Patents
Literature
51 results about "Process isolation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
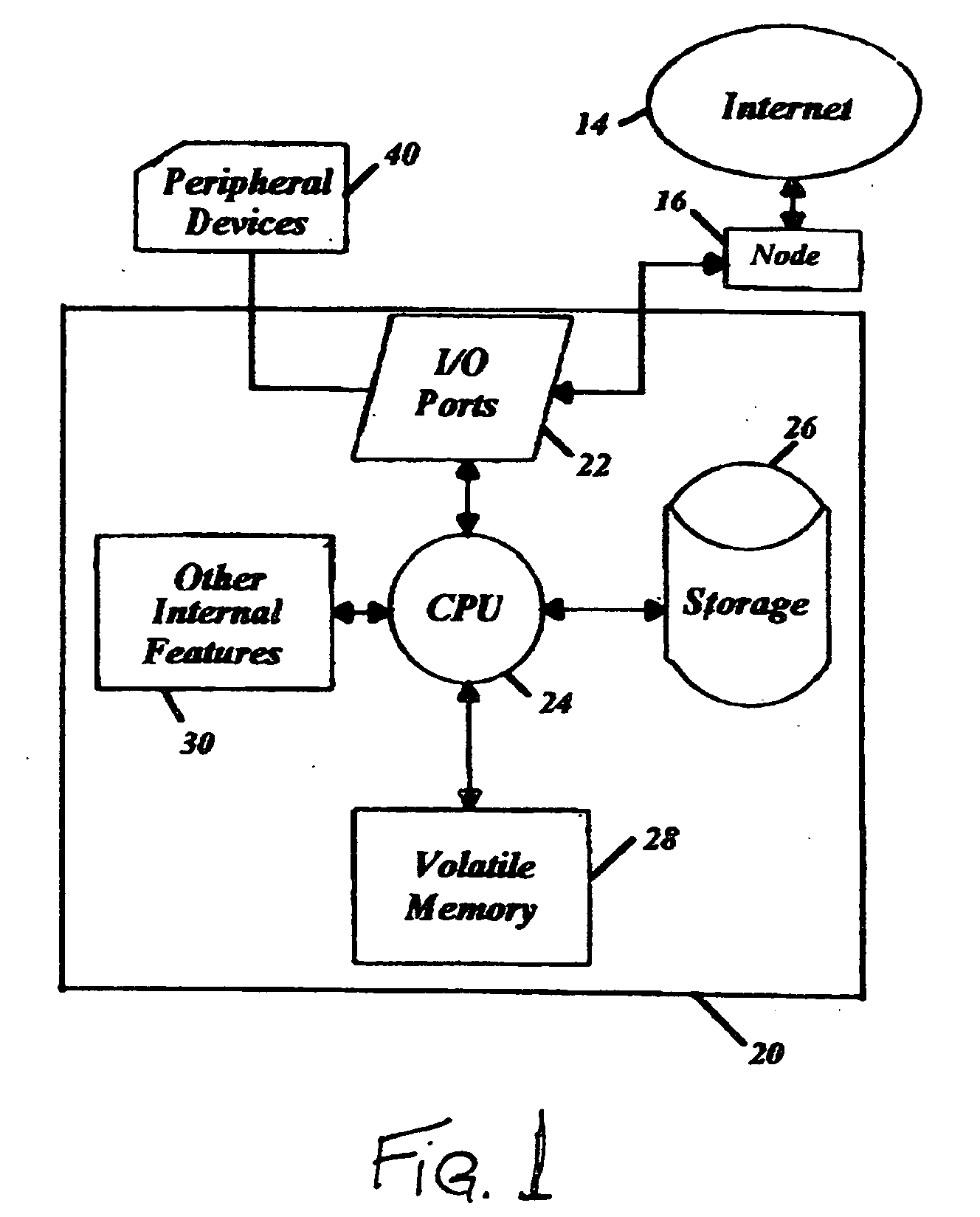
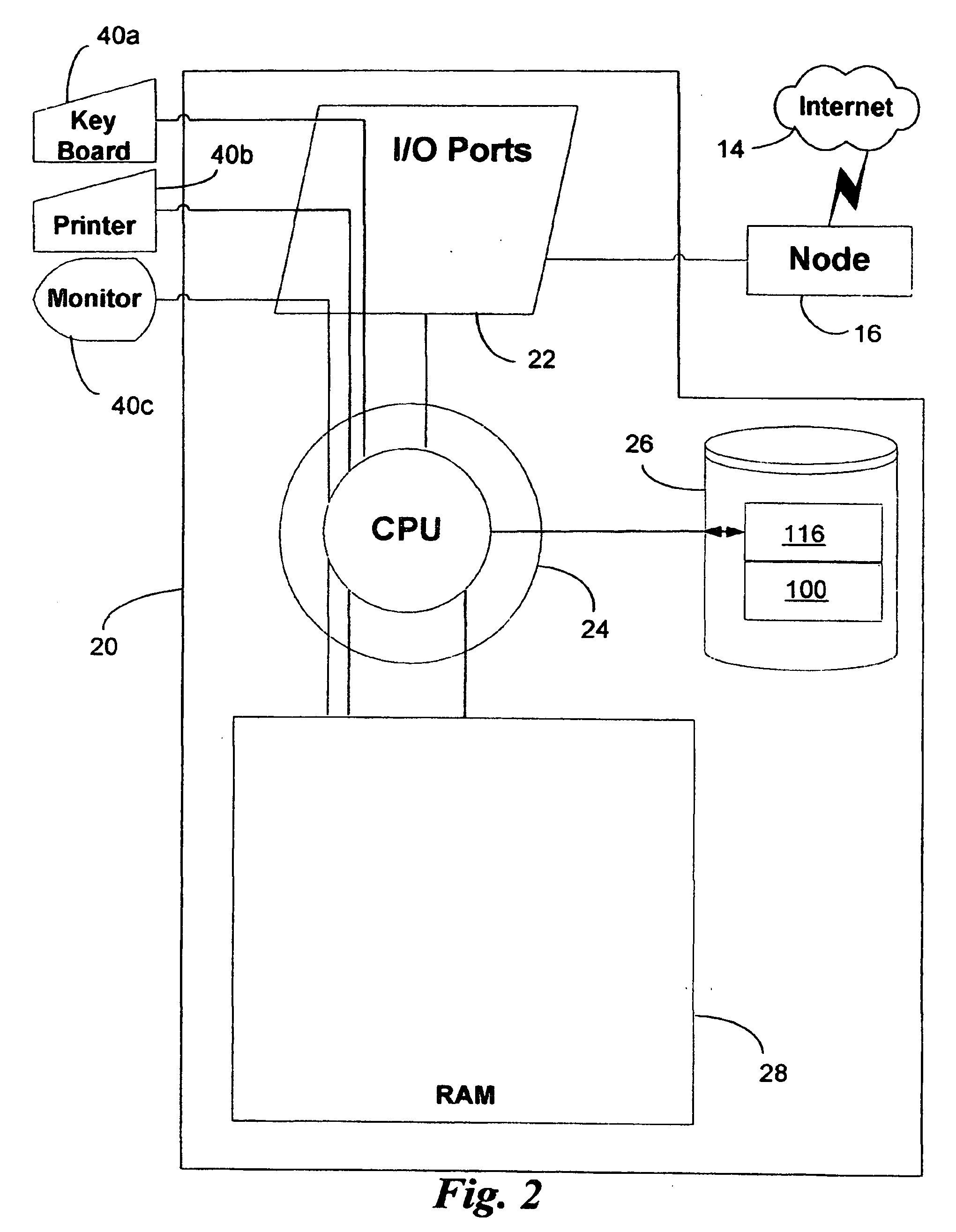
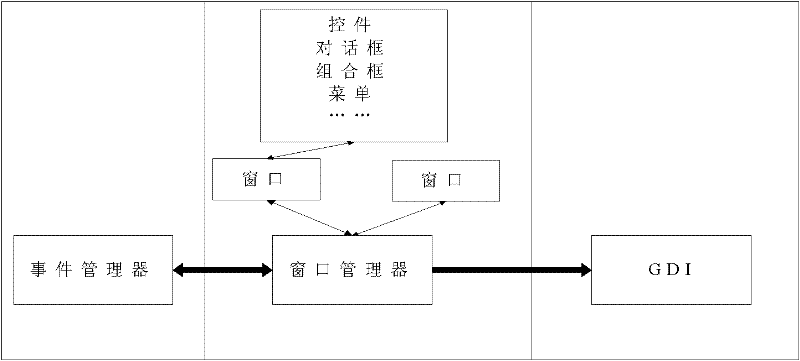
Process isolation is a set of different hardware and software technologies designed to protect each process from other processes on the operating system. It does so by preventing process A from writing to process B.
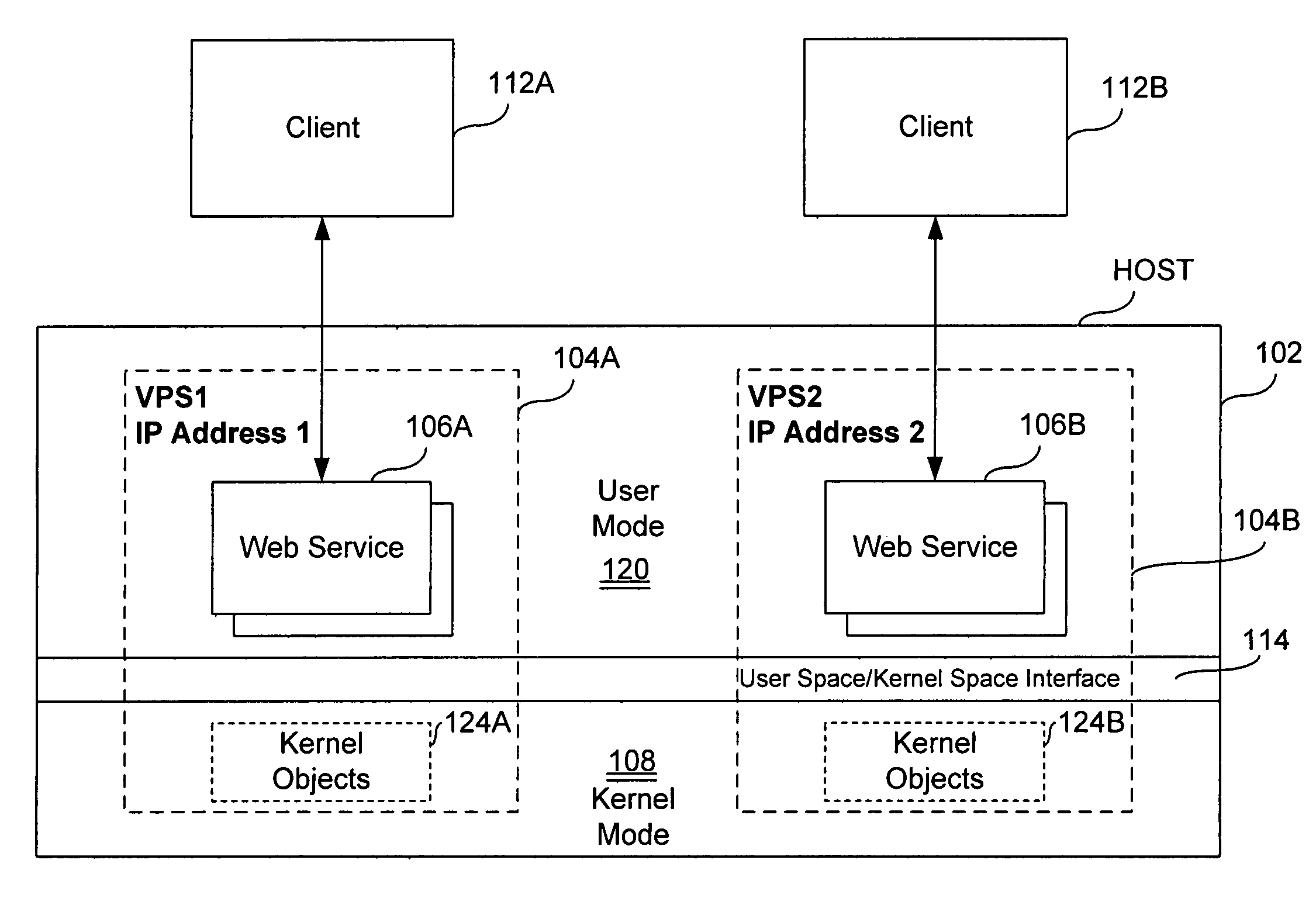
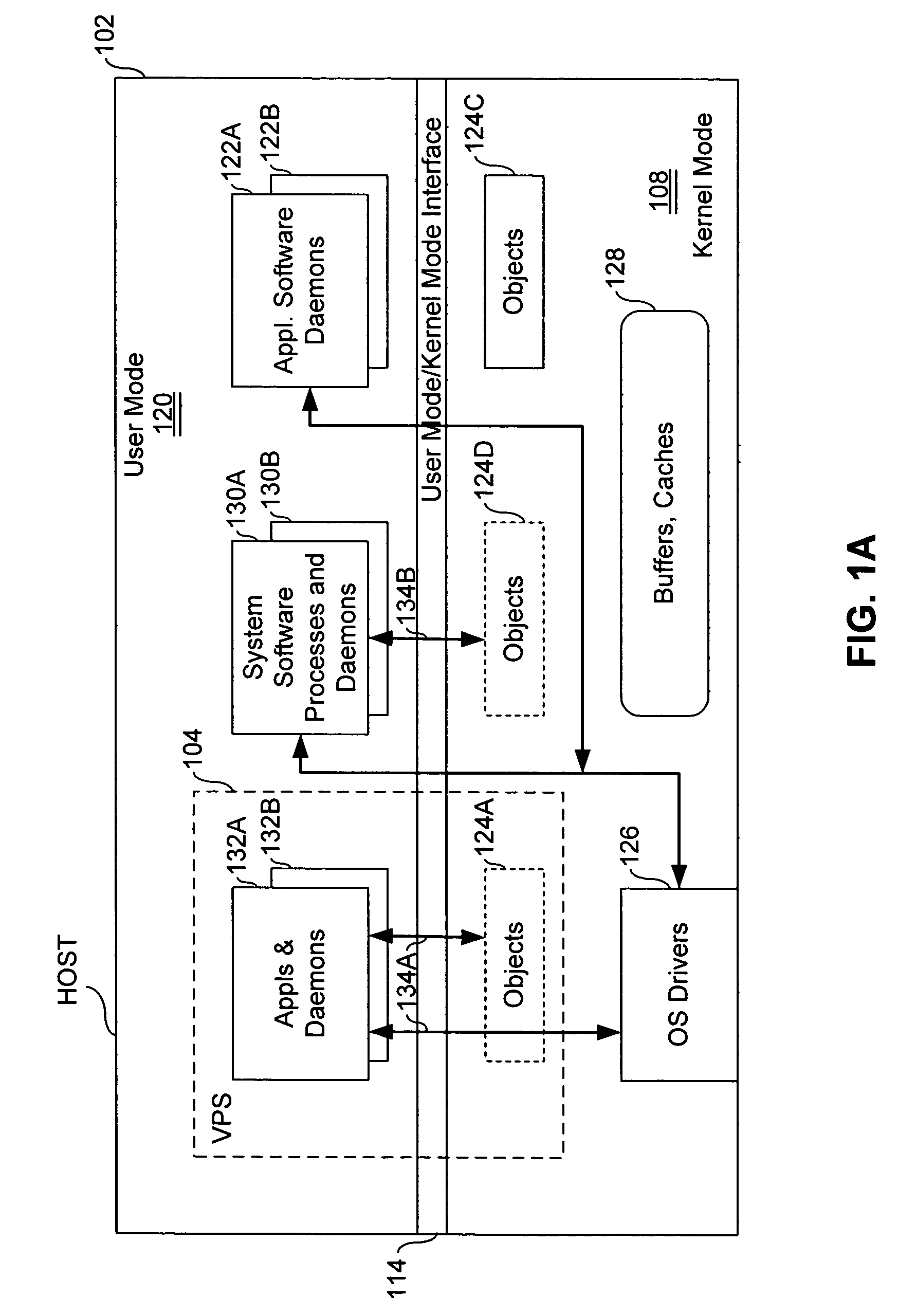
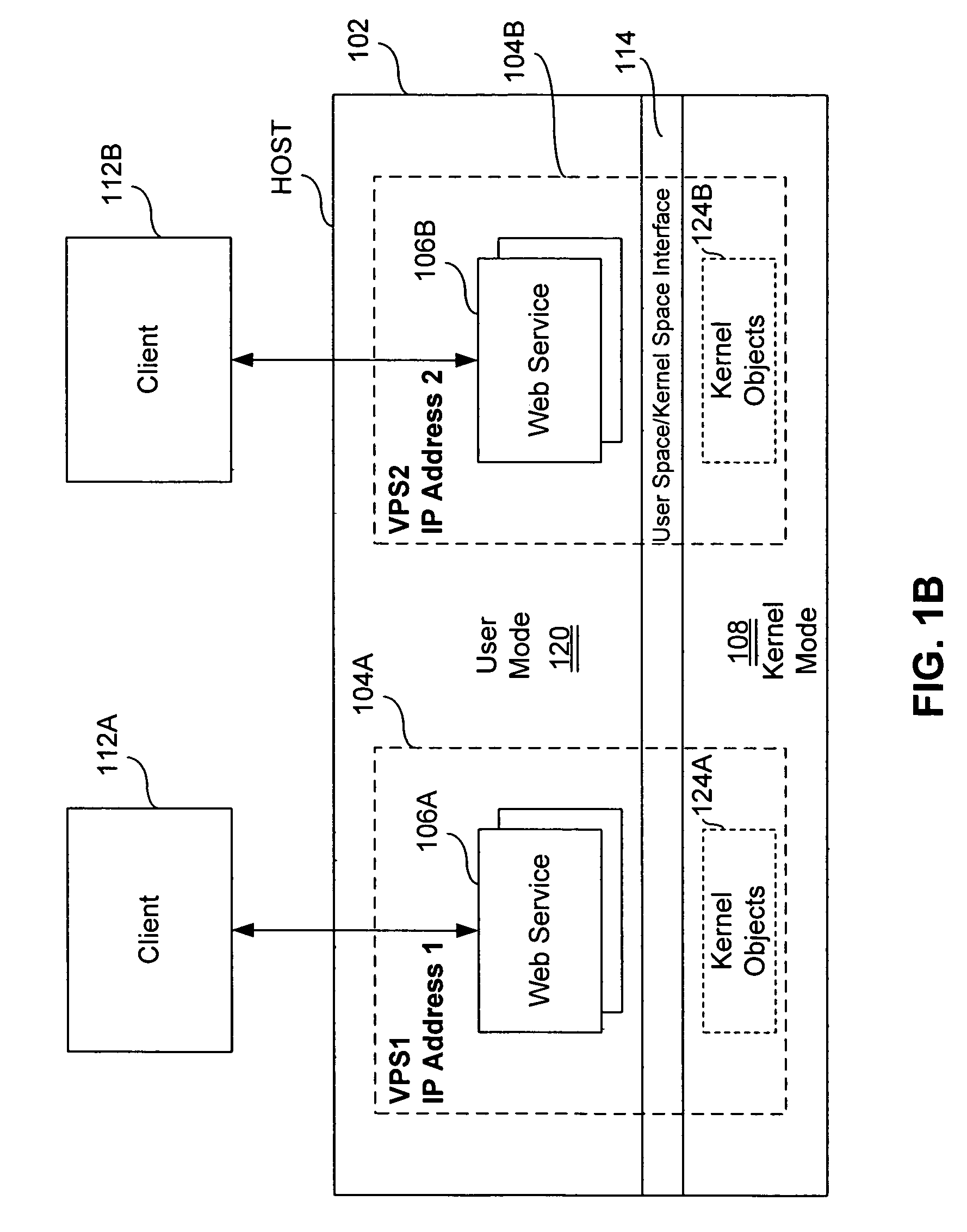
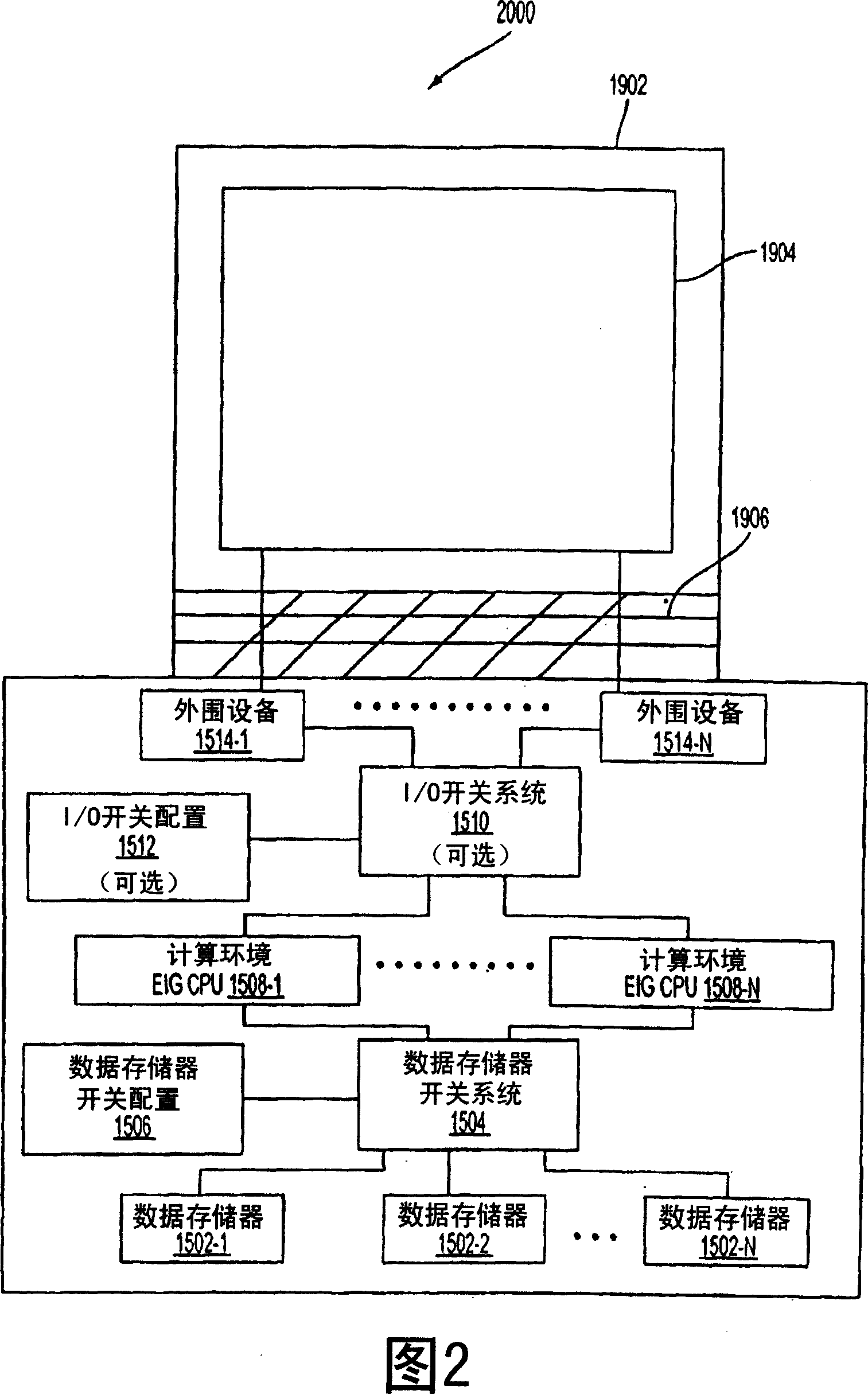
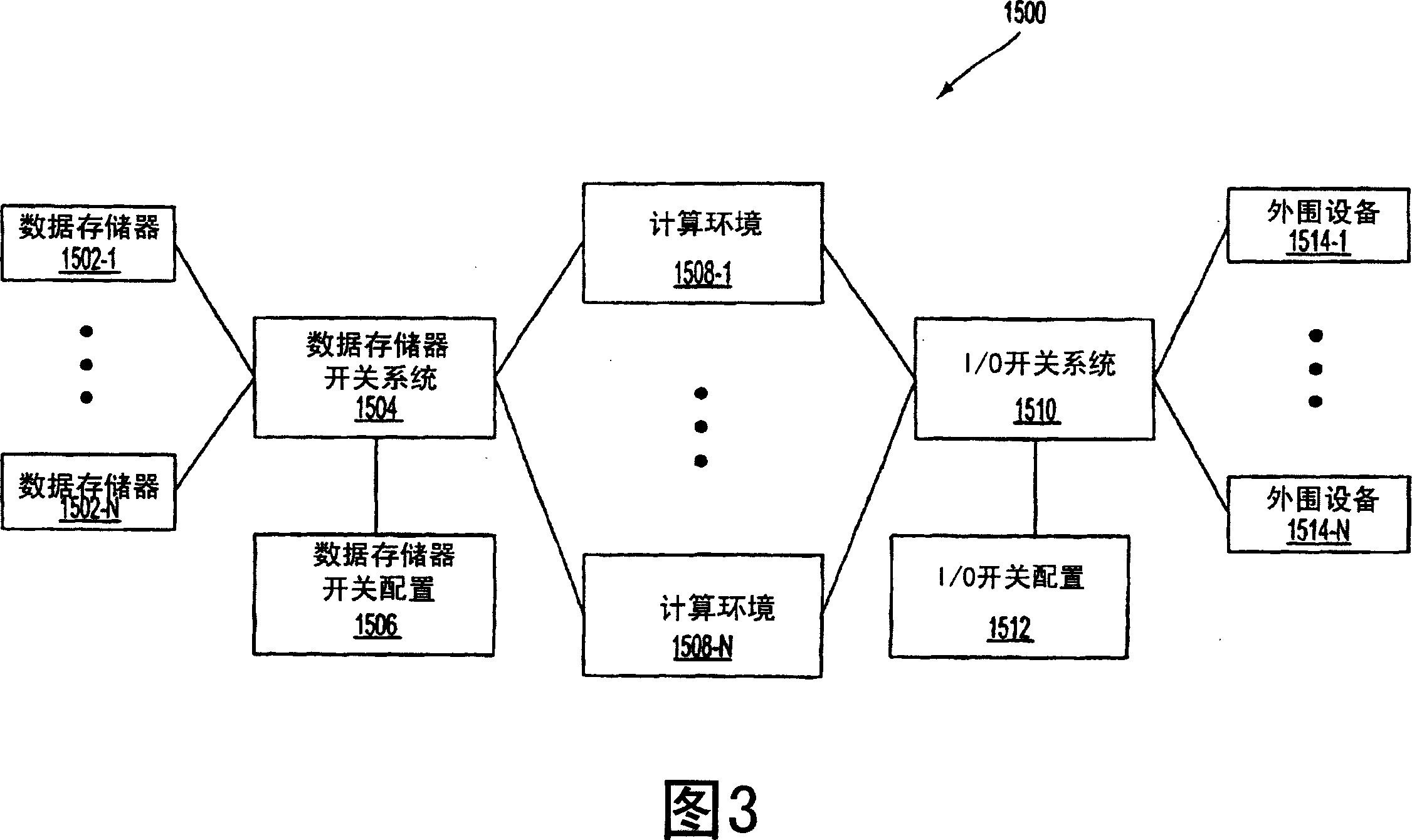
Virtual private server with isolation of system components
ActiveUS7461148B1Eliminate disadvantagesMultiprogramming arrangementsMultiple digital computer combinationsOperational systemUnique identifier
A server includes a host running an operating system kernel. Isolated virtual private servers (VPSs) are supported within the kernel. At least one application is available to users of the VPS. A plurality of interfaces give the users access to the application. Each VPS has its own set of addresses. Each object of each VPS has a unique identifier in a context of the operating system kernel. Each VPS is isolated from objects and processes of another VPS. Each VPS includes isolation of address space of each user from address space of a user on any other VPS, isolation of server resources for each VPS, and failure isolation. The server includes a capability of allocating (or reallocating) system resources to a designated VPS, allocating (or reallocating) system resources to a VPS in current need of such resources, dynamically allocating (or reallocating) VPS resources to a VPS when additional resources are available, and compensating a particular VPS in a later period for a period of under-use or over-use of server resources by the particular VPS in a current period. VPS resources are allocated for each time cycle. All the VPSs are supported within the same OS kernel.
