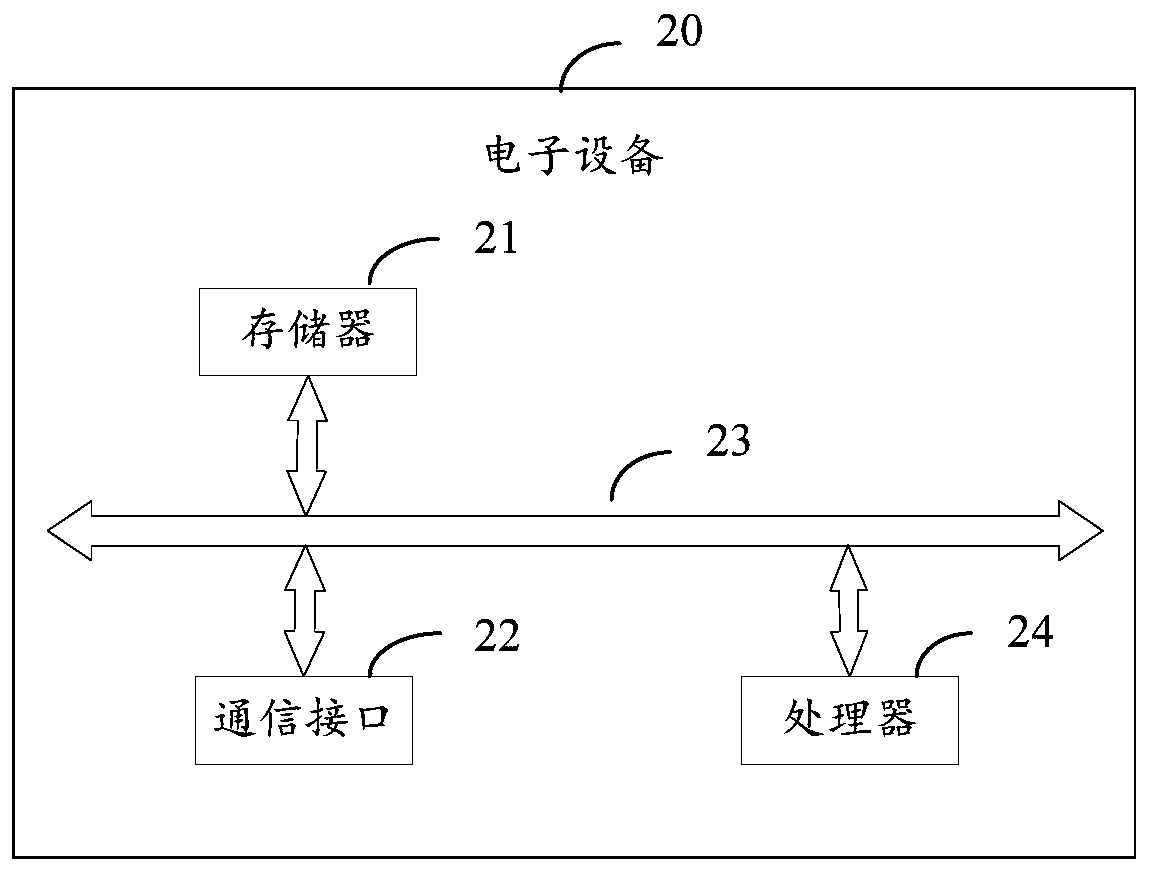
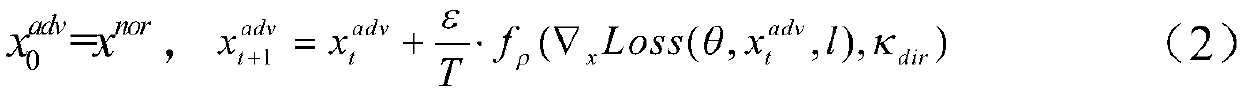Patents
Literature
33results about How to "Effective defense against attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
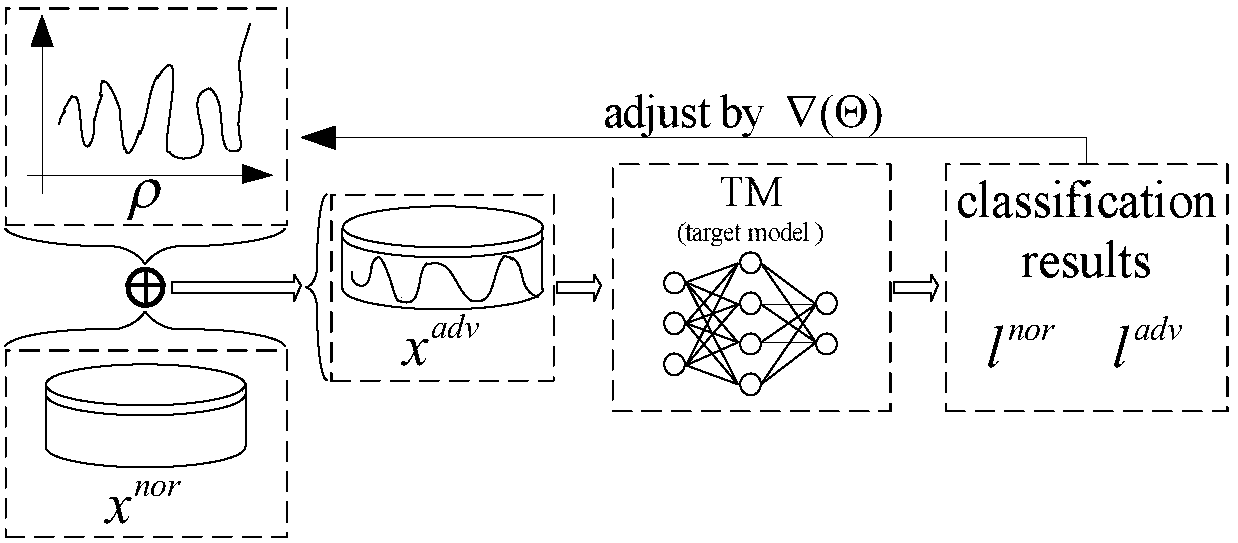
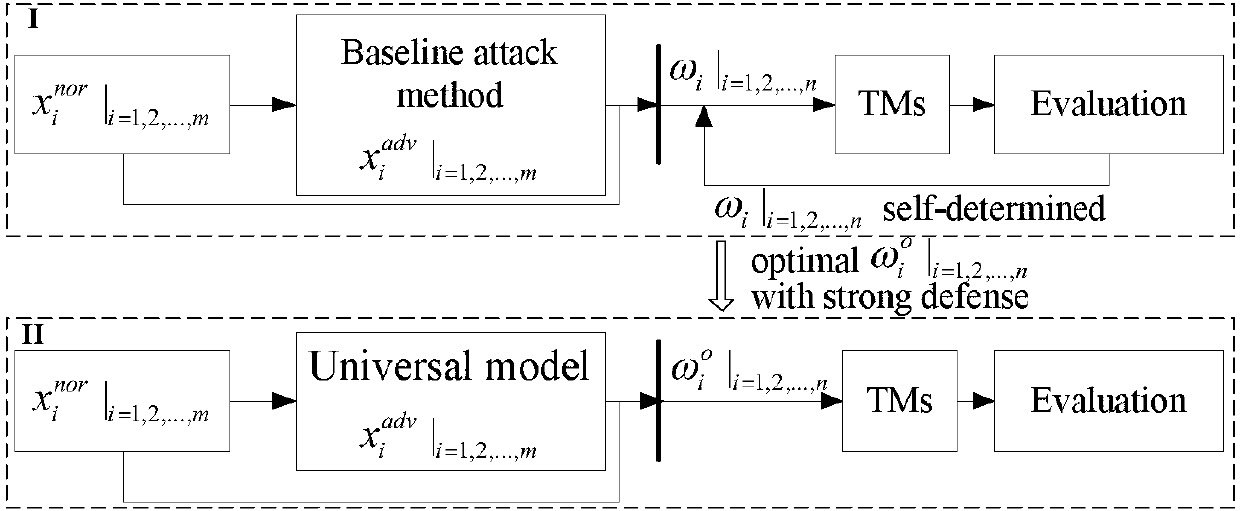
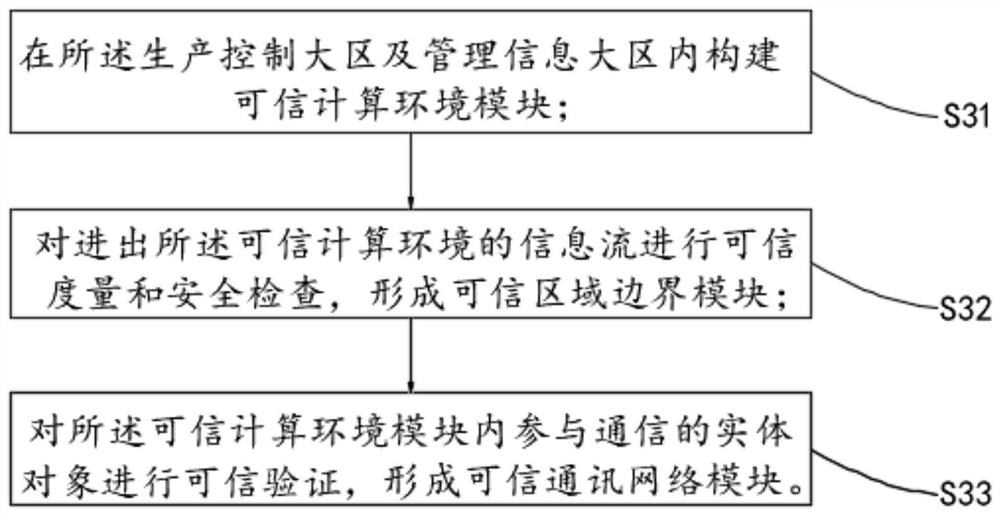
Multi-model cooperative defense method facing deep learning antagonism attack
InactiveCN108446765AEffective defense against attacksAvoid attackCharacter and pattern recognitionNeural learning methodsSubstitution modelAdaBoost
A multi-model cooperative defense method facing deep learning antagonism attack comprises the following steps of: 1) performing unified modeling based on a gradient attack to provide a [Rho]-loss model; 2) according to design of a unified model, for an countering attack of a target model fpre(x), according to a generation result of a countering sample, classifying a basic expression form of an attack into two classes; 3) analyzing the parameters of the model, performing parameter optimization of the [Rho]-loss model and search step length optimization of a disturbance solution model for the countering sample; and 4) for the mystique of a black box attack, designing an experiment based on an adaboost concept, generating a plurality of different types of substitution models, used to achievethe same task, for integration, designing a multi-model cooperative defense method with high defense capability through an attack training generator of an integration model with high defense capability, and providing multi-model cooperative detection attack with weight optimal distribution. The multi-model cooperative defense method is high in safety and can effectively defense the attack of a deep learning model for the antagonism attack.
Owner:ZHEJIANG UNIV OF TECH
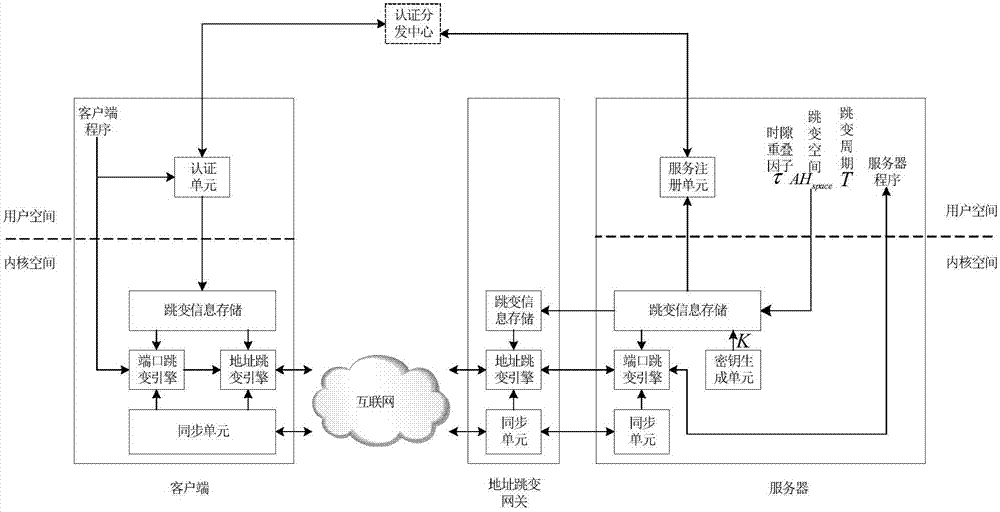
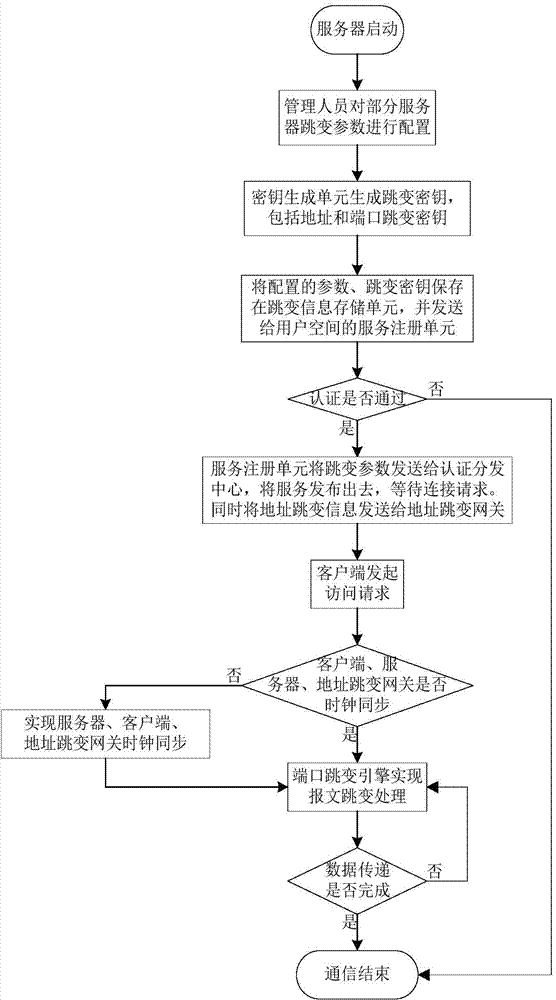
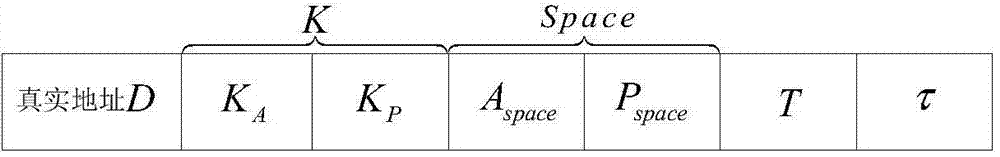
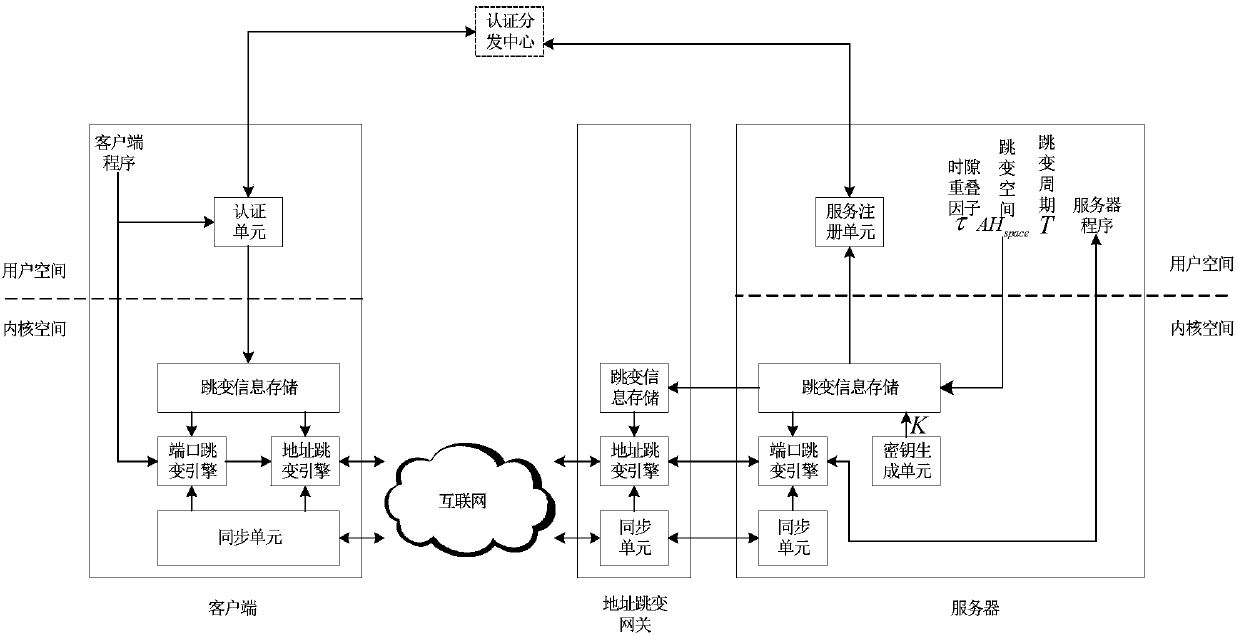
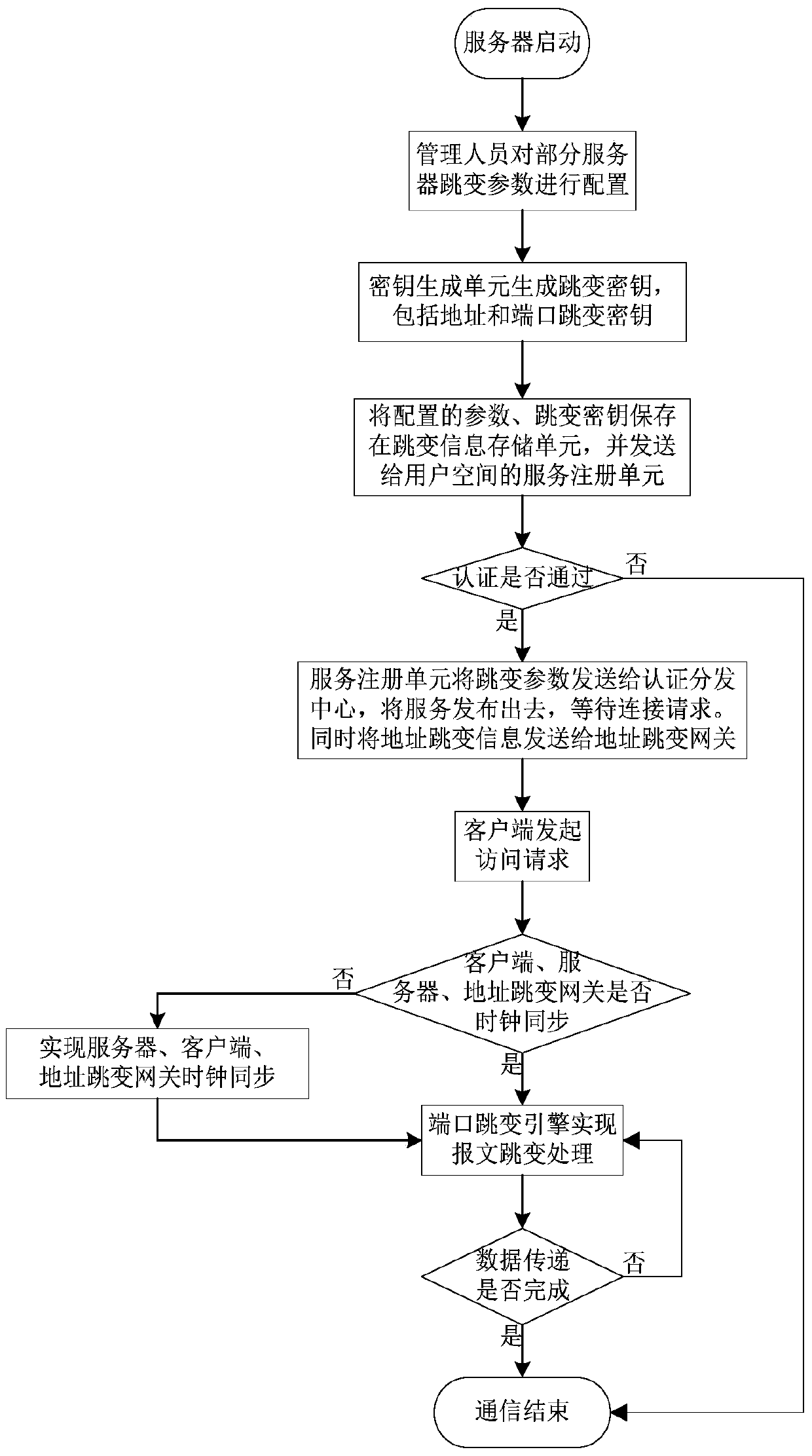
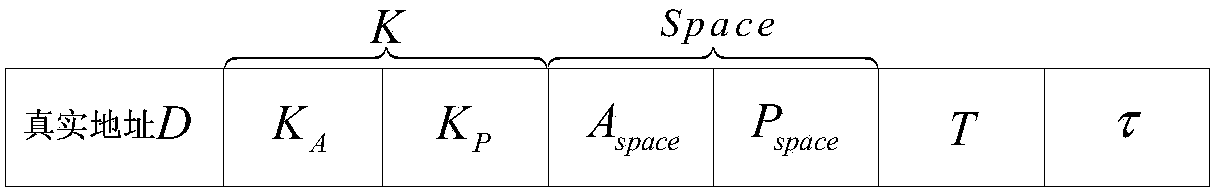
Netfilter-based address and port hopping communication implementation method
ActiveCN104853003AAvoid multiple copiesImprove processing efficiencyTransmissionComputer scienceClock synchronization
The invention provides a netfilter-based address and port hopping communication implementation method, which comprises the steps of 1) initially deploying; 2) configuring the hopping parameters of a server, generating a hopping key, storing the hopping key, and distributing the hopping parameters to an authentication and distribution agent by means of the server; 3) acquiring the hopping parameters of the server by means of a client after the authentication process of the client by an authentication and distribution center; 4) synchronizing the clocks of the client, the server and an address hopping gateway, calculating the current hopping address and the current hopping port of the server, and modifying addresses and ports corresponding to data messages sent and received by a local computer so as to realize the communication; 5) receiving communication messages received by the address hopping gateway from the client and the server, and acquiring the hopping address of the server by an address hopping engine according to the above address hopping parameters, and modifying addresses corresponding to the above messages to complete the message forwarding process; 6) realizing the port hopping function through a port hopping engine by the server, modifying ports corresponding to the messages of an importer / exporter to complete the communication. The method is simple in principle, easy to realize and popularize, and good in safety.
