Patents
Literature
373 results about "Security software" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
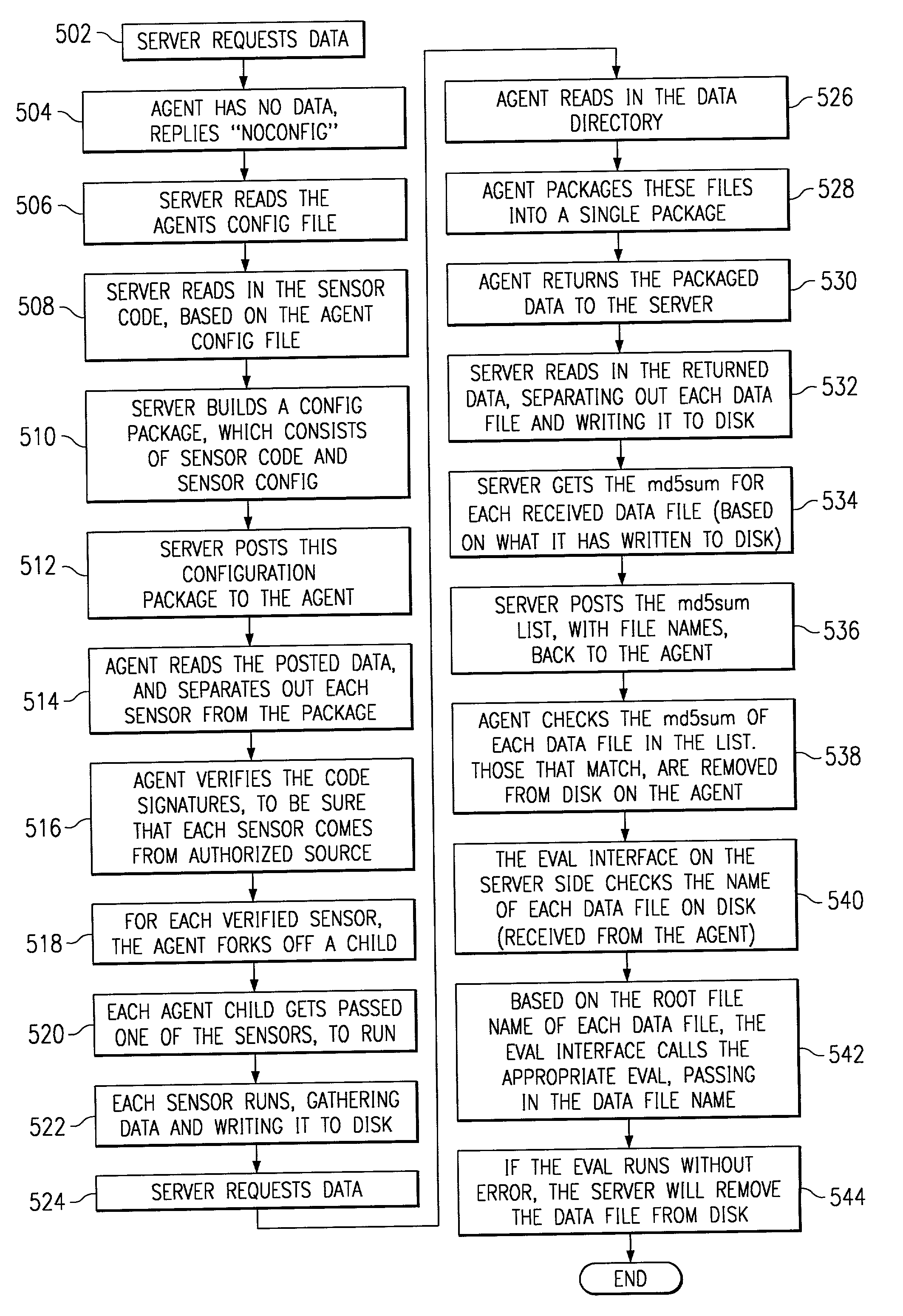
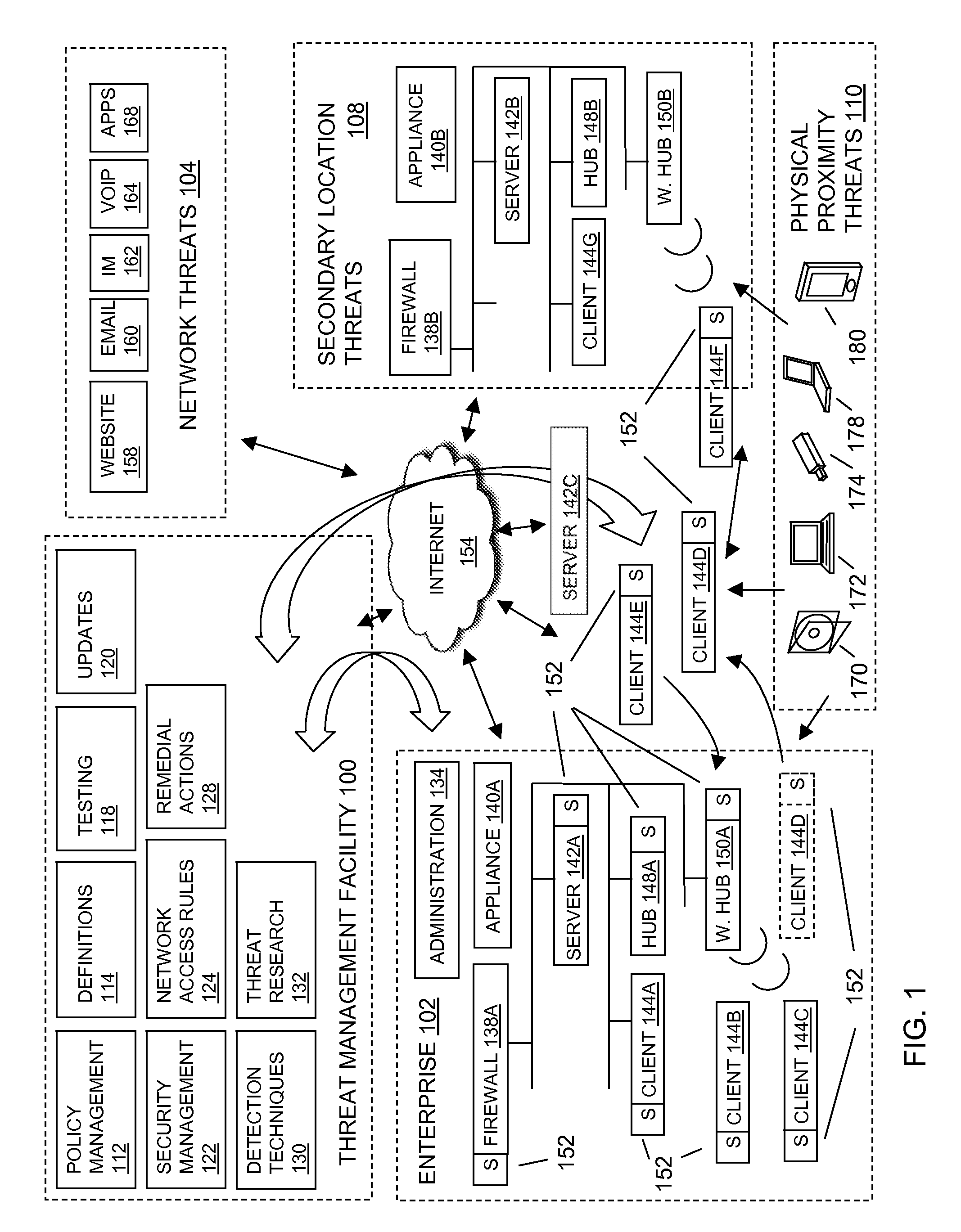
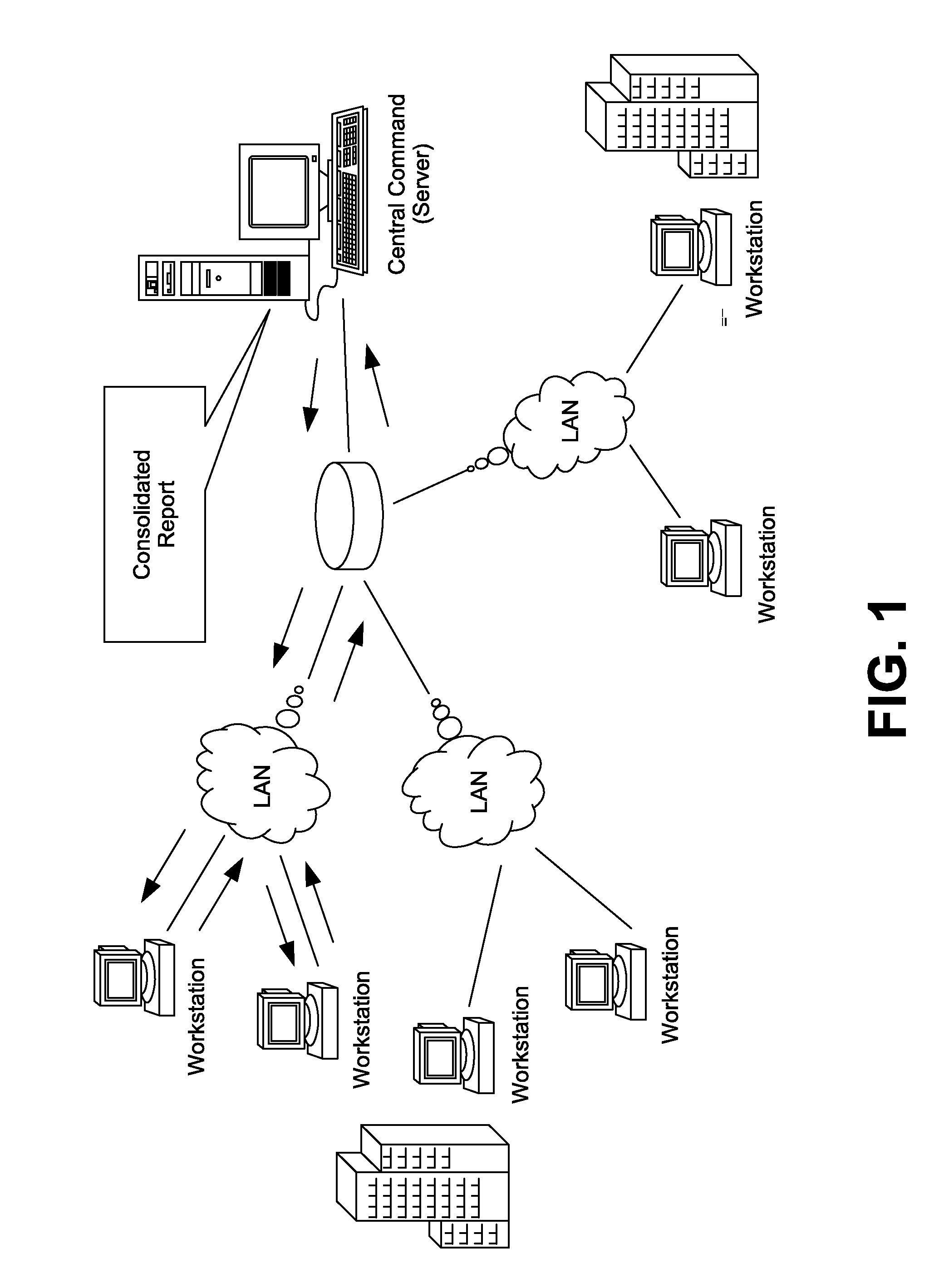
Scalable system for monitoring network system and components and methodology therefore
InactiveUS20020078382A1Memory loss protectionDigital computer detailsScalable systemSecurity software
The present invention is a security software methodology and system that takes an internal approach to mitigating security risks from authorized and unauthorized users. The security software system uses the methodology of monitoring, in great detail, any configuration changes made to information systems within a network. These systems and applications include web servers, firewalls, proxy servers, log servers, intrusion detection software systems, routers and any other device or application which can be considered a part of the enterprise information system infrastructure.
Owner:SECURITY & INTRUSION DETECTION RES LABS
Methods and apparatus for large scale distribution of electronic access clients
ActiveUS20130227646A1Large distributionDigital data processing detailsMultiple digital computer combinationsElectronic accessSecurity software
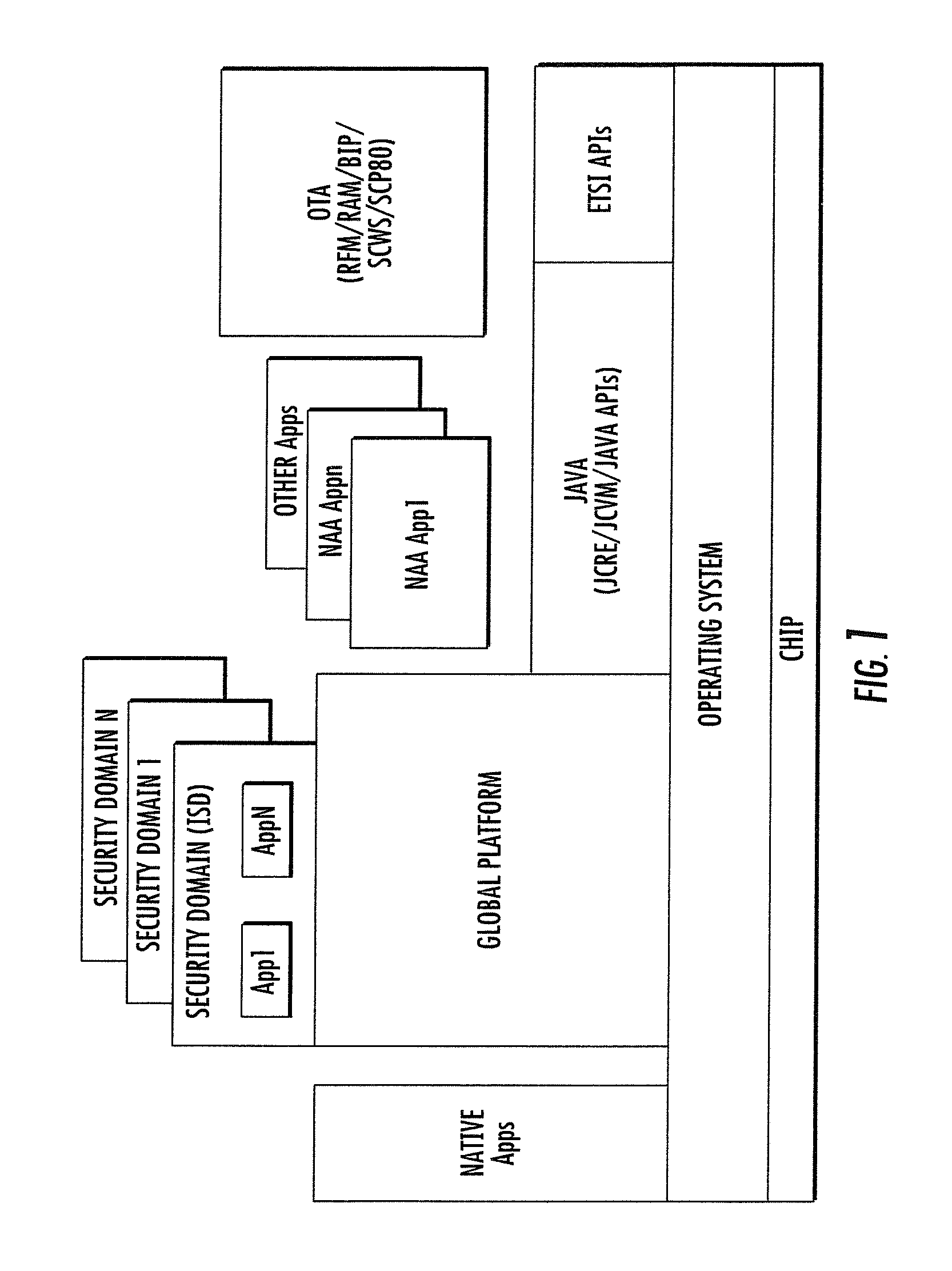
Methods and apparatus for large scale distribution of electronic access control clients. In one aspect, a tiered security software protocol is disclosed. In one exemplary embodiment, a server electronic Universal Integrated Circuit Card (eUICC) and client eUICC software comprise a so-called “stack” of software layers. Each software layer is responsible for a set of hierarchical functions which are negotiated with its corresponding peer software layer. The tiered security software protocol is configured for large scale distribution of electronic Subscriber Identity Modules (eSIMs)
Owner:APPLE INC
Policies for secure software execution
InactiveUS7350204B2Efficiently constrain (or prevent from running) everything on a machineDigital data processing detailsUnauthorized memory use protectionFile systemDigital signature
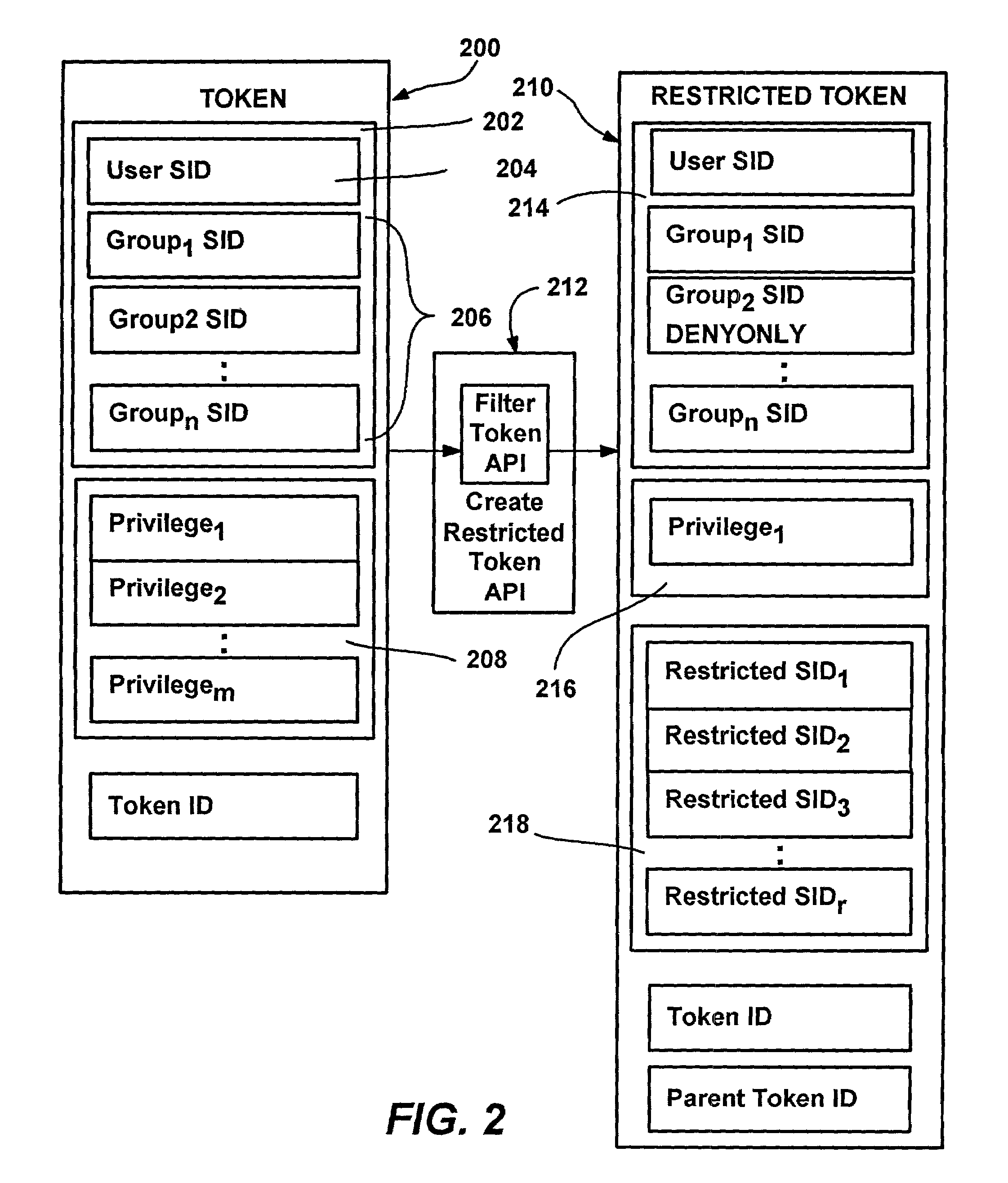
A system and method that automatically, transparently and securely controls software execution by identifying and classifying software, and locating a rule and associated security level for executing executable software. The security level may disallow the software's execution, restrict the execution to some extent, or allow unrestricted execution. To restrict software, a restricted access token may be computed that reduces software's access to resources, and / or removes privileges, relative to a user's normal access token. The rules that control execution for a given machine or user may be maintained in a restriction policy, e.g., locally maintained and / or in a group policy object distributable over a network. Software may be identified / classified by a hash of its content, by a digital signature, by its file system or network path, and / or by its URL zone. For software having multiple classifications, a precedence mechanism is provided to establish the applicable rule / security level.
Owner:MICROSOFT TECH LICENSING LLC
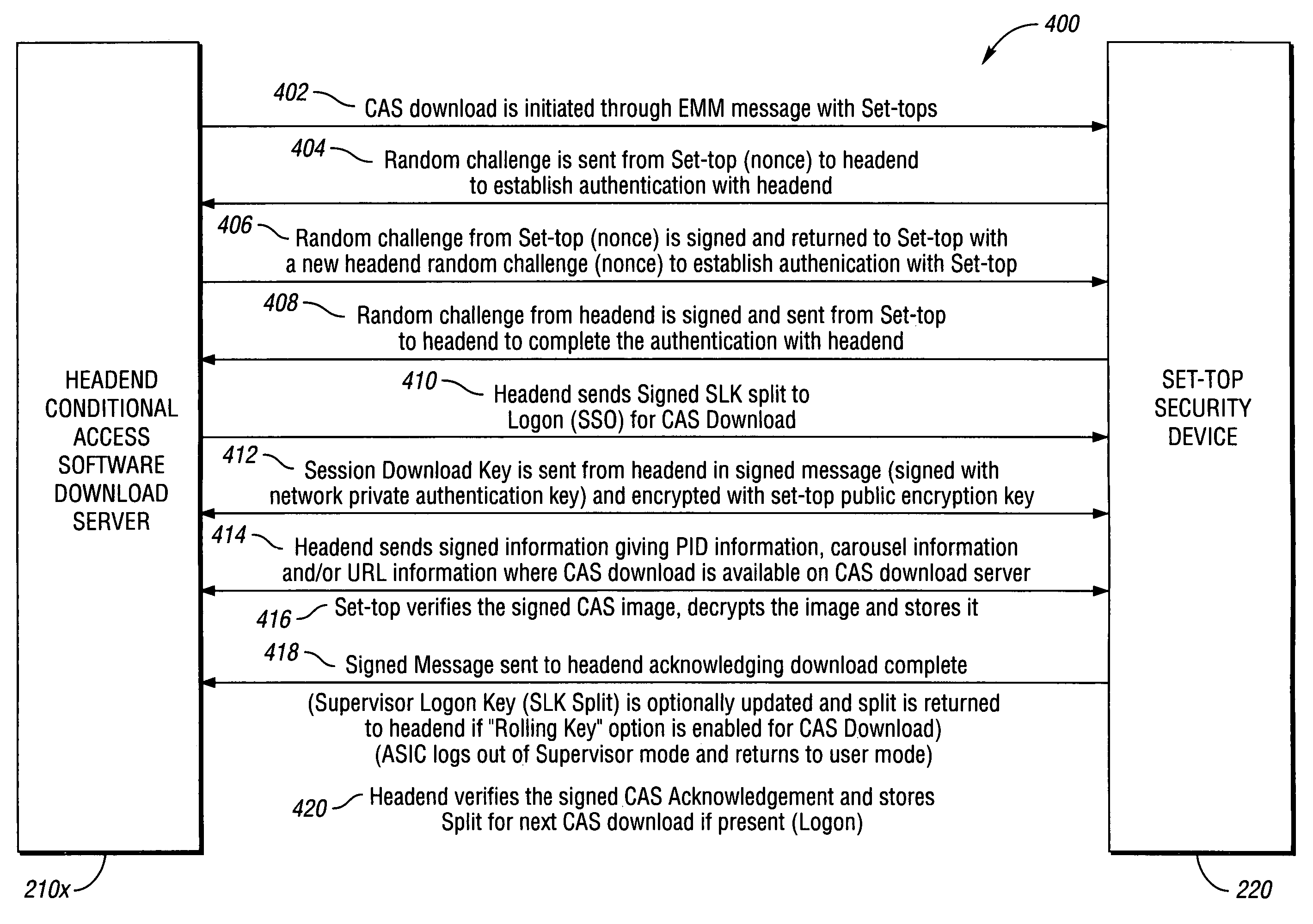
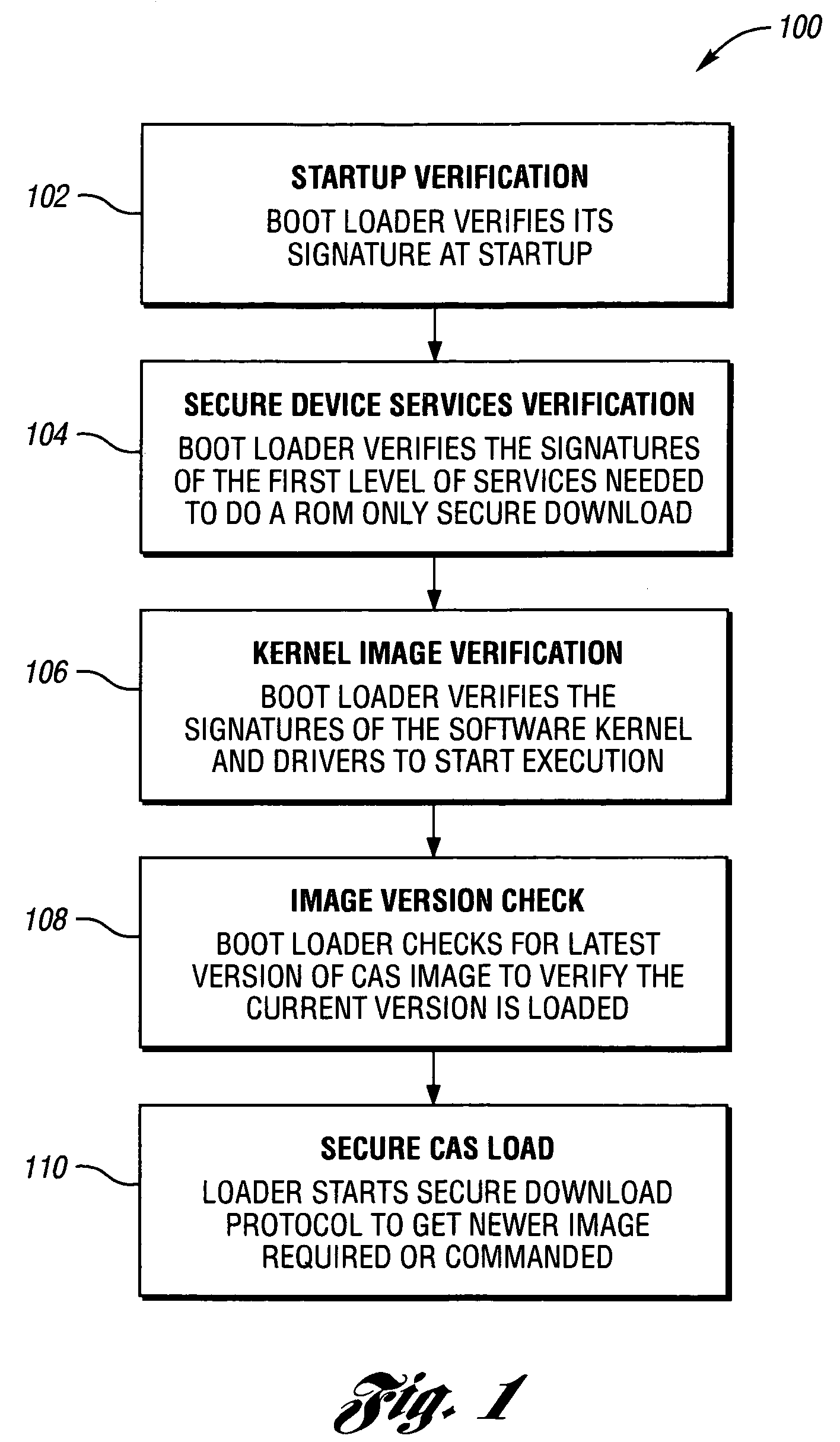
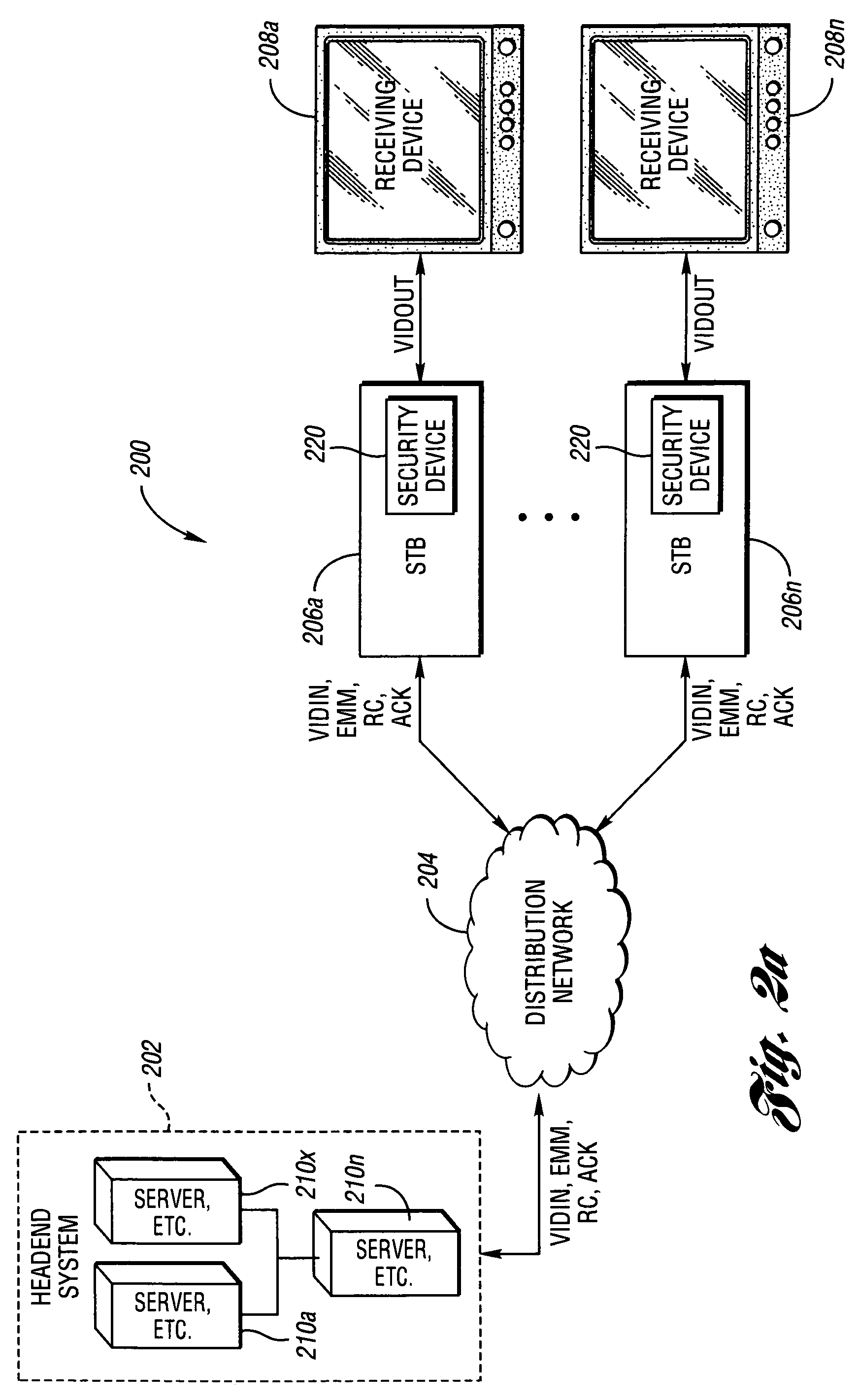