Owner:VIRTUOZZO INT GMBH
Electronic computer system secured from unauthorized access to and manipulation of data
ActiveUS20060069692A1Improve isolationFacilitate redirectionDigital data processing detailsDigital computer detailsSystem callAuthentication
A software security application for a Windows® OS based electronic computer system provides an isolated User environment which protects a User from unauthorized access to and manipulation of data on the system. The security software implements an isolated User file system and provides process / IPC isolation, Windows® registry isolation, network interface isolation, and isolated administrative control on the computer system. Interactive components of the system include an execution hook component that traps system calls, a job object component that creates / destructs, manages and manipulates job objects, a system call hook component for trapping and filtering all Windows registry I / O requests, a file system block device driver for mounting / unmounting the isolated User file system, a file system / filter driver, a network interface / NDIS hook component, and an environment handler. The environment handler provides the overall management interface for other system components, allowing definition of rules, managing authentication and other control / management functions.
Owner:VIIRII LLC
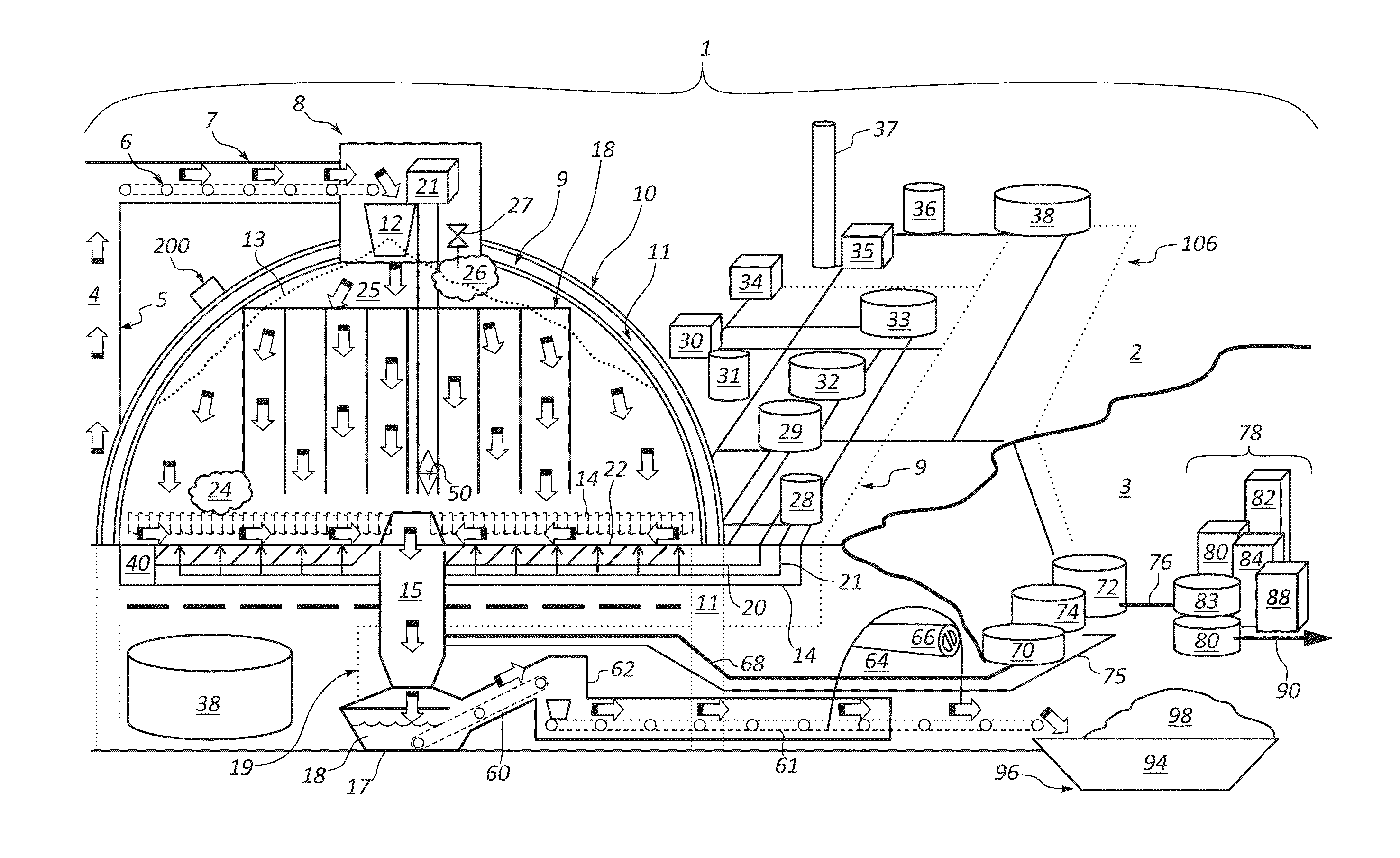
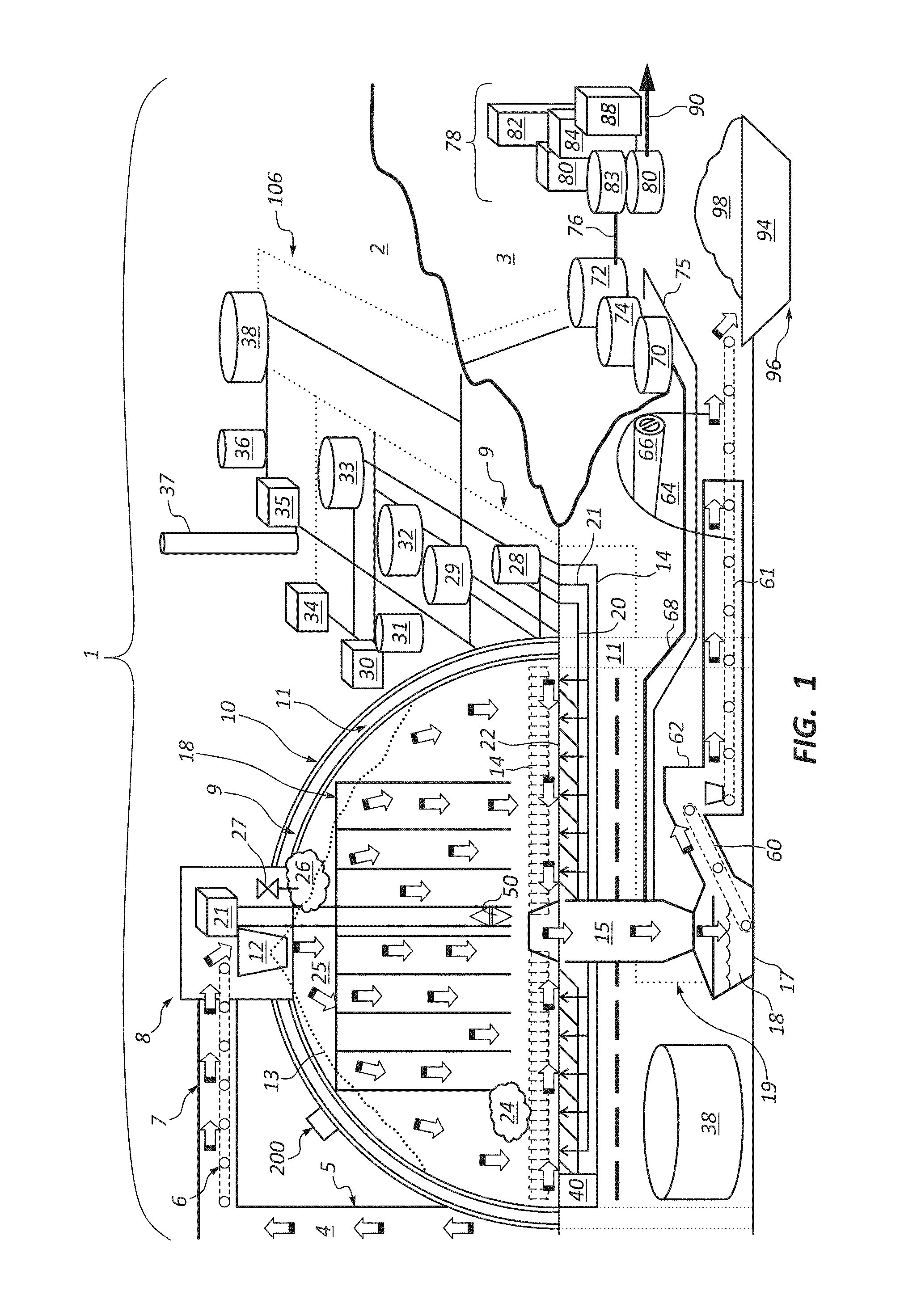
Systems, Apparatus and Methods of a Dome Retort
InactiveUS20110313218A1Increased material throughputLower cost of capitalPressurized chemical processDirect heating destructive distillationBasementControl system
A system, apparatus and method for hydrocarbon extraction from feedstock material that is or includes organic material, such as oil shale, coal, lignite, tar sands, animal waste and biomass. A retort system including at least one retort vessel may include a monolithic dome structure surrounded by a process isolation barrier, the dome structure being sealingly engaged with the process isolation barrier. The dome structure and the process isolation barrier define a retort chamber, at least a portion of which may comprise a subterranean chamber. A lower end of the dome retort structure provides an exit for collected hydrocarbons and spent feedstock material. Systems may include a plurality of such dome retort structures. A control system may be used for controlling one or more operating parameters of a retorting process performed within such a dome retort structure for extraction and collection of hydrocarbons.
Owner:DANA TODD C
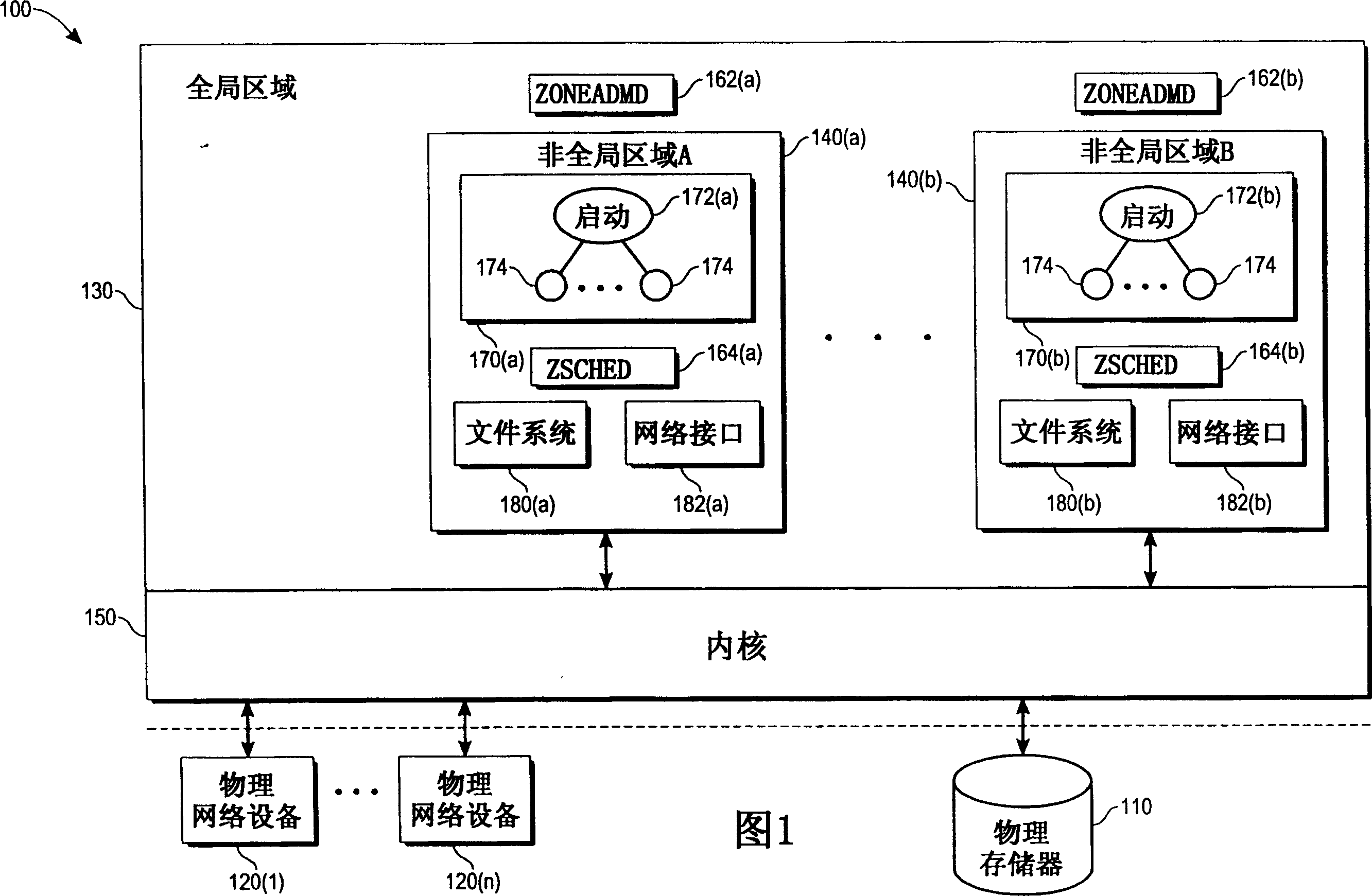
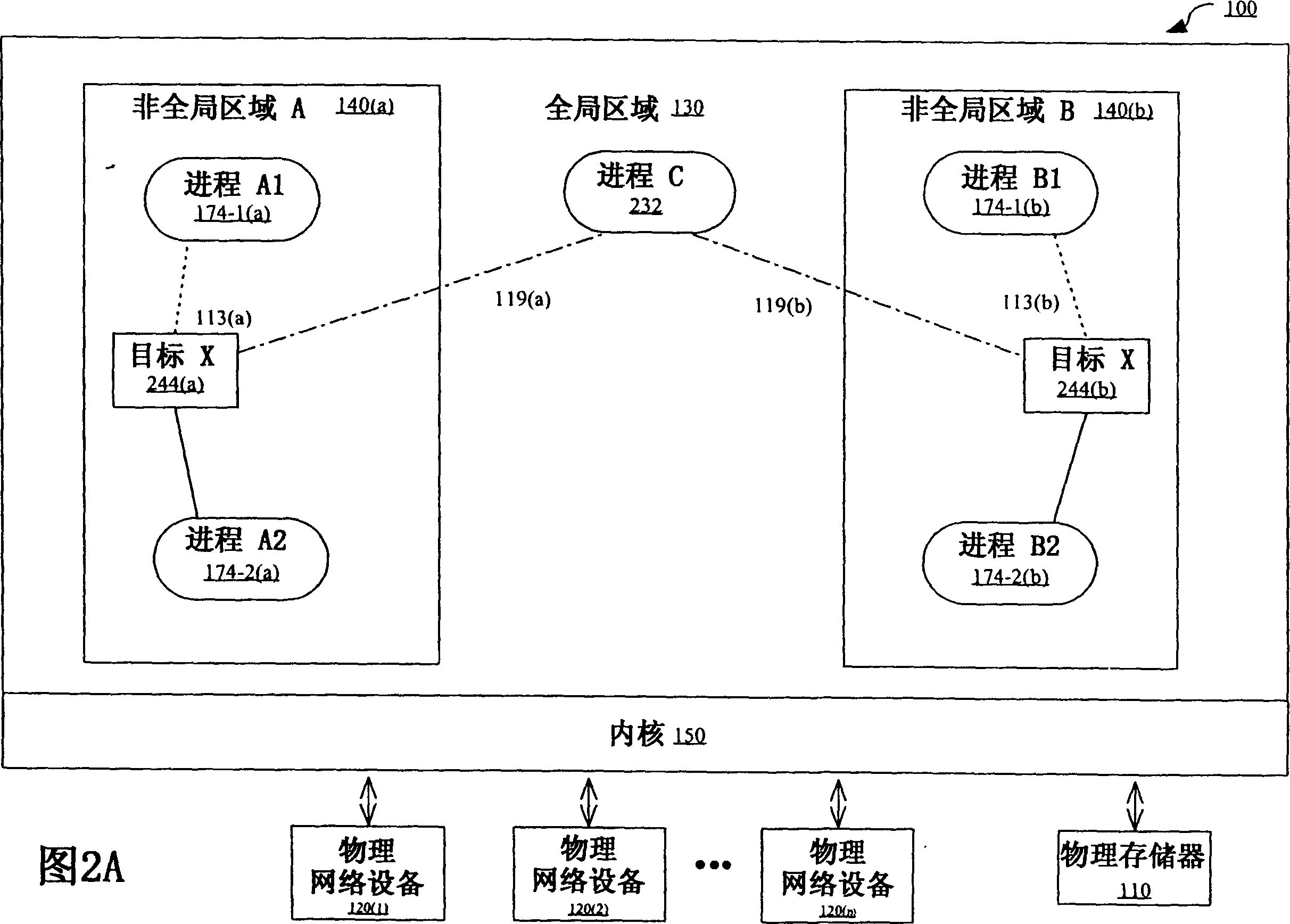
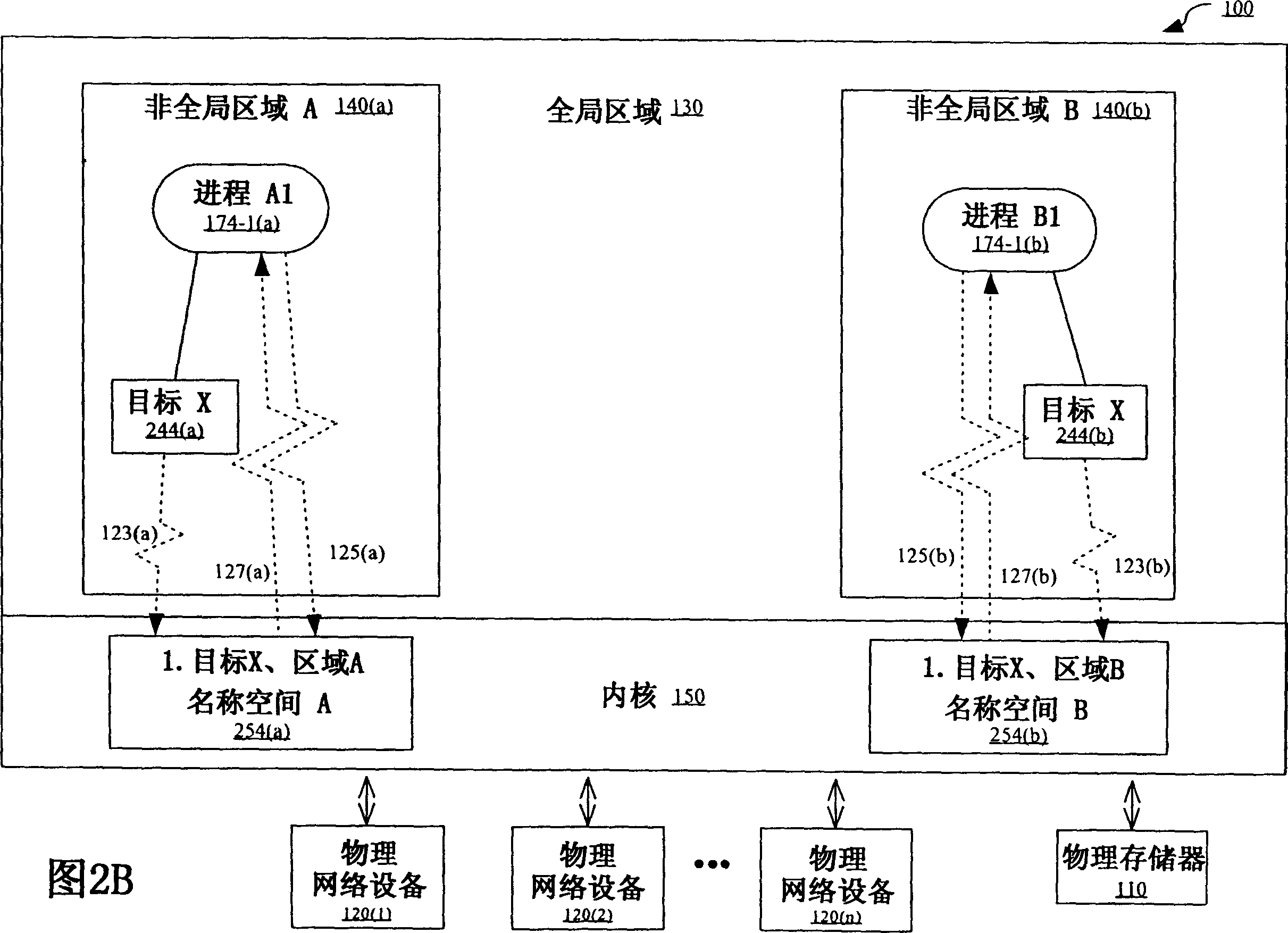
Two-level service model in operating system partitions
ActiveUS7526774B1Data processing applicationsError detection/correctionService modelOperational system
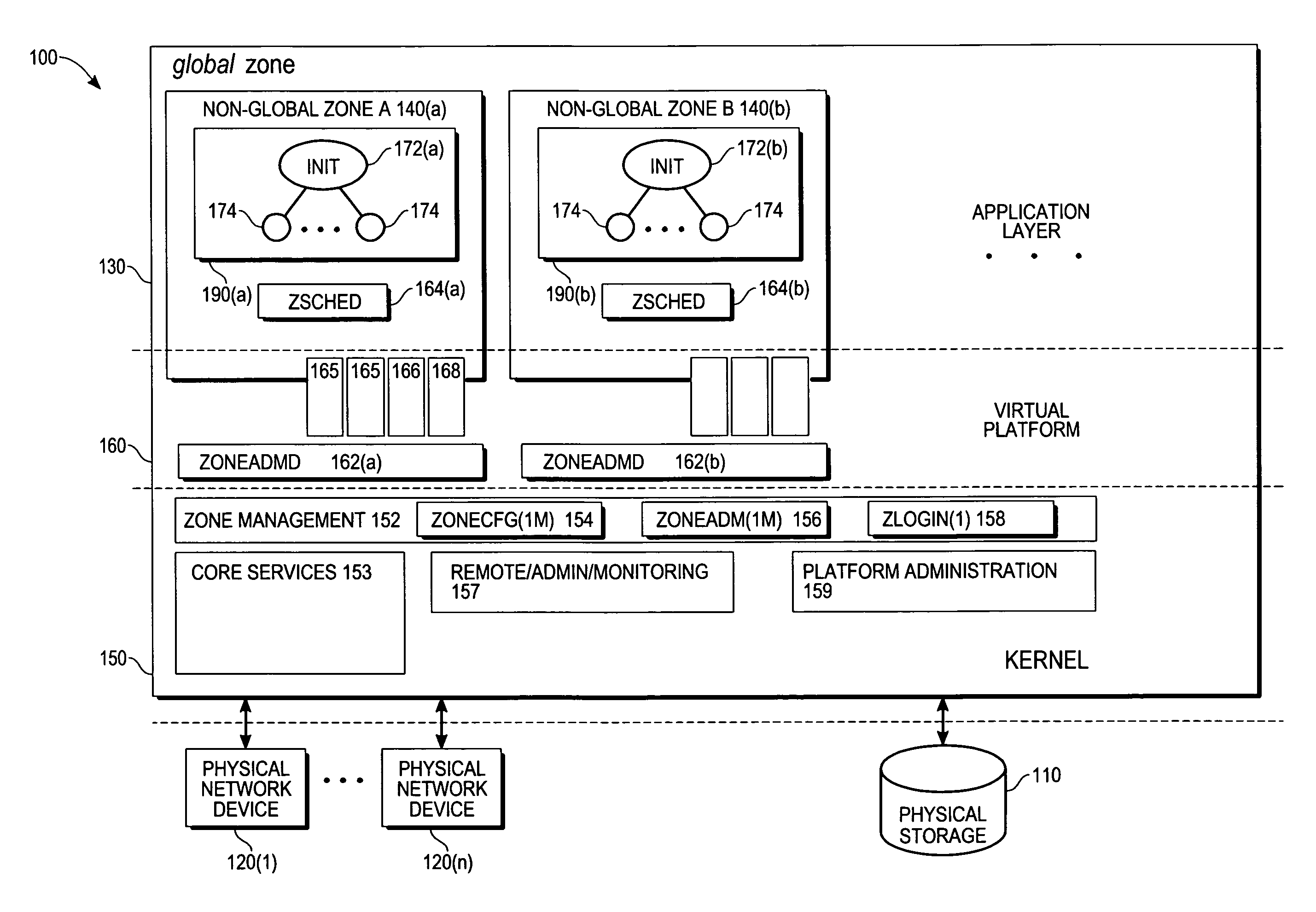
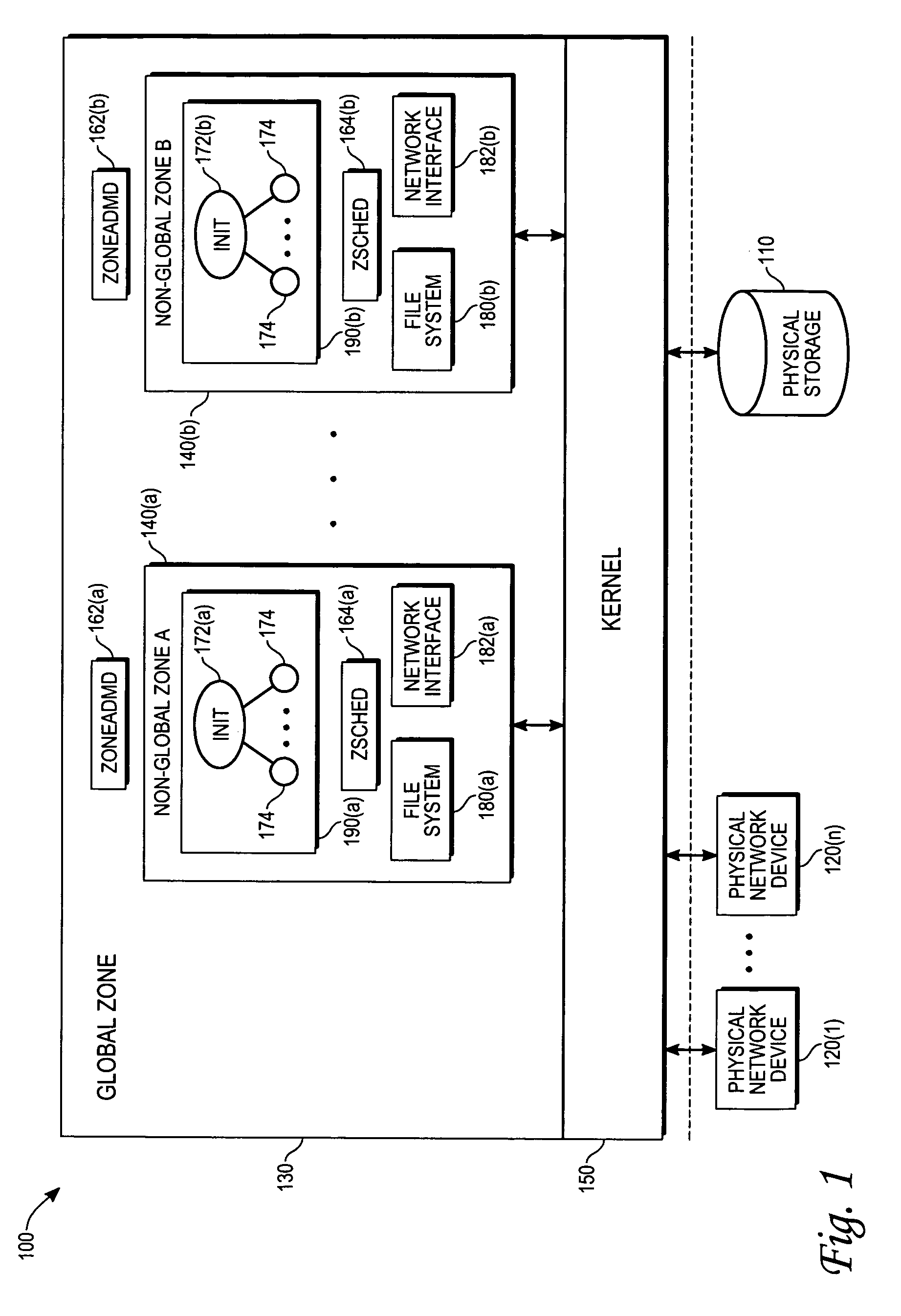
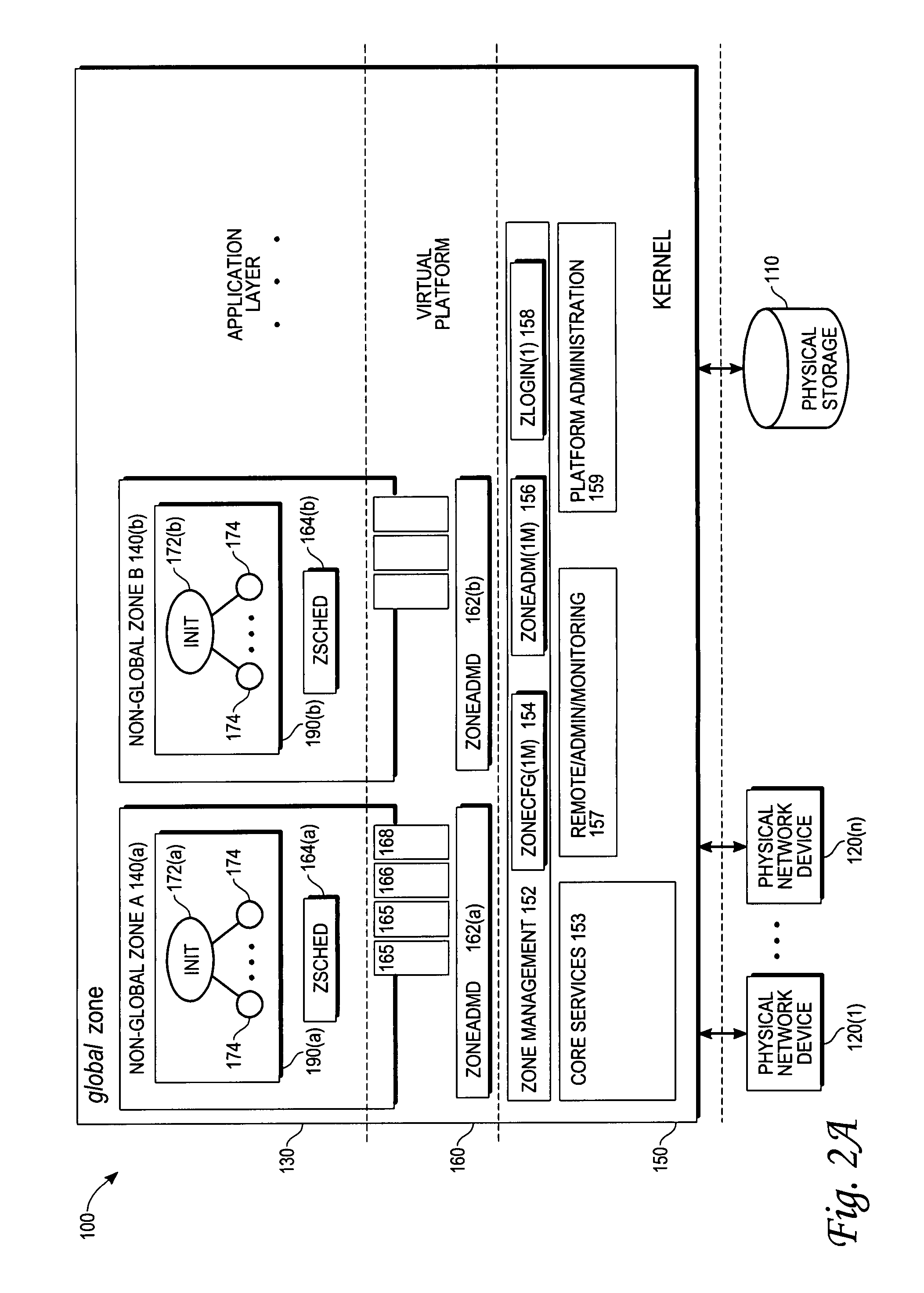
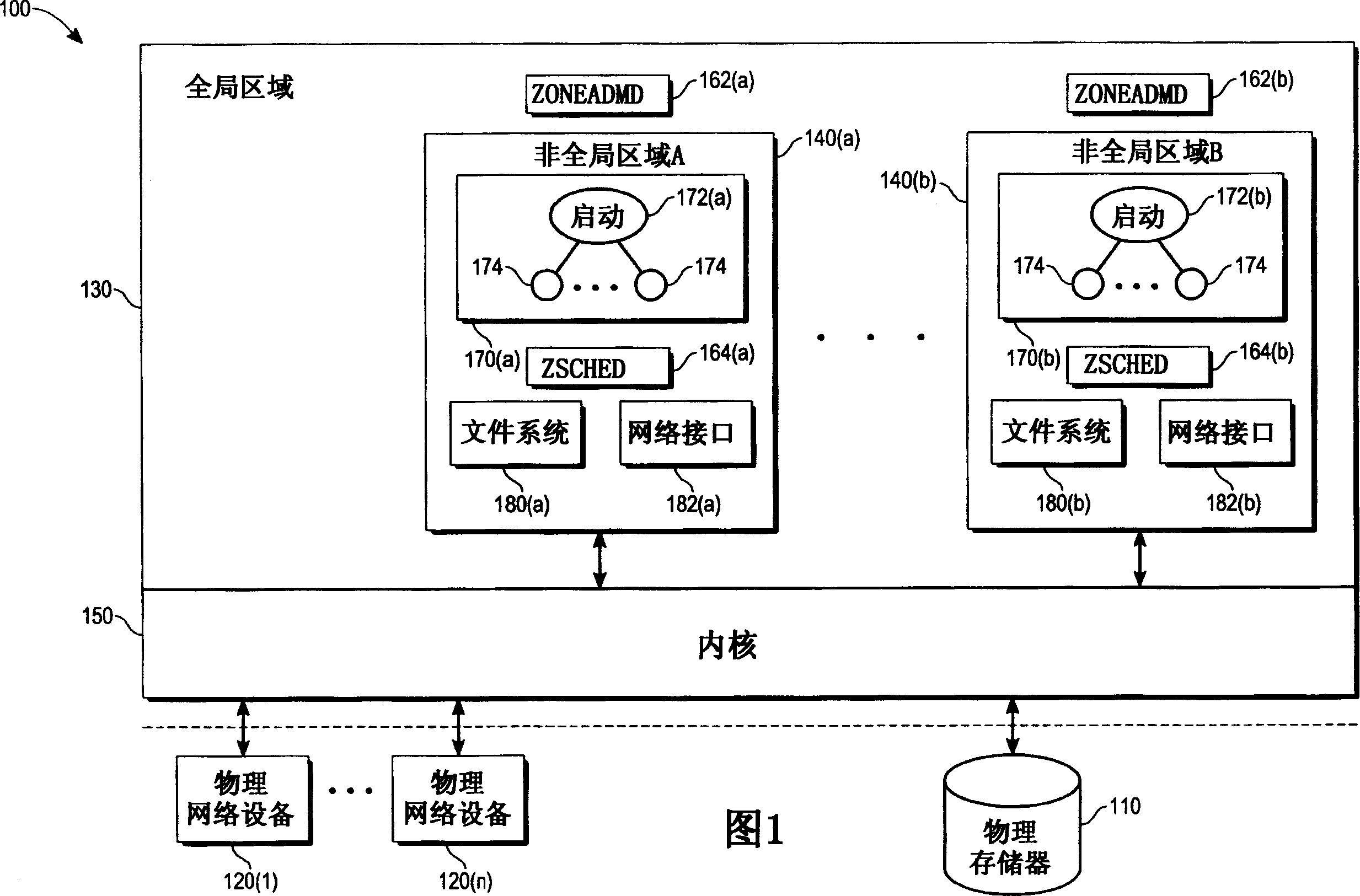
The present invention provides, in one embodiment, a multi-level service model operating system environment that may be partitioned into a global zone and one or more non-global zones to isolate processes from processes executing in association with other non-global zones under control of a single kernel instance. In one embodiment, the multi-level service model includes a virtual platform layer and an application layer. The virtual platform layer may include services and resources for supporting the zones, which can be made accessible to the zones in the form of a virtual platform. The application layer may comprise the non-global zones, including an application environment for maintaining a runtime state for the zone's processes and any zone-constructed objects, such as network connections and shared memory segments. In one embodiment, control and management of non-global zones can be provided by a system of states and transitions.
Owner:ORACLE INT CORP
Automatic isolation of misbehaving processes on a computer system
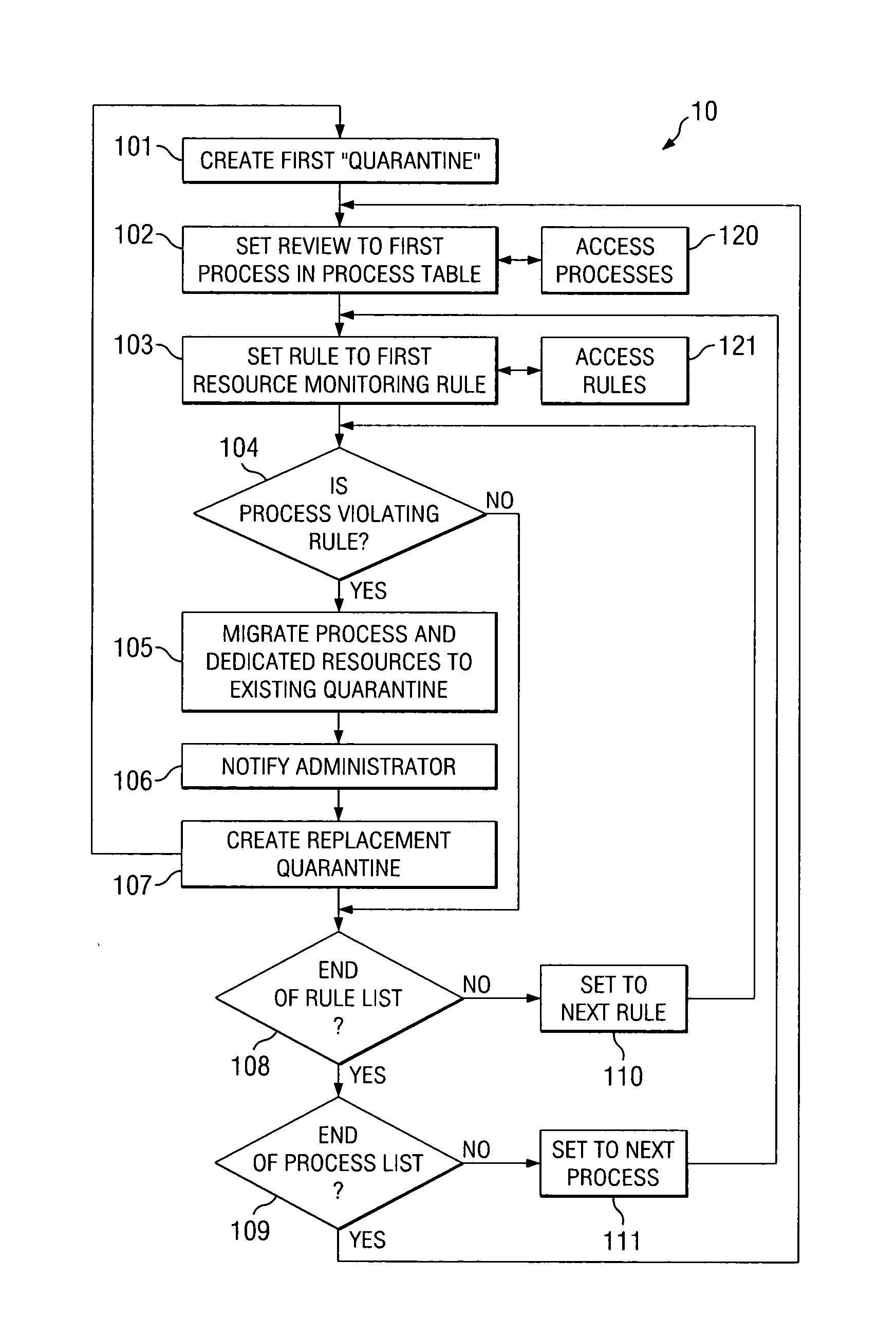
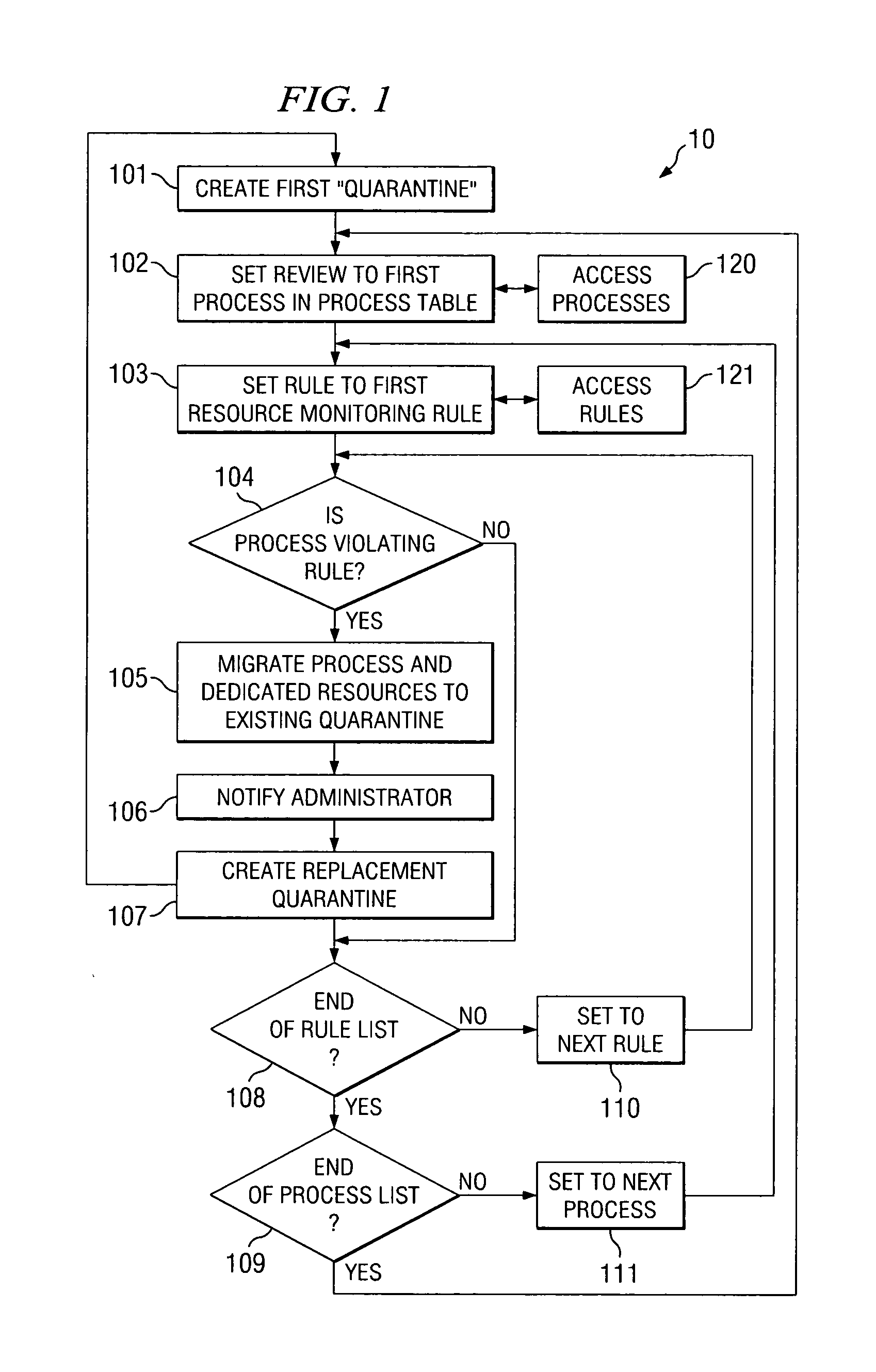
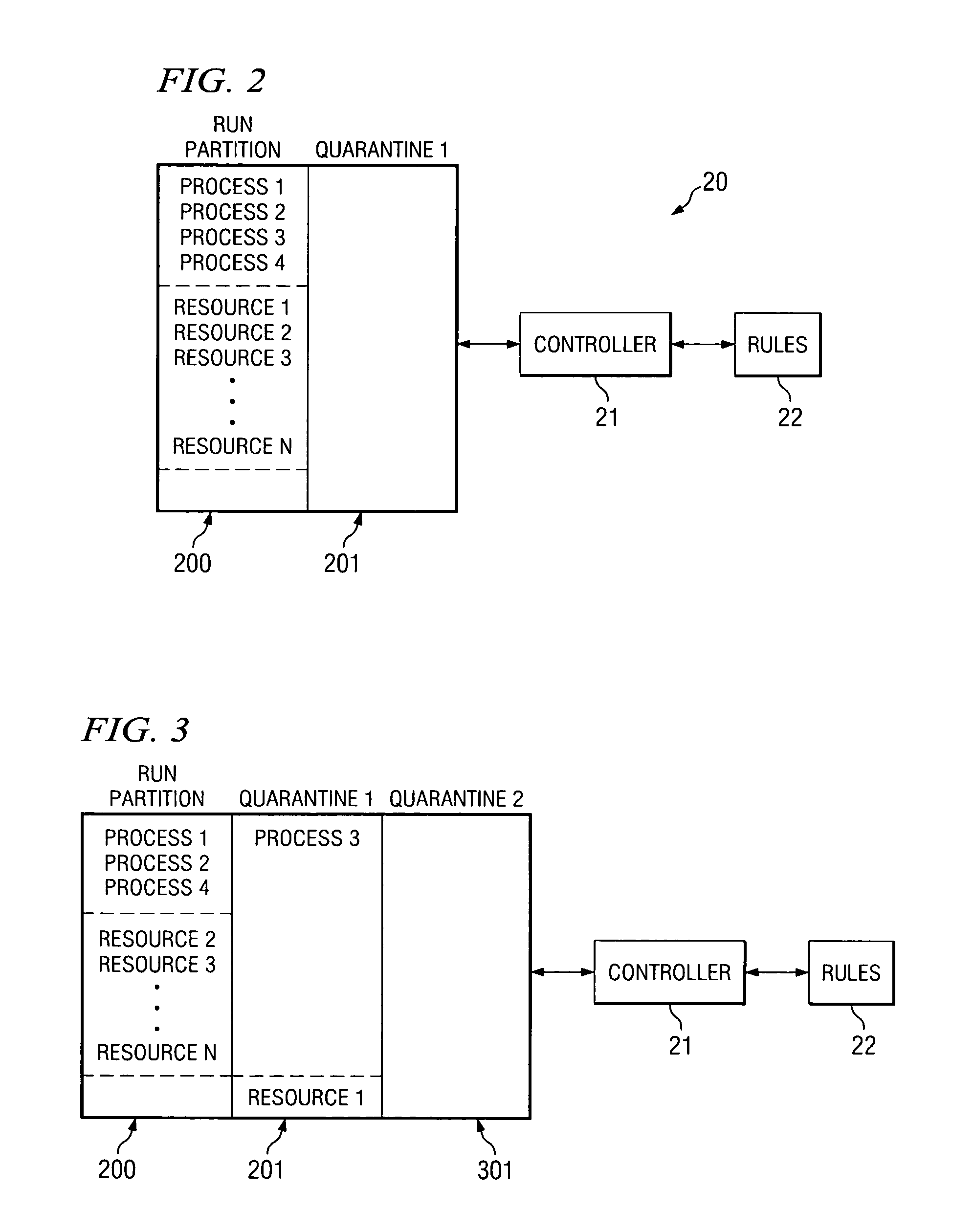
ActiveUS20070250929A1Memory loss protectionError detection/correctionEngineeringIndustrial engineering
