Patents
Literature
32954results about "Software simulation/interpretation/emulation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
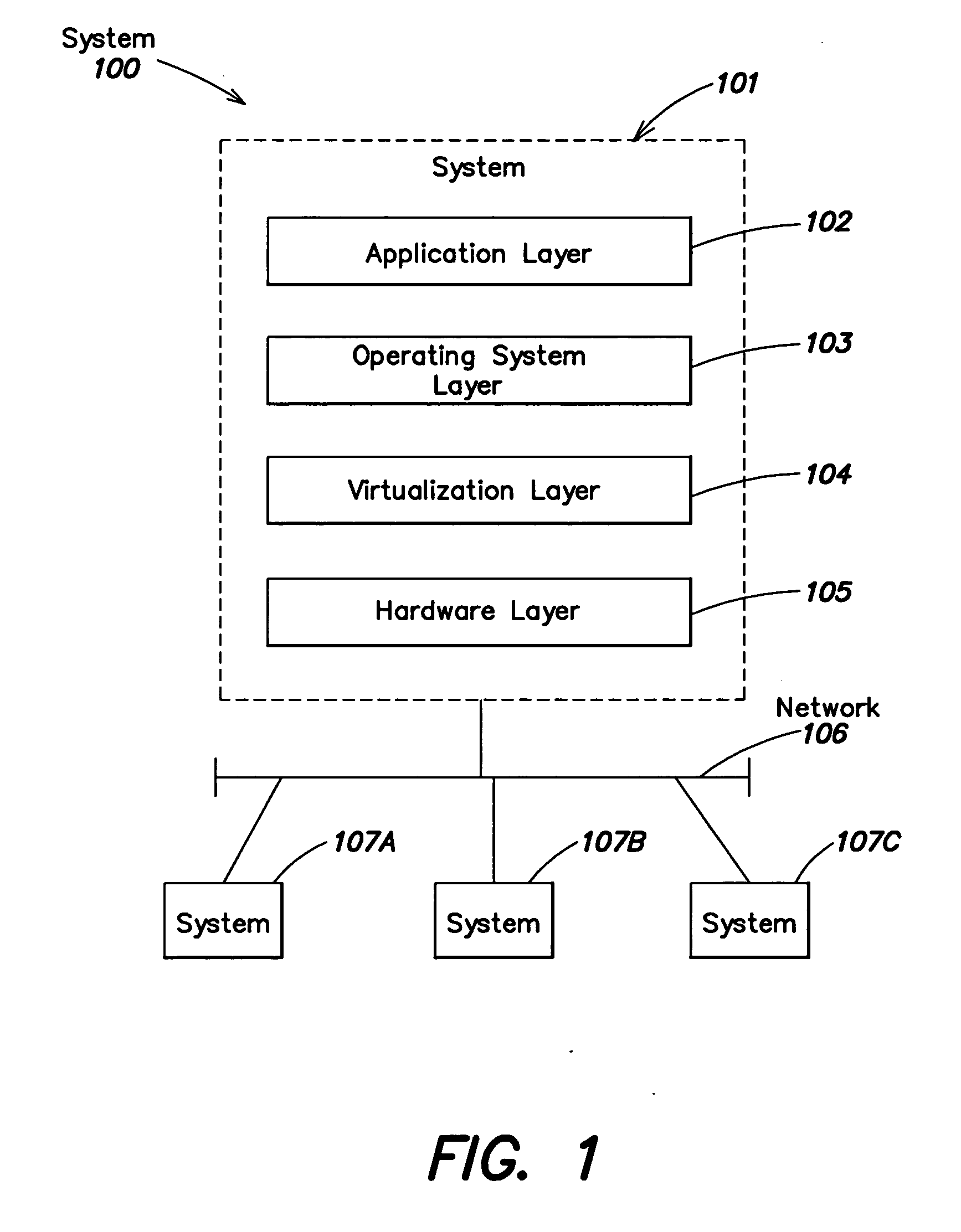
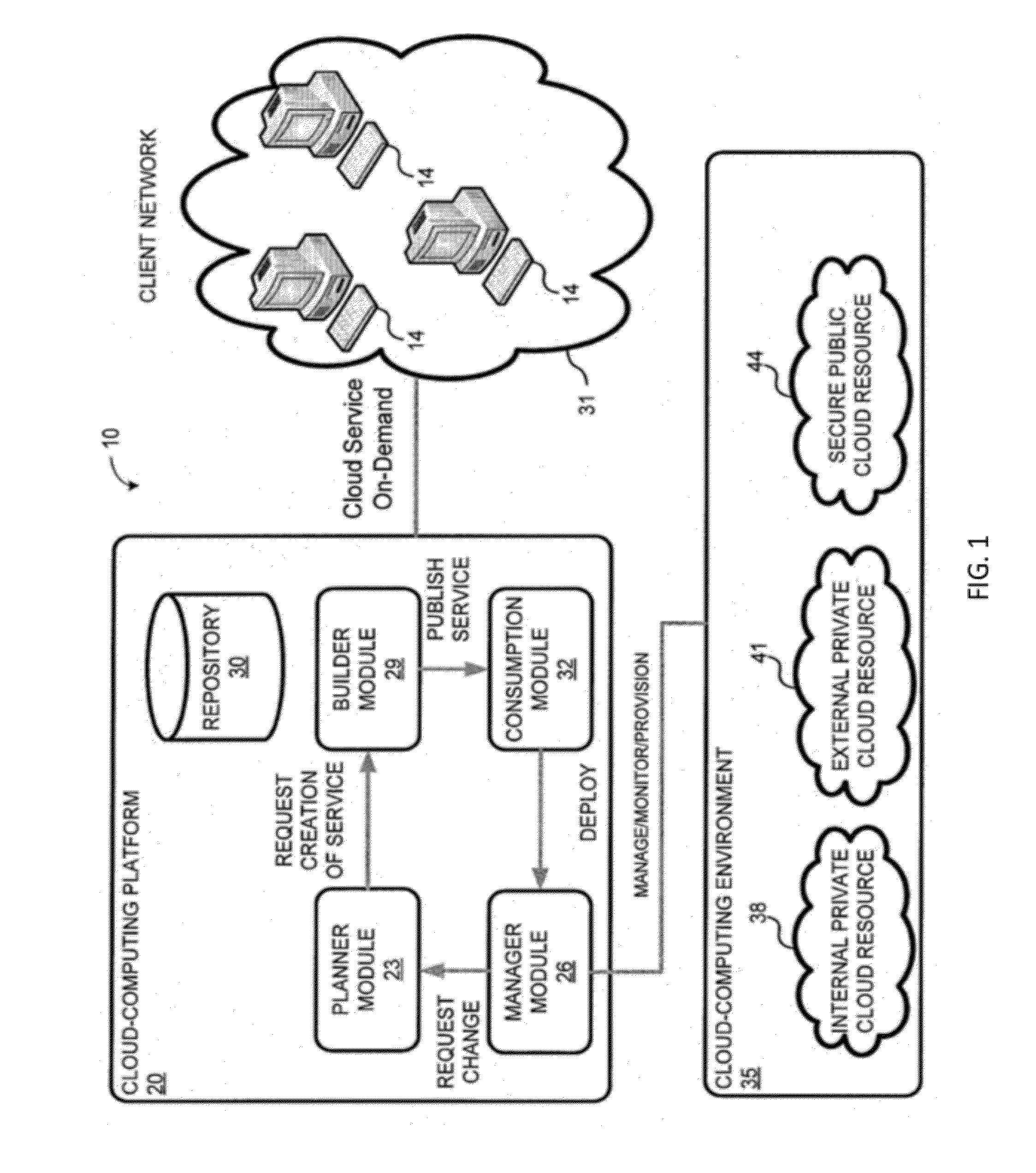
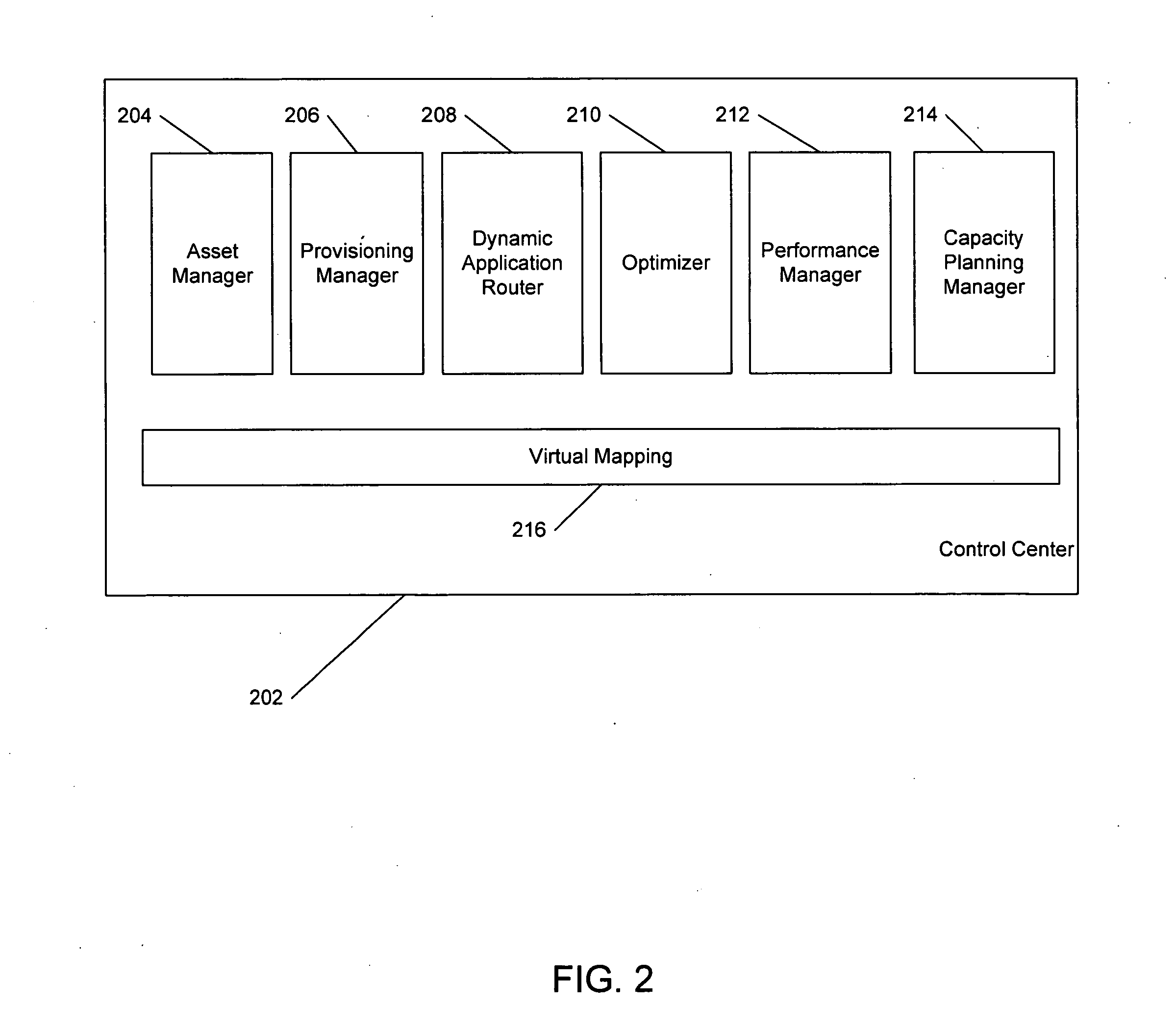
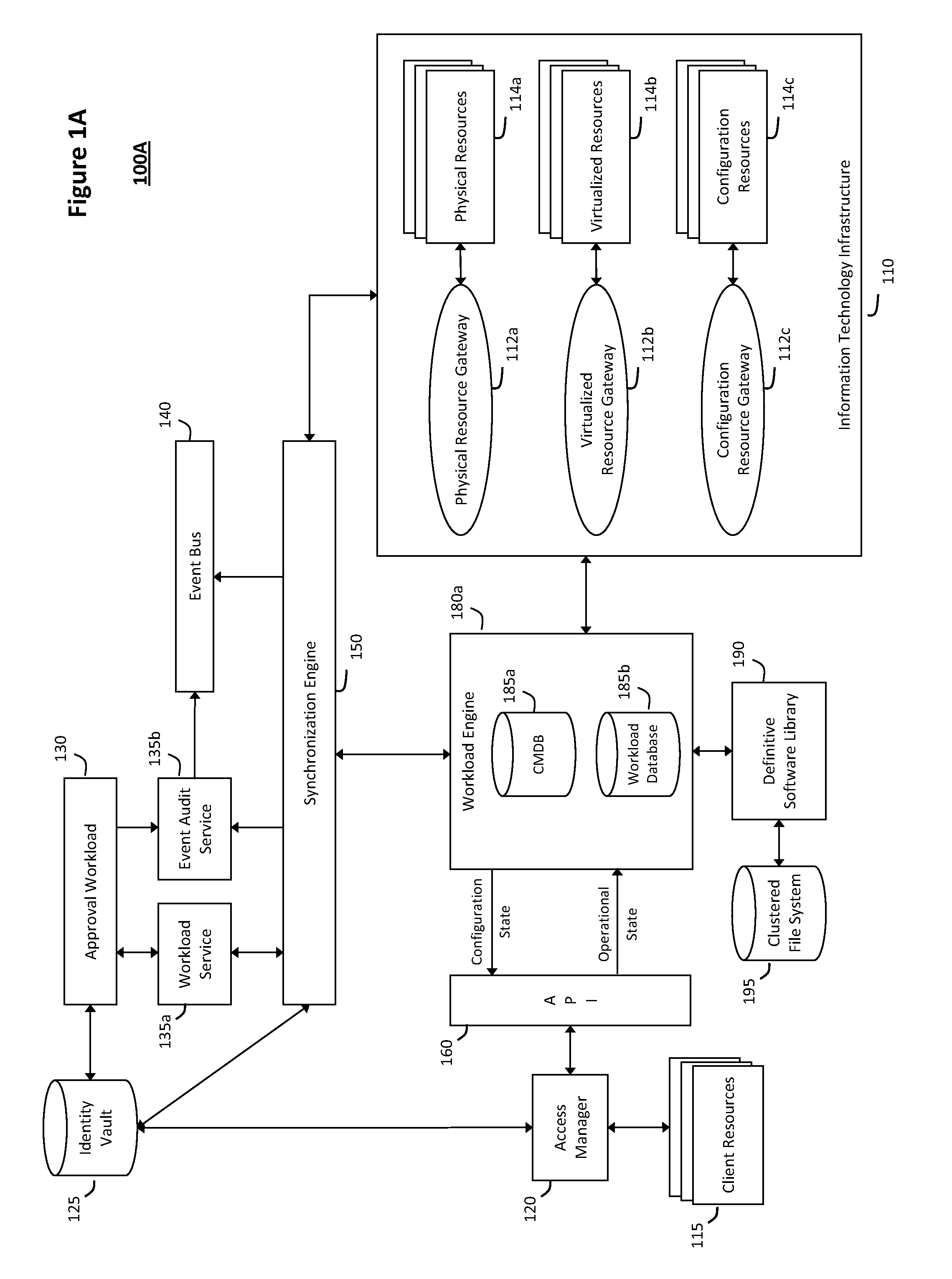
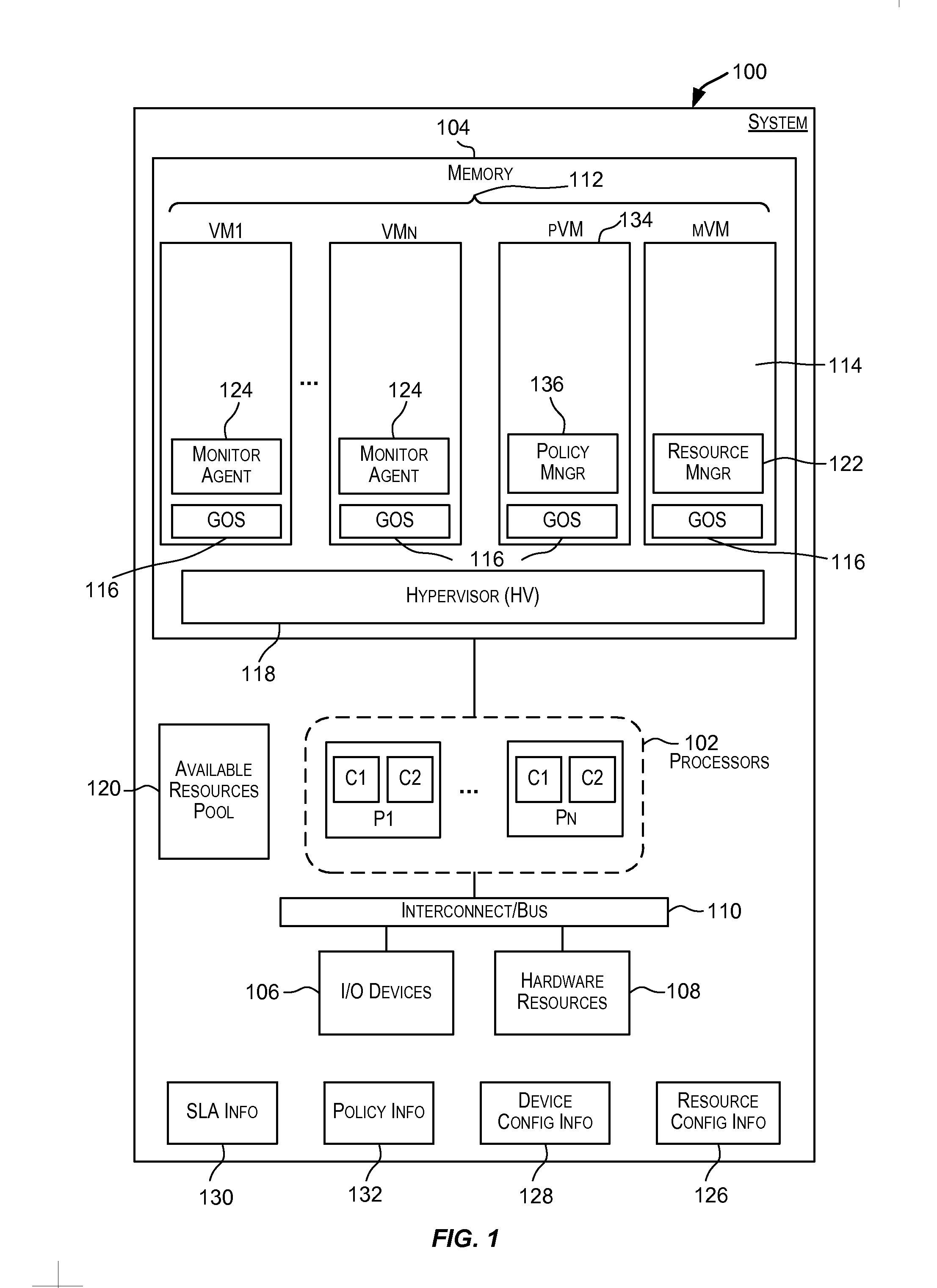
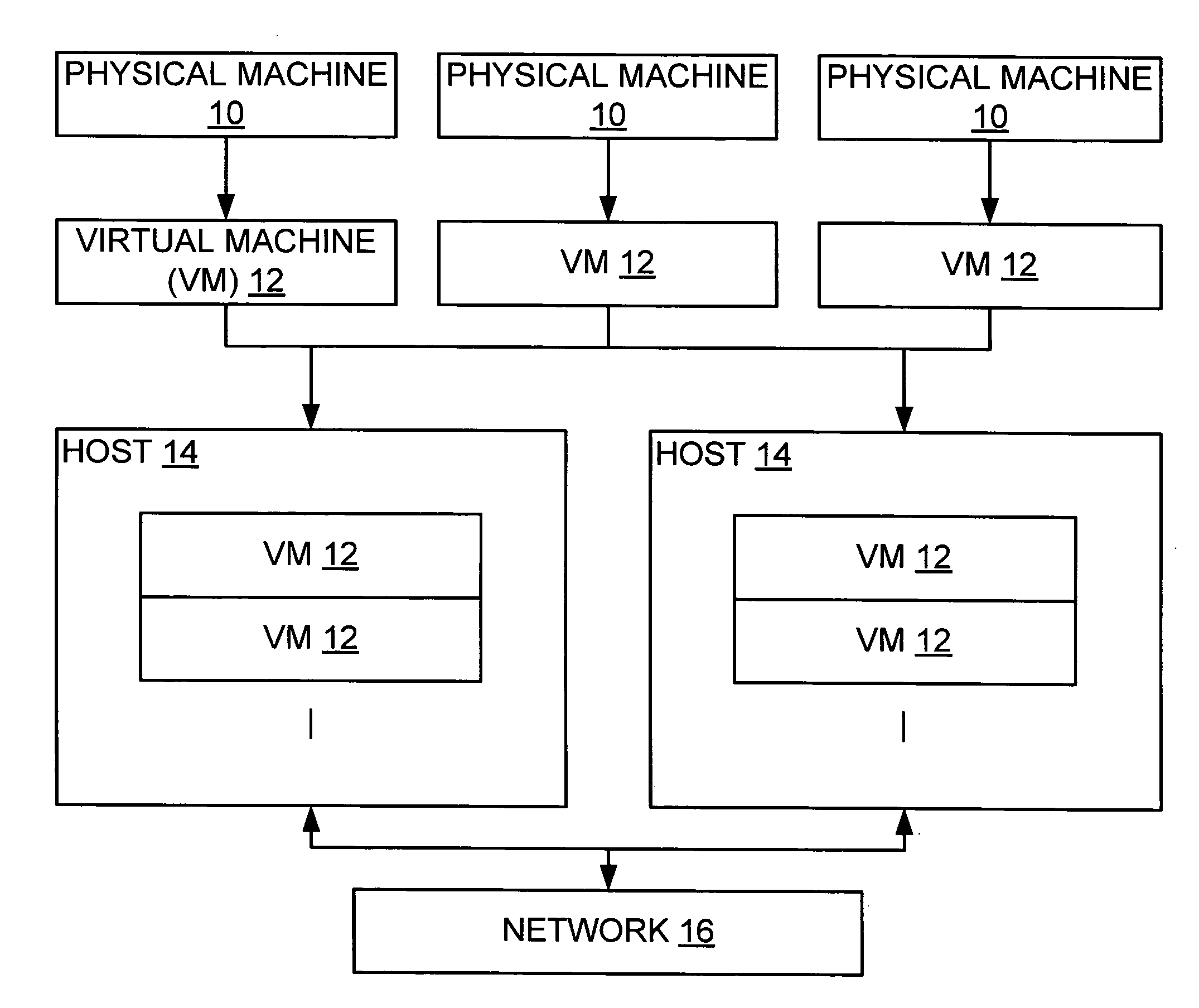
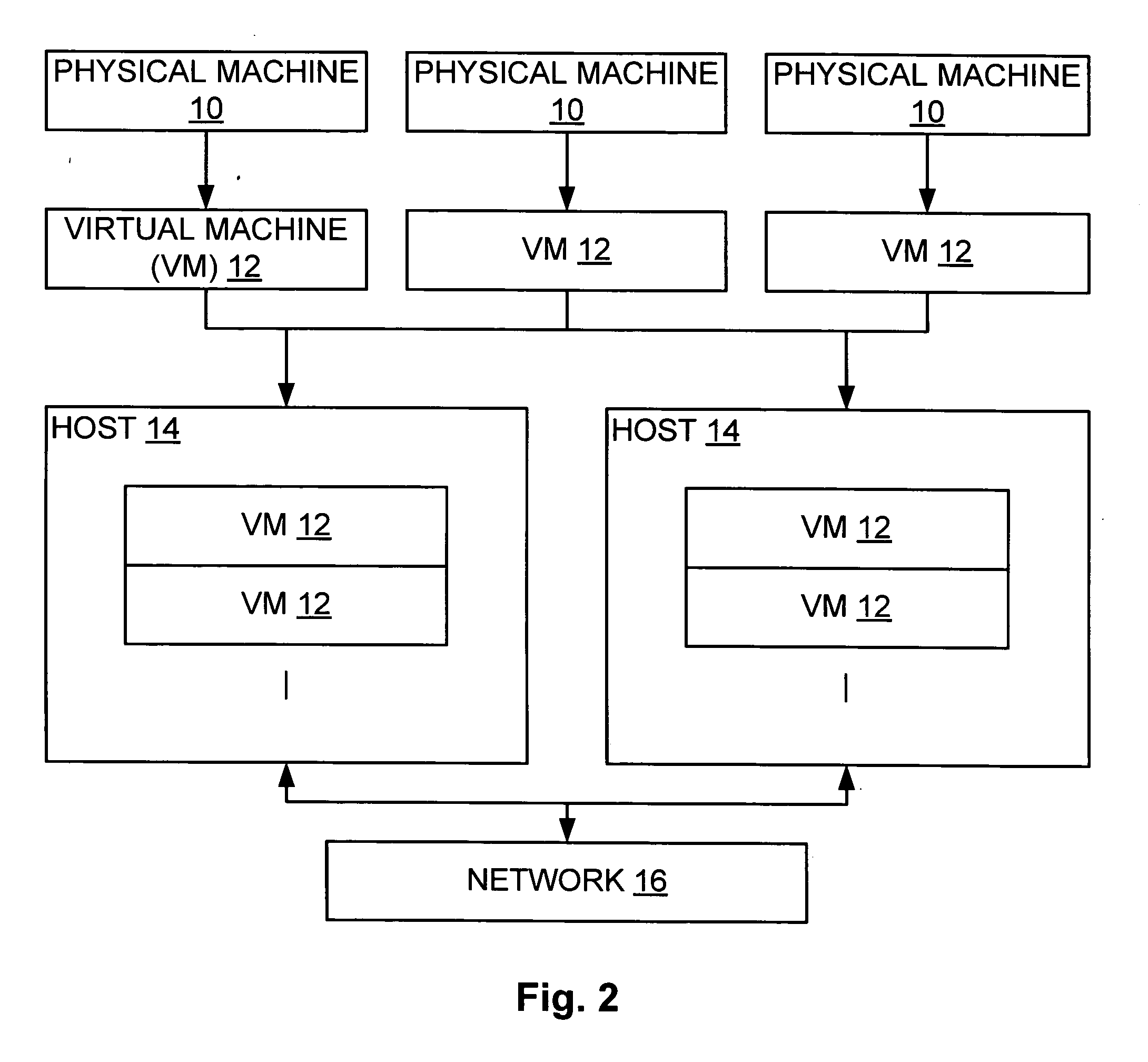
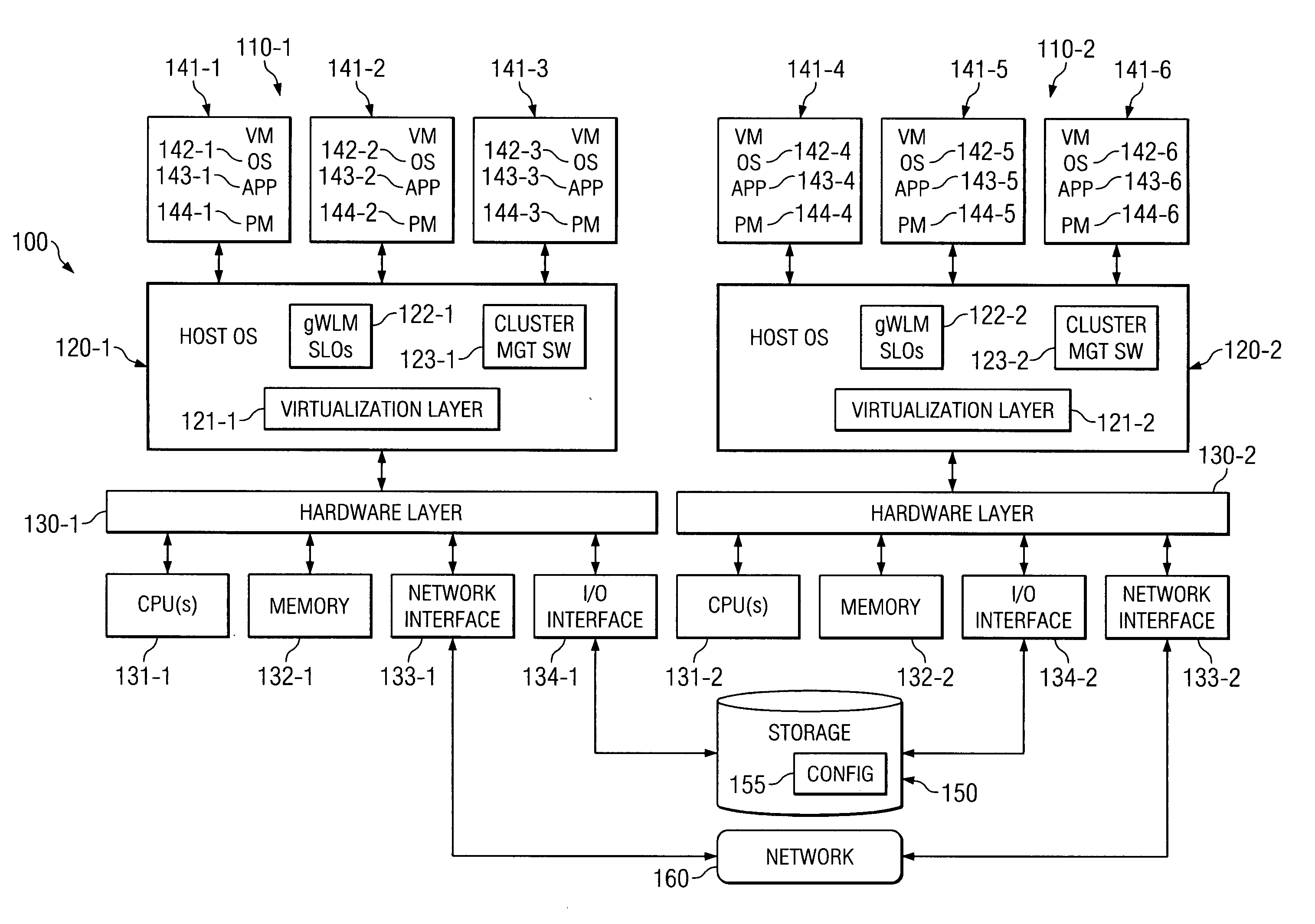
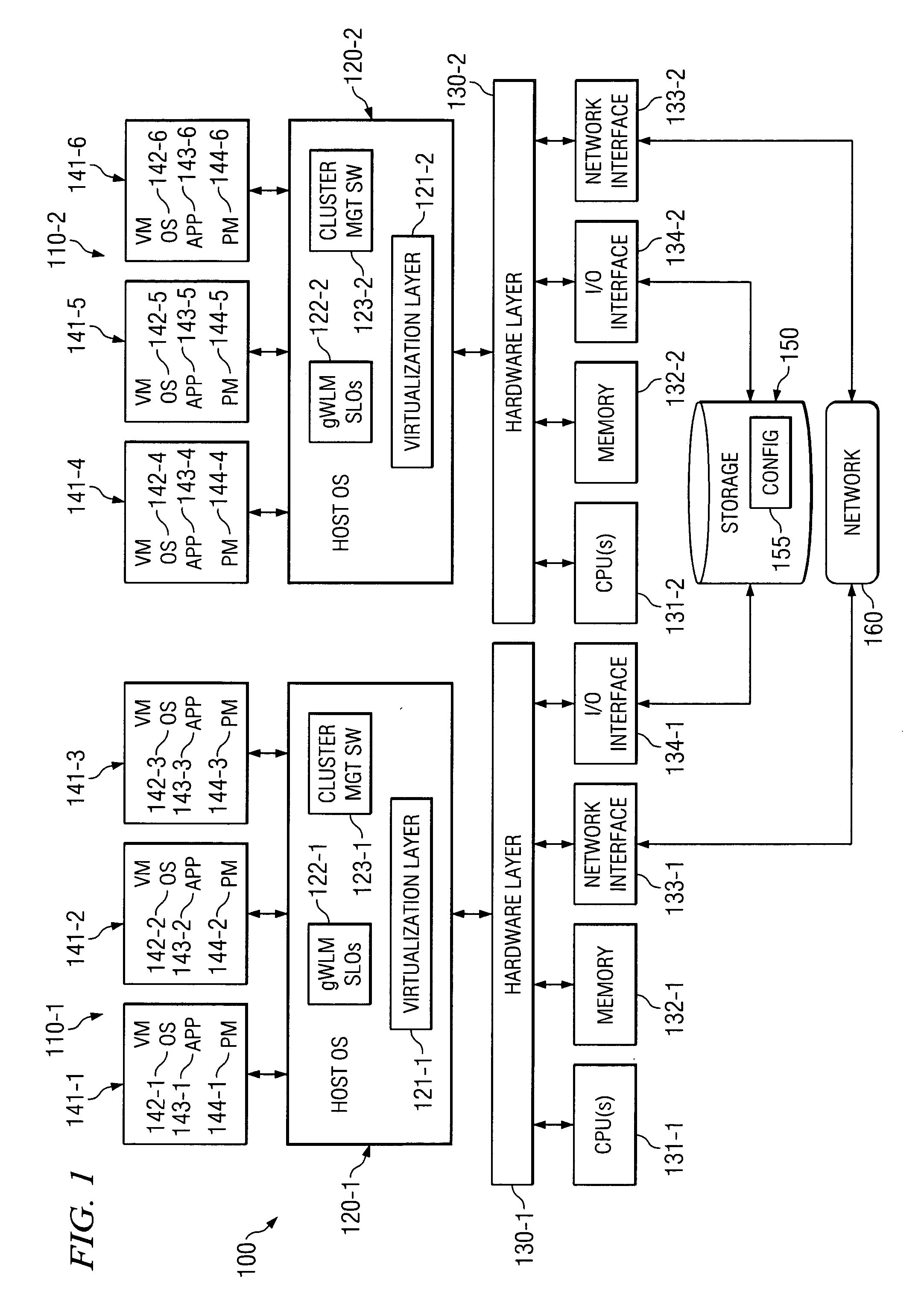
System and method for managing virtual servers
ActiveUS20050120160A1Grow and shrink capabilityMaximize useResource allocationMemory adressing/allocation/relocationOperational systemPrimitive state
A management capability is provided for a virtual computing platform. In one example, this platform allows interconnected physical resources such as processors, memory, network interfaces and storage interfaces to be abstracted and mapped to virtual resources (e.g., virtual mainframes, virtual partitions). Virtual resources contained in a virtual partition can be assembled into virtual servers that execute a guest operating system (e.g., Linux). In one example, the abstraction is unique in that any resource is available to any virtual server regardless of the physical boundaries that separate the resources. For example, any number of physical processors or any amount of physical memory can be used by a virtual server even if these resources span different nodes. A virtual computing platform is provided that allows for the creation, deletion, modification, control (e.g., start, stop, suspend, resume) and status (i.e., events) of the virtual servers which execute on the virtual computing platform and the management capability provides controls for these functions. In a particular example, such a platform allows the number and type of virtual resources consumed by a virtual server to be scaled up or down when the virtual server is running. For instance, an administrator may scale a virtual server manually or may define one or more policies that automatically scale a virtual server. Further, using the management API, a virtual server can monitor itself and can scale itself up or down depending on its need for processing, memory and I / O resources. For example, a virtual server may monitor its CPU utilization and invoke controls through the management API to allocate a new processor for itself when its utilization exceeds a specific threshold. Conversely, a virtual server may scale down its processor count when its utilization falls. Policies can be used to execute one or more management controls. More specifically, a management capability is provided that allows policies to be defined using management object's properties, events and / or method results. A management policy may also incorporate external data (e.g., an external event) in its definition. A policy may be triggered, causing the management server or other computing entity to execute an action. An action may utilize one or more management controls. In addition, an action may access external capabilities such as sending notification e-mail or sending a text message to a telephone paging system. Further, management capability controls may be executed using a discrete transaction referred to as a “job.” A series of management controls may be assembled into a job using one or management interfaces. Errors that occur when a job is executed may cause the job to be rolled back, allowing affected virtual servers to return to their original state.
