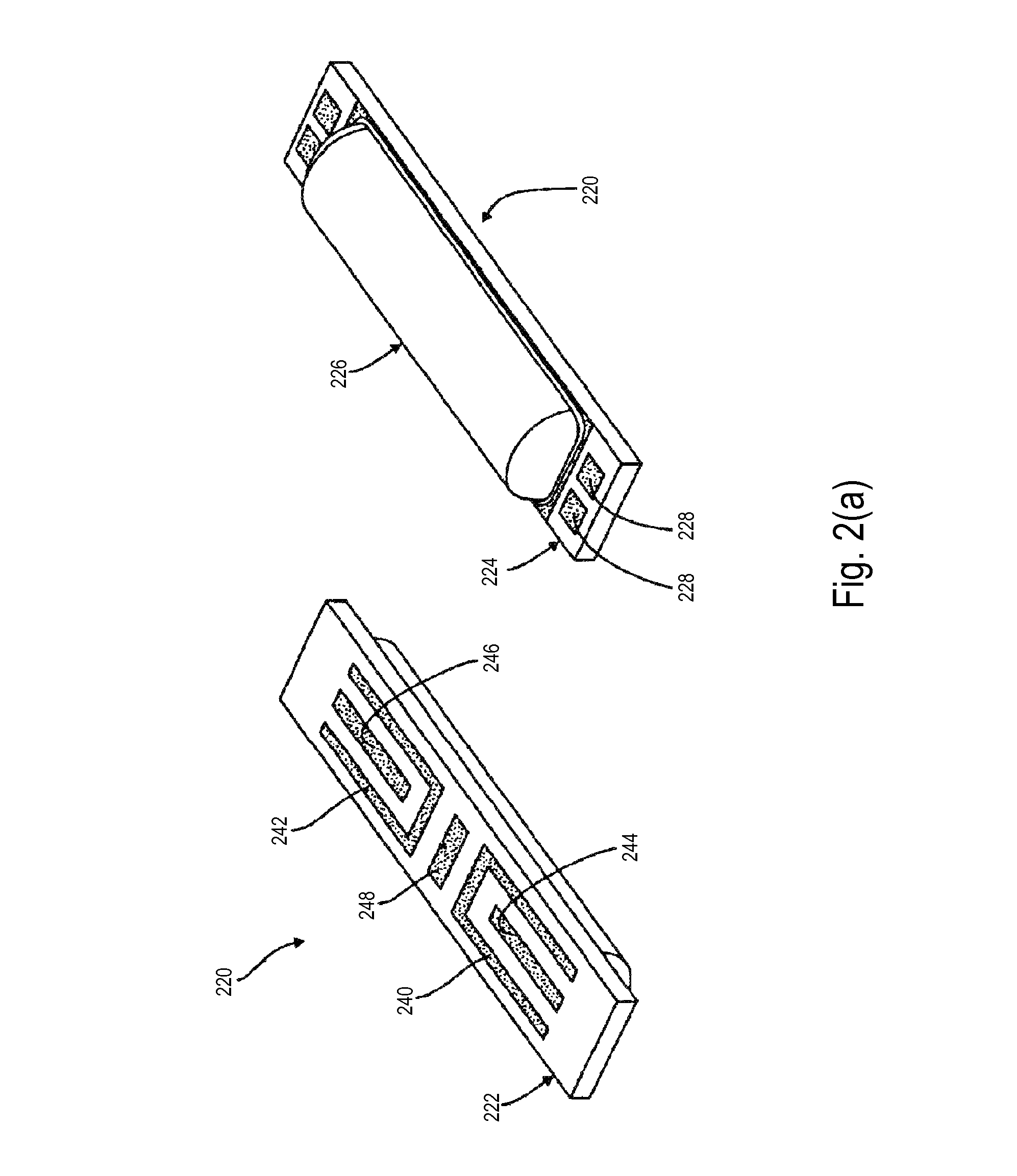
Patents
Literature
701 results about "Remedial action" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A remedial action is a change made to a nonconforming product or service to address the deficiency. Rework and repair are generally the remedial actions taken on products, while services usually require additional services to be performed to ensure satisfaction.
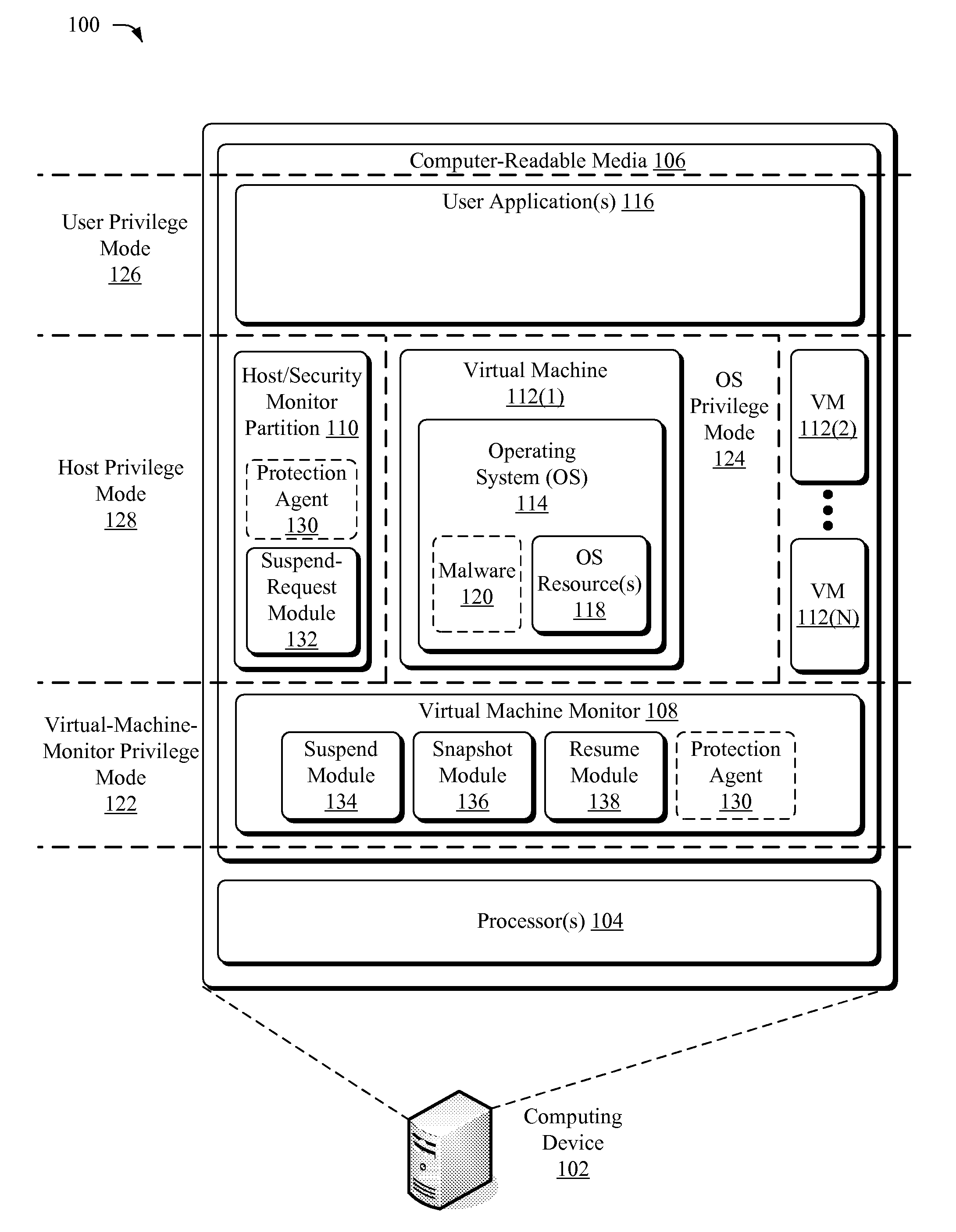
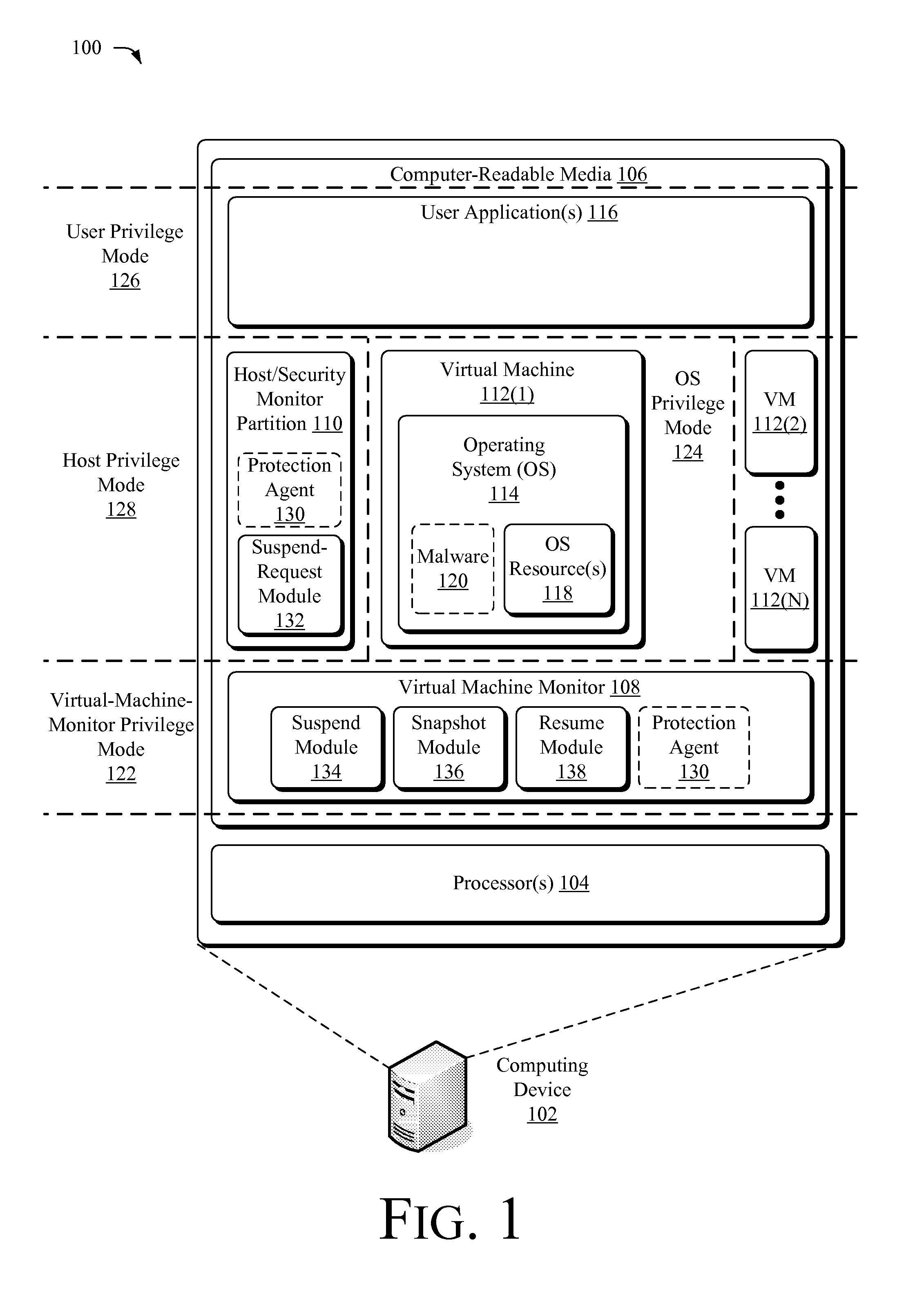
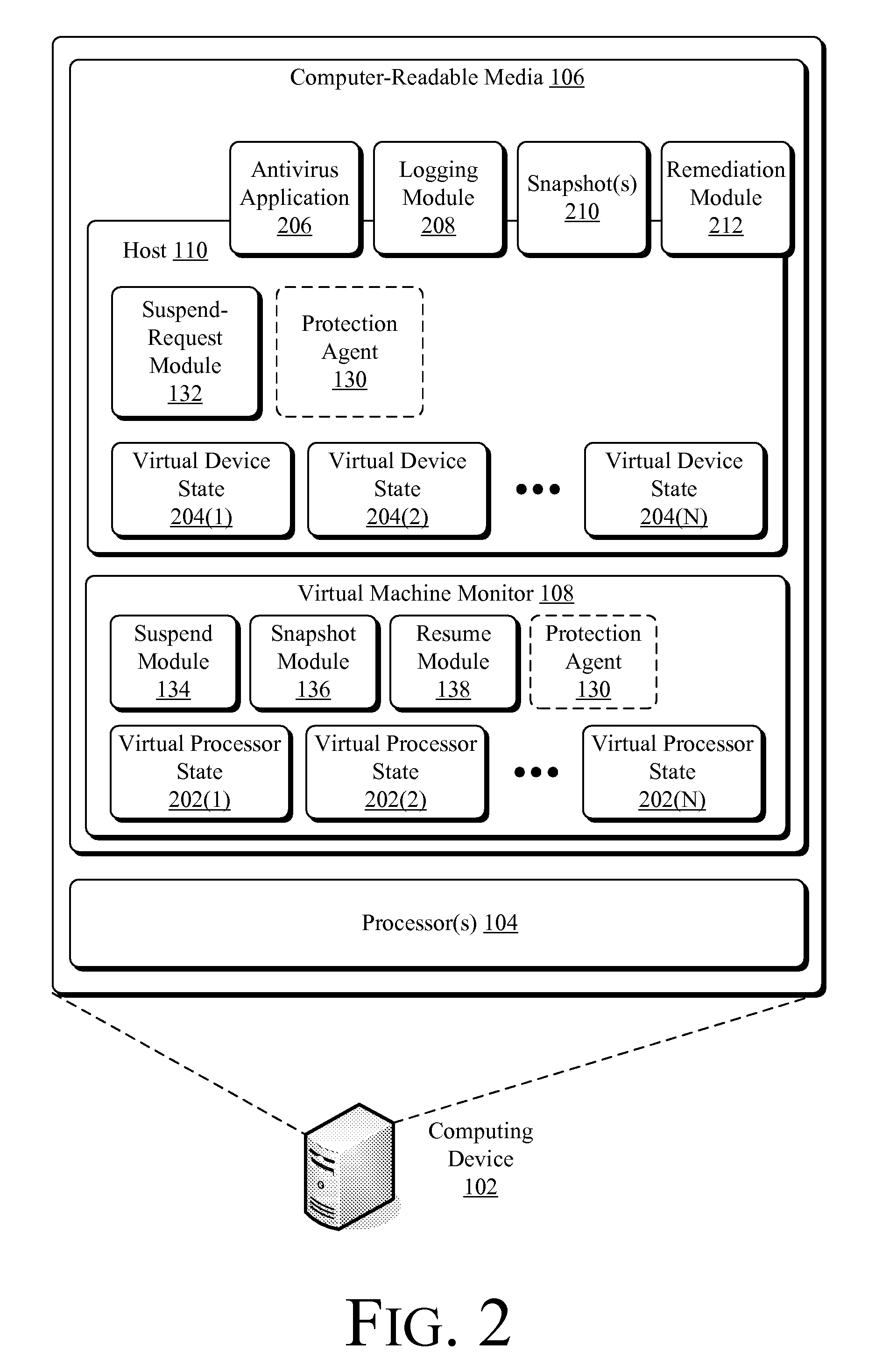
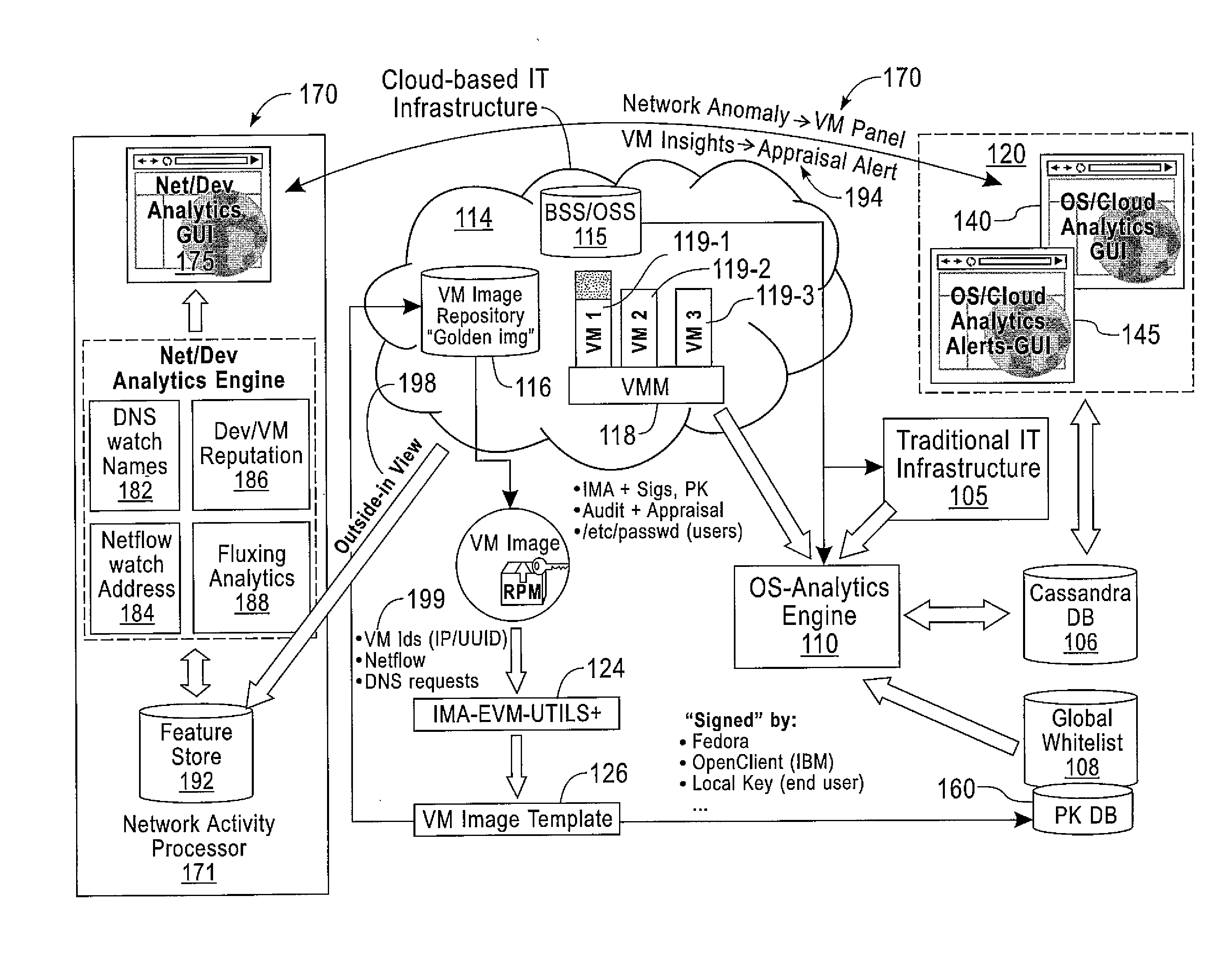
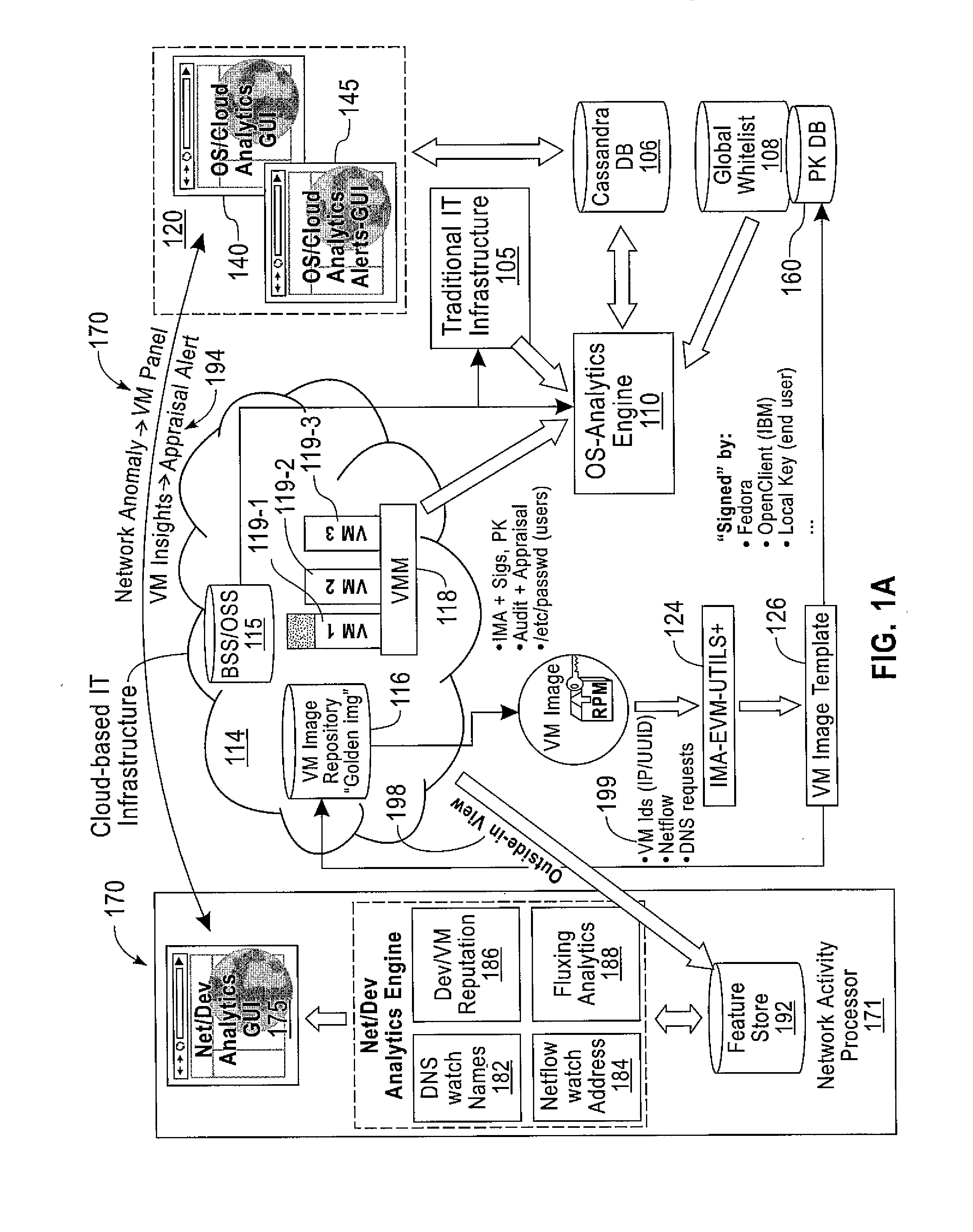
Suspending a Running Operating System to Enable Security Scanning
InactiveUS20090007100A1Well formedUser identity/authority verificationPlatform integrity maintainanceOperational systemRemedial action
Techniques described herein enable virtualizing a processor into one or more virtual machines and suspending an operating system of one of the virtual machines from outside of the operating system environment. Once suspended, these techniques capture a snapshot of the virtual machine to determine a presence of malware. This snapshot may also be used to determine whether an unauthorized change has occurred within contents of the virtual machine. Remedial action may occur responsive to determining a presence of malware or an unauthorized change.
Owner:MICROSOFT TECH LICENSING LLC
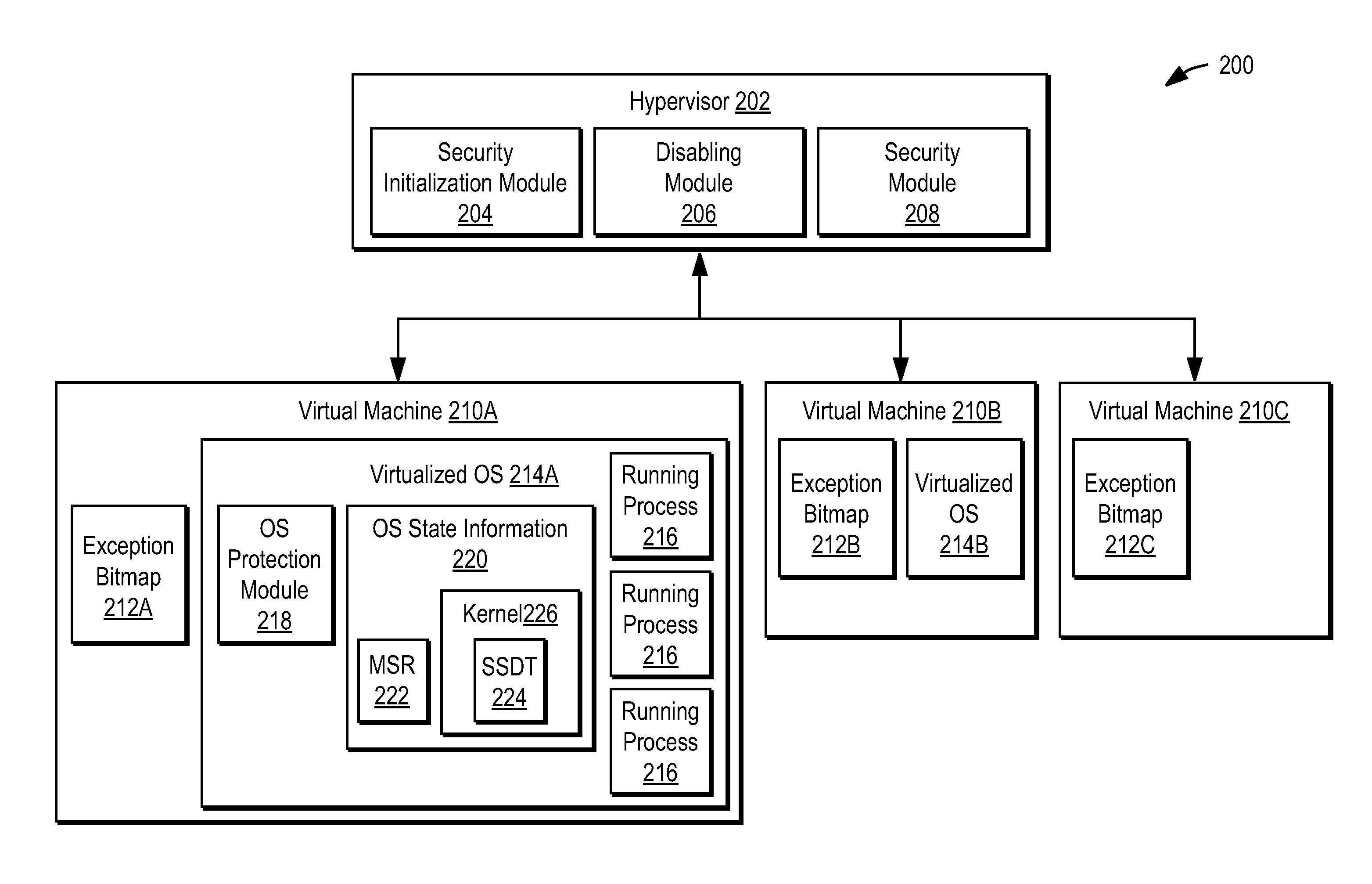
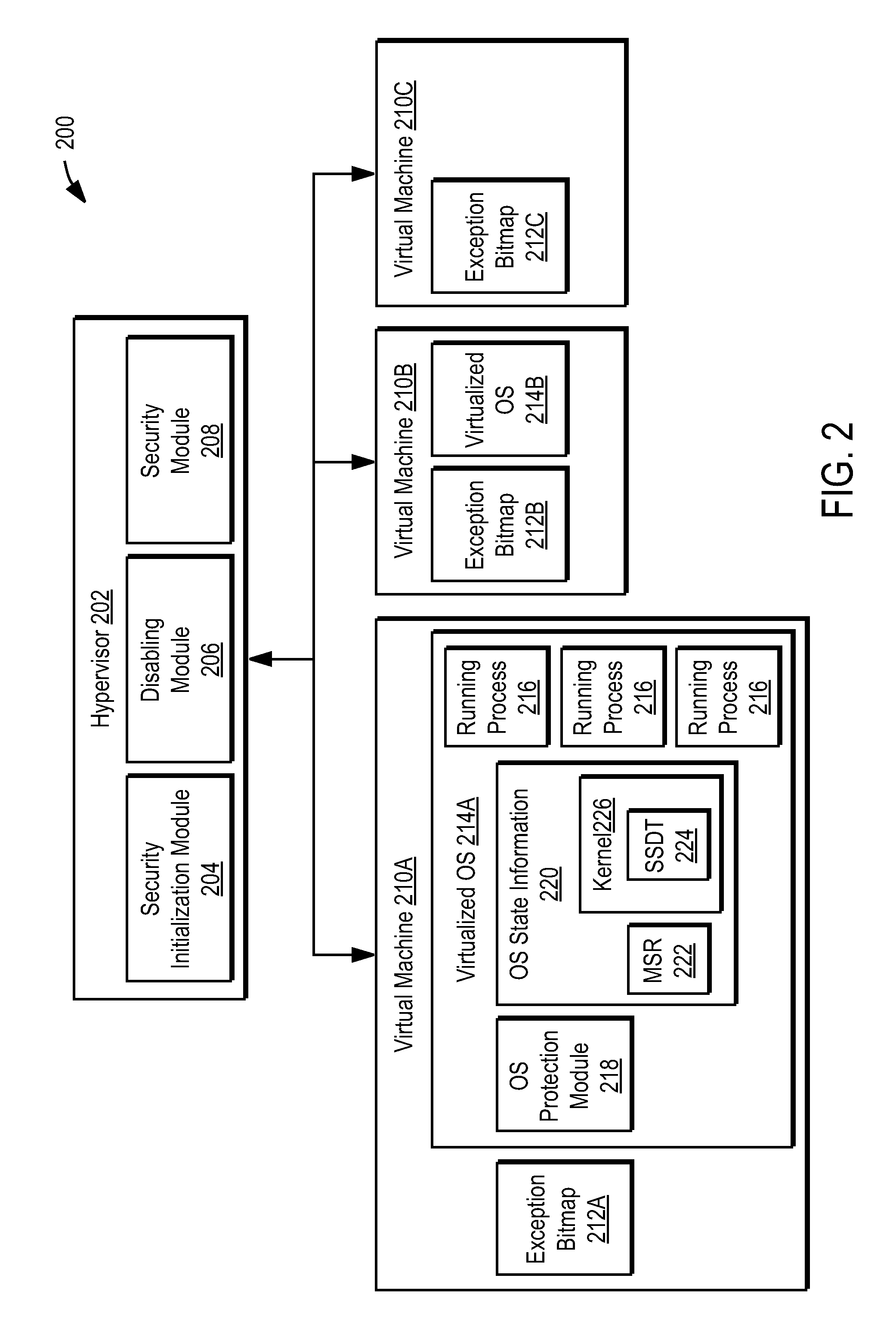
Using a hypervisor to provide computer security
ActiveUS7996836B1Provide securityMemory loss protectionError detection/correctionRemedial actionVirtual machine
A computer includes a virtual machine controlled by a hypervisor. The virtual machine runs a virtualized operating system with running processes. A security initialization module sets the state in the virtual machine to pass execution from the virtual machine to the hypervisor responsive to a process making a system call in the virtualized operating system. Responsive to execution being passed from the virtual machine to the hypervisor, a security module analyzes the process making the system call to determine whether it poses a security threat. If a security threat is found, the security module takes remedial action to address the threat.