Owner:NAT UNIV OF DEFENSE TECH
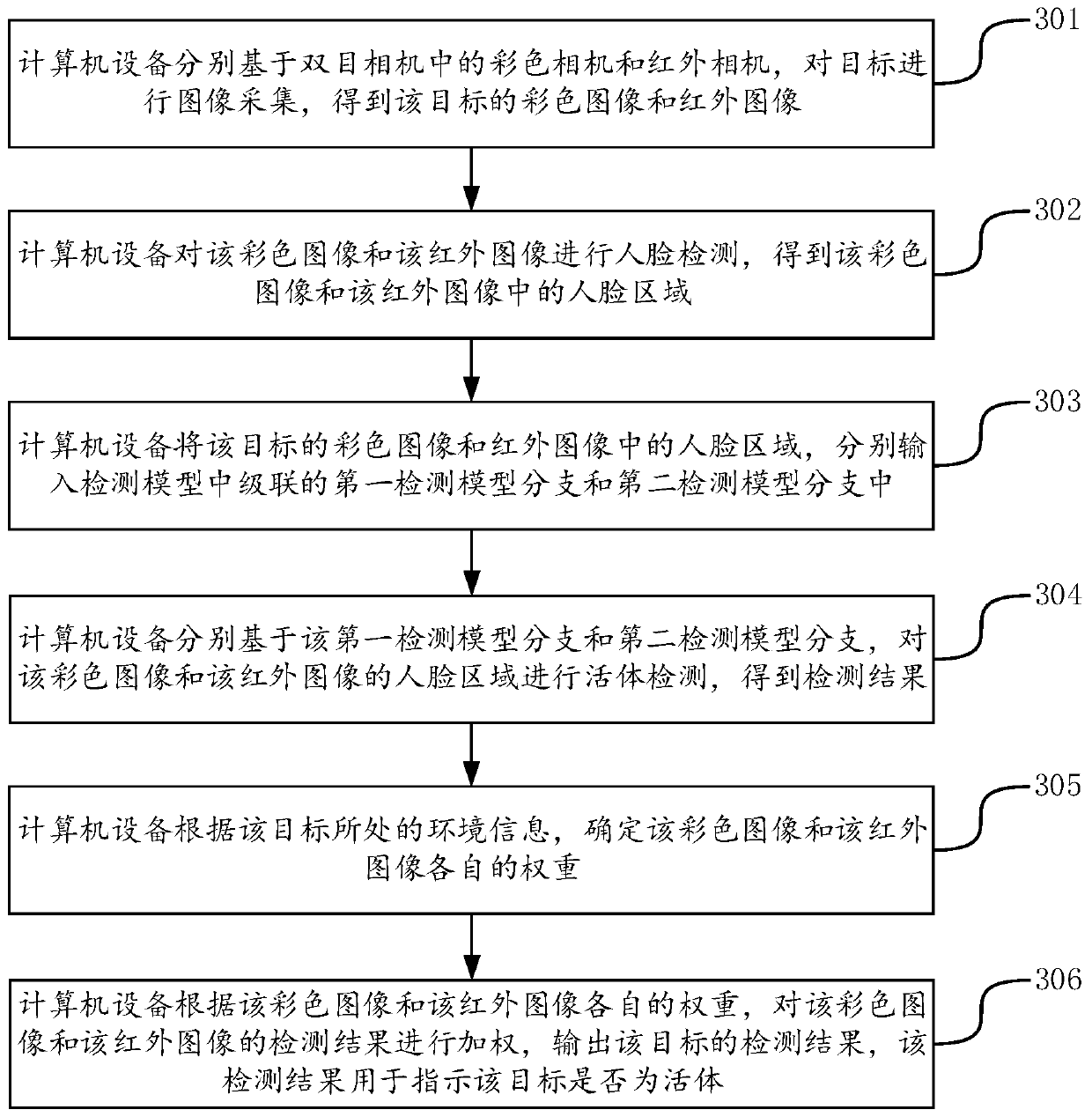
Living body detection method, device and equipment and storage medium
ActiveCN111079576AImprove accuracyEffective attackSpoof detectionColor imageComputer graphics (images)
The invention discloses a living body detection method, device and equipment and a storage medium, and belongs to the technical field of computers. According to the embodiment of the invention, the face areas in the color image and the infrared image of the target are respectively detected through the two cascaded branches in the detection model; whether the target is a living body or not is determined by integrating the detection results of the two images; on one hand, a face region in a color image is detected; according to the method, black-and-white printing and infrared printing images can be effectively defended, detection of a face area in the infrared image is combined, attacks of screen images and color printing images can be effectively defended, and therefore the comprehensive defense effect is achieved, the defense effect is good, practicability is good, and the accuracy of the detection result is good. And on the other hand, different requirements of the two images on theenvironment information are considered in the comprehensive process, and the weight of the two images during combination is determined according to the environment information of the target, so that the accuracy of the detection result obtained by weighting is better, and the defense effect is better.
Owner:TENCENT TECH (SHENZHEN) CO LTD
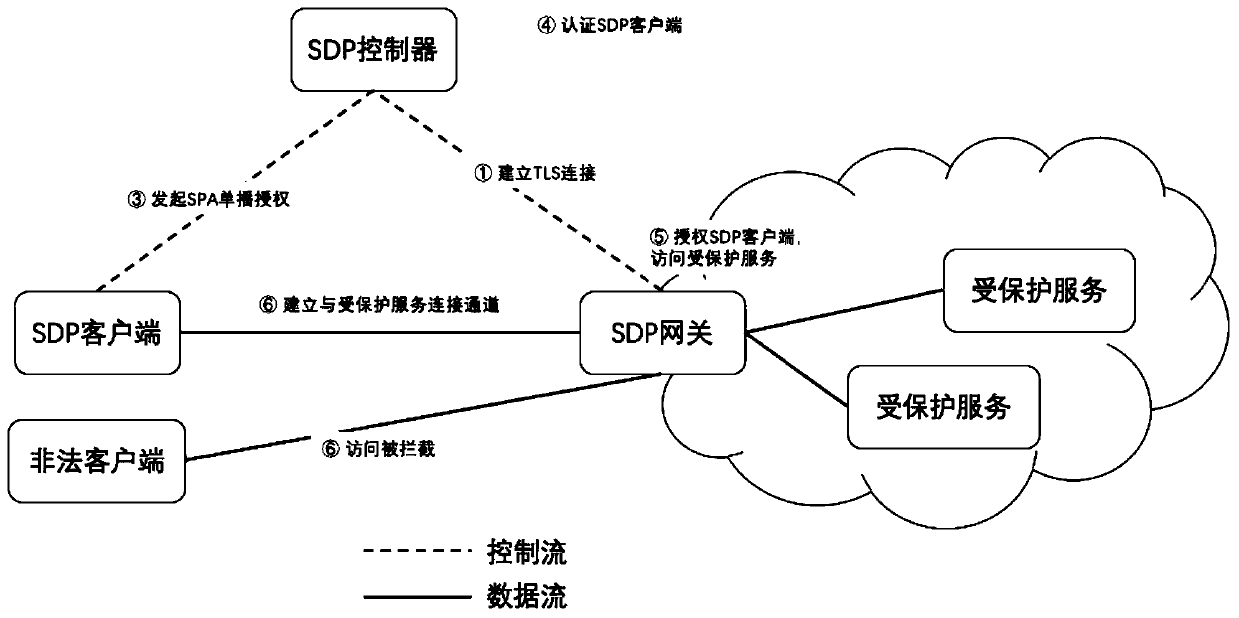
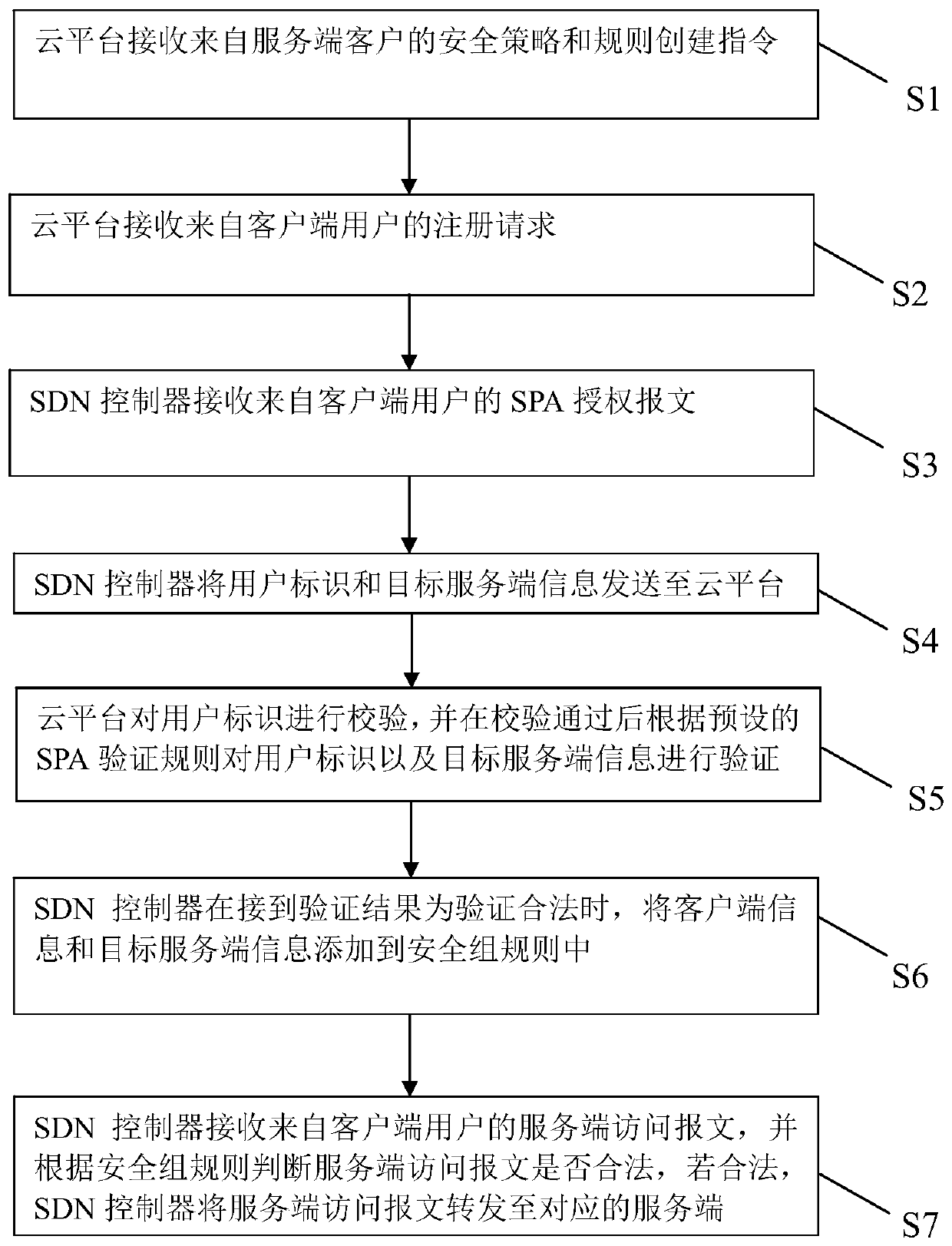
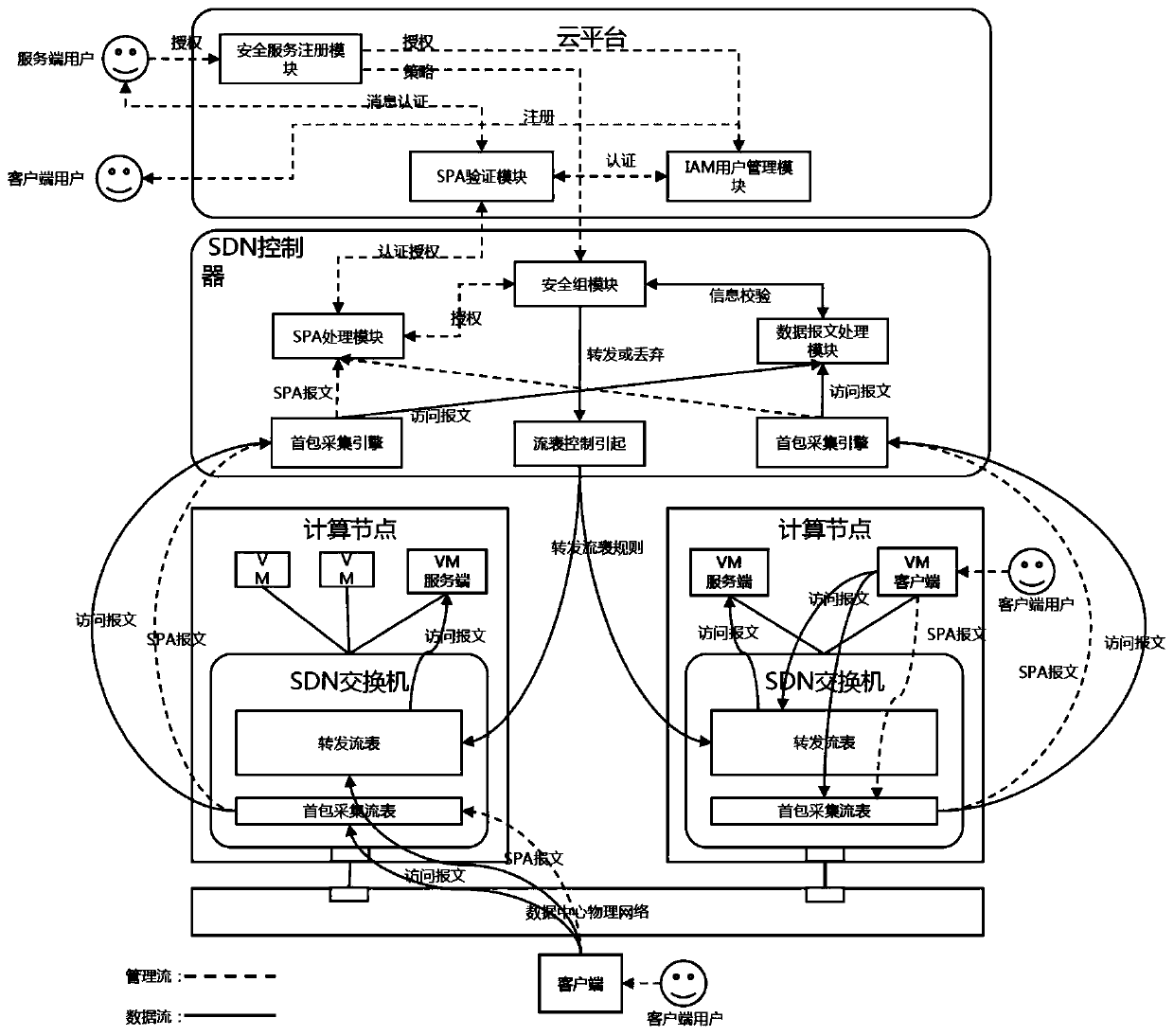
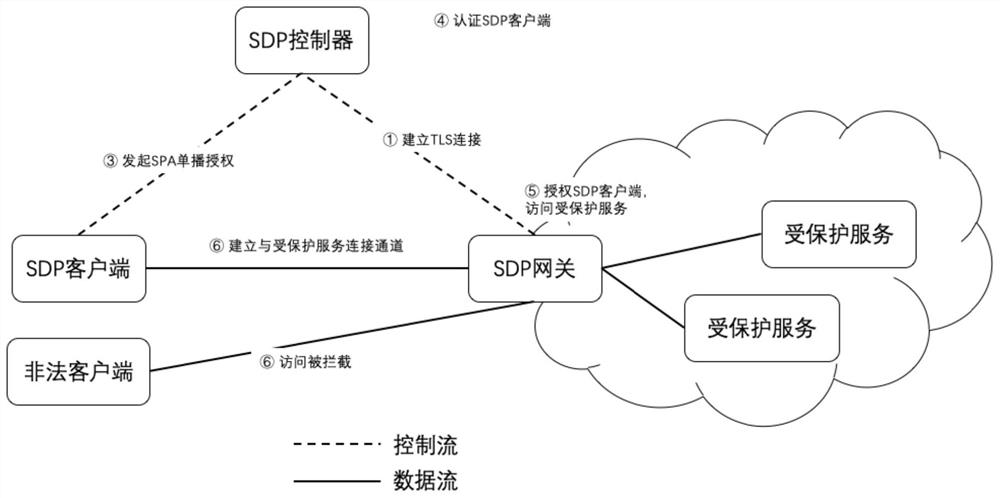
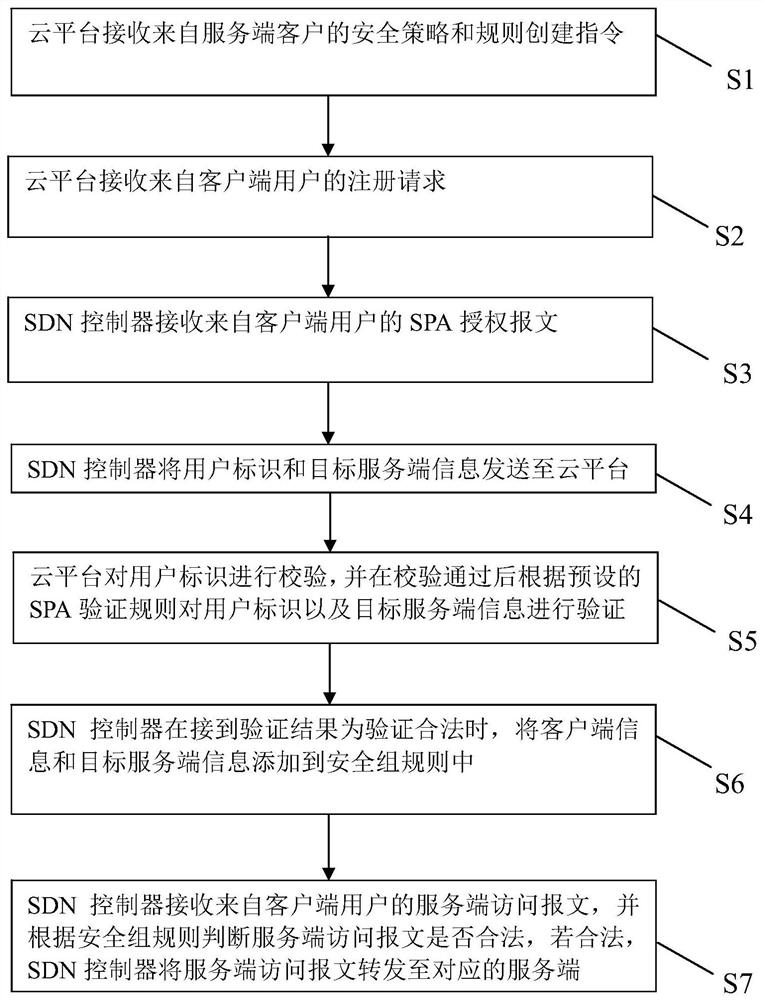
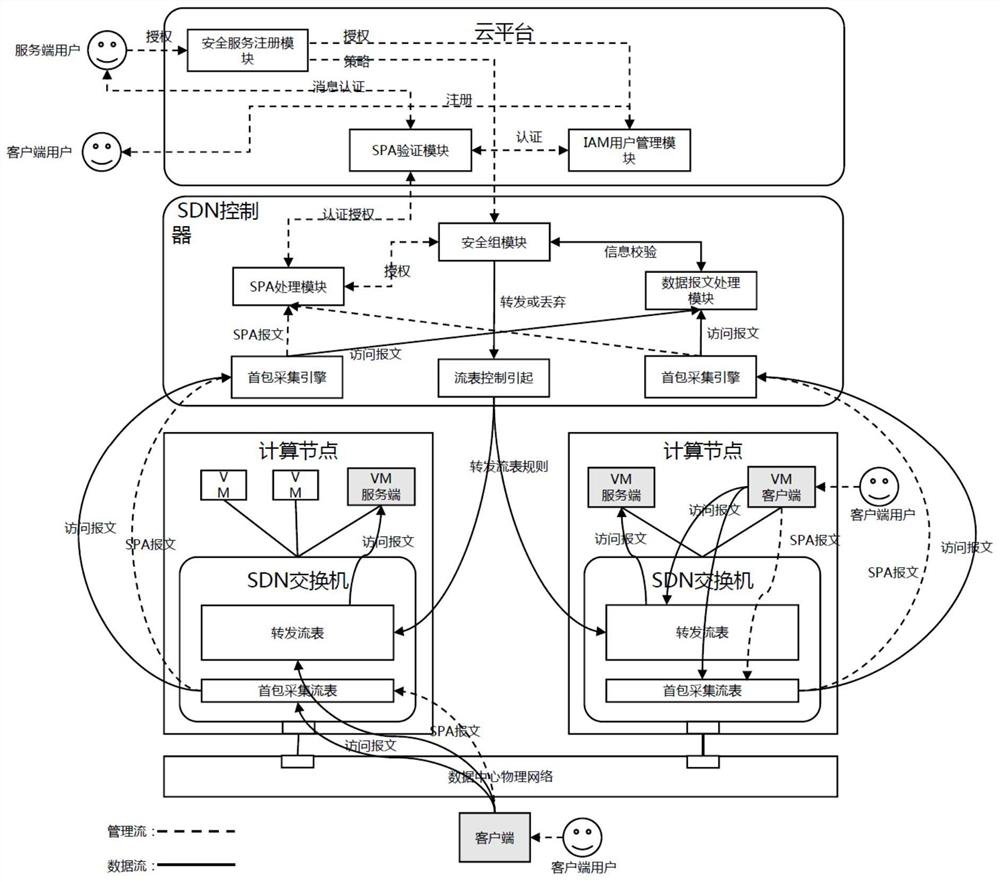
SDN-based SDP security group implementation method and security system
The invention discloses an SDN-based SDP security group implementation method and a security system, and the method achieves SPA single-packet authorization service logic through adoption of a flow table method of an SDN network, and carries out the planning and identity authentication of access authorities of different users through combining with the IAM user management of a cloud platform. According to the invention, the security of the cloud platform security group function is enhanced; accurate control of the security group on external authorization is realized; in combination with the identity authentication technology of the cloud platform and the SDN cloud network, the additional cost of the SDP gateway and the SDP controller is reduced, the SDP technology and the cloud computing security technology are fused, meanwhile, attacks from an internal network can be effectively defended, and comprehensive defense of flow in all directions of the cloud platform can be achieved.