System and method for secure conditional access download and reconfiguration
ActiveUS20060137015A1Overcome deficienciesDigital data processing detailsUser identity/authority verificationSecurity softwareConditional access
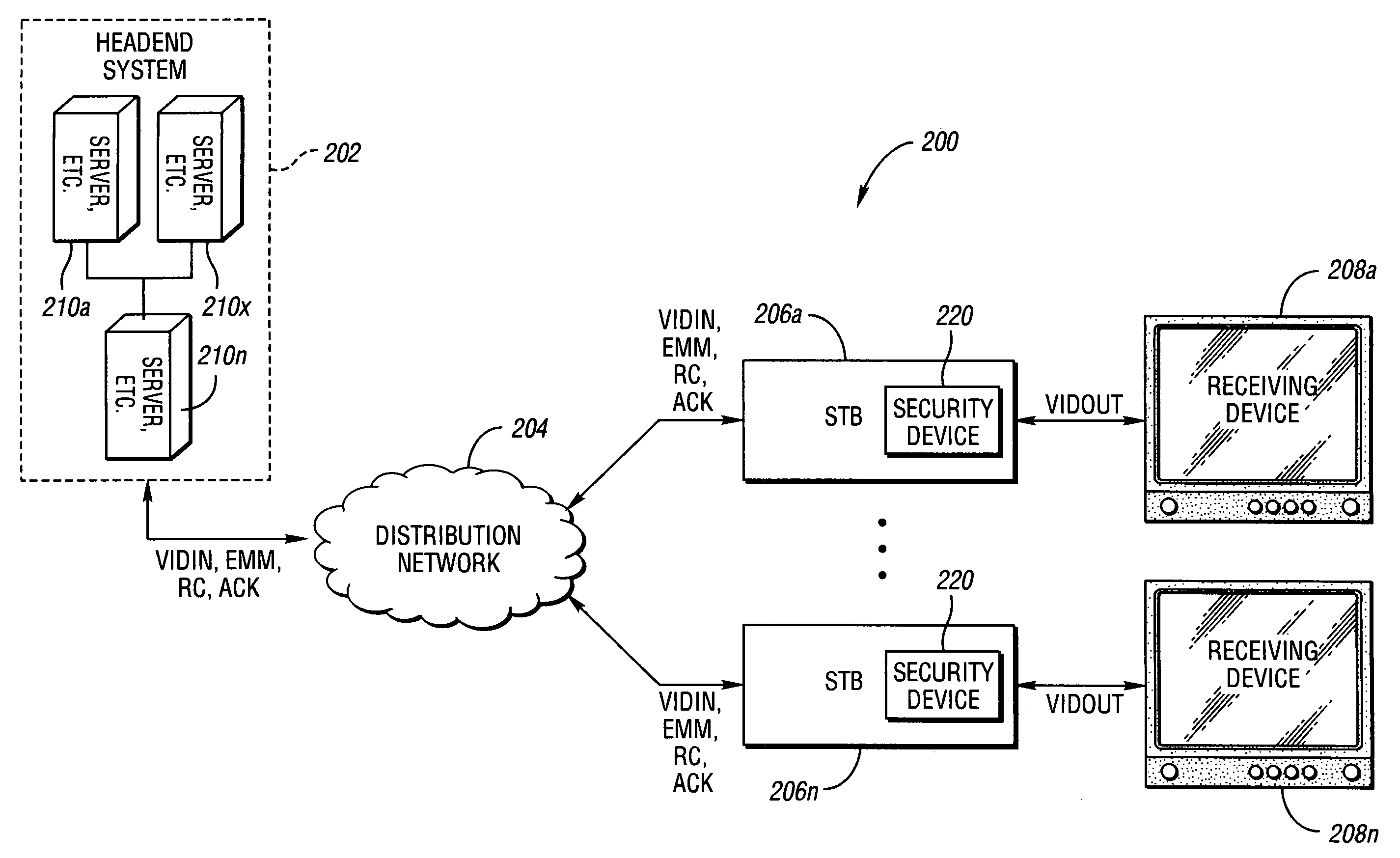
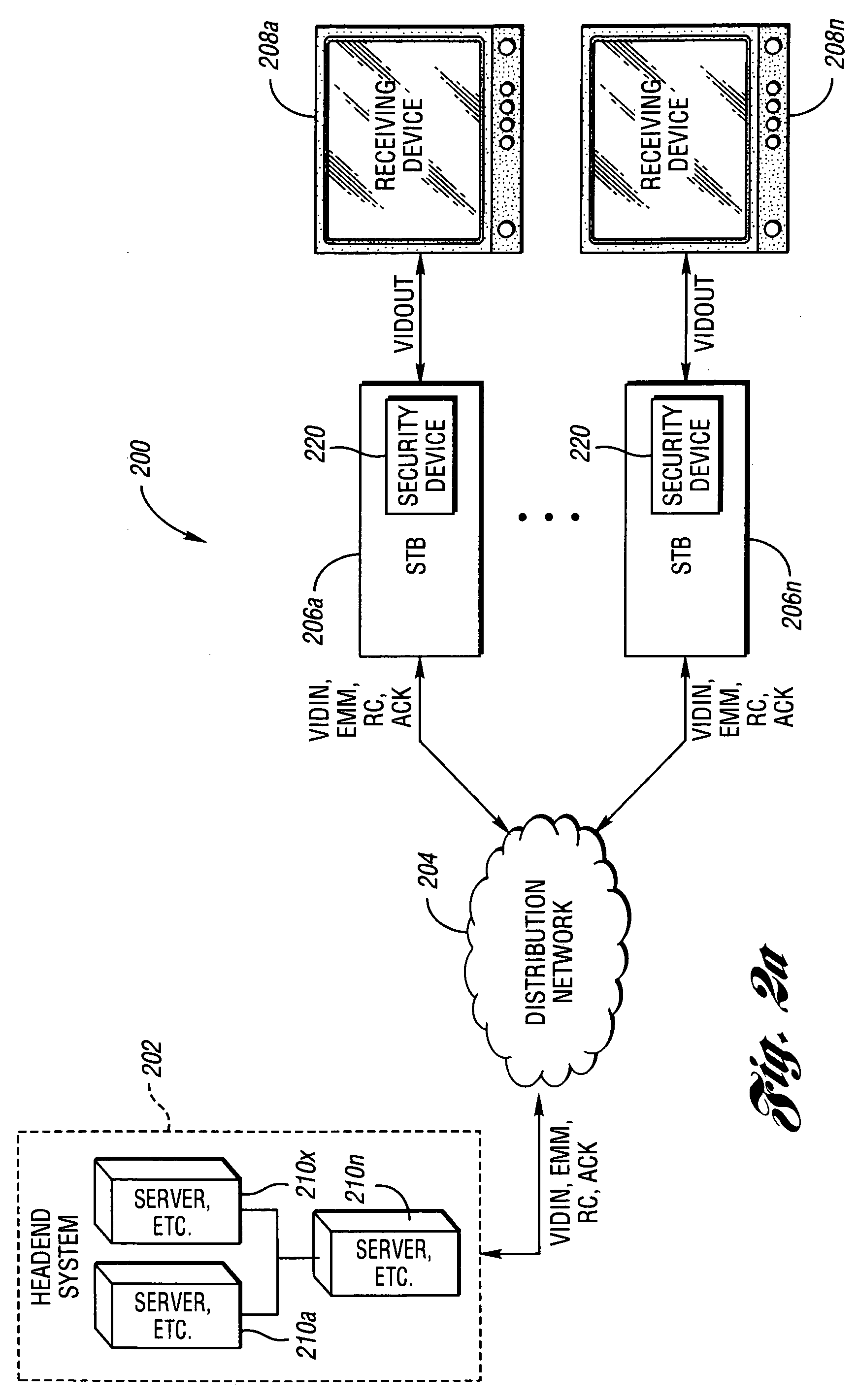
A method of securely downloading at least one of conditional access software (CAS), Digital Rights Management software (DRMS), Trusted Domain Software (TDS), and Gaming Security Software (GSS) includes presenting a specialized entitlement management message (EMM) to initiate the download to a receiver security device using a supervisory logon key (SLK) split to logon with a second split contained inside the receiver security device, presenting a receiver digitally signed random challenge from the receiver security device to a sender security server to establish authentication of the receiver security device to the sender security server, and signing and returning the receiver random challenge from the sender security server to the receiver security device with a sender random challenge to establish authentication of the sender security server to the receiver security device.
Owner:COMCAST CABLE COMM LLC
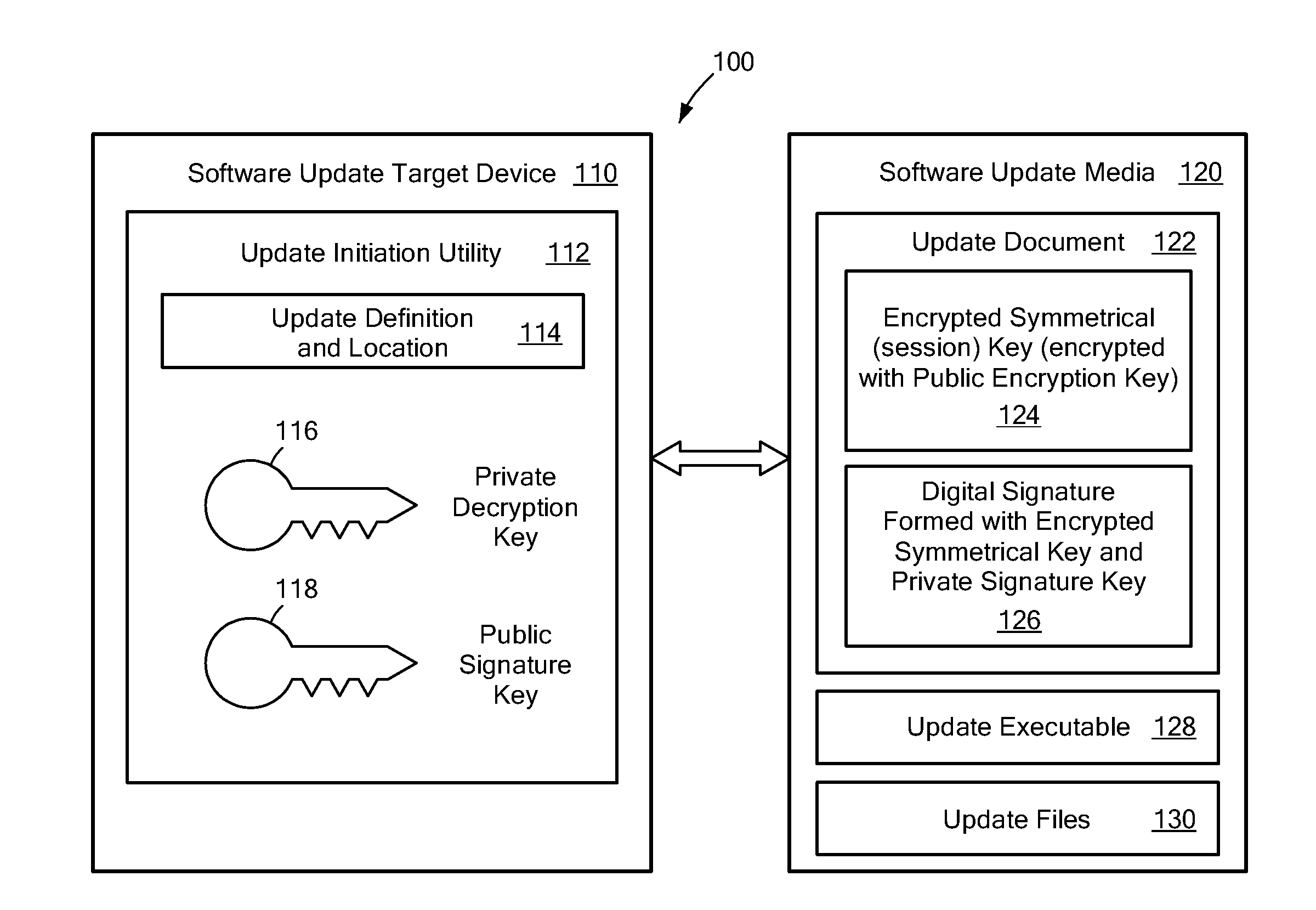
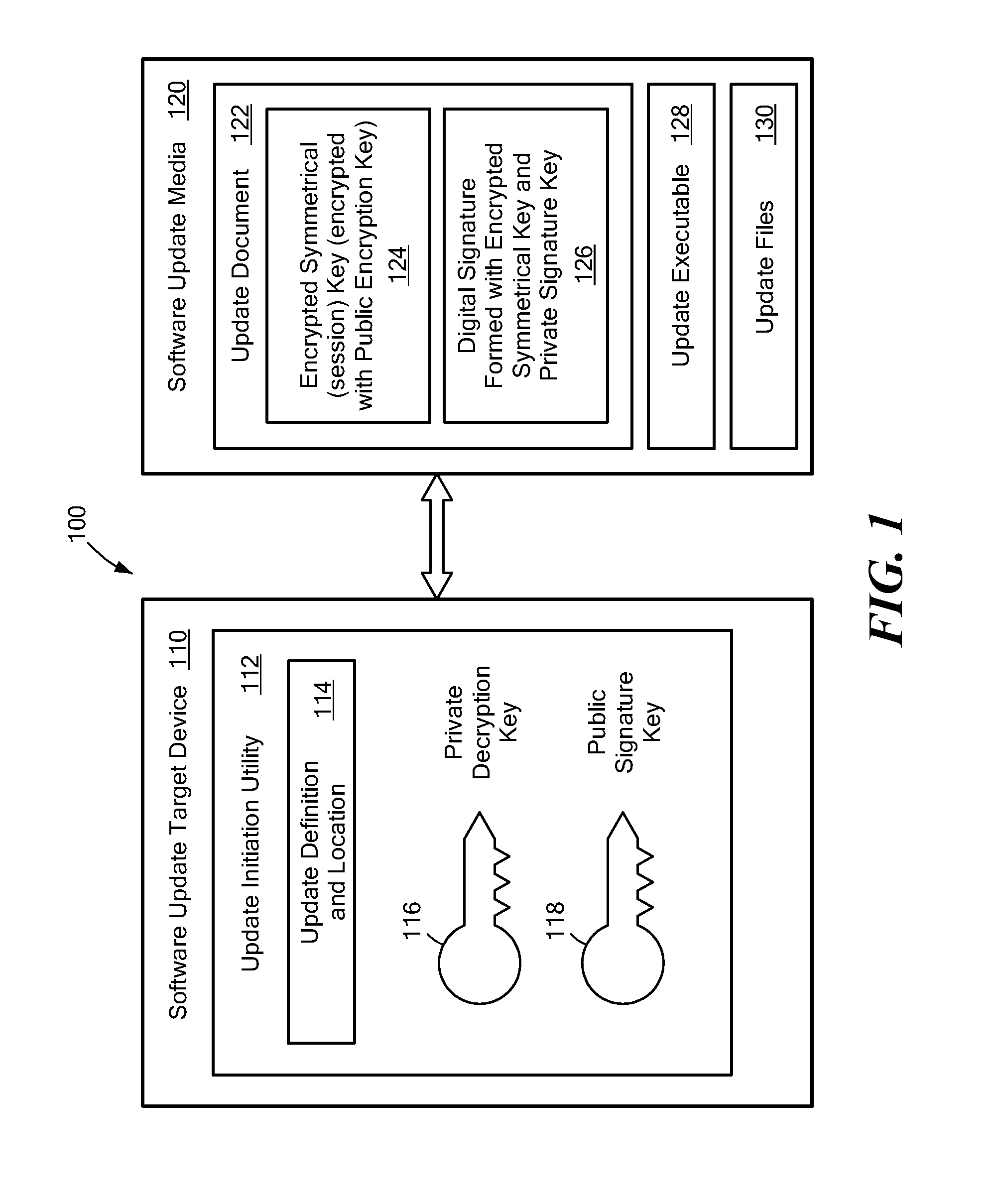
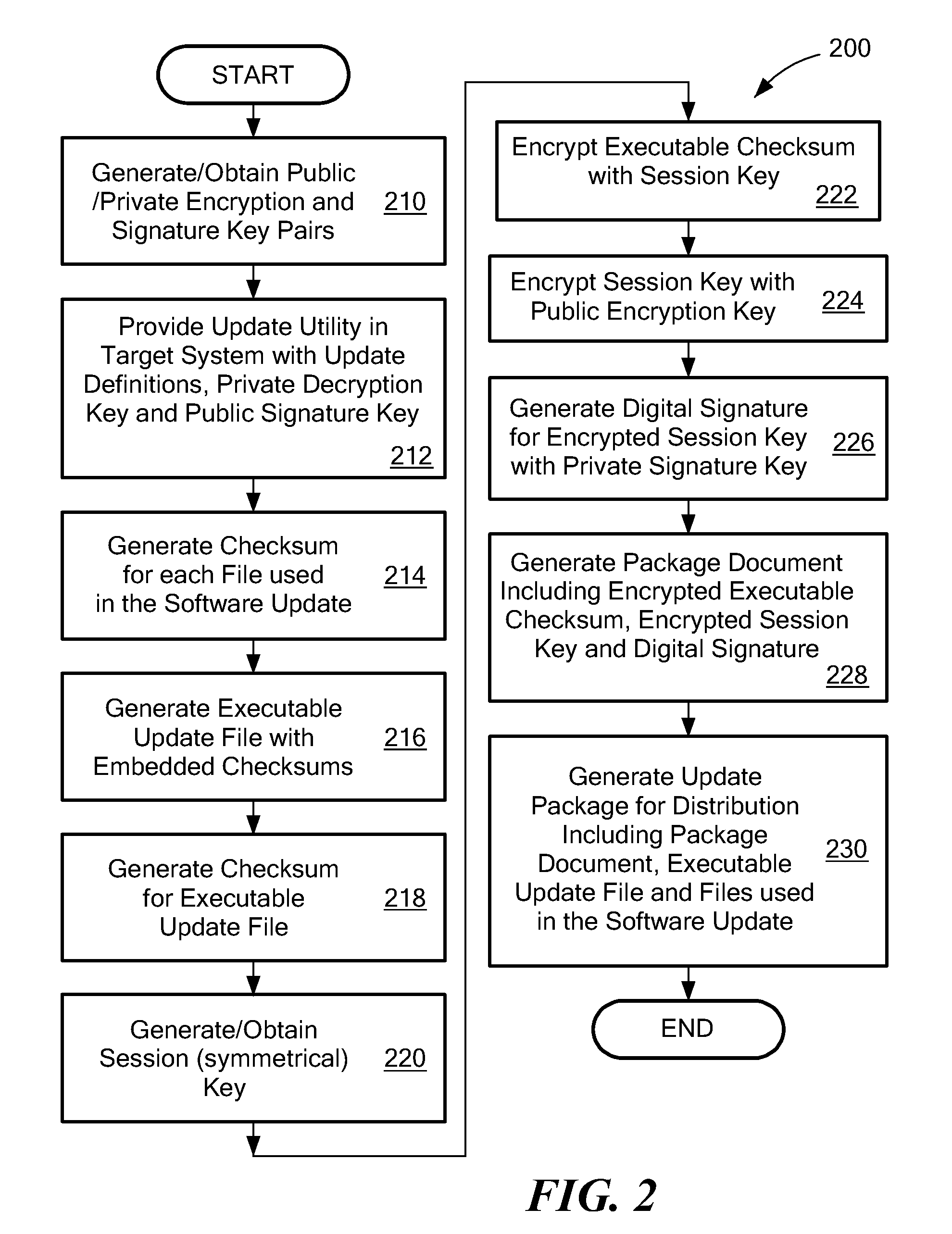
System and Method for Secure Software Update
ActiveUS20130318357A1User identity/authority verificationDigital data protectionThird partySecurity software
A secure software update provides an update utility with an update definition, a private encryption key and a public signature key to a target device. A software update package is prepared on portable media that includes an executable update program, a checksum for the program that is encrypted with a symmetrical key, an encrypted symmetrical key that is encrypted with a public encryption key and a digital signature prepared with a private signature key. The update process authenticates the digital signature, decrypts the symmetrical key using the private encryption key, and decrypts the checksum using the symmetrical key. A new checksum is generated for the executable update program and compared to the decrypted checksum. If inconsistencies are detected during the update process, the process is terminated. Otherwise, the software update can be installed with a relatively high degree of assurance against corruption, viruses and third party interference.
Owner:SIEMENS HEALTHCARE DIAGNOSTICS INC
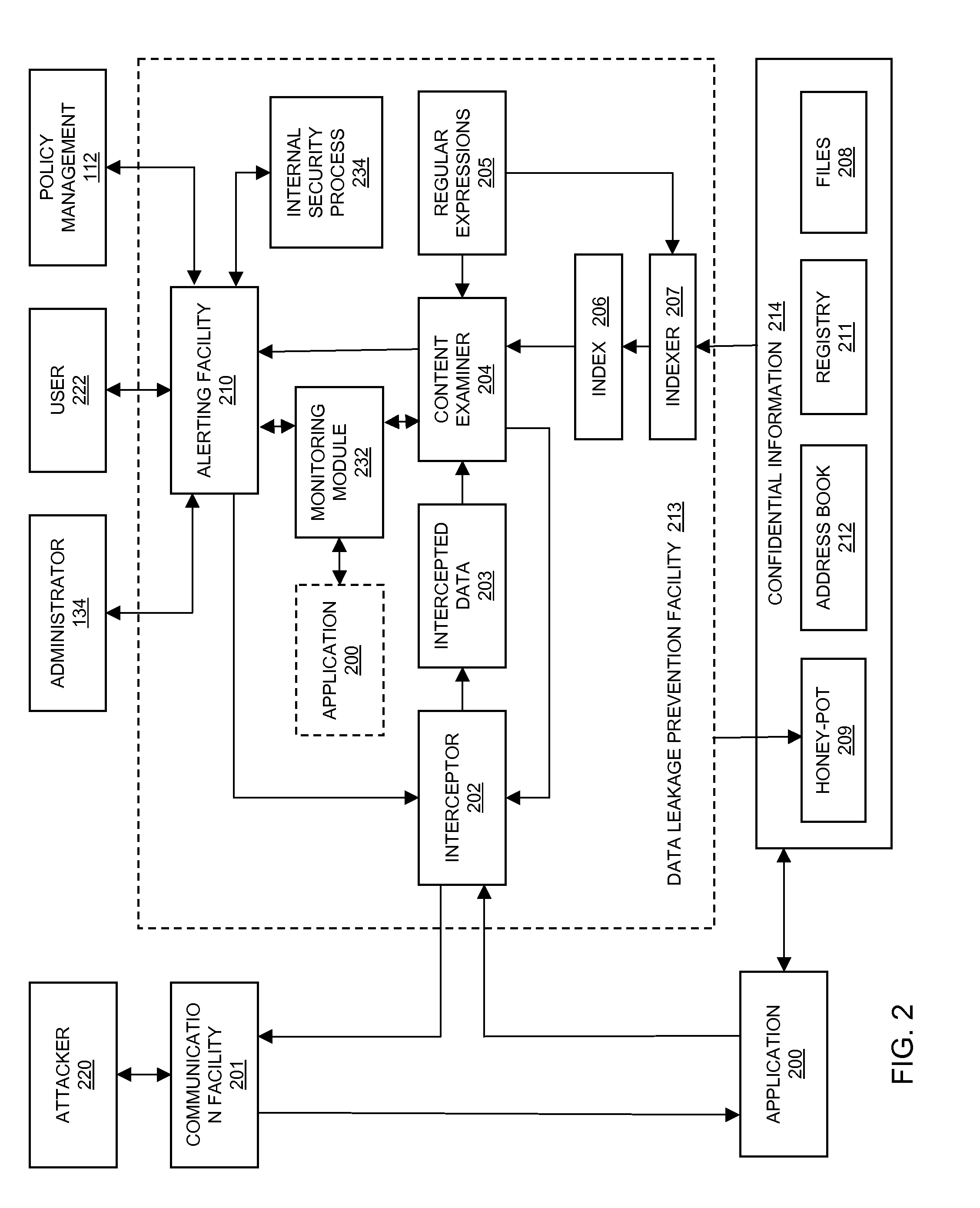
Method and system for preventing data leakage from a computer facilty
InactiveUS20100251369A1Avoid detectionAvoid runningMemory loss protectionError detection/correctionData ingestionSecurity software
In embodiments of the present invention improved capabilities are described for the steps of identifying, through a monitoring module of a security software component, a data extraction behavior of a software application attempting to extract data from an endpoint computing facility; and in response to a finding that the data extraction behavior is related to extracting sensitive information and that the behavior is a suspicious behavior, causing the endpoint to perform a remedial action. The security software component may be a computer security software program, a sensitive information compliance software program, and the like.
