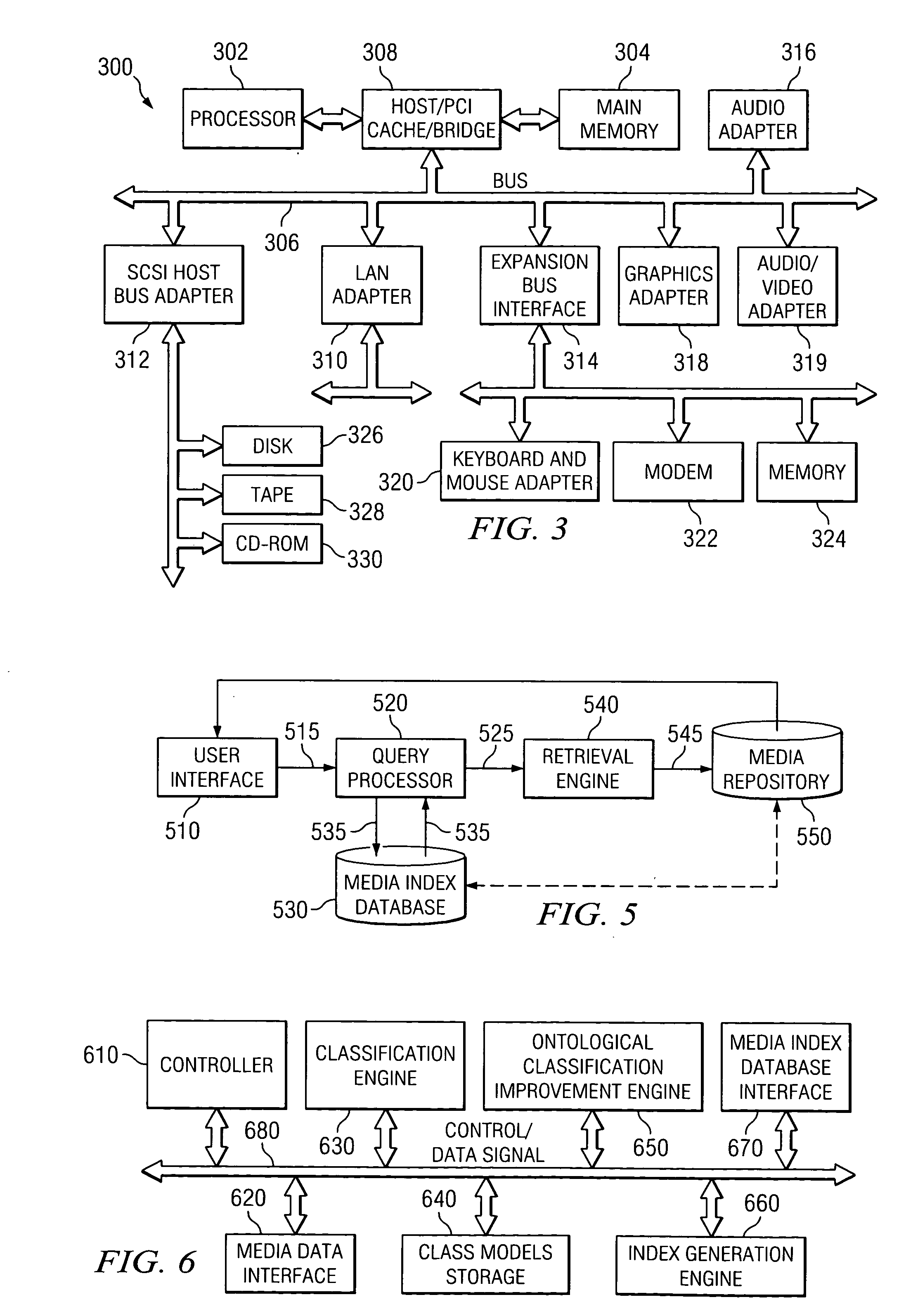
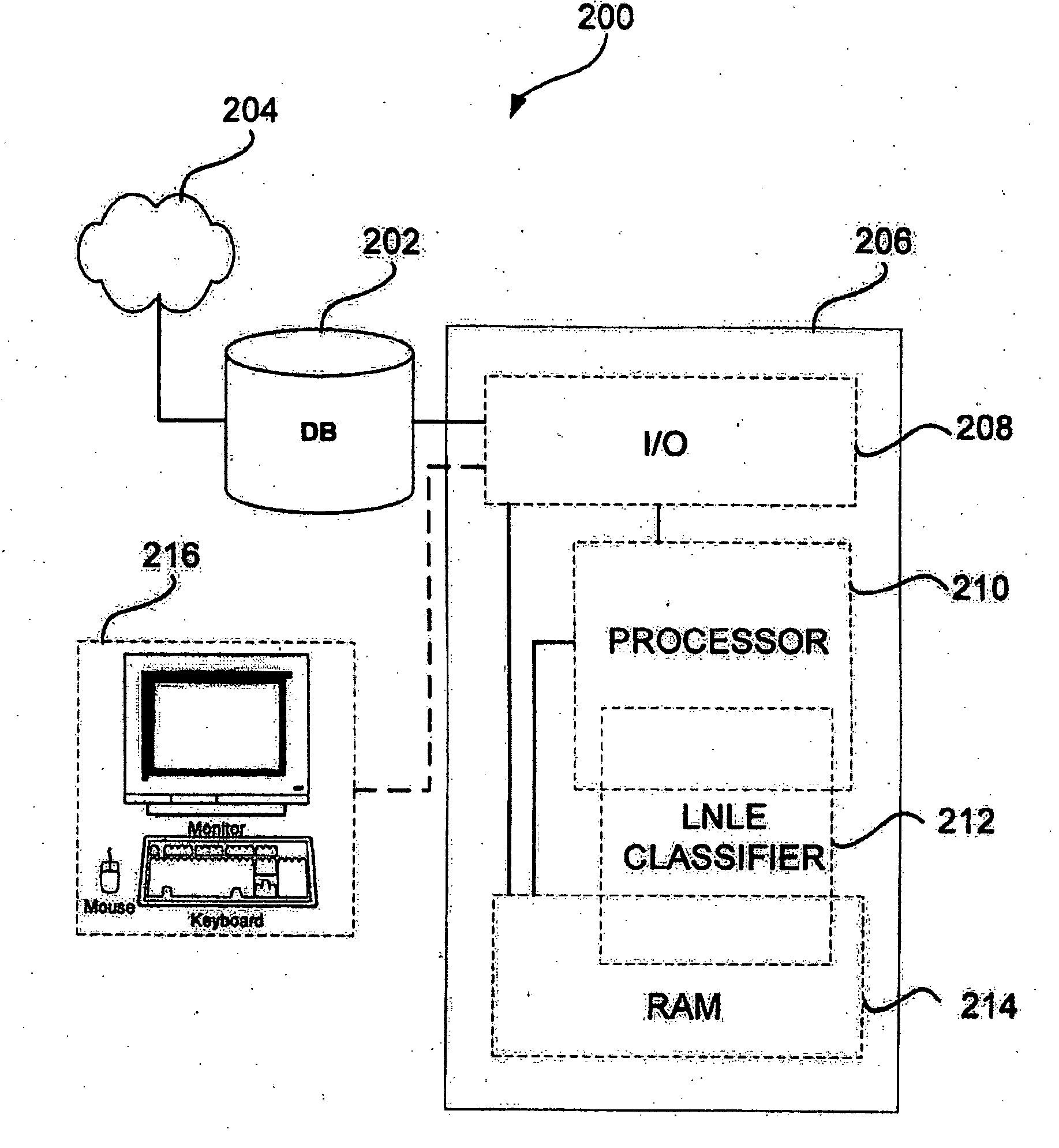
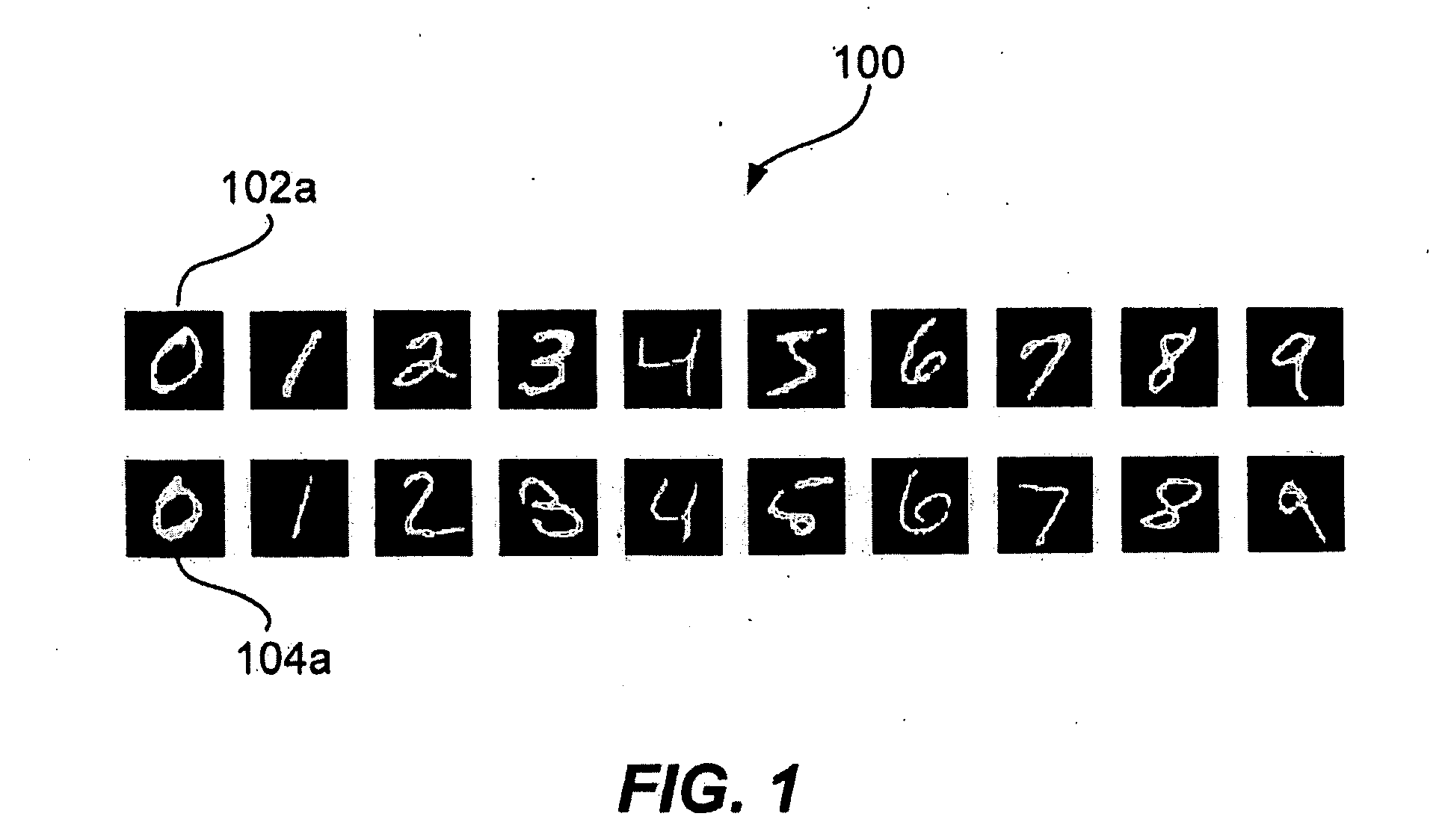
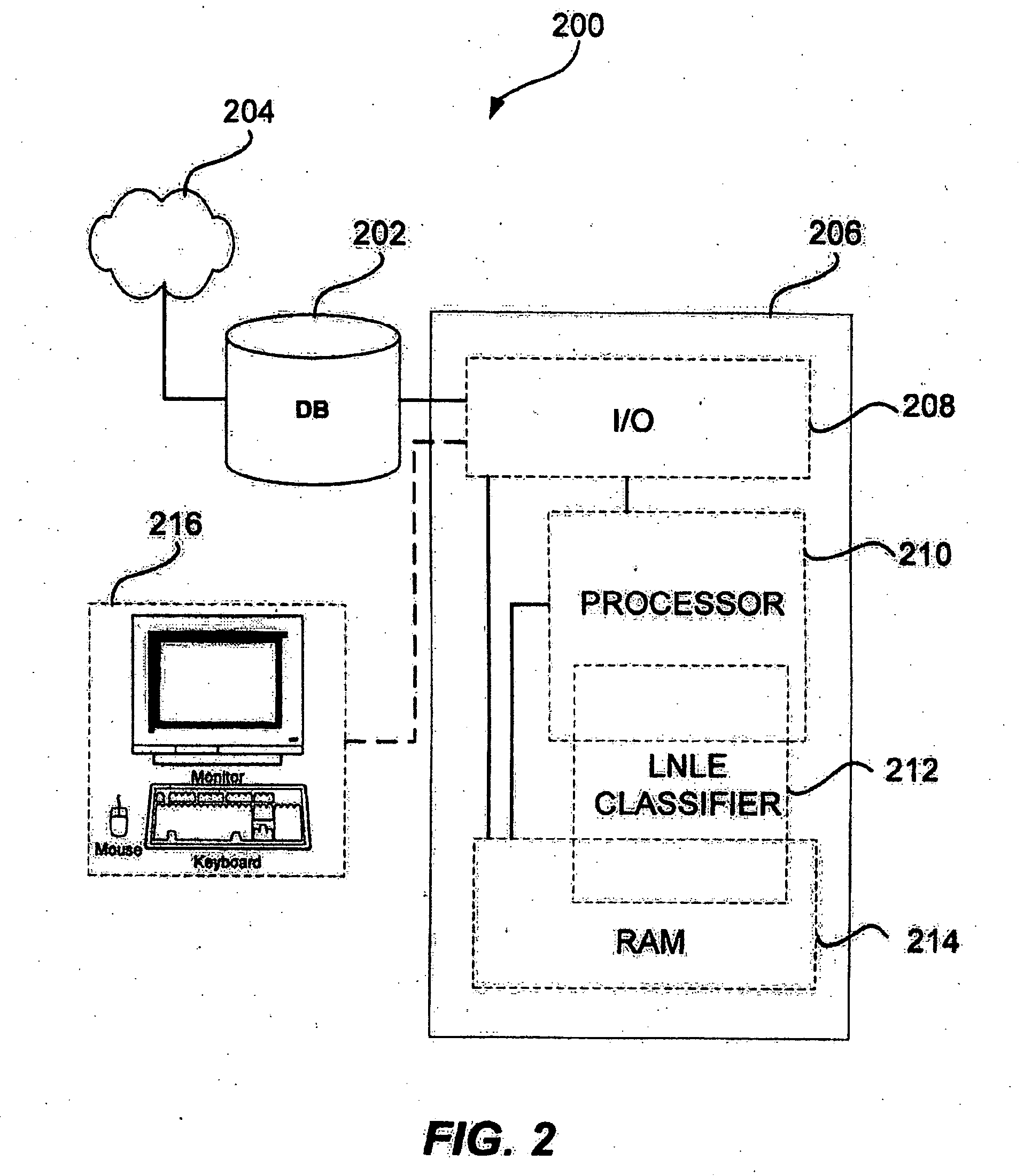
Patents
Literature
2109 results about "Confidence value" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
What is Confidence Value. 1. A function to transform a value into a standard domain, such as between 0 and 1. Learn more in: Classification and Ranking Belief Simplex. 2. A function to transform a value into a standard domain, such as between 0 and 1. Learn more in: Object Classification Using CaRBS.
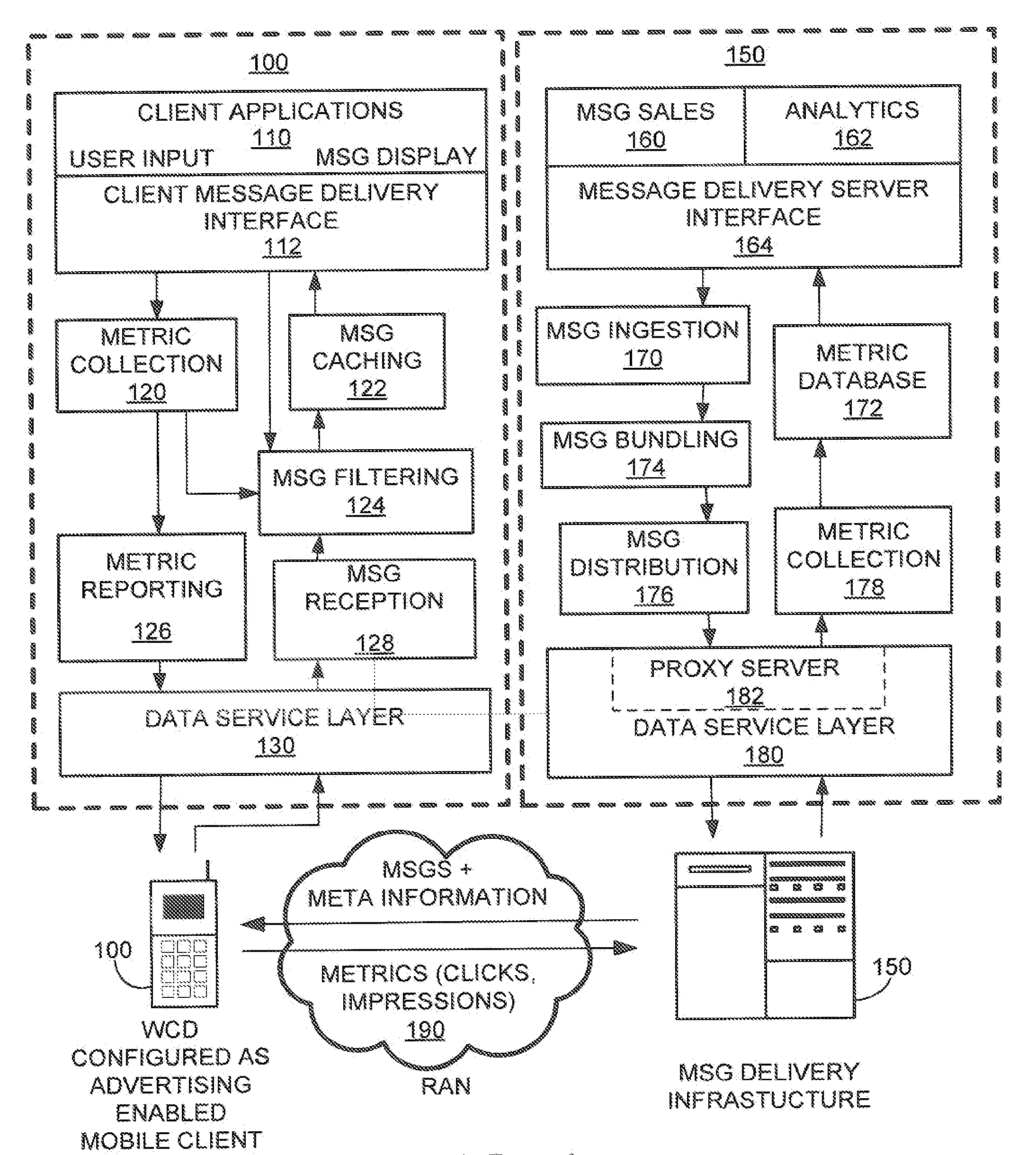
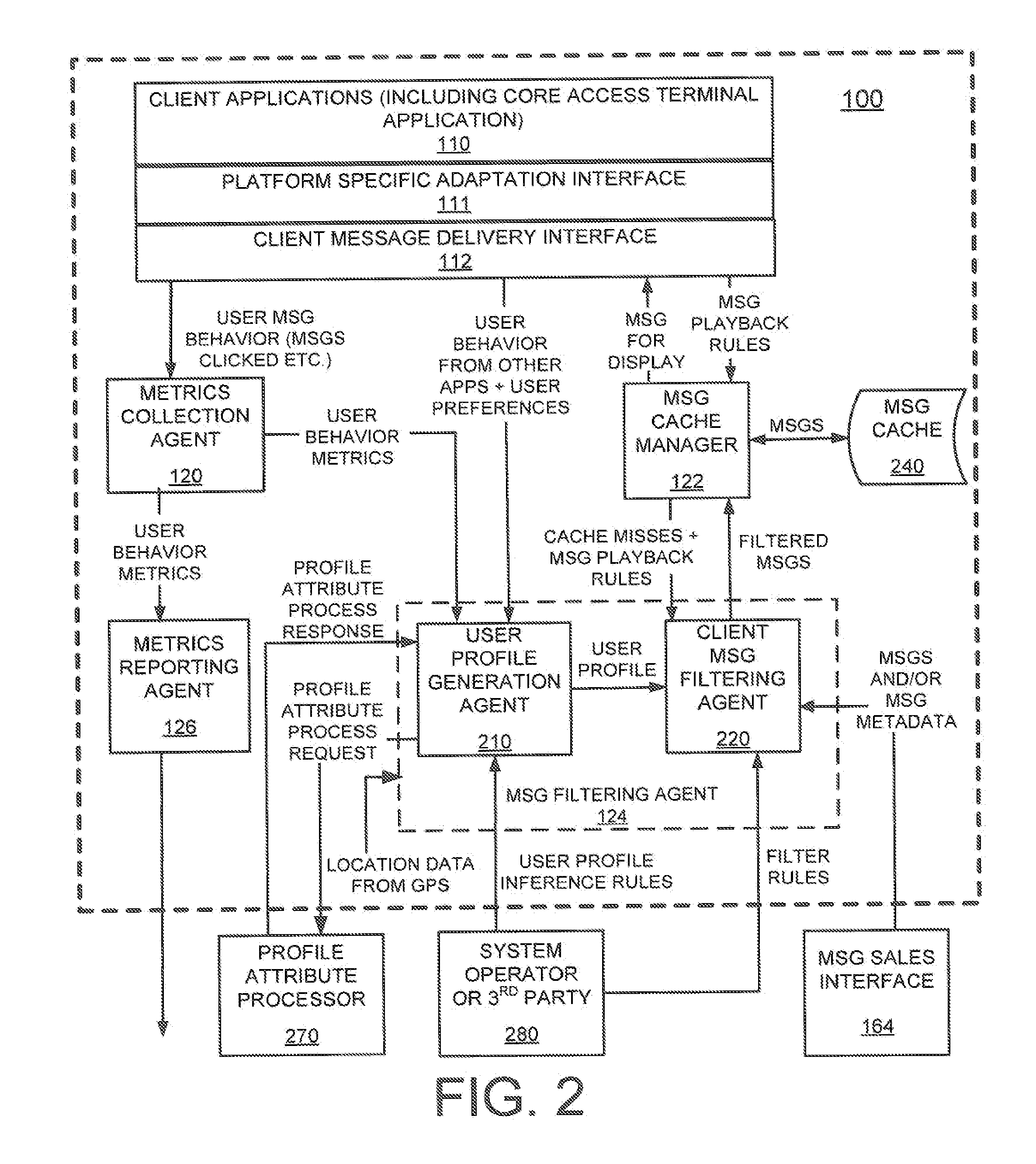
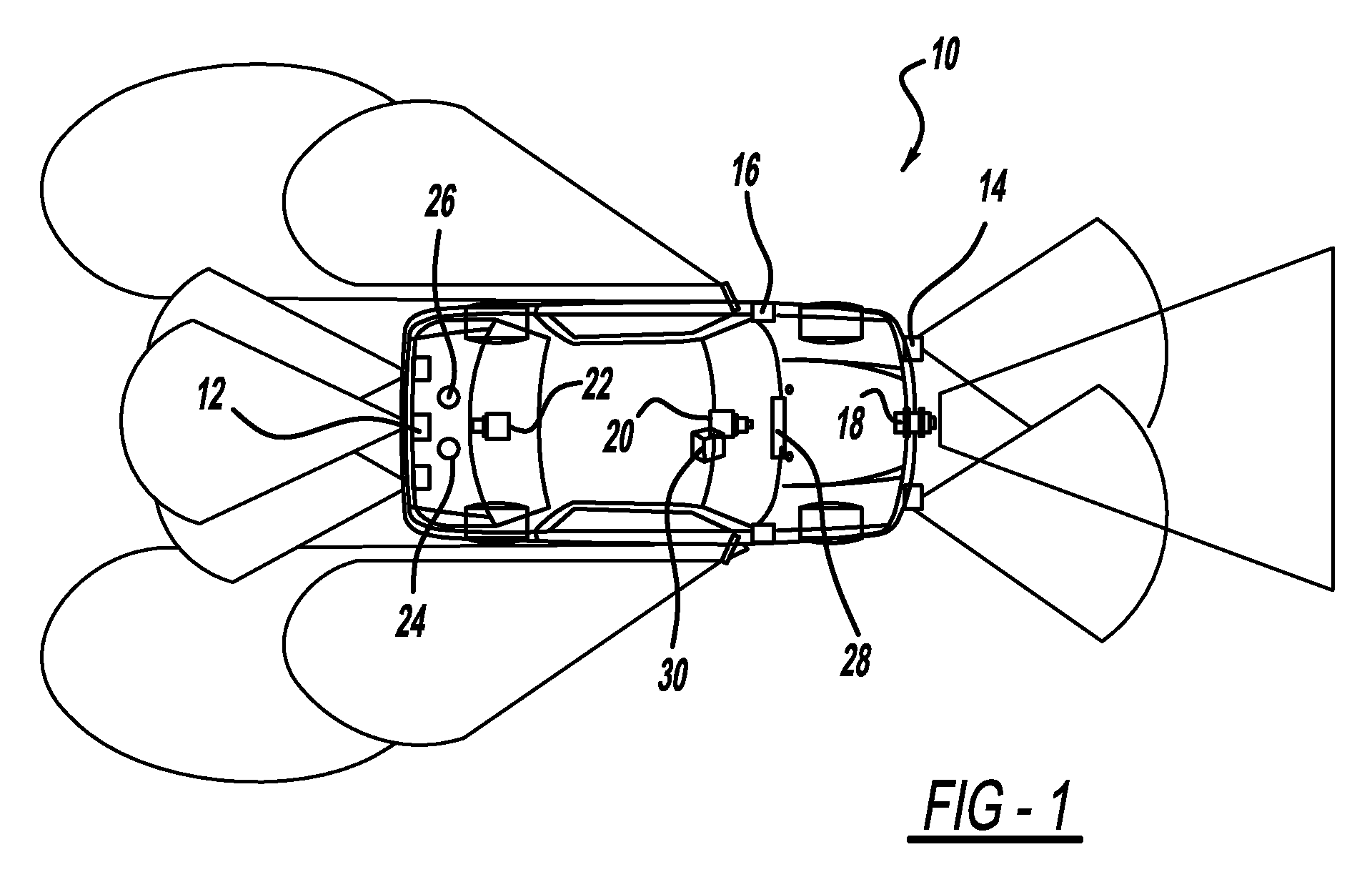
Method and system for user profile match indication in a mobile environment
Methods and systems for determining a suitability for a mobile client to display information are disclosed. For example, a method for determining a suitability for a mobile client to receive a targeted content message includes generating user profile data by the mobile client, receiving a set of target profile data associated with the targeted content message, the set of target profile data being descriptive of the targeted content message, comparing the user profile data with the target set of profile data to produce a set of confidence-level data, a target set of profile data describing the content of a respective targeted-content message, and storing the targeted content message in the mobile client based upon the set of confidence-level data.