When a computer system process is acting contrary to the rules established for that process for the resource it is running on, the process is moved to a quarantined section and its continued operation is isolated from other processes. While in isolation, the quarantined process is tested and appropriate action, such as, for example, rehabilitation, change of the rules, or termination, is performed. The divided quarantined sections are used for each misbehaving process.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Hybrid Field Effect Transistor and Bipolar Junction Transistor Structures and Methods for Fabricating Such Structures
Semiconductor device structures that integrate field effect transistors and bipolar junction transistors on a single substrate, such as a semiconductor-on-insulator substrate, and methods for fabricating such hybrid semiconductor device structures. The field effect and bipolar junction transistors are fabricated using adjacent electrically-isolated semiconductor bodies. During fabrication of the device structures, certain fabrication stages strategically rely on block masks for process isolation. Other fabrication stages are shared during the fabrication process for seamless integration that reduces process complexity.
Owner:IBM CORP
Safe embedded operating system capable of supporting multi-stage loading
ActiveCN102479097AAchieve isolationRealize dynamic loading and runningProgram loading/initiatingProgram/content distribution protectionEnd to end securityGraphical user interface
The invention provides a safe embedded operating system capable of supporting multi-stage loading. The safe embedded operating system supports the dynamic loading operation of an application program of an embedded terminal, realizes the isolation of the application program and an embedded terminal platform and comprises a system management module, a safety management module, a resource management module, a functional unit module, a GUI (Graphical User Interface) module, an application execution engine module, an application program interface (API) module and the like. Meanwhile, the safe embedded operating system is at least divided into a basic stage and an expansion stage by adopting stage treatment on the basis of the traditional Linux inner core, a basic stage module is fixedly loaded, each module and each functional module in the expansion stage are selectively and dynamically loaded according to application requirements under the scheduling of a system management framework, and thus, loading the system by stage is realized. By using the safe embedded operating system, a function of safety management and control for the application program through a safe framework module is achieved, mechanisms such as end-to-end safe issuing and loading of an application, safe operation protection based on an application process isolation and trust mechanism, application operation monitoring and the like are applied, and safe management and control on the whole life cycle of the application from issuing, downloading, loading to operating is realized.
Owner:ZHENGZHOU SEANET TECH CO LTD
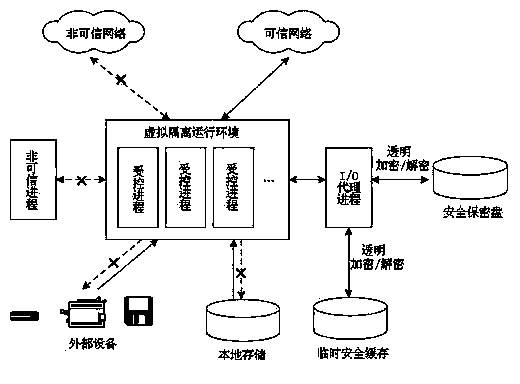
Process isolation and encryption mechanism based security disc model and generation method thereof
InactiveCN104077244ARealize full monitoringFix compatibility issuesUnauthorized memory use protectionComputer hardwareData file
The invention discloses a process isolation and encryption mechanism based security disc model and a generation method thereof. The security disc model comprises a virtual isolating operation module, an I / O agent process encryption / decryption module and a security disc, wherein the virtual isolating operation module is used for acquiring a credible process, and converting the credible process into a controlled process which is forcedly placed in a virtual isolating operation environment for operation; the I / O agent process encryption / decryption module is used for conducting read-write operation on data files in the security disc in the transparent encryption-write / decryption-read manner; the security disc is revealed on a terminal host computer as an ordinary disc partition. The security disc model and the generation method thereof can comprehensively manage and control the credible and controllable operation environment of the terminal security process, the encryption forced filing management of the whole life cycle from storage, conveying, application to destruction of the security files, and the acts of the network, printing, memory leak and the like of a security program operated at the terminal, and realizes whole-process monitoring of the security files.
