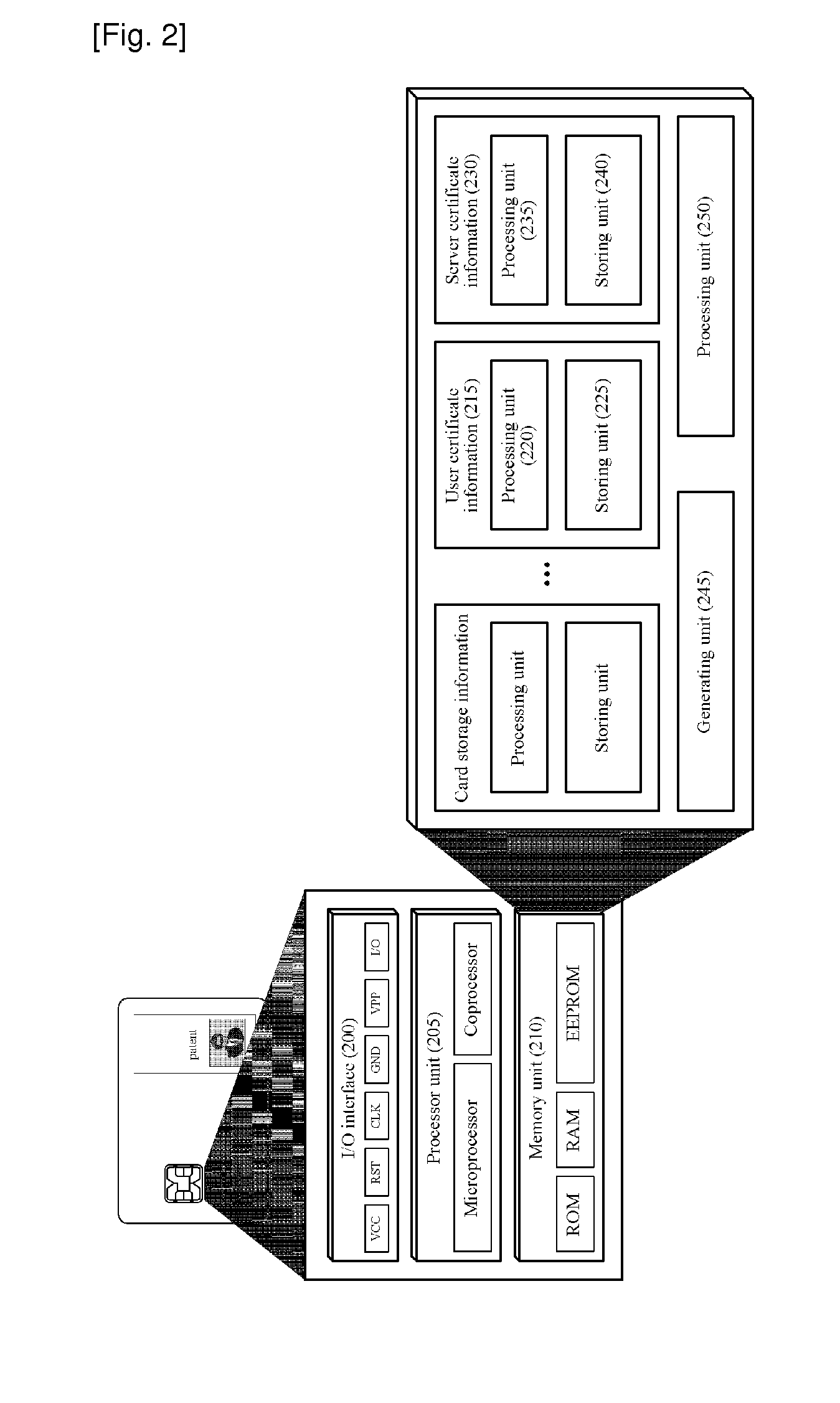
Patents
Literature
144 results about "End to end security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
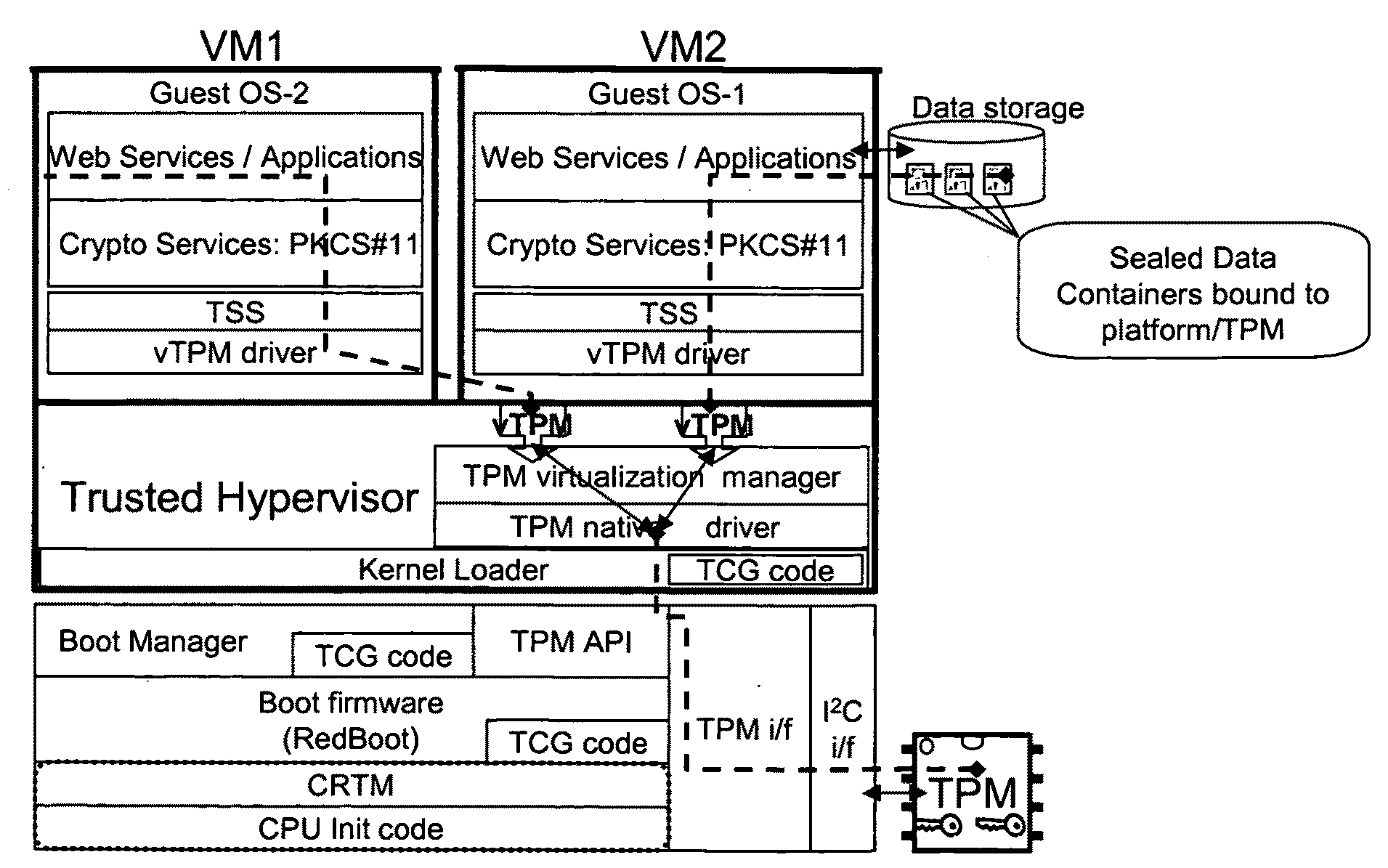
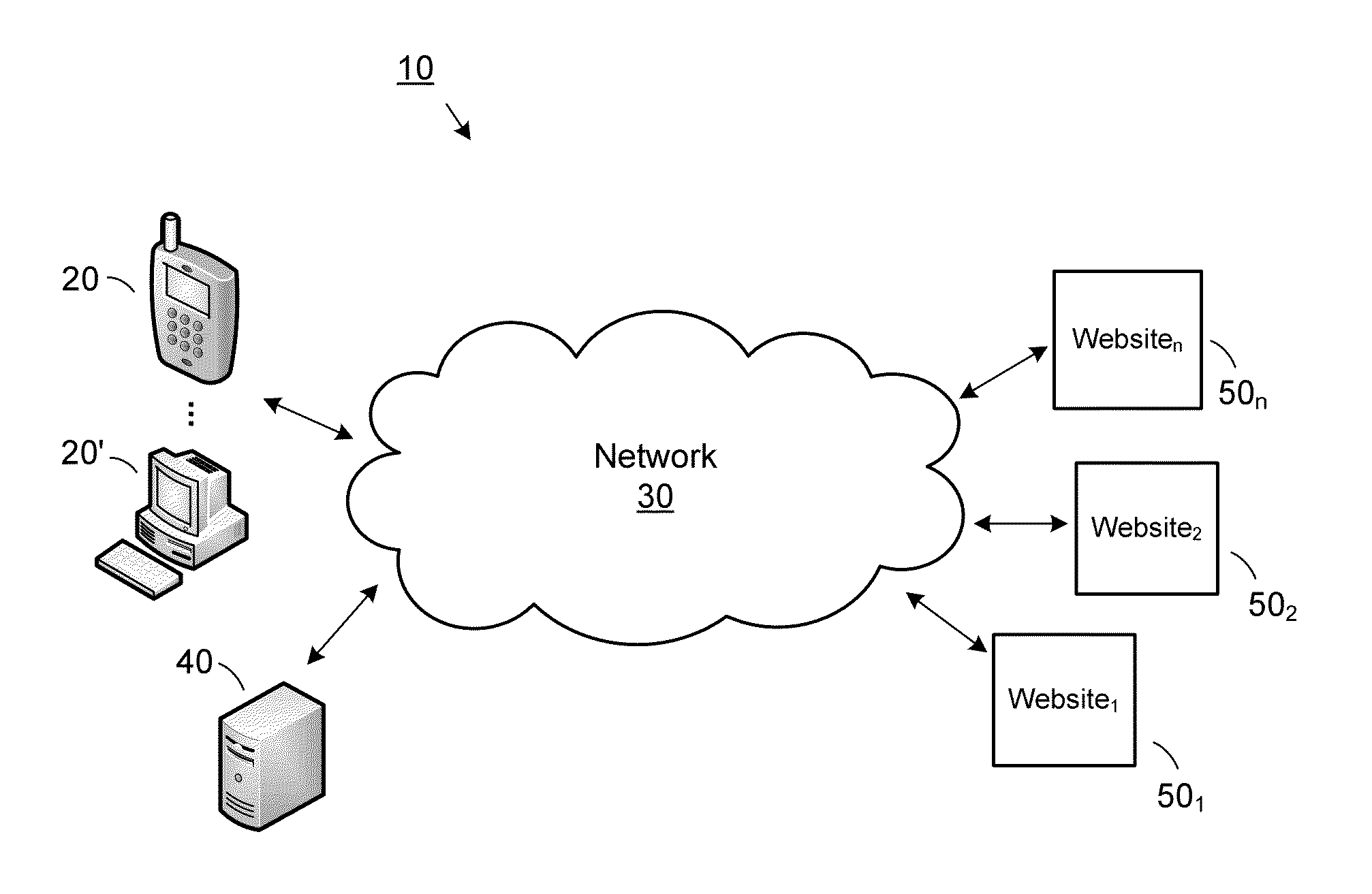
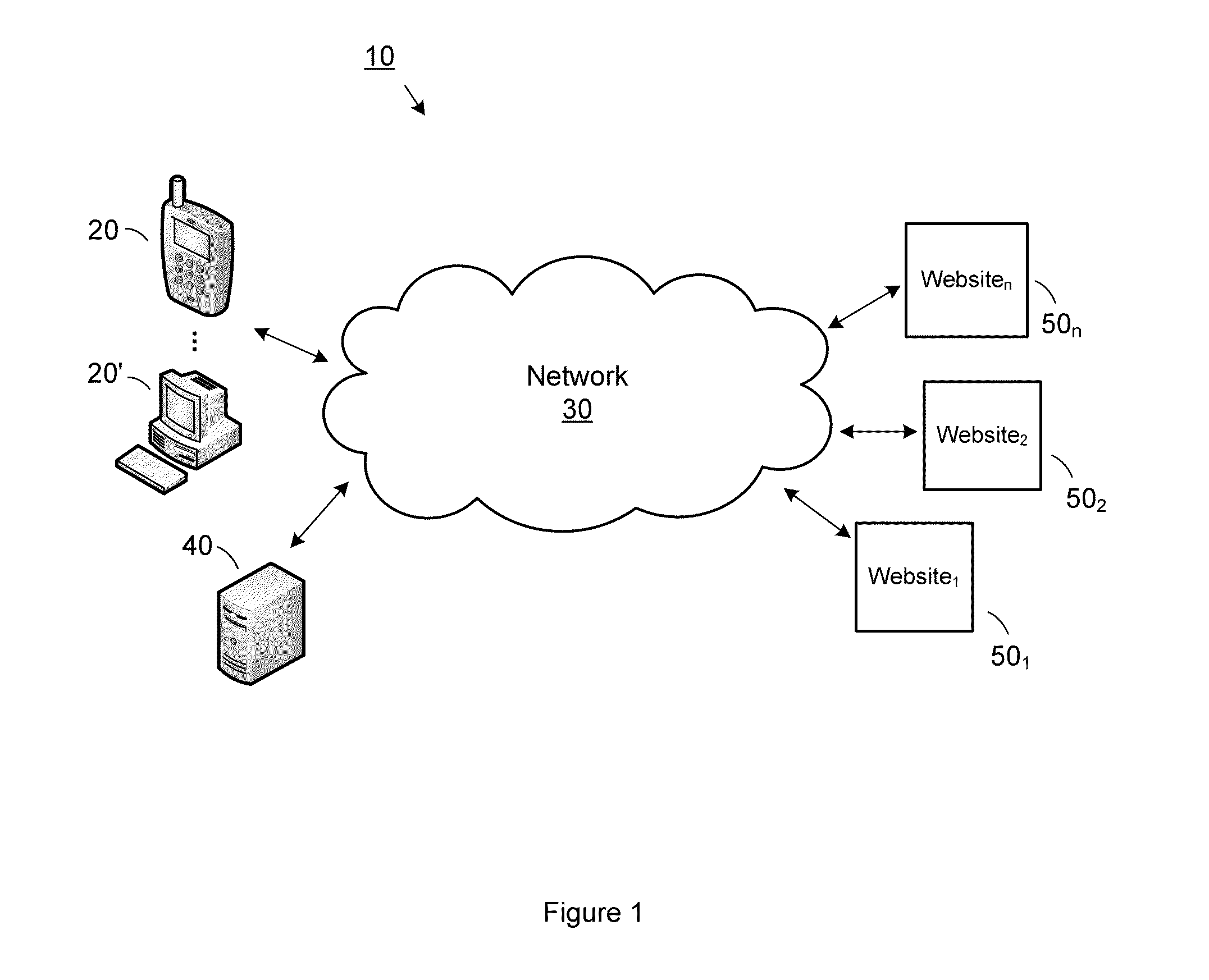
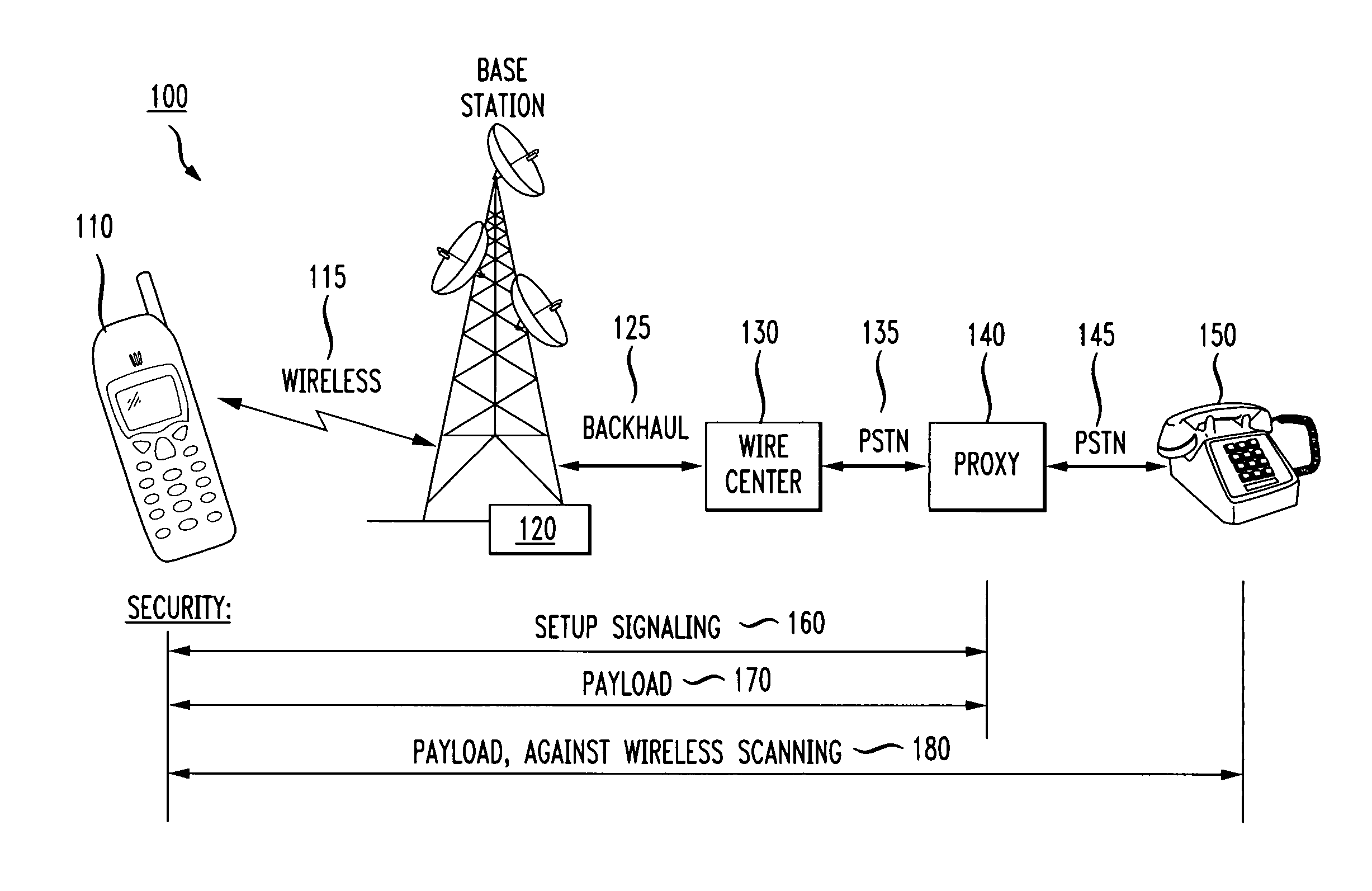
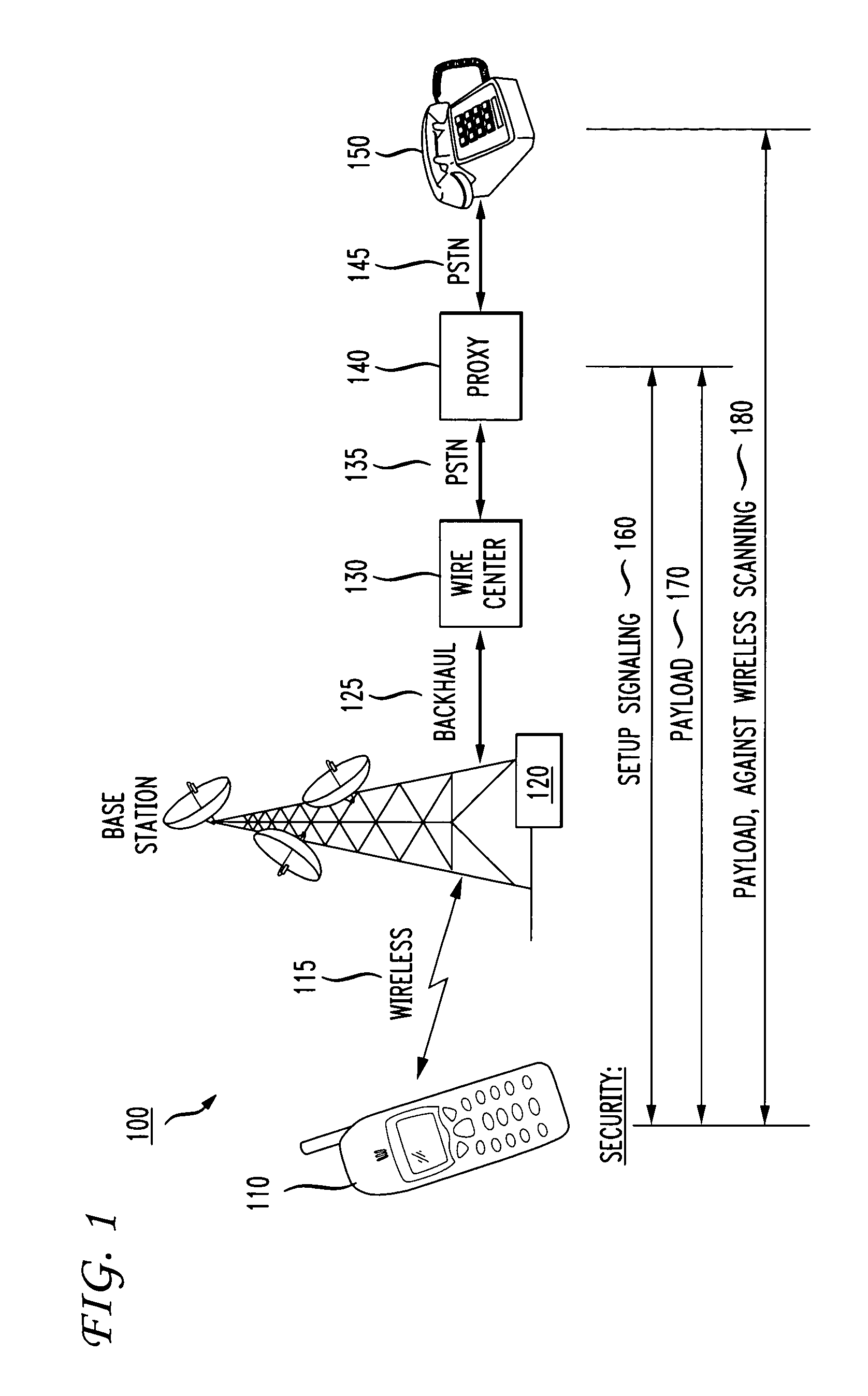
Defining "End". The traditional definition of an endpoint is a client or server. In this definition end-to-end security starts on the client and ends on the server. Given the multitude of applications running in parallel on an operating system, and given increasing virtualization, this definition is usually no longer precise enough.
Distributed trusted virtualization platform
InactiveUS20090204964A1Key distribution for secure communicationMultiple digital computer combinationsVirtualizationEnd to end security
A platform architecture shifts the networked computing paradigm from PC+Network to a system using trusted mobile internet end-point (MIEP) devices and cooperative agents hosted on a trusted server. The MIEP device can participate in data flows, arbitrate authentication, and / or participate in implementing security mechanisms, all within the context of assured end-to-end security. The MIEP architecture improves platform-level capabilities by suitably (and even dynamically) partitioning what is done at the MIEP nodes, the network, and the server based infrastructure for delivering services.
Owner:MOTEGRITY +1
Systems, methods, and computer program products for accelerated dynamic protection of data
InactiveUS7280658B2Sufficient protectionKey distribution for secure communicationSecret communicationComputer resourcesEnd to end security
Owner:SNAP INC
Method and system for providing end-to-end security solutions to aid protocol acceleration over networks using selective layer encryption
The present invention is a method, system, and computer program that provides secure network communication over a network between a first and a second entity wherein data packets are encrypted and transmitted according to previously exchanged encryption command information and wherein TCP accelerators may be used to effectively accelerate the transmission of the data packets. A method, system, and computer program are also shown that provide secure network communication through encrypting a plurality of payloads and embedding encryption command information for each encrypted payload into an options field of a corresponding protocol header while still allowing TCP accelerators to read the protocol headers and effectively accelerate the transmission of the payloads.
Owner:RAGIREDDY KRISHNA +2
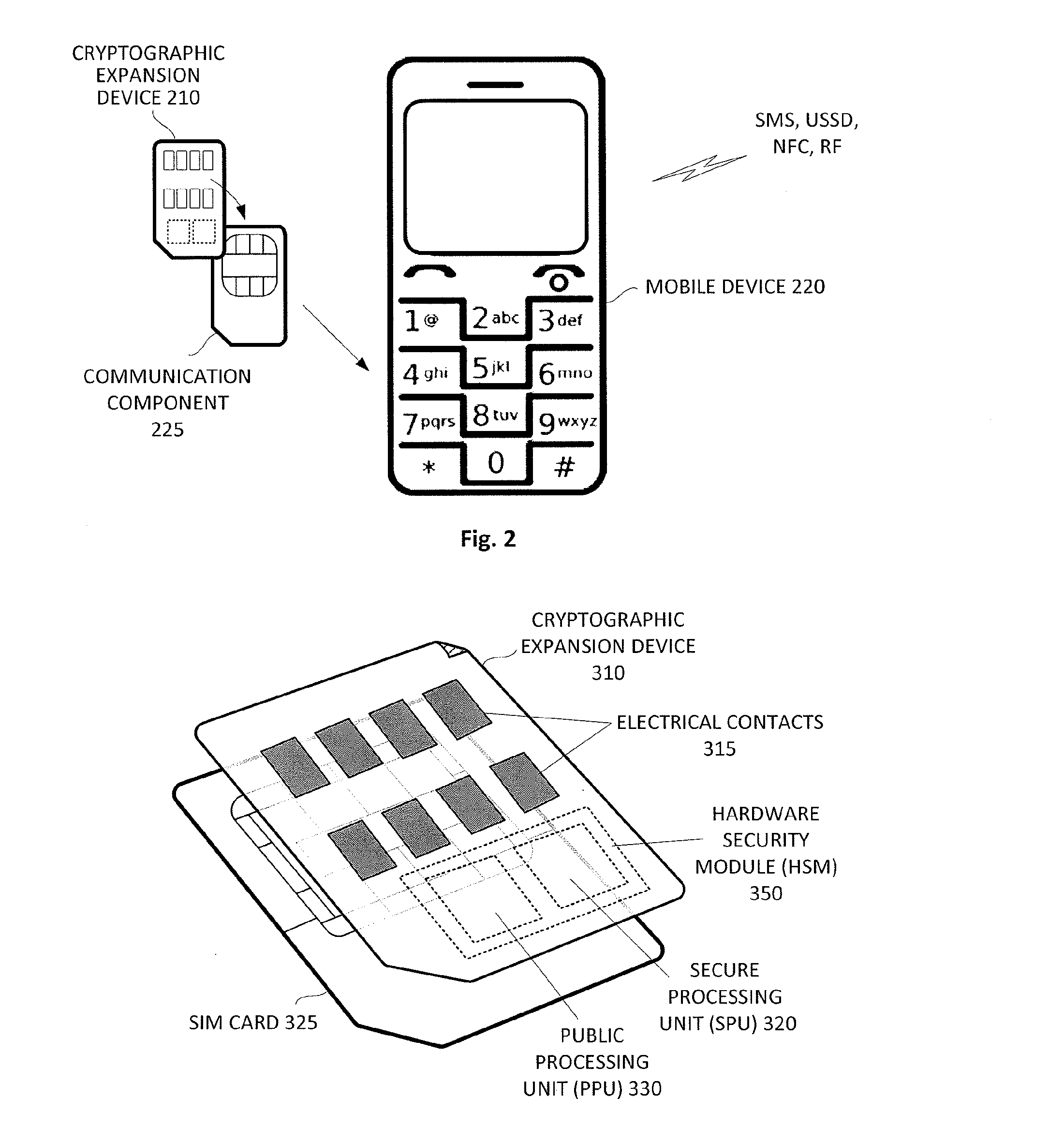
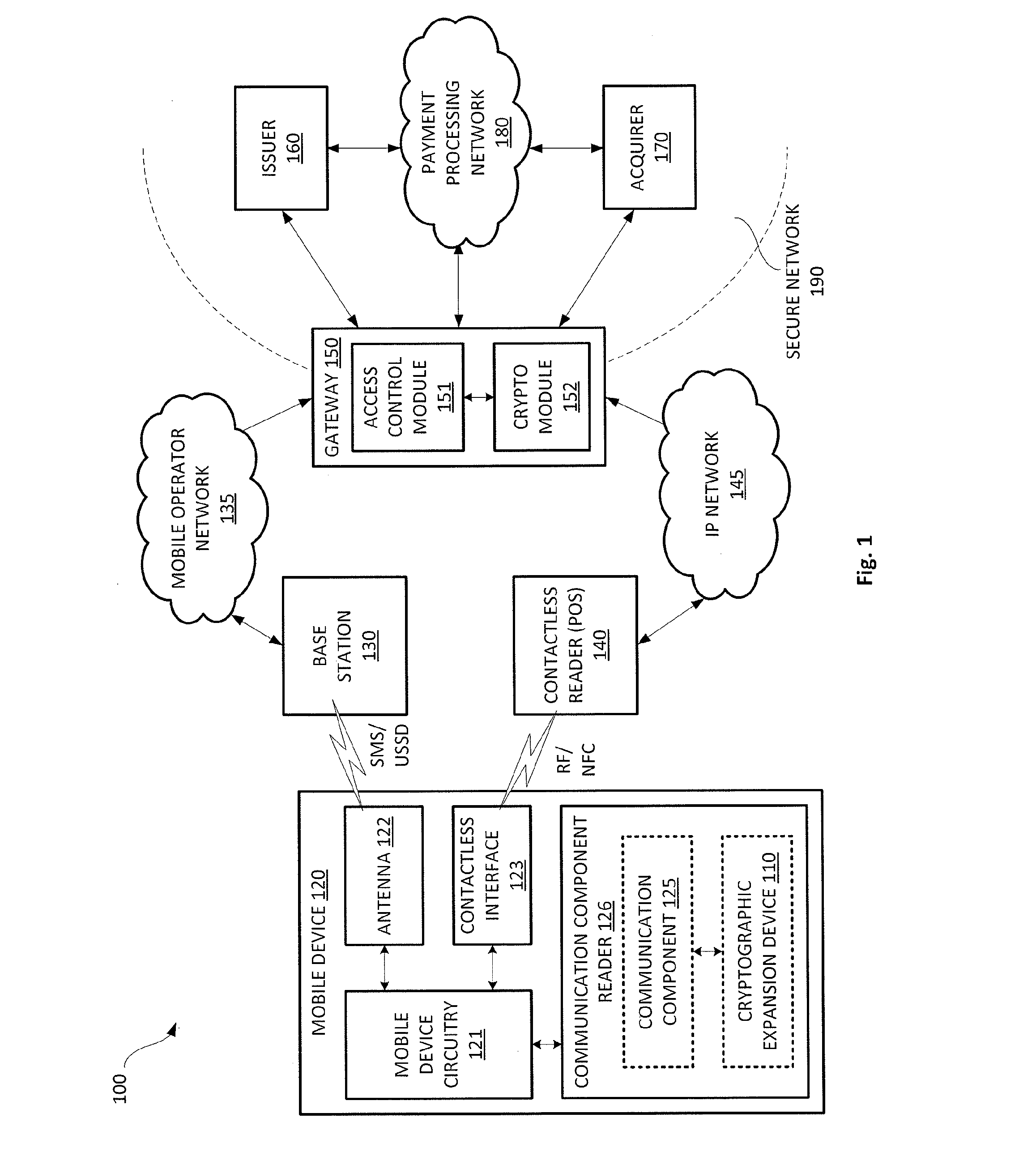
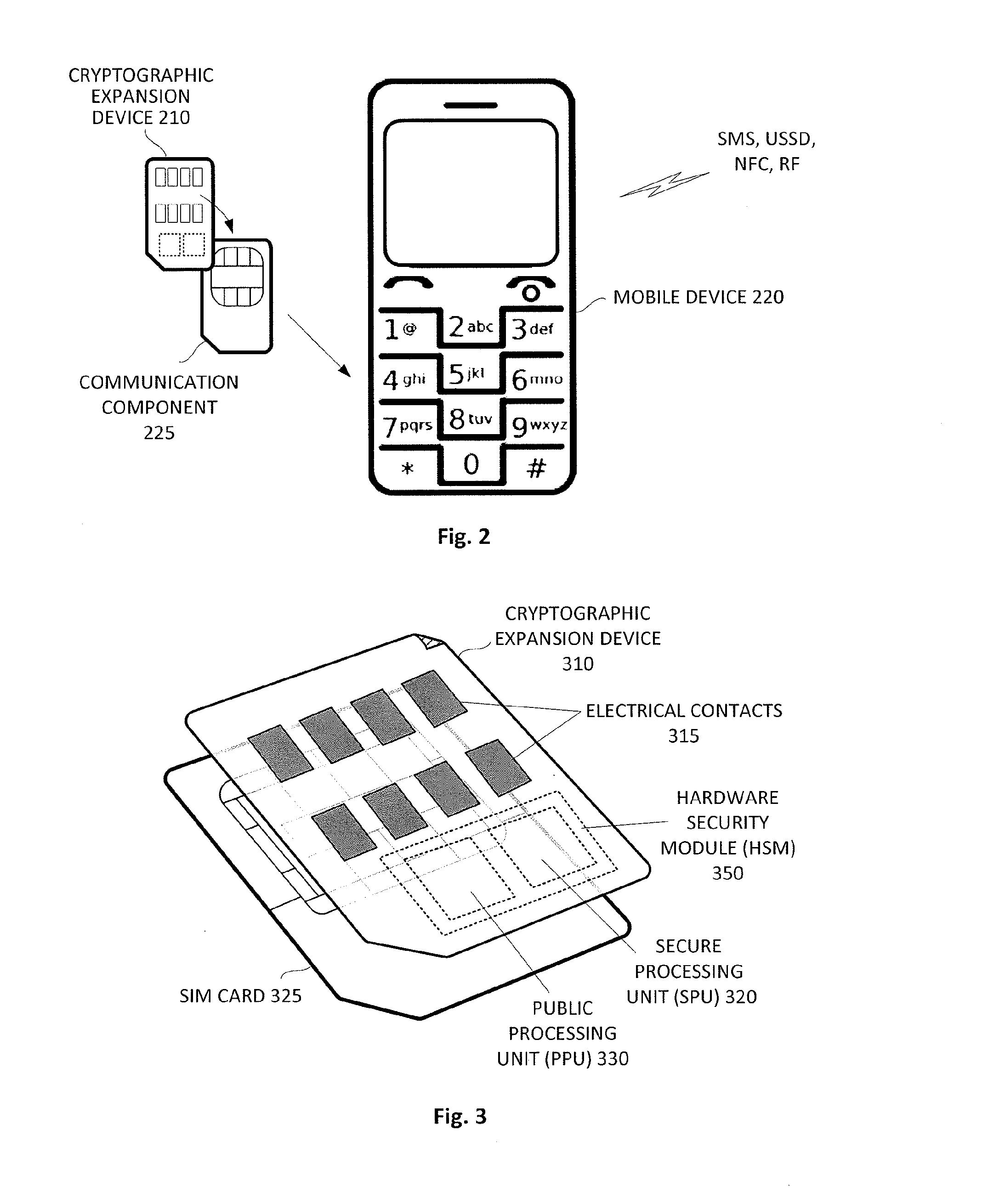
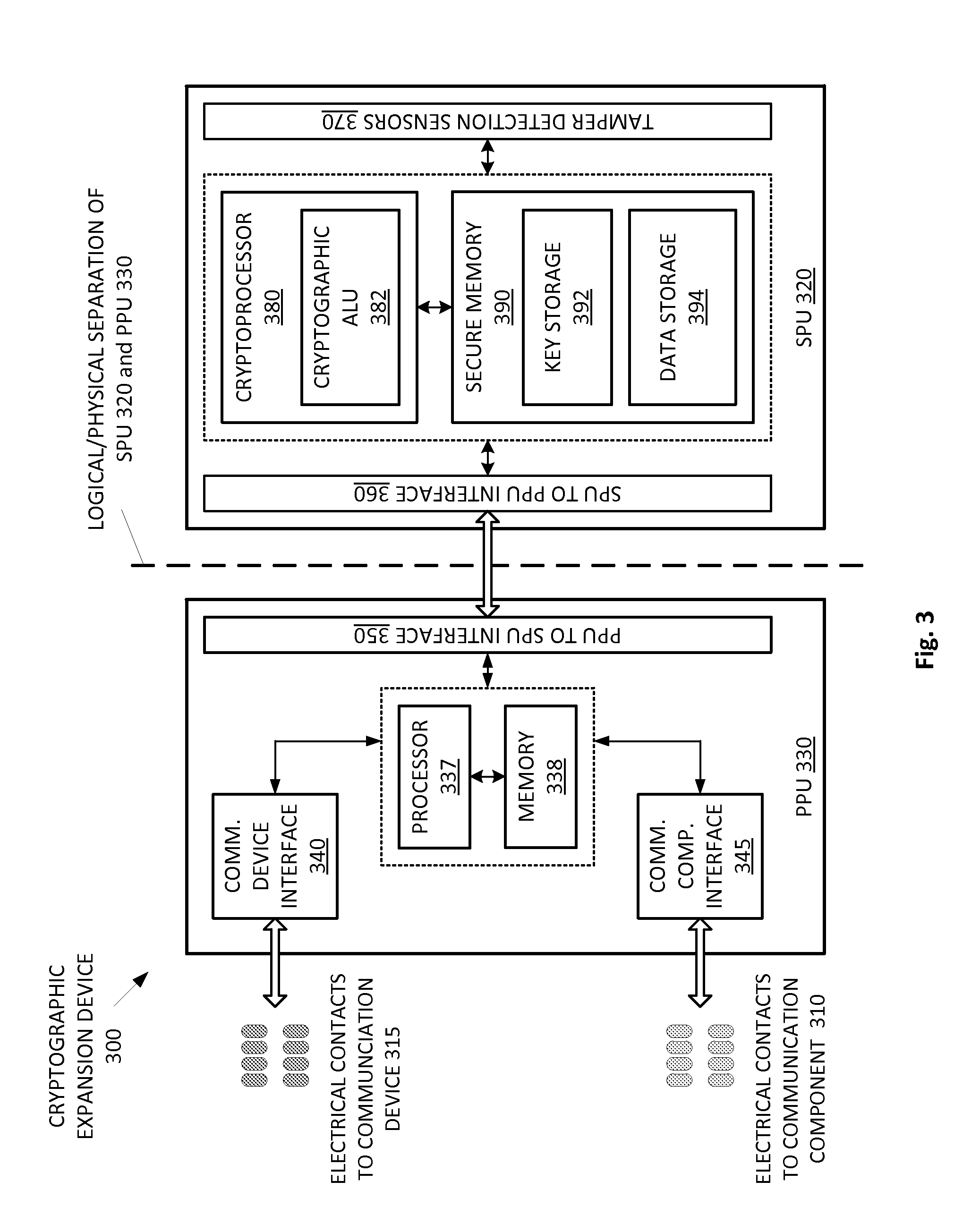
Mobile banking system with cryptographic expansion device
ActiveUS20140188738A1Prevent unauthorized accessPayment protocolsPrinted circuit manufactureSecure communicationComputer hardware
A mobile banking system that uses a cryptographic expansion device attached to a communication component of a mobile device and a secure gateway device to enable end-to-end secure communications between the mobile device and a payment processing network is disclosed. The cryptographic expansion device enables the mobile device to perform cryptographic operations on communications sent to and from the mobile device. The secure gateway device prevents unauthorized accesses to the payment processing network.