Owner:QUALCOMM INC
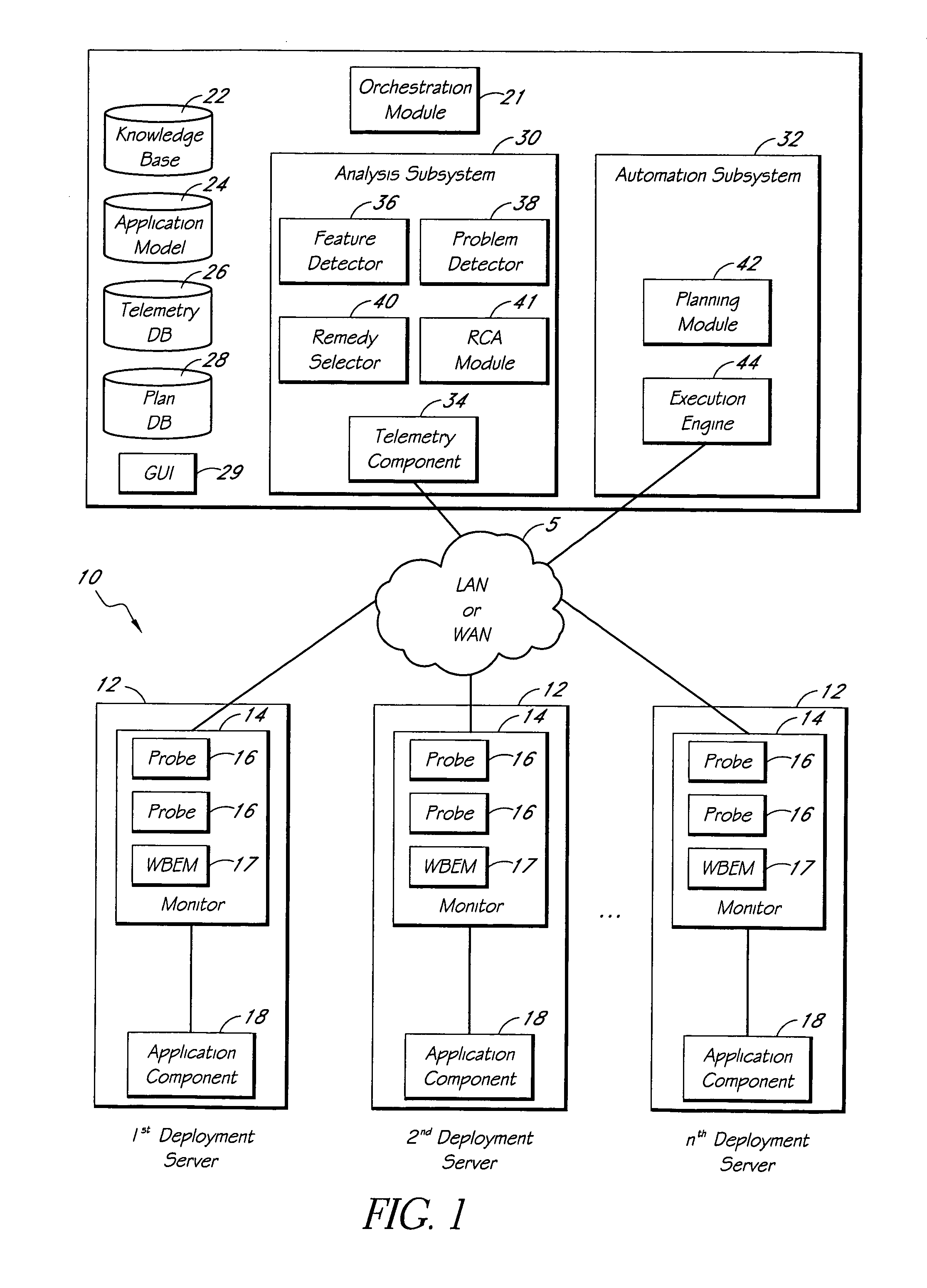
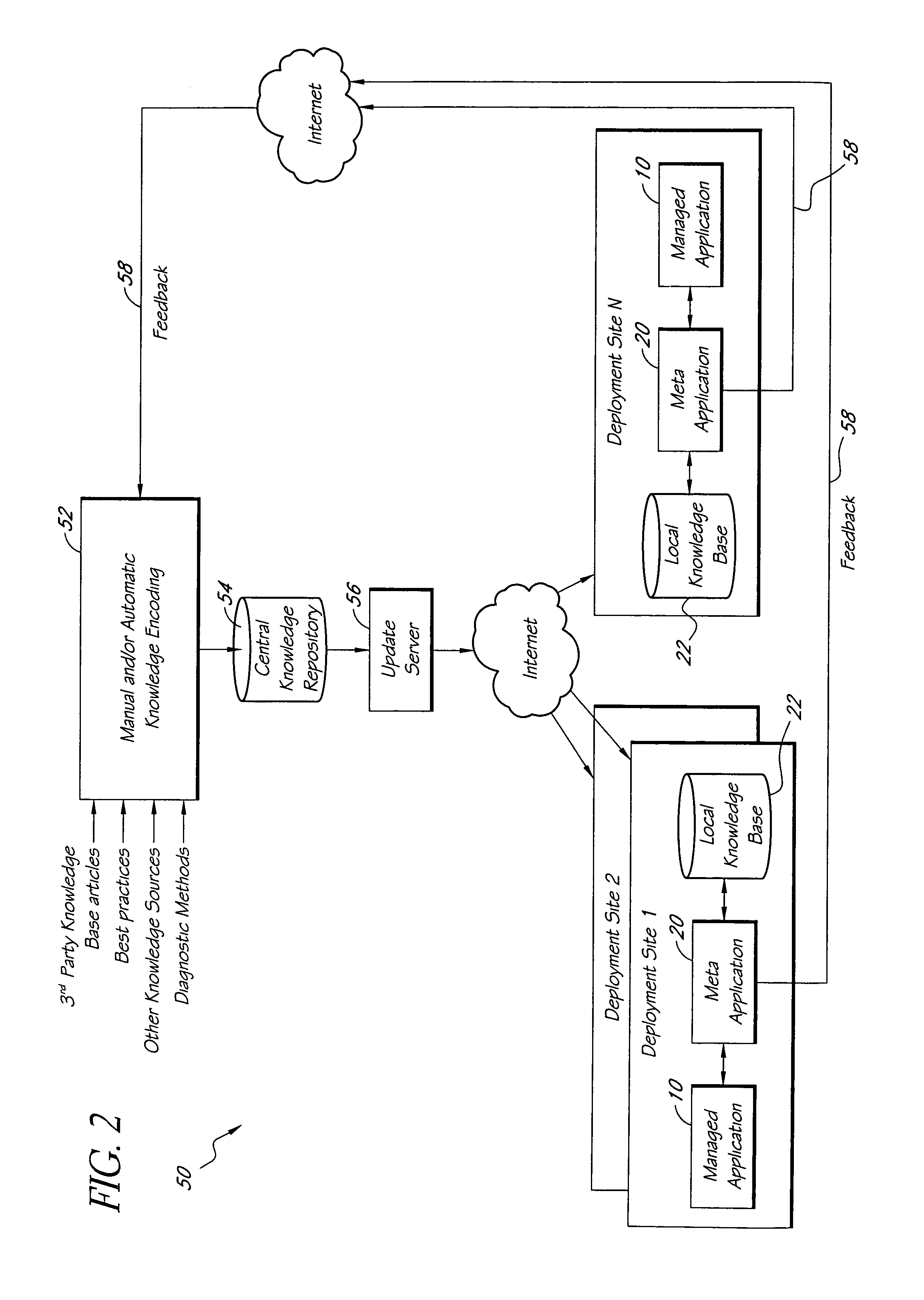
Systems and methods for encoding knowledge for automated management of software application deployments
ActiveUS7490073B1Efficient mappingGreat leverageError detection/correctionChaos modelsKnowledge sourcesSoftware
A method of encoding knowledge is disclosed, which can be used to automatically detect problems in software application deployments. The method includes accessing a source of knowledge describing a problem known to occur in deployments of a particular software application, and which identifies a plurality of conditions associated with the problem. An encoded representation of the knowledge source is generated according to a predefined knowledge encoding methodology. The encoded representation is adapted to be applied automatically by a computer to analyze data representing a current state of a monitored deployment of the software application to detect whether the conditions and the problem exist therein. In various implementations, the encoded representation of the knowledge can include queries for deployment information, information concerning the relative importance of the conditions to a detection of the problem, and / or logical constructs for computing a confidence value in the existence of the problem and for determining whether to report the problem if some of the conditions are not true. The knowledge source can comprise a text document (such as a knowledge base article), a flowchart of a diagnostic troubleshooting method, and the like. Also disclosed are methods of at least partially automating the encoding process.
Owner:CITRIX SYST INC
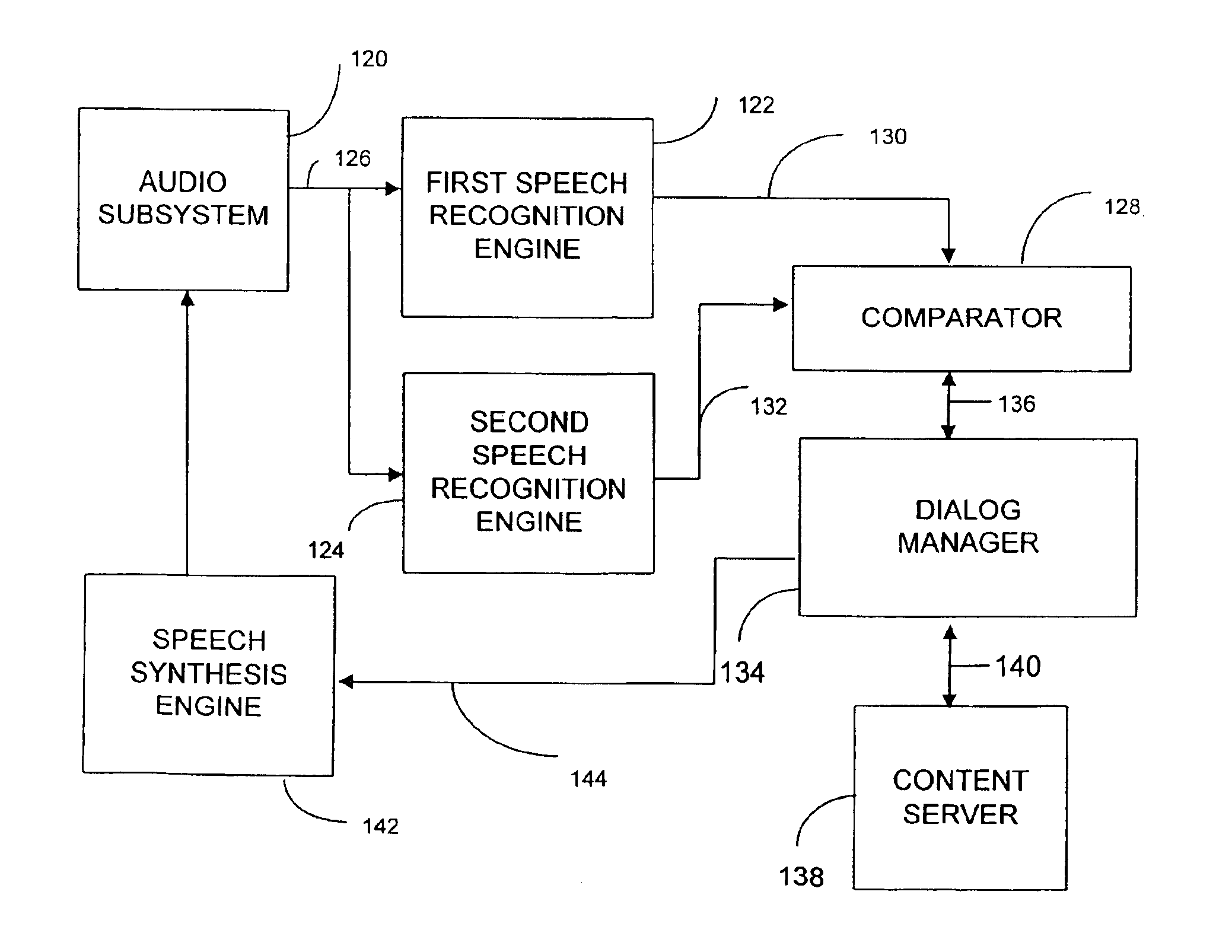
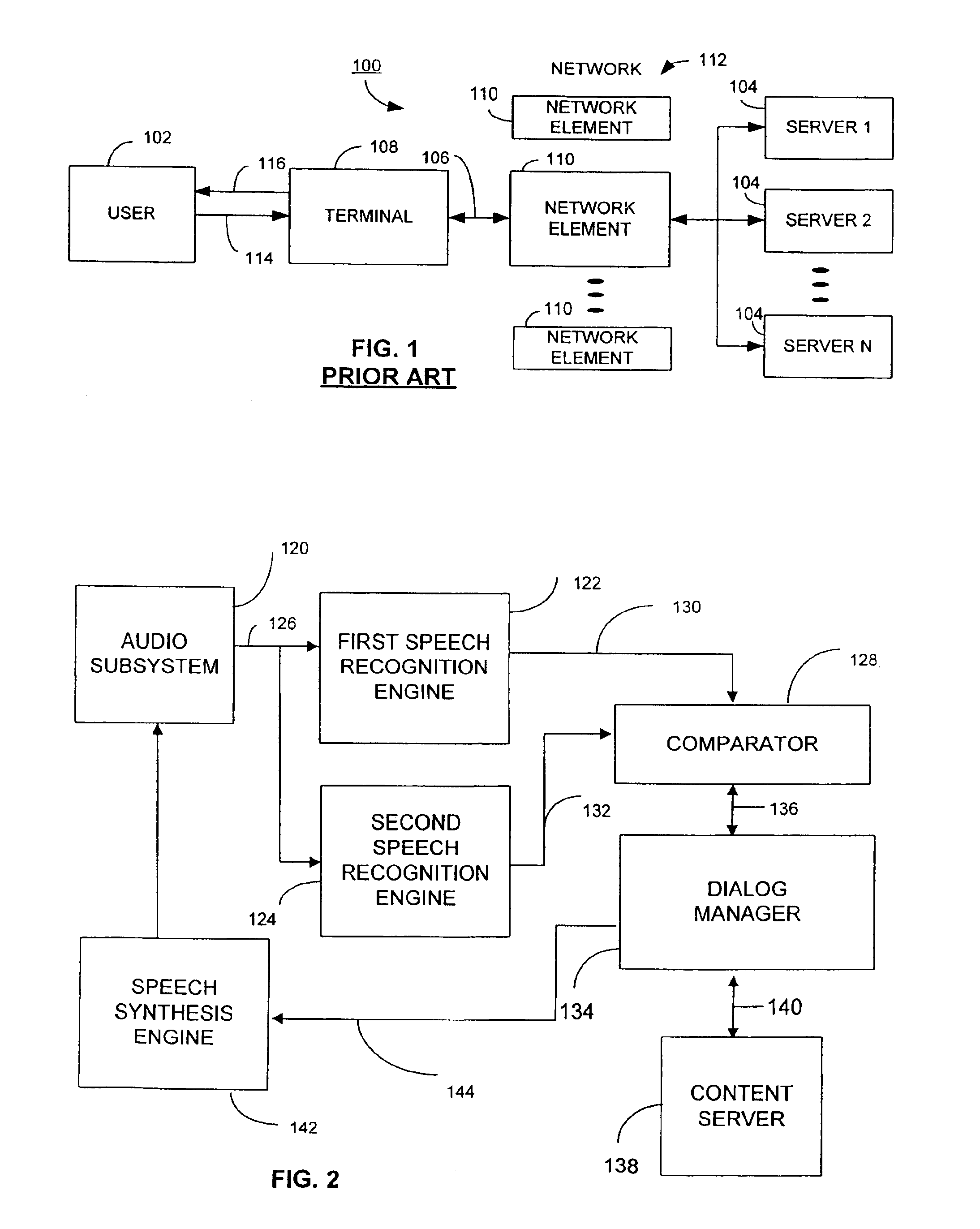
Method and apparatus for multi-level distributed speech recognition
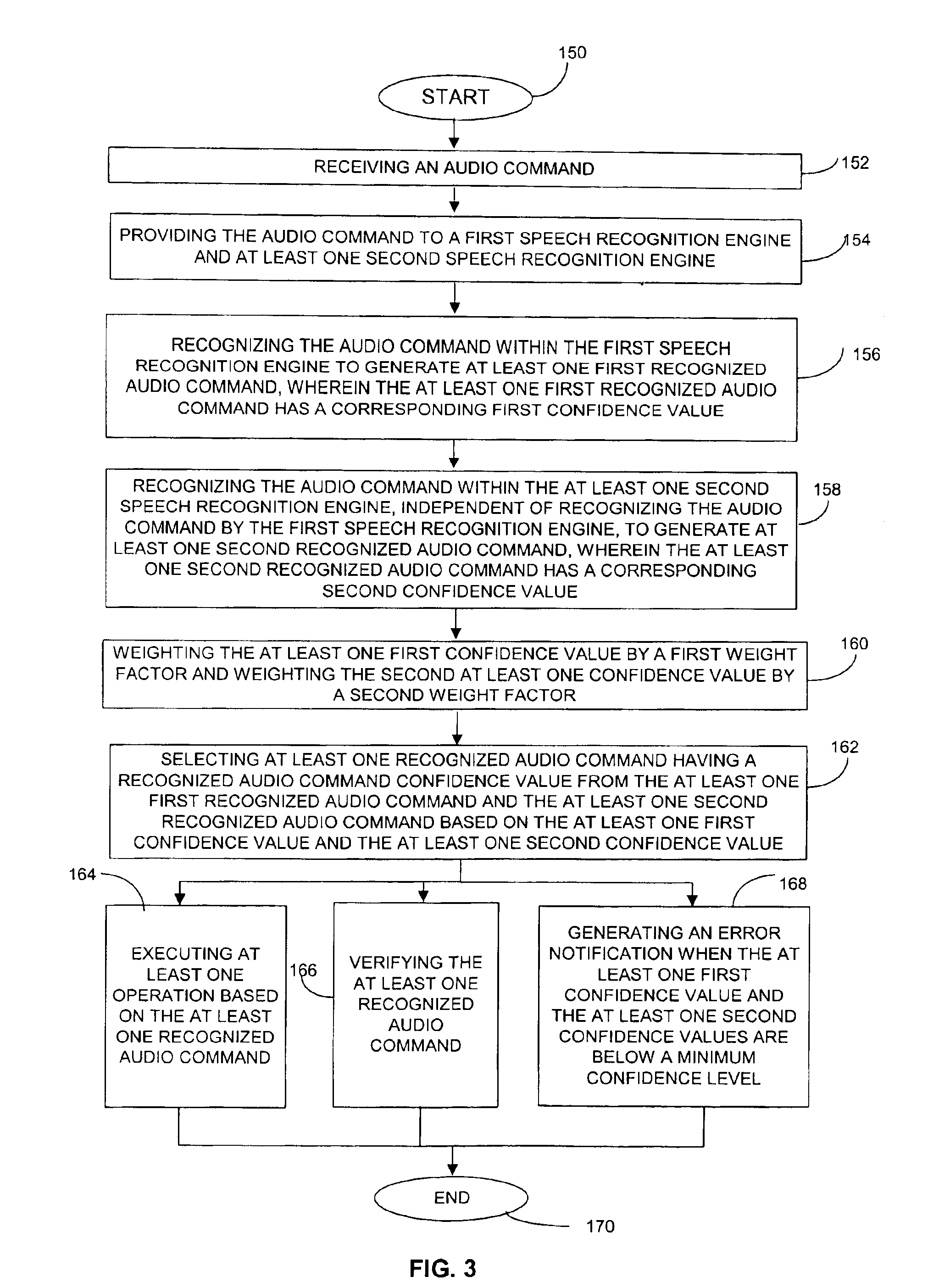
A system and method for multi-level distributed speech recognition includes a terminal (122) having a terminal speech recognizer (136) coupled to a microphone (130). The terminal speech recognizer (136) receives an audio command (37), generating at least one terminal recognized audio command having a terminal confidence value. A network element (124) having at least one network speech recognizer (150) also receives the audio command (149), generating a at least one network recognized audio command having a network confidence value. A comparator (152) receives the recognized audio commands, comparing compares the speech recognition confidence values. The comparator (152) provides an output (162) to a dialog manager (160) of at least one recognized audio command, wherein the dialog manager then executes an operation based on the at least one recognized audio command, such as presenting the at least one recognized audio command to a user for verification or accessing a content server.
Owner:GOOGLE TECH HLDG LLC
Using match confidence to adjust a performance threshold
ActiveUS20050080772A1Improve performanceDecrease in confidenceData processing applicationsWeb data indexingAlgorithmConfidence factor
If some aspect of serving or scoring an ad is subject to a performance (e.g., click-through rate, etc.) threshold, such a threshold may be adjusted using a confidence factor of the ad targeting used. For example, ads served pursuant to a more relaxed notion of match might have to meet a higher performance threshold (e.g., than the threshold applied to ads served pursuant to a stricter notion of match). Alternatively, or in addition, ads served pursuant to a stricter notion of match might be subject to a lower performance threshold (e.g., than the threshold applied to ads served pursuant to a more relaxed notion of match. Thus, in general, a performance threshold could increase as match confidence decreases, and / or a performance threshold could decrease as match confidence increases.
Owner:GOOGLE LLC
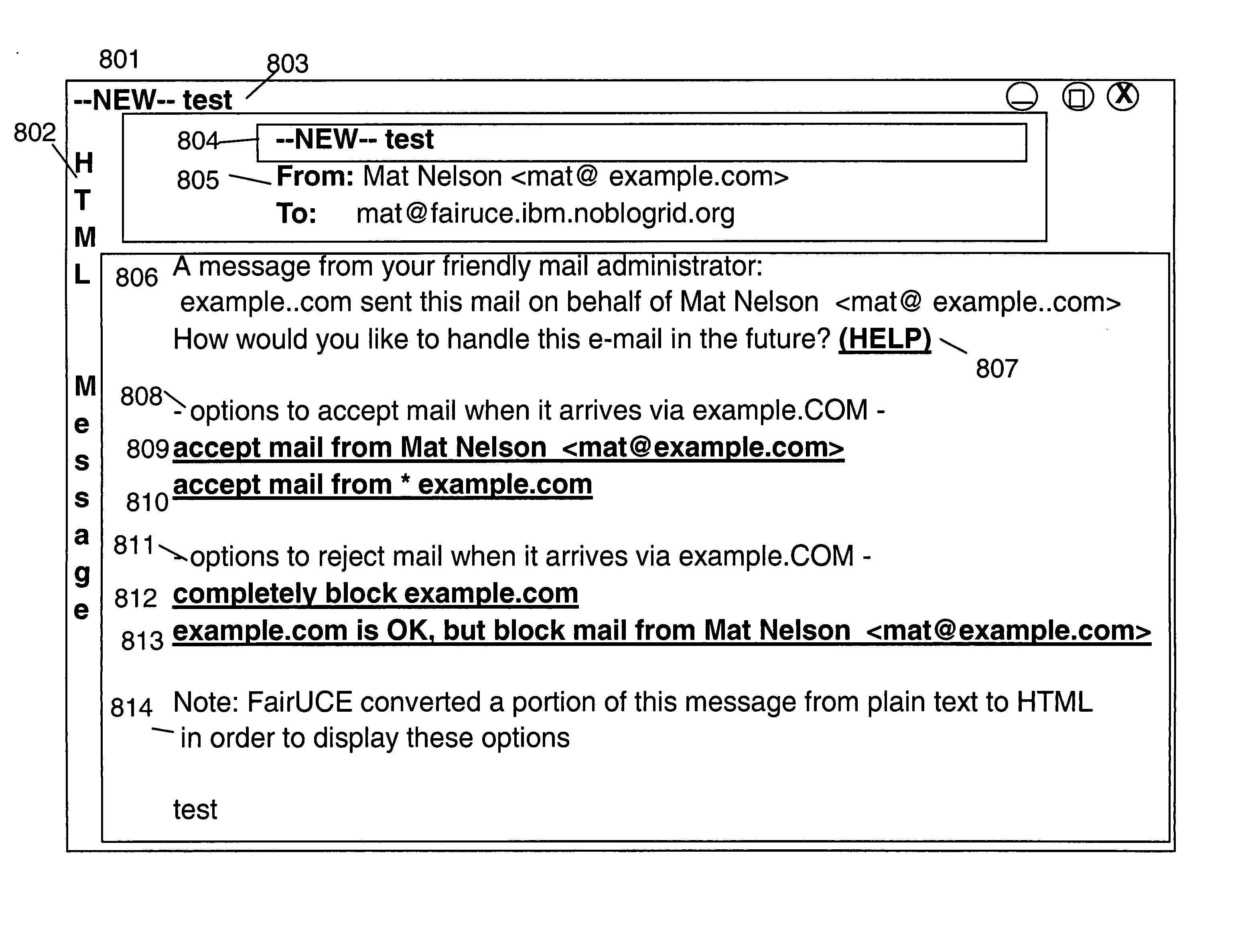
Hiearchically verifying the identity of the sender of an e-mail message
The identity of the sender of an e-mail message is verified by performing a plurality of tests on DNS information. The DNS information is based on a client IP address or a sender address. Each test performed has a corresponding intrinsic confidence value representing the degree of confidence the test provides of the sender identity relationship. If multiple tests are successful the test result with the highest confidence value of the hierarchy of confidence values is used. The confidence value is optionally used in subsequent identity tests as specified by the subsequent test.
Owner:SNAP INC
Location determination techniques
ActiveUS20070149216A1Certain robustnessCope wellPosition fixationTelephonic communicationPosition dependentComputer science
A method for estimating a target object properties, including location, in an environment. A topology model indicates permissible locations and transitions and a data model models a location-dependent physical quantity which is observed by the target object's sensing device. Motion models model specific target object types, obeying the permissible locations and transitions. The target object is assigned a set of particles, each having a set of attributes, including location in relation to the topology model. The attributes estimate the target object properties The particles' update cycles include: determining a degree of belief for each particle to estimate the target object properties; determining a weight for each particle based on at least the determined degree of belief and generating new particles for update cycle n+1 in an evolutionary process.
Owner:OY EKAHAU +2
Compound classifier for pattern recognition applications
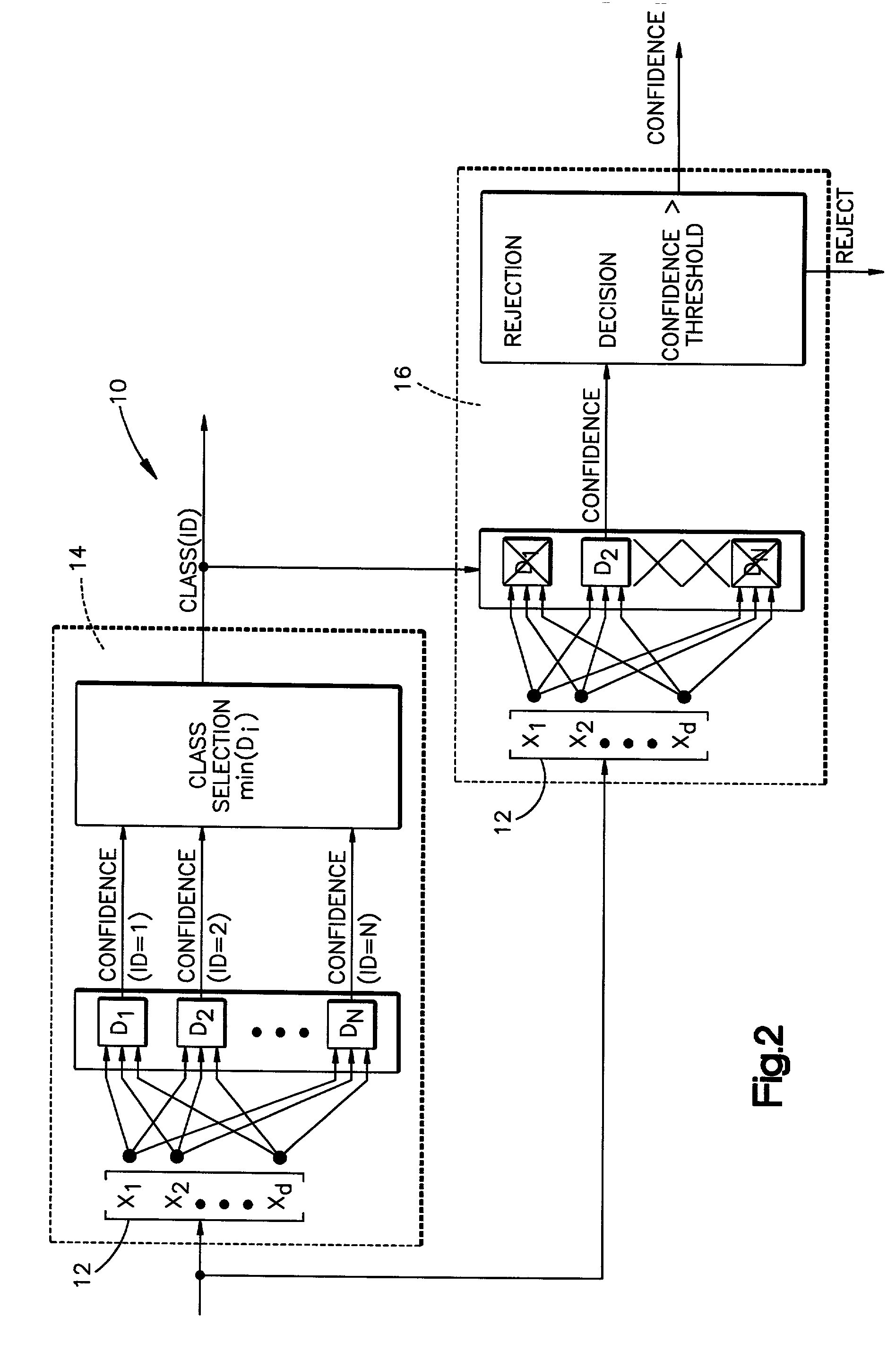
A method is disclosed for classifying an input pattern into an associated class through use of a compound classifier. Data pertaining to preselected features present within the input pattern are extracted. A discriminant value for each of a plurality of classes is then determined via a first classification technique. This value reflects the relative likelihood that a class is the associated class. The class with the highest relative likelihood is selected. A confidence value is generated via a second classification technique. This confidence value is reflective of the a posteriori probability that the selected class is the associated class. The selected class is rejected if the determined confidence value is below a predetermined threshold value.
Owner:LOCKHEED MARTIN CORP
Error correction for speech recognition systems
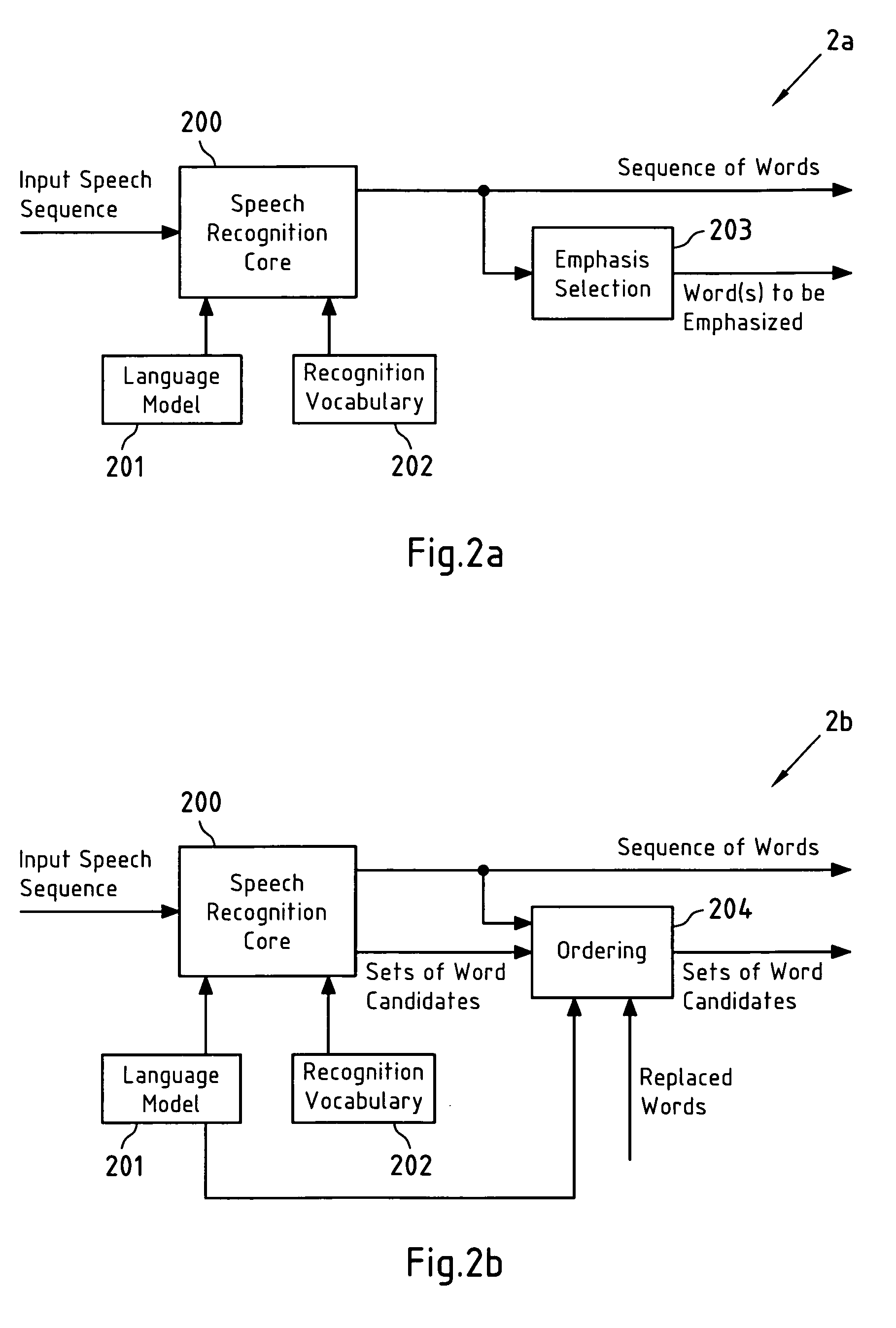
Words in a sequence of words that is obtained from speech recognition of an input speech sequence are presented to a user, and at least one of the words in the sequence of words is replaced, in case it has been selected by a user for correction. Words with a low recognition confidence value are emphasized; alternative word candidates for the at least one selected word are ordered according to an ordering criterion; after replacing a word, an order of alternative word candidates for neighboring words in the sequence is updated; the replacement word is derived from a spoken representation of the at least one selected word by speech recognition with a limited vocabulary; and the word that replaces the at least one selected word is derived from a spoken and spelled representation of the at least one selected word.
