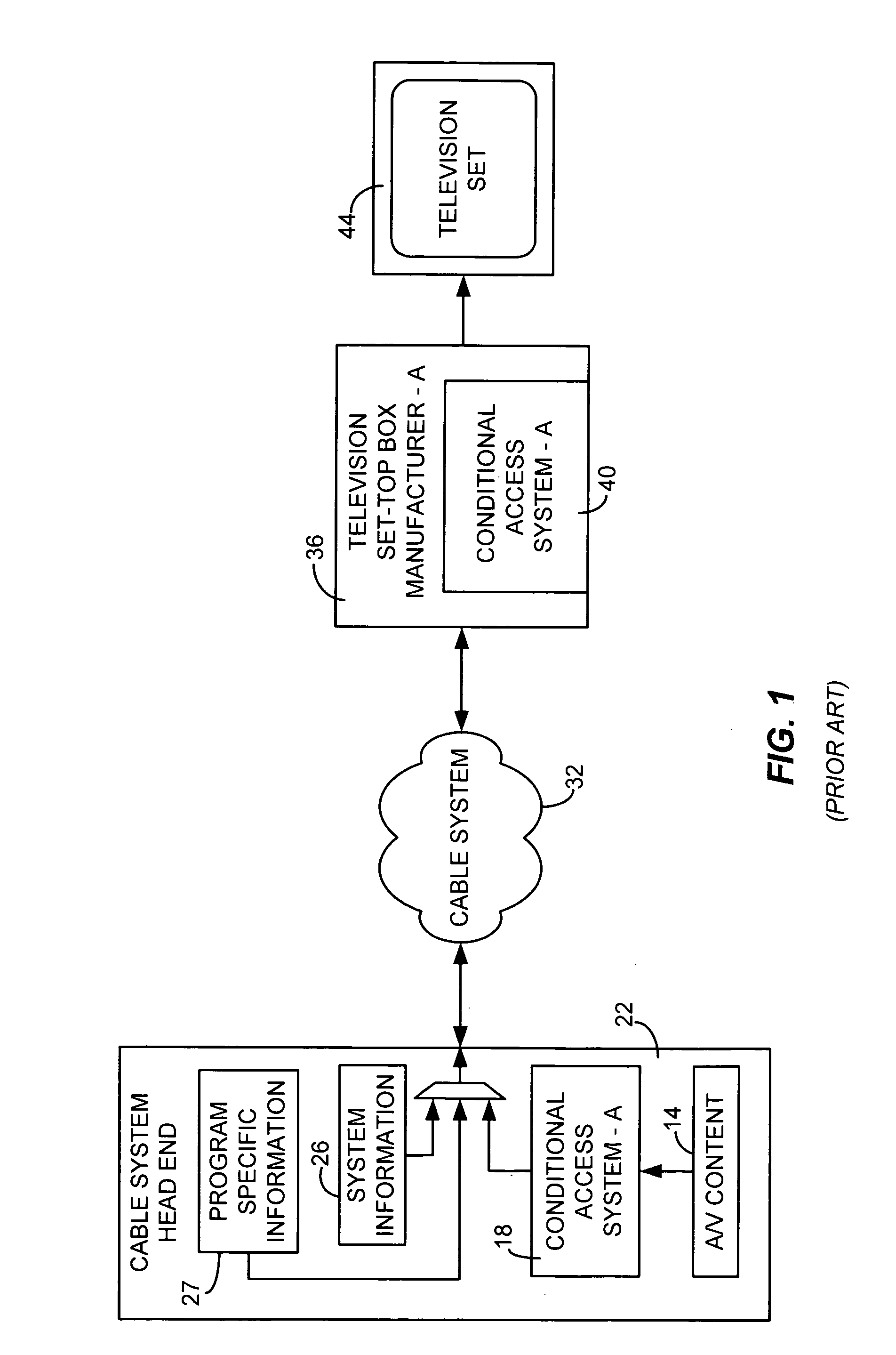
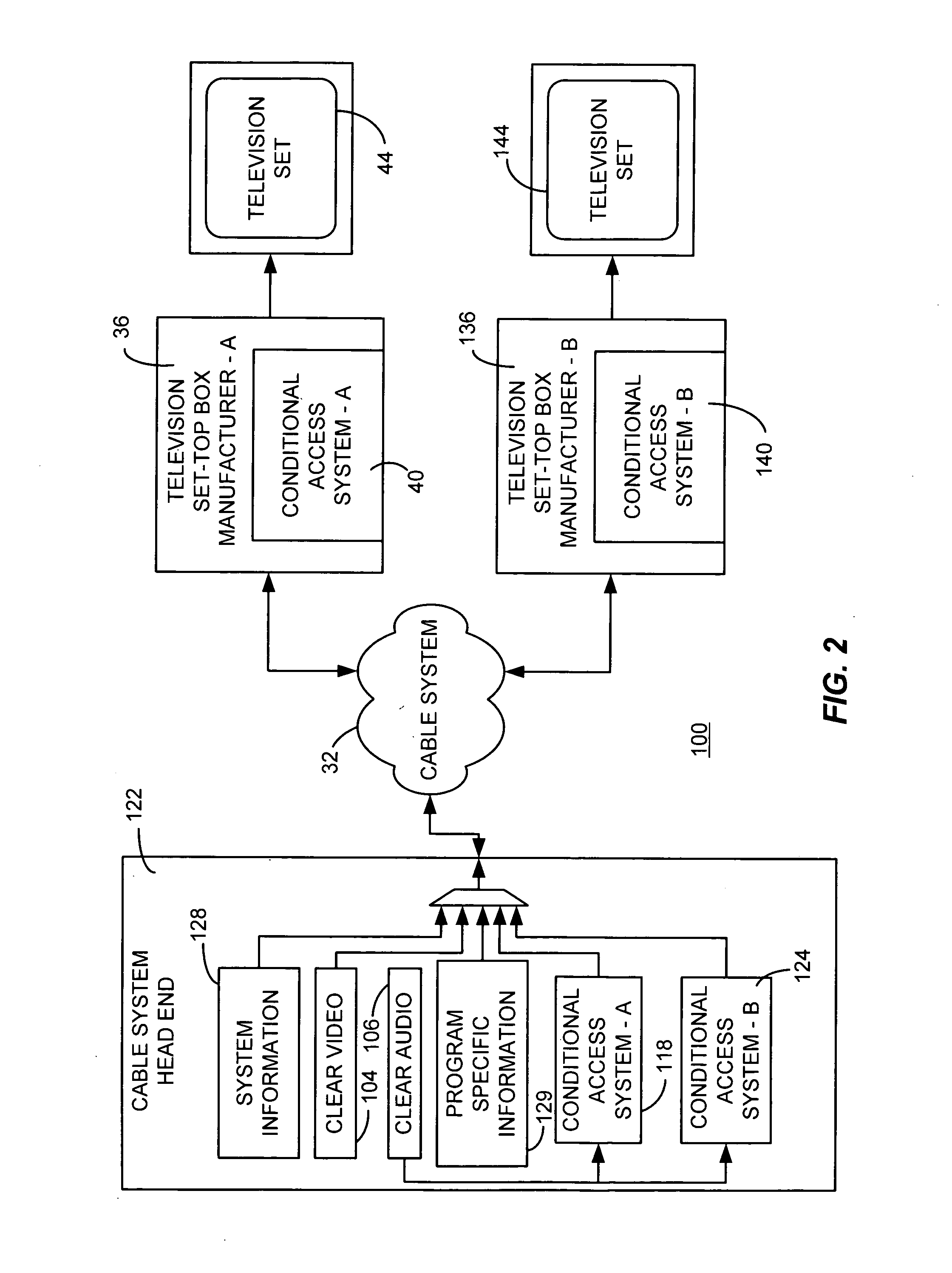
Patents
Literature
356 results about "Multiple encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
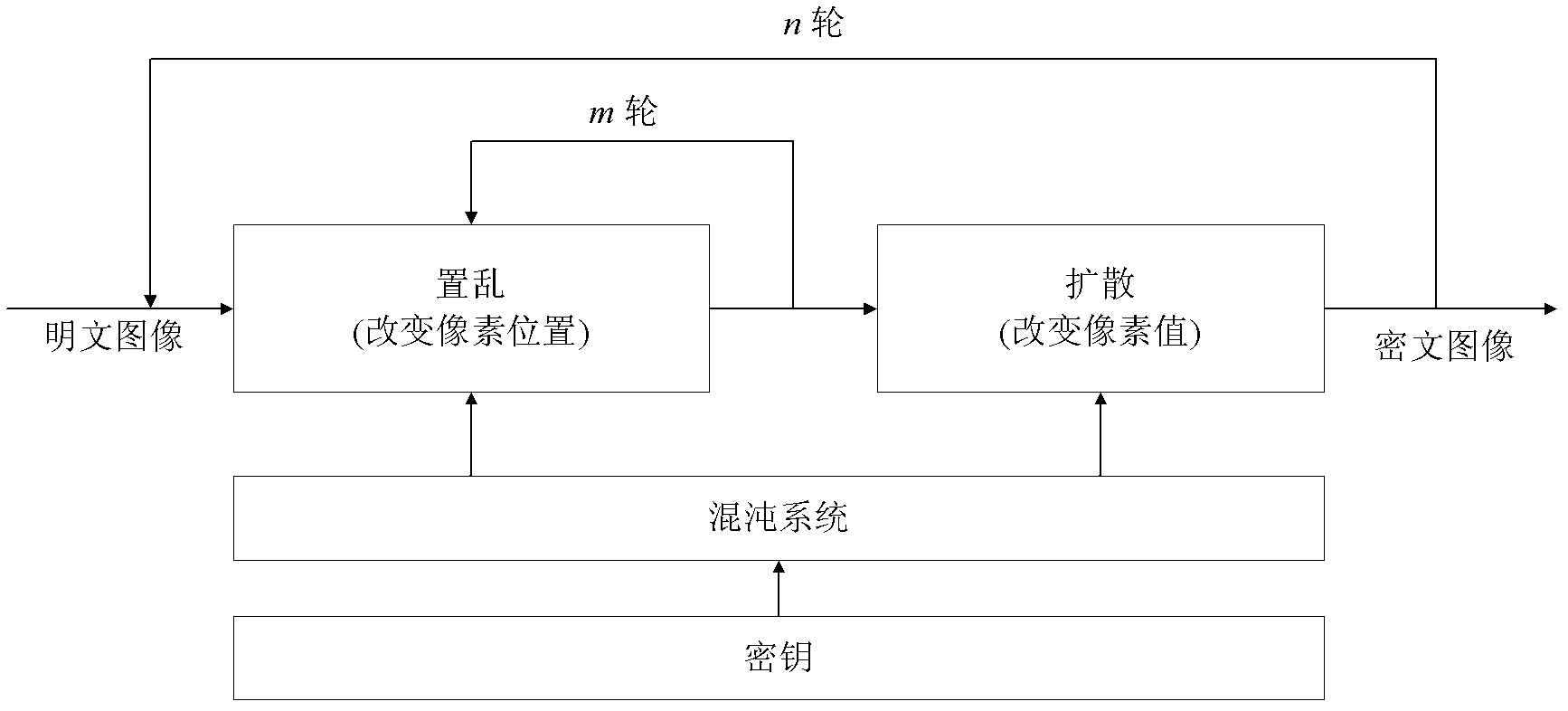
Multiple encryption is the process of encrypting an already encrypted message one or more times, either using the same or a different algorithm. It is also known as cascade encryption, cascade ciphering, multiple encryption, and superencipherment. Superencryption refers to the outer-level encryption of a multiple encryption.
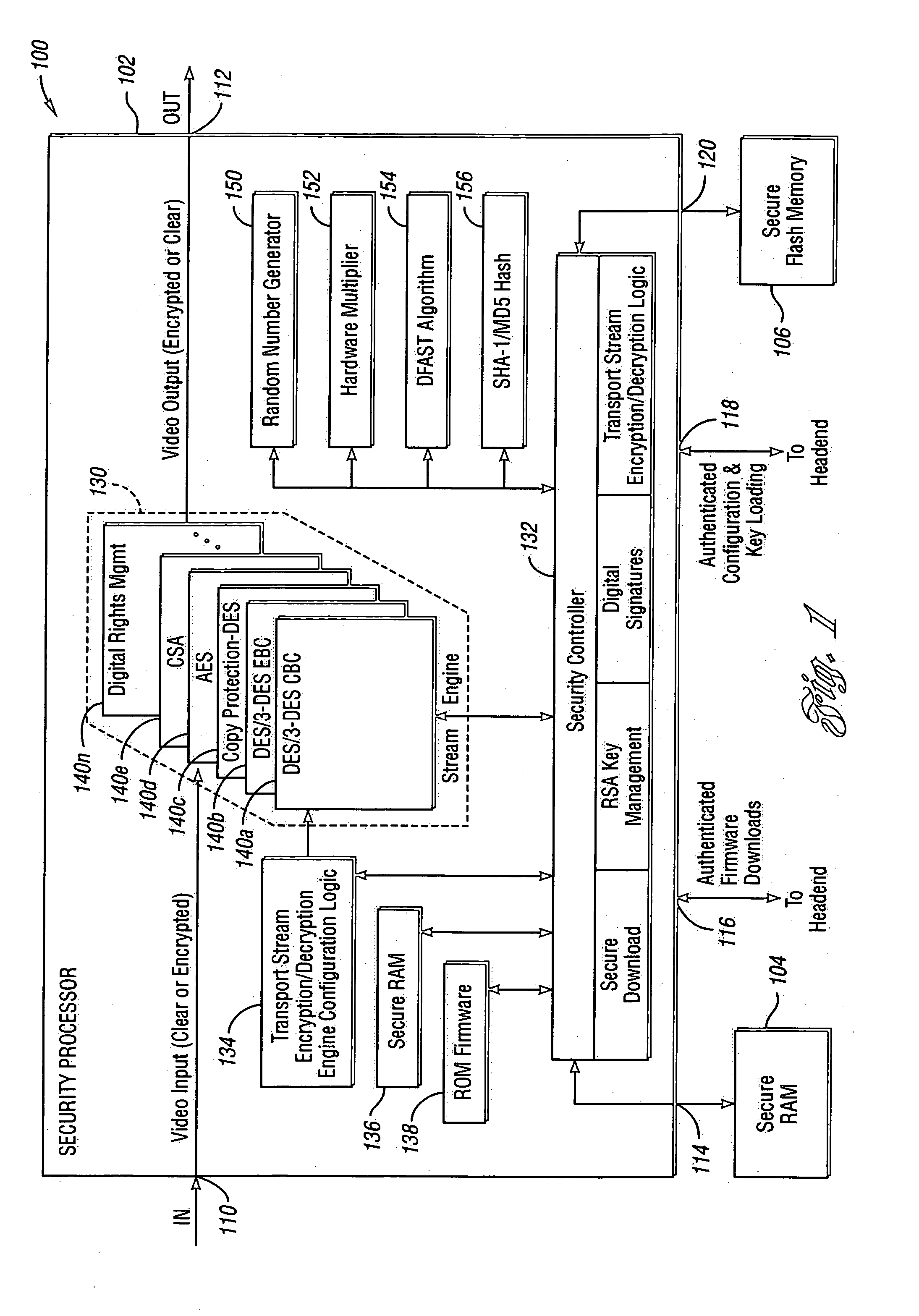
Method and Apparatus for Hardware-Accelerated Encryption/Decryption
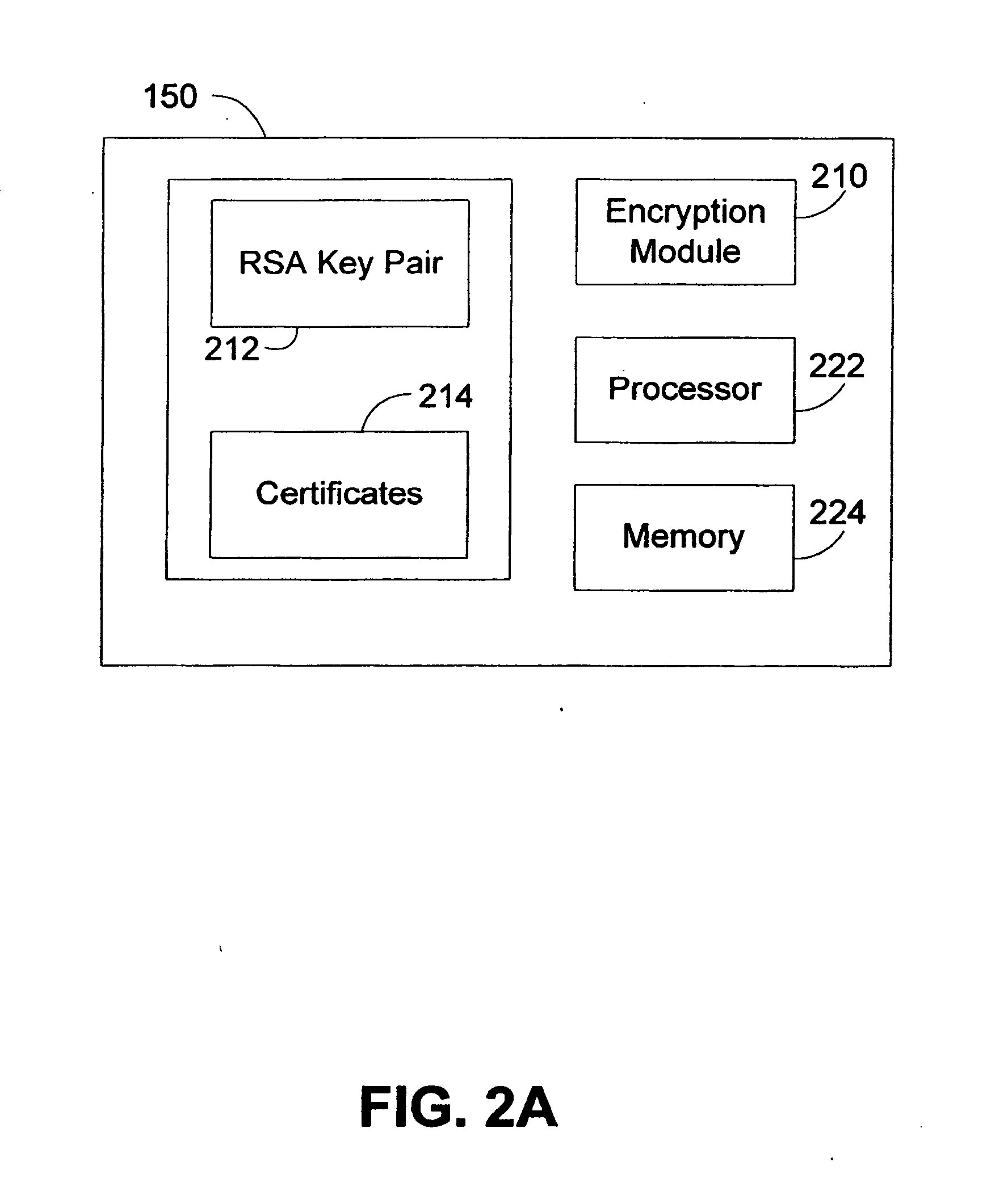
ActiveUS20090060197A1Avoid contactMaximize availabilityEncryption apparatus with shift registers/memoriesSecret communicationMultiple encryptionComputer hardware
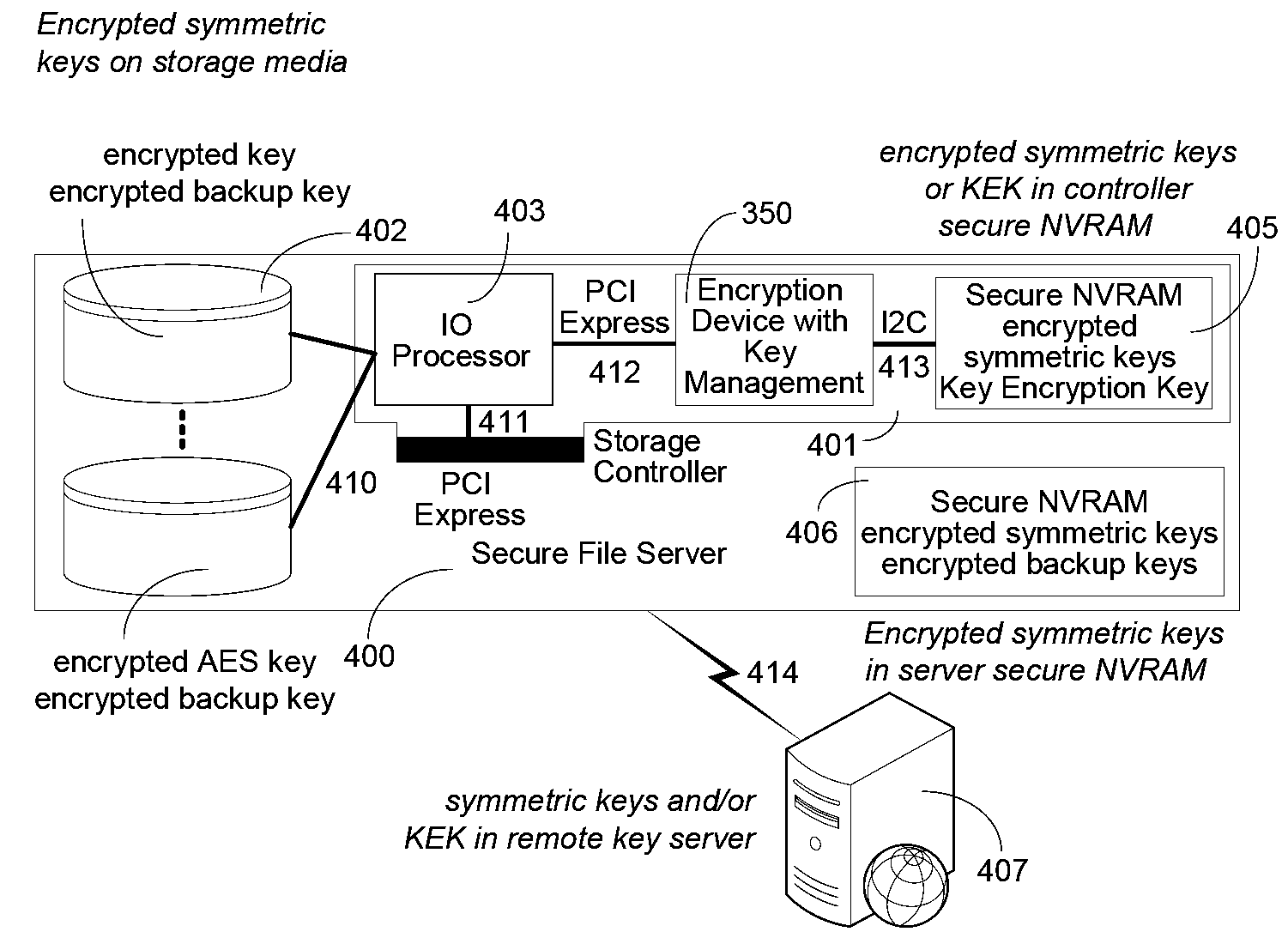
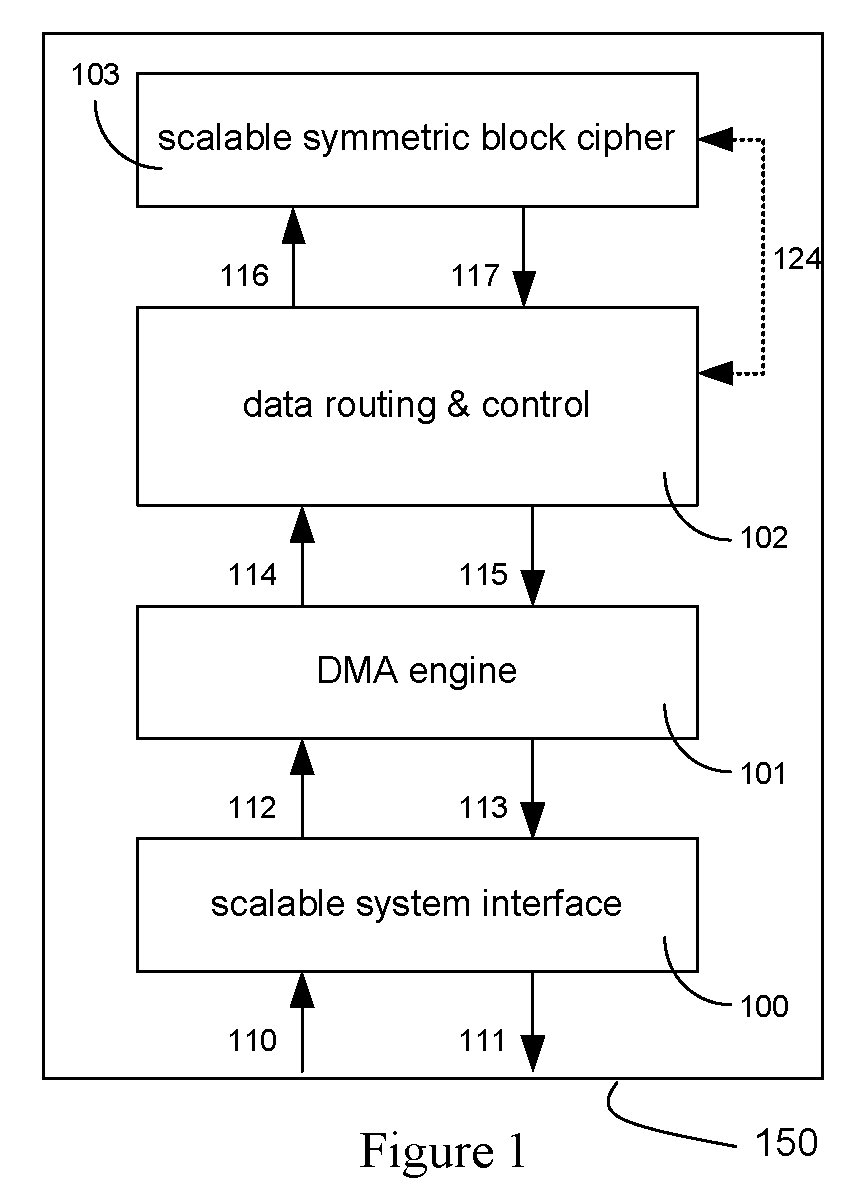
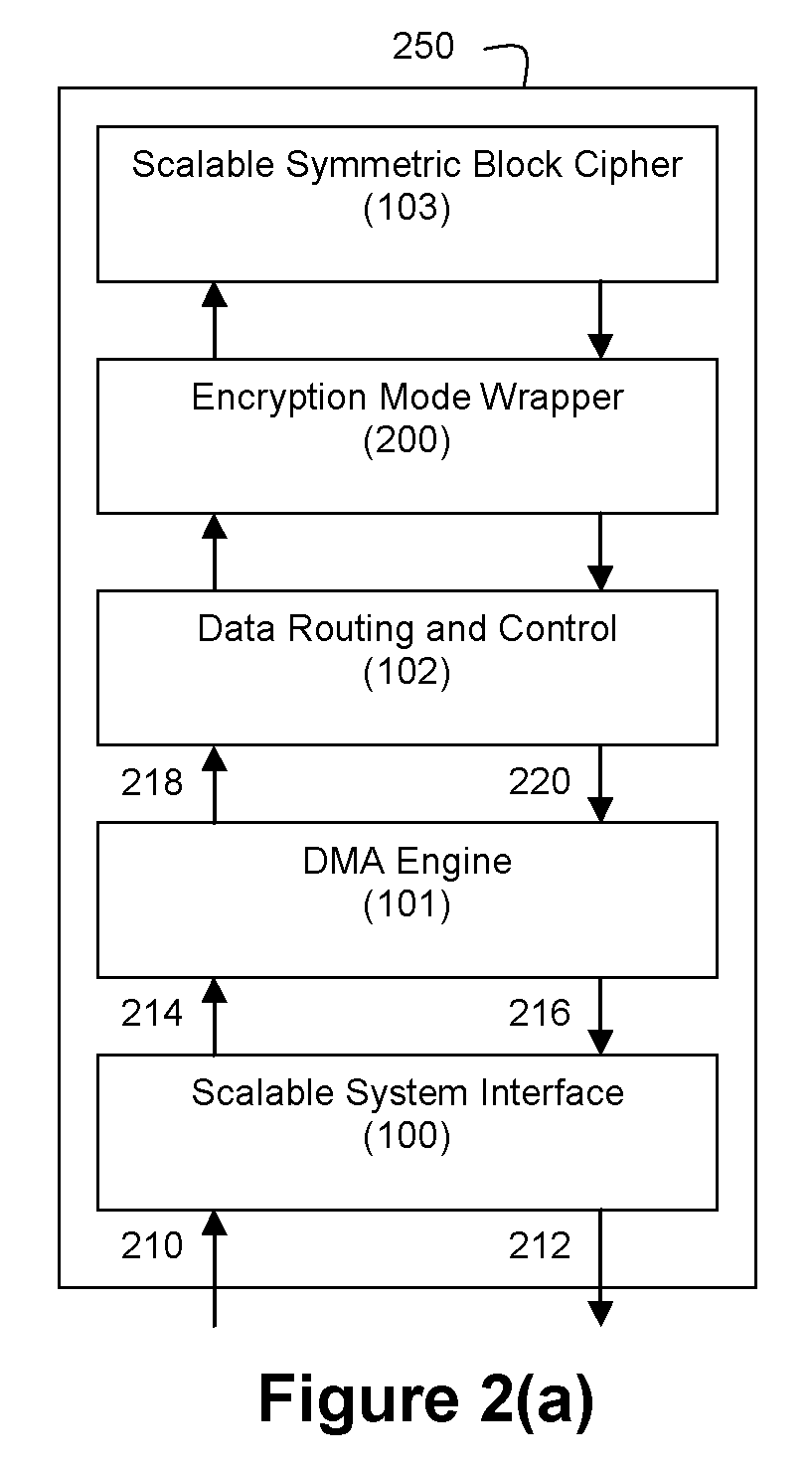
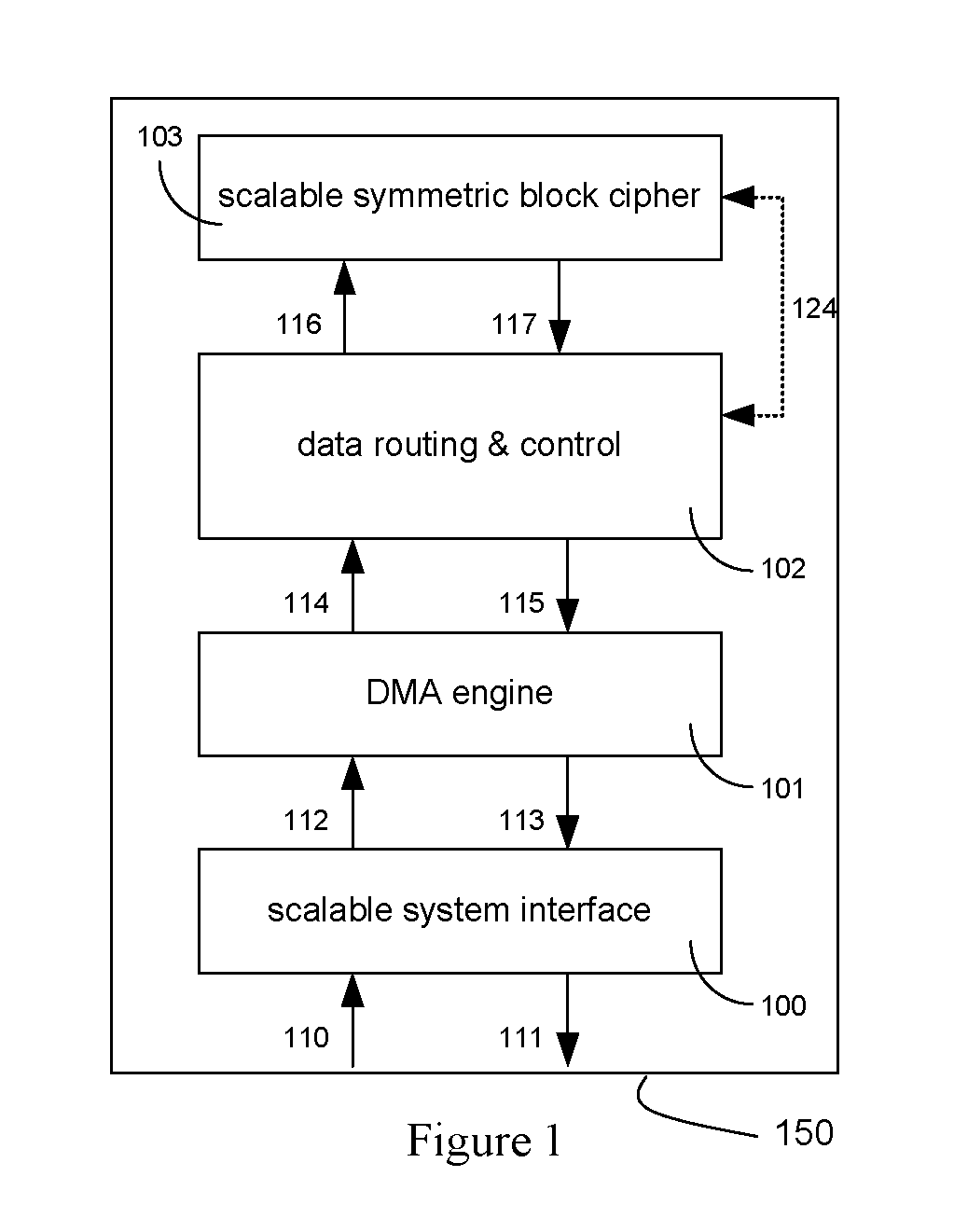
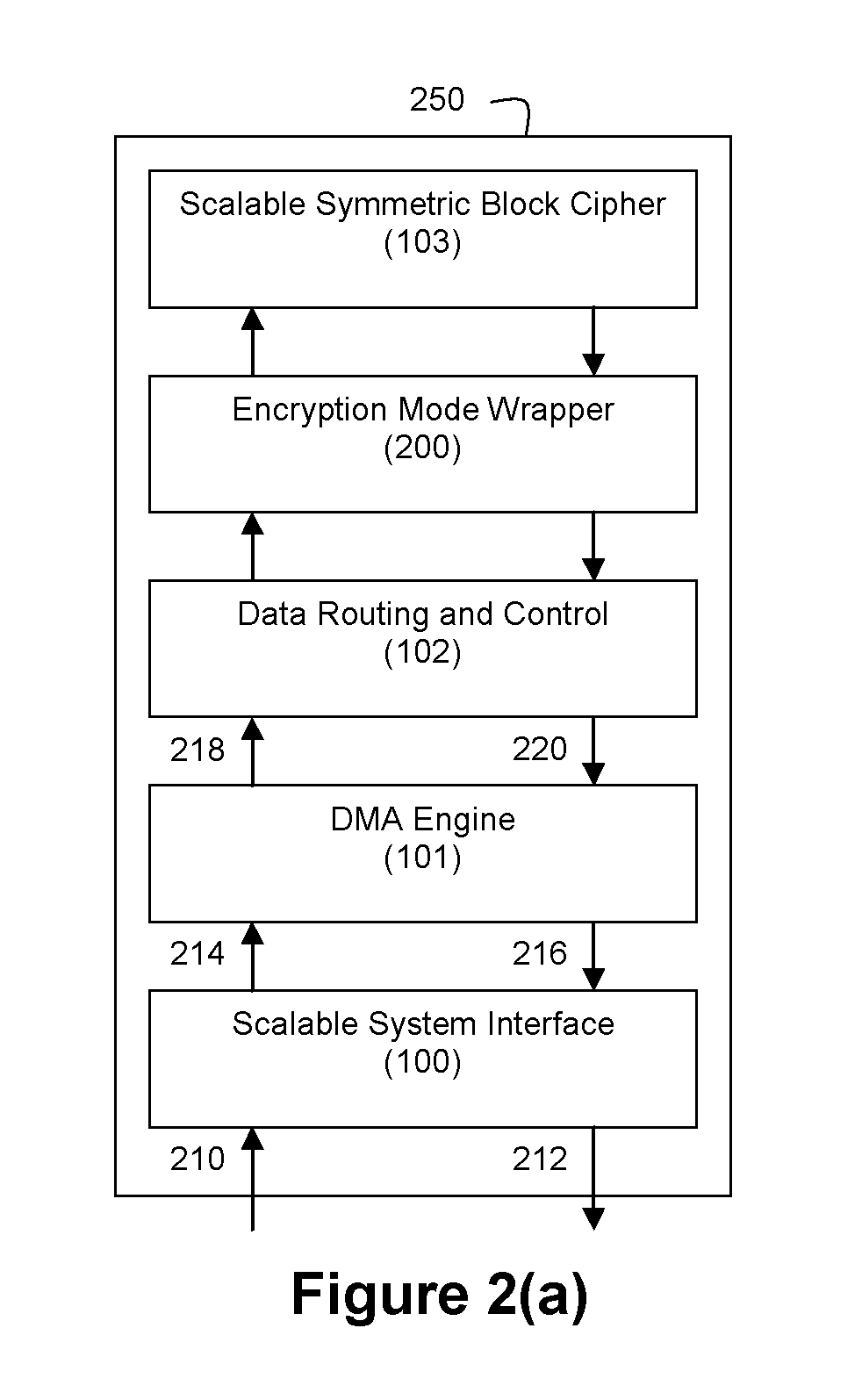
An integrated circuit for data encryption / decryption and secure key management is disclosed. The integrated circuit may be used in conjunction with other integrated circuits, processors, and software to construct a wide variety of secure data processing, storage, and communication systems. A preferred embodiment of the integrated circuit includes a symmetric block cipher that may be scaled to strike a favorable balance among processing throughput and power consumption. The modular architecture also supports multiple encryption modes and key management functions such as one-way cryptographic hash and random number generator functions that leverage the scalable symmetric block cipher. The integrated circuit may also include a key management processor that can be programmed to support a wide variety of asymmetric key cryptography functions for secure key exchange with remote key storage devices and enterprise key management servers. Internal data and key buffers enable the device to re-key encrypted data without exposing data. The key management functions allow the device to function as a cryptographic domain bridge in a federated security architecture.