Owner:ORACLE INT CORP
System and method for a cloud computing abstraction layer with security zone facilities
ActiveUS20120185913A1Rapid and dynamic deployment and scalingShorten the timeComputer security arrangementsHybrid transportVirtualizationAbstraction layer
In embodiments of the present invention improved capabilities are described for a virtualization environment adapted for development and deployment of at least one software workload, the virtualization environment having a metamodel framework that allows the association of a policy to the software workload upon development of the workload that is applied upon deployment of the software workload. This allows a developer to define a security zone and to apply at least one type of security policy with respect to the security zone including the type of security zone policy in the metamodel framework such that the type of security zone policy can be associated with the software workload upon development of the software workload, and if the type of security zone policy is associated with the software workload, automatically applying the security policy to the software workload when the software workload is deployed within the security zone.
Owner:DXC US AGILITY PLATFORM INC
Virtual systems management
Automatic configuration management of a network is provided by determining an inventory of resources at a virtualization layer of a node of the network, assigning prioritization to members of a set of network configuration elements, allocating virtual resources among the set of network configuration elements, establishing a network configuration. The configuration is managed by determining real time performance metrics for the configuration, producing a reallocation of the virtual resources based on the performance metrics that are estimated to change the established configuration, change the performance metrics, and initiating the reallocation of the virtual resources. This Abstract is provided for the sole purpose of complying with the Abstract requirement that allows a reader to quickly ascertain the subject matter of the disclosure contained herein. This Abstract is submitted with the understanding that it will not be used to interpret or to limit the scope or the meaning of the claims.
Owner:TOUTVIRTUAL
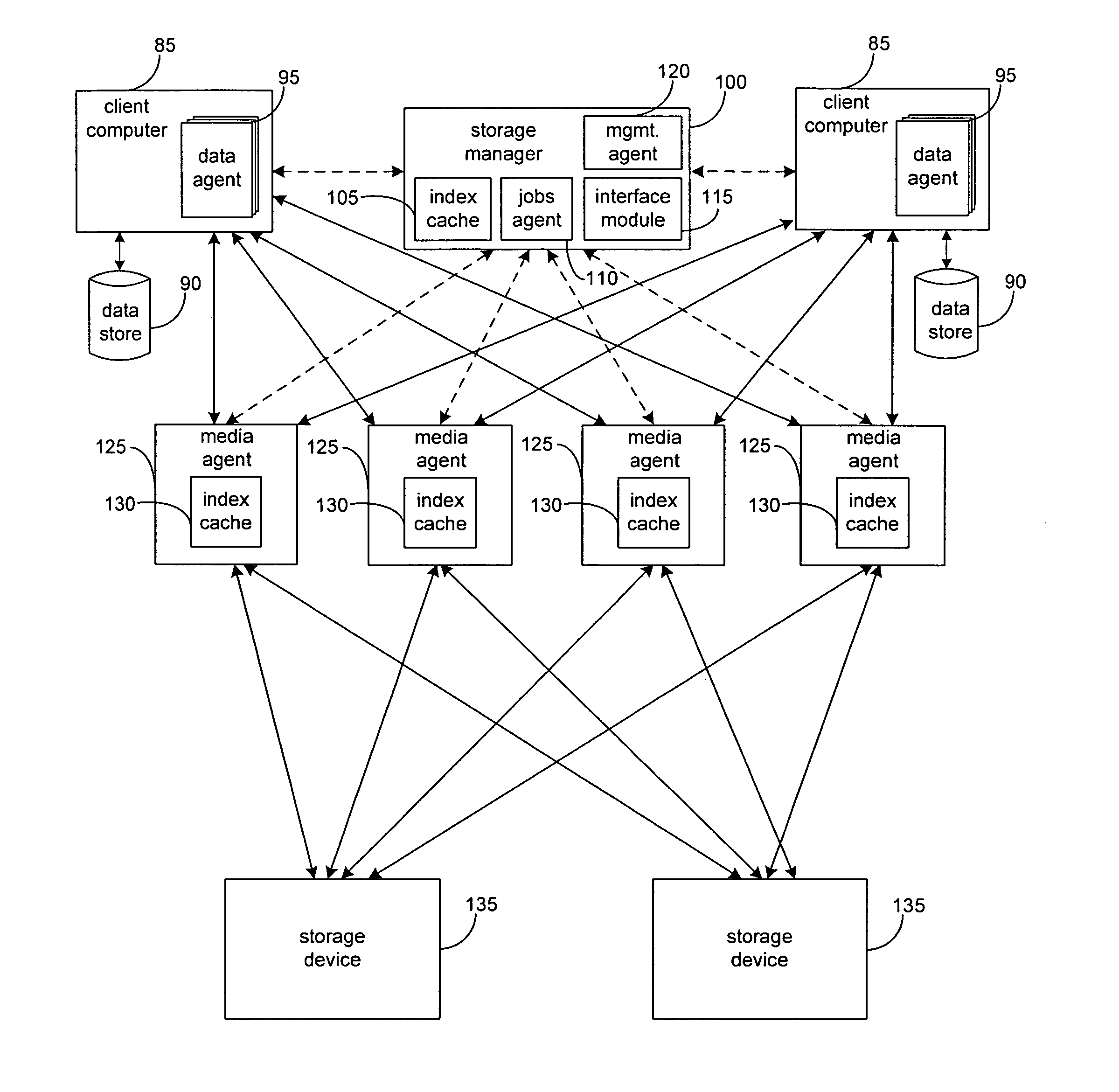
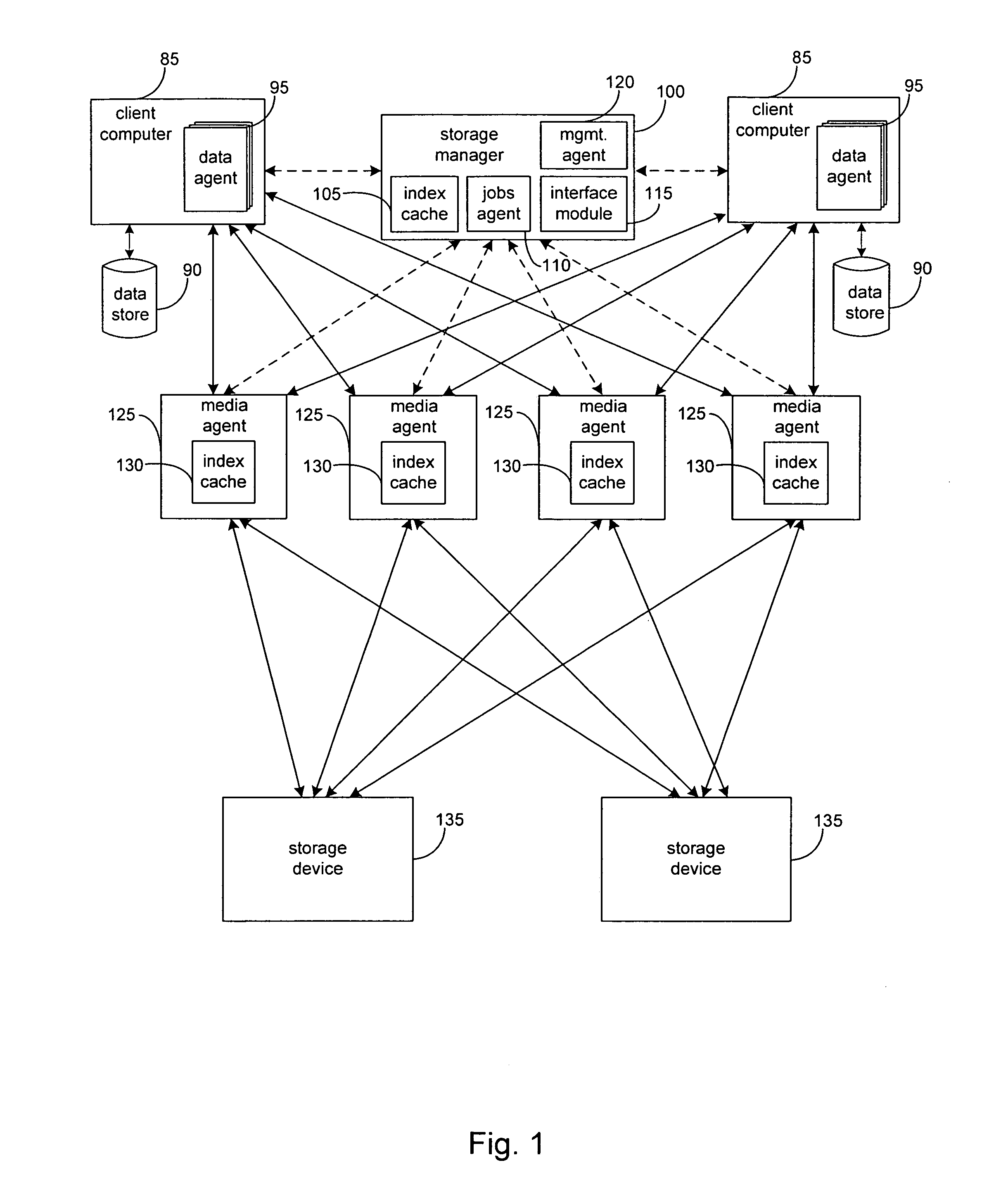
System and method to support simulated storage operations
ActiveUS7536291B1Error detection/correctionMultiple digital computer combinationsOperating systemSimulated data
The present invention includes a system for simulating the performing of data storage operations. The system may include a storage manager component, at least one media management component directed by the storage manager component to manage storage operations to at least one storage device, and a storage emulation module adapted to simulate the characteristics of the at least one storage device. Under the direction of the storage manager, the emulation module may be adapted to simulate storage operations to one or more storage devices performed by one or more of the media management components.
Owner:COMMVAULT SYST INC
Multiple platform support system and method
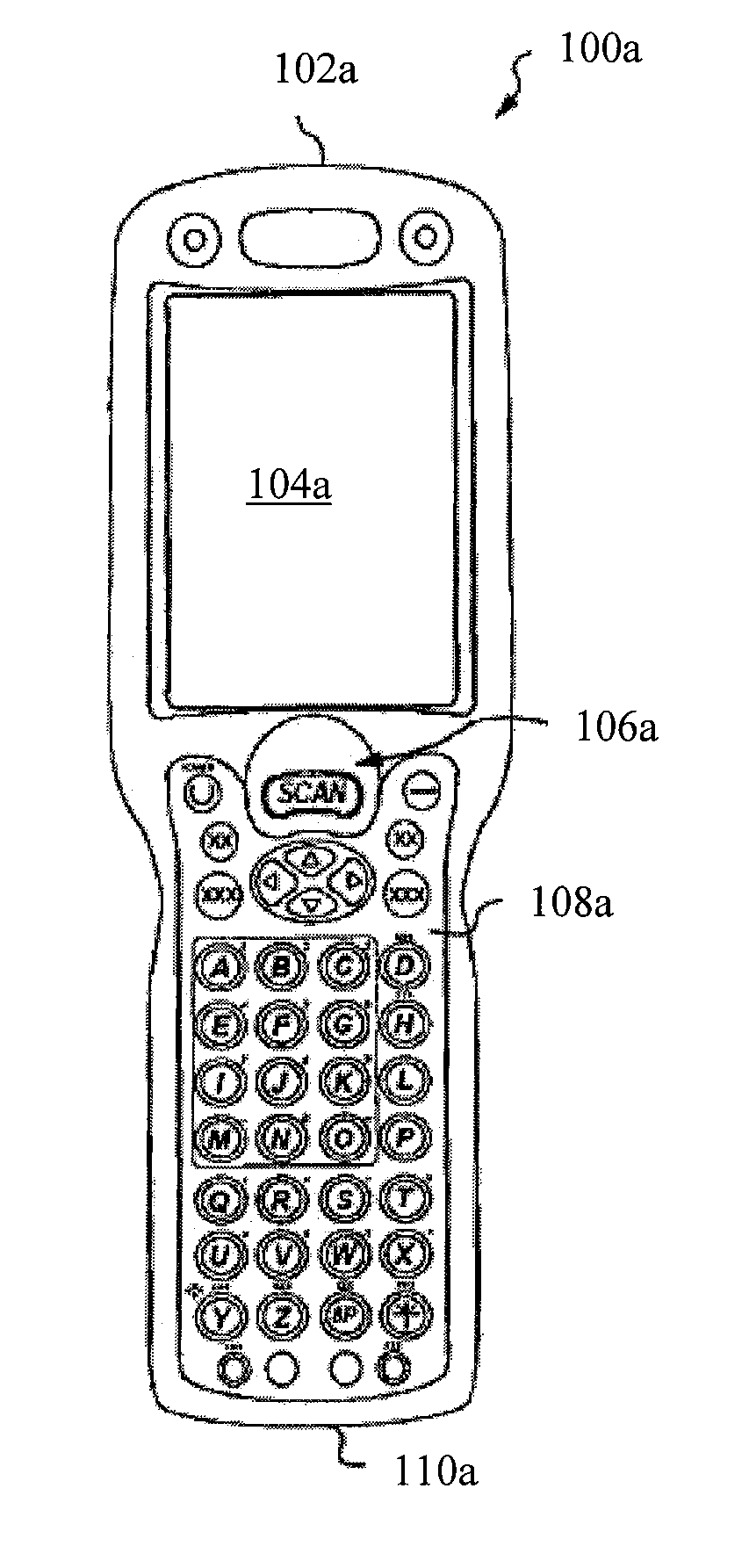
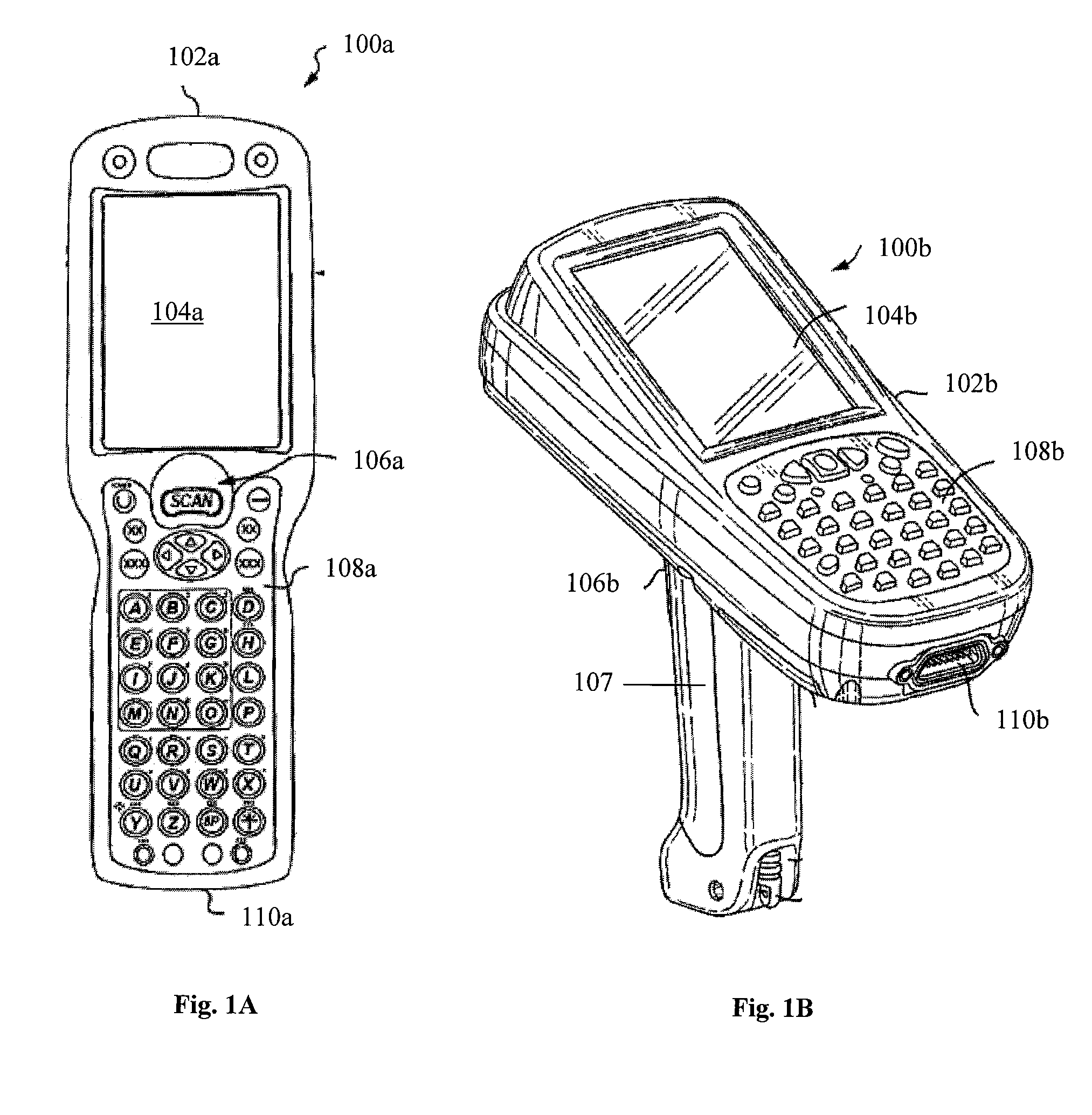
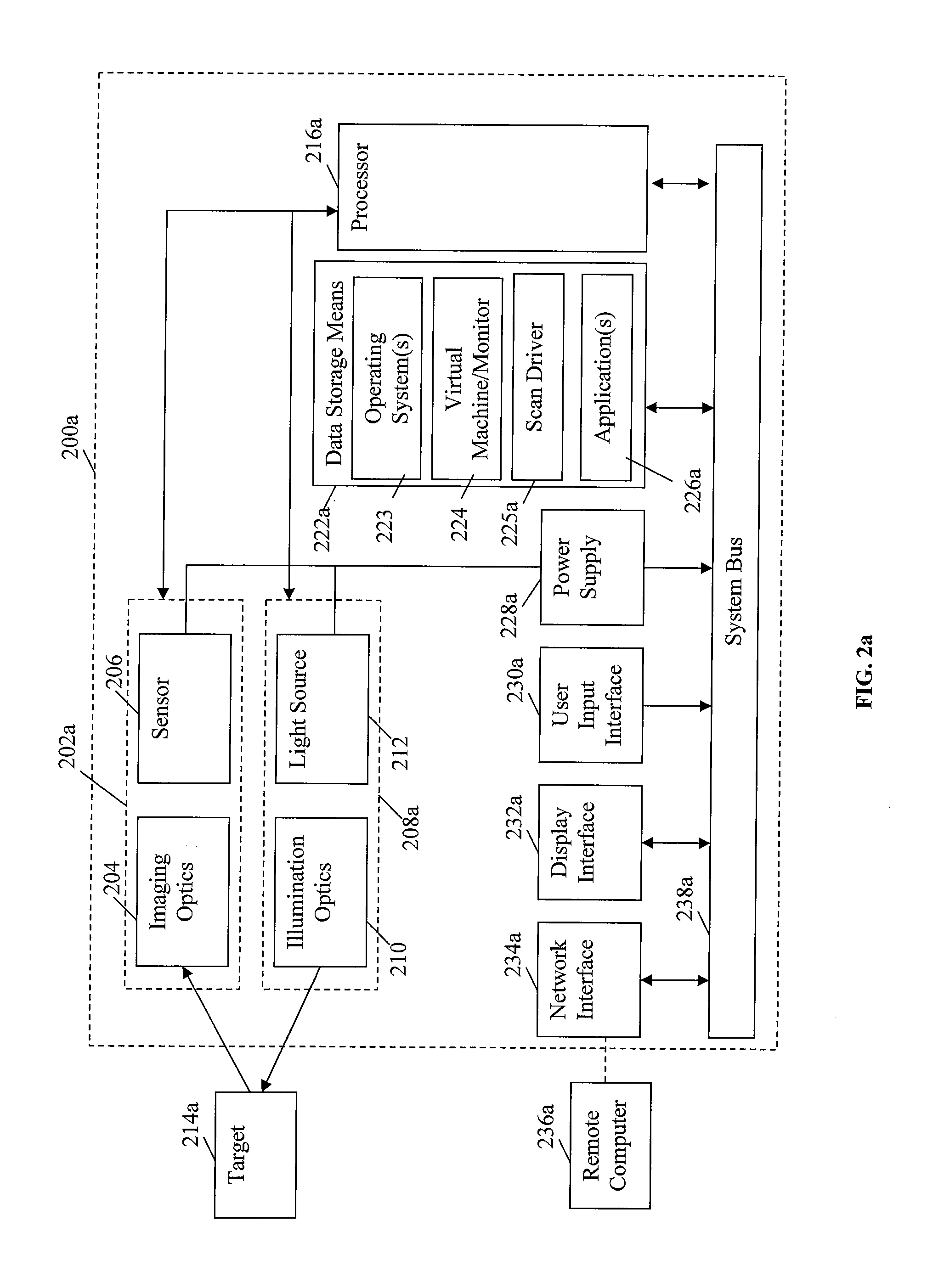
InactiveUS9010641B2Software simulation/interpretation/emulationSpecial data processing applicationsSupporting systemData terminal
A portable data terminal including a processor having an instruction set architecture and data storage means configured to store a plurality of operating systems and a virtual machine monitor application program configured to receive at least one instruction from each operating system, communicate with the processor according to the instruction set architecture, and switch operating system access to the processor upon receipt of an electrical signal representing an event.
Owner:HAND HELD PRODS
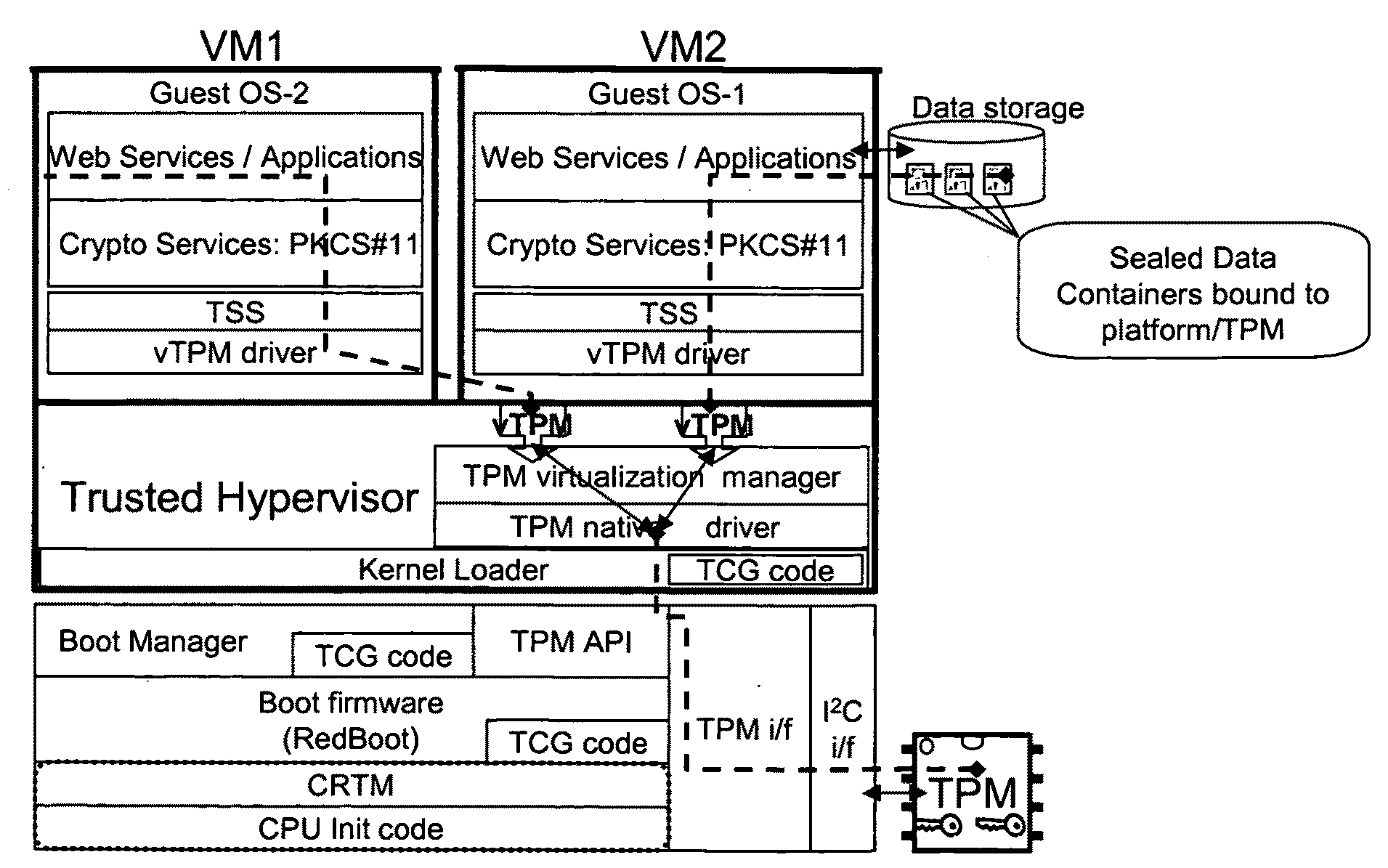
Distributed trusted virtualization platform
InactiveUS20090204964A1Key distribution for secure communicationMultiple digital computer combinationsVirtualizationEnd to end security
A platform architecture shifts the networked computing paradigm from PC+Network to a system using trusted mobile internet end-point (MIEP) devices and cooperative agents hosted on a trusted server. The MIEP device can participate in data flows, arbitrate authentication, and / or participate in implementing security mechanisms, all within the context of assured end-to-end security. The MIEP architecture improves platform-level capabilities by suitably (and even dynamically) partitioning what is done at the MIEP nodes, the network, and the server based infrastructure for delivering services.
Owner:MOTEGRITY +1
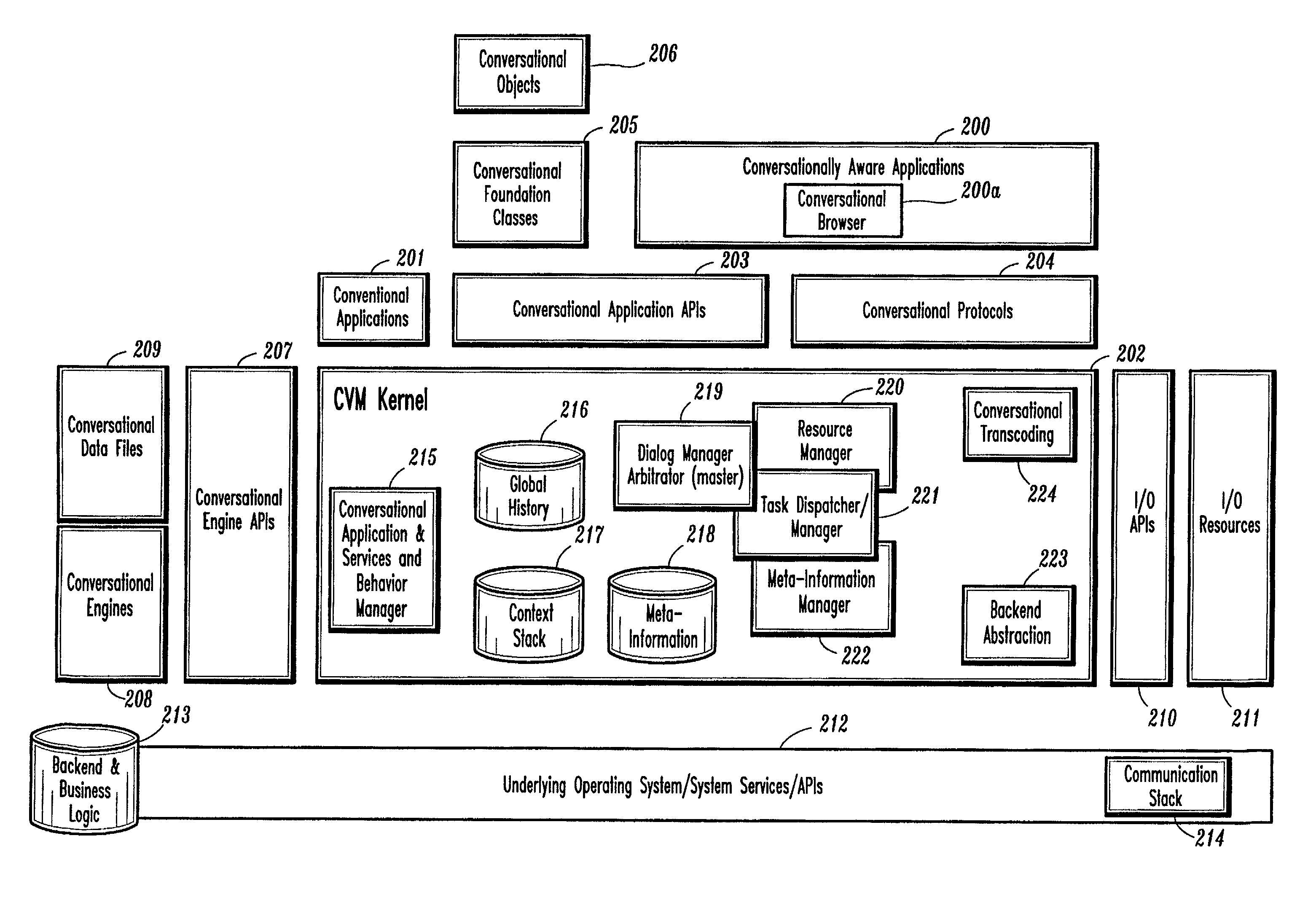
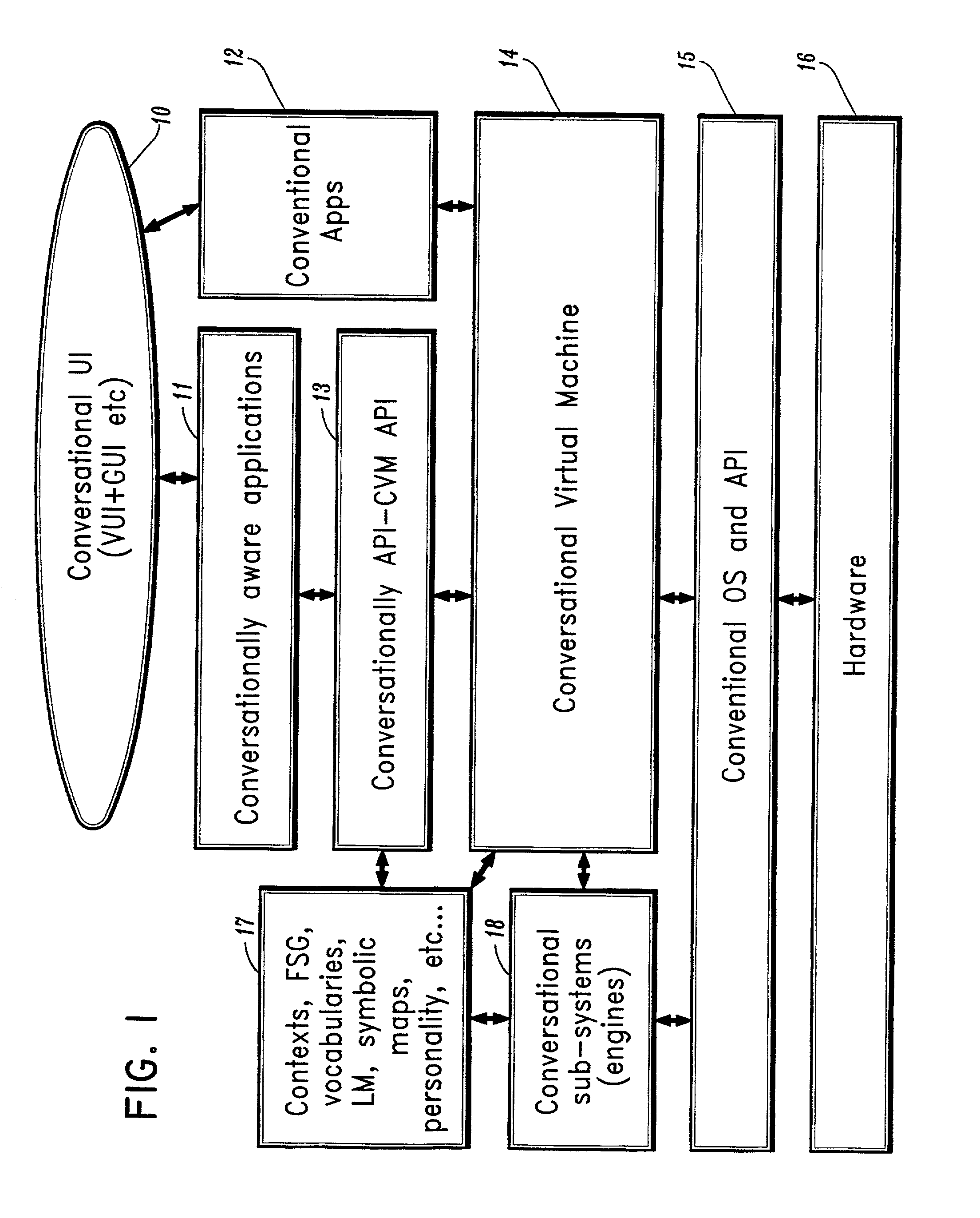
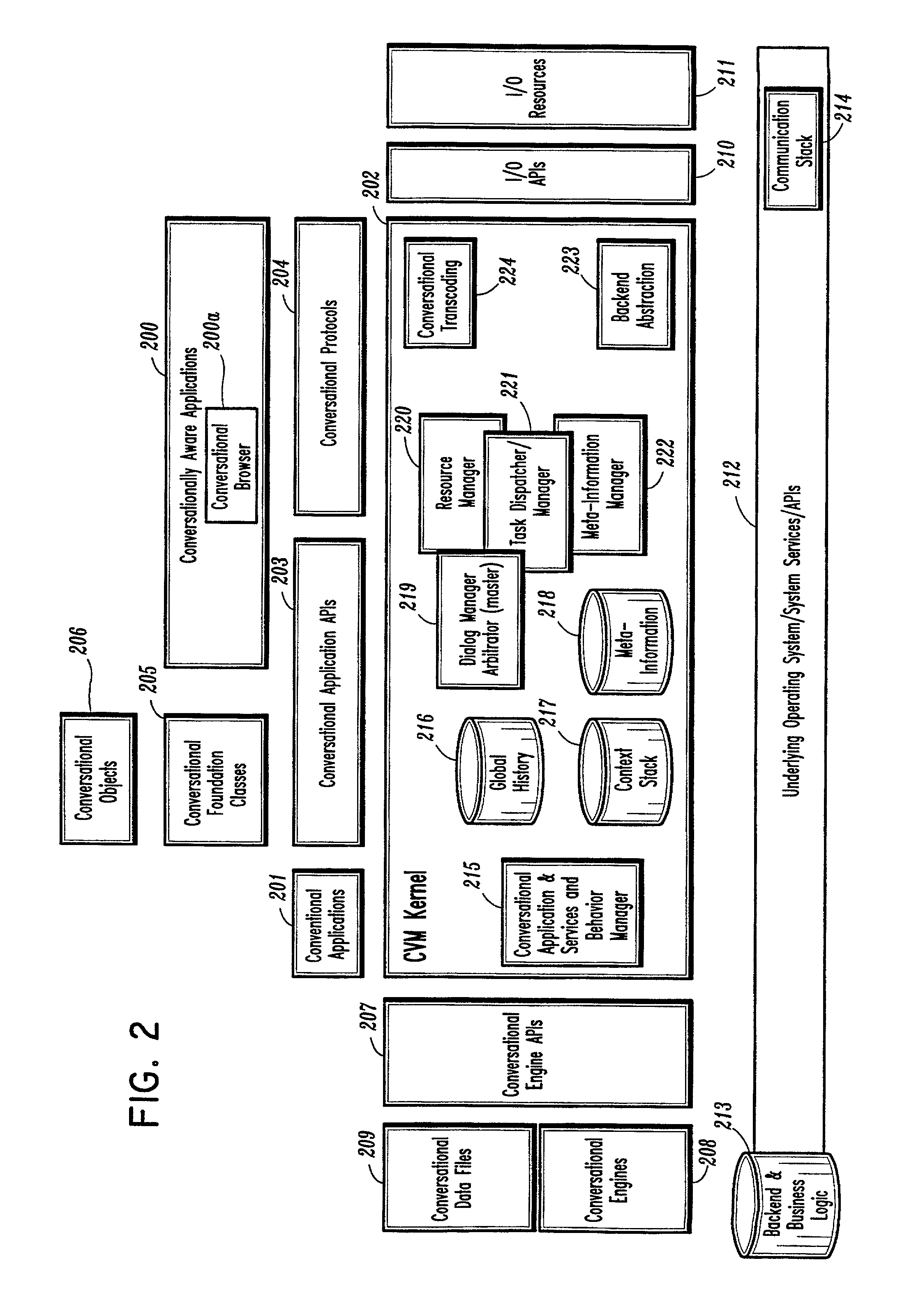
Conversational computing via conversational virtual machine
InactiveUS7137126B1Limitation for transferReduce degradationInterconnection arrangementsResource allocationConversational speechApplication software
A conversational computing system that provides a universal coordinated multi-modal conversational user interface (CUI) (10) across a plurality of conversationally aware applications (11) (i.e., applications that “speak” conversational protocols) and conventional applications (12). The conversationally aware maps, applications (11) communicate with a conversational kernel (14) via conversational application APIs (13). The conversational kernel (14) controls the dialog across applications and devices (local and networked) on the basis of their registered conversational capabilities and requirements and provides a unified conversational user interface and conversational services and behaviors. The conversational computing system may be built on top of a conventional operating system and APIs (15) and conventional device hardware (16). The conversational kernel (14) handles all I / O processing and controls conversational engines (18). The conversational kernel (14) converts voice requests into queries and converts outputs and results into spoken messages using conversational engines (18) and conversational arguments (17). The conversational application API (13) conveys all the information for the conversational kernel (14) to transform queries into application calls and conversely convert output into speech, appropriately sorted before being provided to the user.
