Patents
Literature
294results about How to "Avoid loopholes" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
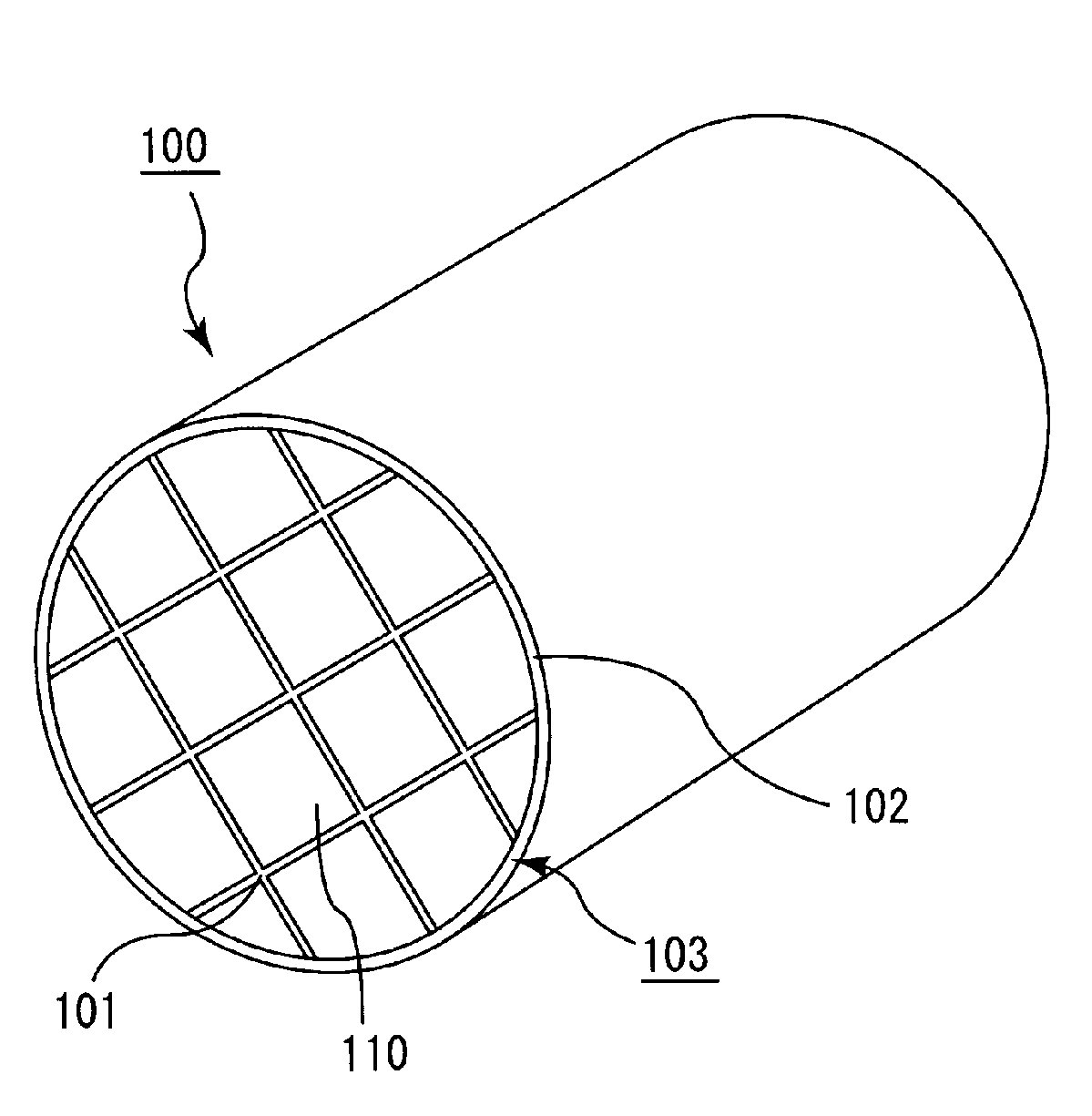
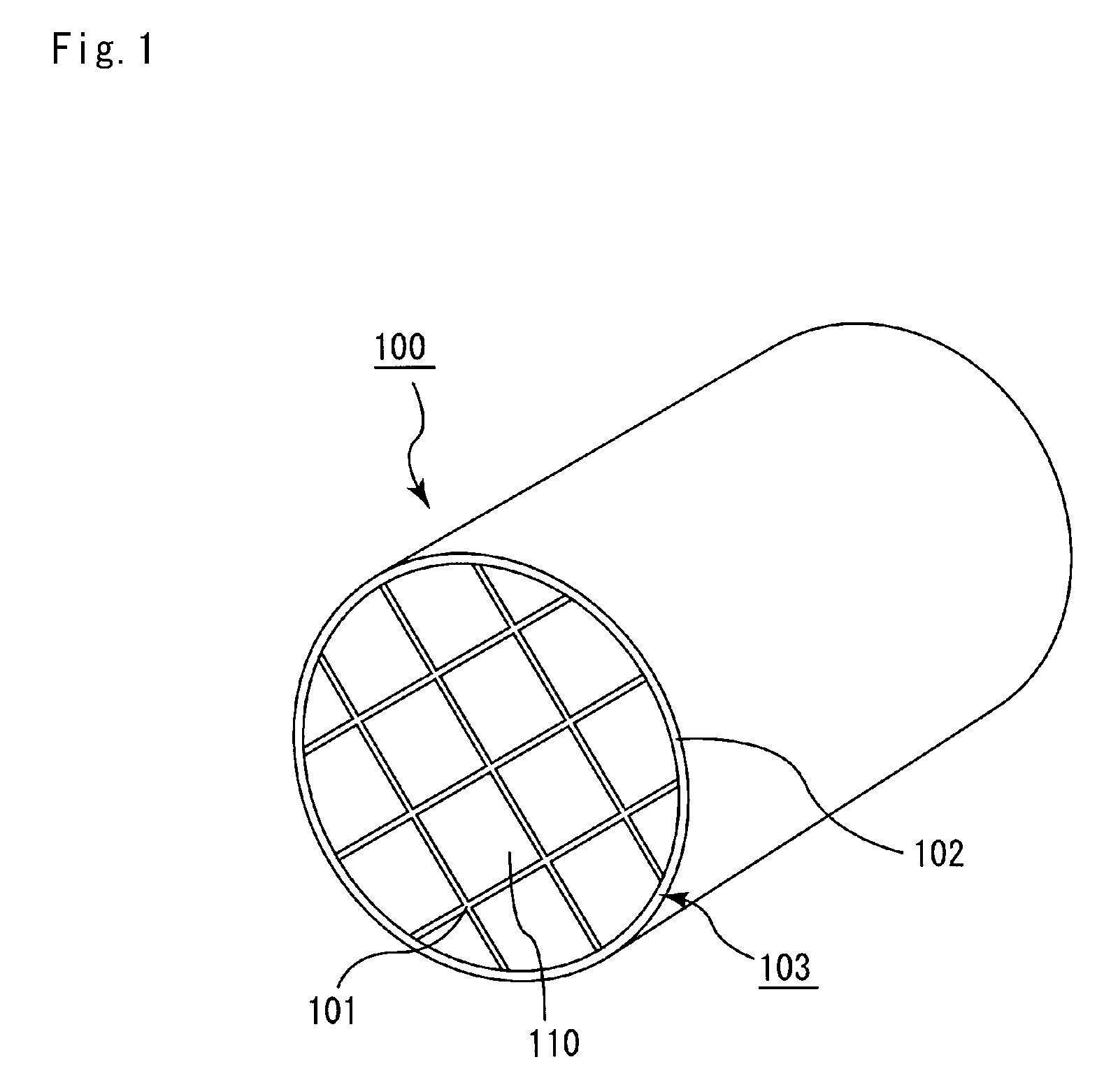
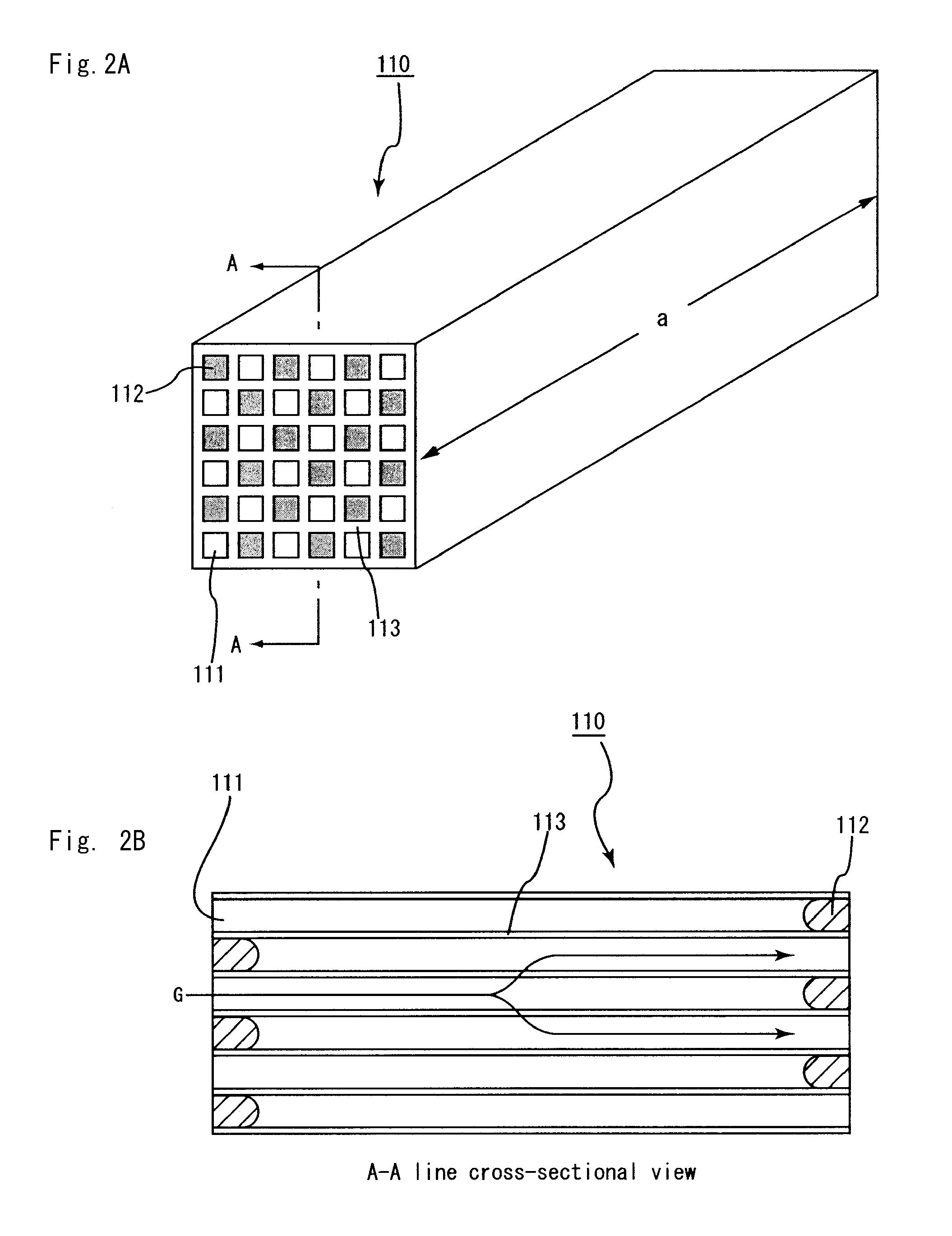
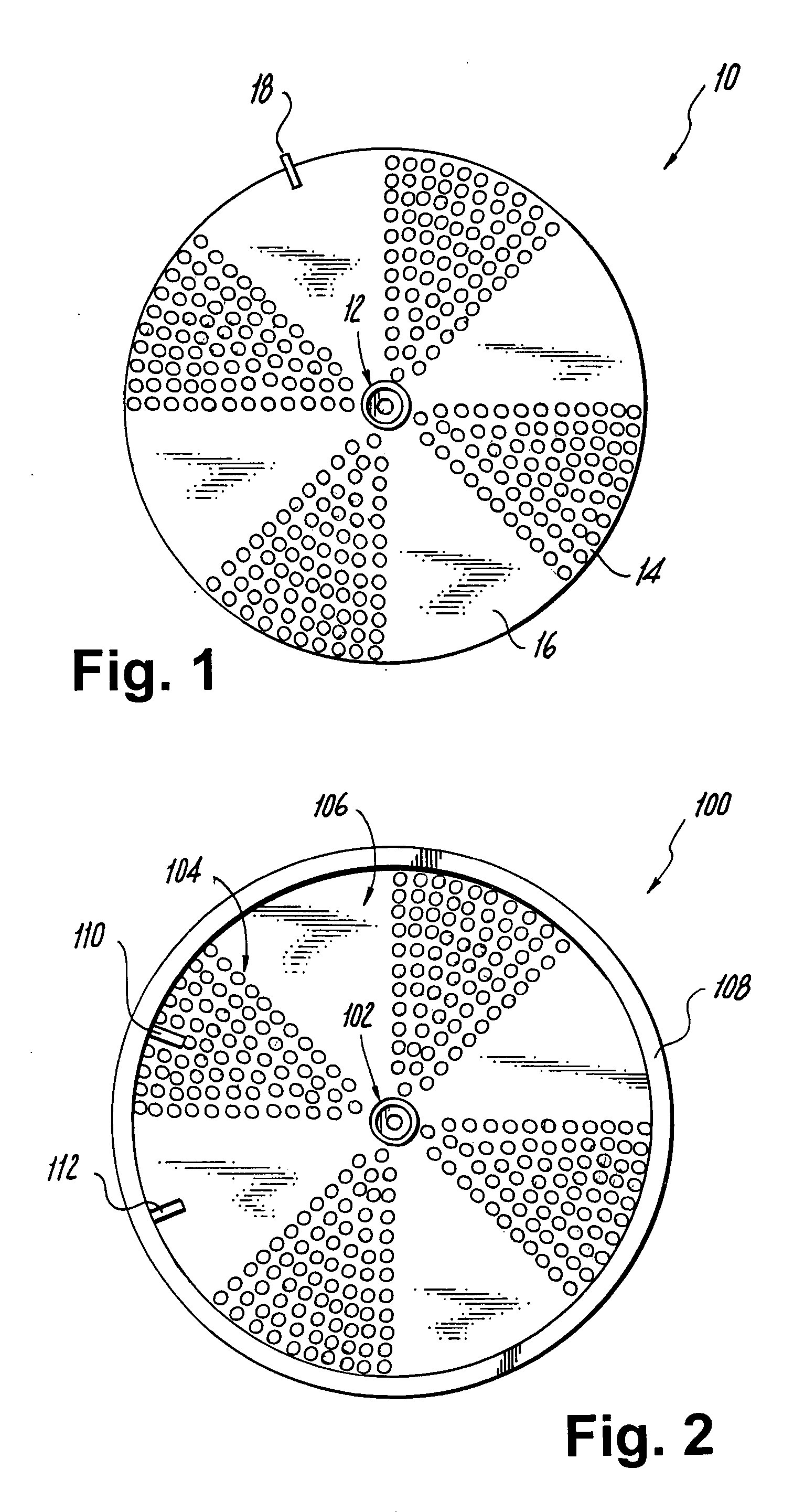
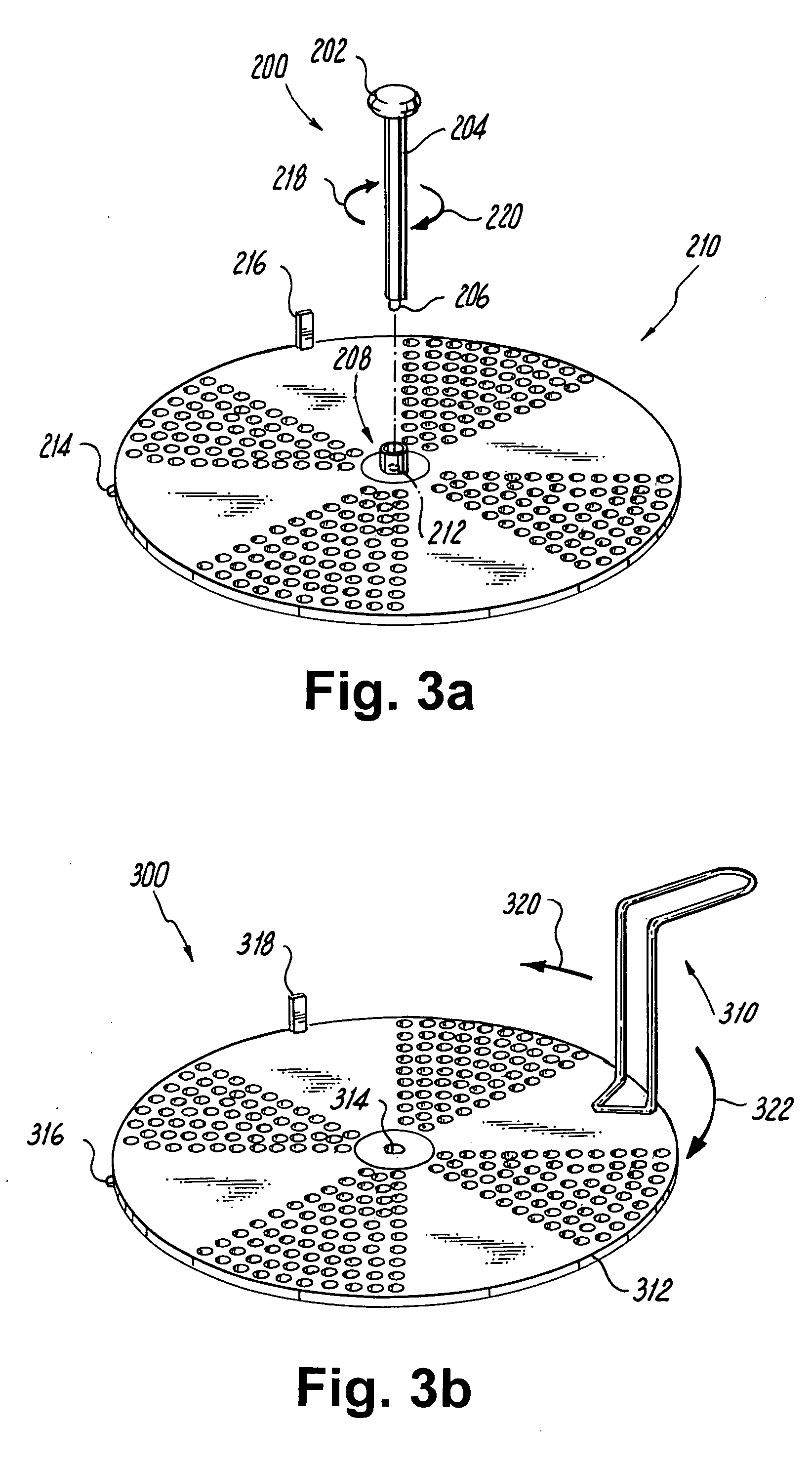
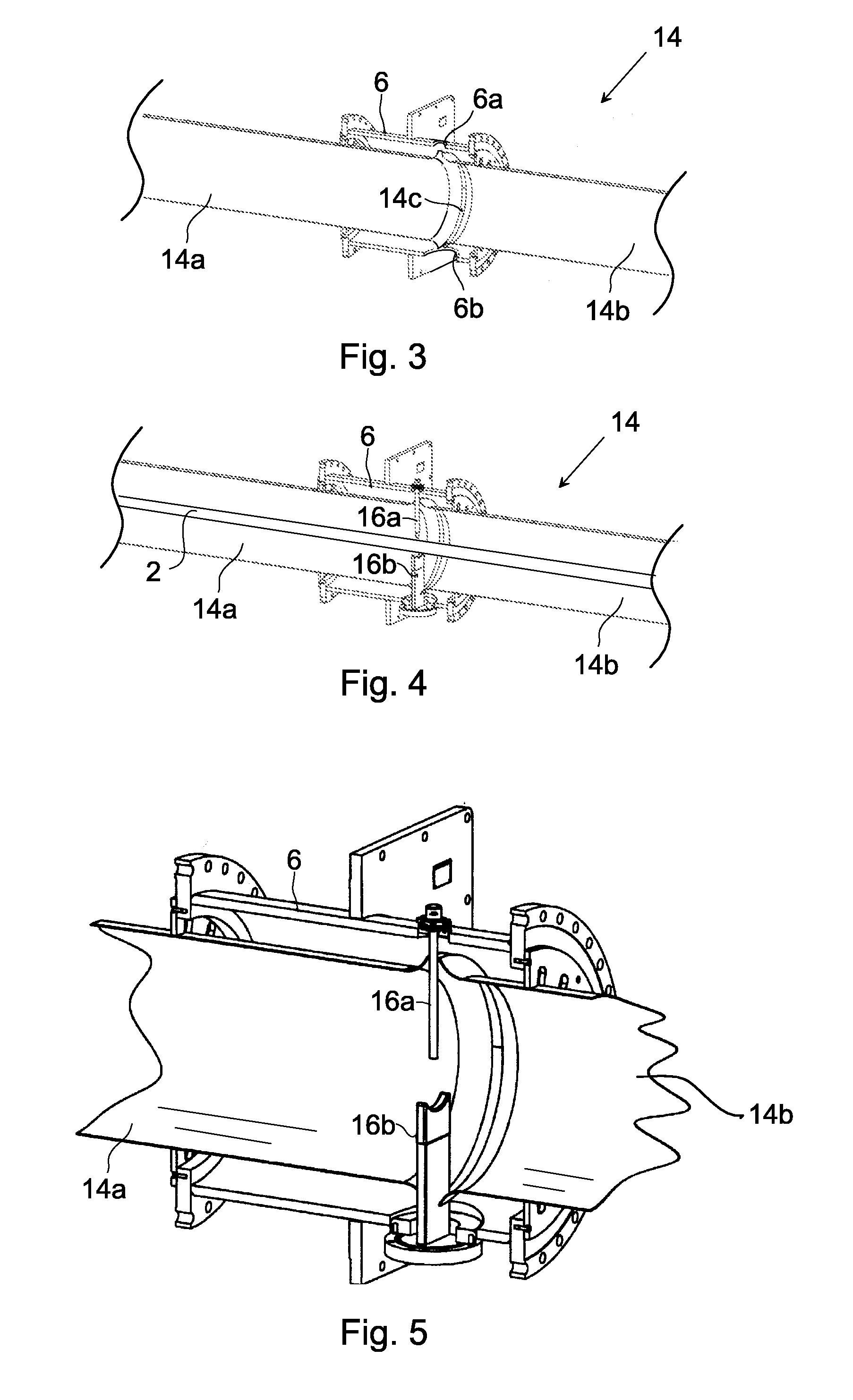
Honeycomb structure and method for manufacturing honeycomb structure
ActiveUS20080318001A1Improve heat resistanceAvoid loopholesDispersed particle filtrationSolid waste managementYoung's modulusCell wall
A honeycomb structure includes a ceramic block and a sealing material layer. The ceramic block includes a plurality of honeycomb fired bodies each having a large number of cells longitudinally disposed substantially in parallel with one another with a cell wall between the cells, an adhesive layer for bonding side faces of the honeycomb fired bodies, and a cavity-holding member placed between the side faces of the honeycomb fired bodies. The sealing material layer is formed on a peripheral face of the ceramic block. The cavity-holding member includes a nonflammable material having Young's modulus of at least about 0.001 GPa and at most about 0.07 GPa.
Owner:IBIDEN CO LTD
Online data encryption and decryption
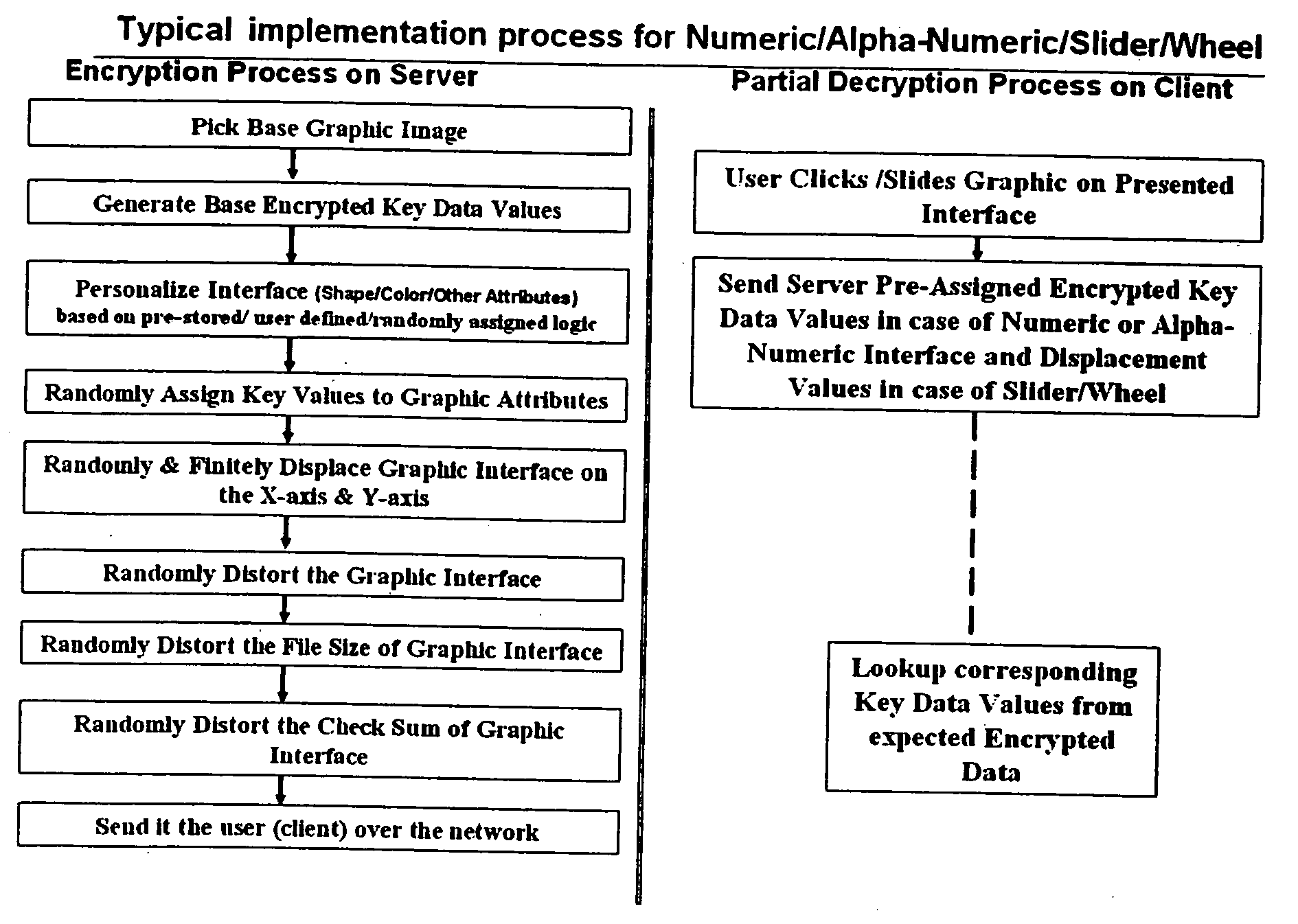
ActiveUS20060020815A1Inhibition of informationAvoid loopholesDigital data authenticationSecret communicationComputer hardwareGraphics
Systems and methods for providing encryption and decryption of data transmitted on a computer implemented network, preferably user authentication identifier data, such as a password, at the point of entry into the user's computer. The systems and methods enable an end user to mentally select a marker from one of the randomly arranged elements on a first portion of a graphical image. A second portion of the graphical image includes an arrangement of possible elements of any individual authentication identifier sequence, and is positioned adjacent to the first portion. The systems and methods prompt a user to enter each element of the identifier by moving the selected marker and the first portion as necessary to substantially align the selected marker with a chosen element of the authentication identifier appearing on the outer portion. According to one embodiment, the image portions are concentric wheels. According to another embodiment, the image portions are arranged in adjacent rows.