Owner:HUNAN LANTOSEC SCI & TECH
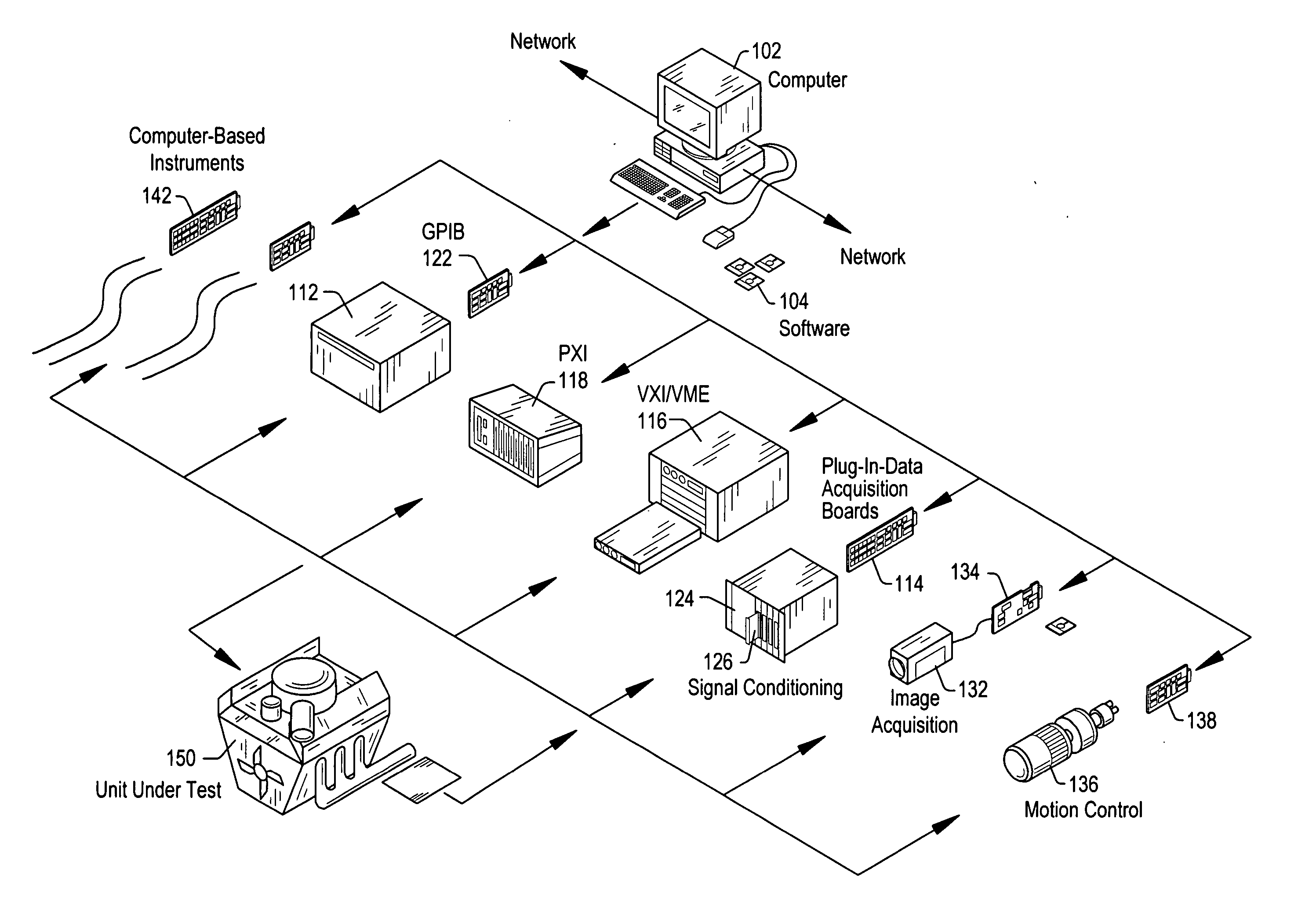
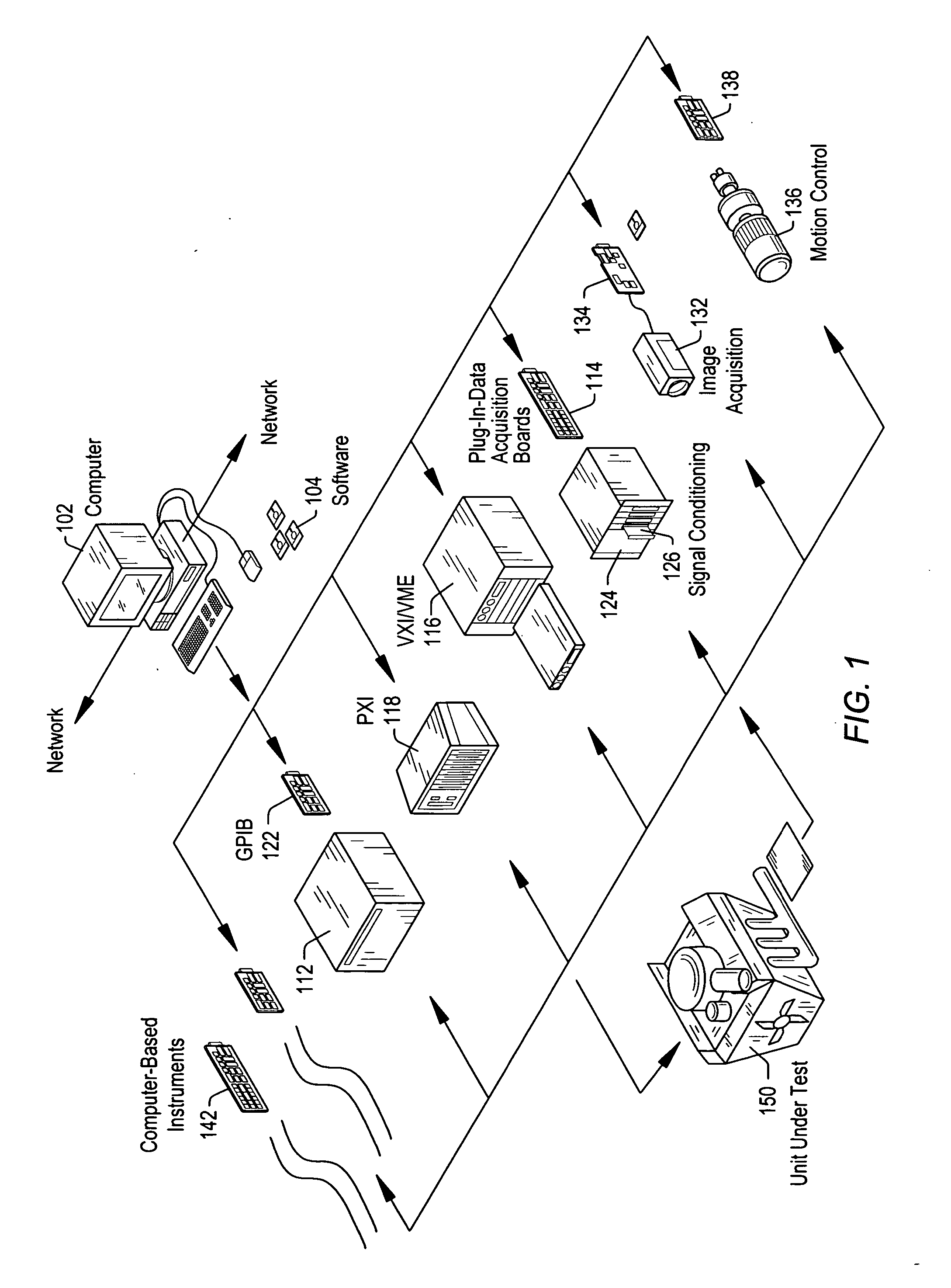
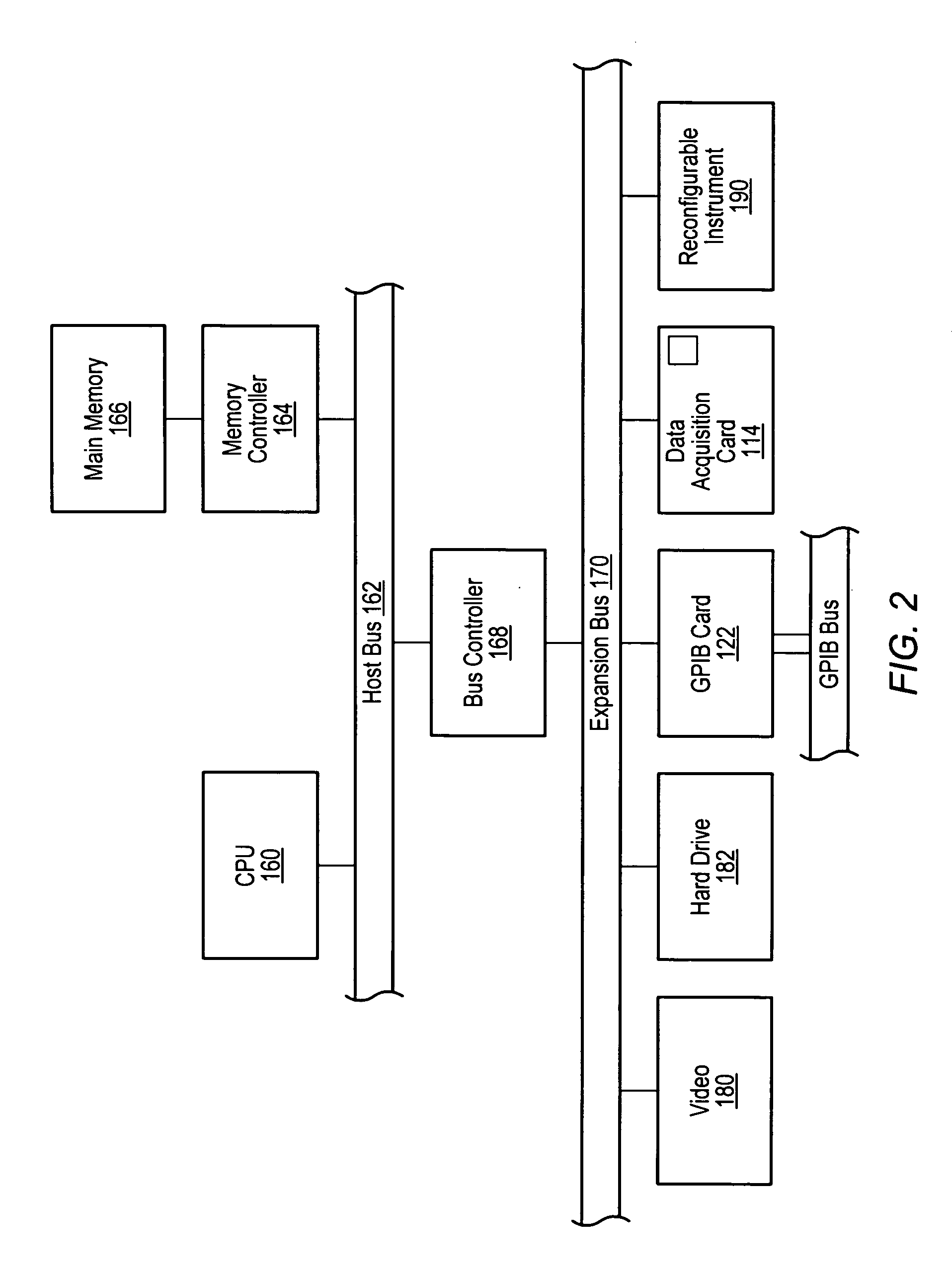
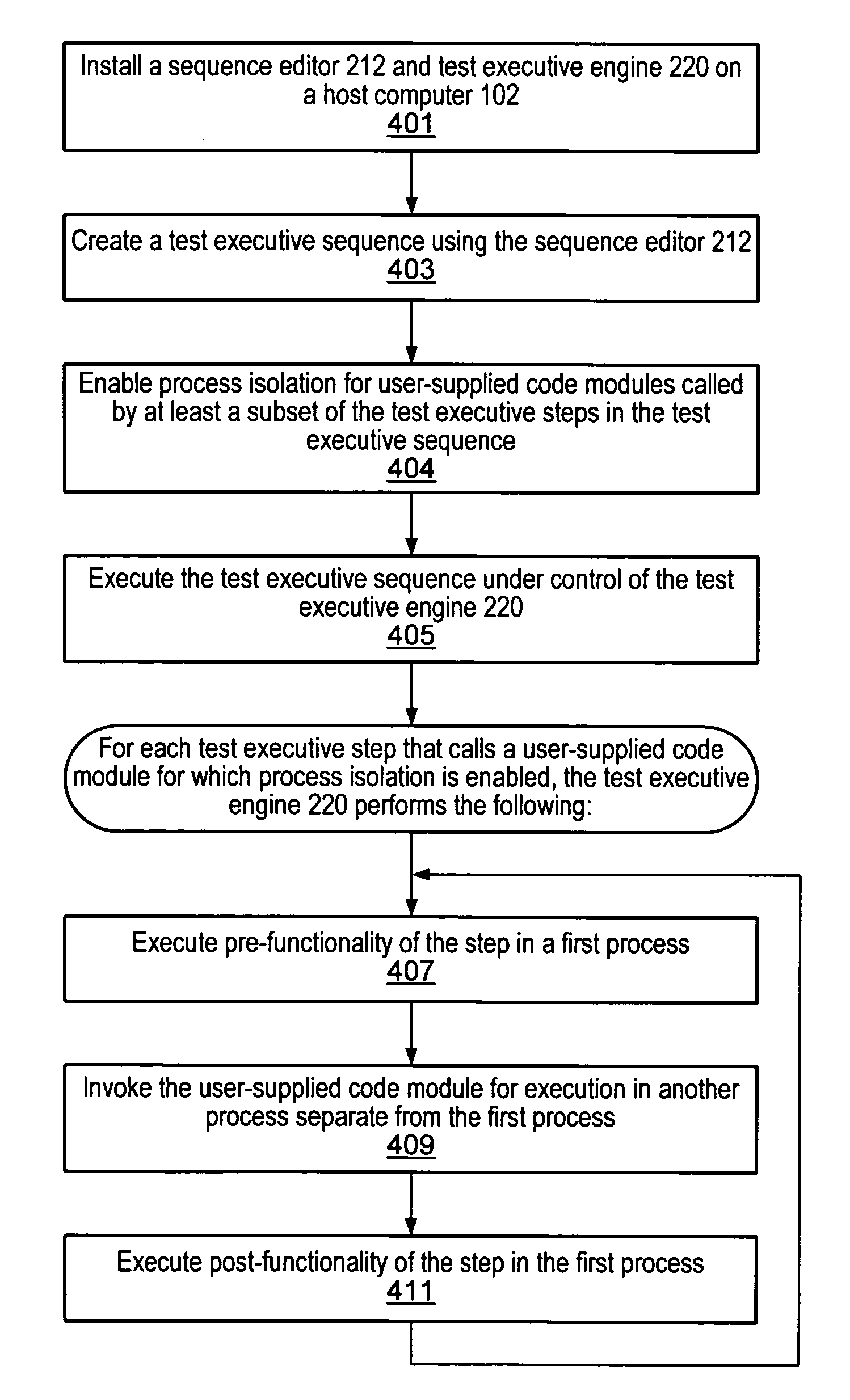
Test executive with external process isolation for user code modules
ActiveUS20060143536A1Resistance/reactance/impedenceError detection/correctionCode moduleTest execution
A system and method for isolating execution of user-supplied code modules that are called by steps of a test executive sequence. The test executive sequence may first be created by including a plurality of test executive steps in the test executive sequence and configuring at least a subset of the steps to call user-supplied code modules. The test executive sequence may then be executed on a host computer under control of a test executive engine. For each step that calls a user-supplied code module, the test executive engine may invoke the user-supplied code module for execution in a separate process other than the process in which the test executive engine executes.
Owner:NATIONAL INSTRUMENTS
Isolated multiplexed multi-dimensional processing in a virtual processing space having virus, spyware, and hacker protection features
InactiveCN1954297AEfficient use ofHardware monitoringInternal/peripheral component protectionPhysics processing unitData memory
Information appliance, computing device, or other processor or microprocessor based device or system provides security and anti-viral, anti-hacker, and anti-cyber terror features, and can automatically create multiple sequentially or concurrently and intermittently isolated and / or restricted computing environments to prevent viruses, malicious or other computer hacking, computer or device corruption and failure by using these computing environments in conjunction with restricted and controlled methods of moving and copying data, combined with a process that destroys malicious code located in computing environments and data stores. Time multiplexed processing streams with system, device, architecture and method for maintaining isolation of multiple processes executing in single physical processor. Virtual multi-dimensional processing space and virtual processing environments. Temporally multiplexed processing is in a single CPU. Process isolation uses address control and mapping. Selecting, configuring, switching, and / or multiplexing multiple processes in physical and / or virtual processing or computing spaces create physical and / or virtual processing or computing environments.
Owner:VIR2US
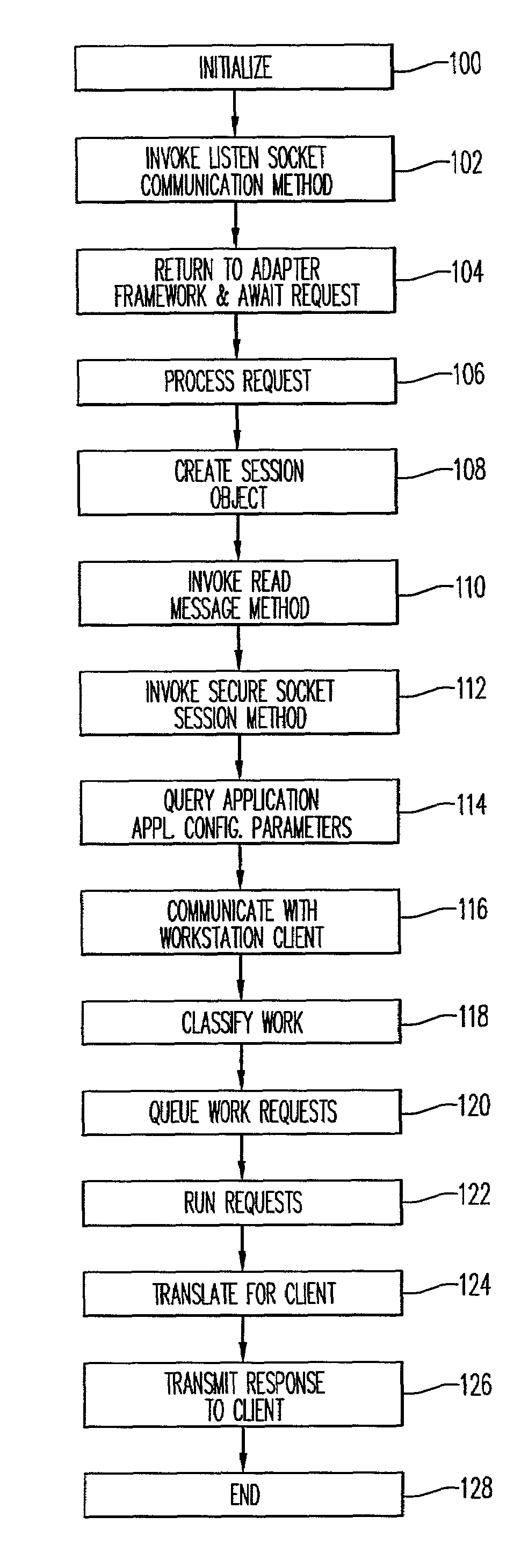
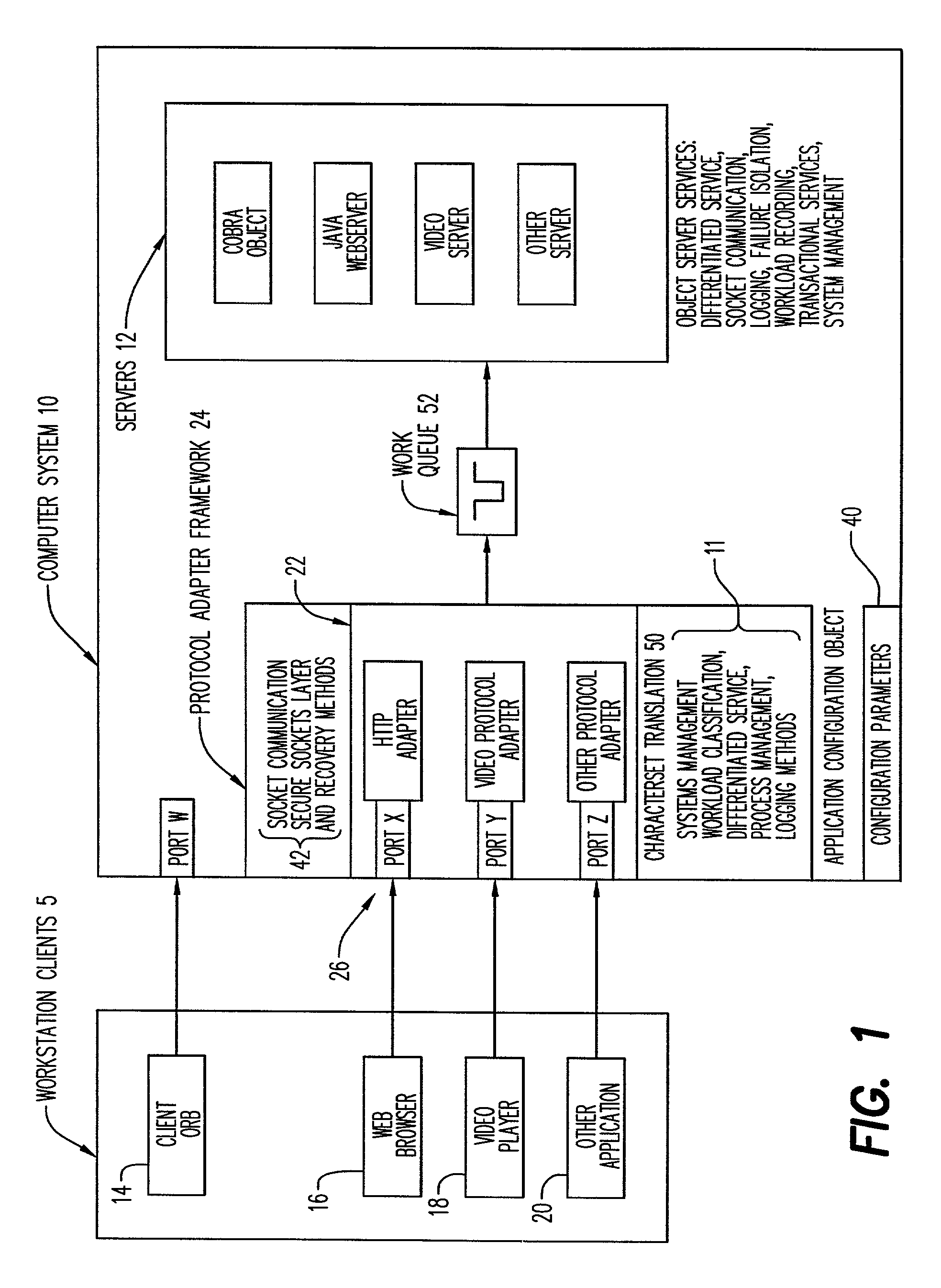
Protocol adapter framework for integrating non-IIOP applications into an object server container
InactiveUS7127517B2Inability to overcomeLessMultiple digital computer combinationsTransmissionDifferentiated servicesSystems management
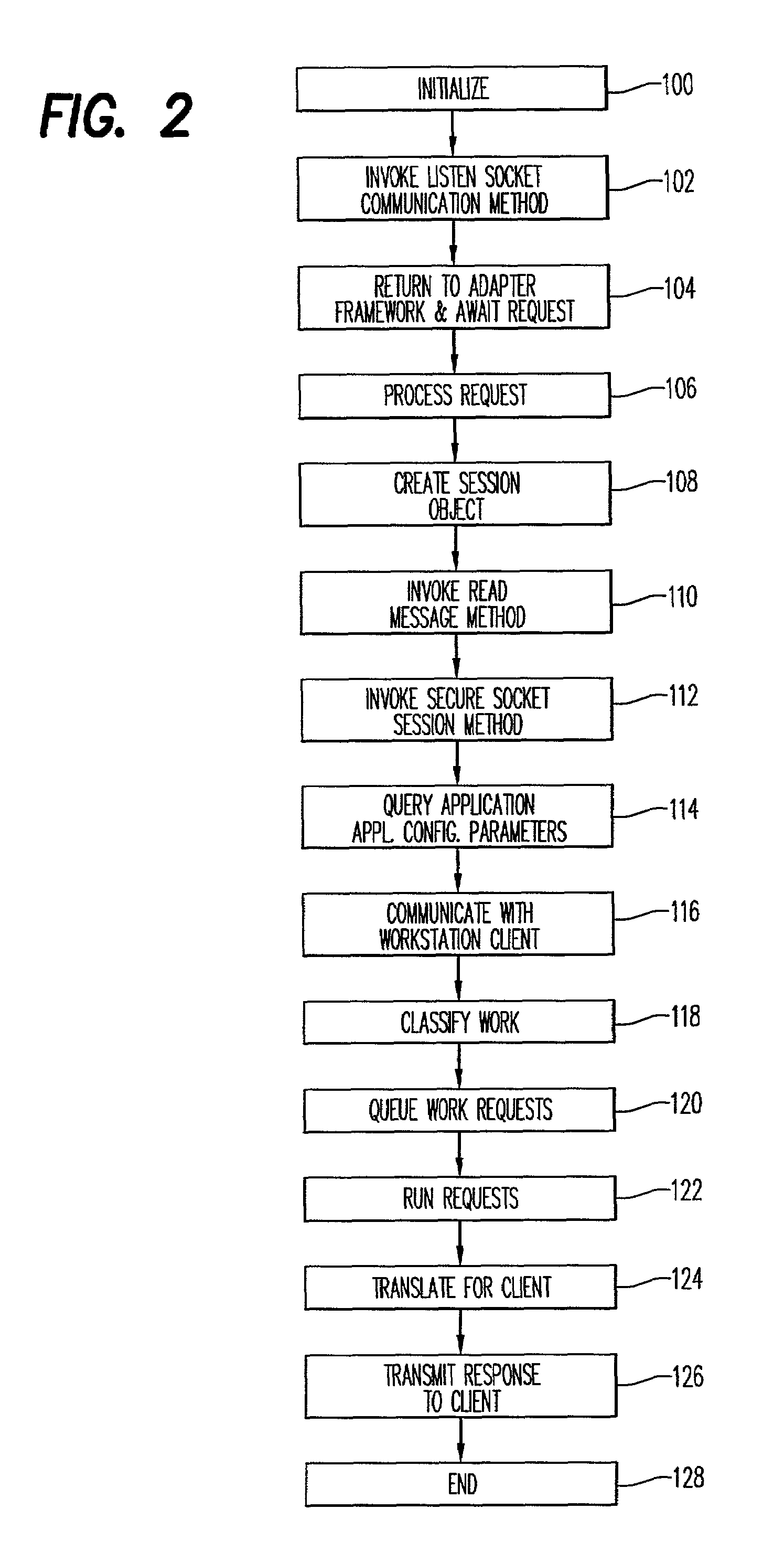
In a computer system containing an object server, a method and apparatus for providing access to objects and methods via arbitrary remote protocols is disclosed. This includes a mechanism known as the protocol adapter framework that allows protocol adapters to manage remote socket sessions, encrypt communication on this session, translate text to the local character set, perform security validation of the remote user, log incoming work requests, classify the incoming work request for differentiated service purposes, and queue the work for execution. Also, included is a mechanism to invoke the protocol adapter in order to manipulate output from the execution of a method on a server object and send it back to the original requester. This allows the implementers of objects and methods that reside in the object server rather than the owner of the object server to provide a protocol adapter that allows communication with remote clients using any arbitrary protocol that the object implementer deems appropriate. In this way, the object implementer can enjoy benefits such as differentiated service, workload recording, server object process management, process isolation, error logging, systems management and transactional services of running objects in a robust object server container.