Owner:UNILOC 2017 LLC
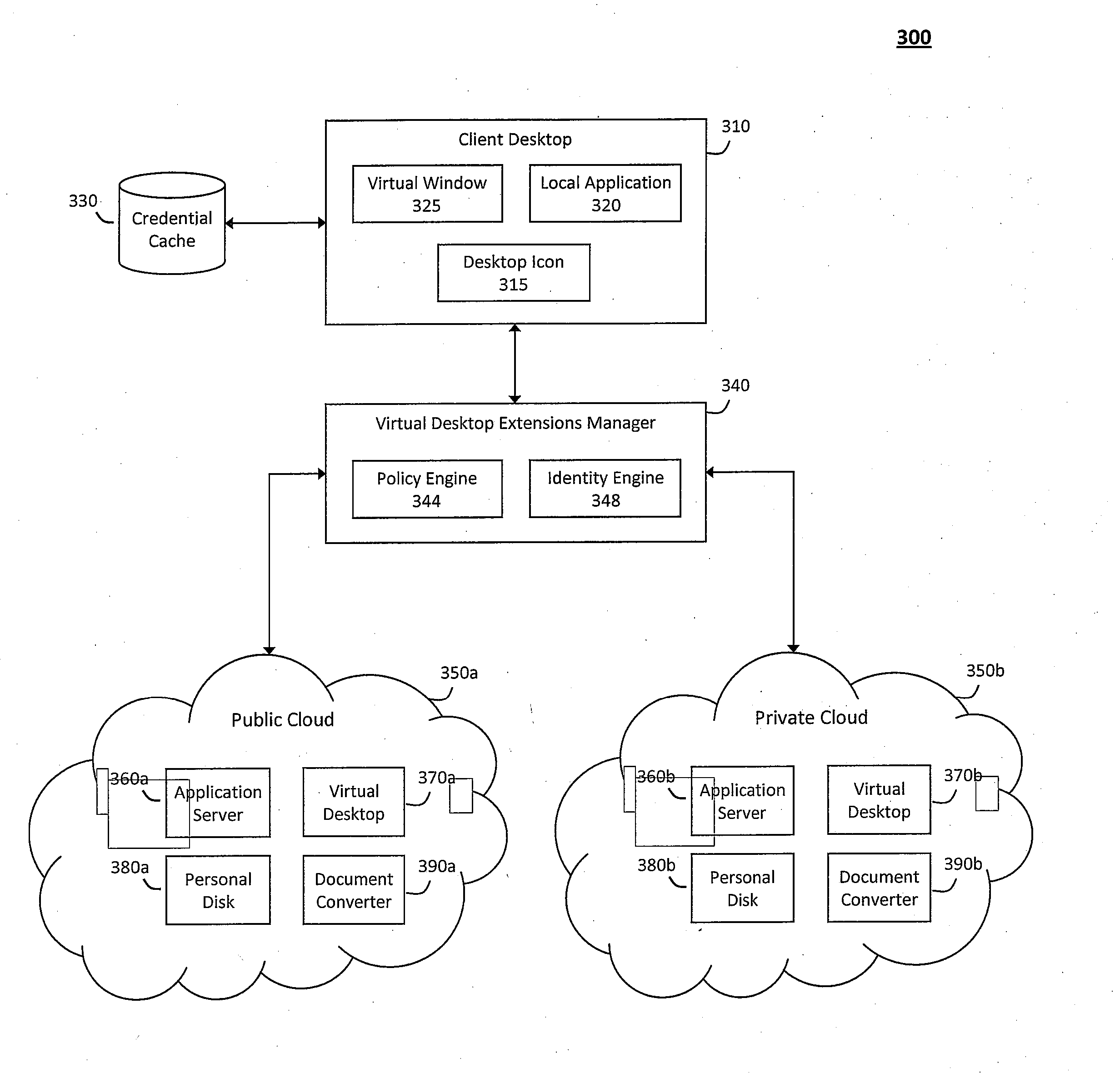
System and method for providing virtual desktop extensions on a client desktop
ActiveUS20110209064A1Simplify complexityProvide capabilityInput/output for user-computer interactionDigital data processing detailsClient-sideCloud computing
The system and method described herein may identify one or more virtual desktop extensions available in a cloud computing environment and launch virtual machine instances to host the available virtual desktop extensions in the cloud. For example, a virtual desktop extension manager may receive a virtual desktop extension request from a client desktop and determine whether authentication credentials for the client desktop indicate that the client desktop has access to the requested virtual desktop extension. In response to authenticating the client desktop, the virtual desktop extension manager may then launch a virtual machine instance to host the virtual desktop extension in the cloud and provide the client desktop with information for locally controlling the virtual desktop extension remotely hosted in the cloud.
Owner:MICRO FOCUS SOFTWARE INC
System and method for centralized software management in virtual machines
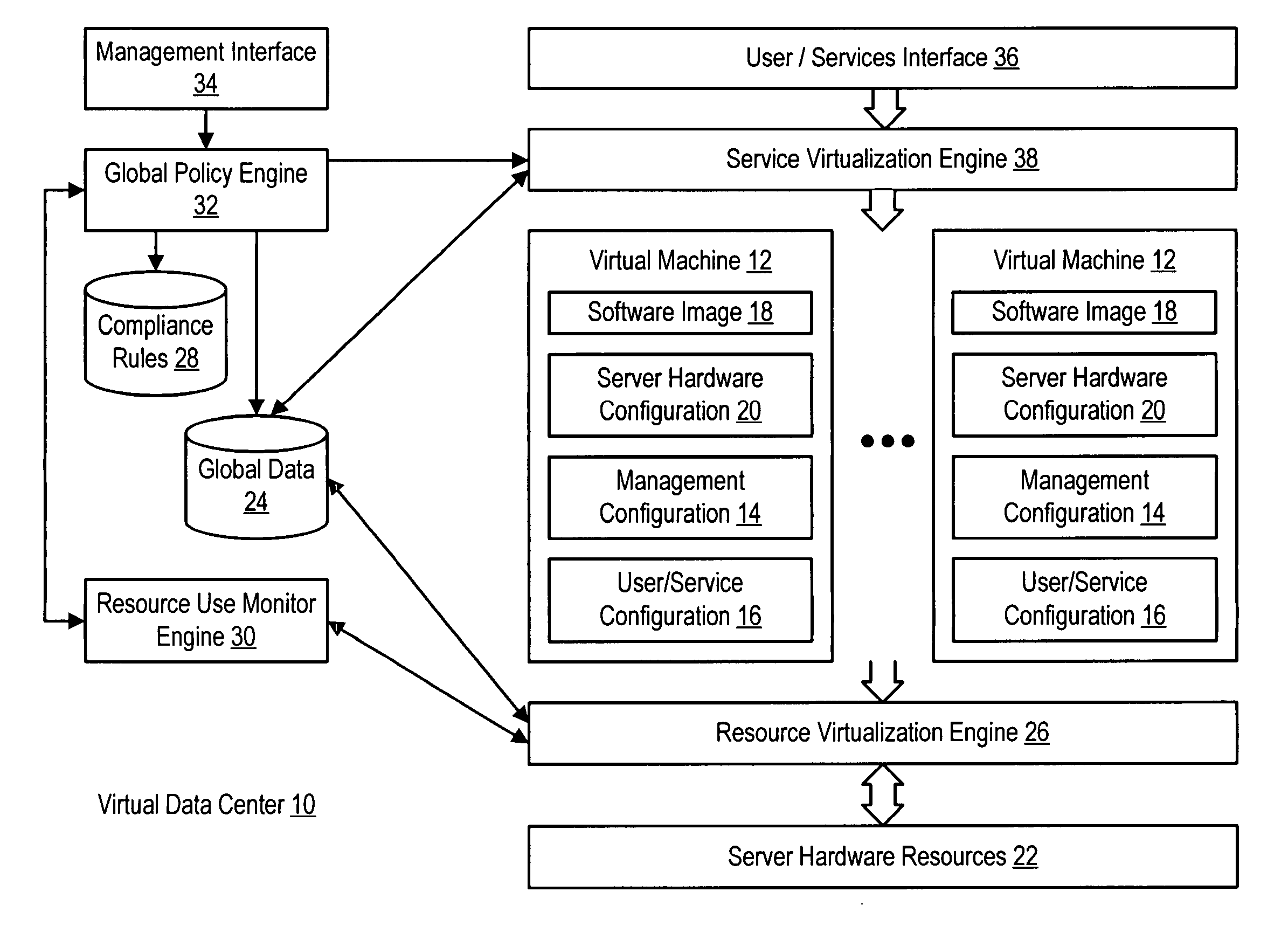
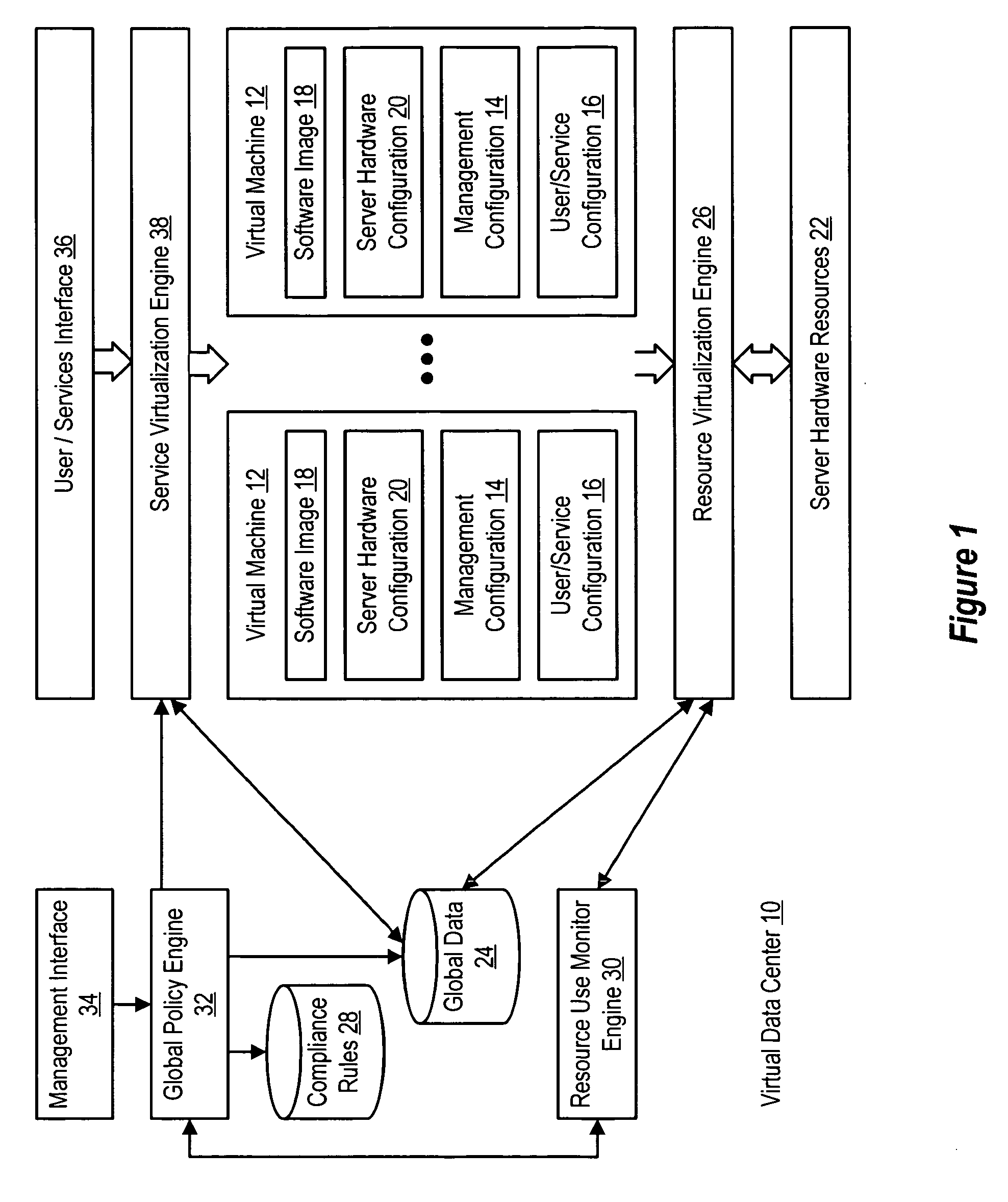
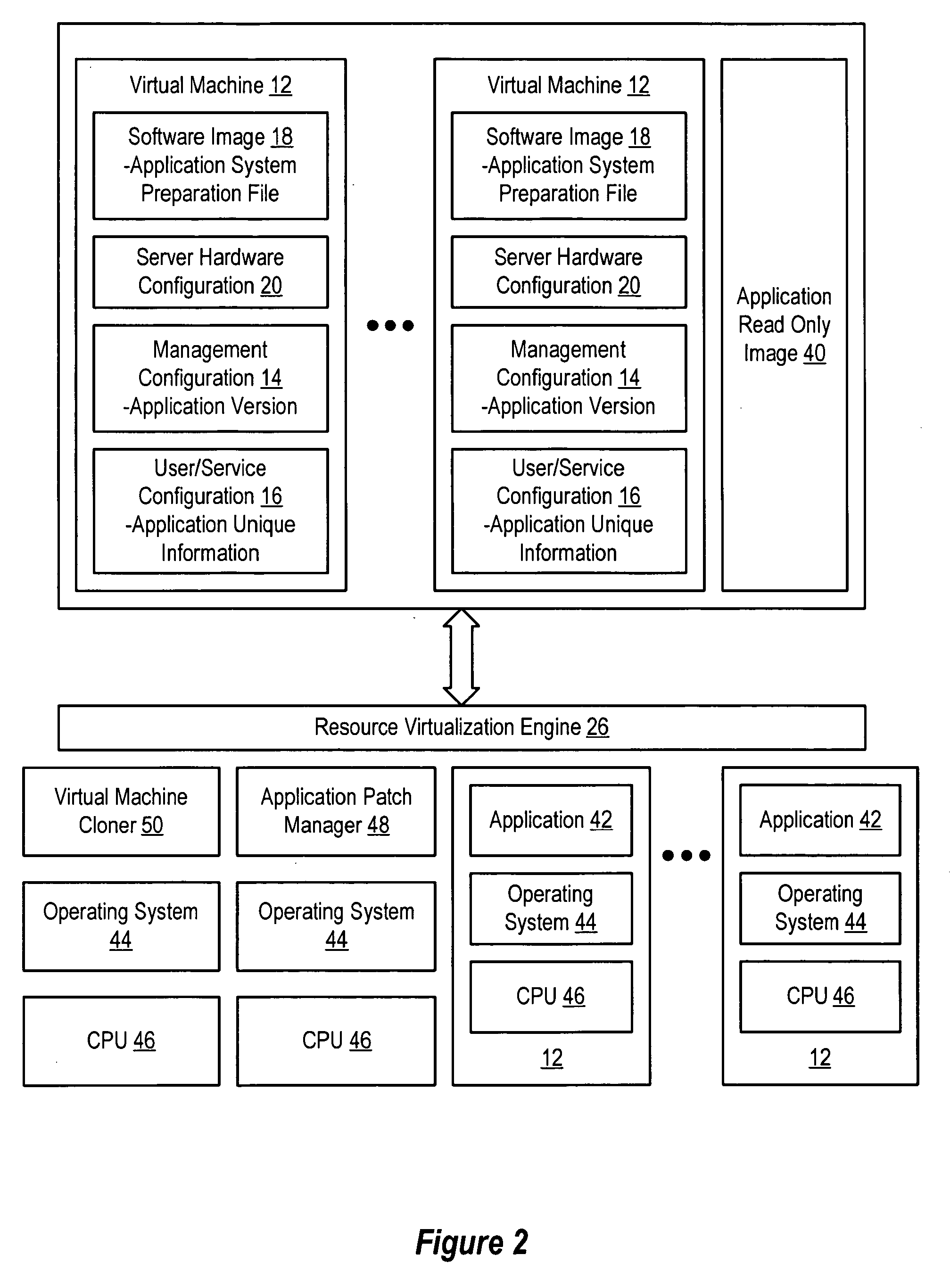
InactiveUS20060184937A1Simplifies management system updateSimple dataSoftware simulation/interpretation/emulationMemory systemsMaintenance releaseData center
Virtual machines of a virtual data center generate runtime instances with a software image, hardware configuration, management configuration and user / service configuration. Virtual data center resource use is monitored by reference to the management configuration of runtime instances, such as for environmental controls like power, cooling and balancing, or for policy limitations on users, software or hardware. Users or services generate runtime instances of stored virtual machines by reference to the user / service configuration, such as pricing or priority. In one example embodiment, the virtual machine software image comprises an application system preparation file that populates a read only application image common to plural virtual machines. Information unique to each virtual machine with respect to the application is maintained in the user / service configuration of the virtual machine and version information is maintained in the management configuration of the virtual machine. Updates to the application across each virtual machine are performed by updating the read only image or any of its configuration information for hardware configuration, management configuration or user / service configuration.
Owner:DELL PROD LP
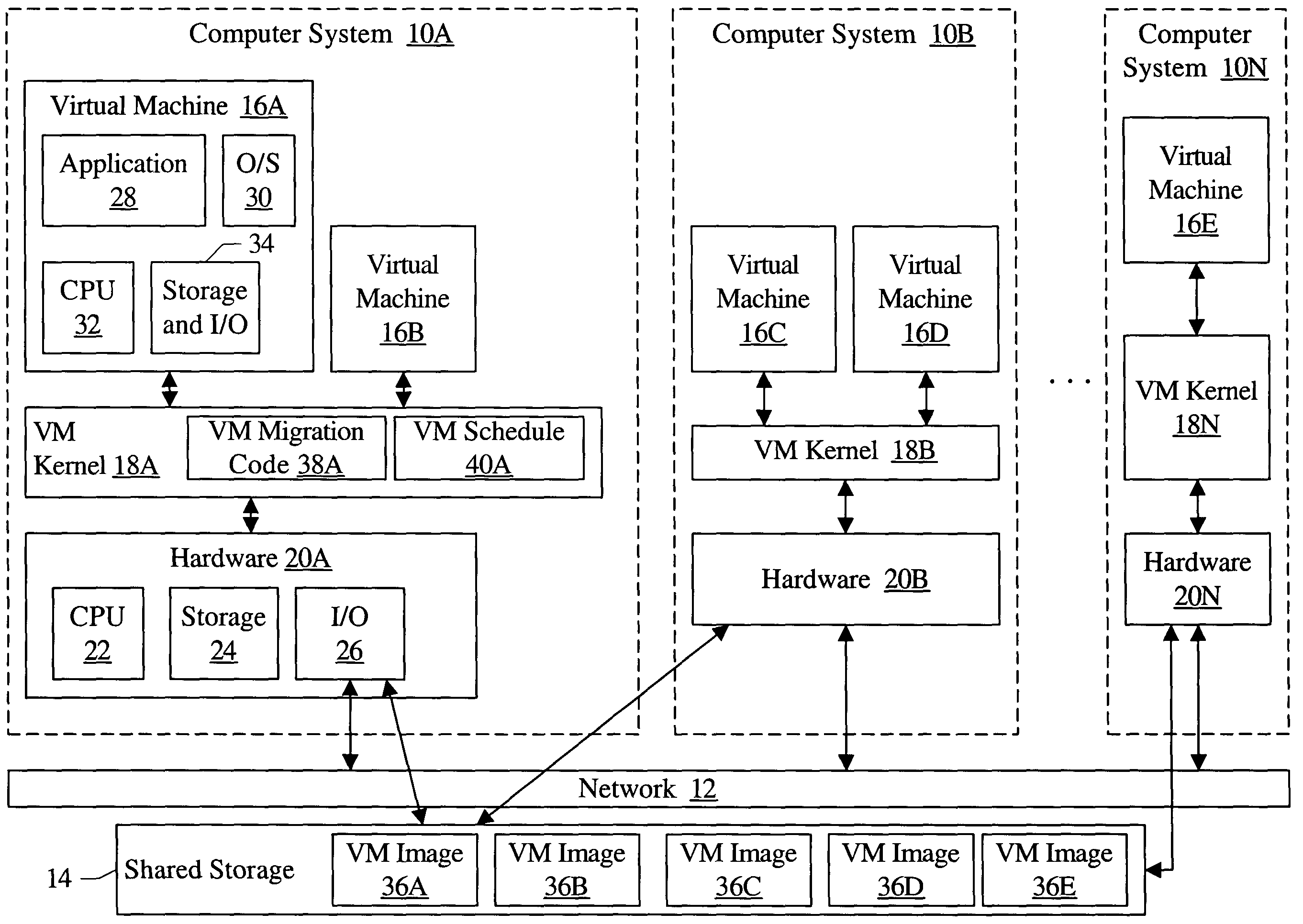
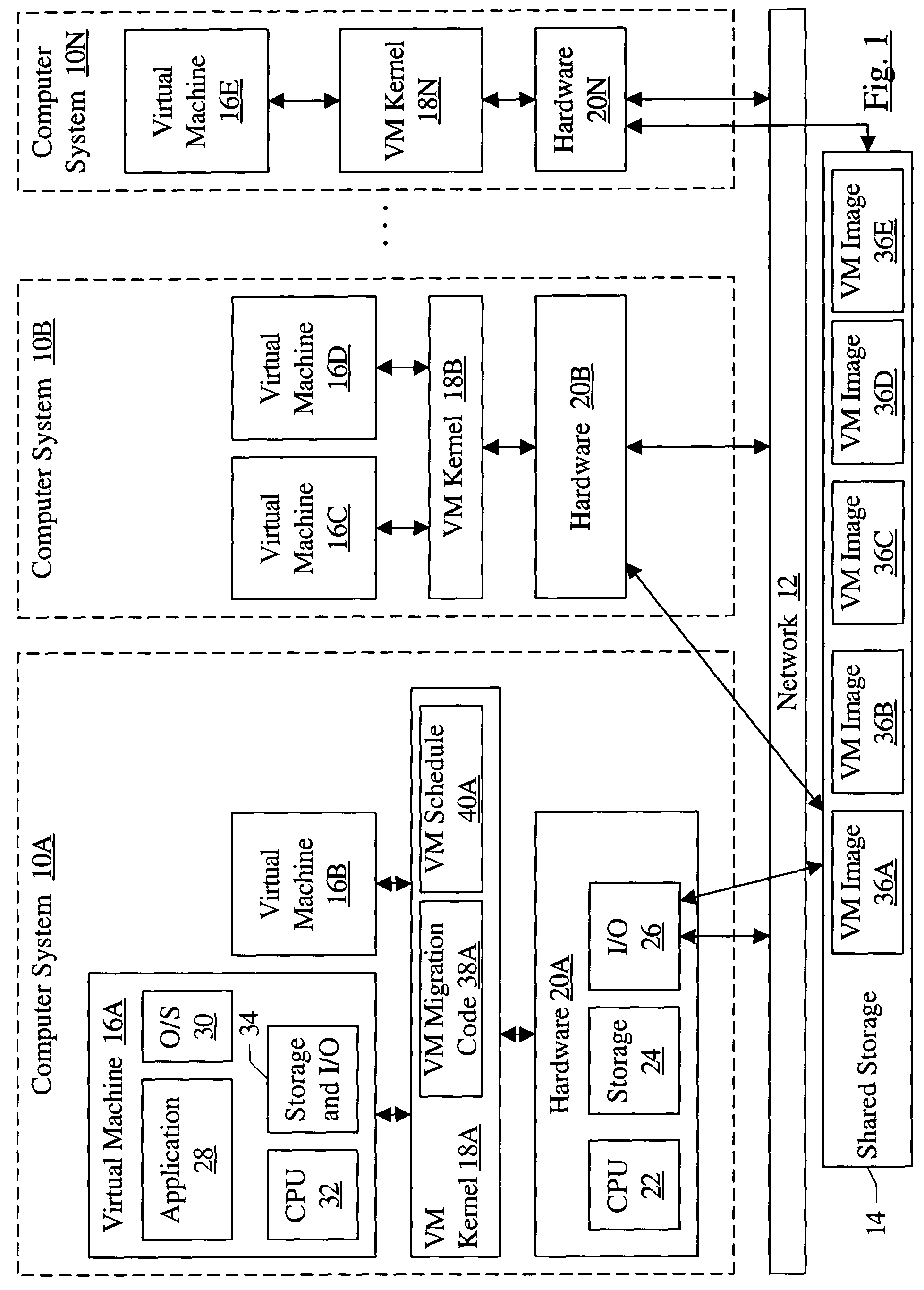
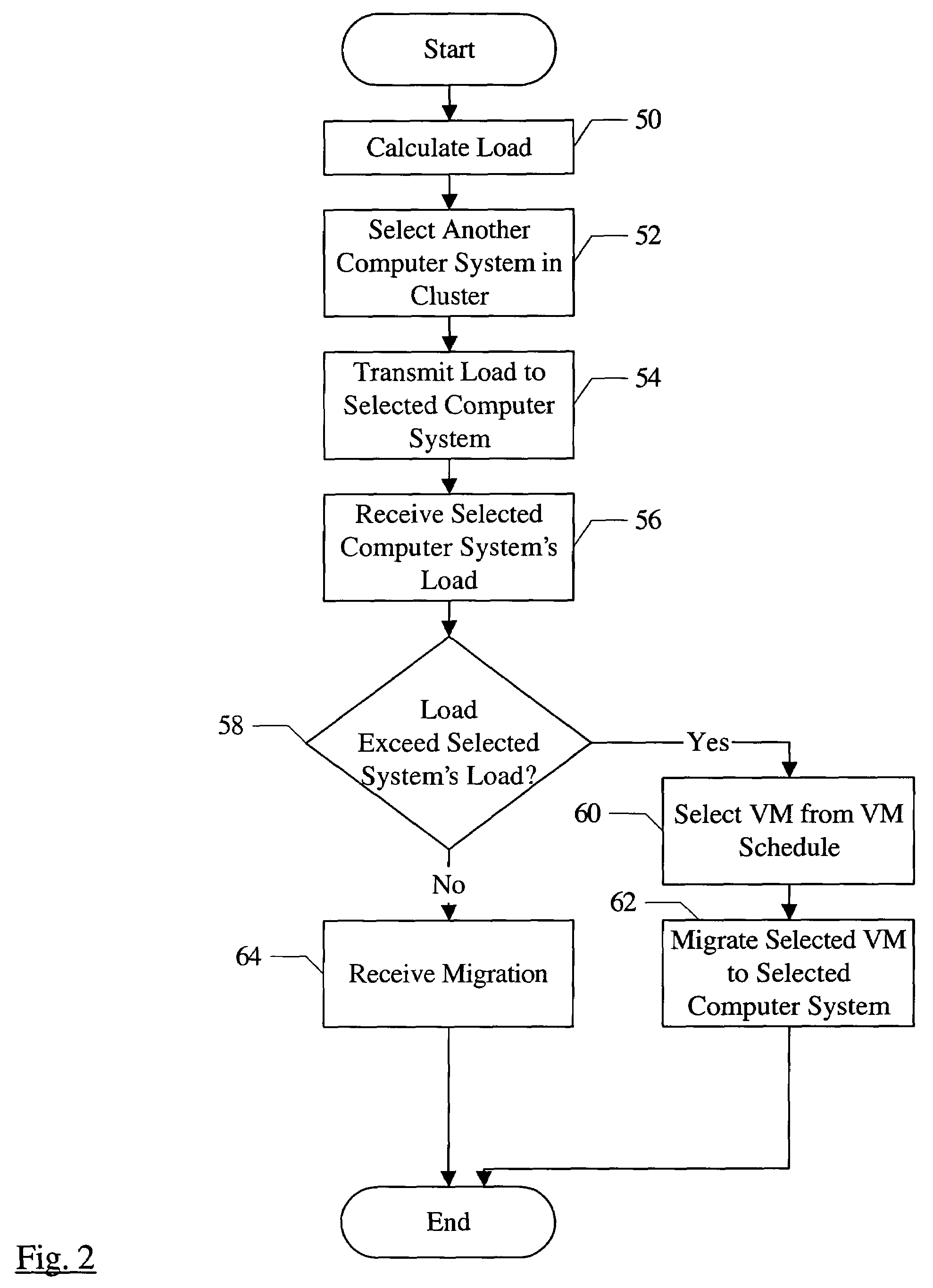
Migrating virtual machines among computer systems to balance load caused by virtual machines
InactiveUS7203944B1Multiprogramming arrangementsSoftware simulation/interpretation/emulationComputerized systemVirtual machine
A cluster comprises a plurality of computer systems, wherein each of the plurality of computer systems is configured to execute one or more virtual machines. Each of the plurality of computer systems comprises hardware and a plurality of instructions. The plurality of instructions, when executed on the hardware, migrates at least a first virtual machine executing on a first computer system of the plurality of computer systems to a second computer system of the plurality of computer systems. The plurality of instructions migrates the first virtual machine responsive to a first load of the first computer system prior to the migration exceeding a second load of the second computer system prior to the migration.