Owner:SOPHOS
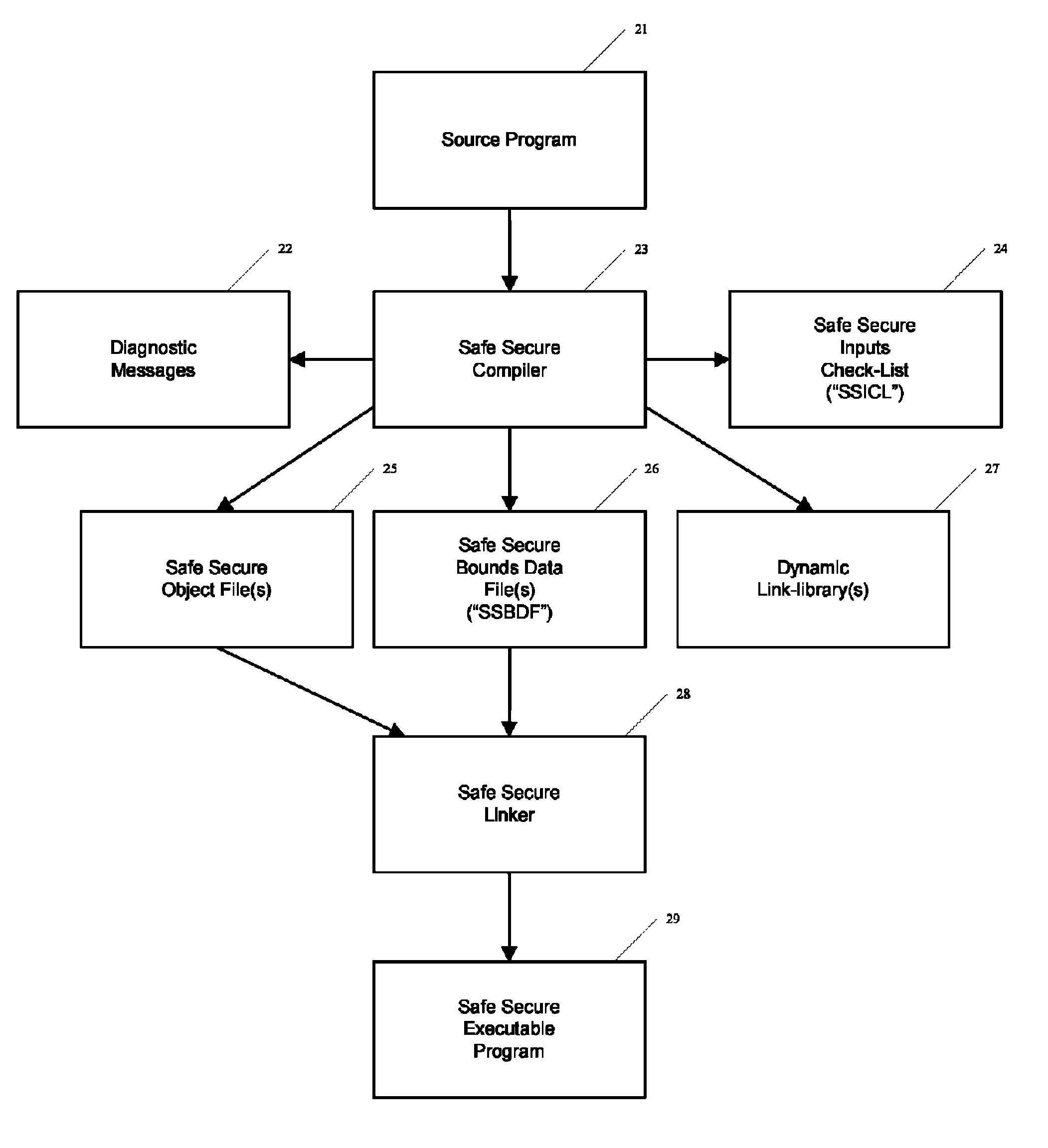
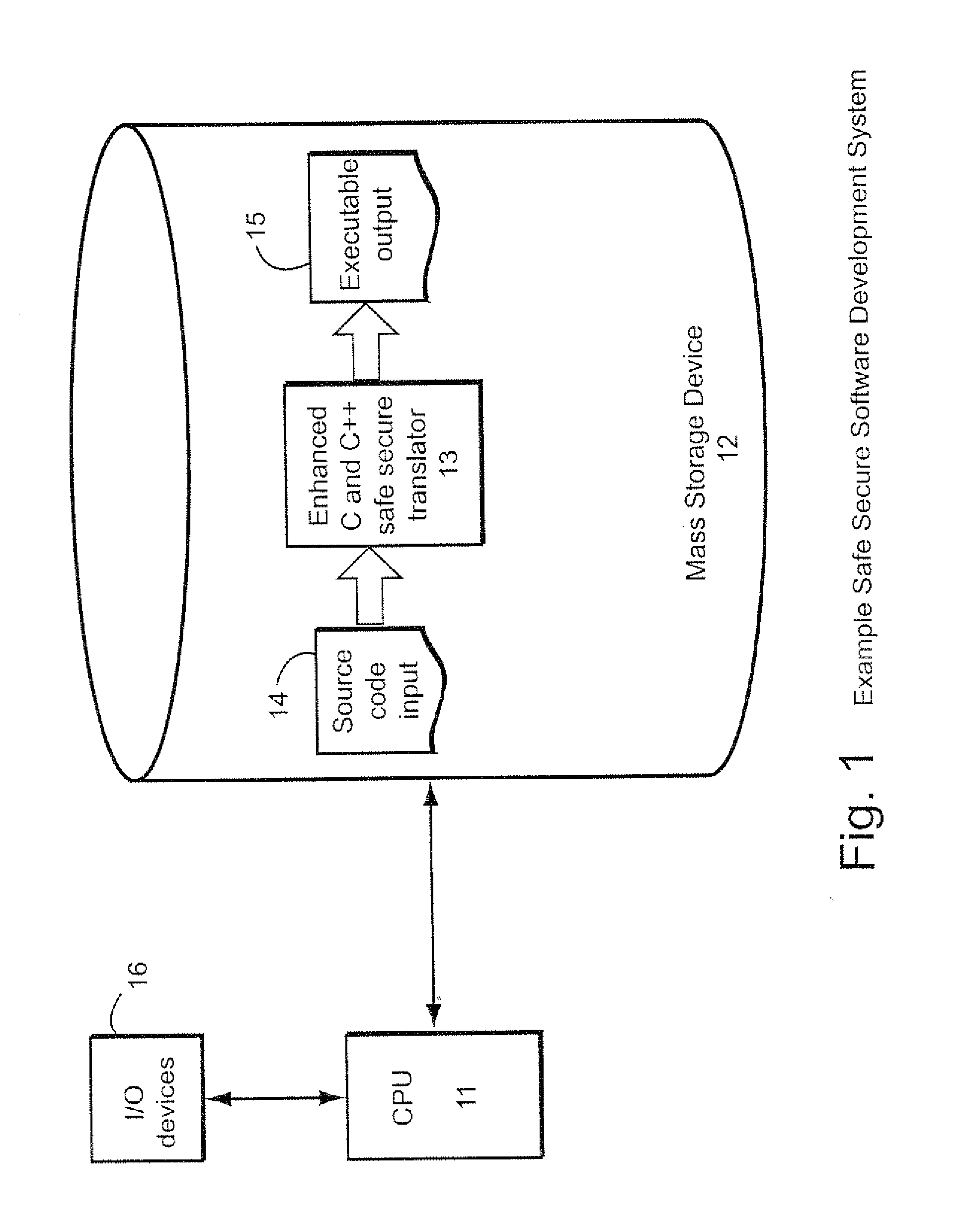
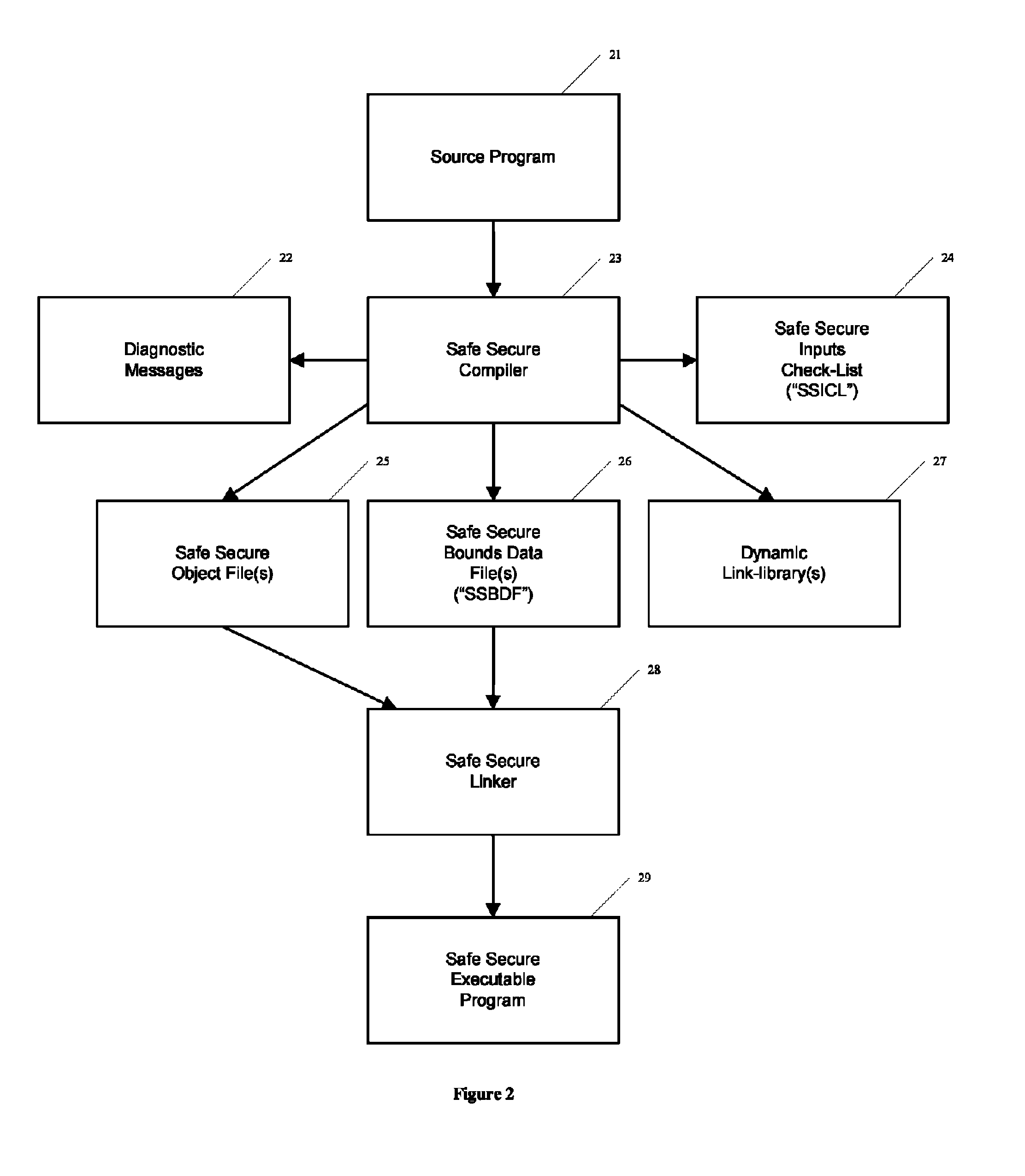
Automated safe secure techniques for eliminating undefined behavior in computer software
InactiveUS7818729B1Behave gracefullyError detection/correctionProgram loading/initiatingSecurity softwareSoftware development
Automated (e.g., compiler implemented) techniques provide safe secure software development including techniques for testing and verifying software for determining and / or certifying that the software had certain characteristics and / or complies with certain properties. In another illustrative implementation, methods are provided whereby the consumer can verify, to any desired level of certainty, that software as delivered truly has the specified properties, and that the compiler used to produce that software can be trusted to provide those assurances.
Owner:T & L PLUM LLC
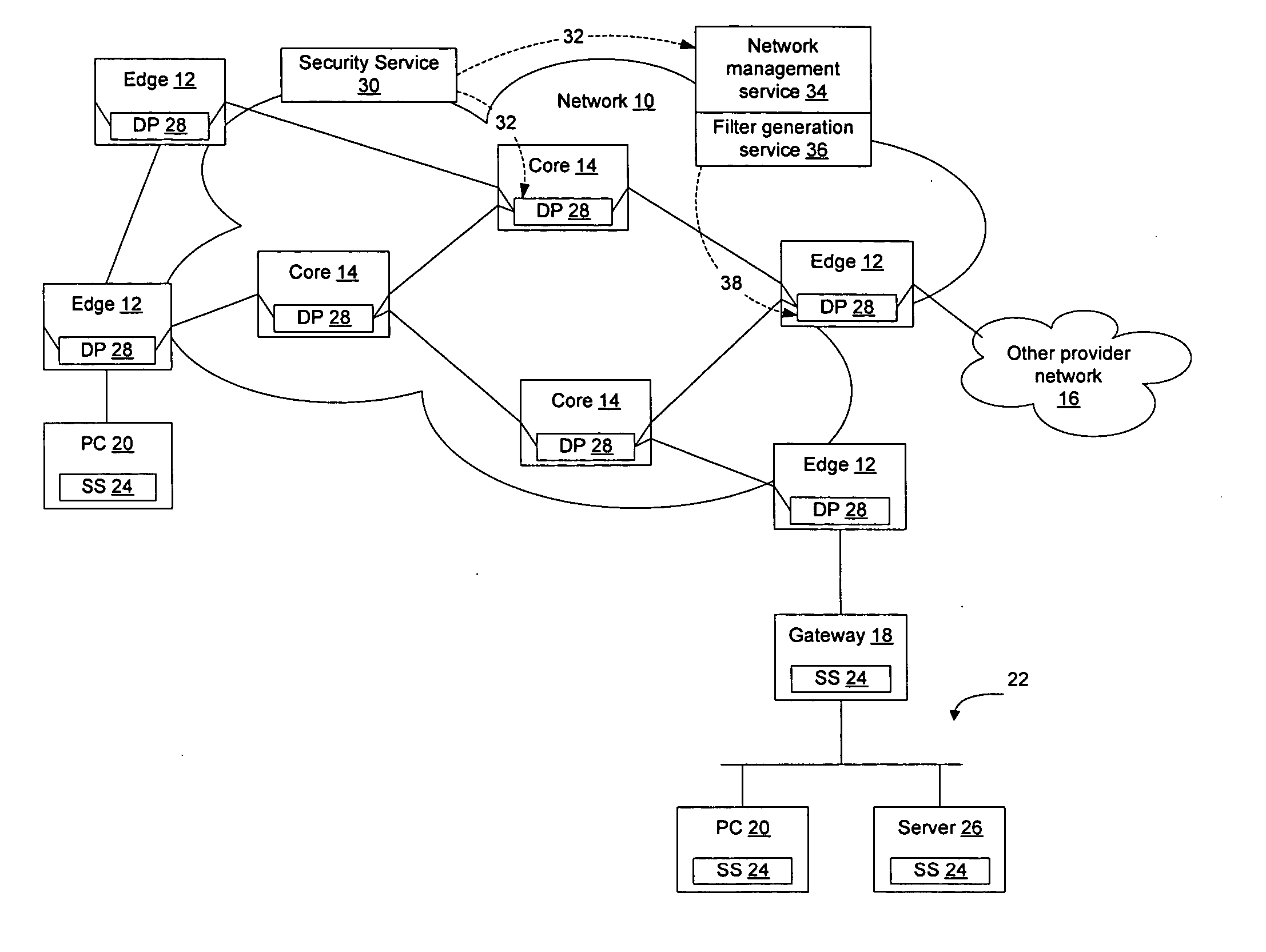
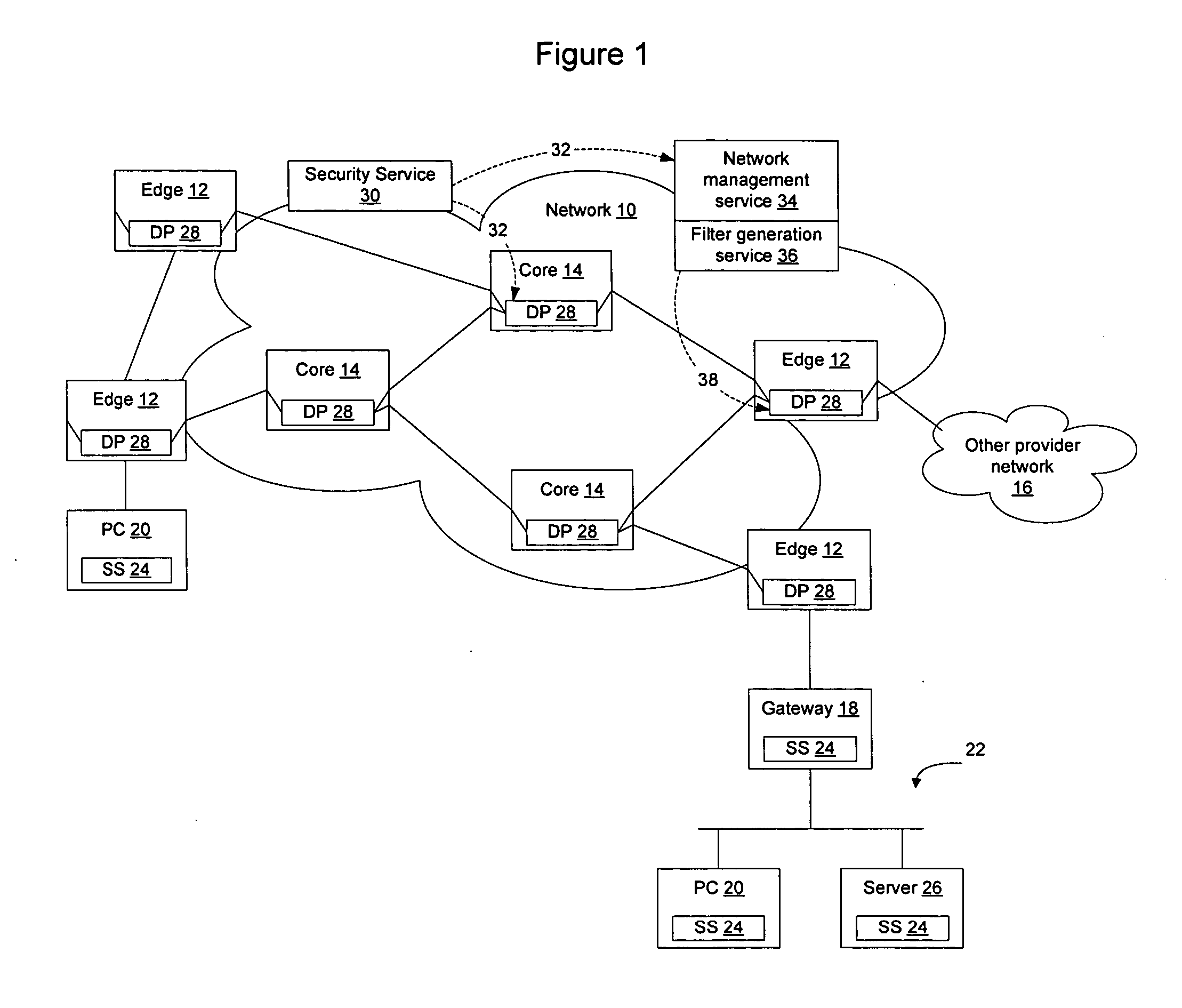
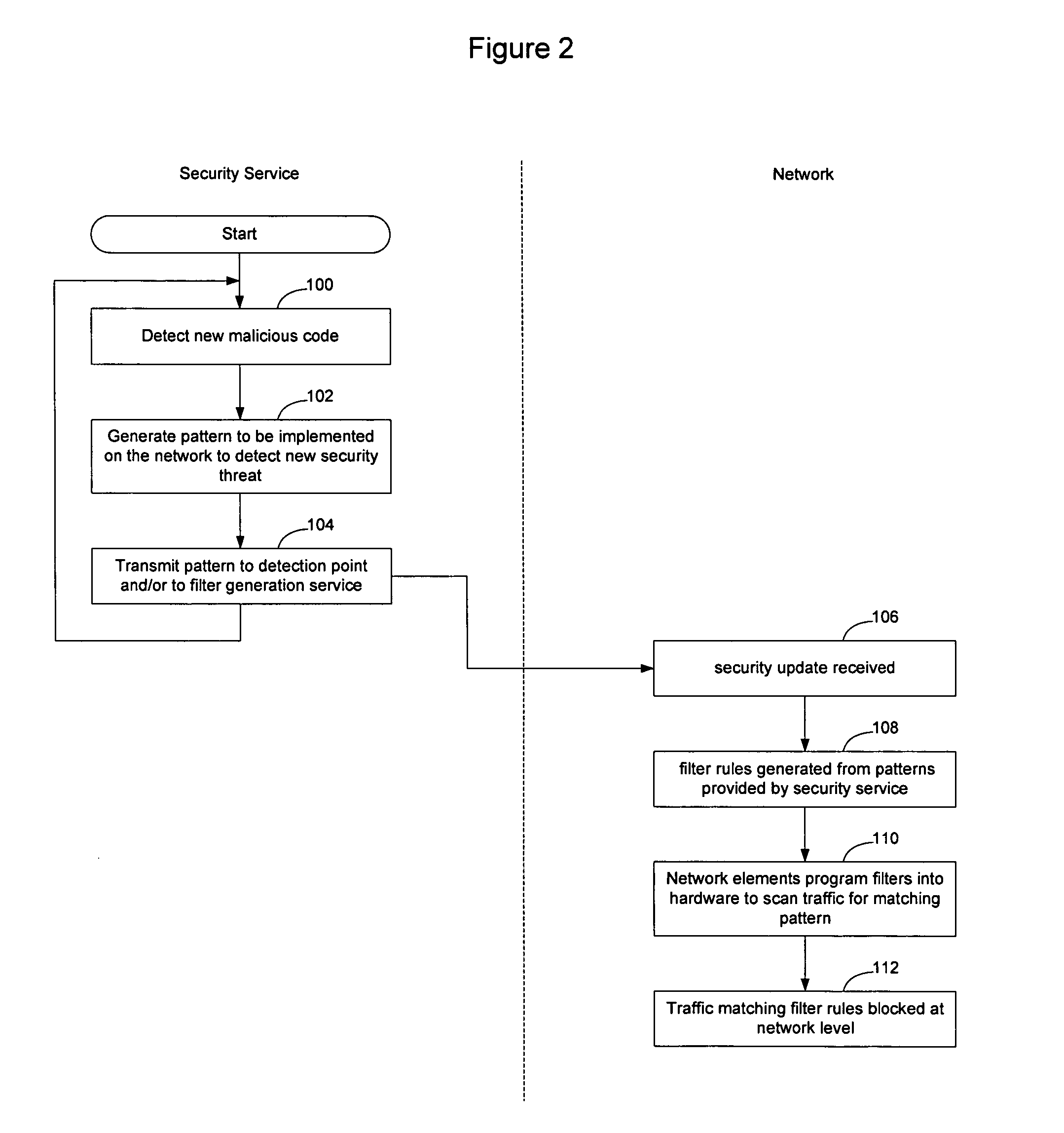
Method and apparatus for network immunization
InactiveUS20060123481A1Avoid dataAvoid spreadingMemory loss protectionError detection/correctionSecurity softwareFiltering rules
Network elements that are configured to perform deep packet inspection may be dynamically updated with patterns associated with malicious code, so that malicious code may be detected and blocked at the network level. As new threats are identified by a security service, new patterns may be created for those threats, and the new patterns may then be passed out onto the network in real time. The real time availability of patterns enables filter rules derived from the patterns to be applied by the network elements so that malicious code may be filtered on the network before it reaches the end users. The filter rules may be derived by security software resident in the network elements or may be generated by a filter generation service configured to generate network element specific filter rules for those network elements that are to be implemented as detection points on the network.
Owner:AVAYA INC
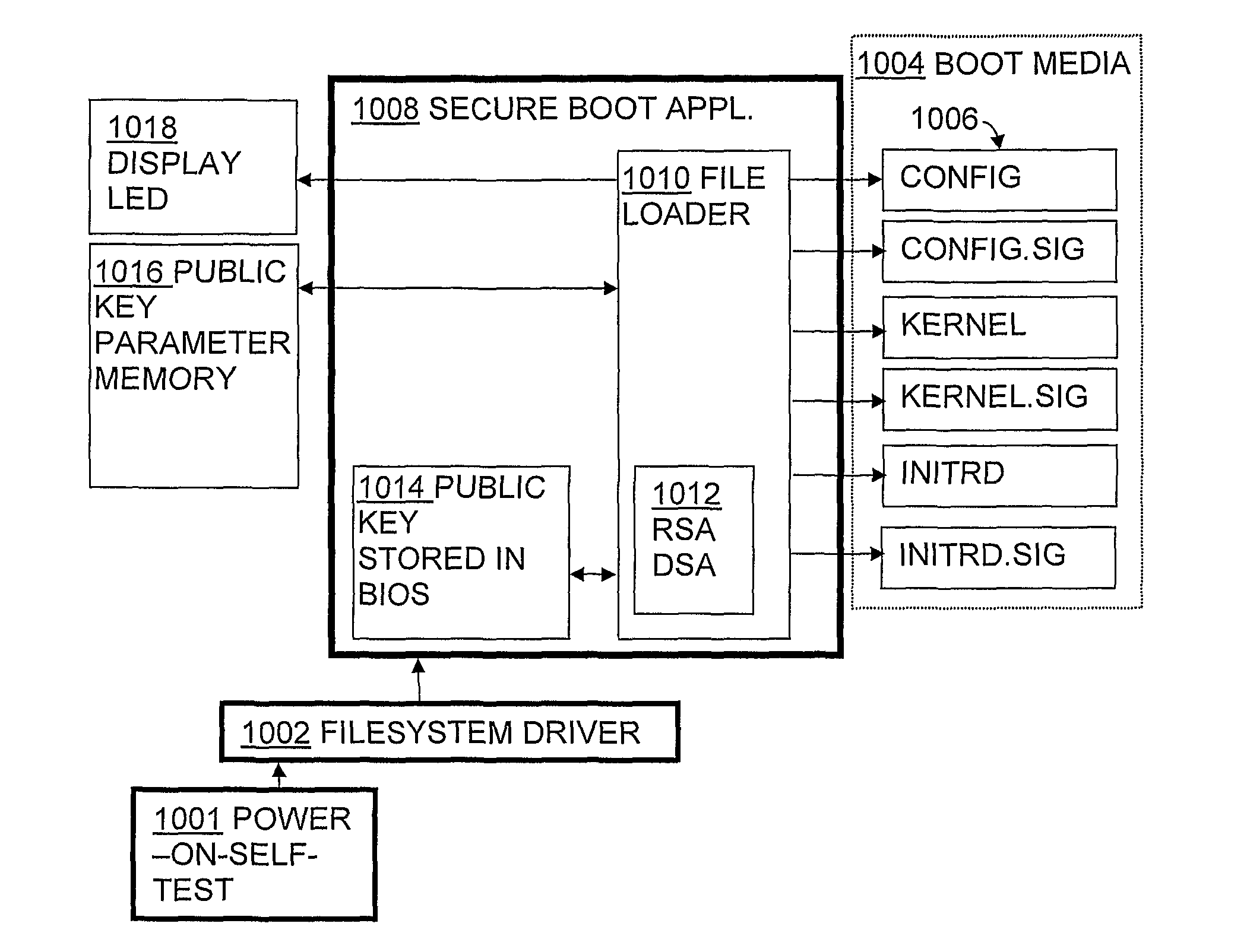
Method and system for secure software provisioning
A method and system for the provisioning of software that enable large scale installation and management of software in computer units in a highly secure manner. The BIOS of the target computer unit is adapted such that upon power up the system attempts to boot from an external media. The BIOS features functions within the code for the implementing a system watchdog for assuring the system remains in a known state, a function for digital signature verification, and loads drivers for a file system. The external media includes the operating system (OS) image and other bootstrap files, each having been digitally signed with an asymmetric private key that corresponds to the public key. A programmable read-only parameter memory on the motherboard is configured to store the public keys and the (failure) state of the system independently of the primary and secondary media enabling reboot from an alternative boot path.