Owner:IBM CORP
Securely and efficiently extending data processing pipeline functionality
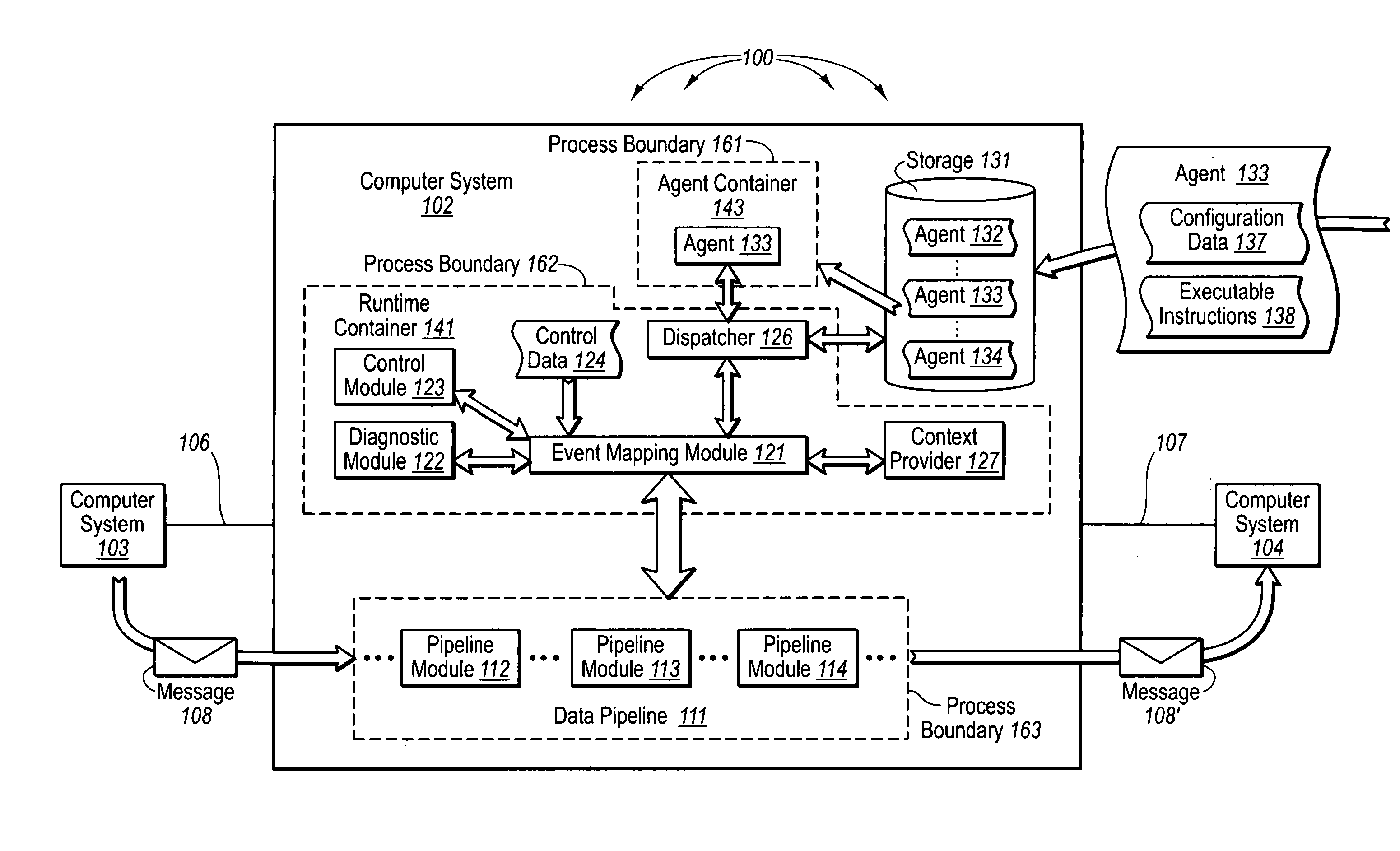
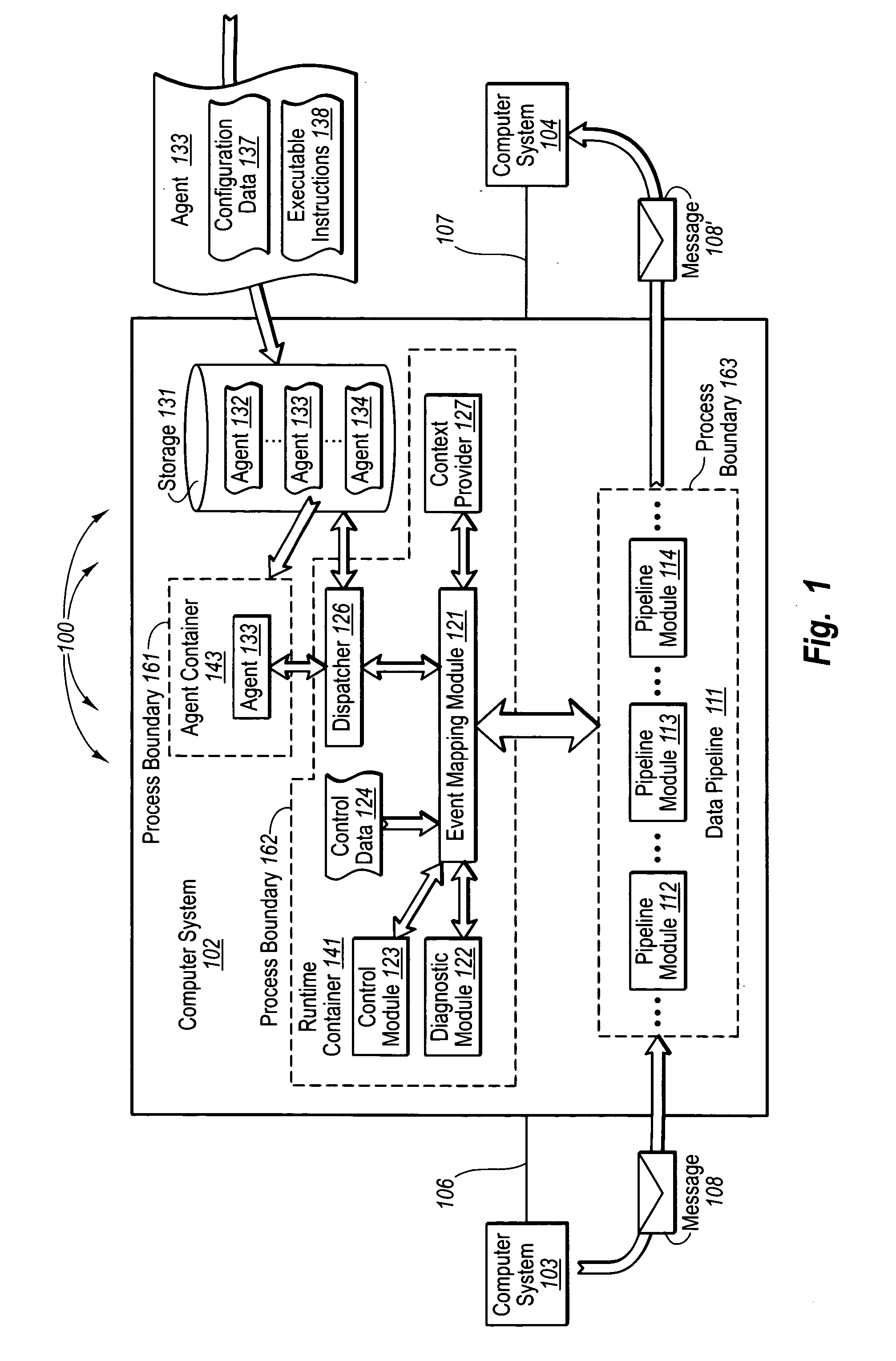
ActiveUS20060069713A1Improve functionalityFunction increaseMultiple digital computer combinationsProgram controlSeparating agentData processing
The present invention extends to methods, systems, and computer program products for securely and efficiently extending data processing pipeline functionality. Data processing agents register, potentially based solely on configuration data contained in the data processing agents, to manipulate data of a data processing pipeline. Configuration data can identify a specified event (e.g., an SMTP verb) the data processing agent is to hook into. Upon detection of a specified event, one or more agents that have registered for the specified event are loaded into secure zones. Process boundaries separate agents from one another and from other processes such that execution of each agent is isolated from other processes. Pipeline related data (e.g., electronic message data) is transferred to each loaded agent. Application Program Interfaces (“APIs”) can be used to transfer data between modules that implement embodiments of the present invention.
Owner:MICROSOFT TECH LICENSING LLC
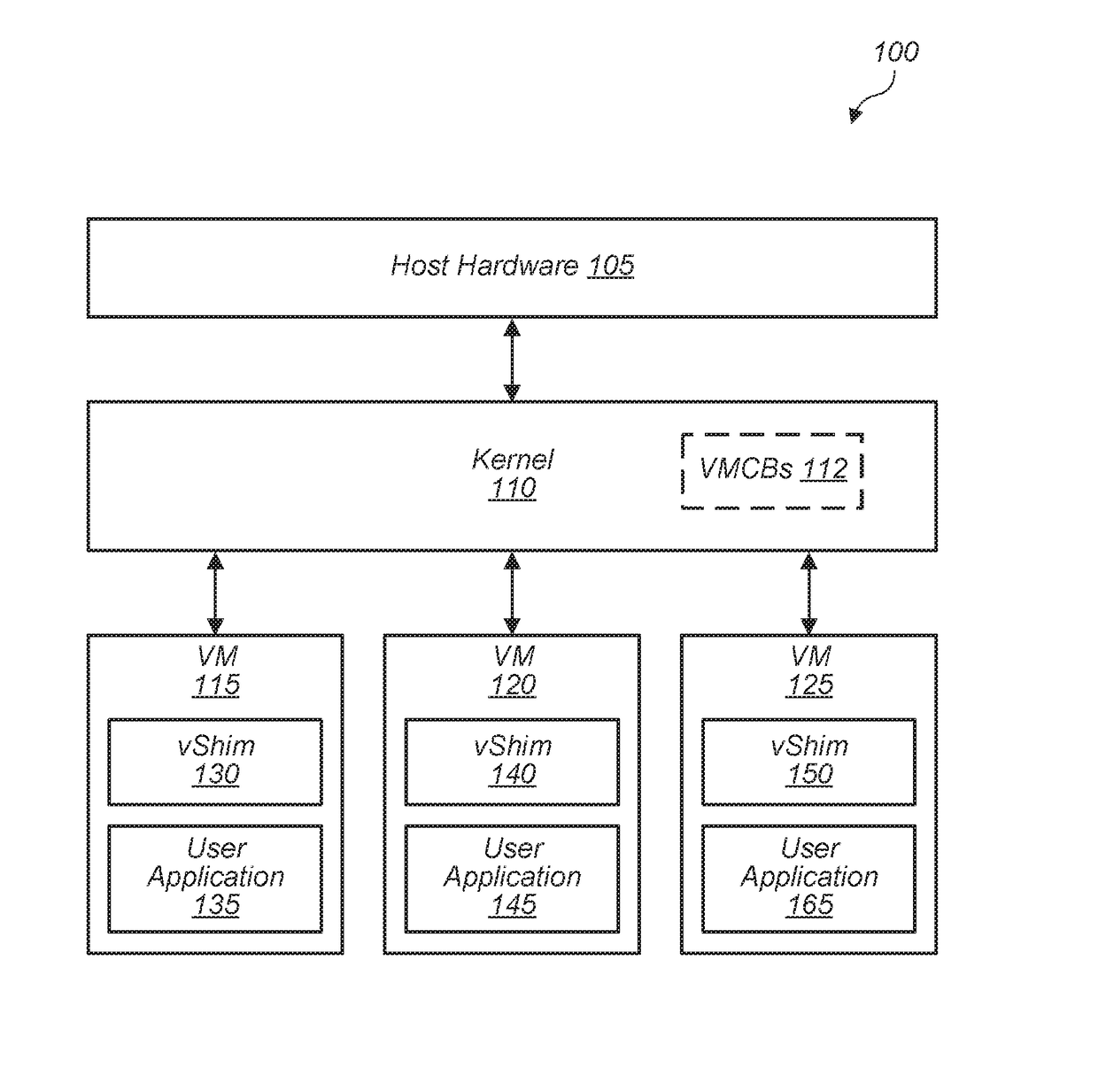
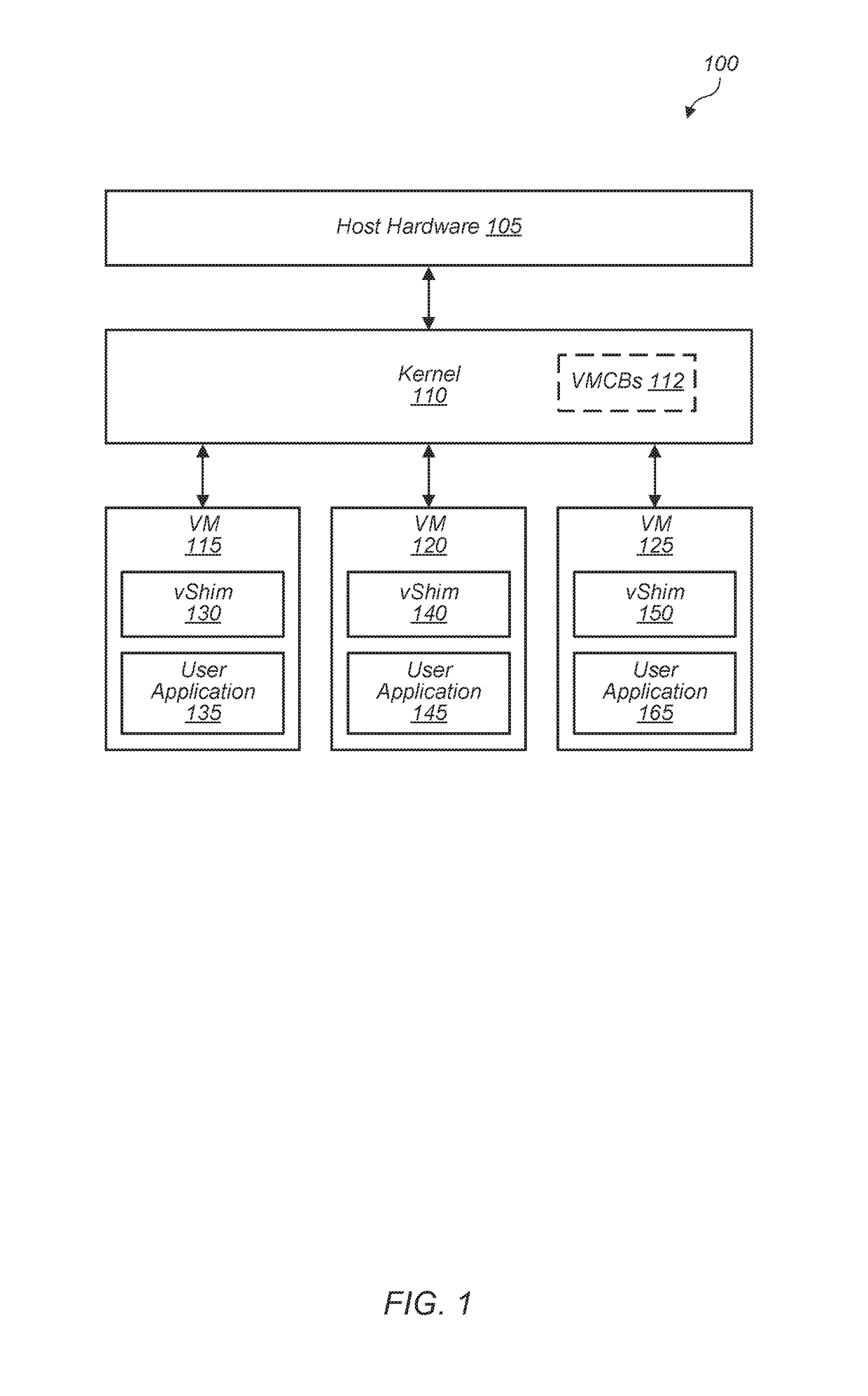
Virtualized process isolation
ActiveUS20180081829A1Memory architecture accessing/allocationUnauthorized memory use protectionVirtualizationPage table
Systems, apparatuses, and methods for implementing virtualized process isolation are disclosed. A system includes a kernel and multiple guest VMs executing on the system's processing hardware. Each guest VM includes a vShim layer for managing kernel accesses to user space and guest accesses to kernel space. The vShim layer also maintains a separate set of page tables from the kernel page tables. In one embodiment, data in the user space is encrypted and the kernel goes through the vShim layer to access user space data. When the kernel attempts to access a user space address, the kernel exits and the vShim layer is launched to process the request. If the kernel has permission to access the address, the vShim layer copies the data to a region in kernel space and then returns execution to the kernel.
Owner:ADVANCED MICRO DEVICES INC
Interprocess communication in operating system partition
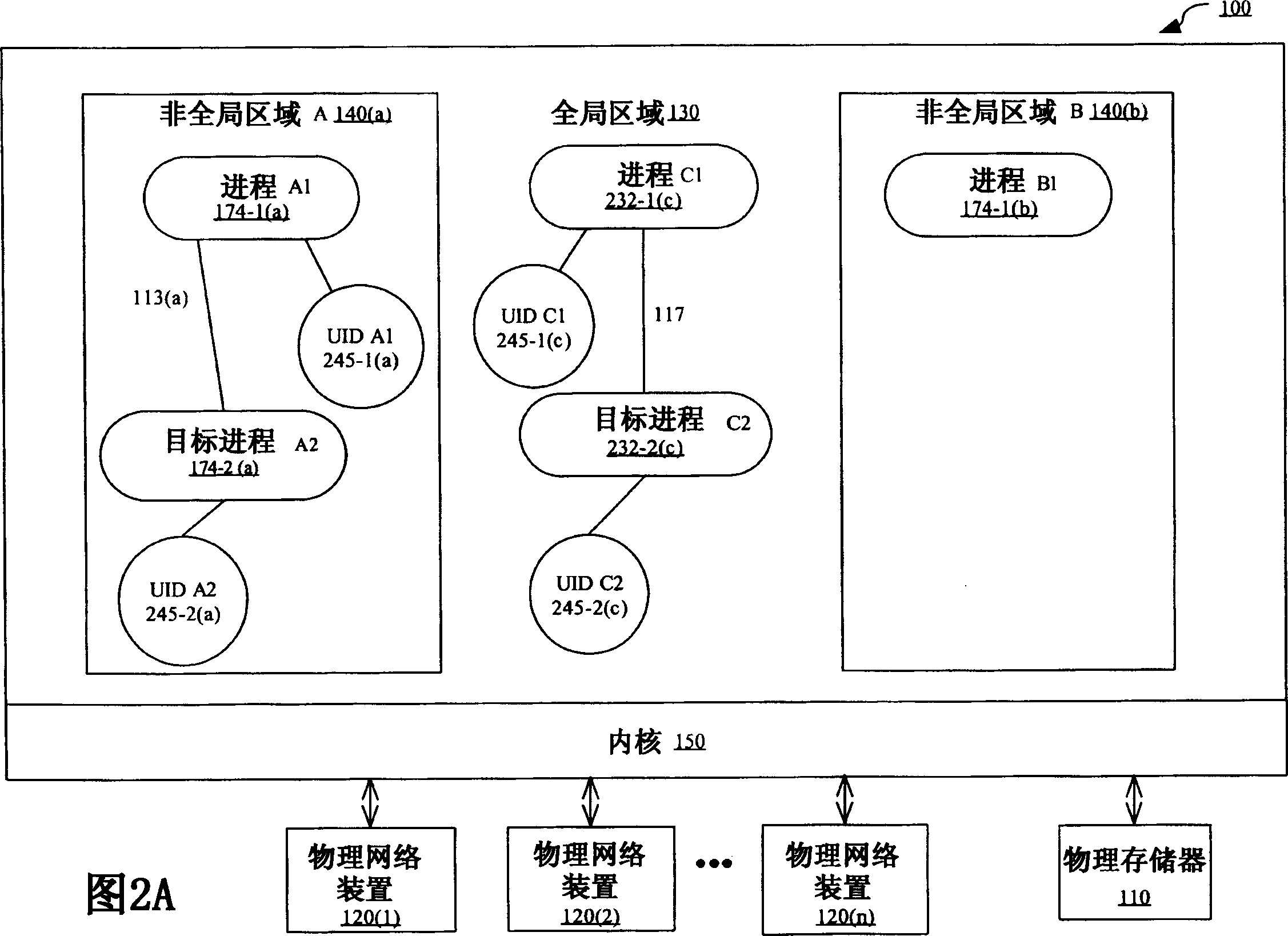
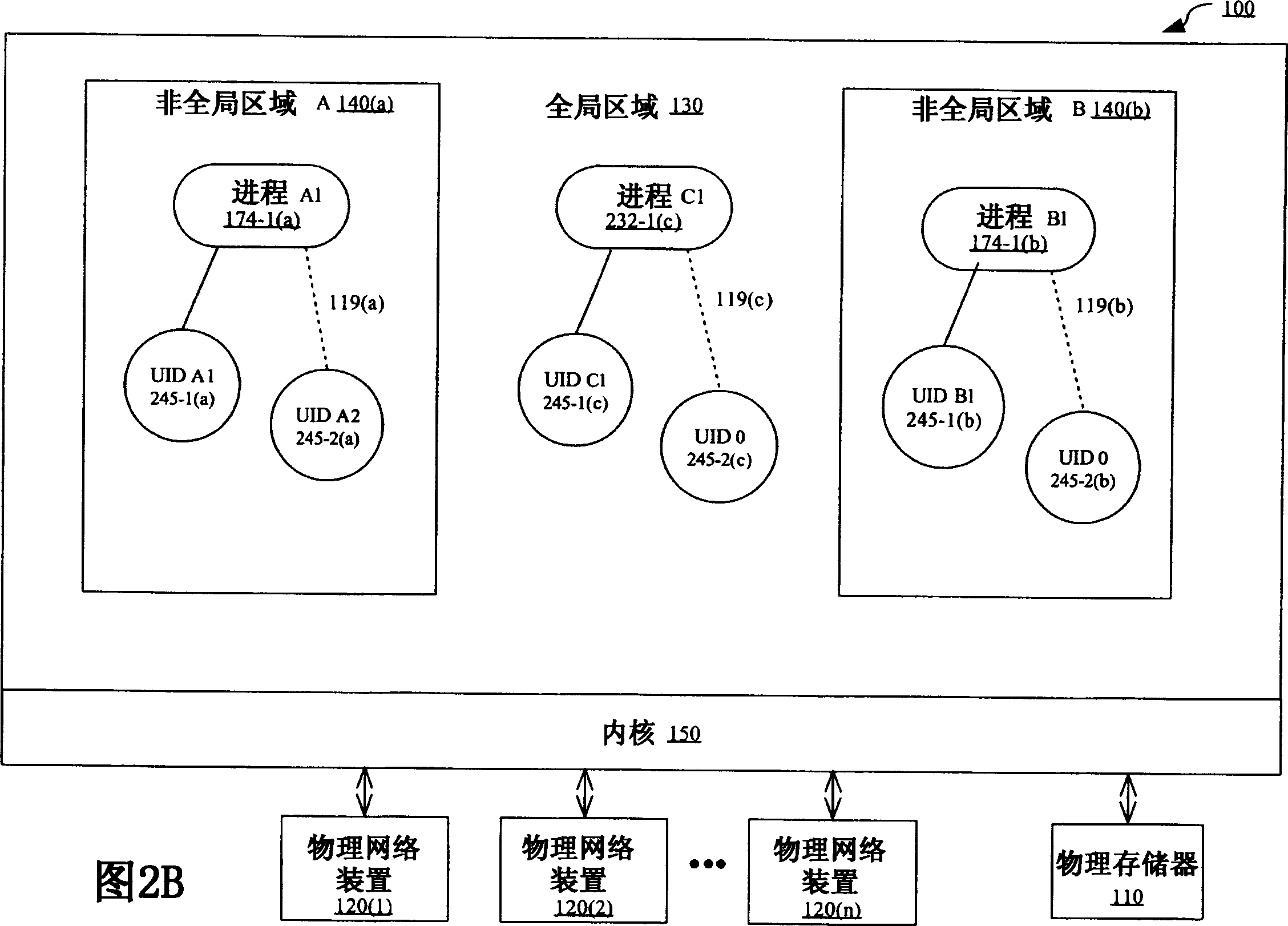
ActiveCN1595363AInterprogram communicationUnauthorized memory use protectionOperational systemUnique identifier
In this method controlling interprocess communication in a single kernel instance operating system partitioned into a global zone and one or more non-global zones, a non-global zone for separating a process from a process in another non-global zone in a global operating system environment controlled by a single kernel instance is established. In compliance with a first request, a communication object having a unique identifier matching the non-global zone of the process making the first request. In compliance with a second request, if it is determined that the process making the second request is associated with the non-global zone having a unique identifier matching that of the communication object, communication is started by using the communication object to the process making the second request.
Owner:SUN MICROSYSTEMS INC
Roll-to-roll continuous thin film PV manufacturing process and equipment with real time online IV measurement
InactiveCN102113092AFinal product manufactureVacuum evaporation coatingQuality dataAtmospheric pressure
Apparatuses and methods are provided for the continuous, roll-to-roll formation of photovoltaic (PV) cells. Apparatuses include reel-to-reel transport chambers, one or more deposition chambers, a differential process isolation unit and a chamber for obtaining real time quality data, including IV data, yield data and uniformity data.
