Patents
Literature
1395 results about "Windows Registry" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
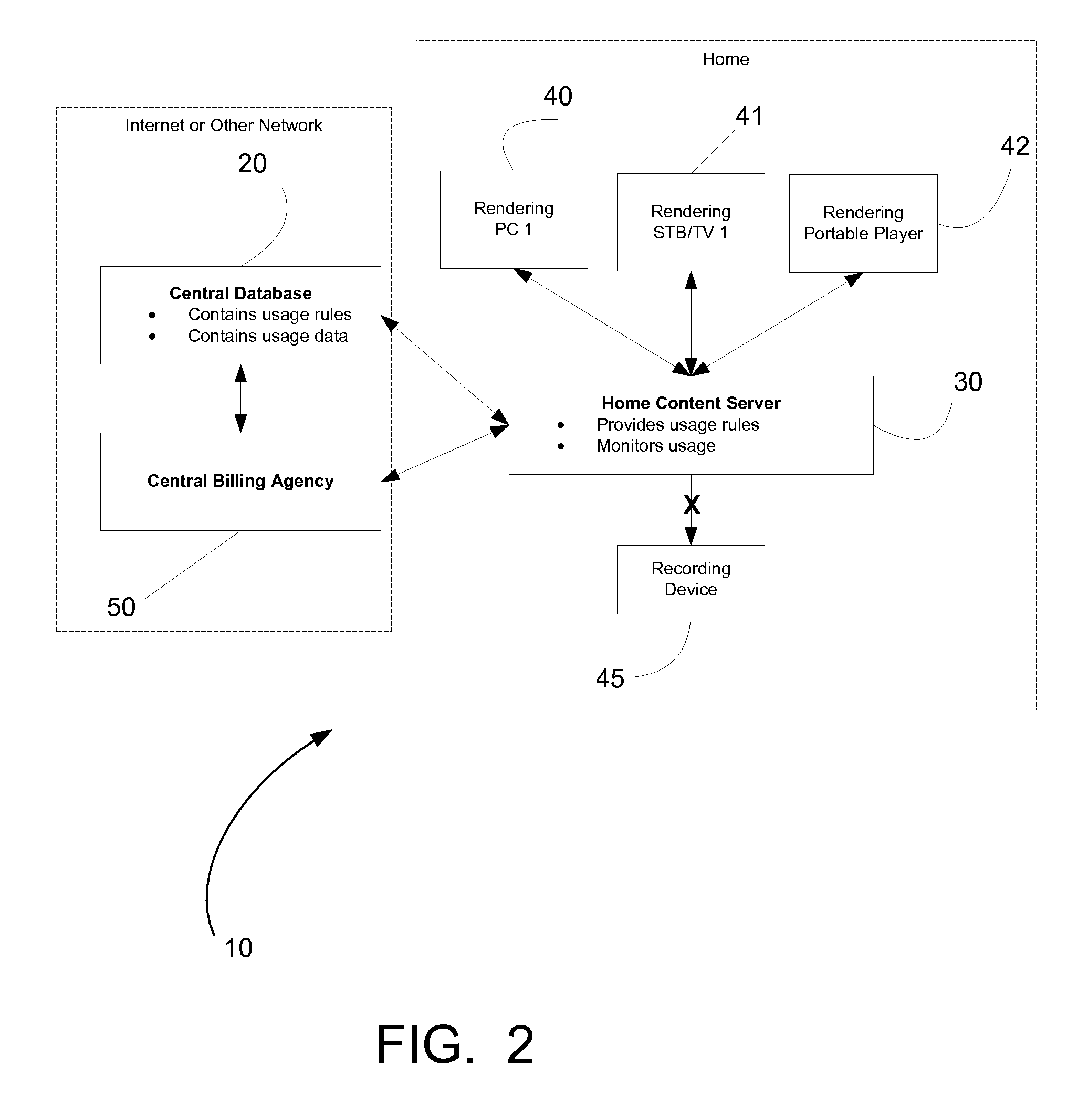
The Windows Registry is a hierarchical database that stores low-level settings for the Microsoft Windows operating system and for applications that opt to use the registry. The kernel, device drivers, services, Security Accounts Manager, and user interface can all use the registry. The registry also allows access to counters for profiling system performance.
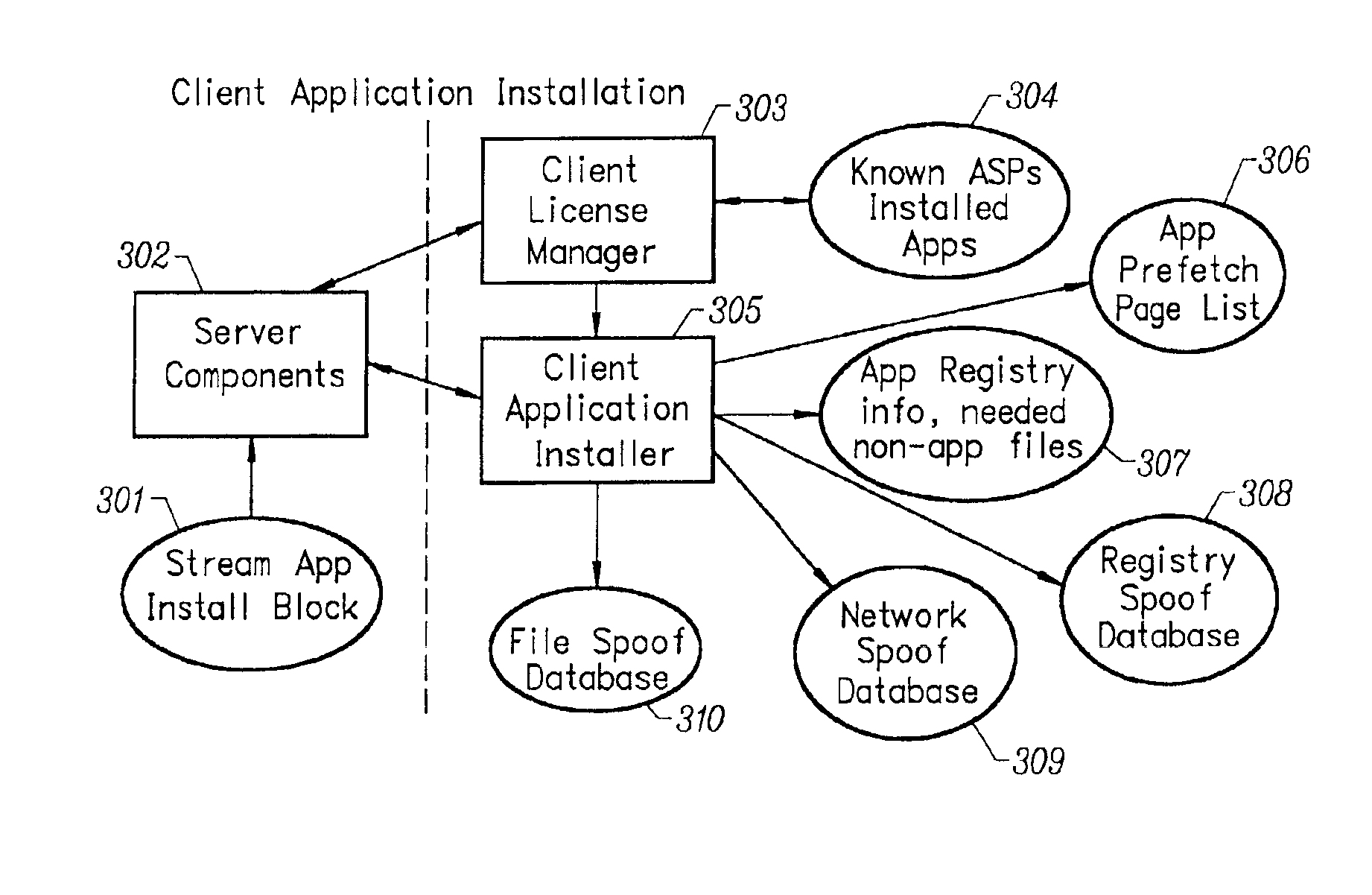
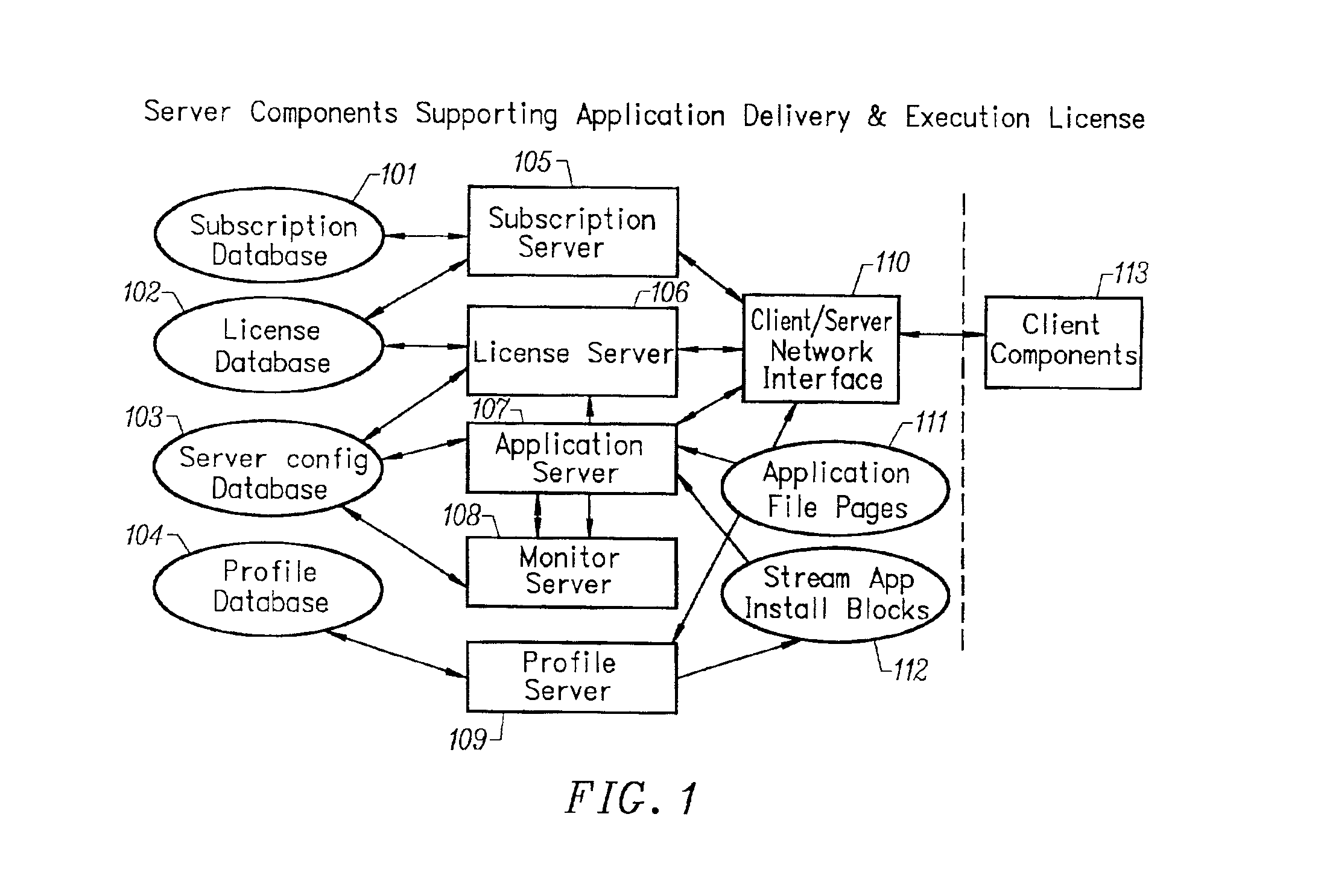
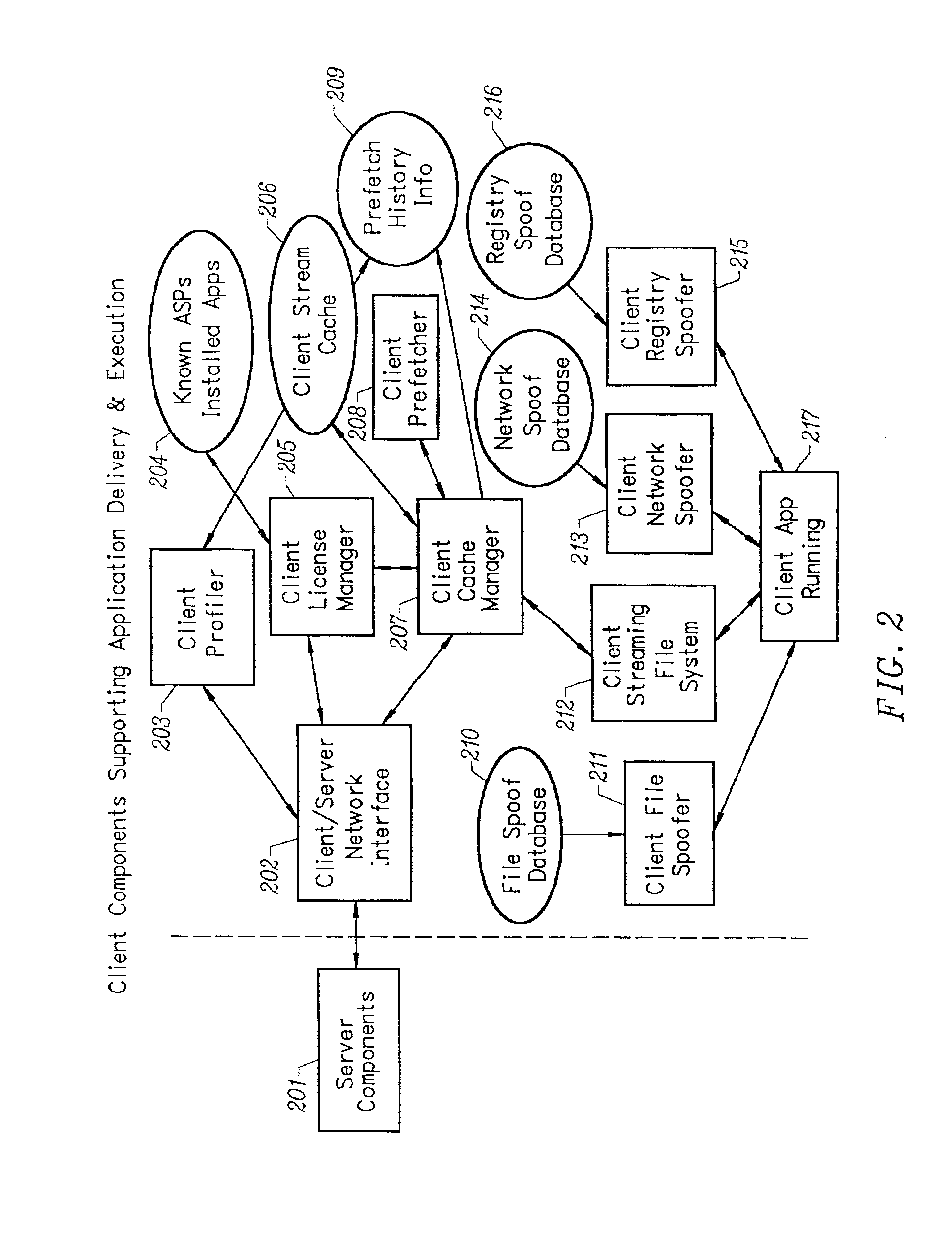
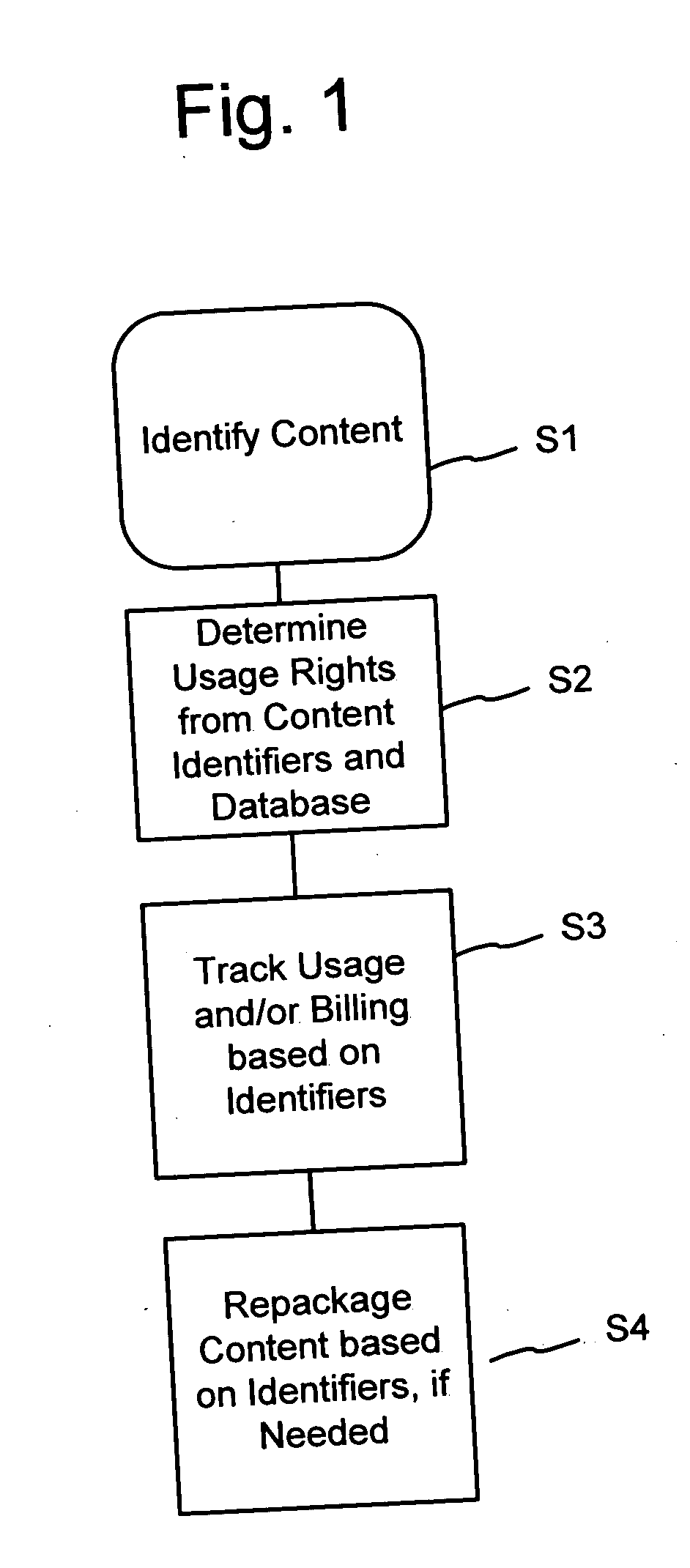
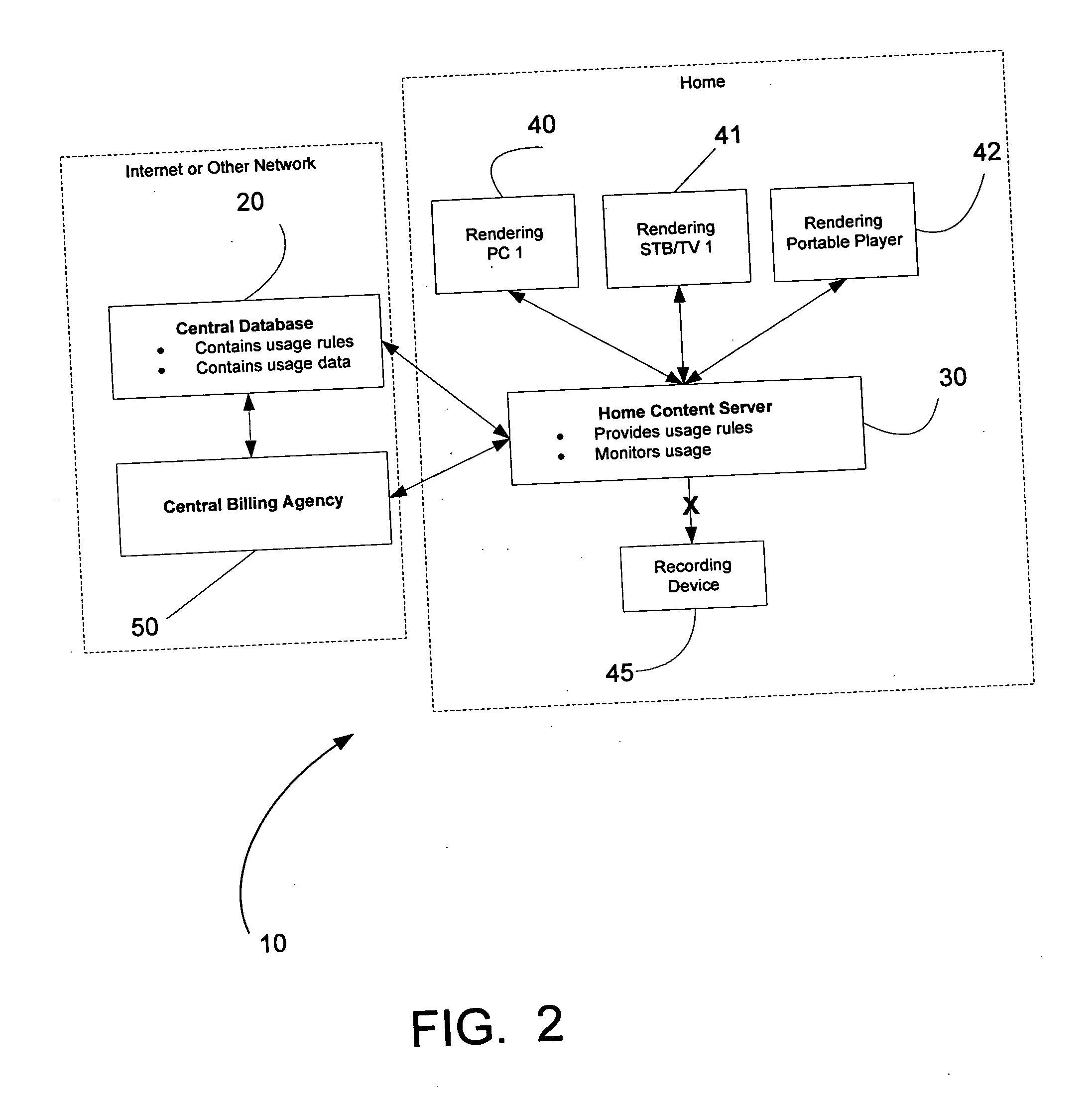
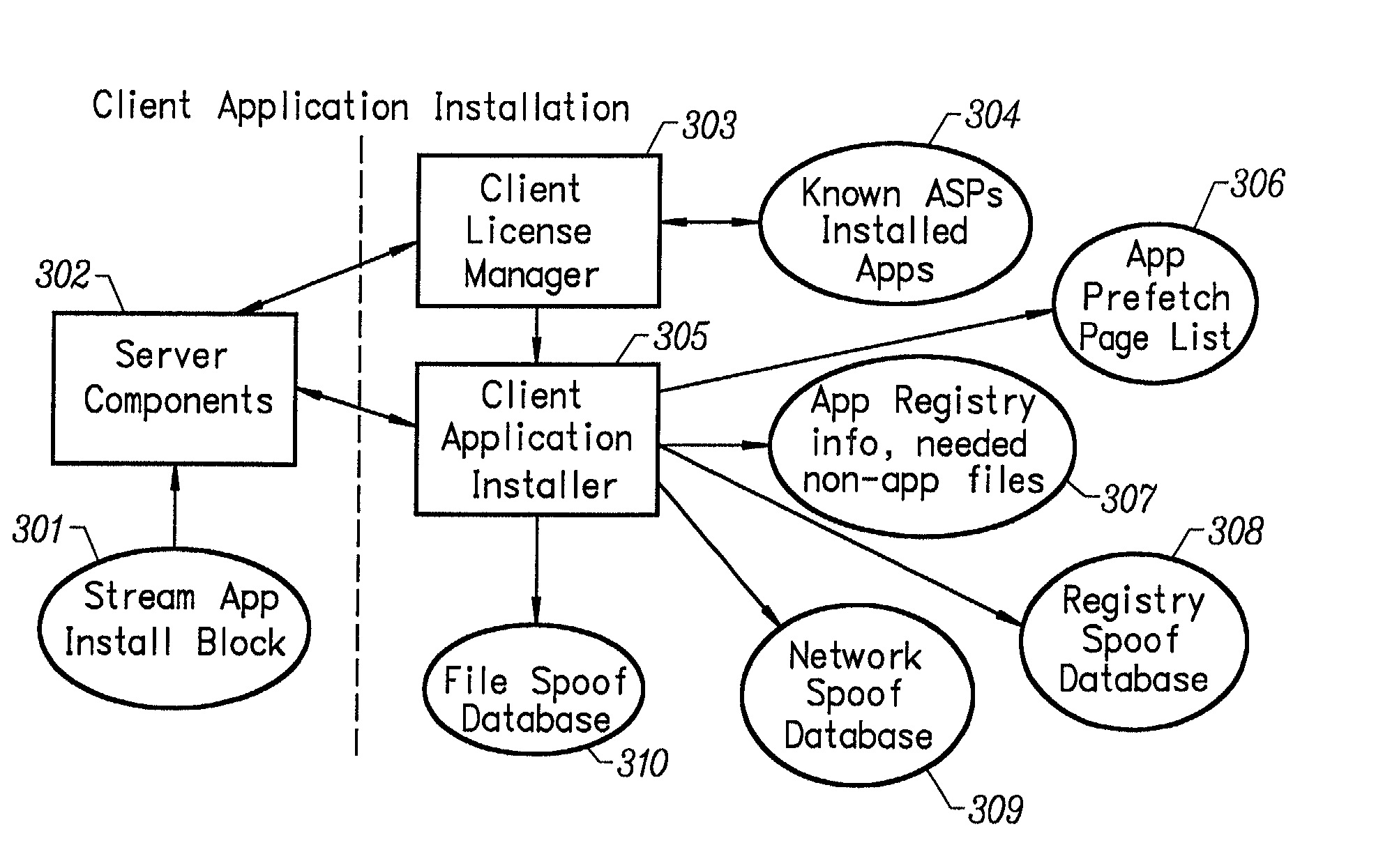
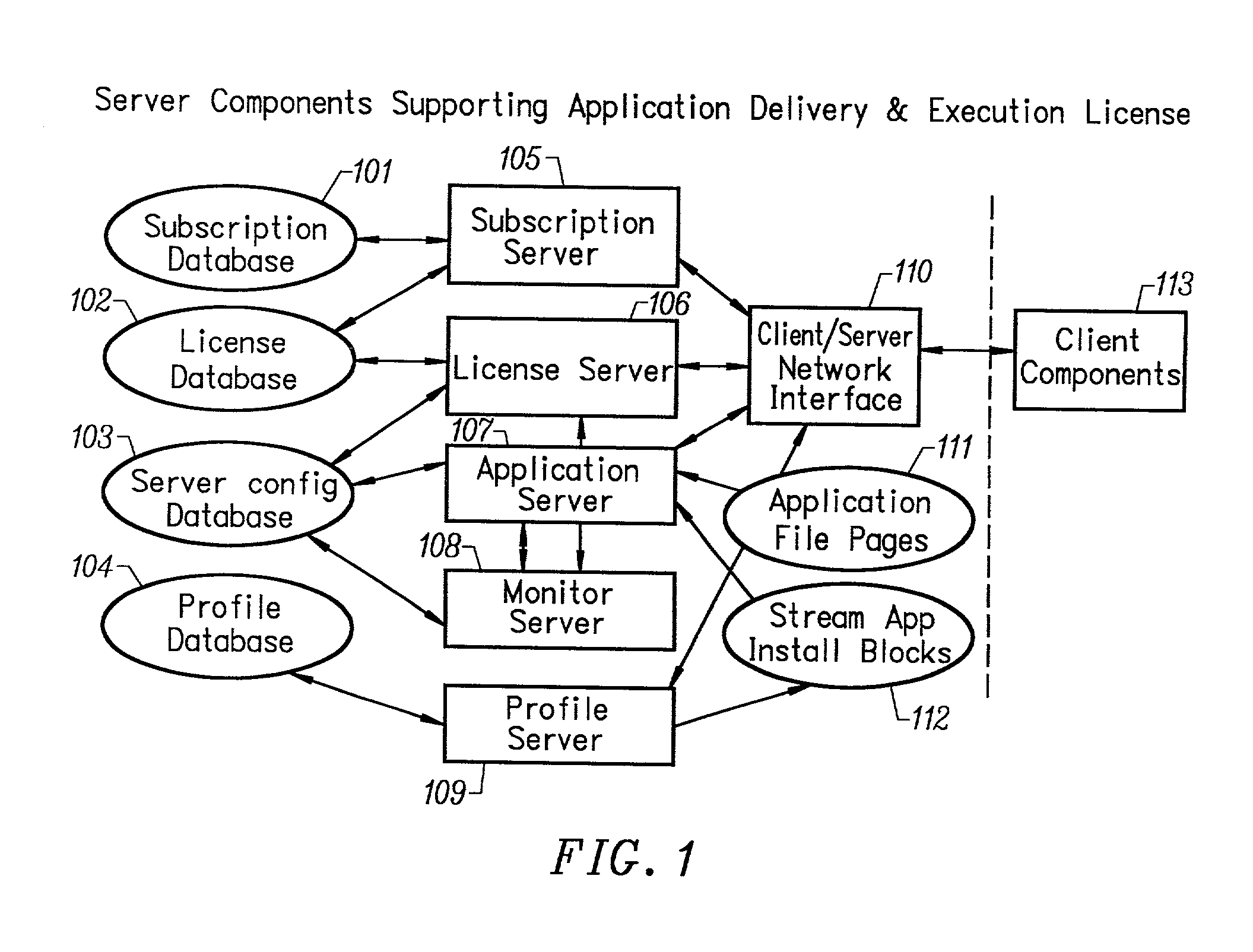
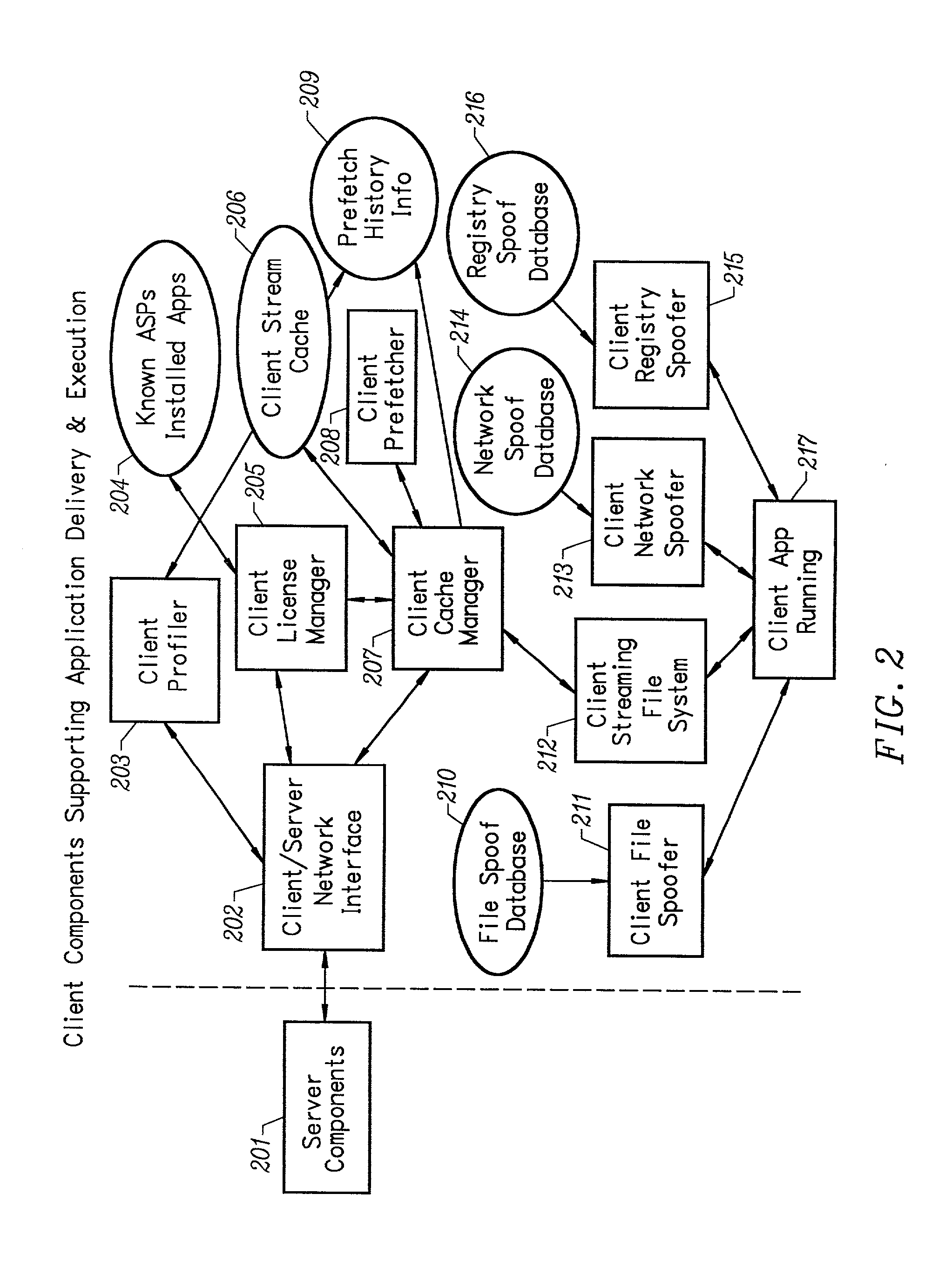
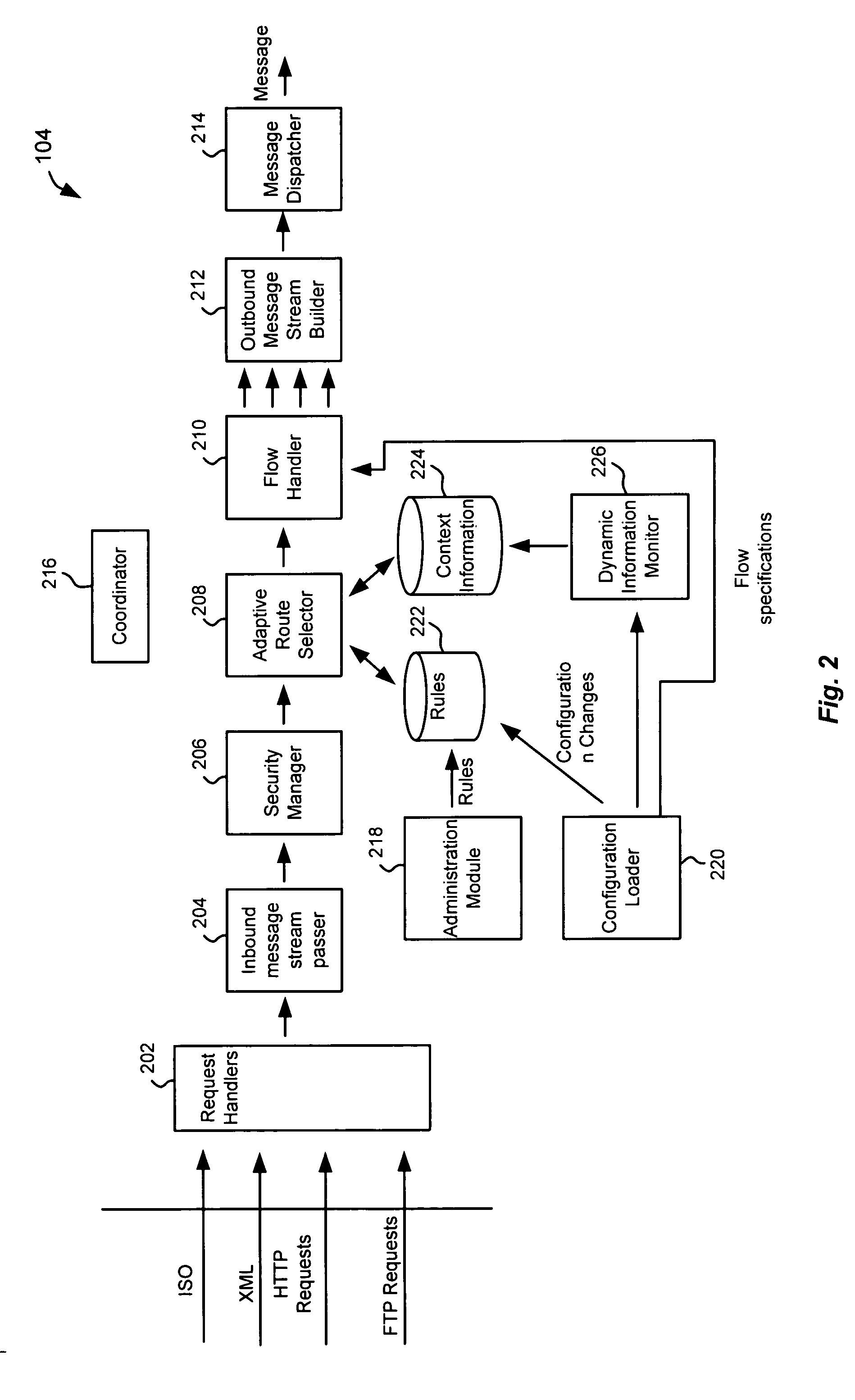
Client installation and execution system for streamed applications
InactiveUS6918113B2Multiple digital computer combinationsProgram loading/initiatingRegistry dataFile system
Owner:NUMECENT HLDG +1
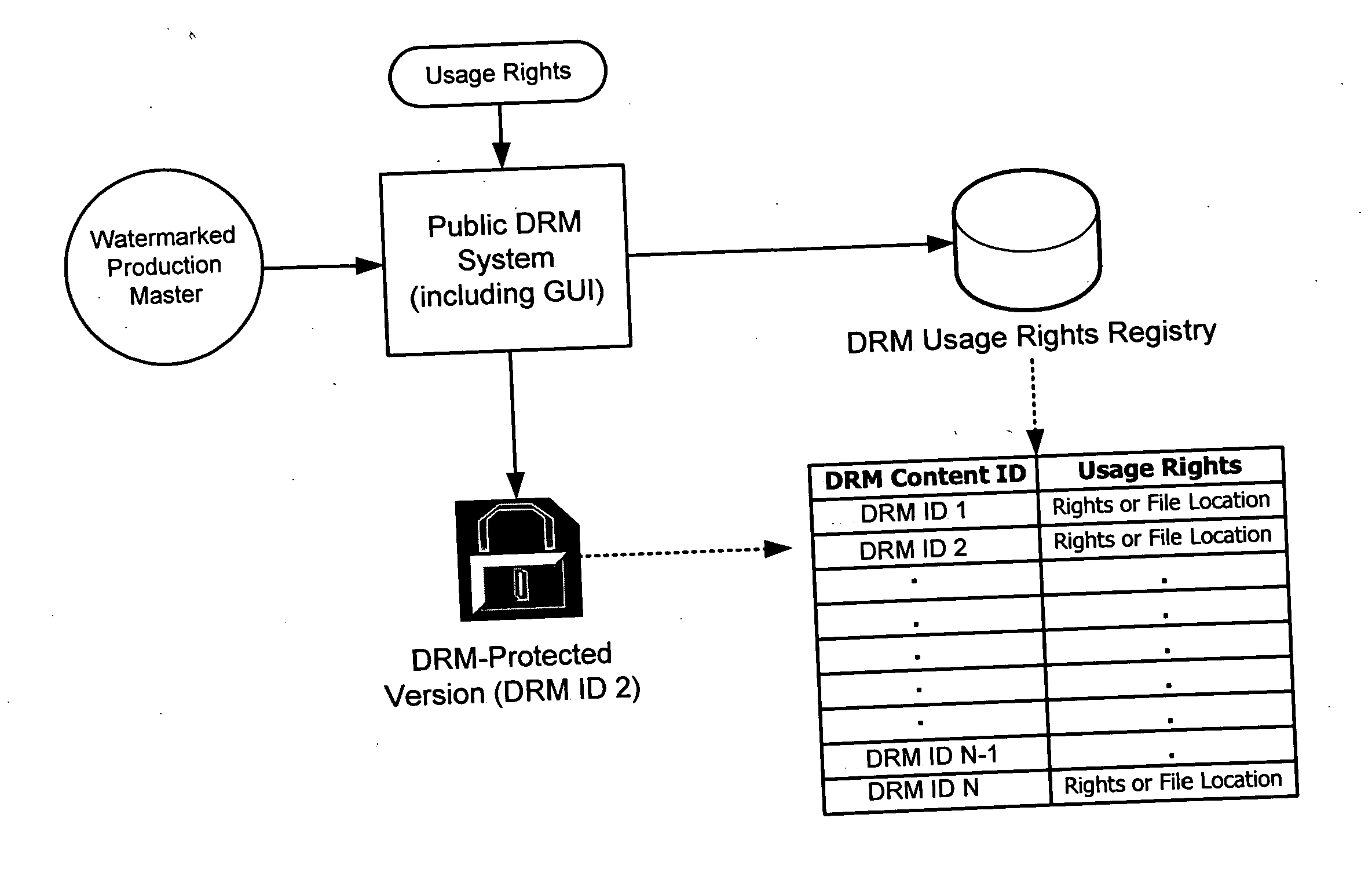
Rights management systems and methods using digital watermarking
ActiveUS20060062426A1Difficult to controlDifficult to trackUser identity/authority verificationAnalogue secracy/subscription systemsContent IdentifierRights management
A digital watermark (DWM) content identifier is steganographically embedded in content. The DWM content identifier provides a link to a rights registry storing usage rights associated with the content. In some implementations the rights registry provides an association between the DWM content identifier and a digital rights management (DRM) content identifier. The DRM content identifier is used to find associated usage rights. The DWM content identifier can also be used to transfer content from a first DRM system to a second DRM system.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