Owner:IP RESERVOIR
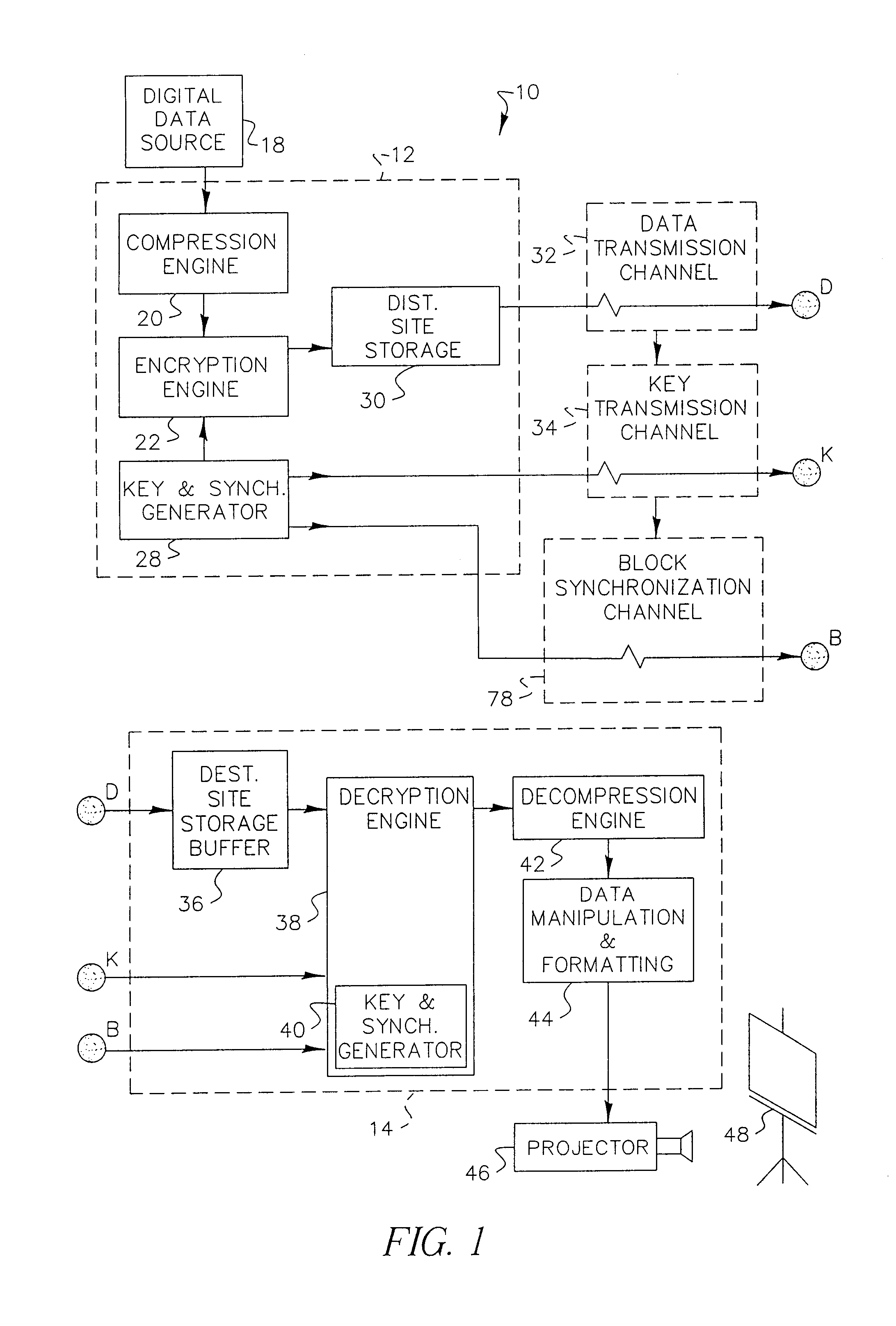
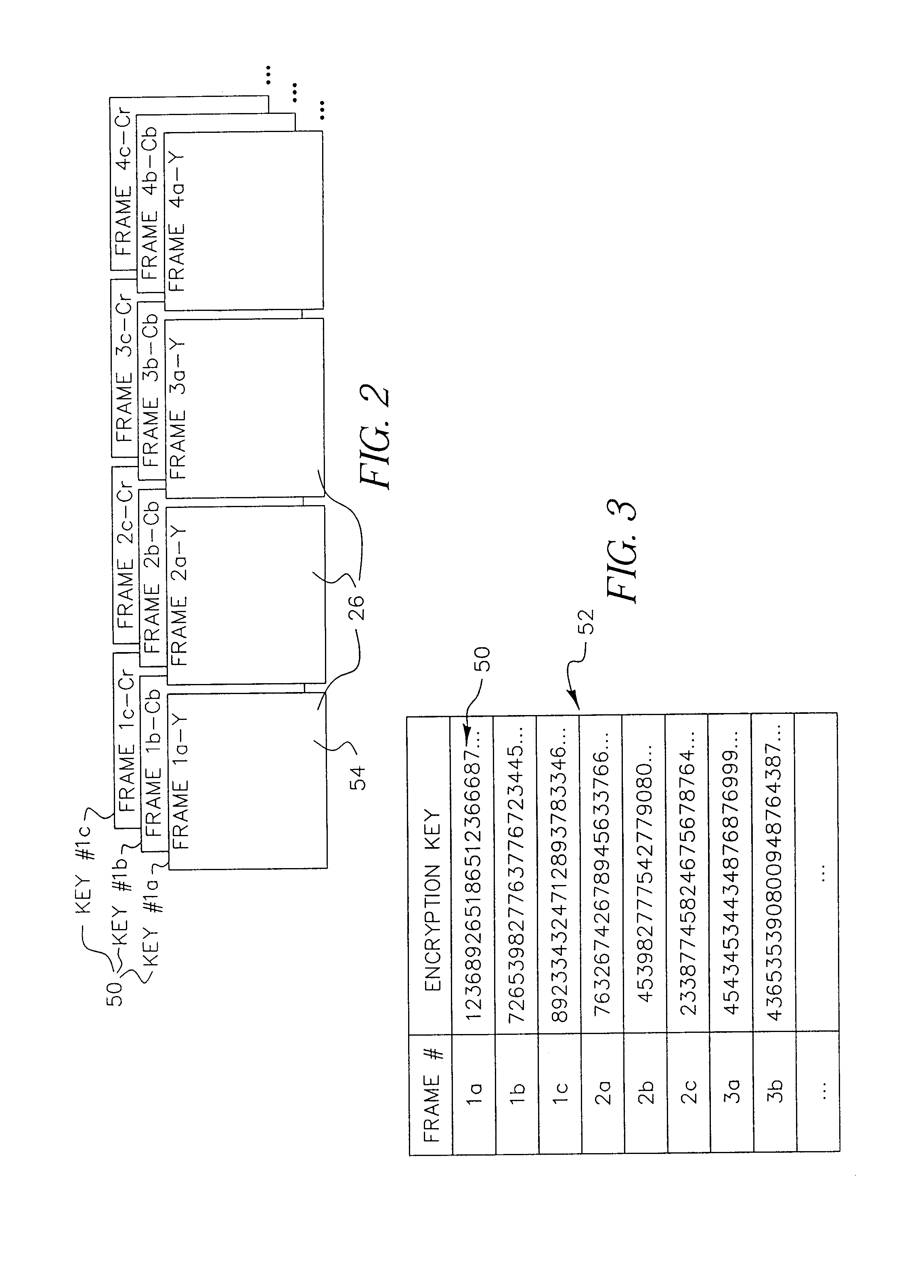
Encryption apparatus and method for synchronizing multiple encryption keys with a data stream
ActiveUS7242772B1Minimized in sizeImprove distributionKey distribution for secure communicationSynchronising transmission/receiving encryption devicesMultiple encryptionComputer hardware
A data stream, such as a digital motion picture, is encrypted in units of one or more blocks, each block having an assigned encryption key. A plurality of encryption keys is assigned to the complete data stream, with a synchronization index provided to map each individual encryption key to its starting data block. Encryption keys and associated synchronization indices are provided separately from the data stream, using one or more additional data transfer mechanisms. An optional offset, randomly generated, allows variation in intervals between data blocks at which encryption by a specific encryption key can be performed.
Owner:MONUMENT PEAK VENTURES LLC
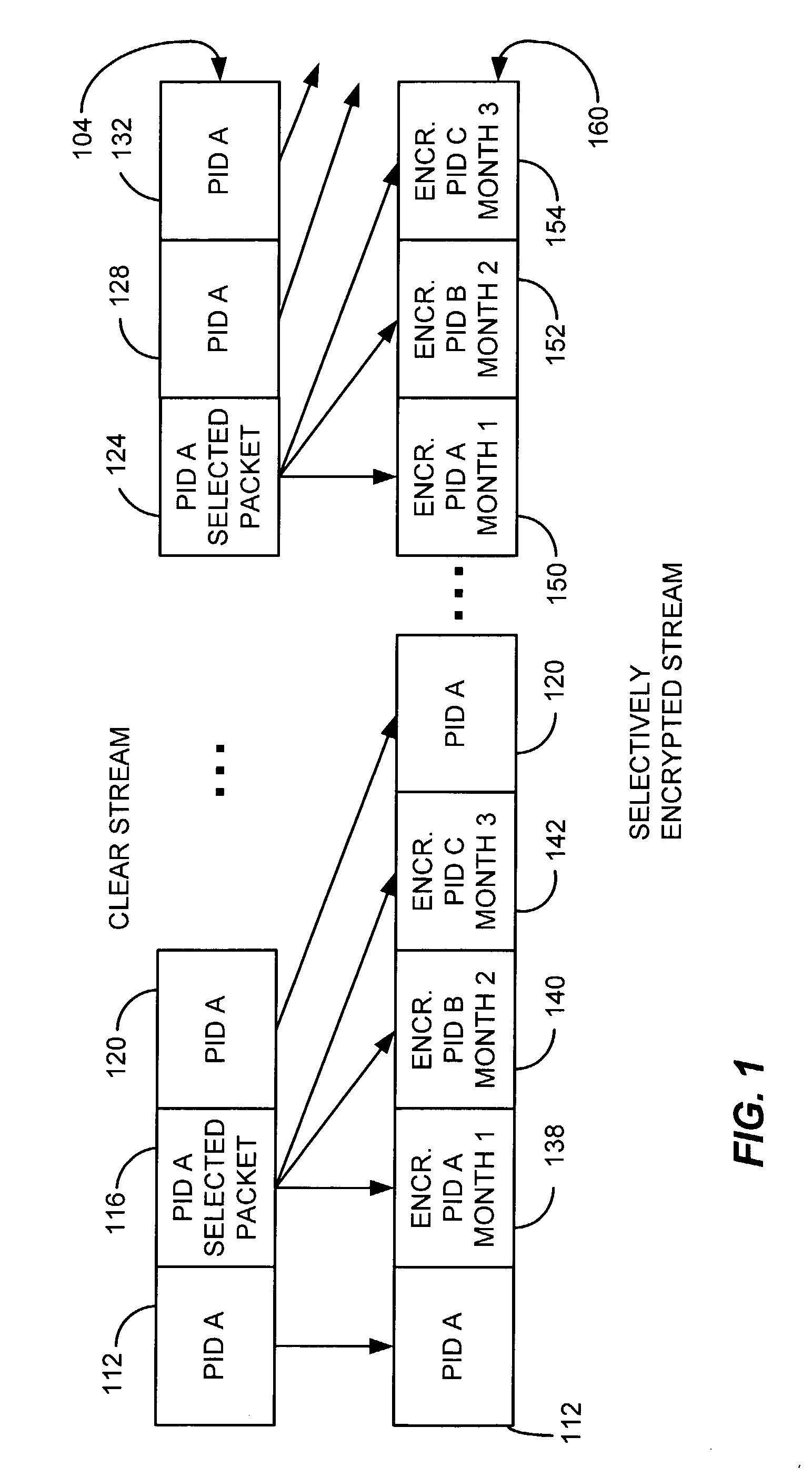
Selective encryption to enable multiple decryption keys
ActiveUS7233669B2Color television with pulse code modulationMultiple keys/algorithms usageComputer hardwareMultiple encryption
A selective encryption method and apparatus consistent with the invention duplicates selected packets in a file or data stream and multiple encrypts the packets using multiple encryption keys. Each encryption key is valid for a specific segment of time so that changes in entitlement keys used for decryption can be made without negatively impacting a customer's ability to access content that has been paid for.
Owner:SONY CORP +1
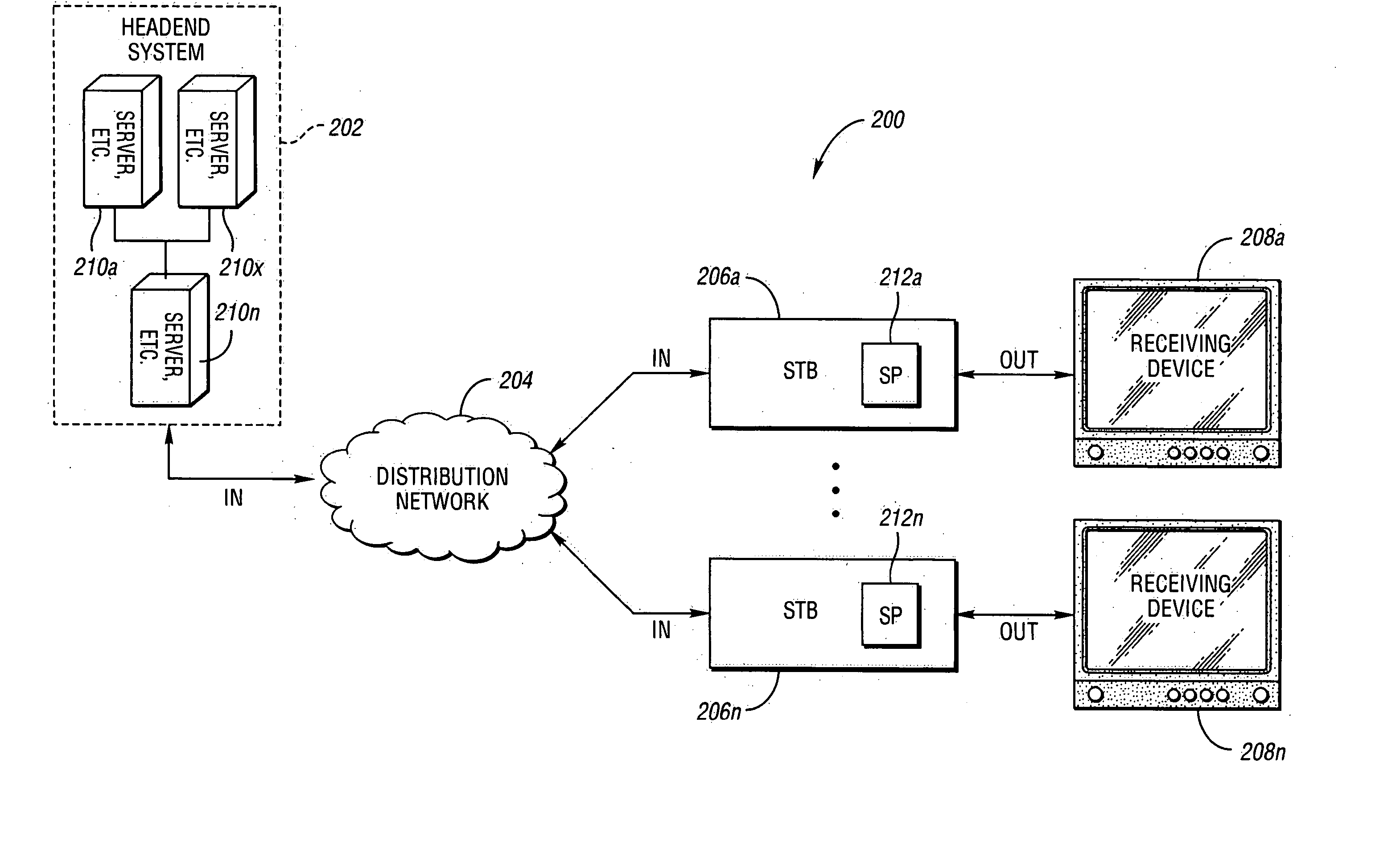
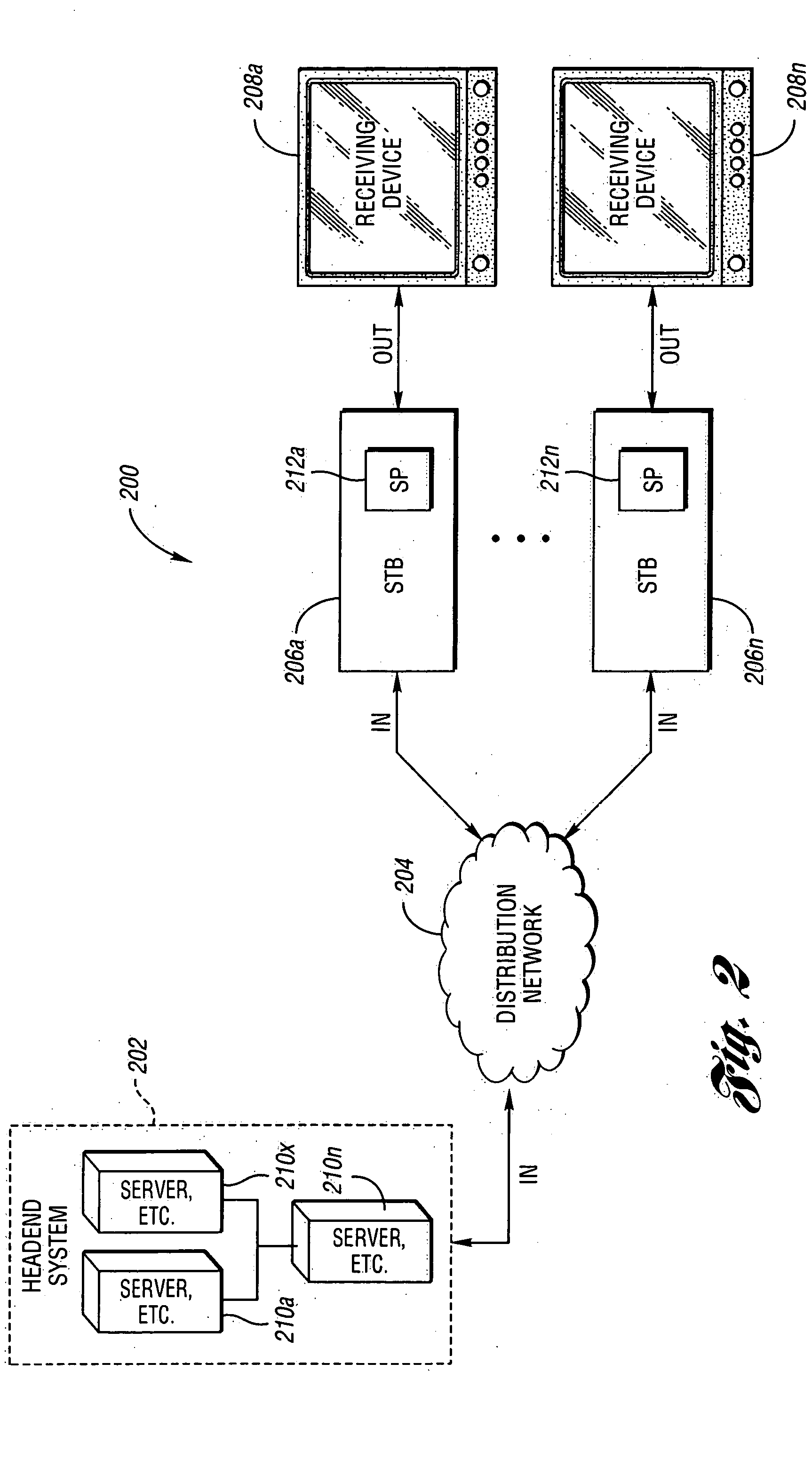
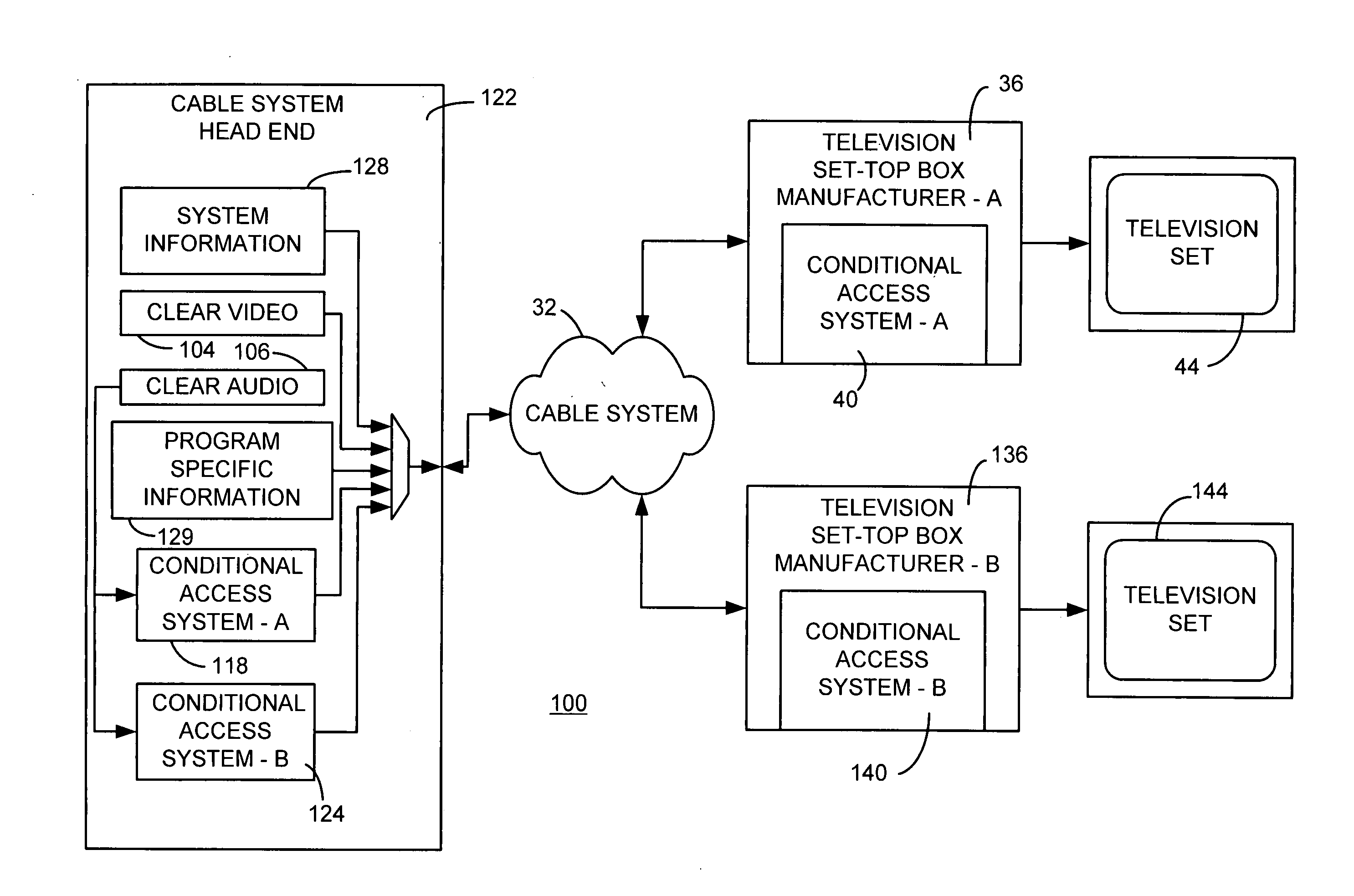
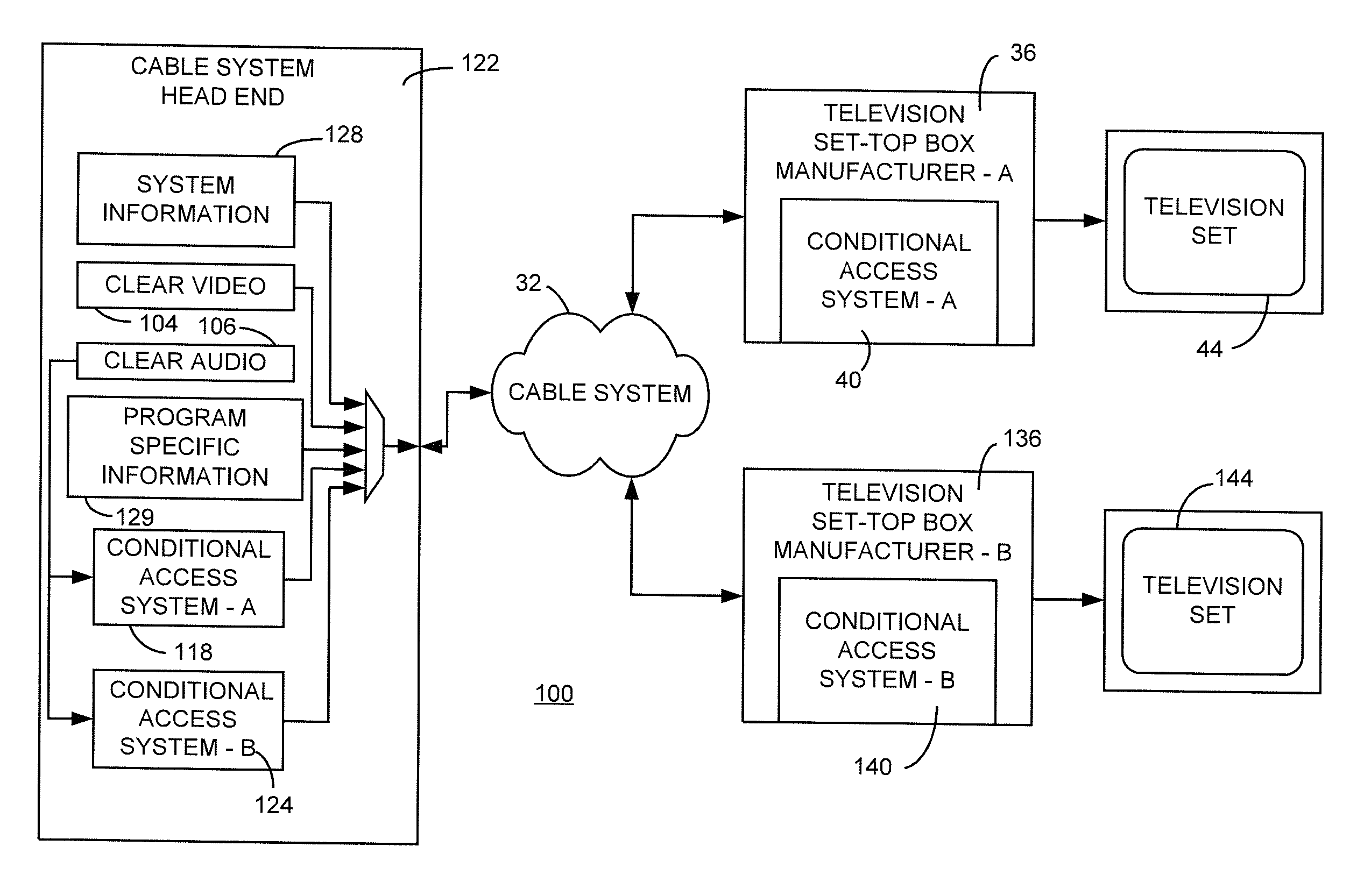
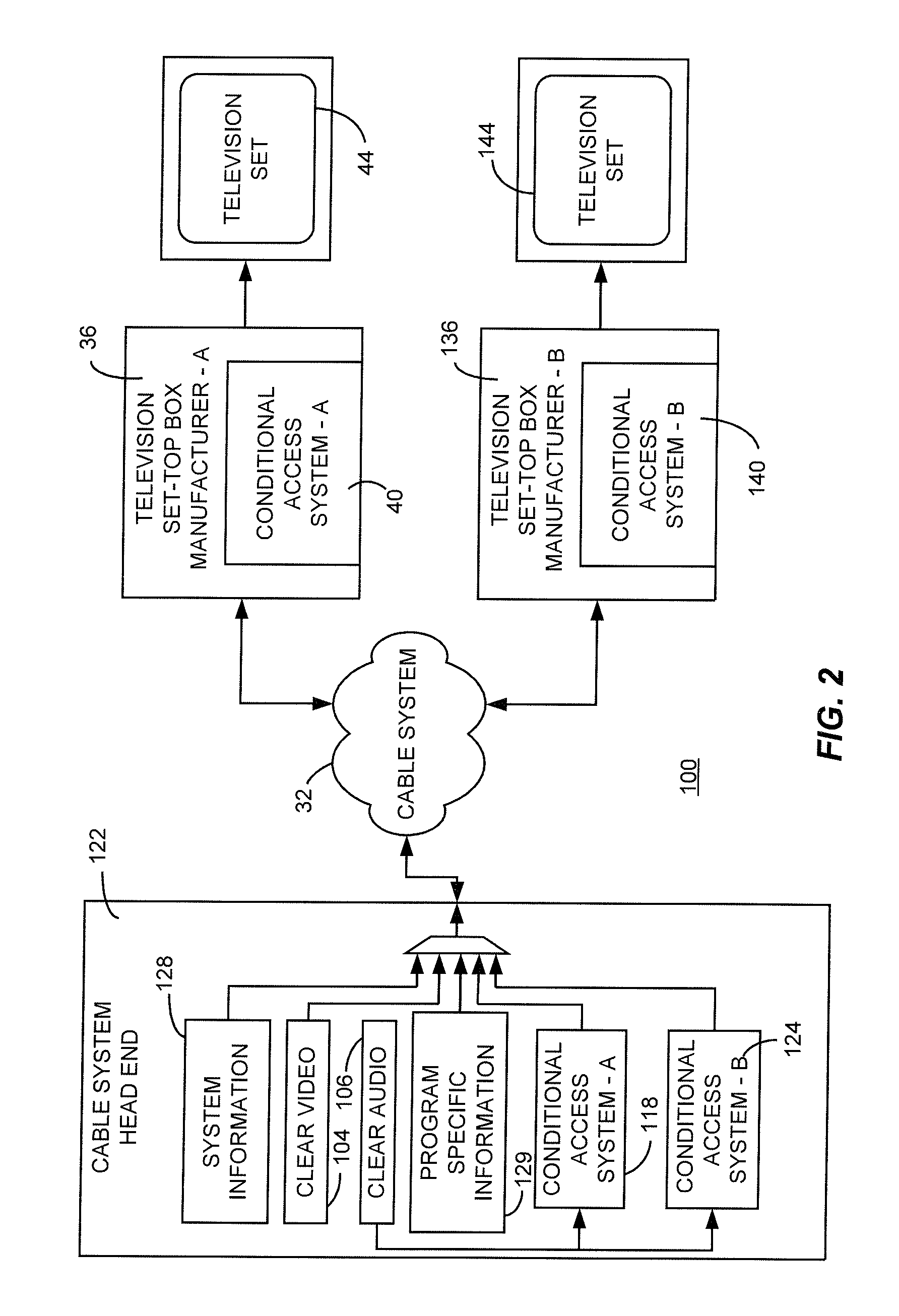
System and method for security processing media streams
ActiveUS20050169468A1Television systemsSelective content distributionComputer hardwareMultiple encryption
A system for multi-stream security processing and distributing digital media streams includes a headend, a network, and at least one receiver. The headend is generally configured to generate encrypted digital media streams. The network may be coupled to the headend and configured to receive the encrypted digital media streams. The at least one receiver may be coupled to the network and configured to receive the encrypted digital media streams and present a decrypted version of the encrypted digital media streams. At least one of the headend and the at least one receiver include a security processor that may be configured to provide at least one of simultaneous multiple encryption and simultaneous multiple decryption processing of the digital media streams.
