Patents
Literature
333 results about "Cyber-attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computers and computer networks an attack is any attempt to expose, alter, disable, destroy, steal or gain unauthorized access to or make unauthorized use of an asset. A cyberattack is any type of offensive maneuver that targets computer information systems, infrastructures, computer networks, or personal computer devices. An attacker is a person or process that attempts to access data, functions or other restricted areas of the system without authorization, potentially with malicious intent. Depending on context, cyberattacks can be part of cyberwarfare or cyberterrorism. A cyberattack can be employed by sovereign states, individuals, groups, society or organizations, and it may originate from an anonymous source.
Detection of Distributed Denial of Service Attacks in Autonomous System Domains
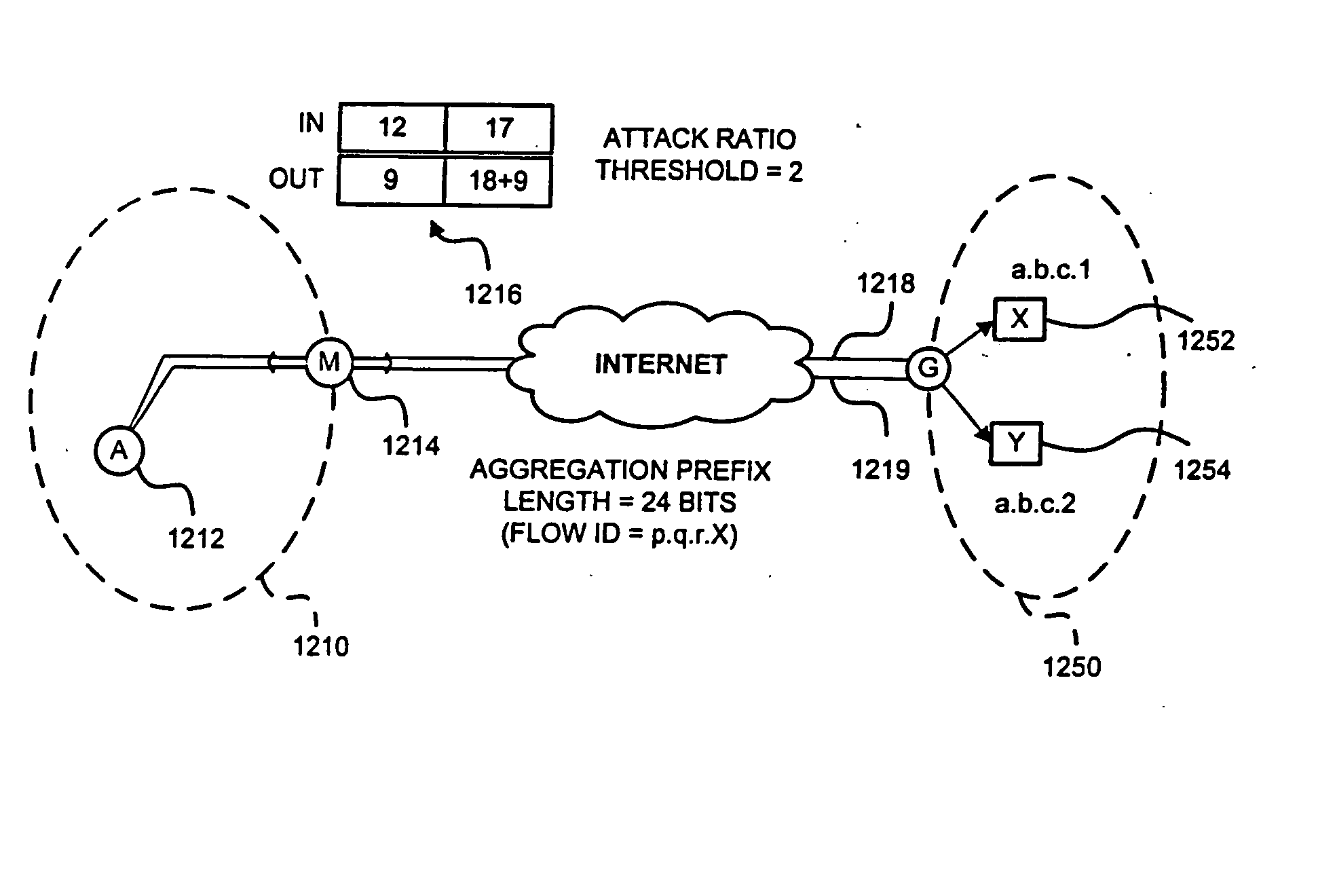
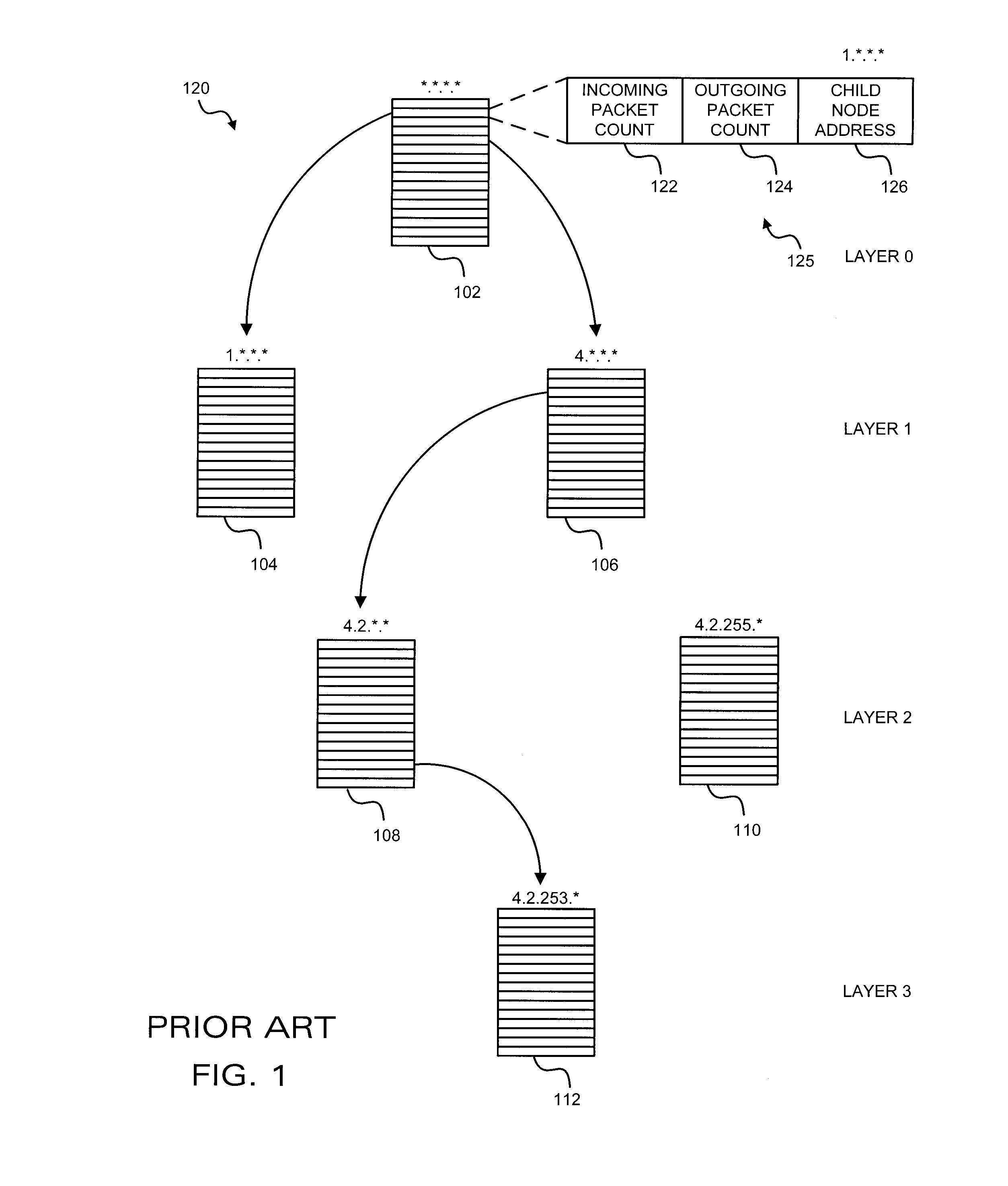
A denial-of-service network attack detection system is deployable in single-homed and multi-homed stub networks. The detection system maintains state information of flows entering and leaving the stub domain to determine if exiting traffic exceeds traffic entering the system. Monitors perform simple processing tasks on sampled packets at individual routers in the network at line speed and perform more intensive processing at the routers periodically. The monitors at the routers form an overlay network and communicate pertinent traffic state information between nodes. The state information is collected and analyzed to determine the presence of an attack.
Owner:MARYLAND UNIV OF
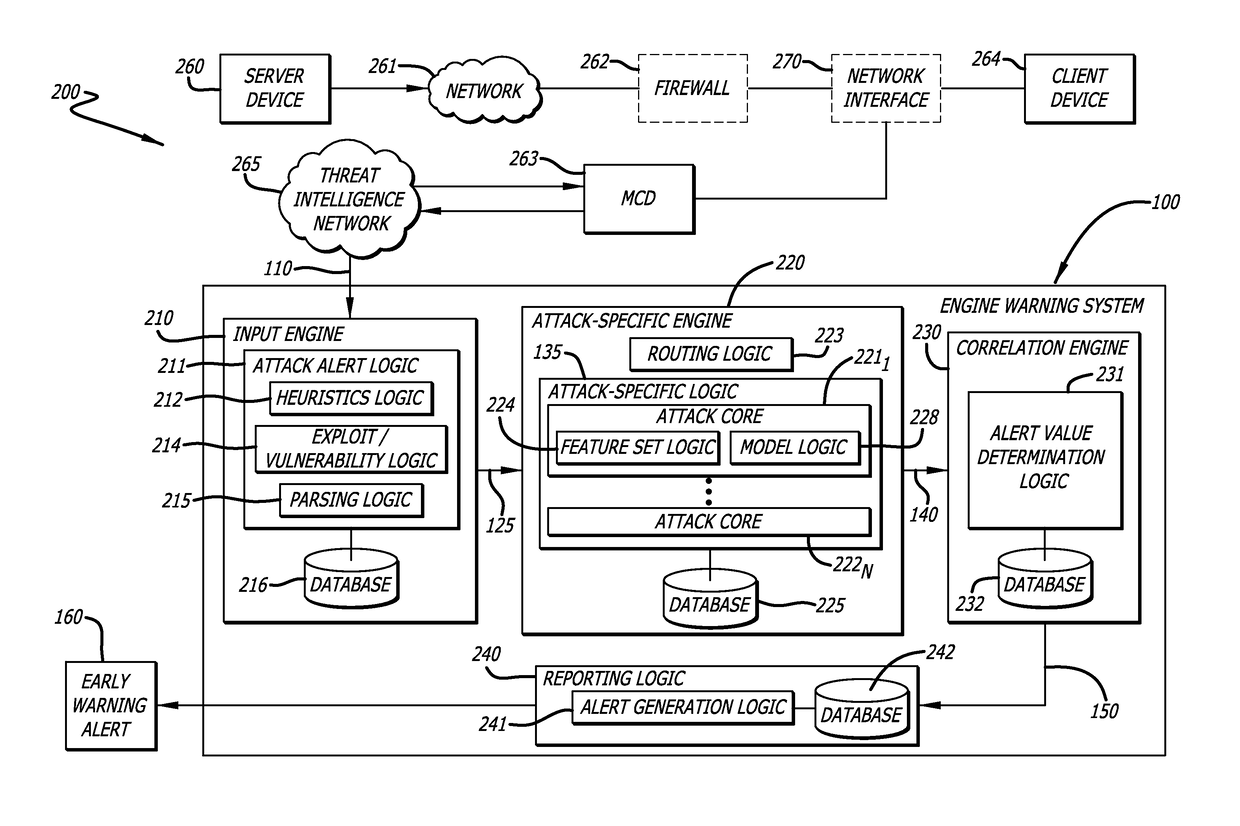
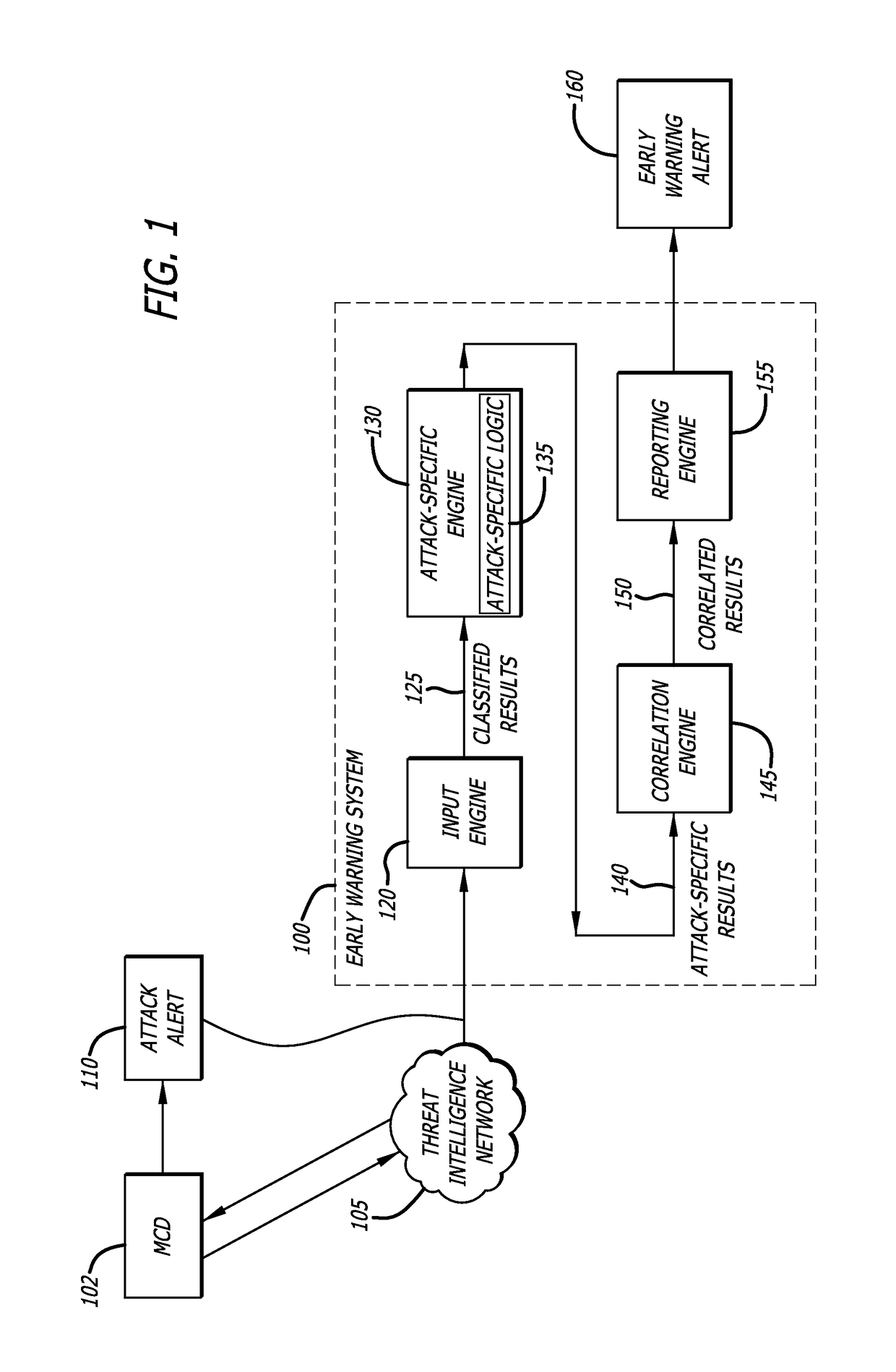
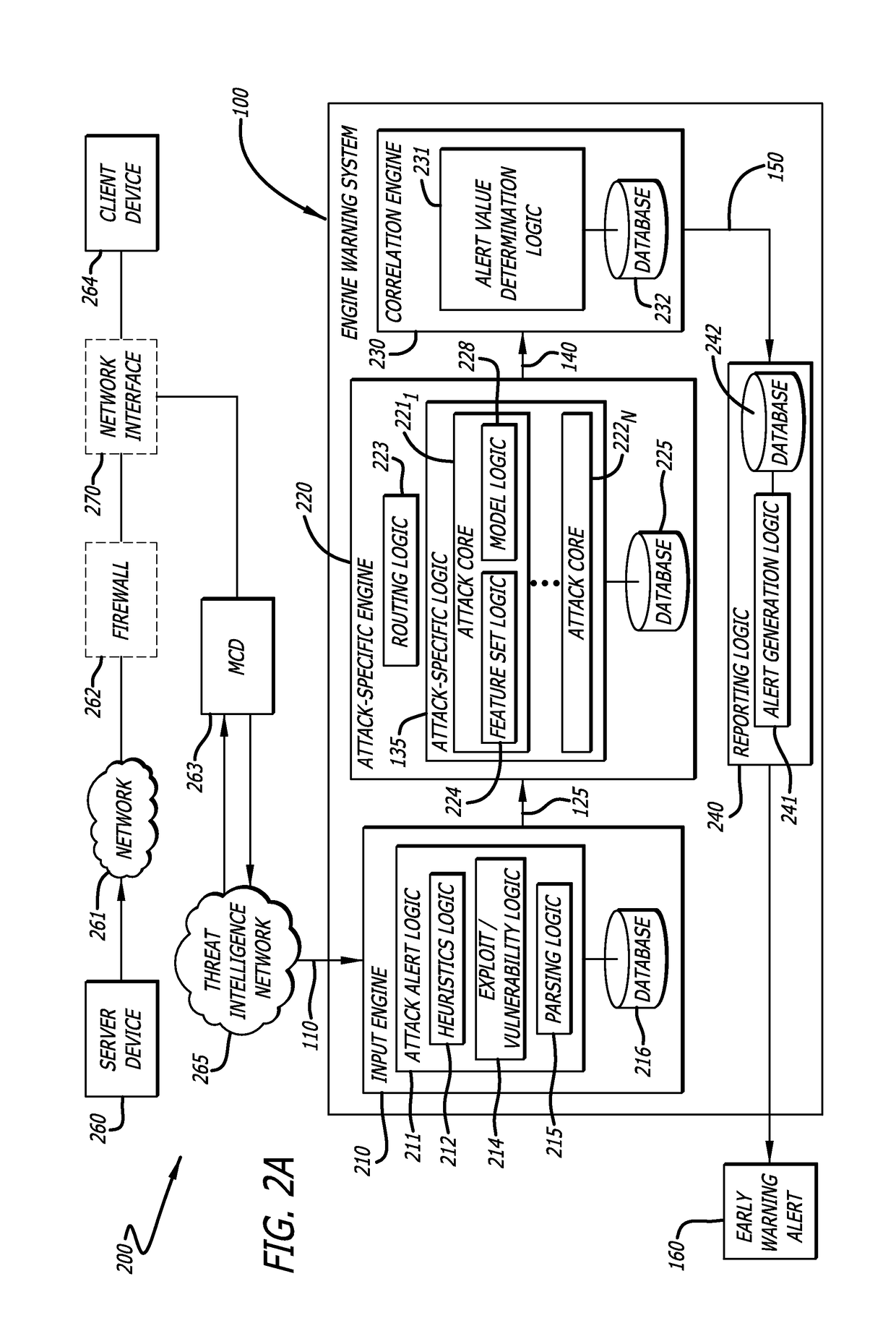
Cyber attack early warning system
An early warning system and method for generating an alert regarding a potential attack on a client device is provided for based on real-time analysis. The early warning system and method generally comprise receiving data associated with an attack alert, wherein the attack alert corresponds to an electrical signal that indicates detection of a malware attack from a remote source. The received data is analyzed using an attack-specific engine that is configured to generate an attack-specific result. An attack value is computed based on the attack-specific result and a consideration of potential attack targets, wherein the attack value is compared to a threshold value so as to determine whether or not to generate an early warning alert. An early warning alert is generated when the attack value matches or exceeds the threshold value.
Owner:FIREEYE SECURITY HLDG US LLC
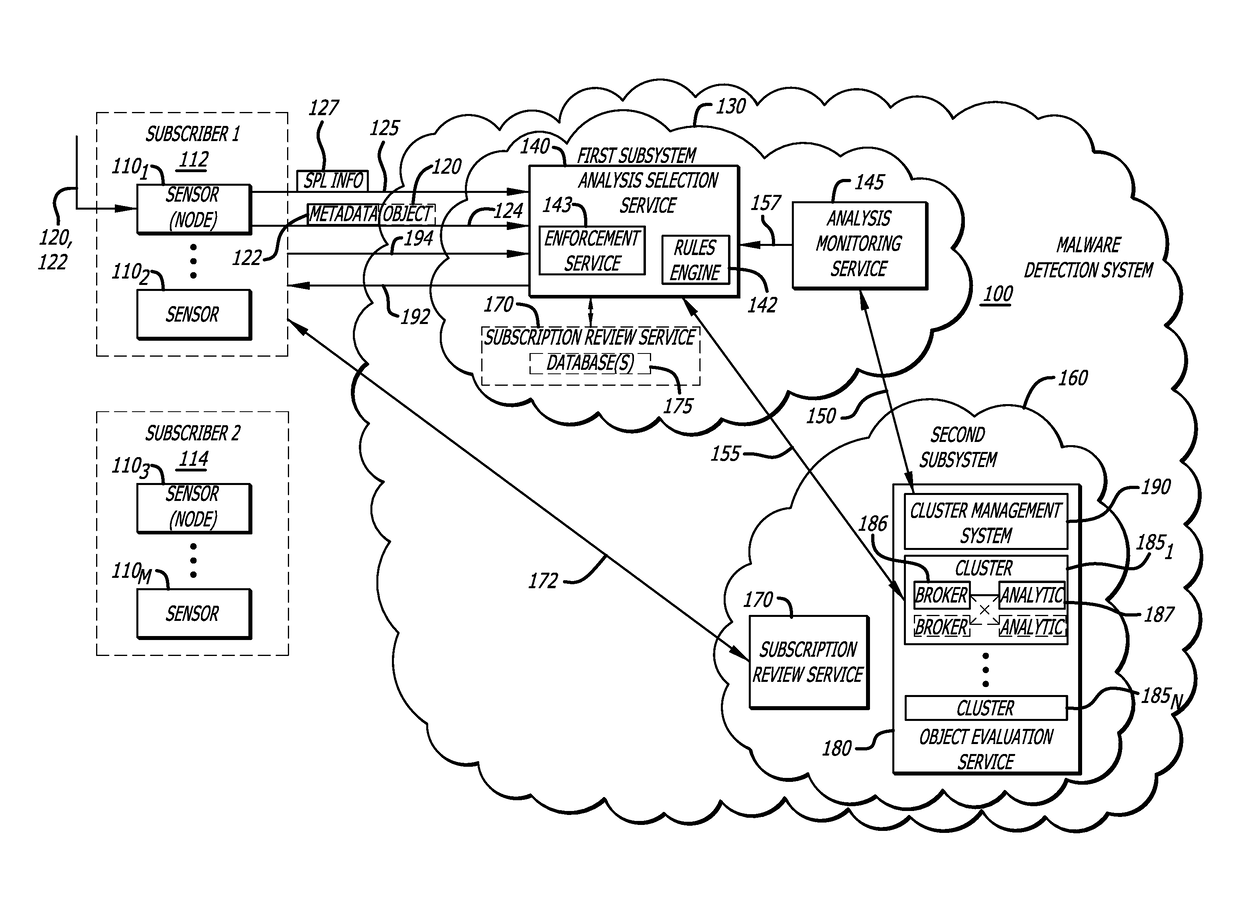
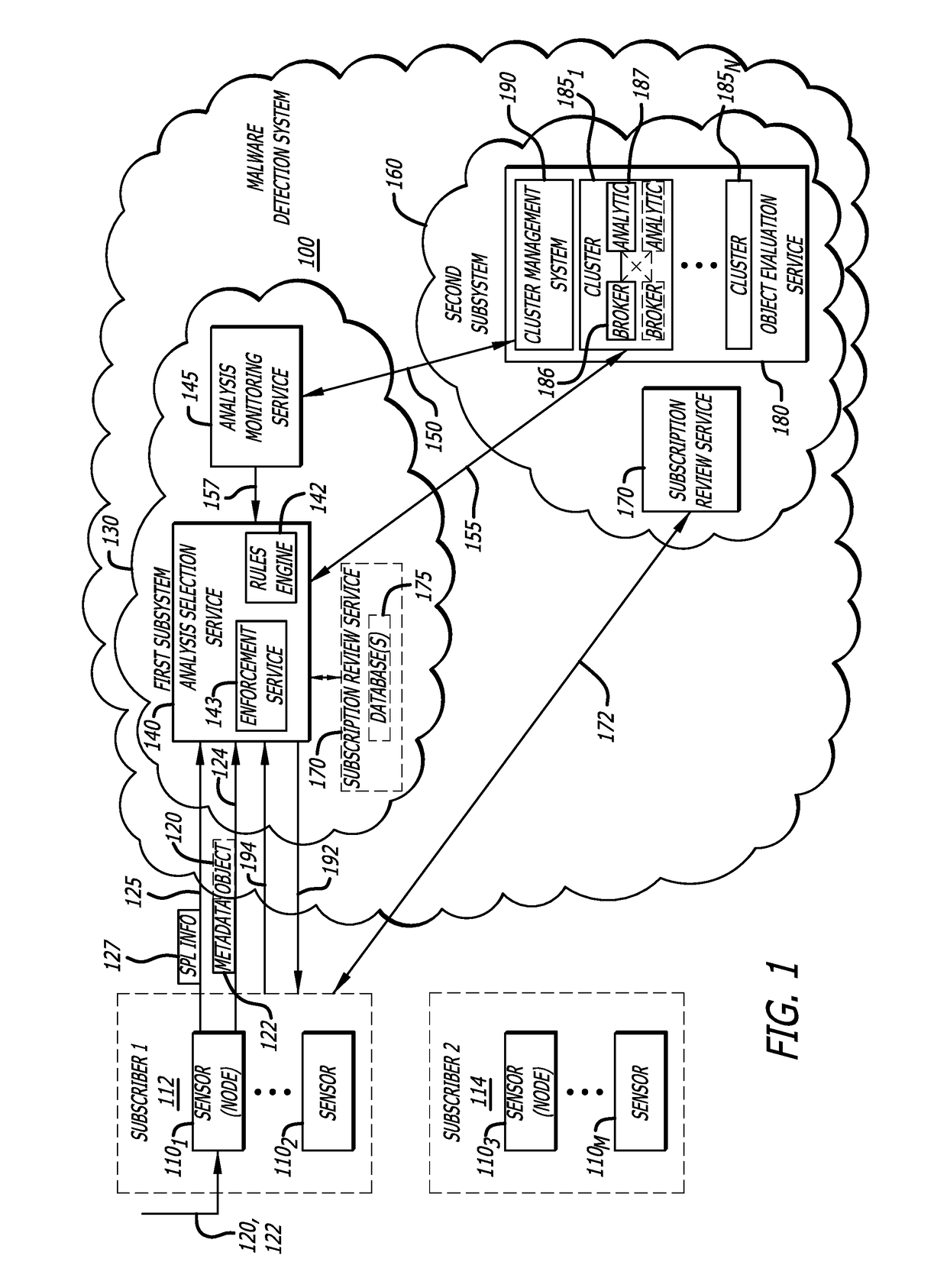
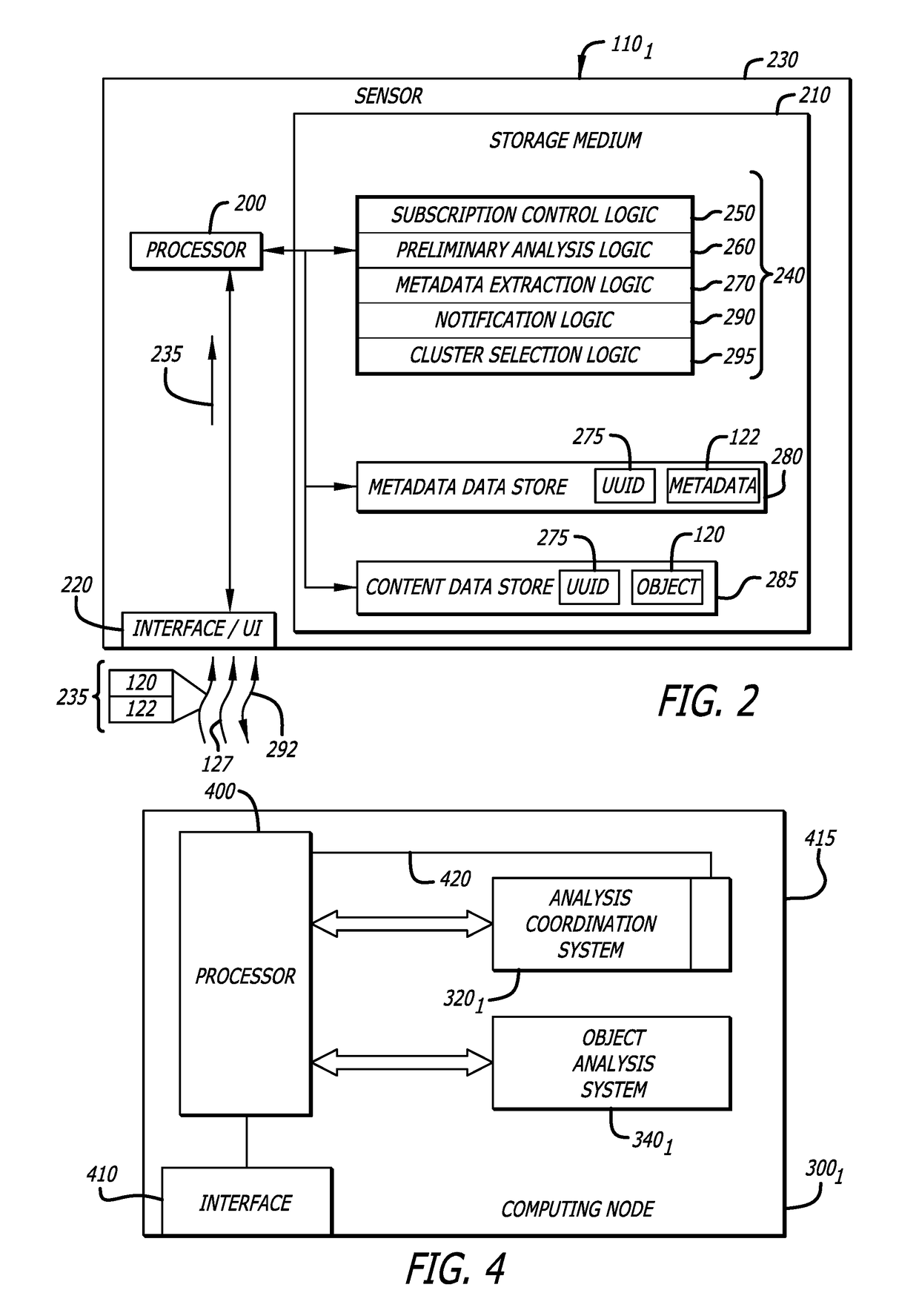
Attribute-controlled malware detection
A computerized method for authenticating access to a subscription-based service to detect an attempted cyber-attack. The method features operations by the cloud broker that include receiving service policy level information and information based on operational metadata. The service policy level information includes at least subscription attributes to identify one or more performance criterion in analyses conducted on one or more objects submitted by a sensor for malware representing an attempted cyber-attack. The operational metadata includes metadata that pertains to an operating state of one or more clusters of a plurality of clusters of the subscription-based service. The cloud broker, using both the service policy level information and the information based on the operational metadata, selecting a cluster of the plurality of clusters to analyze the one or more objects submitted by the sensor and establishes a communication session between the sensor and the cluster via the cloud broker.
