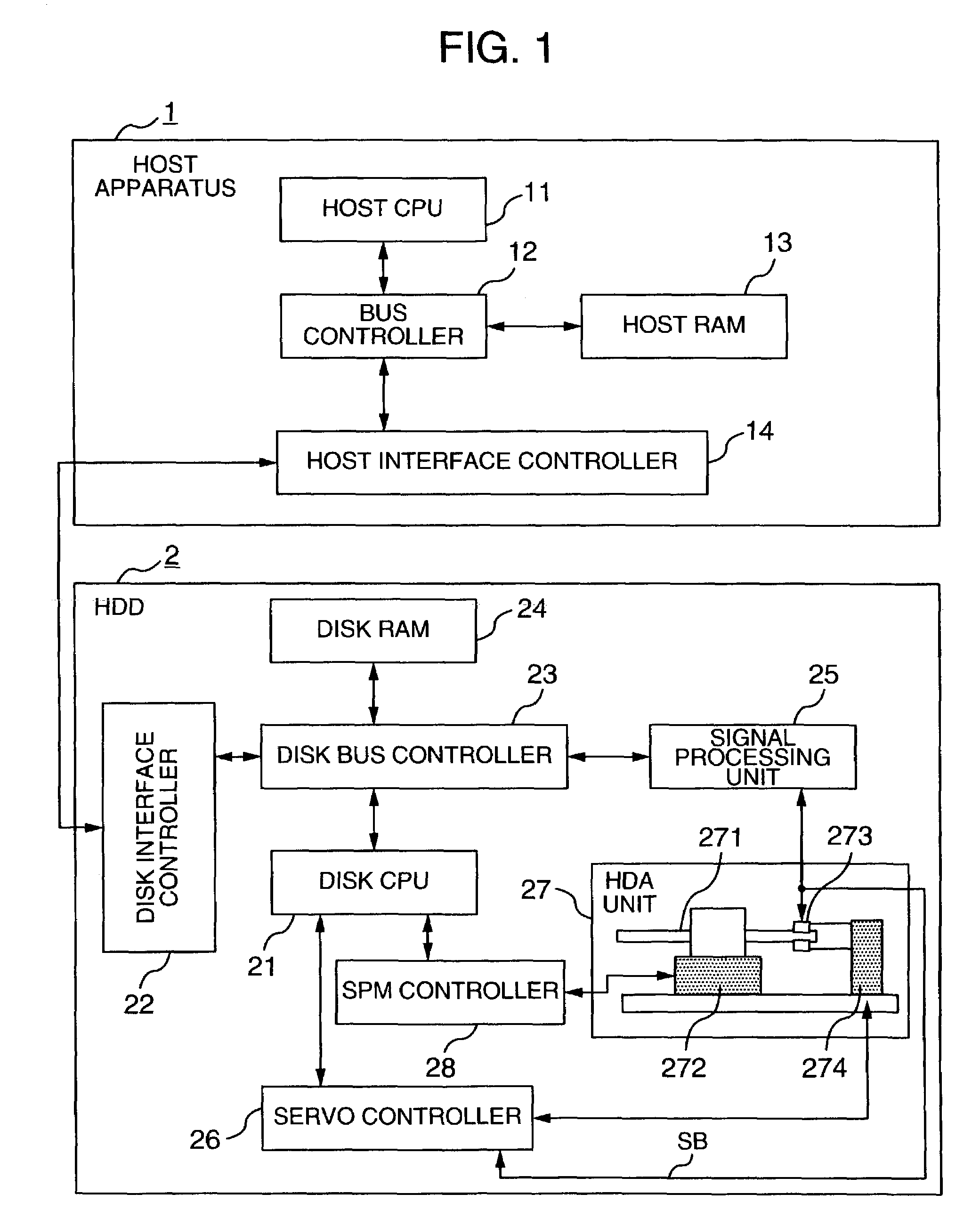
InactiveUS6987635B2Low possible costMore secureDigital data processing detailsFilamentary/web record carriersEngineeringPower dissipation minimization
In a magnetic disk apparatus which is removably mounted or embedded to a host apparatus and intermittently accessed for recording / reproducing data, a RAM contained in the host apparatus is utilized for a portion or entirety of a buffer RAM for use in the intermittent access to accomplish a reduction in size and cost of the magnetic disk apparatus. In addition, the magnetic disk apparatus is controlled to rotate a magnetic disk at a variable rotational speed, and operated at a rotational speed at which the total power consumption is minimized in accordance with the capacity of the utilized buffer RAM and whether an access is made for recording or reproduction, thereby improving a power saving effect.
