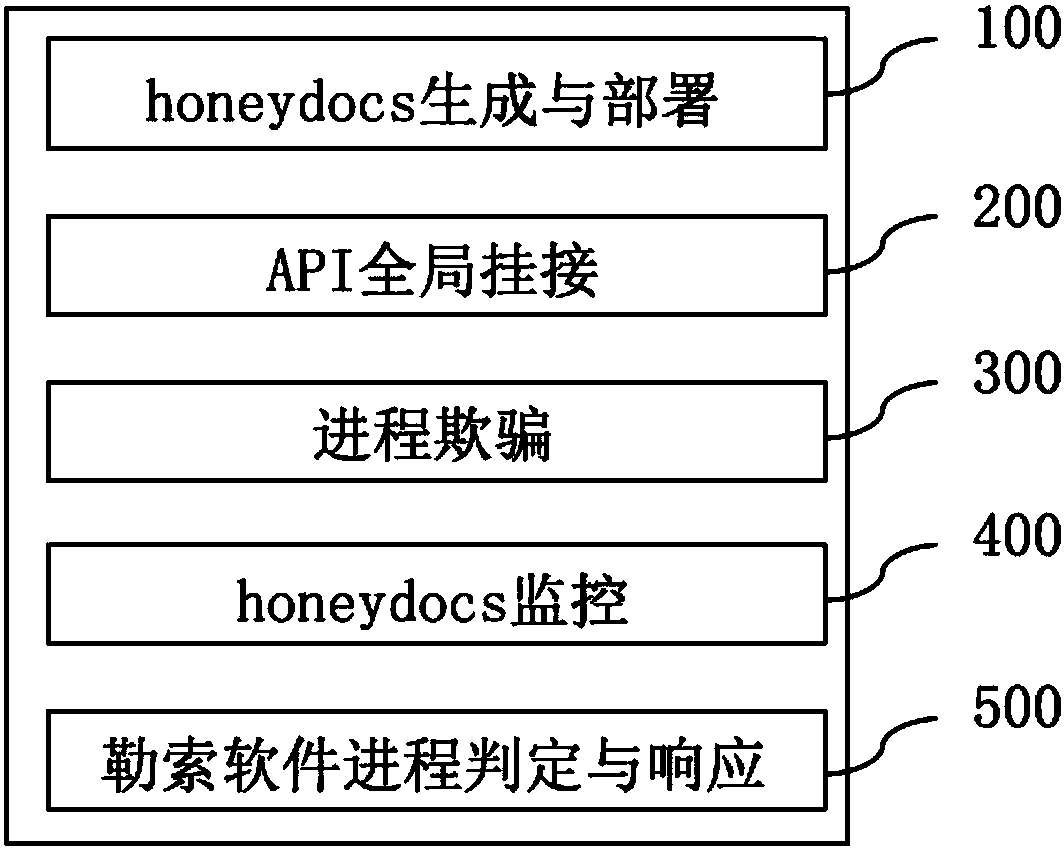
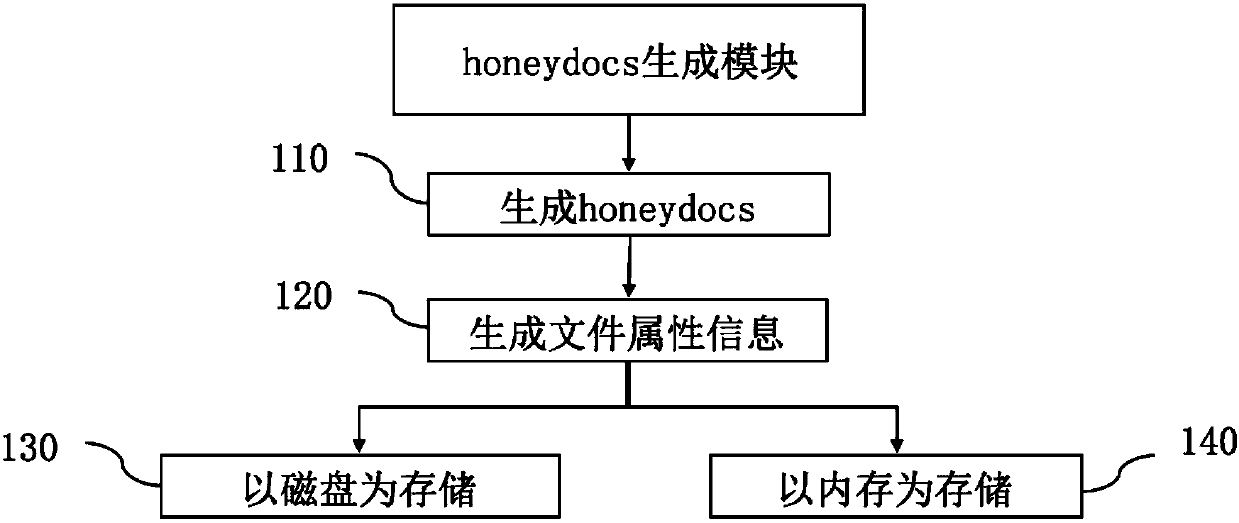
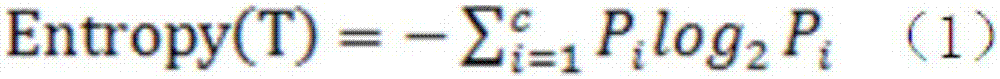Patents
Literature
193 results about "Ransomware" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
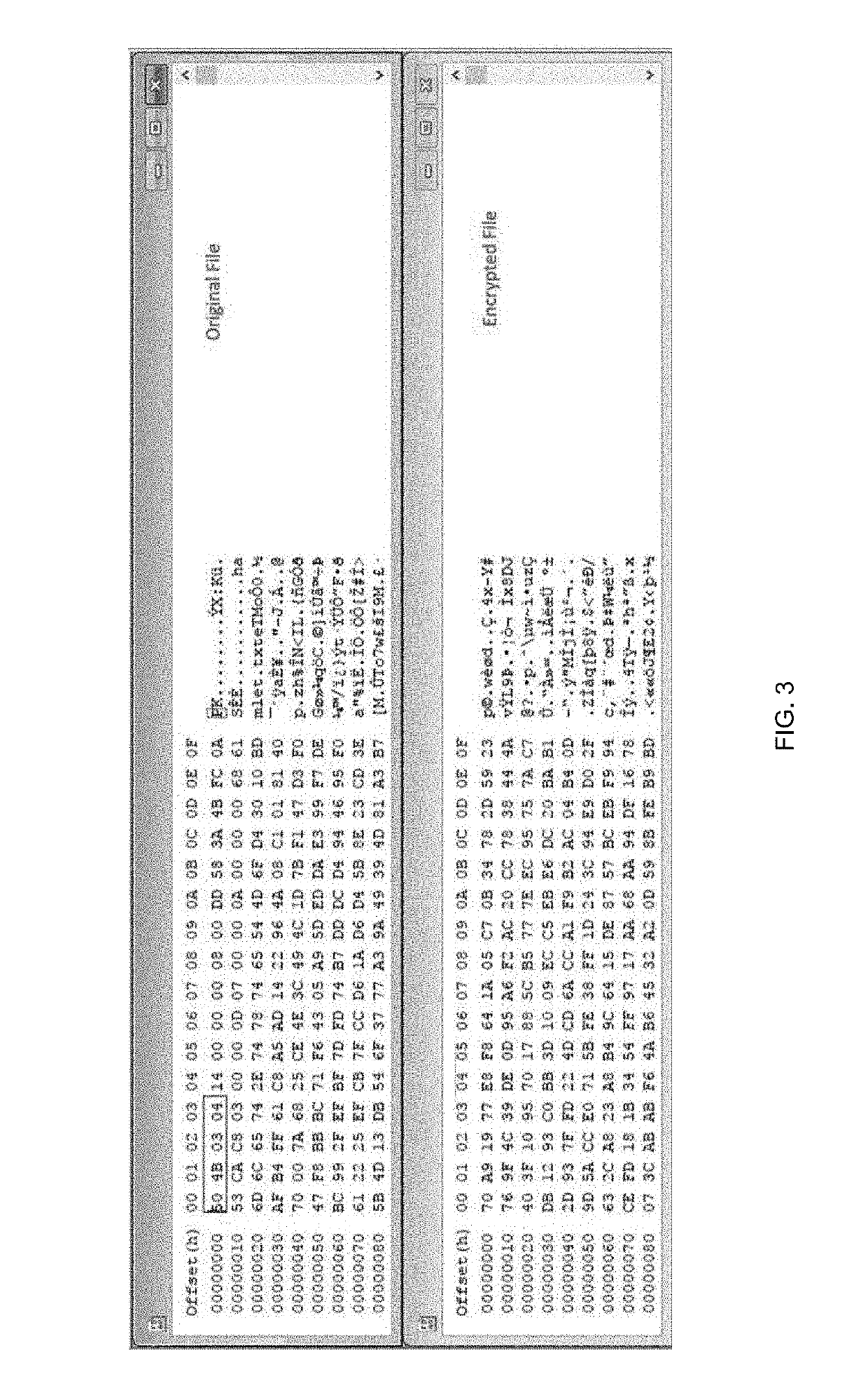
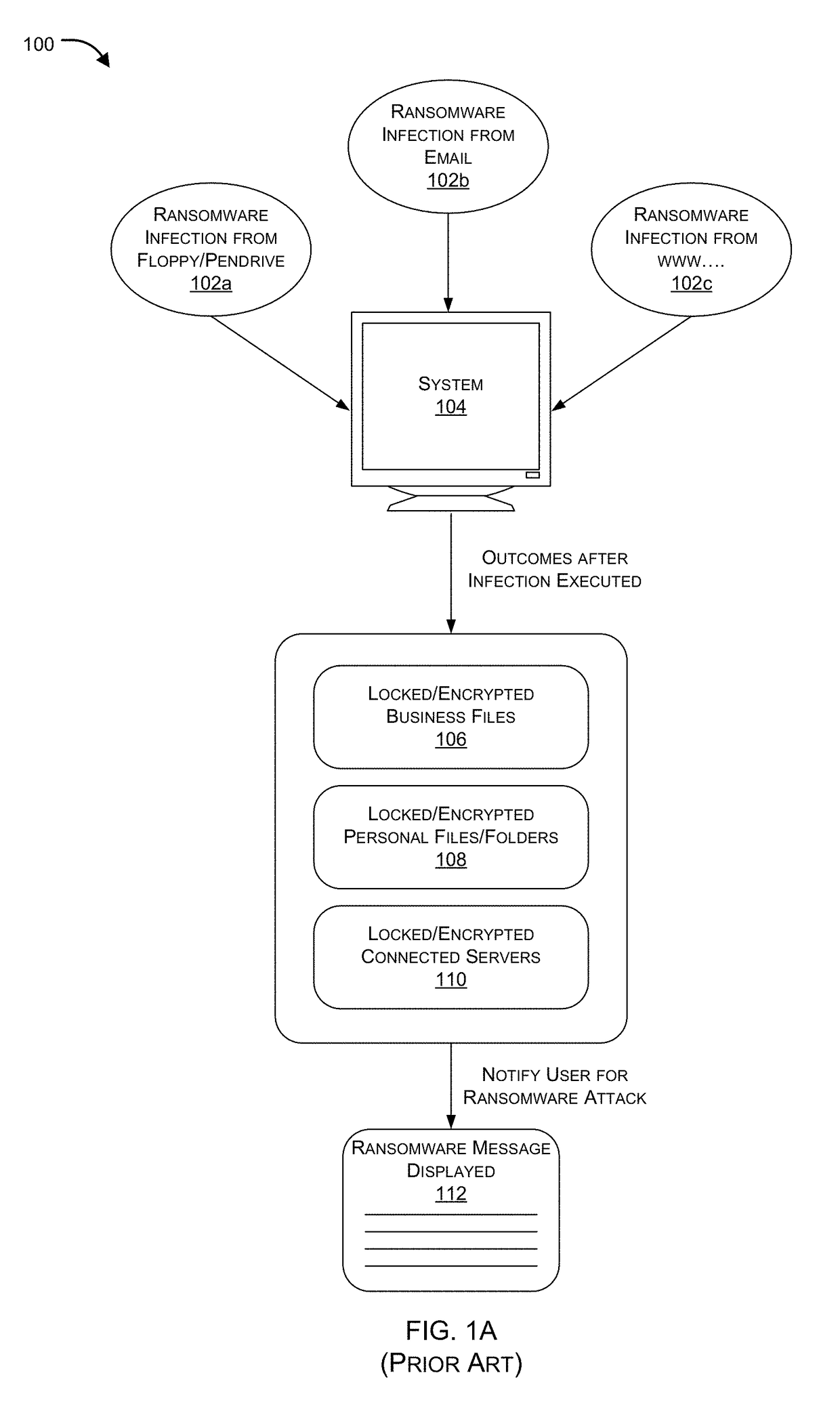
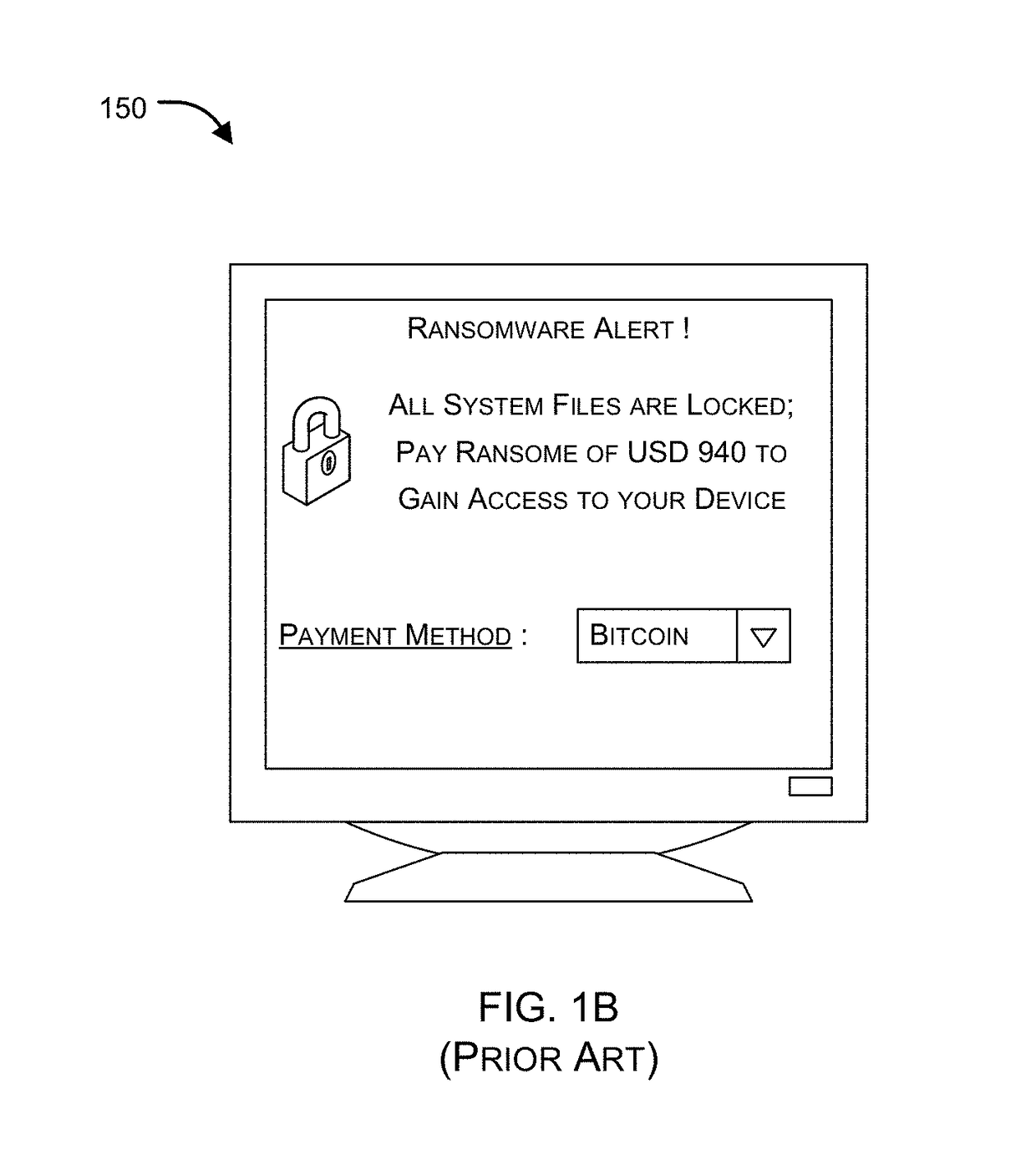
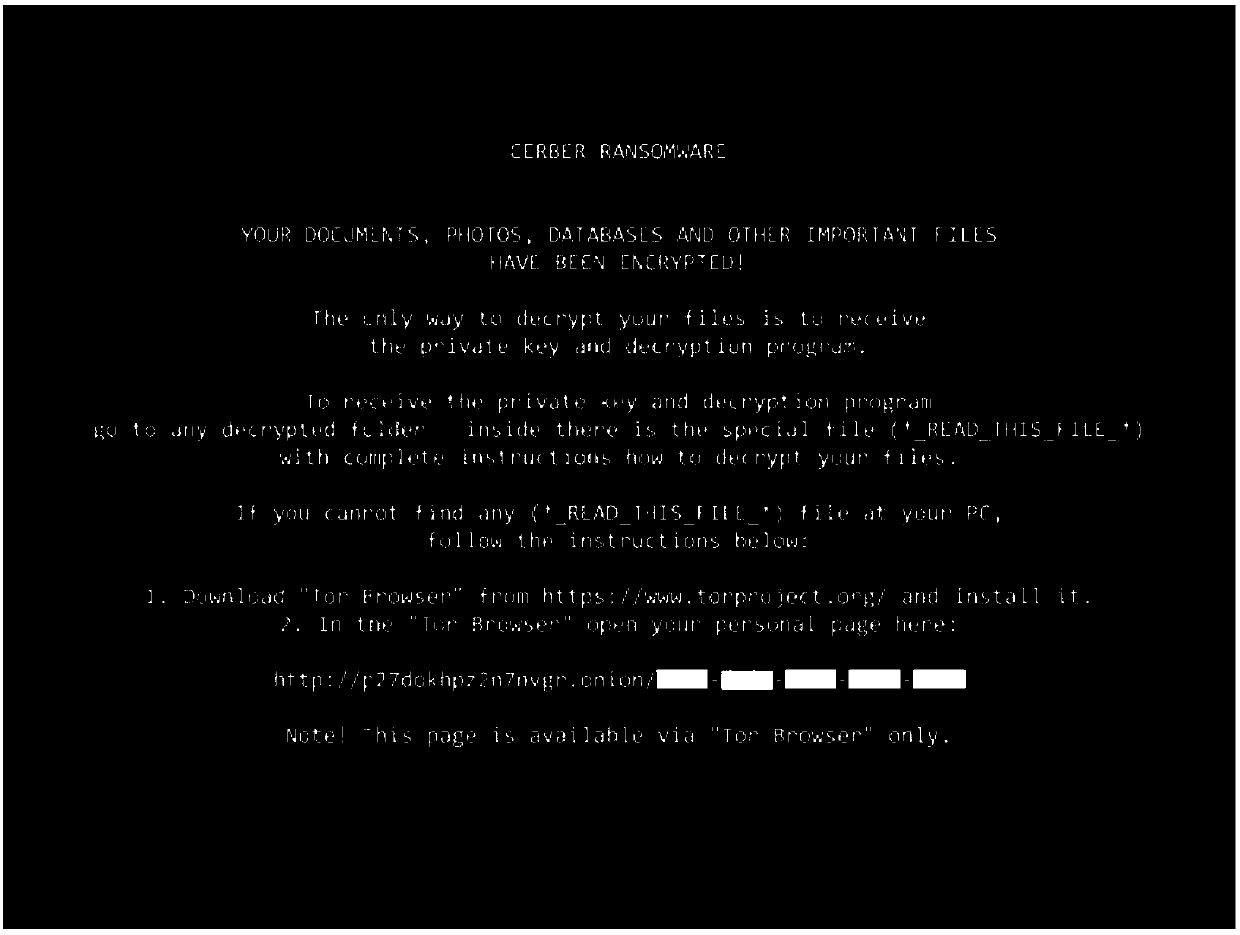
Ransomware is a type of malware from cryptovirology that threatens to publish the victim's data or perpetually block access to it unless a ransom is paid. While some simple ransomware may lock the system in a way which is not difficult for a knowledgeable person to reverse, more advanced malware uses a technique called cryptoviral extortion, in which it encrypts the victim's files, making them inaccessible, and demands a ransom payment to decrypt them. In a properly implemented cryptoviral extortion attack, recovering the files without the decryption key is an intractable problem – and difficult to trace digital currencies such as Ukash or Bitcoin and other cryptocurrency are used for the ransoms, making tracing and prosecuting the perpetrators difficult.