Owner:ONITEO
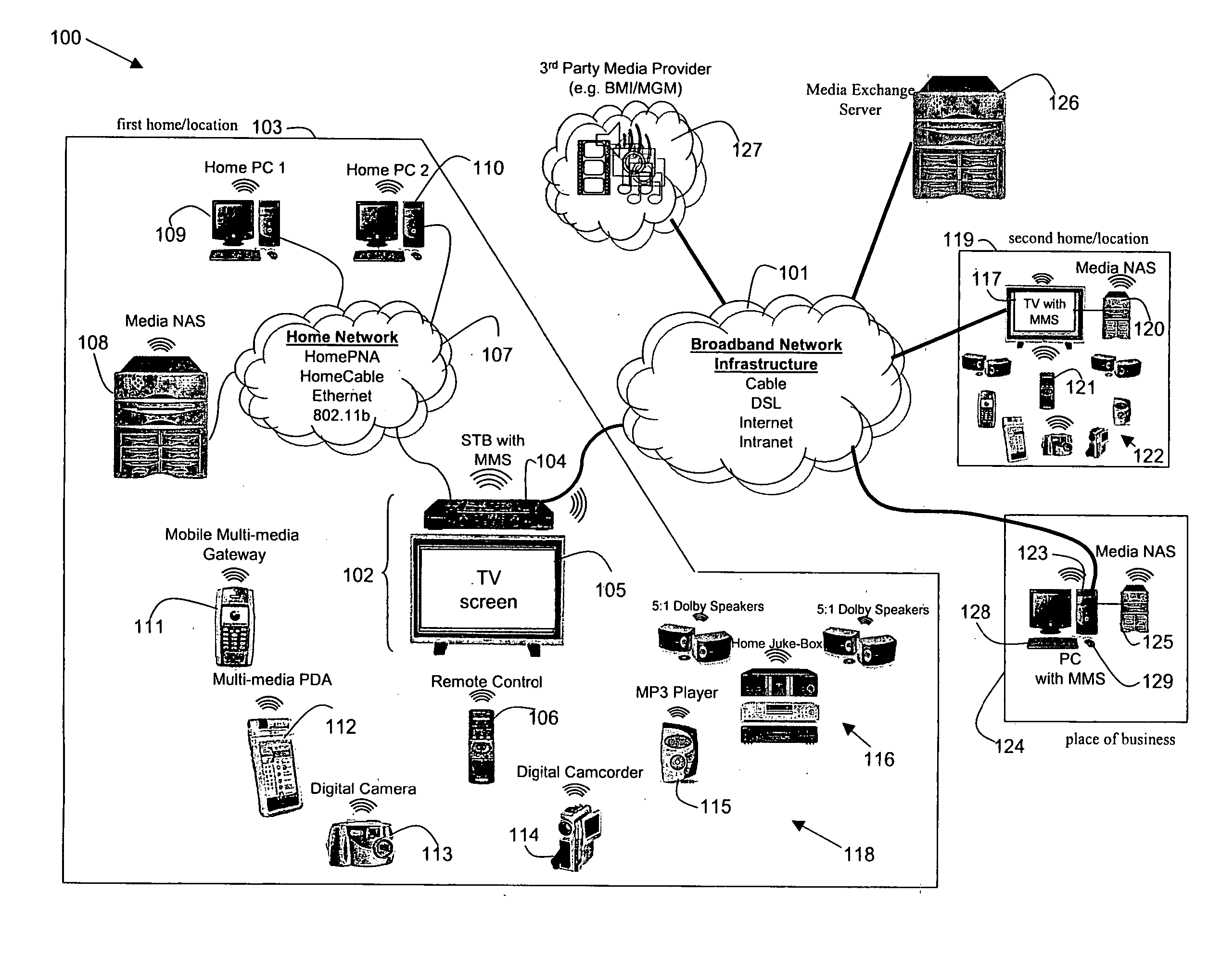
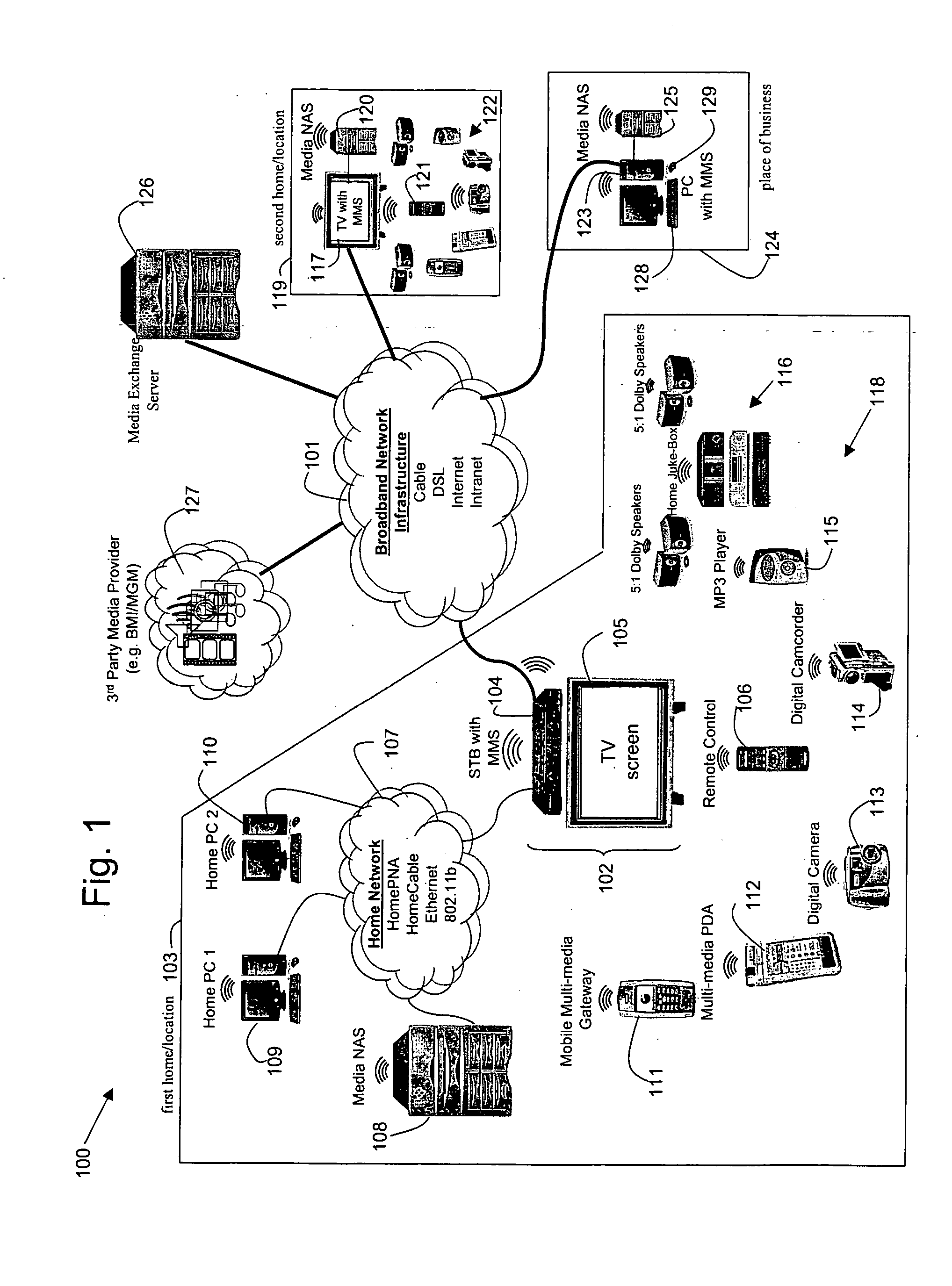
System, method, and apparatus for secure sharing of multimedia content across several electronic devices
InactiveUS20050226170A1Communication securityTelevision system detailsDigital data processing detailsDigital videoDigital data
Disclosed herein is a secure, media exchange network and a method of securely exchanging media between electronic devices across the network. In an embodiment according to the present invention, media may be securely and simultaneously exchanged between friends, family members, business associates, government entities, military entities, law enforcement entities, and 3rd party media providers over a closed and secure media exchange network. The media may include, for example, digital video, digital audio, digital images, digital data, or any other form of digital information. Security features may include security techniques, associated security hardware, and associated security software.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
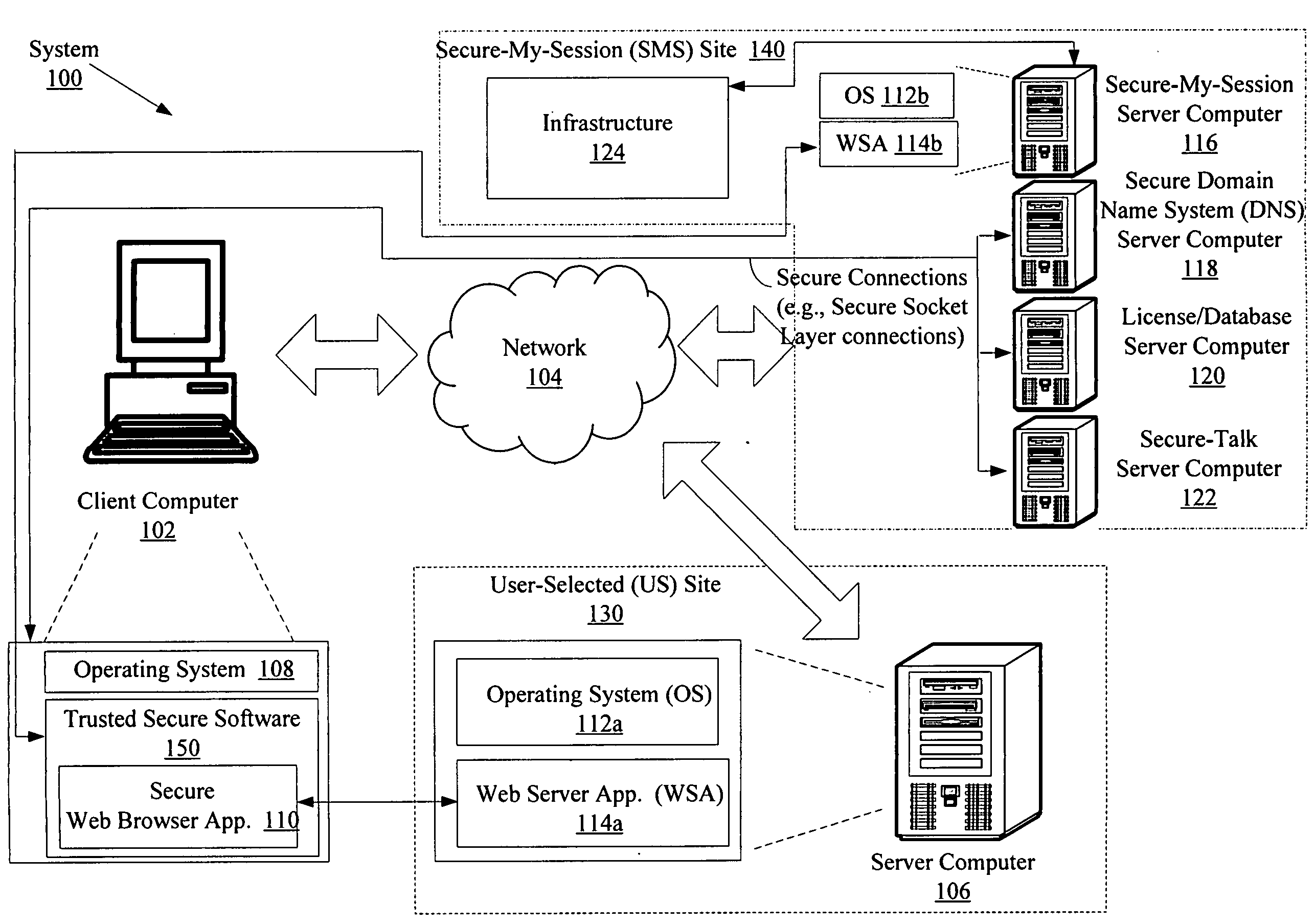
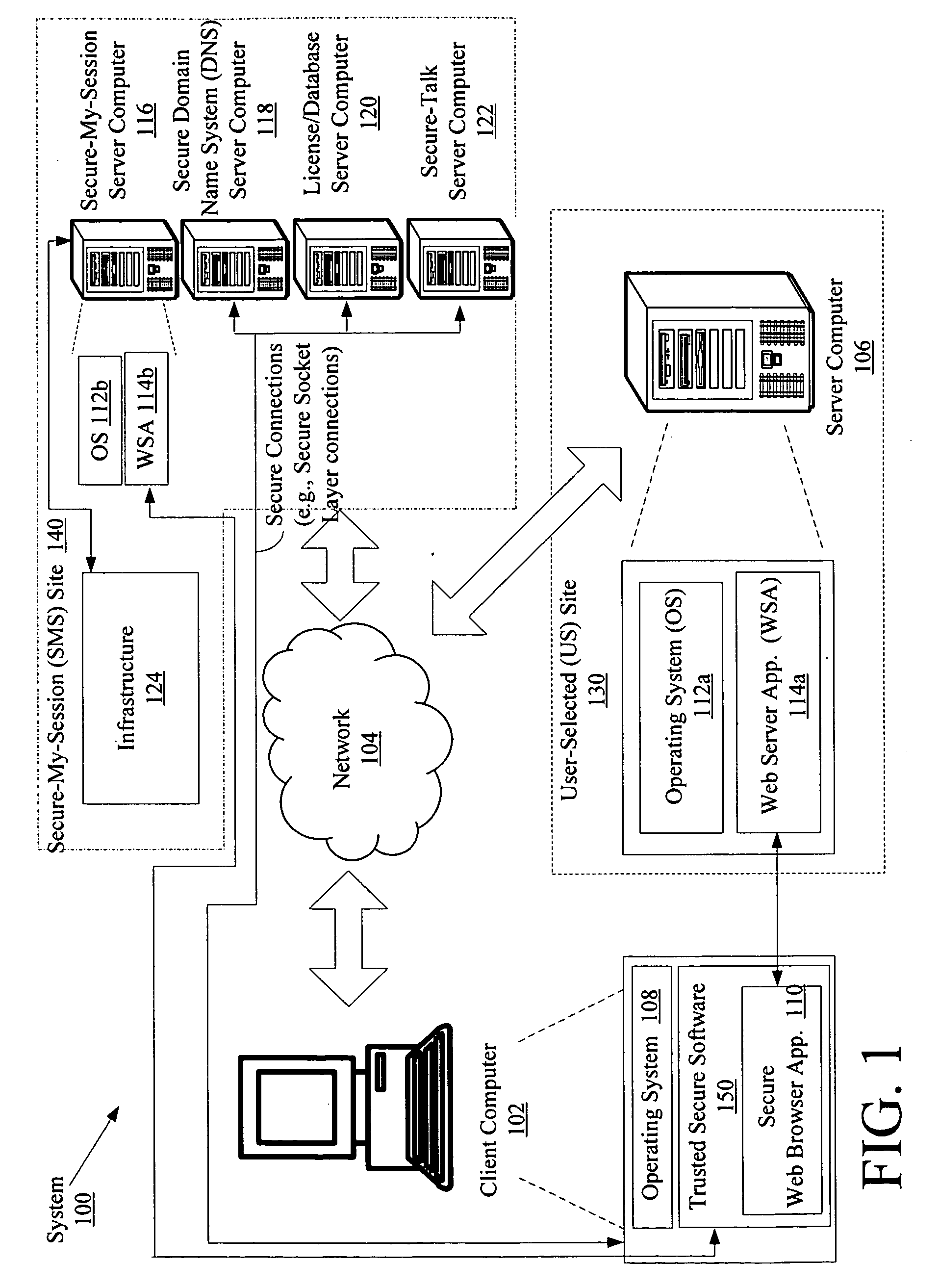
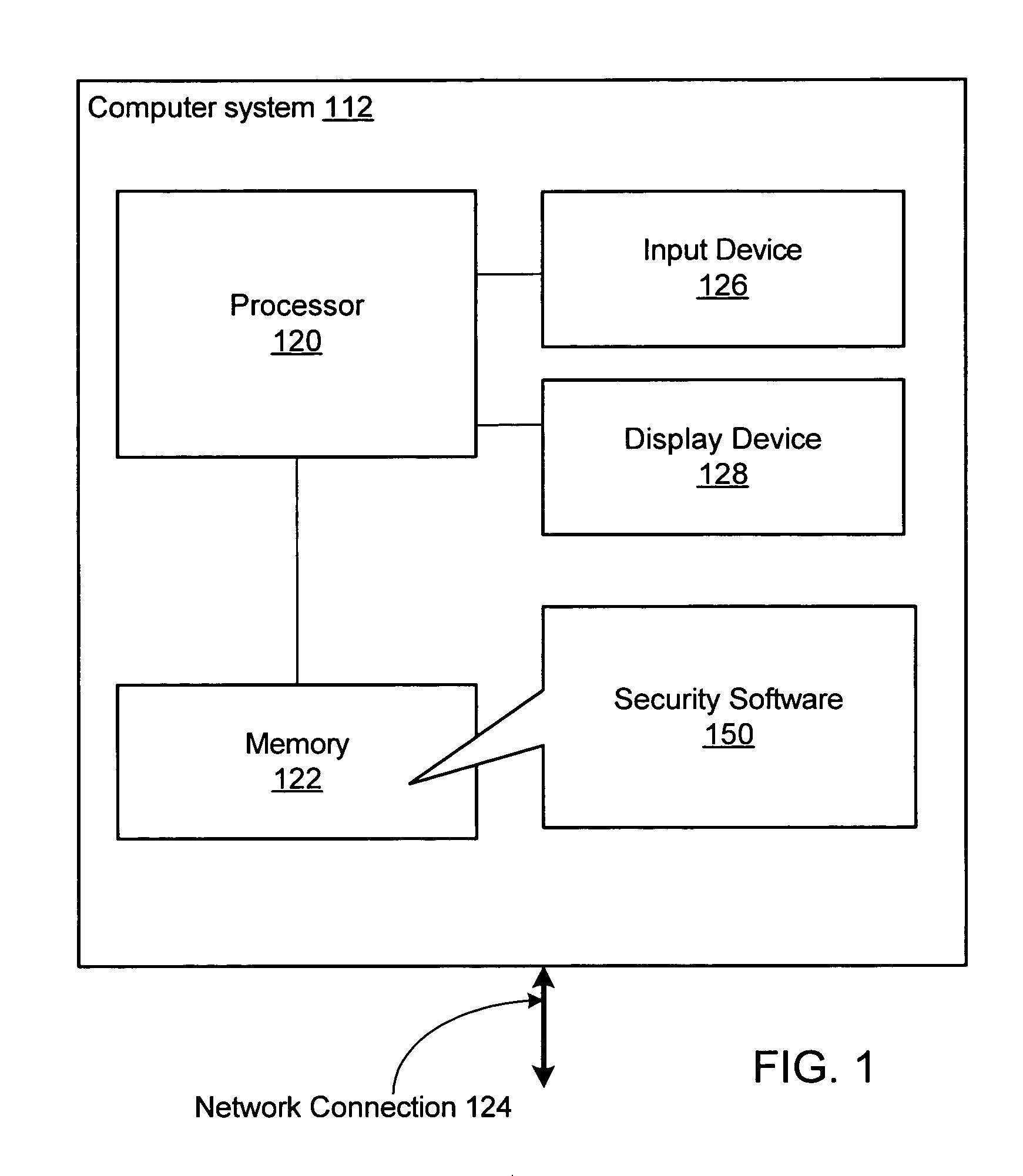
System and method for protecting data accessed through a network connection
ActiveUS20090187763A1Facilitates secure communicationFacilitate gathering of informationPlatform integrity maintainanceSecuring communicationInternal memoryTelecommunications link
Systems (100) and methods (400) for protecting data accessed through a network connection. The methods involve transferring security software (150) from an external memory device of a client computer (102) to an internal memory device of the client computer. The security software is operative to protect data communicated to and from the client computer via communication links. The security software is also operative to provide a web browser (1101, 1102, . . . , 110p) which executes in user mode on a trusted secured desktop (904) configured to run simultaneously with an unsecured desktop (902) of the client computer. The security software is further operative to provide a security service to the web browser. The security service includes at least one service selected from the group consisting of a keylogger prevention service, a code injection prevention service, and a screen scraper protection service.
Owner:WONTOK
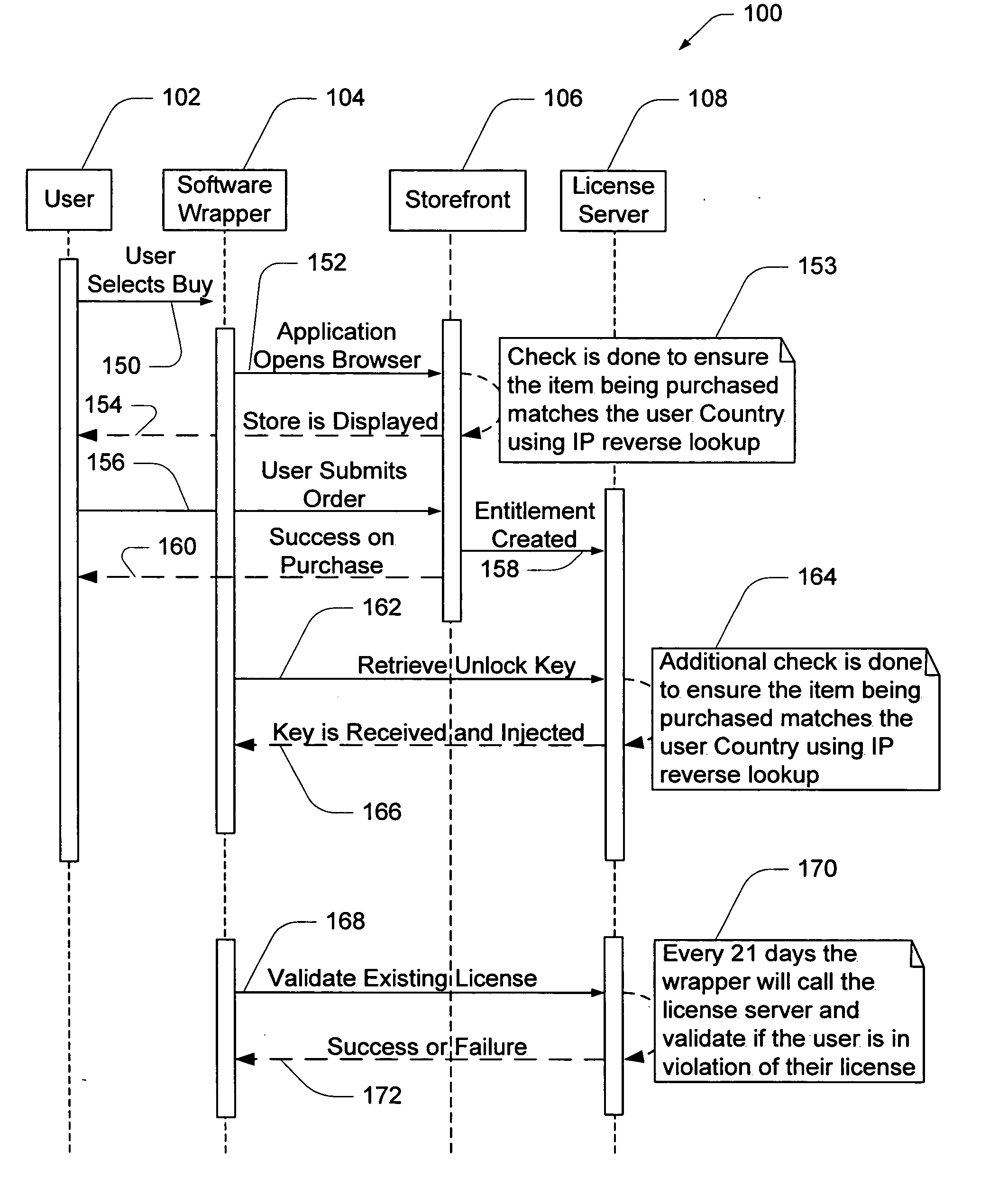
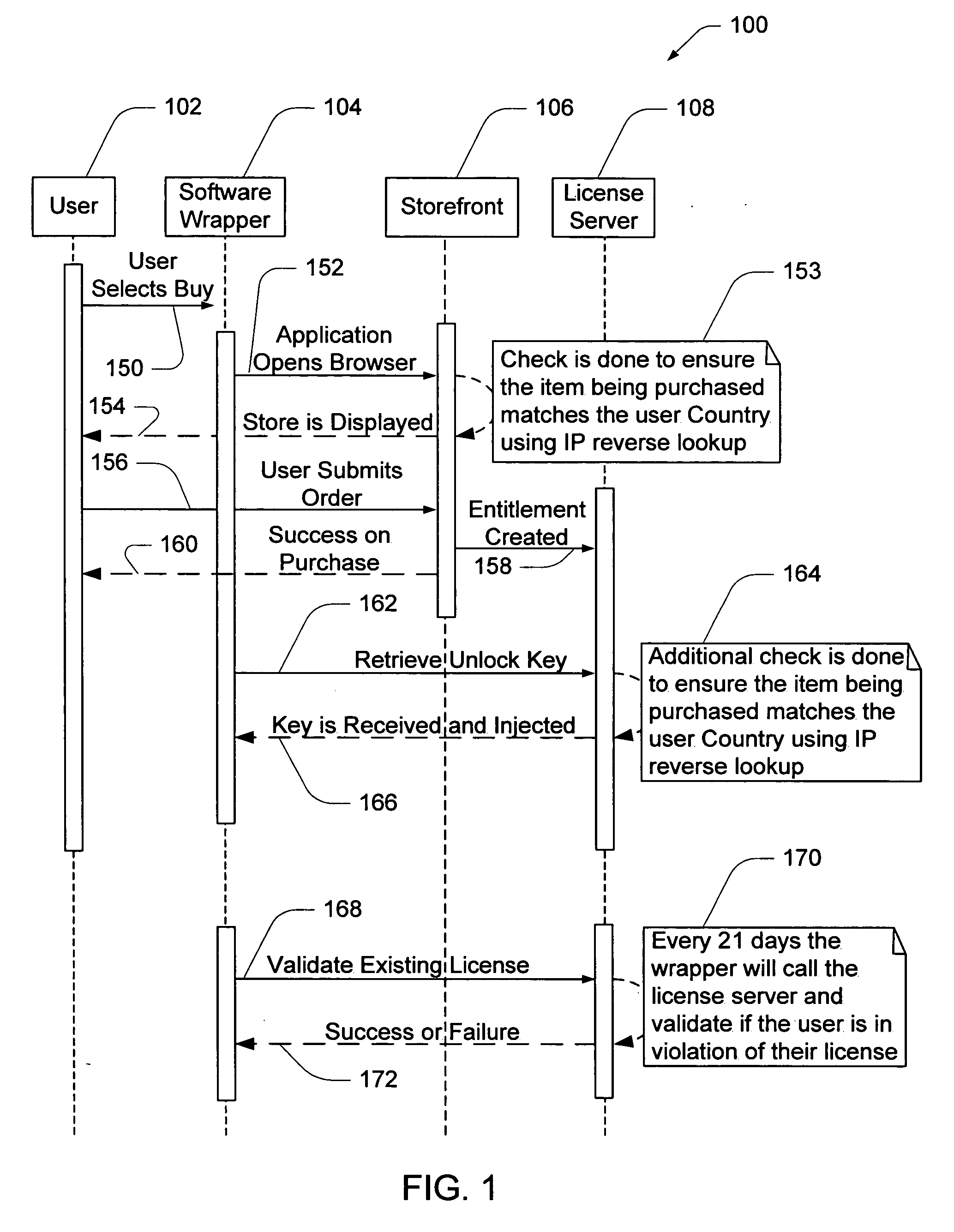
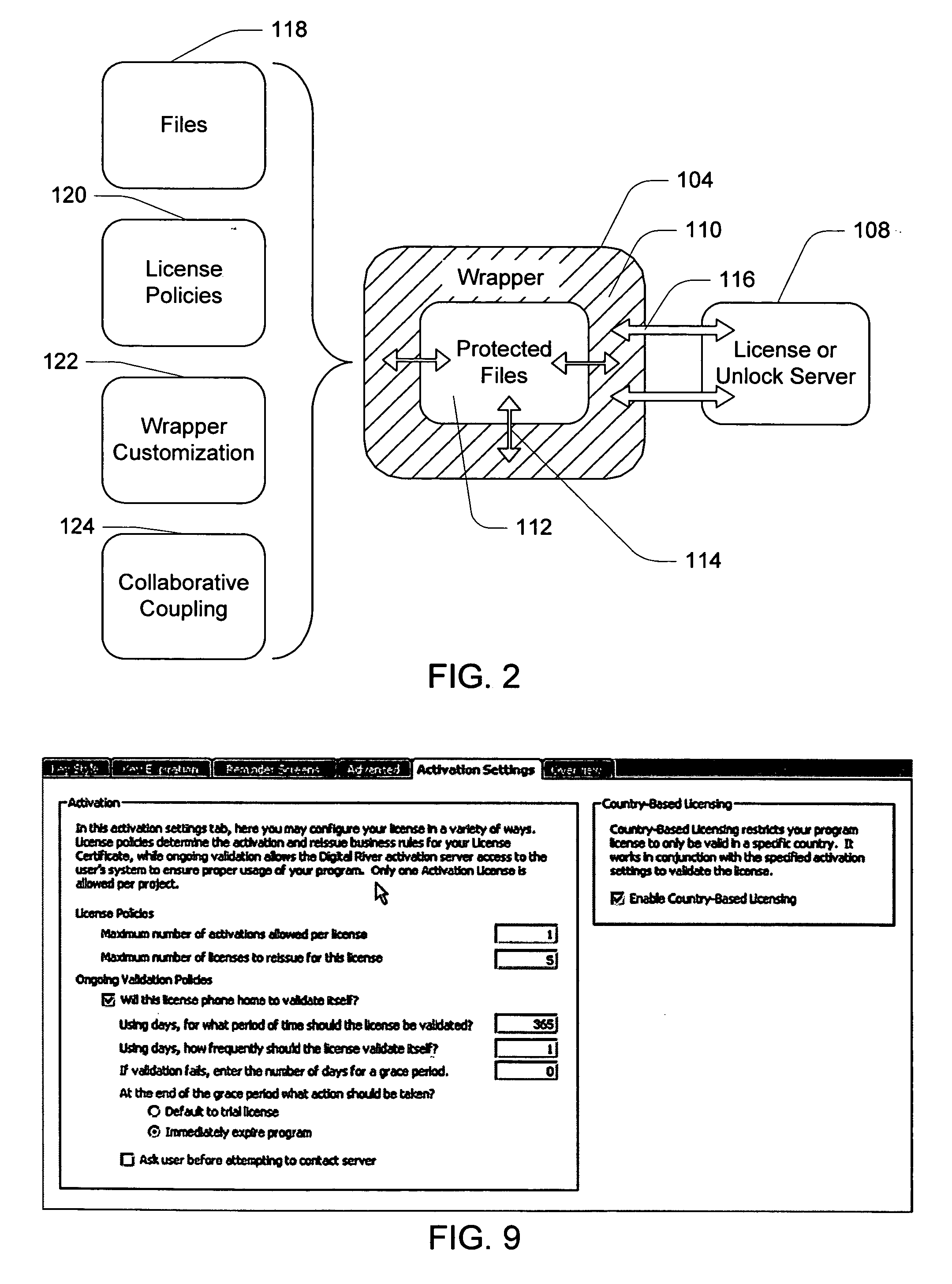
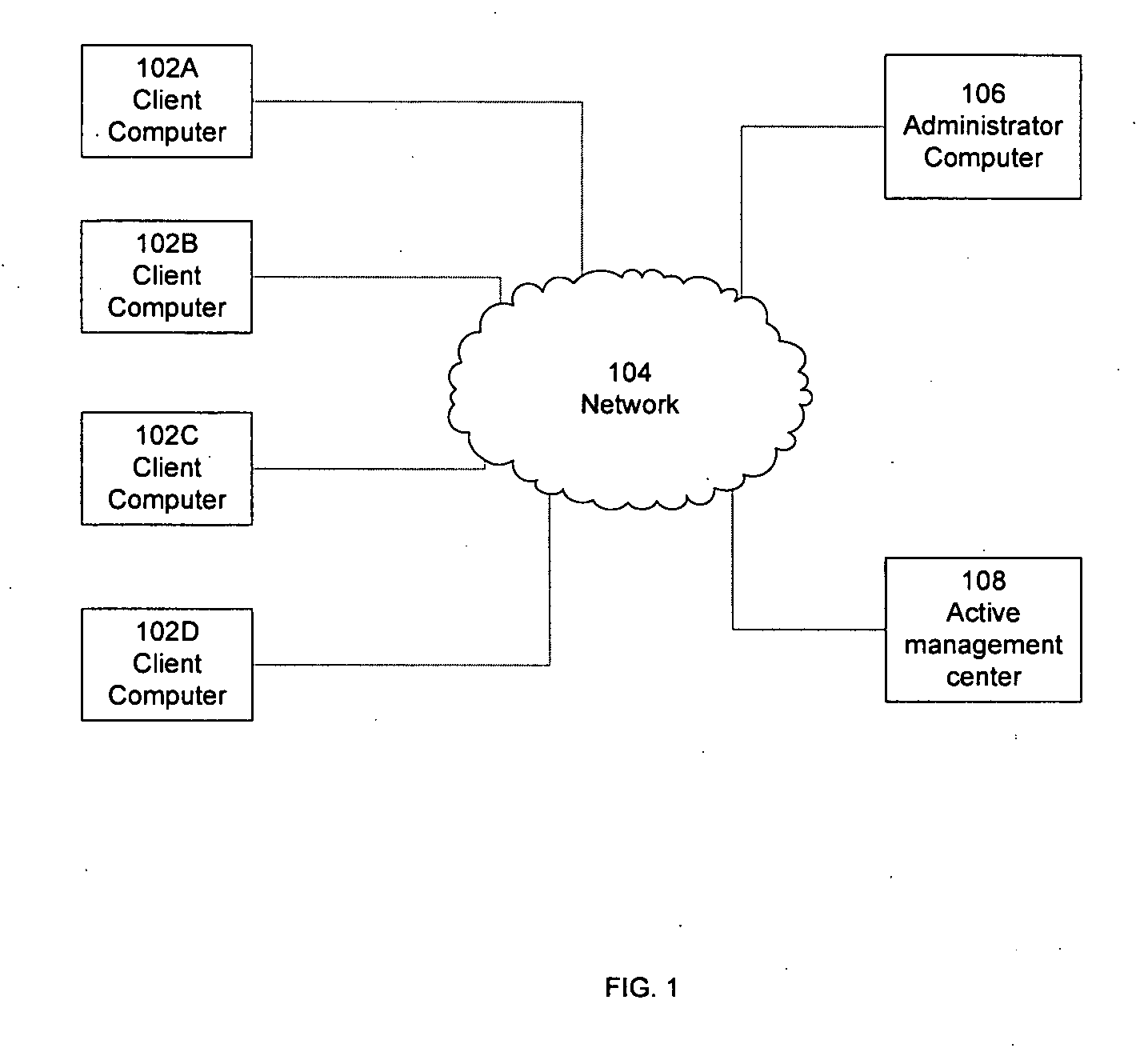
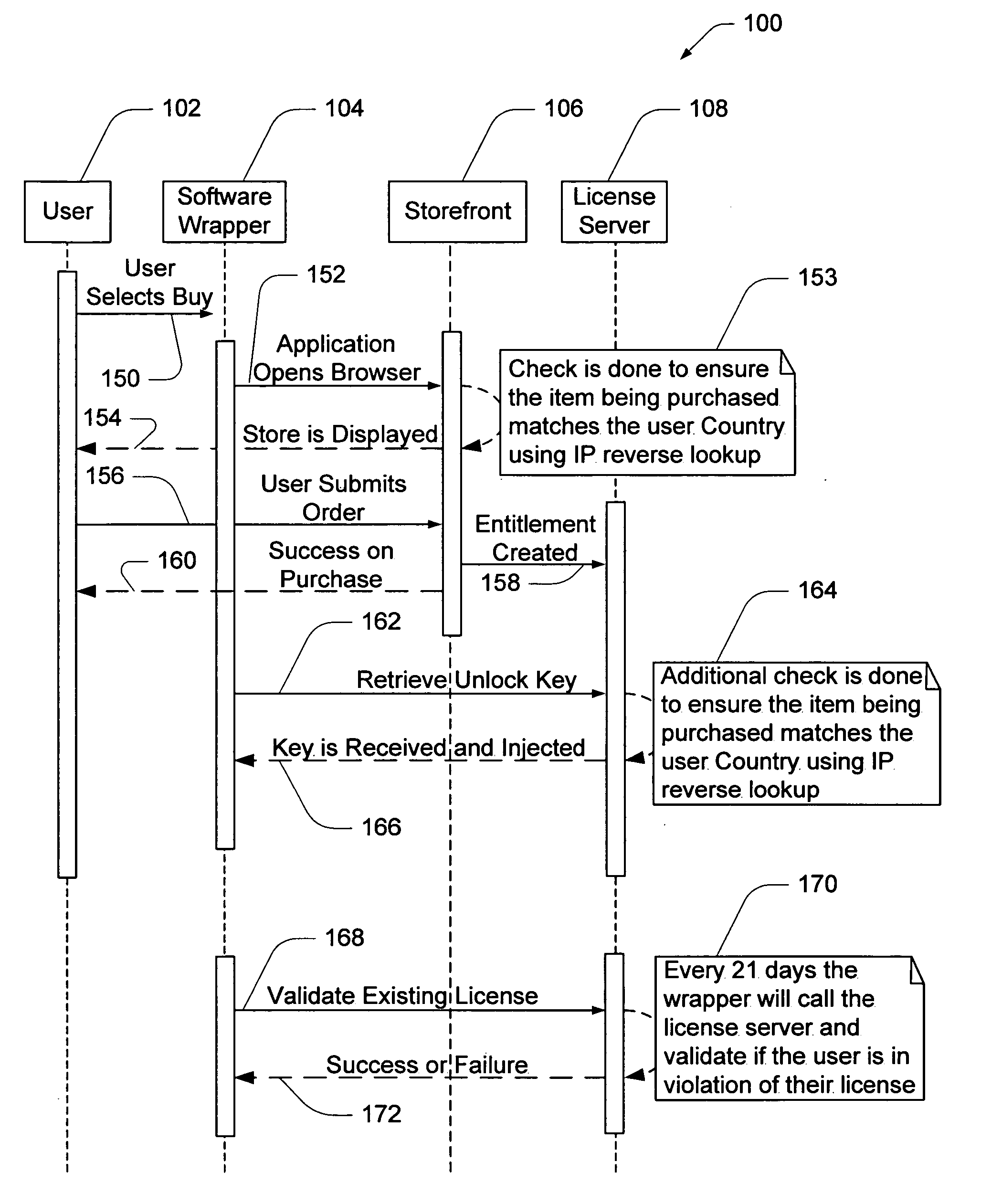
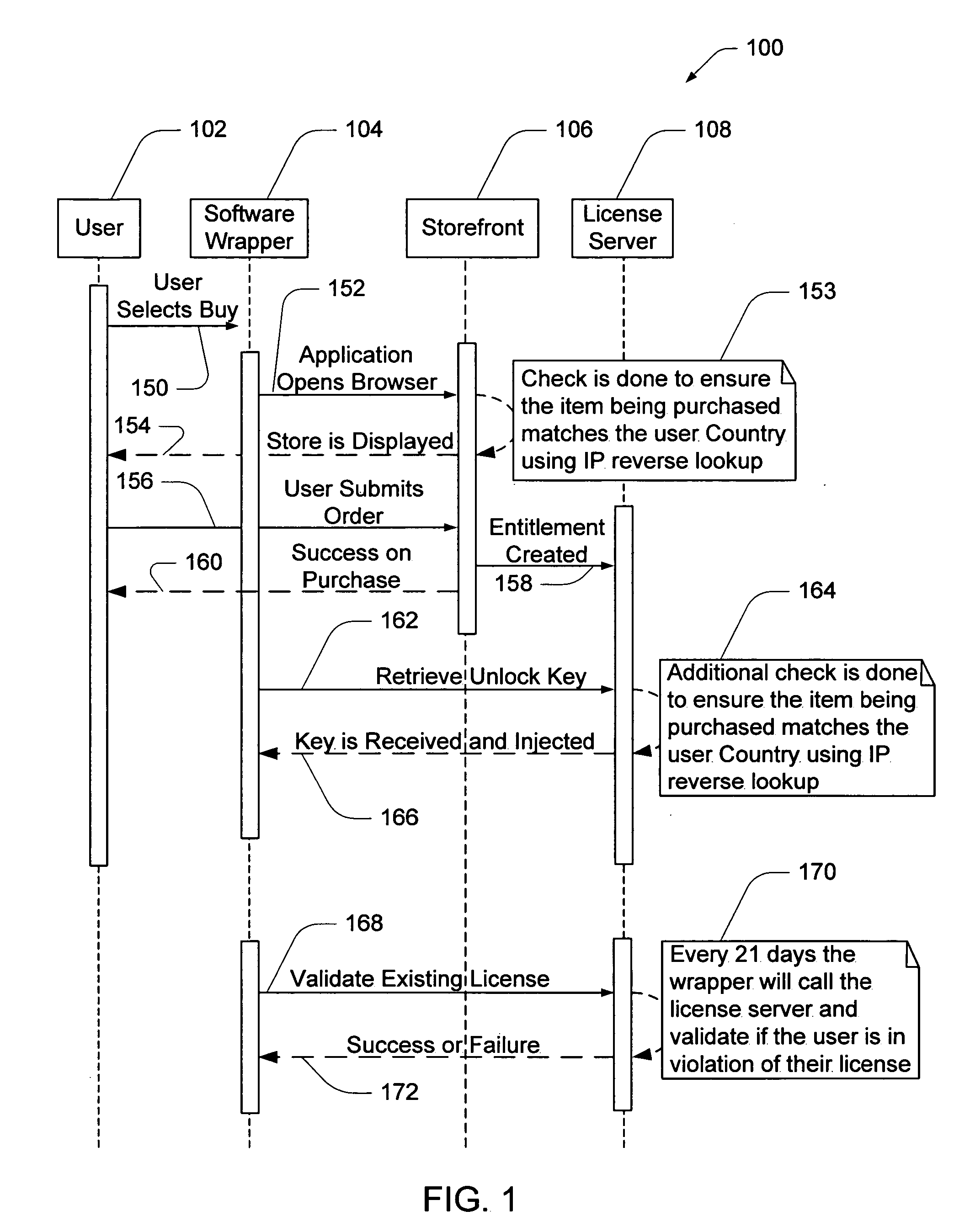
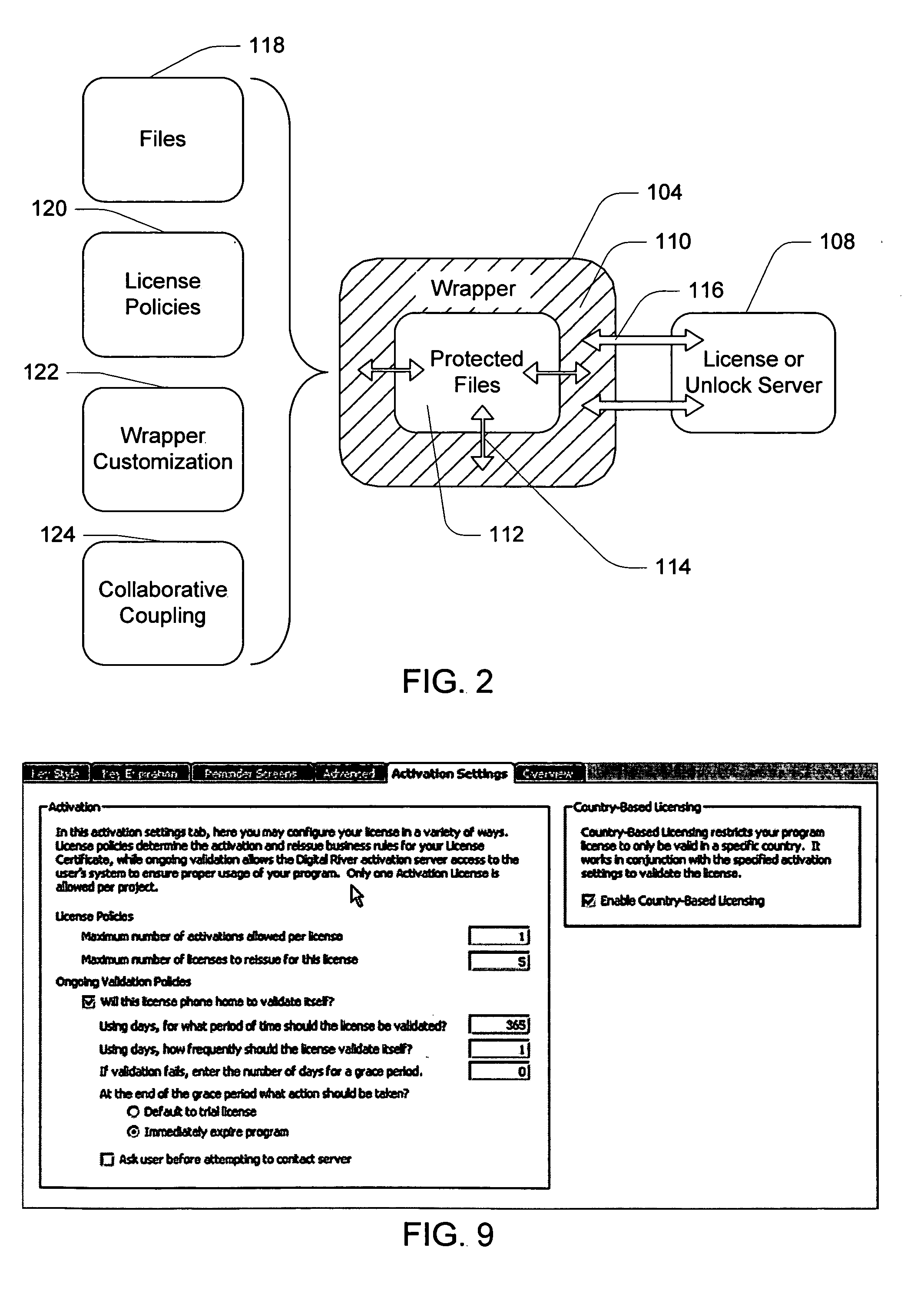
Electronic storefront that limits download of software wrappers based on geographic location
InactiveUS20060059561A1Digital data processing detailsAnalogue secracy/subscription systemsSoftware licenseSecurity software
A computer software license management system wrapper for use in a local computer is described. The software wrapper includes a wrapper interface that provides controlled access to a computer software application file. The software application file is encapsulated by security software code to protect it from unauthorized access. The software wrapper also includes a software license key identifying a license policy specifying a use limitation within a geographic boundary. In addition, the software wrapper includes a license validation mechanism that periodically determines compliance with the license policy. The license validation mechanism permits access by another process operating on the local computer through the wrapper interface in response to a valid license confirmation signal received from the license server. A license server that utilizes and an electronic storefront that sells software license wrappers having software use limitations within a geographic boundary also are described.