Client installation and execution system for streamed applications
InactiveUS20020157089A1Multiple digital computer combinationsProgram loading/initiatingRegistry dataFile system
Owner:NUMECENT HLDG +1
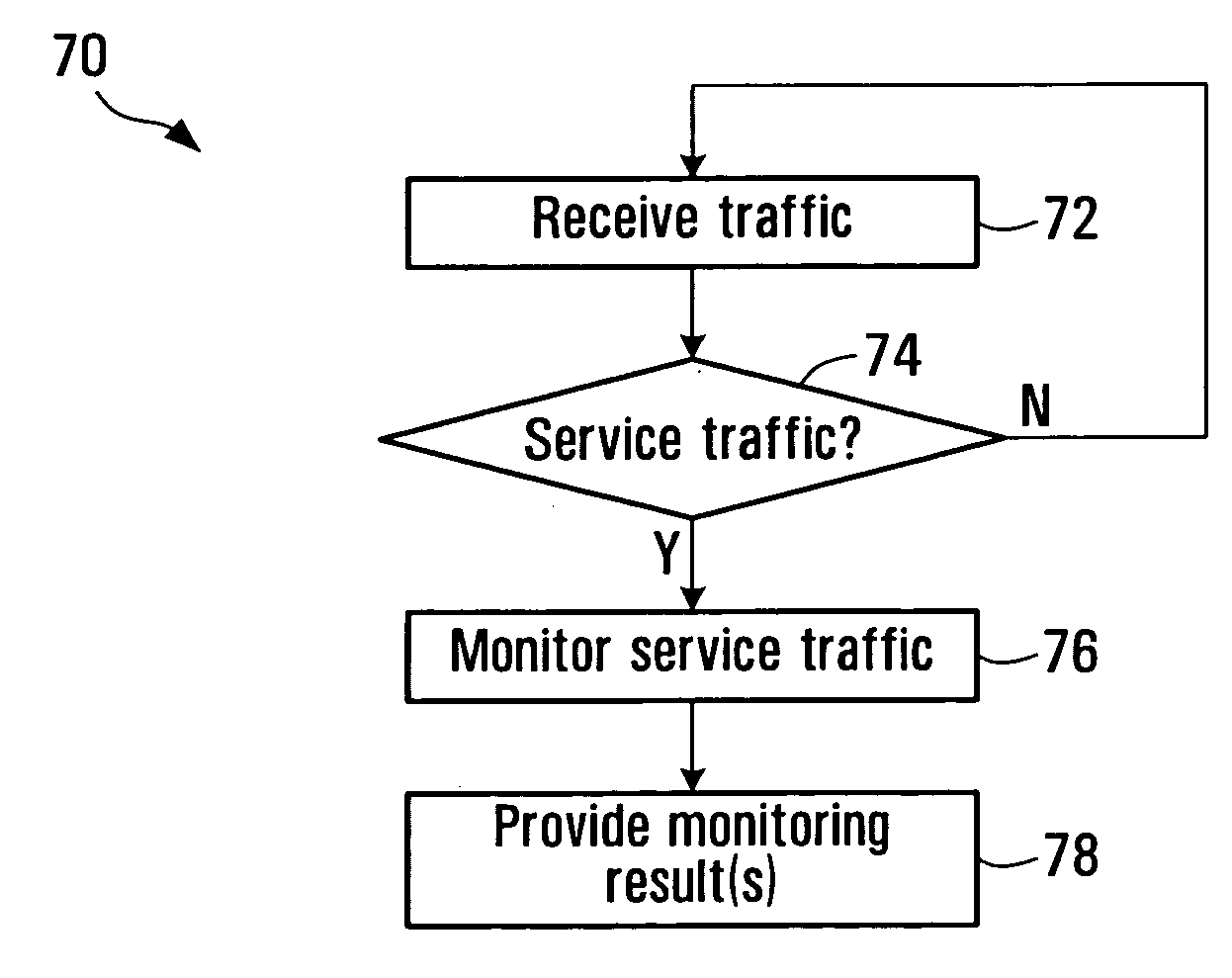
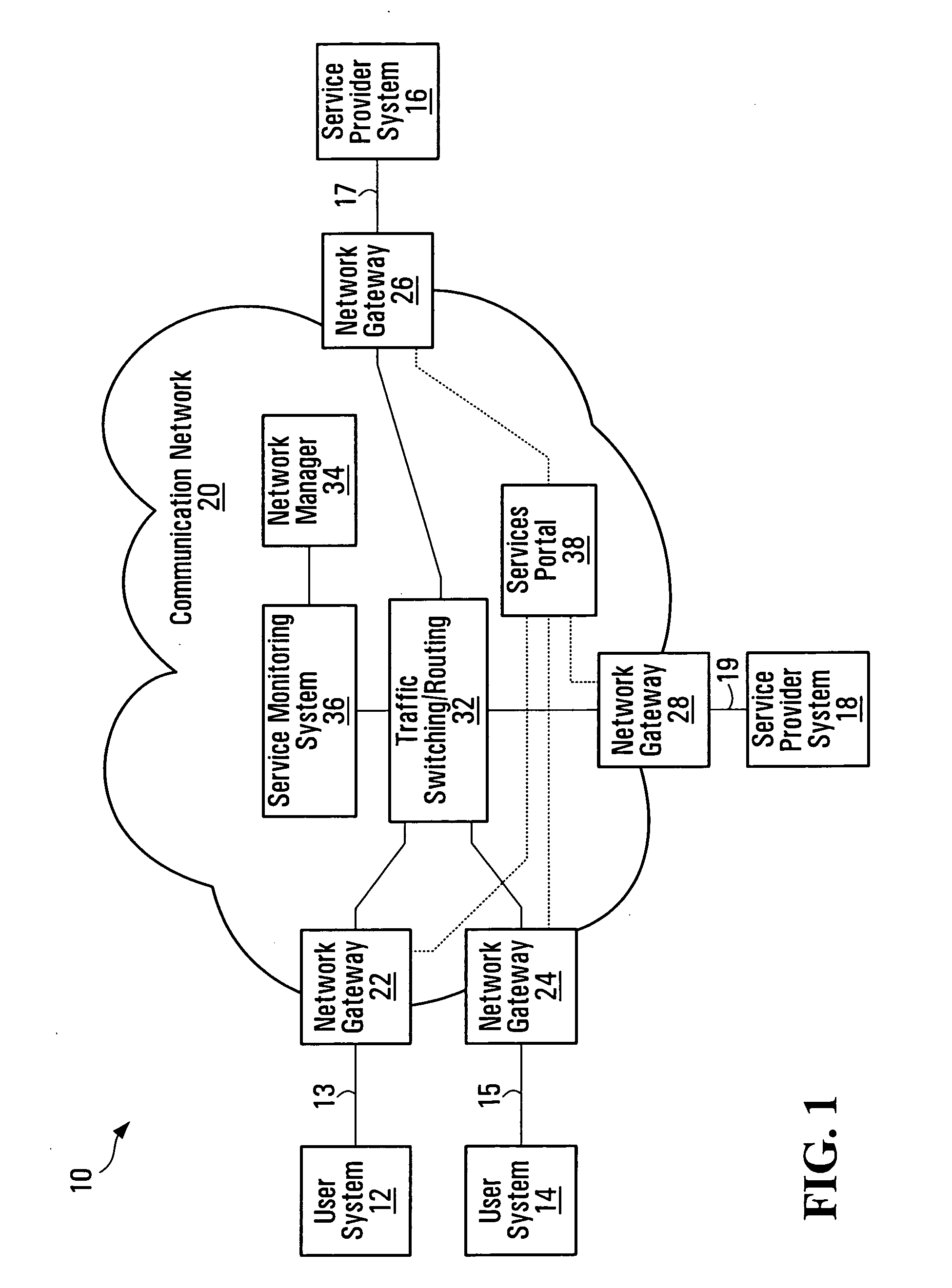
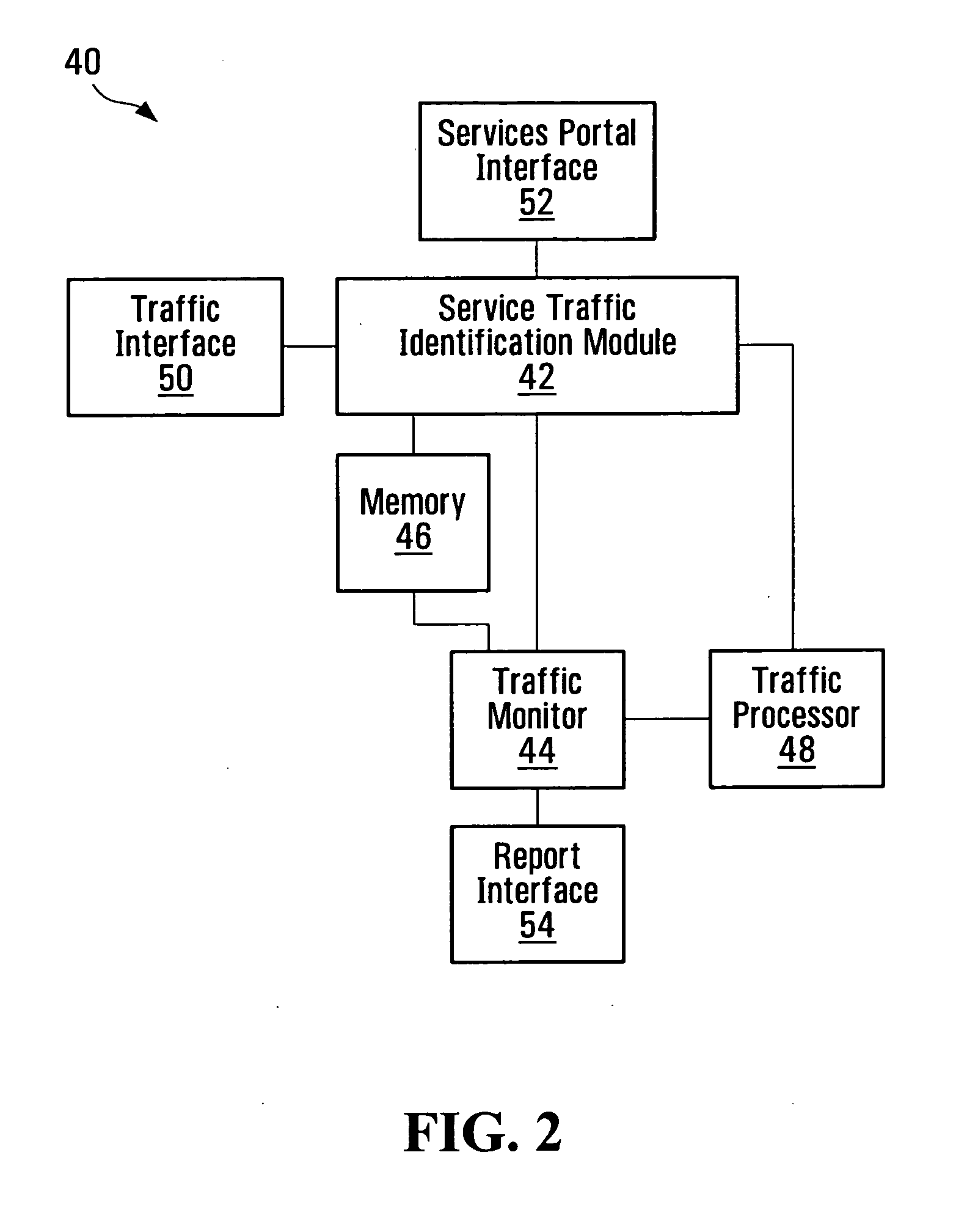
Service-centric communication network monitoring
Service-centric communication network monitoring apparatus and methods are provided. Service traffic, associated with a third-party service provided by an external service provider that is controlled independently of a communication network, is identified in communication traffic that is being transferred through that communication network. The identified service traffic is monitored, for example, to compile service usage statistics, to police usage of the service, to generate billing records for usage of the service, and / or to mirror the identified service traffic. A registry in which the service is registered may interact with a monitoring system of the communication network so as to establish monitoring for the service traffic.
Owner:ALCATEL LUCENT SAS
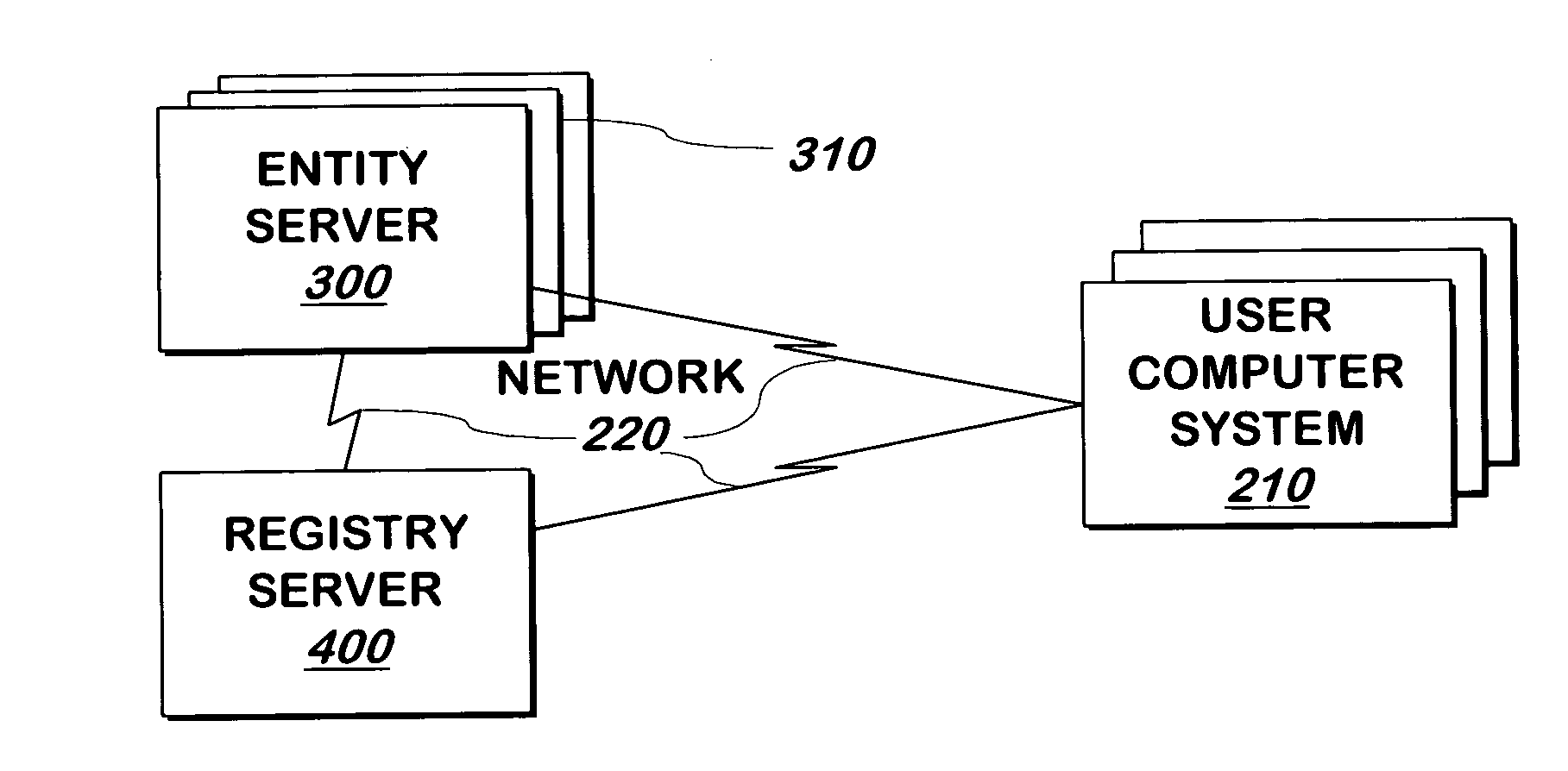
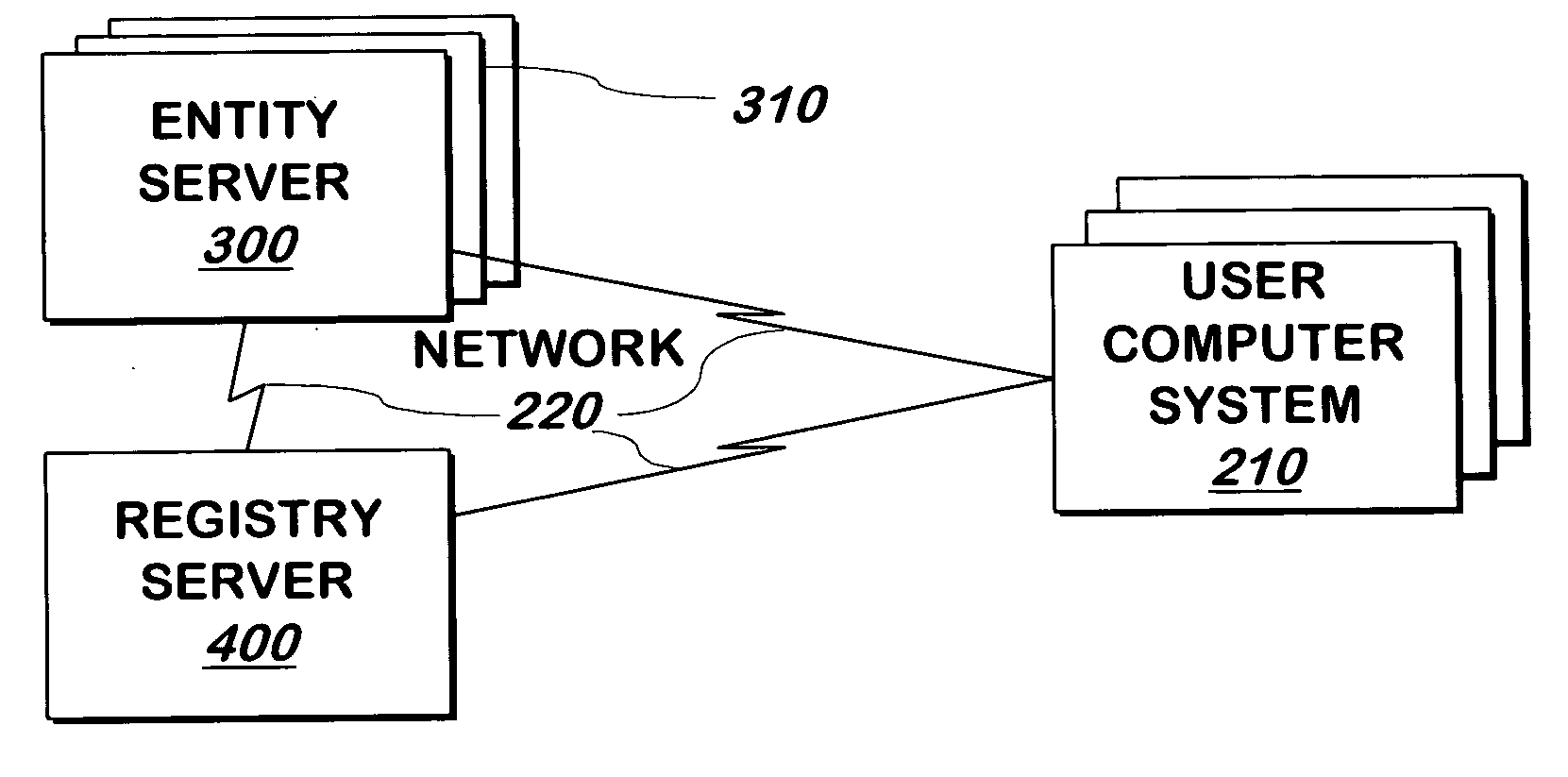
System and method for authenticating entities to users
InactiveUS7562222B2Digital data processing detailsUser identity/authority verificationUser verificationWindows Registry
A system and method communicates information from an entity that a registry can use to authenticate the entity to a user. If the registry authenticates the entity, it displays information that represents a shared secret between the registry and the user.