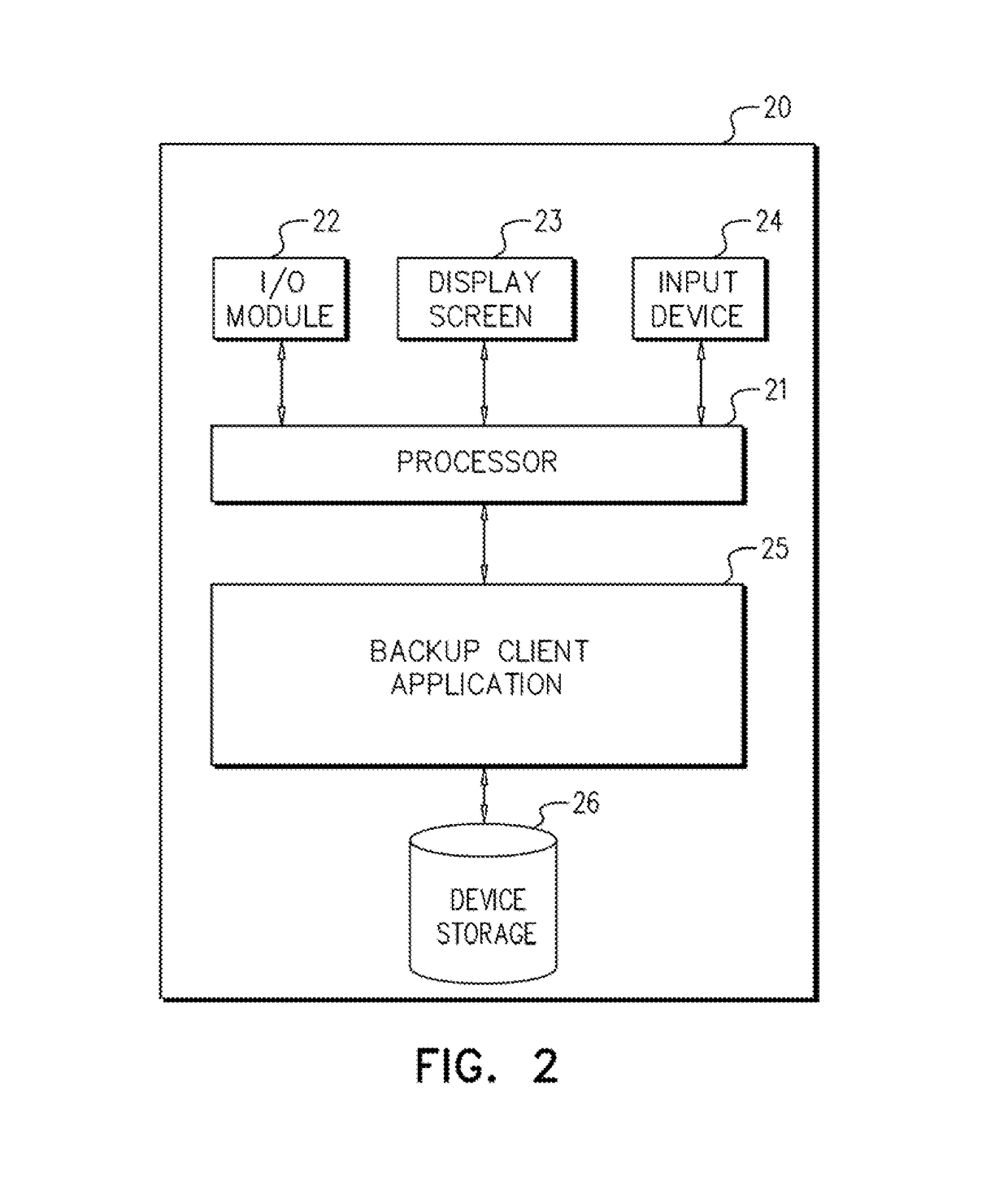
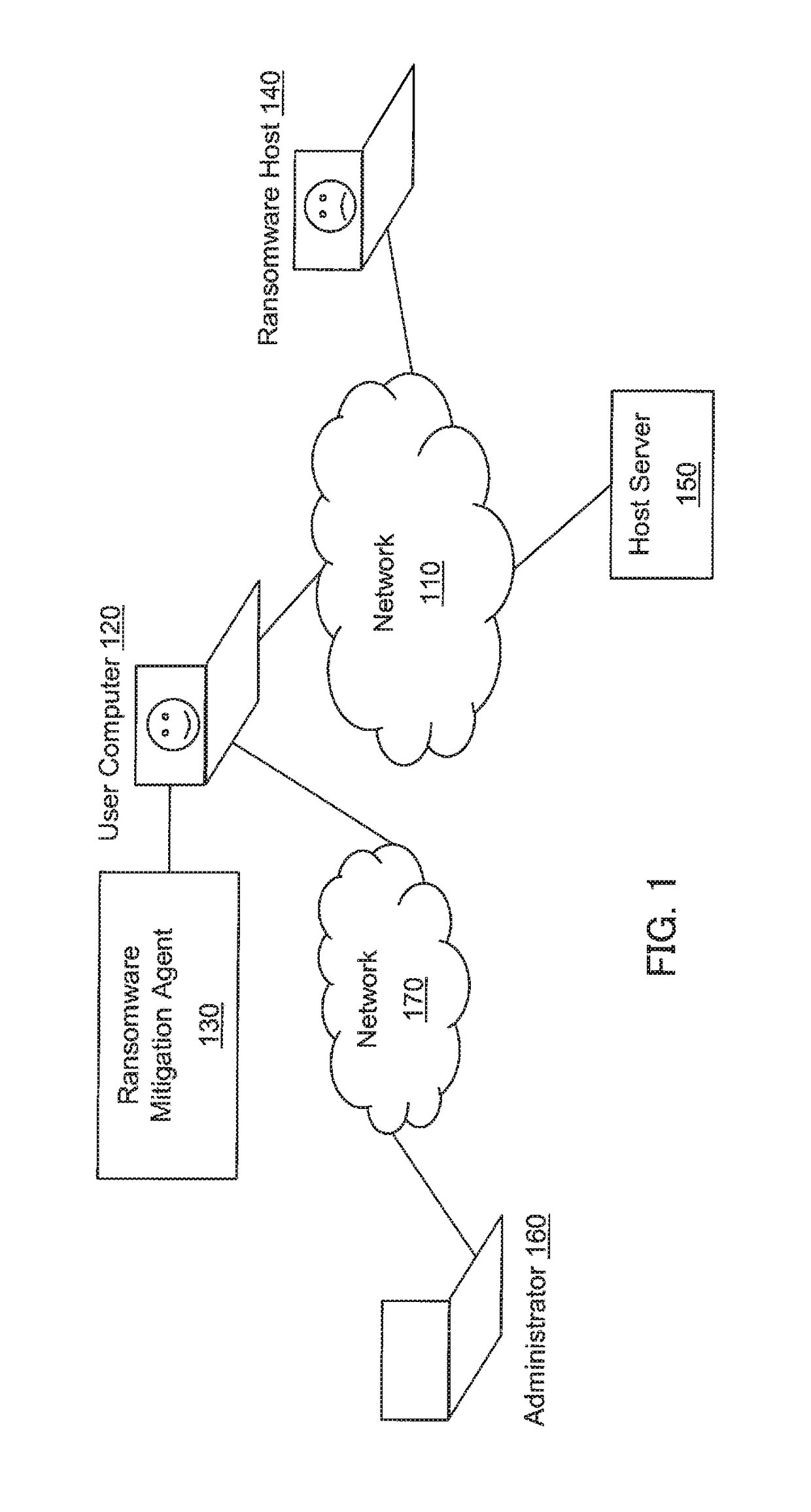
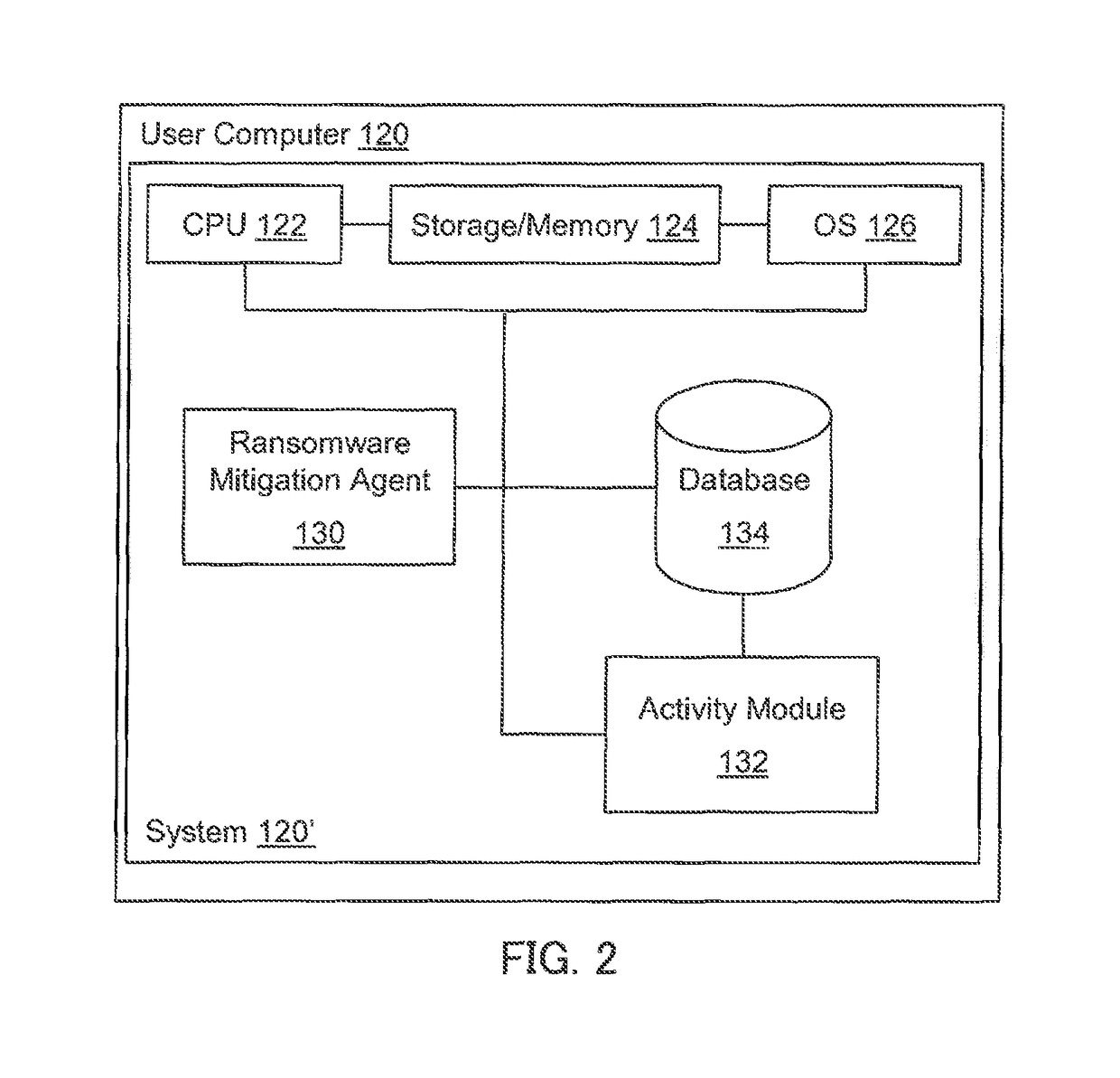
File backup to combat ransomware
ActiveUS9317686B1Prevent encryptionLimited impact on system performancePlatform integrity maintainanceRedundant operation error correctionOperational systemFilename extension
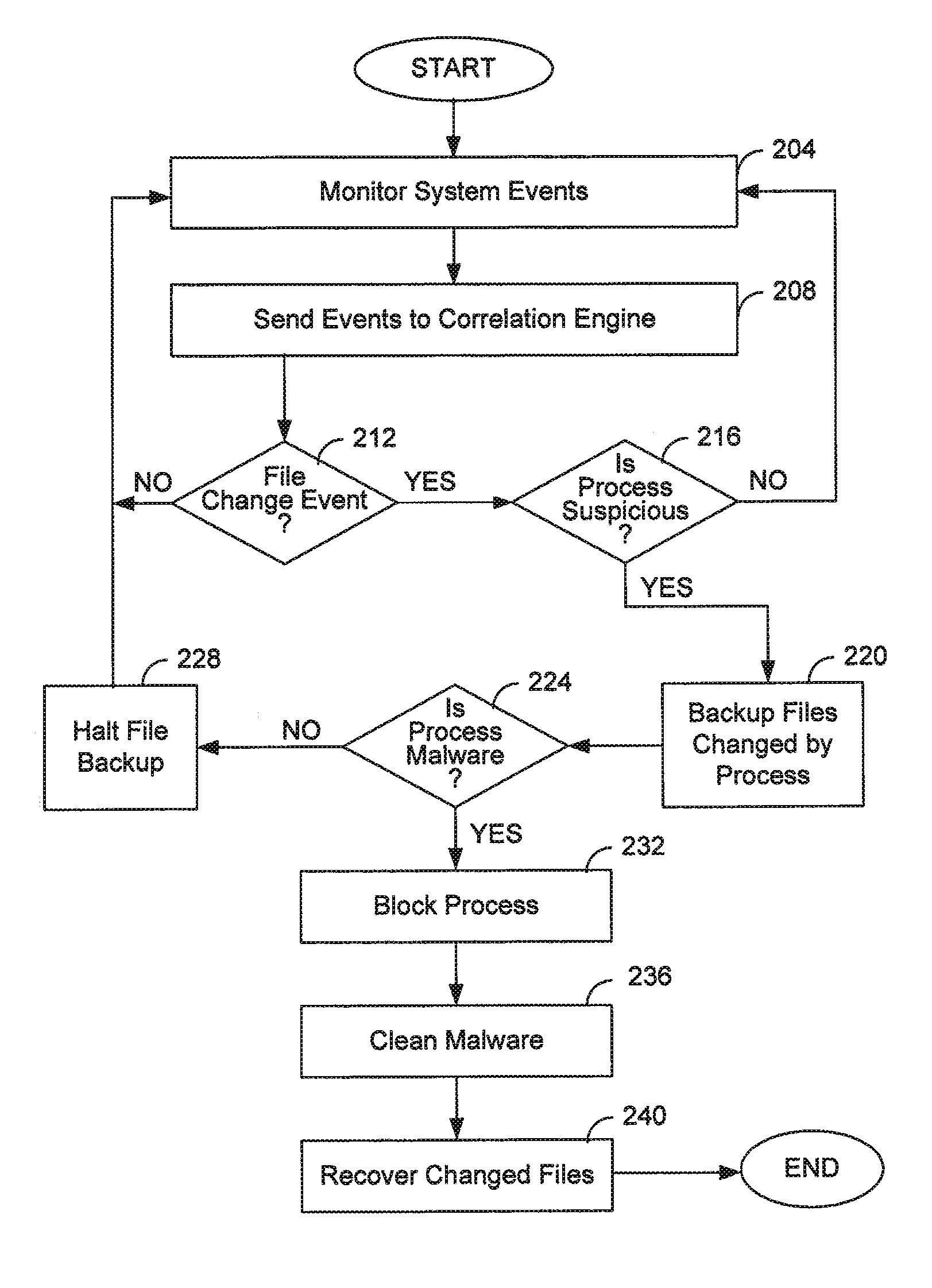
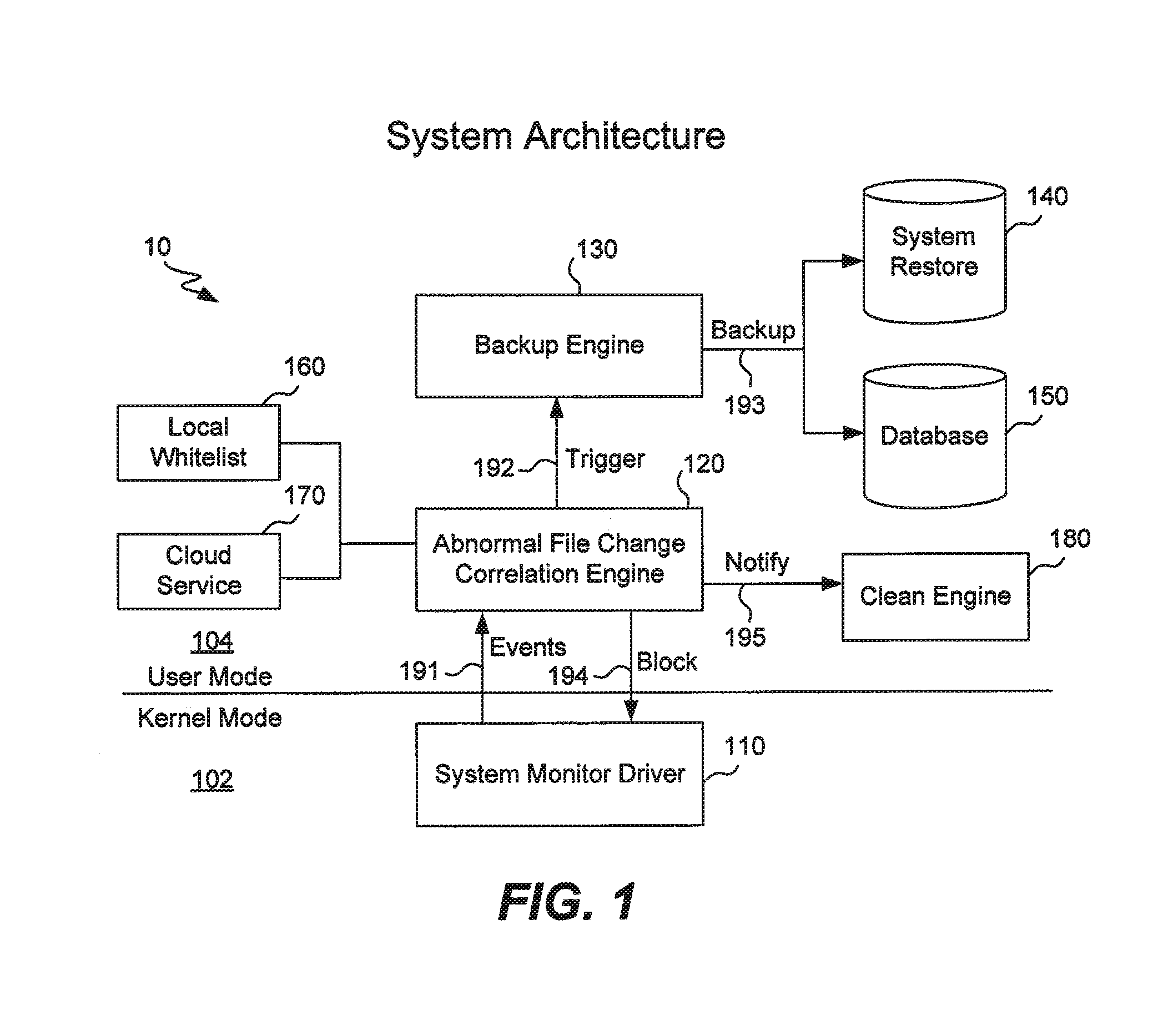
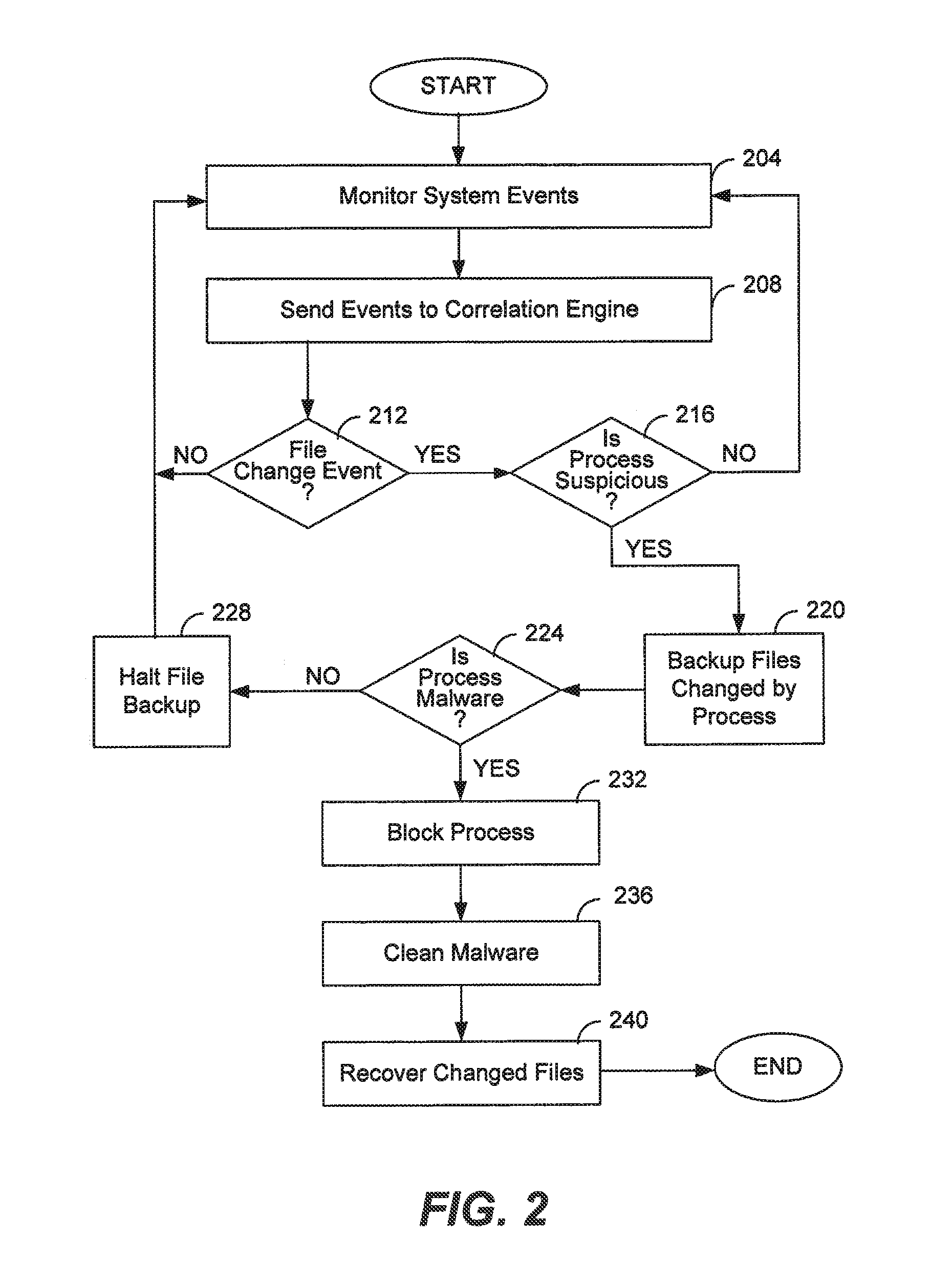
Operating system events are monitored and a file change request of a process is detected. If the process is suspicious, then the file to be changed is backed up and then the process is allowed to change the file as requested. If it is later determined that the process is ransomware, the process is blocked and further file backups are halted. The original file is recovered and the encrypted file is discarded. If it is later determined that the process is not malicious, then further file backups are halted. Any backup files are discarded. Ransomware may be detected by comparing a file extension of the process with file extensions of any files requested to be changed, by comparing file extensions of any files requested to be changed, or by an analysis of behavior of the process itself.
Owner:TREND MICRO INC
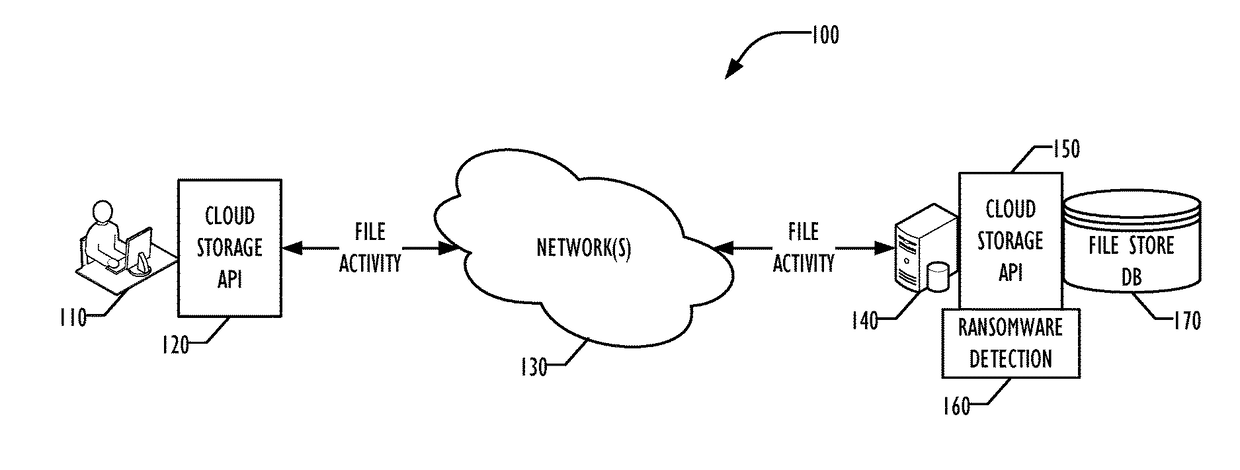
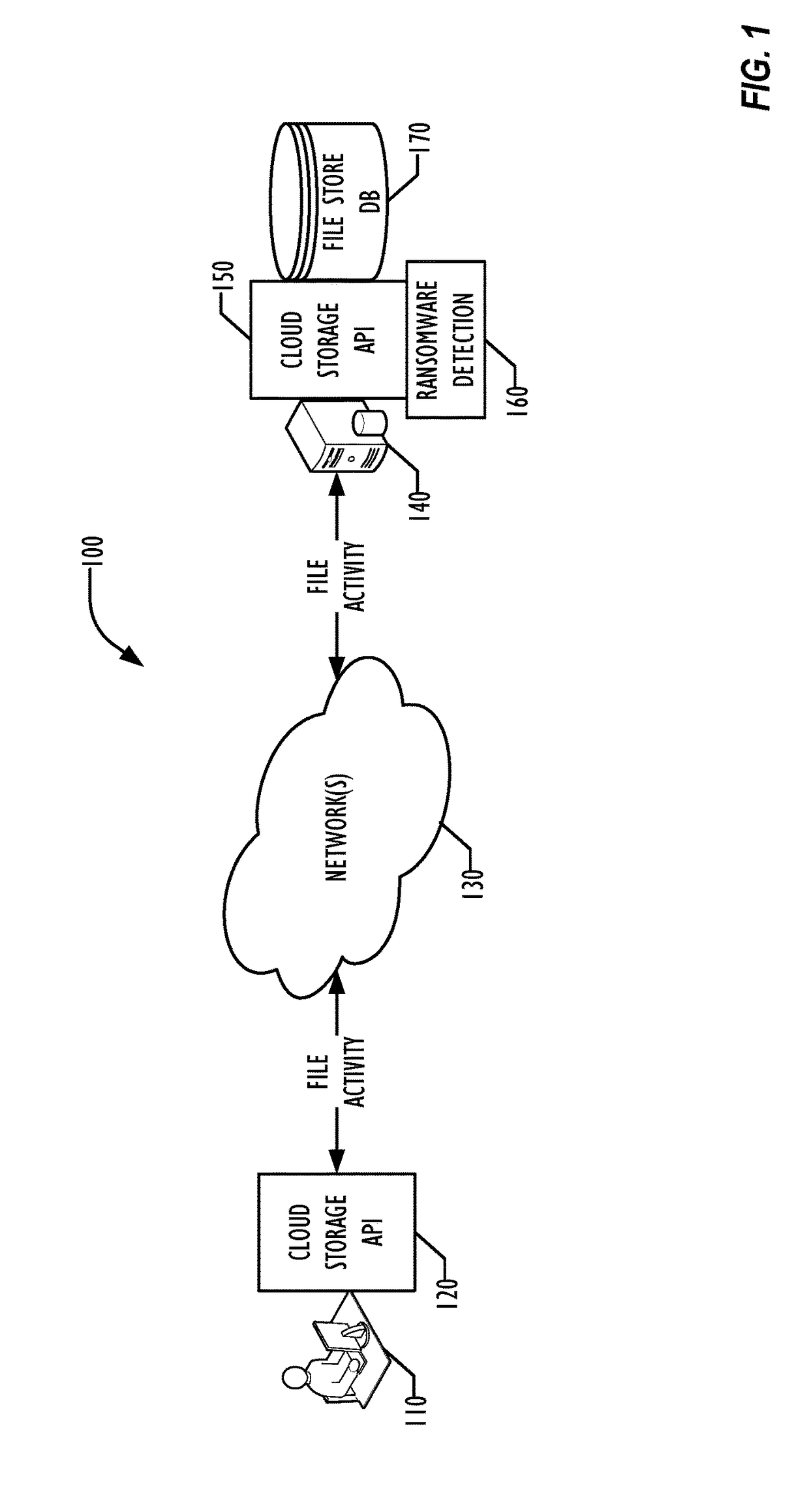
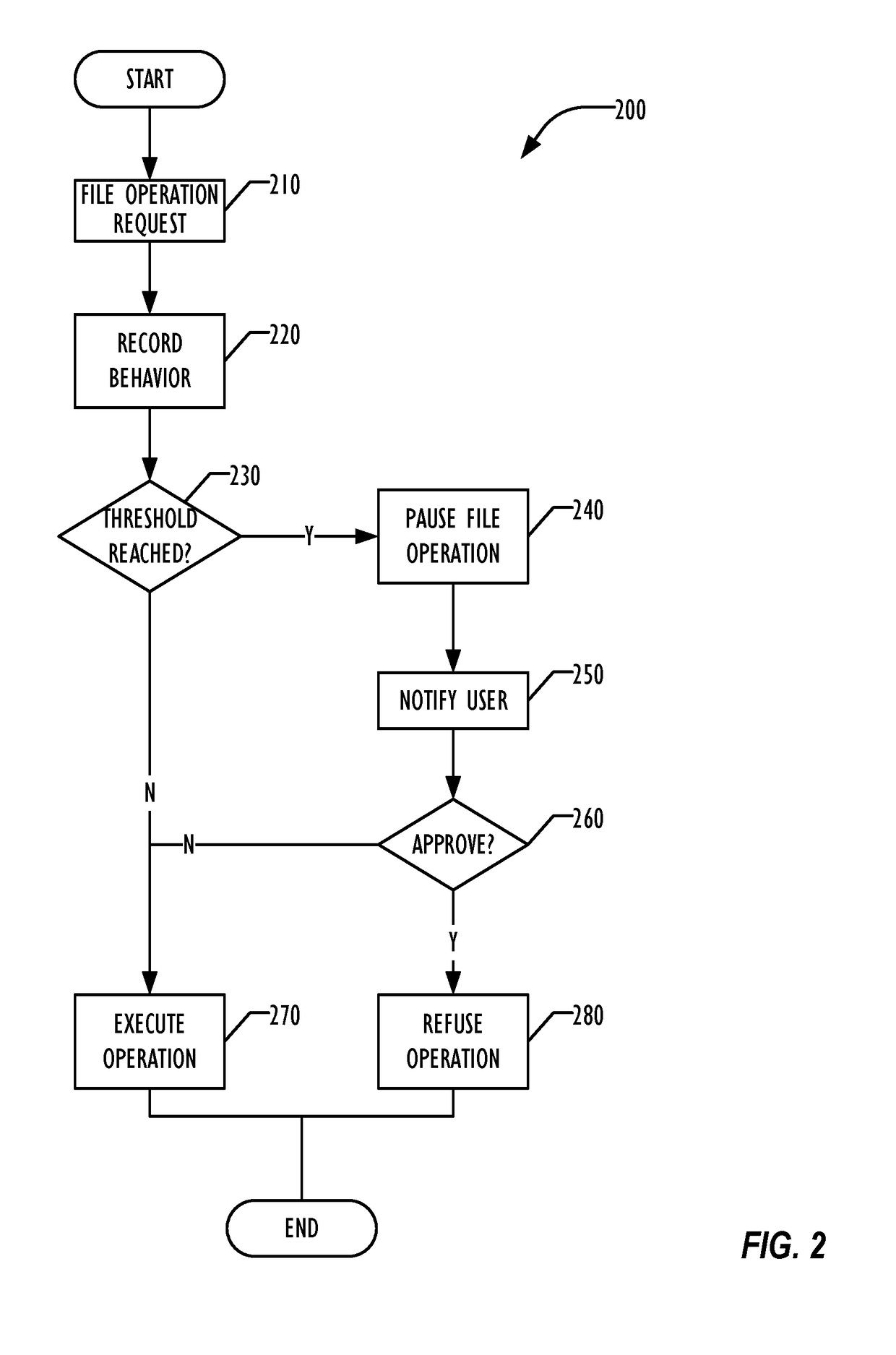
Ransomware Protection For Cloud File Storage
A cloud storage server-based approach allows detection of ransomware activity in cloud storage systems caused by ransomware infections on an endpoint device. A heuristic or rule-based technique is employed for recognizing sequences of file operations that may indicate ransomware activity. In some embodiments, users may be offered an opportunity to approve or disapprove of the possible ransomware activity. In others, cloud system file activity may be suspended or halted for the affected user upon recognition of possible ransomware actions. Enhanced recovery of files affected prior to recognition of the ransomware activity may be performed in some embodiments.
Owner:MCAFEE LLC
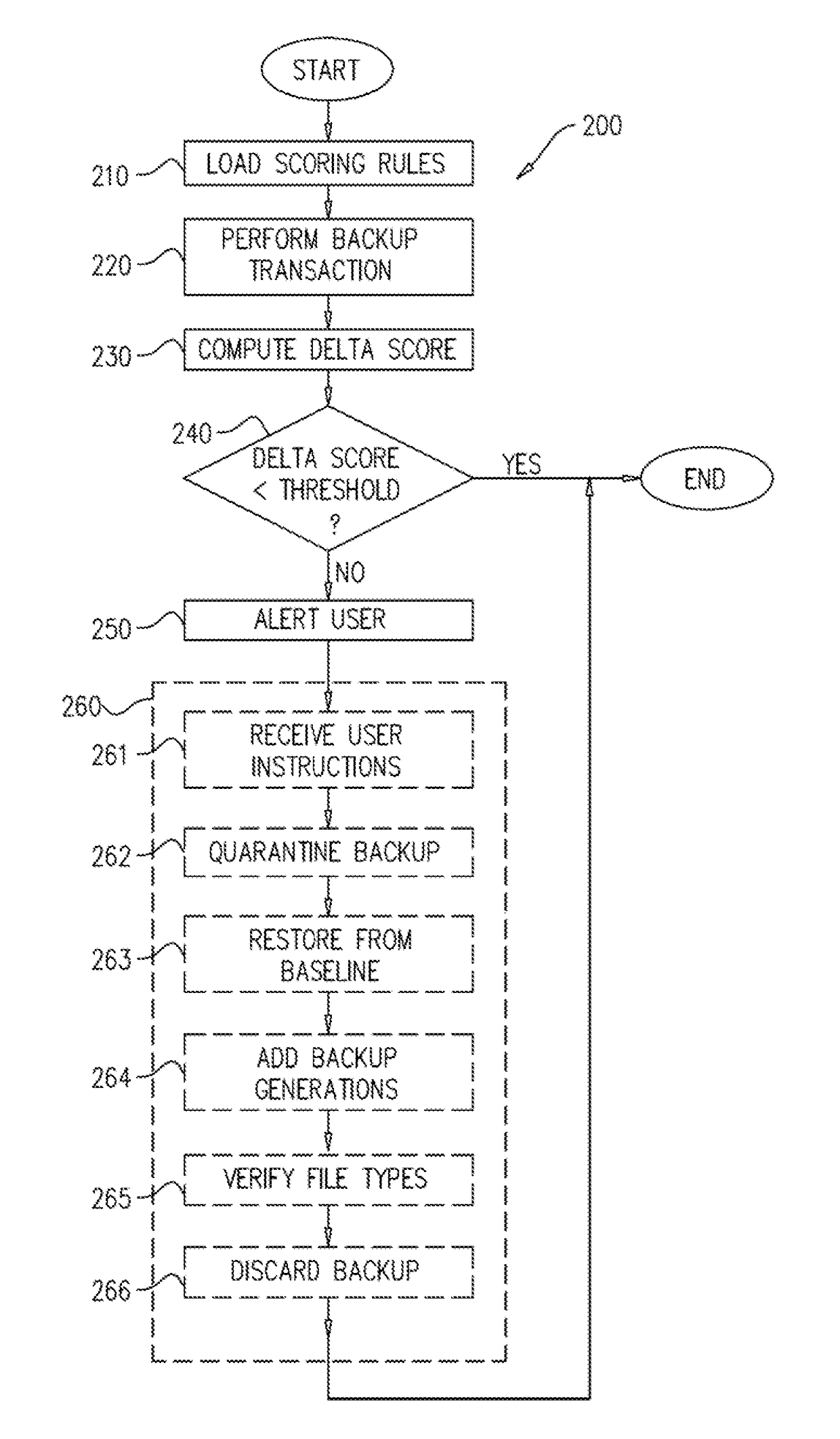
Intelligent backup system
In one embodiment, a method for ransomware-aware file backup is implemented on a computing device and includes: backing up a target population of files from a target file location in a backup transaction, computing a backup delta score for the backup transaction, where the computing comprises comparing backup data from the backup transaction with backup data from a previous backup transaction, determining whether the computer backup delta score exceeds a pre-defined threshold, and upon the computed backup delta score exceeding the pre-defined threshold: determining that the backup transaction is indicative of a ransomware infection, and performing at least one counter-measure in response to the ransomware infection.