Owner:XUNLIGHT CORPORATION
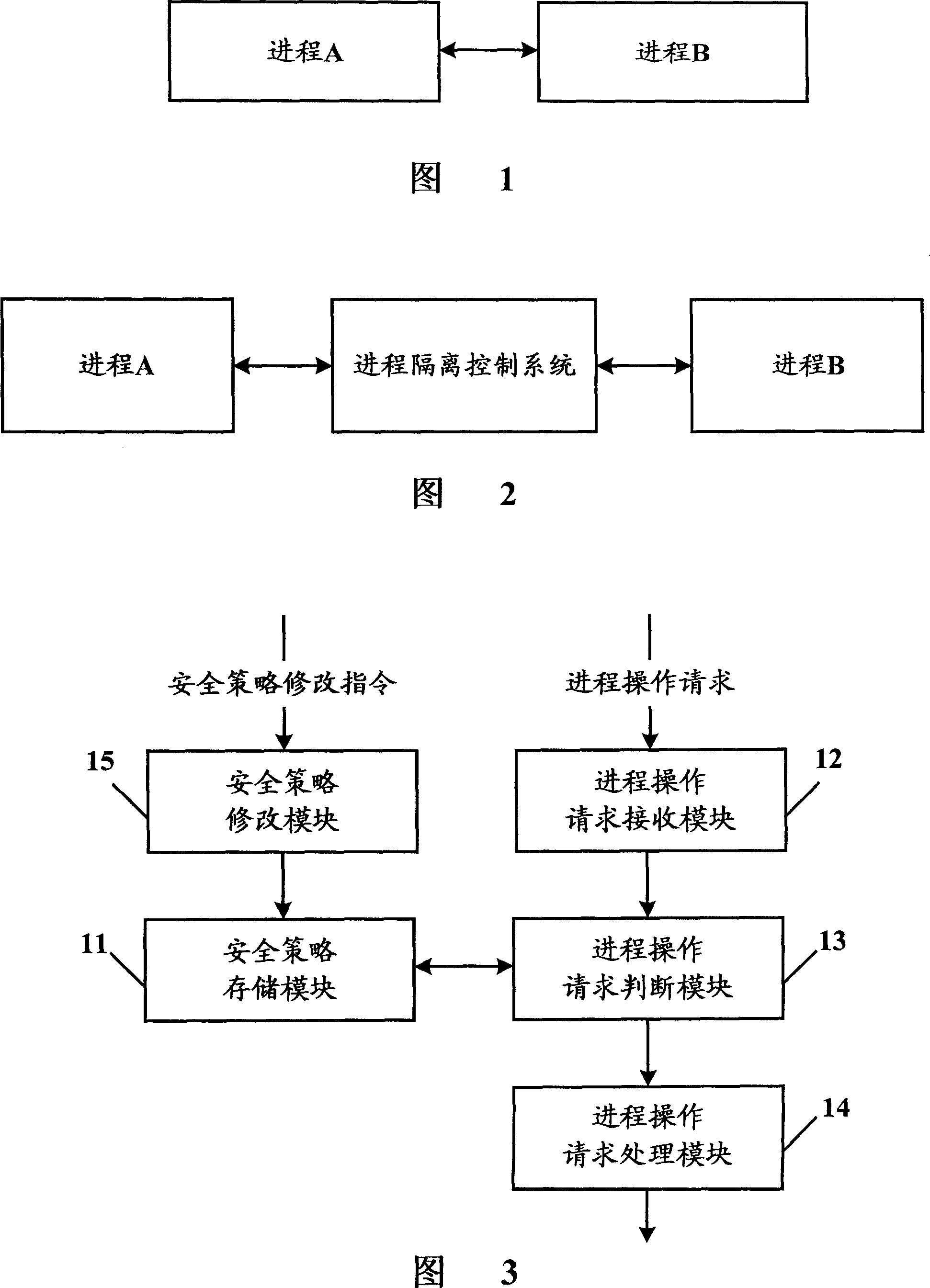
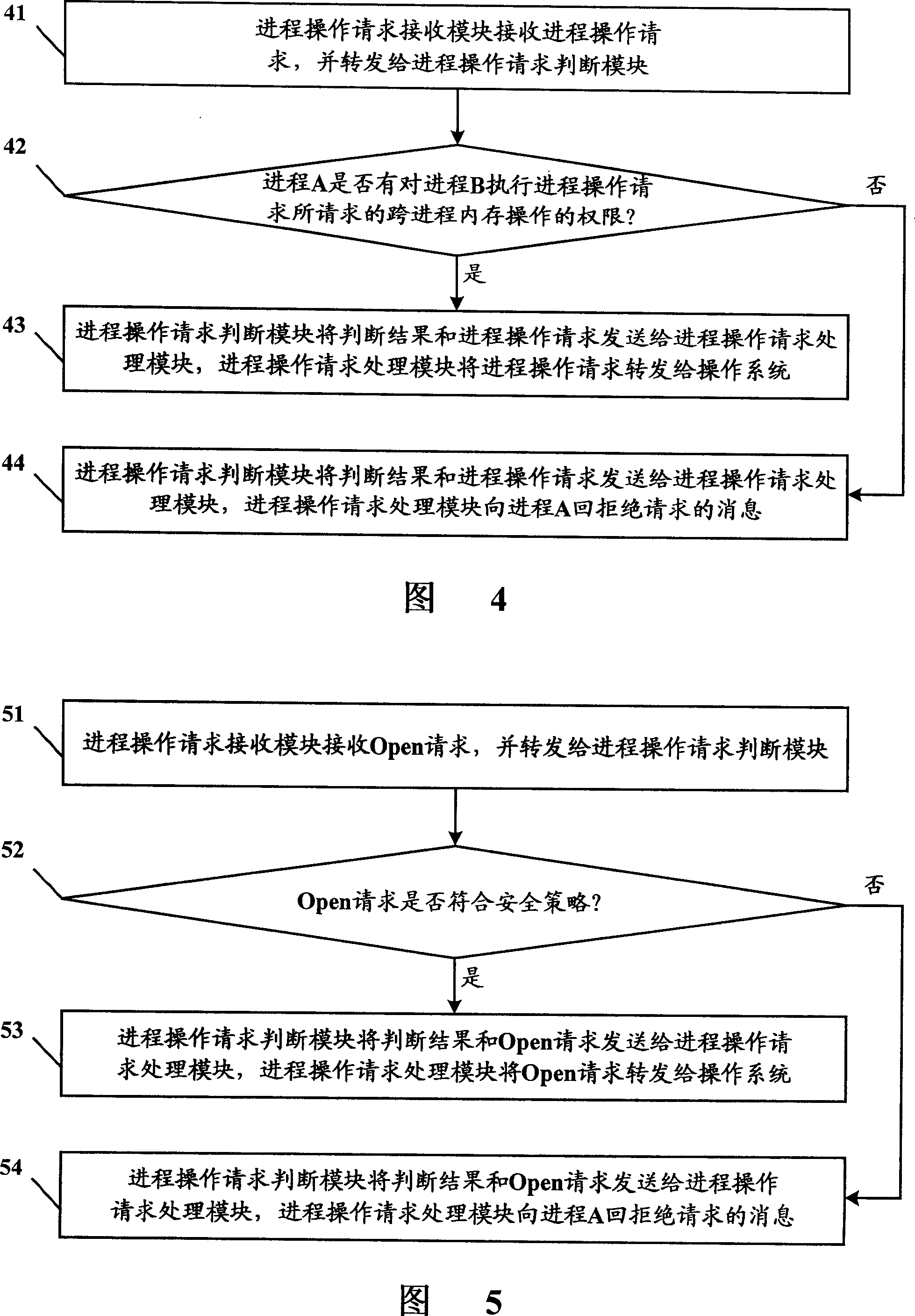
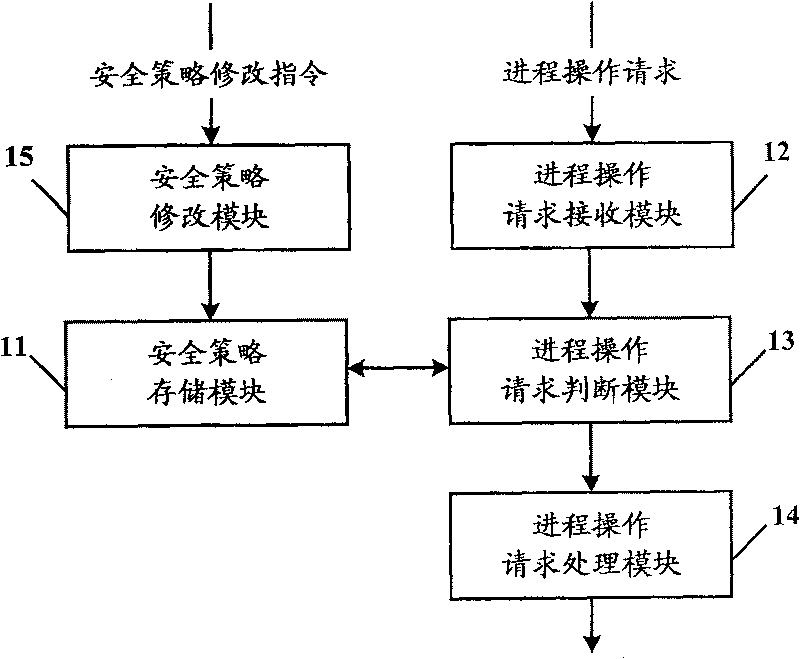
Process-isolation control system and method
ActiveCN101071388AAvoid attackReduce damageMultiprogramming arrangementsProcess memoryOperational system
The invention discloses a process control system and method of isolation. The isolation process and the process control system to connect the operating system, according to security strategy for the judge requested the operation of inter-process memory process operation whether the request meets the requirements, and in accordance with the results described in judgment request the implementation of the process of operating the corresponding treatment. The process of the application of this invention isolation and control systems and methods, only with security strategy can be requested through the process of operation, can effectively monitor the process of inter-operation between the various against unknown viruses and malicious code attacks, will all logic the process of private space protection and isolation, the use of this invention can be virus (malicious code) have reduced the extent of the damage has affected the process will not interfere with the normal operation of another process.
Owner:LENOVO (BEIJING) CO LTD
Process resource distribution method and system for operation system
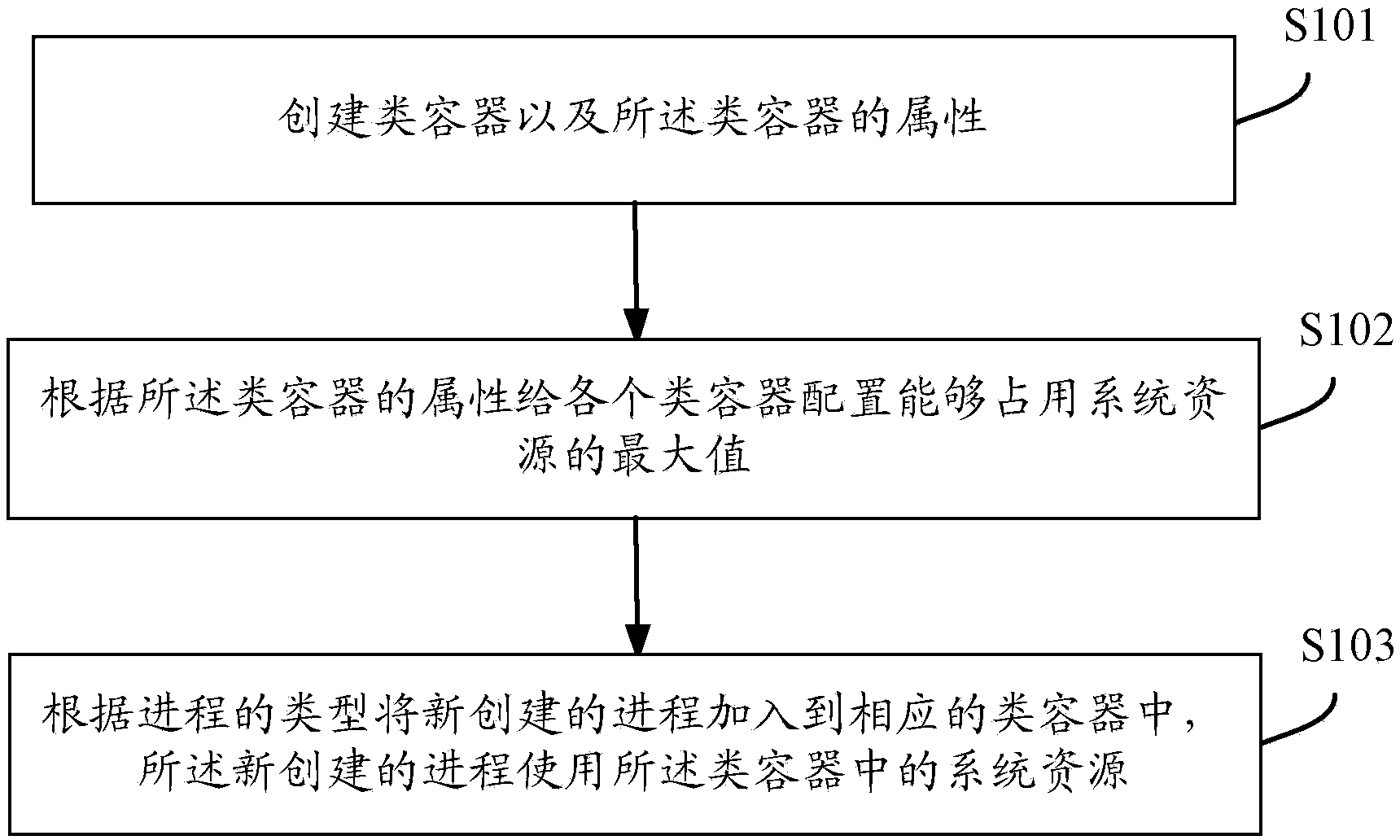
ActiveCN104268022AEfficient use ofImprove performanceResource allocationOperational systemMulti user environment
The invention discloses a process resource distribution method and system for an operation system. The method comprises the following steps: creating like containers and the properties of the like container; configuring the maximum usable system resource value to each like container according to the properties of the like containers; adding the new created process to the corresponding like container according to the type of the process, wherein the new created process can use the system resource in each like container. According to the method and system, the like containers and the processes are classified to separate the processes of different types, thus the processes of the same type can share the resources of the like containers of the same type, and as a result, the system resource can be utilized well and shared to the maximum, and the efficiency of the whole system can be raised; in addition, the process customized by the user is allowed, the user processes are classified, and a multi-user environment and various application programs are supported in the system.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
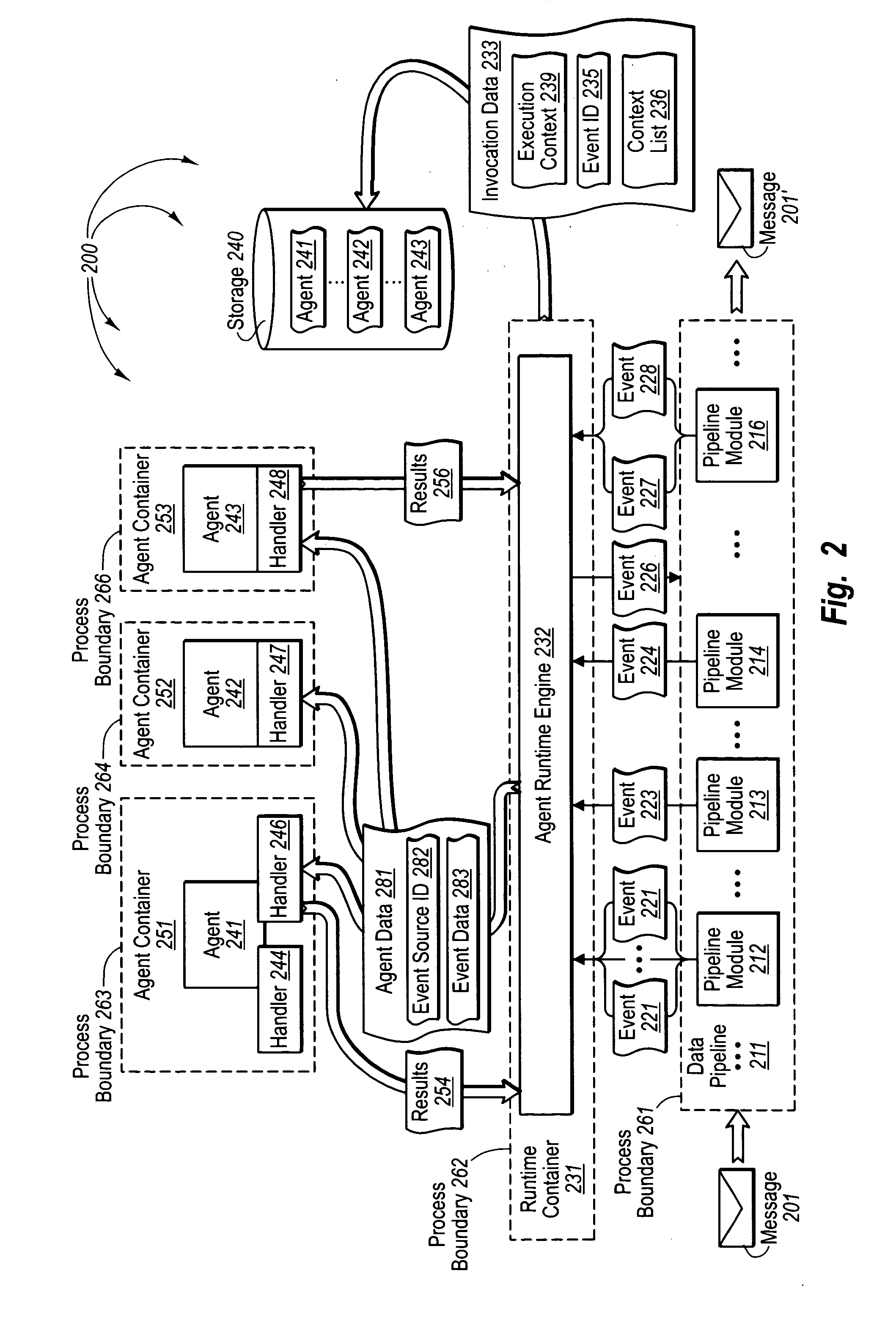
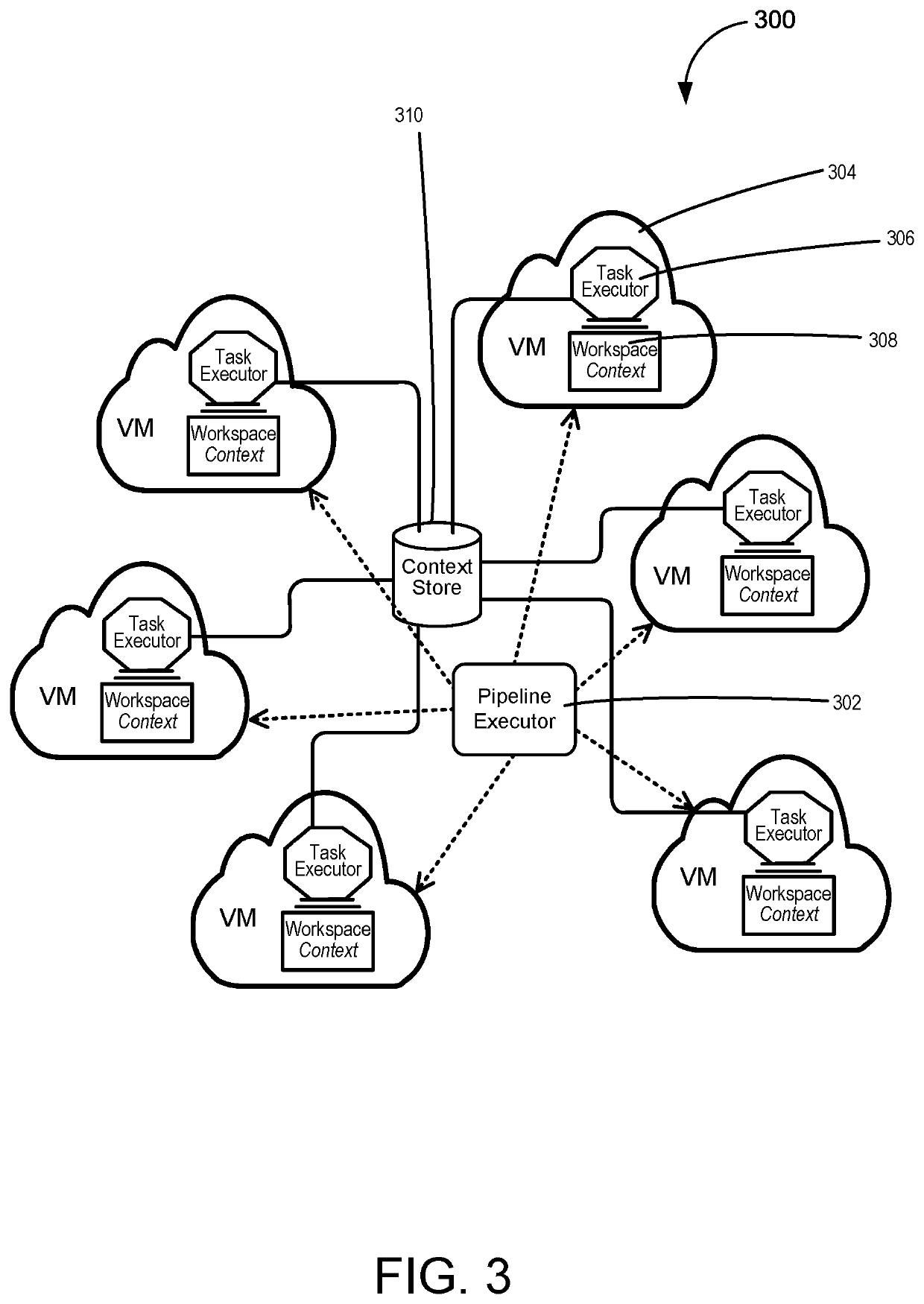
Persistent context for reusable pipeline components
Techniques are provided for managing and isolating build process pipelines. The system can encapsulate all the information needed for each build process step in a build context structure, which may be accessible to the build process step. Each build process step can receive input from the build context, and can generate a child build context as output. Accordingly, the build pipeline may be parallelized, duplicated, and / or virtualized securely and automatically, and the build context can carry, organize, and isolate data for each task. The build context from each step can also be stored and subsequently inspected, e.g. for problem-solving. A computing device can execute a first build step configured to generate the build context including a plurality of output objects. The computing device further executes a second build step based on the build context, which is accessible to the second build step but isolated from other processes.
Owner:ORACLE INT CORP
Fine grain privileges in an operating system
ActiveCN1584843AAccess controlSpecific access rightsProgram initiation/switchingModel managementOperational system
In one embodiment, the present invention provides techniques for managing activities of processes using a fine grained privilege model in an operating system environment partitioned into a global zone and one or more non-global zones for isolating processes from processes executing in association with other non-global zones under control of a single operating kernel instance.
Owner:SUN MICROSYSTEMS INC
Test executive with external process isolation for user code modules
A system and method for isolating execution of user-supplied code modules that are called by steps of a test executive sequence. The test executive sequence may first be created by including a plurality of test executive steps in the test executive sequence and configuring at least a subset of the steps to call user-supplied code modules. The test executive sequence may then be executed on a host computer under control of a test executive engine. For each step that calls a user-supplied code module, the test executive engine may invoke the user-supplied code module for execution in a separate process other than the process in which the test executive engine executes.
Owner:NATIONAL INSTRUMENTS
Roll-to-roll continuous thin film PV manufacturing process and equipment with real time online IV measurement
Owner:XUNLIGHT CORPORATION
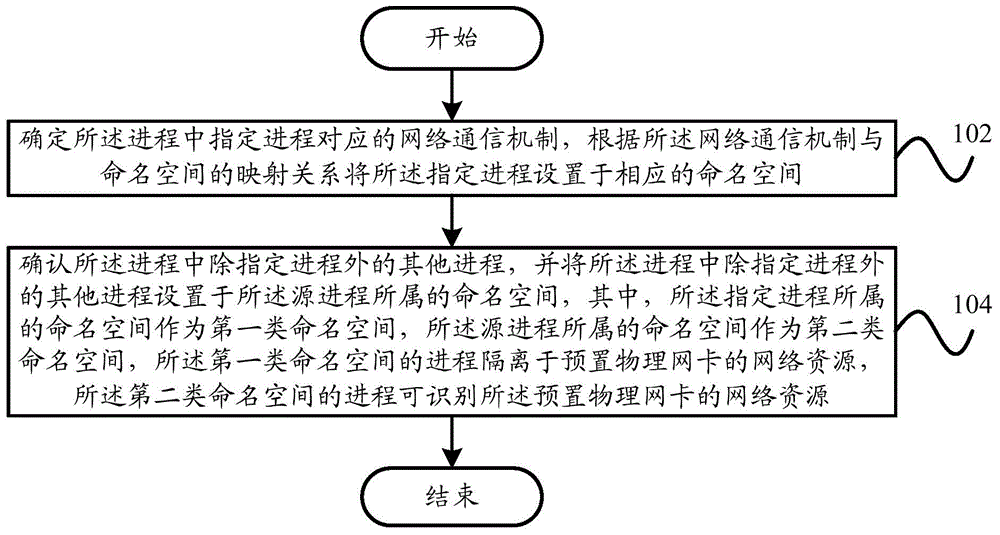
Network resource isolation method, network resource isolation system and mobile terminal