Owner:EMC IP HLDG CO LLC
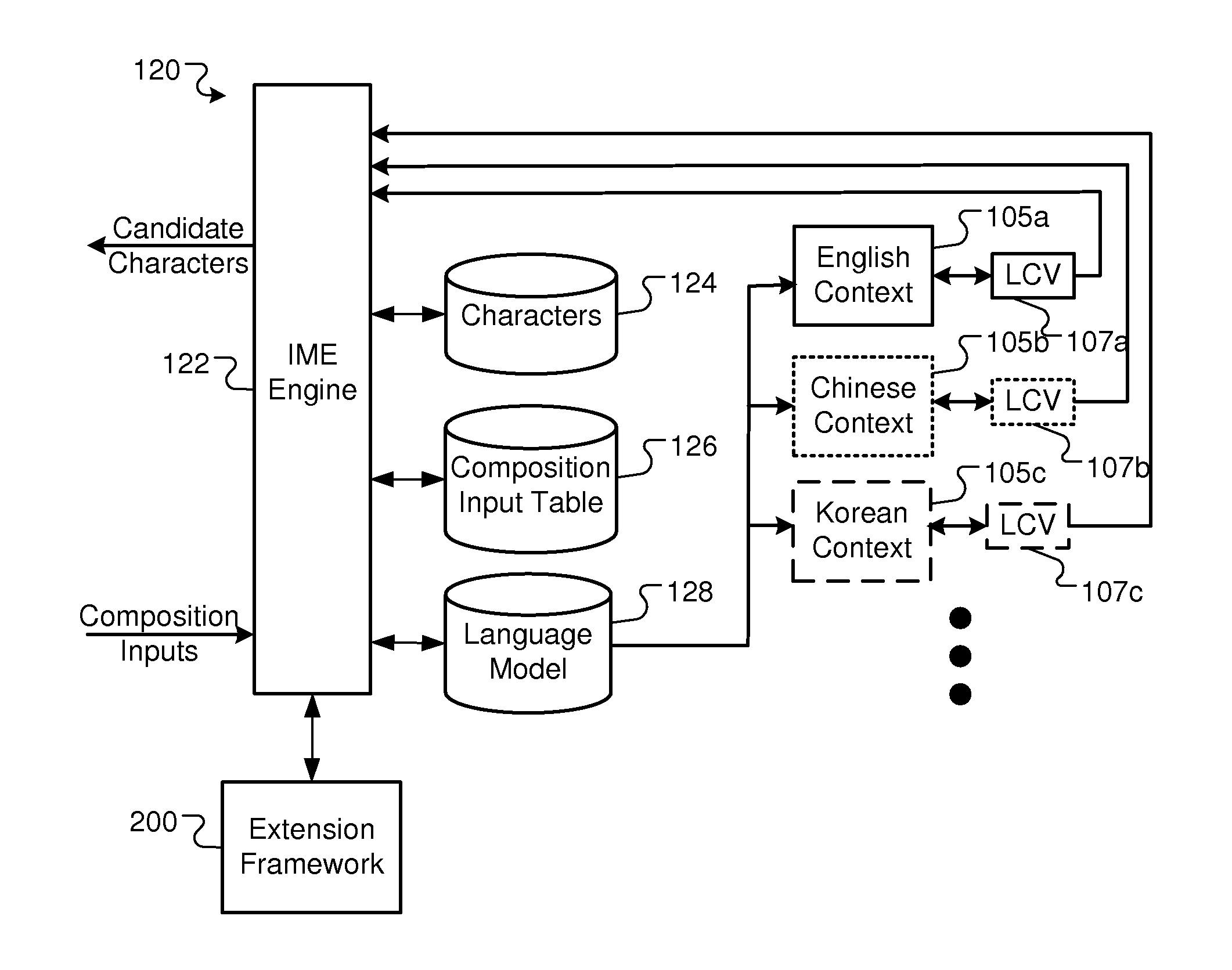
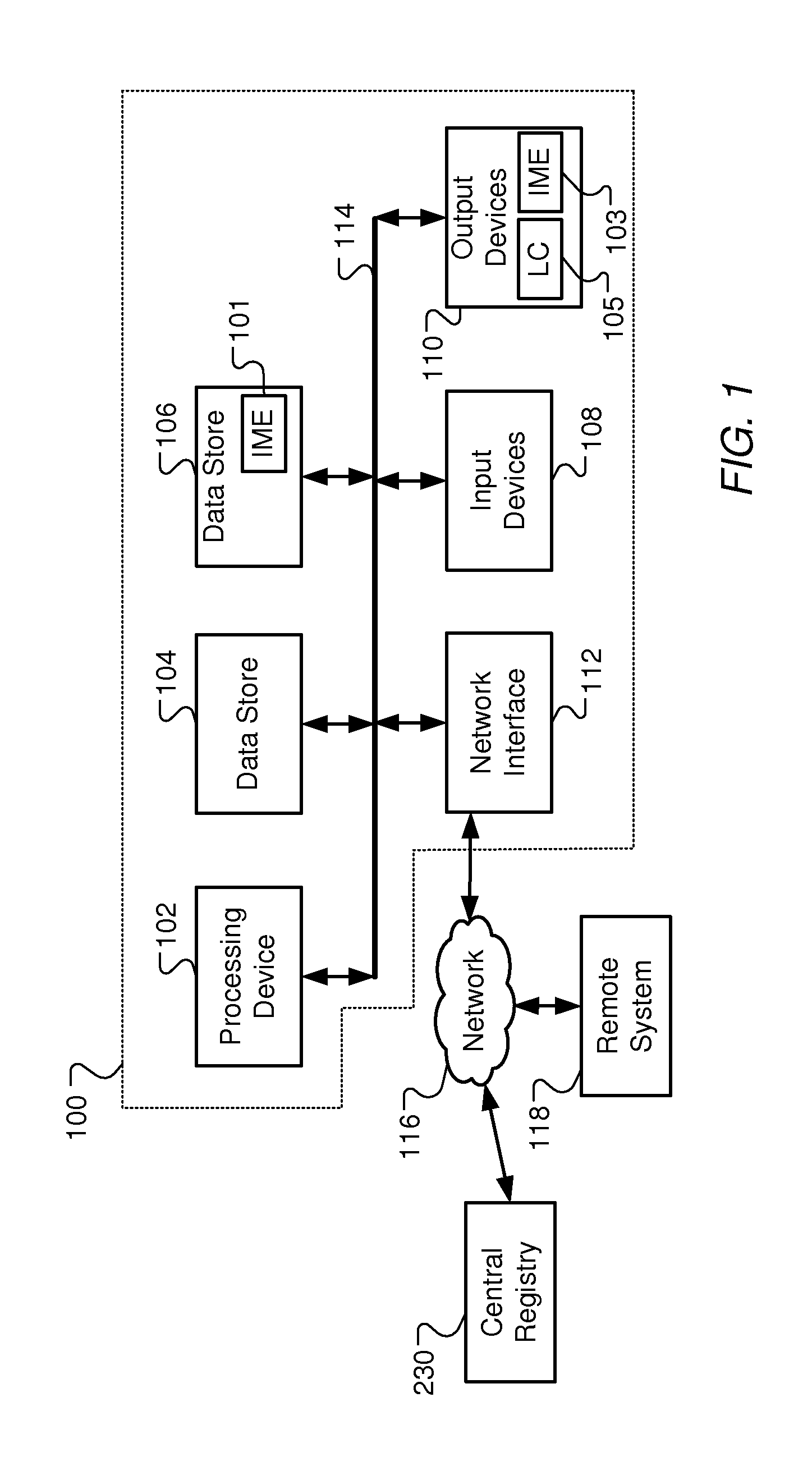
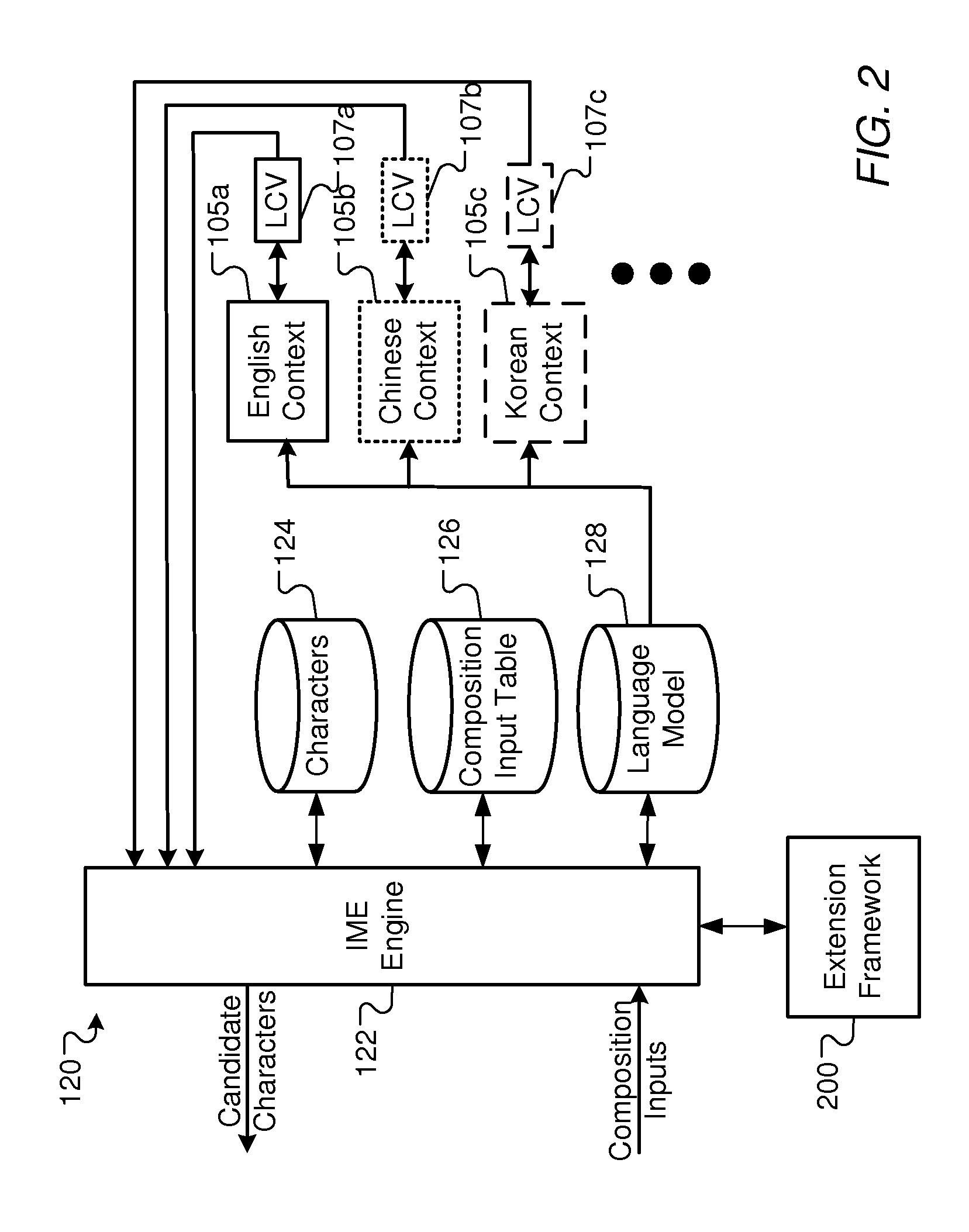
Extension framework for input method editor
Implementations of the present disclosure provide an input method editor (IME) extension framework for extending the functionality of (IMEs). In some implementations, a user input into a user interface of an (IME) is received and is provided to a script engine. A script is selected from a plurality of scripts electronically stored in a script repository. The user input is processed through the script using the script engine to generate one or more candidates, and the one or more candidates are provided to an (IME) engine. In some implementations, a script file is received, the script file being executable by an (IME) system to generate one or more candidates based on a user input into the (IME) system. The script file is electronically stored in a central registry, the central registry including a plurality of scripts, and the plurality of scripts are published for download to and installation on a user device, the user device including the (IME) system.
Owner:GOOGLE LLC
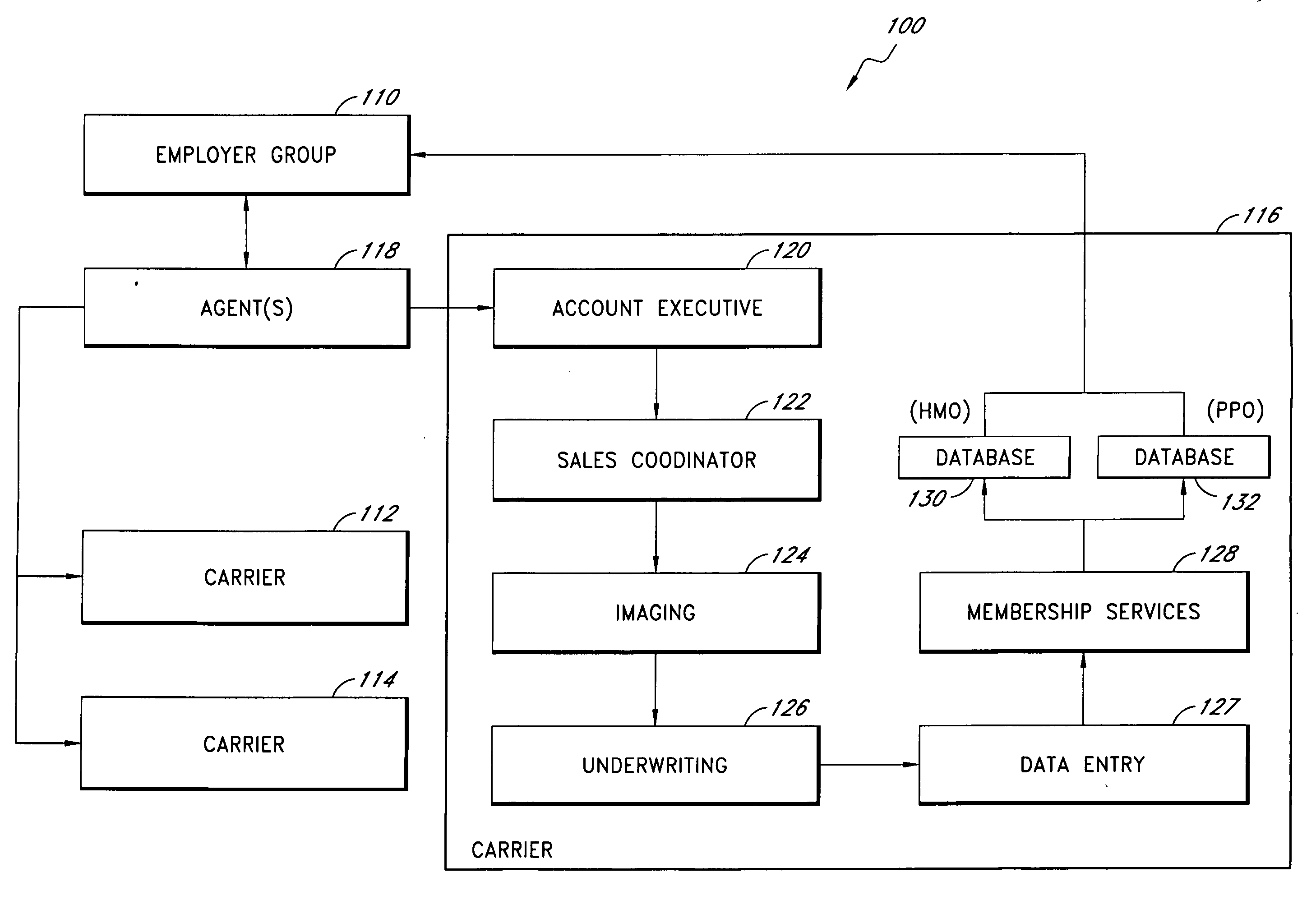
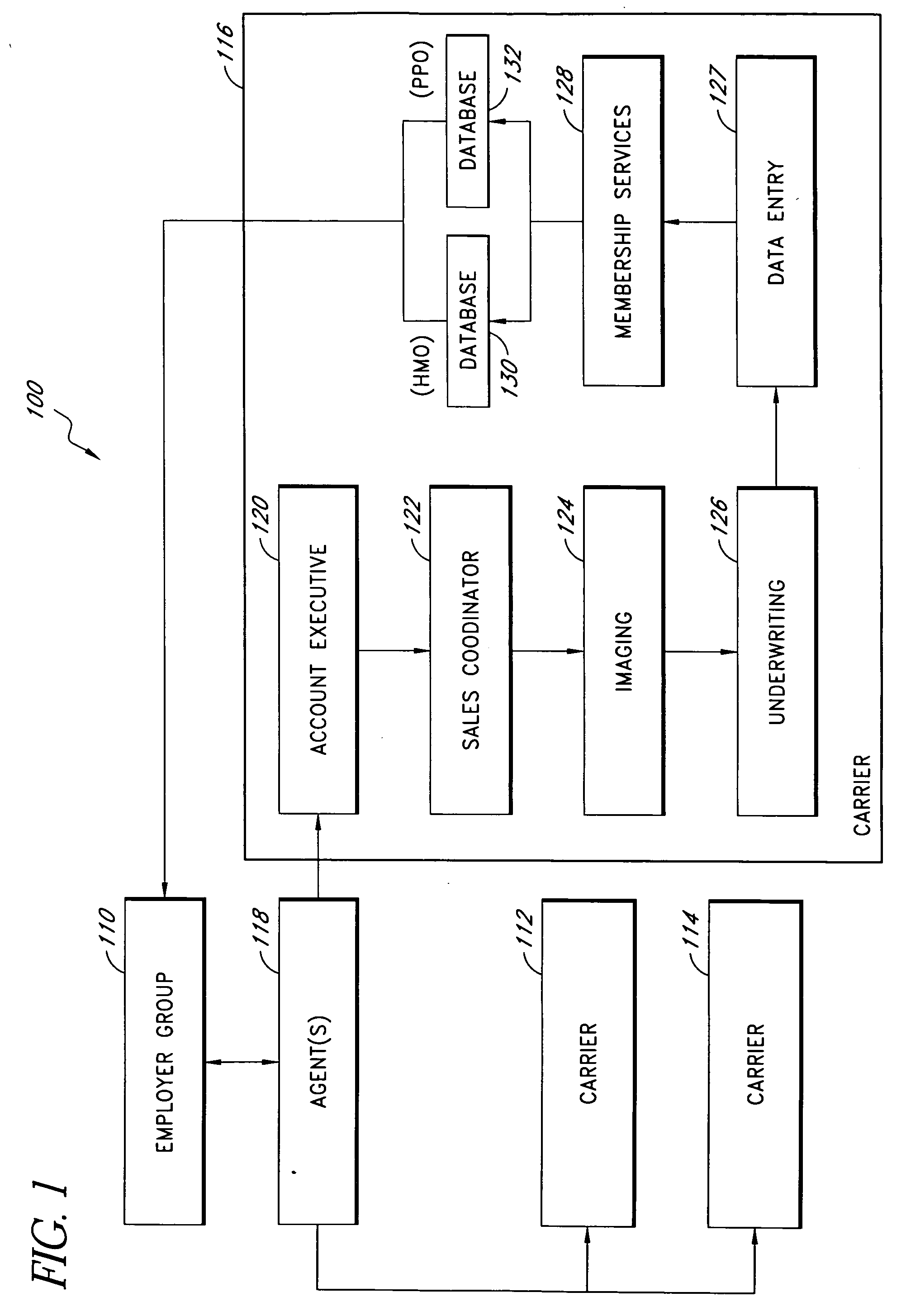
Systems and methods for automating the capture, organization, and transmission of data
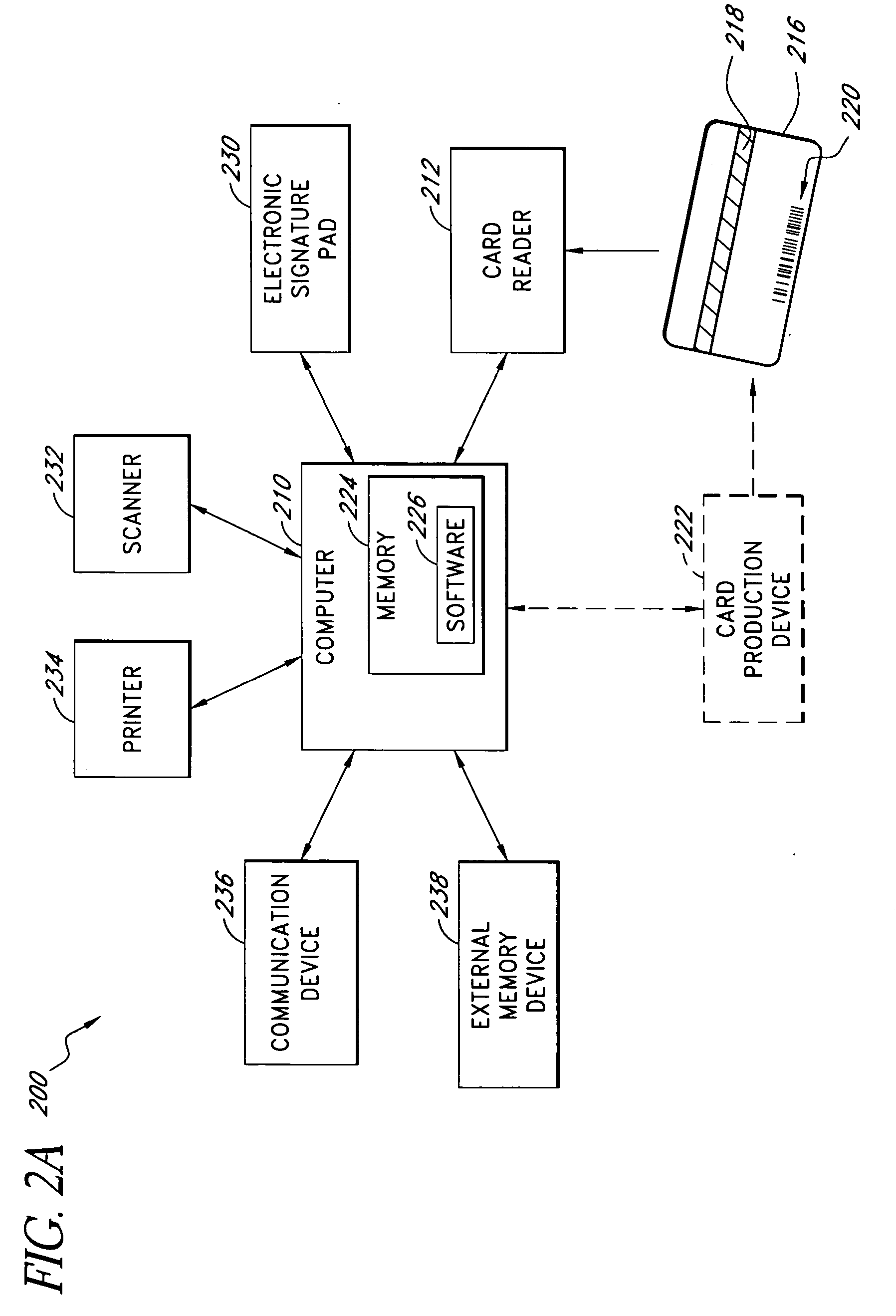
InactiveUS20050080649A1FinanceSpecial data processing applicationsDocumentation procedureData system
Systems and methods automate data entry and processing. Data is automatically entered into a system by reading a user identification card. The data can be supplemented with additional information, if necessary, and processed by the system. In one embodiment, the data is used to register an employee for an employee benefit program offered by a provider such as an insurance carrier. The data read from the identification card is automatically entered into an electronic enrollment form where the user can check it. Documentation corresponding to the enrollment form can be converted to an electronic copy, if necessary, and attached to the enrollment form. Once the enrollment form is complete, the user can electronically sign the enrollment form and send it through a computer network to the provider. The provider may then process the enrollment form, request additional information or corrections from the user, and register the user for the products or services.