Owner:CISCO TECH INC
Method and System for Mitigating the Effects of Ransomware
ActiveUS20170324755A1Reduce the impactAvoid infectionDigital data protectionTransmissionRansomwareSoftware
Computerized methods and systems mitigate the effect of a ransomware attack on an endpoint by detecting access events associated with requests by processes, including ransomware processes, to access data items on the endpoint. The data items are hidden from the operating system processes executed on the endpoint. In response to detecting an access event, an action is taken against the process associated with the access event.
Owner:CHECK POINT SOFTWARE TECH LTD
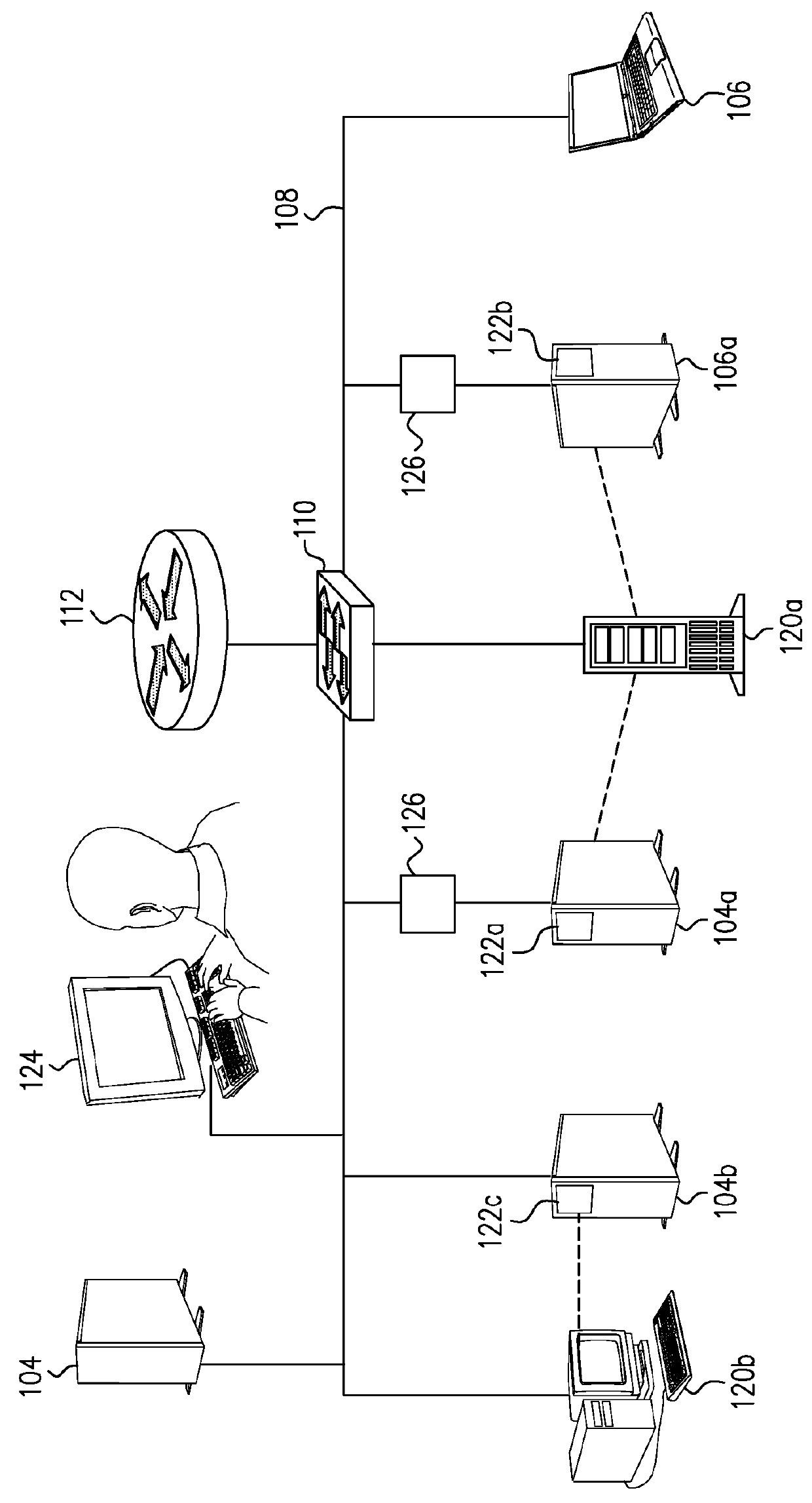
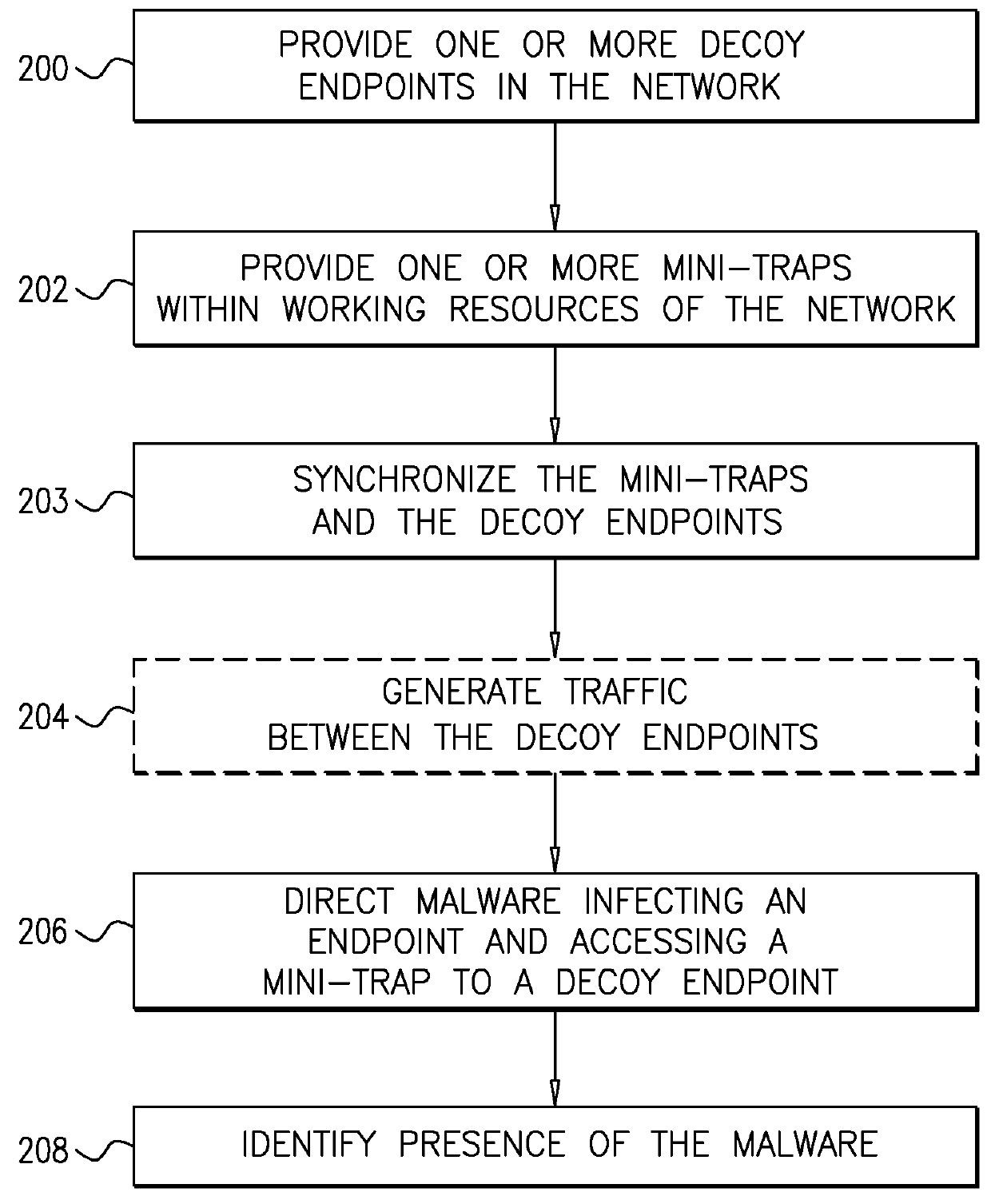
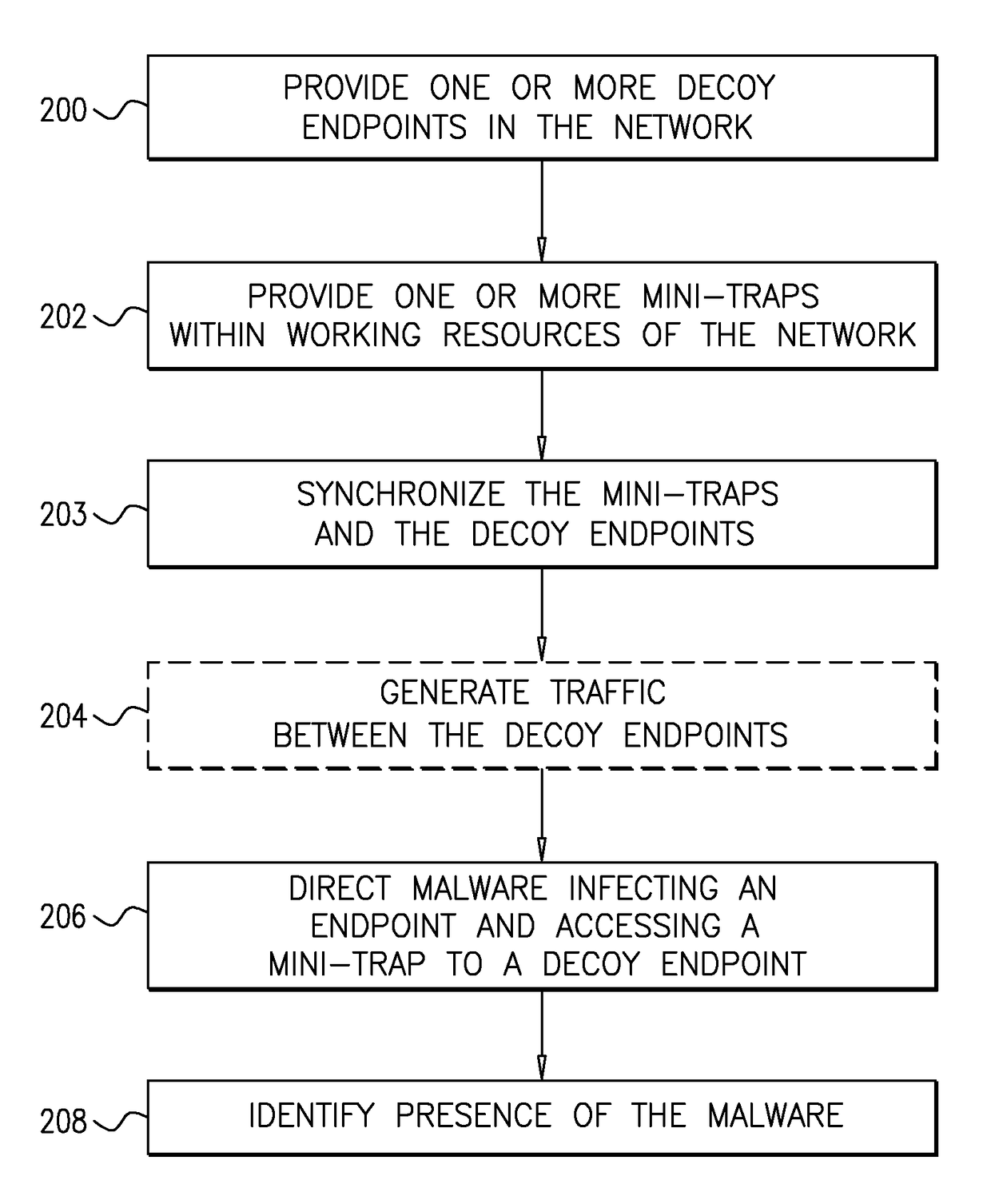
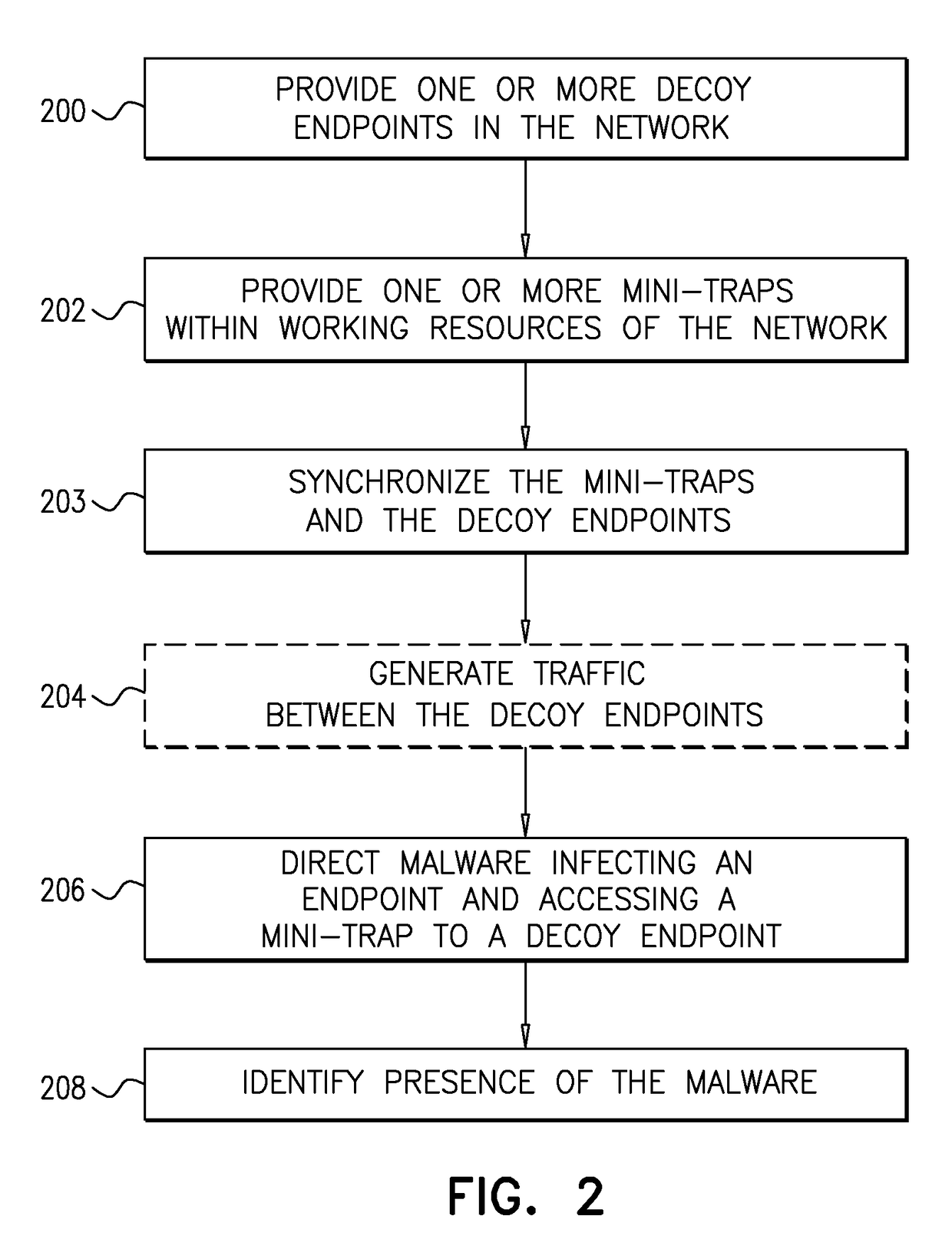
System and a method for identifying the presence of malware and ransomware using mini-traps set at network endpoints
A system and a method for identifying the presence of ransomware on a network including a plurality of resources, and for trapping the ransomware therein.
Owner:FIDELIS SECURITY LLC +1
Method and system for mitigating the effects of ransomware
Computerized methods and systems mitigate the effect of a ransomware attack on an endpoint by detecting access events associated with requests by processes, including ransomware processes, to access data items on the endpoint. The data items are hidden from the operating system processes executed on the endpoint. In response to detecting an access event, an action is taken against the process associated with the access event.
Owner:CHECK POINT SOFTWARE TECH LTD
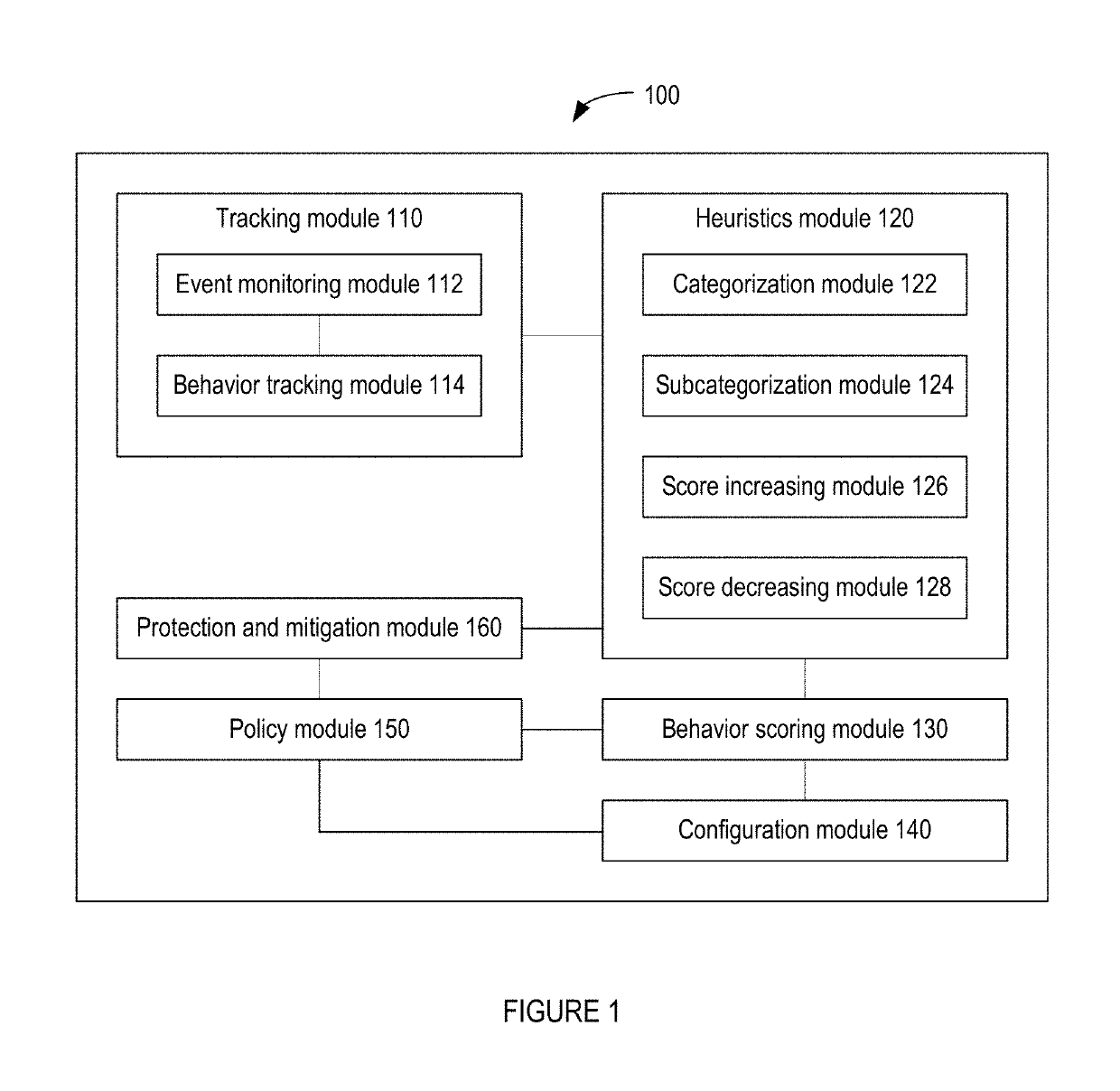
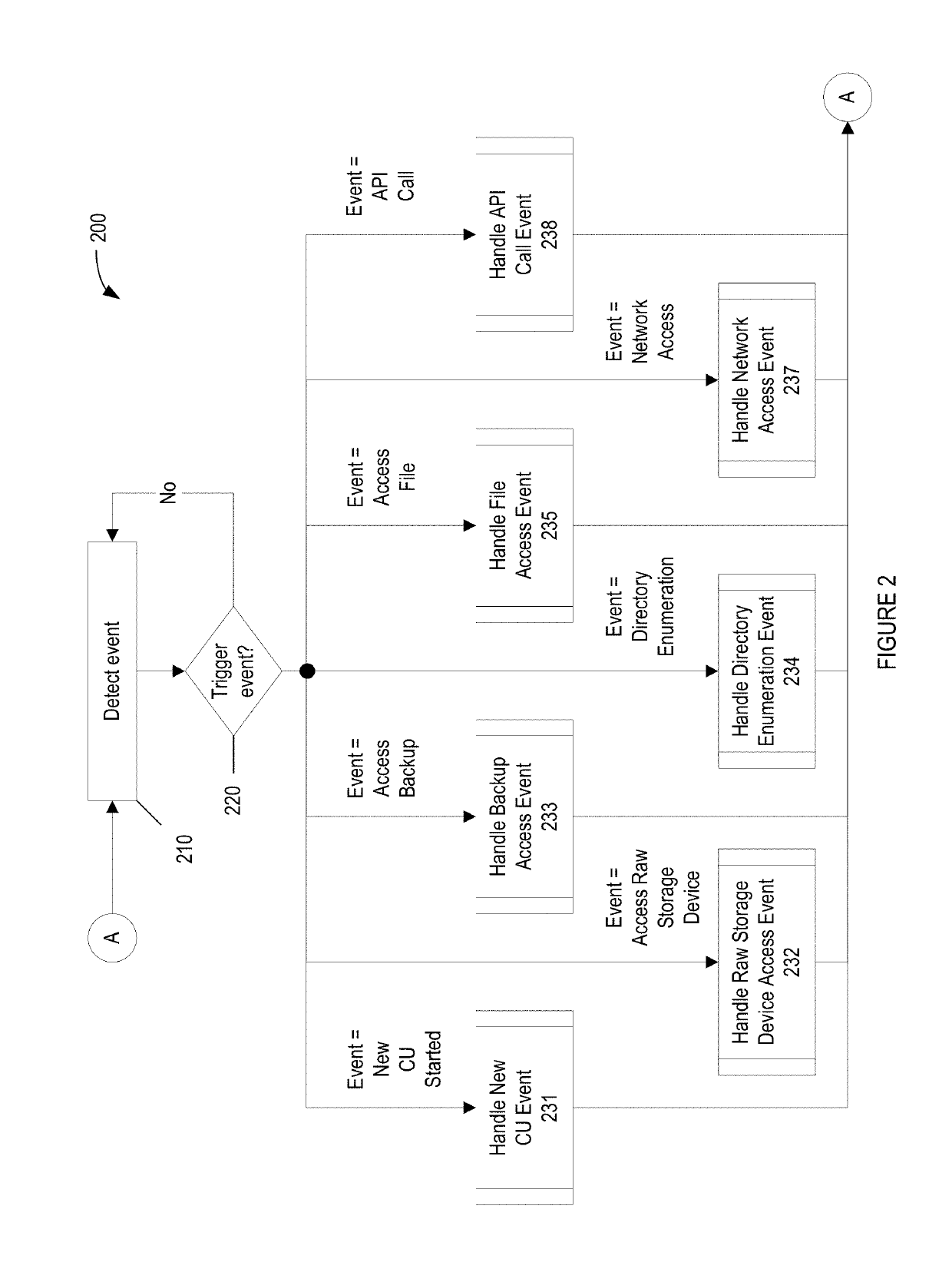
Methods for behavioral detection and prevention of cyberattacks, and related apparatus and techniques
ActiveUS20190121978A1Reduce the amount of calculationReduce false alarm ratePlatform integrity maintainanceTransmissionRansomwareProcess behavior
A security engine may use event-stream processing and behavioral techniques to detect ransomware. The engine may detect process behavior associated with encrypting a file, encrypting a storage device, or disabling a backup file, and may assign a ransomware category to the process based thereon. The engine may initiate protection actions to protect system resources from the process, which may continue to execute. The engine may monitor the process for specific behavior corresponding to its ransomware category. Based on the extent to which such specific behavior is detected, the engine may determine that the process is not ransomware, assign a ransomware subcategory to the process, or adjust the process's threat score. Monitoring of the process may continue, and the threat score may be updated based on the process's behavior. If the threat score exceeds a threshold corresponding to the ransomware category (or subcategory), a corresponding policy action may be initiated.