Owner:SYMANTEC OPERATING CORP
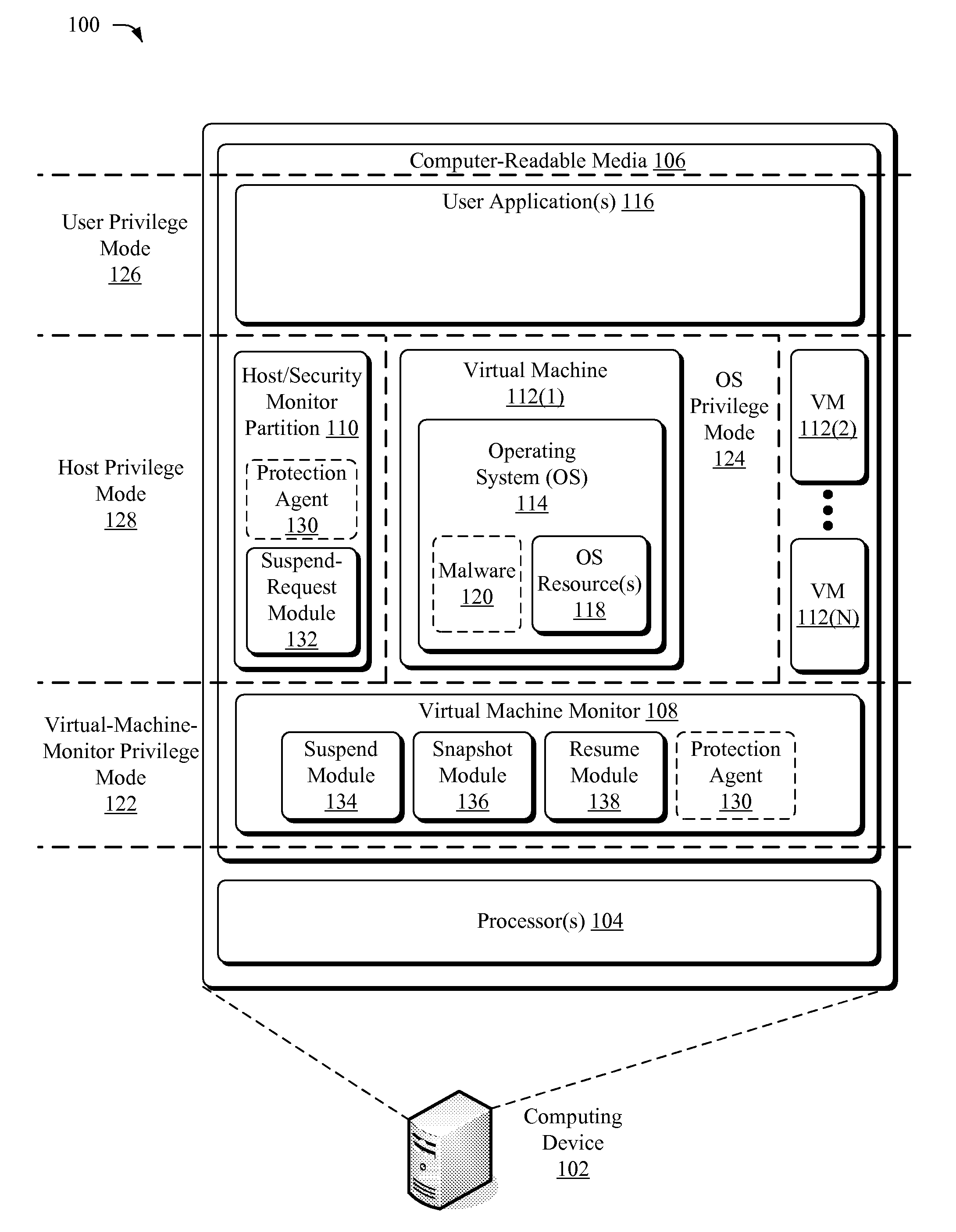
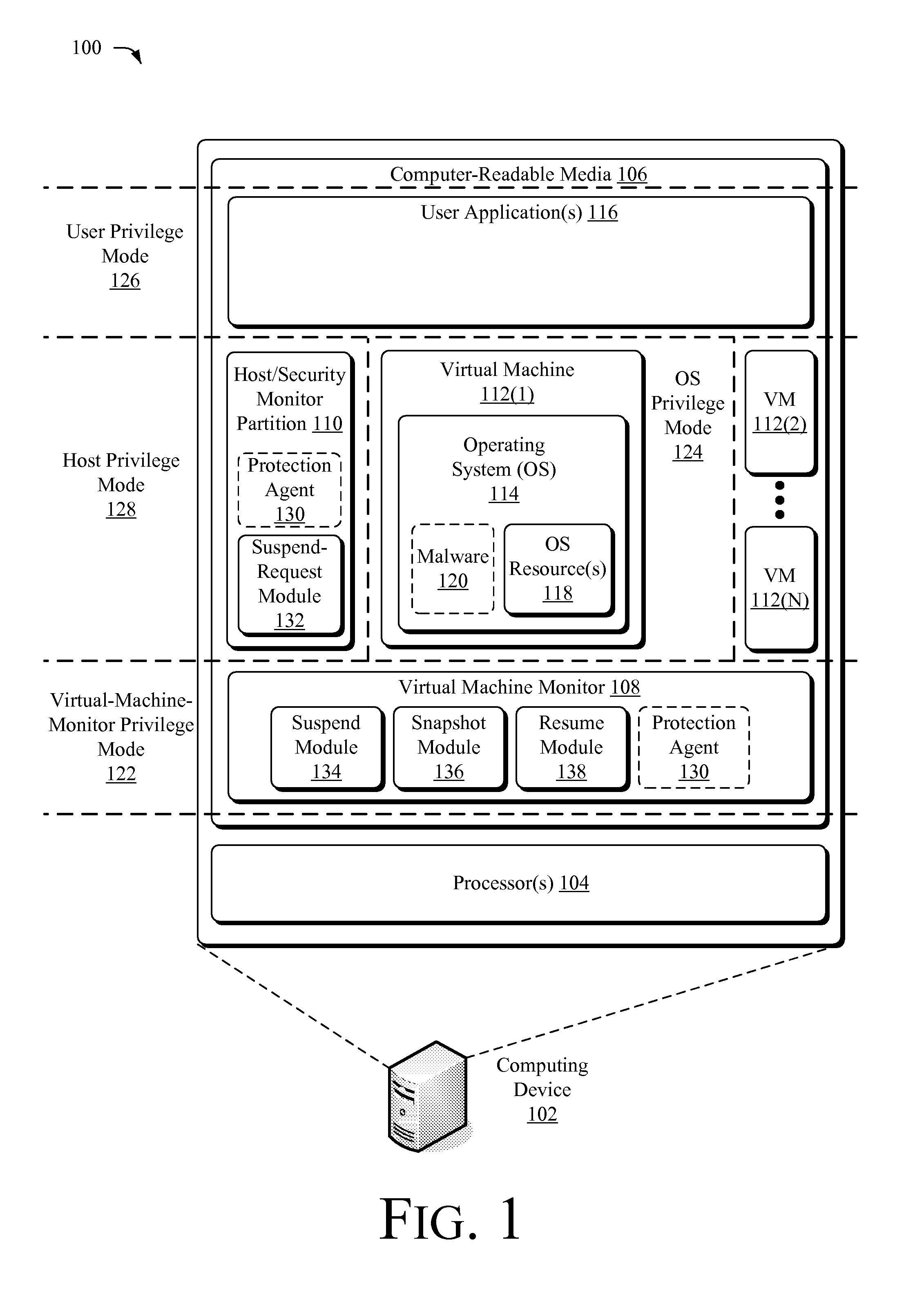
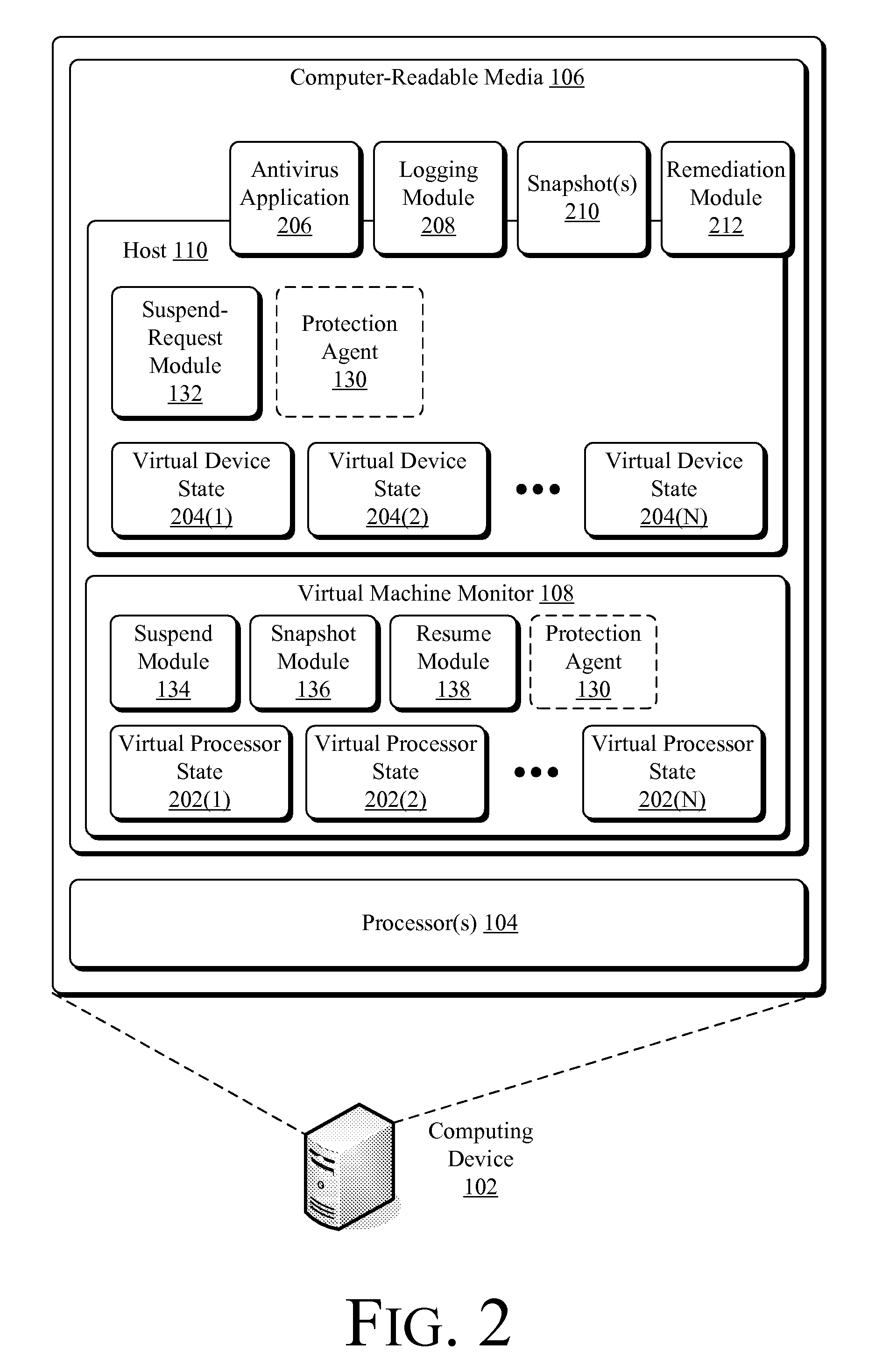
Suspending a Running Operating System to Enable Security Scanning
InactiveUS20090007100A1Well formedUser identity/authority verificationPlatform integrity maintainanceOperational systemRemedial action
Techniques described herein enable virtualizing a processor into one or more virtual machines and suspending an operating system of one of the virtual machines from outside of the operating system environment. Once suspended, these techniques capture a snapshot of the virtual machine to determine a presence of malware. This snapshot may also be used to determine whether an unauthorized change has occurred within contents of the virtual machine. Remedial action may occur responsive to determining a presence of malware or an unauthorized change.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for providing virtual computing services
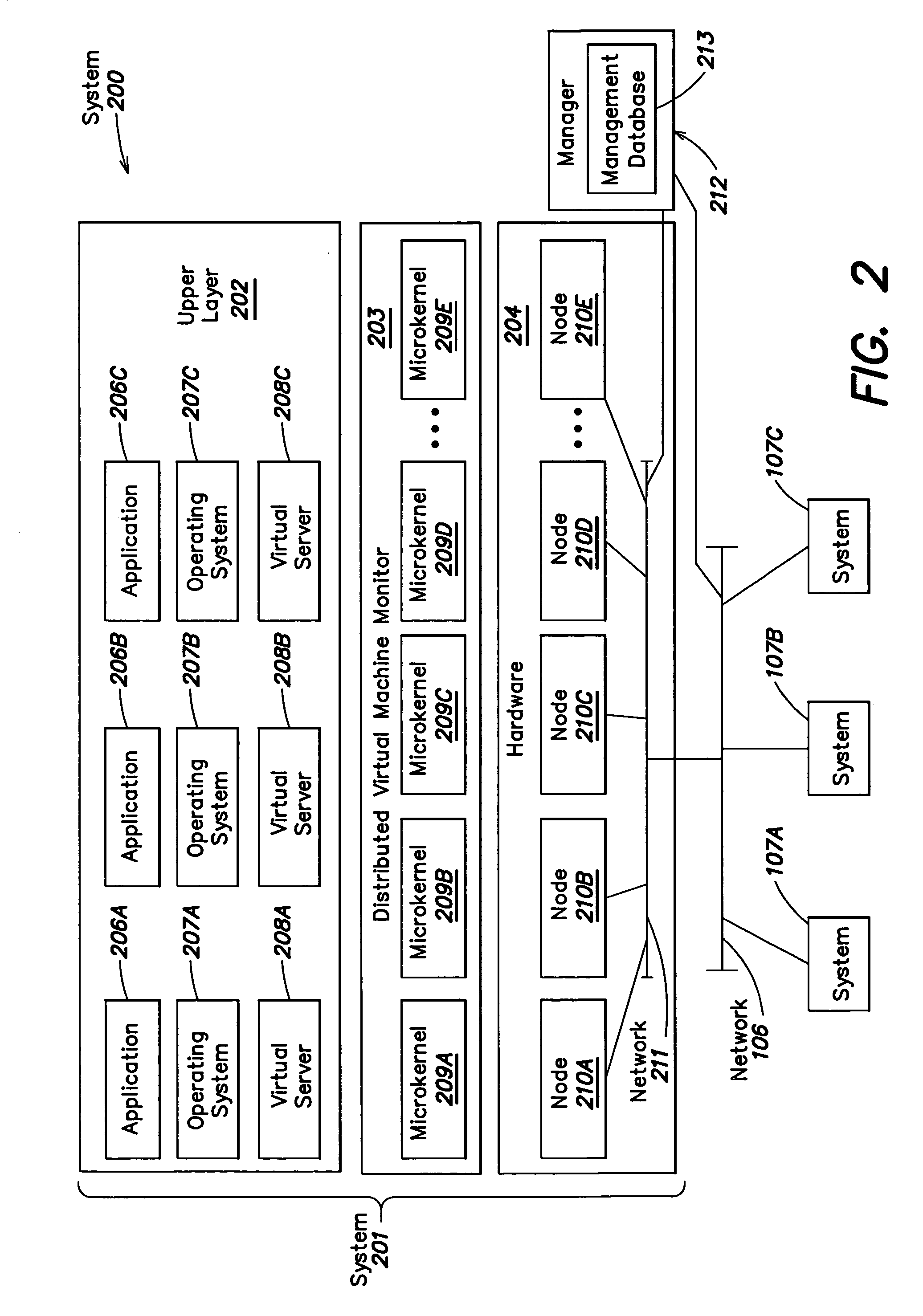
InactiveUS20050044301A1Easy to manageLow costResource allocationMemory adressing/allocation/relocationVirtualizationOperational system
A level of abstraction is created between a set of physical processors and a set of virtual multiprocessors to form a virtualized data center. This virtualized data center comprises a set of virtual, isolated systems separated by a boundary referred as a partition. Each of these systems appears as a unique, independent virtual multiprocessor computer capable of running a traditional operating system and its applications. In one embodiment, the system implements this multi-layered abstraction via a group of microkernels, each of which communicates with one or more peer microkernel over a high-speed, low-latency interconnect and forms a distributed virtual machine monitor. Functionally, a virtual data center is provided, including the ability to take a collection of servers and execute a collection of business applications over a compute fabric comprising commodity processors coupled by an interconnect. Processor, memory and I / O are virtualized across this fabric, providing a single system, scalability and manageability. According to one embodiment, this virtualization is transparent to the application, and therefore, applications may be scaled to increasing resource demands without modifying the application.
Owner:ORACLE INT CORP