InactiveCN105187423AAchieve isolationMeet differentiated needsTransmissionResource isolationNetwork communication
The invention discloses a network resource isolation method, a network resource isolation system and a mobile terminal. The network resource isolation method comprises steps of determining a network communication mechanism corresponding to an appointed process, arranging the appointed process in a corresponding namespace according to the mapping relation between the network communication mechanism and the namespace, determining the other processes except the appointed process in the process, wherein the namespace that the appointed process belongs to is used as a first kind namespace, the namespace that a source process belongs to is used as a second kind namespace, the process of the first kind namespace is isolated from the network resource of a preset physical network and the process of the second kind namespace can recognize the network resource of the preset physic network. The invention can realize the isolation networking mode of the process on the mobile terminal so as to realize the data safety of the terminal user.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
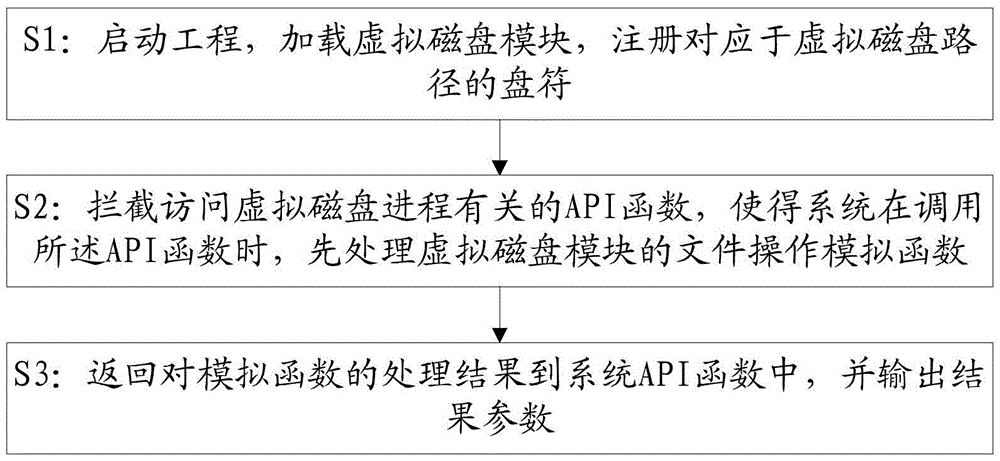
Method and system for accessing to virtual disk
ActiveCN105550582AImprove securityImplement process isolationPlatform integrity maintainanceComputer moduleSoftware engineering
The invention discloses a method and system for accessing to a virtual disk. The method comprises the following steps: starting a project, loading a virtual disk module, and registering a drive corresponding to a virtual disk path; intercepting to access an API function related to a virtual disk process to ensure that the system firstly process a file operation analogue function of the virtual disk module when calling the API function; and returning the analogue function processing result to a system API function and outputting result parameters. Through the manner, the data required for normal access can be integrated and process isolation can be realized at the same time, so that the safety of the virtual disk is improved.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
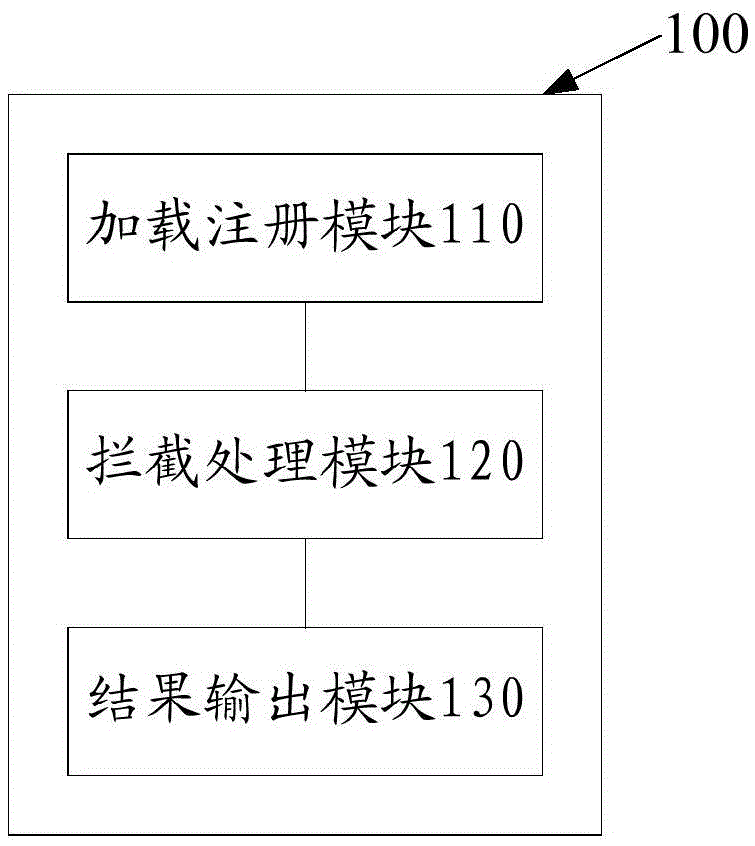
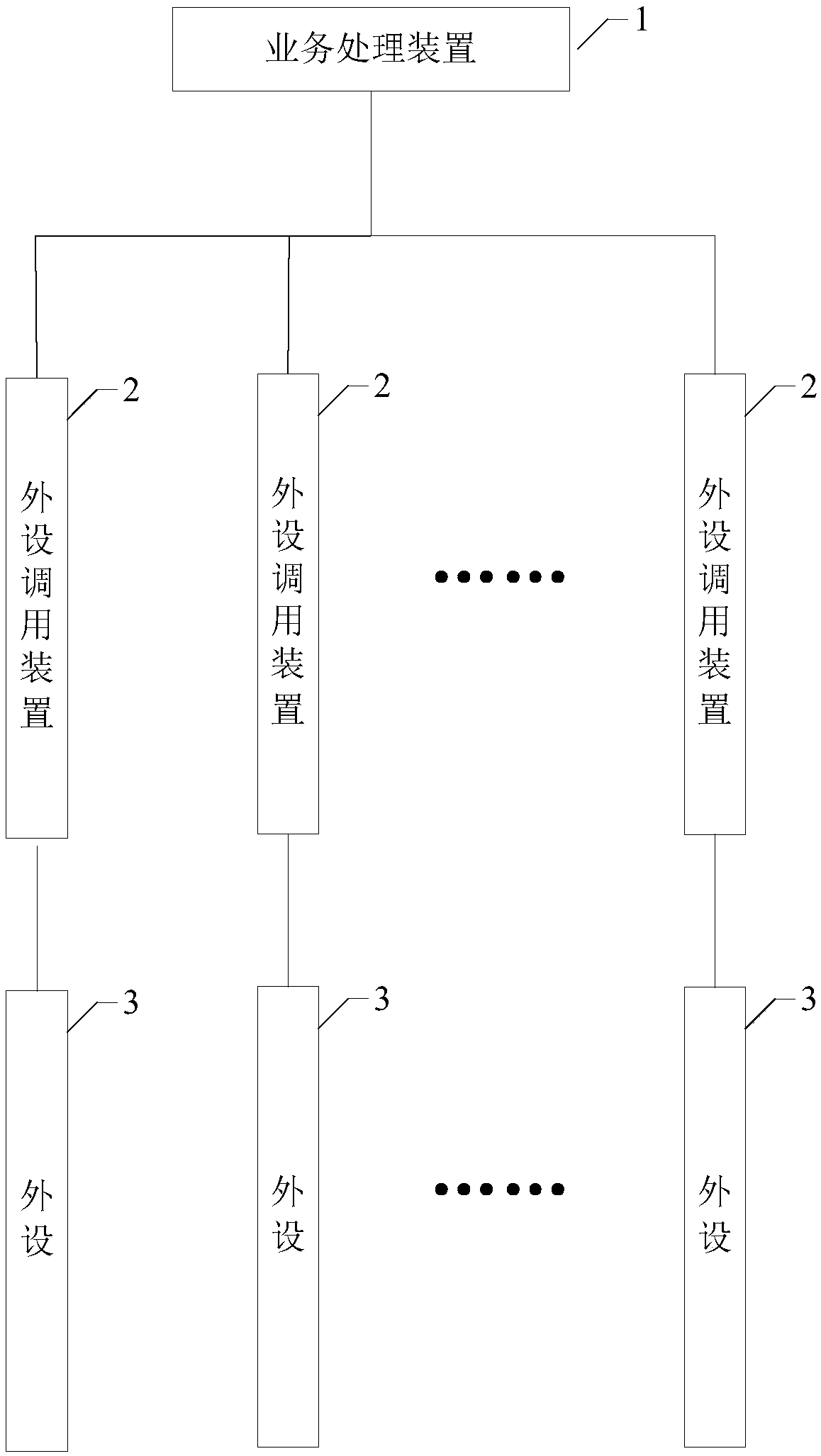
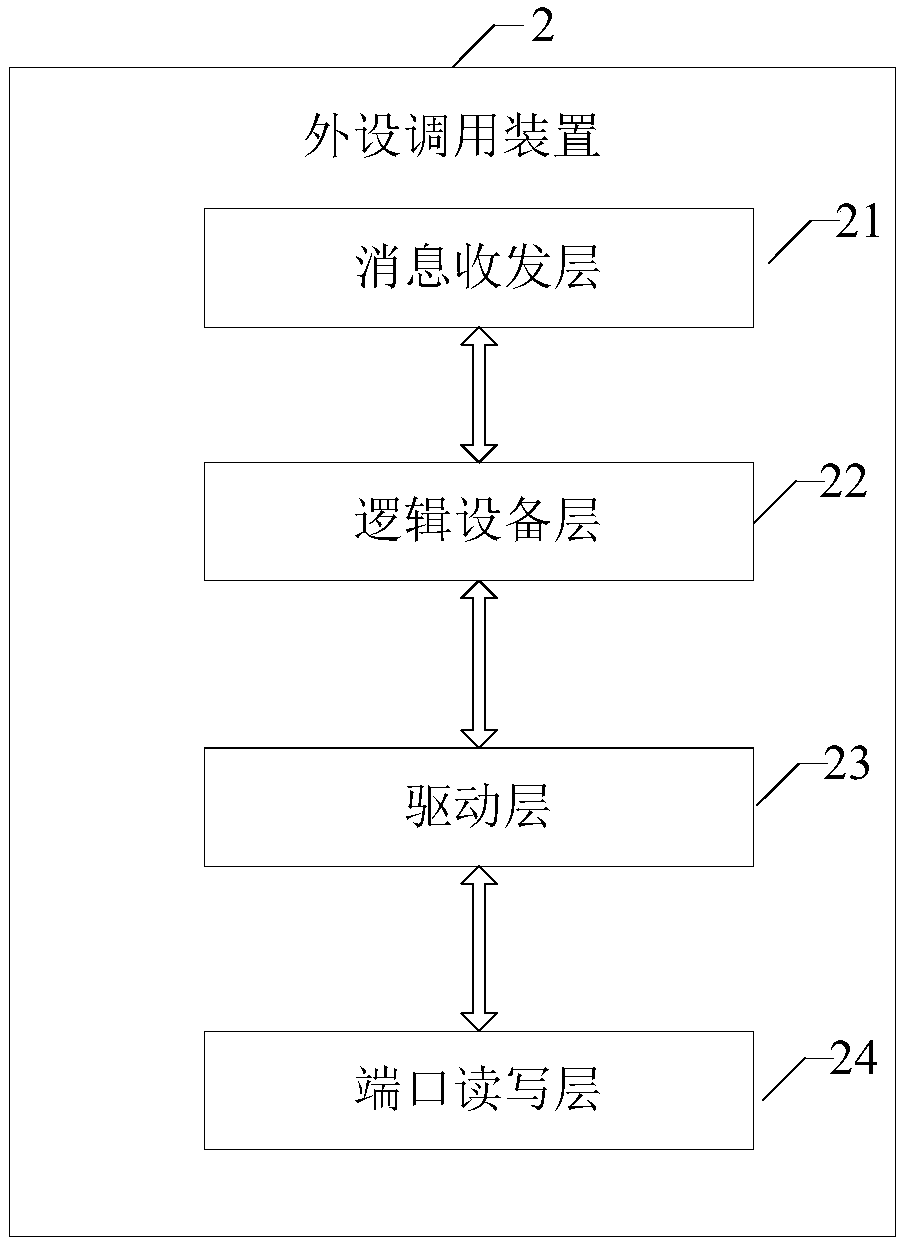
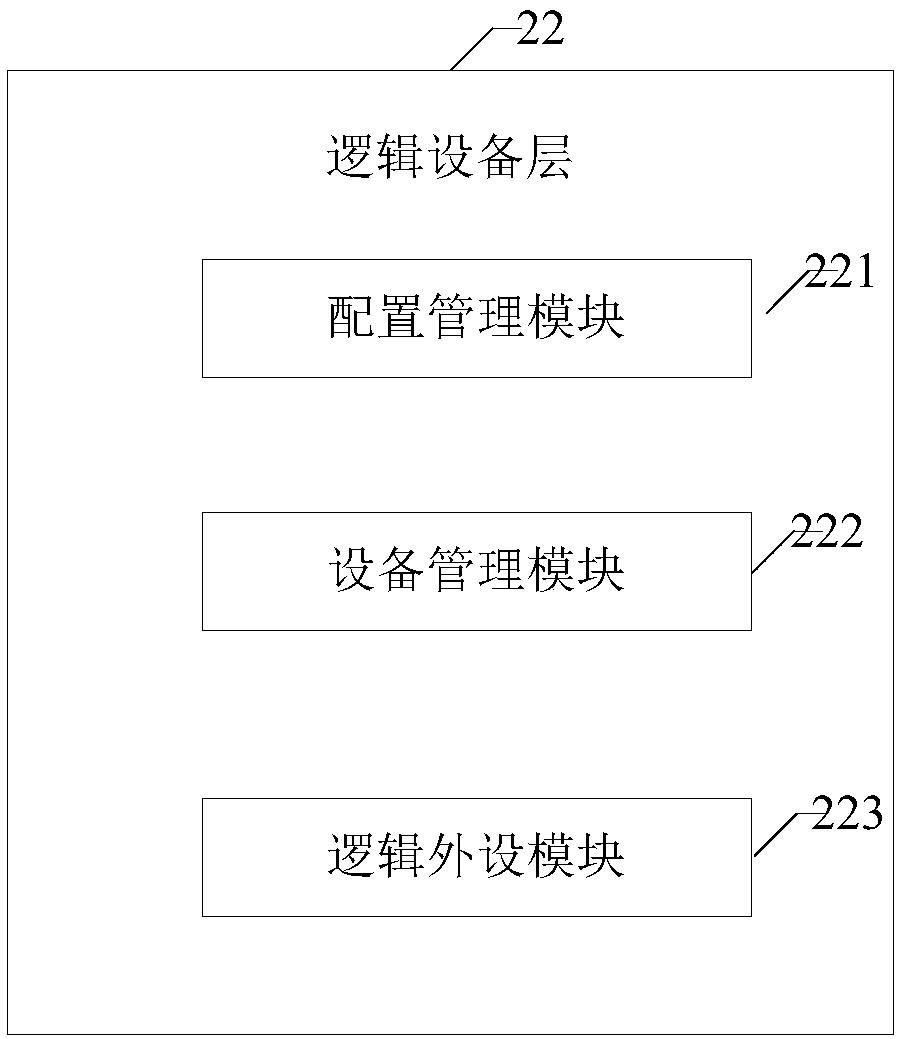
Centralized calling method and system of peripheral equipment and peripheral equipment calling devices
InactiveCN108255757AImprove securityImplement process isolationBootstrappingComputer terminalCentralized management
The invention provides a centralized calling method and system of peripheral equipment and peripheral equipment calling devices, and relates to the technical field of counter terminals. The method comprises the steps that a business processing device sends a peripheral equipment calling message, a message transceiving layer analyzes the peripheral equipment calling message to obtain the peripheralequipment type and the operation type corresponding to the peripheral equipment calling message, when a logic equipment layer judges that peripheral equipment corresponding to the peripheral equipment type is in an idle state, the operation type is sent to a driving layer; the driving layer converts the peripheral equipment calling message into an information format which can be identified by theperipheral equipment corresponding to the peripheral equipment type according to the peripheral equipment type and the operating type, and the information format is sent to the peripheral equipment corresponding to the peripheral equipment type through a port reading-writing layer. By means of the centralized calling method and system of the peripheral equipment and the peripheral equipment calling devices, through the arrangement of the peripheral equipment calling devices, multiple sets of peripheral equipment are centralizedly managed, progress isolation of peripheral equipment operating parties and calling parties is achieved, and the safety of the calling parties is improved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
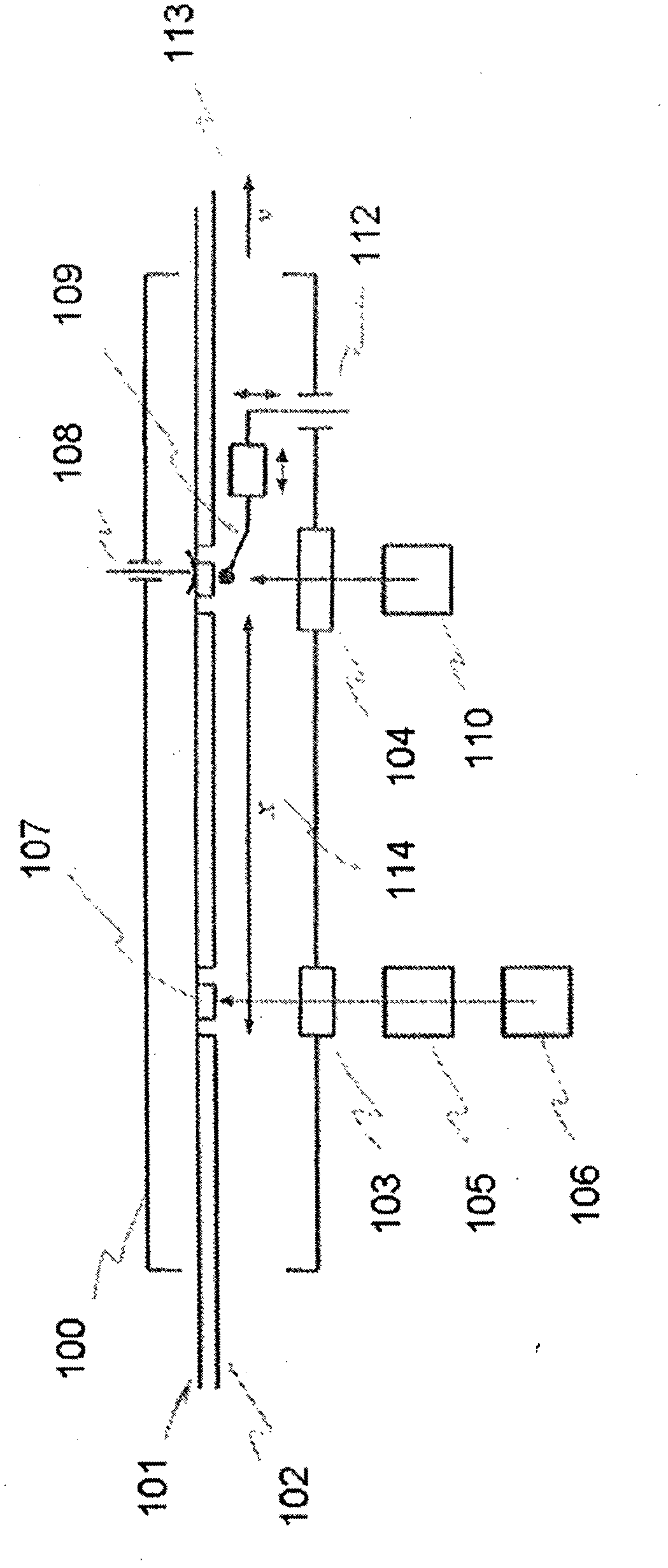
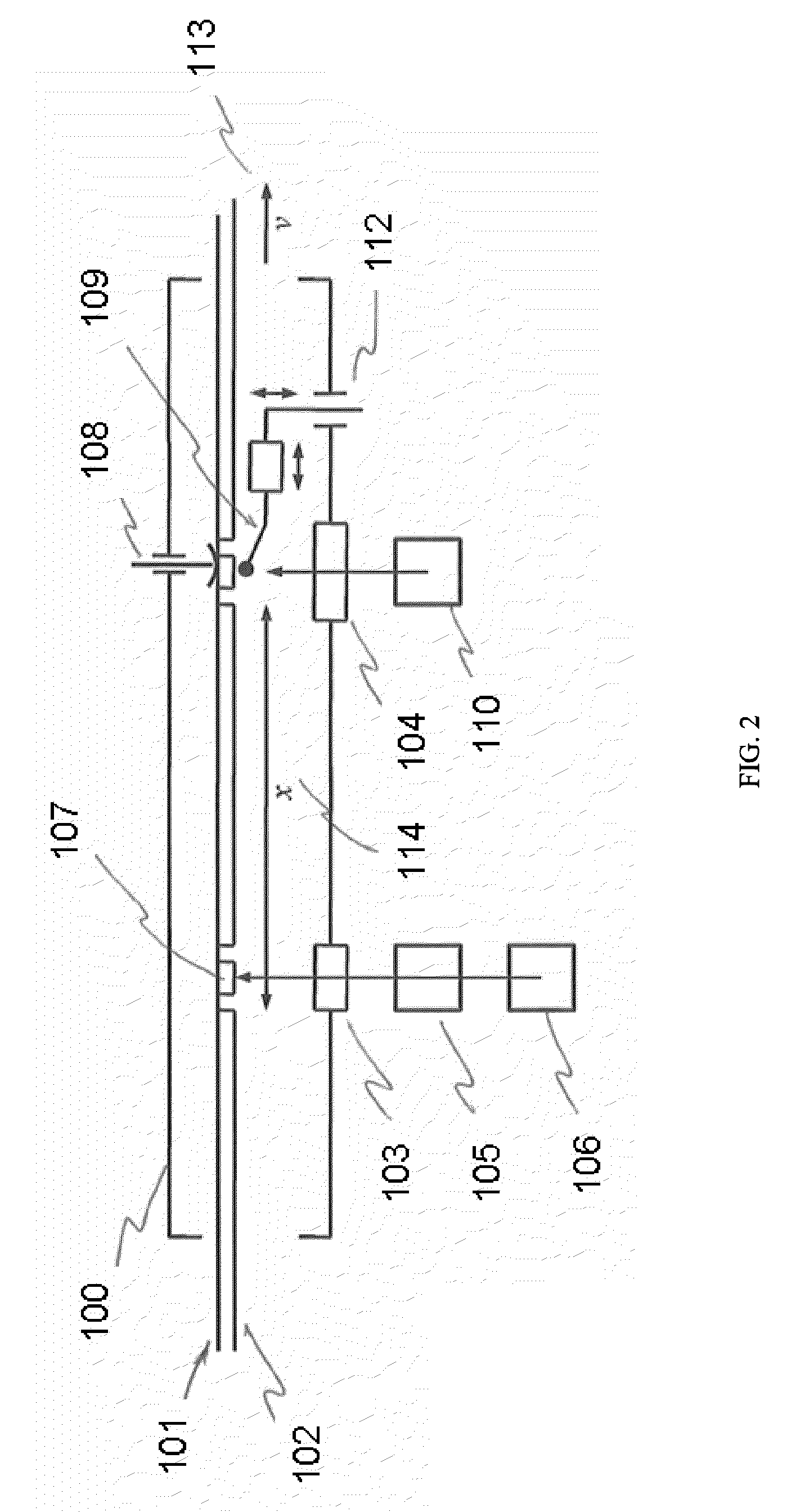
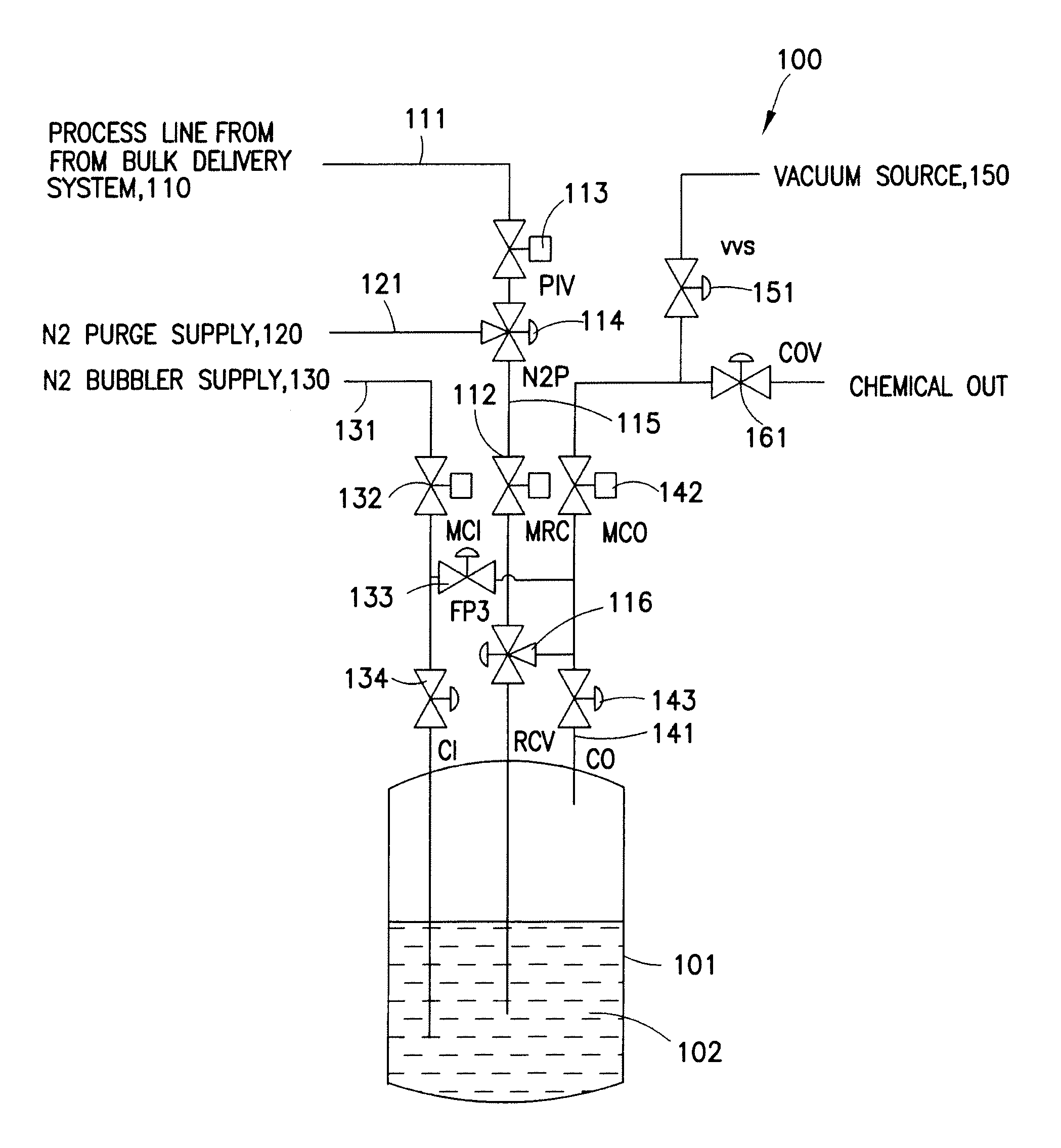
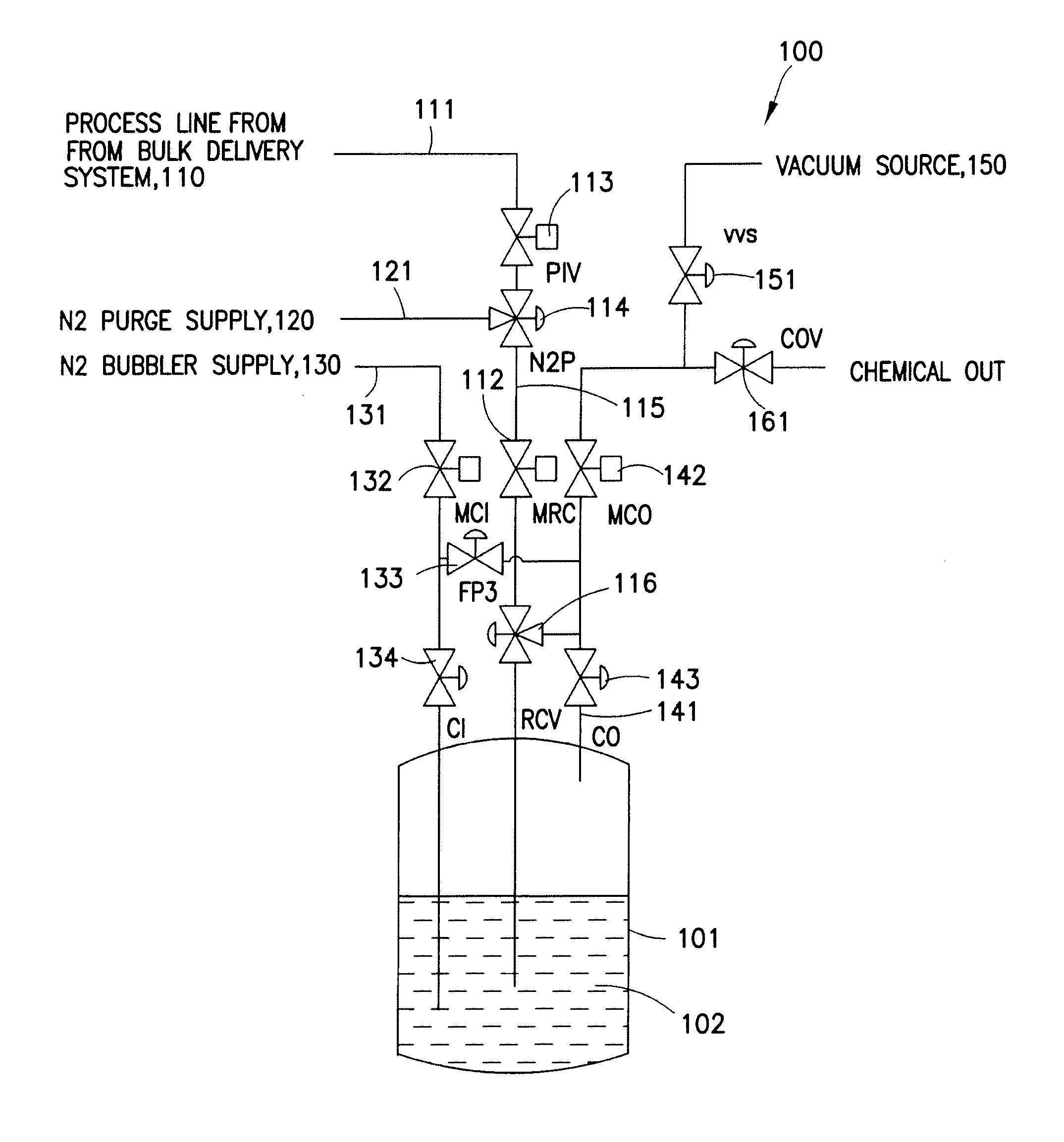
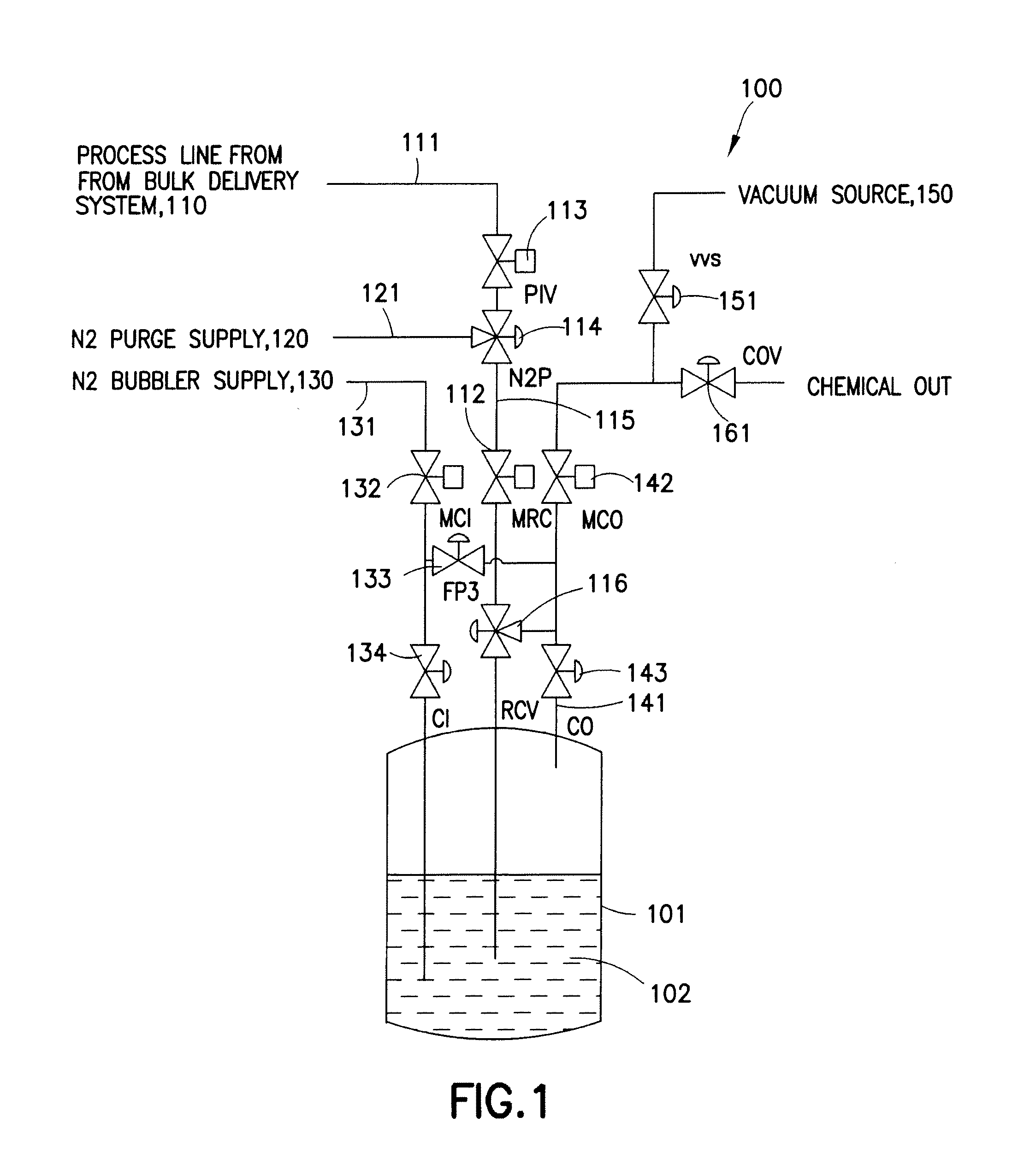
Refillable ampoule with purge capability
A fluid delivery system adapted to isolate an ampoule and / or process line during purge, including an inlet control valve connecting a source of pressurized gas to a refillable ampoule, an outlet control valve connecting the refillable ampoule to a location of use, a process control valve connecting a process line to the refillable ampoule, a process isolation valve, and a purge supply valve, e.g., a three-way purge supply valve, arranged between the process isolation valve and the process control valve. A method of purging a fluid delivery system is also disclosed, including closing a process isolation valve, connecting a process line to a refillable ampoule, supplying a purge gas through a purge supply valve, e.g., a three-way purge supply valve, and cycling open and close at least once a process control valve coupled to the process line. A manifold for use in refilling an ampoule and purging a fluid supply system is also described.