Owner:HITACHI GLOBAL STORAGE TECH JAPAN LTD
Flat panel display device
ActiveUS7279714B2Cross-talk is minimizedMinimize cross-talkSolid-state devicesSemiconductor devicesEngineeringFlat panel display
Owner:SAMSUNG DISPLAY CO LTD
Safe and secure program execution framework
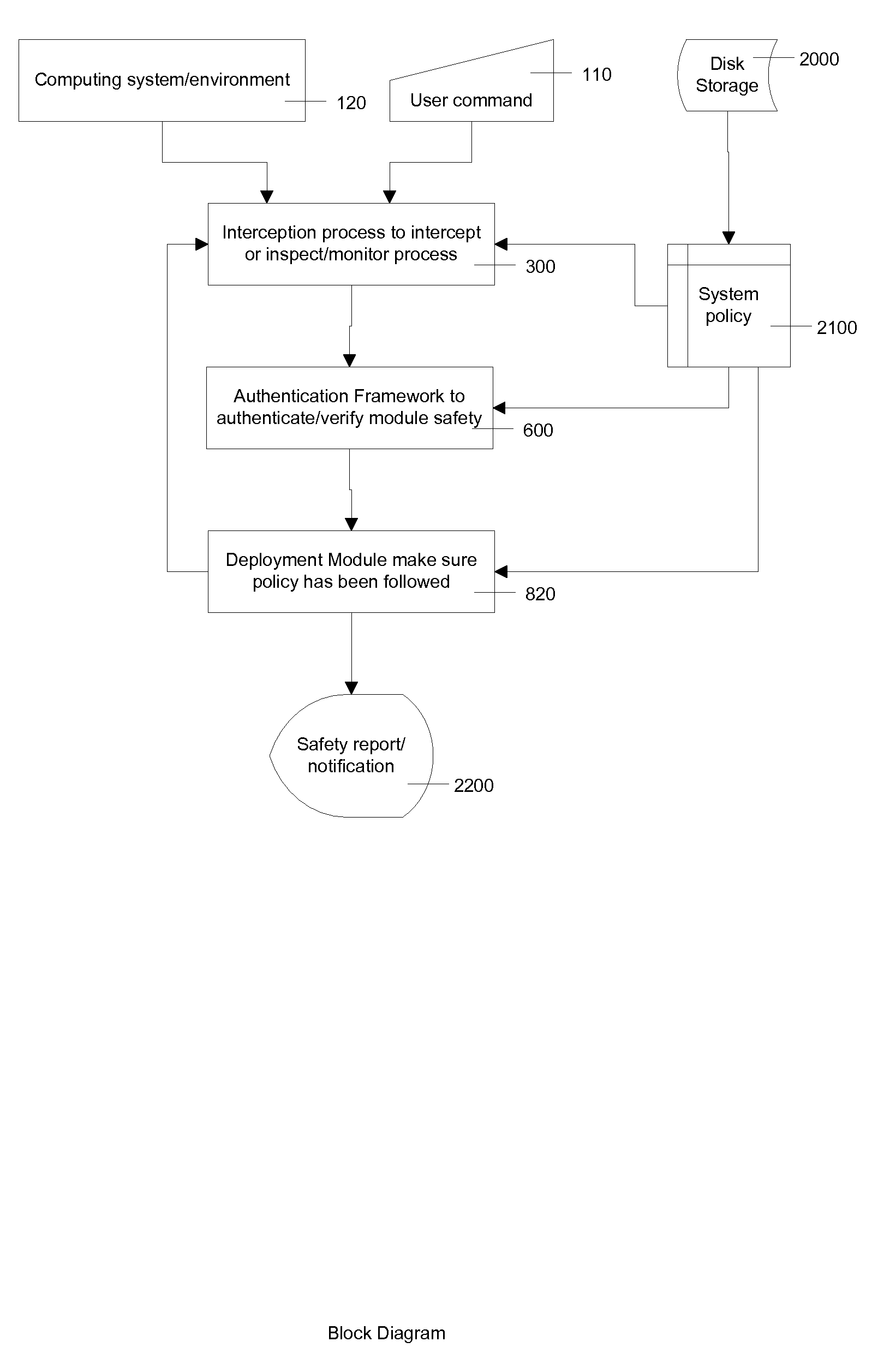
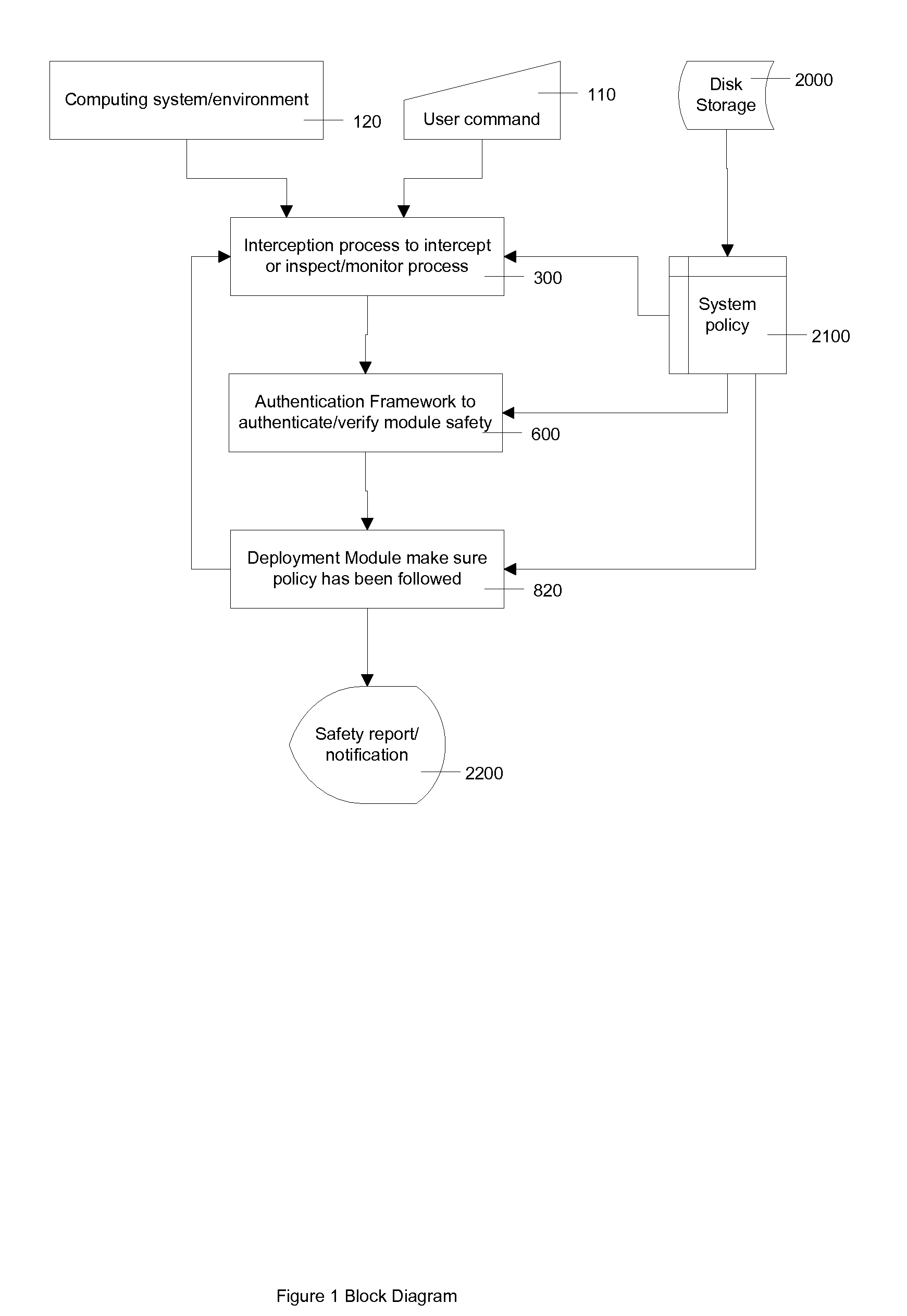
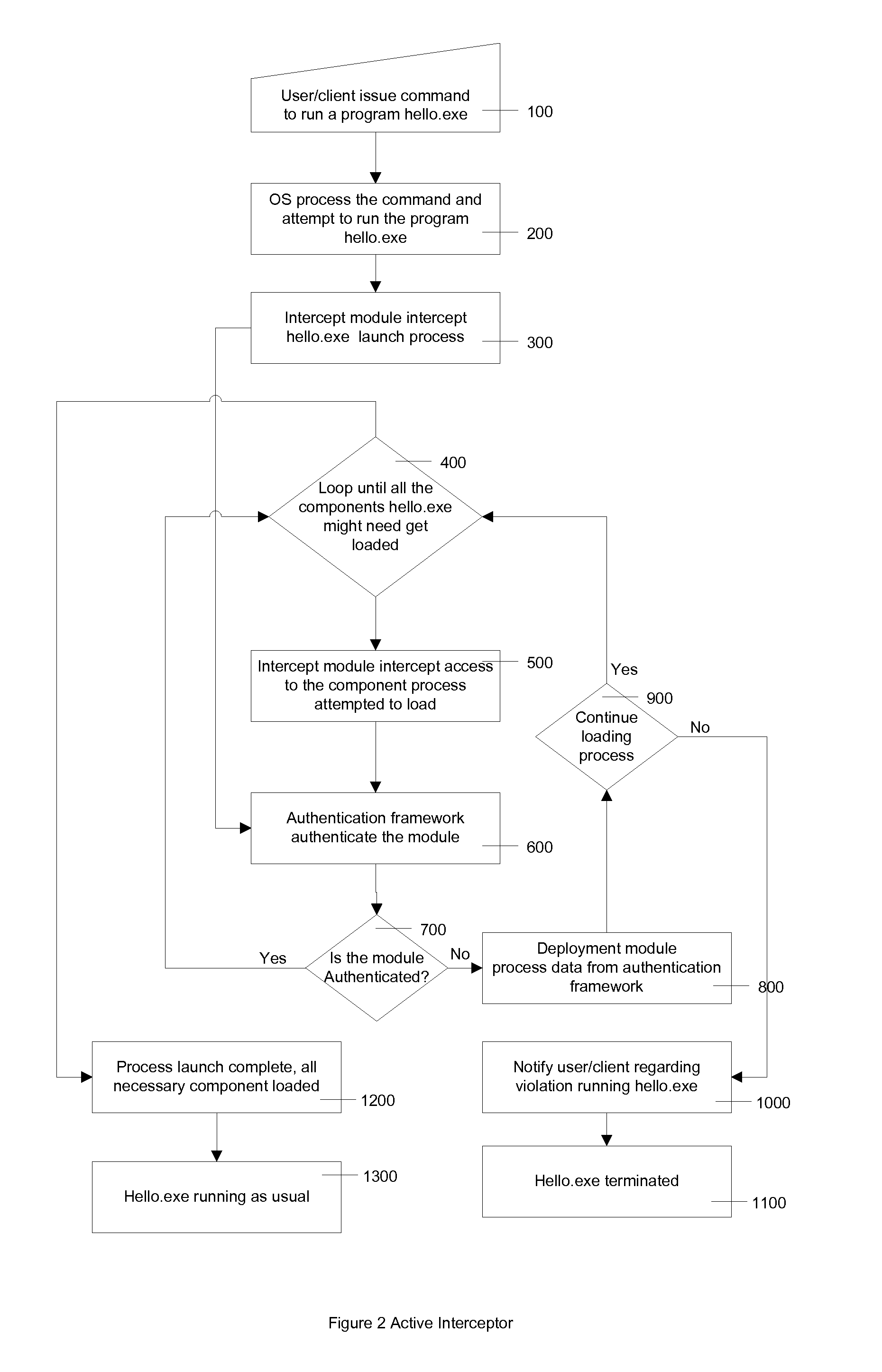
ActiveUS20100031308A1Narrow downReduce the prevalenceMemory loss protectionError detection/correctionMonitoring systemCode segment
A system and method is provided here that can make sure that the instruction sets executing on a computer are certified and secure. The system and method further facilitates a generic way to intercept instruction loading process to inspect loaded code segment 1st before computer get a chance to execute them.Further, a profiling component can monitor all executing process running in a system and profile behavior of the program. If the behavior is suspicious, established by a set of predefined rules, the profiler can take necessary action to notify system administrator and suspend or terminate execution of the program.