Owner:COMCAST CABLE COMM LLC
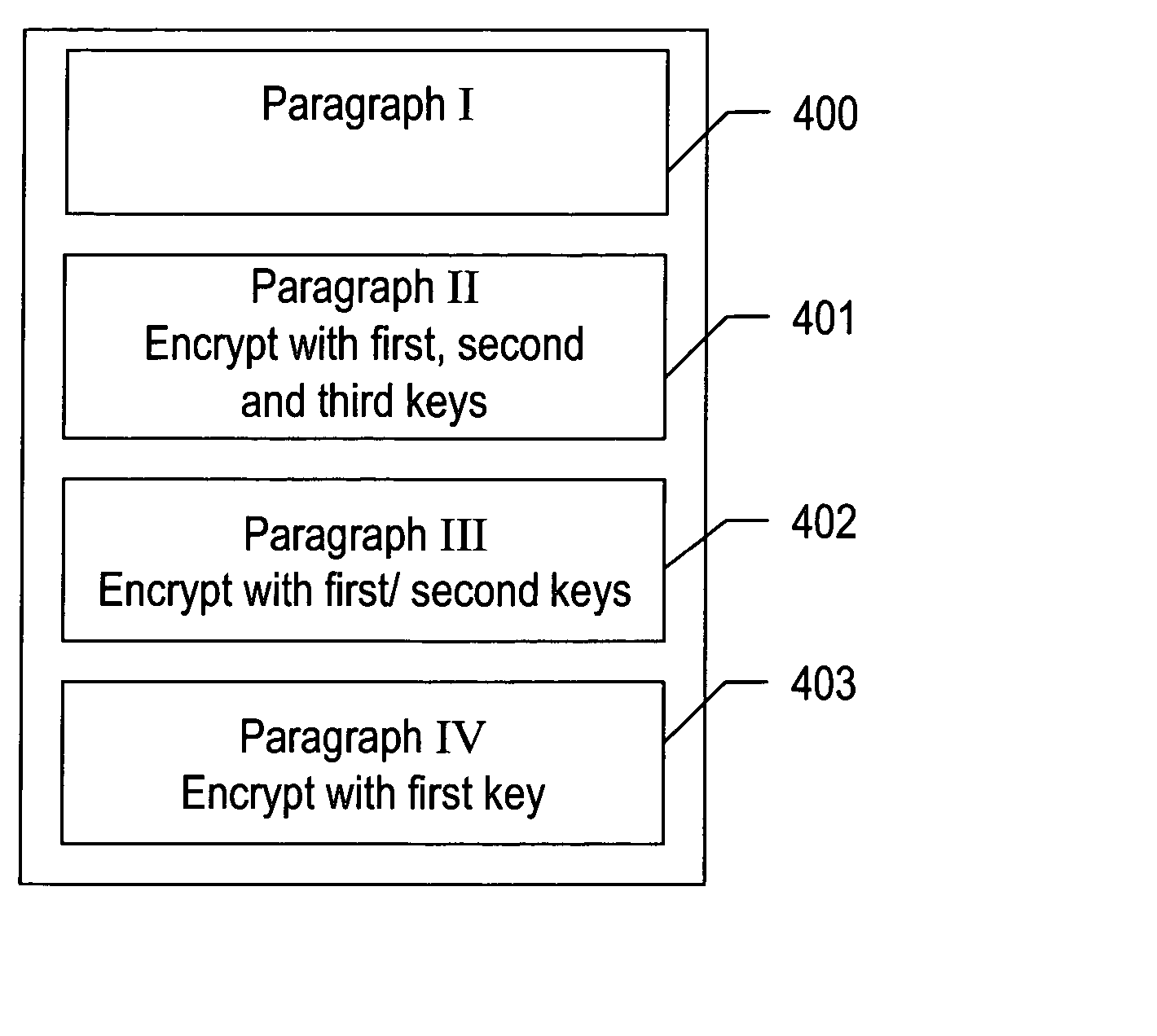
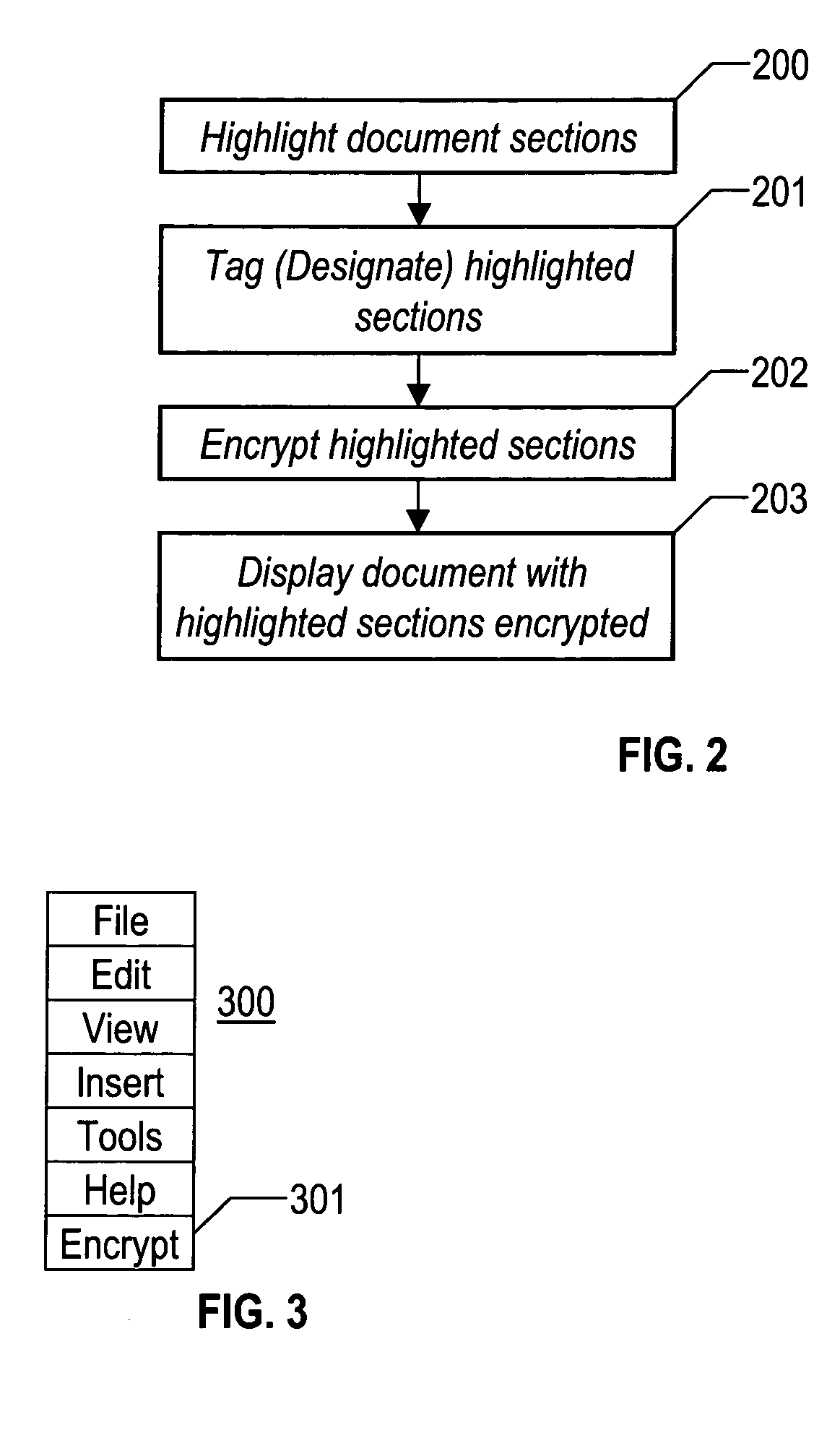
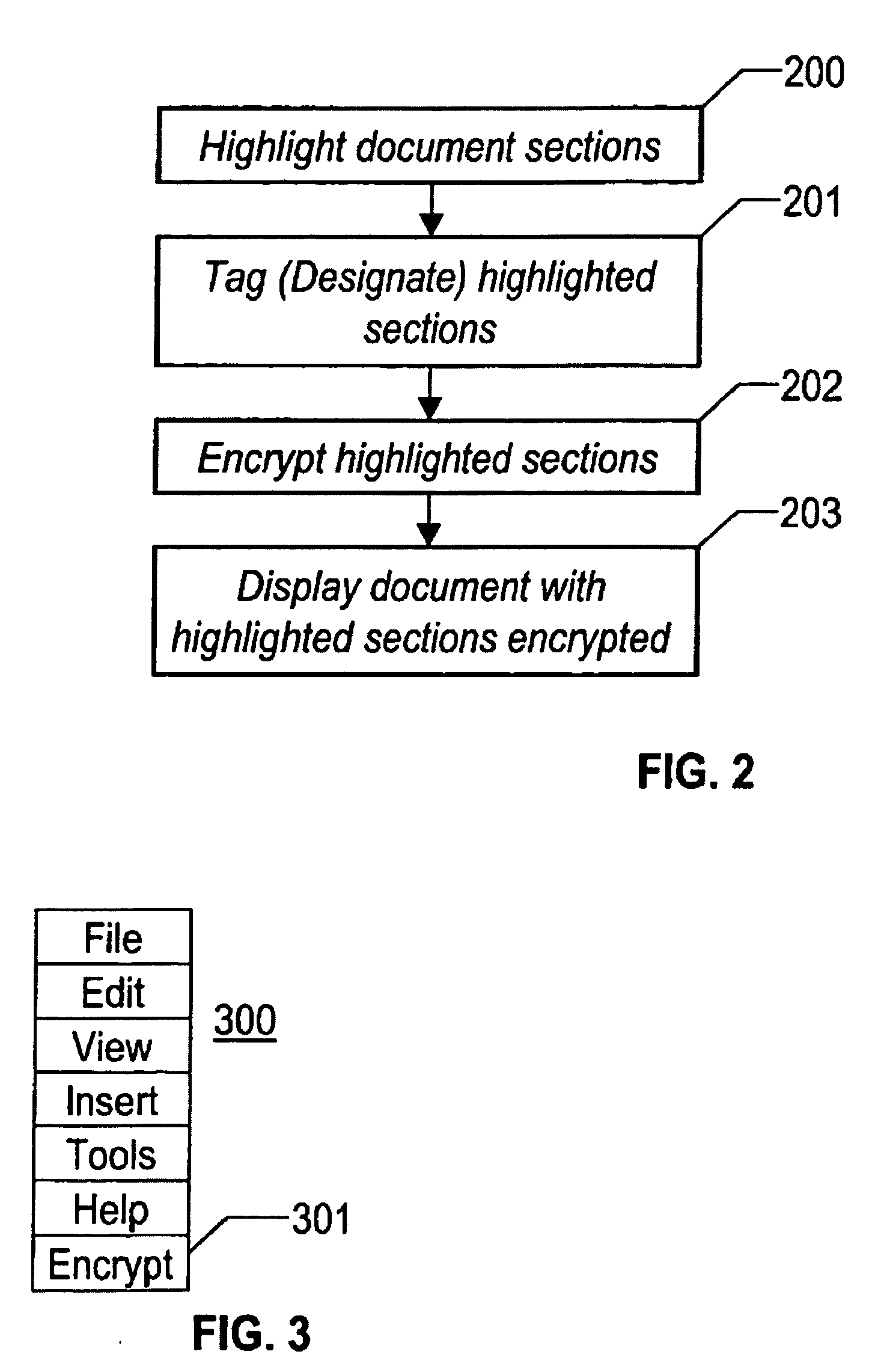
Method for selective encryption within documents
InactiveUS20050235163A1Multiple keys/algorithms usageUser identity/authority verificationMultiple encryptionWord processing
The present invention allows the user (author or creator) of a document to specify that certain portions of a document be selected for encryption while other portions of the document remain displayed as created. In addition, each encrypted section could have multiple encryption keys such that some viewers can review certain parts of the document while other viewers will not have that same access. The user could employ a standard word processing editor technique to highlight (or swipe) portions of a document that the user desires to be encrypted. The highlighted portion would then be ‘tagged’ with a surrounding attribute indicating to the word processor that this highlighted portion of the document is to be encrypted. The highlighted sections would also have encryption keys associated with the highlighted and encrypted section. Any one of the encryption keys for that section would decrypt that section. With proper authorization, any encrypted portion of a document would be displayed as part of the document. Without proper authorization, the display of the document would only contain the unencrypted portions of the document.
Owner:KYNDRYL INC
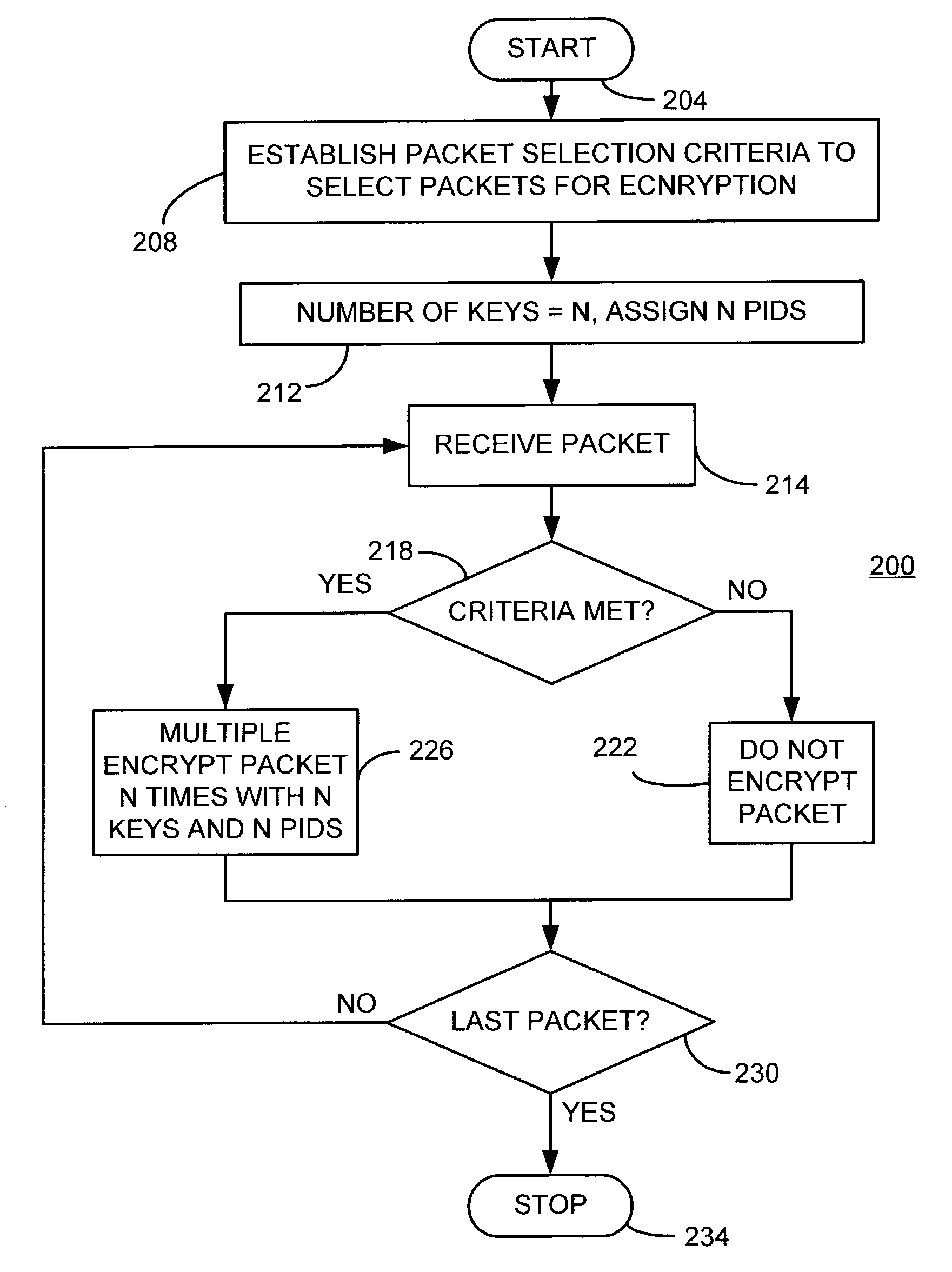
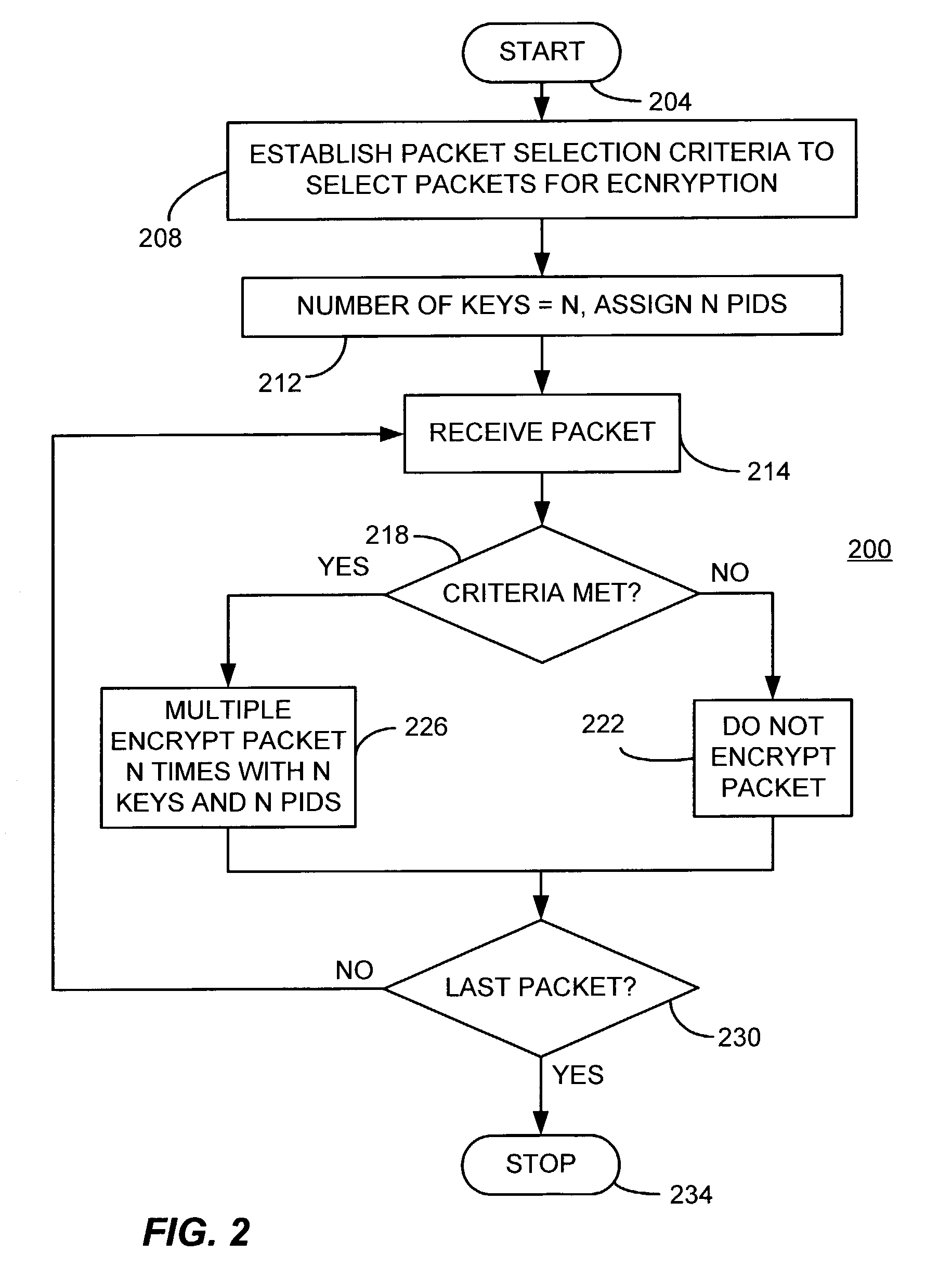
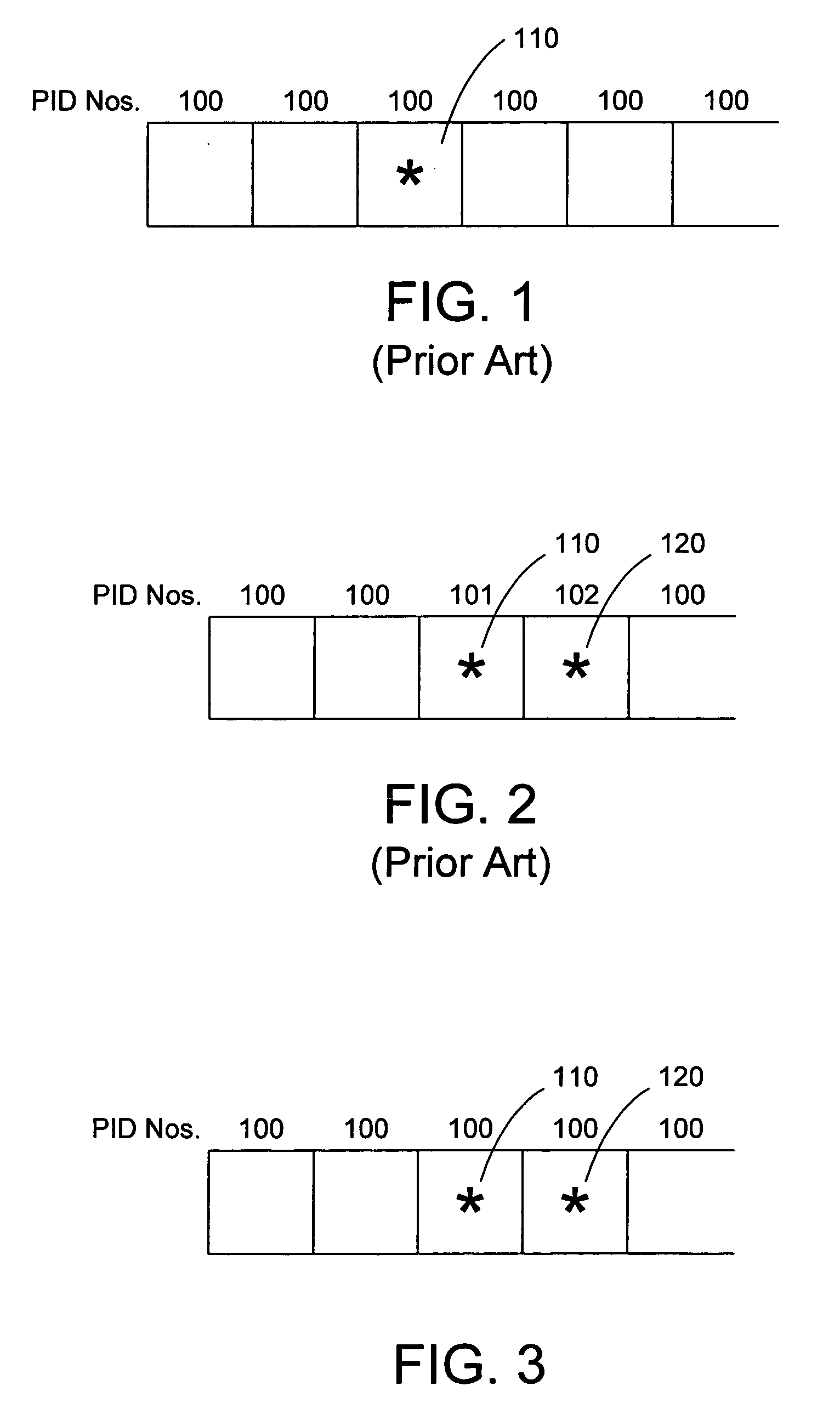
Partial encryption and PID mapping
InactiveUS20060153379A1Analogue secracy/subscription systemsSecret communicationComputer hardwareMultiple encryption
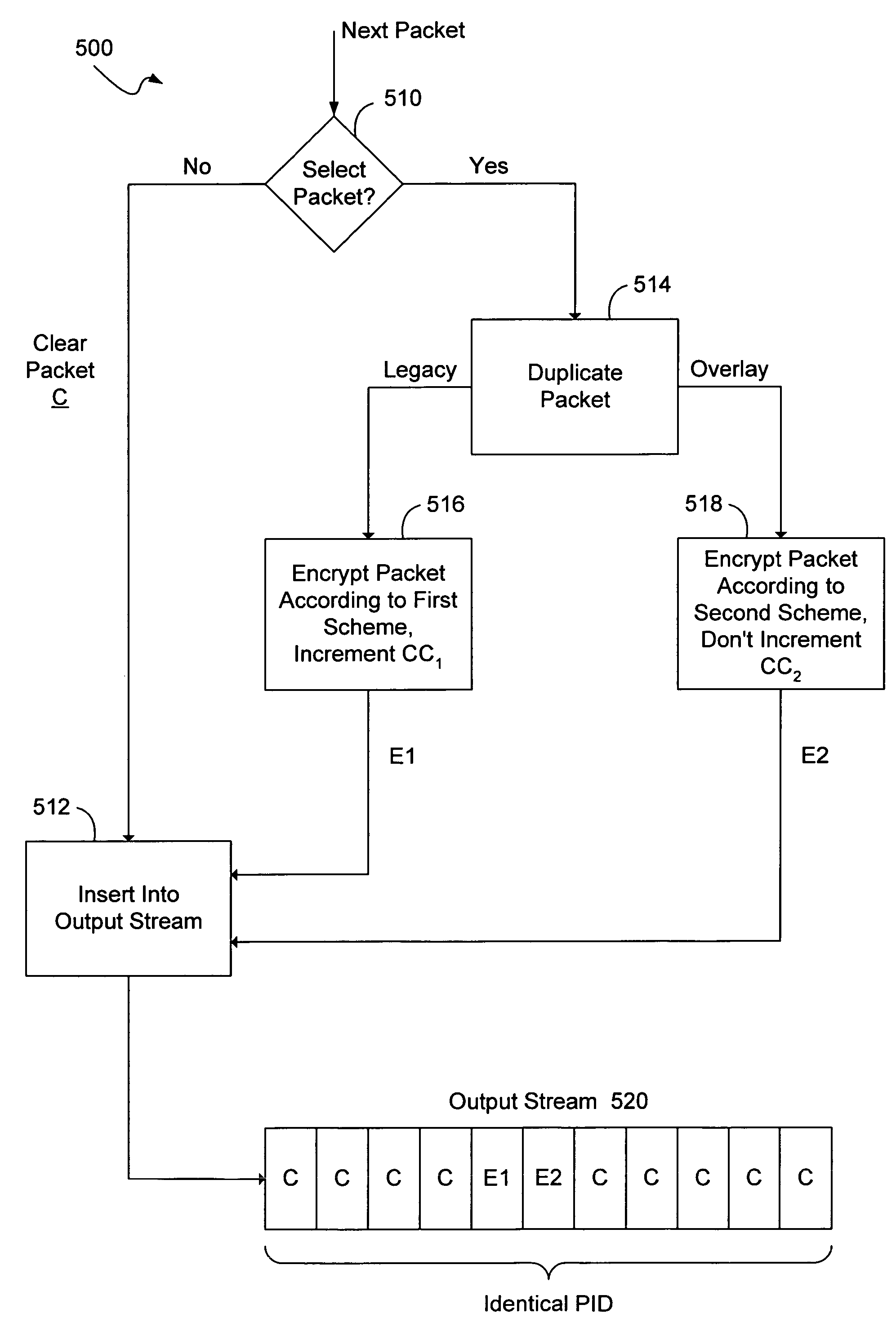
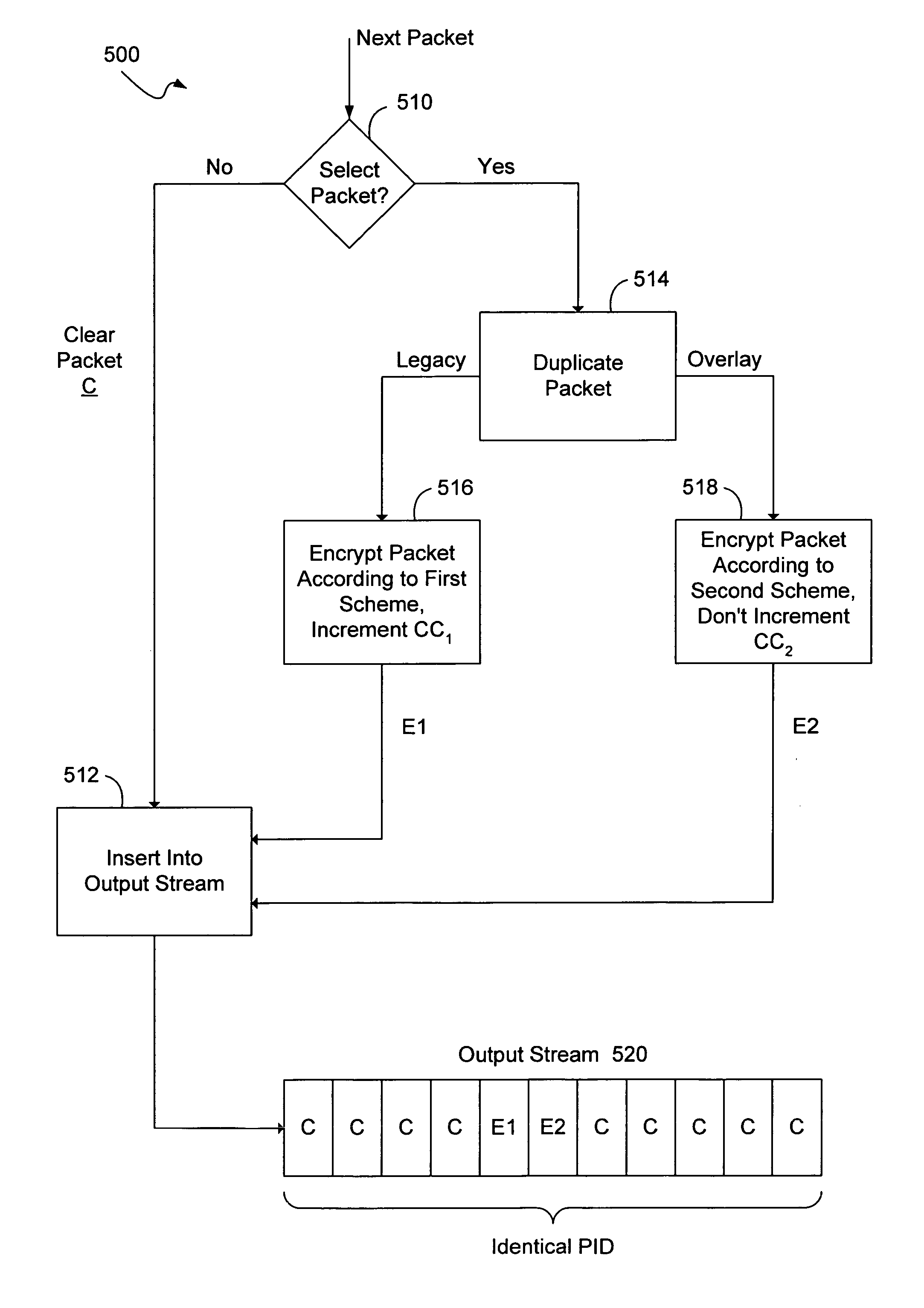
A method consistent with certain embodiments carried out at a television provider headend involves receiving a feed of scrambled television content in the form of a stream of packets; descrambling the scrambled television content to produce a stream of clear packets; selecting a packet for multiple encryption; duplicating the packet to provide first and second packets; re-mapping the first and second packets to first and second packet identifiers; encrypting the first packet under a first encryption algorithm to produce a first encrypted packet; encrypting the second packet under a second encryption algorithm to produce a second encrypted packet; and re-mapping clear packets to the first packet identifier. This abstract is not to be considered limiting, since other embodiments may deviate from the features described in this abstract.