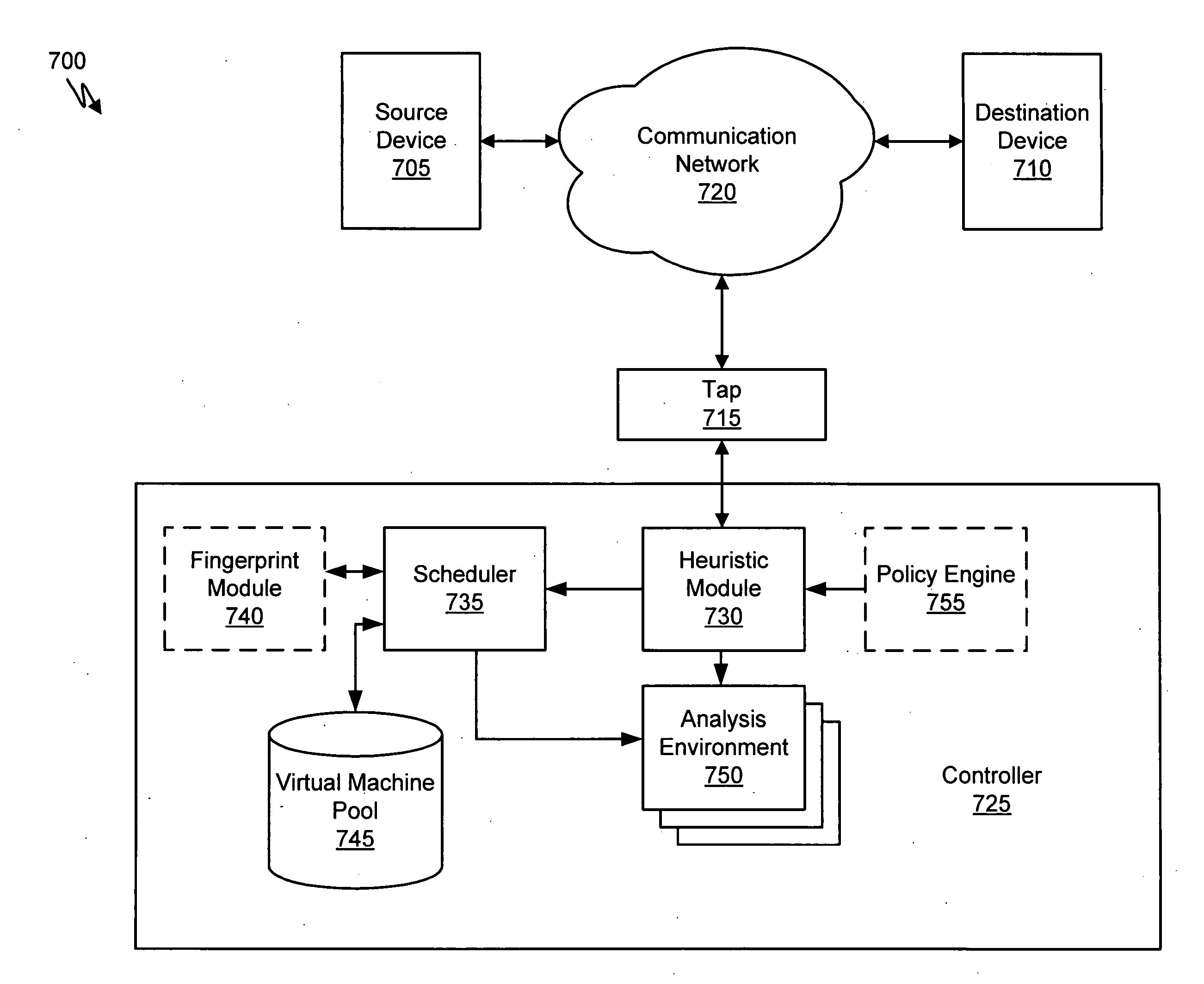
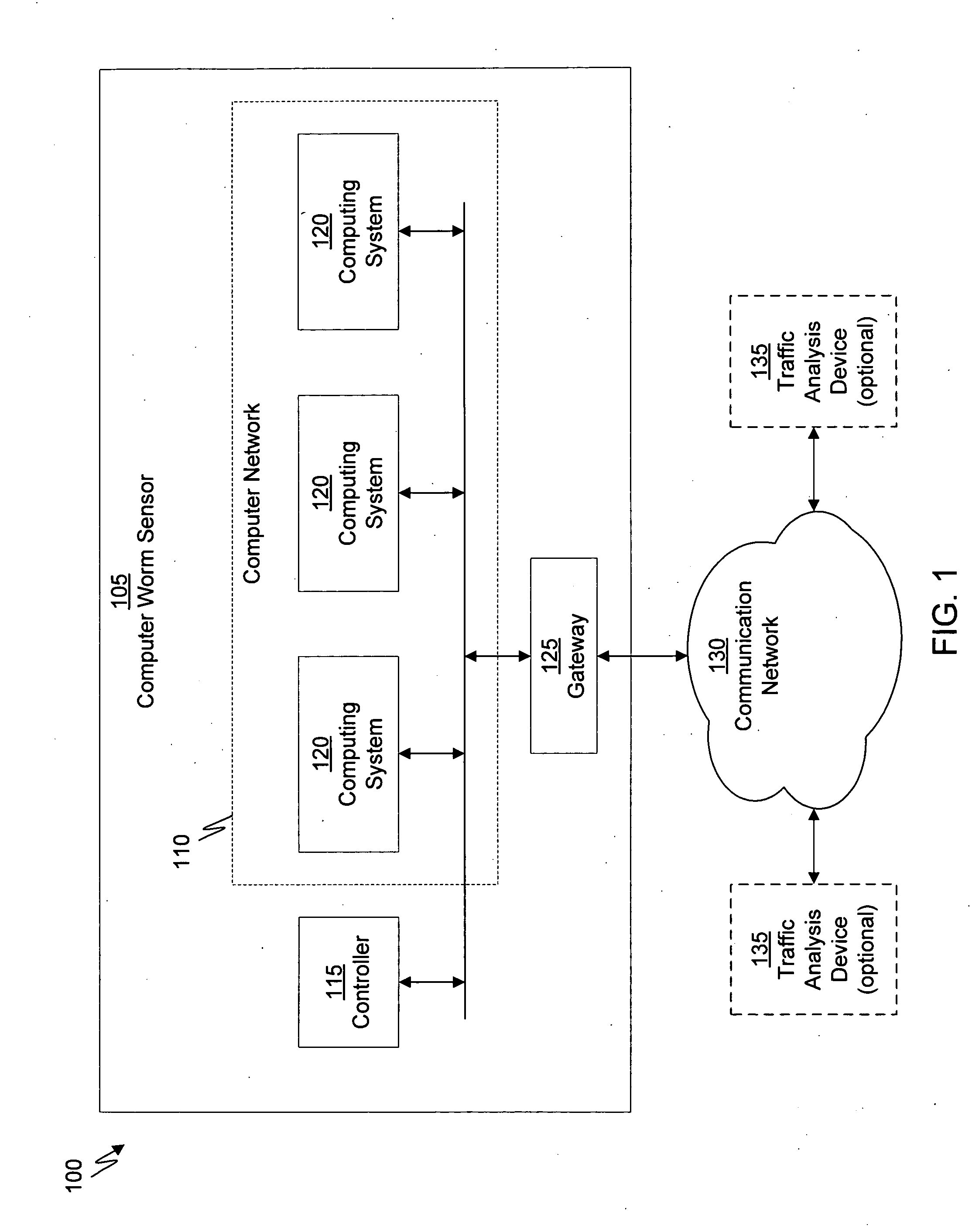
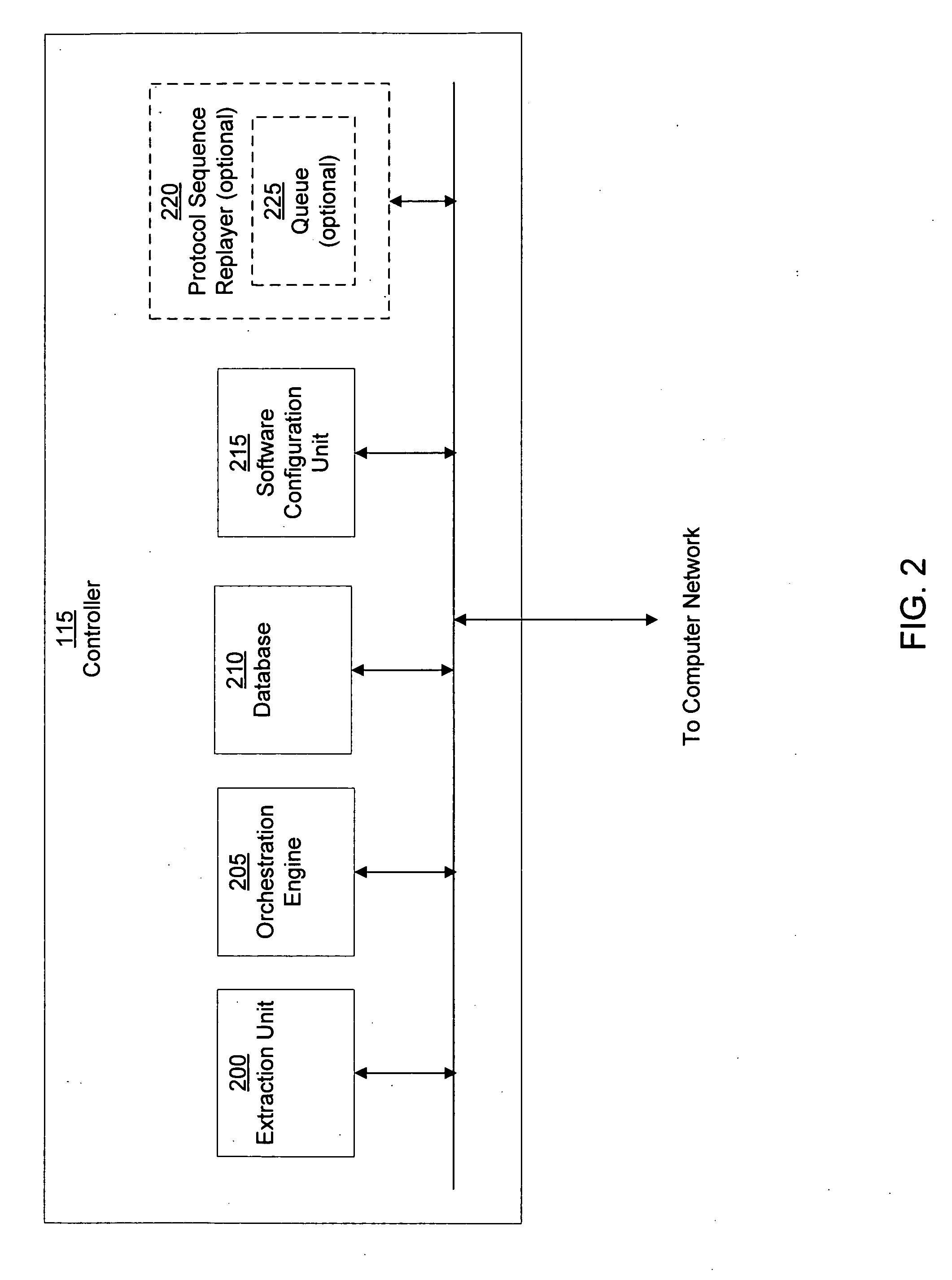
Heuristic based capture with replay to virtual machine
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is coupled to the tap and is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to flag the network data as suspicious, and simulate transmission of the network data to a destination device.
Owner:FIREEYE SECURITY HLDG US LLC
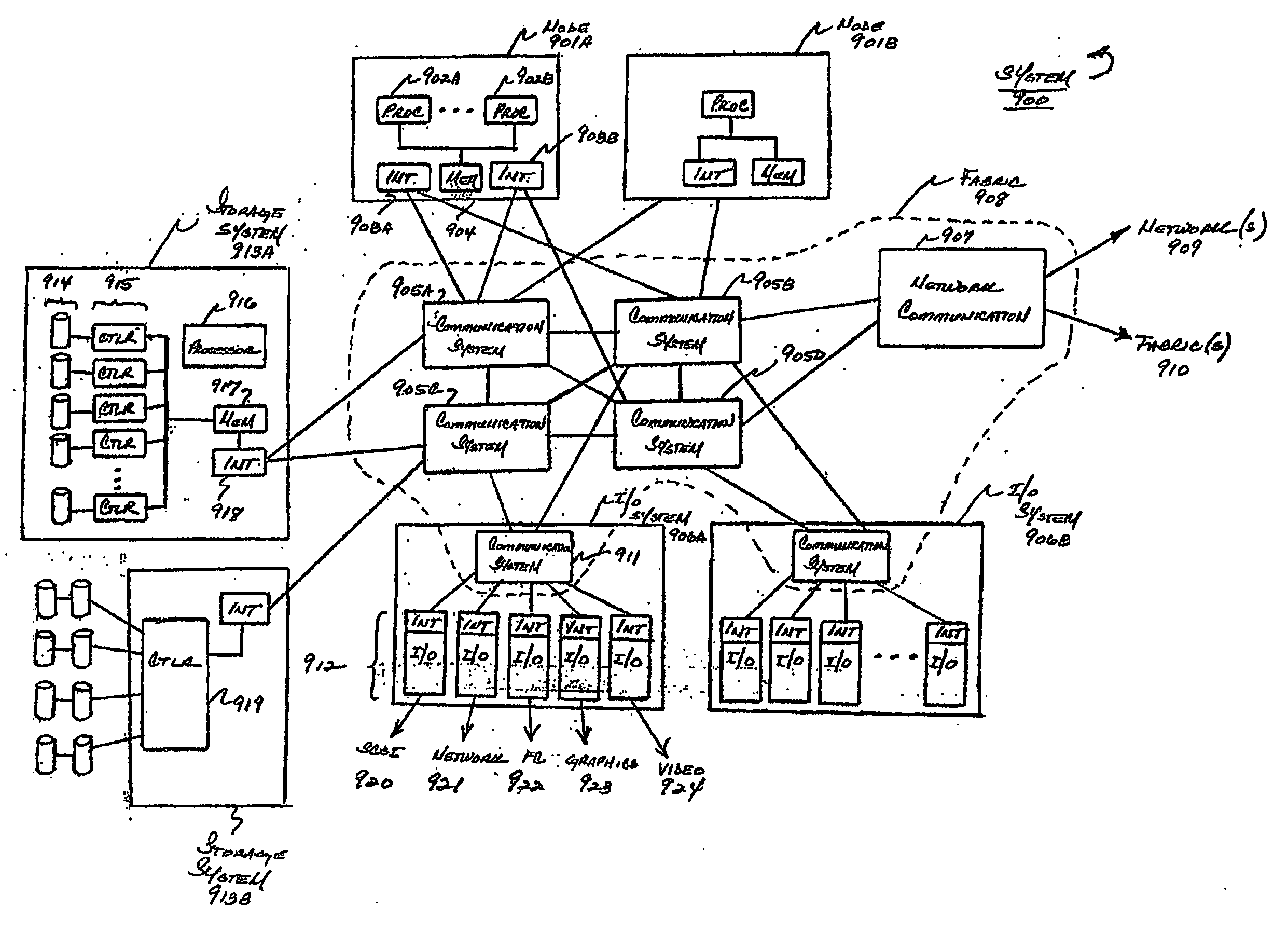
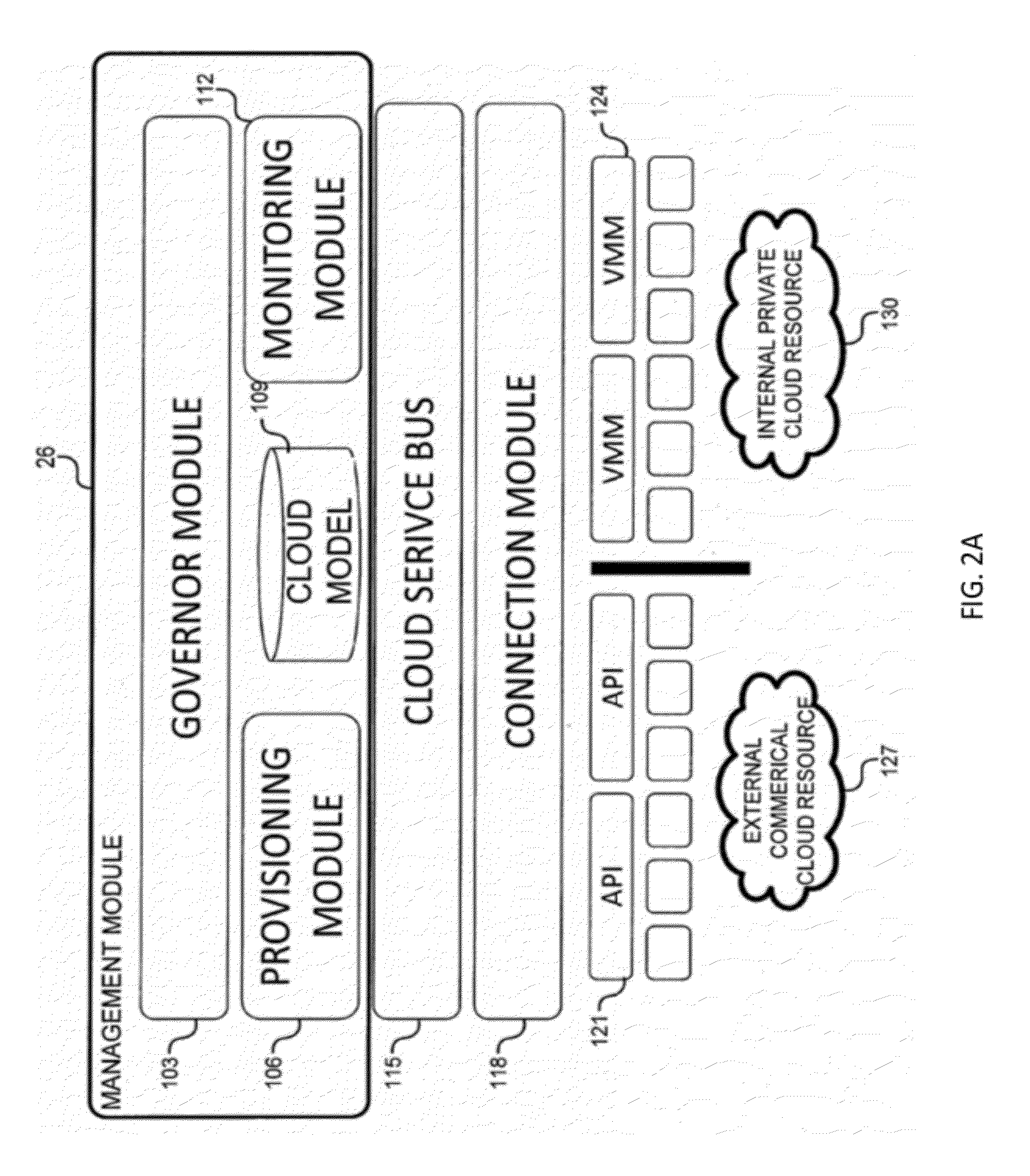
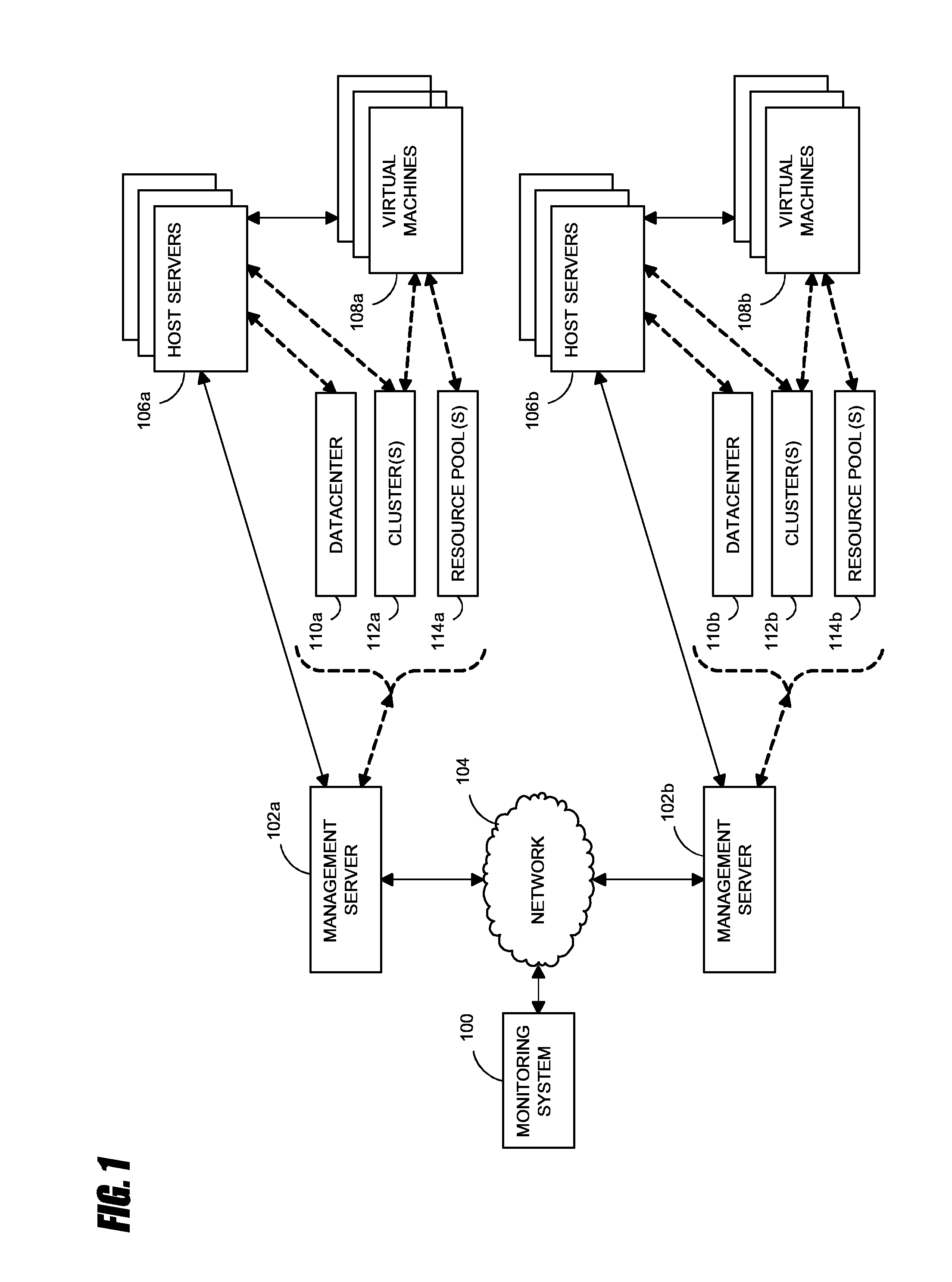
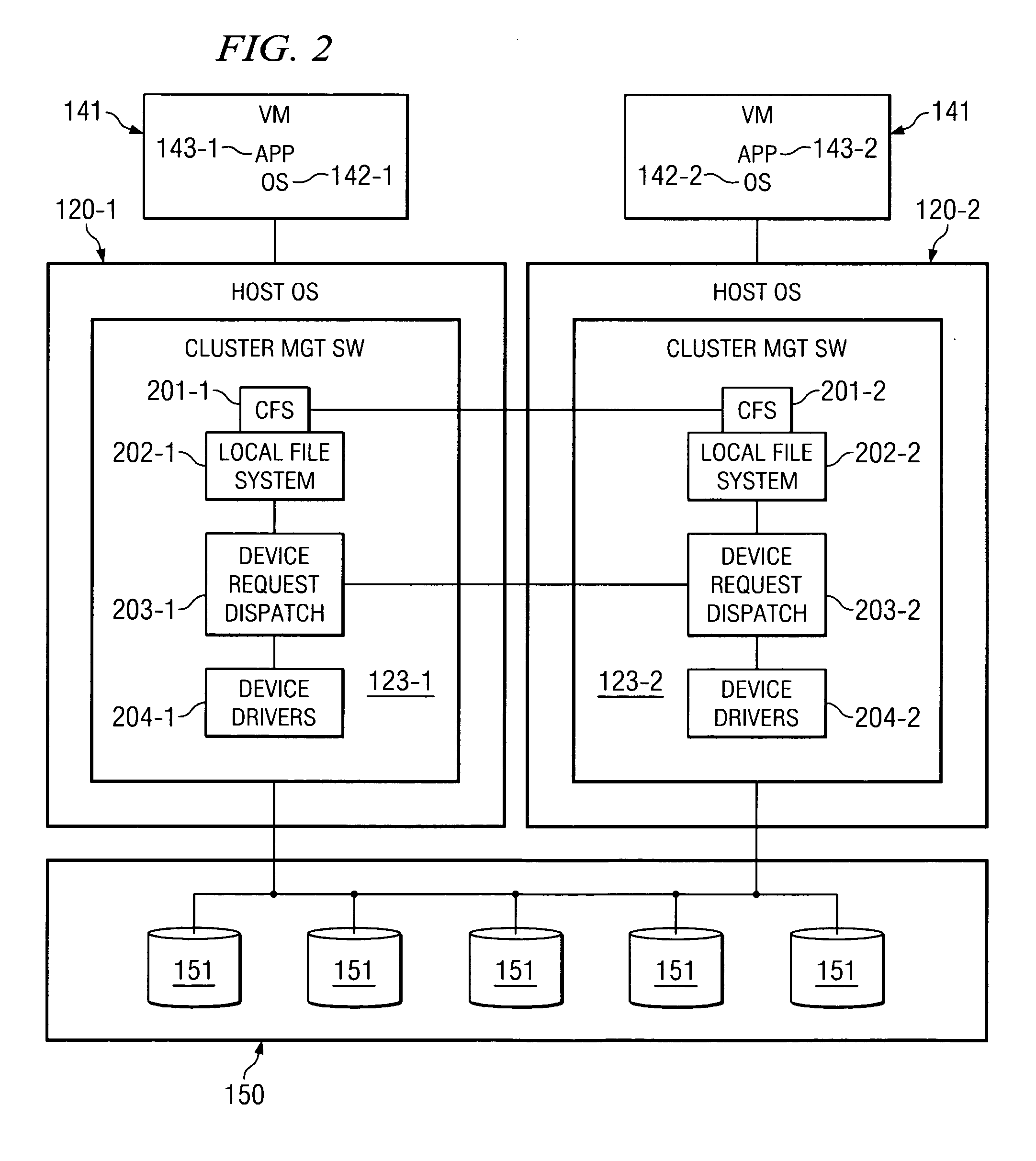
Virtual data center that allocates and manages system resources across multiple nodes
ActiveUS20070067435A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemData center
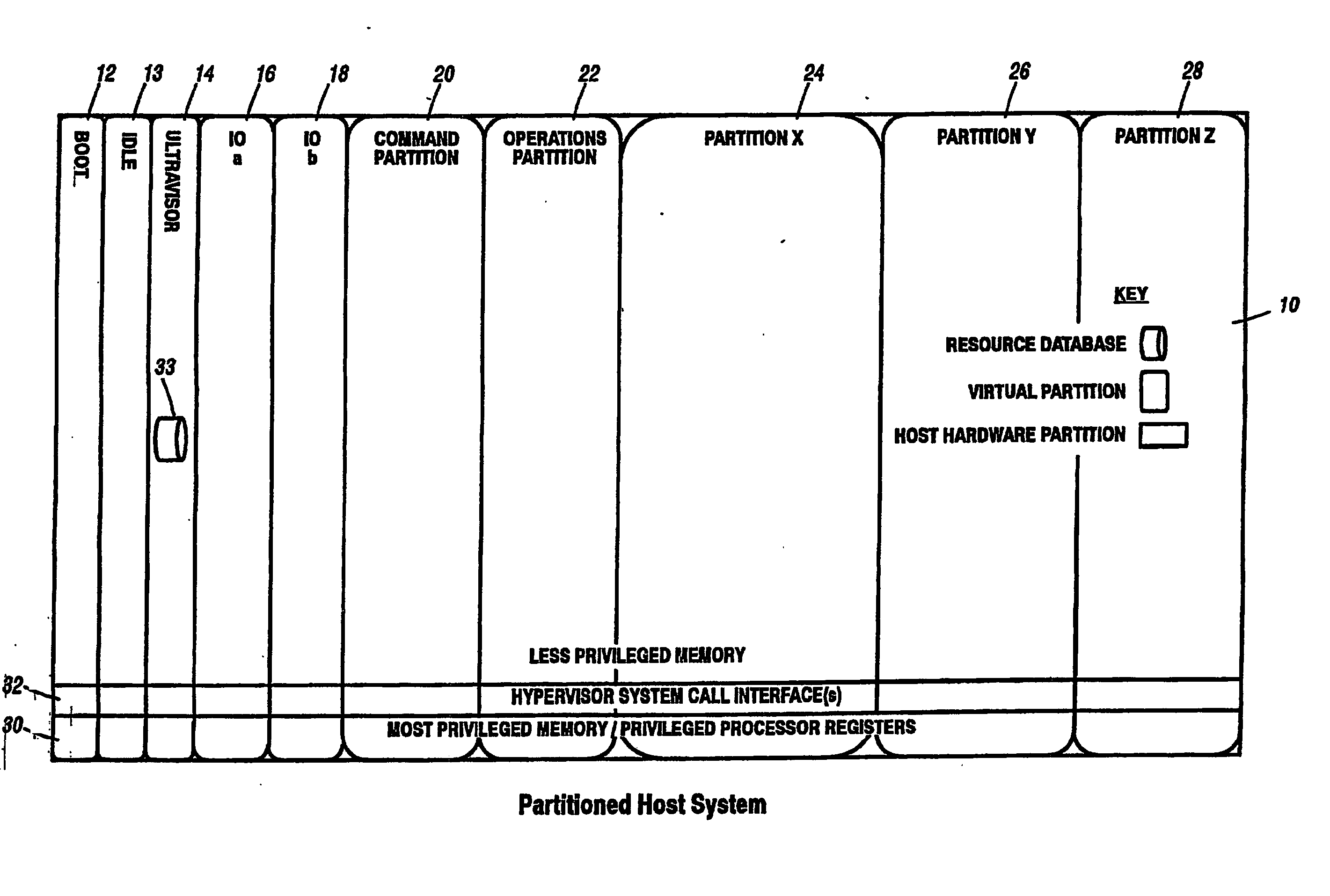
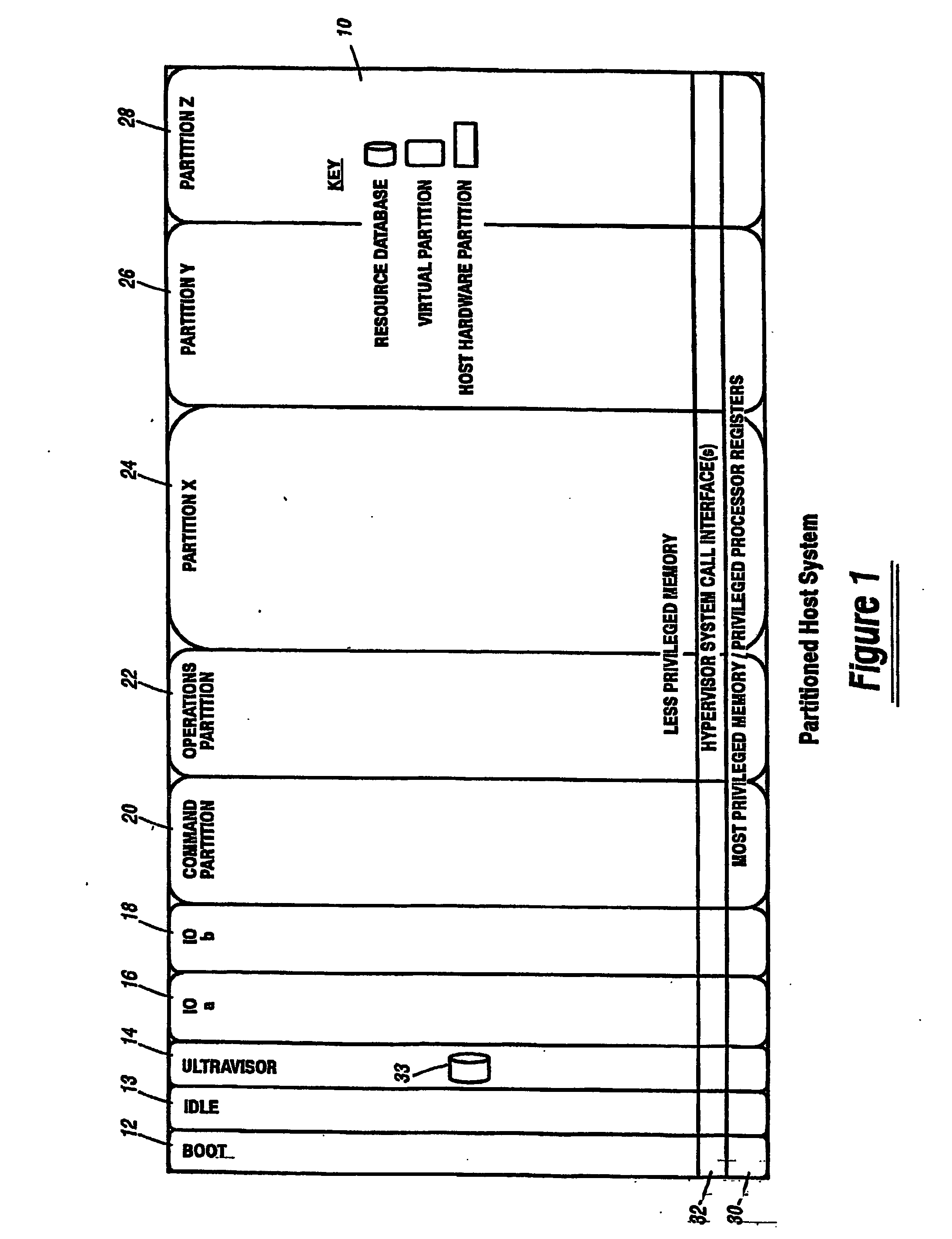
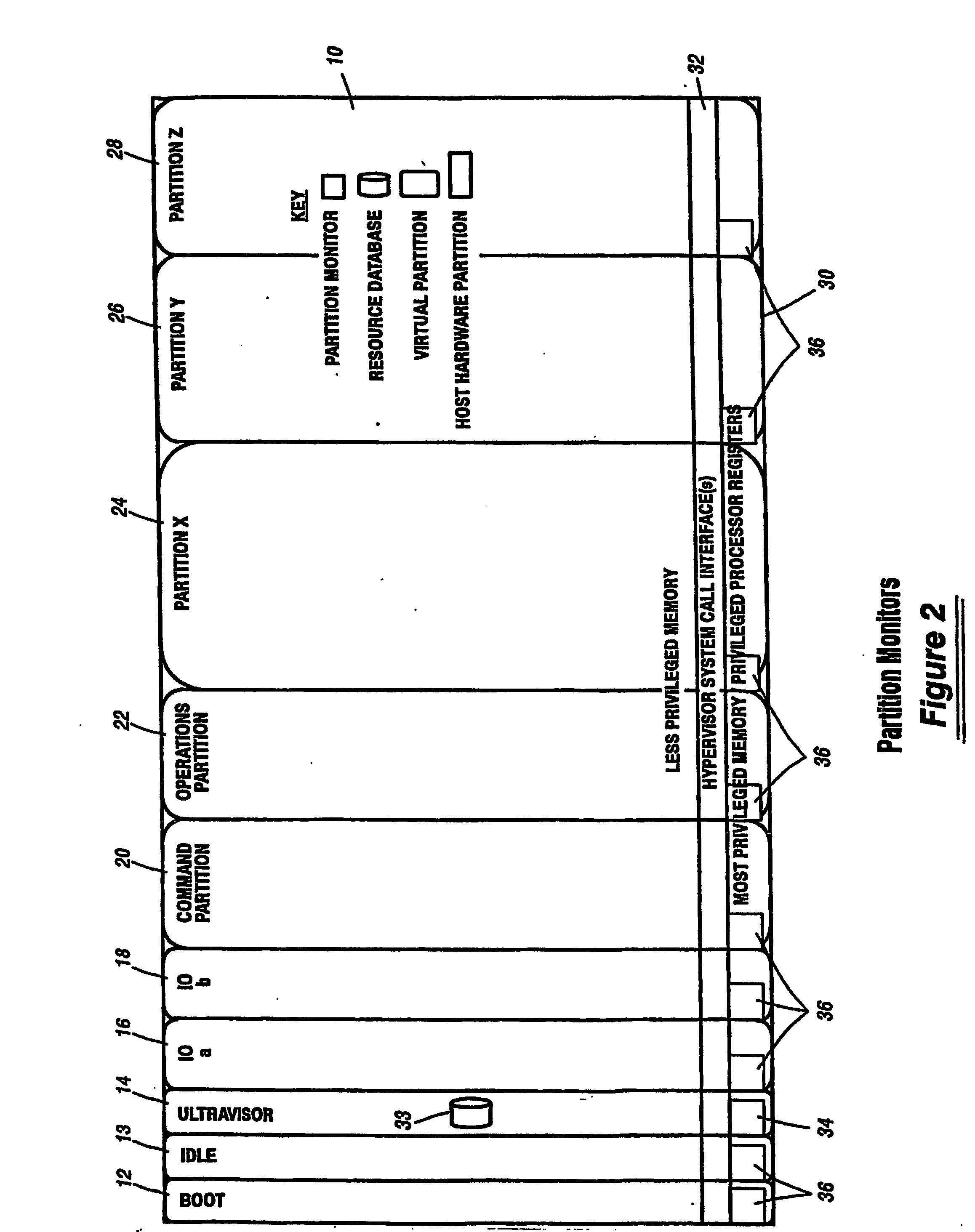
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps. System resources are separated into zones that are managed by a separate partition containing resource management policies that may be implemented across nodes to implement a virtual data center.
Owner:UNISYS CORP
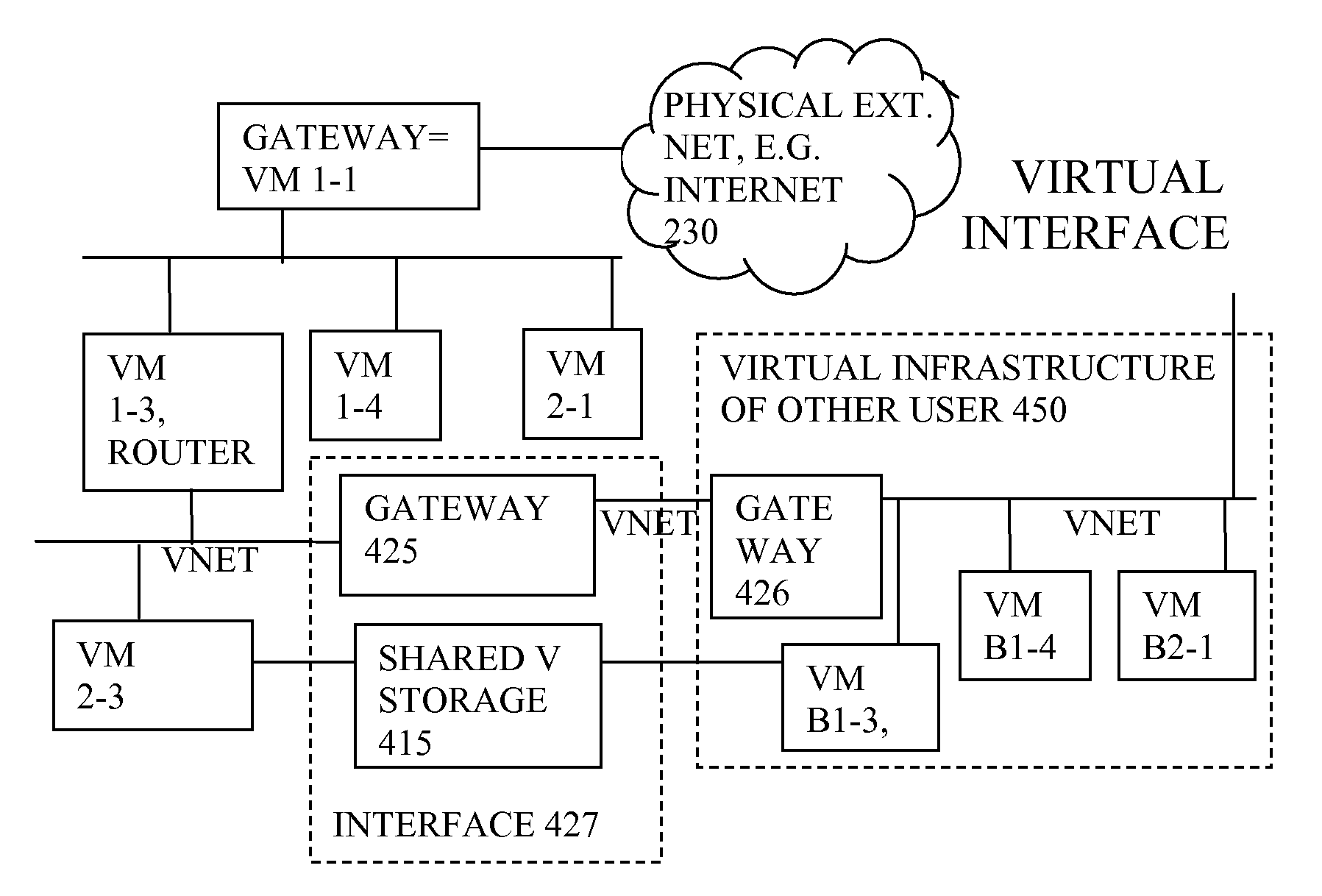
Management and Implementation of Enclosed Local Networks in a Virtual Lab
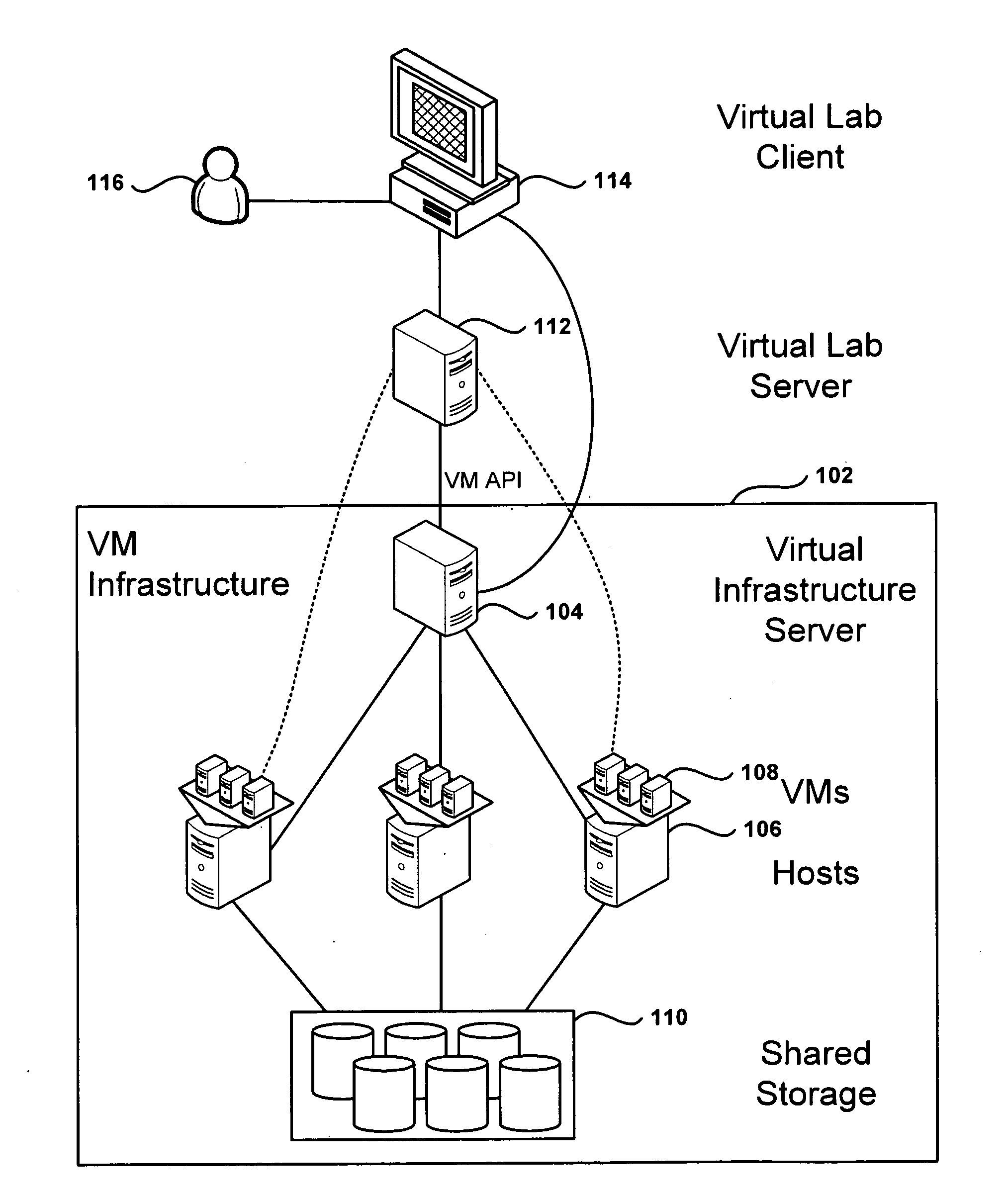
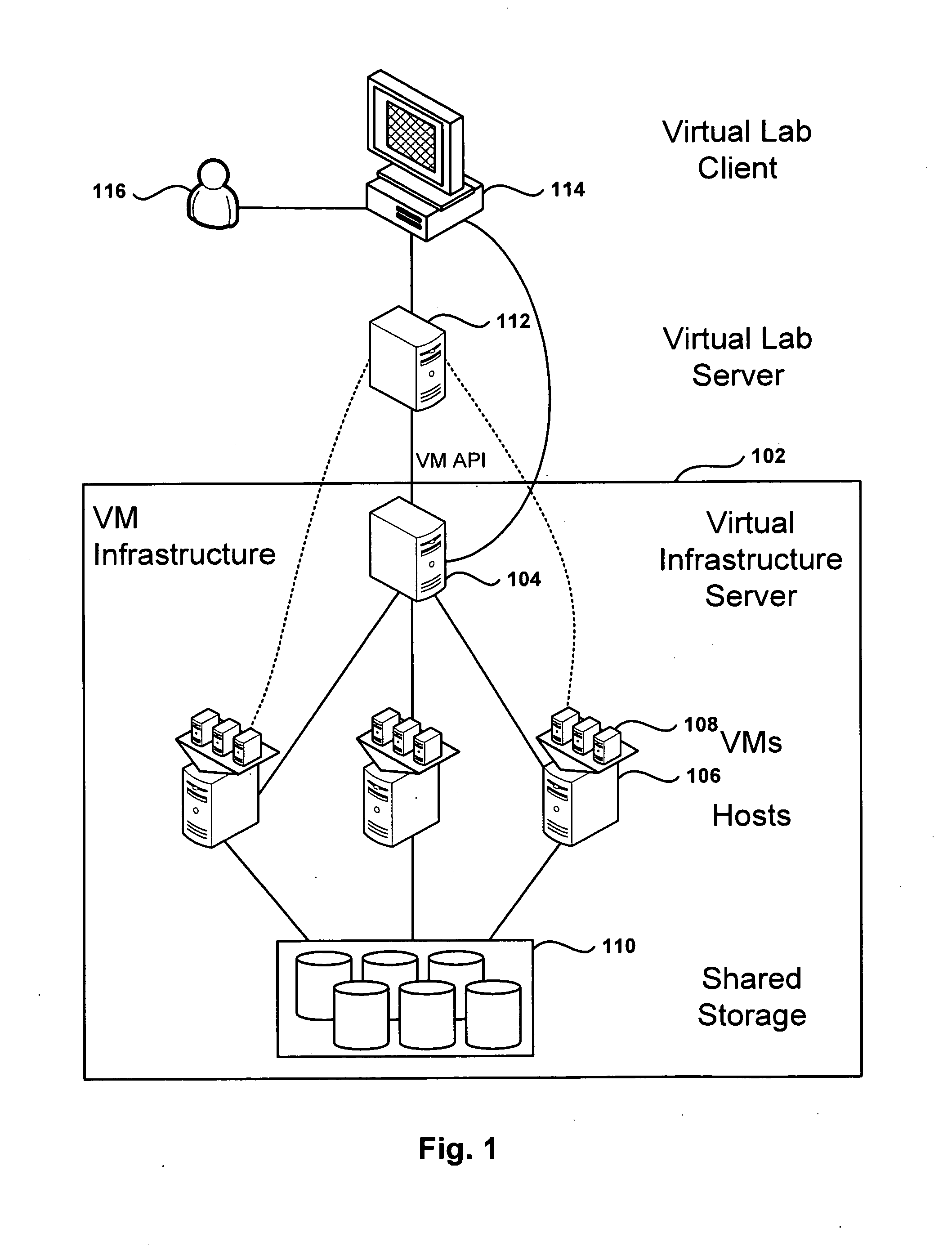
Methods, systems, and computer programs for creating isolated environments that include virtual machines (VM) and networks in a virtual infrastructure are presented. The method includes an operation to define a configuration of a virtual system which includes VMs, virtual network interface cards (VNIC) in the VMs, and configuration local networks (CLN). Further, the method associates each VNIC with one of the CLNs and transmits instructions to the virtual infrastructure for deploying the configuration. Deploying the configuration includes instantiating VMs and CLNs in the virtual infrastructure. Each VM is instantiated in a host monitored by a virtual lab server, and the CLNs are instantiated in the same hosts where the VMs have been instantiated. Only VMs from the configuration can connect to the instantiated CLNs. The method further transmits instructions to the virtual infrastructure to customize the VMs by executing the customization instructions in the guest operating systems of the VMs to configure the VMs' VNICs.