Owner:VISA INT SERVICE ASSOC
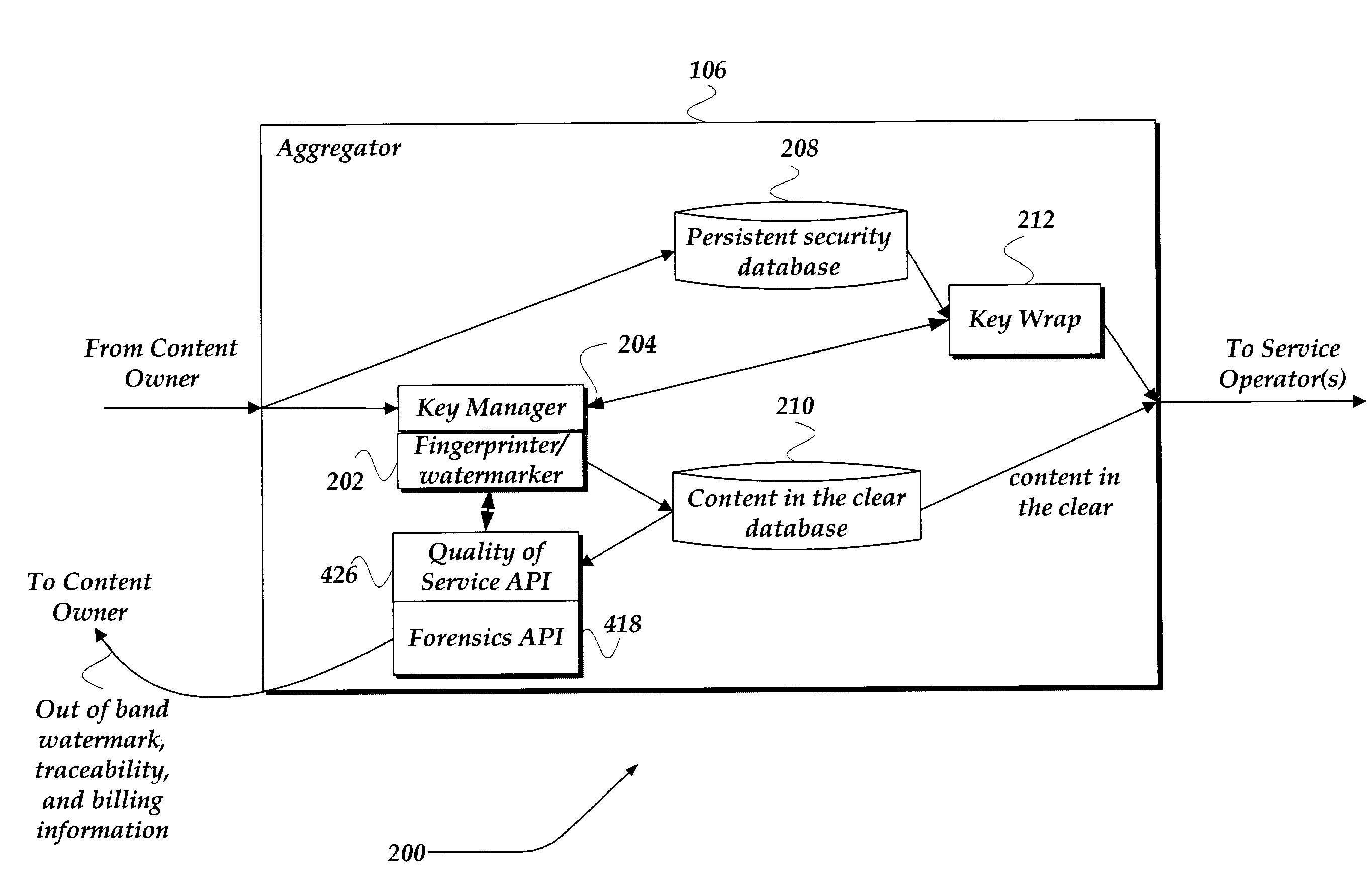
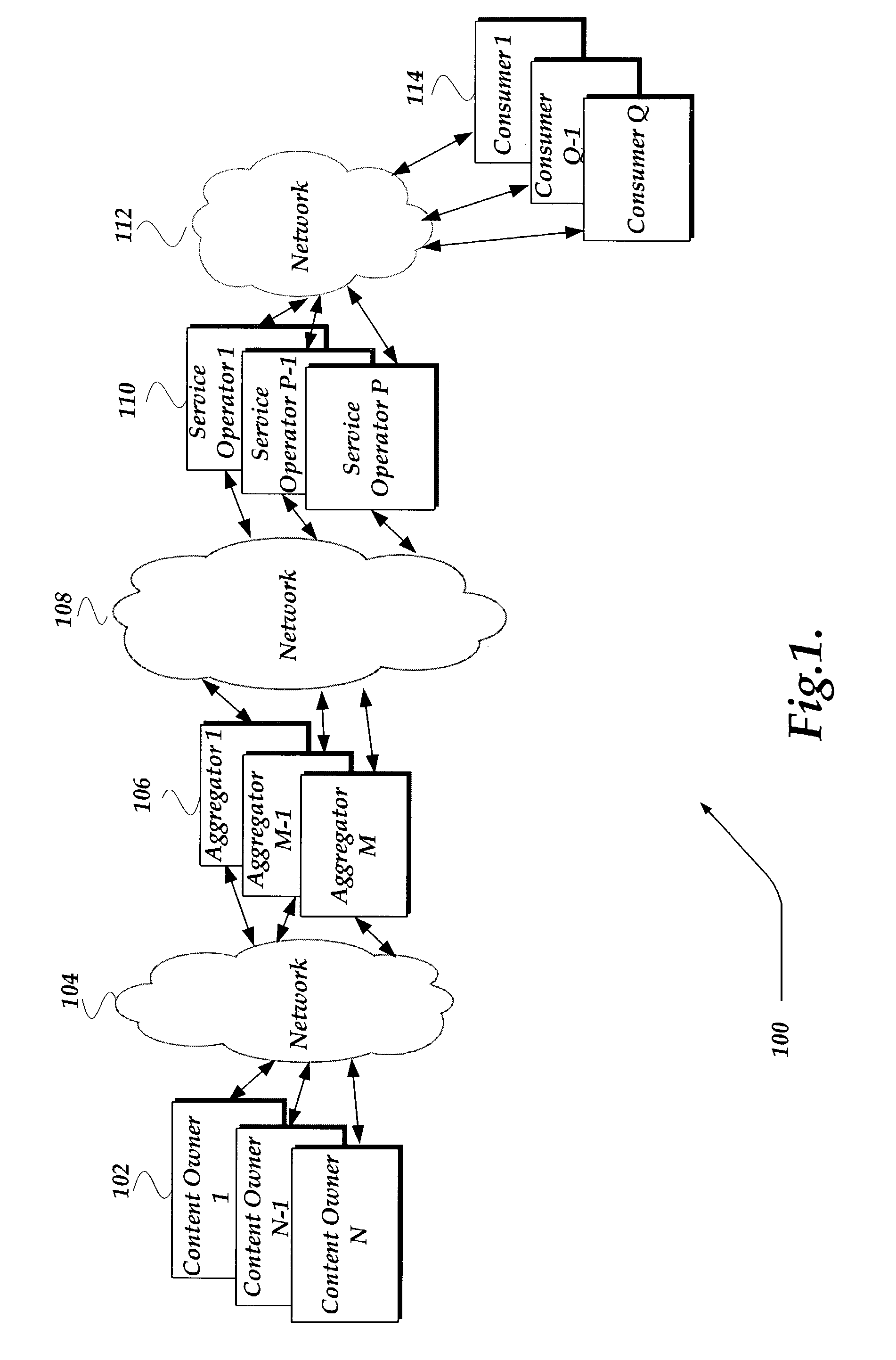
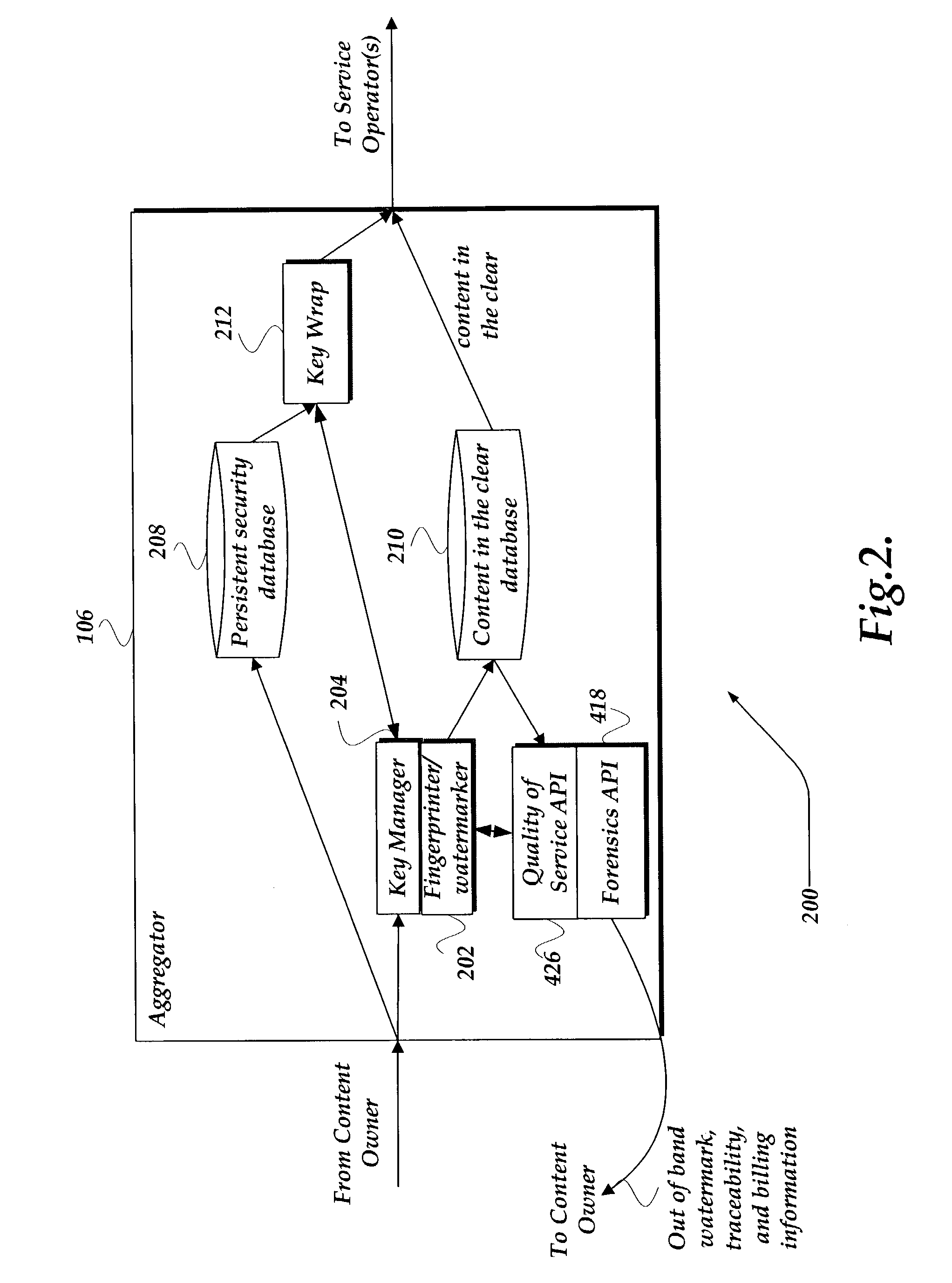
Method and system for end to end securing of content for video on demand
ActiveUS7328345B2Provide securityKey distribution for secure communicationUser identity/authority verificationEnd to end securityMedia transparency
A system and method for providing end-to-end security of content over a heterogeneous distribution chain is provided. A content owner provides content to an aggregator that receives the content and processes the content. The processing may involve decrypting the content and associating at least one of a unique fingerprint and a watermark to the decrypted content. The unique fingerprint and a watermark to the decrypted content provide identifying characteristics to the content. Additional content-based fingerprints may be used to monitor quality of consumer experience for Video and Audio. The content may be sent in a decrypted state to a client or in an encrypted state. When the content is encrypted the aggregator wraps and encrypts the content with a signature such that an end-to-end flow of the content may be determined. Application Level encryption is used to provide network / distribution medium transparency as well as persistent encryption. When the content is transmitted from a consumer to another consumer the transmitting consumer loses rights to the content.
Owner:GOOGLE LLC
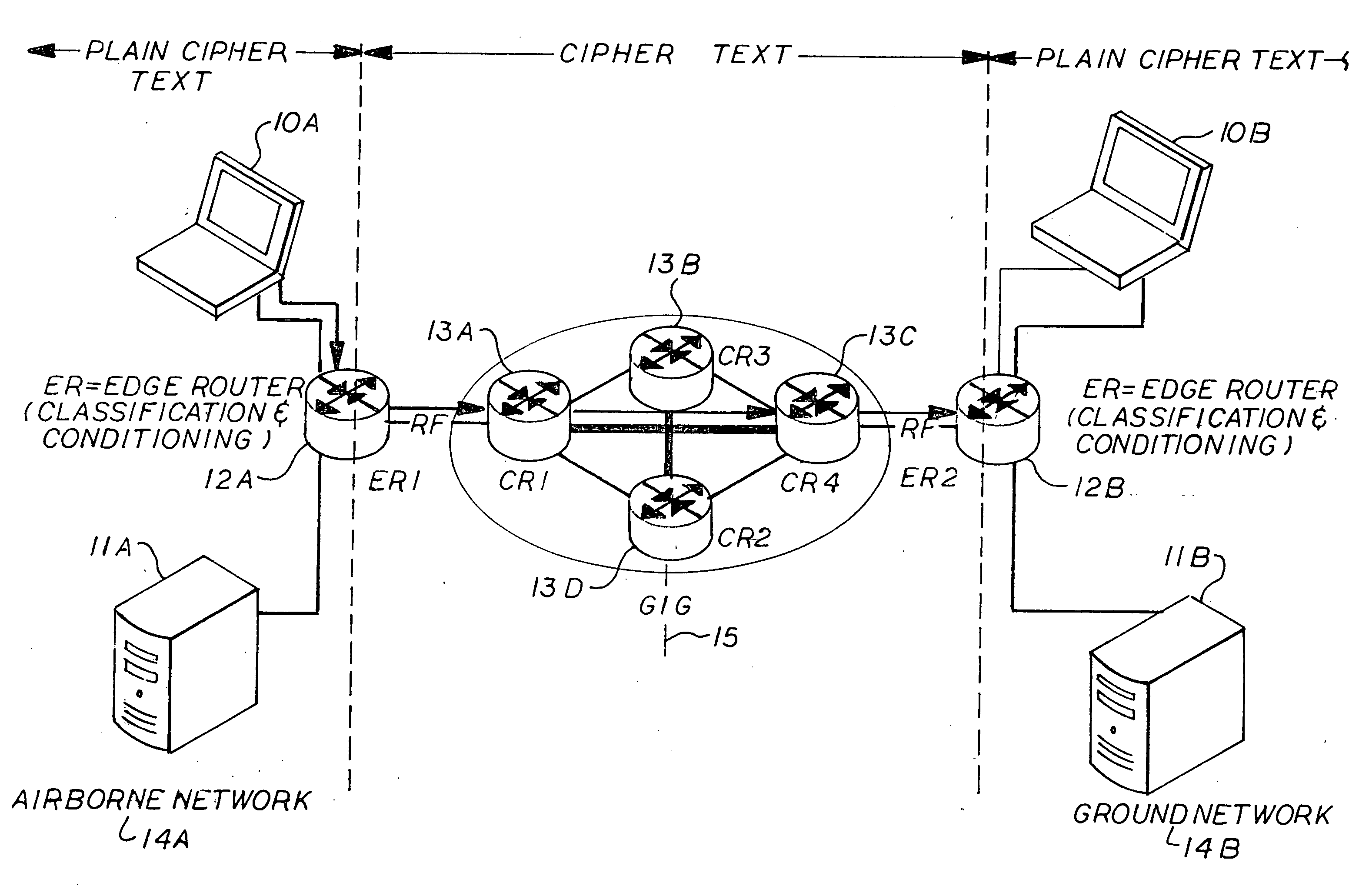
Process for prioritized end-to-end secure data protection
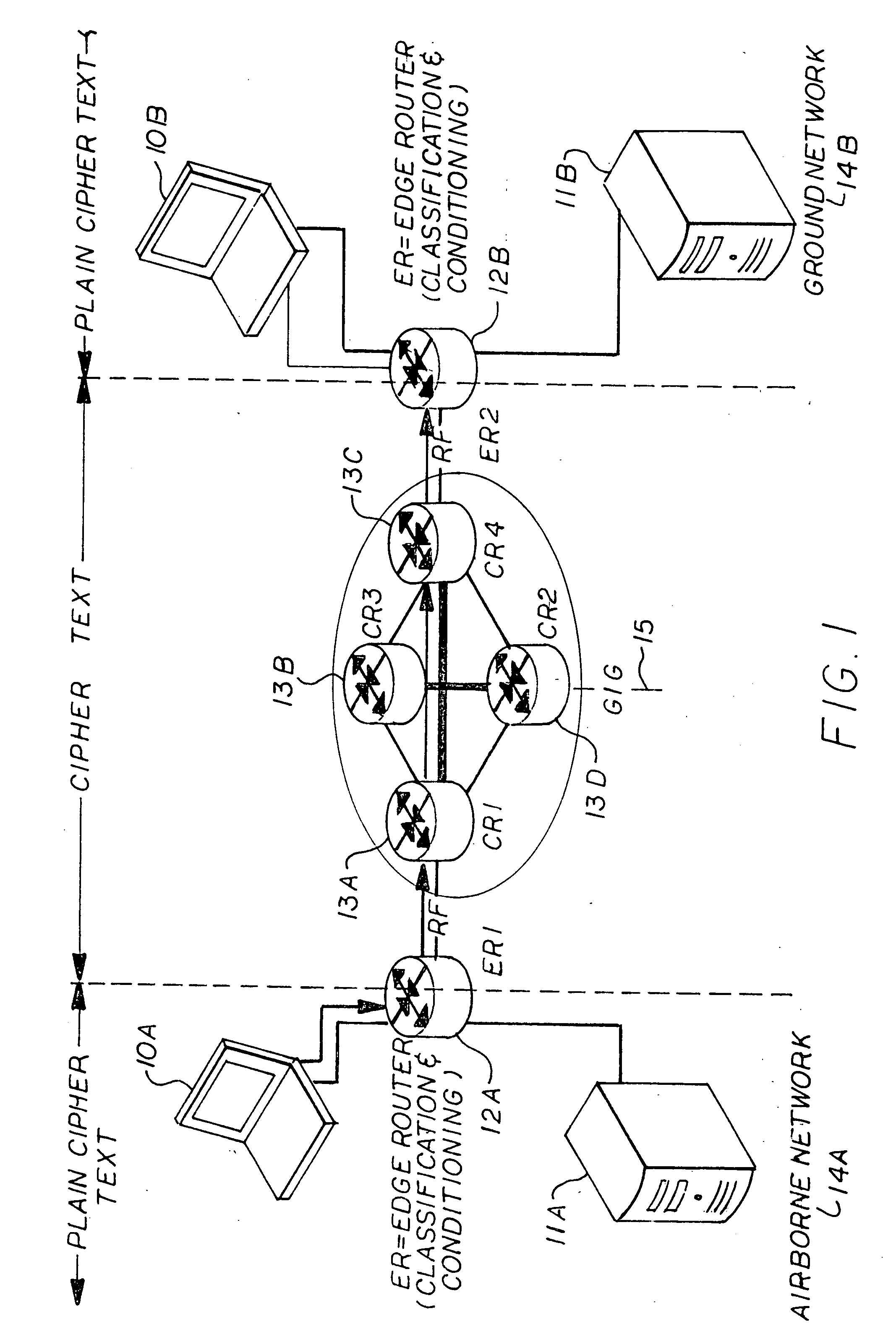
InactiveUS20100135287A1Data augmentationData switching by path configurationEnd to end securityComputerized system
The invention is a process for prioritizing messages from a first computer system having at least one computer connected to a first edge router to be sent to a second computer system having at least one computer connected to a second edge router, the process includes the steps of: 1) providing priority status from the at least one first computer to the at the first edge router; 2) determining the priority status of the message by the first edge router; 3) prioritizing the sending of the message by the first edge router; 4) encrypting the priority status prior to sending the message to the at least one second computer a the selected priority status; and 5) upon receiving the encrypted message, the second edge router decrypts the priority status of the message and sends it to the at least one second computer at the selected priority status.
Owner:NORTHROP GRUMAN CORP
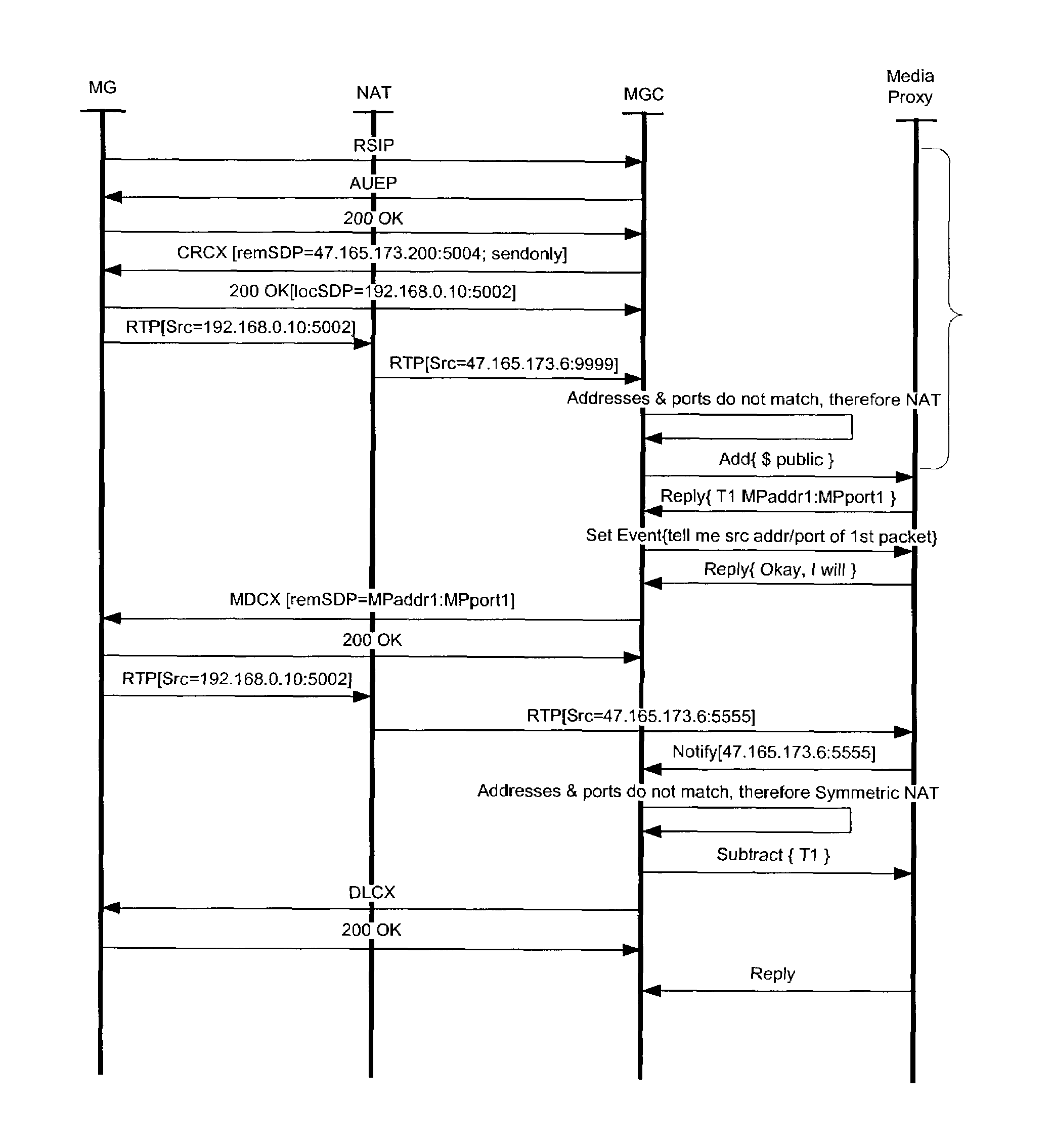
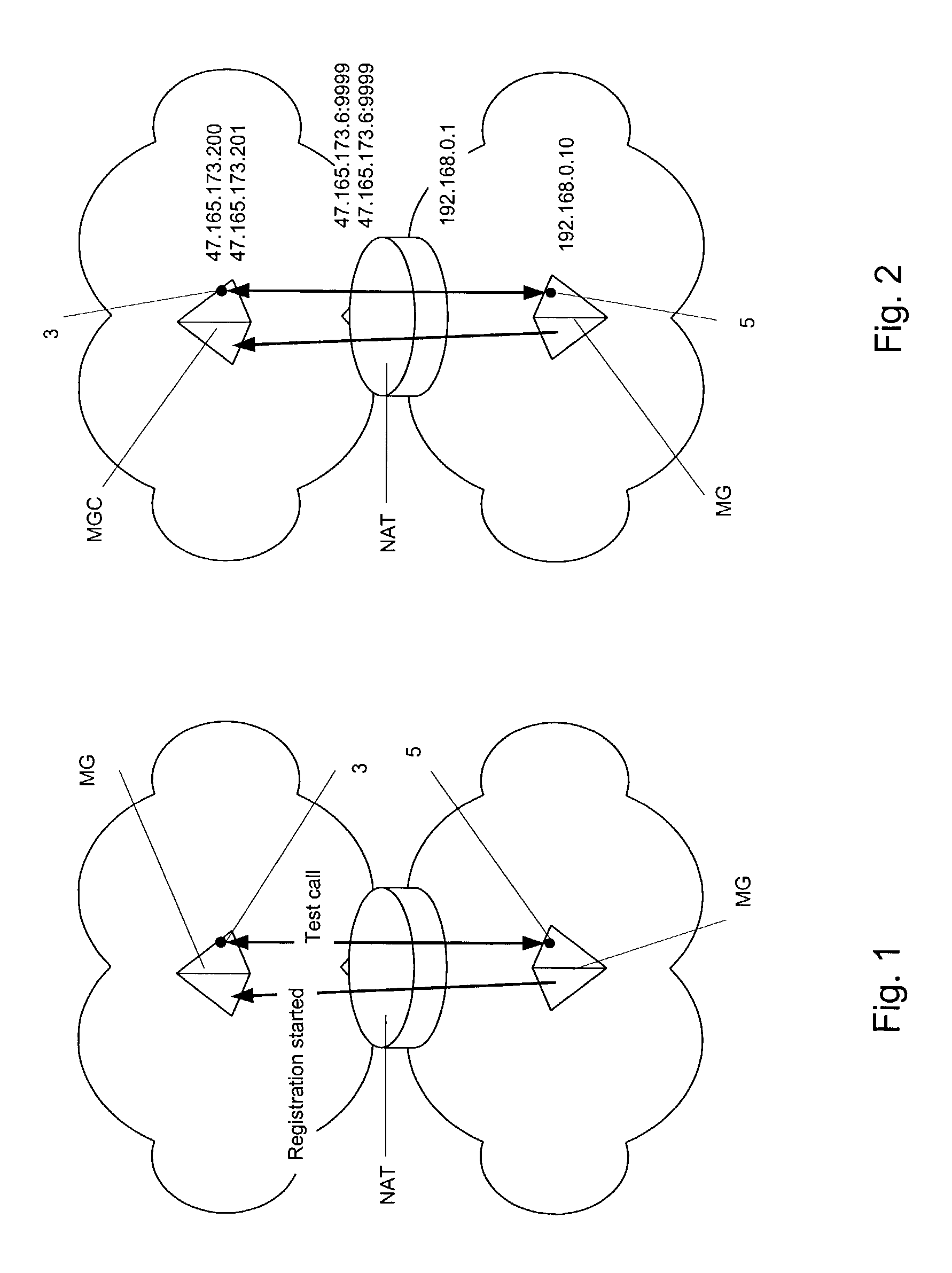
Methods for discovering network address and port translators
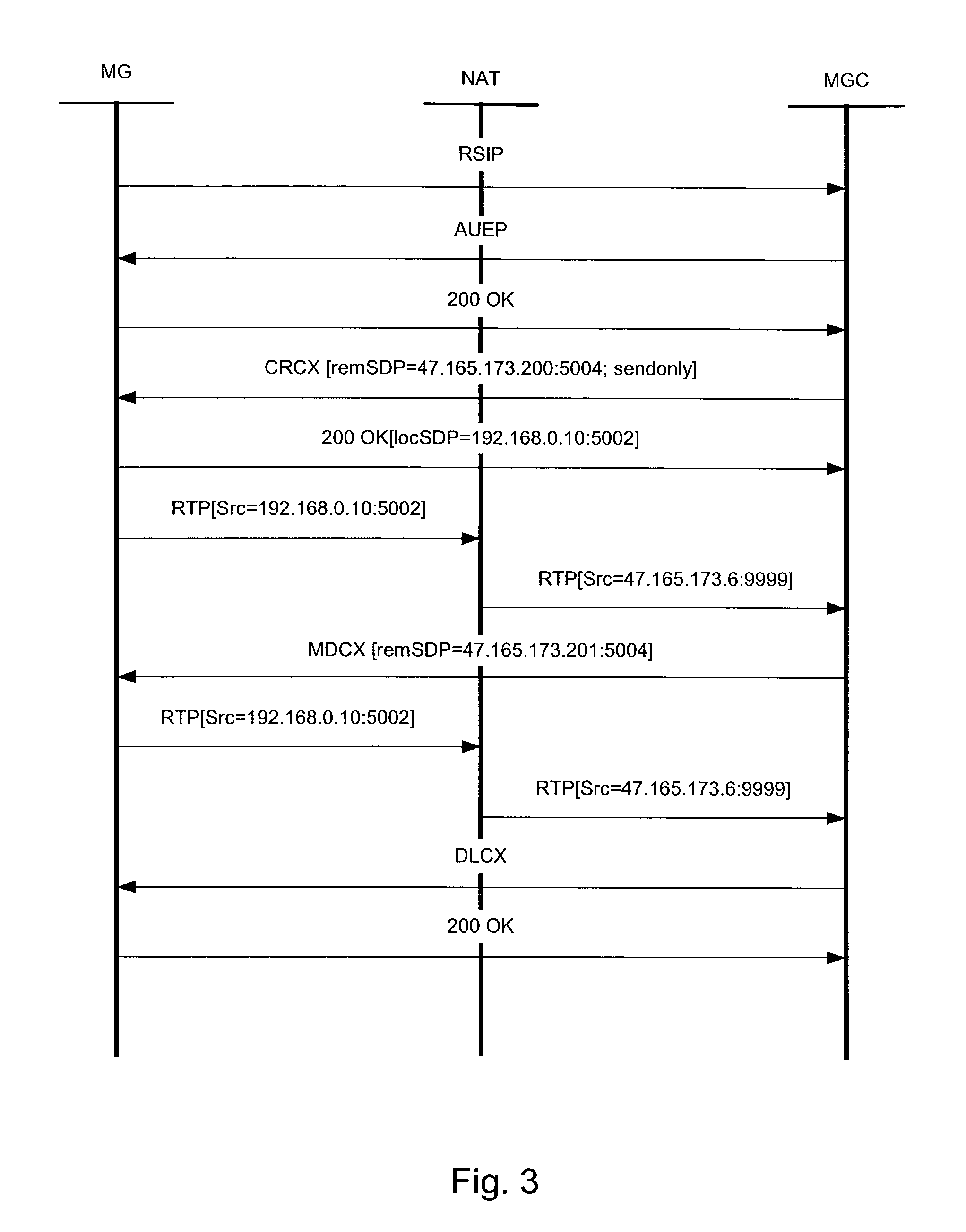
Network Address and Port Translators (NATs) have the potential to interrupt the end-to-end nature of Internet applications, thereby threatening end-to-end security and other end-to-end functions. Thus it is important to be able to discover the existence of NATs and their type. Accordingly there is provided a method of discovering the existence and type of NAT that involves instigating a test call between media endpoints on a Media Gateway (MG) and a Media Gateway Controller (MGC). The MGC is able to deduce the existence of a NAT by examining the media packets sent to its endpoint. If a NAT is determined to be present the MGC instructs the endpoint on the MG to send media packets to another endpoint on the MGC. By comparing the IP addresses and ports of the media packets received at the endpoints of the MGC, the MGC is able to deduce whether the type of NAT is Cone or Symmetric.