Owner:SONY CORP +1
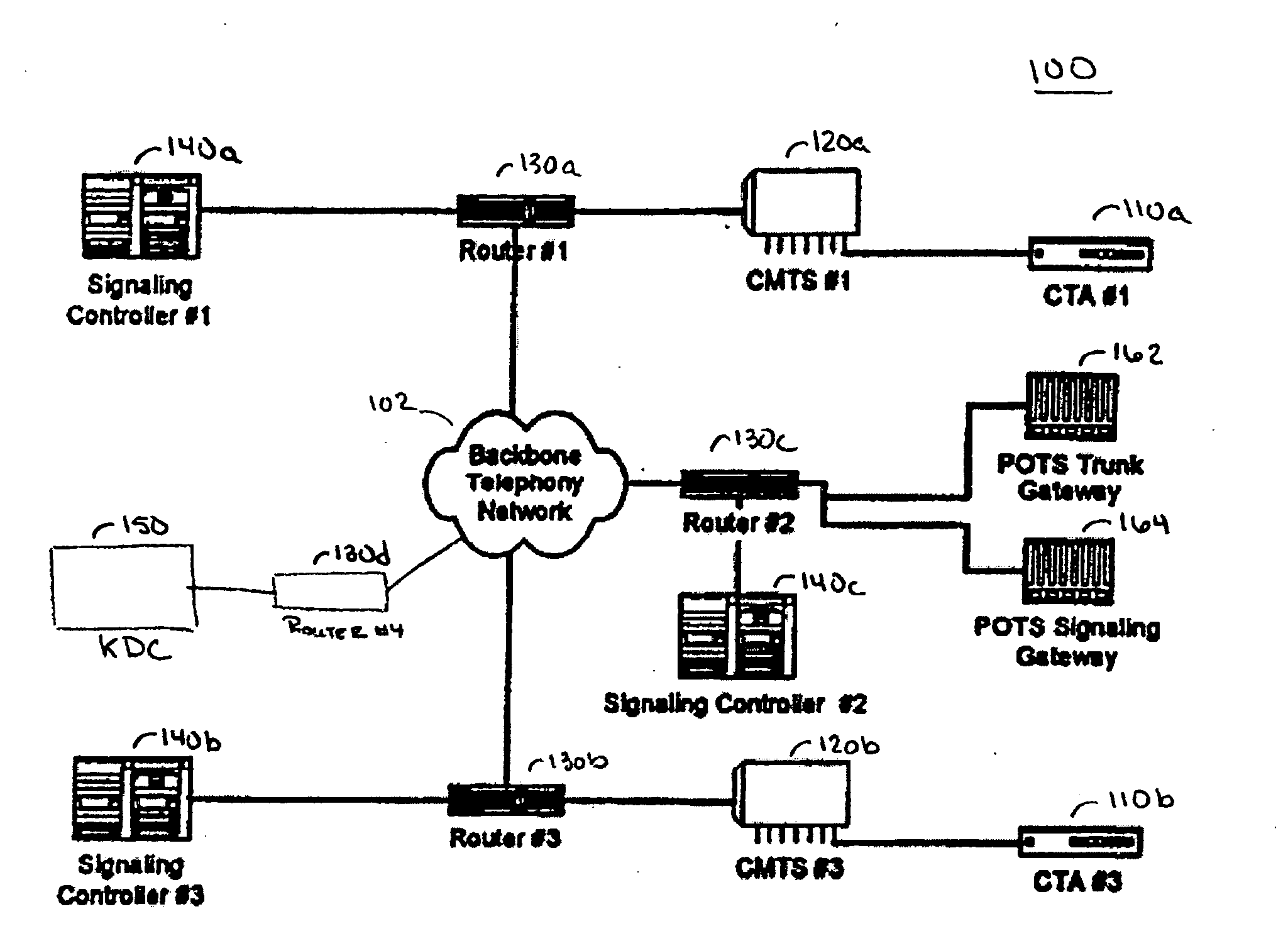
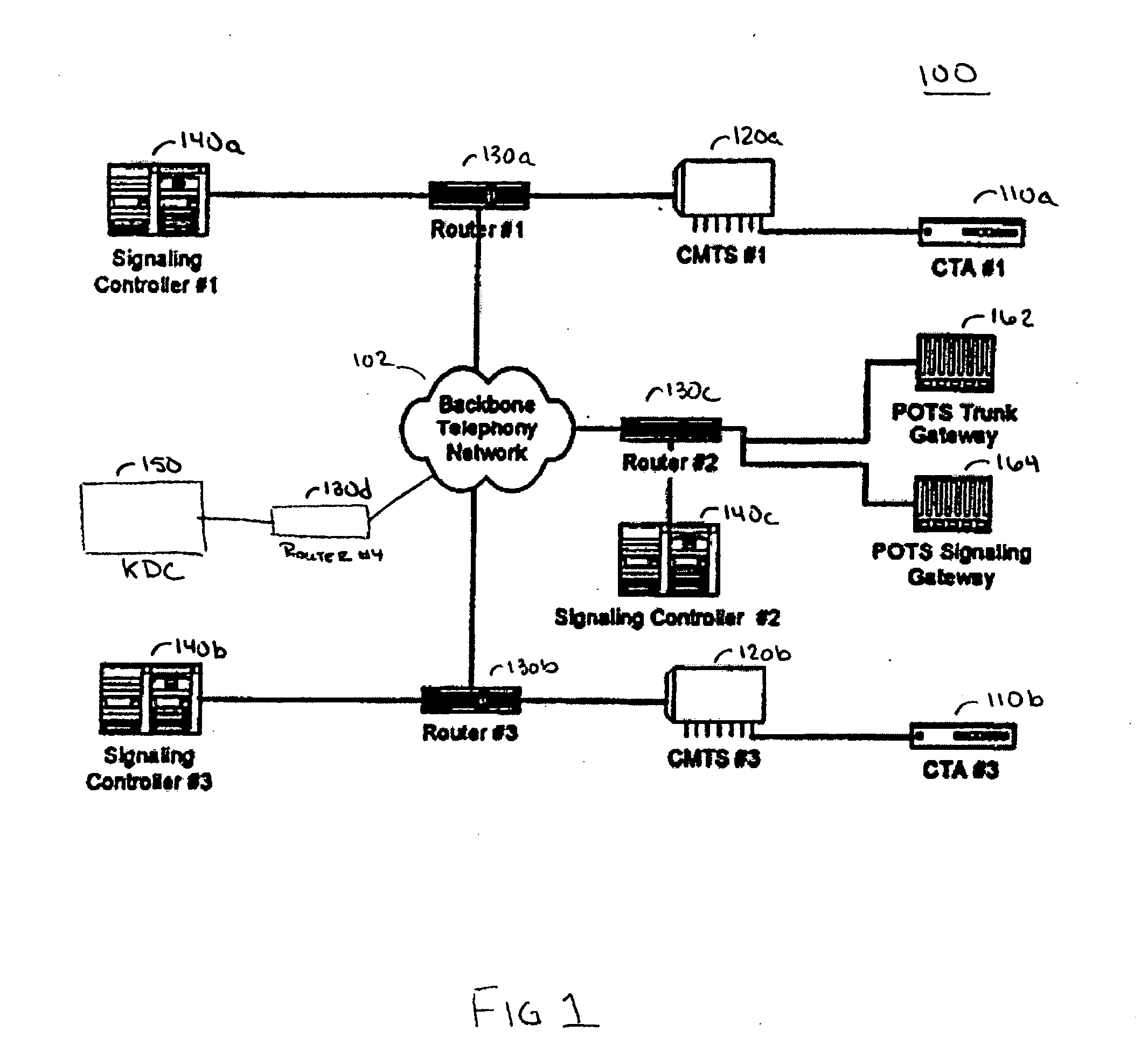
Internet protocol telephony security architecture
InactiveUS20050027985A1Communication securitySpecial service provision for substationKey distribution for secure communicationMultiple encryptionSecure communication
A secure Internet Protocol (IP) telephony system, apparatus, and methods are disclosed. Communications over an IP telephony system can be secured by securing communications to and from a Cable Telephony Adapter (CTA). The system can include one or more CTAs, network servers, servers configured as signaling controllers, key distribution centers (KDC), and can include gateways that couple the IP telephony system to a Public Switched Telephone Network (PSTN). Each CTA can be configured as secure hardware and can be configured with multiple encryption keys that are used to communicate signaling or bearer channel communications. The KDC can be configured to periodically distribute symmetric encryption keys to secure communications between devices that have been provisioned to operate in the system and signaling controllers. The secure devices, such as the CTA, can communicate with other secure devices by establishing signaling and bearer channels that are encrypted with session specific symmetric keys derived from a symmetric key distributed by a signaling controller.
Owner:GOOGLE TECH HLDG LLC
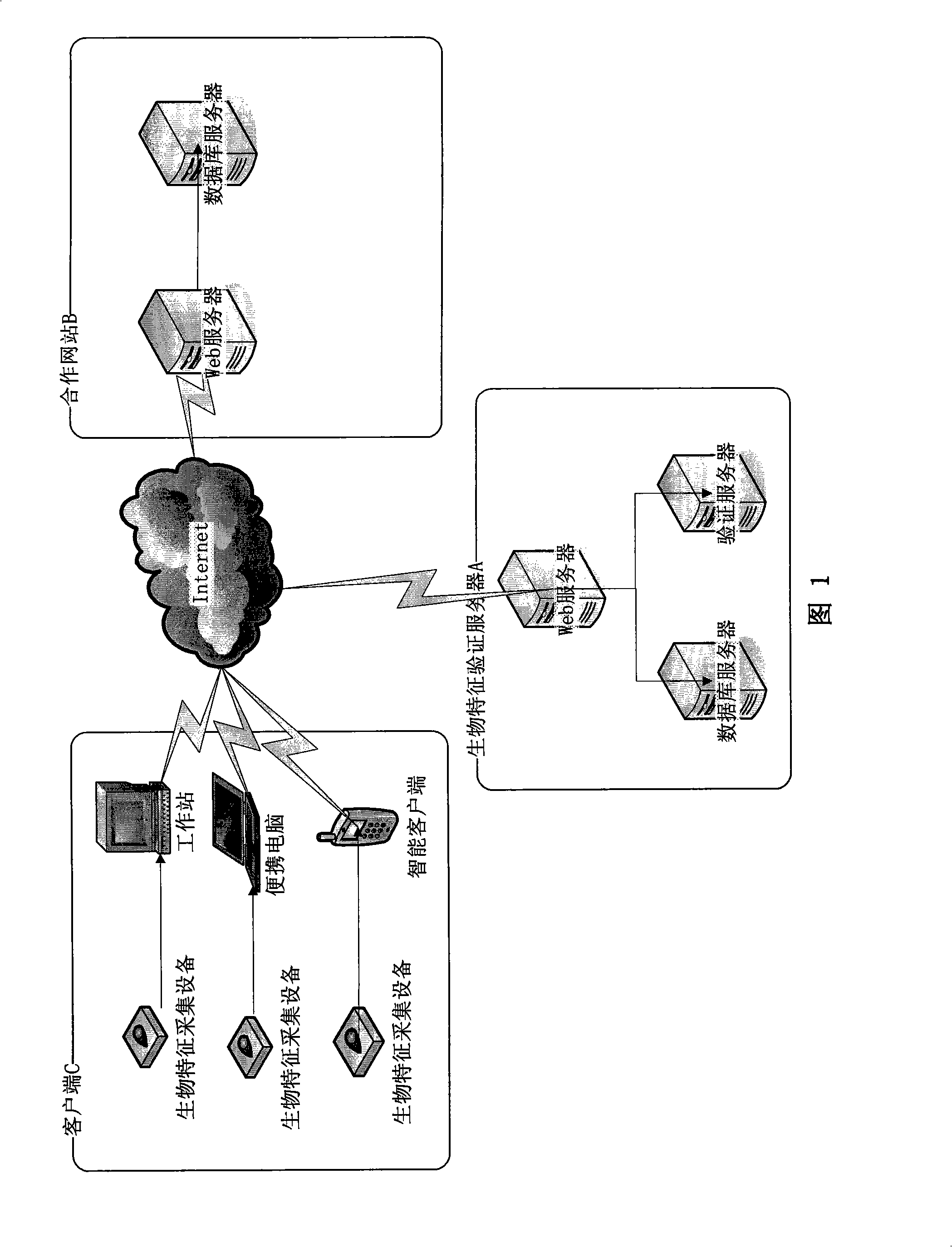
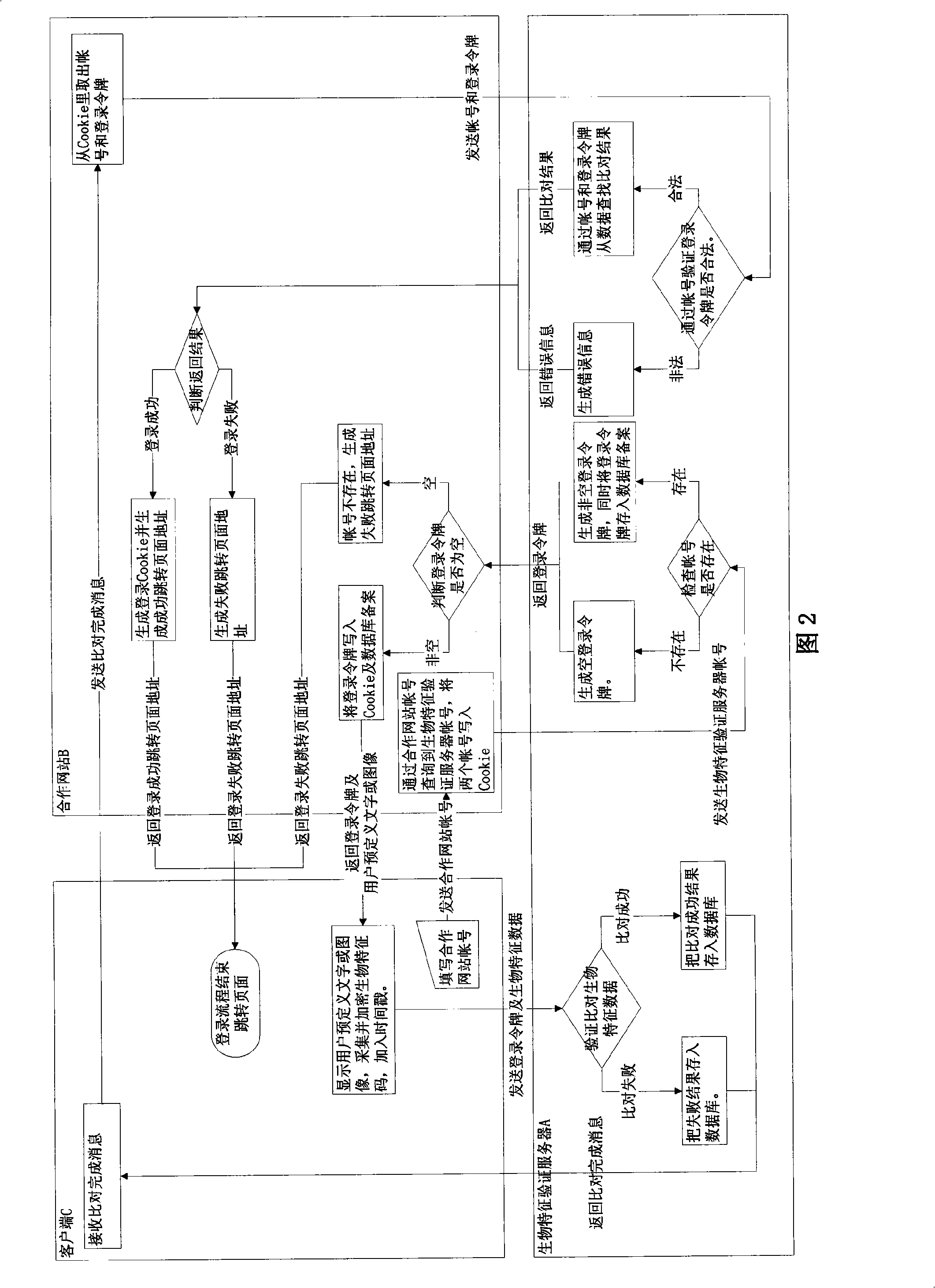
Network identity verification method based on internet third party biological characteristic validation
InactiveCN101316169AGuaranteed reliabilityEnsure safetyUser identity/authority verificationCharacter and pattern recognitionMultiple encryptionApplication software
The invention provides a network identity authentication method based on the biological characteristic authentication of a third party on the Internet. The biological characteristics (fingerprint, human face, iris, lip membrane and so on) are used as the identity identification of the user, the user can obtain an authentication request from the third party by submitting the biological characteristic codes through a client terminal widget provided by the third party, the identity authentication is carried out through the request password process and the matching algorithm, the Internet identity authentication can be carried out through a fully cooperative website or an application program provided by a cooperative network in a self-help mode, the third party provides request interfaces containing the registration, verification, reset of the biological characteristics, binding information,etc., the third party needs not to know the name of the user in the cooperative website or the application program provided by the cooperative network, thus avoiding to obtain the other information of the user in the cooperative website or the application program provided by the cooperative network, the reliability at the service terminal and the communication safety among the three parties can be guaranteed through the complete active service request of the cooperative website or the application program provided by the cooperative network, the Cookie, SSL, multi-encryption, digital signature of the widget, user-defined words or pictures,etc.
Owner:张曌 +2
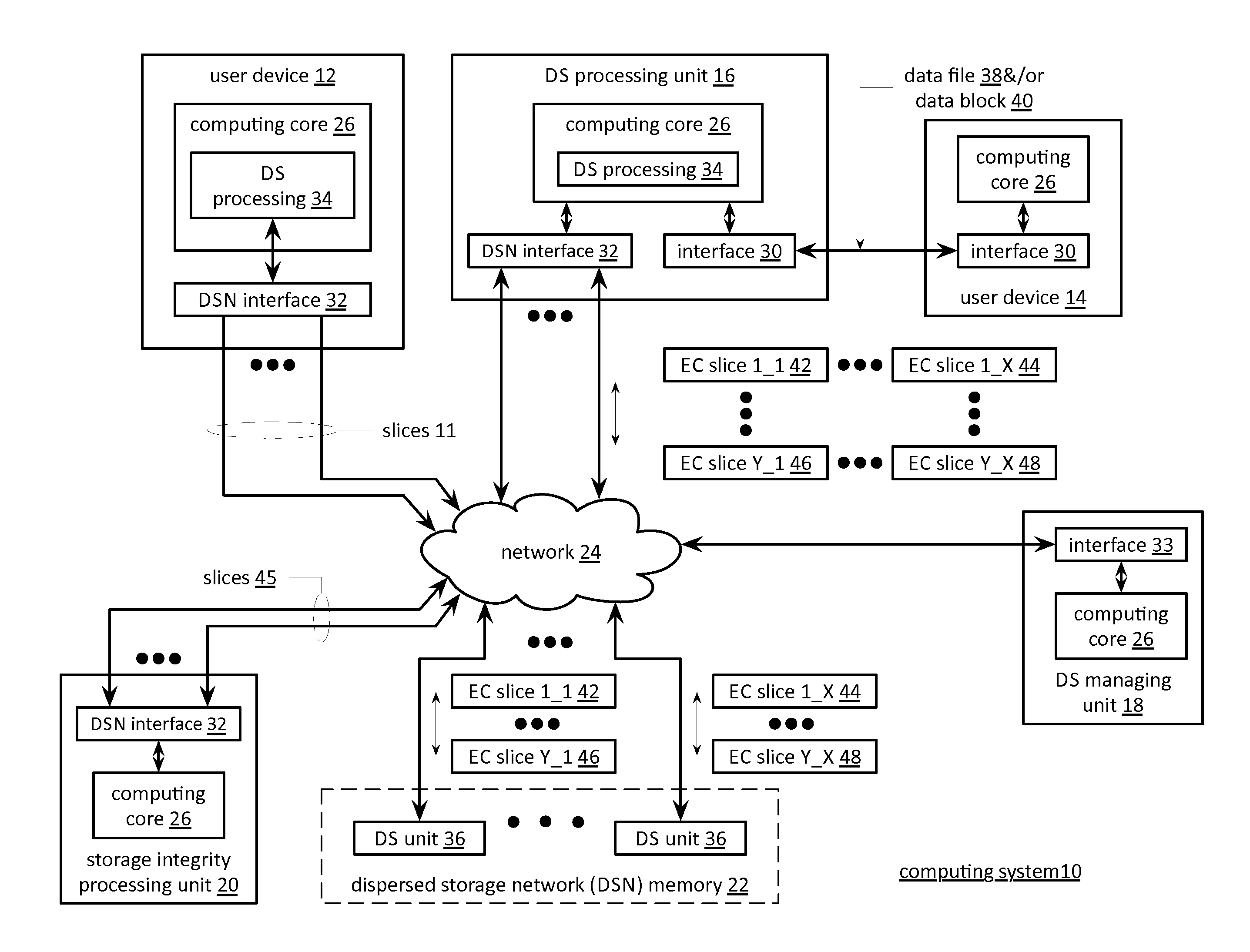
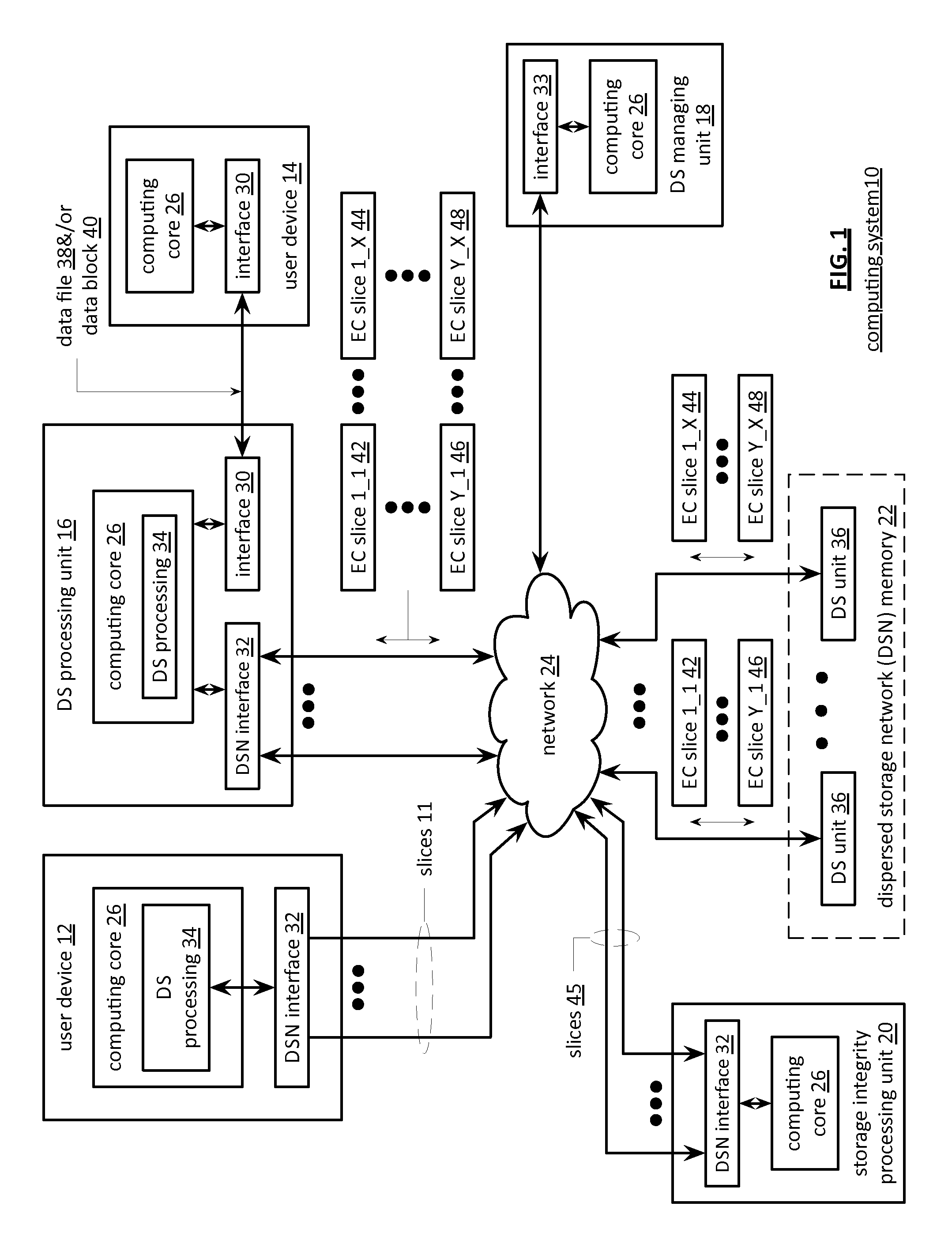
Secure rebuilding of an encoded data slice in a dispersed storage network
ActiveUS20120054500A1Input/output to record carriersUnauthorized memory use protectionMultiple encryptionThreshold number
A method begins by a processing module identifying an encoded data slice to be rebuilt, selecting a decode threshold number of dispersed storage (DS) units of a storage set of DS units, generating a decode threshold number of key pairs, wherein a key pair of the decode threshold number of key pairs corresponds to a DS unit of the decode threshold number of DS units, and sending partial rebuilding requests to the decode threshold number of DS units, wherein a partial rebuilding request of the partial rebuilding requests includes the key pair. The method continues with the processing module receiving encrypted partial encoded data slices, wherein an encrypted partial encoded data slice received from the corresponding DS unit includes a multiple encryption, using the key pair, of a partial encoded data slice and decoding the encrypted partial encoded data slices to rebuild the encoded data slice.
