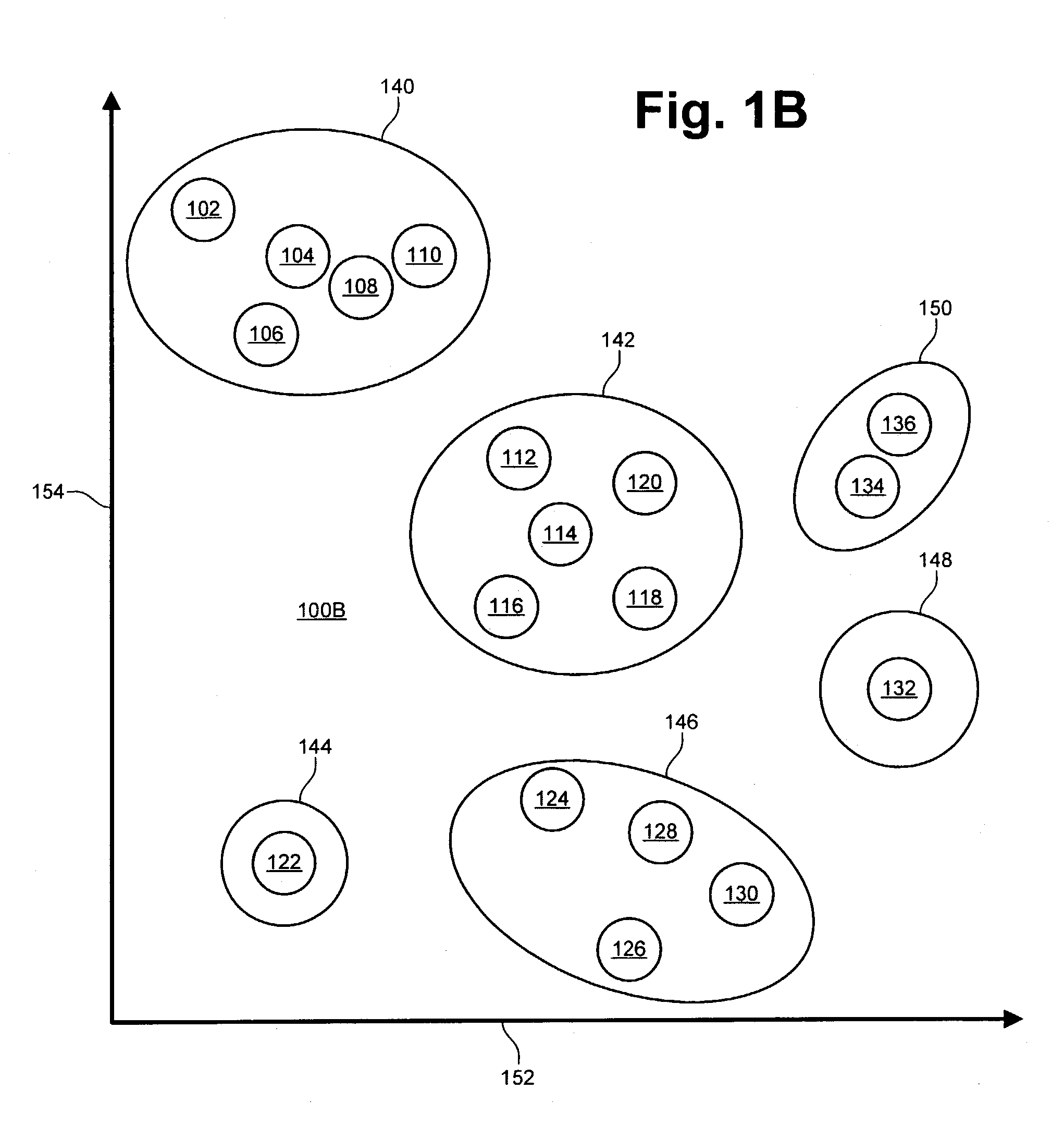
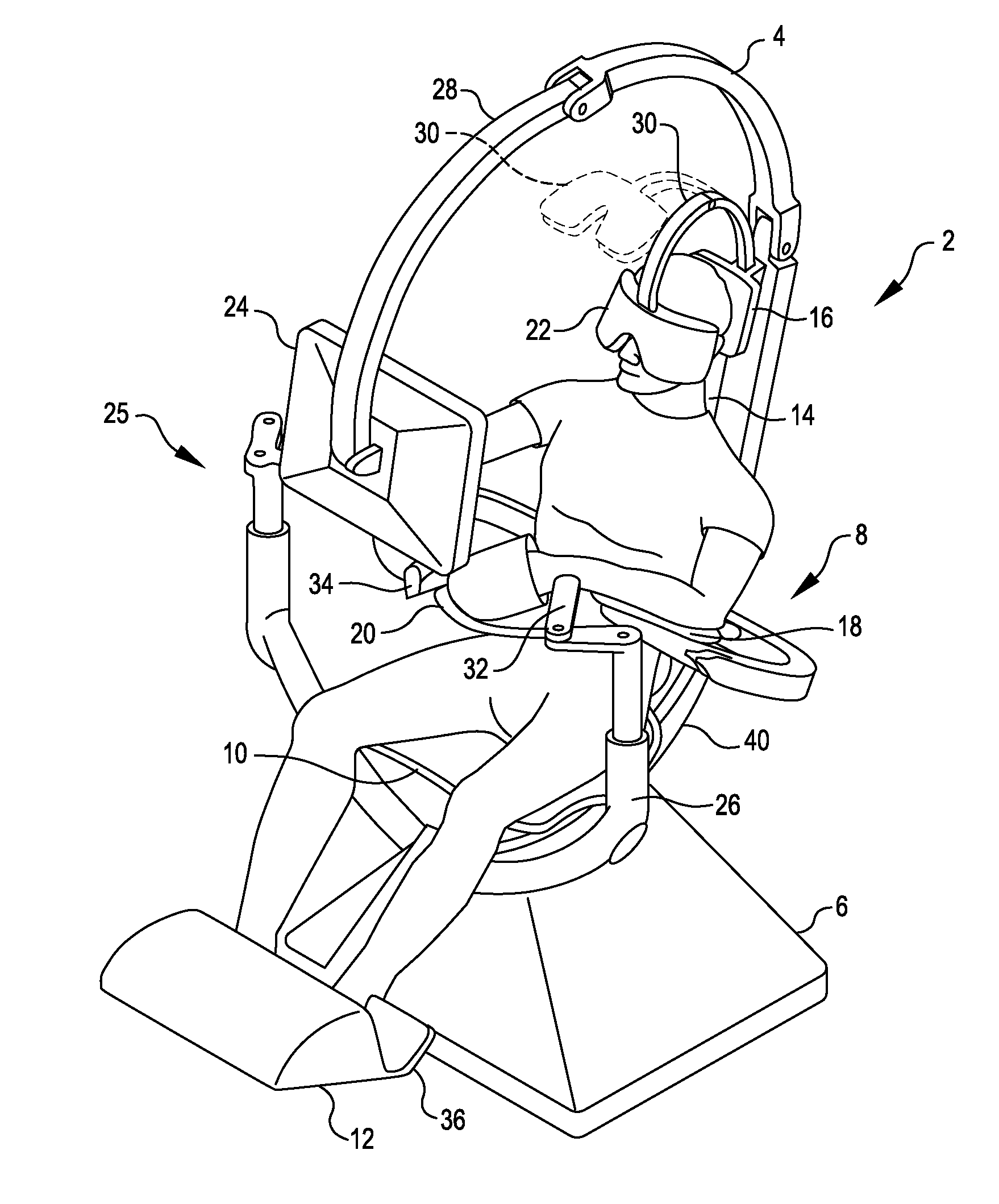
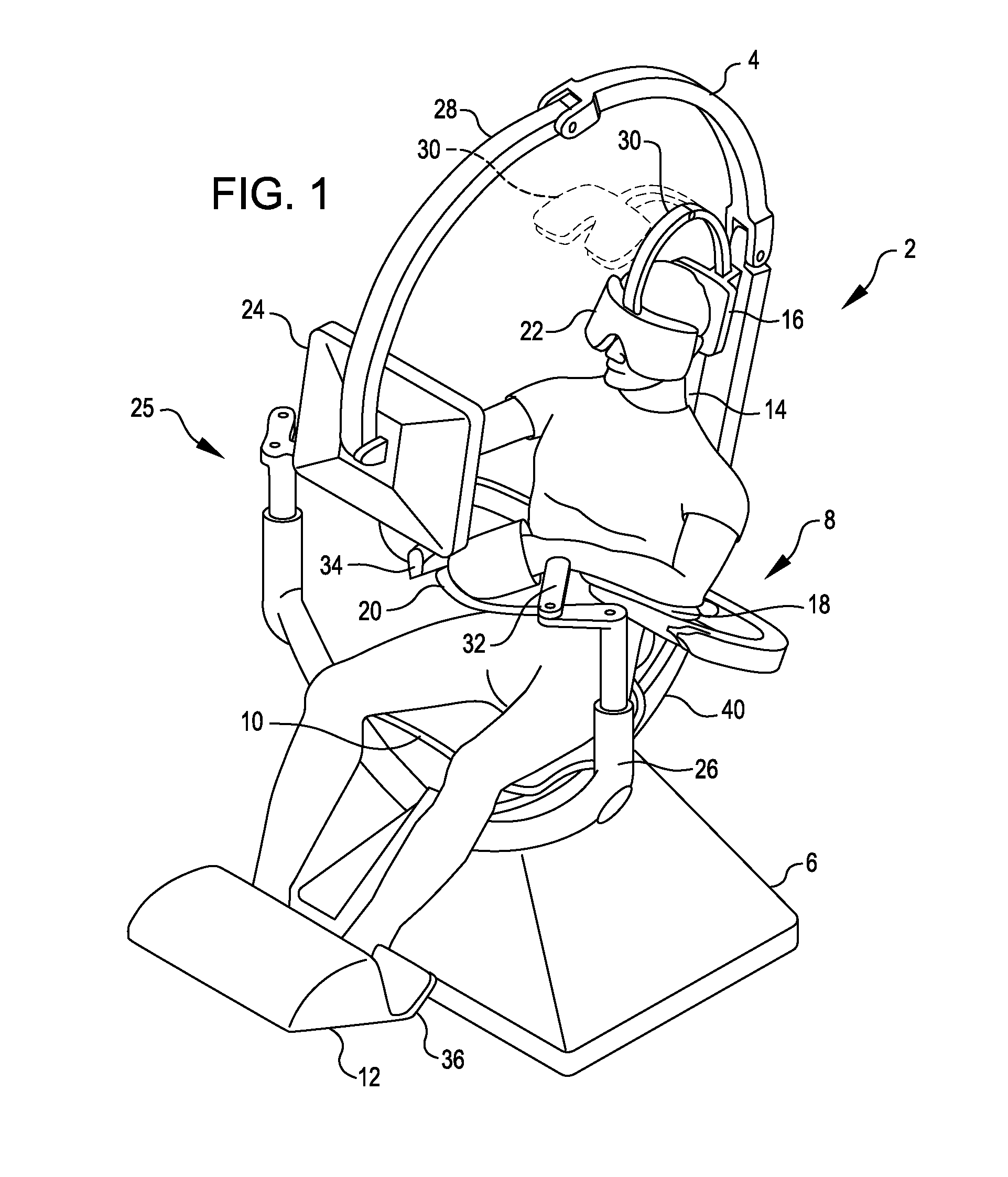
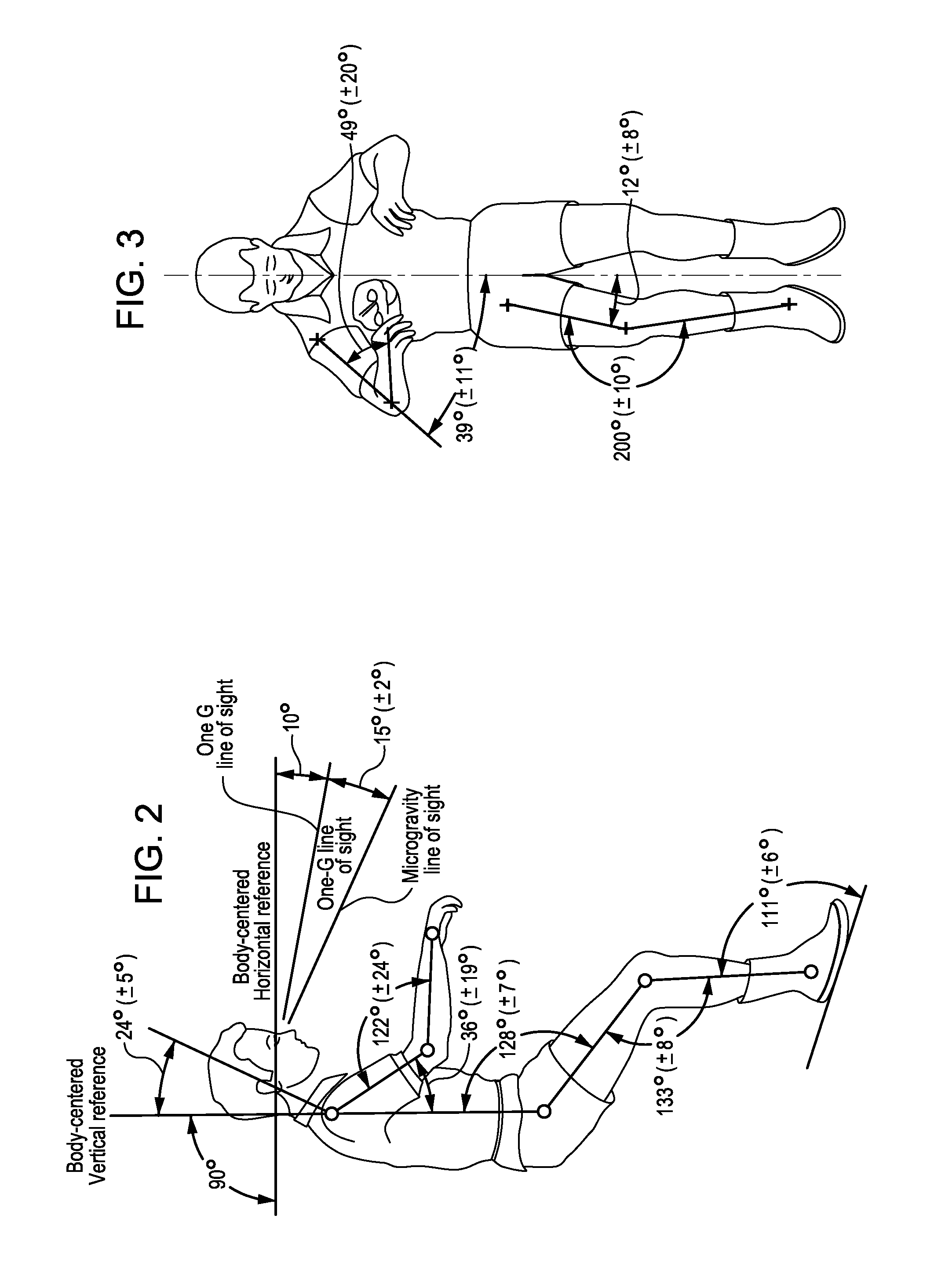
Patents
Literature
510results about How to "Inhibition of information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Context vector generation and retrieval
InactiveUS7251637B1Reduce search timeRapid positioningDigital computer detailsBiological neural network modelsCo-occurrenceDocument preparation
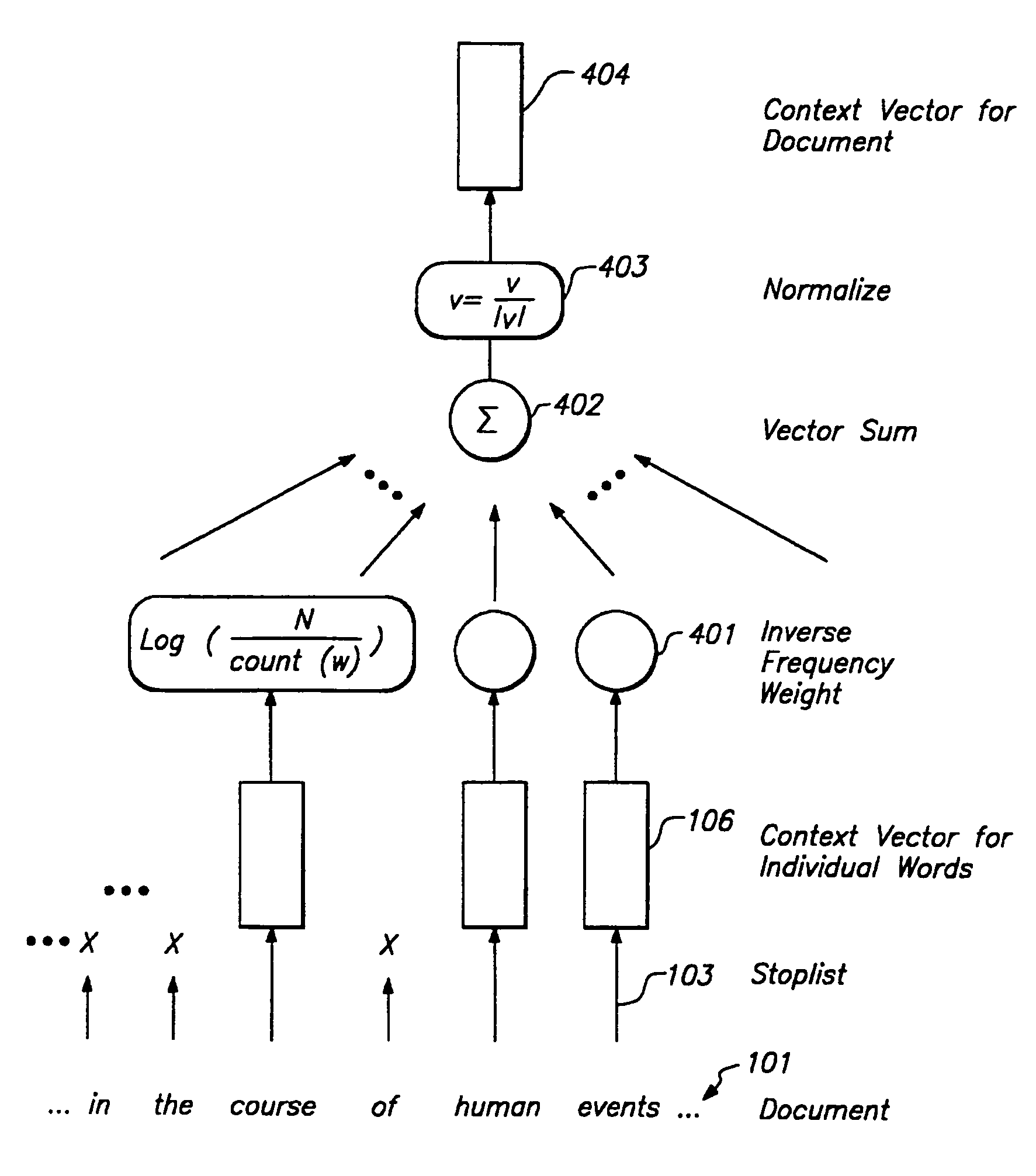
A system and method for generating context vectors for use in storage and retrieval of documents and other information items. Context vectors represent conceptual relationships among information items by quantitative means. A neural network operates on a training corpus of records to develop relationship-based context vectors based on word proximity and co-importance using a technique of “windowed co-occurrence”. Relationships among context vectors are deterministic, so that a context vector set has one logical solution, although it may have a plurality of physical solutions. No human knowledge, thesaurus, synonym list, knowledge base, or conceptual hierarchy, is required. Summary vectors of records may be clustered to reduce searching time, by forming a tree of clustered nodes. Once the context vectors are determined, records may be retrieved using a query interface that allows a user to specify content terms, Boolean terms, and / or document feedback. The present invention further facilitates visualization of textual information by translating context vectors into visual and graphical representations. Thus, a user can explore visual representations of meaning, and can apply human visual pattern recognition skills to document searches.
Owner:FAIR ISAAC & CO INC
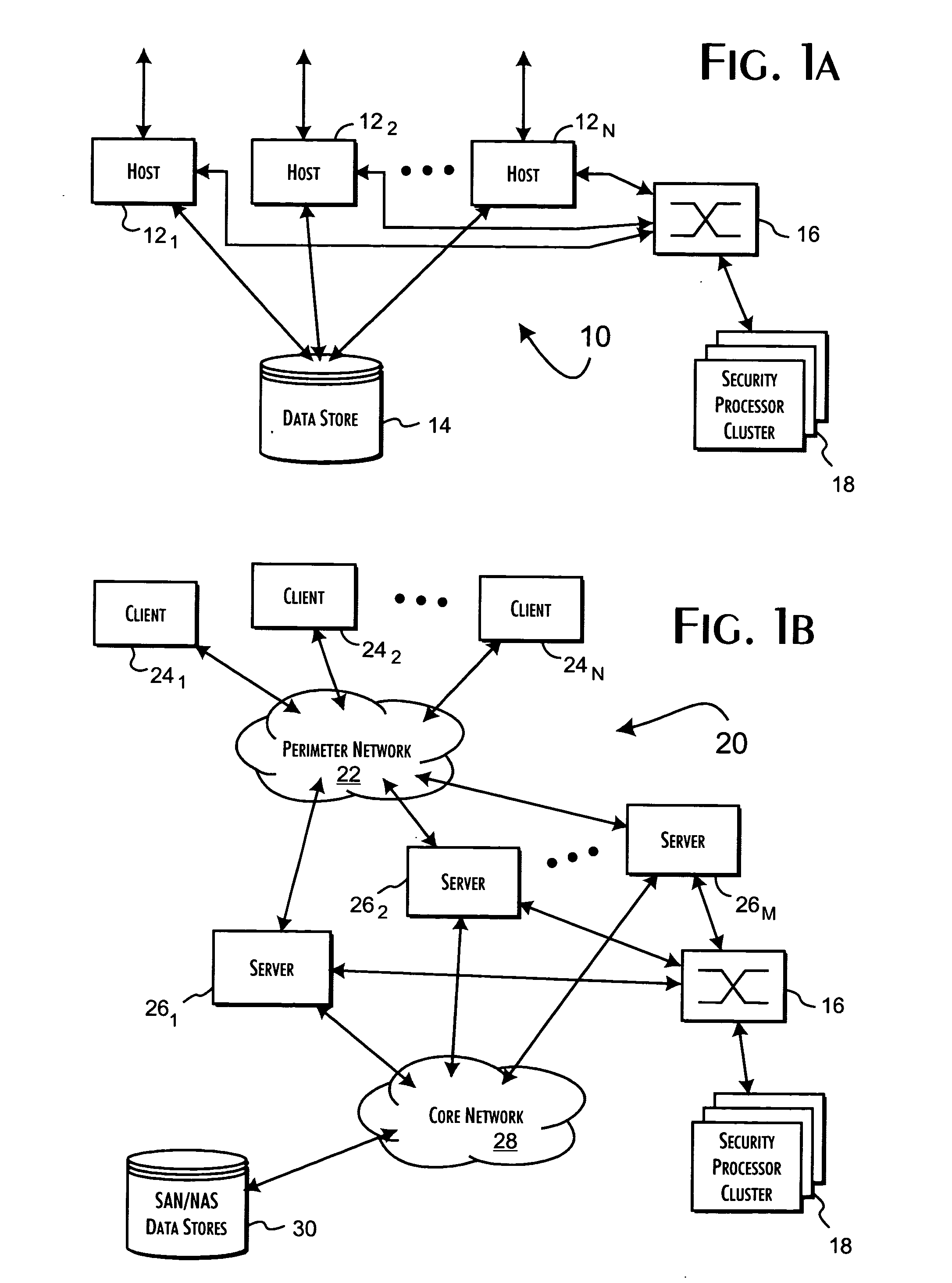
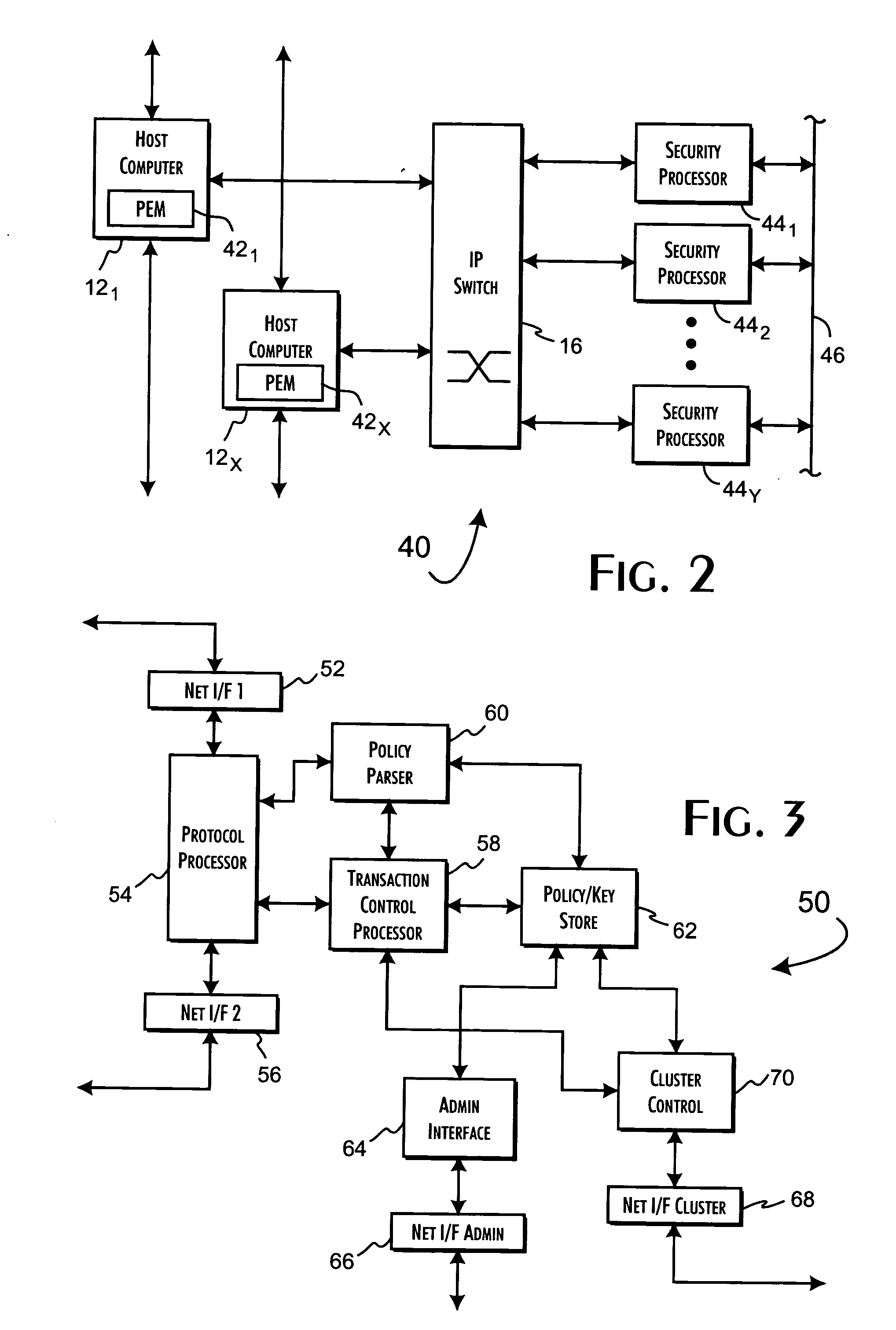
System and methods of cooperatively load-balancing clustered servers
InactiveUS20050027862A1No lost performanceEfficient load balancingDigital computer detailsMultiprogramming arrangementsComputerized systemNetwork service
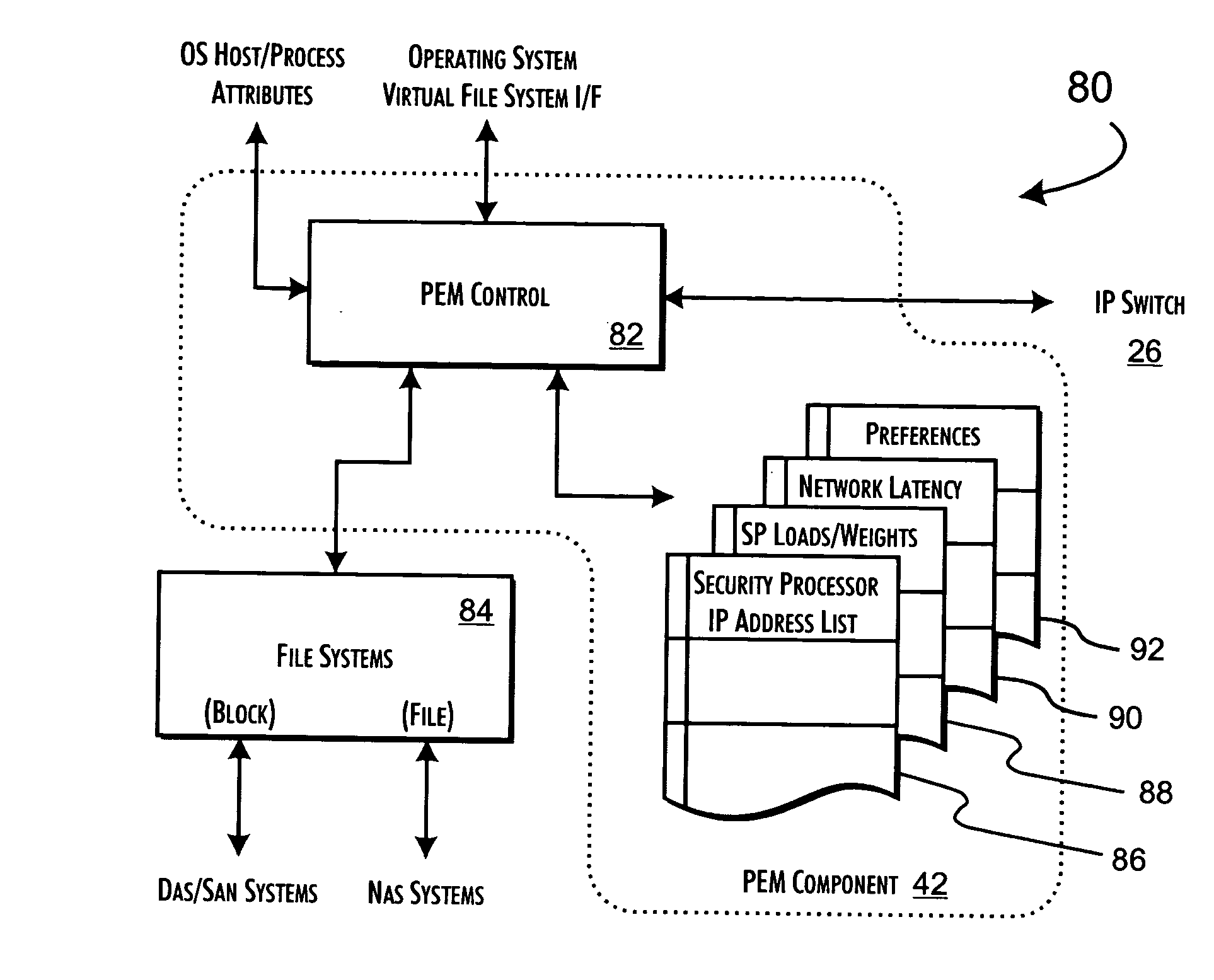
Host computer systems dynamically engage in independent transactions with servers of a server cluster to request performance of a network service, preferably a policy-based transfer processing of data. The host computer systems operate from an identification of the servers in the cluster to autonomously select servers for transactions qualified on server performance information gathered in prior transactions. Server performance information may include load and weight values that reflect the performance status of the selected server and a server localized policy evaluation of service request attribute information provided in conjunction with the service request. The load selection of specific servers for individual transactions is balanced implicitly through the cooperation of the host computer systems and servers of the server cluster.