Owner:NORTONLIFELOCK INC
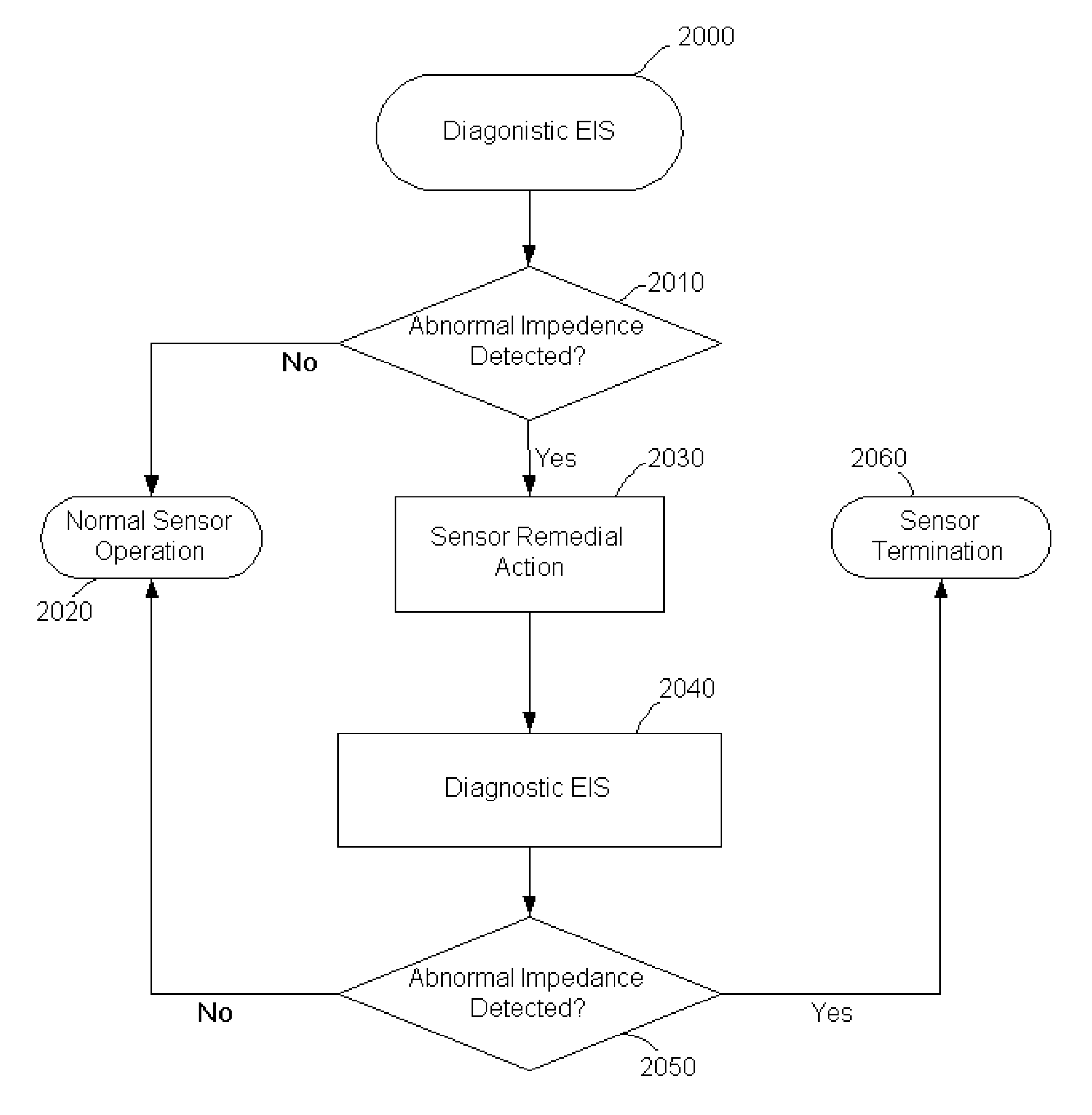
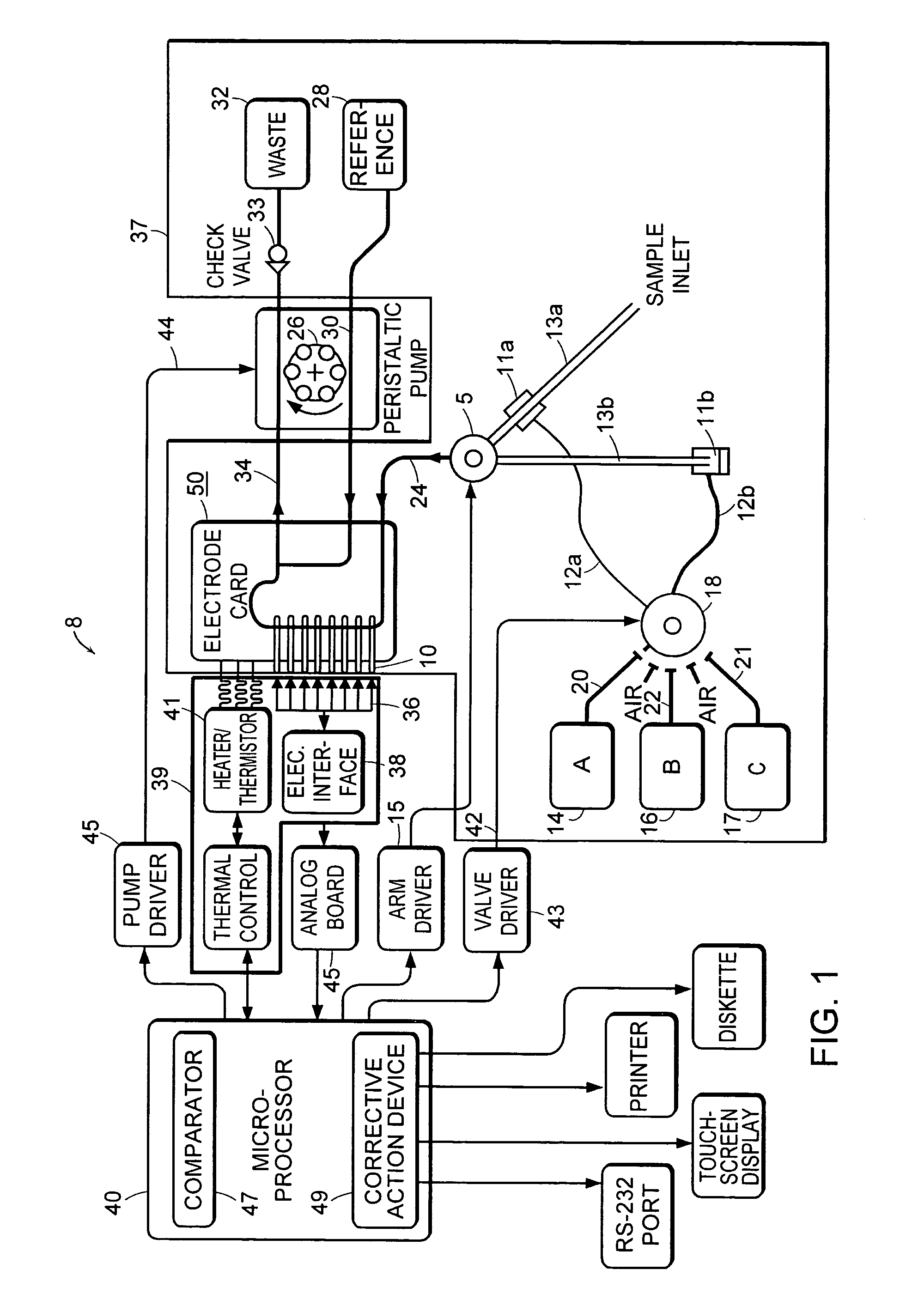
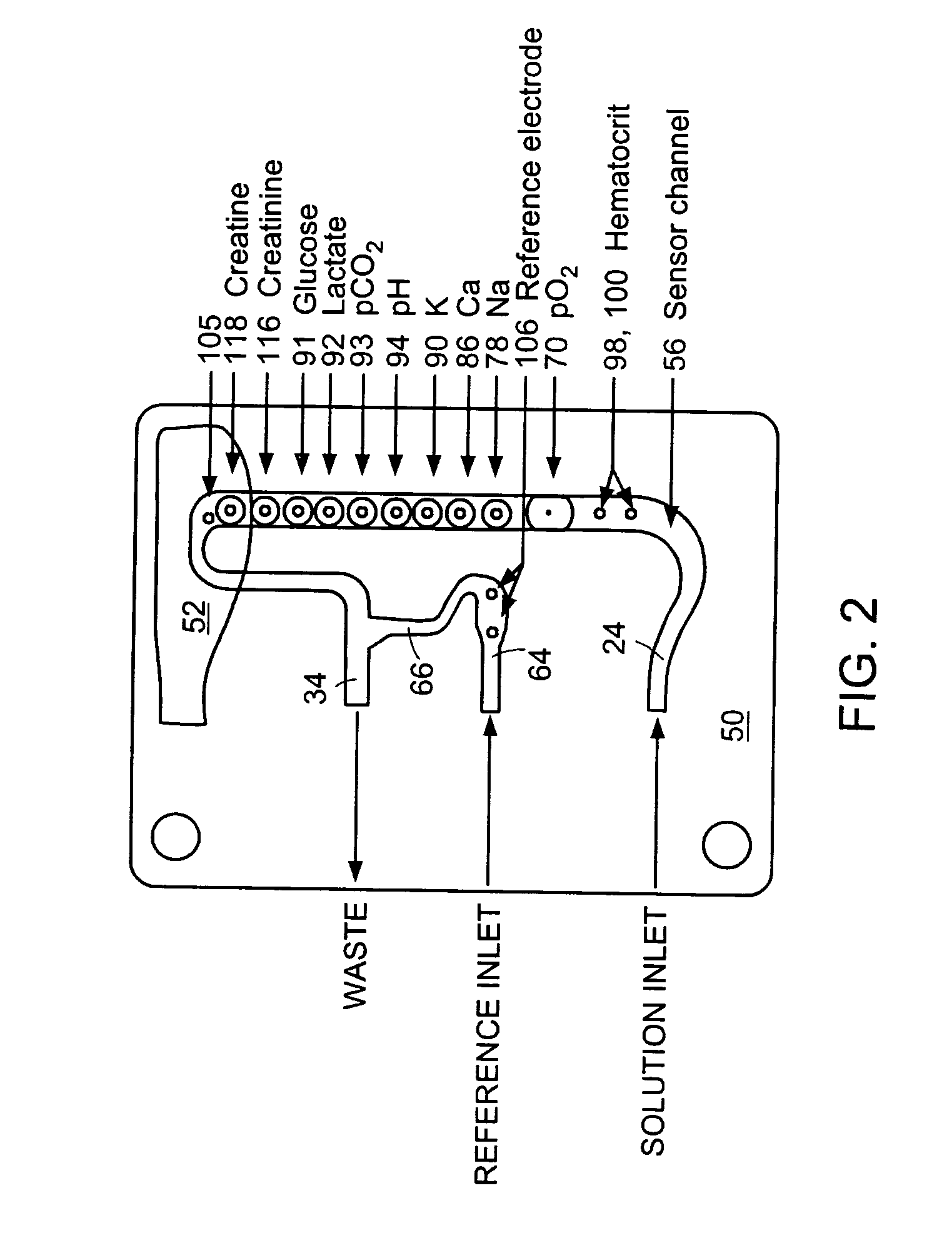
Method and system for remedying sensor malfunctions detected by electrochemical impedance spectroscopy
A method and system that enables a user to maintain a sensor in real time. The present invention involves performing a diagnostic Electrochemical Impedance Spectroscopy (EIS) procedure to measure sensor impedance value in order to determine if the sensor is operating at an optimal level. If the sensor is not operating at an optimal level, the present invention may further involve performing a sensor remedial action. The sensor remedial action involves reversing the DC voltage being applied between the working electrode and the reference electrode. The reversed DC voltage may be coupled with an AC voltage to extend its reach.
Owner:MEDTRONIC MIMIMED INC
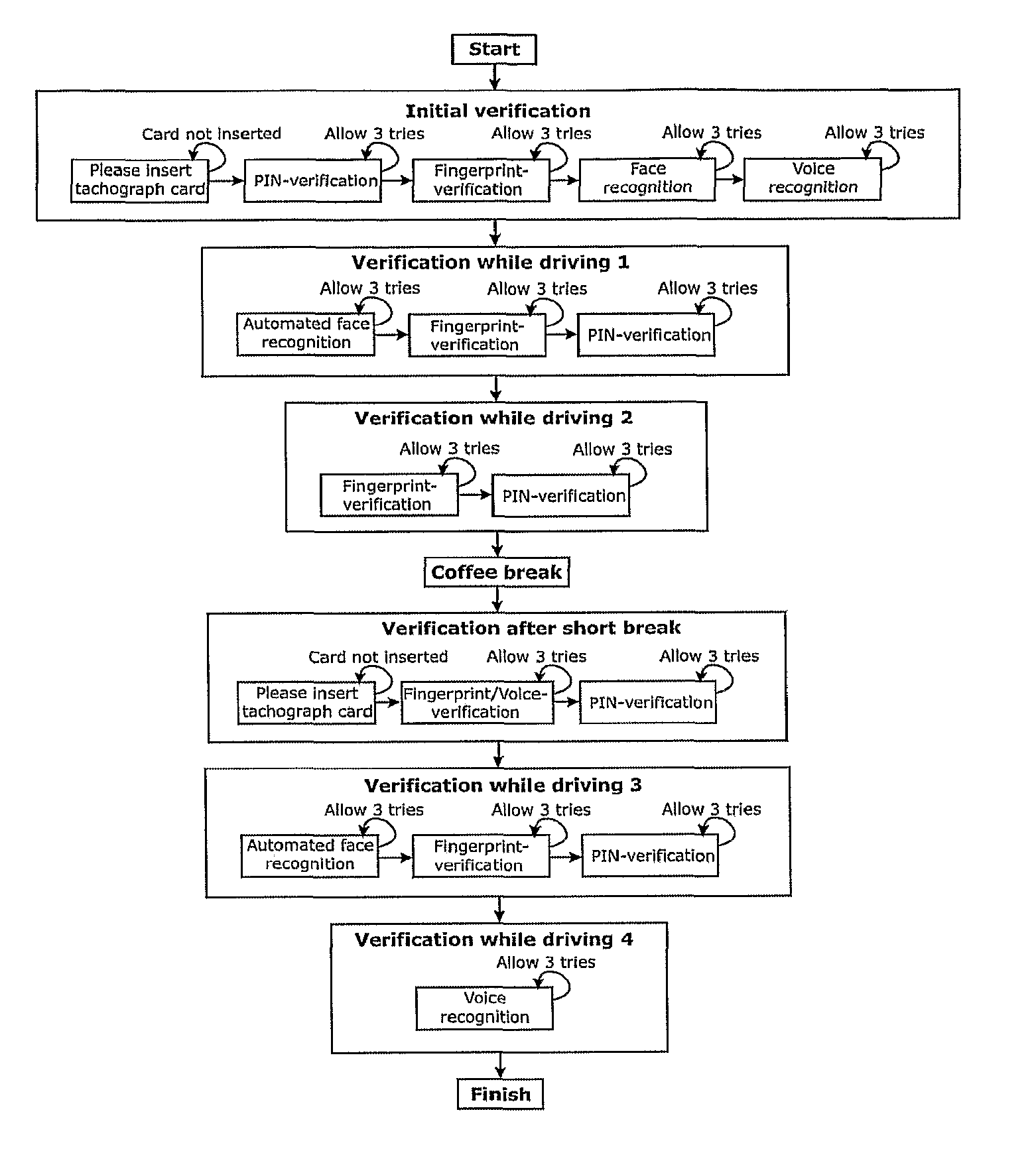
Method for Performing Driver Identity Verification
InactiveUS20080252412A1Improve security levelElectric signal transmission systemsMultiple keys/algorithms usageDriver/operatorRemedial action
Method for assuring that the operator of a vehicle is an authorized driver, the method including utilizing an onboard, multi-mode driver identification system to ascertain whether an operator is an authorized driver. A first driver identification procedure is performed on a present operator of the vehicle and determining whether the present operator is an authorized or unauthorized driver of the vehicle. A second driver identification procedure is performed on the present operator of the vehicle and determining whether the present operator is an authorized or unauthorized driver of the vehicle, wherein the first and second driver identification procedures are performed with a time interval therebetween, the time interval being dependent upon the nature of the work being performed by the operator. A remedial measure is exercised to avert potentially negative impact when the present operator of the vehicle is determined to be an unauthorized driver based upon at least one of the performed identification procedures.
Owner:VOLVO TECH
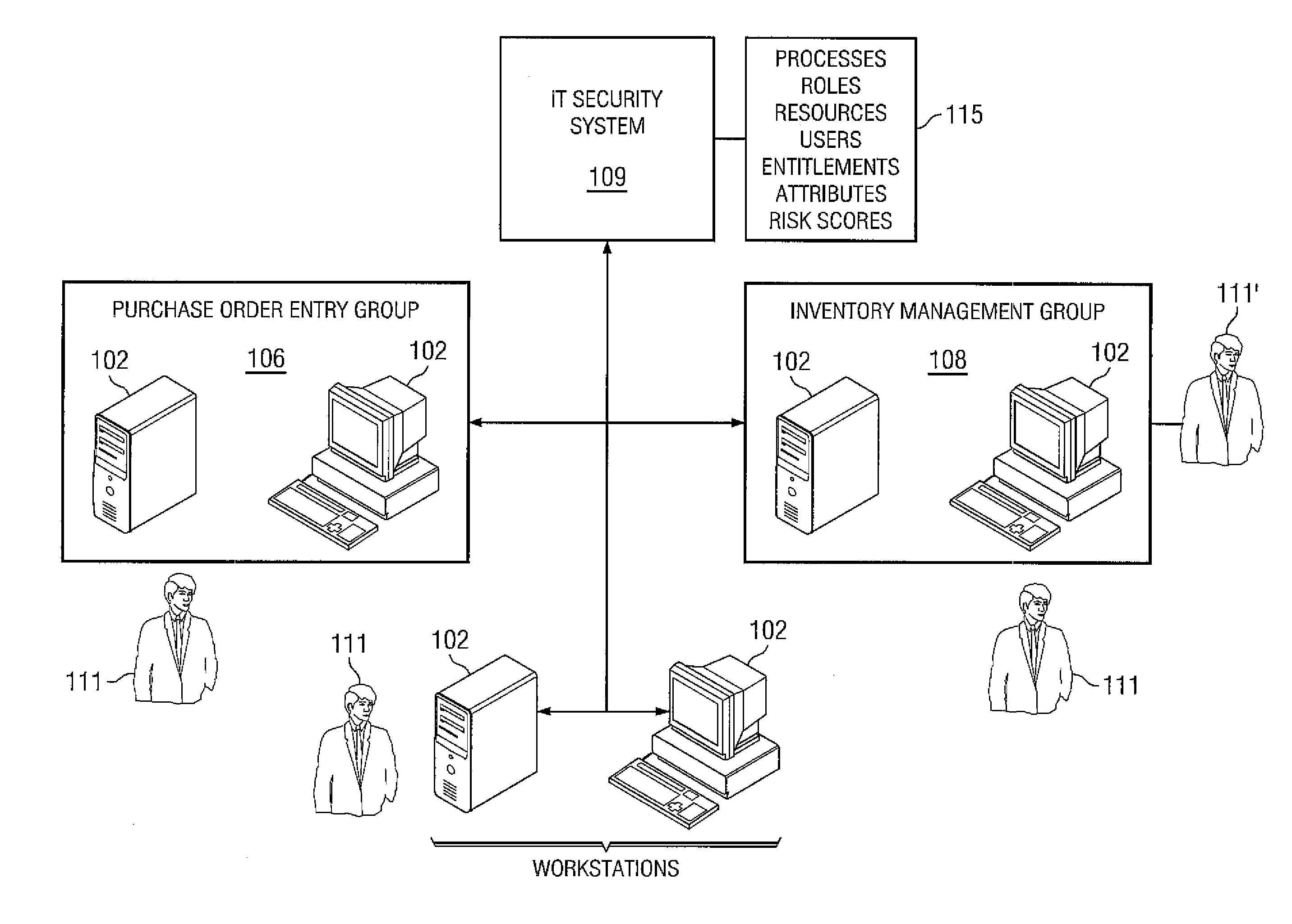
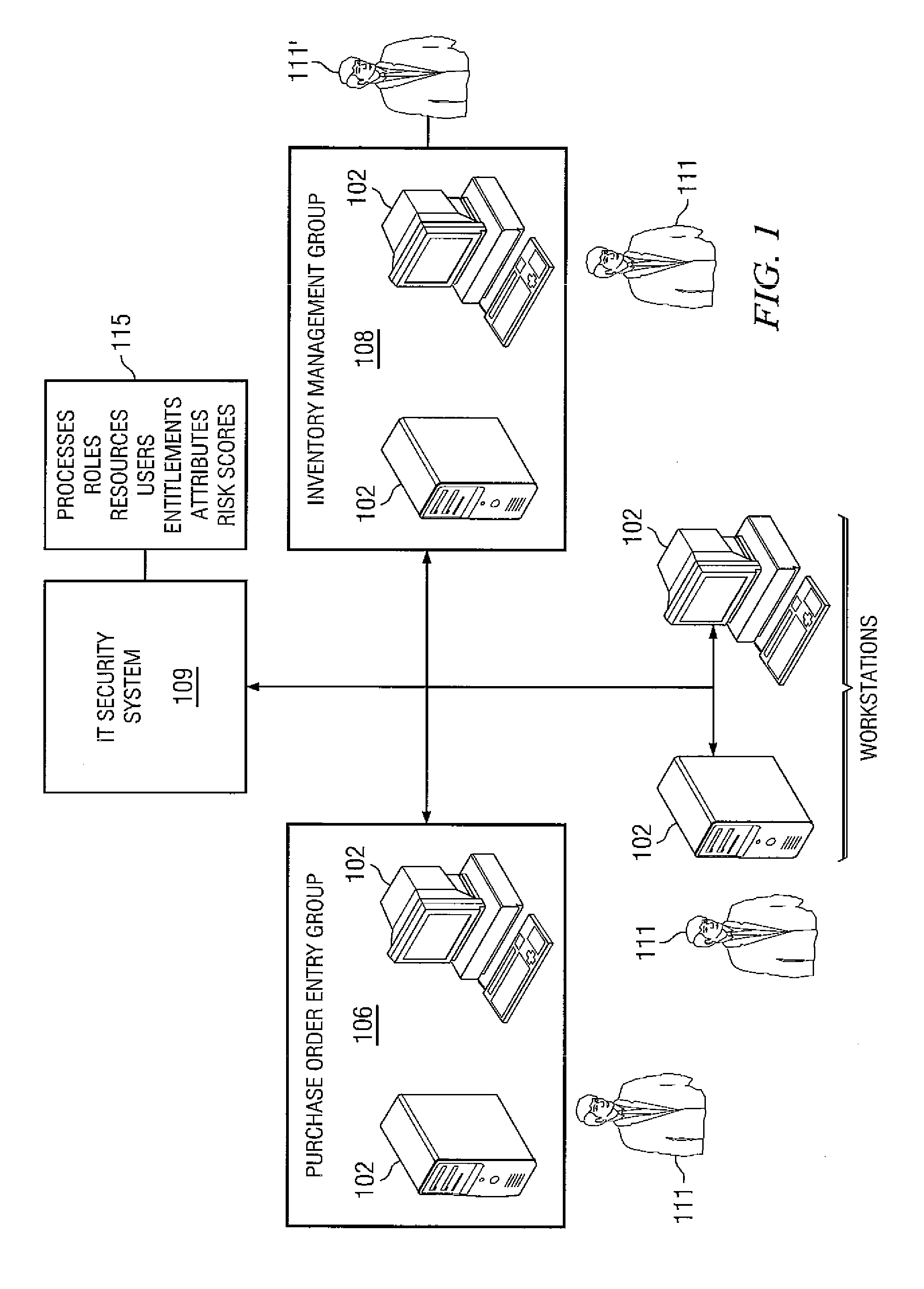
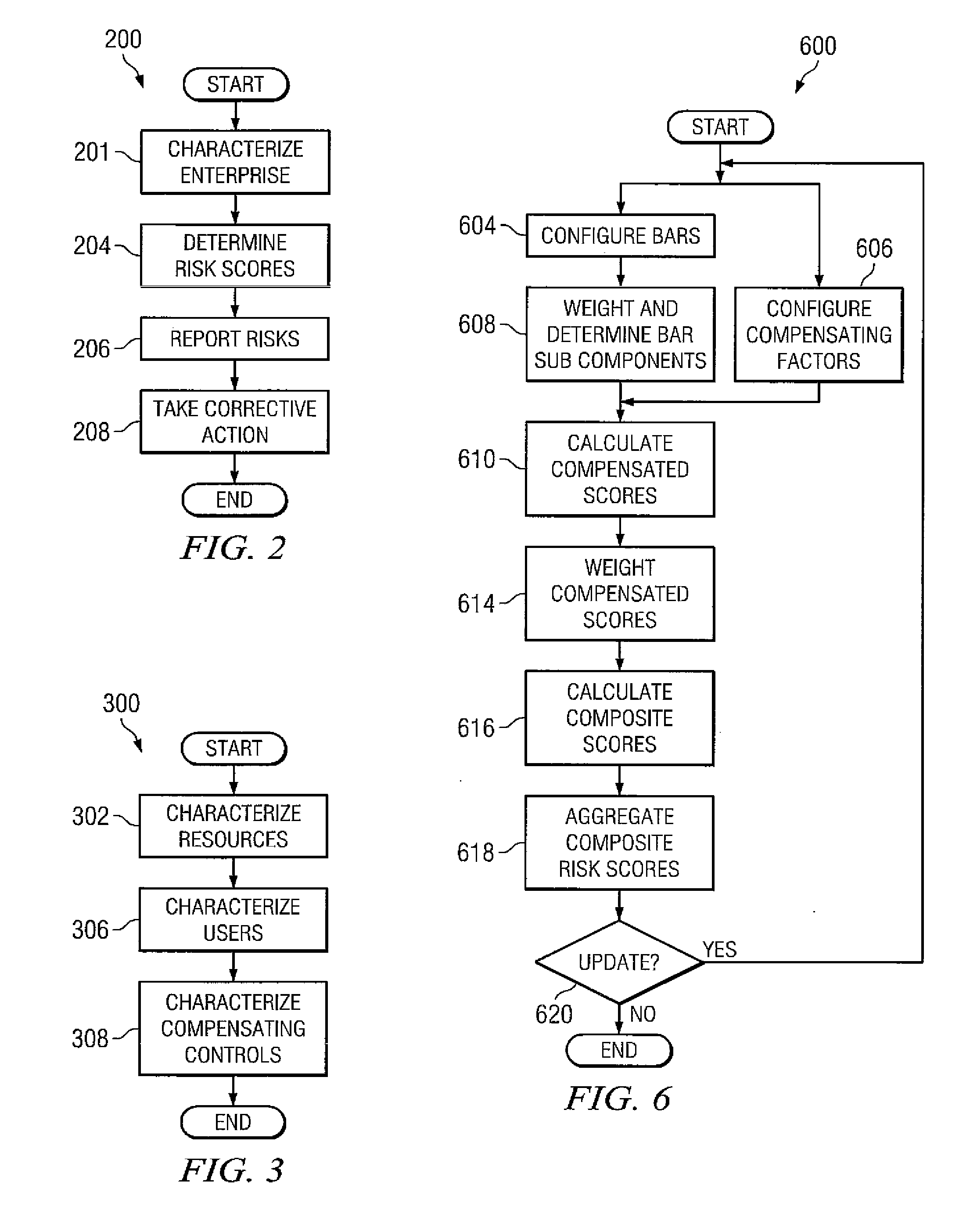
System and method for user access risk scoring
InactiveUS20080288330A1Access risk can be quickly and easilyReduced access riskFinanceResourcesRemedial actionScoring system
Systems and methods for measuring access risk associated with an enterprise having at least one resource accessible by at least one user with at least one entitlement to access the resource. Some embodiments implement a method of identifying the resources, users, and entitlements and associating access risk scores with the entitlements. The method can include combining the access risk scores associated with each user to form composite access risks scores and outputting the composite access risk scores. In some embodiments, the user with the highest composite access risk score can be identified and remedial action taken. The highest access risk user of some embodiments may be a department, a division, a subsidiary, or an organization. The method can occur in real time and an administrator can be alerted to changes in entitlements. Access risk scores can be adjusted for compensating controls and personal factors and attributes of the users.