Owner:ENTEGRIS INC
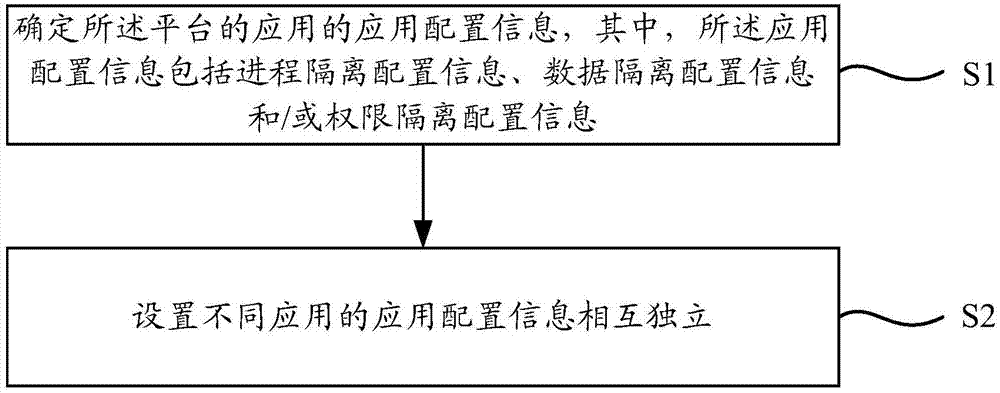
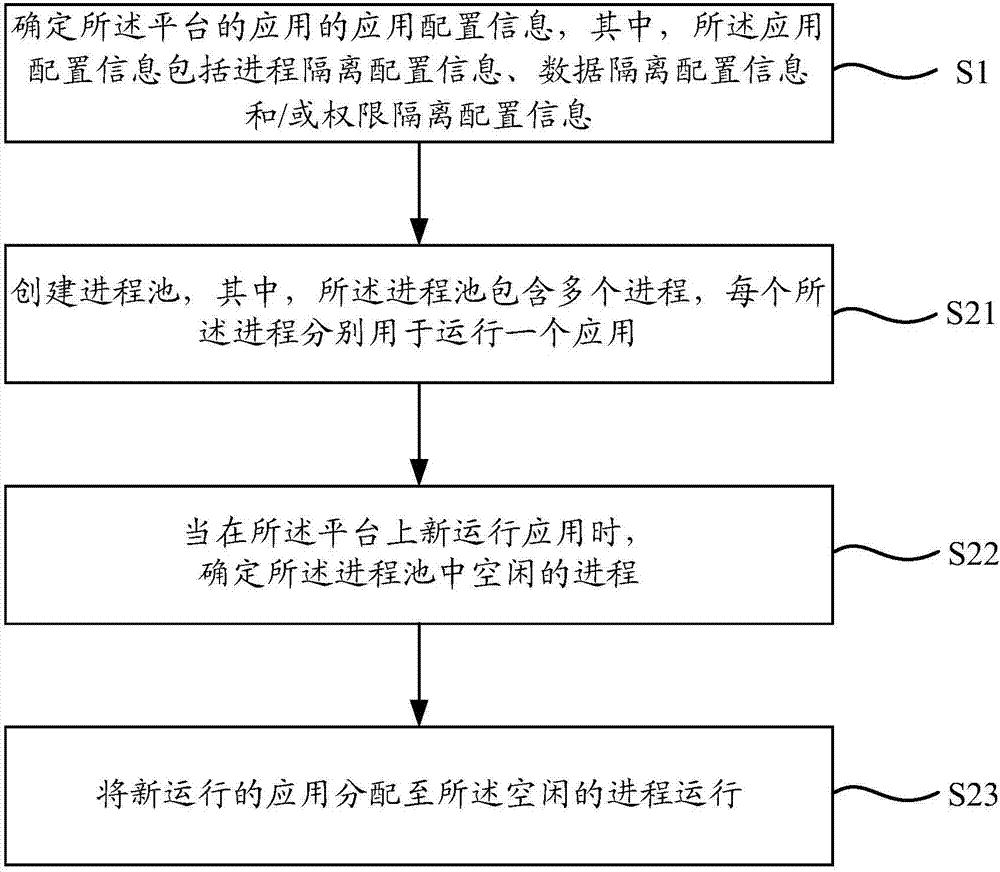
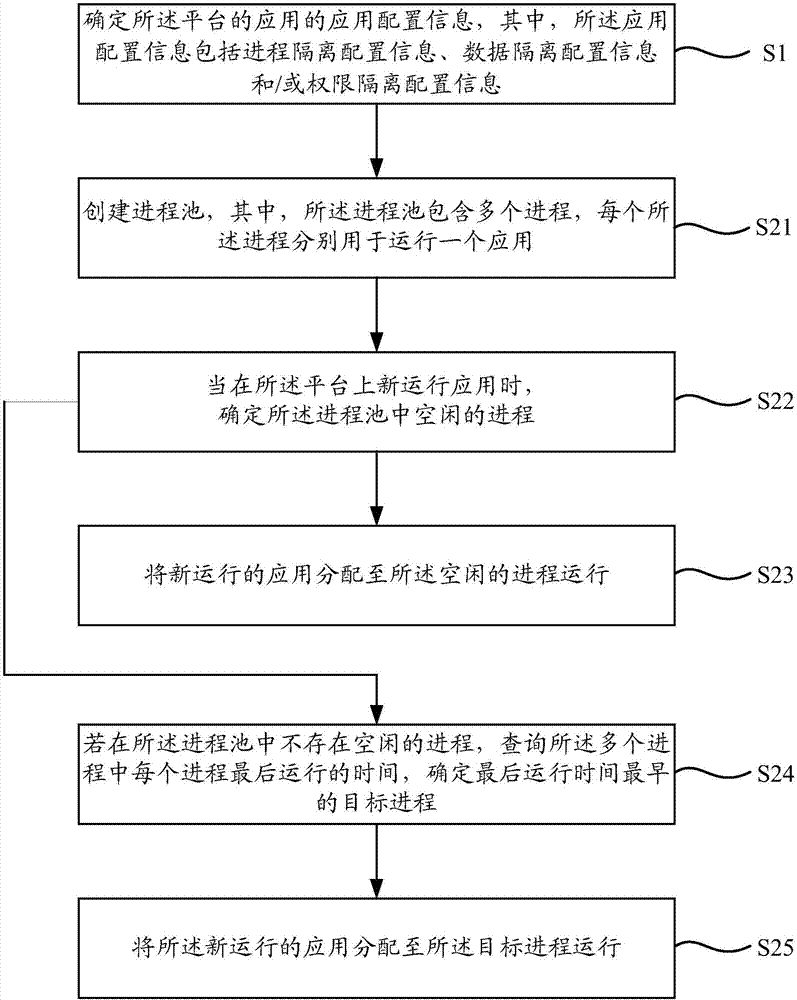
Application management method and application management apparatus
ActiveCN107402784AOrderly and stable operationIndependent assuranceProgram initiation/switchingProgram loading/initiatingSoftware engineeringDatabase
The invention relates to an application management method and an application management apparatus. The application management method is suitable for a platform. The application management method comprises the steps of determining application configuration information of applications of the platform, wherein the application configuration information includes process isolation configuration information, data isolation configuration information and / or permission isolation configuration information; and setting the application configuration information of different applications to be independent mutually. According to the application management method and apparatus, by setting the application configuration information of the different applications of the platform to be independent, different application configuration information of the different applications can be ensured to be independent, so that the interference among the different applications is avoided and the different applications are ensured to run orderly and stably.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Process-isolation control system and method
ActiveCN101071388BAvoid attackReduce damageMultiprogramming arrangementsOperational systemProcess memory
The invention discloses a process control system and method of isolation. The isolation process and the process control system to connect the operating system, according to security strategy for the judge requested the operation of inter-process memory process operation whether the request meets the requirements, and in accordance with the results described in judgment request the implementation of the process of operating the corresponding treatment. The process of the application of this invention isolation and control systems and methods, only with security strategy can be requested throughthe process of operation, can effectively monitor the process of inter-operation between the various against unknown viruses and malicious code attacks, will all logic the process of private space protection and isolation, the use of this invention can be virus (malicious code) have reduced the extent of the damage has affected the process will not interfere with the normal operation of another process.
Owner:LENOVO (BEIJING) LTD
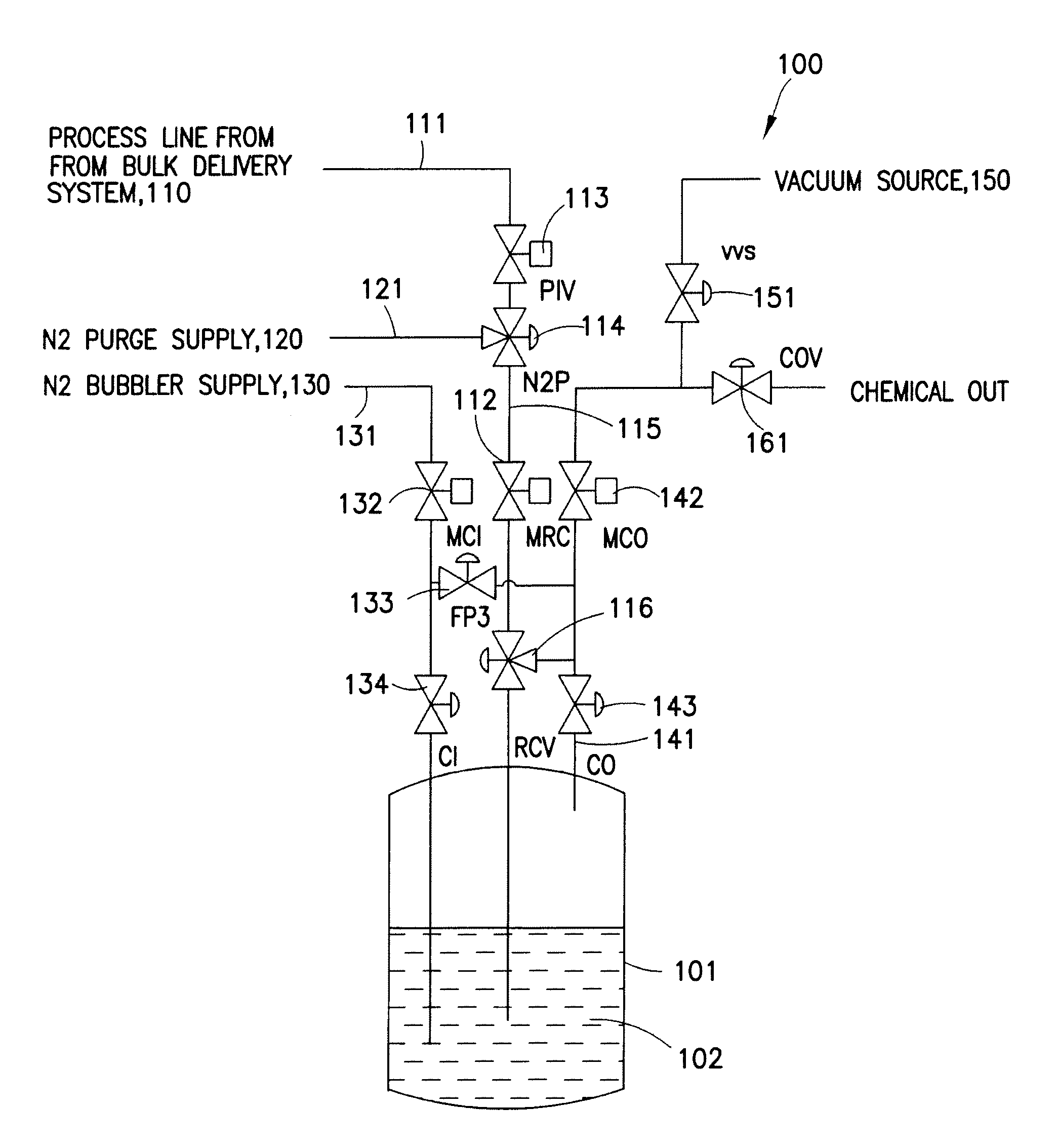
Refillable ampoule with purge capability
A fluid delivery system adapted to isolate an ampoule and / or process line during purge, including an inlet control valve connecting a source of pressurized gas to a refillable ampoule, an outlet control valve connecting the refillable ampoule to a location of use, a process control valve connecting a process line to the refillable ampoule, a process isolation valve, and a purge supply valve, e.g., a three-way purge supply valve, arranged between the process isolation valve and the process control valve. A method of purging a fluid delivery system is also disclosed, including closing a process isolation valve, connecting a process line to a refillable ampoule, supplying a purge gas through a purge supply valve, e.g., a three-way purge supply valve, and cycling open and close at least once a process control valve coupled to the process line. A manifold for use in refilling an ampoule and purging a fluid supply system is also described.
Owner:ENTEGRIS INC
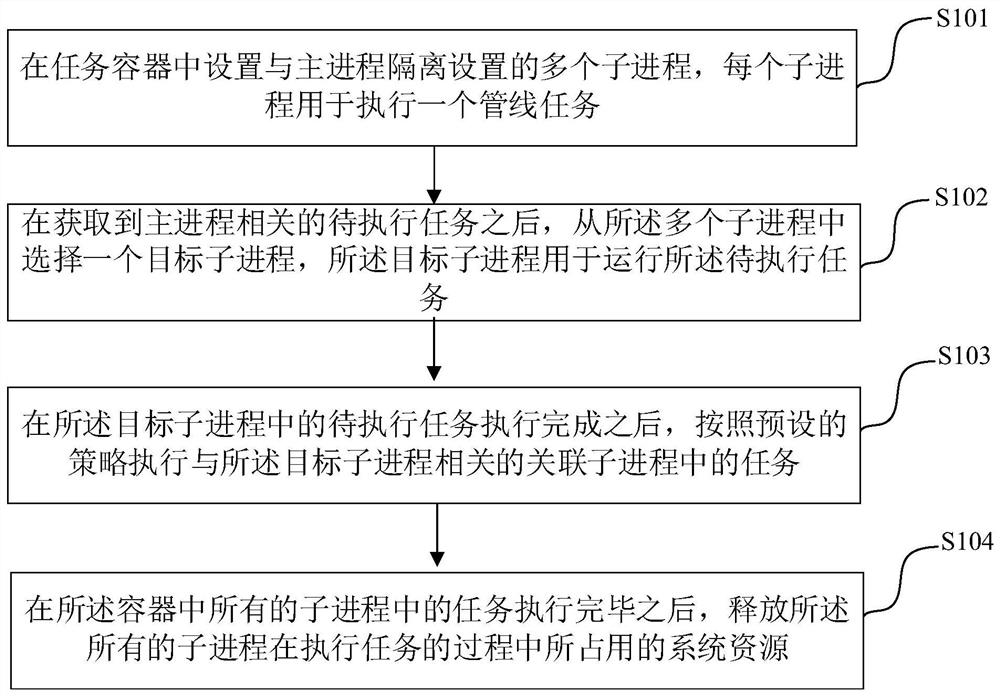
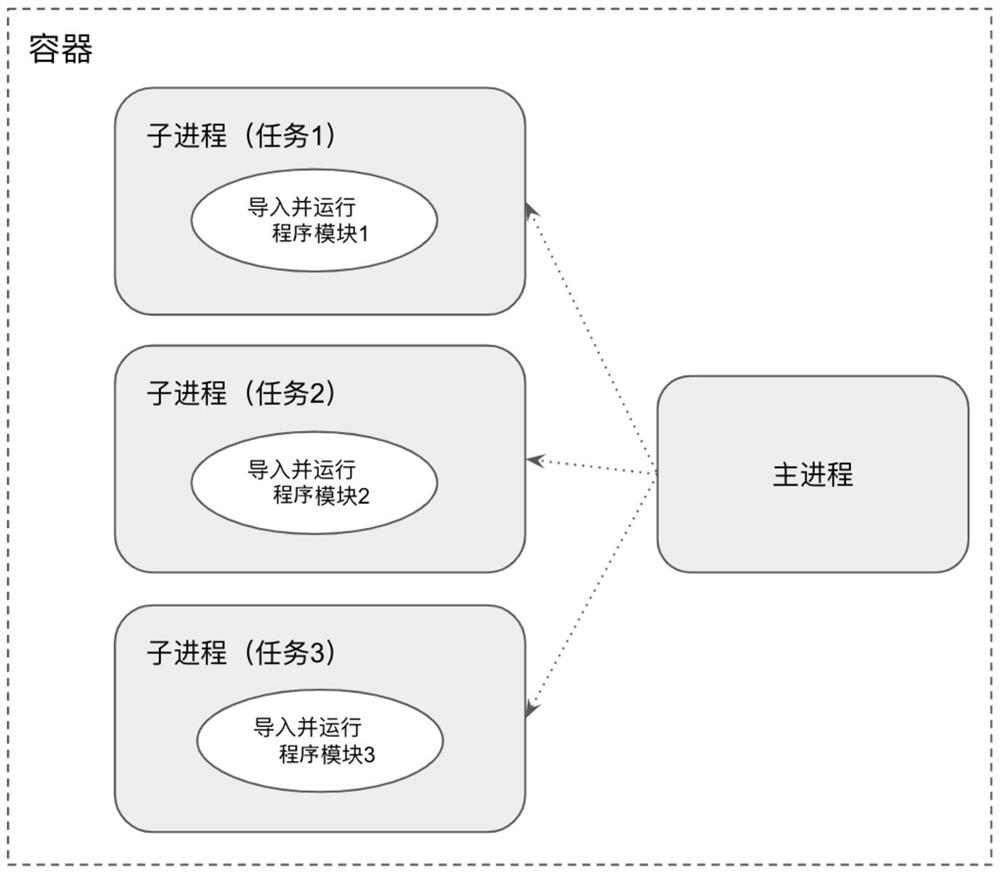
Task pipeline execution method and device and electronic equipment
ActiveCN111625326AImprove execution efficiencySave system resourcesProgram initiation/switchingResource allocationProcess engineeringProcessing
Embodiments of the invention provide a task pipeline execution method and device, and electronic equipment, and belong to data scheduling. The method comprises the steps of setting a plurality of sub-processes isolated from a main process in a task container, each sub-process being used for executing a pipeline task; after a to-be-executed task related to the main process is obtained, selecting atarget sub-processd from the multiple sub-processes, wherein the target sub-process is used for running the to-be-executed task; after the to-be-executed task in the target sub-process is executed, executing a task in an associated sub-process related to the target sub-process according to a preset strategy; and after the tasks in all the sub-processes in the container are executed, releasing system resources occupied by all the sub-processes in the process of executing the tasks. Through the processing scheme disclosed by the invention, the execution efficiency of the task pipeline can be improved.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Application deployment method and device for PaaS platform, server and storage medium
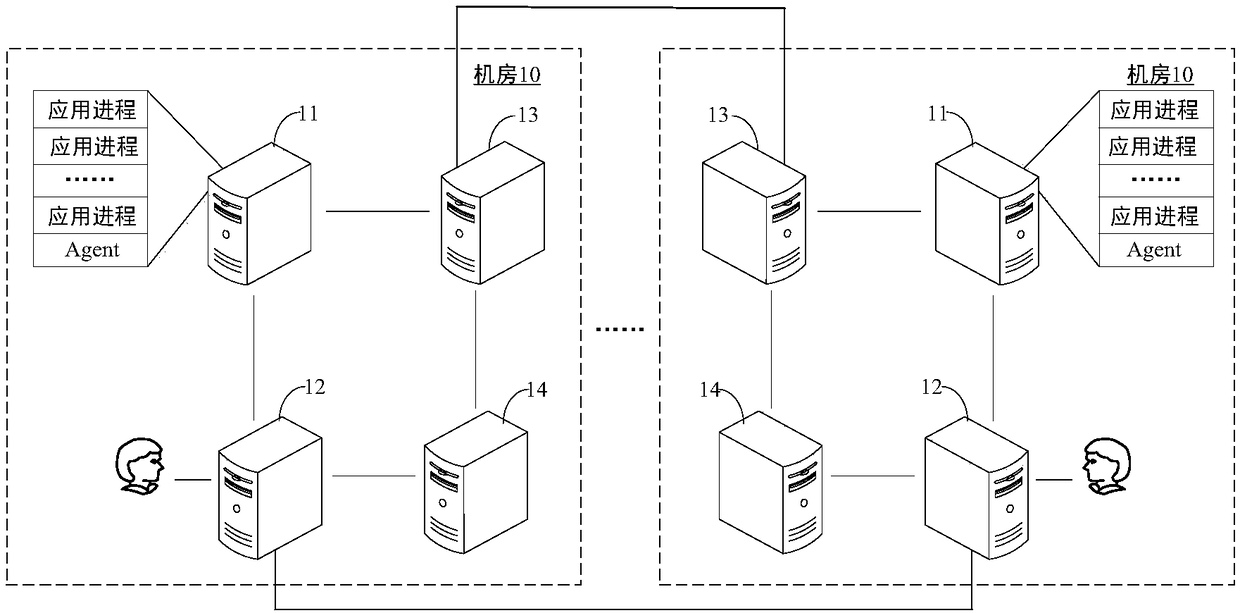
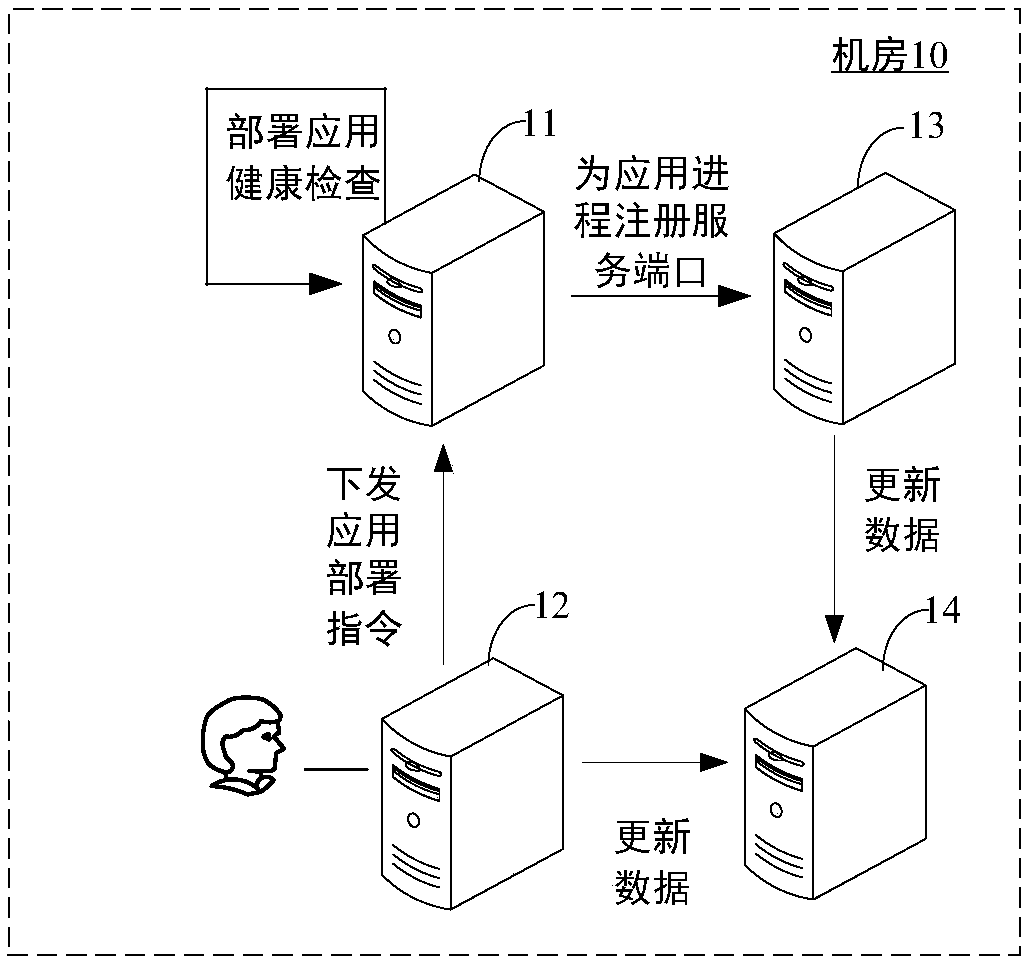
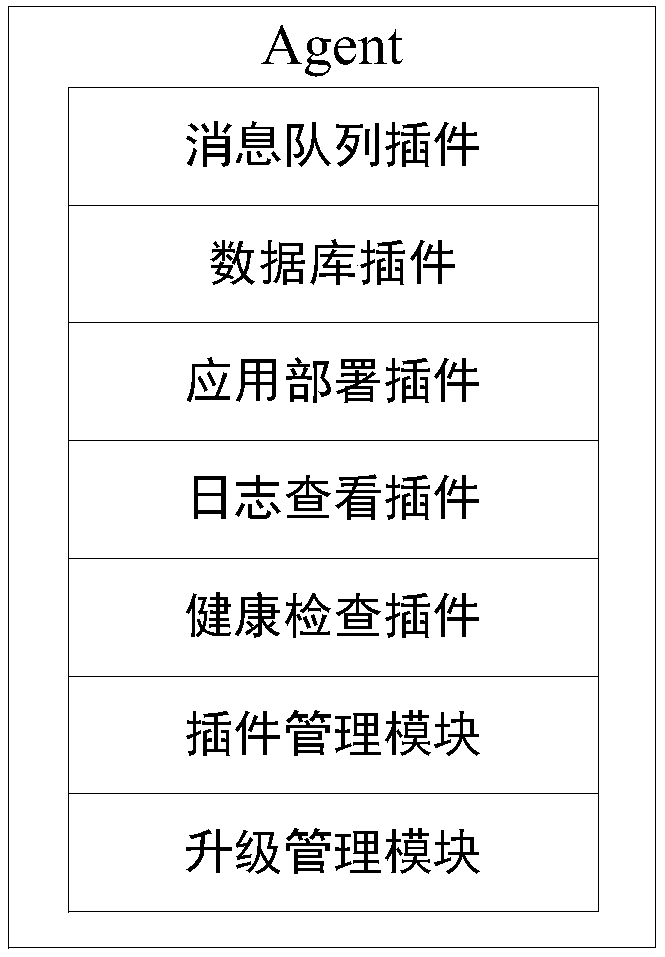
InactiveCN108566432AImplement process isolationImprove securityVersion controlTransmissionApplication serverComputer science
Embodiments of the application disclose an application deployment method and an application deployment device for a PaaS platform, a server and a storage medium, and belong to the field of PaaS platforms. The application deployment method comprises the steps of: receiving an application deployment command transmitted by a management server, wherein the application deployment command is used for indicating an application server to deploy a target application; creating a target account number and a target data directory for the target application according to the application deployment command,wherein the target account number is used for uniquely identifying the target application, the target data directory comprises application data generated by the target application, and different applications are corresponding to different data directories; binding the target application with the target account number and the target data directory; and deploying the target application under the target account number. Through adoption of the application deployment method in the embodiment, different account numbers are distributed to different applications, thus process isolation among the different applications in the same application server is achieved, and data isolation among the different applications in the same application server is also achieved, thereby improving security of the applications in the PaaS platform.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com