Owner:ORACLE INT CORP
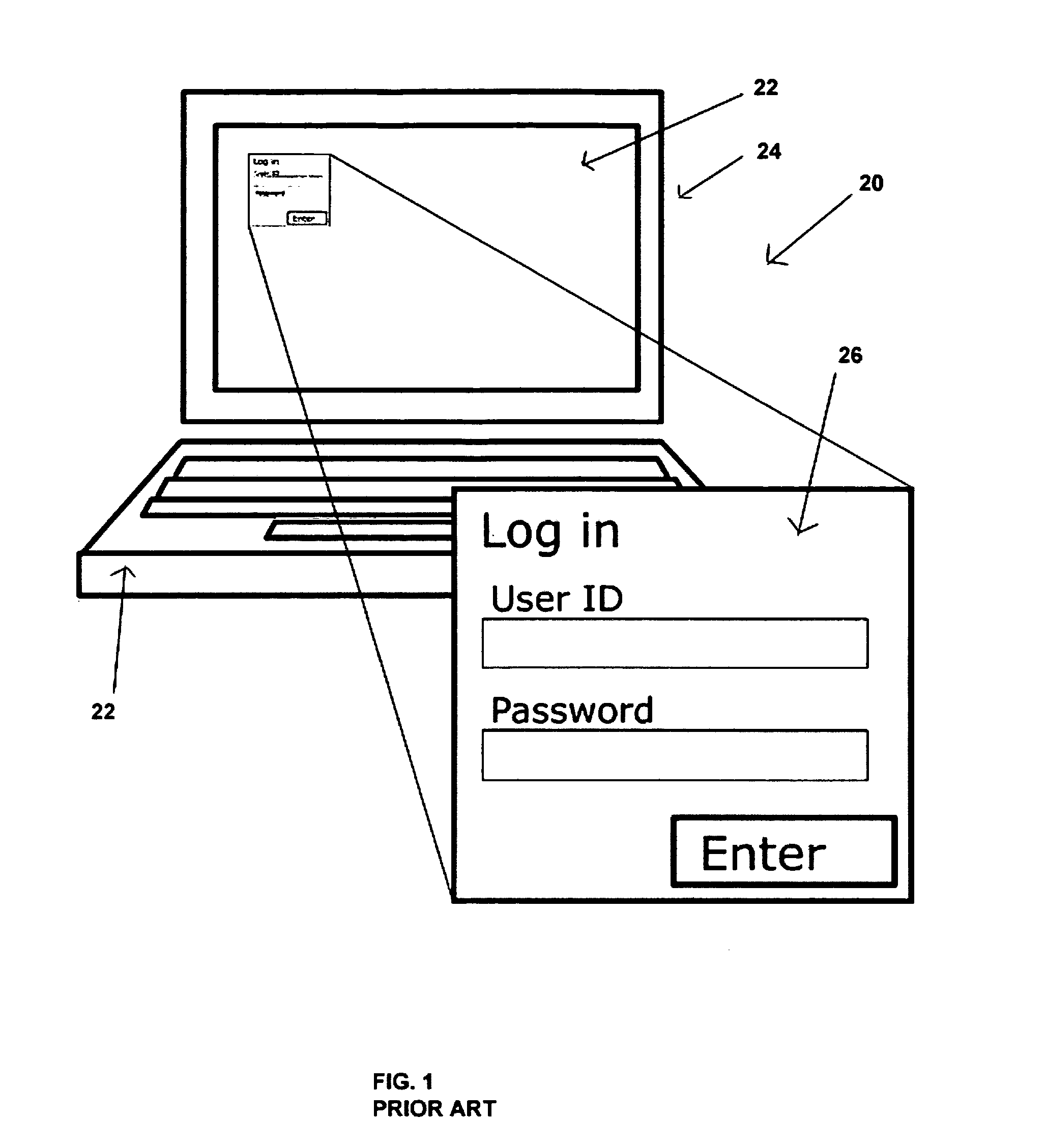
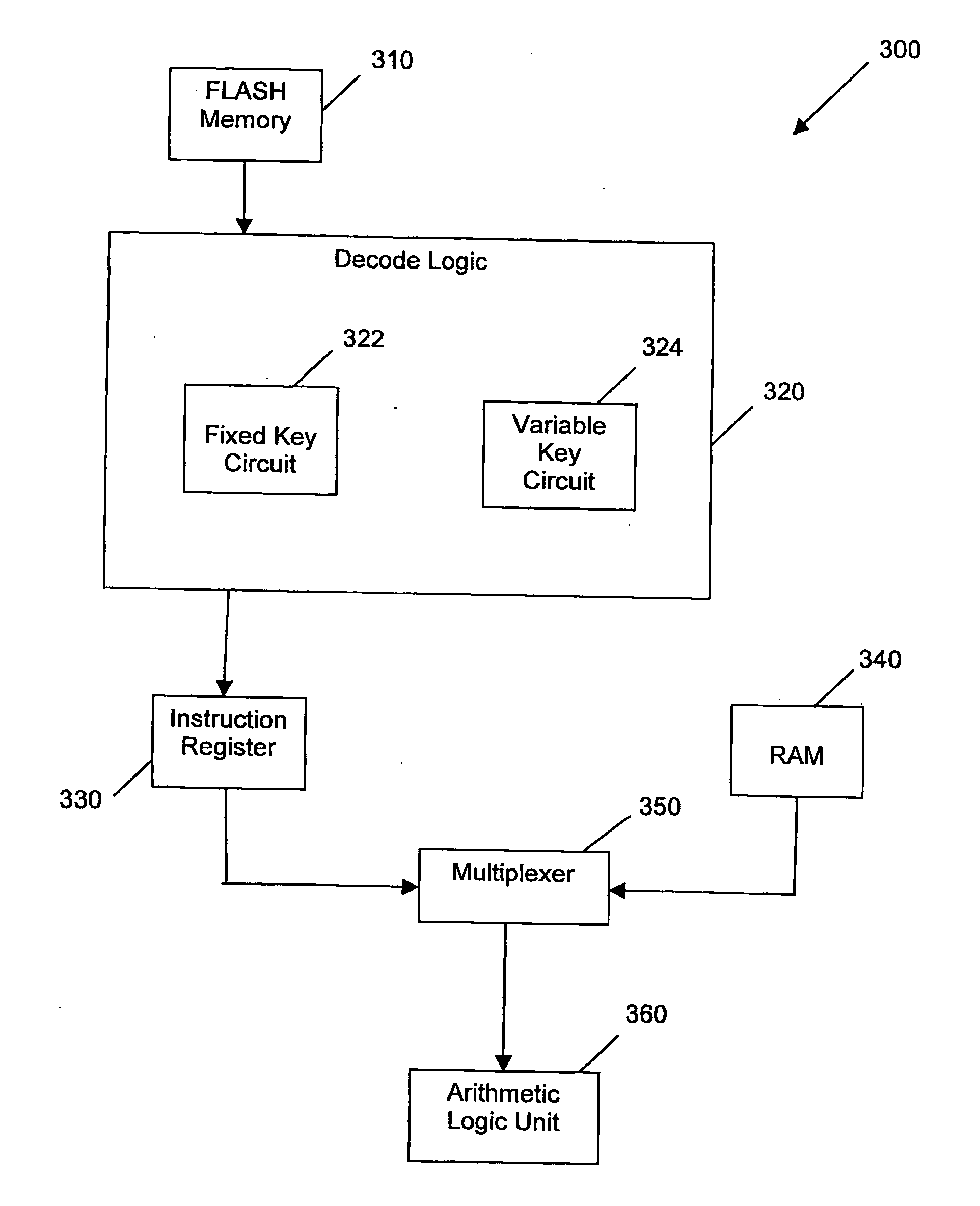
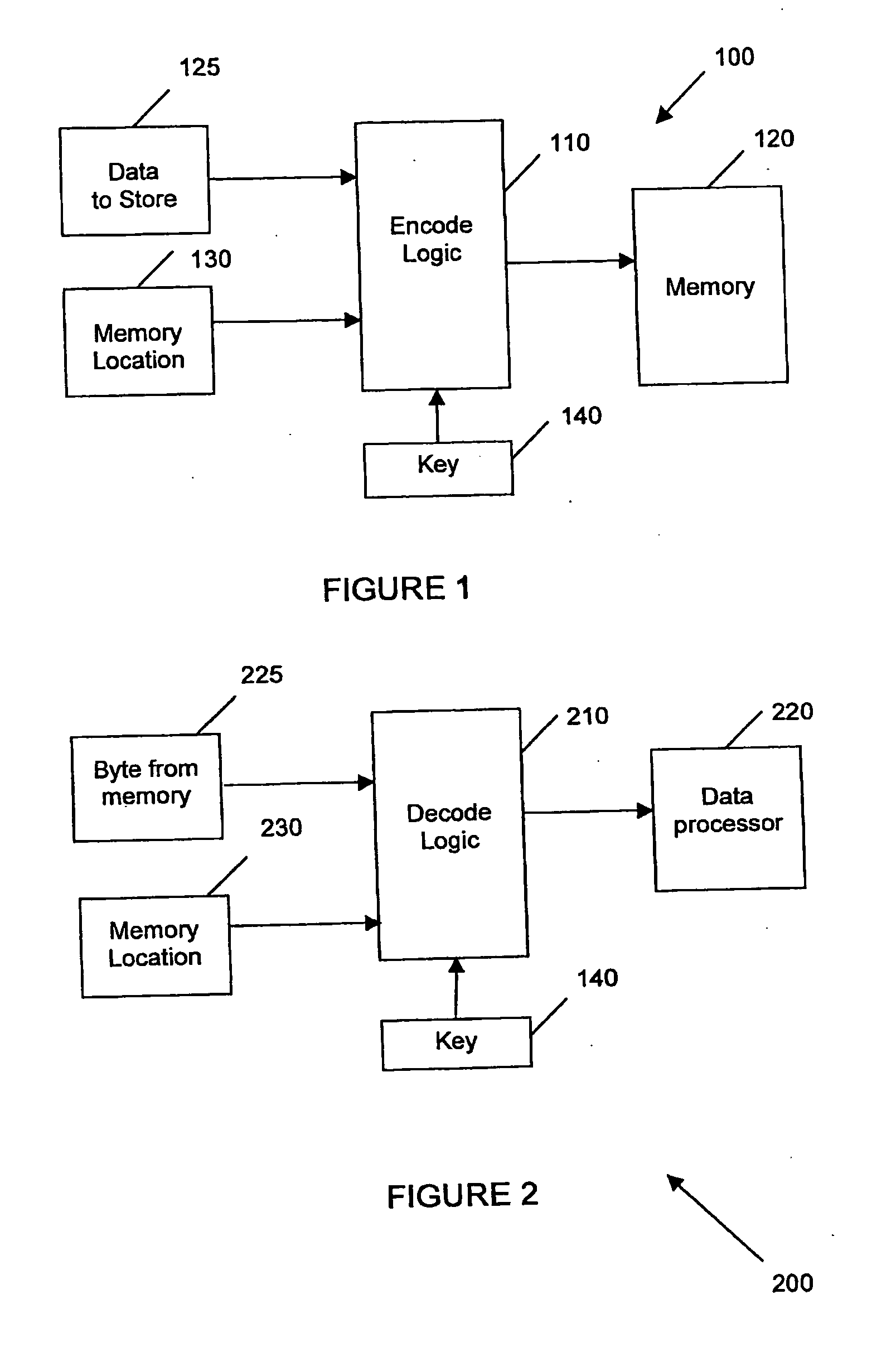
Method and system for microprocessor data security
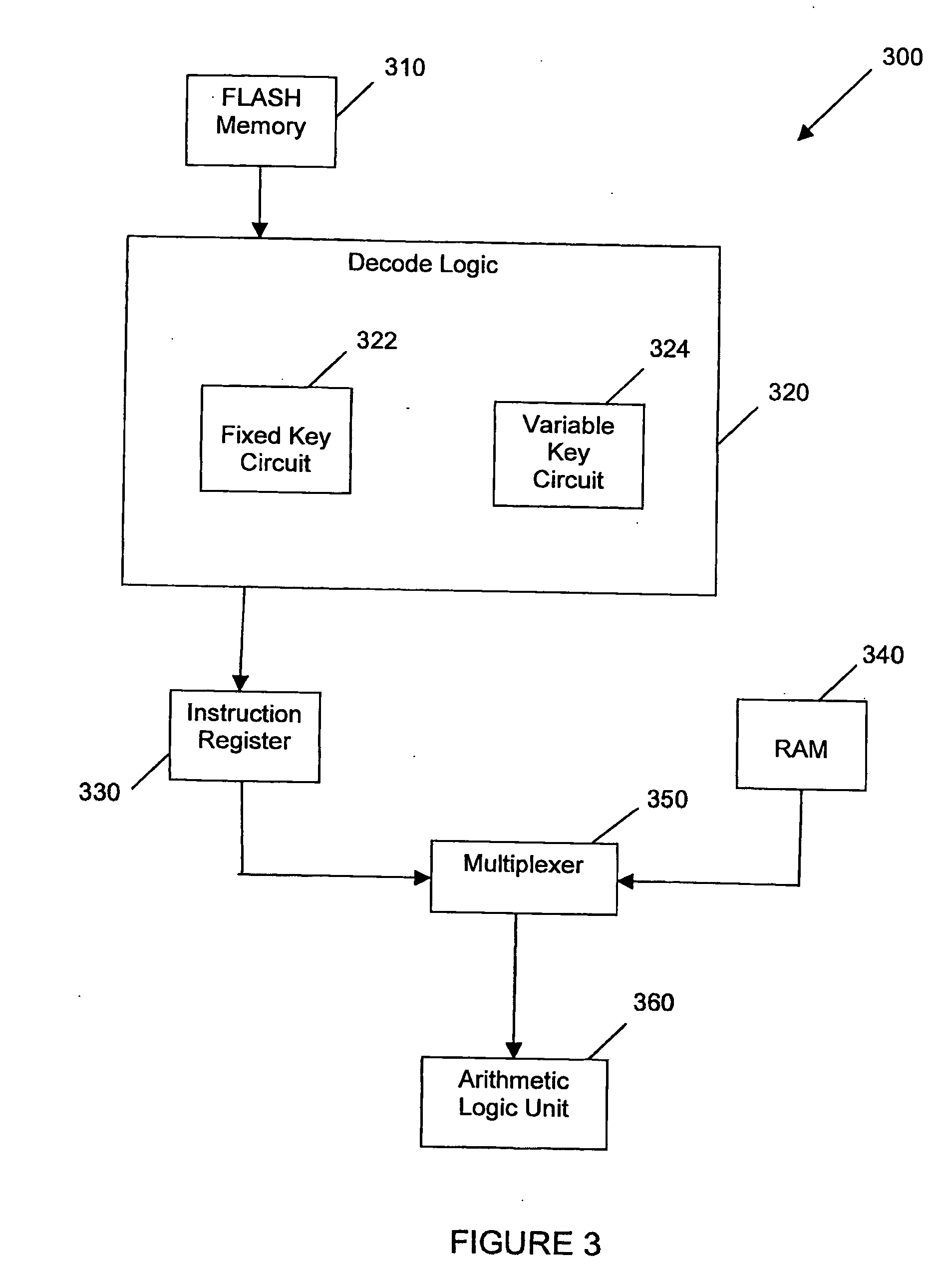
InactiveUS20070172053A1Improve securityAvoid loopholesData stream serial/continuous modificationUser identity/authority verificationByteEncryption
Embodiments of the invention relate generally to methods and systems for microprocessor data security, involving data encryption and decryption of stored data in, or in communication with, a computer microprocessor. Such encryption and decryption can be performed on a per-byte basis. Such encryption and decryption involves performing a logic operation on the byte using a decryption key or encryption key to generate a respective decrypted byte or encrypted byte. The key can be fixed or variable or a combination of both. The key is encoded in a dedicated hard-wired key circuit within the microprocessor and accessible to encryption and decryption circuitry within the microprocessor.
Owner:UNIVERSAL DATA PROTECTION CORP
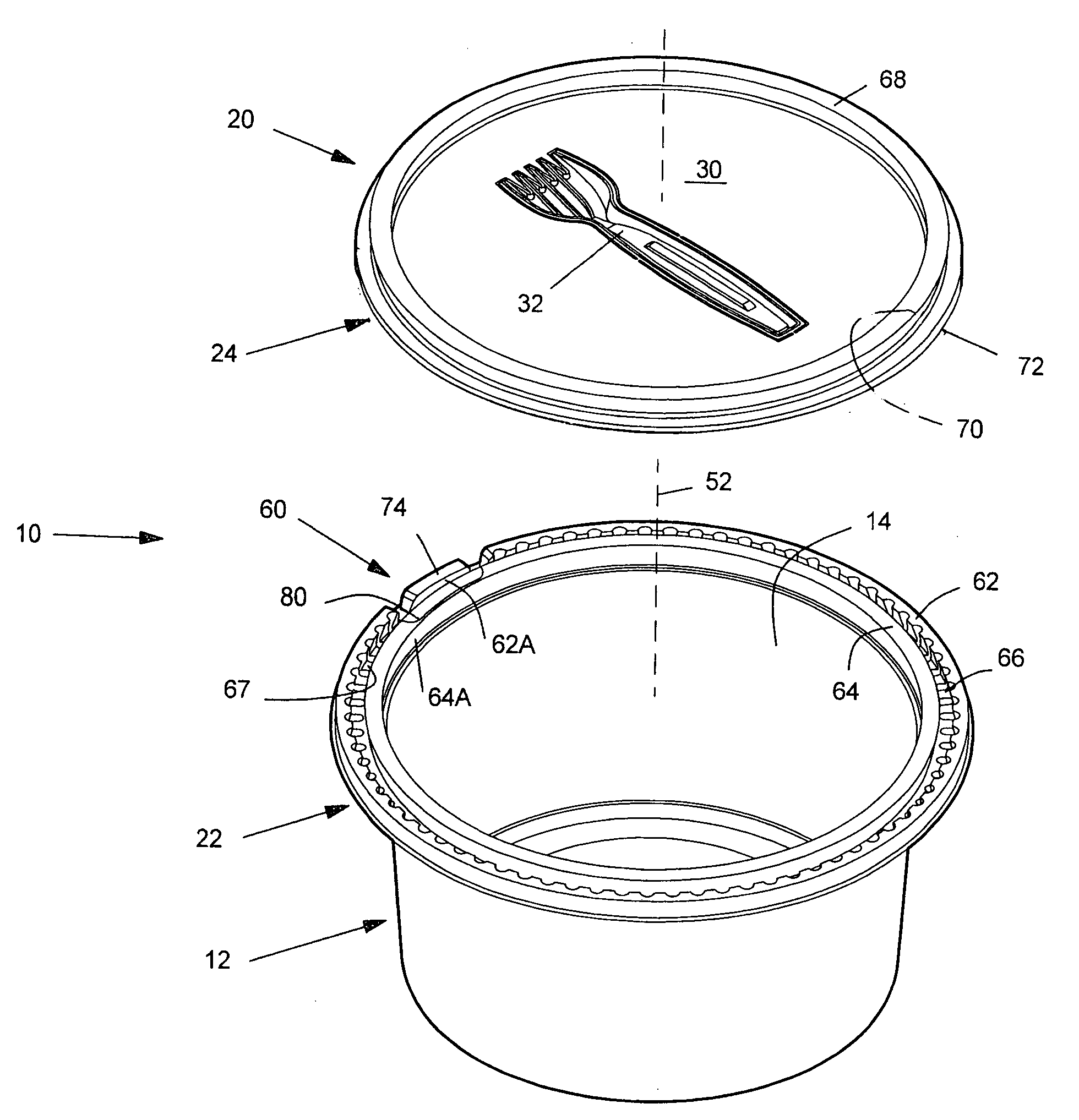
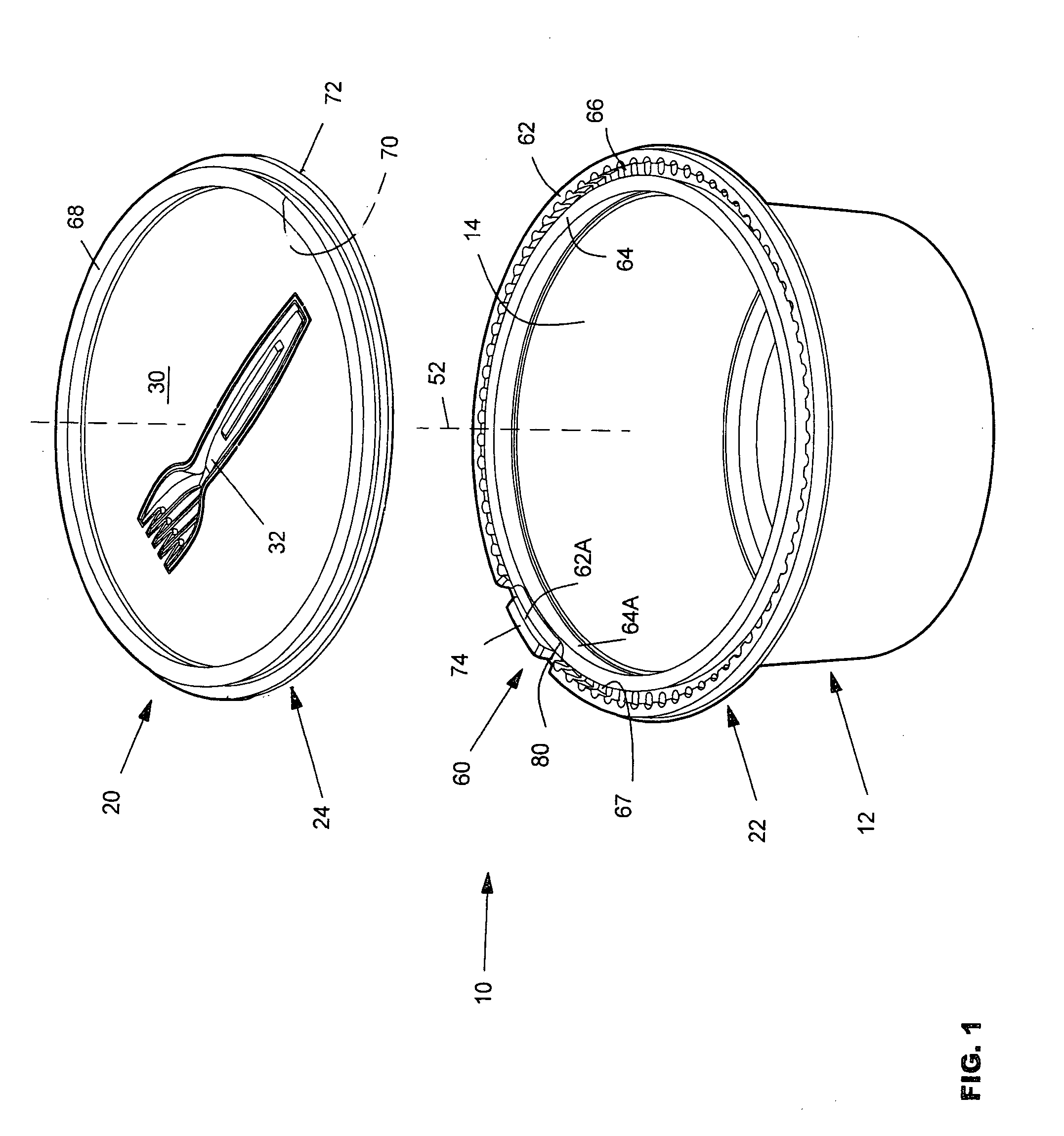
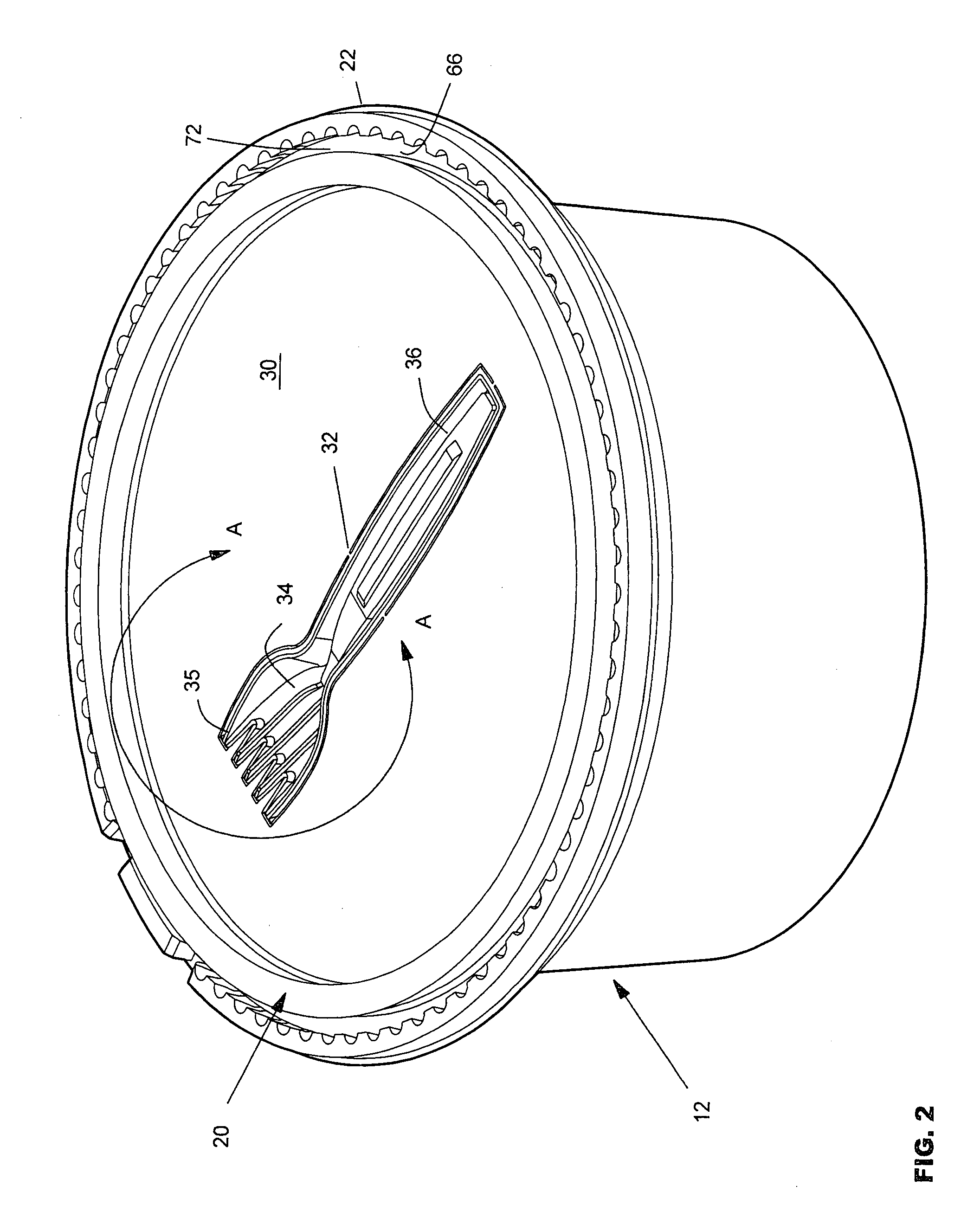
Convenient food container
A food container includes a base (12) with a food-holding cavity (14) and a lid (20) that closes the cavity, each formed of plastic sheeting. The lid defines an eating utensil (32) such as a fork, by a breakaway line that extends around the utensil and that can be easily broken to remove the utensil. The base has radially inner and outer upstanding flanges (64, 62) and an upwardly-opening base groove (66) between them that receives a lid lip (72). At an initial opening section (60) that occupies less than one-fifth of the container perimeter, a section (62A) of the outer base flange is partially separated from the rest of the base by a cut (80) extending along the base groove and by opposite breakable lines. At that section, the inner base flange (64A) is of reduced width to provide more room for a person to grasp the lid, and there is also a smaller interference fit between the base inner flange with walls of the lid groove.