Owner:VORMETRIC INC
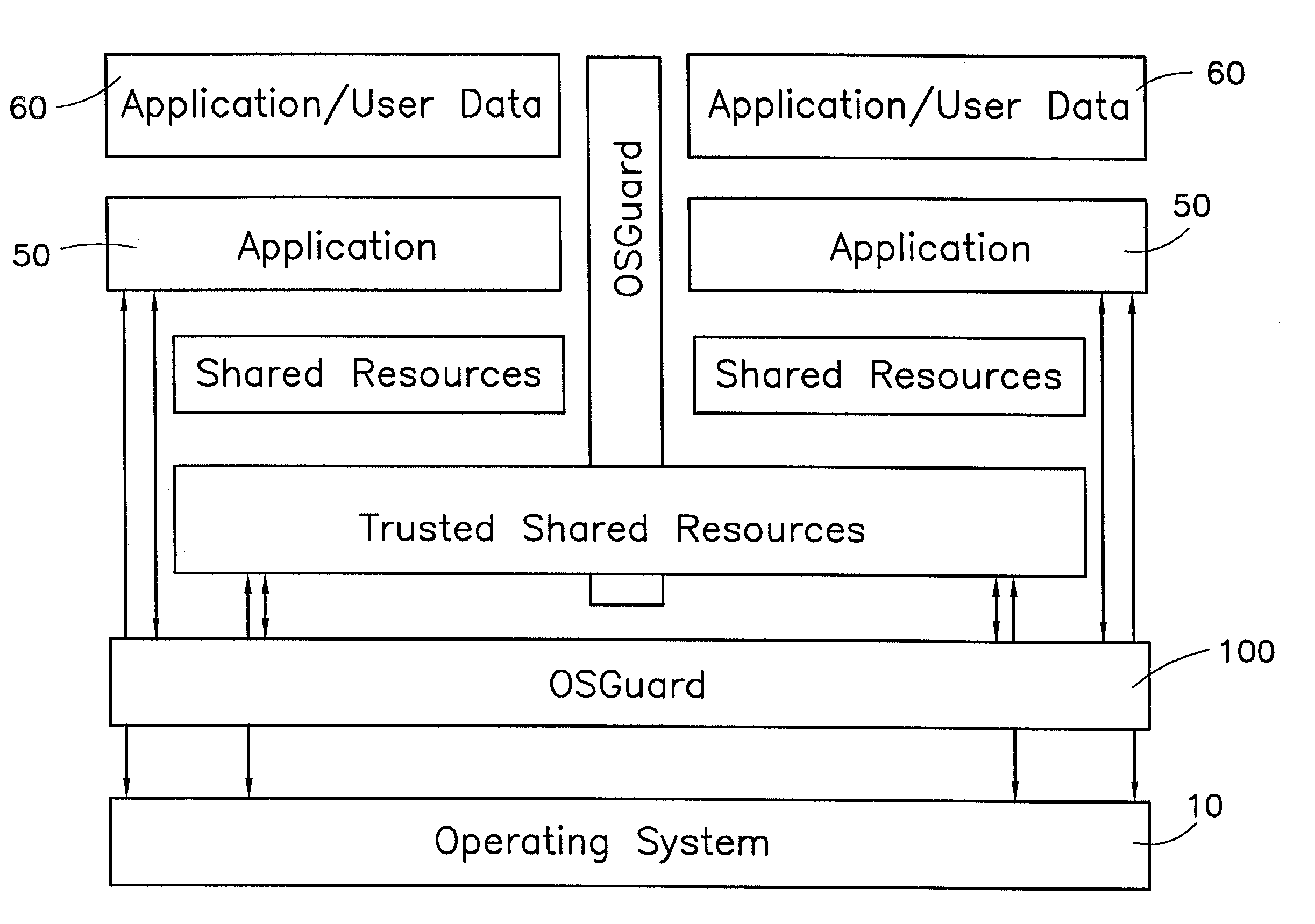
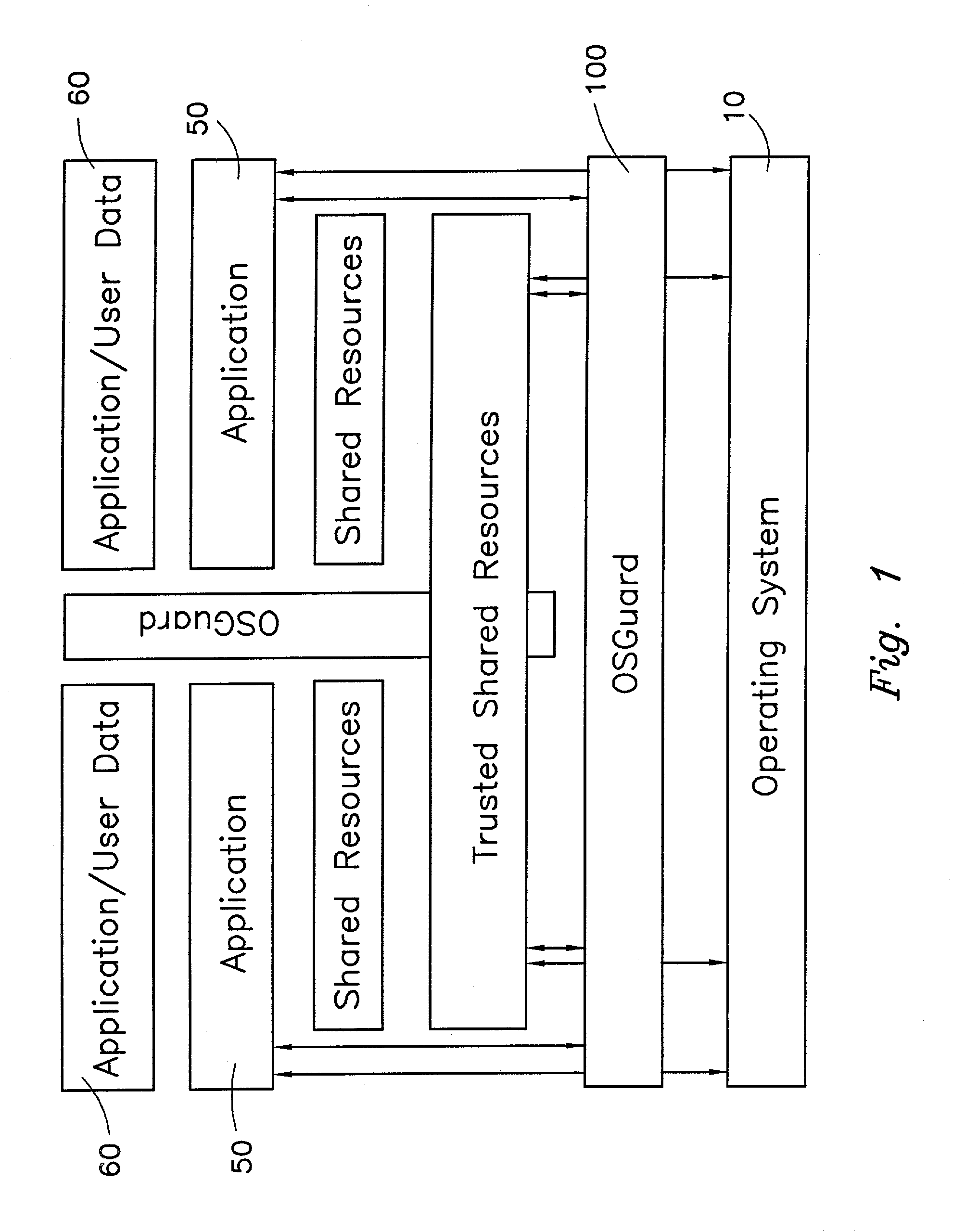
Operating system abstraction and protection layer
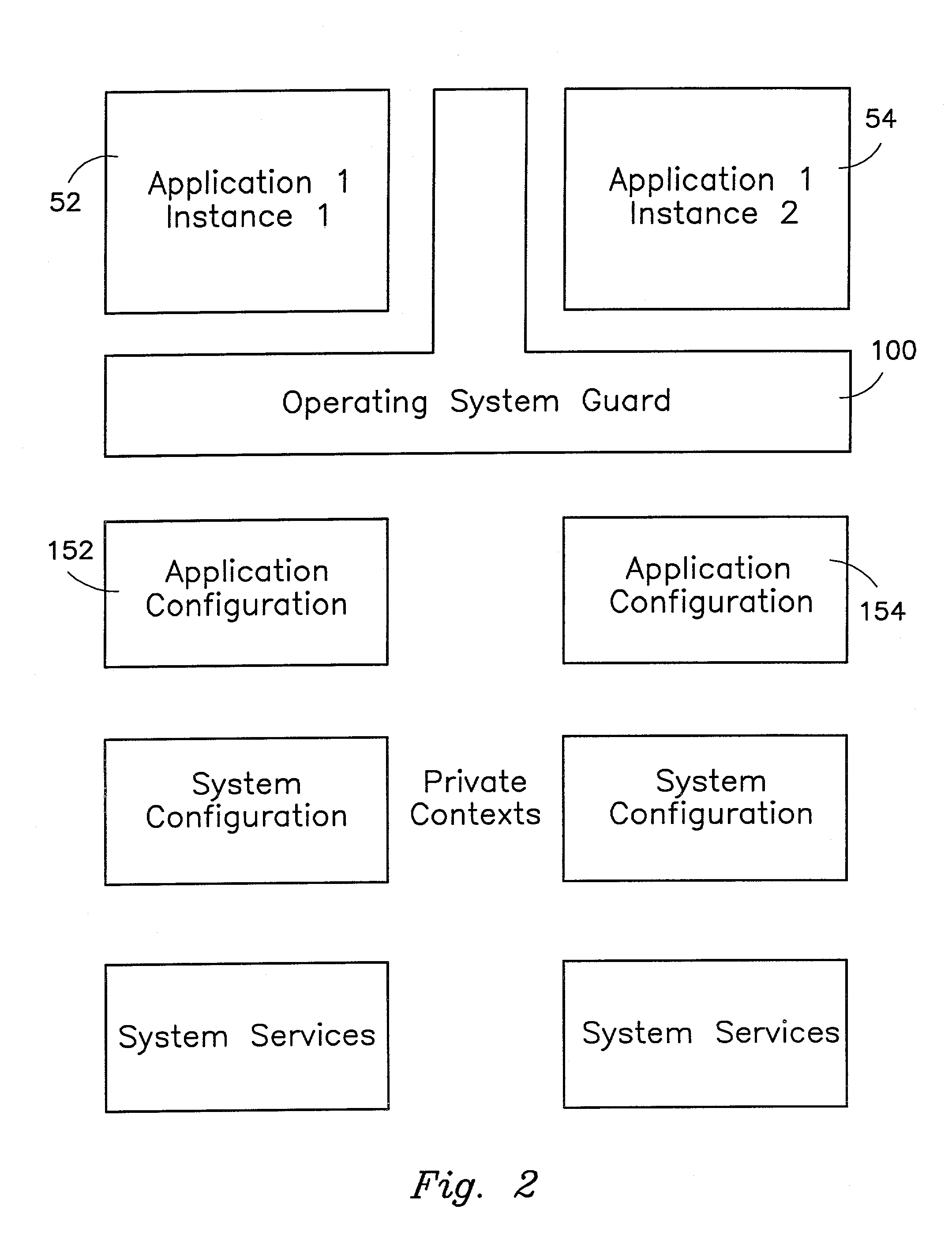
InactiveUS7028305B2Avoid changeInhibition of informationInterprogram communicationDigital computer detailsOperational systemConfiguration item
The present invention provides a system for creating an application software environment without changing an operating system of a client computer, the system comprising an operating system abstraction and protection layer, wherein said abstraction and protection layer is interposed between a running software application and said operating system, whereby a virtual environment in which an application may run is provided and application level interactions are substantially removed. Preferably, any changes directly to the operating system are selectively made within the context of the running application and the abstraction and protection layer dynamically changes the virtual environment according to administrative settings. Additionally, in certain embodiments, the system continually monitors the use of shared system resources and acts as a service to apply and remove changes to system components. The present thus invention defines an “Operating System Guard.” These components cover the protection semantics required by .DLLs and other shared library code as well as system device drivers, fonts, registries and other configuration items, files, and environment variables.
Owner:MICROSOFT TECH LICENSING LLC
Enforcing Geographic Constraints in Content Distribution
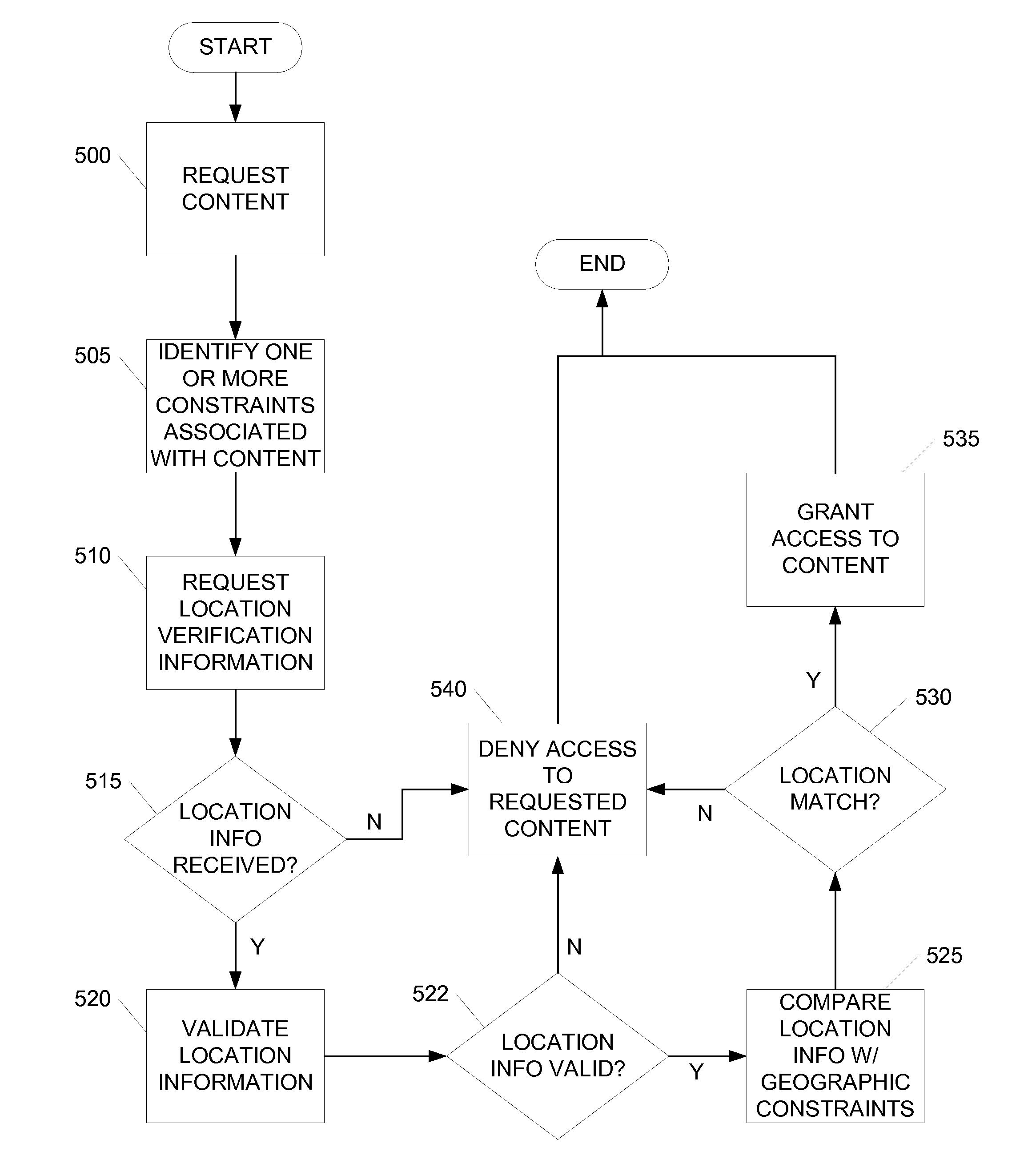
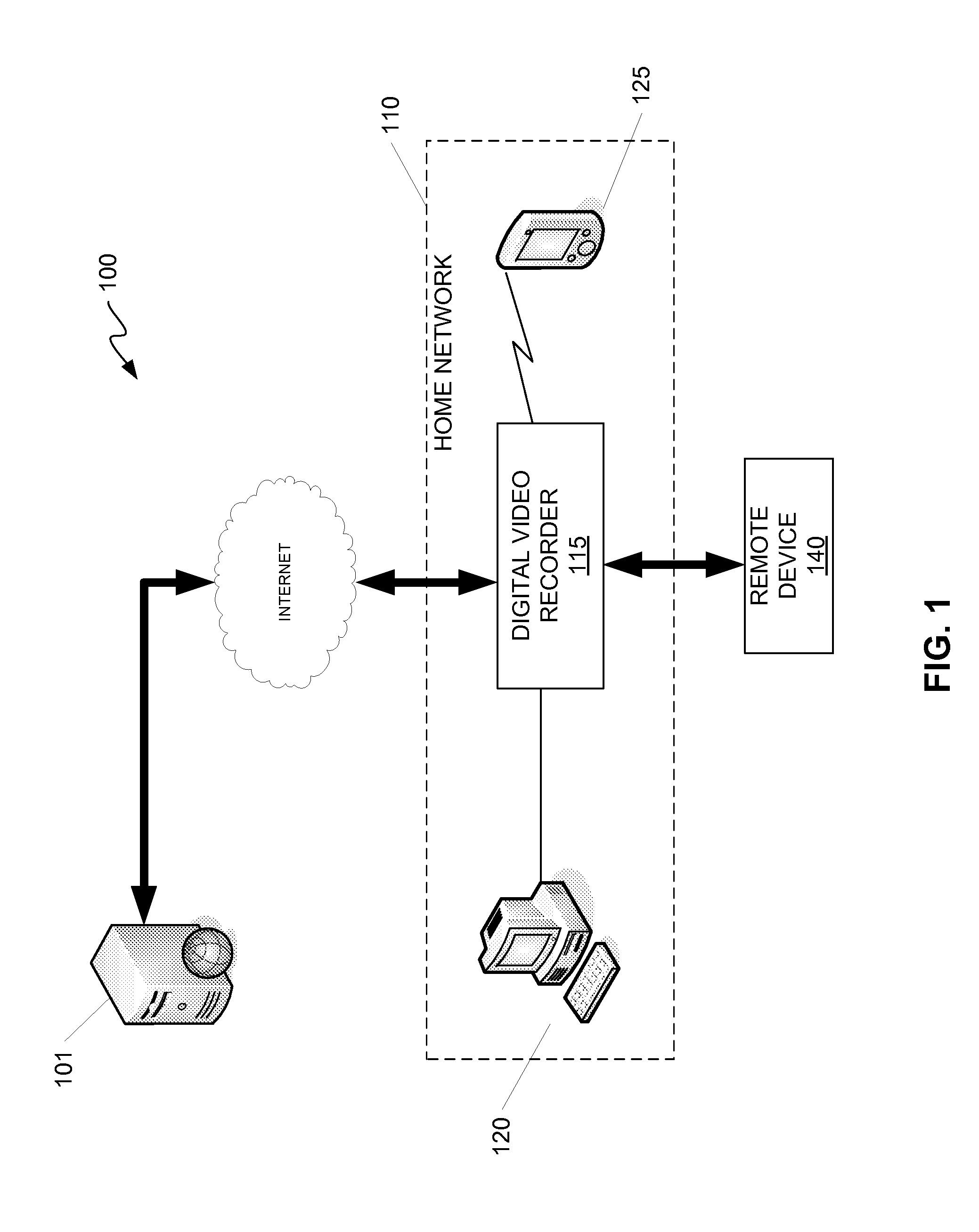
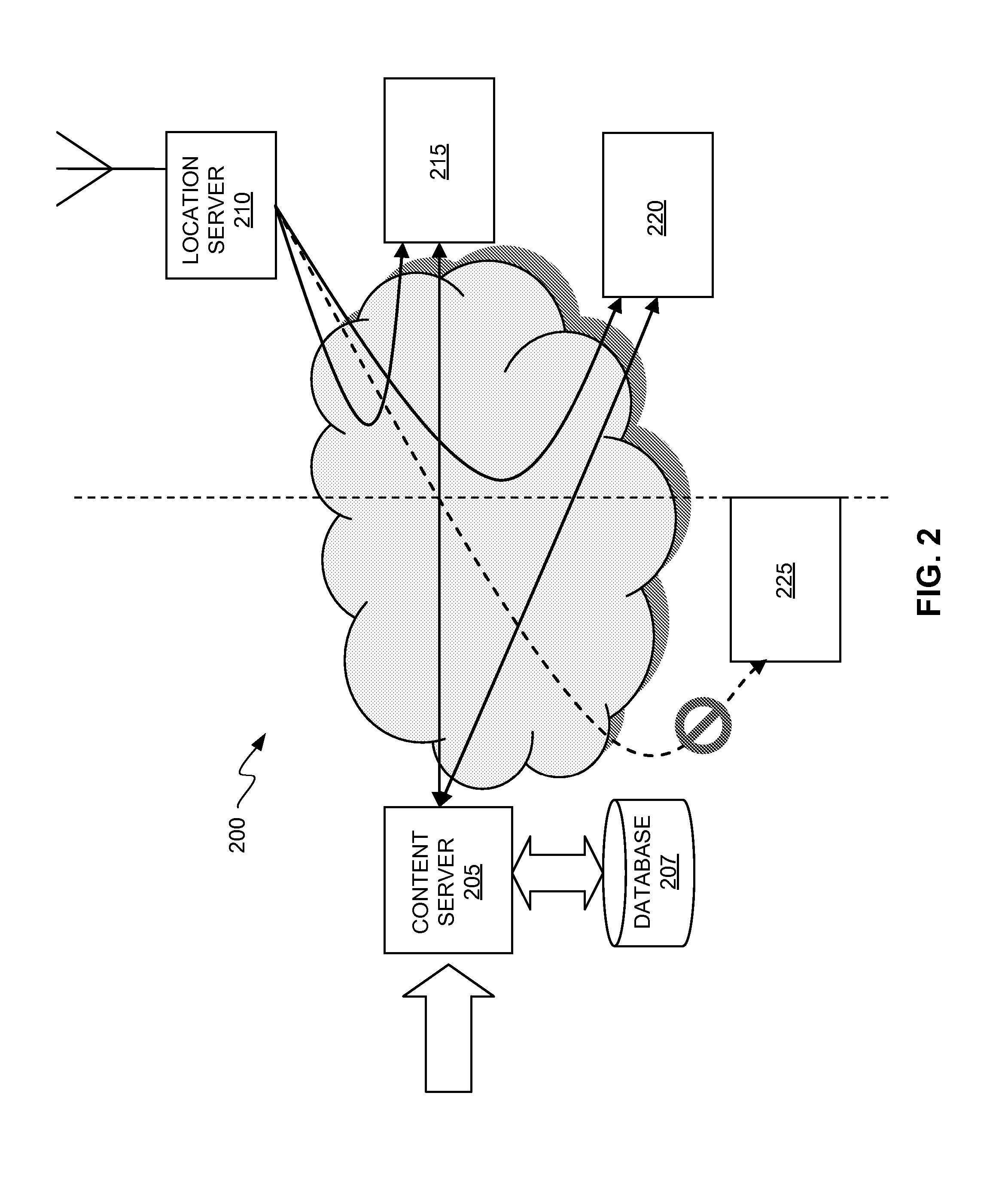
ActiveUS20080022003A1Improve integrityInhibition of informationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsContent distributionProtection mechanism
Enforcement of geographic and location based constraints on content distribution is provided to allow distribution of content to remote devices while preventing unauthorized use and consumption of the content. Content requested by a device may be protected using a variety of content protection mechanisms that support geographic constraints. The requesting device may be required to validate and / or obtain the device's physical location prior to being granted access to the protected content. The requesting device may validate and / or obtain its physical location by requesting location information from a location server or another geographic aware device. The distribution of the location information from the location server may be limited to a predefined proximity. The proximity limit on the dissemination of the location information prevents remote devices from fraudulently using the location information. Location information may be encapsulated and may be formatted as a content file.
Owner:NOKIA TECHNOLOGLES OY
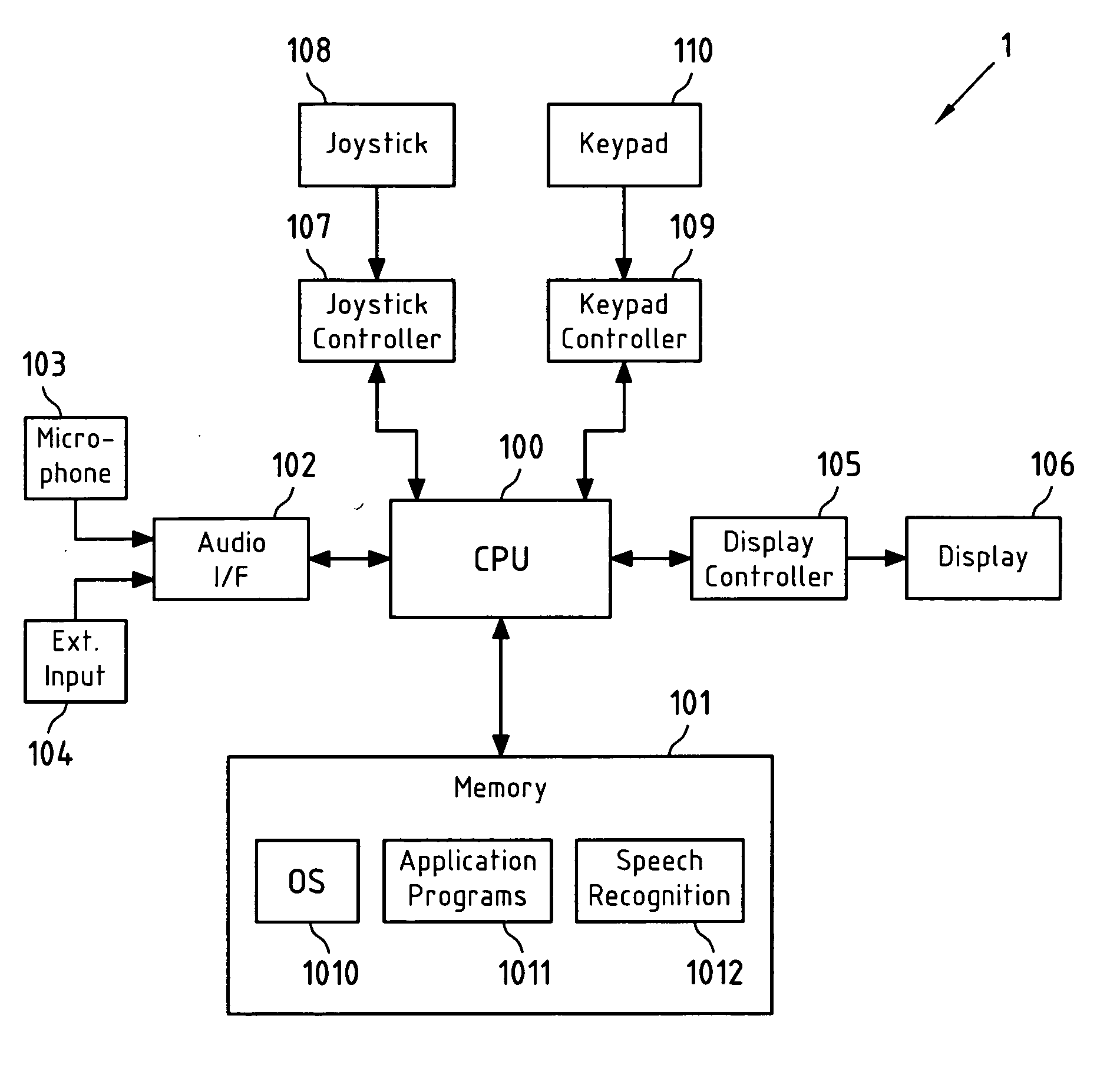
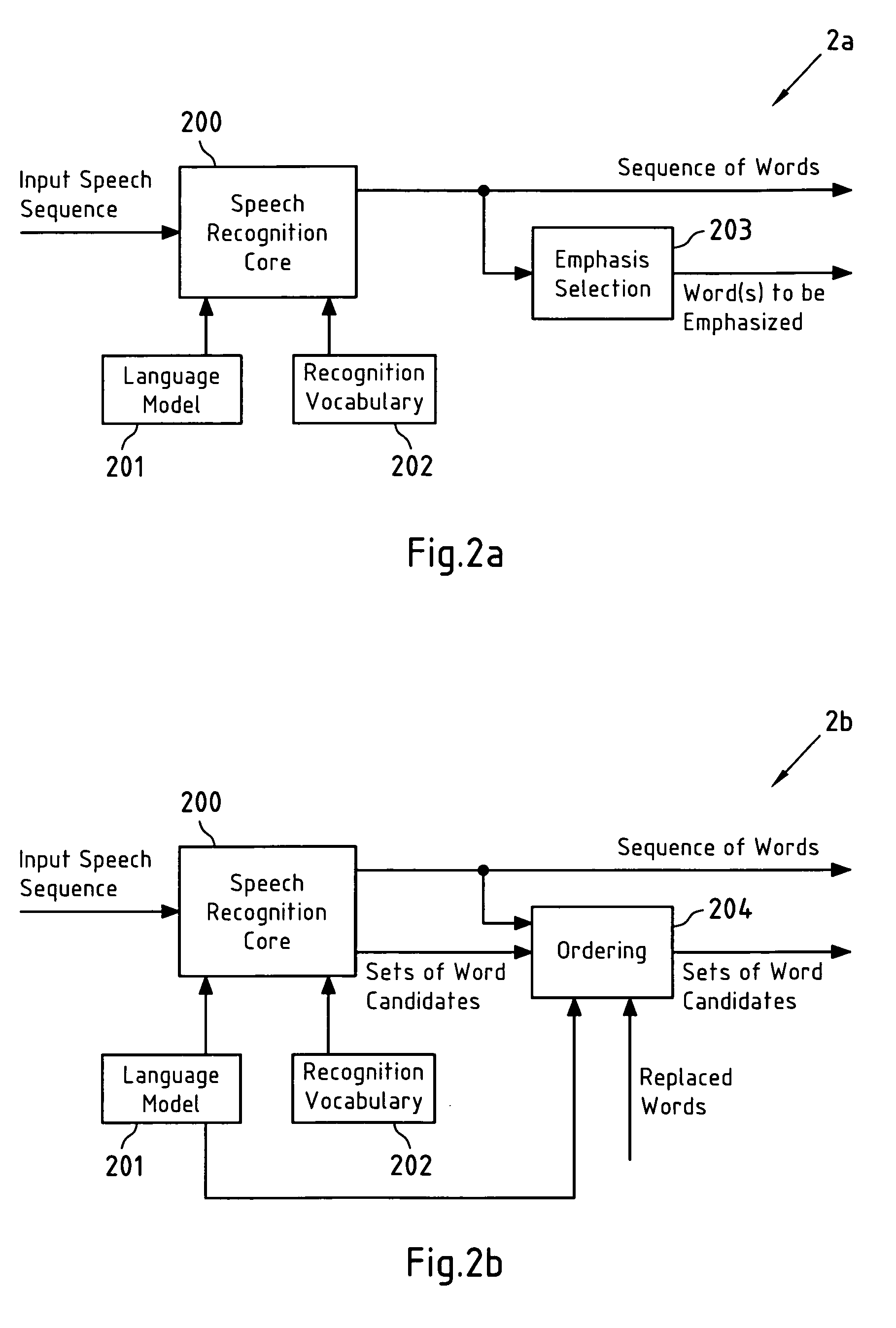
Error correction for speech recognition systems
Words in a sequence of words that is obtained from speech recognition of an input speech sequence are presented to a user, and at least one of the words in the sequence of words is replaced, in case it has been selected by a user for correction. Words with a low recognition confidence value are emphasized; alternative word candidates for the at least one selected word are ordered according to an ordering criterion; after replacing a word, an order of alternative word candidates for neighboring words in the sequence is updated; the replacement word is derived from a spoken representation of the at least one selected word by speech recognition with a limited vocabulary; and the word that replaces the at least one selected word is derived from a spoken and spelled representation of the at least one selected word.