Owner:NOKIA CORP
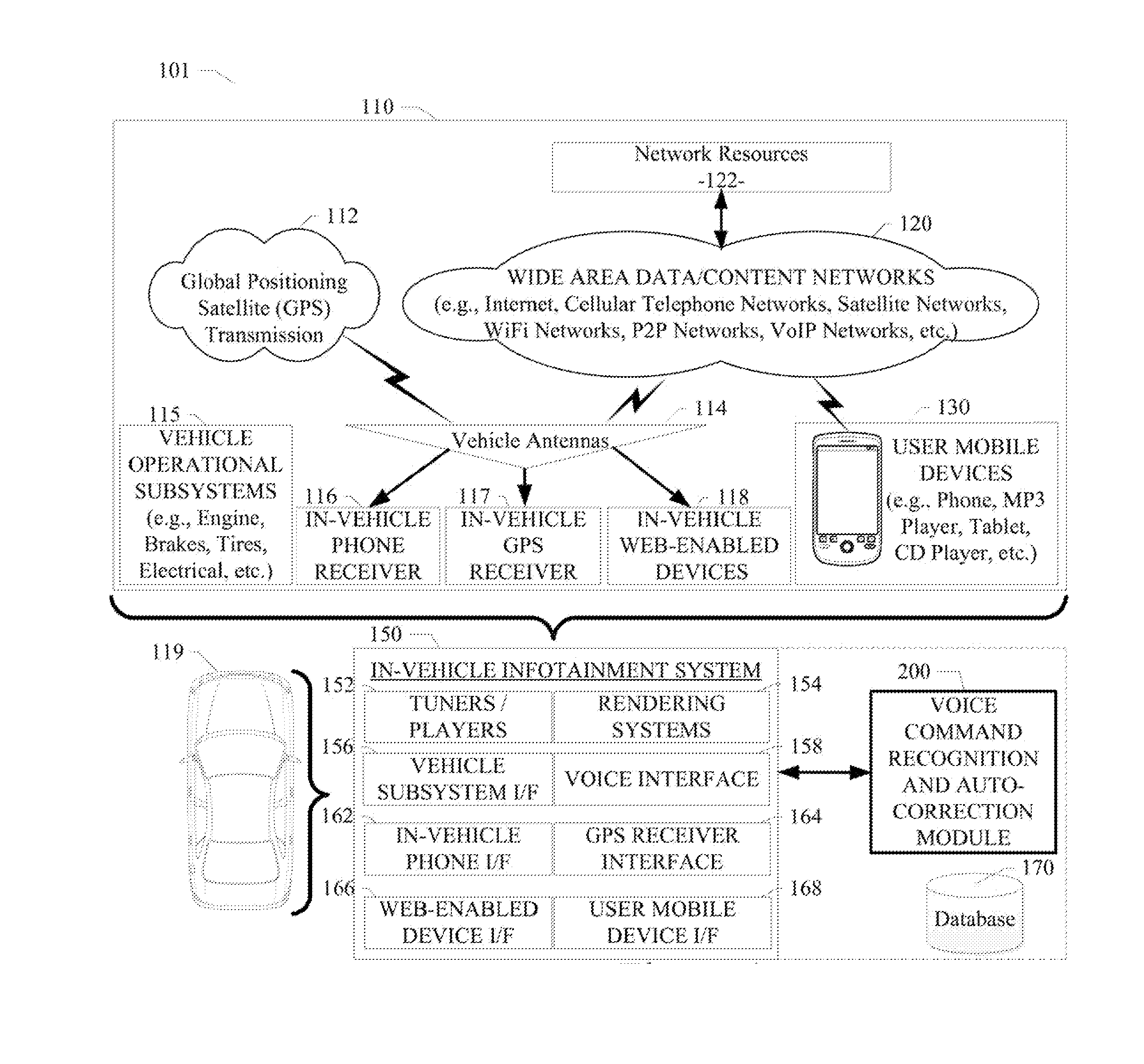
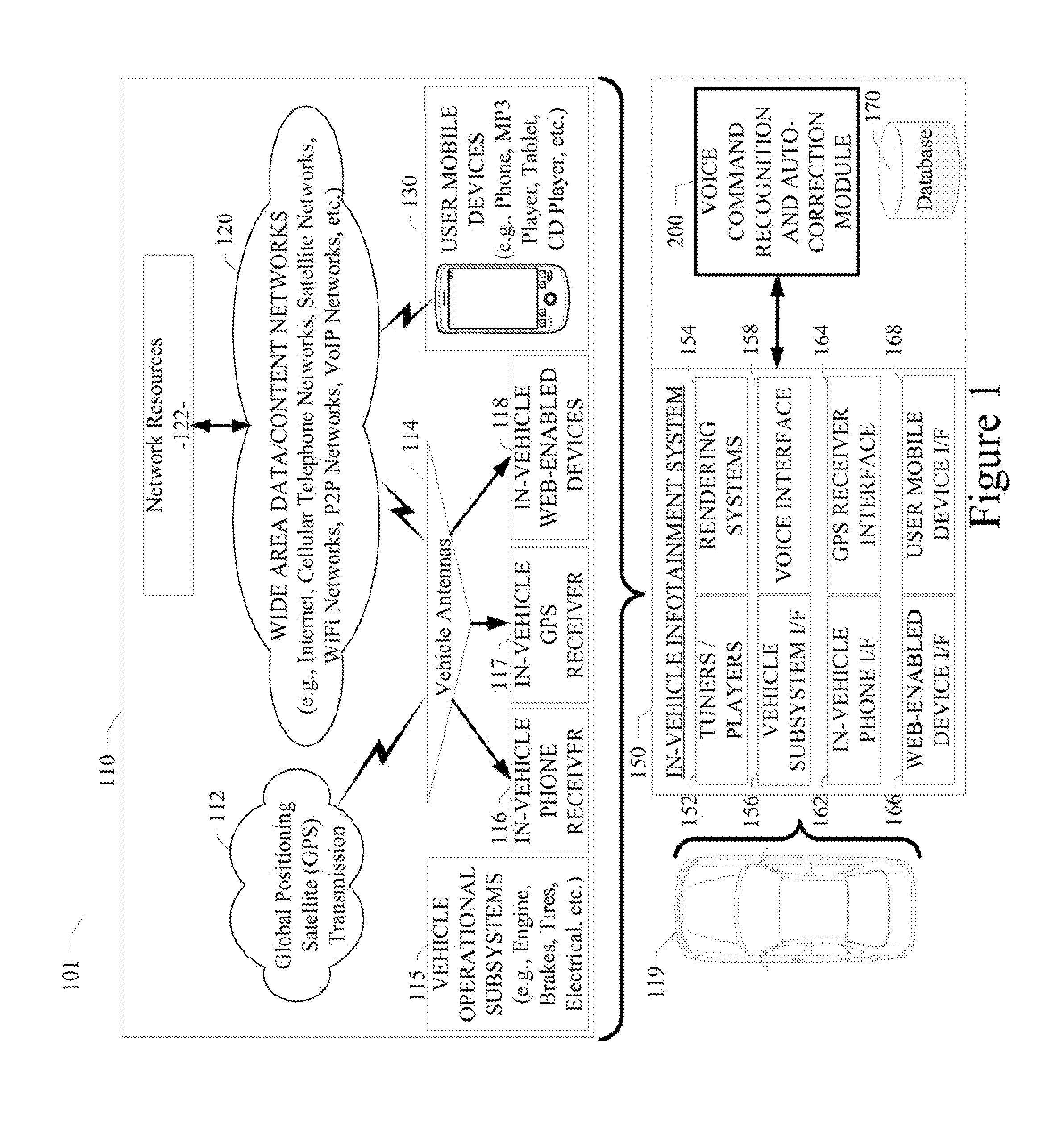
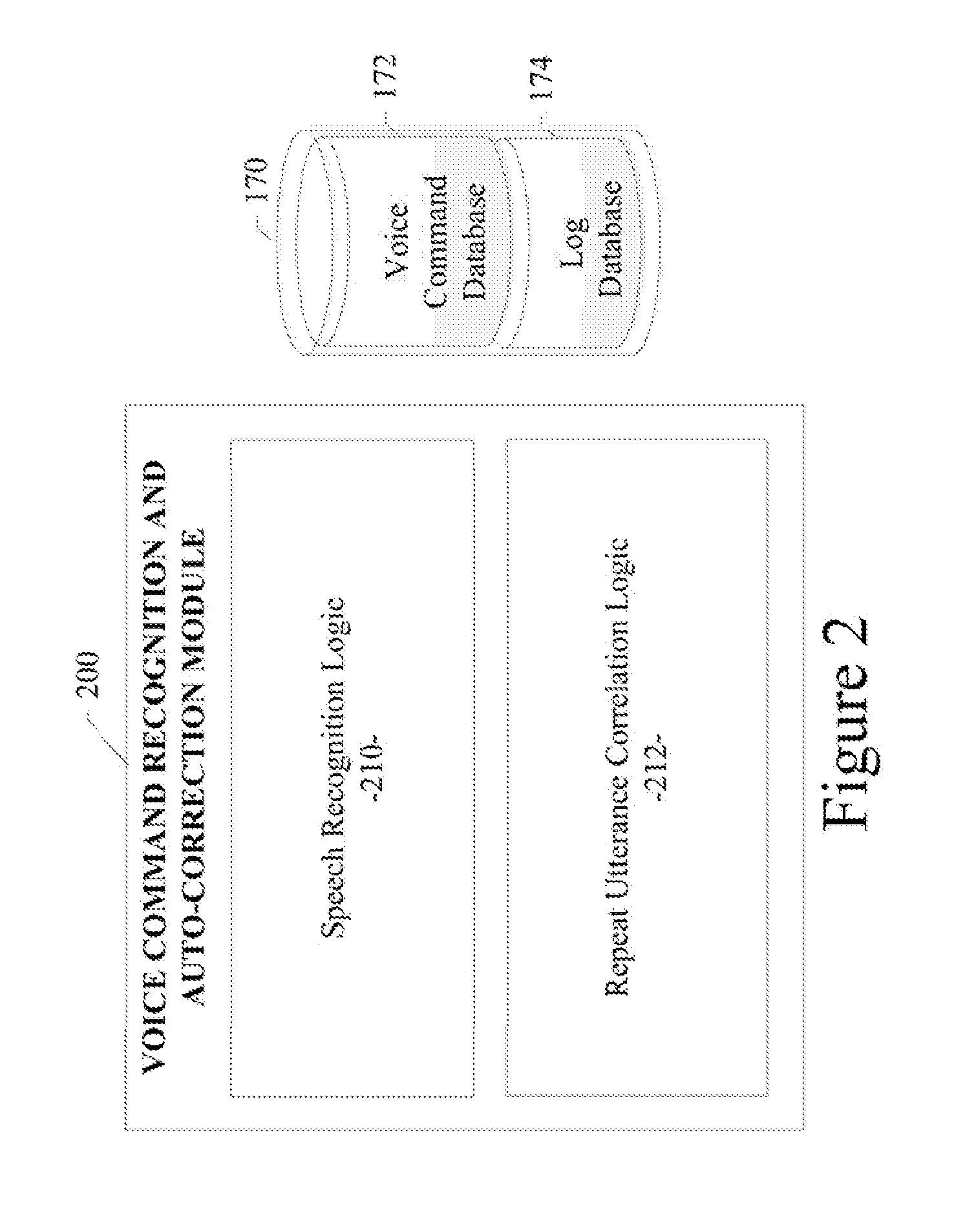
System and method for recognition and automatic correction of voice commands
A system and method for recognition and automatic correction of voice commands are disclosed. A particular embodiment includes: receiving a set of utterance data, the set of utterance data corresponding to a voice command spoken by a speaker; performing a first-level speech recognition analysis on the set of utterance data to produce a first result, the first-level speech recognition analysis including generating a confidence value associated with the first result, the first-level speech recognition analysis also including determining if the set of utterance data is a repeat utterance corresponding to a previously received set of utterance data; performing a second-level speech recognition analysis on the set of utterance data to produce a second result, if the confidence value associated with the first result does not meet or exceed a pre-configured threshold or if the set of utterance data is a repeat utterance; and matching the set of utterance data to a voice command and returning information indicative of the matching voice command without returning information that is the same as previously returned information if the set of utterance data is a repeat utterance.
Owner:LENNY INSURANCE LTD
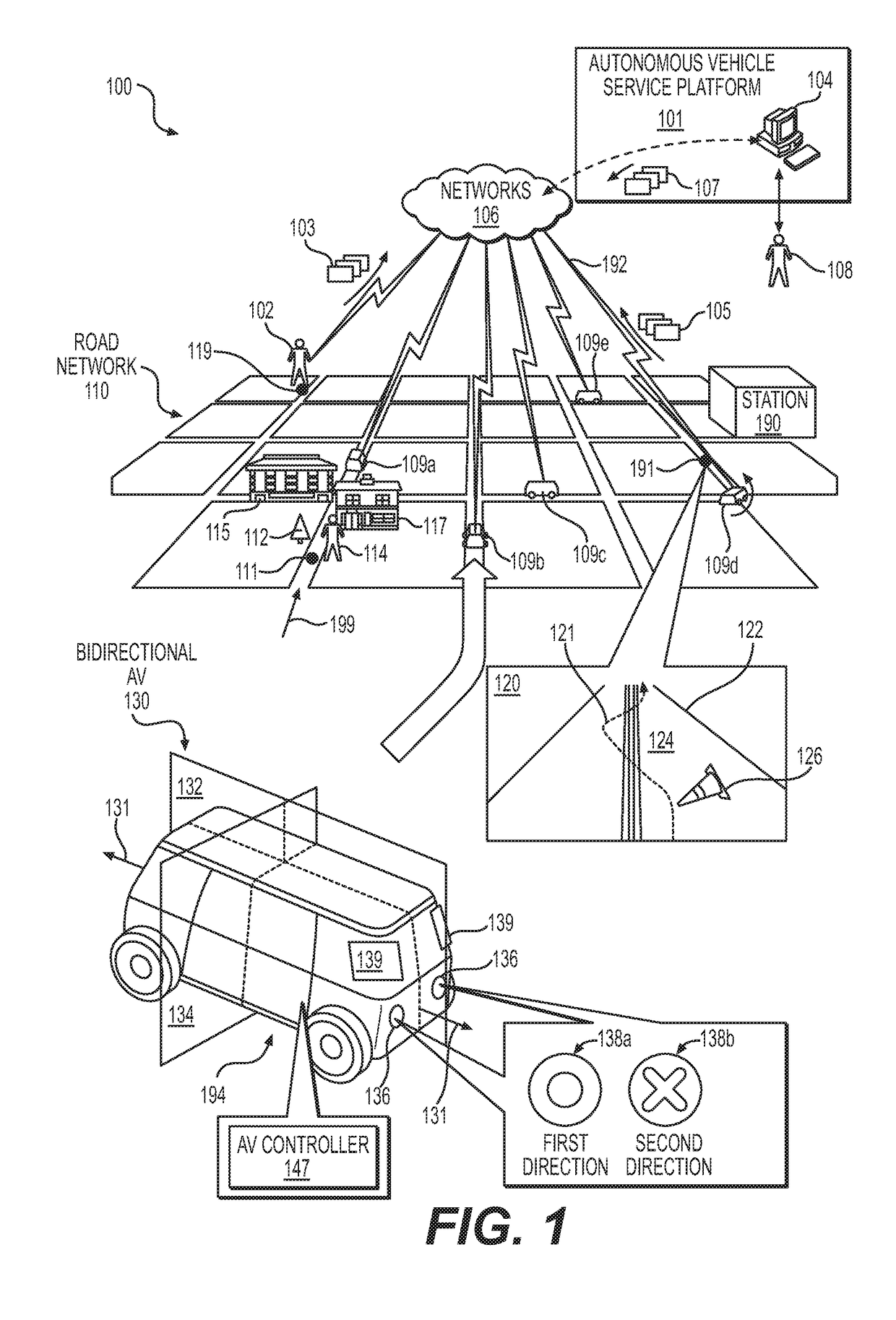
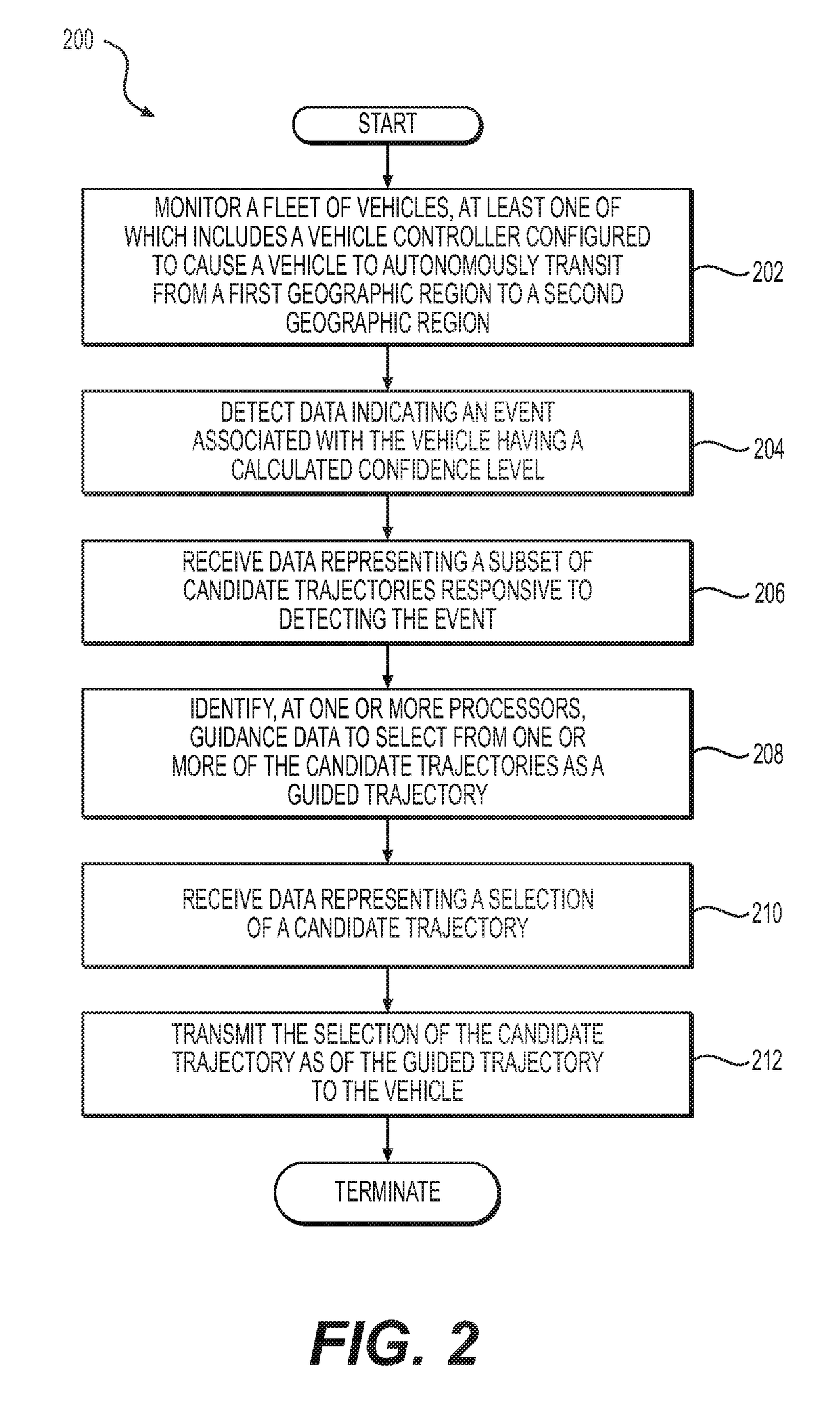
Automated extraction of semantic information to enhance incremental mapping modifications for robotic vehicles
ActiveUS20170316333A1Autonomous decision making processScene recognitionStatistical analysisHeat map
Systems, methods and apparatus may be configured to implement automatic semantic classification of a detected object(s) disposed in a region of an environment external to an autonomous vehicle. The automatic semantic classification may include analyzing over a time period, patterns in a predicted behavior of the detected object(s) to infer a semantic classification of the detected object(s). Analysis may include processing of sensor data from the autonomous vehicle to generate heat maps indicative of a location of the detected object(s) in the region during the time period. Probabilistic statistical analysis may be applied to the sensor data to determine a confidence level in the inferred semantic classification. The inferred semantic classification may be applied to the detected object(s) when the confidence level exceeds a predetermined threshold value (e.g., greater than 50%).
Owner:ZOOX INC
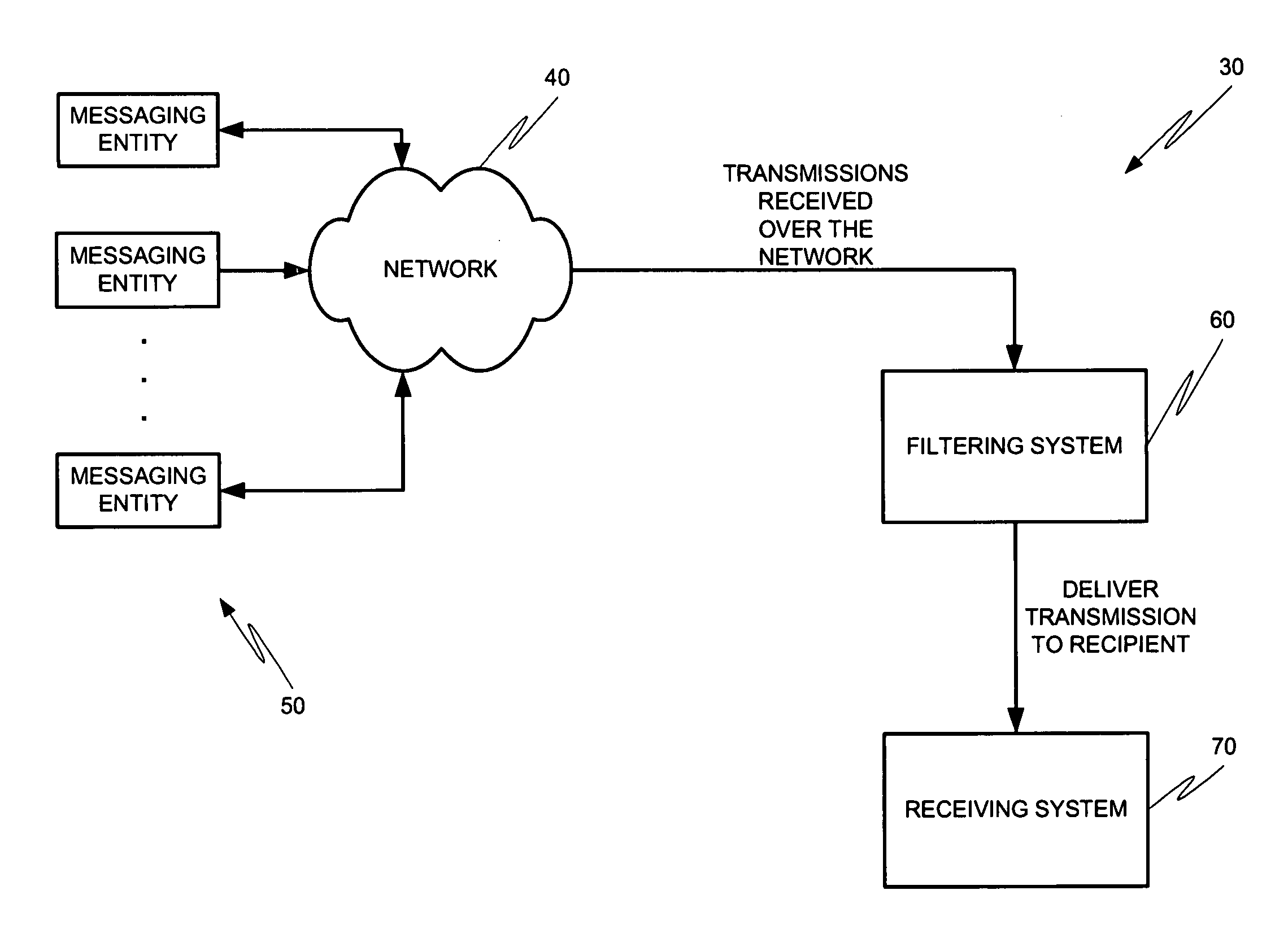
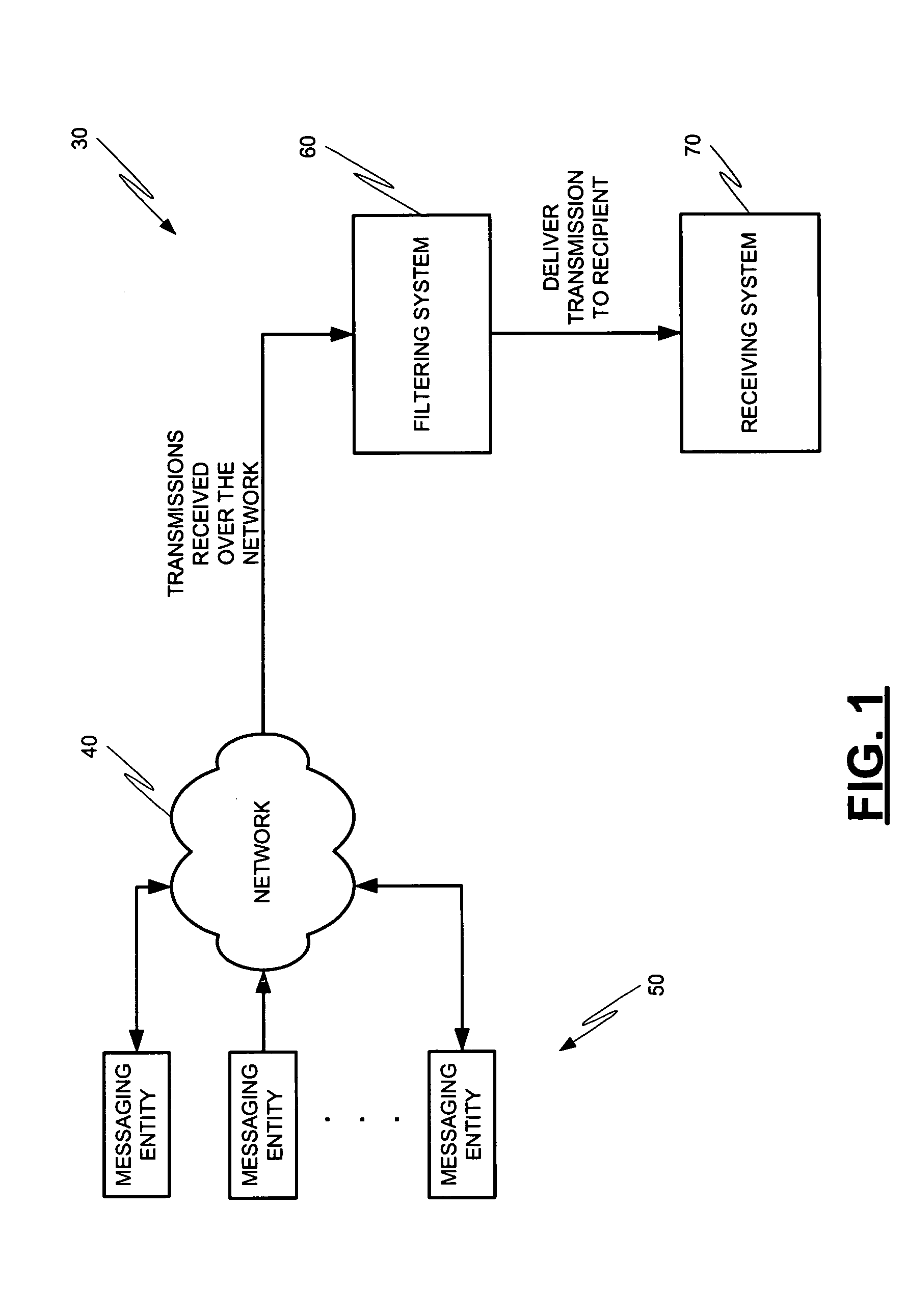
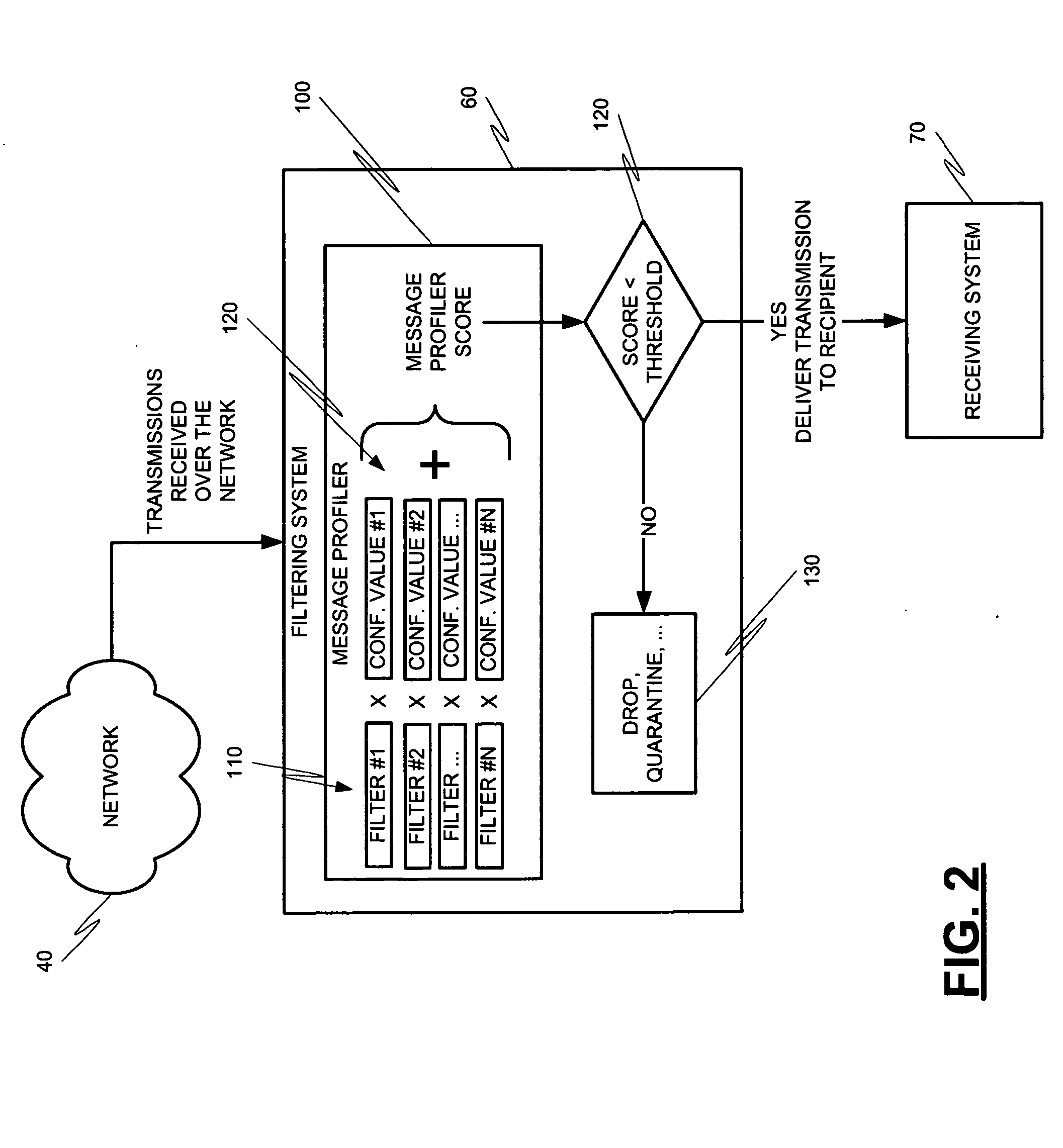
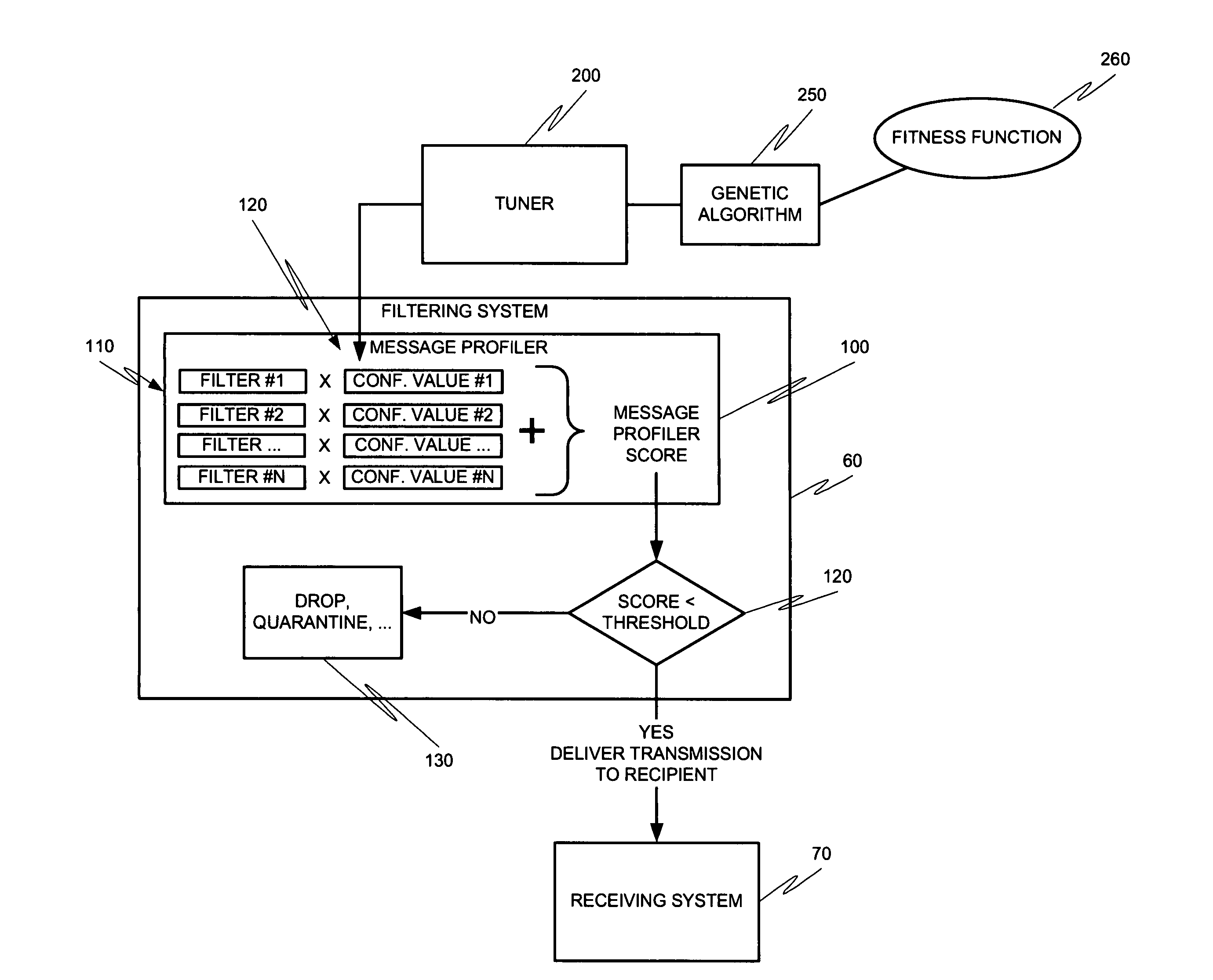
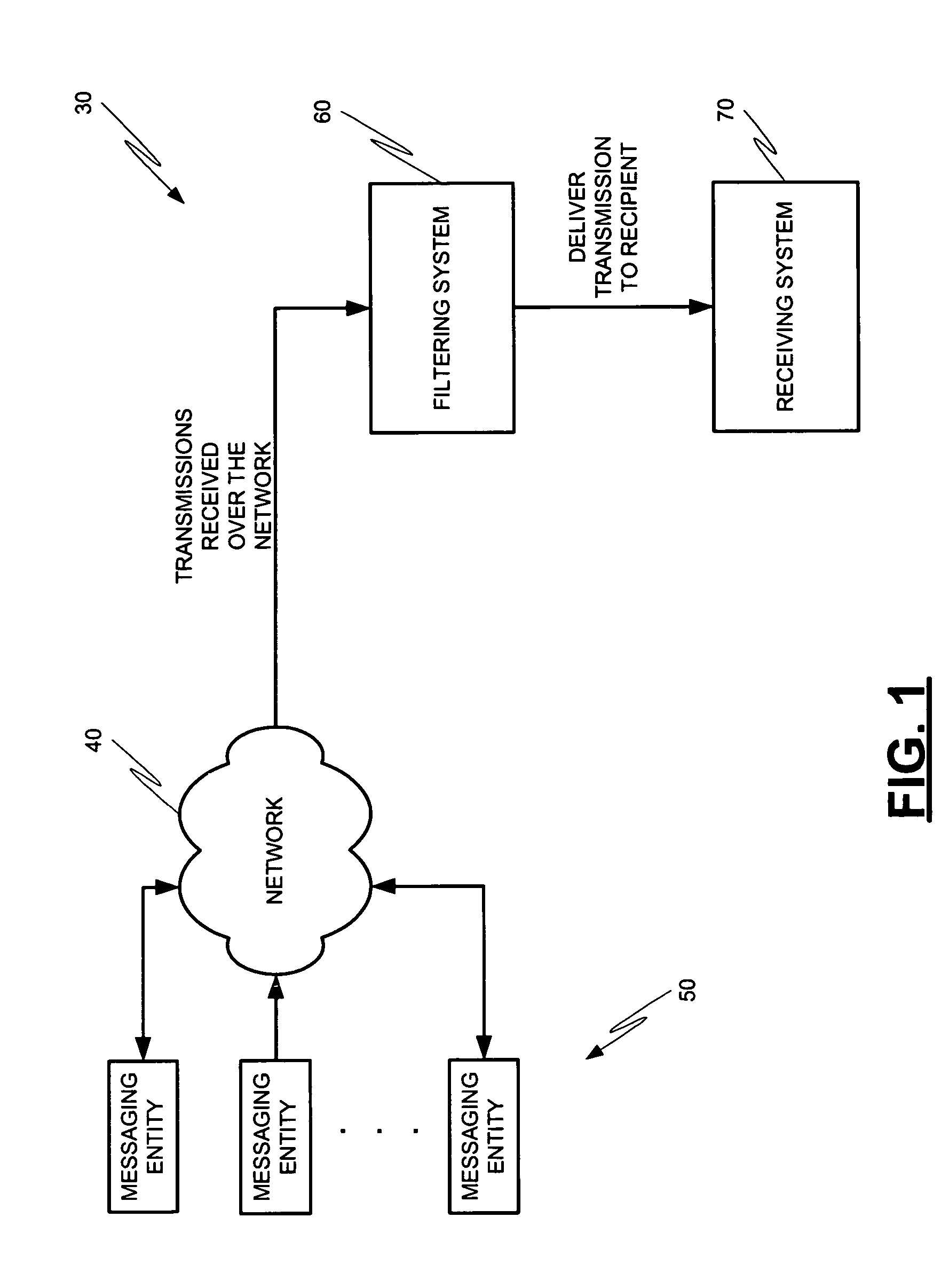
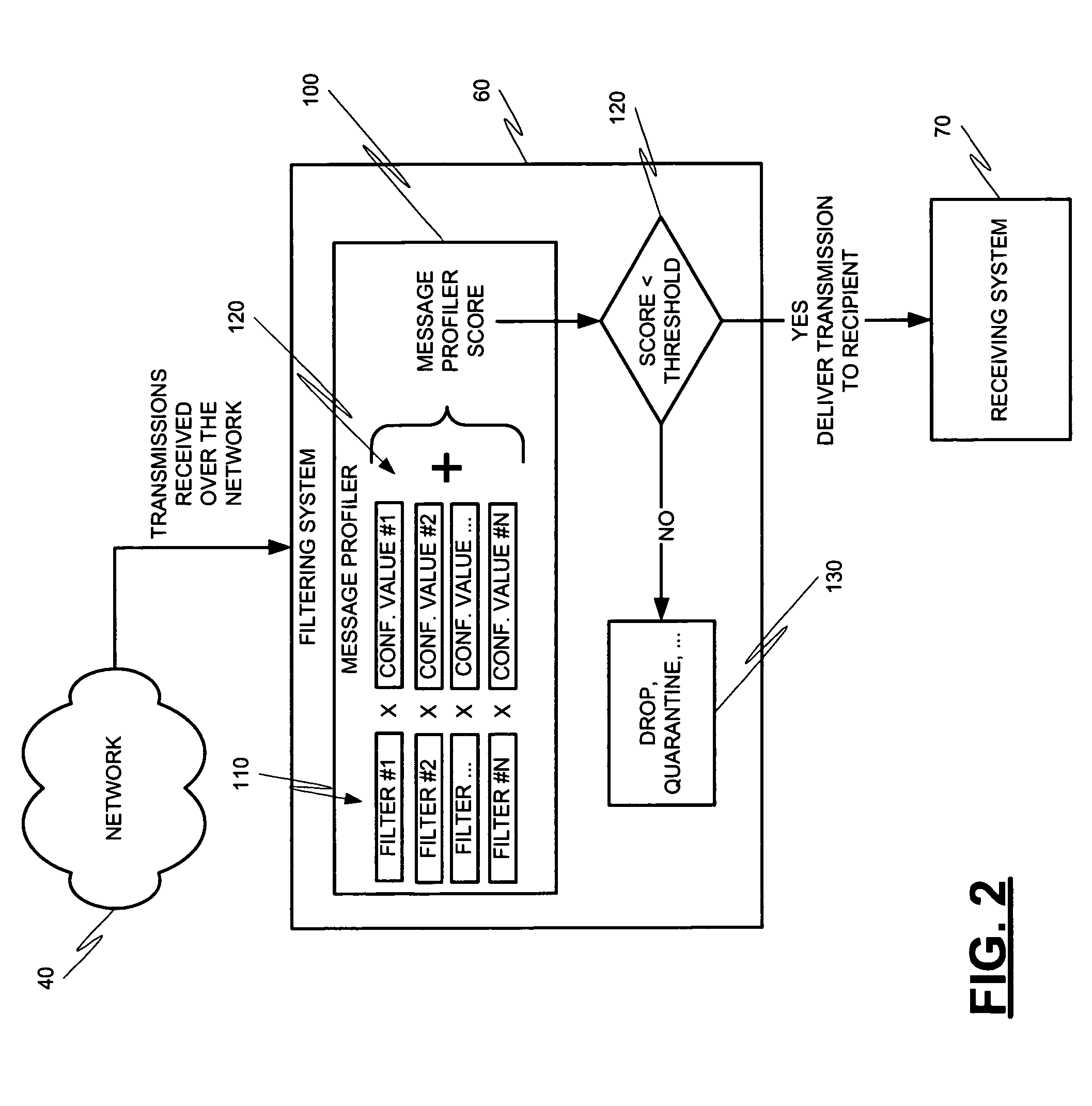
Message profiling systems and methods
Methods and systems for operation upon one or more data processors that classify communications from messaging entities. A method can include receiving a communication that was sent from a messaging entity. A plurality of message classification techniques is used to classify the communication. Each message classification technique is associated with a confidence value which is used in generating a message classification output from the message classification technique. The message classification outputs are combined in order to generate a message profile score. The message Profile score is used in deciding what action is to be taken with respect to the communication associated with the messaging entity.