Owner:CARBON BLACK
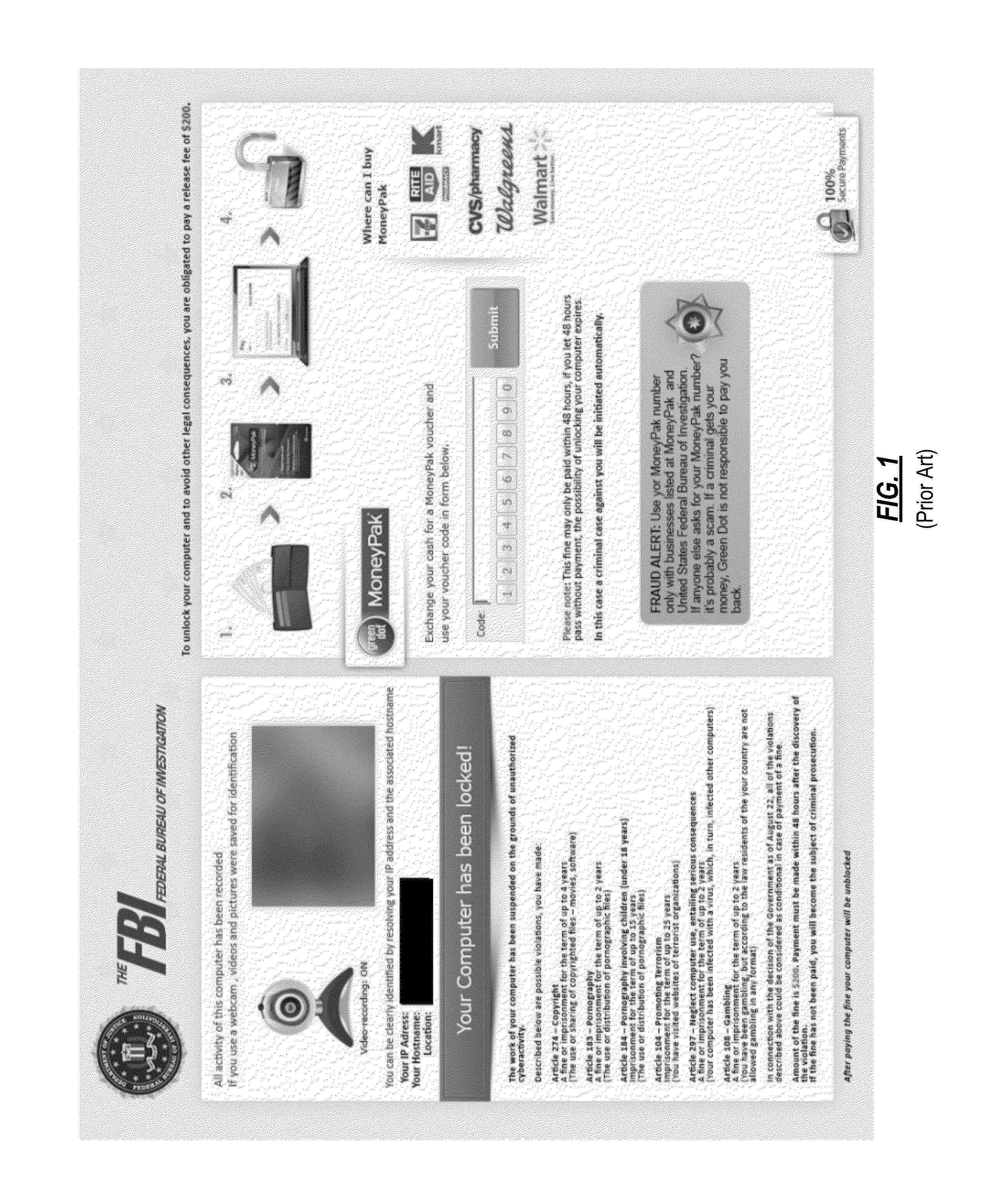
System and method for detecting malware that interferes with the user interface
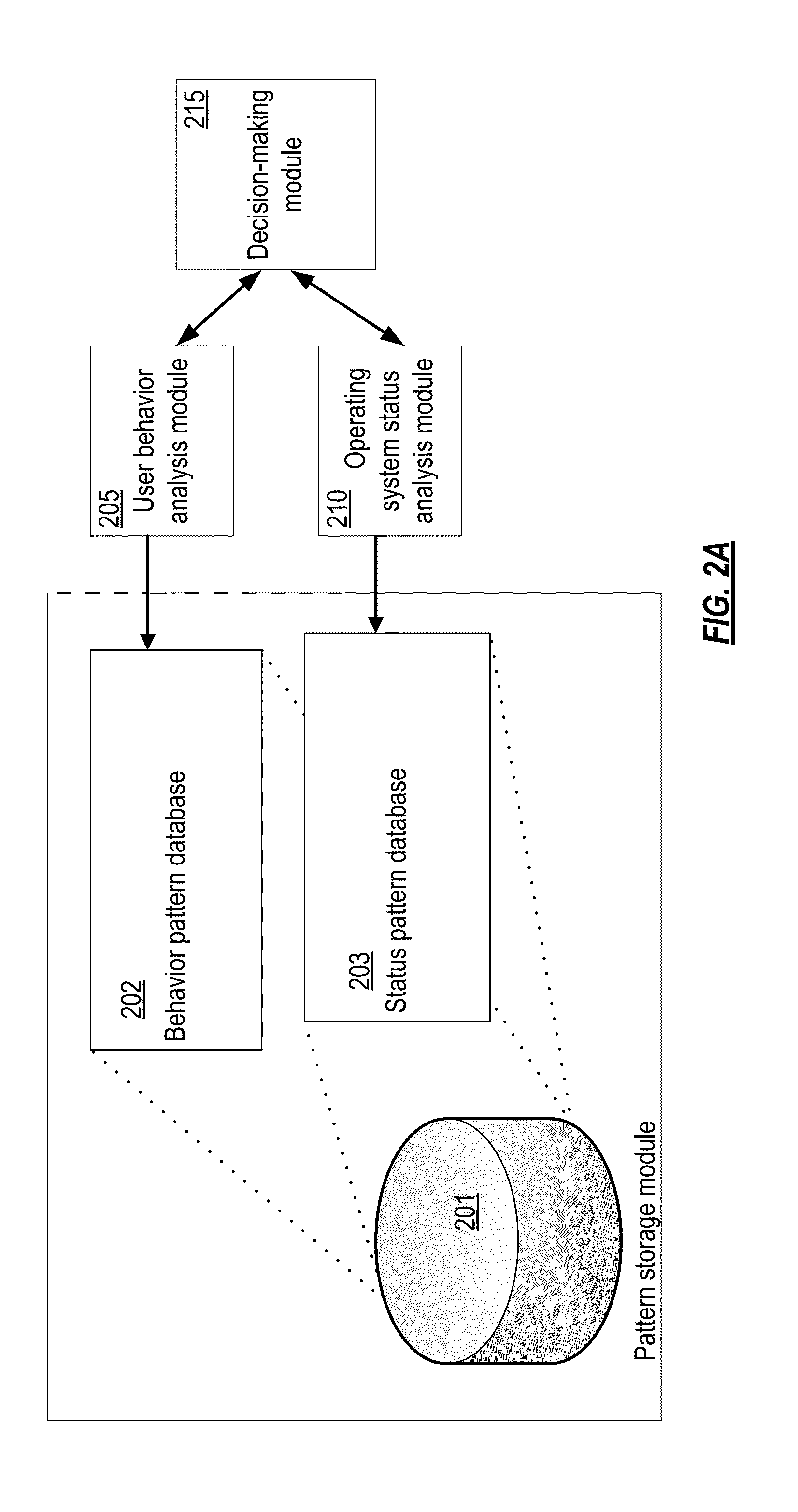
ActiveUS20140181971A1Restore operabilityMemory loss protectionError detection/correctionOperational systemFrustration
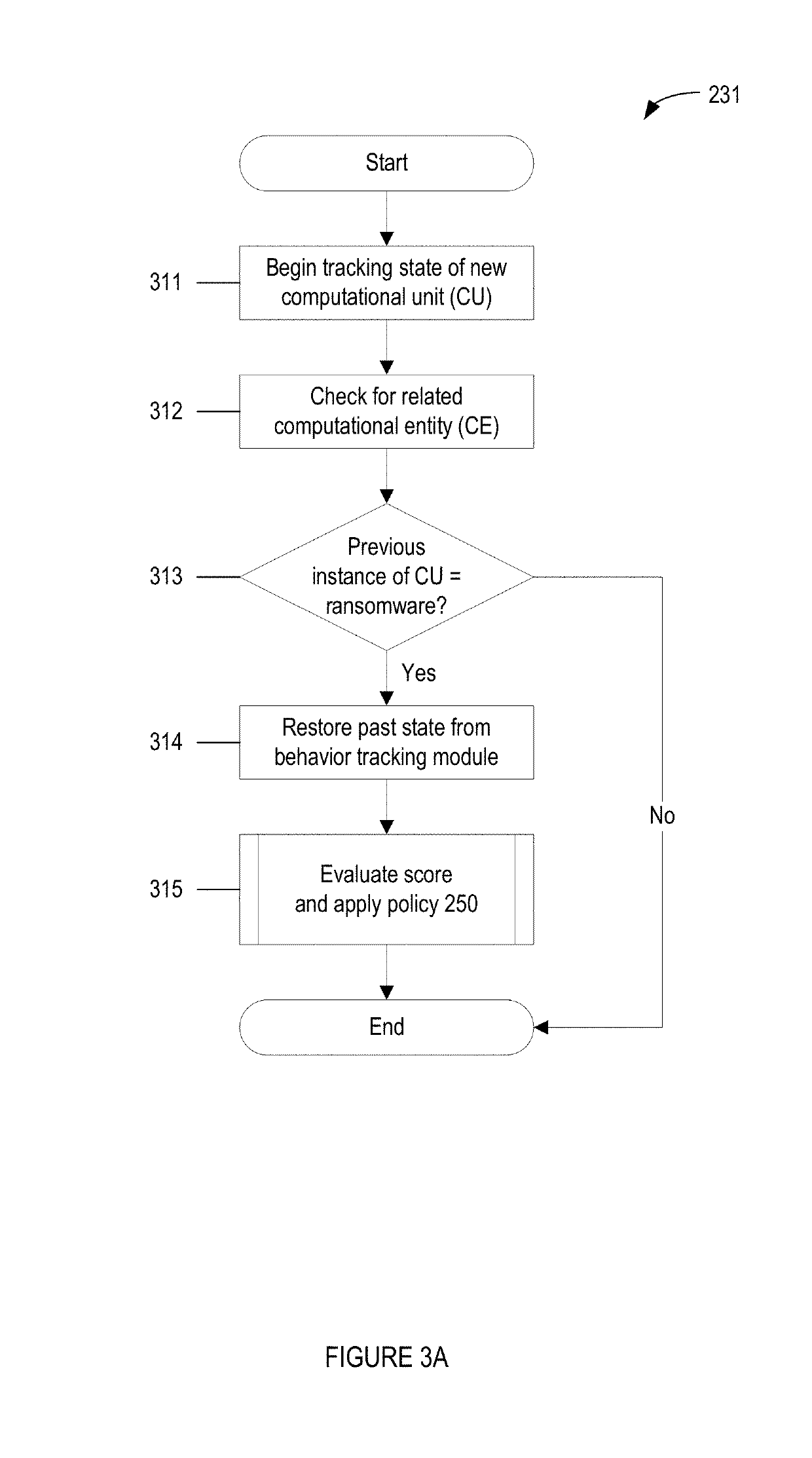
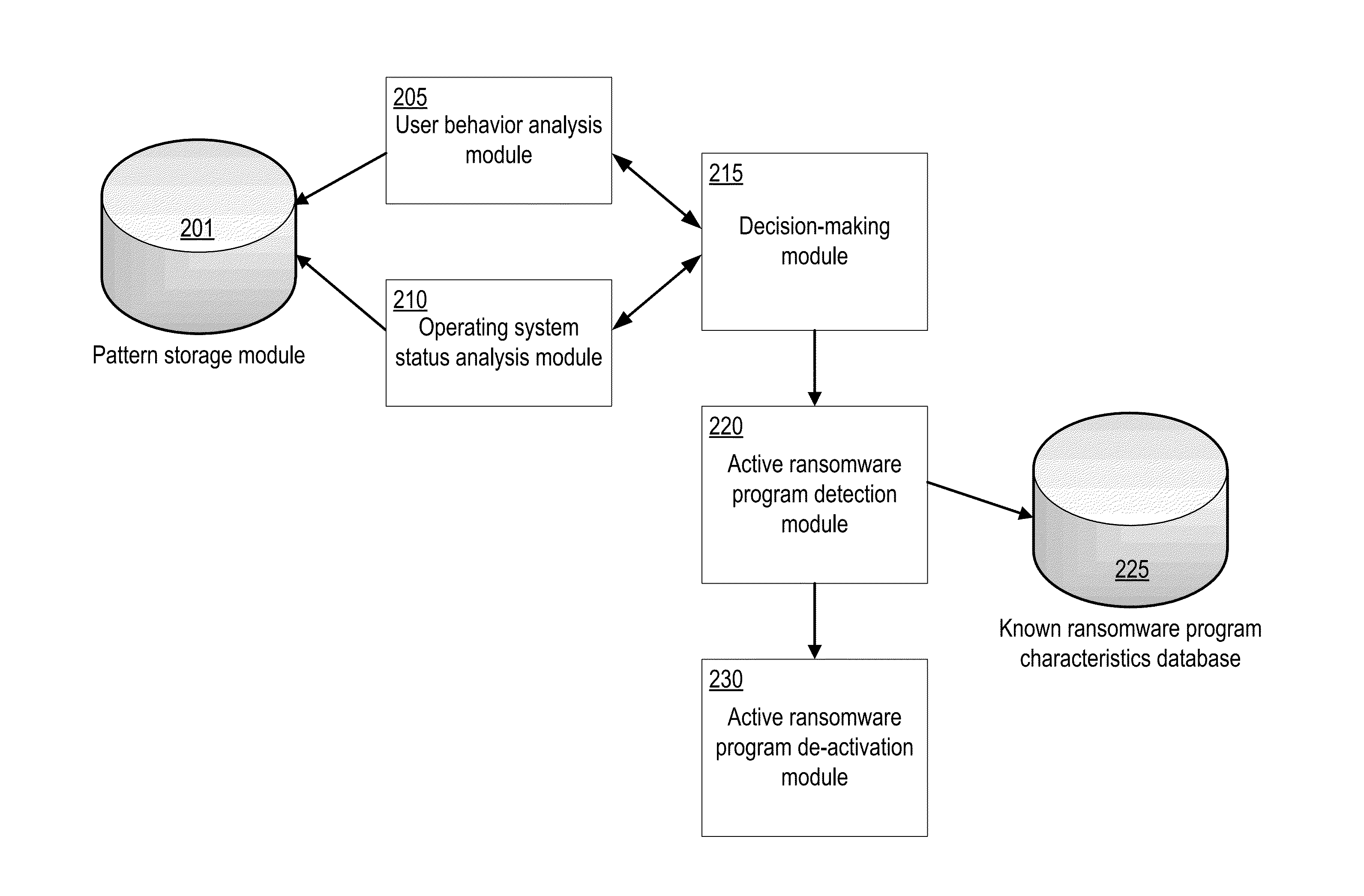
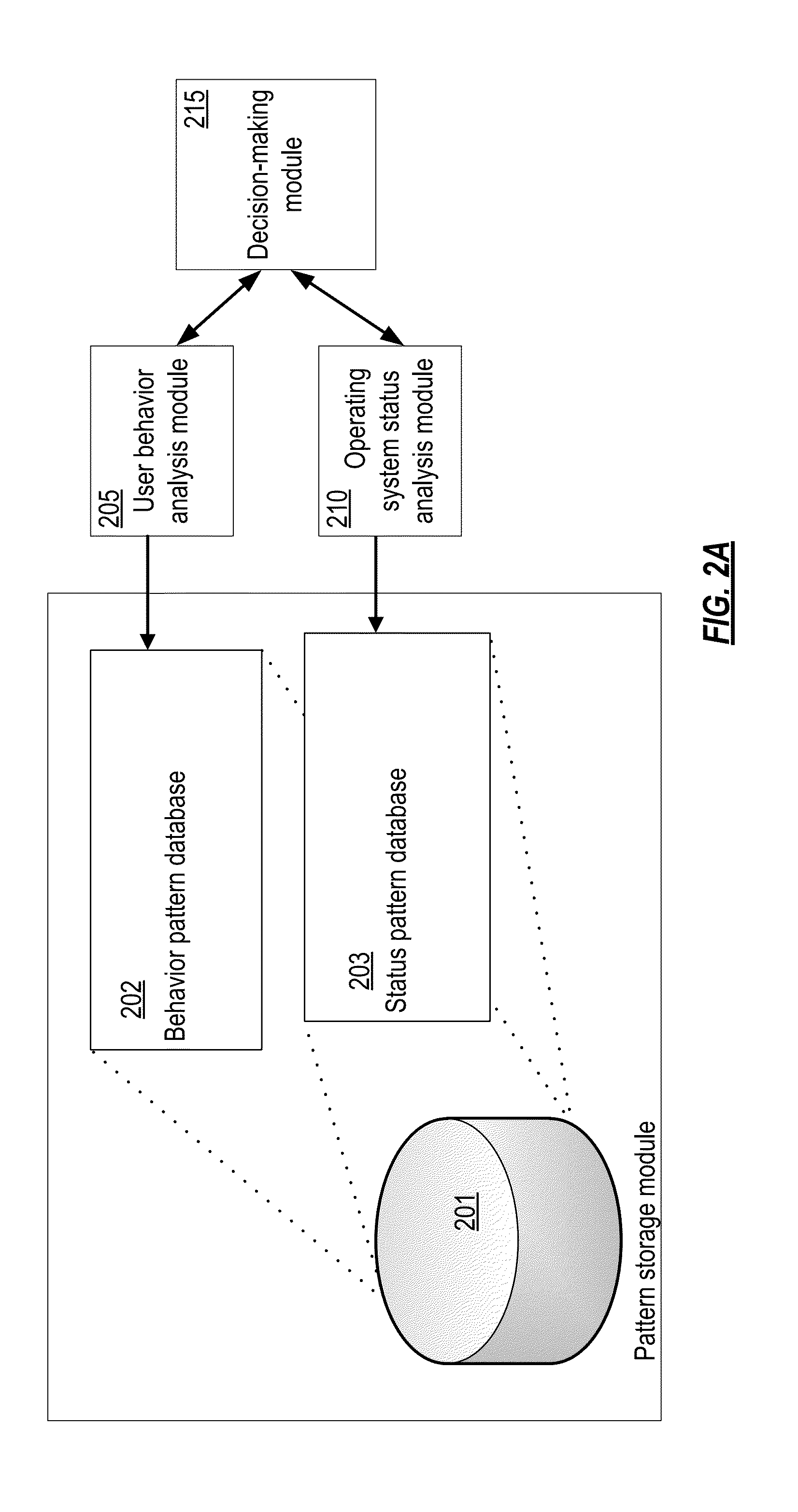
System and method for detecting ransomware. A current user behavior pattern is monitored based on user input via a user input device. The user behavior is compared against a reference set of behavior patterns associated with user frustration with non-responsiveness of the user interface module. A current status pattern of the operating system is also monitored. The current status pattern is compared against a reference set of operating system status patterns associated with predefined ransomware behavior. In response to indicia of current user frustration with non-responsiveness of the user interface, and further in response to indicia of the current status pattern having a correlation to the predefined ransomware behavior, an indication of a positive detection of ransomware executing on the computer system is provided.
Owner:AO KASPERSKY LAB
Ransomware detection and damage mitigation
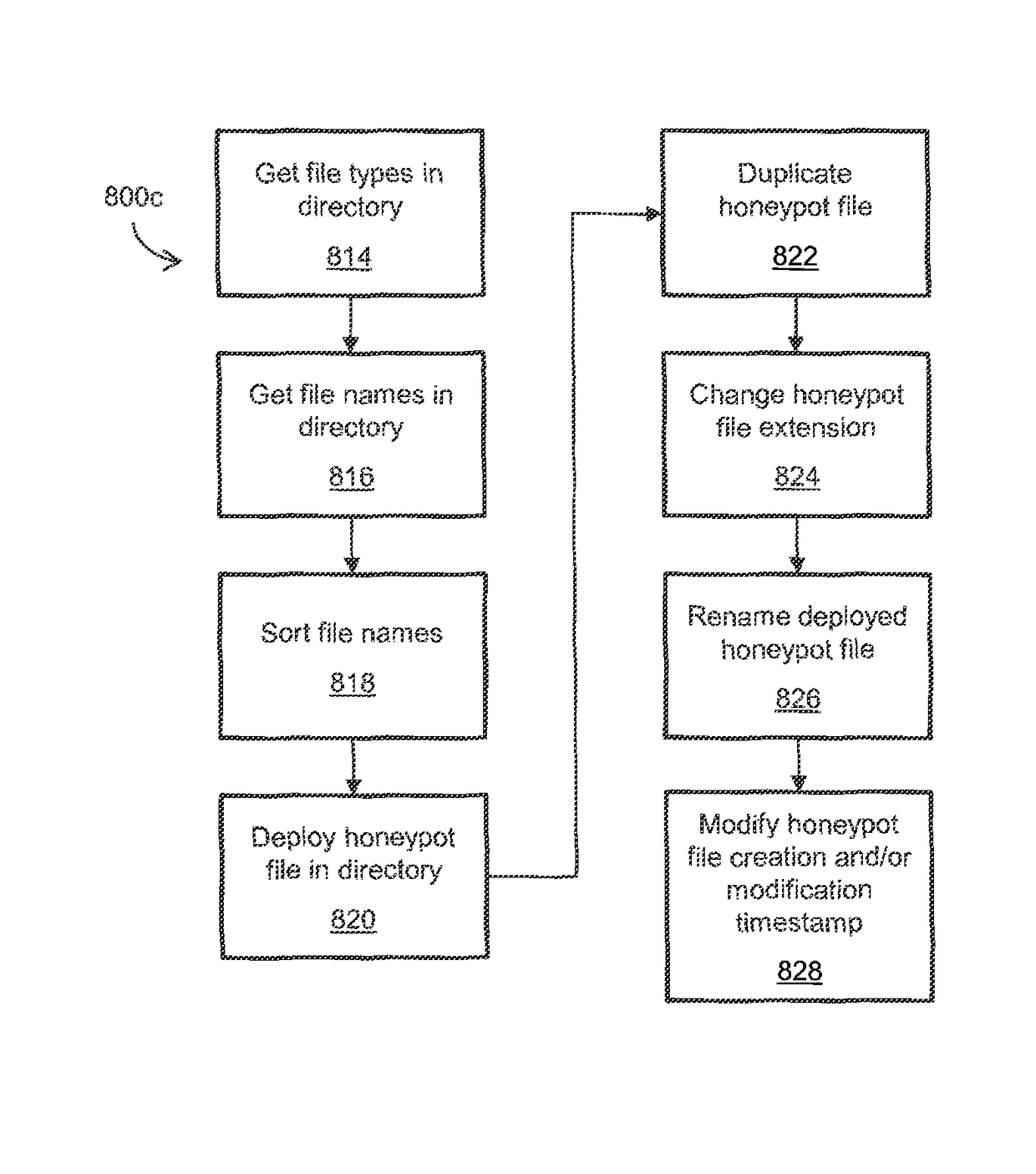
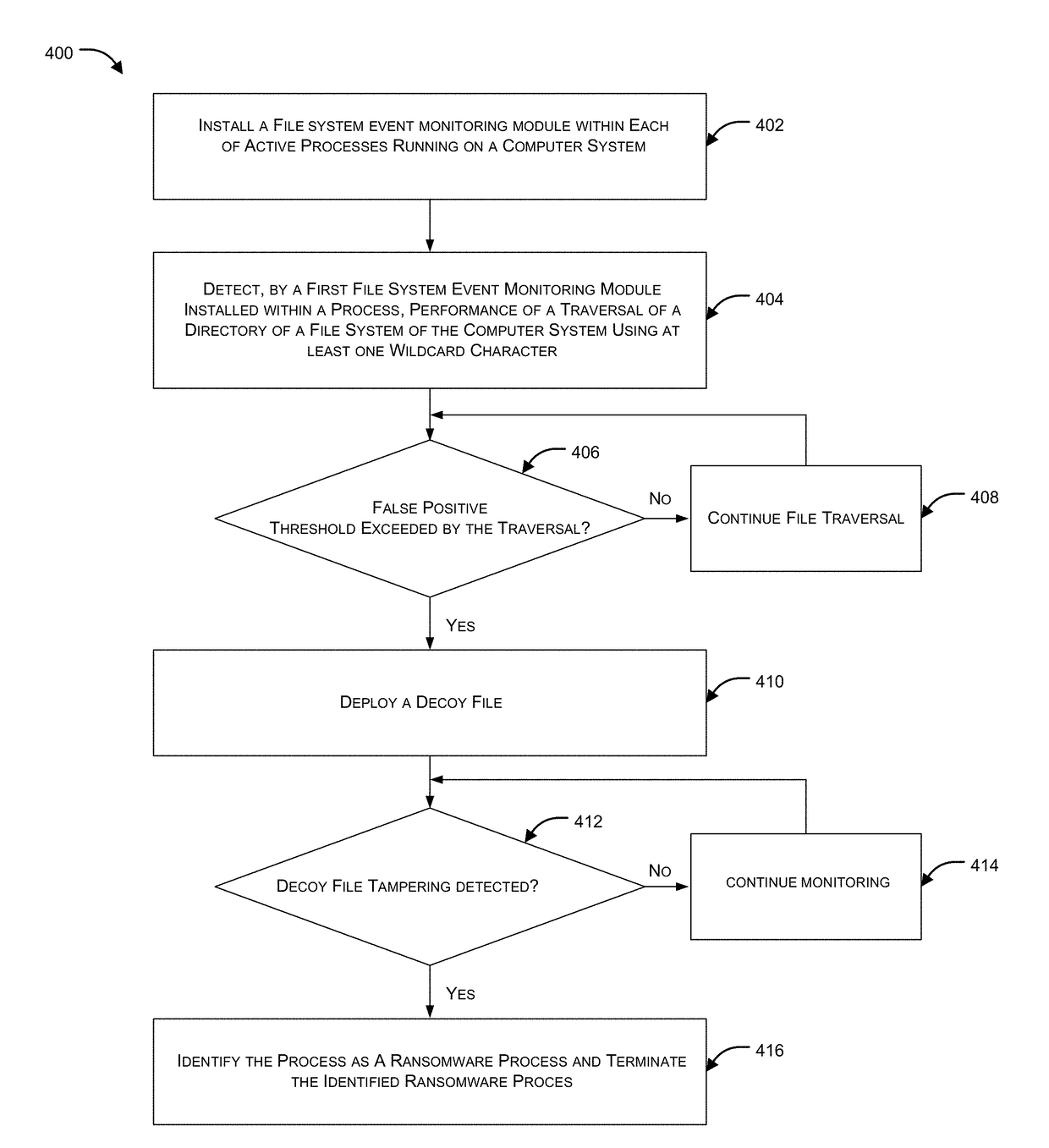
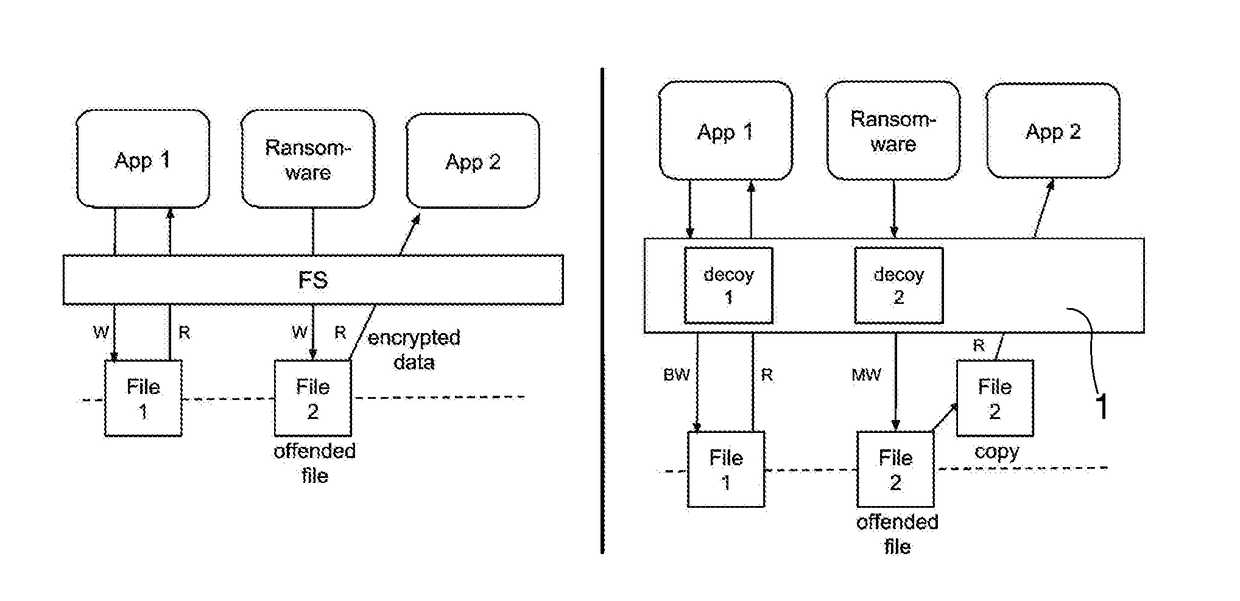
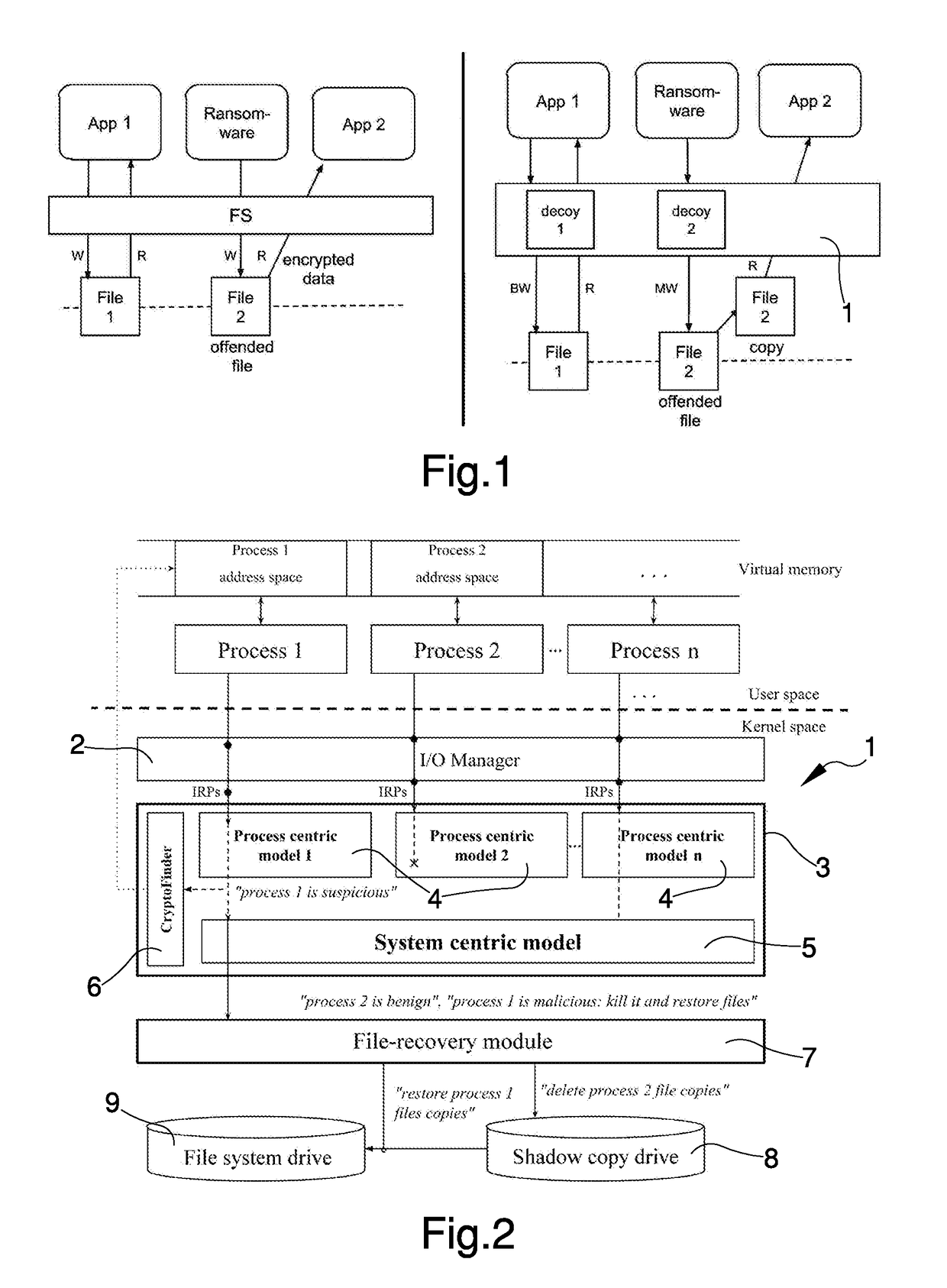
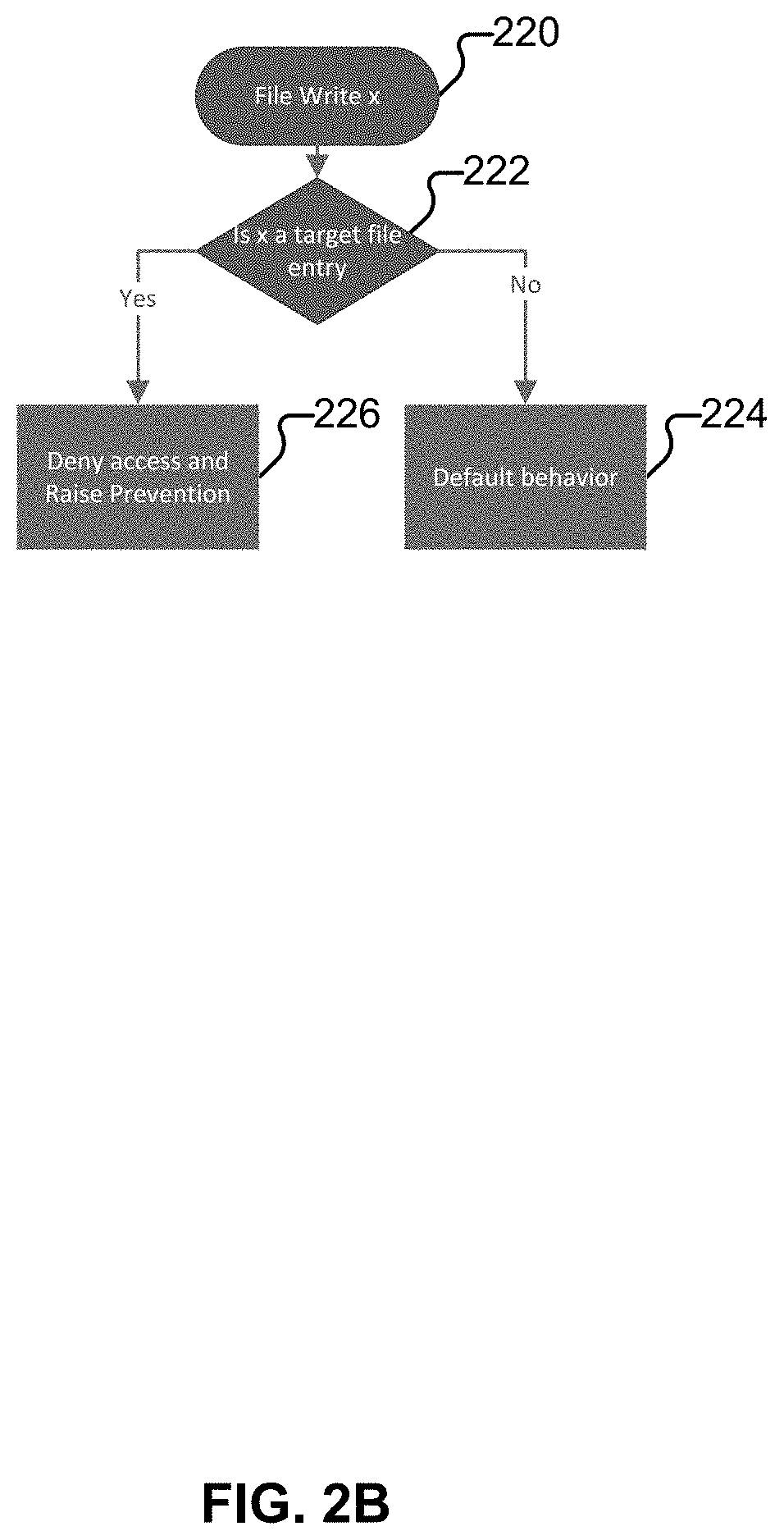
Systems and methods for file encrypting malware detection are provided. According to one embodiment, a monitoring module is installed within active processes running on a computer system by a kernel mode driver. Performance of a directory traversal operation on a directory of the computer system is detected by a monitoring module of a first process of the multiple active processes in which a parameter of the traversal operation includes a wildcard character. When a number of wildcard-based directory traversal operations performed by the first process exceeds a threshold, a decoy file is deployed by the monitoring module within the directory and the driver is notified. The driver monitors for and detects an attempt by the first process to tamper with the decoy file by intercepting and evaluating file system operations. Responsive to detection of the attempt, the first process is confirmed to be a malware process and is terminated.