Owner:NOKIA CORP
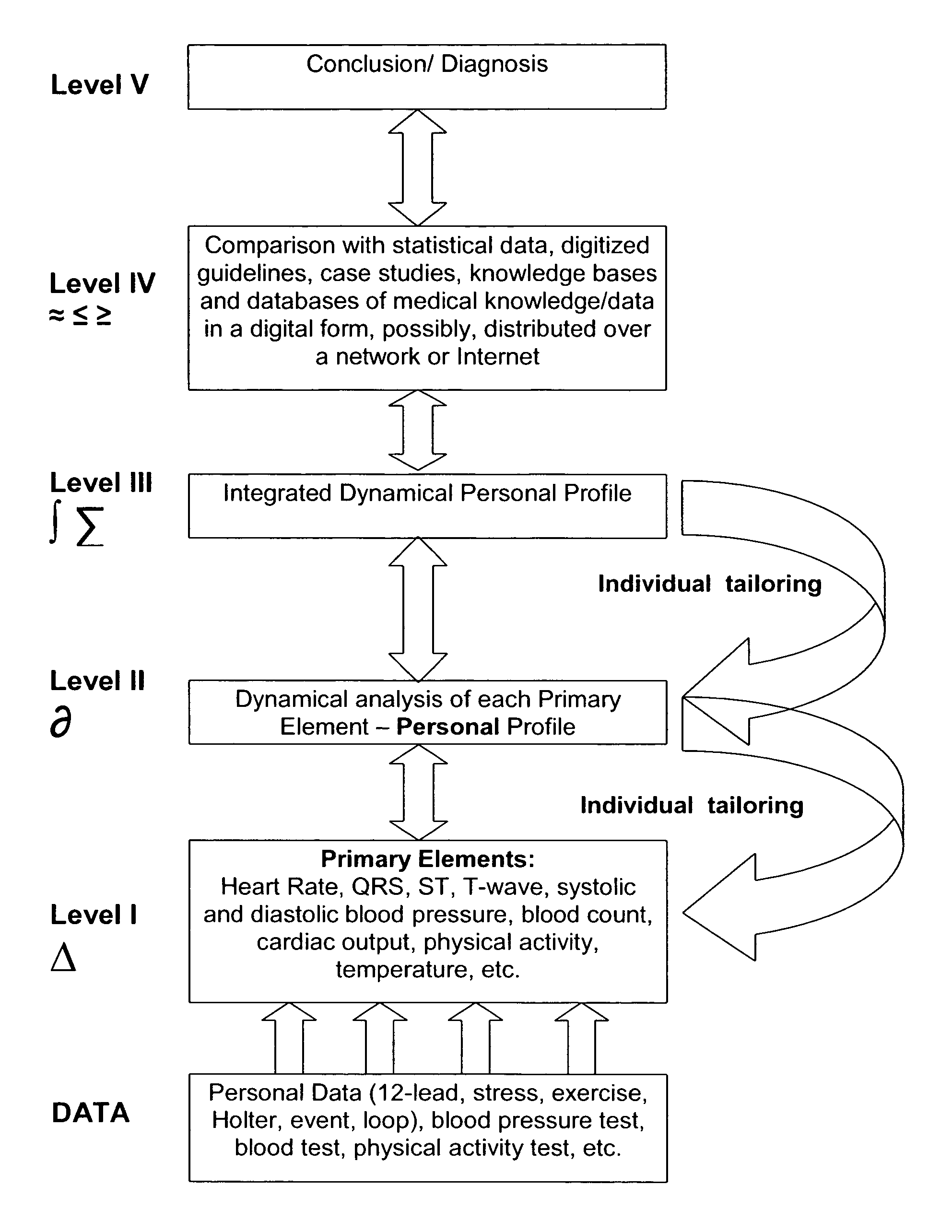
Digital healthcare information management
InactiveUS7801591B1Easy to analyzeImproves and optimizes flowMedical data miningElectrocardiographyPersonal information managementMedical treatment
System for diagnosis, medical decision support, and healthcare information management that performs analysis of serial health data, adapts to the individual data, and represents dynamics of the most significant parameters (indicators), using at least two scales. The system uses the first-scale (low-resolution) analysis of a snapshot measurement of at least one indicator (primary element) such as heart rate or blood pressure and uses a second-scale (higher-resolution) analysis to determine serial changes in each of the said primary elements. The system optimizes information flow, usage of medical knowledge, and improves accuracy of analysis of serial changes, and adaptability to each individual's data. The information can be distributed in parallel to separate databases at different locations.
Owner:SHUSTERMAN VLADIMIR
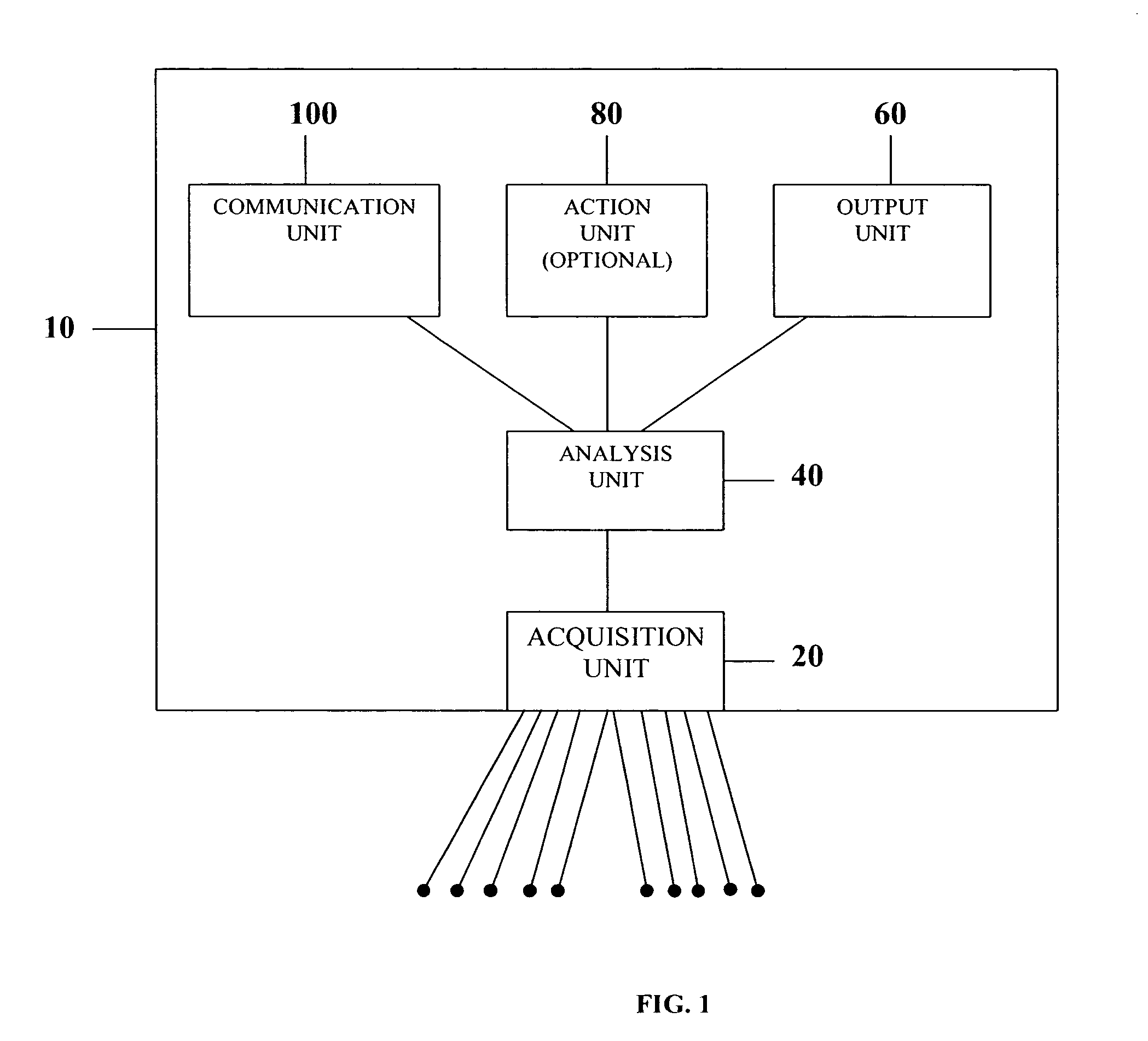
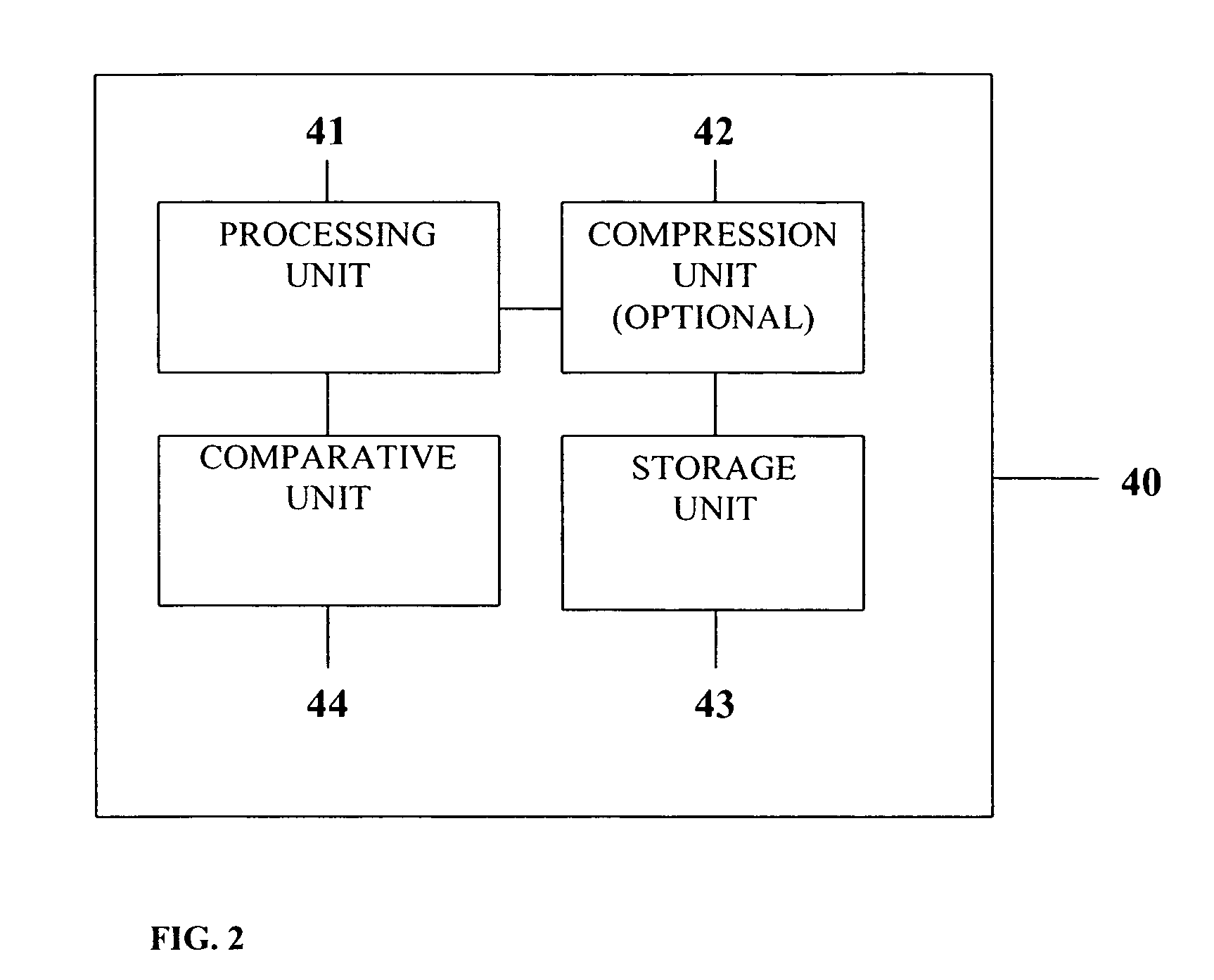
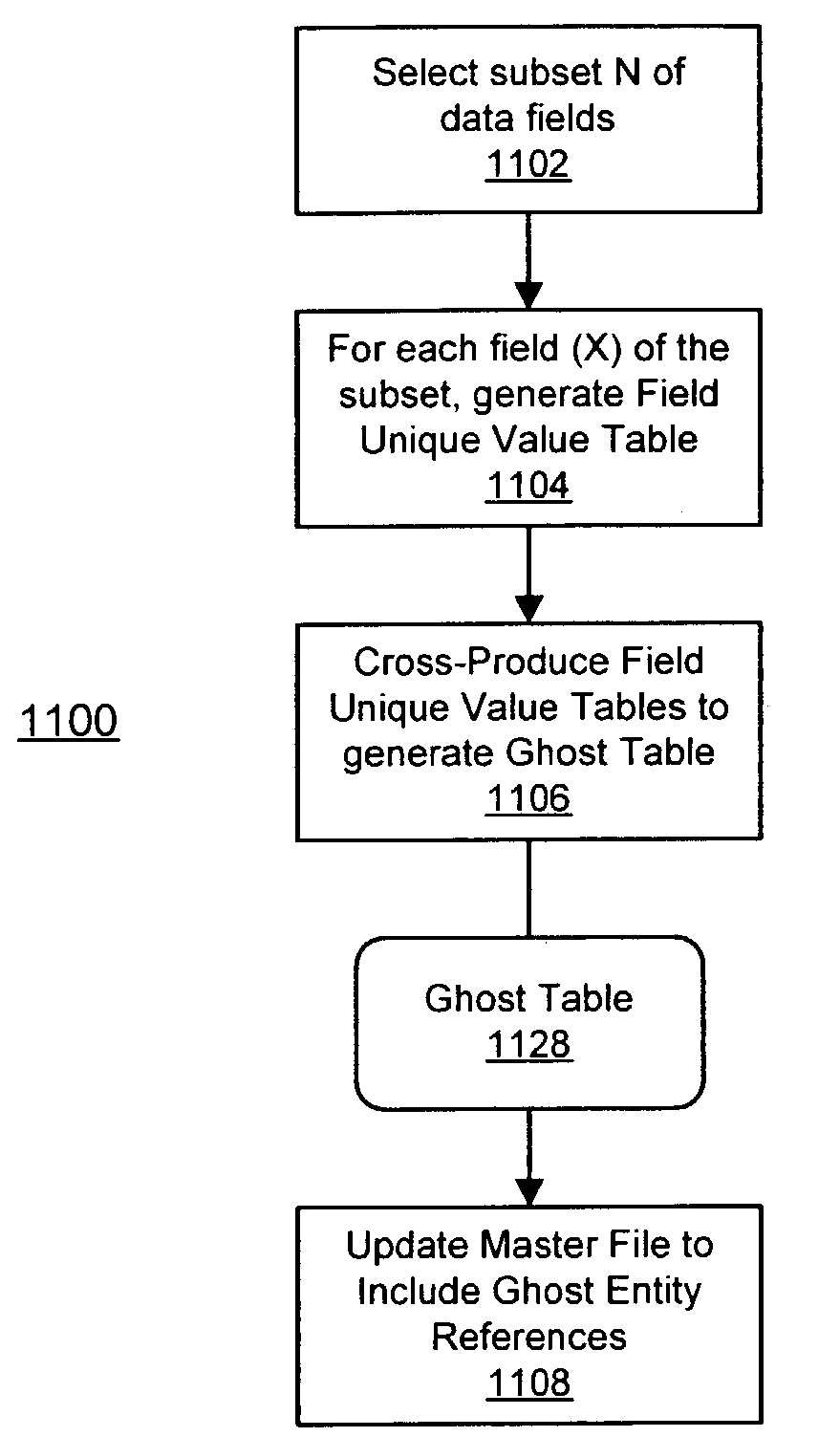
System and method of using ghost identifiers in a database
ActiveUS7720846B1Reduce settingsAvoid it happening againDigital data processing detailsRelational databasesData fieldInformation retrieval
Owner:LEXISNEXIS RISK DATA MANAGEMENT
Surgical Cockpit Comprising Multisensory and Multimodal Interfaces for Robotic Surgery and Methods Related Thereto
InactiveUS20110238079A1Accurately respondEnhanced Situational AwarenessMedical communicationMechanical/radiation/invasive therapiesRemote surgeryCommunications system
Local surgical cockpits comprising local surgical consoles that can communicate with any desired remote surgical module (surgical robot), for example via a shared Transmission Control Protocol / Internet Protocol (TCP / IP) or other unified open source communication protocol or other suitable communication system. The systems and methods, etc., herein can also comprise a modular approach wherein multiple surgical consoles can network supporting collaborative surgery regardless of the physical location of the surgeons relative to each other and / or relative to the surgical site. Thus, for example, an operator operating a local surgical cockpit can teleoperate using a remote surgical module on a patient in the same room as the surgeon, or surgeons located in multiple safe locations can telemanipulate remote multiple surgical robots on a patient in or close to a war zone.
Owner:SPI SURGICAL
Semantic packager
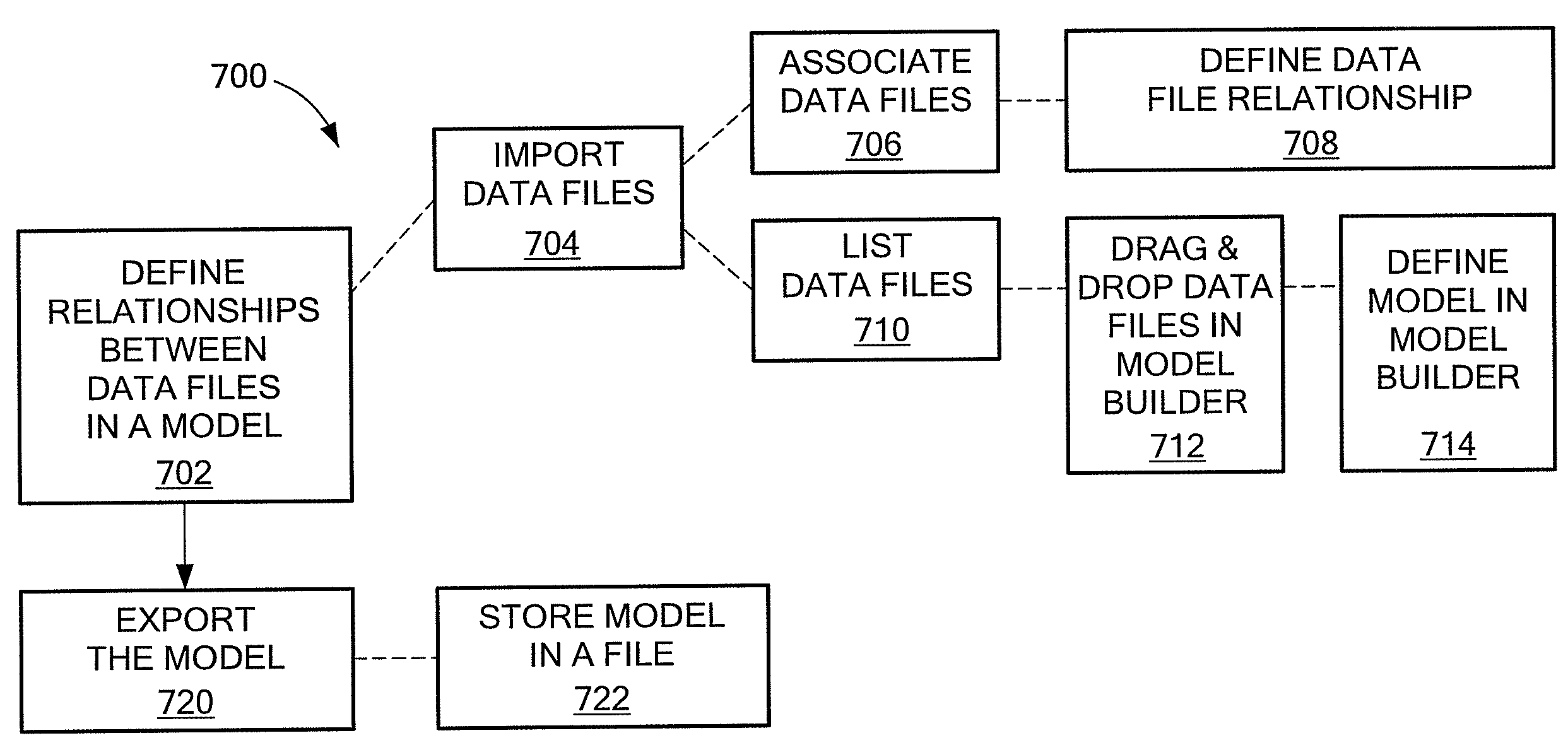
InactiveUS20090282068A1Avoiding file name conflictsEliminate structureSpecial data processing applicationsDocument management systemsData fileSemantics
A system includes a storage medium having stored instructions thereon that when executed by a machine result in the following: a semantic modeler component to define relationships between data files in a semantic model; a viewer component coupled to the semantic modeler component to view the semantic model; and a packager component coupled to the semantic modeler component to export the semantic model and the data files.
Owner:RAYTHEON CO
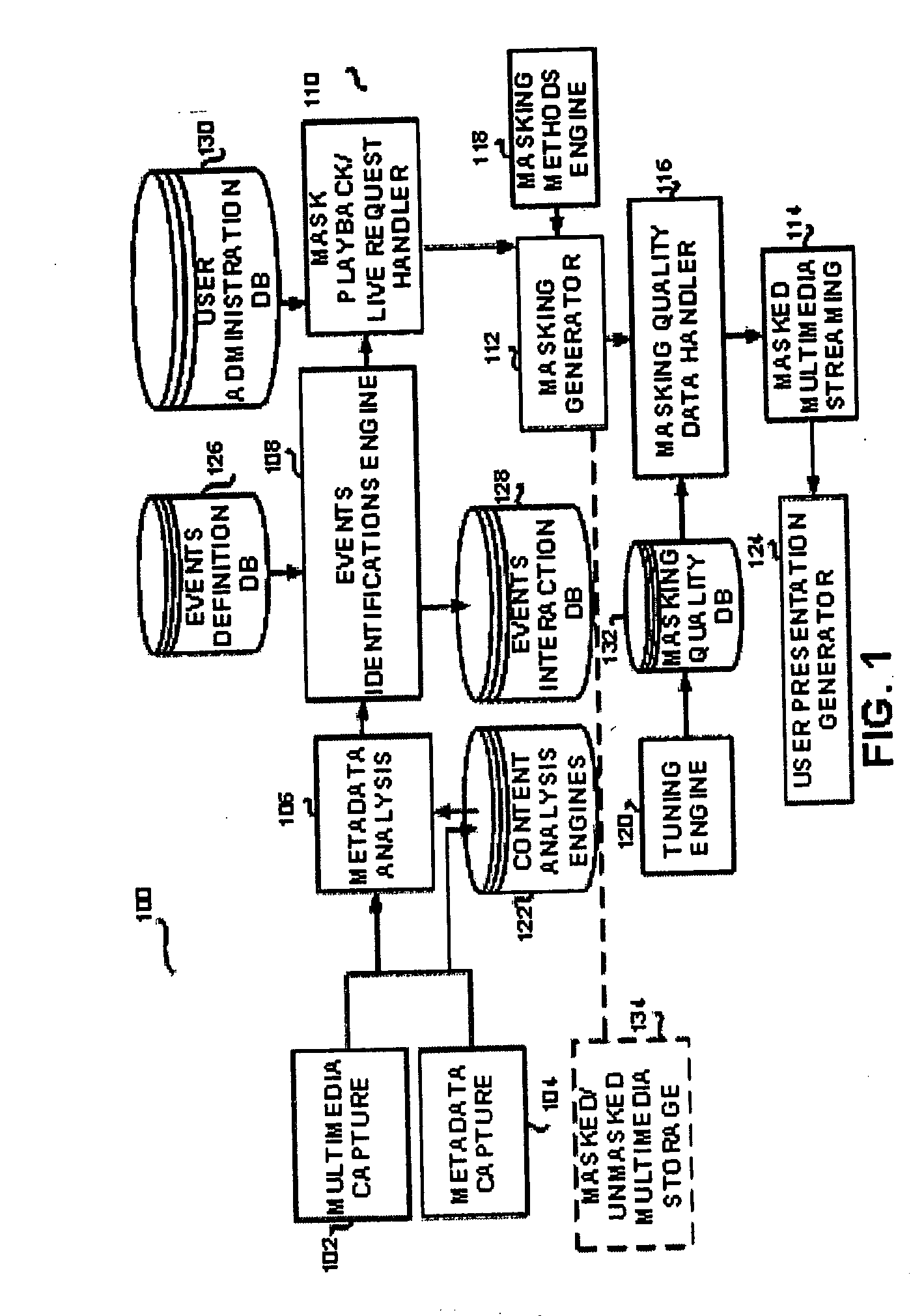
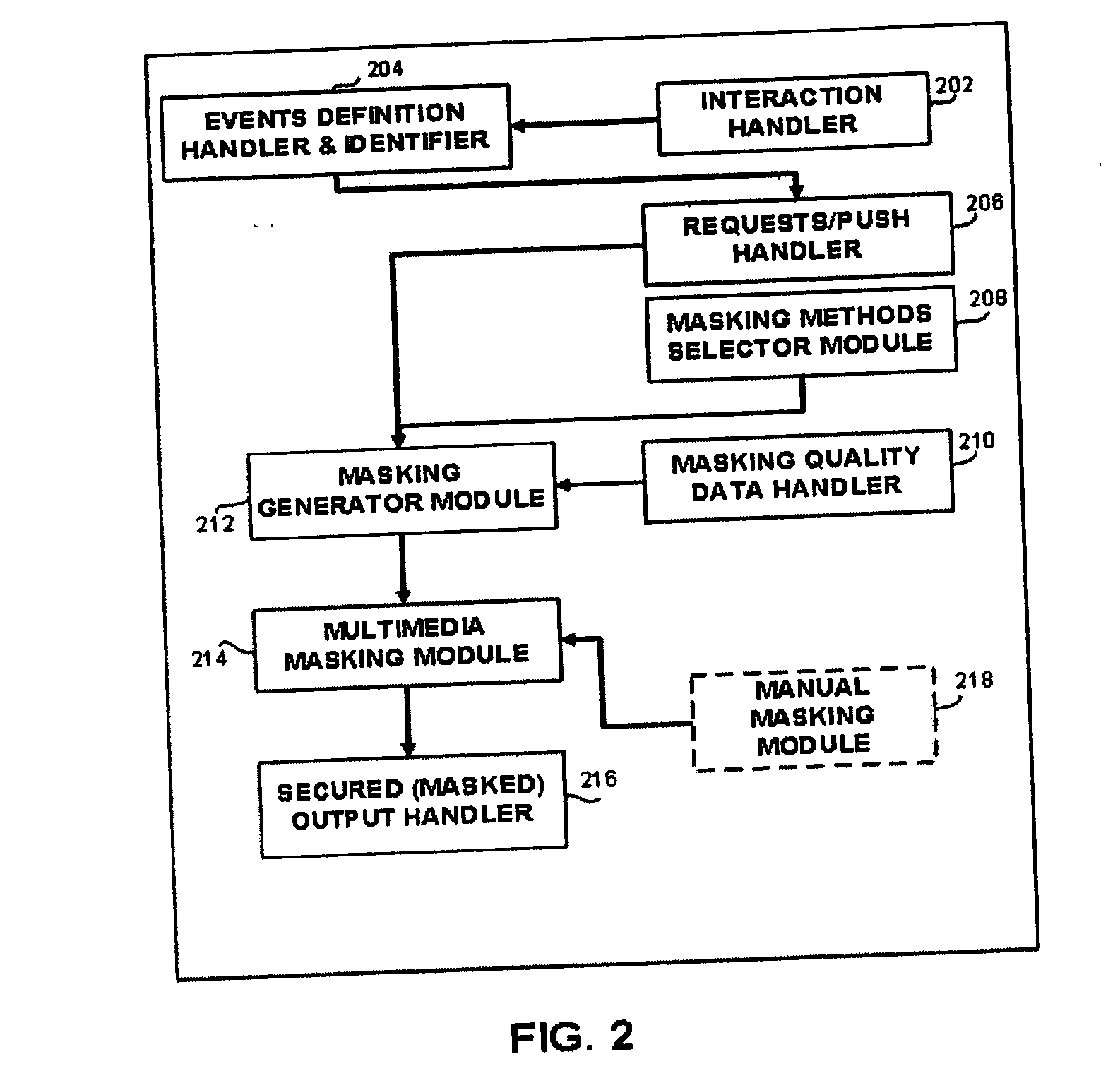
Apparatus and method for multimedia content based manipulation
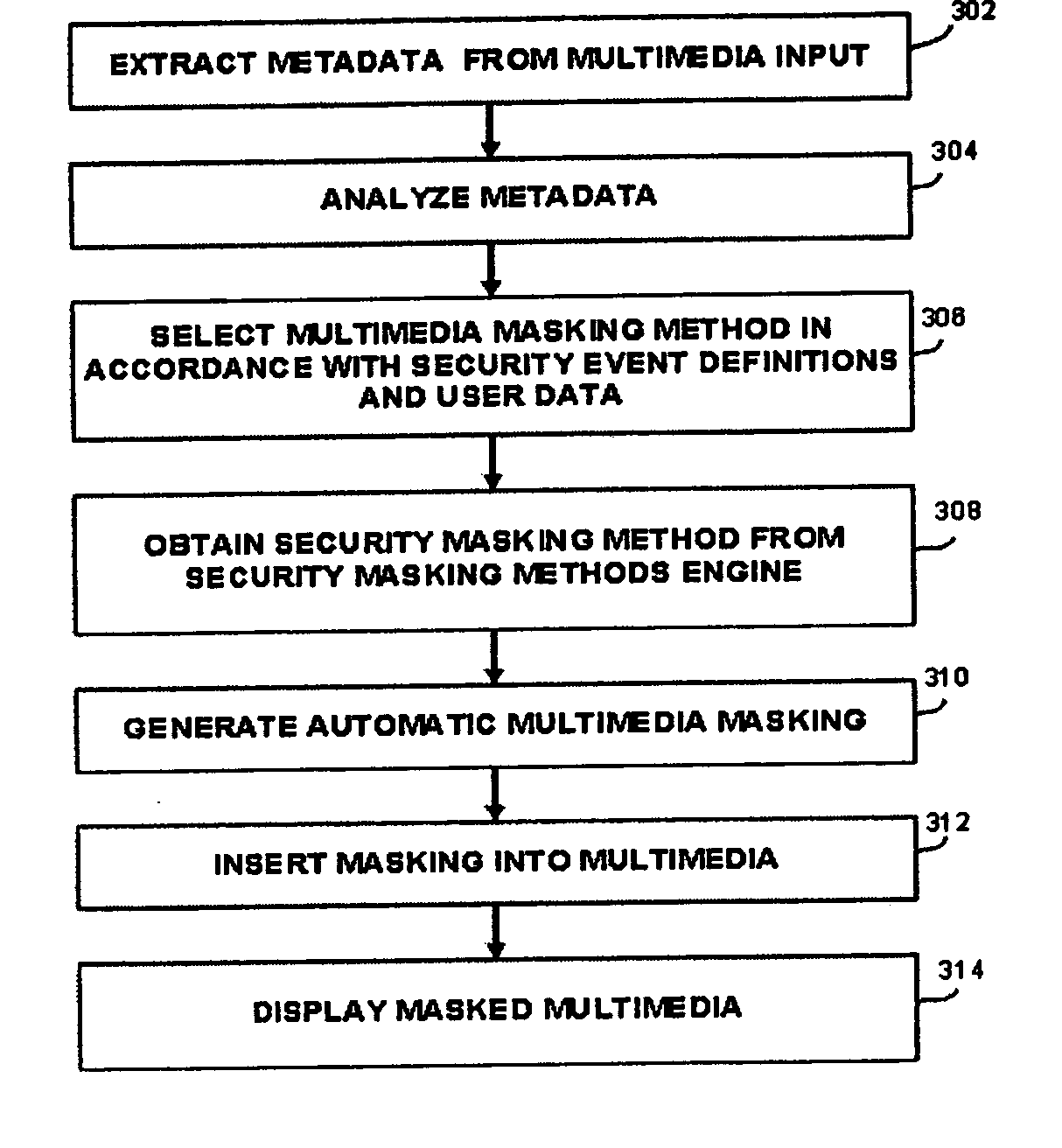
ActiveUS20060028488A1Increase awarenessPreventing information recordedCathode-ray tube indicatorsTransmissionRegion of interestMultimedia
An apparatus and method for multimedia content based manipulation. The method comprises the masking at least one part of the segment of an interaction, said masking can include the hiding, blurring, or alternatively, the enhancing or focusing on a region of interest.