Owner:MCAFEE LLC
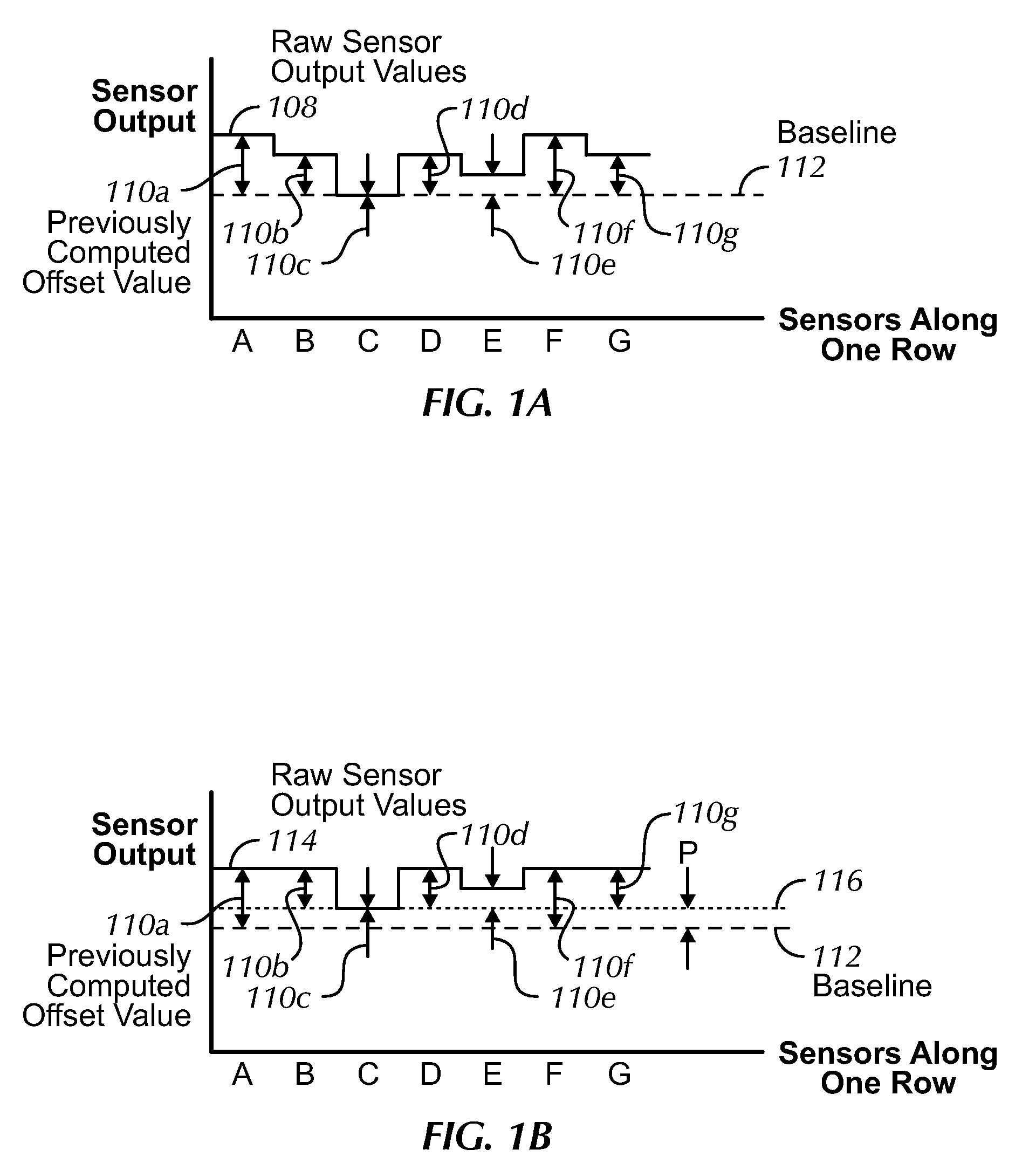
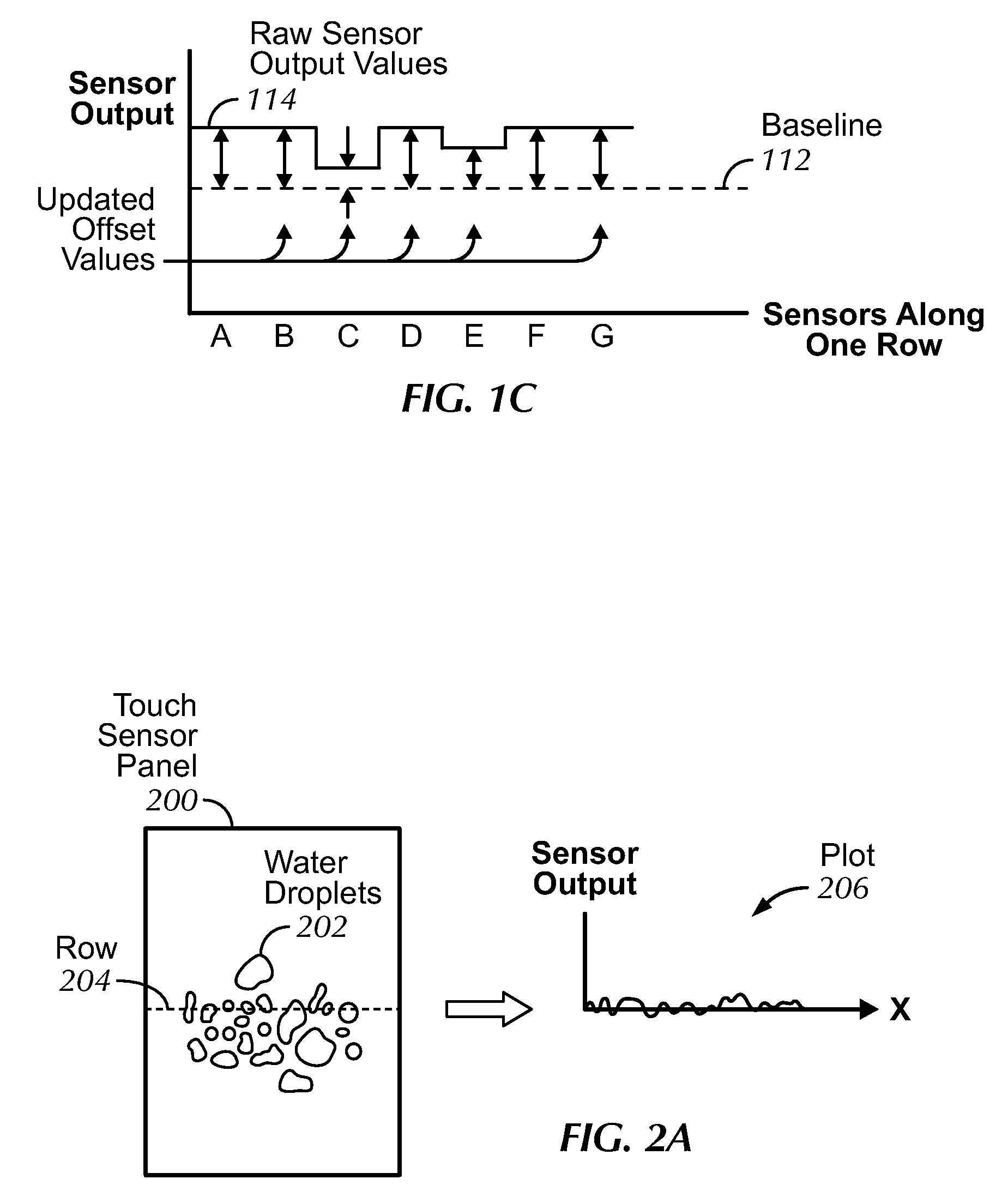
Motion component dominance factors for motion locking of touch sensor data
InactiveUS20090174676A1Improve accuracyDetect presenceImage analysisCharacter and pattern recognitionLine sensorStandardization
An image jaggedness filter is disclosed that can be used to detect the presence of ungrounded objects such as water droplets or coins, and delay periodic baseline adjustments until these objects are no longer present. To do otherwise could produce inaccurate normalized baseline sensor output values. The application of a global baseline offset is also disclosed to quickly modify the sensor offset values to account for conditions such as rapid temperature changes. Background pixels not part of any touch regions can be used to detect changes to no-touch sensor output values and globally modify the sensor offset values accordingly. The use of motion dominance ratios and axis domination confidence values is also disclosed to improve the accuracy of locking onto dominant motion components as part of gesture recognition.
Owner:APPLE INC
Systems and methods for determining the network topology of a network
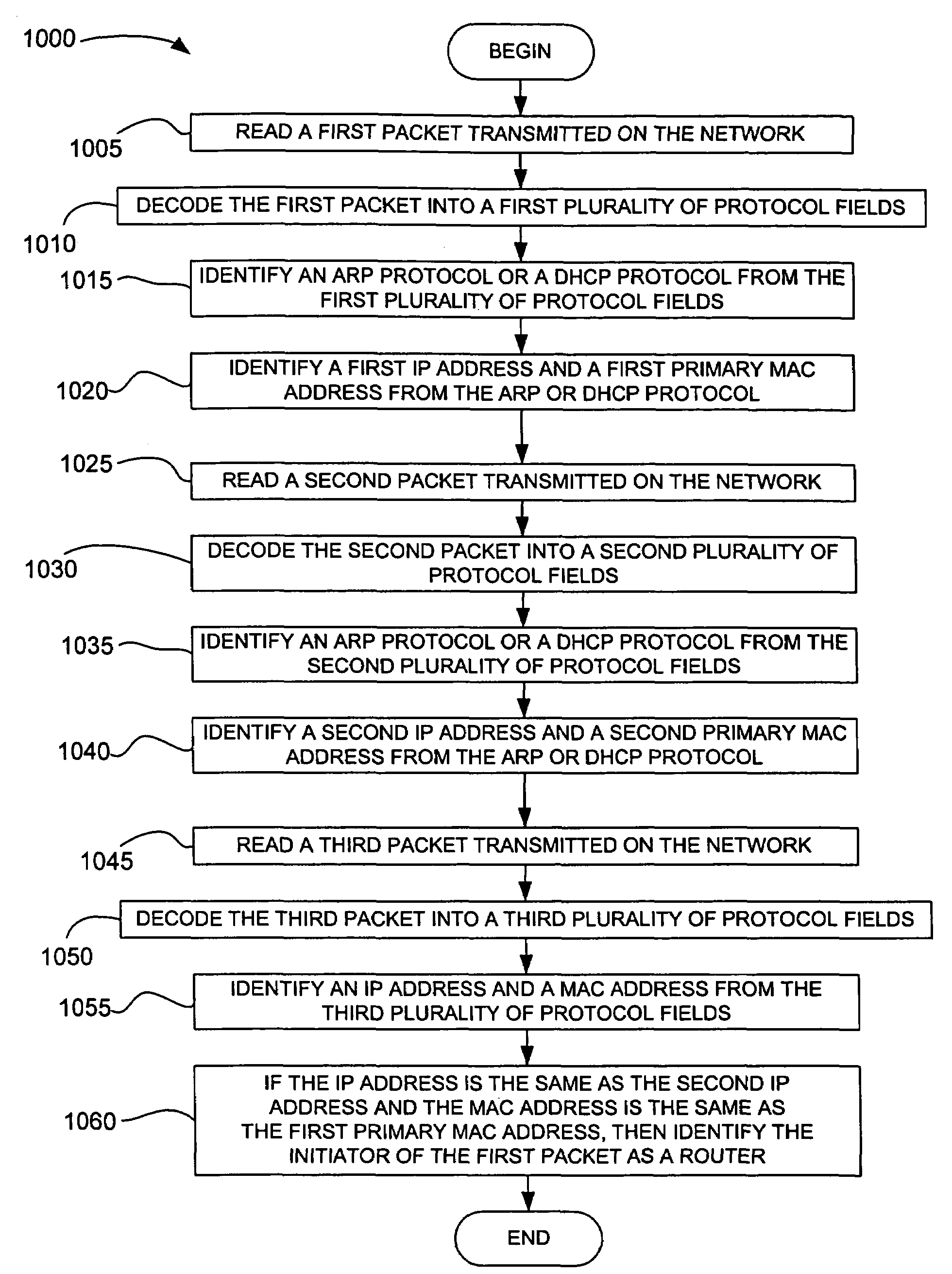
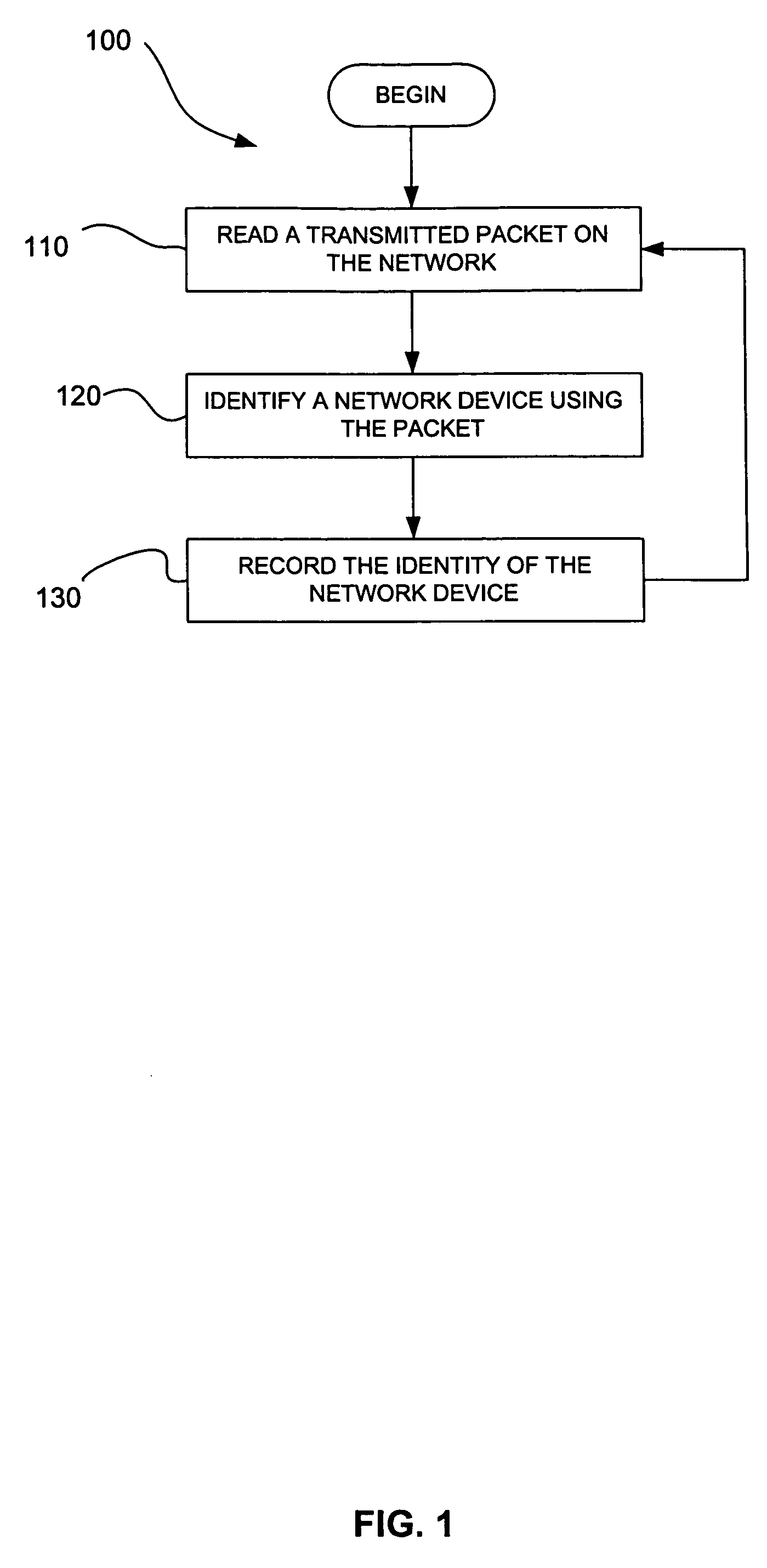
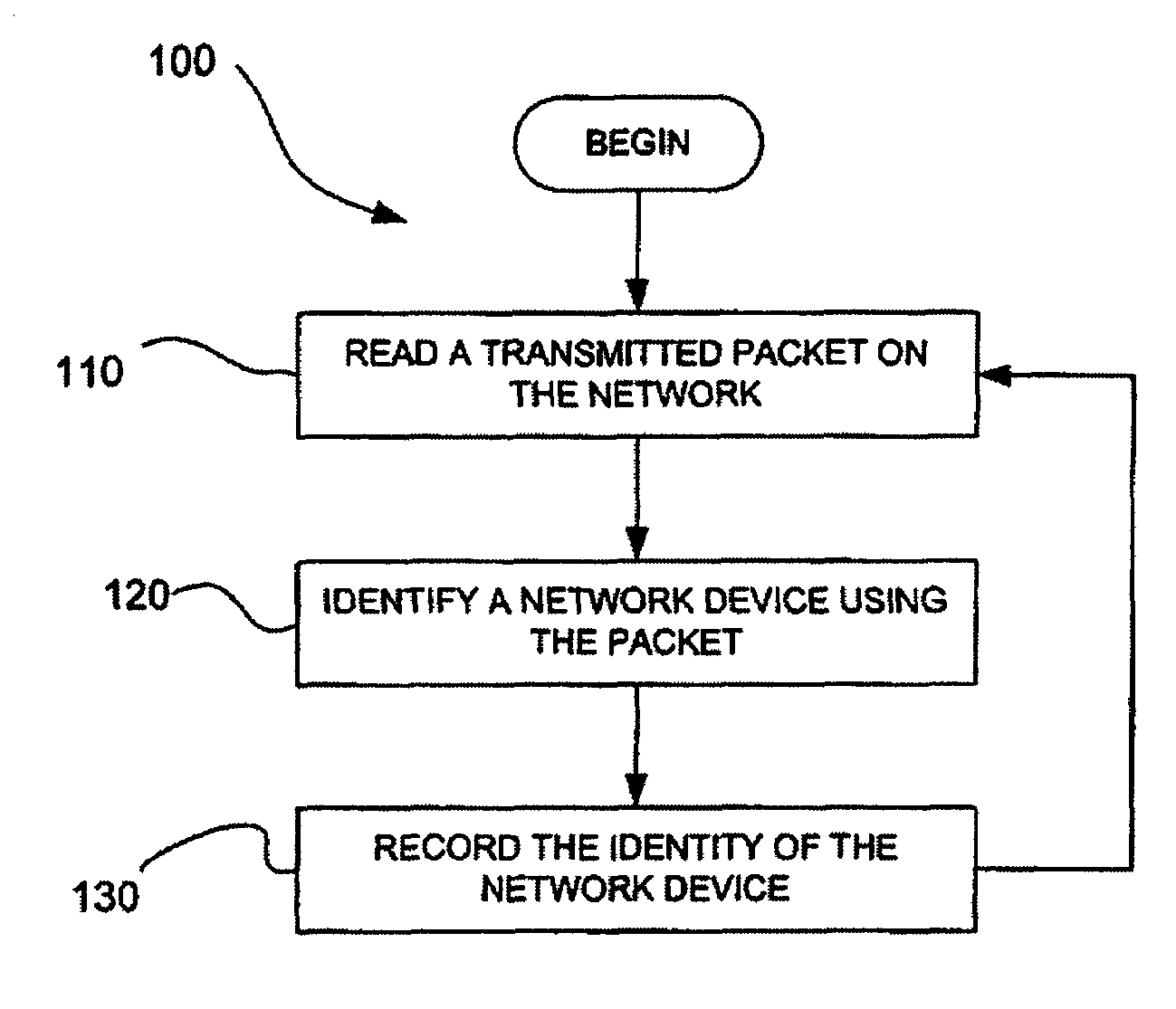
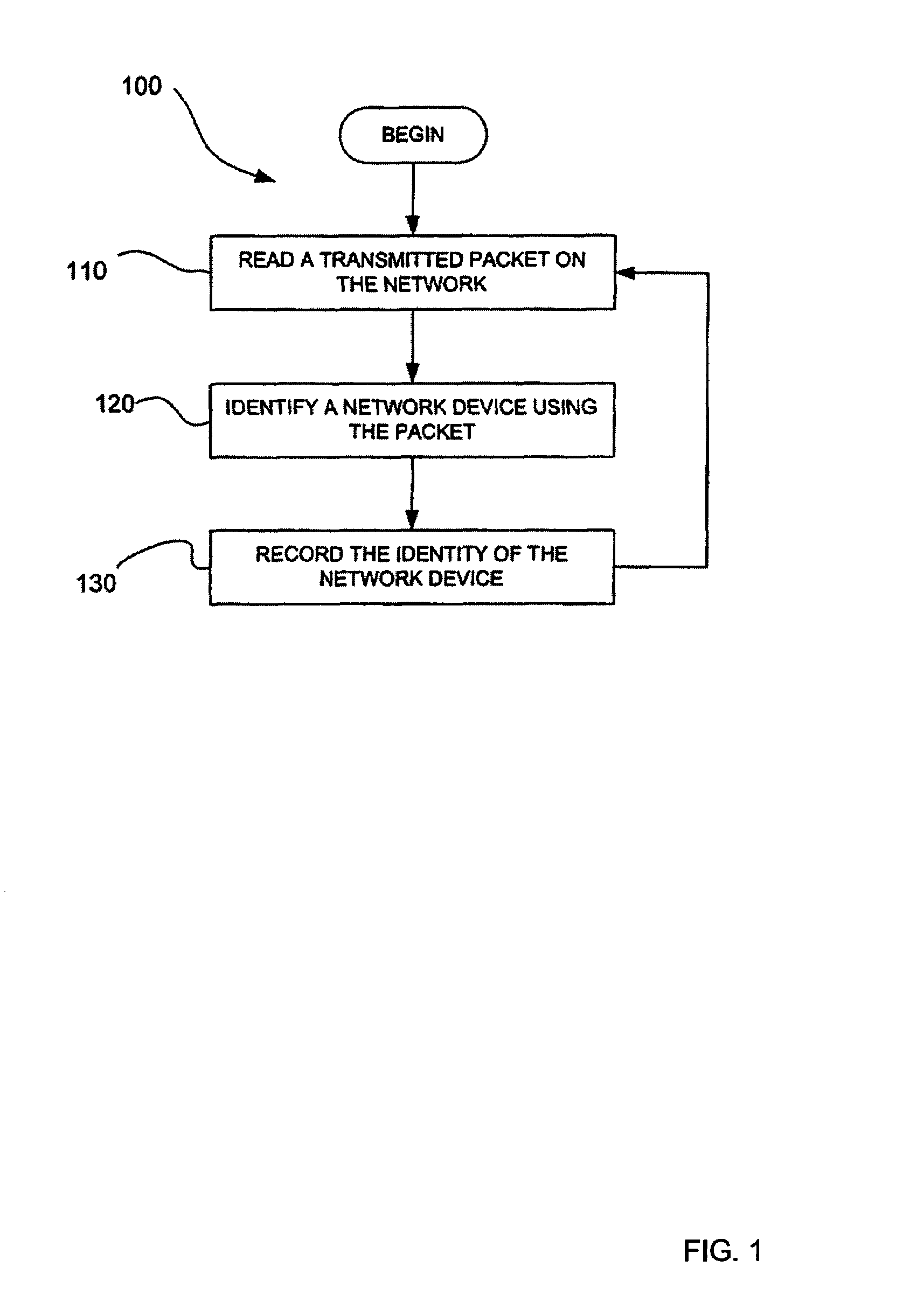
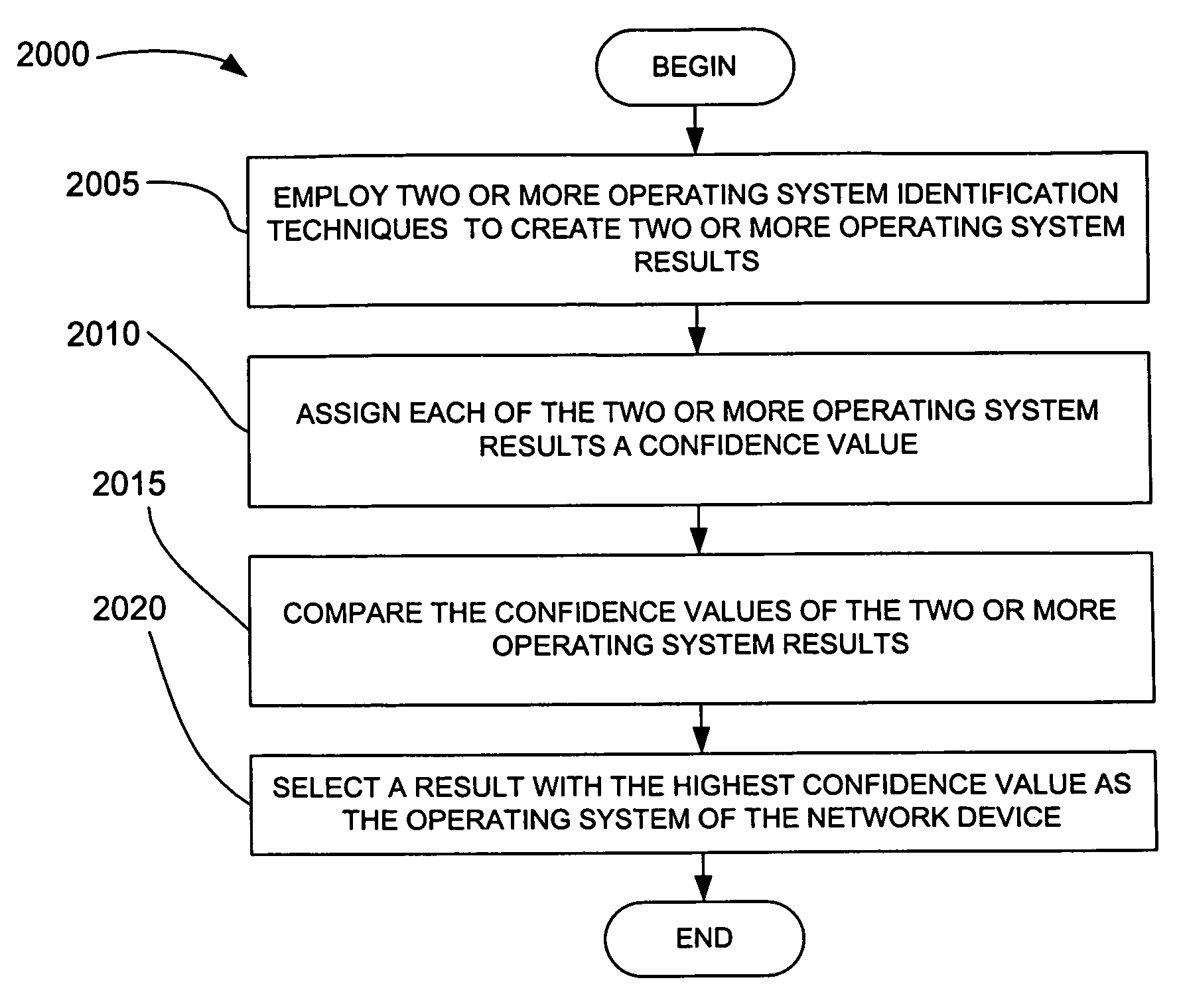
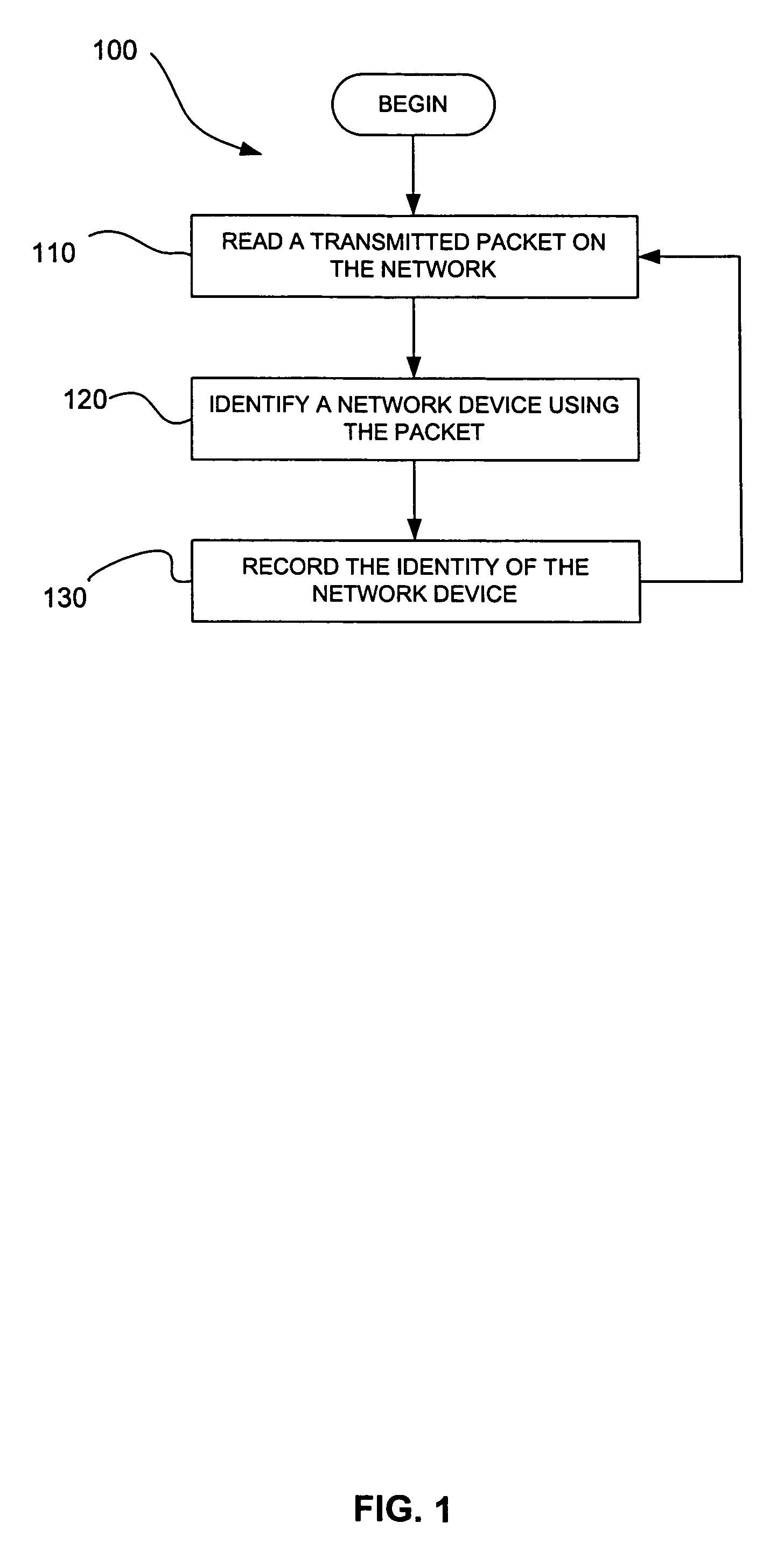
A packet transmitted on a network is read and decoded. A network device and its operating system are identified by analyzing the decoded packet. If more than one operating system is identified from the decoded packet, the operating system is selecting by comparing confidence values assigned to the operating systems identified. A service running on the network device is identified from the decoded packet or subsequent packets that are read, decoded and analyzed. The network topology of a network is determined by reading, decoding, and analyzing a plurality of packets. A flow between two network devices is determined by reading, decoding, and analyzing a plurality of packets. Vulnerabilities are assigned to operating systems and services identified by reading, decoding, and analyzing packets. Network configuration policy is enforced on operating systems and services identified by reading, decoding, and analyzing packets.
Owner:CISCO TECH INC
Systems and methods for identifying the client applications of a network
A packet transmitted on a network is read and decoded. A network device and its operating system are identified by analyzing the decoded packet. If more than one operating system is identified from the decoded packet, the operating system is selecting by comparing confidence values assigned to the operating systems identified. A client application running on the network device is identified from the decoded packet or subsequent packets that are read, decoded and analyzed. The network topology of a network is determined by reading, decoding, and analyzing a plurality of packets. A flow between two network devices is determined by reading, decoding, and analyzing a plurality of packets. Vulnerabilities are assigned to operating systems and client applications identified by reading, decoding, and analyzing packets. Network configuration policy is enforced on operating systems and client applications identified by reading, decoding, and analyzing packets.