Owner:PWP INDS
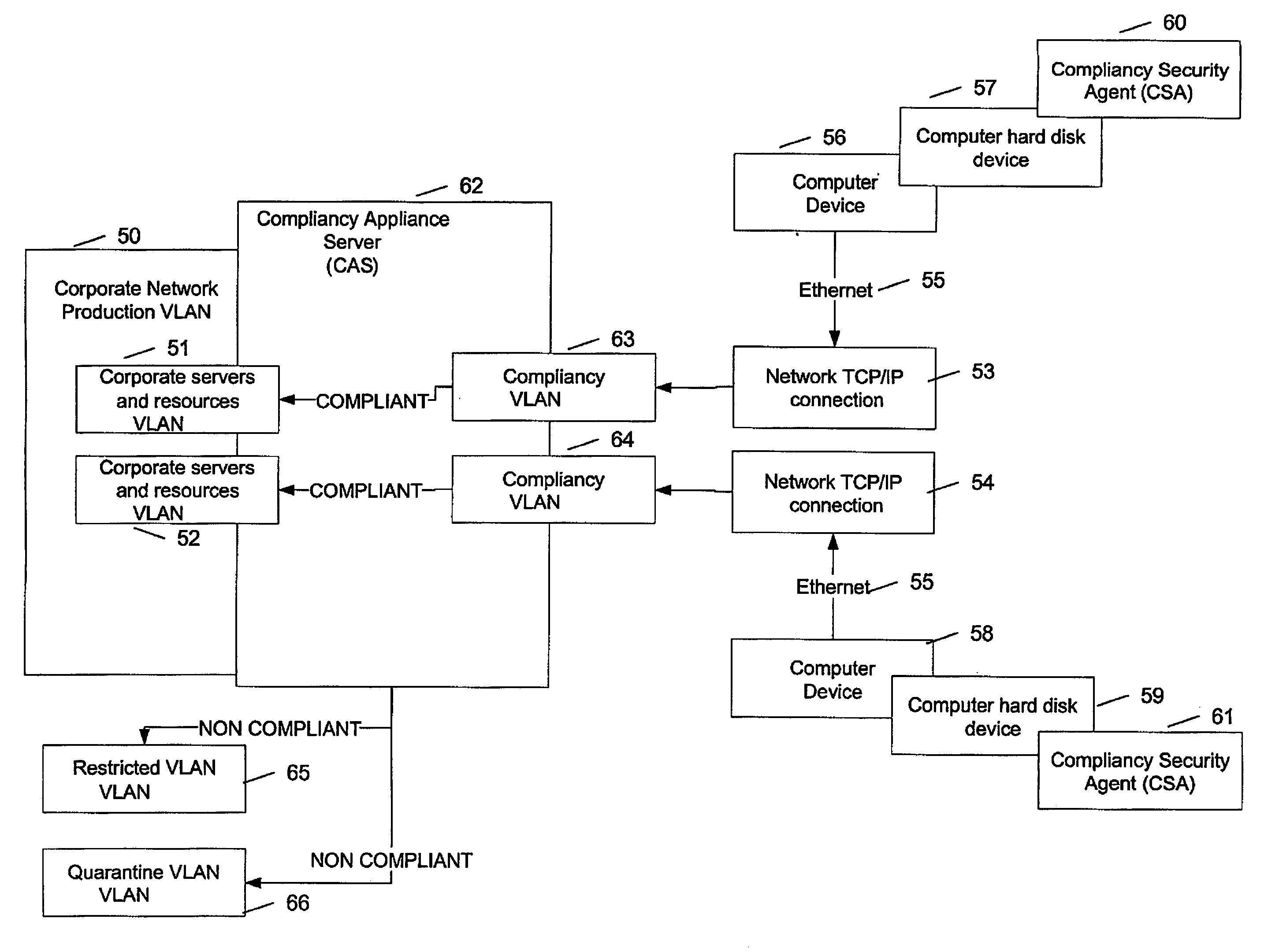
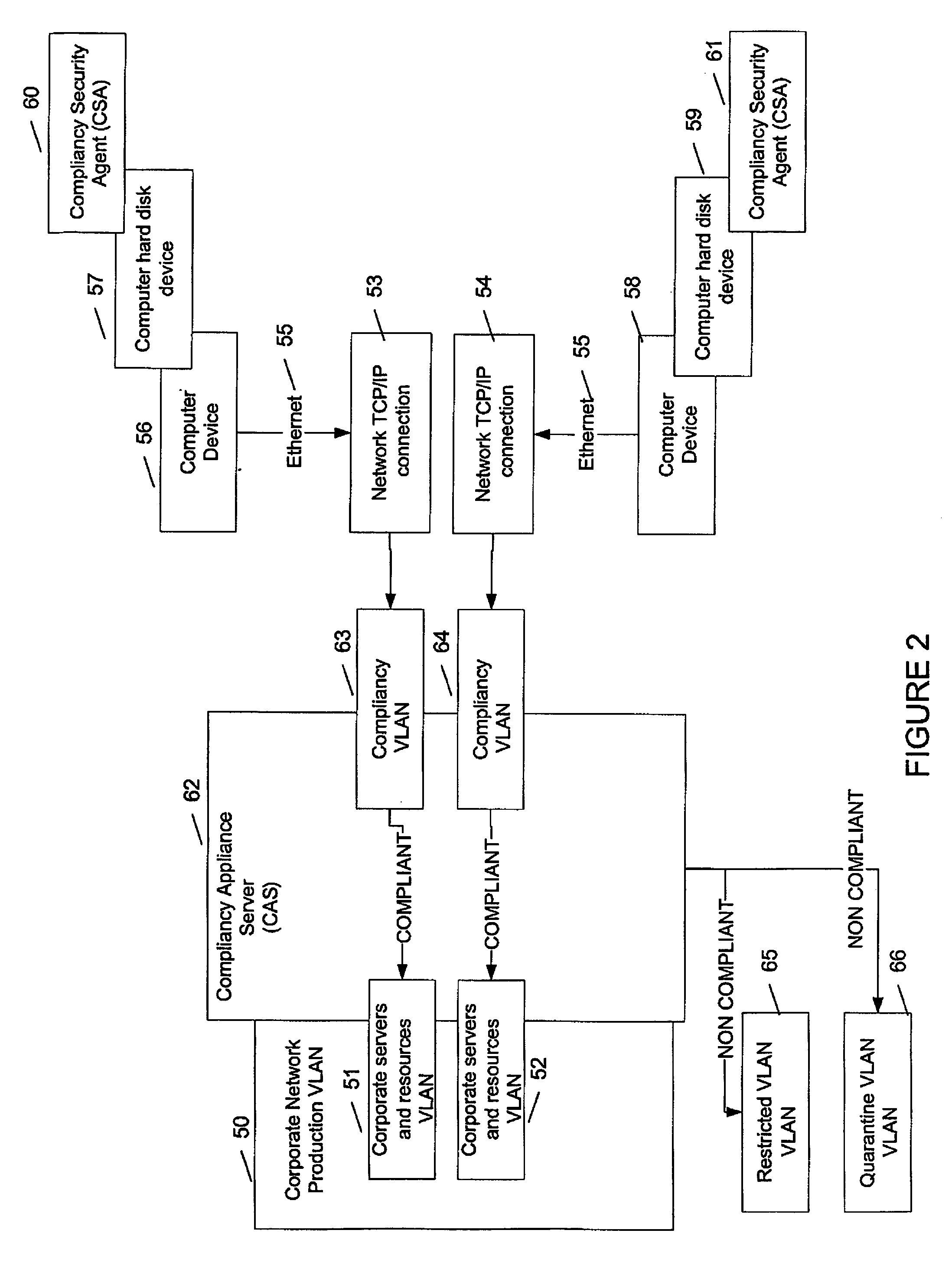
Compliance verification and OSI layer 2 connection of device using said compliance verification
InactiveUS20060203815A1Avoid loopholesPreserving network integrityData switching by path configurationNetwork connectionsCorporate networkIp address
The method comprises installing an agent software on the device; detecting a boot-up of the device; providing the device with a temporary IP address upon boot-up, the temporary IP address being within a compliancy network, logically separate from the corporate network; providing a list of compliance rules to be verified for the device; sending the agent the list of compliance rules; verifying a state of the device for each rule; transmitting a result of the state obtained for each compliance rule; deciding on compliance of the device using the result; instructing a switch port at OSI layer 2 to connect the device to the corporate network if the decision determines compliance; instructing a switch port at OSI layer 2 to connect the device to a network logically separate from the corporate network in case of non-compliance.
Owner:TELUS COMM
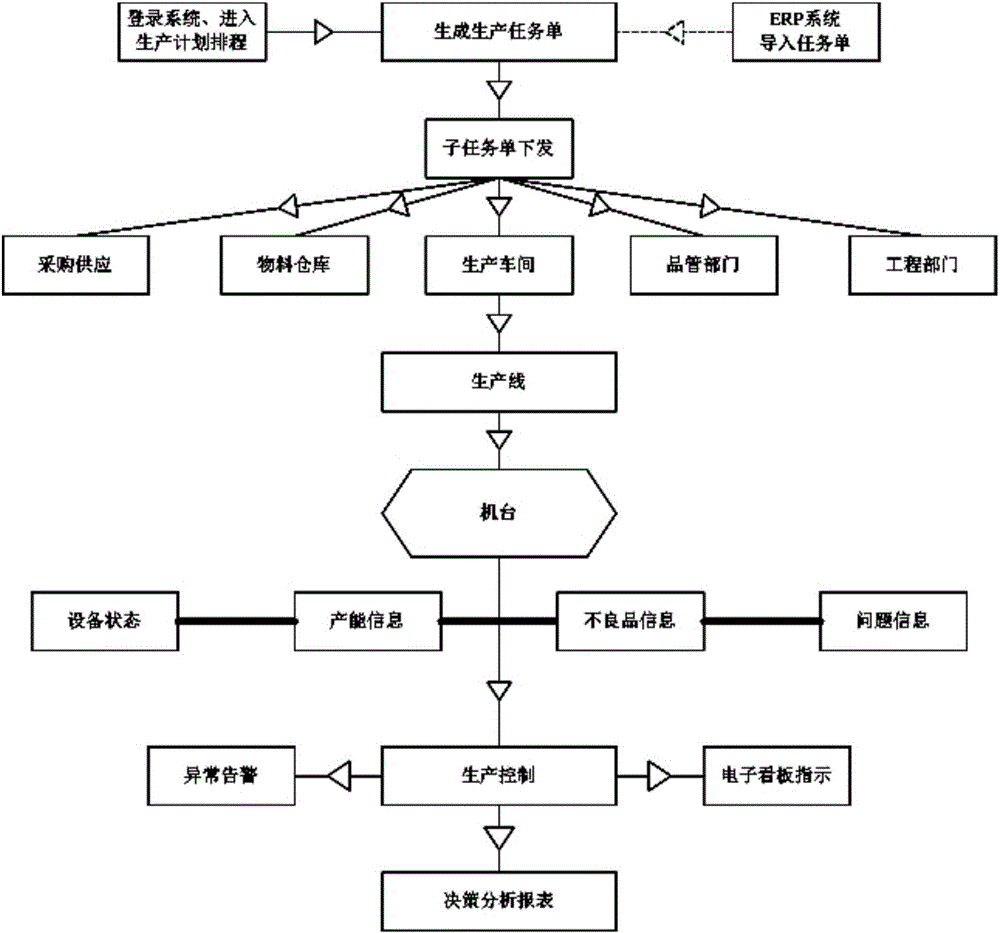
Lean production management kanban system and application method
InactiveCN106779592ASimple designAdvanced architectureOffice automationManufacturing computing systemsData acquisitionPersonal computer
The invention discloses a lean production management kanban system and an application method. The system mainly comprises machine table kanban, comprehensive kanban, a data collector, an industrial personal computer, a server, kanban system software, a call broadcast system, and a special local network. The system has the effects of real-time transmission of production information, transparent management and guarantee of production field work order, and is an effective tool for realizing lean production accurate management.
Owner:林冠良
Crack repair using friction stir welding on materials including metal matrix composites, ferrous alloys, non-ferrous alloys, and superalloys
InactiveUS20050061853A1Avoid loopholesWelding/cutting auxillary devicesAuxillary welding devicesCrazingNuclear reactor
A system and method of using friction stir welding and friction stir processing to perform crack repair or preventative maintenance of various materials and structures, wherein the structures include pipeline, ships, and nuclear reactor containment vessels, wherein the friction stir welding and processing can be performed on various materials including metal matrix composites, ferrous alloys, non-ferrous alloys, and superalloys, and wherein the friction stir welding and processing can be performed remotely and in harsh environments such as underwater or in the presence of radiation.
Owner:BABB JONATHAN A +1
Online data encryption and decryption
ActiveUS20060104446A1Inhibition of informationAvoid loopholesDigital data authenticationSecret communicationComputer hardwareGraphics
Systems and methods for providing encryption and decryption of data transmitted on a computer implemented network, preferably user authentication identifier data, such as a password, at the point of entry into the user's computer. The systems and methods enable an end user to mentally select a marker from one of the randomly arranged elements on a first portion of a graphical image. A second portion of the graphical image includes an arrangement of possible elements of any individual authentication identifier sequence, and is positioned adjacent to the first portion. The systems and methods prompt a user to enter each element of the identifier by moving the selected marker and the first portion as necessary to substantially align the selected marker with a chosen element of the authentication identifier appearing on the outer portion. According to one embodiment, the image portions are concentric wheels. According to another embodiment, the image portions are arranged in adjacent rows.
Owner:ORACLE INT CORP
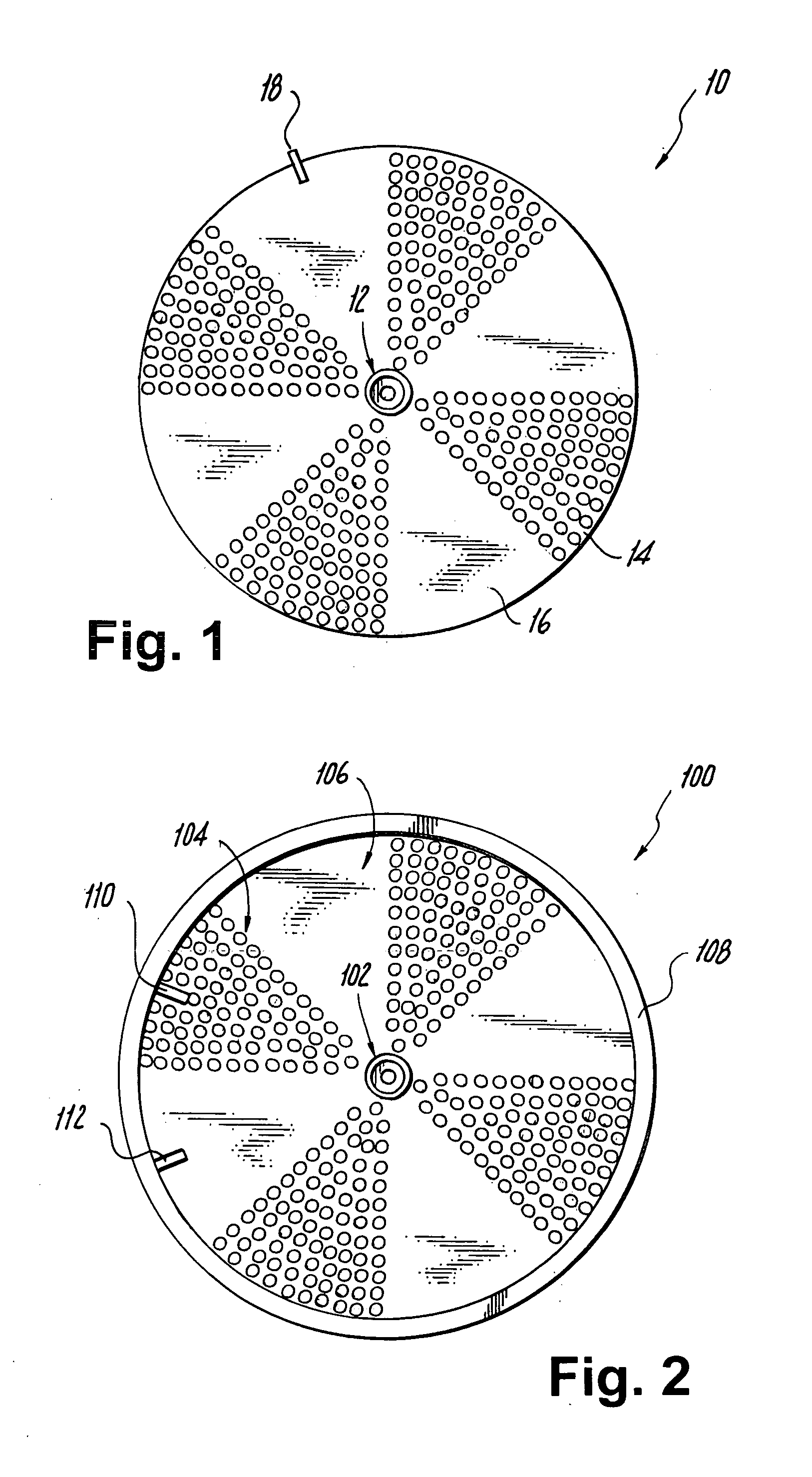
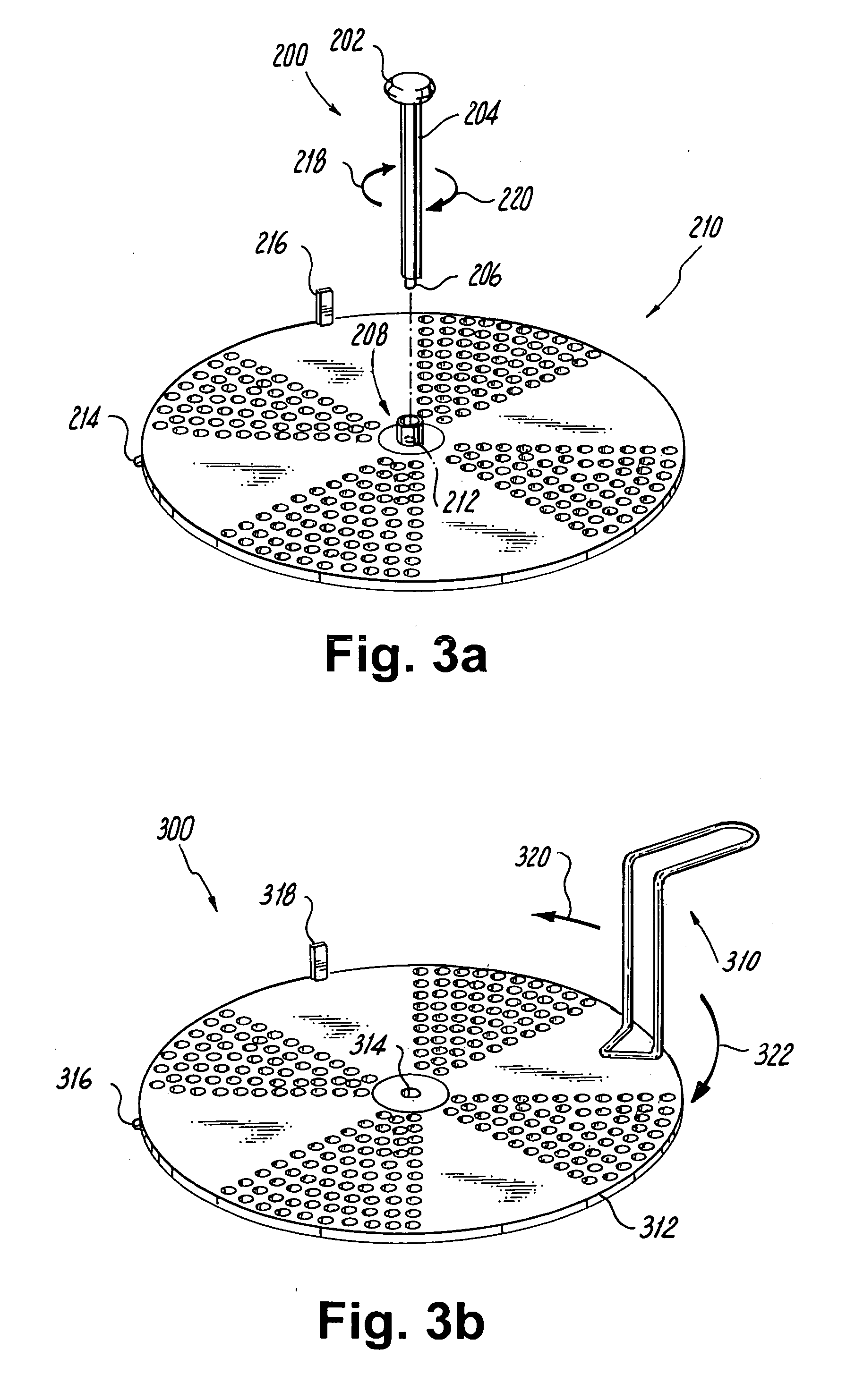
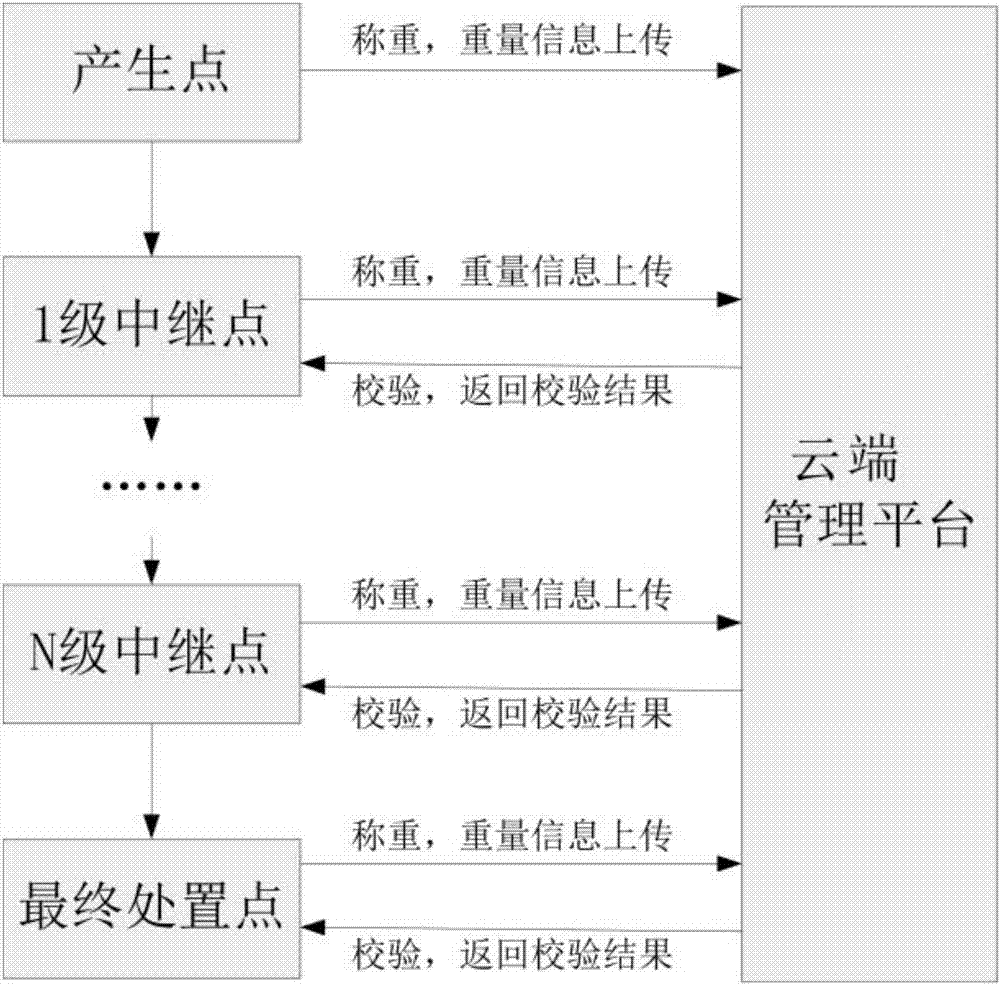
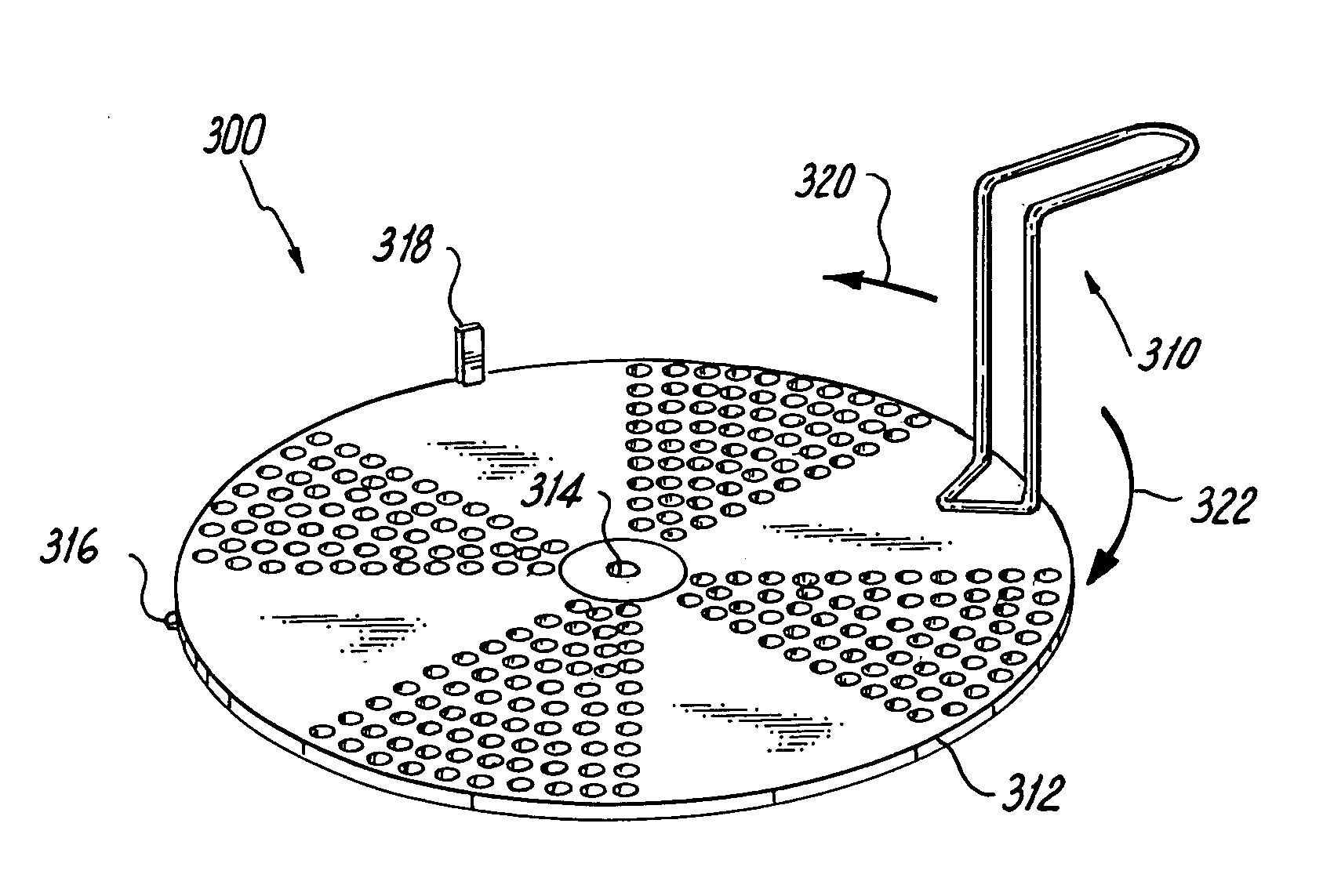
Device and method for removing solids and liquids from a pot
InactiveUS20060254976A1Increase the diameterPrevent fallingFiltration separationCooking insertsEngineering
Owner:COOPER MICHELE
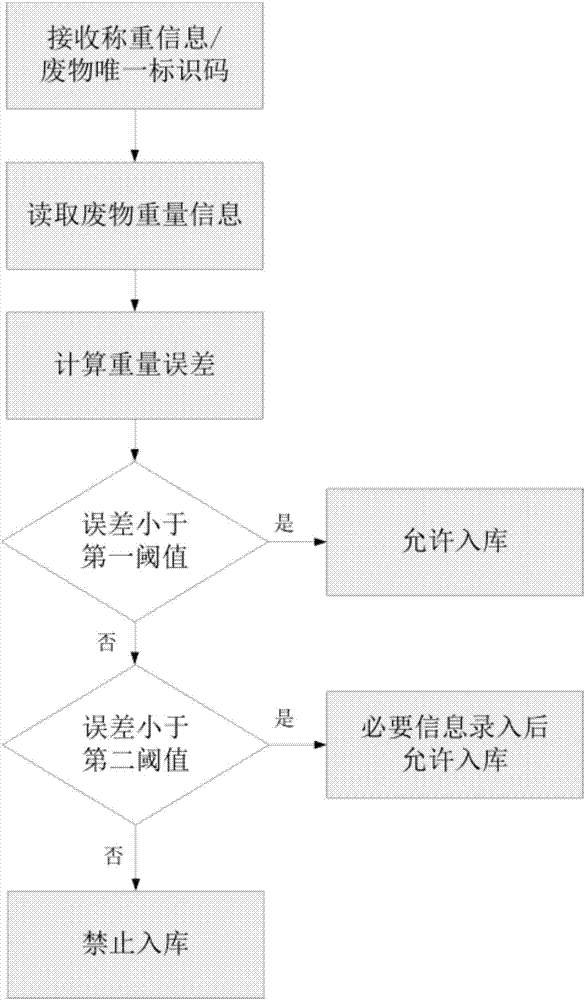
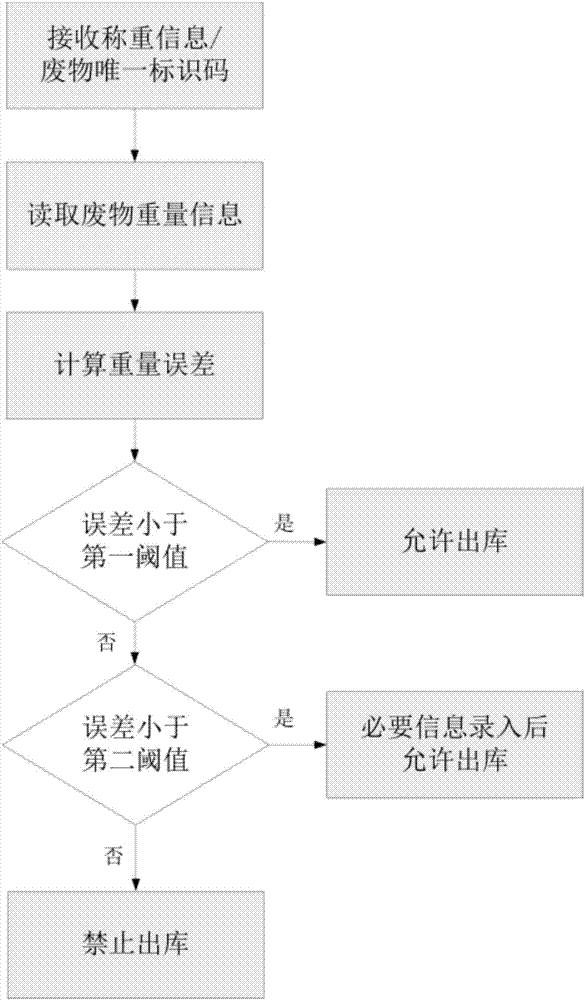
Medical waste management weight verification method