Owner:XENCARE SOFTWARE
Scooter folding structure
InactiveUS20060103096A1Easily and safely changeMore secureFoldable cyclesBicyclesEngineeringFolded structure
Owner:FAR GREAT PLASTICS INDAL
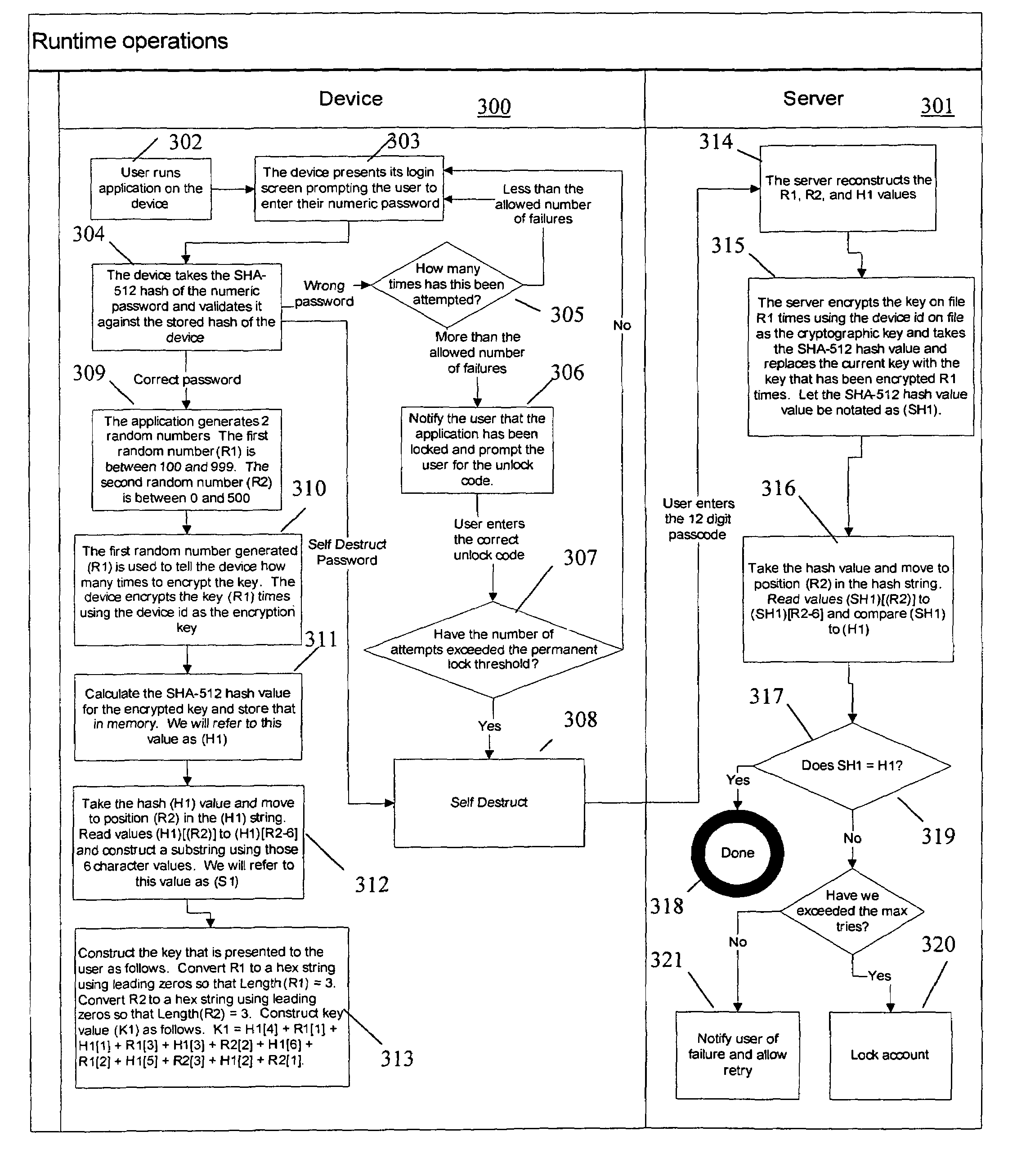
Method and system for generating passwords
InactiveUS20060026439A1More secureMore secure passwordDigital data authenticationSecret communicationThird partyPresent method
An improved method and system of generating passwords wherein Internet search engines are provided a random query and the search results are used to generate a mnemonic password. The password is memorable, yet non-user generated, and the use of search engines allows for a very large set of potential results. The password is more secure than most conventional passwords because it is memorable and not likely to be written down and because it is random. A large set of potential results ensures that the password is unlikely to be determined by a third party. The present method can be used with any device that has access to the Internet. The system can be customized to limit results to a specific language, filter offensive content, and incorporate encryption to limit eavesdropping.