Owner:SAILPOINT TECH INC
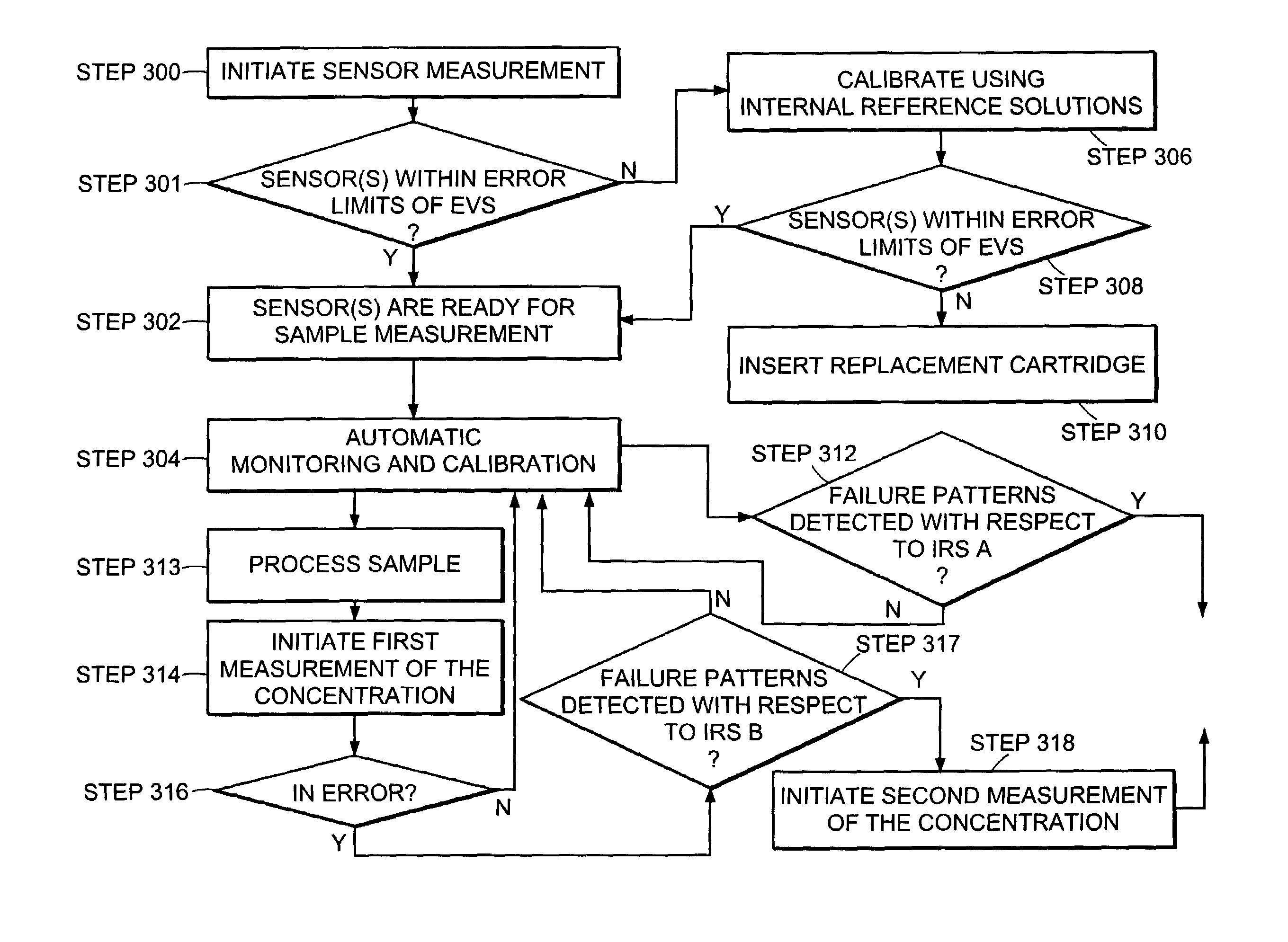
Automated system for continuously and automatically calibrating electrochemical sensors
An electrochemical sensor system that continuously monitors and calibrates the sensors included in the system. The invention also includes a method for determining failure patterns of a sensor and incorporating into an electrochemical sensor system the ability to recognize the failure pattern and initiate remedial action.
Owner:INSTR LAB
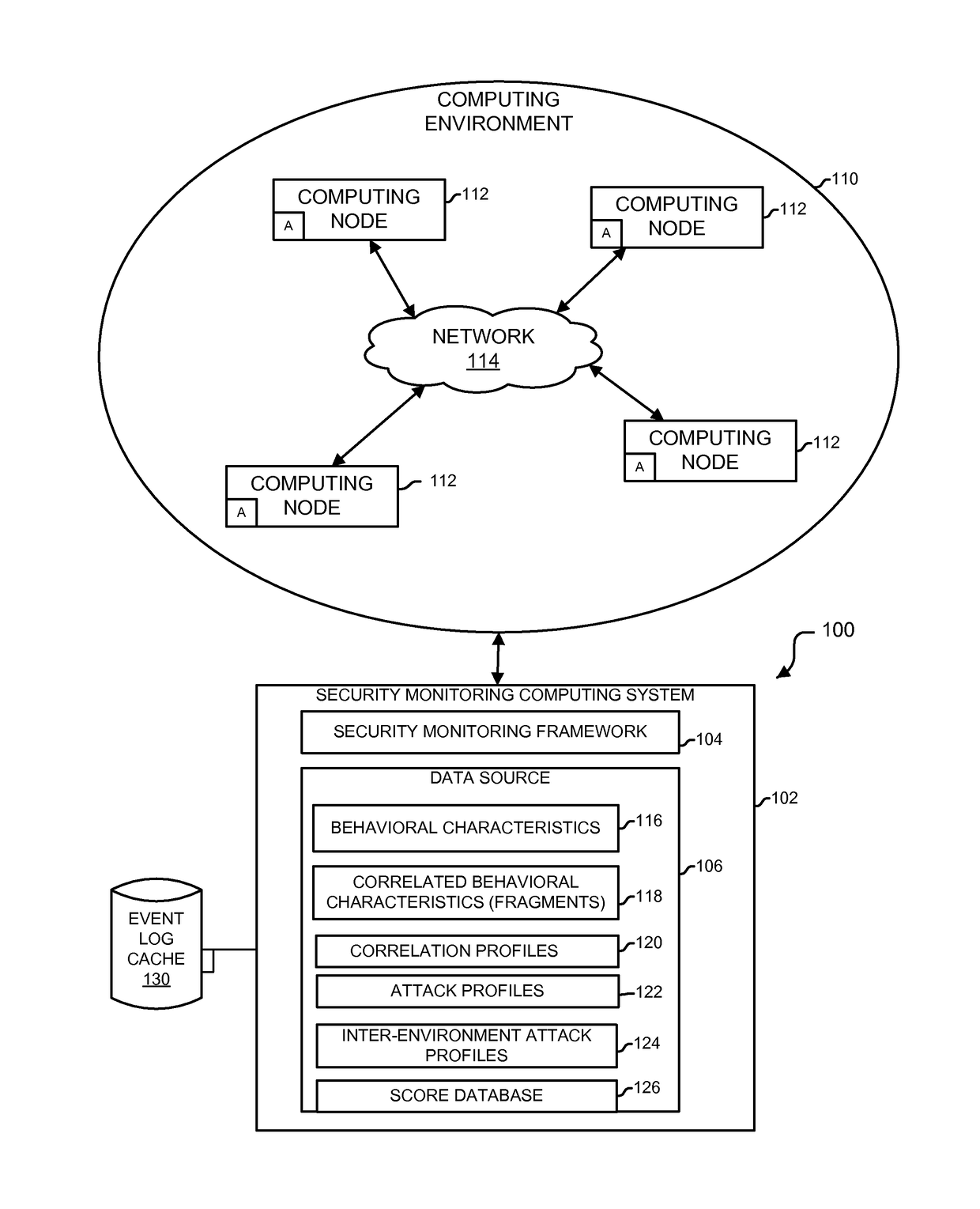
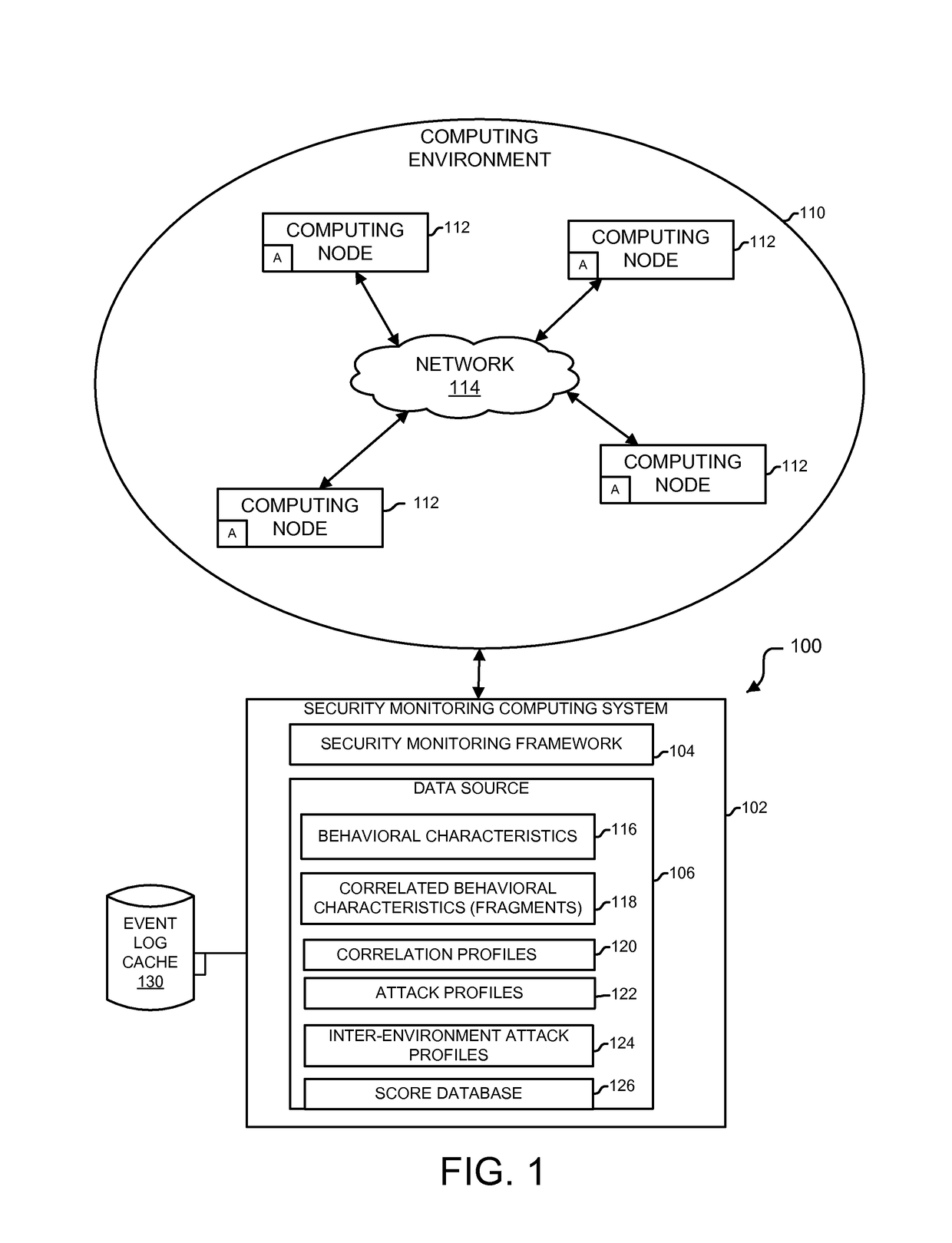
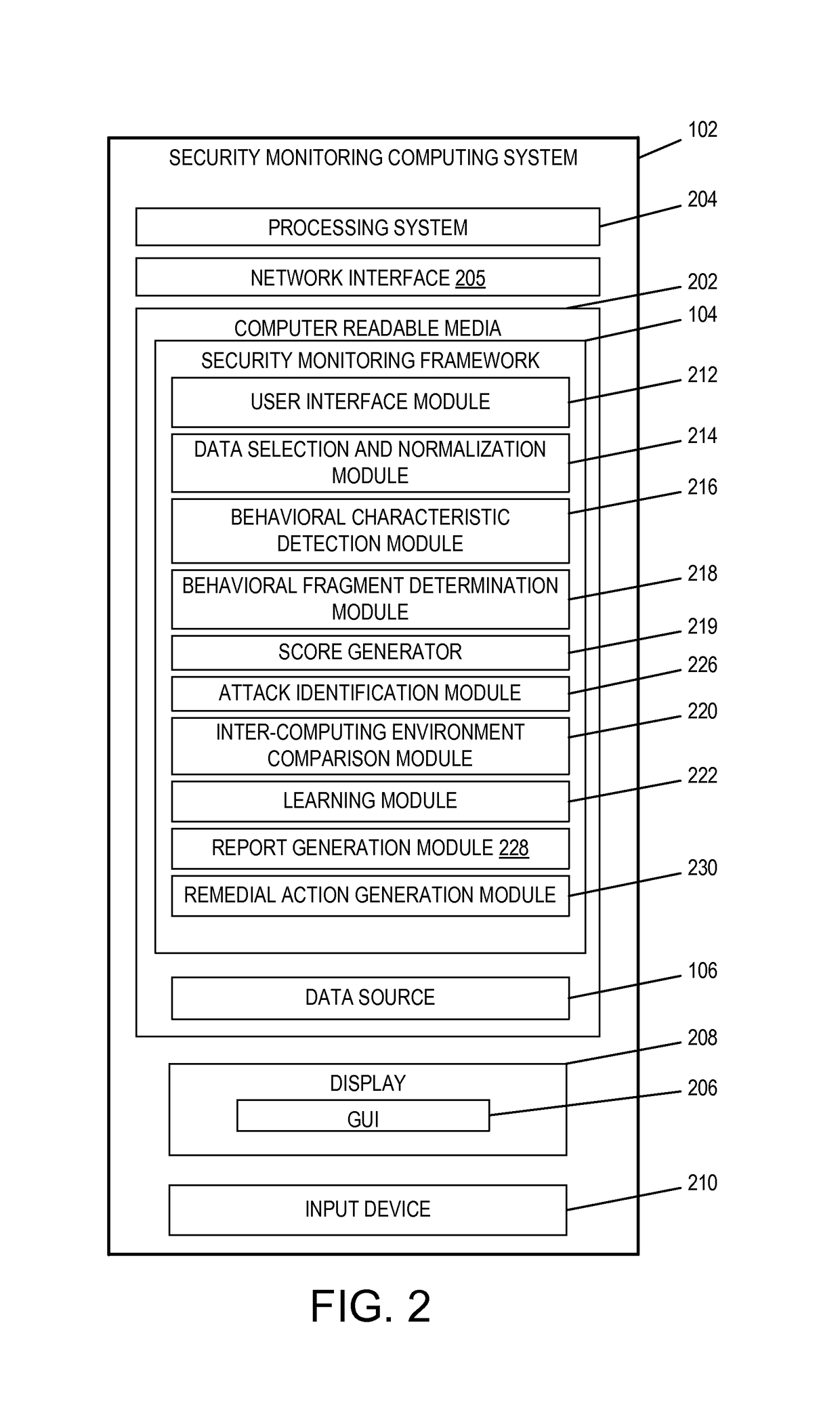
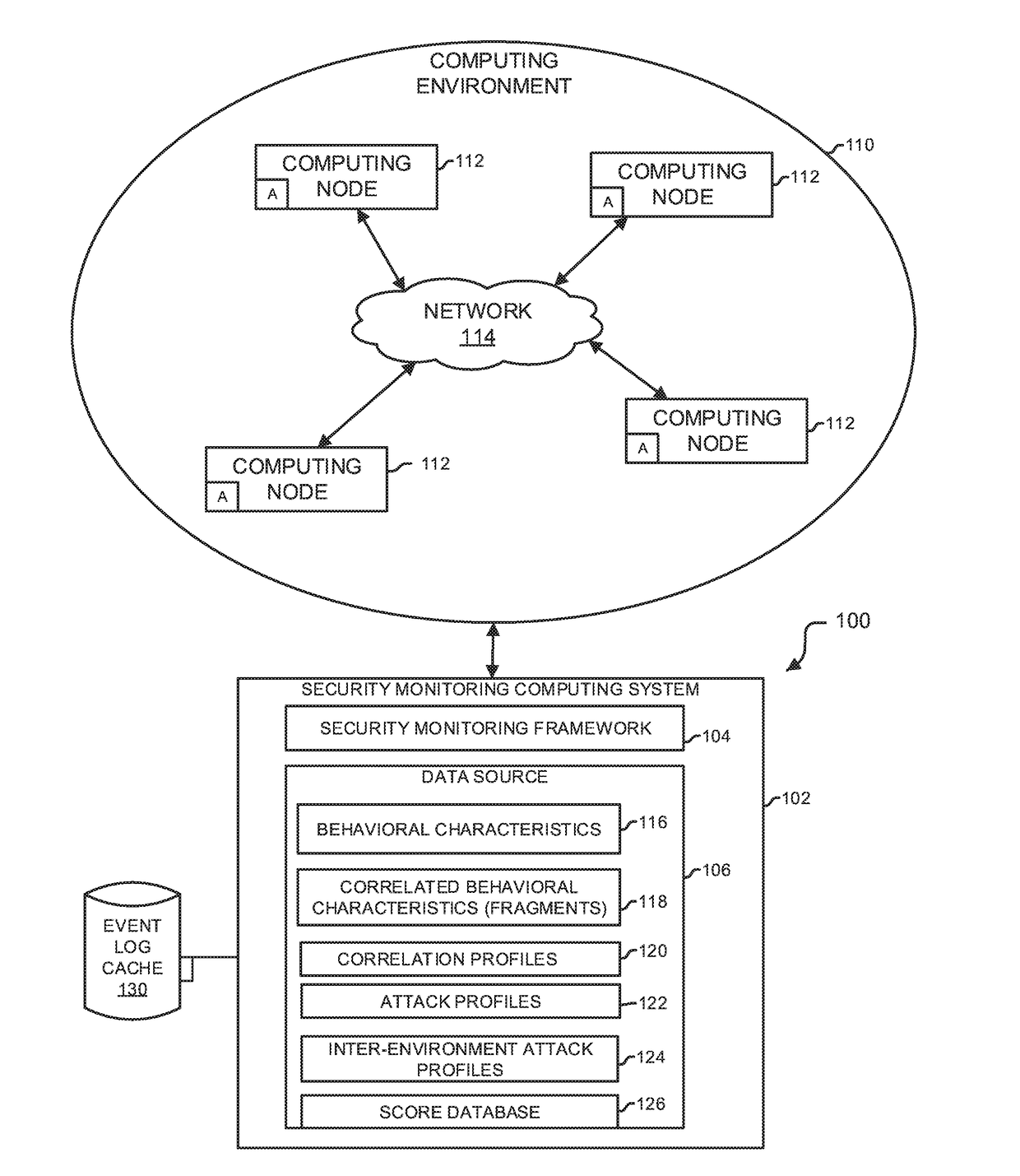
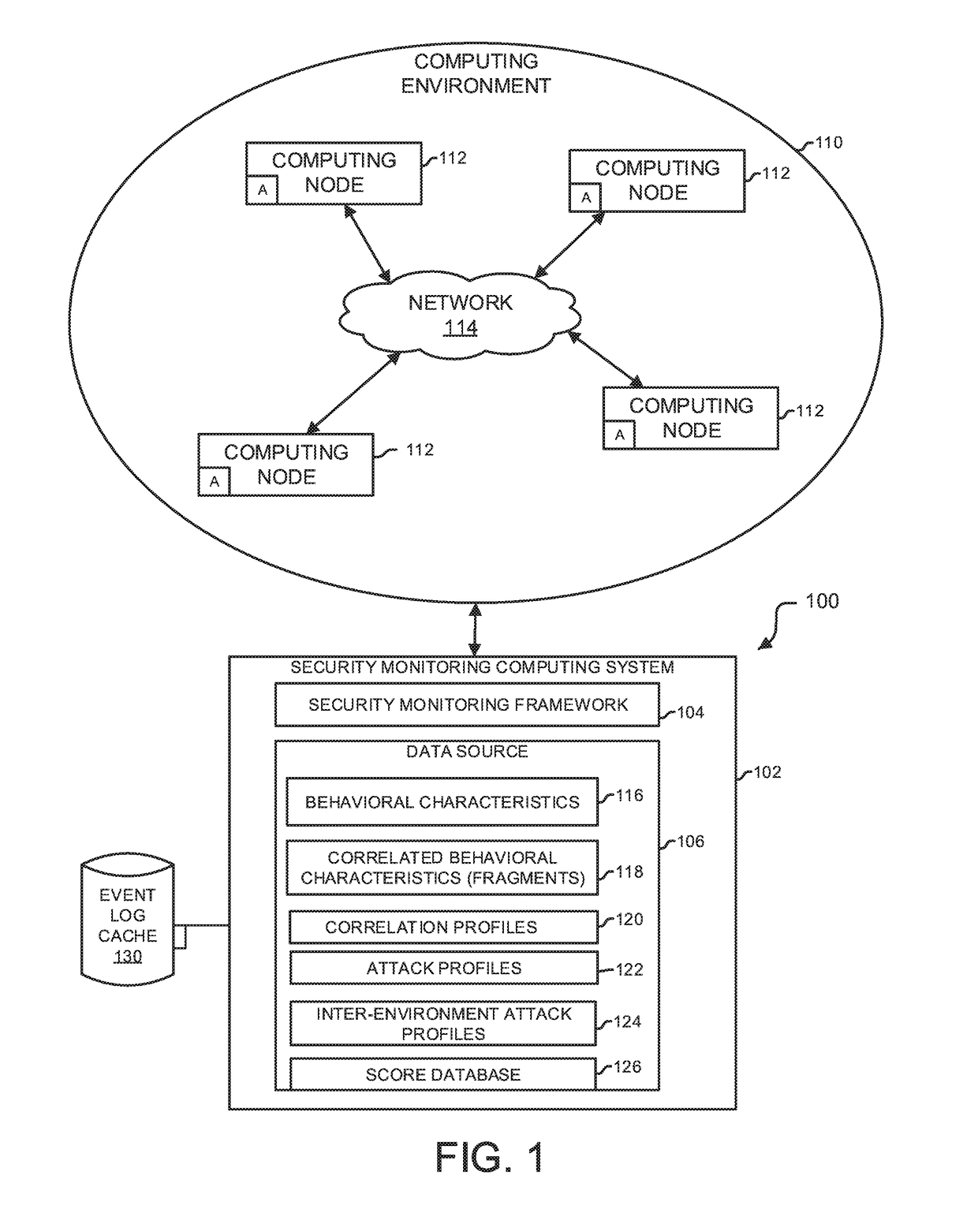
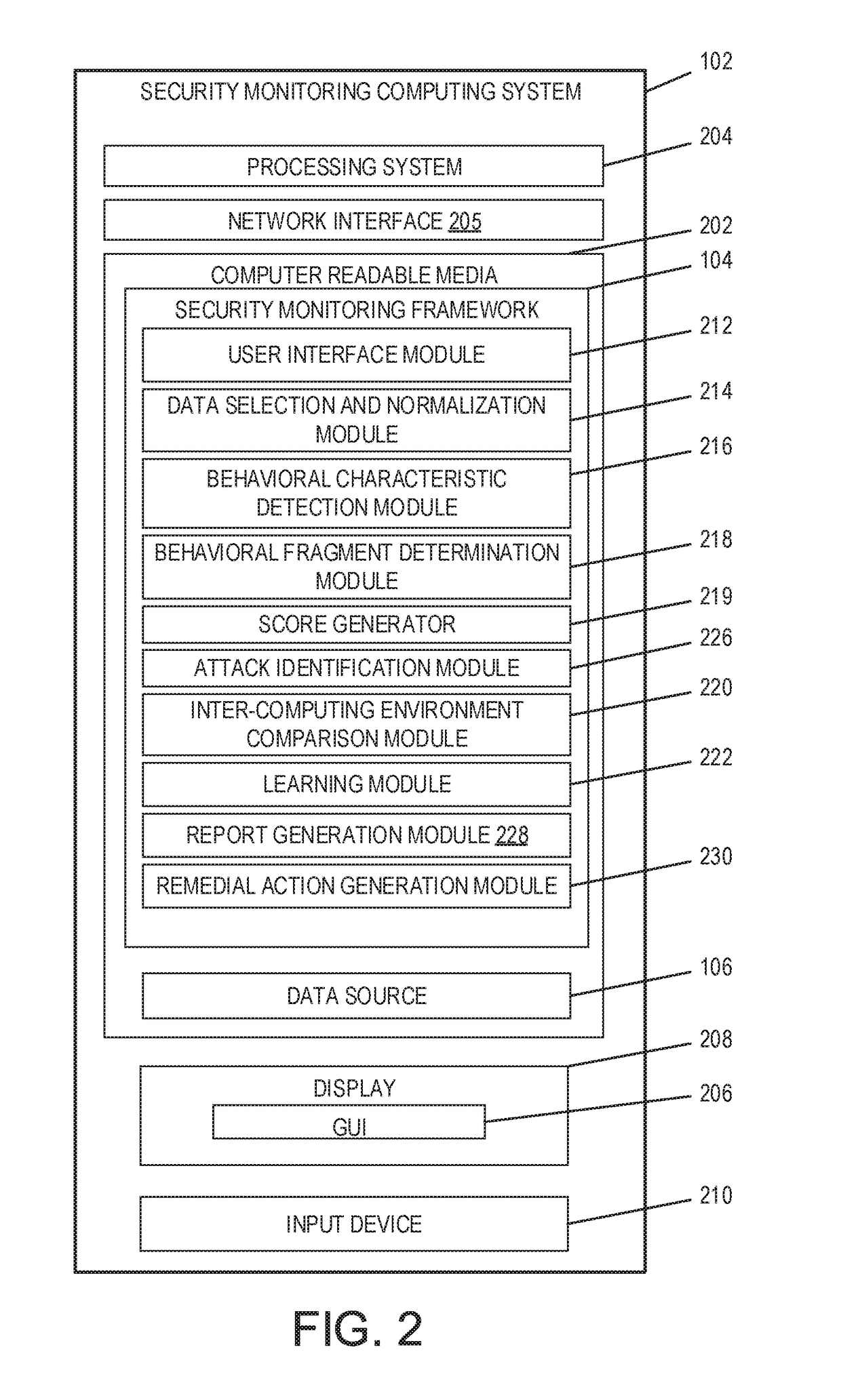
Analytics-based security monitoring system and method
ActiveUS9654485B1Reduce size (quantity)Easy to analyzeMemory loss protectionError detection/correctionRemedial actionSecurity monitoring
An analytics-based security monitoring system includes instructions that may be executed by a computing system to receive data in the form of event logs from one or more network devices transferred through a computing environment, detect a plurality of behavioral characteristics from the received event logs, identify behavioral fragments composed of related behavioral characteristics, and identify an attack by correlating the behavioral fragments against patterns of known malicious attacks. The analytics-based security monitoring system may then perform a learning process to enhance further detection of attacks and perform one or more remedial actions when an attack is identified.
Owner:MANDIANT +1
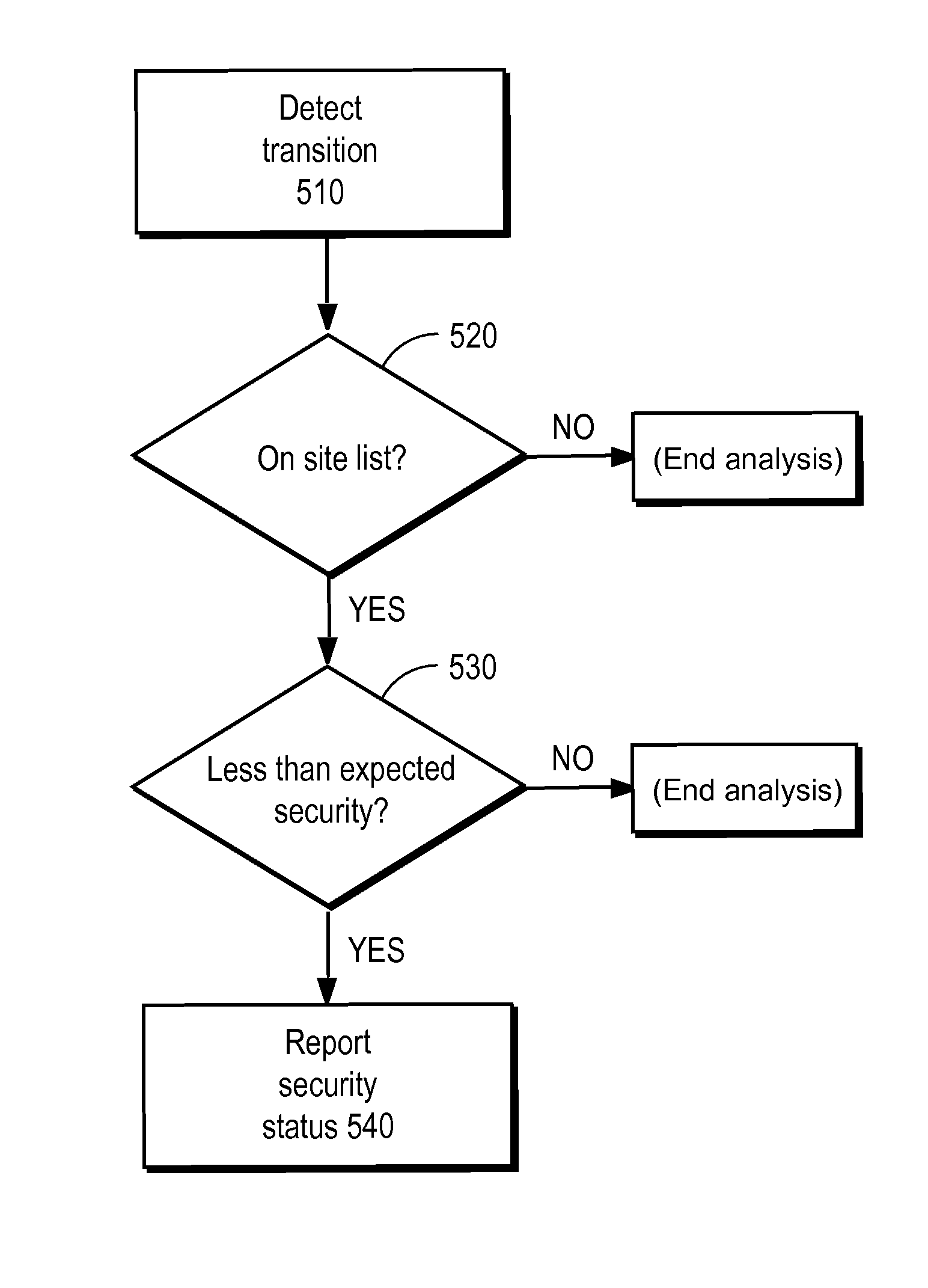
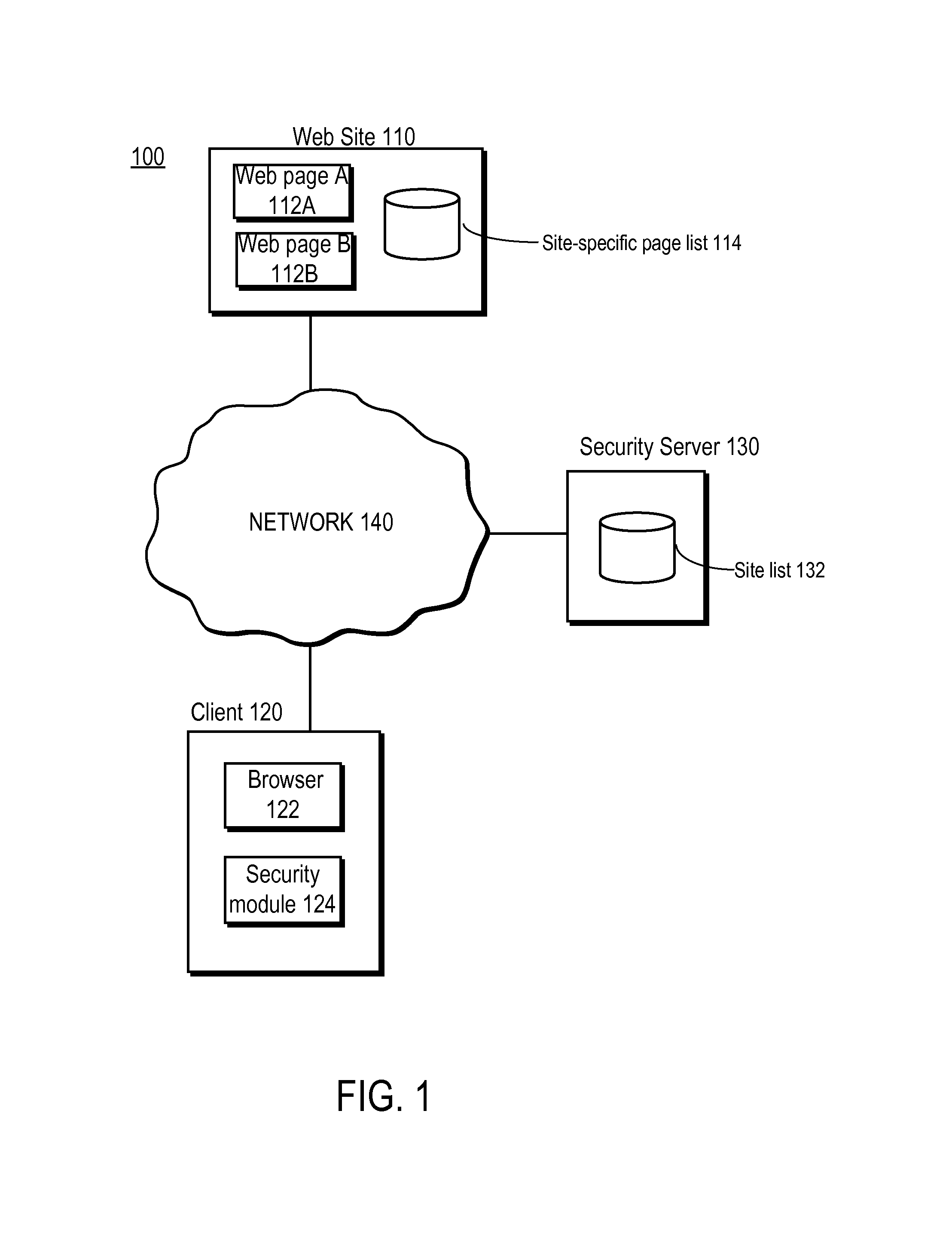
Detecting man-in-the-middle attacks via security transitions
ActiveUS8561181B1Memory loss protectionError detection/correctionMan-in-the-middle attackRemedial action
A page list comprising a list of transitions between network resources is established. Subsequently, a transition is detected between a first network resource and a second network resource. An expected security level associated with the transition is identified based on the page list. Responsive to the detected security level being determined to be lower than the expected security level, a remedial action is performed.
