Virtual device based on multiple encryption cards
A virtual device and encryption card technology, which is applied in the field of encryption cards, can solve the problems of encryption card load balancing, multi-card redundancy backup, etc., and achieve the effects of improving availability and ease of use, improving processing capacity, and improving reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
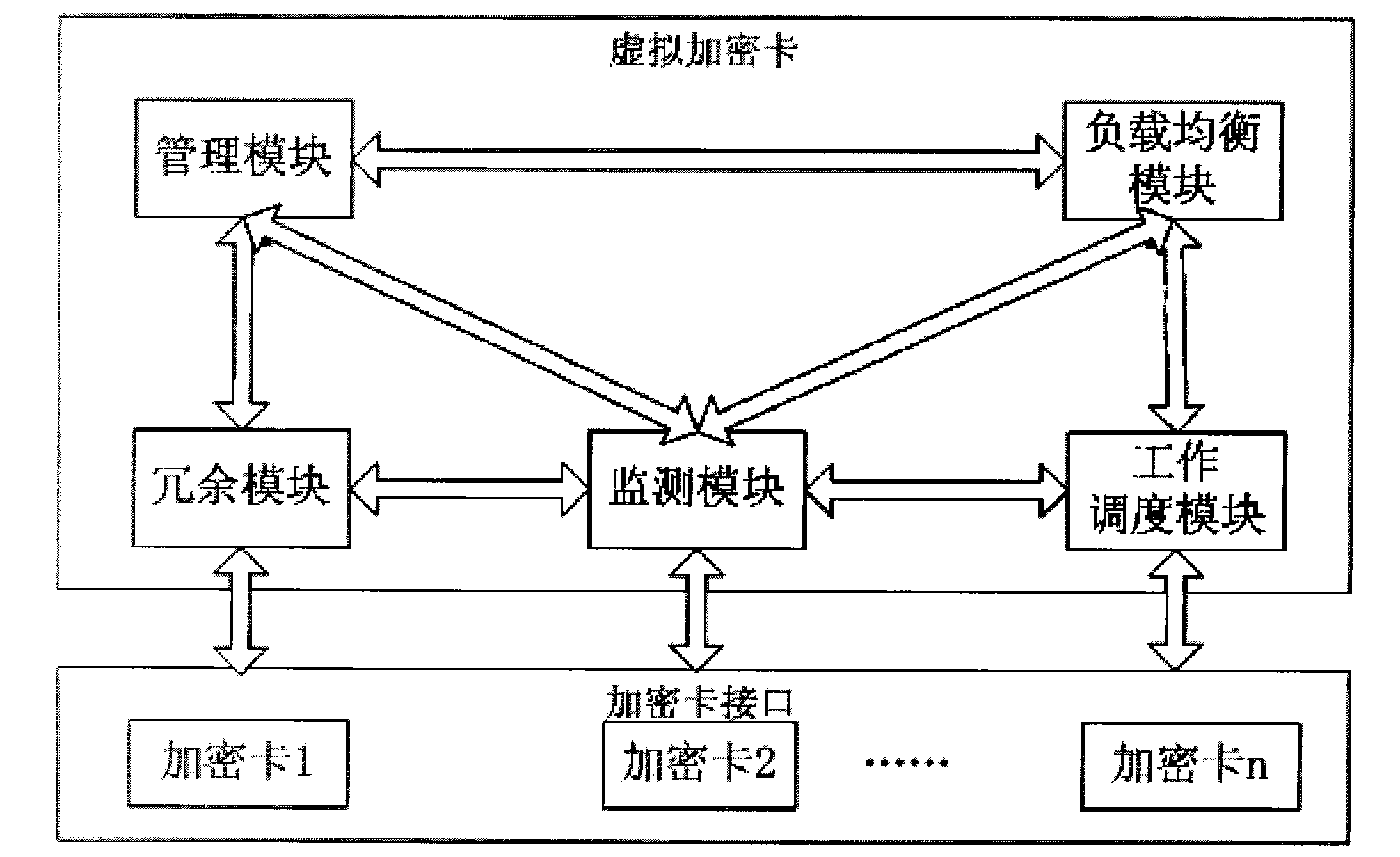
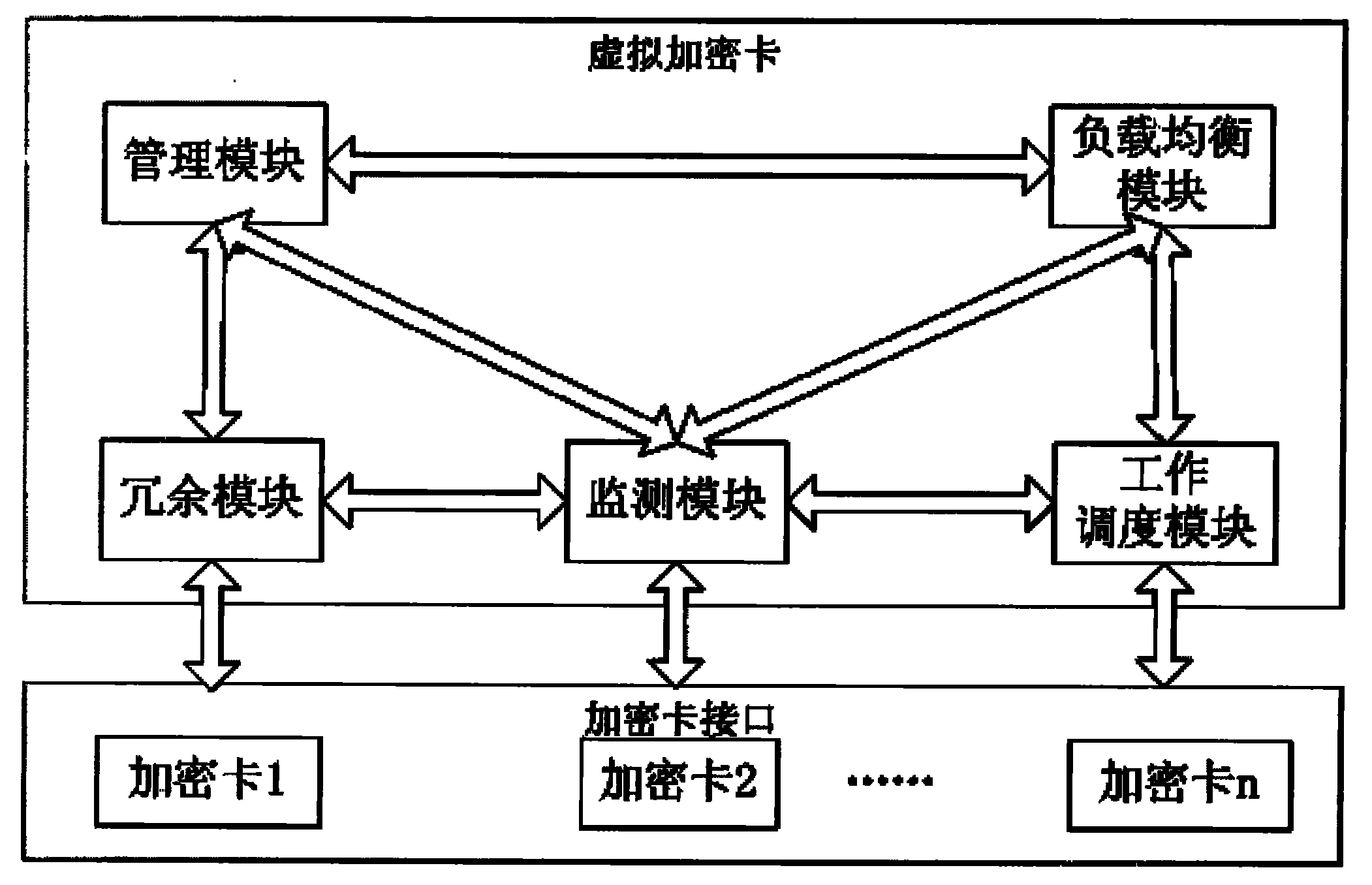
[0015] Each functional module and module communication of the virtual encryption card are as follows:
[0016] Among them, the load balancing module, the redundancy module, the work scheduling module and the monitoring module are modules that are always running, and the other modules are interface modules (interfaces for application and management calls).
[0017] Load balancing is only responsible for the load balancing of each encryption card. The current load of each encryption card is recorded based on the amount of requests being processed by the encryption card. Each request will be distributed to one or several encryption cards with the smallest load in parallel according to whether it can be processed in parallel. (job scheduling module).
[0018] The work scheduling module schedules and completes the requested processing work according to the allocated card resources (which encryption cards), keeps the results that need to be kept and intermediate results, such as key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com