Owner:CISCO TECH INC
Systems and methods for determining characteristics of a network and assessing confidence
A packet transmitted on a network is read and decoded. A network device and its operating system are identified by analyzing the decoded packet. If more than one operating system is identified from the decoded packet, the operating system is selecting by comparing confidence values assigned to the operating systems identified. A service running on the network device is identified from the decoded packet or subsequent packets that are read, decoded and analyzed. The network topology of a network is determined by reading, decoding, and analyzing a plurality of packets. A flow between two network devices is determined by reading, decoding, and analyzing a plurality of packets. Vulnerabilities are assigned to operating systems and services identified by reading, decoding, and analyzing packets. Network configuration policy is enforced on operating systems and services identified by reading, decoding, and analyzing packets.
Owner:CISCO TECH INC
Object recognition using incremental feature extraction
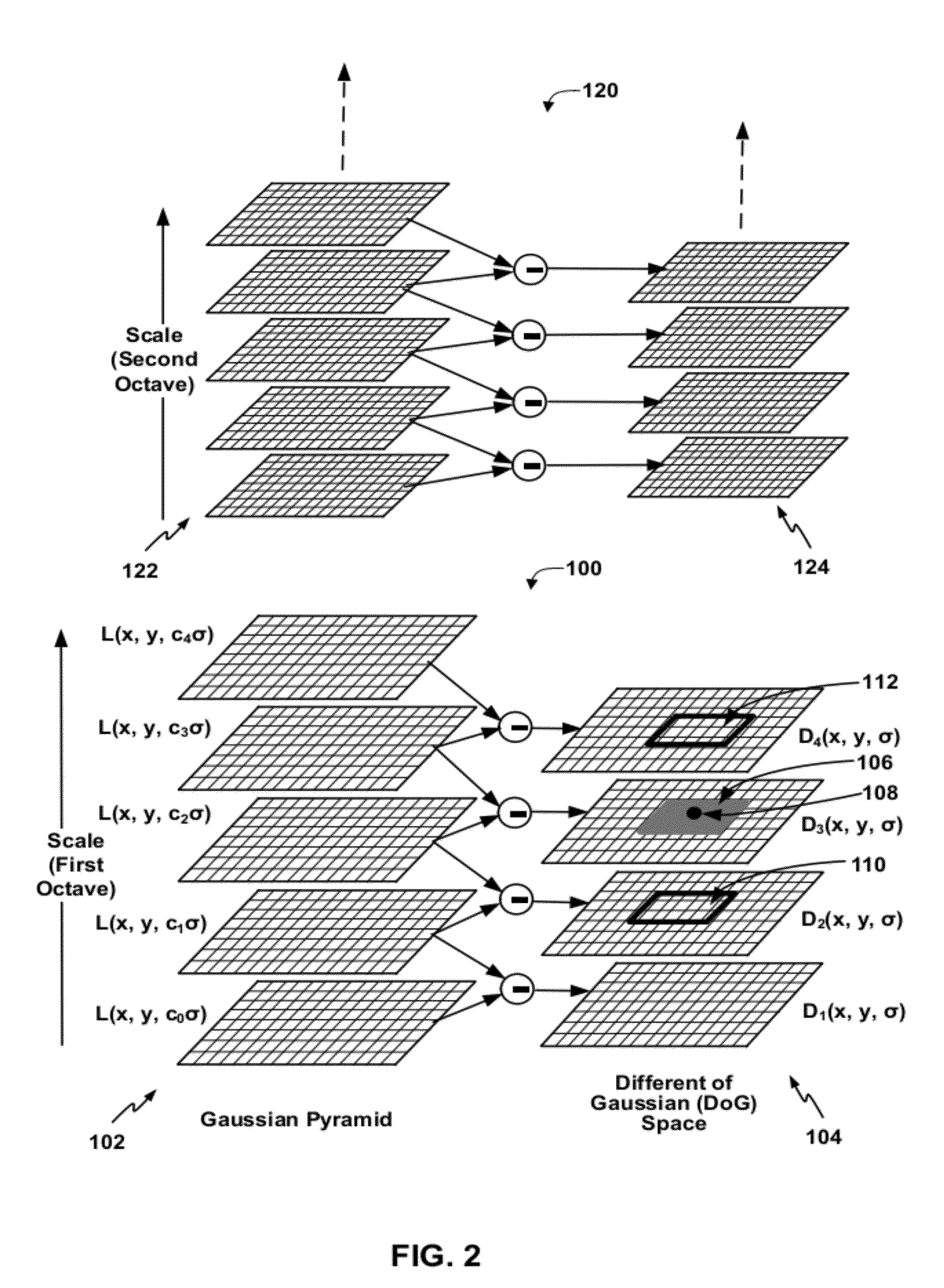
ActiveUS20120027290A1Computational complexity is reducedCharacter and pattern recognitionOctaveDigital image
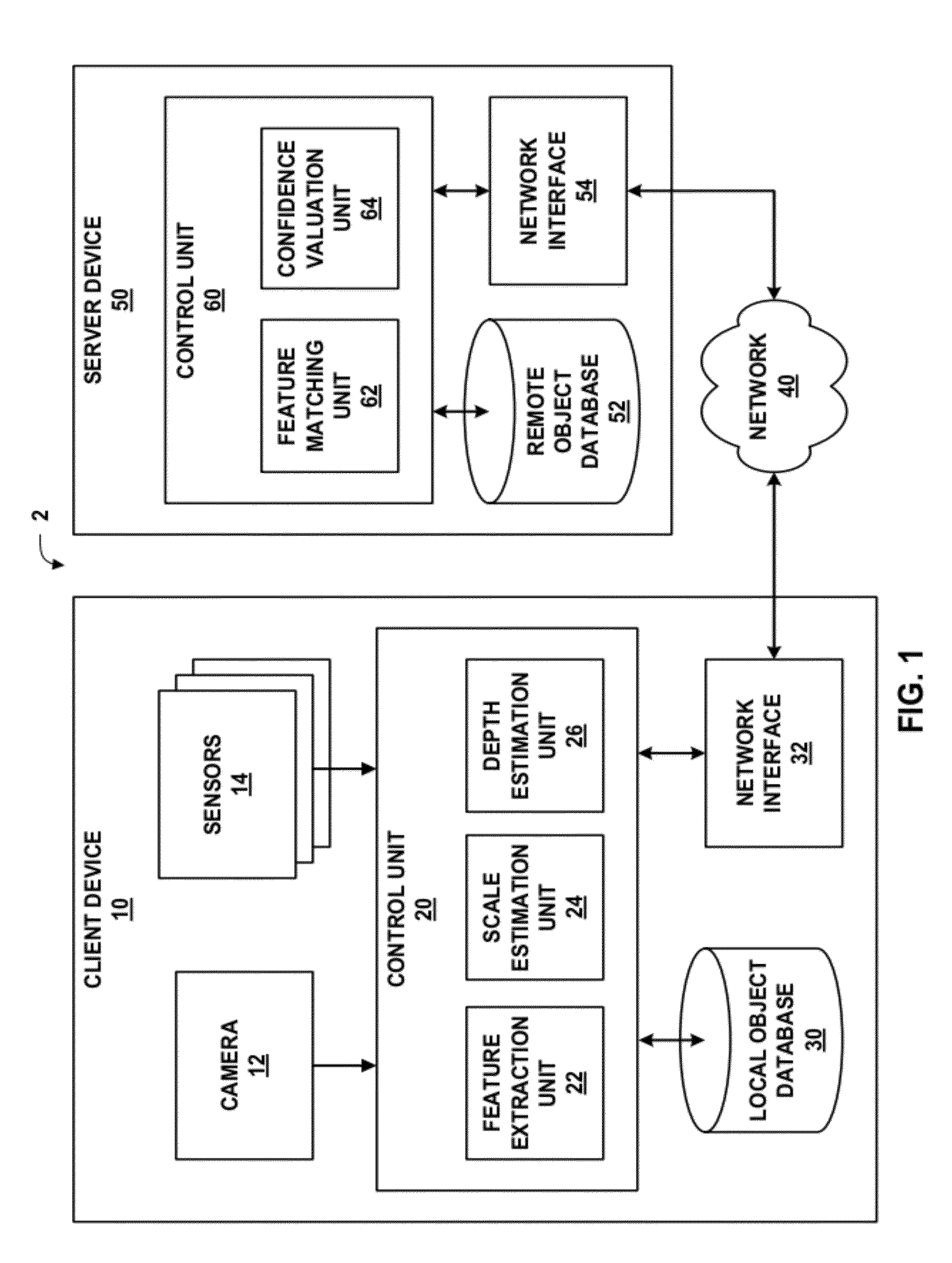
In one example, an apparatus includes a processor configured to extract a first set of one or more keypoints from a first set of blurred images of a first octave of a received image, calculate a first set of one or more descriptors for the first set of keypoints, receive a confidence value for a result produced by querying a feature descriptor database with the first set of descriptors, wherein the result comprises information describing an identity of an object in the received image, and extract a second set of one or more keypoints from a second set of blurred images of a second octave of the received image when the confidence value does not exceed a confidence threshold. In this manner, the processor may perform incremental feature descriptor extraction, which may improve computational efficiency of object recognition in digital images.
Owner:QUALCOMM INC
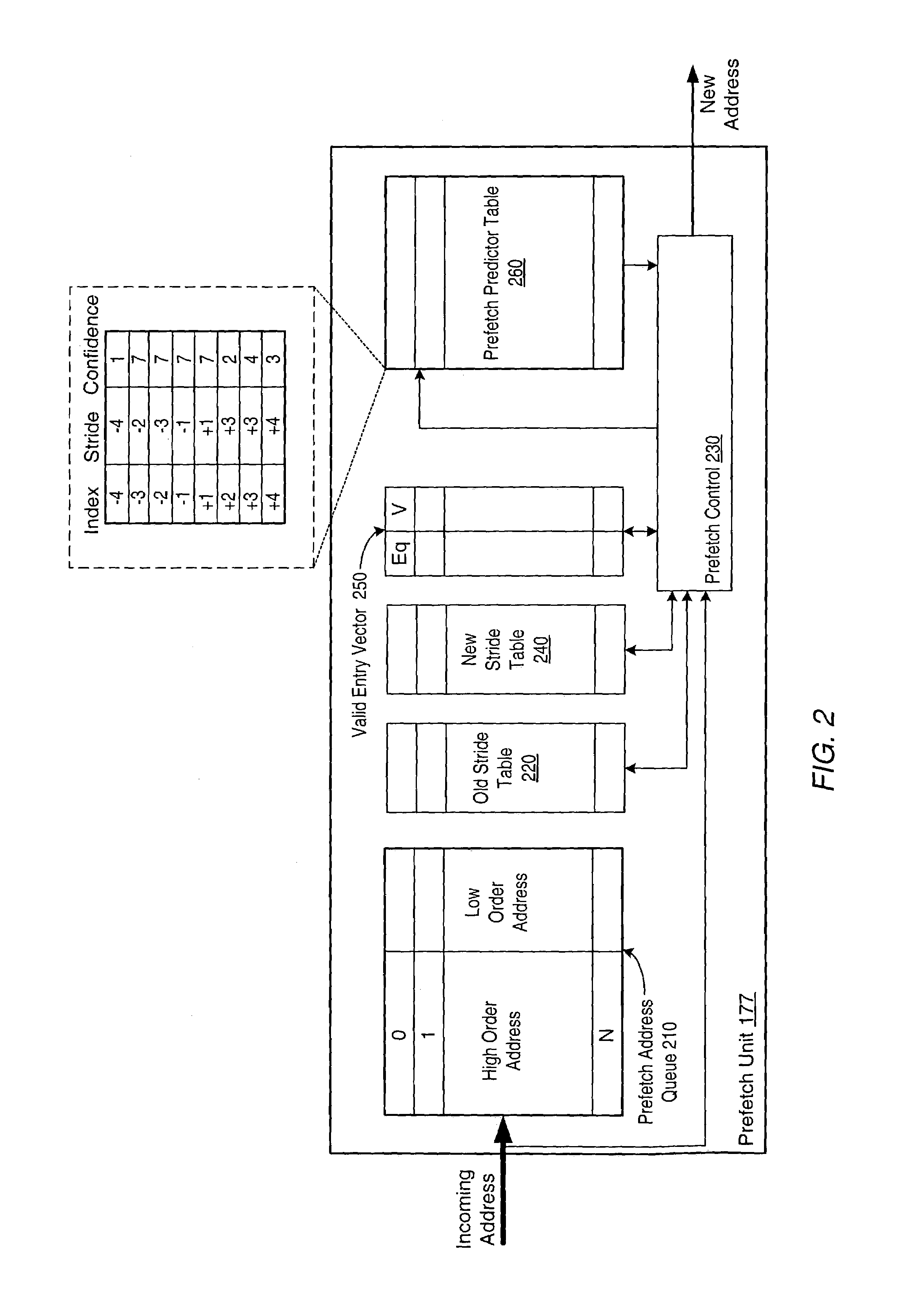
Stride-based prefetch mechanism using a prediction confidence value
ActiveUS6976147B1Memory architecture accessing/allocationMemory adressing/allocation/relocationOperating systemConfidence value
Owner:ADVANCED MICRO DEVICES INC
Selective Location Determination
ActiveUS20110250903A1Maximize accuracyStability of the locationPosition fixationWireless commuication servicesCell IDMedia access control
Methods, program products, and systems for selective location determination are described. A mobile device can determine a location of the mobile device using various techniques. When there is a conflict between the locations determined using different techniques, the mobile device can select a most trustworthy location from the locations, and designate the most trustworthy location as a current location of the mobile device. The mobile device can determine a first location of the mobile device (e.g., a coarse location) using a cell identifier (cell ID) of a cellular network. The mobile device can determine a second location of the mobile device (e.g., a fine location) using one or more media access control (MAC) addresses of a WLAN. The first location and second location can be associated with confidence values that can indicate trustworthiness of the first location and second location.