Owner:CA TECH INC
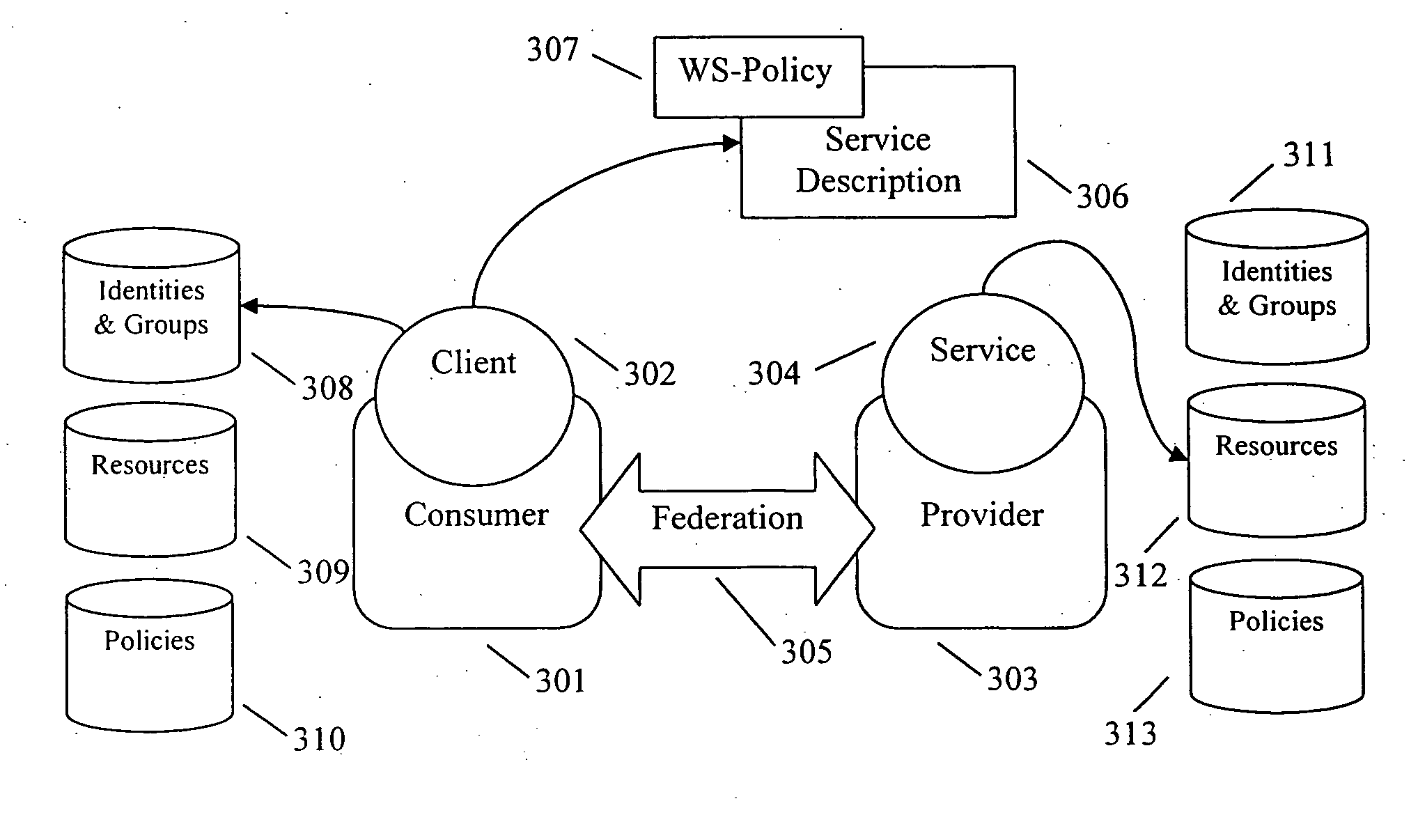
System and method for actively managing service-oriented architecture
InactiveUS20070033194A1MarketingSpecial data processing applicationsRemedial actionService-oriented architecture
A method for managing policy in a service-oriented architecture includes intercepting a communication representing a transaction between a client and a service along a network, interpreting the communication to determine details of the transaction, determining if the transaction complies with policy based on the details of the transaction and remediating where the transaction is determined to not comply with the policy.
Owner:COMP ASSOC THINK INC
Method for performing driver identity verification
InactiveUS8344849B2Improve security levelElectric signal transmission systemsImage analysisRemedial actionEngineering
Method for assuring that the operator of a vehicle is an authorized driver, the method including utilizing an onboard, multi-mode driver identification system to ascertain whether an operator is an authorized driver. A first driver identification procedure is performed on a present operator of the vehicle and determining whether the present operator is an authorized or unauthorized driver of the vehicle. A second driver identification procedure is performed on the present operator of the vehicle and determining whether the present operator is an authorized or unauthorized driver of the vehicle, wherein the first and second driver identification procedures are performed with a time interval therebetween, the time interval being dependent upon the nature of the work being performed by the operator. A remedial measure is exercised to avert potentially negative impact when the present operator of the vehicle is determined to be an unauthorized driver based upon at least one of the performed identification procedures.
Owner:VOLVO TECH
Automated method for identifying and repairing logical data discrepancies between database replicas in a database cluster
InactiveUS8126848B2Digital data processing detailsDatabase distribution/replicationData differencingTransaction log
A method and system for monitoring and maintaining the consistency of replicated databases in a shared-nothing database cluster architecture is presented. The method involves the continuous monitoring of the database transaction logs that are maintained by the autonomous database managers that manage the individual database replicas in the cluster. In the event that data discrepancies are detected via the comparison of the transaction logs of the individual database replicas, remedial action is carried out according to configured rules in the main cluster controller. These remedial actions may include, but are not limited to, making a database node inactive within the cluster, or automatically repairing any data discrepancies that are detected among the database replicas in the cluster.
Owner:WAGNER ROBERT EDWARD
Monitoring system and method for patient care
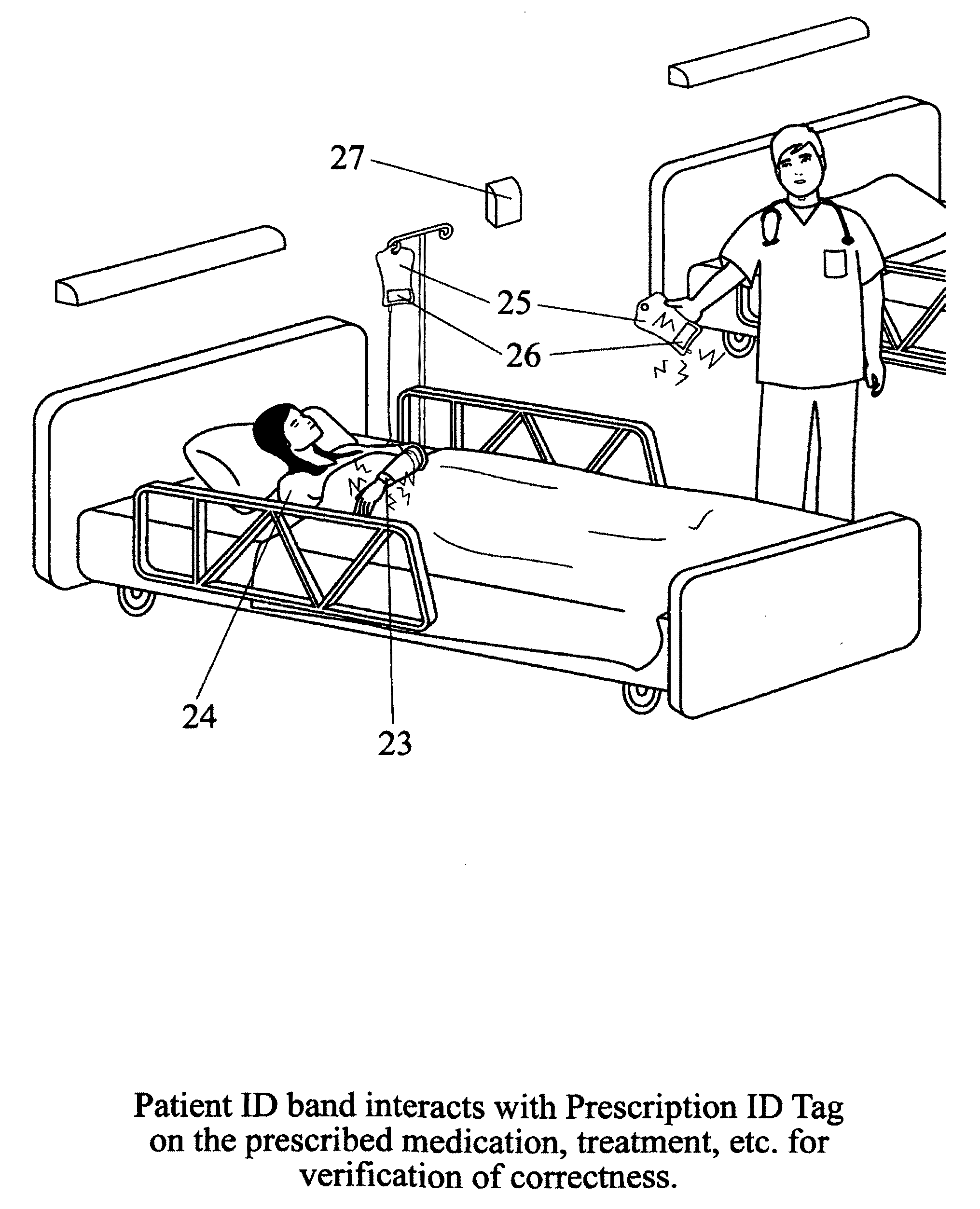
A patient care monitoring system and method employ active RFID devices integrated with digital processing, memory and timing circuitry for patient identification, care giver identification and for identification of each prescribed treatment, procedure, medication and general and / or special care action. At the point-of-care, each care action identity device will match directly with the targeted patient identity device or issue an error warning to prevent mistakes. The patient identity device will also interact with an associated sensor network to proactively prompt care givers to provide general care actions, such as altering a patient's laying position, changing bed pan / clothing / bed sheet, etc. for invalid patients. Also the patient identity tag will furnish periodic records of every care action, mistakes, remedies, care givers' identities and time and date for a central processor of a healthcare facility to monitor the quality of patient care. Such record can also be potentially accessed via the Internet by the responsible regulatory agencies, accreditation associations, insurance firms and even patients' families to ensure patient care is meeting the standards as well as medical billing accuracy.
Owner:HUANG CHING CHING +4
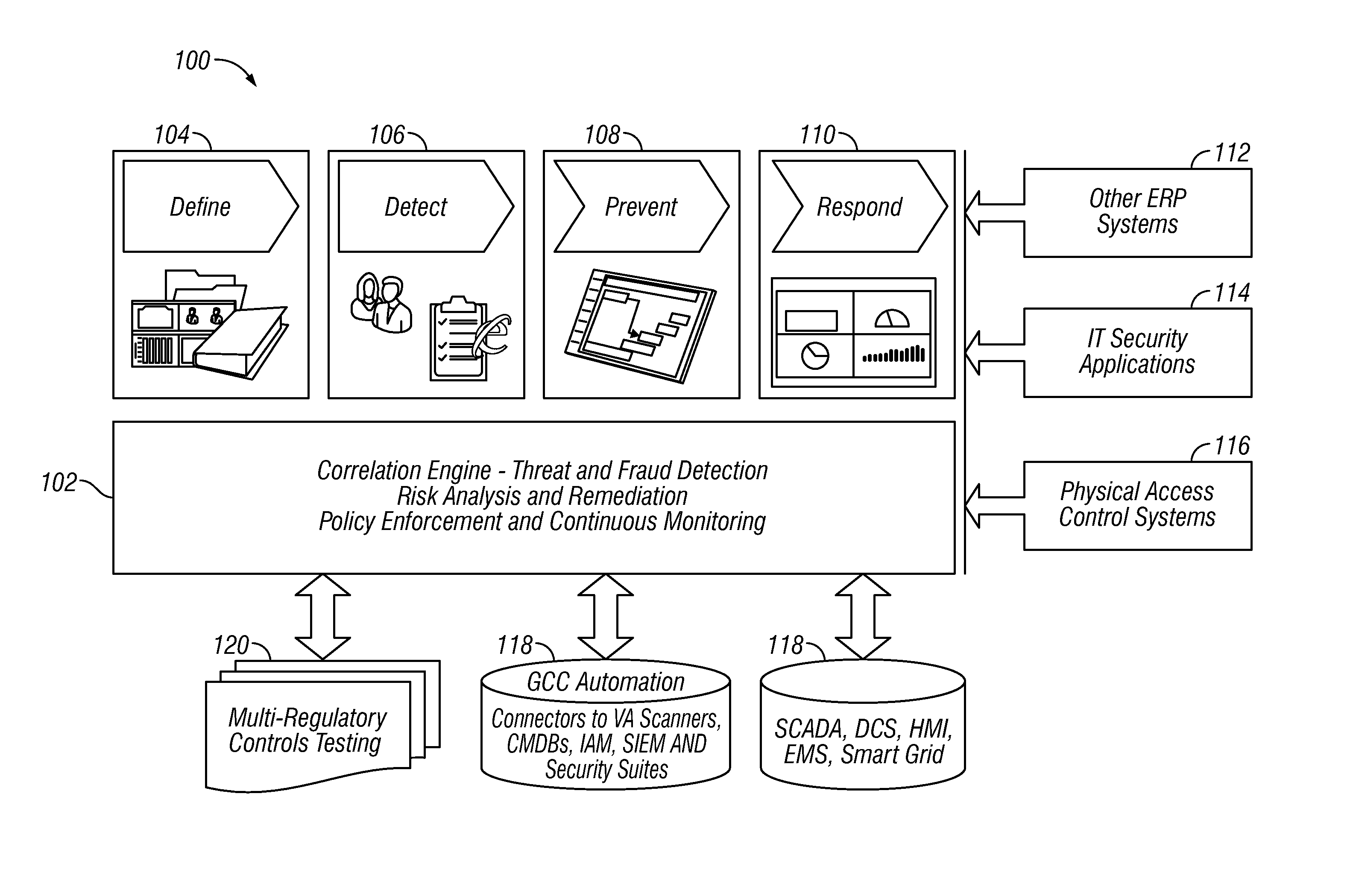
Situational intelligence
ActiveUS20120224057A1Color television detailsClosed circuit television systemsDashboardRemedial action
A method and apparatus is provided that includes techniques for providing complete solutions for role-based, rules-driven access enforcement, the techniques including situational awareness and video surveillance. An embodiment addresses blended risk assessment and security across logical systems, IT applications, databases, and physical systems from a single analytic dashboard, with auto-remediation capabilities. Further, an embodiment provides capability and functionality for co-relating seemingly innocent events and activities to detect real threats and risks, while providing powerful alerting and automated remedial action strategies for decisive action.
Owner:ALERT ENTERPRISE
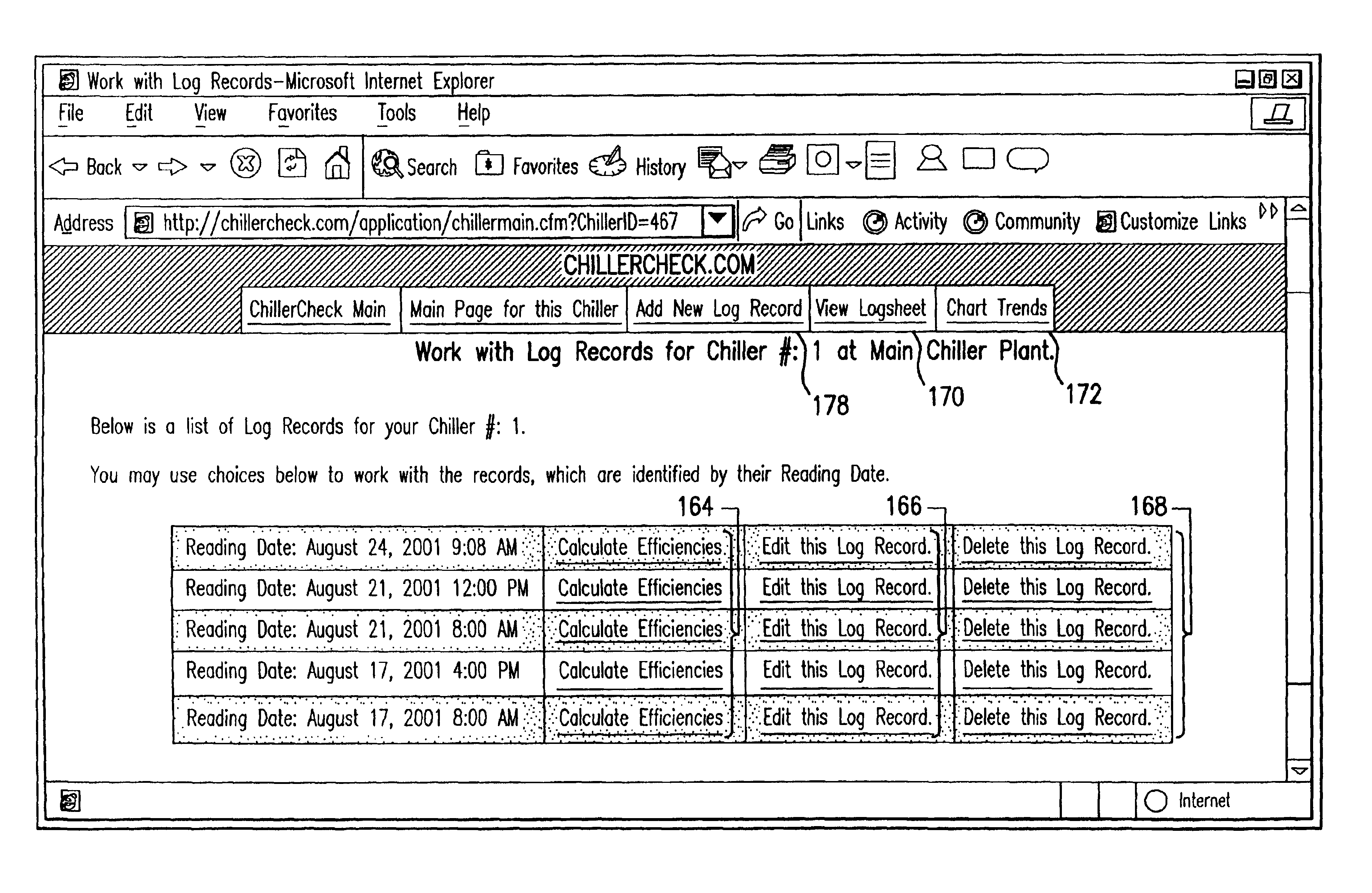
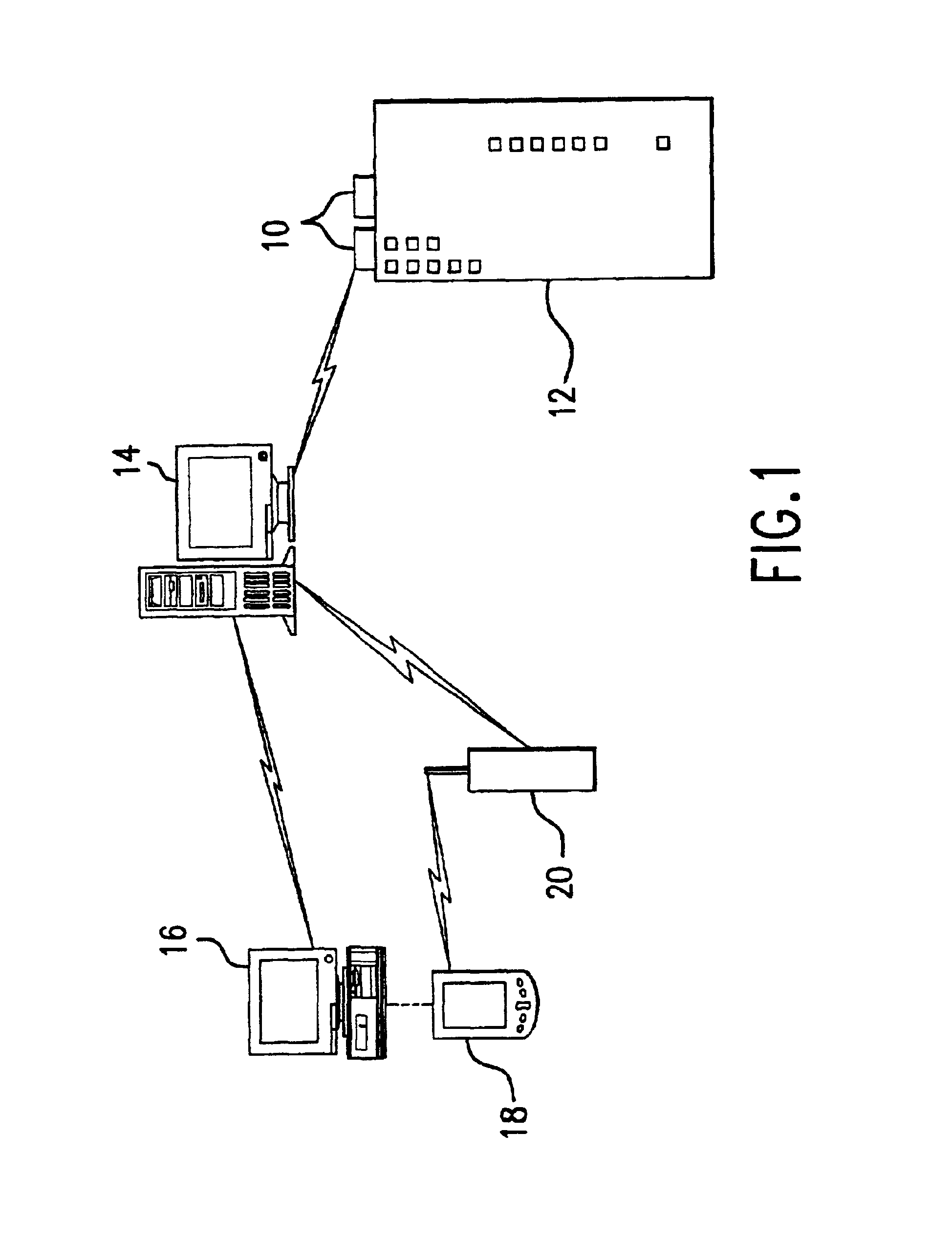
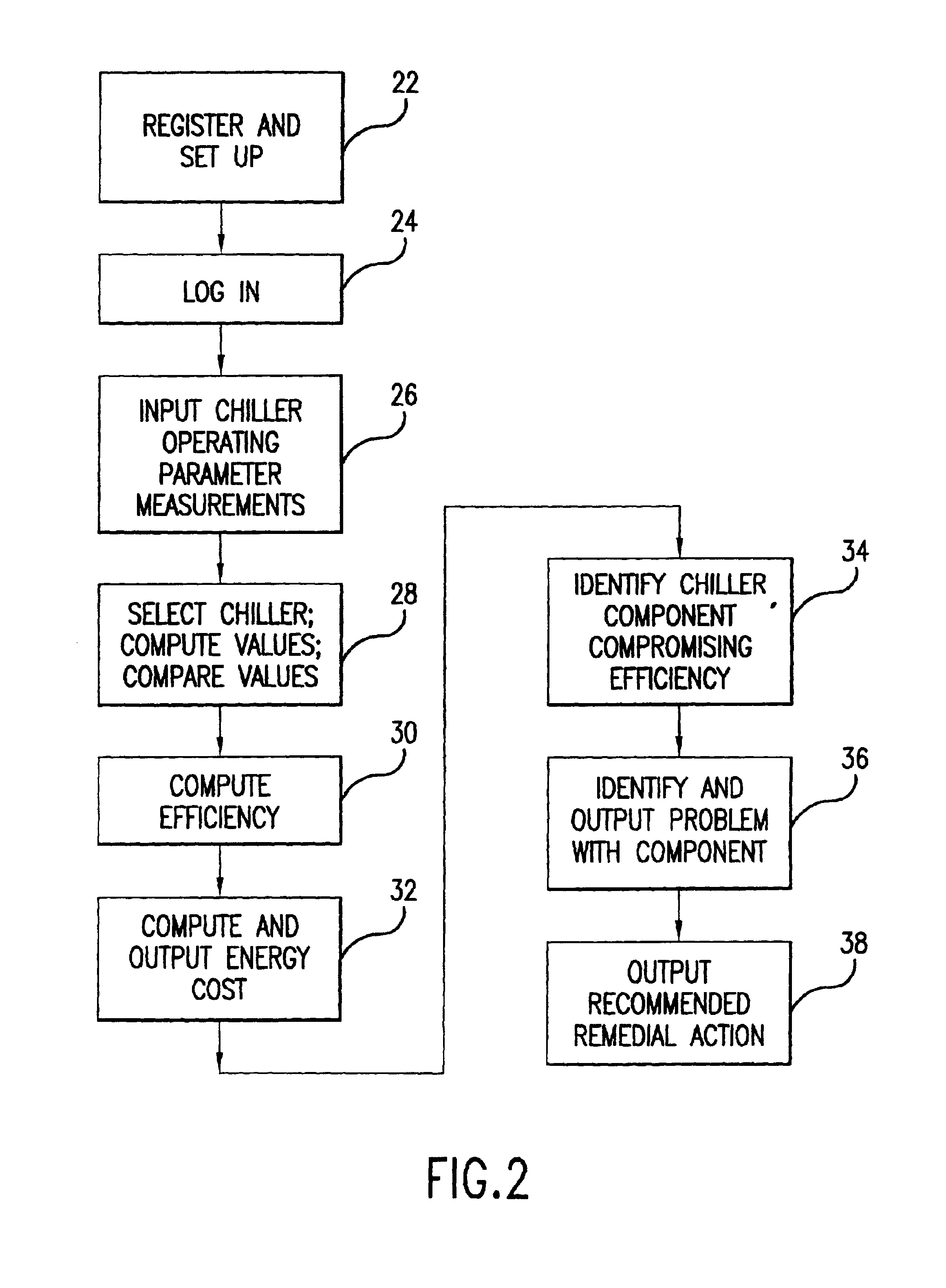
Method and system for evaluating the efficiency of an air conditioning apparatus
InactiveUS6973410B2Computing chiller efficiencySpace heating and ventilationTemperatue controlCurrent loadSimulation
Air conditioning chiller operating efficiency is evaluated in response to chiller operating parameters input to a computing device which calculates separately the efficiencies of the condenser and evaporator components of the chiller. Additional efficiency calculations are performed to identify specific causes of inefficiency in the condenser and evaporator. The computing device also adjusts the efficiency calculations as appropriate to account for actual compressor current load conditions. The device determines whether chiller efficiency is being compromised by poor performance of one or more chiller components, calculates inefficiency values, estimates the cost of the inefficiency, identifies specific causes of the inefficiency, and suggests appropriate remedial actions to restore maximum efficiency of the chiller.