Owner:FIREEYE SECURITY HLDG US LLC
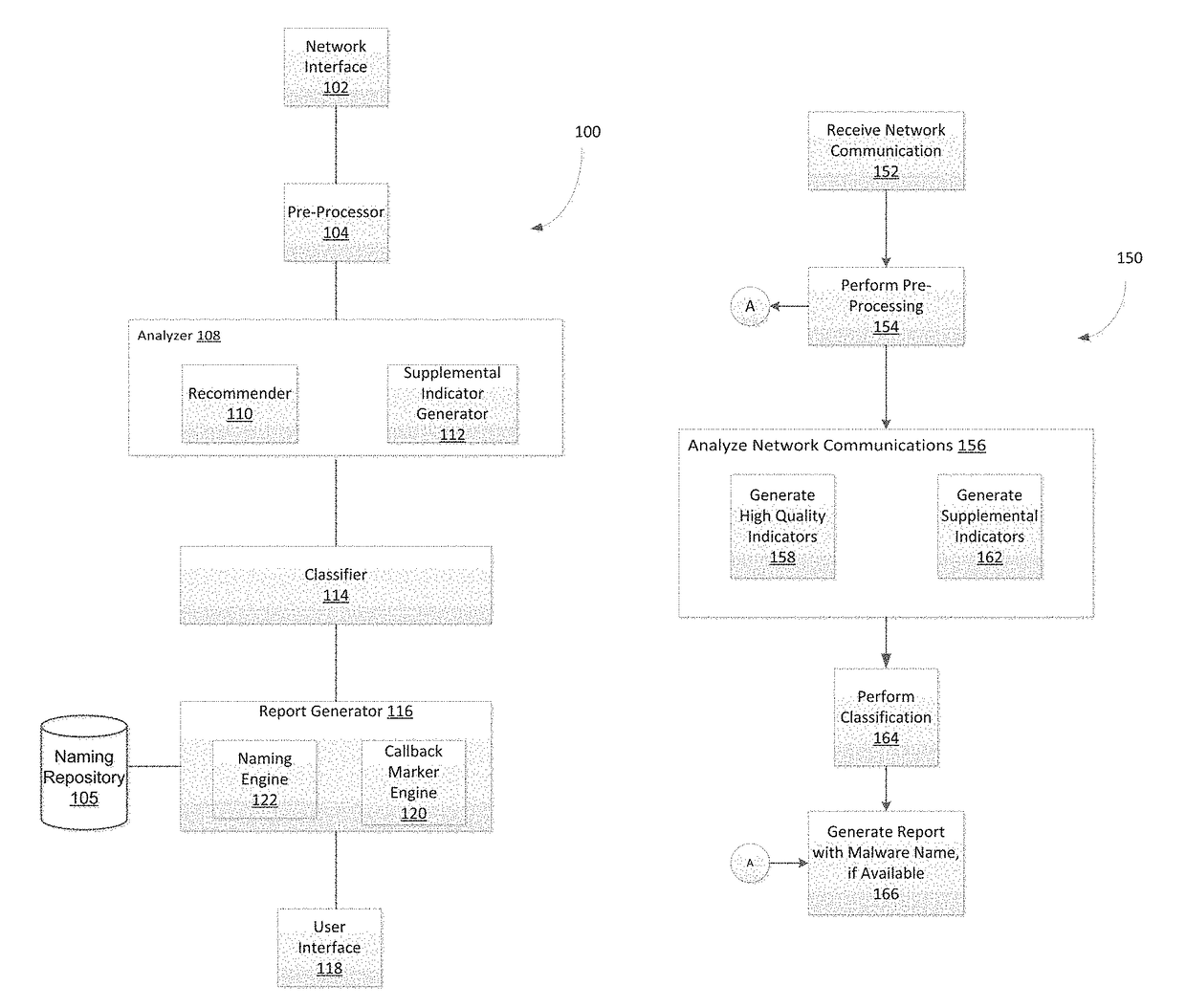
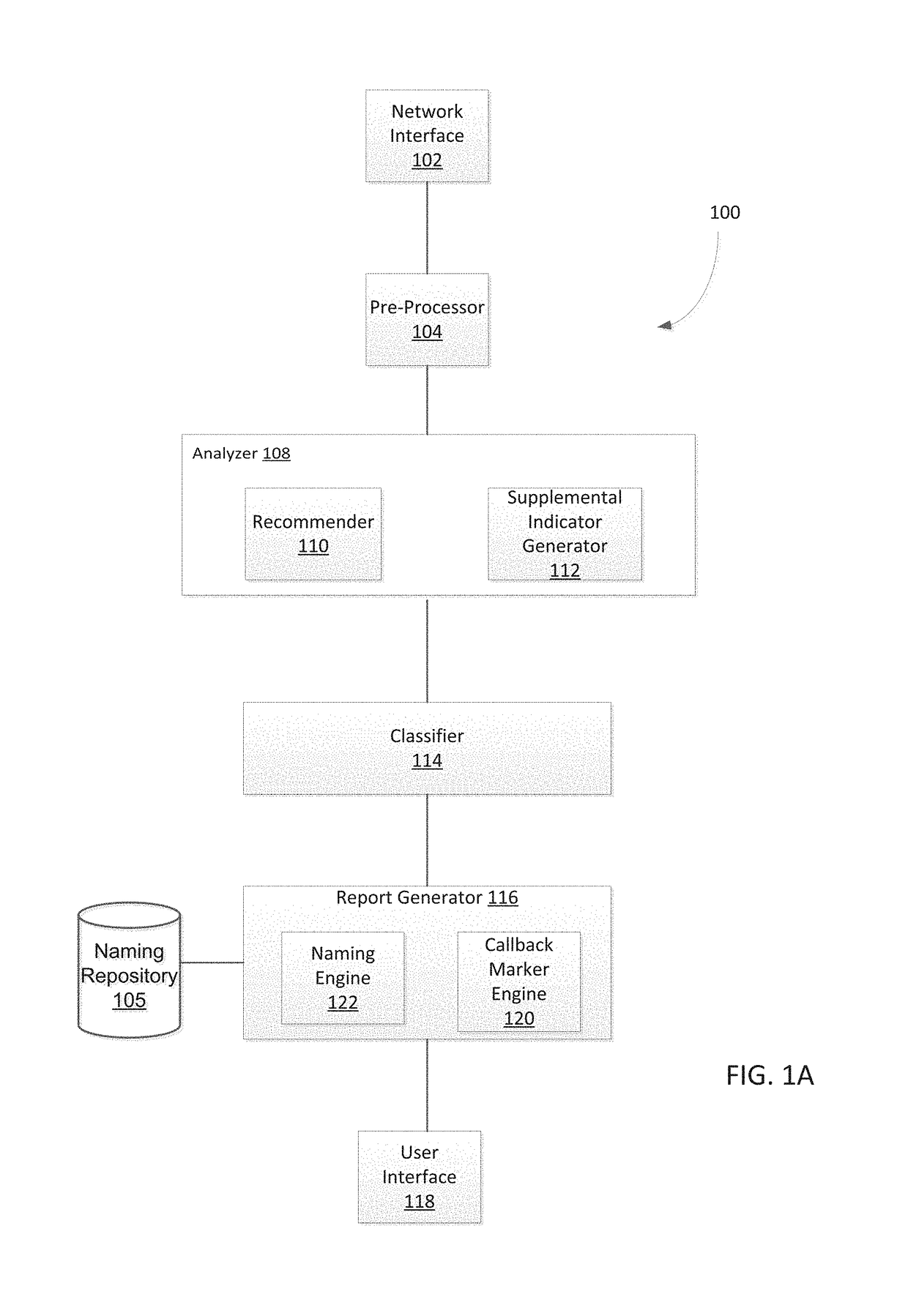
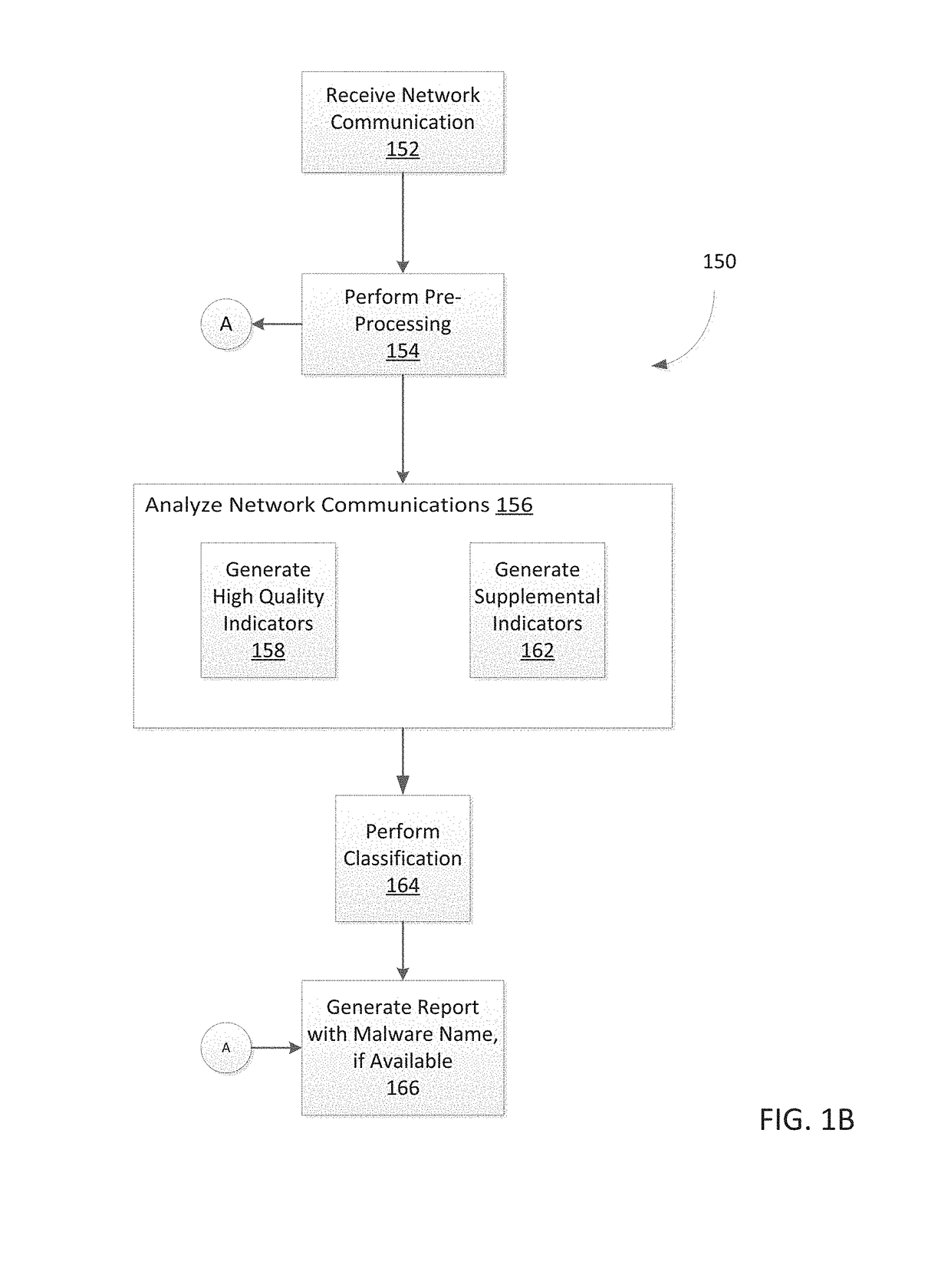
System and method for detecting malicious activity and classifying a network communication based on different indicator types
Owner:FIREEYE SECURITY HLDG US LLC +1
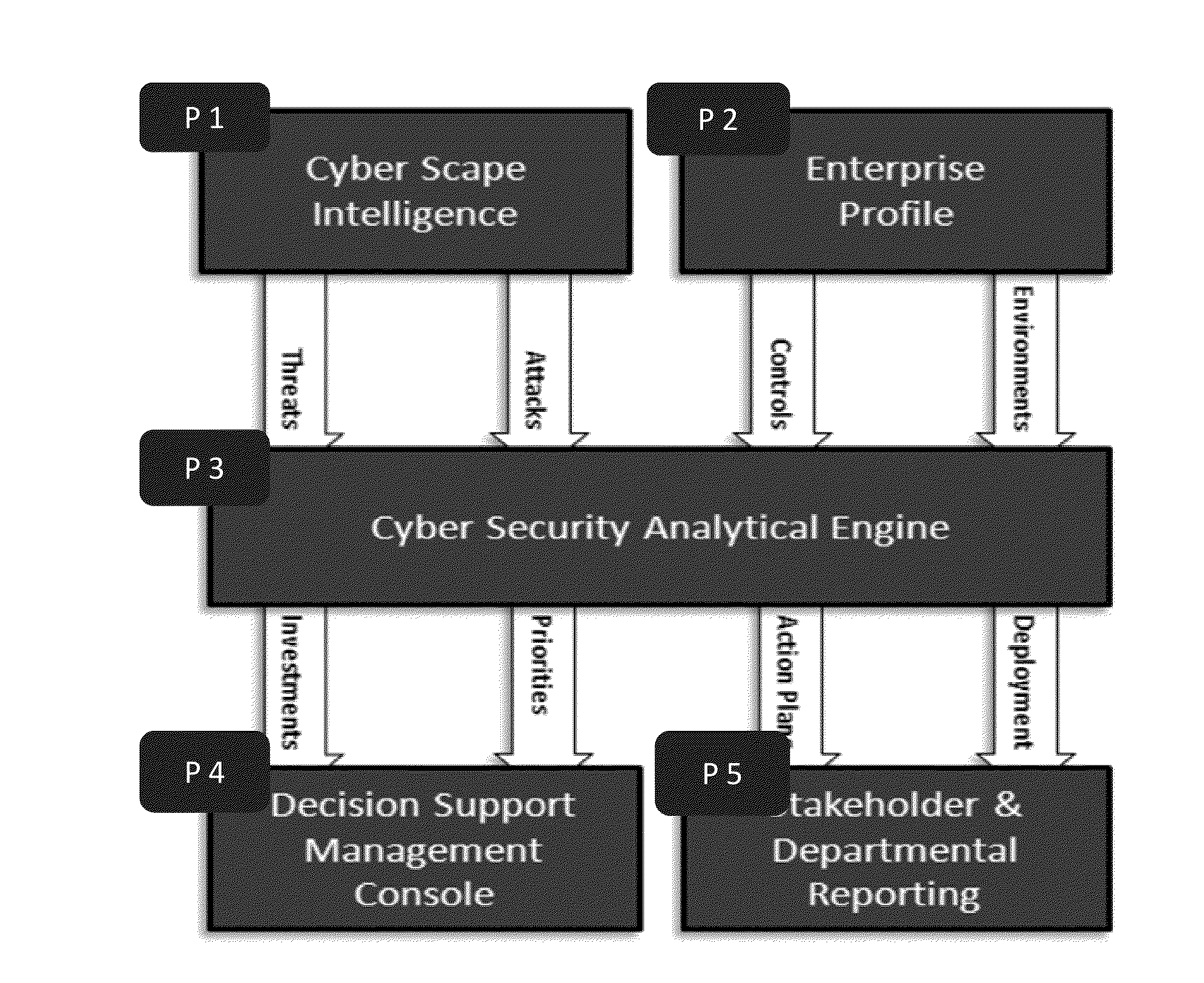
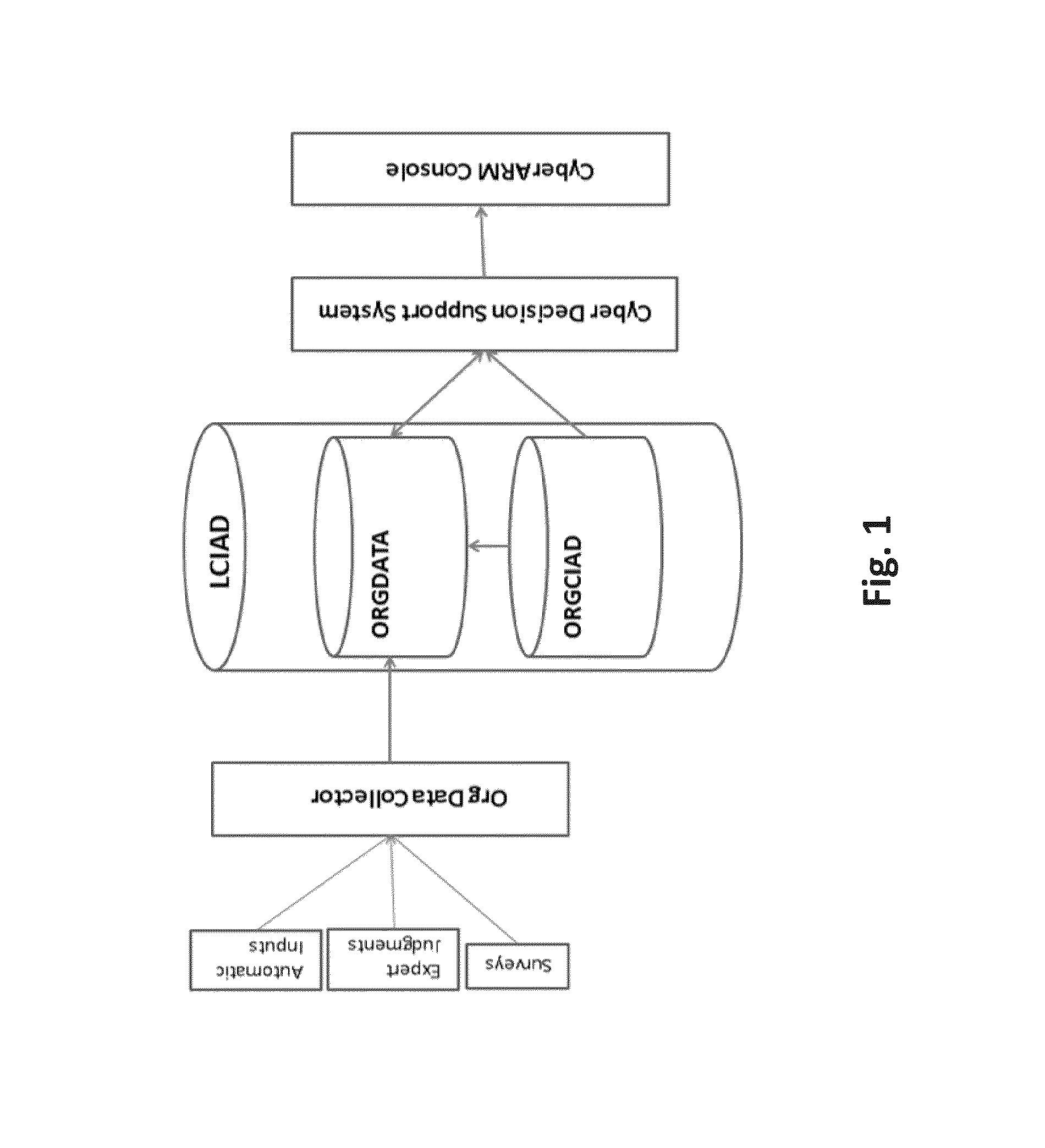
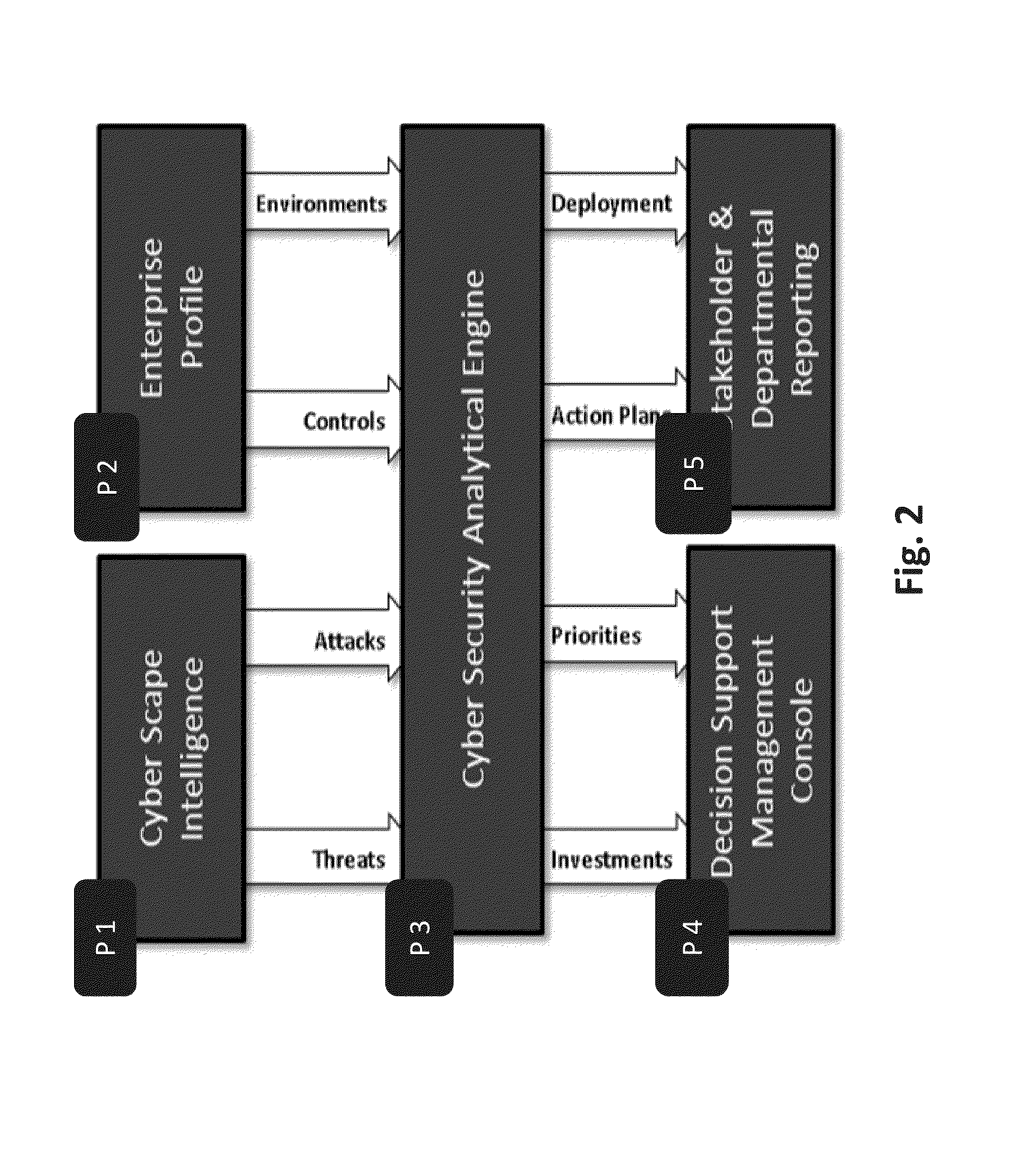
System and method for cyber attacks analysis and decision support
ActiveUS20130227697A1Risk of attack has also grownEasy to controlMemory loss protectionError detection/correctionCyber-attackInternet privacy
A method for cyber attack risk assessment, the method comprising operating at least one hardware processor for: collecting global cyber attack data from a networked resource; collecting organizational profile data from a user, wherein the organizational profile data comprises: types of computerized defensive controls employed by the organization, a maturity of each of the computerized defensive controls, and organizational assets each pertaining to a business environment and each associated with at least one of the computerized defensive controls; and computing a cyber attack risk of the organization in real time, by continuously performing said collecting of global cyber attack data and comparing the global cyber attack data to the organizational profile data, to compute a cyber attack risk score for each of the organizational assets.
Owner:SAUL ACQUISITION SUB LLC
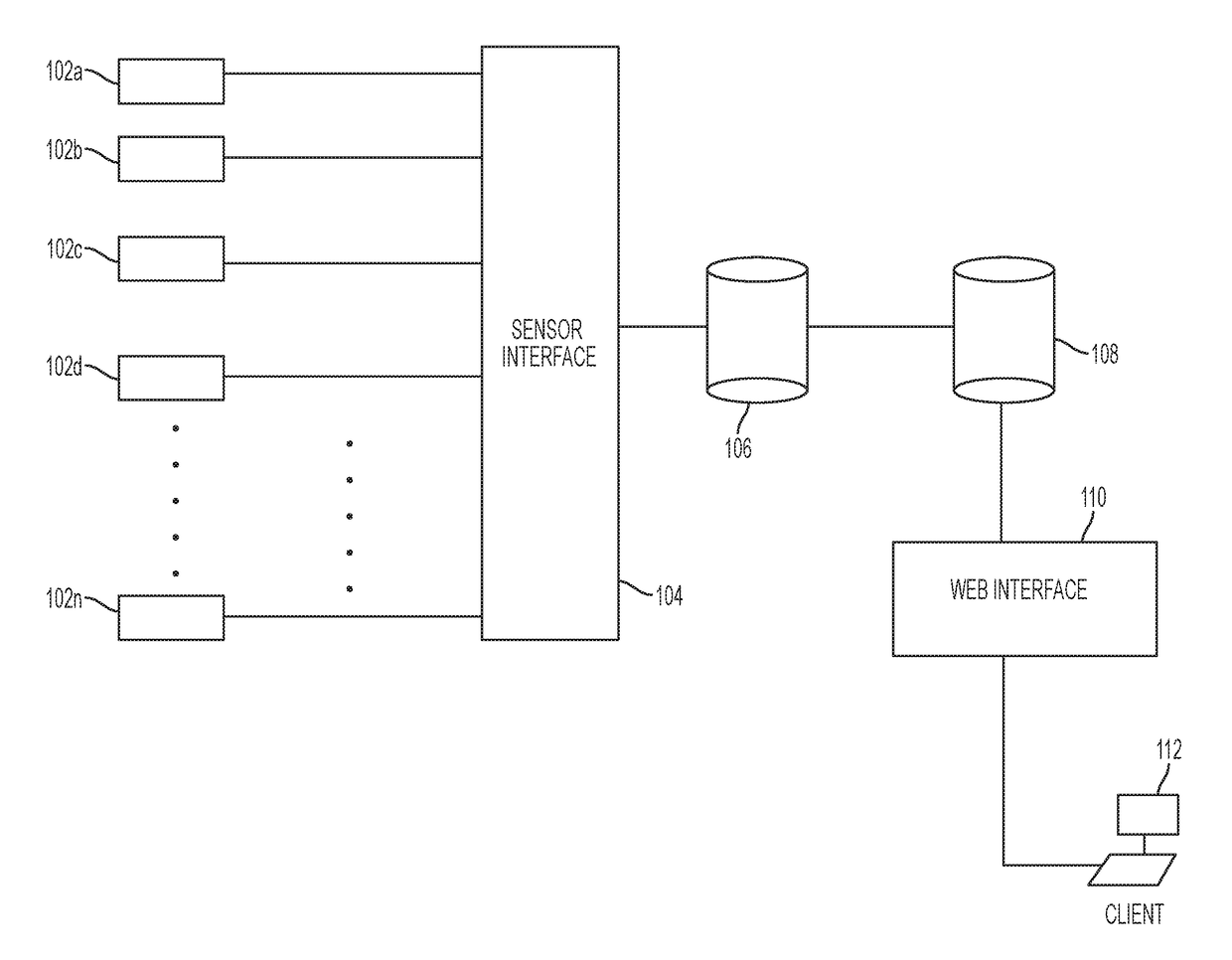
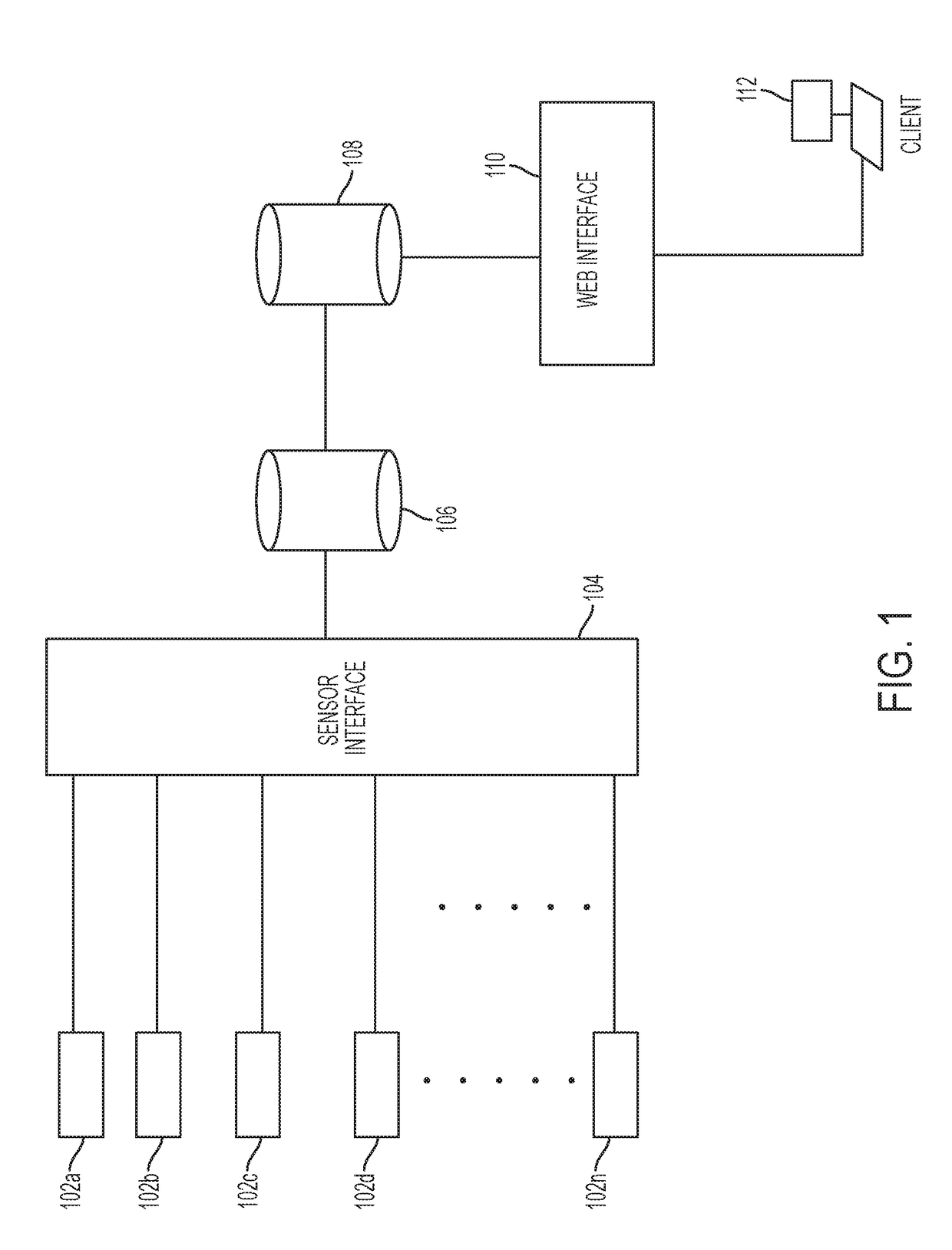
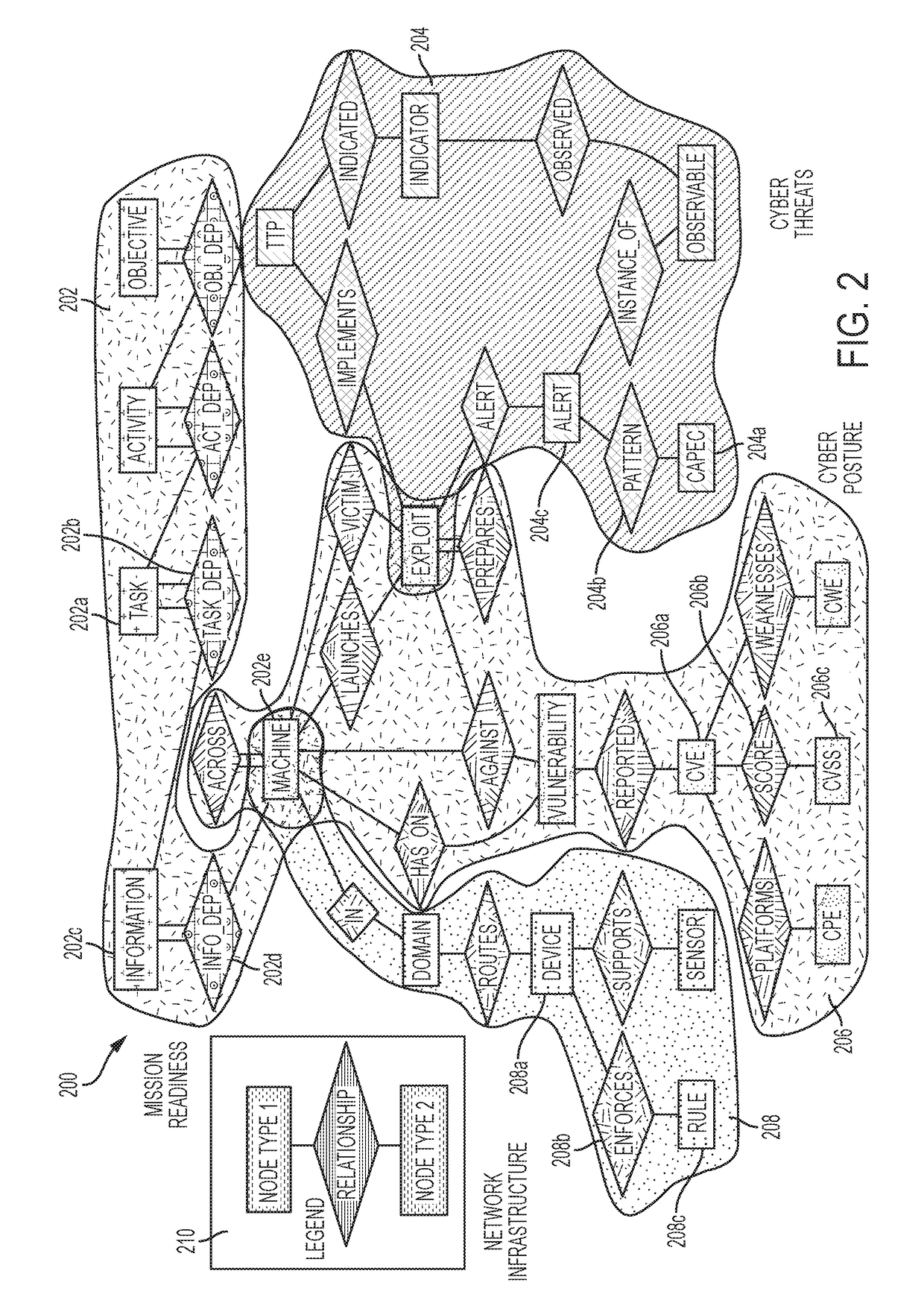
System and method for visualizing and analyzing cyber-attacks using a graph model
A system and method for implementing a graph database to analyze and monitor a status of an enterprise computer network is provided. In one example, a plurality of sensors can be inputted into sensor interface in which all of the data associated with the sensors in converted into a common data format. The data can be parsed into a data model that contains nodes and edges in order to generate a graph database model that can allow a network analyst to analyze the real-time status of a computer network. The graph database model can include multiple layers including an infrastructure layer, a cyber threats layer, a cyber posture layer, and a mission readiness layer. The graph database model can also be queried by a user using a domain-specific query language, so as to provide a user-friendly syntax in generating queries.