Owner:FORTINET
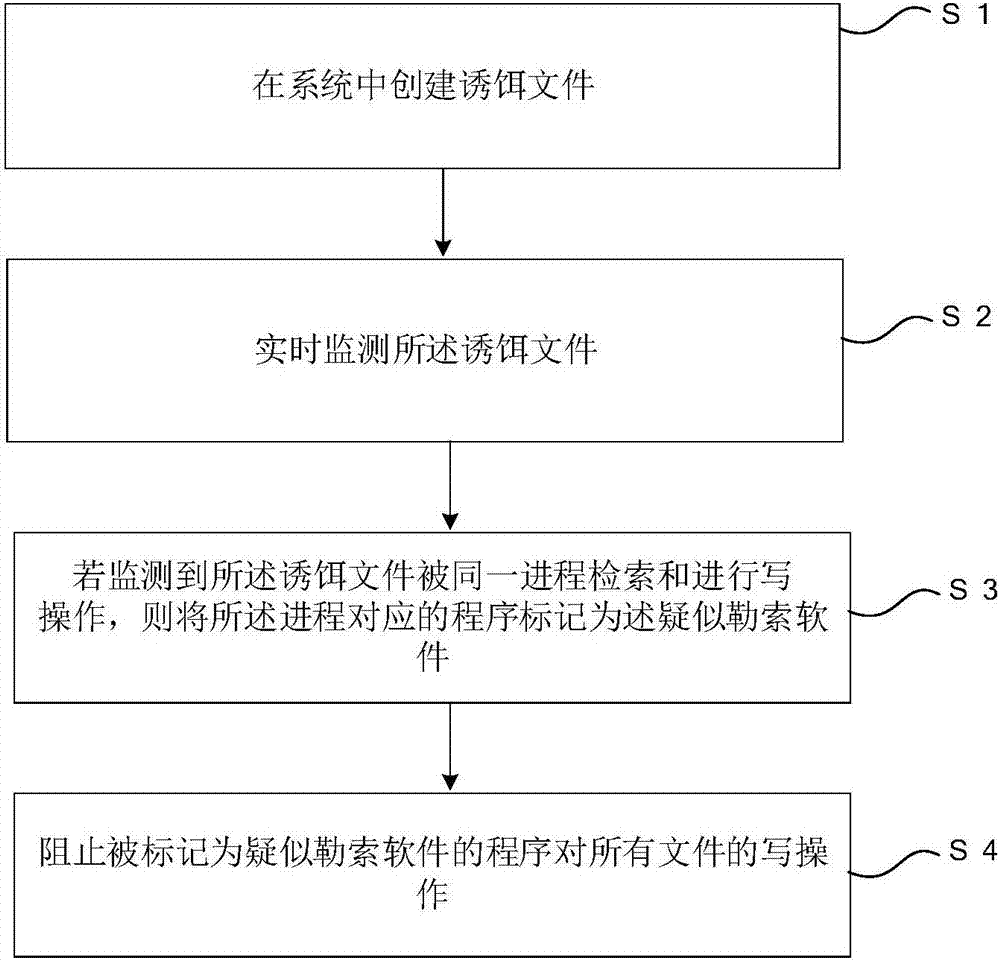
Ransomware prevention method and system
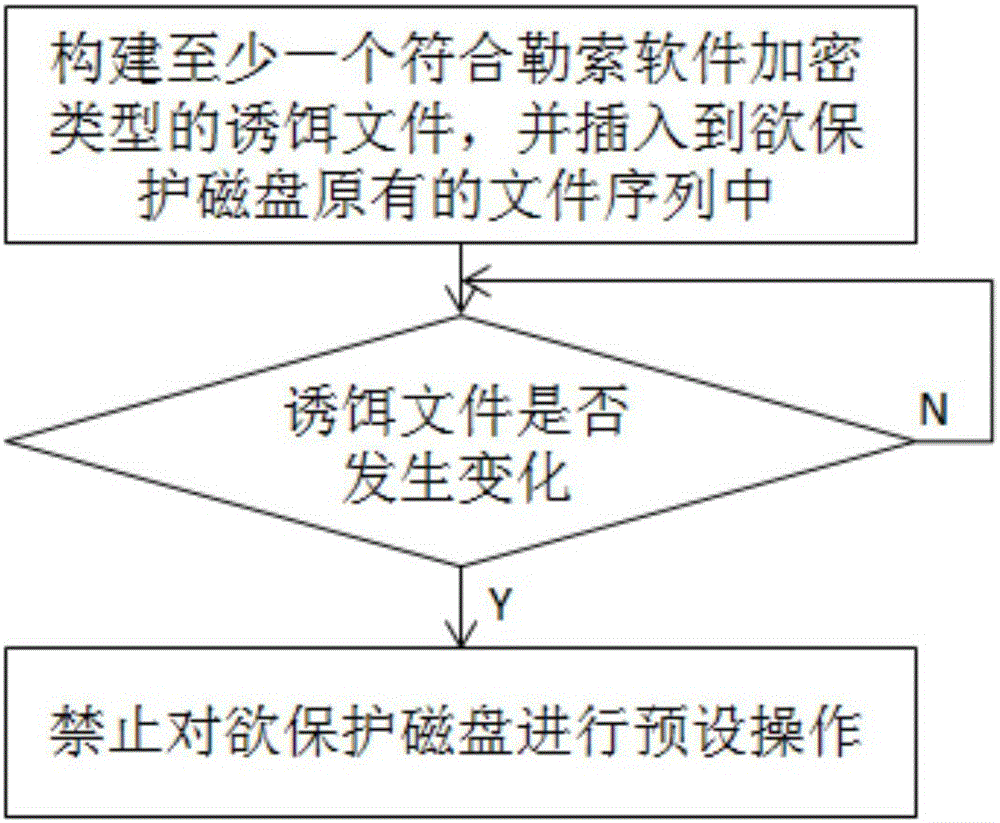
ActiveCN106096397AImprove the accuracy of early warningAvoid Malicious OperationsPlatform integrity maintainanceDecoyRansomware
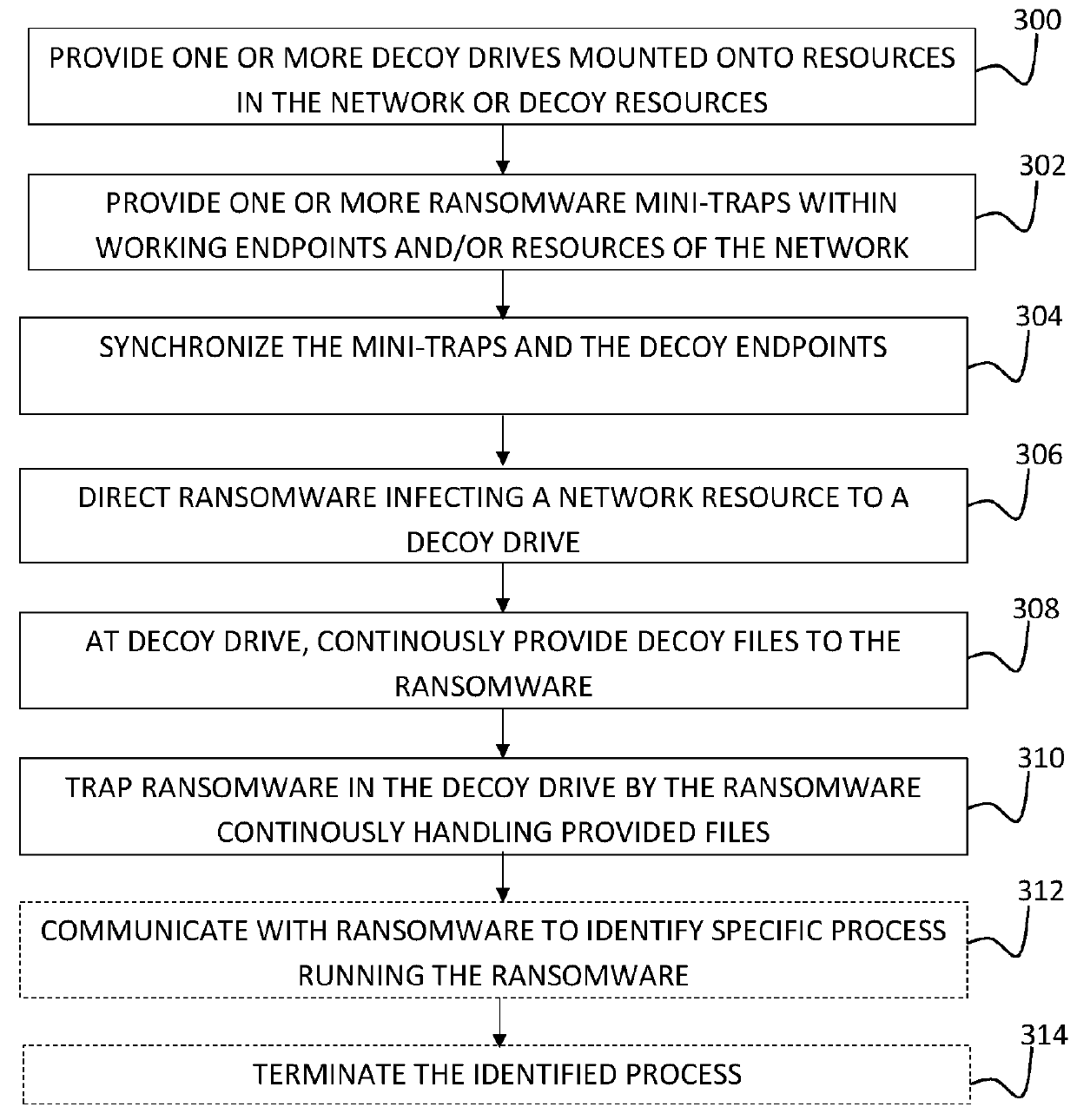
The invention relates to a ransomware prevention method and system. The method comprises the steps of creating at least one bait file with the type conforming to a ransomware encryption type and inserting the bait file into an original file sequence of a to-be-protected disk; judging whether the bait file is changed or not; and prohibiting the to-be-protected disk to be subjected to a preset operation when the bait file is changed. According to the method and the system, the bait file with the type conforming to the ransomware encryption type is created by utilizing a characteristic that ransomware traverses disk files necessarily to search for a file type suitable for encryption, and the bait file is put in the original file sequence of the to-be-protected disk; the effects of prewarning the ransomware and protecting other disk files are achieved by monitoring the bait file; the prewarning accuracy is high; a targeted scheme is designed based on an inevitable common behavior of the ransomware, so that known and unknown ransomware can be detected; and the disk space occupied by the created bait file nearly can be ignored.
Owner:倪茂志
System, Method and Process for Protecting Data Backup from Cyberattack
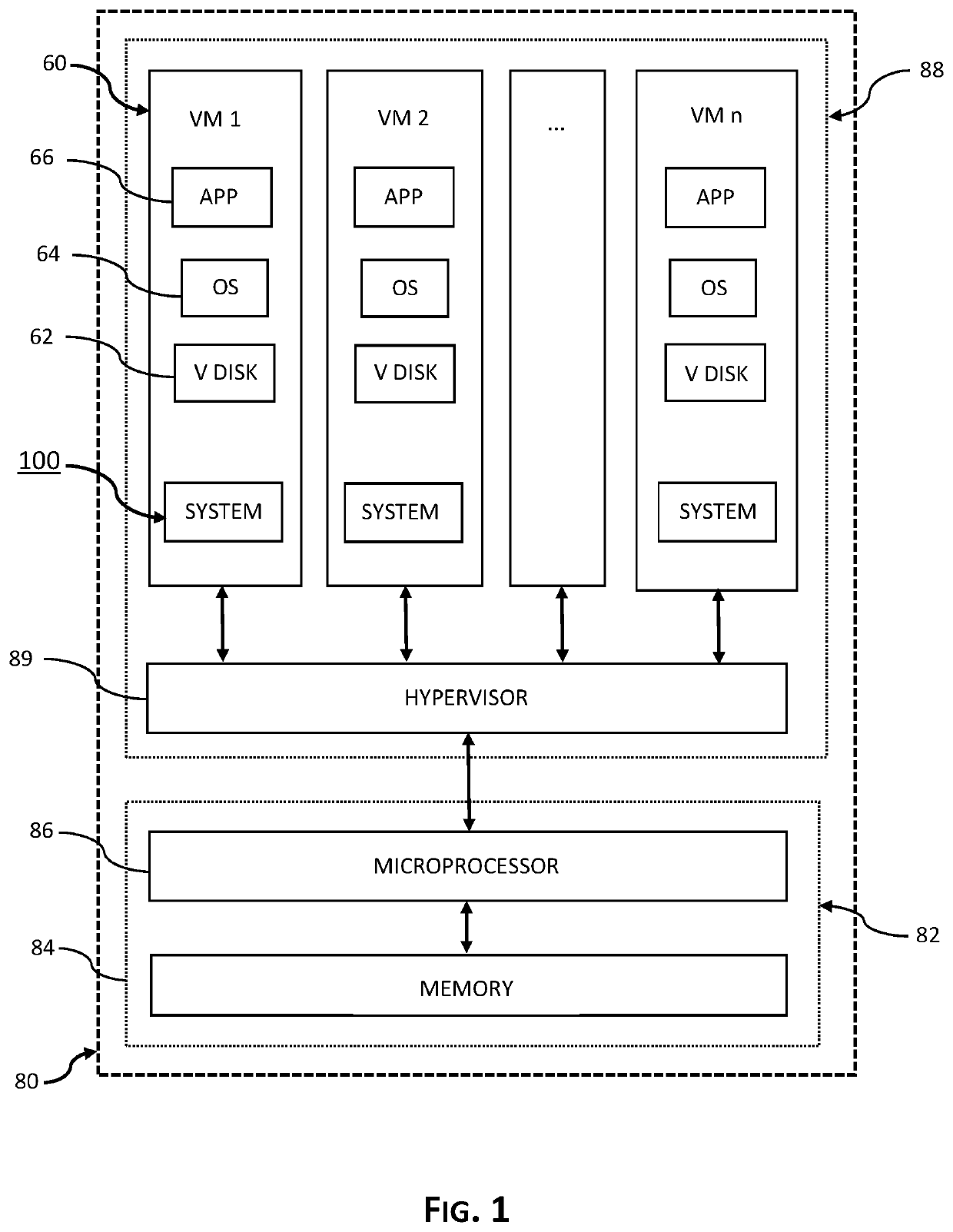
System, method and process for securing and protecting data and data backups from cyberattack and implementing disaster recovery using machine learning and artificial intelligence. Embodiments learn and establish baseline parameters of routine, normal and non-compromised behavior and activity of virtual machines operative in cloud ecosystem, detect and recognize anomalous events related to advanced persistent threats to the instance, such as ransomware, and automatically implement preconfigured actions as determined by a user with the primary objective of protecting data and data backups.
Owner:CLOUD DADDY INC
Lightweight Anti-ransomware system
InactiveUS20190158512A1Reduce stepsComputer security arrangementsTransmissionRansomwareSoftware system
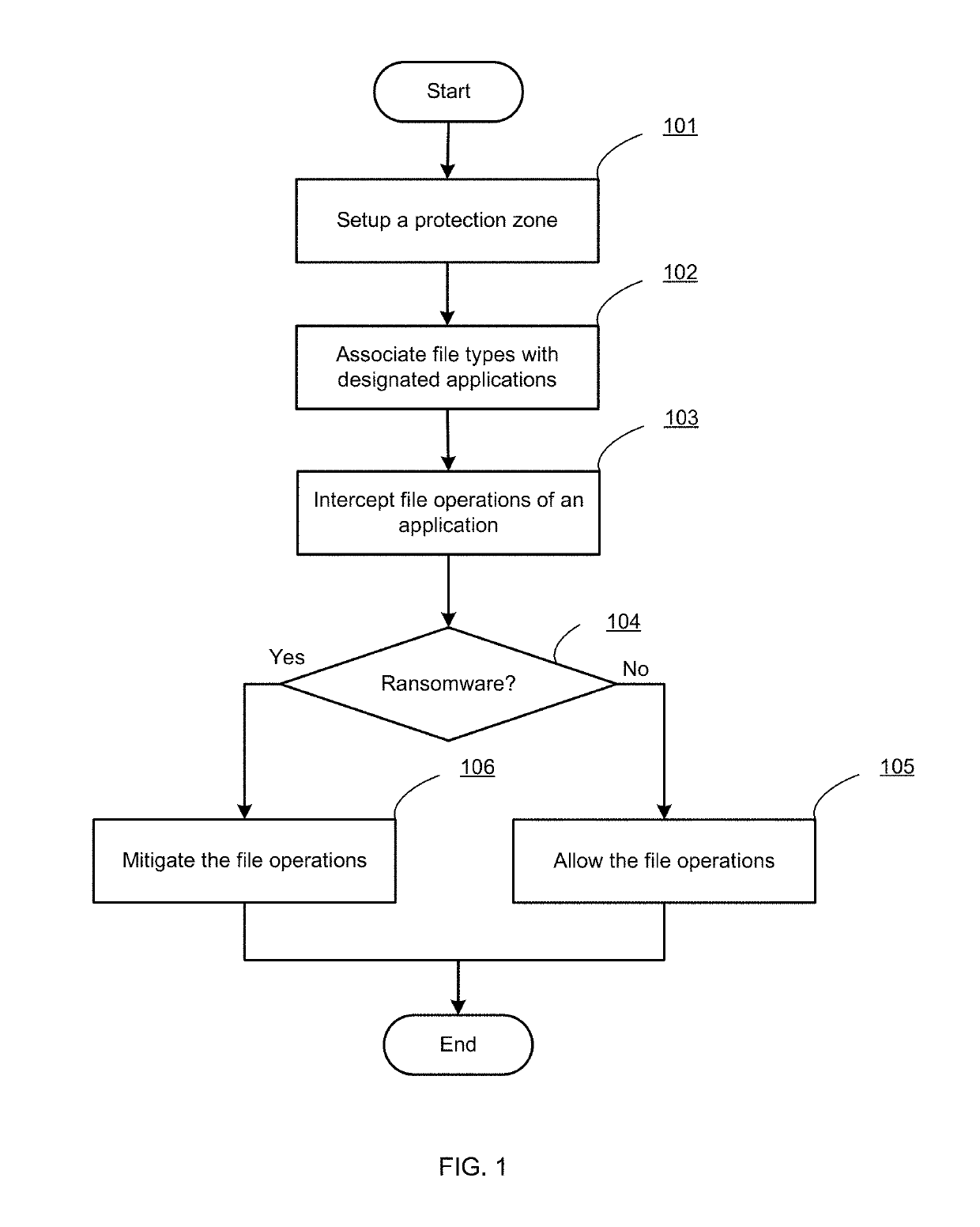
Systems and methods for detecting ransomware are provided. According to one embodiment, a computer device intercepts an operation on a file by an application and determines whether the application is ransomware based on one or more factors. The computer device mitigates the operation to the file when the application is deemed to be ransomware.