Owner:CHILLERGY SYST
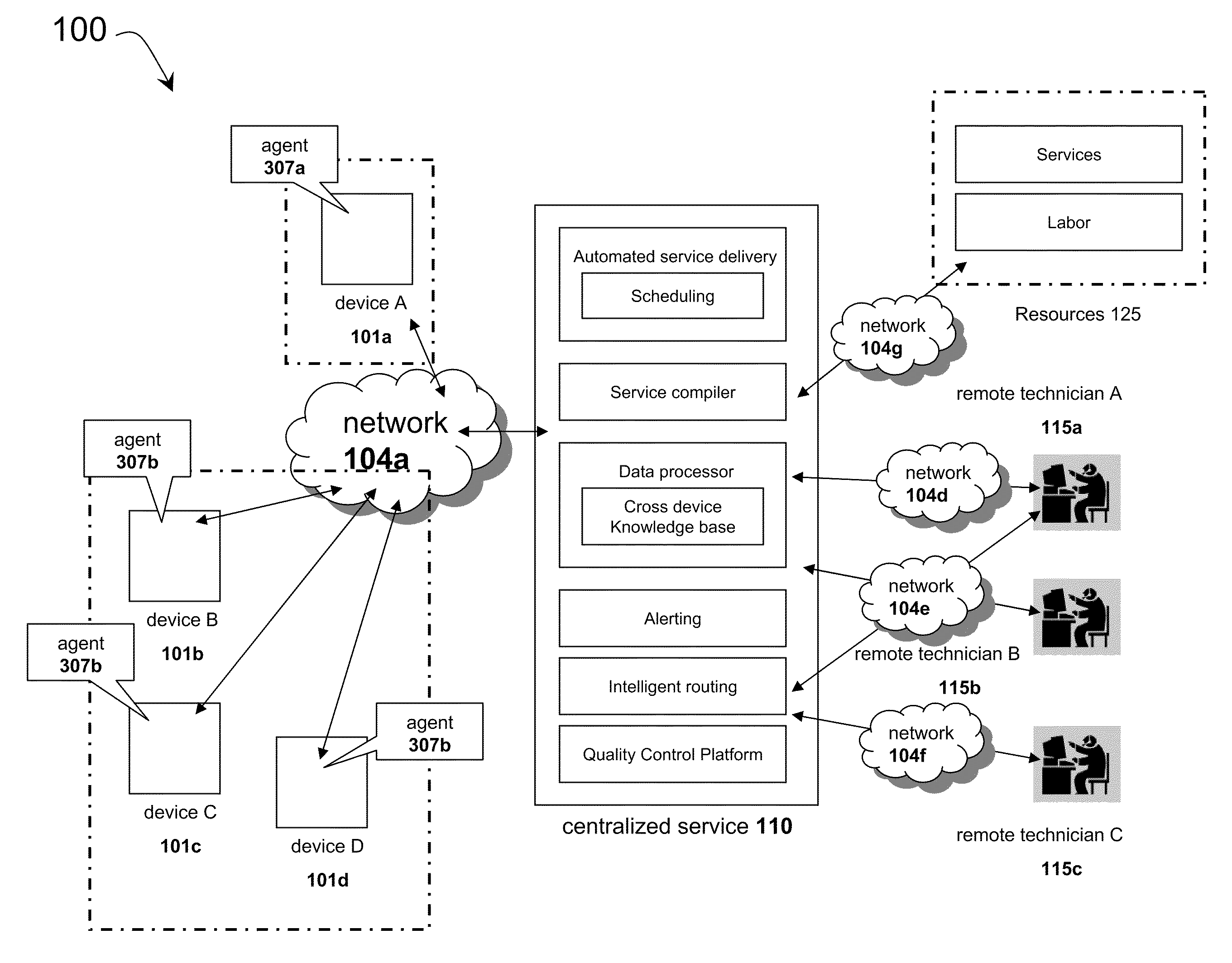
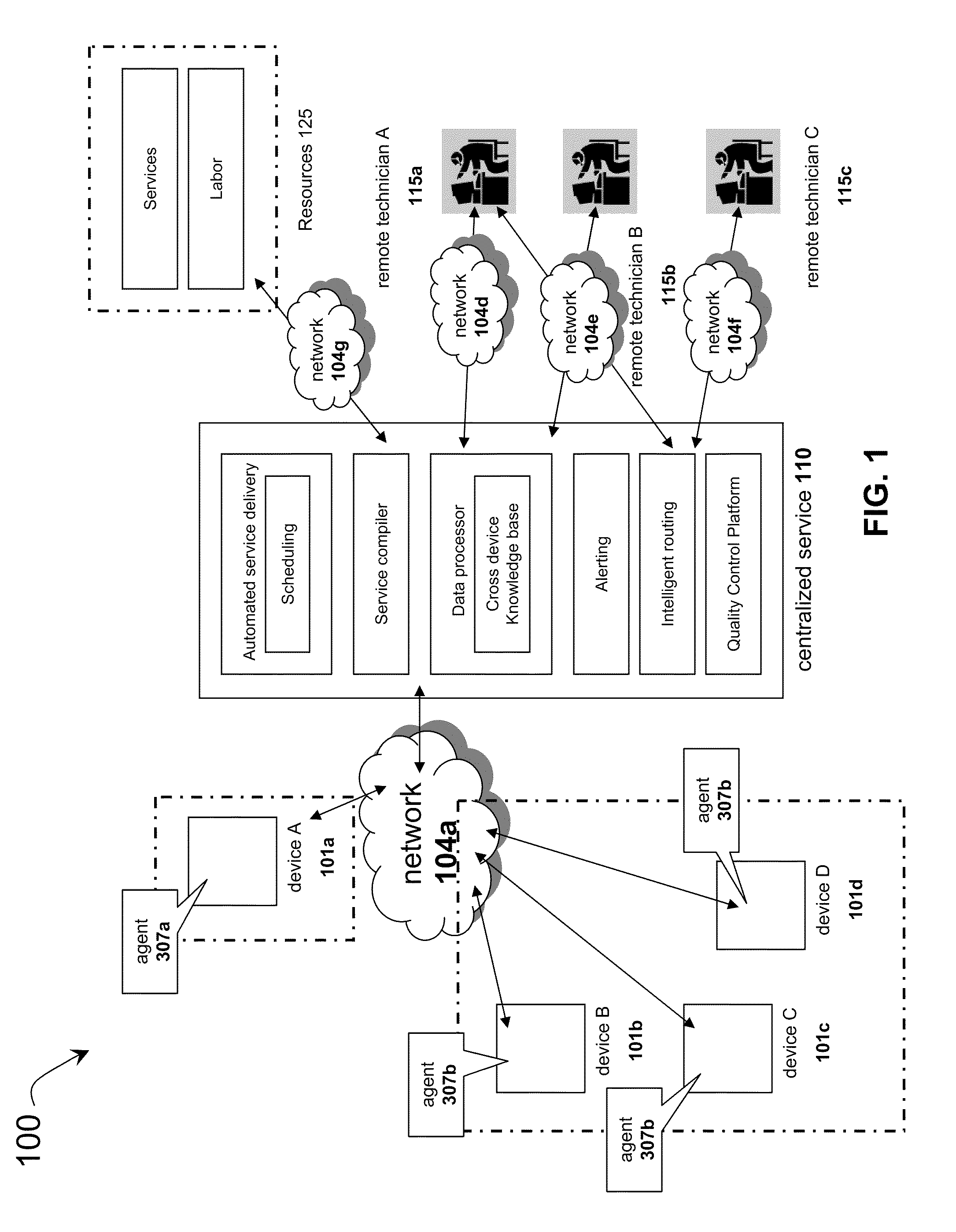
Systems and methods for providing remote services using a cross-device database
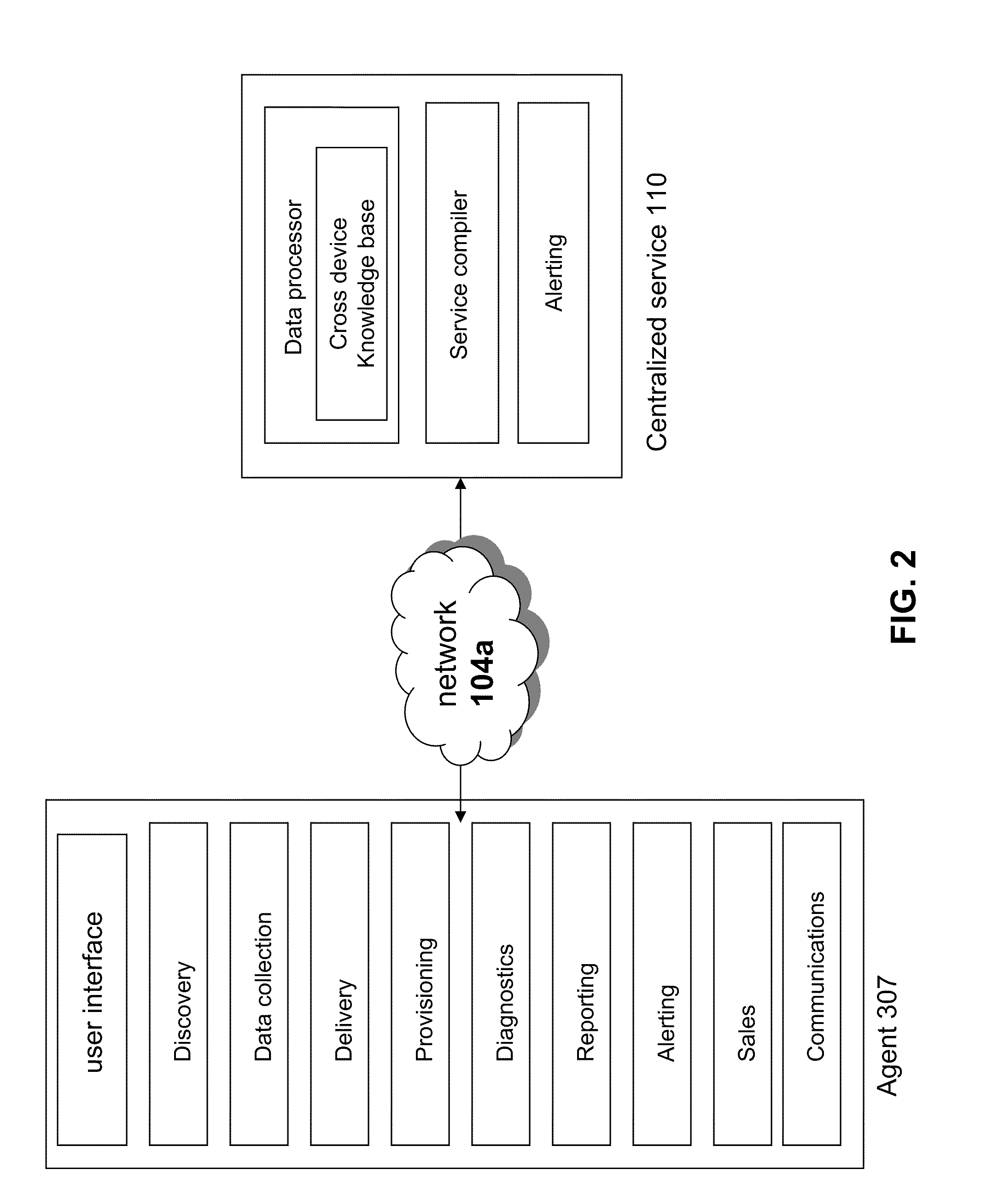
InactiveUS20110022641A1Reduce the burden onEnsure qualityDigital data processing detailsConnection managementComputer networkRemedial action
The solution of the present application provides many types and forms of resources, such as products or services, to an environment of heterogeneous devices. An agent and centralized service may communicate to deliver an optimum package of resources to a device. Each device may include an agent that collects information important to determining the appropriate resources for the device and understanding the environment the devices are contributing to. The information may be stored and analyzed in a cross device knowledge base, and the knowledge base may be consulted to determine resources appropriate for devices. The agent and centralized service may engage in pro-active alerting and provisioning of services, based on any collected information, to minimize the burden of resource procurement on the customer. After delivery of resources, the agent and centralized service may also perform updating, repairing, and healing functions for the resources. Resources may be aggregated into a cohesive platform to be combined and delivered in an optimum manner, and resources may also be maintained and monitored to ensure their quality via escalation or remedial action. Devices may be connected to the resources through intelligent routing.
Owner:PLUMCHOICE
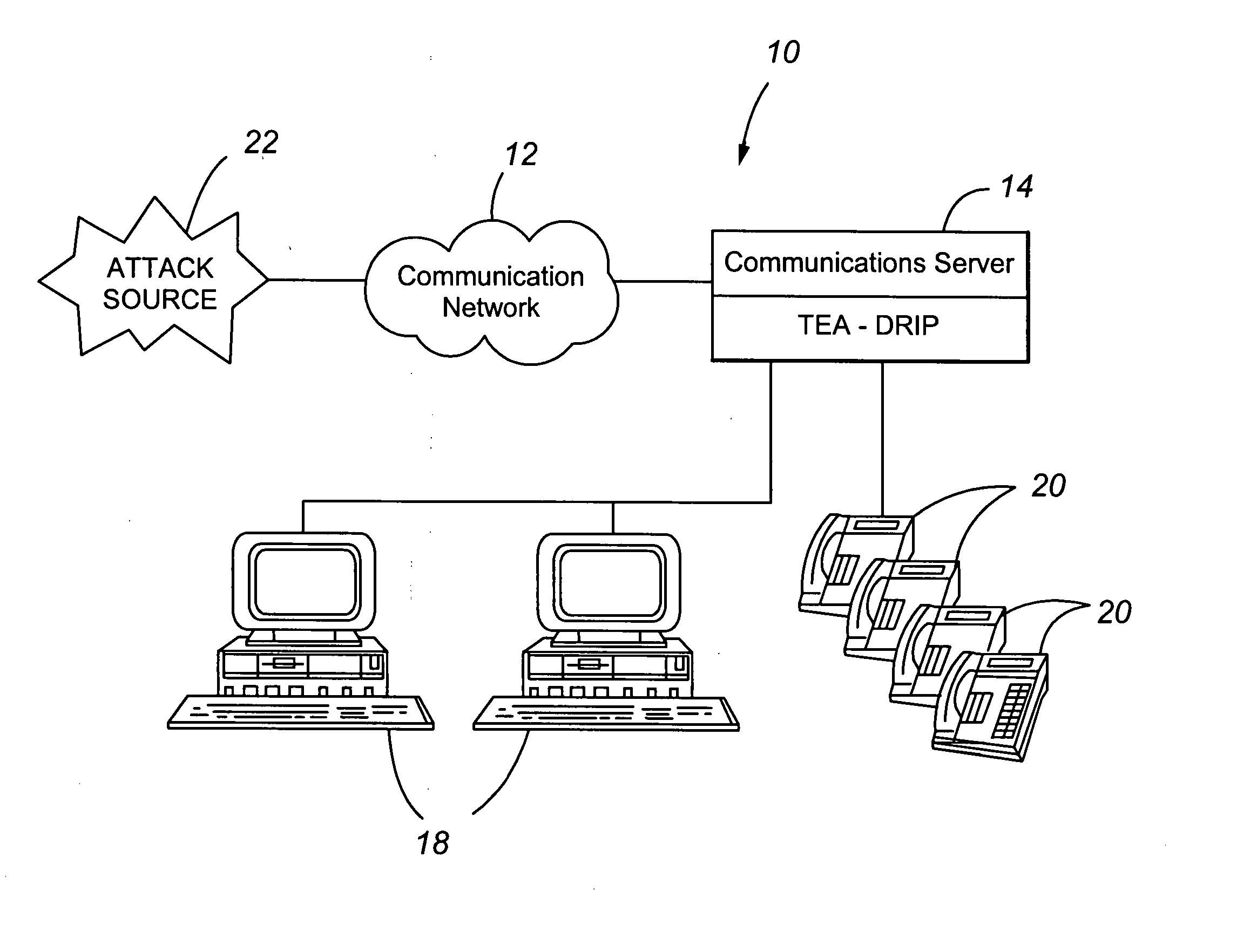
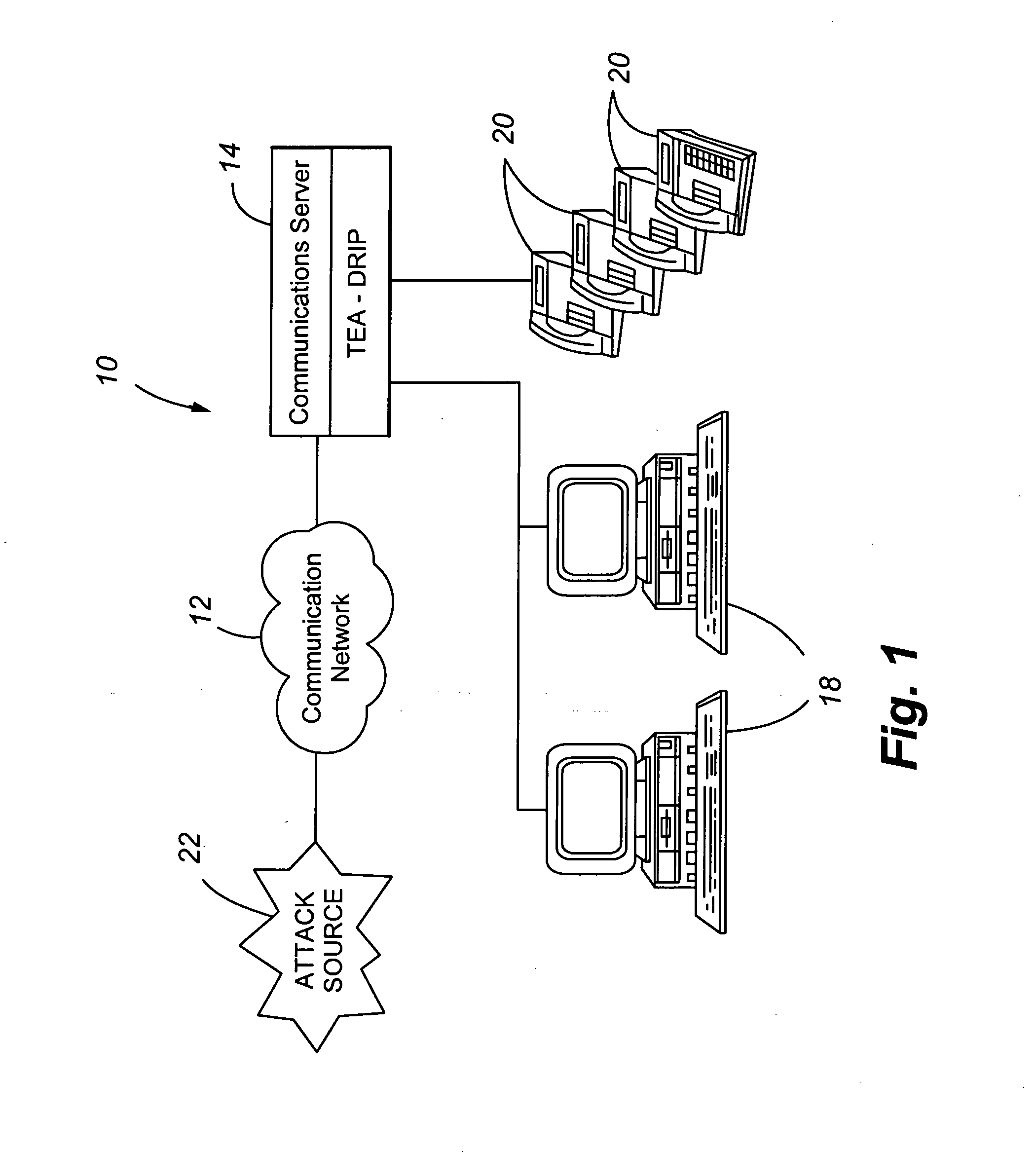
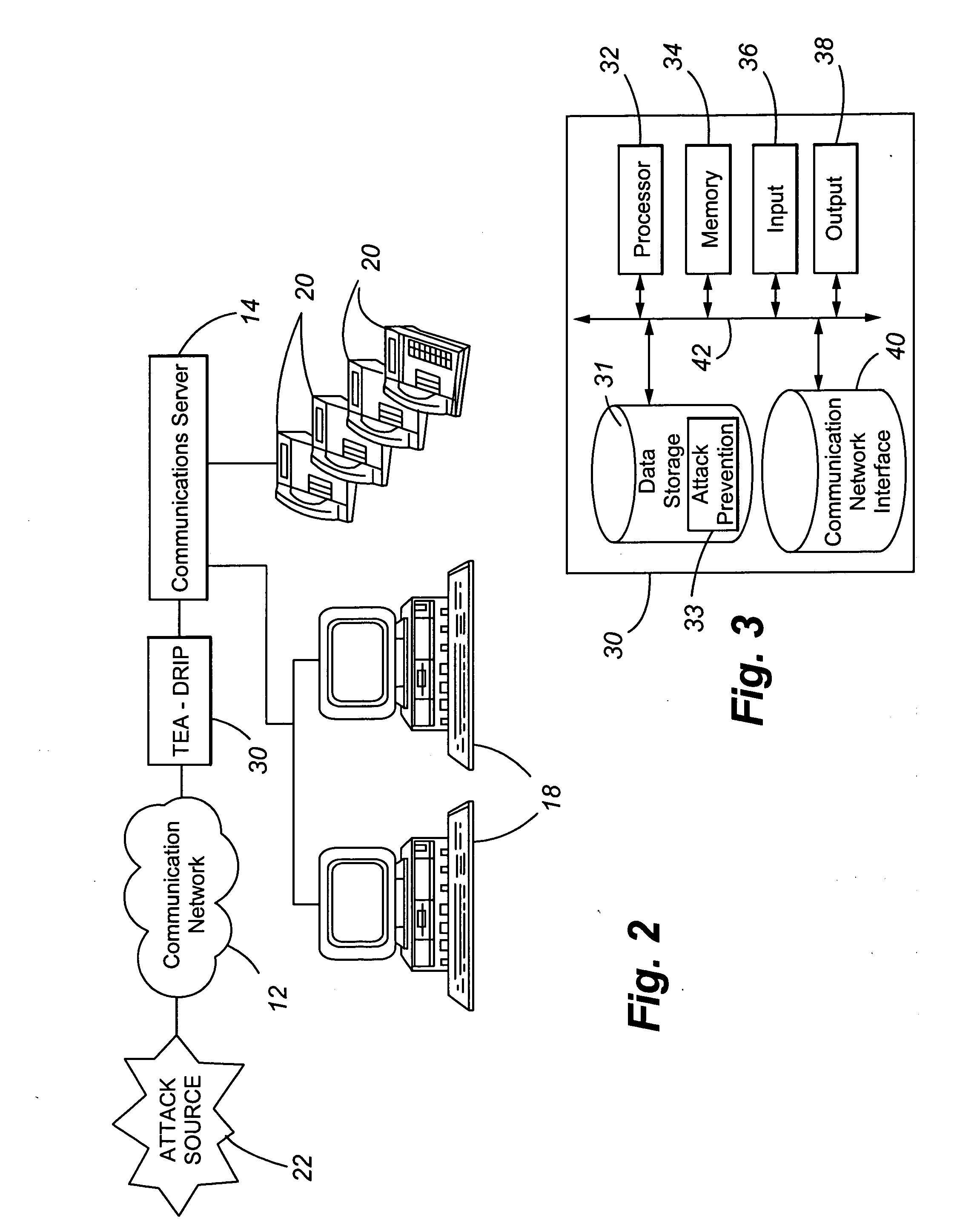
Telephony extension attack detection, recording, and intelligent prevention
ActiveUS20070036314A1Effectively prevent future attackAvoid attackData taking preventionAutomatic exchangesCommunication endpointRemedial action
A system and method are provided for detecting extension attacks made to a communication enterprise, and taking appropriate remedial action to prevent ongoing attacks and future attacks. One or more attributes of a suspect call are analyzed, and a risk is associated with each analyzed attribute. An overall risk or assessment is then made of the analyzed attributes, attack attributes are logged, and one or more remedial actions may be triggered as a result of the analyzed call attributes. The remedial actions may include recording the call, notifying an administrator of a suspect call, or isolating the communication enterprise from the attack by terminating the call or shutting down selected communication endpoints to prevent calls being made to those extensions. Rules may be applied to the analyzed attributes in order to trigger the appropriate remedial action. The call attributes analyzed may include call destination, call direction, call type, time of day of the call, call duration, whether a call source is spoofed, call volume from a particular call source, and hash values created for a suspect media stream.
Owner:AVAYA INC
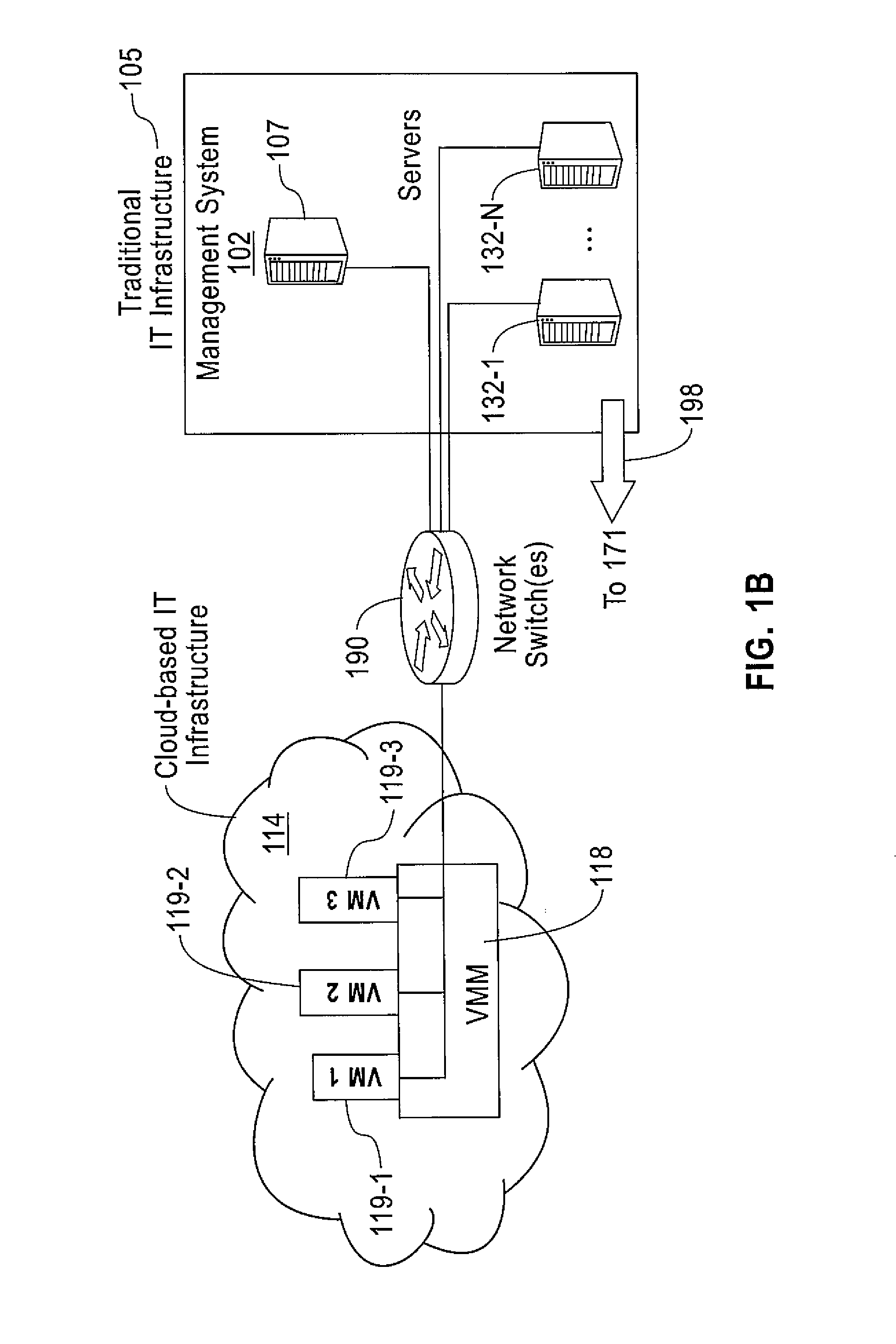
Computer Implemented Techniques for Detecting, Investigating and Remediating Security Violations to IT Infrastructure
A method includes collecting system calls and call parameters invoked by monitored applications for target computer systems. The system calls and call parameters are received from operating system kernels on the plurality of target computer systems. Sequences of systems calls and call parameters of the monitored applications are correlated among different target computer systems to deduce malicious activities. Remedial action(s) are performed in response to malicious activities being deduced as being malicious by the correlating. Another method includes determining that network activity at a specific time is deemed to be suspicious. Using IP addresses involved in the suspicious network activity, computer system(s) are determined that are sources of the suspicious network activity. Based on the specific time and the determined computer system(s), application(s) are determined that are executing on the determined computer system(s) that are causing the suspicious network activity. Remedial action(s) are performed for the determined computer system(s).