Owner:NICE LTD
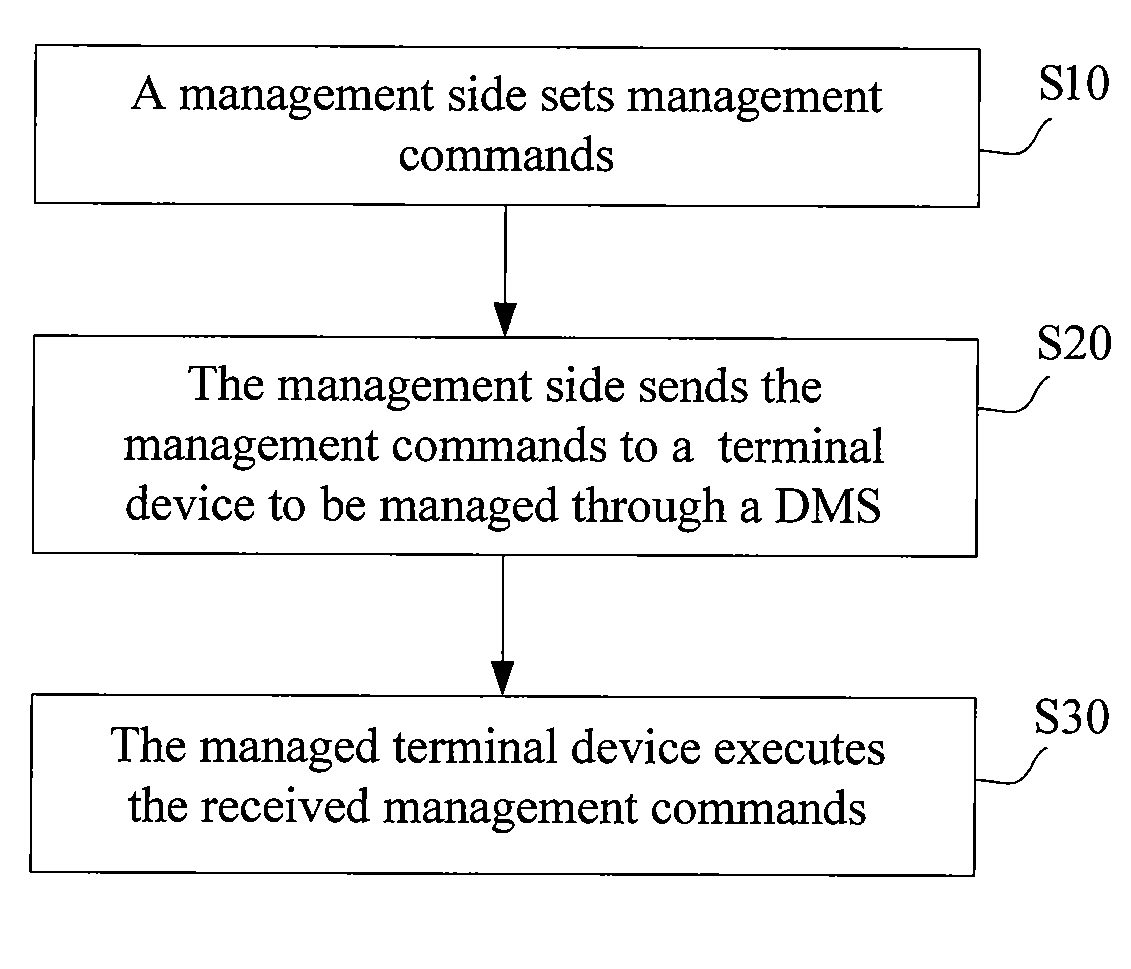
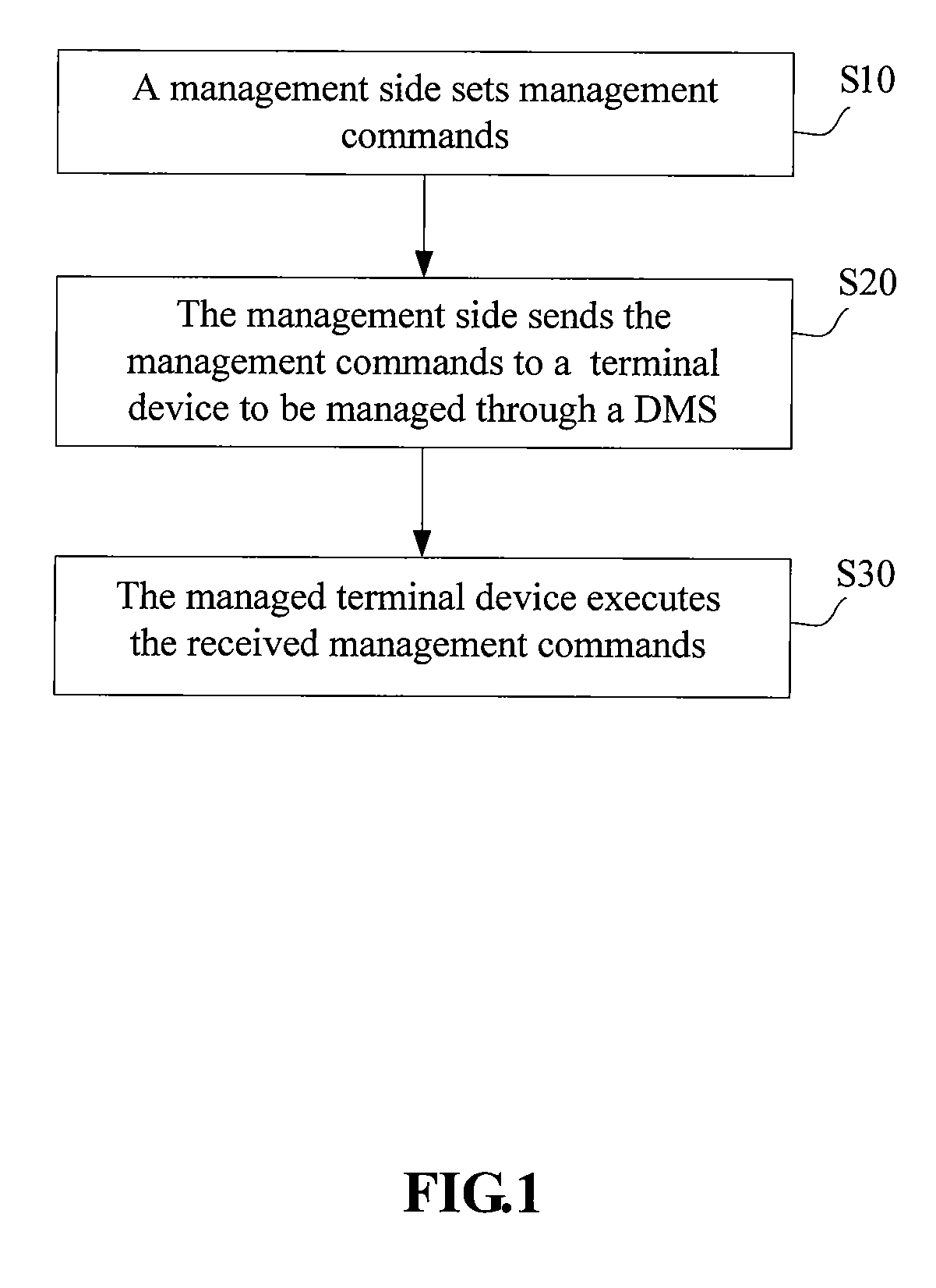
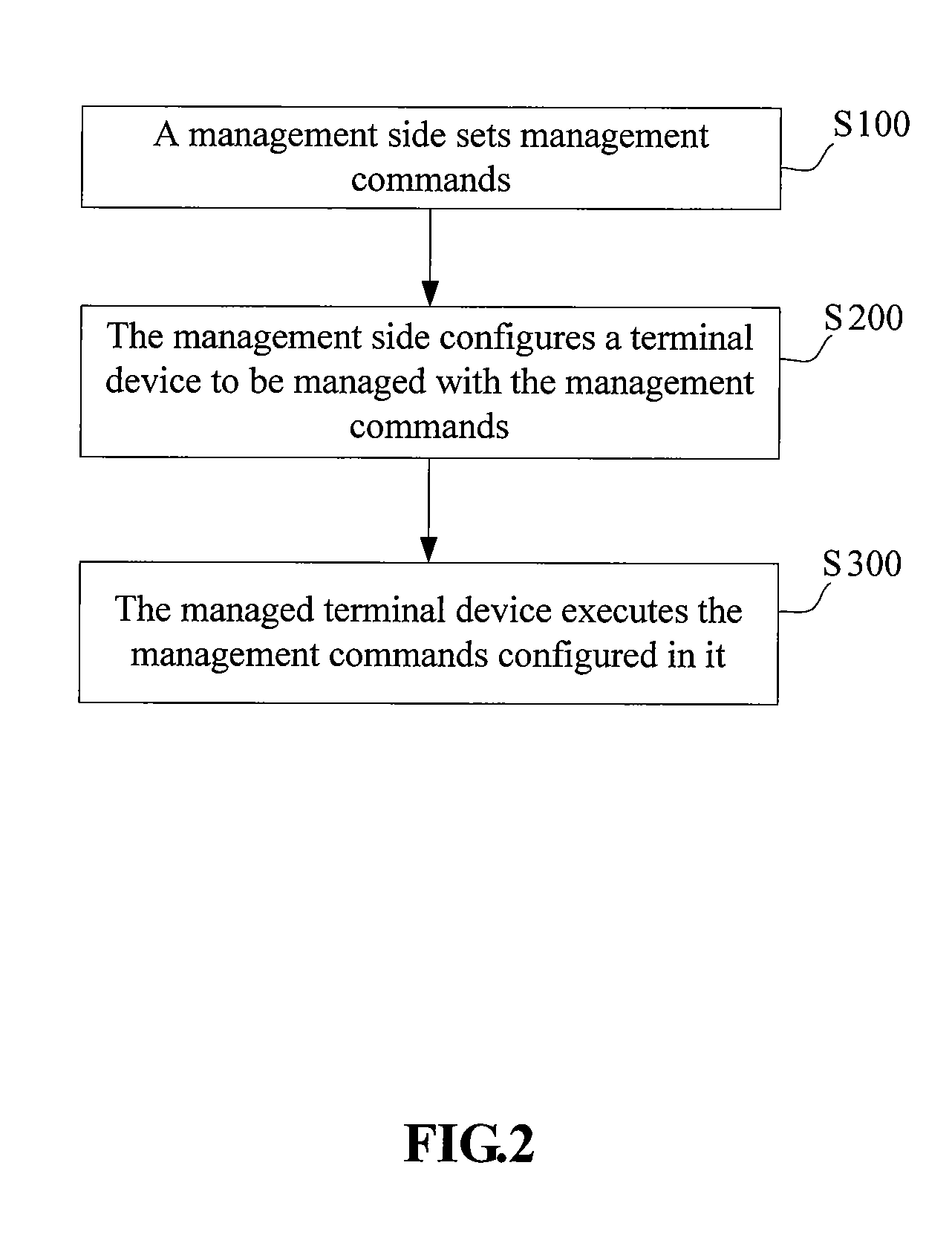
Method for managing a terminal device
ActiveUS20070165654A1Enhanced informationImprove securityData switching by path configurationComputer hardwareTerminal equipment
Owner:HUAWEI TECH CO LTD
Method for the transmission of management data
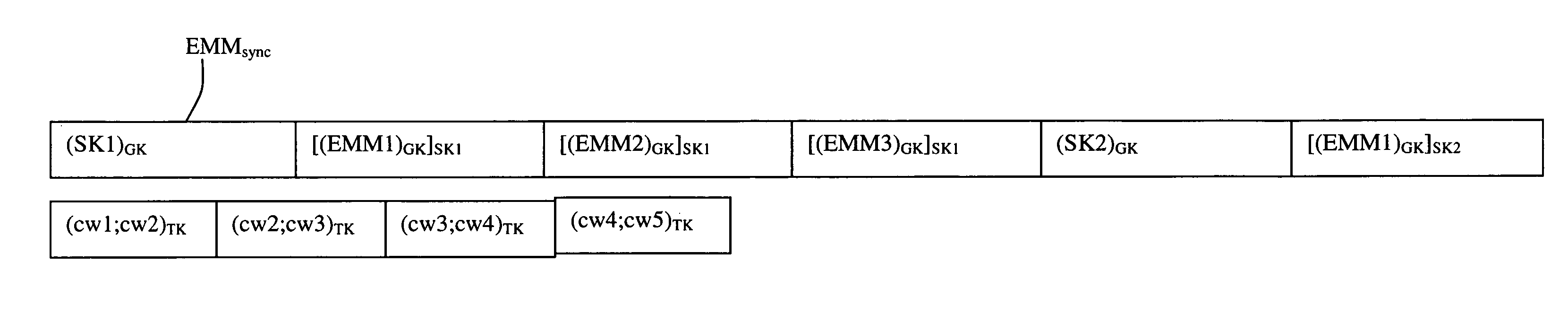
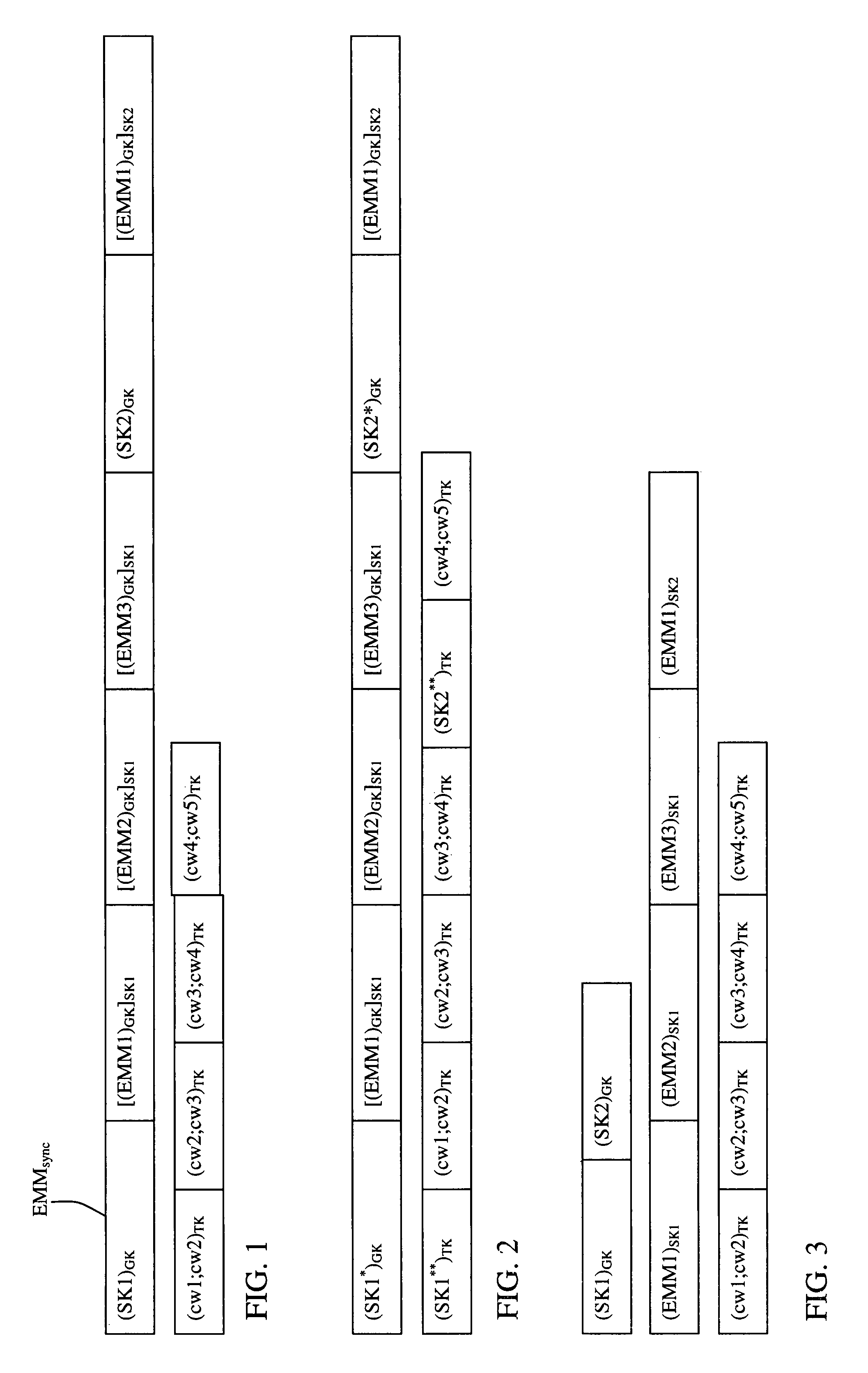
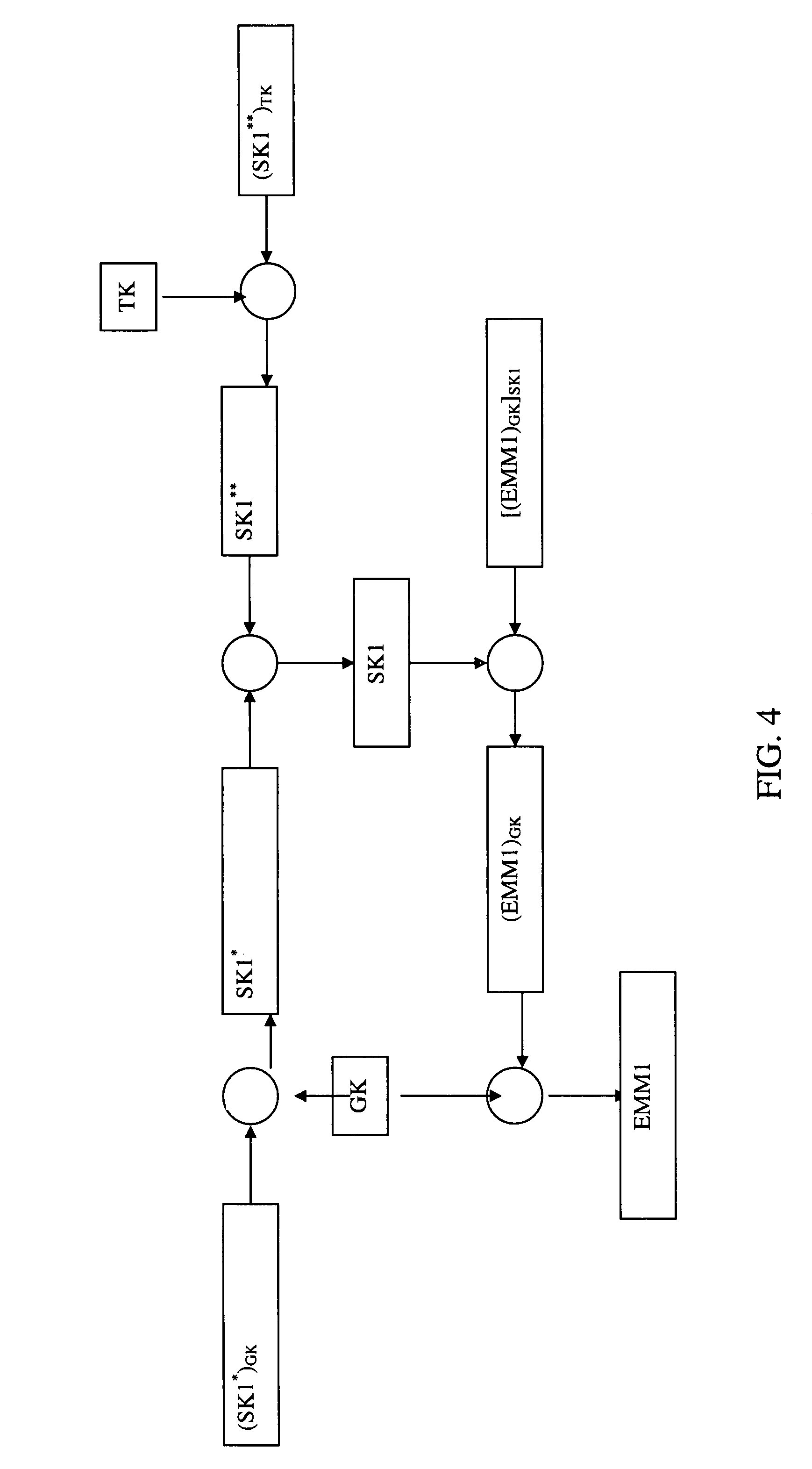
InactiveUS8036387B2Inhibition of informationImprove securityKey distribution for secure communicationPublic key for secure communicationAuthorization
This invention relates to a method for the transmission of management data to at least one multimedia unit or a group of multimedia units. This method is characterized in that said management data is sent in the form of at least one authorization message encrypted by means of at least one synchronization key (SK), the sending of said at least one authorization message being repeated cyclically and intended for said multimedia unit or said group of multimedia units, and in that the synchronization key is modified at least during each cycle.
Owner:NAGRAVISION SA
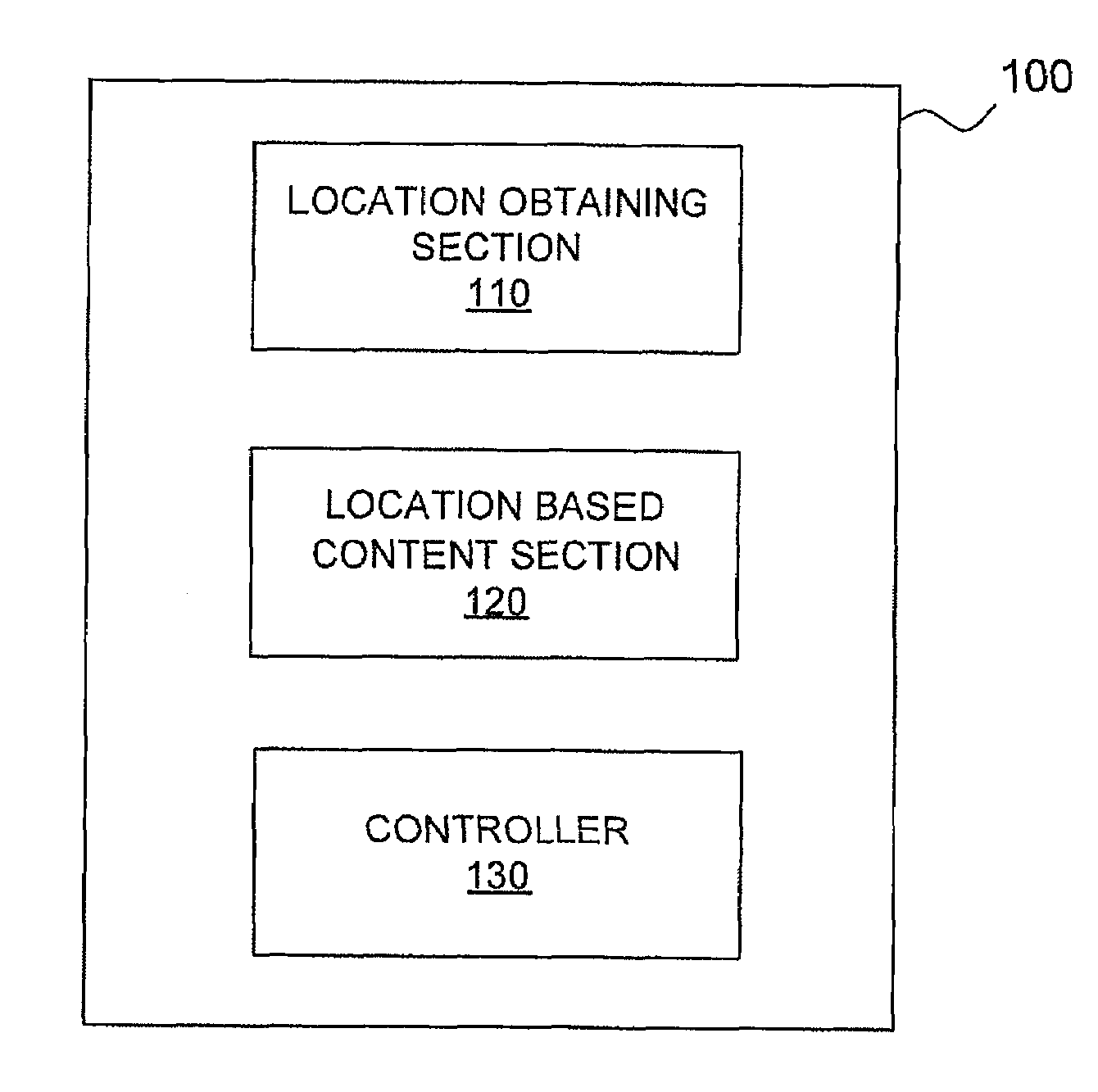
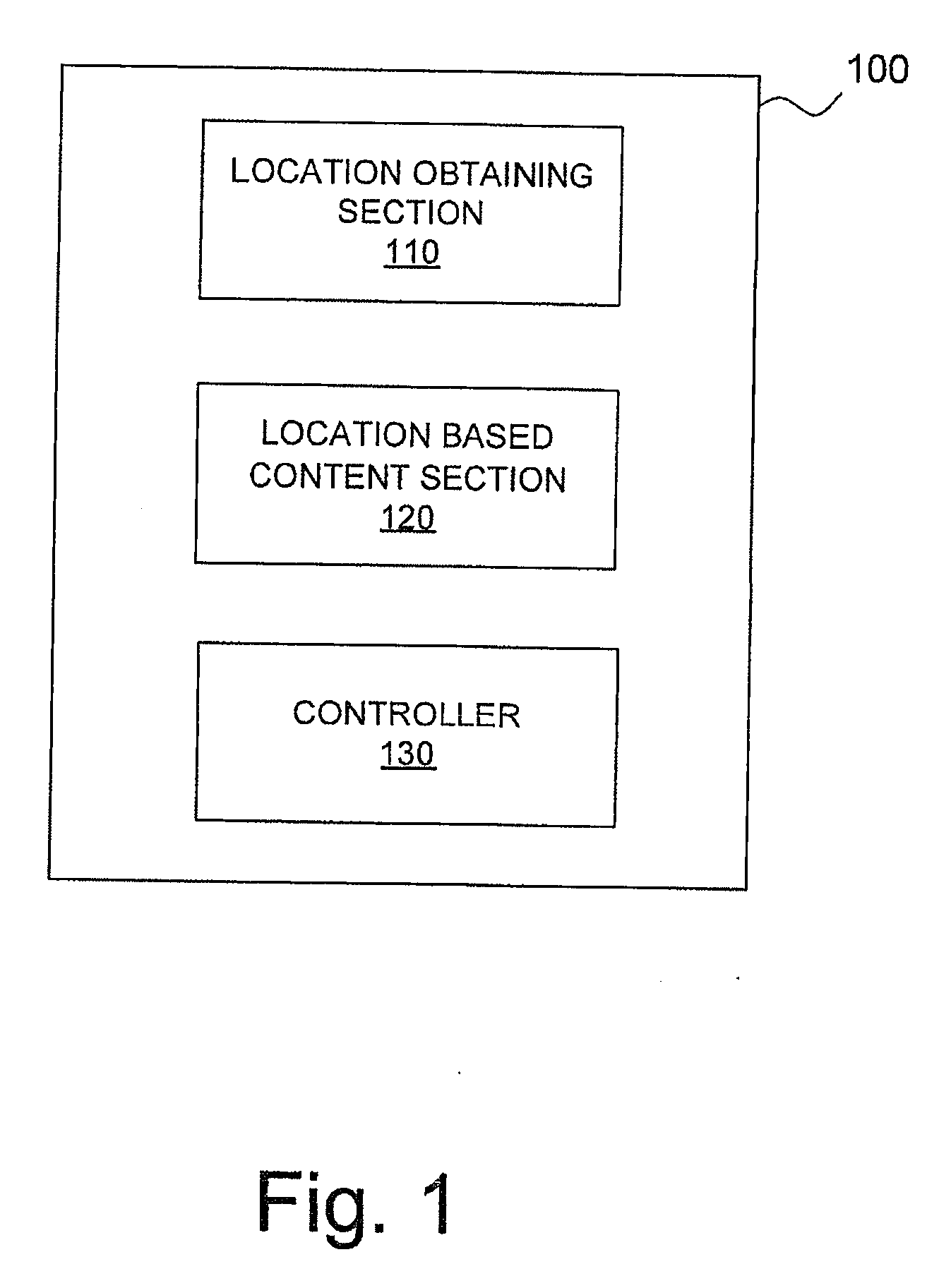
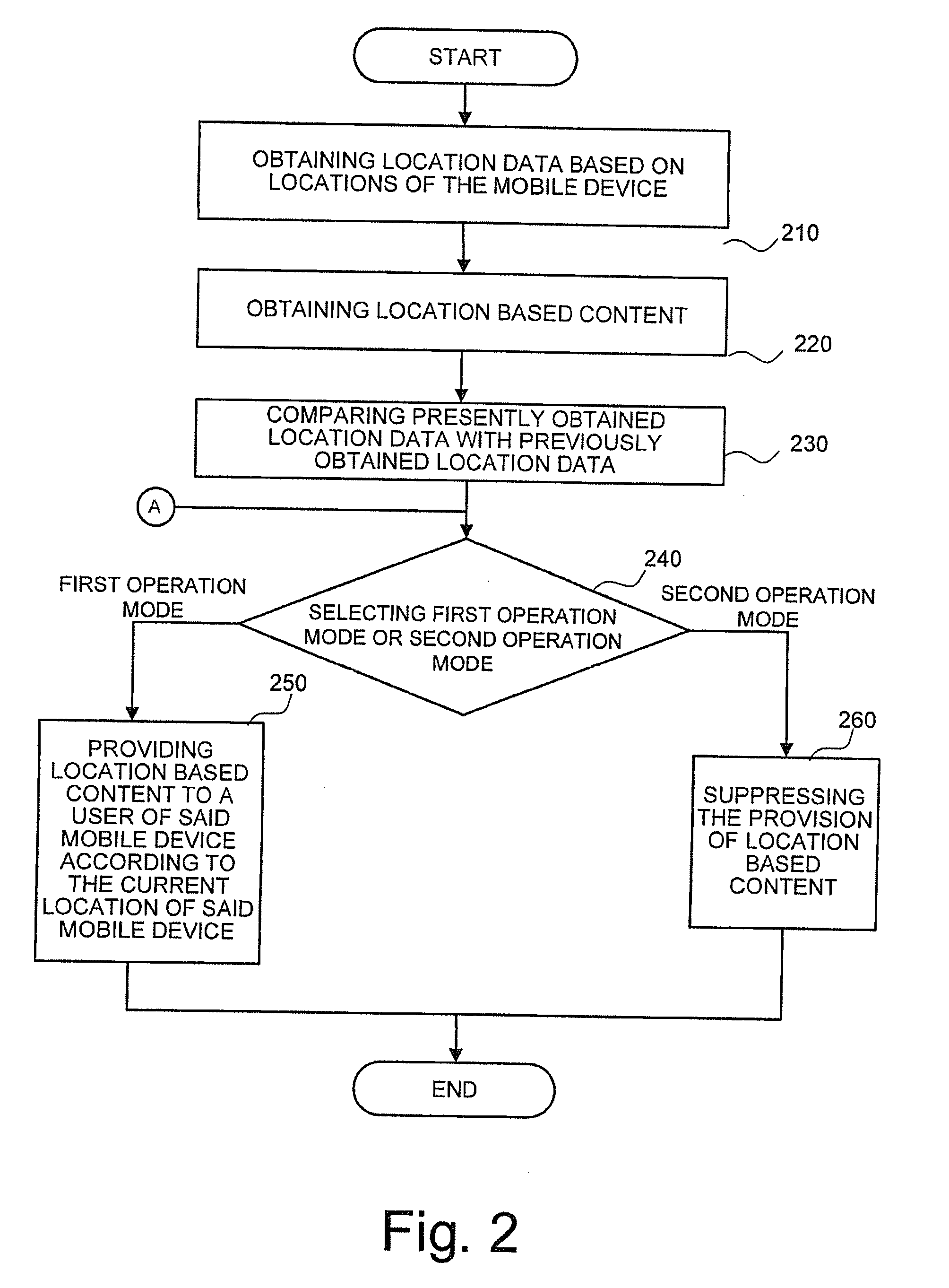
Mobile device and method for providing location based content
ActiveUS20100190513A1Prevent information overloadAvoid constantInformation formatServices signallingOperation modeMobile device
A mobile device and method are disclosed to provide location based content to a user of a mobile device based on the current location, wherein the provision of location based content depends on obtained location data. The mobile device comprises a location obtaining section for obtaining location data based on locations of the mobile device, location based content section for obtaining location based content, and a controller adapted to compare presently obtained location data with previously obtained location data and to select between a first operation mode and a second operation mode according to the comparison, wherein in the first operation mode the location based content section is adapted to provide location based content to a user of the mobile device according to the current location of the mobile device and in the second operation mode providing of location based content is suppressed.