Owner:APPLE INC
System and method for sensor data validation
ActiveUS20060224357A1Mechanical power/torque controlSafety arrangmentsData validationComputer science
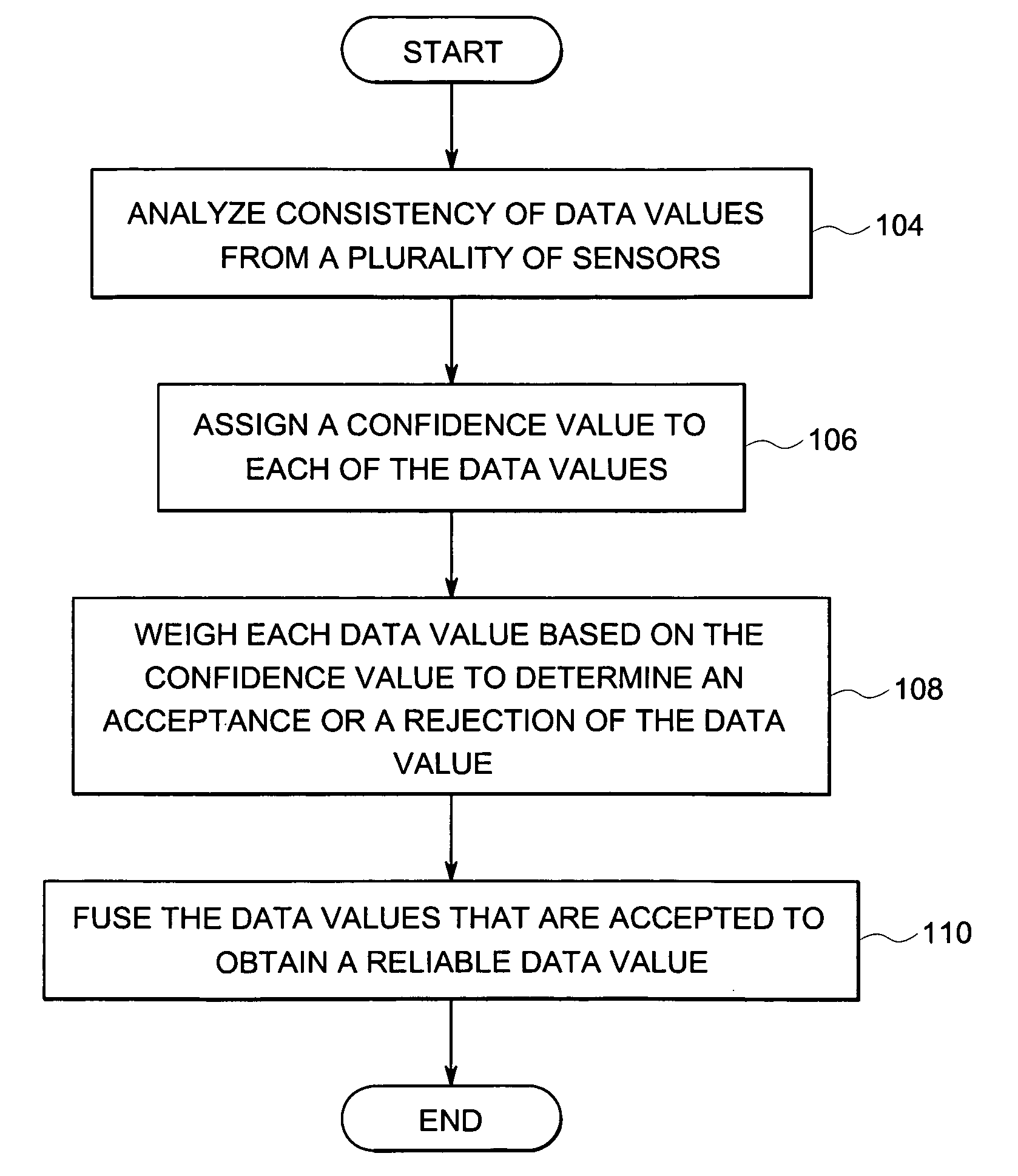
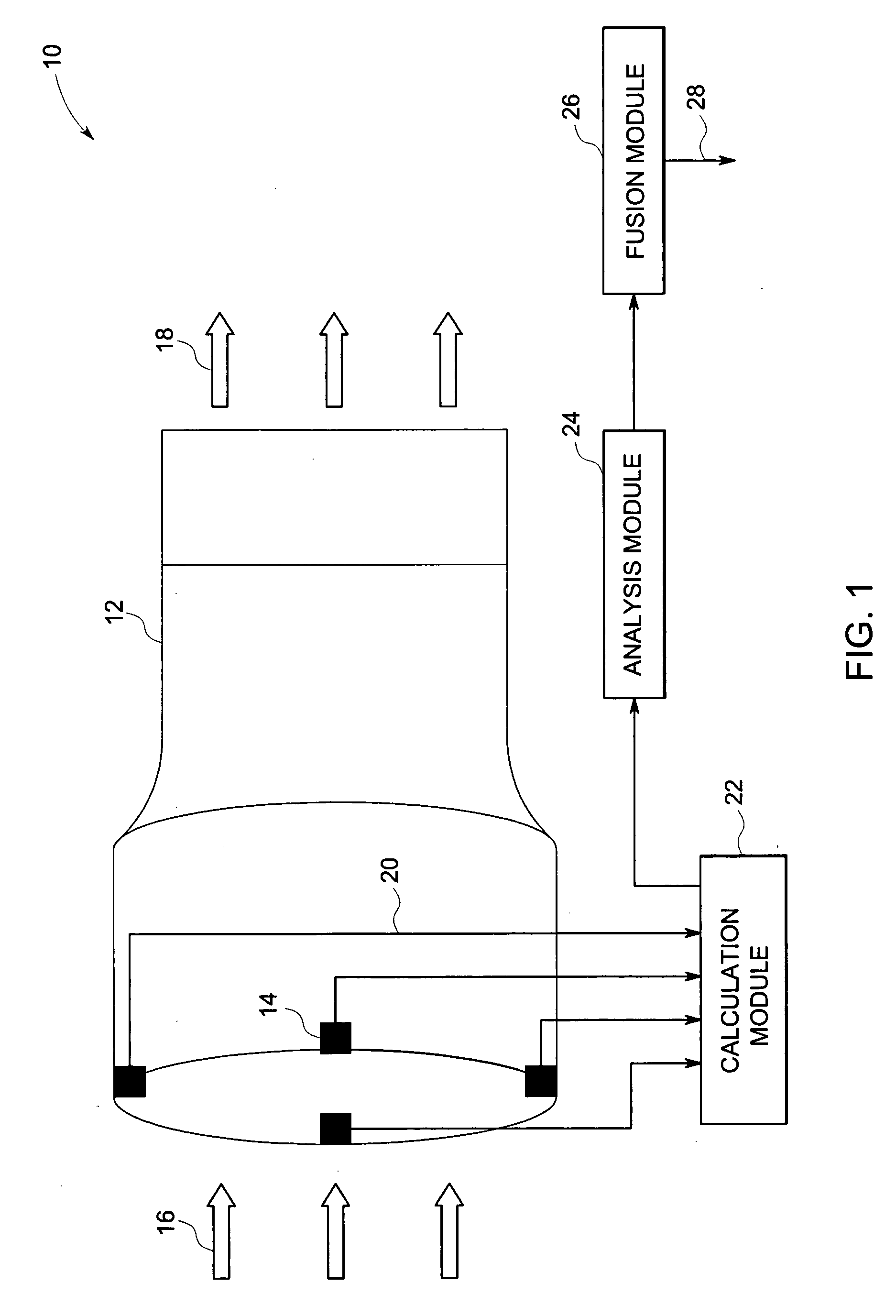
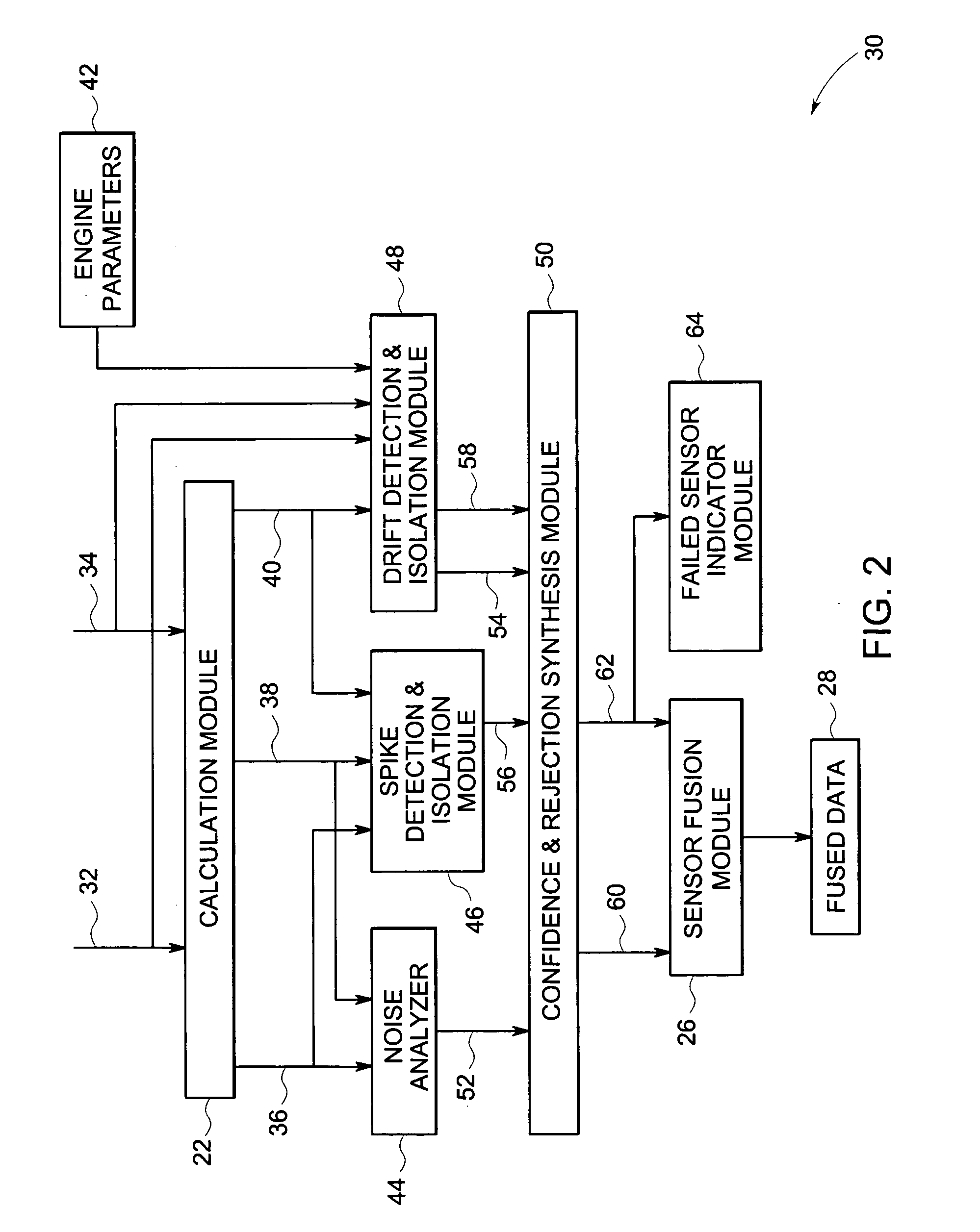
In accordance with an implementation of the present technique, a method for processing data is disclosed. The method involves analyzing consistency of sensor readings obtained from a plurality of sensors monitoring a device, where each sensor reading is indicative of at least one operational parameter of the device. The method also involves assigning a confidence value to each of the sensor readings, where the confidence value is indicative of an operational condition of one of the plurality of sensors that provided the sensor reading. The method also includes weighting each sensor reading based on the confidence value assigned to the sensor reading to determine an acceptance or a rejection of the sensor reading and fusing the sensor readings that are accepted to obtain a fused sensor reading corresponding to the operational parameter measured by the sensors on the device.
Owner:GENERAL ELECTRIC CO
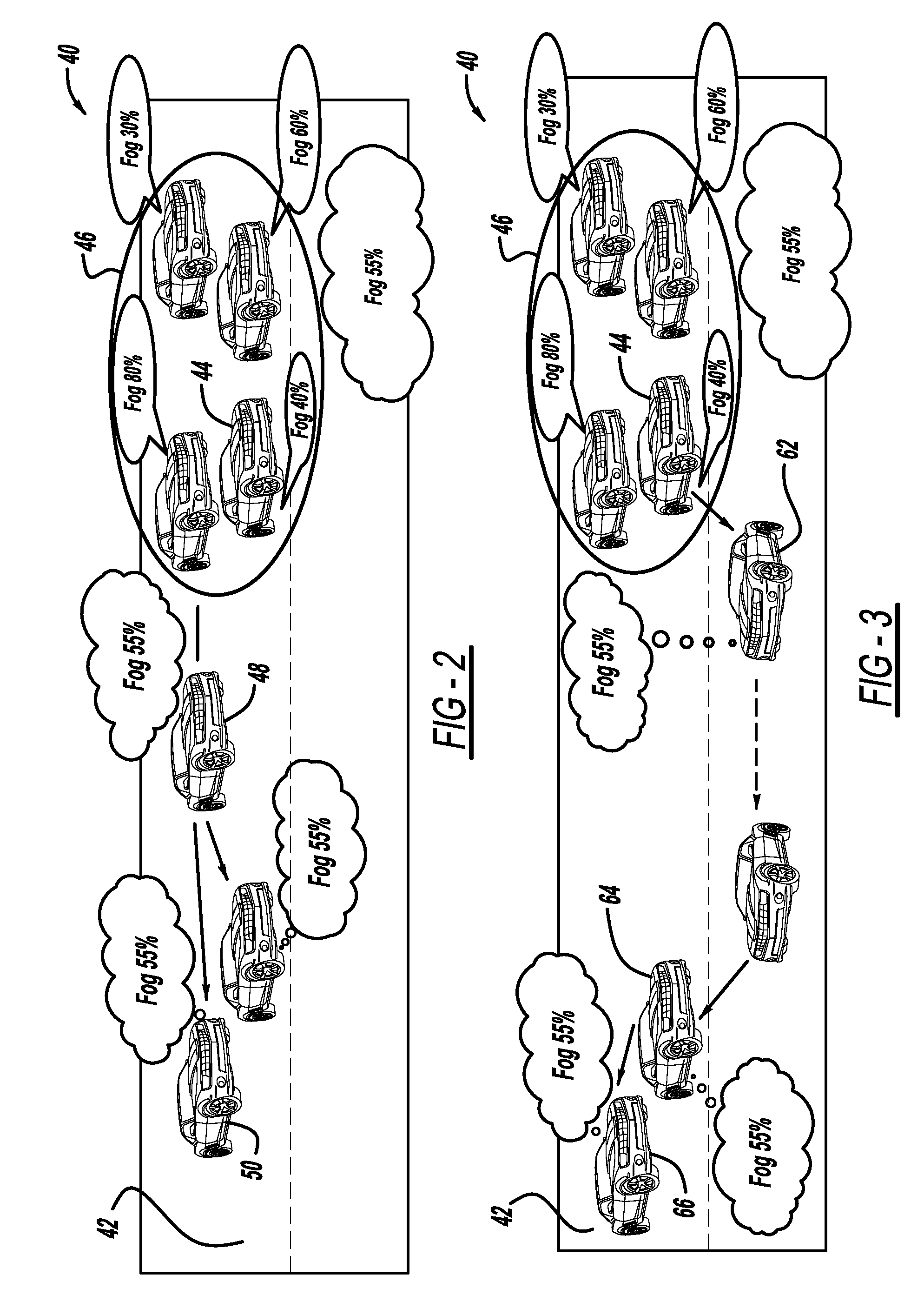
Using v2x-based in-network message generation, aggregation, distribution and processing protocols to enable road hazard condition warning applications
ActiveUS20100250106A1Analogue computers for vehiclesAnalogue computers for trafficTraffic congestionEngineering
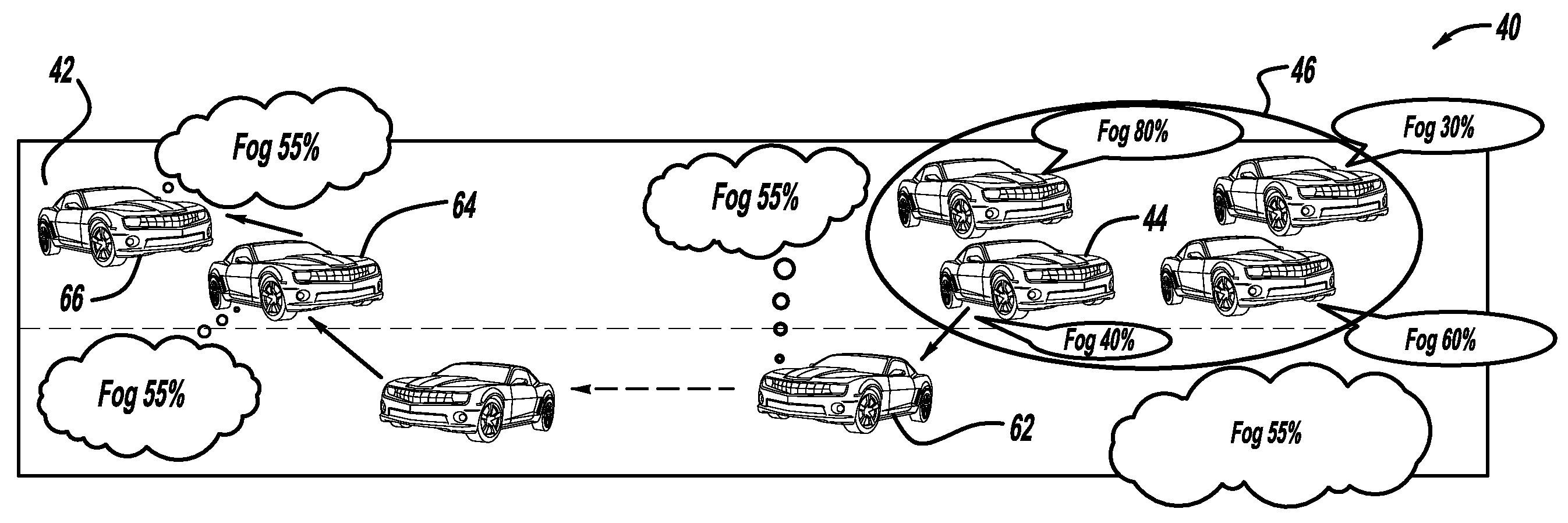
A method for providing messages indicating potential hazardous road conditions using a wireless communications network. Vehicles using the network include sensors that are able to detect various potentially hazardous road conditions, such as rain, fog, icy road conditions, traffic congestion, etc. A plurality of vehicles that detect a specific road condition provide a confidence value that the condition exists. The confidence value is then aggregated by the vehicles with the confidence value of the detected condition from the other vehicles to provide an aggregated result that identifies the probability that the detected road condition is occurring. The aggregated result is then transmitted to other vehicles approaching the road condition, possibly in a multi-hop manner. Alternately, the confidence value from all of the vehicles that detect the condition can be transmitted to approaching vehicles who will provide the aggregated result identifying the potential that the condition exists.
Owner:GM GLOBAL TECH OPERATIONS LLC
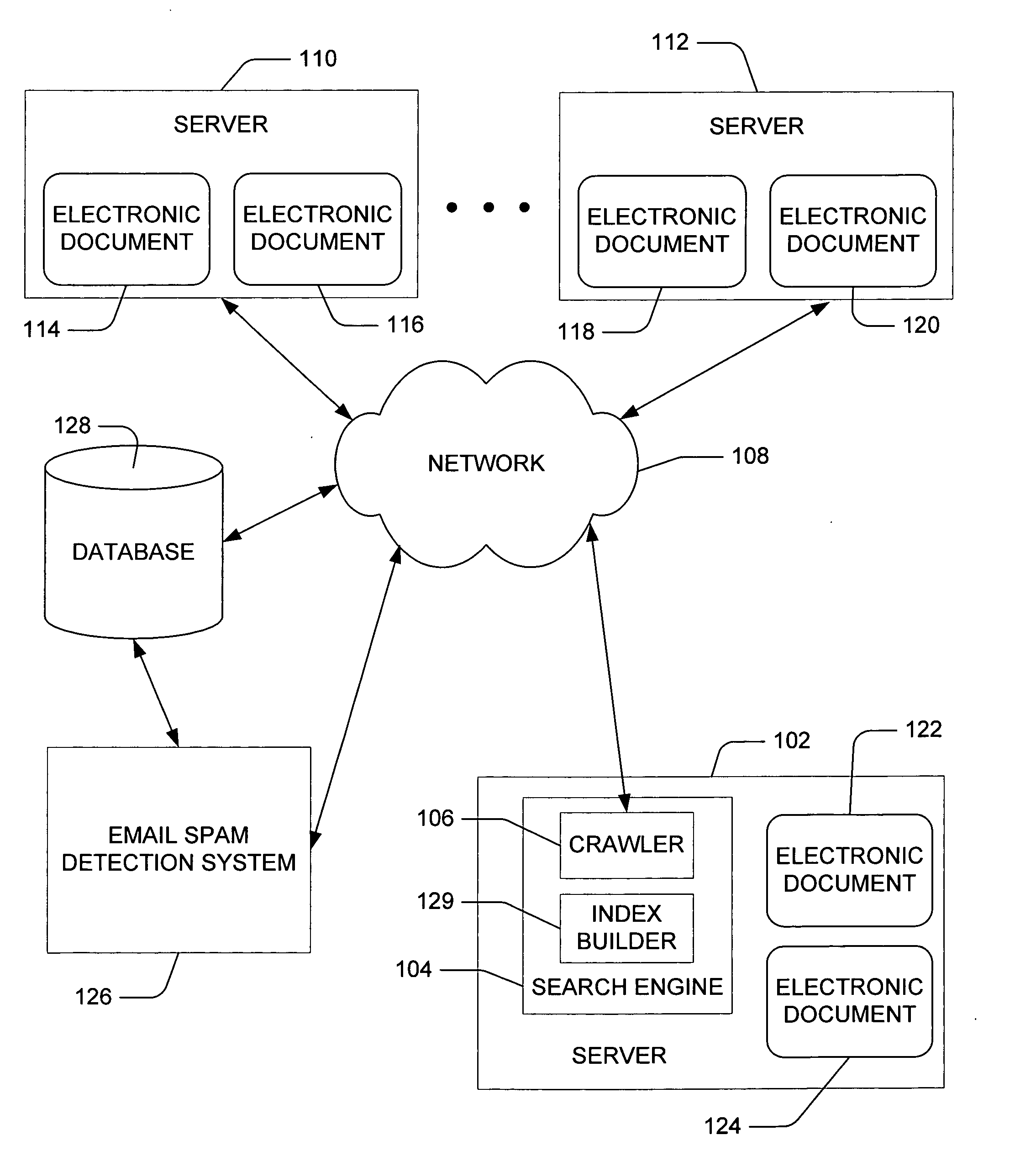
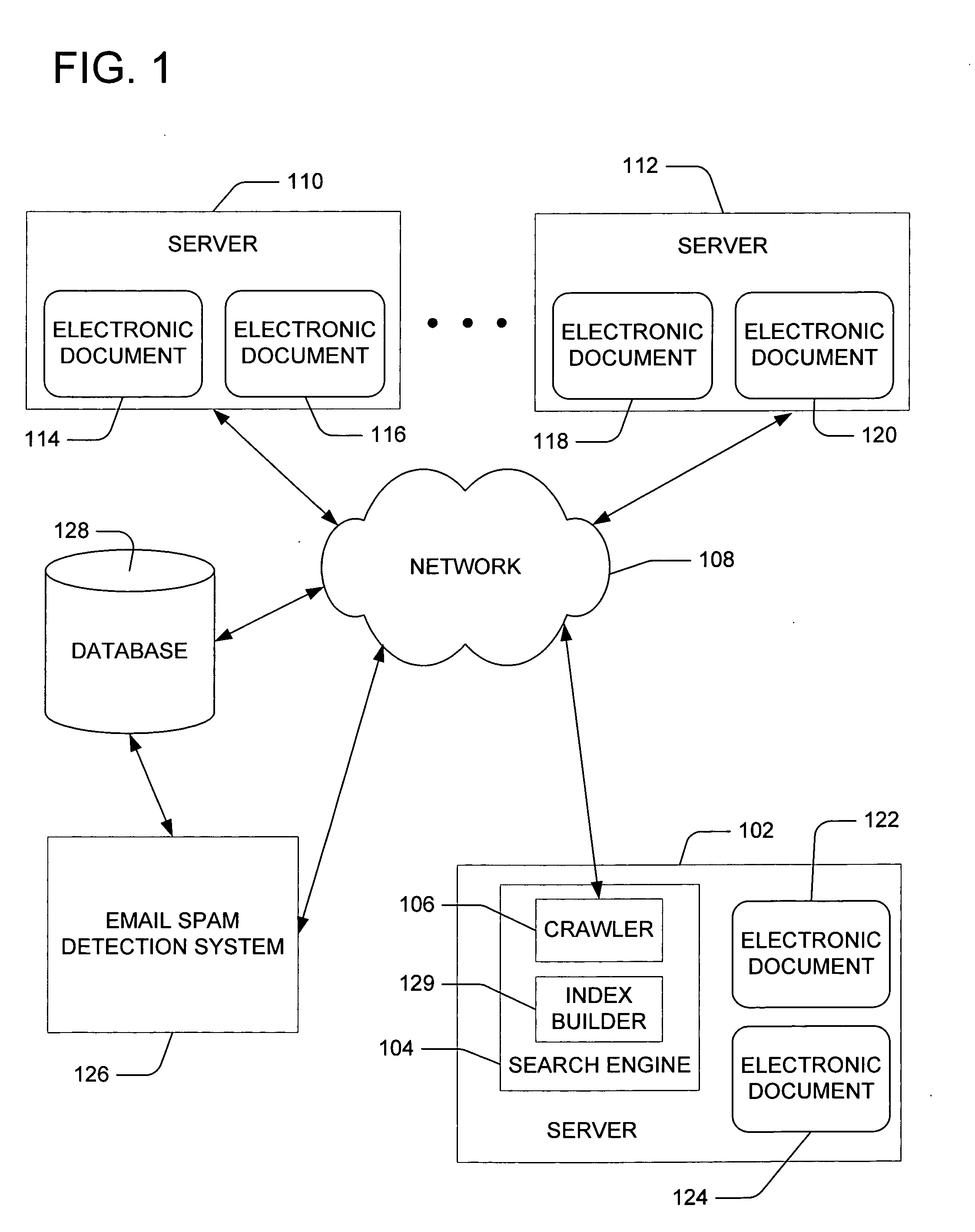
Search engine spam detection using external data
InactiveUS20060004748A1Search engine resultImprove trustData processing applicationsDigital data information retrievalElectronic documentExternal data
Evaluating an electronic document in connection with a search. An external source provides data for use in evaluating an electronic document retrieved by a search engine. A first confidence level of the electronic document is determined based on the externally provided data. The first confidence level indicates a likelihood that the electronic document is undesirable. A second confidence level of the electronic document is determined based on attributes of the electronic document. The second confidence level indicates a likelihood that the electronic document is unsatisfactory with respect to a search. A rating for the electronic document generated as a function of the determined first confidence level and the determined second confidence level is used to categorize the electronic document as unsatisfactory in connection with a received search request.