Owner:IBM CORP
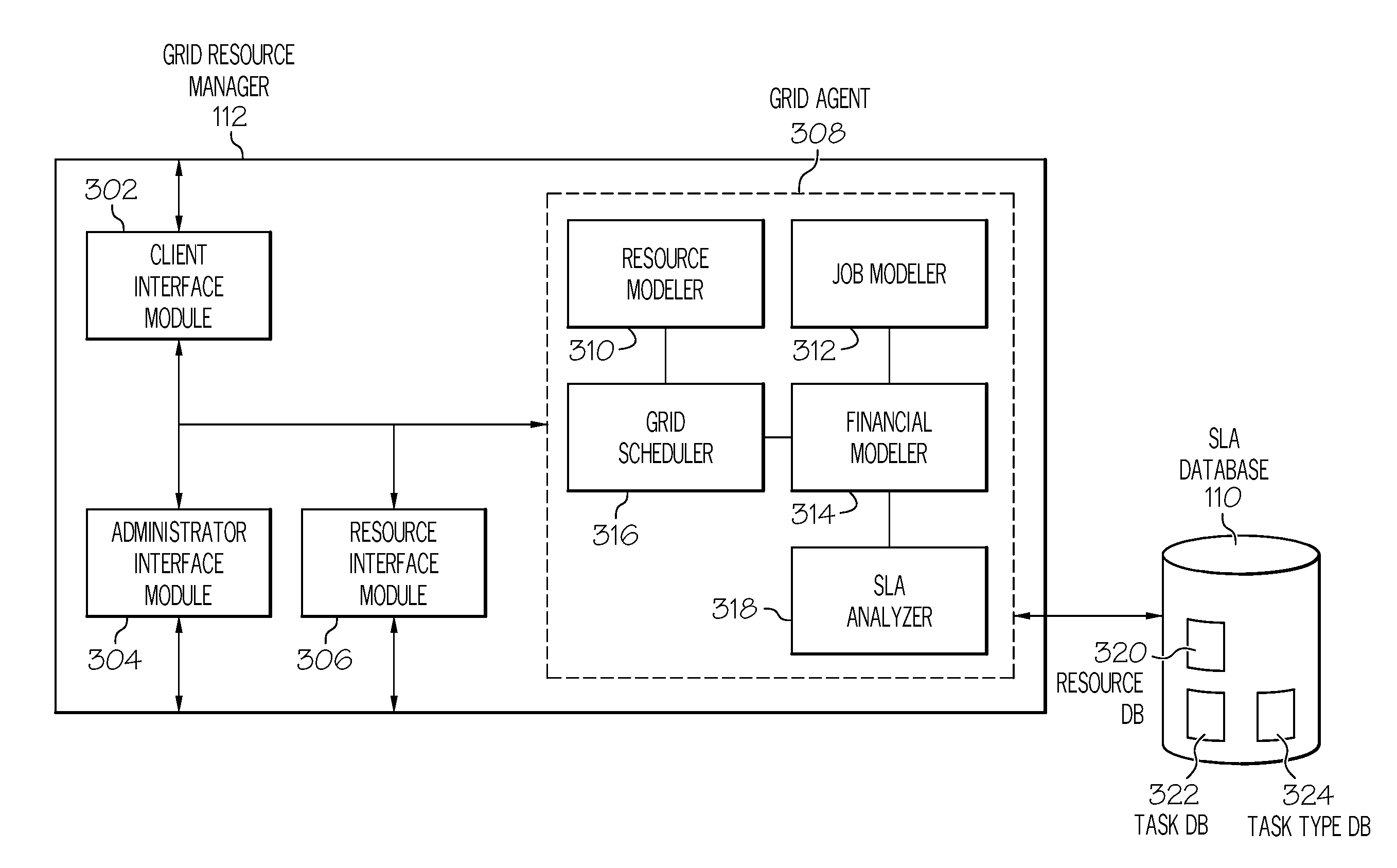
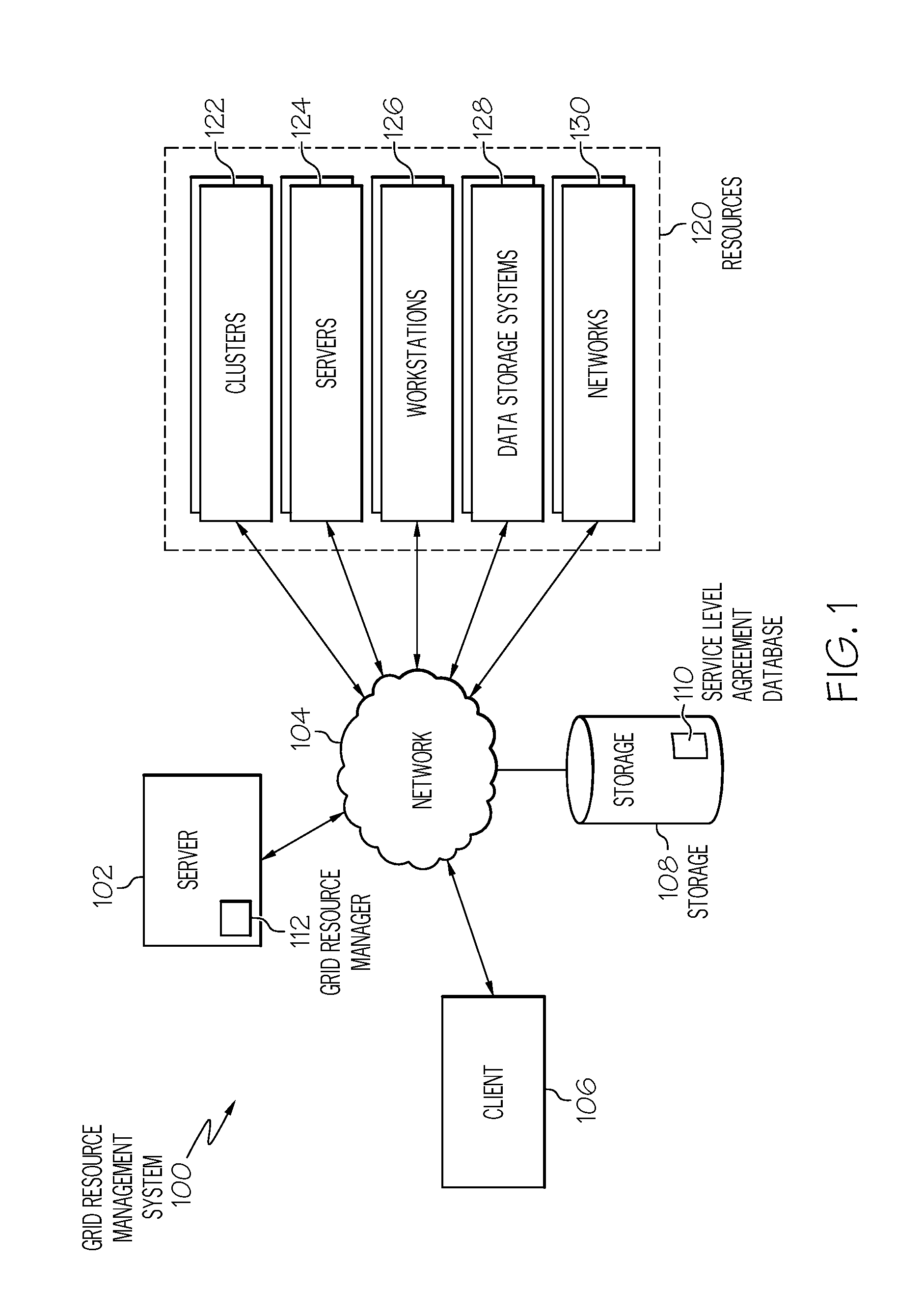
Management of grid computing resources based on service level requirements
InactiveUS20080320482A1Multiprogramming arrangementsTransmissionService level requirementRemedial action
Generally speaking, systems, methods and media for management of grid computing resources based on service level requirements are disclosed. Embodiments of a method for scheduling a task on a grid computing system may include updating a job model by determining currently requested tasks and projecting future task submissions and updating a resource model by determining currently available resources and projecting future resource availability. The method may also include updating a financial model based on the job model, resource model, and one or more service level requirements of an SLA associated with the task, where the financial model includes an indication of costs of a task based on the service level requirements. The method may also include scheduling performance of the task based on the updated financial model and determining whether the scheduled performance satisfies the service level requirements of the task and, if not, performing a remedial action.
Owner:IBM CORP
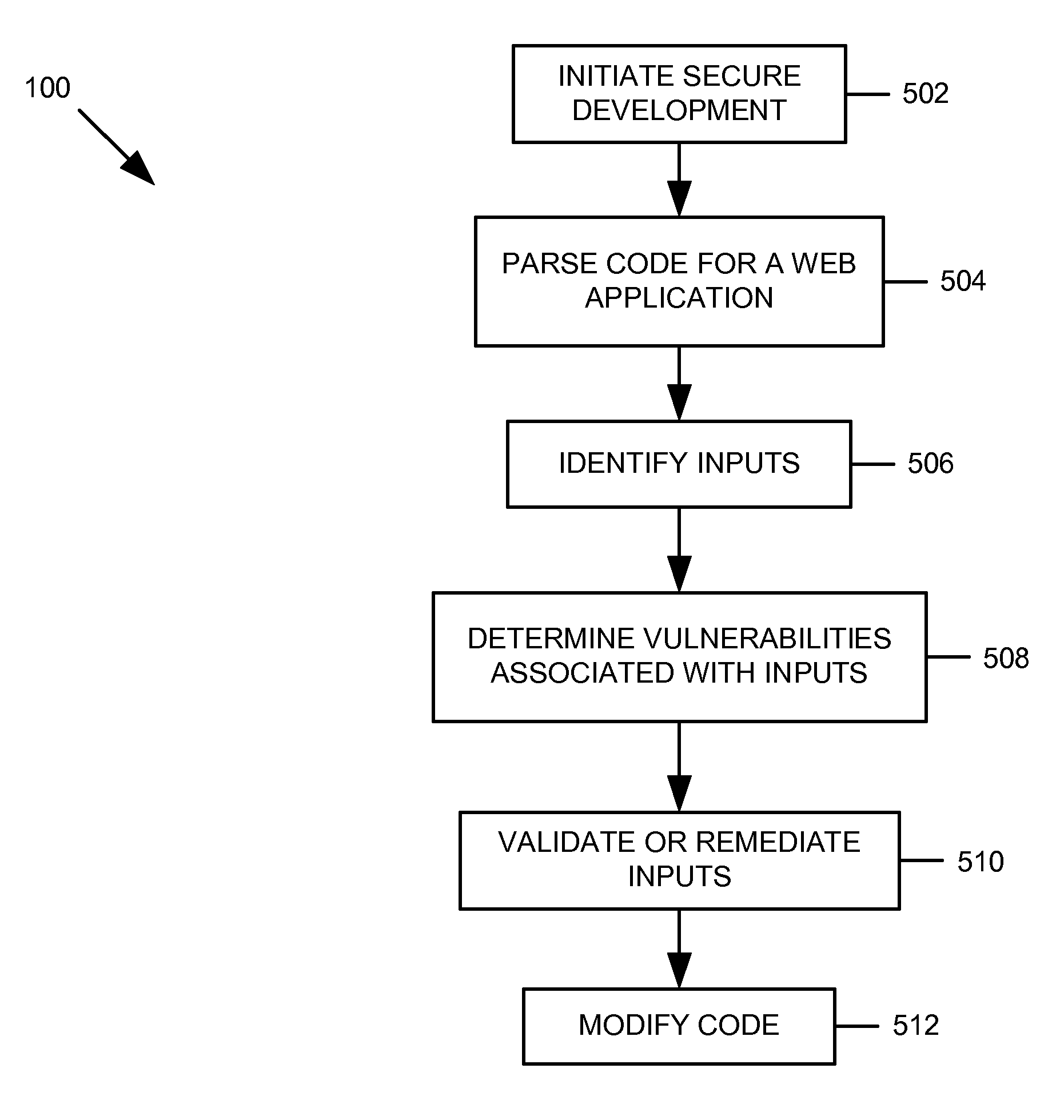
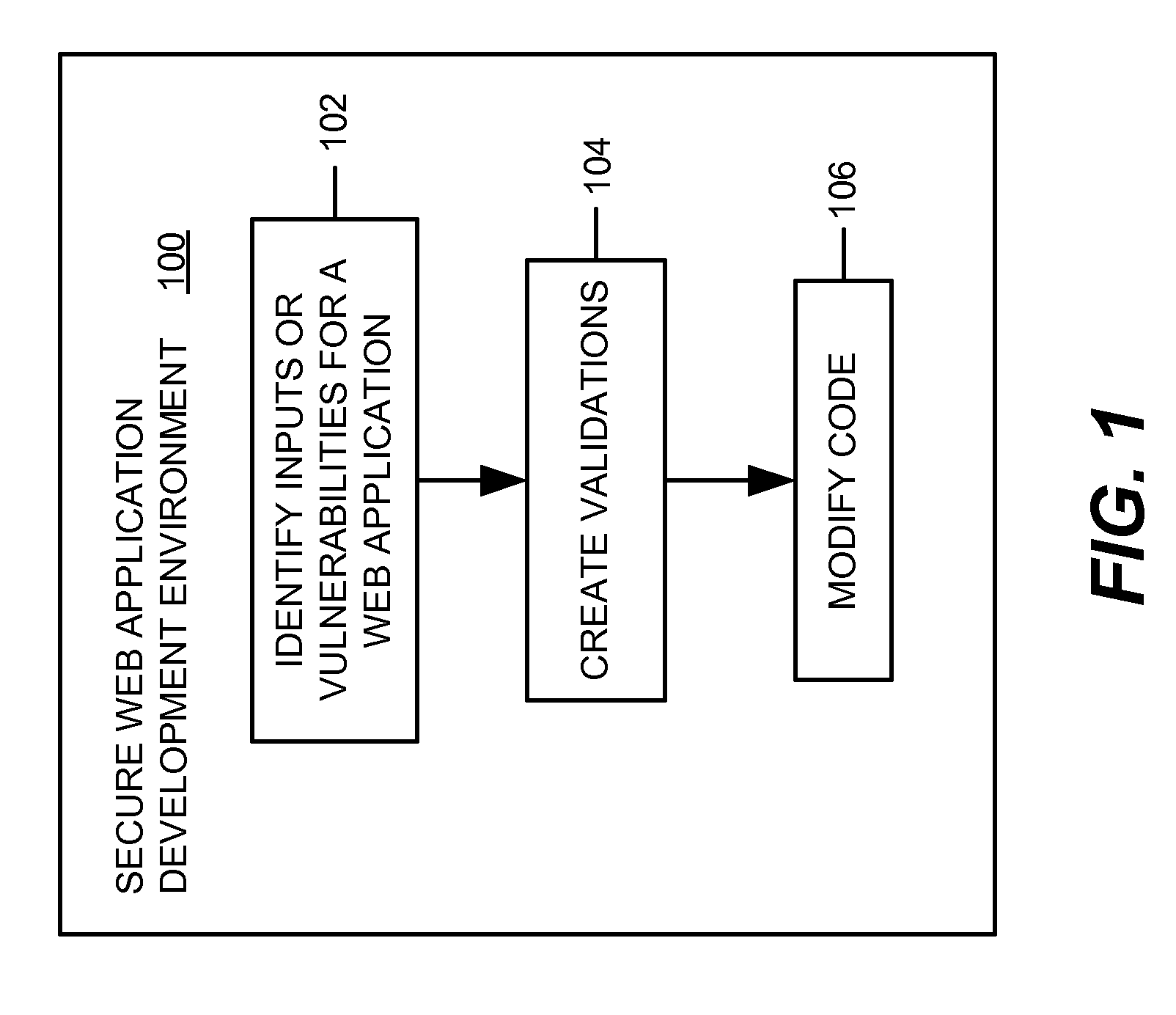
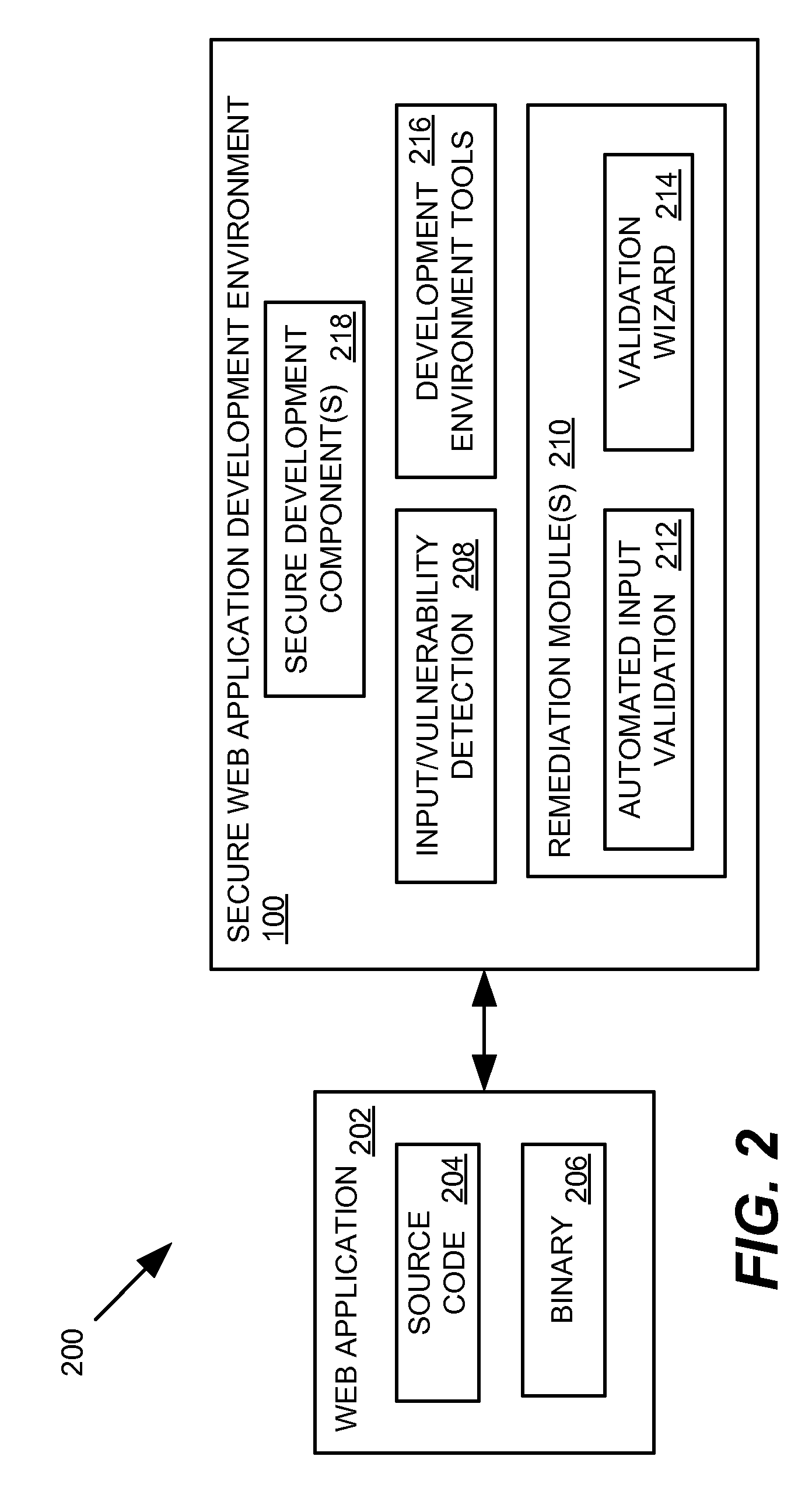
Secure web application development and execution environment
ActiveUS20060282897A1Memory loss protectionError detection/correctionWeb applicationSoftware engineering
Providing secure web application development and operation. In a web development environment, code developed for the web application is analyzed to identify vulnerabilities and remedial actions are identified. The remedial actions may be automatically invoked or a developer can be prompted to take particular actions to remediate the vulnerability.
Owner:MICRO FOCUS LLC
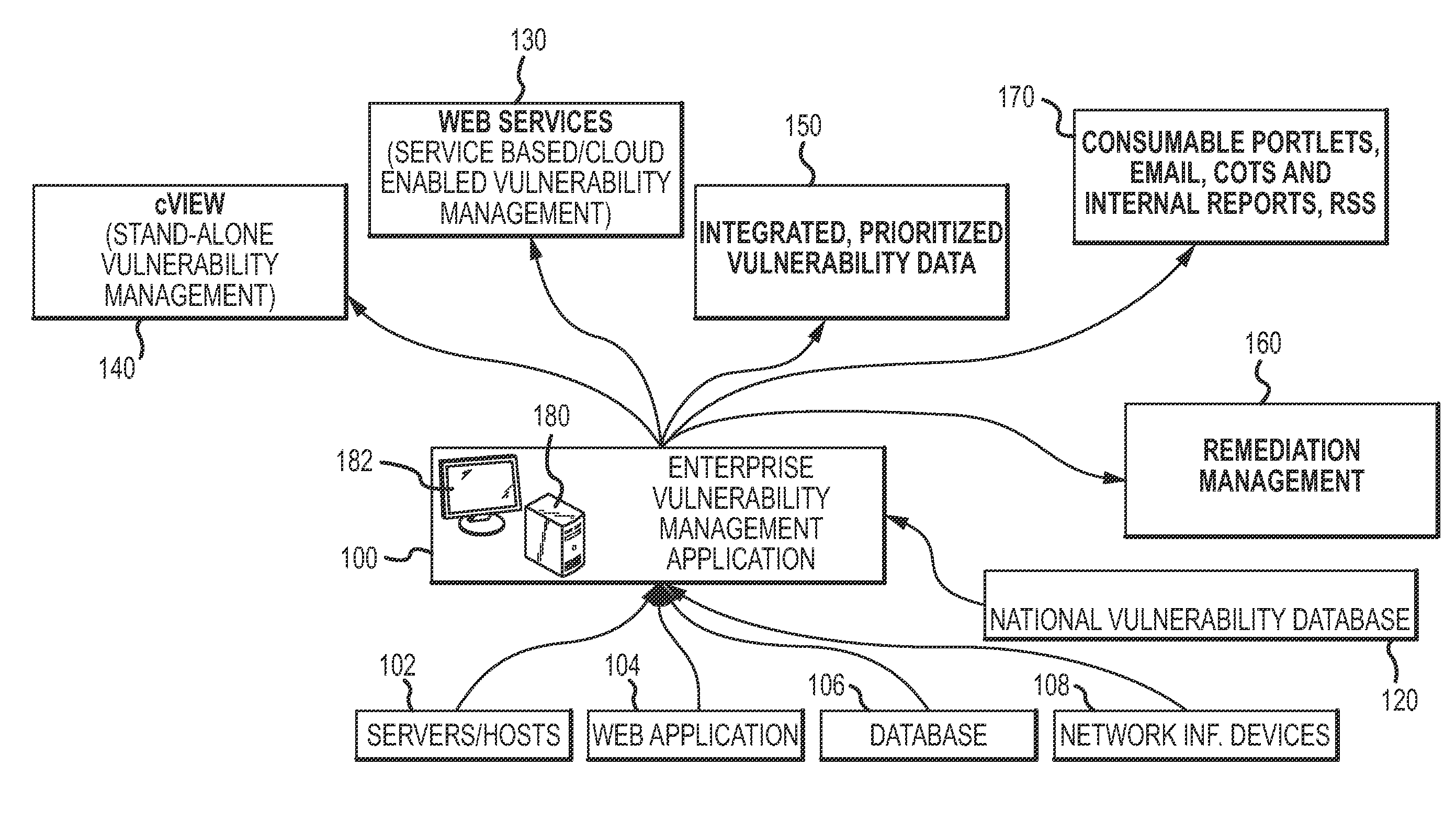
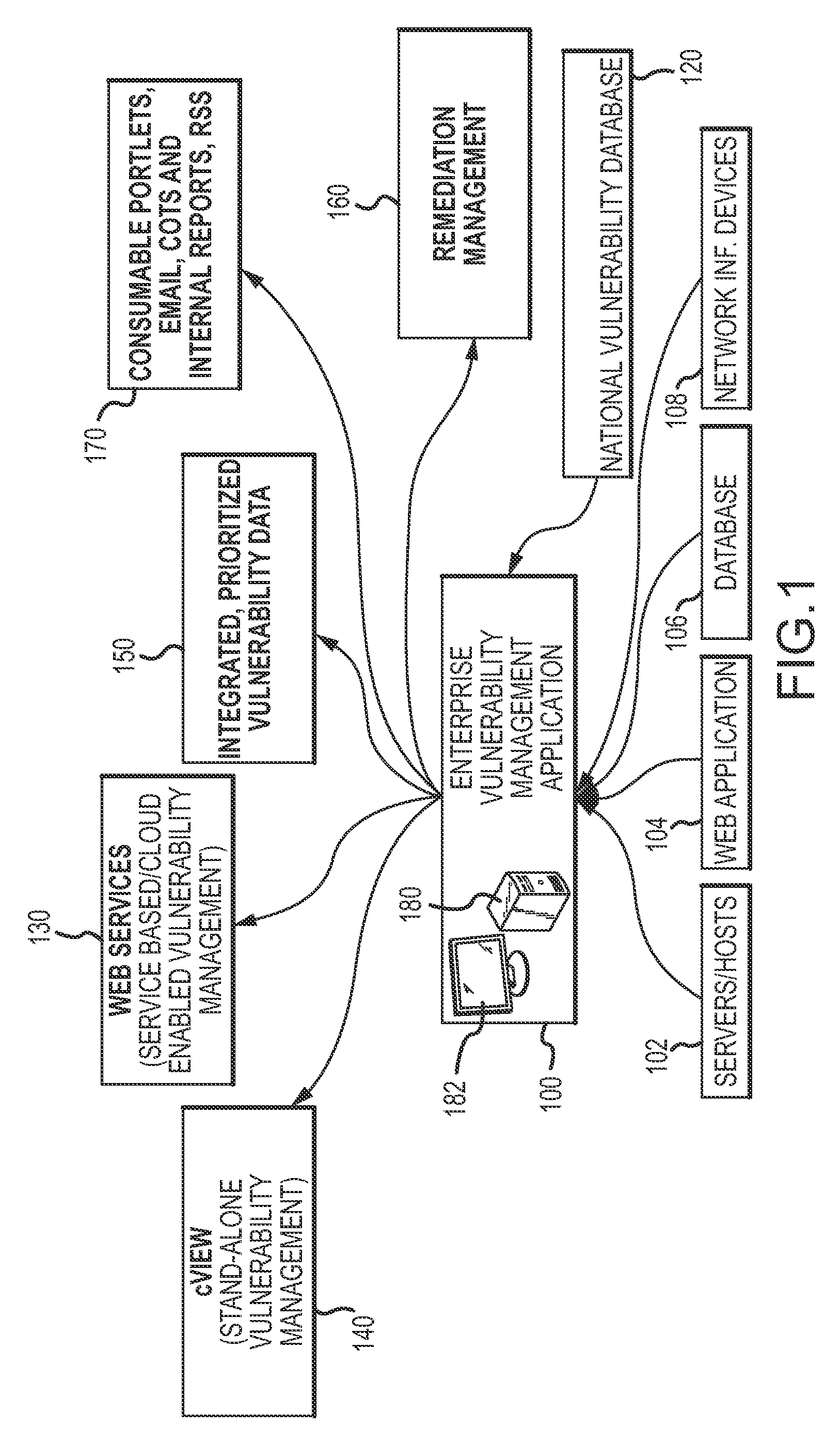
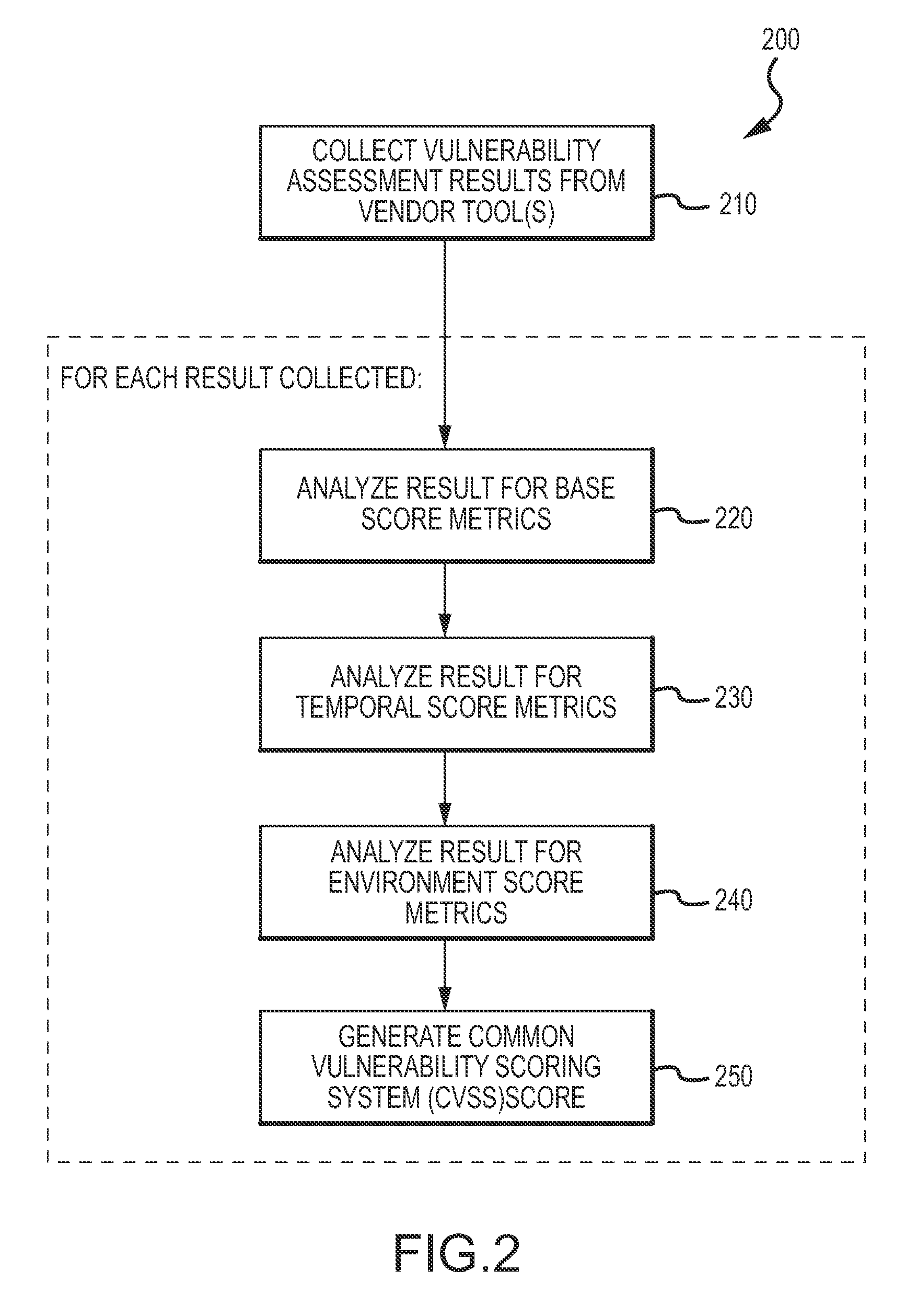
Enterprise vulnerability management
ActiveUS20120304300A1Fast data analysisEasy to addMemory loss protectionError detection/correctionVulnerability managementRemedial action
An enterprise vulnerability management application (EVMA), enterprise vulnerability management process (EVMP) and system. In one embodiment, the EVMP may include executing computer software code on at least one computer hardware platform to receive login information from a user, inventory current information technology assets of the enterprise, conduct vulnerability scanning of the inventoried information technology assets, analyze vulnerability correlation and prioritization of the information technology assets, remediate one or more vulnerabilities of the information technology assets, and report to the user about the vulnerabilities and remediation undertaken. As part of the analysis, one or more vulnerability scores such as, for example, Common Vulnerability Scoring System (CVSS) scores, may be generated from base score metrics, temporal score metrics and environment score metrics.