Owner:RPX CLEARINGHOUSE
Methods, devices and systems for establishing end-to-end secure connections and for securely communicating data packets
ActiveUS20140143855A1Guaranteed availabilityImprove efficiencyMultiple digital computer combinationsProgram controlEnd to end securityCommunications system
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
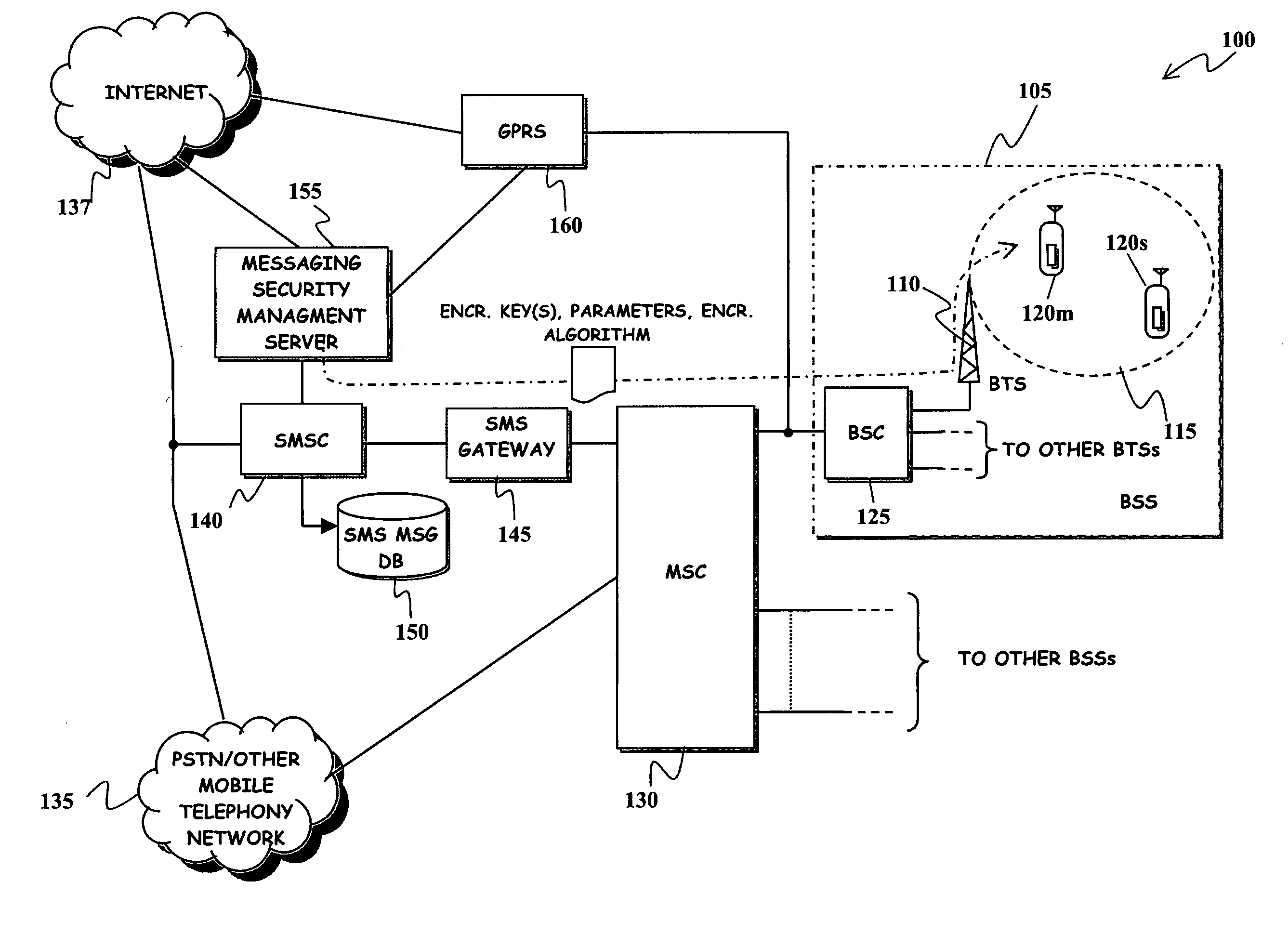
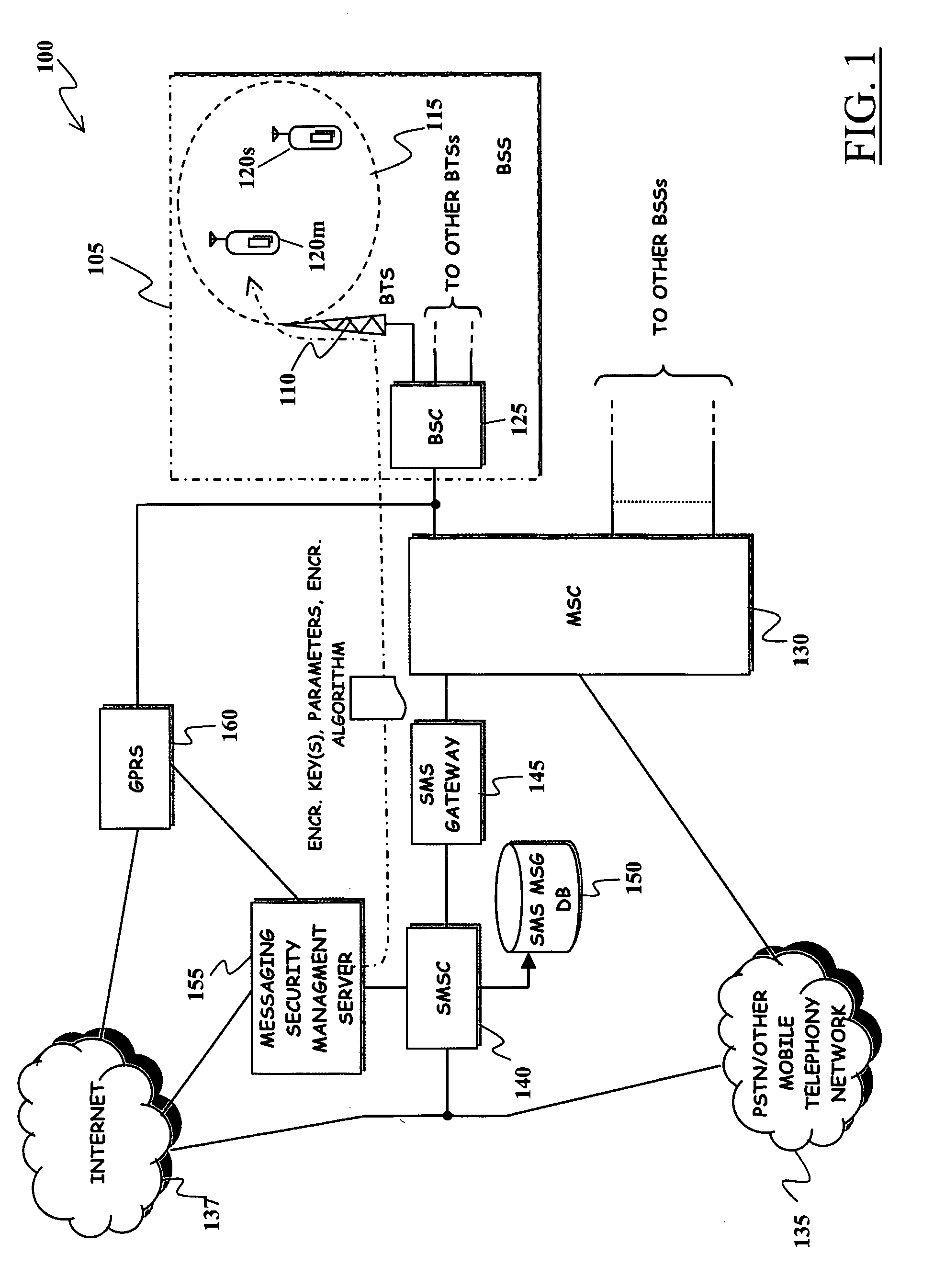
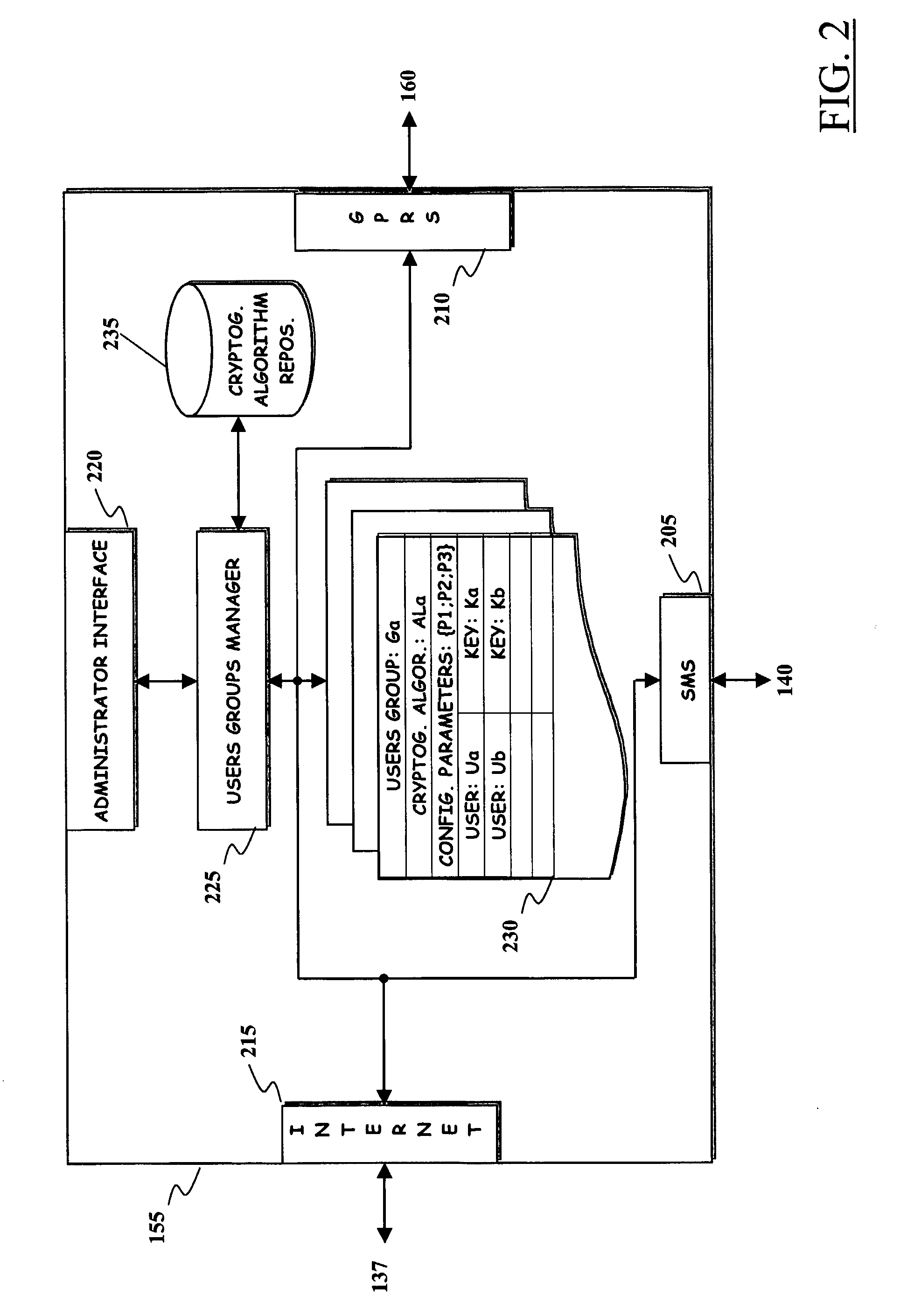
Method and System for Improving Robustness of Secure Messaging in a Mobile Communications Network
ActiveUS20080292101A1Increase flexibilityImprove robustnessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareEnd to end security
A mobile communications network has mobile communications capabilities and supports a secure messaging service, such as an SMS messaging service, that allows a message sender and at least one message receiver (at least one among the message sender and the message receiver being a user of the mobile communications network) to exchange messages encrypted by means of a cryptographic process performed by the message sender, so as to obtain an encrypted message that can be decrypted by a corresponding cryptographic process performed by the intended message receiver. End-to-end security of the exchanged message is thus achieved. A cryptographic algorithm, exploited by the user of the mobile communications network for performing the cryptographic process, is modified by exploiting the mobile communications capabilities of the mobile communications network. Robustness and reliability over time of the end-to-end security messaging is improved.
Owner:TELECOM ITALIA SPA
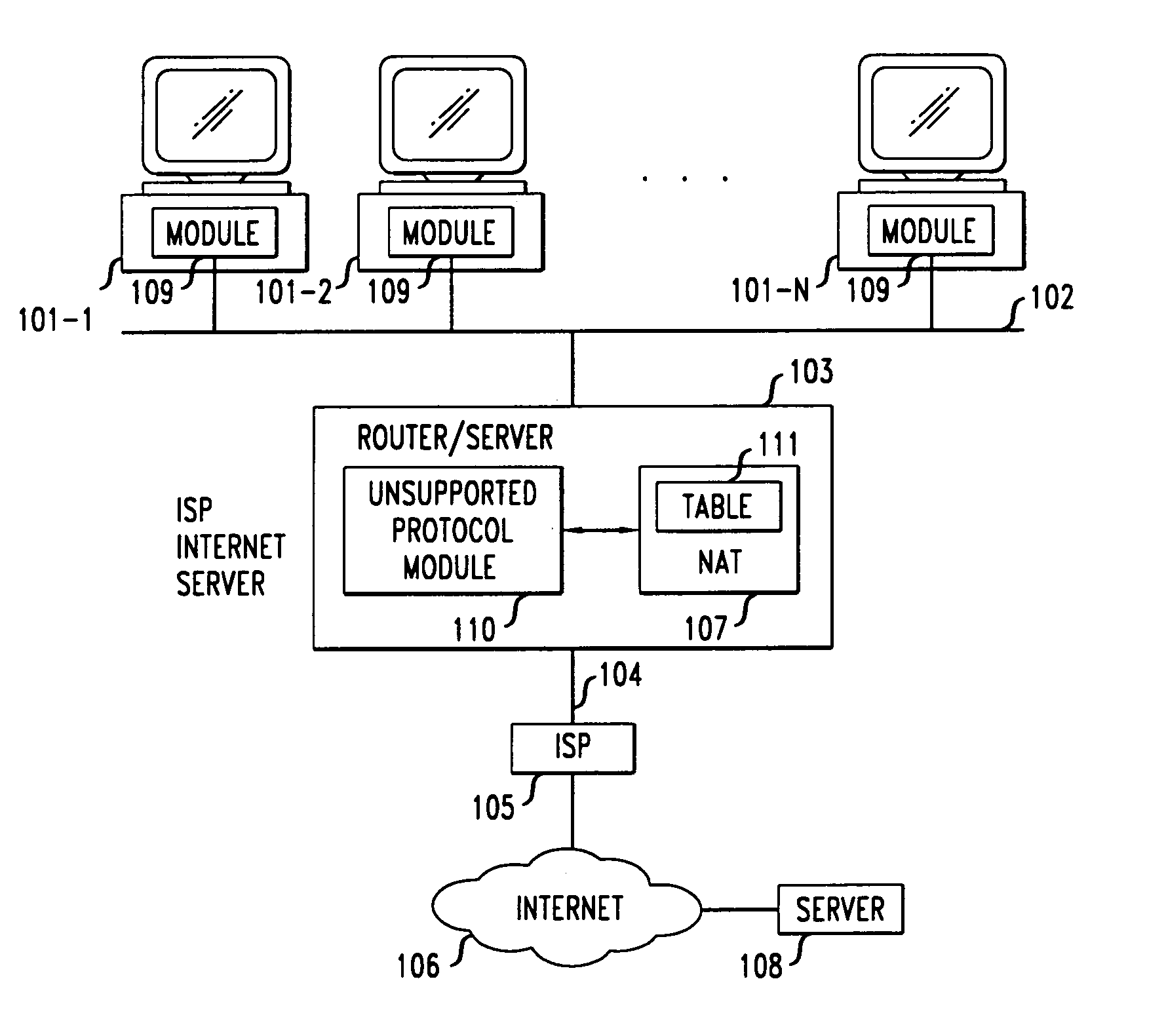
Method and apparatus for application-independent end-to-end security in shared-link access networks
InactiveUS6963982B1Multiple digital computer combinationsProgram controlExpiration TimeEnd to end security
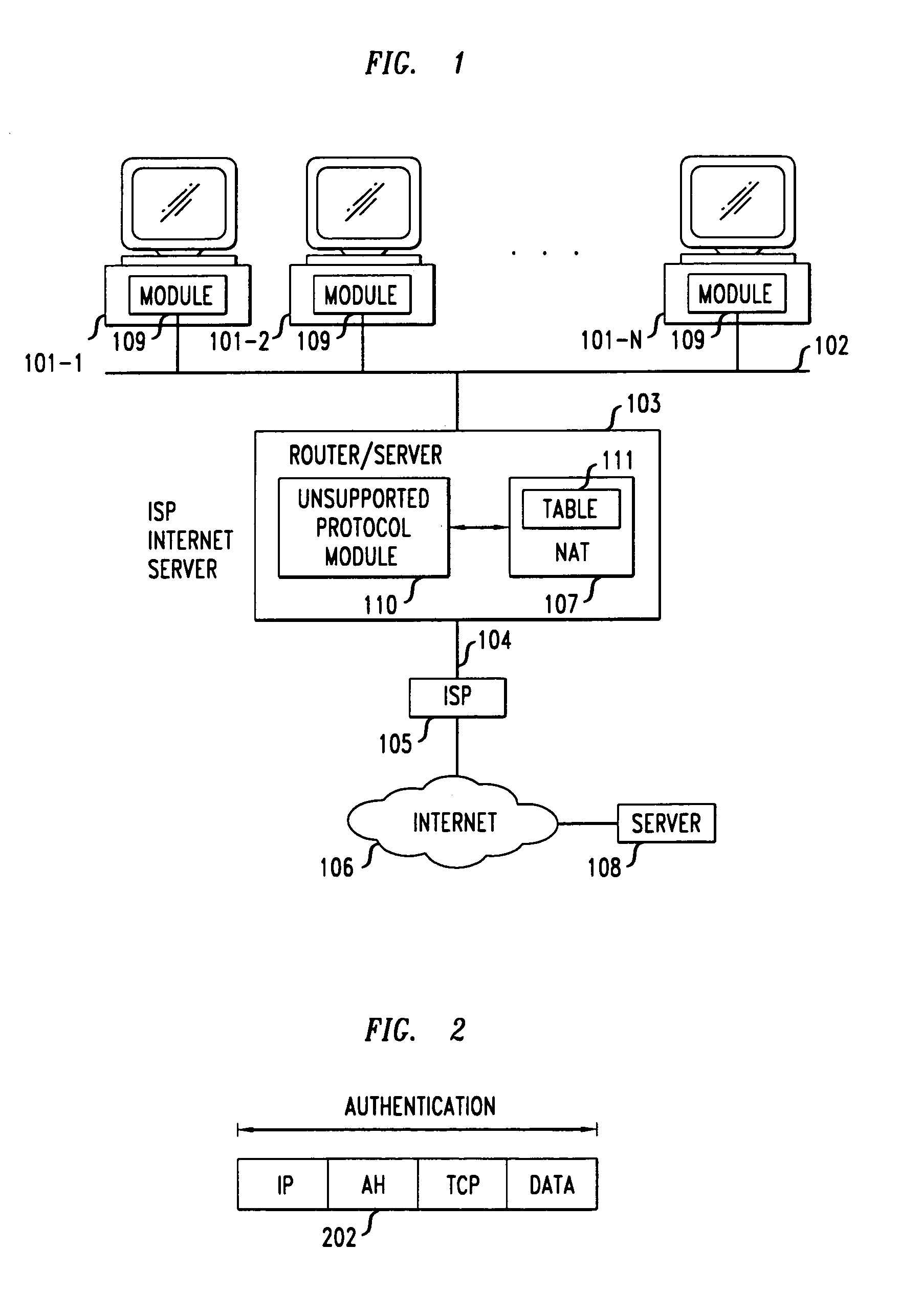
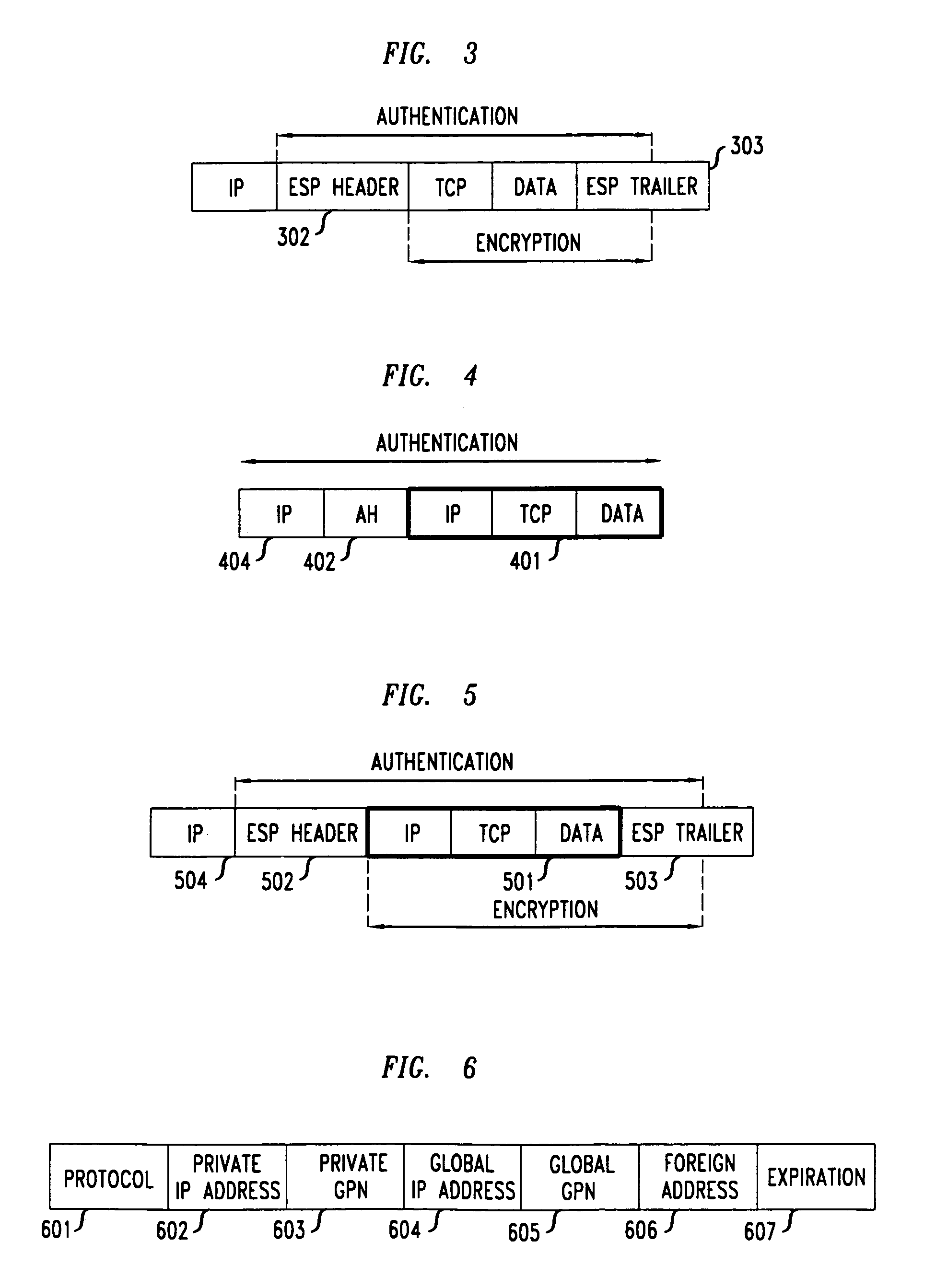
Clients that are connected on a private network and which are assigned a private IP address that is not routable on the Internet can connect to the Internet through a router / server that includes a network address translator (NAT). For outgoing packets, the NAT translates the client's private source IP address and generalized port number (GPN) to the NAT's global IP address and GPN. For incoming packets sent to the NAT's global IP address and GPN, the NAT translates the global destination IP address and GPN to the client's private IP address and GPN. For protocols which cannot be directly supported by the NAT, such as those in the IPSec security protocol suite, the NAT is extended by creating in the NAT's translation table an entry that associates, for a specific unsupported protocol, a client's private IP address and GPN, the NAT's global IP address and GPN, and a foreign address on the Internet, that is valid until a specified or default expiration time. Outgoing packets from the client to that foreign address and incoming packets from that foreign address to the NAT's global IP address and GPN are translated according to the entry until the entry expires. In associations with these translations to outgoing and incoming packets, the client implements any Application Layer Gateway (ALG) that would otherwise be implemented at the NAT. Further, at the client, outgoing packets are modified before being transmitted so as to pre-compensate for the effects of the translations. Incoming packets at the client from the NAT are similarly modified so as to post-compensate for the effects of the translations. For the IPSec protocol, these modification include adjusting the checksum in the TCP or UDP header to account for IP address and TCP or UDP port number translations.