Owner:MITRE SPORTS INT LTD
System and method for forensic cyber adversary profiling, attribution and attack identification
A system and method is provided for identifying and analyzing cyber-attacks and profiling adversaries responsible for such attacks. The system and method allows for the quantitative measurement of adversary attack behavior. The system and method is able to extract quantitative data from raw attack data and compare the quantitative data to a database of quantifiable metrics associated with known adversaries. This allows for the possible linking of a cyber-attack to a known adversary or known adversary behavior.
Owner:PARKER THOMAS W
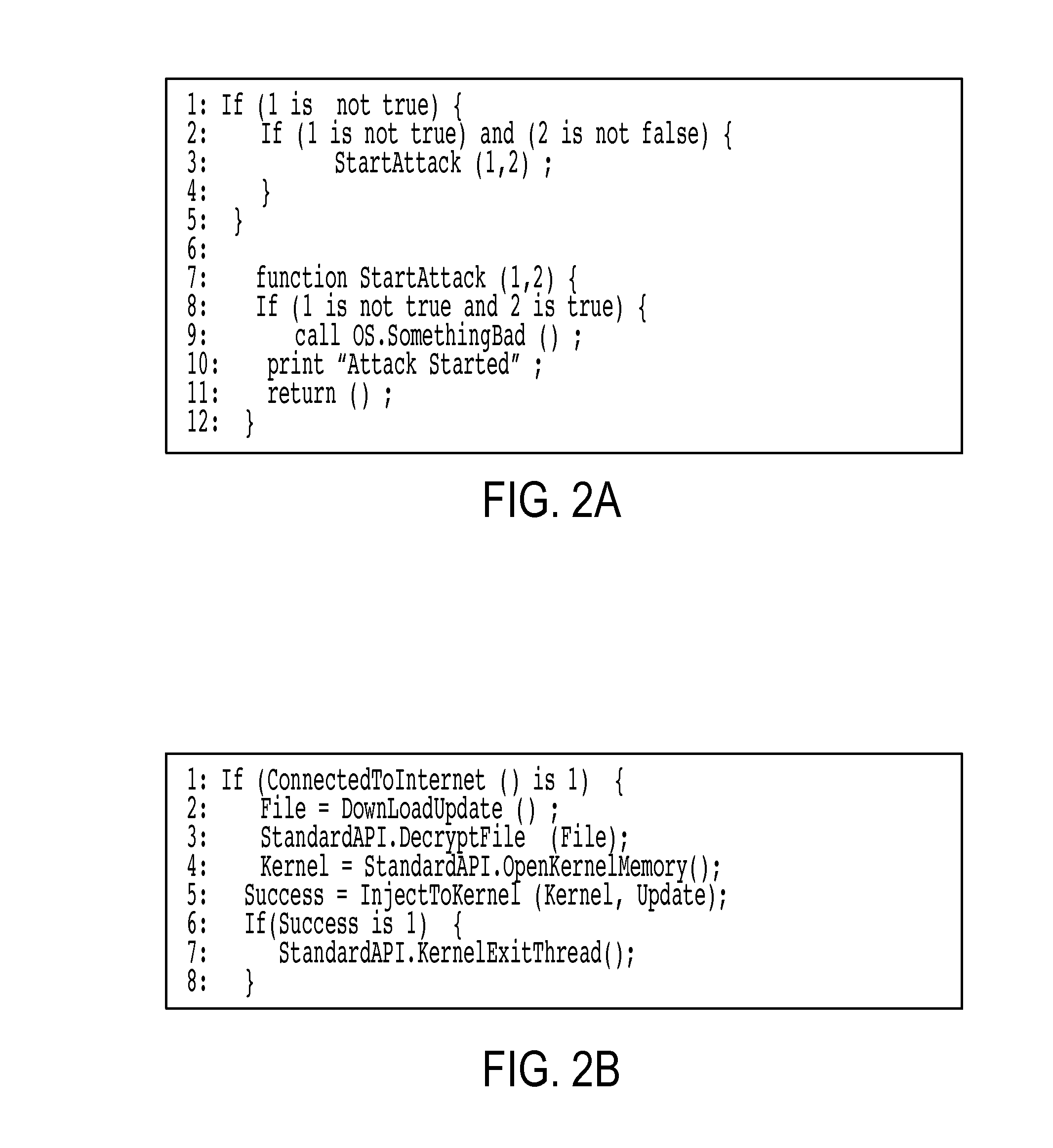
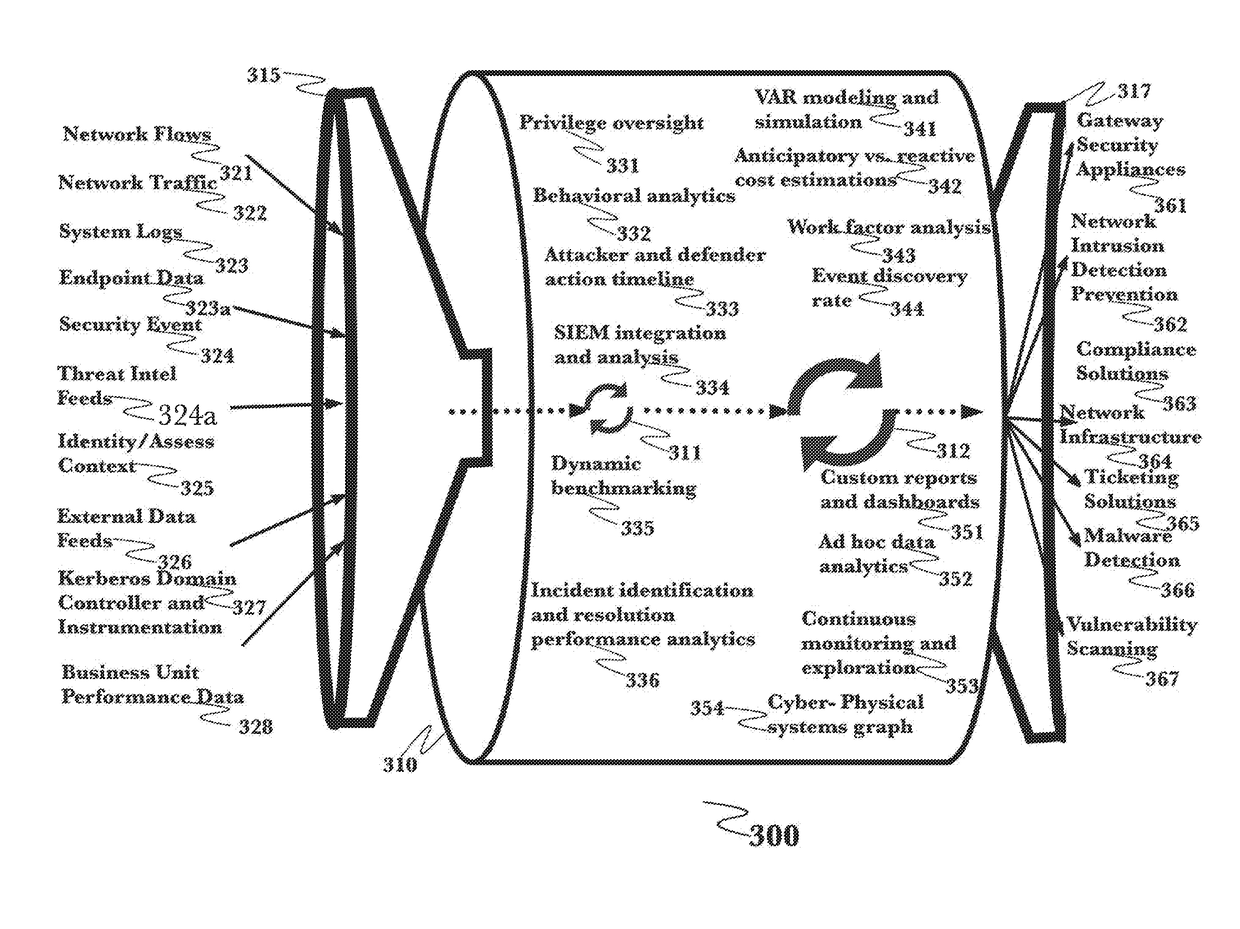
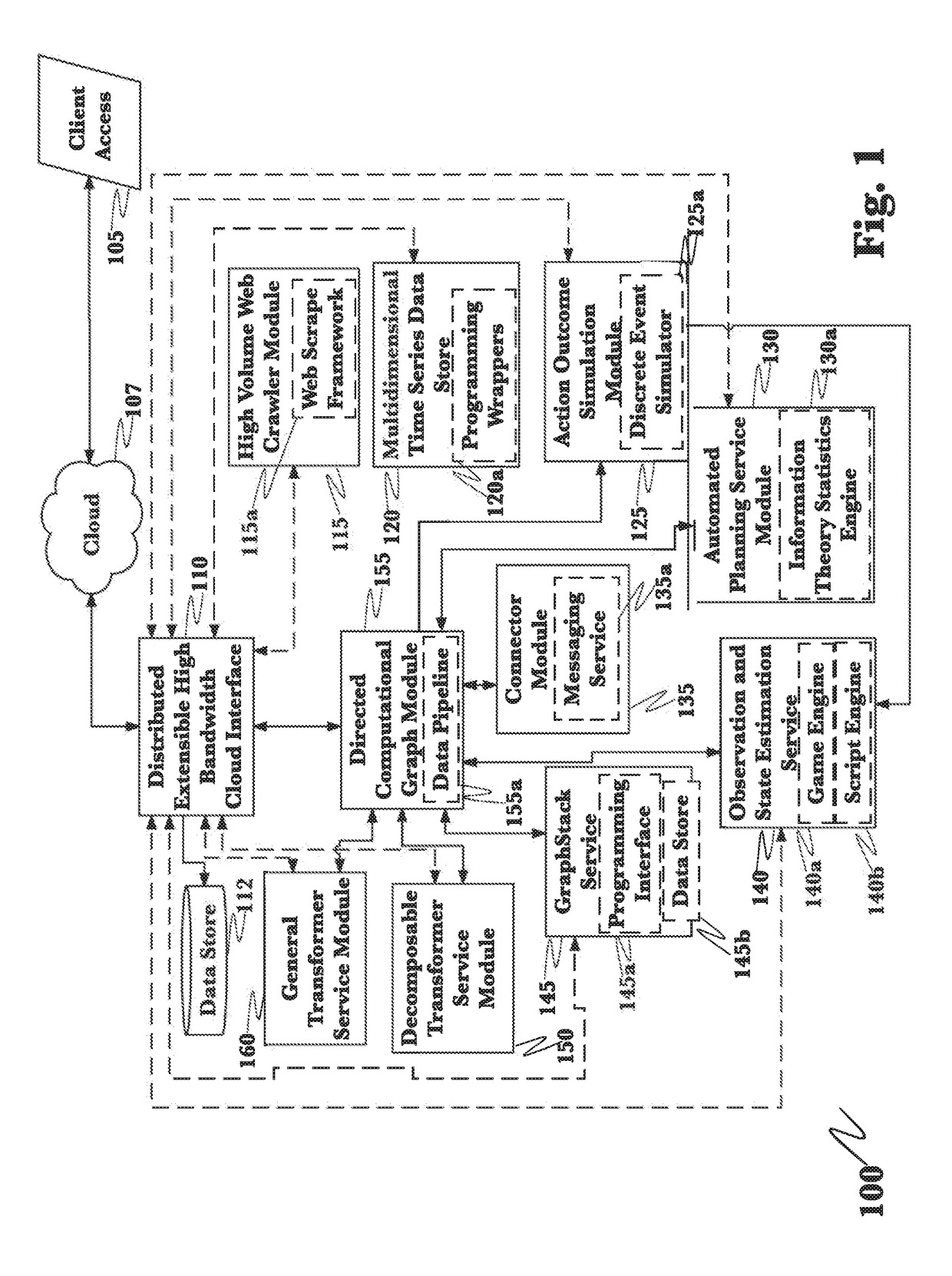
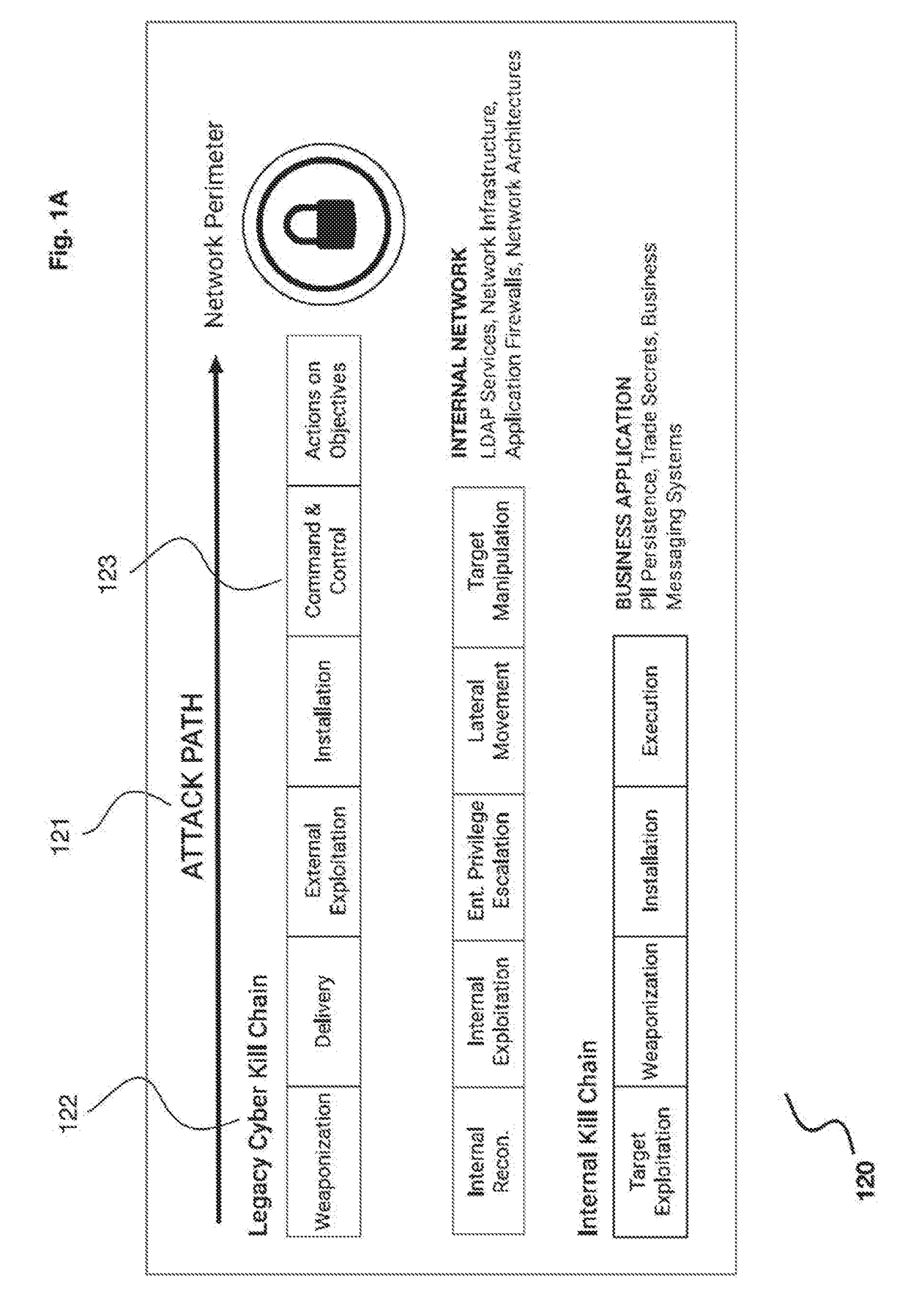
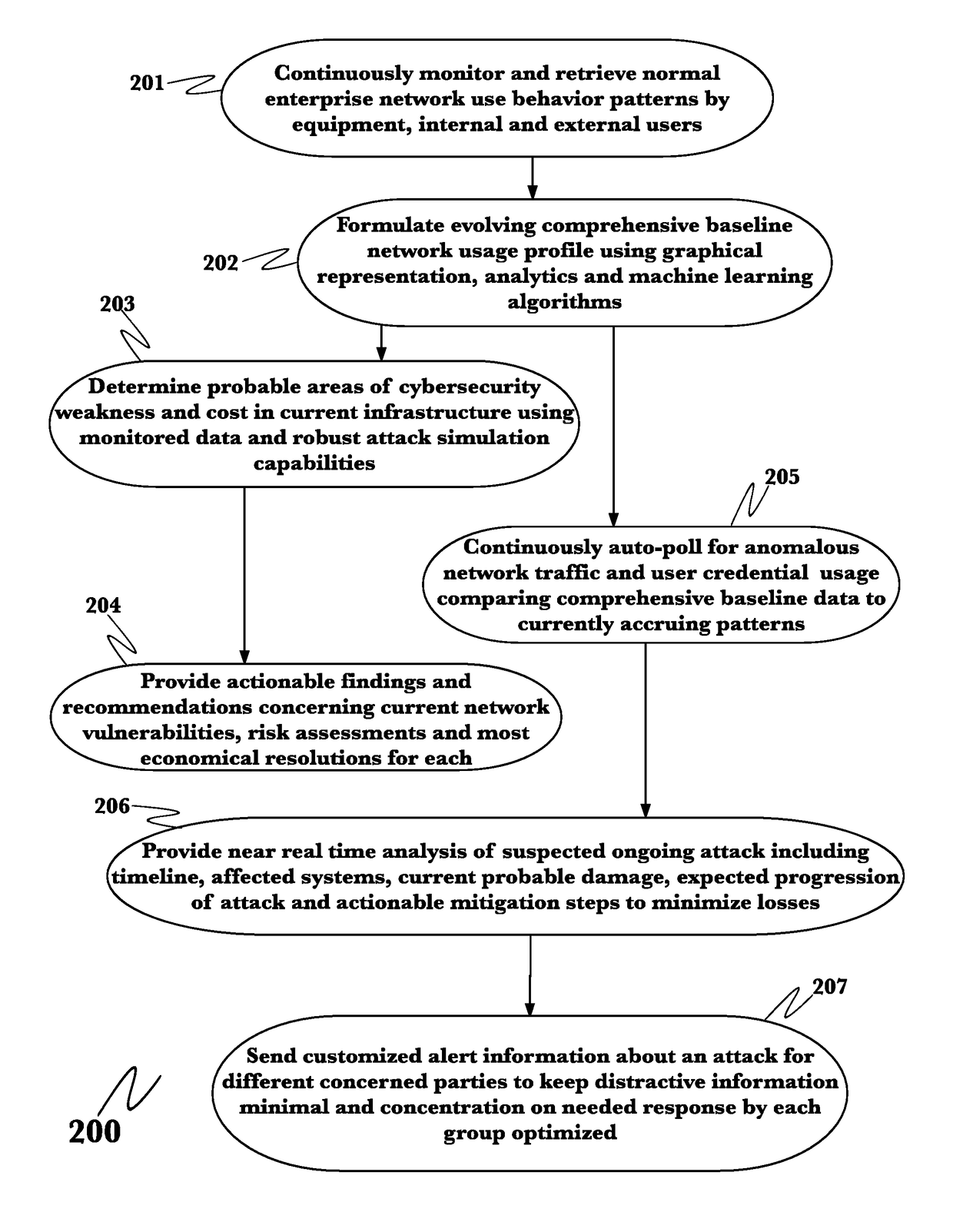
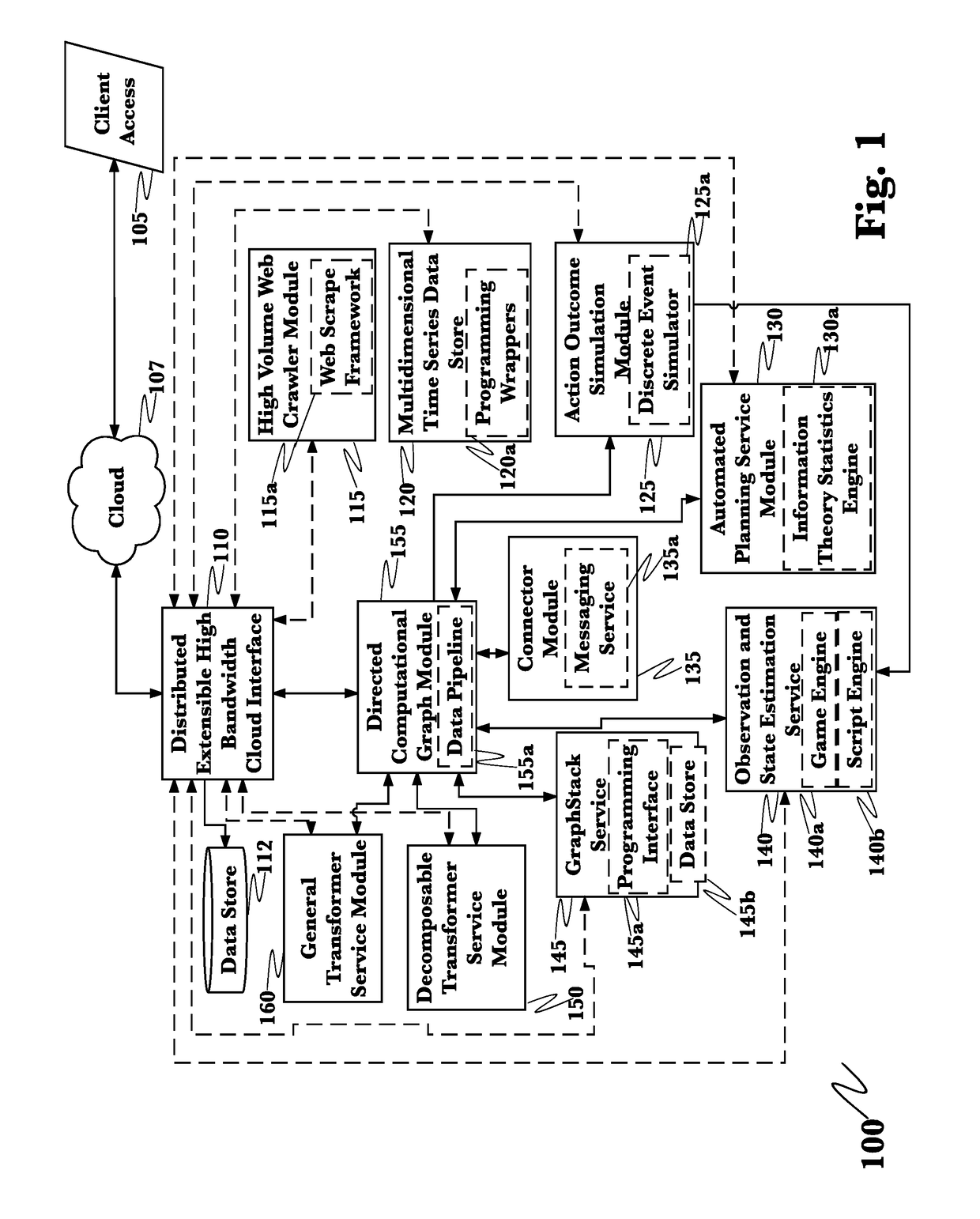
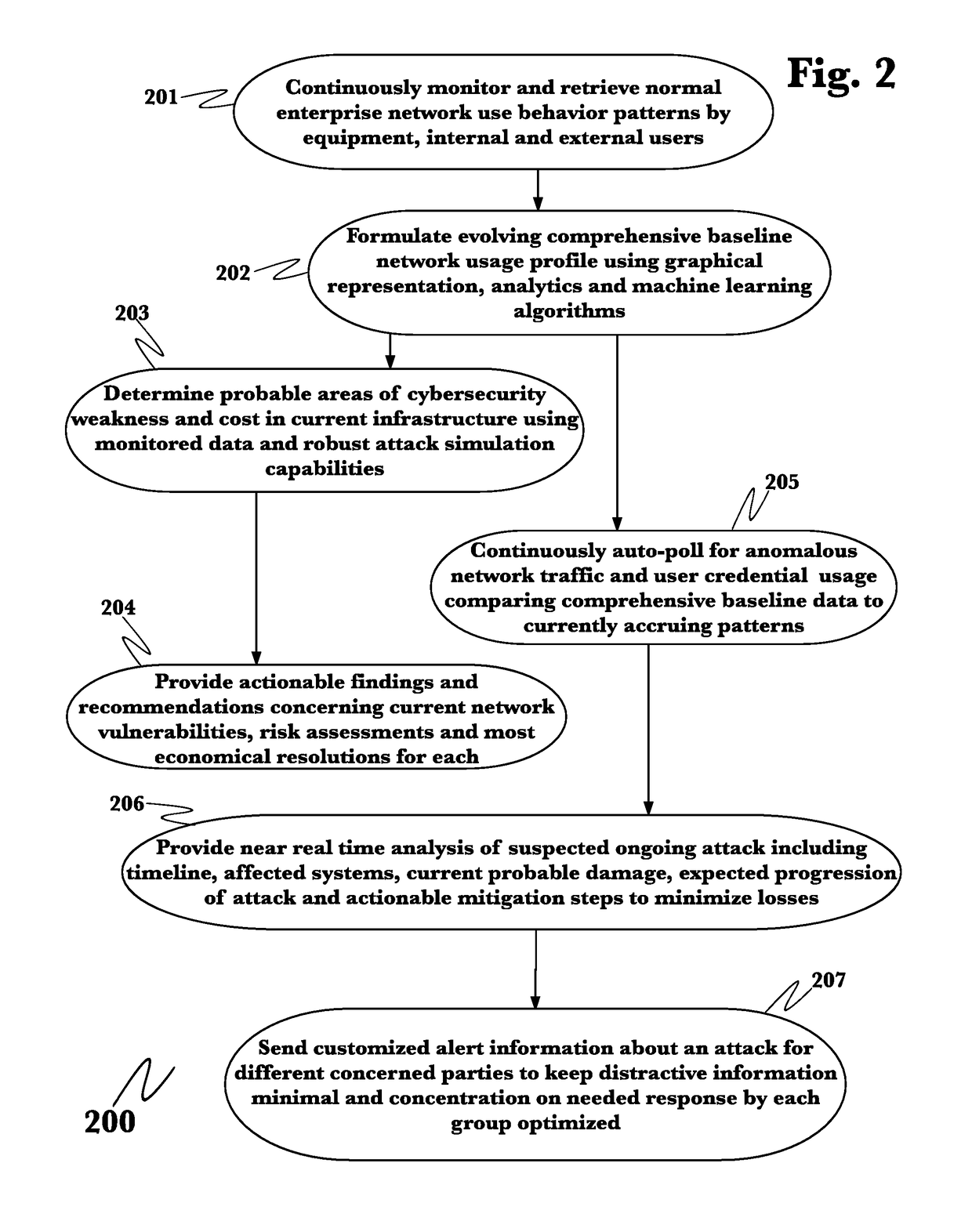
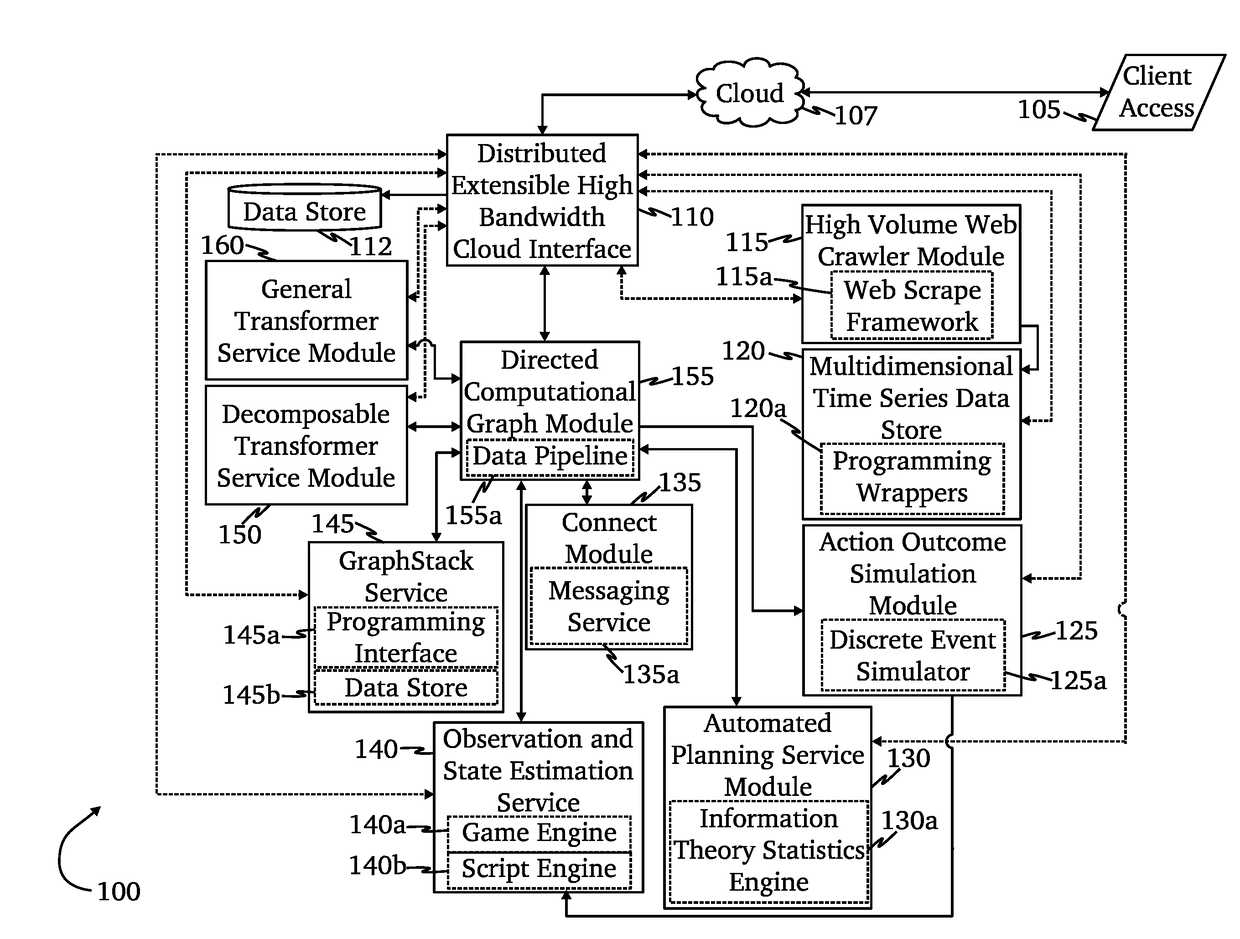
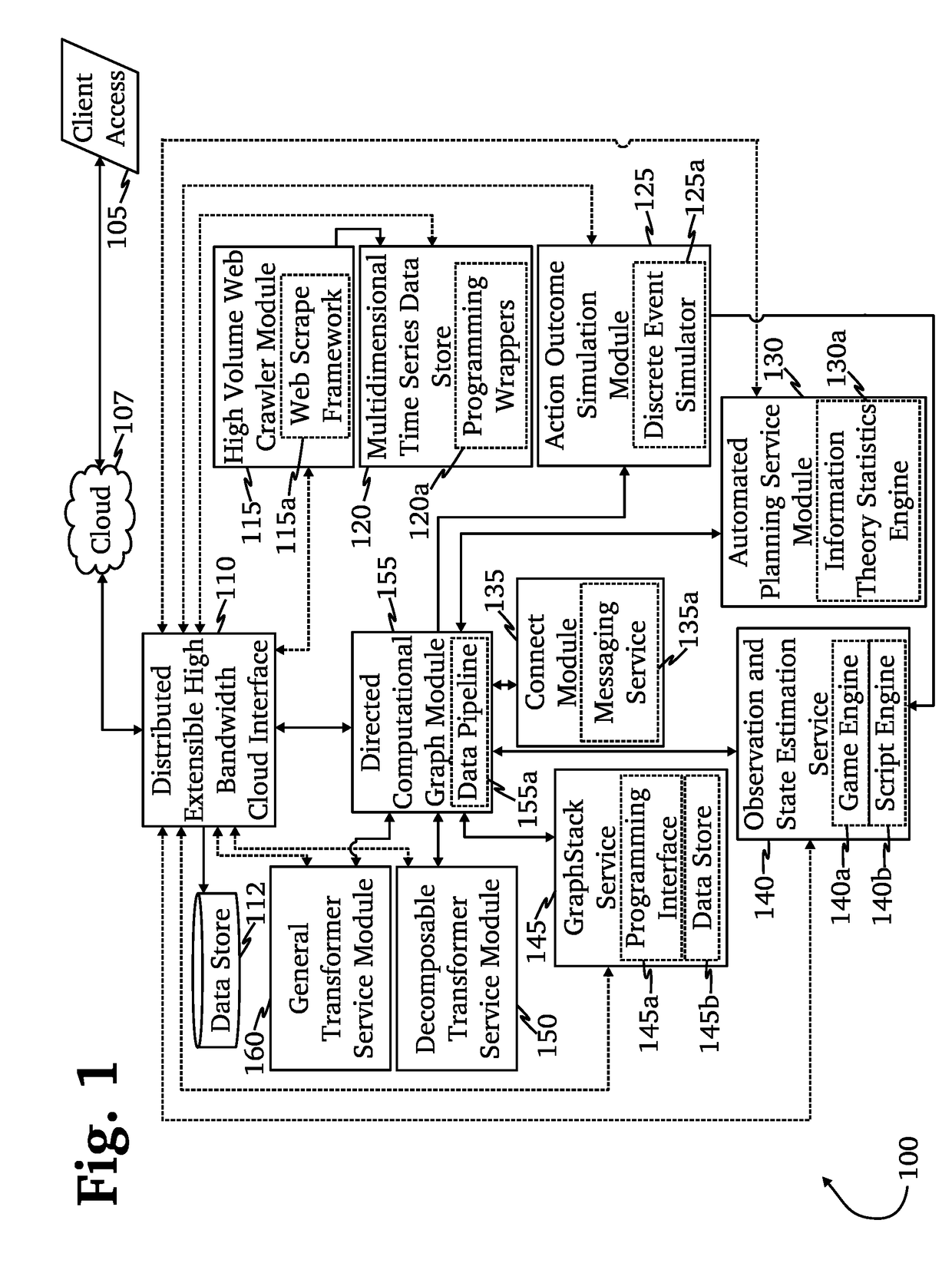
Application of advanced cybersecurity threat mitigation to rogue devices, privilege escalation, and risk-based vulnerability and patch management
A system for mitigation of cyberattacks employing an advanced cyber decision platform comprising a time series data store, a directed computational graph module, an action outcome simulation module, and observation and state estimation module, wherein the state of a network is monitored and used to produce a cyber-physical graph representing network resources, simulated network events are produced and monitored, and the network events and their effects are analyzed to produce security recommendations.