Owner:BENEFITSDOMAIN COM INSURANCE SERVICES
System and Method for Smart Registration of Wireless Power Receivers in a Wireless Power Network
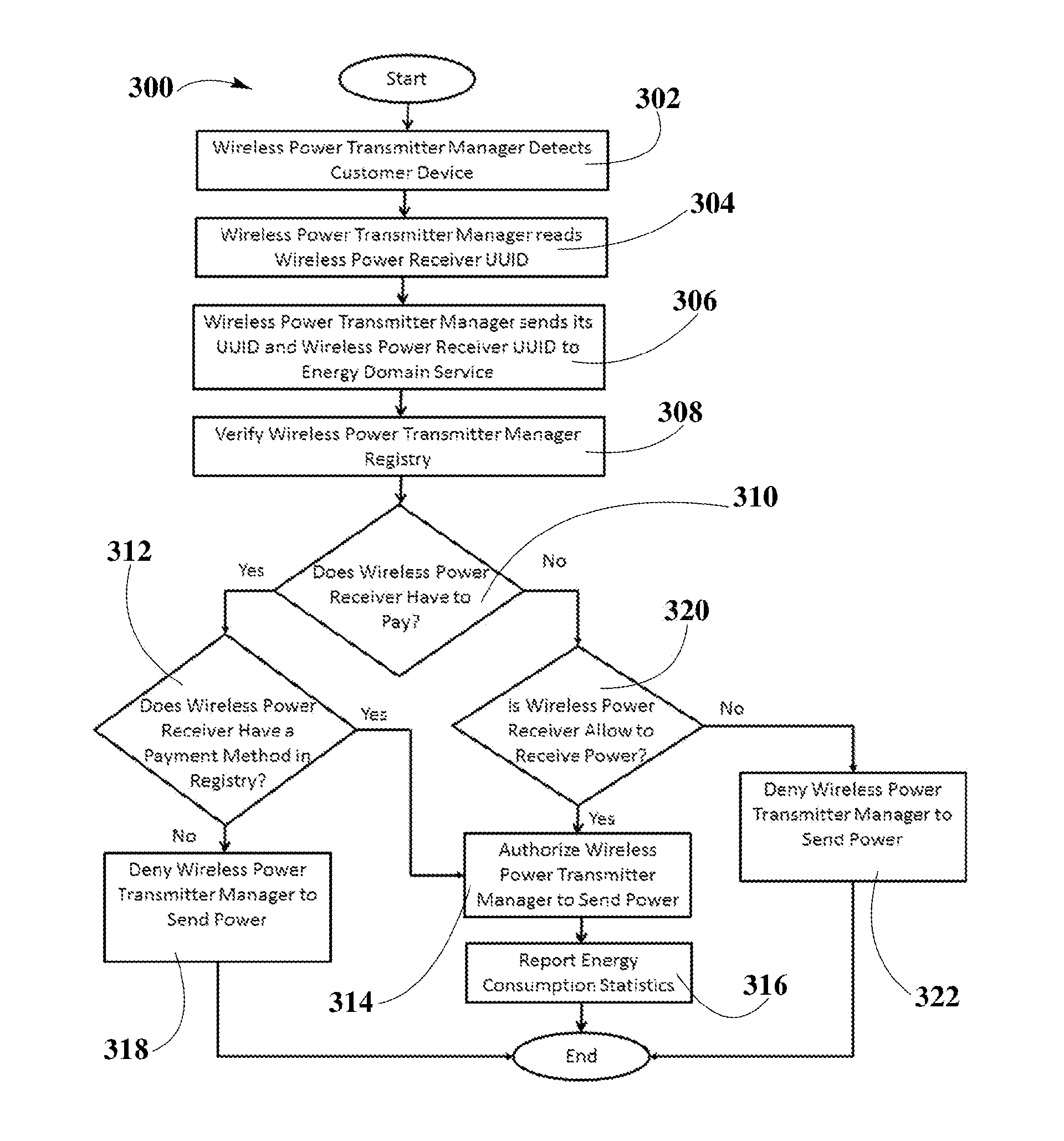
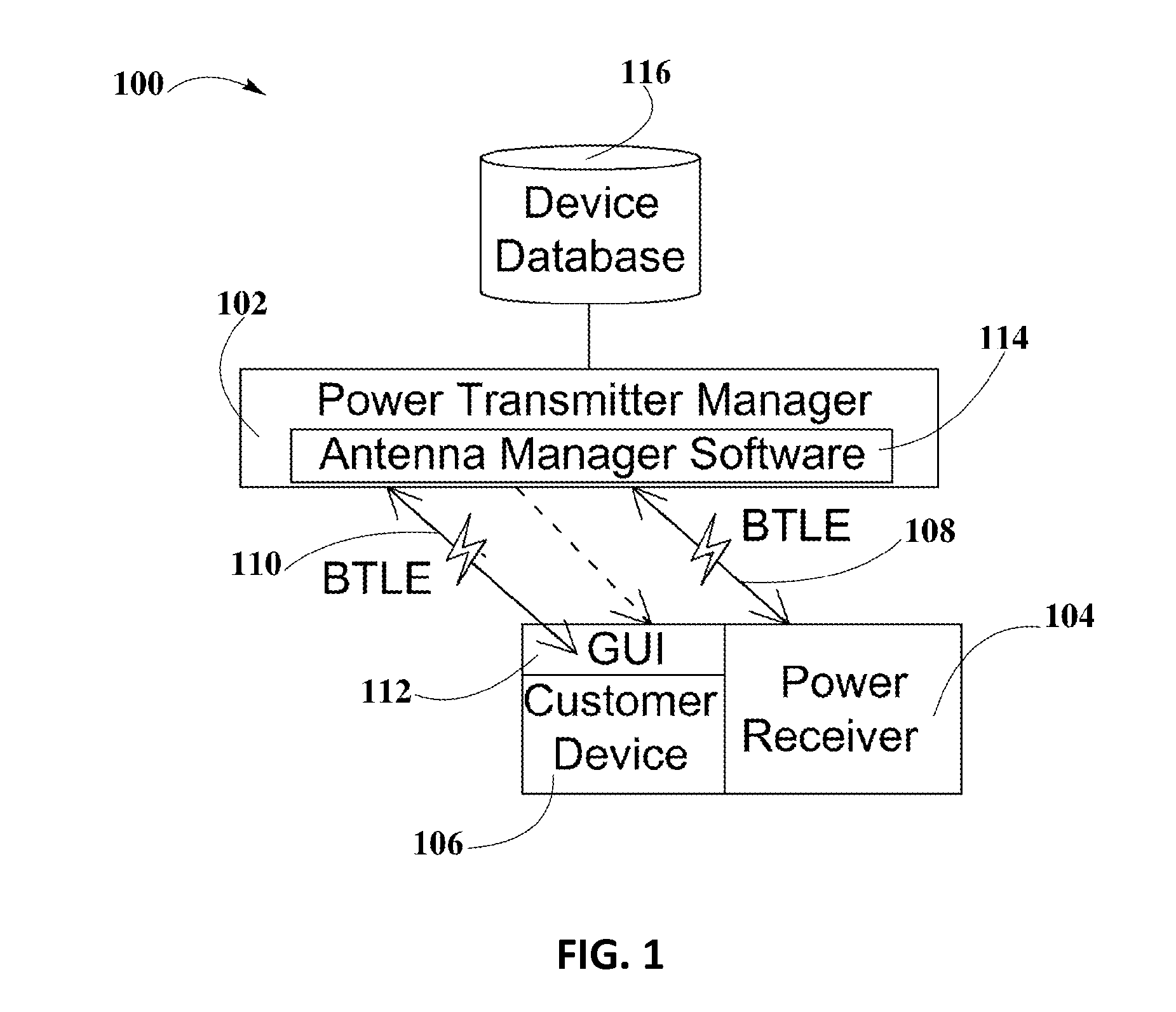
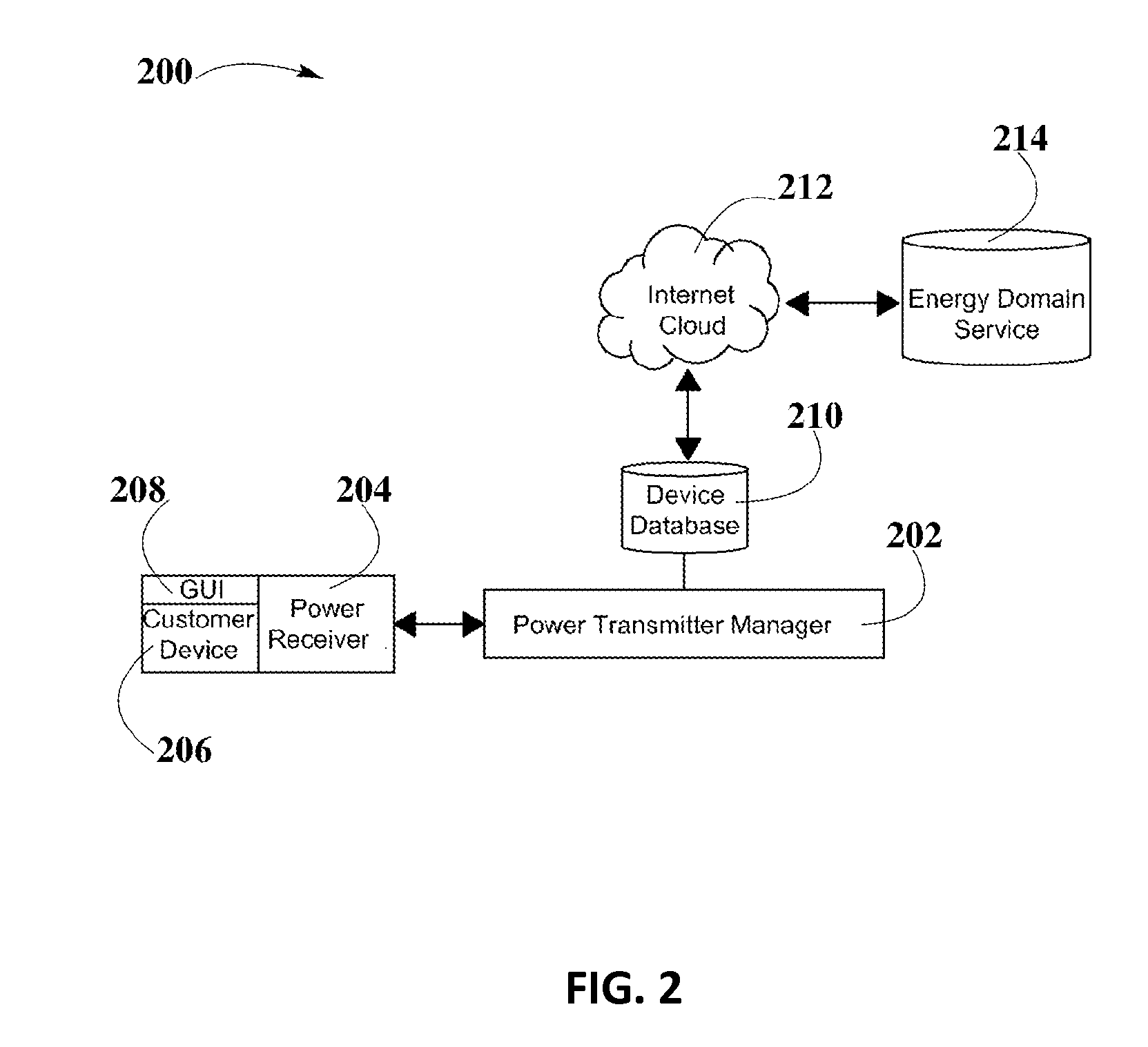
ActiveUS20160020649A1Avoid abuseNear-field transmissionElectromagnetic wave systemElectric power transmissionUniversally unique identifier
A system and method for smart registration of wireless power receivers within a wireless power network is disclosed. Each wireless power device may include a universally unique identifier (UUID). Each wireless power device bought by a customer may be registered, at the time of purchase or later. The registry may be stored in an energy domain service, where energy domain service may be one or more cloud-based servers. The method for smart registration may include the steps of detecting a customer device; establishing a connection with a wireless power receiver to read its UUID; sending wireless power transmitter manager's UUID and wireless power receiver's UUID to energy domain service; inspecting wireless power transmitter manager registry; verifying wireless power receiver registry; authorizing power transfer to wireless power receiver; and reporting energy consumption for subsequent billing of customer depending on billing policy of wireless power transmitter manager specified within registry.
Owner:ENERGOUS CORPORATION
Preparing output XML based on selected programs and XML templates
Owner:ORACLE INT CORP
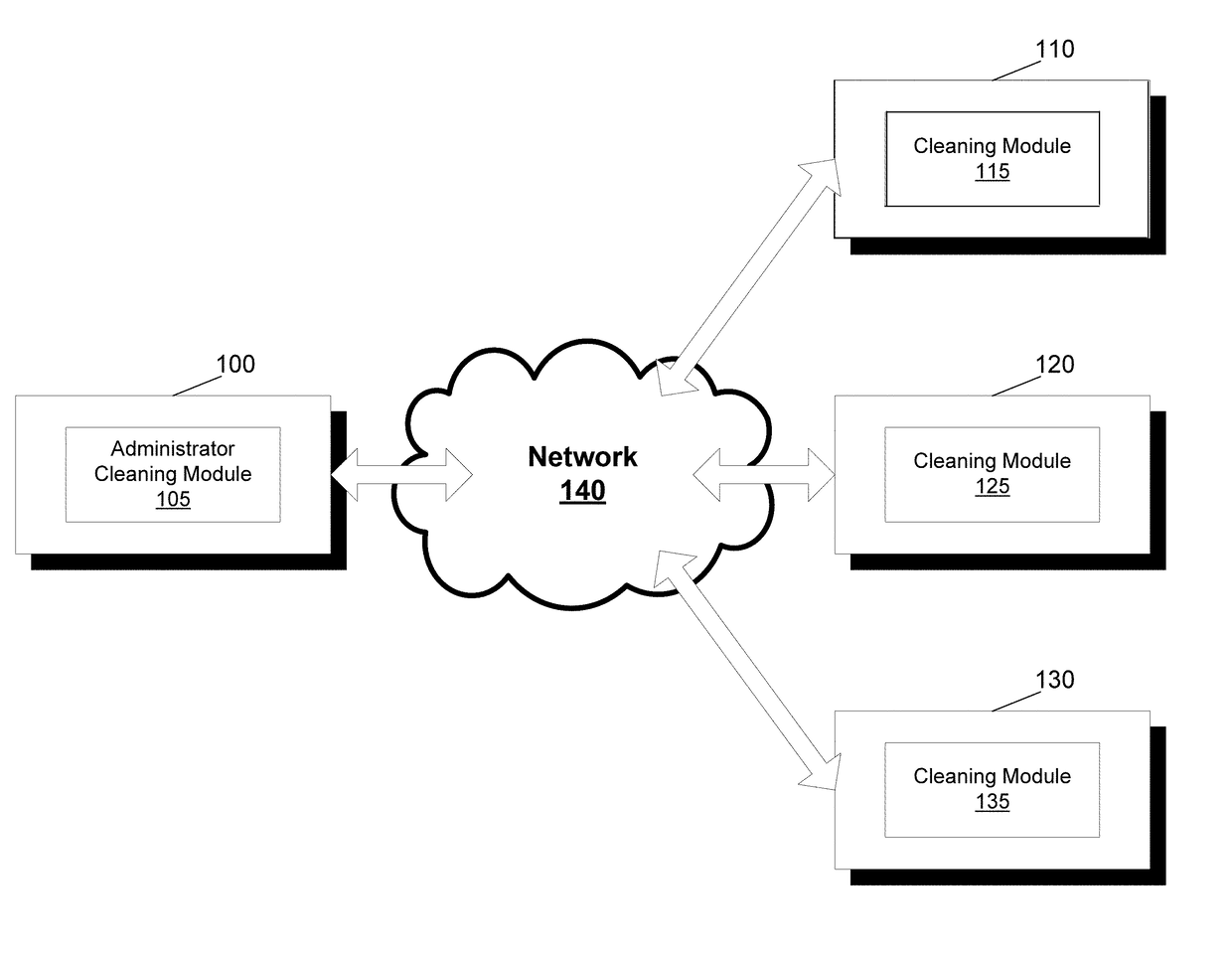
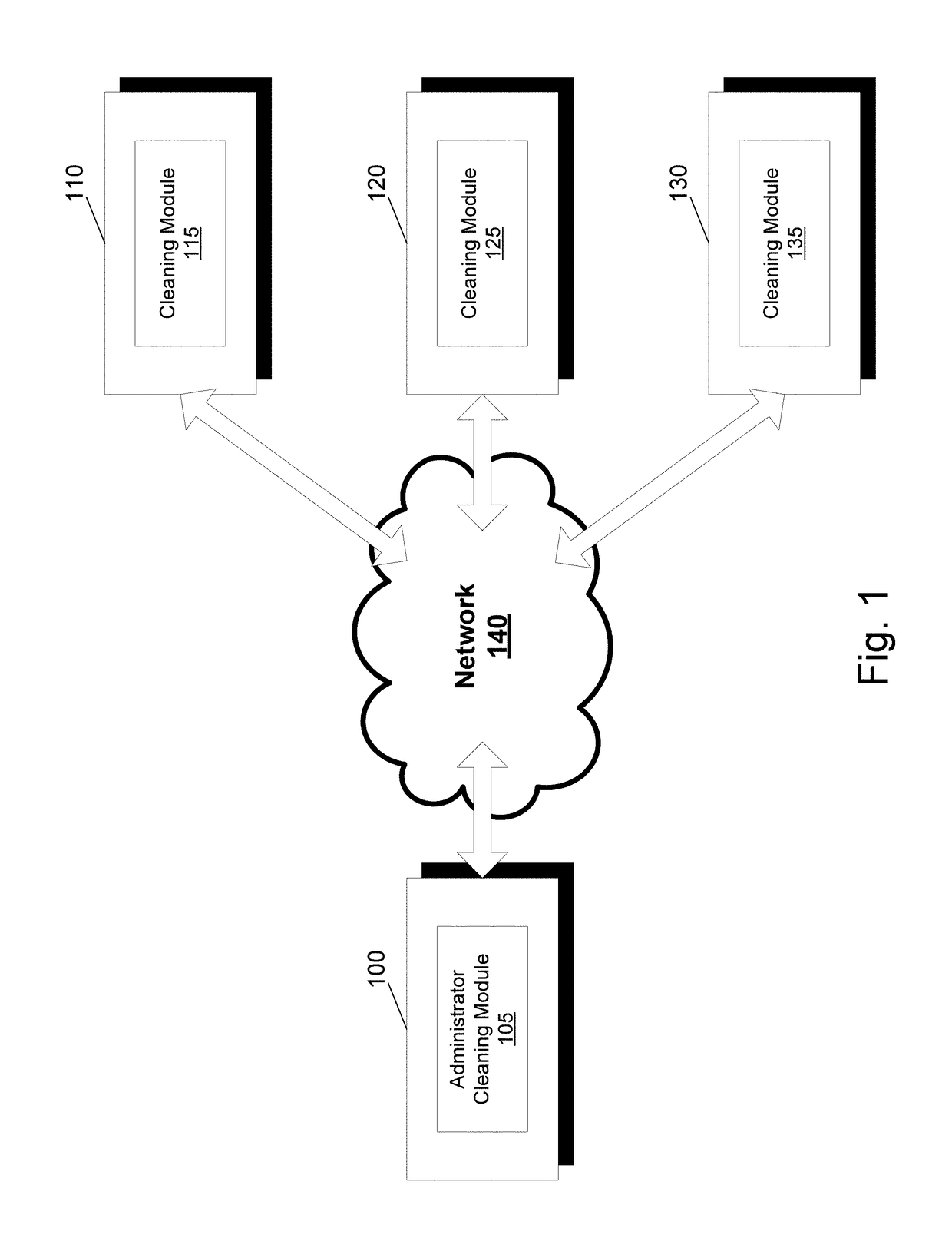
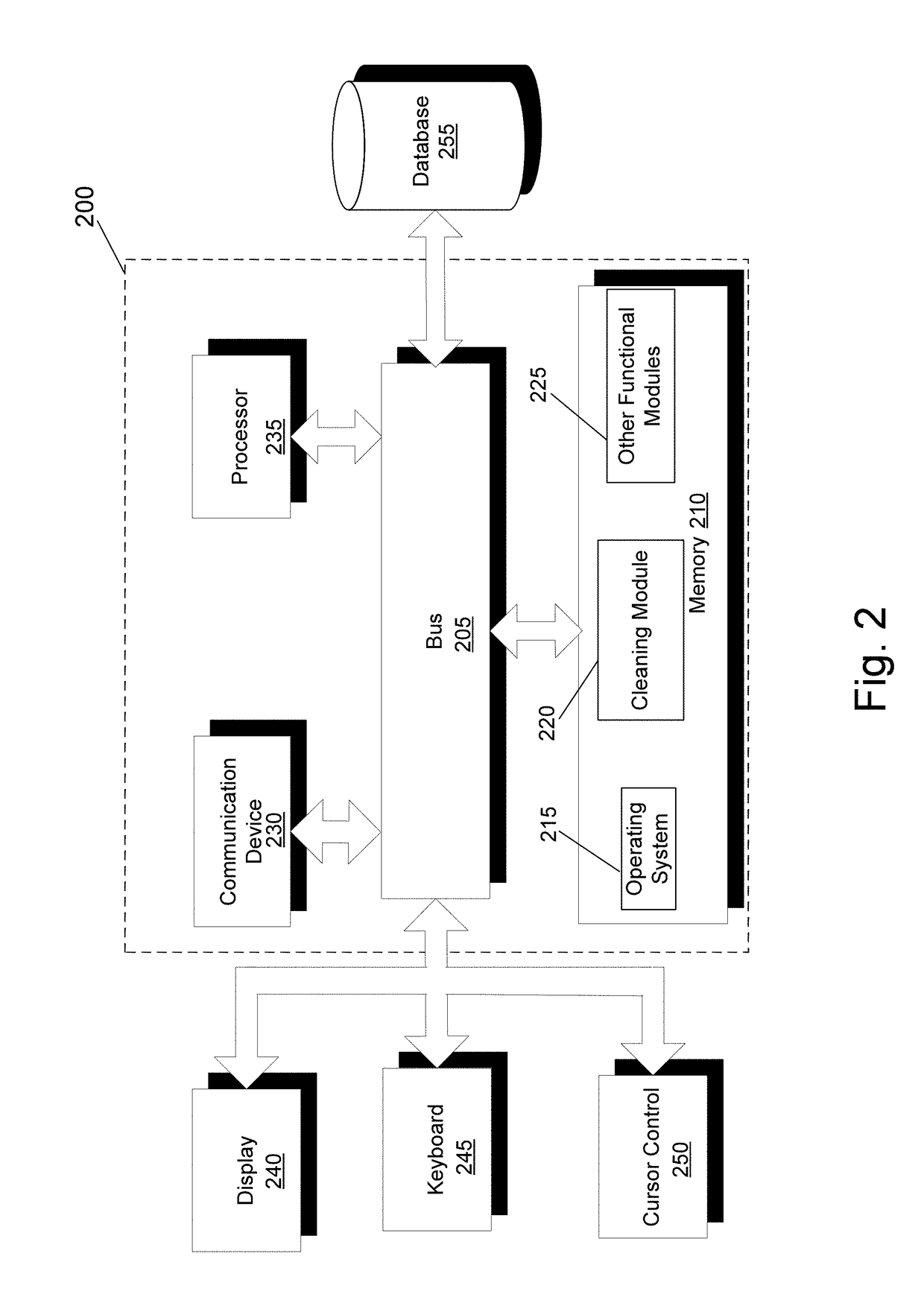
Multiple user profile cleaner
ActiveUS9798749B2Digital data information retrievalSpecial data processing applicationsUser profileWindows Registry
A cleaning application that can clean, for one or more user profiles, at least one of one or more files of a computer or a registry of the computer is provided. The cleaning application can include a cleaning module. The cleaning module can select a plurality of user profiles of the computer. The cleaning module can further select at least one of a file location or a user profile hive for each user profile of the plurality of user profiles. The cleaning module can further clean at least one of one or more files stored within the file location or a registry stored within the user profile hive for each user profile of the plurality of user profiles.
Owner:PIRIFORM SOFTWARE LTD
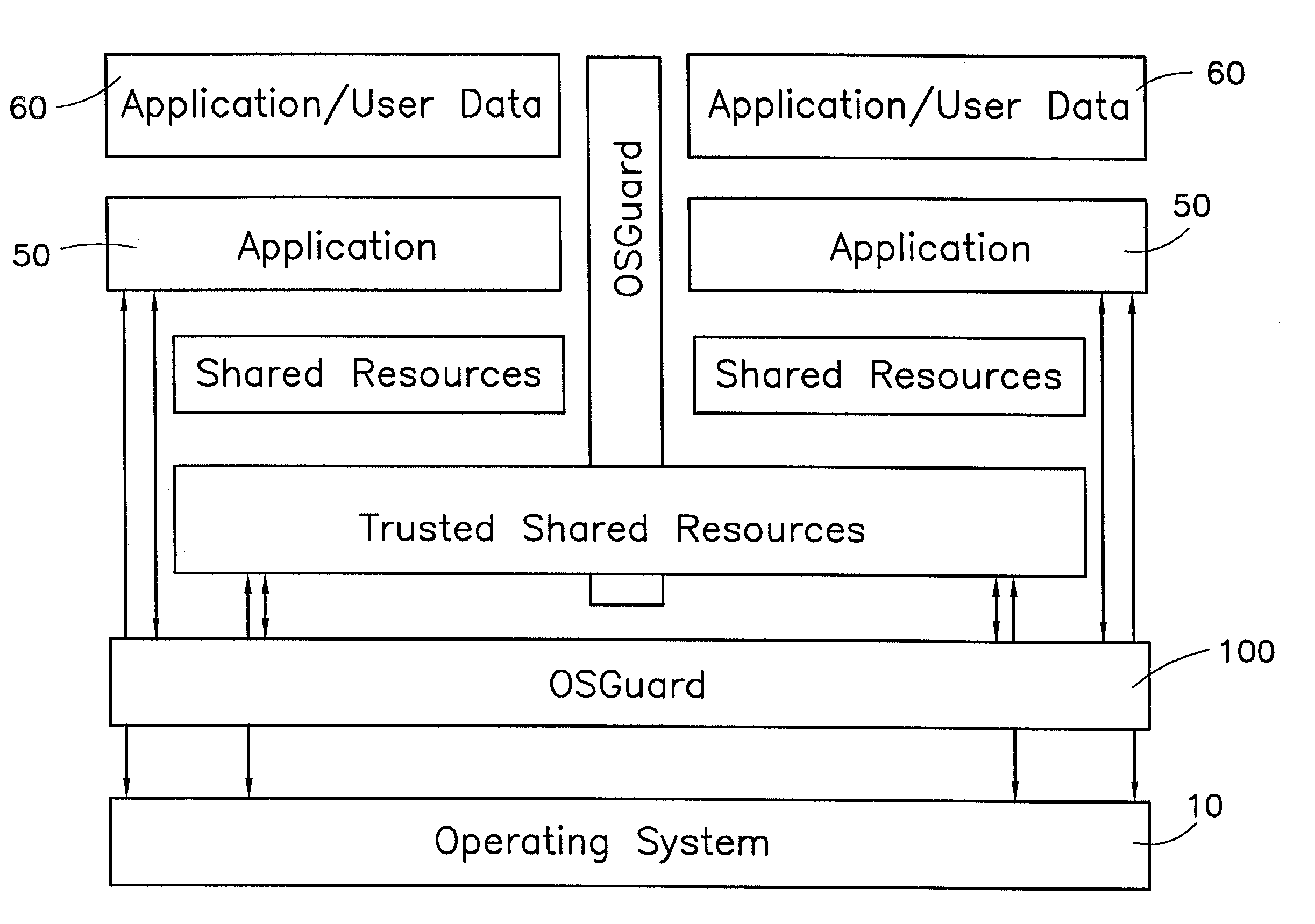
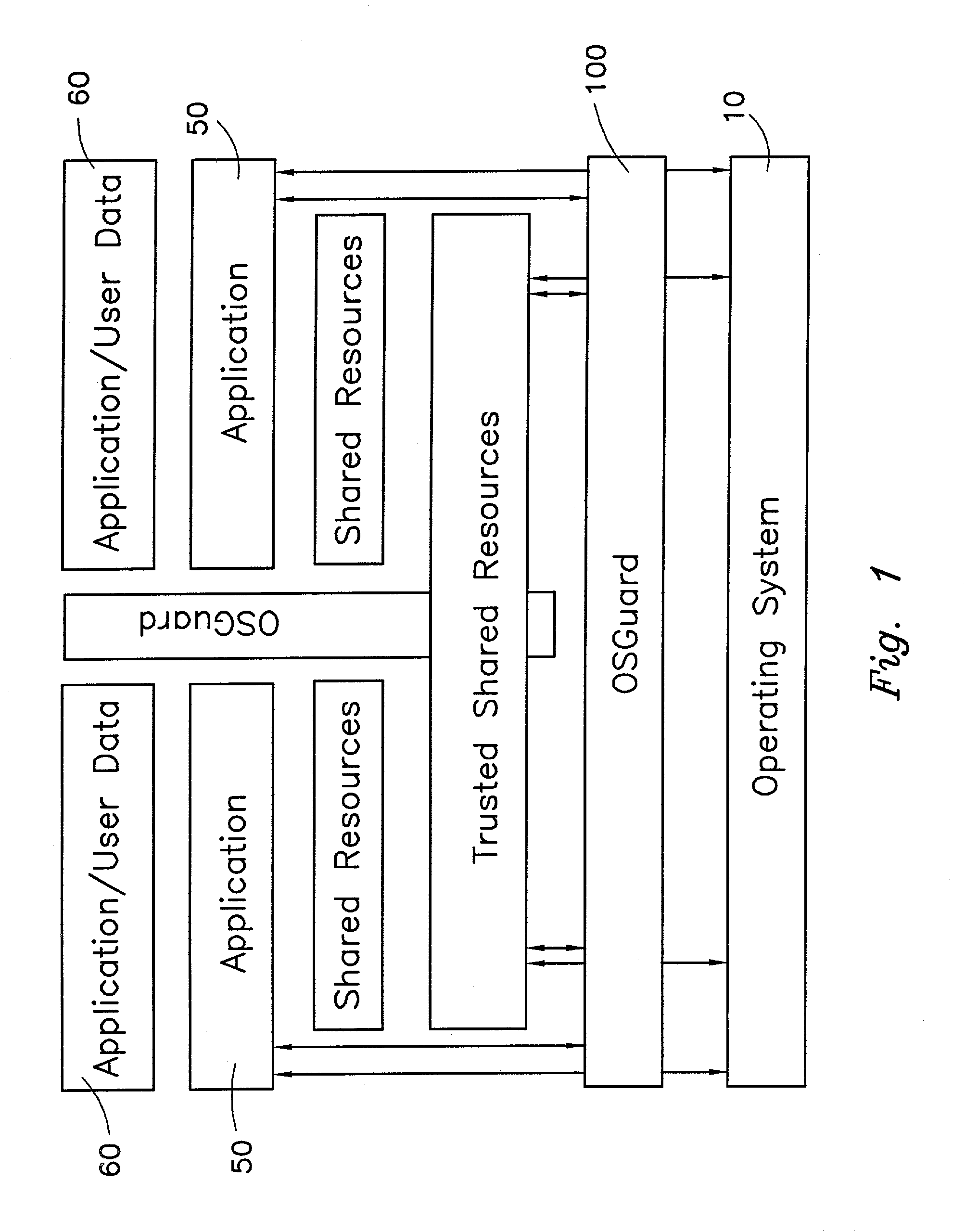
Operating system abstraction and protection layer
InactiveUS7028305B2Avoid changeInhibition of informationInterprogram communicationDigital computer detailsOperational systemConfiguration item
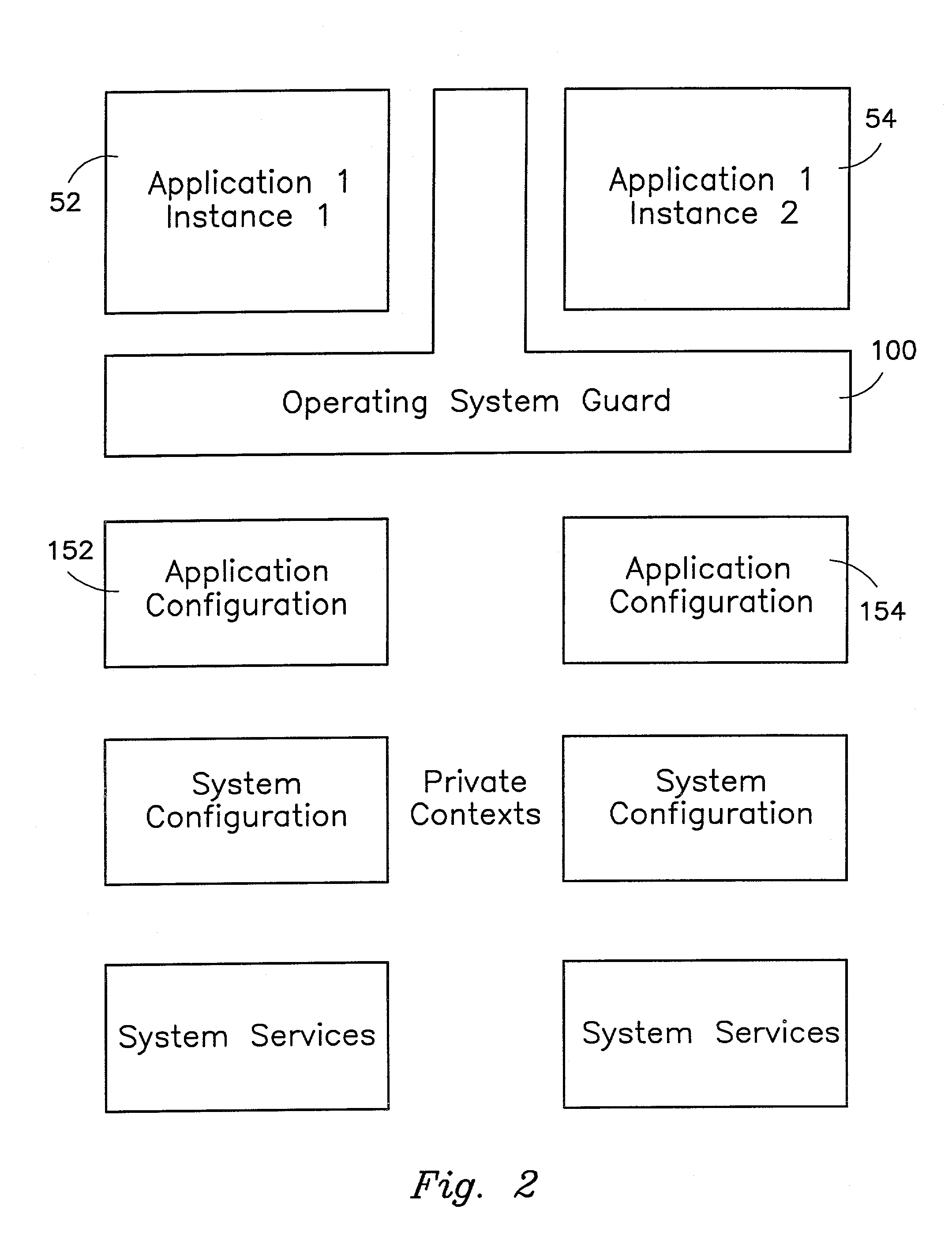
The present invention provides a system for creating an application software environment without changing an operating system of a client computer, the system comprising an operating system abstraction and protection layer, wherein said abstraction and protection layer is interposed between a running software application and said operating system, whereby a virtual environment in which an application may run is provided and application level interactions are substantially removed. Preferably, any changes directly to the operating system are selectively made within the context of the running application and the abstraction and protection layer dynamically changes the virtual environment according to administrative settings. Additionally, in certain embodiments, the system continually monitors the use of shared system resources and acts as a service to apply and remove changes to system components. The present thus invention defines an “Operating System Guard.” These components cover the protection semantics required by .DLLs and other shared library code as well as system device drivers, fonts, registries and other configuration items, files, and environment variables.