Owner:SONY CORP
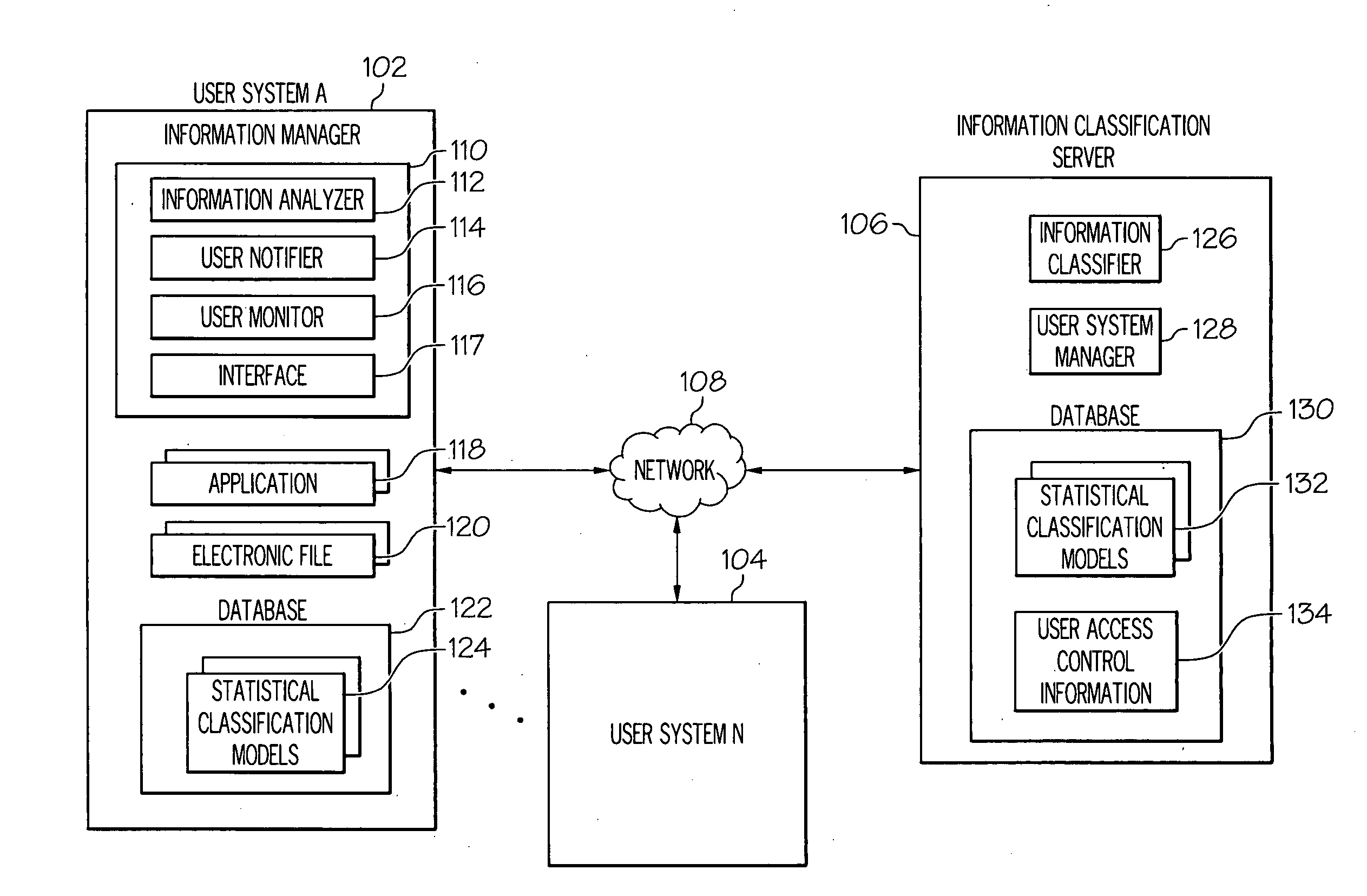
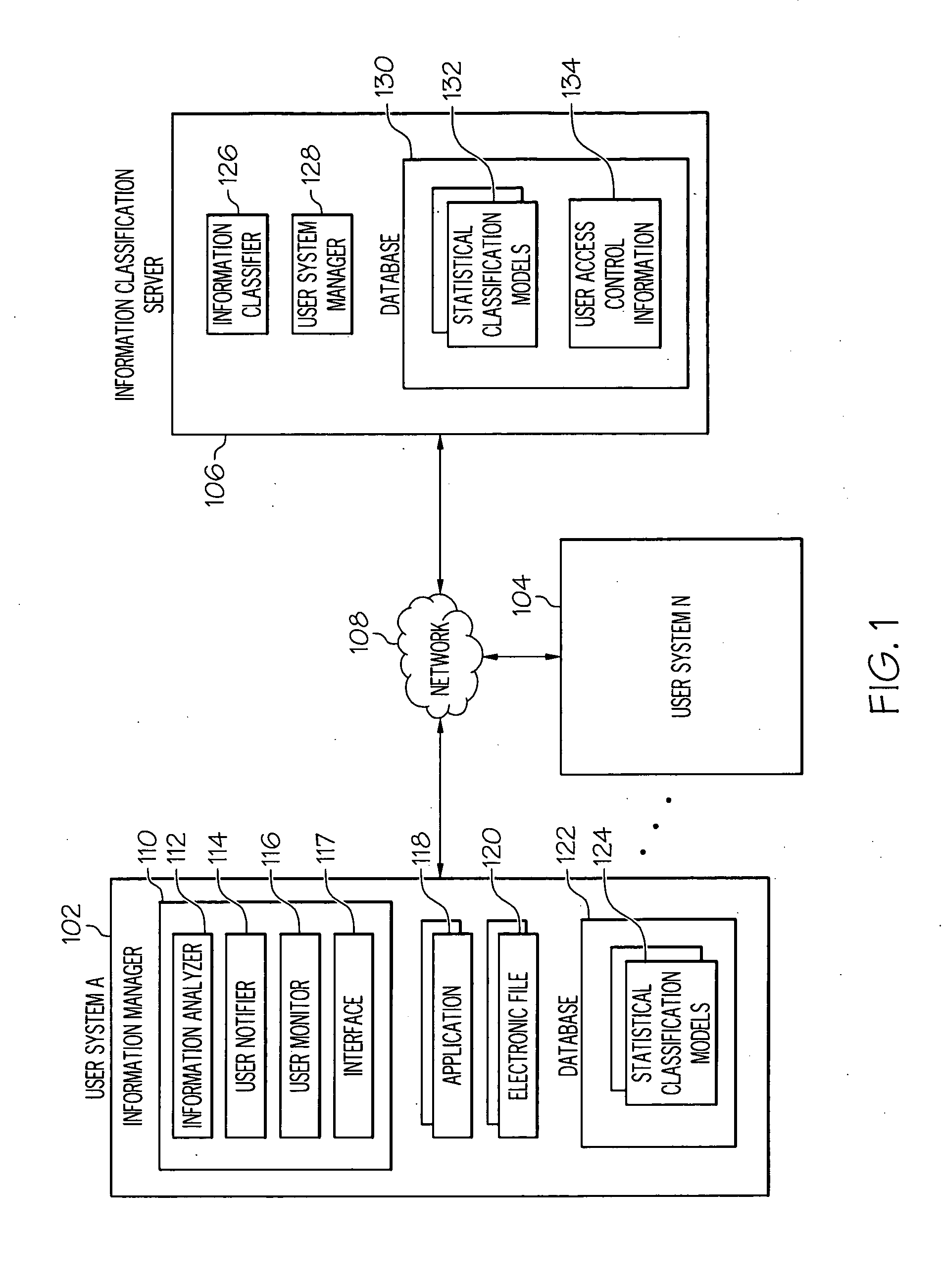
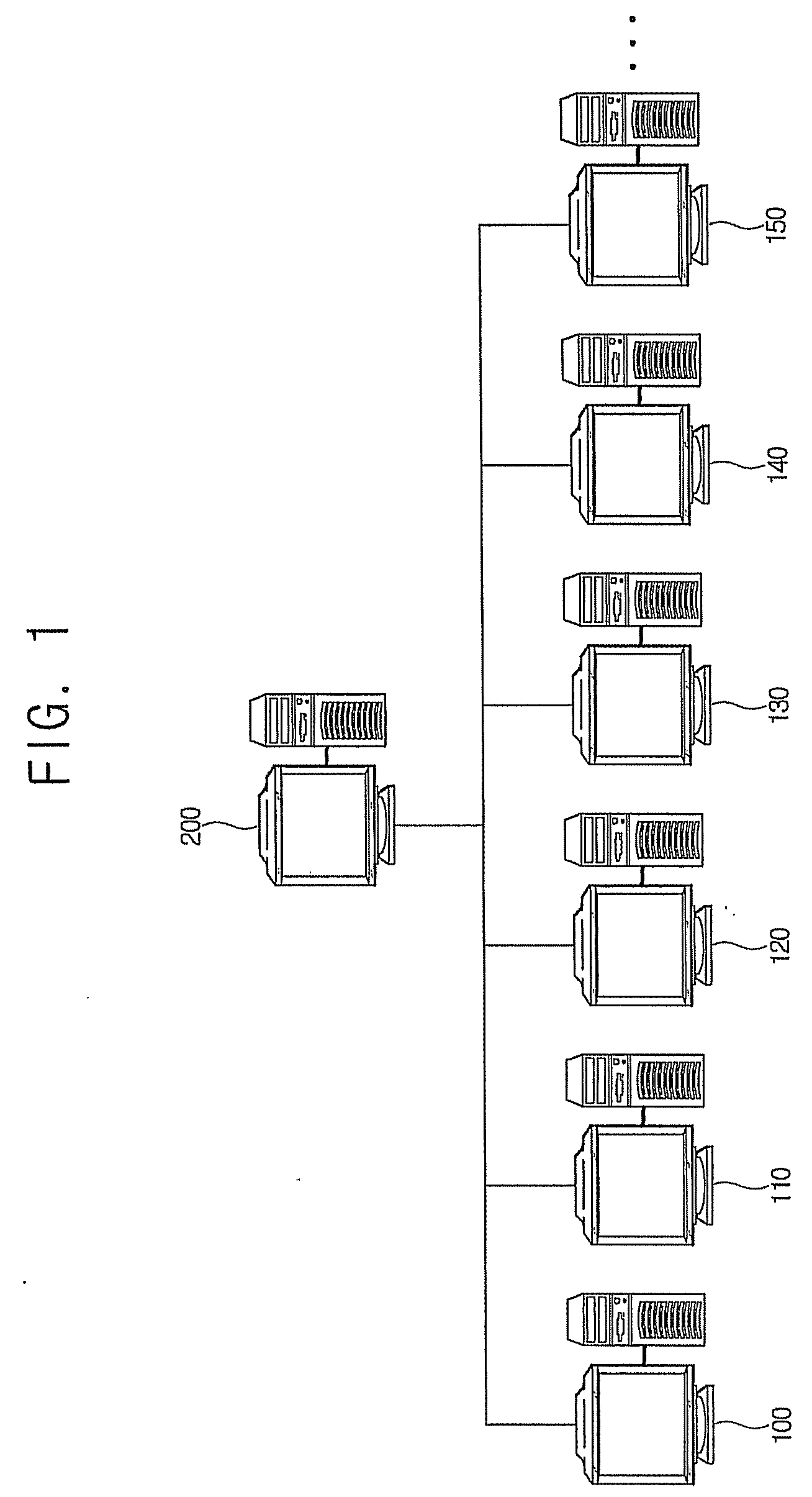
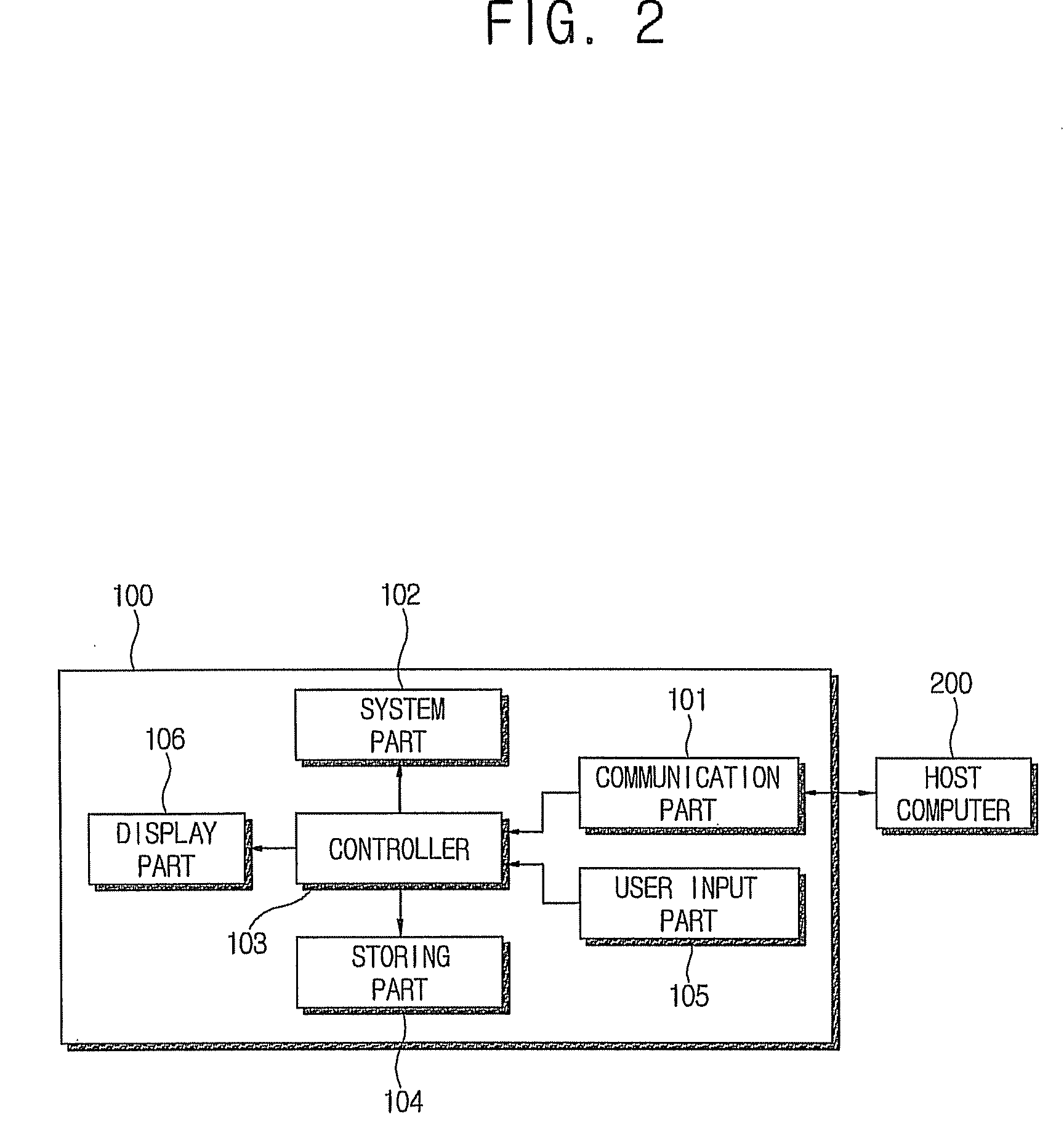
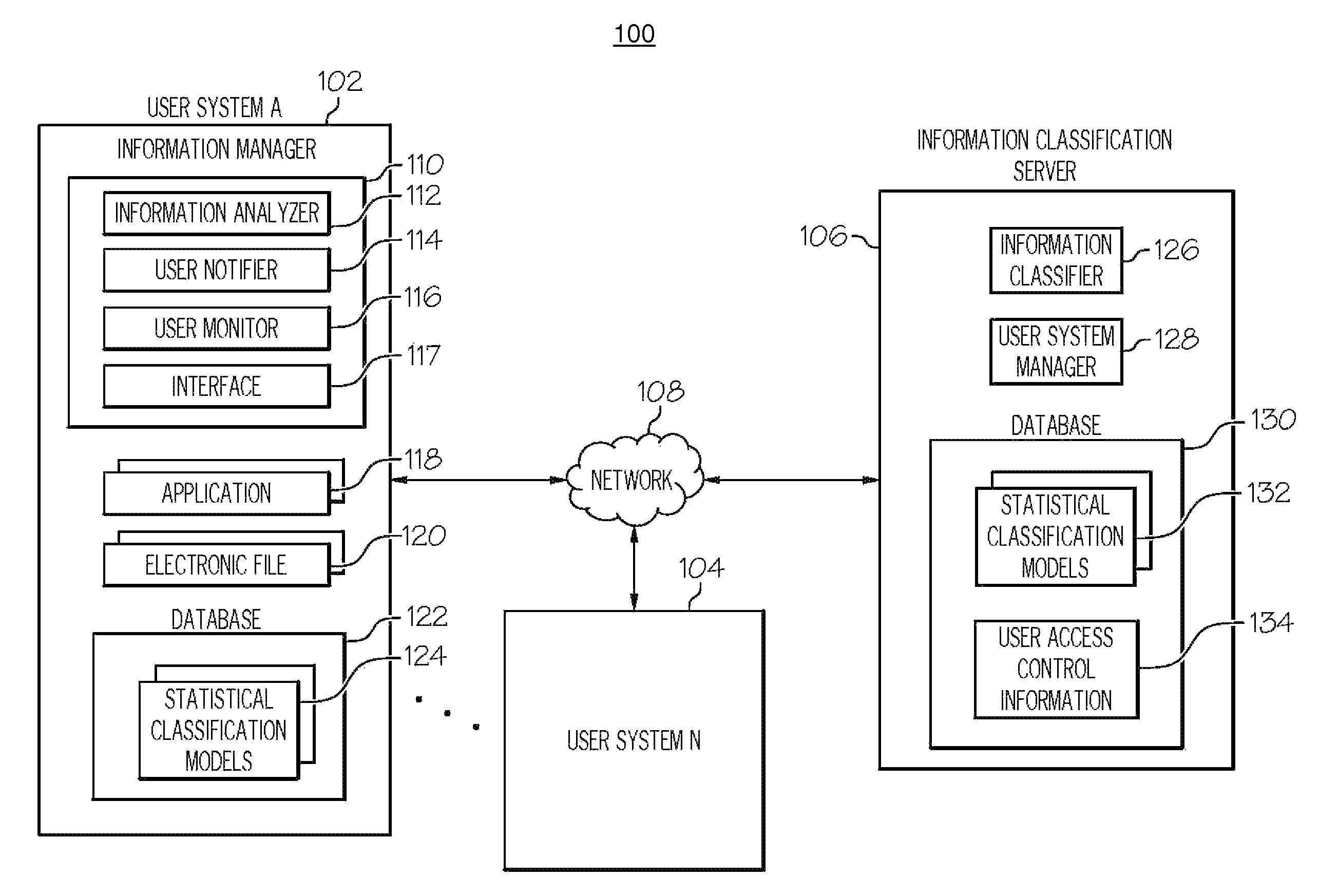
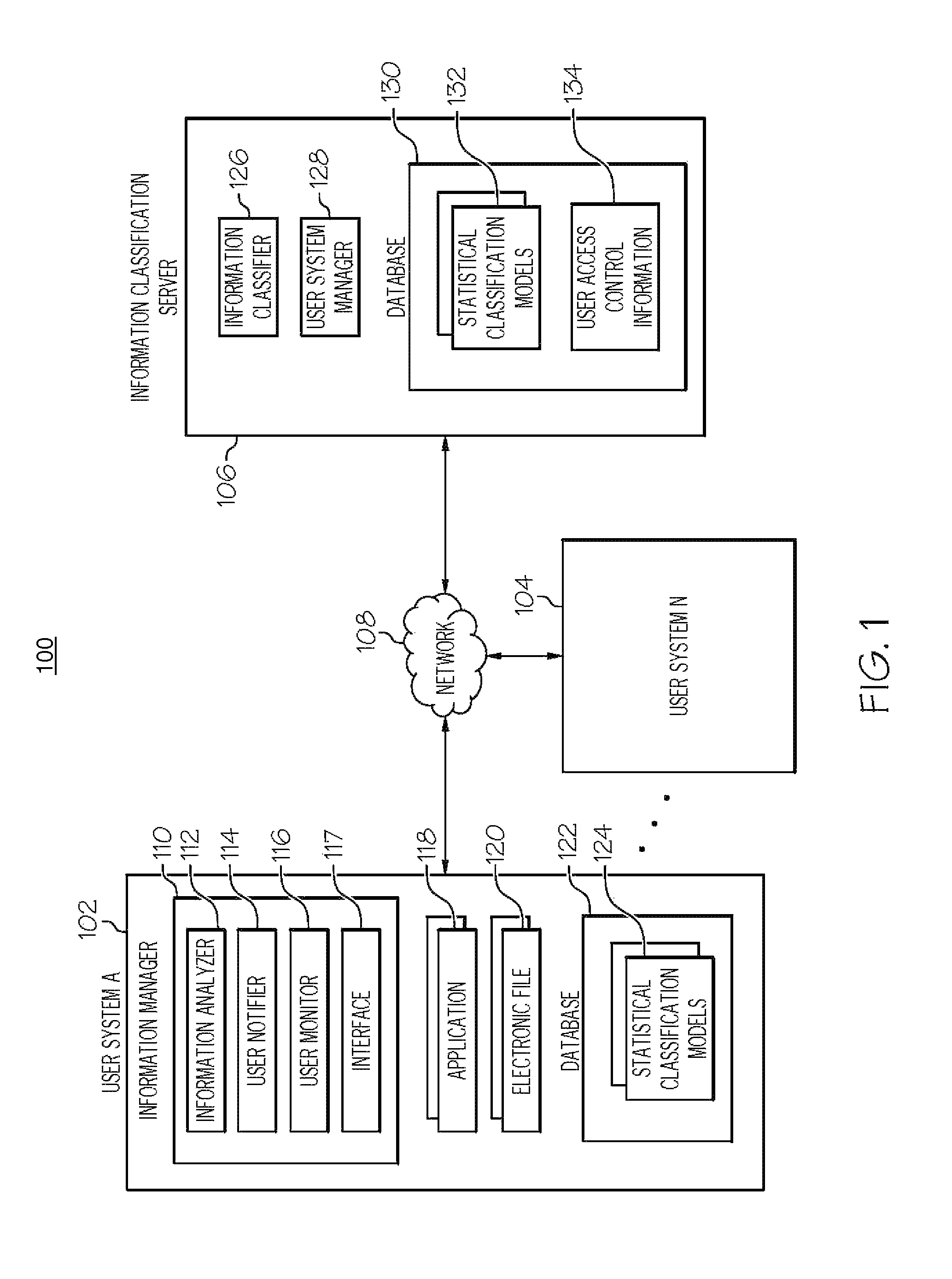
Managing the creation, detection, and maintenance of sensitive information
InactiveUS20100011000A1Prevent sensitive informationInhibition of informationDigital data processing detailsAnalogue secracy/subscription systemsInformation handling systemStatistical classification
A method, information processing system, and computer program storage product for managing information within an electronic file are provided. A plurality of information sets within an electronic file is analyzed. At least one of the information sets is compared to at least one statistical classification model. The statistical classification model includes one or more probabilities associated with a plurality of analyzed information sets that indicate a likelihood that a respective analyzed information set is classified sensitive information. The at least one information set is determined to substantially match at least one analyzed information set in the statistical classification model. The probability associated with the at least one analyzed information set is determined whether to be above a threshold. The at least one information set is classified as sensitive information in response to determining that the probability is above the threshold.
Owner:IBM CORP
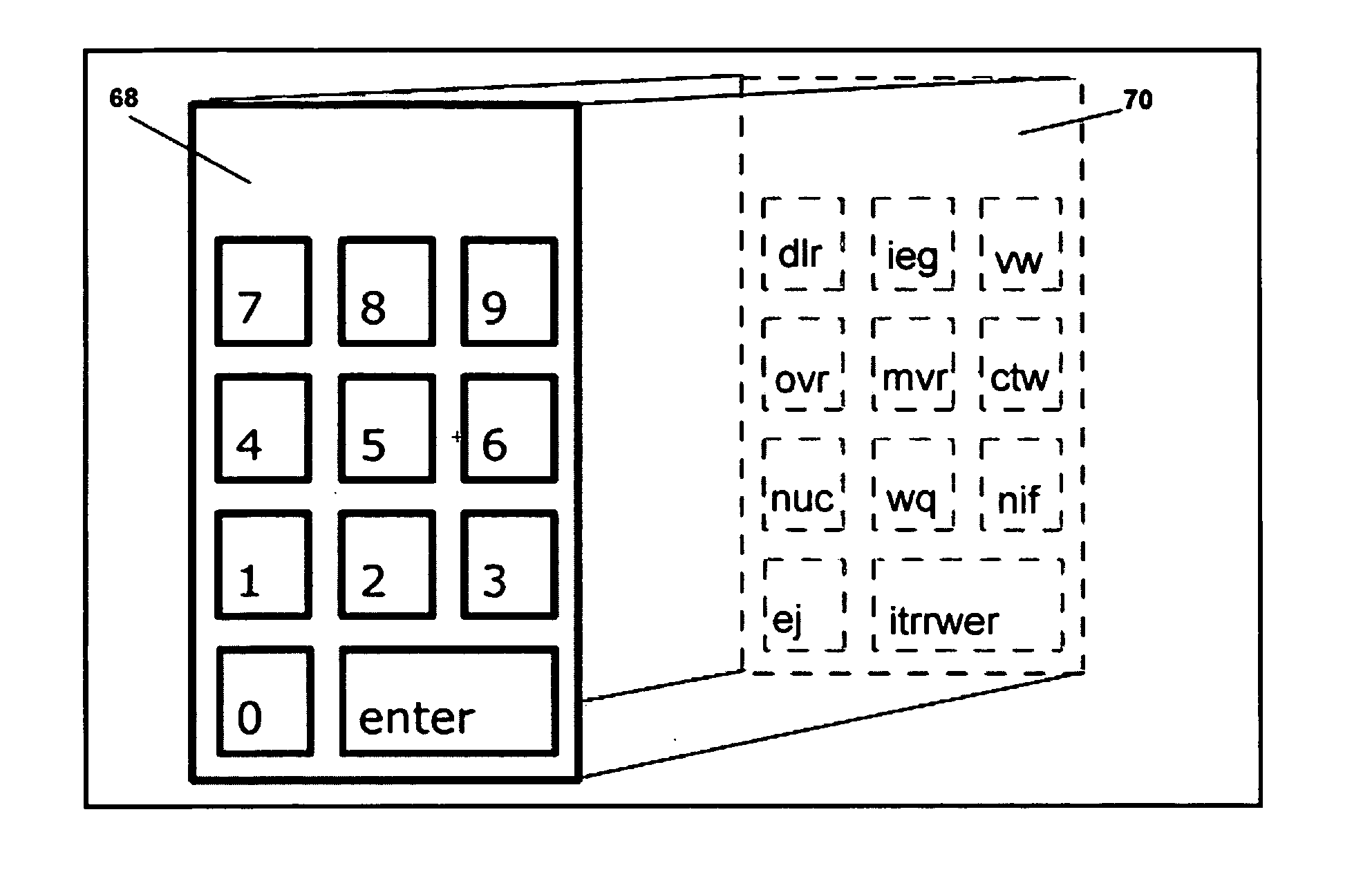
Online data encryption and decryption
ActiveUS20060020815A1Inhibition of informationAvoid loopholesDigital data authenticationSecret communicationComputer hardwareGraphics
Systems and methods for providing encryption and decryption of data transmitted on a computer implemented network, preferably user authentication identifier data, such as a password, at the point of entry into the user's computer. The systems and methods enable an end user to mentally select a marker from one of the randomly arranged elements on a first portion of a graphical image. A second portion of the graphical image includes an arrangement of possible elements of any individual authentication identifier sequence, and is positioned adjacent to the first portion. The systems and methods prompt a user to enter each element of the identifier by moving the selected marker and the first portion as necessary to substantially align the selected marker with a chosen element of the authentication identifier appearing on the outer portion. According to one embodiment, the image portions are concentric wheels. According to another embodiment, the image portions are arranged in adjacent rows.
