Process-isolation control system and method
A process isolation and control system technology, applied in the direction of multi-programming devices, etc., can solve the problems of attacks, interfere with the process, cannot guarantee the security of the operating environment, etc., and achieve the effect of preventing attacks and reducing the degree of damage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] In the embodiment of the present invention, two processes (process A and process B) are taken as an example for illustration.
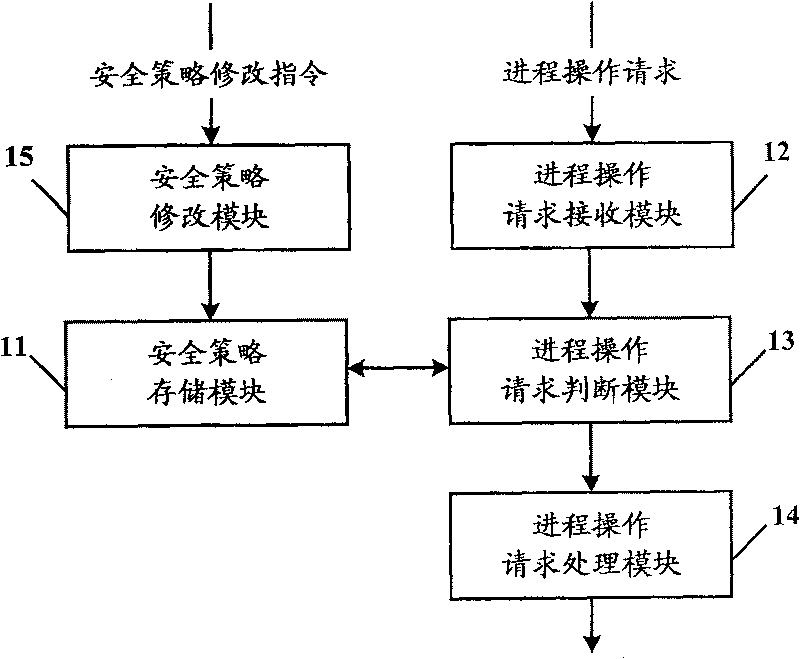
[0033] like figure 2 As shown, the process isolation control system of the present invention is connected to the system process (process A and process B), and is also connected to the operating system (not shown in the figure) at the same time, and is used to control the cross-process (process A and process B) according to the security policy. Between memory operations, such as image 3 As shown, it specifically includes a security policy storage module 11, a process operation request receiving module 12, a process operation request judging module 13, and a process operation request processing module 14, wherein:
[0034] The security policy storage module 11 is used to store a security policy, and the security policy is used to determine whether the first process has the authority to perform cross-process memory operations on the second proc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com