Owner:GUANGZHOU BINGO SOFTWARE
Driven malware defence method and device
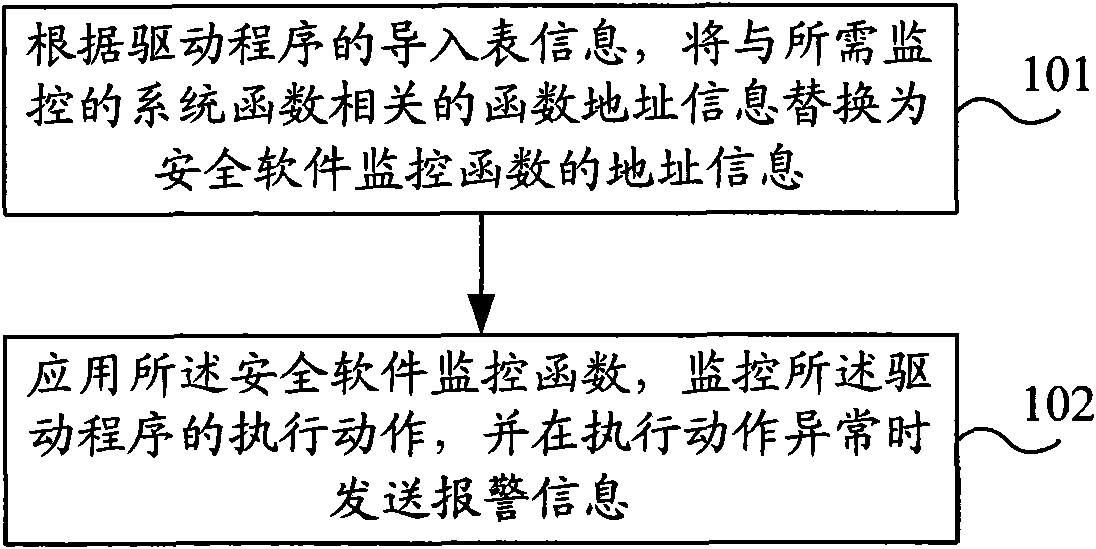
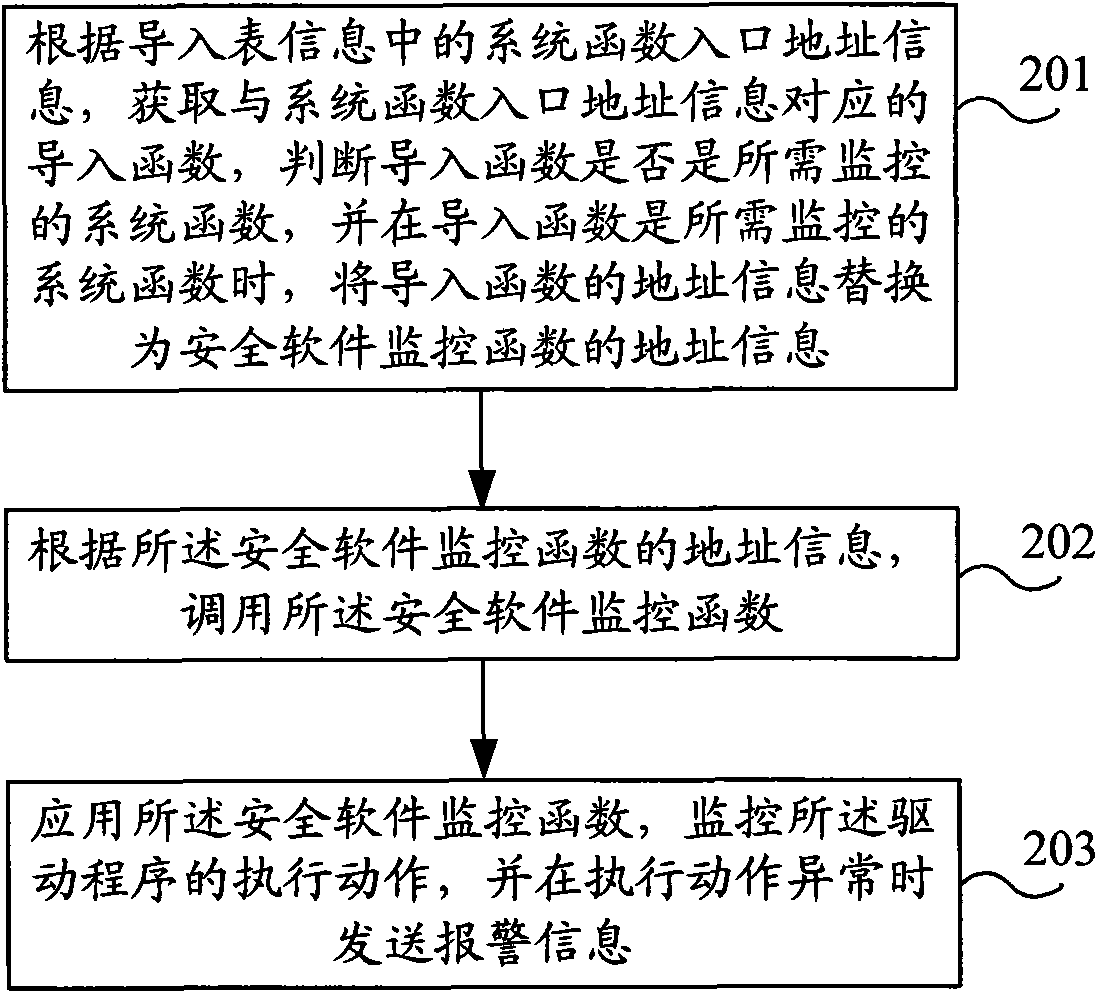
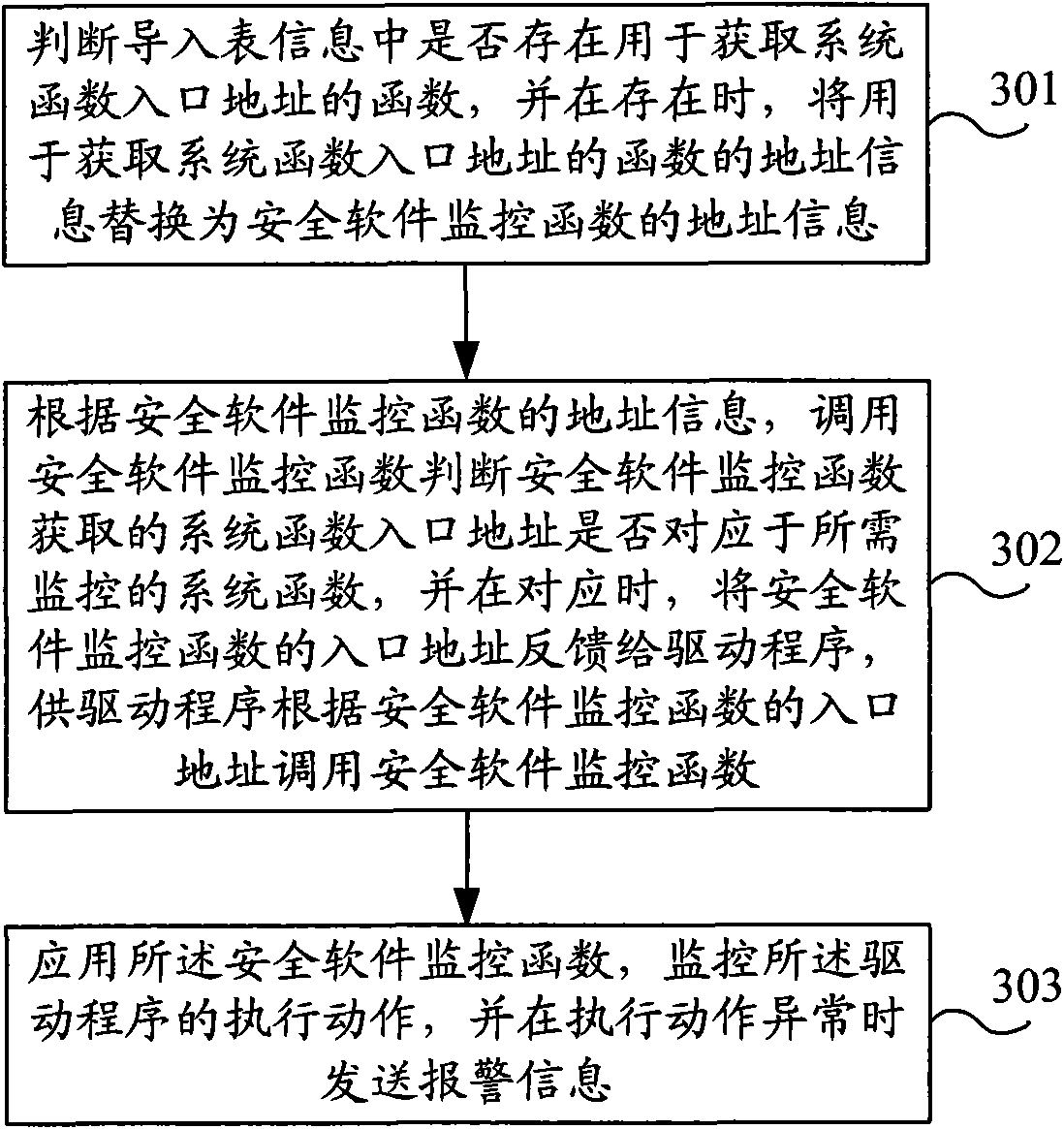
InactiveCN101599113AMonitor execution actionsEffective defense against attacksMultiprogramming arrangementsPlatform integrity maintainanceAlarm messageSecurity software
The invention discloses a driven malware defense method and a device; the method comprises the following steps: according to import table information of a driver, replacing function address information related to a system function needing monitoring with address information of a security software monitoring function; using the security software monitoring function to monitor executing action of the driver and send alarm information when the executing action is abnormal. The device comprises a replacement processing module and a monitoring processing module; according to the import table information of the driver, the replacement processing module is used for replacing the function address information related to the system function needing monitoring with the address information of the security software monitoring function; the monitoring processing module is used for using the security software monitoring function replaced by the replacement processing module to monitor the executing action of the driver and sending the alarm information when the executing action is abnormal. The invention has the characteristics of intellectuality, safe and reliable defense performance, unlikeliness of being restored, no influence on the system performance and the like while effectively carrying out defense on the driven malware.
Owner:北京东方微点信息技术有限责任公司
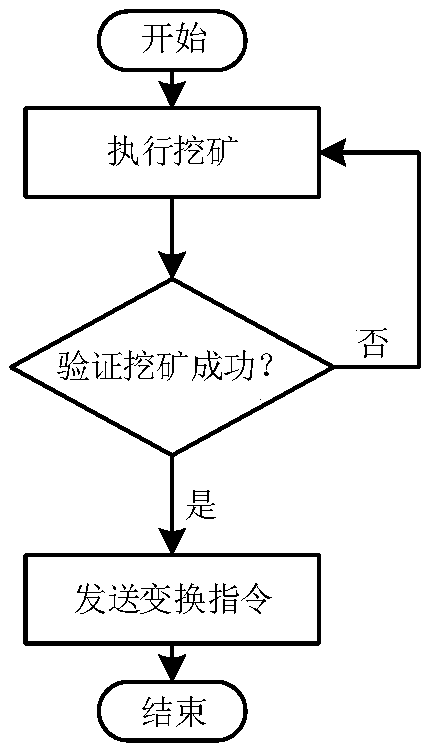
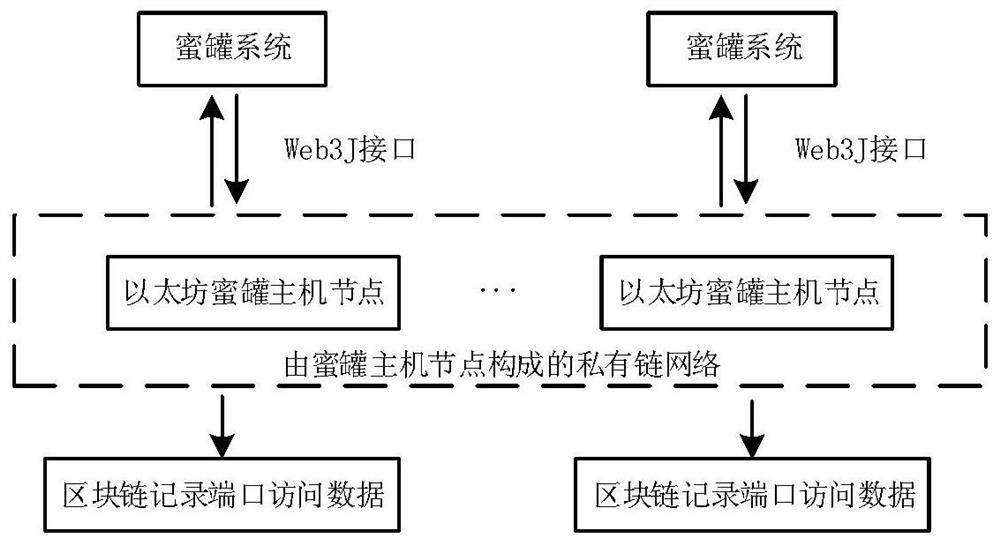
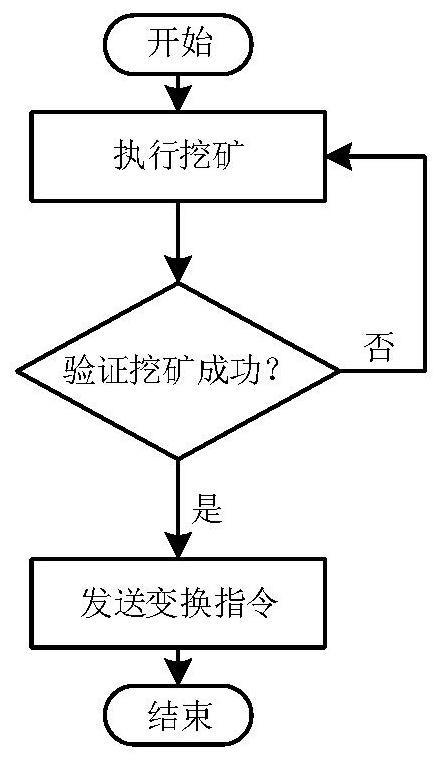
Array honey pot cooperative control method based on block chain
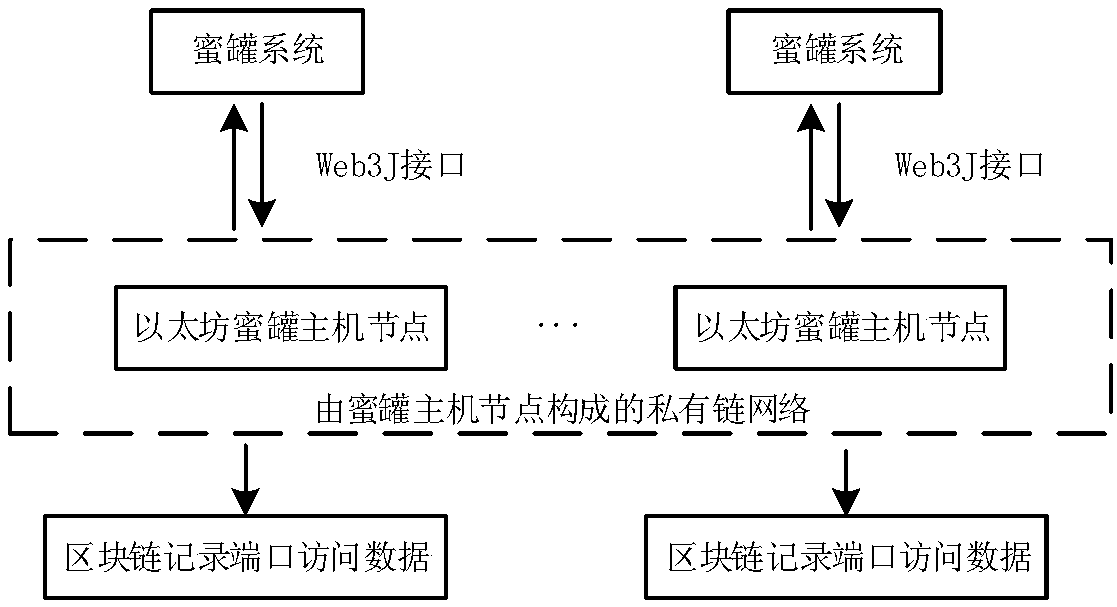
ActiveCN108521426AEffective defense against attacksResist attackPublic key for secure communicationTamper resistanceDigital evidence
The invention relates to an array honey pot cooperative control method based on a block chain. The method comprises the following steps: constructing a private chain by using an Ethereum platform, andrealizing de-centralized cooperative operation thought of a honey pot host cluster through a mining way; constructing a topological structure consistent with the Ethereum platform starting from a P2Pnetworking model, and realizing the communication through web3J. Each host in the array executes the mining, the host acquiring an accounting charging right can holds the post of a honey pot serviceconversion task at one periodic time, conversion information is sent through an encryption mechanism, and other host receives and executes the corresponding conversion instruction. Furthermore, external port request access data is stored in the block chain by using the tamper resistance of the block chain information, thereby obtaining the digital evidence for implementing the attack by an attacker. Through the method disclosed by the invention, the cooperative operation of the array honey pot host cluster is guaranteed, thereby trapping the attacker by using the true-false service in dynamicconversion, and the network security active defense aim is realized.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
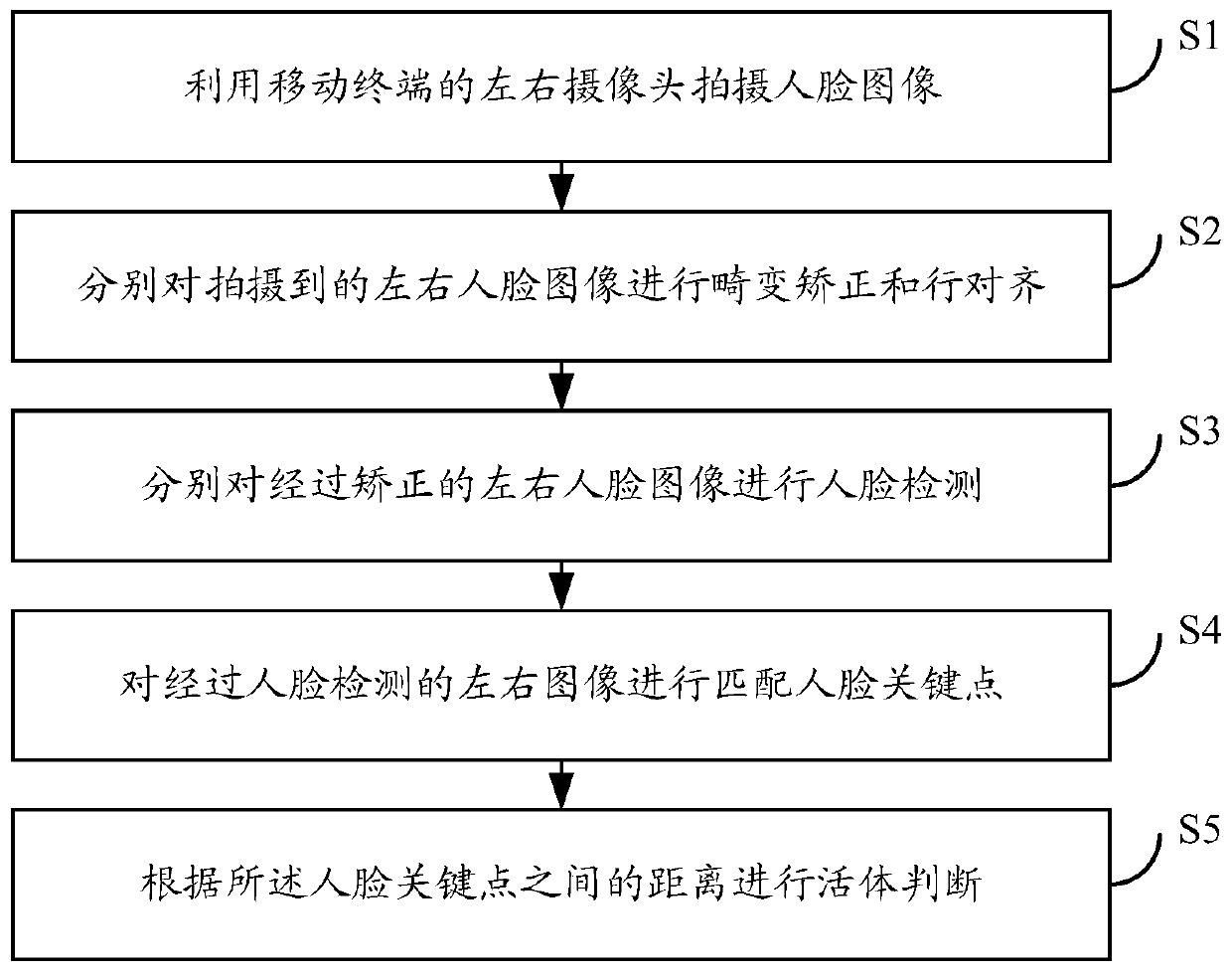
Human face living body verification method and device, mobile terminal and readable storage medium
ActiveCN110059590AEffective defense against attacksImprove experienceSpoof detectionHigh level techniquesFace detectionPattern recognition
The invention discloses a human face living body verification method and device, a mobile terminal and a computer readable storage medium, which are applied to the field of mobile terminals, and comprise the following steps: shooting a human face image by utilizing left and right cameras of the mobile terminal; performing distortion correction and line alignment on the shot left and right face images respectively; respectively carrying out face detection on the corrected left and right face images; matching the left image and the right image subjected to face detection with face key points; and carrying out living body judgment according to the distance between the face key points. According to the embodiment of the invention, when face recognition authentication is used, attacks of images, videos and the like can be effectively resisted,. The method is simple, reliable and mature, the speed is high, potential safety hazards are reduced, and the user experience is improved.