ActiveCN107358398APutting an end to the ways of stealing medical waste for profitAvoid loopholesSustainable waste treatmentSolid waste disposalClosed loopMedical waste
The invention relates to a medical waste management weight verification method. The method performs weight management on medical wastes from a generation point to a final disposal point through relay nodes at various levels, weighs the medical wastes at the generation point, pastes a waste information Label, uploads initial weight information to a cloud management platform, reweighs the medical wastes during in-warehouse and out-warehouse processes at the relay points and the disposal points, and enables the cloud management platform match and verify the weight and the initial weight of the medical wastes. The method controls the entire life cycle of the medical wastes from generation to disposal, performs weight control and repeated verification in the whole process of production, storage, transportation and disposal so as to prevent leaks, enhance the safety of a closed-loop system, and eliminates opportunities for criminals to take advantage.
Owner:JIANGSU SUPERSENSE TECH CO LTD
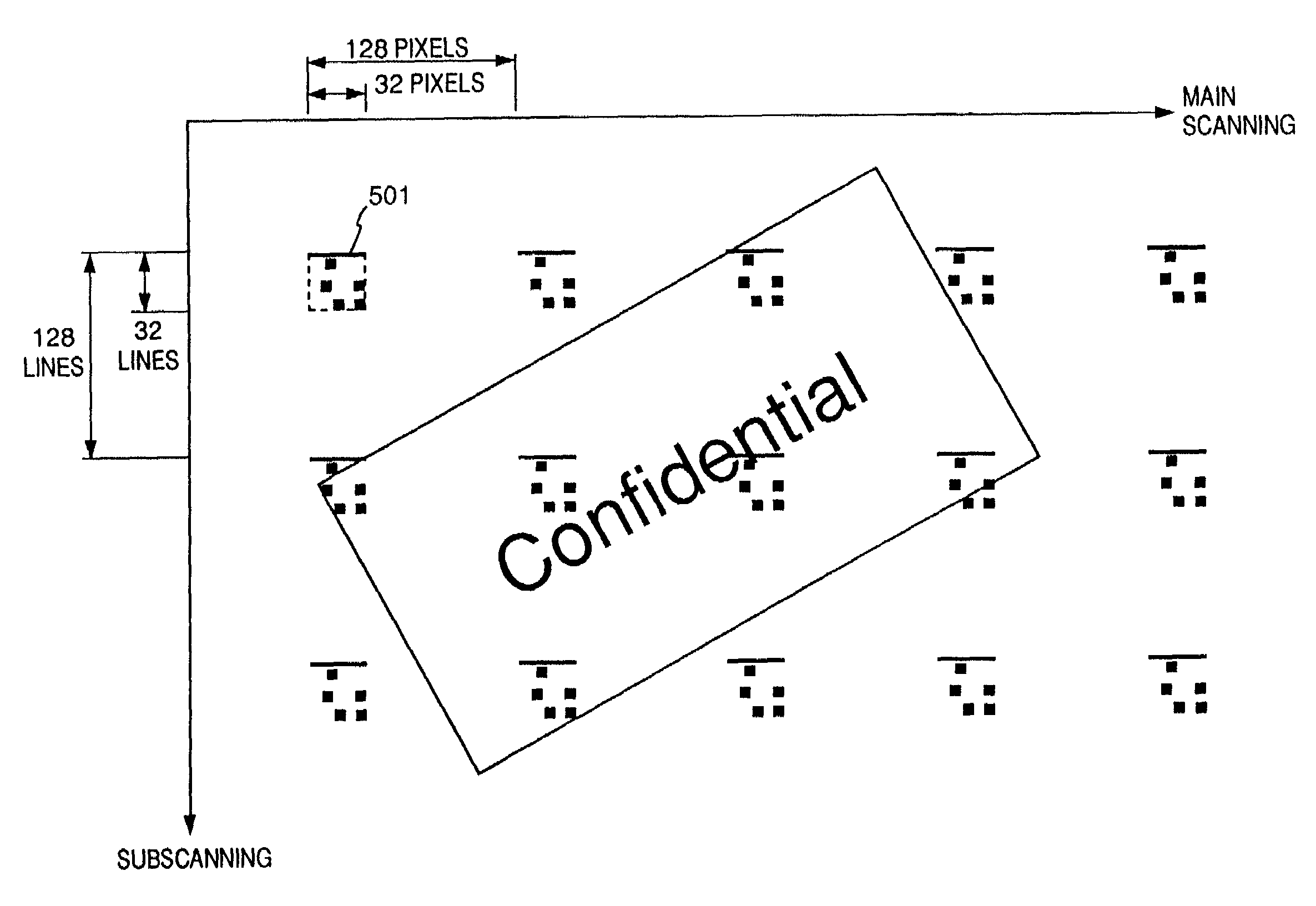
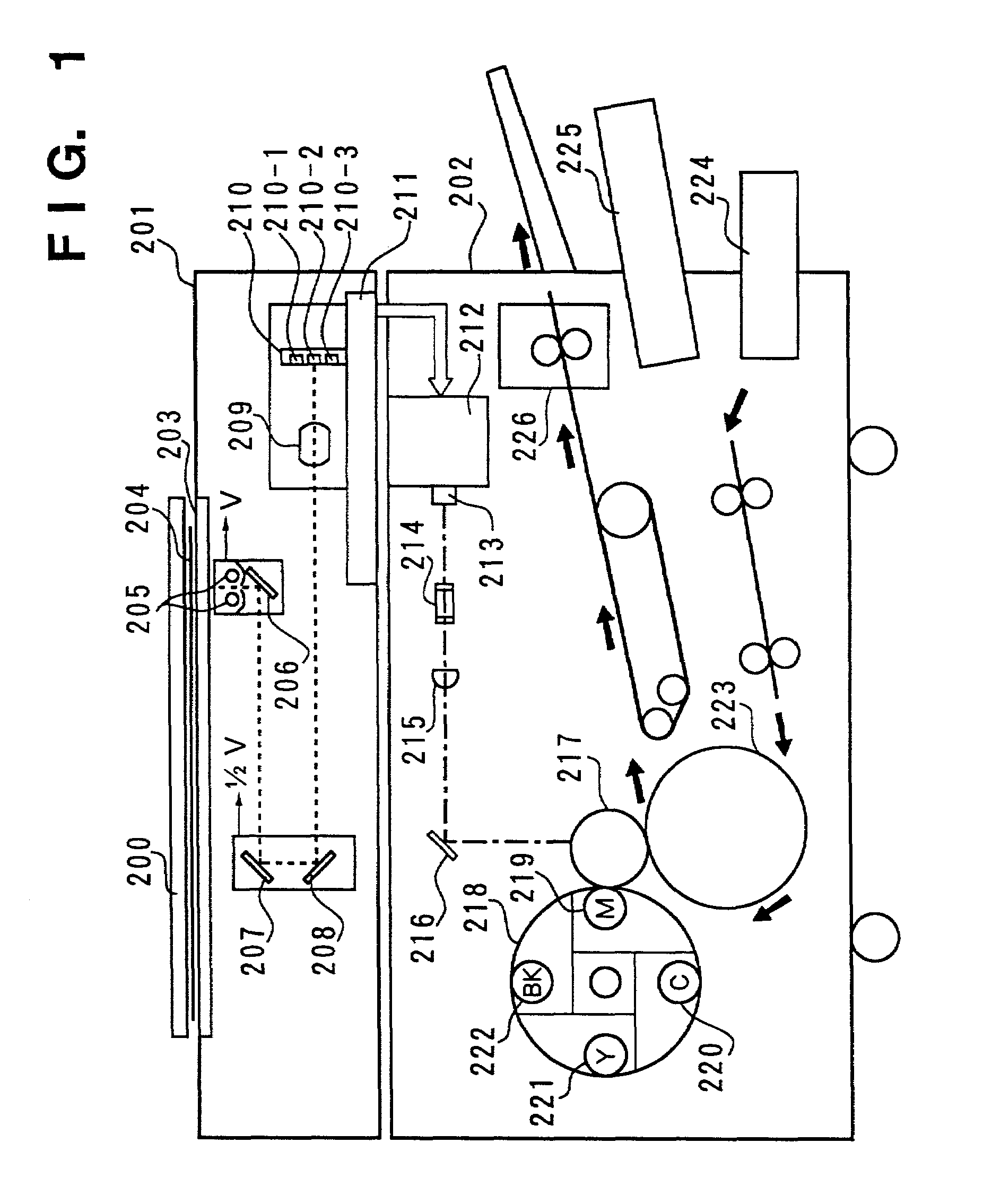
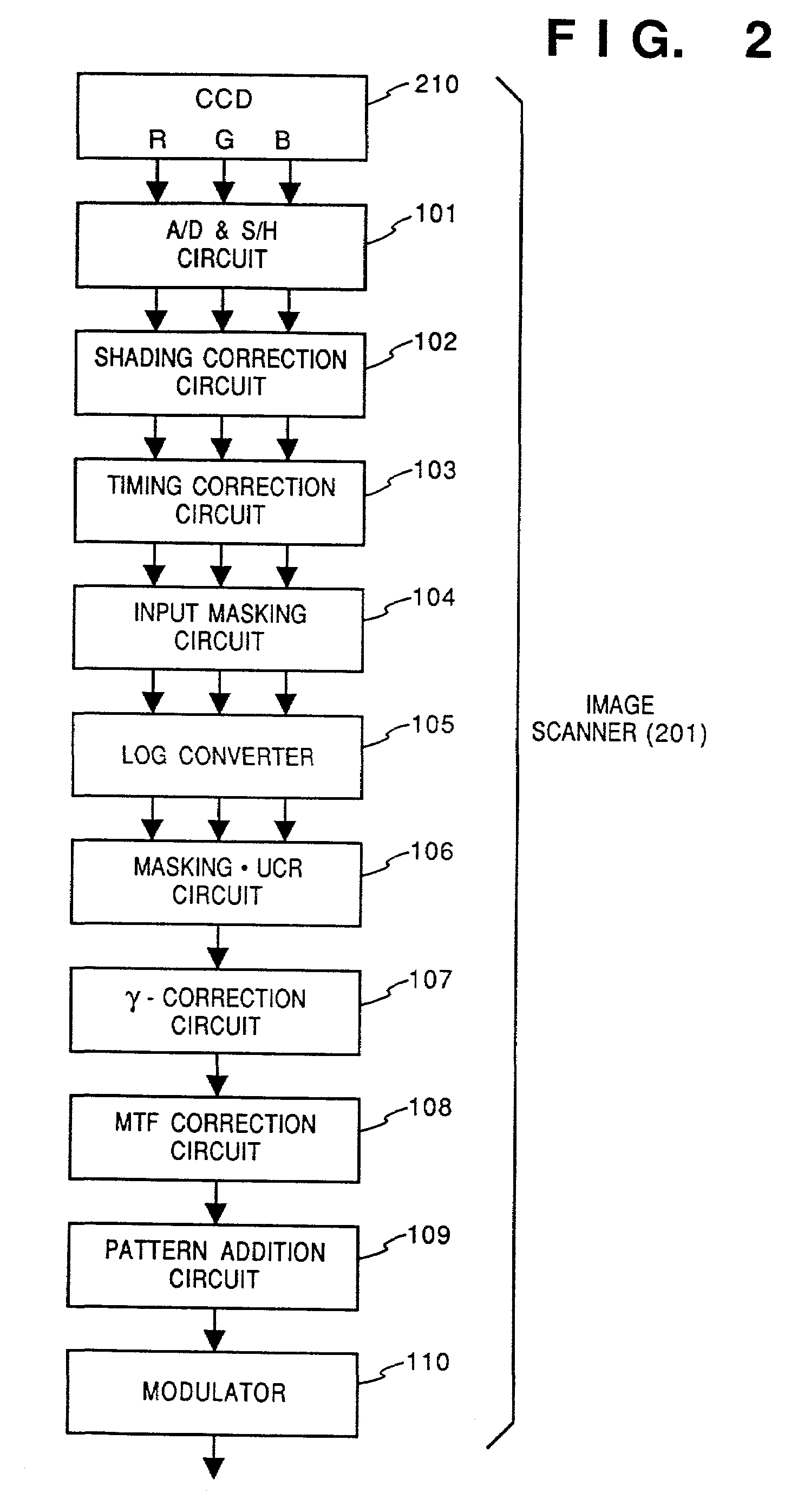
Image processing apparatus and method using image information and additional information or an additional pattern added thereto or superposed thereon
InactiveUS7061652B2Avoid loopholesIncrease patternOther printing matterVisual presentationImaging processingComputer graphics (images)
Owner:CANON KK
Intelligent storage cabinet capable of refrigerating for fresh food delivery, and monitoring method thereof
ActiveCN103854344ASmall footprintFlexible placementIndividual entry/exit registersFresh foodThe Internet
The invention relates to an intelligent storage cabinet capable of refrigerating for fresh food delivery, and a monitoring method of the intelligent storage cabinet. The intelligent storage cabinet comprises a monitoring system which is arranged in a storage box body provided with a box liner; the storage box body is also provided with an intelligent control system and a refrigerating system which are connected with each other; the intelligent control system is connected with the internet; the internet is connected with a far-end network monitoring system and a short message platform; the monitoring system is connected with the intelligent control system. The intelligent storage cabinet is combined with the monitoring method, so that the defects of being large in occupied land area, small in volume of a refrigerating cabinet, high in labor cost and not capable of providing 24-hour pickup service, and easily causing mistakes and omissions can be effectively reduced.
Owner:NANJING INFOL TECH
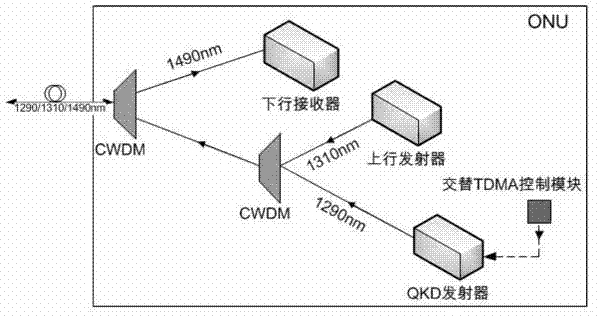
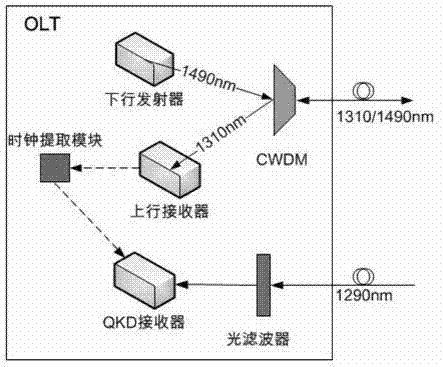
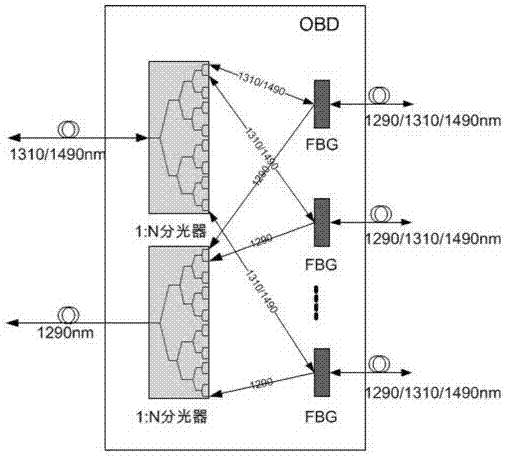
Optical access passive network supportive of quantum communication
ActiveCN103118308AAvoid interferenceAvoid loopholesMultiplex system selection arrangementsKey distribution for secure communicationGratingPassive networks
Disclosed is an optical access passive network supportive of quantum communication. The network is supportive of bidirectional data communication of a GPON (gigabit passive optical network) accordant with the ITU (International Telecommunication Union)-T G.984 standard or an EPON (Ethernet passive optical network) accordant with the IEEE802.3 (Institute of Electrical and Electronics Engineers) standard and quantum key distribution (QKD) of uplink direction. An improved optical network unit is adopted in the network to add a QKD emitter and an alternating time-division multiple-address access control module on a basis of an original GPON or EPON, an improved optical line terminal is adopted to add a QKD receiver and a clock extraction module on a basis of the original GPON or EPON, and an improved passive optical splitter is adopted and comprises two 1: N optical splitters and N Bragg gratings (N is the number of the optical network unit). The network integrally greatly avoids inferences, on quantum signals, of high-light signals to enable the QKD to be capable of coexisting with the GPON or EPON. The optical access passive network supportive of quantum communication can thoroughly improve potential security loopholes of common optical access networks and provides a feasible scheme for popularizing the quantum communication technology to a fiber to house (building) FTTx (fiber to the x) access network.