Owner:PURE STORAGE
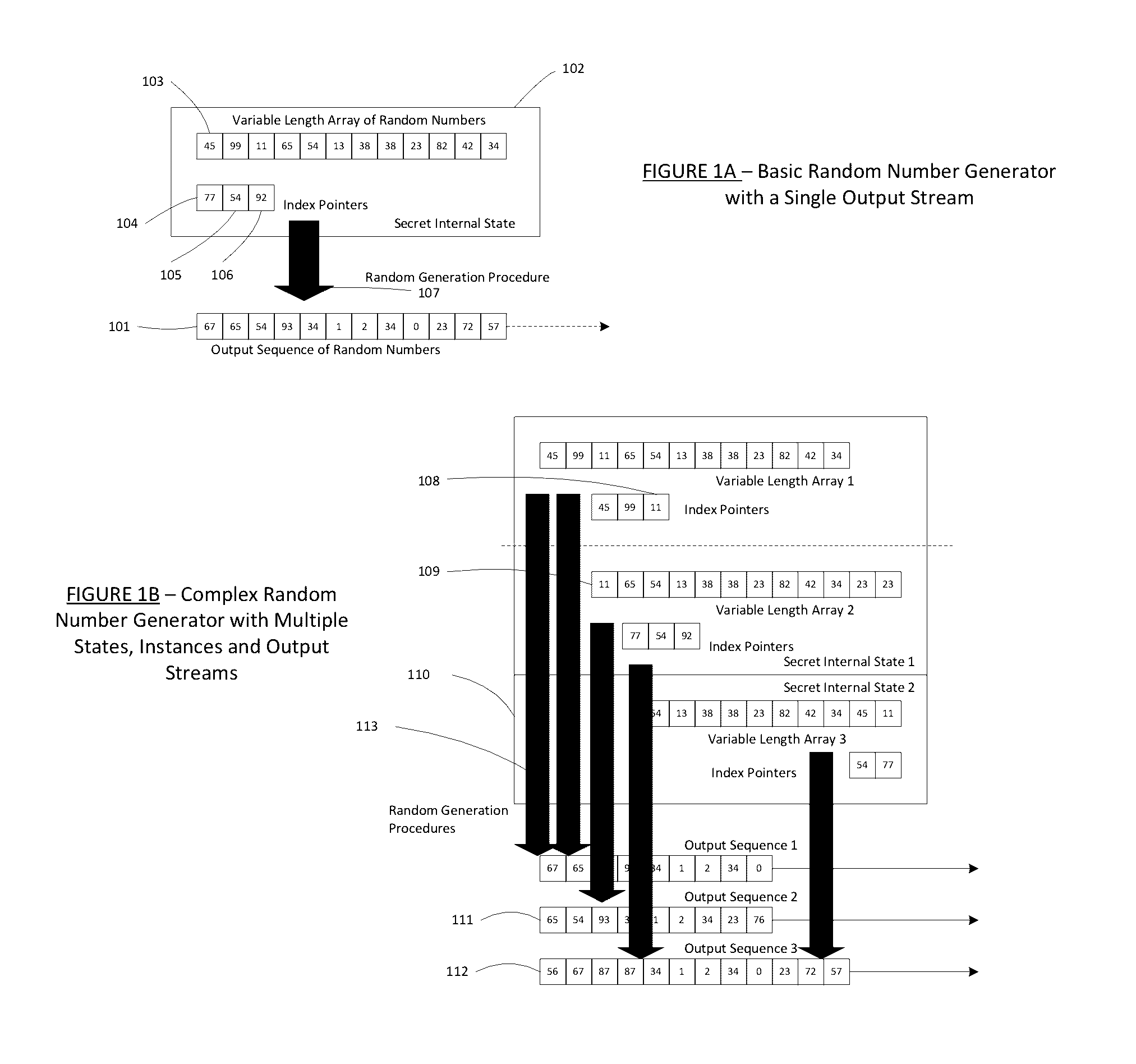
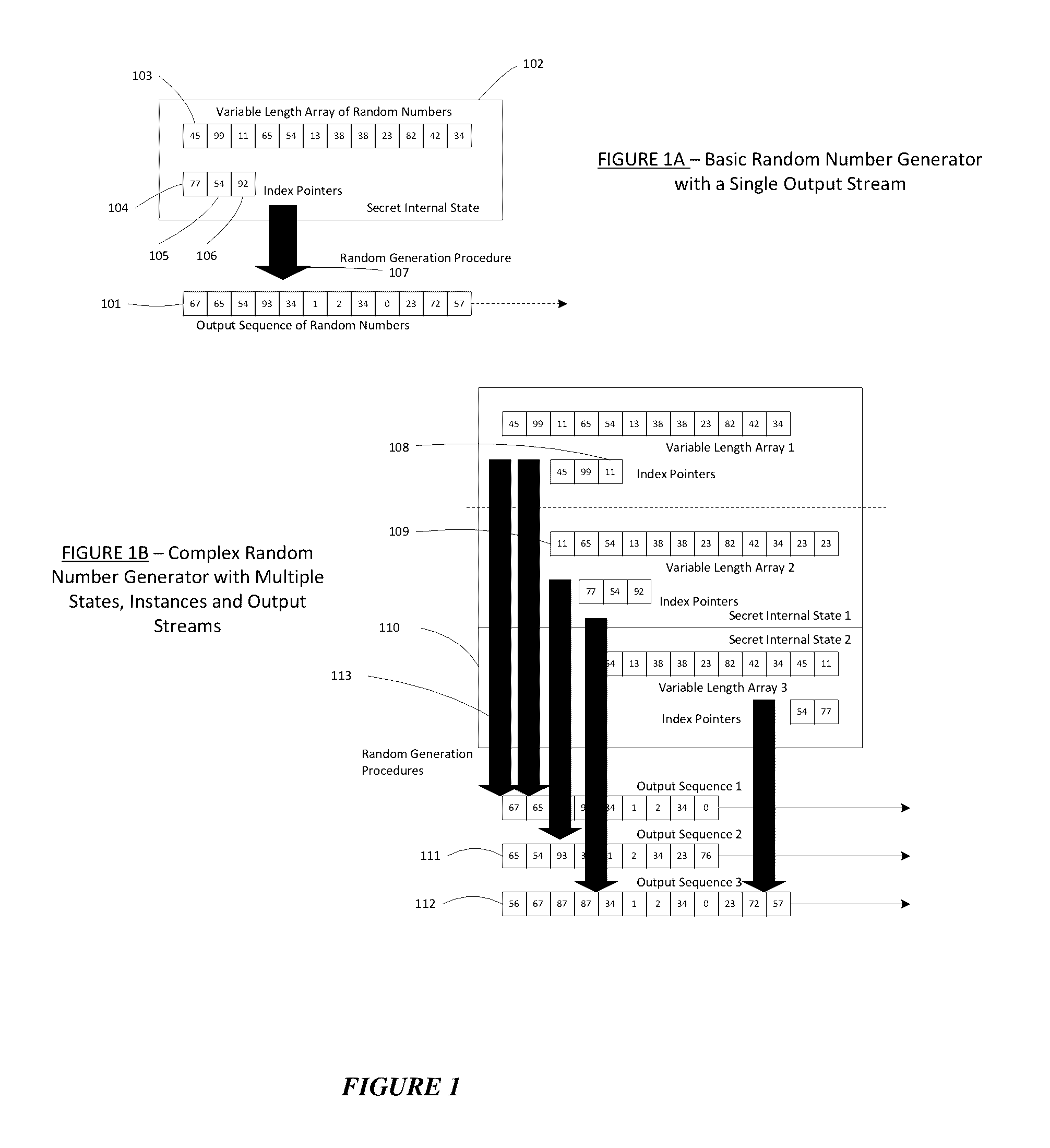
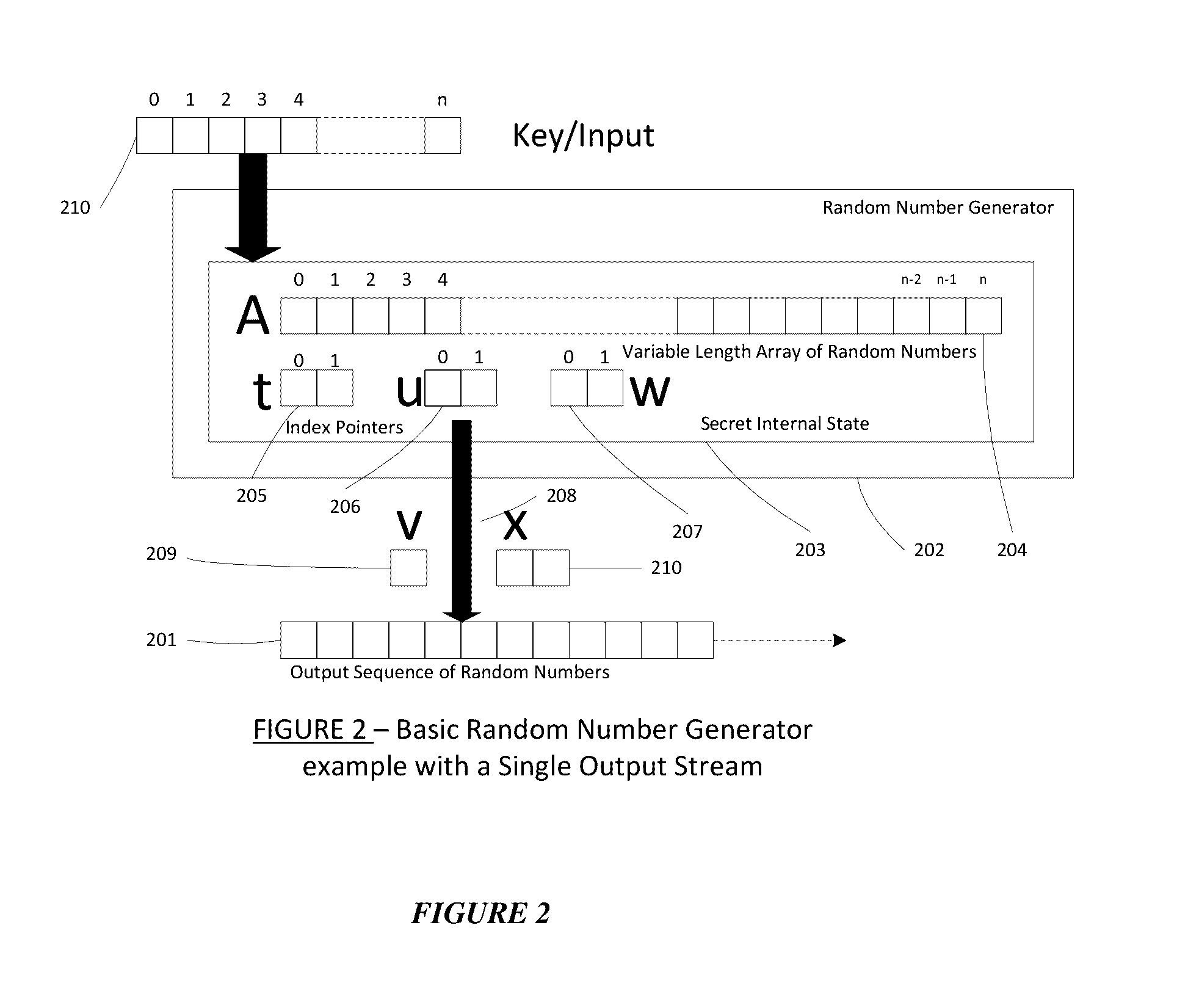
Method for a Dynamic Perpetual Encryption Cryptosystem
A dynamic computer communication security encryption method or system using an initial seed key and multiple random number generators of a specific design, whereby a sequence of independent random entropy values is produced by one set of random number generators and encrypted along with the message stream using the initial seed key, or the output of a second set of random number generators initialized with the initial seed key, and following the subsequent transmission of the variable encrypted entropy / message block, the entropy values are used to symmetrically or identically augment or increase the current uncertainty or entropy of the cryptosystem at both the sender and the receiver, prior to the next encryption block operation. The encryption process effectively entailing the use of multiple encryption ciphers, and the entropy augmentation process entailing the encryption or application of various logical mathematical operations on the already dynamic but deterministic internal state values of the second set of random number generators, effectively altering their deterministic outputs in a random probabilistic manner.Random length message value sequences from one or more data sources is combined with one or more random length entropy value sequences from an independent source, following which the entropy “updates” may also be used to alter, or change any cryptosystem variable, value or component in a randomly determined manner. In addition, whilst ensuring synchronization, the random entropy sequences also serve to “pollute” the cipher-stream and thereby hinder most current forms of cryptanalysis, whilst simultaneously injecting additional entropy into the cryptographic system and allowing for its propagation to affect any connected system nodes, and thereby introducing unpredictable entropy into the system pseudorandom number generator outputs, and thereby ensuring the perpetual generation of unpredictable random numbers.Super-encryption mechanics are independent of the user data, simple, fast and efficient, and can incorporate compression, error correction and asymmetric encryption authentication routines. But most importantly, super-encryption ensures resistance to brute force attacks (not possible to verify if a message was even sent), an ability to exceed “perfect secrecy” requirements, and an improvement on previous super-encipherment design, since overhead can be dramatically reduced from 100% overhead.Communication links previously established by system nodes with central authorities may be used for secure node authentication and registration, whilst allowing the central authority to broker and synchronize communication channels and providing mutual authentication and other security functions between the system nodes.
Owner:FIGUEIRA HELDER SILVESTRE PAIVA
Partial Multiple Encryption
InactiveUS20110311045A1Television system detailsPulse modulation television signal transmissionComputer hardwareMultiple encryption
A partial multiple encryption device consistent with certain embodiments has an input adapted to receive a unencrypted video signal. An encryption arrangement produces a partially multiple encrypted video signal from the unencrypted video signal. An output is adapted to provide the partially multiple encrypted video signal. This abstract is not to be considered limiting, since other embodiments may deviate from the features described in this abstract.
Owner:SONY CORP +1
Conditional access overlay partial encryption using MPEG transport continuity counter
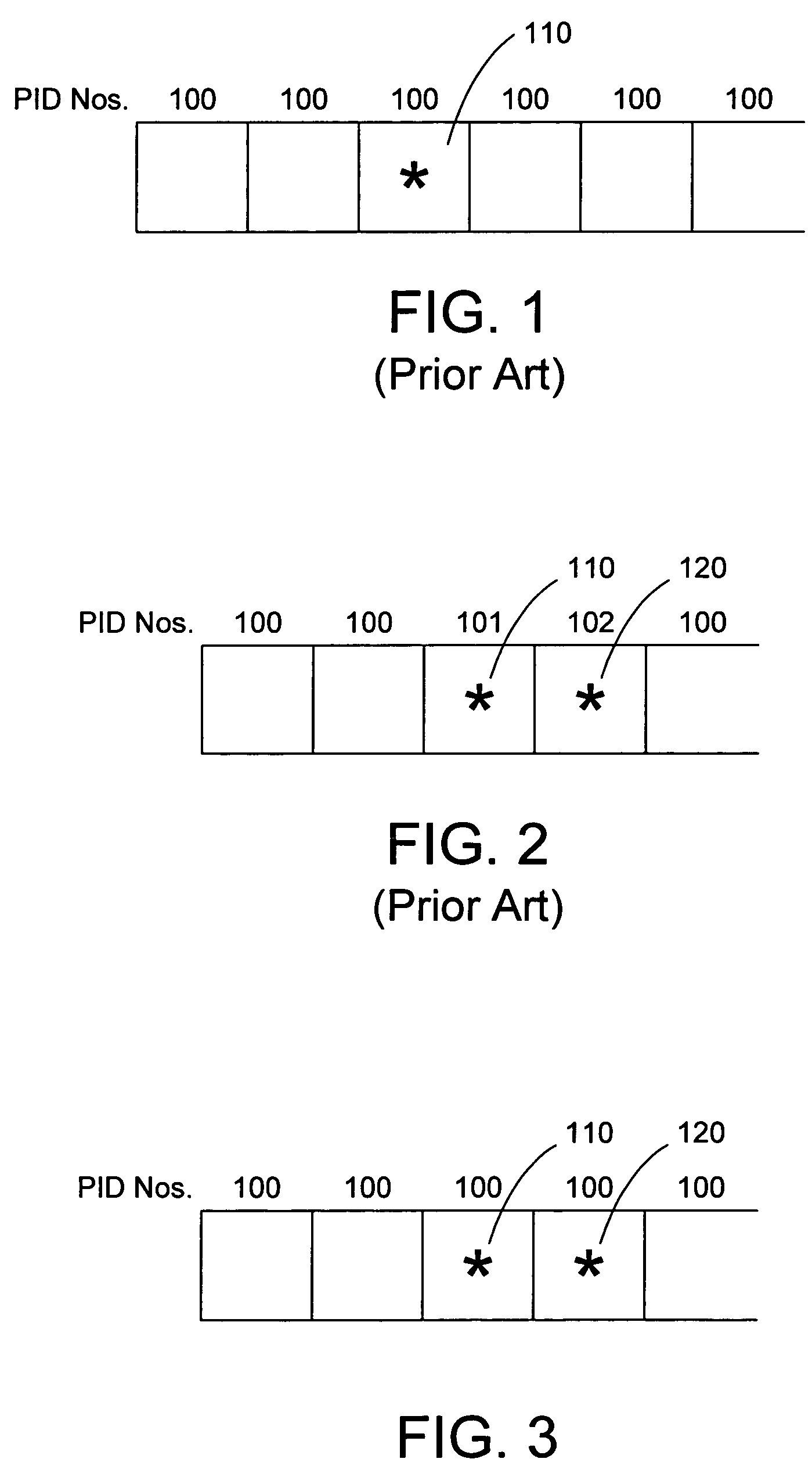
InactiveUS7490236B2User identity/authority verificationUnauthorized memory use protectionMultiple encryptionPlaintext
A conditional access overlay system utilizing partial encryption without requiring additional program identifiers. The conditional access overlay system generates duplicate critical packets for separate encryption that are sent using the same packet identifier. The rest of the content stream is sent in the clear. However, these duplicated packets are sent without incrementing a continuity counter relative to one another. The overlay packets with non-incremented continuity counter are sent as the second packet immediately following the original critical packet. At the receivers, the incumbent set-top will use the first of the two encrypted packets while the overlay set-top is programmed to use the second of the two encrypted packets. Therefore, methods for verifying alignment of associated packets may be used to distinguish between multiple encryption methods in conditional access overlay systems.
Owner:CISCO TECH INC
Method and apparatus for hardware-accelerated encryption/decryption
ActiveUS8879727B2Maximize availabilityLimited operating lifeKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMultiple encryptionKey exchange
An integrated circuit for data encryption / decryption and secure key management is disclosed. The integrated circuit may be used in conjunction with other integrated circuits, processors, and software to construct a wide variety of secure data processing, storage, and communication systems. A preferred embodiment of the integrated circuit includes a symmetric block cipher that may be scaled to strike a favorable balance among processing throughput and power consumption. The modular architecture also supports multiple encryption modes and key management functions such as one-way cryptographic hash and random number generator functions that leverage the scalable symmetric block cipher. The integrated circuit may also include a key management processor that can be programmed to support a wide variety of asymmetric key cryptography functions for secure key exchange with remote key storage devices and enterprise key management servers. Internal data and key buffers enable the device to re-key encrypted data without exposing data. The key management functions allow the device to function as a cryptographic domain bridge in a federated security architecture.
Owner:IP RESERVOIR
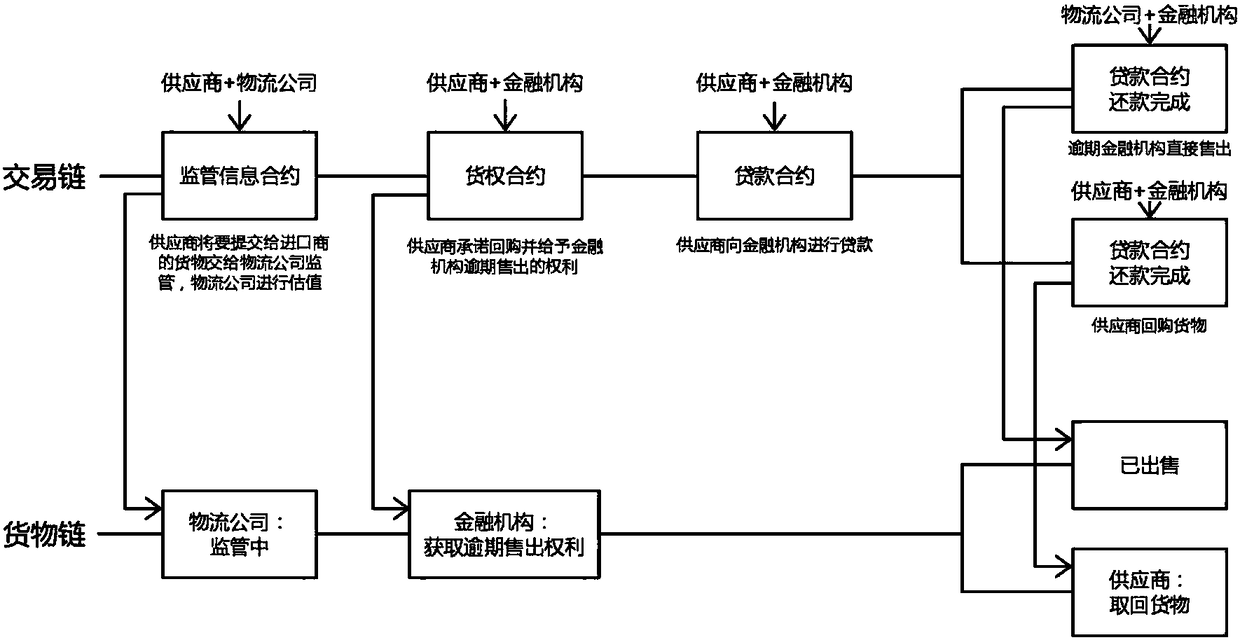
Blockchain-based supply chain financial anti-counterfeiting traceability method
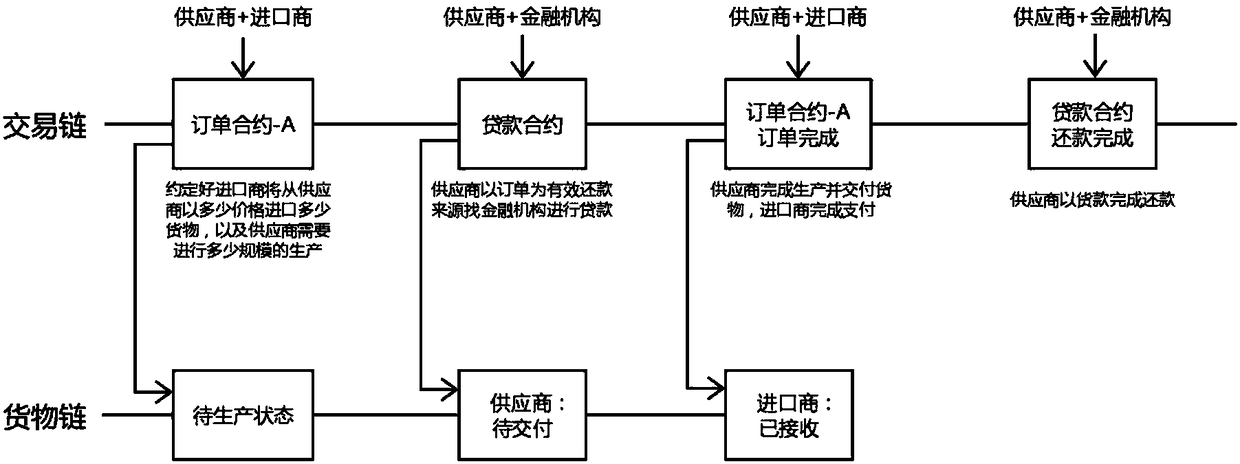
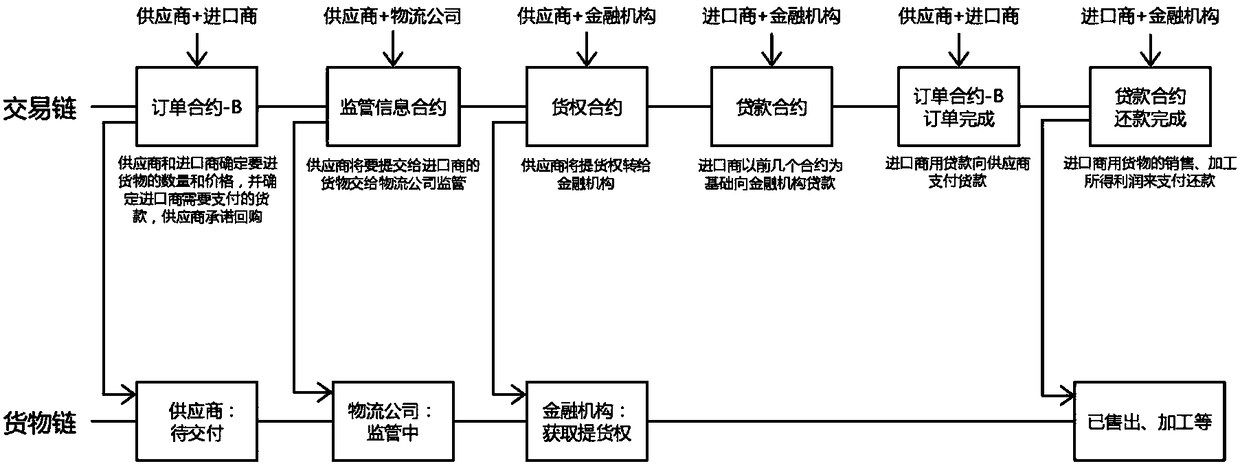
InactiveCN108229981ASolve difficultySolve possible shortcomings such as fraud and fraudFinanceDigital data protectionMultiple encryptionThird party
The invention discloses a blockchain-based supply chain financial anti-counterfeiting traceability method. The method utilizes the advantages of blockchain decentralization, no need for a third-partytrust system, multiple encryption algorithms and the like, the method is achieved through smart contracts in supply chain finance, and the defect of a traditional anti-counterfeiting traceability method can be better solved. By using the characteristic that a blockchain cannot be distorted, all of the content of the contracts including the state of goods can be clearly found, and the defects thatthe traditional anti-counterfeiting traceability method needs to be transferred by a paper certificate, a third-party guarantee or certification institution is needed, the fundraising difficulty of small and medium size enterprises is large, cheating and fraud might exist and the like are solved. Contractual agreement, logistics supervision and financial evaluation between buyers and sellers are achieved through the smart contracts, paper contracts are not needed because all of the contracts are finished in a system, complicated procedures are reduced, and the process is accelerated.
Owner:HANGZHOU YUNXIANG NETWORK TECH
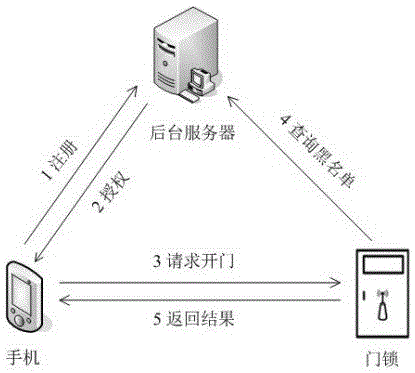
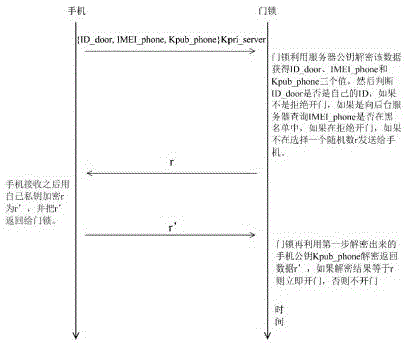
Mobile phone door lock system based on asymmetric secret key and realization method thereof
InactiveCN105139499AImprove securitySimple structureIndividual entry/exit registersMultiple encryptionBlack list
The invention discloses a mobile phone door lock system based on an asymmetric secret key and a realization method thereof, and belongs to a mobile phone door lock. The system comprises an intelligent mobile phone, a door lock and a server; data transmission among the intelligent mobile phone, the door lock and the server is carried by network; the server is used for storing a mobile phone identification number blacklist, and encrypting door opening permission serial data after the verification is valid and sending the serial data to the mobile phone; the intelligent mobile phone is used for sending the door opening permission serial data of the mobile phone to the door lock, and the door opening authority serial data at least comprises a door lock ID, a mobile phone identification number, etc.; the encrypted permission serial data and black list verification and multiple encryption and decryption verifications are carried out between the mobile phone, the door lock and the server, thereby solving the technology problem that the prior mobile phone door lock product cannot withstand replay attack and the invalid unlocking risk is high, providing a complete permission distribution, authentication and cancel process, greatly improving safety performance of the mobile phone door lock product, and promoting the development of the mobile phone door lock industry.
Owner:蔡炜
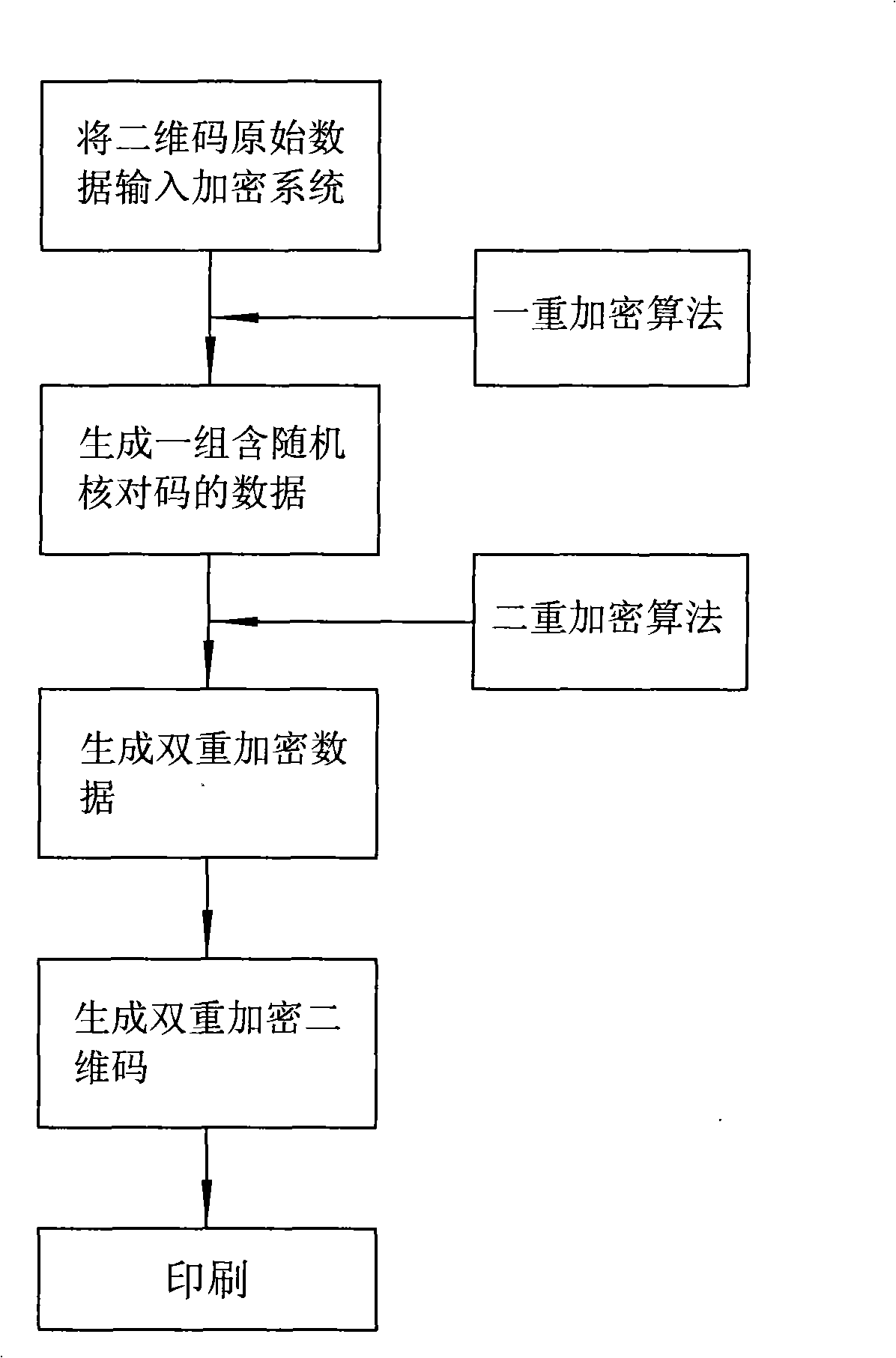
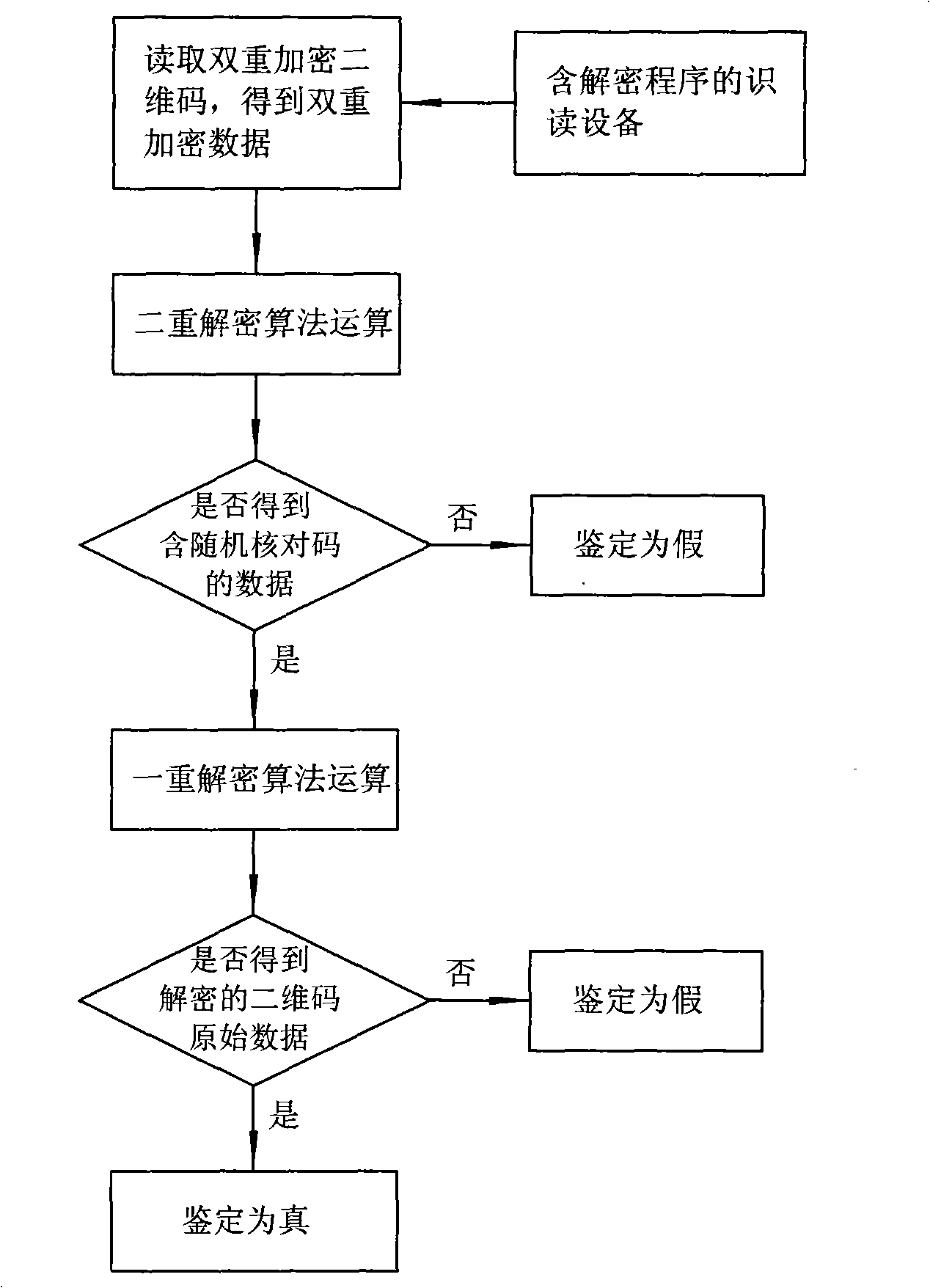
Two-dimensional code multi-enciphering anti-fake printing method
ActiveCN101295343ASolve the problem of getting the information in the QR codeImprove confidentialityDigitally marking record carriersSensing record carriersMultiple encryptionConfidentiality
The invention relates to the anti-counterfeiting printing technical field, in particular to a multi-encryption and anti-counterfeiting printing method for a two-dimensional code which is applicable to the two-dimensional code and has encryption requirements on the information of the two-dimensional code, and the multi-encryption and anti-counterfeiting printing method is carried out according to the following steps: (1) original data of the two-dimensional code to be encrypted is input to an encryption system; (2) the encryption system takes out one or a plurality of bits from the original data of the two-dimensional code to carry out a first encryption algorithm calculation, thus obtaining a group of random check codes; (3) the group of random check codes are arranged in the original data of the two-dimensional code, thus generating a group of data containing the random check codes; (4) the obtained data containing the random check codes is carried out a second encryption algorithm calculation, thus generating the dual-encryption data; (5) the obtained dual-encryption data is utilized for generating the dual-encryption two-dimensional code; (6) the dual-encryption two-dimensional code is transmitted to a digital printing system for printing. The method can effectively prevent others from utilizing the existing two-dimensional code reading device to decode the encrypted content, thus obtaining the information in the two-dimensional code and having good confidentiality.