Owner:LEIDOS INNOVATIONS TECH INC
System and method for controlling movement of vehicles
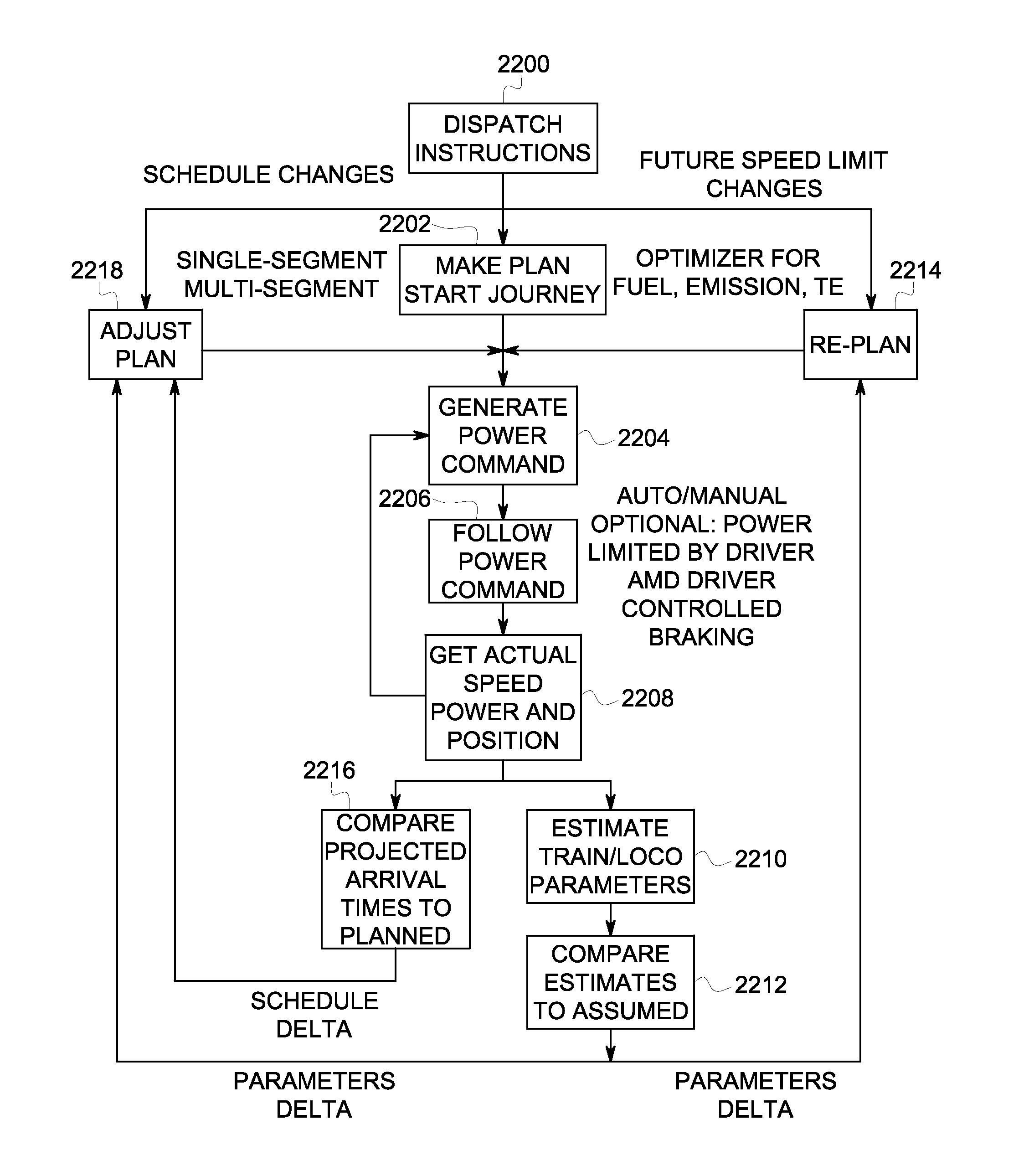
ActiveUS20120277940A1Improve performanceSave fuelDigital data processing detailsTraffic regulationRemedial actionTransport network
A method includes determining an operational parameter of a first vehicle traveling with a plurality of vehicles in a transportation network and / or a route in the transportation network, identifying a failure condition of the first vehicle and / or the route based on the operational parameter, obtaining plural different sets of remedial actions that dictate operations to be taken based on the operational parameter, simulating travel of the plurality of vehicles in the transportation network based on implementation of the different sets of remedial actions, determining potential consequences on travel of the plurality of vehicles in the transportation network when the different sets of remedial actions are implemented in the travel that is simulated, and based on the potential consequences, receiving a selection of at least one of the different sets of remedial actions to be implemented in actual travel of the plurality of vehicles in the transportation network.
Owner:GE GLOBAL SOURCING LLC
Method and system for preventing data leakage from a computer facilty
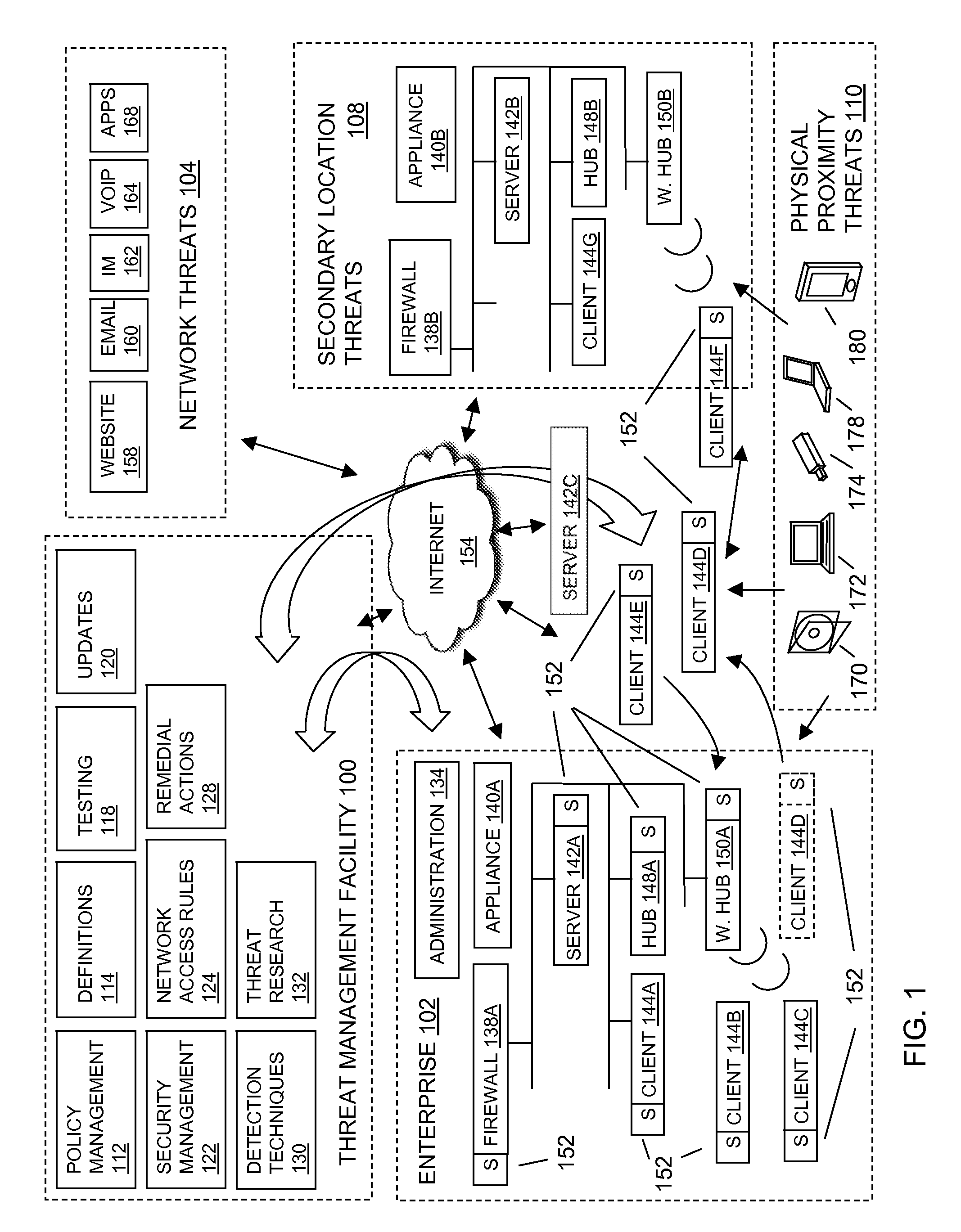
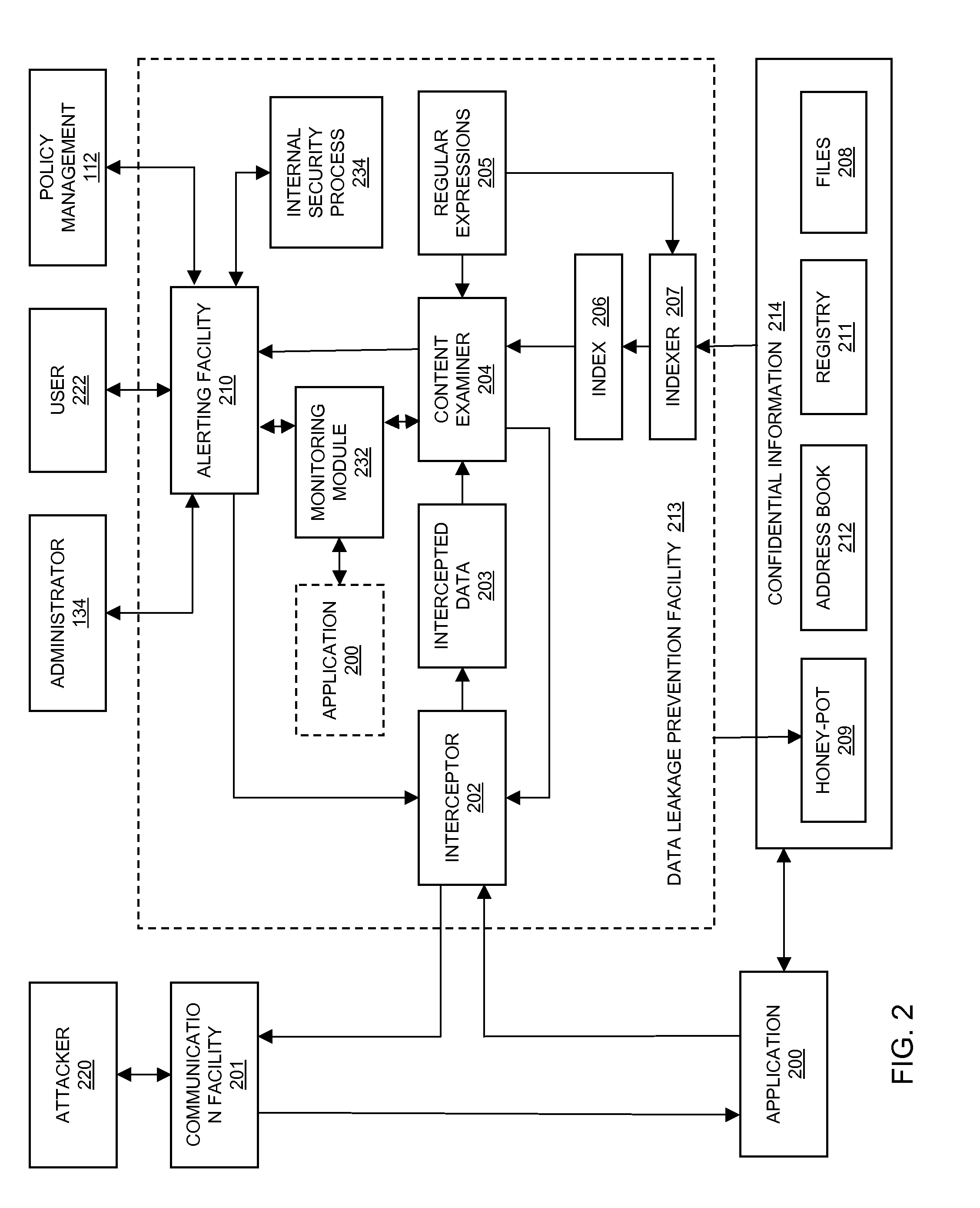
InactiveUS20100251369A1Avoid detectionAvoid runningMemory loss protectionError detection/correctionData ingestionSecurity software
In embodiments of the present invention improved capabilities are described for the steps of identifying, through a monitoring module of a security software component, a data extraction behavior of a software application attempting to extract data from an endpoint computing facility; and in response to a finding that the data extraction behavior is related to extracting sensitive information and that the behavior is a suspicious behavior, causing the endpoint to perform a remedial action. The security software component may be a computer security software program, a sensitive information compliance software program, and the like.
Owner:SOPHOS
Analytic-based security with learning adaptability
ActiveUS10104102B1High attackReliable identificationMachine learningTransmissionRemedial actionSecurity monitoring
An analytics-based security monitoring system is adapted to receive data, such as in the form of event logs, from one or more network devices transferred through a computing environment, detect a plurality of behavioral characteristics from the received event logs, identify behavioral fragments composed of related behavioral characteristics, and identify an attack by correlating the behavioral fragments against patterns of known malicious attacks. The analytics-based security monitoring system may then perform a learning process to enhance further detection of attacks and perform one or more remedial actions when an attack is identified.
Owner:FIREEYE SECURITY HLDG US LLC +1
Early warning near-real-time security system
InactiveUS6873261B2Road vehicles traffic controlAnti-theft devicesDigital videoGeneral Packet Radio Service
An early-warning security system for monitoring and tracking in real-time or at least in near-real-time the activities and movements associated with prescribed personnel, personal property, mobile vehicles, and buildings. The system comprises a plurality of in situ local controllers having a microprocessor and a coordinated plurality of conspicuous and clandestine digital video cameras for continuously producing digital audio and visual signals, uplinking such signals via a suitable wireless telecommunications device to a satellite, general packet radio service, the Internet, intranet or extranet, and then downlinking these signals to a plurality of control centers for recording and analysis thereof. Uplinking of these digital signals may occur continuously or may be activated by a manual or predefined trigger event. Preventive or remedial action is immediately taken when perturbations from normal behavior or activities are observed in the recorded audio and visual signals.
Owner:ANTHONY ERIC +1
System and method monitoring and characterizing manual welding operations
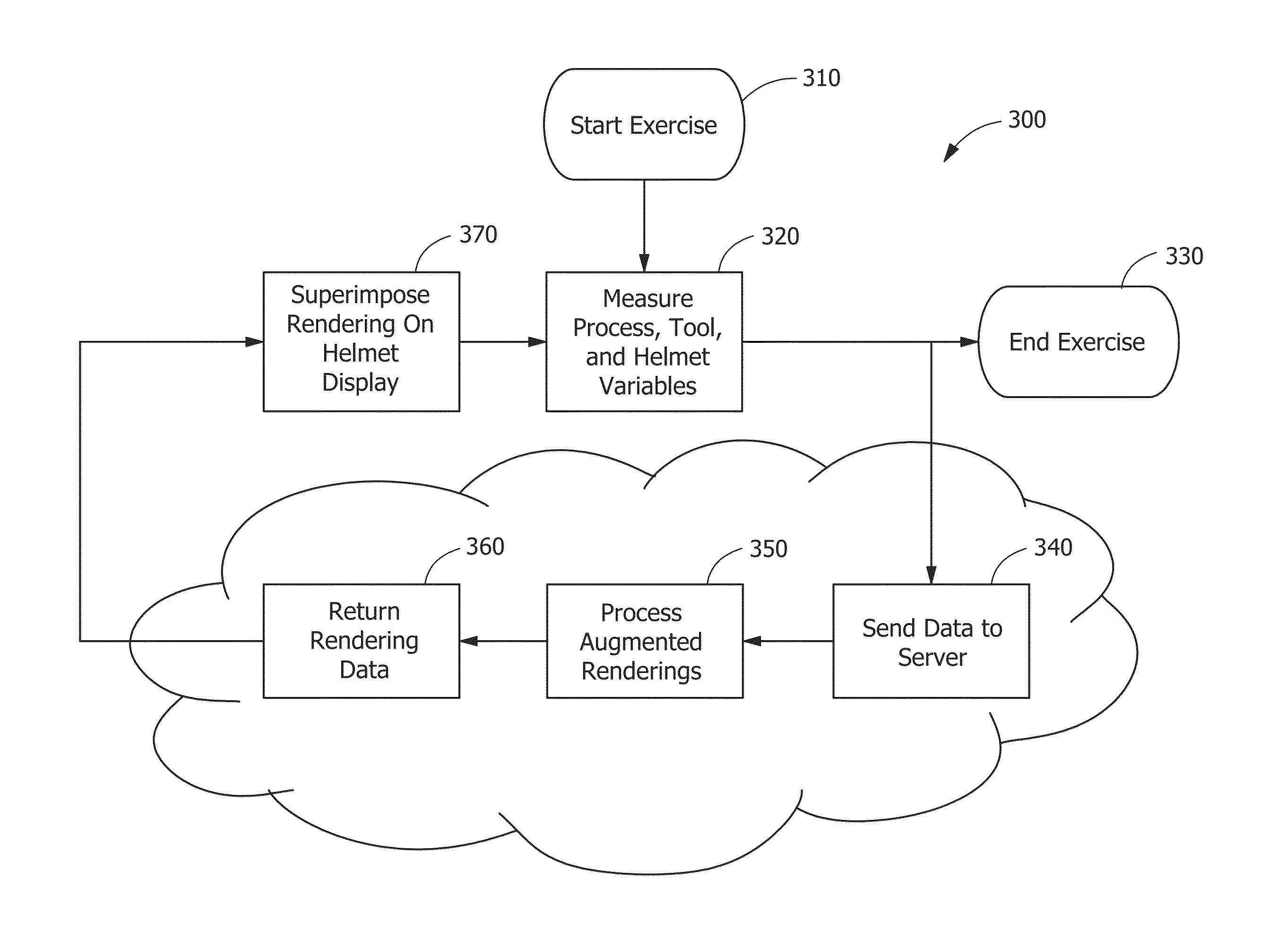
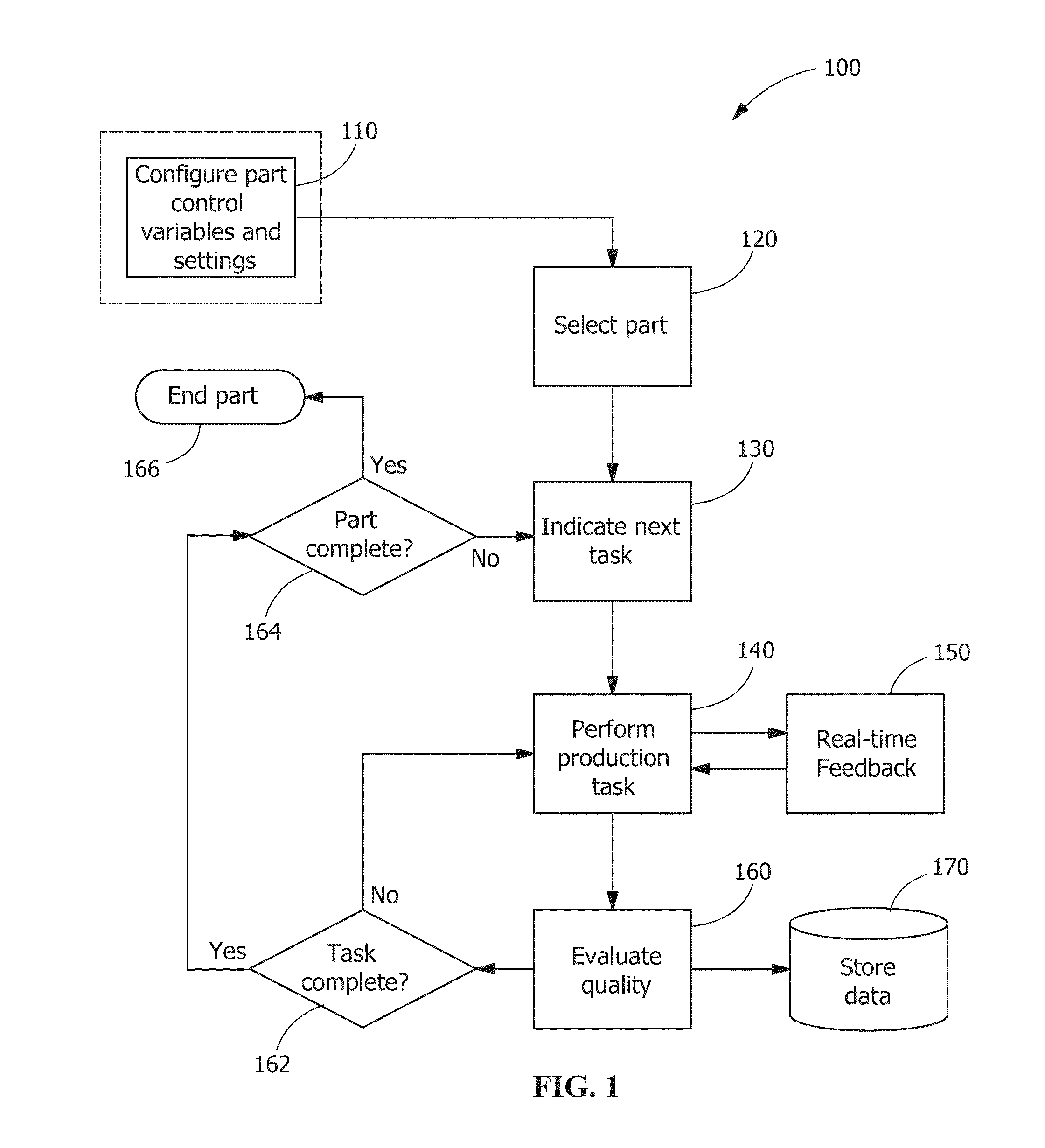
A system and method for monitoring manual welding that includes a welding system that further includes hardware and software components for gathering and processing data in real time, wherein the data is derived from an actual welding exercise conducted by a welder; providing the system with part information, process variable control targets, and acceptability limits; selecting a part to be welded from the part information; indicating a production task to be completed on the part; performing the indicated production task; providing real-time feedback to the welder performing the task; evaluating the quality of the welder's performance of the task based on the process variable control targets and acceptability limits; if necessary, requiring remedial action with regard to the quality of the performance of the task; and storing data gathered from the evaluation of the performance of the task.
Owner:LINCOLN GLOBAL INC
Automated Malware Detection and Remediation
ActiveUS20110247071A1Avoid detectionMemory loss protectionError detection/correctionState variationRemedial action
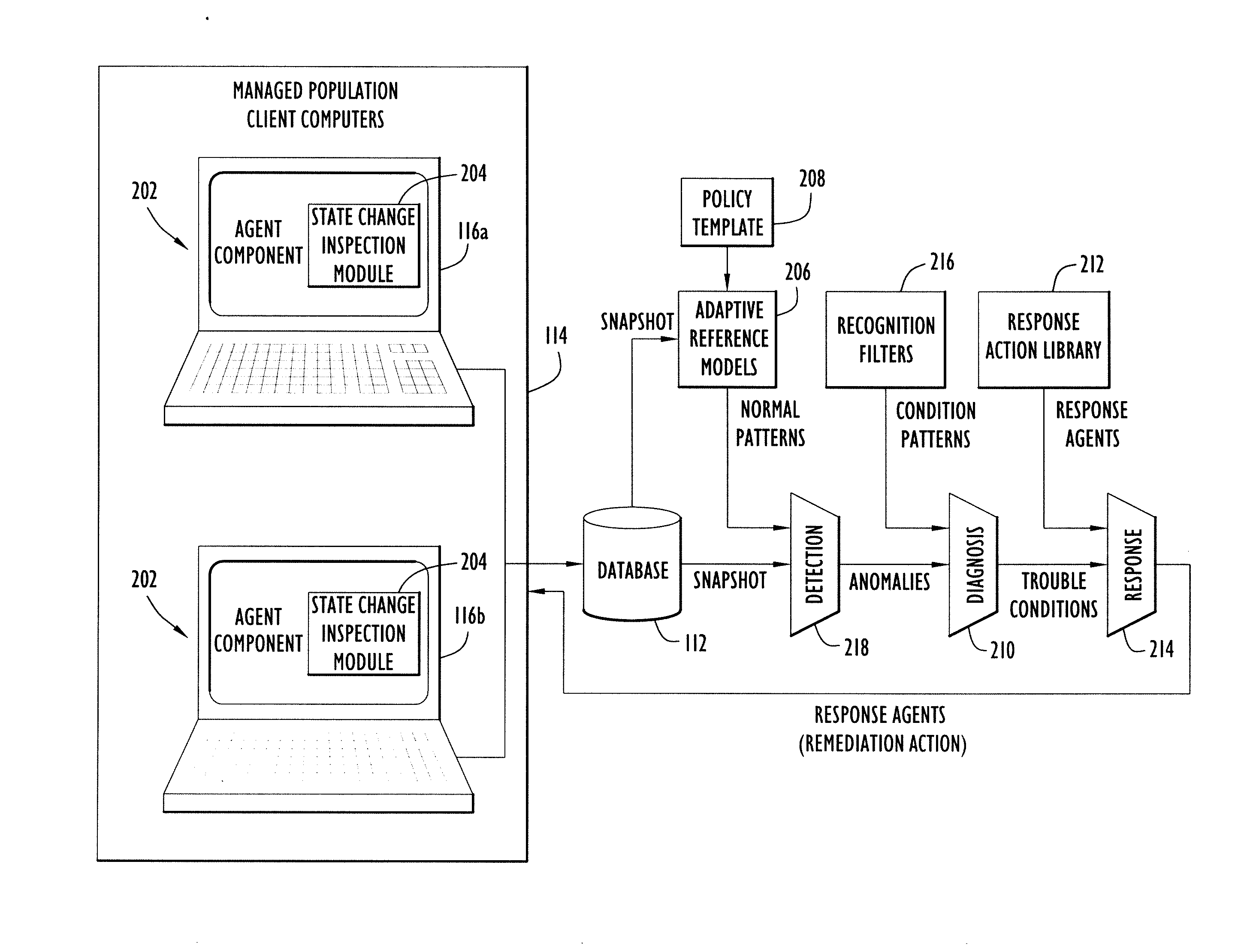
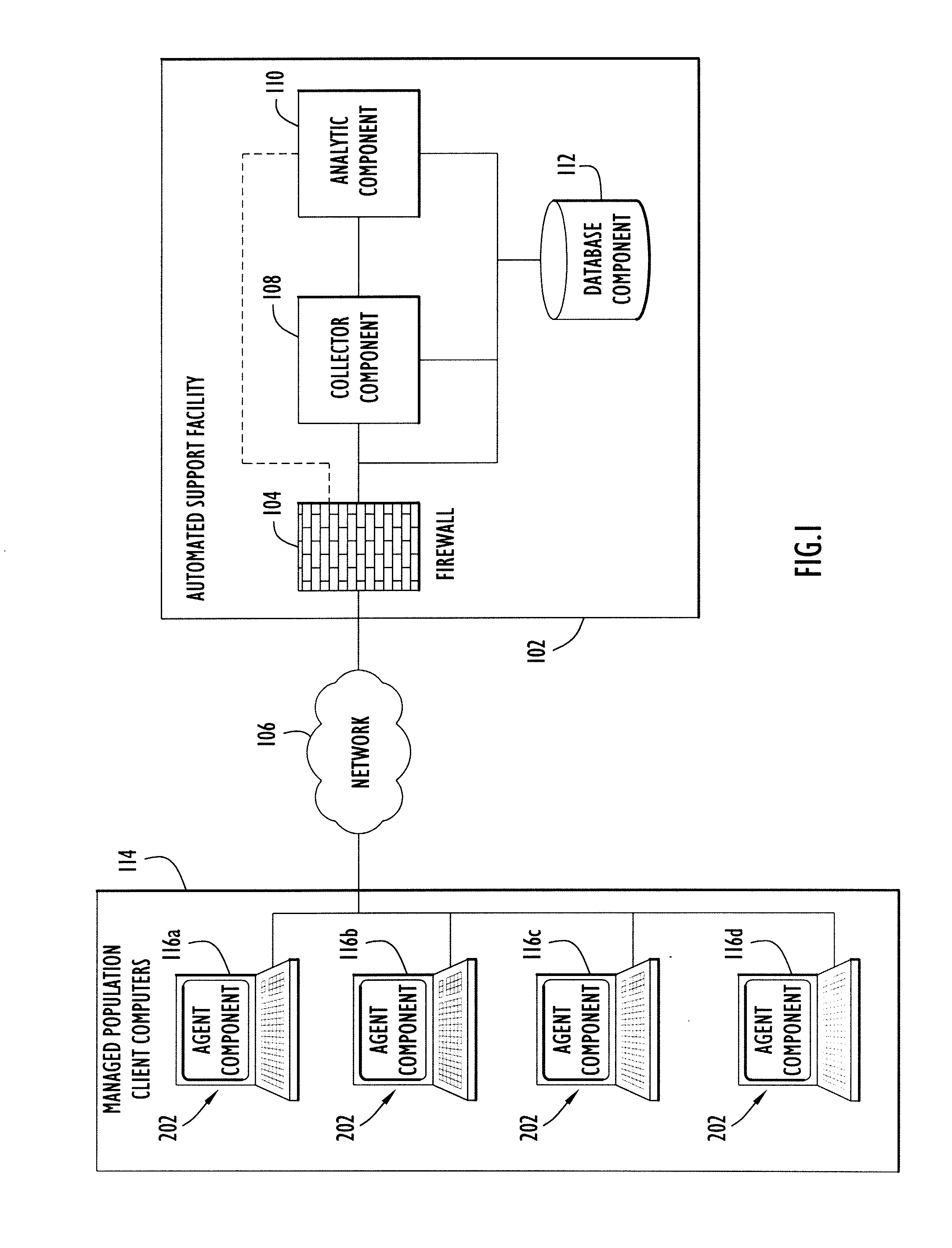
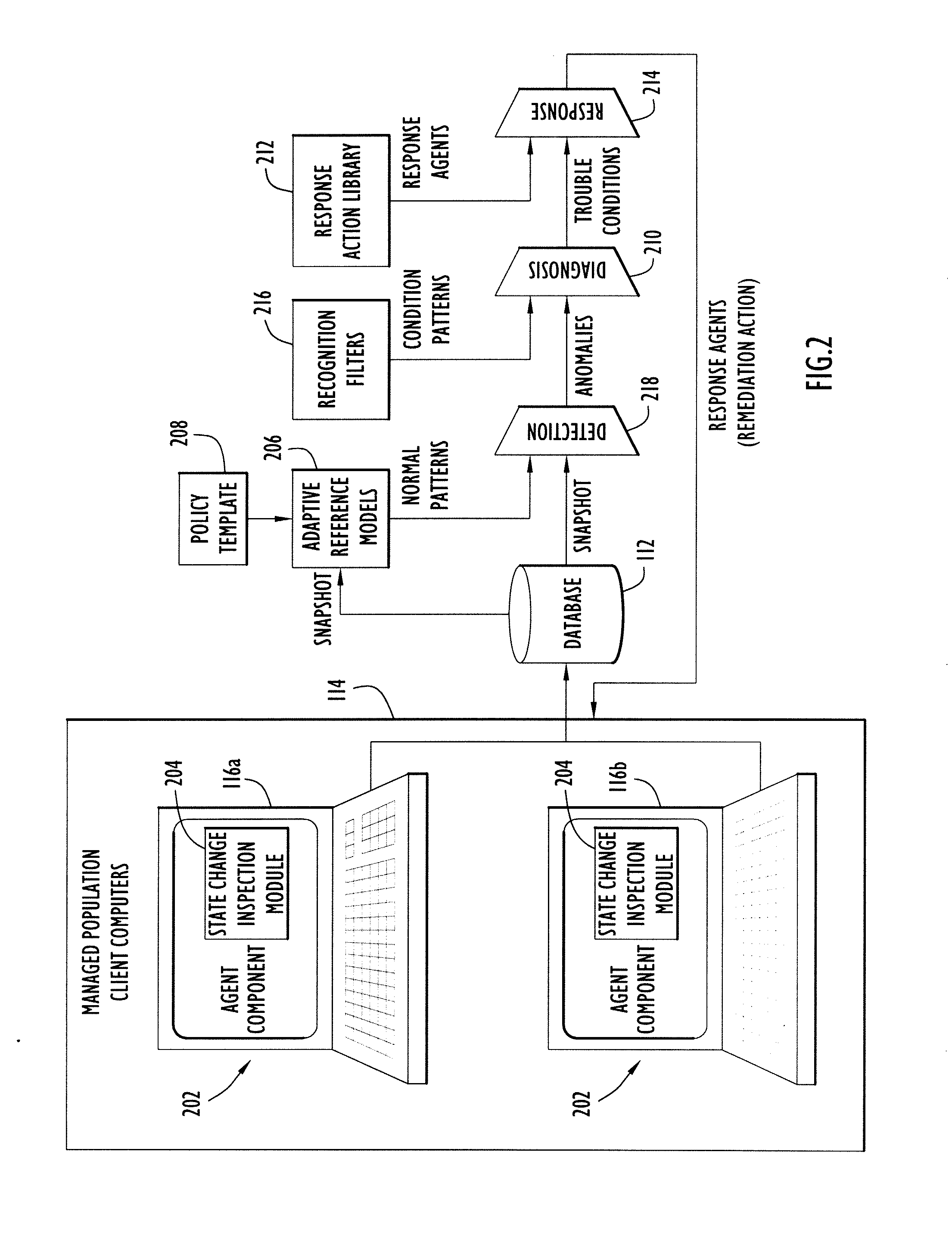
Systems and methods for detecting malware in a selected computer that is part of a network of computers. The approach includes inspecting a predetermined set of operational attributes of the selected computer to detect a change in a state of the selected computer. In response to a detected change in state, the selected computer is scanned to create a snapshot of the overall state of the selected computer. The snapshot is transmitted to an analytic system wherein it is compared with an aggregated collection of snapshots previously respectively received from a plurality of computers in the computer network. Based on the comparison, anomalous state of the selected computer can be identified. In turn, a probe of the selected computer is launched to gather additional information related to the anomalous state of the selected computer so that a remediation action for the anomalous state of the selected computer can be generated.