Owner:ALCATEL-LUCENT USA INC
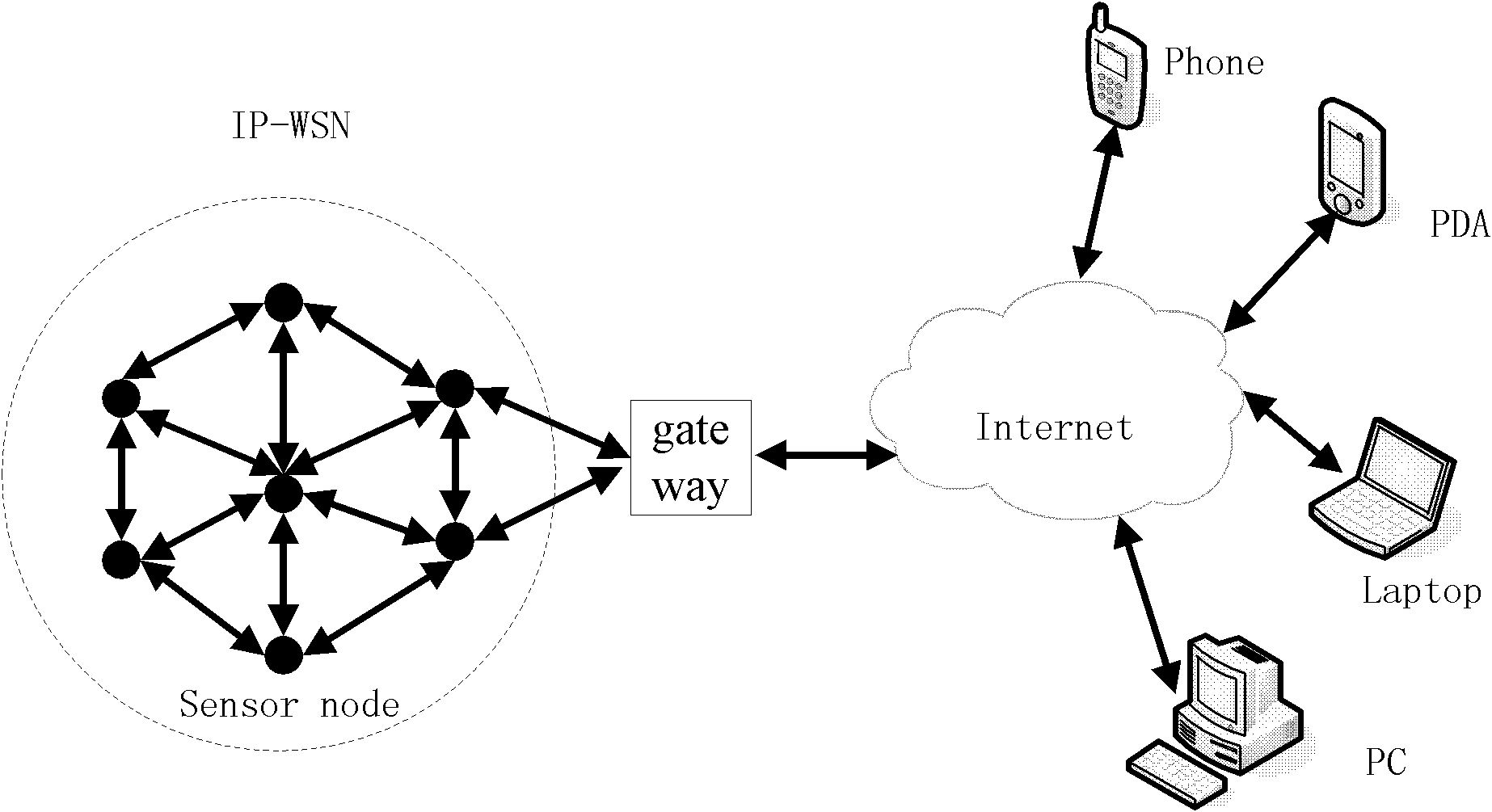
End-to-end security assurance method under IoT (Internet of Things) cloud environment
ActiveCN107919956AGuarantee the legitimacy of identityReduce computational overheadKey distribution for secure communicationPublic key for secure communicationSecure communicationEnd to end security
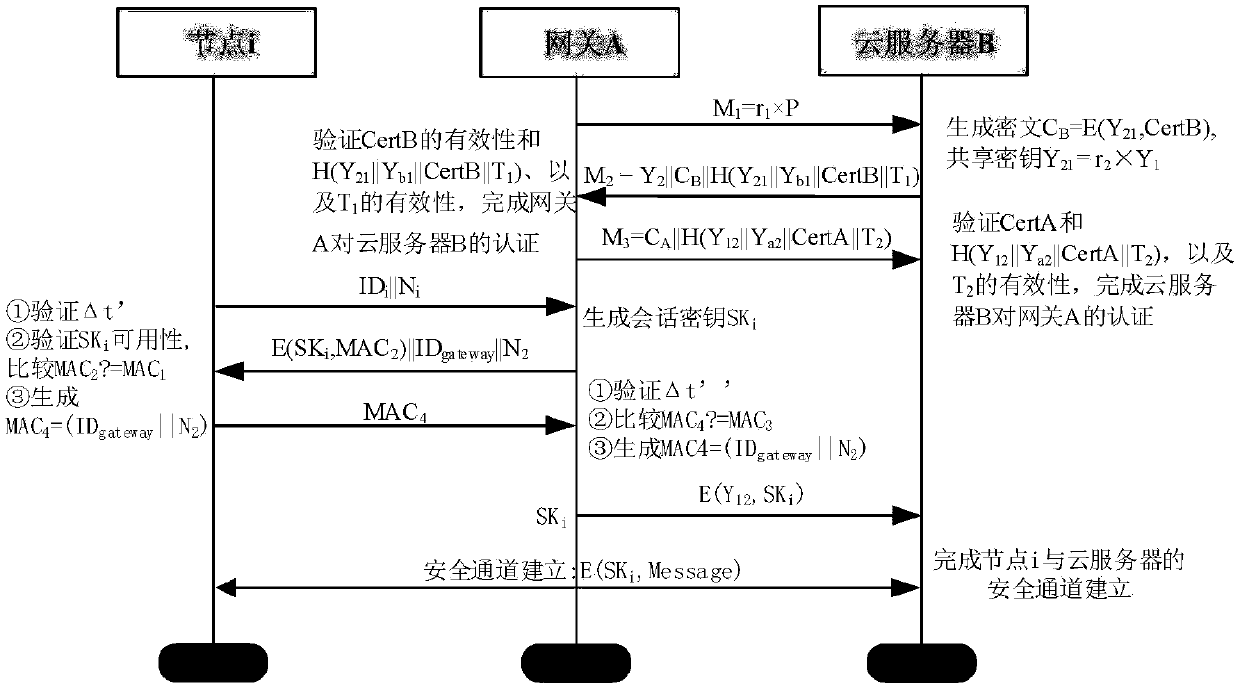
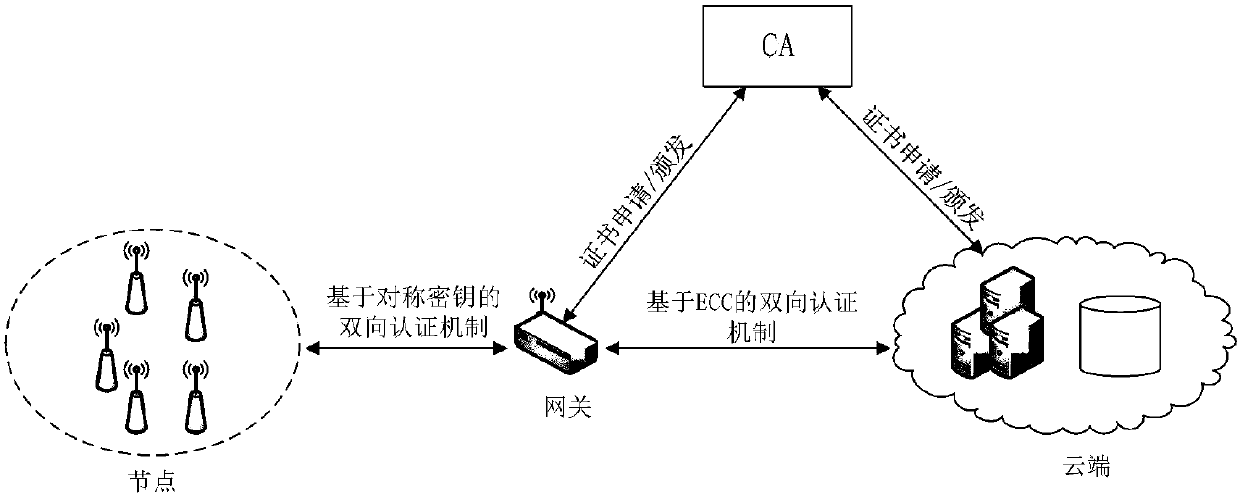
The invention relates to an end-to-end security assurance method under an IoT (Internet of Things) cloud environment, belonging to the fields of loT and cloud computing. Firstly, a PKI authenticationmechanism based on an ellipse curve algorithm is used to realize the authentication and key negotiation of a gateway and a cloud server, and establish a secure channel between the gateway and the cloud server; then the bidirectional authentication protocol based on the modified symmetric key is used to realize the authentication and key negotiation of a resource-limited node and the gateway; and finally a session key between the gateway and the cloud server is used to encrypt a session key between the node and the gateway, and the encrypted session key is sent to the cloud server, thus completing the establishment of the secure channel between the terminal node and the cloud server. The invention guarantees the identity validity of the node and the cloud server, and meanwhile, effectivelyreduces the computing cost of the sensor node. The authentication of the cloud server is indirectly realized by the gateway, thus reducing the authentication times between the gateway and the cloud server, and realizing the secure communication between the terminal node and the cloud server.
Owner:INST OF IND INTERNET CHONGQING UNIV OF POSTS & TELECOMM
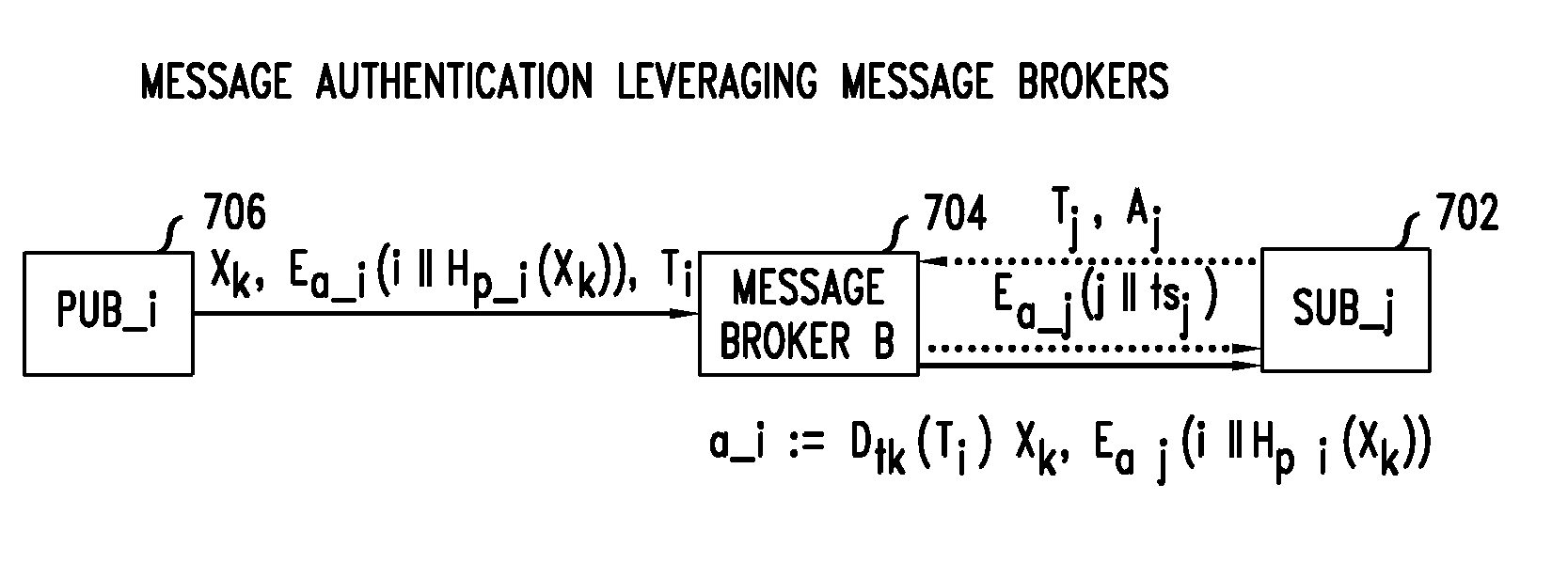
Method and apparatus for resilient end-to-end message protection for large-scale cyber-physical system communications
InactiveUS20140129838A1Reduce overheadCompromising scalabilityKey distribution for secure communicationUser identity/authority verificationEnd to end securityPhysical system
To address the security requirements for cyber-physical systems, embodiments of the present invention include a resilient end-to-end message protection framework, termed Resilient End-to End Message Protection or REMP, exploiting the notion of the long-term key that is given on per node basis. This long term key is assigned during the node authentication phase and is subsequently used to derive encryption keys from a random number per-message sent. Compared with conventional schemes, REMP improves privacy, message authentication, and key exposure, and without compromising scalability and end-to-end security. The tradeoff is a slight increase in computation time for message decryption and message authentication.
Owner:WSOU INVESTMENTS LLC
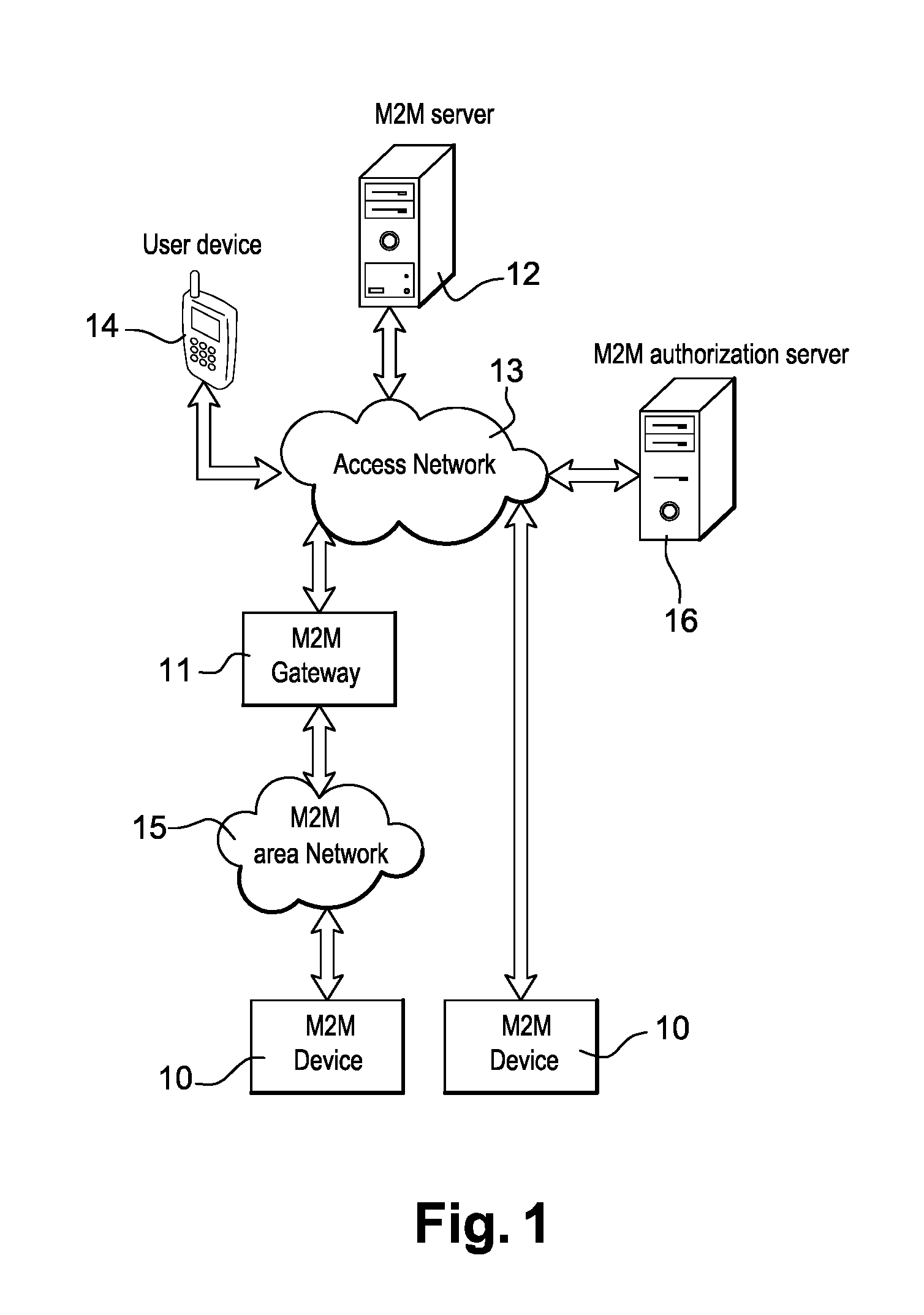
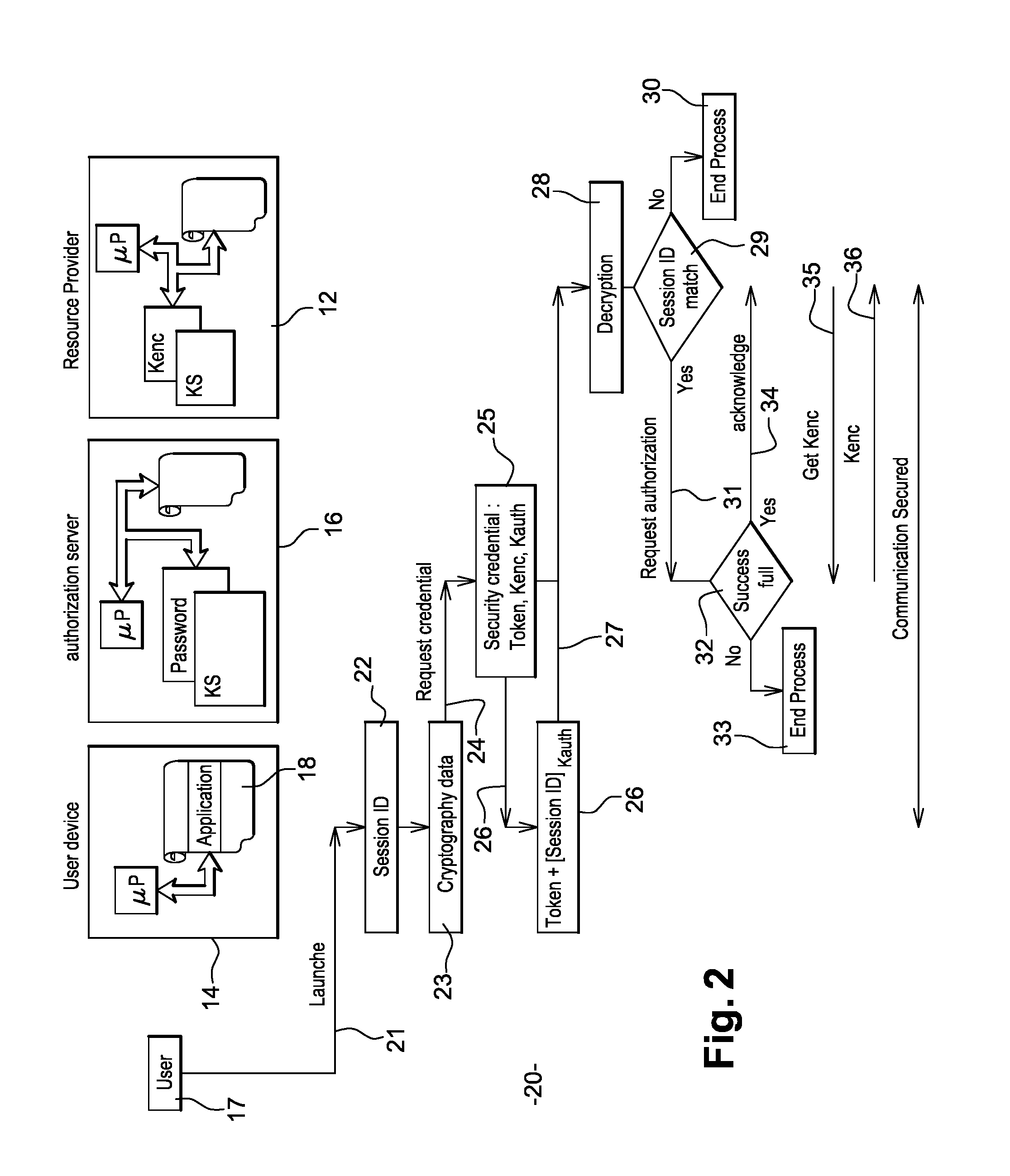
System and method for securing machine-to-machine communications
ActiveUS20160337354A1Improve securityEasy accessWireless commuication servicesTransmissionEnd to end securityData source
This invention concerns the implementation of end-to-end security for the communication between objects in the domain of the Internet of Things (or Internet of Objects). The purpose of the patent is dealing with the setup of secure authorized information channel between data source (M2M device) and data consumers (consumer entity). According to the present invention, the access to a M2M device by a consumer entity (consumer application) is controlled by a M2M authorization server. The M2M authorization server is the entity in charge of managing access rights for the M2M device and makes the decision regarding the access to the resource by the consumer entity (consumer application). The M2M server is an entity that enforces the decision and enables the access to the M2M device. When a consumer application needs to communicate with a M2M device, the present invention proposes a method for authorizing a consumer application to access a M2M device and for encrypting the communication between the consumer application and the M2M device. The M2M authorization server computes security credentials which are sent to the consumer application.
Owner:GEMPLU
Cryptographic expansion device and related protocols
InactiveUS20140214687A1Payment architecturePrinted circuit manufactureComputer hardwareSecure communication
A cryptographic expansion device that can be attached to a communication component of a communication device to enable the communication device to perform cryptographic operations on communications sent to and from the communication device is described. When used with a communication device, the cryptographic expansion device enables the communication device to send and received end-to-end secure encrypted communications. The cryptographic expansion device can be used with a communication device without requiring any changes to the internal software or hardware of the communication device and without requiring any modification to the communication protocols of the communication device. In some embodiments, the end-to-end secure communications enabled by the cryptographic expansion device can be utilized by a user of the communication device to perform financial and / or banking transactions.
Owner:VISA INT SERVICE ASSOC
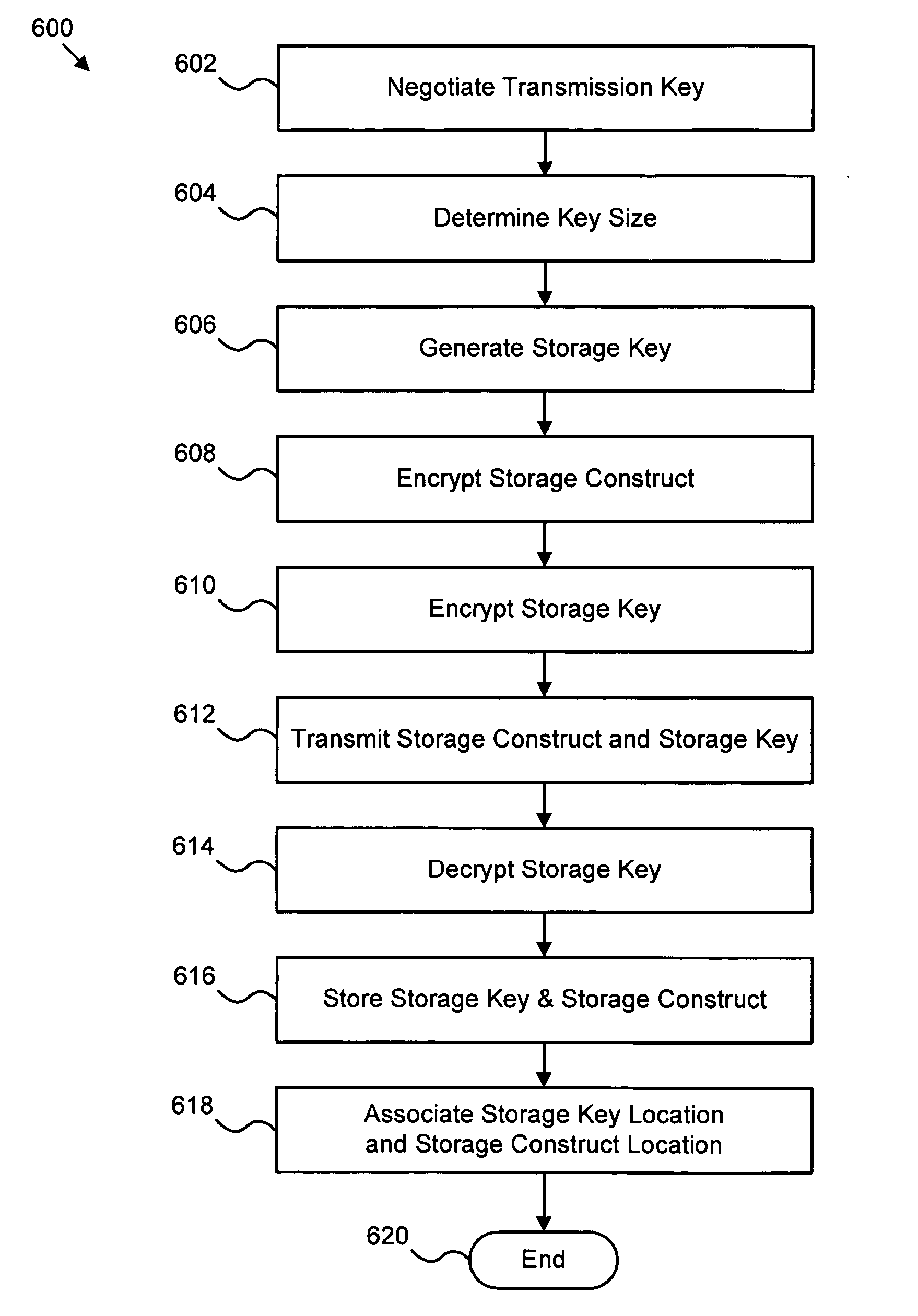
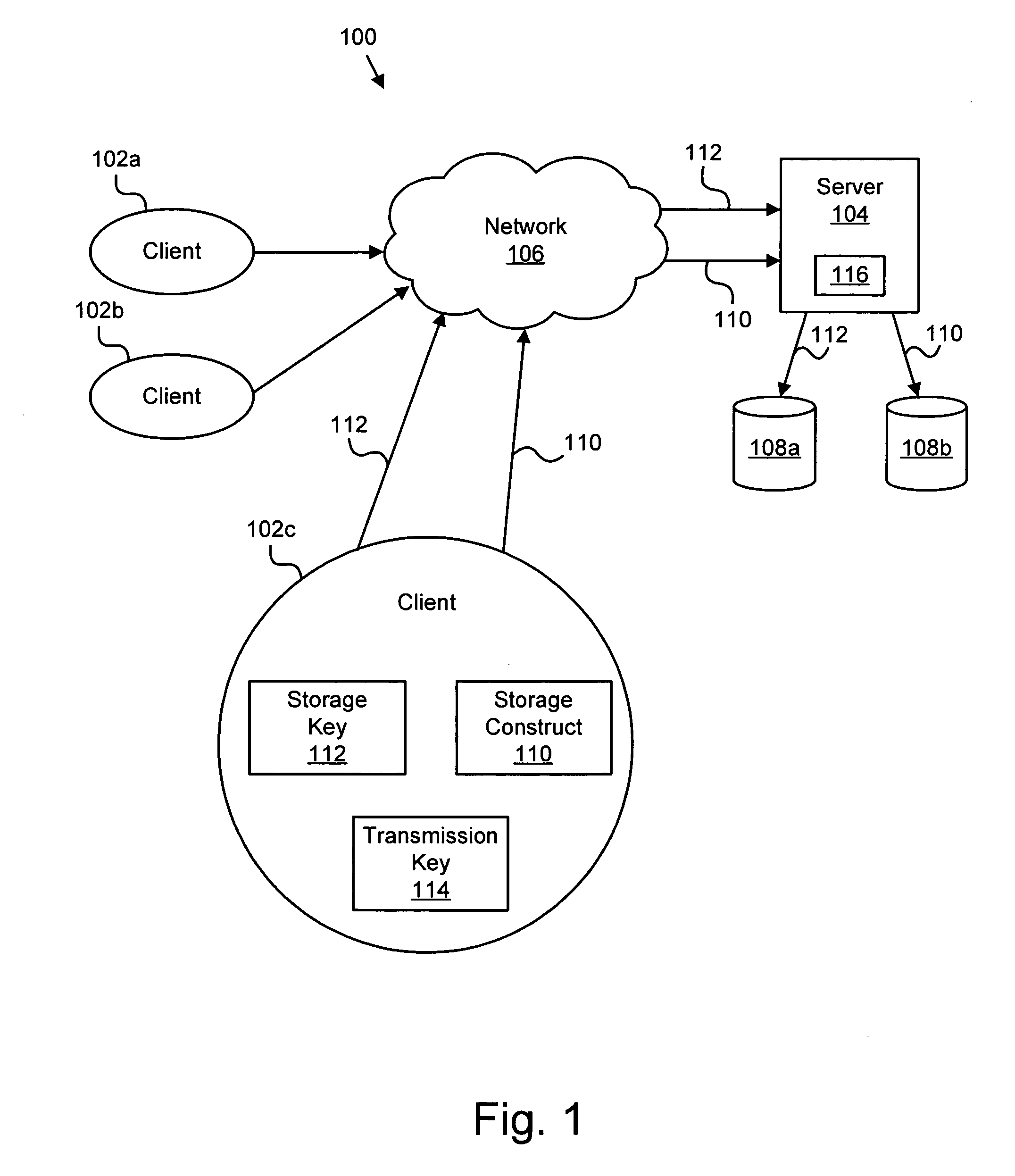
Apparatus, system, and method for transparent end-to-end security of storage data in a client-server environment
InactiveUS20060126850A1Transparent end-to-end security of storage dataKey distribution for secure communicationSecret communicationComputer hardwareKey server
The present invention includes one or more clients in communication with a server. The client desires to send a storage construct to the server for storage. The client negotiates a transmission key with the server. The client generates a storage key associated specifically with the storage construct. The client encrypts the storage construct using the storage key and encrypts the storage key using the transmission key. The encrypted storage construct and encrypted storage key are sent to the server. The server decrypts the storage key using the transmission key. The server stores the storage construct on a storage device separate from a storage device storing the storage key. Preferably, any changes to the storage construct location, the storage key location, or the storage construct name are tracked and proper modifications are made to an association relating the location of the storage construct and the location for the corresponding storage key.
Owner:IBM CORP
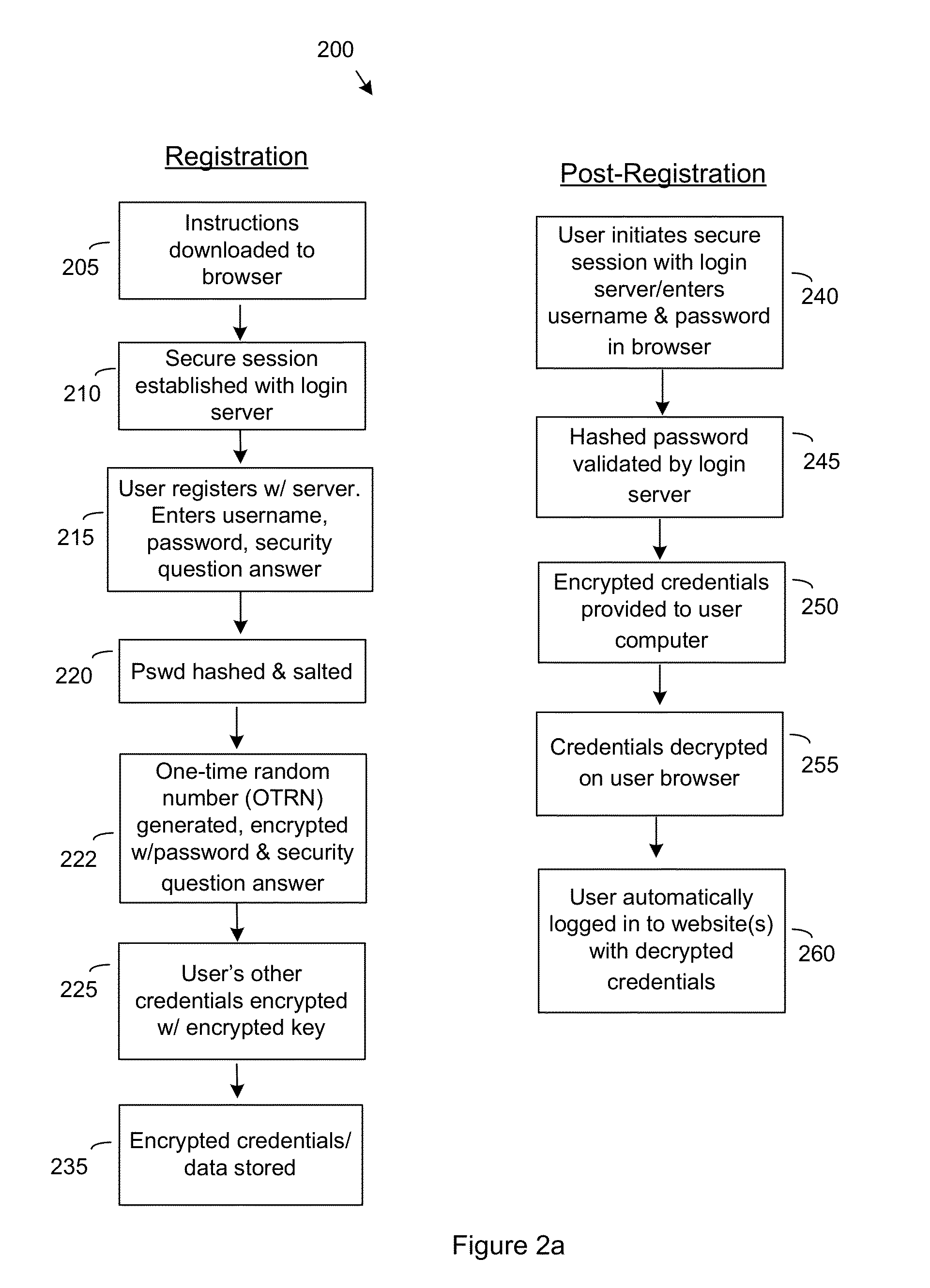
Methods for single signon (SSO) using decentralized password and credential management
ActiveUS8819444B2Decentralized credential managementShorten the timeComputer security arrangementsSecuring communicationEnd to end securityPassword
A method for single sign-on (SSO) that provides decentralized credential management using end-to-end security. Credential (and other personal user information) management is decentralized in that encryption is performed locally on the user's computer. The user's encrypted credentials may be stored by the login server and / or a plurality of distributed servers / databases (such as a cloud). The login server never has access to the user's credentials or other personal information. When the user wants to use single sign-on, he enters his password into his browser and the browser submits the encrypted / hashed password to the login server for validation. Upon validation, the browser receives the user's encrypted credentials. The credentials are decrypted by the browser and provided to relevant websites to automatically log the user in.