Owner:HONGBO CO LTD
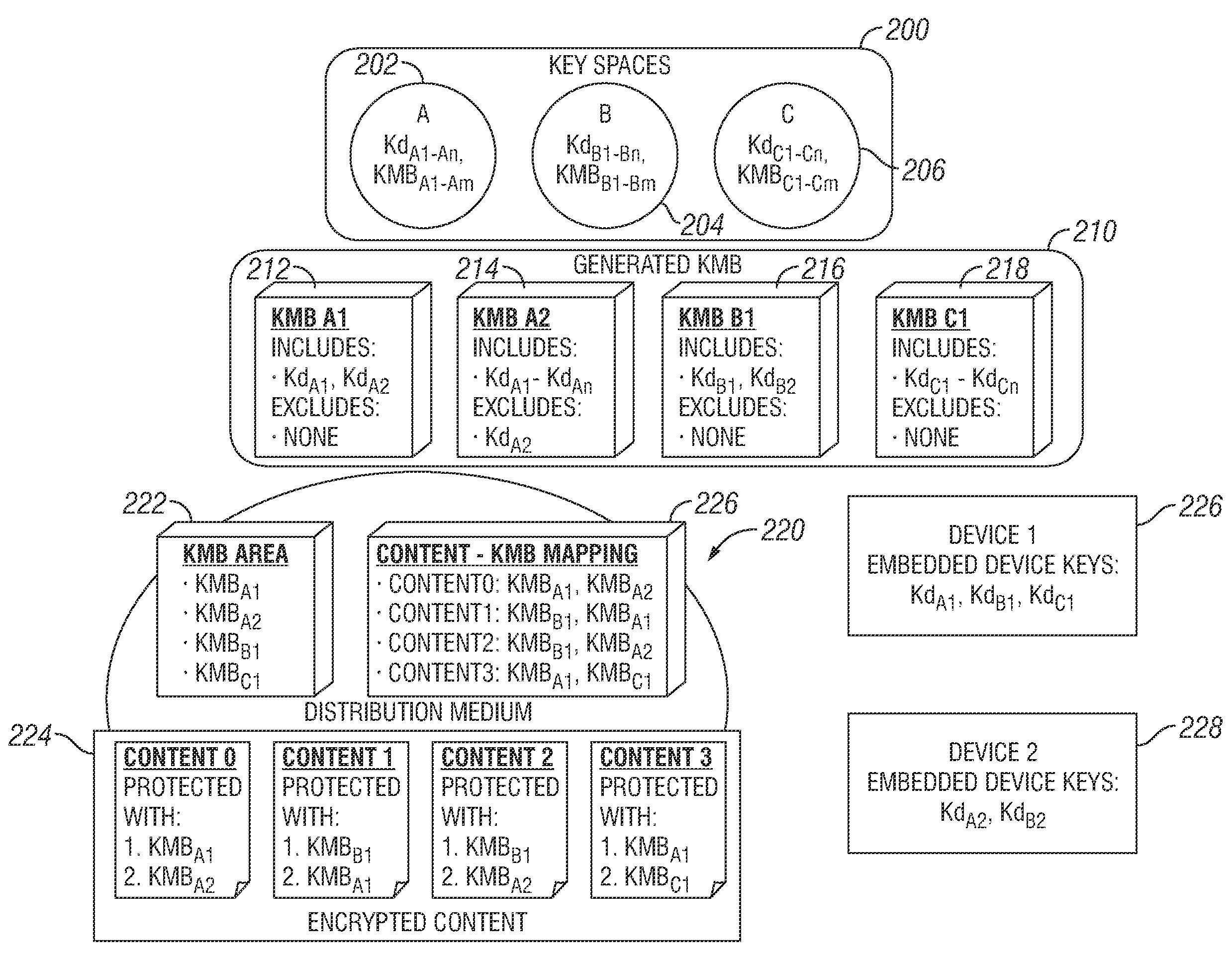
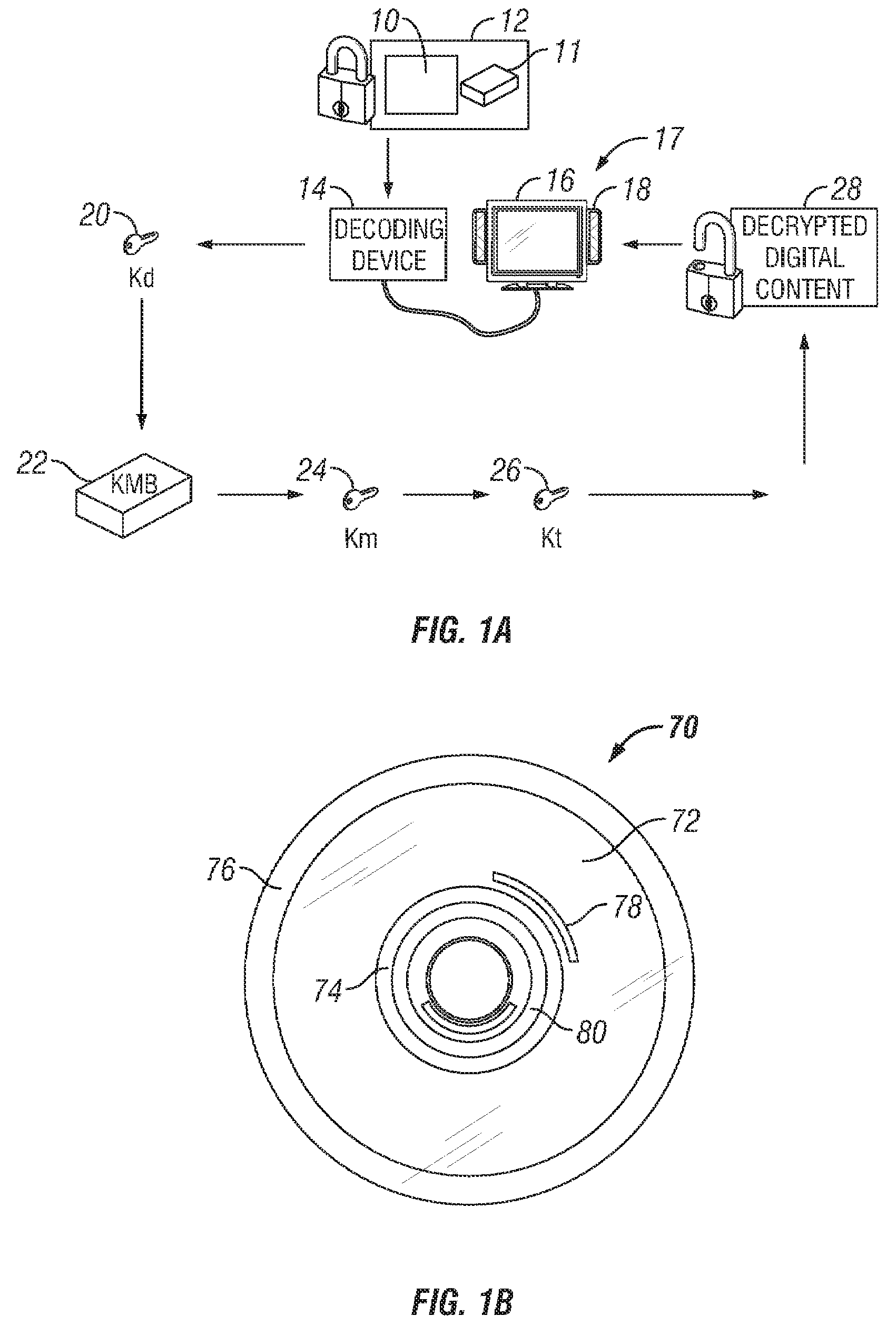
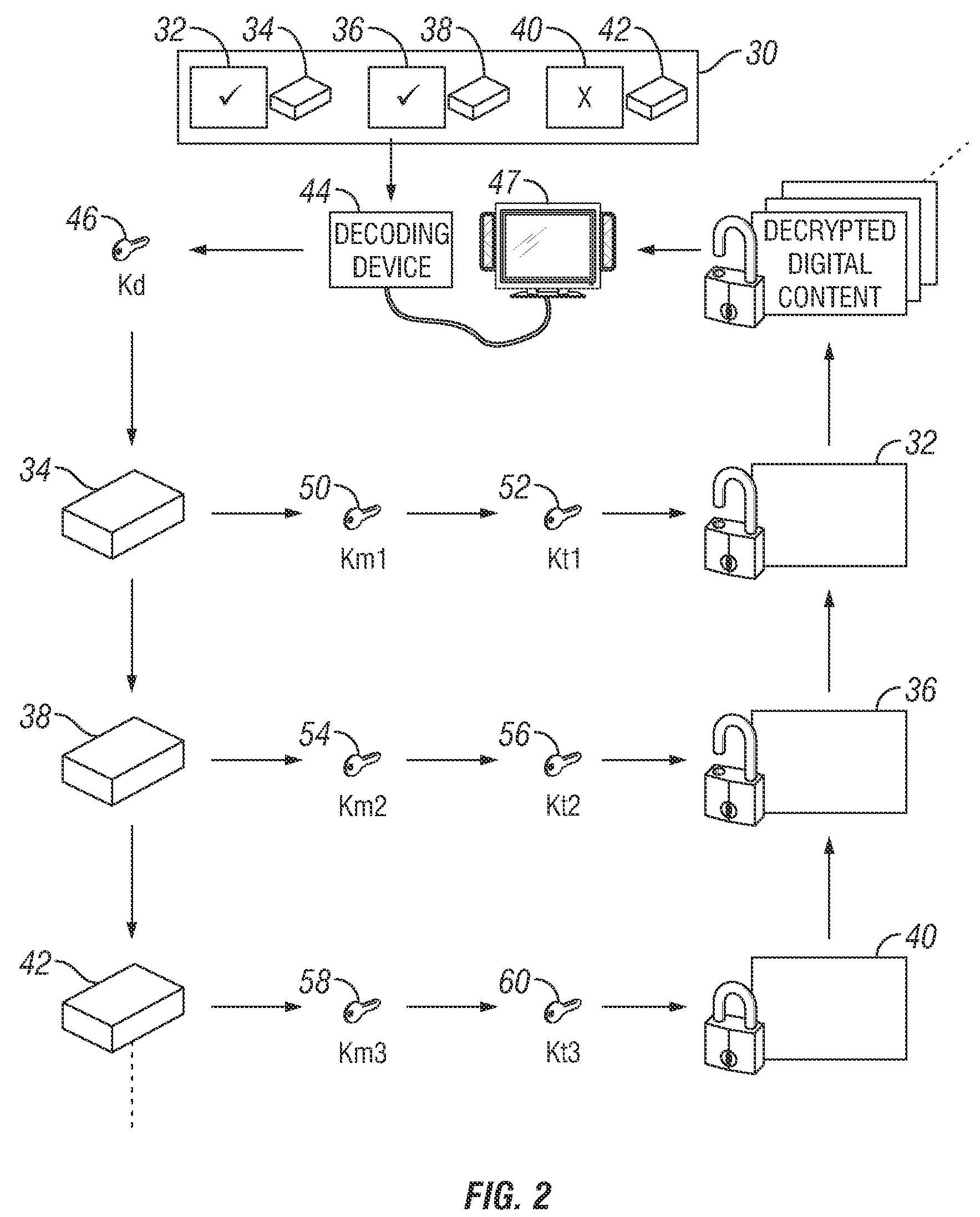
Method for controlling access to encrypted content using multiple broadcast encryption based control blocks
An apparatus and a method are provided for selectively accessing digital content carried on a distribution medium such as a physical medium or a broadcast medium. In one embodiment, a plurality of digital content items are encrypted under a plurality of different key management blocks, wherein each key management block is associated with a different set of device keys. The plurality of content items may be provided together on a single distribution medium to devices having assigned device keys, so that devices may selectively access content as determined by the different key management block used to encrypt the various content items and by the device keys assigned to the devices. Depending on the association between the device key and the key management blocks, the decoding device may decode all of the content items, some of the content items, or none of the content items. To provide greater security, each content item may be multiple encrypted using multiple key management blocks per content item.
Owner:IBM CORP
Digital image encryption method based on chaotic orbit perturbation
InactiveCN102360488AImprove diffusion abilityImprove abilitiesImage data processing detailsMultiple encryptionPlaintext
The invention relates to a digital image encryption method based on chaotic orbit perturbation and relates to the field of encryption systems. The method comprises the following steps of: scrambling a plaintext image by adopting a generalized discrete Baker mapping-based method; diffusing the scrambled image by adopting a Logistic mapping-based method, and changing the pixel value of each point in the image; and performing multiple encryption according to the requirement on encryption strength. According to the method, a key flow is related to a key and a plaintext by introducing a chaotic orbit perturbation mechanism related to the plaintext, so that the diffusing effects of an encryption system are effectively improved, and the known plaintext resistance is obviously improved. Certain pixel value is changed in the diffusion process depending on the cumulative effect of all the encrypted pixel values before the pixel, so that the tiny change of one pixel value can be effectively diffused to all the subsequent pixels in the image. The method has short encryption time.
Owner:付冲 +1
Conditional access overlay partial encryption using MPEG transport continuity counter
InactiveUS20050152548A1User identity/authority verificationUnauthorized memory use protectionPlaintextMultiple encryption
A conditional access overlay system utilizing partial encryption without requiring additional program identifiers. The conditional access overlay system generates duplicate critical packets for separate encryption that are sent using the same packet identifier. The rest of the content stream is sent in the clear. However, these duplicated packets are sent without incrementing a continuity counter relative to one another. The overlay packets with non-incremented continuity counter are sent as the second packet immediately following the original critical packet. At the receivers, the incumbent set-top will use the first of the two encrypted packets while the overlay set-top is programmed to use the second of the two encrypted packets. Therefore, methods for verifying alignment of associated packets may be used to distinguish between multiple encryption methods in conditional access overlay systems.
Owner:CISCO TECH INC
Method for Selective Encryption Within Documents
ActiveUS20080270807A1Multiple keys/algorithms usageUser identity/authority verificationMultiple encryptionWord processing
Owner:KYNDRYL INC
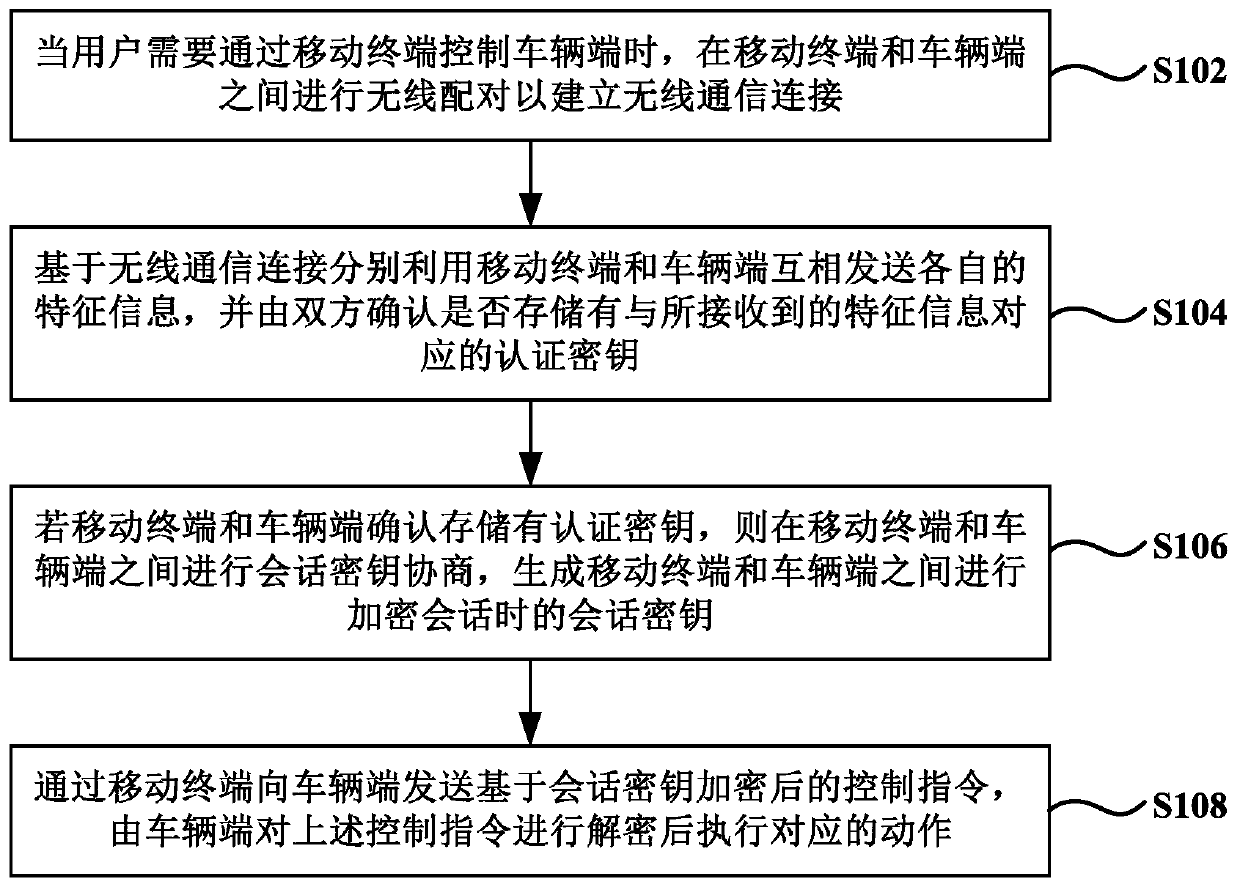
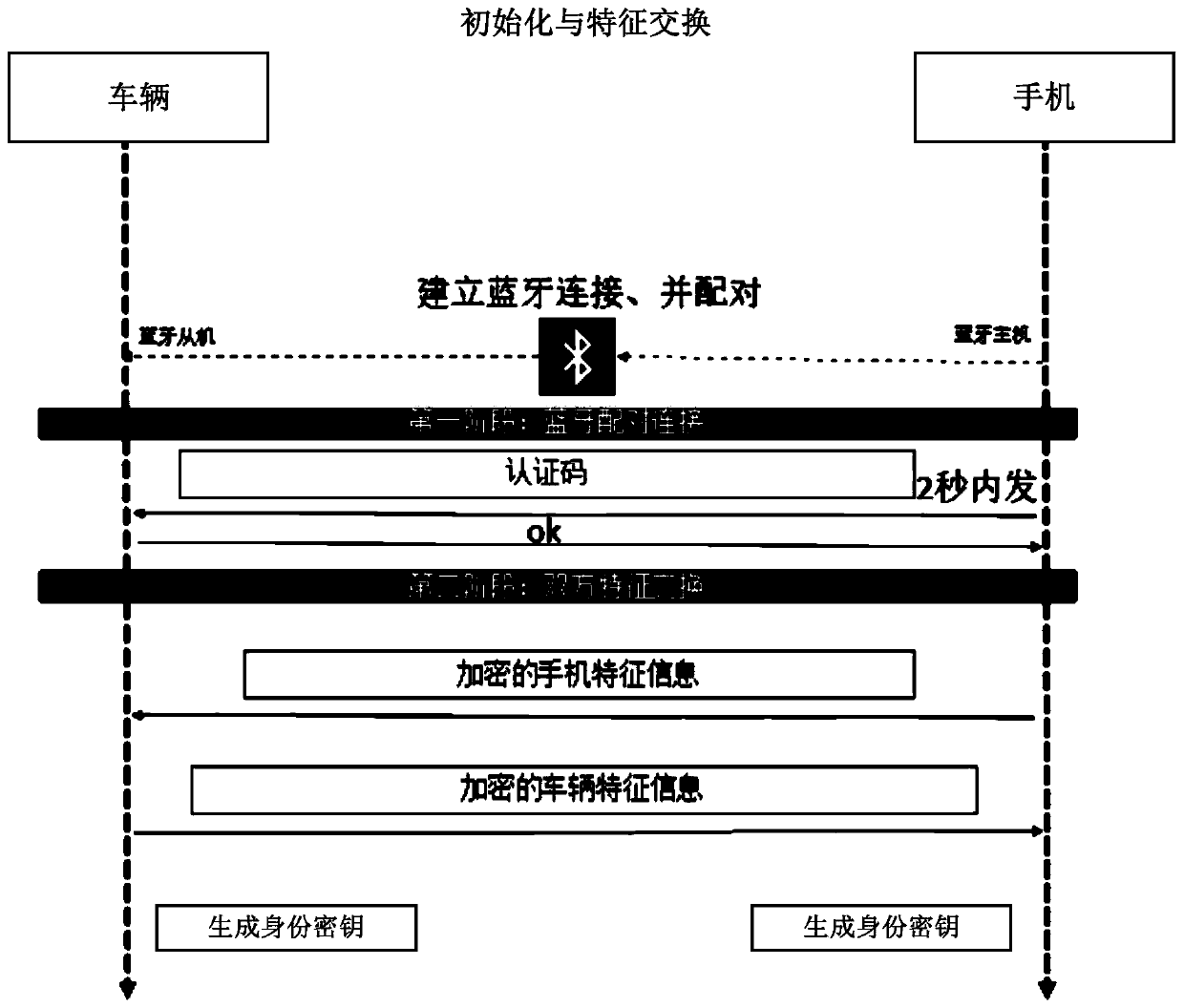
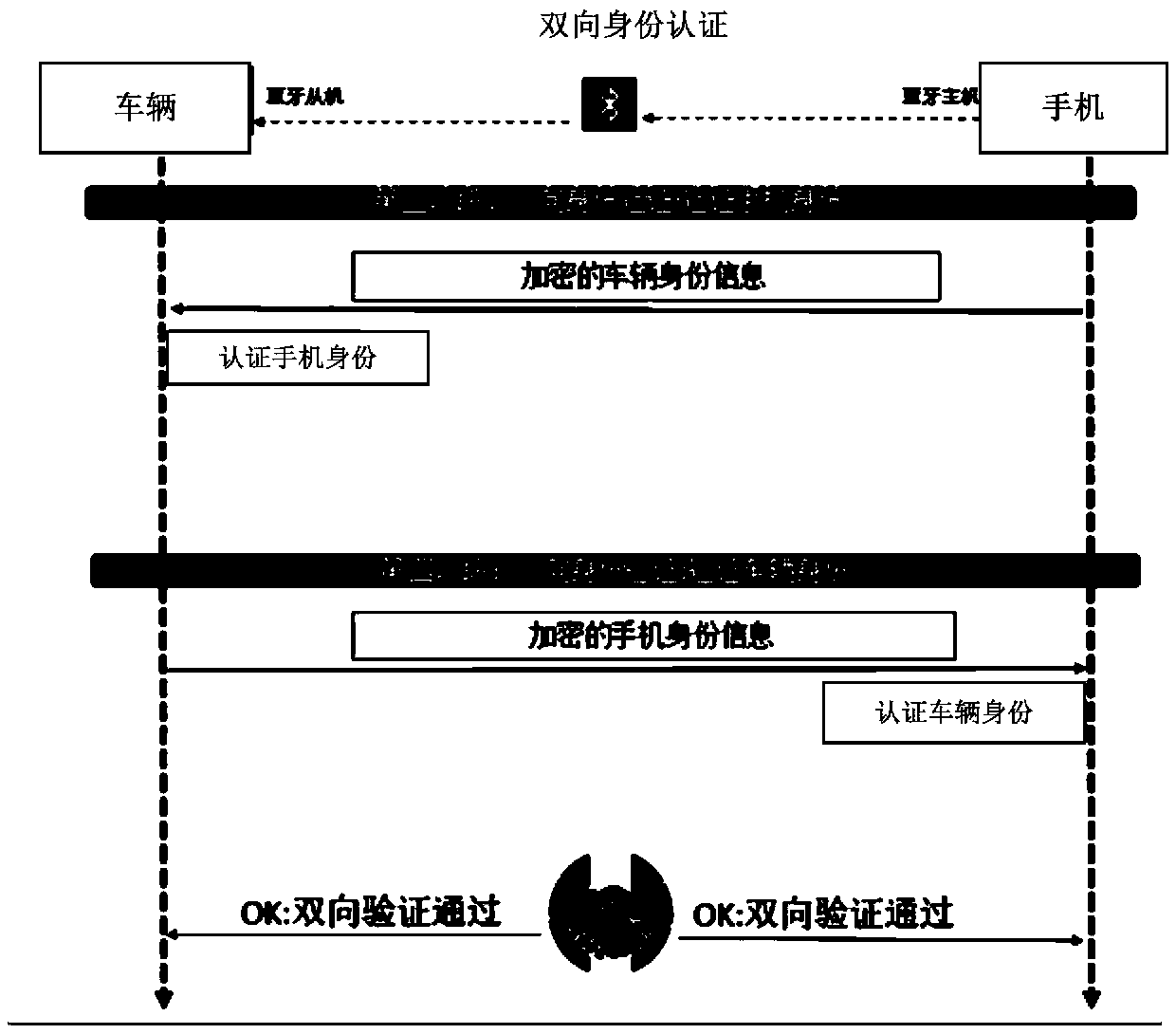
Wireless control method and system for vehicle
ActiveCN110177354AEnsure safetyImprove securityParticular environment based servicesVehicle wireless communication serviceMultiple encryptionWireless control
The invention provides a vehicle wireless control method and system, and the method comprises the steps: carrying out the wireless pairing between a mobile terminal and a vehicle end when a user needsto control the vehicle end through the mobile terminal, so as to build wireless communication connection; based on the wireless communication connection, utilizing the mobile terminal and the vehicleend to mutually send respective feature information, and confirming whether an authentication key corresponding to the received feature information is stored or not by the two parties; if the mobileterminal and the vehicle end confirm that the authentication key is stored, performing session key negotiation between the mobile terminal and the vehicle end, and generating a session key when an encryption session is performed between the mobile terminal and the vehicle end; and sending a control instruction encrypted based on the session key to the vehicle end through the mobile terminal, and decrypting the control instruction by the vehicle end and then executing a corresponding action. Based on the scheme provided by the invention, multiple encryption authentications are adopted to ensurethe safety of the vehicle digital key.
Owner:ECARX (HUBEI) TECHCO LTD
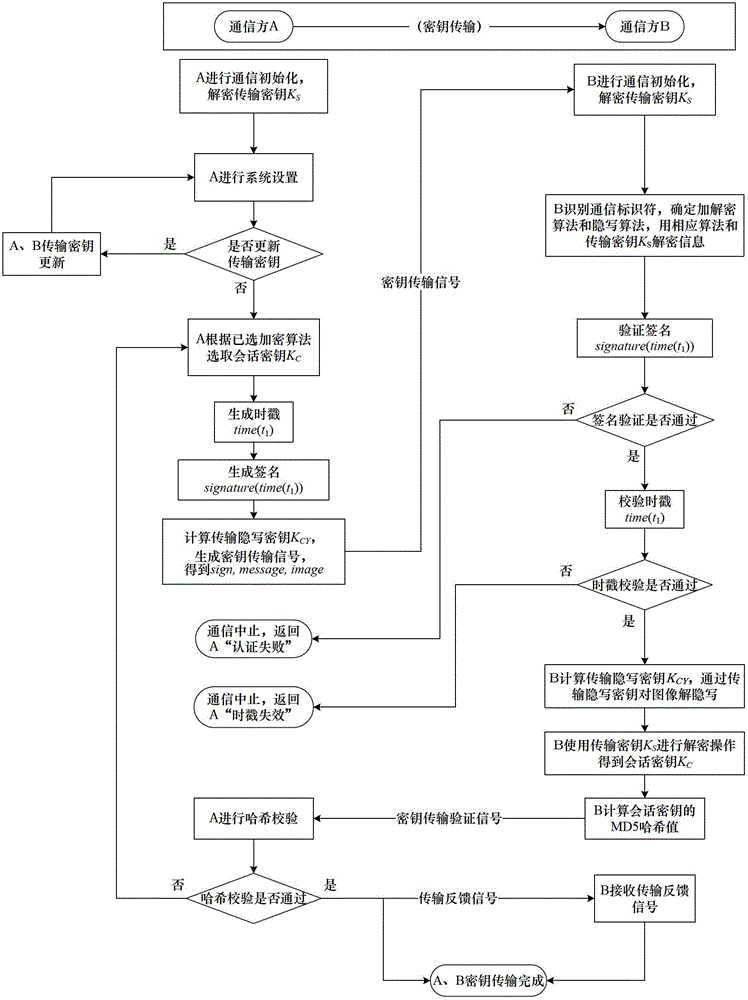
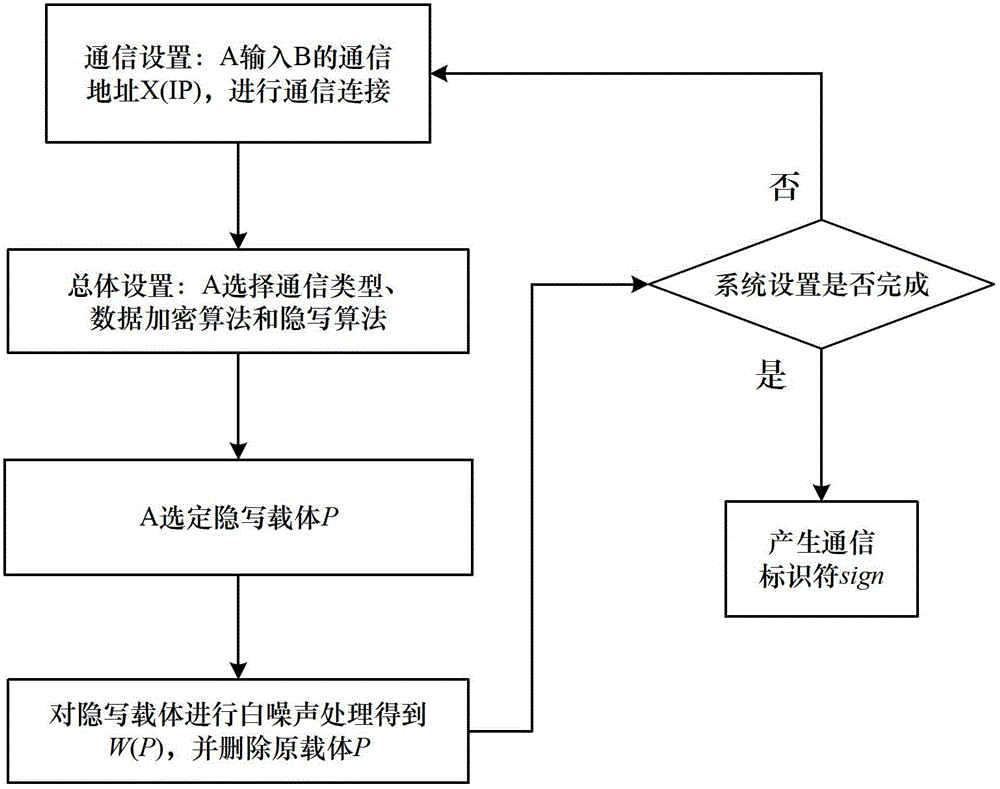
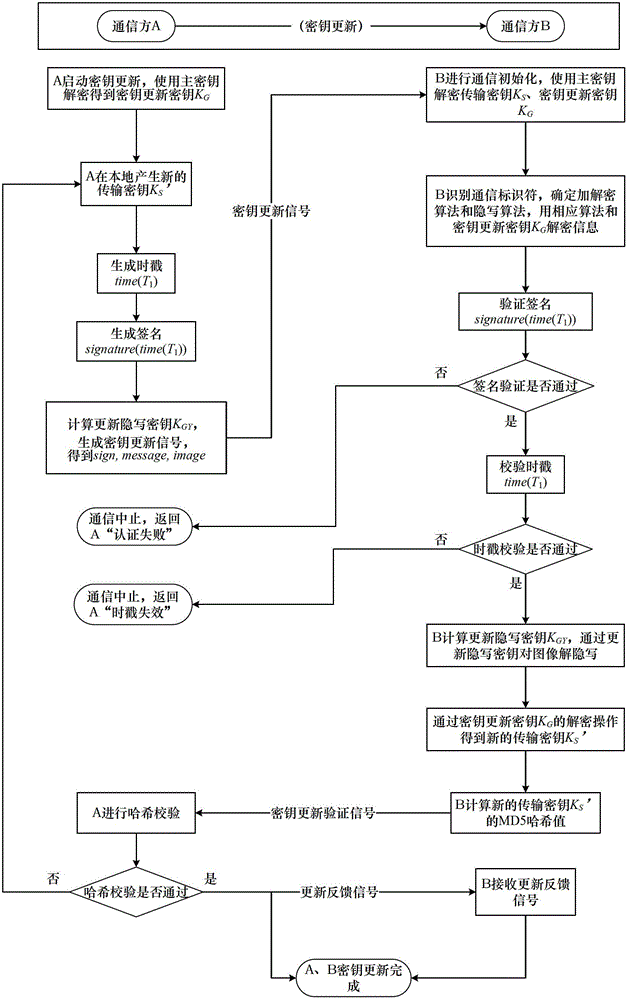
Steganography-based key transmission and key updating method
ActiveCN102724041AEffective verification of identity informationImprove authentication strengthEncryption apparatus with shift registers/memoriesUser identity/authority verificationMultiple encryptionCiphertext
The invention provides a steganography-based key transmission and key updating method, which is applied to the field of information safety. The method comprises the steps that a communication party A sets a communication type, an encryption algorithm an steganography algorithm, selects a steganography carrier and generates a communication identifier and then performs the updating of a transmission key or the transmission process of a conversion key; a new transmission key is selected when in updating, a time stamp and a signature are generated to encrypt and steganograph the transmission key, the key updating information is generated to be transmitted to a communication party B, and the communication party B performs the verification, de-staganography and deciphering to obtain the transmission key; and the conversion key is selected in transmission to generate a time stamp and a signature so as to encrypt and steganograph the conversion key, the key transmission information is generated to be transmitted to the communication party B, and the communication party B performs the verification, de-steganography and deciphering to obtain the conversation key. The key is concealed by utilizing the steganography, so that an encrypted data format in the key transmission process and the key updating process can be effectively protected, and the safety transmission of multiple encryption and decryption algorithm conversation keys can be realized.