Owner:DIGITAL RIVER INC
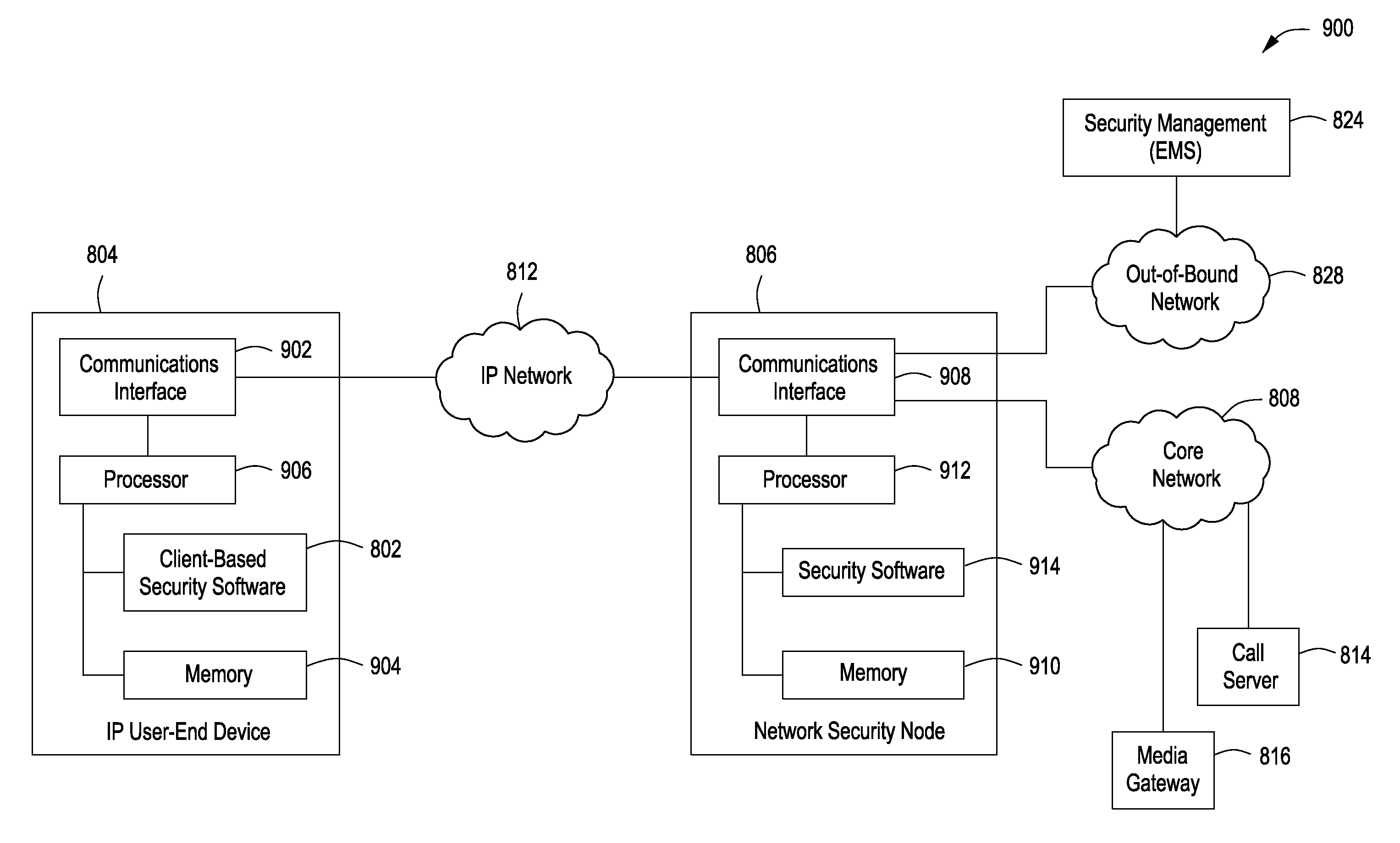
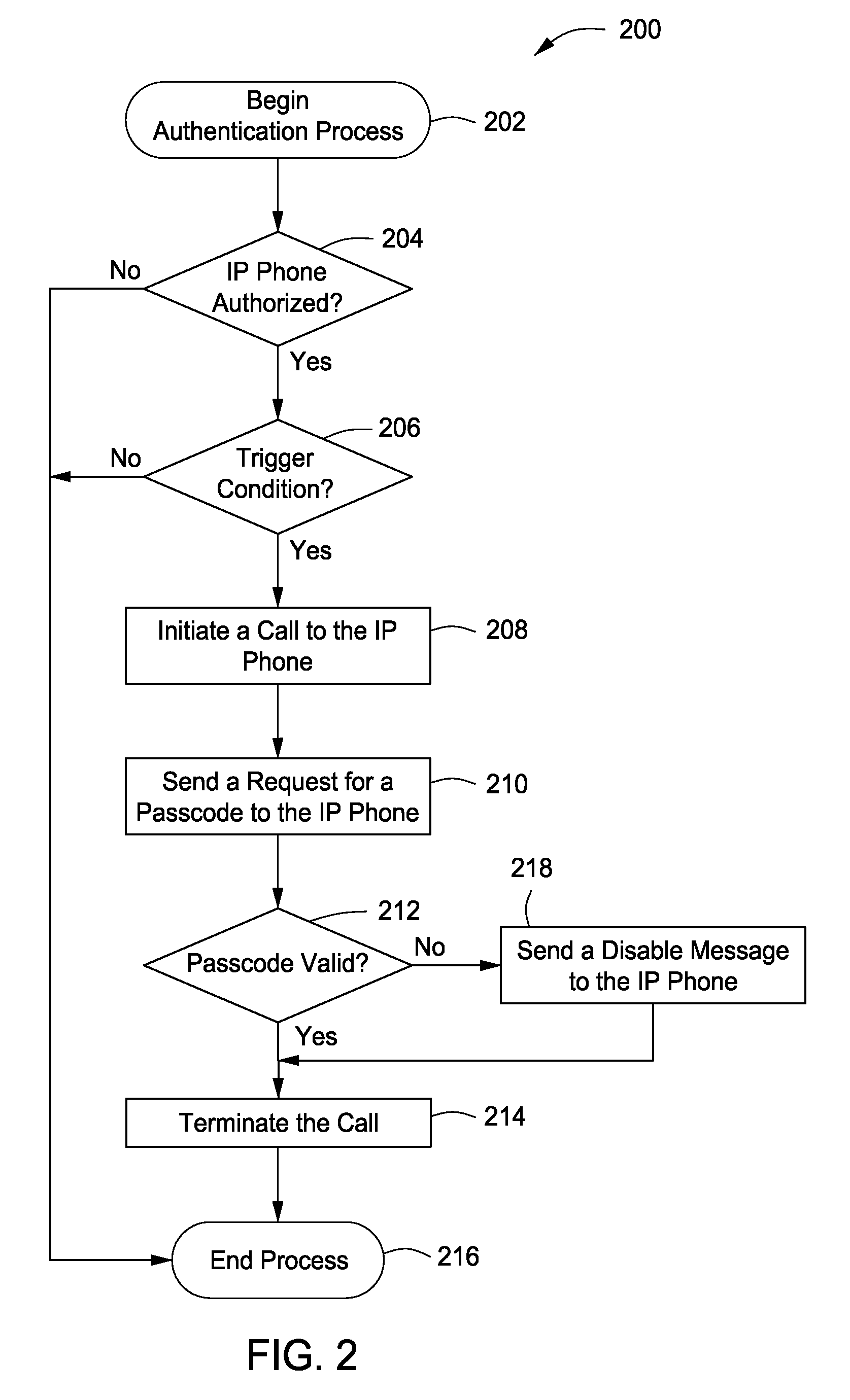
System, method and apparatus for authenticating and protecting an IP user-end device
ActiveUS20100107230A1Raise security concernsInterconnection arrangementsUnauthorised/fraudulent call preventionInternet privacyAttack
A system, method and apparatus authenticates and protects an Internet Protocol (IP) user-end device by providing a client-based security software resident on the IP user-end device, authenticating the IP user-end device using the client-based security software and a network security node communicably coupled to the IP user-end device, authenticating a user of the IP user-end device whenever a trigger condition occurs using an in-band channel between the client-based security software and the network security node, and protecting the IP user-end device by: (a) screening incoming IP traffic to the IP user-end device using the client-based security software, and (b) detecting an attack or a threat involving the IP user-end device using the network security node.
Owner:AVAYA INC
System and method for secure conditional access download and reconfiguration
ActiveUS7383438B2Overcome deficienciesUser identity/authority verificationSecret communicationSecurity softwareConditional access
A method of securely downloading at least one of conditional access software (CAS), Digital Rights Management software (DRMS), Trusted Domain Software (TDS), and Gaming Security Software (GSS) includes presenting a specialized entitlement management message (EMM) to initiate the download to a receiver security device using a supervisory logon key (SLK) split to logon with a second split contained inside the receiver security device, presenting a receiver digitally signed random challenge from the receiver security device to a sender security server to establish authentication of the receiver security device to the sender security server, and signing and returning the receiver random challenge from the sender security server to the receiver security device with a sender random challenge to establish authentication of the sender security server to the receiver security device.
Owner:COMCAST CABLE COMM LLC
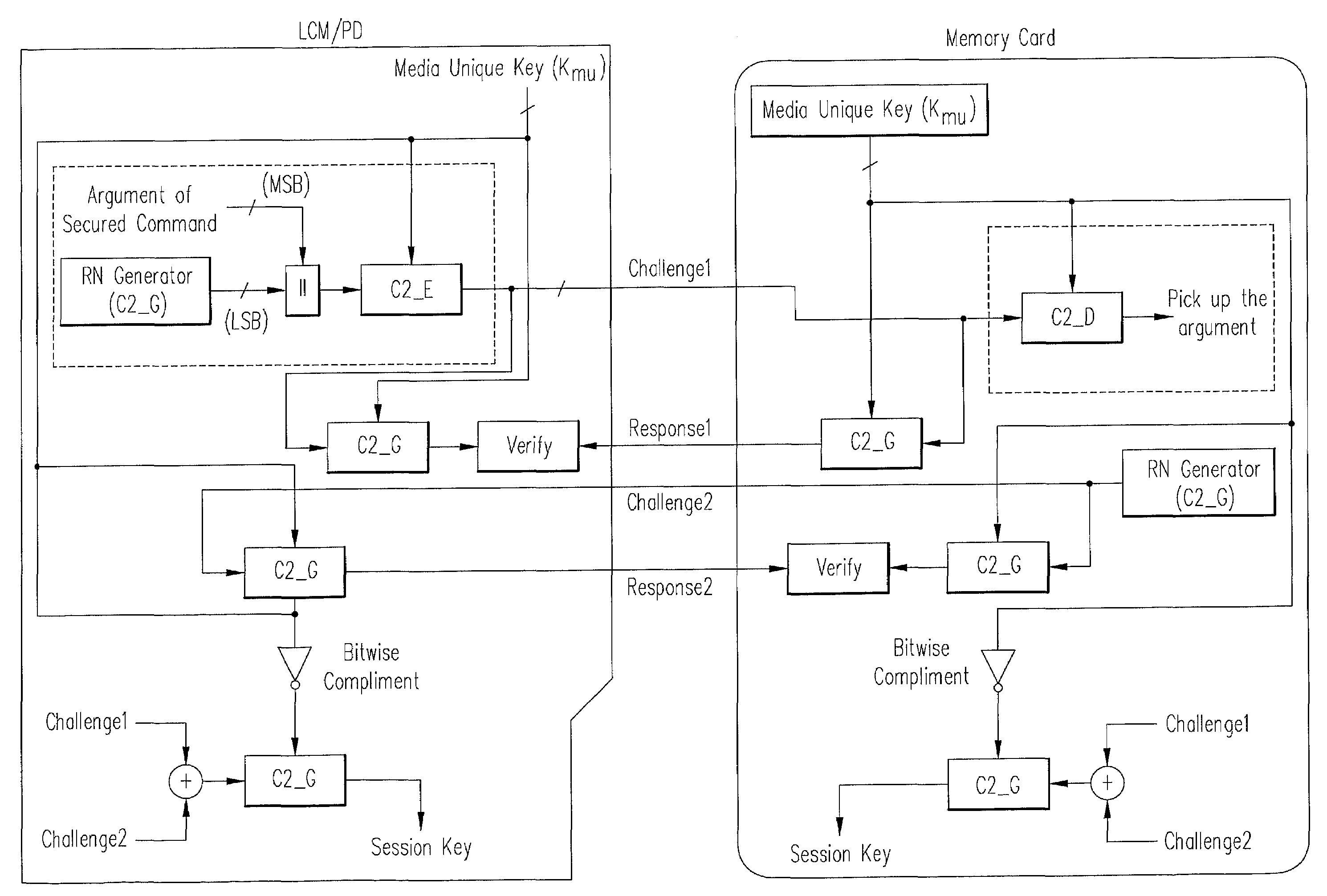
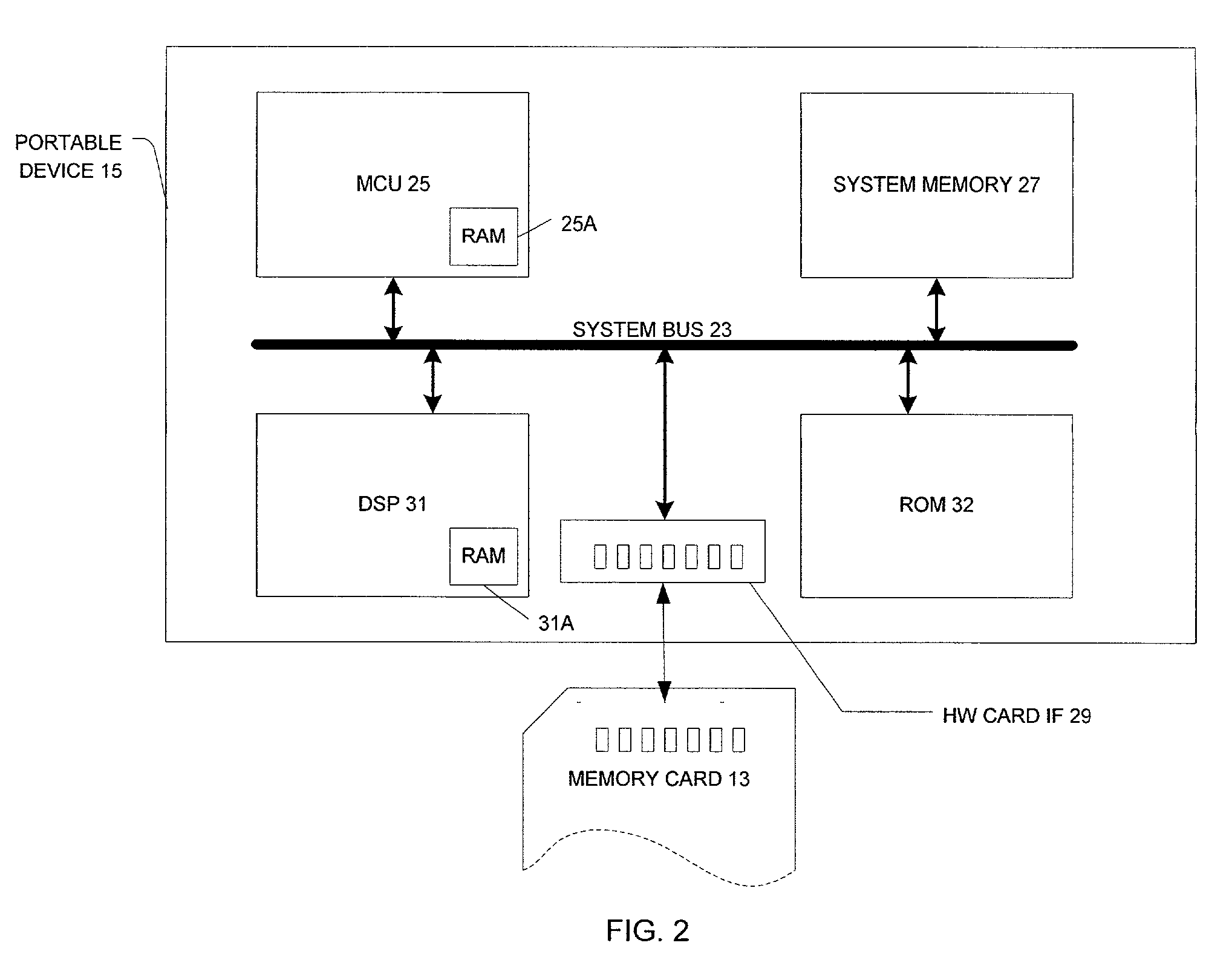
System, method, and device for playing back recorded audio, video or other content from non-volatile memory cards, compact disks or other media
InactiveUS7227952B2Minimize exposureDifficult to accessTelevision system detailsKey distribution for secure communicationSoftware systemSecurity software
A secure software system for a portable device or computer that provides a simple interface to the device or computer and that retrieves and dynamically decrypts keys and content from a secure media while minimizing exposure of the keys and eliminating the need for manufacturers of the device or computer to create a their own system to manage these complex processes.
Owner:SANDISK TECH LLC
Electronic computer system secured from unauthorized access to and manipulation of data
ActiveUS20060069692A1Improve isolationFacilitate redirectionDigital data processing detailsDigital computer detailsSystem callAuthentication
A software security application for a Windows® OS based electronic computer system provides an isolated User environment which protects a User from unauthorized access to and manipulation of data on the system. The security software implements an isolated User file system and provides process / IPC isolation, Windows® registry isolation, network interface isolation, and isolated administrative control on the computer system. Interactive components of the system include an execution hook component that traps system calls, a job object component that creates / destructs, manages and manipulates job objects, a system call hook component for trapping and filtering all Windows registry I / O requests, a file system block device driver for mounting / unmounting the isolated User file system, a file system / filter driver, a network interface / NDIS hook component, and an environment handler. The environment handler provides the overall management interface for other system components, allowing definition of rules, managing authentication and other control / management functions.