Owner:FORTINET
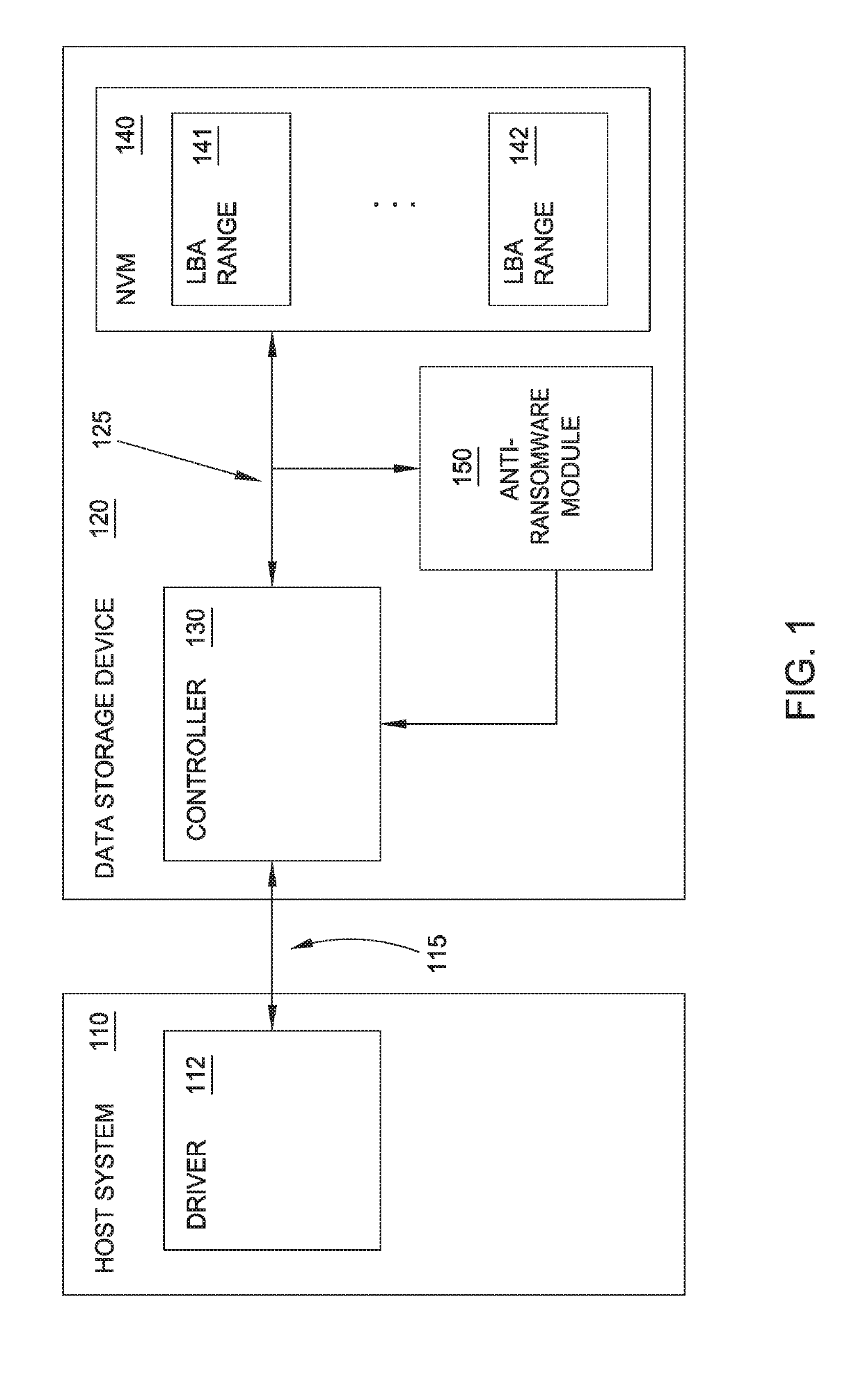
Device-based Anti-malware
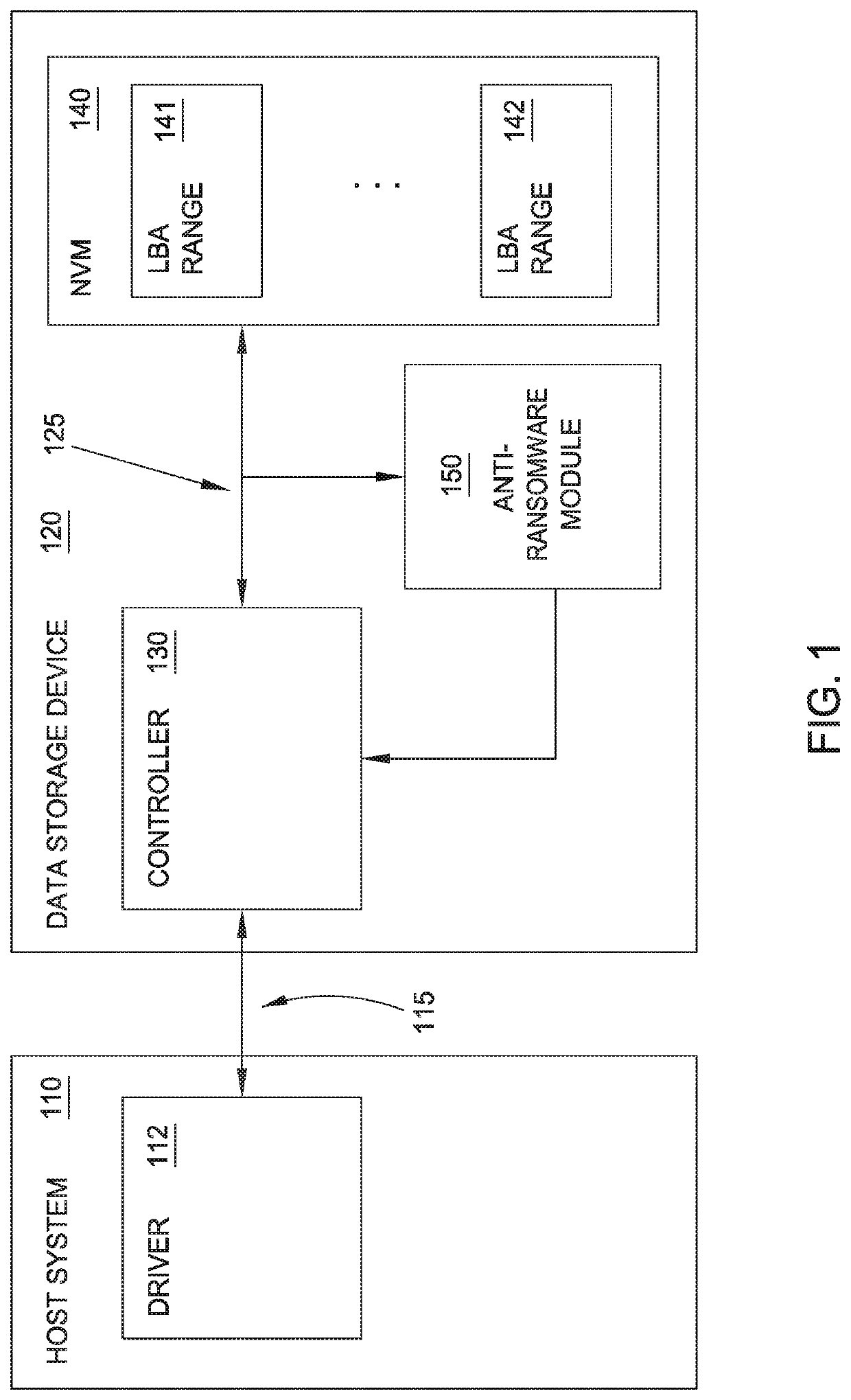
ActiveUS20190130097A1Internal/peripheral component protectionPlatform integrity maintainanceData setRansomware
Methods and equipment for determining whether a ransomware attack is suspected include a data storage device including a controller; non-volatile memory; a data path between the controller and the non-volatile memory; and an anti-ransomware module configured to monitor the data path. Methods and equipment also include monitoring a data path between a controller and a non-volatile memory on a data storage device; calculating an entropy of a data set to be written to the non-volatile memory; analyzing the calculated entropy; and determining whether a malware attack is suspected. Methods and equipment also include monitoring a data path between a controller and a non-volatile memory on a data storage device; identifying activity indicative of ransomware; once activity indicative of ransomware has been identified, calculating an entropy of a data set to be written to the non-volatile memory; analyzing the calculation; and determining whether a ransomware attack is suspected.
Owner:WESTERN DIGITAL TECH INC
Protection system and method for protecting a computer system against ransomware attacks
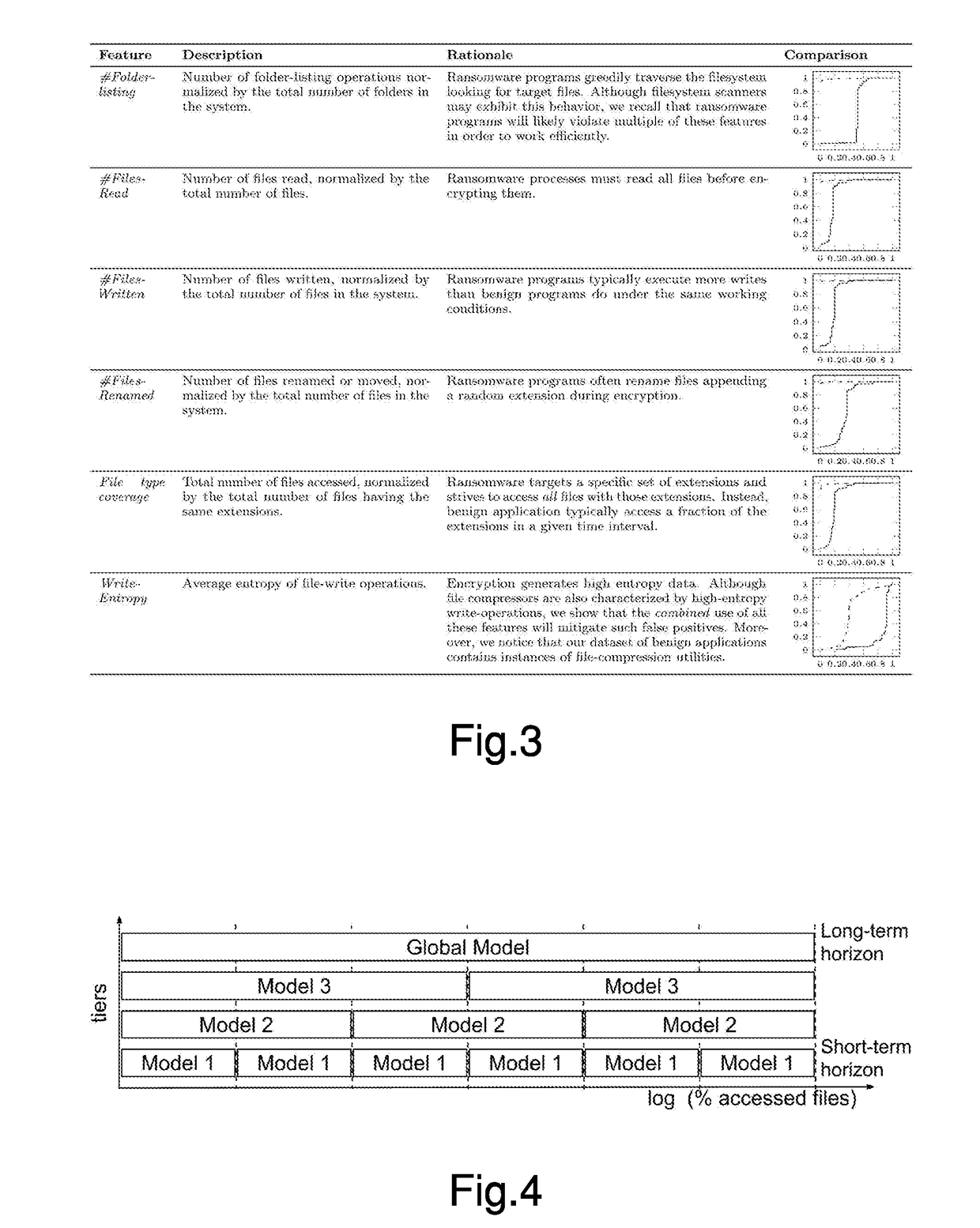
InactiveUS20180157834A1Efficient detectionFile system administrationPlatform integrity maintainanceRansomwareFile system
A protection system and a protection method for protecting a computer system against ransomware attacks is provided. The system and method effectively detect the effects of ransomware attacks by combining automatic detection and transparent file-recovery capabilities at the filesystem level.
Owner:POLITECNICO DI MILANO
System and method for detecting malware that interferes with the user interface
ActiveUS8856542B2Restore operabilityMemory loss protectionDigital computer detailsUser inputFrustration
System and method for detecting ransomware. A current user behavior pattern is monitored based on user input via a user input device. The user behavior is compared against a reference set of behavior patterns associated with user frustration with non-responsiveness of the user interface module. A current status pattern of the operating system is also monitored. The current status pattern is compared against a reference set of operating system status patterns associated with predefined ransomware behavior. In response to indicia of current user frustration with non-responsiveness of the user interface, and further in response to indicia of the current status pattern having a correlation to the predefined ransomware behavior, an indication of a positive detection of ransomware executing on the computer system is provided.
Owner:AO KASPERSKY LAB
Ransomware detection method
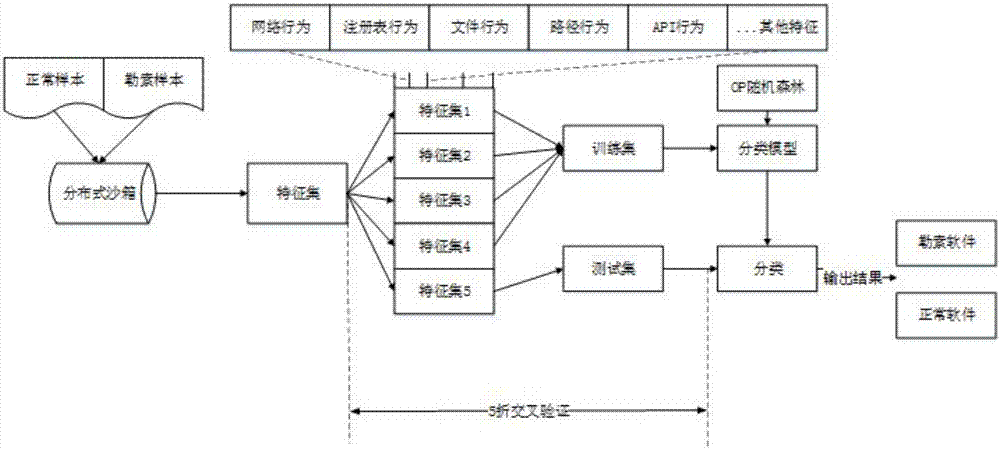
InactiveCN107273747AReduce dimensionalityReduce complexityPlatform integrity maintainanceTransmissionFeature setRansomware
The invention discloses a ransomware detection method, which is divided into two parts executed in sequence. The method comprises the following steps that: 1) training a ransomware detection model: firstly, determining a training set for training the ransomware detection model, and utilizing a distributed sandbox to carry out dynamic analysis on samples in the training set, wherein the training set is divided into two subsets including a ransomware sample set 1) and a normal sample set 2); and 2) testing the ransomware detection model: according to a feature construction algorithm, establishing a feature set, adopting a five-fold crossover method to train and test the model, and using an index with the accuracy to measure model performance. By use of the method, the defects in the prior art that ransomware is difficult in detection, the characteristics of different types of ransomware can not be deeply researched, a detected result is more and more seriously interfered and a constructed algorithm is high in dimension and complexity can be solved.
Owner:CHINESE PEOPLE'S PUBLIC SECURITY UNIVERSITY
Active network backup device
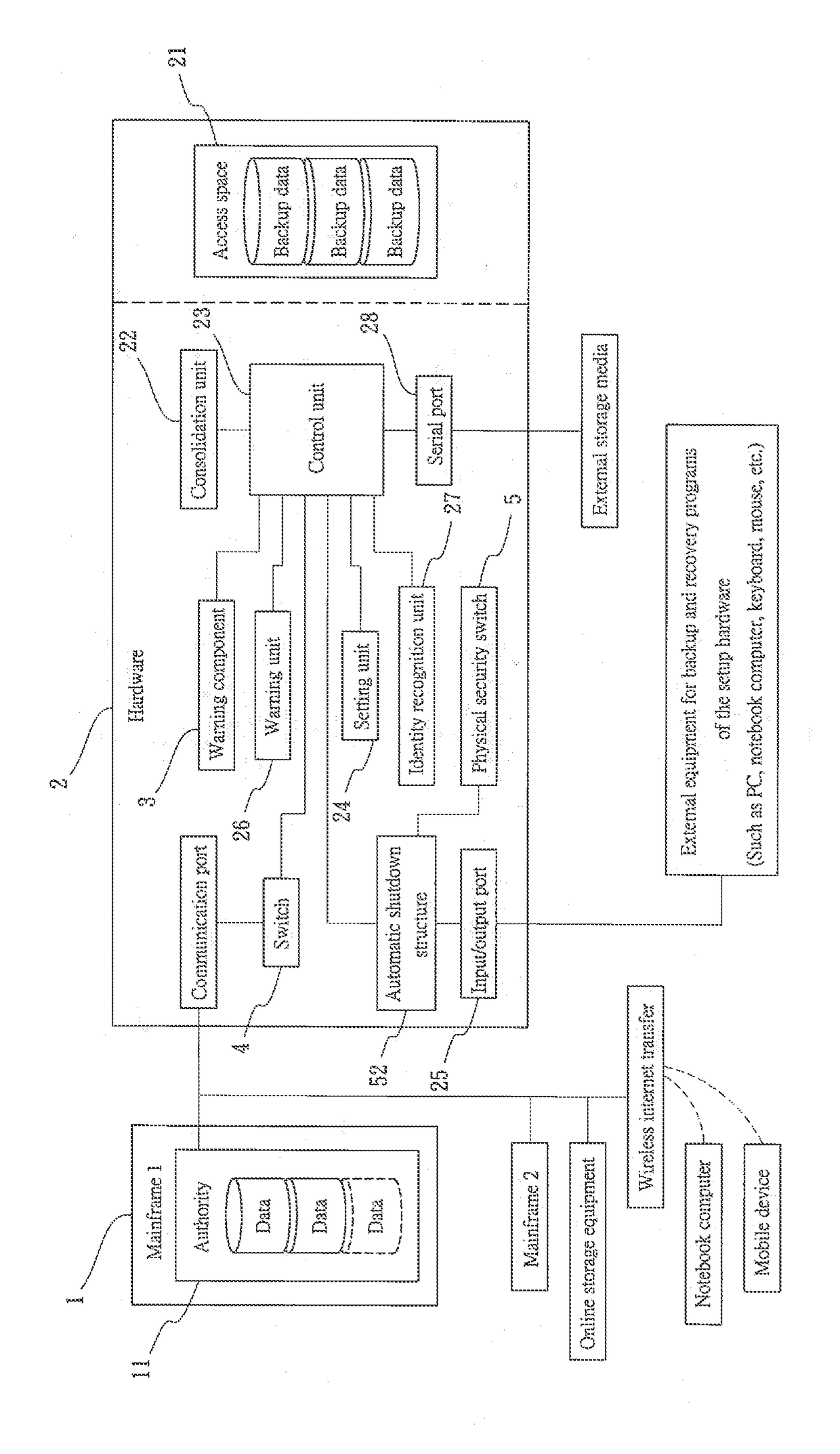
InactiveUS20180375826A1Widely promotedEasily causes data corruption or blackmailInput/output to record carriersTransmissionRansomwareSoftware
An active network backup device includes at least a mainframe and a hardware. The mainframe and other network devices cannot log in, create settings and access data of the hardware. Hence, the hardware can practically prevent and block viruses, ransomware and attacks by hackers; moreover, the device has a physical security switch design for switching on and off a port to ensure personal operation of the administrator and prevent the hardware from being hacked by robot program. Most importantly, the hardware cannot execute destructive instructions and thereby viruses cannot be executed or run in the hardware, which also prevents accidental deletion due to setting errors, or any ransomware or malicious programs in the disguise of setting programs being downloaded and executed by careless users.
Owner:CHANG SHENG HSIUNG +1
Method and system for preventing ransomware
ActiveCN107480527AQuickly discover cryptographic operationsDiscover cryptographic operationsPlatform integrity maintainanceRansomwareVirus
The invention relates to a method and system for preventing ransomware. The method includes the steps of creating a bait file in the system, and monitoring the bait file in real time; if monitoring that the bait file is retrieved and written by the same process, labeling a program corresponding to the process as suspected ransomware; preventing the program labeled as the suspected ransomware from conducting write operations on all files. The method and system for preventing ransomware can accurately and quickly discover the encrypted operation of the ransomware virus on the disk files, and prevent in time.
Owner:SHENZHEN LEAGSOFT TECH
System and a method for identifying the presence of malware and ransomware using mini-traps set at network endpoints
Owner:FIDELIS SECURITY LLC
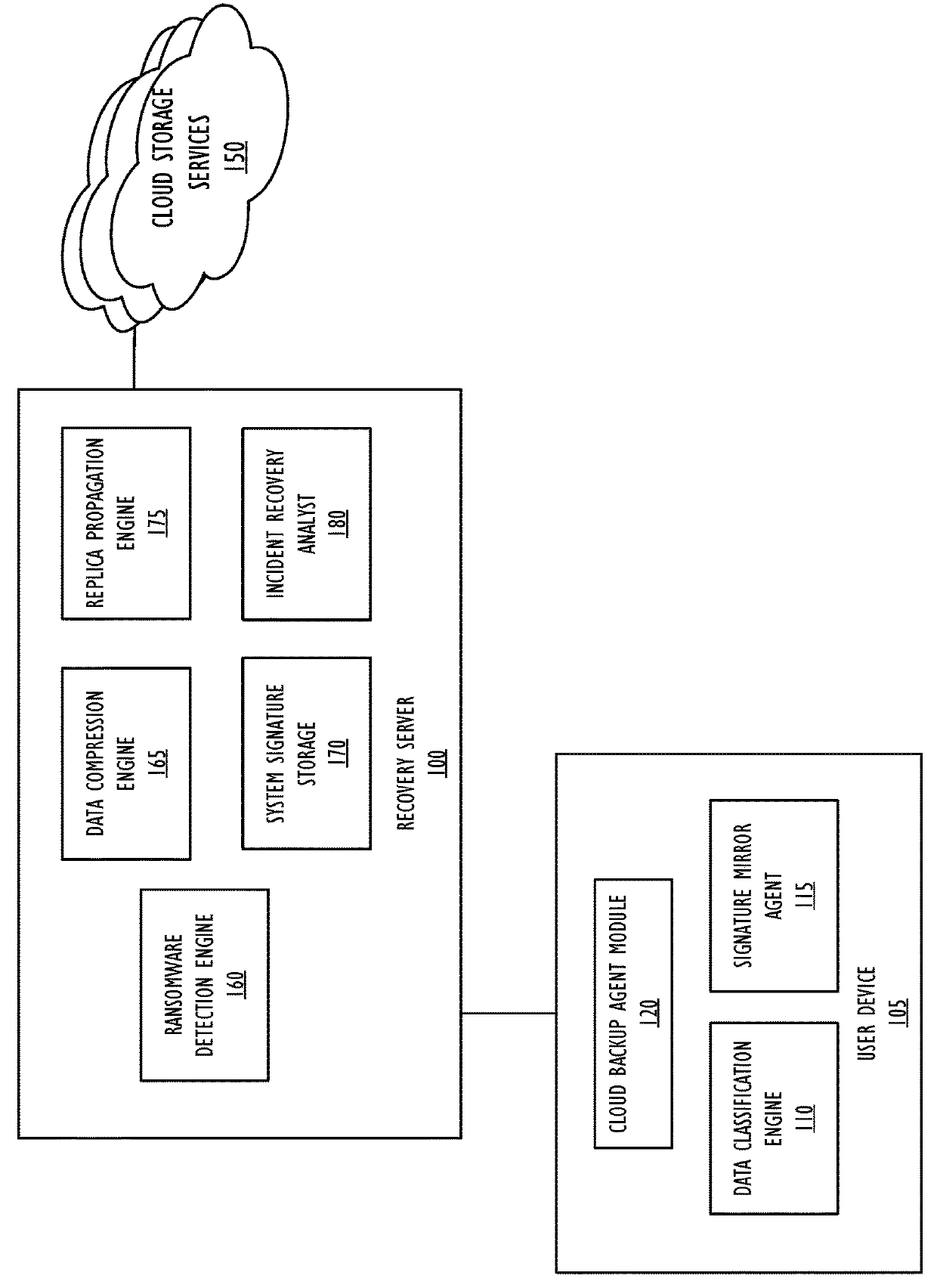
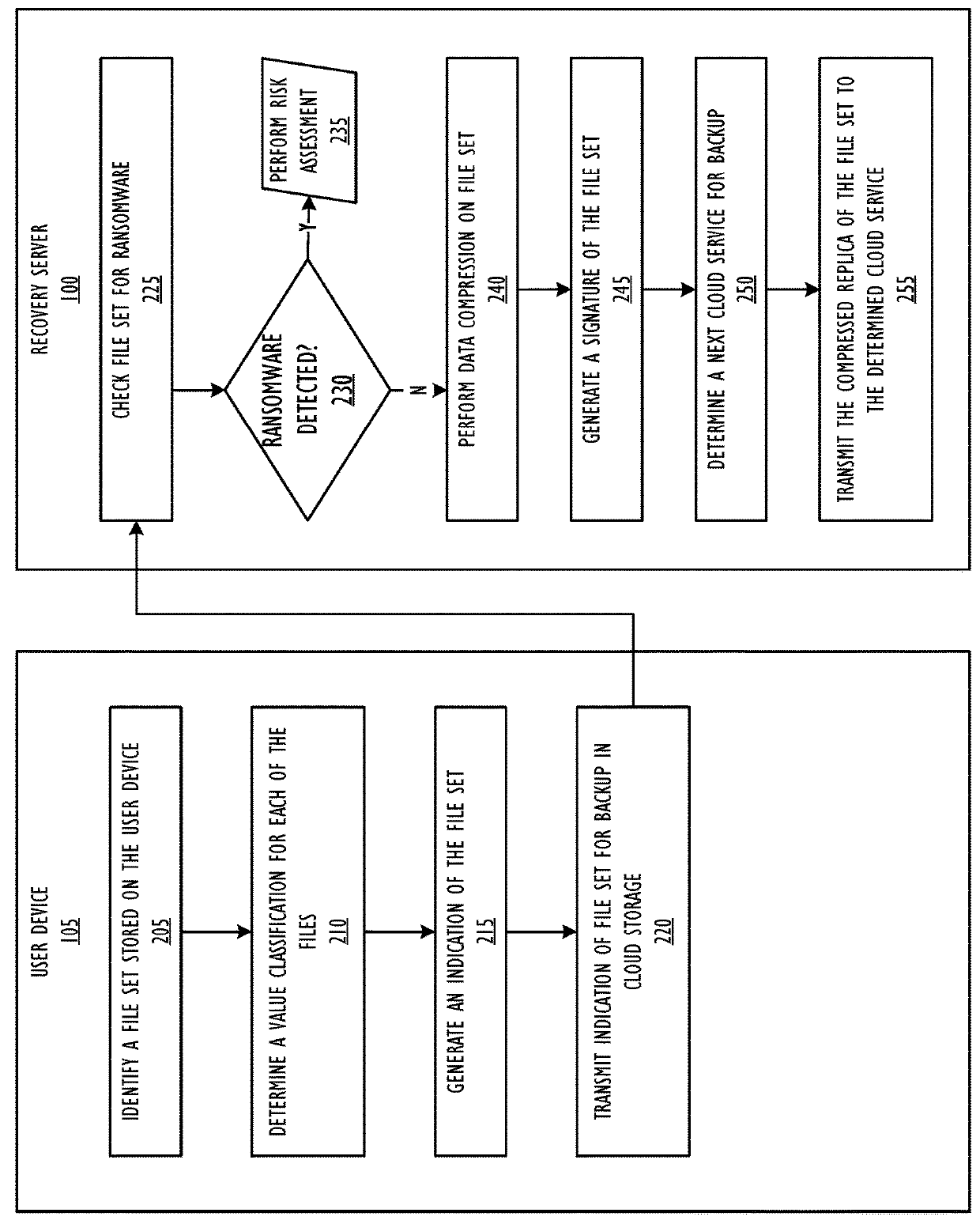
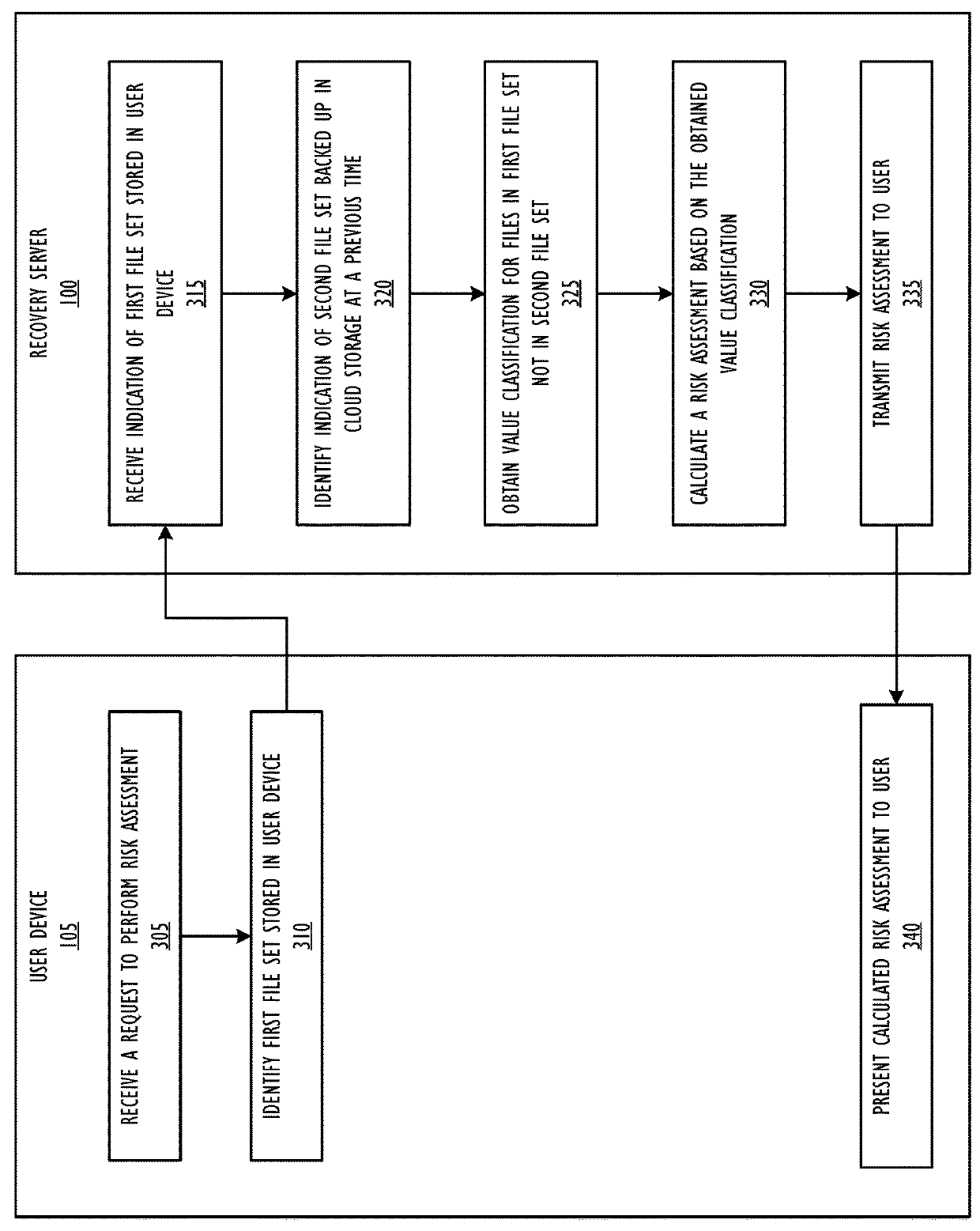
Method for ransomware impact assessment and remediation assisted by data compression
Assessing ransomware impact includes receiving an indication of a first plurality of files stored on a user device and a classification for each of the first plurality of files, determining a second plurality of files stored in a remote storage, wherein the second plurality of files corresponds to an indication of files stored on the user device at a first prior time, wherein each of the second plurality of files are associated with a second classification, determining a third plurality of files comprising files included in the first plurality of files and not included in the second plurality of files, and calculating a risk assessment based on classifications for each of the third plurality of files.