Owner:BEIHANG UNIV
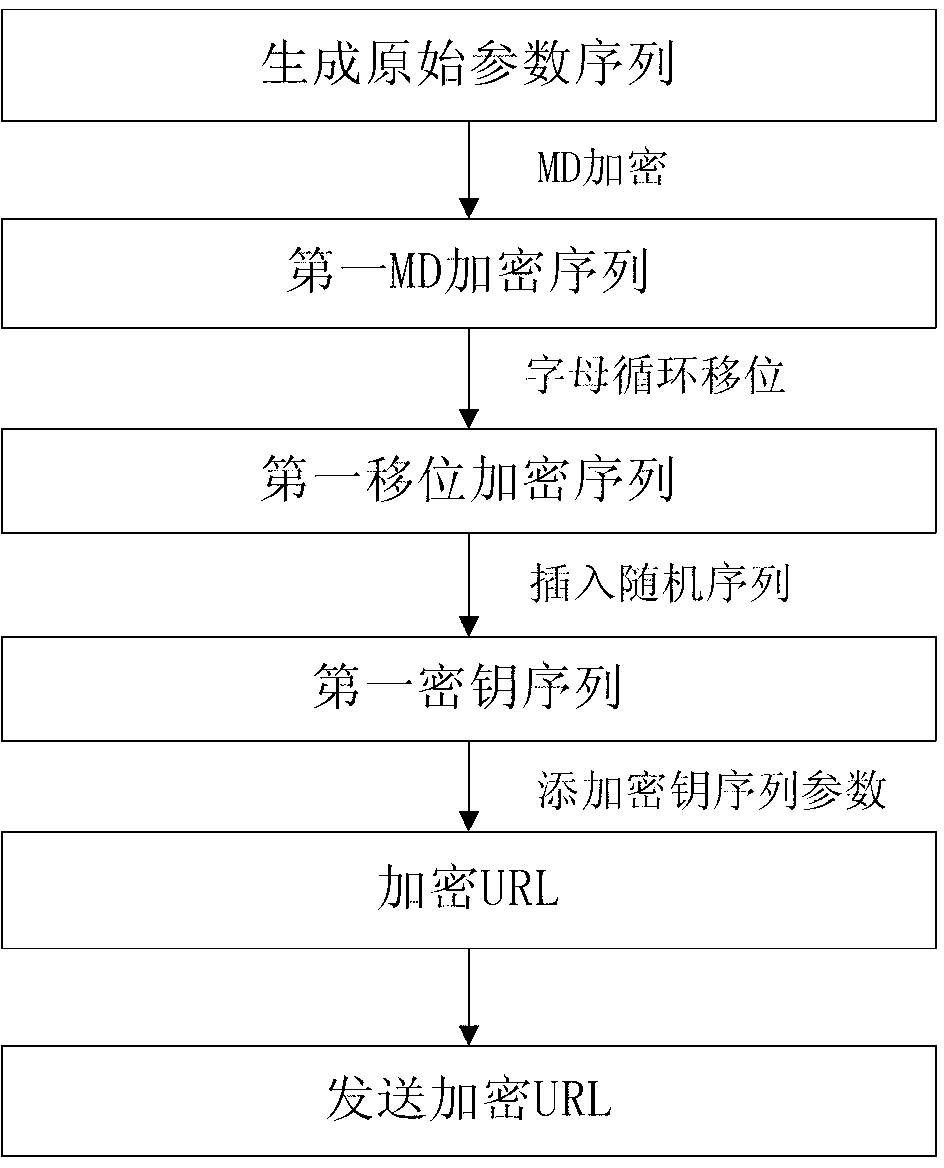
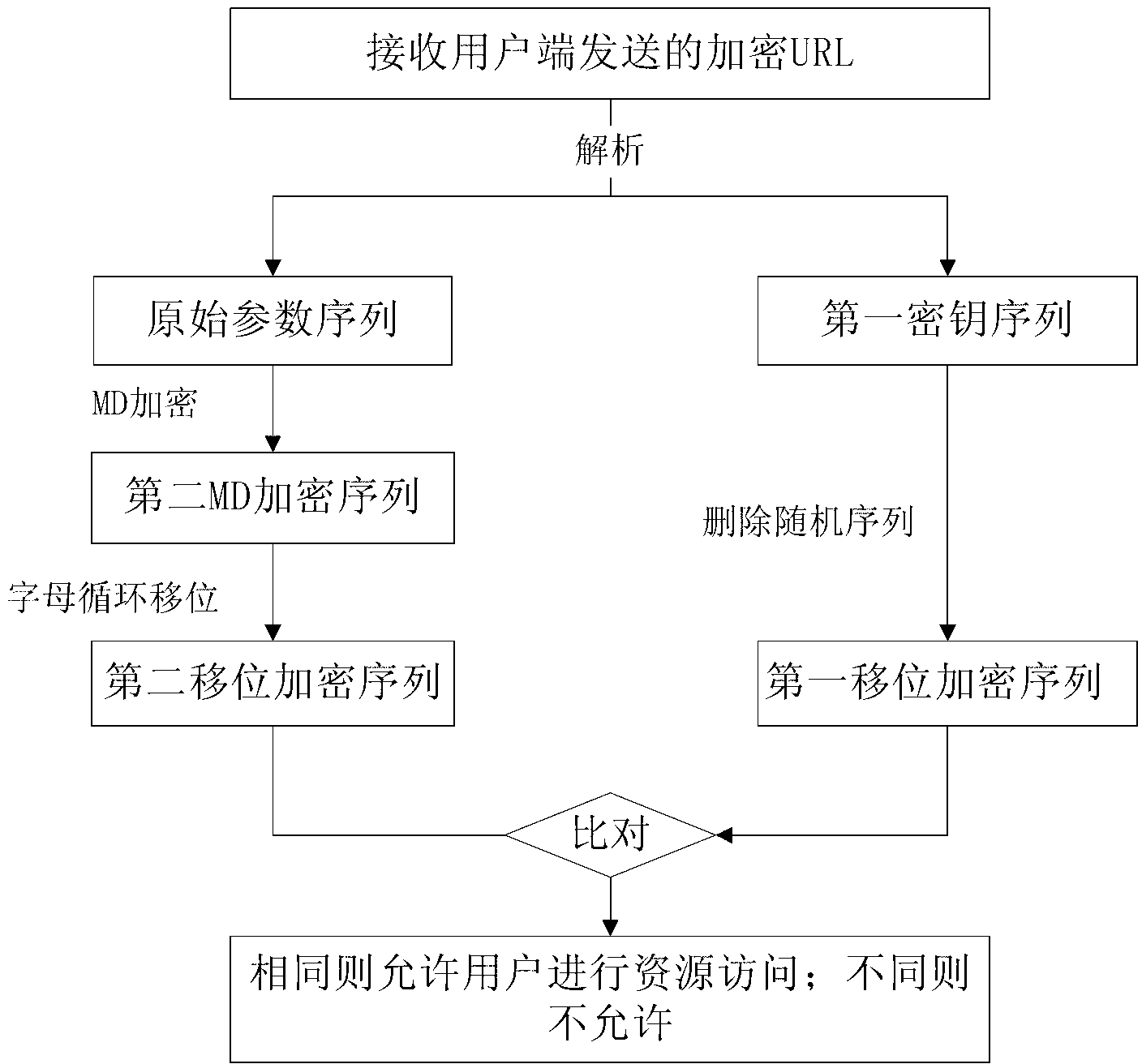
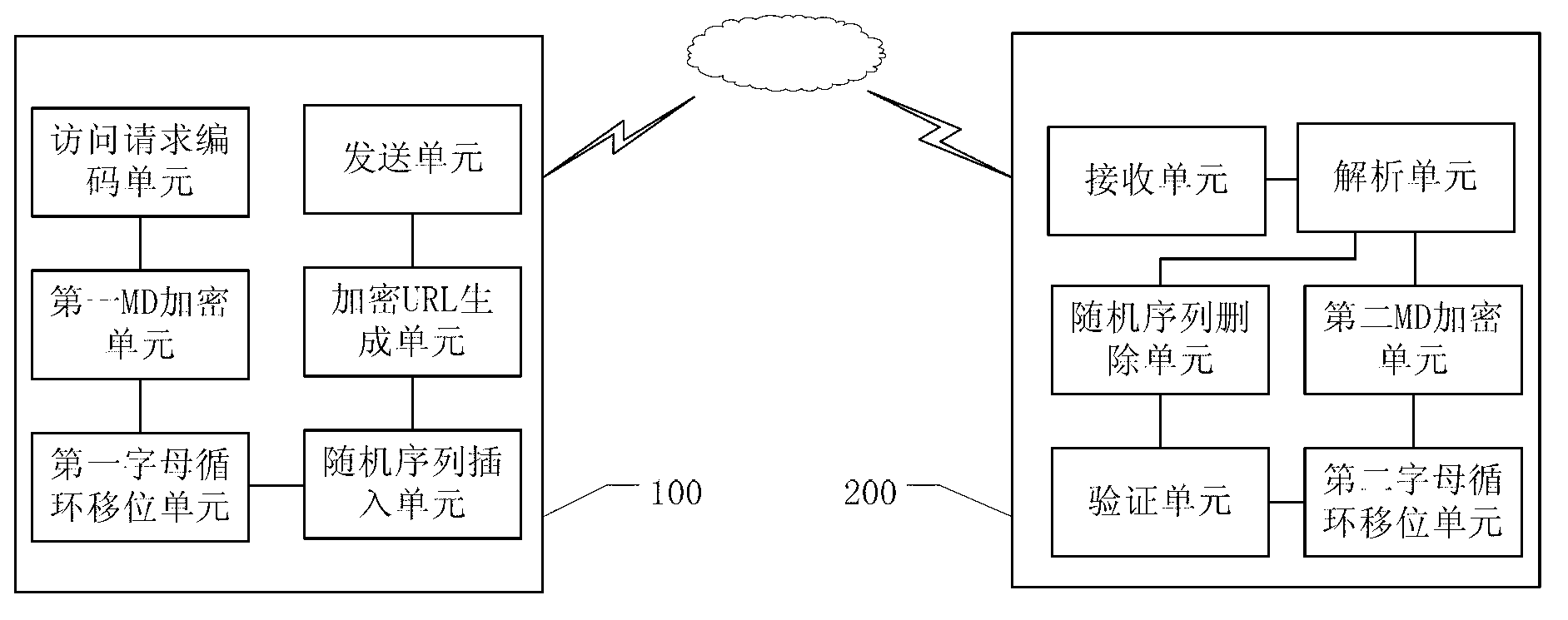
Uniform resource locator (URL) encryption and validation method for mobile internet user resource access and device provided with the same
ActiveCN103067156AEncryption apparatus with shift registers/memoriesSecurity arrangementMultiple encryptionValidation methods
The invention provides a uniform resource locator (URL) encryption and validation method for mobile internet user resource access and a device provided with the URL encryption and validation method for the mobile internet user resource access. A user side responses to a resource access request from a user, a request parameter set is obtained, an original parameter sequence of the resource access request is generated, a first secret key sequence is obtained after mini disk (MD) encryption, transposition and inserting of a random sequence, and added to the request parameter set, and further, an encryption URL is generated. A terminal receiving encryption URL is provided in the content of the invention embodiment, and the original parameter sequence and the first secret key sequence are extracted from the terminal receiving encryption URL. An encryption processing similar to an encryption processing of the user side is performed on the original parameter sequence, and then the original parameter sequence is compared with the first secret key sequence, if the original parameter sequence is consistent with the first secret key sequence, the user is allowed to access resource, and otherwise, the user is not allowed to access the resource. A multiple encryption technology is adopted for generating of request parameters, encrypted parameters have timeliness and uncrackable performance, and therefore when the user requests for the access of a resource class URL, the security of resource URL access request can be guaranteed, and request information is prevented from being hotlinked or falsified.
Owner:MDC TELECOM CO LTD
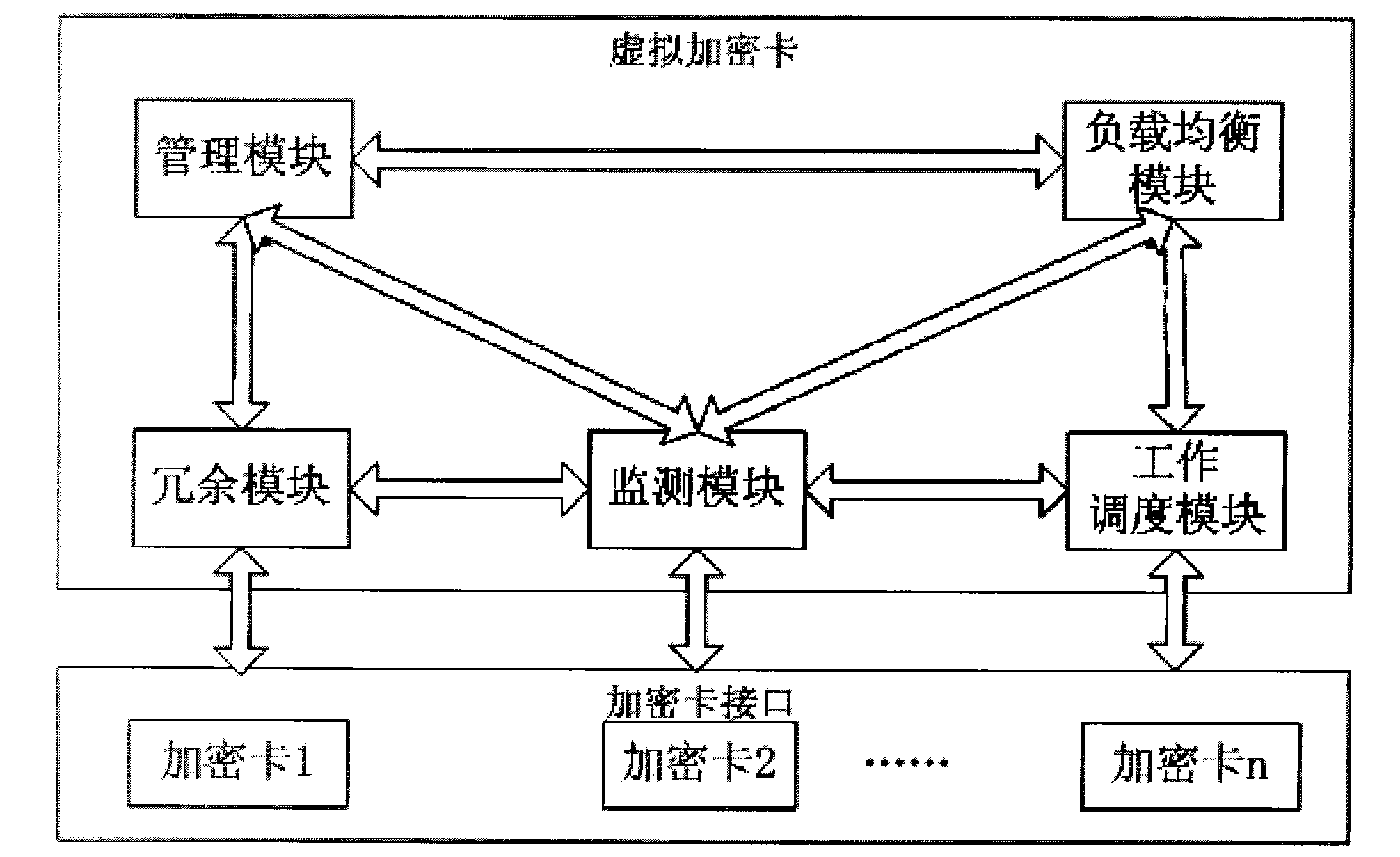
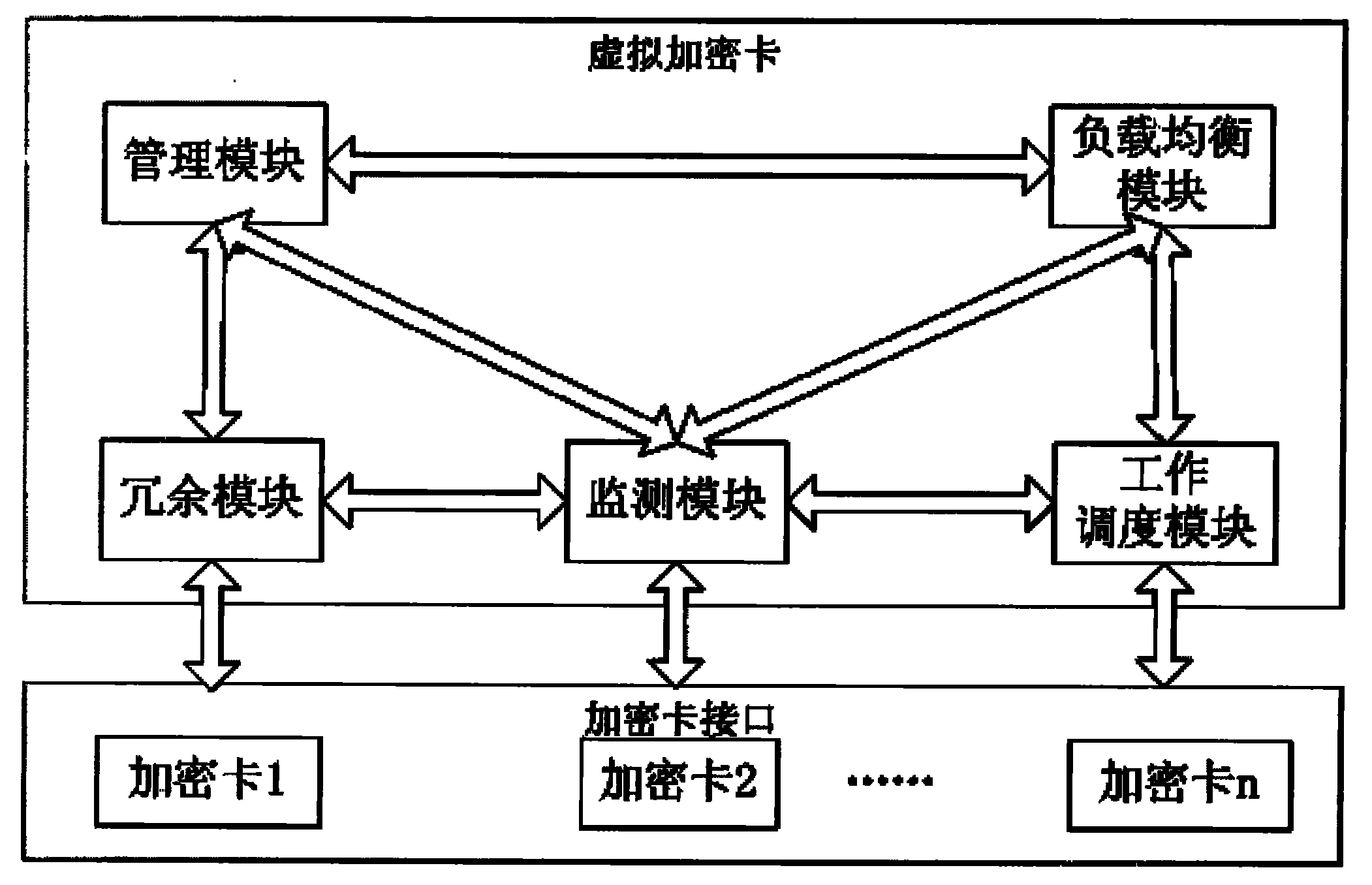
Virtual device based on multiple encryption cards
InactiveCN102023888AEasy to manageImprove usabilitySoftware simulation/interpretation/emulationMultiple encryptionUsability
The invention provides a virtual encryption card based on multiple encryption cards, which comprises a plurality of encryption cards, a load balancing module, a monitoring module, a management module, a redundancy module and a work scheduling module. The invention simplifies the management of the virtual encryption cards, and can concurrently process the concurrent requests among the encryption cards, thereby greatly enhancing the processing capacity; in the aspect of load balancing, the invention realizes load balanced allocation among the cards for each request; by using the multiple card redundancy, the request can switch among multiple cards in a seamless way, thereby greatly enhancing the availability and usability; and in the aspect of multiple card scheduling, the invention completely differs from the traditional request and card binding relation, realizes the independence of requests from cards, reduces the coupling property between requests and cards, greatly enhances the reliability of the encryption card, and can not influence the processing of the application requests due to the abnormity of a certain encryption card.
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
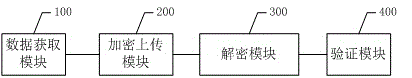
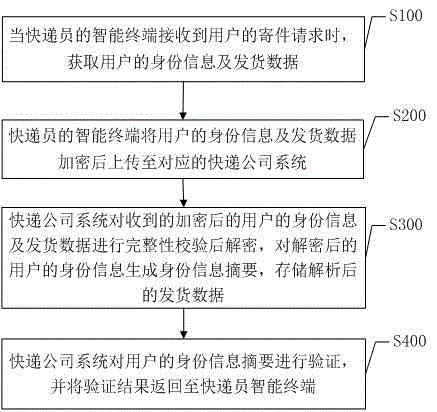
Identity real-name authentication method and authentication system based on express sending
InactiveCN105554032AImprove securityPrevent leakageDigital data authenticationTransmissionMultiple encryptionInformation transmission
The invention discloses an identity real-name authentication method and authentication system based on express sending. The method comprises: when an intelligent terminal of a courier receives a sending request of a user, acquiring identity information of the user and sending data; by the intelligent terminal of the courier, uploading the identity information of the user and the sending data to a corresponding express company system after encrypting the identity information of the user and the sending data; by the express company system, carrying out decryption after carrying out integrity checking on the received encrypted identity information of the user and the received encrypted sending data, generating an identity information abstract on the decrypted identity information of the user, and storing the analyzed sending data; and by the express company system, carrying out real-name authentication on the identity information abstract of the user, storing the identity information abstract after successfully carrying out real-name authentication, and returning an authentication result to the intelligent terminal of the courier. According to the identity real-name authentication method and authentication system based on express sending, which are disclosed by the invention, a multiple encryption method is adopted, so that safety of user identity information transmission is improved; and the courier is prompted whether to send an express item to the user according to an identity checking result, so that data leakage is prevented, and convenience is provided for the user.
Owner:深圳支付界科技有限公司
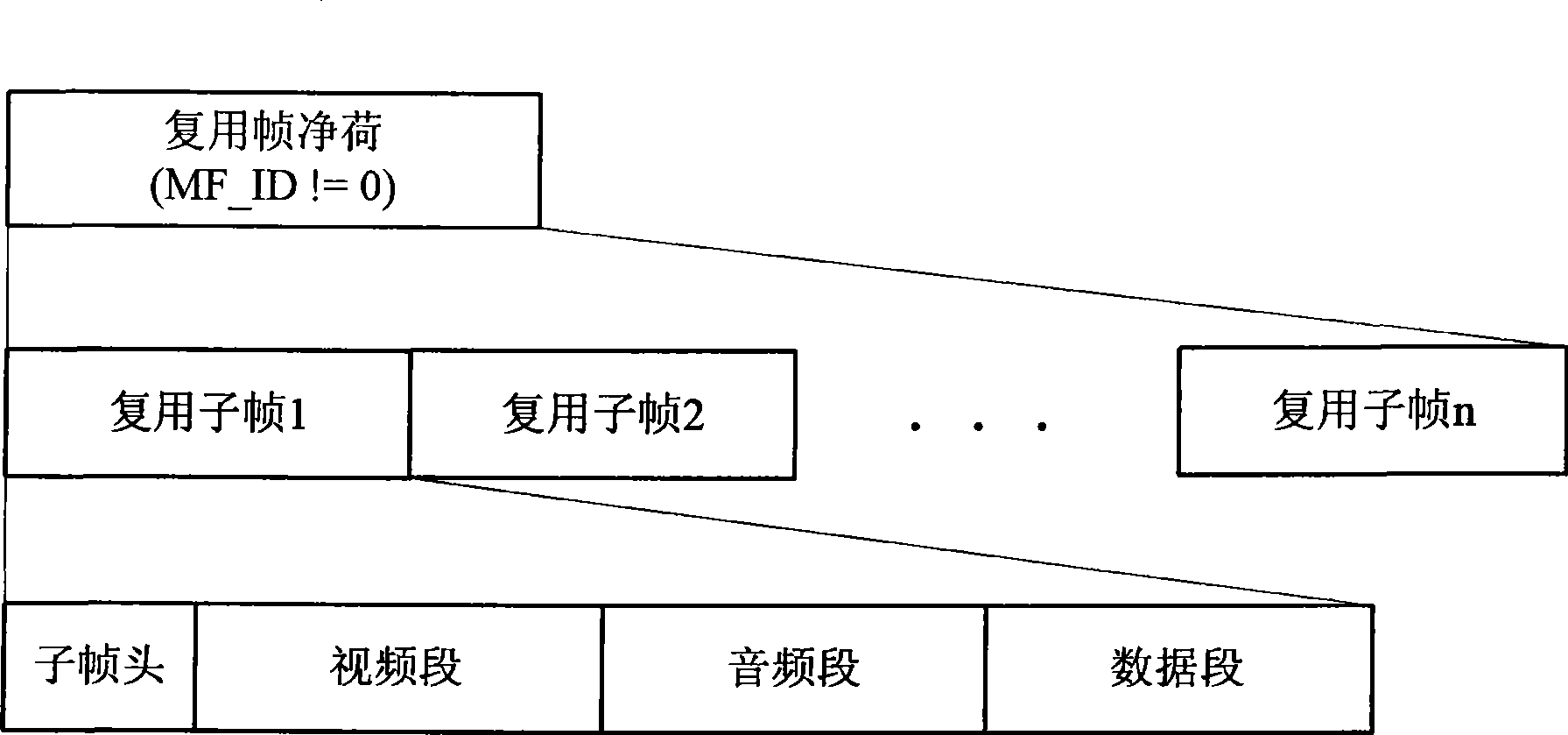
Implementation method and apparatus for multimedia broadcast multiple ciphering and deciphering
InactiveCN101478544AEasy to expandImplement multi-level encryptionKey distribution for secure communicationSpecific information broadcast systemsMultiple encryptionComputer hardware
The invention provides a multimedia broadcasting multiple encryption and decryption method and an apparatus for improving the safety of a mobile multimedia broadcasting system. The encryption method comprises: performing a first order scrambling to a coded program stream and / or data pack, performing a first order encryption and second a order encryption to a used cipher key when scrambling, wherein the first scrambling employs the program stream and / or data pack as objects, the first encryption is to encrypt the cipher key during the first scrambling and to obtain a first entitlement control message (ECM1) and a first entitlement management message (EMM1), the second order encryption comprises twice encryption, the first encryption employs a second cipher key to encrypt the obtained ECM1 and the EMM1 after the last order encryption, the second encryption is to encrypt the second cipher key; encapsulating the encryption of the scrambled program stream and / or data pack and the obtained results after the second encryption to service integration frames, allocating a control information table and encapsulating the table to a control integration frame; modulating the encapsulated integration frame to an electromagnetic wave on a physical channel and transmitting the electromagnetic wave to the air.