Owner:ORACLE INT CORP
Antenna selection control circuitry
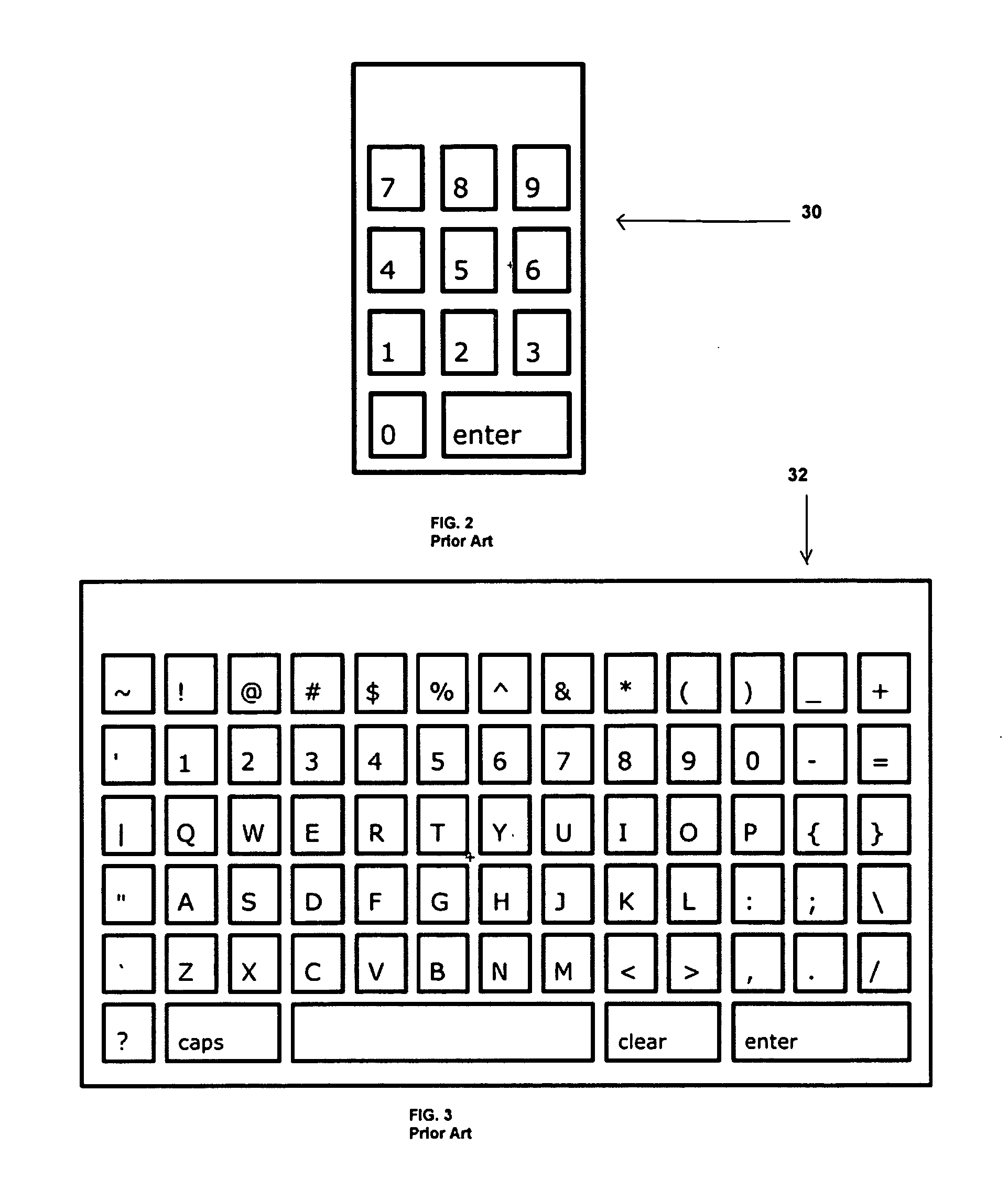
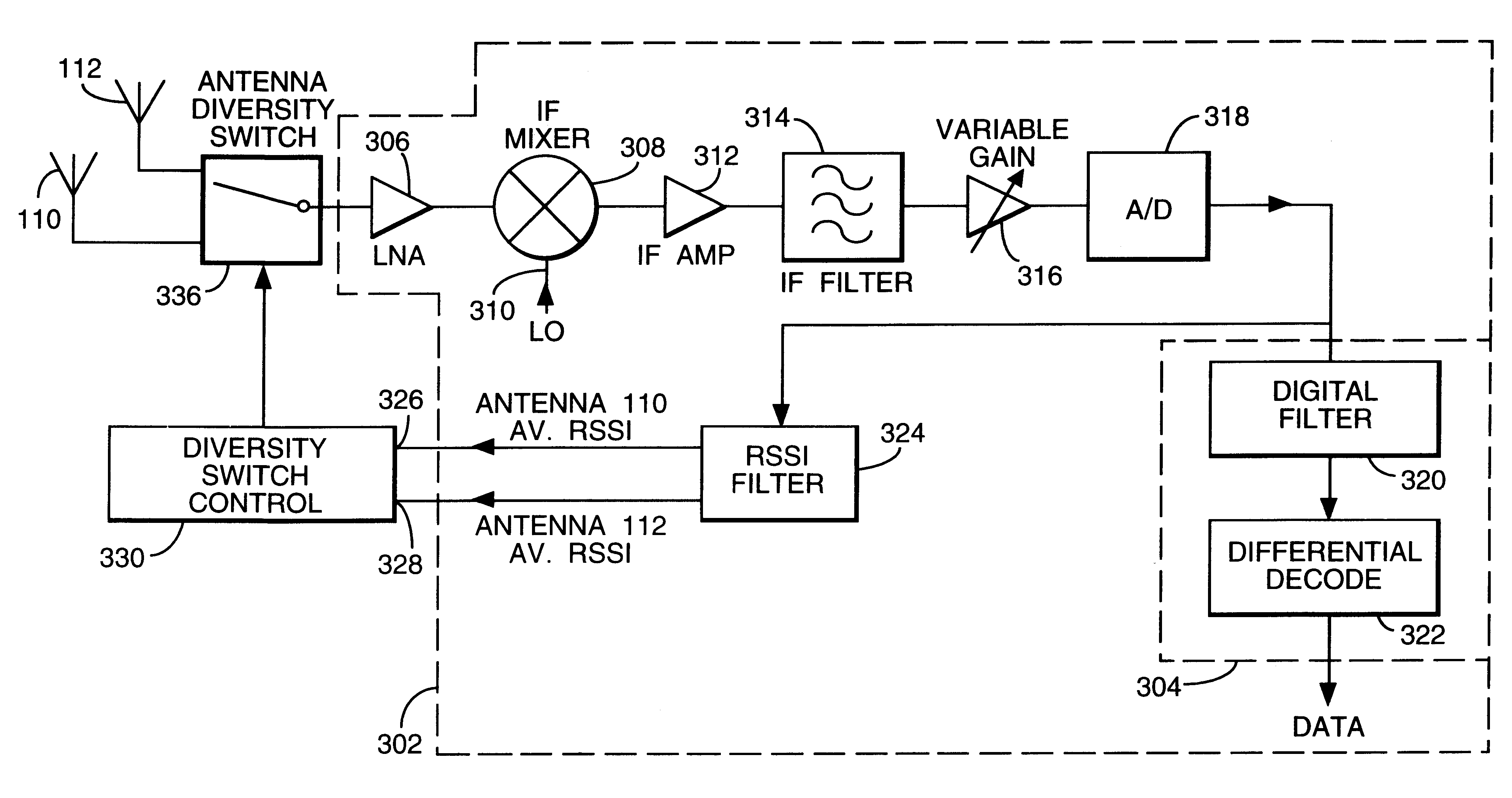
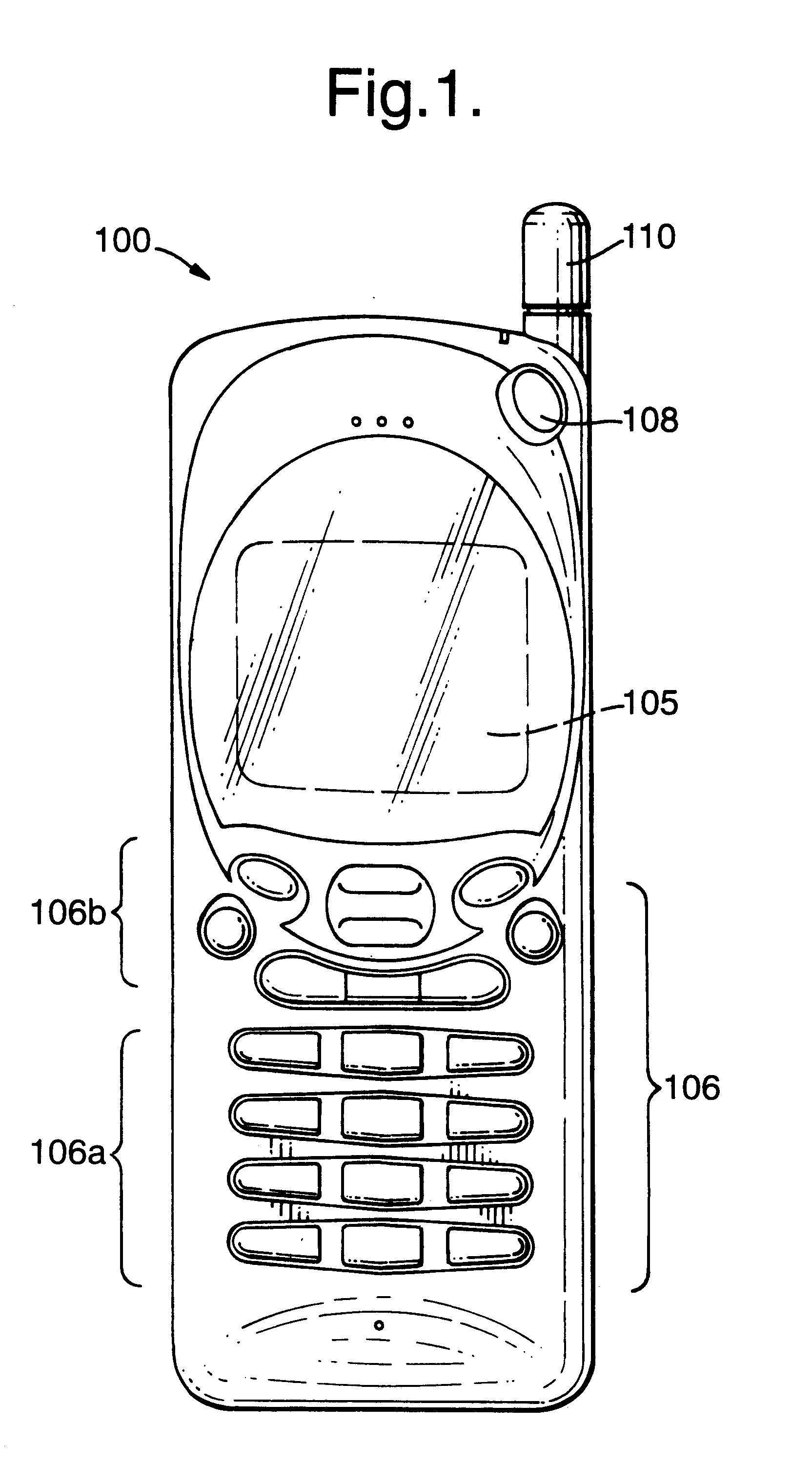
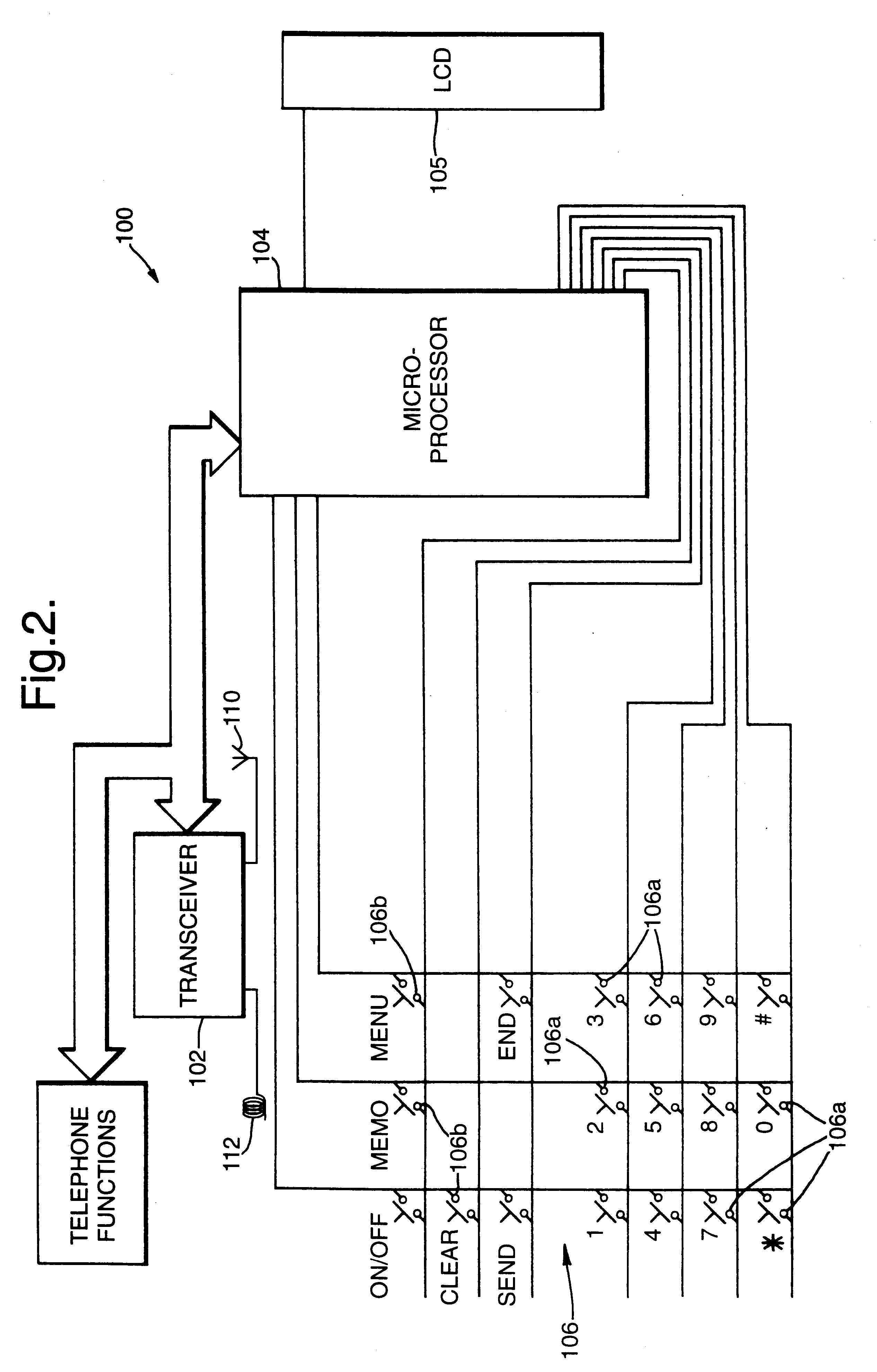
InactiveUS6330433B1Avoid interferenceSimple signalSpatial transmit diversityRadio transmission for post communicationSignal qualityControl circuit
Apparatus and method are described for selecting for subsequent use an antenna from a plurality of antennas. The selection is biased in favor of the antenna most likely to receive subsequent signals having best signal quality. In a preferred embodiment the signal quality comprises received signal strength.
Owner:NOKIA MOBILE PHONES LTD
Information processing device, virtual machine creation method, and application distribution system
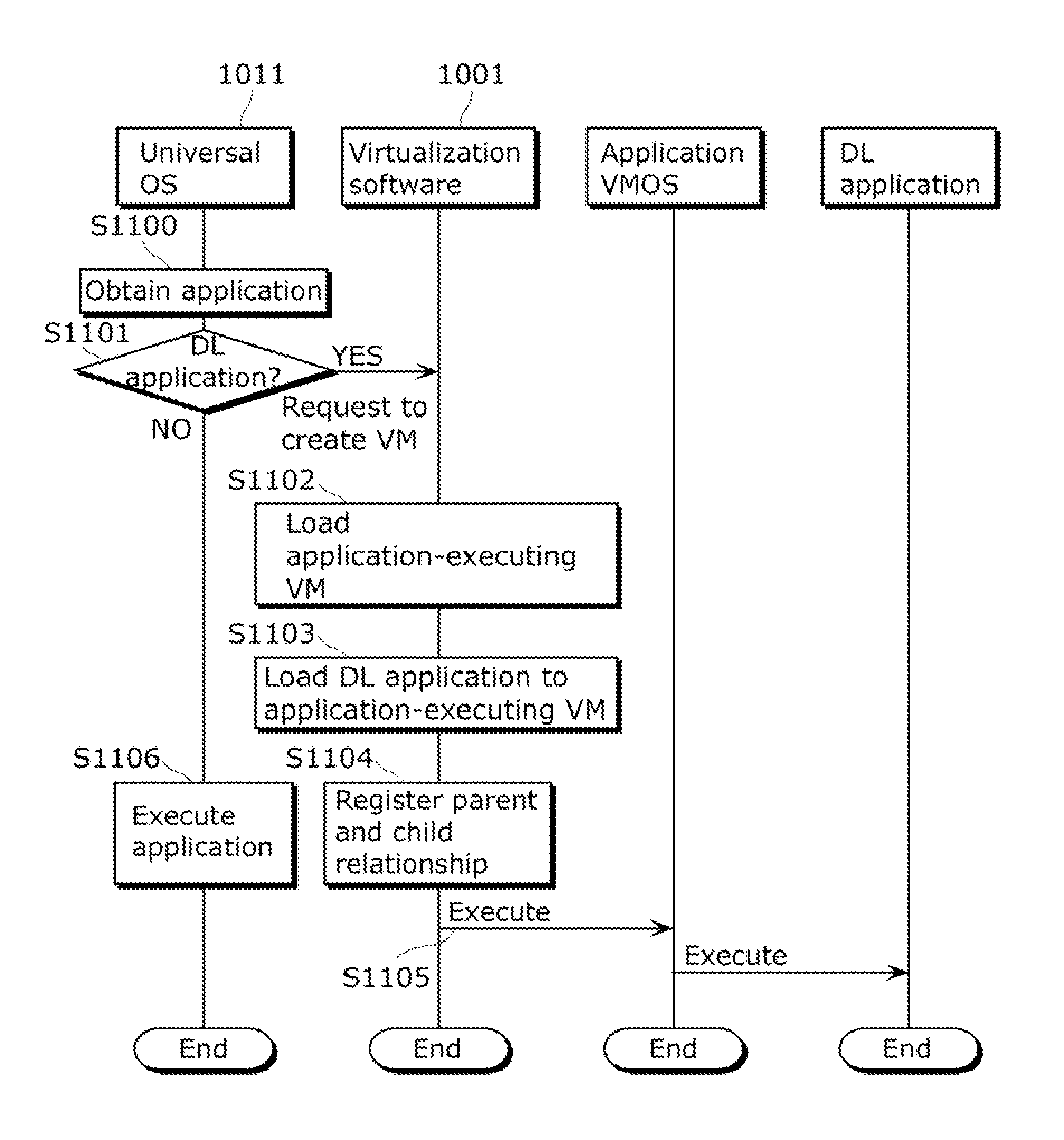
ActiveUS20120260250A1Prevent access to informationInhibition of informationMultiprogramming arrangementsPlatform integrity maintainanceInformation processingVirtualization
A device (110) according to an implementation of the present invention, having a plurality of virtual machines (1002, 1003, 1004, and 1005), includes a virtualization software (1001) which manages the virtual machines. The virtualization software includes an application VM creating unit (1300) which creates a virtual machine for executing a program. A first virtual machine (1002) determines whether a first program is to be executed on the first virtual machine or to be executed on a virtual machine other than the first virtual machine. When the first virtual machine determines that the first program is to be executed on the other virtual machine, the application VM creating unit creates a second virtual machine for executing the first program.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
Mutual for reporting a theft in an authentication system
ActiveUS20090328162A1Inhibition of informationMemory loss protectionDigital data processing detailsThird partyPassword
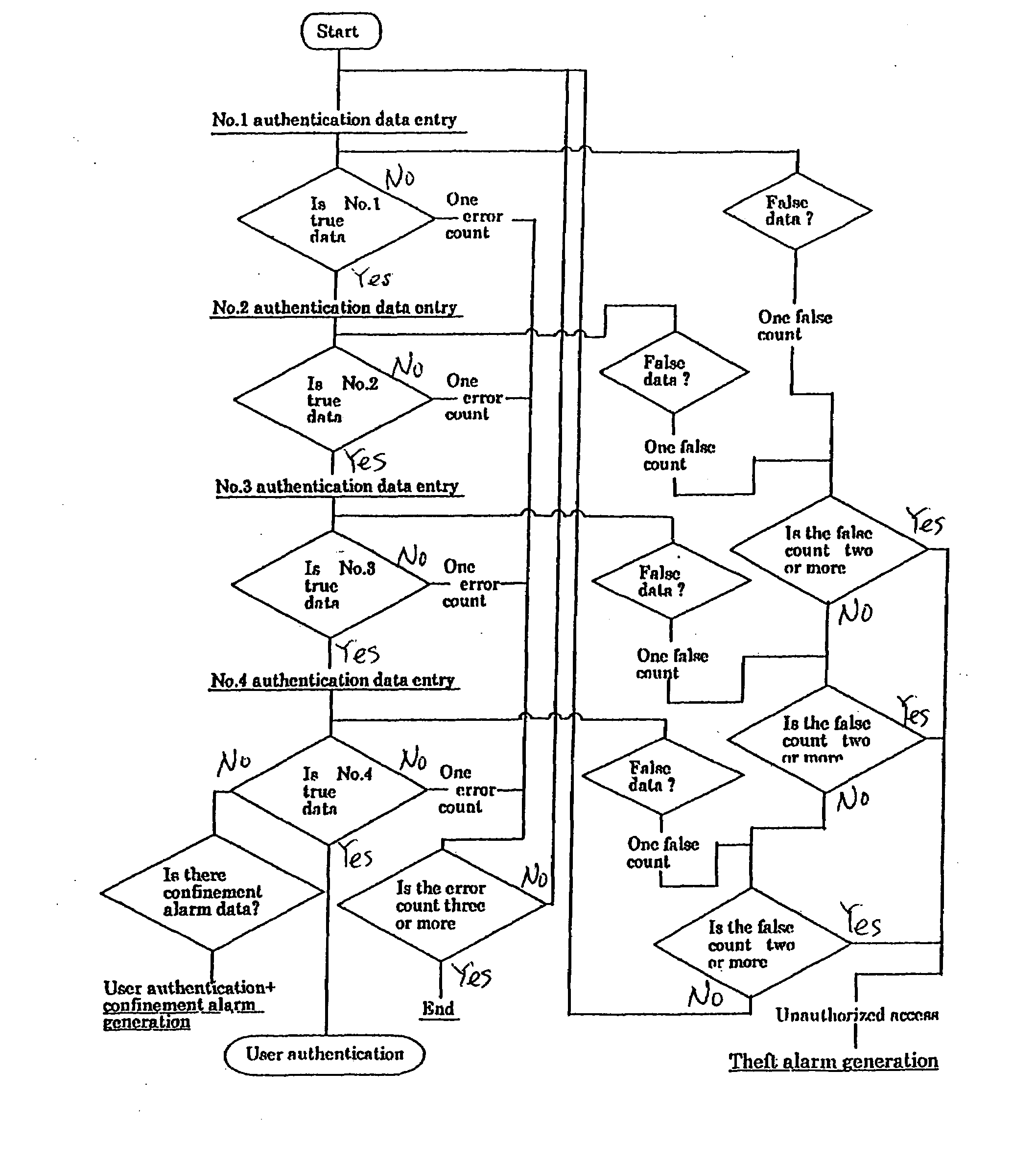
Disclosed are protection of secret information including an encryption key and a system for reporting an emergency such as theft or confinement when secret information is accessed. Secret information includes a large quantity of decoy data and a piece / pieces of true and correct data mixed into the decoy data. The secret data including the decoy data and the true and correct data is two-dimensional code data the code of which is composed of groups of cells having different areas. The positions and order of storage of the true and correct data dispersedly mixed in the decoy data are determined and reported to the user. The user adds a predetermined alerting signal when inputting the password to tell that the user is under control of a third party. The system can detect the alerting signal and know that the user is in an abnormal state, performs normal identification procedures, and takes protection / preservation measures. Part of decoy data is specified as confinement report data and added to the true and correct data. Consequently at least a piece of confinement report data is included and therefore the user himself is judged to be under control of the third party. Then the user is identified and a confinement report alert is issued.
Owner:MNEMONIC SECURITY
Method and apparatus for authenticating area biometric scanners
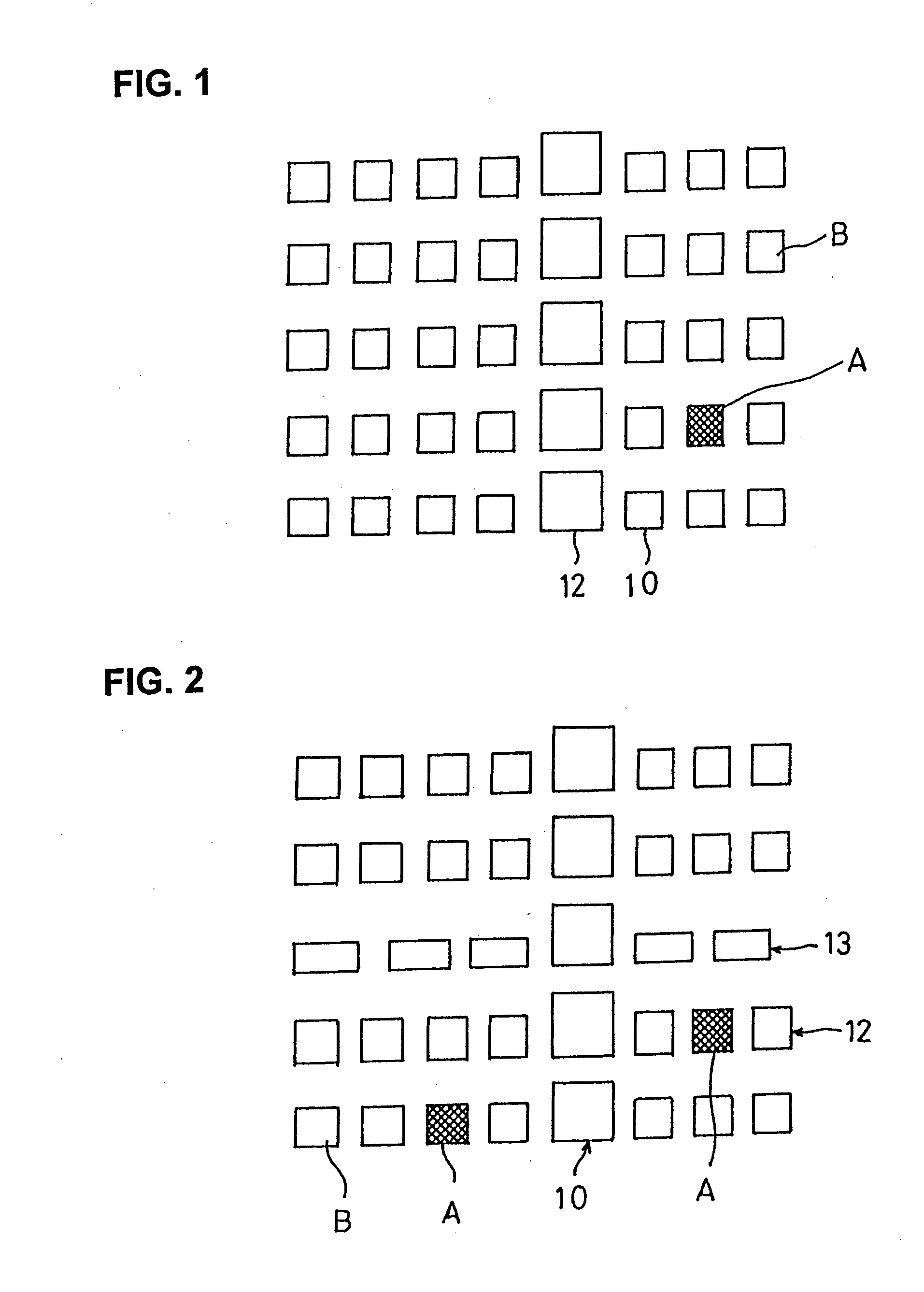
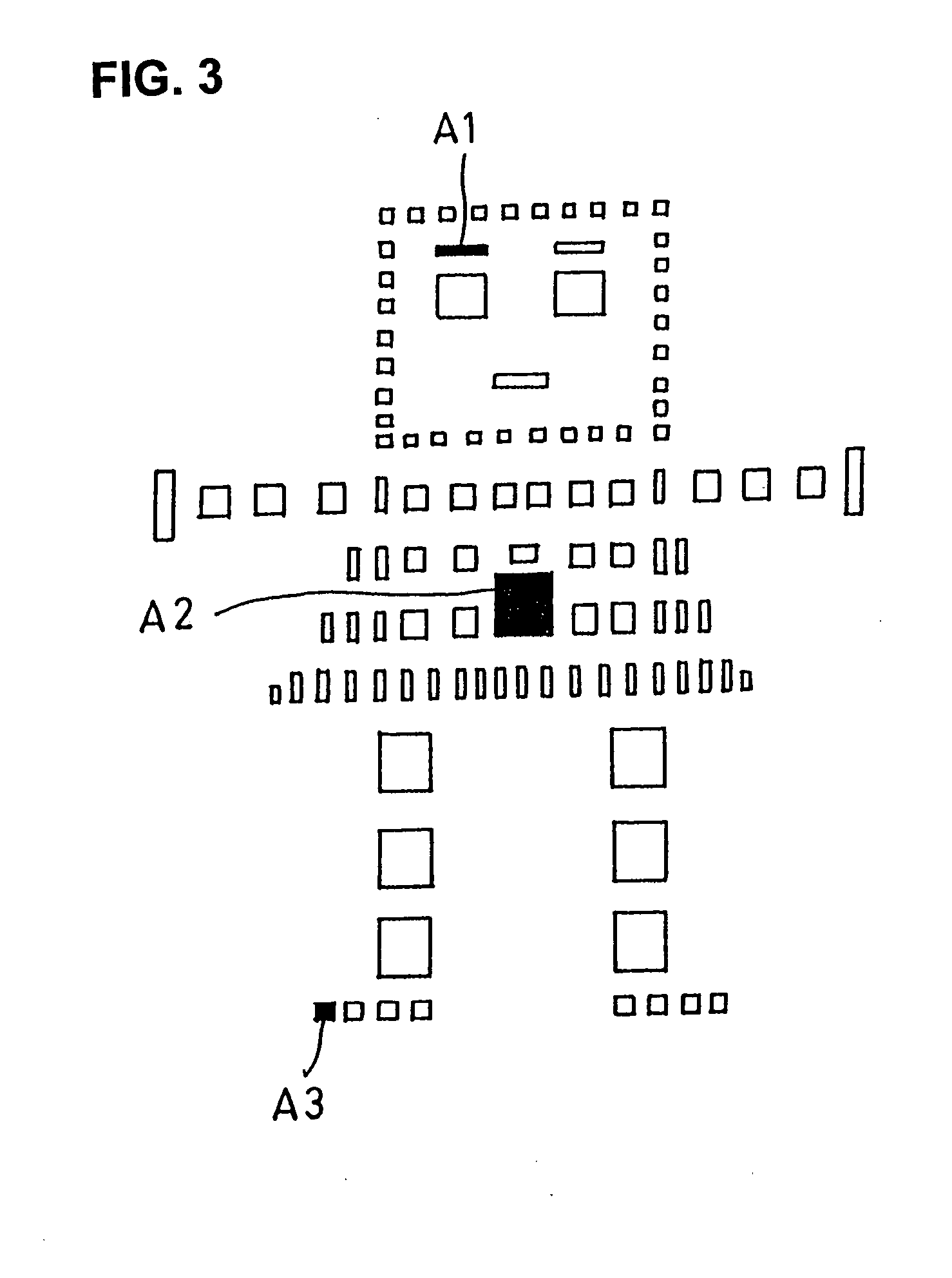
ActiveUS20120300988A1Improve security levelEasy to be stolenImage enhancementPrint image acquisitionImaging processingUser authentication
Methods and apparatuses for authenticating a biometric scanner, such as area type finger print scanners, involves estimating unique intrinsic characteristics of the scanner (scanner pattern), that are permanent over time, and can identify a scanner even among scanners of the same manufacturer and model. Image processing and analysis are used to extract a scanner pattern from images acquired with the scanner. The scanner pattern is used to verify whether the scanner that acquired a particular image is the same as the scanner that acquired one or several images during enrollment of the biometric information. Authenticating the scanner can prevent subsequent security attacks using counterfeit biometric information on the scanner, or on the user authentication system.