Owner:MICROSOFT TECH LICENSING LLC
Method, system, and medium for classifying category of photo
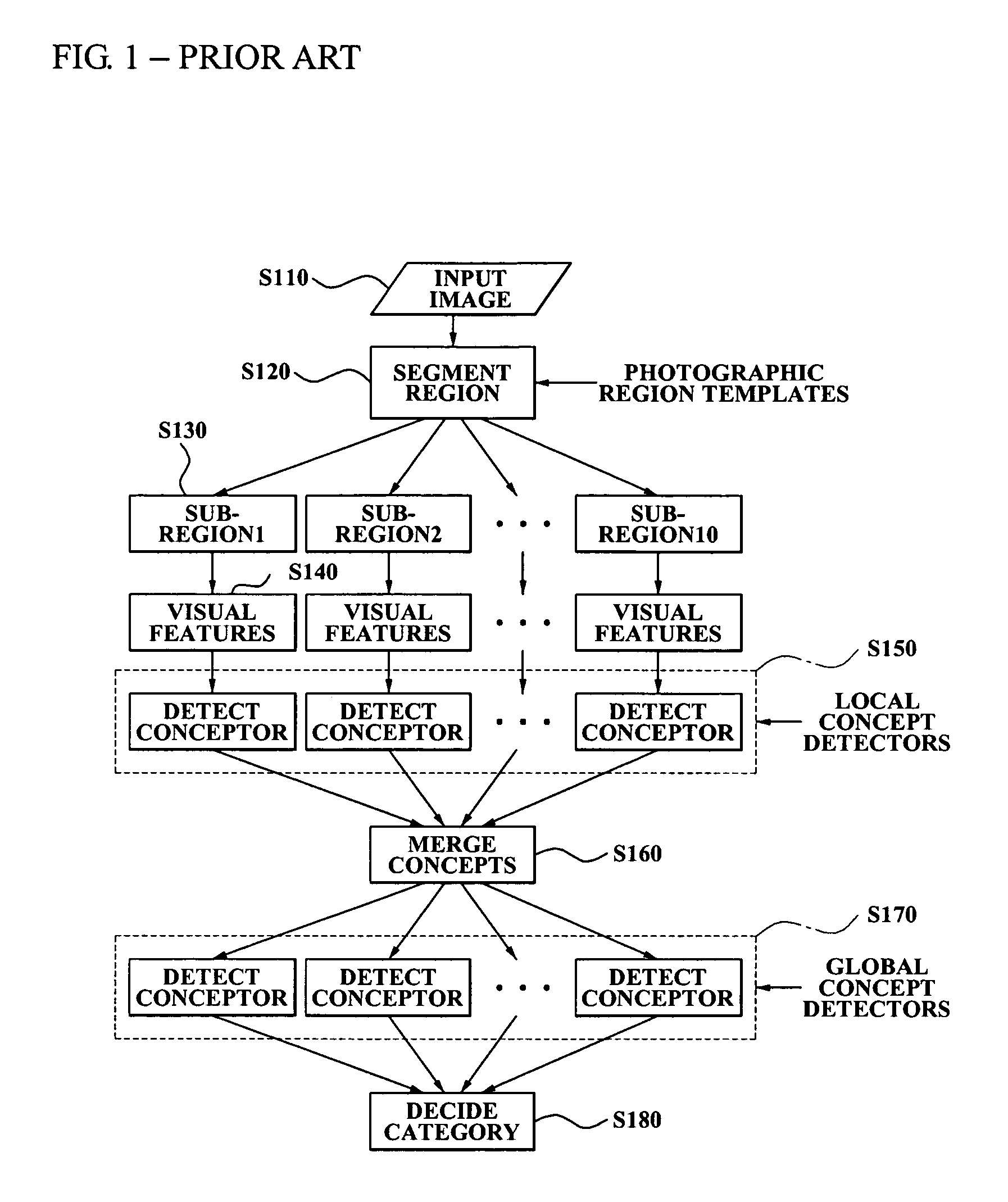
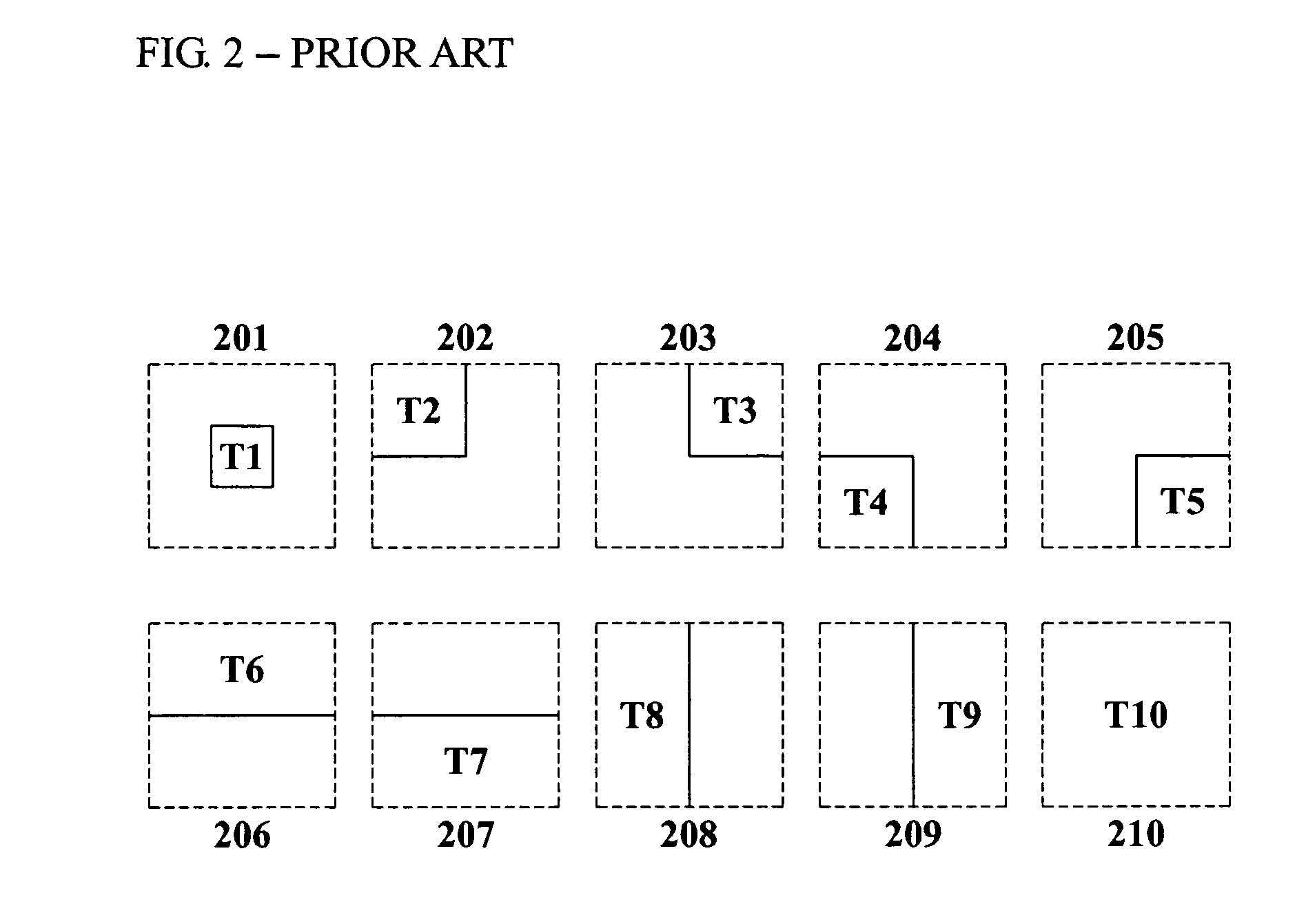
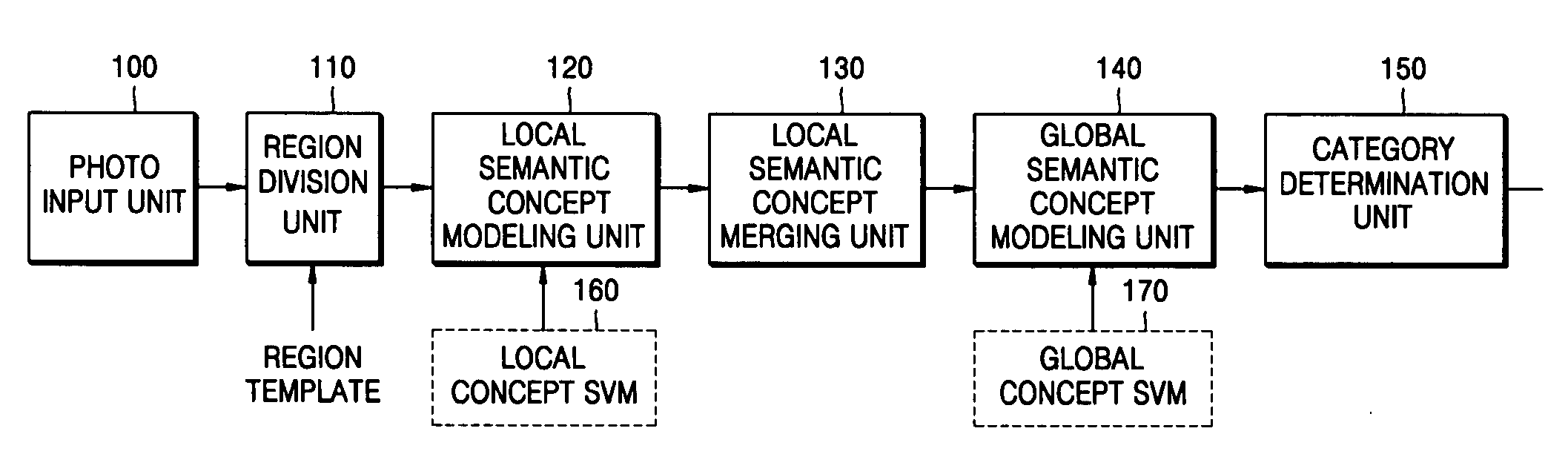
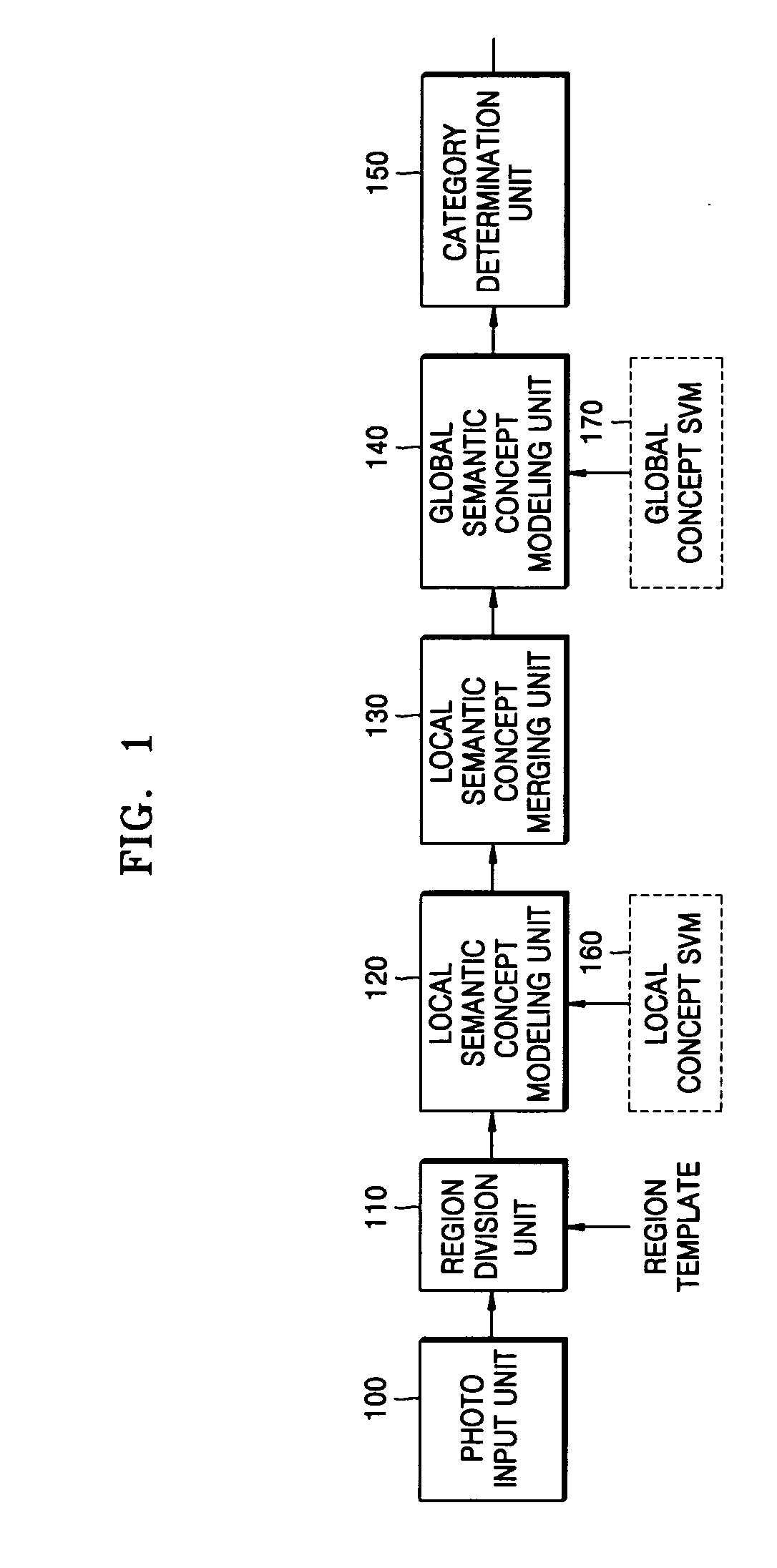
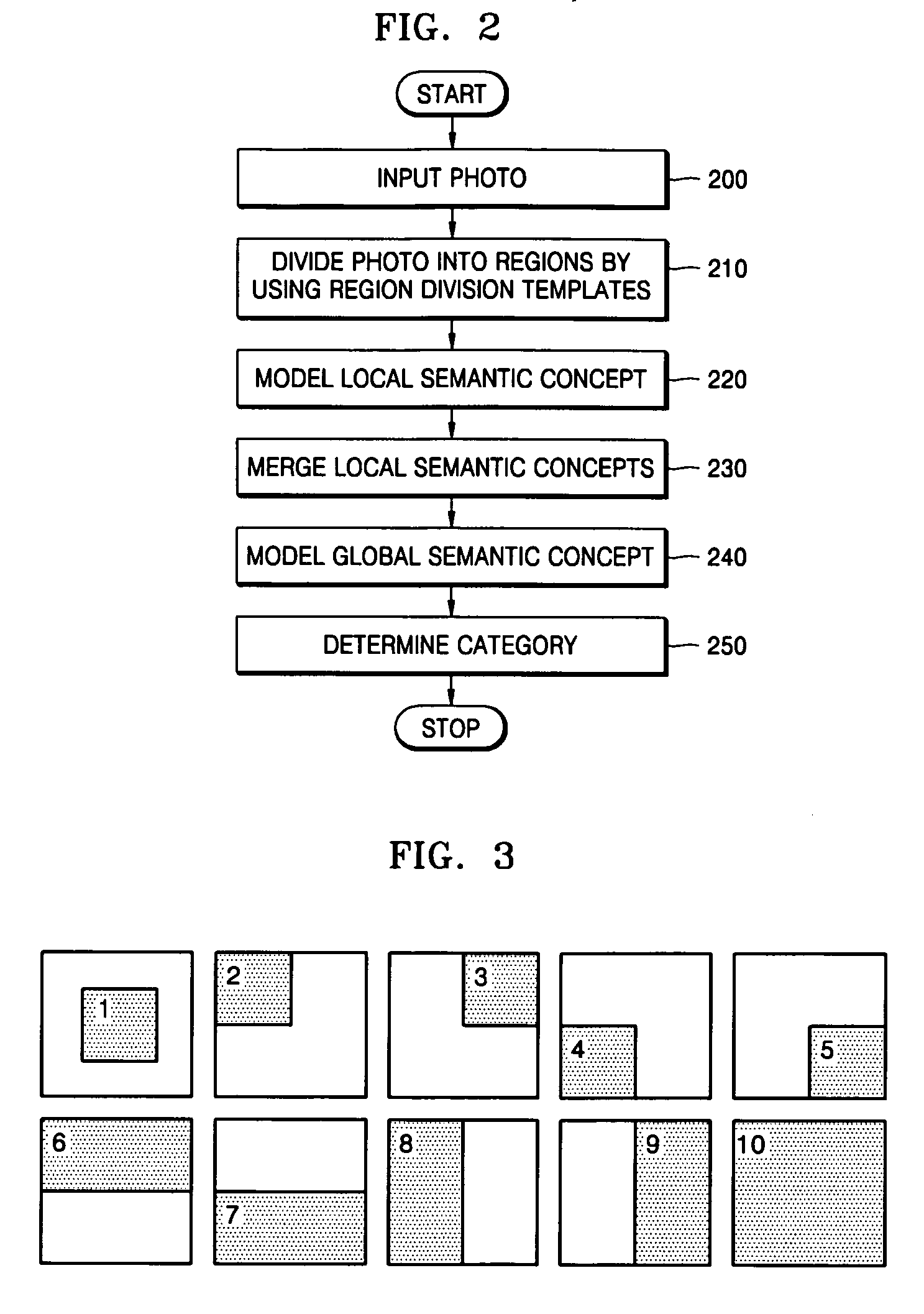
InactiveUS20080013940A1Amount of timeMinimally deteriorating category classification performanceImage analysisProcessed material treatmentRegression analysisClassification methods
A photo category classification method including dividing a region of a photo based on content of the photo and extracting a visual feature from the segmented region of the photo, modeling at least one local semantic concept included in the photo according to the extracted visual feature, acquiring a posterior probability value from confidence values acquired from the modeling of the at least one local semantic concept by normalization using regression analysis, modeling a global semantic concept included in the photo by using the posterior probability value of the at least one local semantic concept; and removing classification noise from a confidence value acquired from the modeling the global semantic concept.
Owner:SAMSUNG ELECTRONICS CO LTD
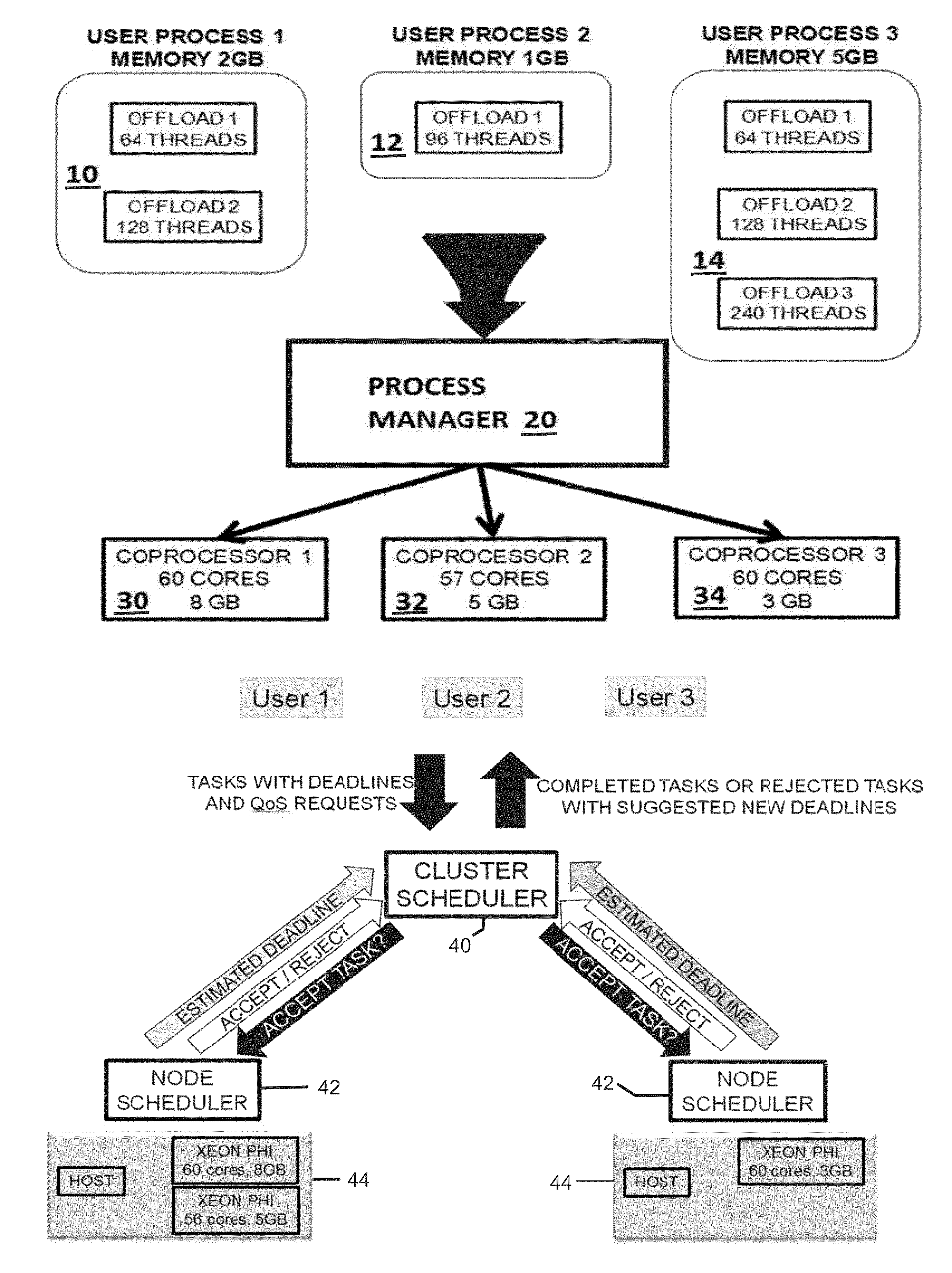
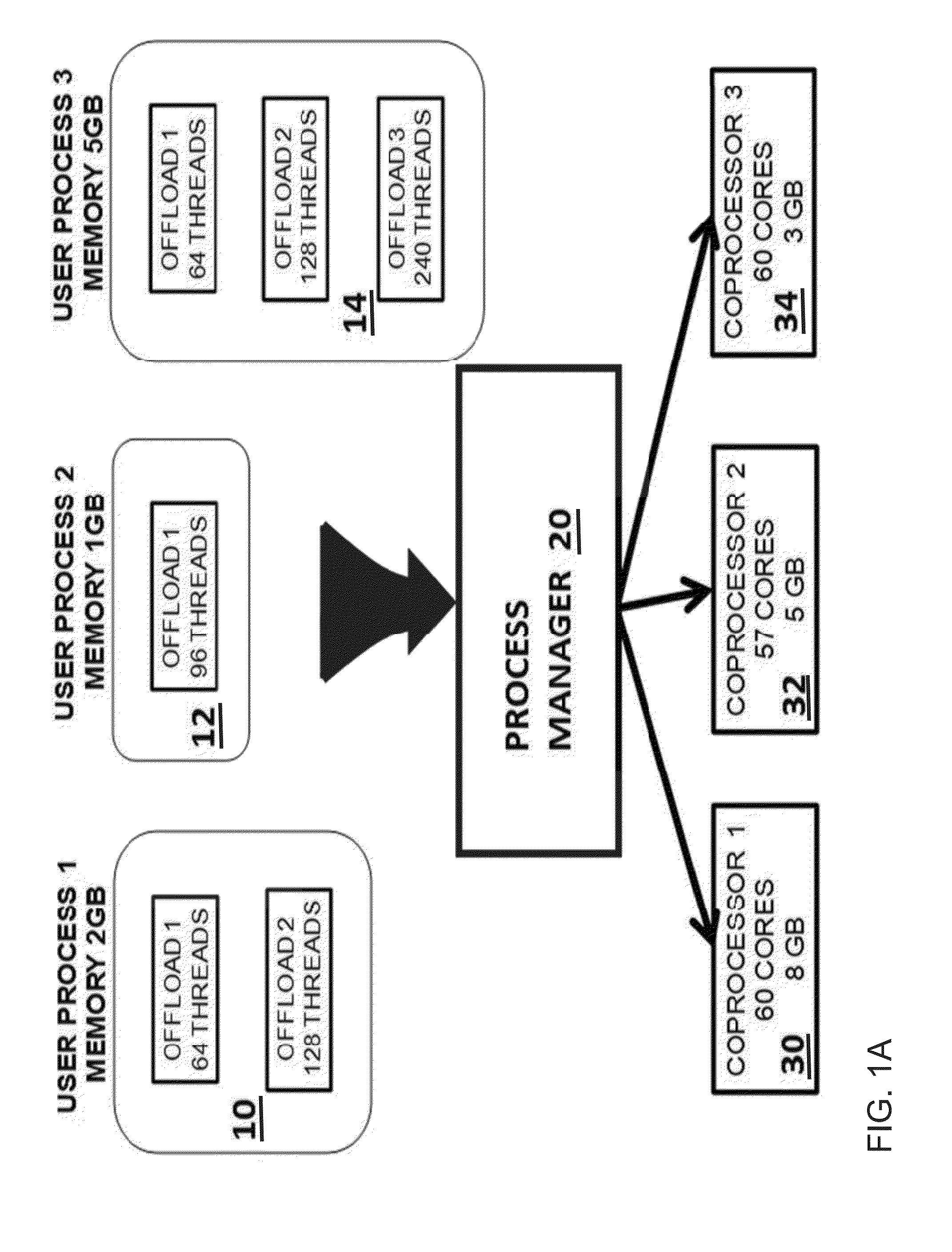
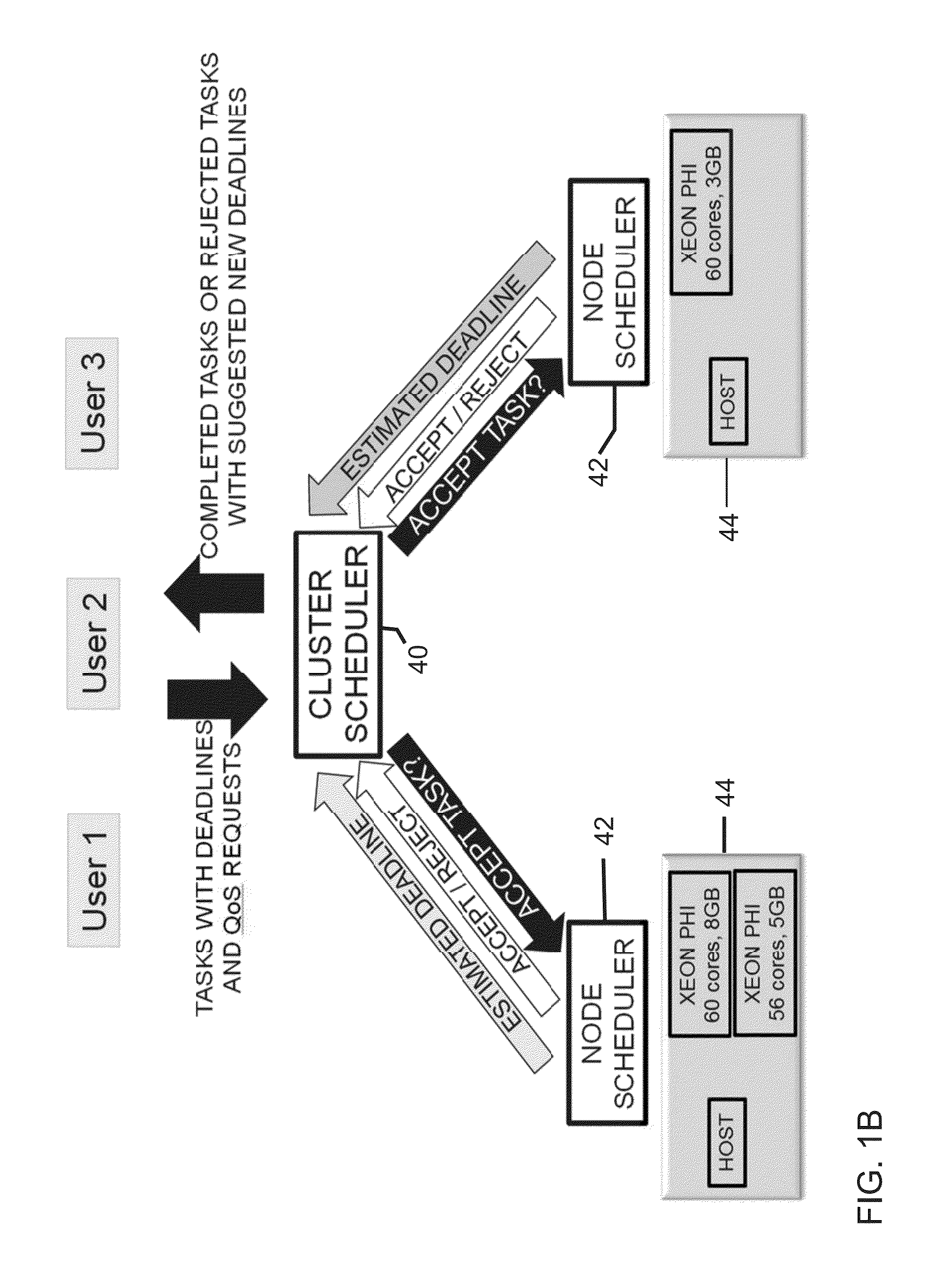
Simultaneous scheduling of processes and offloading computation on many-core coprocessors
Methods and systems for scheduling jobs to manycore nodes in a cluster include selecting a job to run according to the job's wait time and the job's expected execution time; sending job requirements to all nodes in a cluster, where each node includes a manycore processor; determining at each node whether said node has sufficient resources to ever satisfy the job requirements and, if no node has sufficient resources, deleting the job; creating a list of nodes that have sufficient free resources at a present time to satisfy the job requirements; and assigning the job to a node, based on a difference between an expected execution time and associated confidence value for each node and a hypothetical fastest execution time and associated hypothetical maximum confidence value.
Owner:NEC CORP
Message profiling systems and methods
Methods and systems for operation upon one or more data processors that classify communications from messaging entities. A method can include receiving a communication that was sent from a messaging entity. A plurality of message classification techniques is used to classify the communication. Each message classification technique is associated with a confidence value which is used in generating a message classification output from the message classification technique. The message classification outputs are combined in order to generate a message profile score. The message profile score is used in deciding what action is to be taken with respect to the communication associated with the messaging entity.
Owner:MCAFEE LLC
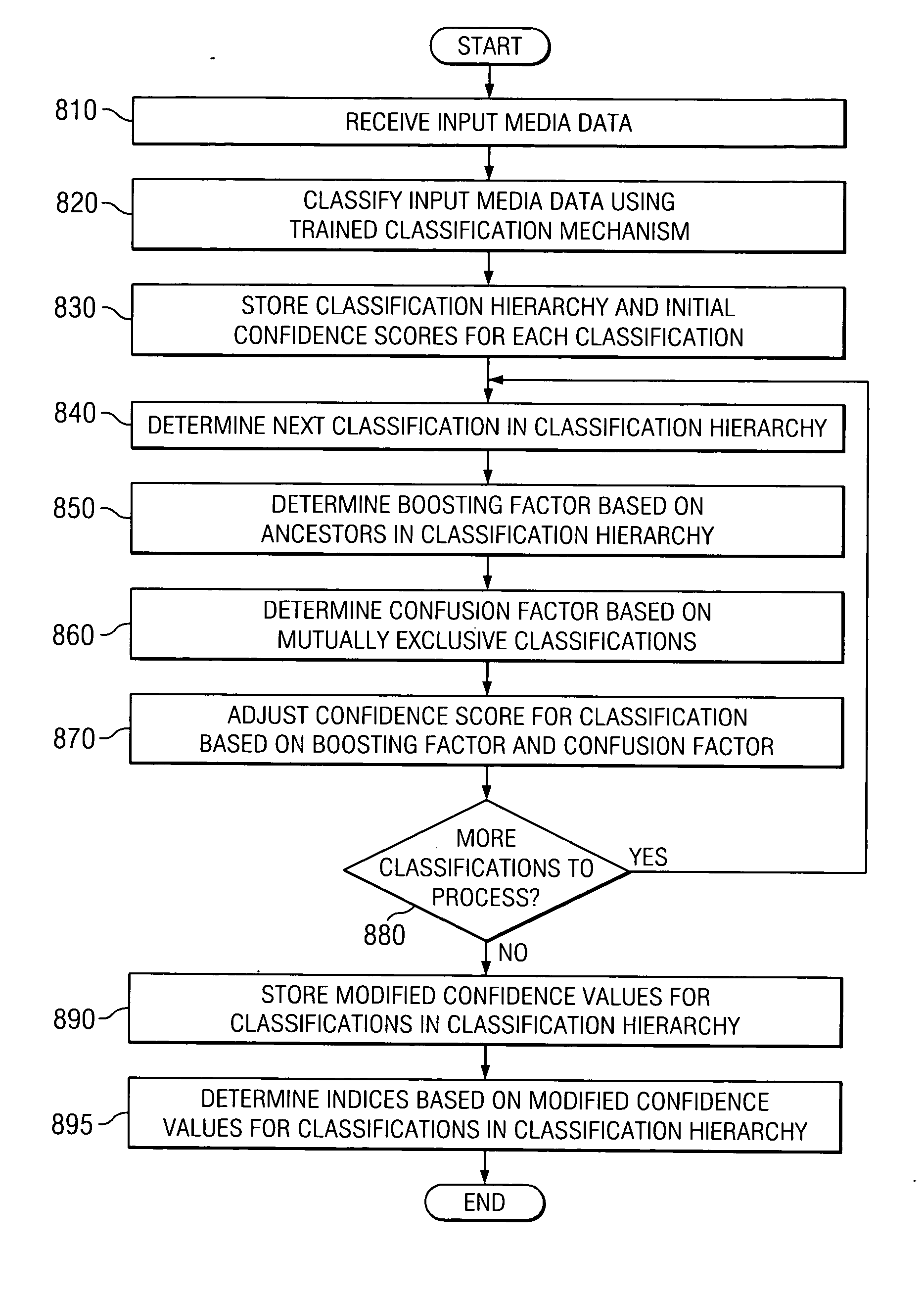
Method and apparatus for ontology-based classification of media content
ActiveUS20060031217A1Improve accuracyBoosting factorCharacter and pattern recognitionNatural language data processingConfidence factorConfusion
A method and apparatus for ontology-based classification of media content are provided. With the method and apparatus, initial confidence values of classifiers in a hierarchical classification structure are modified based on relationships between classifiers. A confidence value for a classifier is boosted by a boosting factor based on a correspondence between the confidence value and confidence values of ancestor classifiers in the hierarchical classification structure. A confidence value for a classifier is modified by a confusion factor based on a correspondence between the confidence value of the classifier and the confidence values of mutually exclusive classifiers in the hierarchical classification structure. In this way, a more accurate representation of the actual confidence that media content falls within the classification associated with the classifier is obtained. From this improved classification mechanism, indices for media content may be generated for use in accessing the media content at a later time.
Owner:SINOEAST CONCEPT
Partially supervised machine learning of data classification based on local-neighborhood Laplacian Eigenmaps
InactiveUS20060235812A1FastEasily extended into SSII algorithmDigital computer detailsCharacter and pattern recognitionData setDecomposition
A local-neighborhood Laplacian Eigenmap (LNLE) algorithm is provided for methods and systems for semi-supervised learning on manifolds of data points in a high-dimensional space. In one embodiment, an LNLE based method includes building an adjacency graph over a dataset of labelled and unlabelled points. The adjacency graph is then used for finding a set of local neighbors with respect to an unlabelled data point to be classified. An eigen decomposition of the local subgraph provides a smooth function over the subgraph. The smooth function can be evaluated and based on the function evaluation the unclassified data point can be labelled. In one embodiment, a transductive inference (TI) algorithmic approach is provided. In another embodiment, a semi-supervised inductive inference (SSII) algorithmic approach is provided for classification of subsequent data points. A confidence determination can be provided based on a number of labeled data points within the local neighborhood. Experimental results comparing LNLE and simple LE approaches are presented.