Owner:QOMPLX INC
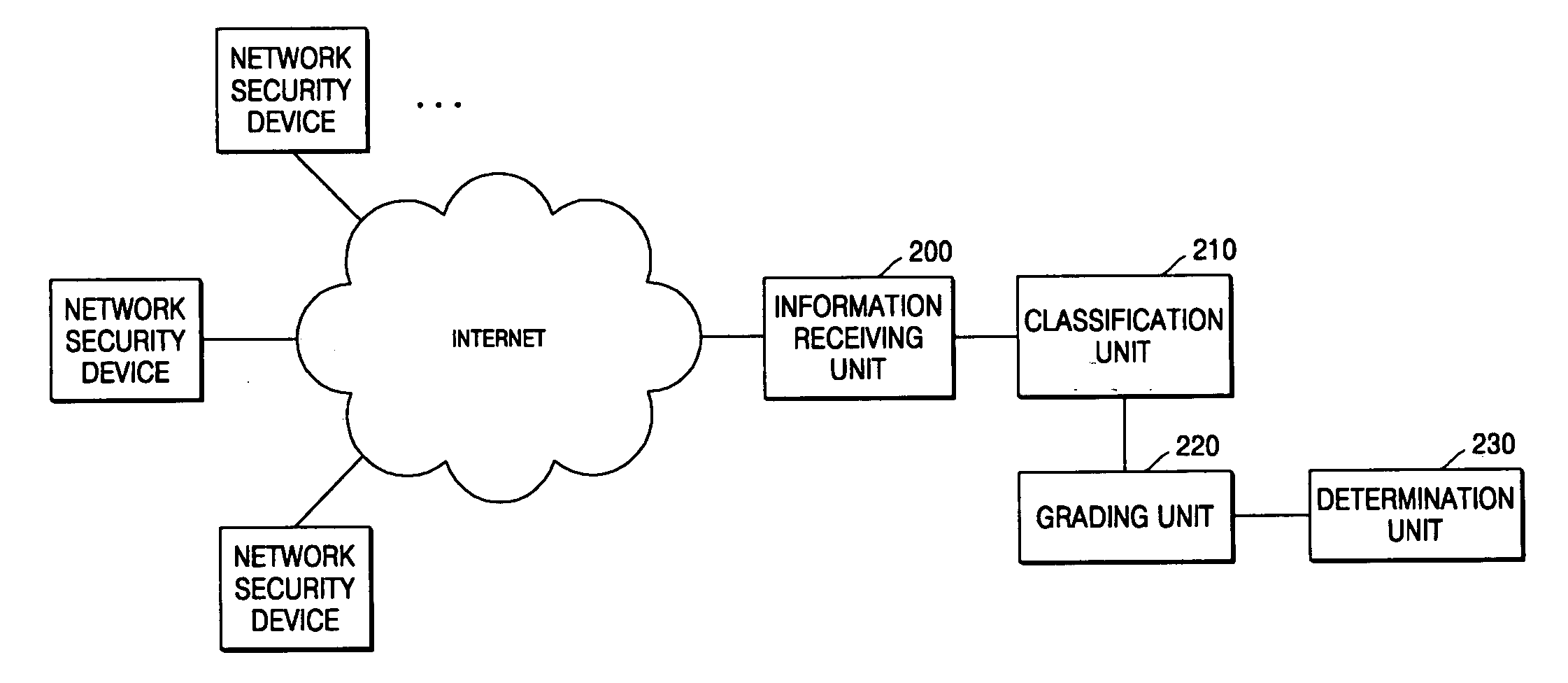
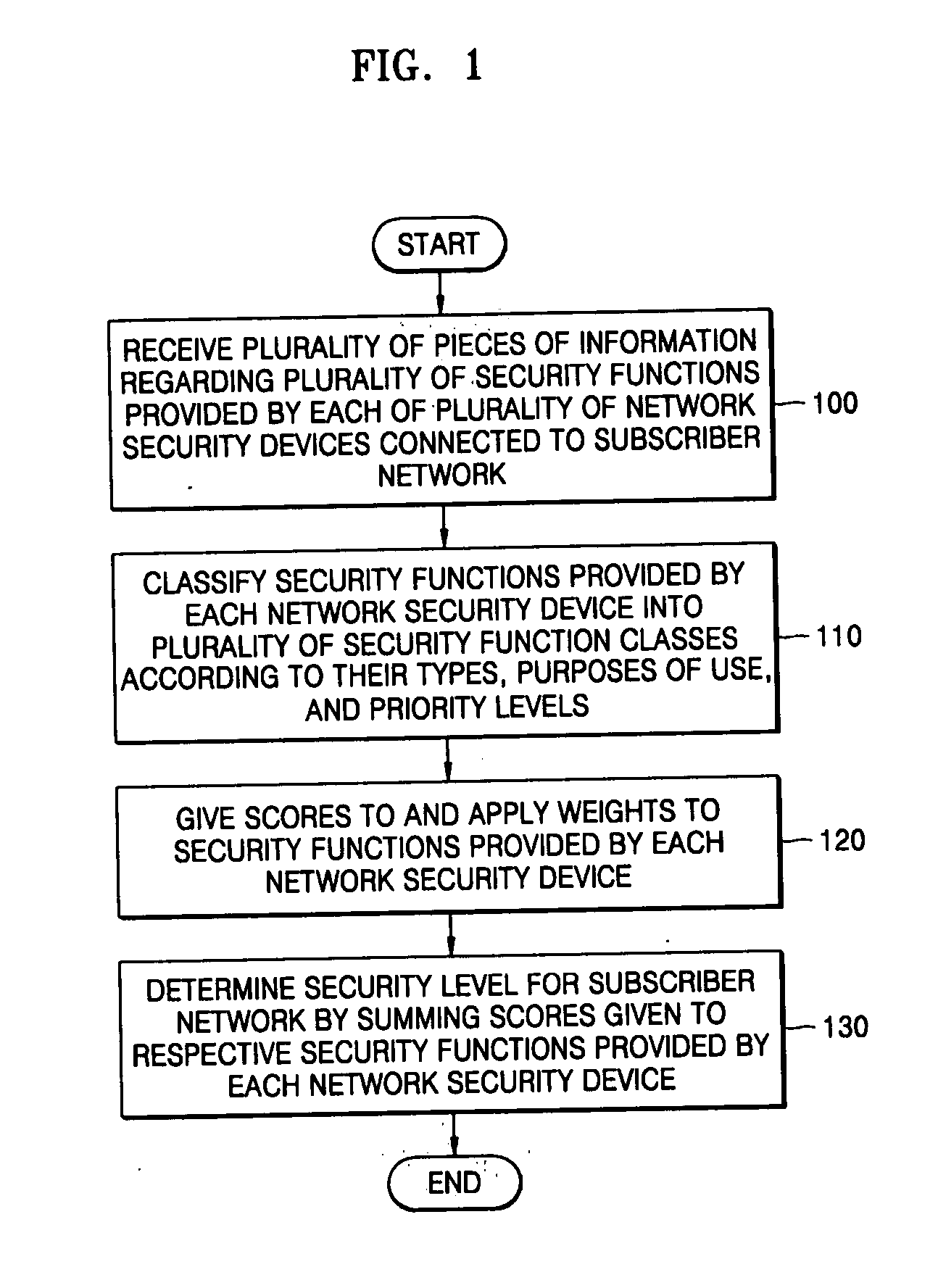
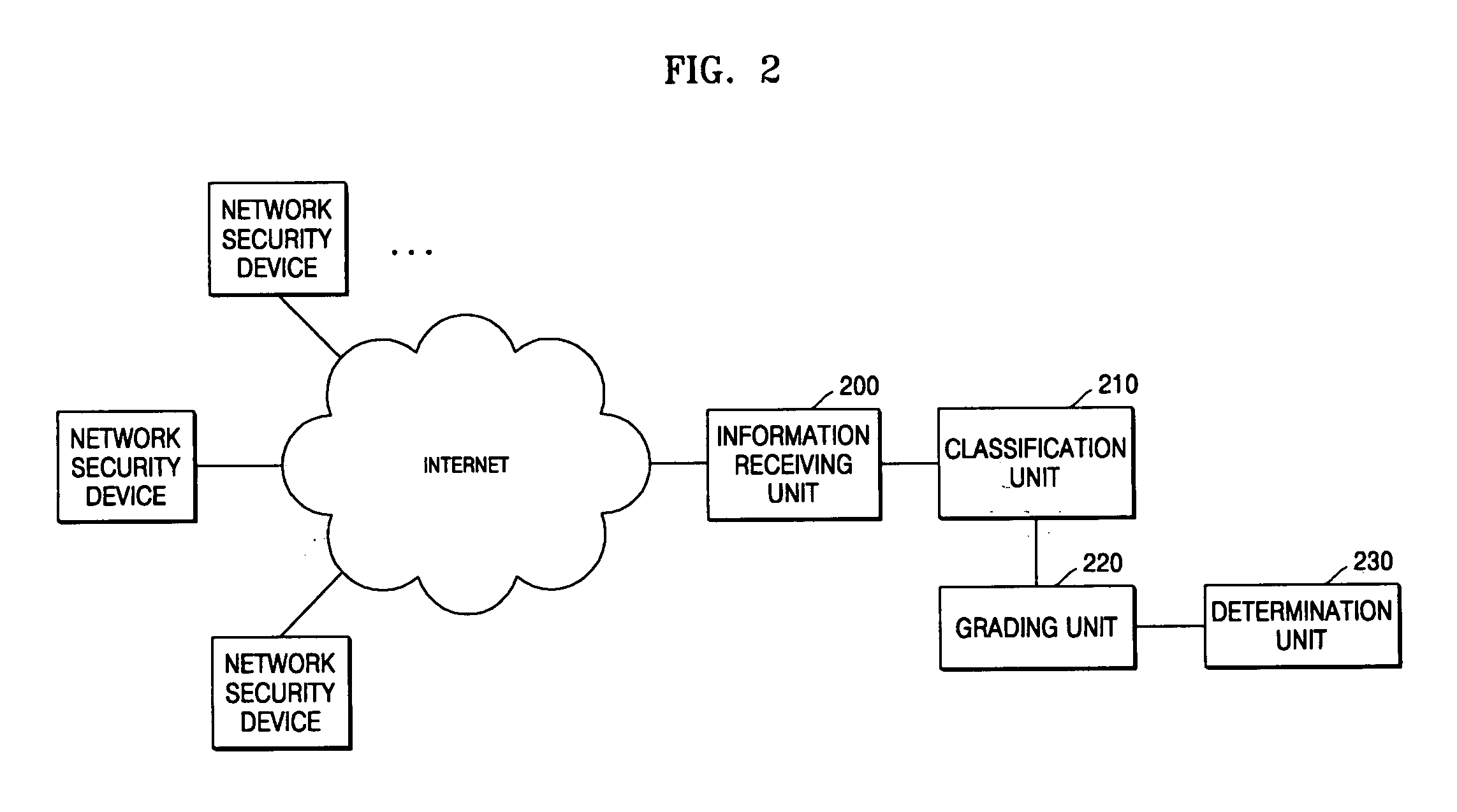
Method and apparatus for evaluating security of subscriber network
InactiveUS20060129810A1Effective risk controlCarry-out efficiently and effectivelySecuring communicationCyber-attackSecurity level
A method and apparatus for evaluating the security of a subscriber network are provided. In the method and apparatus for evaluating the security of a subscriber network, pieces of information regarding a plurality of security functions provided by each of a plurality of network security devices connected to a network are collected, and the security functions are classified according to their types, purposes of use, and priority levels. Scores are given to the security functions using weights with reference to the classification results, and a security level for the network is determined by summing the scores of the security functions. Therefore, it is possible to objectively evaluate how secure a network is against cyber attacks launched internally or externally upon the network. In addition, it is possible to evaluate security functions provided by network security devices in a network in advance and enhance the performance of the security functions based on the evaluation results.
Owner:ELECTRONICS & TELECOMM RES INST
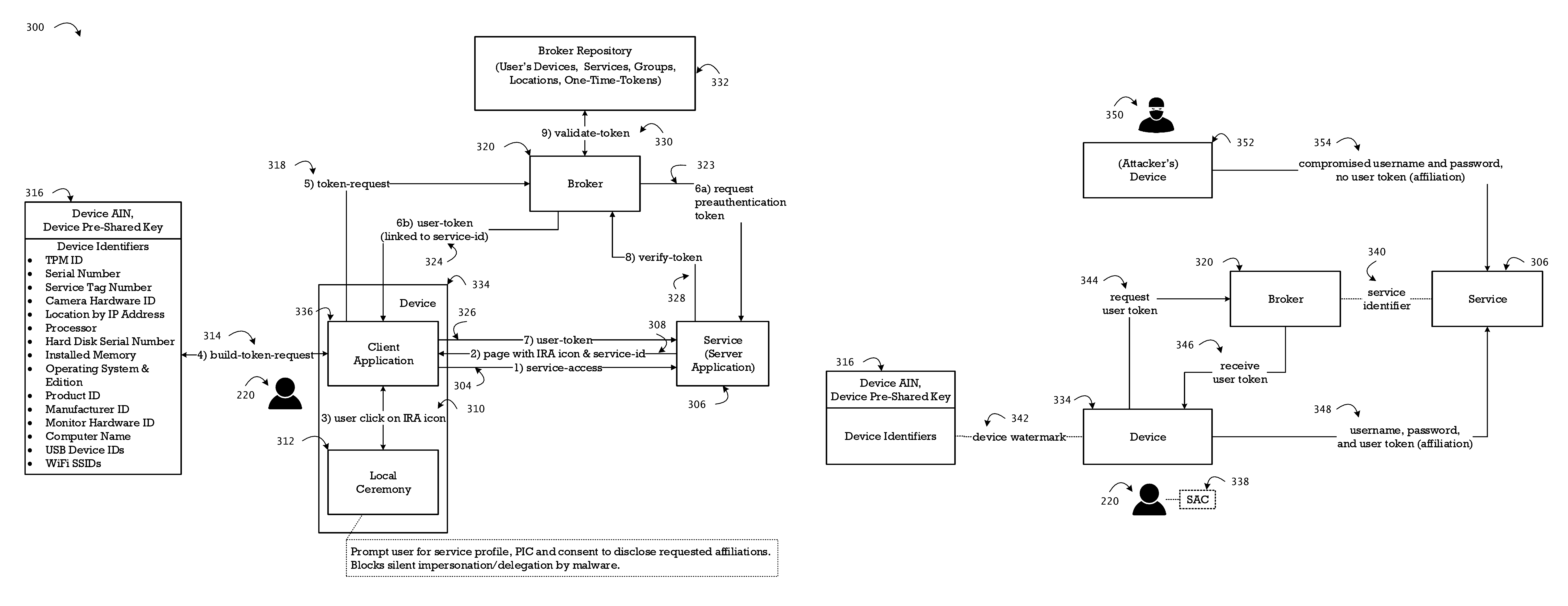
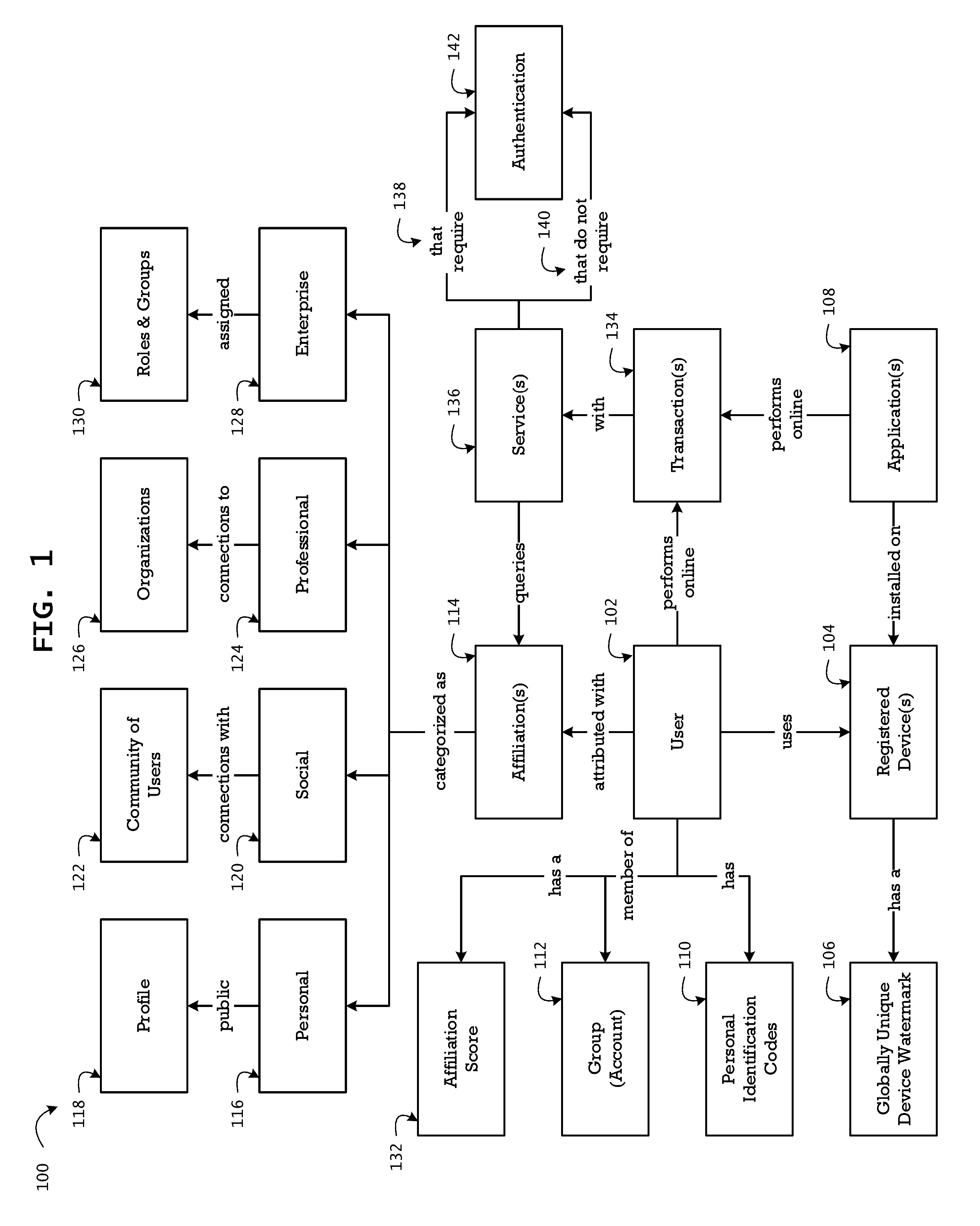
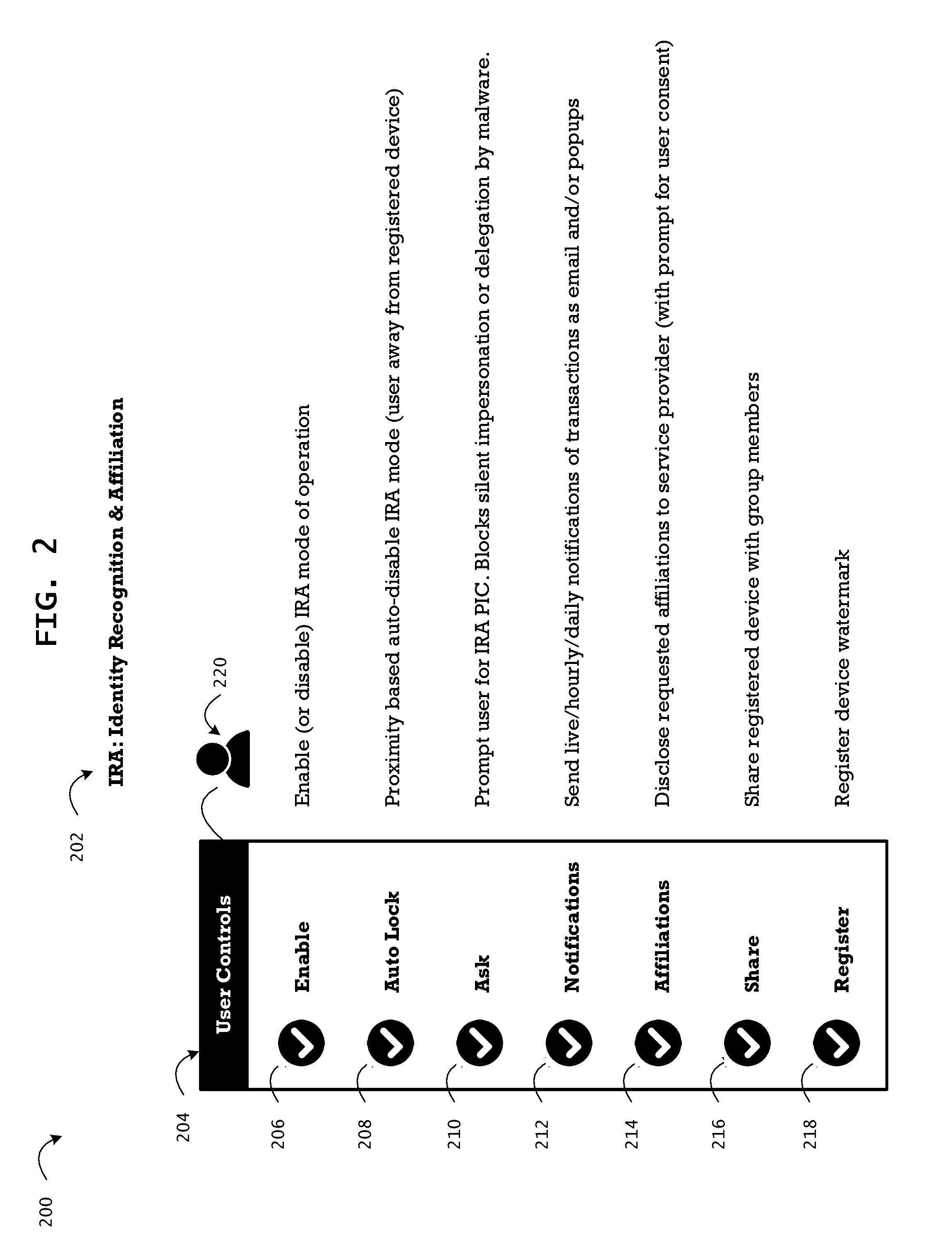
System and method for identity recognition and affiliation of a user in a service transaction
The method integrates the dynamic and authoritative posture of an authenticated user, a registered device, and a registered service provider as a conclusive proof of identity recognition for affiliation of associated contextual attribution and referential integrity. In addition to relieving the user of the burden of remembering multiple passwords for a plurality of services, the method provides a means to facilitate an affiliation oriented architecture for a broad spectrum of web and cloud based services with affiliation aware content streaming, leveraging the affiliation score as a key trust metric. The method provides protection from user-agnostic delegation and impersonation of identity, social engineering, and compromised passwords, which are exploited by numerous strains of landed malware to launch multi-stage coordinated cyber-attacks on consumer accounts and enterprise systems. The method of affiliation based on identity recognition provides authoritative, contextual, and consensual user information, of relevance in a live transaction, to the service provider.
Owner:KUMAR SRINIVAS +2
Method for detecting sophisticated cyber attacks
InactiveUS20060265748A1Memory loss protectionError detection/correctionCyber-attackInformation networks
Owner:UT BATTELLE LLC
Advanced cybersecurity threat mitigation using behavioral and deep analytics
A system for mitigation of cyberattacks employing an advanced cyber decision platform comprising a time series data store, a directed computational graph module, an action outcome simulation module, and observation and state estimation module, wherein the state of a network is monitored and used to produce a cyber-physical graph representing network resources, simulated network events are produced and monitored, and the network events and their effects are analyzed to produce security recommendations.
Owner:QOMPLX INC
Computerized system and method for securely distributing and exchanging cyber-threat information in a standardized format
Computerized systems and methods for sharing identified cyber-threat information in a standardized and secure format. The sharing of cyber-threat information assists in preventing malicious actors from replicating successful cyber-attacks by informing potential targets of the methods employed by the malicious actors, and the defensive measures that those targets should to implement to prevent those methods from succeeding. By distributing cyber-threat information in a standardized format, the systems and methods enable participating entities to automatically analyze and implement defensive measures for cyber-threat information shared by any other participating entities. The systems and methods also permit an entity to control which threat information it shares and which other entities it shares it with in a secure manner in order to preserve that entity's security and reputation.