Owner:VIIRII LLC
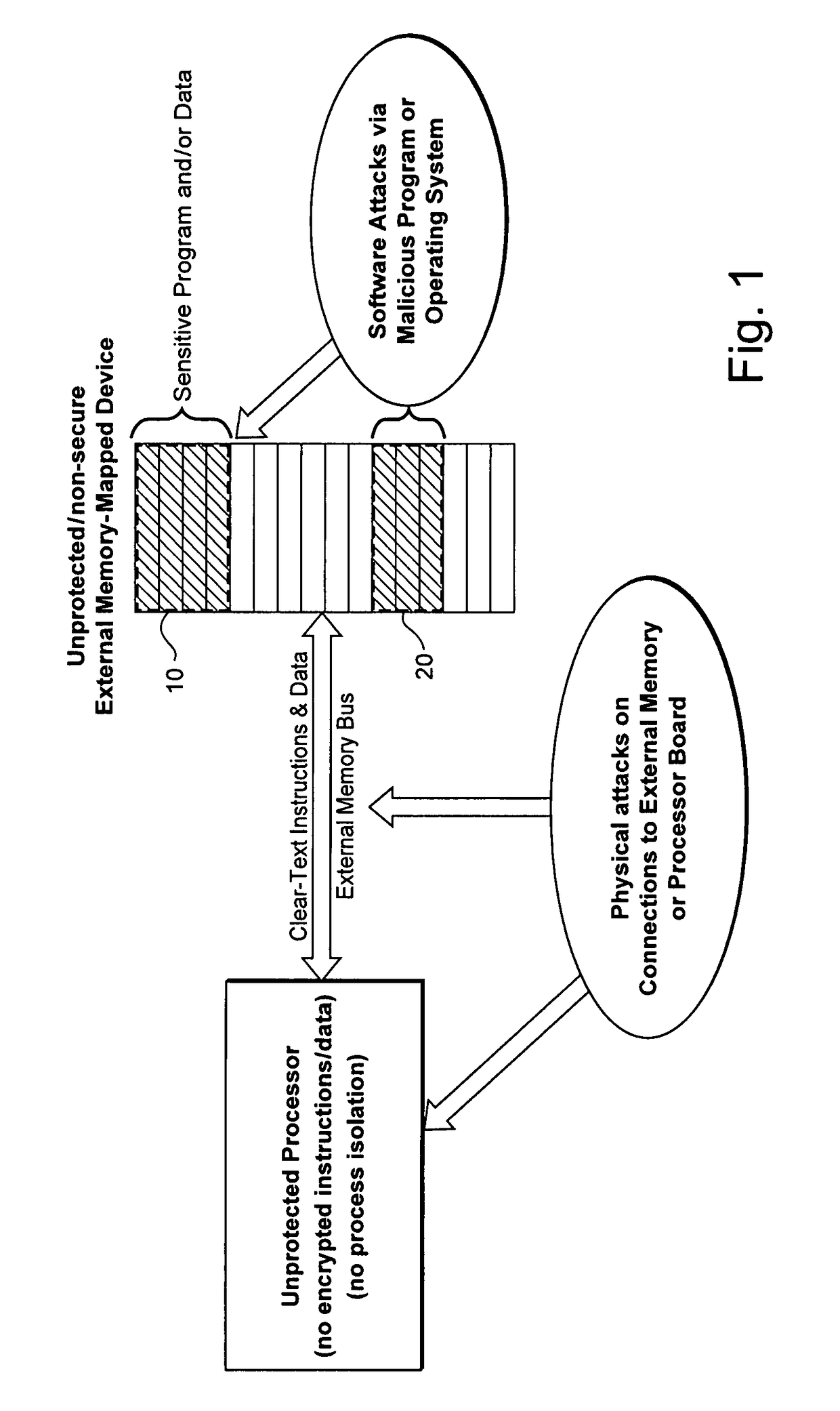
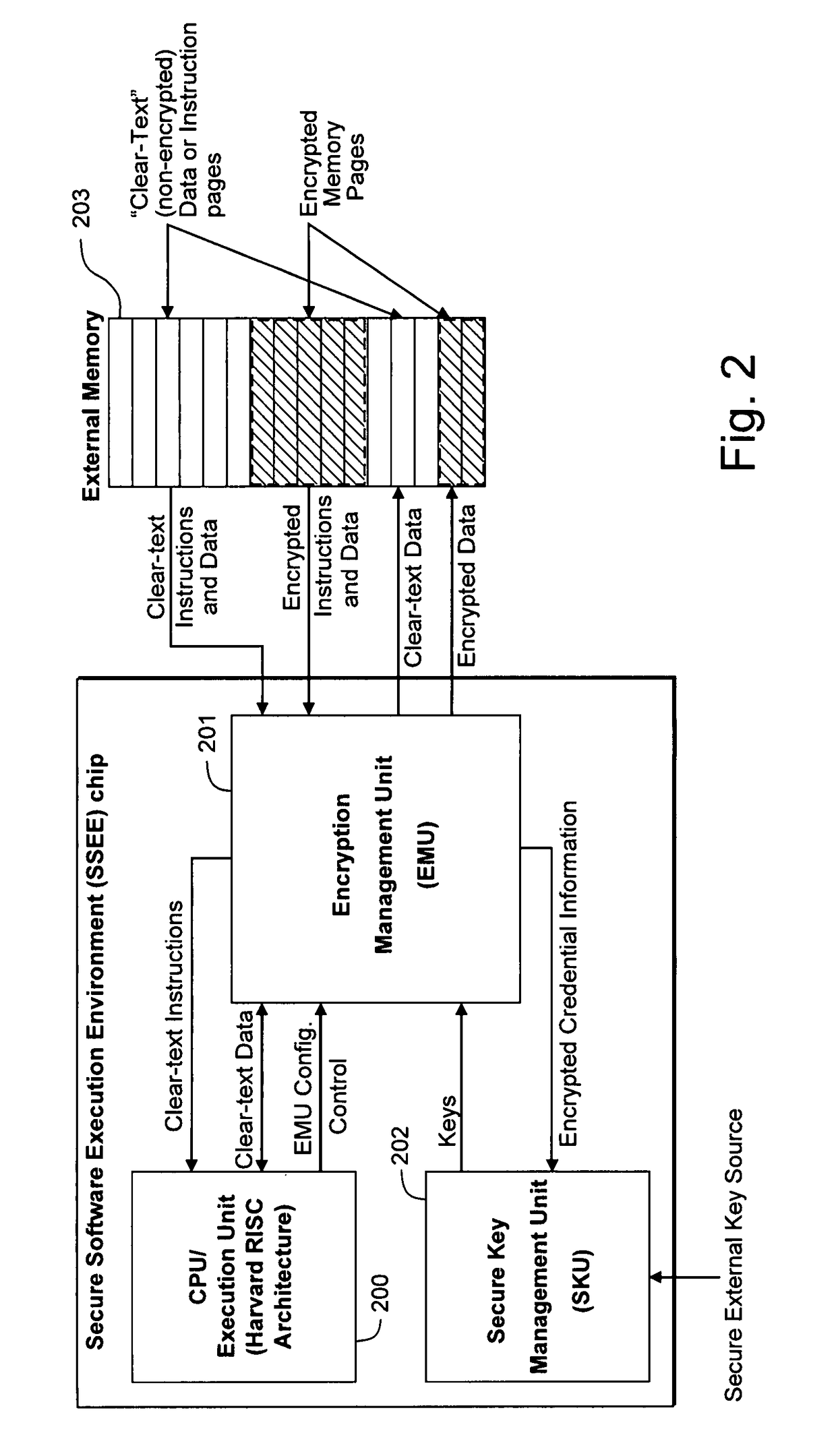
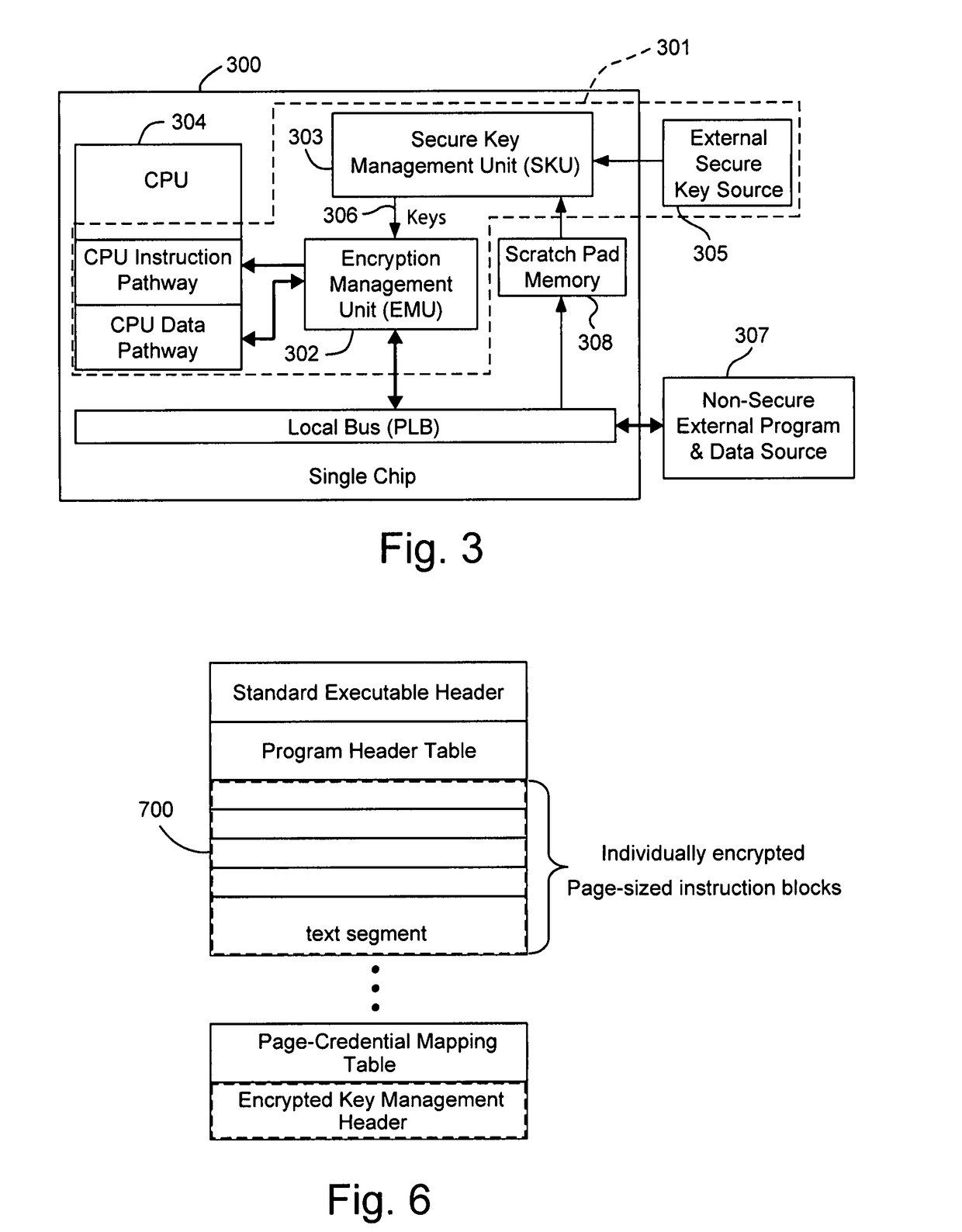
Hardware-facilitated secure software execution environment
InactiveUS8473754B2Avoid unwanted disclosureProvide confidentialityUser identity/authority verificationUnauthorized memory use protectionConfidentialityKey management
A hardware-facilitated secure software execution environment provides protection of both program instructions and data against unauthorized access and / or execution to maintain confidentiality and integrity of the software or the data during distribution, in external memories, and during execution. The secure computing environment is achieved by using a hardware-based security method and apparatus to provide protection against software privacy and tampering. A Harvard architecture CPU core is instantiated on the same silicon chip along with encryption management unit (EMU) circuitry and secure key management unit (SKU) circuitry. Credential information acquired from one or more sources is combined by the SKU circuitry to generate one or more security keys provided to the EMU for use in decrypting encrypted program instructions and / or data that is obtained from a non-secure, off-chip source such as an external RAM, an information storage device or other network source. In a non-limiting illustrative example implementation, the EMU decrypts a single memory page of encrypted instructions or data per a corresponding encryption key provided by the SKU. Although instantiated on the same chip, the CPU core does not have direct access to the SKU circuitry or to encryption key information generated by the SKU.
Owner:MACAULAY BROWN +1
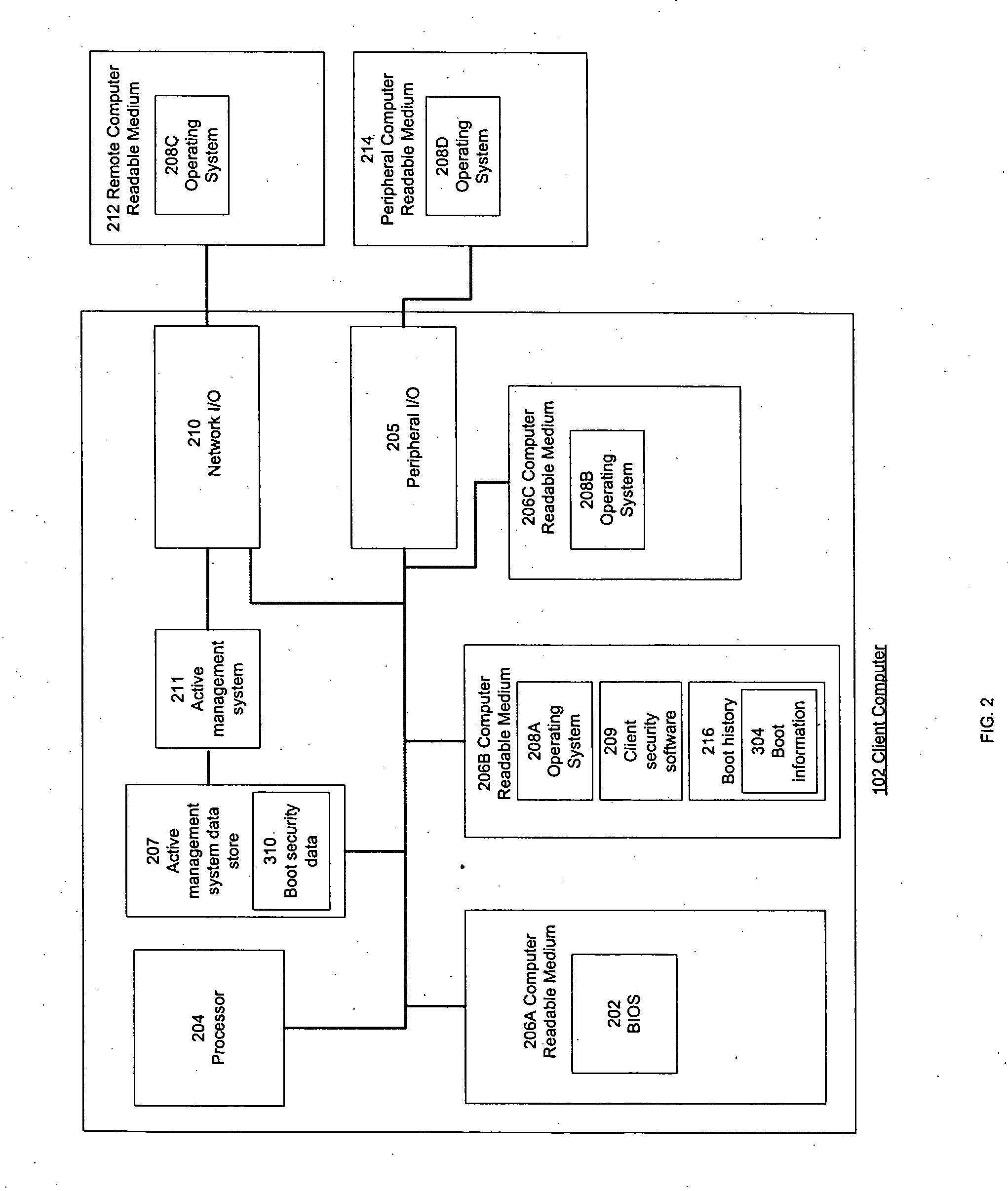
System and method for detecting unauthorized boots
InactiveUS20070136807A1Memory loss protectionError detection/correctionOperational systemSecurity software
A system and method for detecting unauthorized boots and adjusting security policy. According to one embodiment of the present invention, the BIOS stores boot information in a data store from which it can later be distributed on a network and / or accessed by security software. The security software compares a signature of the operating system booted by the computer to a signature of a trusted, or authorized, operating system. The security software is capable of determining whether an attempted boot is authorized and can adjust security policy in response to the boot information.
Owner:CISCO TECH INC
Software wrapper having use limitation within a geographic boundary
ActiveUS20060059099A1Payment architectureProgram/content distribution protectionSecurity softwareSoftware license
A computer software license management system wrapper for use in a local computer is described. The software wrapper includes a wrapper interface that provides controlled access to a computer software application file. The software application file is encapsulated by security software code to protect it from unauthorized access. The software wrapper also includes a software license key identifying a license policy specifying a use limitation within a geographic boundary. In addition, the software wrapper includes a license validation mechanism that periodically determines compliance with the license policy. The license validation mechanism permits access by another process operating on the local computer through the wrapper interface in response to a valid license confirmation signal received from the license server. A license server that utilizes and an electronic storefront that sells software license wrappers having software use limitations within a geographic boundary also are described.
Owner:DIGITAL RIVER INC
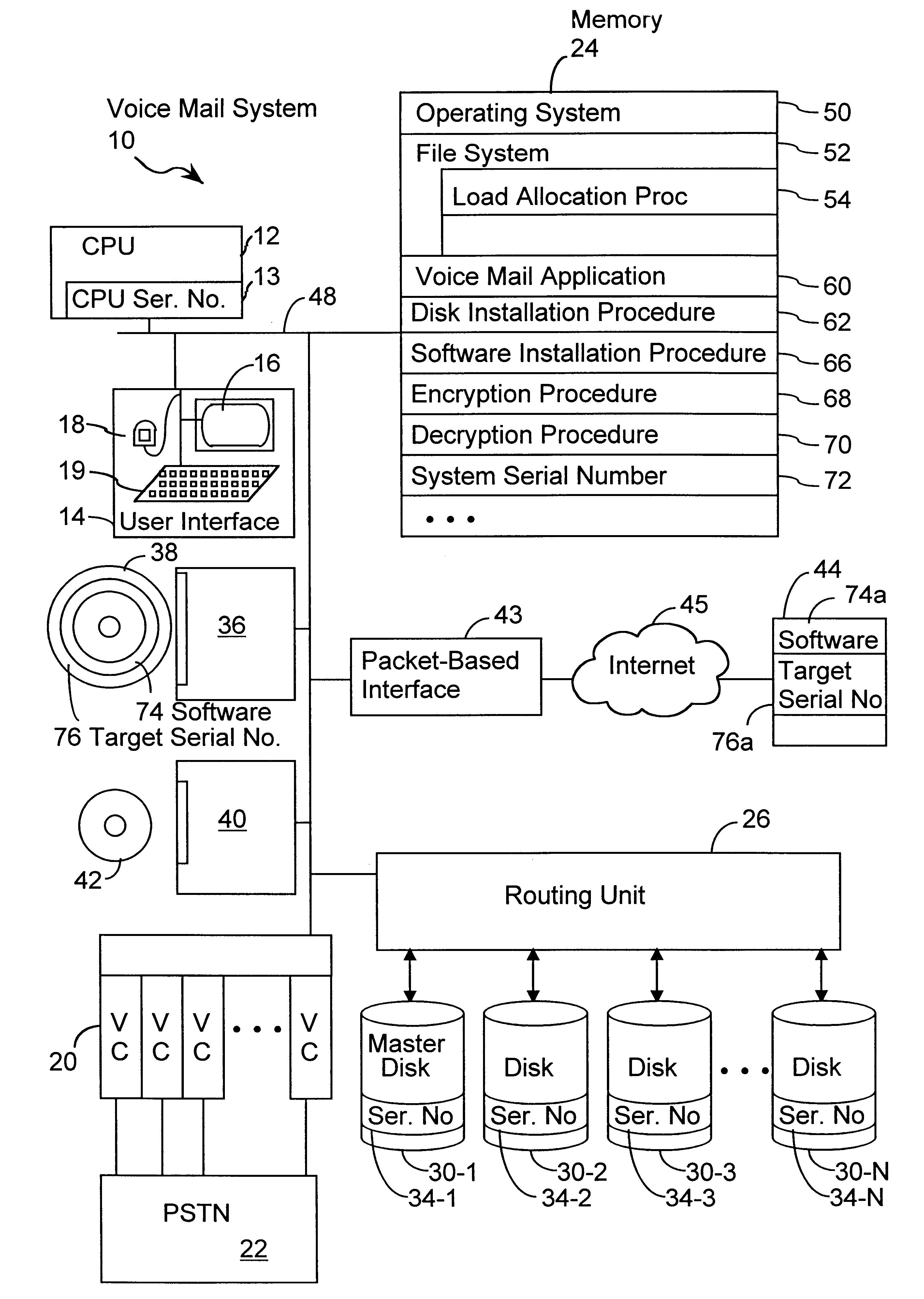
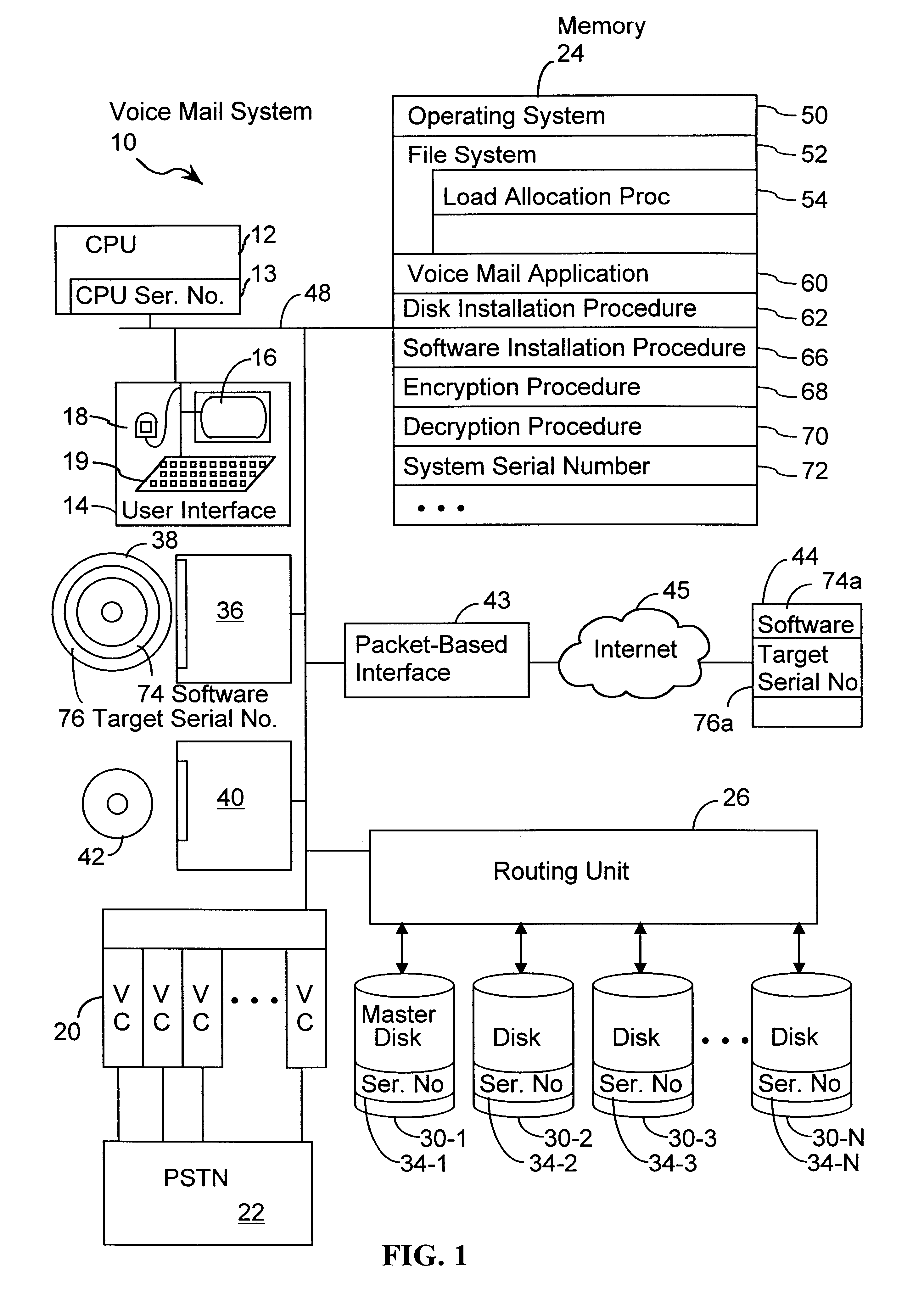
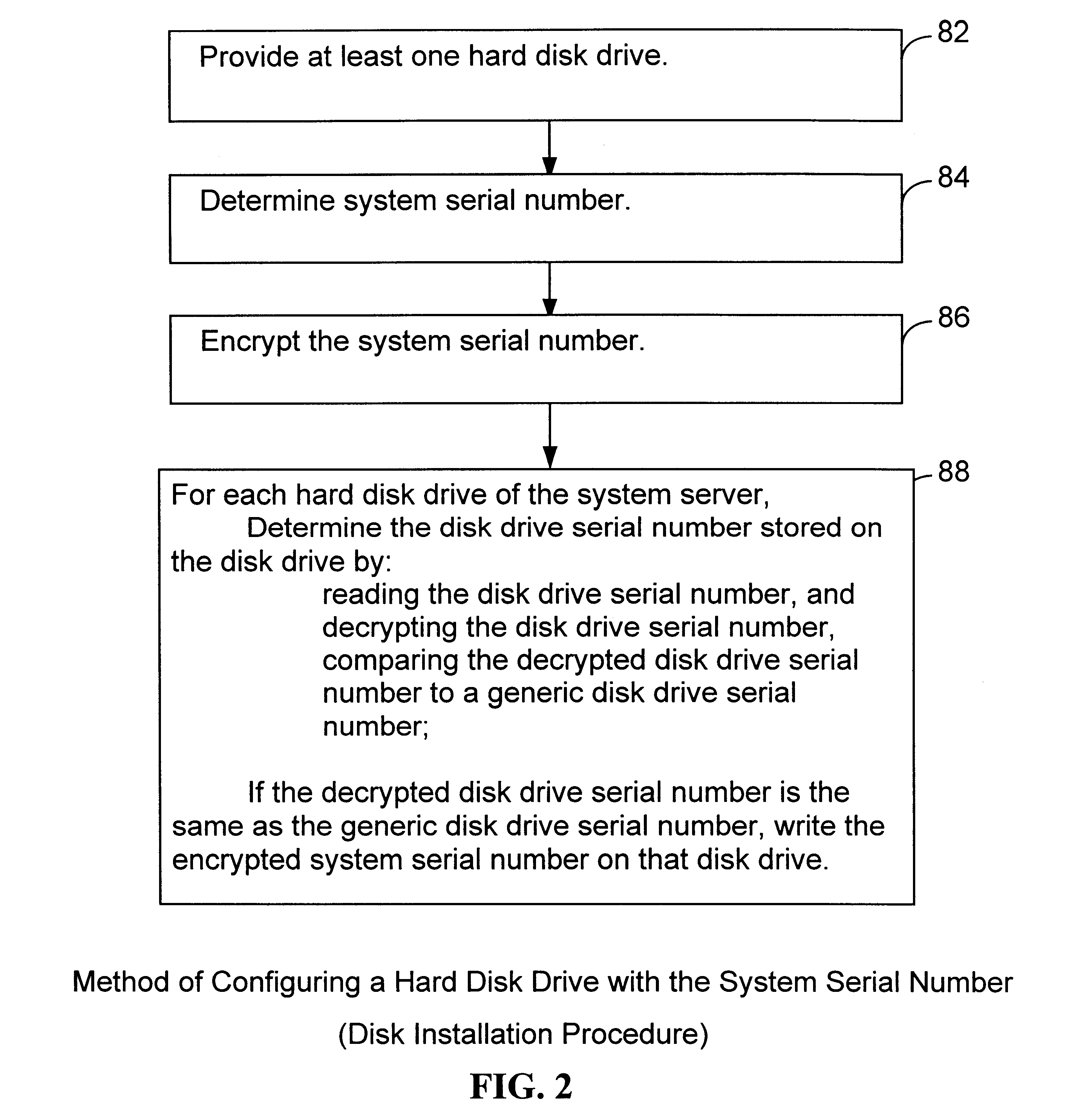
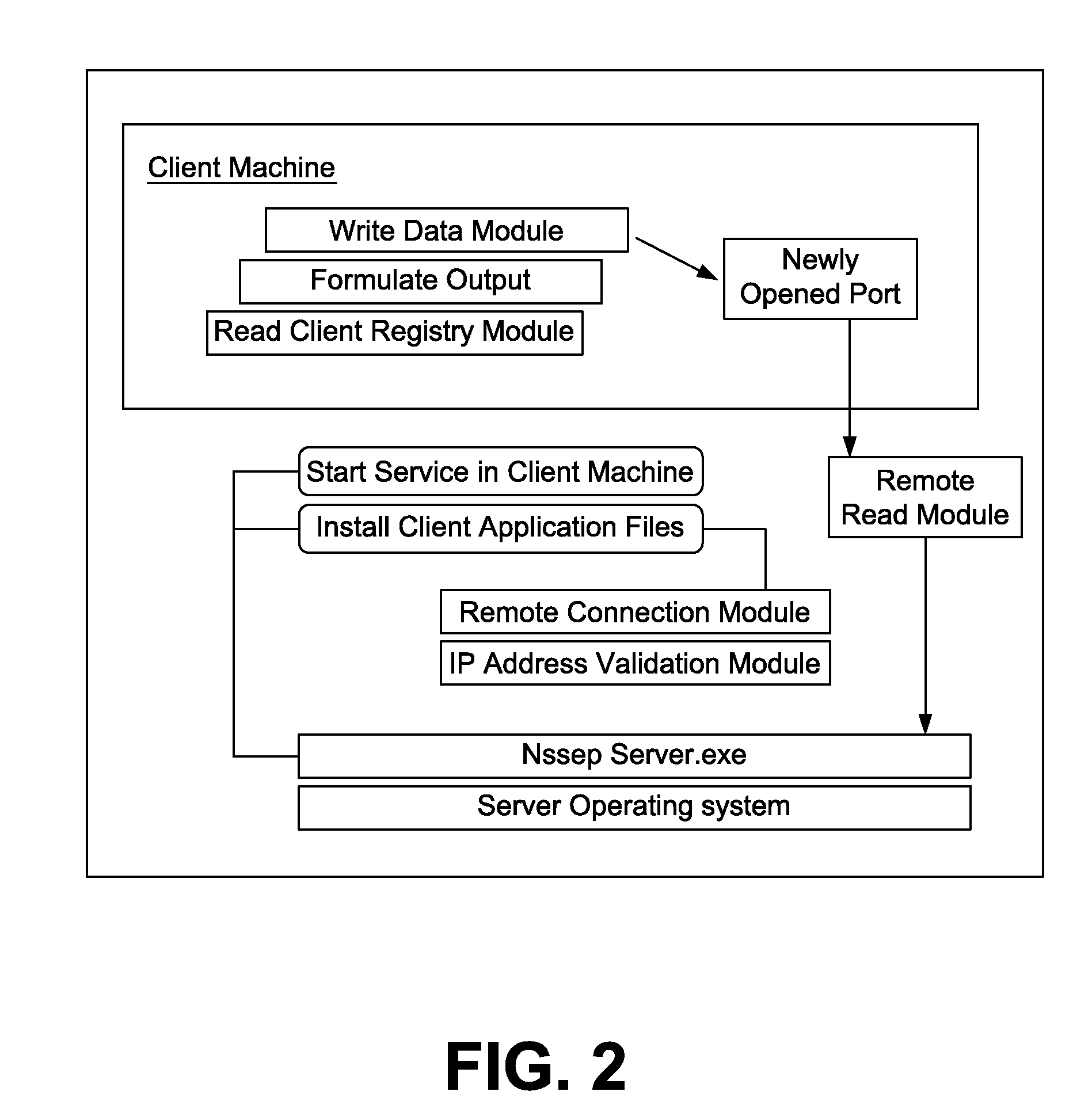
System and method for secure software installation
InactiveUS6725205B1Reduce effortImprove securityDigital computer detailsUnauthorized memory use protectionSecurity softwareComputerized system
A method secures software in a computer system that has one or more fixed disk drives. Each fixed disk drive is configured with a predetermined system serial number, such that each fixed disk drive has the same system serial number. Software is received with an associated target serial number. The associated target serial number is compared to the system serial number on every fixed disk drive. The file is installed when the system serial number on every fixed disk drive is the same as the associated target serial number. A computer program product embodies the method described above.