Owner:HONDA MOTOR CO LTD
Method and device for recognizing voices
ActiveCN103971680AConfidence thresholds can be flexibly adjustedImprove speech recognition rateSpeech recognitionSpeech soundVoice data
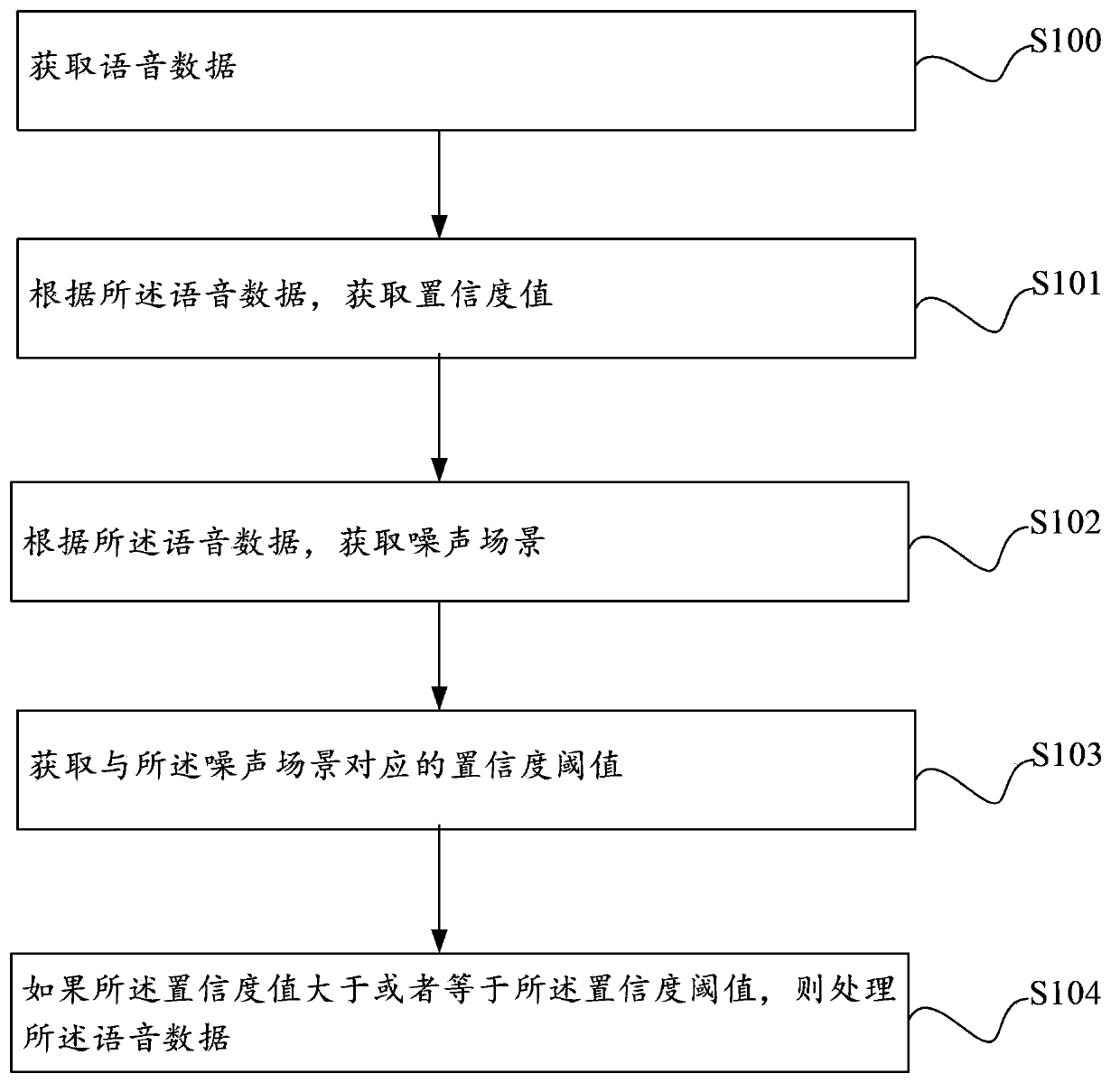
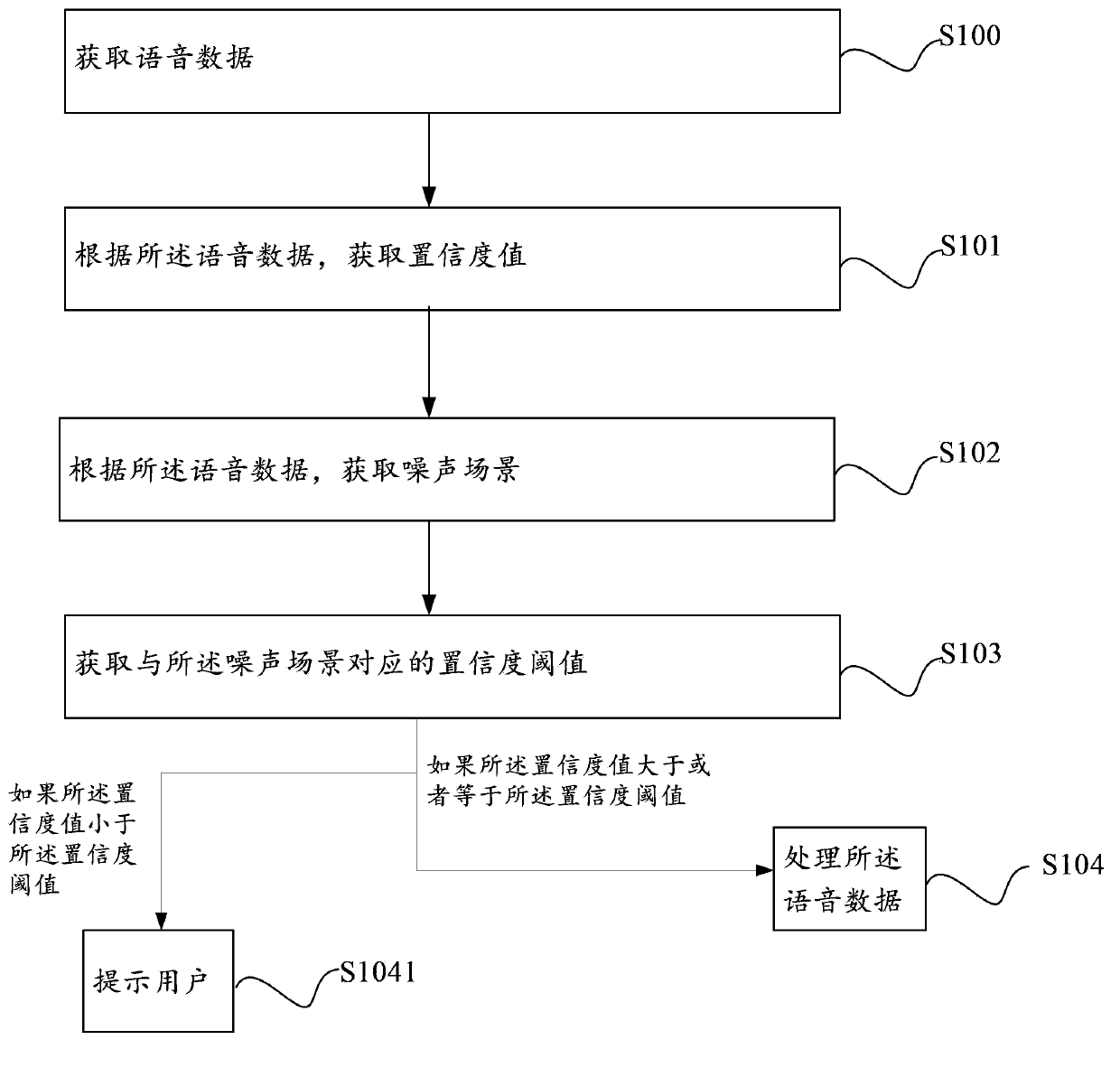
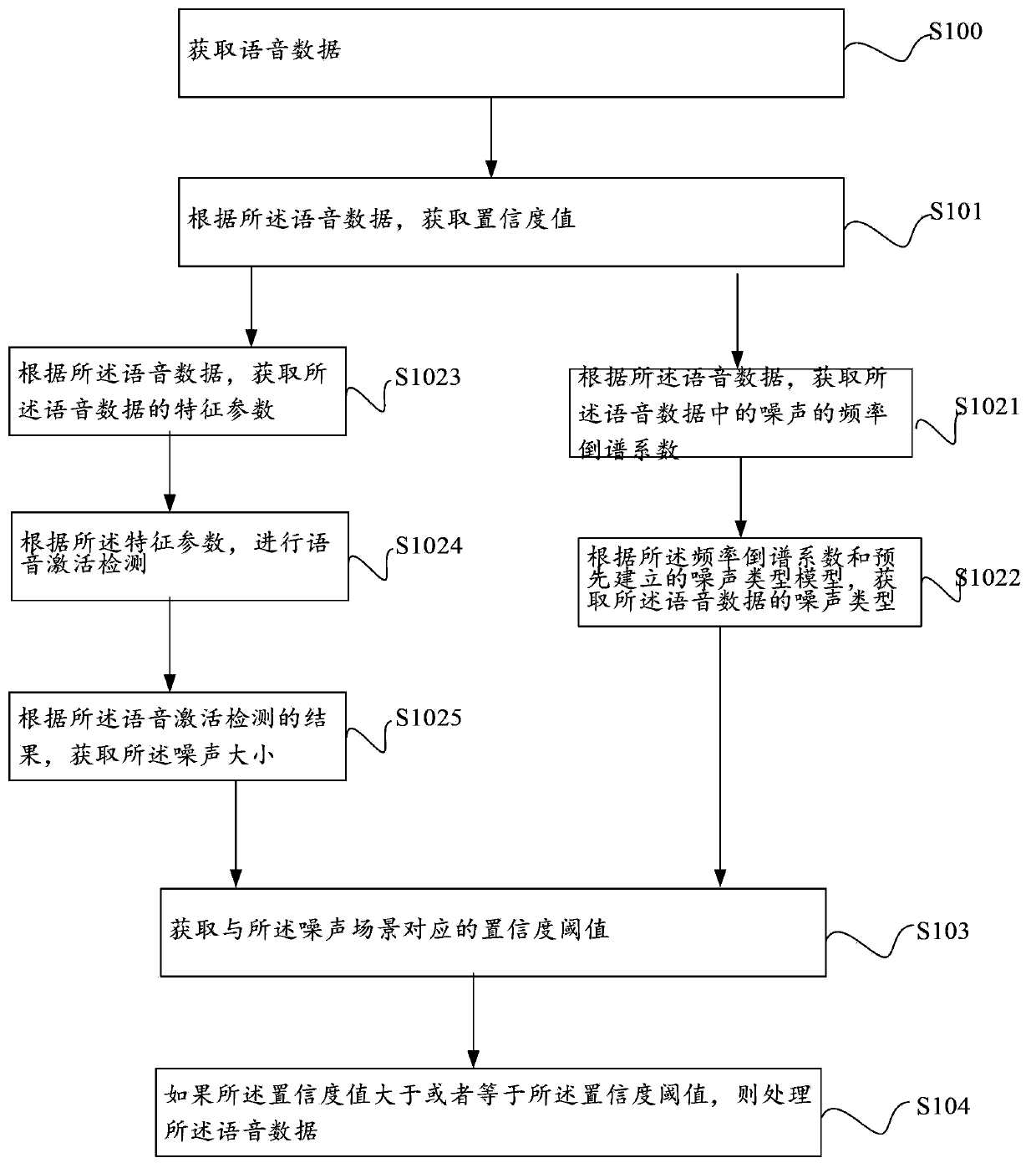
Embodiments of the present invention provide a voice identification method, which includes: obtaining voice data; obtaining a confidence value according to the voice data; obtaining a noise scenario according to the voice data; obtaining a confidence threshold corresponding to the noise scenario; and if the confidence value is greater than or equal to the confidence threshold, processing the voice data. An apparatus is also provided. The method and apparatus that flexibly adjust the confidence threshold according to the noise scenario greatly improve a voice identification rate under a noise environment.
Owner:HUAWEI DEVICE CO LTD
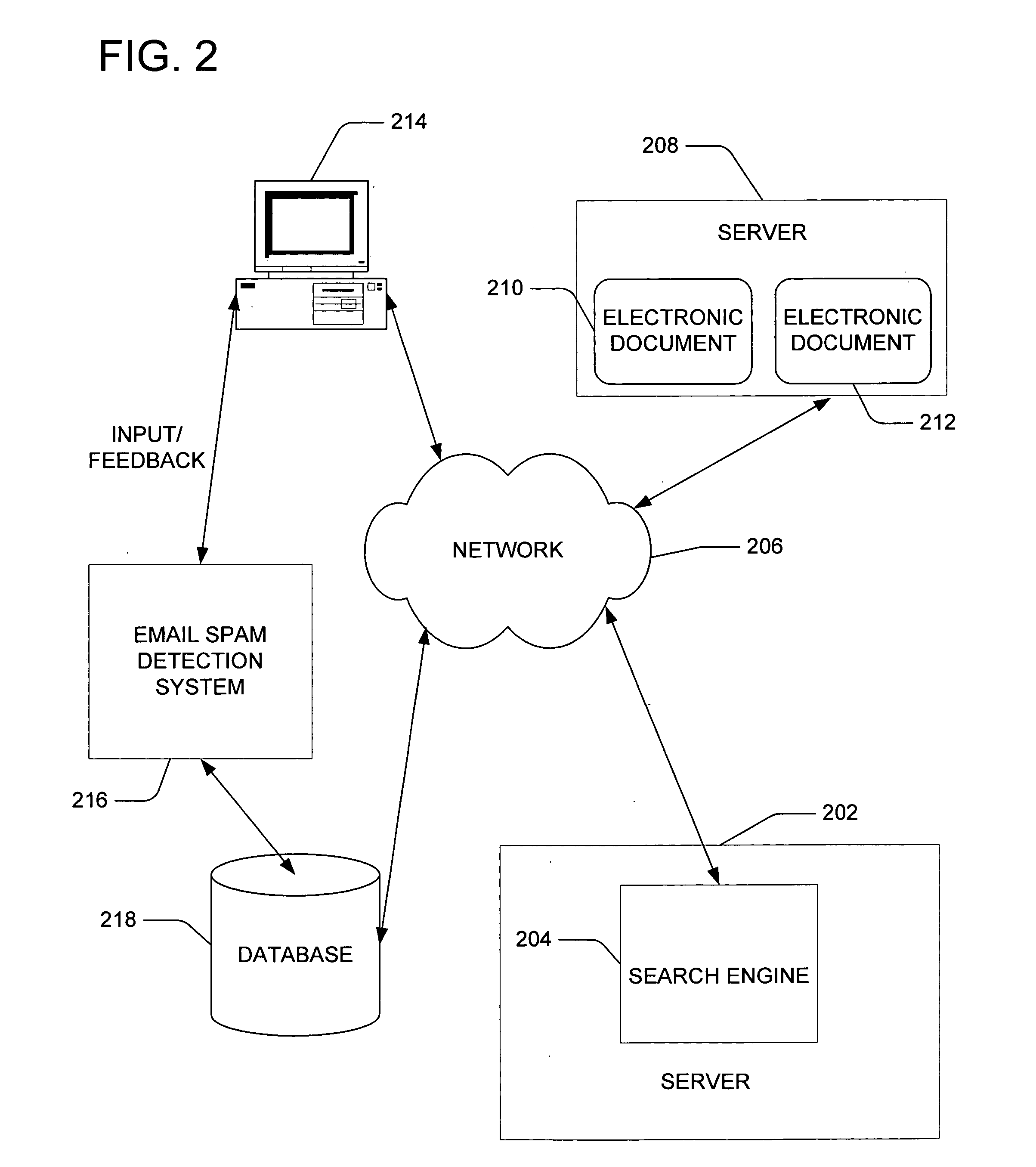
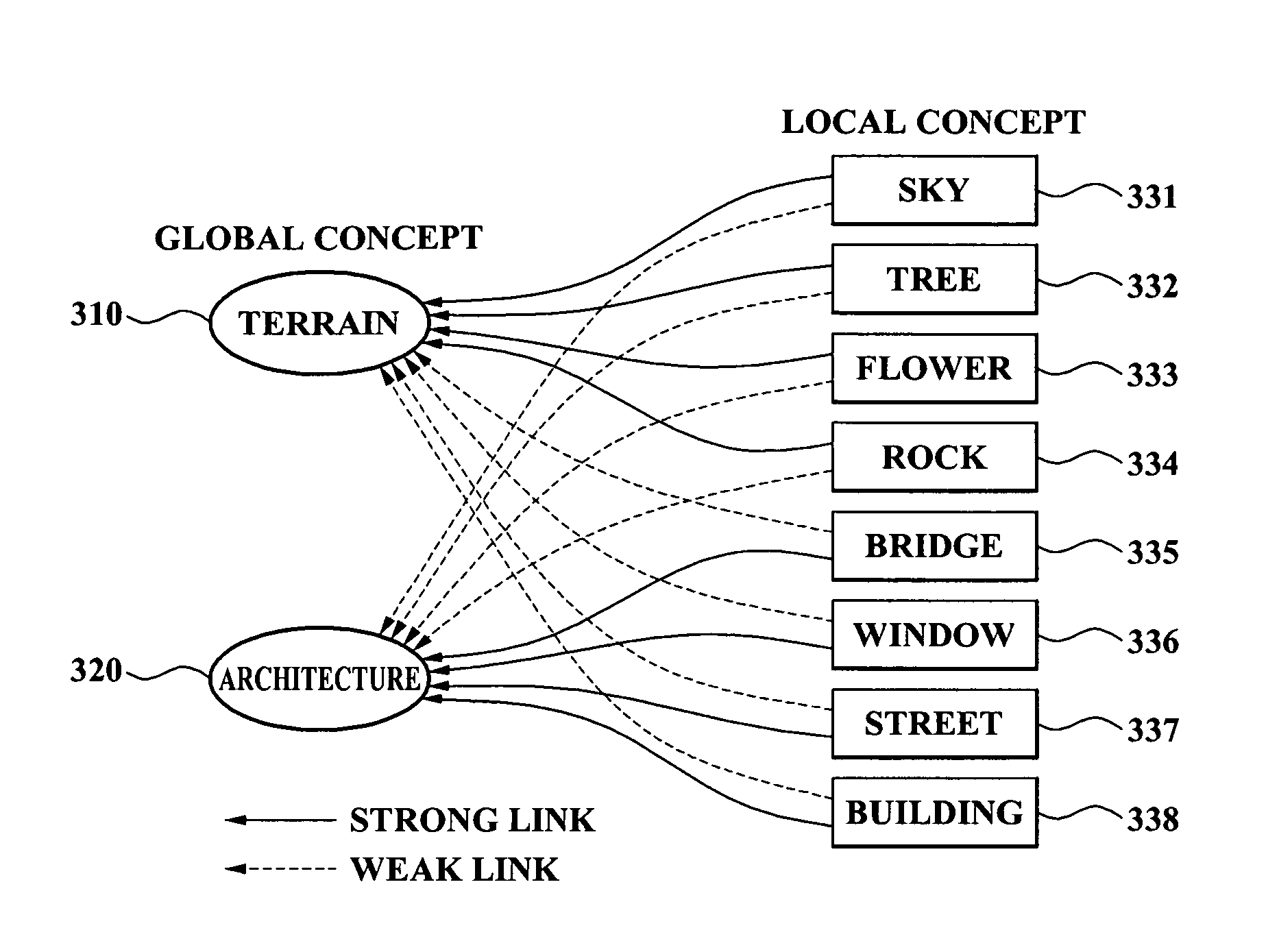
Method, medium, and apparatus with category-based clustering using photographic region templates
InactiveUS20060159442A1Character and pattern recognitionExposure controlMultiple categoryConfidence value
A clustering method, medium, and apparatus using region division templates. According to the method, medium, and apparatus, in order to more reliably extract semantic concepts included in a photo, multiple content-based feature values can be extracted from region images divided by using region division templates, and the confidence degree of an input image in relation to the local semantic concept, defined by using the feature values, is measured. With respect to the confidence degree, the local semantic concepts of the photo can be merged and a more reliable local semantic concept can be extracted. By using the merged local semantic concept, the confidence degree of a global semantic concept is measured, and according to the confidence, multiple category concepts included in the input photo are extracted. By doing so, photo data can be quickly and effectively used to generate an album.
Owner:RES & INDAL COOPERATION GROUP +1
Image data normalization for a monitoring system
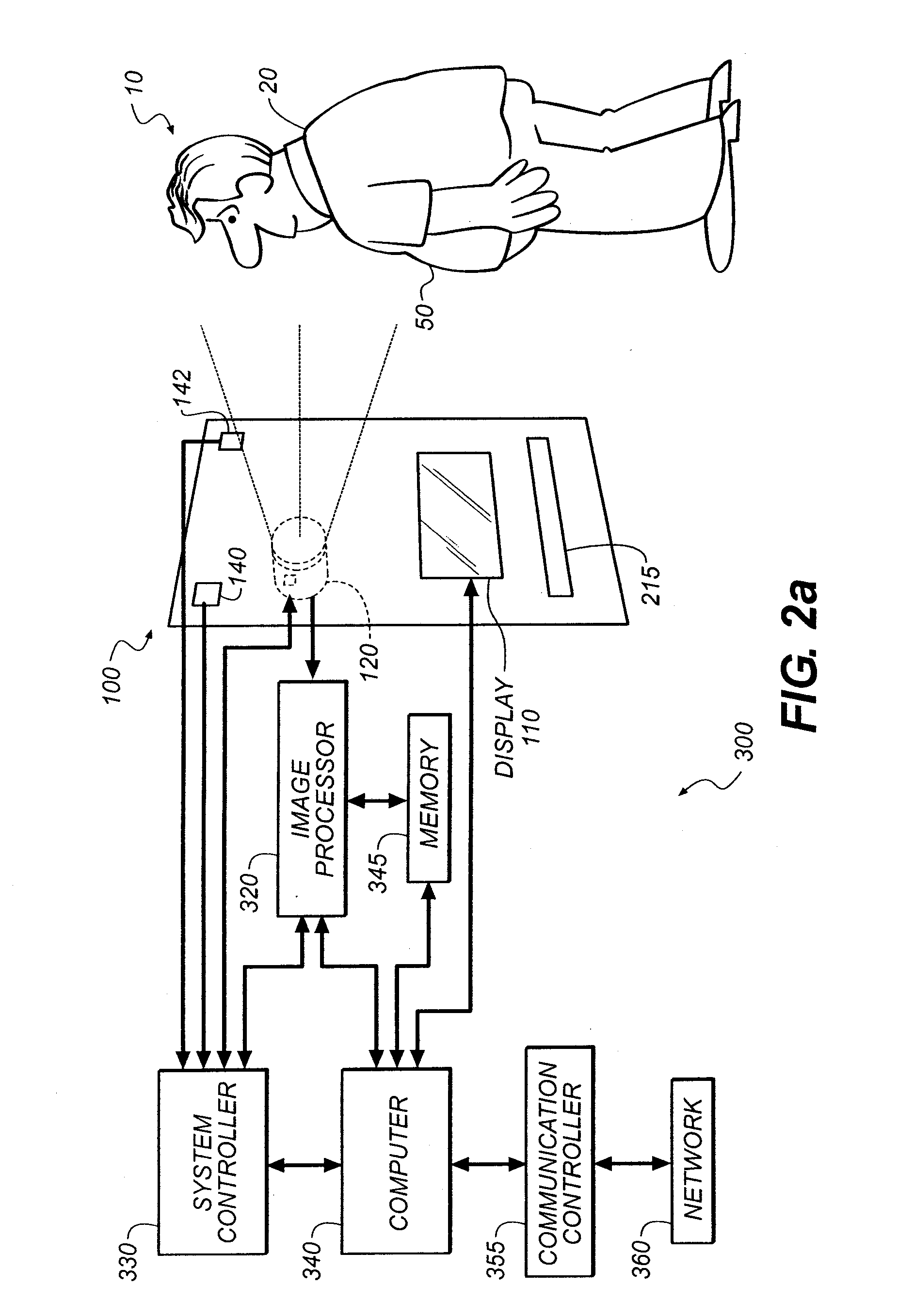
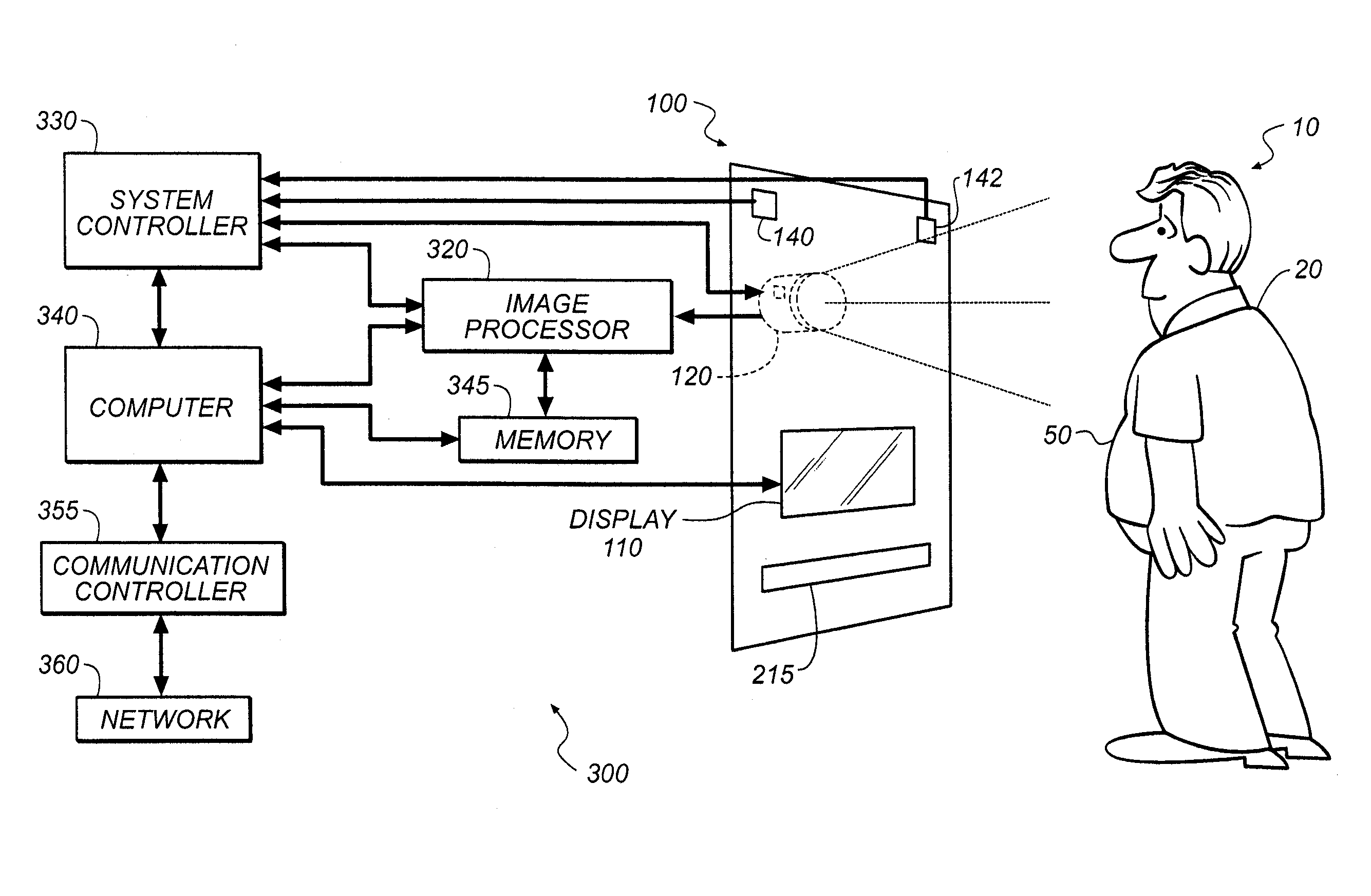
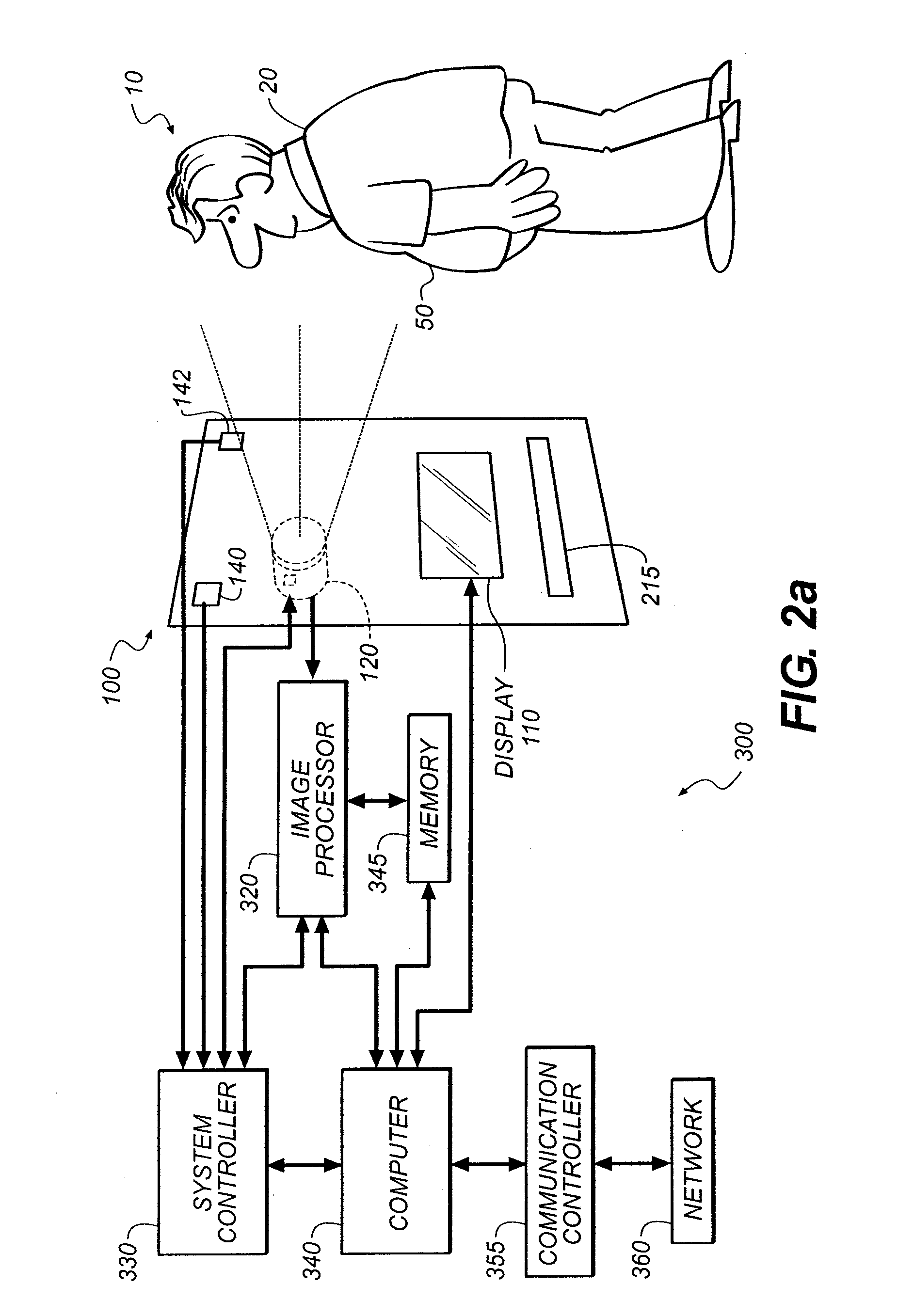
InactiveUS20080294017A1Increase valueEasy to useTelevision system detailsTelemedicineMonitoring systemPhysiological monitoring
A method for providing normalized physiological monitoring data of an individual with a measure of the quality of the normalization, including providing a reference feature based on a physiological attribute of the individual for which an attribute value can be determined; unobtrusively capturing physiological monitoring data for the individual during a series of capture events and determining the capture conditions present during each capture event; detecting the presence of the reference feature in the series of captured physiological monitoring data and determining associated attribute values for each capture event; normalizing the captured physiological monitoring data from each capture event according to differences in the attribute values associated with each event and previously calculated attribute values; and calculating normalization confidence values for the individual at the series of capture events, based on capture conditions, normalization transforms, or semantic data, wherein the confidence values statistically measure the quality of the normalization.
Owner:EASTMAN KODAK CO
Image data normalization for a monitoring system
InactiveUS7972266B2Increase valueEasy to useTelevision system detailsTelemedicinePhysiological monitoringMonitoring system
A method for providing normalized physiological monitoring data of an individual with a measure of the quality of the normalization, including providing a reference feature based on a physiological attribute of the individual for which an attribute value can be determined; unobtrusively capturing physiological monitoring data for the individual during a series of capture events and determining the capture conditions present during each capture event; detecting the presence of the reference feature in the series of captured physiological monitoring data and determining associated attribute values for each capture event; normalizing the captured physiological monitoring data from each capture event according to differences in the attribute values associated with each event and previously calculated attribute values; and calculating normalization confidence values for the individual at the series of capture events, based on capture conditions, normalization transforms, or semantic data, wherein the confidence values statistically measure the quality of the normalization.
Owner:EASTMAN KODAK CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com