Owner:CELERIUM INC
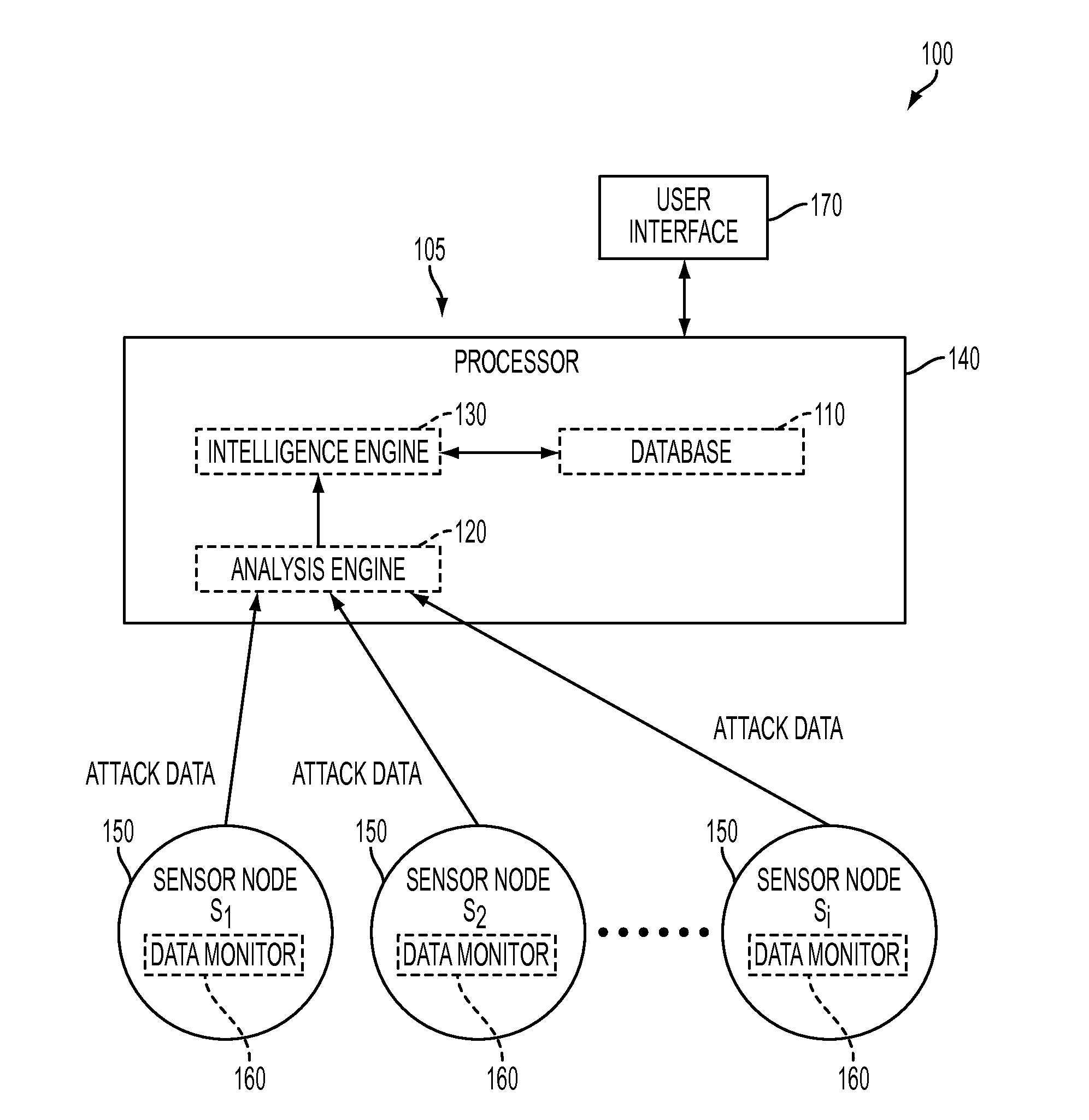
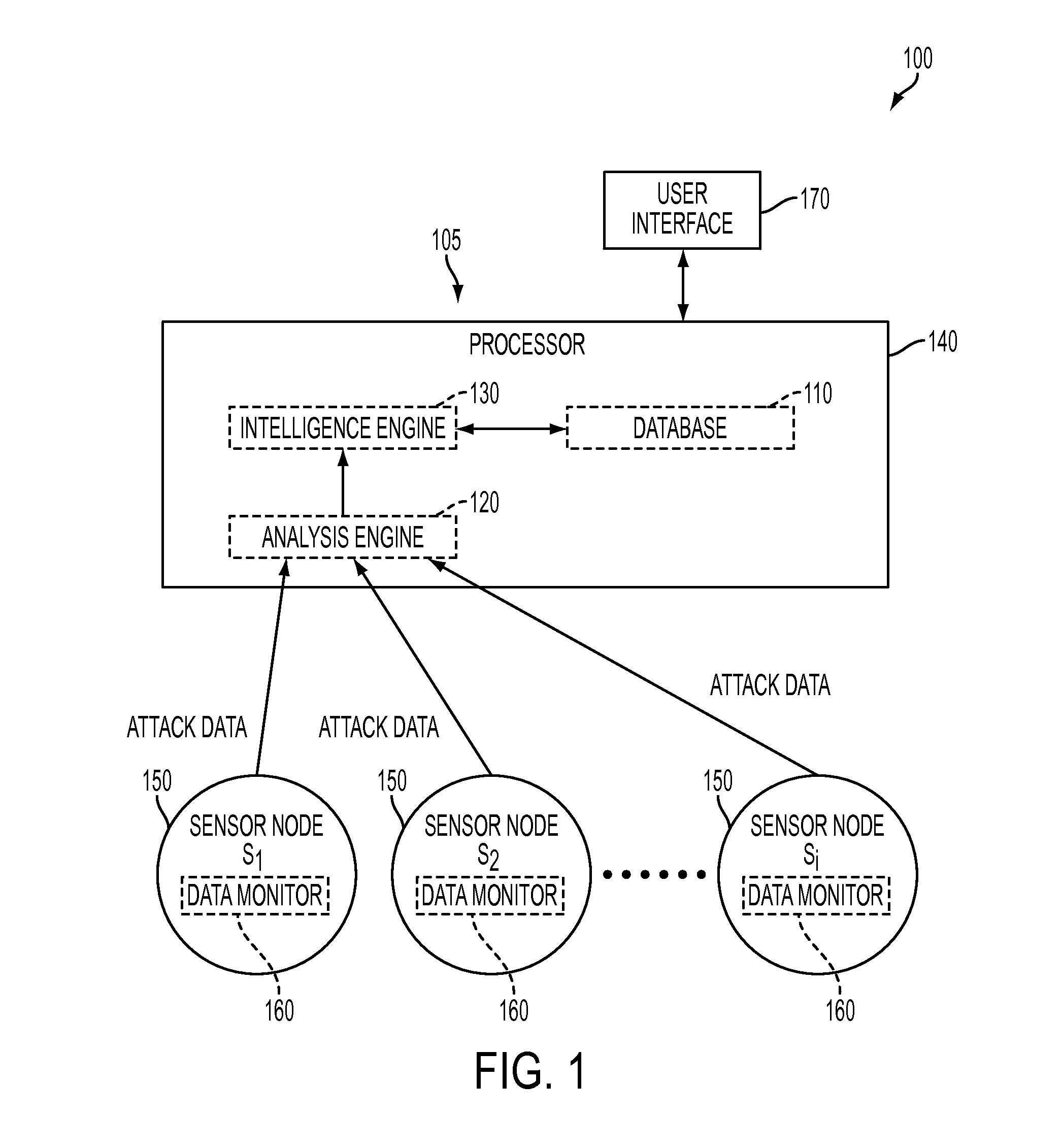
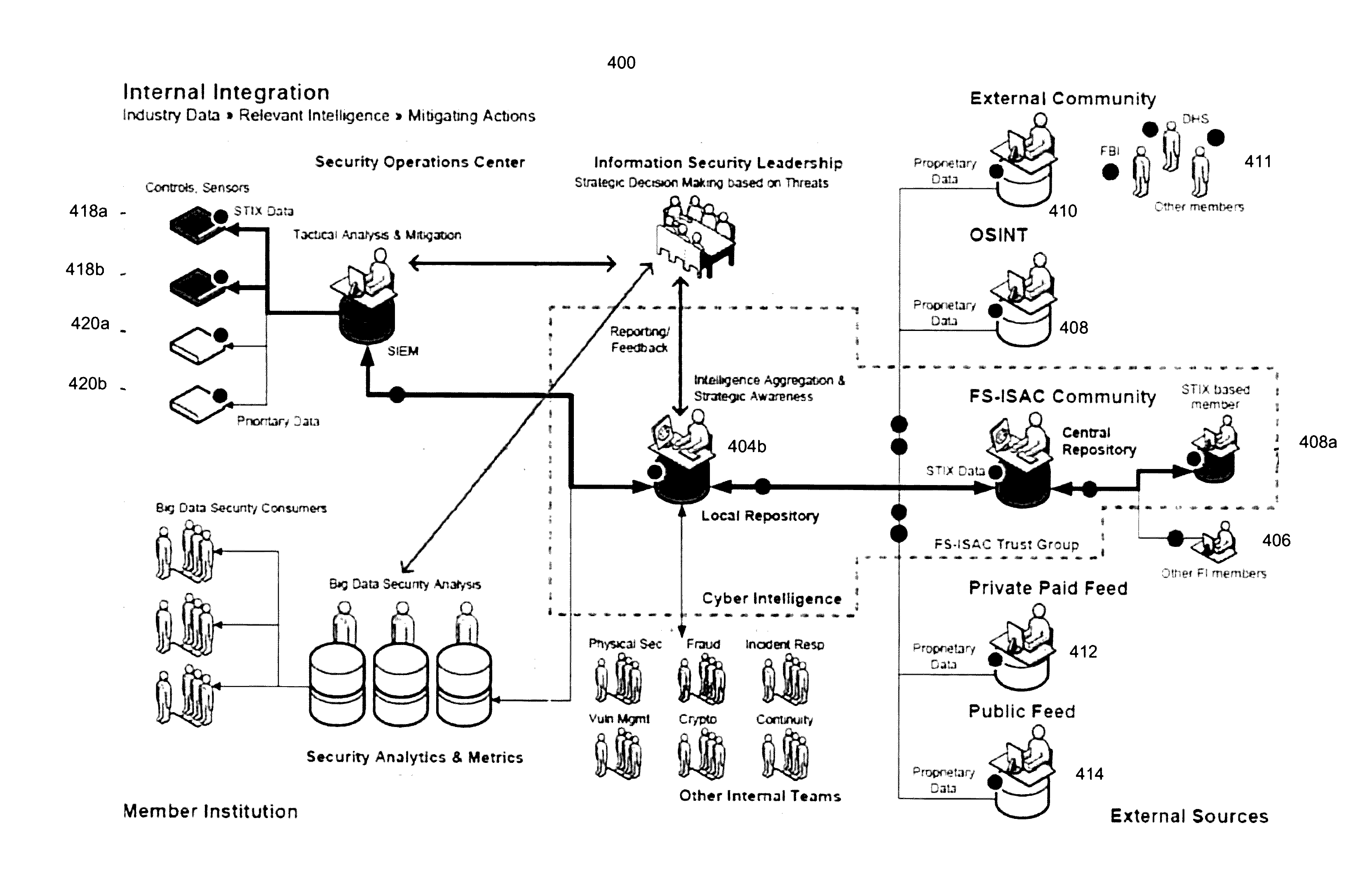
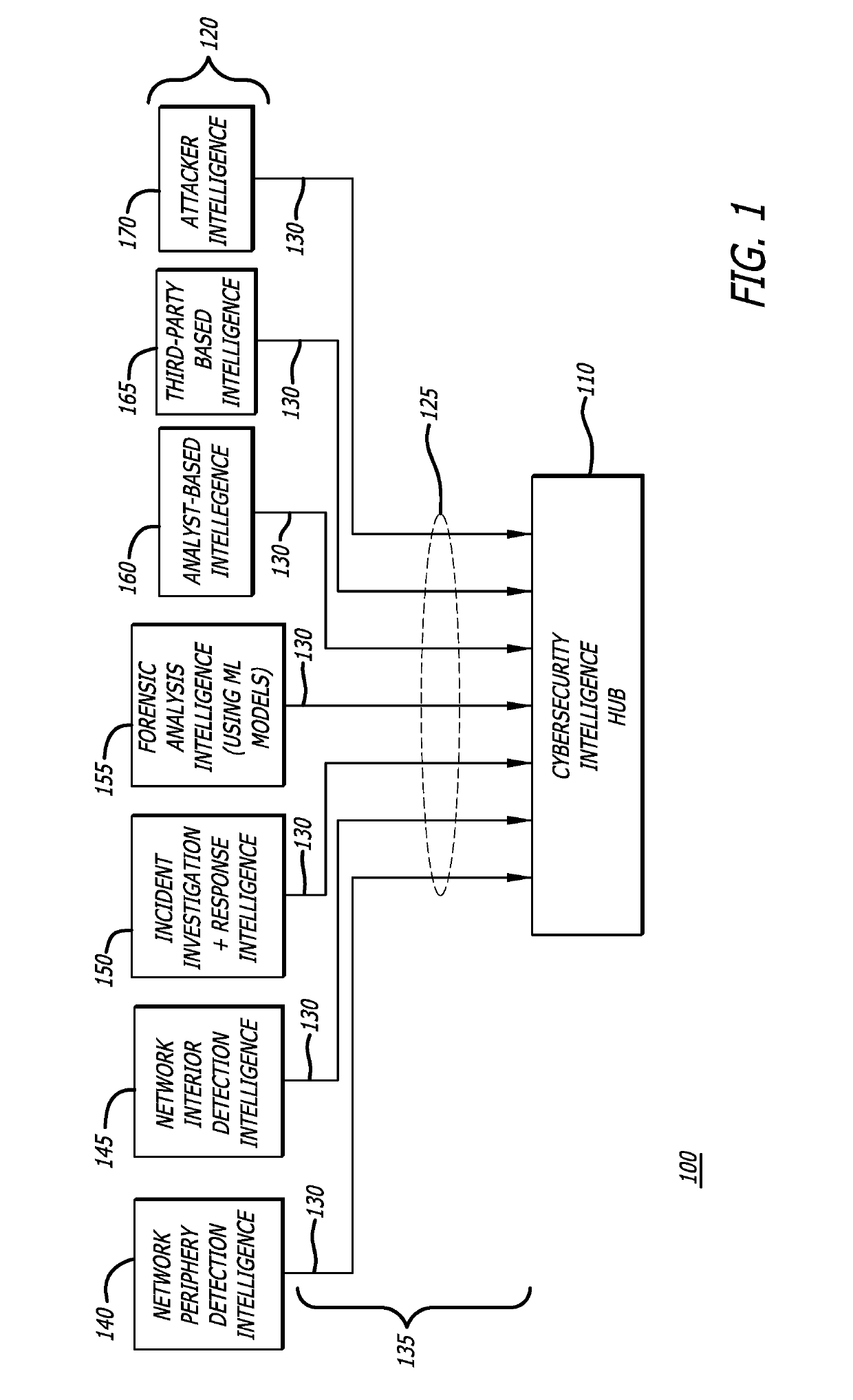
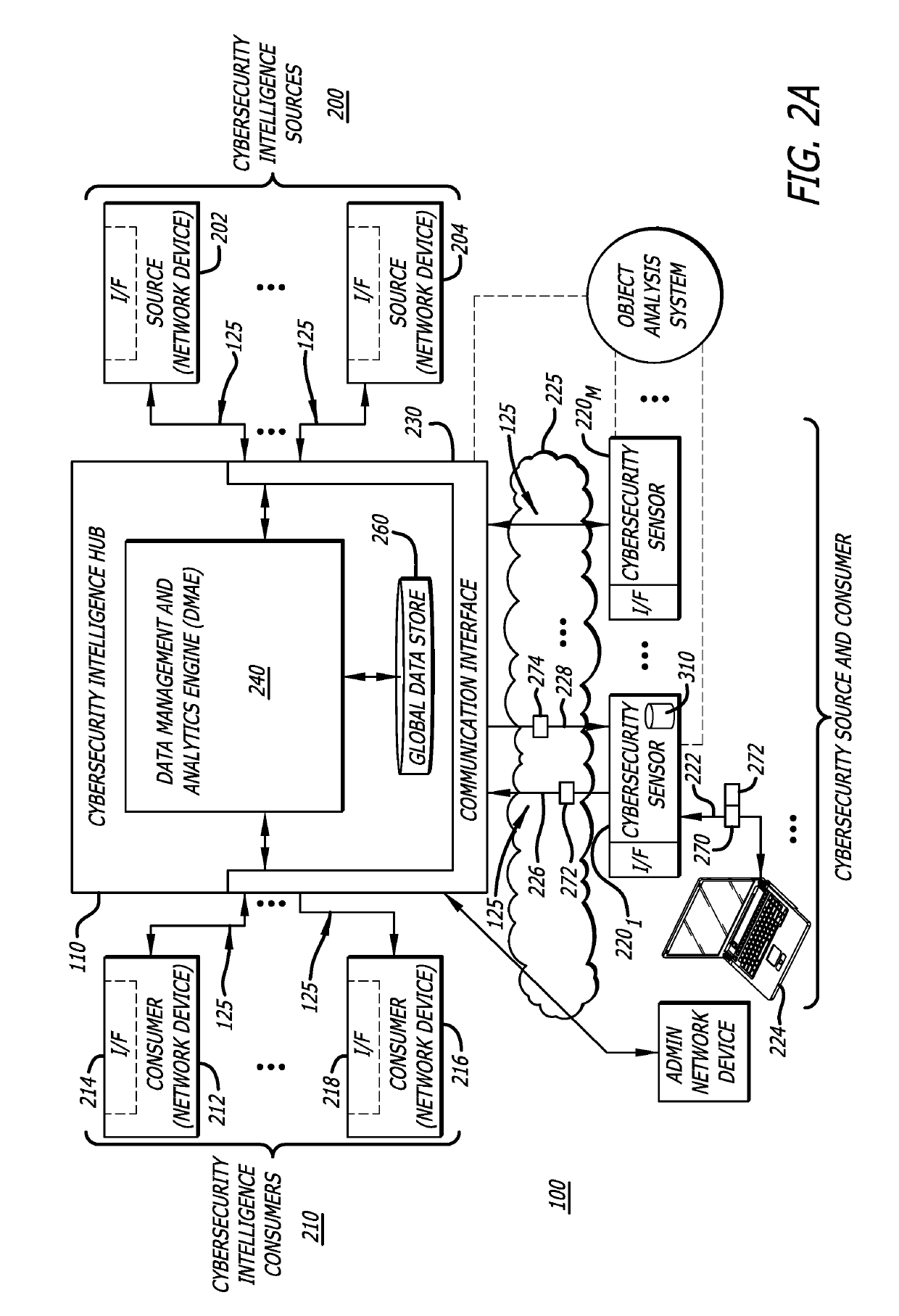
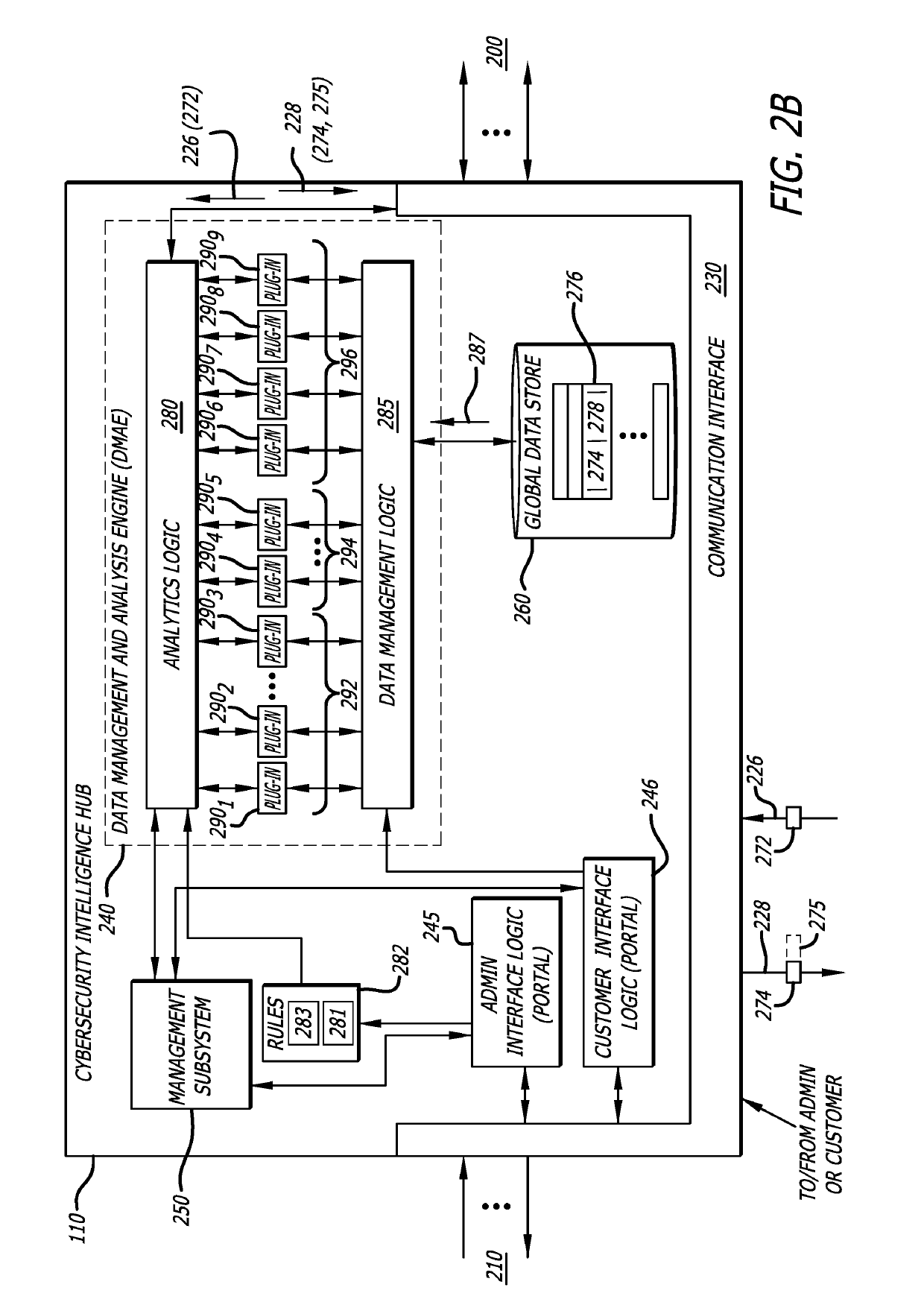
Platform and Method for Enhanced Cyber-Attack Detection and Response Employing a Global Data Store
A system for detecting artifacts associated with a cyber-attack features a cybersecurity intelligence hub that includes a data store with stored meta-information associated with each artifact of a plurality of artifacts and each stored meta-information includes a verdict classifying an artifact corresponding to the stored meta-information as a malicious classification or a benign classification. The hub is configured to (i) receive meta-information associated with a first artifact from a cybersecurity sensor, and (ii) determine a verdict for the first artifact based on an analysis of meta-information associated with the first artifact stored meta-information associated with each of the plurality of artifacts. A verdict for the first artifact is returned to the cybersecurity sensor in response to a detected match between a portion of stored meta-information and a portion of the meta-information associated with the first artifact.
Owner:FIREEYE SECURITY HLDG US LLC
Density estimation network for unsupervised anomaly detection
Systems and methods for preventing cyberattacks using a Density Estimation Network (DEN) for unsupervised anomaly detection, including constructing the DEN using acquired network traffic data by performing end-to-end training. The training includes generating low-dimensional vector representations of the network traffic data by performing dimensionality reduction of the network traffic data, predicting mixture membership distribution parameters for each of the low-dimensional representations by performing density estimation using a Gaussian Mixture Model (GMM) framework, and formulating an objective function to estimate an energy and determine a density level of the low-dimensional representations for anomaly detection, with an anomaly being identified when the energy exceeds a pre-defined threshold. Cyberattacks are prevented by blocking transmission of network flows with identified anomalies by directly filtering out the flows using a network traffic monitor.
Owner:NEC CORP
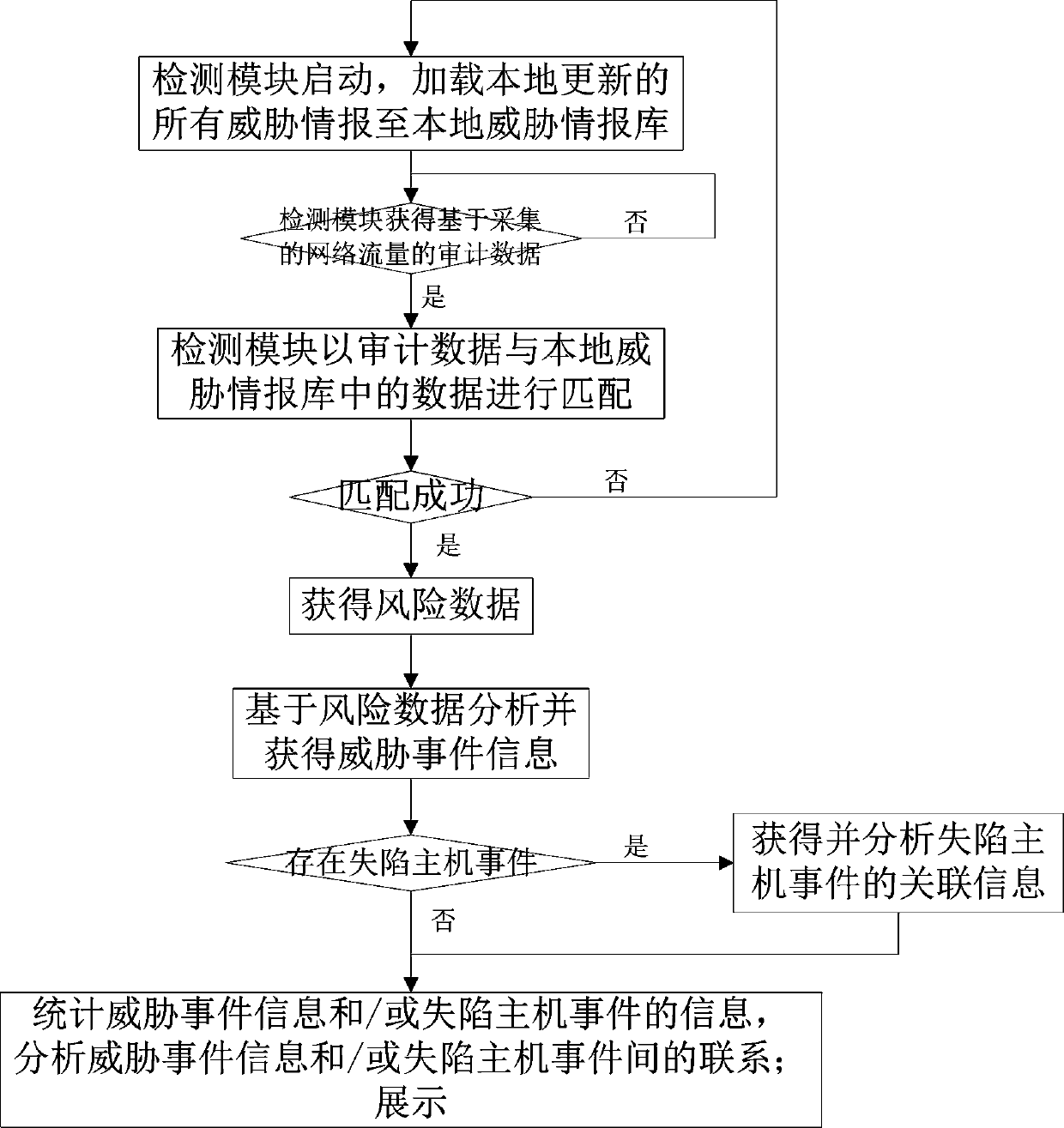
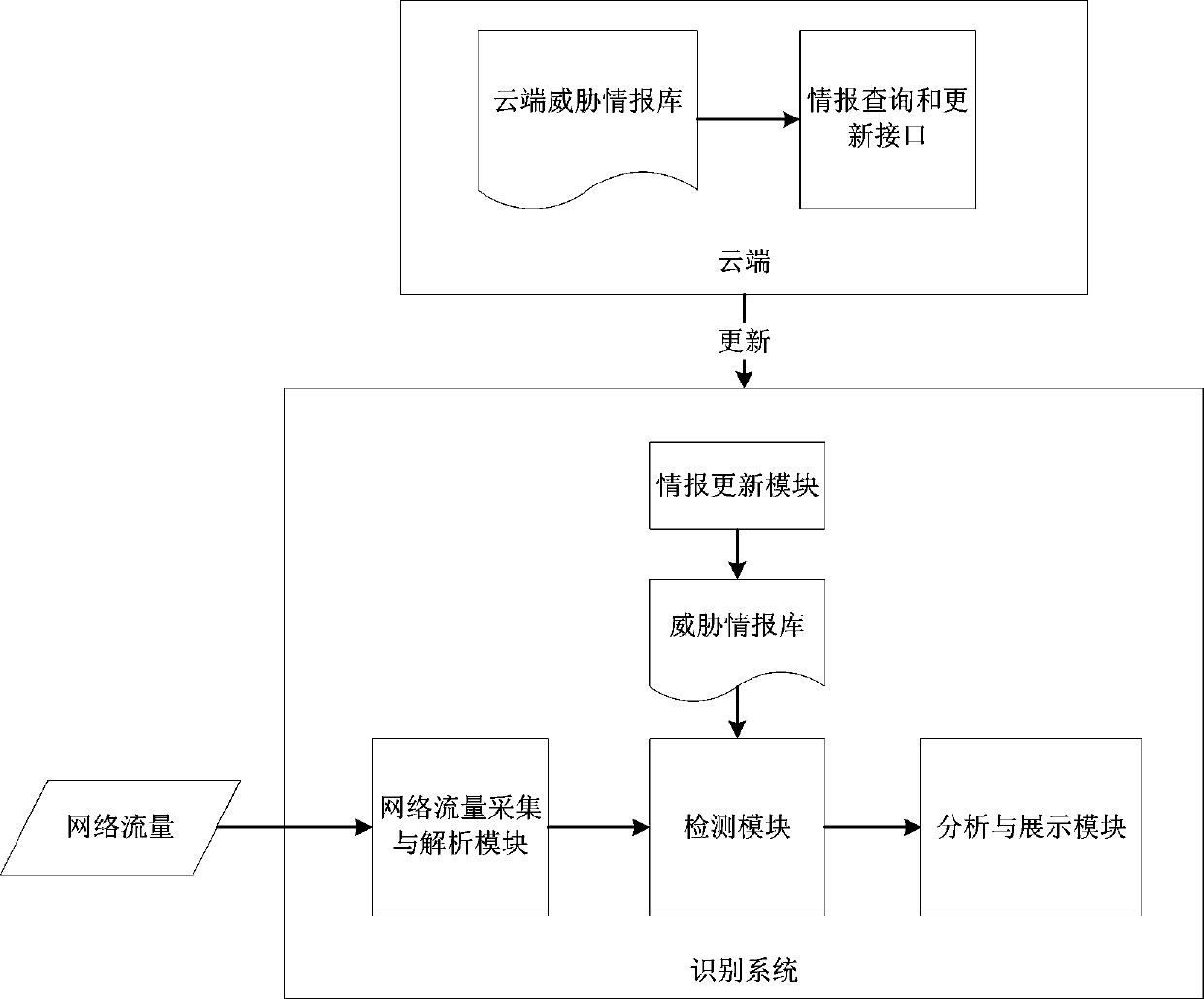
Threat intelligence-based network threat identification method and identification system
The invention relates to a threat intelligence-based network threat identification method and identification system. The method includes: after the detection module is started, loading all the threatinformation updated by the information updating module to the local; acquiring the collected and analyzed audit data, matching the audit data with data in a threat intelligence library, analyzing andacquiring threat event information based on risk data through an analysis and display module if the audit data is successfully matched with the data in the threat intelligence library, acquiring and analyzing associated information of possible lost host events, and counting, analyzing and displaying the relationship between the events. According to the invention, the threat condition of the wholenetwork is analyzed and displayed from two perspectives of threat event information and a lost host event; a collapsed host is determined, targeted attacks are accurately recognized, correlation analysis and display are carried out on the threats, the efficiency of processing network attack events is improved, the false alarm rate is low, potential threats can be found, tracing and post-processingof the threat events are greatly facilitated, attacks possibly occurring in the future are predicted, and therefore truly valuable attack events are deeply analyzed and found.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
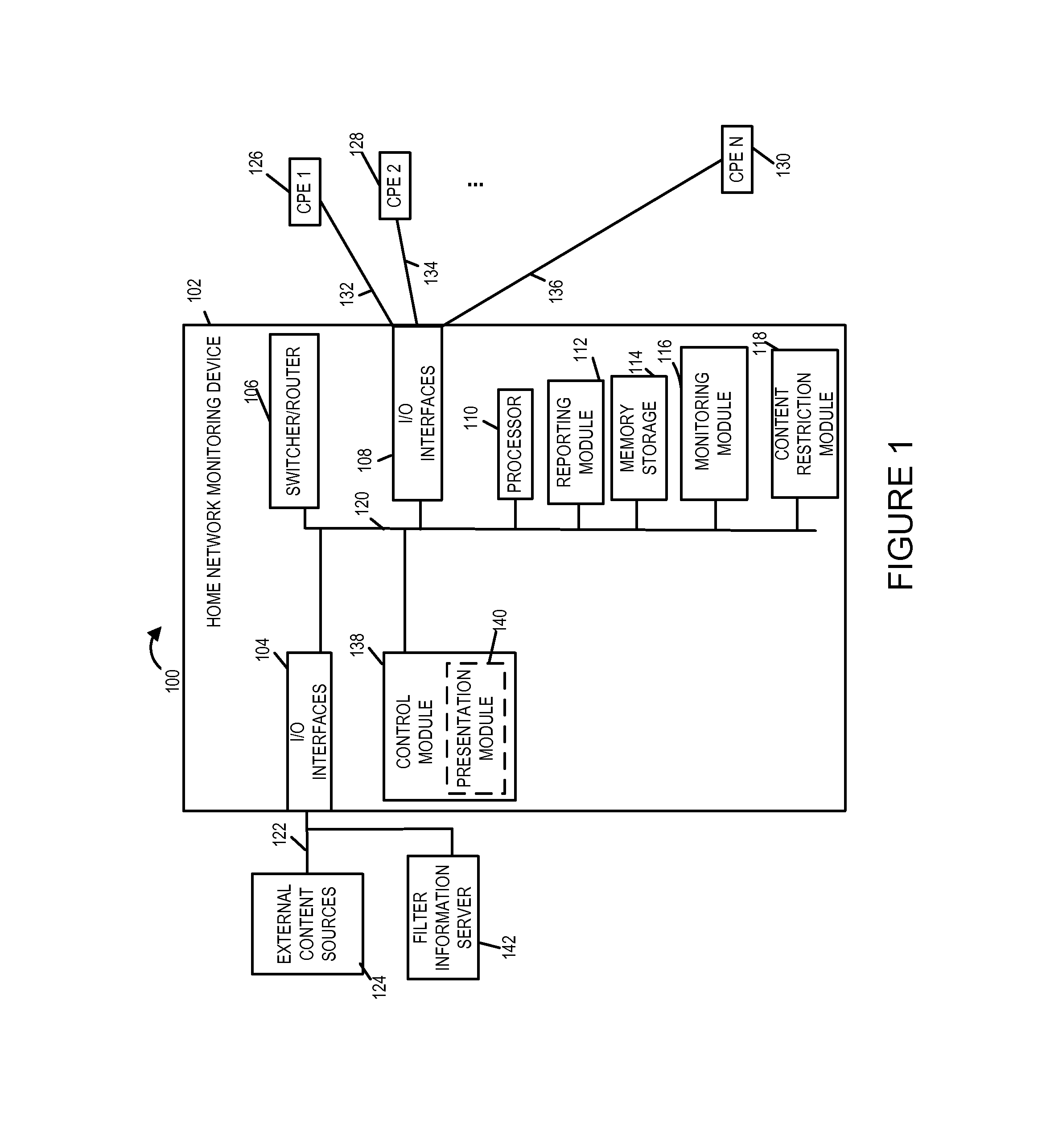
Methods and apparatus for providing parental or guardian control and visualization over communications to various devices in the home
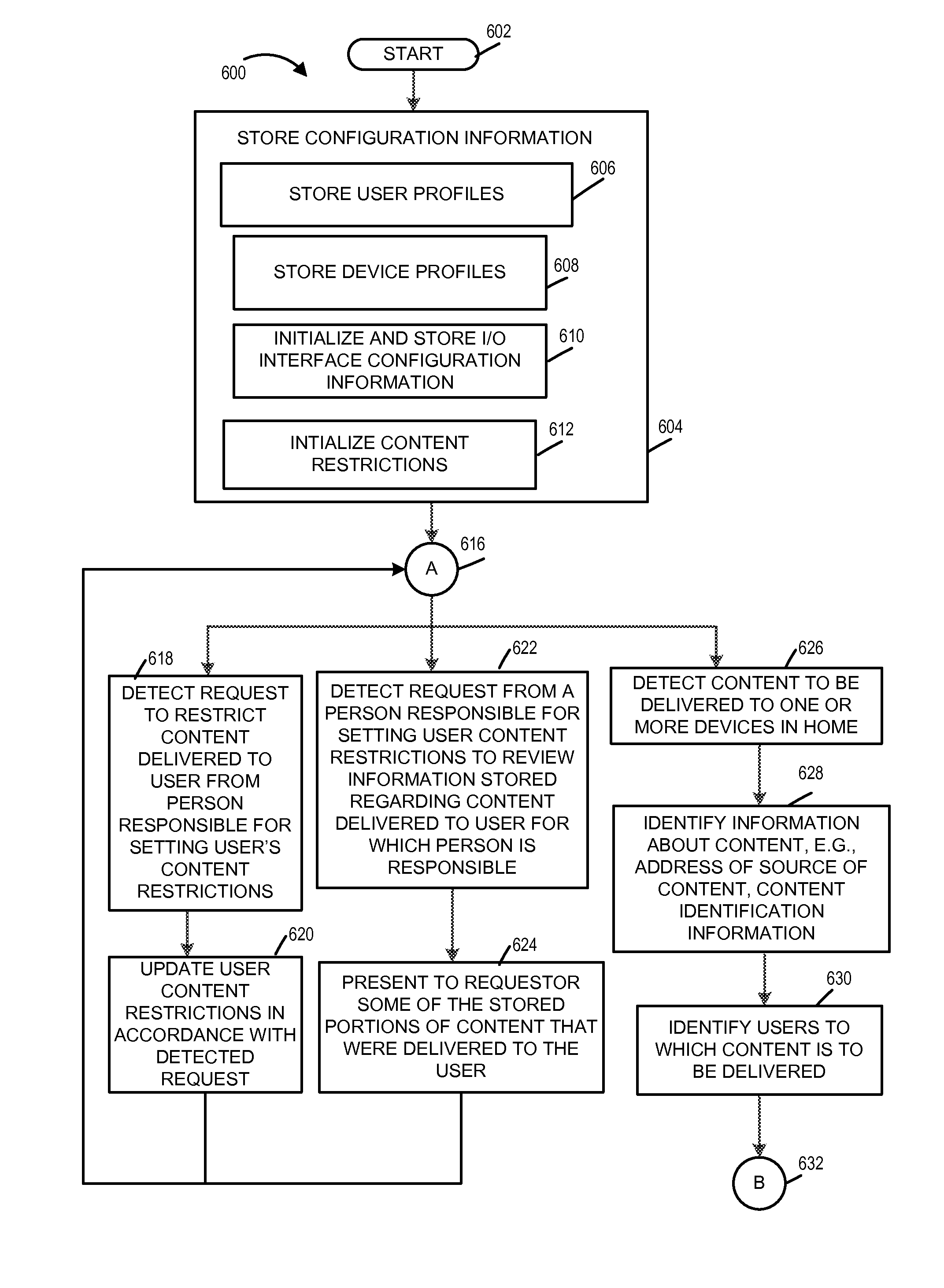
ActiveUS8843953B1Analogue secracy/subscription systemsSelective content distributionCyber-attackFamily network
Methods and apparatus for providing a supervisor such as a parent or guardian with a way to monitor and control the delivery of content, e.g., video and audio programs, to users of devices within a home. Exemplary embodiments include methods and apparatus for operating a home network monitoring device located in a home including detecting delivery of content to one or more users in the home, storing, in the home, portions of content delivered to a first user, presenting some of the stored portions of content to a person responsible for setting content restrictions applicable to the first user, and subjecting further content delivery to the first user via the home network to restrictions established by the person responsible for setting content restrictions applicable to the first user. Some embodiments also detect and report potential attacks, e.g., cyber attacks, on the home network.