Owner:SHAHBAZI MAJID +1
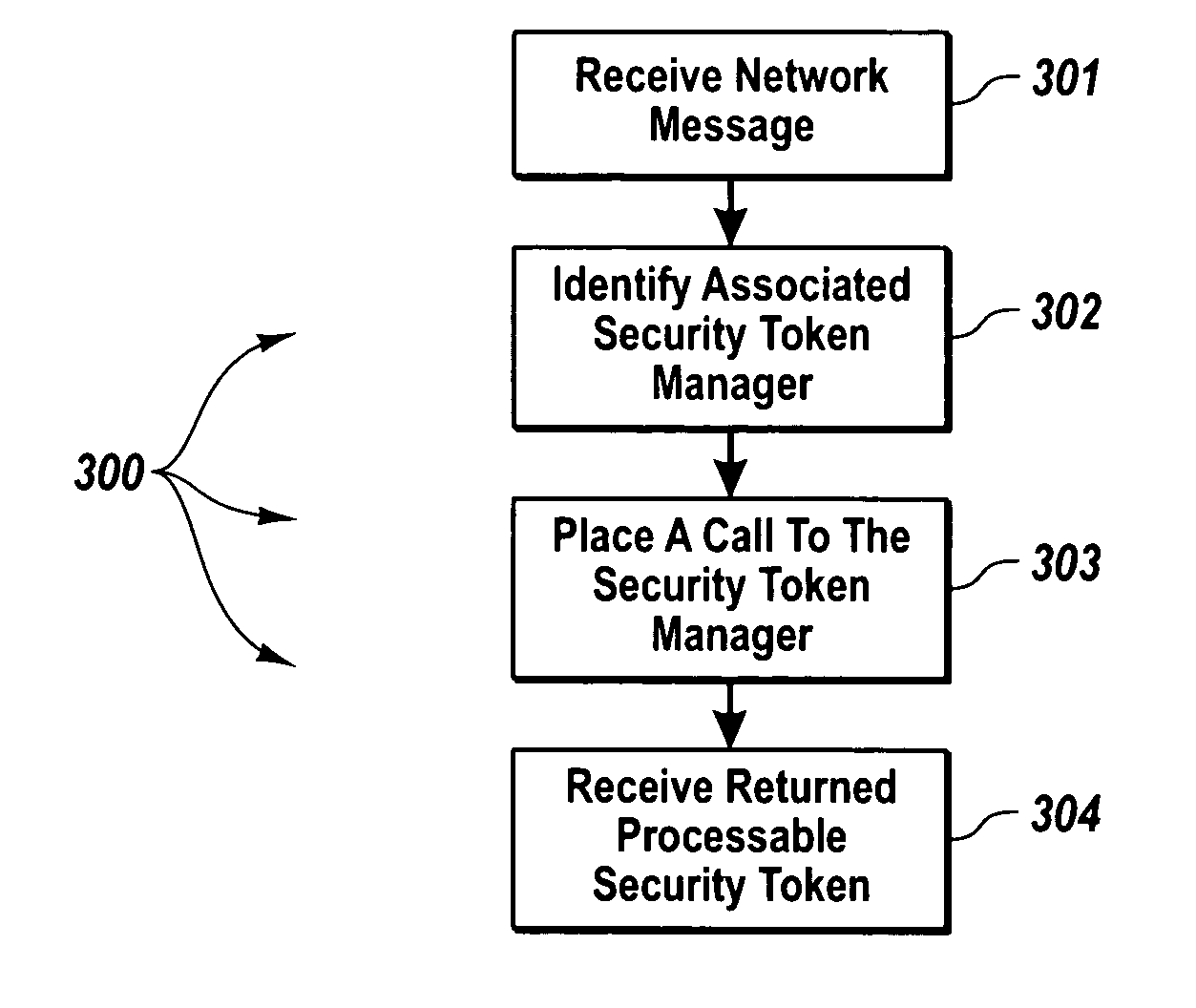
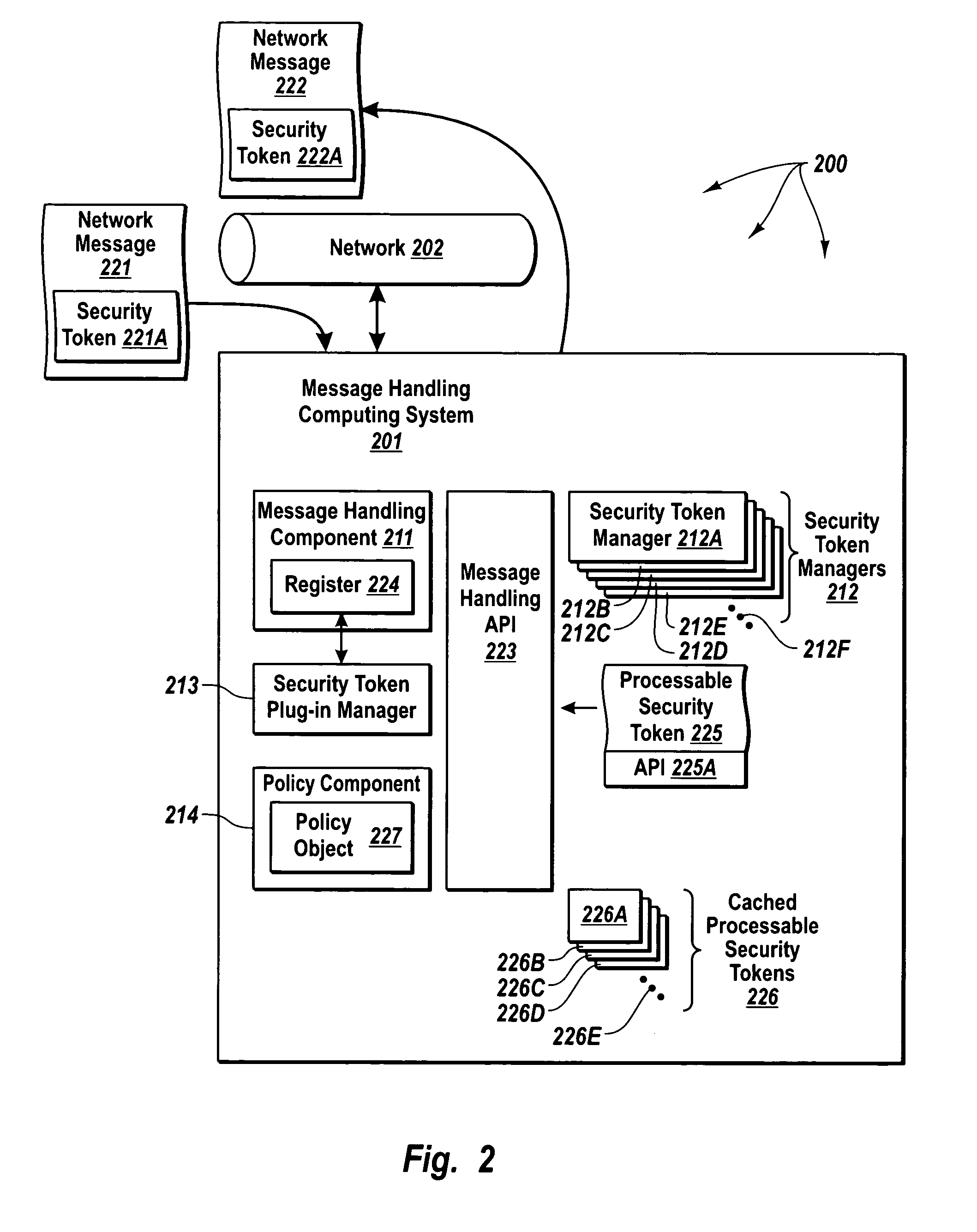
Extendible security token management architecture and secure message handling methods
InactiveUS20060015932A1Conveniently addedDigital data processing detailsUser identity/authority verificationEnd to end securityMessage handling
A message handling computing system that provides security across even transport-independent communication mechanisms, and which allows for convenient extension of security to different security token types, and may provide end-to-end security across different transport protocols. The message handling computing system includes a message handling component configured to send and receive network messages having security tokens. The message handling component interfaces with an expandable and contractible set of security token managers through a standardized application program interface. Each security manager is capable of providing security services for messages that correspond to security tokens of a particular type. A security token plug-in component registers new security token managers with the message handling component.
Owner:MICROSOFT TECH LICENSING LLC
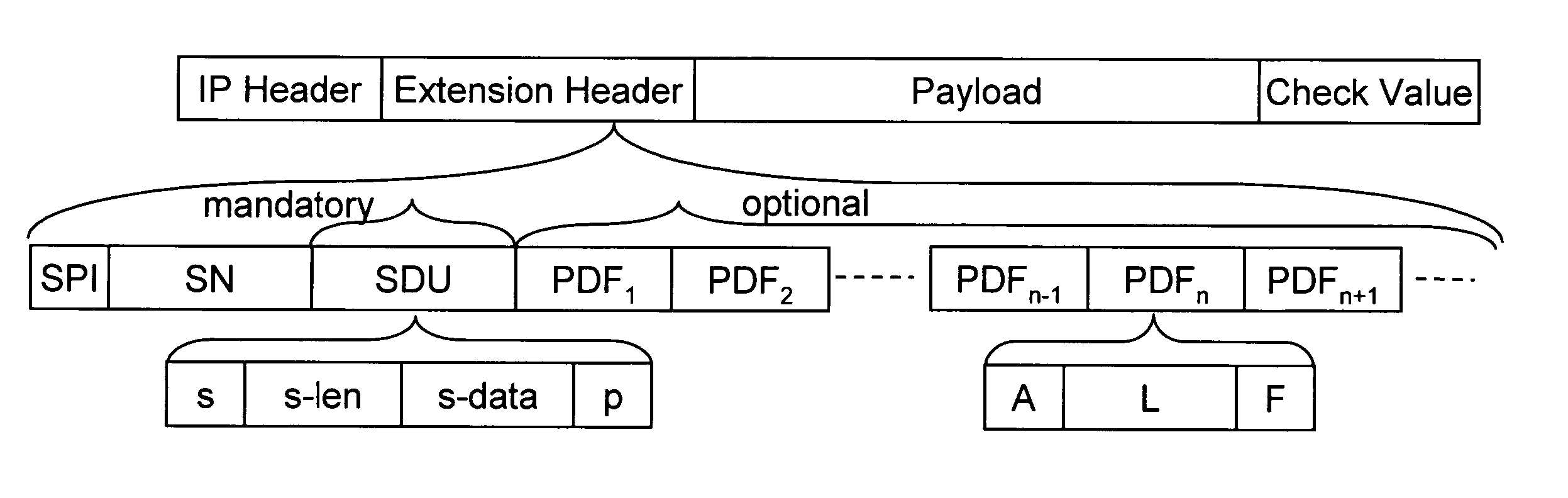
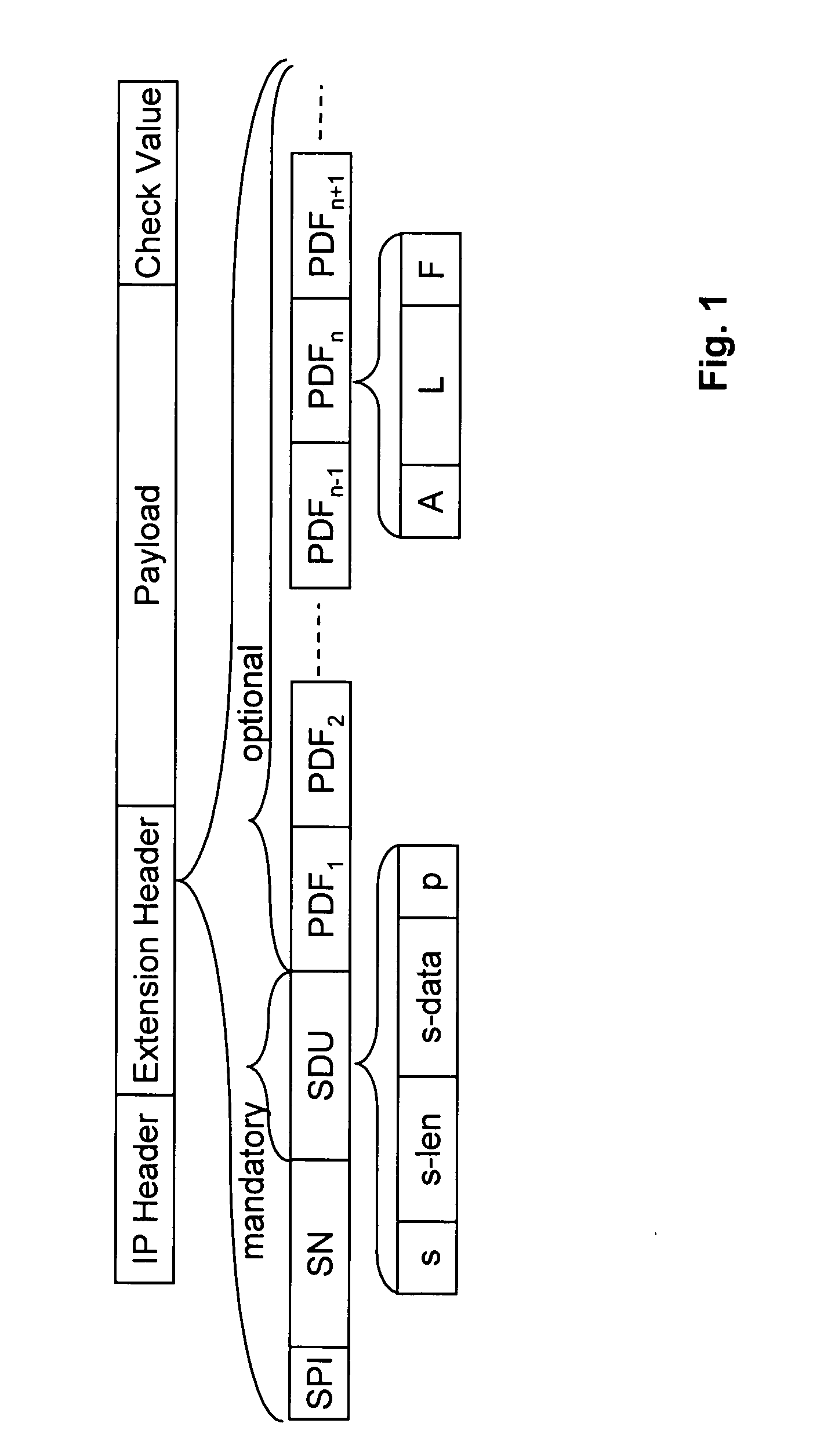
Intermediate node aware IP datagram generation
InactiveUS20050102504A1Digital data processing detailsMultiple digital computer combinationsPlaintextData pack
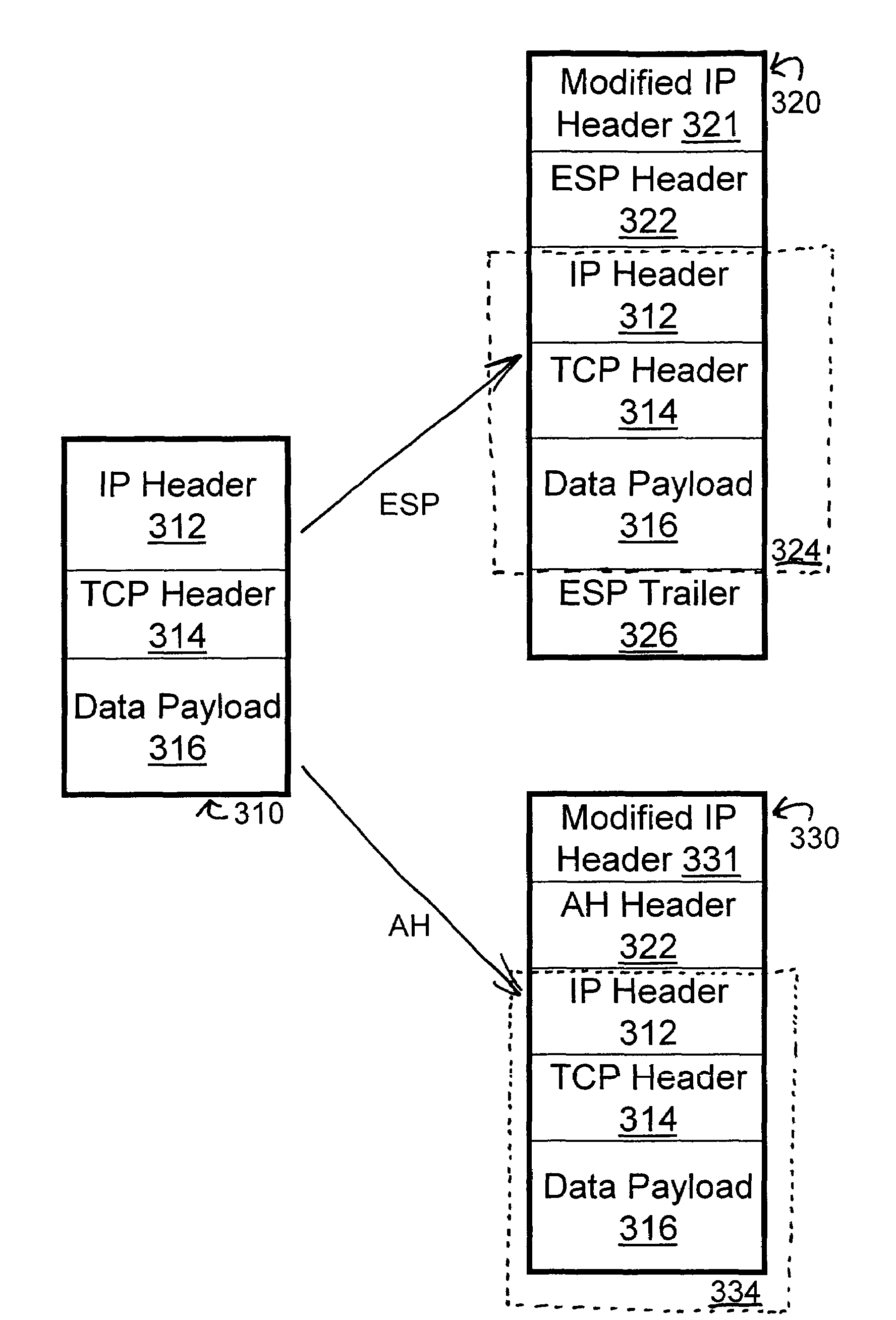
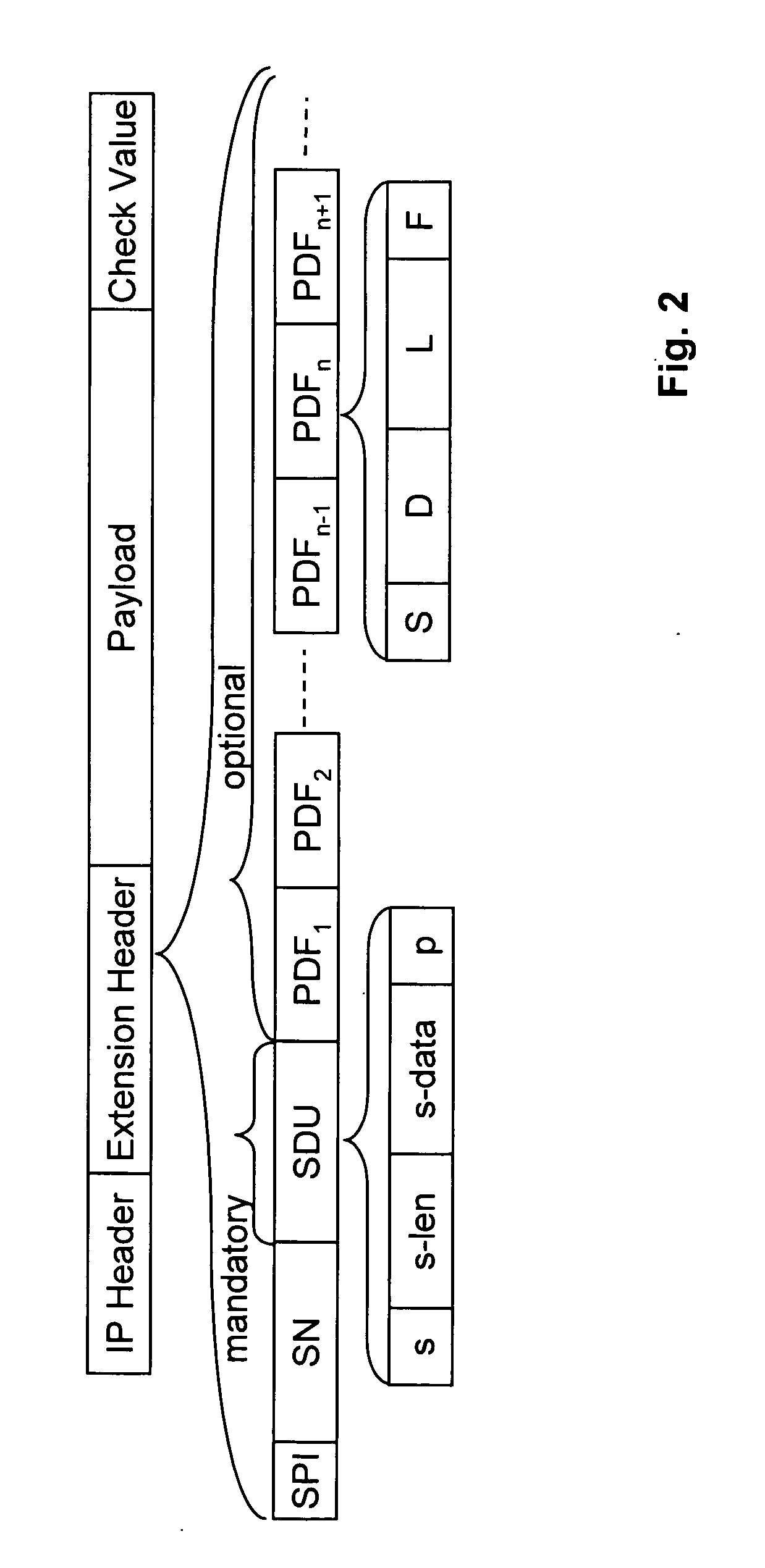
According to the invention, information in clear text is added to a data packet transmitted from a sender to a receiver with end-to-end security in an IP network, which information indicate encrypted data fields in payload data of the packet and / or instruct an intermediate node located on a path between the sender and the receiver how to process the packet, wherein the part of the packet in which the information is provided is different from payload data.
Owner:WSOU INVESTMENTS LLC
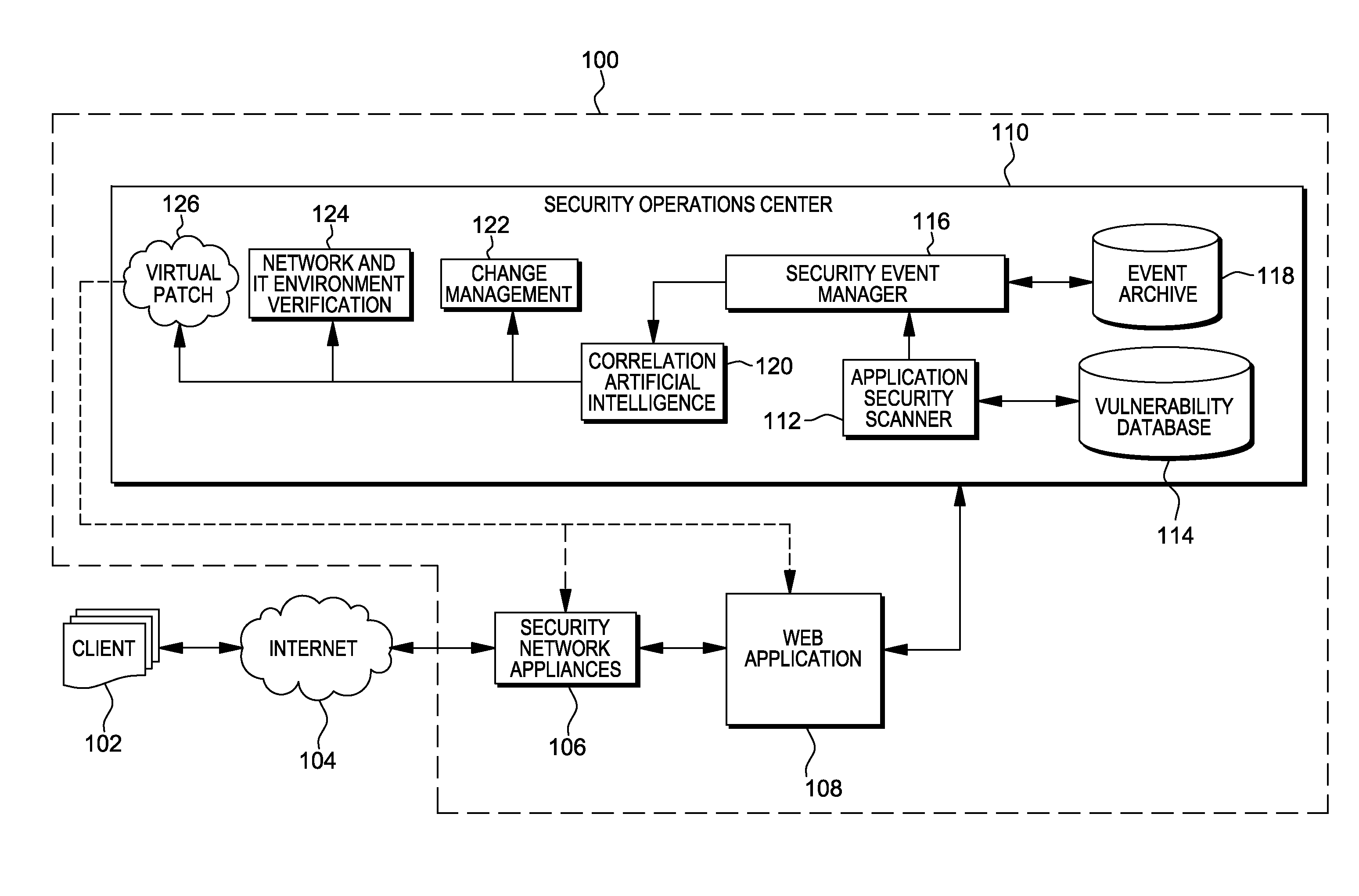
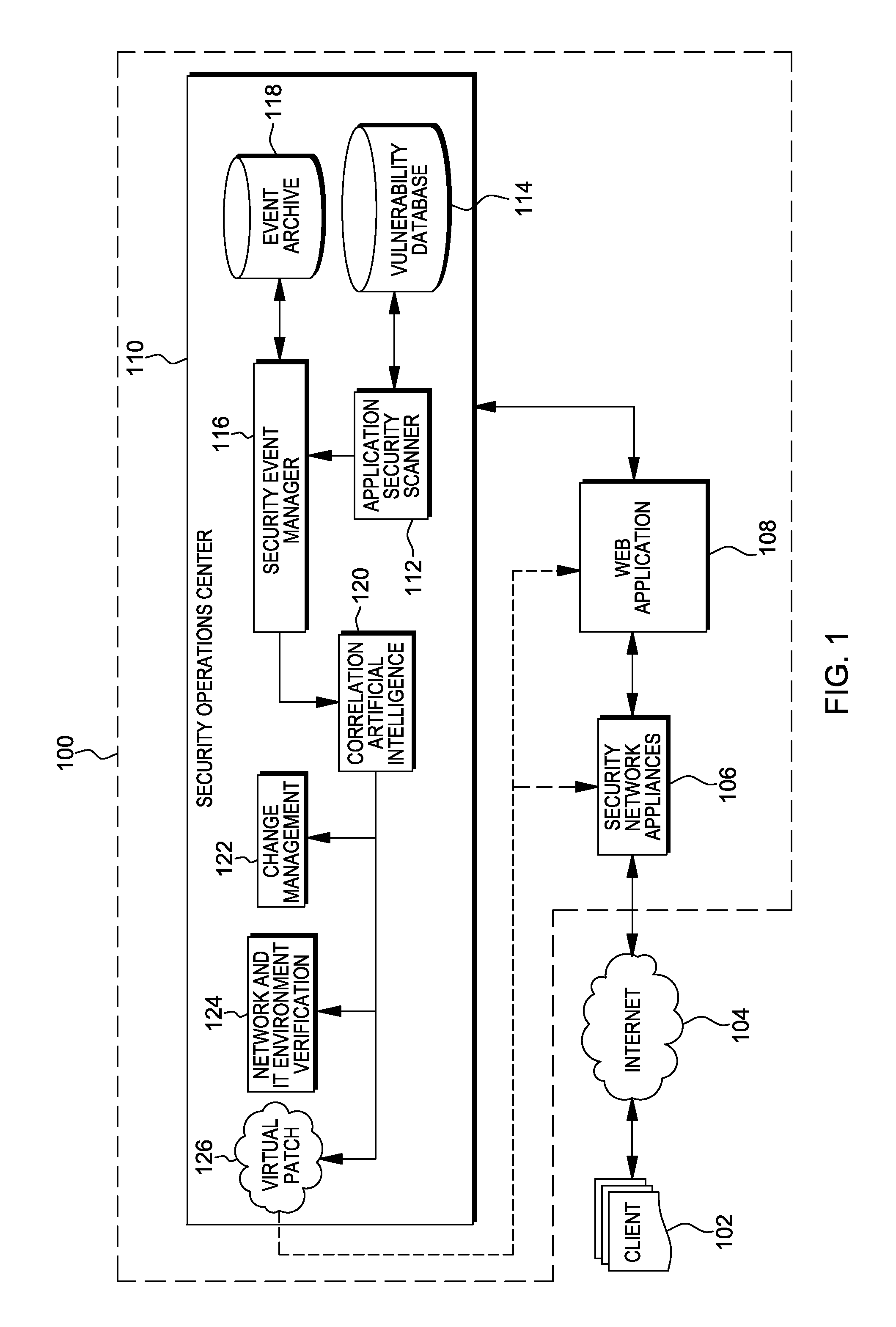
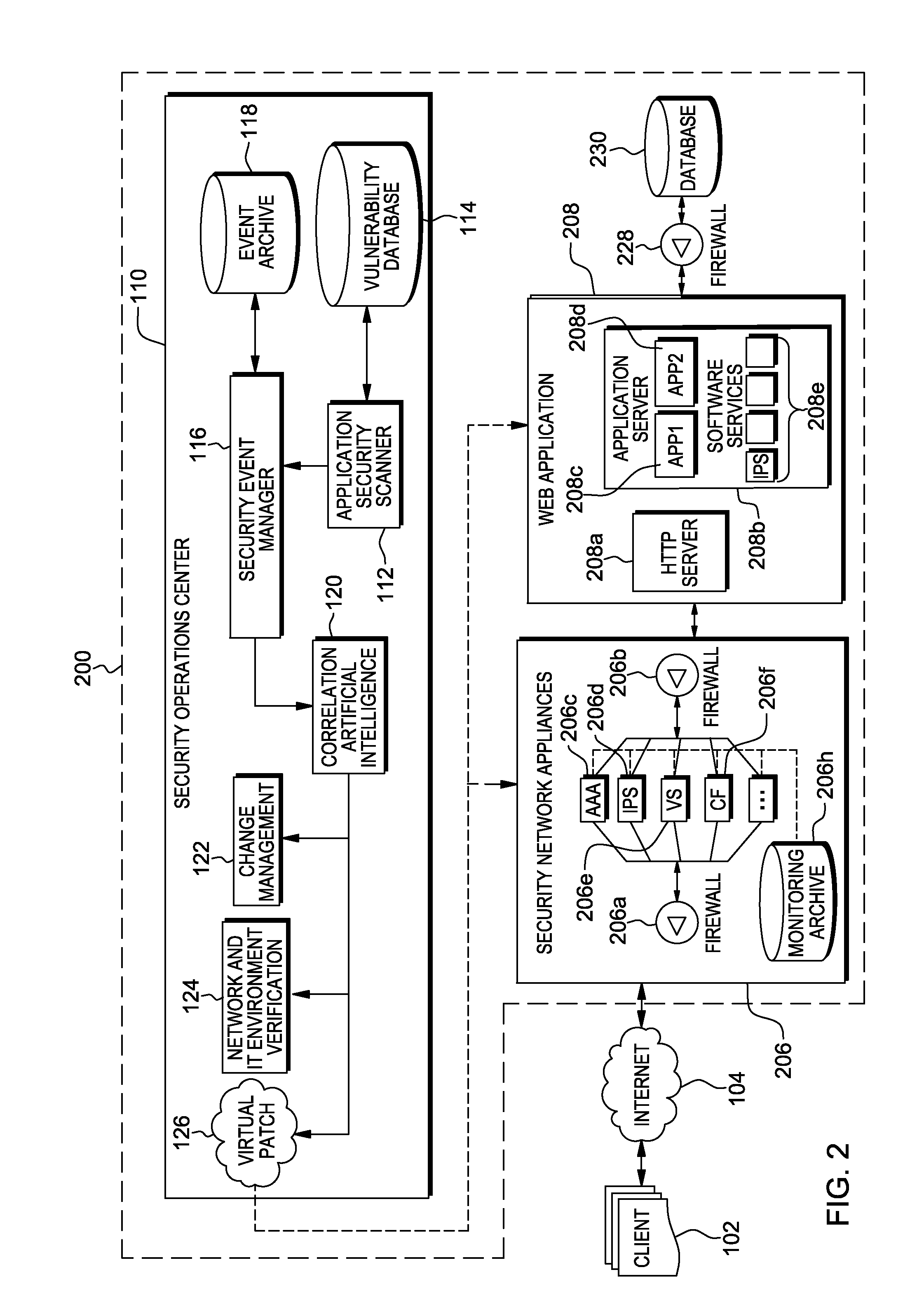
Web application exploit mitigation in an information technology environment
ActiveUS20130086688A1Improve protectionMemory loss protectionUnauthorized memory use protectionEnd to end securityProgram management
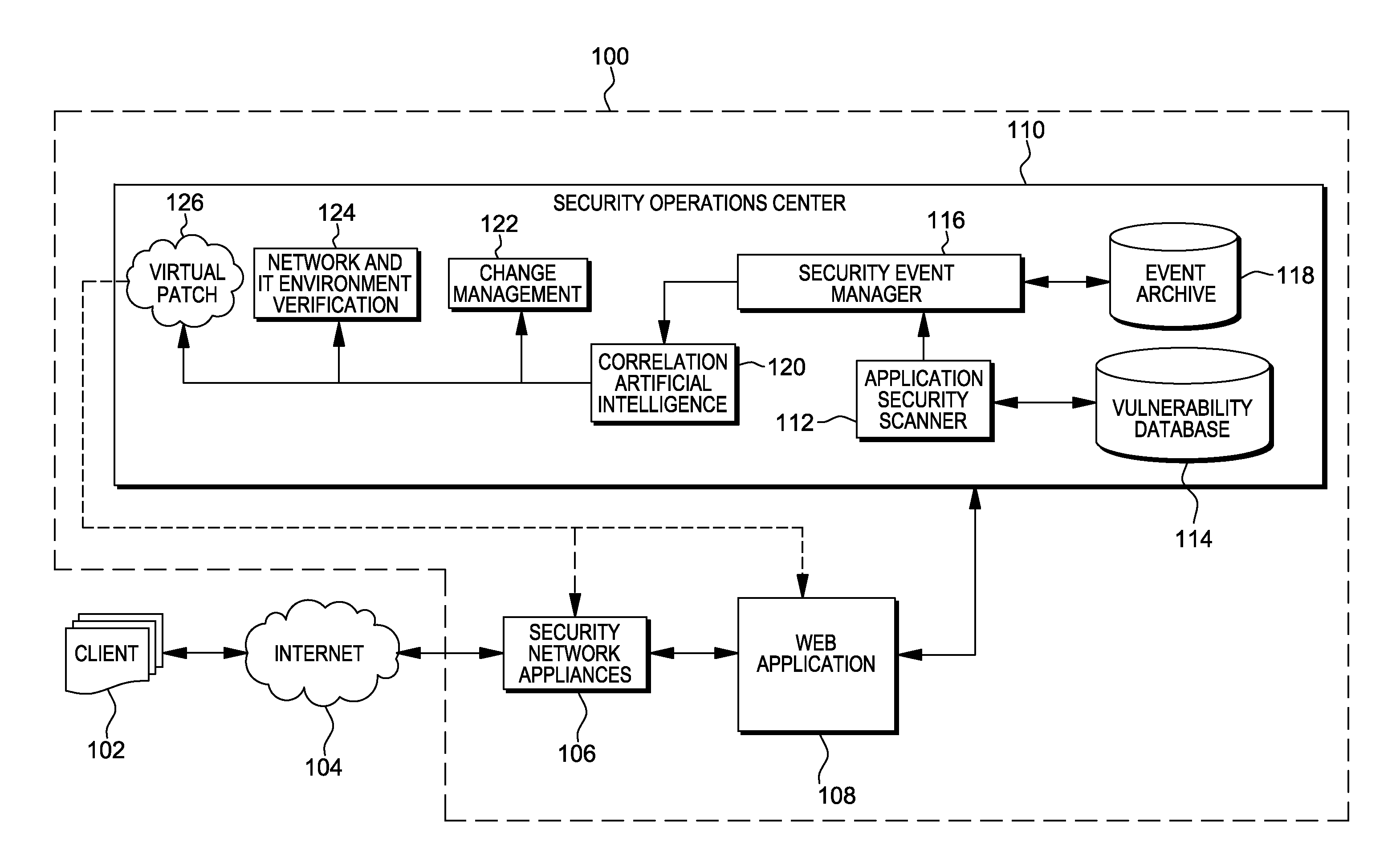
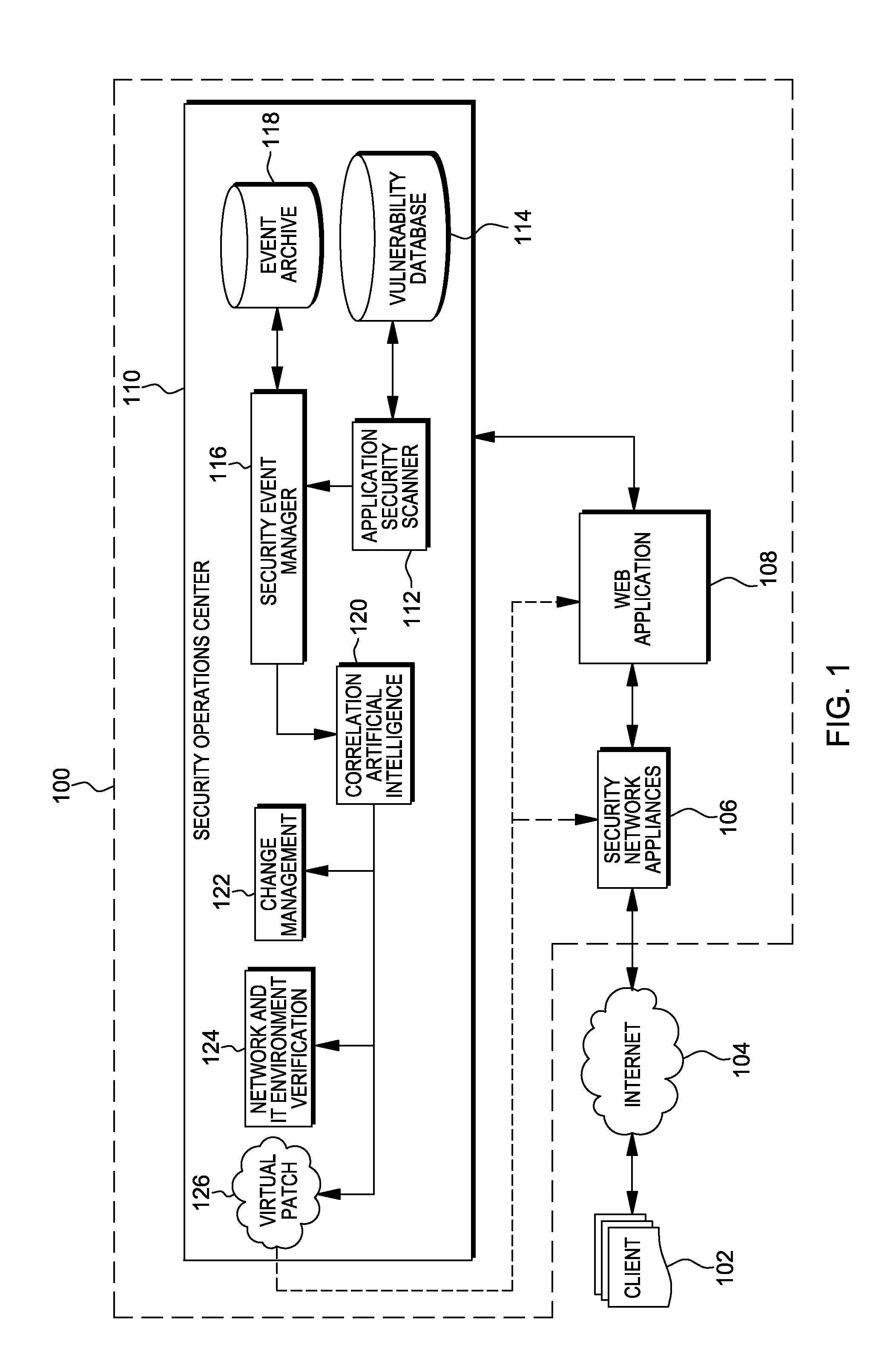
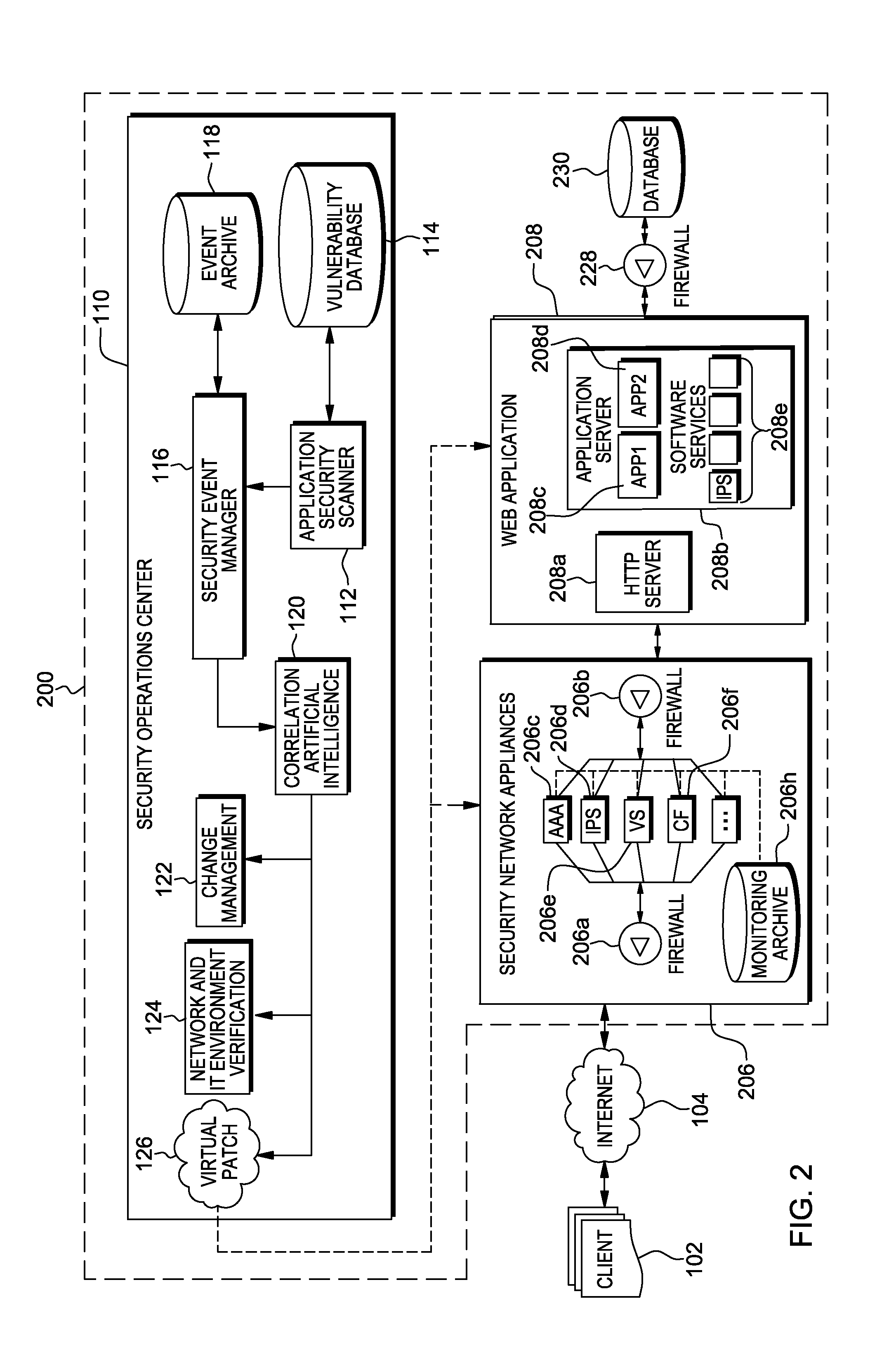
Methods, systems, and computer program products are provided herein for facilitating security in an information technology environment. Web application security vulnerabilities are discovered and addressed by means of virtual patches deployed to components of the information technology environment. An intelligent feedback loop is created to fill the void in the security of the web application when implemented in the specific information technology environment, thereby providing end-to-end security application management through dynamic, pre-emptive, and proactive security awareness and protection in the information technology environment. As new web application security vulnerabilities are discovered, the vulnerability is diagnosed and resolved to preemptively prevent exploitation of the security vulnerability.
