Systems and methods for ransomware detection and mitigation
a ransomware and detection system technology, applied in the field of cybersecurity technology, can solve problems such as improper cryptovariable reuse, shortening the time of encryption, and affecting the implementation of encryption algorithms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
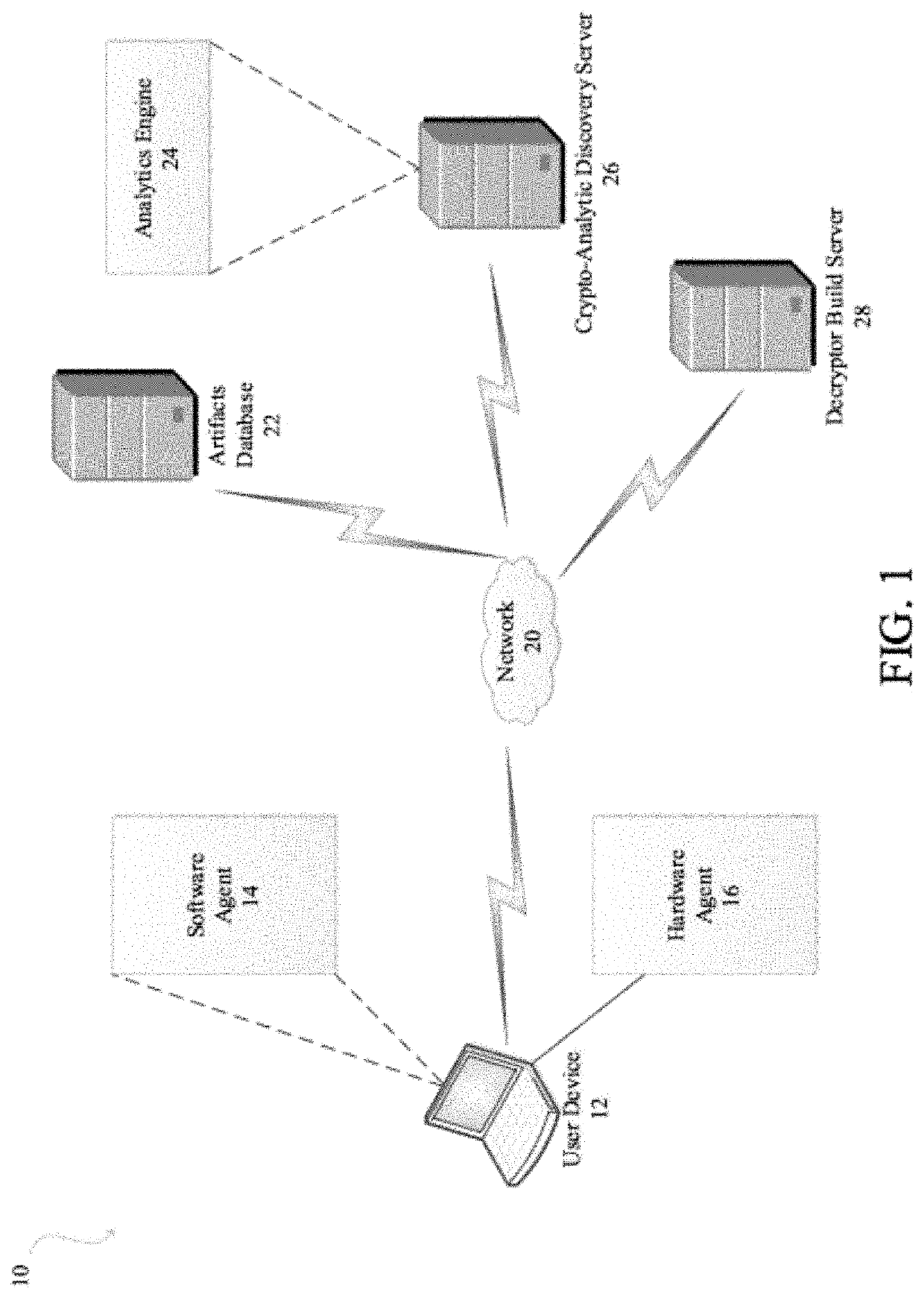
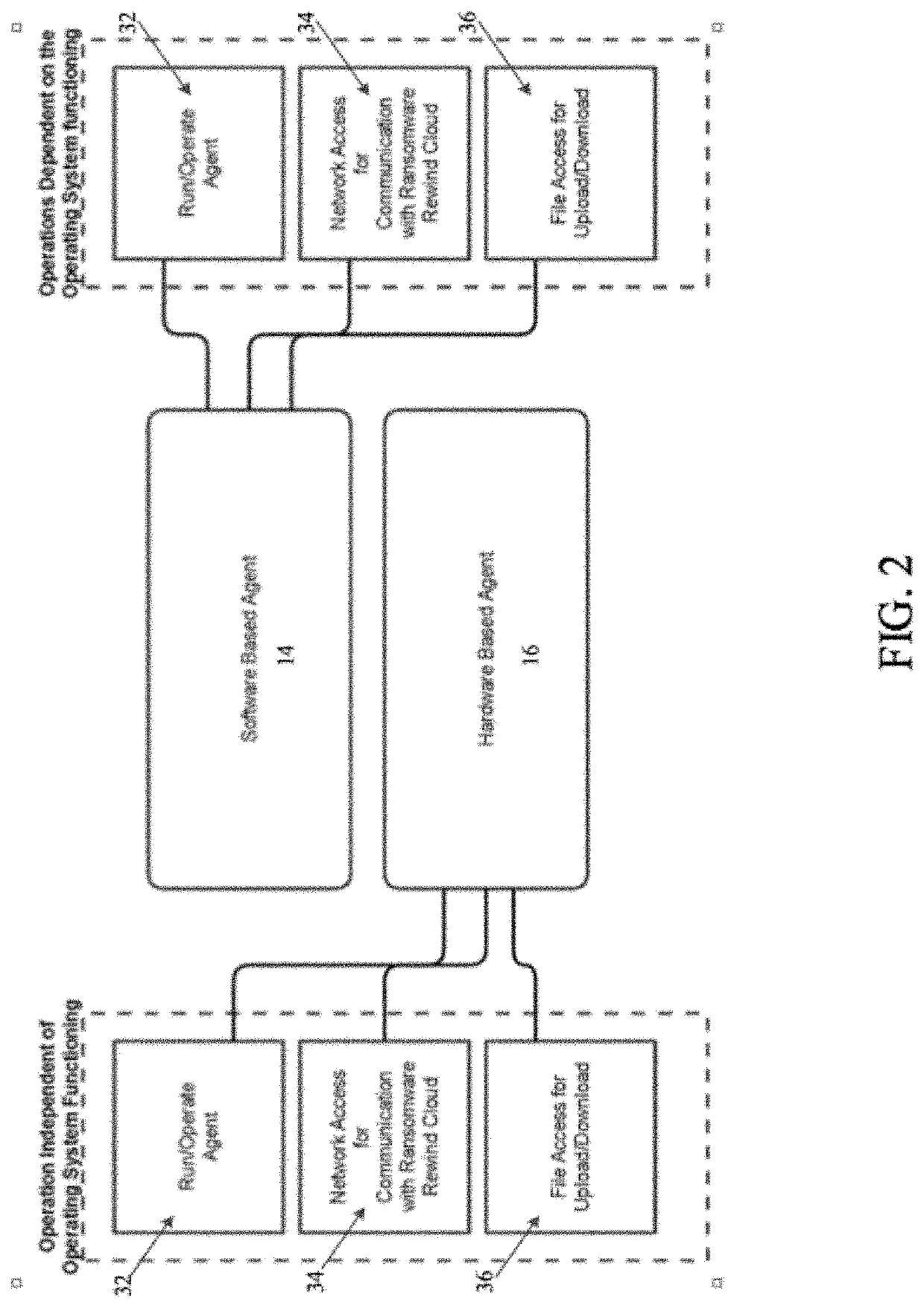
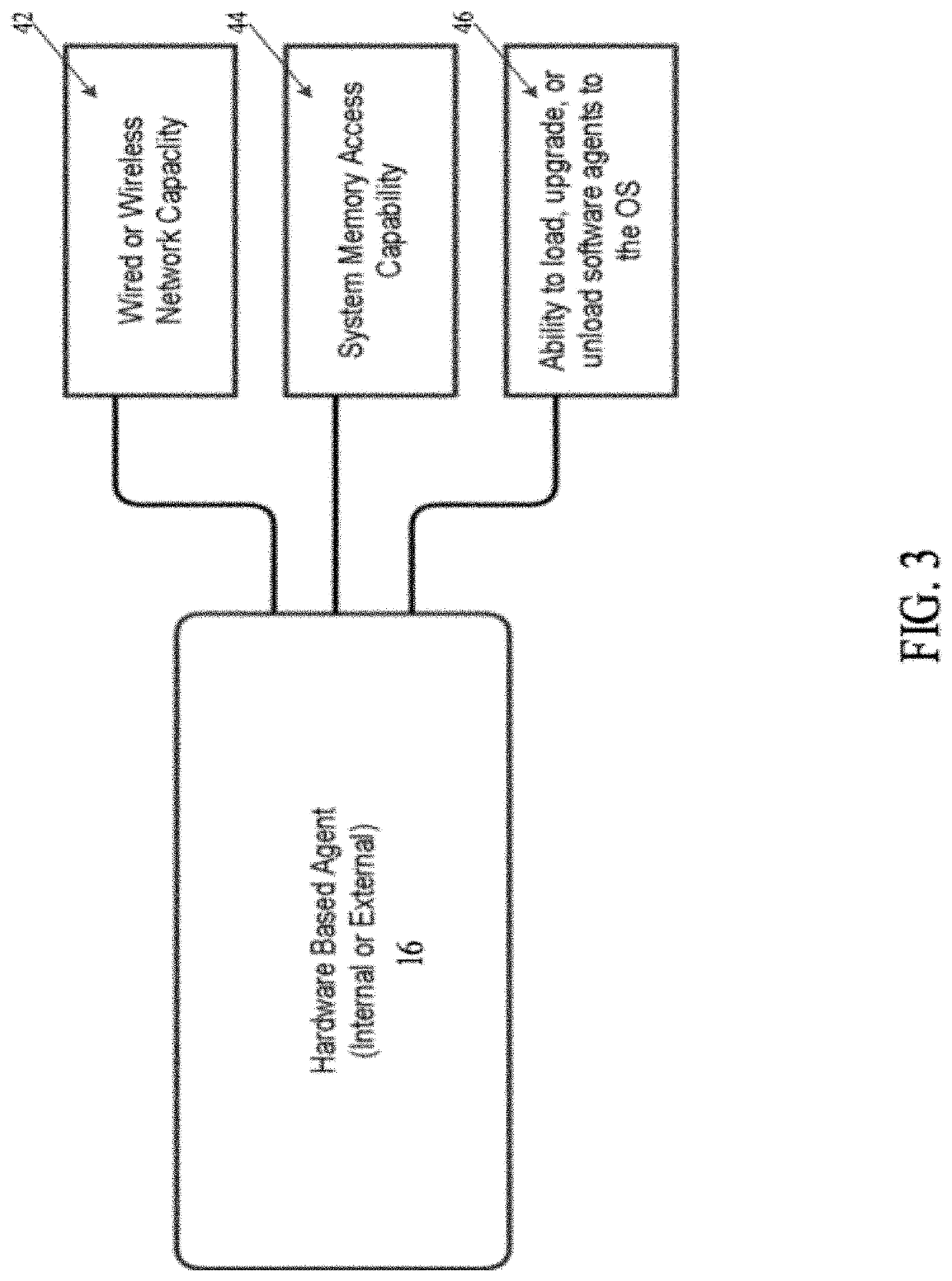
[0034]The present invention relates to systems and methods for ransomware detection and protection, as described in detail below in connection with FIGS. 1-11.
[0035]A part of the ransomware behavior detection strategy is the use of monitored artifacts placed on the system. One such artifact is a trap file positioned within a filing system used by an operating system of a computing device, including a processing node or machine, a client, a server or a stand-alone workstation. Access to a trap file indicates a probability of a ransomware attack. These artifacts are placed by position, content, and quality to enable a very high probability of both detection of ransomware activity and behavior of the ransomware activity, and a very low probability of users encountering the artifacts.
[0036]In one embodiment, the present invention relates to systems and methods for automatically discovering the start of a ransomware attack based on access to trap files and defeating an attacker's encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com