Owner:NUBIA TECHNOLOGY CO LTD
Malicious code detection method, data interaction method and related equipment
ActiveCN112685739AImprove recognition rateEffective defense against attacksPlatform integrity maintainanceNeural learning methodsIdentification rateEngineering
Owner:卓尔智联(武汉)研究院有限公司
Keyword ciphertext generation method and device for cloud storage data
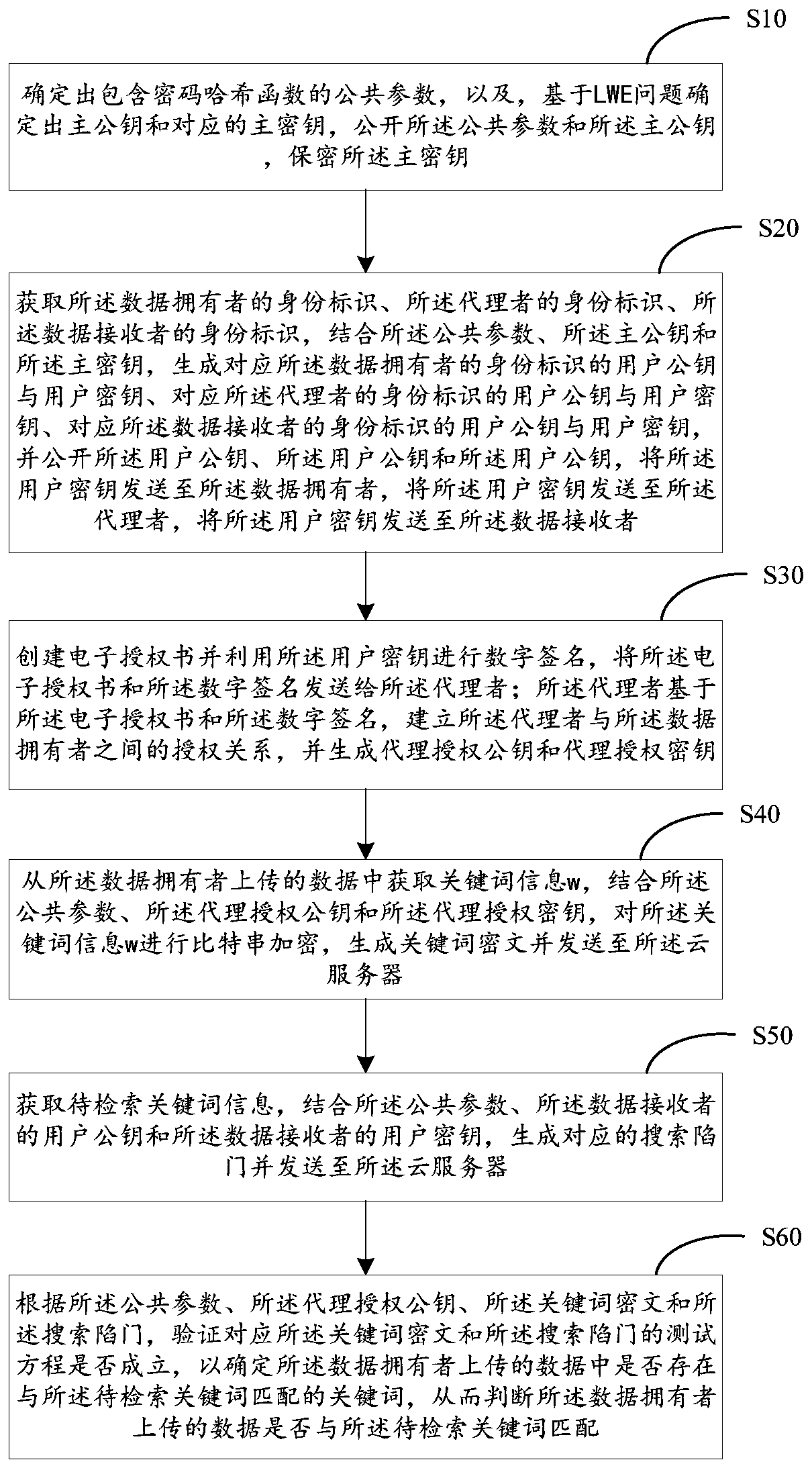
ActiveCN110266490AImprove securityStrong practical application advantagesKey distribution for secure communicationUser identity/authority verificationCiphertextCloud storage system
The invention provides a keyword ciphertext generation method and device for cloud storage data, a cloud storage anti-quantum computing public key searchable encryption method, a cloud storage system, a storage medium and electronic equipment. The cloud storage data keyword ciphertext generation method comprises the steps of acquiring keyword information from data uploaded by a data owner; determining a random bit string; performing bit string encryption on the keyword information to determine a first component; performing bit string encryption on the random bit string to determine a second component; determining a third component according to the first component and an agent authorization public key and an agent authorization key between the agent and the data owner; and determining the keyword ciphertext based on the first component, the second component and the third component of the keyword ciphertext. By adopting the bit string encryption mode, the binary bit string encryption of the keyword information can be realized, the data security is improved, and the bit string encryption also has stronger practical application advantages and stronger practicability.
Owner:SOUTHWEST PETROLEUM UNIV +1
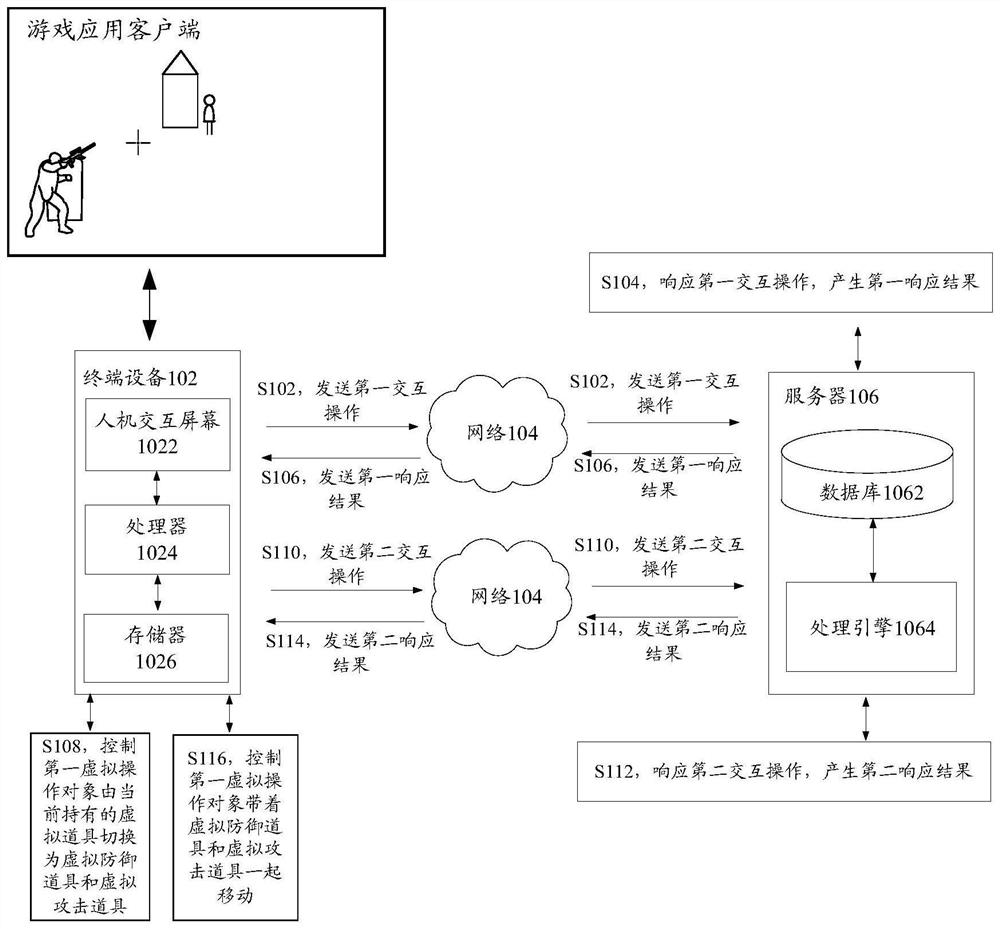
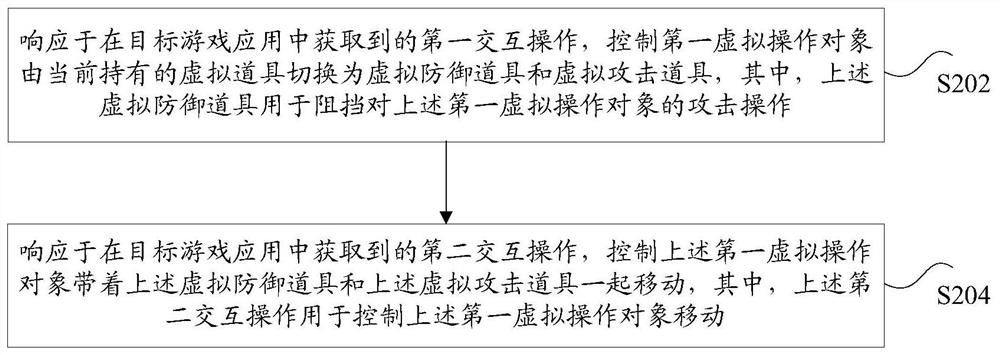
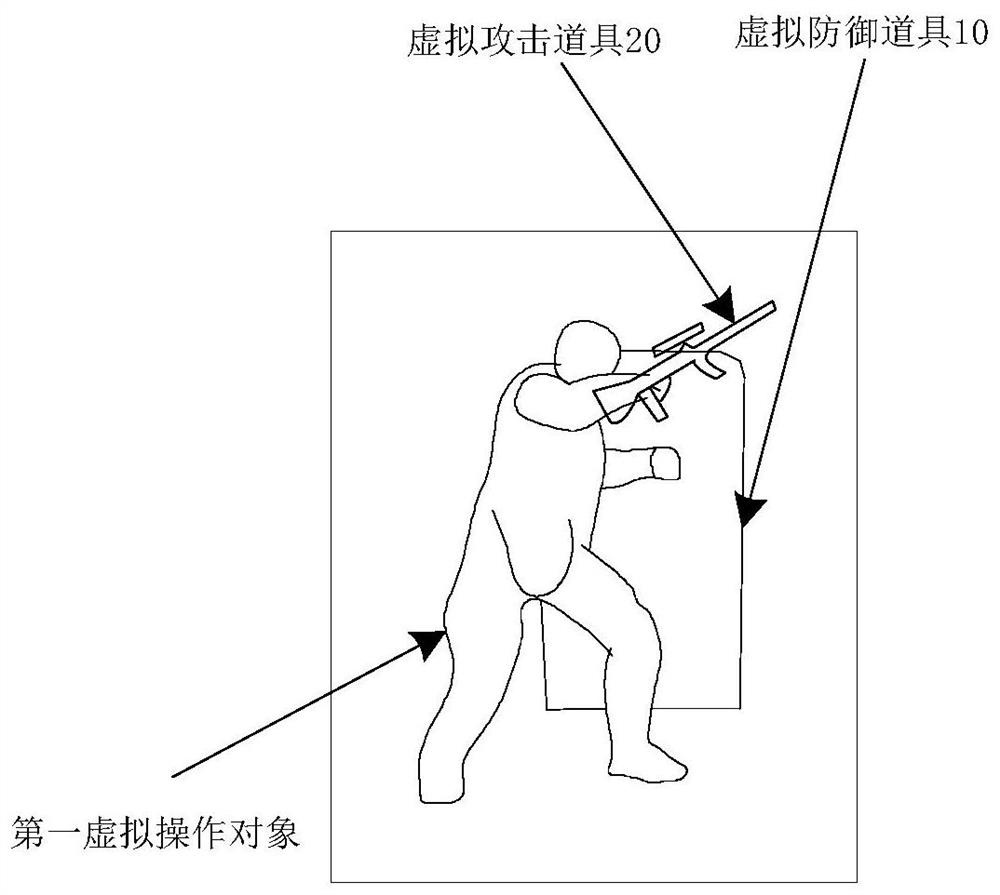
Virtual prop control method and device, storage medium and electronic equipment
The invention discloses a virtual prop control method and device, a storage medium and electronic equipment. The method comprises the steps that in response to a first interaction operation obtained in a target game application, a first virtual operation object is controlled to be switched from a currently held virtual prop to a virtual defense prop and a virtual attack prop, and the virtual defense prop is used for blocking an attack operation on the first virtual operation object; and in response to a second interaction operation obtained in the target game application, the first virtual operation object is controlled to move together with the virtual defense prop and the virtual attack prop, and the second interaction operation is used for controlling the first virtual operation objectto move. By the adoption of the technical scheme, the technical problem that in the prior art, a defensive shield in a traditional mode is poor in protection effect on game characters is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
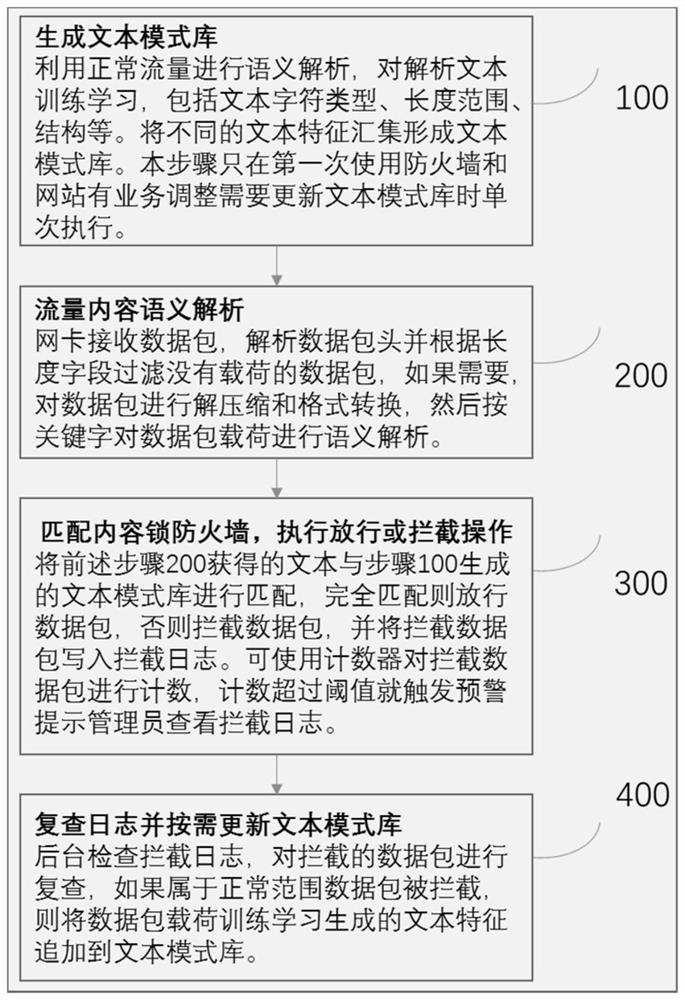
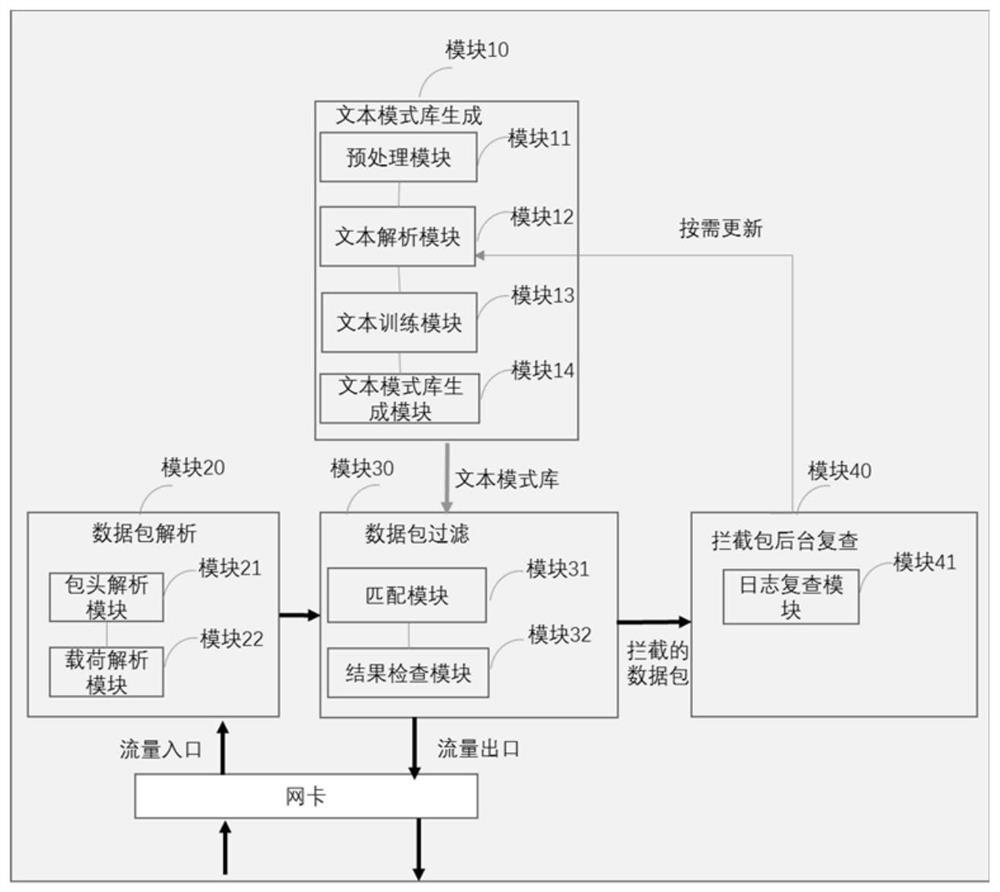
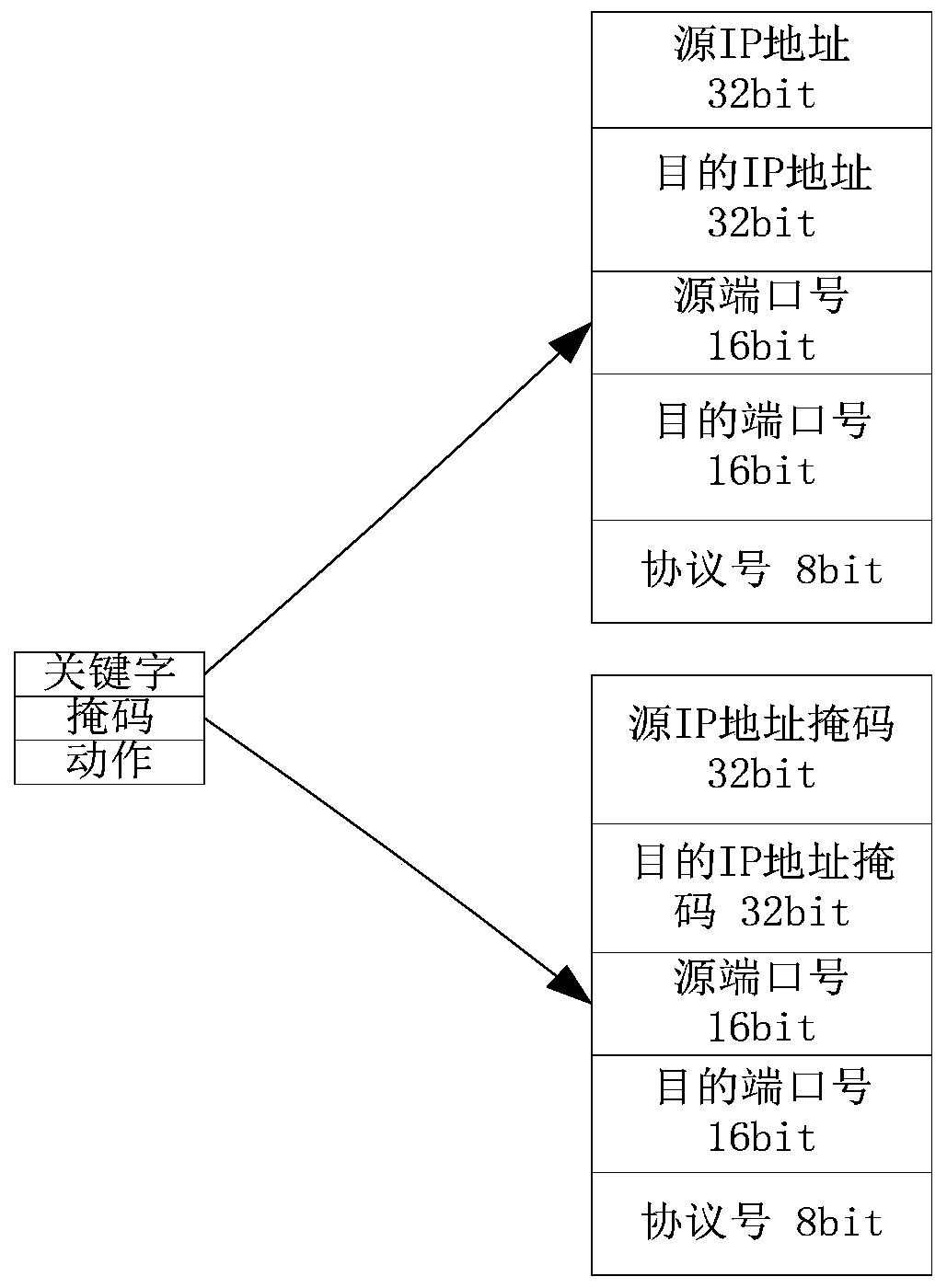
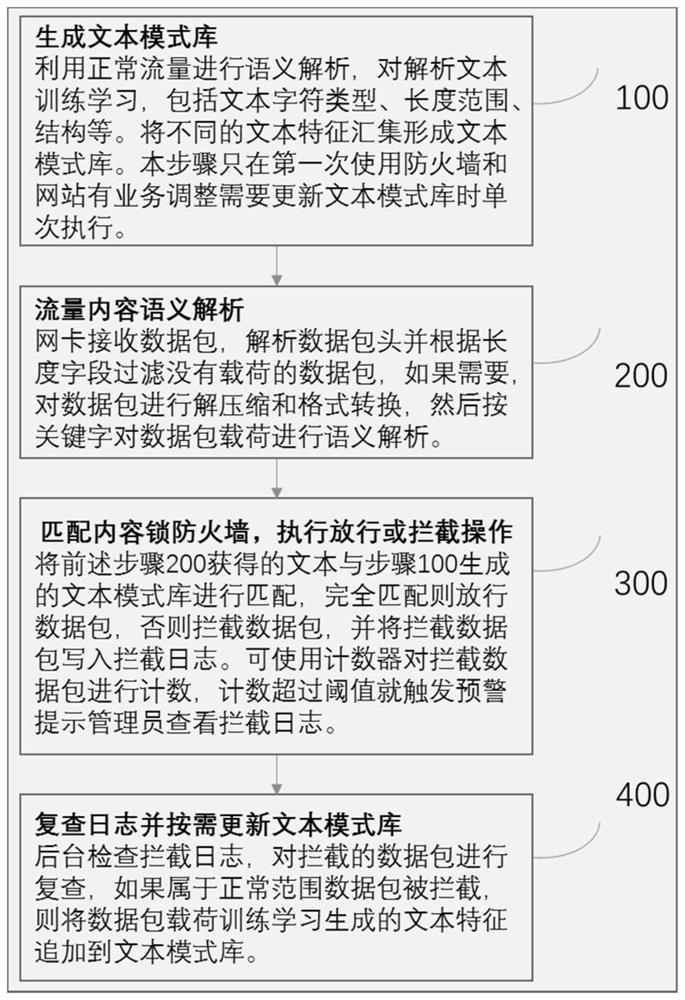
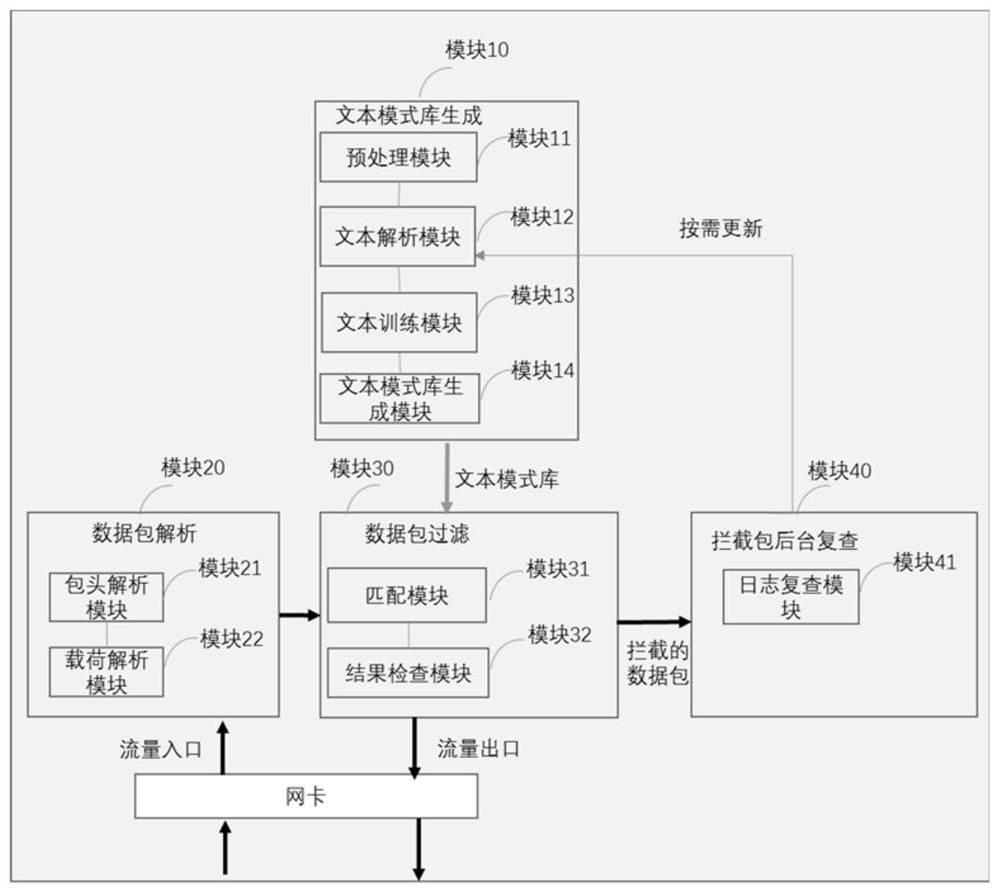
Content lock firewall method and system based on white list