Owner:RPX CORP
Remote monitoring diagnostics
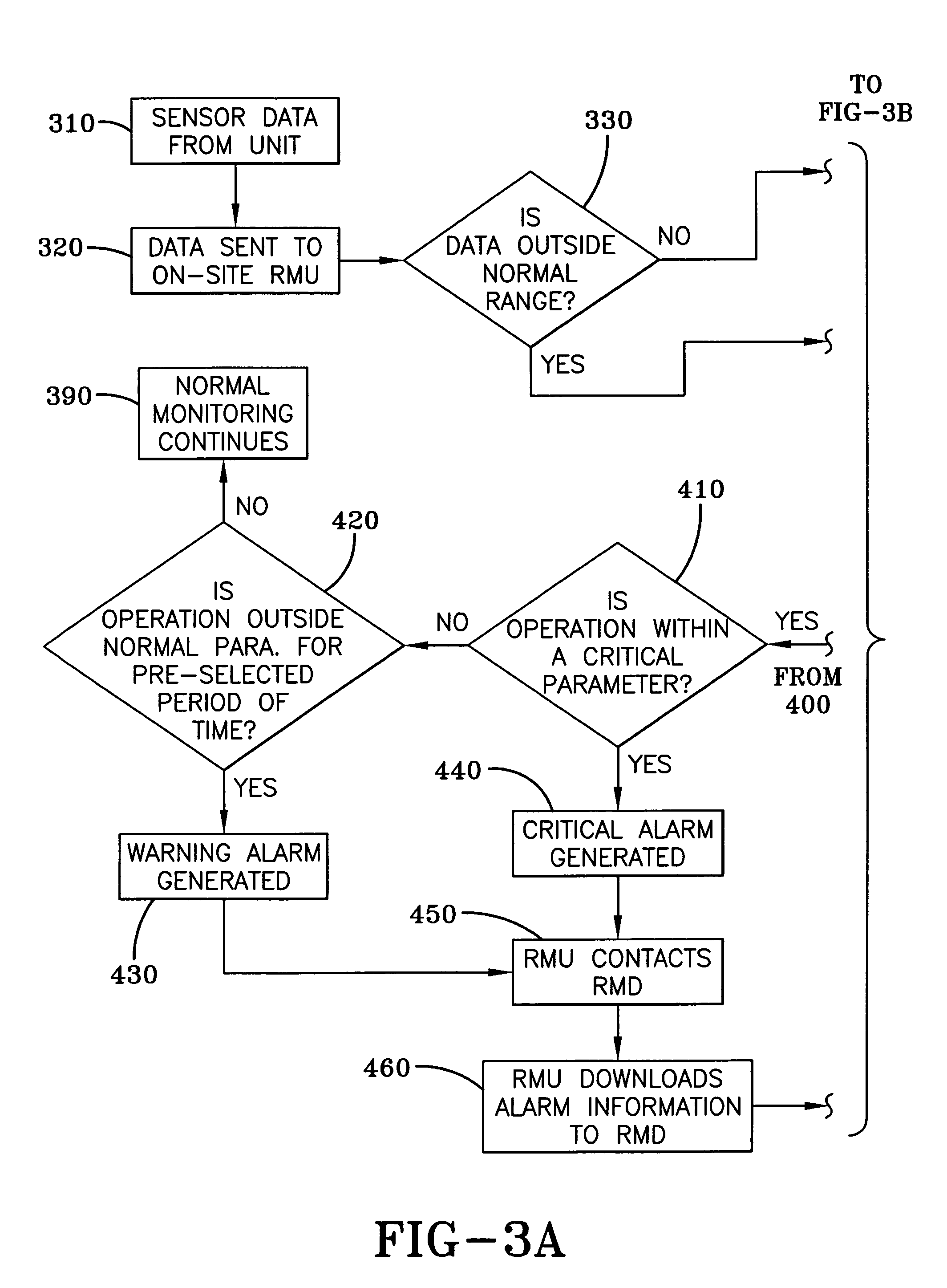
InactiveUS6955302B2Reduce needMinimize the numberMechanical apparatusSpace heating and ventilation safety systemsRemedial actionSystem usage
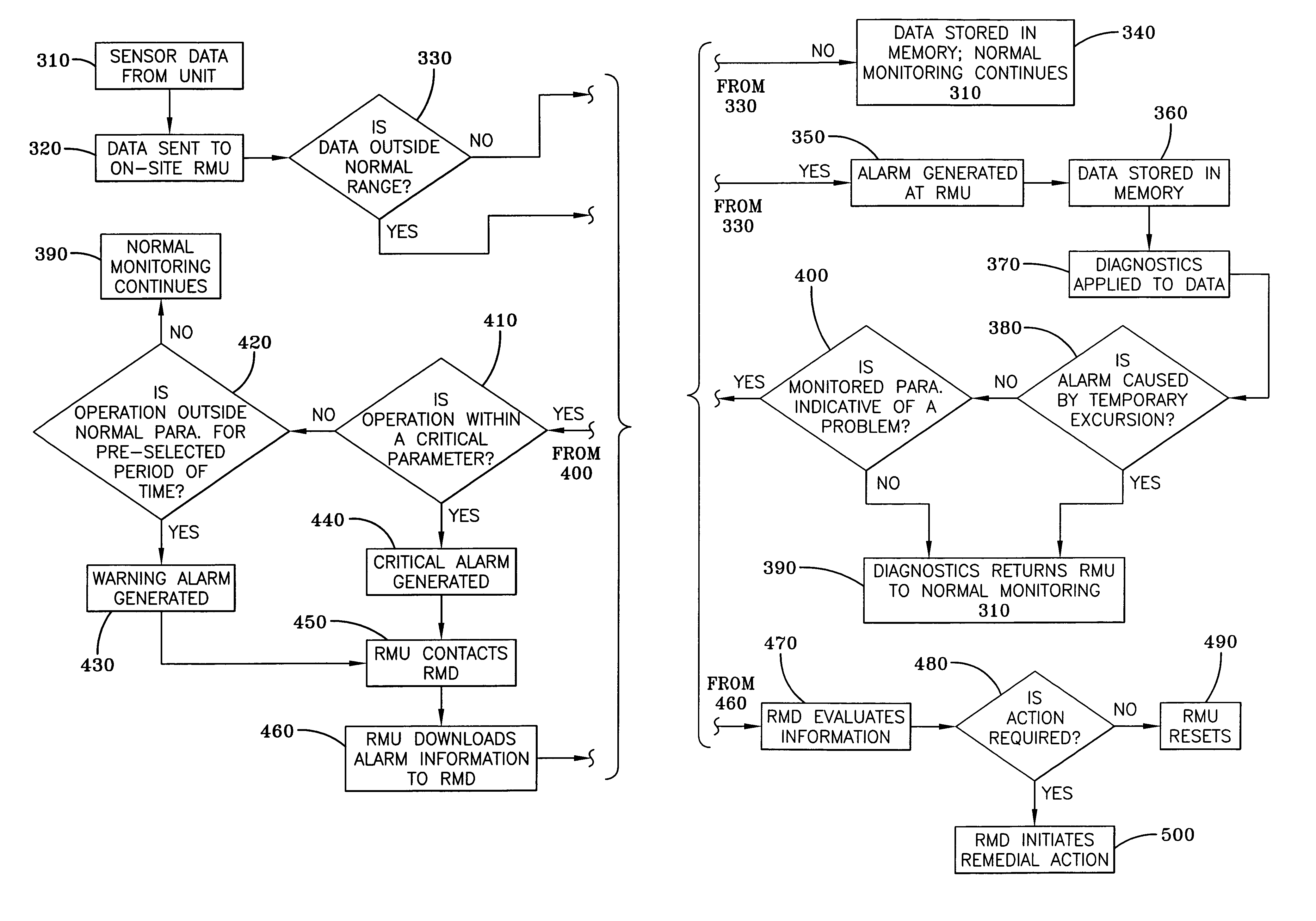
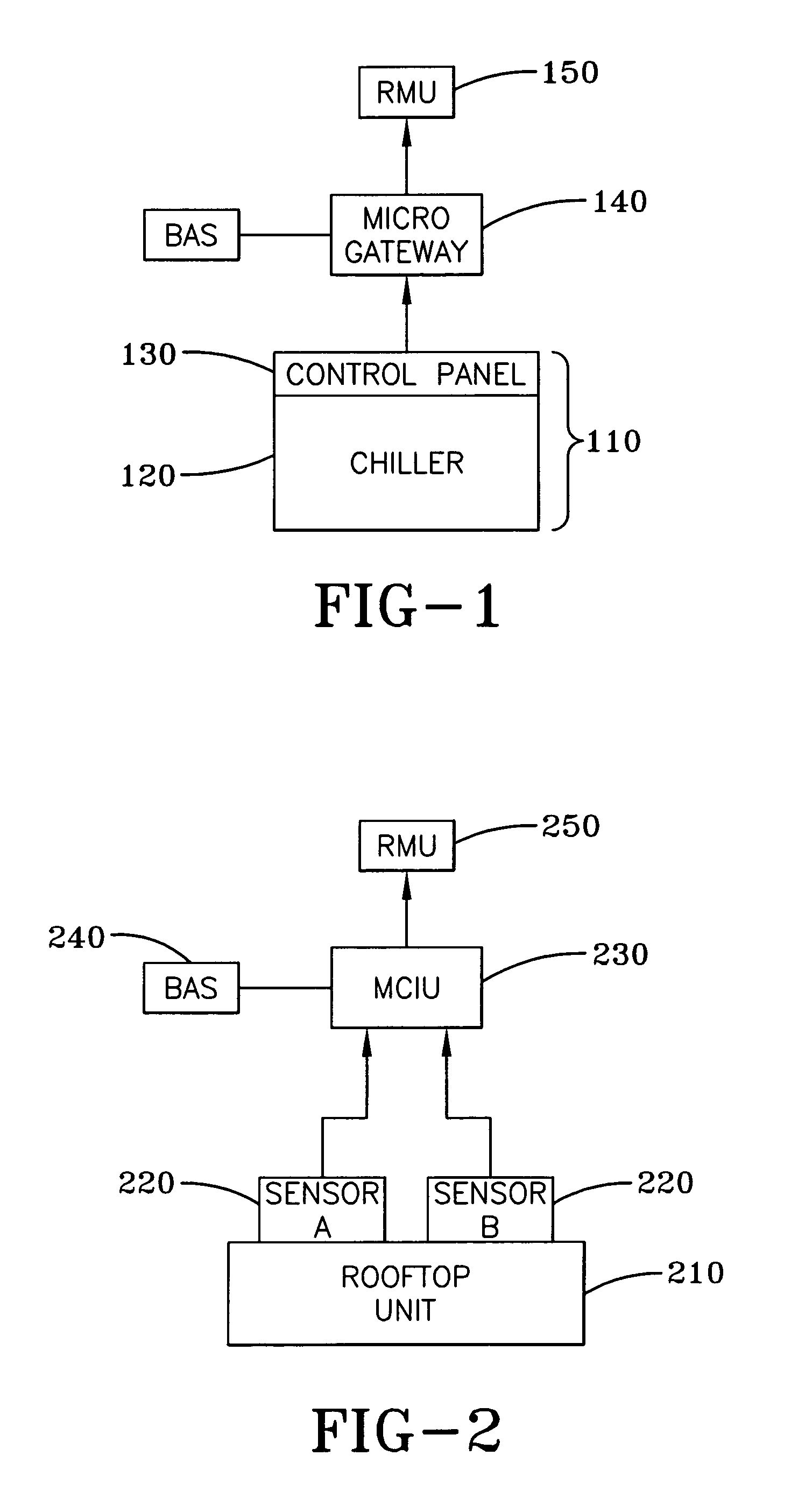
A system for remotely monitoring operations of an HVAC system such as a chiller system having a control center, or a rooftop unit. The system utilizes a remote monitoring unit (RMU) located on-site. The RMU is in one-way communication with the component of the air conditioning system and receives data indicative of the operation of the component and determines whether the component is operating outside the normal operating parameters. When the RMU determines, from the data, that there is a problem that is within a critical parameter range, then a critical alarm is generated and the RMU opens a line of communication with a remote monitoring diagnostics device (RMD) located at the facility of the HVAC or refrigeration manufacturer and downloads the information to the RMD which determines whether remedial action is required and initiates remedial action if required.
Owner:YORK INT CORP
Drilling components and systems to dynamically control drilling dysfunctions and methods of drilling a well with same
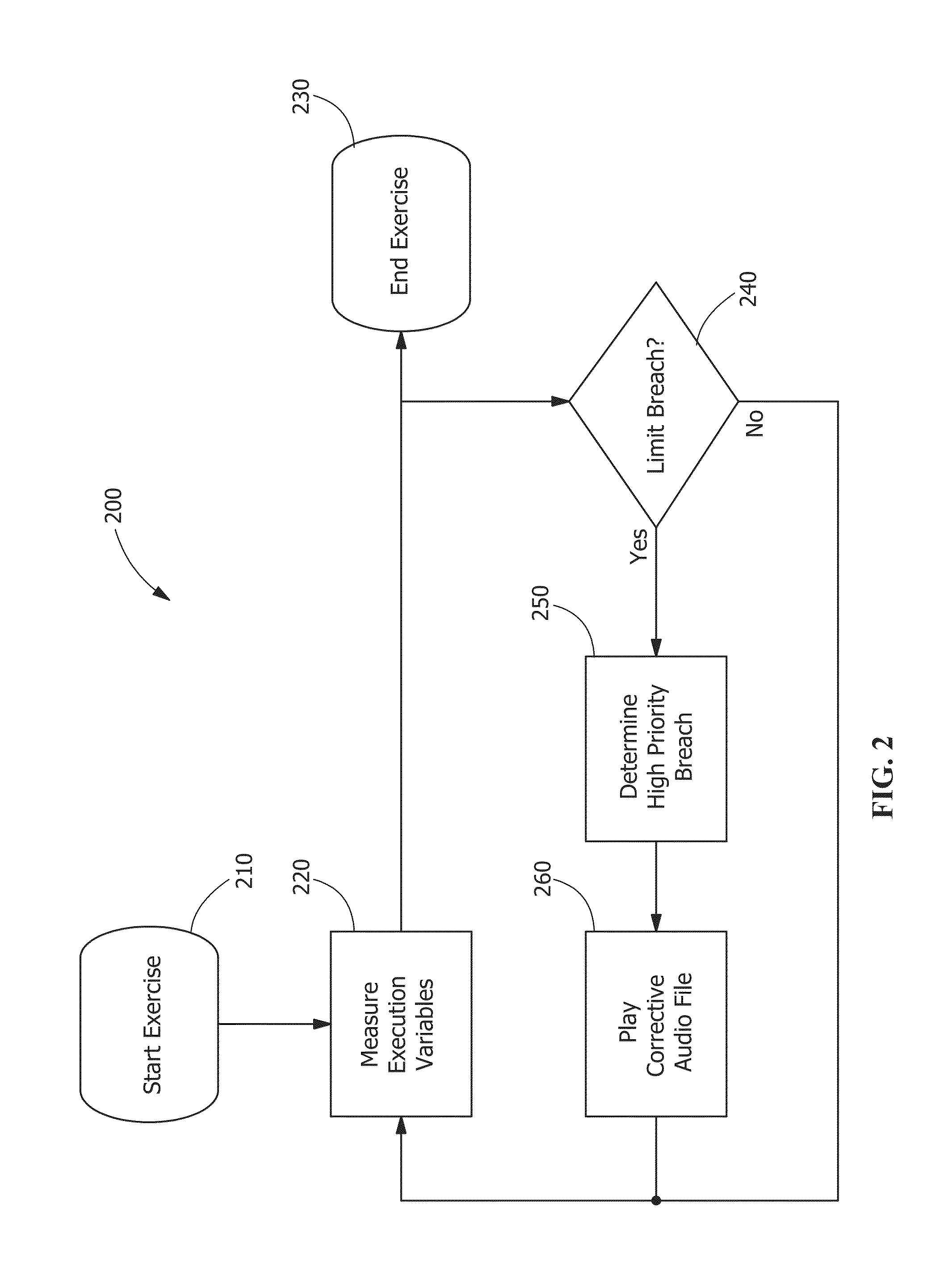
Drilling tools that may detect and dynamically adjust drilling parameters to enhance the drilling performance of a drilling system used to drill a well. The tools may include sensors, such as RPM, axial force for measuring the weight on a drill bit, torque, vibration, and other sensors known in the art. A processor may compare the data measured by the sensors against various drilling models to determine whether a drilling dysfunction is occurring and what remedial actions, if any, ought to be taken. The processor may command various tools within the bottom hole assembly (BHA), including a bypass valve assembly and / or a hydraulic thruster to take actions that may eliminate drilling dysfunctions or improve overall drilling performance. The processor may communicate with a measurement while drilling (MWD) assembly, which may transmit the data measured by the sensors, the present status of the tools, and any remedial actions taken to the surface.
Owner:BAKER HUGHES INC
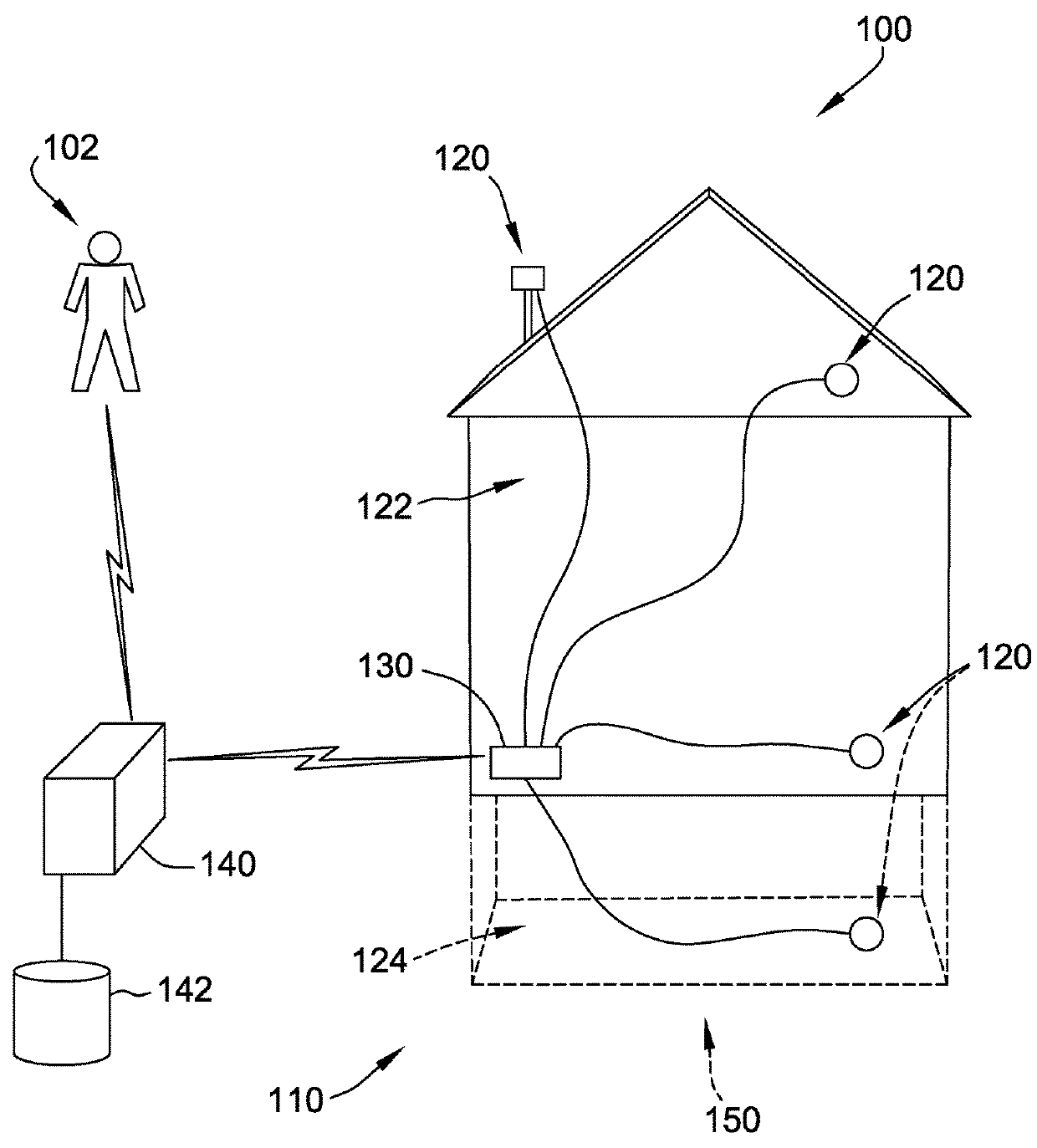
Systems and methods for monitoring building health
ActiveUS10042341B1Early detectionDetection of fluid at leakage pointWallsArchitectural engineeringRemedial action
A building monitoring computer system for monitoring building integrity may be provided. Various types of sensors may be embedded throughout or within certain portions of different types of building or construction material making up the building, such as within roofing, foundation, or structural materials. The sensors may be in wireless communication with a home controller. The sensors may be water, moisture, temperature, vibration, or other types of sensors, and may detect unexpected or abnormal conditions within the home. The sensors and / or home controller may transmit alerts to a mobile device of the home owner associated with the unexpected condition, and / or that remedial actions may be required to repair the home or mitigate further damage to the home. The sensor data may also be communicated to an insurance provider remote server to facilitate the insurance provider communicating insurance-related recommendations, updating insurance policies, or preparing insurance claims for review for home owners.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
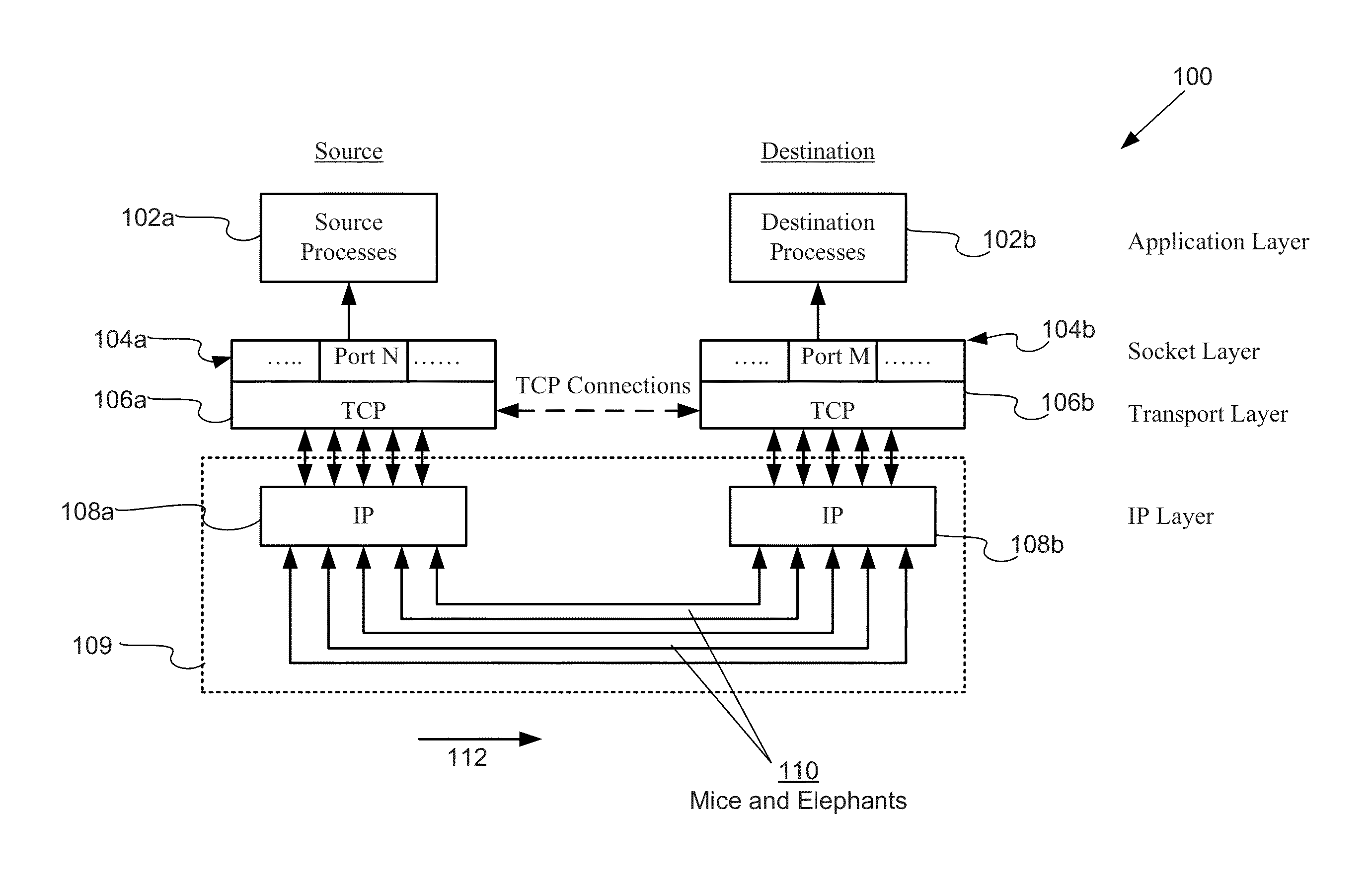
Methods and systems for detecting, locating and remediating a congested resource or flow in a virtual infrastructure
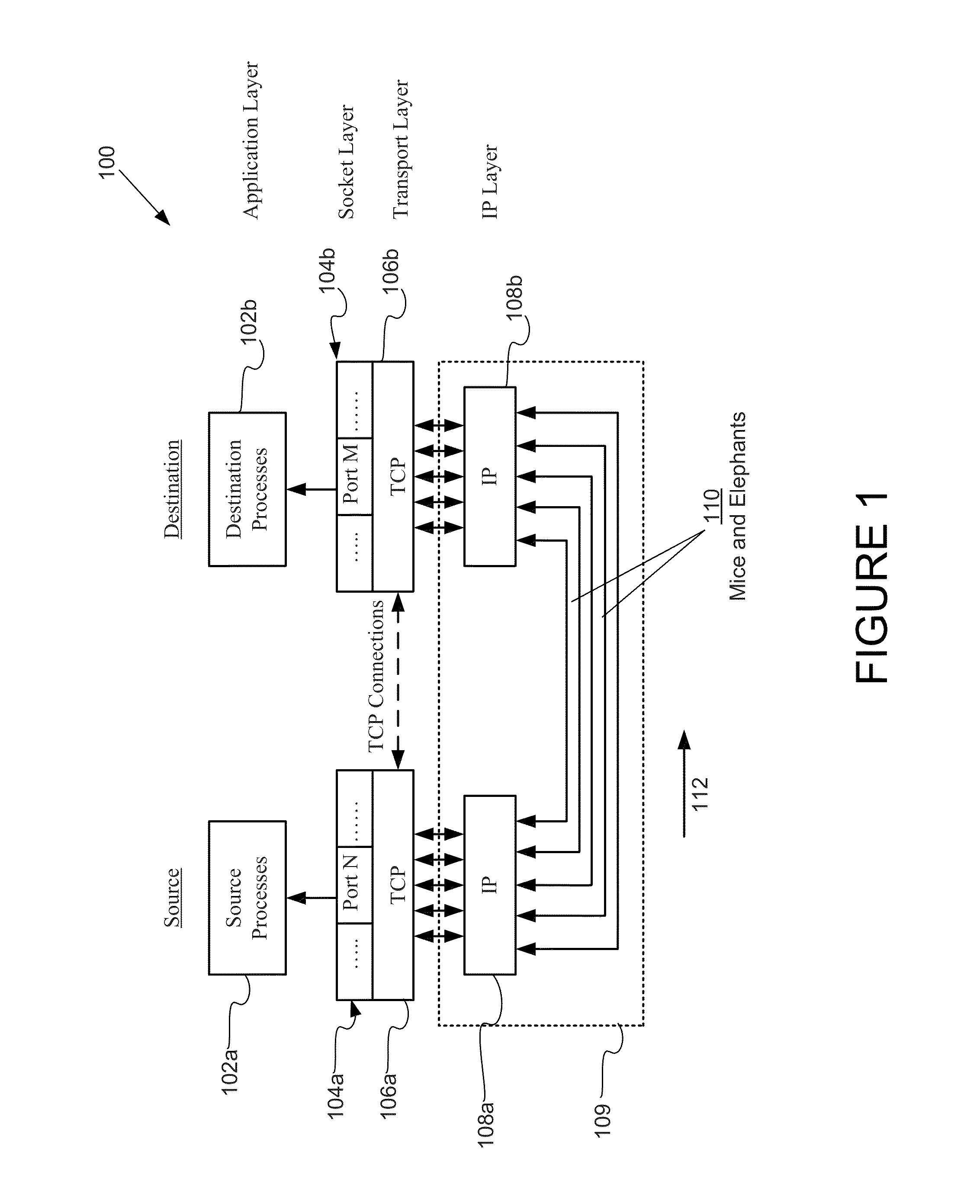
InactiveUS20140215077A1Well formedDigital computer detailsData switching networksRemedial actionDistributed computing
Once a potential bottleneck is identified, the system provides a methodology for locating the bottleneck. The methodology involves checking in order each of the application, transport and network layers of a sender and receiver nodes for performance problems. Conditions are defined for each of the layers at the sender and receiver nodes that are indicative of a particular type of bottleneck. When the conditions are met in any one of the layers, the system can be configured to stop the checking process and output a message indicating the presence of a bottleneck in the layer and its location. In addition, the system can be configured to generate and output a remedial action for eliminating the bottleneck. The system can be configured to perform the action automatically or after receiving a confirmation from the user.
Owner:F5 NETWORKS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com