Owner:TIME WARNER CABLE ENTERPRISES LLC
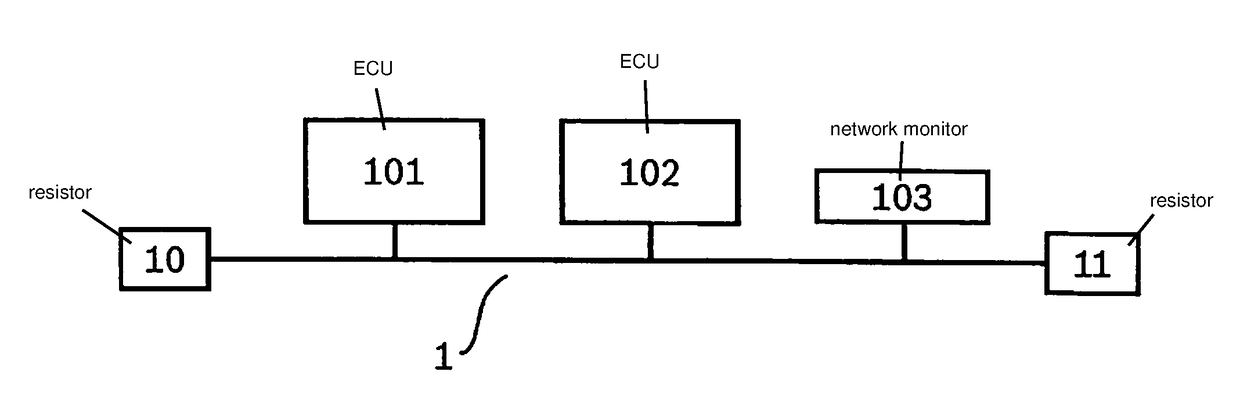
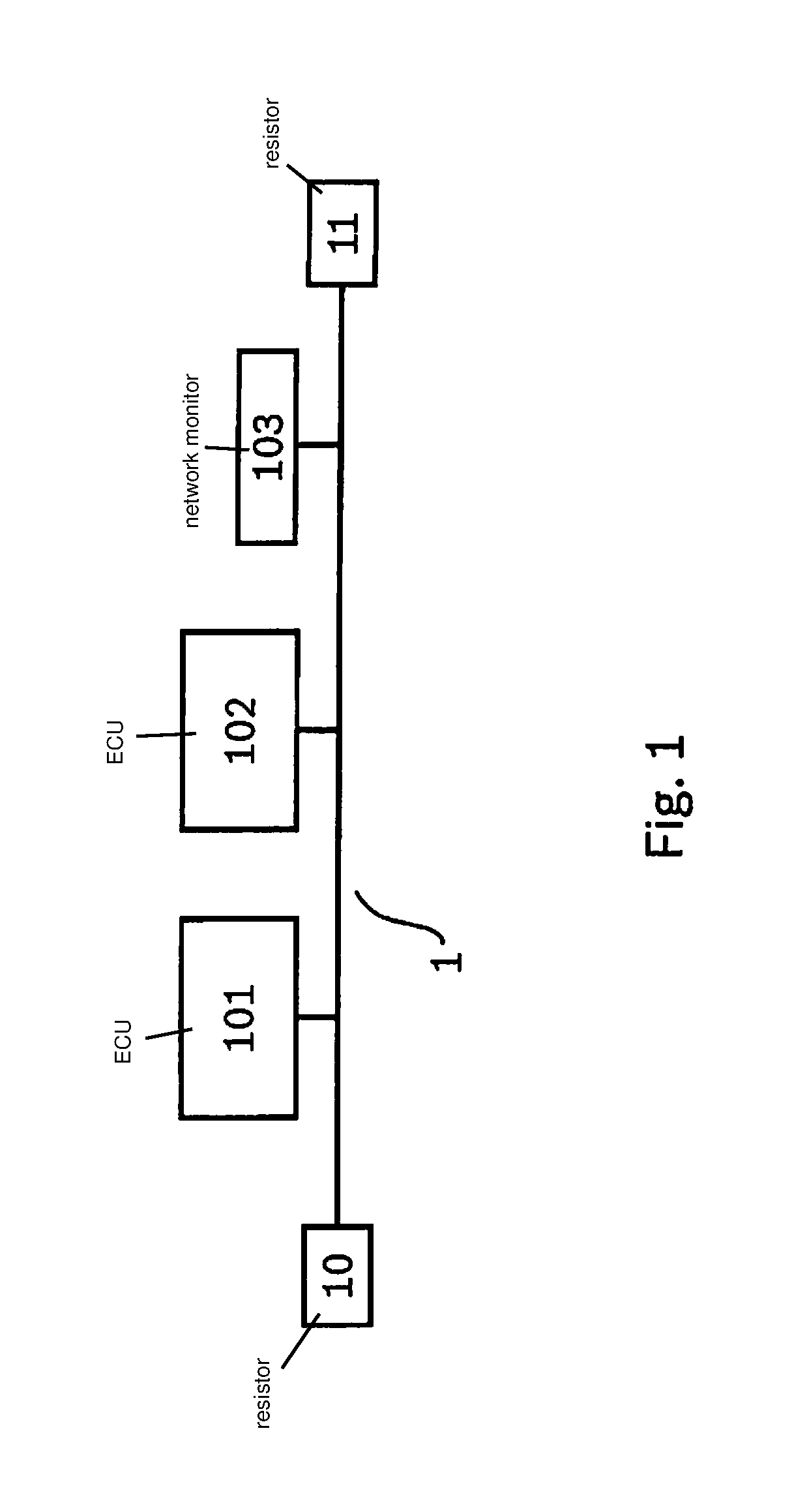
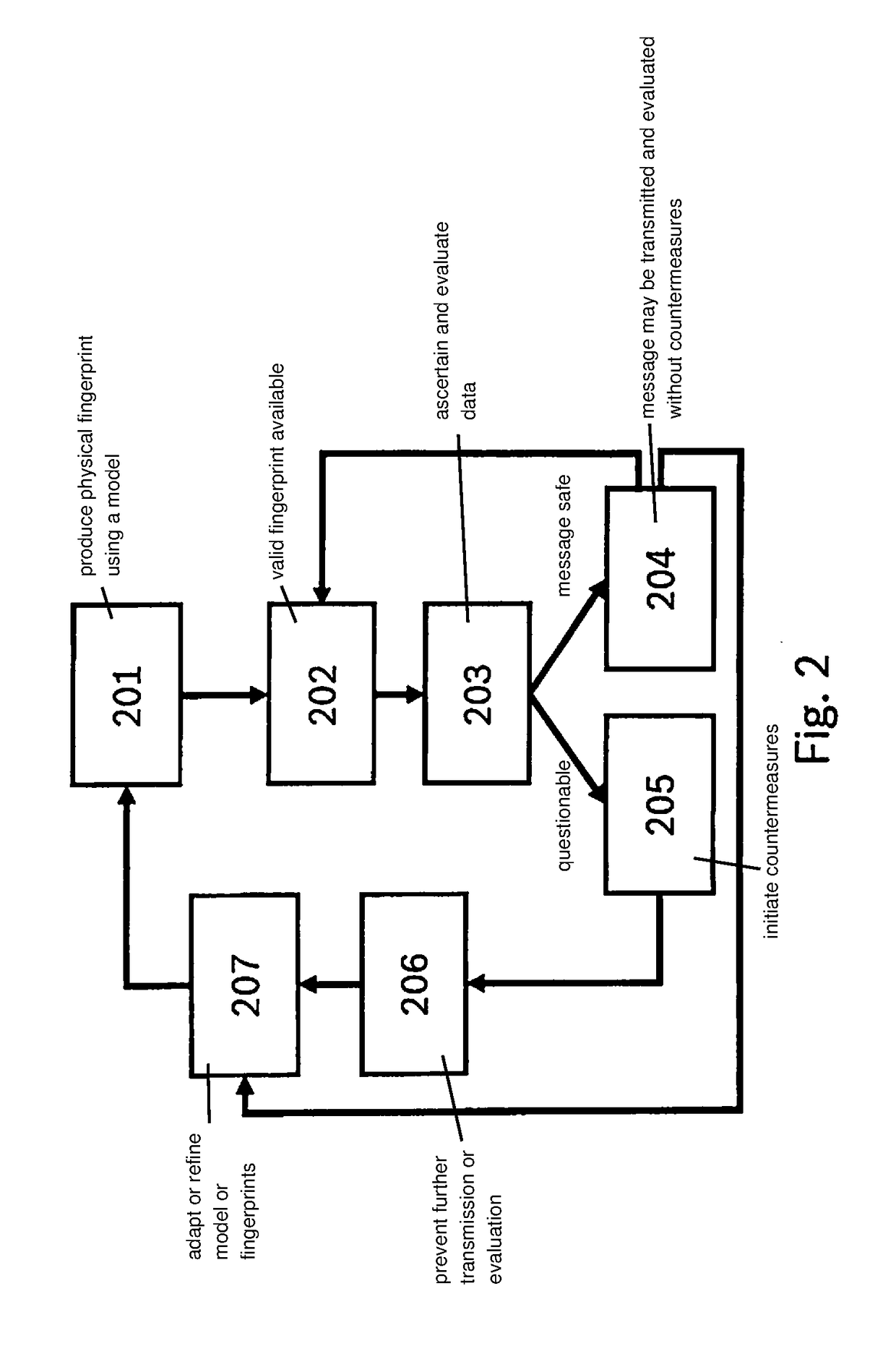
Method for protecting a network against a cyberattack
InactiveUS20180337938A1Improve reliabilityImprove protectionParticular environment based servicesDigital data protectionComputer hardwareCyber-attack
A method for protecting a network against a cyberattack, in which for a message in the network first characteristics of a first transmission of the message are determined and an origin of the message in the network is determined by a comparison of the first characteristics with at least one fingerprint of at least one subscriber or a segment of the network or a transmission route. If a manipulation of the message is detected, a point of attack of the cyberattack in the network is detected and localized in particular on the basis of the origin of the message.
Owner:ROBERT BOSCH GMBH
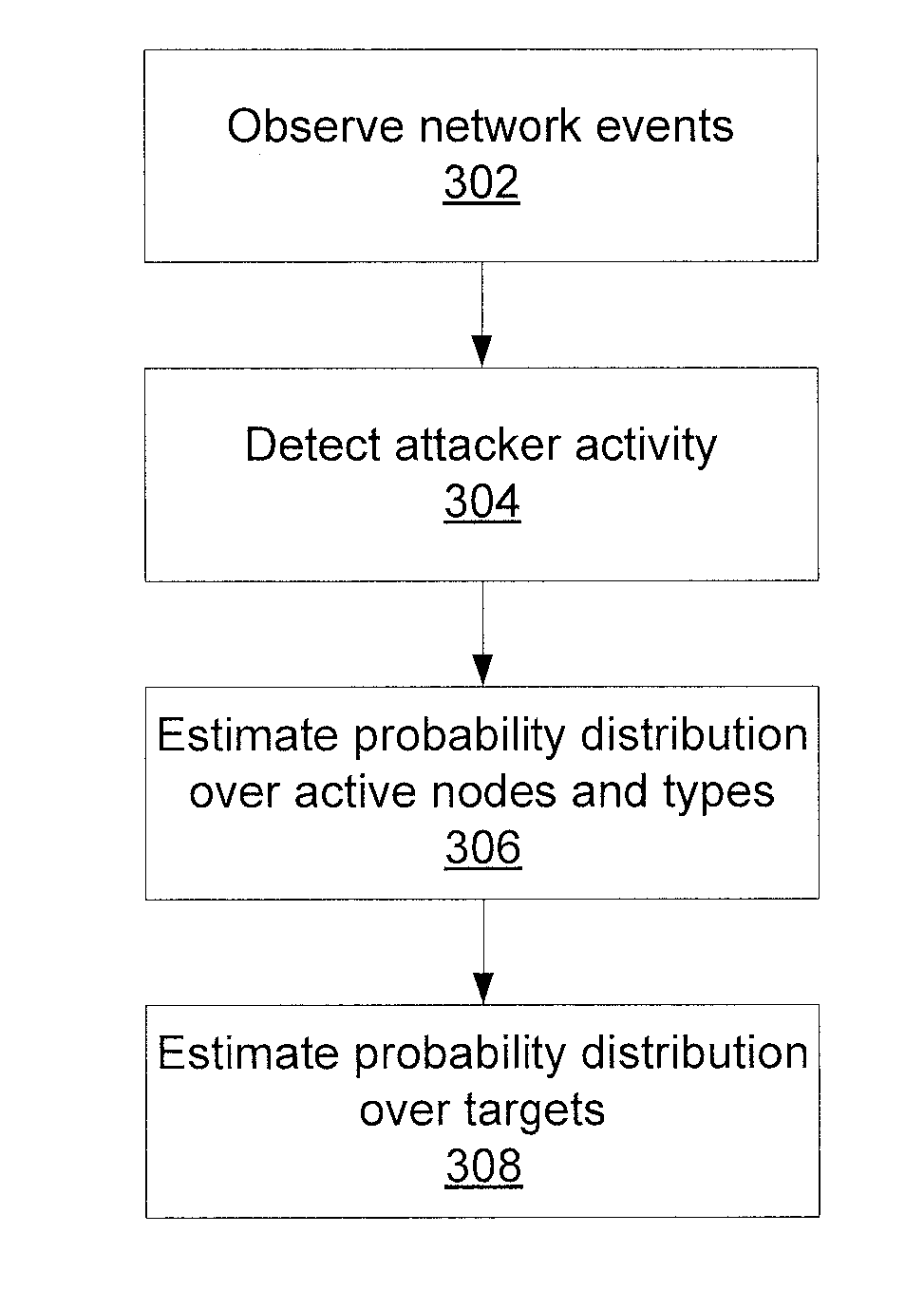
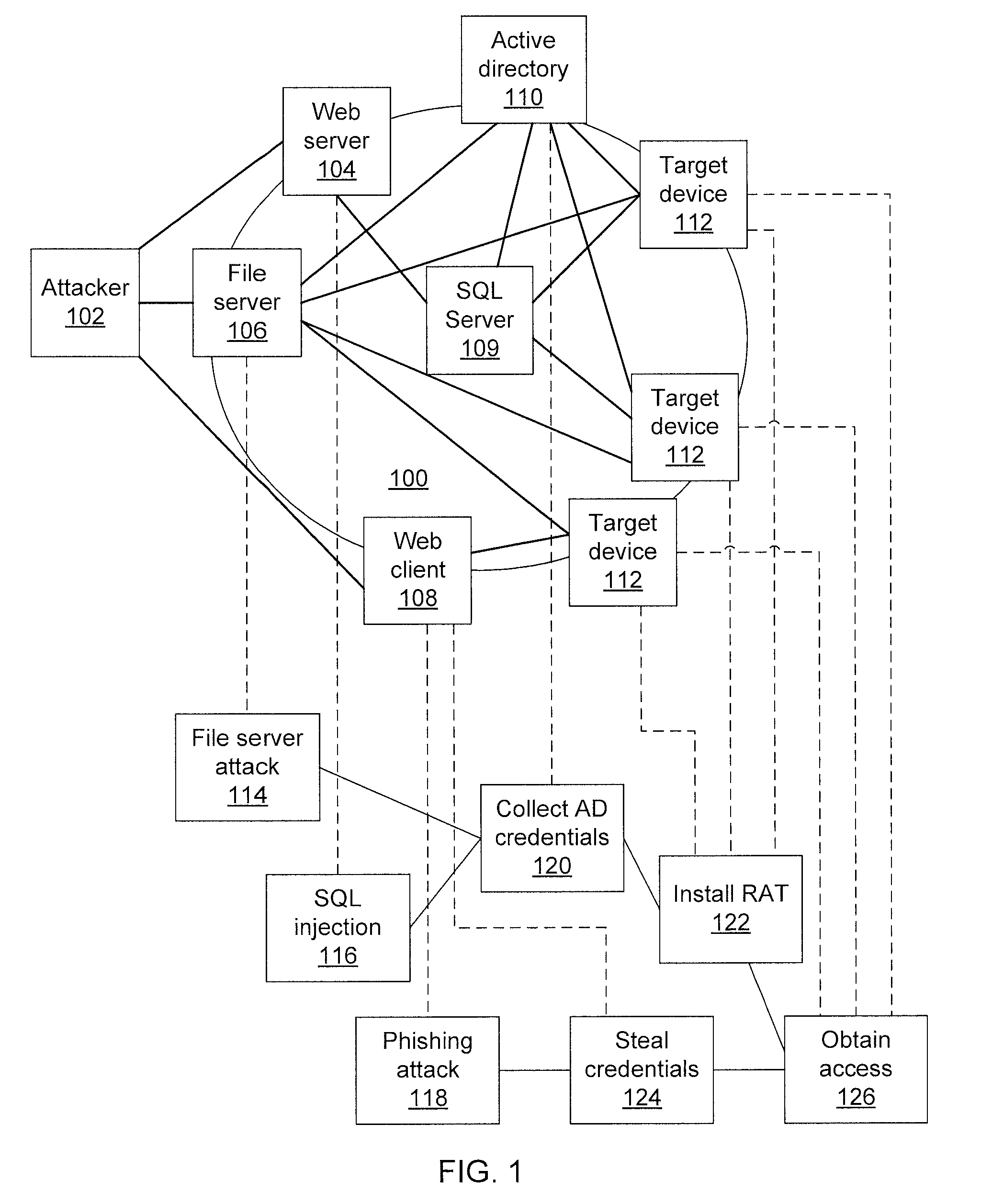
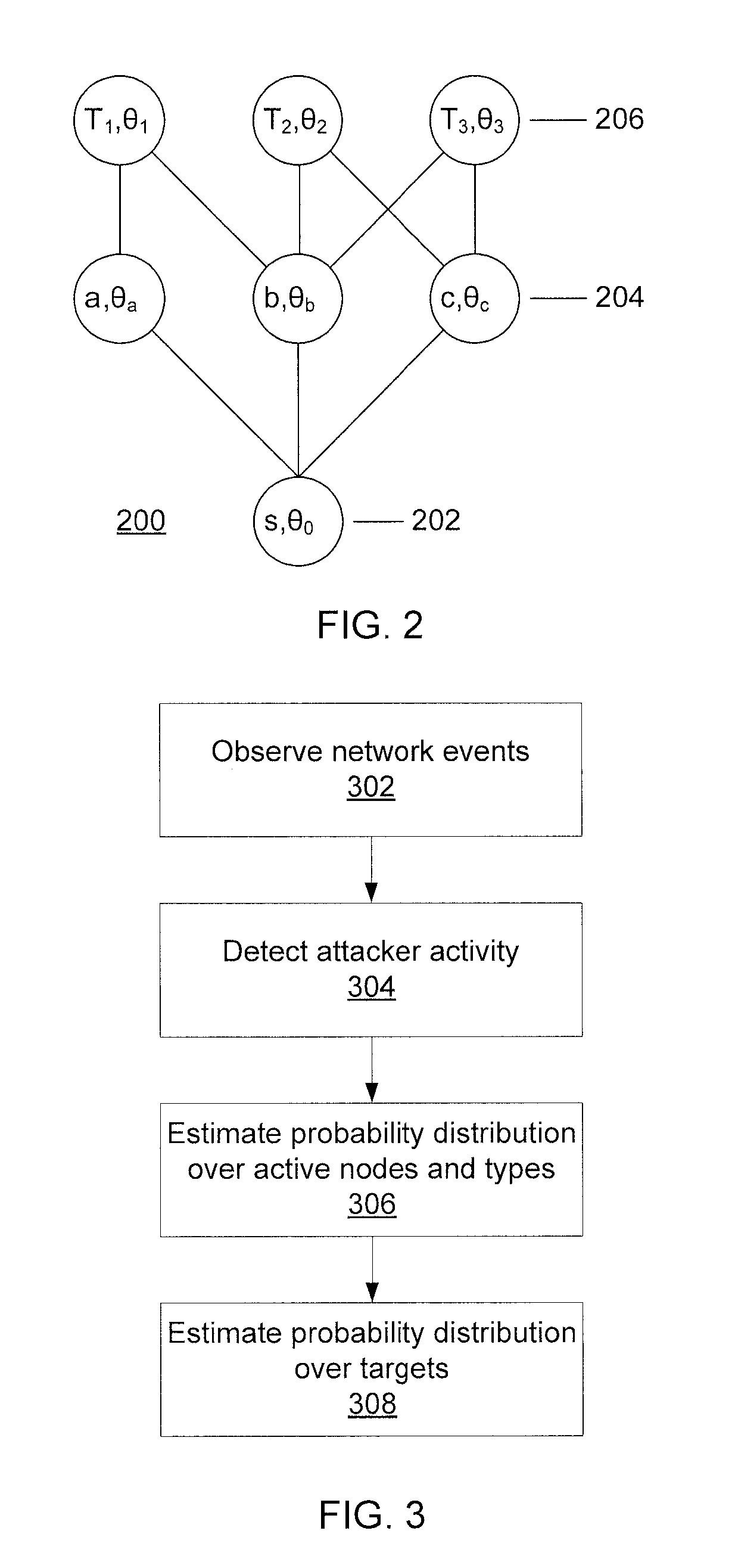
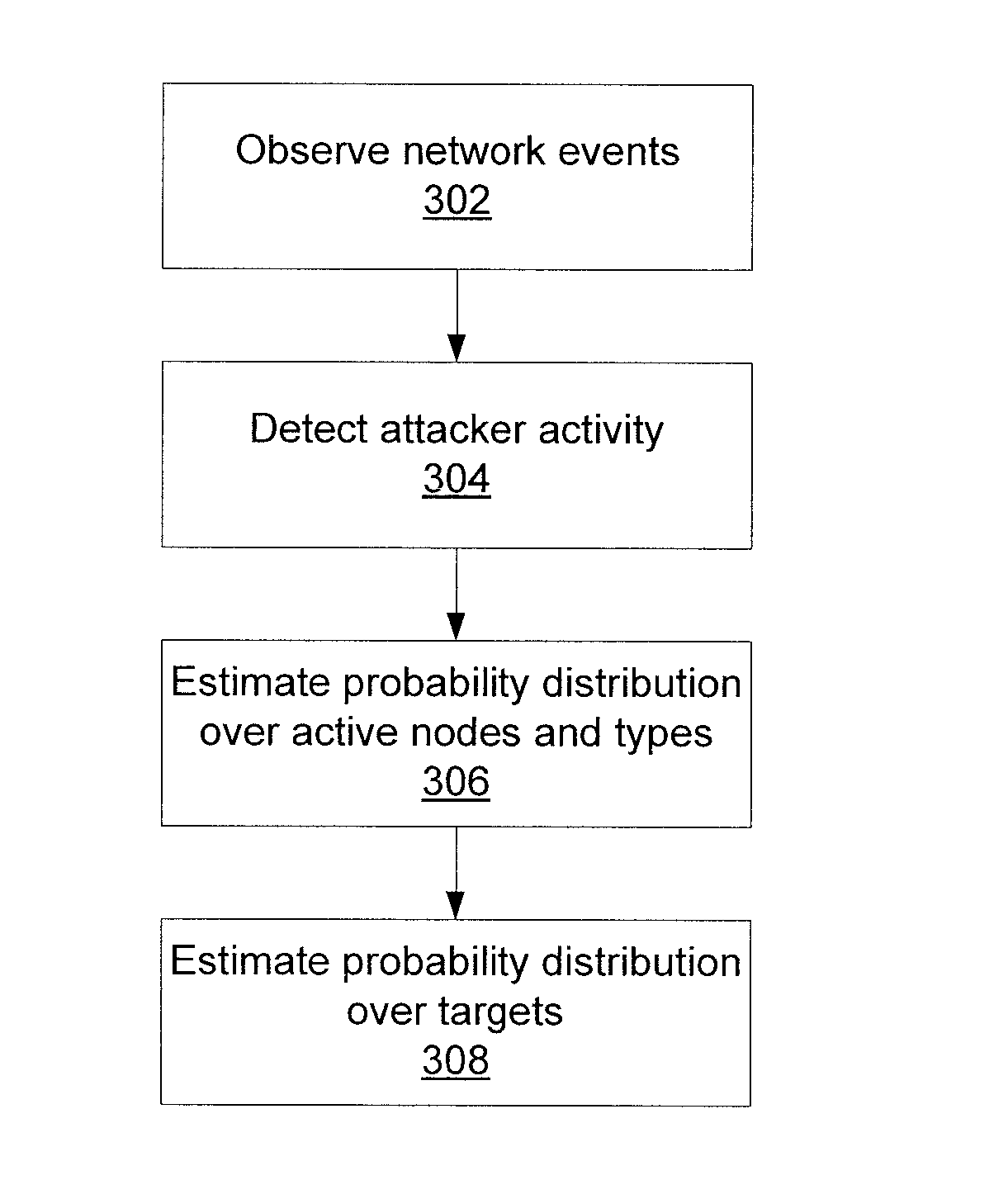
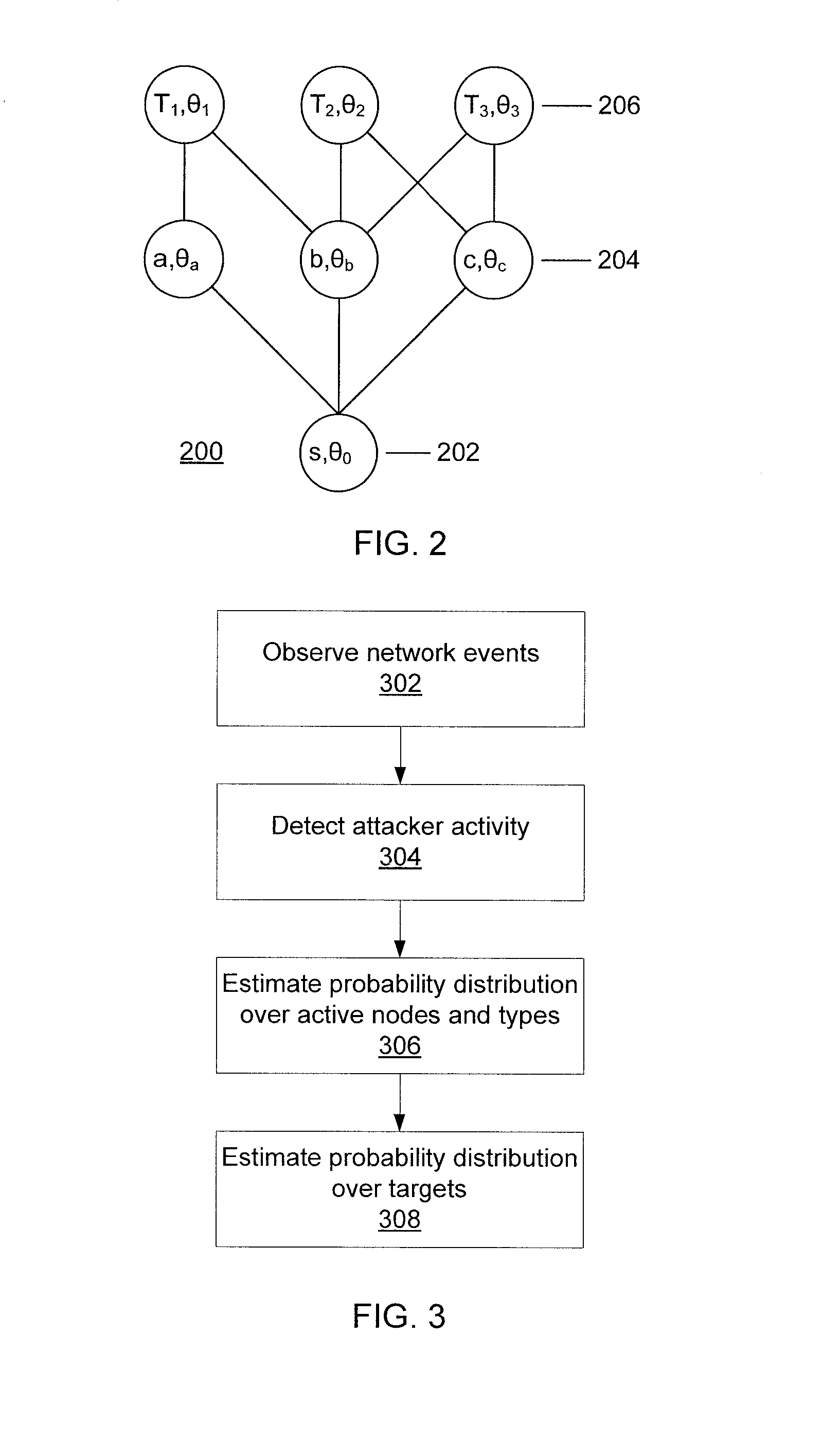
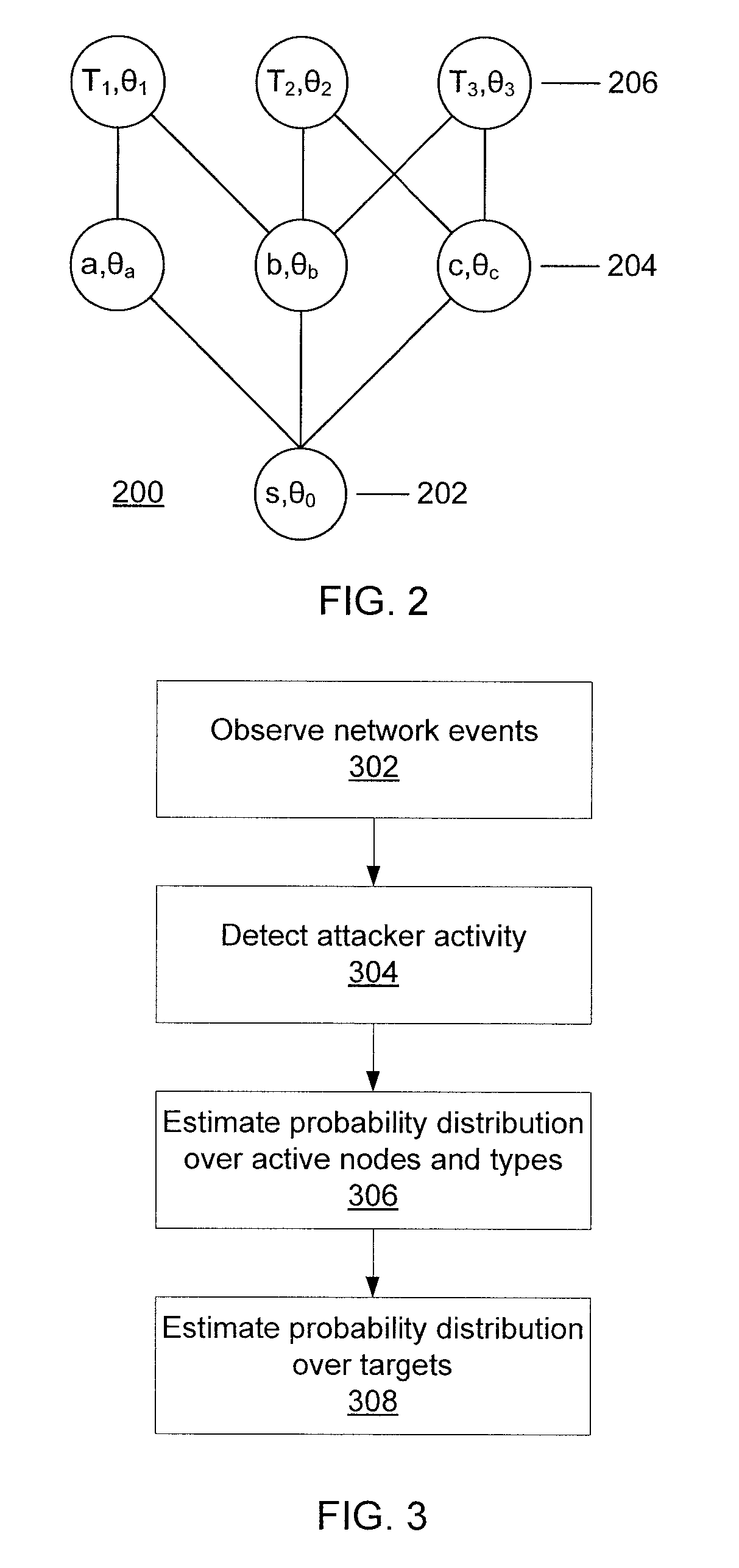
Predicting attacks based on probabilistic game-theory
InactiveUS20130318616A1Minimizes a defender's expected uncertainty over the potential targetsMemory loss protectionError detection/correctionCyber-attackNetwork management
Systems for determining cyber-attack target include a network monitor module configured to collect network event information from sensors in one or more network nodes; a processor configured to extract information regarding an attacker from the network event information, to form an attack scenario tree that encodes network topology and vulnerability information including a plurality of paths from known compromised nodes to a set of potential targets, to calculate a likelihood for each of the paths, to calculate a probability distribution for the set of potential targets to determine which potential targets are most likely pursued by the attacker, to calculate a probability distribution over a set of nodes and node vulnerability types already accessed by the attacker, and to determine a network graph edge to remove that minimizes a defender's expected uncertainty over the potential targets; and a network management module configured to remove the determined network graph edge.