Owner:ZHEJIANG UNIV OF TECH
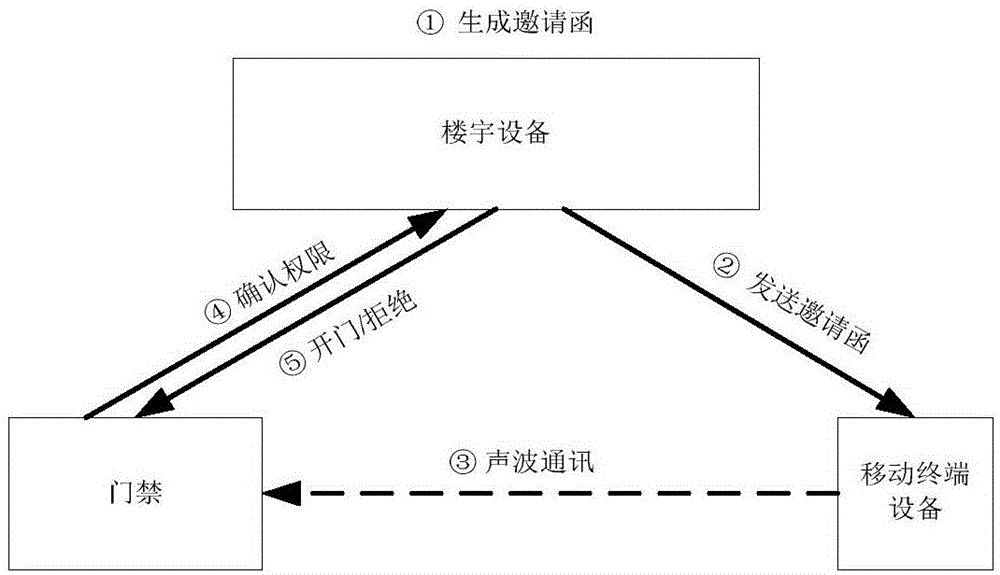
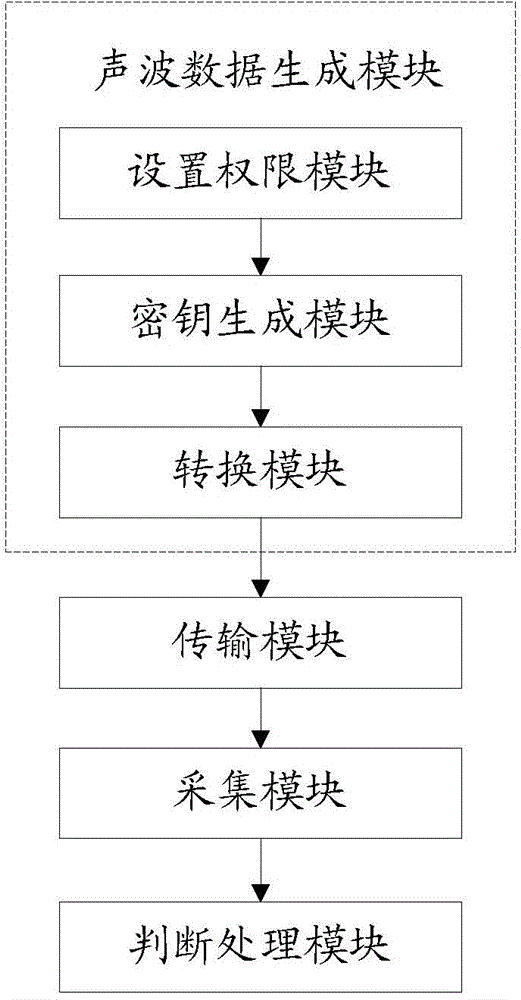
Long-distance door access control method and long-distance door access control system utilizing acoustic wave communication
ActiveCN104954121AConvenient for temporary accessLow costKey distribution for secure communicationUser identity/authority verificationControl systemTerminal equipment
The invention provides a long-distance door access control method utilizing acoustic wave communication. The method comprises the following steps: 1, according to the temporary visit required authority of a visitor, generating a secret key, and then, converting the secret key into acoustic wave data through coding; 2, sending the acoustic wave data to mobile terminal equipment of the visitor; 3, collecting the acoustic wave data sent by the mobile terminal equipment through a built-in sound sensor of a door access; 4, analyzing the acoustic wave data by the door access or building equipment to recover the secret key, and then, judging whether a door is opened or not by the building equipment according to the authority corresponding to the secrete key. The invention also provides a long-distance door access control system utilizing the acoustic wave communication, and the temporary authorization way of the door access control system low in cost, convenient and fast is realized.
Owner:FUJIAN STAR NET COMM
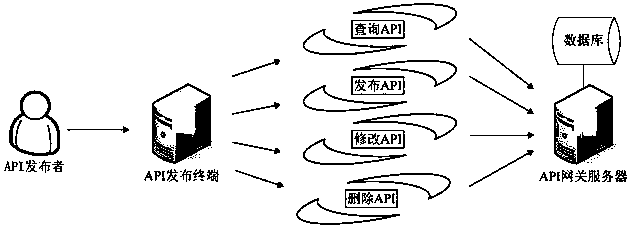
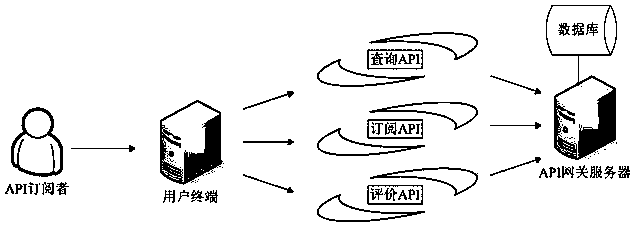
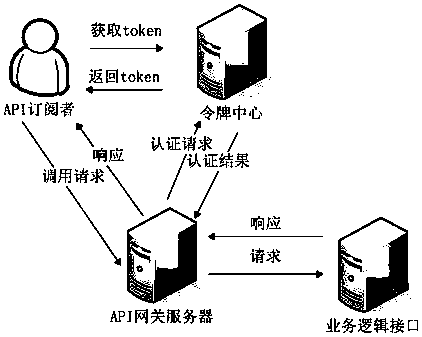
Security management method and system for application programming interface
ActiveCN109150805AProtection controllabilityPlay a protective effectUser identity/authority verificationApplication programming interfaceIp address
The application provides a security management method and system for an application programming interface. On a gateway server side, the method includes the following steps that: service logical interface information submitted by a publisher is received; an interface external access address which is published to the outside is generated according to a preset format on the basis of the IP address of the gateway server and a port number allocated to the publisher, an association relationship between the interface external access address and the service logic interface information is established;an interface call request sent by a subscriber is received; and a request token center authenticates the identity of the subscriber that sends the interface call request, if the identity of the subscriber passes the authentication, the interface call request is forwarded to a corresponding service logical interface according to the association relationship between the interface external access address and the service logical interface information, and the execution result of the service logic interface is returned to the subscriber. With the above technical schemes of the invention adopted, the problem that illegal access to service data through an API cannot be blocked in the prior art can be solved.
Owner:亿阳安全技术有限公司
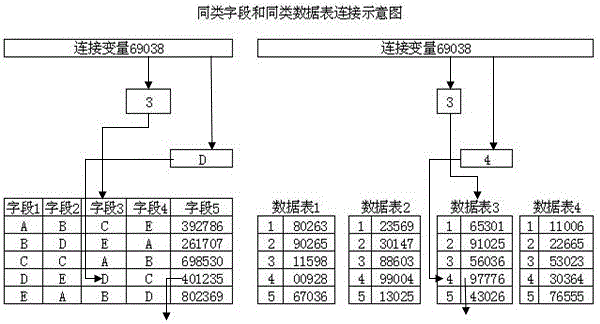
Digital encryption algorithm
ActiveCN106161006AEnsure safetyLow costKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPasswordServer-side
A digital encryption algorithm uses a connection variable to connect a same kind field or a same kind data table and performs encryption on source data; the encryption method needs hardware data to participate and enables a password to be complex through multiple times of encryption and expanding encrypted data; and the biggest characteristic of the password is that the encrypted data is not completely stored, so that cracking on the server terminal is very difficult.
Owner:湖南瀚洲智能科技有限公司
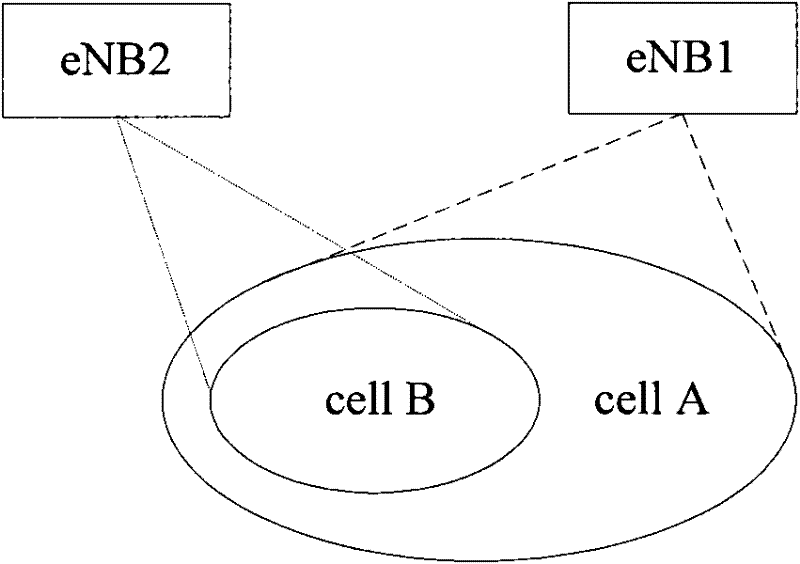
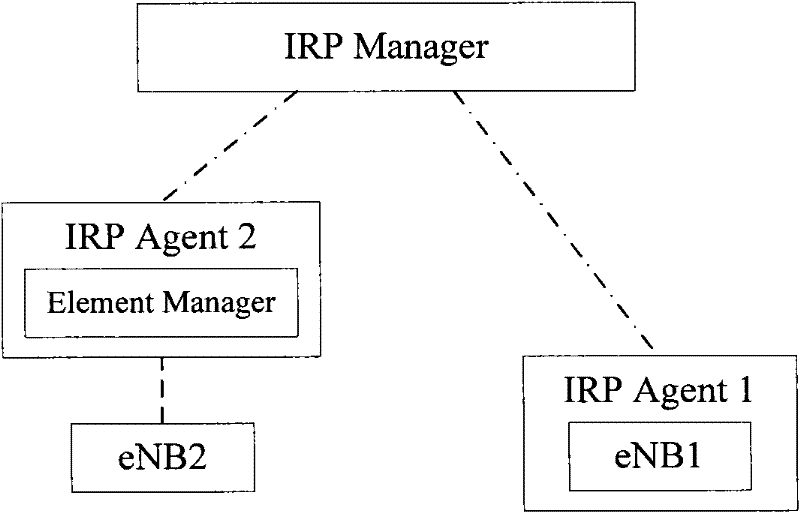
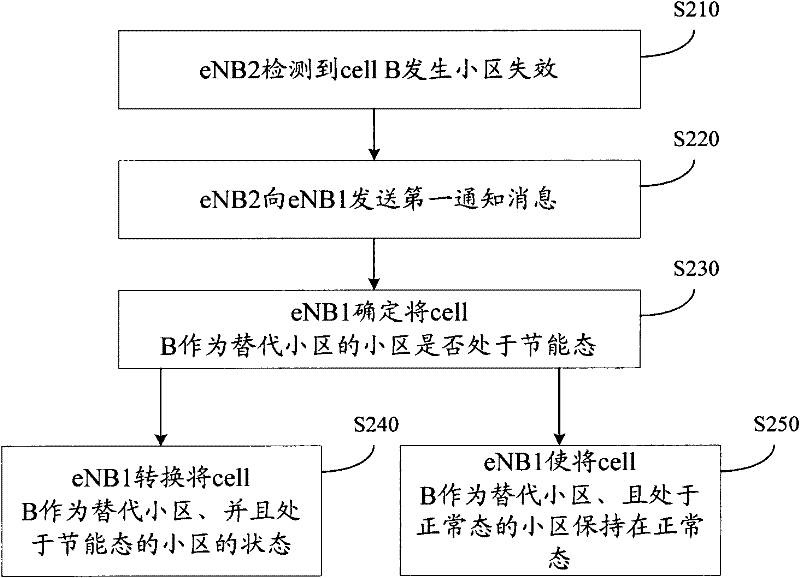
Method and equipment for processing cell outage
ActiveCN102238595AAvoid loopholesPower managementEnergy efficient ICTBiological activationComputer science
The embodiment of the invention provides a method and equipment for processing cell outage. The method comprises the steps as follows: a first base station receives an energy saving activation message sent by a second base station when a second cell is subjected to cell outage, wherein the energy saving activation message is used for forbidding the energy saving function; and the first base station converts the status of a first cell from the energy saving status to the normal status according to the energy saving activation message or maintains a third cell in the normal status until the first base station learns that the cell outage of the second cell has been solved. By using the method, the problem of faulty network coverage caused by the condition that the first cell self is in the energy saving status and the second cell supporting the network coverage of the first cell is subjected to cell outage or the problem of faulty network coverage caused by the condition that the third cell enters the energy saving status when the second cell is subjected to cell outage can be avoided.
Owner:HUAWEI TECH CO LTD
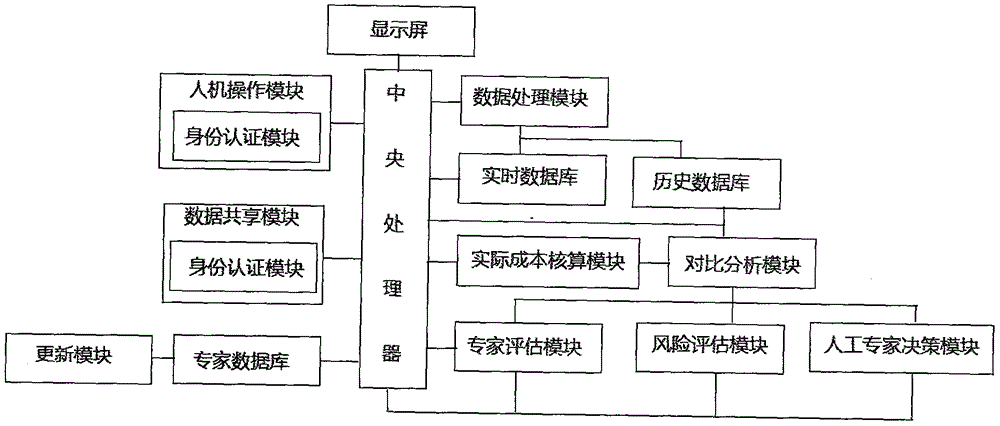
Economic management cost control system
The invention discloses an economic management cost control system, including a man-machine operation module internally provided with an identity authentication module, a central processing unit, a data processing module, an actual cost accounting module, a contrastive analysis module, a risk assessment module, an expert assessment module and an artificial expert decision module. The system can avoid various loopholes which occur in a cost control process, and can give different disposal decisions according to different situations, and entering of each data carries identity information of an entering person, thereby realizing traceability of data, data are assessed in multiple aspects, a management requirement of related personnel for cost control is ensured, and a requirement for information sharing in all aspects can be met.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
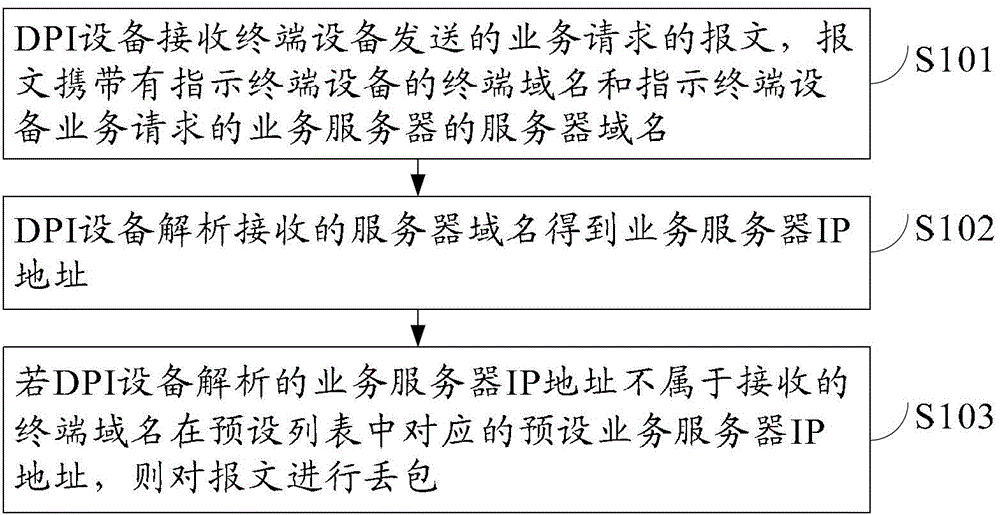
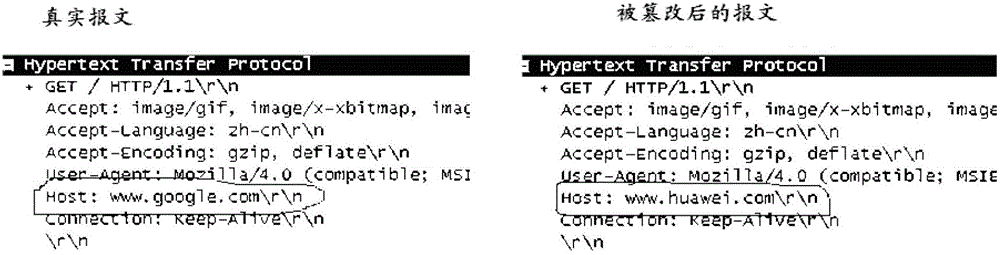
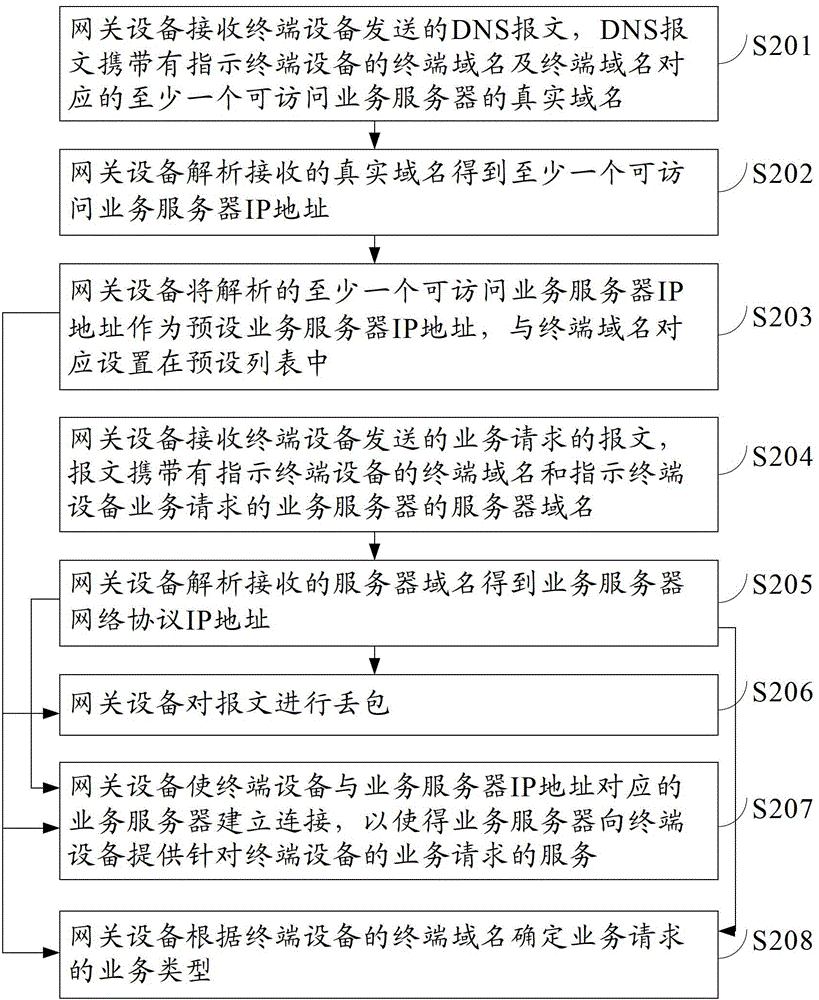
Message receiving method, deep packet inspection device, and system
Embodiments of the invention provide a message receiving method, a deep packet inspection device, and a system, relating to the field of communication, and by the method, the device and system, the message identification capacity of the deep packet inspection device is improved, thereby preventing bugs caused by insufficient identification. The message receiving method comprises: receiving a service request message sent by a terminal device, the message carrying a terminal domain name indicating the terminal device and a server domain name of a service server indicating the service request of the terminal device; analyzing the received server domain name so as to obtain an internet protocol (IP) address of the service server; and if the IP address of the service server does not belong to preset service server IP addresses corresponding to the received terminal domain name in a preset list, dropping the massage. Embodiments of the invention are used for processing messages.