Owner:INTELLECTUAL VENTURES I LLC
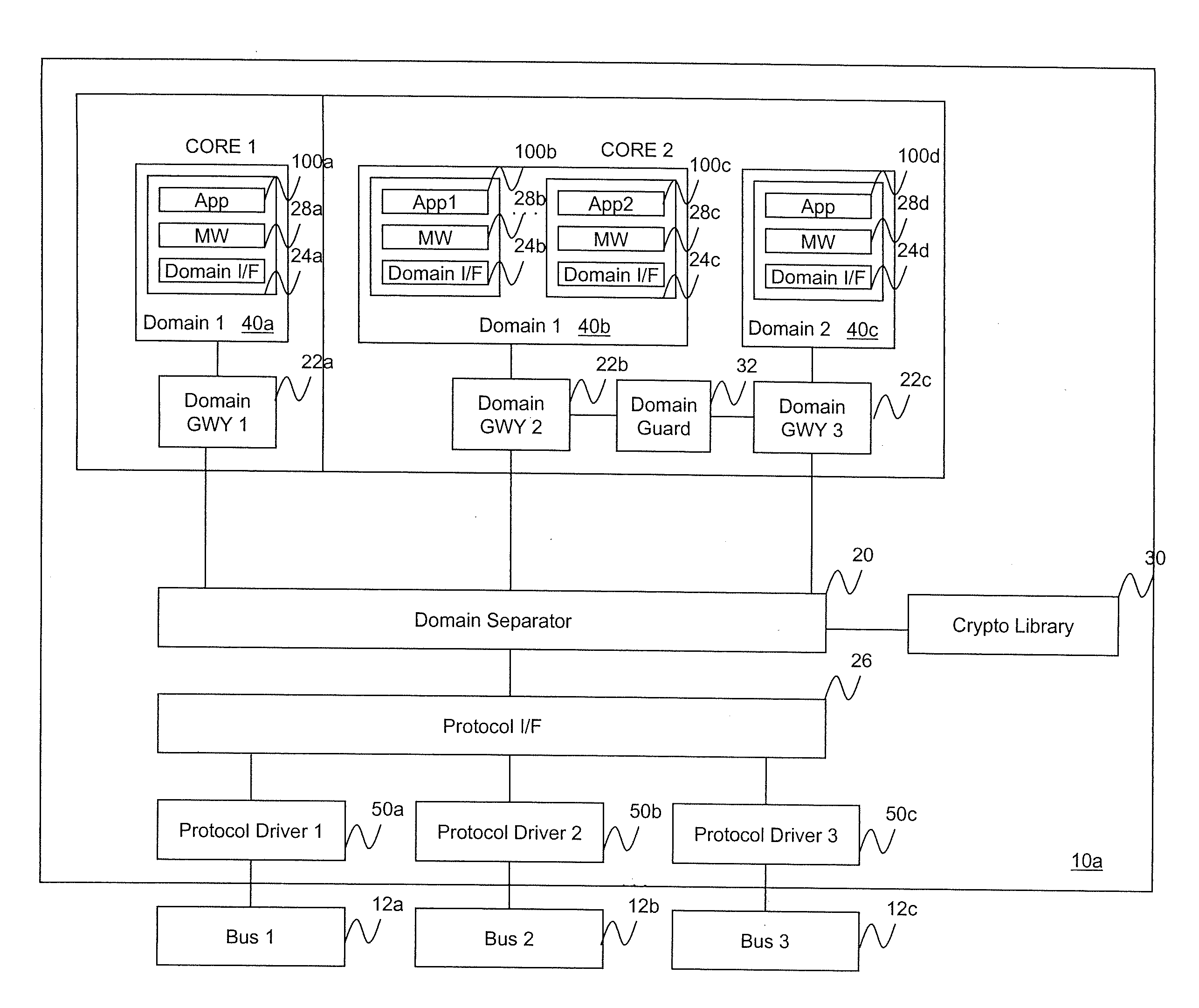
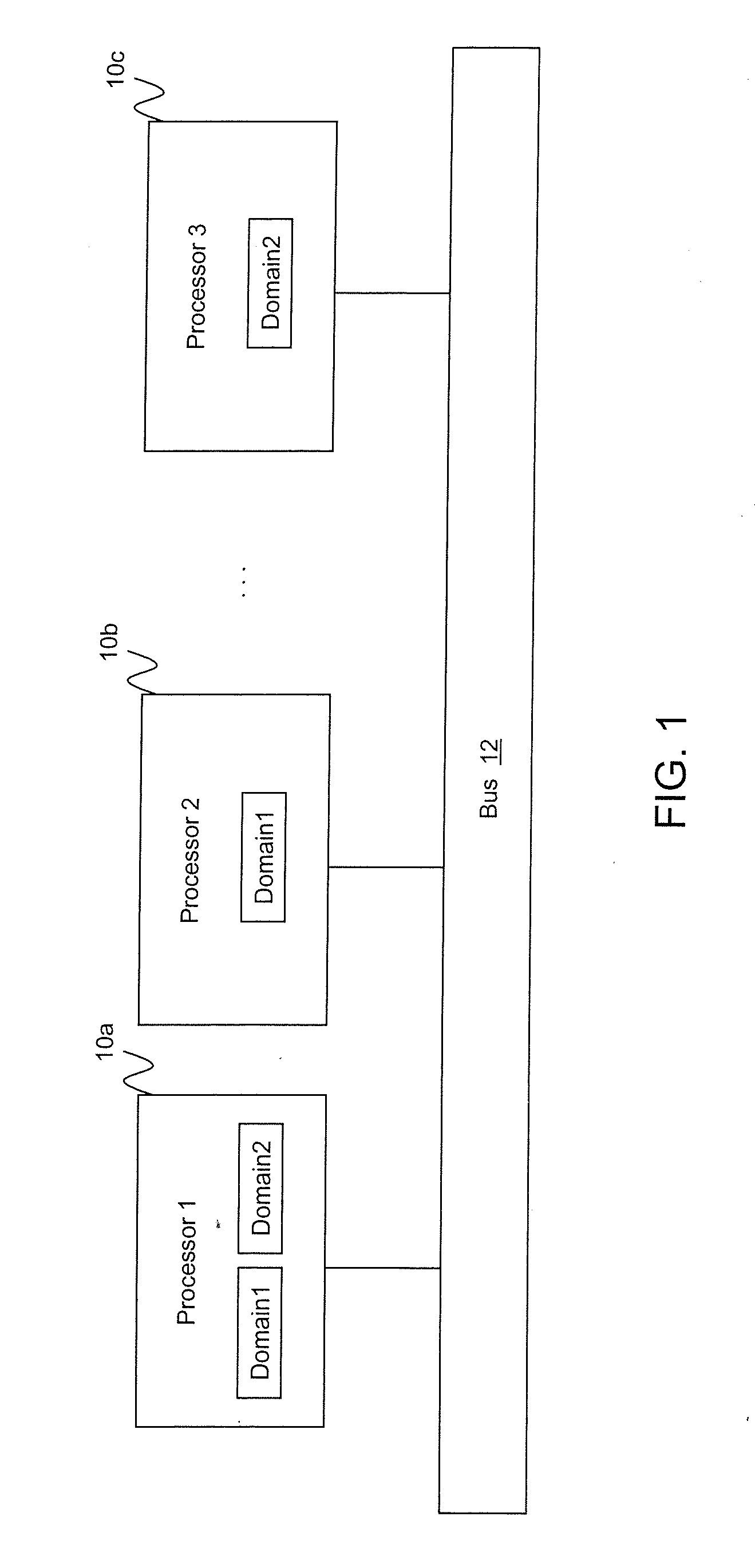
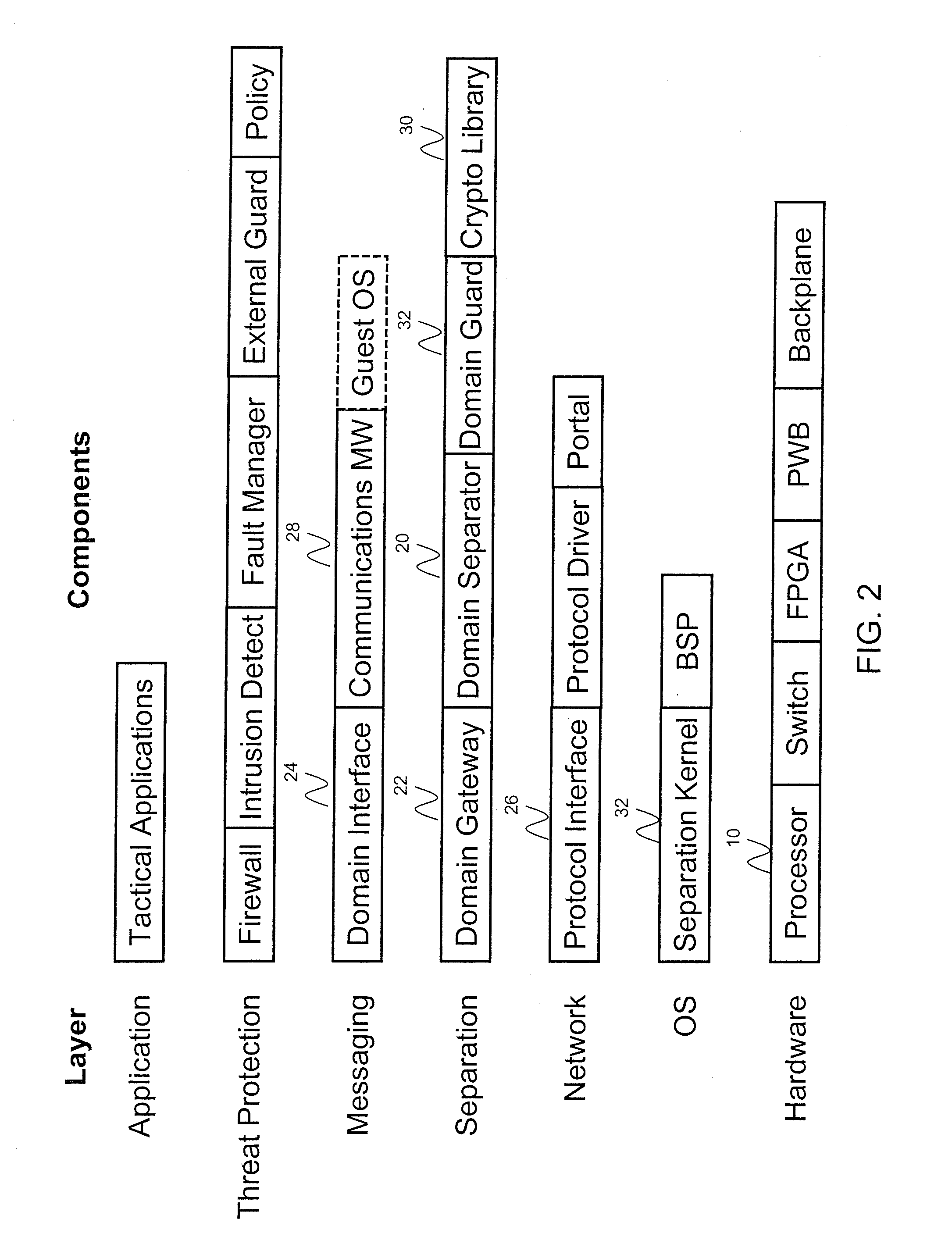
Multi-level security software architecture
ActiveUS20120066509A1Unauthorized memory use protectionHardware monitoringSecurity softwareFull data
A multi-level security software architecture includes various components configured to provide full data separation across multiple processors while limiting the number and size of high assurance components. The architecture includes a domain separator for ensuring that messages exchanged between domains that are distributed on different microprocessors are securely routed between domain members. The domain separator verifies a message label including a domain identifier provided by a domain gateway and cryptographically binds the message label to each message via cryptographic keys. This prevents misrouting messages caused by accidental or malicious corruption of message labels. Additionally, the domain separator can encrypt messages as necessary to enforce data separation on shared network buses. The domain separator is also responsible for managing the cryptographic keys used to label or encrypt messages.
Owner:FORCEPOINT FEDERAL
Network security scanner for enterprise protection
ActiveUS20080276295A1Improve virus prevention processImprove engineer-productivityPlatform integrity maintainanceTransmissionOperational systemNetwork connection
A method of monitoring levels of security conformity and preparedness of a plurality of network connected computing machines, obtains a report by remotely scanning the machines in segments. The machines might already be connected to commercial security software and a patch dispenser. The report includes definition dates and any files quarantined by the commercial security software, patch-management-software communication present and the patches received. The method uses the report and software (not installed on the scanned machines) to produce a Network Security Scanner for Enterprise Protection output to perform a security-preparedness audit of the scanned machines. The audit non-intrusively ascertains. If the scanned machines conform to user-defined fields and policies, and assists in selective security updating of the machines. The scanning, unrecognized by the scanned machines may be configured to suit their OS, and done periodically as desired. A computer readable medium executing the method is included.
Owner:WIPRO LTD
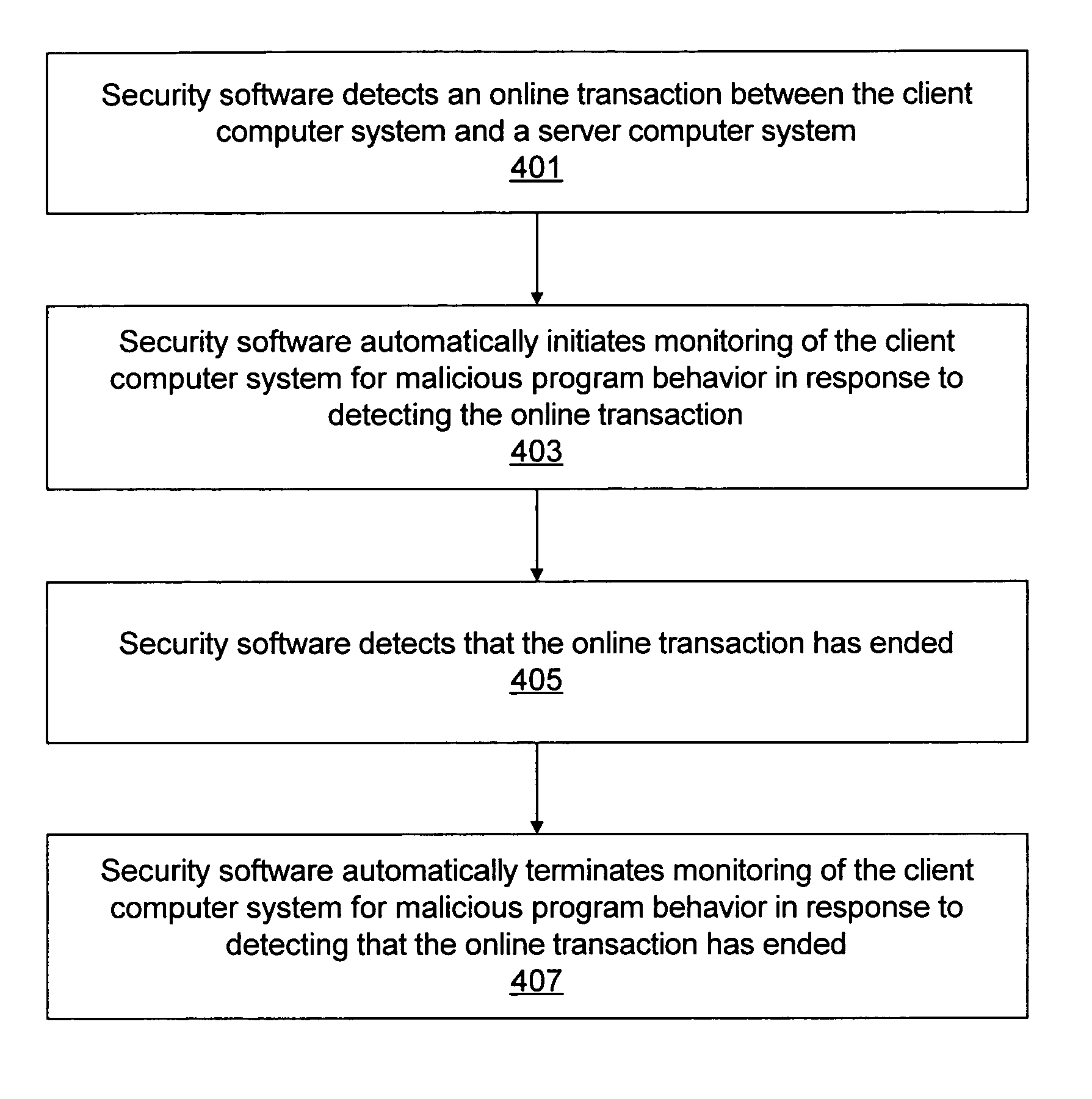
Method, system, and computer program product for blocking malicious program behaviors
InactiveUS7818800B1Memory loss protectionError detection/correctionSecurity softwareComputerized system
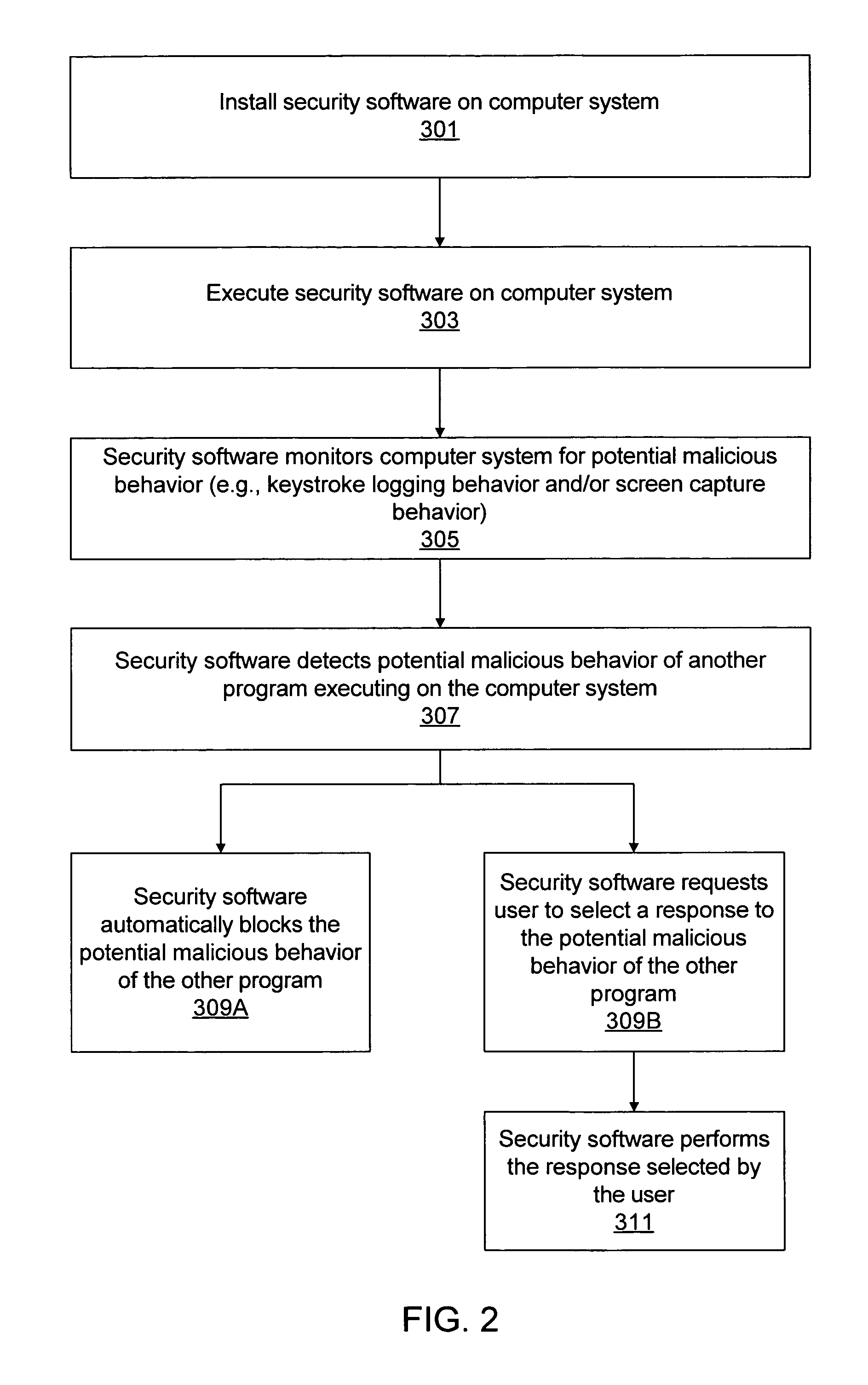
Various embodiments of a system and method for blocking malicious program behaviors, such as keystroke logging behavior or screen capture behavior, are disclosed. Security software may execute on a computer system, where the security software is operable to monitor the computer system to detect malicious program behavior. In response to detecting a first condition indicating that monitoring of the computer system to detect malicious program behavior should be initiated, the security software automatically initiates monitoring of the computer system to detect malicious program behavior. After initiating the monitoring for malicious program behavior, the security software may detect malicious program behavior of a second program executing on the computer system and block the malicious program behavior of the second program.
Owner:CA TECH INC
Safe software revision for embedded systems
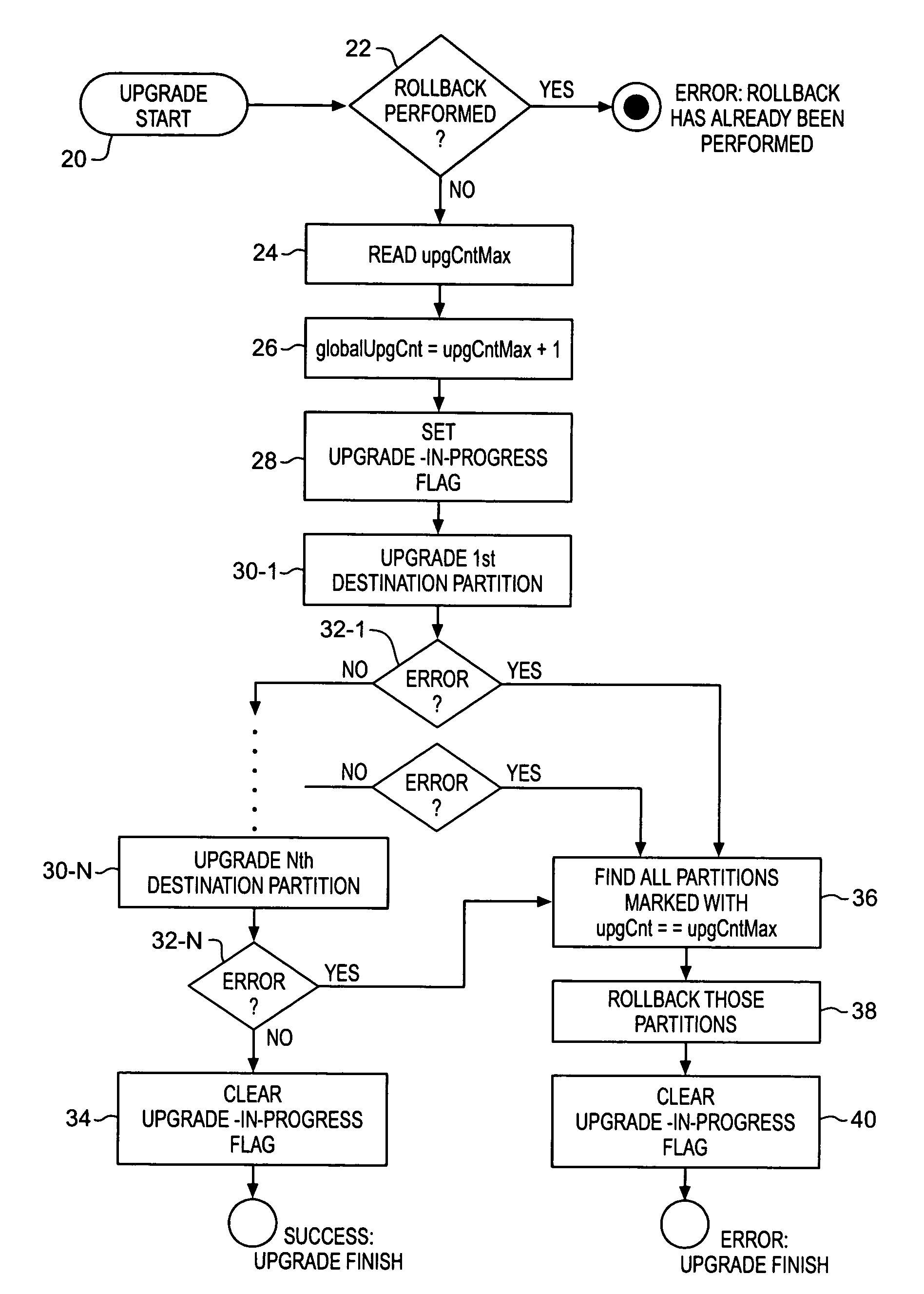
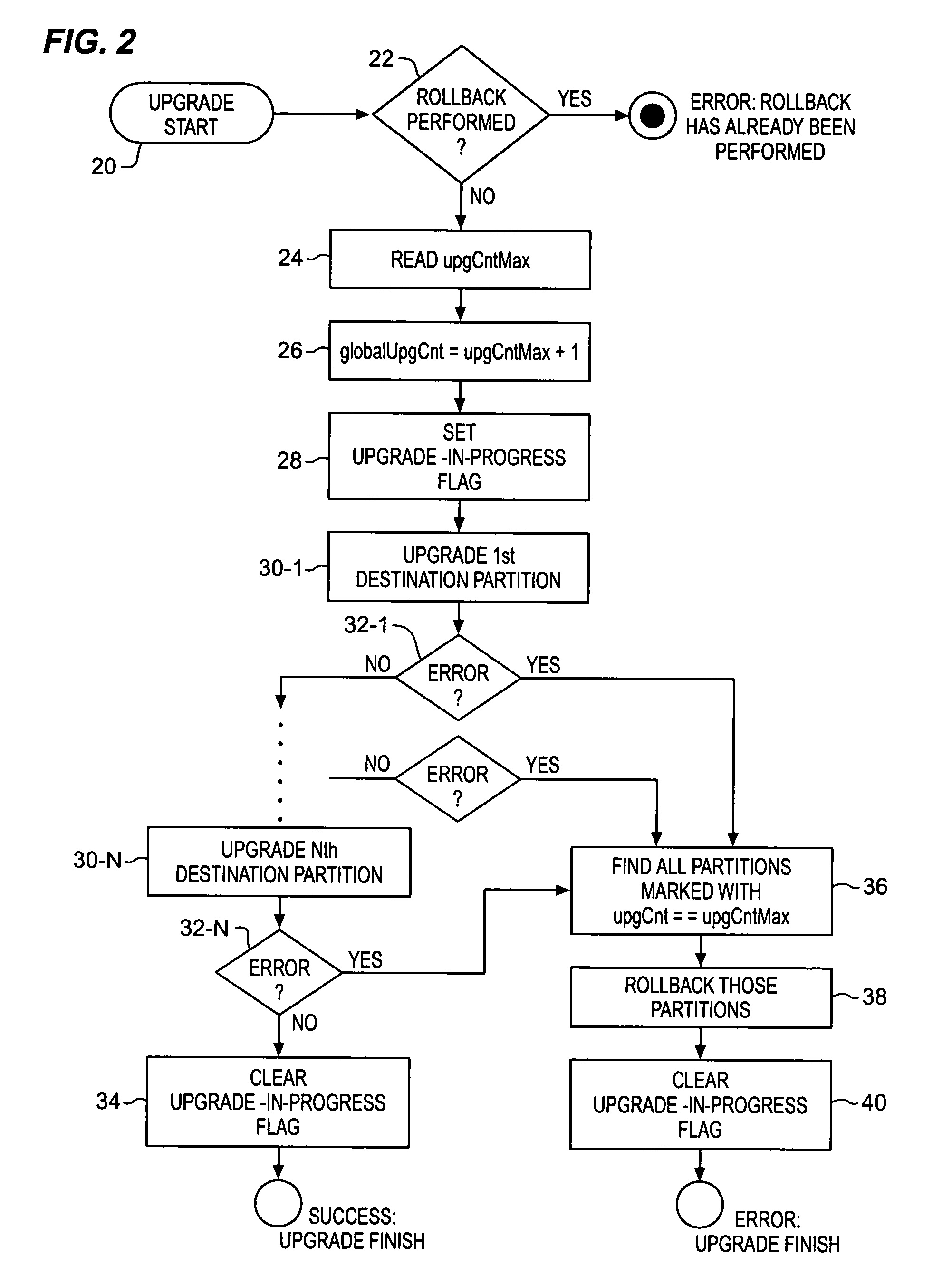
InactiveUS20080270677A1Memory adressing/allocation/relocationSpecific program execution arrangementsSecurity softwareEmbedded system
The present invention, in one embodiment includes identifying a first partition of an embedded program memory, reading a description associated with the first partition, identifying a second partition of an embedded program memory, reading a description associated with the second partition, comparing descriptions, selecting an embedded program memory partition using the comparison, and writing program code to the selected program memory partition.
