Content lock firewall method and system based on white list
A technology of white list and firewall, which is applied in the field of firewall and network security, can solve the problems of high cost and achieve the effect of defending against new network attack modes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
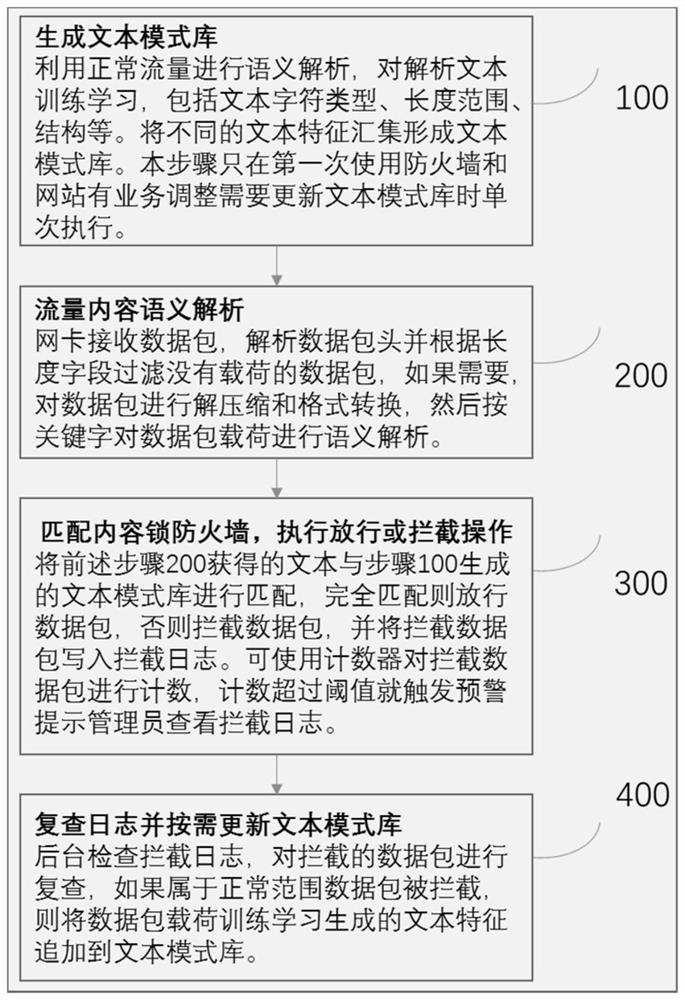
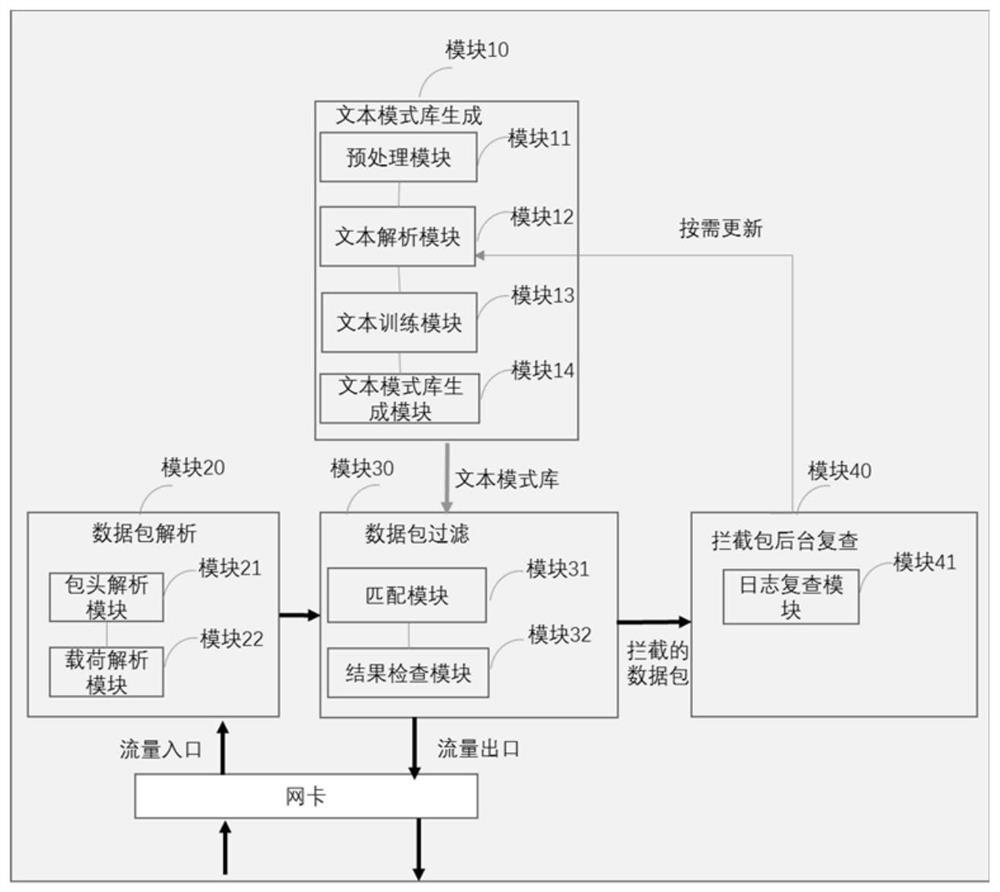
[0039] As introduced in the background art, the traditional firewall technology has problems such as slow response or high maintenance cost, so a more convenient and quicker method is needed. For this reason, the inventor of this patent proposes a data packet filtering method based on a whitelist-based content lock, which uses a text pattern library as a whitelist, and only allows trusted text content to pass through the firewall. This method utilizes the regular and followable characteristics of the normal traffic content of the website, conducts text analysis and training on the normal traffic content, learns to generate a text pattern library, and only allows the data packets completely matched by the text pattern library to pass through the firewall during the content detection process , and perform background review on unmatched data packets, and update the text pattern library as needed to prevent false interception. figure 1 A flowchart of an embodiment of the method is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com