Owner:VMWARE INC
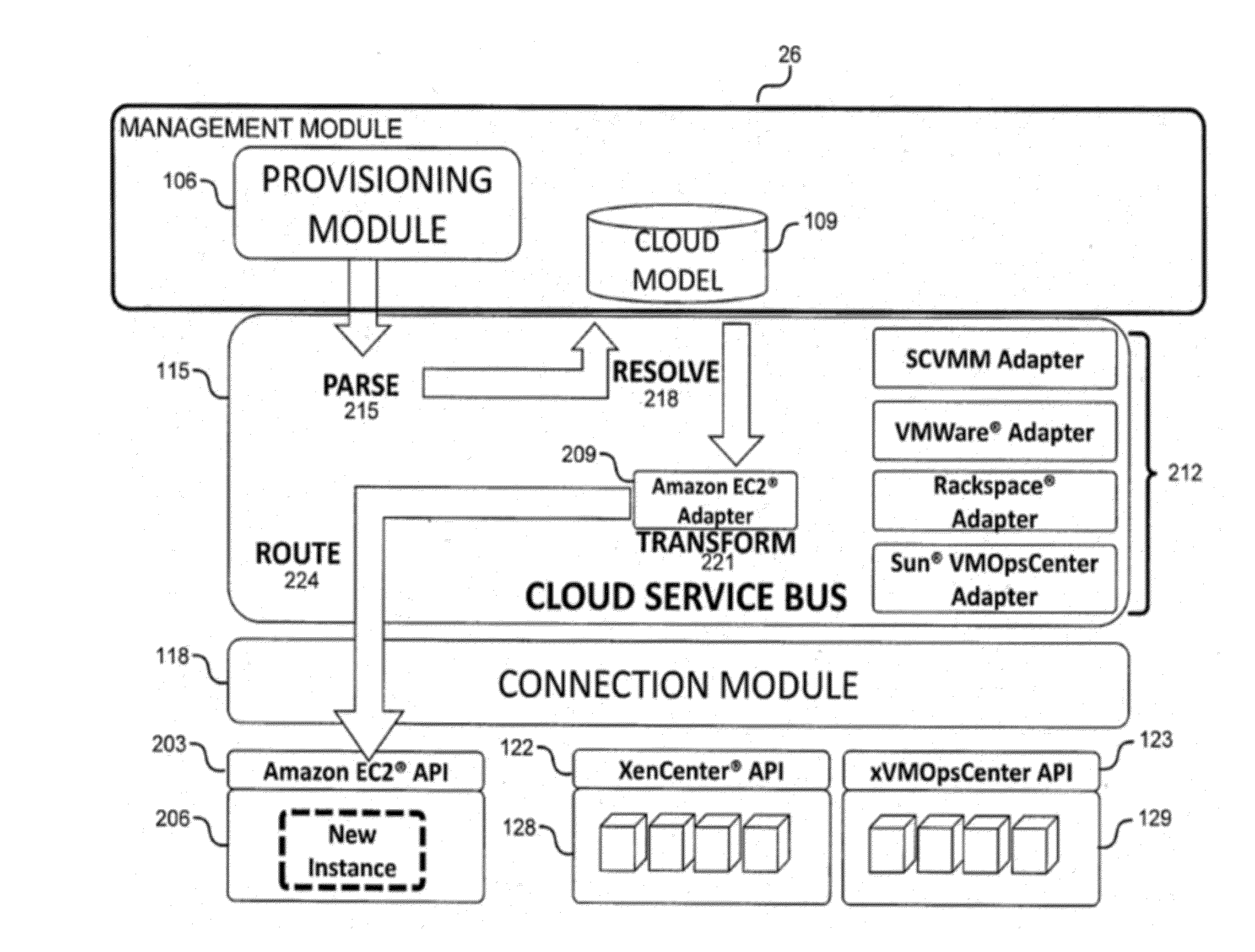
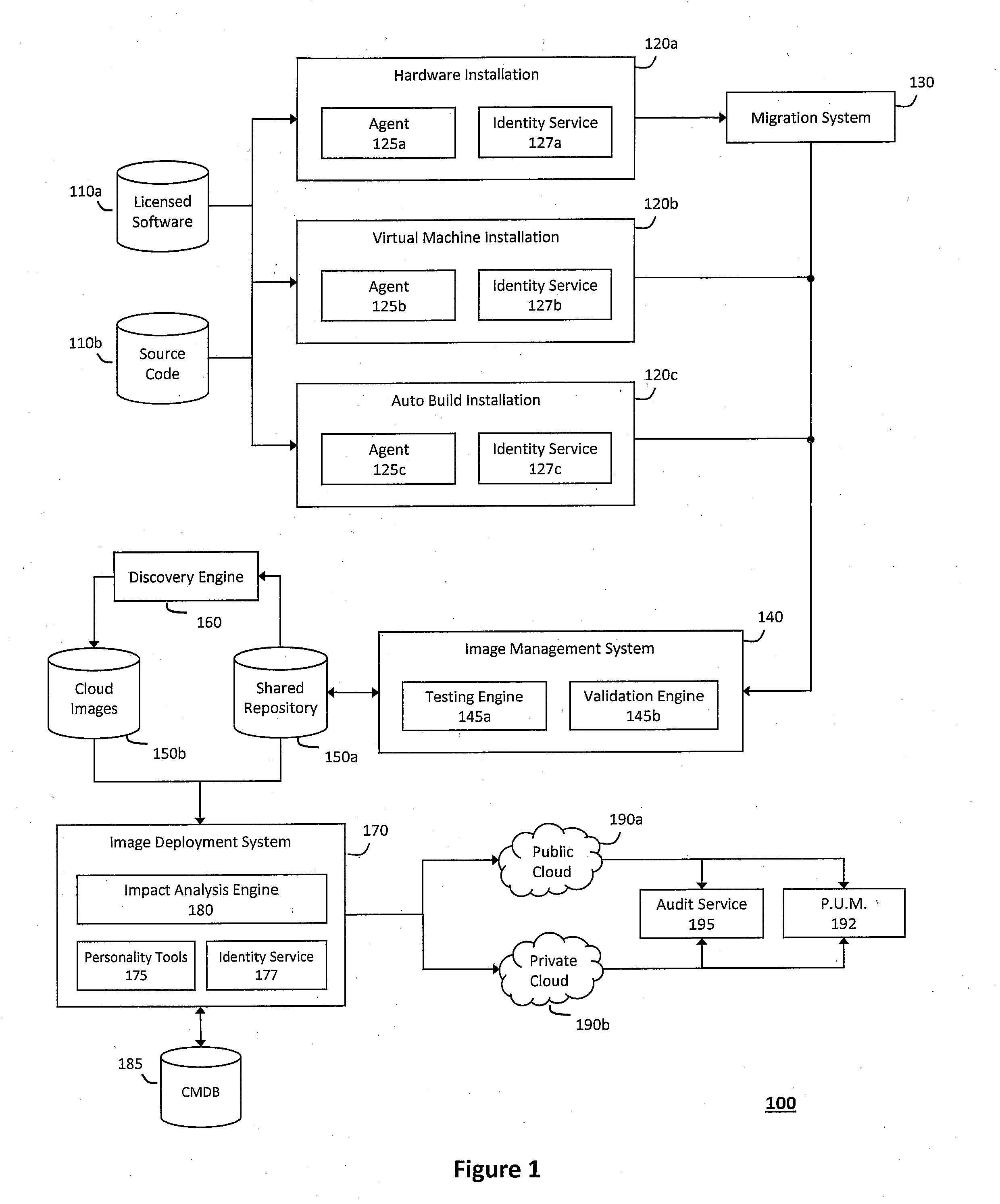
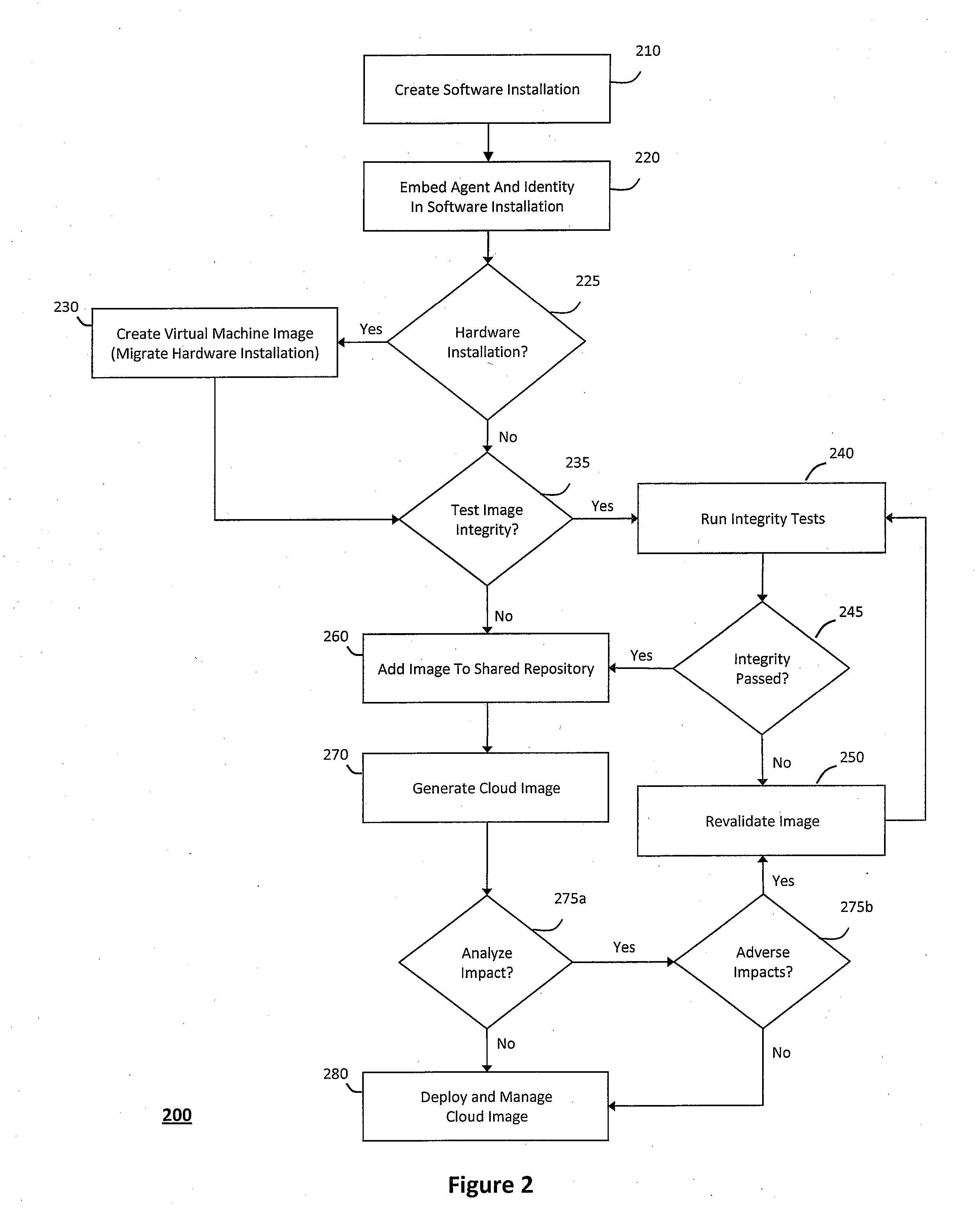
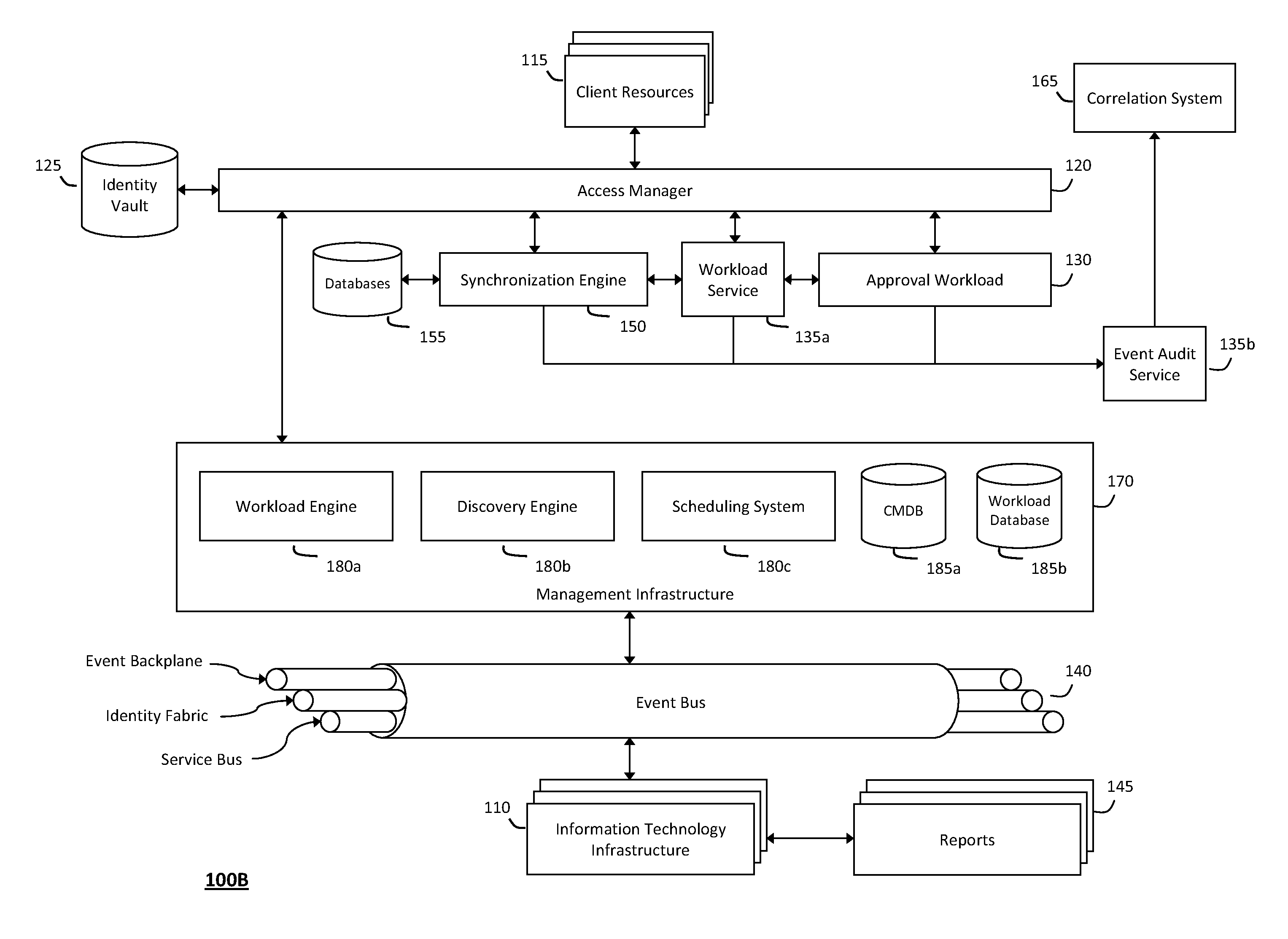
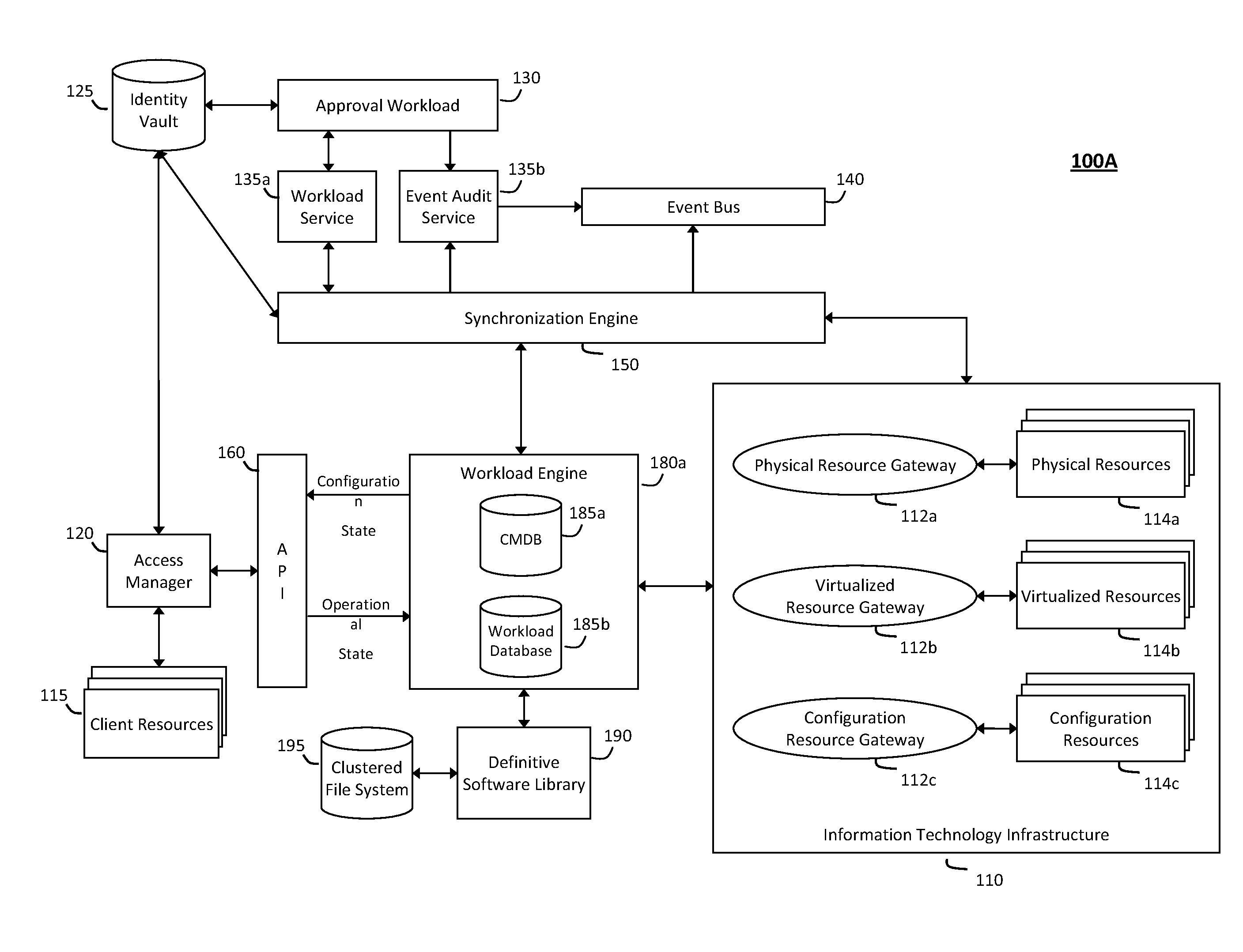
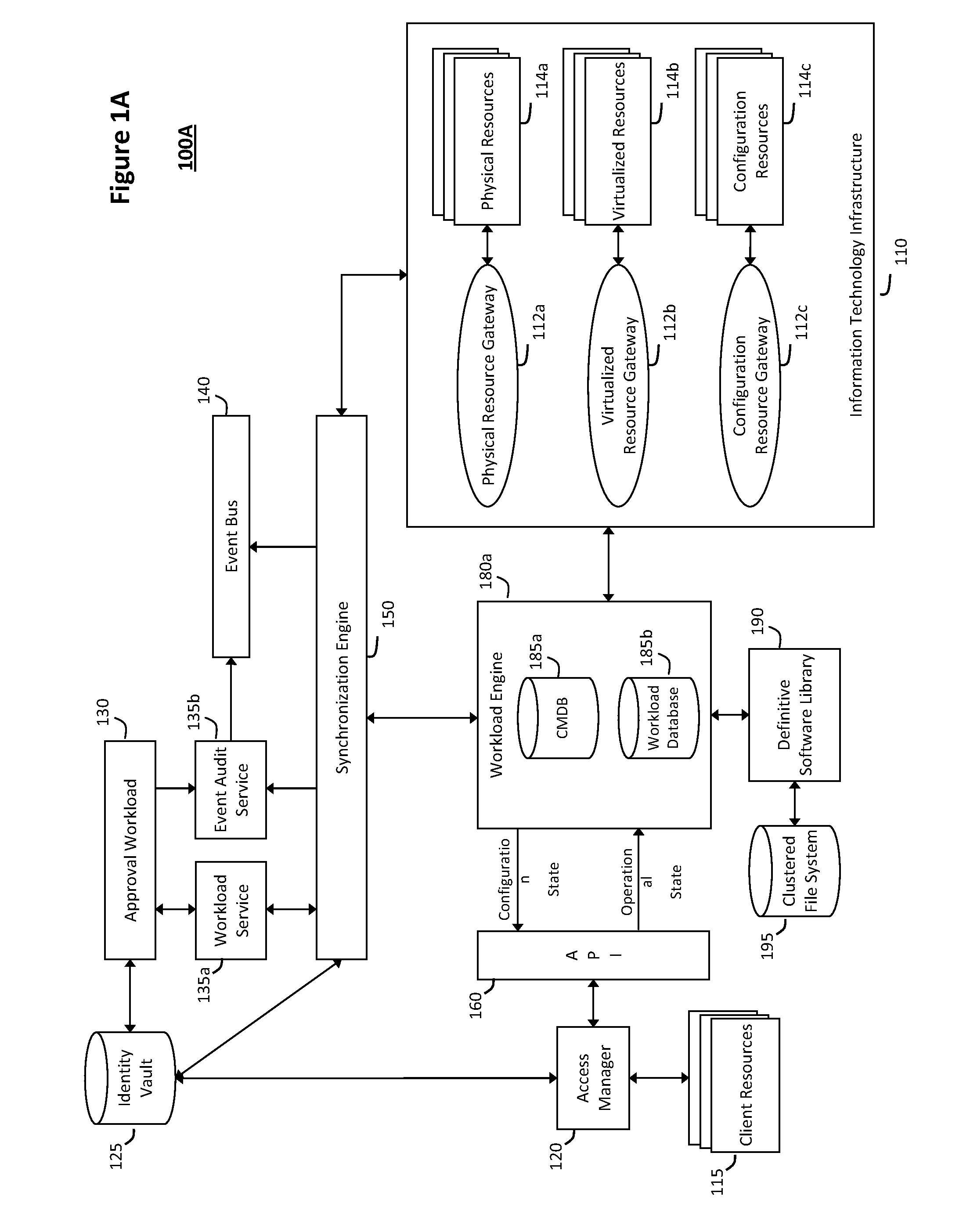
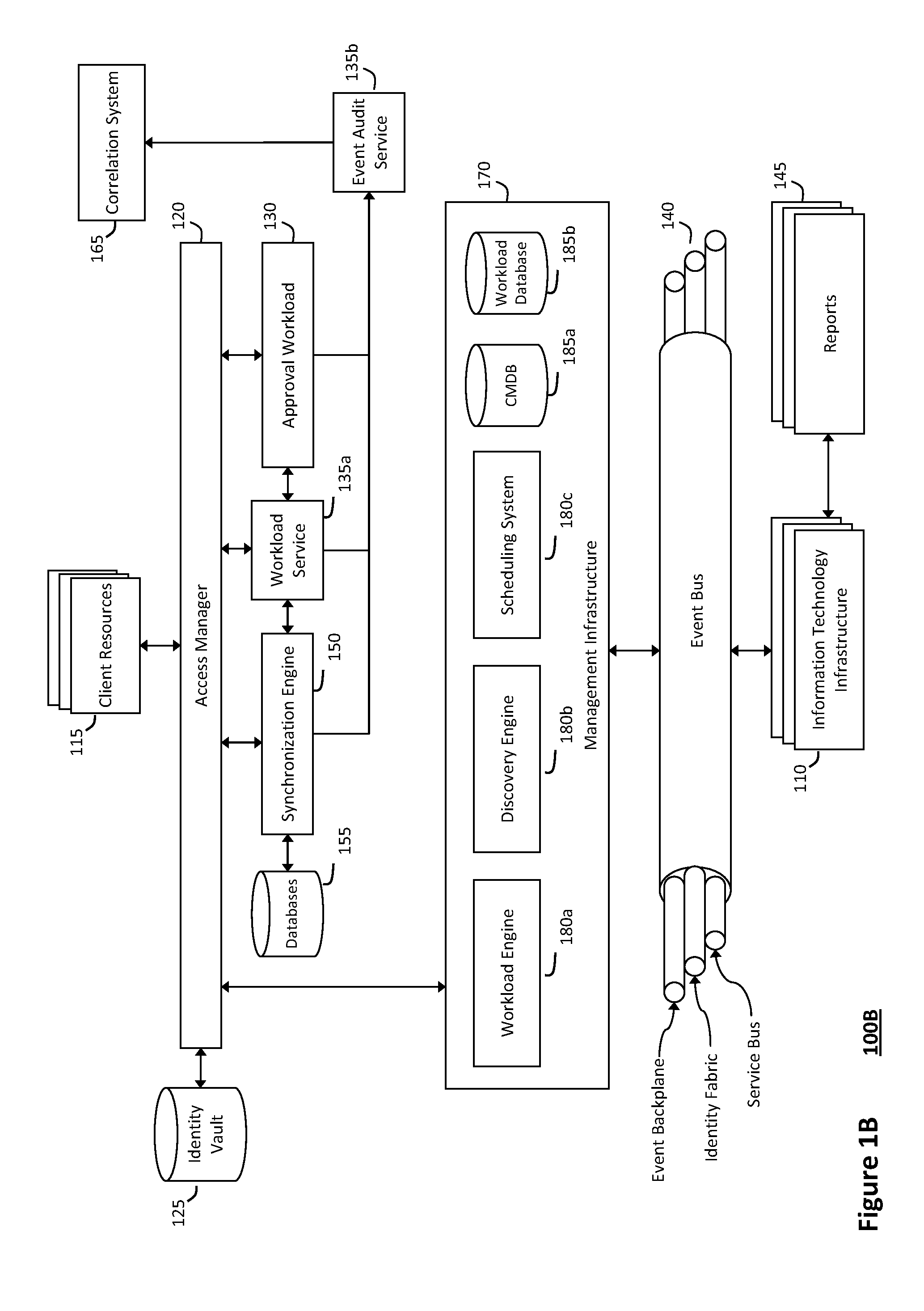
System and method for controlling cloud and virtualized data centers in an intelligent workload management system
InactiveUS20110126197A1Free computational resourceAgile and flexible managementDigital computer detailsDigital data authenticationData centerService-oriented architecture
The system and method for controlling cloud and virtualized data centers described herein may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads, and further to creating cloud images having embedded management agents and identity services for validating the cloud images prior to deployment into the cloud and virtualized data centers and controlling, monitoring, and auditing activity associated with the cloud images following deployment into the cloud and virtualized data centers.
Owner:MICRO FOCUS SOFTWARE INC
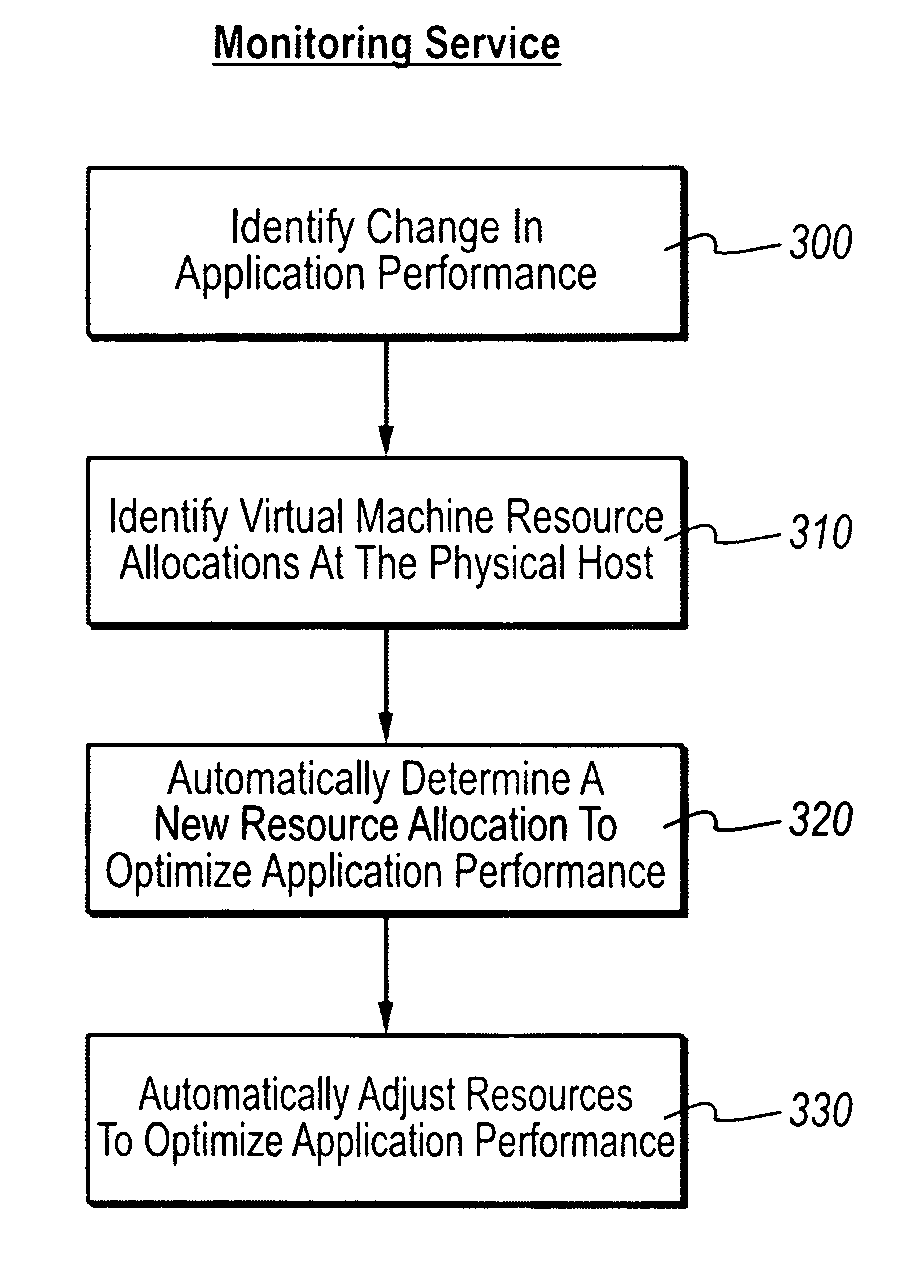
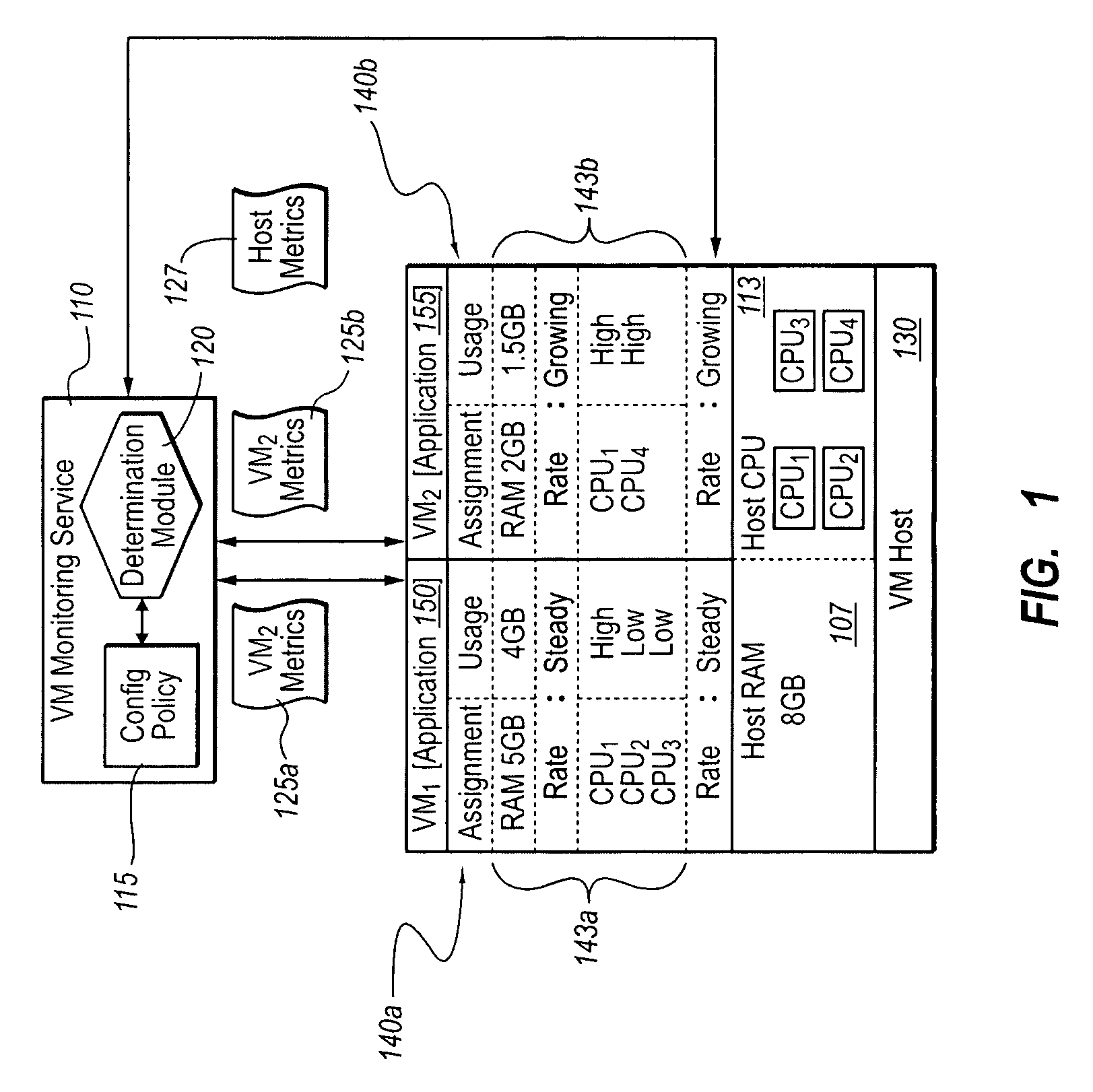
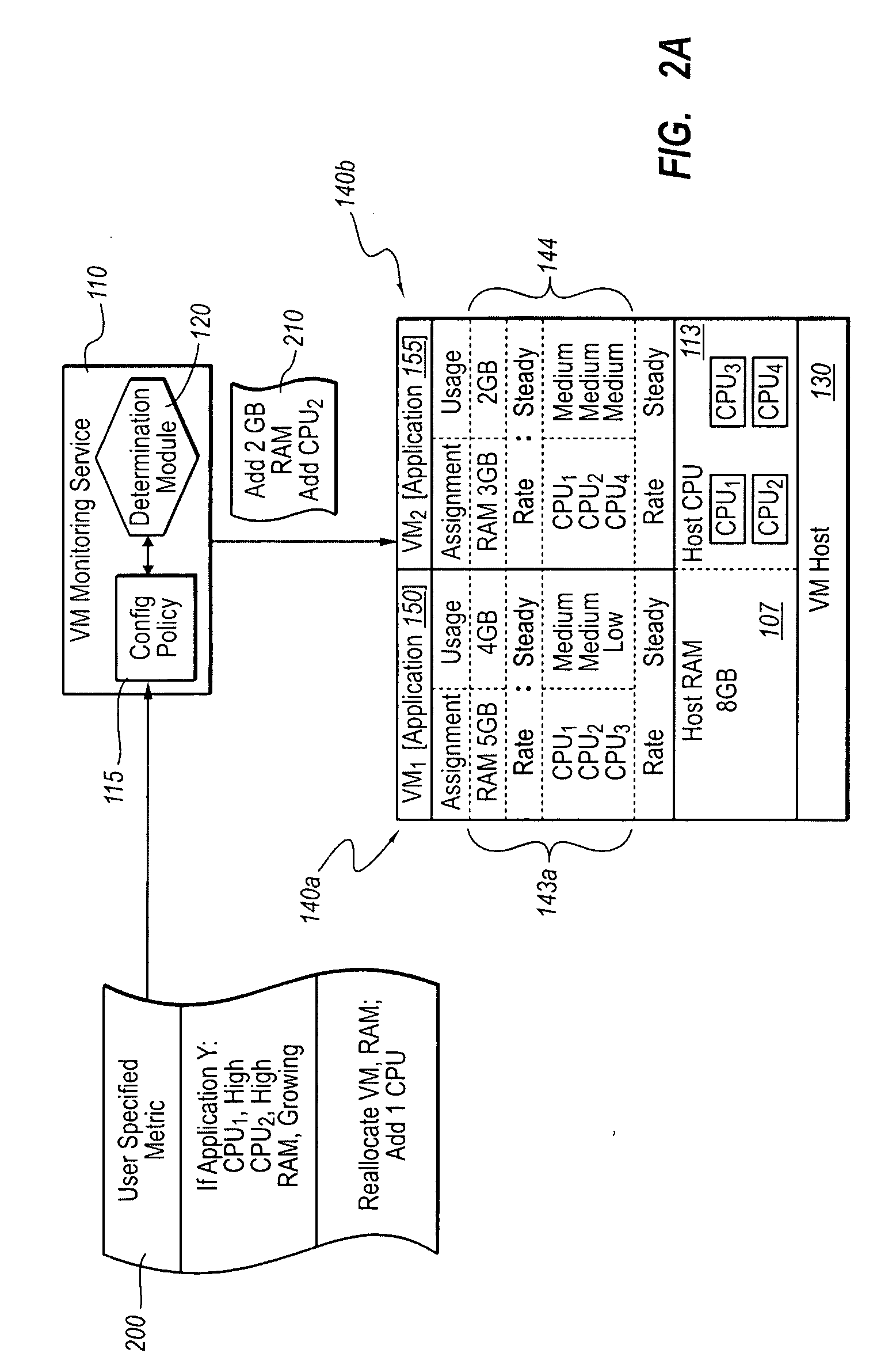
Optimizing application performance on virtual machines automatically with end-user preferences
InactiveUS20090265707A1Improve performanceError detection/correctionMultiprogramming arrangementsUser inputResource utilization
A virtual machine management / monitoring service can be configured to automatically monitor and implement user-defined (e.g., administrator-defined) configuration policies with respect to virtual machine and application resource utilization. In one implementation, the monitoring service can be extended to provide user-customized alerts based on various particularly defined events that occur (e.g., some memory or processing threshold) during operation of the virtual machines and / or application execution. The user can also specify particularly tailored solutions, which can include automatically reallocating physical host resources without additional user input on a given physical host, or moving / adding virtual machines on other physical hosts. For example, the monitoring service can be configured so that, upon identifying that a virtual machine's memory and processing resources are maxed out and / or growing, the monitoring service adds memory or processing resources for the virtual machine, or adds a new virtual machine to handle the load for the application program.
Owner:MICROSOFT TECH LICENSING LLC
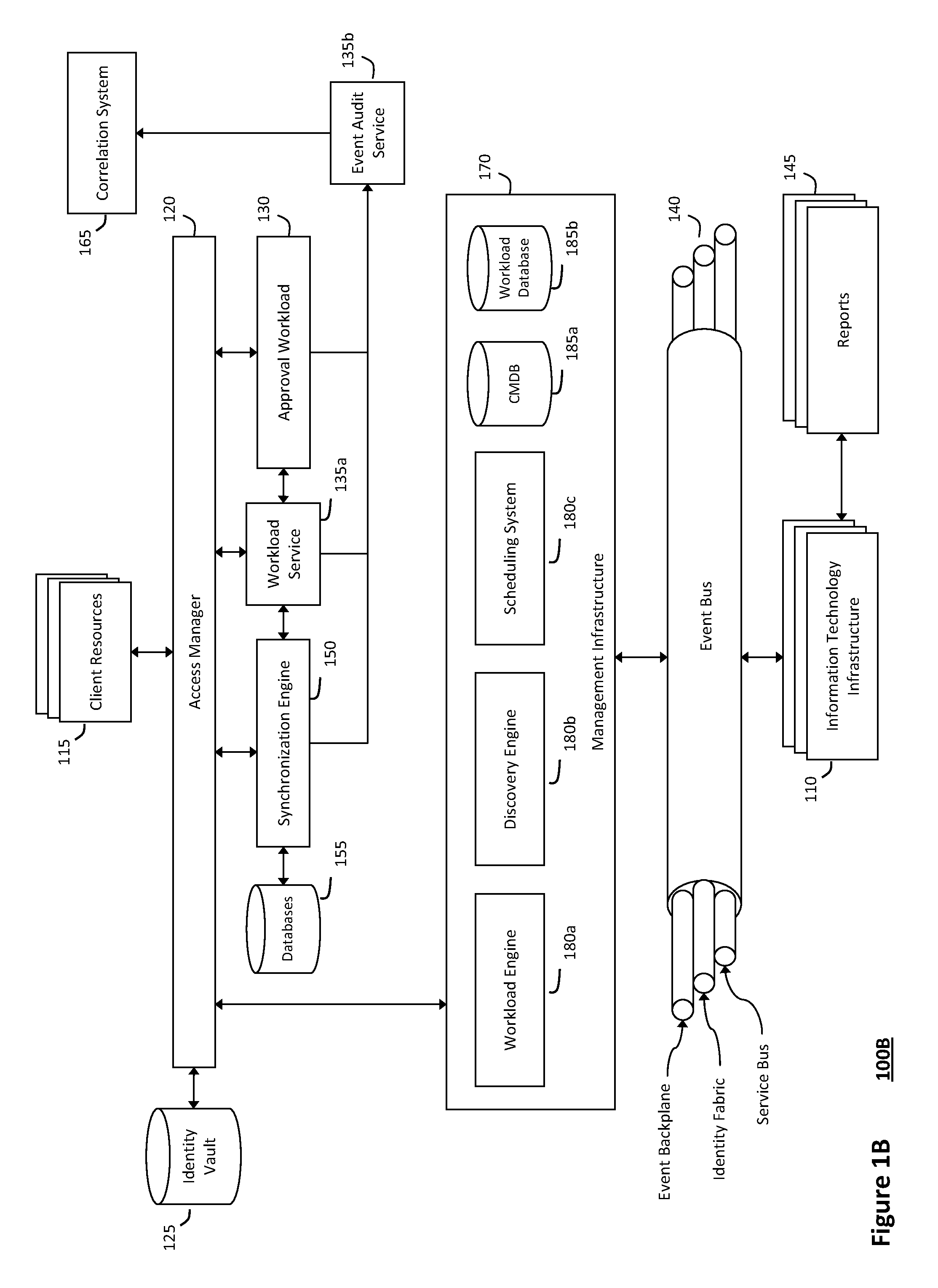
System and method for discovery enrichment in an intelligent workload management system
InactiveUS20110126275A1Free computational resourceAgile and flexible managementDigital data processing detailsUser identity/authority verificationVirtualizationService-oriented architecture
The system and method described herein for discovery enrichment in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for managing identities and access credentials, which may provide information that can enrich discovery of physical and virtual infrastructure resources. For example, a discovery engine may reference federated identity information stored in an identity vault and enrich a discovered infrastructure model with the federated identity information. Thus, the model may generally include information describing physical and virtualized resources in the infrastructure, applications and services running in the infrastructure, and information derived from the federated identity information that describes dependencies between the physical resources, the virtualized resources, the applications, and the services.