Owner:INTEL CORP
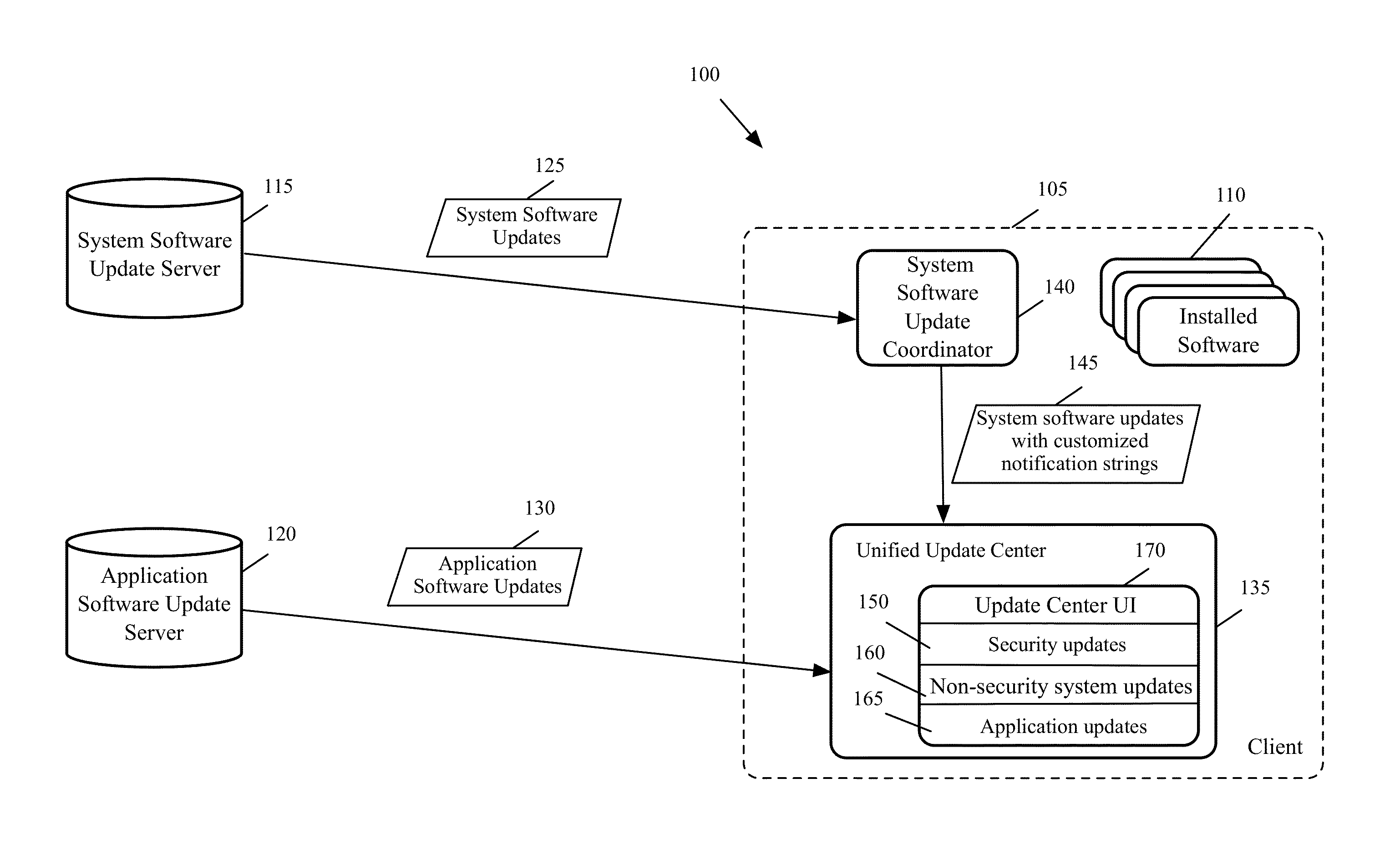
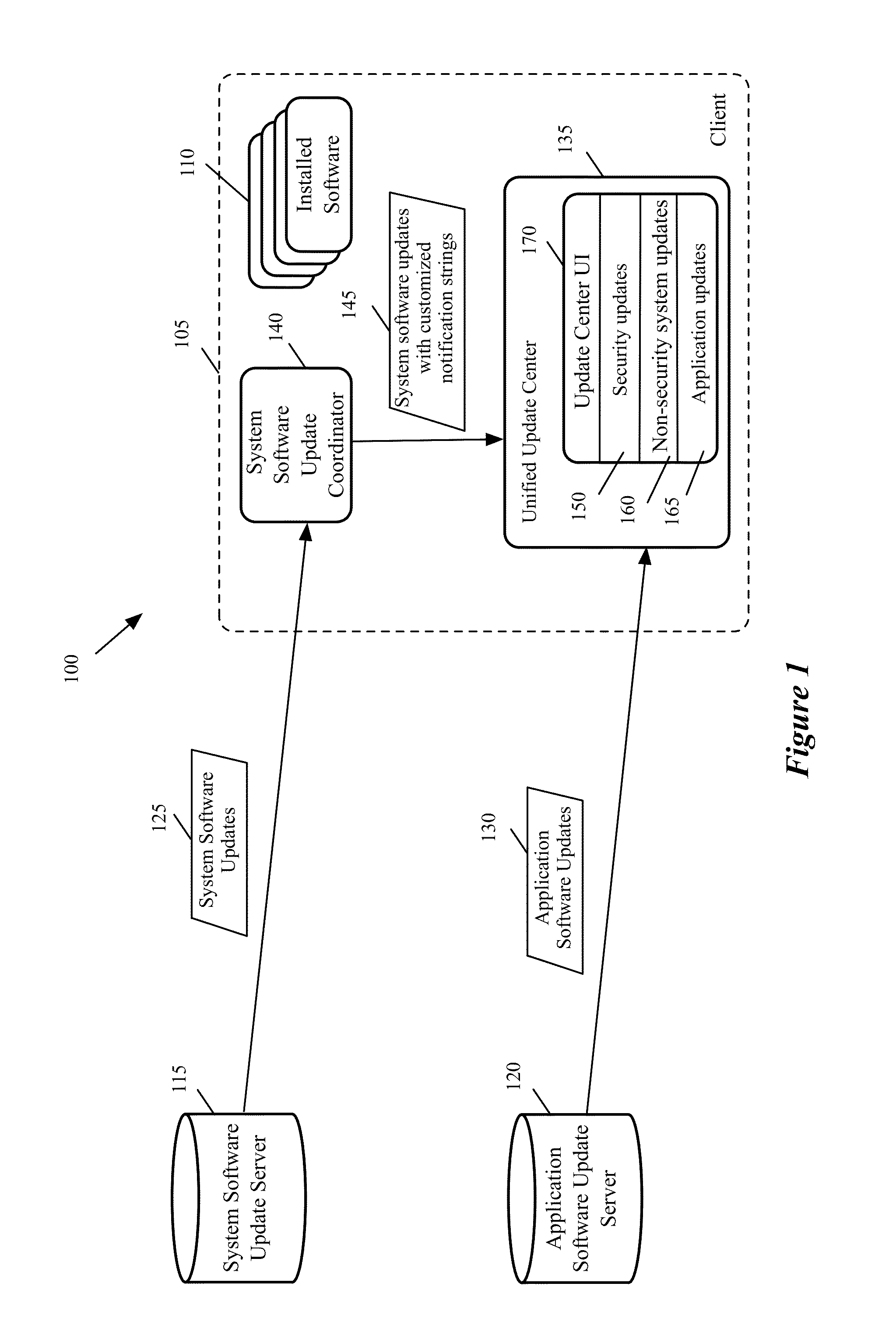
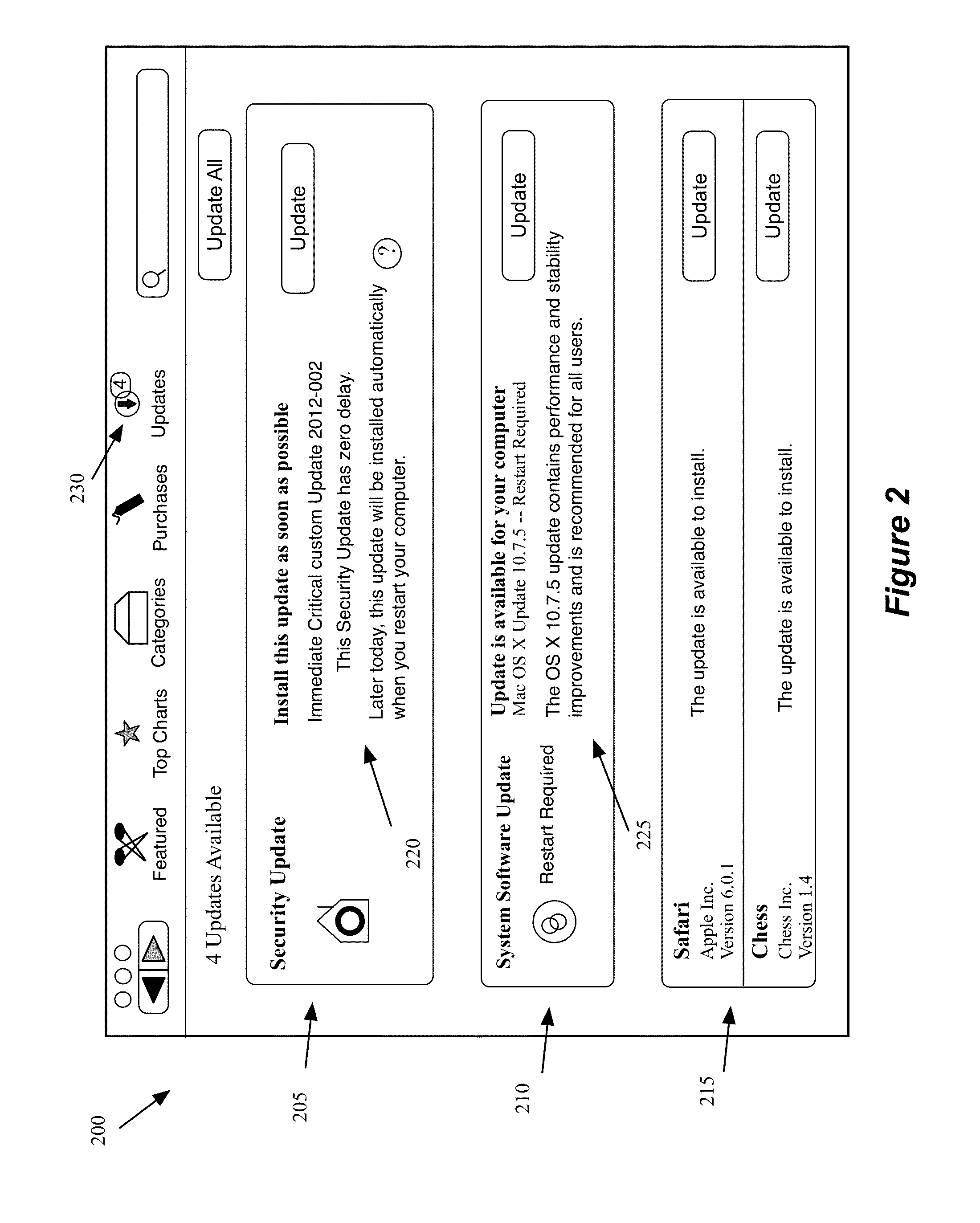
Providing A Unified Update Center for Security Software Updates and Application Software Updates
A graphical user interface (GUI) for a unified software update display center is provided. The GUI includes a first display area for displaying a set of available security system software updates. The GUI includes a second display area for displaying a set of available non-security system software updates. The GUI includes a third display area for displaying a set of available application software updates. The GUI includes a single selection tool for installing all available security updates without installing any updates displayed in the second and third display areas. The GUI includes individual selection tools for installing individual updates displayed in the second and third display areas. The GUI includes a selection tool to receive further updates from a system update server and an application update server. The critical security updates are displayed with different display attributes or in different sections to distinguish them from other types of updates.
Owner:APPLE INC
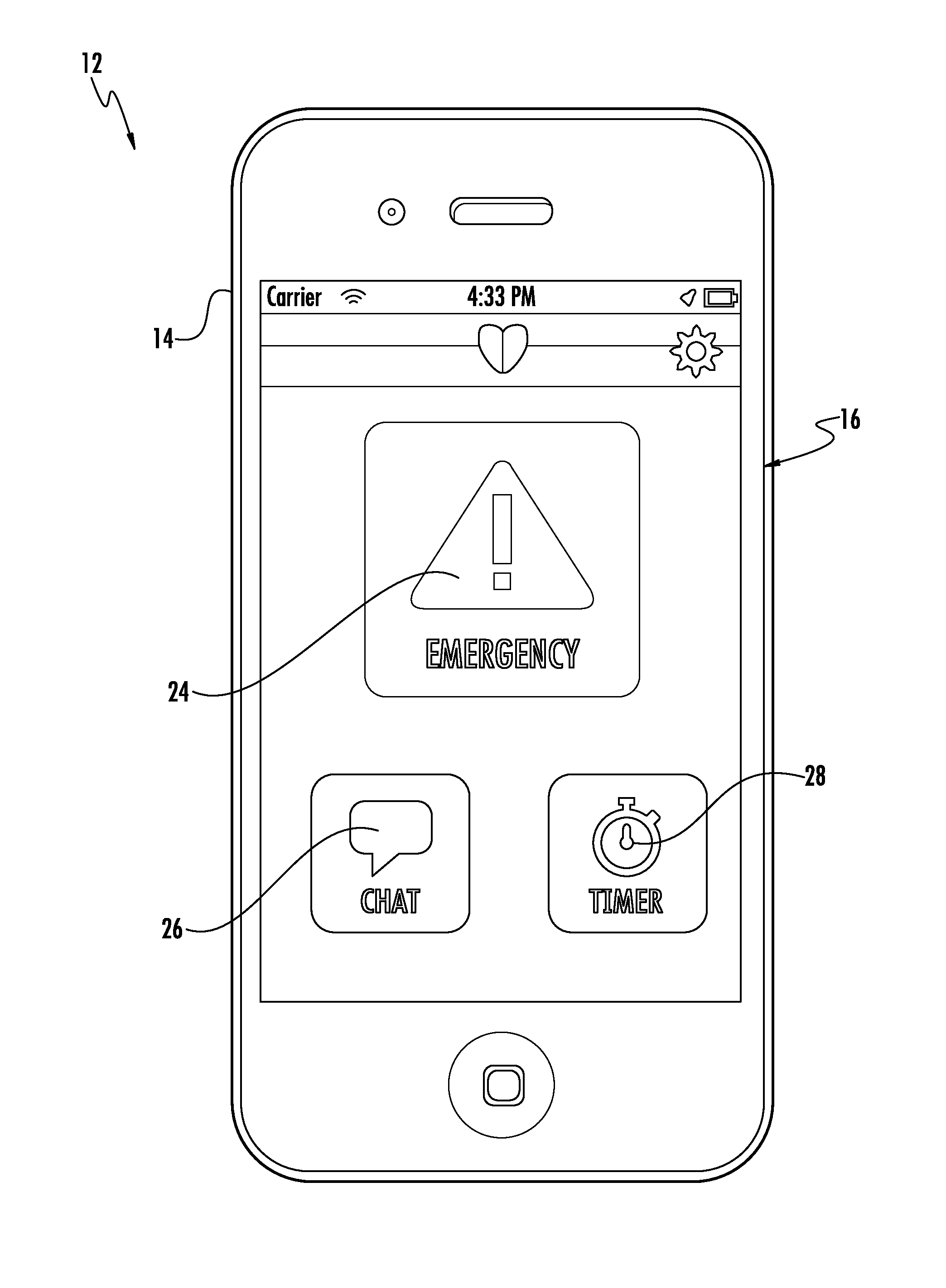
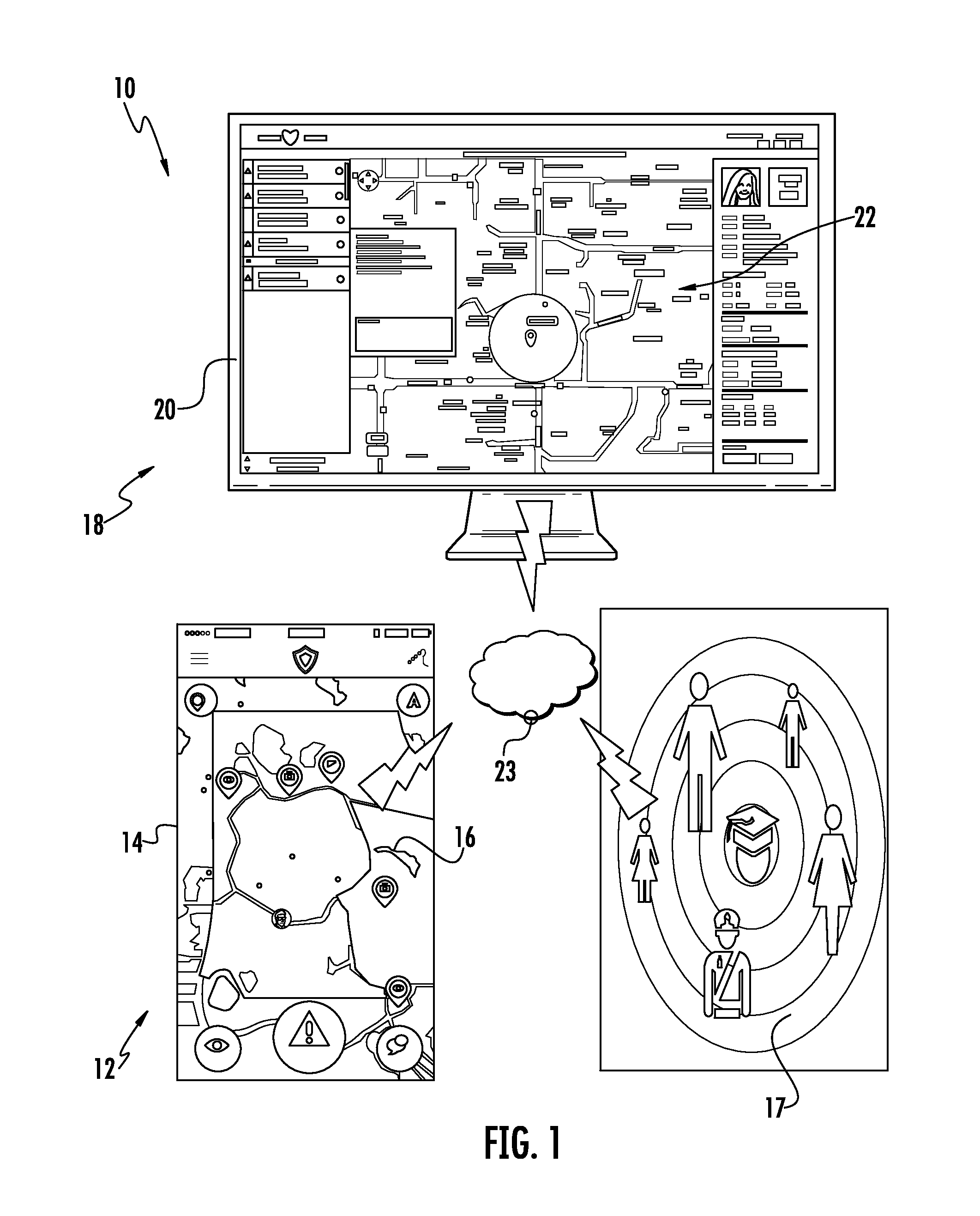
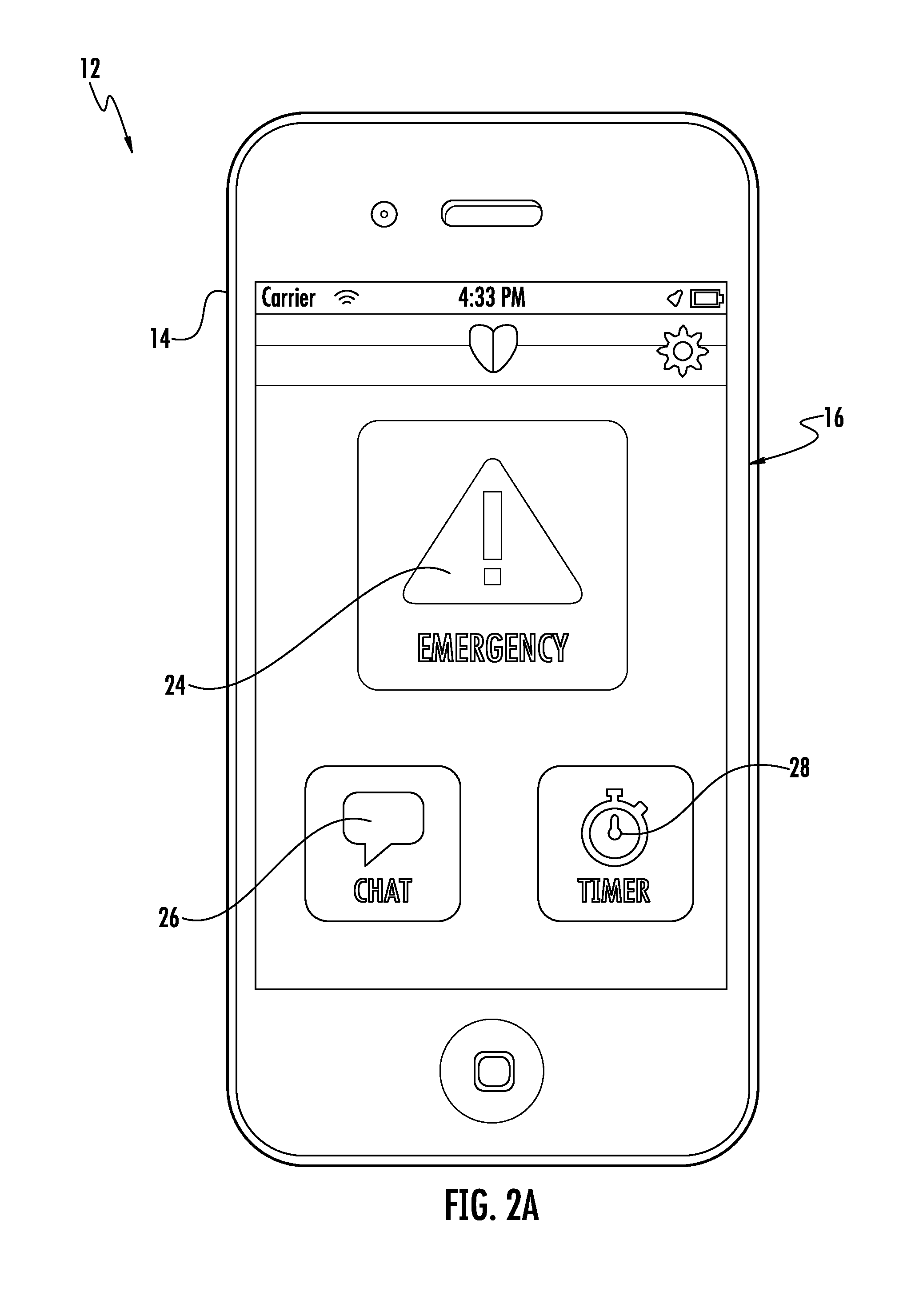
System and method for signaling and responding to an emergency situation
InactiveUS9426638B1Fast and easy and reliableEmergency connection handlingTelephonic communicationThird partyService personnel
Disclosed is a system and method for signaling the presence of an emergency situation. The system includes a personal emergency device in communication with a dispatch station over a wireless network. Upon encountering an emergency situation, a user signals an alert using the personal emergency device, which includes a mobile device running custom security software. The device subsequently transmits information about the users location and personal characteristics to the dispatch station, where it is interpreted by a computer running custom emergency alert monitoring and reporting software, enabling a dispatcher to notify emergency service personnel about the location and characteristics of the user in an emergency situation. The system further enables a user to communicate with emergency personnel and other predetermined third parties in real time during the emergency situation.
Owner:TAPSHIELD LLC
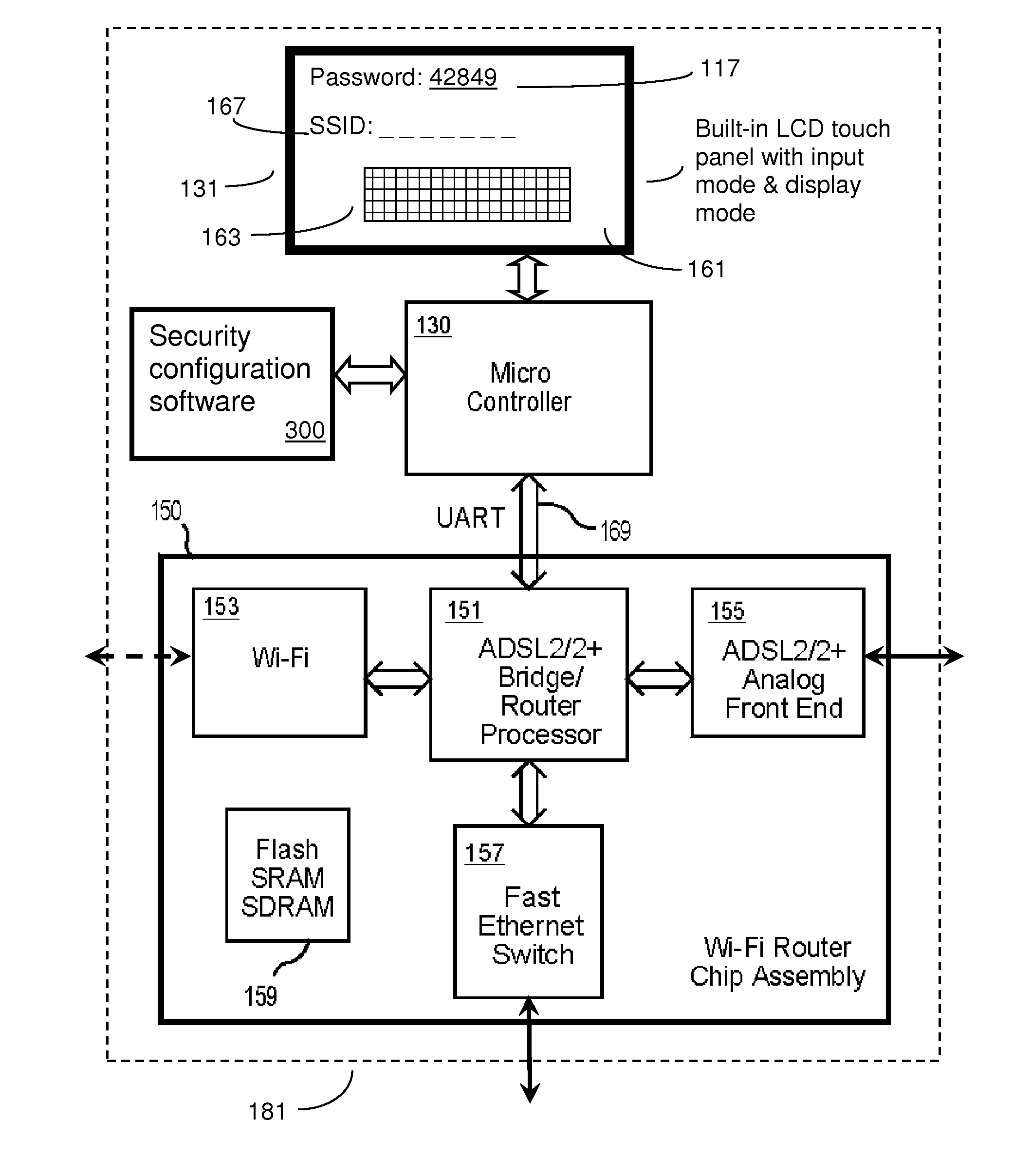
Wi-fi router with integrated touch-screen and enhanced security features
ActiveUS20120239916A1Easy to reconfigureNetwork securityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsWi-FiPassword
A Wi-Fi router with an integrated configuration touch-screen, and method to use this integrated touch screen to provide enhanced security features. The Wi-Fi router, which has a wired or optical network interface, may be factory pre-configured with hard to anticipate passwords and encryption codes, thus making even its default Wi-Fi settings difficult to attack. Besides displaying interactive menus on the touch-screen, the router may also generate touch sensitive dynamic alphanumeric virtual keypads to enable administrators to interact with the device without the need of extra computers or software. Inexperienced administrators secure in the knowledge that they may access and change even difficult to remember security settings at any time through the built-in touch-screen controller and simplified user interface, are encouraged to set up secure Wi-Fi systems. The device may optionally include security software that, upon touch of a button, can provide new randomized or otherwise obfuscated router settings.
Owner:SECURIFI INC
Finger sensing apparatus performing secure software update and associated methods
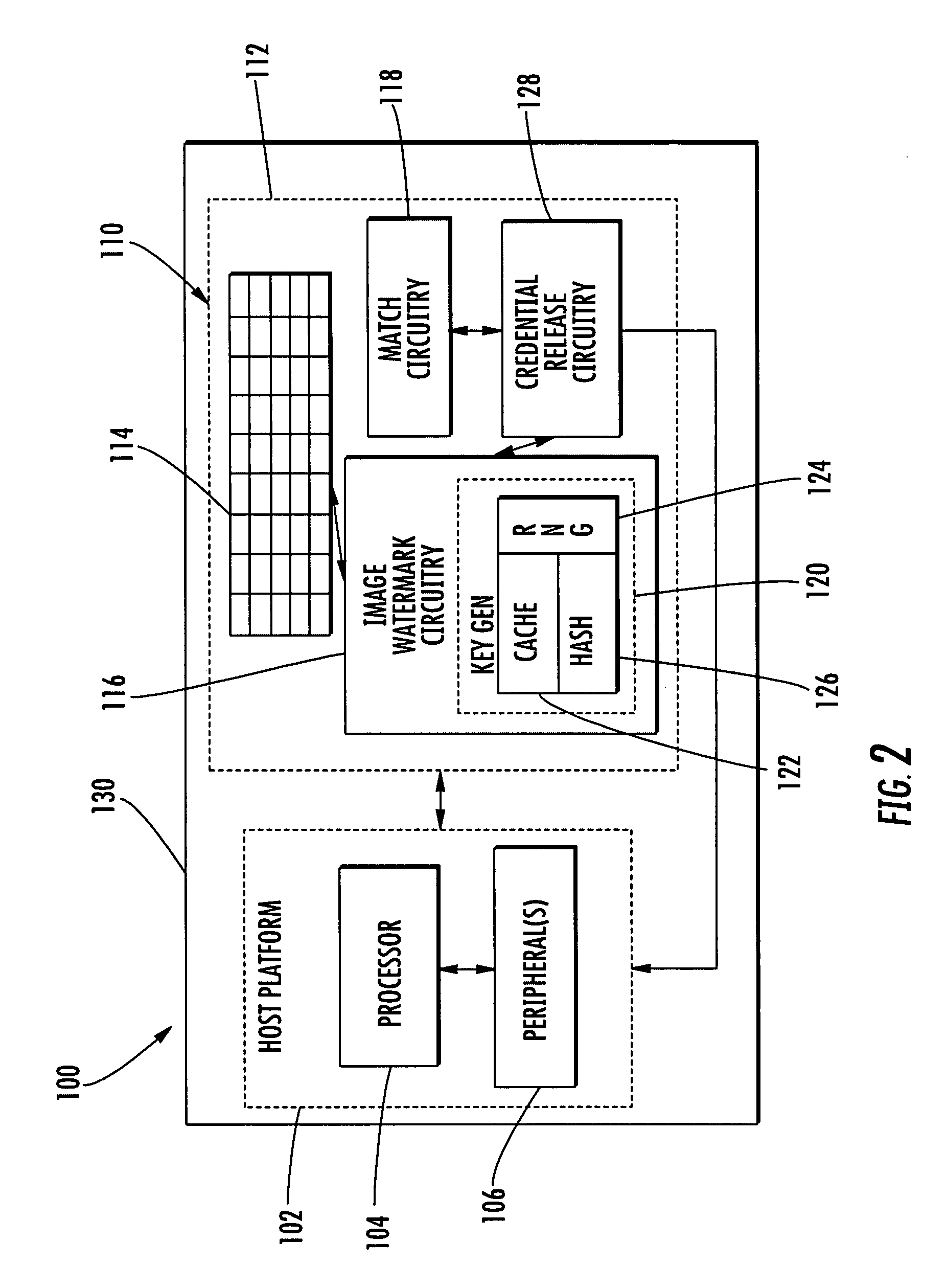
ActiveUS20090067689A1Improve methodImprove securityCharacter and pattern recognitionInternal/peripheral component protectionComputer hardwareSoftware update
A finger sensing apparatus may include a finger sensor having an integrated circuit (IC) substrate, an array of finger sensing elements on the IC substrate, and secure software update circuitry on the IC substrate. In addition, the finger sensing apparatus may include a host platform external from the finger sensor and hosting software associated with the finger sensor. The host platform may cooperate with the secure software update circuitry to authorize an attempted software update.
Owner:APPLE INC
Electro-mechanic USB locking device
InactiveUS20150020189A1Safe removalFlexibility and securityDigital data processing detailsCoupling device detailsSecurity softwareUSB
USB ports present risk of data leak from computers. The invention provides an electromechanical USB port protection device capable of mechanically block unused USB port, thus preventing the connection of any USB device to that port. Removal of the device requires electrically energizing the lock using security code. Security software provides scalable and secure centralized keys management. The device provides clear and continuous user visual indications when device is secure. Device derivative secures USB cable to the computer USB port. Another device derivative filters and secures a connected user peripheral device, for example a USB locking device that only allows a connection of USB mouse or keyboard.
Owner:HIGH SEC LABS LTD
Apparatus and method for unilaterally loading a secure operating system within a multiprocessor environment
InactiveUS7024555B2Memory loss protectionVolume/mass flow measurementInformation repositoryOperational system
An apparatus and method for unilaterally loading a secure operating system within a multiprocessor environment are described. The method includes disregarding a received load secure region instruction when a currently active load secure region operation is detected. Otherwise, a memory protection element is directed, in response to the received load secure region instruction, to form a secure memory environment. Once directed, unauthorized read / write access to one or more protected memory regions are prohibited. Finally, a cryptographic hash value of the one or more protected memory regions is stored within a digest information repository as a secure software identification value. Once stored, outside agents may request access to a digitally signed software identification value in order to establish security verification of secure software within the secure memory environment.
Owner:INTEL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com