Owner:ZTE CORP
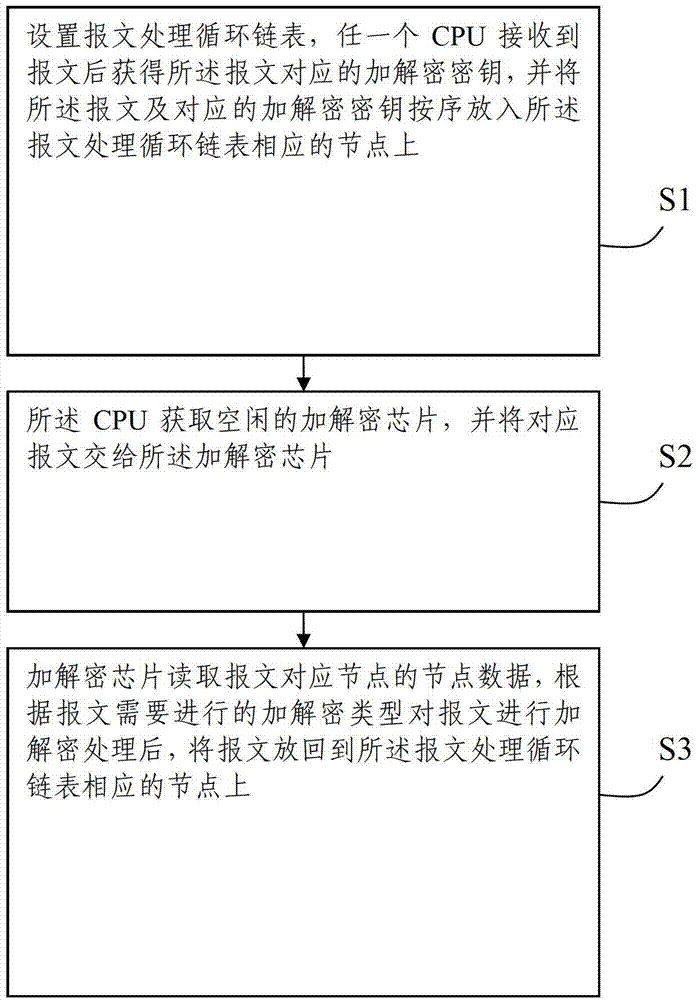
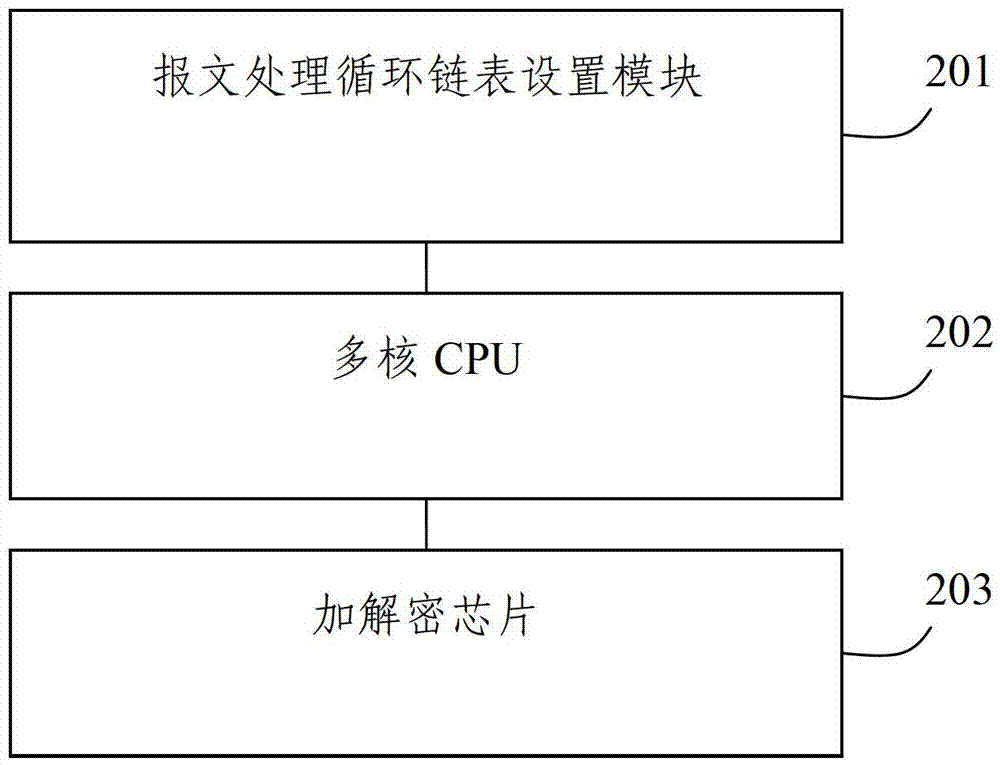
Order-preserving method and system for encrypting and decrypting messages by multiple encryption and decryption chips in parallel
The invention discloses an order-preserving method for encrypting and decrypting messages by multiple encryption and decryption chips in parallel. The order-preserving method comprises the following steps of: S1, setting a message processing cyclic chain table, after any central processing unit (CPU) receives a message, acquiring an encryption and decryption key corresponding to the message, and putting the messages and the corresponding encryption and decryption keys to corresponding nodes of the message processing cyclic chain table; S2, acquiring idling encryption and decryption chips by the CPU, and sending the corresponding messages to the encryption and decryption chips; and S3, reading node data of the nodes corresponding to the messages, encrypting and decrypting the messages according to encryption and decryption types of the messages, and putting the messages back to the corresponding nodes of the message processing cyclic chain table. The invention also discloses an order-preserving system implementing the order-preserving method. By the method and the system, the order of the messages can be guaranteed when multiple encryption and decryption chips encrypt and decrypt the messages at the same time, and a disorder phenomenon during sending of the messages is avoided.
Owner:OPZOON TECH
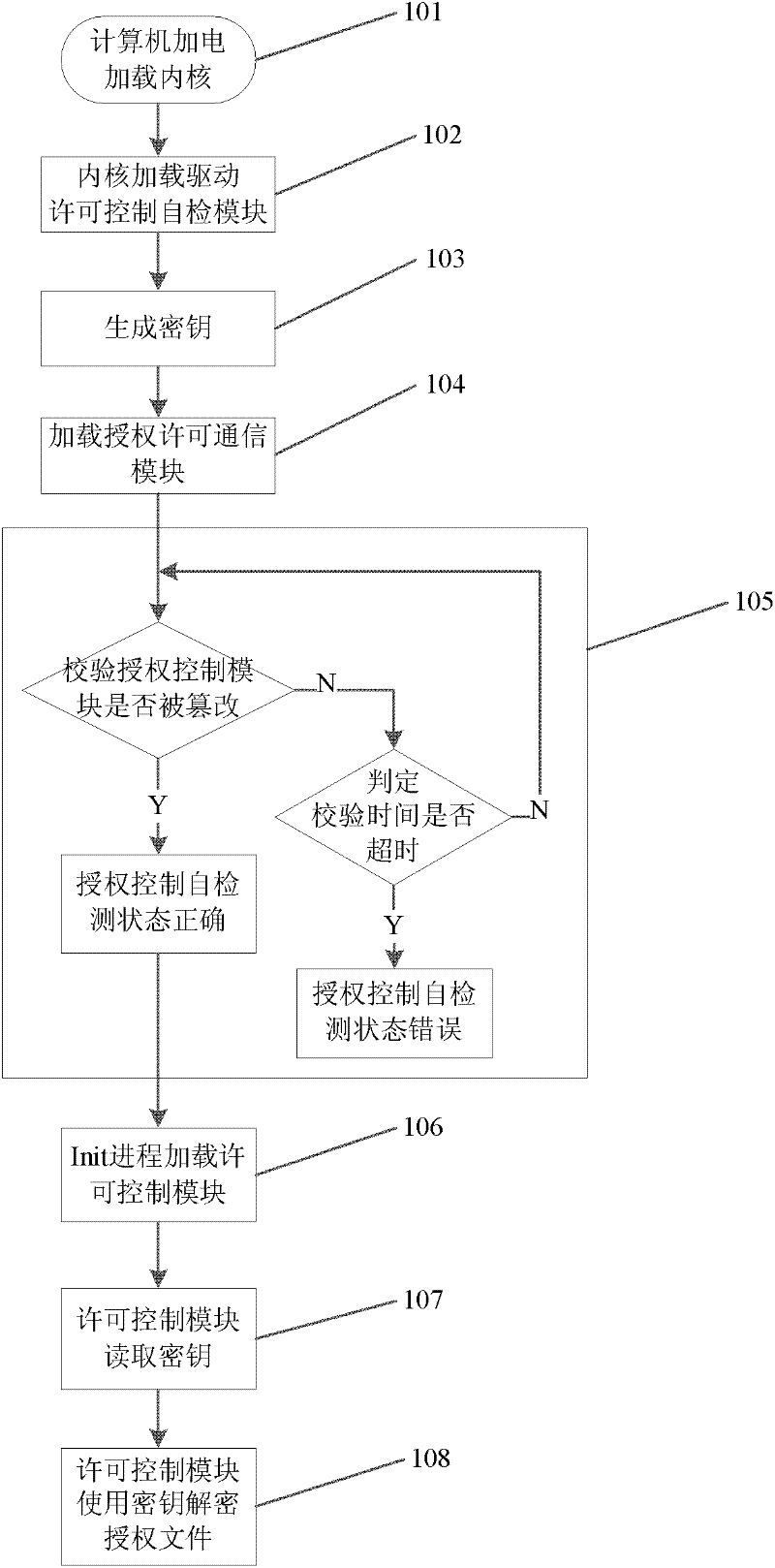
Method and system for license control of Linux operating system
ActiveCN102456111AGuaranteed operabilityGuaranteed normal startupDigital data protectionMultiple encryptionOperational system
The invention relates to a method for the license control of a Linux operating system. The method comprises two parts, namely a self protection mechanism and a license management mechanism respectively, wherein the self protection mechanism is implemented by both a kernel layer license control self-inspection module and an application layer license communication module; and the license management mechanism is implemented through a license communication module by an application layer license control module and an application layer license distribution module. The self protection mechanism loads the license control self-inspection module into a kernel space by utilizing the loading of a Linux system kernel, and the license control self-inspection module finishes integrity inspection on the license control function of the system and performs corresponding processing according to an inspection result. By the method, the problem that the license control function of the conventional software or system is cancelled can be effectively solved, and the validity of a license file in a distribution process can be ensured by multiple encryption, so the license file is prevented from being randomly falsified. The method has universality, and can be used for realizing user license control in a Linux environment.
Owner:CHINA STANDARD SOFTWARE
Medical data encryption transmission system and method
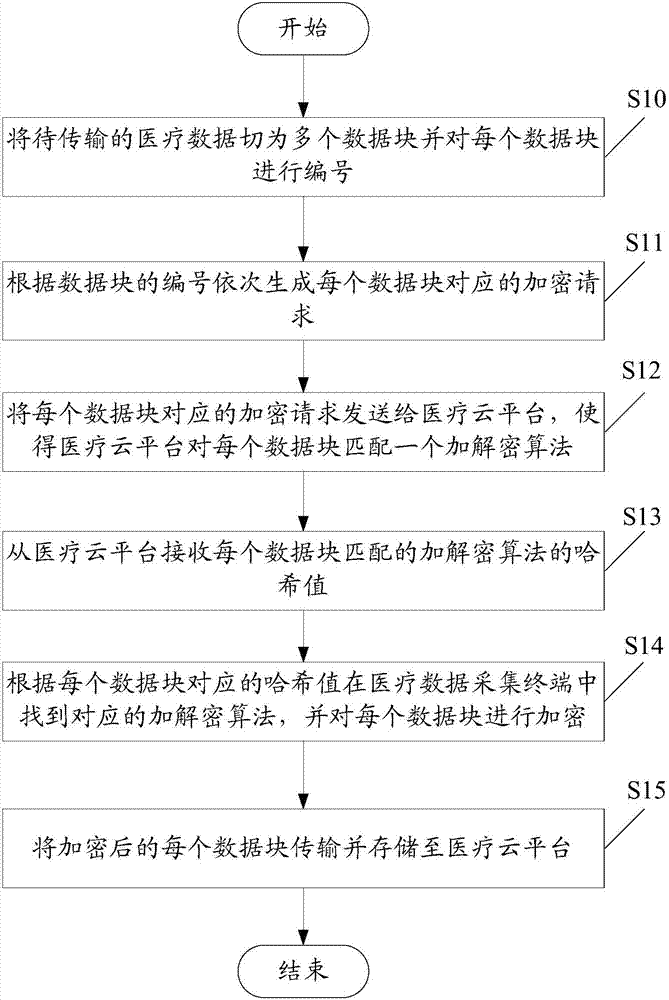
InactiveCN107018145AImprove information securityPrevent leakageTransmissionMultiple encryptionData acquisition
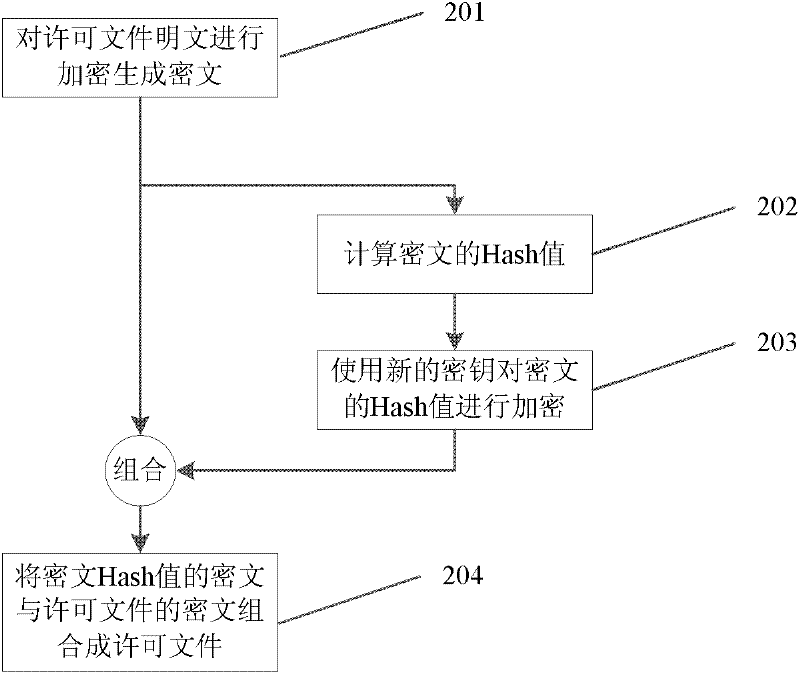
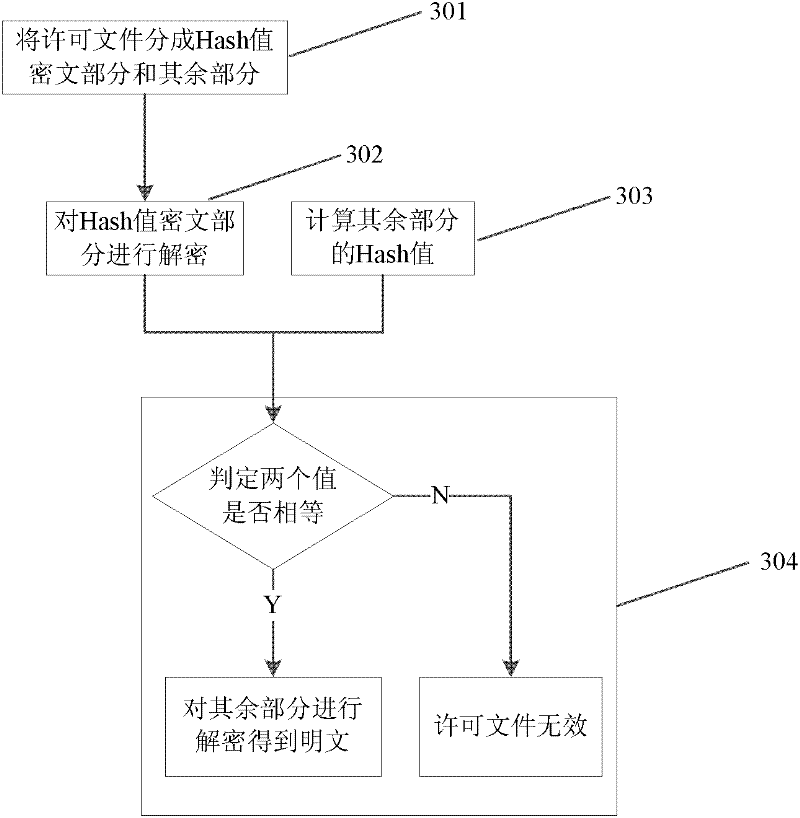
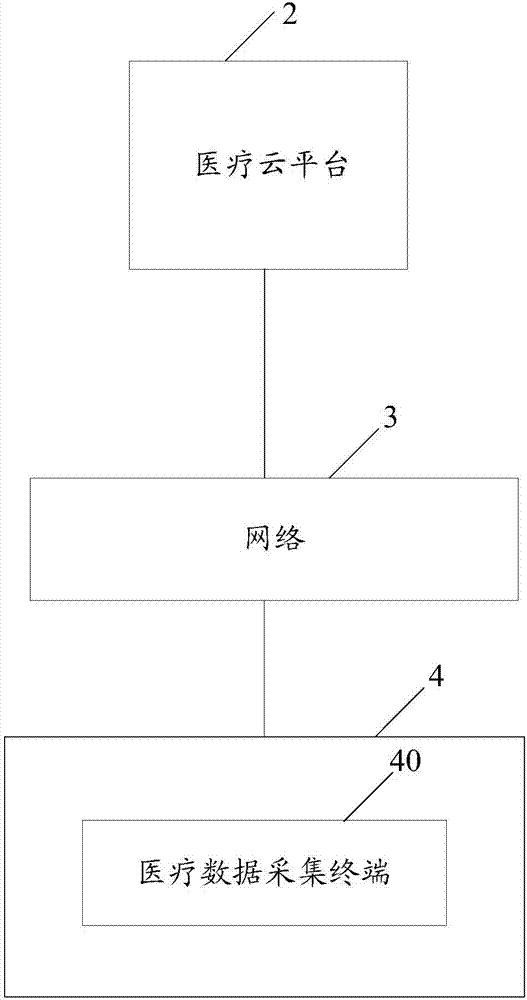
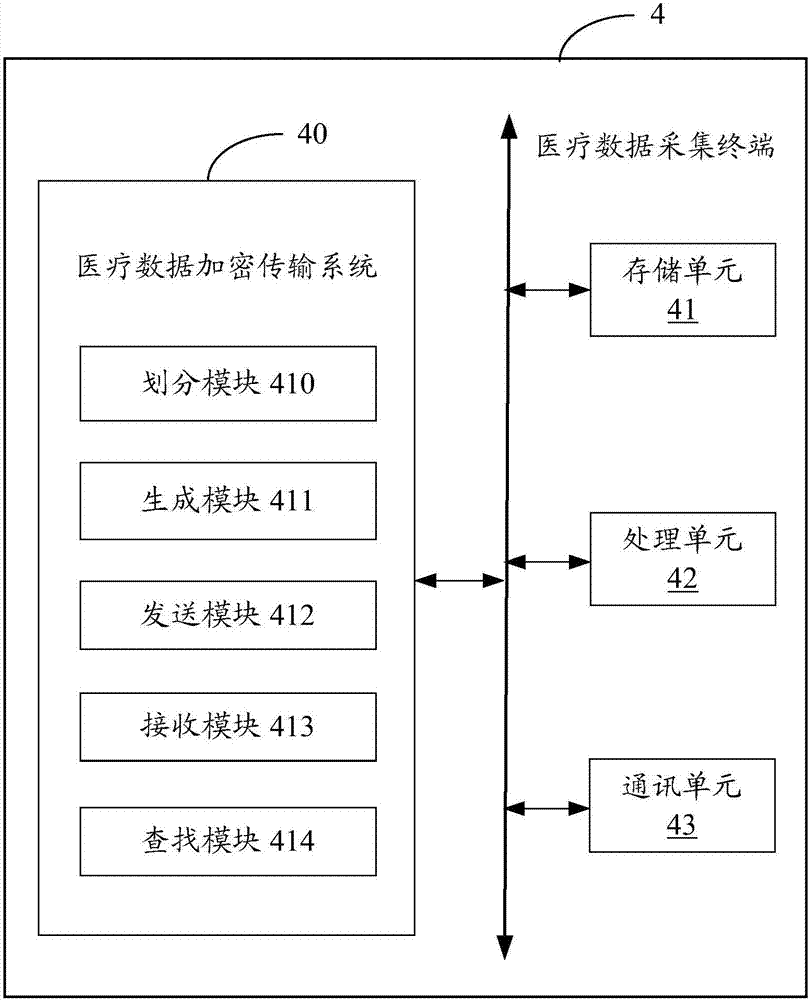
The invention provides a medical data encryption transmission system and method. The method comprises the following steps: cutting the medical data to be transmitted into multiple data blocks and numbering each data block; sequentially generating an encryption request corresponding to each data block according to the number of the data blocks; sending the encryption request corresponding to each data block to a medical cloud platform to ensure that the medical cloud platform matches an encryption-decryption algorithm for each data block; receiving the harsh value of the encryption-decryption algorithm matched with each data block from the medical cloud platform; finding the corresponding encryption-decryption algorithm from a medical data acquisition terminal according to the harsh value corresponding to each data block, and encrypting each data block; and transmitting and storing each encrypted data block into the medical cloud platform. According to the implementation of the medical data encryption transmission system and method provided by the invention, the transmitted medical data is encrypted and decrypted by using a dynamic encryption-decryption algorithm, the same batch of medical data is encrypted by multiple encryption and decryption algorithms, and thus the information security of the medical data can be further improved, and secret leakage events can be avoided.
Owner:ANYCHECK INFORMATION TECH
Cloud intelligent lock system based on multiple encryption mode and secret key management method
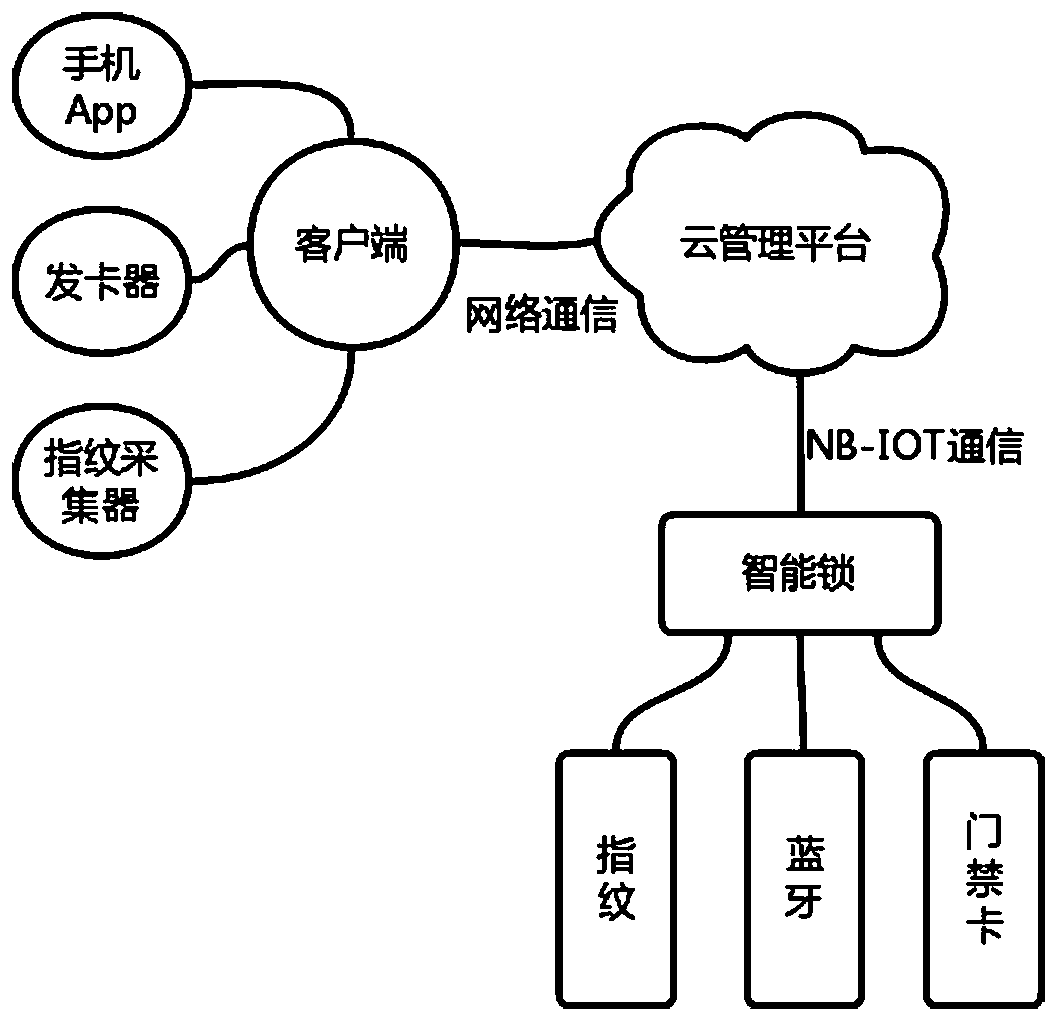
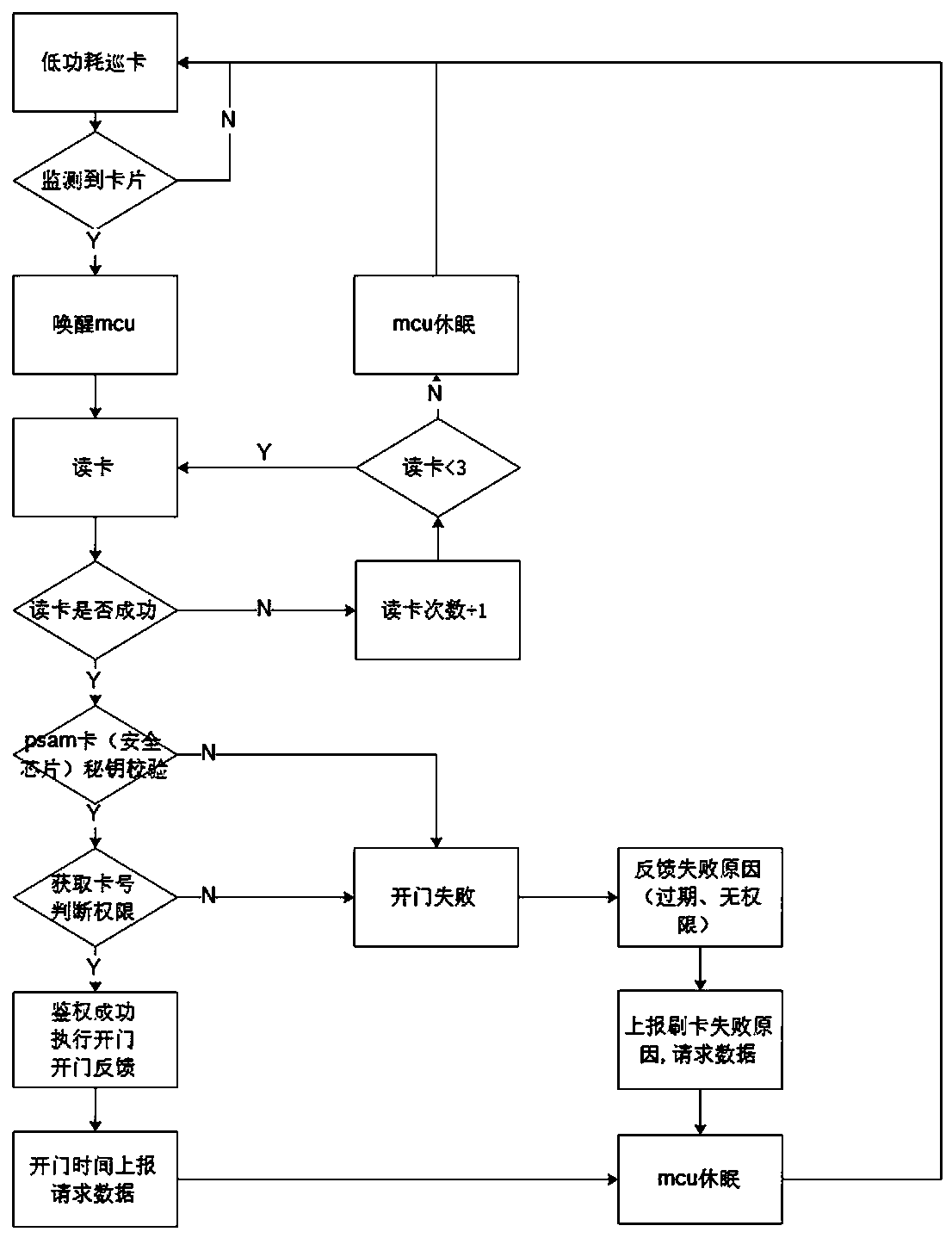
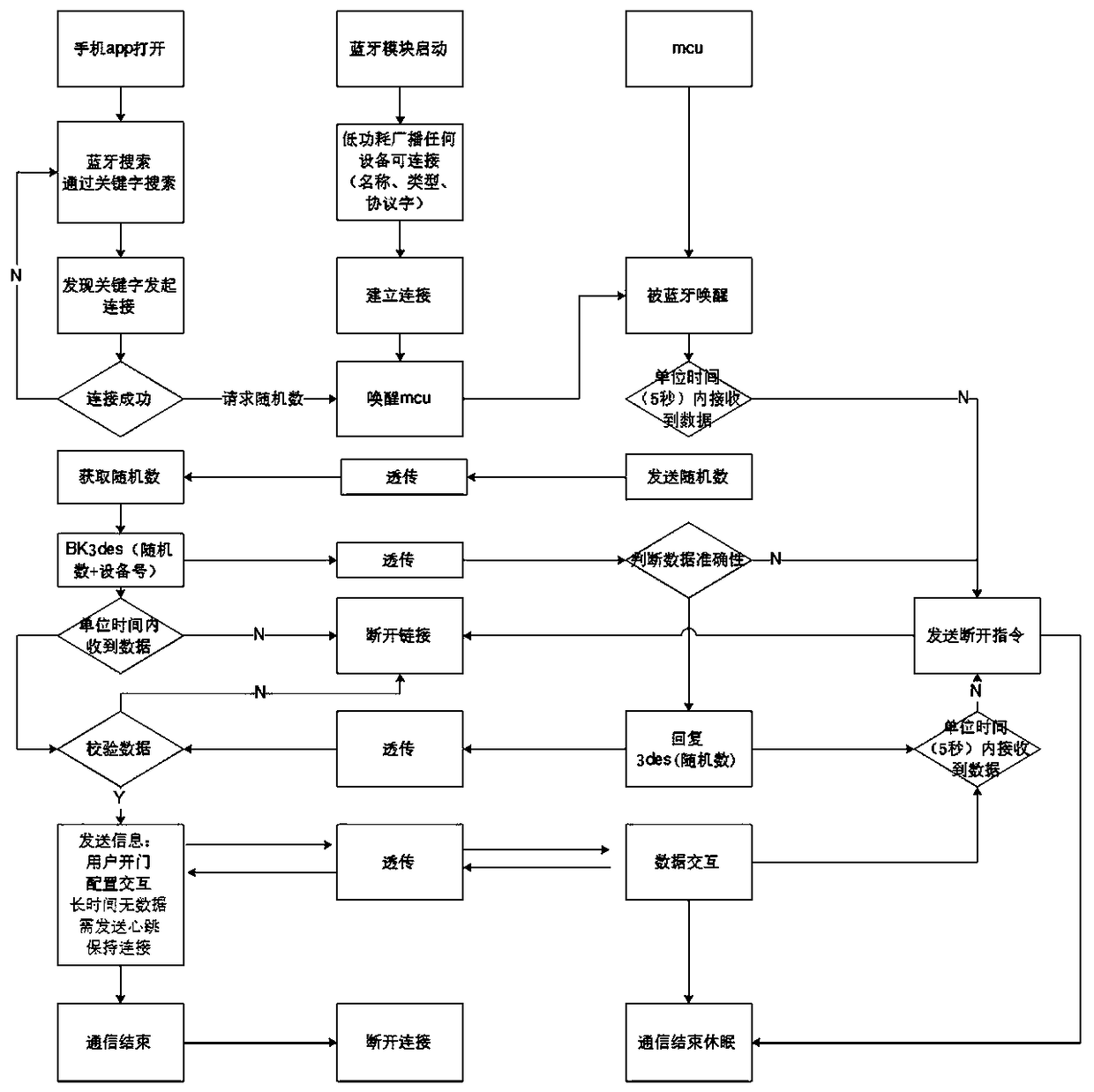
PendingCN109448197AReal-time monitoring of operationEasy to manage centrallyIndividual entry/exit registersTransmissionMultiple encryptionCiphertext
The invention relates to a cloud intelligent lock system based on a multiple encryption mode and a secret key management method. The cloud intelligent lock system comprises an intelligent lock, a cloud management platform and a client, the intelligent lock is registered to the cloud management platform by adopting networking authentication registration through a NB-IOT (Narrow Band-Internet of Things) network, the client binds the authority information of fingerprints, an entrance guard card and bluetooth of a user in a matched mode according to the identity information of the user, the authority information is enabled to generate ciphertext to be sent to the corresponding intelligent lock through communication secret keys of the intelligent lock and an encryption algorithm, and the cloudmanagement platform adopts a secret key dispersing algorithm to disperse corresponding Managekeys so as to form modes of one lock to one secret key, one card to one secret key and one bluetooth to onesecret key. According to the cloud intelligent lock system based on a multiple encryption mode and the secret key management method, the intelligent lock is registered to the cloud management platform by adopting a networking authentication mode, so that networking of intelligent lock equipment is realized, centralized management is facilitated, particularly for hotels and public renting housings, personnel and safety management is facilitated, different encryption secret keys for different door opening modes and different encryption secret keys for the same door opening mode are adopted, andtherefore the safety is fully guaranteed.
Owner:HANGZHOU GOGENIUS TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com