Owner:JPMORGAN CHASE BANK N A AS ADMINISTATIVE AGENT
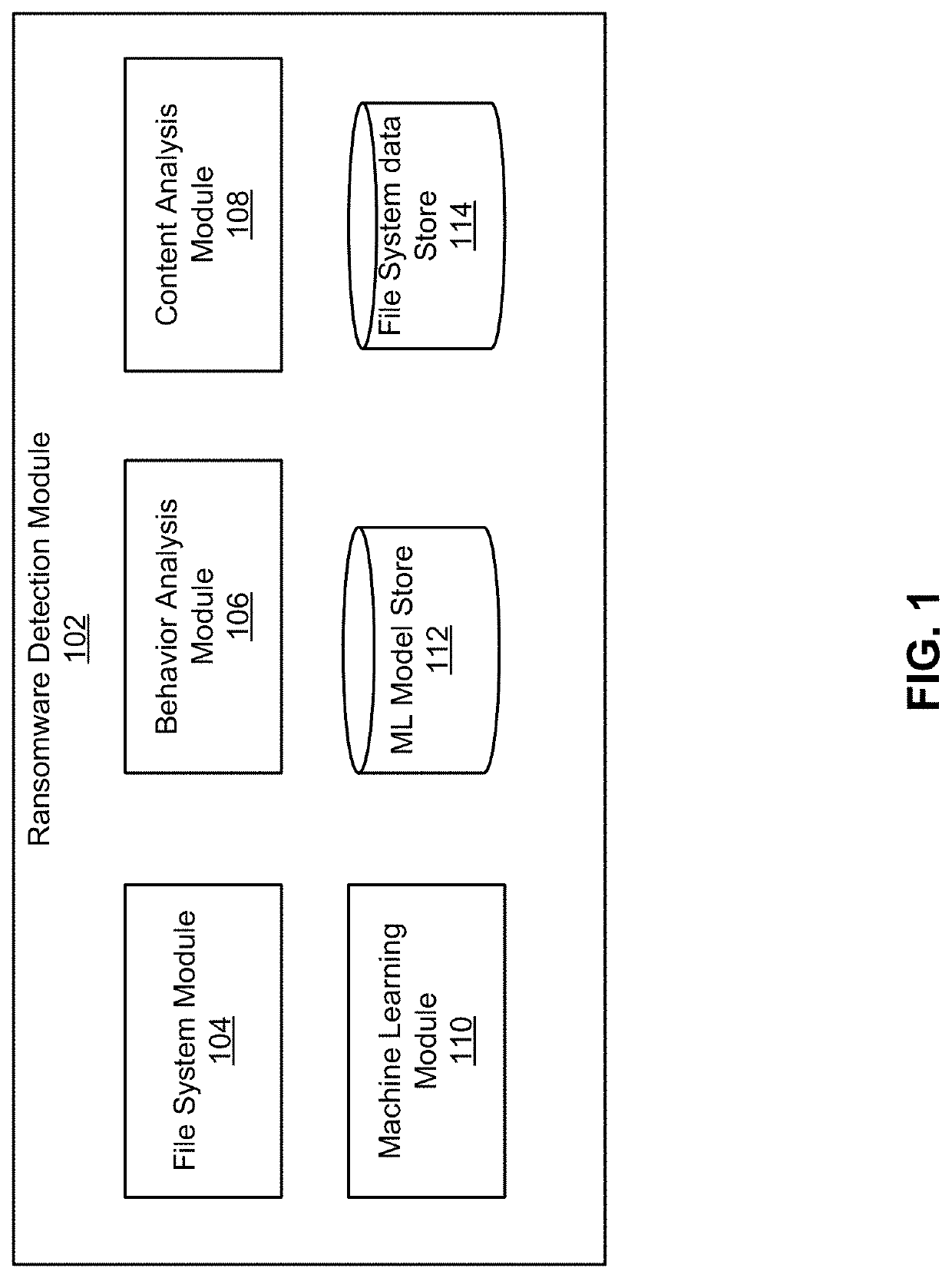
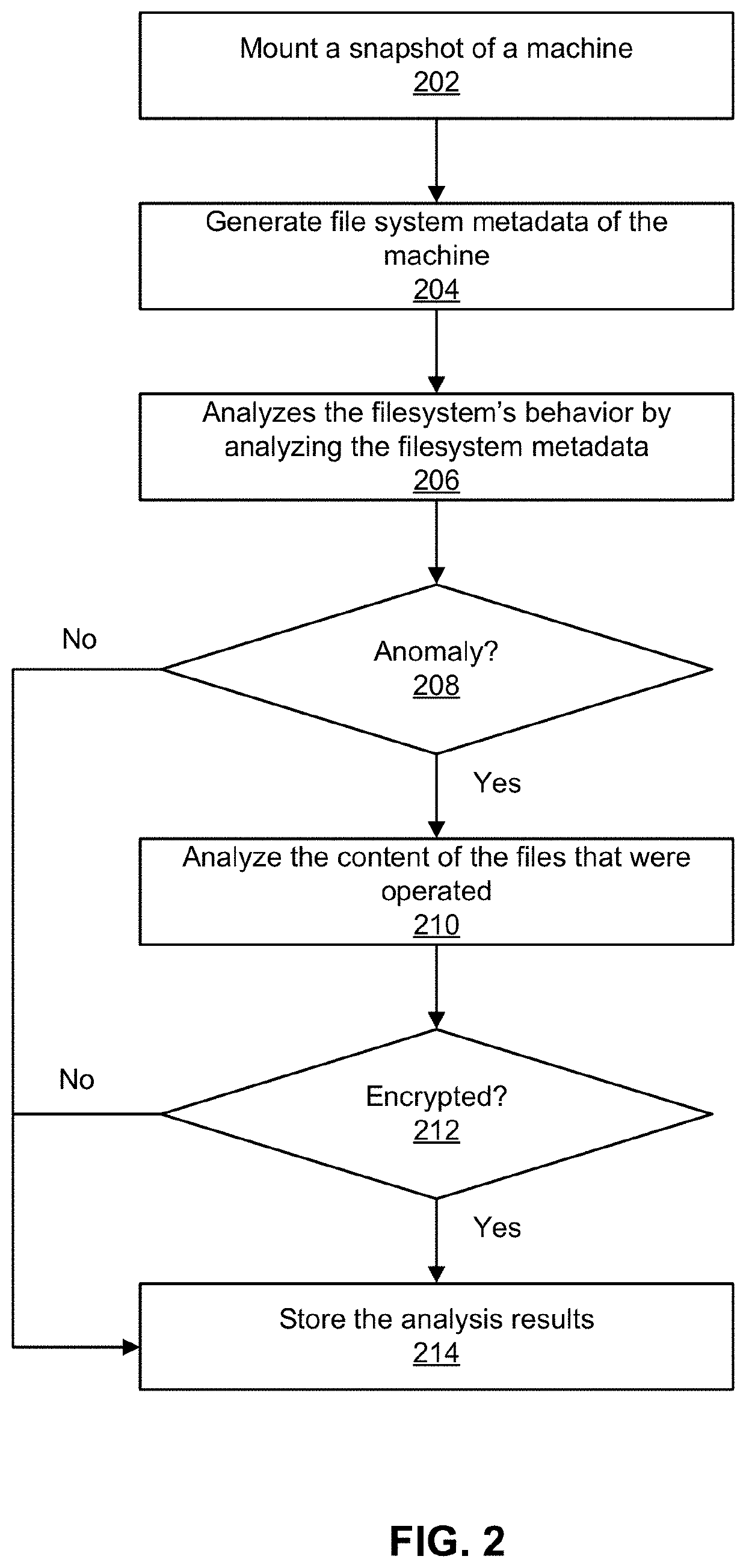
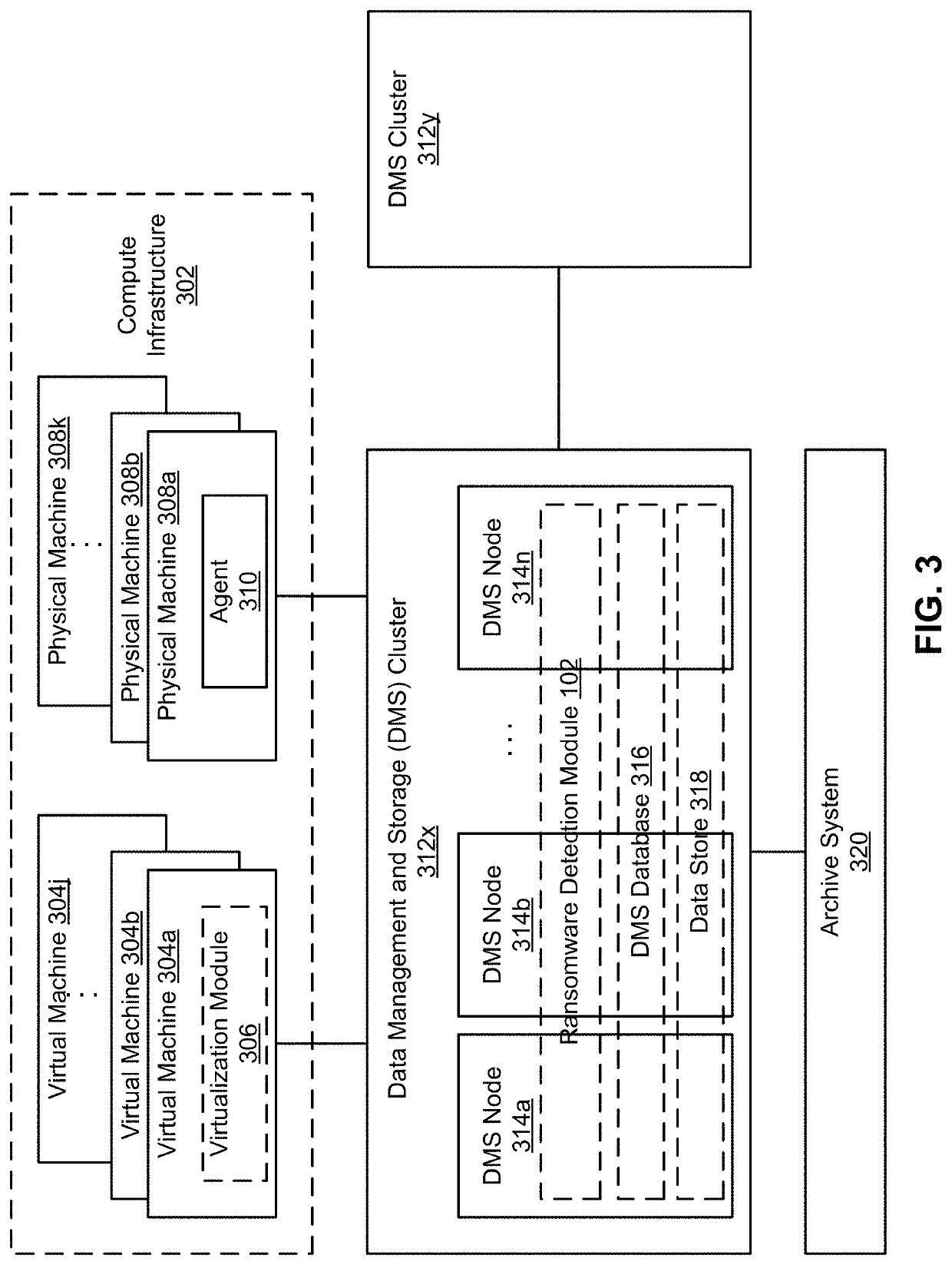
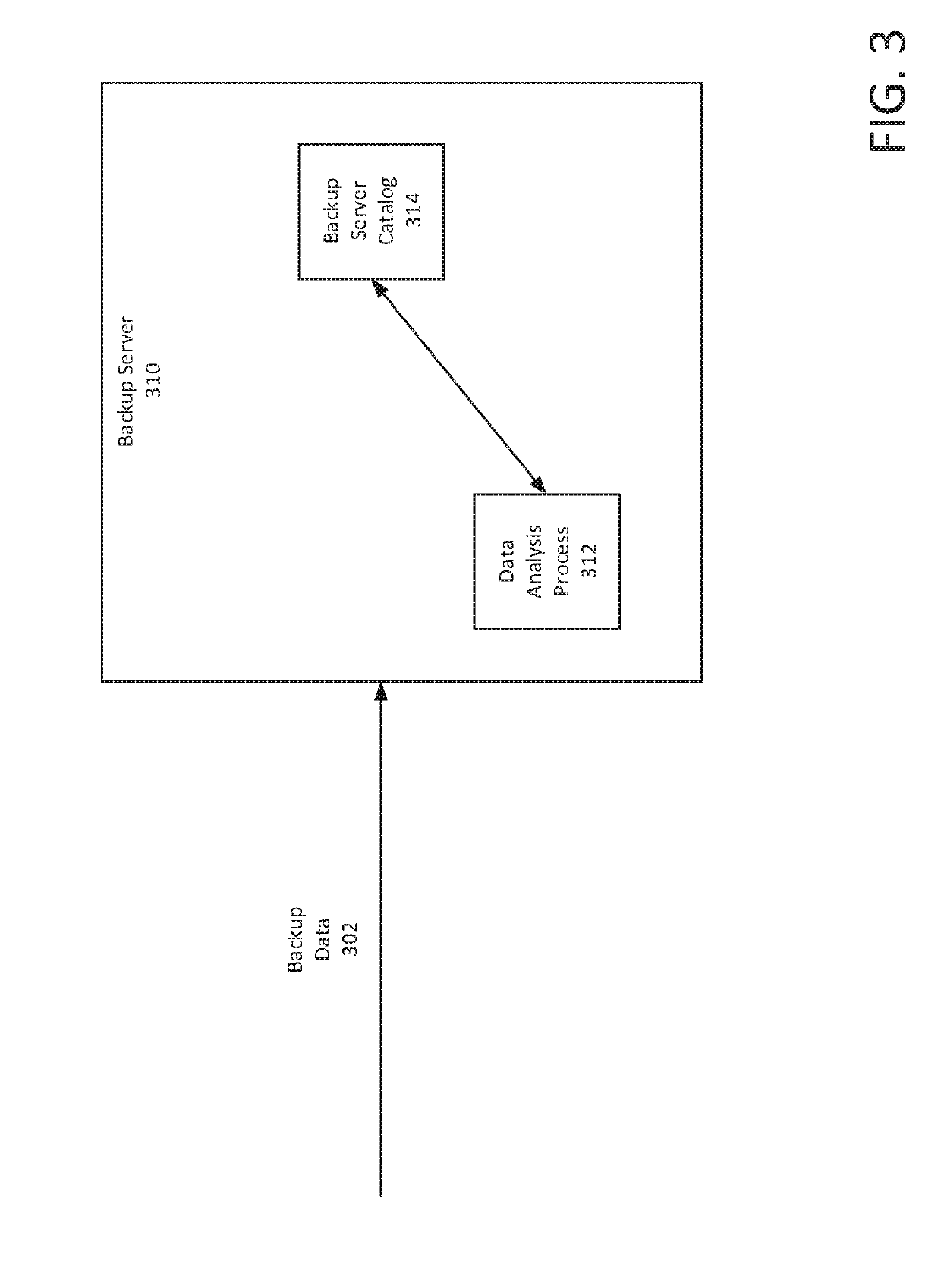
Ransomware infection detection in filesystems
Described herein is a system that detects ransomware infection in filesystems. The system detects ransomware infection by using backup data of machines. The system detects ransomware infection in two stages. In the first stage, the system analyzes a filesystem's behavior. The filesystem's behavior can be obtained by loading the backup data and crawling the filesystem to create a filesystem metadata including information about file operations during a time interval. The filesystem determines a pattern of the file operations and compares the pattern to a normal patter to analyze the filesystem's behavior. If the filesystem's behavior is abnormal, the system proceeds to the second stage to analyze the content of the files to look for signs of encryption in the filesystem. The system combines the analysis of both stages to determine whether the filesystem is infected by ransomware.
Owner:RUBRIK INC
Device-based anti-malware
ActiveUS10733290B2Internal/peripheral component protectionPlatform integrity maintainanceData setRansomware
Methods and equipment for determining whether a ransomware attack is suspected include a data storage device including a controller; non-volatile memory; a data path between the controller and the non-volatile memory; and an anti-ransomware module configured to monitor the data path. Methods and equipment also include monitoring a data path between a controller and a non-volatile memory on a data storage device; calculating an entropy of a data set to be written to the non-volatile memory; analyzing the calculated entropy; and determining whether a malware attack is suspected. Methods and equipment also include monitoring a data path between a controller and a non-volatile memory on a data storage device; identifying activity indicative of ransomware; once activity indicative of ransomware has been identified, calculating an entropy of a data set to be written to the non-volatile memory; analyzing the calculation; and determining whether a ransomware attack is suspected.
Owner:WESTERN DIGITAL TECH INC
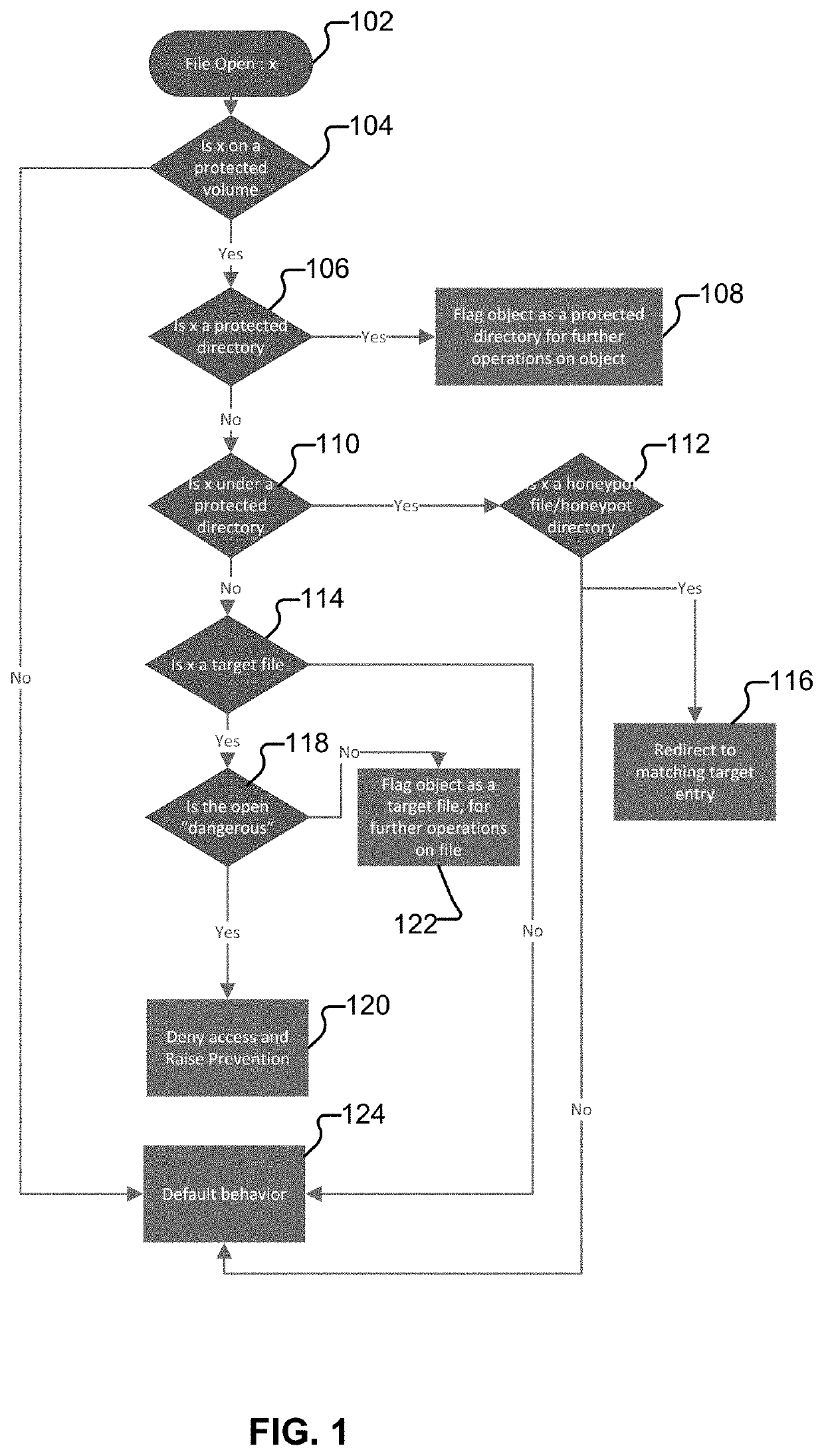
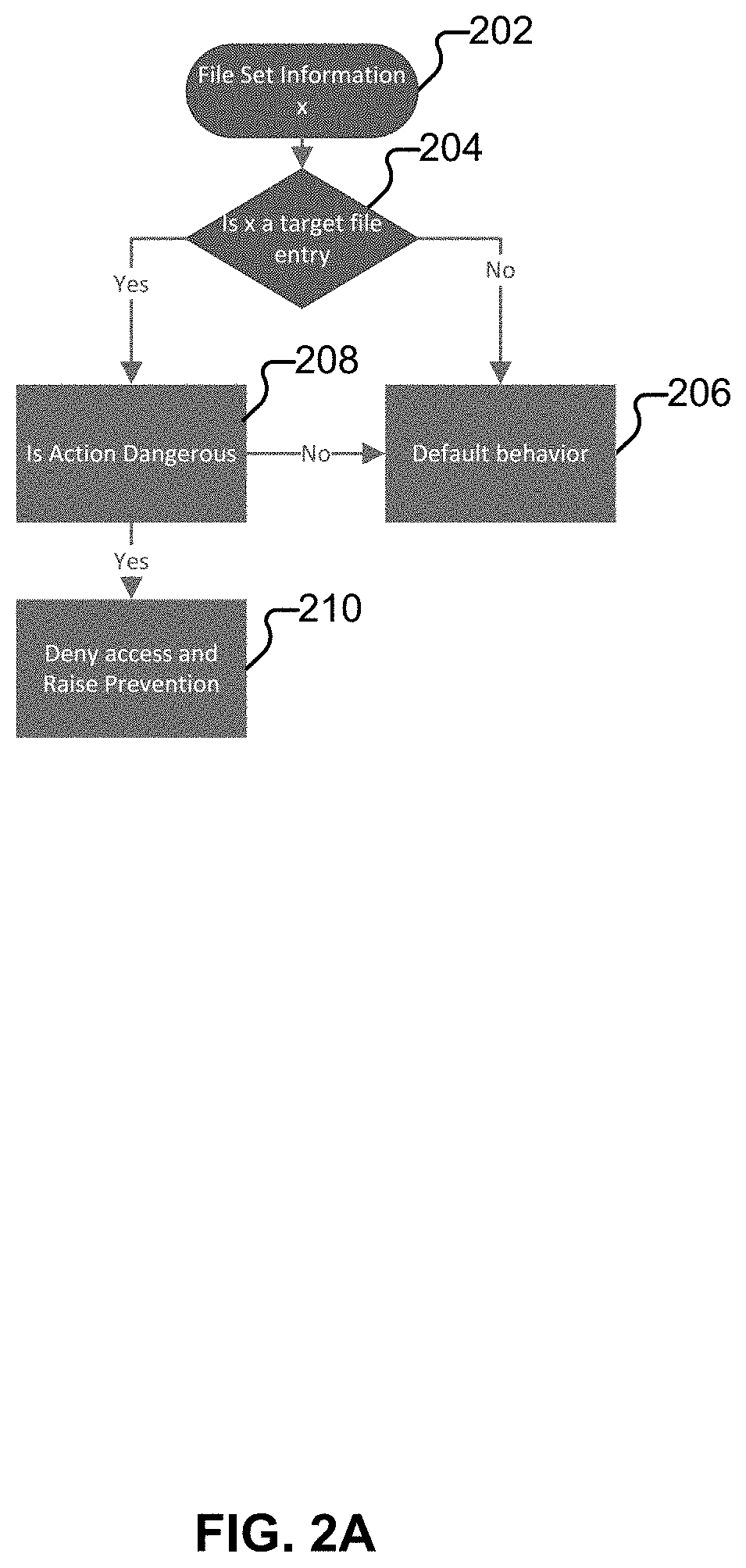
Preventing ransomware from encrypting files on a target machine
Techniques for preventing ransomware from encrypting files on a target machine are disclosed. In some embodiments, a system / process / computer program product for preventing ransomware from encrypting files on a target machine includes monitoring file system activities on a computing device; detecting an unauthorized activity associated with a honeypot file or honeypot folder; and performing an action based on a policy in response to the unauthorized activity associated with the honeypot file or honeypot folder.
Owner:PALO ALTO NETWORKS INC
Ransomware detection and damage mitigation
Systems and methods for file encrypting malware detection are provided. According to one embodiment, a monitoring module is installed within active processes running on a computer system by a kernel mode driver. Performance of a directory traversal operation on a directory of the computer system is detected by a monitoring module of a first process of the multiple active processes in which a parameter of the traversal operation includes a wildcard character. When a number of wildcard-based directory traversal operations performed by the first process exceeds a threshold, a decoy file is deployed by the monitoring module within the directory and the driver is notified. The driver monitors for and detects an attempt by the first process to tamper with the decoy file by intercepting and evaluating file system operations. Responsive to detection of the attempt, the first process is confirmed to be a malware process and is terminated.
Owner:FORTINET
Ransomware real-time detecting and defending method based on file request monitoring
InactiveCN107563199AEnsure consistencyDamage minimizationPlatform integrity maintainanceRansomwareOperational behavior
The invention provides a ransomware real-time detecting and defending method based on file request monitoring, and belongs to the technical field of system security. The method includes the steps of monitoring whether a tested program has operation behaviors on a user file or not in a user host, if yes, mirroring the file to a protected storage area, operating the file in the area, recording the complete operation information, judging whether the program is ransomware or not in combination with a dubiety measuring mechanism based on the file content and operation behavior analysis, if yes, deleting the file in the protected area and deleting the program, and if not, updating and synchronizing the file according to the file in the protected area so that the consistency of data under normalcircumstances can be ensured. Through the process, the malicious ransomware can be effectively detected, the damage of malicious codes to user data is minimized, and the aim of improving the securityand defending capacity of a server host system is achieved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
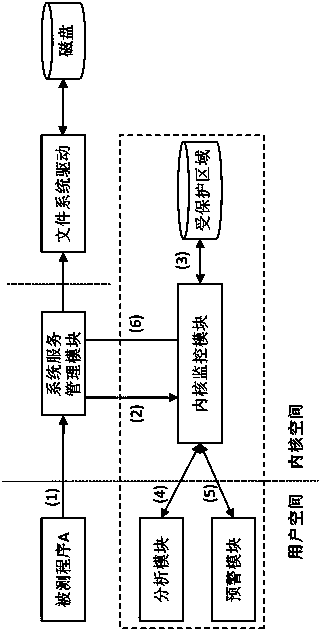
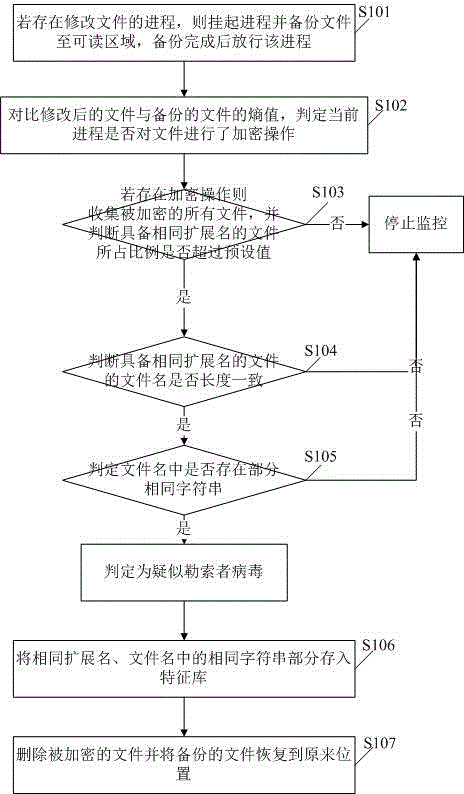
Ransomware detection method and system
The invention discloses a ransomware detection method and system. The method comprises the steps of suspending a process and backing up files to a readable region if the file modification process exists, and releasing the process after the backup is finished; comparing entropy values of modified files and the backed-up files, and judging whether the current process performs encryption operation on the files or not; if the encryption operation exists, collecting all the encrypted files, and judging whether a proportion of the files with the same expanded names exceeds a preset value or not; if yes, continuing to judge whether the file names of the files with the same expanded names are consistent in length and part of same character strings exist or not; and if yes, judging that the files are suspected ransomware. According to the technical scheme, the ransomware can be effectively identified, the false alarm rate is reduced, and the operation of normal software on the files is not influenced.