Owner:IBM CORP
Predicting attacks based on probabilistic game-theory
ActiveUS20130318615A1Minimizes a defender's expected uncertainty over the potential targetsMemory loss protectionError detection/correctionCyber-attackAlgorithm
Methods for determining cyber-attack targets include collecting and storing network event information from sensors to extract information regarding an attacker; forming an attack scenario tree that encodes network topology and vulnerability information including paths from known compromised nodes to a set of potential targets; calculating a likelihood for each of the paths using a processor; calculating a probability distribution for the set of potential targets to determine which potential targets are most likely pursued by the attacker; calculating a probability distribution over a set of nodes and node vulnerability types already accessed by the attacker; determining a network graph edge to remove which minimizes a defender's expected uncertainty over the potential targets; and removing the determined network graph edge.
Owner:IBM CORP
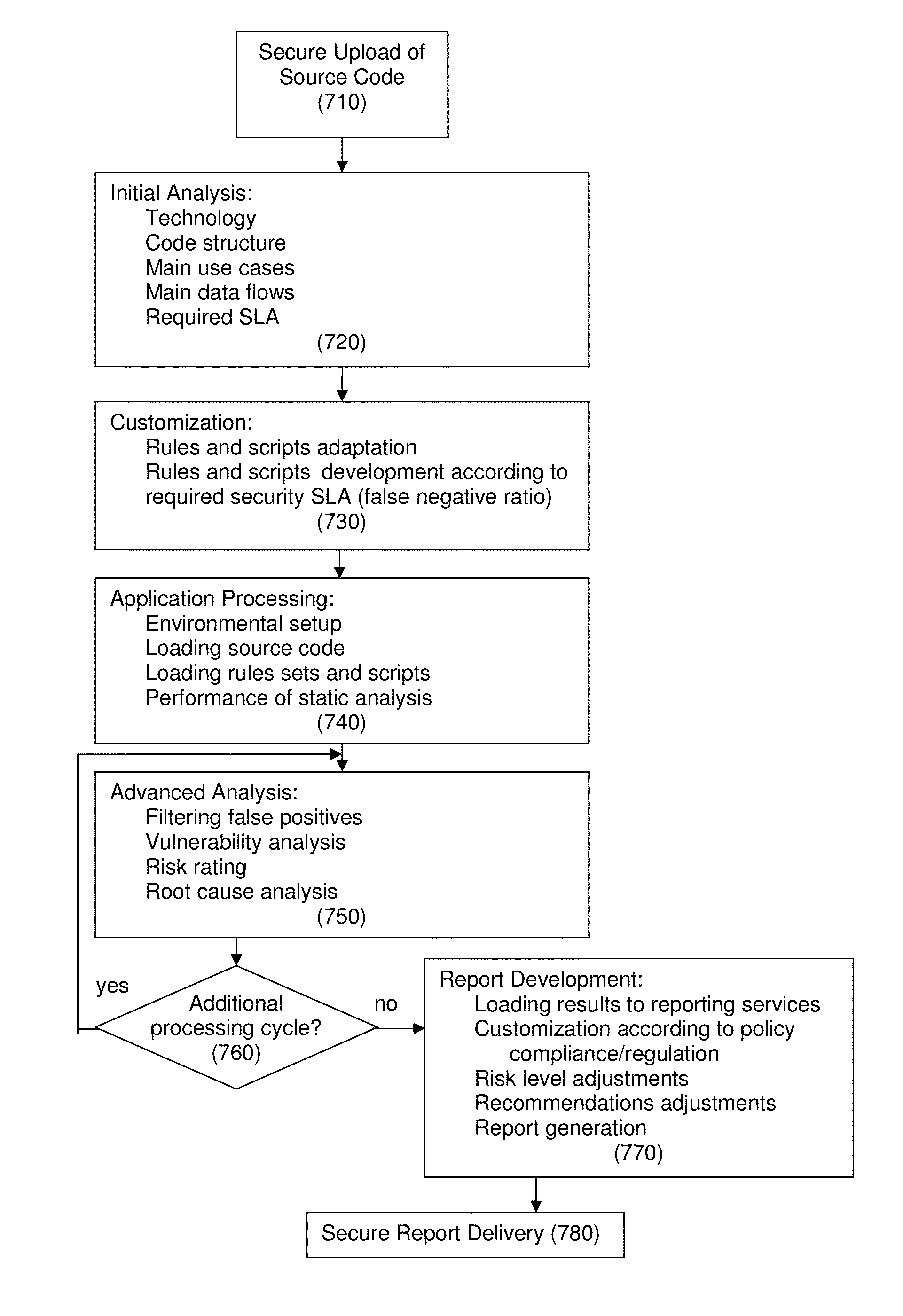
Systems and methods for defending against cyber attacks at the software level
InactiveUS20150121532A1Minimizing false negative rateEliminating false positiveMemory loss protectionError detection/correctionCyber-attackHigh level analysis
A method for a customized, scalable and cost-efficient solution to enable source code level solutions to provide zero percentage false positives as well as a controlled false negative ratio to detect software security vulnerabilities accurately and in time. The method includes secure uploading of the source code, initial analysis and customizing according to accuracy and depth defined to enable control of the false negative ratio. The method also includes application processing, advanced analyzing, performing report development and delivering a secure report. The initial analysis provides for a human analyst “built-in” as part of the process that performs the analysis on initial results and the filtering of the results to contain ONLY relevant security vulnerabilities
Owner:COMSEC CONSULTING
System, Method and Process for Protecting Data Backup from Cyberattack
System, method and process for securing and protecting data and data backups from cyberattack and implementing disaster recovery using machine learning and artificial intelligence. Embodiments learn and establish baseline parameters of routine, normal and non-compromised behavior and activity of virtual machines operative in cloud ecosystem, detect and recognize anomalous events related to advanced persistent threats to the instance, such as ransomware, and automatically implement preconfigured actions as determined by a user with the primary objective of protecting data and data backups.
Owner:CLOUD DADDY INC
Pattern detection in sensor networks
InactiveUS20160156652A1Memory loss protectionError detection/correctionAugmented lagrange multiplierData set
A method of detecting an anomaly in a sensor network for diagnosing a network attack may include receiving a data set comprising a plurality of vector-valued measurements from a plurality of sensors, and decomposing the data set into a low-rank component L and a sparse component S using an Augmented Lagrange Multiplier (ALM) method. In one embodiment, at least one of L or S can be determined using an exact minimizer of a Lagrangian in the ALM method, L can represent patterns that occur in a relatively large number of the plurality of sensors, and S can represent patterns that occur in a relatively small number of the plurality of sensors. The method may also include ascertaining, using the computer system, the anomaly in the data set based on the patterns in the sparse component S.
Owner:NUMERICA CORP
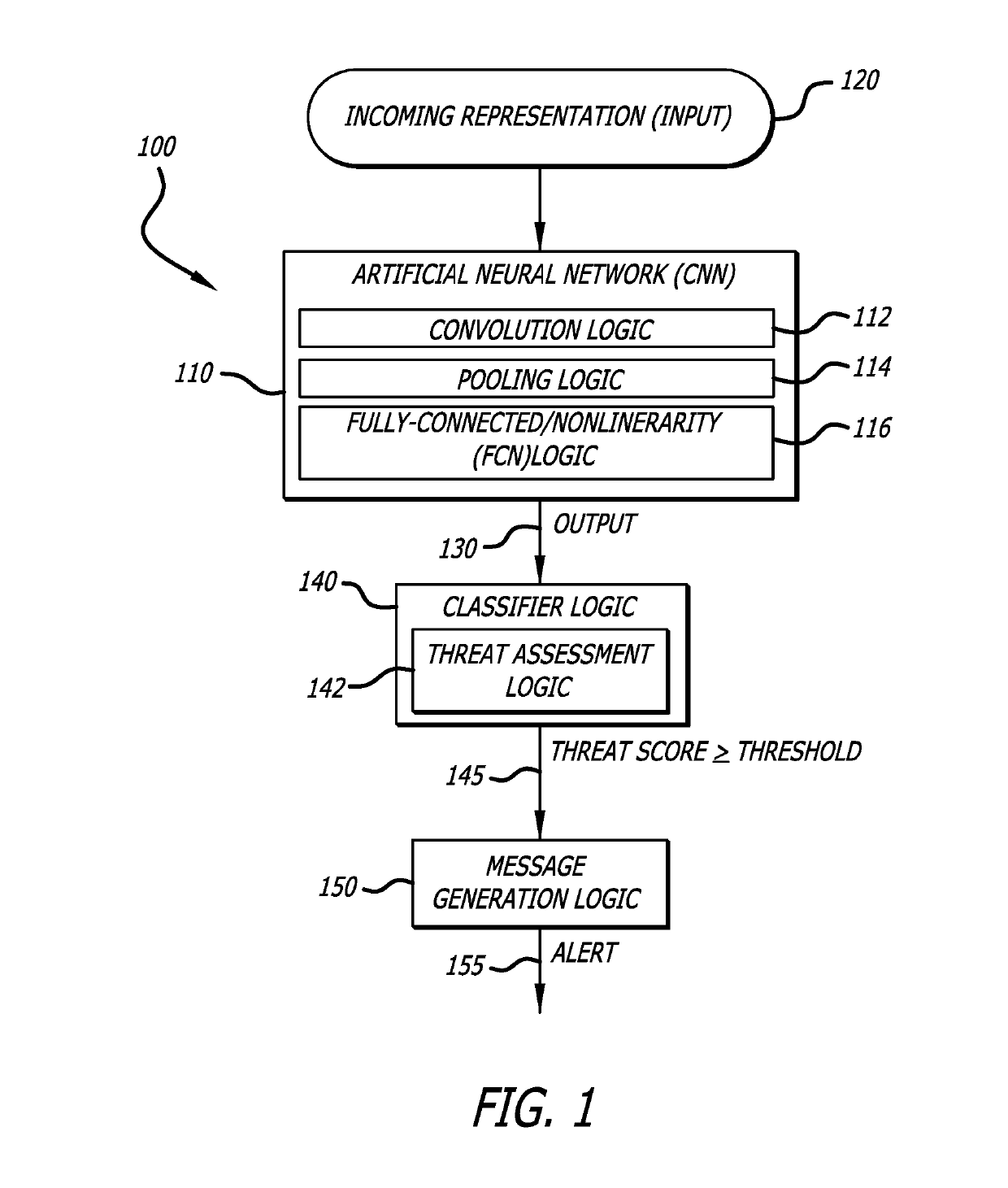
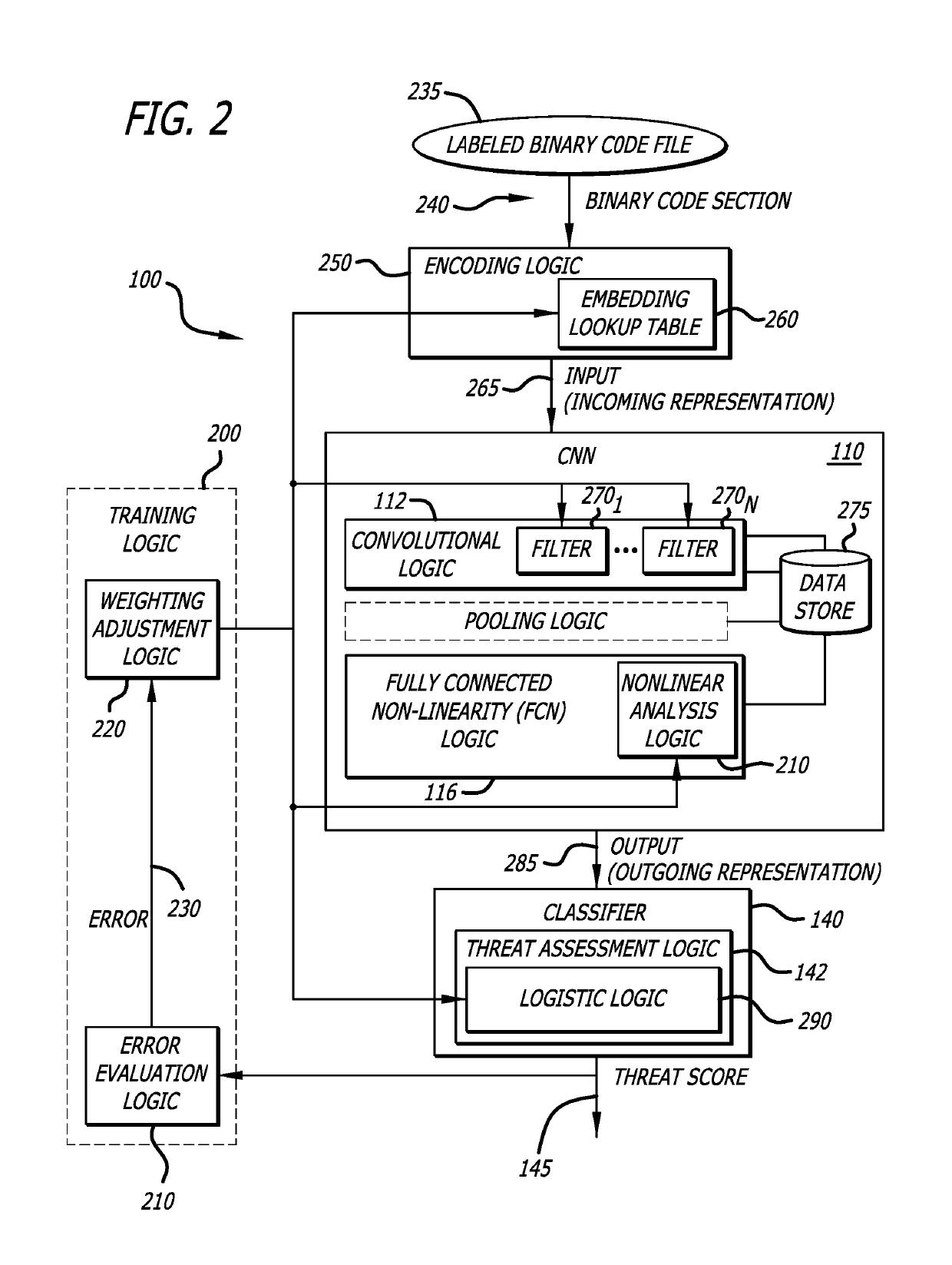
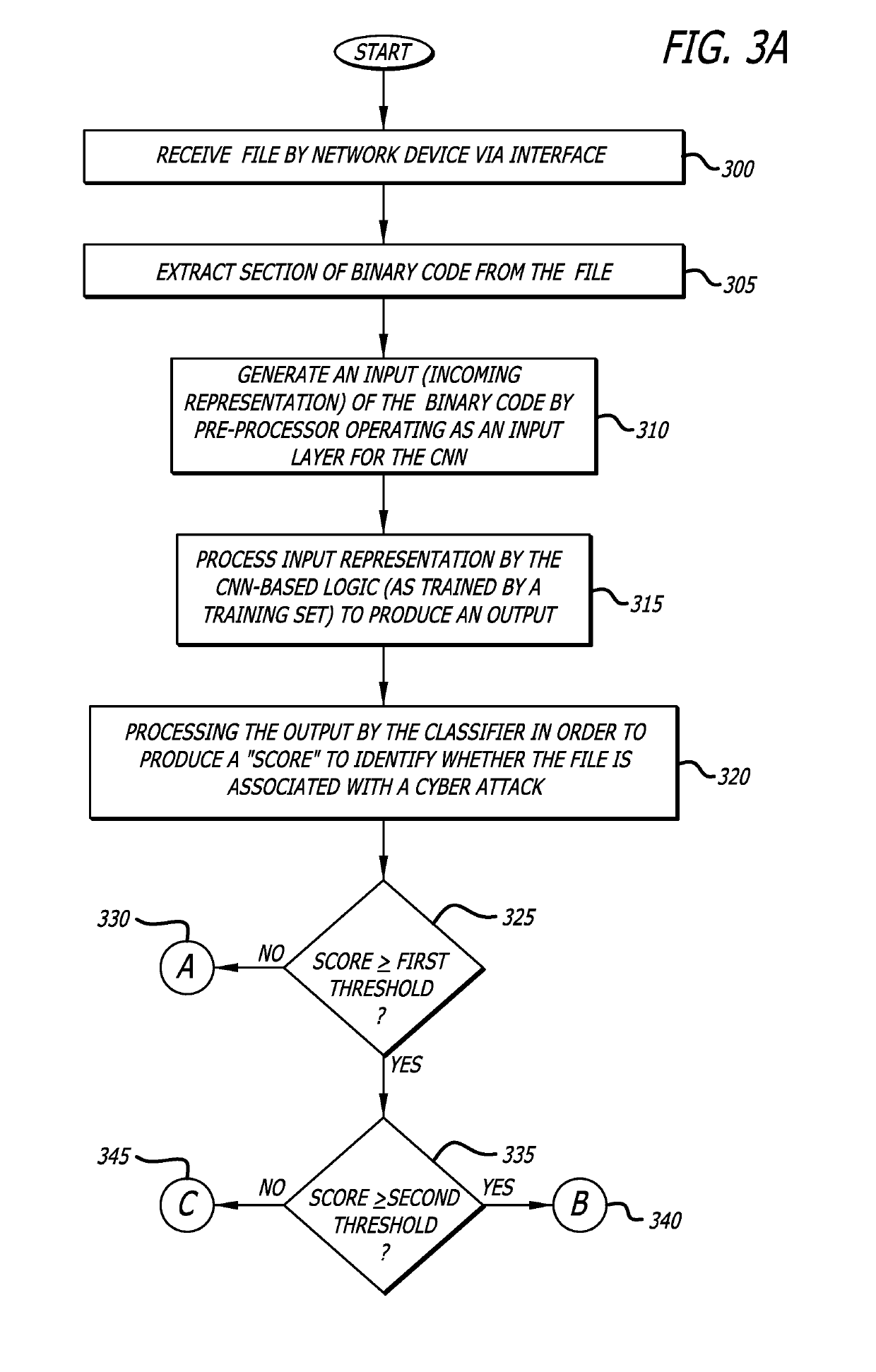
System and method for analyzing binary code for malware classification using artificial neural network techniques
A system for detecting whether a file including content s associated with a cyber-attack is described. The content may include an executable file for example. The system includes an intelligence-driven analysis subsystem and a computation analysis subsystem. The intelligence-driven analysis subsystem is configured to (i) receive the file, (ii) inspect and compute features of the file for indicators associated with a cyber-attack, and (iii) produce a first output representing the detected indicators. The computational analysis subsystem includes an artificial neural network to (i) receive a network input being a first representation of at least one section of binary code from the file as input, and (ii) process the first representation of the section to produce a second output. The first output and the second output are used in determination a classification assigned to the file.
Owner:GOOGLE LLC
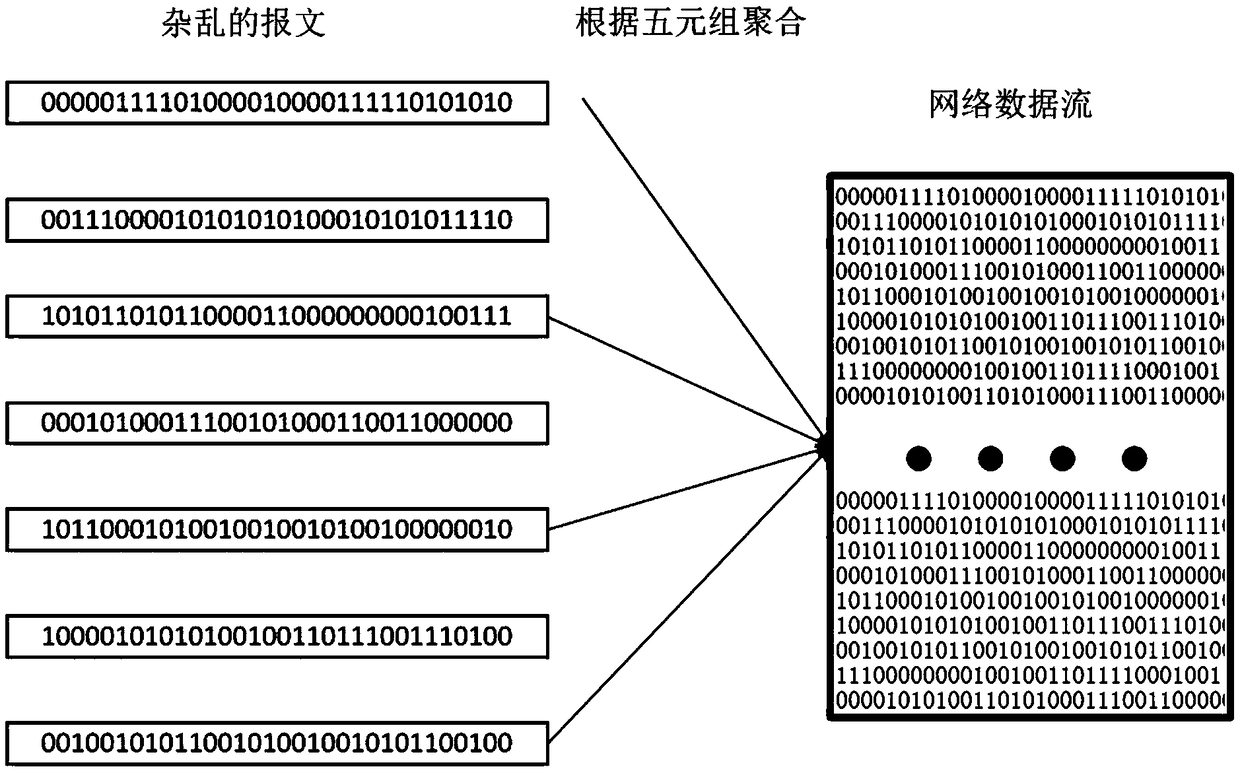
Data stream anomaly detection system based on empirical features and convolution neural network
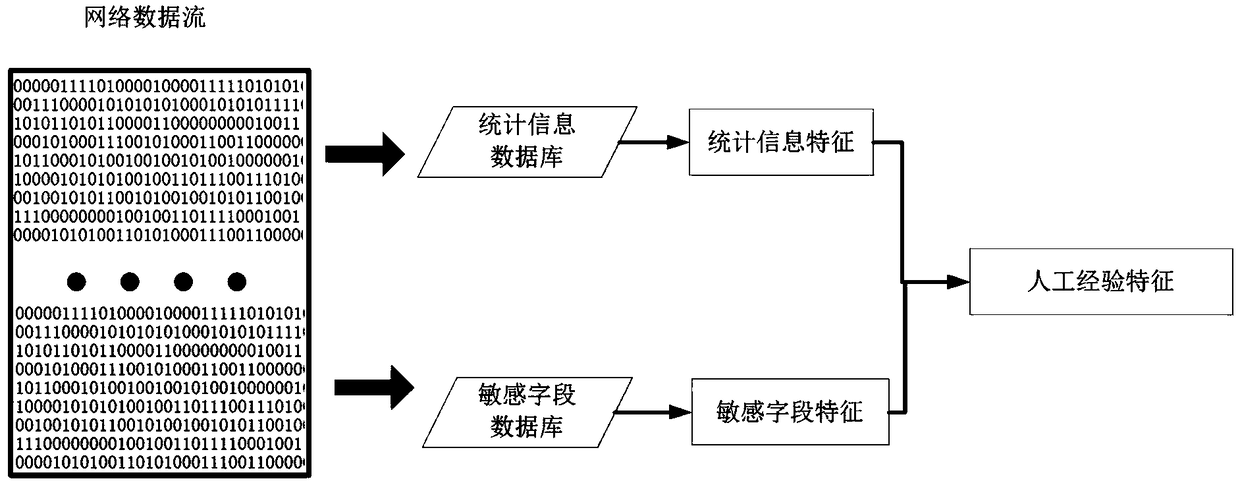
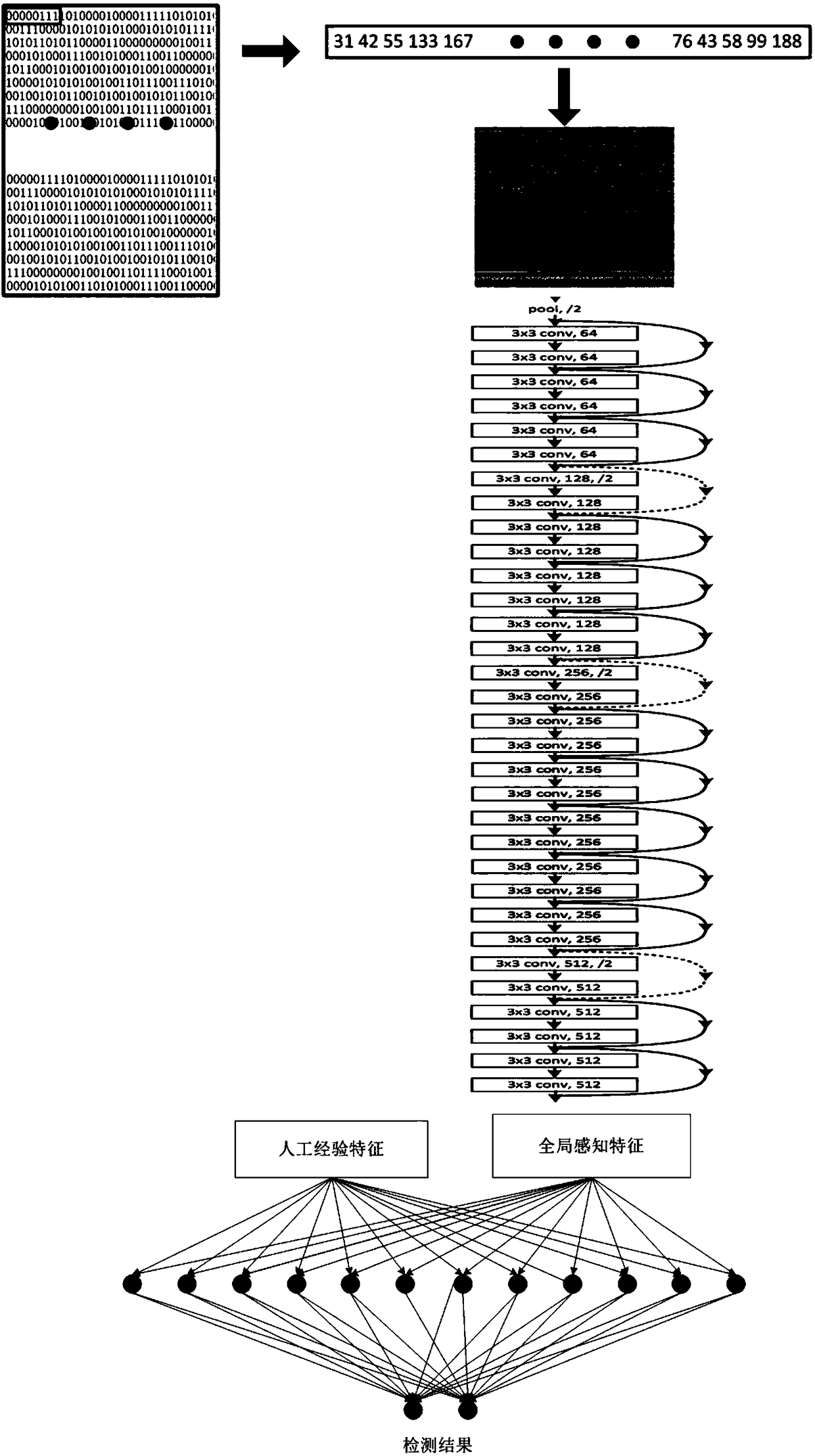
ActiveCN109284606AEasy to detectMeet real-time requirementsCharacter and pattern recognitionPlatform integrity maintainanceDistillationComplex network
The invention discloses a data stream anomaly detection system based on empirical characteristics and convolution neural network. The system includes an empirical feature extraction module, which is used to identify statistical features and header features as features based on artificial experience, which play a more important role in data packet anomaly recognition; a bit stream conversion picture module used to convert the data stream into the form of two-dimensional gray-scale picture, and then through the convolutional neural network perception, the global high-level perception features are extracted; a fusion splicing module used for fusing the above modules as the data stream characteristics and identifying abnormal data streams by using the full connection layer of the neural network; a distillation model module that replaces complex networks in actual deployment; a concept drift fine-tuning module updates the detection model of concept drift; an update experience database module adding new network attacks or hidden attack instructions to the artificial experience database. The invention accurately and efficiently detects abnormal behaviors such as network failure, user misoperation, network attack and the like.