Owner:UNIV OF MARYLAND BALTIMORE
Electronics device system and electronics device
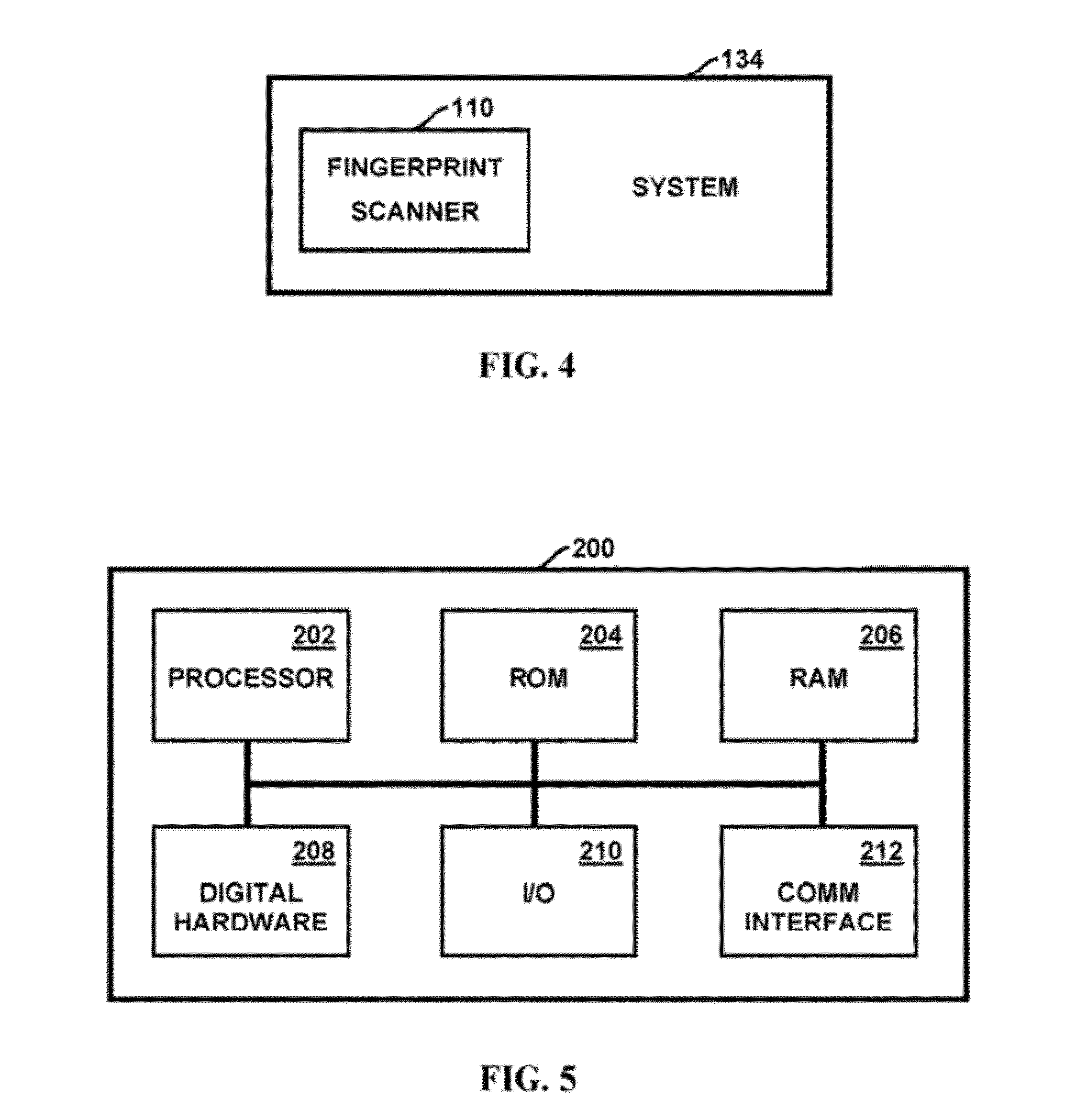
InactiveUS20070077063A1Prevent image informationOperational securityTelevision system detailsSubstation/switching arrangement detailsCamera lensComputer terminal
A camera comprises a lens unit and a camera body to which the lens unit is attached by a rotational operation. The camera body is provided with terminals including a specific terminal. Arrangement of the specific terminal is different from that of the other terminals. In detaching the lens unit from the camera body, the specific terminal is adapted to be disconnected earlier relative to the other terminals while the other terminals are connected. After the disconnection of the specific terminal has been detected, the other terminals are set to high impedance.
Owner:FUJIFILM HLDG CORP +1
Secured medical sign-in
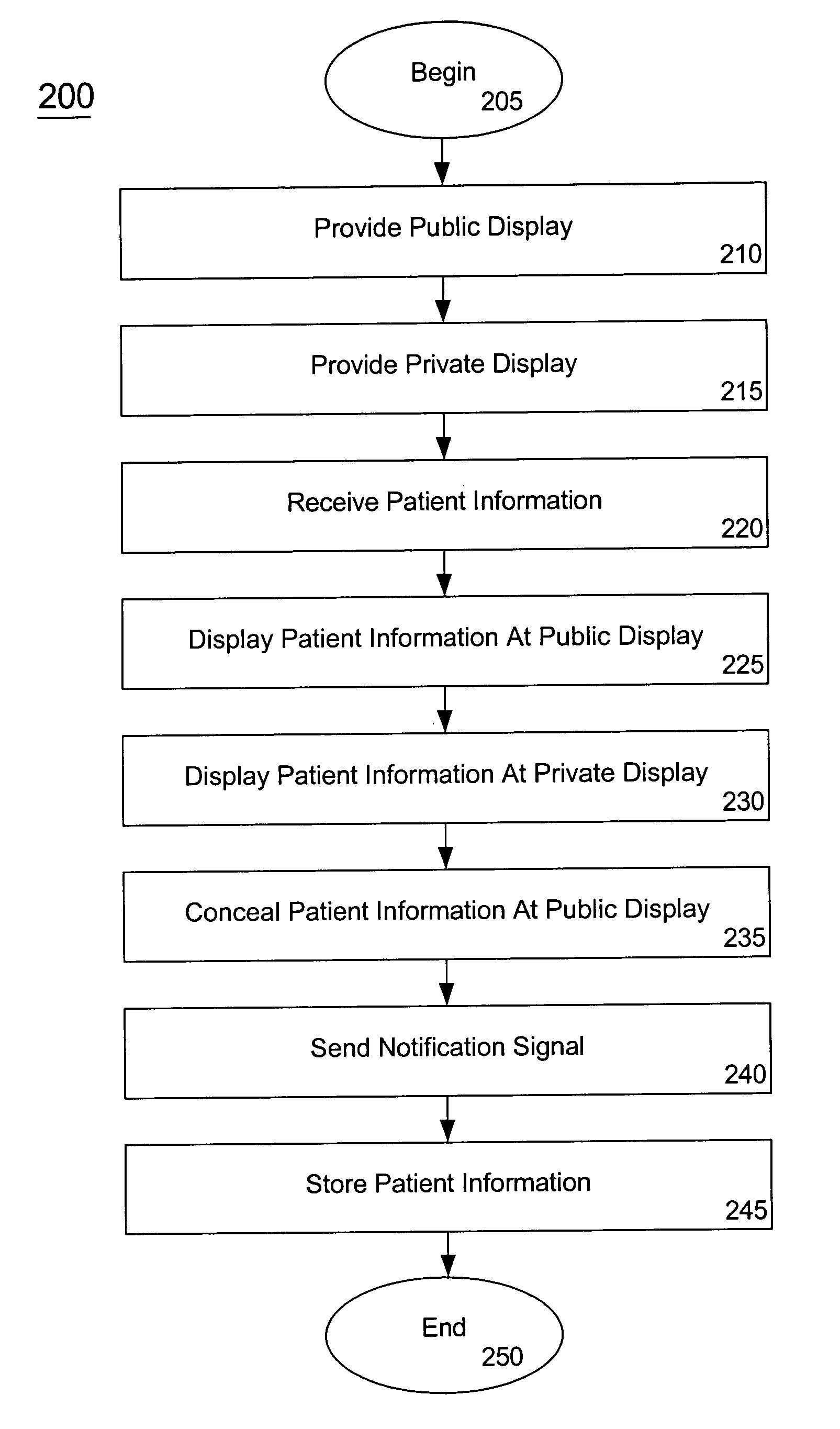
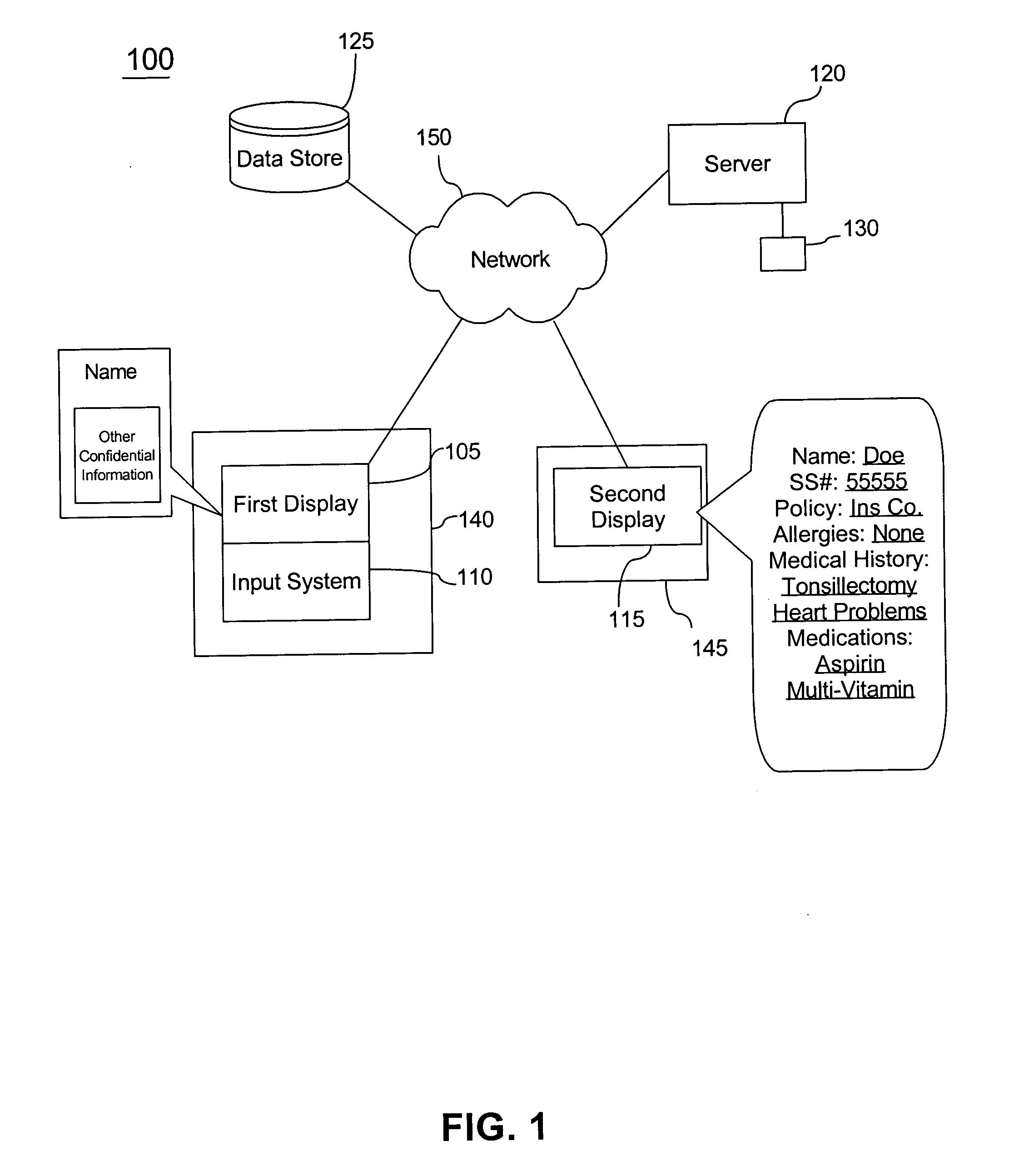
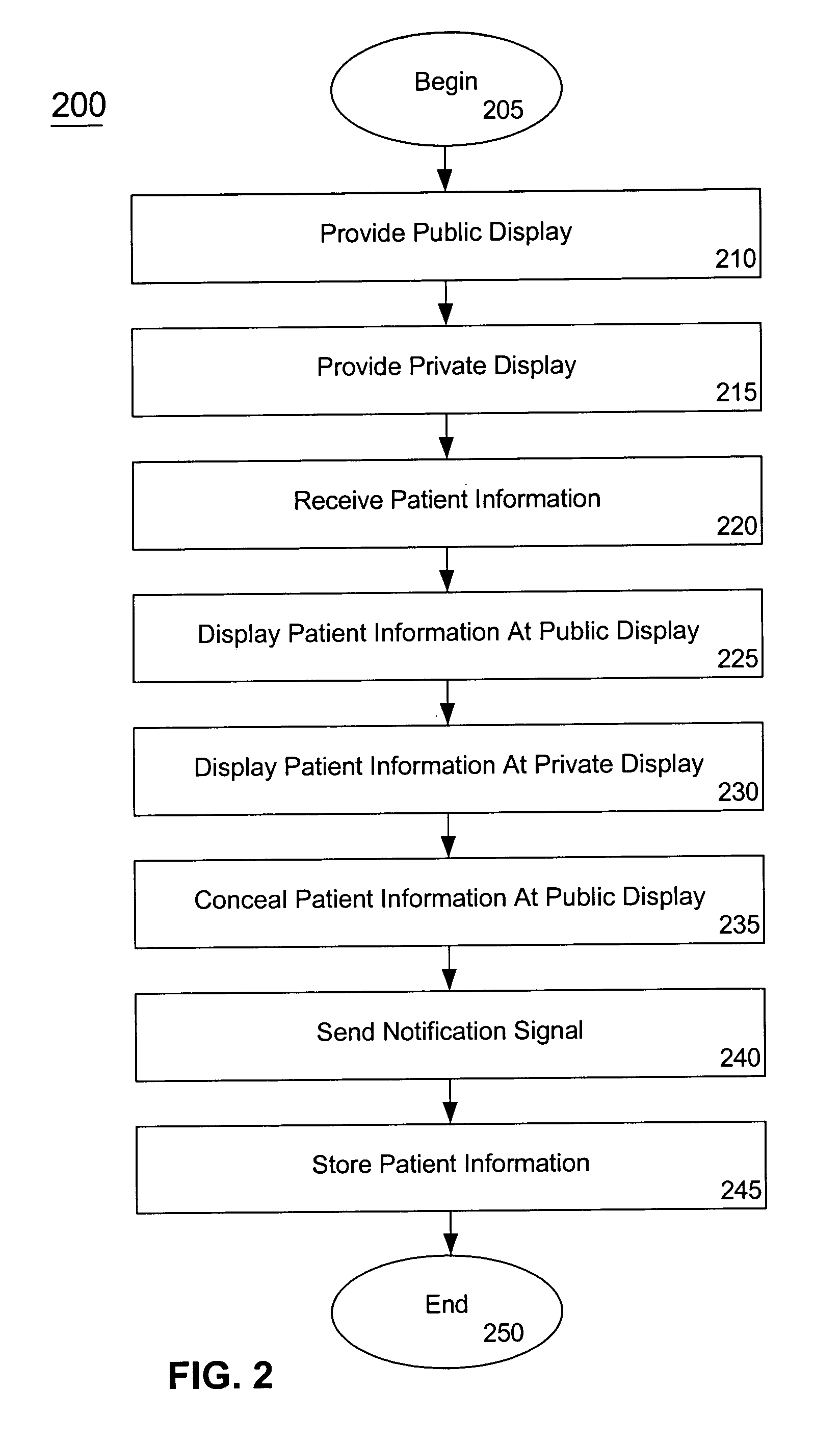
ActiveUS20050071188A1Prevent access to informationInhibition of informationOffice automationMedical equipmentInternet privacyDisplay device
A method for concealing displayed confidential information includes providing one or more publically accessible displays and one or more private displays, receiving confidential information, displaying at least a portion of the confidential information at the private display, and displaying at least a portion of the confidential information at the publically accessible display for an amount of time determined by an occurrence of an event where the event includes at least one of an expiration of a time period and a user request. The method can also include sending a notification signal where the notification signal can be sent to a health care professional and storing at least a portion of the confidential information. The method can also include concealing at least a portion of the confidential information at the publically accessible display where the concealing step is responsive to a user request.
Owner:TWITTER INC
Client computer, remote control system, and remote control method
ActiveUS20080040786A1Prevent leakageAvoid dataEnergy efficient ICTUser identity/authority verificationRemote controlControl system
Owner:SAMSUNG ELECTRONICS CO LTD
Managing the creation, detection, and maintenance of sensitive information
InactiveUS8346532B2Inhibition of informationDigital data processing detailsAnalogue secracy/subscription systemsInformation processingStatistical classification
A method, information processing system, and computer program storage product for managing information within an electronic file are provided. A plurality of information sets within an electronic file is analyzed. At least one of the information sets is compared to at least one statistical classification model. The statistical classification model includes one or more probabilities associated with a plurality of analyzed information sets that indicate a likelihood that a respective analyzed information set is classified sensitive information. The at least one information set is determined to substantially match at least one analyzed information set in the statistical classification model. The probability associated with the at least one analyzed information set is determined whether to be above a threshold. The at least one information set is classified as sensitive information in response to determining that the probability is above the threshold.
Owner:INT BUSINESS MASCH CORP
Prevention of side channel attacks against block cipher implementations and other cryptographic systems
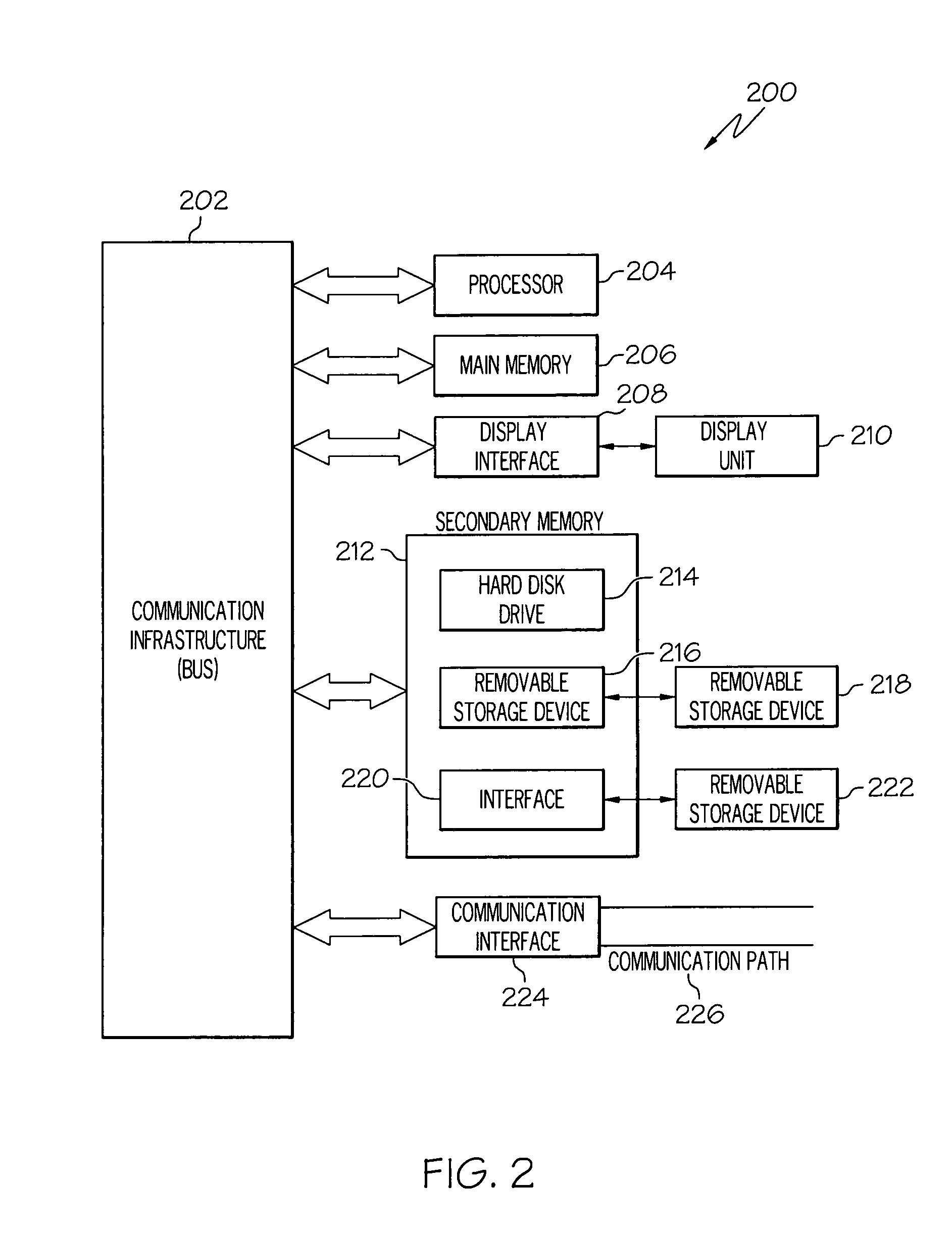
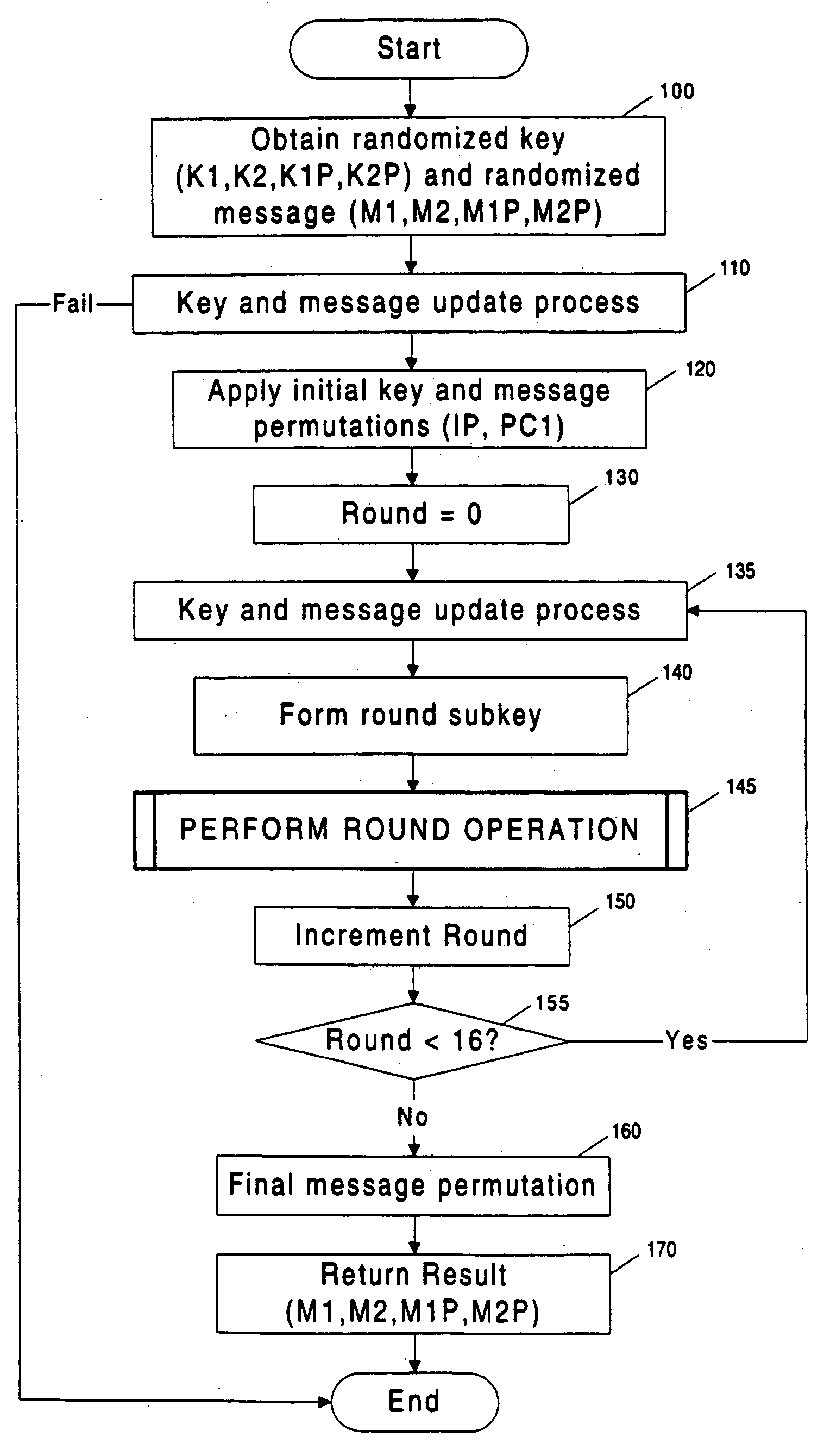
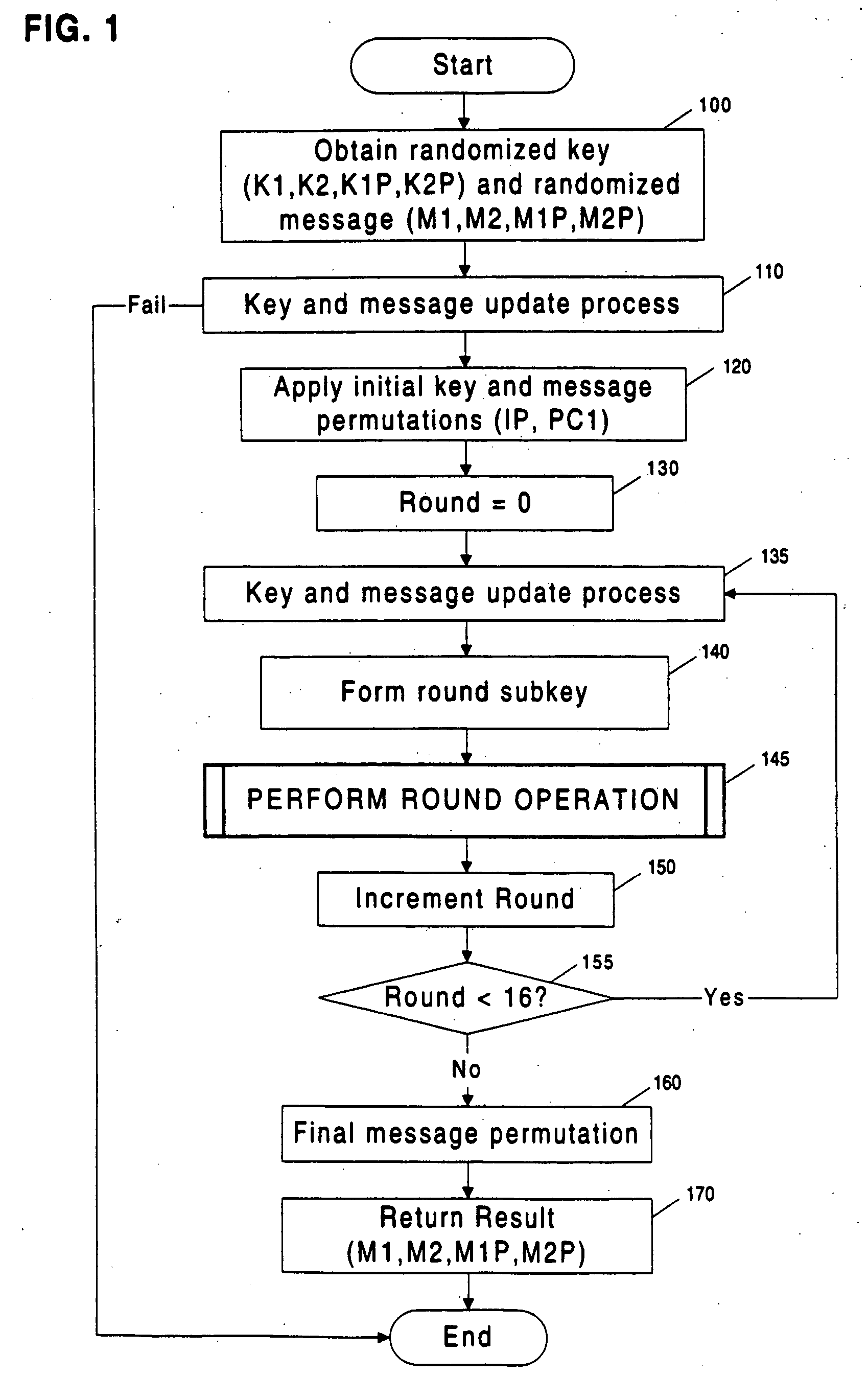
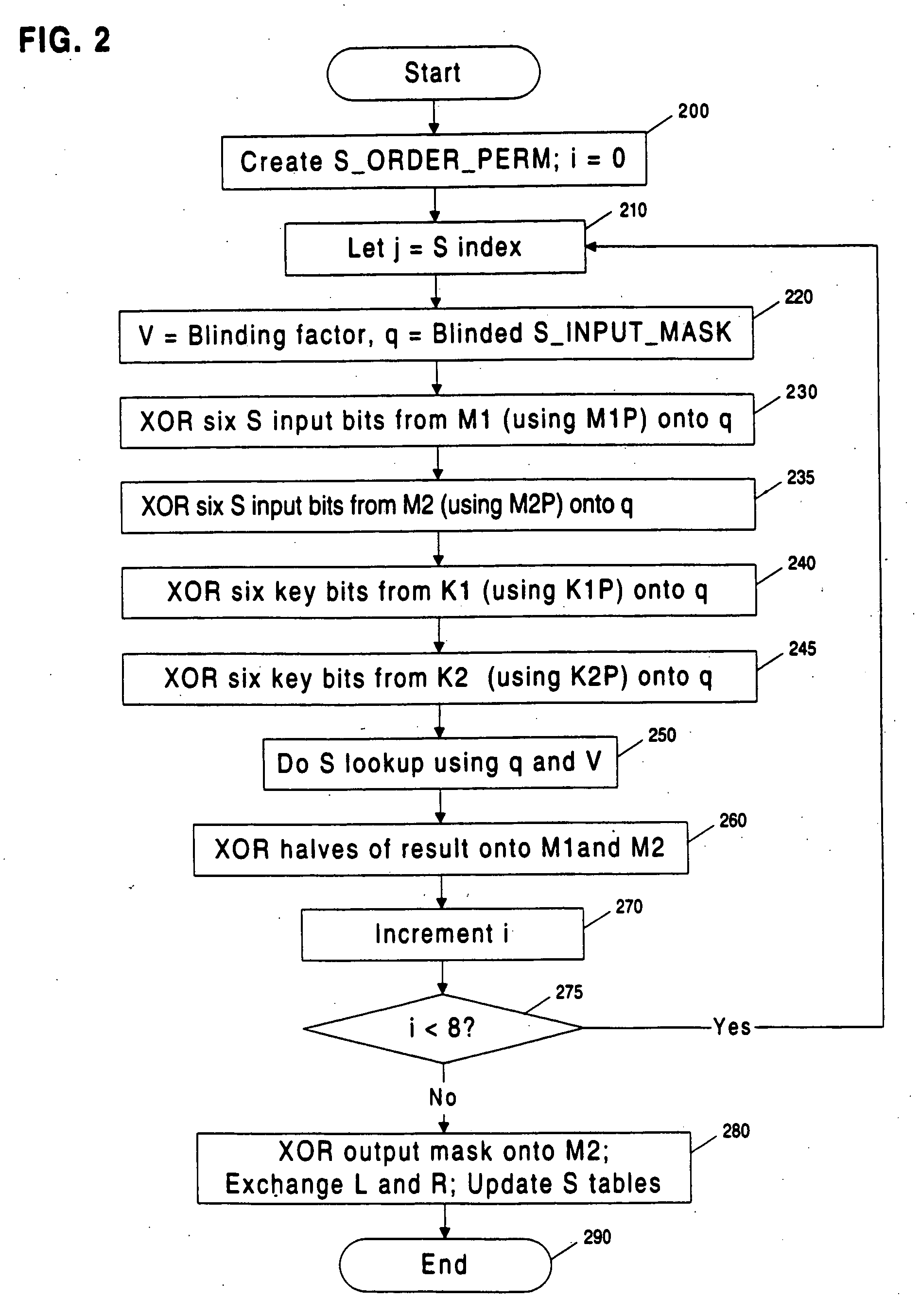
InactiveUS20060045264A1Safe leakageEasy to convertEncryption apparatus with shift registers/memoriesDigital data processing detailsPlaintextSignal-to-noise ratio (imaging)
Methods and apparatuses are disclosed for improving DES and other cryptographic protocols against external monitoring attacks by reducing the amount (and signal-to-noise ratio) of useful information leaked during processing. An improved DES implementation of the invention instead uses two 56-bit keys (K1 and K2) and two 64-bit plaintext messages (M1 and M2), each associated with a permutation (i.e., K1P, K2P and M1P, M2P) such that K1P{K1} XOR K2P{K2} equals the “standard” DES key K, and M1P{M1} XOR M2P{M2} equals the “standard” message. During operation of the device, the tables are preferably periodically updated, by introducing fresh entropy into the tables faster than information leaks out, so that attackers will not be able to obtain the table contents by analysis of measurements. The technique is implementable in cryptographic smartcards, tamper resistant chips, and secure processing systems of all kinds.