Owner:MOSELEY BRETT E
Operating method for push authentication system and device
ActiveUS20180337783A1Facilitate transmissionProtection attackUser identity/authority verificationMan-in-the-middle attackApplication server
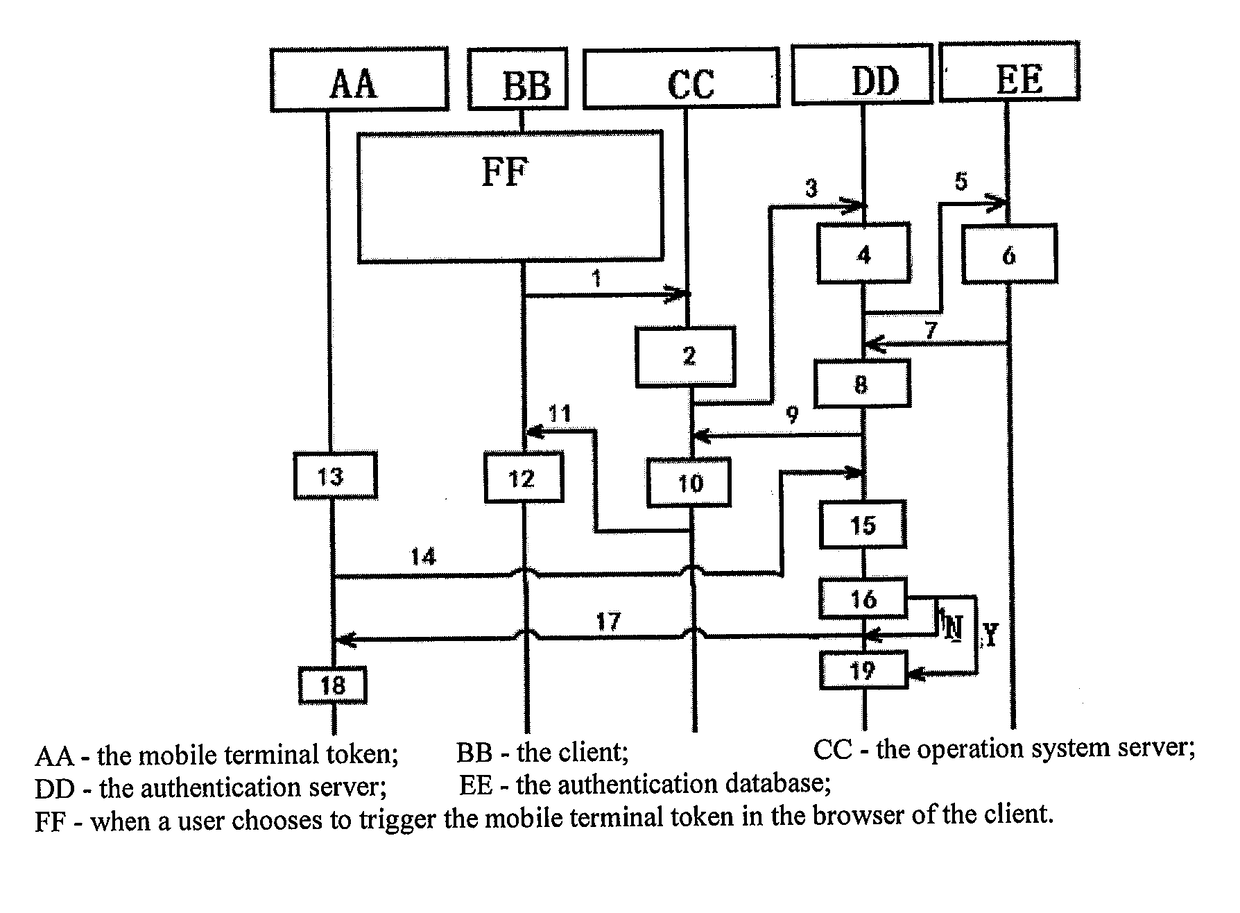
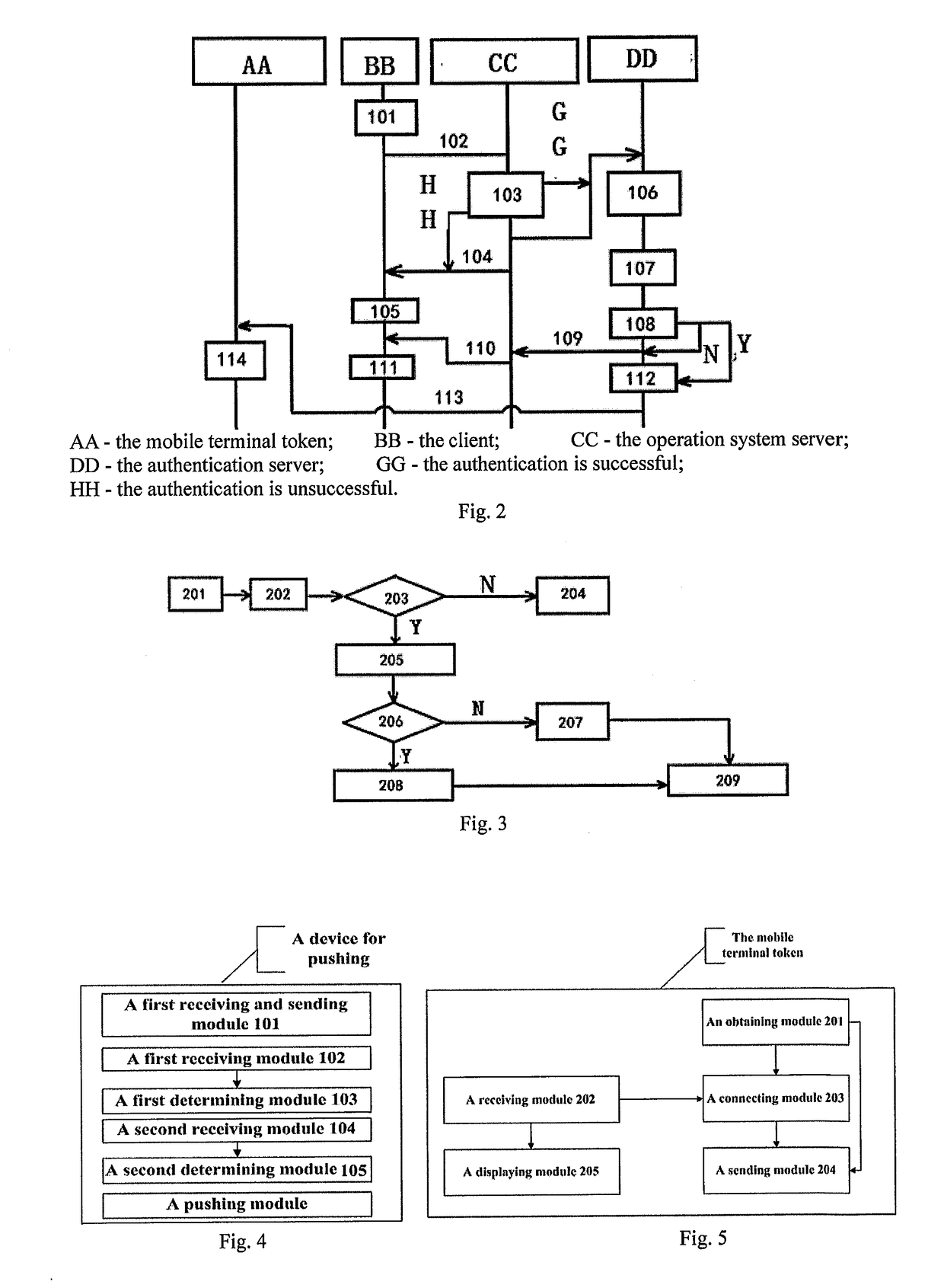
An operating method for a push authentication system and device, belonging to the field of information security. The method comprises: an application interface receiving user information and sending same to an application server; the application server sending the user information and an application identifier to an authentication server; the authentication server generating a push authentication request according to a generated challenge value, token information, the user information and an application name corresponding to the application identifier and sending same to a mobile terminal token; the mobile terminal token generating login information according to the push authentication request, and generating a first response value according to the challenge value when a user selects to confirm login and sending same to the authentication server; and the authentication server generating a second response value according to the challenge value, and returning a authentication success result to the application server when the first response value and the second response value are the same. The present invention can improve the data transmission speed of traditional authentication, and a user does not need to participate in the input of a password, thereby preventing the man-in-the-middle attack and improving the security of authentication.
Owner:FEITIAN TECHNOLOGIES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com