Owner:HUAWEI TECH CO LTD
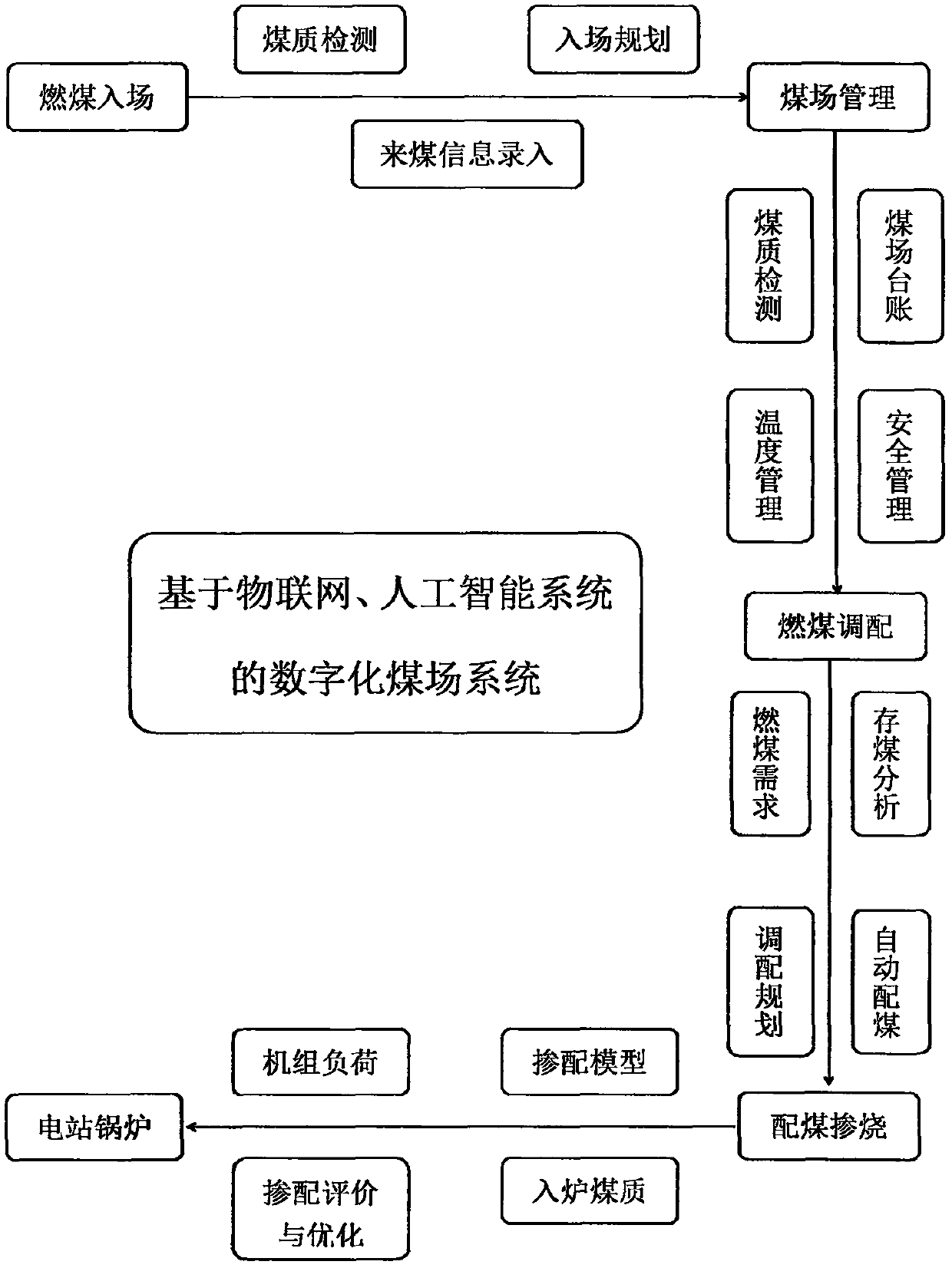
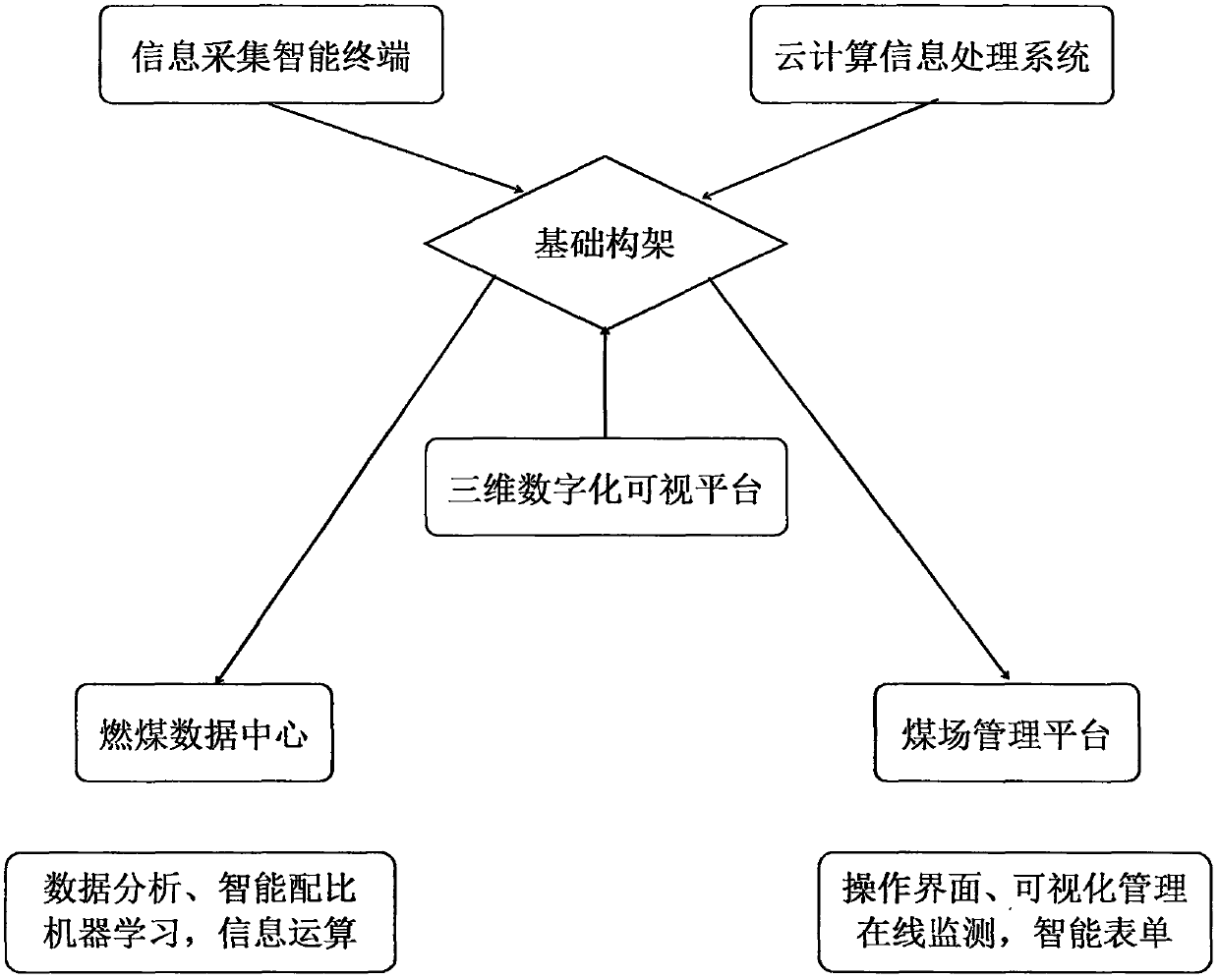
Digitized coal yard system based on Internet of Things and artificial intelligence system
PendingCN109583699AHigh degree of digitizationEasy to deployOffice automationResourcesData centerClosed loop
The invention provides a digitalized coal yard system based on Internet of Things and an artificial intelligence system, relates to the technical field of fuel management, digitalized factories and power generation, and particularly relates to a digitalized management system of a coal yard. The method is based on the Internet of Things. The invention discloses a digital coal yard system of an artificial intelligence system. Digitization and intelligentization of coal yard and fire coal data are achieved by means of an artificial intelligence system, coal quality test equipment and entrance detection equipment are combined by means of coal yard related equipment and an information acquisition intelligent terminal, fire coal digital management is achieved, a data reference basis is providedfor coal blending combustion and fire coal planning, and actual economic benefits are brought to enterprises. According to the invention, a management chain from entry to evaluation is required to beestablished, and closed-loop management of fuel is realized, so that a coal yard management platform and a coal-fired data center are provided on the basis of an overall scheme architecture, and digitalization, visualization and intelligentization of coal yard management of power generation enterprises are realized through construction of the coal yard management platform and the coal-fired data center.
Owner:天津市容创智行节能科技有限公司
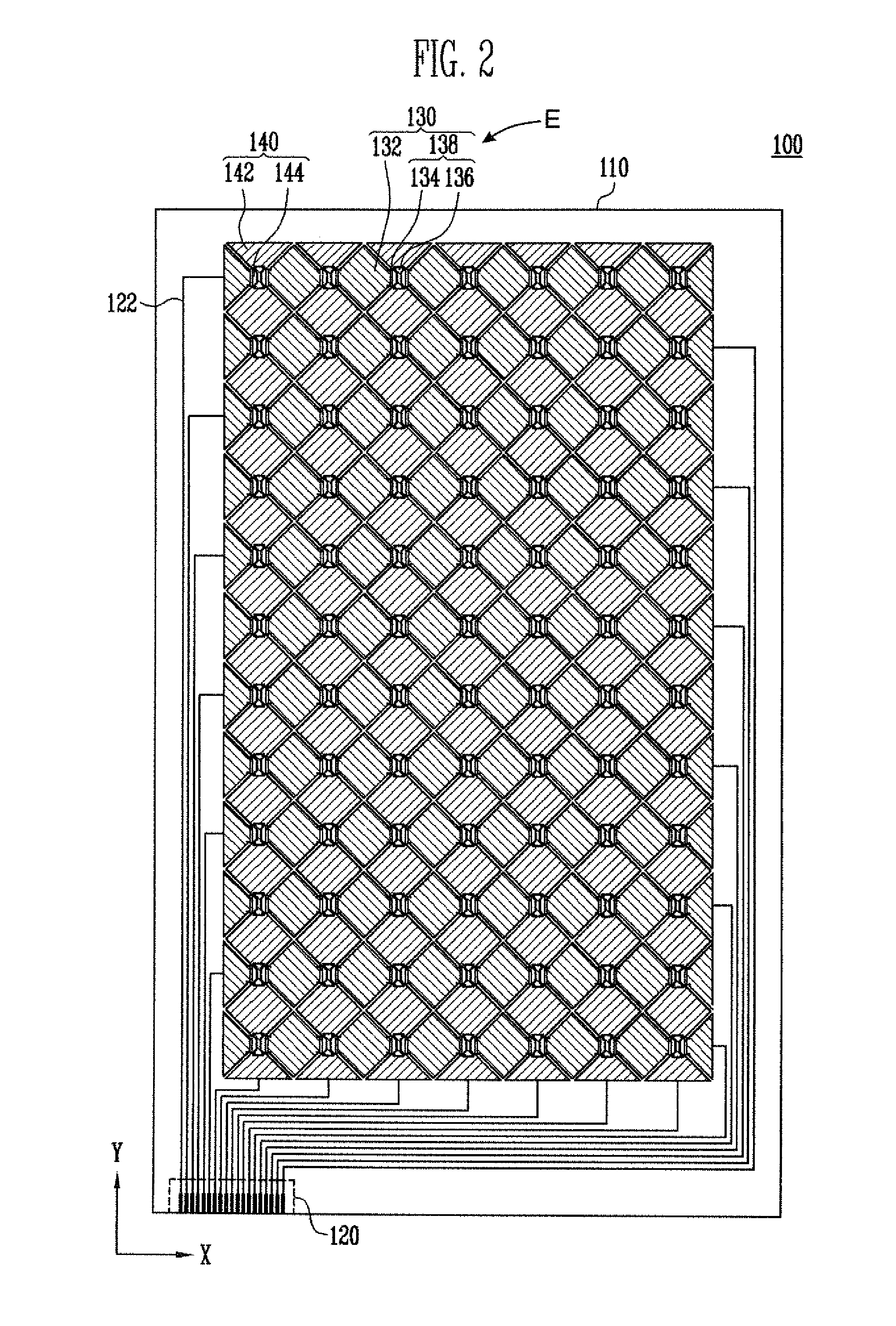
Touch screen panel and display device having the same
ActiveUS8698768B2Increase awarenessAvoid loopholesInput/output processes for data processingDisplay deviceTouchscreen
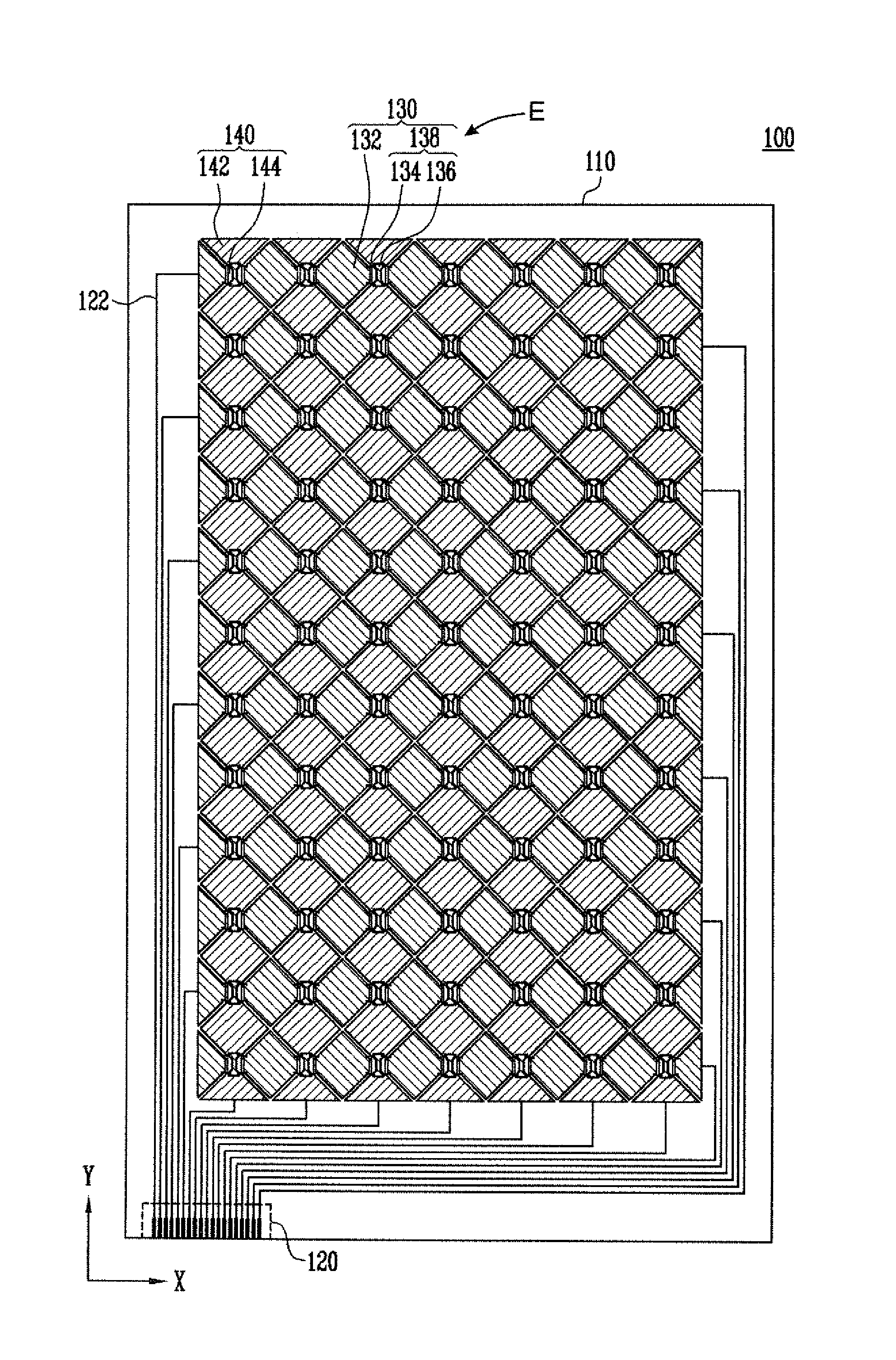
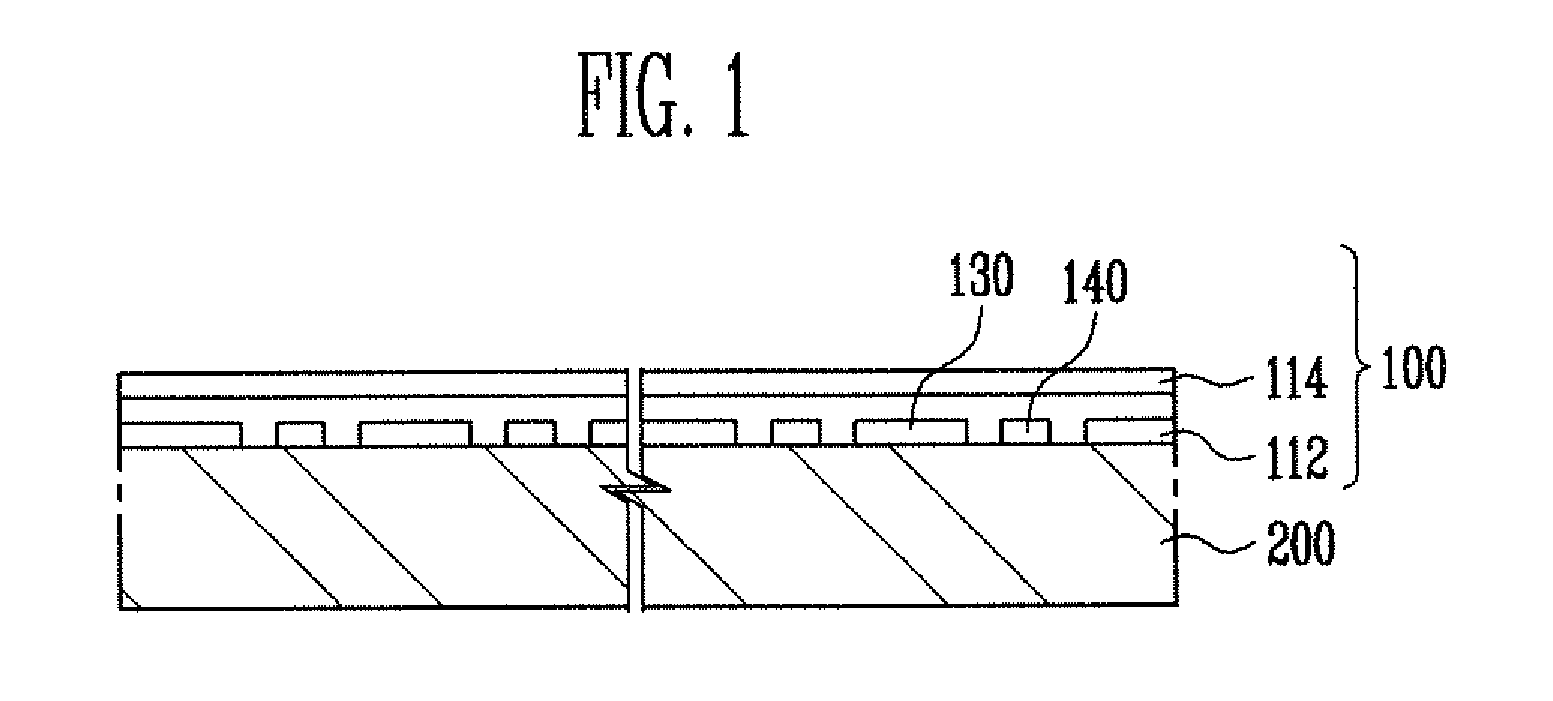
A touch screen panel comprises a first sensing pattern provided with first sensing cells arranged on one row along a first direction on a transparent substrate, and a first connection pattern through which adjacent first sensing cells are electrically connected to each other. A second sensing pattern is provided with second sensing cells arranged so as to be spaced apart from the first sensing cells on one column along a second direction on the transparent substrate, and a second connection pattern through which adjacent second sensing cells are electrically connected to each other. The first connection pattern includes at least two pairs of metal patterns arranged so as to be spaced apart from one another, and a transparent pattern formed in the shape of an island in the second sensing pattern so as to be electrically connected to one or the other end of each of the metal patterns.
Owner:SAMSUNG DISPLAY CO LTD
Crack repair using friction stir welding on materials including metal matrix composites, ferrous alloys, non-ferrous alloys, and superalloys
InactiveUS7225968B2Avoid loopholesWelding/cutting auxillary devicesAuxillary welding devicesCrazingEngineering
A system and method of using friction stir welding and friction stir processing to perform crack repair or preventative maintenance of various materials and structures, wherein the structures include pipeline, ships, and nuclear reactor containment vessels, wherein the friction stir welding and processing can be performed on various materials including metal matrix composites, ferrous alloys, non-ferrous alloys, and superalloys, and wherein the friction stir welding and processing can be performed remotely and in harsh environments such as underwater or in the presence of radiation.
Owner:BABB JONATHAN A +1
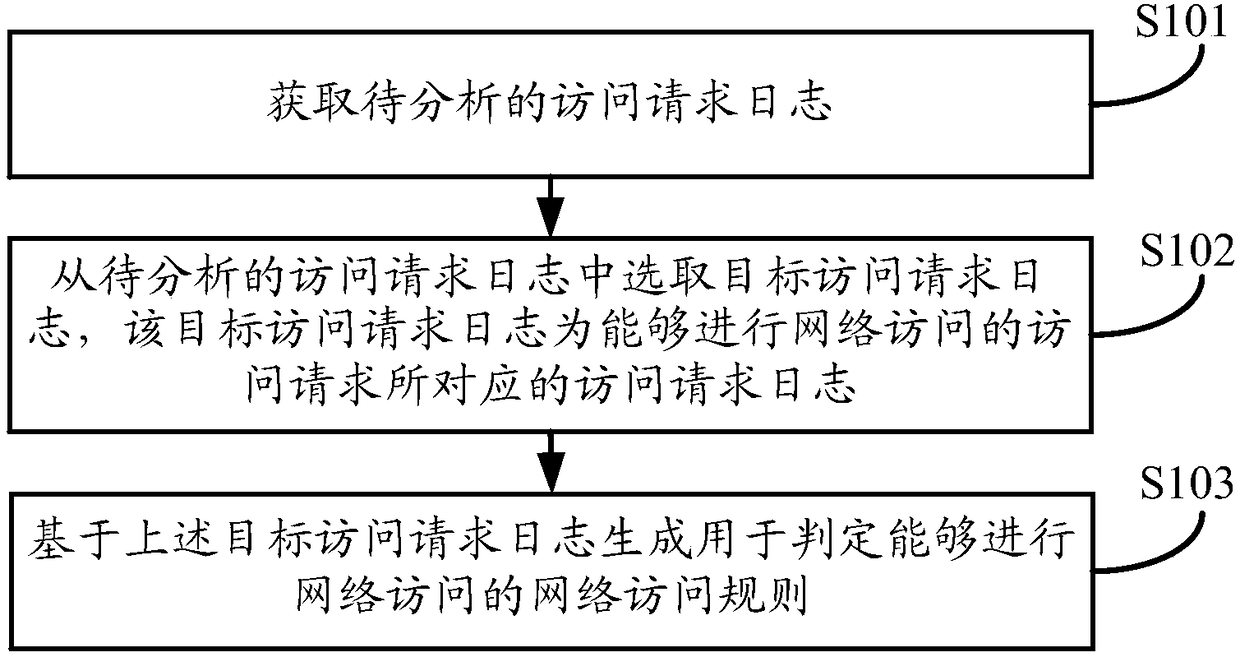
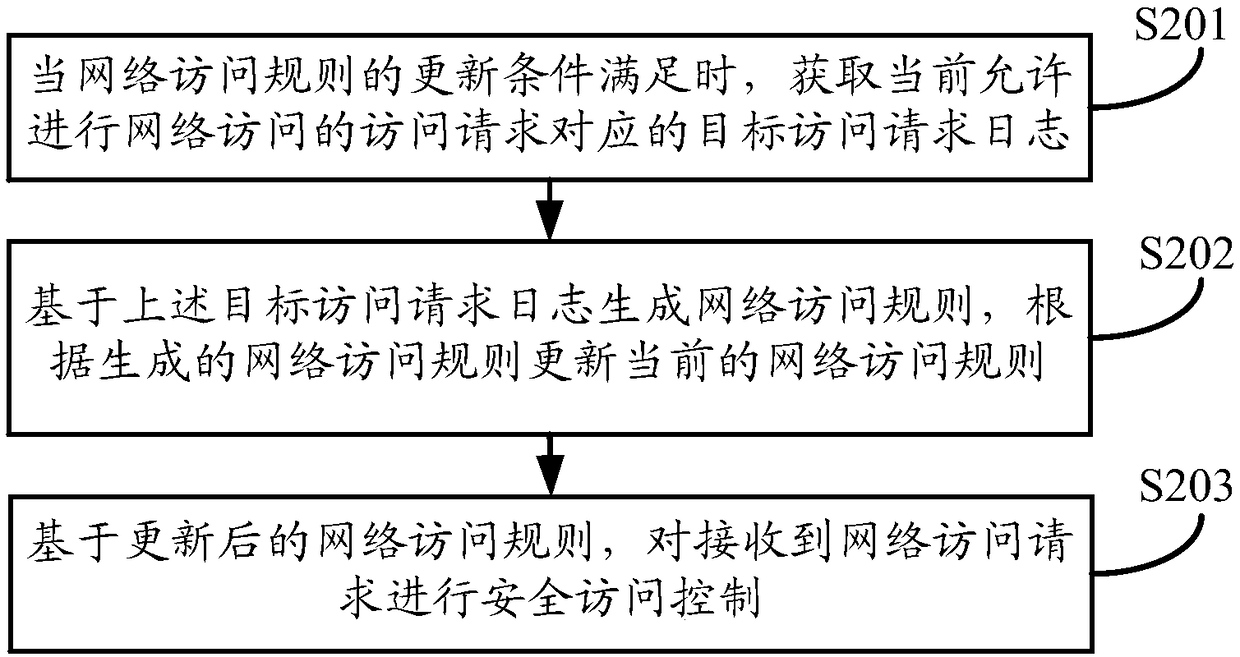
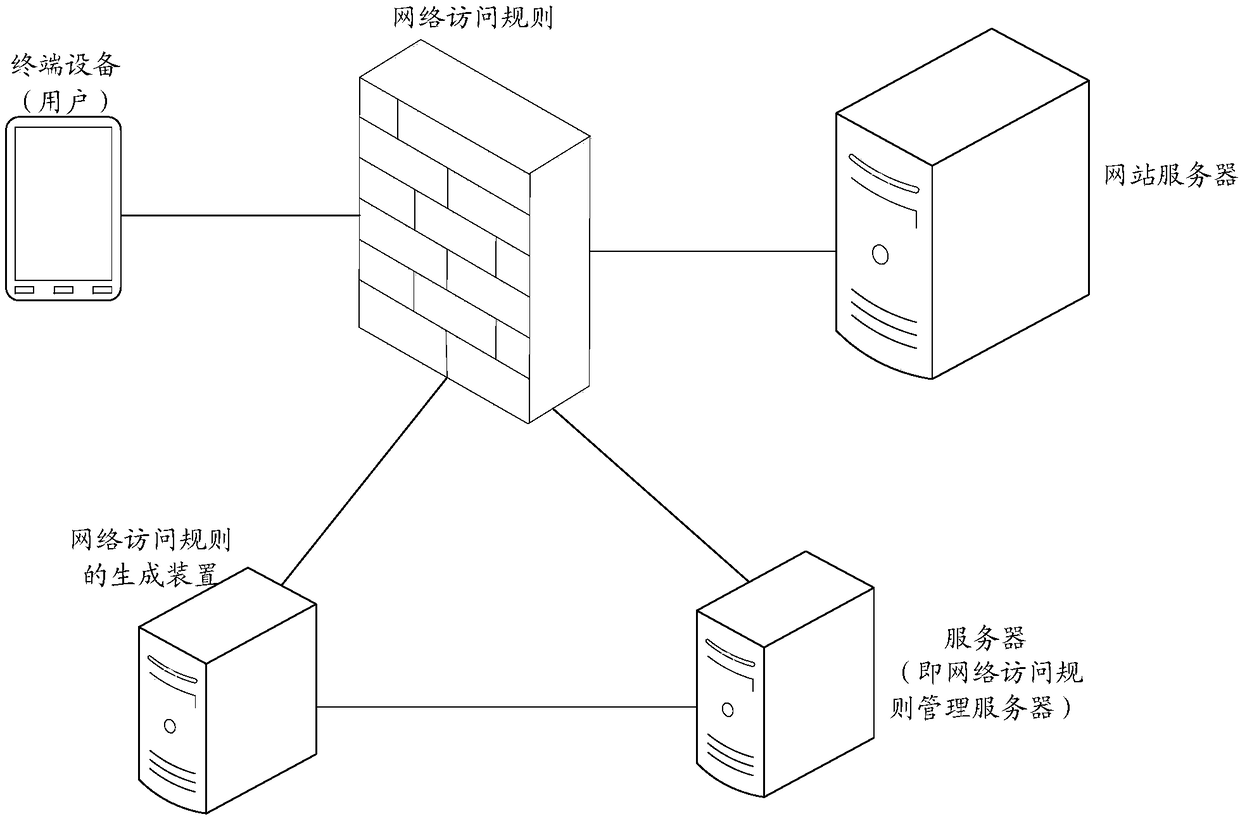
Security access control and network access rule generation method, device and equipment
The embodiment of the invention discloses a security access control and a network access rule generation method, device and equipment. The method comprises the steps: obtaining a target access requestlog corresponding to an access request that is currently allowed to access a network when an update condition of the network access rule is met; generating a network access rule based on the target access request log, and updating the current network access rule according to the generated network access rule; performing security access control of the received network access request based on the updated network access rule. Through the embodiment of the invention, the method can be used for detecting and determining whether to respond to the access request through the generated network accessrule (i.e., white list) for determining that the network access can be performed, so that only the access request that satisfies the network access rule can be responded to avoid new vulnerabilities or missed reports caused by new network attack patterns and improve the security of network access.