Owner:MICRO FOCUS SOFTWARE INC
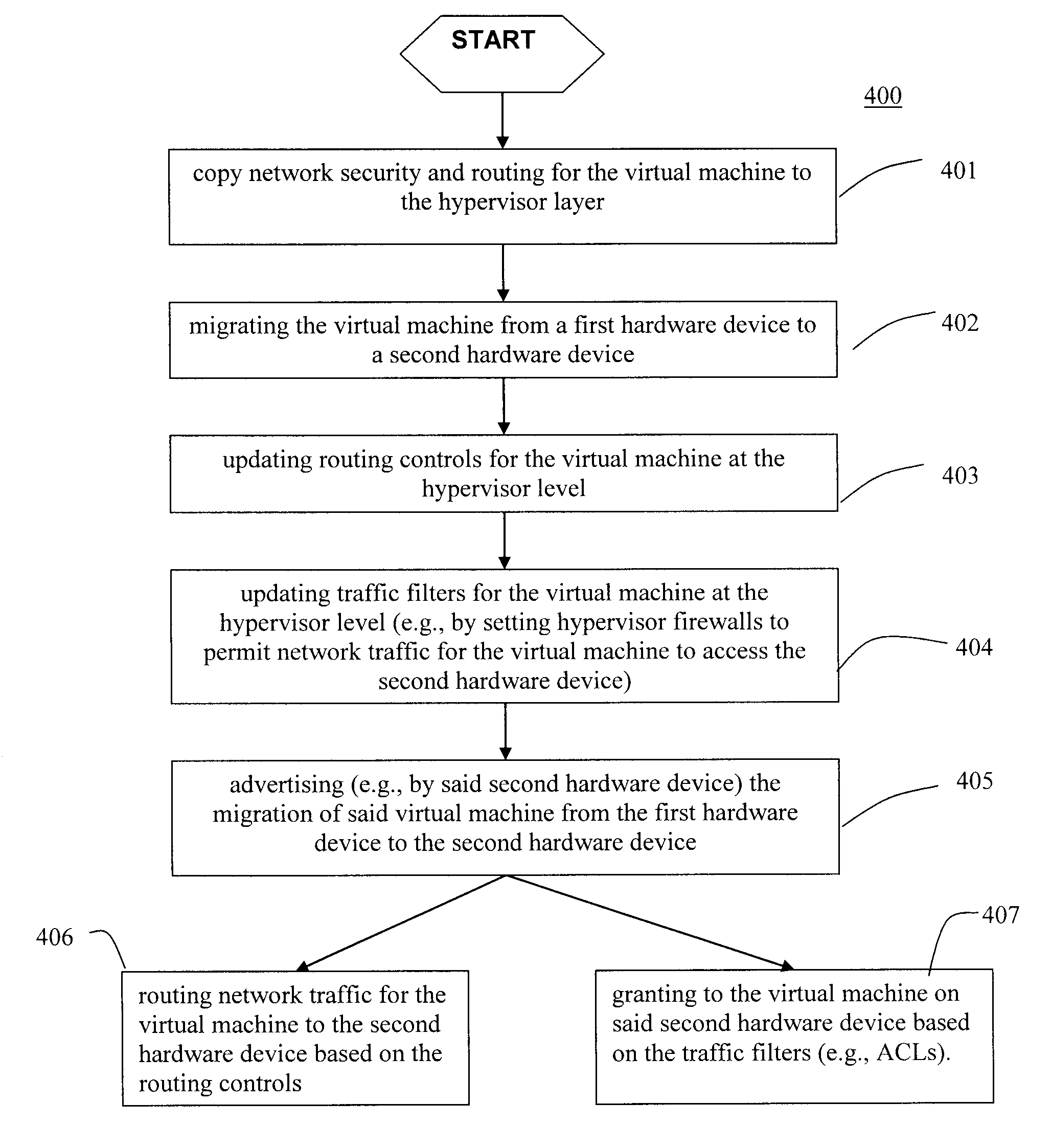
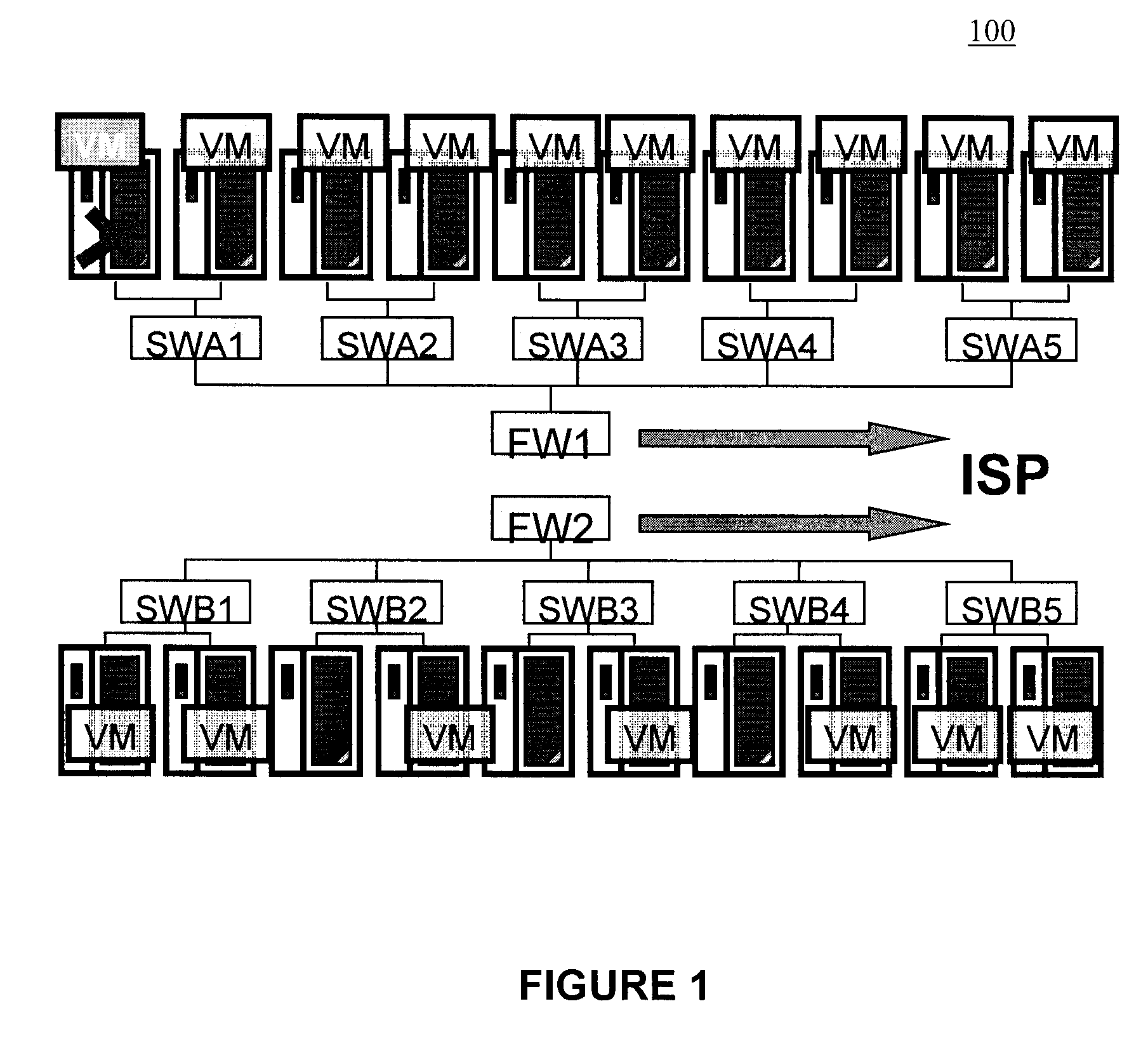
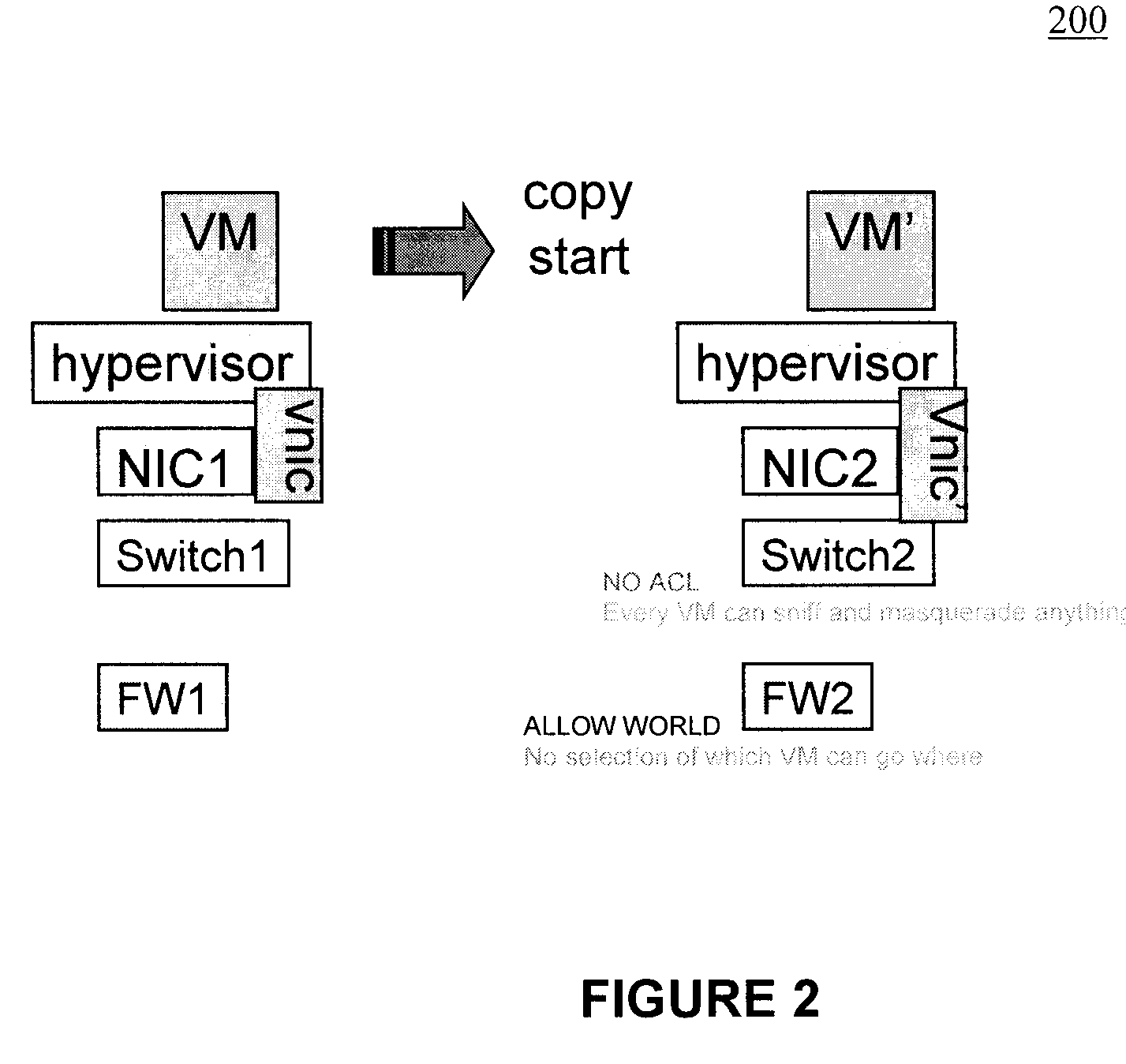
Moveable access control list (ACL) mechanisms for hypervisors and virtual machines and virtual port firewalls
ActiveUS20080163207A1Efficient responseRapid deploymentSemiconductor electrostatic transducersMicrophone structural associationVLAN access control listAccess control list
A method (and system) which provides virtual machine migration with filtered network connectivity and control of network security of a virtual machine by enforcing network security and routing at a hypervisor layer at which the virtual machine partition is executed, and which is independent of guest operating systems.
Owner:DAEDALUS BLUE LLC
System and method for intelligent workload management
ActiveUS20110125894A1Free computational resourceAgile and flexible managementDigital data processing detailsUser identity/authority verificationAuthentication serverService-oriented architecture
The system and method for intelligent workload management described herein may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads, wherein the management threads may converge information for managing identities and access credentials, enforcing policies, providing compliance assurances, managing provisioned and requested services, and managing physical and virtual infrastructure resources. In one implementation, an authentication server may generate authentication tokens defining access credentials for managed entities across a plurality of authentication domains, wherein the authentication tokens may control access to resources in an information technology infrastructure. For example, a management infrastructure may create service distributions for the managed entities, which may include virtual machine images hosted on physical resources. Further, the authentication tokens may be embedded in the service distributions, whereby the embedded authentication tokens may control access to the resources in the information technology infrastructure.
Owner:MICRO FOCUS SOFTWARE INC
Systems and methods for performing backup operations of virtual machine files
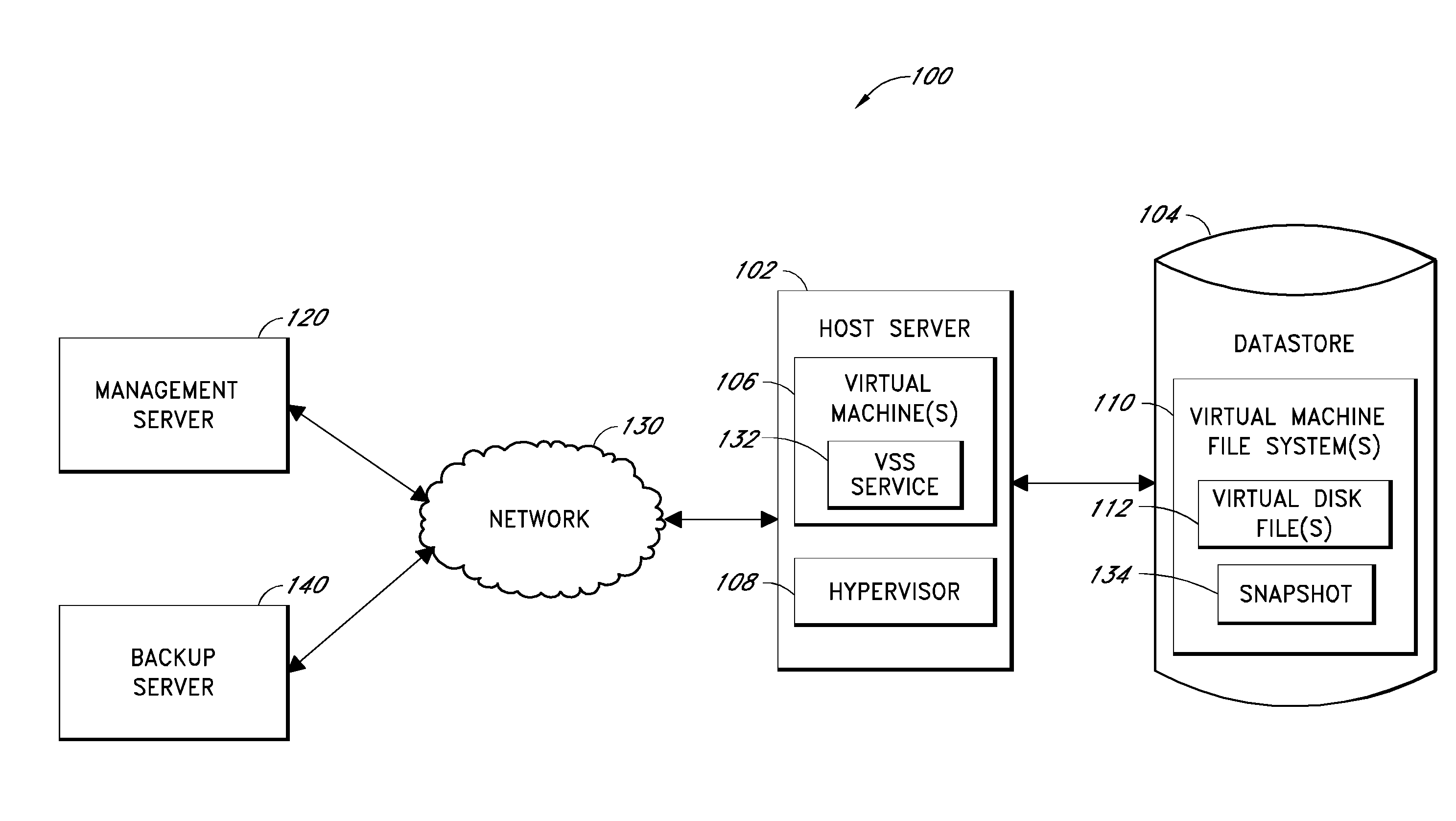
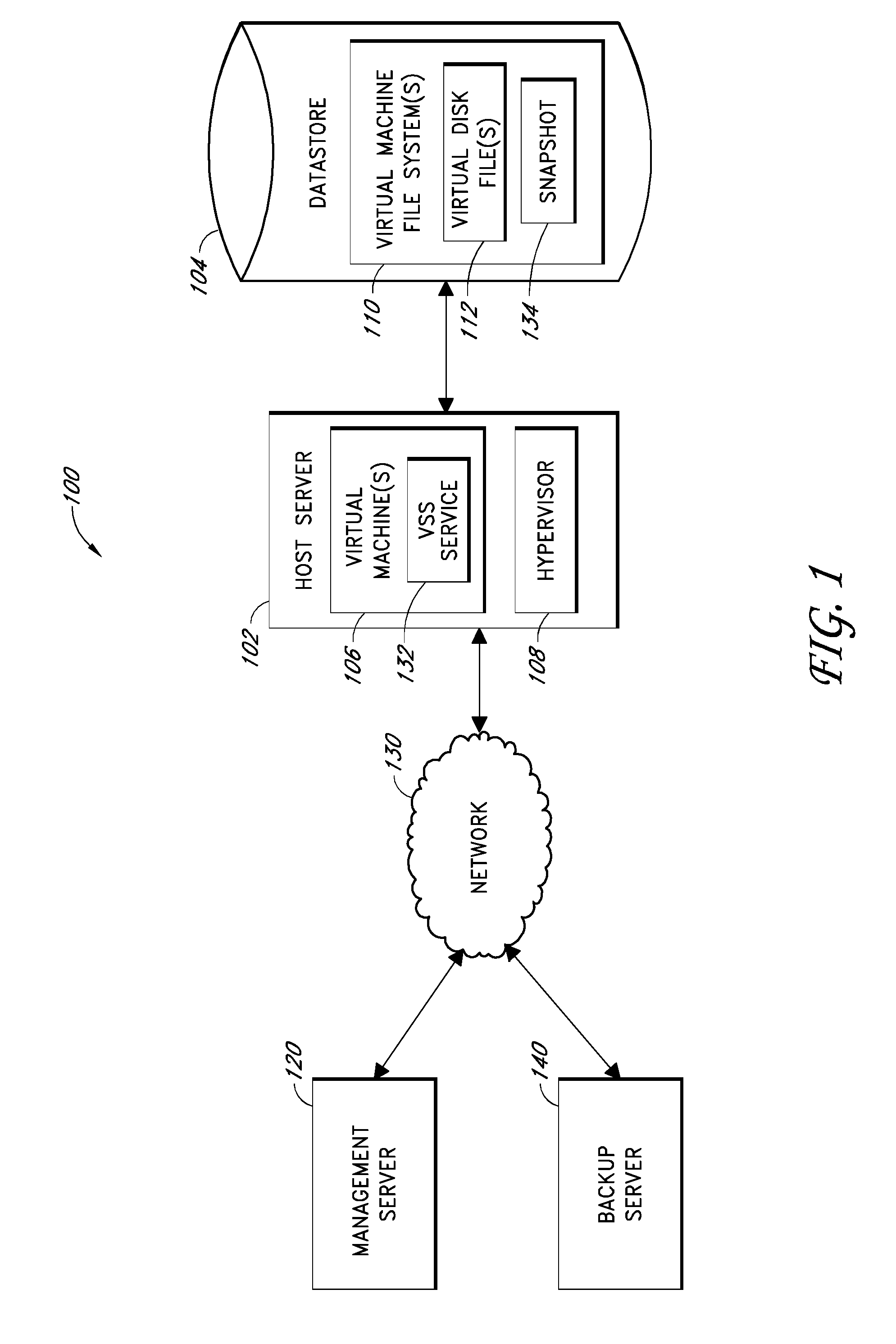
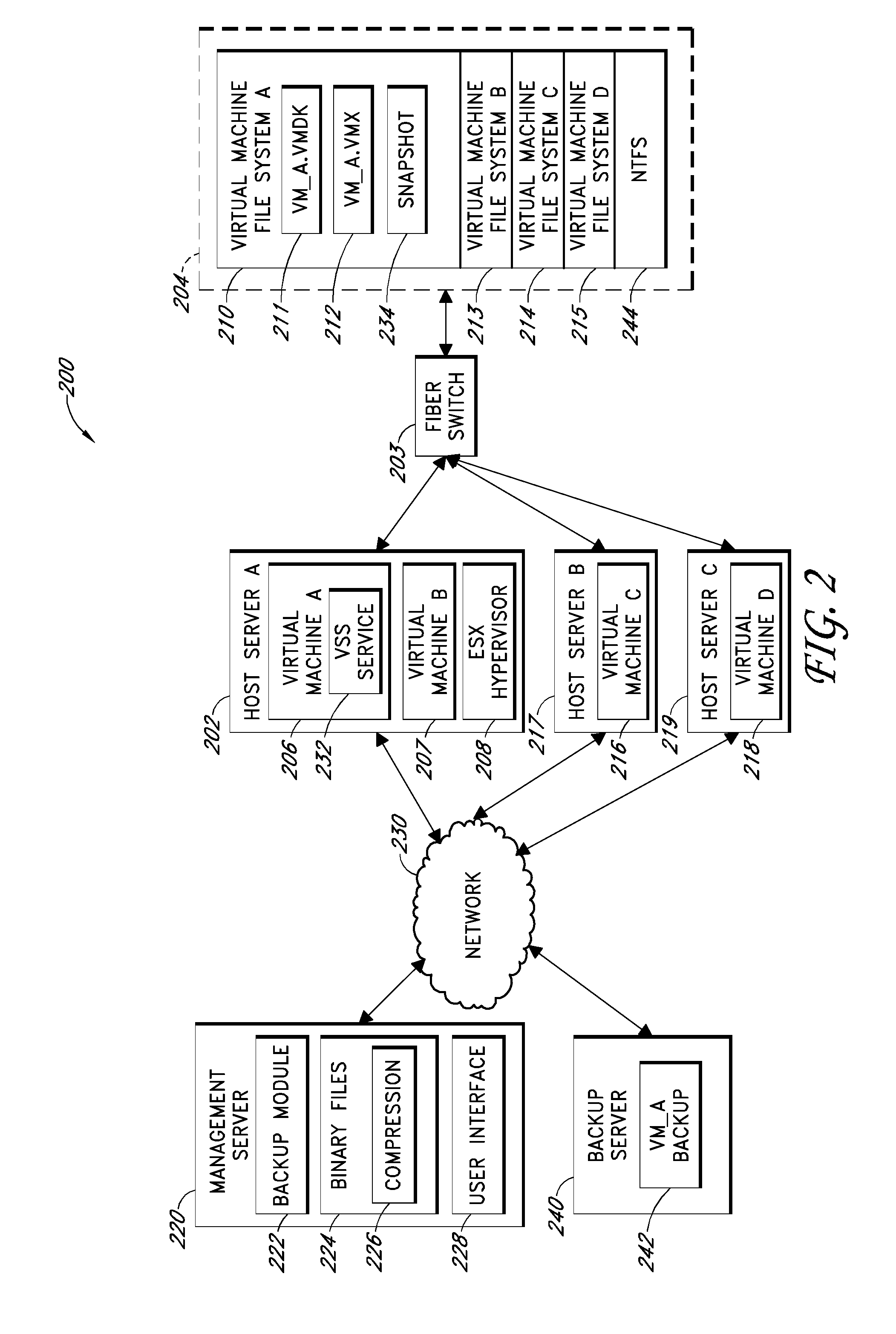
ActiveUS20100011178A1Memory loss protectionError detection/correctionCommunications managementOperational system
Backup systems and methods are disclosed for a virtual computing environment. Certain examples include a system having a backup management server that communicates with a host server having at least one virtual machine. The management server coordinates with the host server to perform backup copies of entire virtual machine disks from outside the guest operating system of the virtual machine. In certain examples, such backup systems further utilize a volume shadow copy service executing on the host server to quiesce virtual machine applications to put data in a consistent state to be backed up. The backup system then utilizes hypervisor snapshot capabilities of the host server to record intended changes to the virtual machine disk files while such files are being copied (e.g., backed up) by the host server. Such recorded changes can be later committed to the virtual machine disk files once the backup operation has completed.
Owner:QUEST SOFTWARE INC
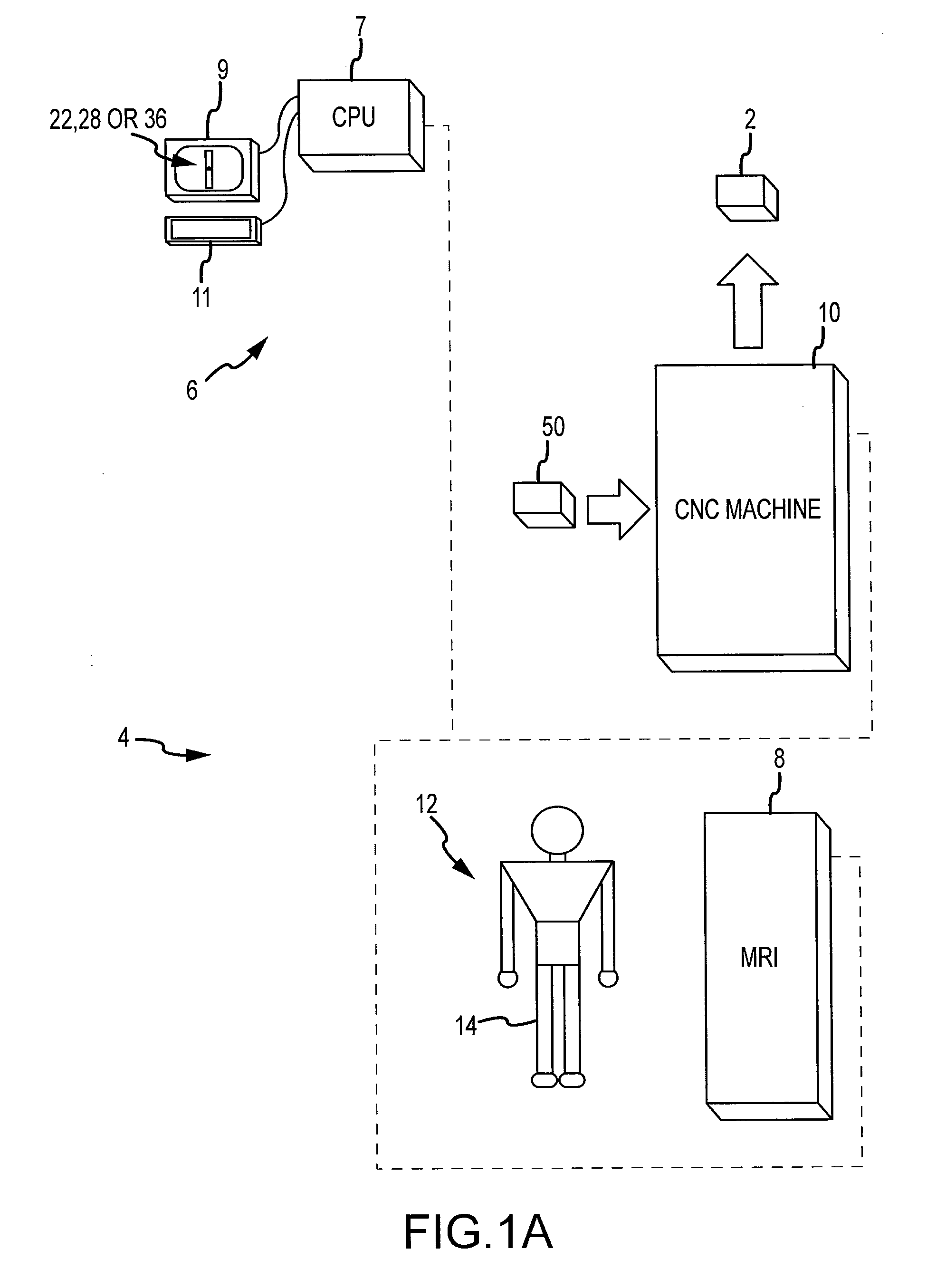
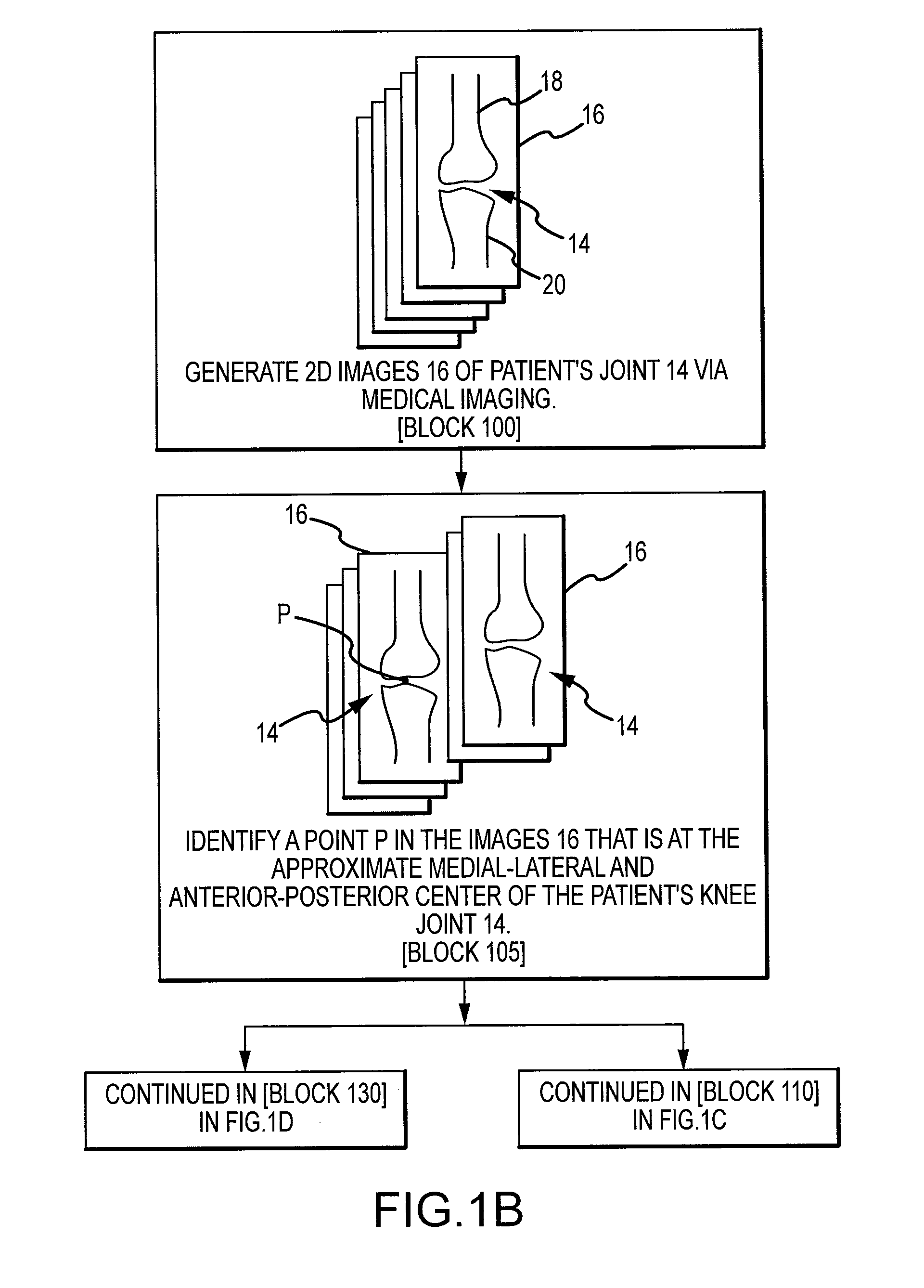
Generation of a computerized bone model representative of a pre-degenerated state and useable in the design and manufacture of arthroplasty devices
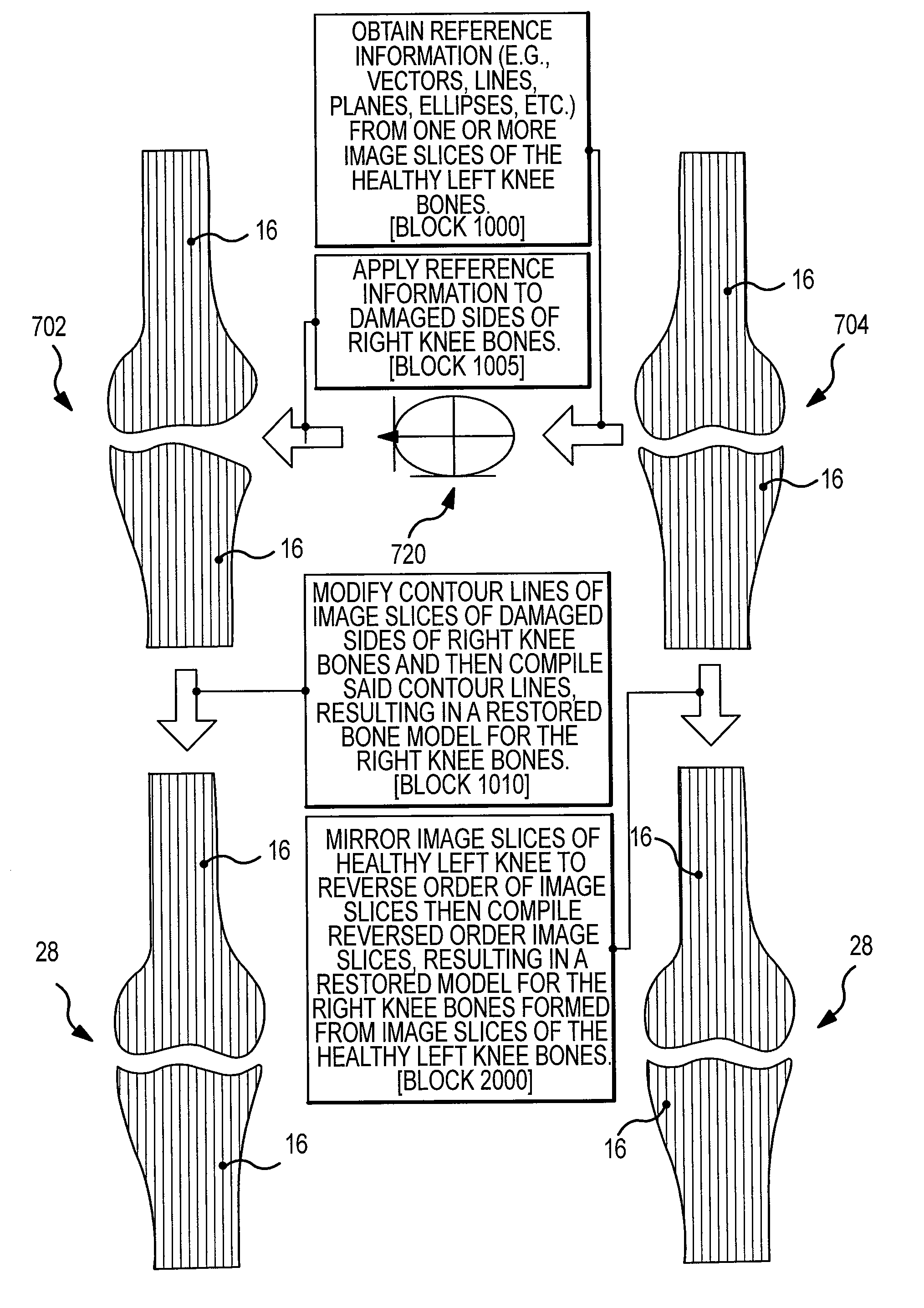
ActiveUS20090270868A1Reduce the possibilityIncrease success rateDiagnosticsAnalogue computers for chemical processesKnee JointProsthesis
Disclosed herein is a method of generating a computerized bone model representative of at least a portion of a patient bone in a pre-degenerated state. The method includes: generating at least one image of the patient bone in a degenerated state; identifying a reference portion associated with a generally non-degenerated portion of the patient bone; identifying a degenerated portion associated with a generally degenerated portion of the patient bone; and using information from at least one image associated with the reference portion to modify at least one aspect associated with at least one image associated the generally degenerated portion. The method may further include employing the computerized bone model representative of the at least a portion of the patient bone in the pre-degenerated state in defining manufacturing instructions for the manufacture of a customized arthroplasty jig. Also disclosed herein is a customized arthroplasty jig manufactured according to the above-described method. The customized arthroplasty jig is configured to facilitate a prosthetic implant restoring a patient joint to a natural alignment. The prosthetic implant may be for a total joint replacement or partial joint replacement. The patient joint may be a variety of joints, including, but not limited to, a knee joint.