The invention provides a content lock firewall method based on a white list, and the method comprises the steps: step 200, carrying out the semantic analysis of a data package load received by a website, and obtaining an analysis text of a received data package; step 300, matching the parsed text of the data packet received by the website with a text pattern library to determine whether to forwardor intercept the received data packet, the text pattern library comprising value domains and structural features of a plurality of keywords. Based on the method disclosed in the embodiment of the invention, for websites with relatively fixed functions, known and novel network attacks can be effectively defended by deploying the firewall, the websites can run with vulnerabilities under the condition of guaranteeing normal functions, and high-cost upgrading is not needed.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
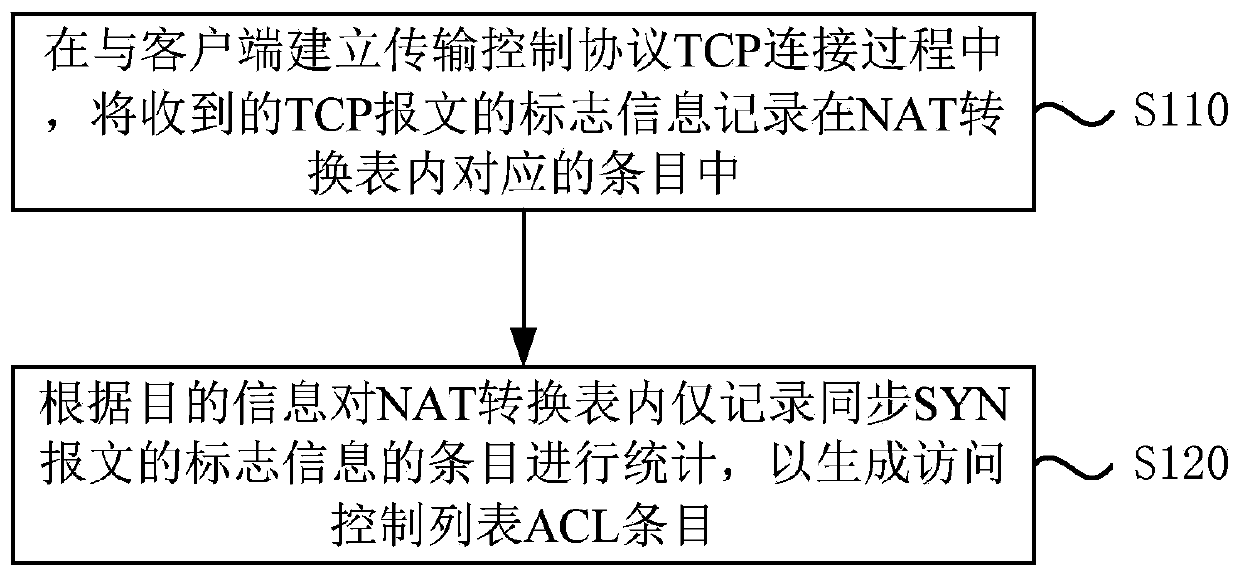
Method, system and equipment for defending attack message
ActiveCN109962918AEffective defenseEffective defense against attacksTransmissionNetwork deploymentNetwork address translation
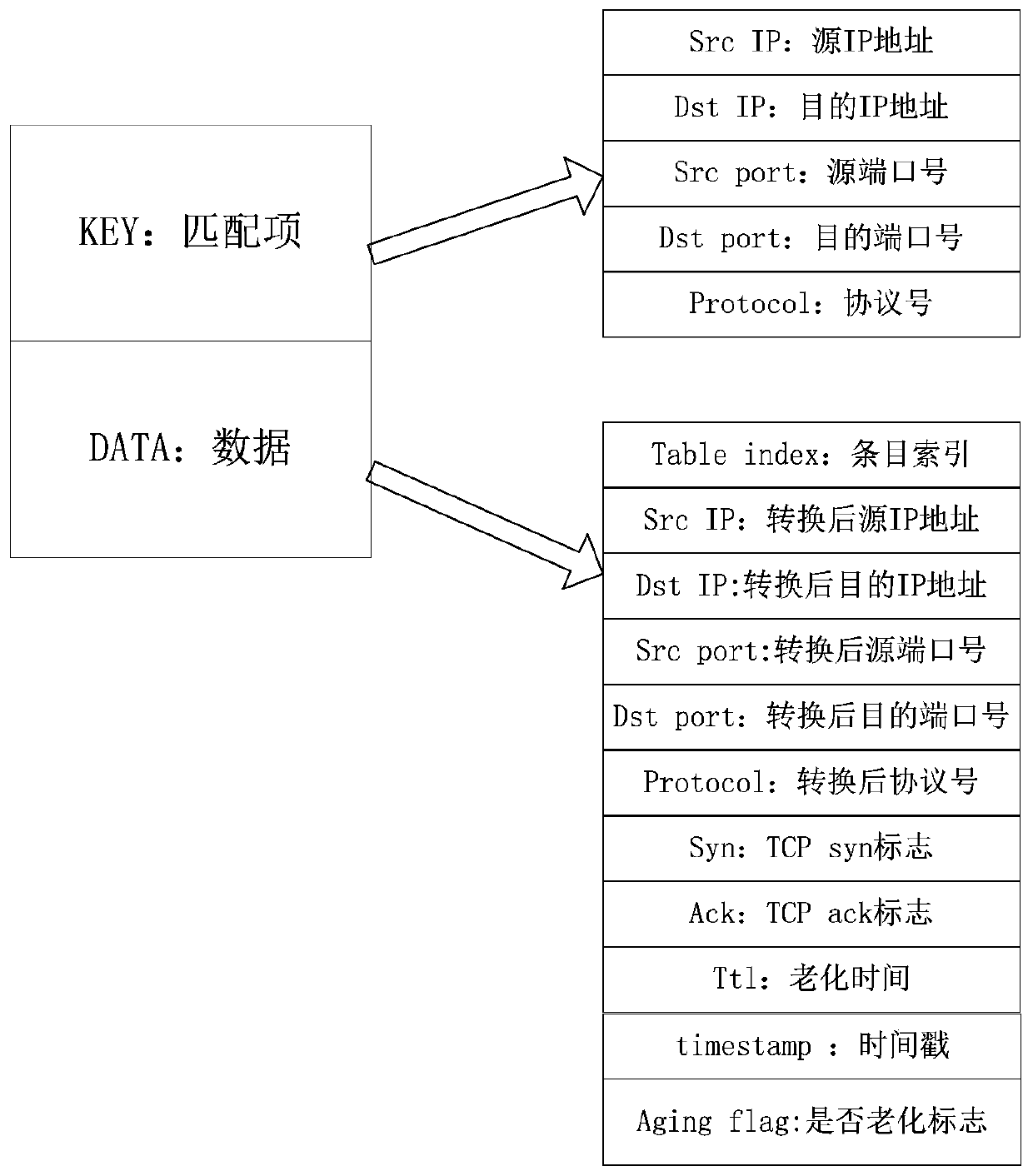
The invention discloses a method, a system and equipment for defending against an attack message, and relates to the technical field of communication. The method for defending against the attack message comprises the following steps: recording mark information of a received TCP message in a corresponding entry in a network address translation (NAT) table in a process of establishing transmission control protocol (TCP) connection with a client; and according to the destination information, statistics is carried out on entries which only record the mark information of the SYN message in the NATconversion table, so that an access control list ACL entry can be generated. Attack messages are effectively defended, the network deployment is simplified, and the cost is reduced.
Owner:FENGHUO COMM SCI & TECH CO LTD
Identification authentication method based on N-dimension sphere
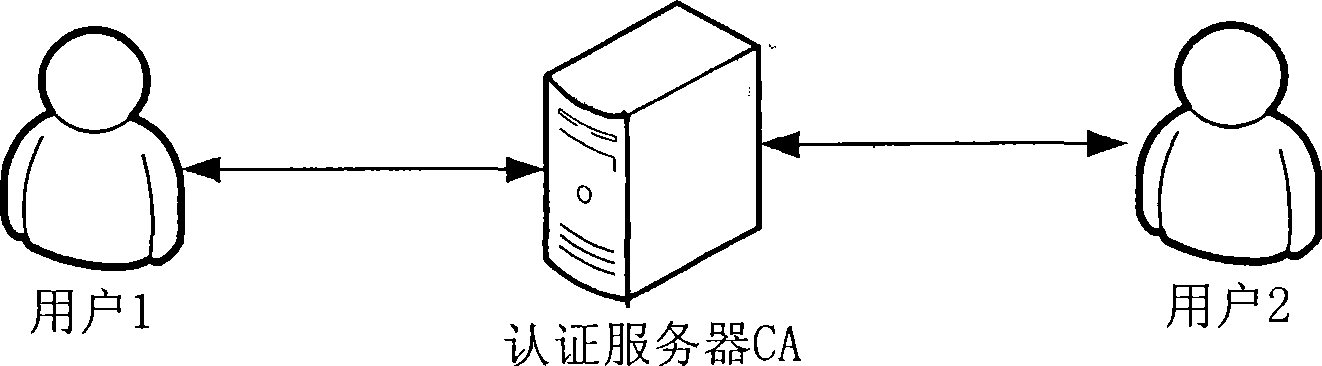
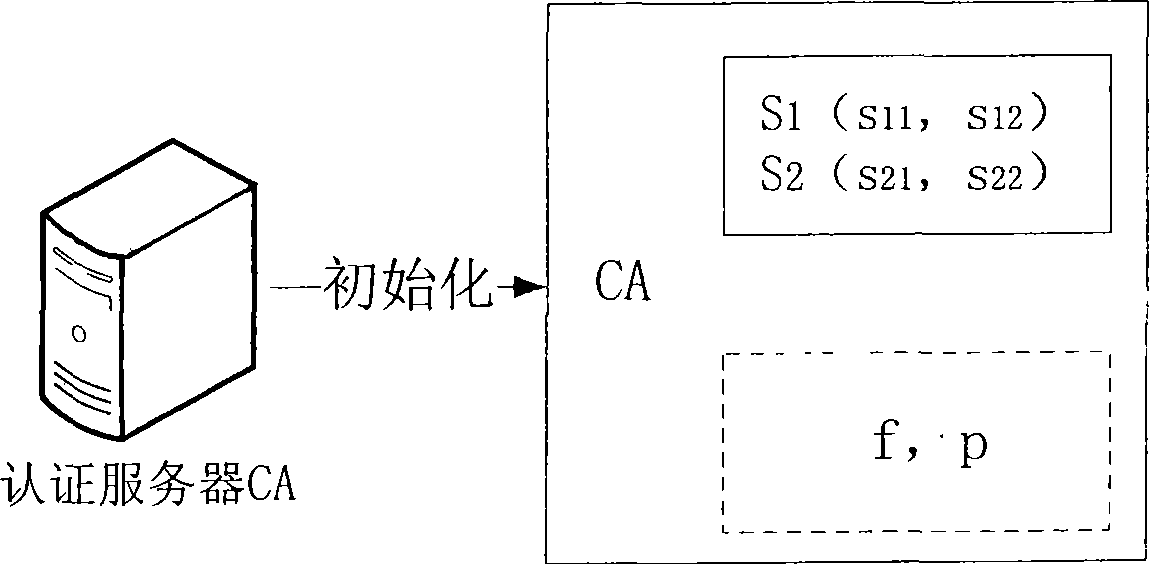
InactiveCN101510875AShorten the timeRealize verificationPublic key for secure communicationUser identity/authority verificationPasswordInternet privacy
The invention discloses an identity authentication method based on an N-dimensional spherical surface, which comprises: an authentication server receives registration and identity authentication of users after being initialized; when a new user registers, the user calculates a vector by a safe one-way function according to passwords selected and submits the vector to the authentication server; the authentication server specifies an IDg for the user as the identification of the identity of the user; the authentication server combines a self secrete vector with the vector submitted by the user to determine the N-dimensional spherical surface; the authentication server randomly selects a plurality of different points on the N-dimensional spherical surface to form an encrypted file which is sent to the user through a safe channel; when the user requires identity authentication, the passwords and the encrypted file containing identity identification are utilized to calculate; the result of calculation is sent to the authentication server; and the authentication server checks and determines whether to accept the identity of the user after calculation. The method can effectively reduce the stored information and calculation load of the authentication server and prevent imitating the authentication server.