Owner:MICROSOFT TECH LICENSING LLC
System and method for event subscriptions for CORBA gateway
InactiveUS7010586B1Improve performanceImprove scalabilityData switching by path configurationMultiple digital computer combinationsEvent typeInternet traffic
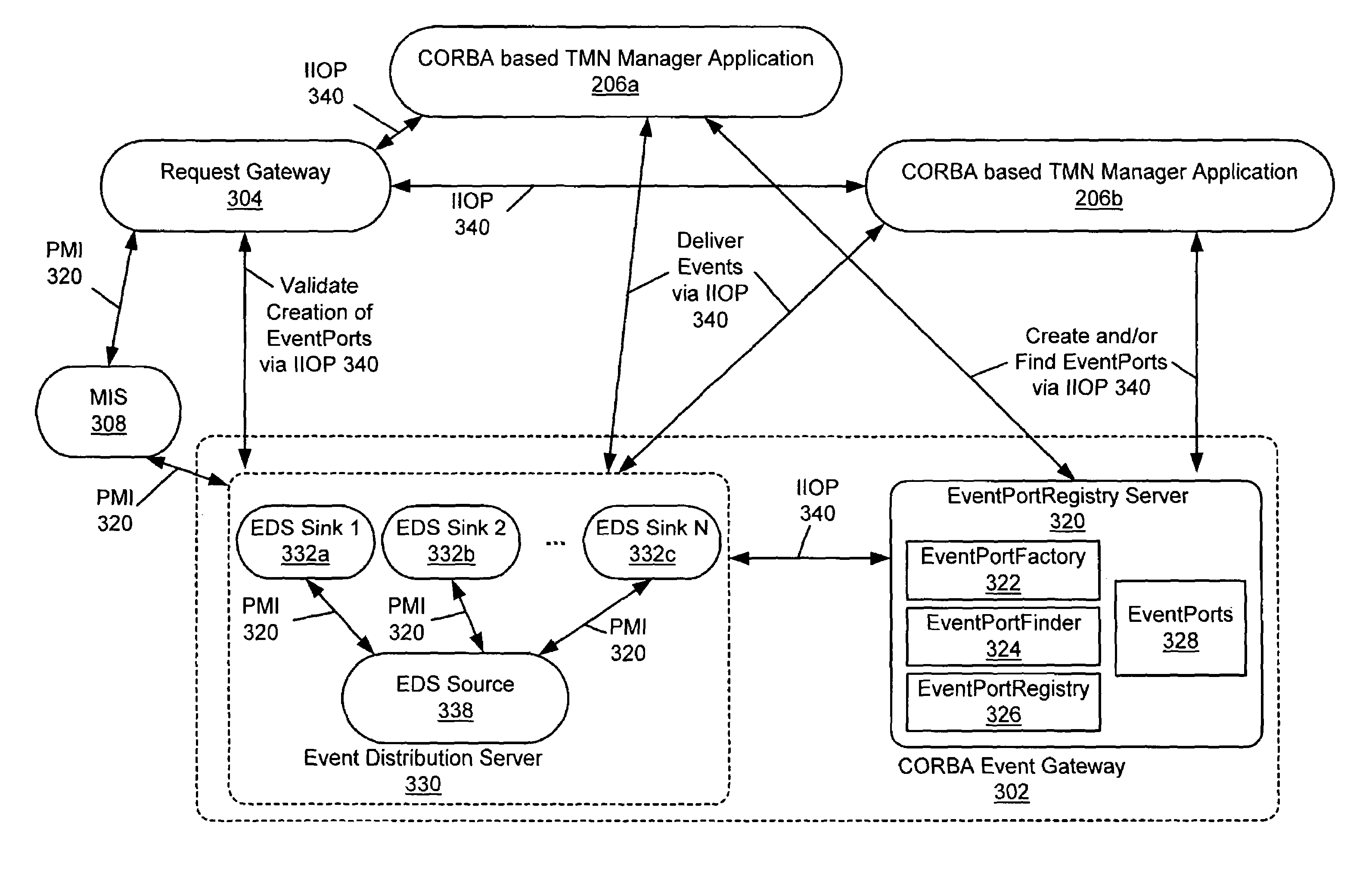
A CORBA Gateway between CORBA-based applications and an enterprise manager may be configurable to manage various networked objects, such as printers, scanners, copiers, telephone systems, cell phones, phone systems, faxes, routers, switches, etc., which may be interconnected via networks. Various embodiments of the CORBA Gateway may include an Event Gateway which manages object events. The CORBA Event Gateway is designed to leverage existing Event Distribution Server (EDS) sinks to provide EDS filtering functionality and EDS object level access control functionality. The approach leverages existing EDS solutions by providing a common sink for all events / notifications and using a unique Event Port Registry to manage the subscriptions of various TMN clients that subscribe for such events / notifications. Generally, the approach described provides the capability to filter events according to criteria presented by client event subscriptions. In one embodiment, the events may be filtered to enforce policy-based access control on TMN events / notifications, determining which CORBA client applications have access to which events. The filtering of events at the sink based upon client subscriptions decreases unnecessary network traffic in that events may be “pushed” to the client, rather than delivered upon client request. In addition, the approach may provide easy-to-use IDL APIs that allow CORBA clients to directly subscribe / unsubscribe to events based on criteria such as object class, object instance, and event type.
Owner:ORACLE INT CORP
System and method for authenticating entities to users
InactiveUS20050268100A1Digital data processing detailsUser identity/authority verificationUser verificationWindows Registry
A system and method communicates information from an entity that a registry can use to authenticate the entity to a user. If the registry authenticates the entity, it displays information that represents a shared secret between the registry and the user.
Owner:EMC IP HLDG CO LLC
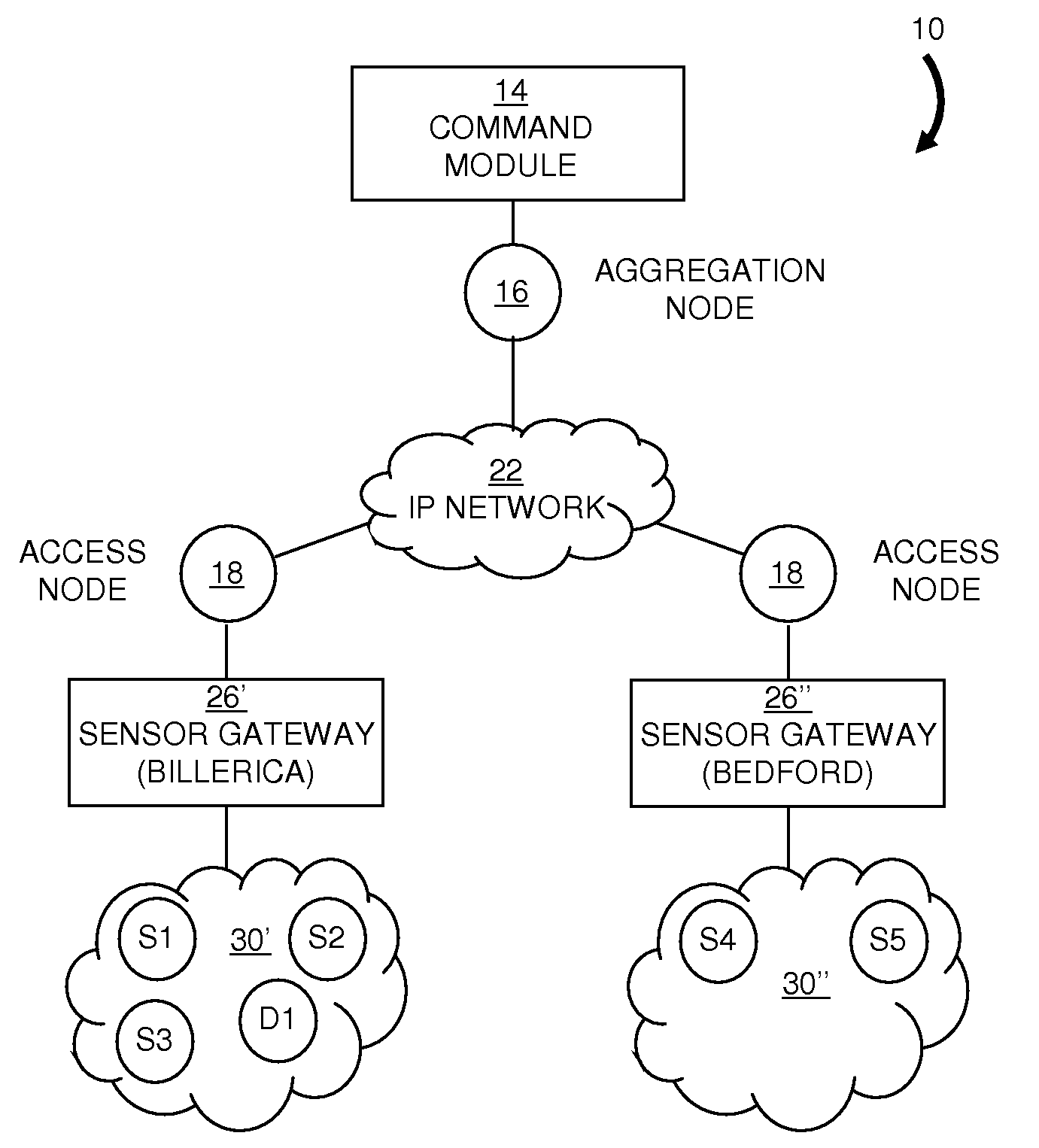
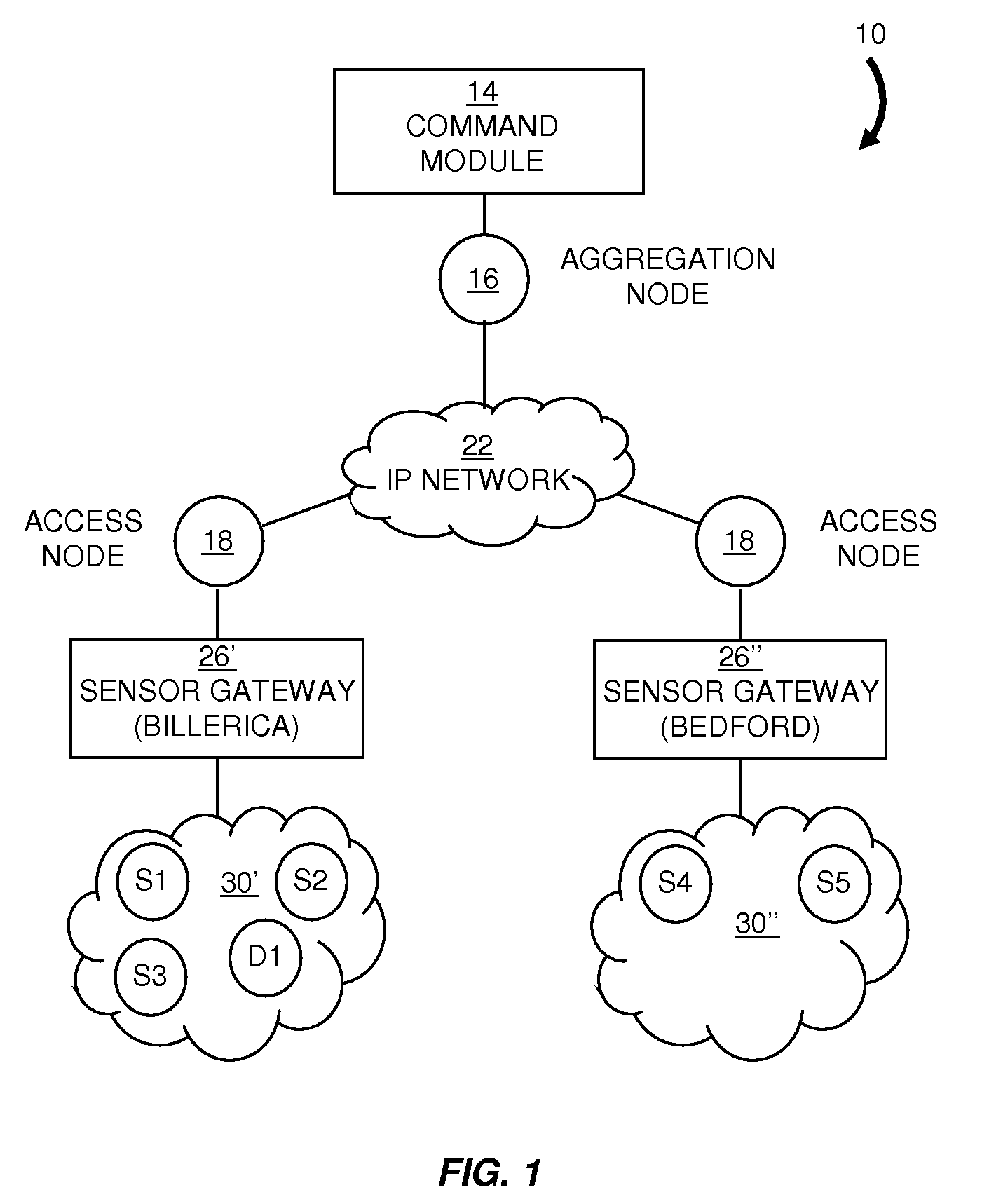
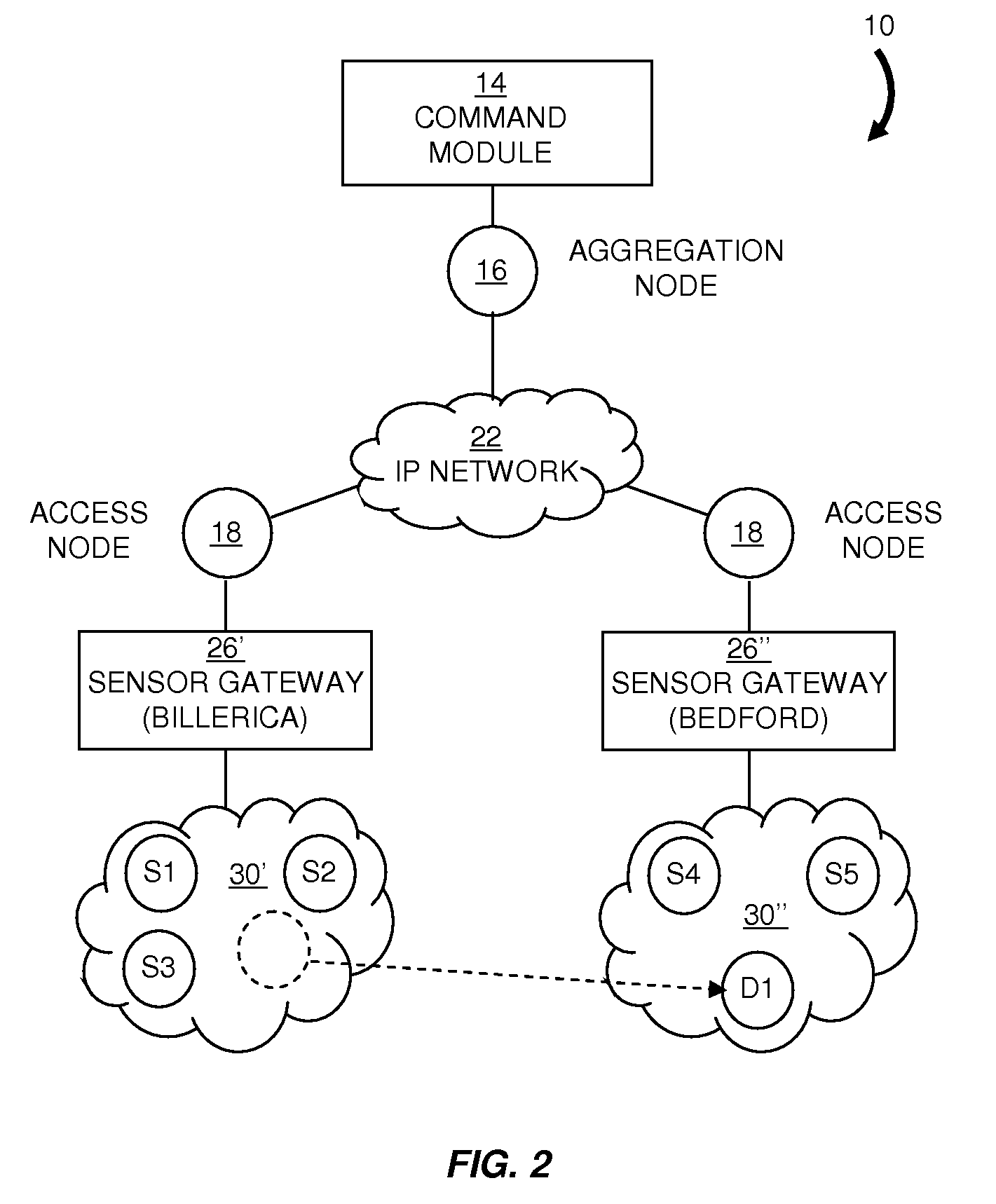
Dynamic sensor network registry
InactiveUS20090222541A1User identity/authority verificationNetwork topologiesNetwork connectionNetwork architecture
A scalable network architecture adapted to interface with various sensor types and sensor access mechanisms while providing real-time access to sensor data for distributed applications and organizations is described. A centralized sensor network service manages the registration, capabilities, near real-time status of the sensors and their current network connections. New sensors are discovered automatically through messaging between network access nodes and the sensor registry. The registry service can be made available to distributed sensor applications and sensor middleware, and facilitates the sharing of sensors across organizations. The sensor registry is automatically updated by network software and does not require manual configuration or reconfiguration each time a sensor is added to or relocated within the network. Authentication and authorization policies can be implemented to ensure that only authorized applications can query and view the registry. The registry can be implemented for multi-vendor sensor networks and can accommodate multiple addressing schemes.
Owner:RPX CLEARINGHOUSE
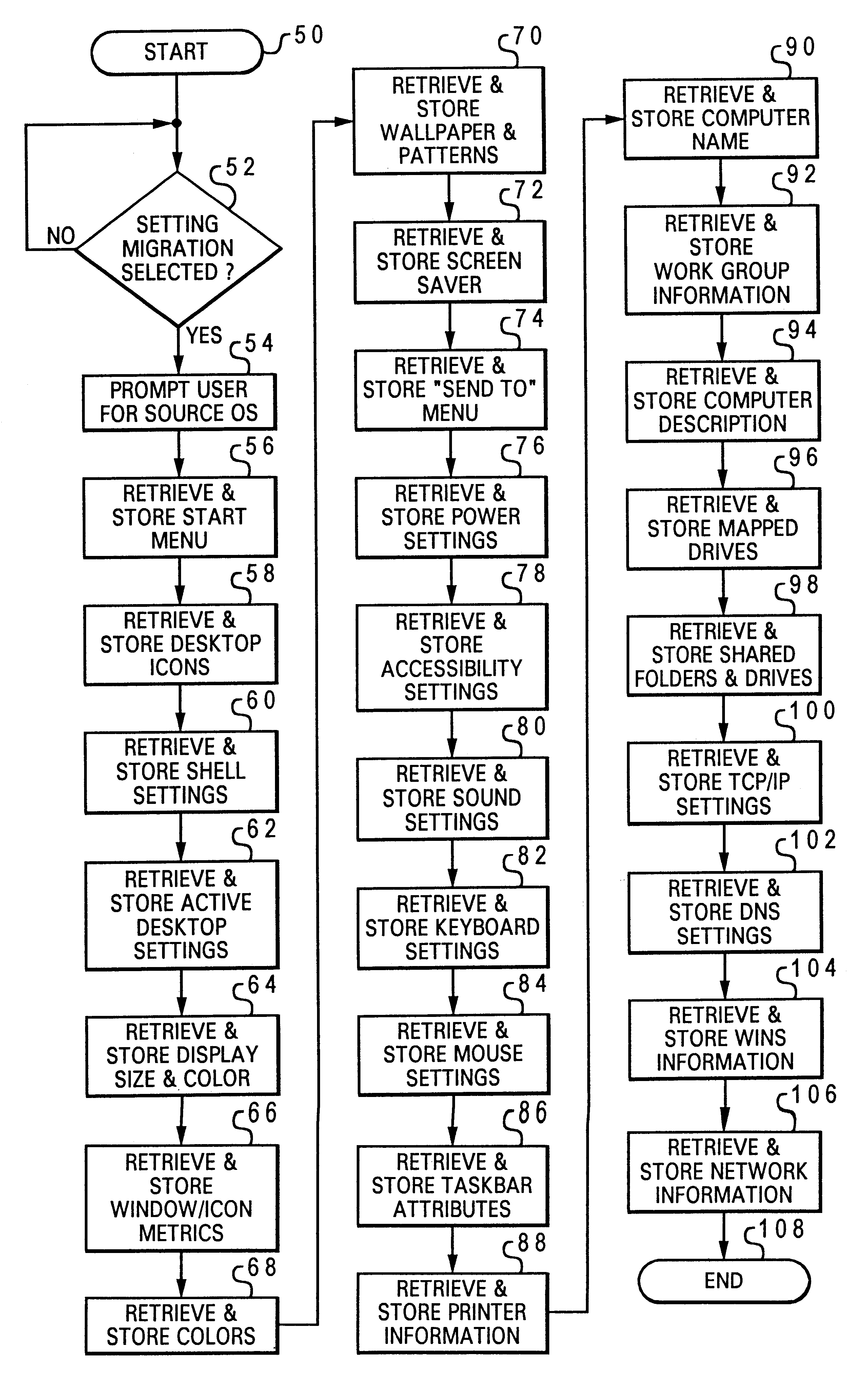
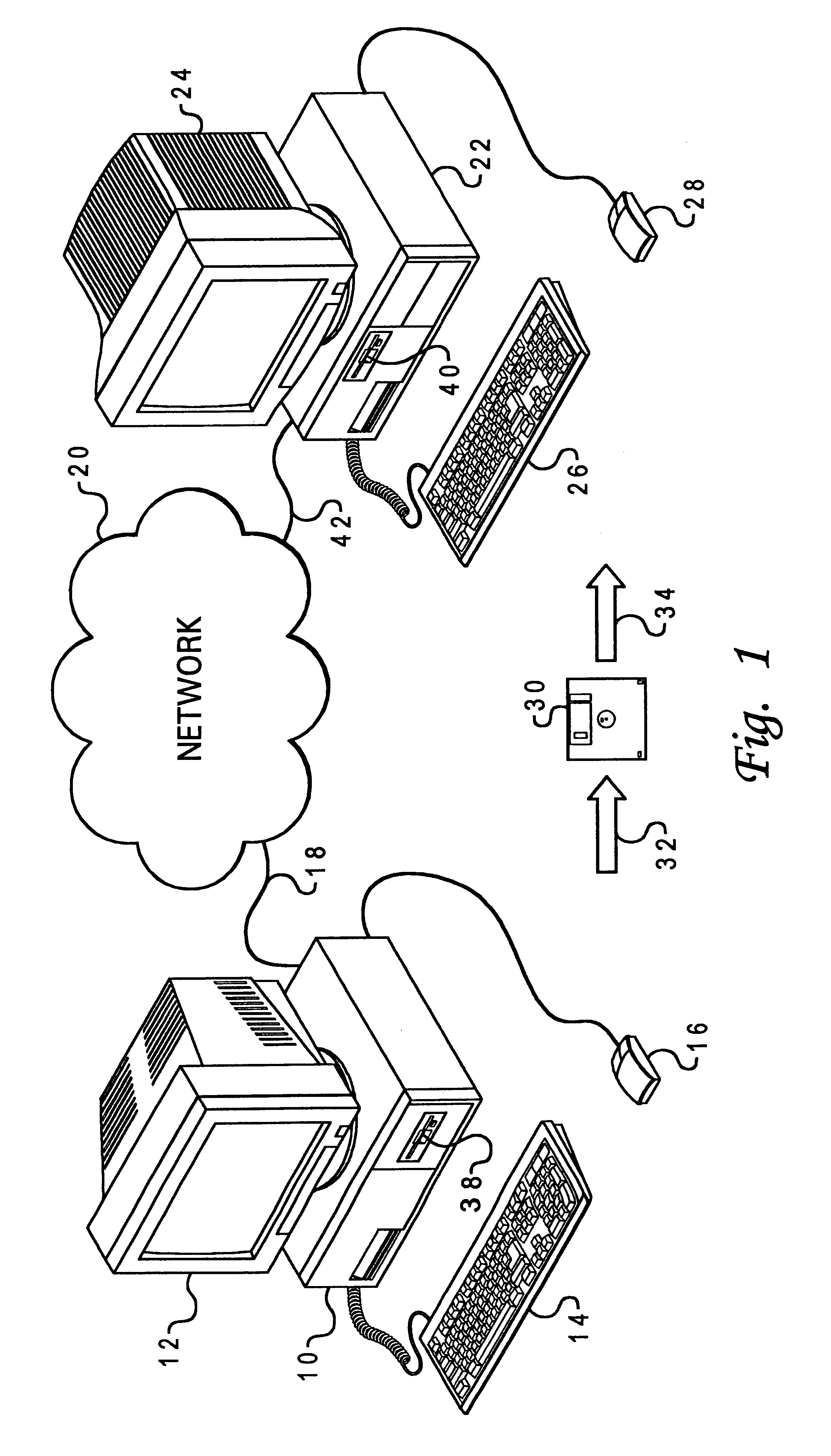
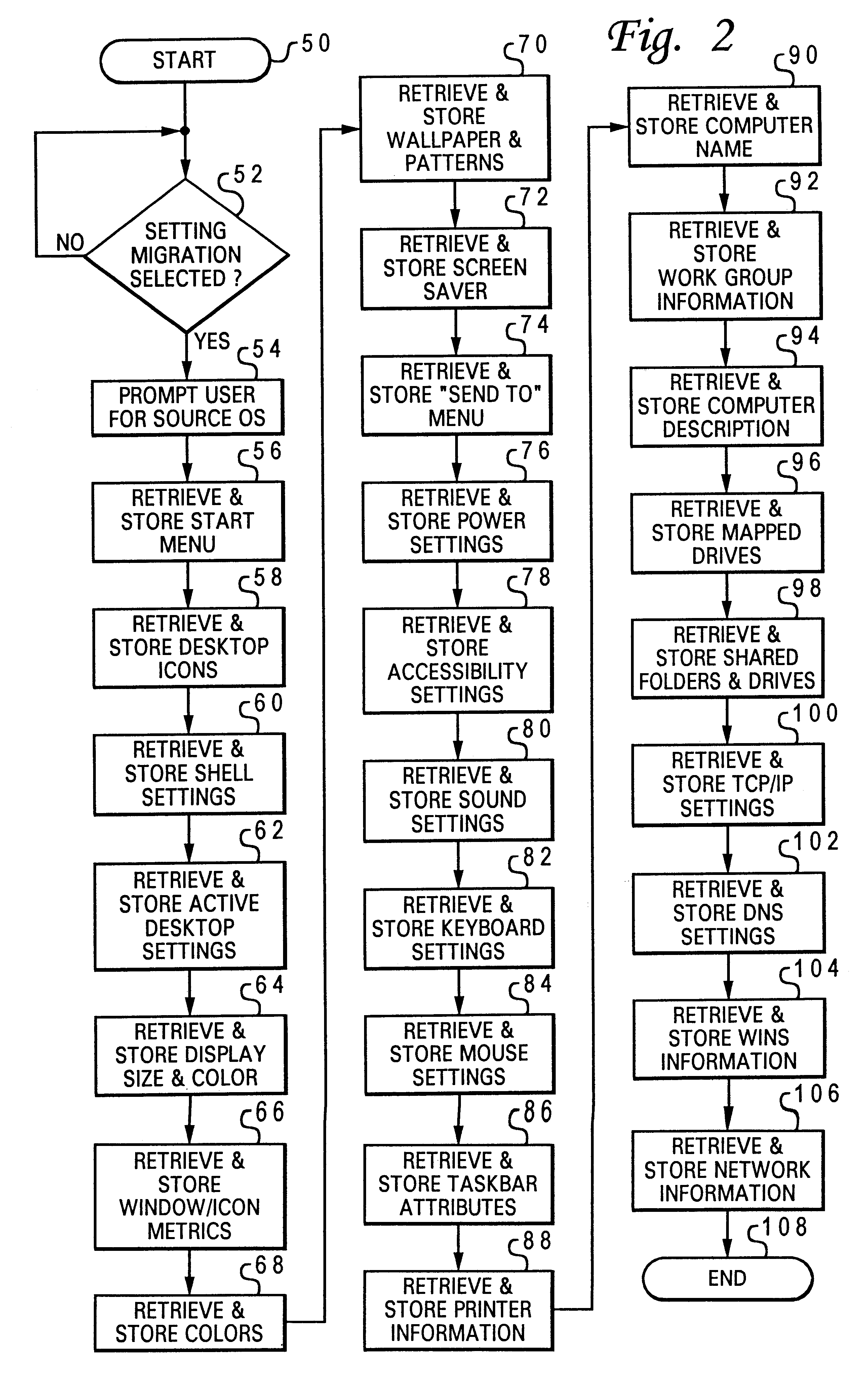
Method and system for automated migration of user settings to a replacement computer system
A method and system are disclosed for automating migration of user system settings from an existing computer system to a replacement computer system in response to a user input. Selected portions of the registry, or central hierarchial data base within the existing computer system are automatically copied and stored in response a user input. A plurality of application program interface (API) routines are then initiated to retrieve and store selected settings within the existing computer system. Adapter binding information for all adapters within the existing computer system are retrieved and stored. The selected portions of the registry, selected settings and adapter binding information are then transferred to the replacement computer system and copied into appropriate registry keys, directories and files, effectively transferring the system settings from the existing computer system to the replacement computer system.