Owner:ALIBABA GRP HLDG LTD
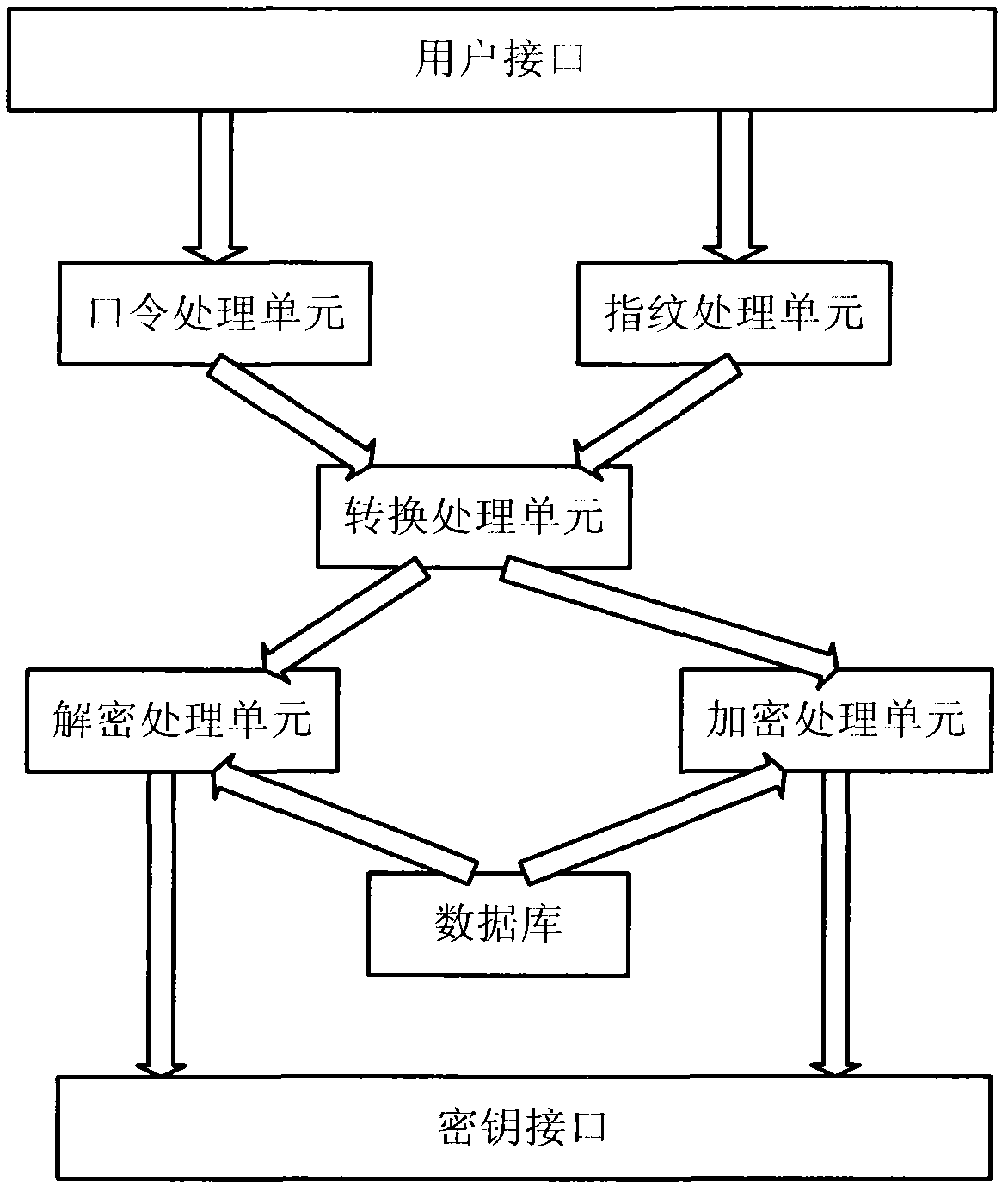
Fingerprint encryption-based identity authentication system and implementation method thereof
ActiveCN102004872AAvoid loopholesImprove securityCharacter and pattern recognitionDigital data authenticationAuthentication systemFingerprint
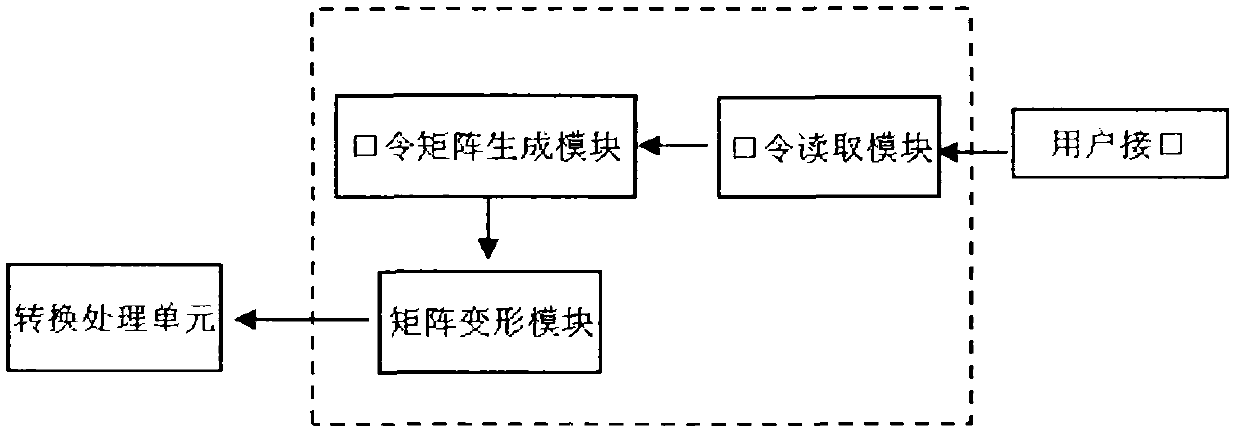
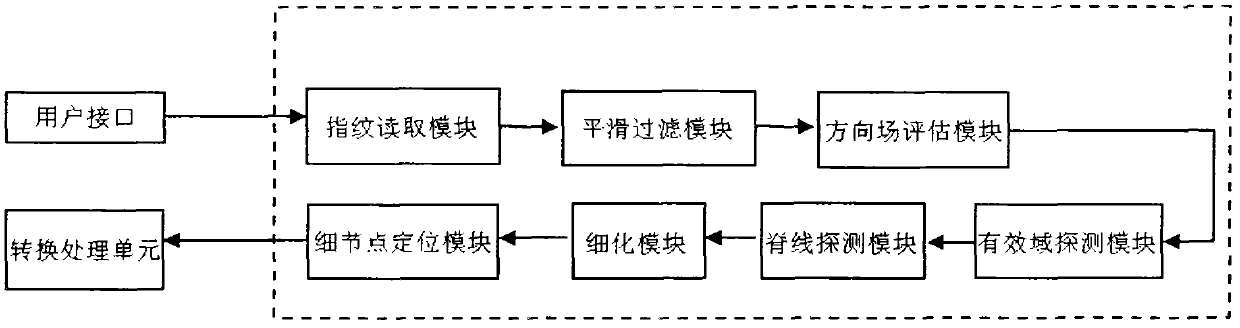
The invention discloses a fingerprint encryption-based identity authentication system. The system comprises a user interface, a key interface, a database, a password processing unit, a fingerprint processing unit, a conversion processing unit, a decryption processing unit and an encryption processing unit, wherein the user interface is connected with the password processing unit and the fingerprint processing unit respectively; the password processing unit, the fingerprint processing unit, the decryption processing unit and the encryption processing unit are connected with the conversion processing unit respectively; and the decryption processing unit and the encryption processing unit are connected with the database and the key interface respectively. The invention also discloses an implementation method of the fingerprint encryption-based identity authentication system, which comprises the steps of encryption and decryption. The system and the method have the advantages that: a biological characteristic password can be allowed to be cancelled and can be reset for unlimited times, the safety is high, cross-comparison bugs are prevented, and the like.
Owner:武汉欧微优科技有限公司
High voltage bushing
ActiveUS20100018752A1High voltageEasy to operateHigh-tension/heavy-dress switchesMetal working apparatusEngineeringHigh pressure
Owner:HITACHI ENERGY SWITZERLAND AG
Light-emitting semiconductor device using gallium nitride compound semiconductor
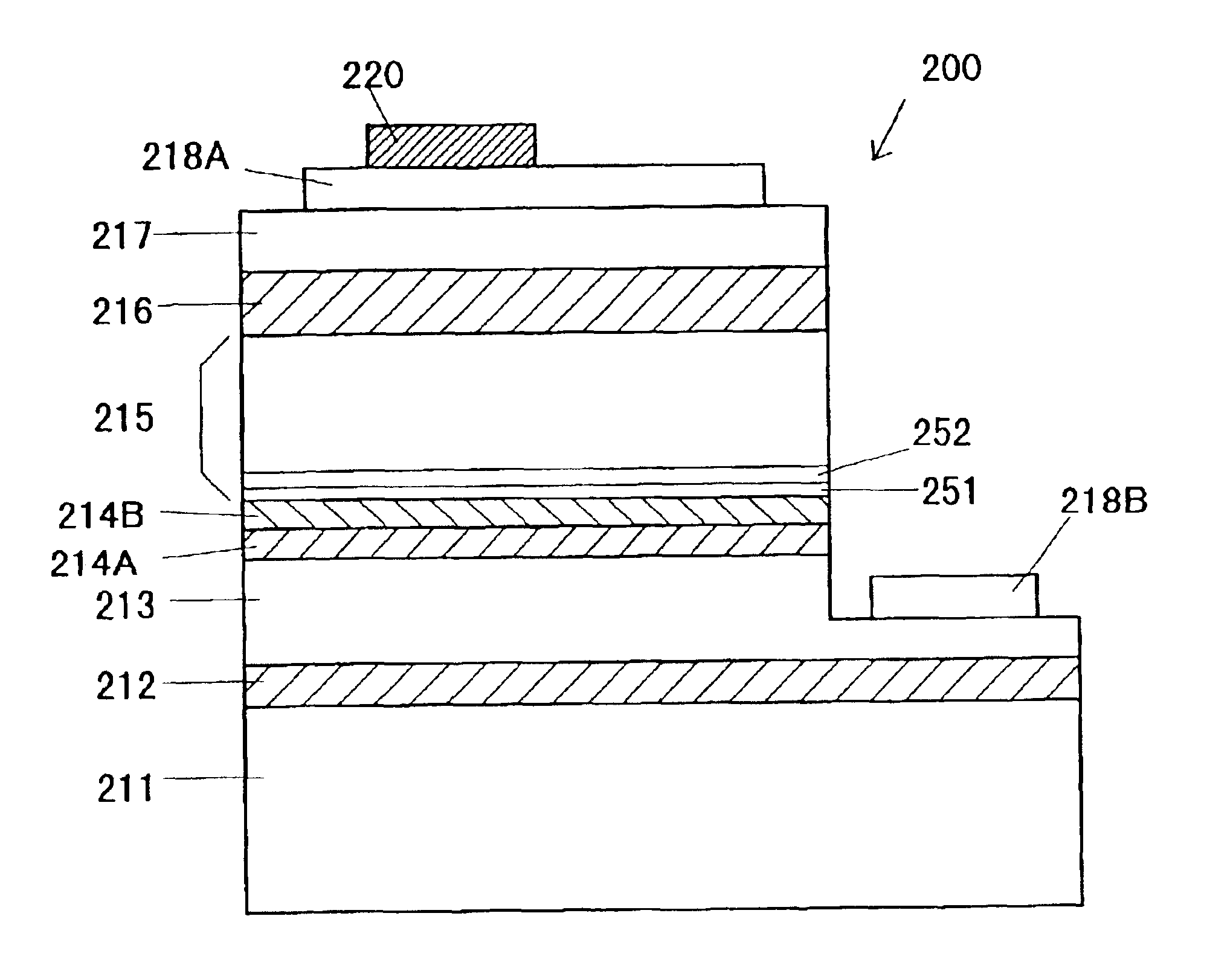
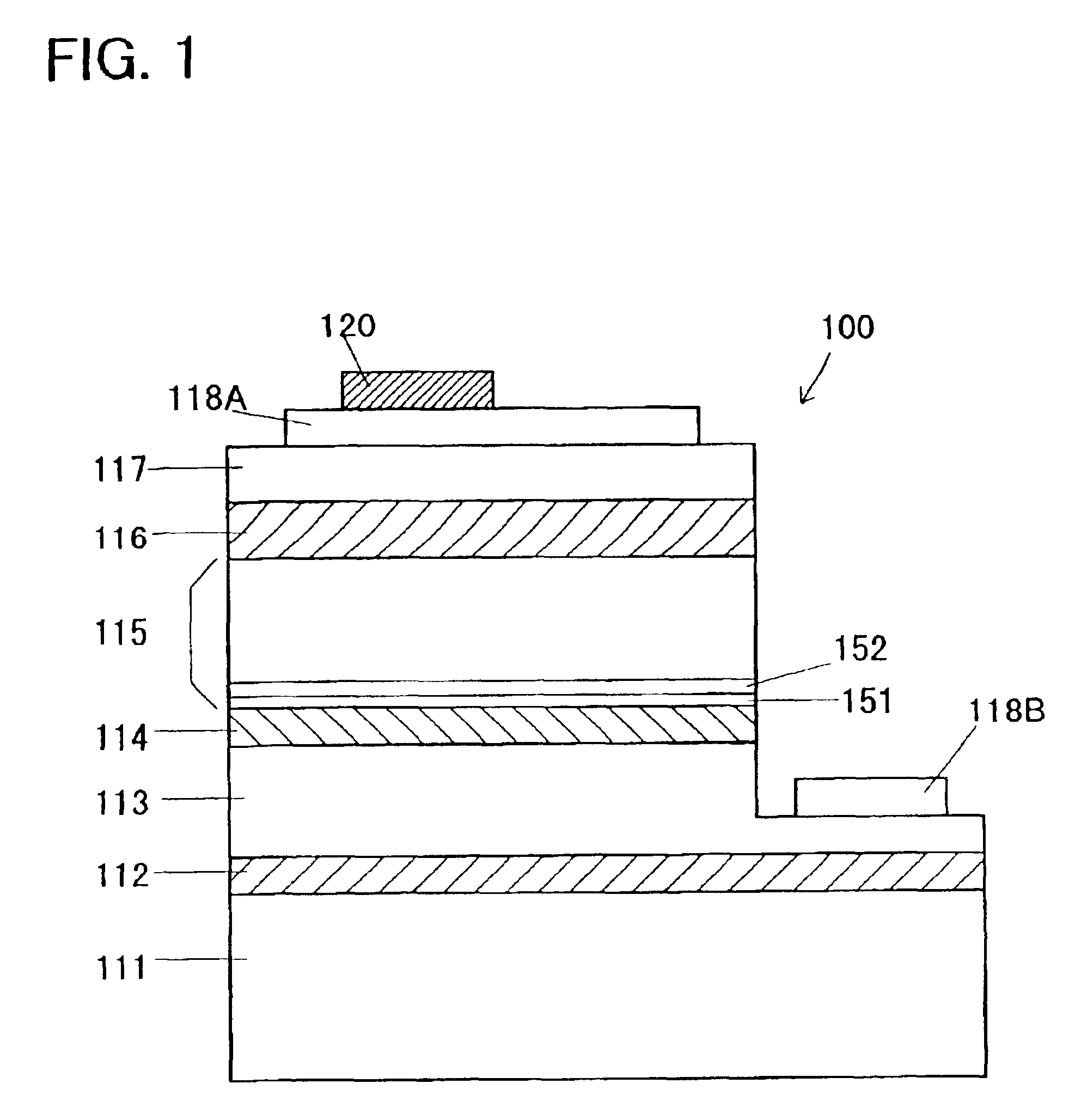
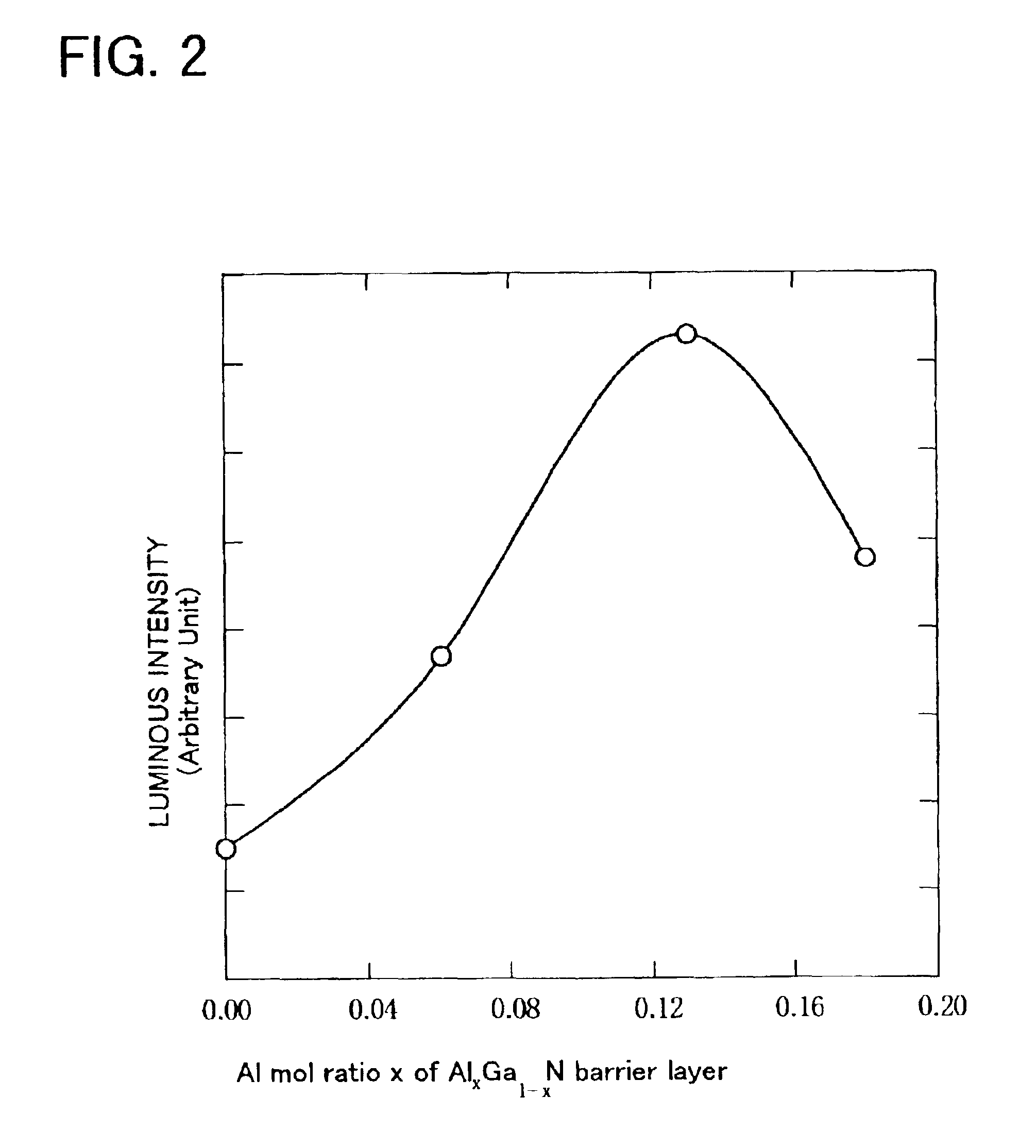
InactiveUS6853009B2Improve luminous efficiencyLarge band gap energySolid-state devicesNanoopticsLuminous intensityQuantum well
A barrier layer made of AlxGa1-xN (0<x≦0.18) is formed in a light-emitting semiconductor device using gallium nitride compound having a multi quantum-well (MQW) structure. By controlling a composition ratio x of aluminum (Al) or thickness of the barrier layer, luminous intensity of the device is improved.An n-cladding layer made of AlxGa1-xN (0<x≦0.06) is formed in a light-emitting semiconductor device using gallium nitride compound. By controlling a composition ratio x of aluminum or thickness of the n-cladding layer, luminous intensity of the device is improved.A p-type layer and an n-type layer are formed in a light-emitting semiconductor device using gallium nitride compound having a double-hetero junction structure. By controlling a ratio of a hole concentration of the p-type layer and an electron concentration of the n-type layer approximates to 1, luminous intensity of the device is improved.