Owner:ARMY ENG UNIV OF PLA
Predicting attacks based on probabilistic game-theory
ActiveUS8863293B2Minimizes a defender's expected uncertainty over the potential targetsMemory loss protectionError detection/correctionNODALCyber-attack
Methods for determining cyber-attack targets include collecting and storing network event information from sensors to extract information regarding an attacker; forming an attack scenario tree that encodes network topology and vulnerability information including paths from known compromised nodes to a set of potential targets; calculating a likelihood for each of the paths using a processor; calculating a probability distribution for the set of potential targets to determine which potential targets are most likely pursued by the attacker; calculating a probability distribution over a set of nodes and node vulnerability types already accessed by the attacker; determining a network graph edge to remove which minimizes a defender's expected uncertainty over the potential targets; and removing the determined network graph edge.
Owner:INT BUSINESS MASCH CORP
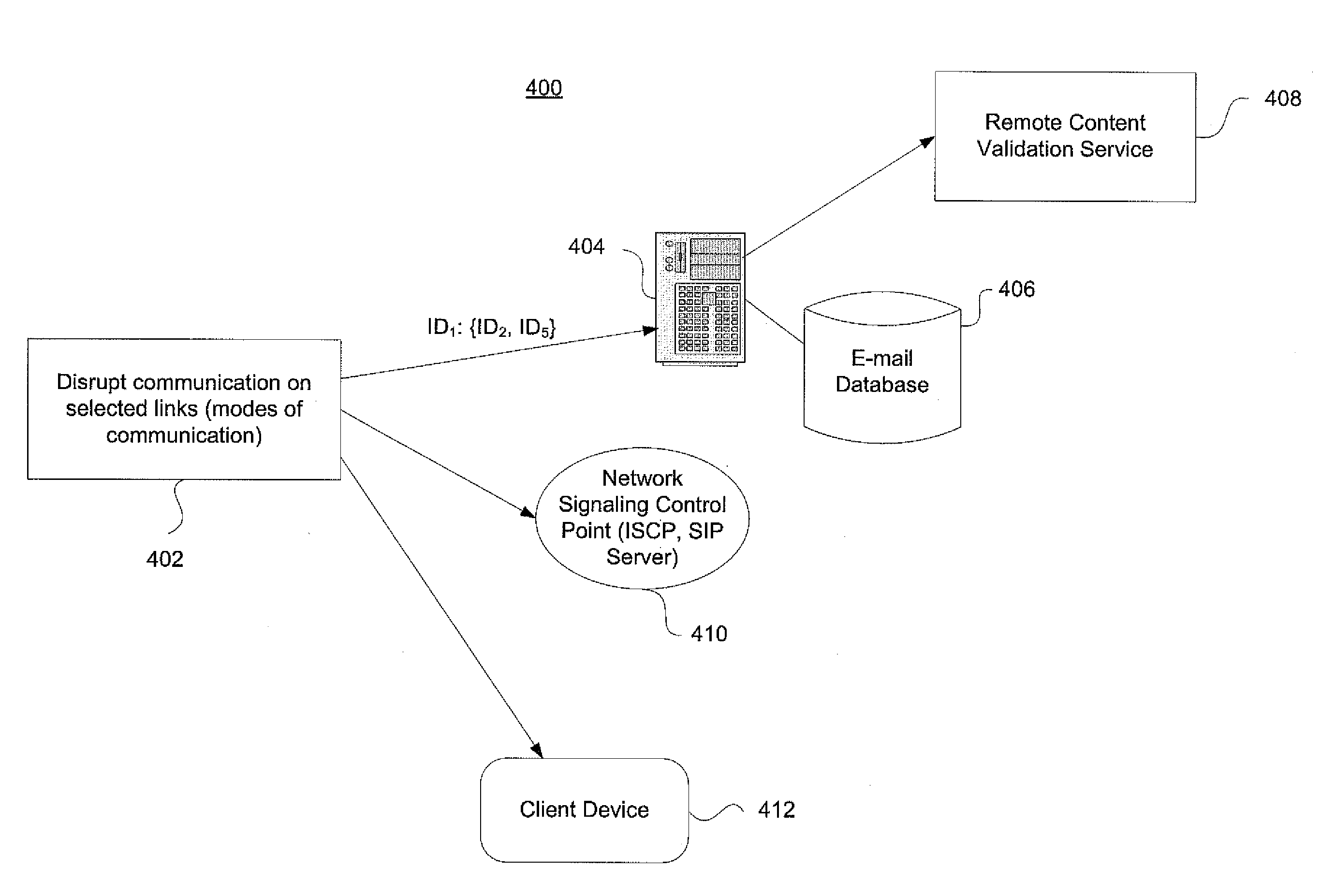
Societal-scale graph-based interdiction for virus propagation slowdown in telecommunications networks
InactiveUS20110295982A1Disrupting spreadExtended durationMemory loss protectionError detection/correctionCyber-attackTelecommunications network
Embodiments of the invention enable very rapid intervention on detection of computer network attacks by viruses or other malicious code. Targeted disruption of links between selected nodes in the network is used to hinder the spread of such malicious code. This applies to e-mail and other modes of communication. For instance, identification of and response to an attack may occur within 5-10 minutes instead of the hours or days timescale associated with known signature-based virus protection techniques. Aspects of the invention directly adapt to observed patterns of social contacts and exchanges to provide a substantial increase, e.g., on the order of a 10-fold increase, in the time until a virus affects 70-80% of network users. This provides anti-virus inoculation mechanisms significant time, for instance on the order of 1-2 additional days, before an attack disrupts worldwide communication networks.
Owner:TT GOVERNMENT SOLUTIONS
Method for mitigation of cyber attacks on industrial control systems
ActiveUS20170054751A1Way accurateEffectively respondsTesting/monitoring control systemsPlatform integrity maintainanceCyber-attackNetwork behavior
Methods and systems for detecting a potential compromise of cyber security in an industrial network are disclosed. These methods and systems comprise elements of hardware and software for establishing a baseline of site-acceptable network behavior comprising a list of network states and transition probabilities, wherein a transition probability denotes an estimated probability of a first network state being followed temporally by a second network state during normal network operation; establishing a threshold representing tile probability below which a sequence of network states is anomalous; determining a probability for the occurrence of a sequence of network states as obtained from a particular stream of packets, according to the baseline of site-acceptable network behavior; and, taking protective action according to whether the determined probability is below the established threshold.
Owner:MICROSOFT TECH LICENSING LLC
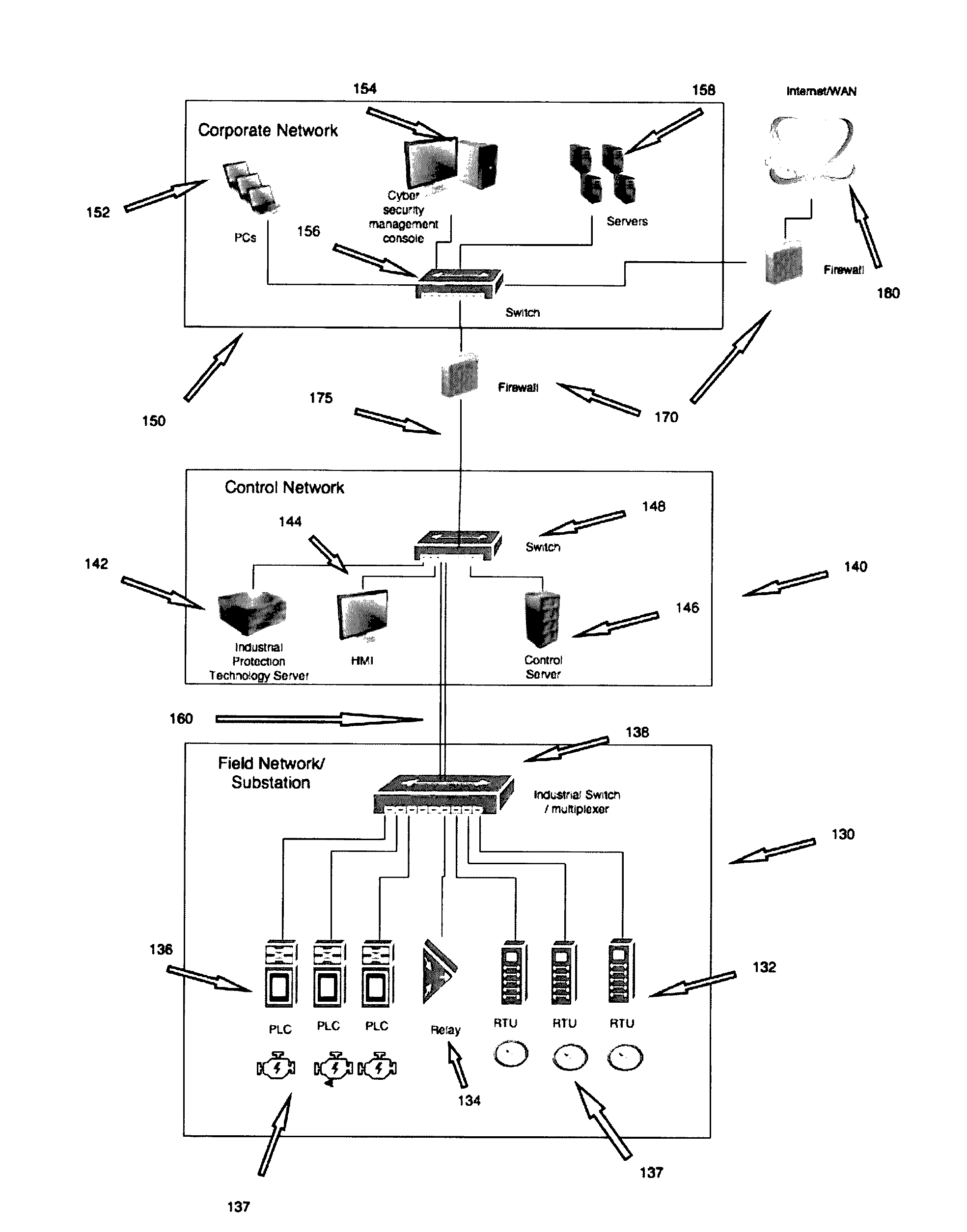
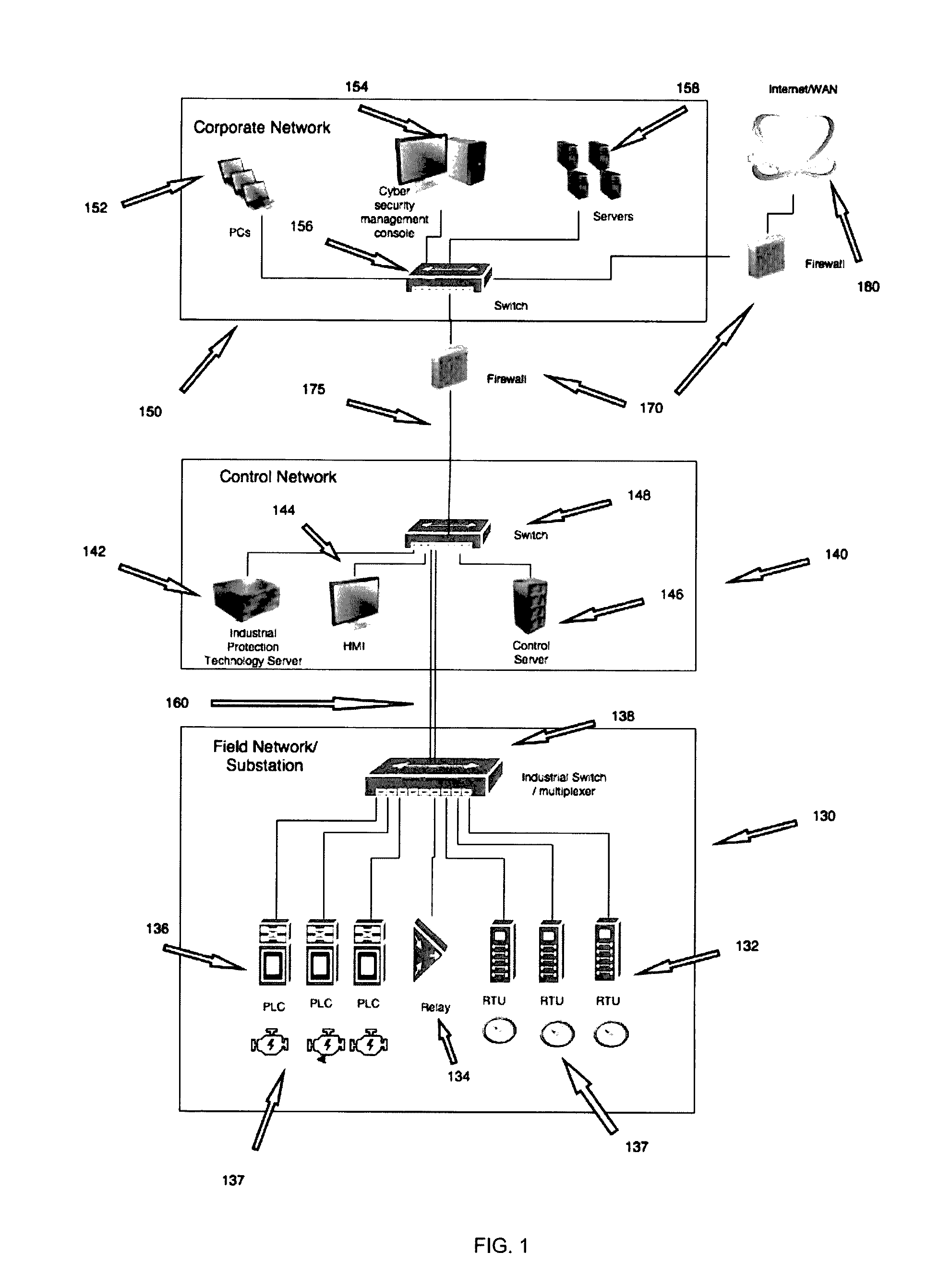
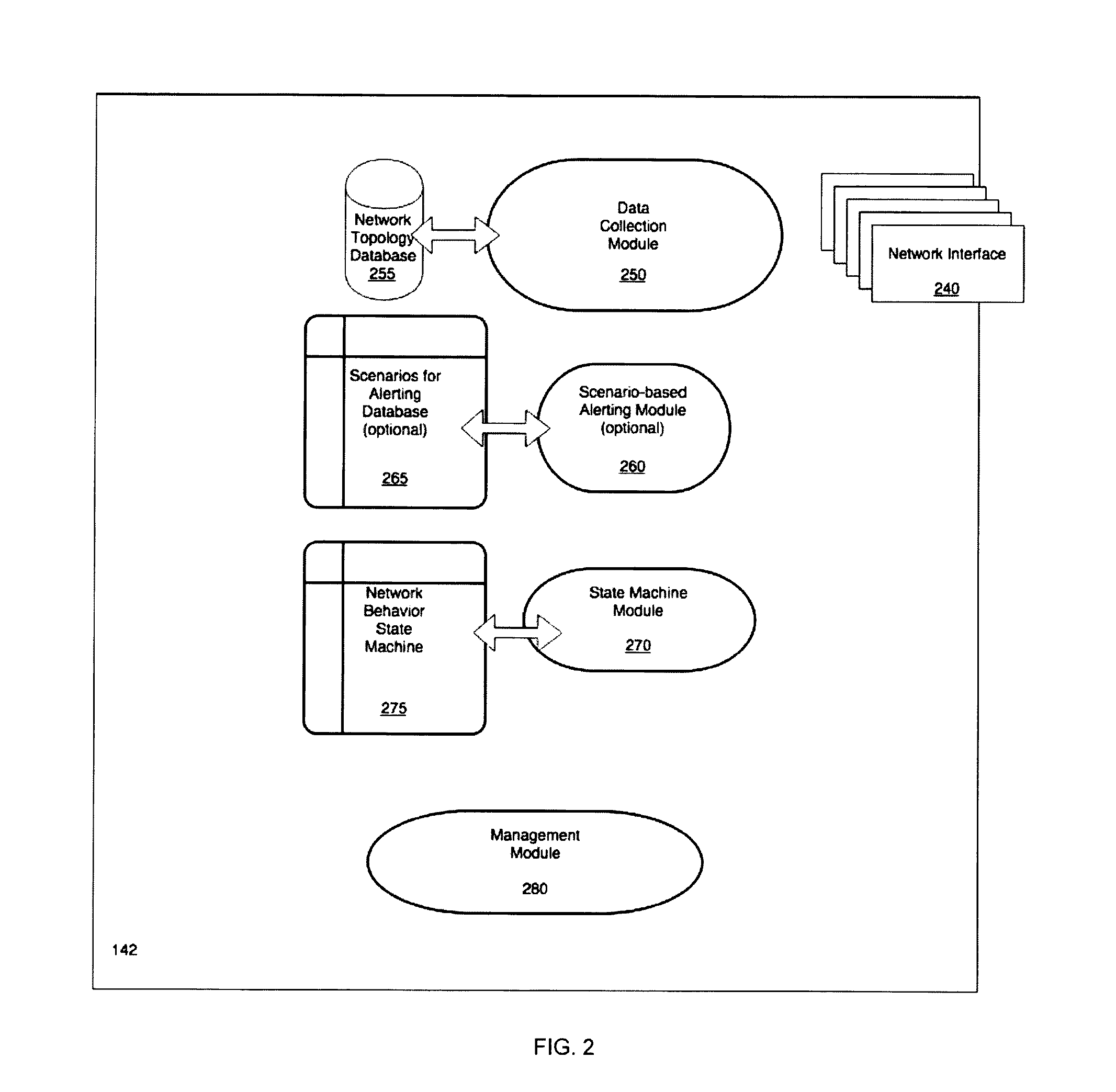
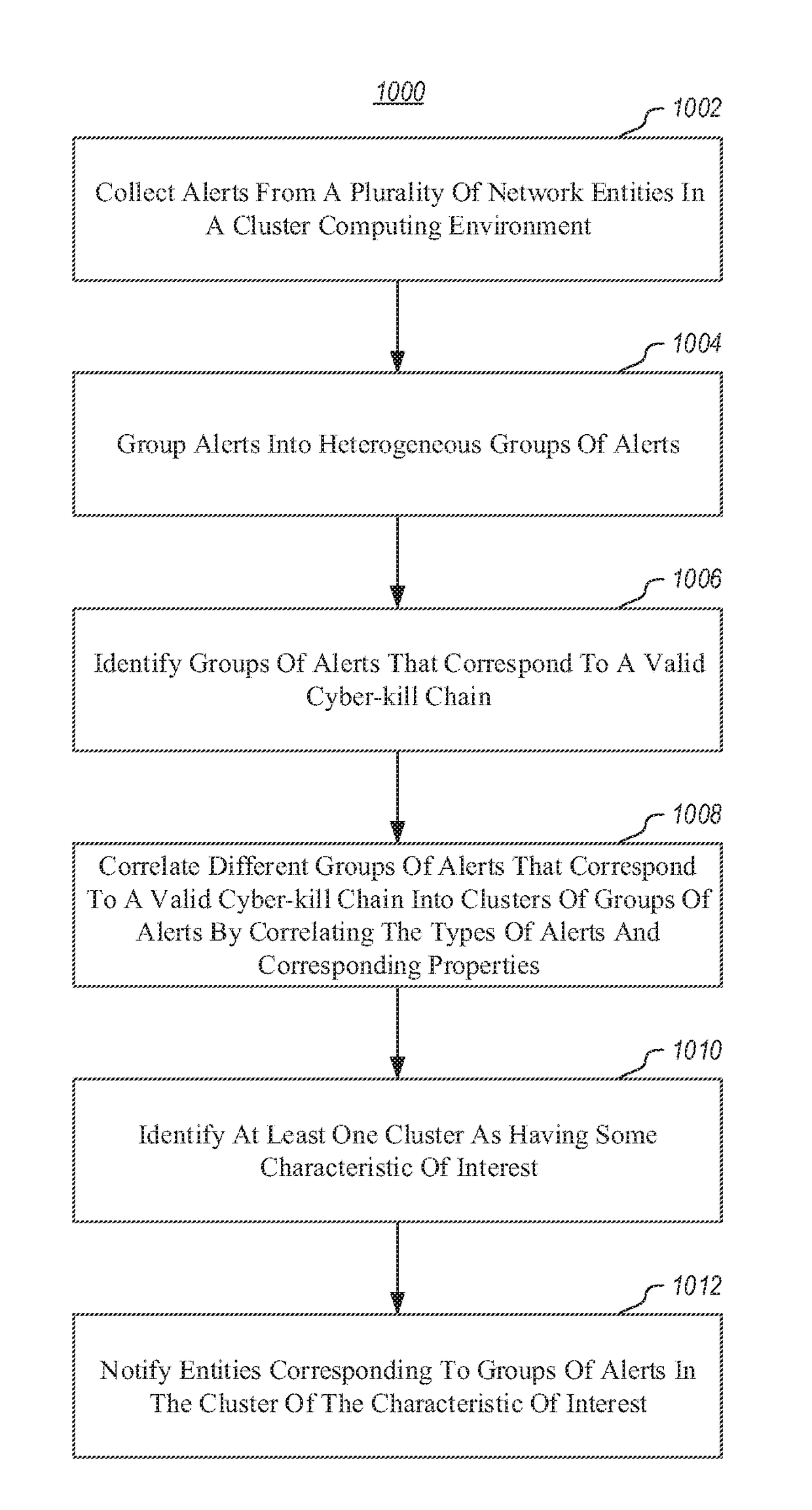
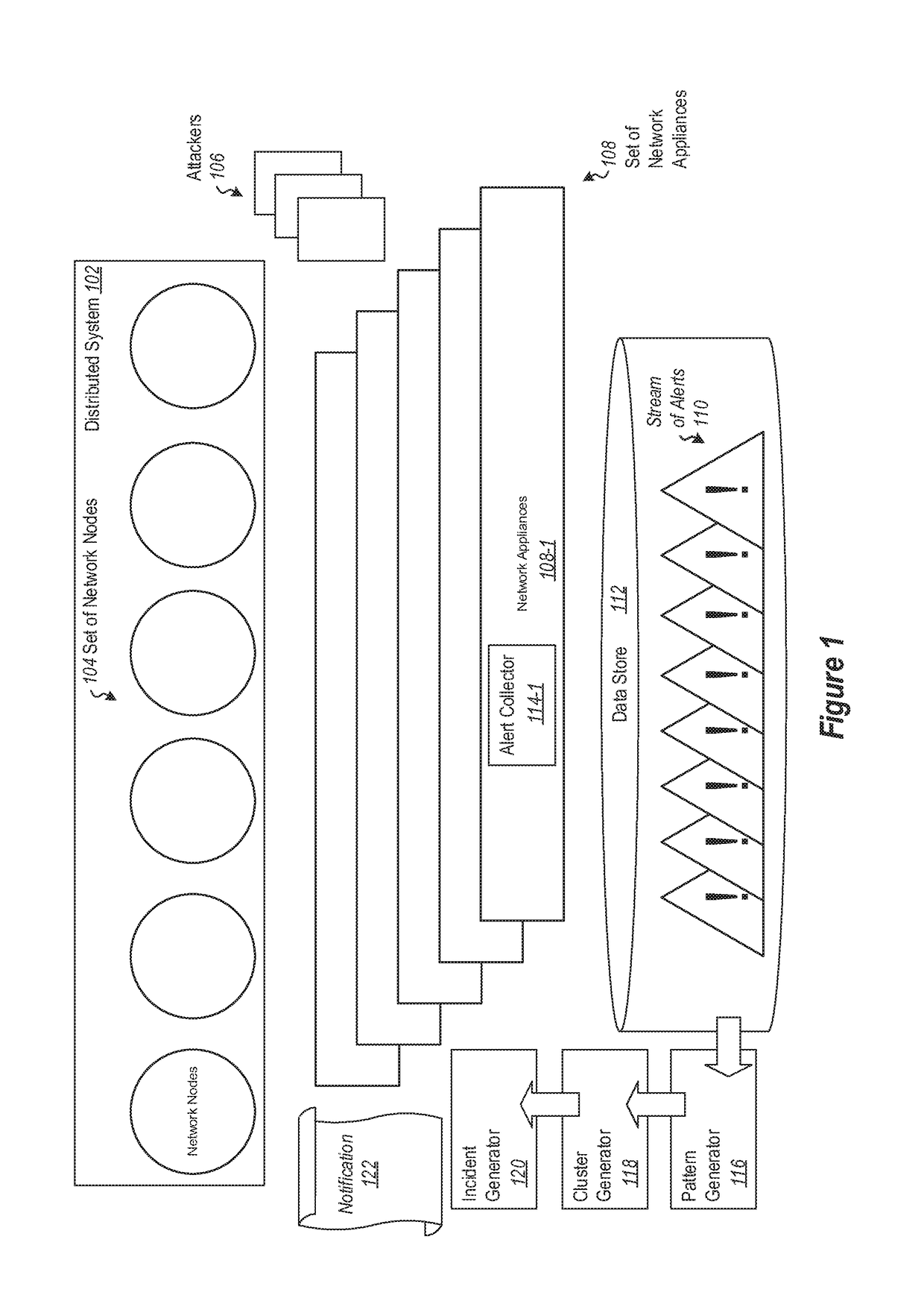
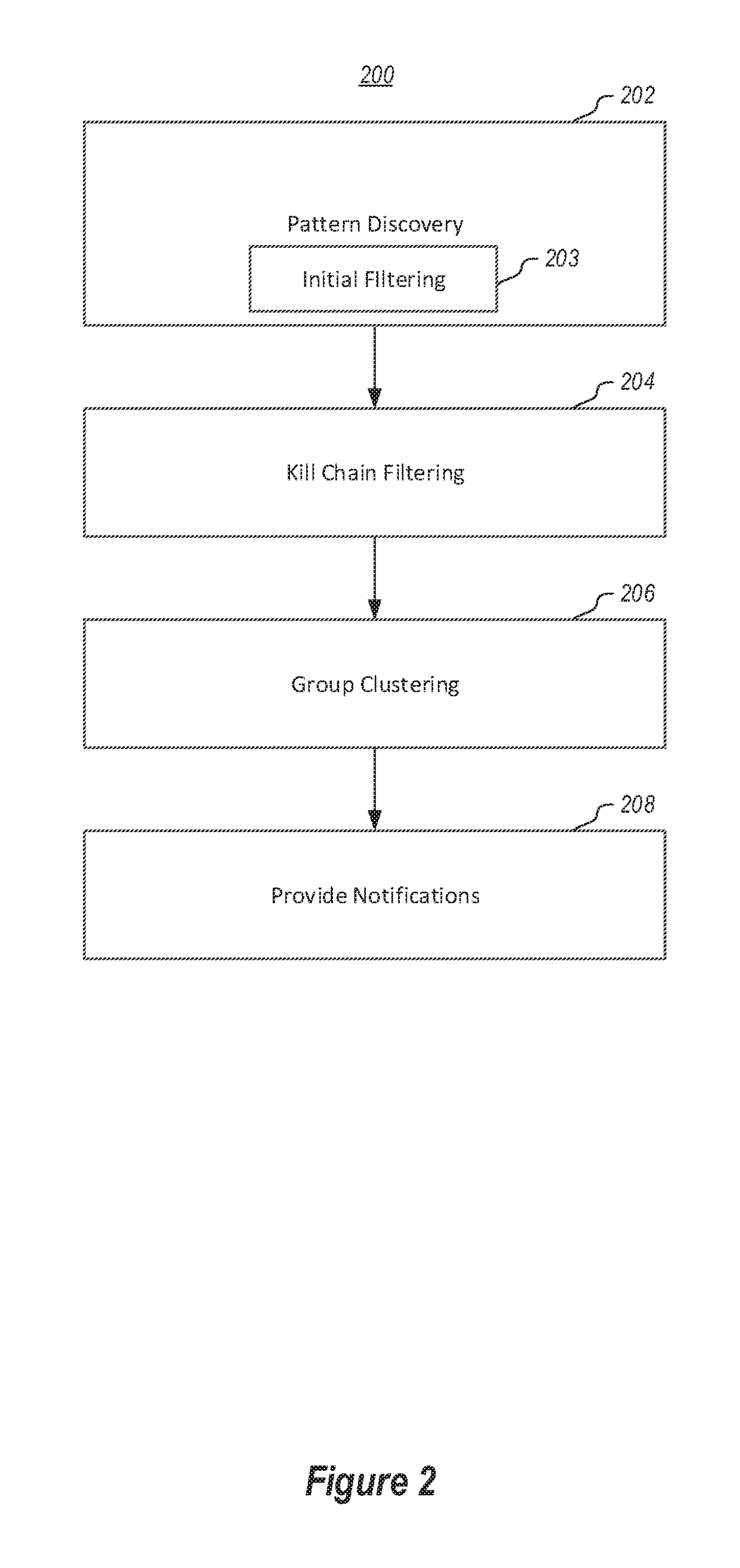
Detecting Cyber Attacks by Correlating Alerts Sequences in a Cluster Environment
ActiveUS20180248893A1Well formedComputer security arrangementsMachine learningCyber-attackHeterogeneous group
Providing network entities with notifications of attacks on the entities. A method includes collecting alerts from a plurality of network entities in a cluster computing environment. Alerts are grouped into heterogeneous groups of alerts. Each group includes a plurality of different types of alerts. Each alert has corresponding properties, including at least one property identifying the type of alert. Each group of alerts corresponds to a timeline of alerts for a particular entity. Groups of alerts that correspond to a valid cyber-kill chain are identified. Different groups of alerts that correspond to a valid cyber-kill chain are correlated into clusters of groups of alerts by correlating the types of alerts and corresponding properties. At least one cluster is identified as having some characteristic of interest. Entities corresponding to groups of alerts in the cluster are notified of the characteristic of interest.
Owner:MICROSOFT TECH LICENSING LLC
Advanced cybersecurity threat mitigation for inter-bank financial transactions
ActiveUS20180013771A1Reduce decreaseFinanceDesign optimisation/simulationCyber-attackFinancial transaction
A system for mitigation of cyberattacks employing an advanced cyber decision platform comprising a time series data store, a directed computational graph module, an action outcome simulation module, and observation and state estimation module, wherein the state of a network is monitored and used to produce a cyber-physical graph representing network resources, simulated network events are produced and monitored, and the network events and their effects are analyzed to produce security recommendations.
Owner:QOMPLX LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com