Owner:LENOVO PC INT
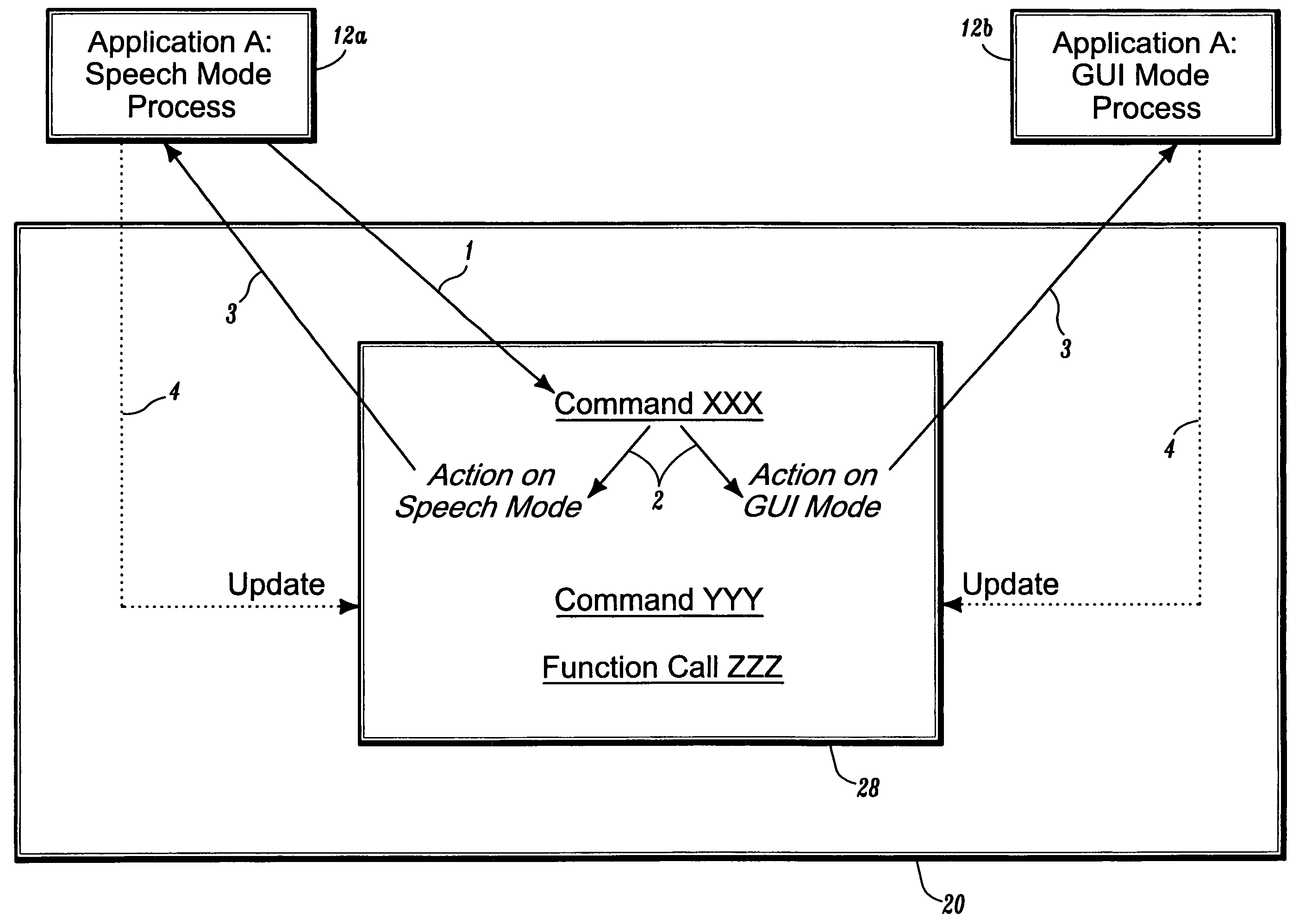
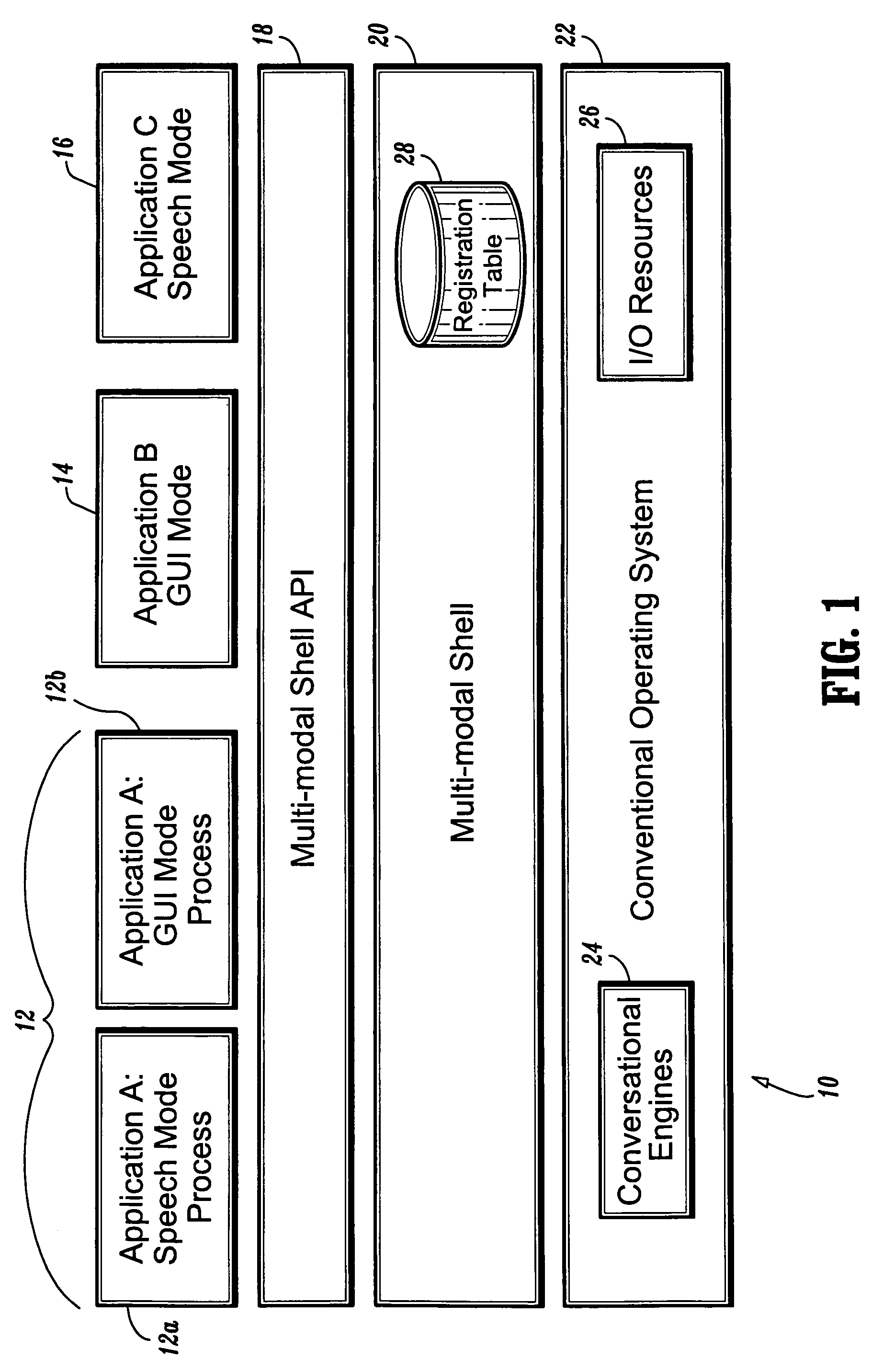
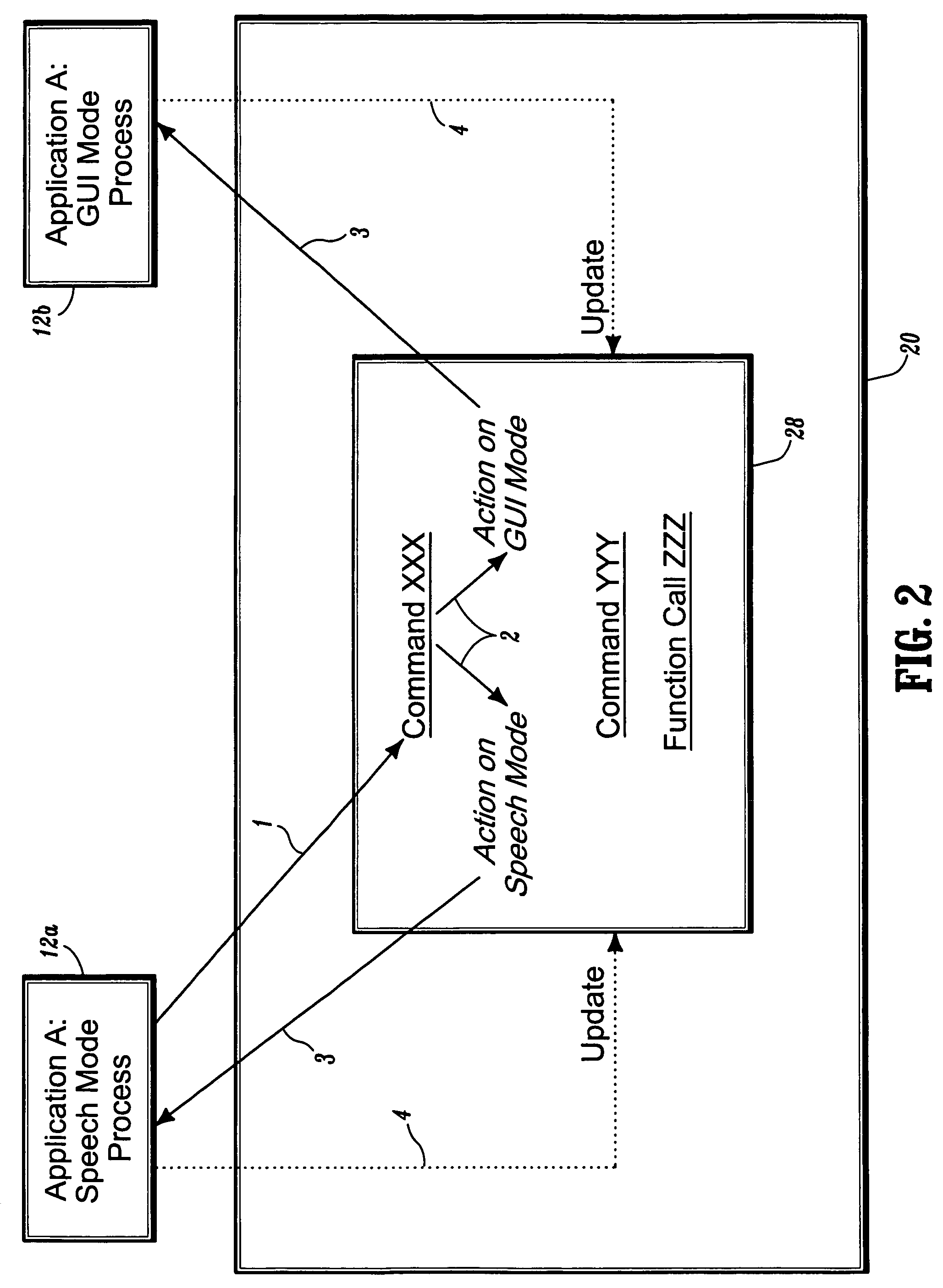
Systems and methods for synchronizing multi-modal interactions
System and methods for synchronizing interactions between mono-mode applications, different modes of a multi-modal application, and devices having different UI modalities. In one aspect, a multi-modal shell coordinates multiple mode processes (i.e. modalities) of the same application or multiple applications through API calls, whereby each mode process registers its active commands and the corresponding actions in each of the registered modalities. The multi-modal shell comprises a registry that is implemented with a command-to-action table. With the execution of a registered command, each of the corresponding actions are triggered to update each mode process accordingly, and possible update the registry to support new commands based on the change in state of the dialog or application. In another aspect, separate applications (with UI of different modalities) are coordinated via threads (e.g., applets) connected by socket connections (or virtual socket connections implemented differently). Any command in one mode triggers the corresponding thread to communicate the action to the thread of the other application. This second thread modifies accordingly the state of the second process mode. The threads are updated or replaced by new threads.
Owner:UNILOC 2017 LLC
Optimizing cloud service delivery within a cloud computing environment
This invention provides a system or method to provide dynamically packaged Cloud services to customers via a Cloud services registry. The Cloud services registry is dynamic and operates by polling different Cloud service providers and Cloud service databases to ensure that the Cloud services registry is up to date with the latest available Cloud services. The Cloud services registry is available for queries from Cloud customers and abstracts multiple Cloud service providers. By abstracting the Cloud services, the dynamic Cloud services registry creates a modular package of different services from different Cloud service providers based on the query and requested priority for services. The dynamic Cloud registry is dynamically updated based on the level of services that the provider has available. The dynamic registry determines what service best matches the requirements from a Cloud service request (CSR) and returns a personalized set of matching services.
Owner:IBM CORP
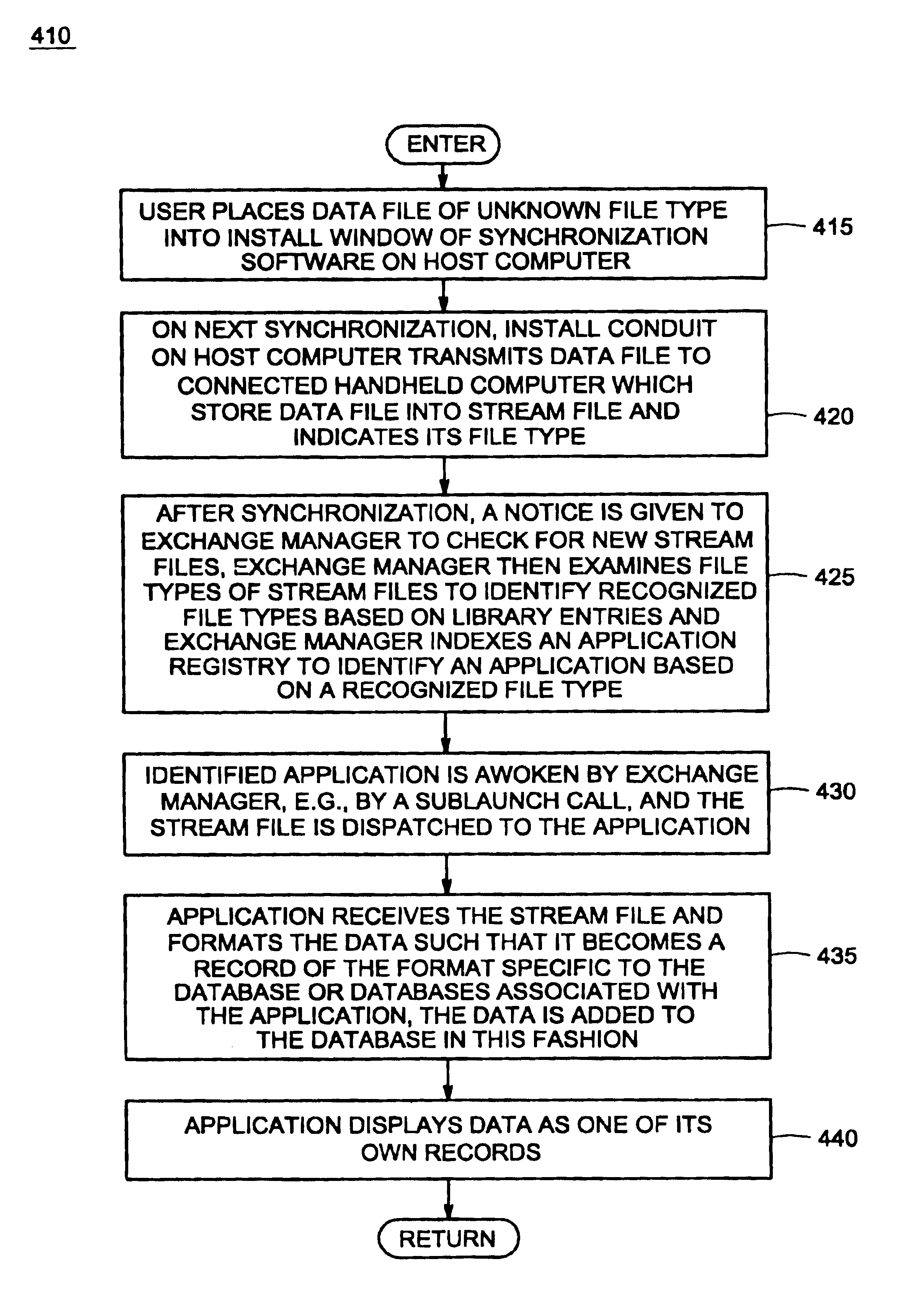
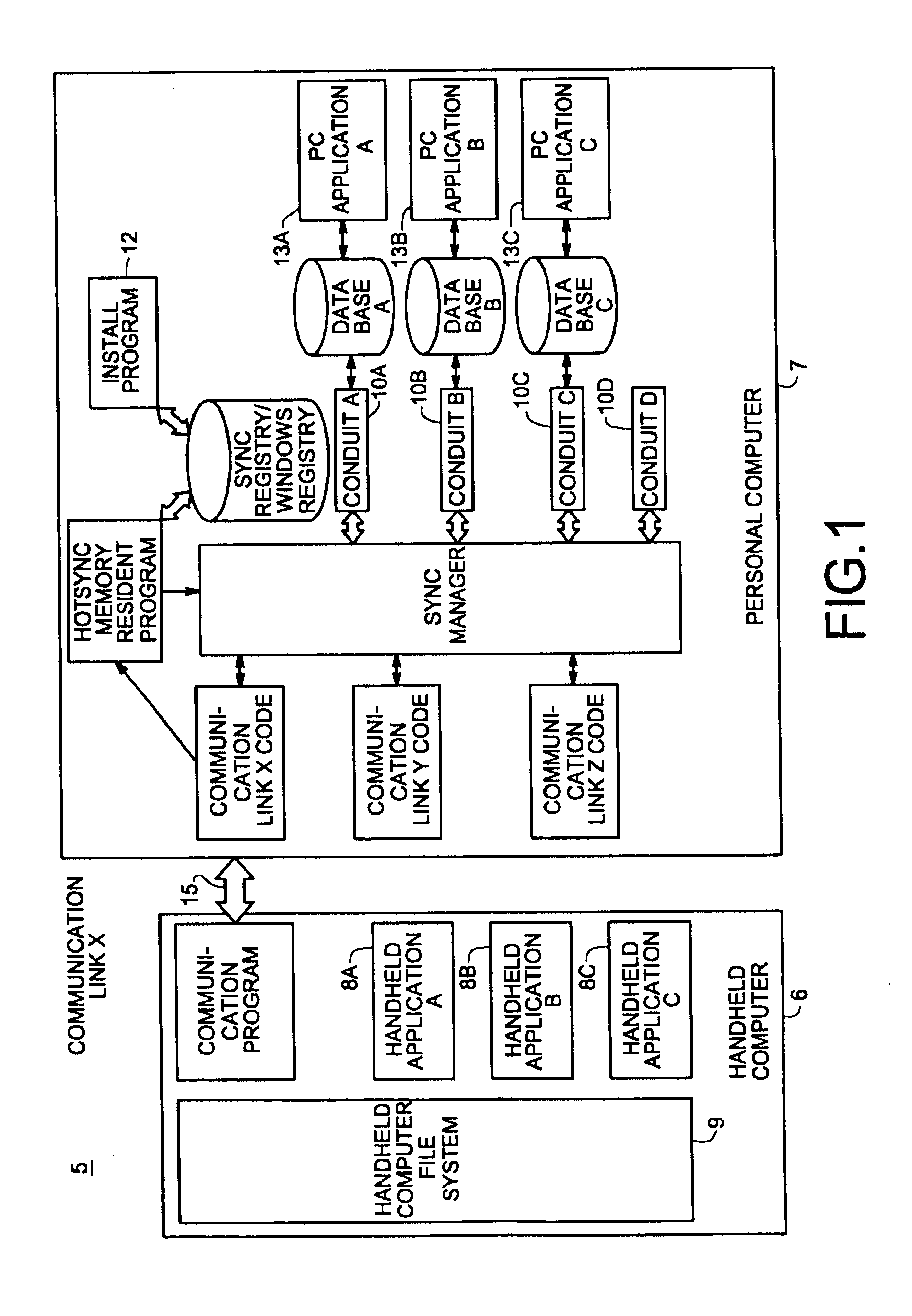
Data exchange between a handheld device and another computer system using an exchange manager via synchronization
InactiveUS6868451B1Data processing applicationsMultiple digital computer combinationsElectronic systemsComputerized system
A method and electronic system for exchanging data between a handheld device and another computer system are described. A data file is transferred to the handheld device using the install application of a synchronization manager. The transferred file is stored as a digital stream file with its native data encoding. After synchronization, a message is sent to notify the exchange manager about the data file. The exchange manager then uses an application registry to identify the application program that corresponds to the stream file based on the extension of the stream file. The pertinent application program is then invoked and the stream file is dispatched to the application for processing. During processing, the pertinent application then formats the stream file such that the data file becomes a record within the database file that is associated with the pertinent application.
Owner:ACCESS
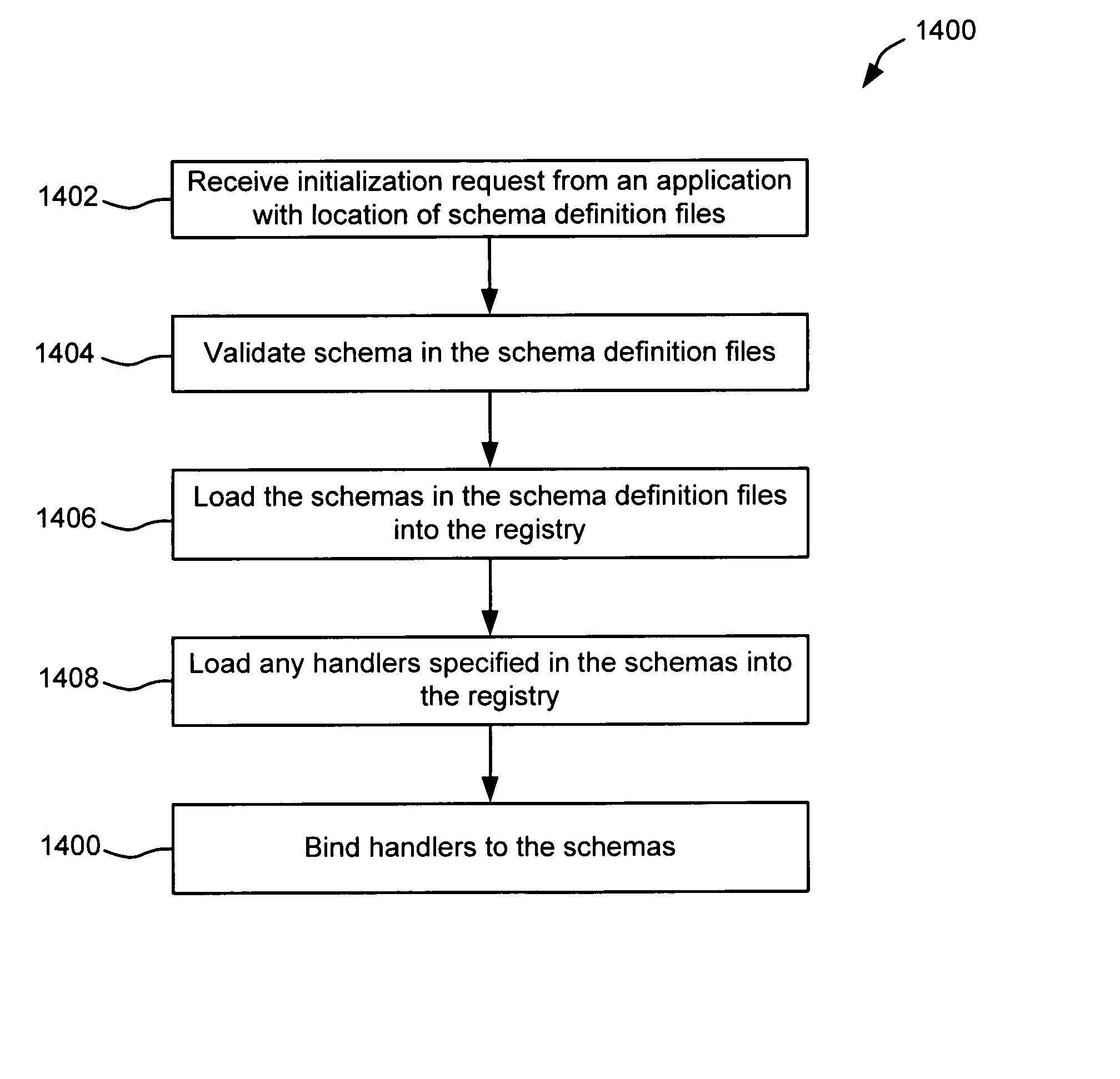
Schema-based dynamic parse/build engine for parsing multi-format messages
ActiveUS20070005613A1Limiting memory neededImprove performanceNatural language analysisDigital data processing detailsWindows RegistryCharacter encoding
A parse / build engine that can handle multi-format financial messages. The engine converts the different format messages into a common format, and the common format message is then processed by the business service application. A parser examines the message and determines an appropriate schema for the particular format of message received. The schema is a data structure in a schema registry that includes a grammar structure for the received format as well as pointers to handlers for converting the different fields of the message into the internal message format using the grammar structure (the “grammar” can include field sequence, field type, length, character encoding, optional and required fields, etc.). The handlers are individually compiled. As formats change, new formats or changes to old formats can be dynamically added to the parse / build engine by loading new schema and handlers.