Owner:SOUTH CHINA UNIV OF TECH
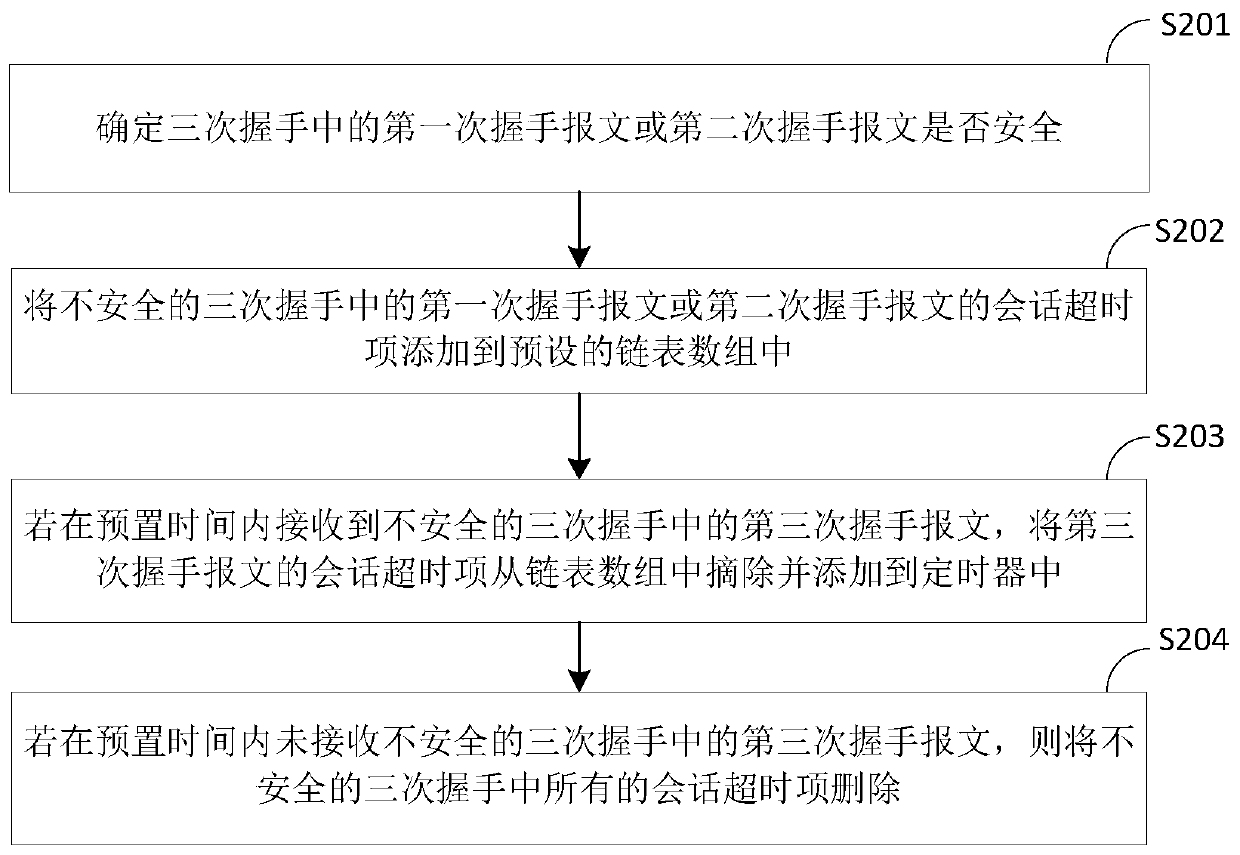
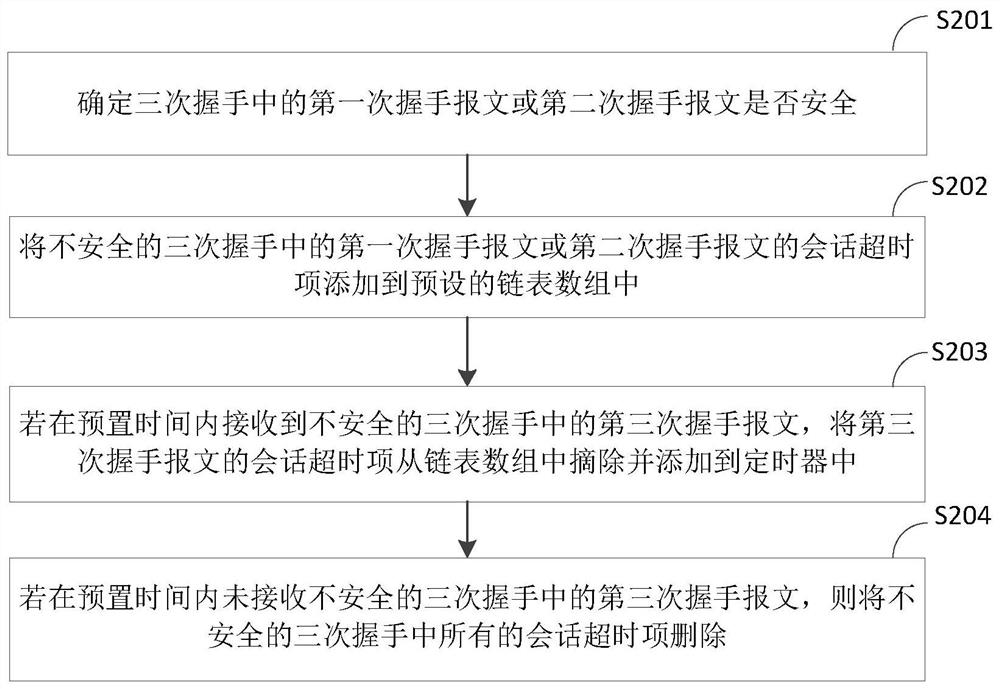
Session table entry processing method and device in multi-core system and related product
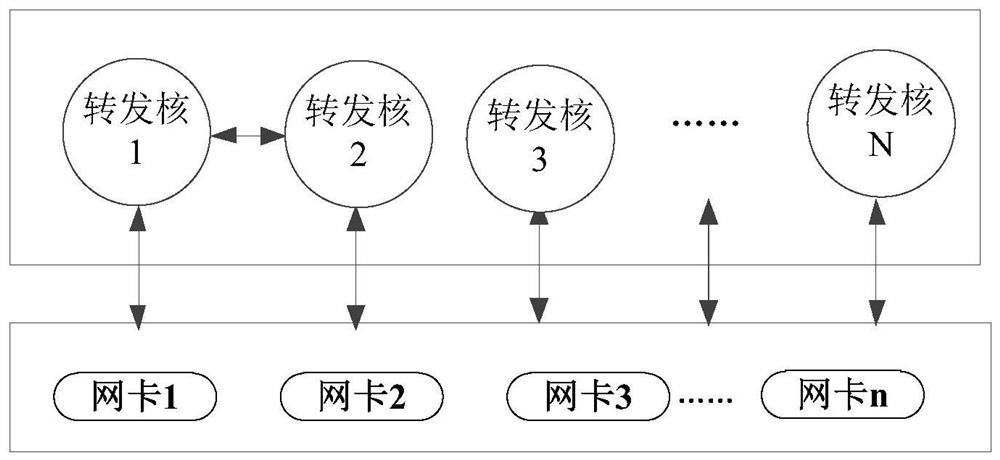
ActiveCN110381032AProcessing is normalSave processing resourcesTransmissionArray data structureTimer
The embodiment of the invention discloses a session table entry processing method and device in a multi-core system. Whether a message is safe or not is firstly determined after a forwarding core receives a first handshake message or a second handshake message when the forwarding core receives the message. When the message is an unsafe first handshake message or an unsafe second handshake message,the session timeout item of the message is added into the link table list array; and the session timeout item of the message is processed by utilizing the link table list array; therefore, the situation that when the received message is the attack message, the timer of the forwarding core is used for processing the session timeout item of the attack message is avoided, attacks are effectively defended, processing resources of the timer of the forwarding core can be saved, the forwarding core can normally process the security message, and the overall forwarding performance is improved. In addition, each forwarding core is configured with a linked list array, so that lock-free processing of the multi-core system is realized.
Owner:NEUSOFT CORP
A kind of anti-riot helmet and preparation method thereof
InactiveCN107296318BReduce weightStrong penetration resistanceFibre typesOrganic non-macromolecular adhesiveAdhesiveAlloy
The invention discloses an antiriot helmet and a preparing method thereof. The antiriot helmet comprises an inner helmet body and an outer helmet body arranged on the inner helmet body in a sleeving mode. The inner helmet body and the outer helmet body are attached together through an adhesive. The outer helmet body is prepared through injection molding after melting of PC / ABS alloy aggregates. The inner helmet body is prepared through molding of multiple layers of aramid fiber fabric layers dipped with modified phenolic resin. The antiriot helmet effectively resists the attacks of bullets, edge tools, clubs, non-explosive projectiles and chemical liquid and effectively protects the head, face and neck of a human body.
Owner:FUJIAN QUANZHOU HAIBIN PROTECTIVE ARMANMENTS CO LTD
Intrusion detection method and system based on honeynet arrangement, and storage medium
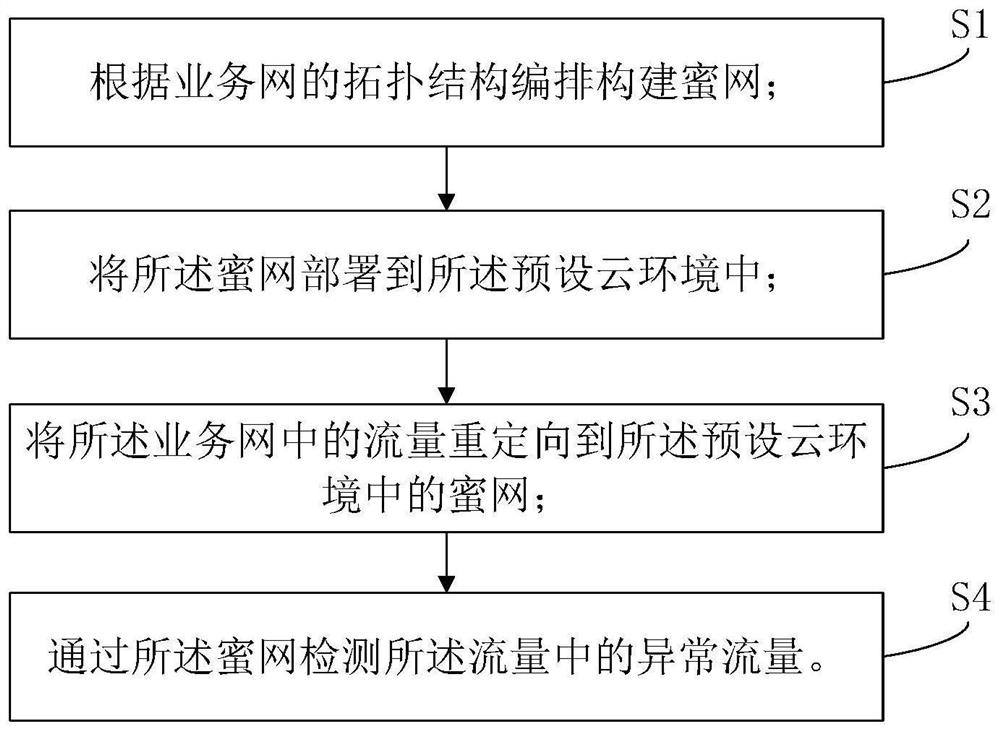
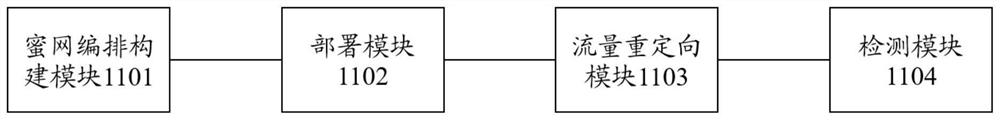
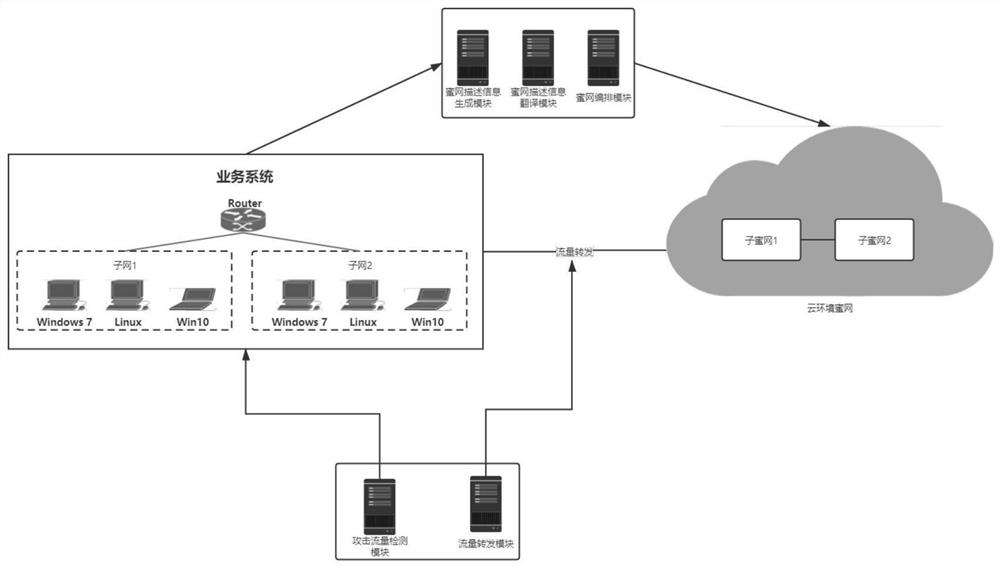
InactiveCN114221815ASolve problems that require pinning physical server resourcesRapid deploymentSecuring communicationAttackNetwork structure
The invention discloses an intrusion detection method based on a honeynet arrangement, a storage medium and a system, and relates to the field of network security. The method comprises the following steps: arranging and constructing a honeynet according to a topological structure of a service network, deploying the honeynet to a preset cloud environment, redirecting traffic in the service network to the honeynet in the preset cloud environment, detecting abnormal traffic in the traffic through the honeynet, constructing the honeynet based on a real network topology of the service network, the system has a real network structure, the authenticity and the cheating ability of the honeynet are remarkably improved, and interaction is carried out through the honeynet and a service attacker to identify used strategies and tools, excavate unknown rules to cope with attacks and effectively defend unknown attack modes.
Owner:北京国腾创新科技有限公司 +1
Low-orbit satellite security authentication method based on spatial channel characteristics
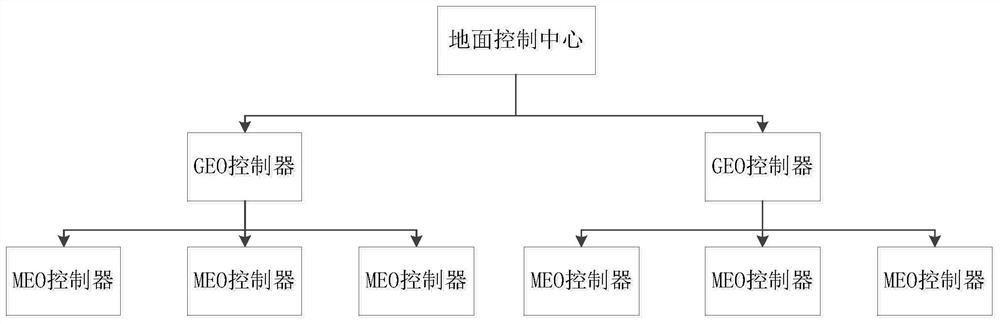
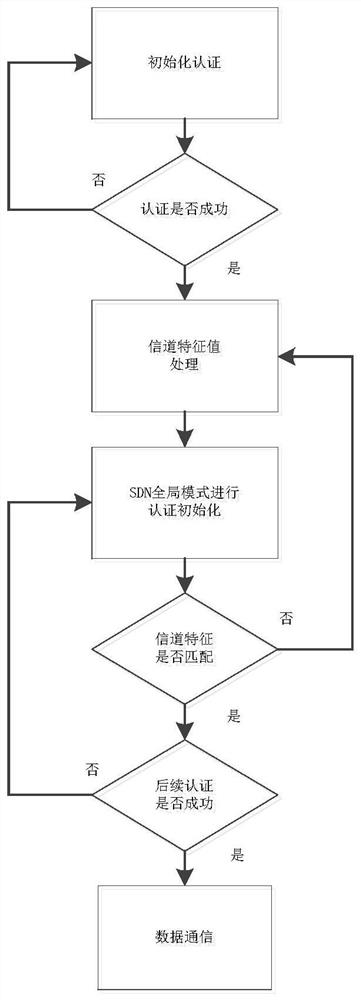
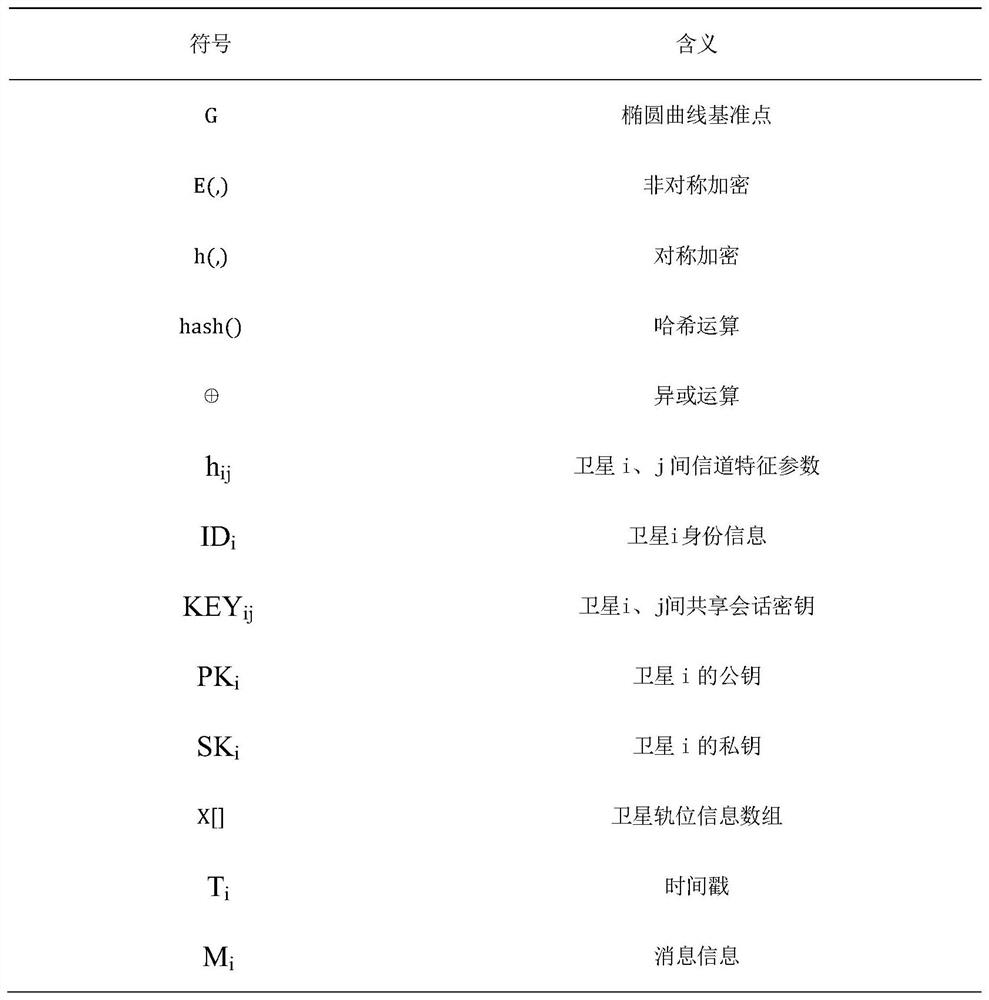
PendingCN113949517AIrreversibleEffective defense against attacksPublic key for secure communicationUser identity/authority verificationCentriolar satelliteEngineering
The invention relates to the technical field of spatial information, and discloses a low-orbit satellite security authentication method based on spatial channel characteristics. The method comprises a three-layer SDN distributed control structure consisting of a ground control center, a GEO satellite controller and an MEO satellite controller. In the whole authentication process, key agreement contains timestamp information, so that the freshness of the message is ensured. After the timestamp T is acquired, whether the timestamp T is within an allowable time range delta T is detected, if the timestamp T is valid, the acquired secret key is fresh, replay attacks can be effectively resisted, symmetric secret keys generated in the subsequent authentication process are iteratively generated based on the initial KEYab, and the shared secret key needs to be updated again every time a session is ended. The new secret key is based on the Hash operation of the channel characteristic value and the message and has randomness, so that even if an attacker obtains the current shared secret key, a subsequent new secret key cannot be generated, and the independence of the authentication process is guaranteed.