Owner:FINJAN BLUE INC
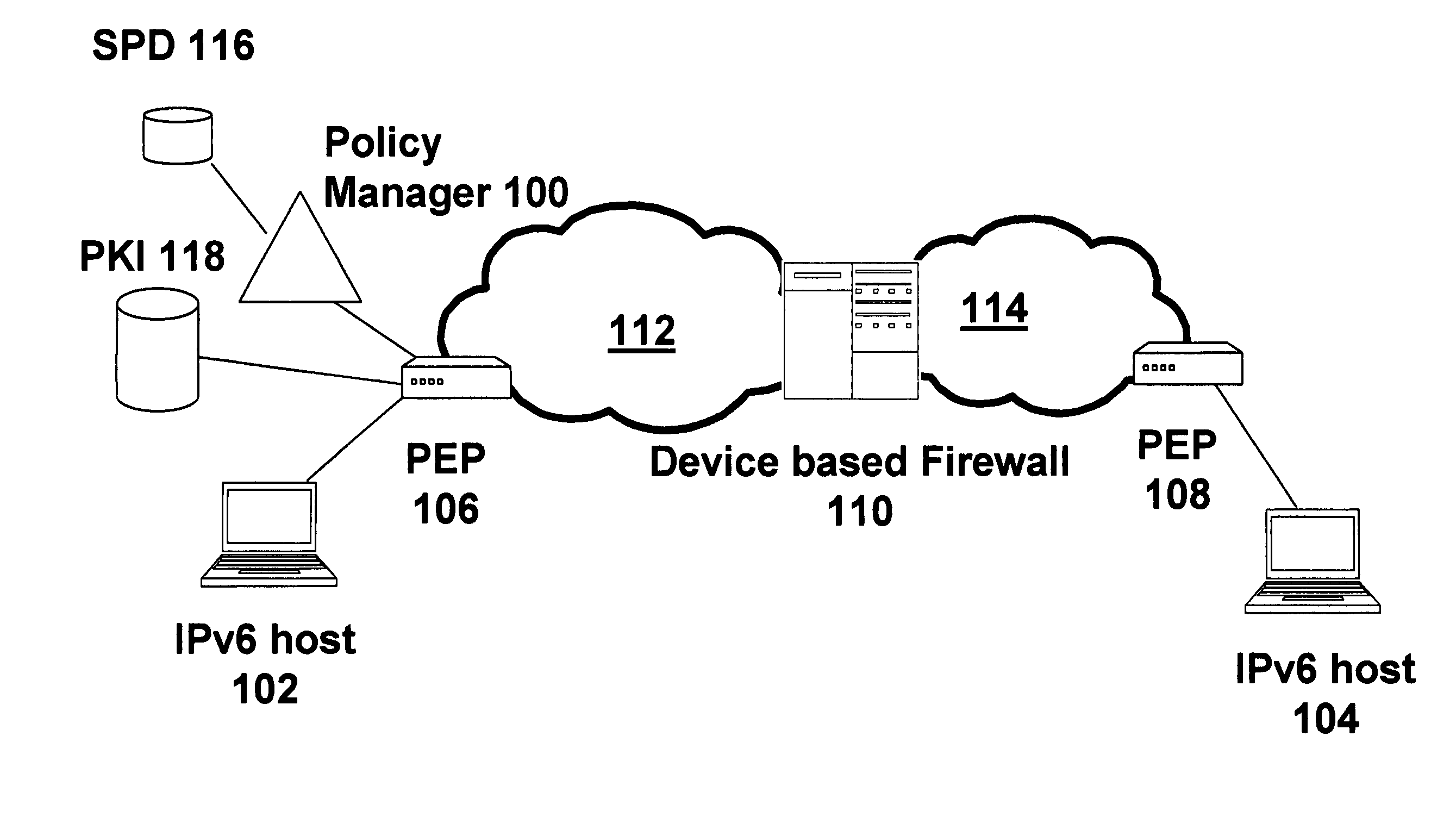
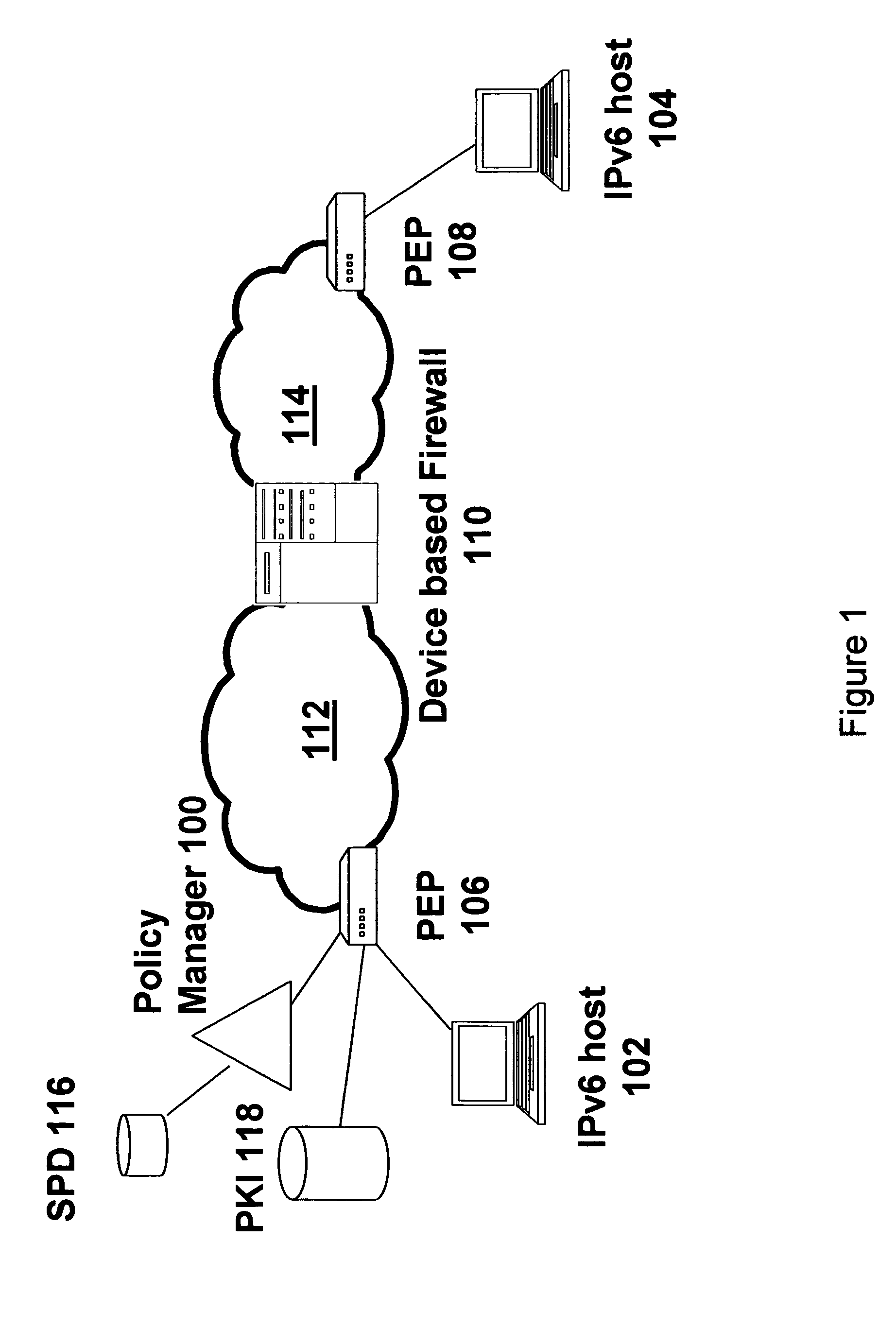
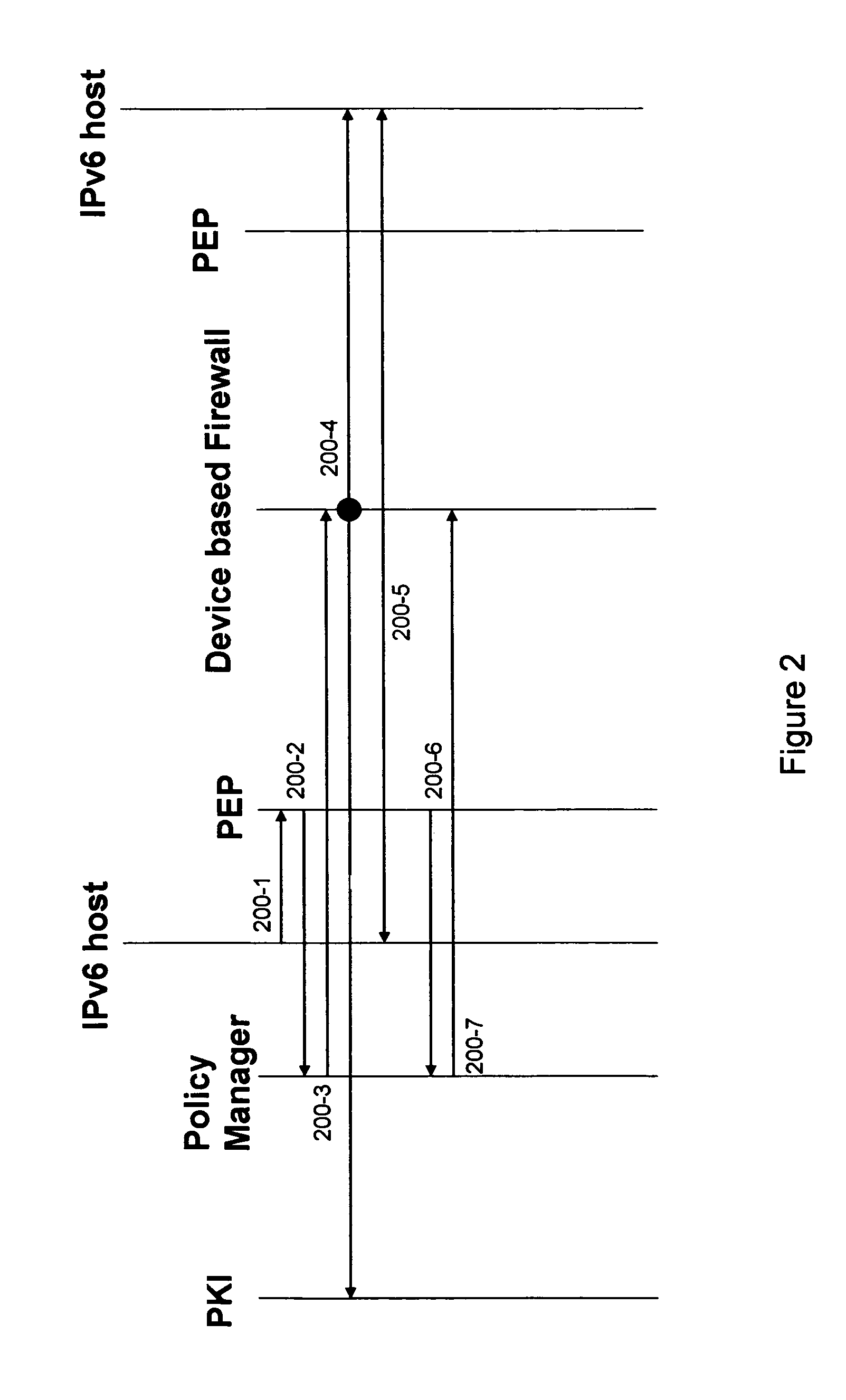
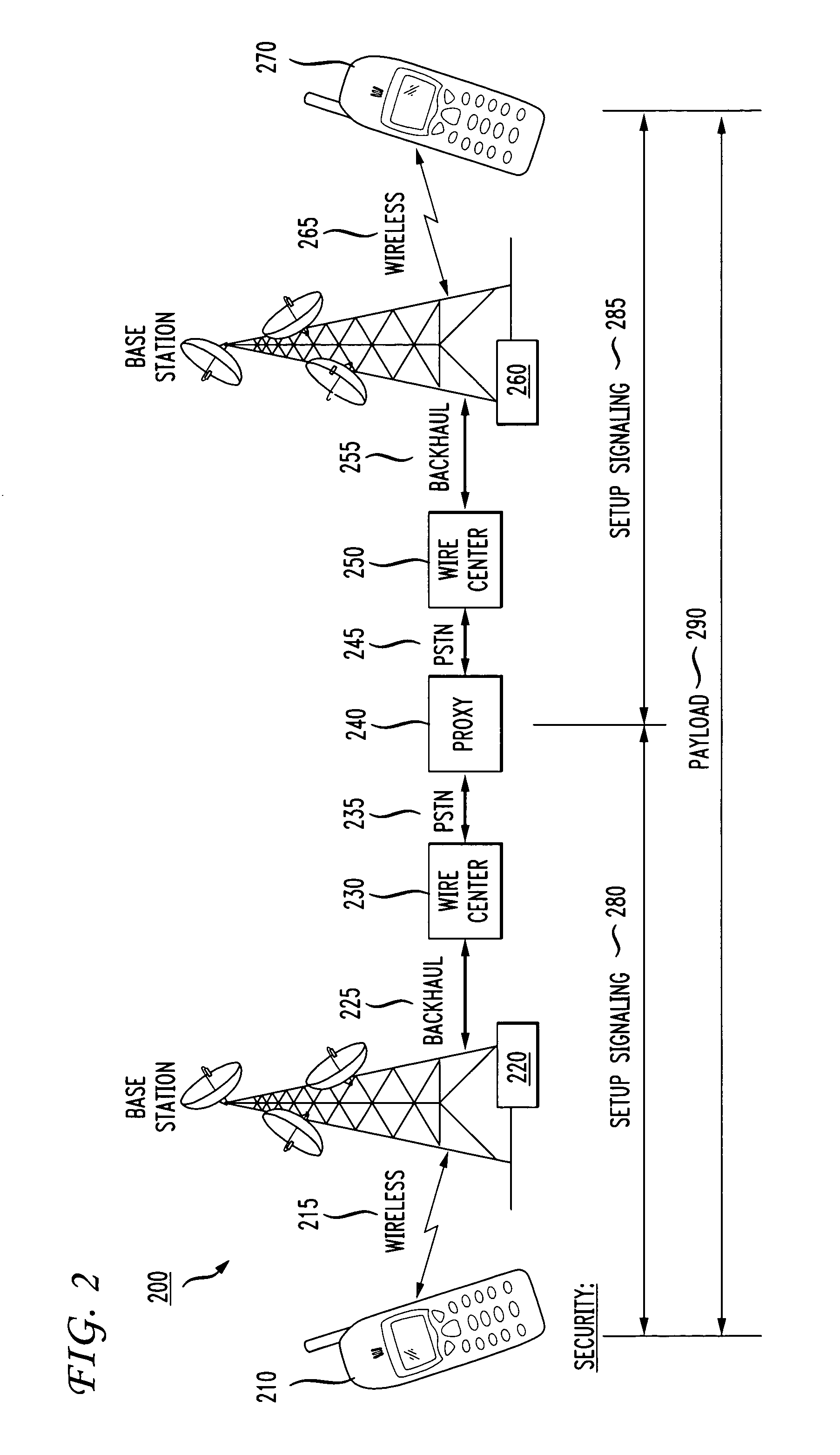
End-to-end IP security
ActiveUS7739728B1Synchronising transmission/receiving encryption devicesMultiple digital computer combinationsEnd to end securitySecurity association
End-to-end security is established automatically for network communications. In one embodiment a first host is associated with a policy manager that determines, for the first host, whether a secure session is permissible. If the secure session is determined to be permissible then the policy manager signals to intermediate devices in order to prompt establishment of SA / DA pinholes. In an alternative embodiment a neutral policy broker determines, for both first and second hosts, whether the secure session is permissible and signals to the intermediate devices to establish the pinholes if the secure session is permissible. In another embodiment the end-to-end session includes back-to-back tunnel mode sessions linked by at least one intermediate device. The intermediate device is operative to decrypt and re-encrypt traffic in the session, and may be configured by a policy manager or policy broker. Further, another security association can be nested in one or more segments of the session in a manner that permits one host to access a third host or secure resource which is shielded from the second host.
Owner:AVAYA INC
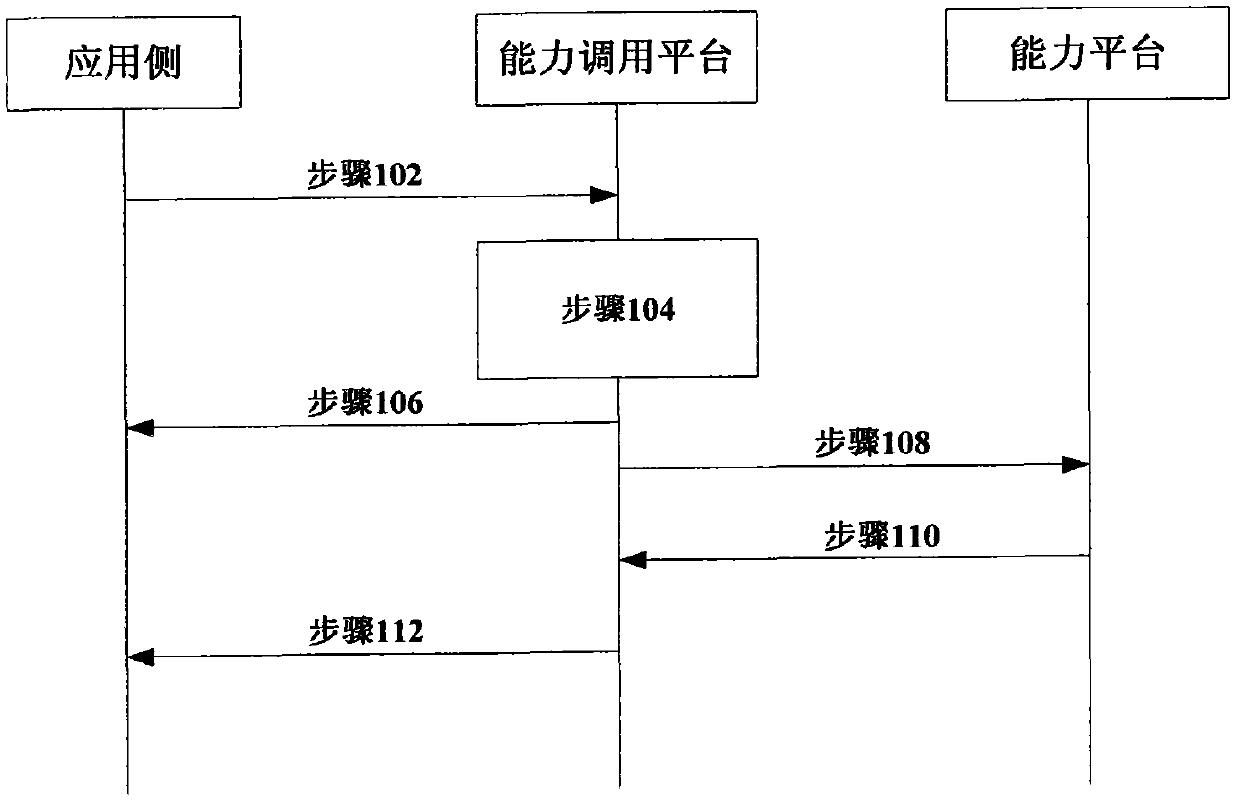
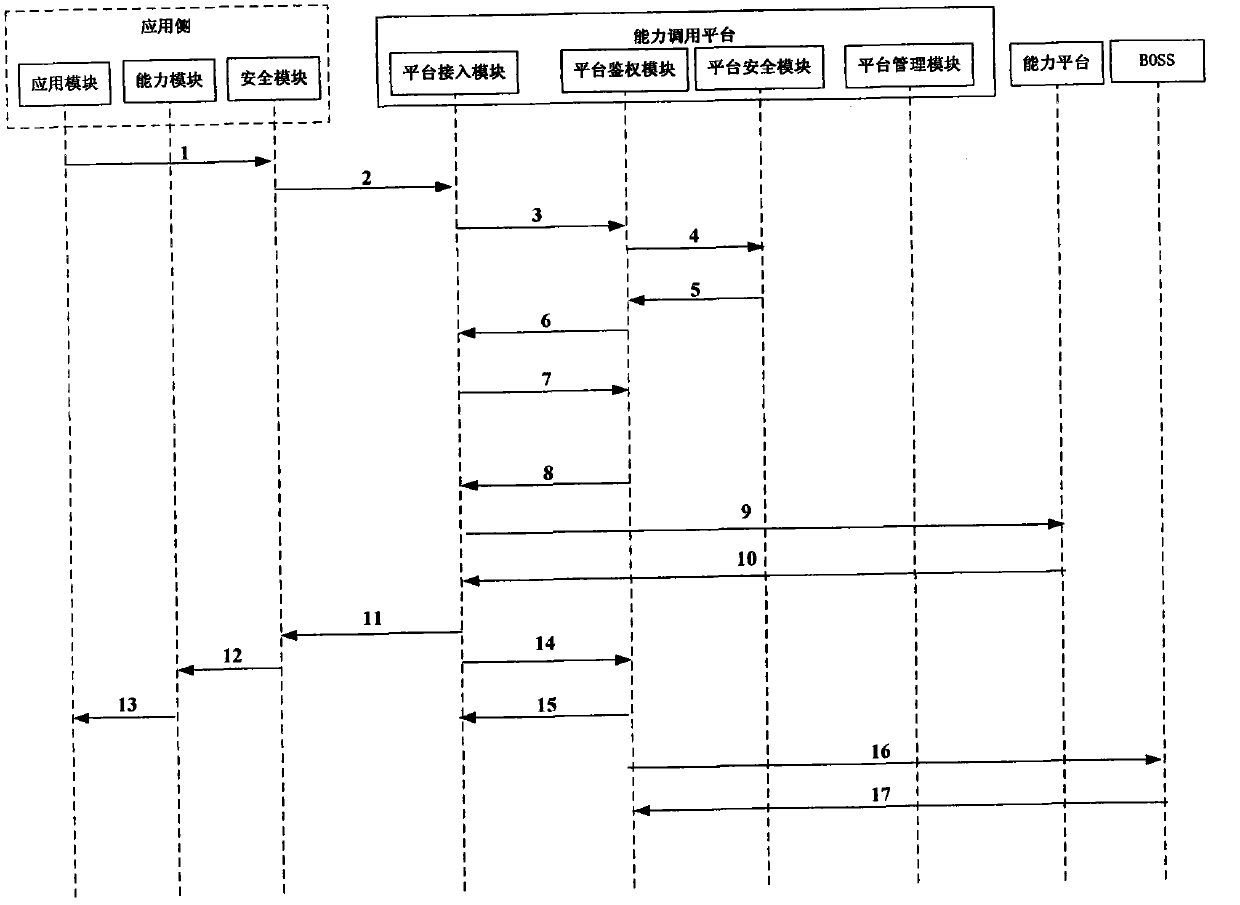
Capability safety calling method, device and system
InactiveCN102571693AImprove securityEnsure safetyUser identity/authority verificationEnd to end securityThe Internet
The invention discloses a capability safety calling method, a device and a system, wherein the capability safety calling method comprises the following steps of: verifying an application identity authentication Token in a received capability calling request which is sent by an application side; and after successfully verifying, calling a capability from a corresponding capability platform for the application side. According to the capability safety calling method, the device and the system disclosed by the invention, the security of capacity opening of an Internet platform is improved by verification of the capability calling request of the application side. Furthermore, the invention provides a safe framework comprising the application side and a capability calling platform side. The end-to-end security of opening the capability is ensured by interaction of the application side and the capability calling platform side.