Owner:VISA USA INC (US)
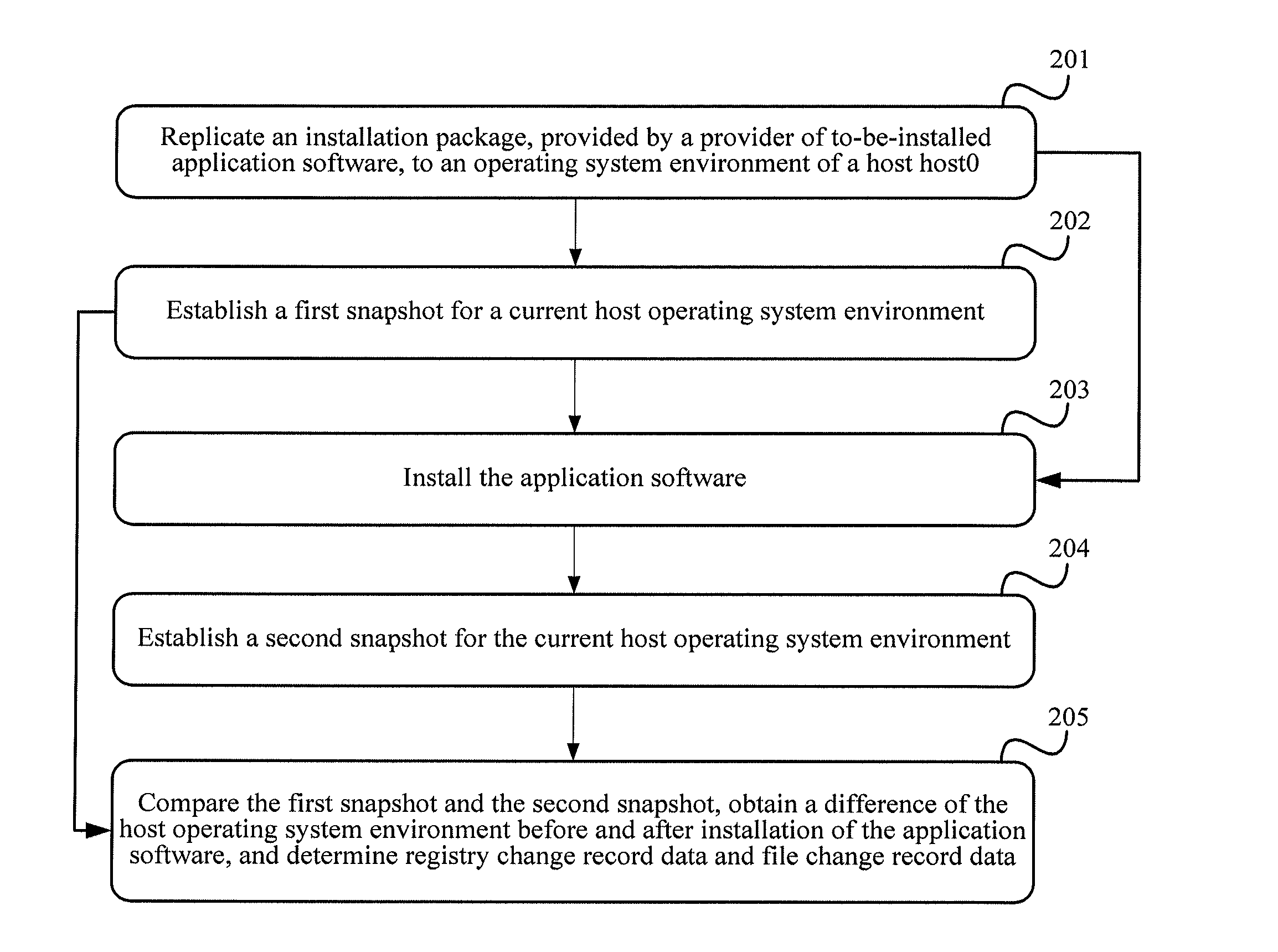
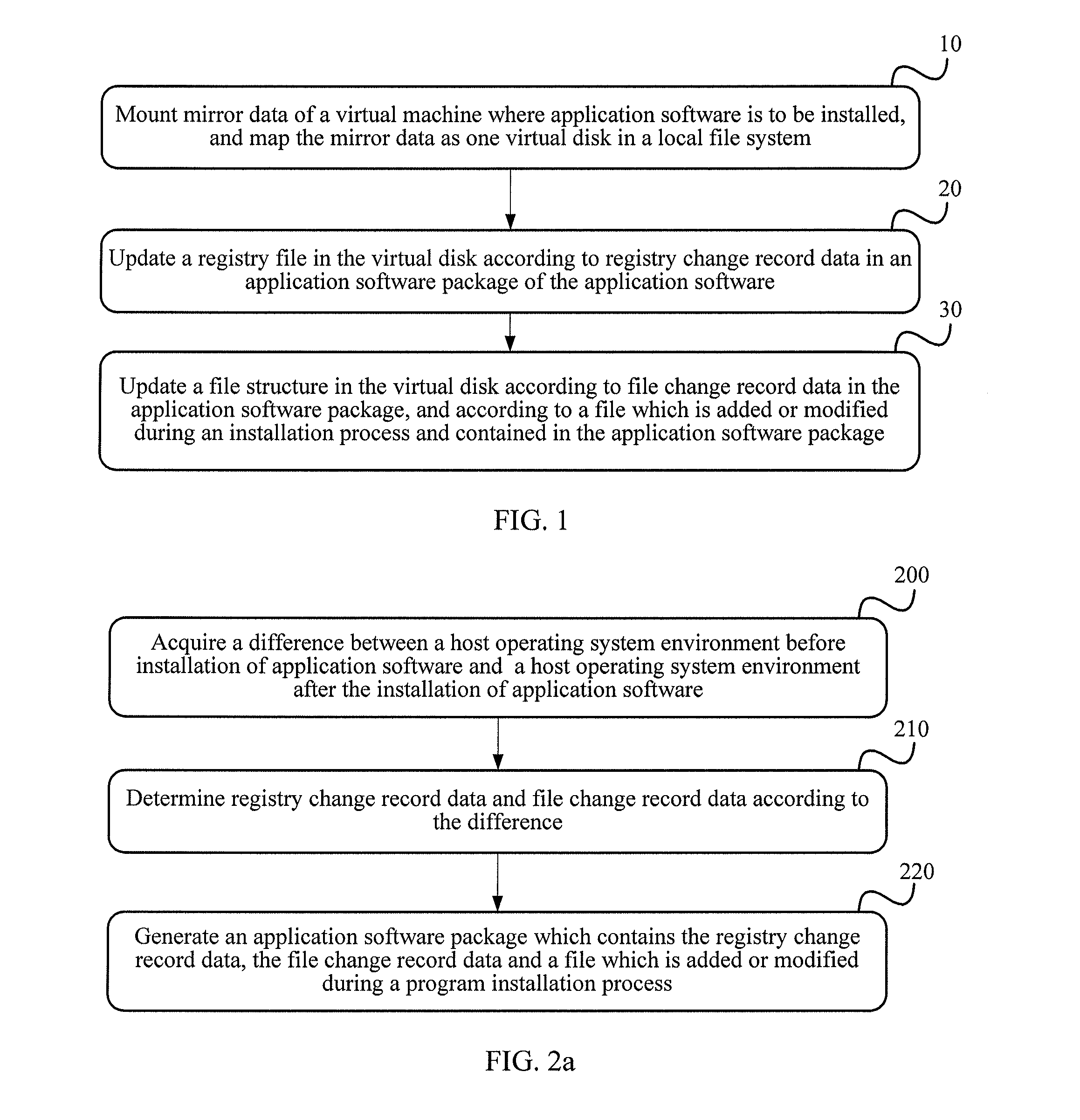
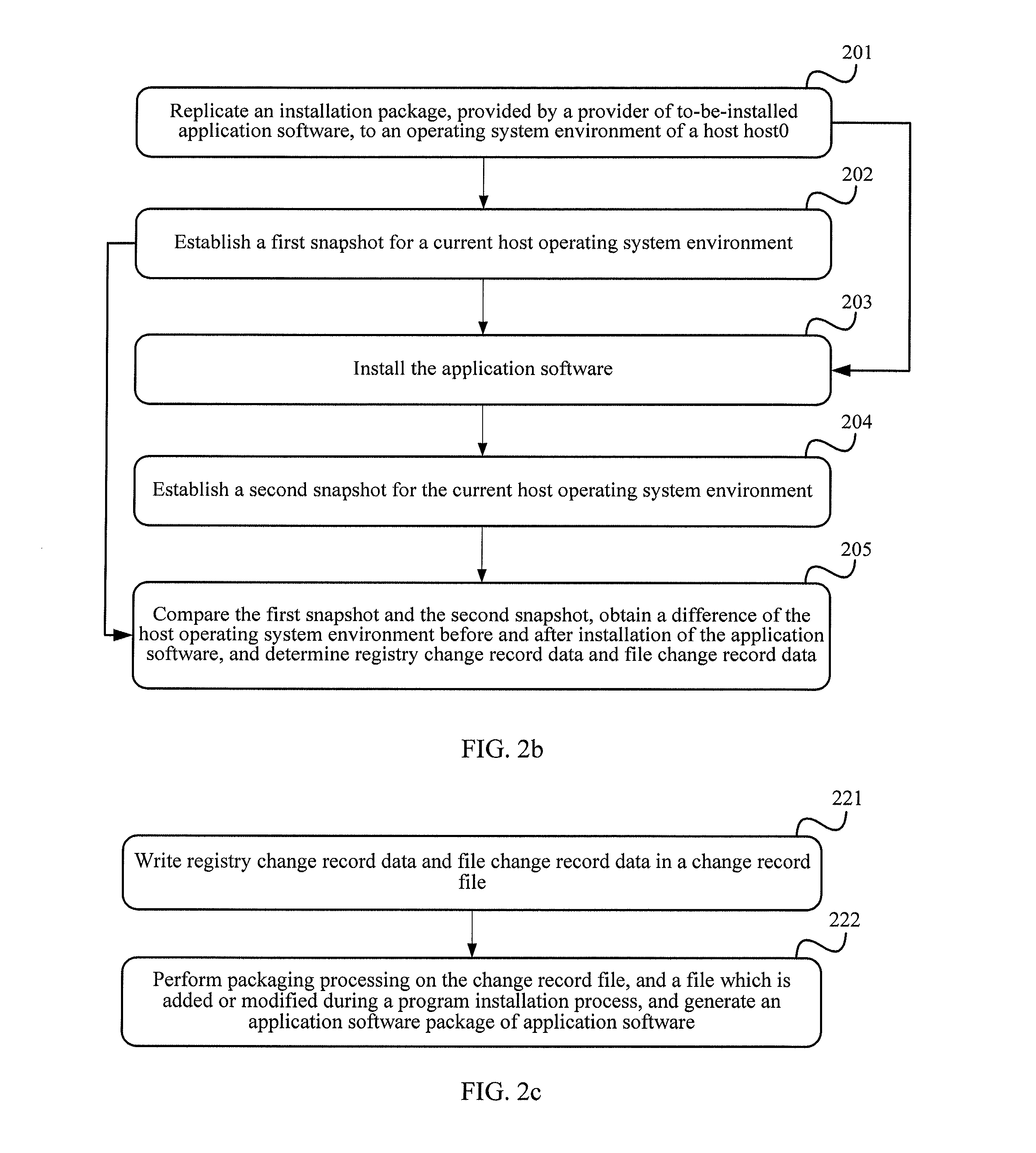
Application software installation method and application software installation apparatus
ActiveUS20130132942A1Reducing software installation difficultyComplicated operationProgram loading/initiatingMemory systemsFile systemSoftware engineering
An application software installation method and an application software installation apparatus are used to solve problems of operation complexity and high implementation difficulty in an existing installation process of application software. The method includes: mounting mirror data of a virtual machine, and mapping the mirror data as one virtual disk in a local file system; updating a registry file in a virtual disk according to registry change record data in an application software package; and updating a file structure in the virtual disk according to the file change record data and the file in the application software package, thereby implementing installation of the application software in the virtual machine. In the process of installing the application software, a user of the virtual machine does not need to perform complex operations, thereby reducing software installation difficulty.
Owner:HUAWEI TECH CO LTD
Multiple service bindings for a real time data integration service
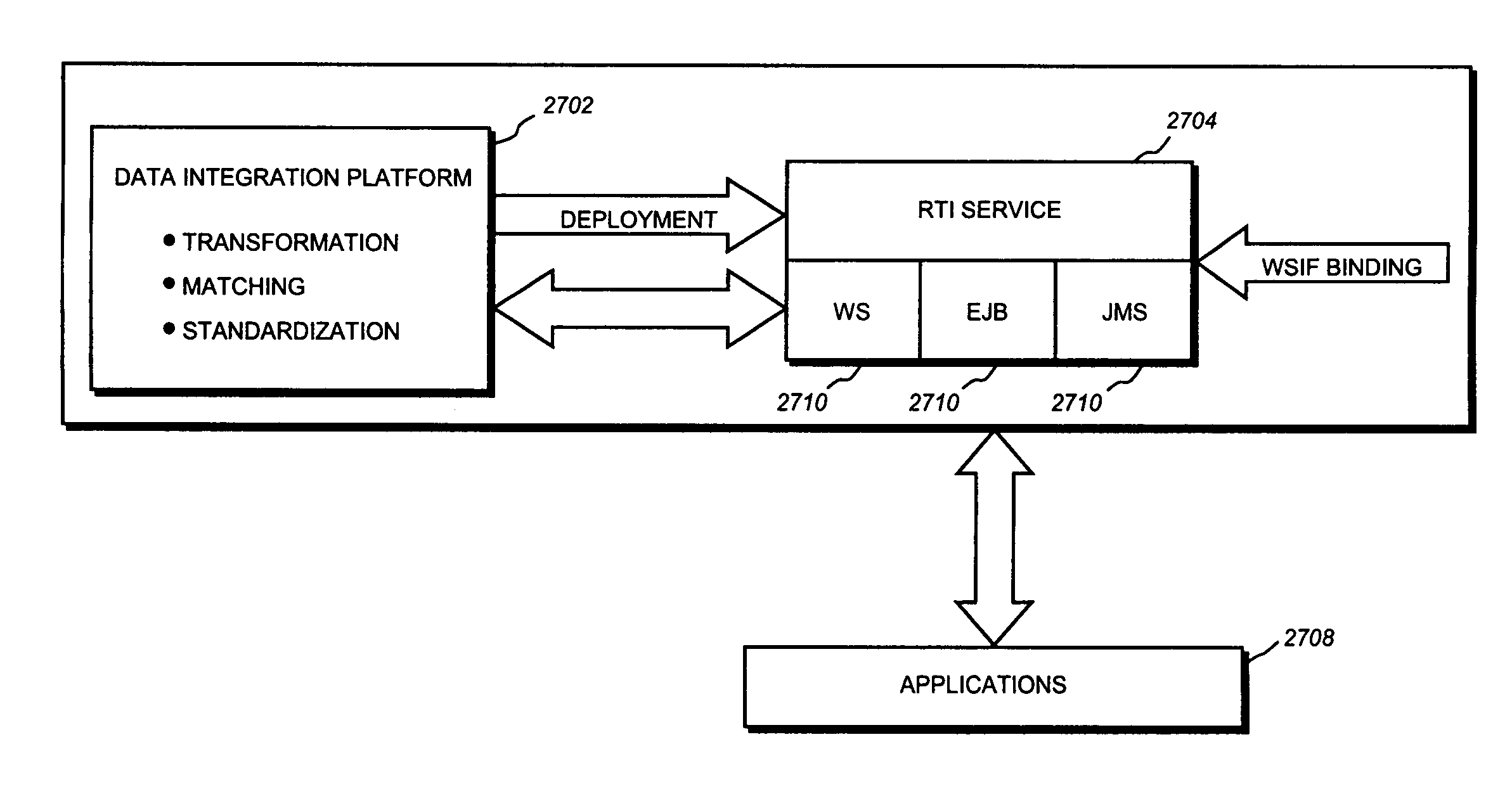
InactiveUS7814470B2Easy accessSimple interfaceDigital data information retrievalDigital data processing detailsData transformationMetadata management
Real time data integration jobs are deployed in a services oriented architecture as services that allow multiple service bindings. In one aspect, a method includes providing a code module executing a data integration job and a registry of services for storing the code module. When the code module is identified in the registry, access is provided to the code module in the registry of services, in real time wherein the code module may be accessed by more than one type of service binding such that different applications can utilize the real-time integration service using different protocols to invoke the real-time integration service. At least one of the types of service bindings may be an EJB binding, a SOAP binding, a JMS binding, and a web service binding. The data integration job may include an extraction job, a data transformation job, a loading job, a metadata management job, and a data quality job.
Owner:INT BUSINESS MASCH CORP
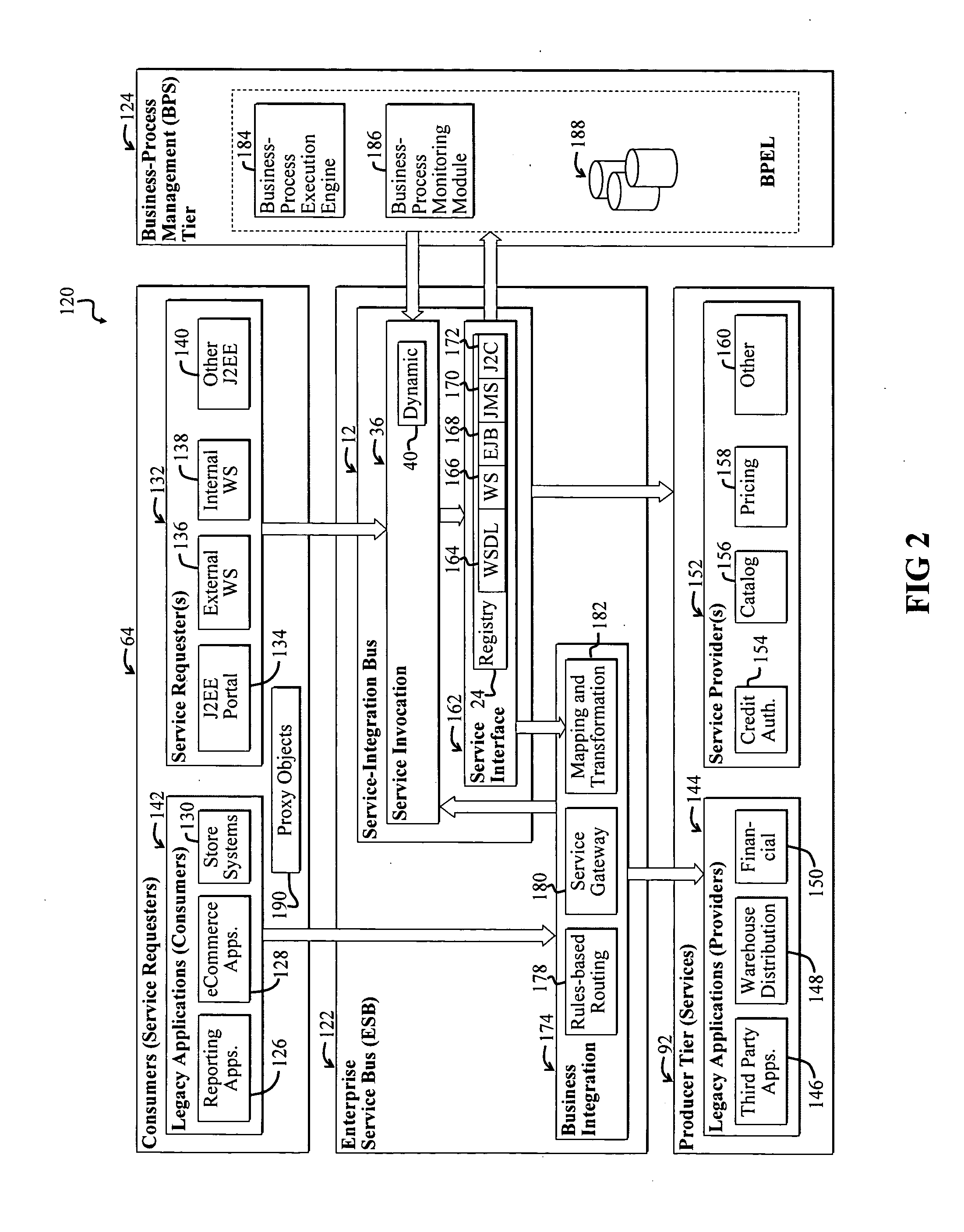
Service-oriented architecture
InactiveUS20070011126A1ModificationEasy to adaptData processing applicationsKnowledge representationService implementationReusability
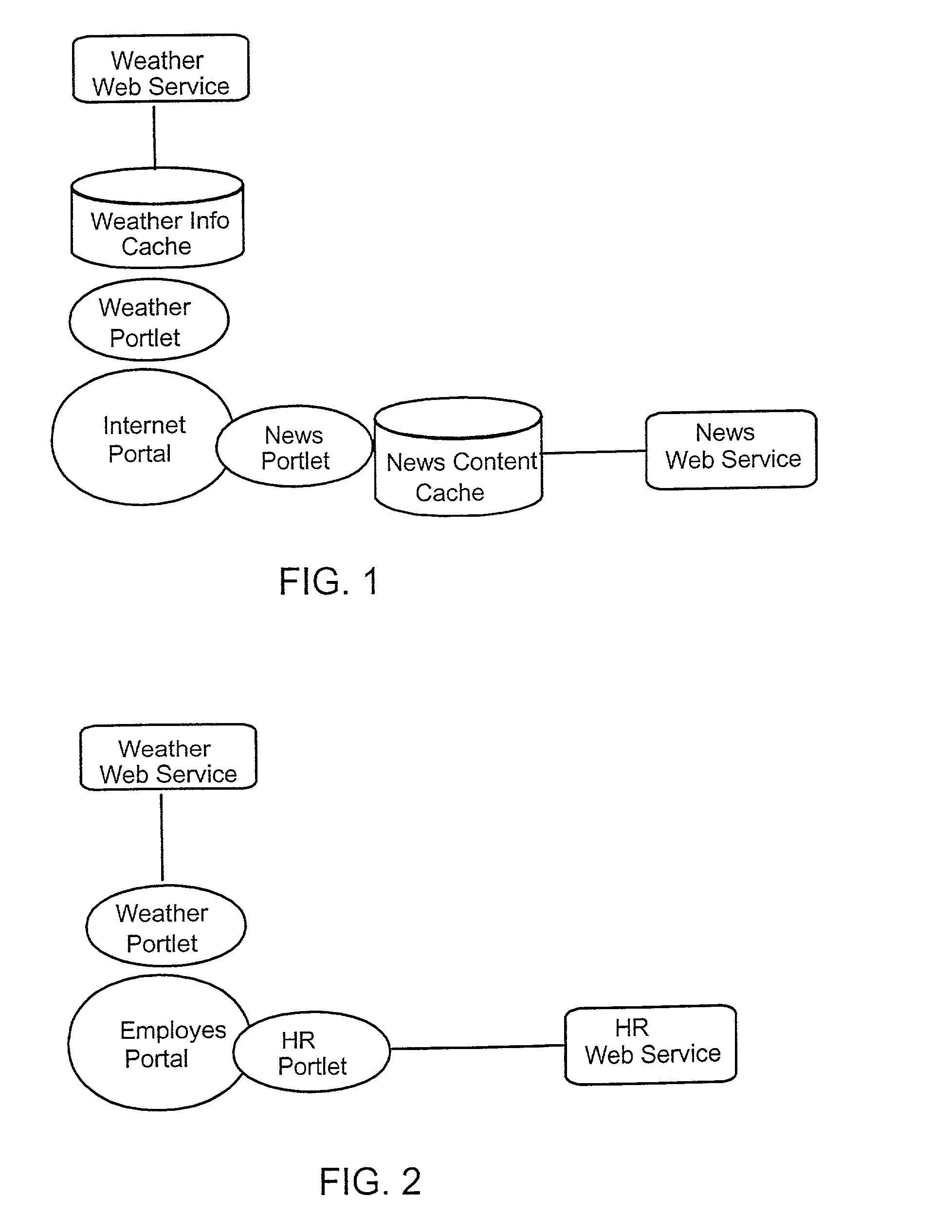
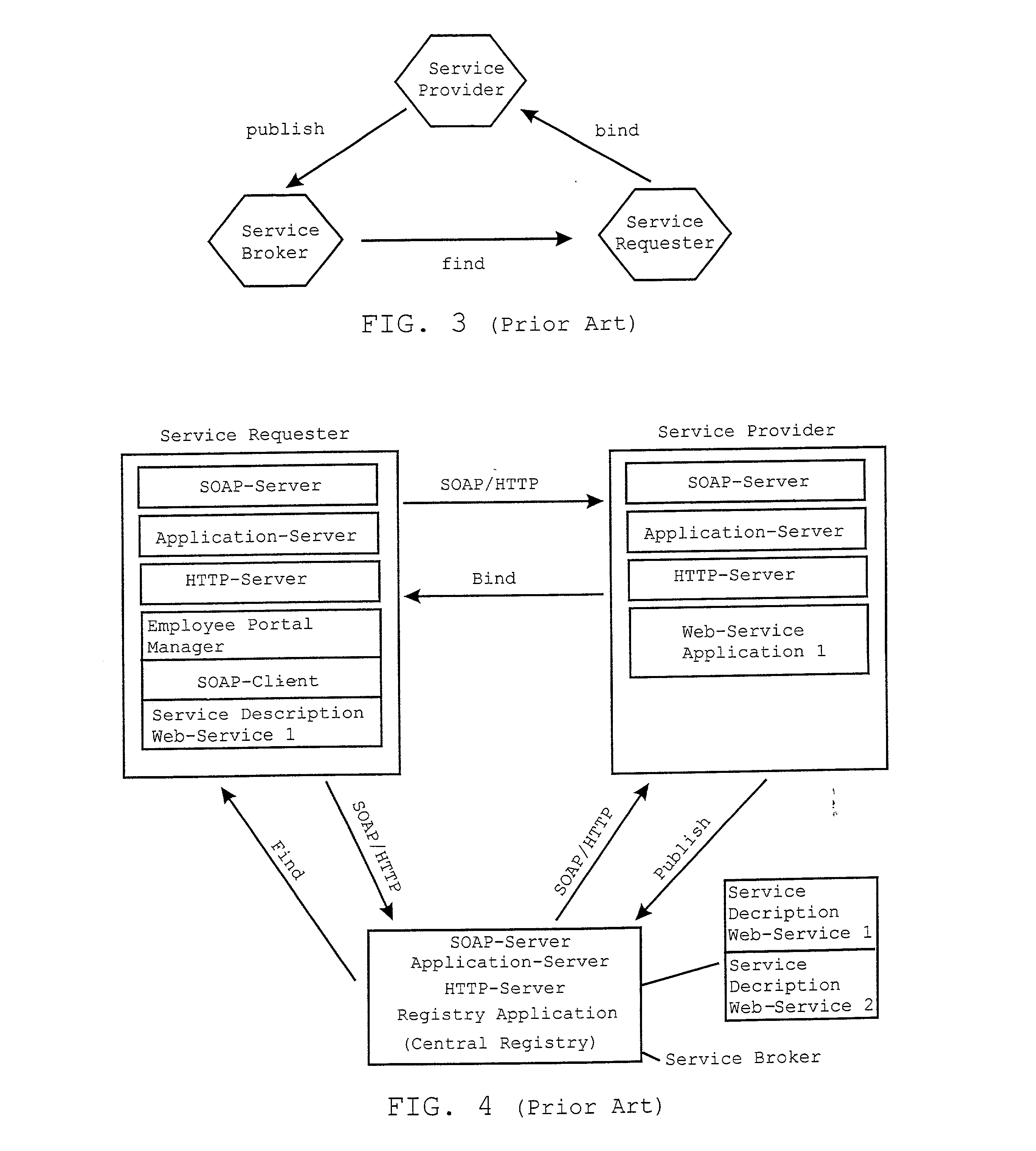
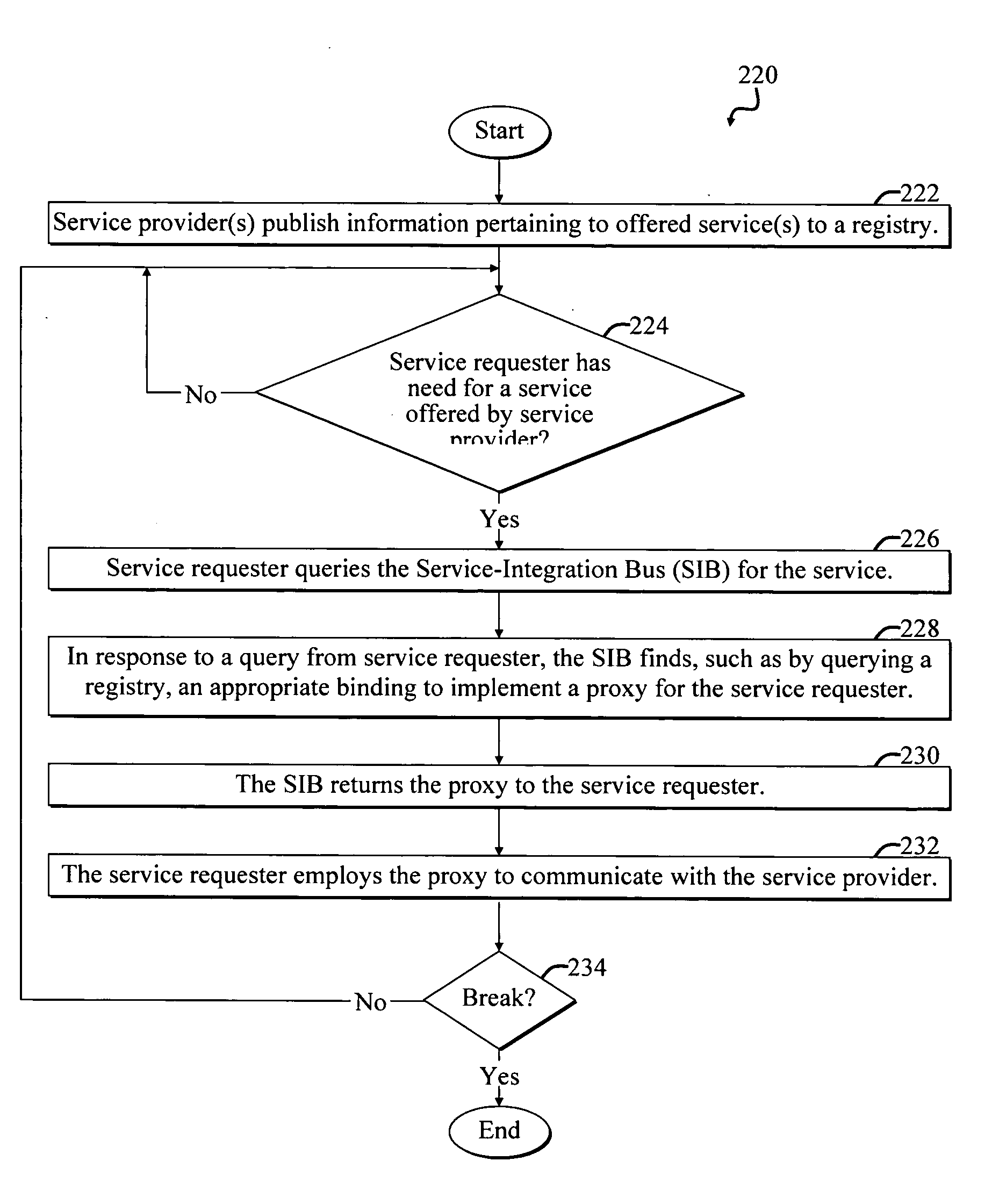
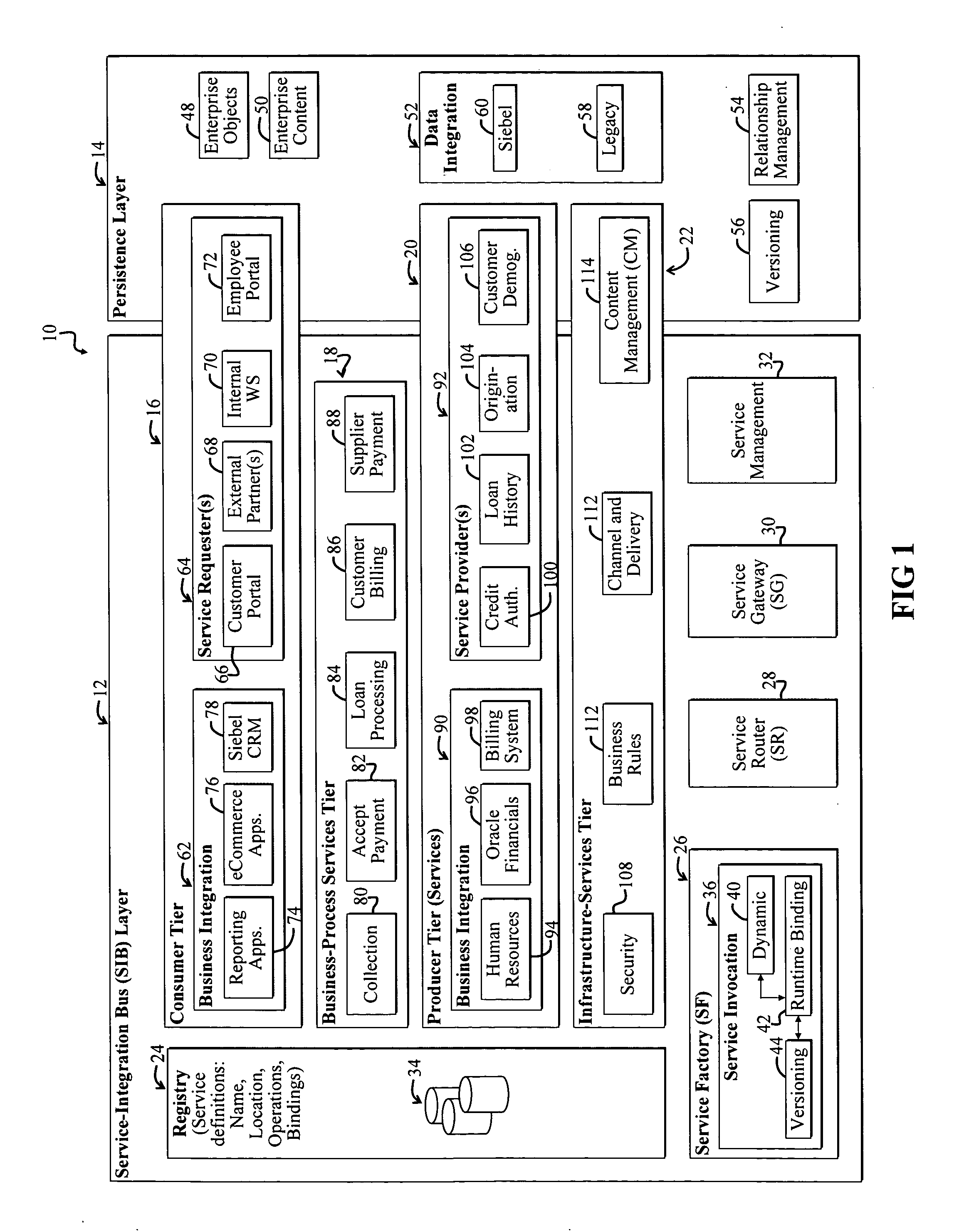
A Service-oriented architecture (SOA) and accompanying method. In one embodiment, the SOA includes one or more service requesters coupled to one or more service providers via a bus. The bus includes runtime-binding functionality to facilitate interaction between the one or more service requesters and the one or more service providers. A registry, which stores information pertaining to a service provided by the one or more service providers, communicates with one or more service providers and / or requesters and the bus. In a more specific embodiment, bus includes a Service-Integration Bus (SIB) that includes a Service-Factory (SF) module for facilitating implementing the runtime binding functionality and for selectively invoking the service. Functionality of the SOA is strategically organized into various tiers and layers, including a requester tier, a provider tier, a business-process services tier, an infrastructure-services tier, an SIB layer, a persistence layer, and so on, to optimize system reusability, adaptability, and other desirable properties. A service interface pattern is described whereby a change in service implementation does not require modification to the manner in which the service is invoked by a requester
Owner:PRIMITIVE LOGIC
Secure sharing of personal devices among different users
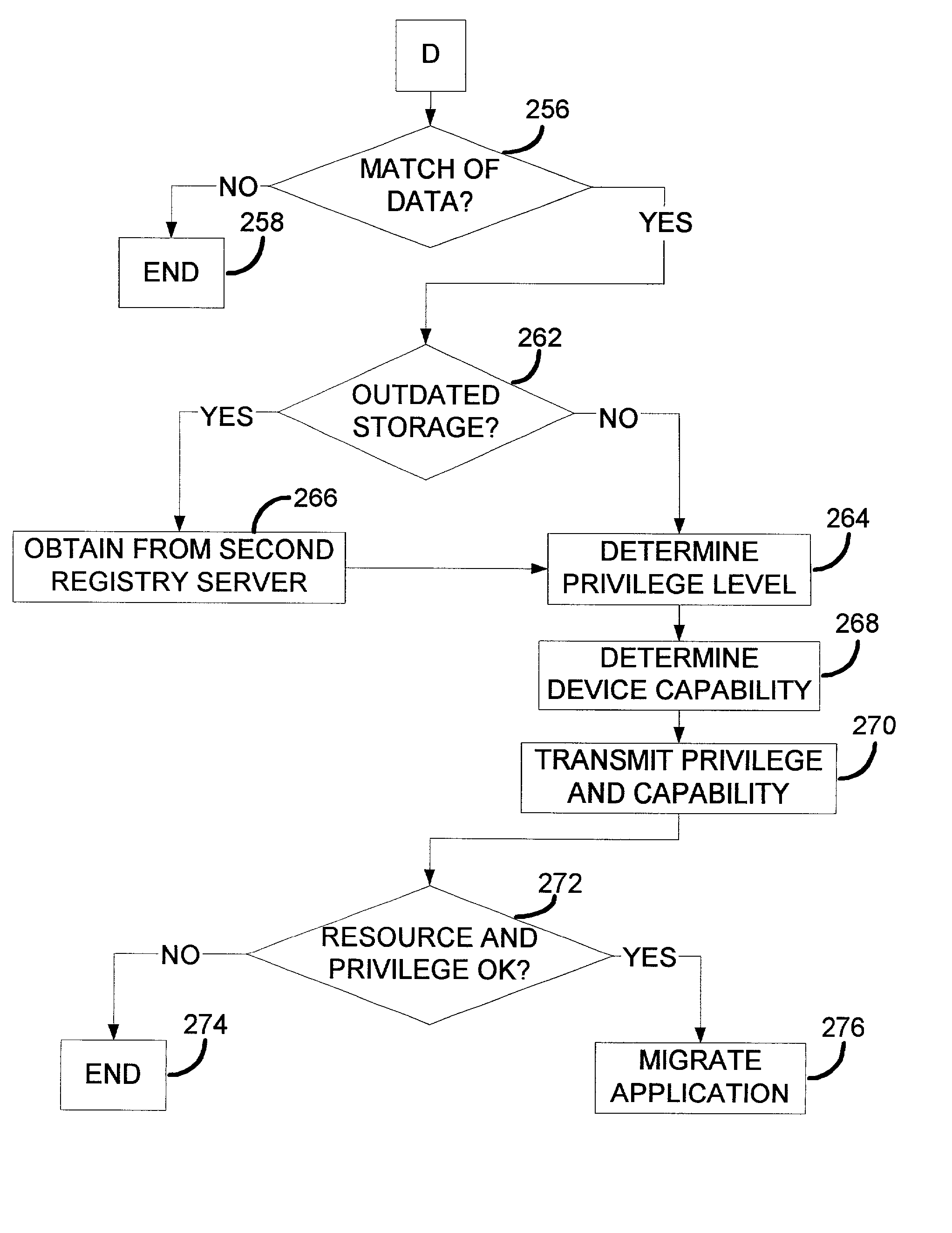
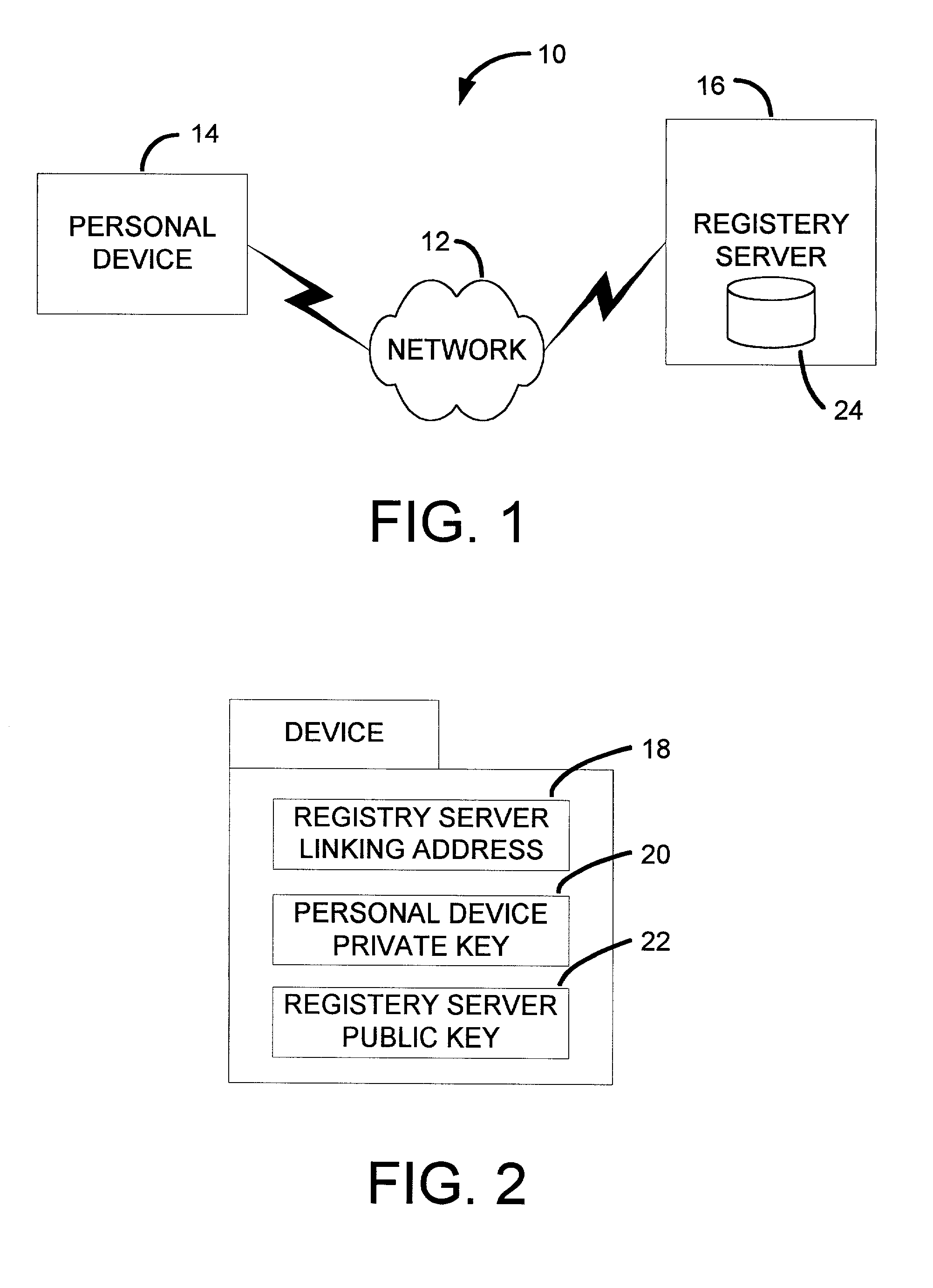
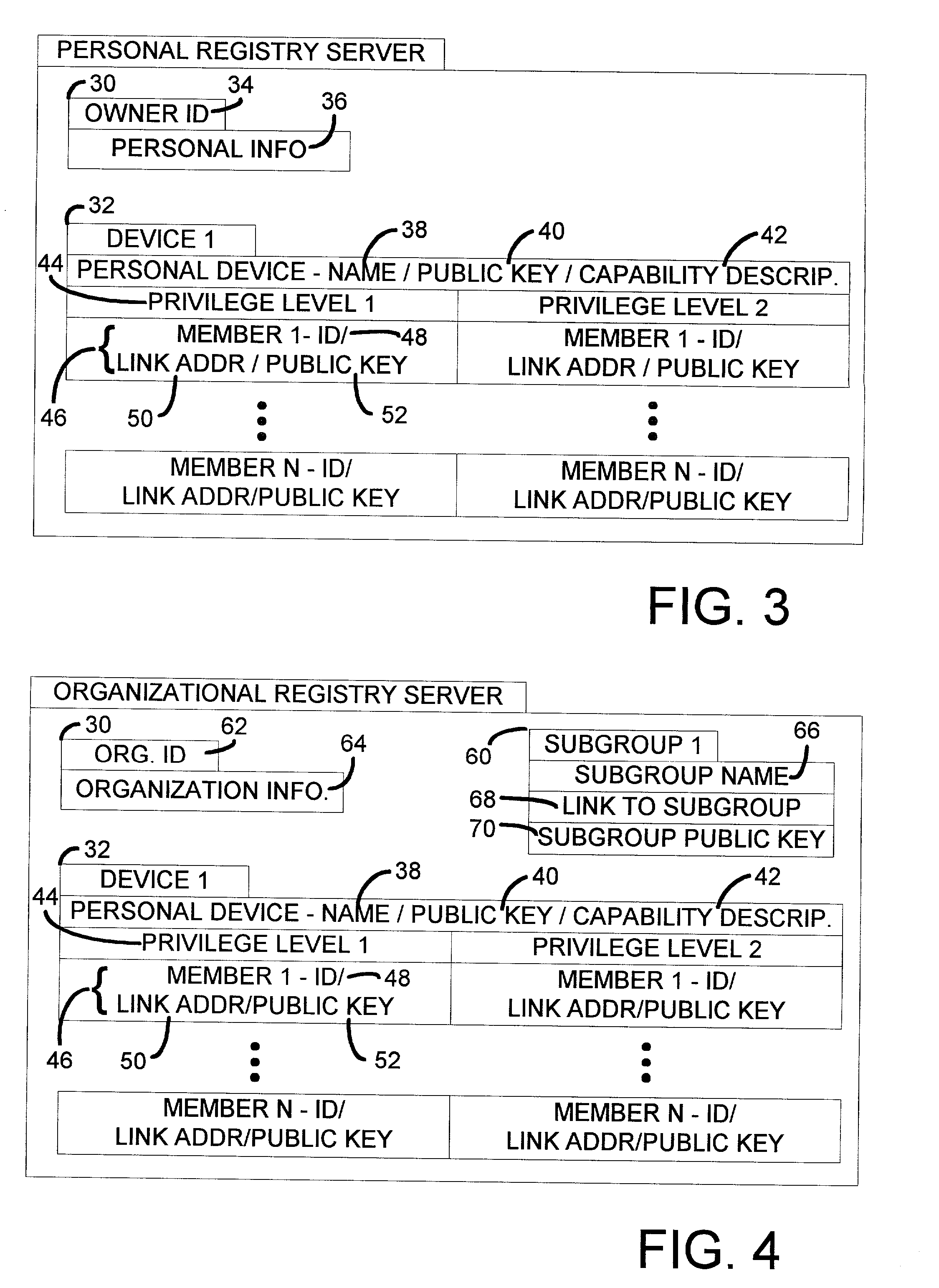
ActiveUS20030065947A1Improve privacyImprove scalabilityMemory loss protectionError detection/correctionDevice registerInternet privacy
A registry architecture for securely sharing personal devices among different users is disclosed. The registry architecture is a distributed architecture that includes at least one registry server communicating over a network with at least one personal device. The architecture provides verification and authorization of users and applications on personal devices registered with the registry server. In addition, secure migration of applications between a first personal device and at least one second personal device may be performed as a function of the registry architecture. Further, the ability to securely share a personal device among different users is provided by identification of potential users of the personal device within the registry architecture.
Owner:NTT DOCOMO INC
Method and apparatus for identifying the existence of differences between two files