Owner:CRYPTOGRAPHY RESEARCH
Methods and systems related to trading engines
Owner:PORTWARE LLC
Automated Media Analysis And Document Management System
InactiveUS20080183710A1Prevent information overloadSacrificing coverageData processing applicationsDigital data processing detailsManagement toolDocument preparation
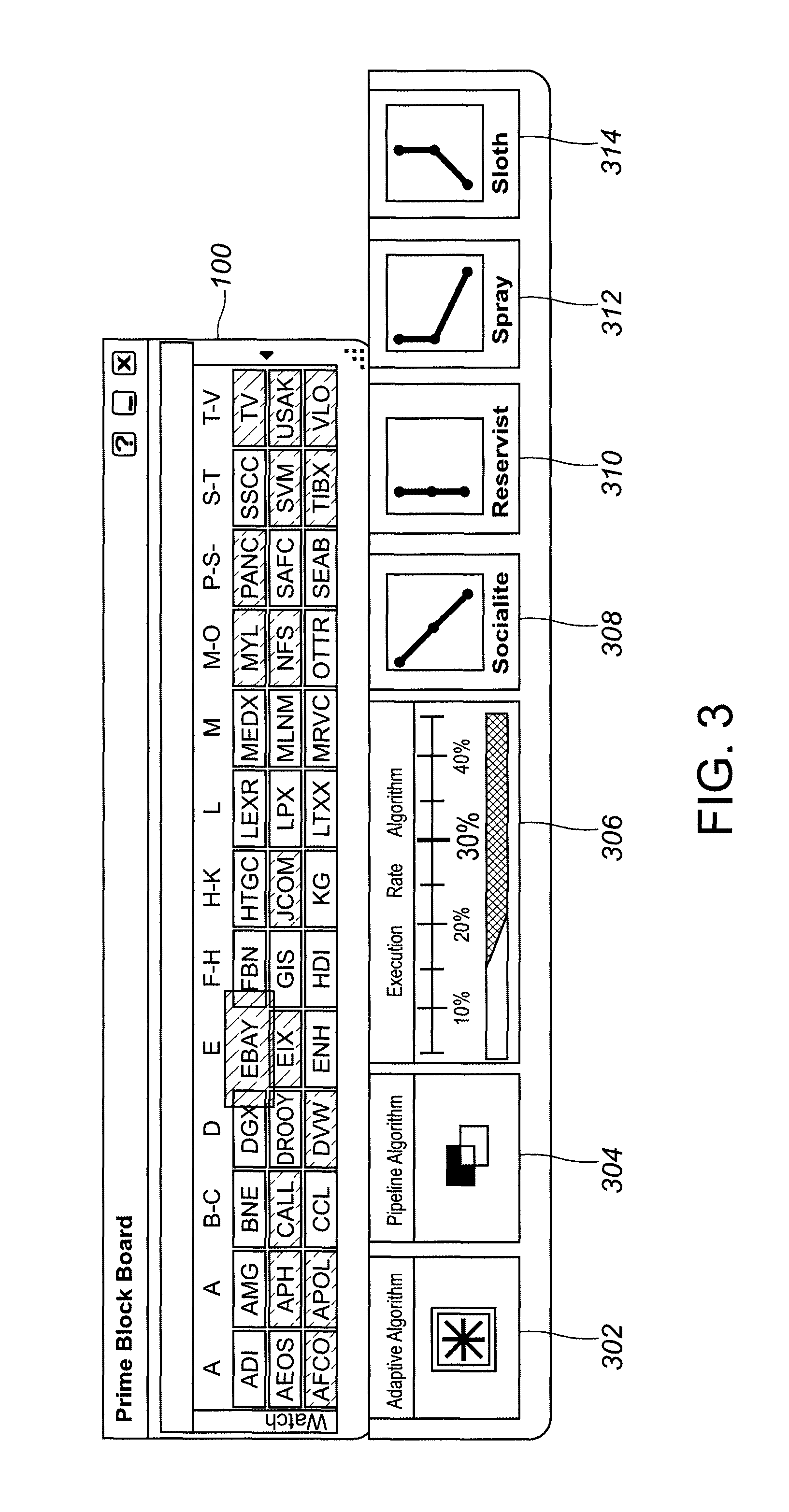
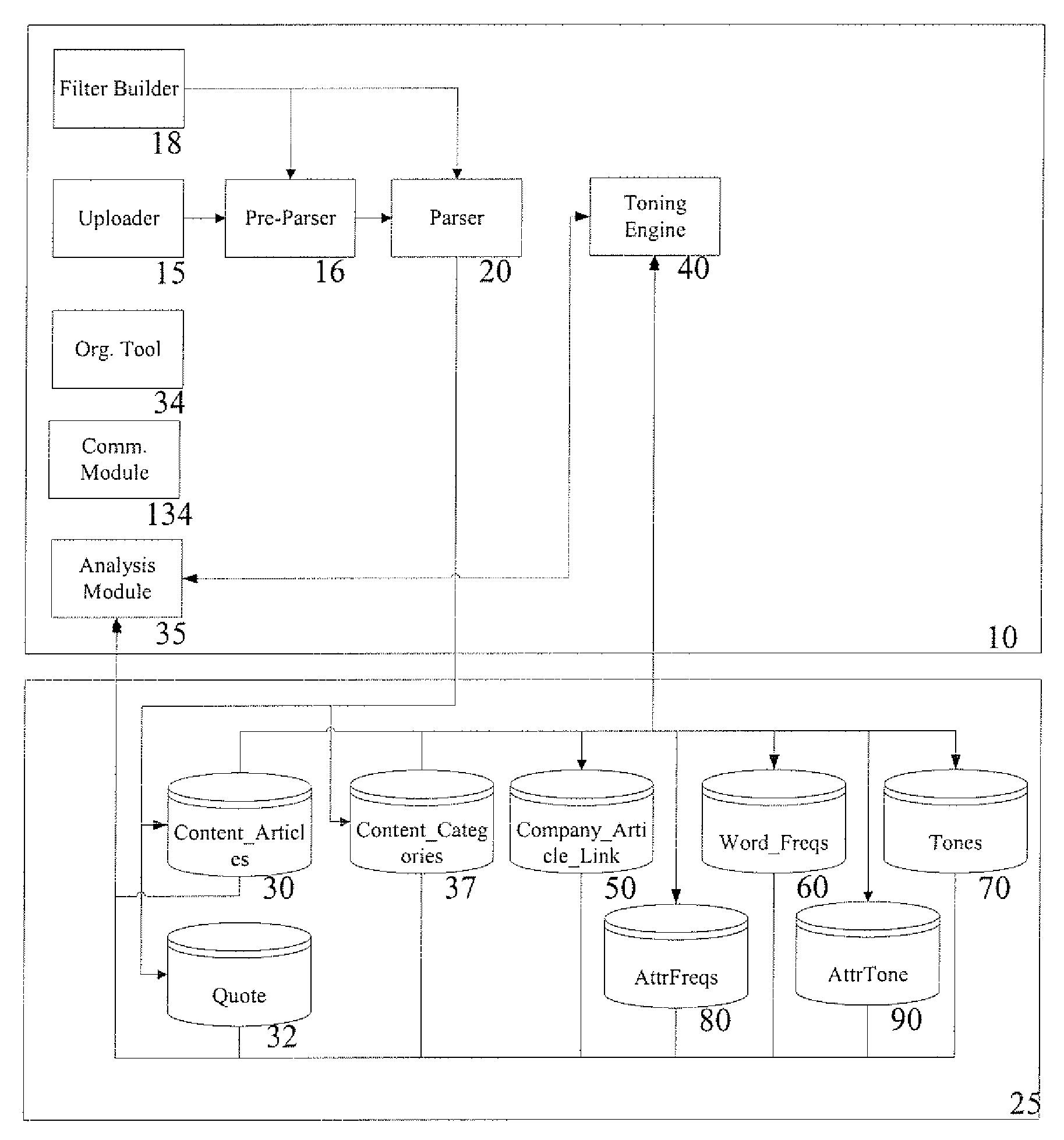
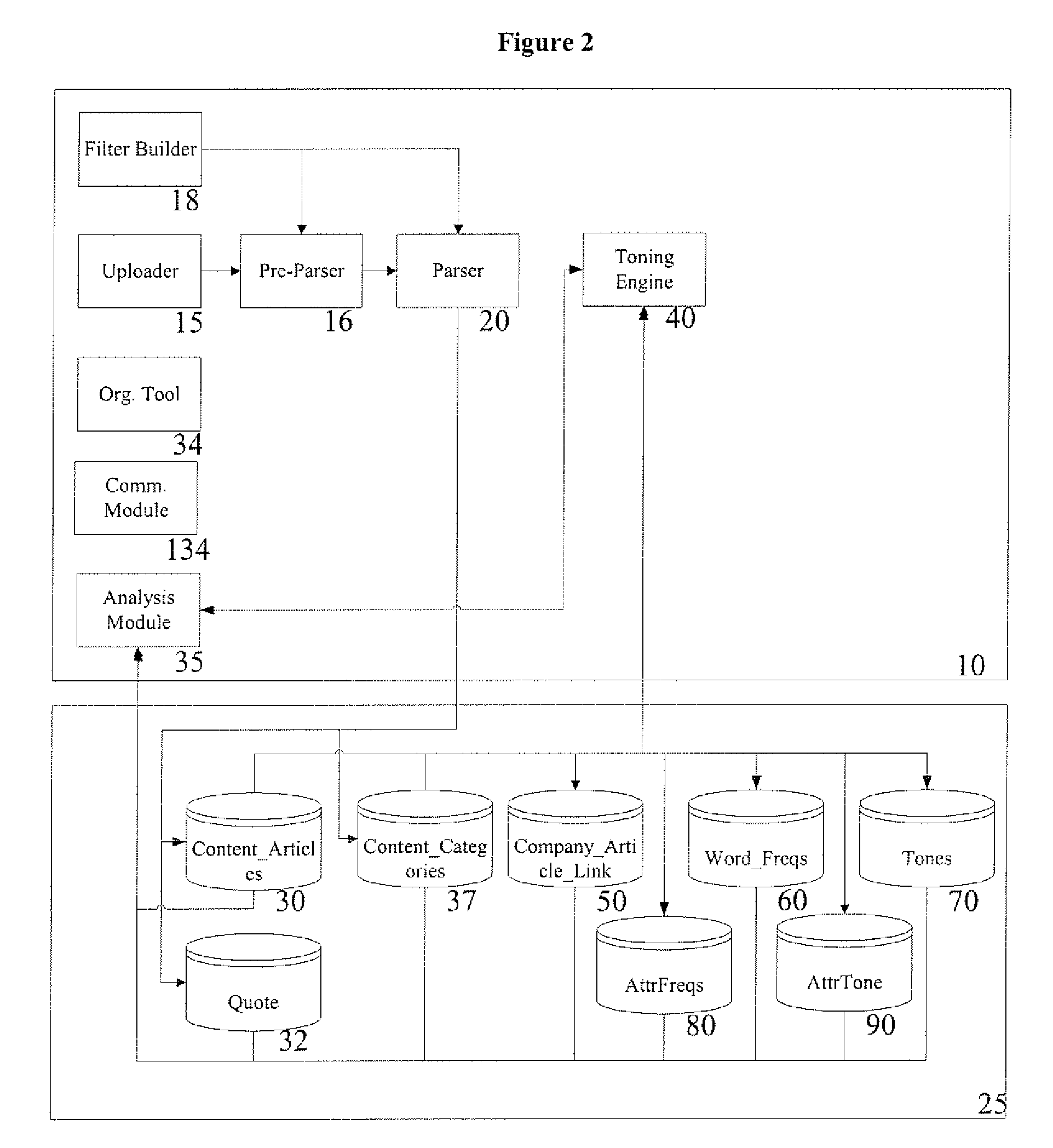
A web-based media analysis system, consisting of automated media analysis and document management tools, which processes news articles by parsing the news contents or documents and assigning, relating, and extracting information from the news contents for media analysis and relationally storing them in at least one database. The system further comprises a toning engine for toning articles accurately, based on words, attributes and categories of the article, and optionally based on the author of the article, if applicable.
Owner:MEDIAMISER
Method and system for text summarization and summary based query answering
InactiveUS20100287162A1Easy to useQuick understandingDigital data information retrievalSemantic analysisSemanticsUnique identifier
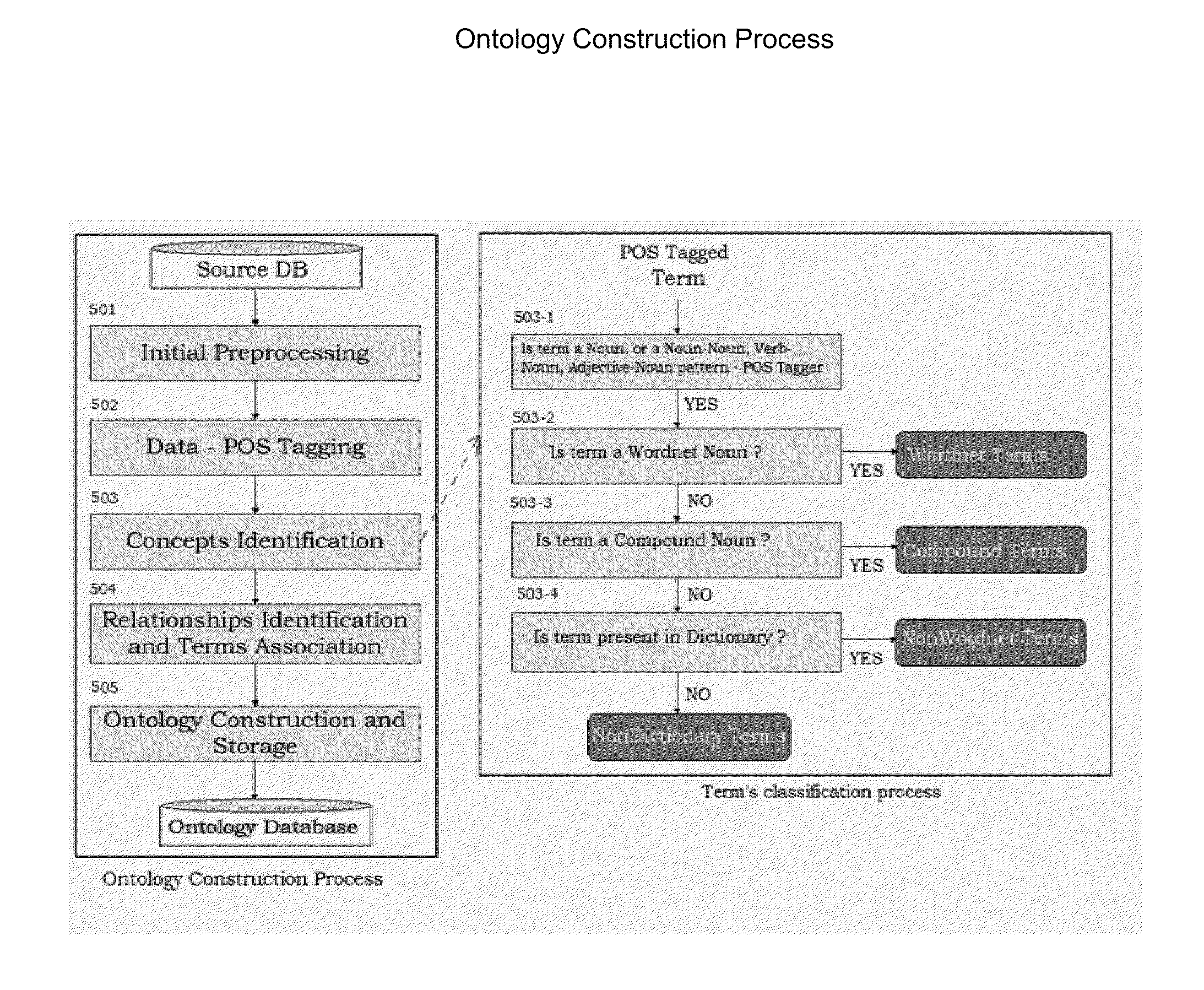
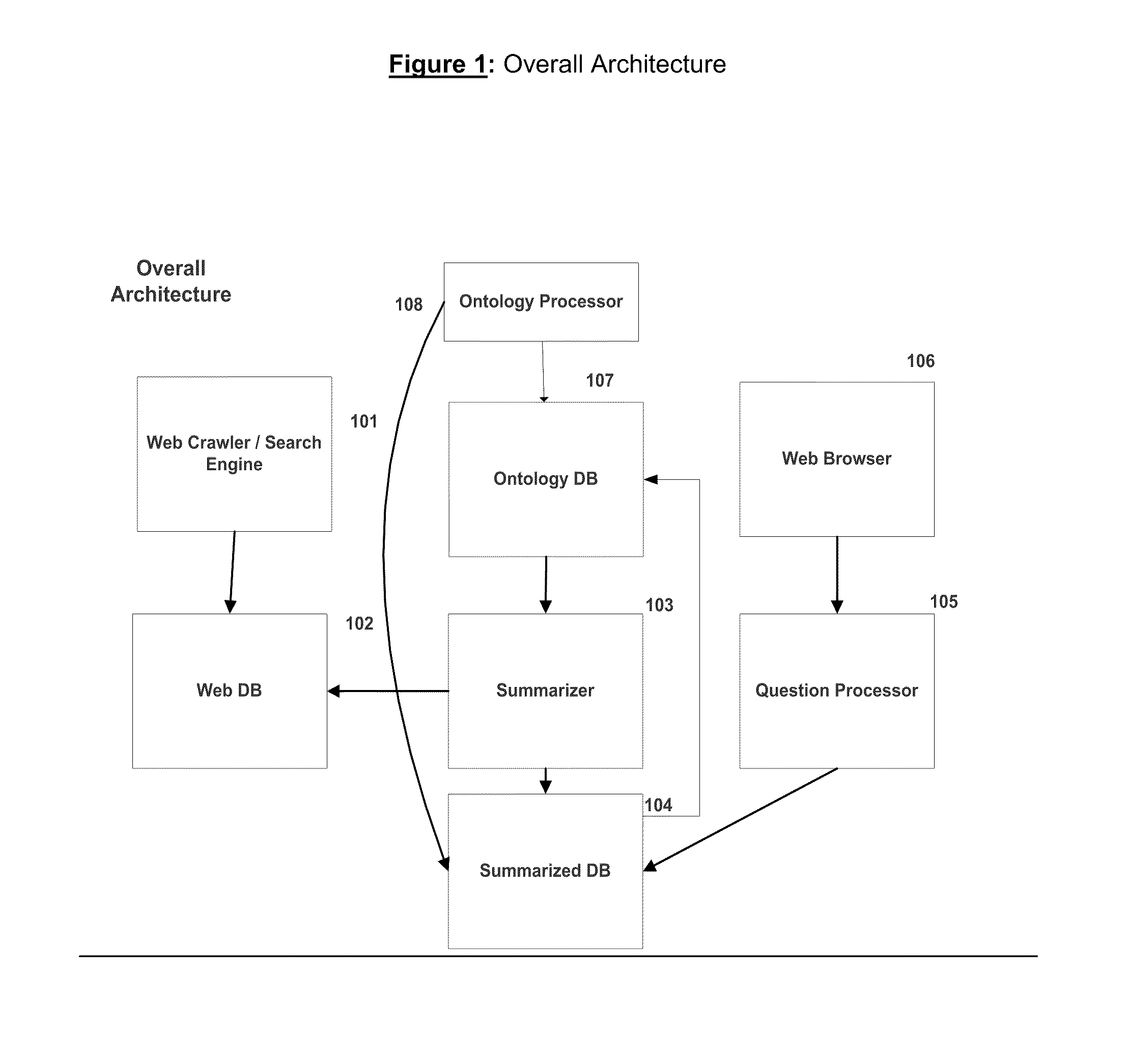
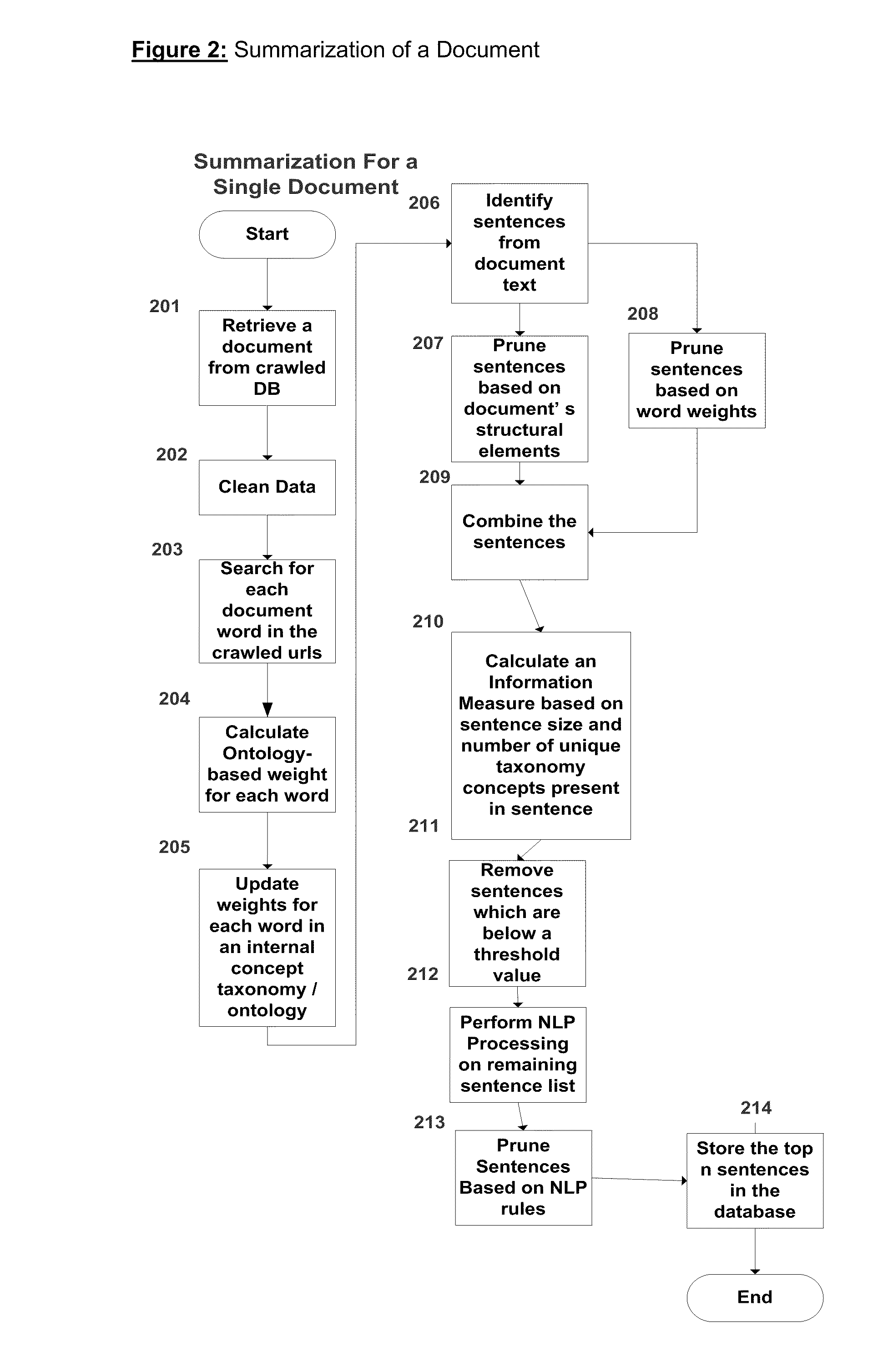
A method and system for generating answers to questions based on electronic data summary which is itself derived on context and semantics of a corpus of authoritative documents and its subsequent usage is disclosed. The method and system provides for generating a taxonomy of concepts, assigning unique-identifiers and weights to the taxonomy concepts using a given corpus of electronic data, using the taxonomy to identify the semantics of the document to be summarized, generating an ontology from a summarized authoritative text, having the ontology generation and the summary generation in a feedback loop, selecting text from a given document based on the weights of unique-identifiers in the taxonomy / ontology, sentences as a summary and pruning of the list based upon an entropy threshold, and the presence of a probability distribution, publishing of the summary in a known format on server or any other software / hardware platform with or without monetization for consumption, usage of the summary to generate answers which can be configured using an ontology and thus prevent denial of information / information overload.
Owner:SHIRWADKAR SANIKA
Methods of assessing and designing an application specific measurement system
ActiveUS20070282647A1Great confidenceReliable and economical to developMarket predictionsSpectrum investigationAnalysis dataEngineering
Methods of assessing feasibility of a project include receiving a datum from a customer; designing an application specific system based on the datum; analyzing the datum; evaluating a set of input parameters to determine an applicability of the application specific system to a customer process; and providing feedback for the customer process with the application specific system.
Owner:HALLIBURTON ENERGY SERVICES INC
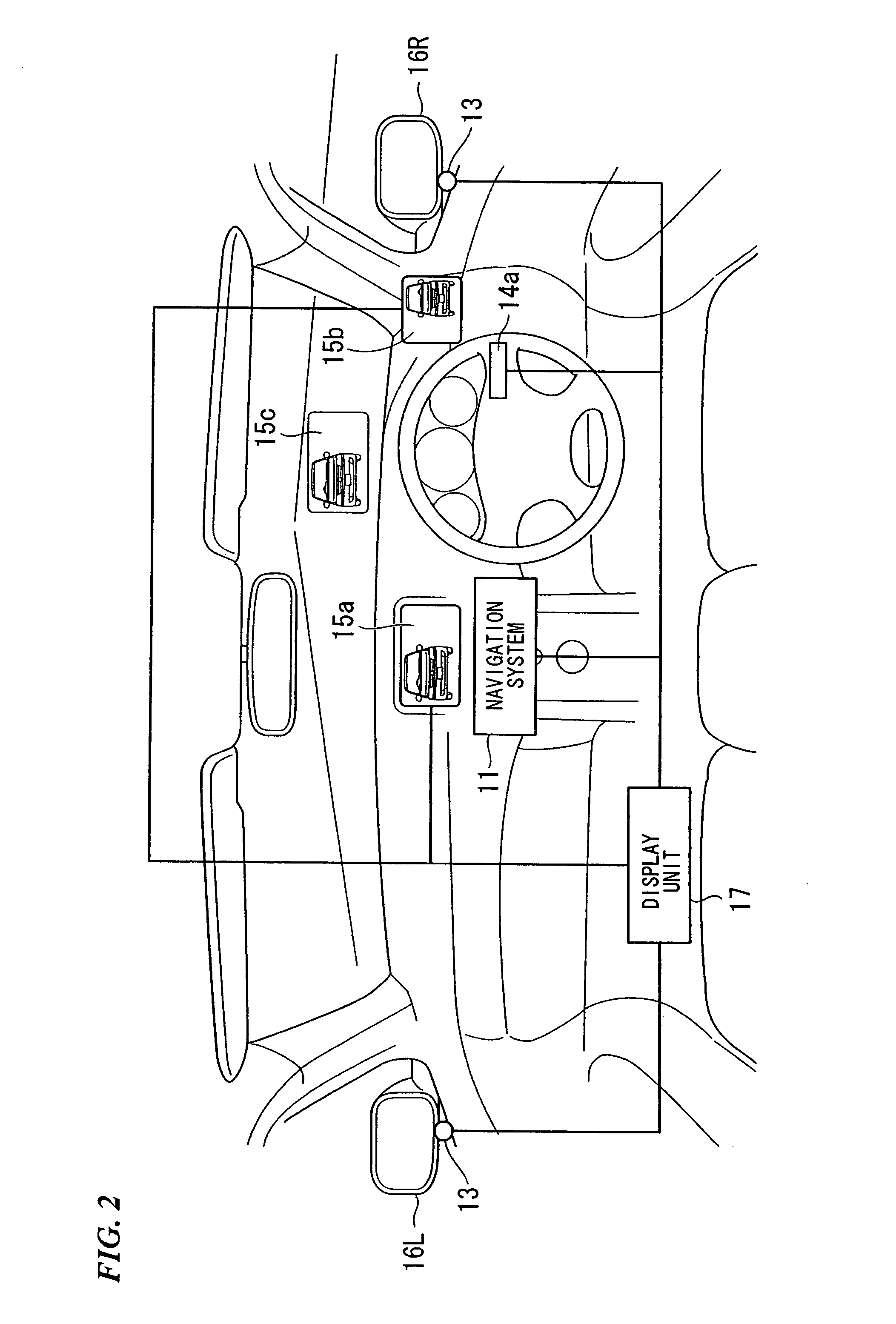
Driving support apparatus
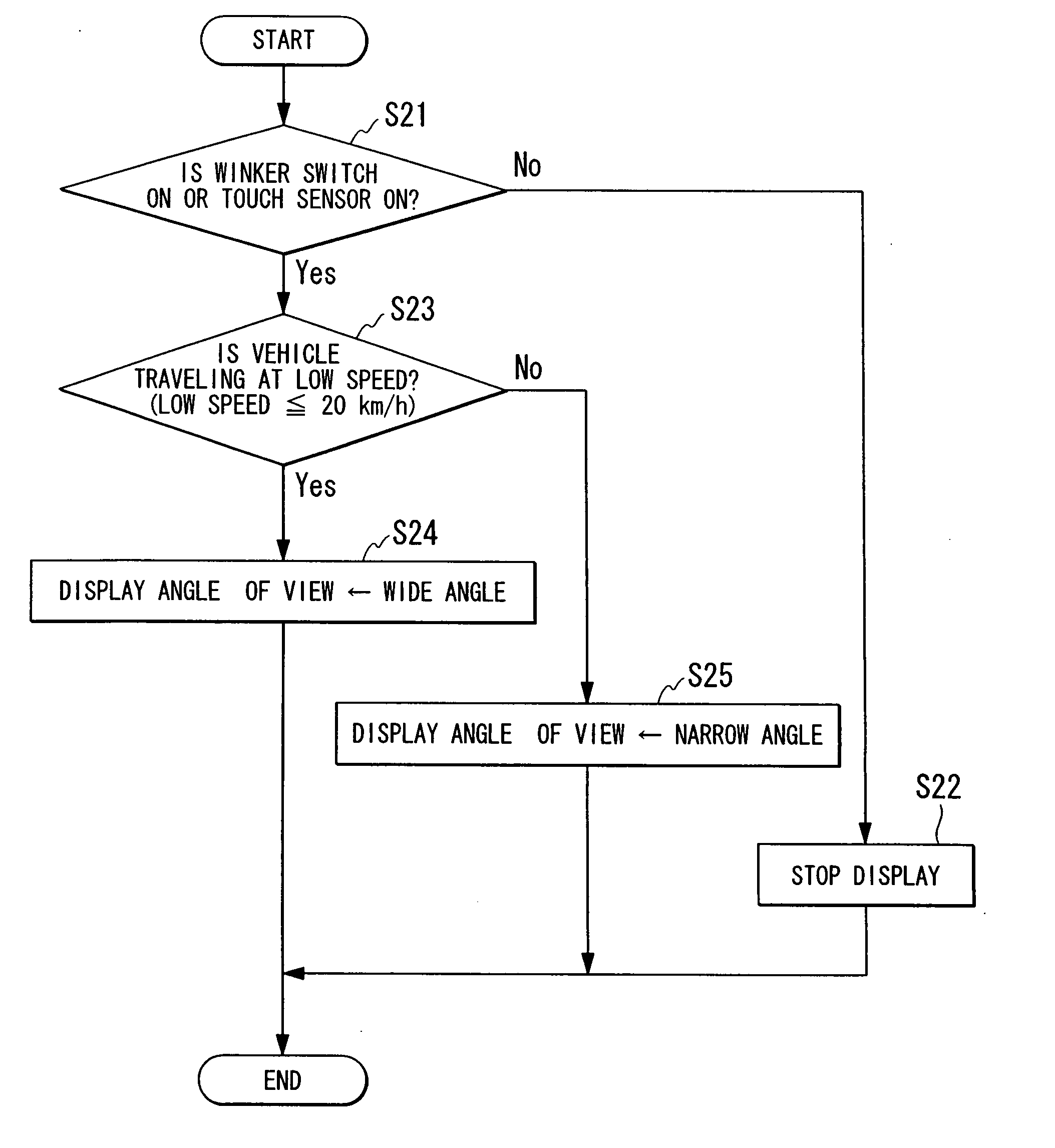
InactiveUS20080007428A1Increase awarenessInhibition of informationAnti-collision systemsAutomatic initiationsDriver/operatorVideo image
A driving support apparatus includes: an image sensing device that photographs side region of a vehicle and rearward region of a vehicle while altering an angle of view; a display unit that displays video images photographed by the image sensing device so as to be visible to a driver of the vehicle; a display determination device that determines a running state of the vehicle, and determines whether or not an alteration of the display angle of view is required; and an angle of view adjustment device that switches the angle of view of the image sensing device, in accordance with a display method decided by the display determination device, between either one of a wide angle that enables the side region and the rearward region to be photographed, and a narrow angle that only allows the rearward region to be photographed.
Owner:HONDA MOTOR CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com