Owner:CHINA MOBILE COMM GRP CO LTD
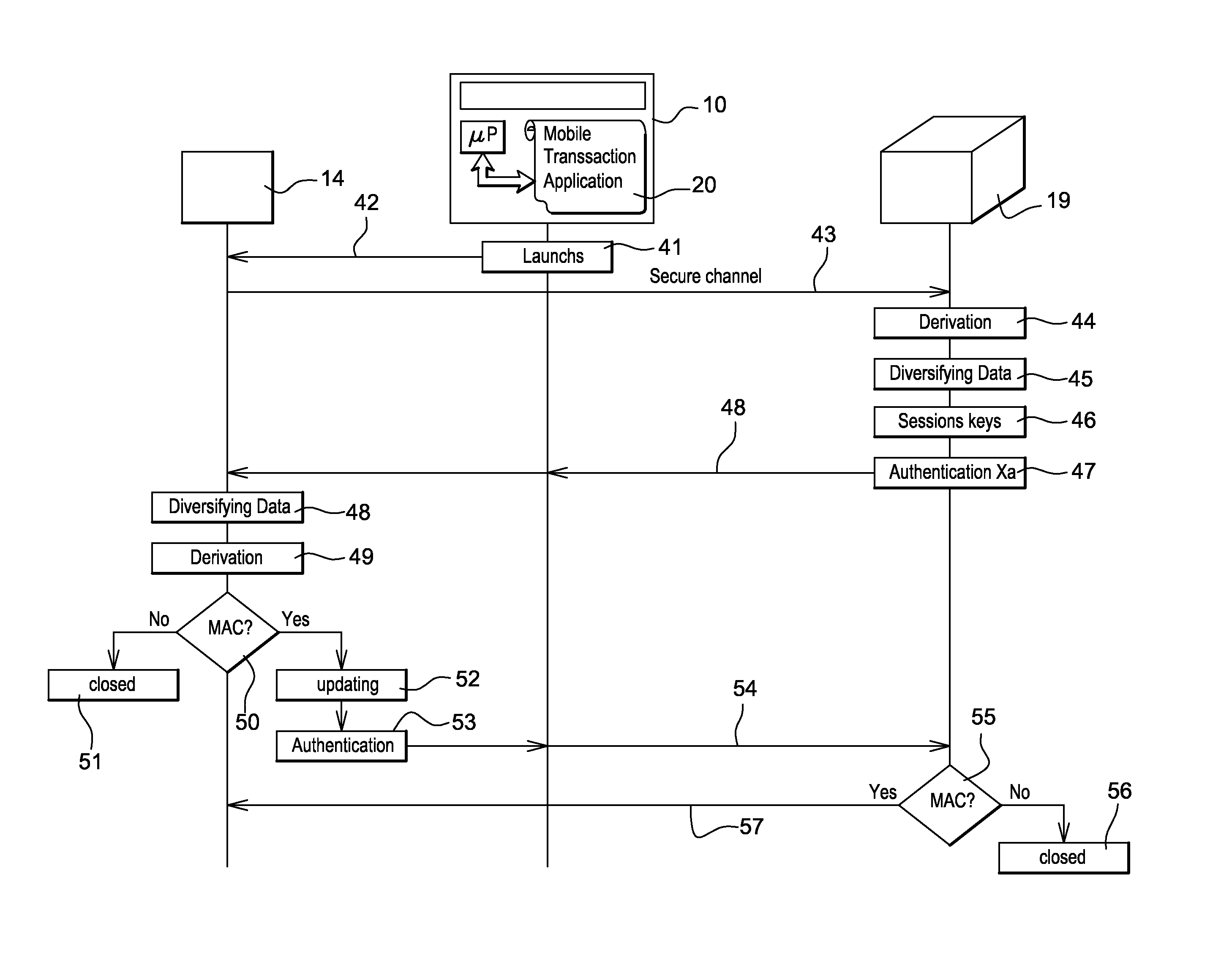
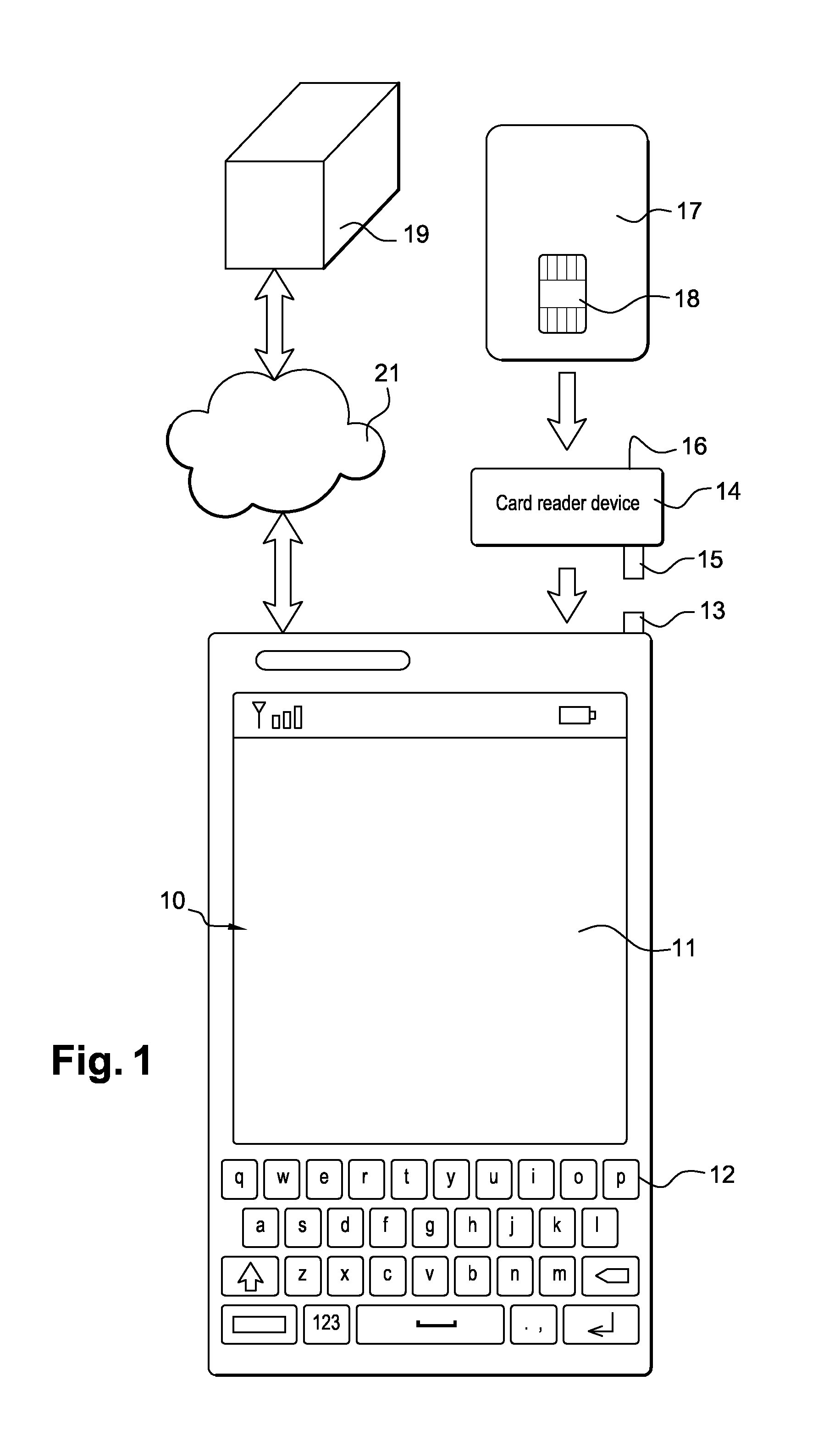
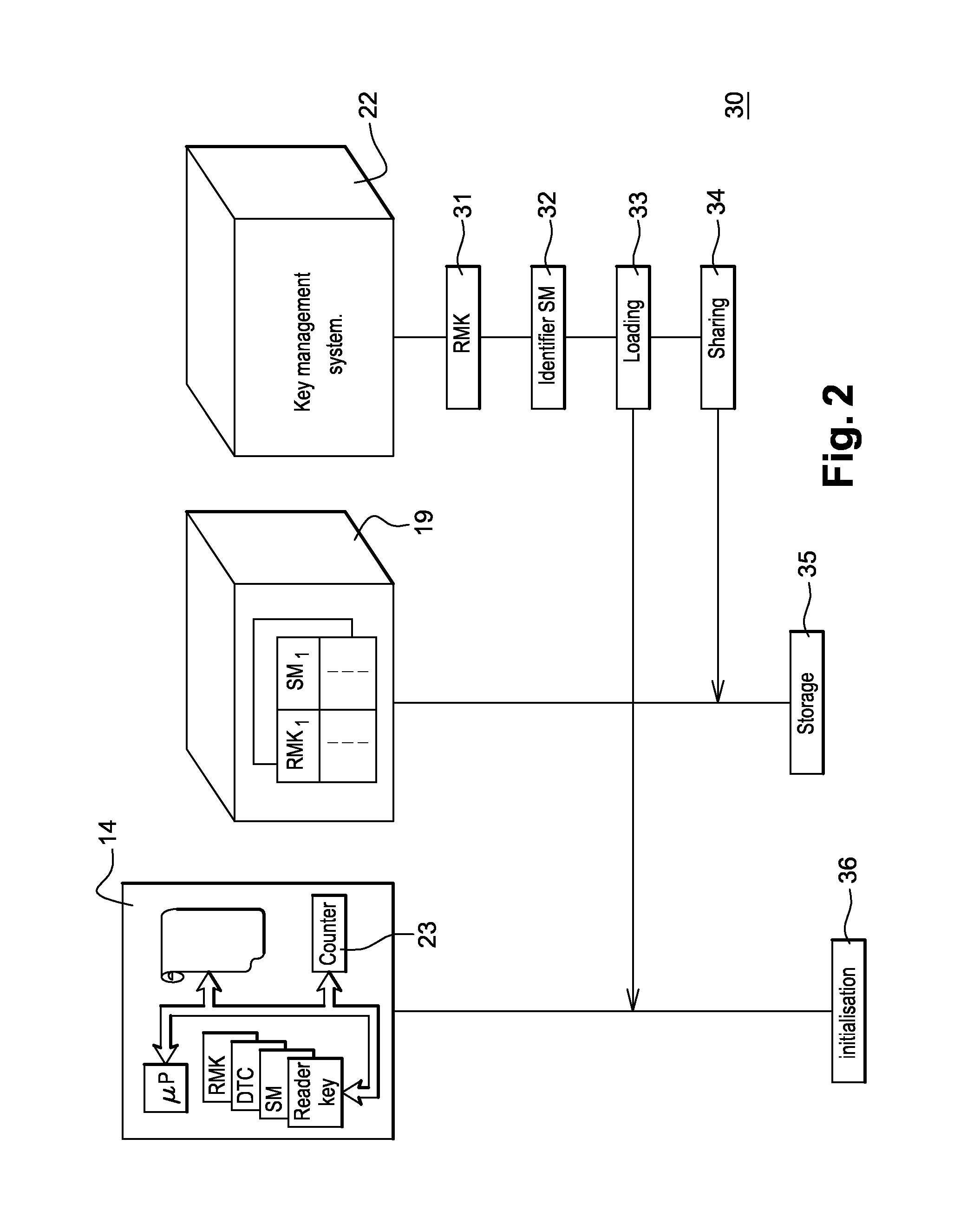
System and method for securing communications between a card reader device and a remote server
InactiveUS20160295404A1Reduced flexibilityImprove securityKey distribution for secure communicationSecurity arrangementSecure communicationEnd to end security
The present invention concerns the implementation of end-to-end security for the communication between a low cost card reader and the remote server. The purpose of the present invention is the establishment of a secure channel between the card reader and the remote server through an un-trusted communication device (e.g. a smart phone or a tablet) that is intrinsically resistant to some basic differential side-channel analysis in a context where there is no secure random number generator and no source of entropy in the card reader, while providing the following characteristics:—Mutual authentication between the card reader and the server—Secure channel based on session keys such that the keys of the secure channel related to a past transaction cannot be re-played, or the session keys of a future transaction cannot be pre-computed by the card reader and later re-use by the card reader in a legitimate transaction.
Owner:GEMPLU
Safe embedded operating system capable of supporting multi-stage loading
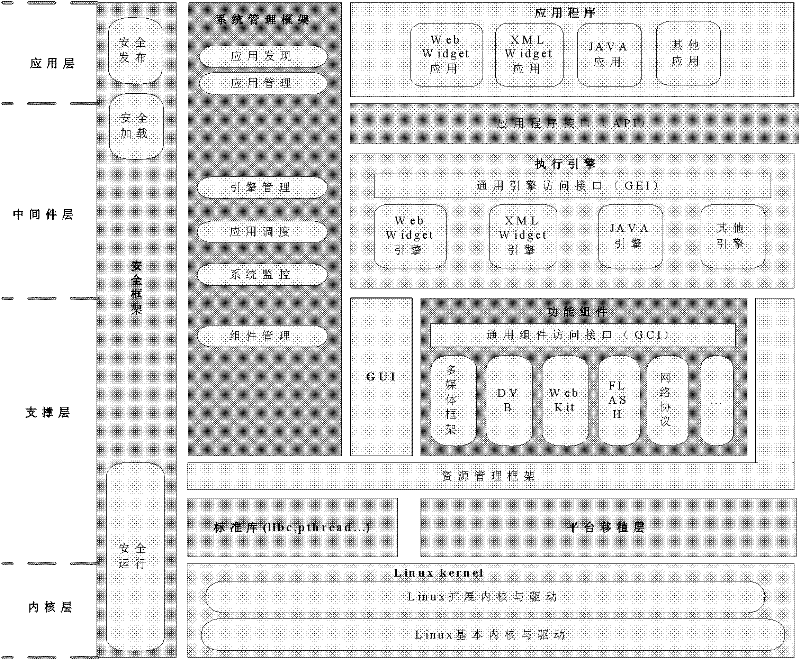
ActiveCN102479097AAchieve isolationRealize dynamic loading and runningProgram loading/initiatingProgram/content distribution protectionEnd to end securityGraphical user interface
The invention provides a safe embedded operating system capable of supporting multi-stage loading. The safe embedded operating system supports the dynamic loading operation of an application program of an embedded terminal, realizes the isolation of the application program and an embedded terminal platform and comprises a system management module, a safety management module, a resource management module, a functional unit module, a GUI (Graphical User Interface) module, an application execution engine module, an application program interface (API) module and the like. Meanwhile, the safe embedded operating system is at least divided into a basic stage and an expansion stage by adopting stage treatment on the basis of the traditional Linux inner core, a basic stage module is fixedly loaded, each module and each functional module in the expansion stage are selectively and dynamically loaded according to application requirements under the scheduling of a system management framework, and thus, loading the system by stage is realized. By using the safe embedded operating system, a function of safety management and control for the application program through a safe framework module is achieved, mechanisms such as end-to-end safe issuing and loading of an application, safe operation protection based on an application process isolation and trust mechanism, application operation monitoring and the like are applied, and safe management and control on the whole life cycle of the application from issuing, downloading, loading to operating is realized.
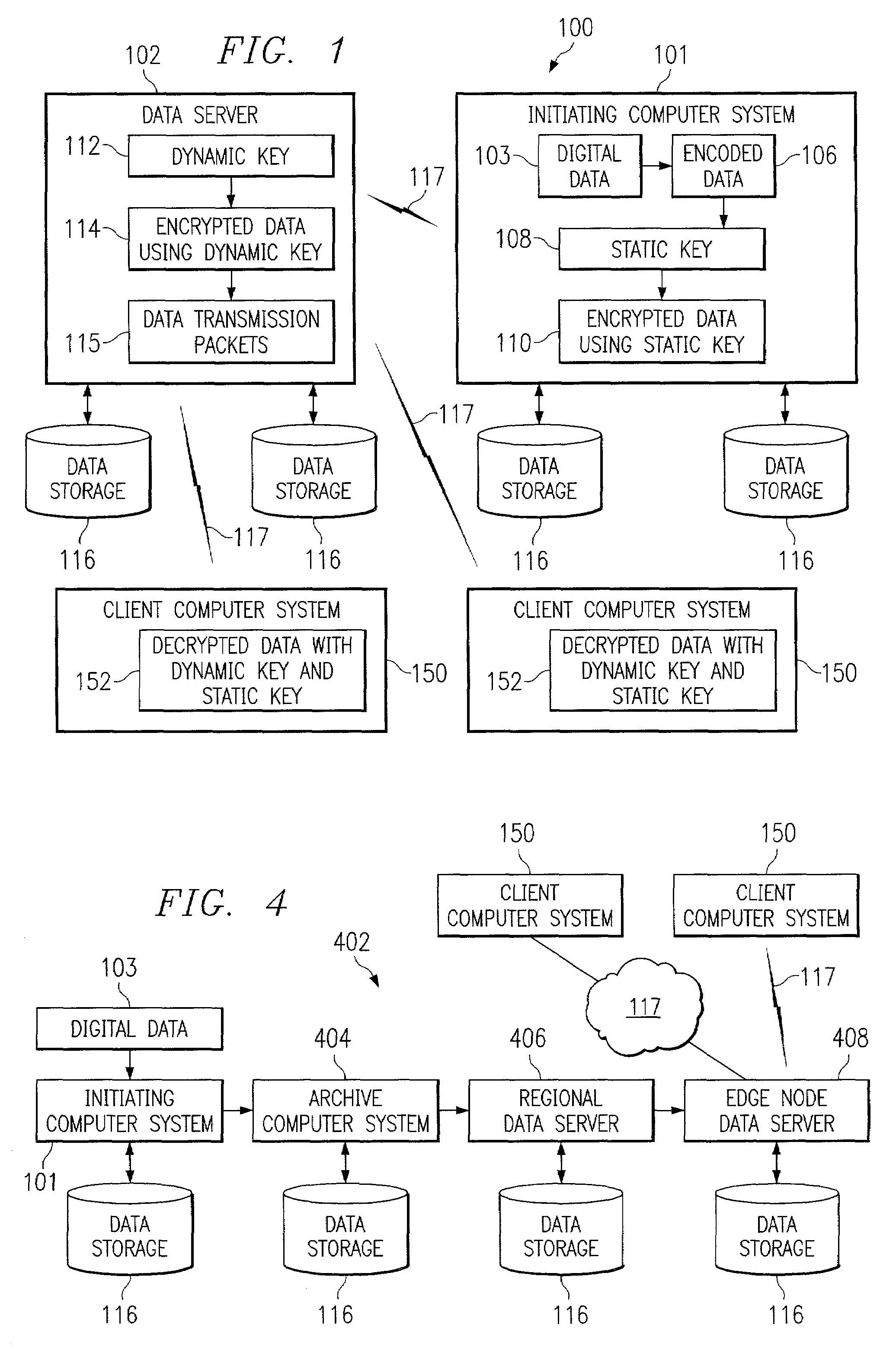
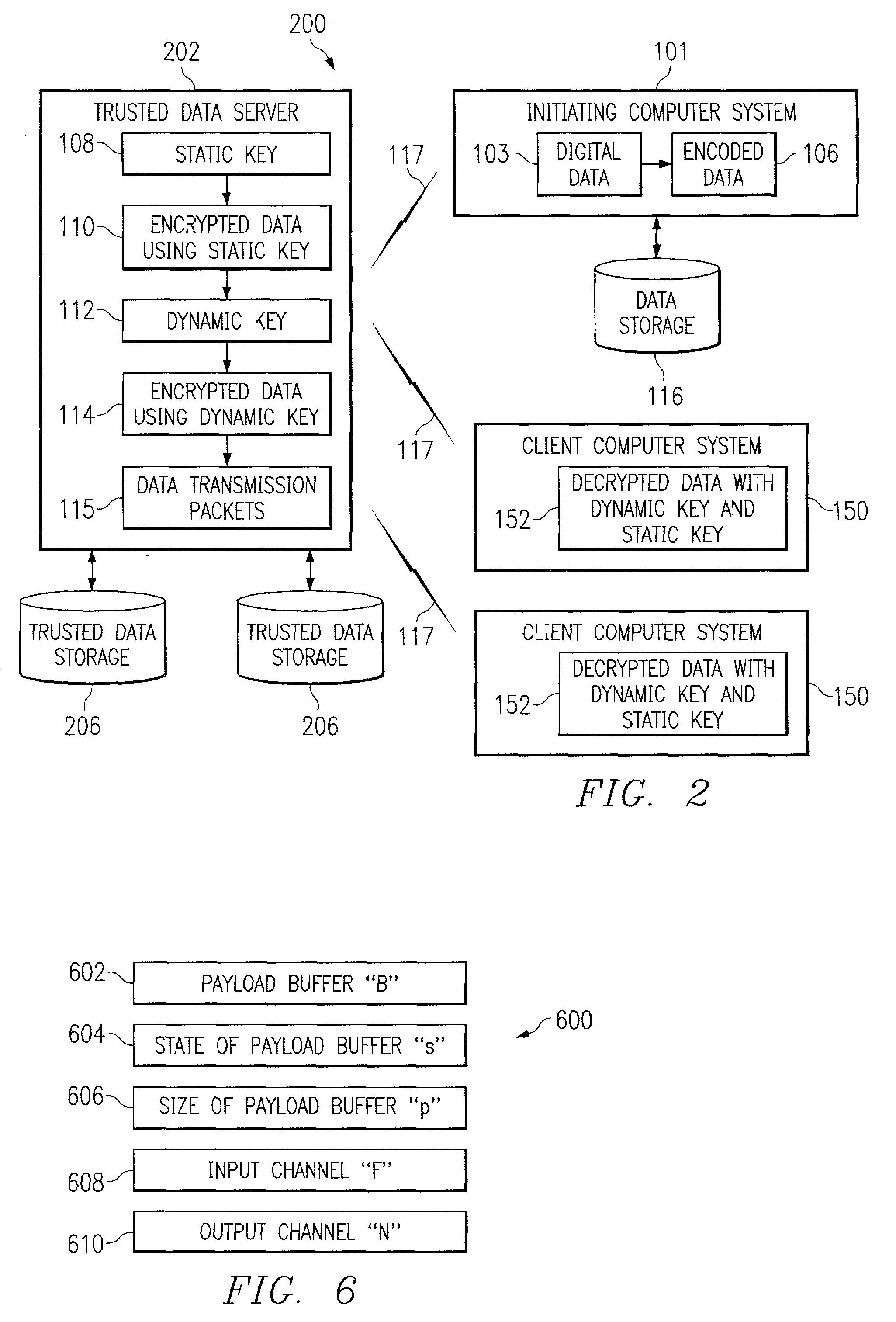
Owner:ZHENGZHOU SEANET TECH CO LTD
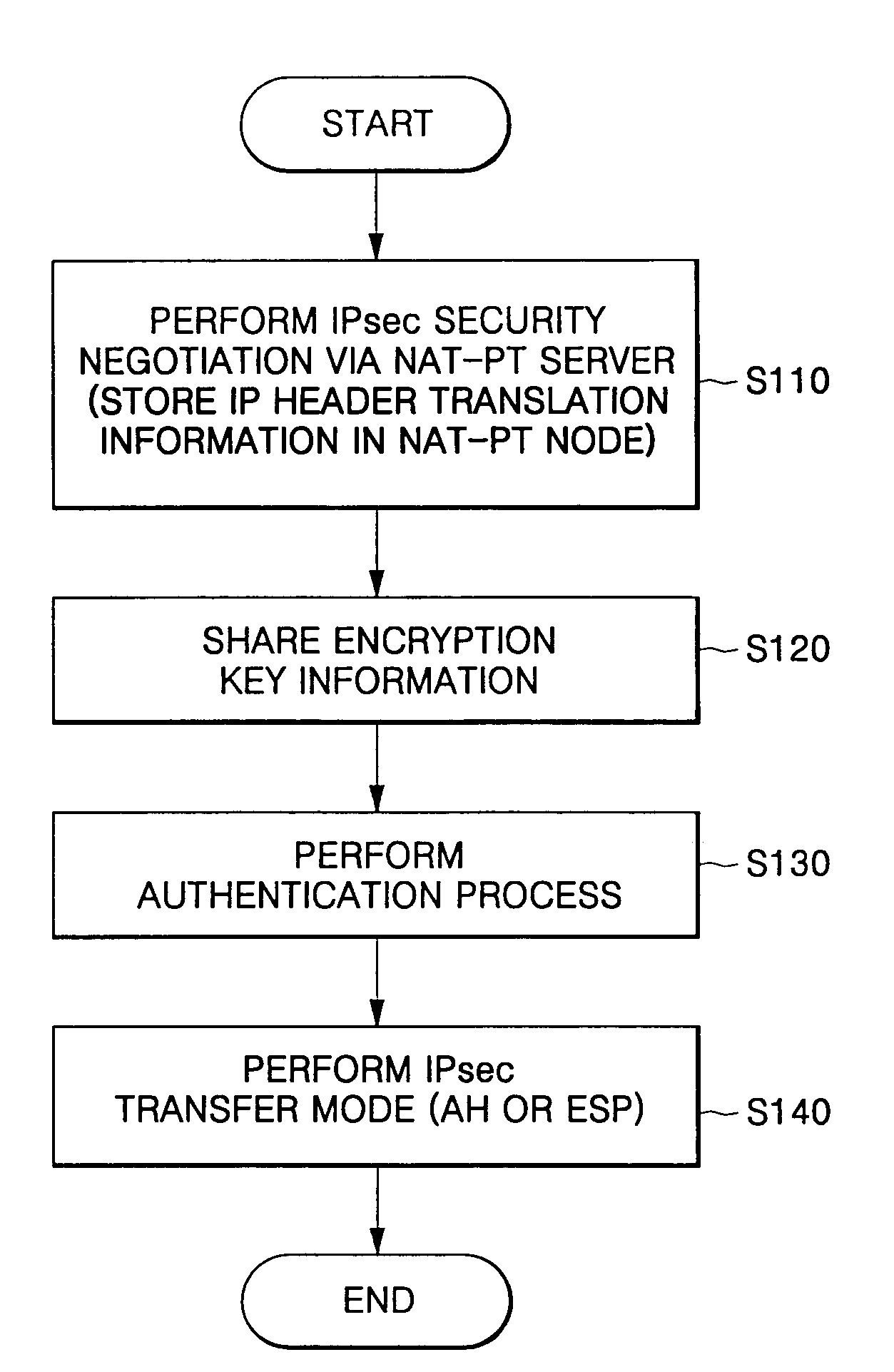
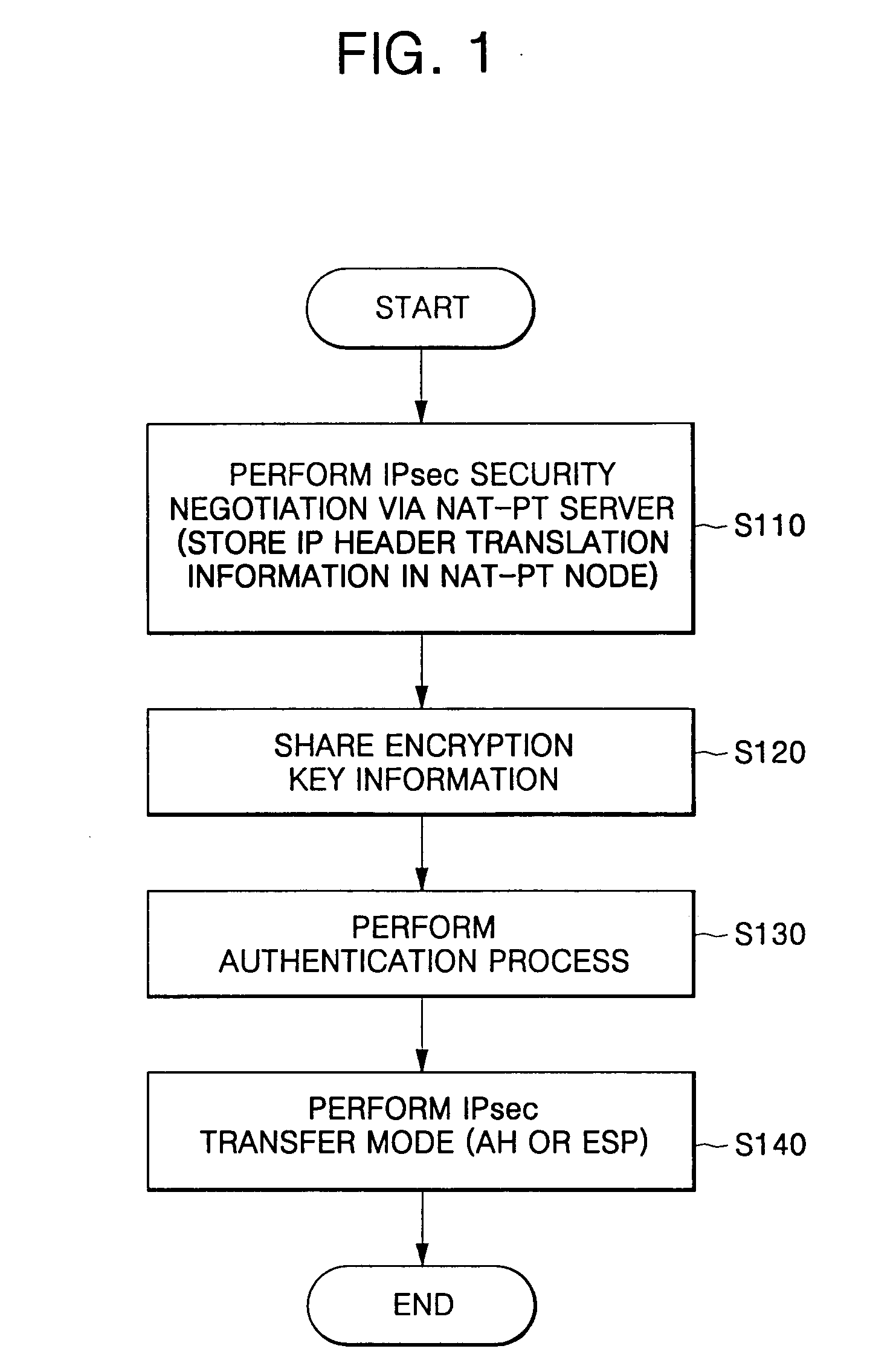
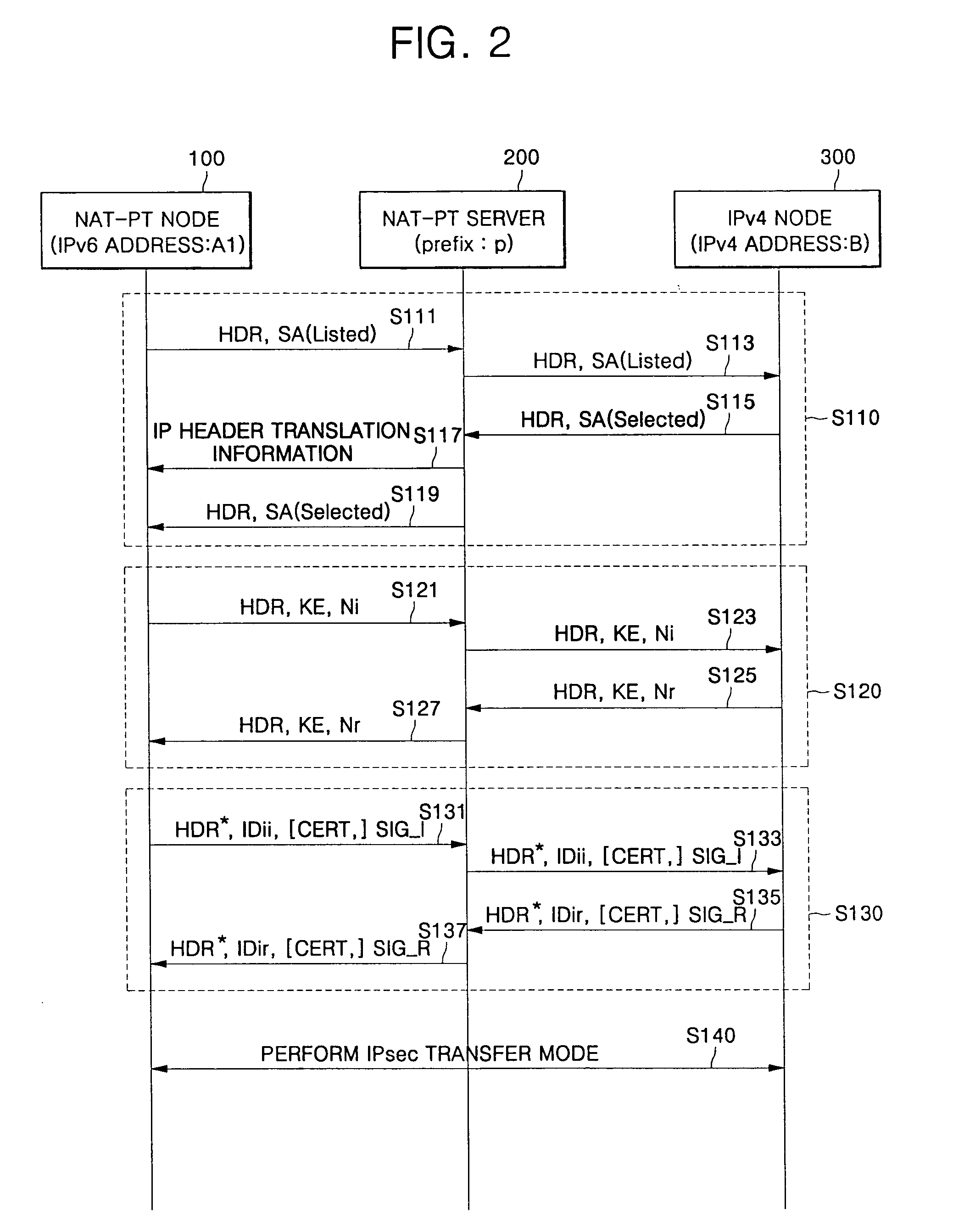
Method for providing end-to-end security service in communication network using network address translation-protocol translation
A method for providing end-to-end security service in a communication network having an NAT-PT function comprises: performing security negotiation between a first node included in a first communication network having the network address translation-protocol translation function and a second node included in a second communication network operating with a protocol different from the first communication network; storing protocol translation information generated when the security negotiation is performed in the first node; and performing security transmission between the first and second nodes using the stored protocol translation information. The method transmits the address translation information to the ends in advance, thereby being capable of applying the security service using the address information on transmitting the data between hosts in the communication network using the address translation method.