Owner:HARBIN ANTIY TECH
Systems and methods for ransomware detection and mitigation
PendingUS20210026961A1Platform integrity maintainanceSpecial data processing applicationsOperational systemFile system
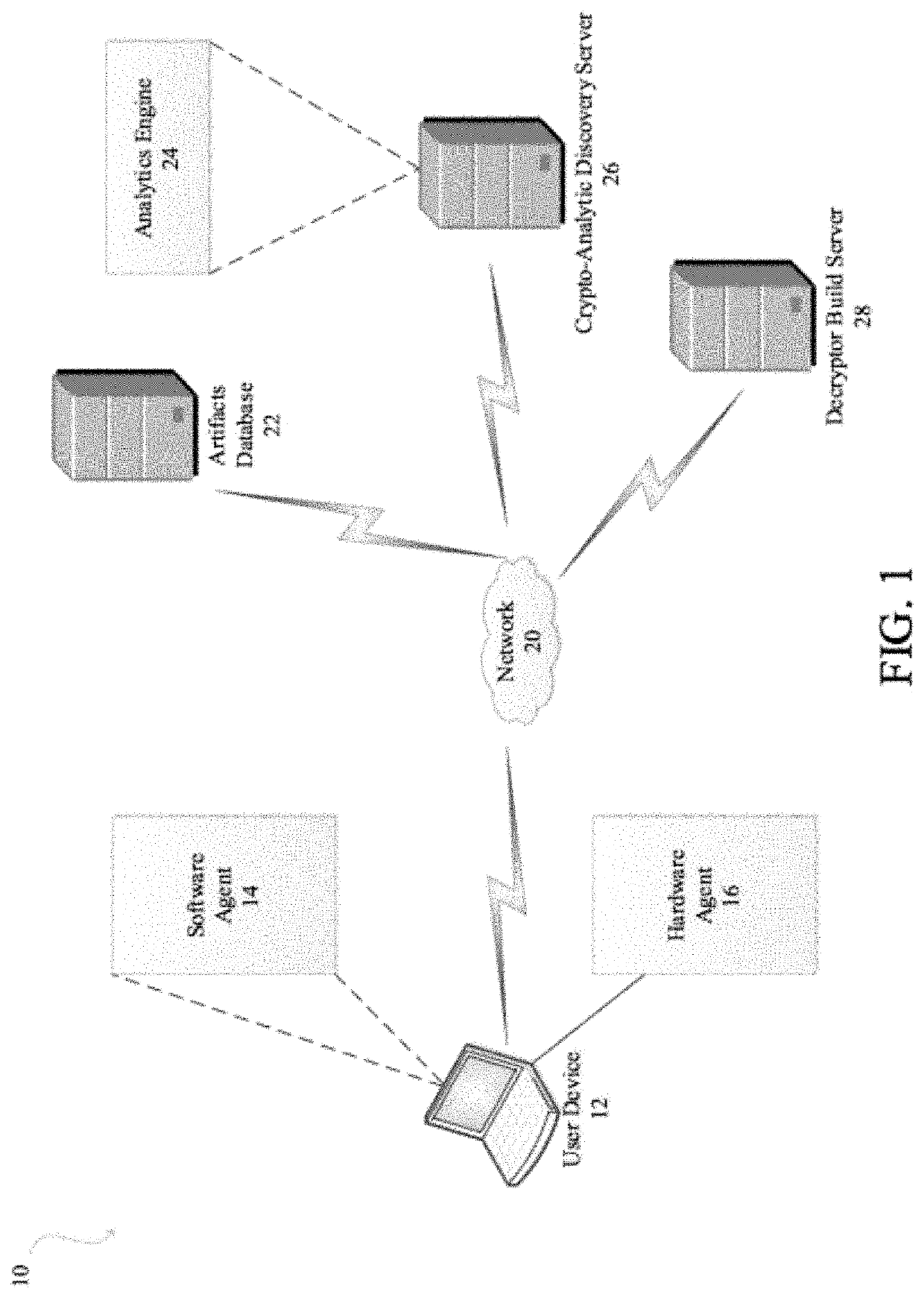
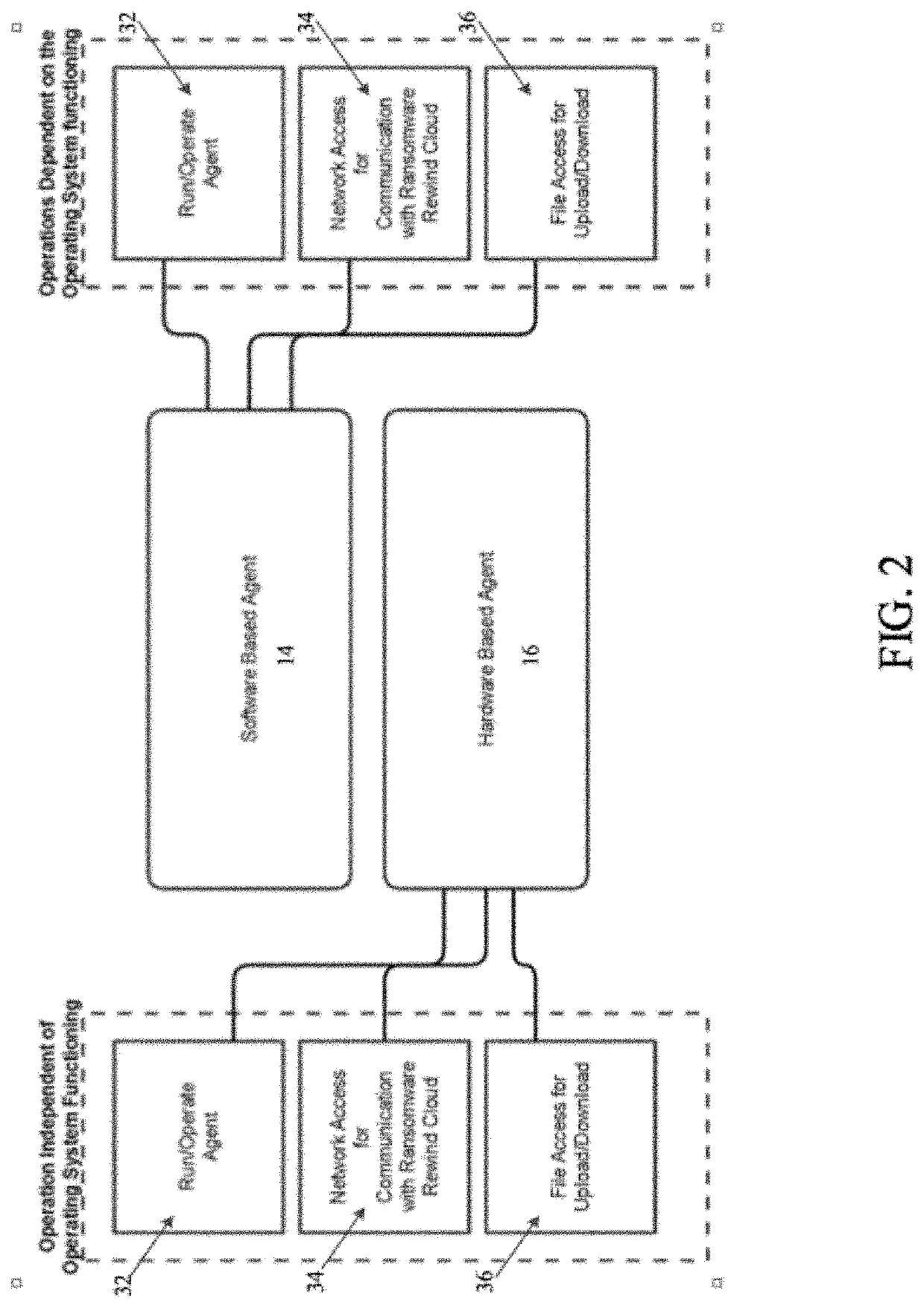
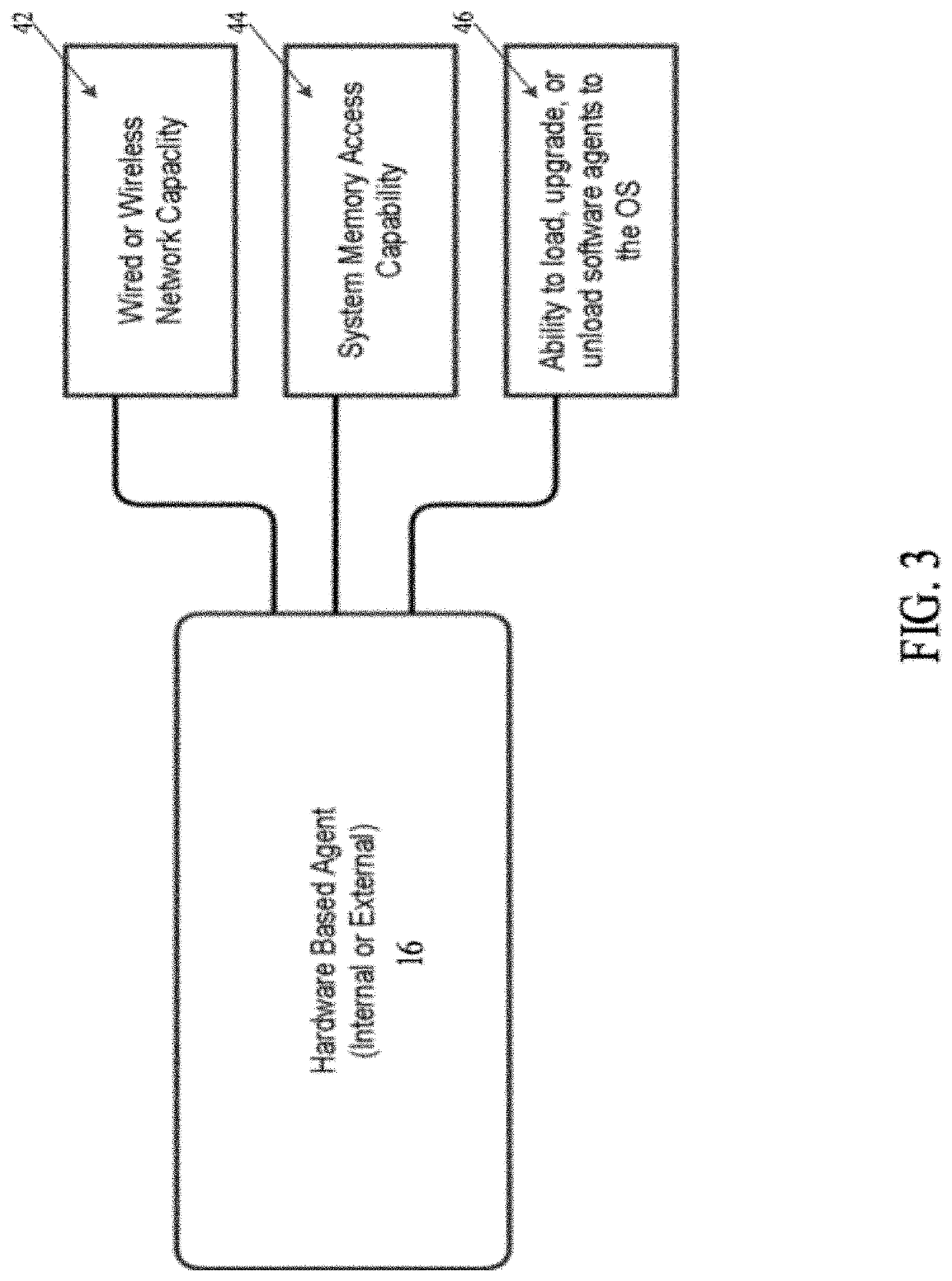
System and method for protecting a computing device of a target system against ransomware attacks employs a file system having a data structure used by an operating system of the computing device for managing files. A software or a hardware installed agent in the computing device performs one or more actions autonomously on behalf of the target system. The agent autonomously creates one or more trap files in the data structure of the filing system. A trap file is a file access to which indicates a probability of ransomware attack. The agent monitors access to the one or more trap files. Upon detecting access to a trap file, remedial action is performed by the target system against the probability of ransomware attack.
Owner:CYBER CRUCIBLE
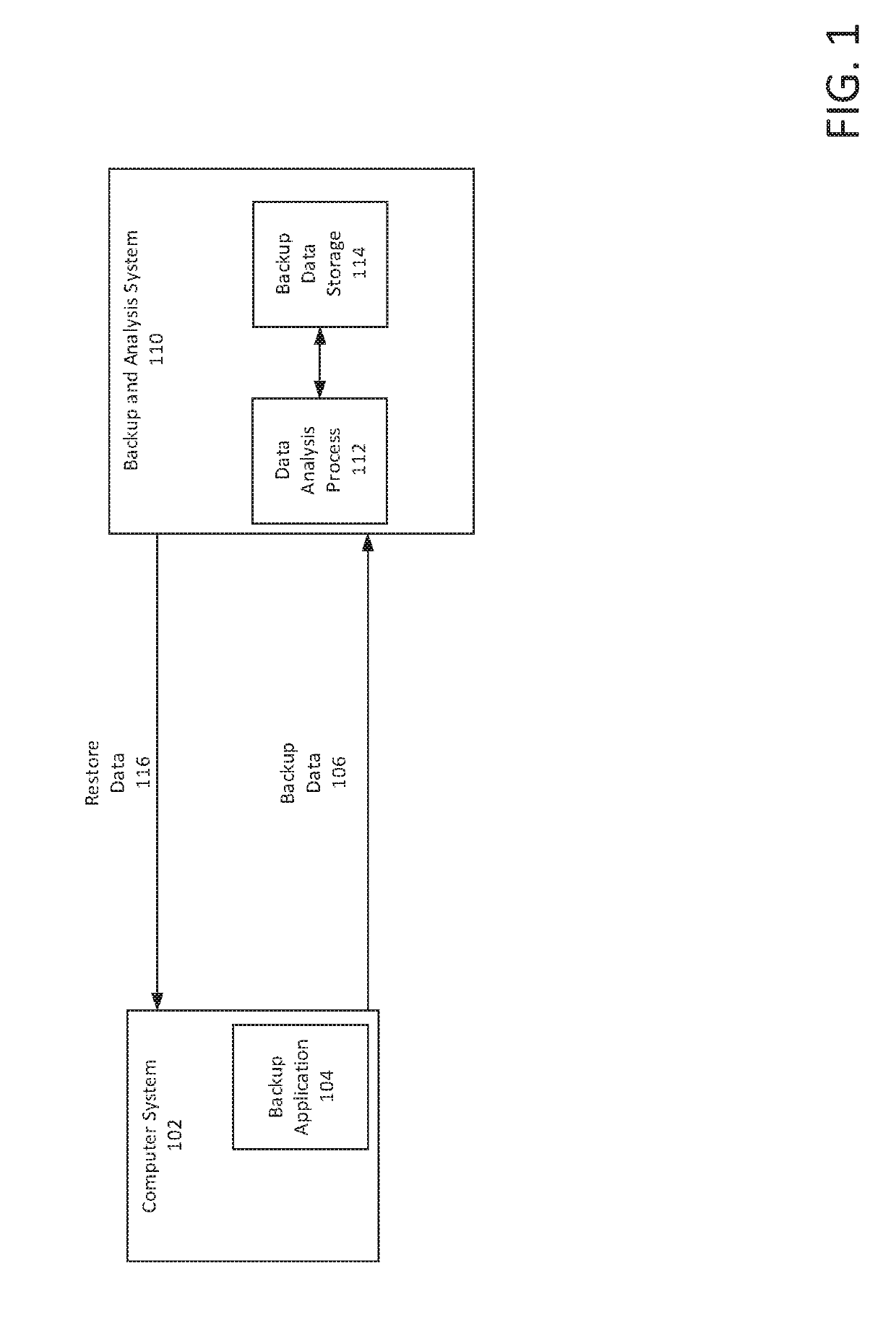
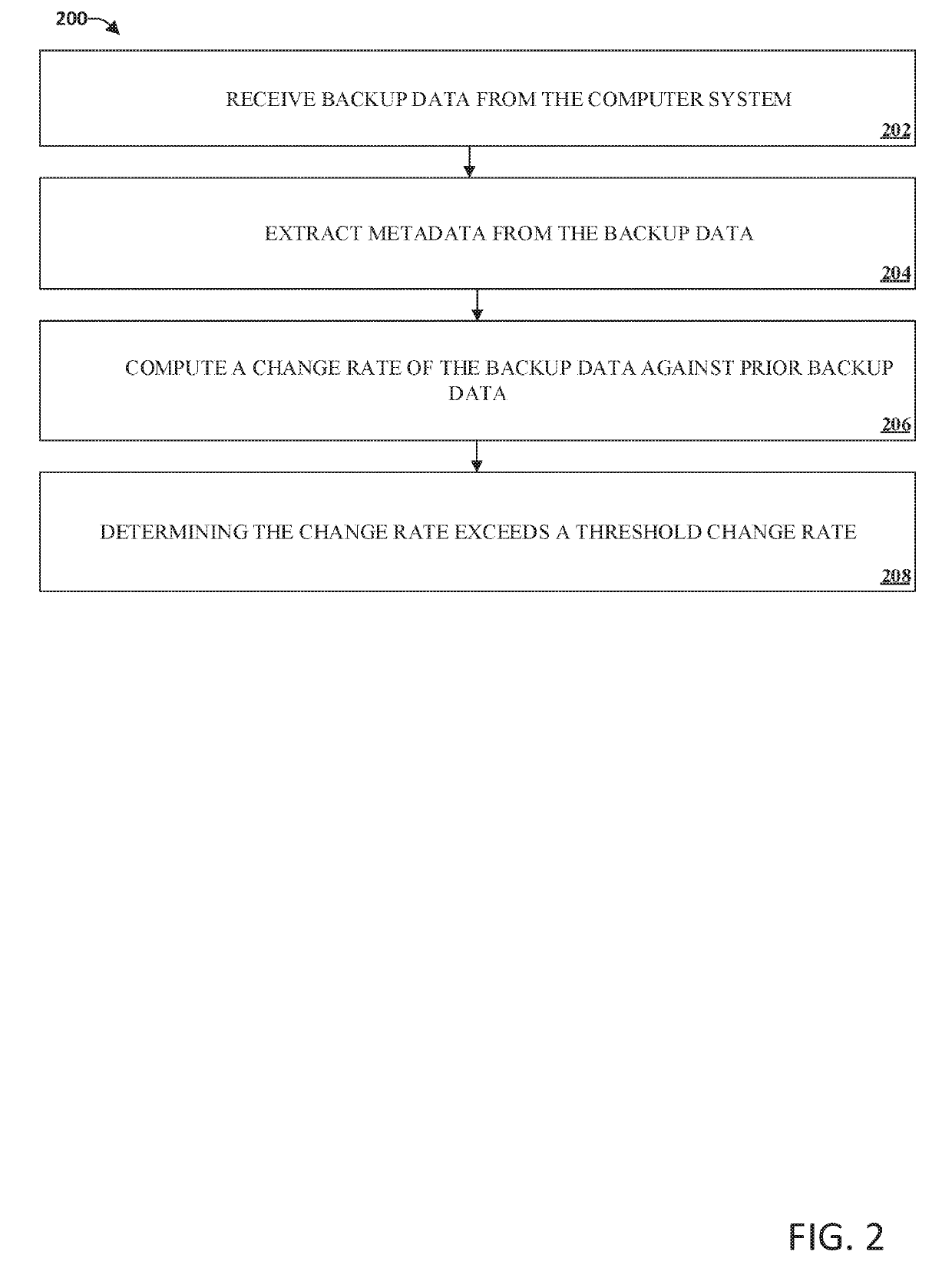
Detection of and recovery from ransomware in backup data
InactiveUS20190236274A1Improve data storage processImprove securityPlatform integrity maintainanceRedundant operation error correctionRansomwareComputerized system
Systems, methods, and computer-readable media can present improved detection of ransomware in a computer system. Embodiments can provide receiving backup data from the computer system. Metadata may be extracted from the backup data. Change rates of the backup metadata against prior backup data may be computed. Ransomware may be then detected by determining that the change rate exceeds a threshold change rate.
Owner:EMC IP HLDG CO LLC
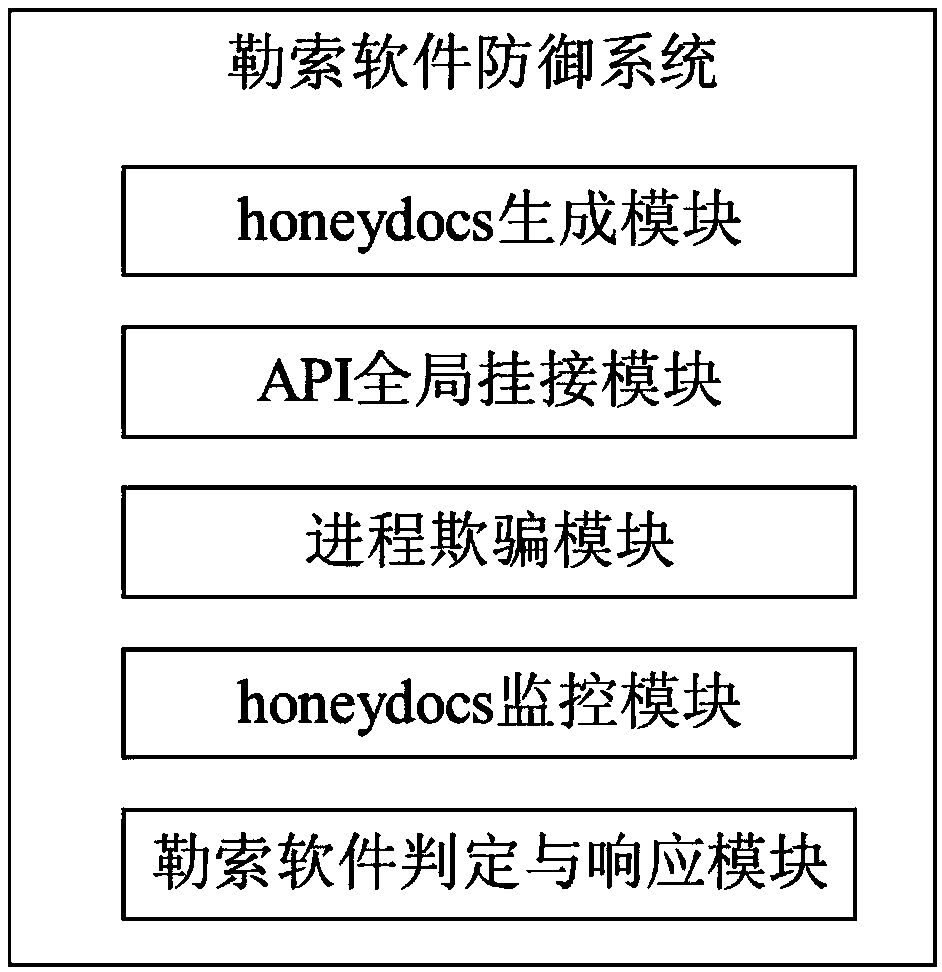
Ransomware defense method and system
ActiveCN107729752ANo normal file system effectsGuaranteed lossDigital data protectionPlatform integrity maintainanceRansomwareFinite segment
The invention relates to a ransomware defense method and system. The method comprises the following steps that 1, overall hooking is performed on an API which must be called by ransomware in the kernel mode or the user mode of an operation system; 2, finite segment cheating data is generated and deployed; 3, when a process is subjected to file traversal operation, a certain amount of cheating datais inserted into the traversal result and returned back to the process so as to cheat the process; 4, when the API obtained after overall hooking finds that the process operates the cheating data, whether the cheating data is abnormally changes or not is monitored so that whether the process is a malicious act of the ransomware or not is determined; 5, if the process is the malicious act of the ransomware, the process is ended and the user is informed. Under the condition of low consumption and zero loss, real-time detection and termination can be performed on the process of the ransomware, and users' and enterprises' data and property safety are protected.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
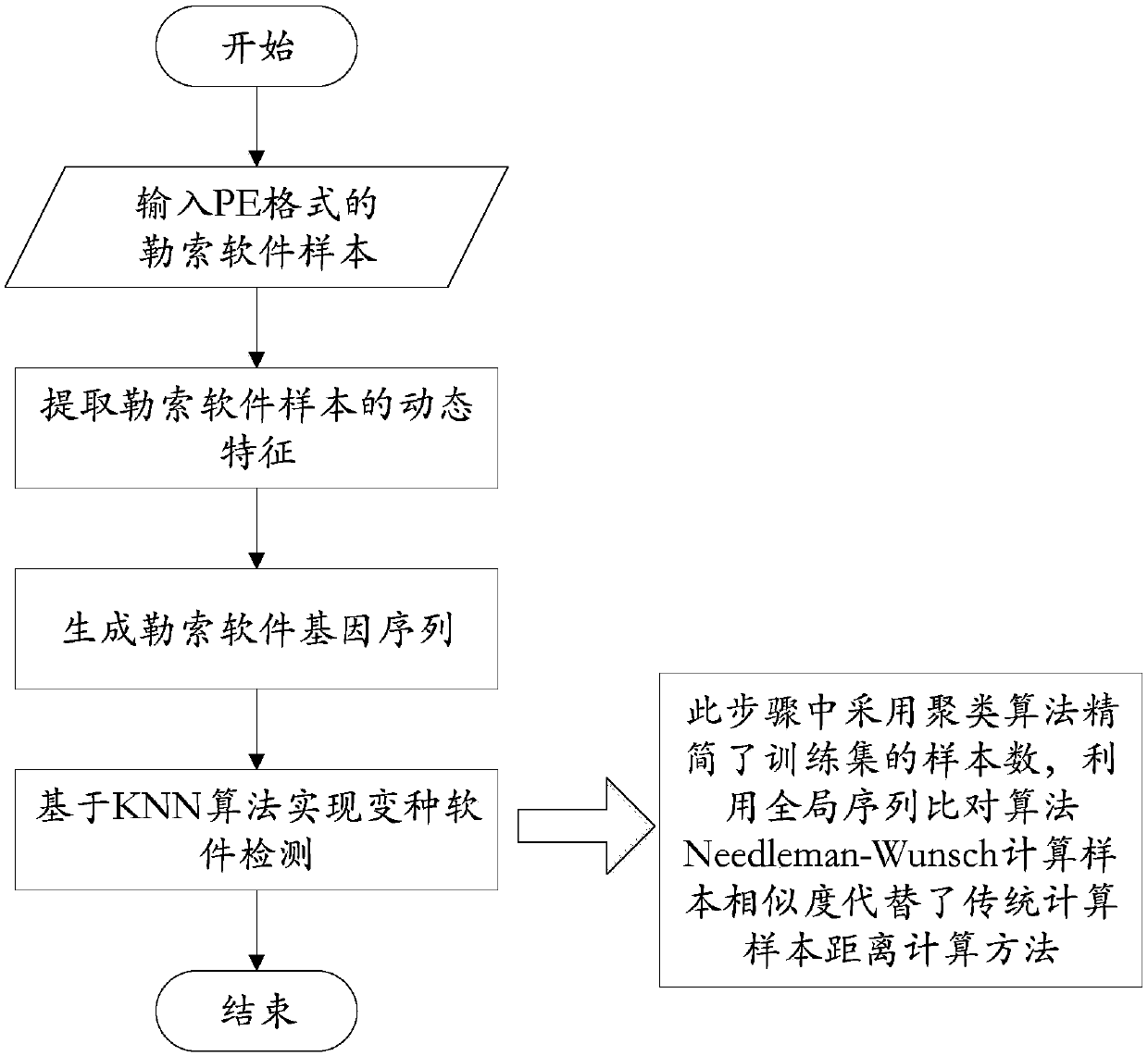
Ransomware variation detection method based on sequence alignment algorithm
ActiveCN107679403AAchieve exact alignmentReduced sample sizeCharacter and pattern recognitionPlatform integrity maintainanceSequence alignment algorithmSequence processing
The invention provides a ransomware variation detection method based on a sequence alignment algorithm. The method comprises the specific steps of inputting a ransomware sample, extracting a sample feature sequence, processing the sample feature sequence into a gene sequence, and detecting a ransomware variation. The step of variation detection specifically comprises the sub-steps of clustering each gene sequence in a sample set, extracting clustering result information to acquire various ransomware families; using the sequence alignment algorithm Needleman-Wunsch to compute similarity betweena sample to be detected and a class cluster center sample of various ransomware families, screening out clusters with the similarity more than a preset threshold, and using the screened clusters to form a new ransomware training sample set; determining the ransomware family class to which the sample to be detected belongs b using the newly screened training sample set in combination with the sequence alignment algorithm and a KNN classification algorithm to achieve variation detection. According to the method, the purpose of quickly achieving ransomware variation detection is achieved by combining the sequence alignment algorithm with the existing classification algorithm.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com