Owner:南京审计大学金审学院
Biometric feature living body recognition detection method and device based on depth image
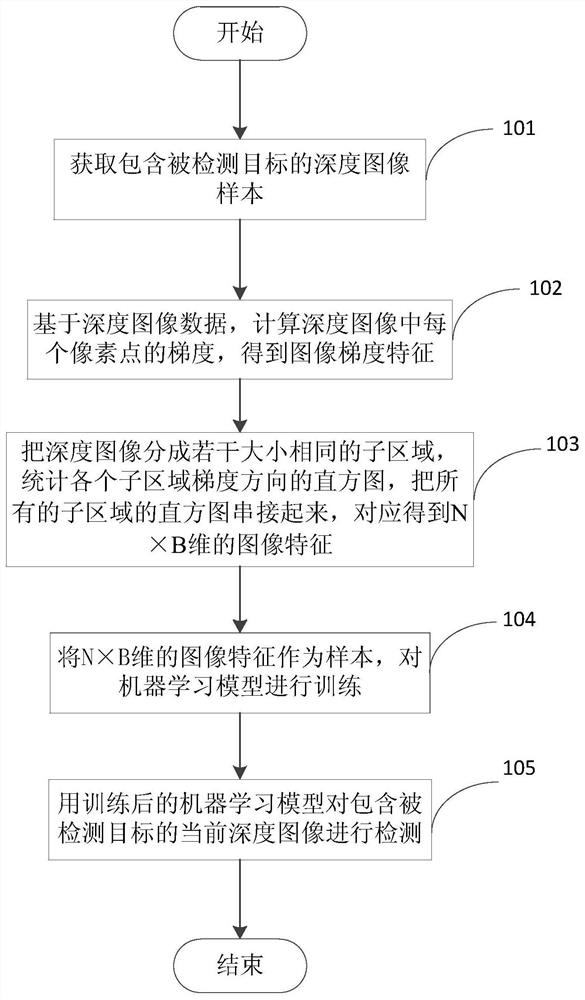
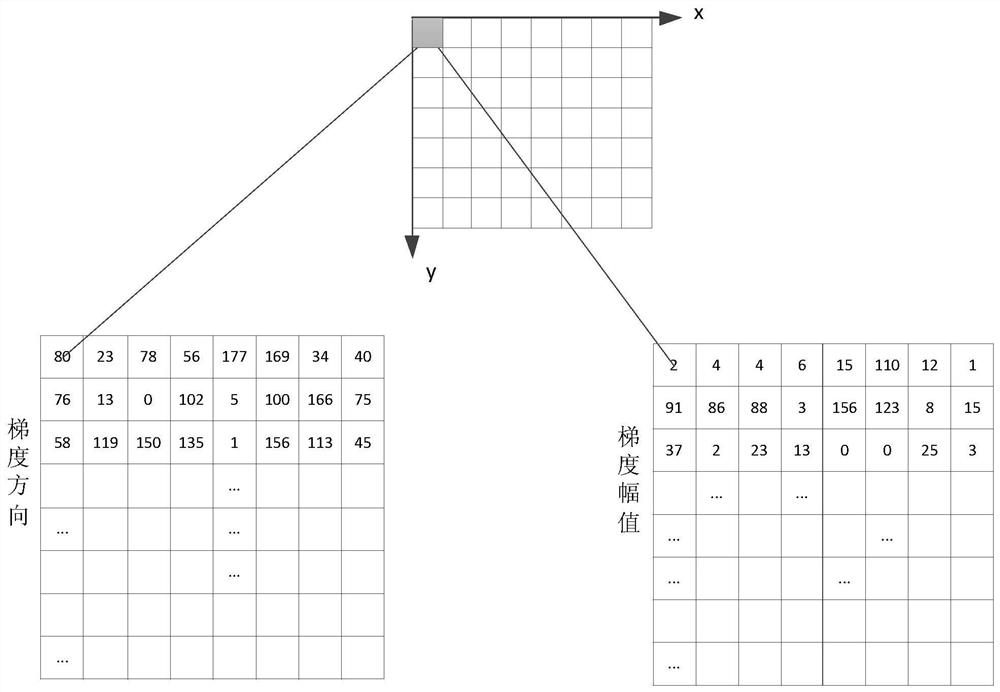
PendingCN112668370ARobustnessTaking into account efficiencyCharacter and pattern recognitionMachine learningImaging FeatureImage gradient
The invention discloses a biometric feature living body recognition and detection method based on a depth image, and the method comprises the steps: obtaining the depth image of a detected target which currently comprises biometric features, and carrying out living body recognition of the current depth image based on a trained machine learning model, calculating the gradient of pixel points in the depth image based on the depth image sample, and obtaining image gradient features representing the change degree of the image depth value; obtaining a sub-region gradient direction histogram of the gradient amplitude of at least one sub-region image distributed in the gradient direction according to the image gradient characteristics; connecting all the sub-region gradient direction histograms in series to obtain extracted image features; and taking the image features as a sample of the machine learning model, and training the machine learning model. The invention is simple in algorithm and short in response time, realizes presentation attack detection, and improves the security of identification equipment.
Owner:HANGZHOU HIKVISION DIGITAL TECH
System and method for facial expression detection
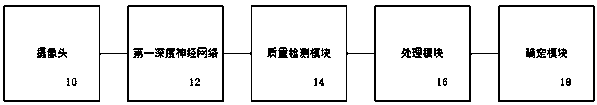
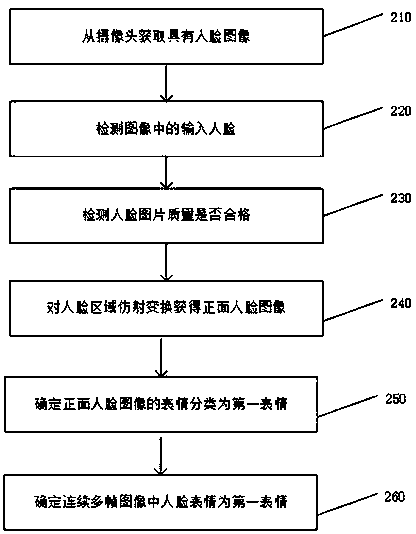
PendingCN110674770APrivacy protectionEffective securityAcquiring/recognising facial featuresRadiologySurveillance camera
The present invention provides a system and method for facial expression detection. The system comprises a camera used for acquiring an image with an input face; a first deep neural network used for detecting the input face in the image; a quality detection module used for judging whether the detected input human face is a human face picture with qualified quality or not, and sending a trigger signal if the detected input human face is the human face picture with qualified quality; a processing module used for intercepting a face area from the image when receiving the trigger signal sent by the quality detection module, and carrying out affine transformation on the face area to obtain a front image corresponding to the input face; and a determination module used for determining the expression classification of the front image as a first expression through a second deep neural network, and when the input faces in more than a preset number of continuous multi-frame images are all the first expressions, determining the input faces as the first expressions, so that the problem of face expression detection in a monitoring camera scene can be solved.
Owner:SHANGHAI YITU NETWORK SCI & TECH
A session entry processing method, device and related products in a multi-core system
ActiveCN110381032BProcessing is normalSave processing resourcesSecuring communicationAttackEngineering
Owner:NEUSOFT CORP
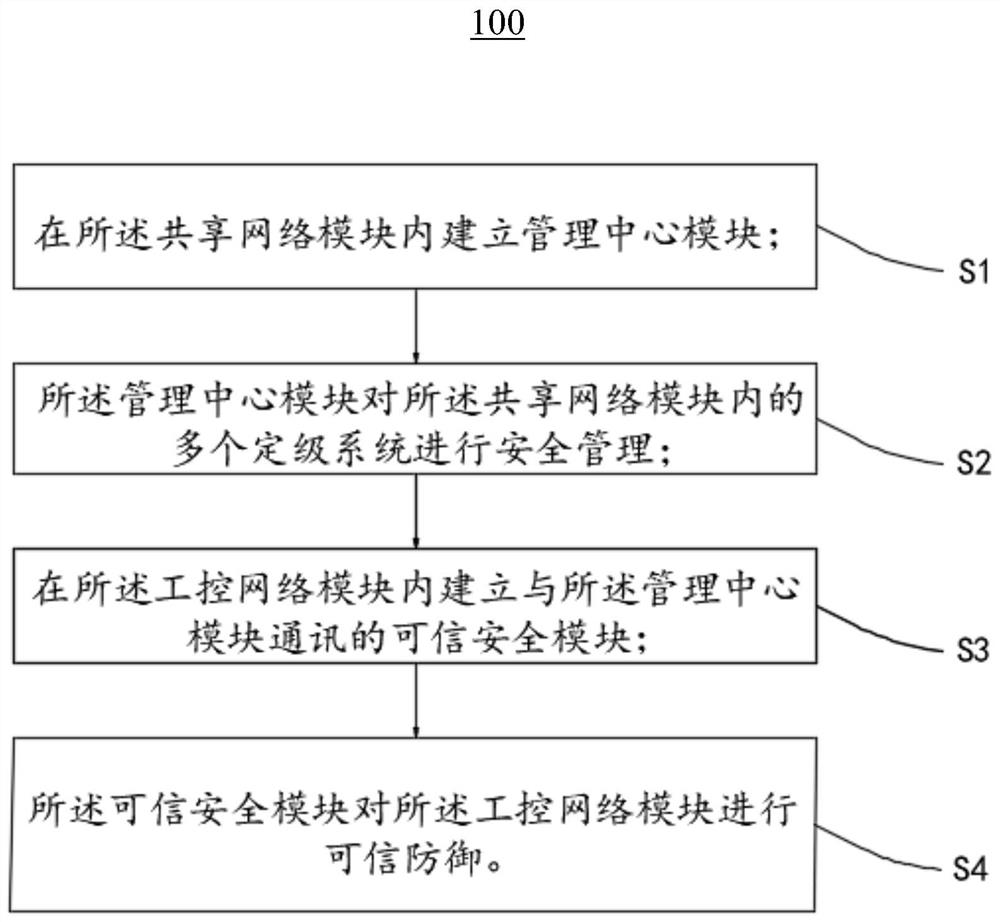
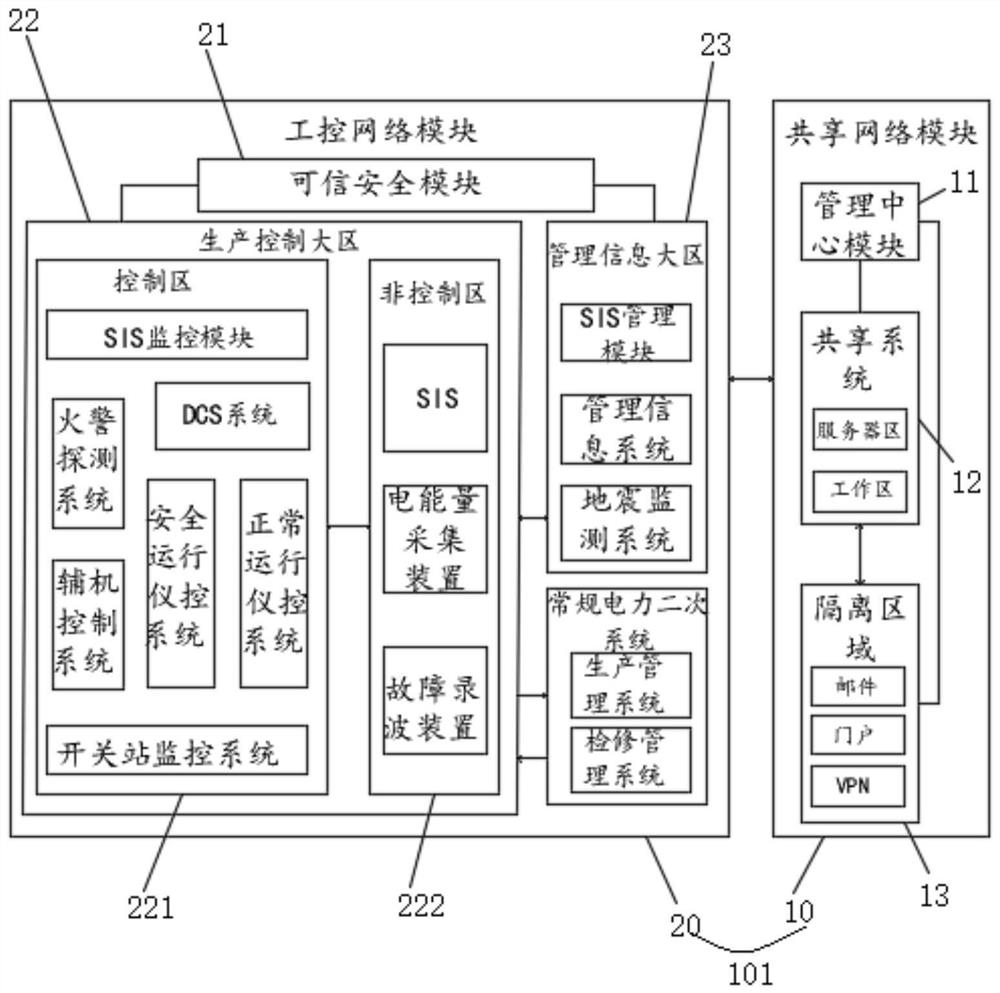
Security defense method and system for industrial control system network
ActiveCN112073431BAvoid security issuesMeet the requirements of relevant standards for graded protectionTransmissionRating systemComputer network
The present invention provides a security defense method for an industrial control system network. The industrial control system network includes a shared network module and an industrial control network module. The security defense method includes the following steps: establishing a management center module in the shared network module; The management center module performs security management on multiple grading systems in the shared network module; a trusted security module communicating with the management center module is established in the industrial control network module; the trusted security module controls all rating systems The above-mentioned industrial control network module conducts trusted defense. The invention also provides a security defense system for the industrial control system network. The security defense method and system of the industrial control system network provided by the present invention realizes the transformation of the defense method from passive "blocking and killing" to active immunity, and can effectively resist organized attacks while meeting the requirements of high real-time and high reliability. , Targeted attacks.
Owner:中广核工程有限公司 +1
A method of identity authentication based on n-dimensional sphere
InactiveCN101510875BShorten the timeRealize verificationPublic key for secure communicationUser identity/authority verificationPasswordAuthentication server
An identity authentication method based on N-dimensional sphere is provided by the present invention. An authentication server accepts a user registration and an identity verification after initialization; when a new user registers, the user computes a vector via a security one-way function according to a password selected by himself and submits it to the authentication server, the authentication server appoints an IDg as an identifier of the user identity for the user; the authentication server determines a N-dimensional sphere by combining its own secret vectors and the vector submitted by the user; the authentication server selects several different points on the N-dimensional sphere randomly, forms an encrypted file with them and sends it to the user via a security channel; when requiring for identity authentication, the user performs computation by using his own password and the encrypted file containing the identity authentication identifier, and transmits the result to the authentication server. After performing computation, the authentication server verifies and determines whether the user identity should be accepted. The present invention can reduce the storing information and the calculation amount of the authentication server efficiently, and can prevent fake authentication servers.
Owner:SOUTH CHINA UNIV OF TECH
Method and system for content-locking firewall based on whitelist
The present invention provides a whitelist-based content locking firewall method, comprising: step 200: performing semantic analysis on the data packet load received by the website, and obtaining the parsed text of the received data packet; step 300: receiving the website The parsed text of the data packet is matched with a text pattern library to decide whether to forward or intercept the received data packet, and the text pattern library contains value domains and structural features of multiple keywords. Based on the embodiment of the present invention, for websites with relatively fixed functions, the firewall can effectively defend against known and new network attacks by deploying the firewall, and can run with loopholes while ensuring normal functions, without expensive upgrades.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
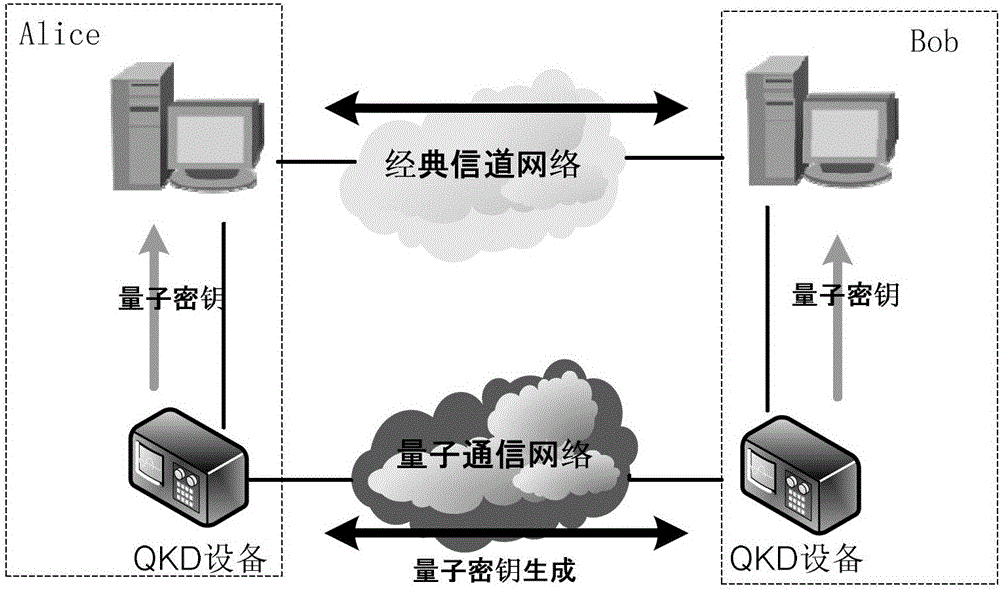
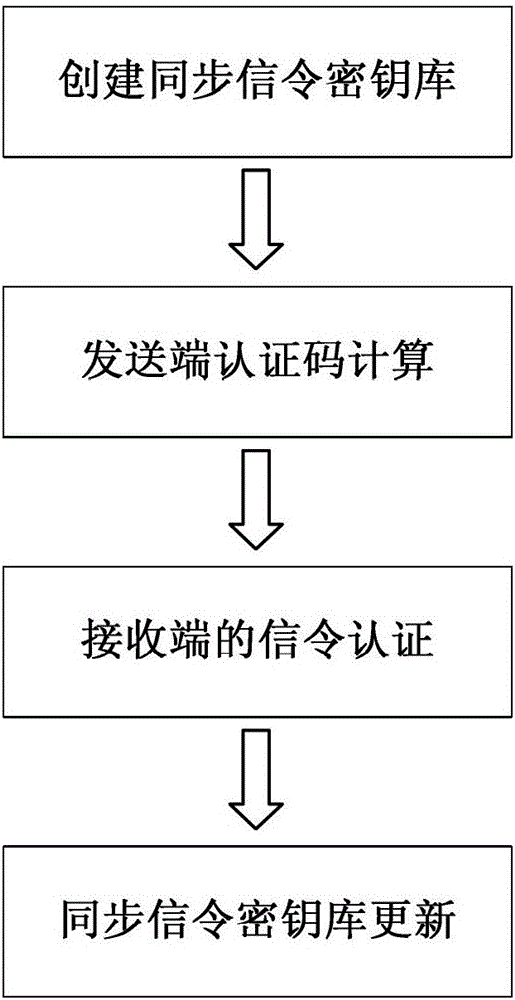
An authentication method for network signaling between quantum secure network devices
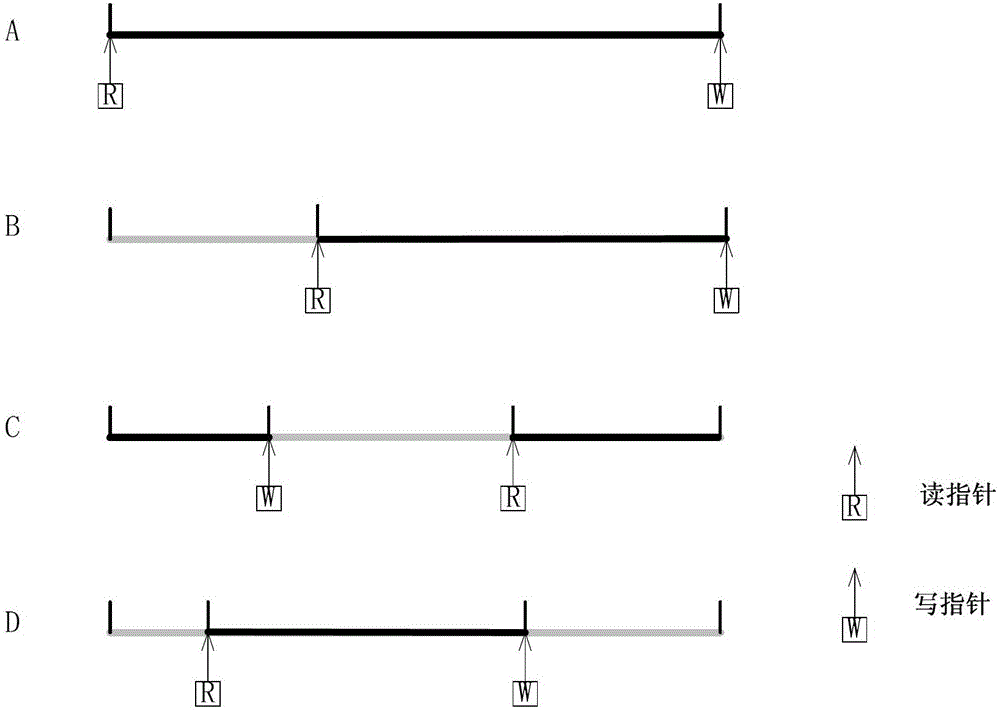
ActiveCN103095461BFast operationWith absolute securityKey distribution for secure communicationError preventionNetwork packetQuantum network
The invention discloses an authentication method for network signaling between quantum safety network equipment. The authentication method includes the following steps: creating synchronous signaling key stores used for signaling authentication for both sides between the communicated network equipment, wherein the synchronous signaling key stores are divided into an encrypting signaling key store and a decrypting signaling key store, and setting a read indicator and a write indicator for each signaling key store; a sending end calculating related hash operation message authentication codes H of keys based on key data and a read indicator offset address of the encrypting signaling key store of the sending end, and sending a corresponding signaling data packet to a receiving end; the receiving end receiving the signaling data packet, acquiring a read indicator offset address in the signaling data packet, and judging whether the key data of the read indicator offset address of the decrypting signaling key store of the receiving end is already used or not; and if the key data is not used, calculating H and verifying the content of the signaling data packet. The authentication method for the network signaling between the quantum safety network equipment has the advantages that the authentication is fast, and the method has a certain preventive effect on distributed denial of service (DDoS) attacks, can achieve true one-time-one-key encrypting authentication and is absolutely safe theoretically.