Owner:HOWMEDICA OSTEONICS CORP
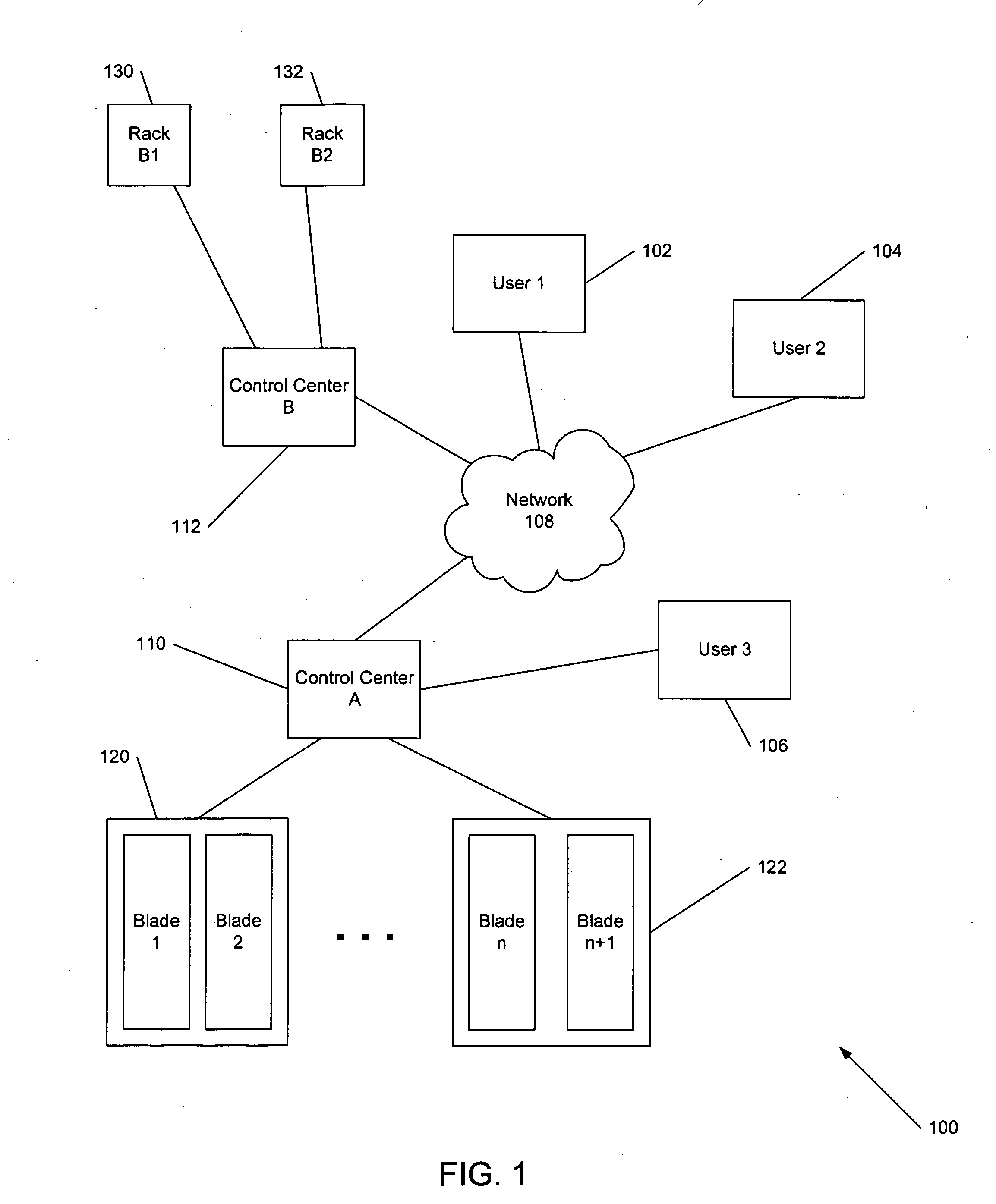
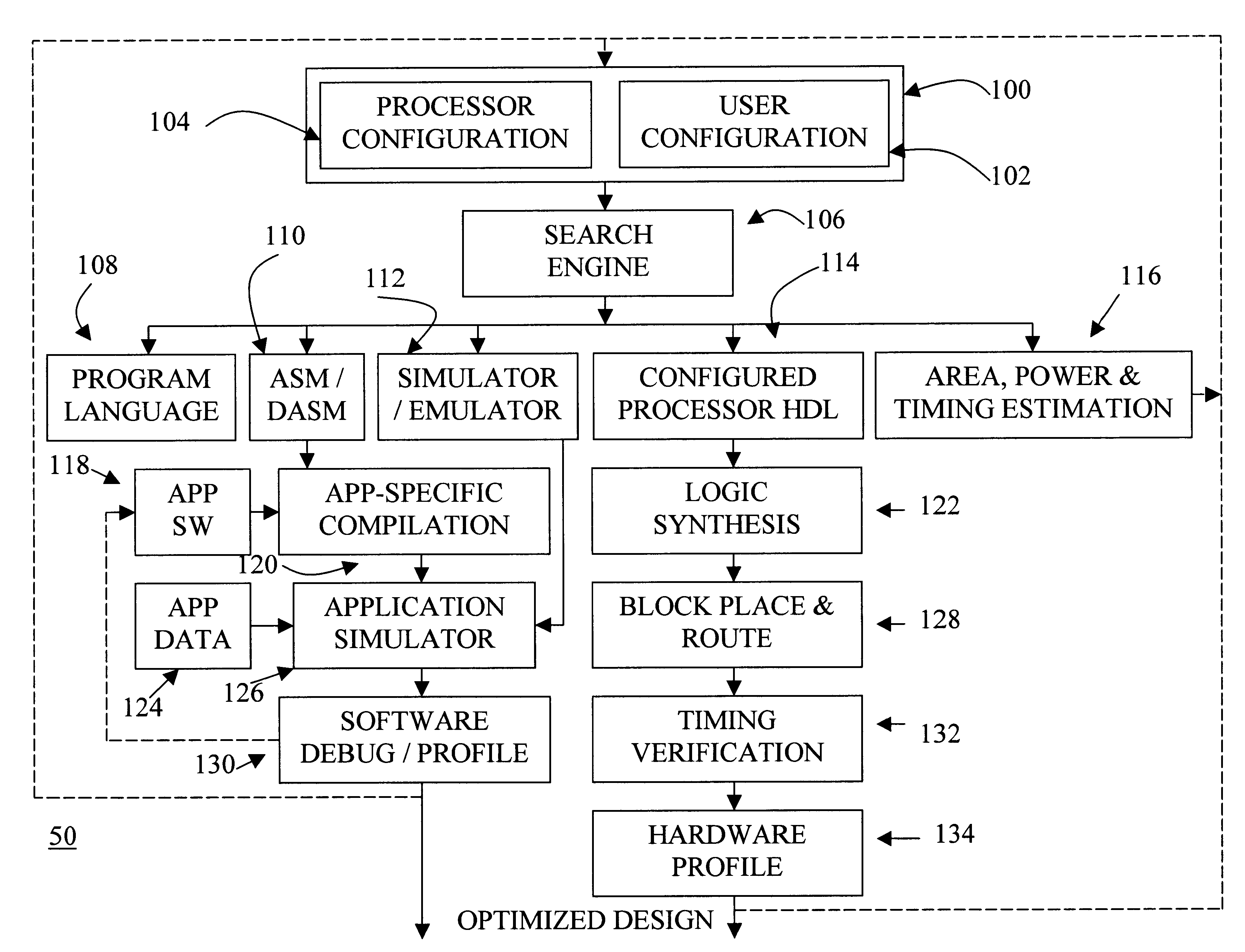
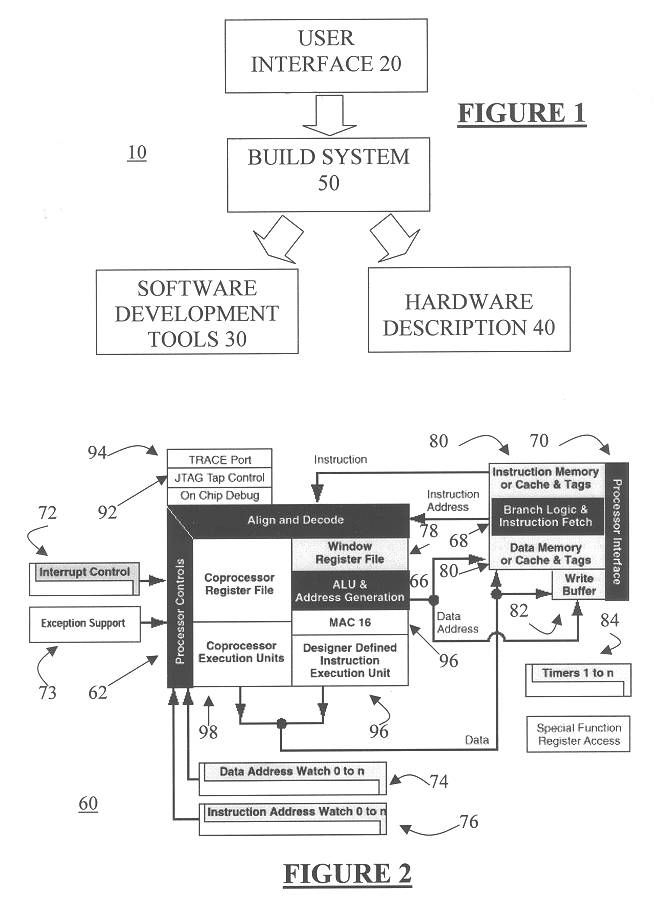
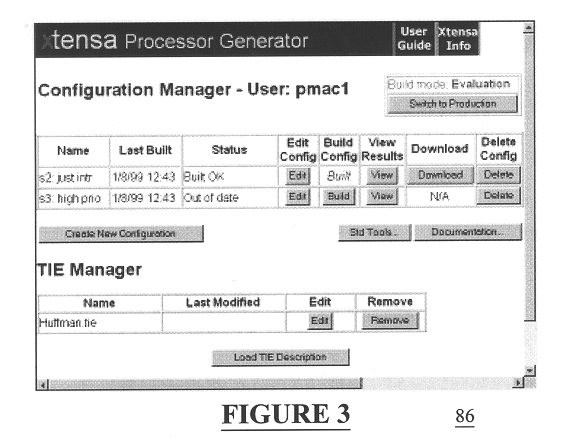
Automated processor generation system for designing a configurable processor and method for the same
InactiveUS6477683B1Decompilation/disassemblyCAD network environmentApplication softwareProcessor design
An automated processor design tool uses a description of customized processor instruction set extensions in a standardized language to develop a configurable definition of a target instruction set, a Hardware Description Language description of circuitry necessary to implement the instruction set, and development tools such as a compiler, assembler, debugger and simulator which can be used to develop applications for the processor and to verify it. Implementation of the processor circuitry can be optimized for various criteria such as area, power consumption, speed and the like. Once a processor configuration is developed, it can be tested and inputs to the system modified to iteratively optimize the processor implementation. By providing a constrained domain of extensions and optimizations, the process can be automated to a high degree, thereby facilitating fast and reliable development.
Owner:TENSILICA
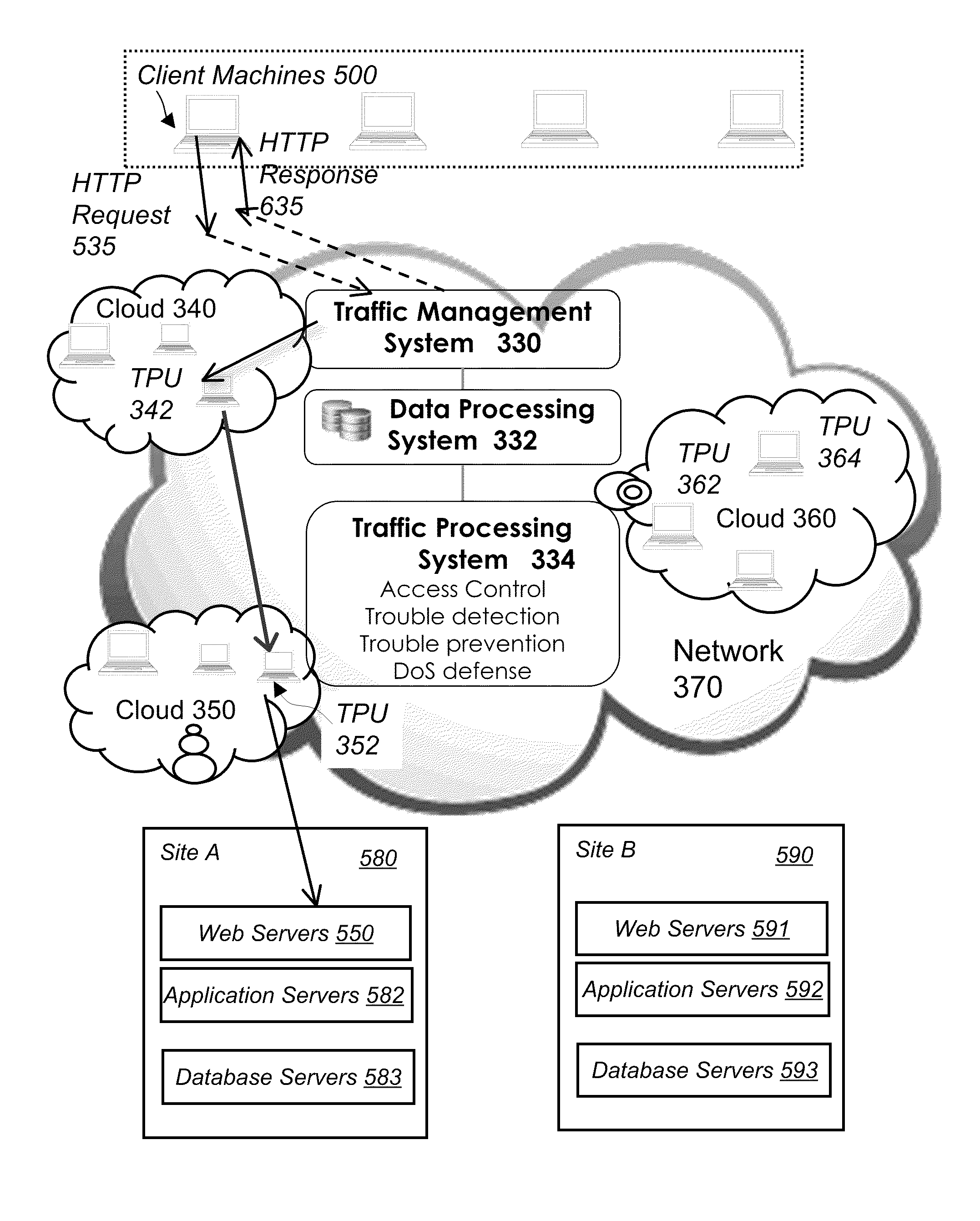
System and method for network traffic management and load balancing
InactiveUS20100223364A1Improve application performanceImprove availabilityMultiple digital computer combinationsLocation information based serviceTraffic capacityFailover
A method for providing load balancing and failover among a set of computing nodes running a network accessible computer service includes providing a computer service that is hosted at one or more servers comprised in a set of computing nodes and is accessible to clients via a first network. Providing a second network including a plurality of traffic processing nodes and load balancing means. The load balancing means is configured to provide load balancing among the set of computing nodes running the computer service. Providing means for redirecting network traffic comprising client requests to access the computer service from the first network to the second network. Providing means for selecting a traffic processing node of the second network for receiving the redirected network traffic comprising the client requests to access the computer service and redirecting the network traffic to the traffic processing node via the means for redirecting network traffic. For every client request for access to the computer service, determining an optimal computing node among the set of computing nodes running the computer service by the traffic processing node via the load balancing means, and then routing the client request to the optimal computing node by the traffic processing node via the second network.
Owner:YOTTAA
Heuristic detection of malicious computer code by page tracking
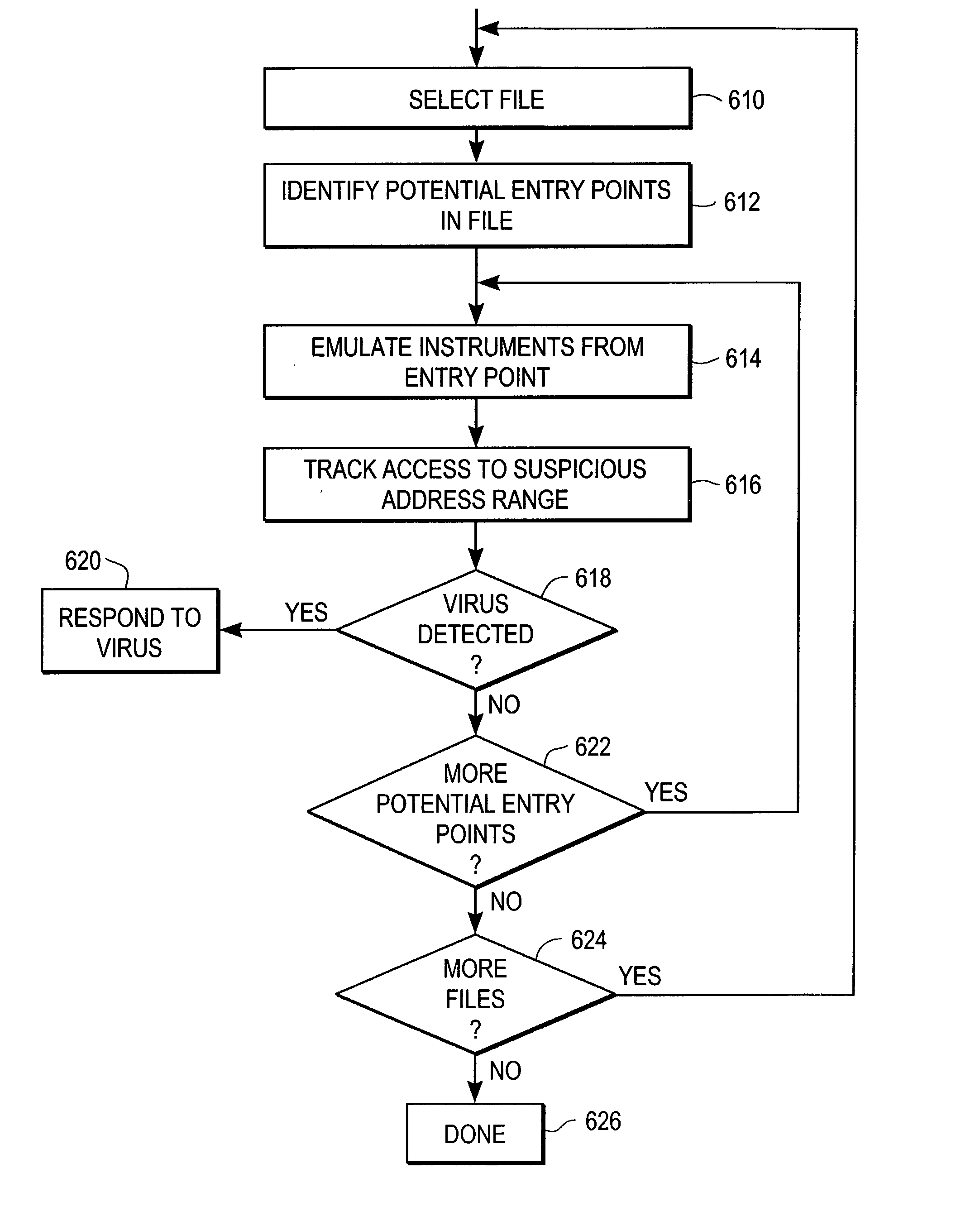
To detect a computer virus in a host file (100), an emulating module (414) emulates the host file (100) in a virtual machine (422) having a virtual memory (426). While emulating the host file (100), the system (400) tracks the host file's access of the virtual memory (426). Responsive to an access in a non-normal address range of the virtual memory (426) by the host file (100), a flag recording module (522) sets a flag. A virus reporting module (526) declares a potential virus based on whether the flag is set.
Owner:CA TECH INC
Systems and methods for analyzing performance of virtual environments
InactiveUS8175863B1Effective and efficient diagnosisResource allocationError detection/correctionMonitoring systemSmart surveillance
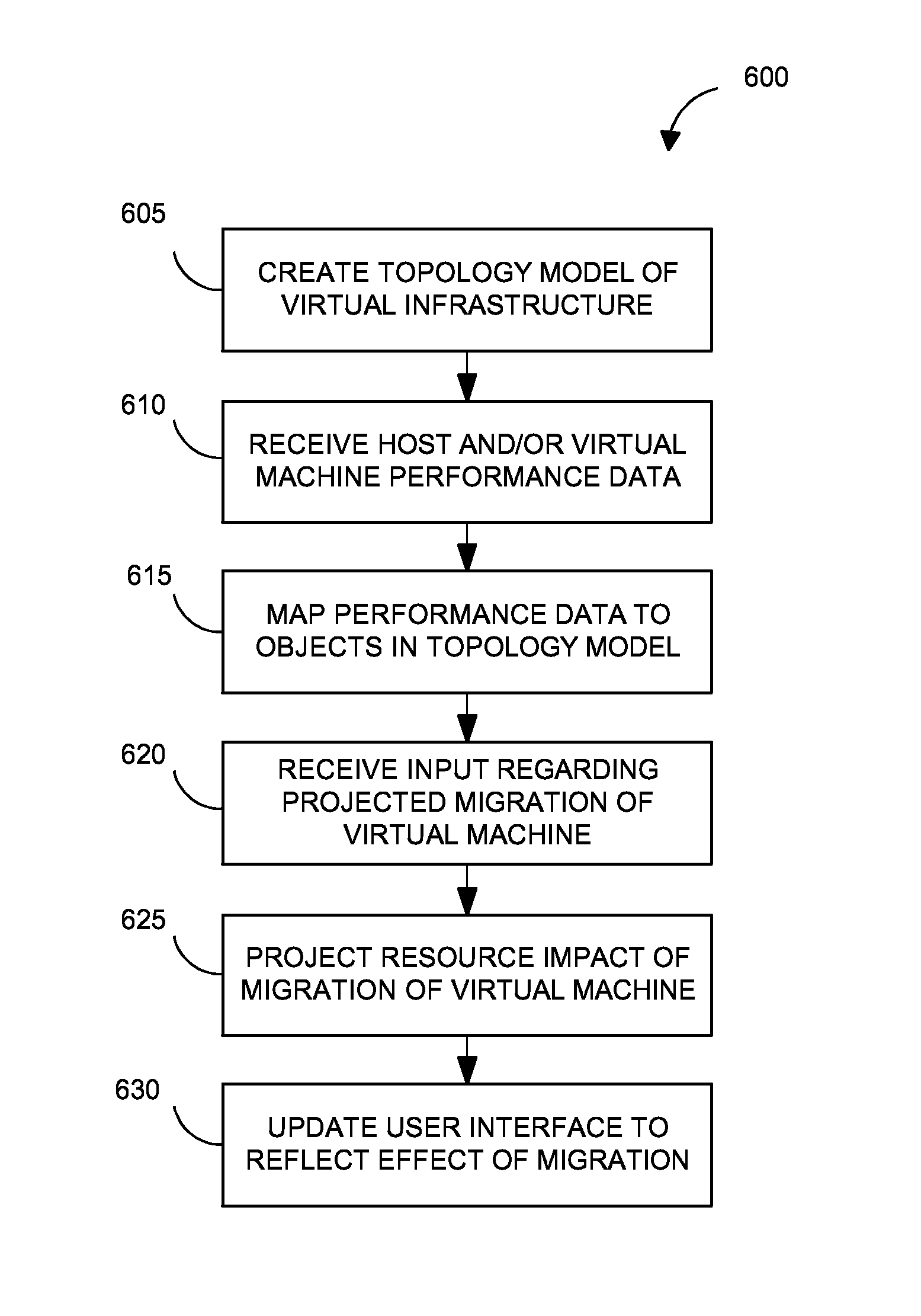
Intelligent monitoring systems and methods for virtual environments are disclosed that understand various components of a virtual infrastructure and how the components interact to provide improved performance analysis to users. In certain examples, a monitoring system assesses the performance of virtual machine(s) in the context of the overall performance of the physical server(s) and the environment in which the virtual machine(s) are running. For instance, the monitoring system can track performance metrics over a determined period of time to view changes to the allocation of resources to virtual machines and their location(s) on physical platforms. Moreover, monitoring systems can utilize past performance information from separate virtual environments to project a performance impact resulting from the migration of a virtual machine from one physical platform to another.
Owner:QUEST SOFTWARE INC
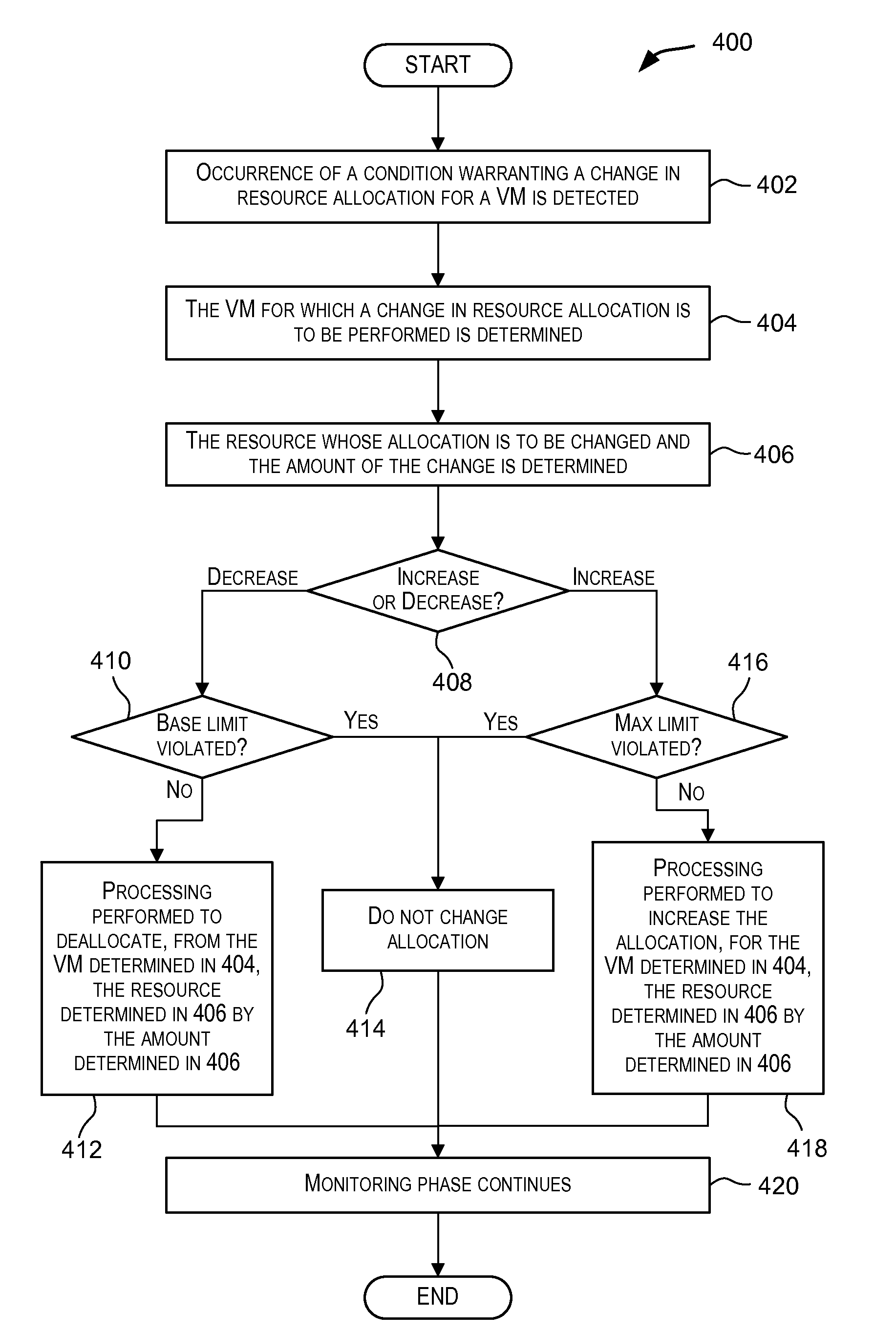
Dynamic resource allocation for virtual machines
InactiveUS20140007097A1Increase the amount of resourcesReduce the amount of solutionSoftware simulation/interpretation/emulationMemory systemsFailoverService-level agreement
Certain embodiments enable resources assigned or allocated to an operating virtual machine (VM) to be modified while the VM is operating and without having to stop, restart, or reboot the VM. The modification may correspond to increasing or decreasing the amount of a resource being assigned to the VM. In this manner, resources assigned to a VM at the time of creation of the VM are not static and can instead be dynamically changed while the VM is operating without having to stop, reboot, or restart the VM. In some embodiments, the changes to the resources allocated to one or more VMs provided for a user (e.g., a customer) may be made according to or in response to a Service Level Agreement (SLA) entered into by the user, in response to an event such as a failover or switchover event, and the like.
Owner:AVAGO TECH INT SALES PTE LTD
Deploying virtual machine to host based on workload characterizations
InactiveUS20070271560A1Convenient to accommodateSoftware simulation/interpretation/emulationMemory systemsWorkloadVirtual machine
Owner:MICROSOFT TECH LICENSING LLC
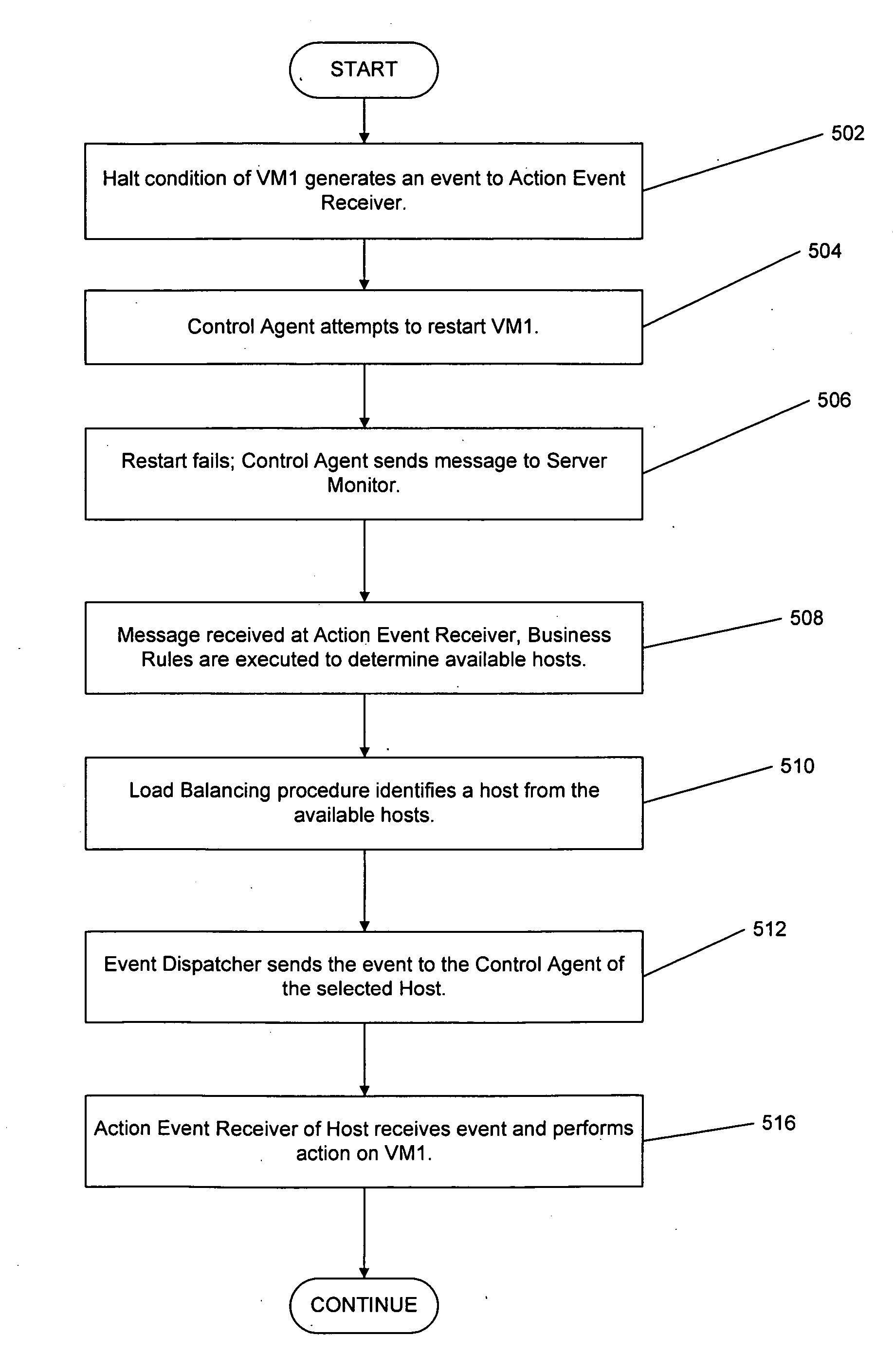
System and method for migrating virtual machines on cluster systems
ActiveUS20060195715A1Satisfactory operationError detection/correctionDigital computer detailsManagement processCluster systems
In one embodiment, a method comprises executing a plurality of virtual machines on a plurality of nodes of a cluster computing system, wherein at least one application is executed within each of the plurality of virtual machines, generating data that is related to performance of applications in the virtual machines, analyzing, by a management process, the data in view of parameters that encode desired performance levels of applications, and migrating, by the management process, a virtual machine on a first node to a second node of the plurality of nodes in response to the analyzing.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
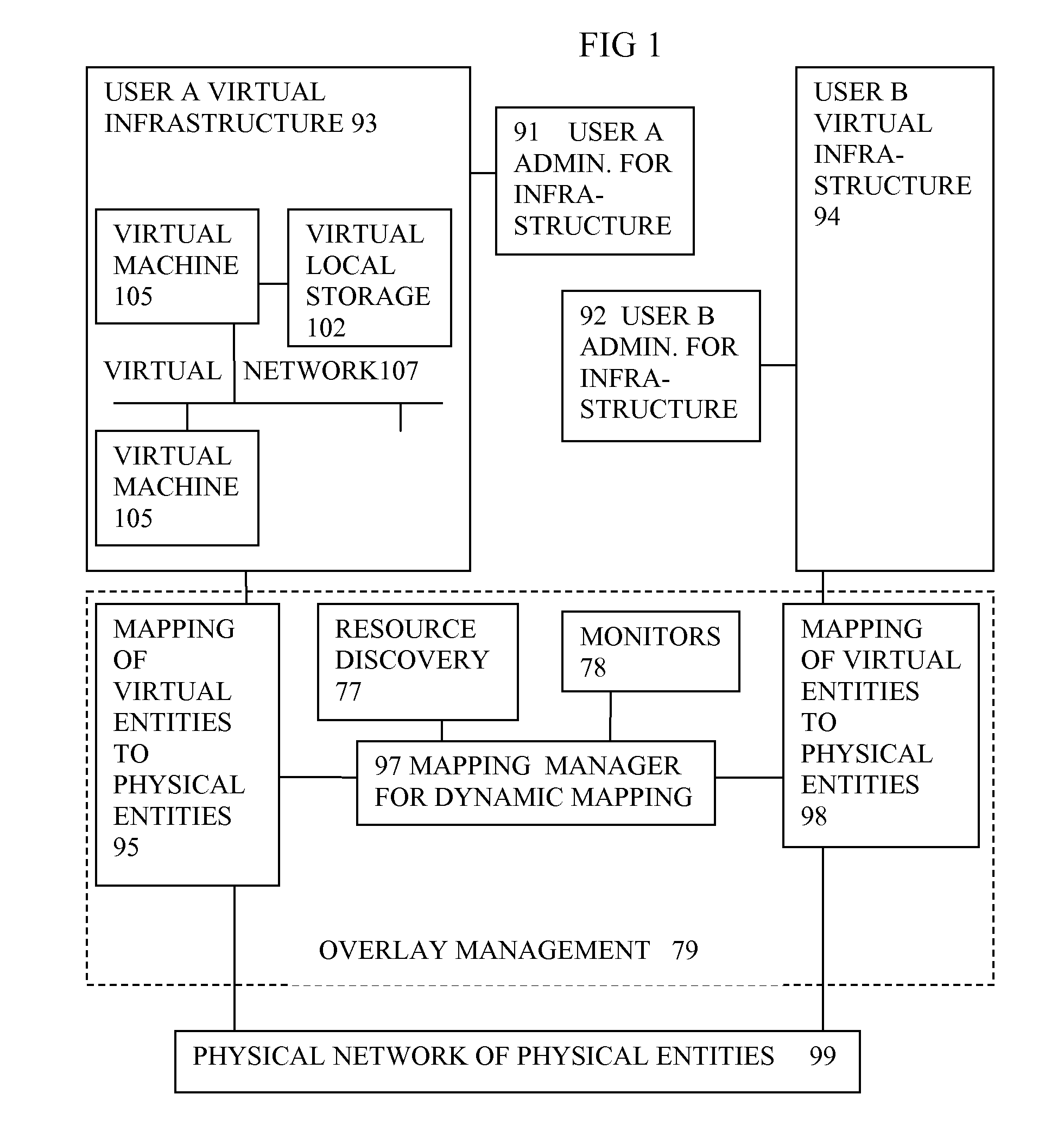
Virtual computing infrastructure
InactiveUS20090199177A1Overcome disadvantagesCritical applicationResource allocationTransmissionVirtualizationNetwork communication
A system has a virtual overlay infrastructure mapped onto physical resources for processing, storage and network communications, the virtual infrastructure having virtual entities for processing, storage and network communications. The system has a mapping manager to dynamically alter the mapping for balancing, performance, and redundancy. There can be more independence from the underlying physical configuration, compared to known methods of virtualizing only some of the entities. The mapping manager can be distributed across a number of entities on different physical servers arranged to cooperate with each other.
Owner:HEWLETT PACKARD DEV CO LP
Popular searches
Data switching by path configuration Network connections Input/output processes for data processing Sensing by electromagnetic radiation Interprogram communication Subscriber signalling identity devices Speech recognition Digital voice transmission telephone sets Speech synthesis Web data browsing optimisation
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com