Owner:SAMSUNG ELECTRONICS CO LTD
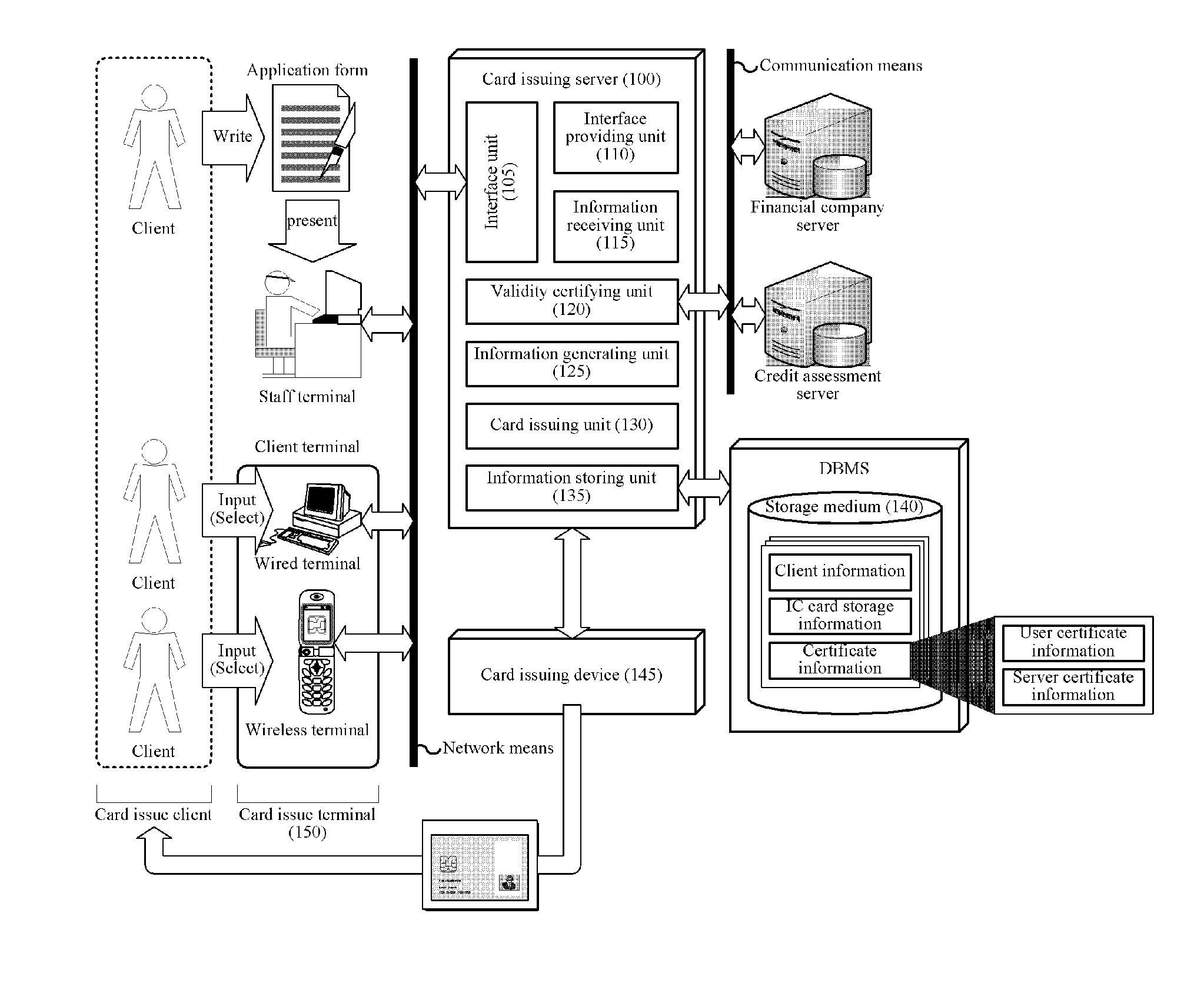
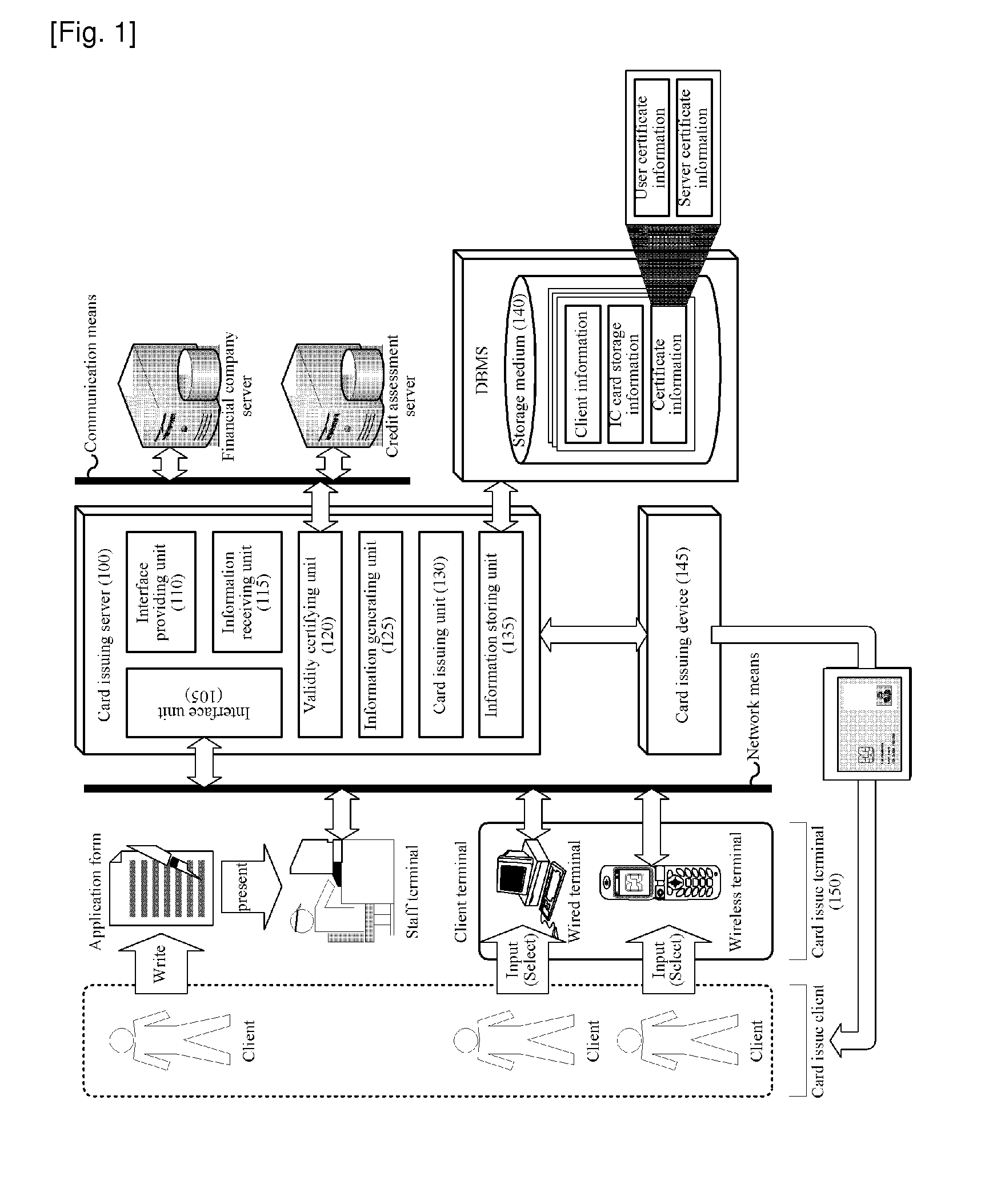
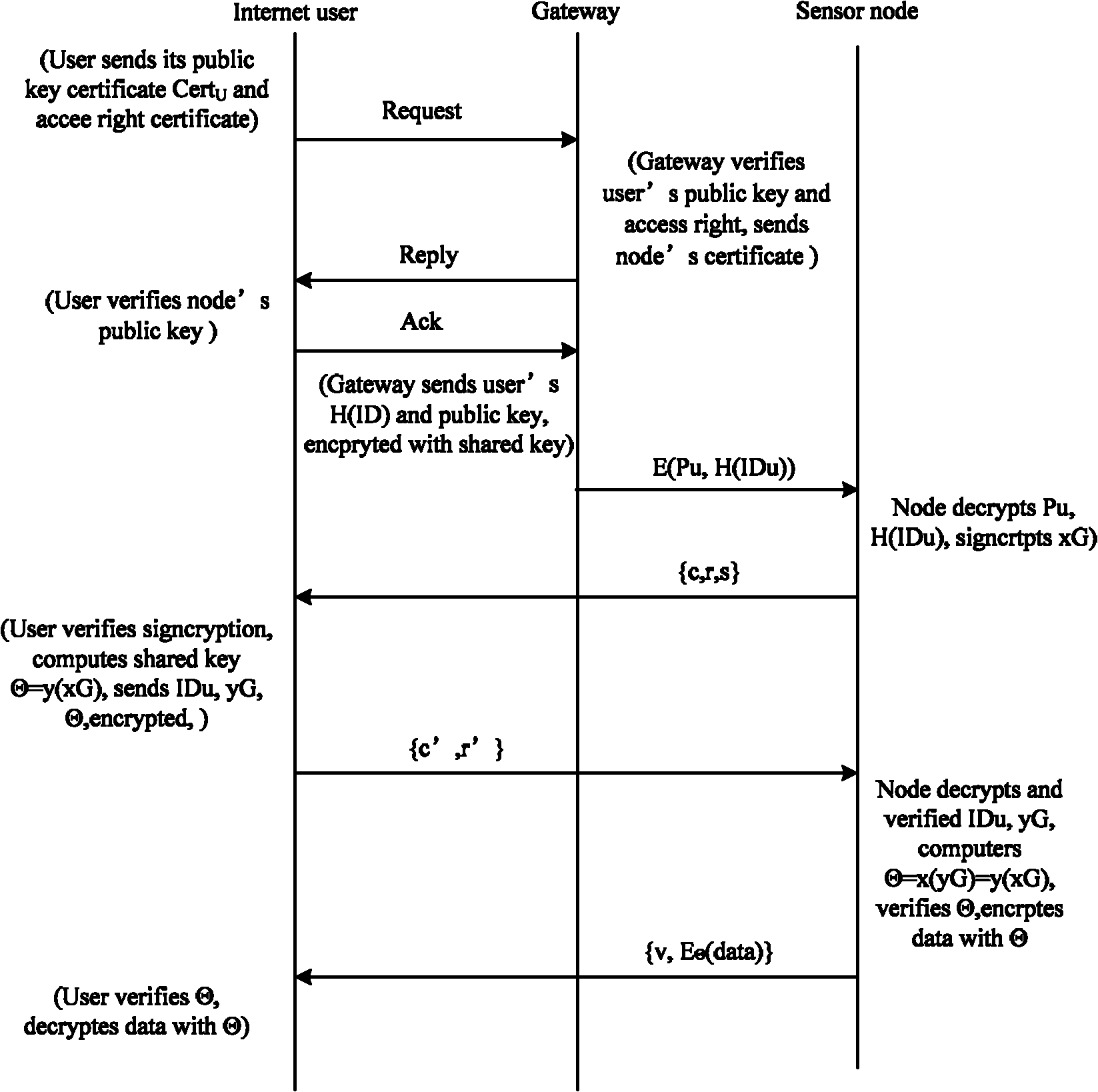
System and Method for Operating End-to-End Security Channel Between Server and IC Card
ActiveUS20100287375A1Avoid dangerPowerful security functionUser identity/authority verificationPayment circuitsComputer hardwareEnd to end security
The present invention relates to a system and method for operating an end-to-end security channel between an IC card and a server on a communication network. A method for connecting an end-to-end security channel between an IC card and a server on a communication network includes the steps of: generating, by the server, a random number Rs for transmission to the IC card, generating an E(Rs) by encrypting the random number Rs by a user public key, and transmitting the E(Rs) to the IC card through the communication network; receiving, by the IC card, the E(Rs) through the communication network and extracting the random number Rs by decrypting the E(Rs) by a user private key; generating, by the IC card, a random number Rc to be transmitted to the server, generating a session key K′ by the random number Rs and the random number Rc, and generating a first card verifier MAC by encrypting the random number Rs by the session key K′; transmitting, by the IC card, the random number Rc and the first card verifier MAC to the server through the communication network; receiving, by the server, the random number Rc and the first card verifier MAC through the communication network, generating a session key K by the random number Rs and the random number Rc, and generating a first server verifier MAC by encrypting the random number Rs by the session key K; and comparing, by the server, the first card verifier MAC and the first server verifier MAC to certify the session key K.
Owner:LEE SUNG MAN
Web application exploit mitigation in an information technology environment
ActiveUS8572750B2Improve protectionMemory loss protectionError detection/correctionEnd to end securityProgram management
Methods, systems, and computer program products are provided herein for facilitating security in an information technology environment. Web application security vulnerabilities are discovered and addressed by means of virtual patches deployed to components of the information technology environment. An intelligent feedback loop is created to fill the void in the security of the web application when implemented in the specific information technology environment, thereby providing end-to-end security application management through dynamic, pre-emptive, and proactive security awareness and protection in the information technology environment. As new web application security vulnerabilities are discovered, the vulnerability is diagnosed and resolved to preemptively prevent exploitation of the security vulnerability.
Owner:FINJAN BLUE INC
End-to-end secure wireless communication for requesting a more secure channel
InactiveUS7873350B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsEnd to end securitySecurity Measure
The present invention is a system and method for establishing a secure connection using a public a wireless telephone network. The method utilizes a proxy base station and establishes an encrypted session over the public wireless network between a wireless handset and the proxy base station. The proxy base station further establishes a connection with second communication station such as a landline phone. The proxy base station determines a most secure channel between the base station and the second communication station by consulting a database of channels and associated measures of security.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
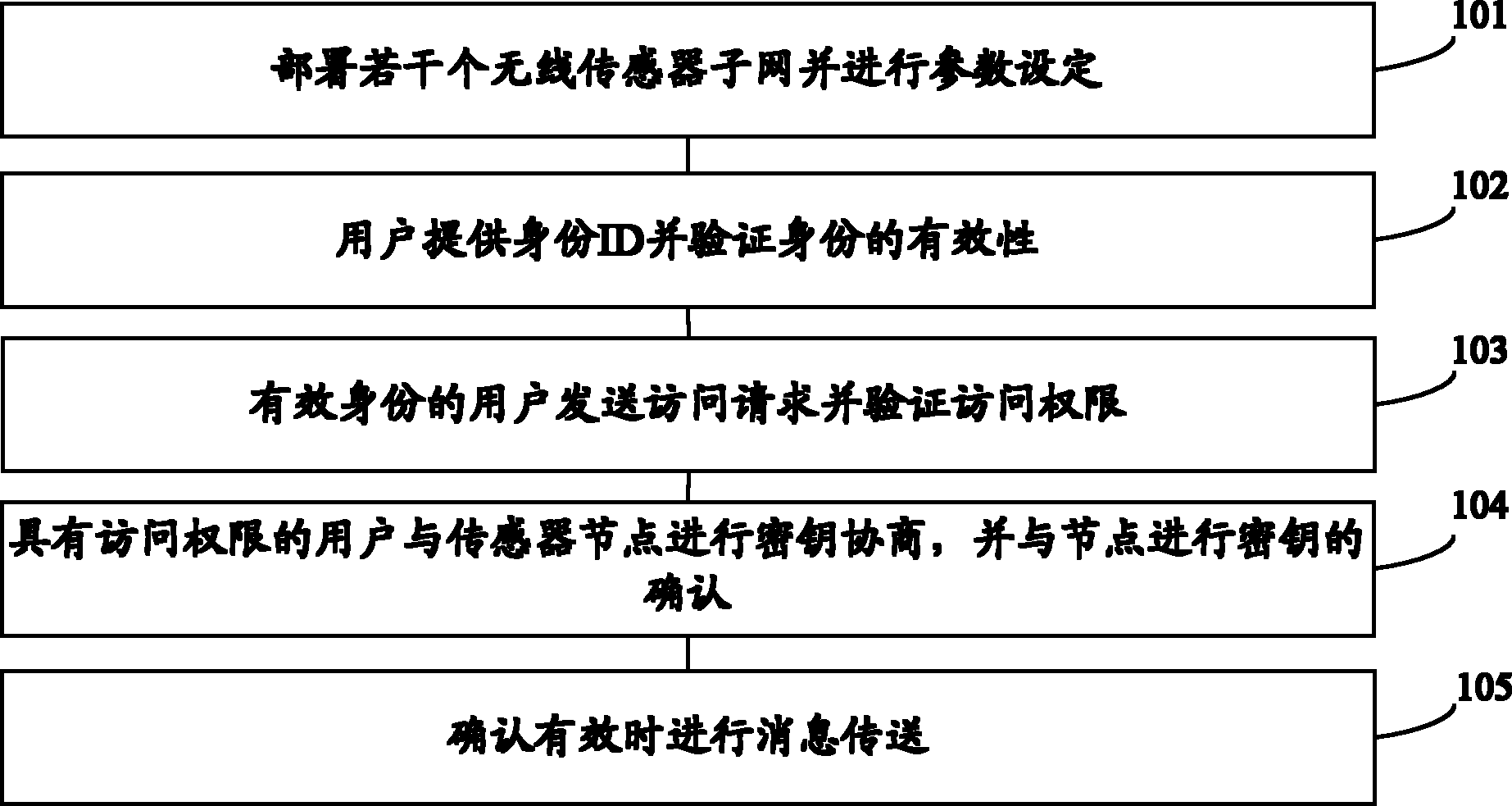
End-to-end safety control method for wireless sensor network and internet intercommunication
InactiveCN102546650AReduce energy consumptionEnhanced Access ControlKey distribution for secure communicationUser identity/authority verificationEnd to end securityWireless mesh network
The invention provides an end-to-end safety control method for wireless sensor network and internet intercommunication. Part of the certification and access control work is transferred to the gateway of the wireless sensor network, an asymmetric key negotiation mode based on elliptic-curve signcryption technology is adopted to place unsigncryption operation with large computing amount in an Internent remote terminal, and the symmetric key decryption operation is placed in the sensor nodes. Compared with the improved ECC (Elliptic Curve Cryptography)-based SSL (Security Socket Layer) protocol and the improved TLS (Transport Layer Security) protocol based on elliptic-curve identity, the energy consumption of the sensor nodes is effectively reduced, access control and privacy protection are enhanced and Dos (Disk Operating System) attack can be resisted.
Owner:BEIJING UNIV OF TECH
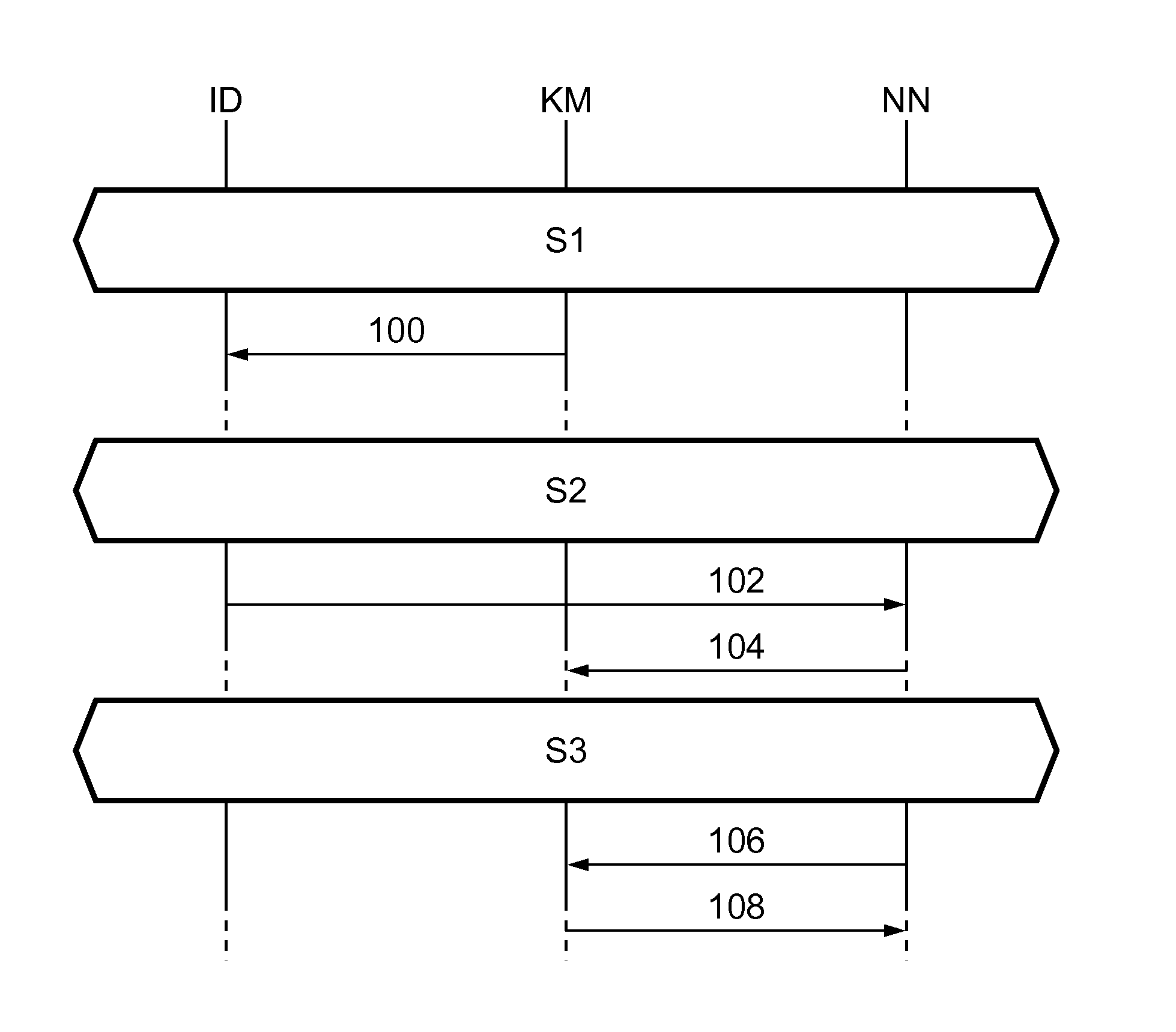
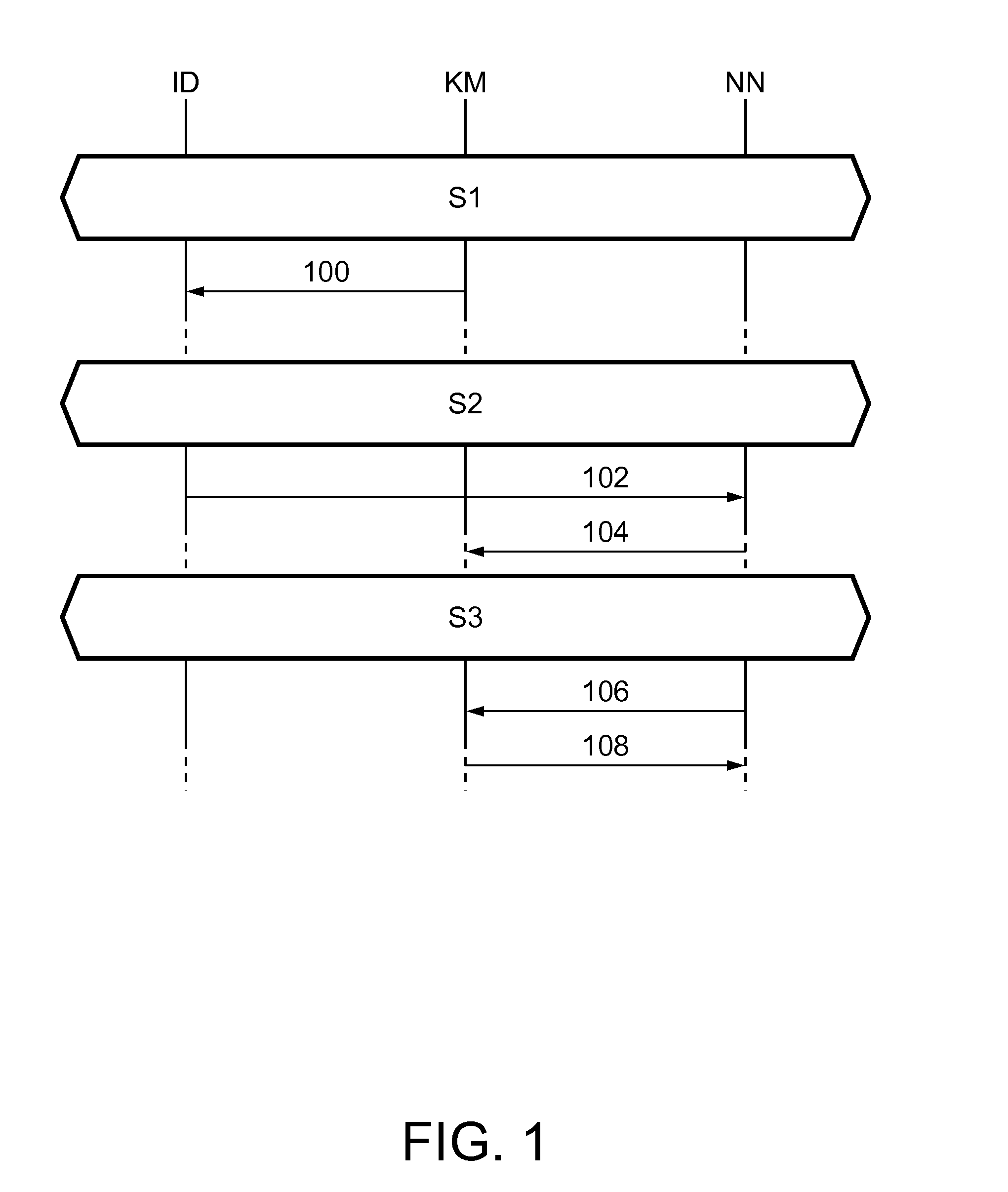
Method for establishing secure communication between nodes in a network, network node, key manager, installation device and computer program product
ActiveUS20130312072A1Easy—yet secure—installation of new nodesDigital data processing detailsMultiple digital computer combinationsSecure communicationEnd to end security
According to an aspect of the invention, a method for establishing secure communication between nodes in a network is conceived, wherein the network comprises a key manager which accommodates a key-manager-specific public key and a corresponding key-manager-specific private key; wherein a copy of the key-manager-specific public key is stored in an installation device; wherein the installation device provides a new node with the copy of the key-manager-specific public key; and wherein said new node is registered with the key manager by providing a node-specific public key and an identifier of said new node to the key manager, such that other nodes in the network may setup end-to-end secure connections with said new node by requesting the node-specific public key of said new node from the key manager.
Owner:NXP BV
Image data security transmission system with support of transparent transcoding
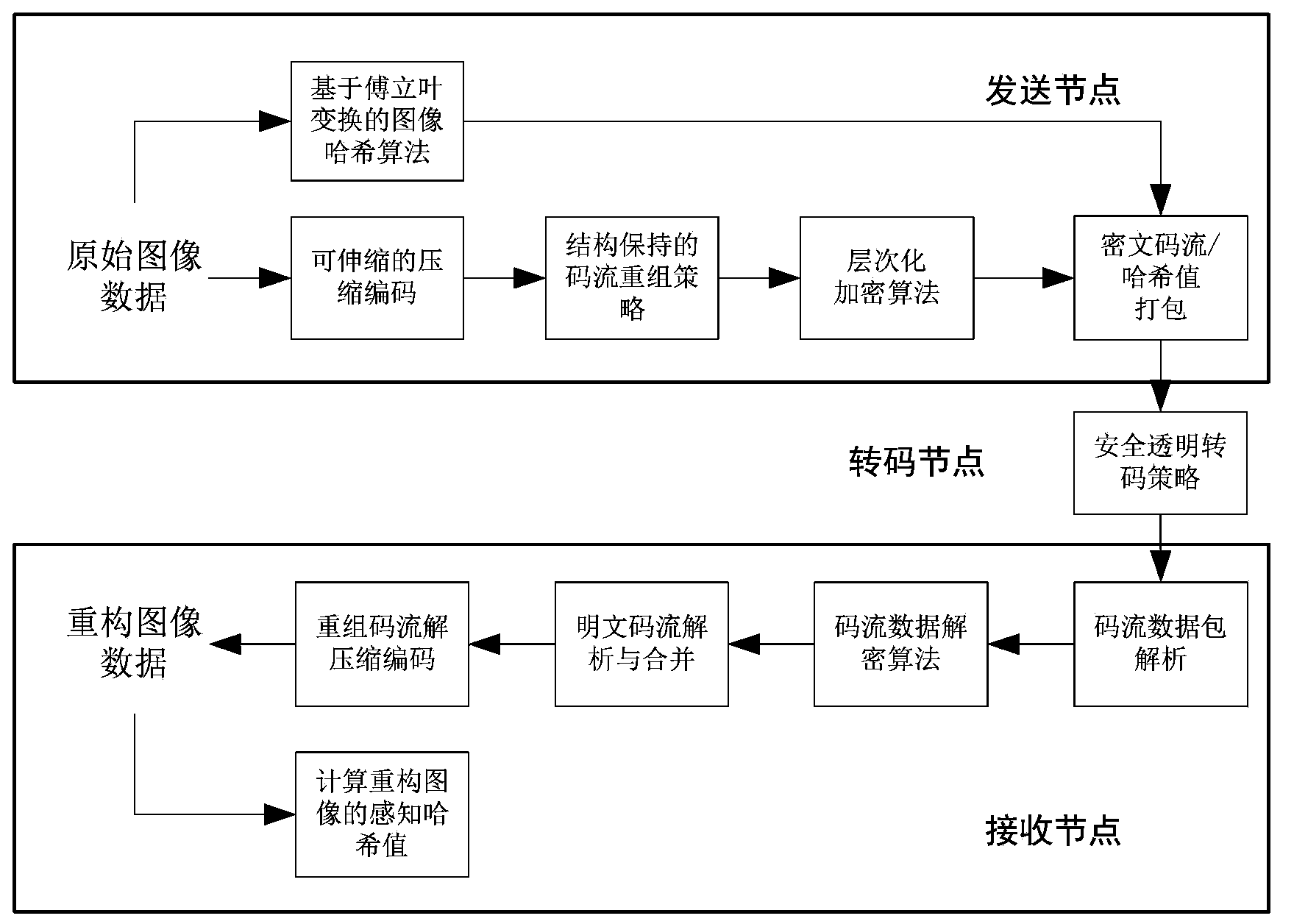
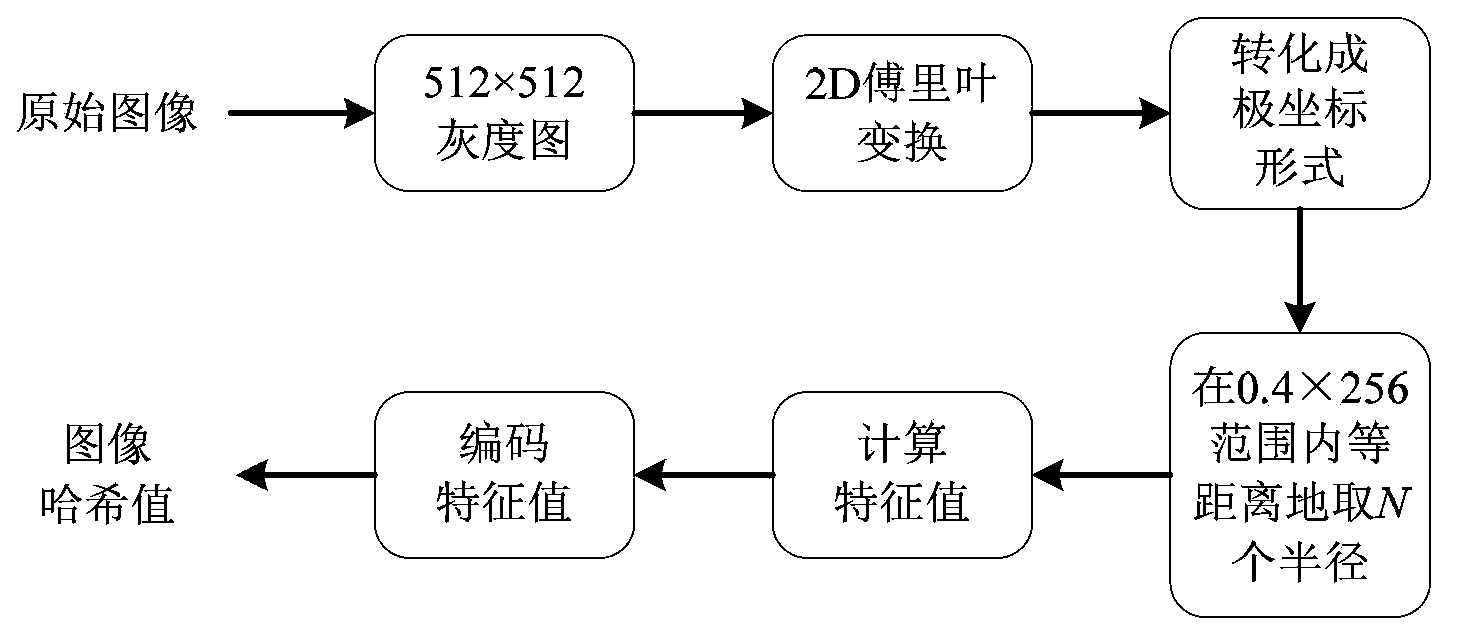
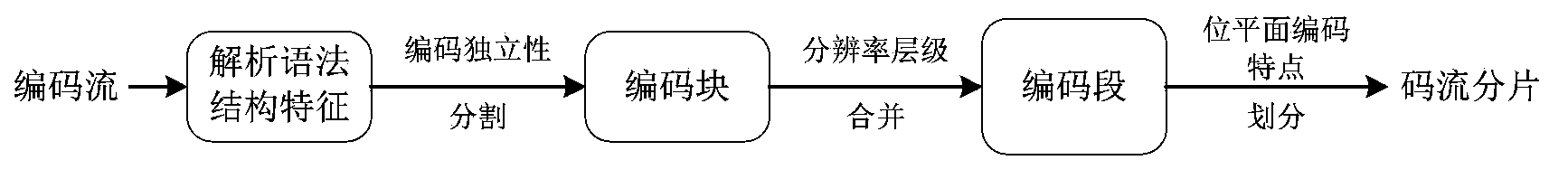
InactiveCN103414686ARealize end-to-end security authenticationAchieve reorganizationTransmissionComputer hardwareEnd to end security
The invention provides an image data security transmission system with the support of transparent transcoding. The system comprises three kinds of nodes which are a sending node, an intermediate transcoding node and a receiving node. The sending node is an image data server. The receiving node comprises different types of terminal devices. The sending node is provided with a calculation sensing Hash module of the sending node, a compression encoding module, a bit stream recomposition module, a hierarchical encryption module, and a bit stream package module. The intermediate node is provided with a safe transparent transcoding module. The receiving point is provided with a packet analysis module, a bit stream decoding module, an analysis bit stream module, a decompression encoding module and a computation perception Hash module of the receiving node. According to the system, a network intermediate node can directly carry out code rate conversion on a ciphertext domain bit stream, the decoding and decompression of the bit stream before the encoding of a converted bit stream is not needed, the end to end safety transmission of image data is realized, the safety transmission comprises the confidentiality, integrity and non-repudiation protection of an image, and the cost of transcoding is greatly reduced.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com