Owner:SHANDONG INST OF QUANTUM SCI & TECH +2
A method and security system for implementing SDP security group based on SDN
The invention discloses an SDN-based SDP security group implementation method and a security system, and the method achieves SPA single-packet authorization service logic through adoption of a flow table method of an SDN network, and carries out the planning and identity authentication of access authorities of different users through combining with the IAM user management of a cloud platform. According to the invention, the security of the cloud platform security group function is enhanced; accurate control of the security group on external authorization is realized; in combination with the identity authentication technology of the cloud platform and the SDN cloud network, the additional cost of the SDP gateway and the SDP controller is reduced, the SDP technology and the cloud computing security technology are fused, meanwhile, attacks from an internal network can be effectively defended, and comprehensive defense of flow in all directions of the cloud platform can be achieved.
Owner:GUANGZHOU BINGO SOFTWARE
A realization method of address and port hopping communication based on netfilter
ActiveCN104853003BAvoid multiple copiesImprove processing efficiencyTransmissionComputer scienceClock synchronization
The invention provides a netfilter-based address and port hopping communication implementation method, which comprises the steps of 1) initially deploying; 2) configuring the hopping parameters of a server, generating a hopping key, storing the hopping key, and distributing the hopping parameters to an authentication and distribution agent by means of the server; 3) acquiring the hopping parameters of the server by means of a client after the authentication process of the client by an authentication and distribution center; 4) synchronizing the clocks of the client, the server and an address hopping gateway, calculating the current hopping address and the current hopping port of the server, and modifying addresses and ports corresponding to data messages sent and received by a local computer so as to realize the communication; 5) receiving communication messages received by the address hopping gateway from the client and the server, and acquiring the hopping address of the server by an address hopping engine according to the above address hopping parameters, and modifying addresses corresponding to the above messages to complete the message forwarding process; 6) realizing the port hopping function through a port hopping engine by the server, modifying ports corresponding to the messages of an importer / exporter to complete the communication. The method is simple in principle, easy to realize and popularize, and good in safety.
Owner:NAT UNIV OF DEFENSE TECH
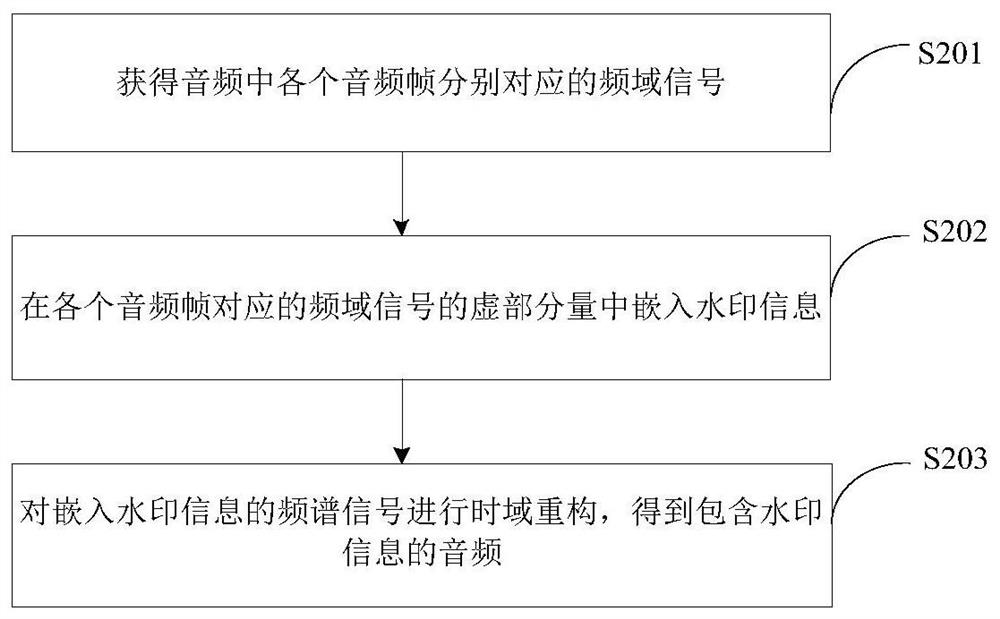
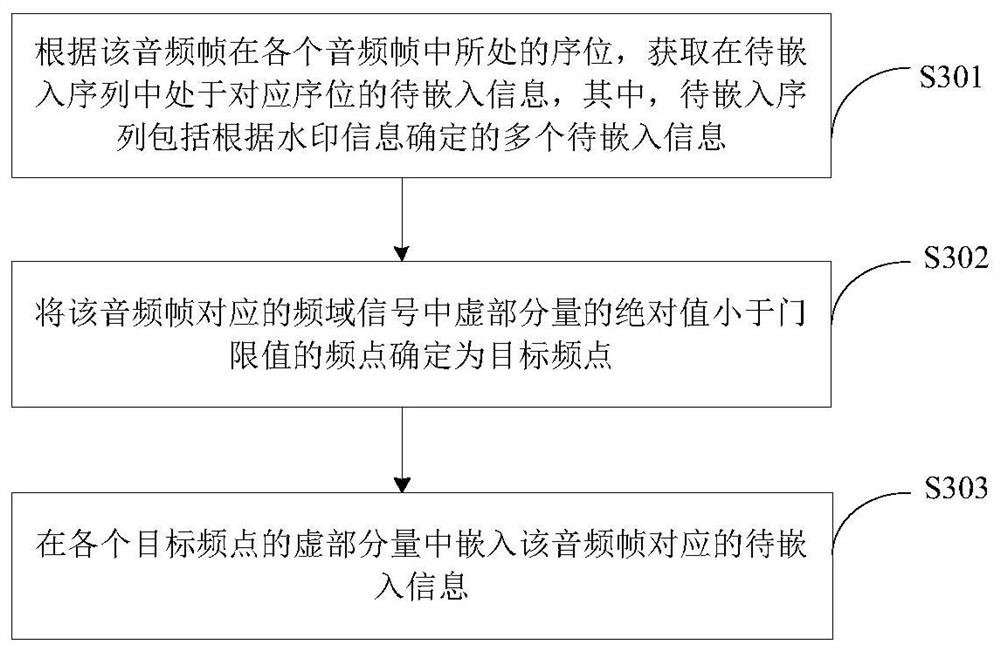
Audio watermark processing method and device, electronic equipment and storage medium
PendingCN113362835AGuaranteed sound qualityAccurate extractionSpeech analysisPattern recognitionTime domain
The invention discloses an audio watermark processing method and device, electronic equipment and a storage medium, wherein the energy for embedding a watermark can be reduced, the accurate extraction of the watermark can be ensured, and better robustness and concealment can be obtained. The method comprises the following steps: acquiring frequency domain signals respectively corresponding to each audio frame in audio; embedding watermark information into the imaginary component of the frequency domain signal corresponding to each audio frame; and performing time domain reconstruction on the frequency spectrum signal embedded with the watermark information to obtain an audio containing the watermark information.
Owner:HANGZHOU NETEASE CLOUD MUSIC TECH CO LTD
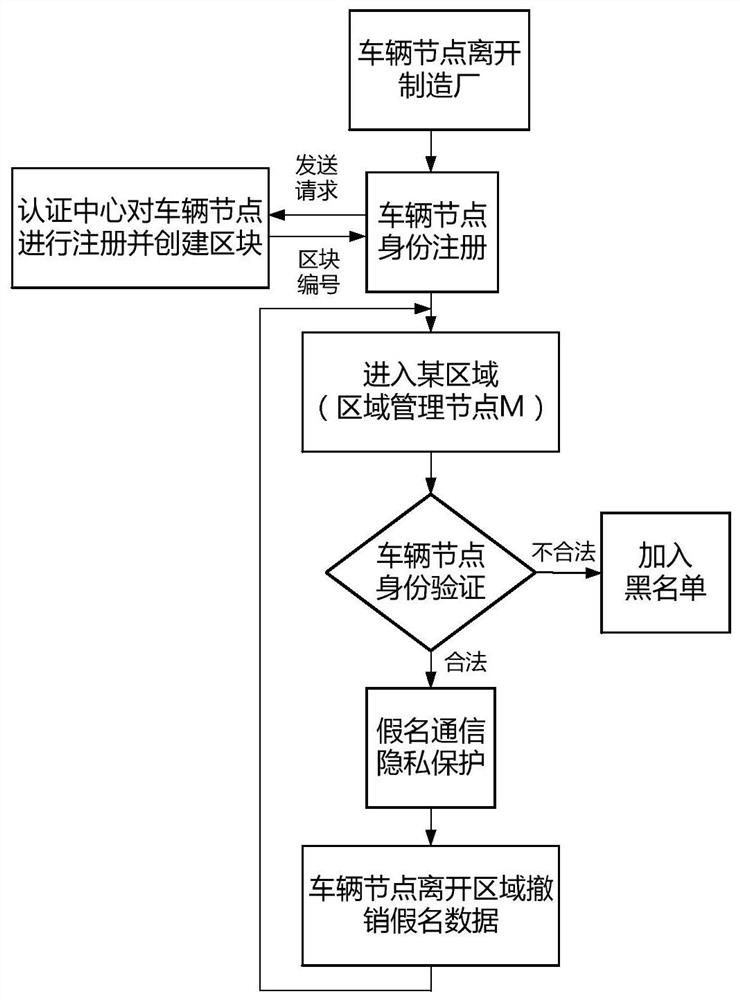
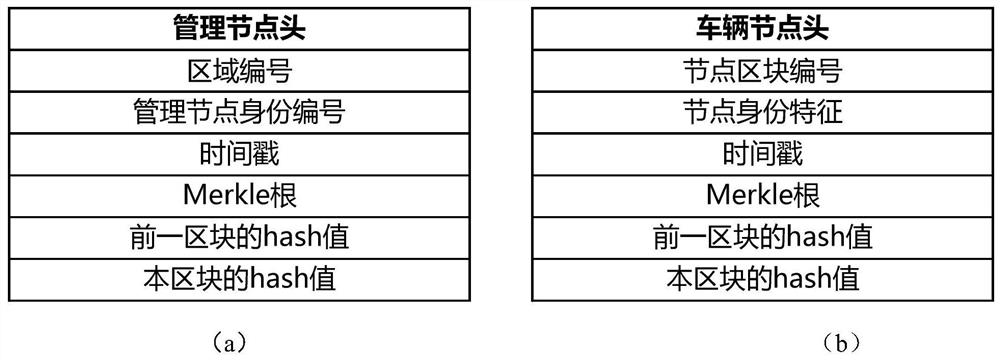
Low altitude node identity authentication and privacy protection method based on hash chain
ActiveCN109194480BGuarantee data securityGuaranteed confidentialityUser identity/authority verificationCommunications managementConfidentiality
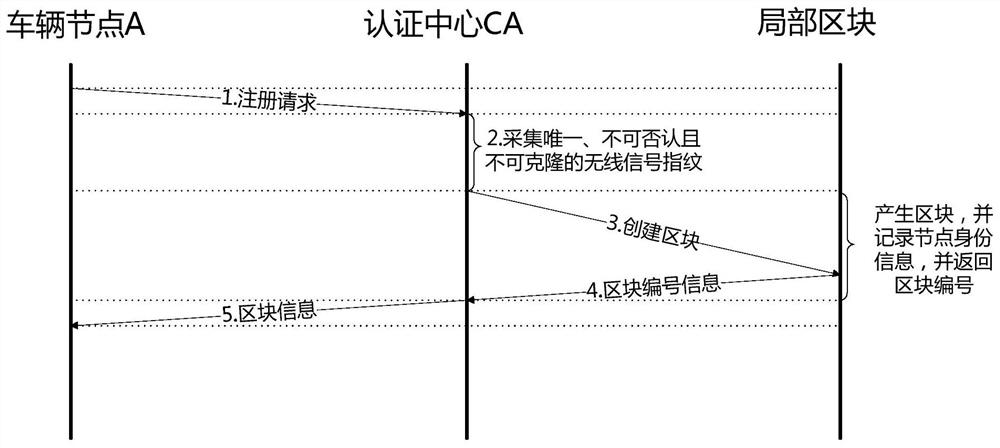
The present invention discloses a low-altitude node identity authentication and privacy protection method based on a Hash chain. The method comprises the steps of: when a vehicle node enters a space-air-ground integral network at the first time, taking unique and undeniable wireless signal fingerprints which cannot be cloned as identity features of the vehicle node, and creating a Hash block for the vehicle node while performing identity registration of the vehicle node by an authentication center; when communication of the vehicle node is performed in an area, performing identity authentication based on block content by a management node; in order to protect the identity privacy, employing a pseudonym generated by the management node to perform communication by the vehicle node; and recording key motions or information of different nodes at different time in the area by the management node, and recording the key motions or the information of the vehicle node itself at different areasat different time by the vehicle node. The method can effectively defense various attacks such as the sybil attack, the denial of service attack and the replay attack. Besides, the data safety of thenetwork is guaranteed, namely, the confidentiality, integrity, availability and non-repudiation of the data in the network.
Owner:XIAMEN UNIV
Face recognition method and device based on binocular camera and storage medium
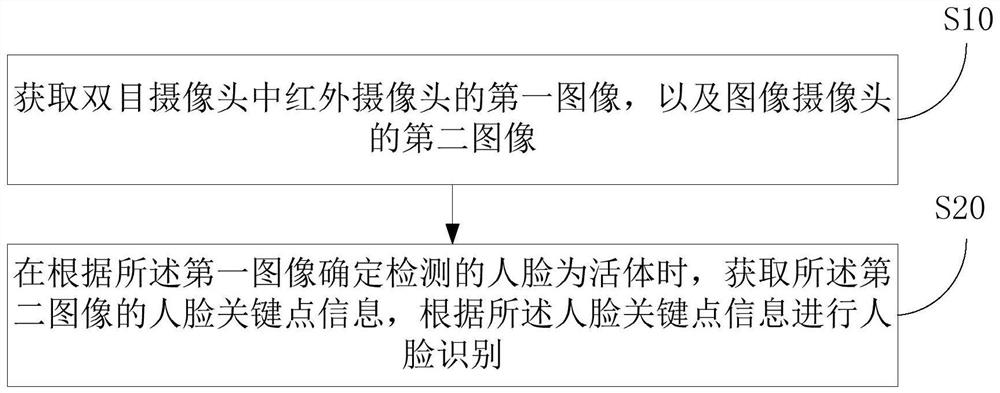
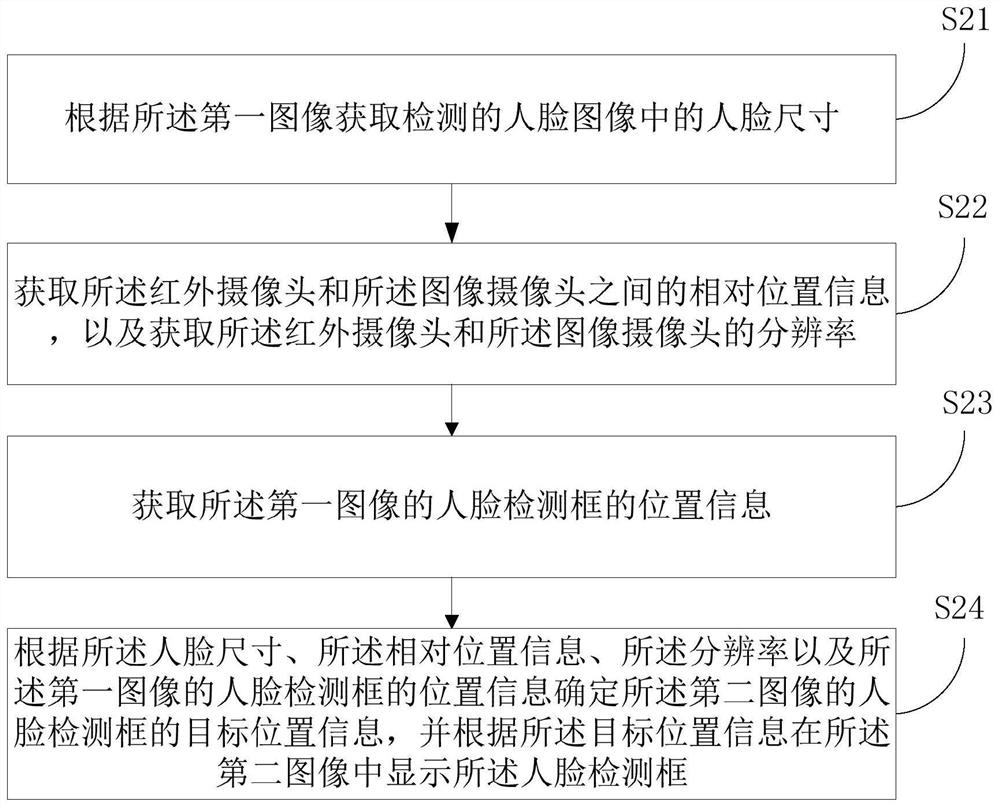
PendingCN113673378AImprove securityEffective defense against attacksCharacter and pattern recognitionComputer graphics (images)Radiology
The invention discloses a face recognition method and device based on a binocular camera and a storage medium. The face recognition method based on the binocular camera comprises the steps that a first image of an infrared camera in the binocular camera and a second image of an image camera are acquired; and when it is determined that the detected face is a living body according to the first image, face key point information of the second image is acquired, and face recognition is performed according to the face key point information. Face recognition is carried out by using the binocular camera, so that attacks of photos, videos, 3D printing and the like can be effectively resisted, and the safety of face recognition is improved.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
A collaborative control method for array honeypots based on blockchain
ActiveCN108521426BEffective defense against attacksResist attackPublic key for secure communicationTamper resistanceAttack
The invention relates to an array honey pot cooperative control method based on a block chain. The method comprises the following steps: constructing a private chain by using an Ethereum platform, andrealizing de-centralized cooperative operation thought of a honey pot host cluster through a mining way; constructing a topological structure consistent with the Ethereum platform starting from a P2Pnetworking model, and realizing the communication through web3J. Each host in the array executes the mining, the host acquiring an accounting charging right can holds the post of a honey pot serviceconversion task at one periodic time, conversion information is sent through an encryption mechanism, and other host receives and executes the corresponding conversion instruction. Furthermore, external port request access data is stored in the block chain by using the tamper resistance of the block chain information, thereby obtaining the digital evidence for implementing the attack by an attacker. Through the method disclosed by the invention, the cooperative operation of the array honey pot host cluster is guaranteed, thereby trapping the attacker by using the true-false service in dynamicconversion, and the network security active defense aim is realized.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com