Owner:TOYODA GOSEI CO LTD
Method and device for defending DOM-Based-XSS vulnerability and client
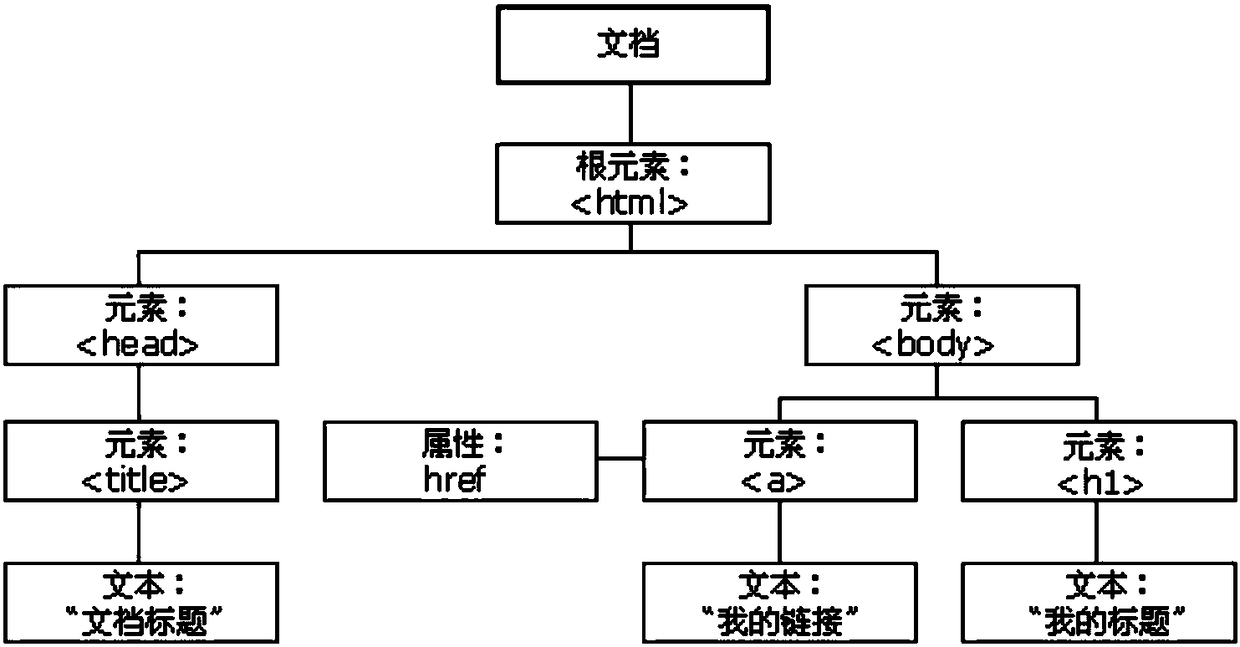
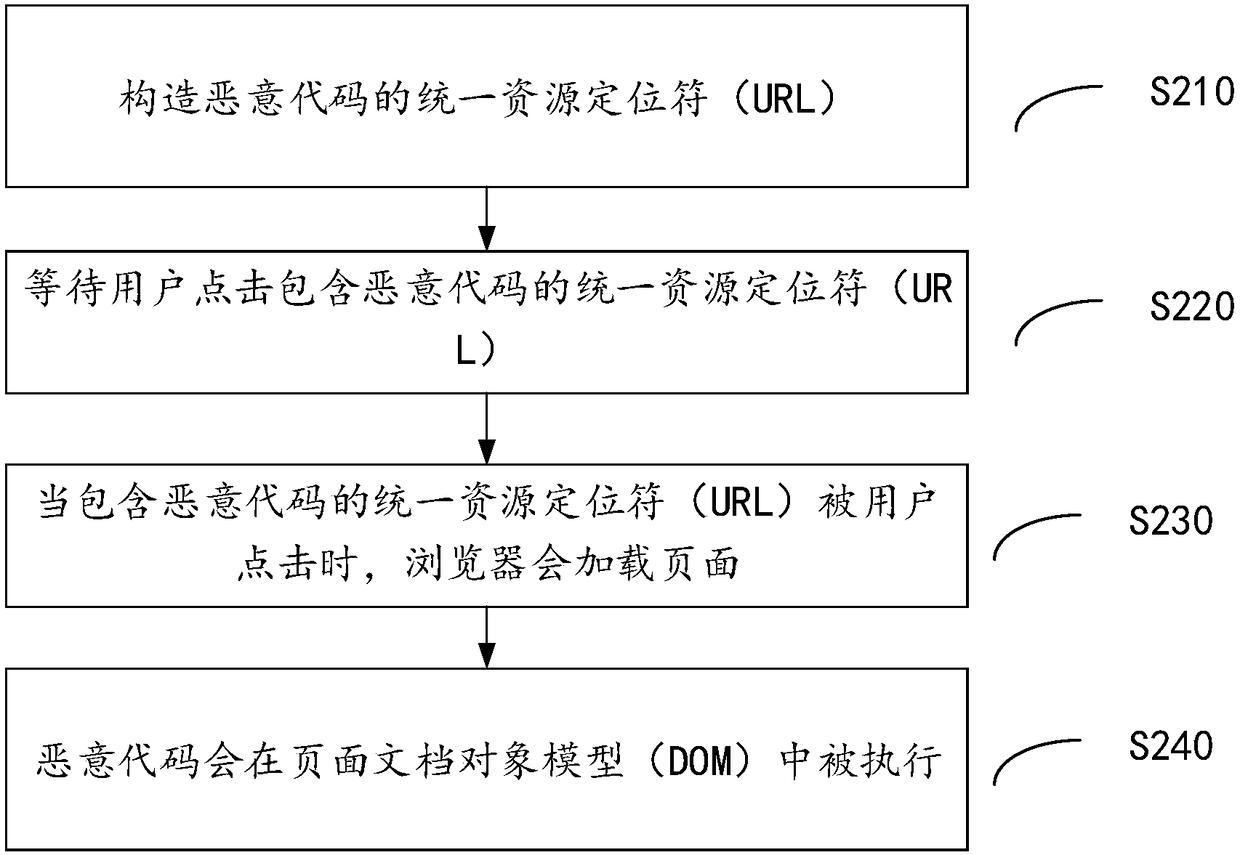
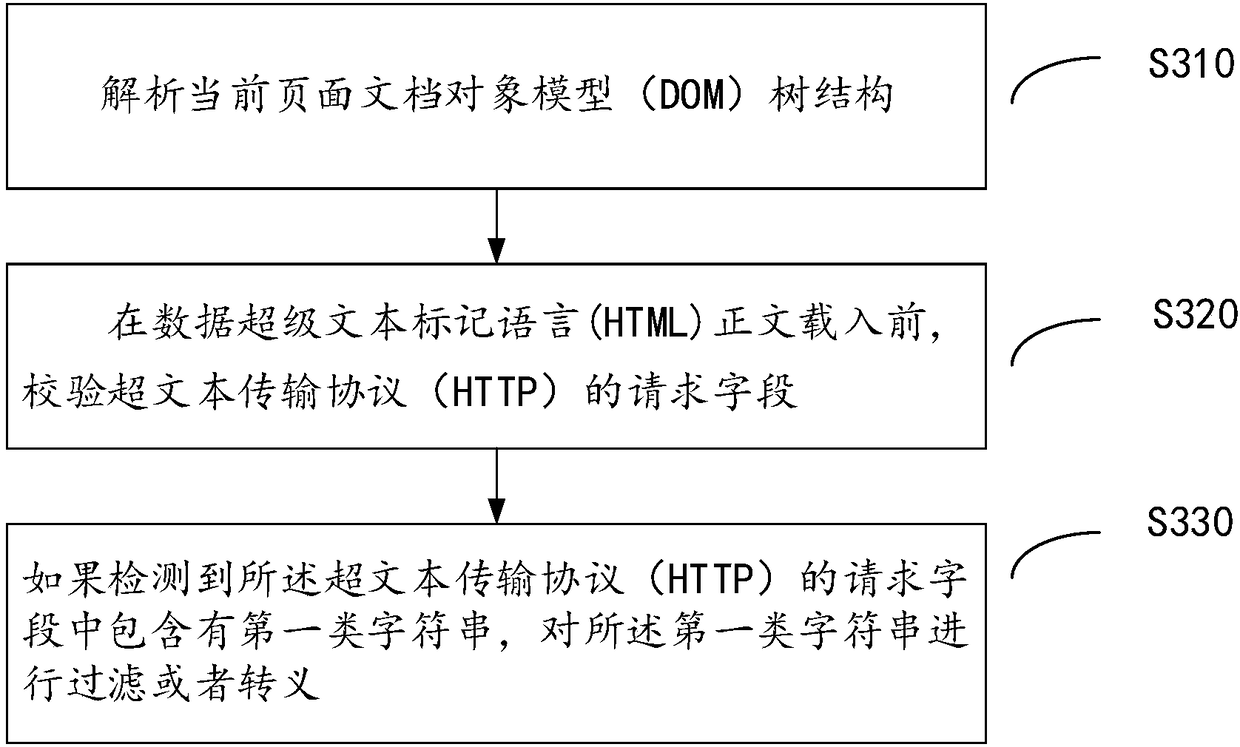
ActiveCN108881101ARealize verificationHas the whole station defense effectTransmissionUniform resource locatorClient-side
The invention provides a method and device for defending a document object model based cross site scripting (DOM-Based-XSS) vulnerability and a client. The method comprises the steps of: parsing a tree structure of a current page DOM; before a data hypertext markup language (HTML) text is loaded, checking a request field related to the DOM tree in a hypertext transfer protocol; and if the requestfield comprises a first category of character strings, carrying out filtering or escaping on the first category of character strings. According to the invention, at a moment before the data HTML textis loaded, the request field in the hypertext transfer protocol is verified, so that verification on a uniform resource locator (URL) can be comprehensively and efficiently implemented; the DOM-Based-XSS vulnerability is repaired; and the method and the device have a full-site defense effect and are helpful for controlling the online service increment DOM-Based-XSS vulnerability and preventing newDOM-Based-XSS vulnerability.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for manufacturing semiconductor device
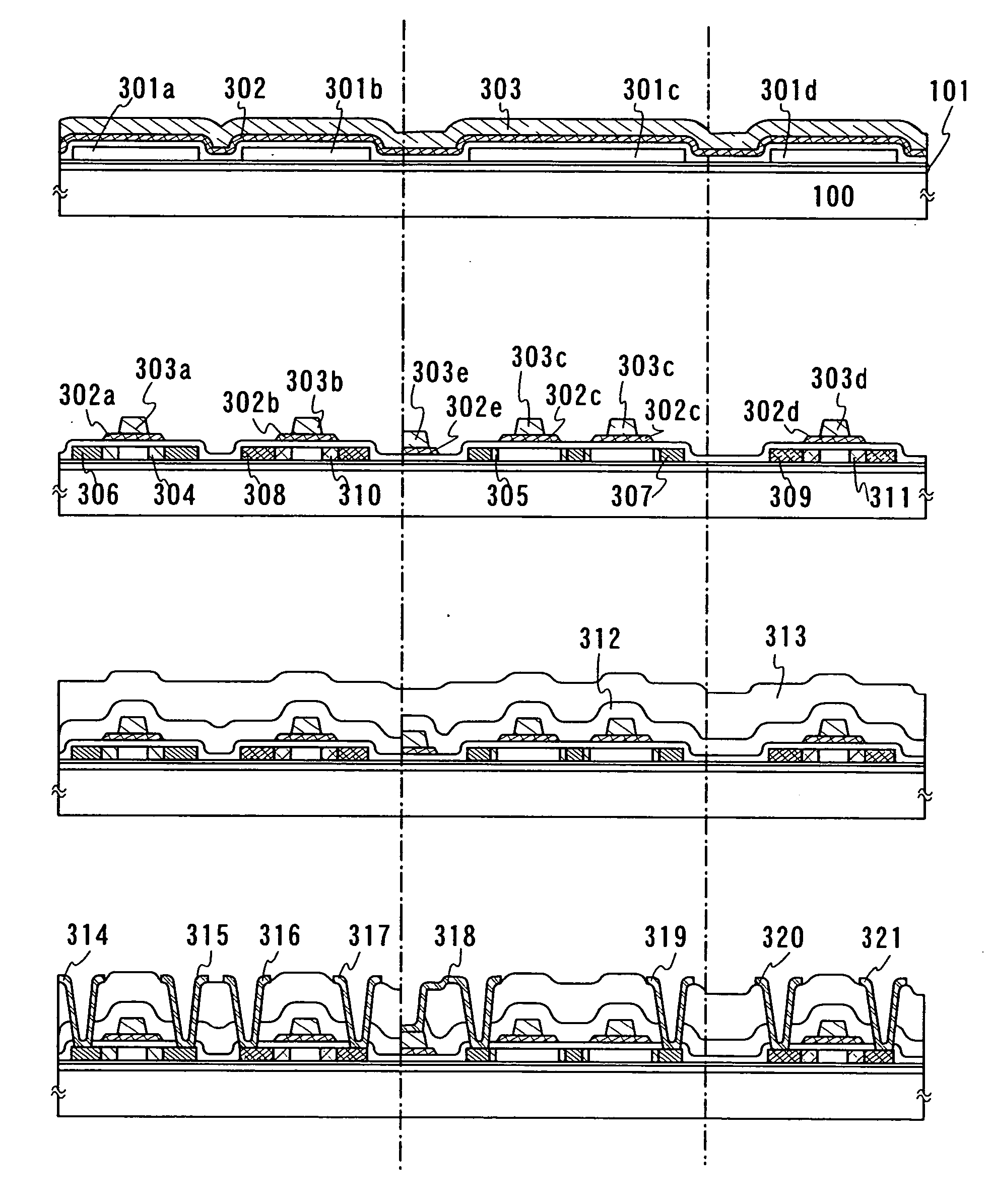
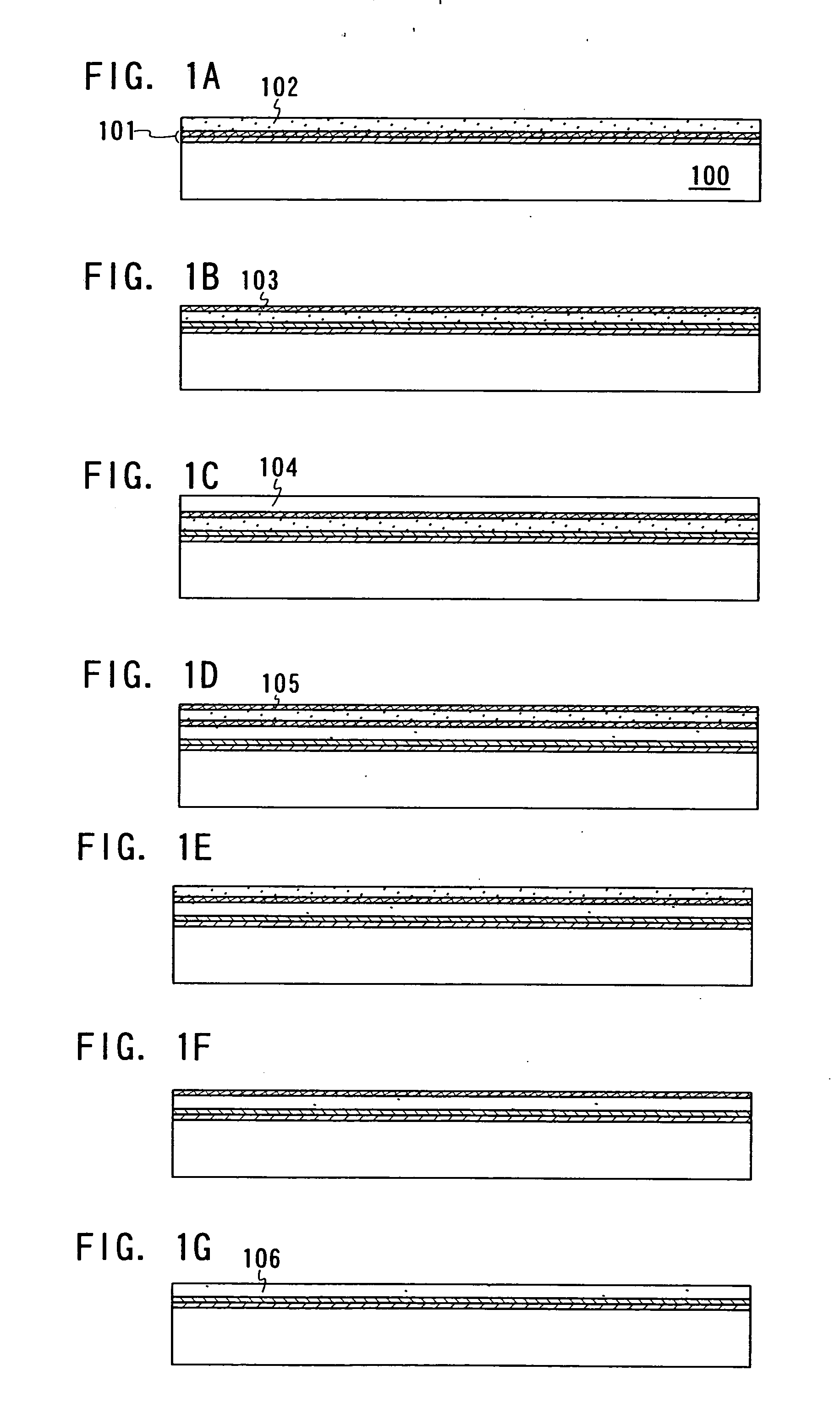
InactiveUS20060134891A1Yield and reliability be improveHigh reliableSolid-state devicesSemiconductor/solid-state device manufacturingSilicon oxideCrystalline semiconductor
An object of the present invention is to provide a method for manufacturing a semiconductor device in which, after crystallizing by using an element that promotes crystallization, holes are prevented from being generated in a crystalline semiconductor film with a concentration of the element in the crystalline semiconductor film decreased by performing gettering. To solve the problem, as a feature of the structure of the invention, in the case of removing a silicon oxide film formed over the semiconductor film, an etchant made of a solution containing fluorine and a substance having surface activity is used.
Owner:SEMICON ENERGY LAB CO LTD
System and method for allocating resources in a communication system
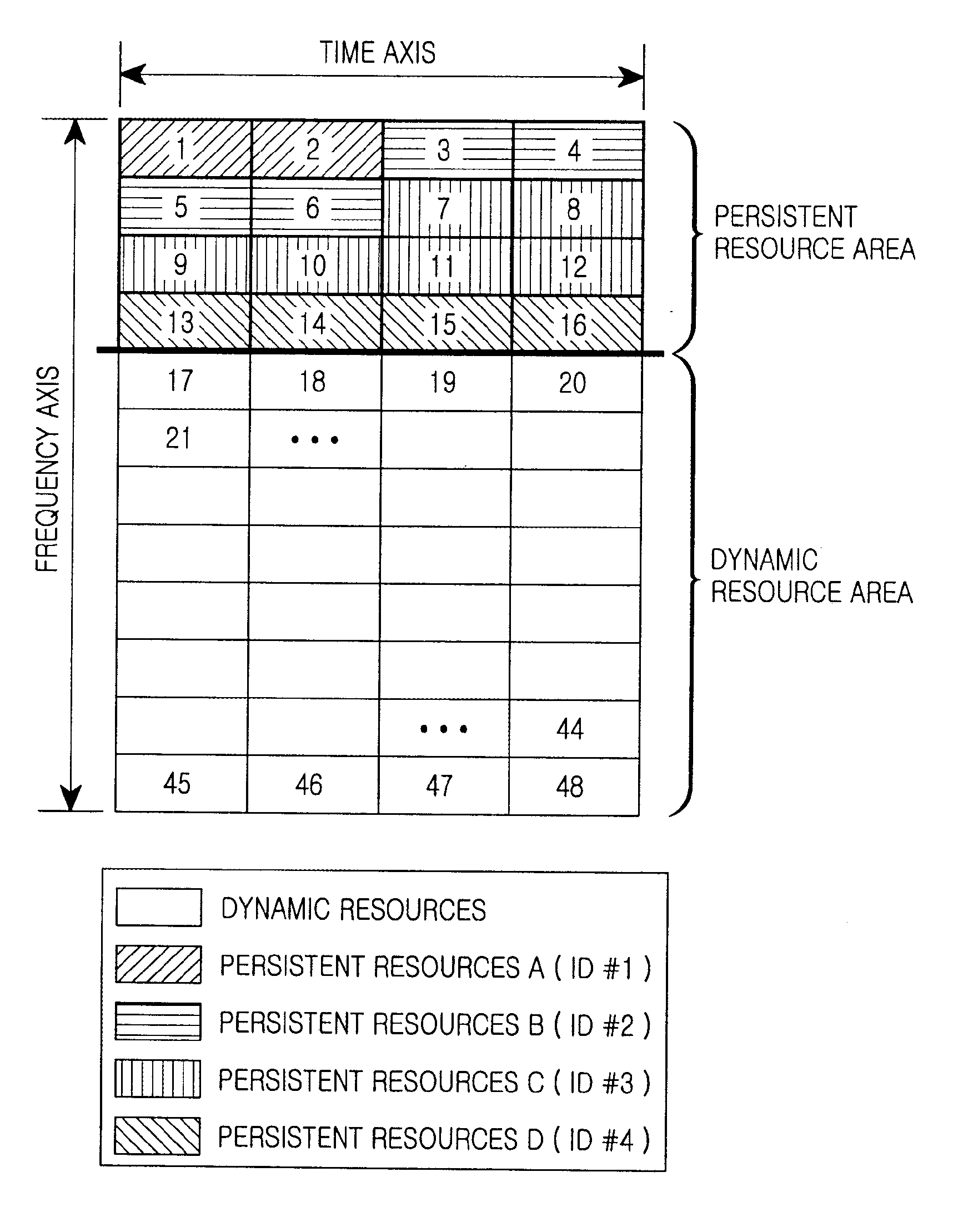
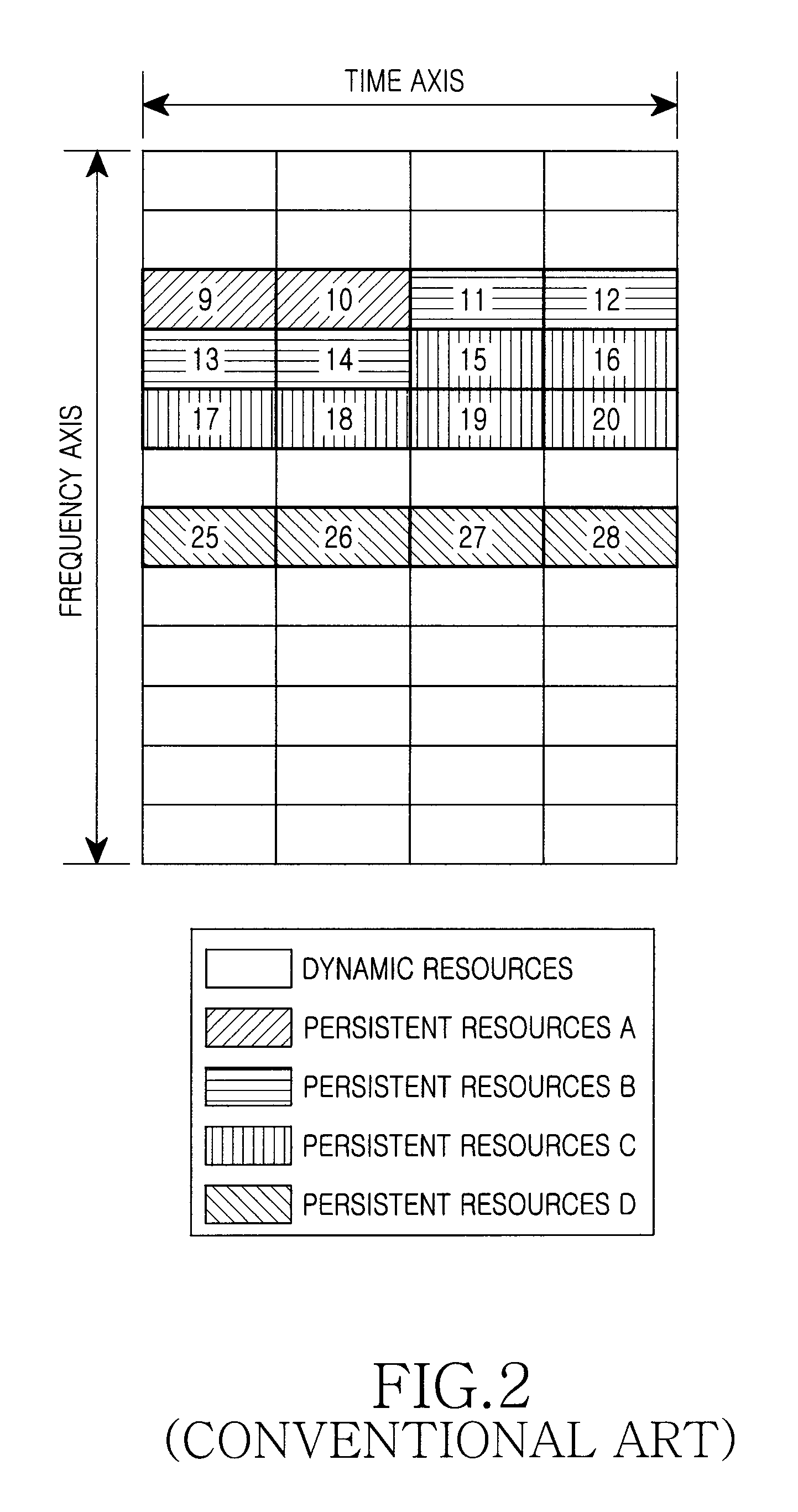
InactiveUS20090122754A1Avoid loopholesWireless commuication servicesCommunications systemDynamic resource
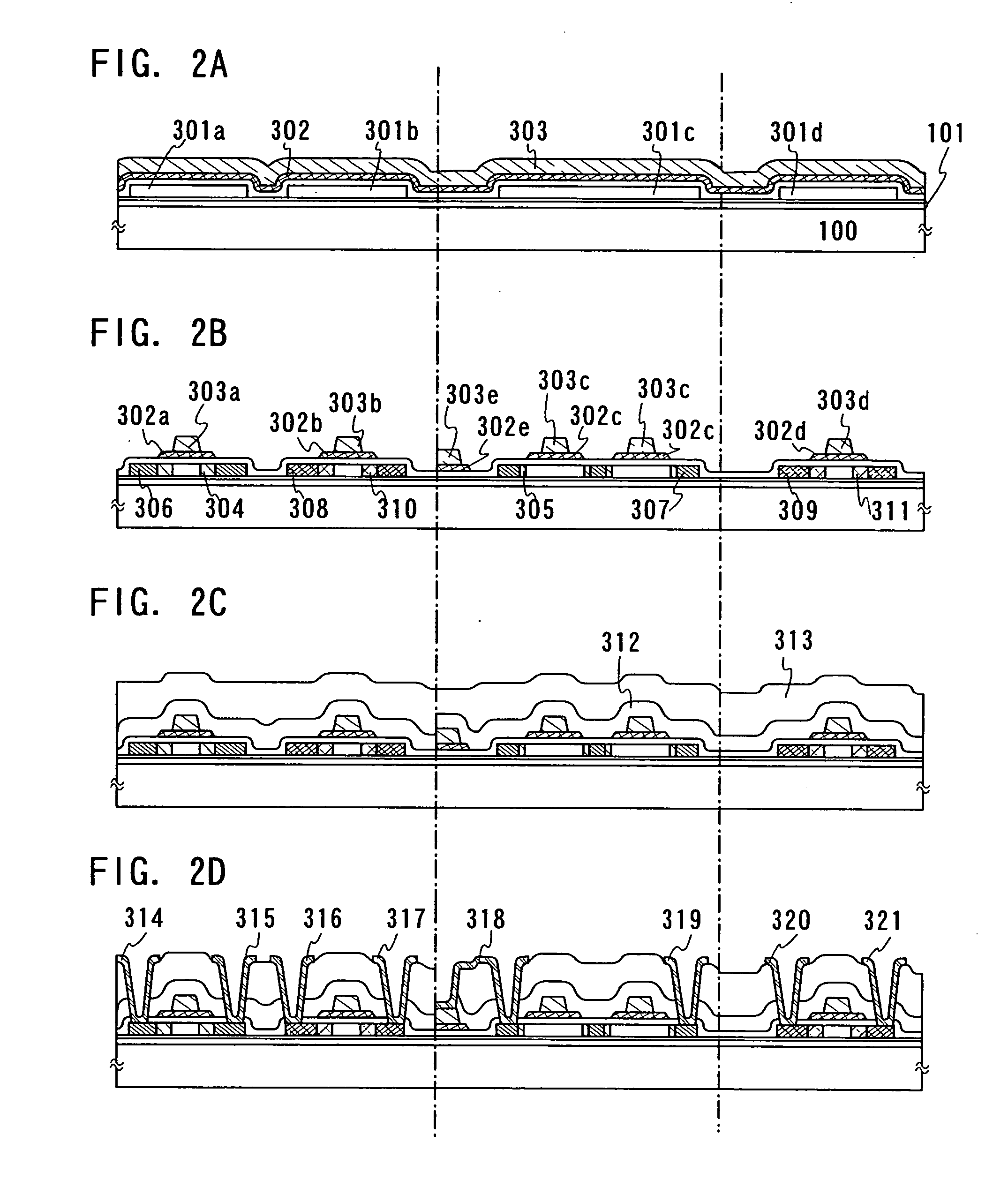
A method and system for allocating resources in a communication system are provided. The system includes a Base Station (BS) for allocating persistent resources included in a persistent resource area to one or more a Mobile Stations (MS) using the persistent resource area, for allocating an Identifier (ID) indicating an allocation order of the persistent resources to each of the one or more the MS using the persistent resource area, for transmitting resource allocation information including the ID and the number of slots included in the persistent resources to each of the one or more MSs using the persistent resource area, and for allocating dynamic resources to one or more MSs using a dynamic resource area, after the persistent resource allocation is completed for all of the one or more MSs using the persistent resource area. The persistent resource area includes successive persistent resources along a time axis and along a frequency axis.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com