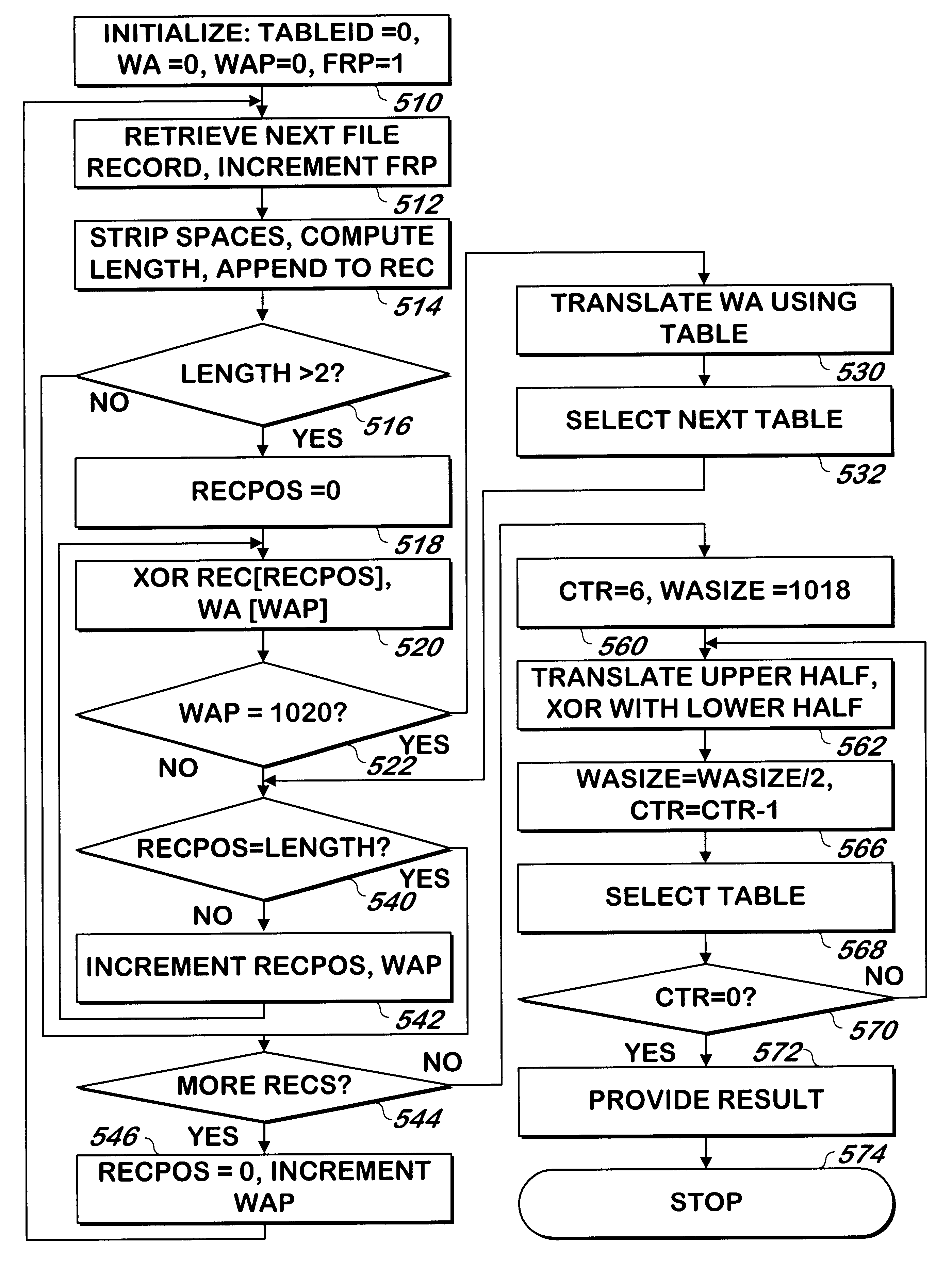
InactiveUS6393438B1Reduce probabilityData processing applicationsDigital data processing detailsHigh probabilityPersonal computer
A method and apparatus identifies the existence of differences between two files on a personal computer, such as two versions of a Windows registry file. Portions of each of the files are hashed into a four byte value per portion to produce a set of hash results, and the set of hash results is combined with a four byte size of the portion of the file from which the hash was generated to produce a signature of each file. If the two files are different versions of a Windows registry file, the portion of the file hashed are the values of the Windows registry file. If the two files are different, there is a high probability that the signatures of the two files will be different. The signatures may be compared to provide a strong indicator whether the two files are different. Each four-byte hash from one file can be compared against its counterpart from the other file to determine the portion or portions of the files that differ. Stored portions of one file that are determined to differ may be inserted into corresponding portions of the other file to cause the two files to be equivalent.
Owner:SERENA SOFTWARE
Rights Management Systems and Methods Using Content Identifiers
InactiveUS20080140433A1Difficult to controlDifficult to trackRecord information storageAnalogue secracy/subscription systemsContent IdentifierRights management
Owner:DIGIMARC CORP
Creating a virtual machine image with a software deployment system
InactiveUS20080307414A1Deficiency correctedSoftware simulation/interpretation/emulationMemory systemsState switchingSoftware deployment
A novel method is disclosed for capturing an installed state of a conventional application and converting the captured state into a virtual application. The novel method starts with a bare machine in a known state, preferably soon after the OS was installed. Installation scripts are used to install one or more software applications along with required components and dependencies. Other artifacts can be added and configured such as files, trees, directories, entries, data, values, among others. These also may include updates to various system databases, such as the Windows registry in which certain metadata is stored. The installed applications are tested and verified to work as desired. Undesired artifacts can be deleted manually or removed by the OS. The state of the virtual machine with the installed applications is captured. The installed applications can be tested on the frozen virtual machine. If the user determines that the installed applications are working properly, a virtual machine image is prepared and then written out. The resulting output is a new populated virtual application container that encapsulates the applications installed and configured by the user. If the user determines that one or more installed applications do not work properly during testing, then the frozen virtual machine can be unfrozen and any deficiencies corrected. The virtual machine image is stored as a launch document and a set of shards. The virtual machine image represents the state of the virtual machine along with the installed applications at the time the preparation virtual machine was frozen.
Owner:IBM CORP
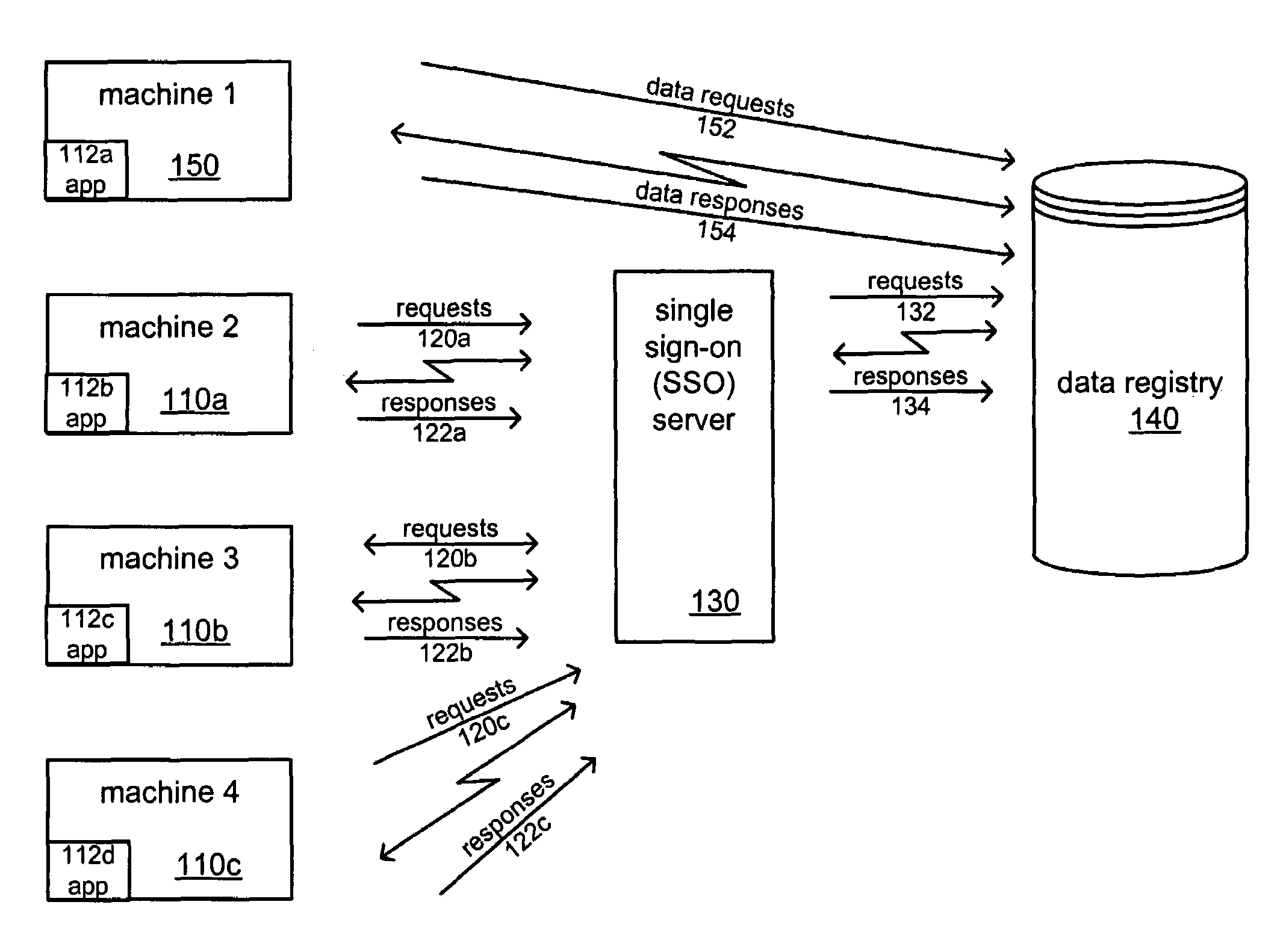
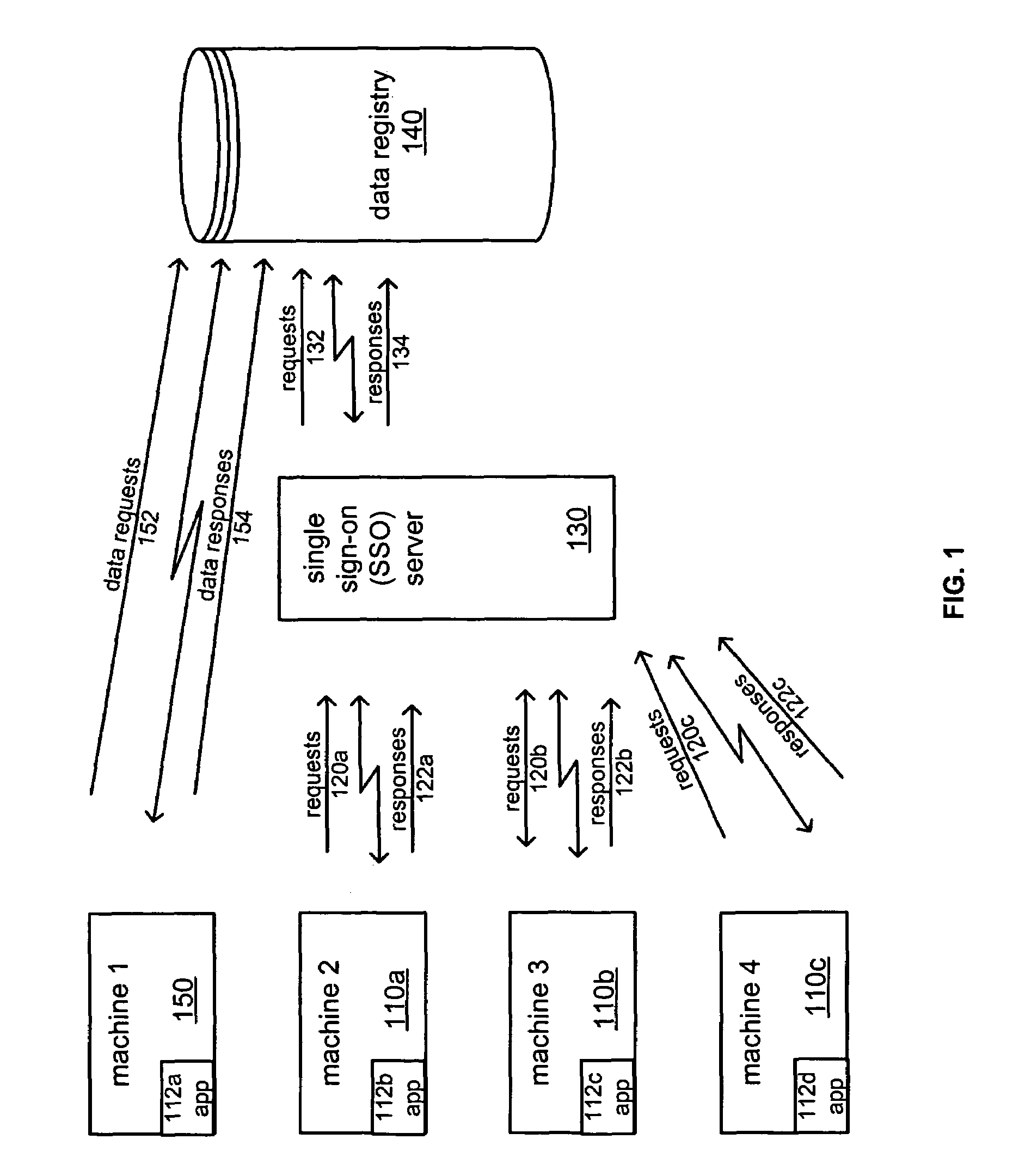
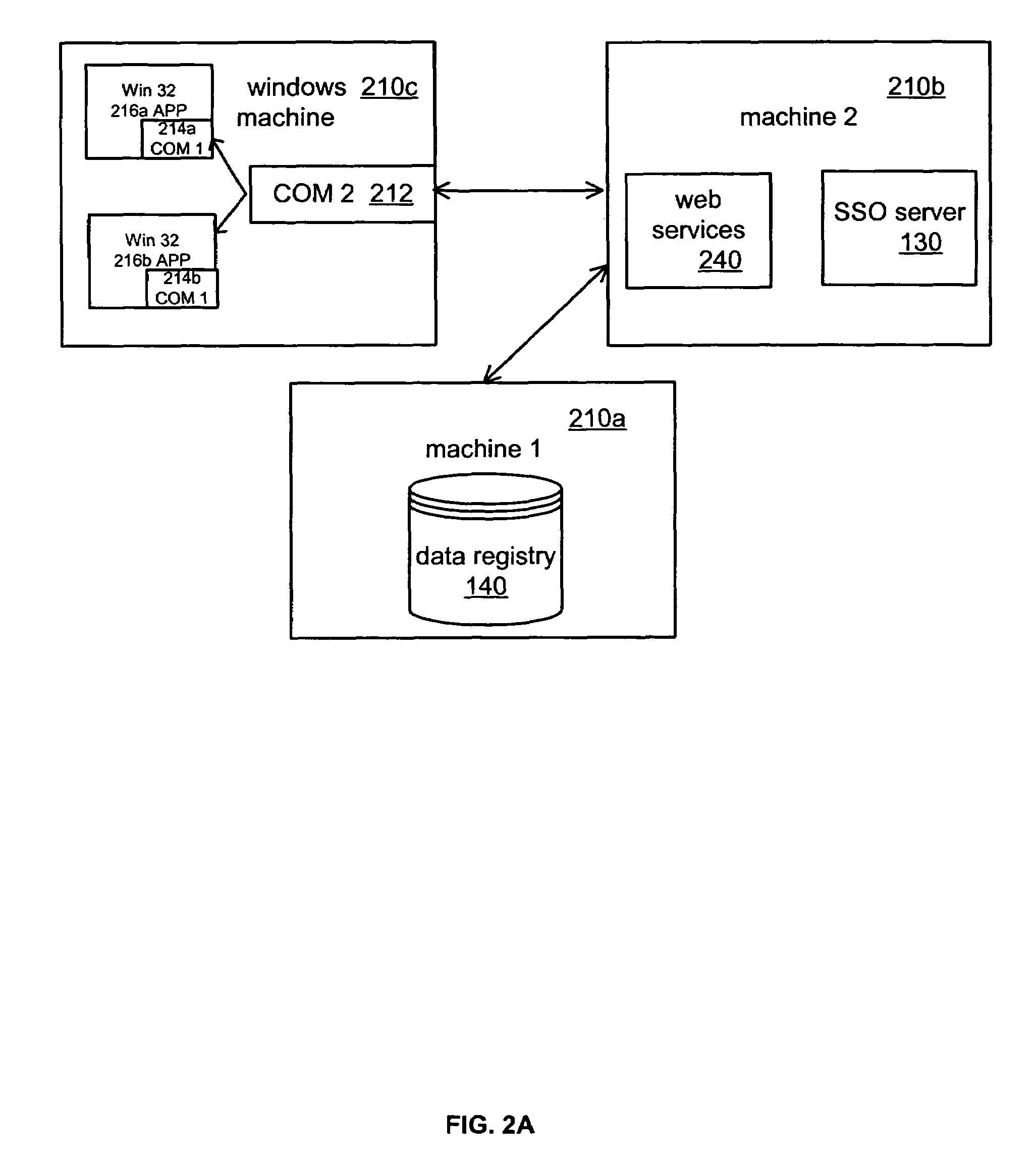
Cross-platform single sign-on data sharing
ActiveUS7509672B1Digital data processing detailsMultiple digital computer combinationsEnterprise computingApplication software
Systems and methods of authentication and data sharing across applications and platforms based on a single authentication are described. The systems and methods allow a user, based on a single log on to an application, to be automatically logged on to other applications and to fetch and store preference, state, and setting data across enterprise computing systems that include multiple computing platforms and applications. A data registry stores authentication and non-authentication data. An interface for automatically executing authentication transactions for the applications and facilitating the share of non-authentication data is also provided. The non-authentication data is user configurable to provide flexible application support across the enterprise, such as through the preservation of state information, preferences, settings, and application data across multiple computers.
Owner:BMC SOFTWARE
Open registry for provenance and tracking of goods in the supply chain
InactiveUS20180108024A1Avoid flowEncryption apparatus with shift registers/memoriesCryptography processingThird partyThe Internet
An identity system for the Internet of Things (IOT) that enables users and machines to identify, authenticate and interact with items / goods without relying on a third-party-controlled authentication service. The system includes tags having alphanumeric values and coupled to items / goods and an open registry database and ledger where digital records associated with the items / goods is able to be stored. The open registry enables public access to the items / goods and data combined with item registration anonymity.
Owner:CHRONICLED INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com